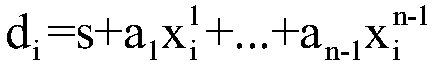Patents
Literature
744results about How to "Realize verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
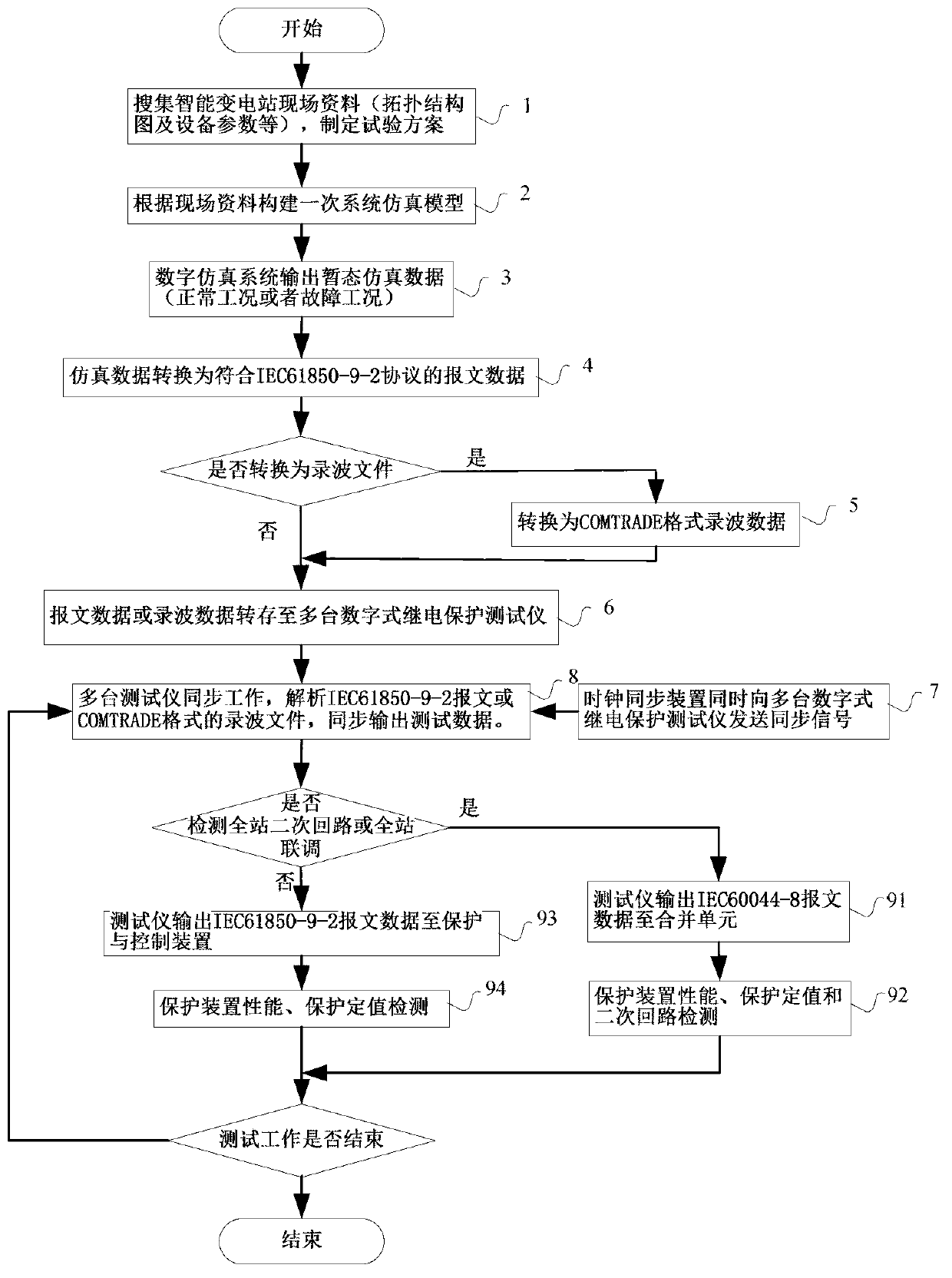
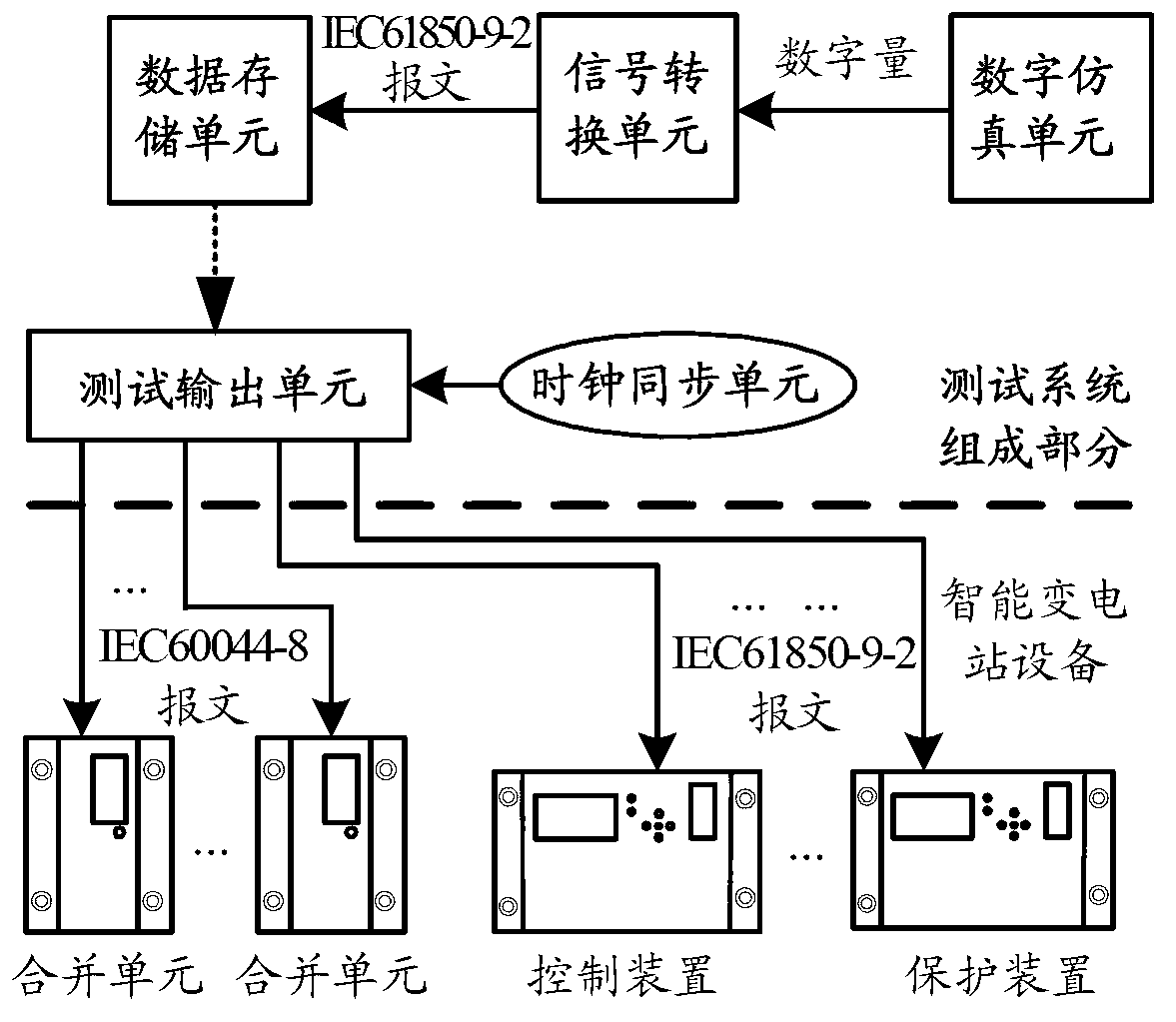
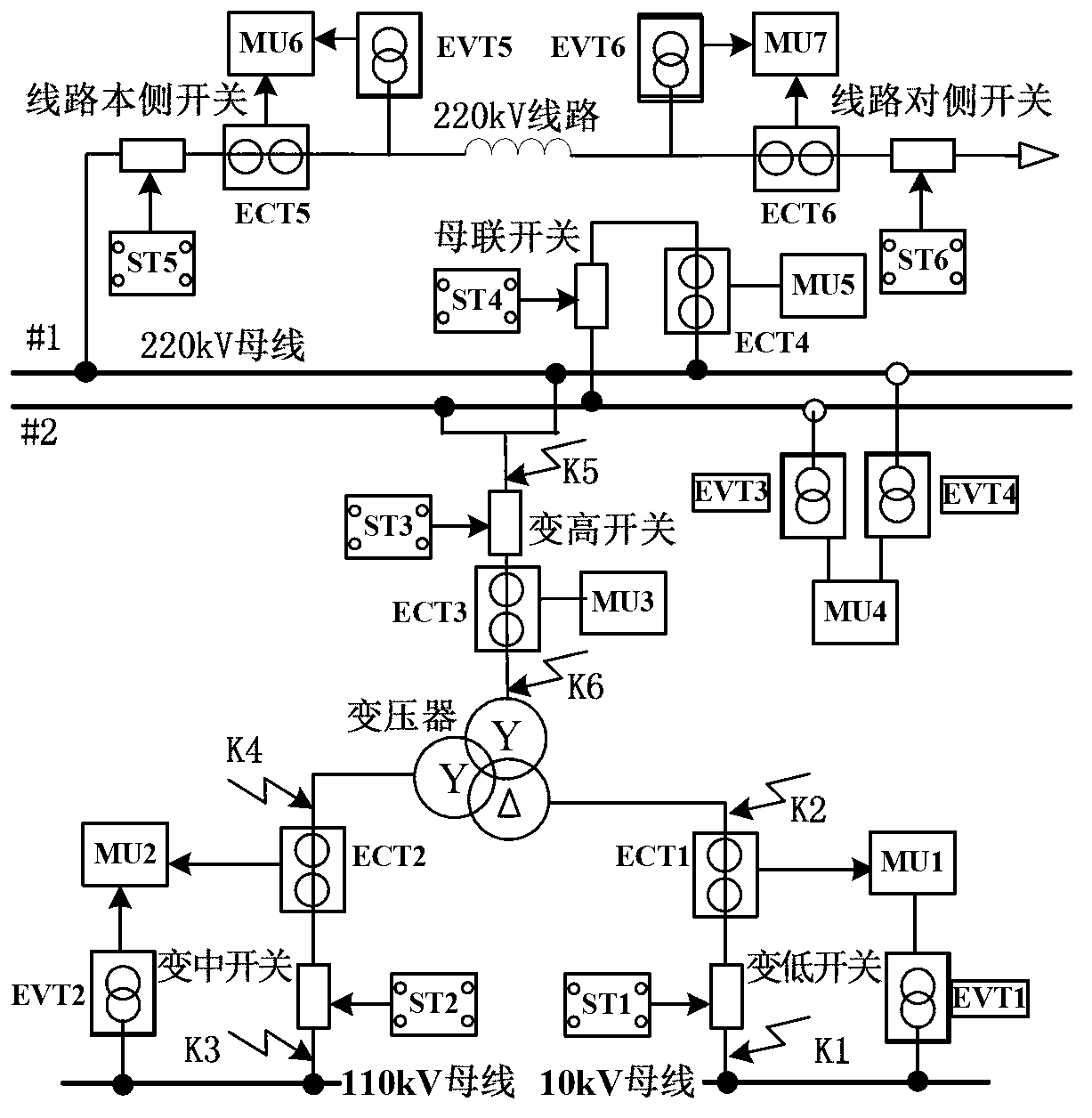
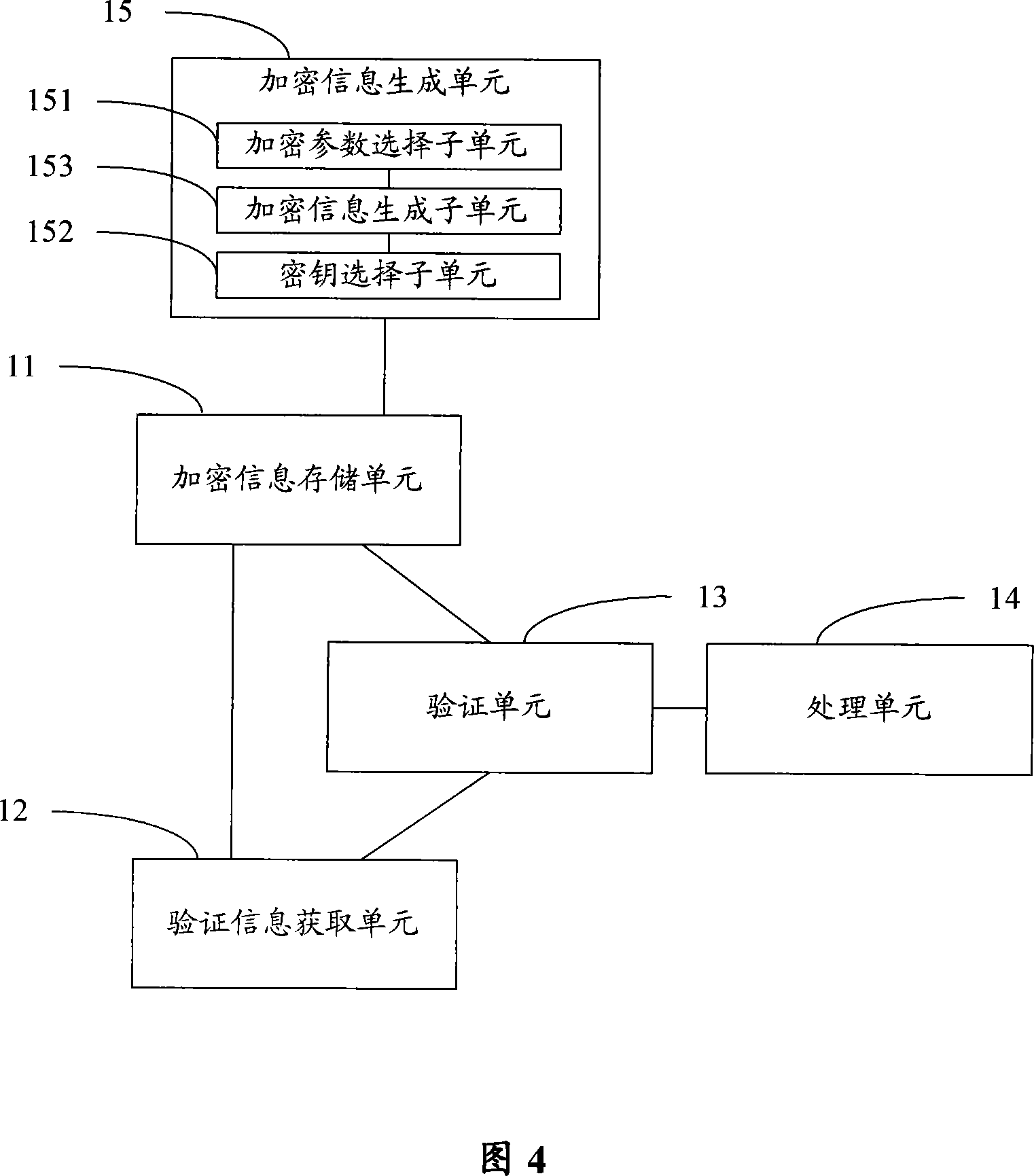
Detection method and detection system of intelligent relay protection device
ActiveCN103105550ARealize verificationPowerfulCircuit interrupters testingInformatizationTransient state
The invention provides a detection method and a detection system of an intelligent relay protection device. Aiming at the situation that compared with the prior art, dynamic properties of the relay protection device cannot be detected effectively in an intelligent substation spot, and starting from the feature of sharing of digitalization and informatization of an intelligent substation secondary system, the detection method which regards a digit simulation system as a data source and regards synchronous working of a plurality of digitized relay protection testers is provided and the detection system of the intelligent relay protection device is constructed. Various operating situations which probably happen in a transformer substation can be simulated according to an actual electric topological structure of an intelligent substation and device parameters construction and simulation models in a lab, simulating calculation can be conducted, transient test data which have higher similarity with the actual operating situations can be achieved by transforming, the transient test data can be output in the intelligent substation spot in a playback mode, and detection of the dynamic properties of the relay protection device and checkout work of protection definite value can be carried out.
Owner:STATE GRID CORP OF CHINA +2
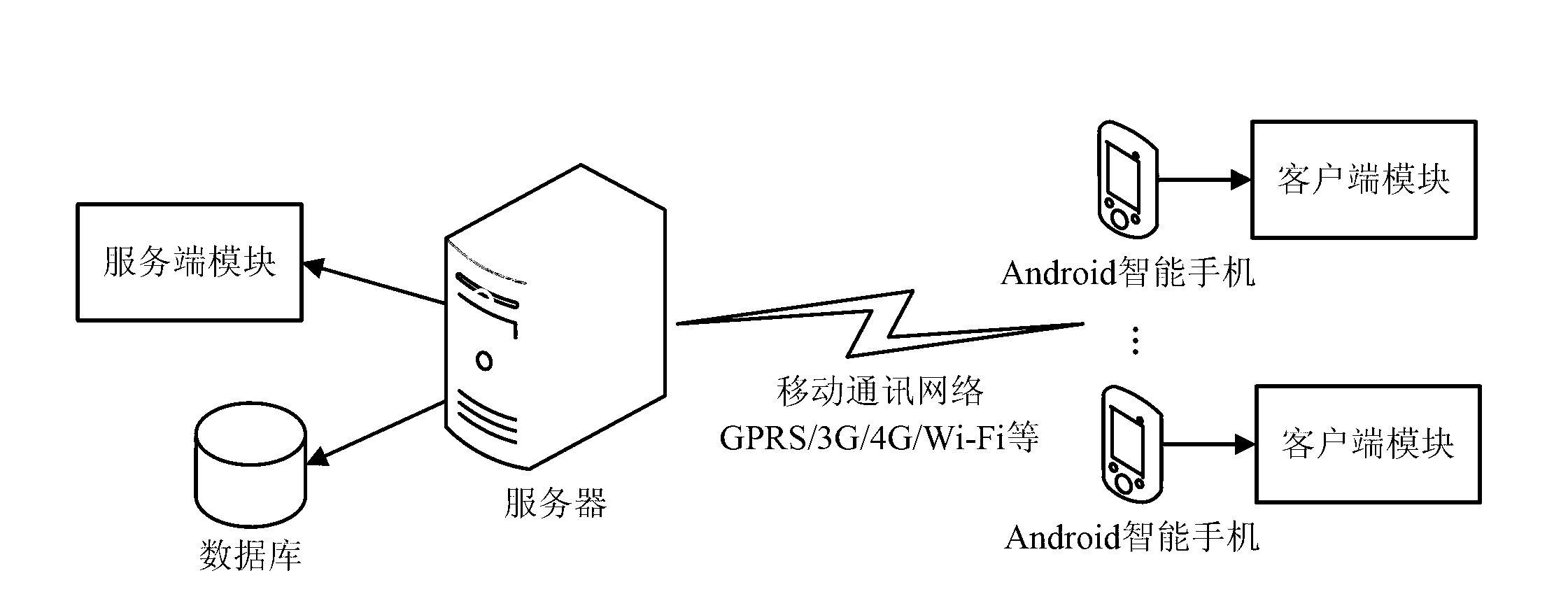
Authentication system and method based on intelligent mobile communication equipment
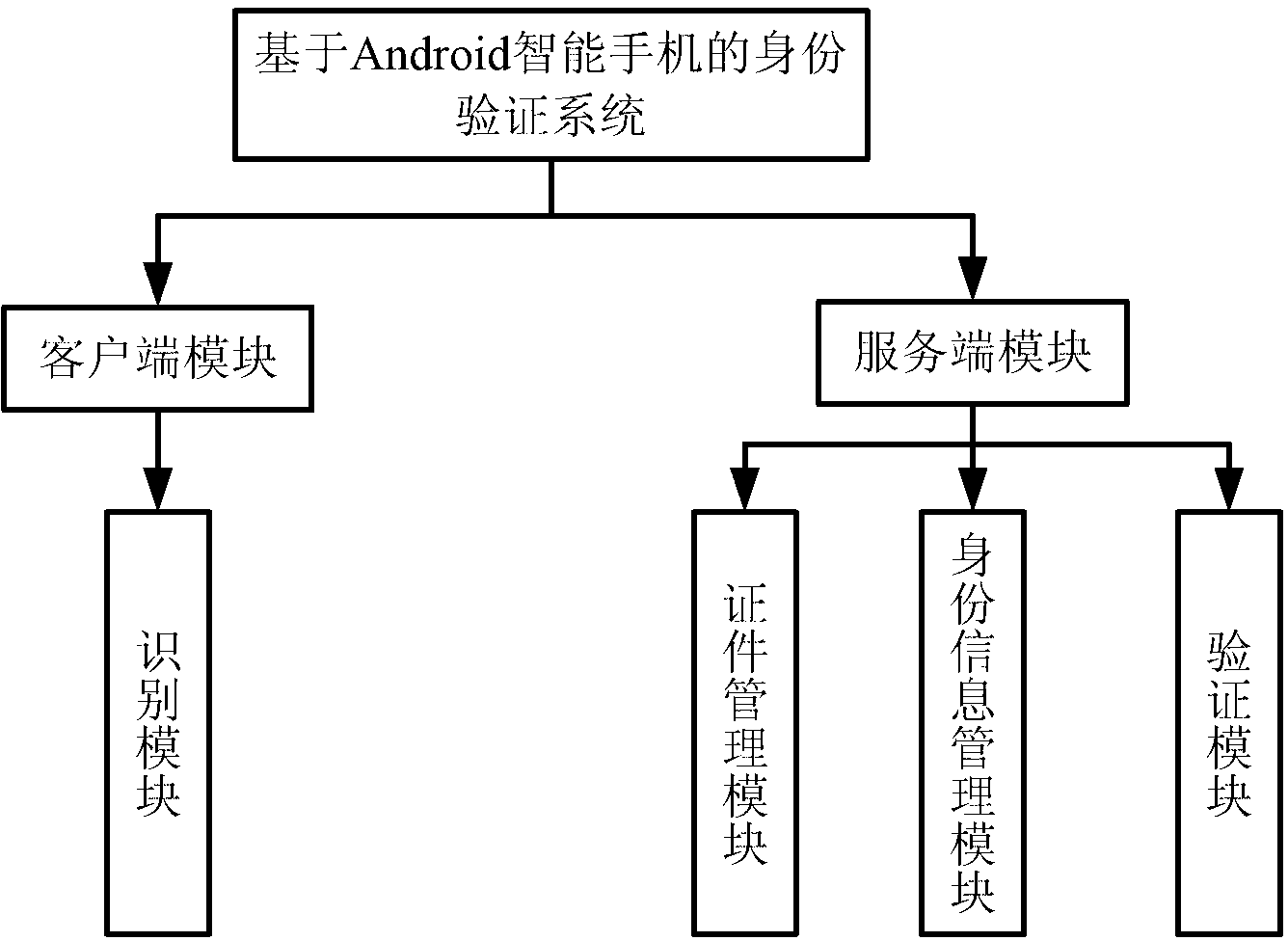
InactiveCN102801528AVerification is achieved quicklyRealize verificationUser identity/authority verificationSecurity arrangementComputer moduleE communication
The invention provides an authentication system based on intelligent mobile communication equipment. The authentication system comprises more than one intelligent mobile communication equipment, more than one server, a client-side module and a server-side module; the client-side module is arranged in the intelligent mobile communication equipment and comprises an identification module, wherein the identification module is used for submitting an authentication request, acquiring identity information, identifying elements in the identity information and querying an authentication result; the server-side module is arranged in the server and comprises a certificate management module, an identity information management module and an authentication module and is used for realizing format and content management of various certificates, management of the identity information and authentication of effectiveness of the elements; the identity information comprises at least one element; and the client-side module and the server-side module are in data communication through a mobile communication network. The invention further provides an authentication method based on the intelligent mobile communication equipment. Due to adoption of the authentication system and method, the identity authentication can be rapidly, conveniently and accurately carried out.
Owner:ZHUHAI ZAIZHOU SOFTWARE TECH
Data integrity authentication information generation method and device as well as data integrity authentication method and device
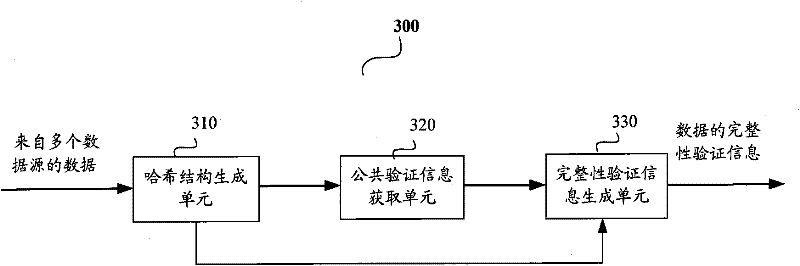
InactiveCN102413313AEffective Integrity ProtectionAchieve protectionTelevision system detailsColor television detailsComputer hardwareData integrity
The invention provides a data integrity authentication information generation method and device. The device comprises a Hash structure generation unit, a common authentication information acquisition unit and an integrity authentication information generation unit, wherein the Hash structure generation unit can generate a Hash structure corresponding to a specific time period according to Hash values of data sections contained in multiple data sources in the specific time period, so that the Hash value in each data section can respectively represent a child node at the lowest level of the Hash structure in order to calculate a root Hash value of the child node; the common authentication information acquisition unit can acquire the common authentication information according to the root Hash values; the integrity authentication information generation unit can generate the integrity authentication information of the data sections contained in the multiple data sources in the specific time period for the multiple data sources, wherein the integrity authentication information of each data section comprises common authentication information, path information containing from the Hash value of the data section of the leaf node at the lowest level in the Hash structure to the root node, and the relevant node Hash value of the child node in the path. The invention also provides a data integrity authentication device and method.
Owner:SONY CORP
Information interaction method and device and electronic equipment
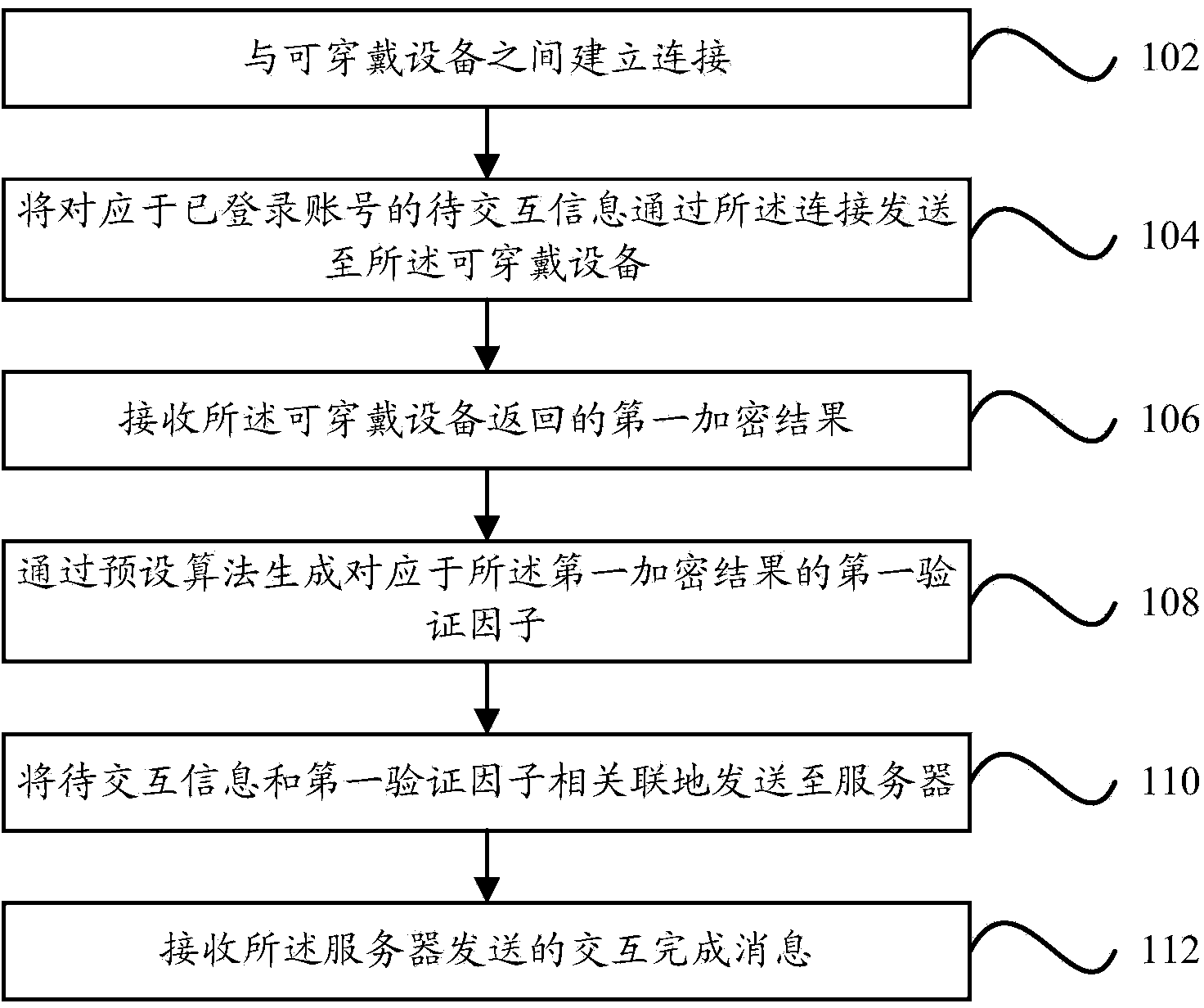
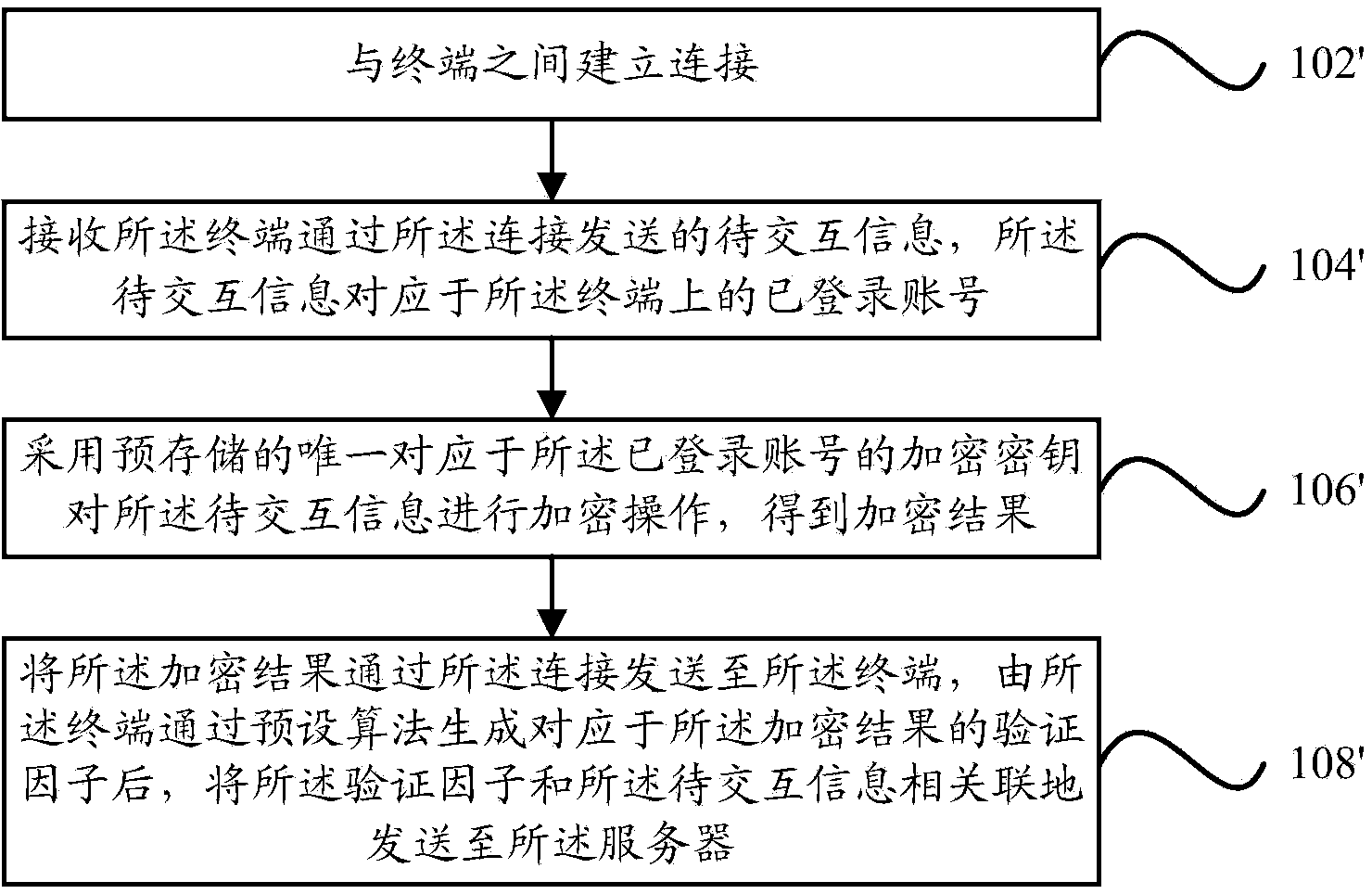
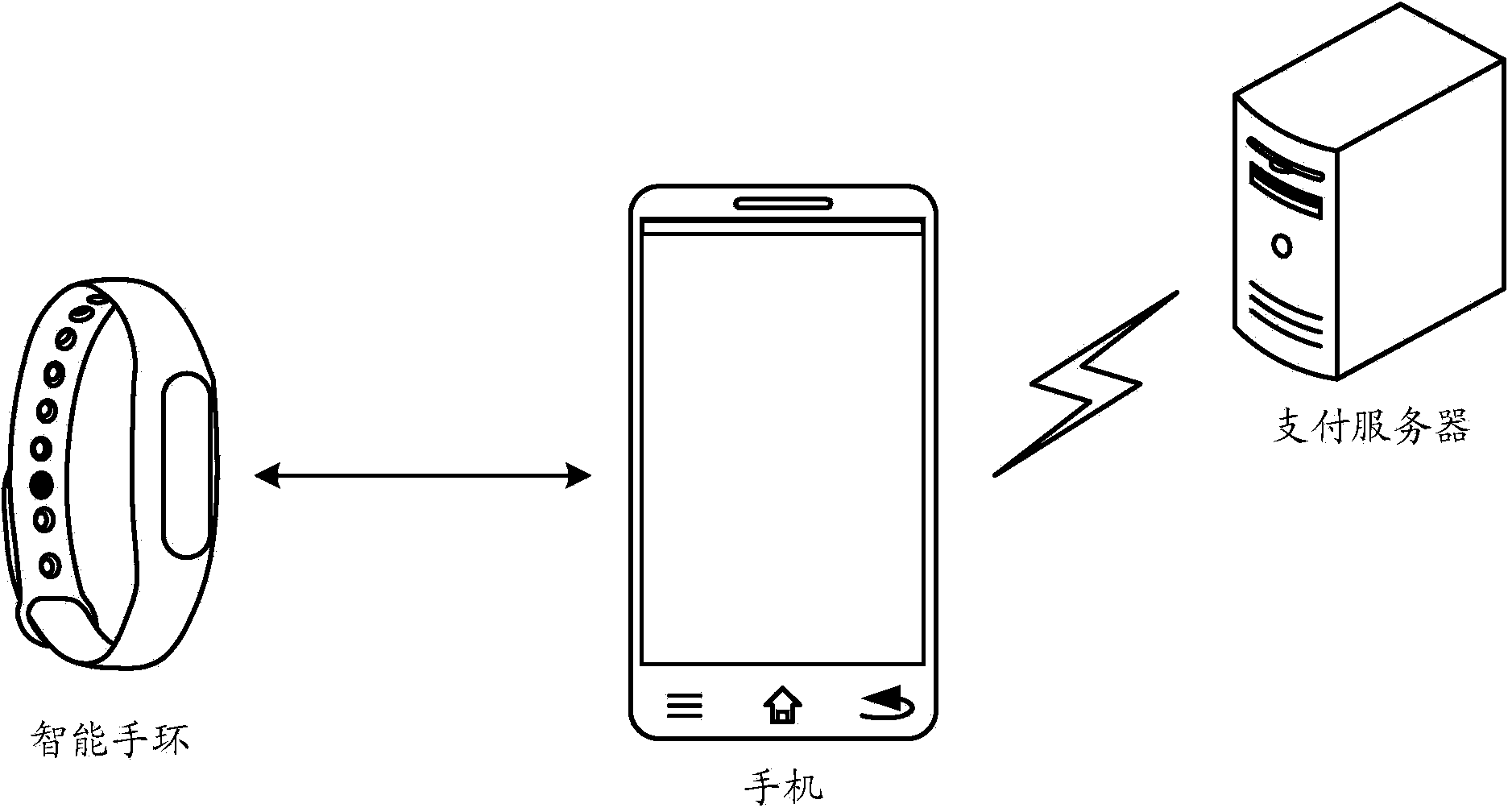
ActiveCN104243484AImprove interaction efficiencyRealize verificationUser identity/authority verificationPayment architectureComputer hardwareEncryption
The invention relates to an information interaction method and device and electronic equipment. The method includes: building a connection with wearable equipment; transmitting to-be-interacted information corresponding to a logged-in account to the wearable equipment through the connection; by the wearable equipment, returning a first encrypted result; generating a first verification factor corresponding to the first encrypted result according to a preset algorithm; transmitting the to-be-interacted information and the first verification factor to a server in an associated manner; receiving an interaction completed message transmitted by the server, wherein the interaction completed message is transmitted when the server obtains a second encrypted result by using a pre-stored encryption key to encrypt the to-be-interacted information and determines that a second verification factor which is generated by using the preset algorithm and corresponds to the second encrypted result is identical with the first verification factor. By the method, user identification can be achieved on the basis of the wearable equipment, and information interaction efficiency is increased favorably.
Owner:BEIJING XIAOMI PAYMENT TECH CO LTD
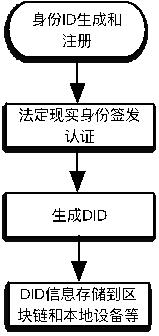
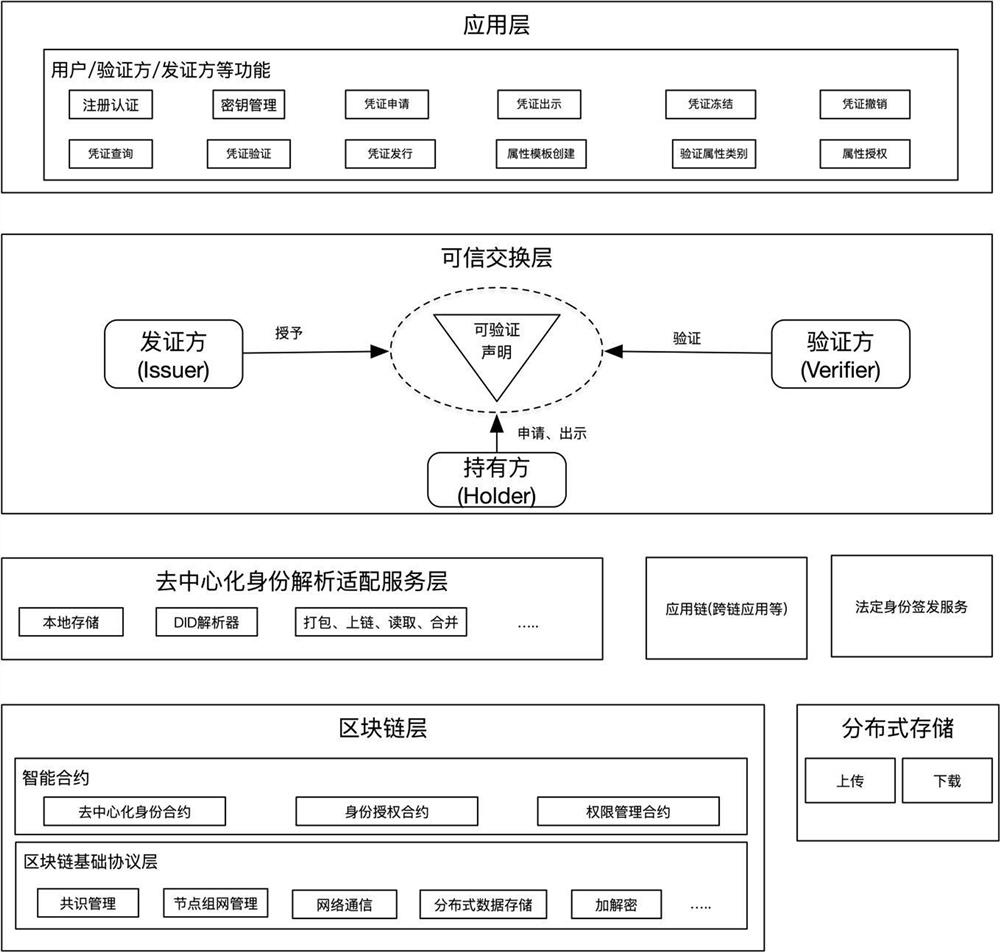
Multi-dimensional digital identity authentication system based on block chain
InactiveCN112580102ASupport large-scale accessSupport for customizable identity certificatesDigital data protectionDigital data authenticationEngineeringData store
The invention discloses a multi-dimensional digital identity authentication system based on a block chain, and relates to the technical field of block chains. The system comprises: a block chain layerused for storing and anchoring a DID document and other data needing distributed storage content; a decentralized identity analysis adaptation service layer which is used for providing a unified DIDdocument analysis service for the block chain layer, and the service can be connected with other application chains at the same time to carry out cross-chain application; a trusted exchange layer which is used for obtaining a DID document through an identity on a user agent registration chain, applying for various verifiable certificates to a certificate issuer by depending on the DID document, and finally providing the DID and the verifiable certificates to a verifier to complete a verification process; and an application layer which is used for constructing a web, wherein an application of the mobile client is provided for a terminal user to use. The system supports cross-chain and cross-platform interoperation, and can be expanded in various different modes.
Owner:ZHENGZHOU UNIV
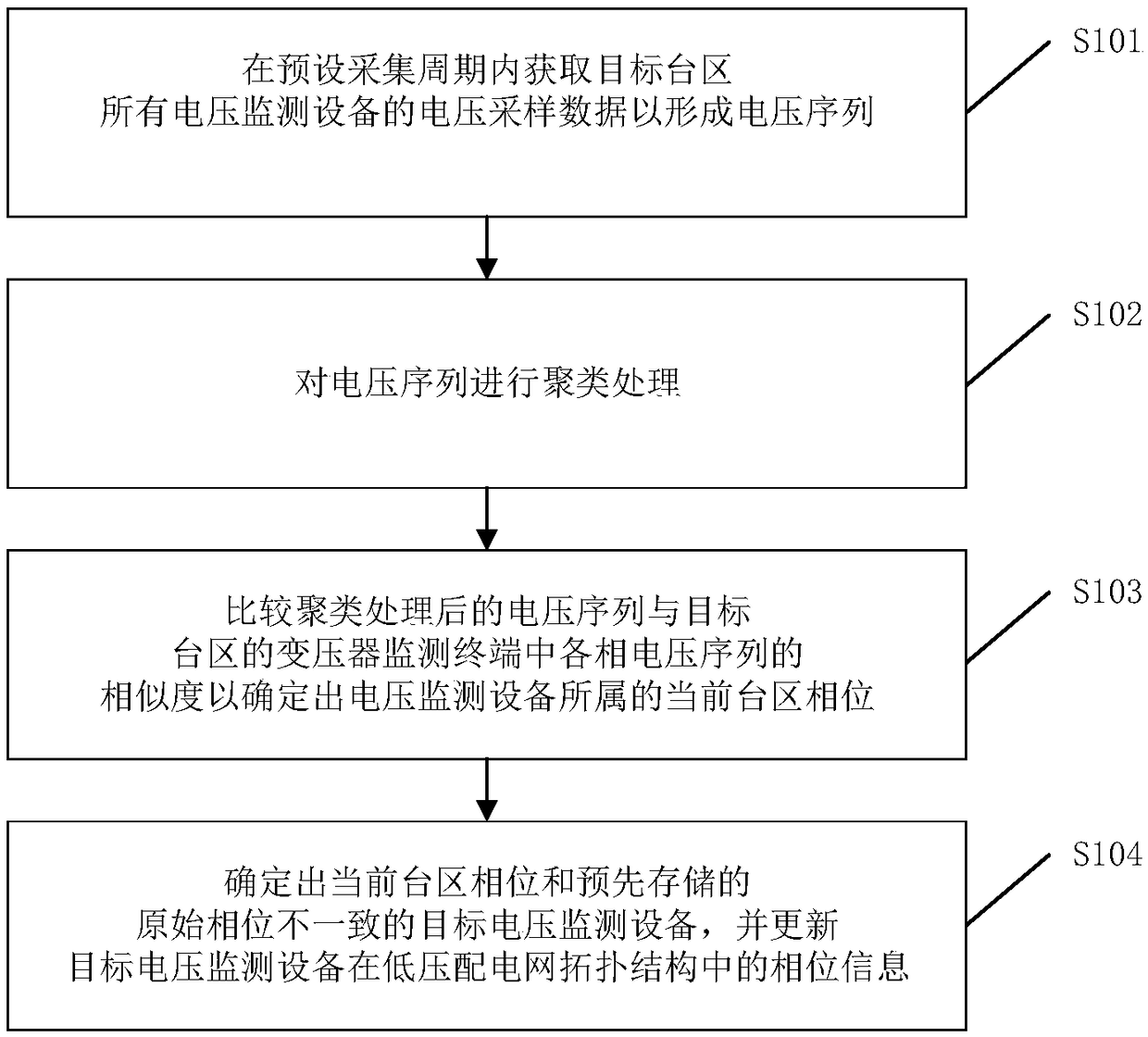
Low-voltage distribution network topology structure verification method, device and equipment and storage medium
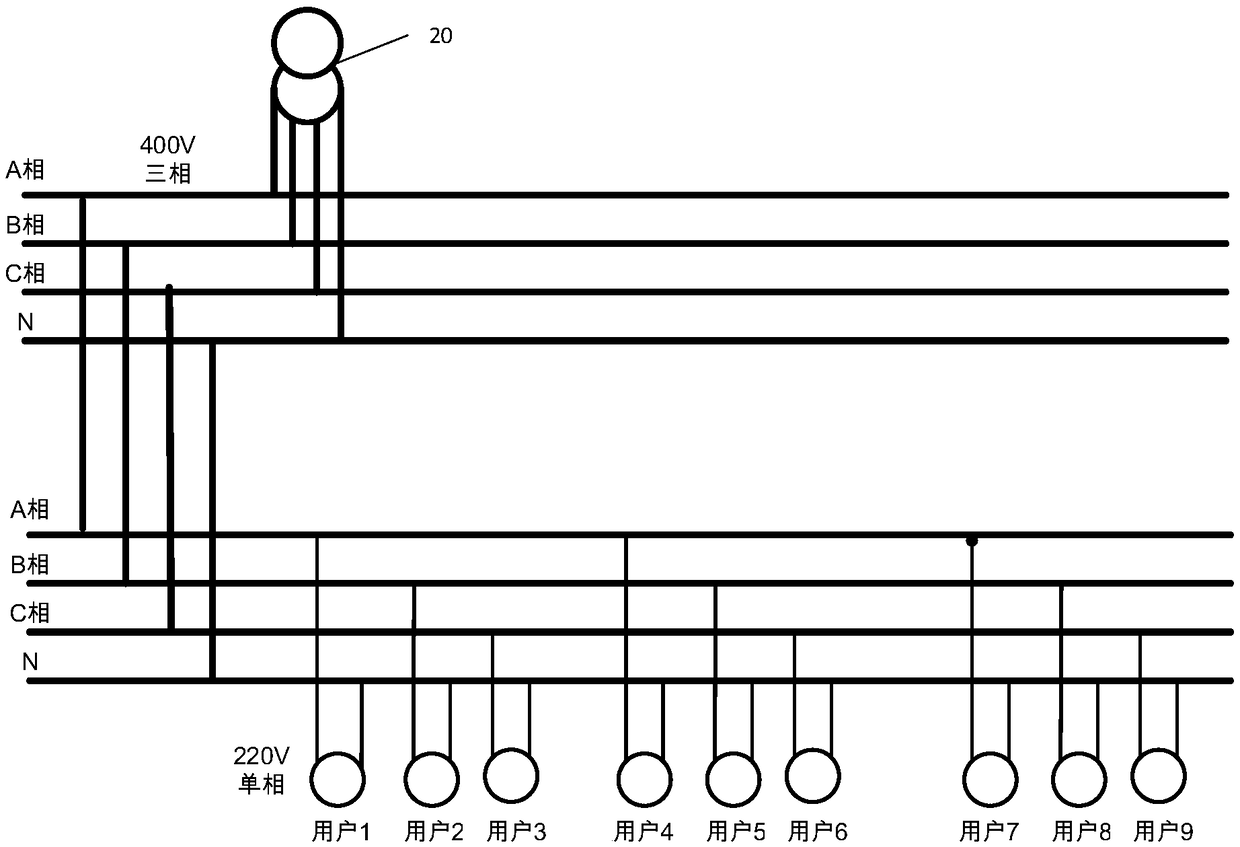
PendingCN109325545AEasy to manageEasy to save energyData processing applicationsCharacter and pattern recognitionTransformerLow voltage
The invention discloses a low-voltage distribution network topology structure verification method. After a voltage sequence is formed, the voltage sequence is clustered, namely, the voltage sequence is clustered into three groups. Then by comparing the similarity between the voltage sequence after clustering processing and the voltage sequence of each phase in the transformer monitoring terminal of the target station area, the current station area phase to which the voltage monitoring equipment belongs can be determined. Finally, the target voltage monitoring equipment with phase change is determined, and the phase of the target voltage monitoring equipment is updated, so as to achieve the verification of the low-voltage distribution network topology. This method not only determines the station information of voltage monitoring equipment but also determines the phase information of each voltage monitoring equipment, which can improve the accuracy of low-voltage distribution network topology verification, and thus is conducive to the management of low-voltage distribution network and loss reduction and energy conservation. In addition, the invention also discloses a low-voltage distribution network topology structure verification device and equipment and a storage medium, which have the effects above.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
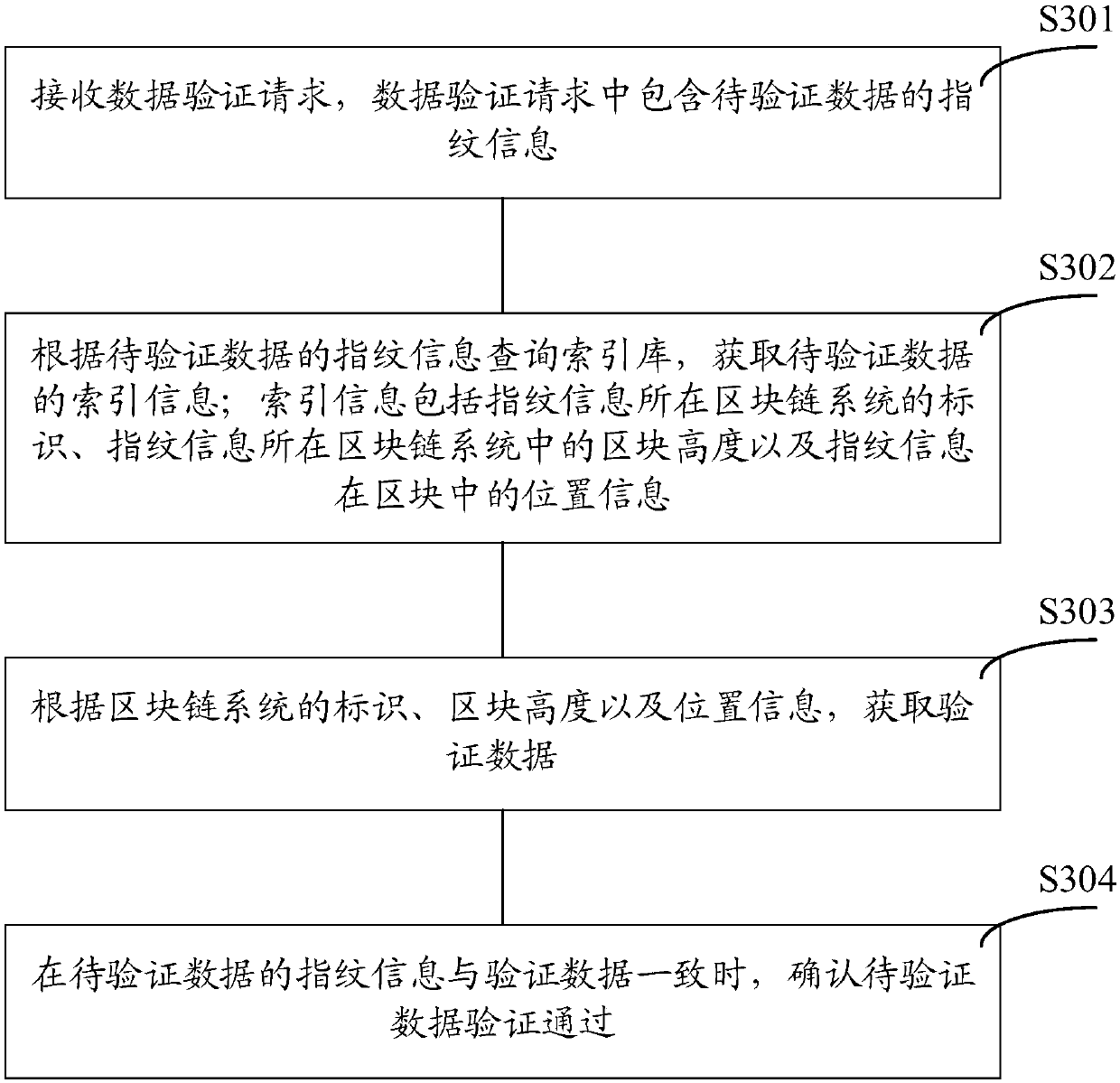
Index database generation method, data verification method and device and platform
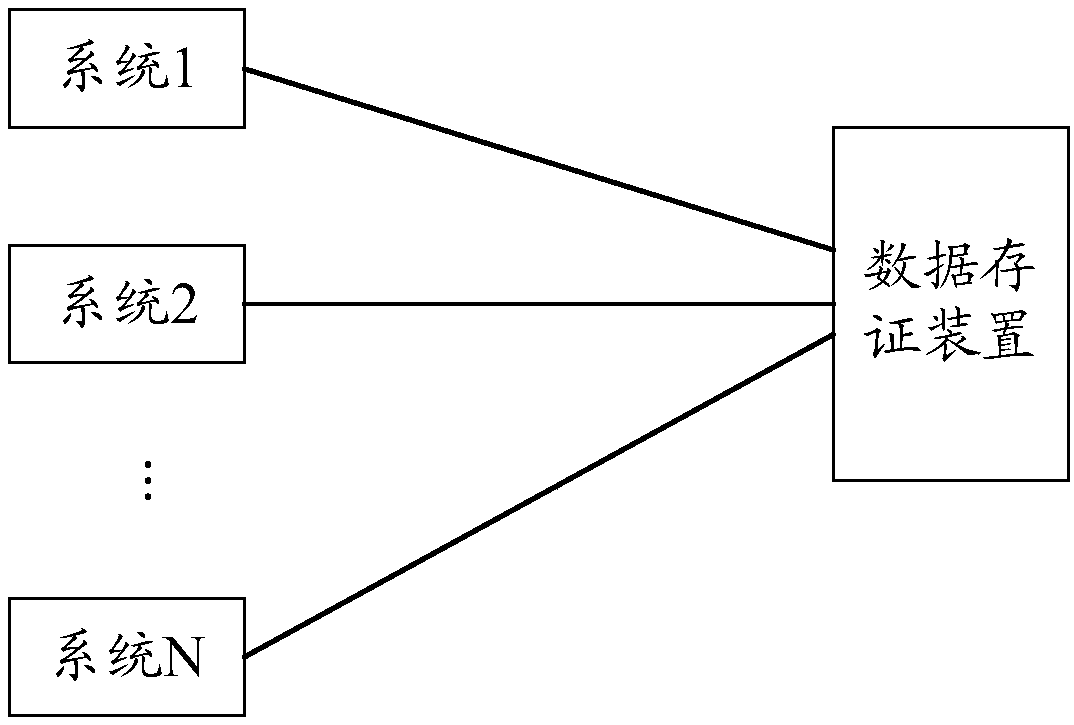
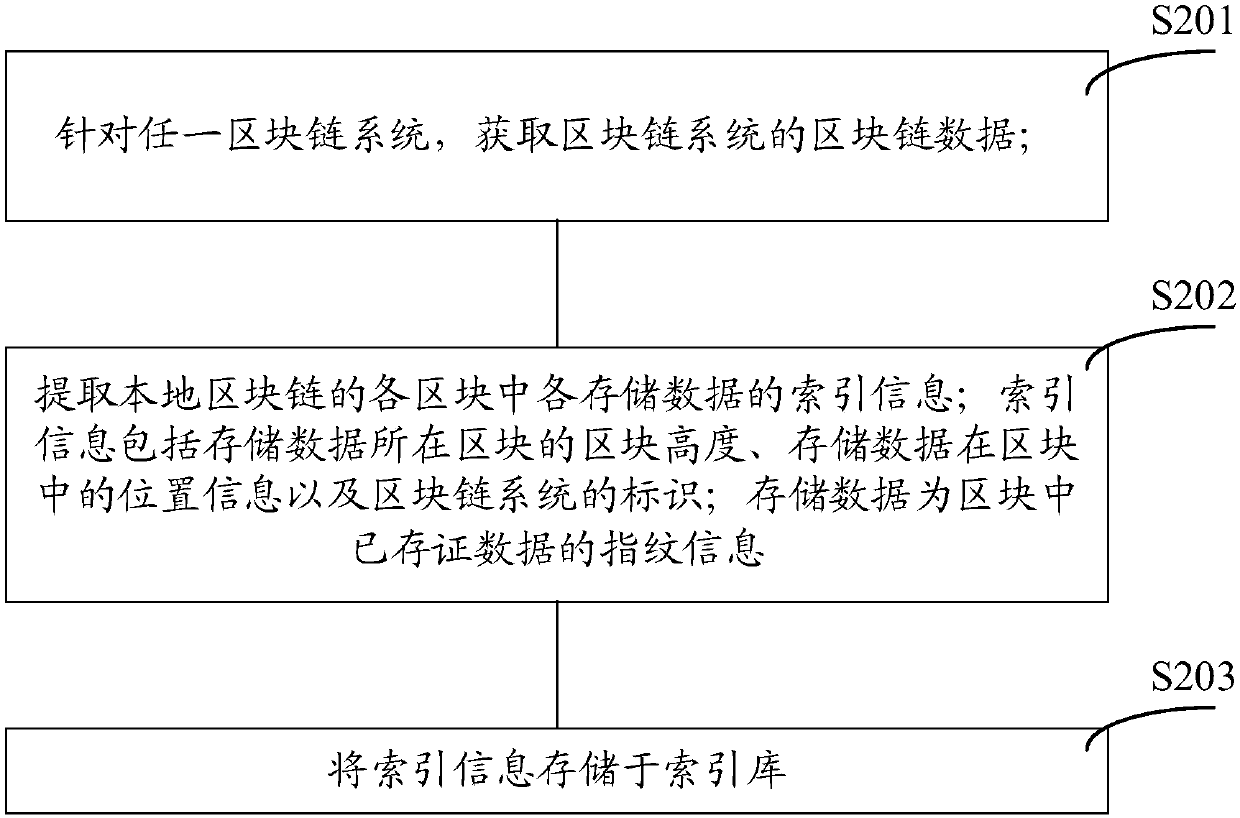
ActiveCN107729383AAchieve positioningRealize verificationOther databases queryingSpecial data processing applicationsSource Data VerificationData storing
The invention discloses an index database generation method, a data verification method and device and a platform. The platform comprises N blockchain systems, wherein N is larger than or equal to 1.The index database generation method comprises the steps that blockchain data of each blockchain system is obtained; index information of all storage data in all blocks of a local blockchain is extracted, wherein the index information comprises the block height of the block where the storage data is located, the position information of the storage data in the block and the identifier of the blockchain system, and the storage data is fingerprint information of the data stored and verified in the blocks; the index information is stored in an index database. Each piece of storage data in the blockchains can be precisely positioned through the block height, the position information and the identifier of the blockchain system in the index information so that quick verification in the multi-blockchain system can be achieved.
Owner:UNION MOBILE PAY
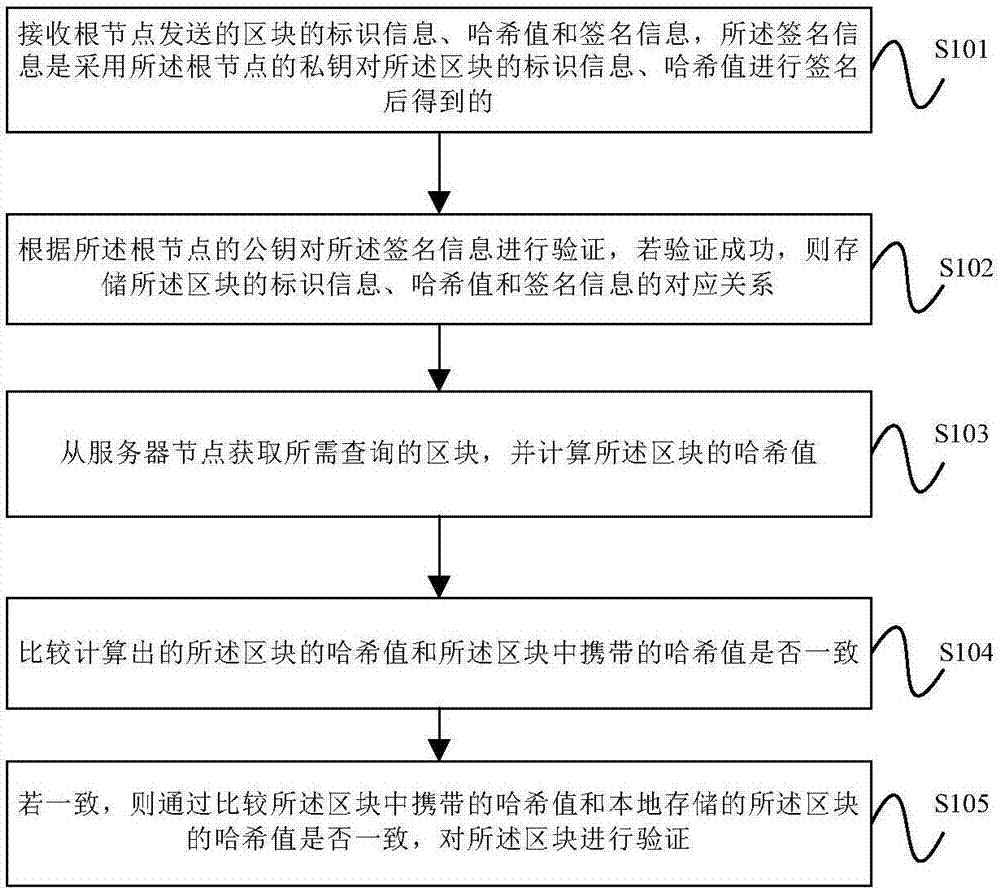
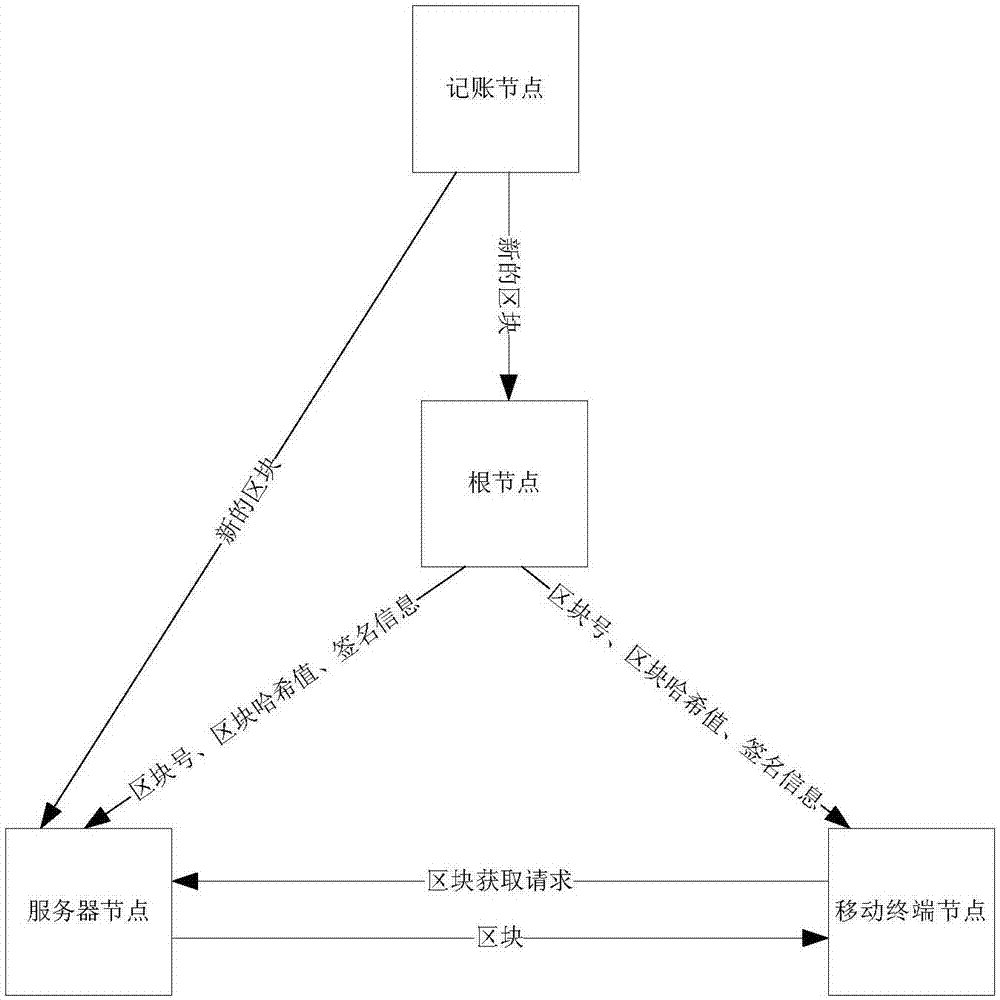
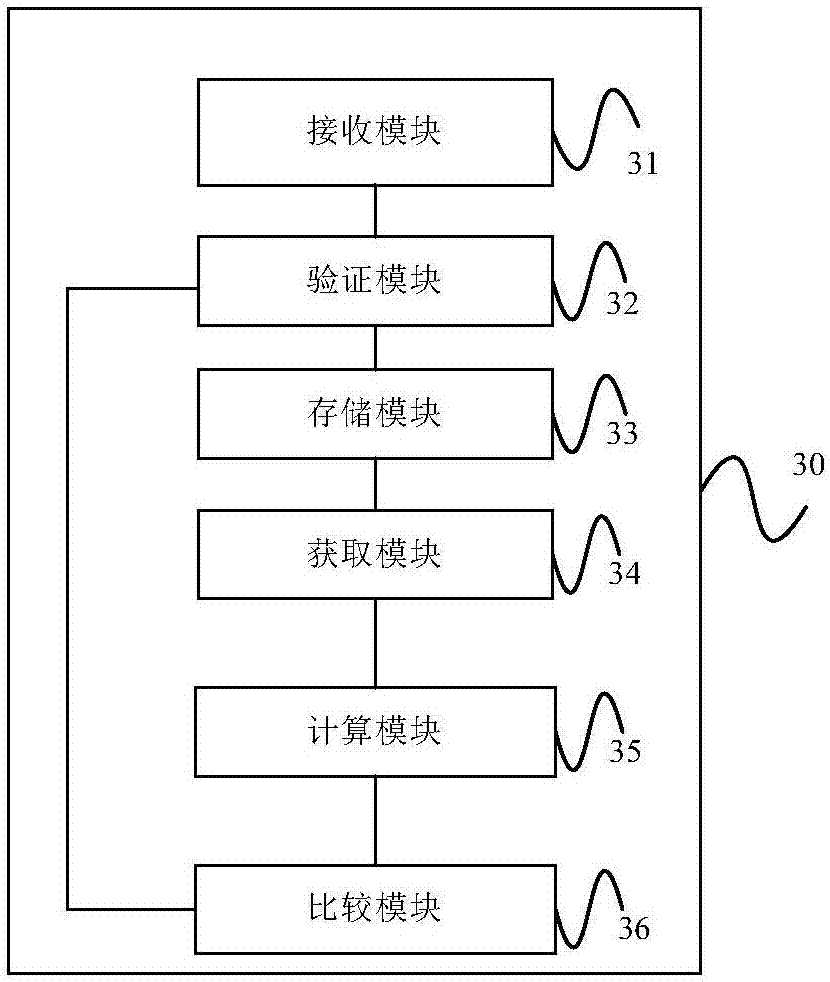
Block verification method and device
ActiveCN107396360ARealize verificationKey distribution for secure communicationUser identity/authority verificationValidation methodsComputer security
The embodiment of the invention provides a block verification method and device. The method comprises the steps that the identification information, the hash value and the signature information of a block sent by a root node are received; the signature information is verified according to the public key of the root node; if the verification is successful, the corresponding relationship among the identification information, the hash value and the signature information of the block are stored; a block to be queried is acquired from a server node; and the block is verified by comparing whether the hash value carried in the block is consistent with the hash value of a locally stored block. According to the embodiment of the invention, a mobile terminal node receives the identification information, the hash value and the signature information of the block sent by the root node, and stores the corresponding relationship among the identification information, the hash value and the signature information; and when the mobile terminal node acquires the block to be queried from the server node, the node verifies the block by comparing whether the hash value carried in the block is consistent with the hash value of the locally stored block.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
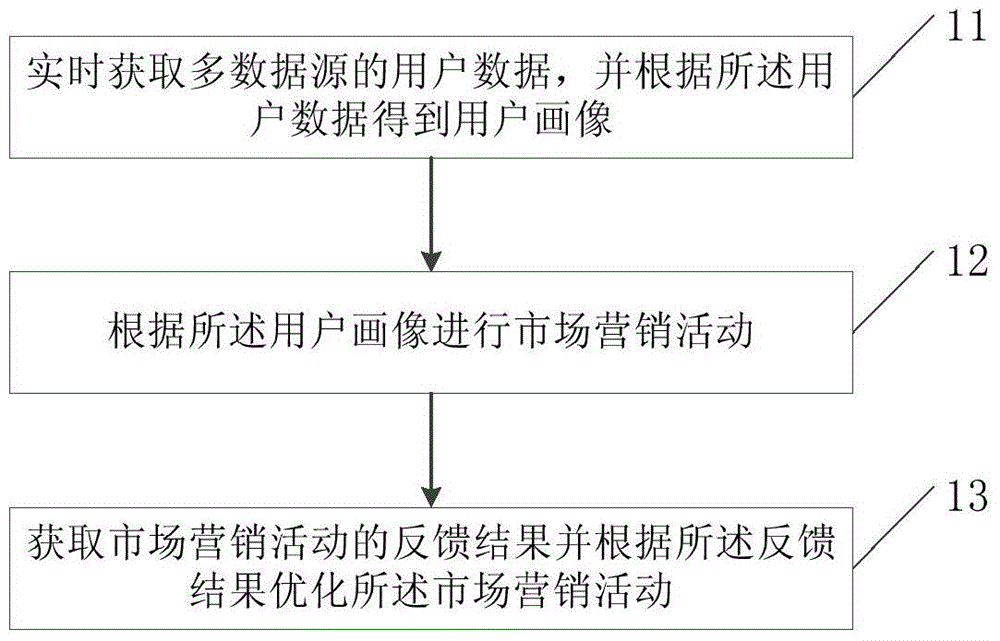
Method and apparatus for applying cross-data-source marketing crowds to marketing
Embodiments of the invention provide a method and an apparatus for applying cross-data-source marketing crowds to marketing. The method comprises the steps of obtaining user data of multiple data sources in real time and obtaining user portraits according to the user data; performing marketing activities according to the user portraits; and obtaining feedback results of the marketing activities and optimizing the marketing activities according to the feedback results. Therefore, an objective data basis is provided for each marketing link, and high-quality data and marketing experience are accumulated.
Owner:北京百分点科技集团股份有限公司
Heterogeneous unmanned aerial vehicle cluster target tracking system and method based on biosocial force
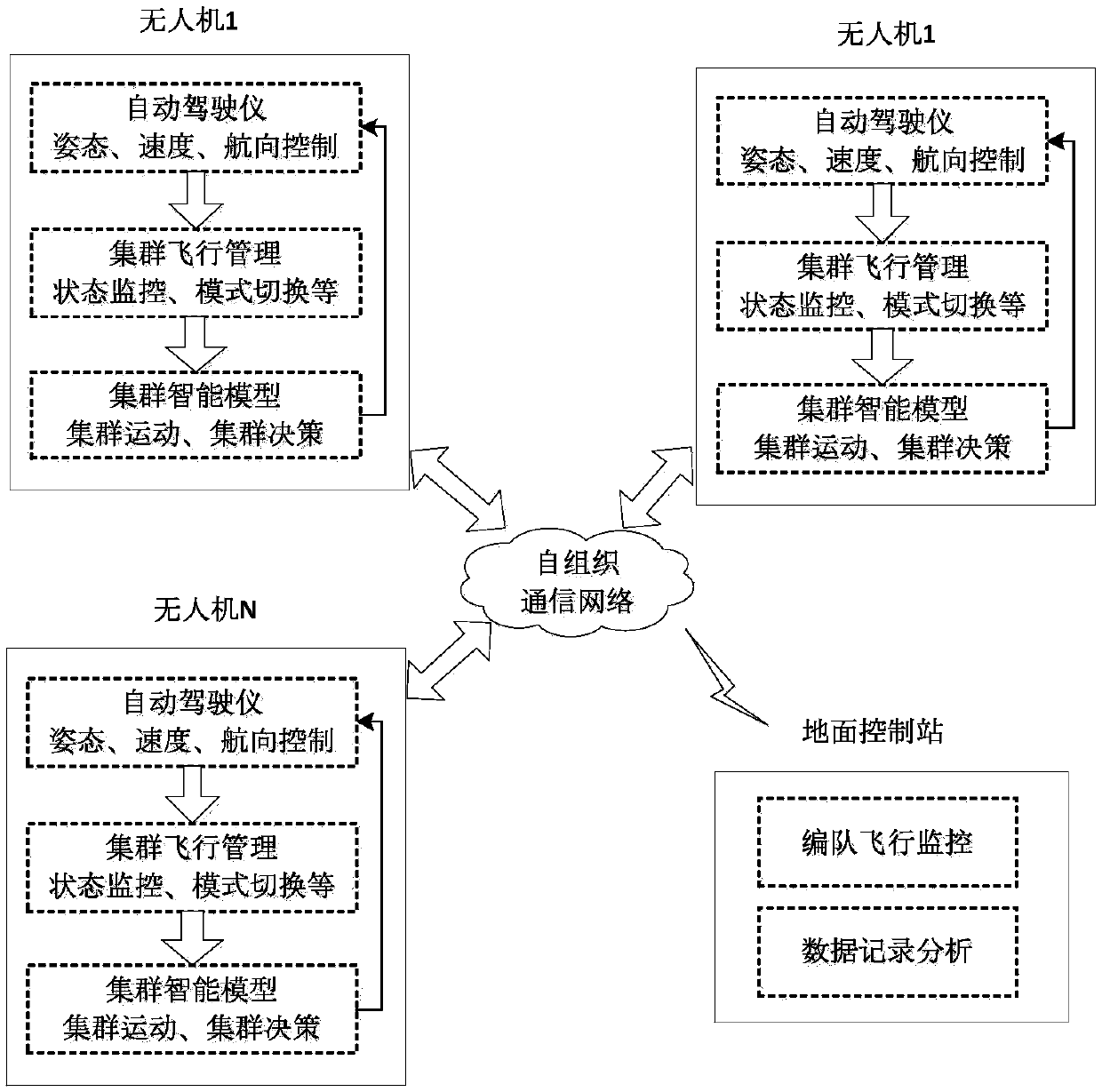
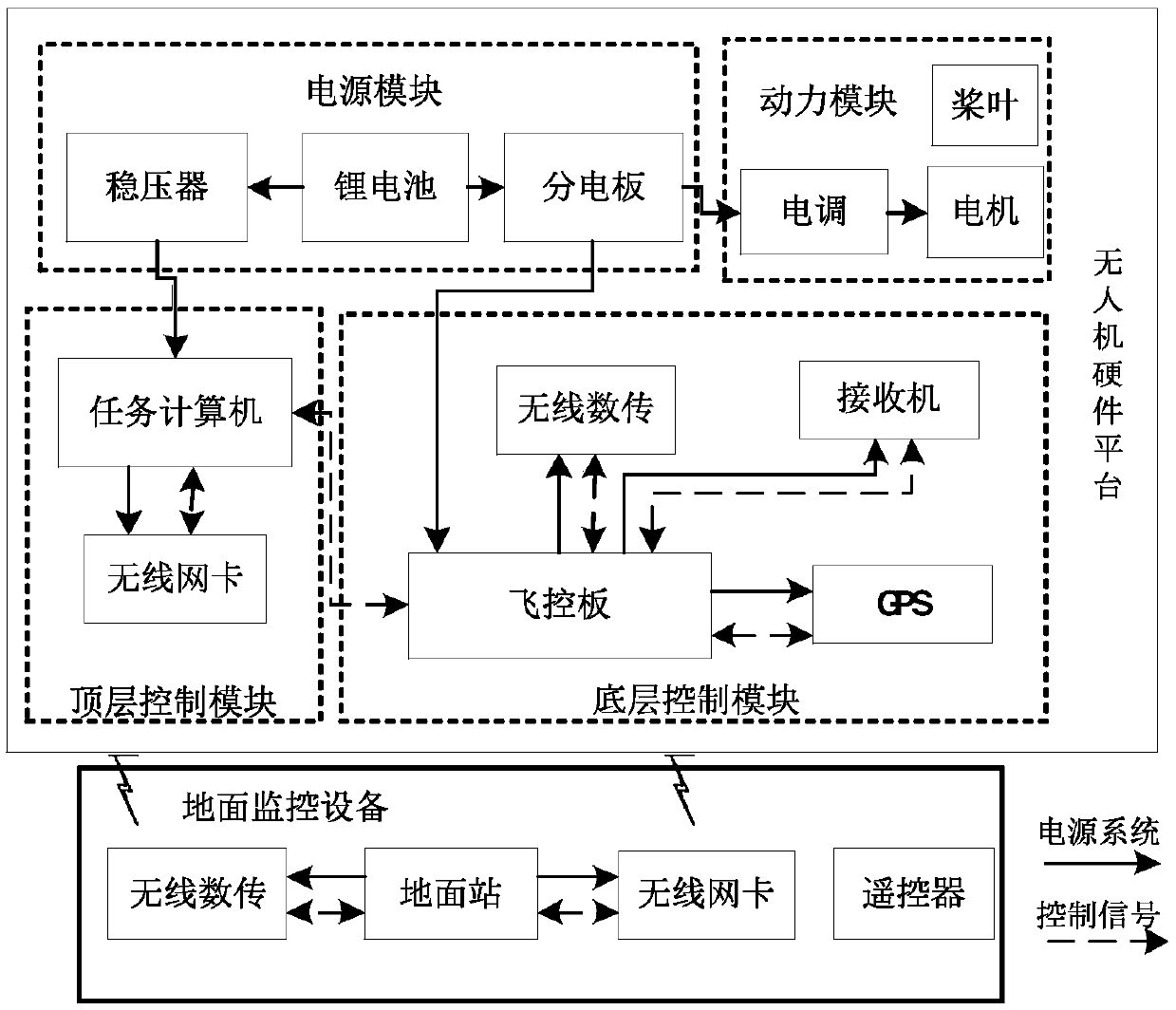
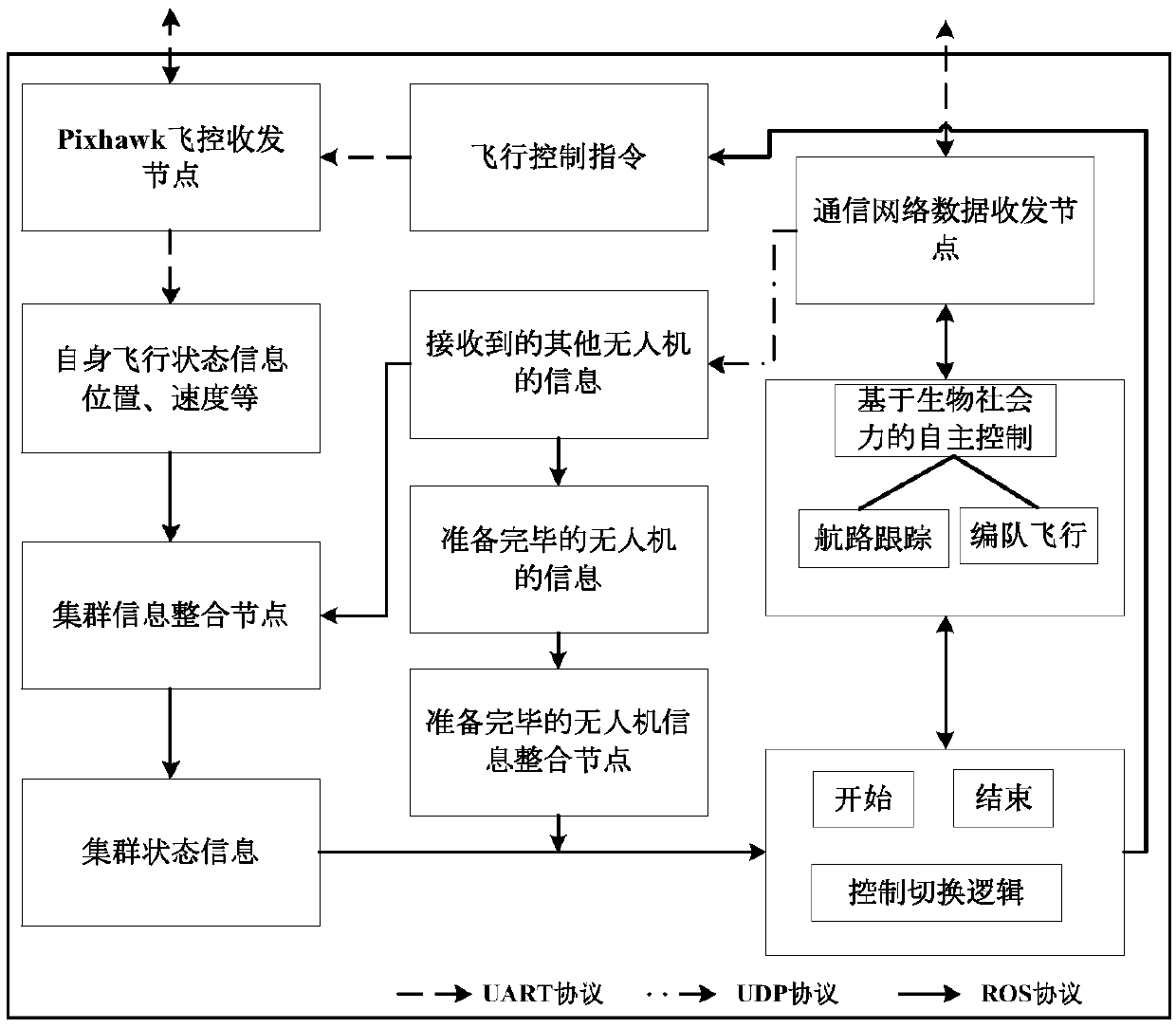
ActiveCN109613931AAchieve goal trackingRealize verificationTarget-seeking controlPosition/course control in three dimensionsCommunications systemControl system
The invention discloses a heterogeneous unmanned aerial vehicle cluster target tracking system and method based on biosocial force. The target tracking system includes a cluster hardware system architecture, a cluster software system architecture, a cluster communication system architecture and a cluster flight management and control system. The method comprises the following steps that 1, modeling of an unmanned aerial vehicle state is carried out; 2, a consistency protocol is designed; 3, unmanned aerial vehicle control instructions are designed based on a phase difference consistency algorithm; 4, trajectory tracking based on non-linear guidance is carried out; 5, a heterogeneous unmanned aerial vehicle cluster system based on the biosocial force is described; and 6, heterogeneous unmanned aerial vehicle cluster target tracking based on the biosocial force is carried out. The heterogeneous unmanned aerial vehicle cluster target tracking system and method based on the biosocial forcehas the advantages that the heterogeneous unmanned aerial vehicle cluster target tracking is realized, the speed of controlling an unmanned aerial vehicle to gradually converge to an expected path isincreased, and the system of the whole target tracking system is complete, the functions are perfect, and the verification of targets in different task scenes can be realized.
Owner:BEIHANG UNIV
Identity verification method and device
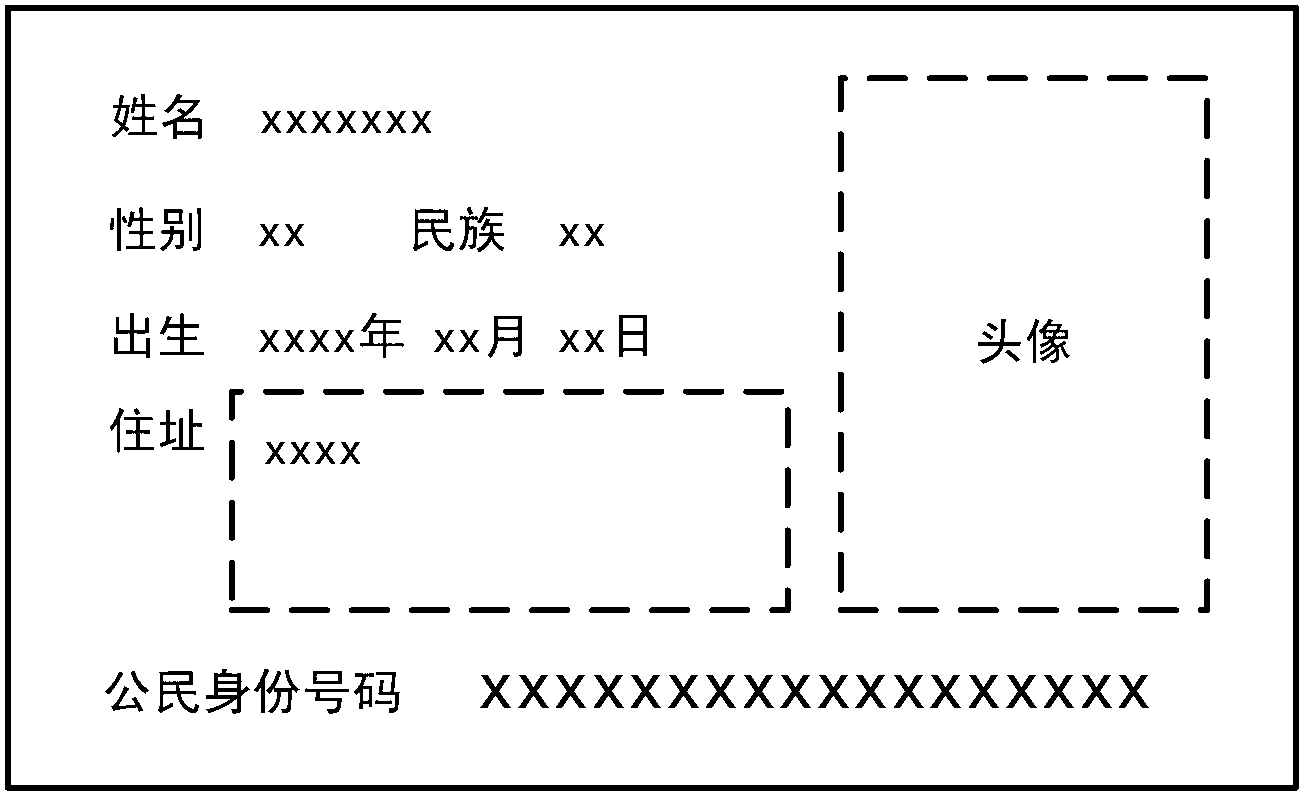
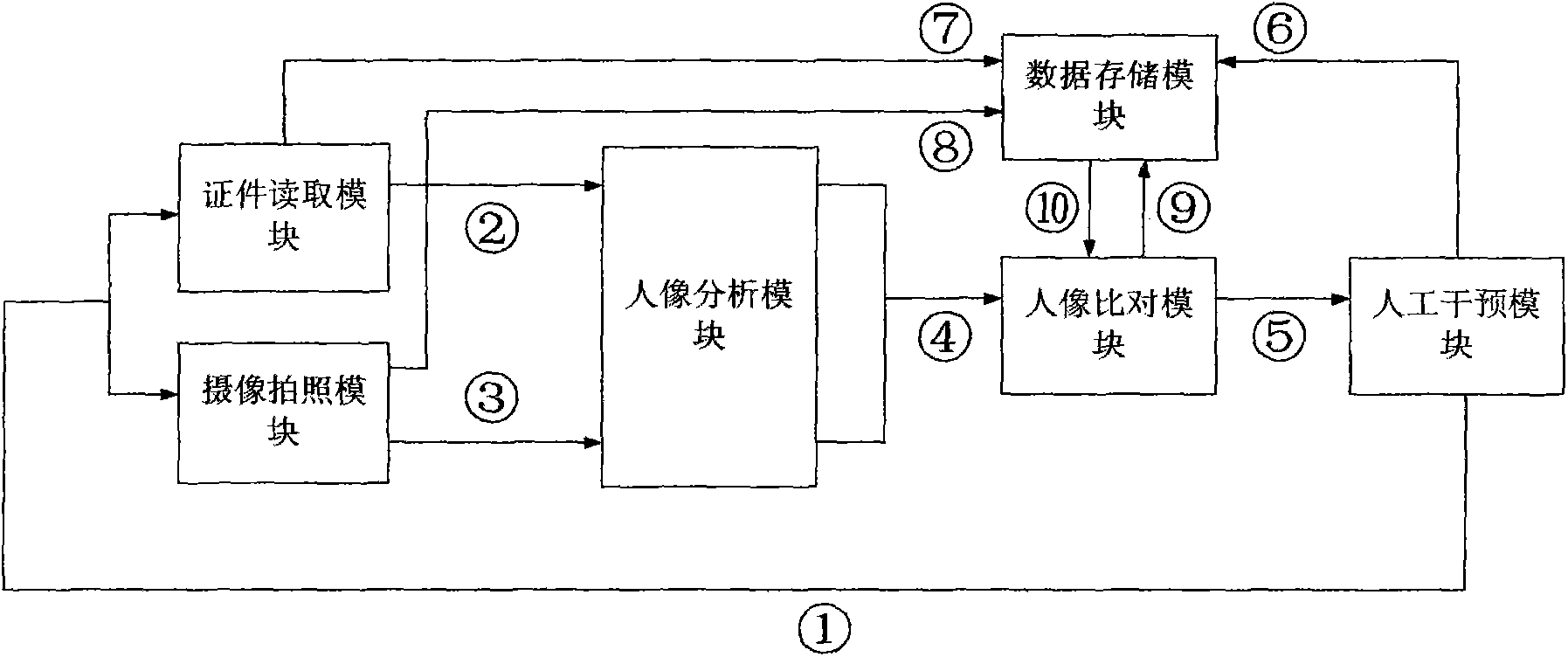
ActiveCN104112114ARealize verificationTo achieve the goal of "integration of witnesses and witnesses"Character and pattern recognitionImaging analysisRadiology
The invention relates to an identity verification device comprising a certificate reading module, an image-photographing module, a human image analysis module, a human image comparison module, an artificial intervention module and a data storage module. The certificate reading module and the image-photographing module are respectively connected with the human image analysis module. The certificate reading module and the image-photographing module are also respectively connected with the data storage module. The human image analysis module is connected with the human image comparison module. The human image comparison module is respectively connected with the artificial intervention module and the data storage module. The artificial intervention module is respectively connected with the data storage module, the certificate reading module and the image-photographing module. Consistency of a certificate holder and a certificate can be rapidly verified.
Owner:BEIJING ANJIETIANDUN TECH DEV
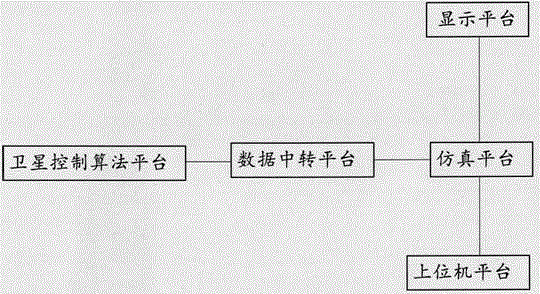
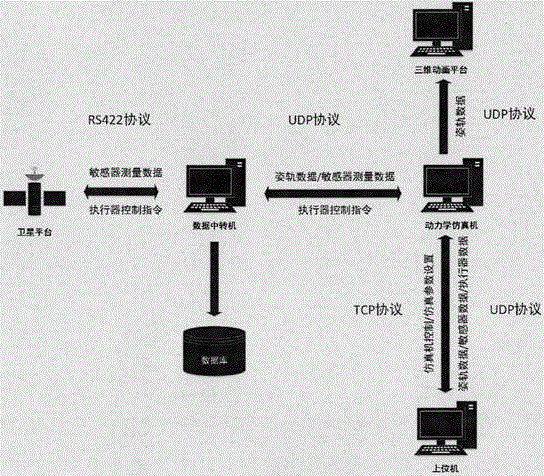
Digital satellite attitude and orbit control algorithm ground simulation verification system
InactiveCN106647335ARealize closed-loop controlRealize verificationSimulator controlSimulationVerification system
The invention provides a digital satellite attitude and orbit control algorithm ground simulation verification system. The digital satellite attitude and orbit control algorithm ground simulation verification system comprises a simulation platform, a host computer platform, a data transfer platform, and a satellite control algorithm platform. The simulation platform is suitable for acquiring control information of a satellite attitude and orbit algorithm, and is operated in a preset simulation environment according to a dynamical model to generate an actual attitude and an actual orbit of a satellite, and then is used to output satellite simulation information. The host computer platform is suitable for receiving the satellite simulation information, and based on the setting of the satellite simulation information and parameters related to the dynamical model, and is used to transmit operation information of operating the simulation platform to the simulation platform according to an instruction input by a user. The satellite control algorithm platform is suitable for determining the satellite attitude and orbit algorithm according to the satellite simulation information, and is used to transmit control information of executing the satellite attitude and orbit algorithm to the simulation platform. The linked operation of the satellite simulation verification system is realized, and a satellite simulation integration level is improved.
Owner:王洋
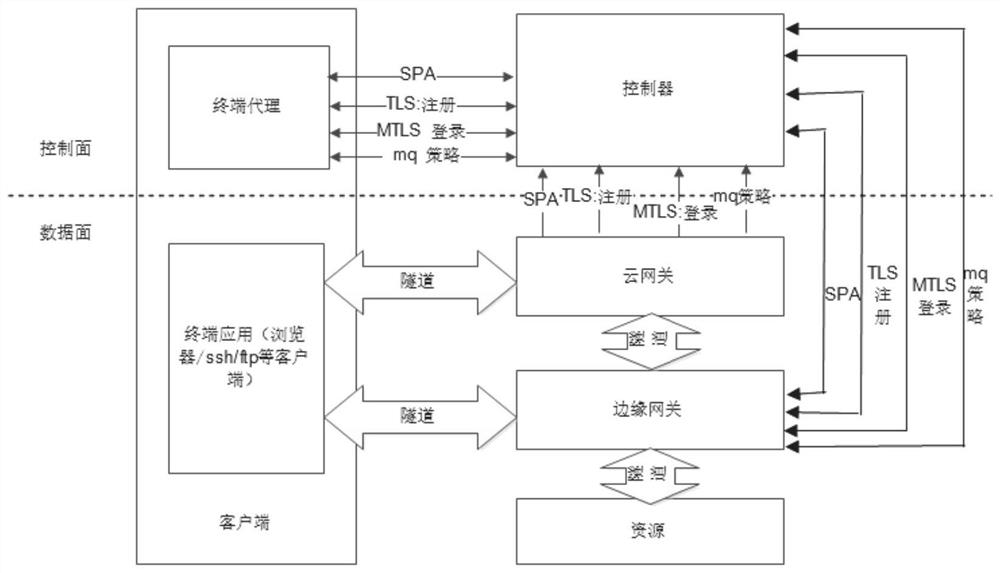
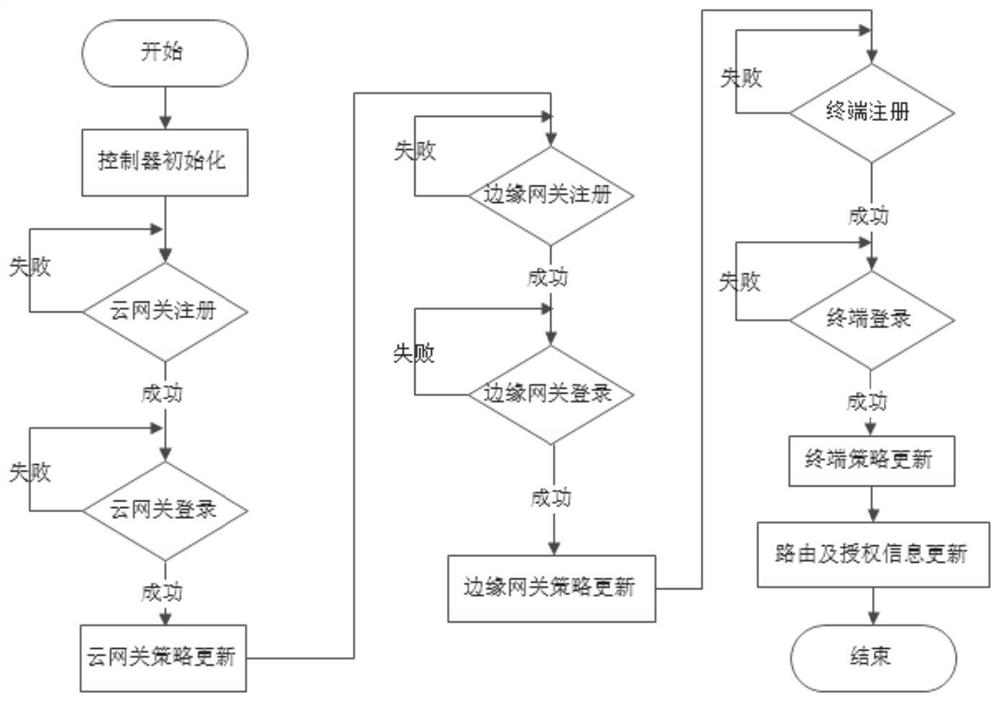
Zero-trust network architecture and construction method
ActiveCN113572738AAvoid security threatsBlock network attacksData switching networksHigh level techniquesBusiness enterpriseNetwork architecture
The invention provides a zero-trust network architecture and a construction method. The zero-trust network architecture comprises a controller, a cloud gateway, an edge gateway and a terminal agent, the edge gateway is in communication connection with the cloud gateway, the cloud gateway, the edge gateway and the terminal agent are respectively in communication connection with the controller, and the cloud gateway and the edge gateway are respectively in communication connection with the client; the controller is used for controlling registration and login processes of the client, the cloud gateway and the edge gateway and issuing a routing strategy and an authorized access control strategy; the edge gateway is used for controlling resource security access, and the cloud gateway is used for routing when a client accesses resources across regions; the terminal agent is deployed at a client, establishes a tunnel with the cloud gateway and the edge gateway, and performs secure access on authorized resources; the network position boundary no longer determines the access authority, all access subjects need to be subjected to identity authentication and authorization before access is allowed, and the security threat brought by the enterprise network architecture with the fuzzy boundary at present is solved.
Owner:中孚安全技术有限公司
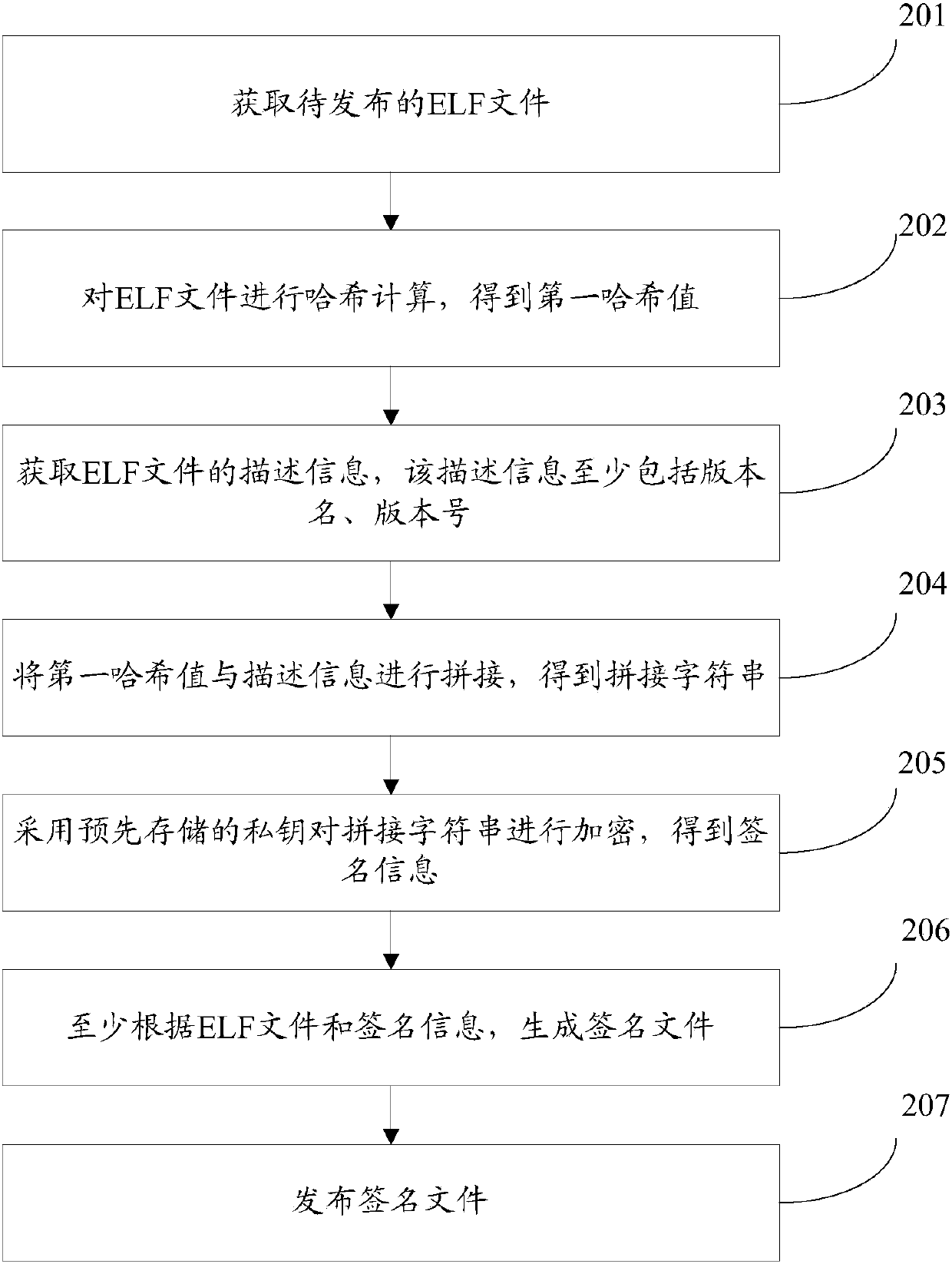
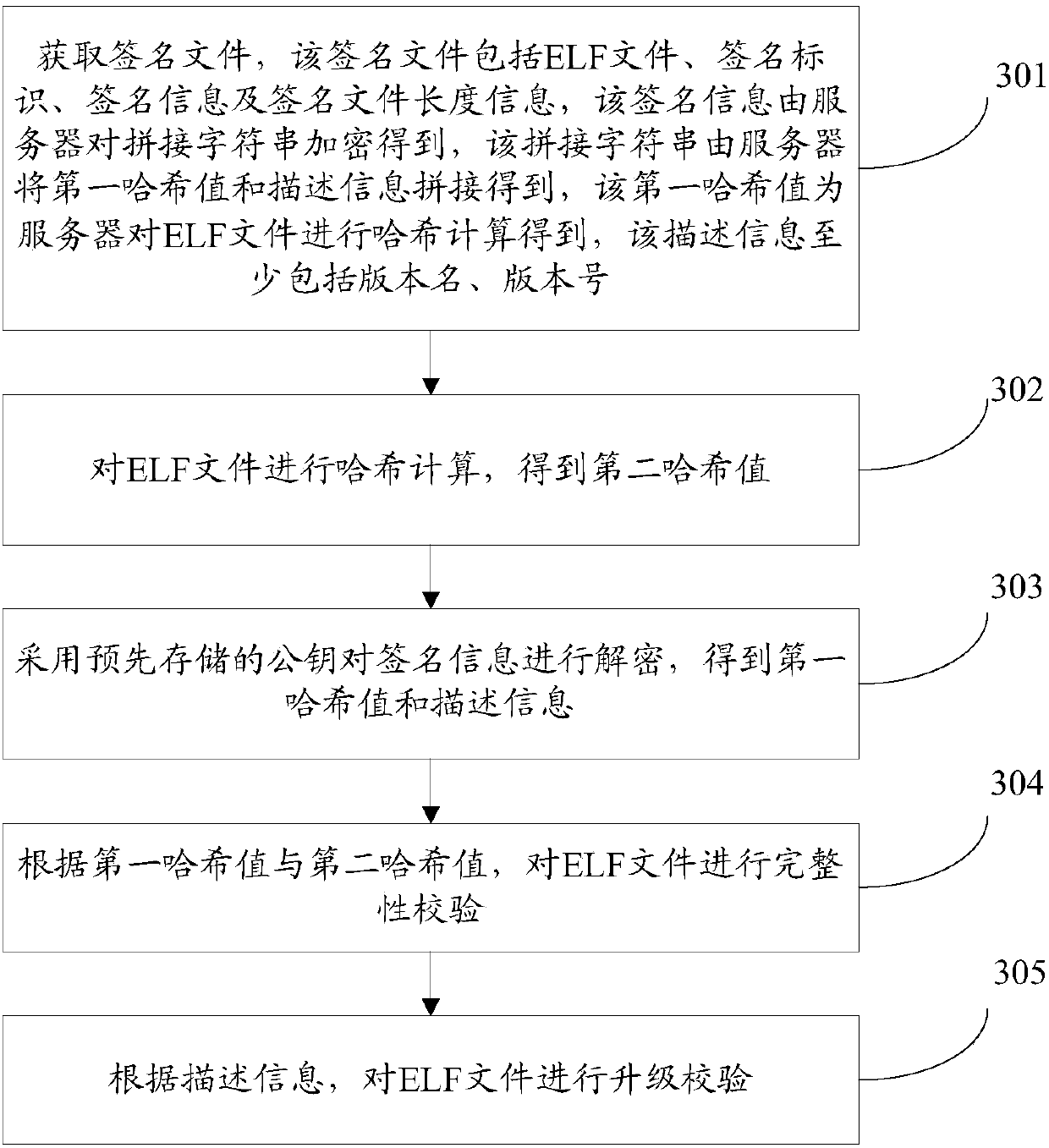
ELF file release method, ELF file verification method, server and terminal
ActiveCN107786504AThe verification result is accurateGood adaptabilityEncryption apparatus with shift registers/memoriesUser identity/authority verificationLocal memoriesFile verification
The invention discloses an ELF file release method, an ELF file verification method, a server and a terminal, and belongs to the technical field of the Internet. The server splices a first hash valueobtained by performing hash calculation on an ELF file with description information to obtain a spliced character string, encrypts the ELF file and the spliced character string to obtain signature information, generates a signature file and releases the signature file. As the released signature file is generated according to the whole ELF file, after obtaining the signature file released by the server, the terminal can verify the whole ELF file, so that the verification result is more accurate and is independent from the verification mode based on byte encryption and decryption, no matter thesystem of the terminal supports the byte encryption and decryption or not, the terminal can verify the ELF file, so that the adaptability is better. In addition, by means of the description information in the signature file, the terminal can also perform upgraded verification on the ELF file stored in a local memory, thereby enriching the verification contents.
Owner:TENCENT TECH (SHENZHEN) CO LTD
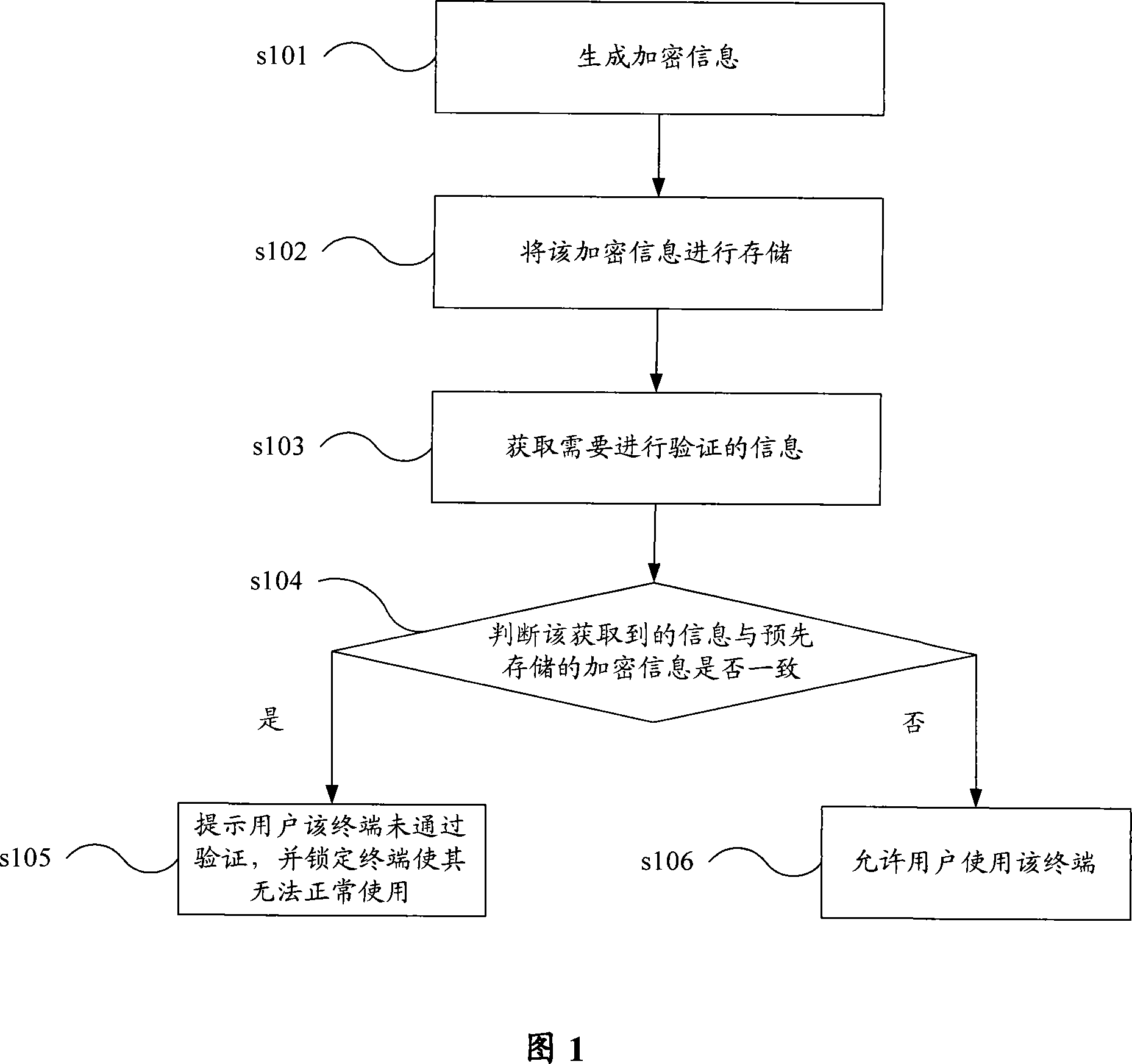
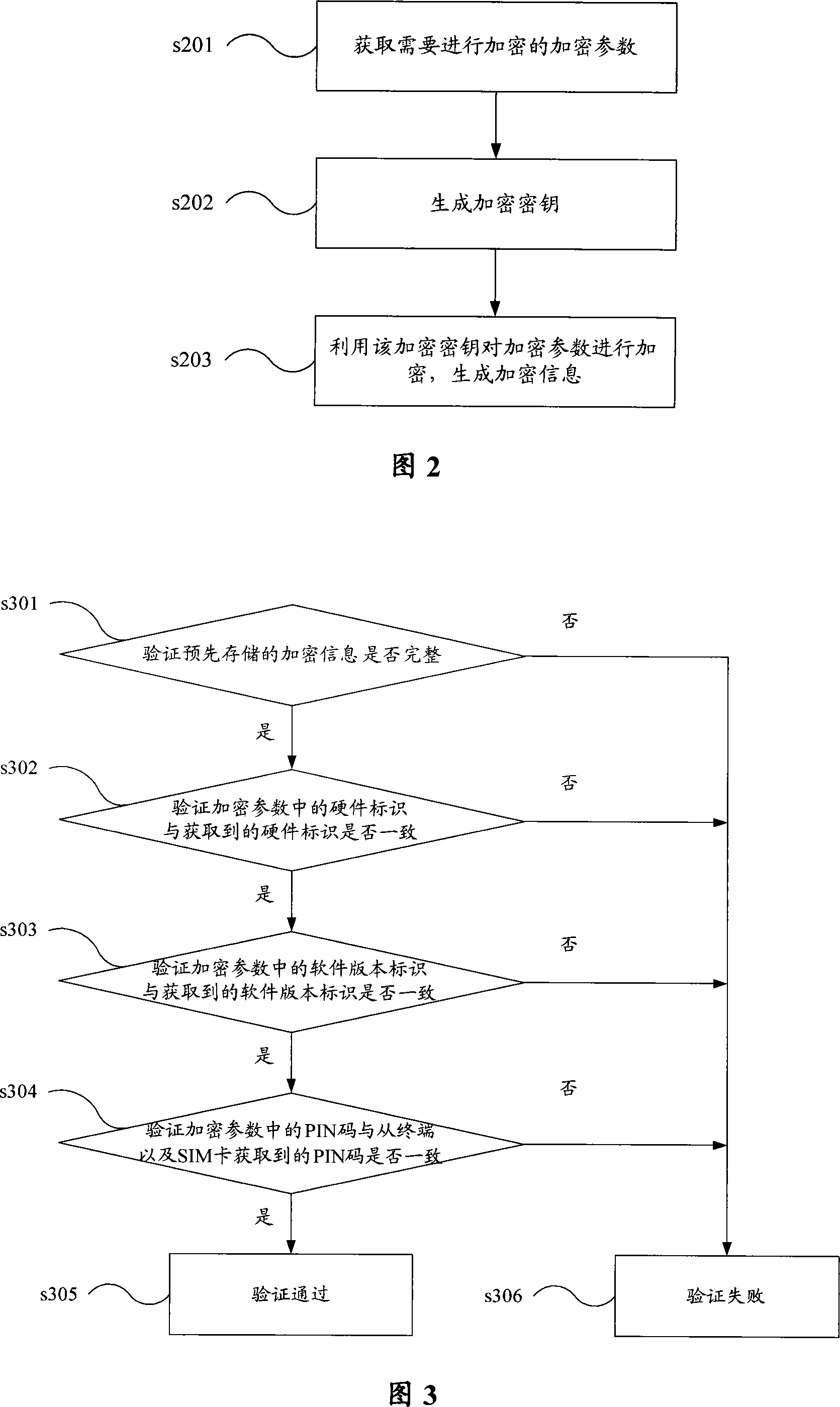
Terminal verification method and device
InactiveCN101102574ARealize verificationAvoid crackingRadio/inductive link selection arrangementsSecurity arrangementComputer hardwareValidation methods
The method comprises: when receiving the request for using the terminal; getting the information to be authenticated; deciding if obtained information is consistent with the pre-saved encryption information; if yes, then allowing using the terminal; otherwise rejecting to use the terminal. The invention also reveals an apparatus thereof.
Owner:HUAWEI TECH CO LTD
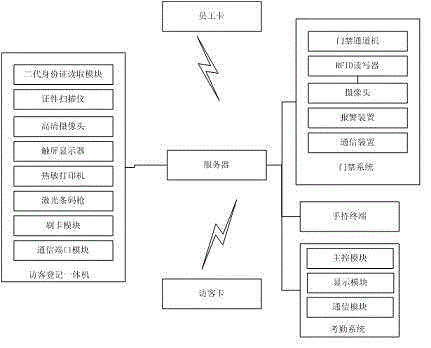
Visitor ingress-egress registration management system and method
InactiveCN104680622ARealize verificationRealize on-site photo retentionIndividual entry/exit registersLate developmentHand held
The invention discloses a visitor ingress-egress registration management system. The system comprises a visitor registration all-in-one machine, an access control system, a hand-held terminal, a visitor card and a server, the visitor registration all-in-one machine, the access control system, the hand-held terminal and the server are connected by a network, a RFID label with visitor information is arranged in the visitor card, the visitor registration all-in-one machine is arranged at an entrance guard and is used for visitor information registration, through cooperation of the visitor registration all-in-one machine and the hand-held terminal, information confirmation is realized, and the access control system is installed at an inlet / outlet of an enterprise and is used for blocking external staffs. The disclosed management system can realize automated management of visitors, greatly saves labor, simultaneously realizes data long-term preservation and provides data for later development.
Owner:NANJING ZHENGU PHOTOELECTRICITY & TECH CO LTD
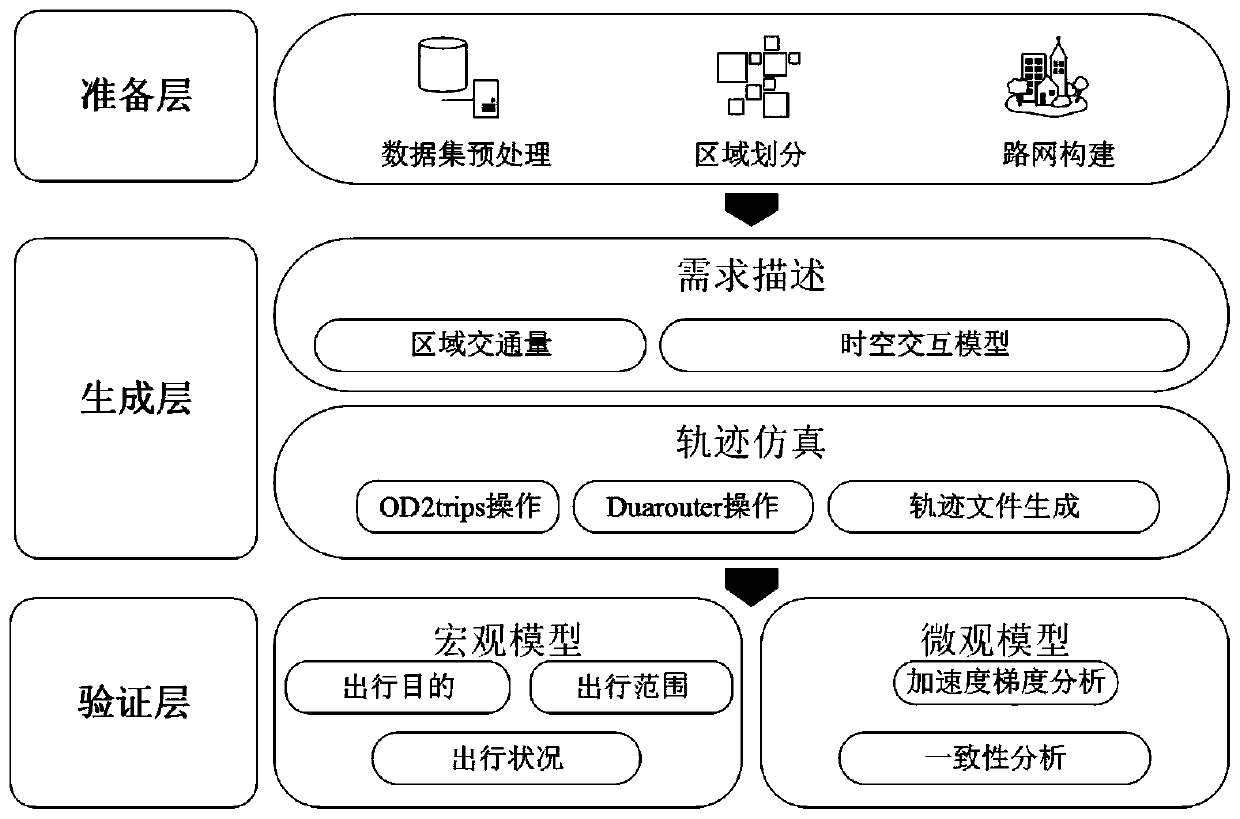
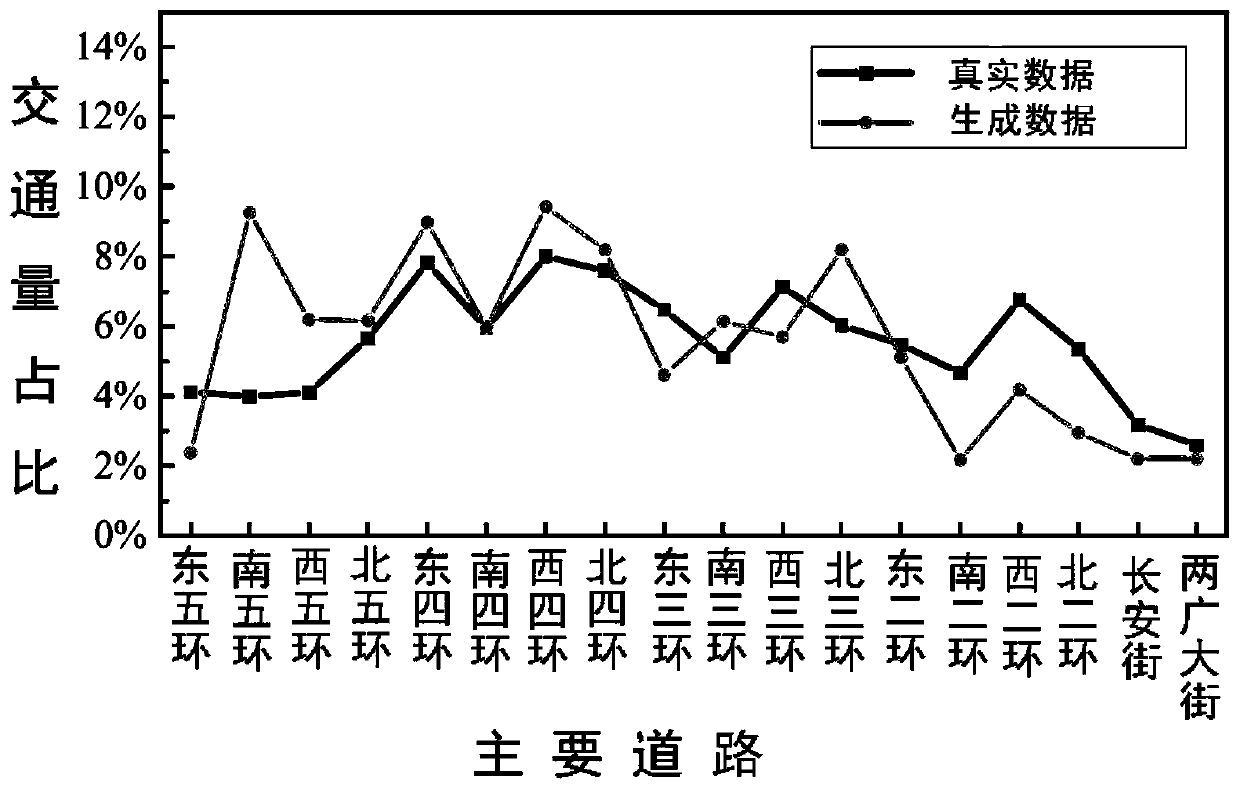
Urban traffic track data set generation method based on taxi data and urban road network
The invention discloses an urban traffic track data set generation method based on taxi data and an urban road network, and belongs to the field of traffic transportation. The model is composed of a preparation layer, a generation layer and a verification layer. Track data of private cars are generated based on taxi data and urban road network information for the first time, and meanwhile a complete verification method is provided for verifying the accuracy of a generated data set. The invention provides an urban functional region division method based on an adjacent road division method. Theurban functional region division method comprises the steps of dividing a city into different functional regions; meanwhile, providing a regional population weight opportunity model, and a populationmovement mode can be more accurately depicted. In order to verify the authenticity and the accuracy of the method, a macroscopic angle-based model and a microscopic angle-based model are respectivelyprovided on a verification layer to verify the authenticity and the accuracy of a data set generated by the model. Through verification of the verification layer, the track data of the private car generated according to the taxi GPS data and the urban vehicle network information are high in authenticity and accuracy.
Owner:DALIAN UNIV OF TECH
Logistics state monitoring method and system based on combination of sensors
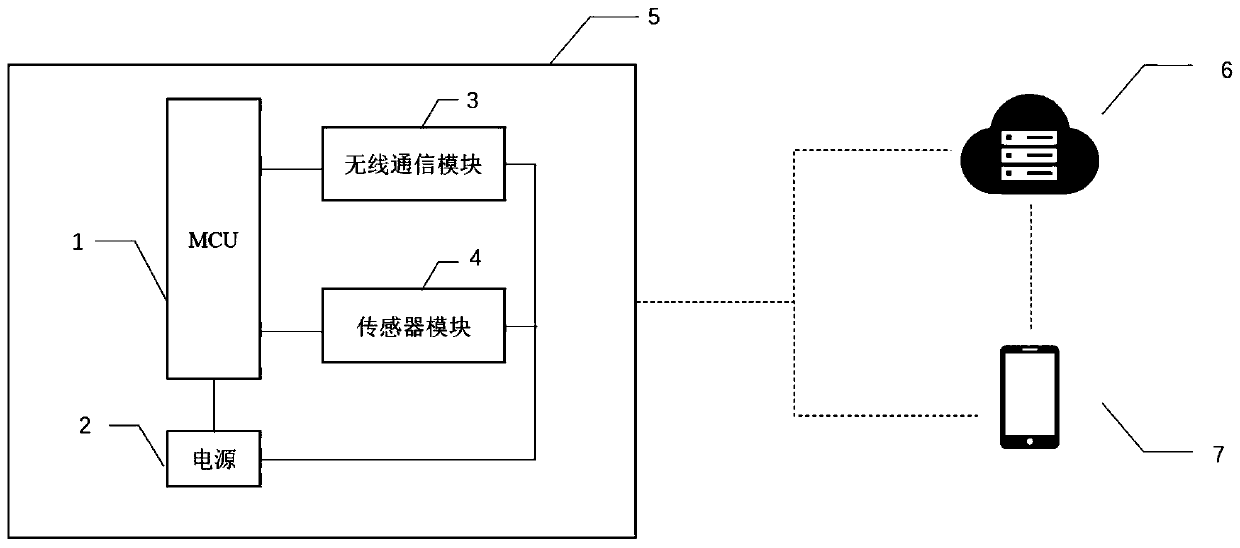
ActiveCN109947007AImprove transportation efficiencyImplement updateProgramme controlMeasurement devicesMicrocontrollerLogistics management
The invention discloses a logistics state monitoring method and system based on combination of sensors. The system comprises intelligent labels, each intelligent label is composed of a label casing, amicrocontroller, a sensor module, a wireless communication module and a power supply module, the label casing is mounted in the surface of a transport cargo, the microcontroller is responsible for work task scheduling of the whole system, via interconnection of different types of sensors, the sensor module can realize sensor data collection and event modeling calculation in the cargo transport environment, events include shocking, collision, overturning, falling off, unsealing and temperature and humidity imbalance, and the wireless communication module sends the sensor data, time label and event record to a monitoring mobile terminal or remote cloud server. Thus, real-time state and event record information of cargoes in the production material transmission and logistics transport process can be monitored effectively, alarm is raises against damage of cargoes timely, and safe transport of sensitive products can be monitored accurately and effectively.
Owner:ZHEJIANG UNIV
Method for obtaining digital siguature and realizing data safety
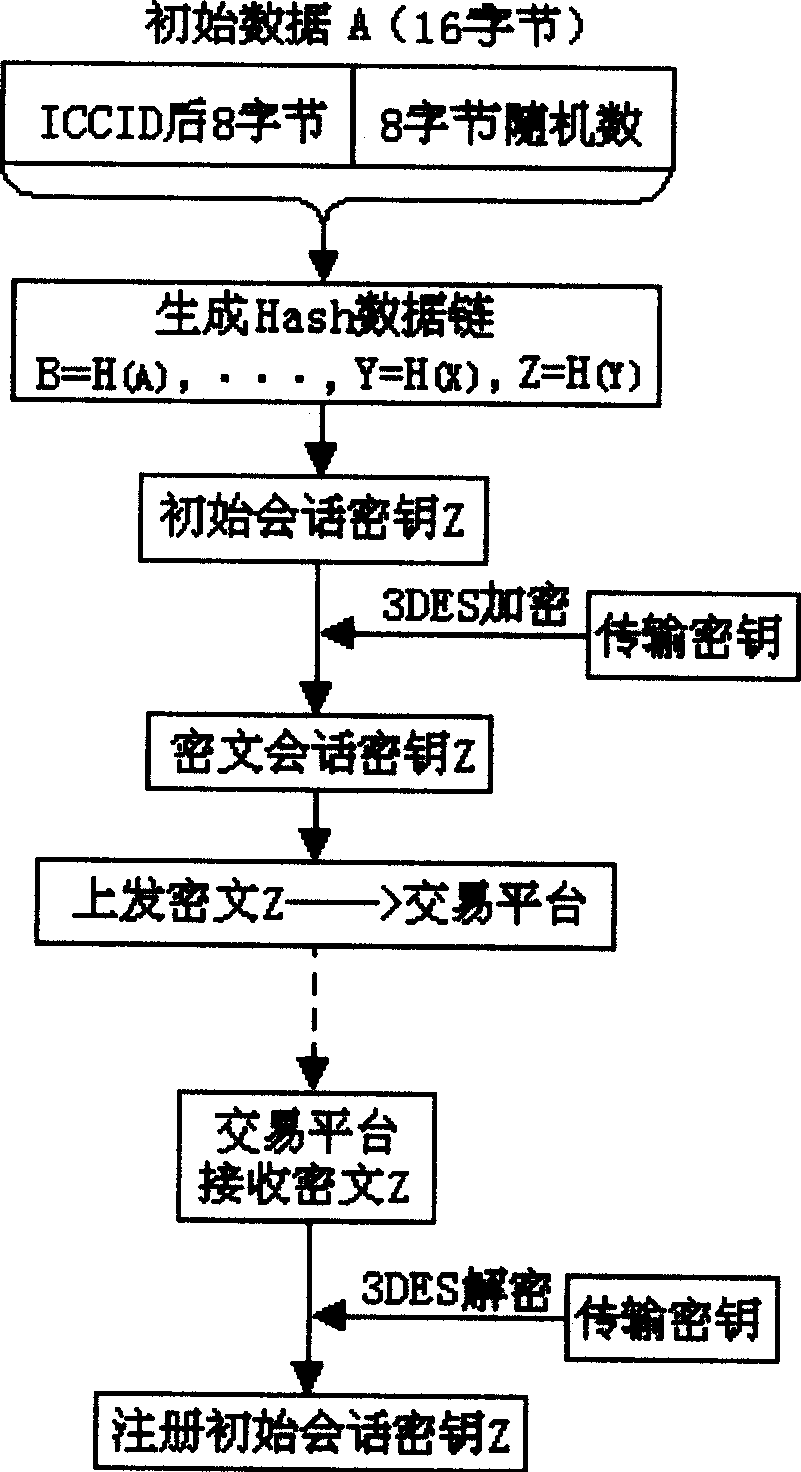
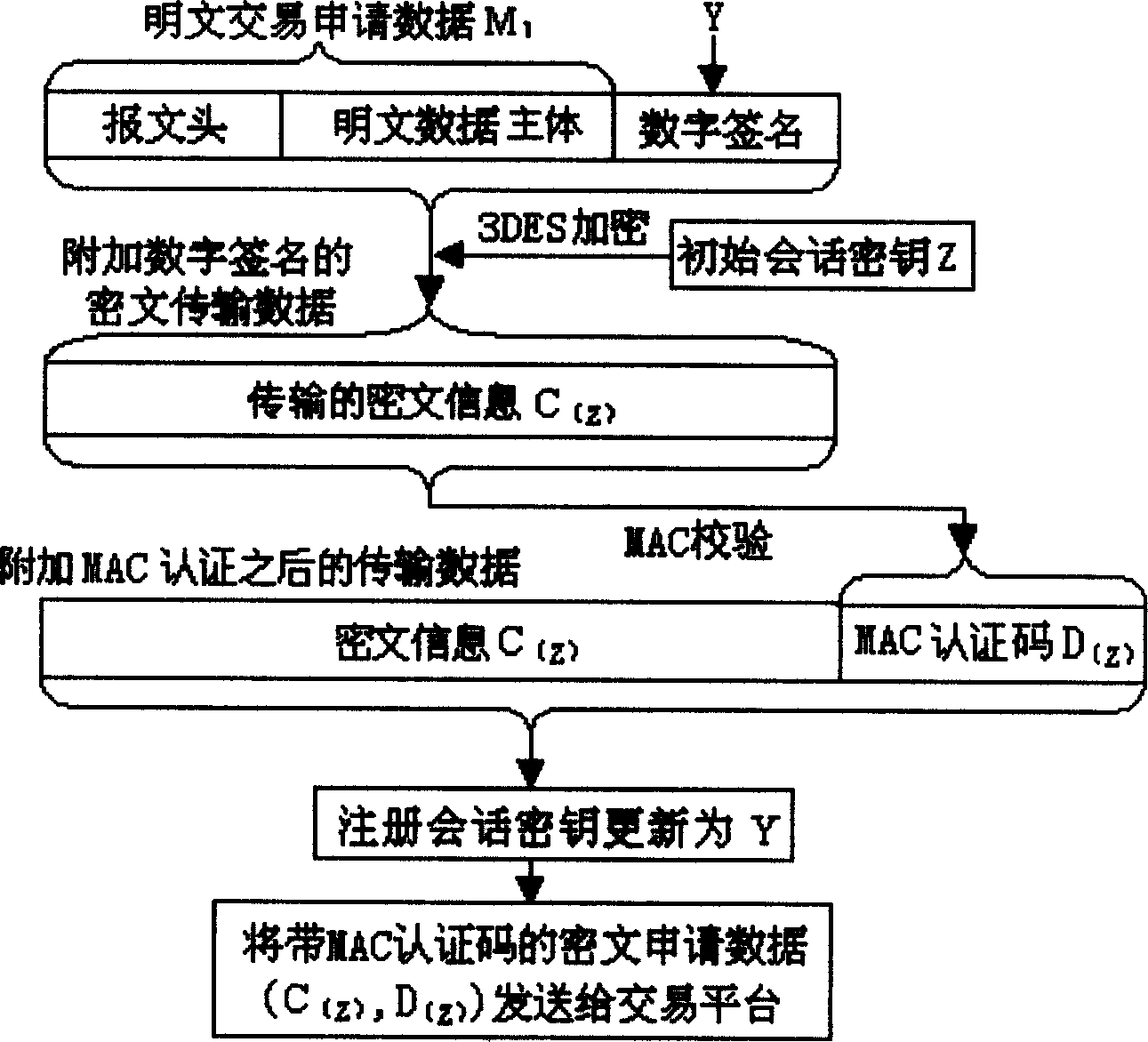
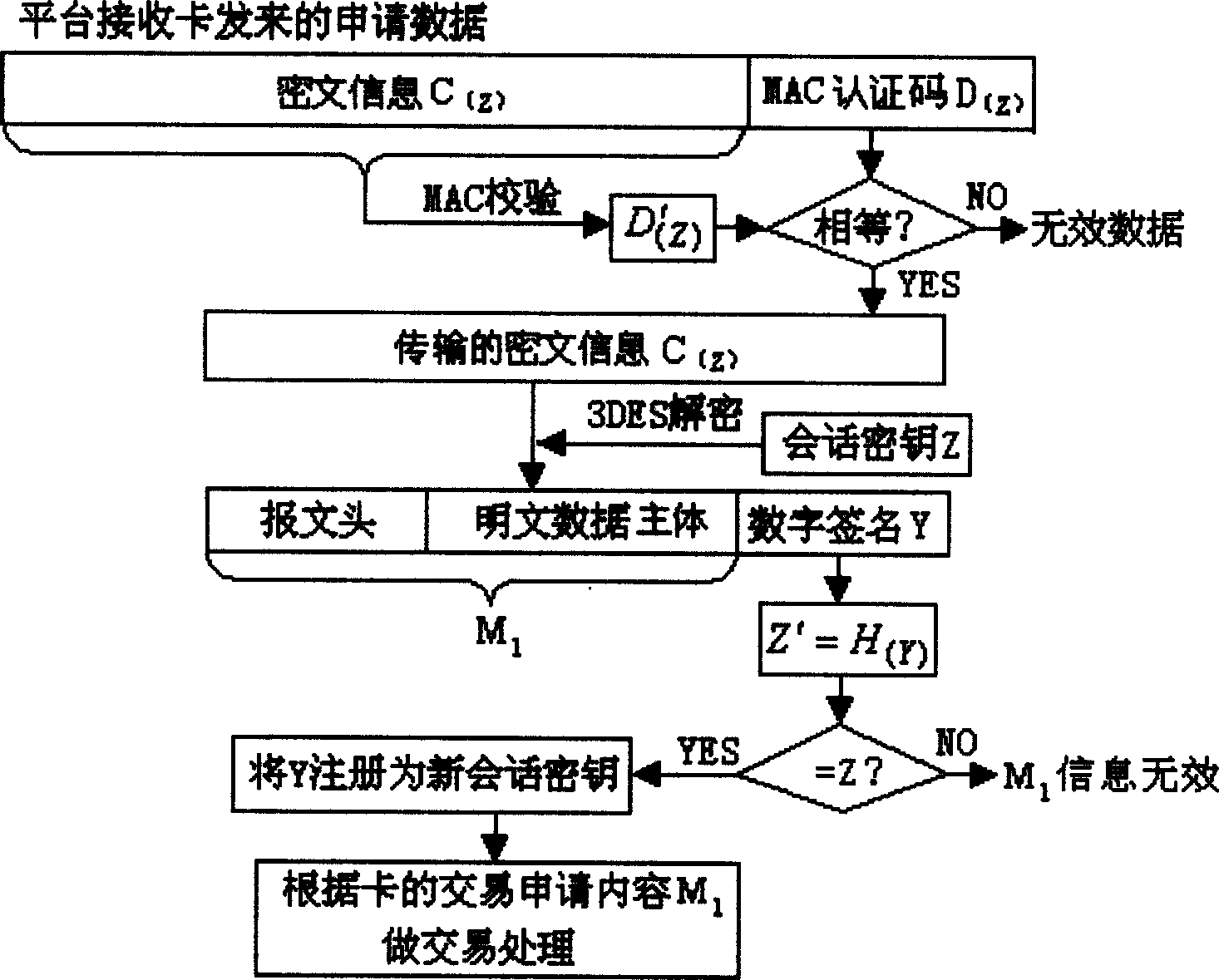
InactiveCN1532726AGuaranteed confidentialityGuaranteed security authenticationRandom number generatorsRadio/inductive link selection arrangementsDigital signatureMobile communication systems
The method of obtain digital signature and realizing data safety used especially in mobile communication system to ensure safe data transmission includes: adopting one-way inreversible predication algorithm to generate one-way inreversible data chain for cipher key management and to make the conversation cipher key for enciphering and deciphering changeable; adopting the one-way inreversible predication algorithm for digital signature of the conservation cipher key generated dynamically; and adopting symmetrical enciphering algorithm and verifying code confirming process in verifying the enciphered information to further ensure the security and integrality of the information. The method has lowered requirement in the data processing speed and capacity of the processor and is especially suitable for the application field with relatively high safety and speed requirement in mobile communication system.
Owner:DATANG MICROELECTRONICS TECH CO LTD
Method and device for performing multi-party security calculation through certificate issuing
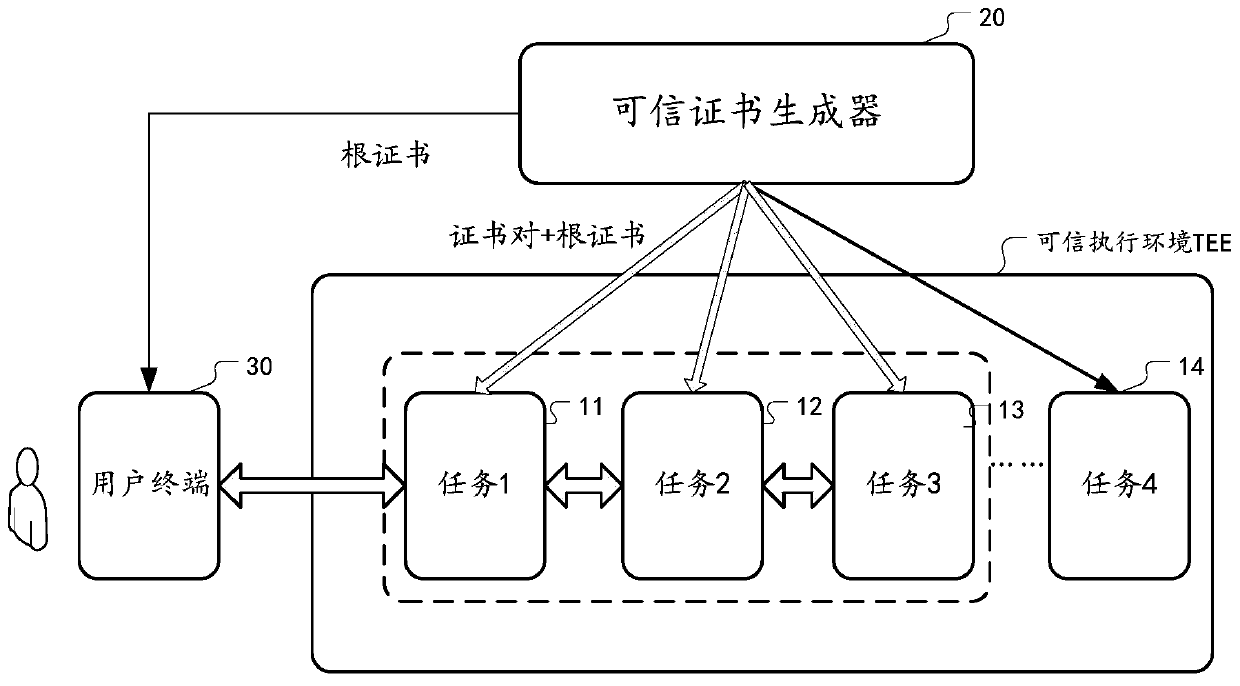
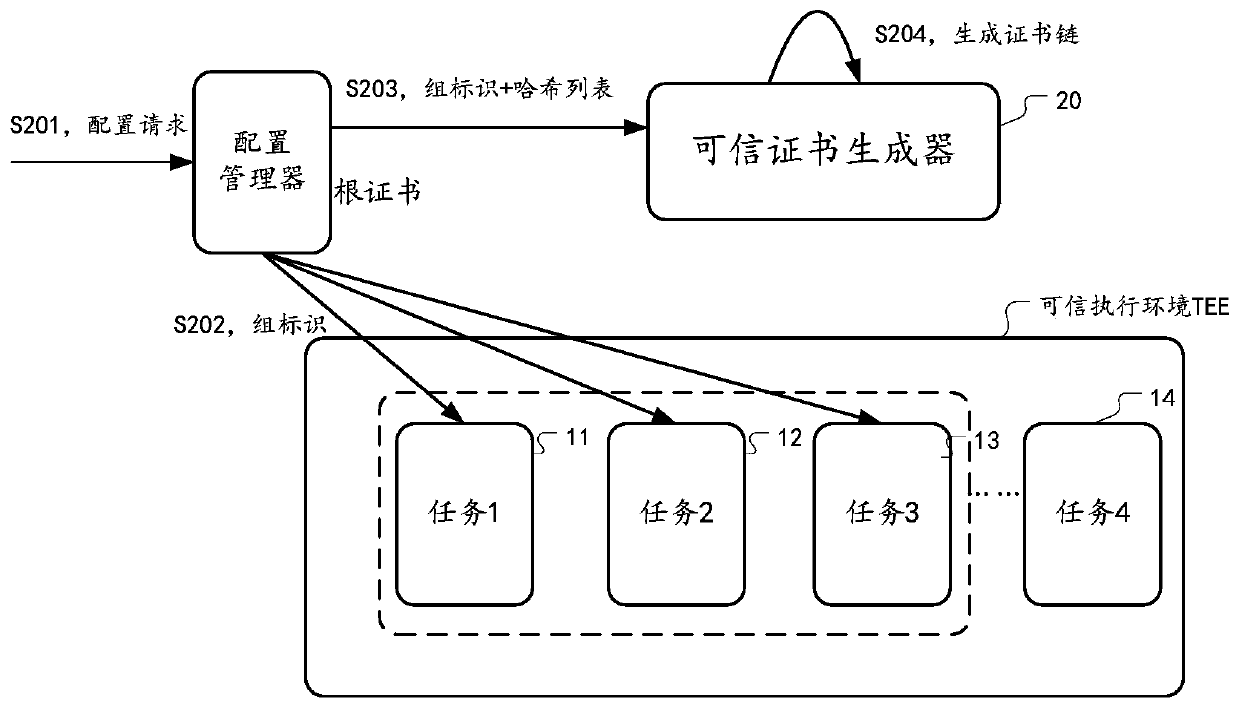
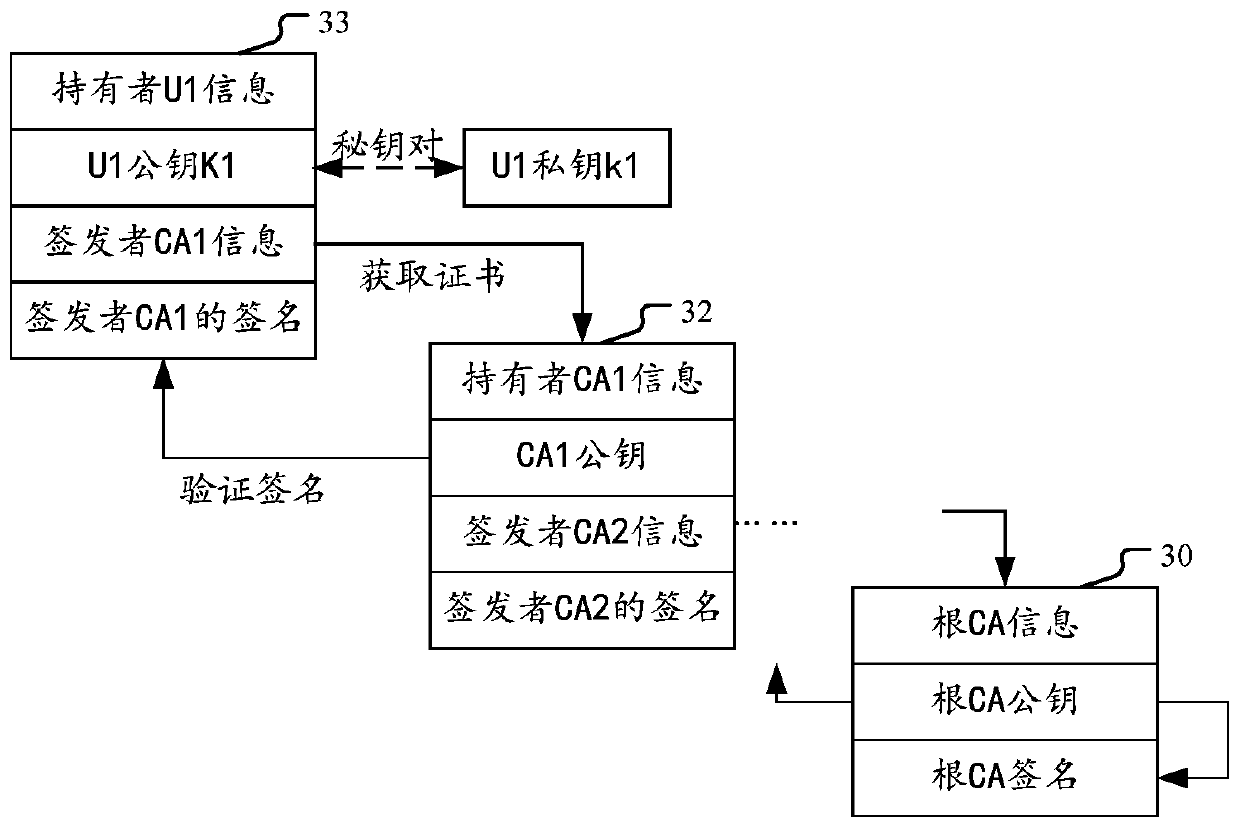
ActiveCN110535628AAchieve securityRealize verificationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesRoot certificateSecure communication
The embodiment of the invention provides a method and device for performing multi-party secure computing by distributing certificates. According to the scheme, task groups are formed through pre-configuration, and group identifiers are allocated. A trusted certificate generator generates a set of certificate chain and a private key for a group identifier, the certificate chain comprises a root certificate and a corresponding public key certificate, and the public key certificate is matched with the private key to form a certificate pair. And then, the trusted certificate generator distributesthe root certificate and the certificate pair to each trusted computing unit which is authenticated and runs each computing task corresponding to the group of identifiers. And on the other hand, the root certificate is distributed to the user terminal requesting the computing service of the task group. Thus, the user terminal with the root certificate and the trusted computing unit with the root certificate and the certificate pair can perform multi-party secure communication in a TLS protocol mode.
Owner:ADVANCED NEW TECH CO LTD
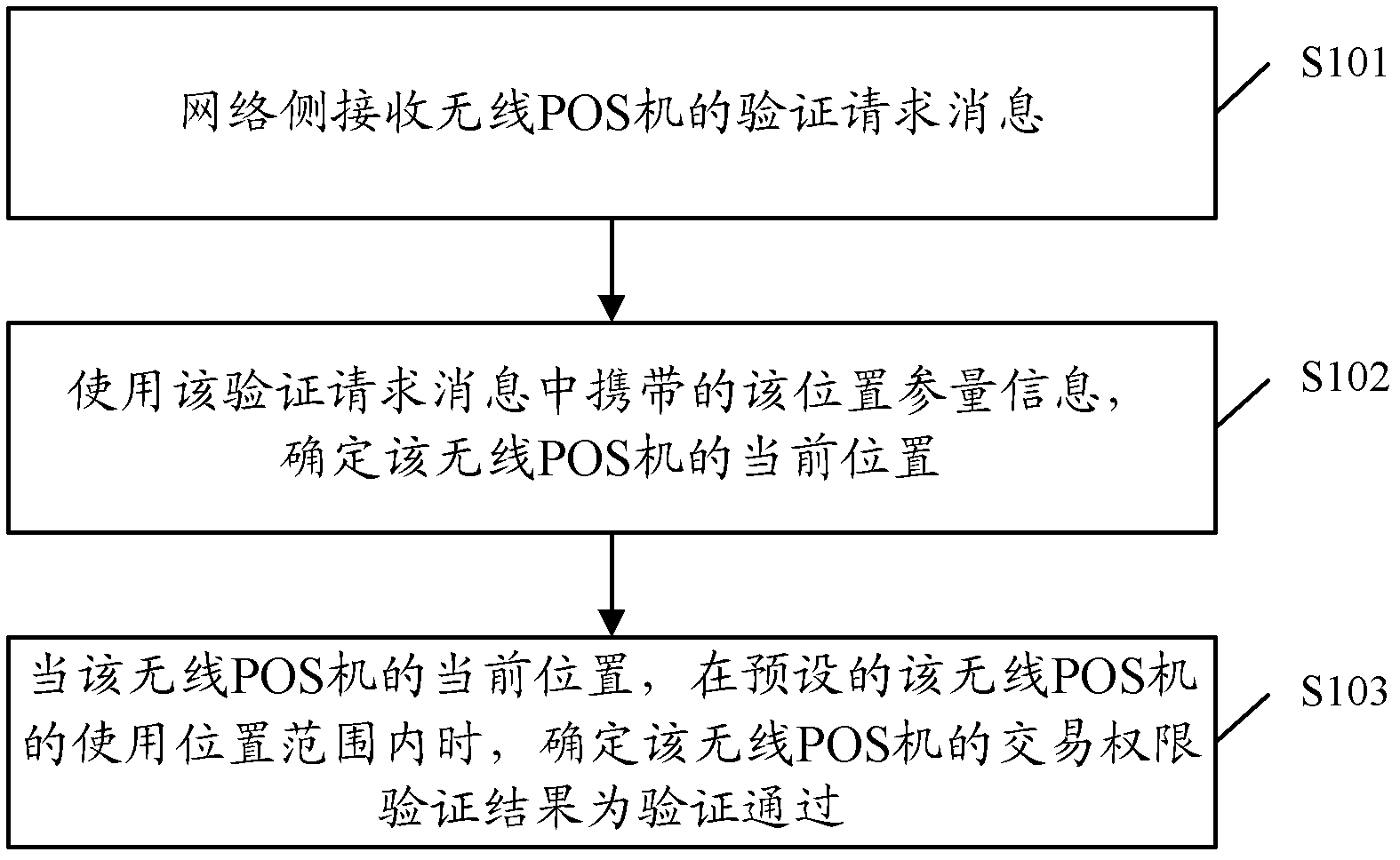
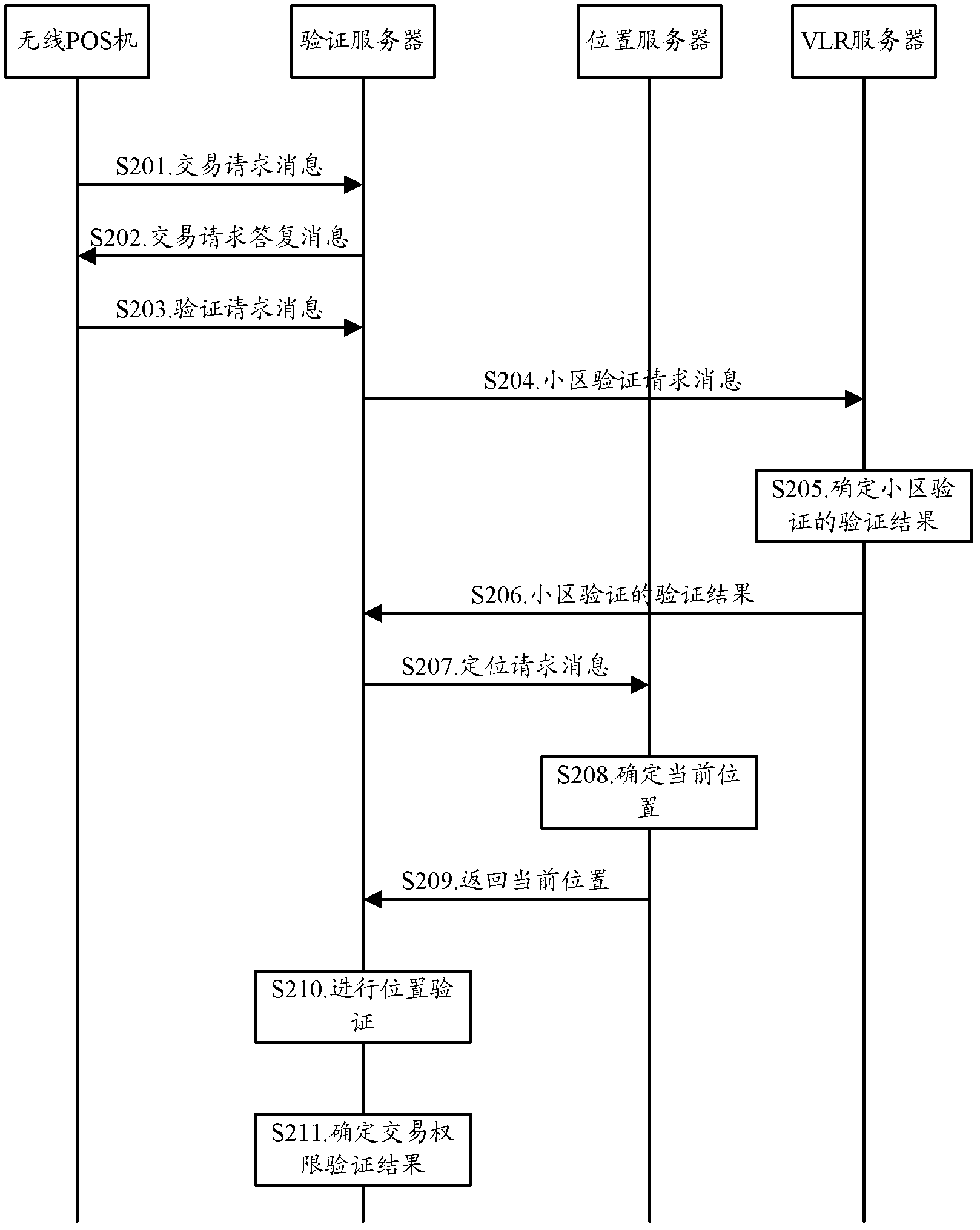
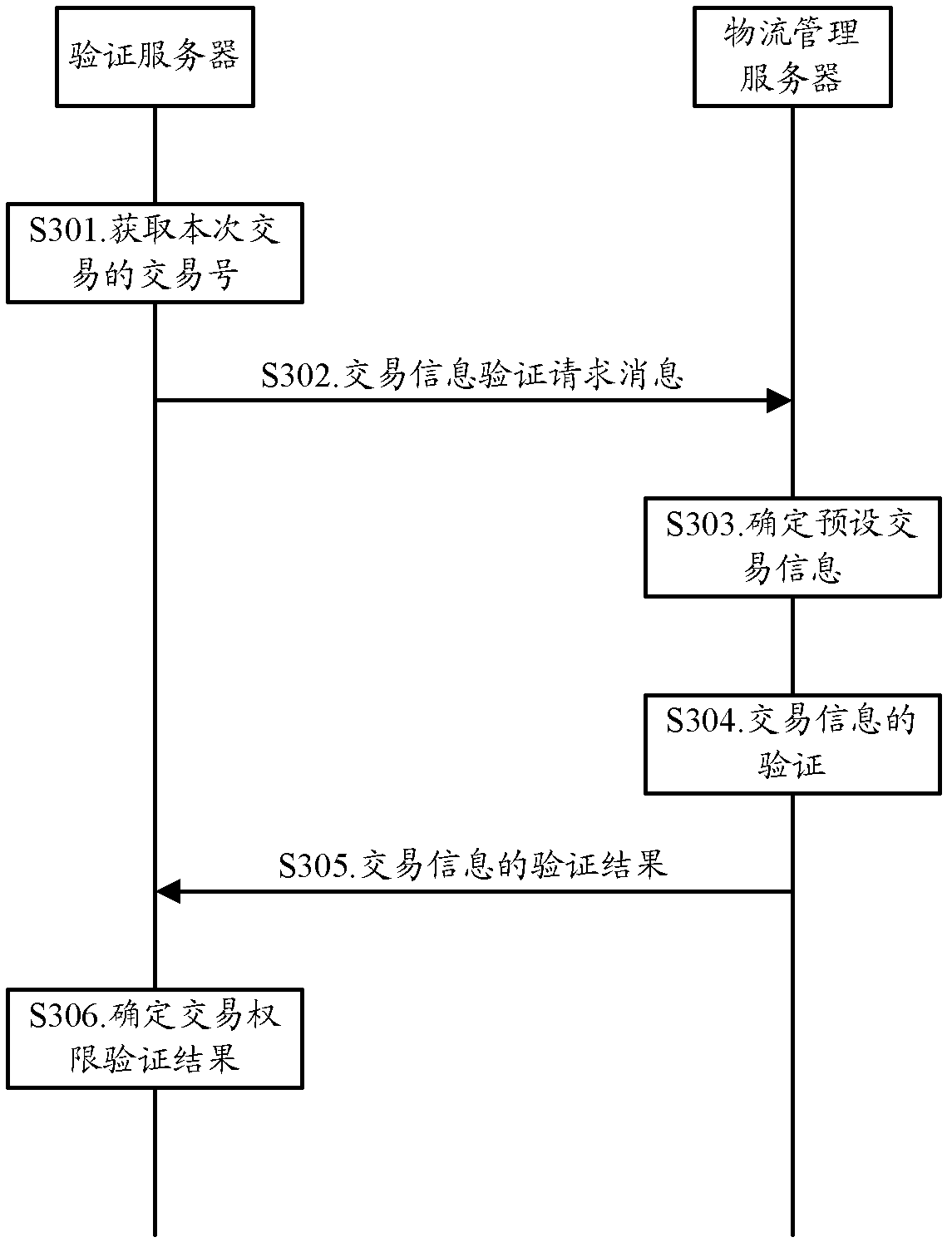
Method, device and system for verifying transaction permission of wireless point-of-sale (POS) machine
ActiveCN103035081ARealize verificationUser identity/authority verificationCash registersPaymentValidation methods
The invention discloses a method, device and system for verifying transaction permission of a wireless point-of-sale (POS) machine. The method includes that a network side receives verifying request information of the wireless POS machine, and the verifying request information carries position parameter information required for determining a current position of the wireless POS machine; the current position of the wireless POS machine is determined by using the position parameter information carried in the verifying request information; and when the current position of the wireless POS machine is in a preset use position range of the wireless POS machine, a transaction permission verifying result of the wireless POS machine is determined as that verification passes. By means of the scheme of an embodiment of the method, device and system, the network side achieves verification of transaction permission of the wireless POS machine in a transaction payment process on the basis of the current position of the wireless POS machine.
Owner:CHINA MOBILE COMM GRP CO LTD
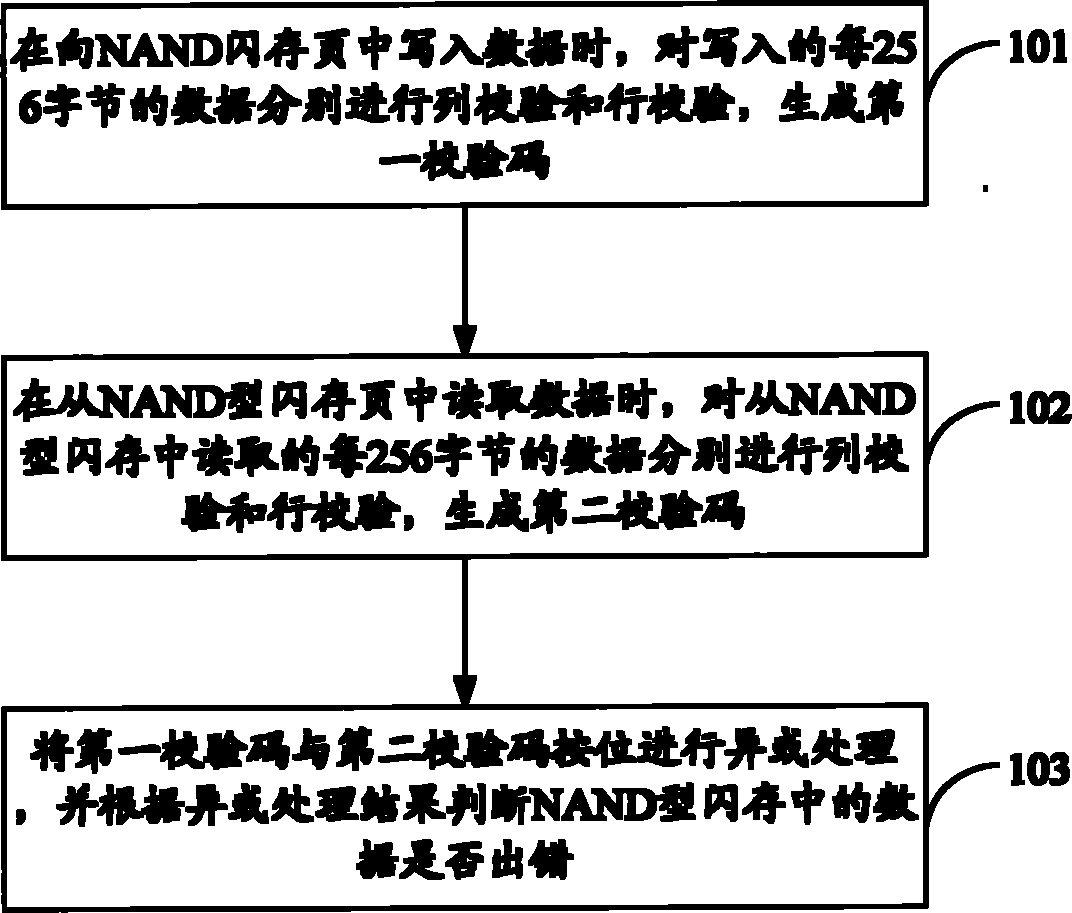
NAND flash memory as well as data checking method and device thereof
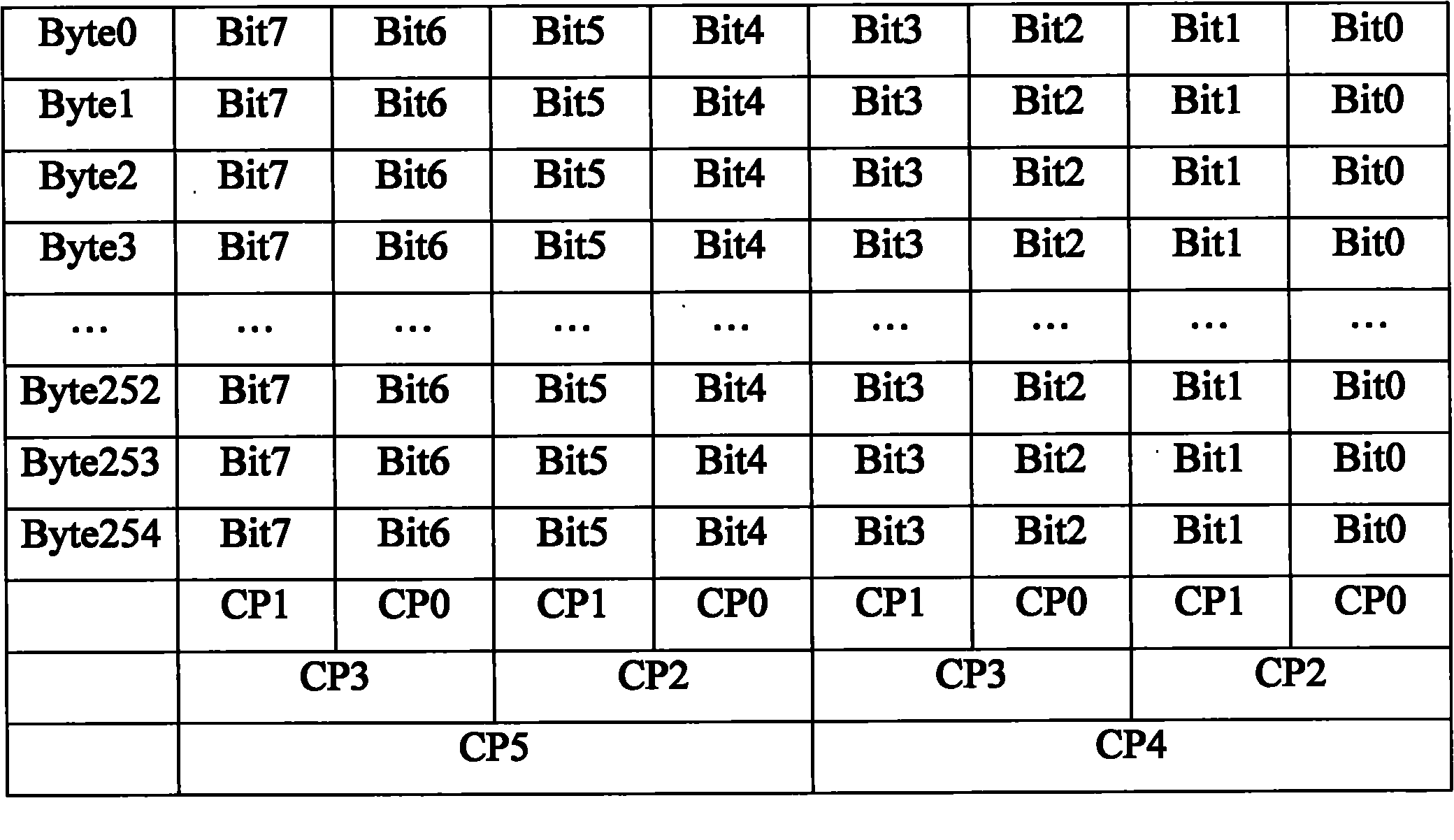
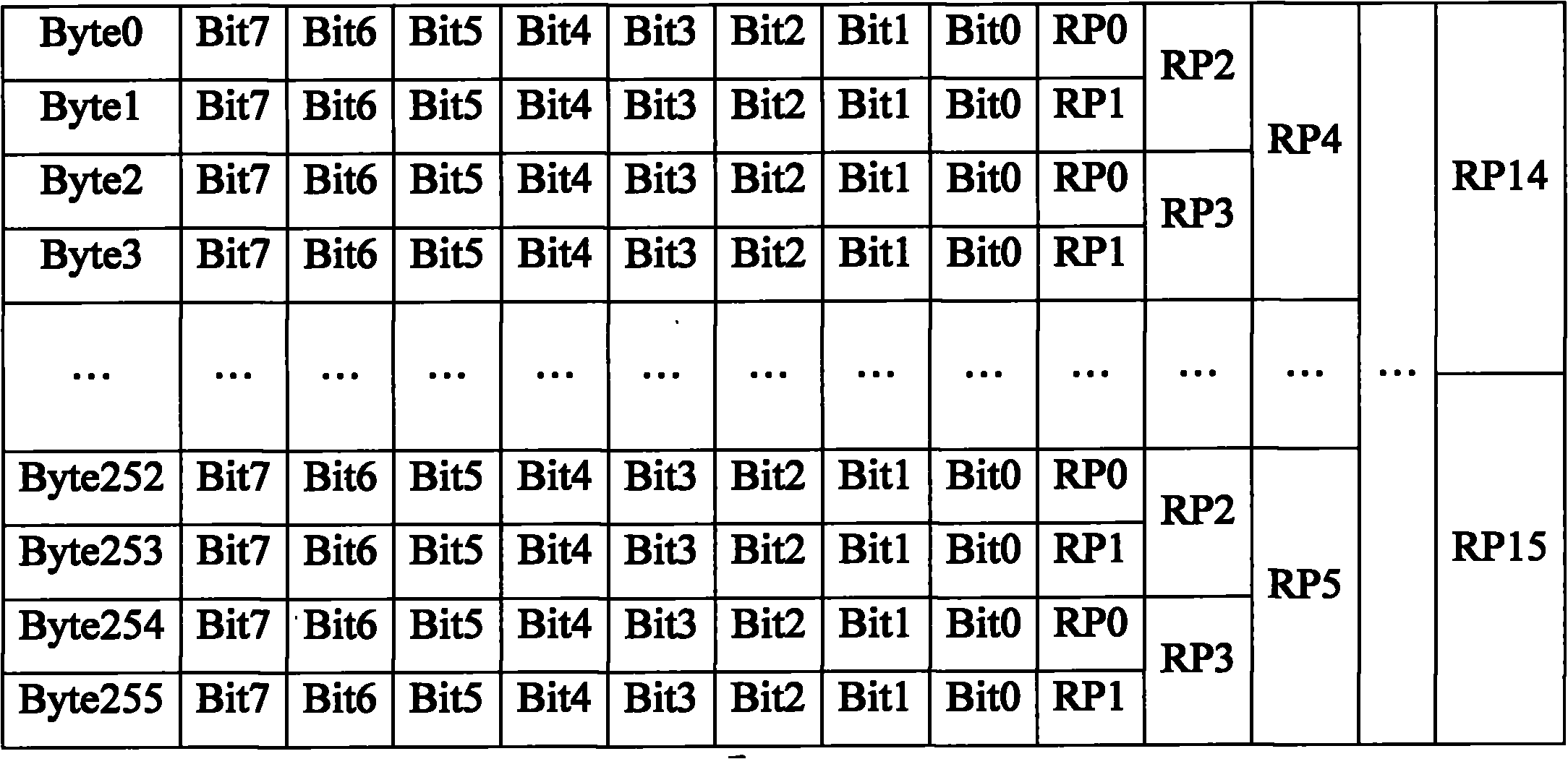
The invention is suitable for the memory field, and provides an NAND flash memory as well as a data checking method and device thereof. The method comprises the following steps: checking the row and the column of each 256-byte datum written to an NAND flash memory file to generate a first check code; checking the row and the column of each 256-byte datum read from the NAND flash memory file to generate a second check code; and processing the first check code and the second check code by XOR treatment, and determining whether the datum in the NAND flash memory has a fault according to the XOR treatment result. According to the embodiment of the invention, the method can check the data in the NAND flash memory in the software form, and is suitable for any platform.
Owner:KONKA GROUP
Privacy protection method based on blockchain cloud outsourcing computing data
ActiveCN108712429AOvercoming scalabilityOvercome securityPublic key for secure communicationExtensibilityData privacy protection
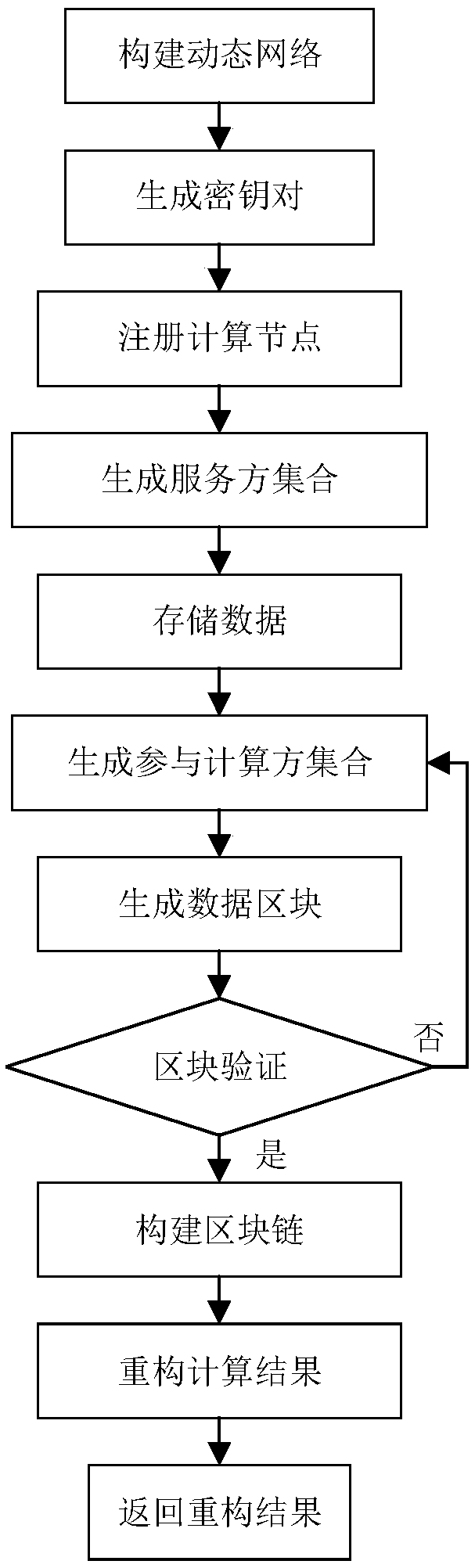
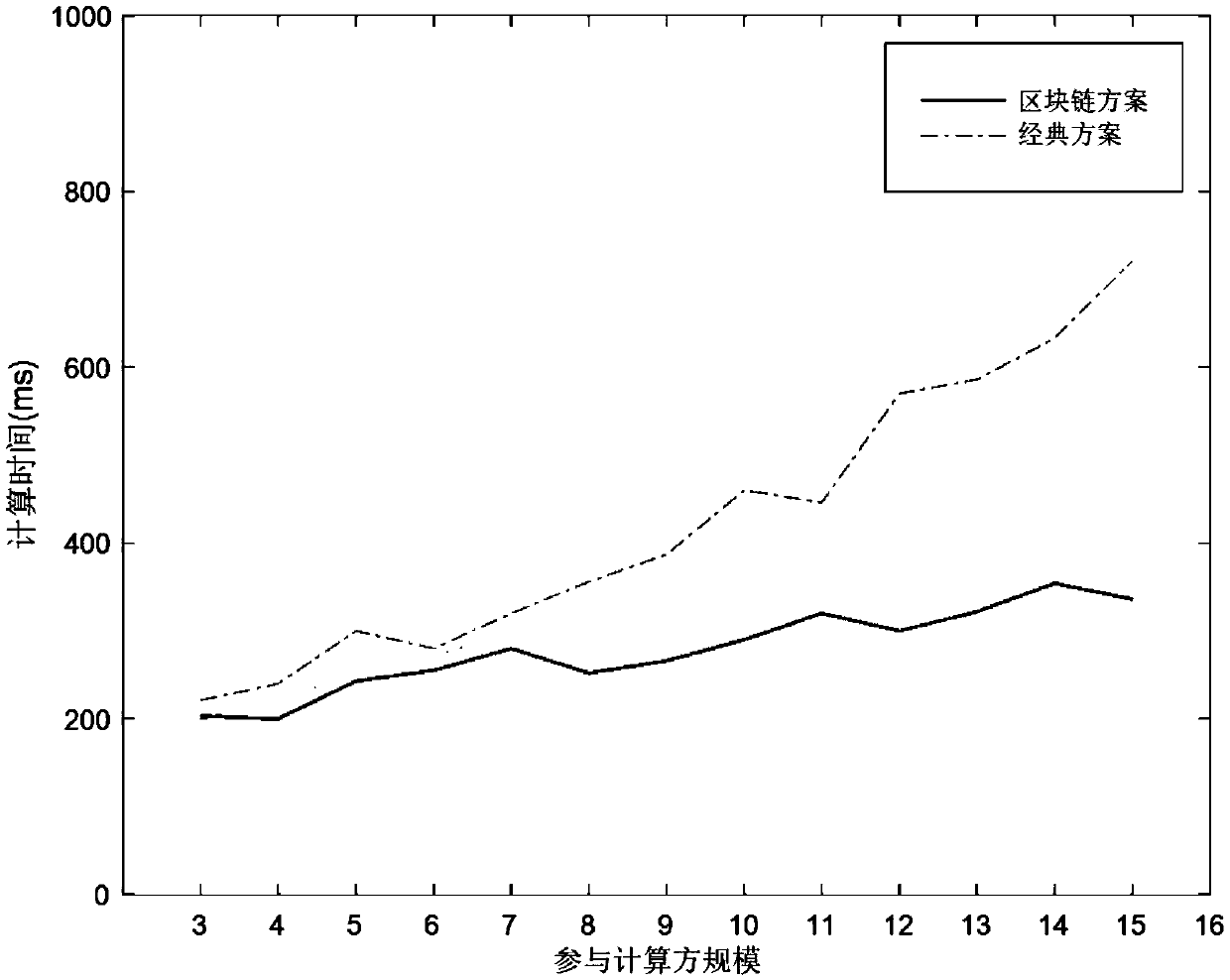
The invention discloses a privacy protection method based on blockchain cloud outsourcing computing data, and mainly solves the problem of high time complexity and scalability of the data privacy protection technology in the current cloud outsourcing computing process. The technical scheme is of using log information of a computing node to construct a blockchain, and using the blockchain technology to perform secure storage verification of the computing data; using the quorum technology to select a suitable computing node set for each round of computing to complete the computing task; and adopting a secure multi-party computing method based on threshold secret sharing to segment and reconstruct secret information. The privacy protection method based on blockchain cloud outsourcing computing data in the invention overcomes the problem that in the prior art, the computing network lacks the scalability and security and the complexity of the data verification process is high; and the scalability of the computing network and the efficiency of the computing process are greatly improved while the data privacy can be effectively ensured.
Owner:XIDIAN UNIV
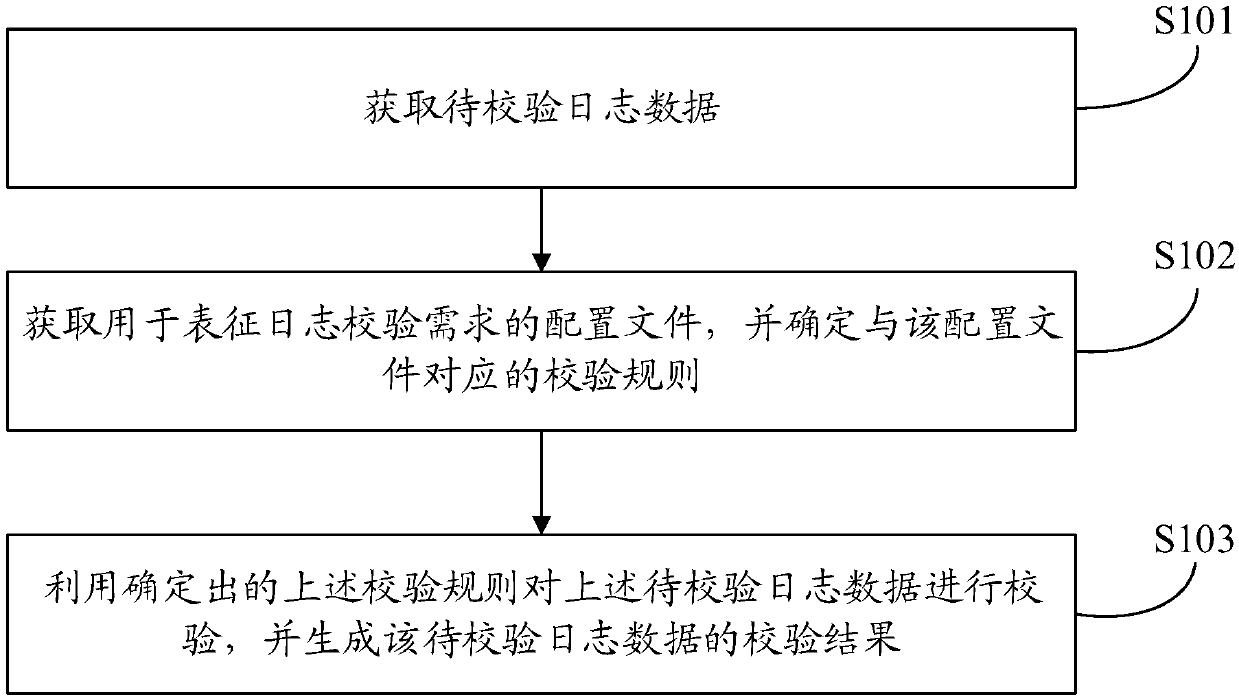
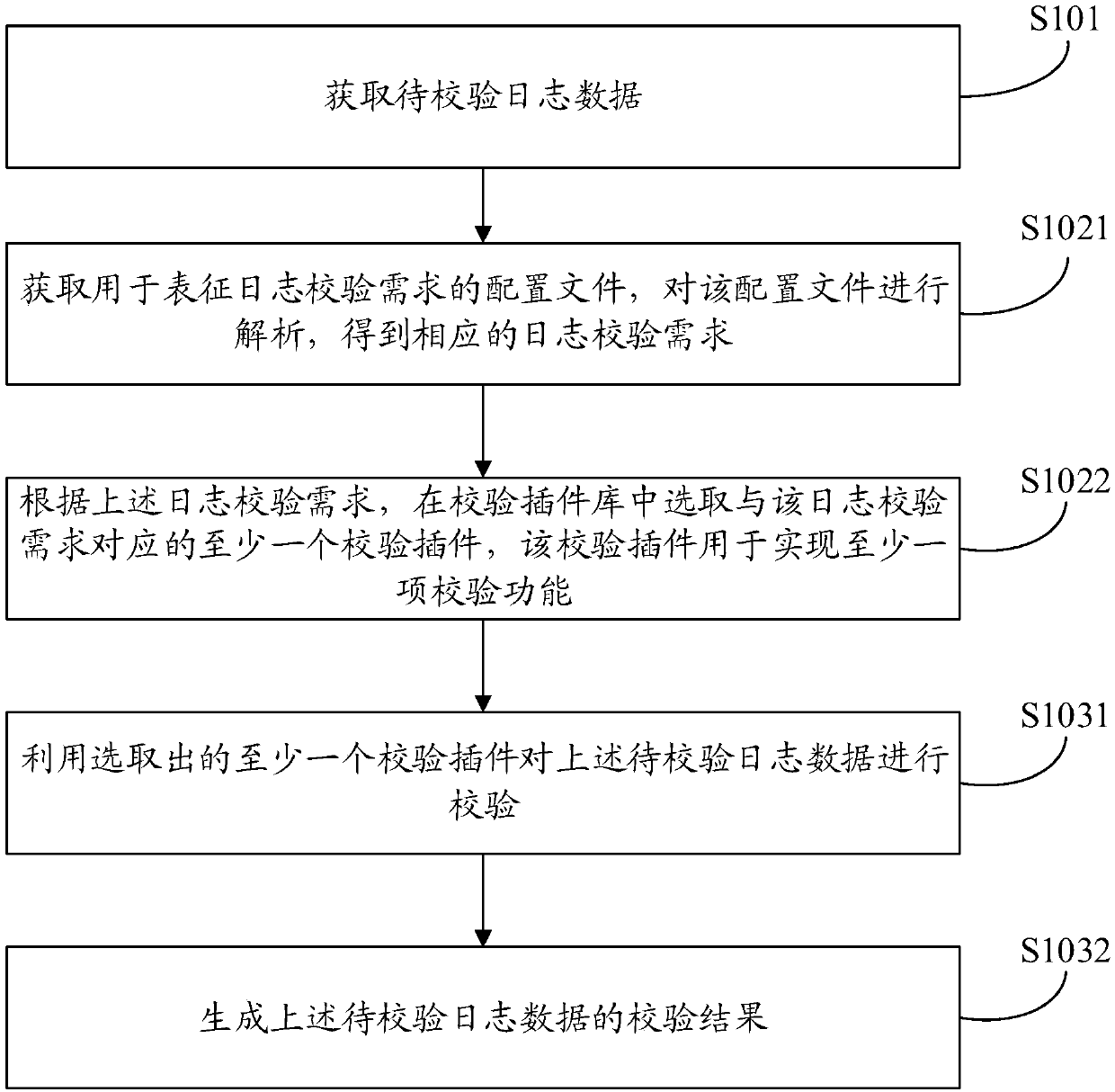
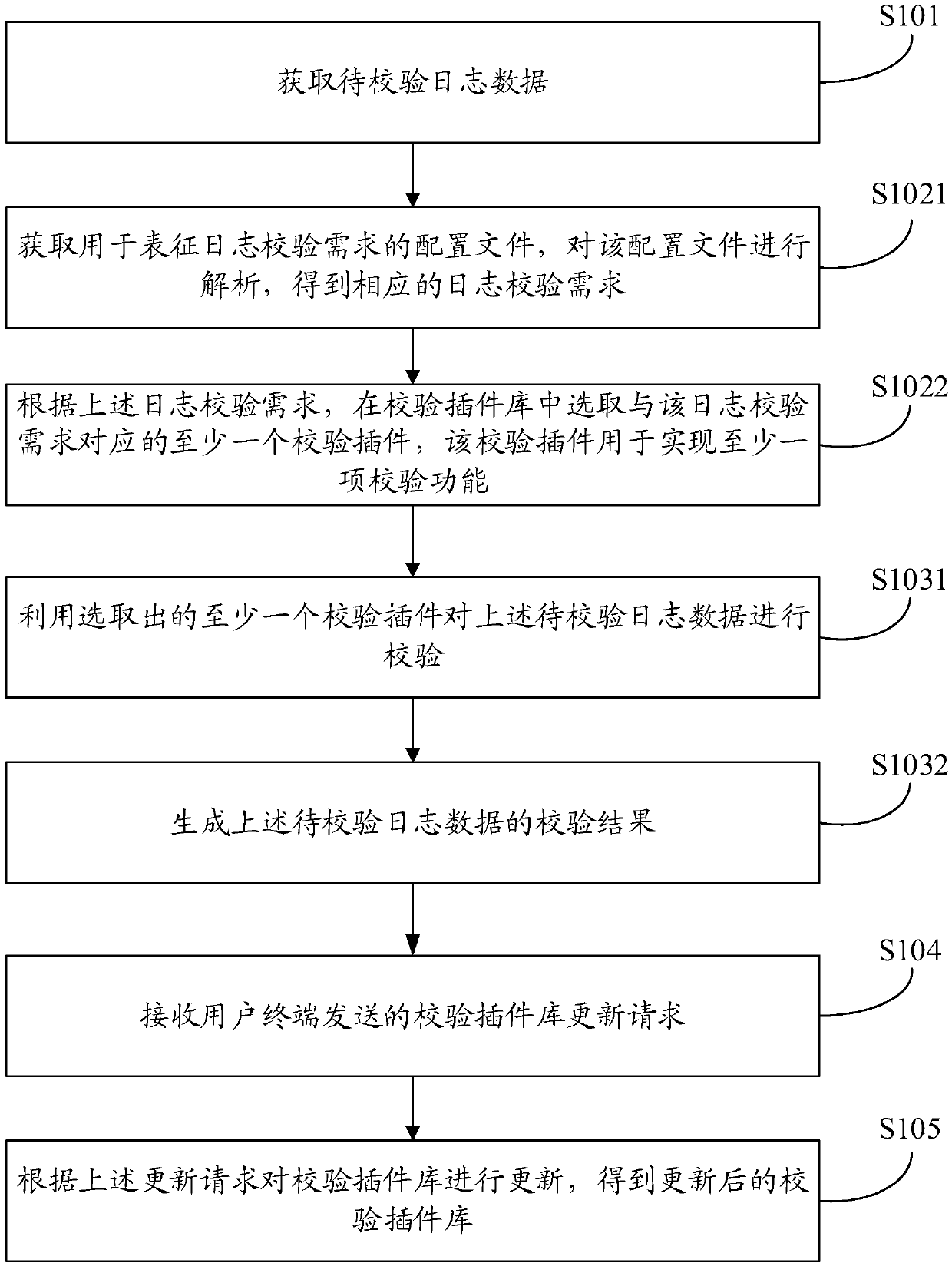
Checking methods and devices of log data
ActiveCN107844400ARealize verificationIncrease flexibilityHardware monitoringProgram loading/initiatingData miningService system
The embodiment of the application provides checking methods and devices of log data. One of the methods includes: acquiring to-be-checked log data; acquiring a configuration file used for characterizing log checking requirements, and determining checking rules corresponding to the configuration file; and utilizing the determined checking rules to check the to-be-checked log data, and generating achecking result of the to-be-checked log data. Compared with an artificial log checking manner or a checking manner, of which checking rules are fixed and invariable, in the related art, the checkingmethods and devices of the log data provided by the embodiment of the application can automatically match the checking rules according to the actual checking requirements of a user, thus achieve an effect that the checking rules can be freely configured, then utilize the checking rules to realize automatic checking of the log data, improve flexibility and variability of the log checking manners, and can realize, without the need for modifying an application program of a service system, an effect of combining the different checking requirements and adopting the corresponding checking rules to check the log data.
Owner:ADVANCED NEW TECH CO LTD
Satellite multiple attitude control mode test system based on double gimbal control moment gyroscope (DGCMG) structure
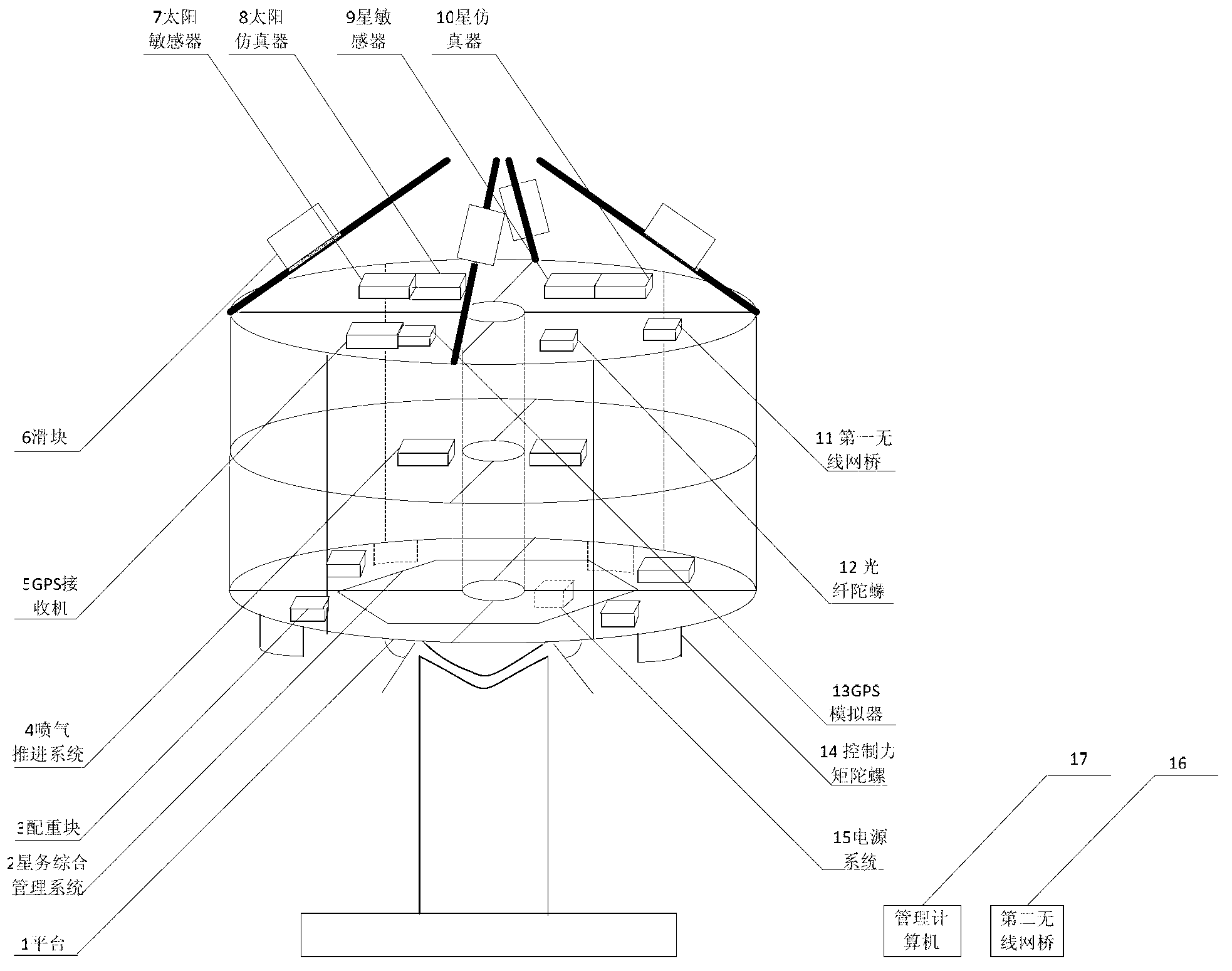
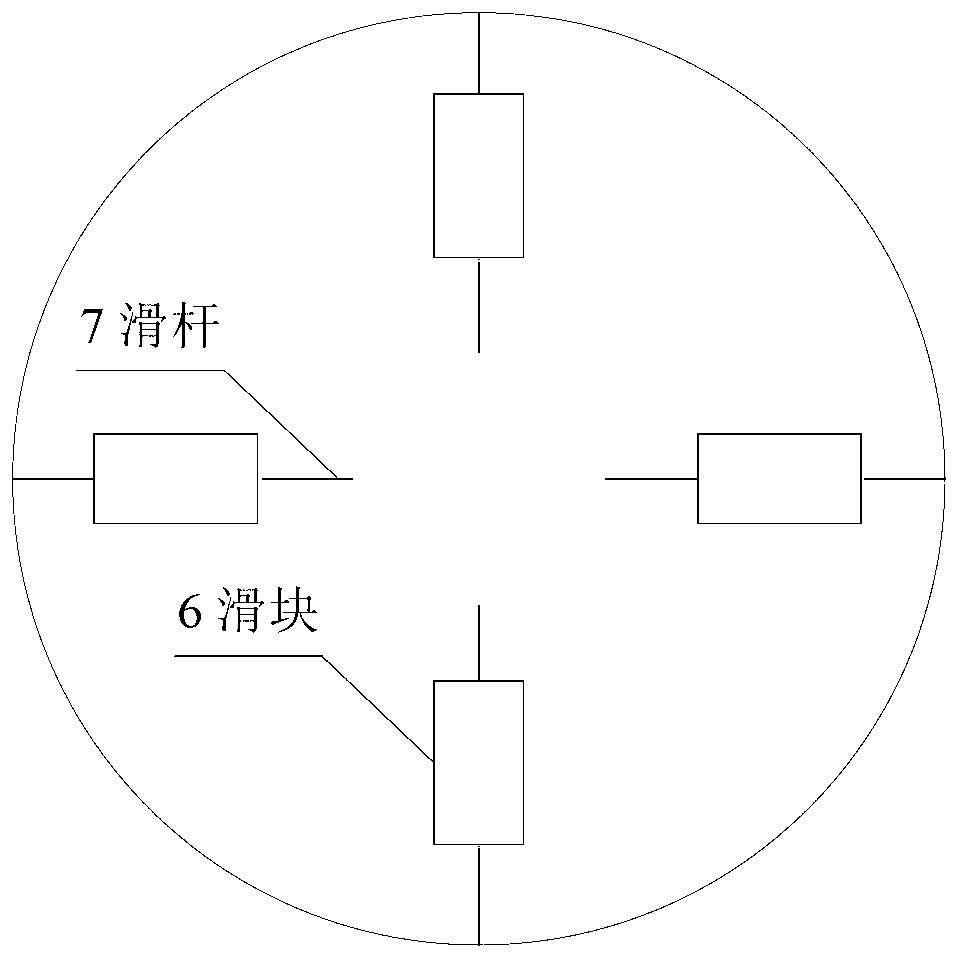
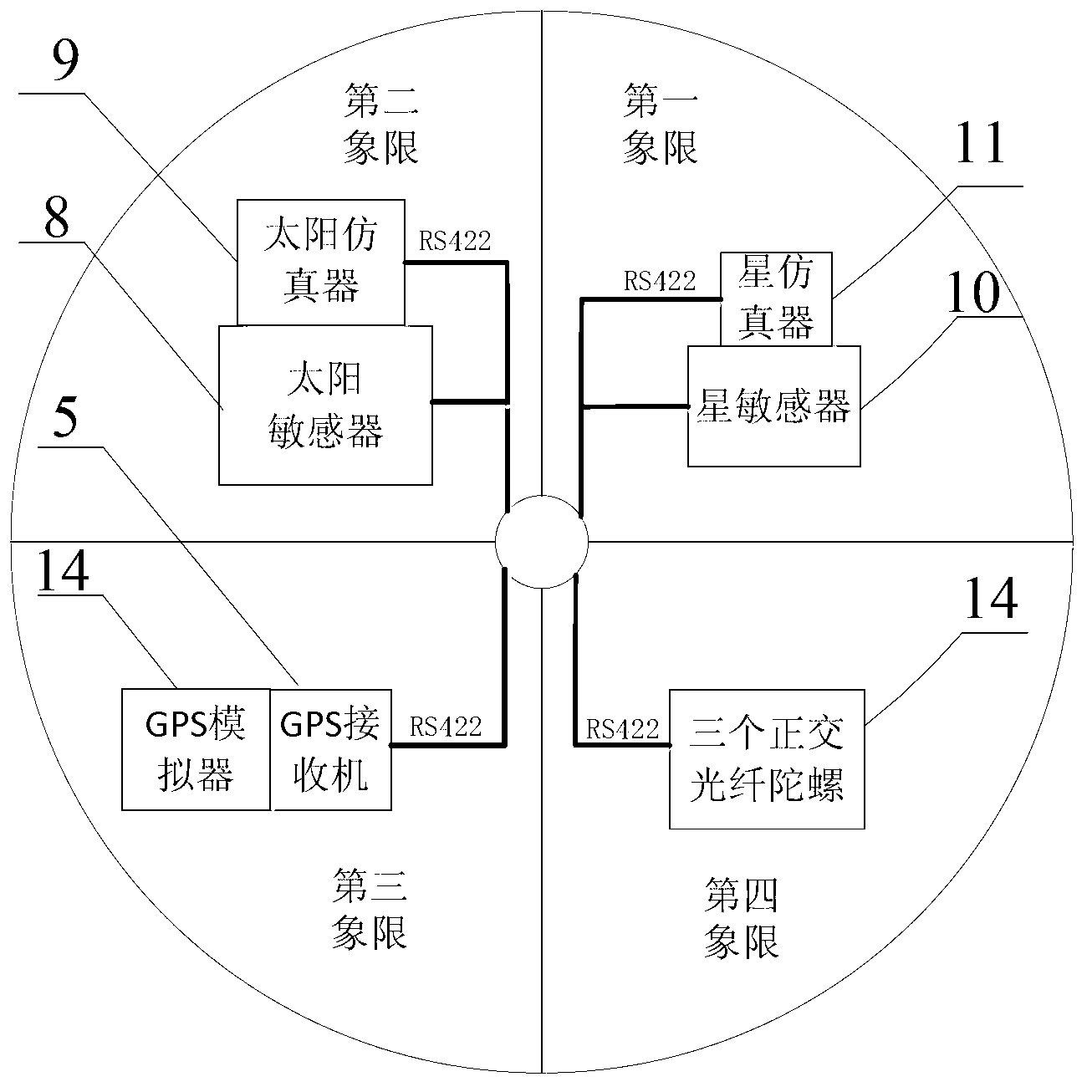
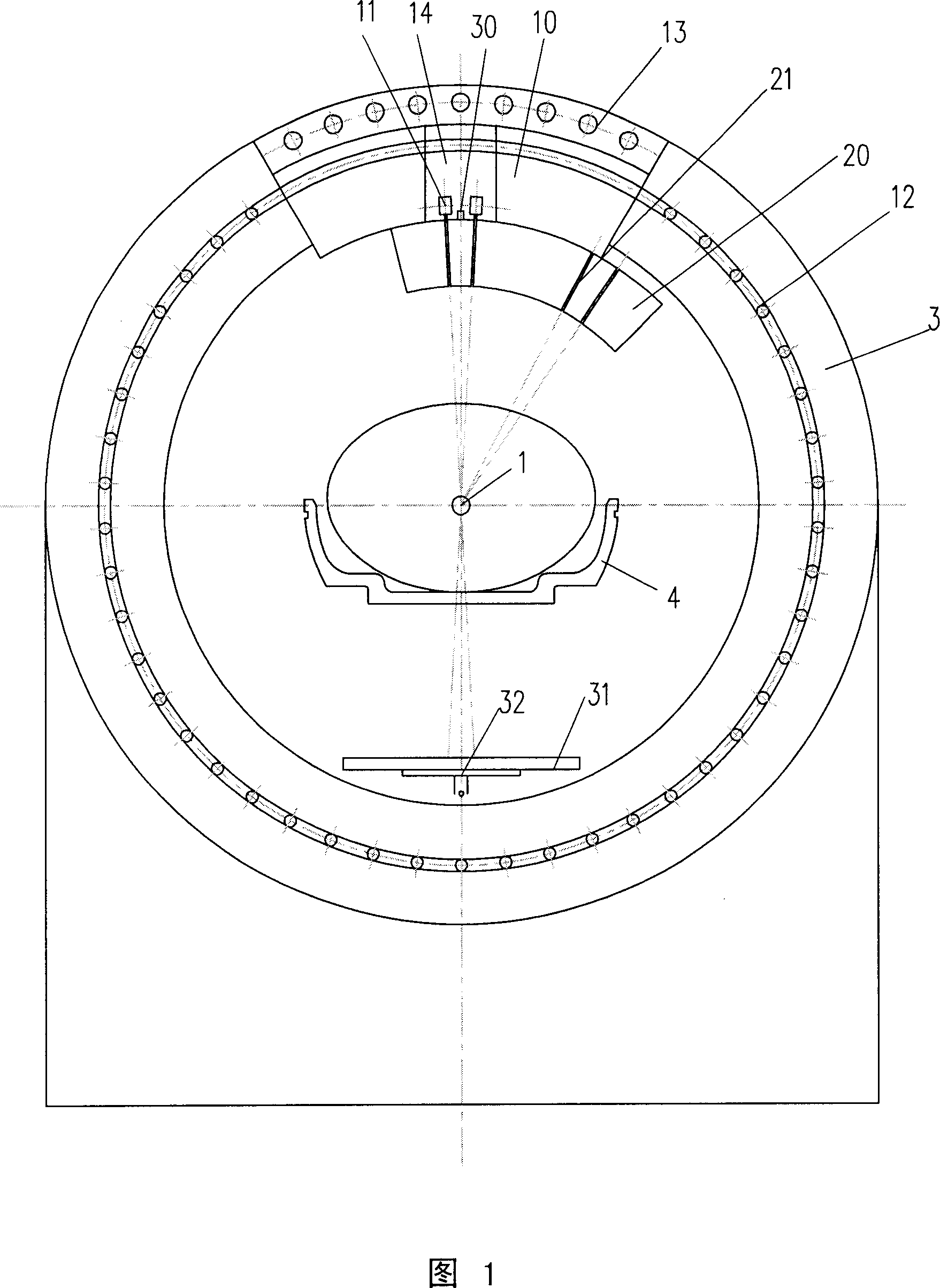
The invention relates to a satellite multiple attitude control mode test system based on a double gimbal control moment gyroscope (DGCMG) structure. Performance of three satellite attitude control systems which are based on a DGCMG, a single gimbal control moment gyroscope (CMG) and a flywheel is tested and verified through a DGCMG actuating mechanism. The satellite multiple attitude control mode test system based on the DGCMG structure comprises a platform system, the satellite attitude control system, a space environment simulation system and a ground station system. The platform system is composed of a tri-axial air bearing table, a satellite service comprehensive management system, a power source and a wireless bridge and used for simulating satellite dynamic characteristics and information management. The satellite attitude control system is composed of a jet propulsion system, the DGCMG, a fiber-optic gyroscope, a star sensor, a sun sensor and a global position system (GPS) receiver and used for determination of an attitude and an orbit and control of a satellite platform. The space environment simulation system is composed of a GPS simulator, a sliding block which is of a pyramidal structure, a sun simulator and a star simulator and used for simulating space interference torque, and part performance of a GPS satellite and a celestial body. The satellite multiple attitude control mode test system based on the DGCMG structure can provide ground testing and verification for multiple attitudes of a satellite.
Owner:BEIHANG UNIV
Radiation therapeutical device
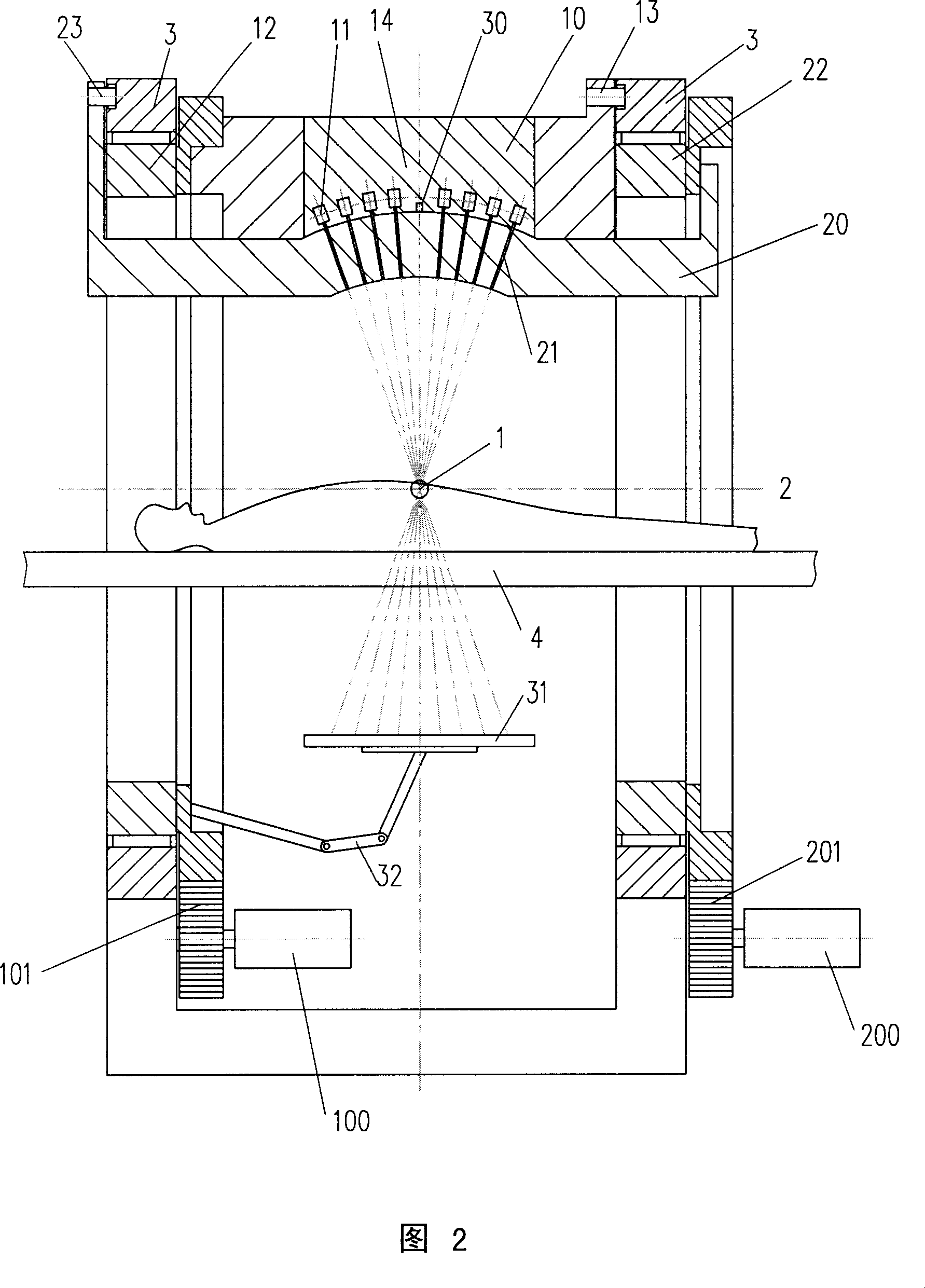
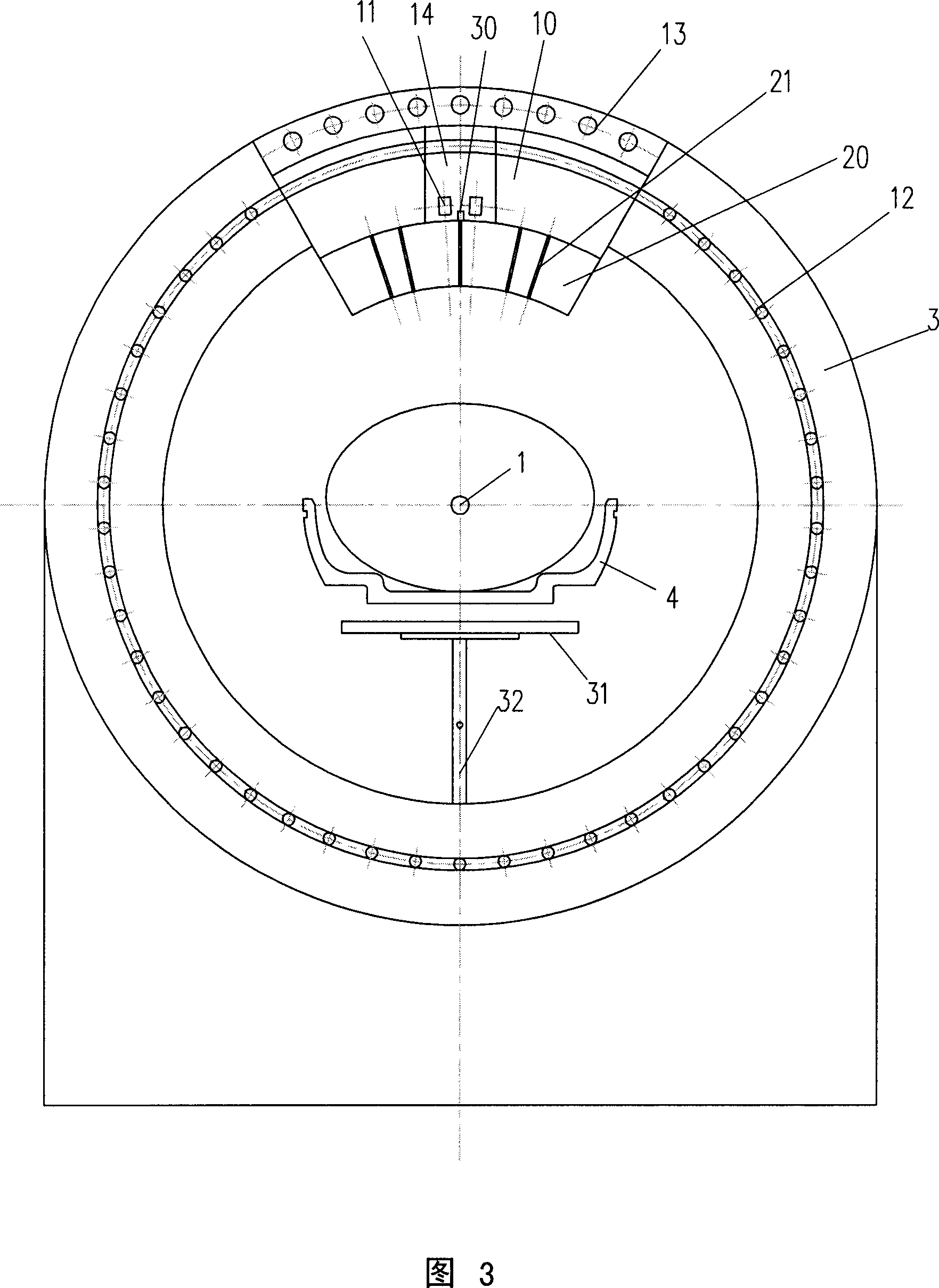
ActiveCN1919372AGood effectRealize verificationRadiation diagnosticsX-ray/gamma-ray/particle-irradiation therapyTherapeutic bedGamma ray
The invention relates to a radiotherapy device and method of gamma ray rotation and focusing, which comprises the following steps: main control unit, driver, radiation device, therapeutic bed and so on, wherein the therapeutic bed and rotatable barrier are set in the rotating ring and radiation device separately, the rotating support ring is fixed on two ends of rotating stand with the axial of rotating support ring matching rotating ring positionally, the relating radiation device is set between two rotating rings, whose the rotatable barrier center fixes a rotatable cylindrical alignment.
Owner:SHEN ZHEN HYPER TECH SHENZHEN
Fingerprint identification method and apparatus
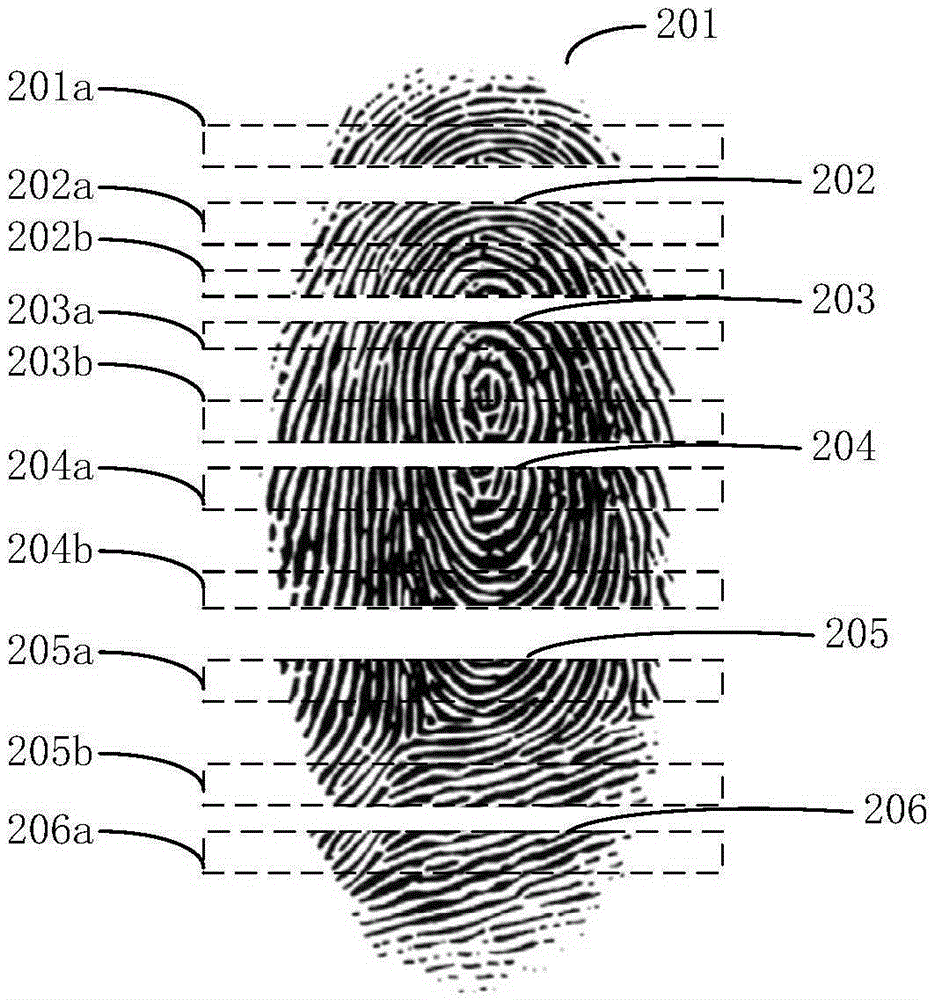
InactiveCN105354544AFree up free spaceEasy to useCharacter and pattern recognitionPattern recognitionTerminal equipment
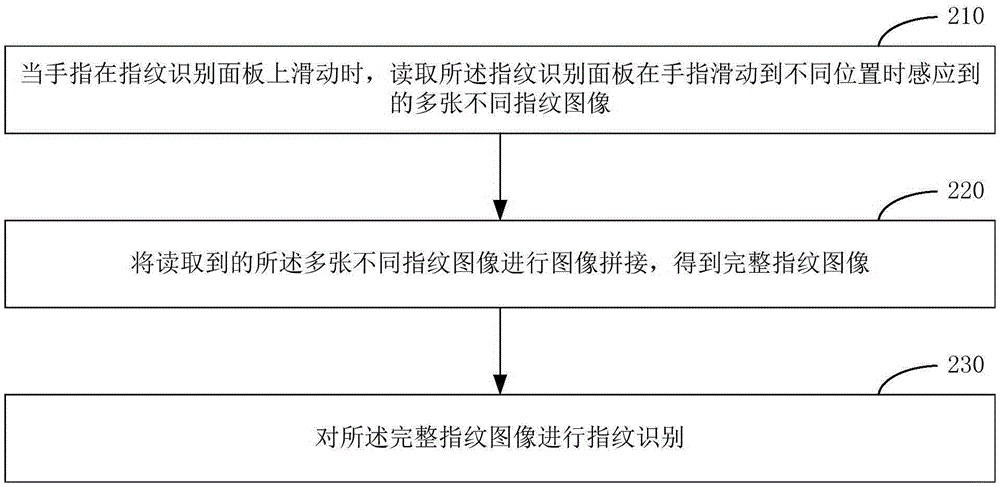
The present disclosure relates to a fingerprint identification method and apparatus. The method comprises: when a finger slides on a fingerprint identification panel, reading a plurality of different fingerprint images sensed by the fingerprint identification panel when the finger slides to different positions; performing image stitching on the plurality of different read fingerprint images to obtain a complete fingerprint image; and performing fingerprint identification on the complete fingerprint image. The complete fingerprint image does not need to be obtained only by touching the fingerprint identification panel for once and the method and the apparatus have no special requirement for the size of the fingerprint identification panel, and thus, even if the fingerprint identification panel is narrow, the complete fingerprint image also can be obtained by finger sliding and image stitching to finish fingerprint identification, thereby releasing an available space of terminal equipment.
Owner:XIAOMI INC
Second-generation ID card online inquiry system and method based on secure network
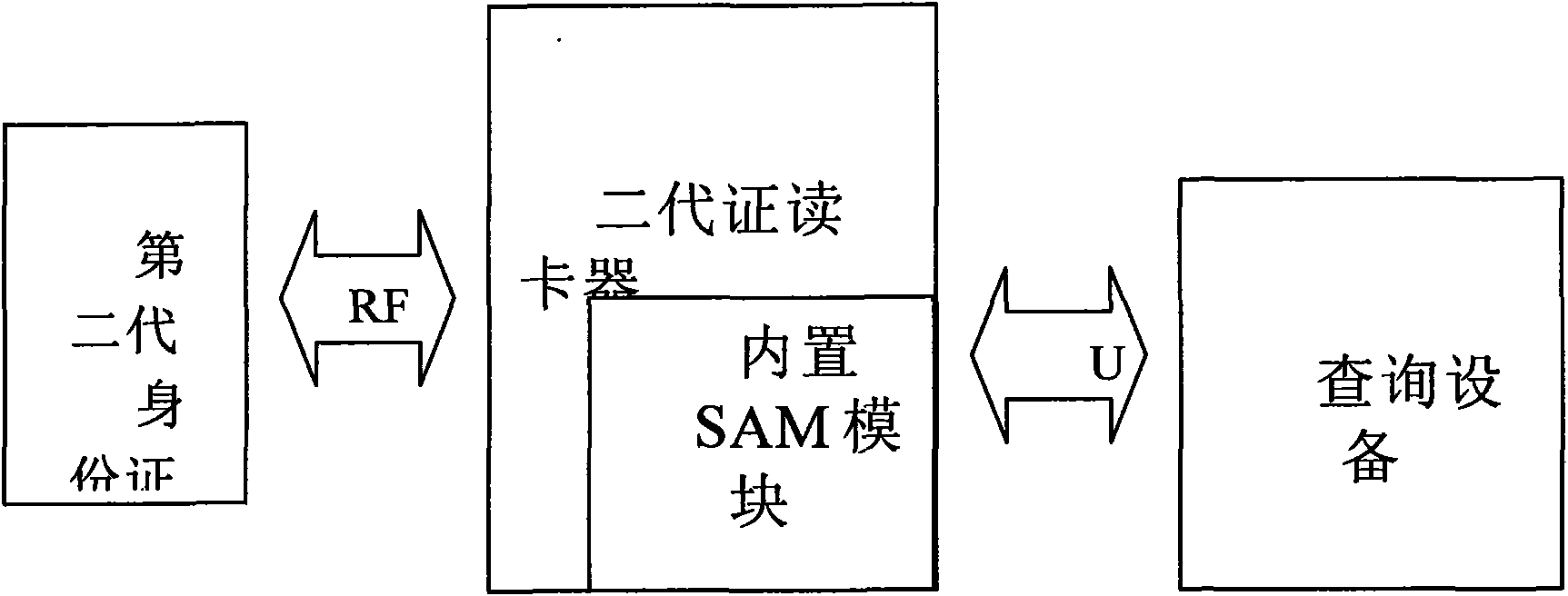
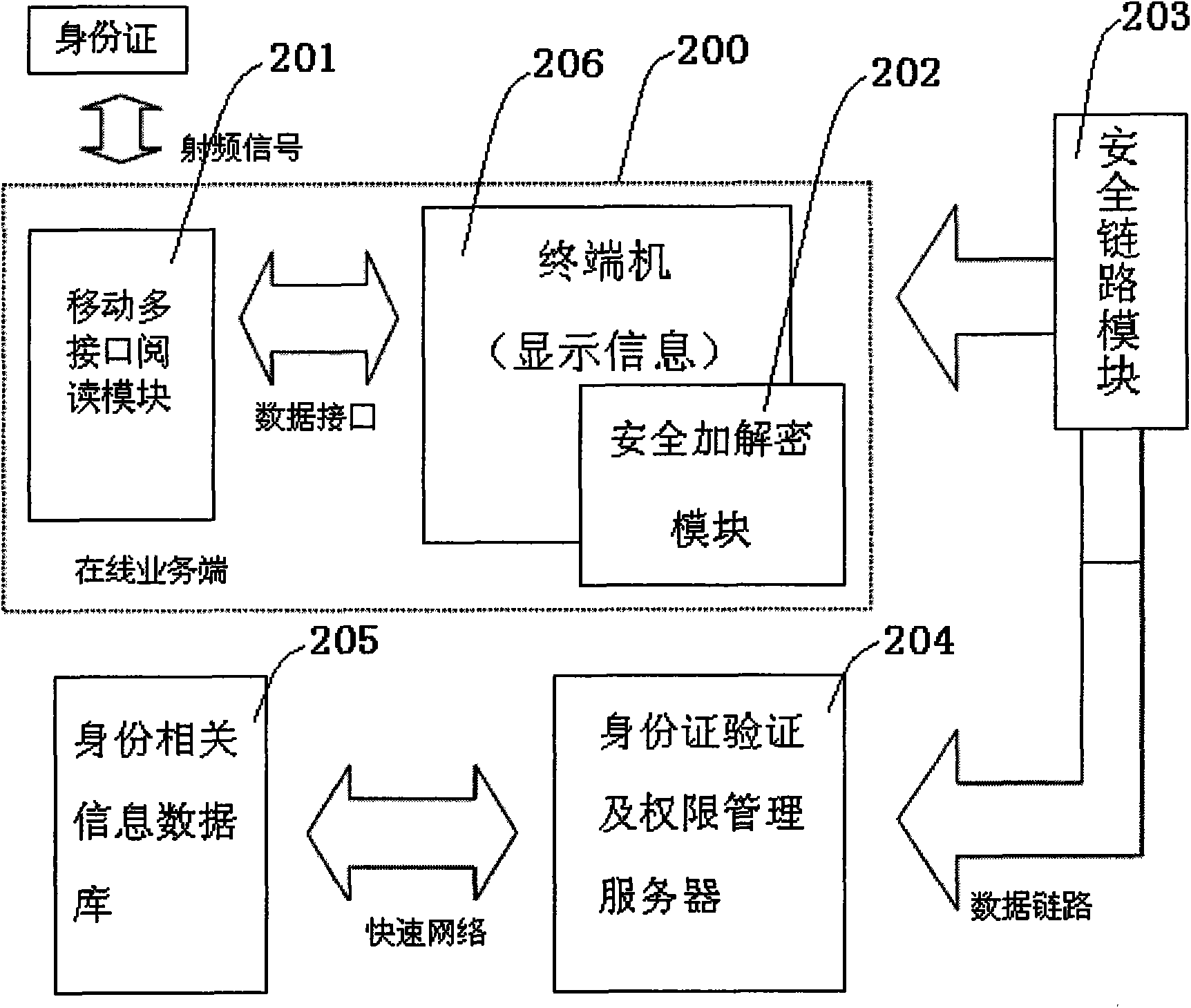
InactiveCN101656748ASolving the full range of mobile online applicationsRealize remote secure deliveryUser identity/authority verificationSpecial data processing applicationsRelevant informationNetwork link
The invention discloses a second-generation ID card online inquiry system based on a secure network, comprising an on-line service terminal, a secure network link module, an identification authentication and right management server and an identification relevant information database, wherein the on-line service terminal comprises a mobile multi-interface read module, a secure coding and decoding module and a terminal set, wherein the mobile multi-interface read module and the secure coding and decoding module are both connected to the same terminal set; the terminal set is connected with the identification authentication and right management server through the secure network link module; and a high-speed data link exists between the identification authentication and right management serverand the identification relevant information database. After the mobile multi-interface read module finishes reading a second-generation ID card, an identification information authentication inquiry request initiated from the terminal set by an operator is coded by the secure coding and decoding module and sent to the identification authentication and right management server by the secure networklink module, then information is obtained from the identification relevant information database after identification authentication and right judgment, and the information is fed back from the securenetwork link module to the terminal, thereby movably finishing the on-line authentication and inquiry of personal information with high security.
Owner:上海申远投资管理有限公司
Inter-system subscriber identity authentication system and method
InactiveCN101651671AGuarantee system securityLighten the login verification operationUser identity/authority verificationClient-sideSystem safety
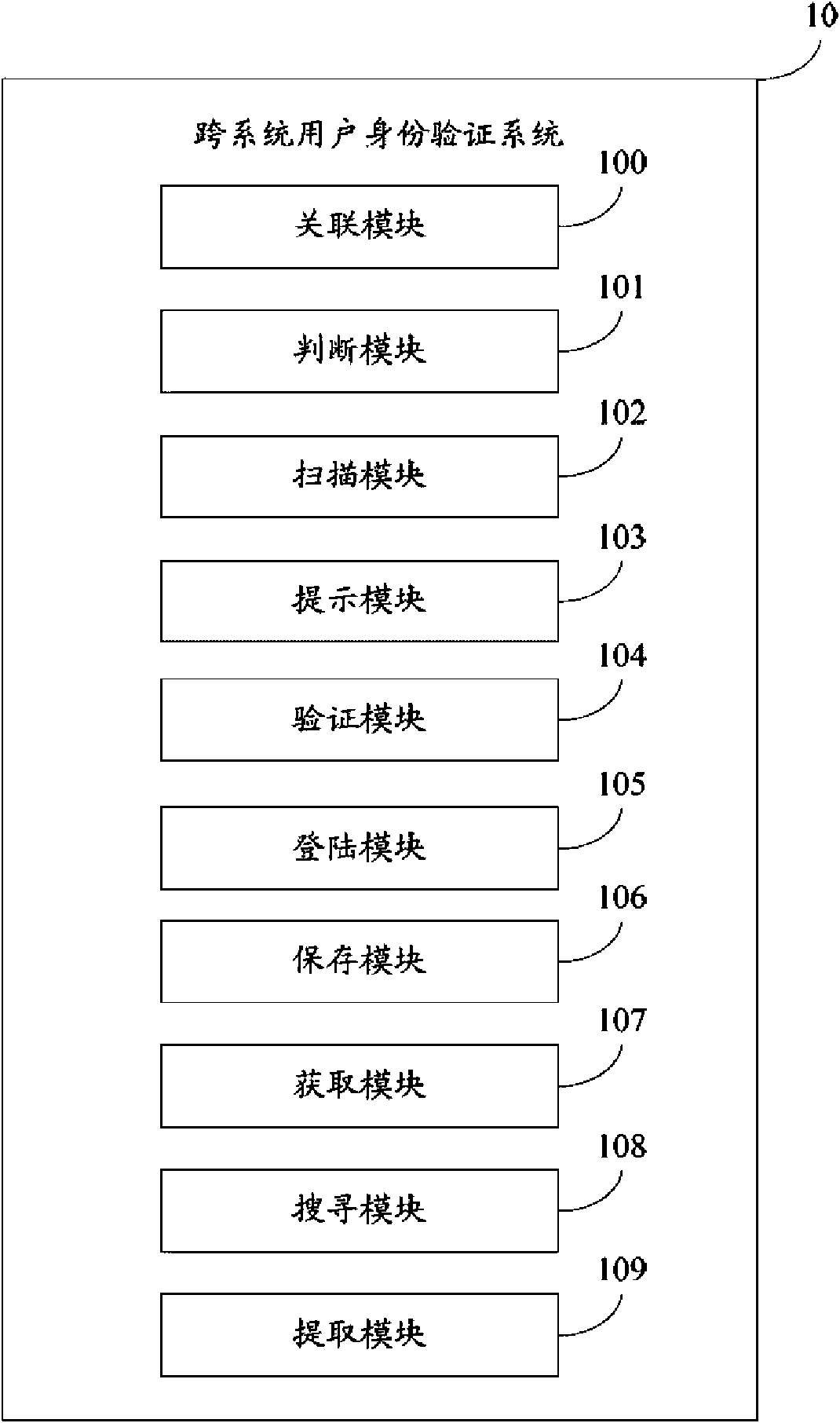
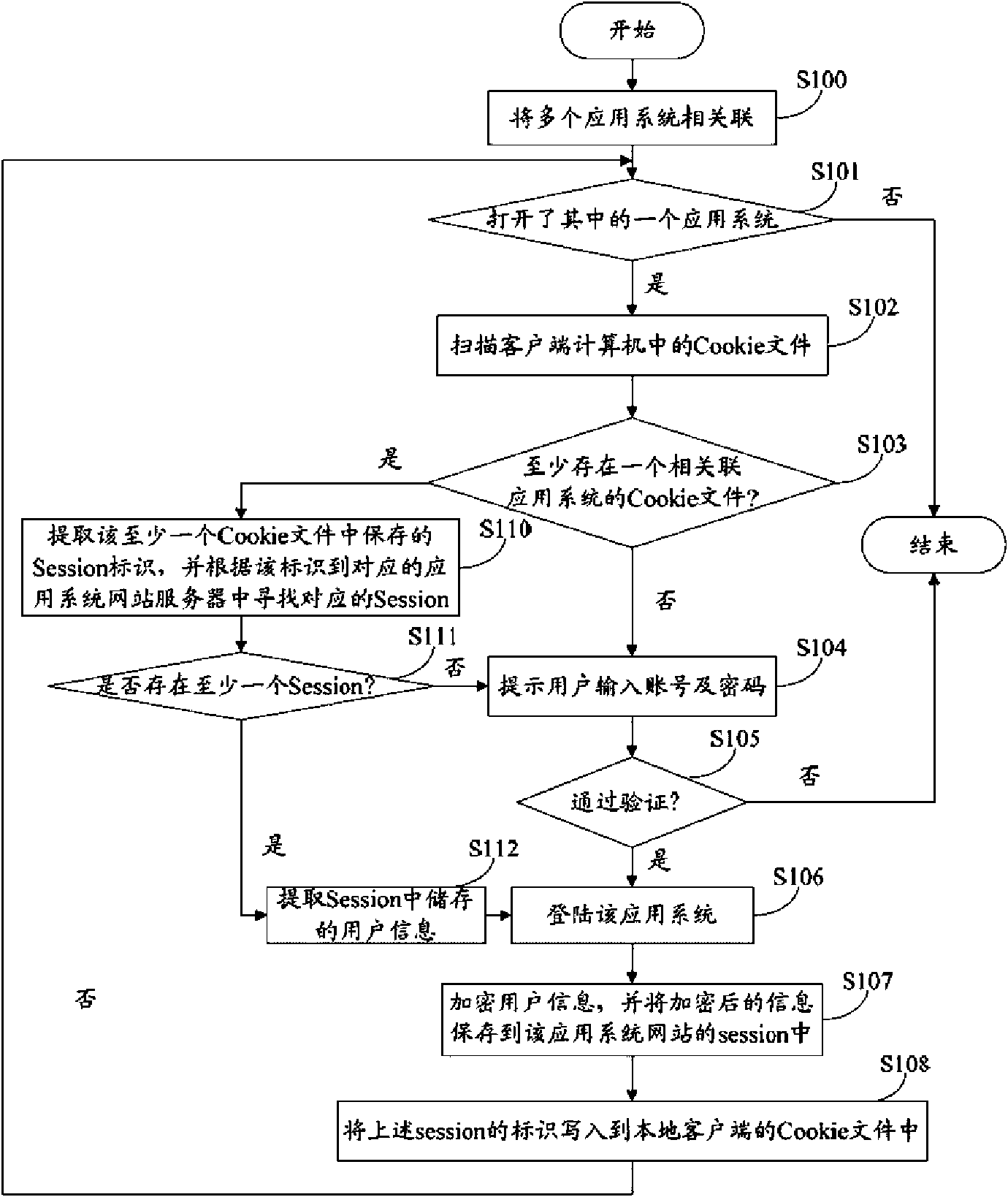
The invention provides an inter-system subscriber identity authentication system, comprising an association module, a scanning module, an acquisition module, a searching module, an extracting module and a logging-in module; the association module is used for associating a plurality of application systems; the scanning module is used for scanning and judging, when a user opens an application system, whether Cookie files of other application systems associated with the application system exist in a client computer; the acquisition module is used for acquiring Session markers in the Cookie fileswhen the Cookie files exist; the searching module is used for searching for Session files in the network servers of application systems according to the Session markers; the extracting module is usedfor extracting user basic information stored in the Session files; and the logging-in module is used for automatically logging in the application system according to the extracted user basic information. The invention also provides an inter-system subscriber identity authentication method. The invention can simultaneously guarantee system security and reduce user operation.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Fault-tolerant directory cache controller
ActiveCN105740168AAvoid failurePerformance priorityMemory systemsSystem structureElectromagnetic environment
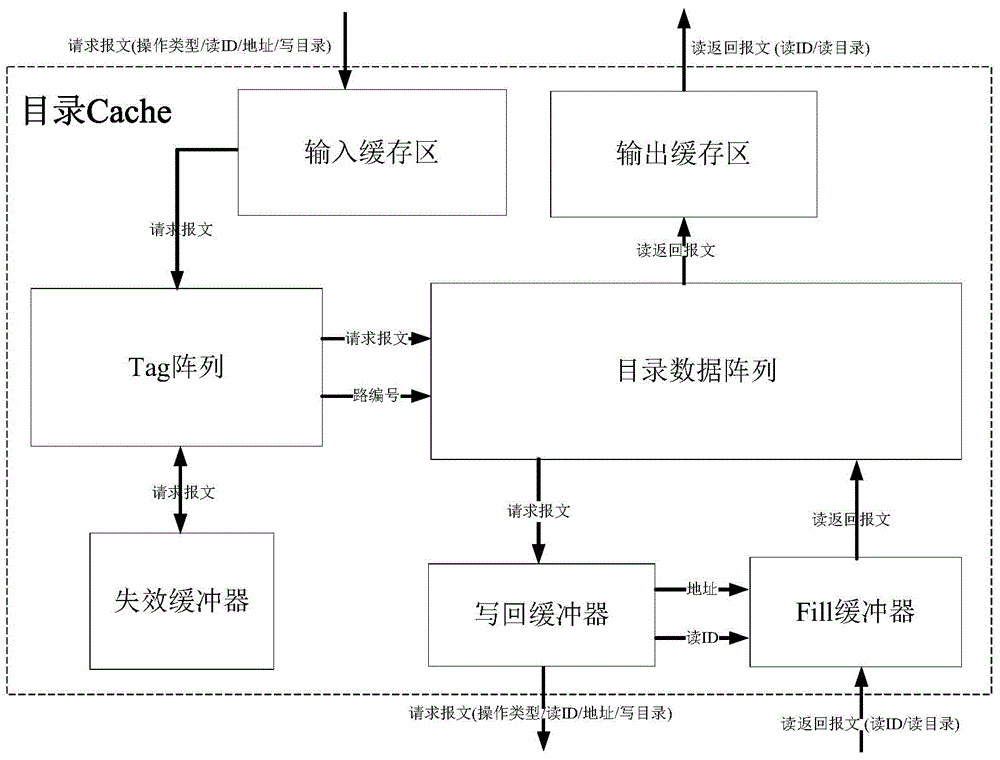
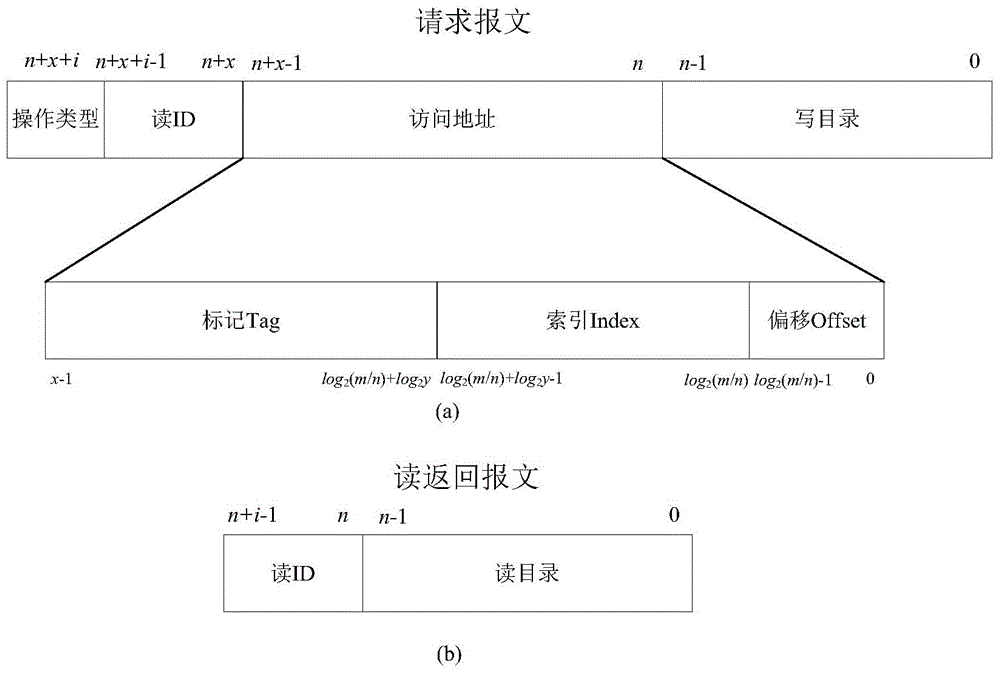
The invention discloses a fault-tolerant directory cache controller for the problem that a conventional directory cache is poor in fault tolerance and low in reliability, and cannot meet the requirements of a spatial environment or a complicated electromagnetic environment. The fault-tolerant directory cache controller comprises four identical directory cache bodies, a directory access bypass, a directory access crossbar switch, an access crossbar switch and a configuration register. By designing the four directory cache bodies, the configuration register, the full interconnected access crossbar switch and the directory access crossbar switch, two working modes can be flexibly configured, so that both the performance and the fault tolerance are preferred. By designing a directory access bypass module, the complete failure of a directory Cache function in a bad condition such as a space high-radiation environment is prevented, so that the reliability is enhanced. Compared with the conventional directory Cache, the fault-tolerant directory cache controller has the advantages that a multilevel fault-tolerant technology from a system structure level to a circuit design level is adopted, so that on the premise of no performance loss, the fault tolerance and reliability of the directory Cache are remarkably improved.
Owner:NAT UNIV OF DEFENSE TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com