Method and device for performing multi-party security calculation through certificate issuing
A certificate and root certificate technology, which is applied in the field of distributed computing and secure computing, can solve problems such as high cost, complicated and cumbersome multi-party computing communication process, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0136] The solutions provided in this specification will be described below in conjunction with the accompanying drawings.
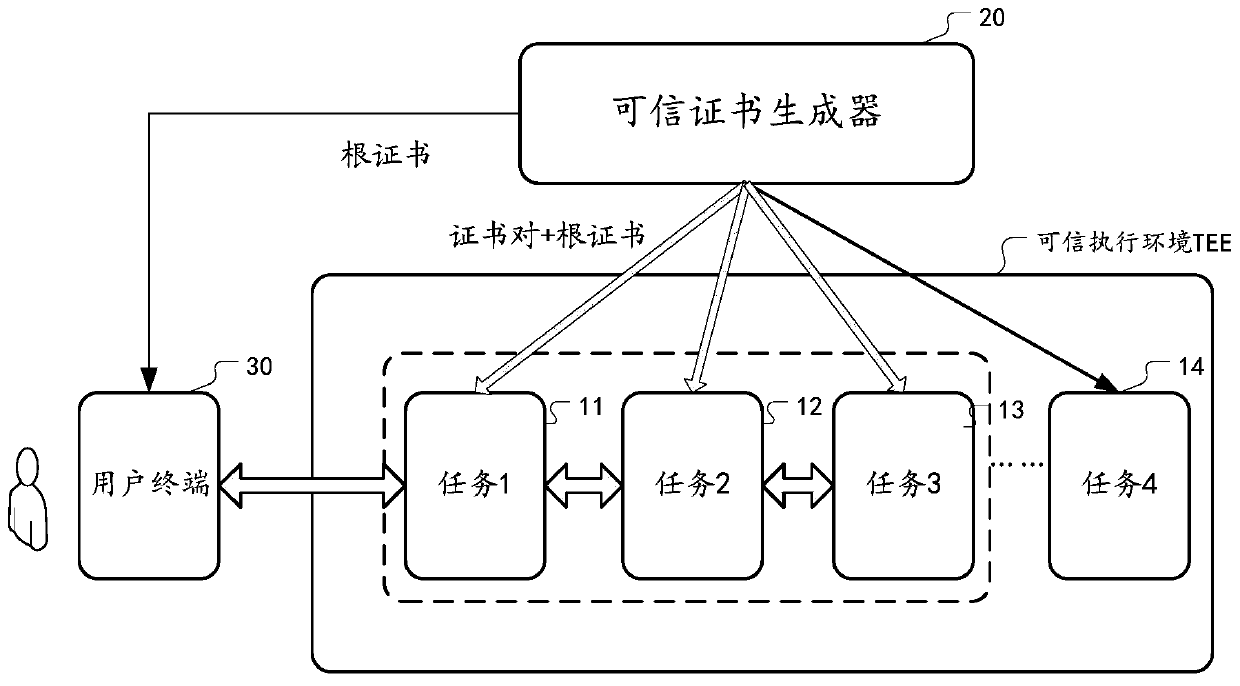
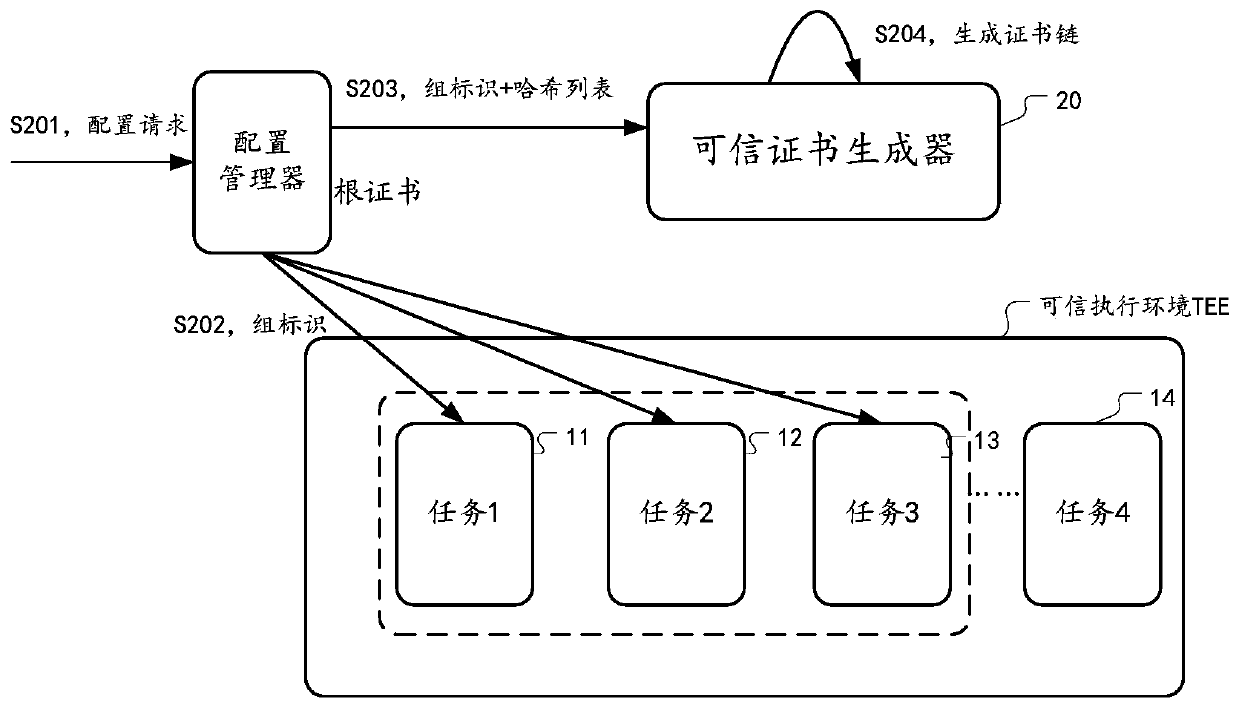
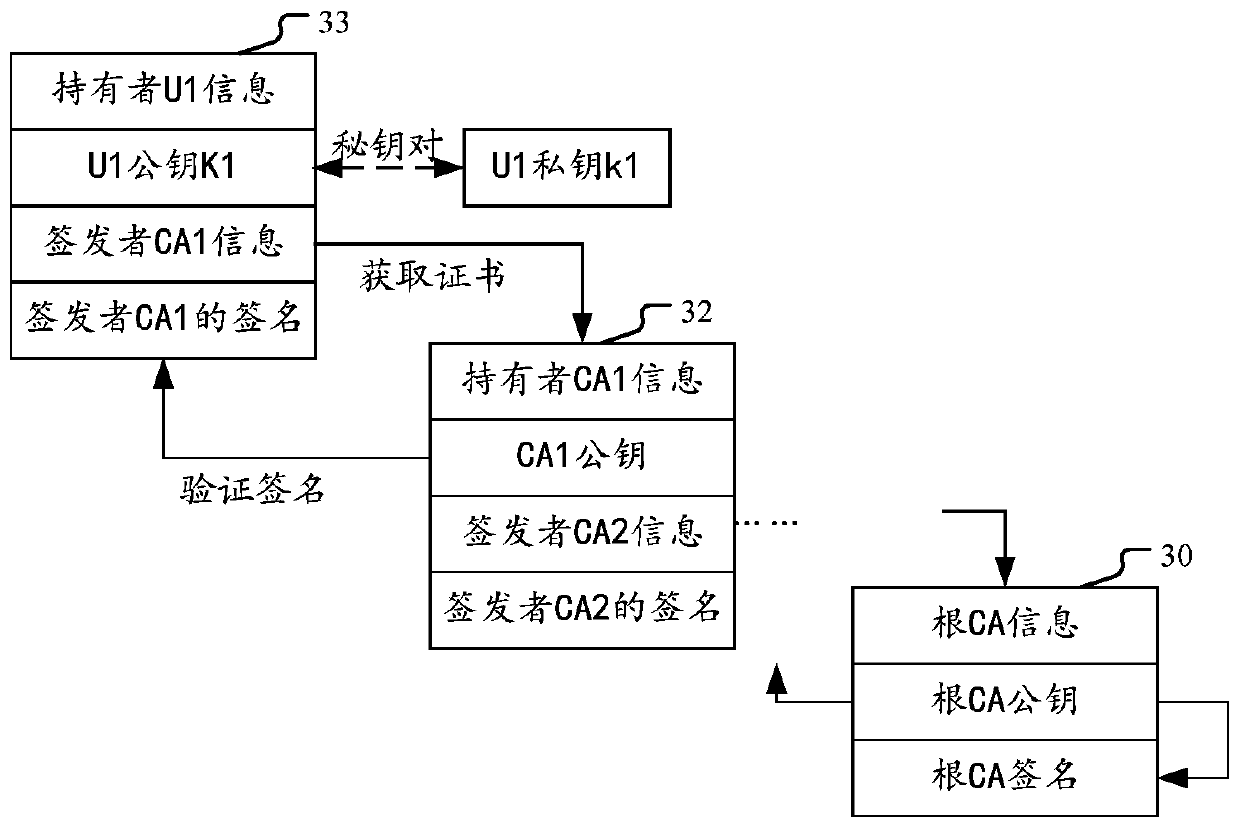
[0137] figure 1 It is a schematic diagram of an implementation scenario of an embodiment disclosed in this specification. As shown in the figure, the required computing tasks can be executed by the trusted computing units in the trusted execution environment TEE. A trusted computing unit can be a computing module or computing device that has a certain isolation capability to ensure computing security, such as a trusted computing enclave Enclave, such as implemented by using technologies such as SGX or Trust Zone. For example, according to SGX technology, by providing a series of CPU instruction codes, allowing user code to create a private memory area with high access rights to form a computing enclave Enclave. Other applications, including the operating system OS, BIOS system, virtual machine system, etc., cannot access the data in the Enclave, and ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com