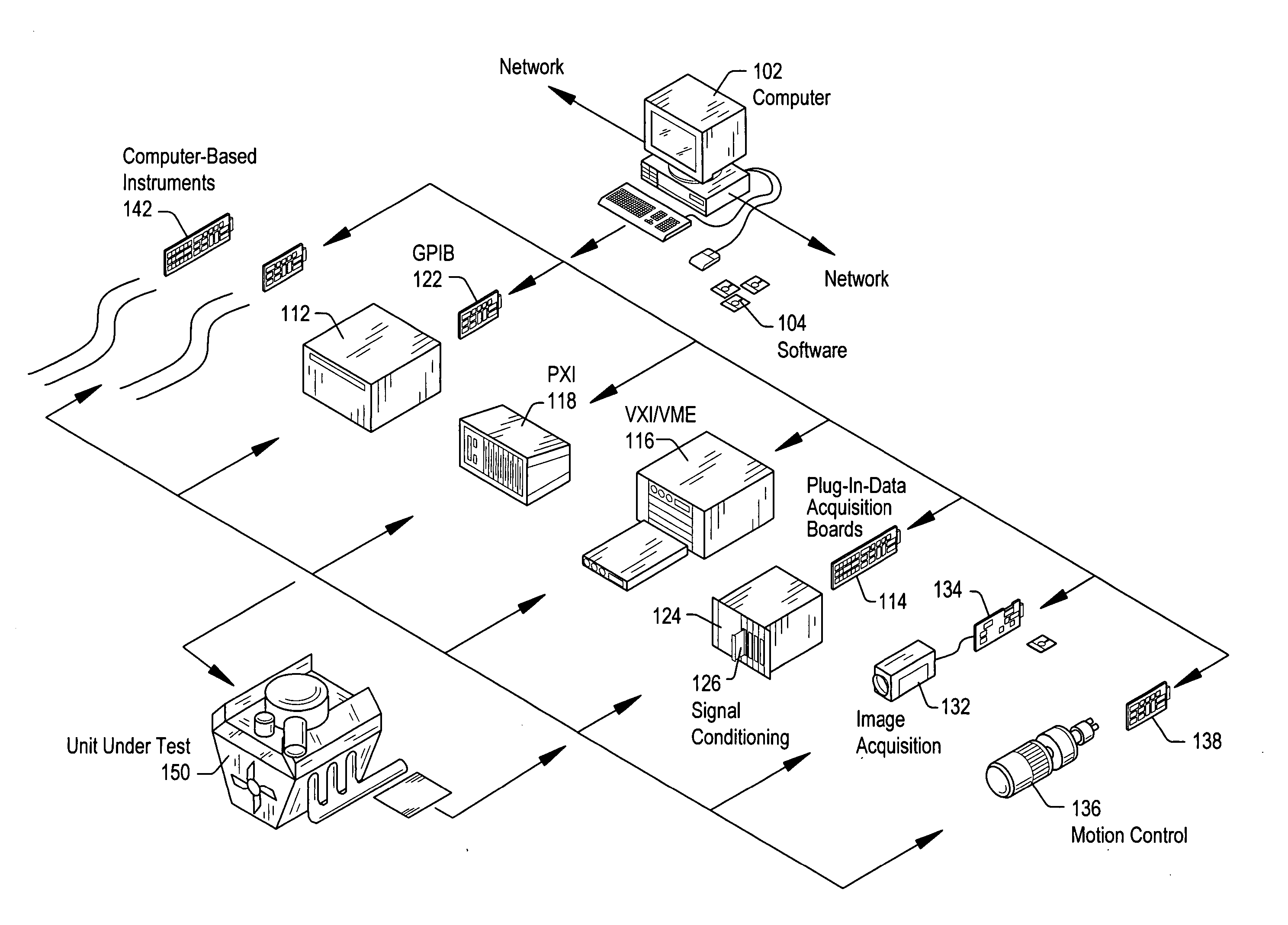
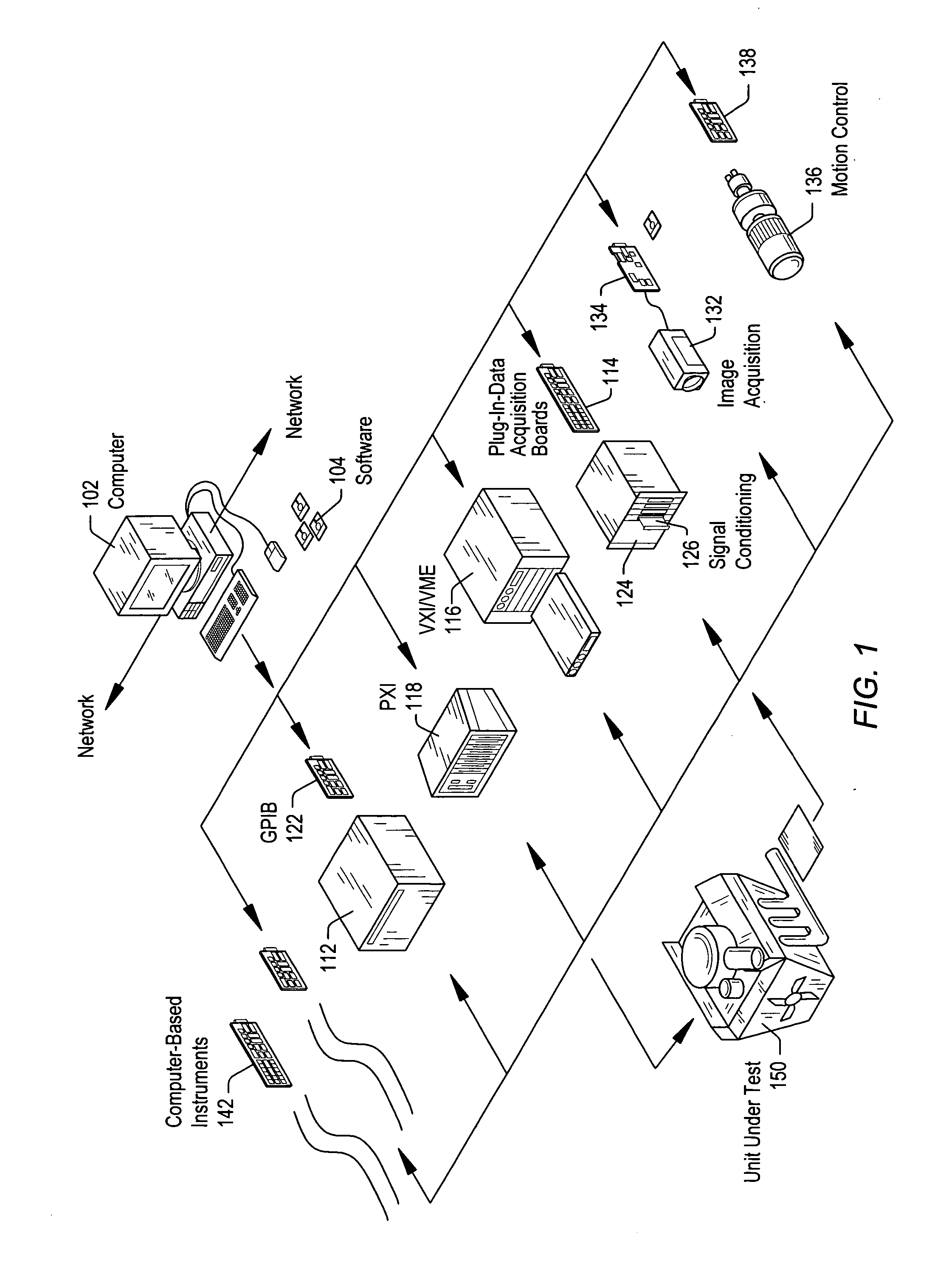
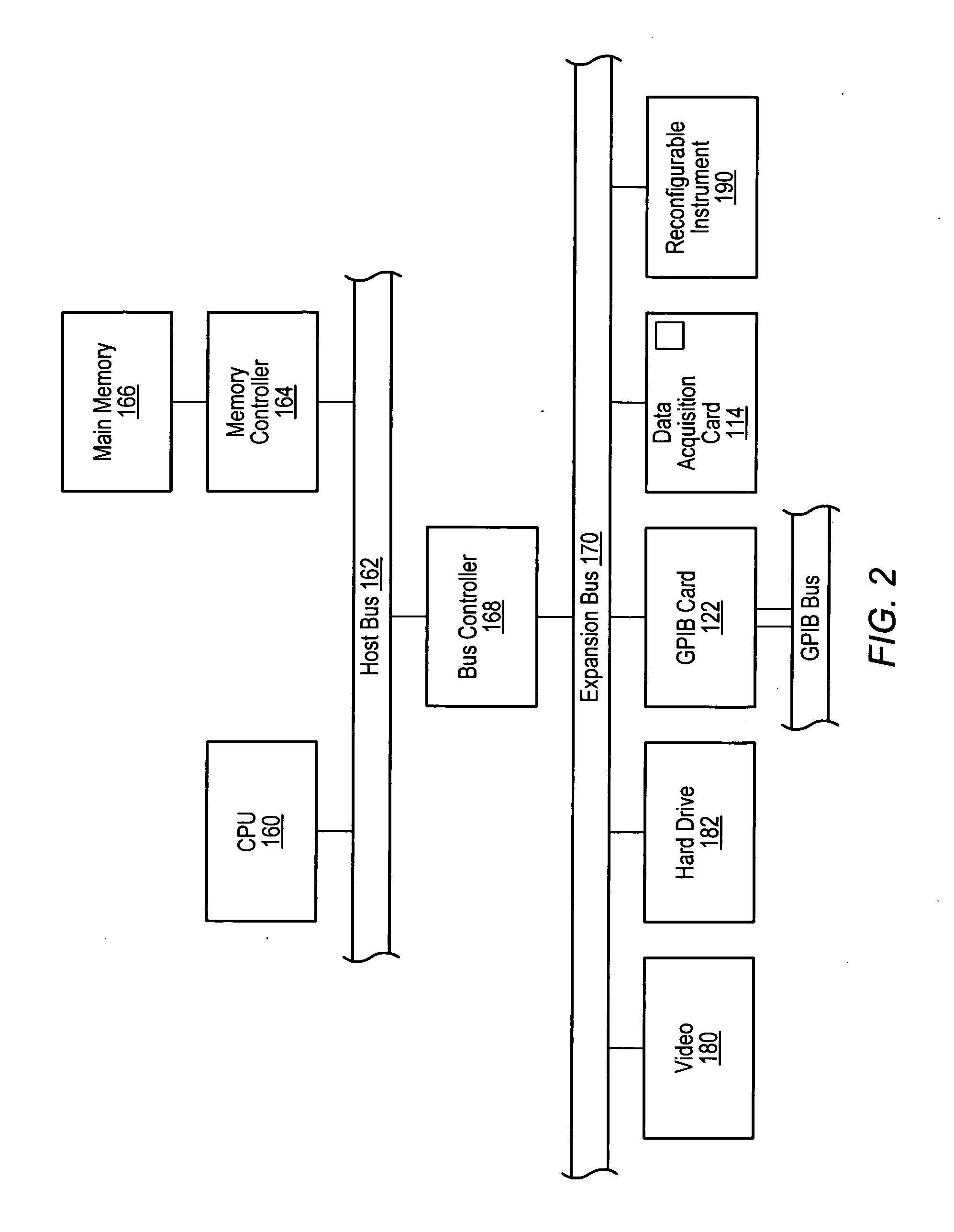
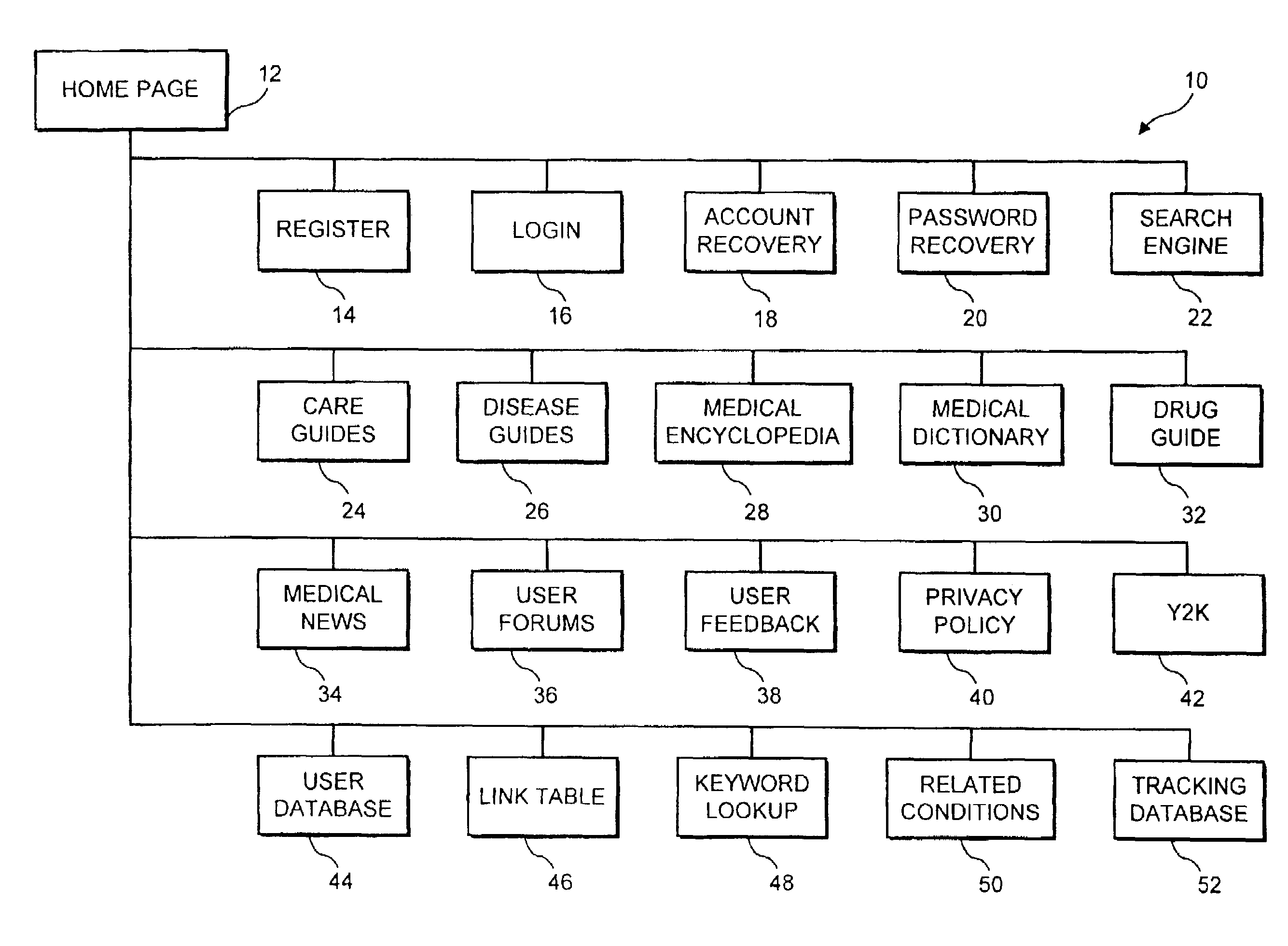
Patents
Literature
459 results about "User code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The User Code is one of the key pieces of information used for identifying users and their accounts when requesting support. You should note down your User Code just in case you need help, but cannot access your game. Your User Code can be seen from Menu > Player Info.
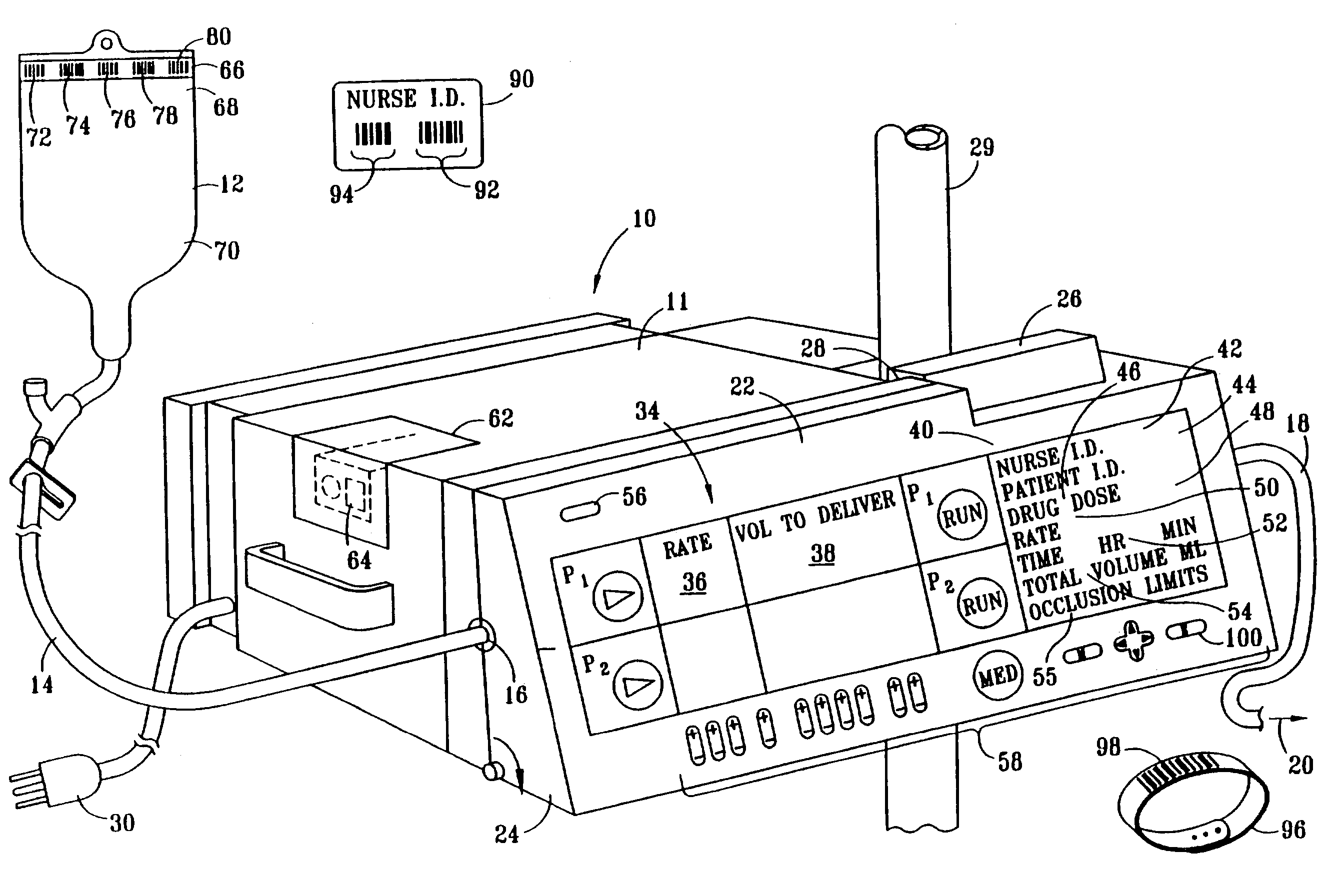
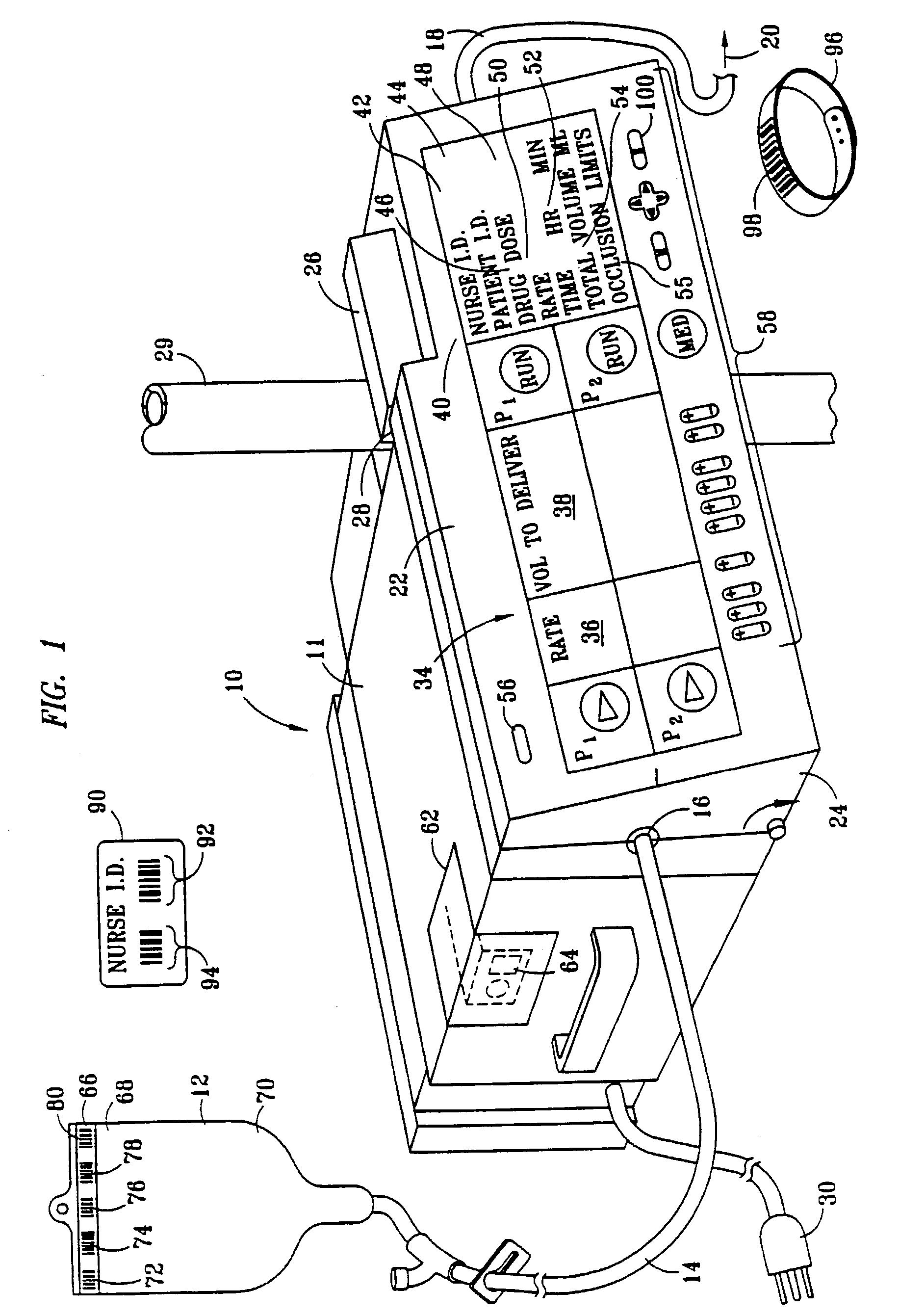
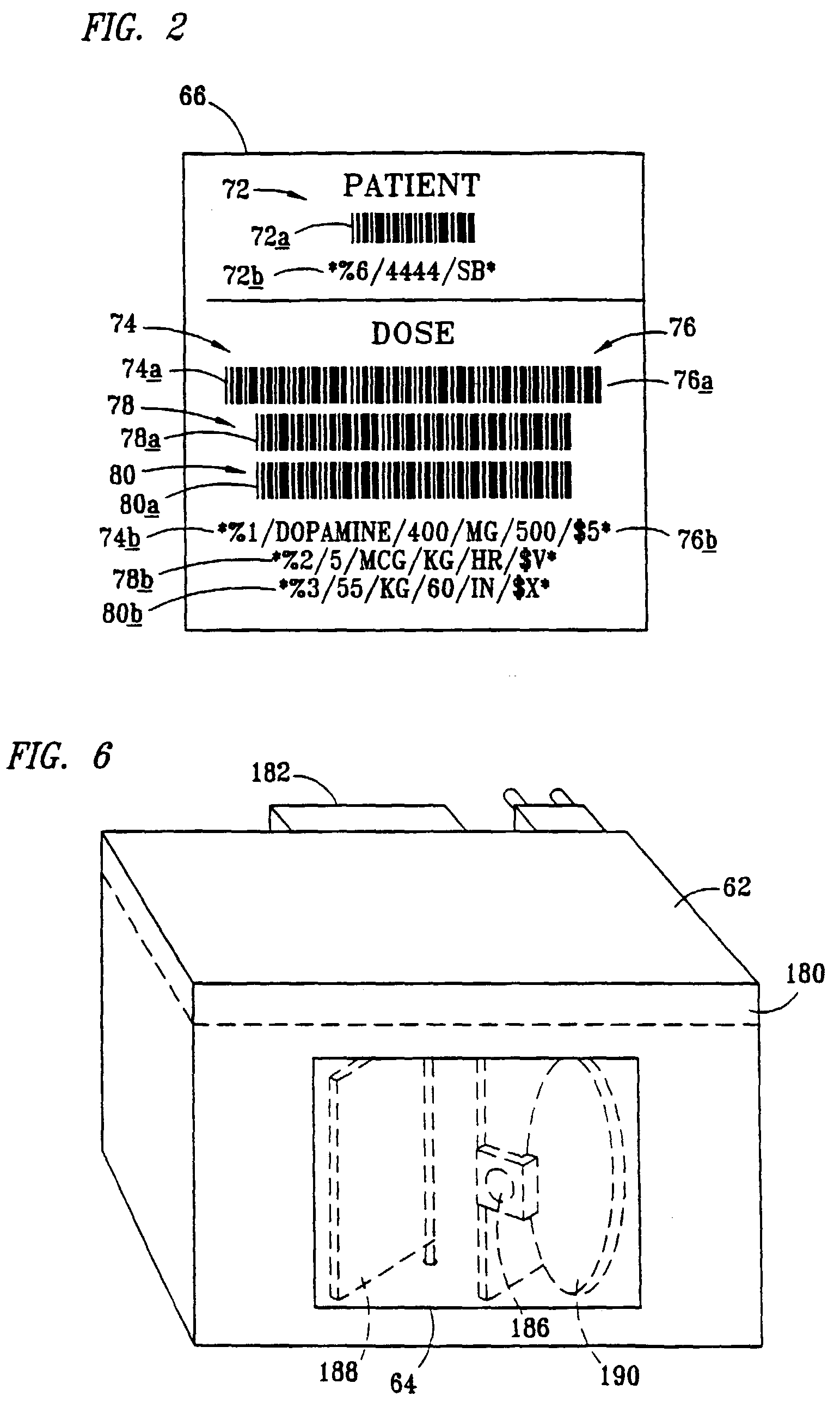
Security infusion pump with bar code reader
InactiveUS7236936B2Improve accuracyImprove securityDrug and medicationsMedical devicesData operationsBarcode
A medical infusion pump with a bar code reader having simplified and enhanced security features. The infusion pump with bar code reader is comprised of an infusion pump with a housing, a control display screen and control software for operating the infusion pump according to input infusion data. A bar code reader is contained in the infusion pump housing and operatively attached to communicate scanned bar code infusion data to the pump display screen and to the control software. At least one initialization button for starting execution of a bar code scanning program is operatively connected through circuitry in the pump, the program activating the bar code reader to scan for an authorized user code, for an authorized user ID code, for a patient ID code, and for infusion data compatible for operating the infusion pump. A confirmation program and confirmation buttons manually operable by the authorized user. Acceptable scanning of authorization code, authorized user ID code, patient ID code and infusion data must be manually confirmed by the authorized user prior to activating the pump to infuse fluids according to the infusion data.
Owner:B BRAUN MEDICAL
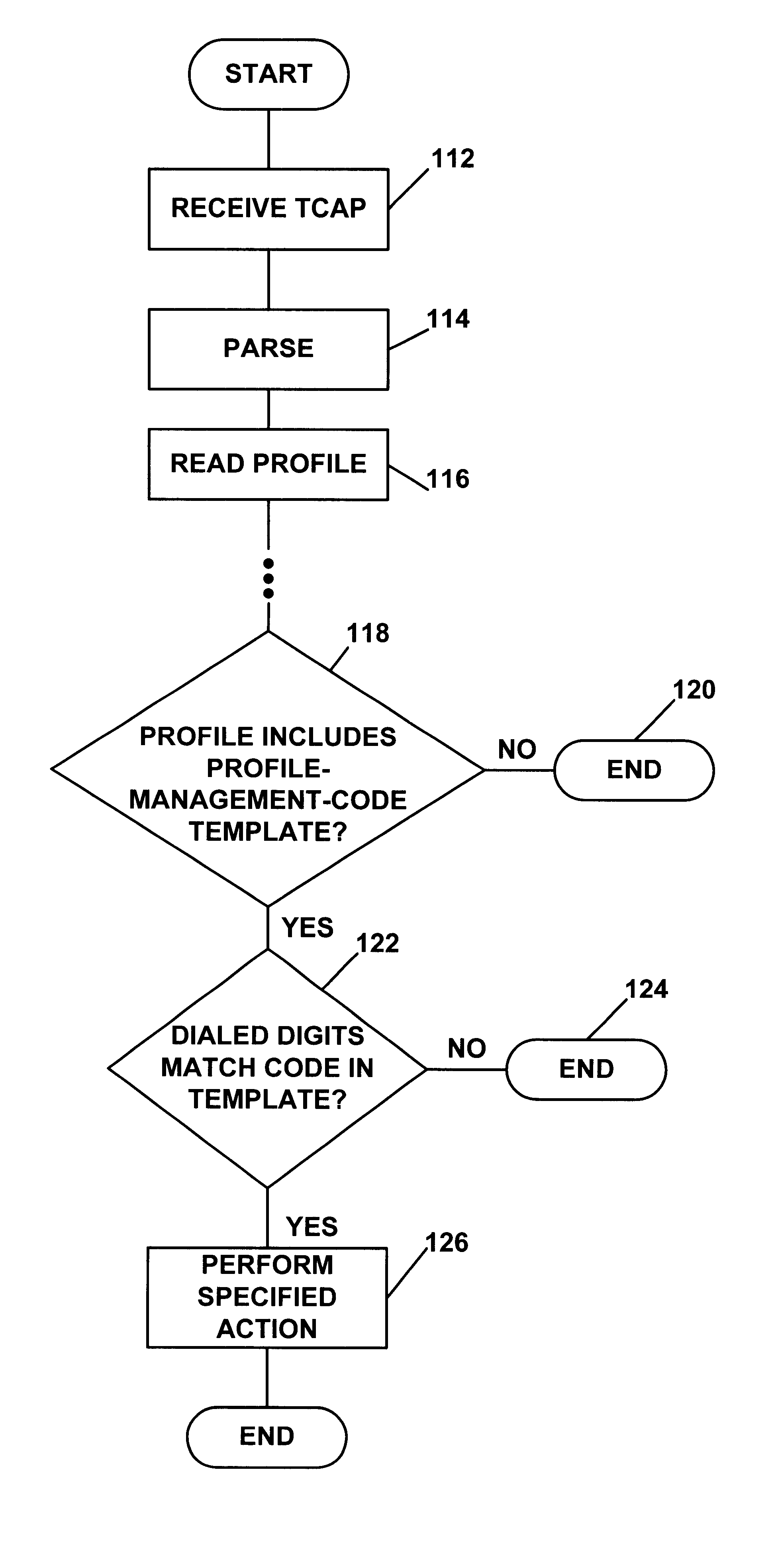
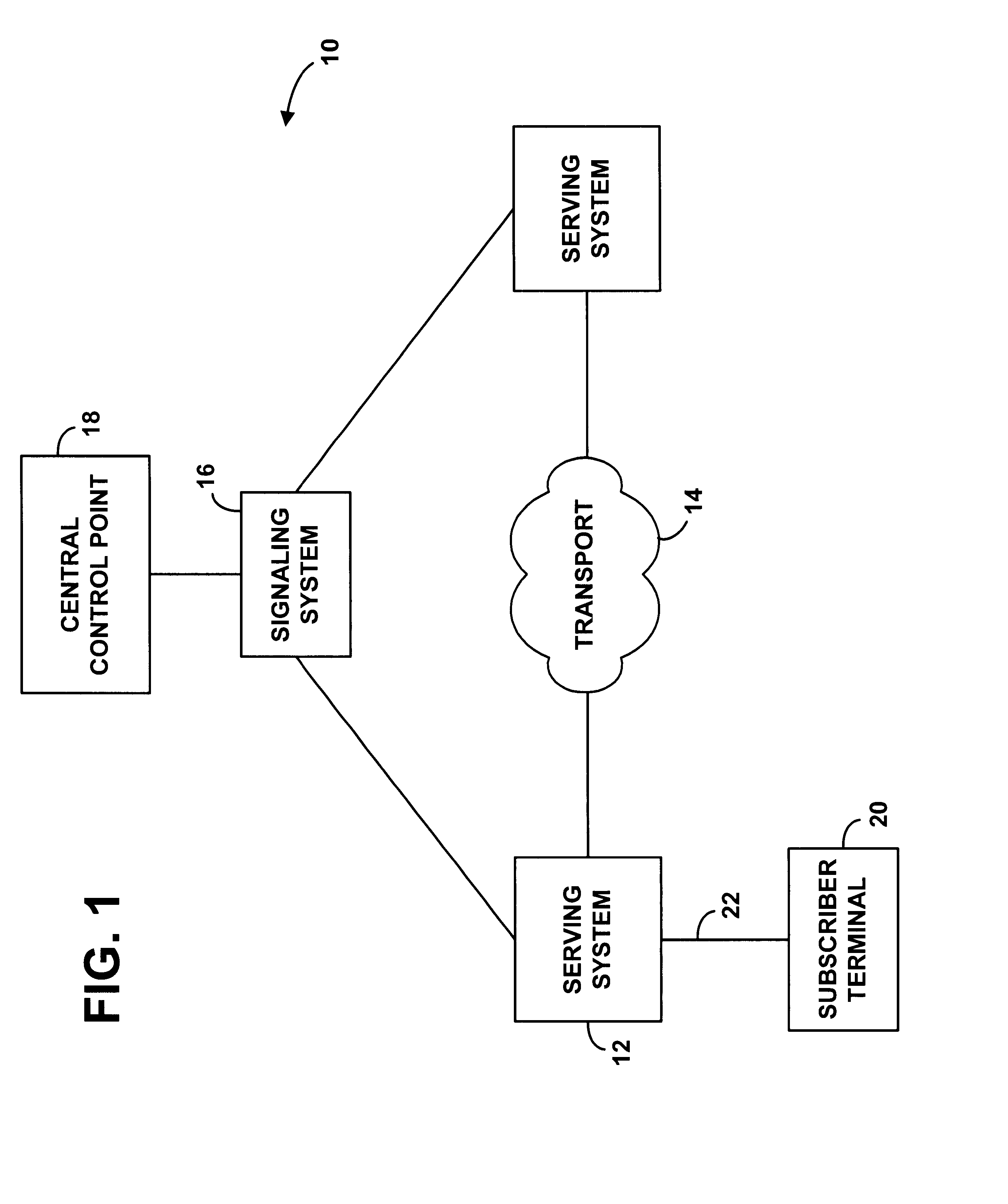
System for managing telecommunications services through use of customized profile management codes
InactiveUS6522876B1Multiplex system selection arrangementsAccounting/billing servicesThird partyIntelligent Network
A service management system based on customized profile management codes. In an advanced intelligent network, a central control point includes a set of logic that defines profile management codes customized for individual subscribers or groups of subscribers. When the central control point receives a profile management code for a particular subscriber, for instance, the central control point may interpret the profile management code altogether differently than it does for the same code from another subscriber. For instance, the logic in a single central control point may indicate for one subscriber that the code "11" means to "activate call forwarding," and the logic may indicate for another subscriber that the code "11" means to "bill the call to a specified third party account."
Owner:SPRINT SPECTRUM LLC
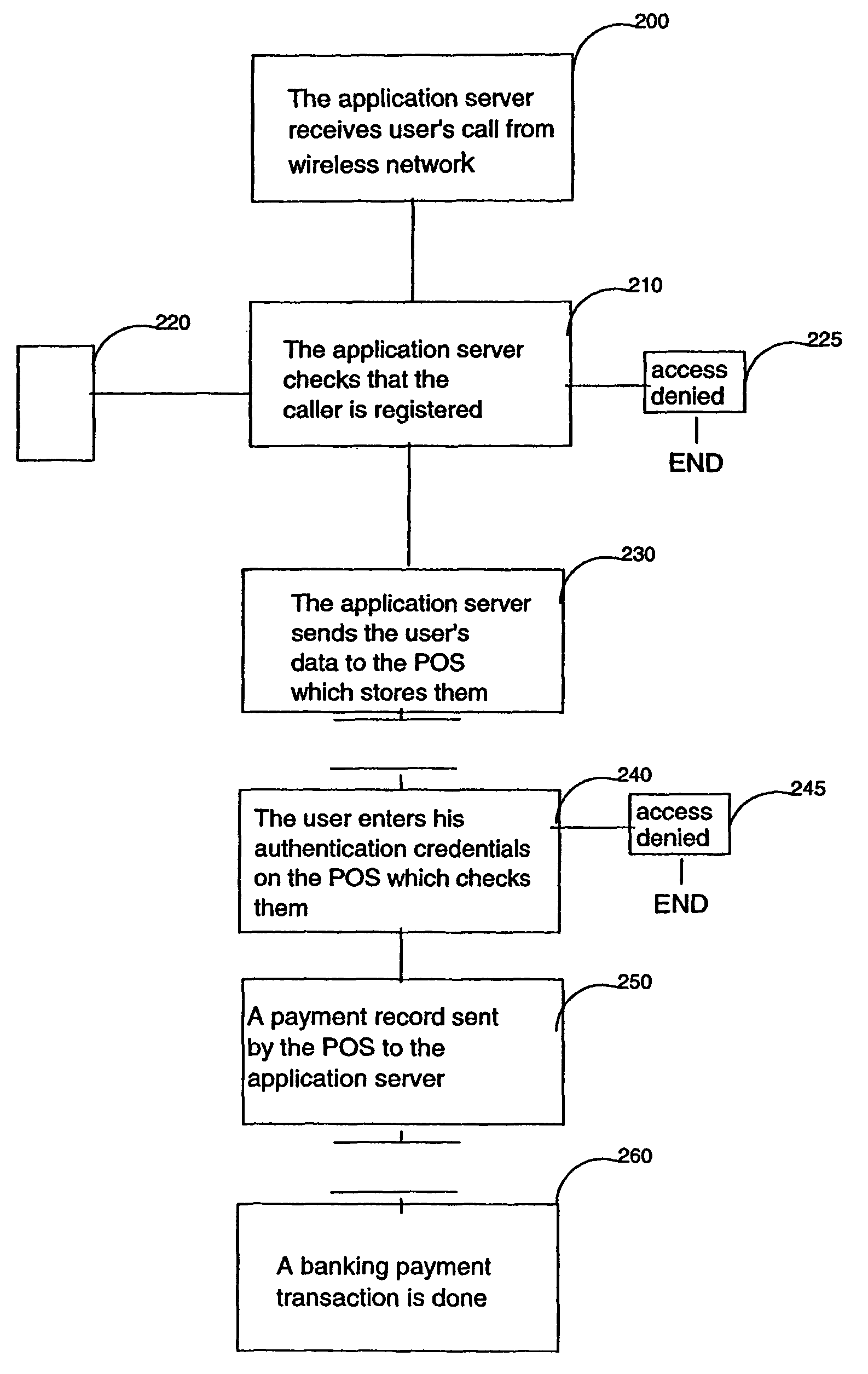
Method and system for secured transactions over a wireless network
InactiveUS8352360B2Easy to implementAccurate interactionHand manipulated computer devicesFinancePaymentClient-side
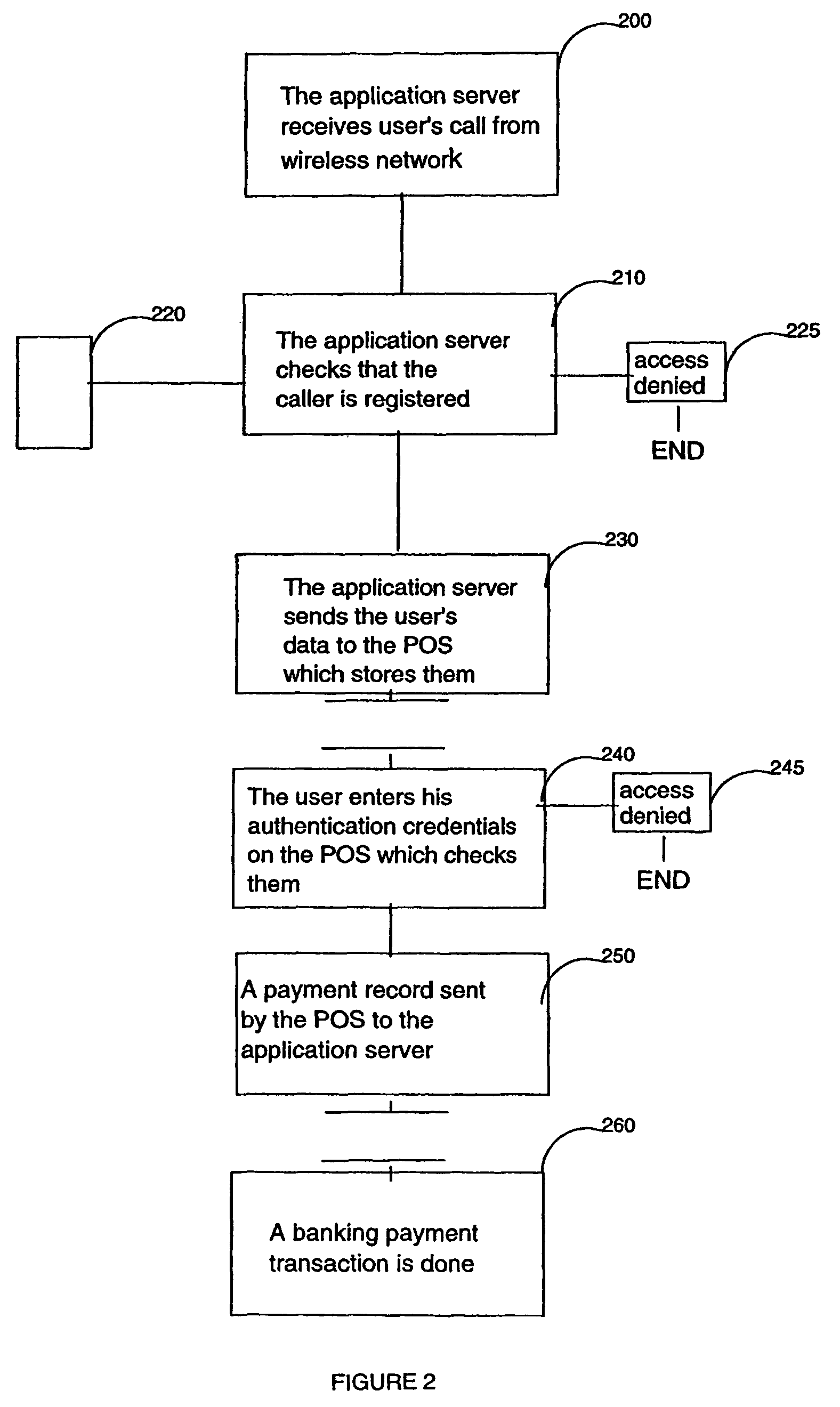
A method and system are disclosed for booking and paying a retailer having a POS, which can be a low cost thin client computer system, connected to a transaction server storing confidential user information including a retailer identification, a user code and a user wireless device phone number, said method comprising the steps of receiving at the transaction server, from the user wireless device which can be a common cellphone, an SMS containing a retailer identification, reading at the transaction server the phone number of the wireless device communicated by the carrier transporting the SMS, authentifying said phone number and retailer identification with the stored confidential user information and sending the user confidential information to the retailer POS, the user entering on the POS the user code and the POS reading and authentifying the user code with the user confidential information received from the transaction server, the retailer entering the payment information on the POS and sending it with user information to the transaction server.
Owner:TOSHIBA GLOBAL COMMERCE SOLUTIONS HLDG
Vehicle Range Finder
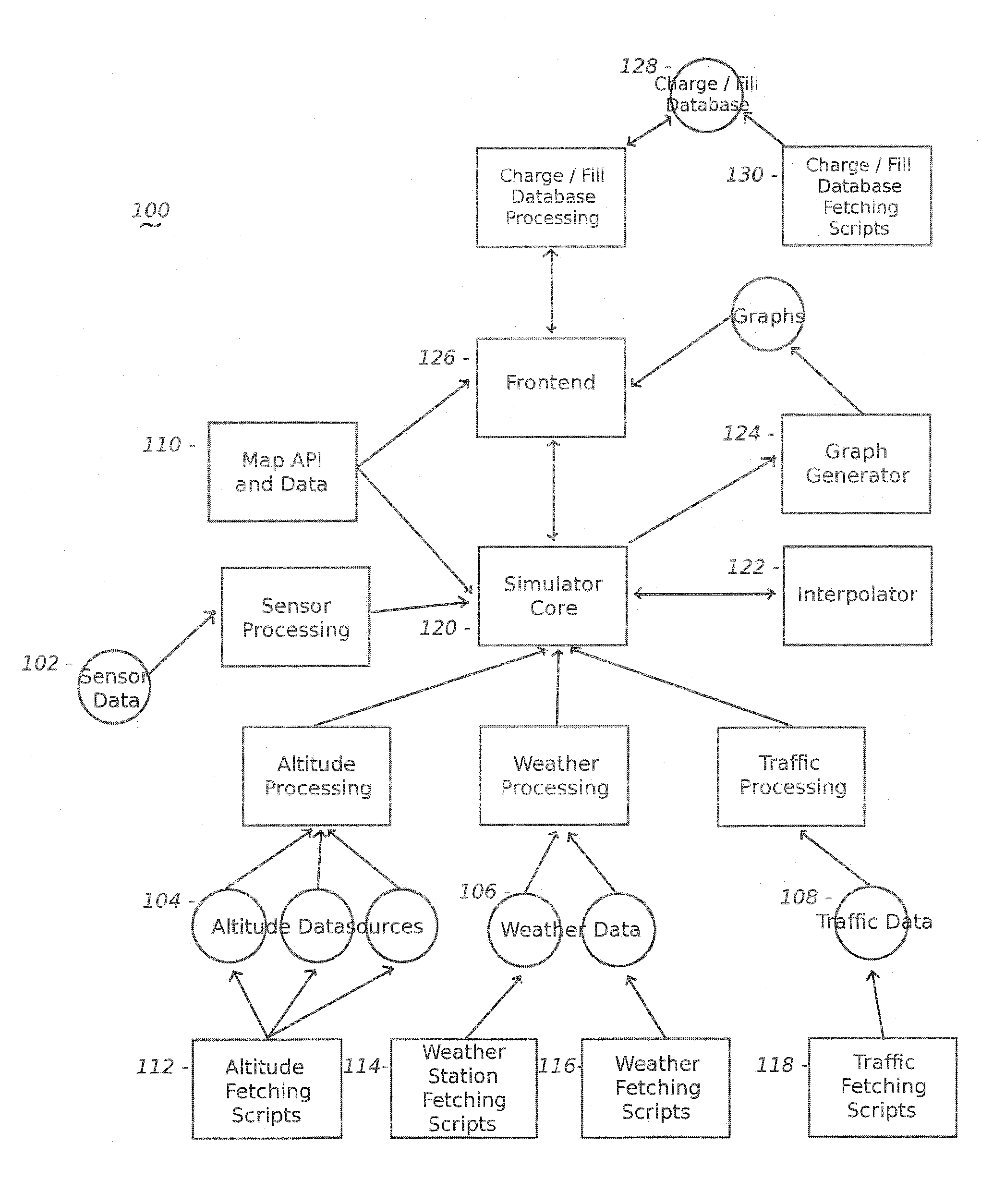
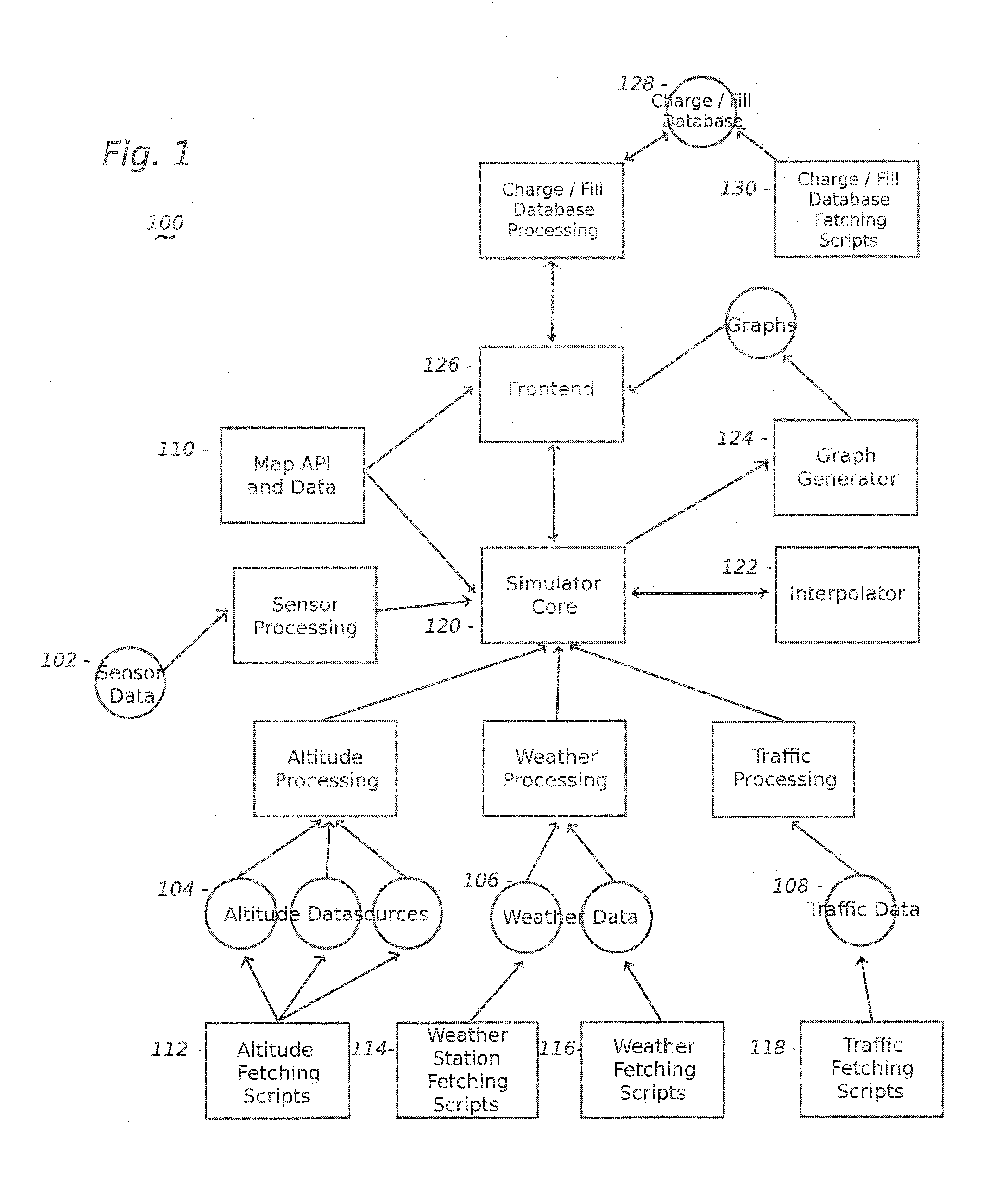
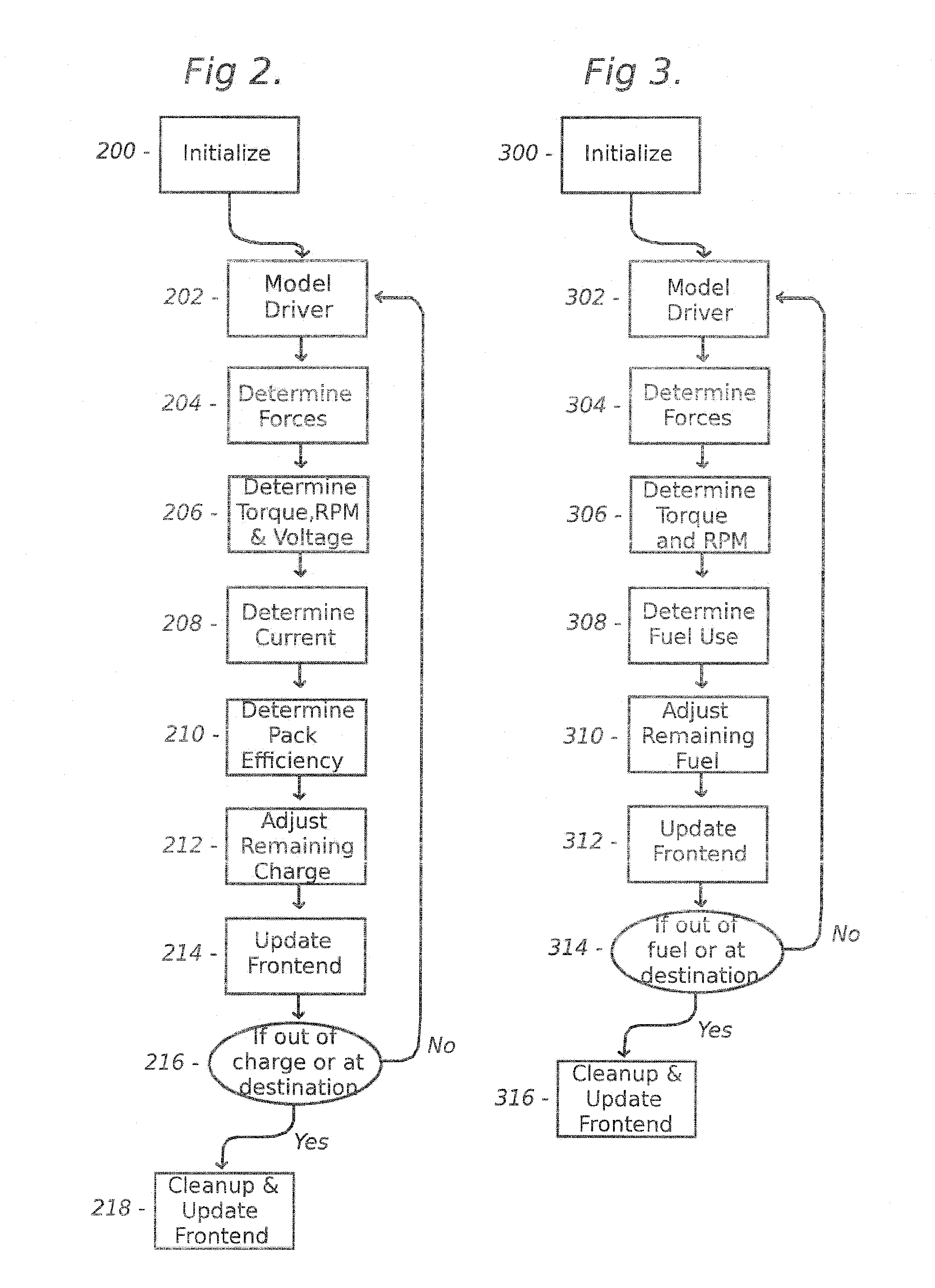
The present invention includes, among other embodiments, a system embedded in a vehicle including several inputs. The inputs may include one hard coded data, data from sensors on the vehicle, data from external sensors, user coded data, data received from remote databases, data received from broadcast data steams or data that has been accumulated during use of the vehicle. The inputs provide information regarding vehicle speed, motor rpm, motor torque, battery voltage, battery current, and battery charge level, etc. The embedded system also includes a processor unit that receives information from the plurality of inputs and calculates at least an expected vehicle range. The results of any calculations completed by the processing unit is supplied as an output to a display unit, which then displays the information to the user.
Owner:CELADON APPL
Hybrid Transactional Memory System (HybridTM) and Method
InactiveUS20110119452A1Simple/cost-effective hardware designAdd supportNon-redundant fault processingMemory systemsOperational systemHandling system
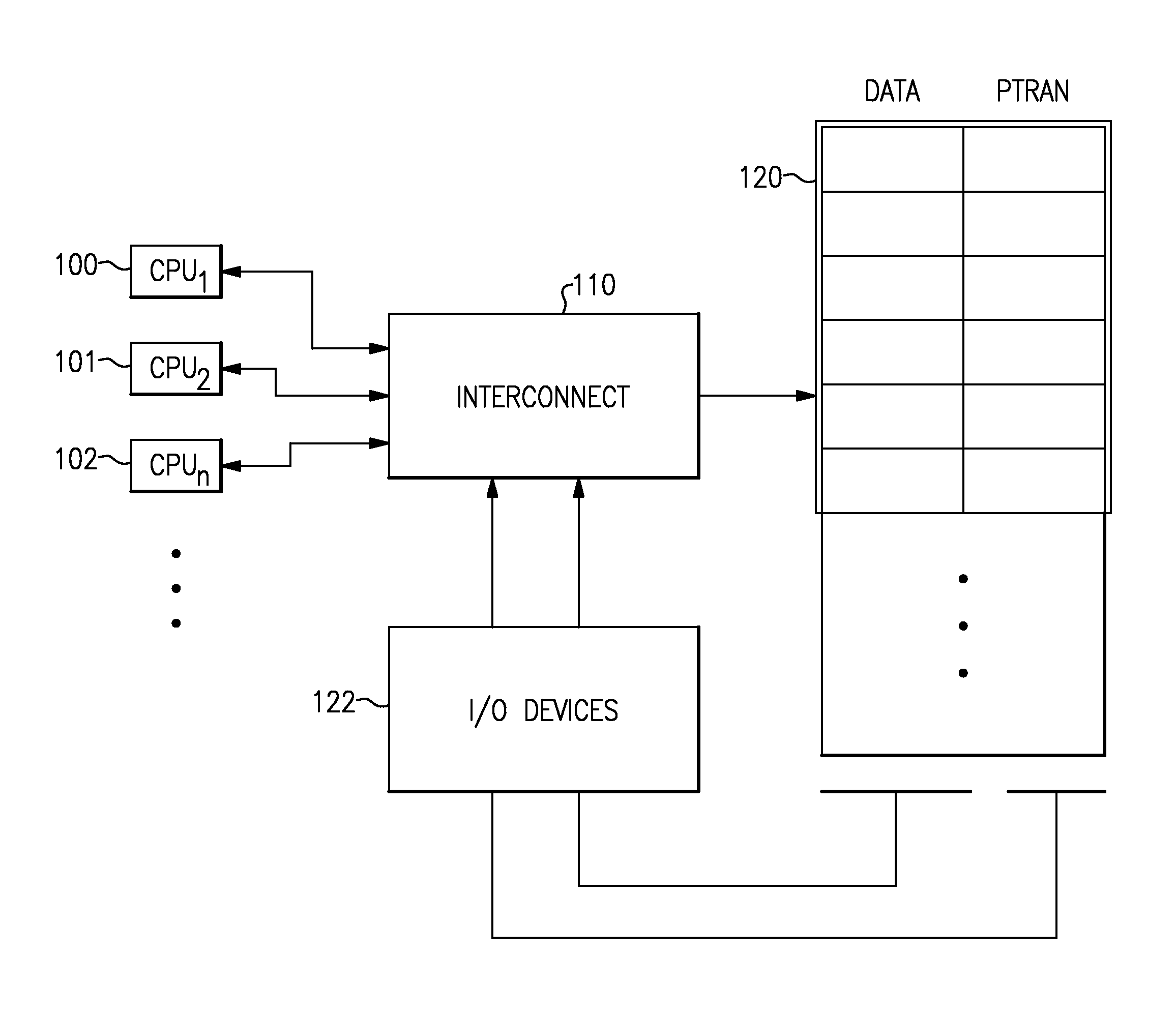
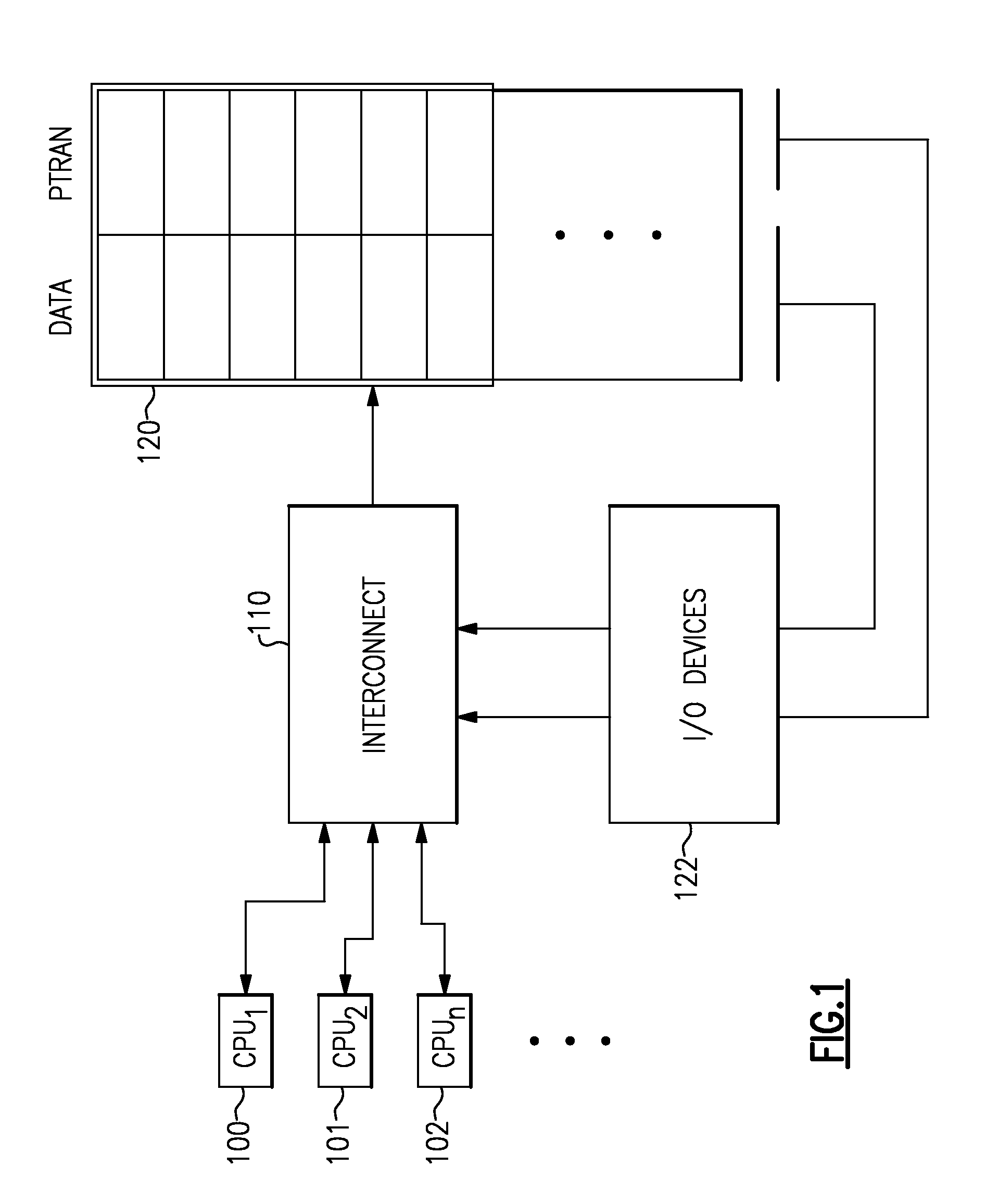
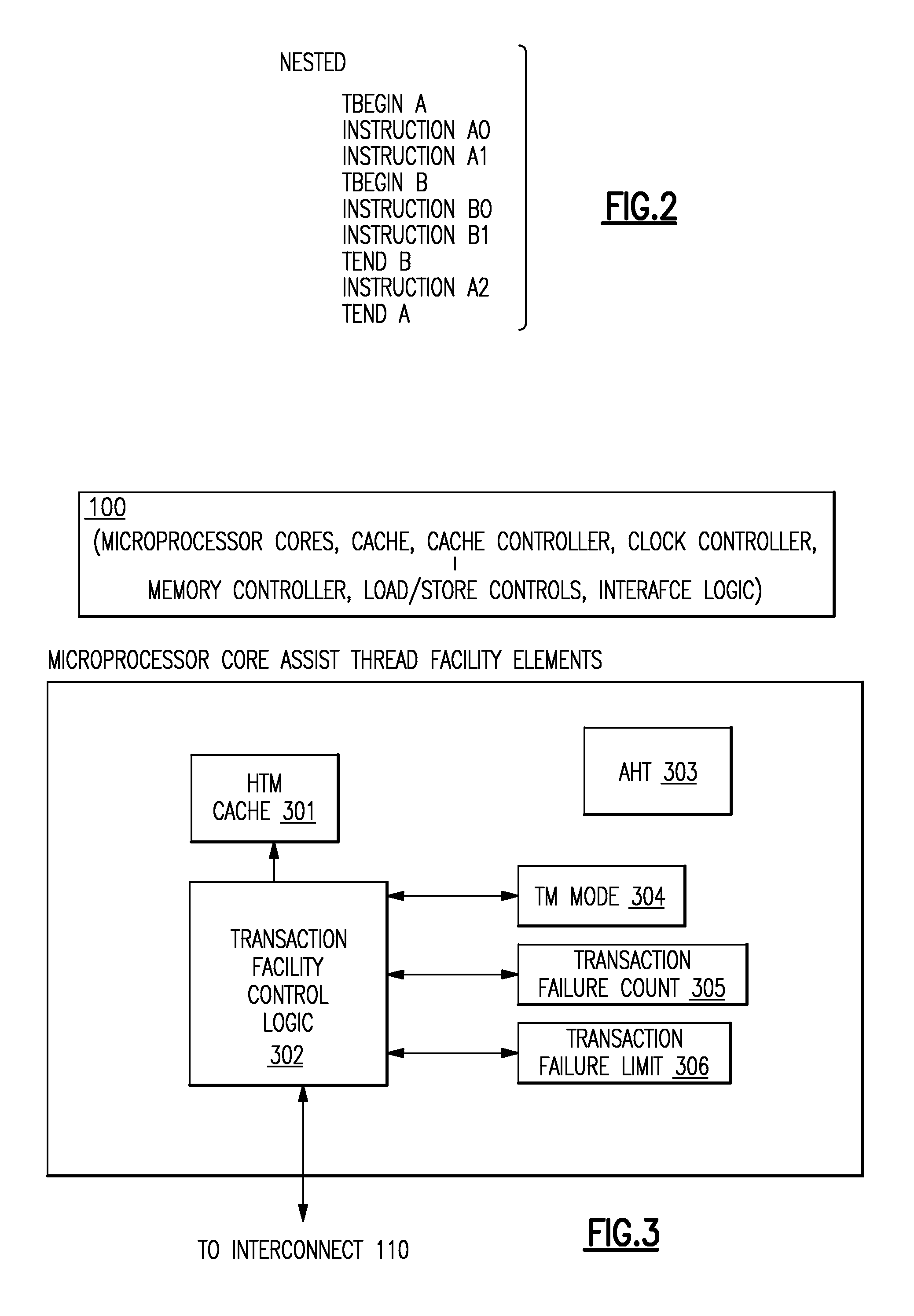
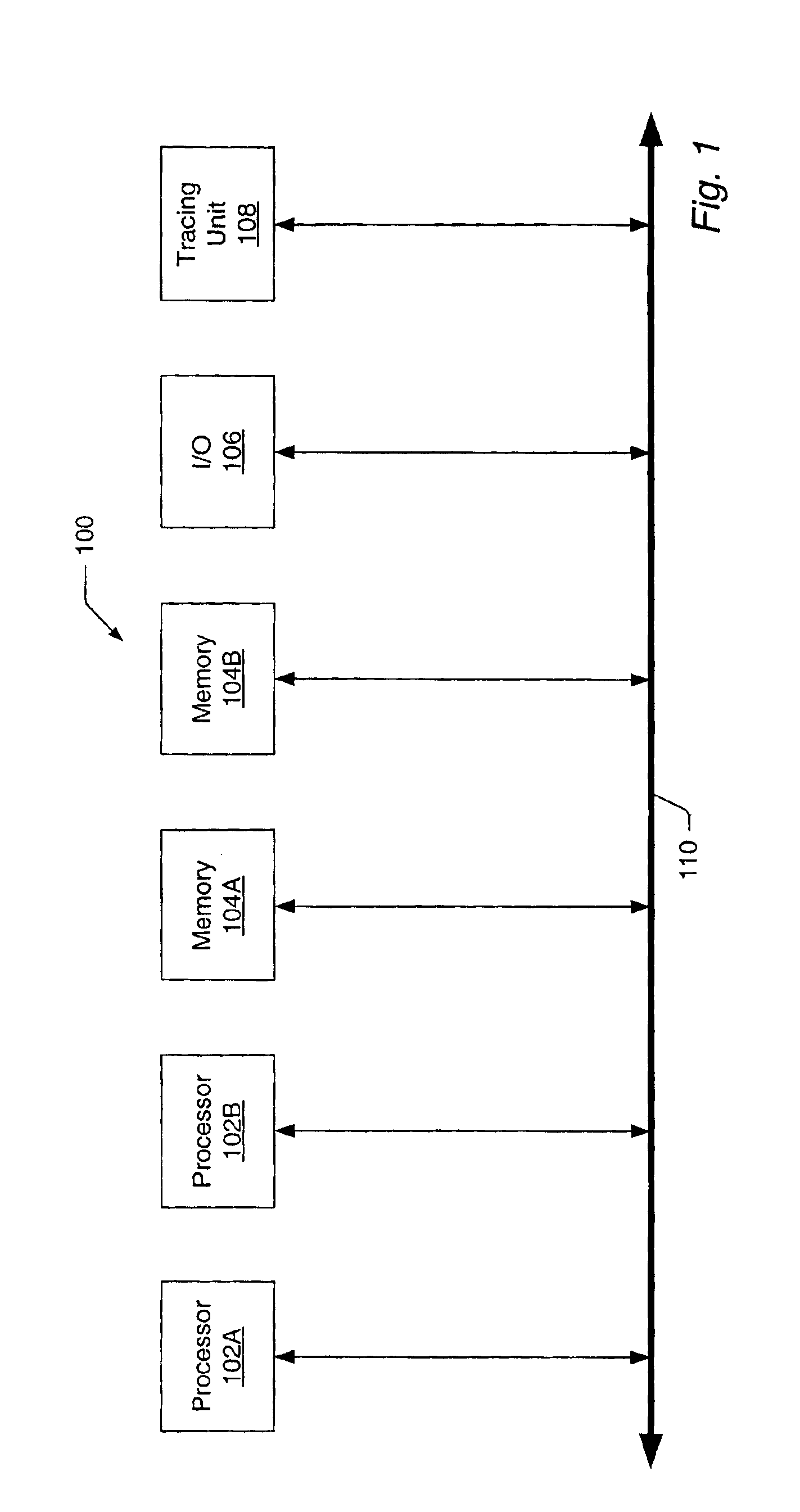
A computer processing system having memory and processing facilities for processing data with a computer program is a Hybrid Transactional Memory multiprocessor system with modules 1 . . . n coupled to a system physical memory array, I / O devices via a high speed interconnection element. A CPU is integrated as in a multi-chip module with microprocessors which contain or are coupled in the CPU module to an assist thread facility, as well as a memory controller, cache controllers, cache memory, and other components which form part of the CPU which connects to the high speed interconnect which functions under the architecture and operating system to interconnect elements of the computer system with physical memory, various 1 / 0, devices and the other CPUs of the system. The current hybrid transactional memory elements support for a transactional memory system that has a simple / cost effective hardware design that can deal with limited hardware resources, yet one which has a transactional facility control logic providing for a back up assist thread that can still allow transactions to reference existing libraries and allows programmers to include calls to existing software libraries inside of their transactions, and which will not make a user code use a second lock based solution.
Owner:IBM CORP
Annotations for transaction tracing
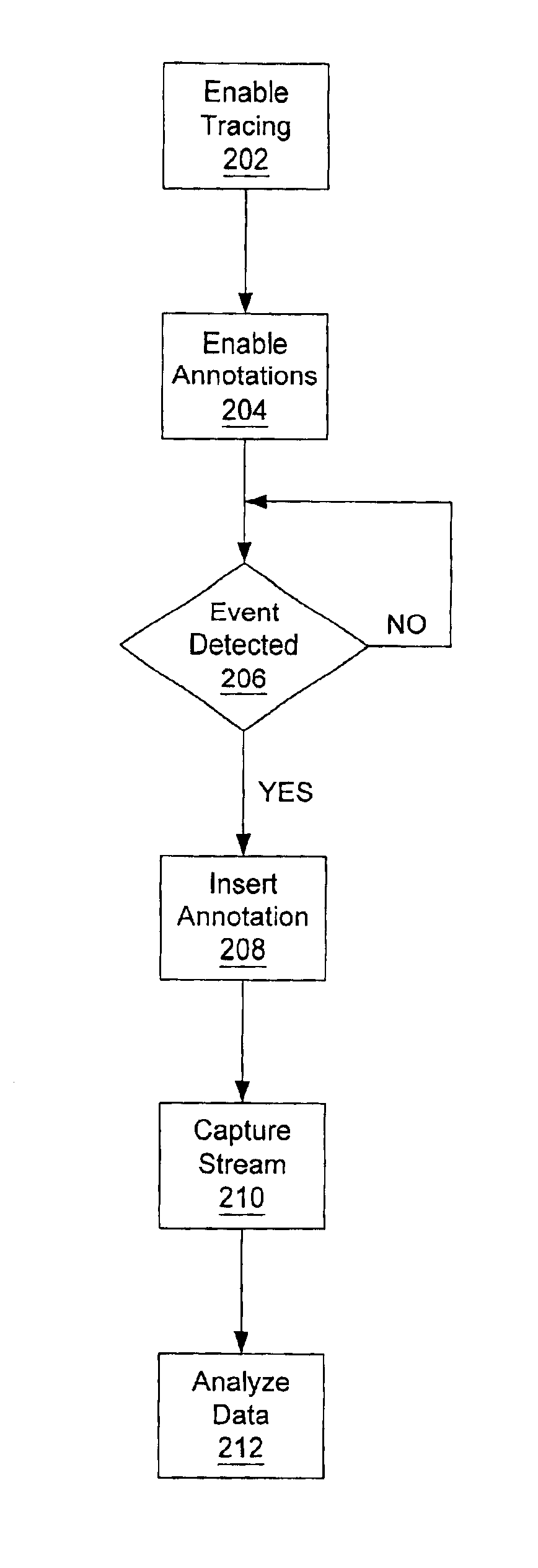
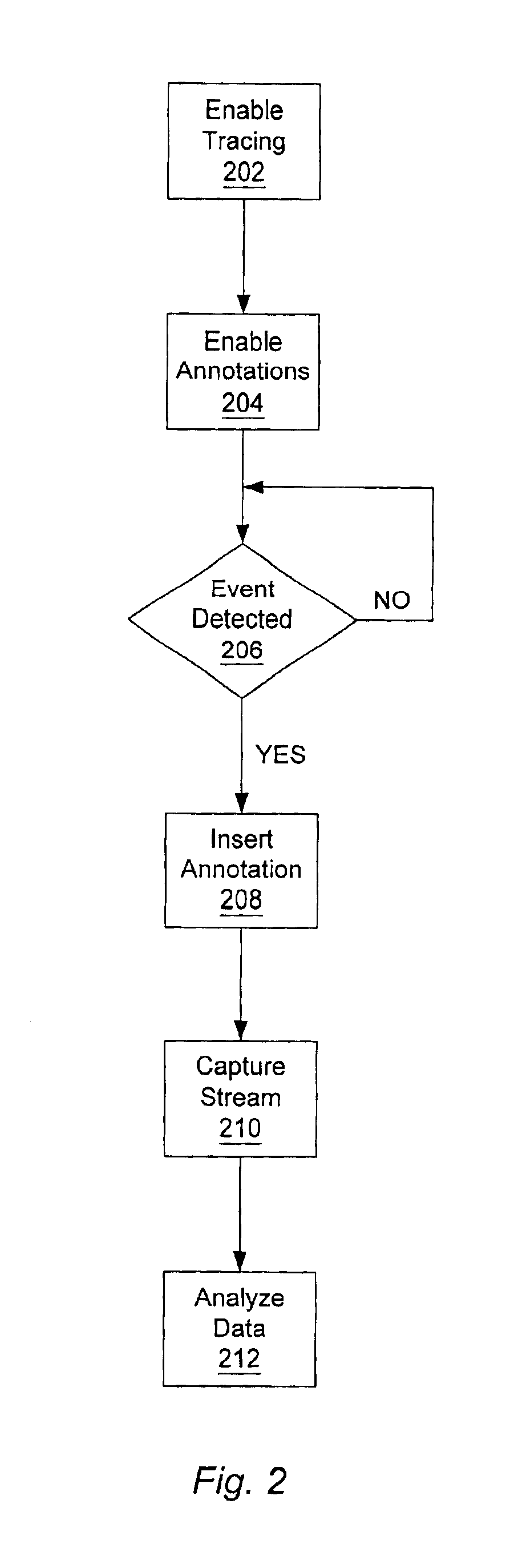
InactiveUS6883162B2Enhanced debugEnhanced performance analysisDigital computer detailsHardware monitoringTimestampOperational system
A method and mechanism for annotating a transaction stream. A processing unit is configured to generate annotation transactions which are inserted into a transaction stream. The transaction stream, including the annotations, are subsequently observed by a trace unit for debug or other analysis. In one embodiment, a processing unit includes a trace address register and an annotation enable bit. The trace address register is configured to store an address corresponding to a trace unit and the enable bit is configured to indicate whether annotation transactions are to be generated. Annotation instructions are added to operating system or user code at locations where annotations are desired. In one embodiment, annotation transactions correspond to transaction types which are not unique to annotation transactions. In one embodiment, an annotation instruction includes a reference to the trace address register which contains the address of the trace unit. Upon detecting the annotation instruction, and detecting annotations are enabled, the processing unit generates an annotation transaction addressed to the trace unit. In one embodiment, annotation transactions may be used to indicate context switches, processor mode changes, timestamps, or address translation information.
Owner:ORACLE INT CORP
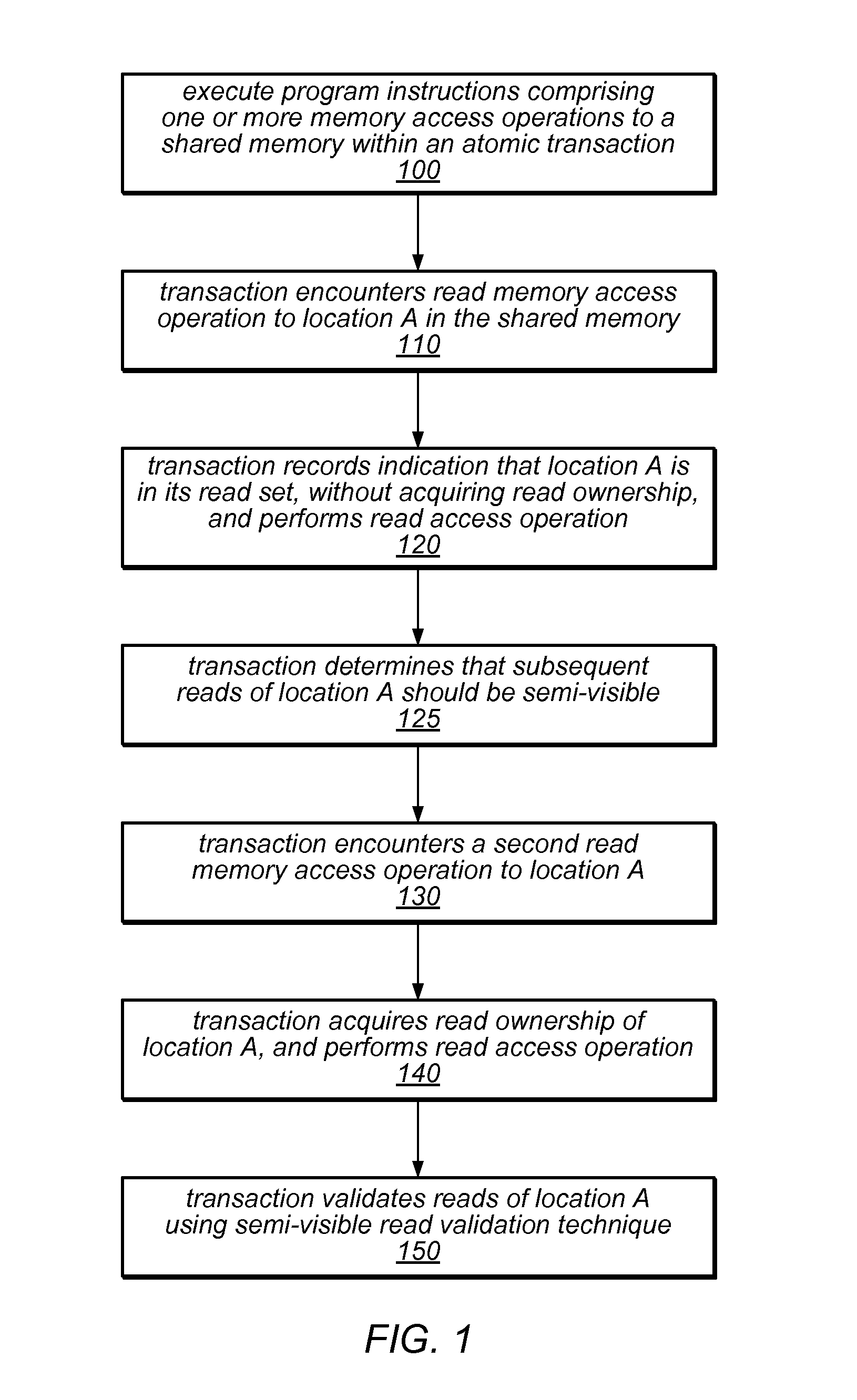
System and Method for Committing Results of a Software Transaction Using a Hardware Transaction
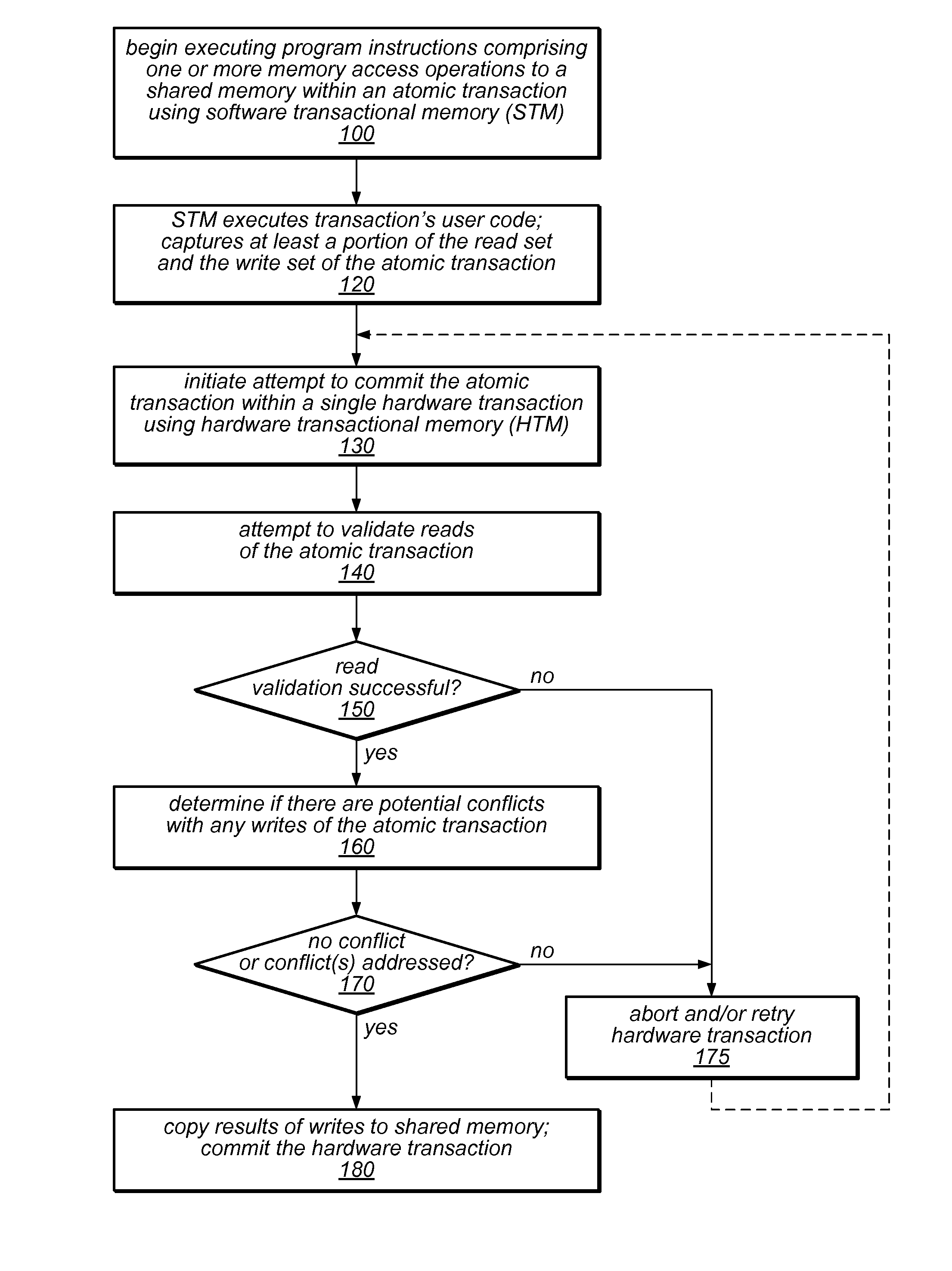
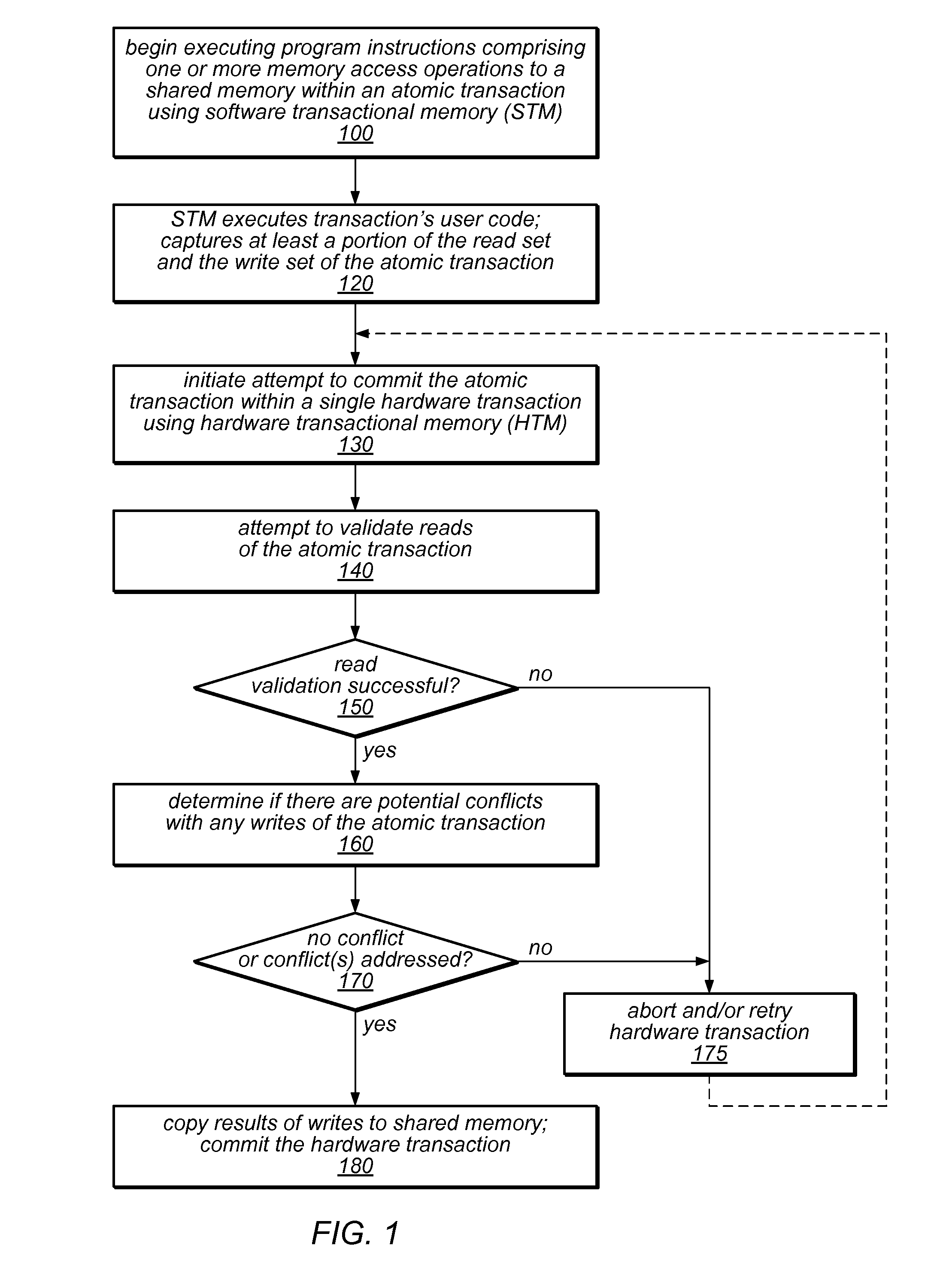
ActiveUS20110246725A1Improve software performanceReduce overheadMemory loss protectionError detection/correctionRemedial actionUser code
The system and methods described herein may exploit hardware transactional memory to improve the performance of a software or hybrid transactional memory implementation, even when an entire user transaction cannot be executed within a hardware transaction. The user code of an atomic transaction may be executed within a software transaction, which may collect read and write sets and / or other information about the atomic transaction. A single hardware transaction may be used to commit the atomic transaction by validating the transaction's read set and applying the effects of the user code to memory, reducing the overhead associated with commitment of software transactions. Because the hardware transaction code is carefully controlled, it may be less likely to fail to commit. Various remedial actions may be taken before retrying hardware transactions following some failures. If a transaction exceeds the constraints of the hardware, it may be committed by the software transactional memory alone.
Owner:ORACLE INT CORP
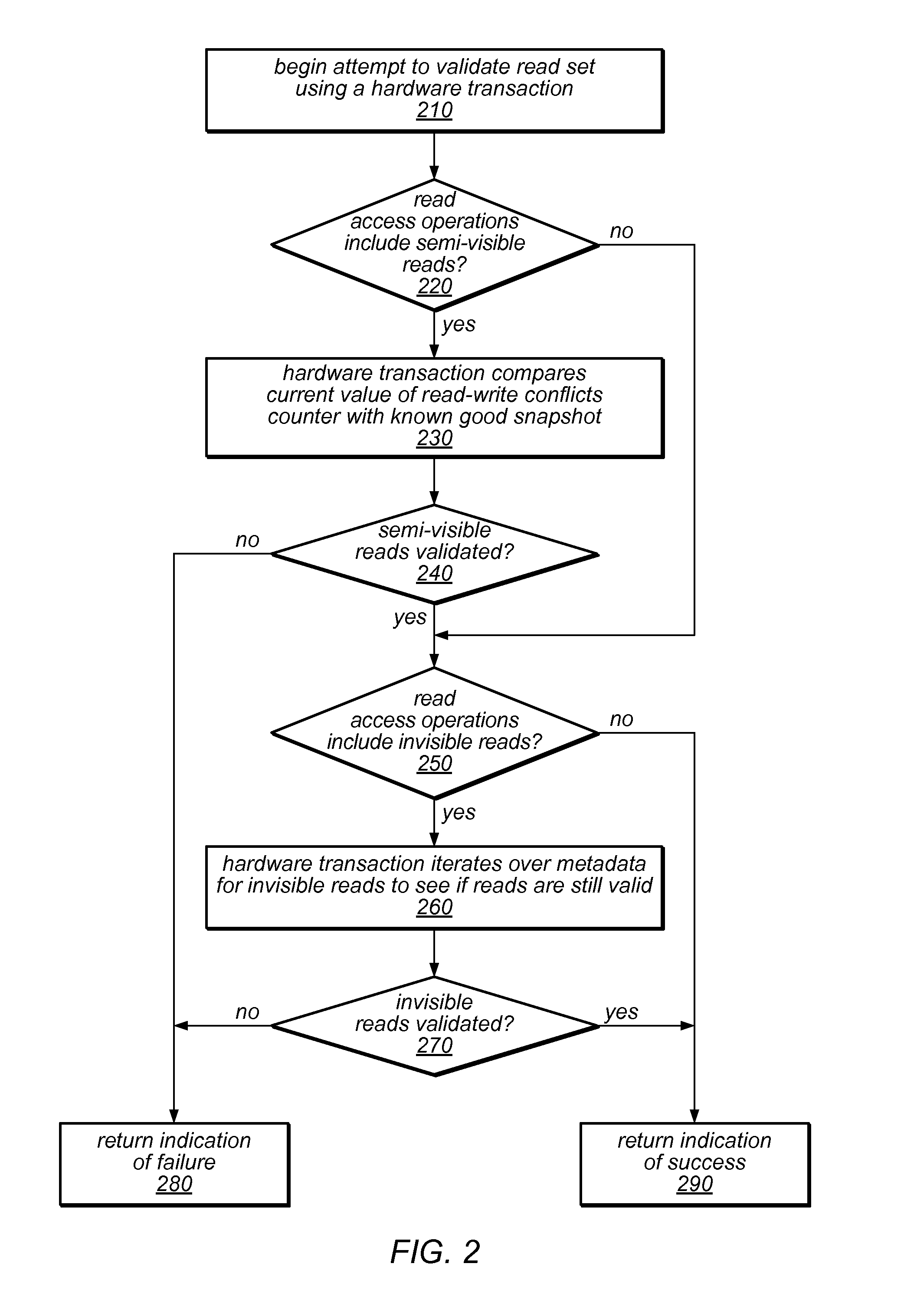
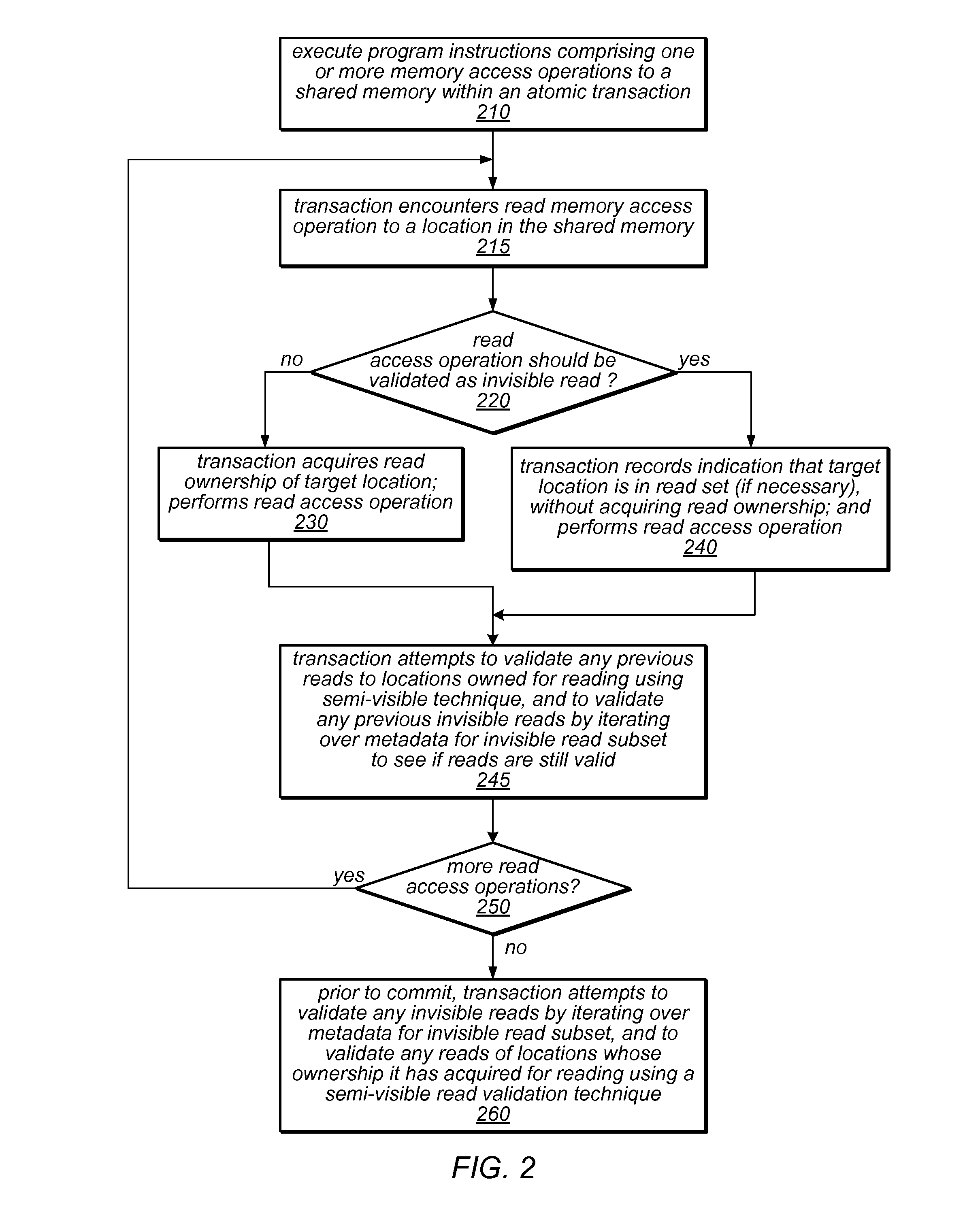
System and Method for Performing Dynamic Mixed Mode Read Validation In a Software Transactional Memory
ActiveUS20110125973A1Management costMemory adressing/allocation/relocationUnauthorized memory use protectionMixed modeUser code
The transactional memory system described herein may apply a mix of read validation techniques to validate read operations (e.g., invisible reads and / or semi-visible reads) in different transactions, or to validate different read operations within a single transaction (including reads of the same location). The system may include mechanisms to dynamically determine that a read validation technique should be replaced by a different technique for reads of particular locations or for all subsequent reads, and / or to dynamically adjust the balance between different read validation techniques to manage costs. Some of the read validation techniques may be supported by hardware transactional memory (HTM). The system may delay acquisition of ownership records for reading, and may acquire two or more ownership records back-to-back (e.g., within a single hardware transaction). The user code of a software transaction may be divided into multiple segments, some of which may be executed within a hardware transaction.
Owner:ORACLE INT CORP
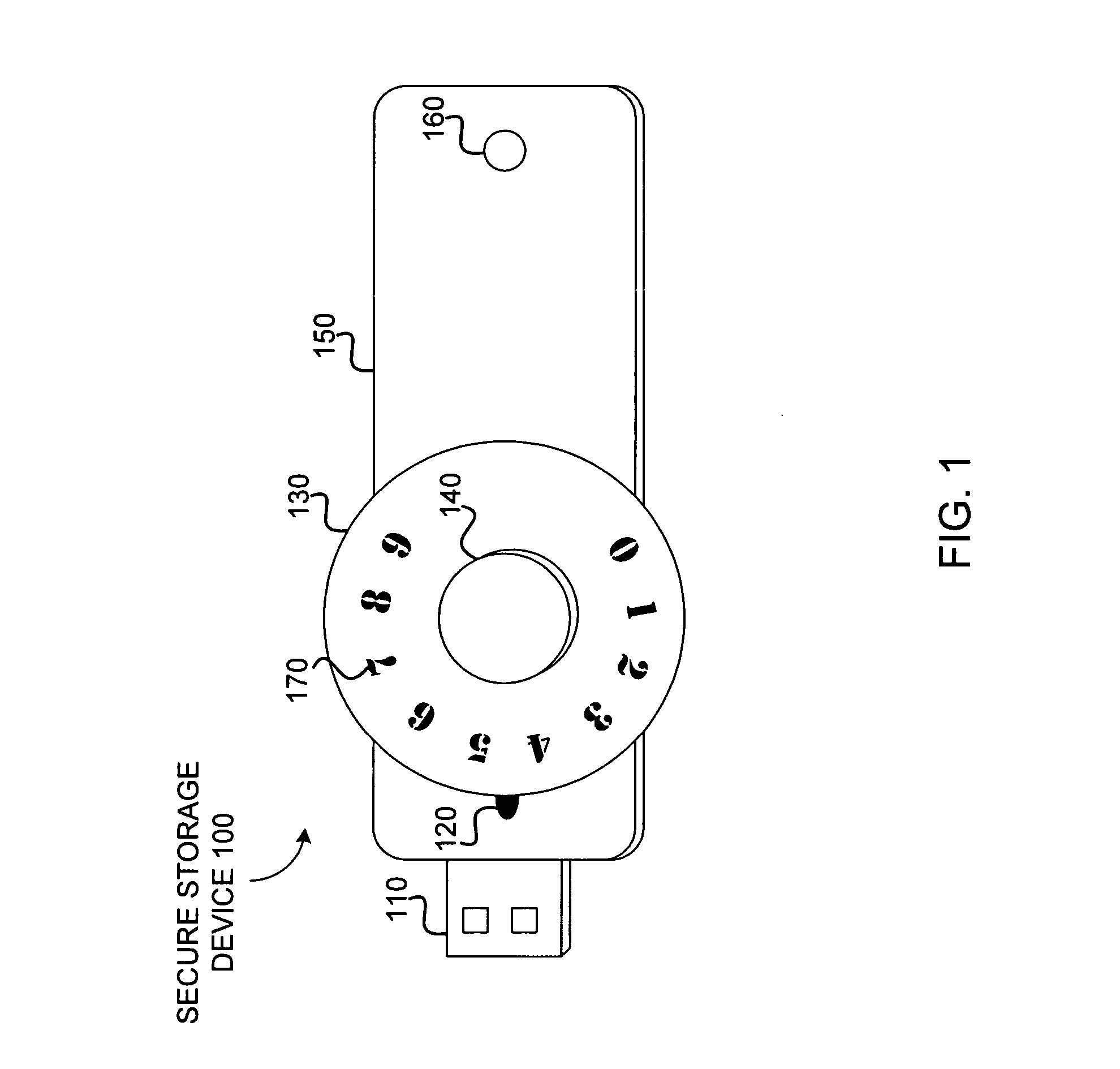
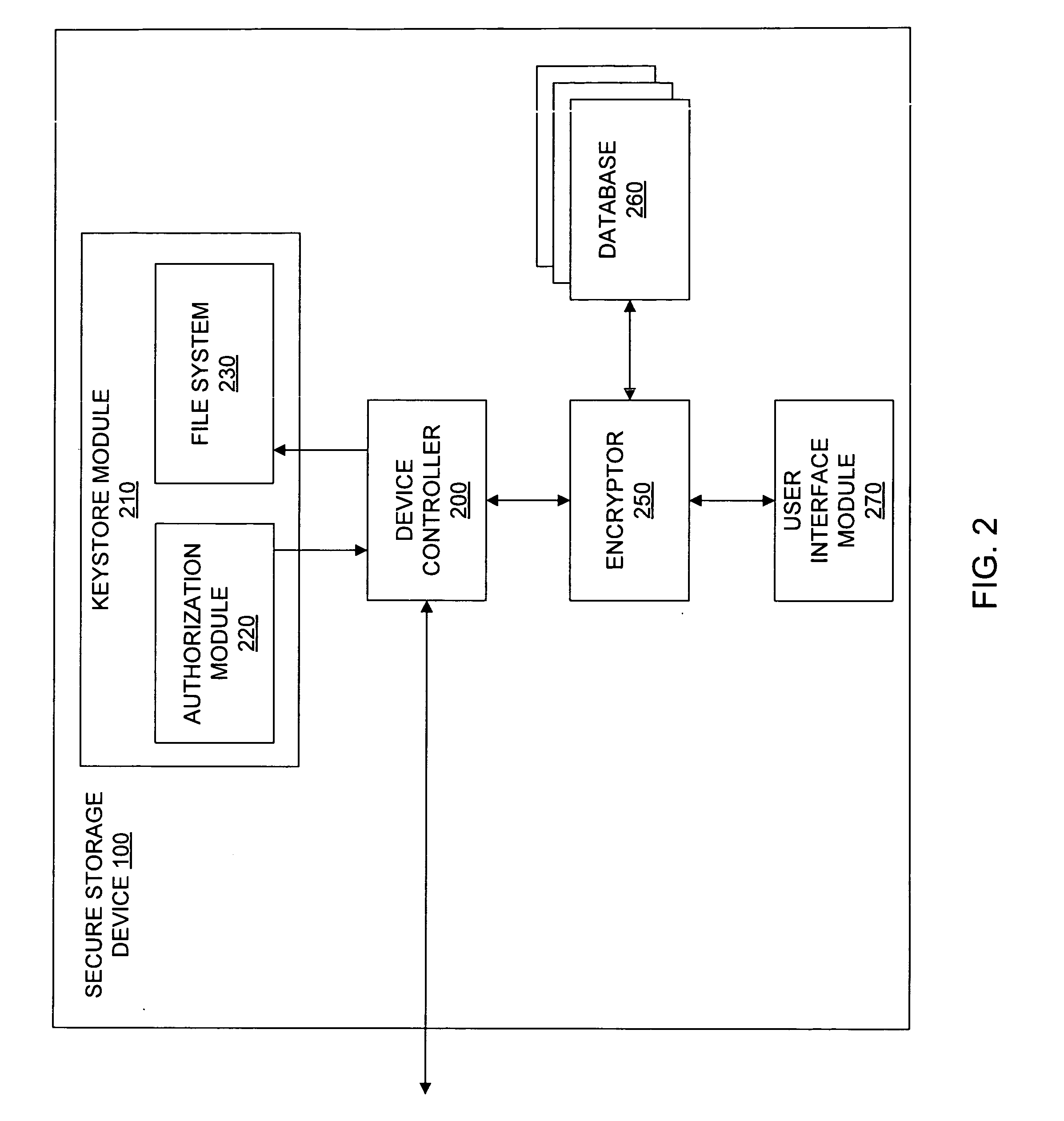
Secure storage device with offline code entry
ActiveUS20070016743A1Digital data processing detailsUnauthorized memory use protectionData storeUser code
A system to authorize access to secured data storage can compromise a user interface configured to receive a user code offline from a user to allow access to stored data, circuitry configured to authorize access to the stored data based, at least in part, on the user code and provide access to the stored data, and a storage system configured to store the stored data.
Owner:KINGSTON DIGITAL CO LTD
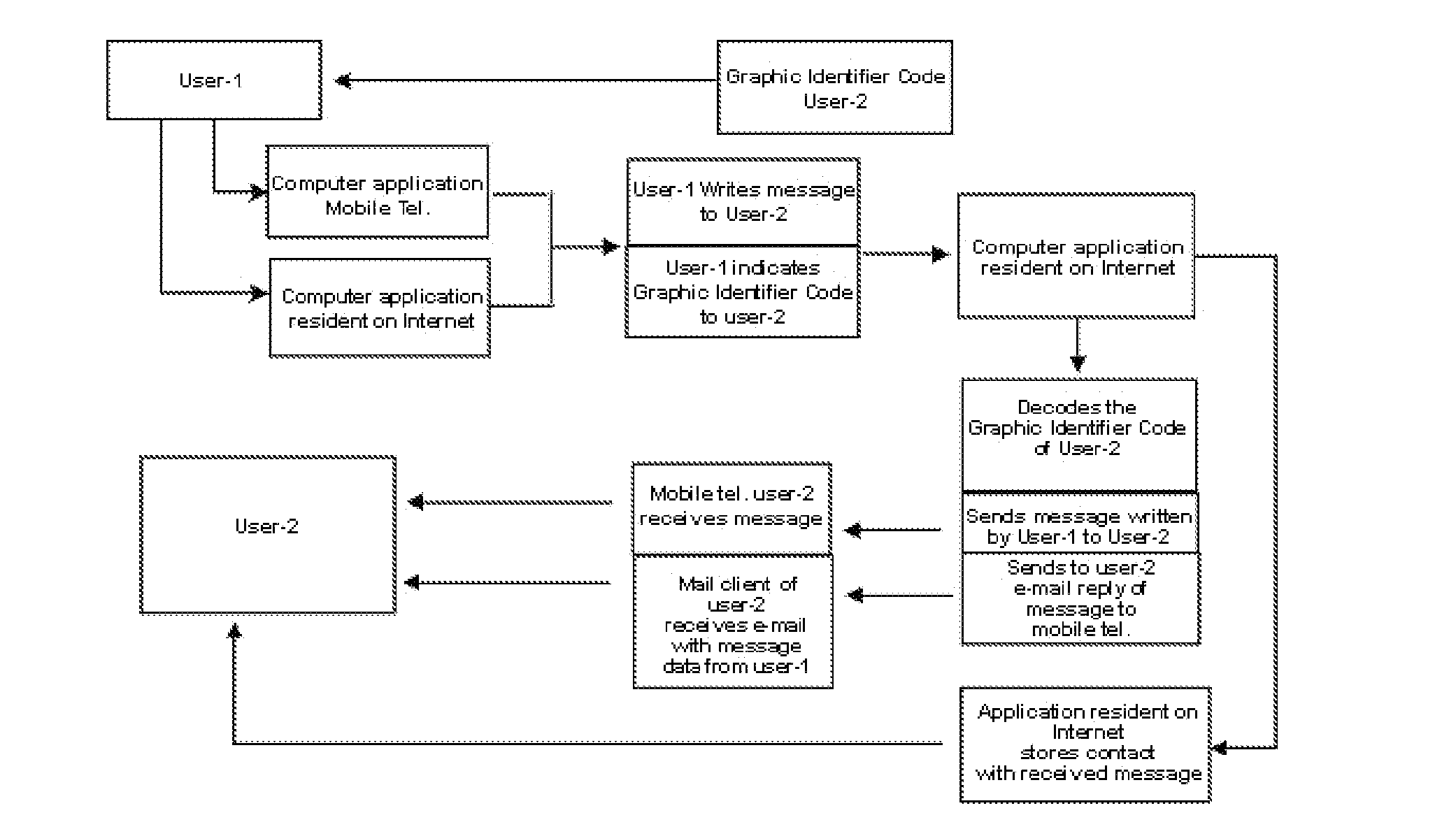
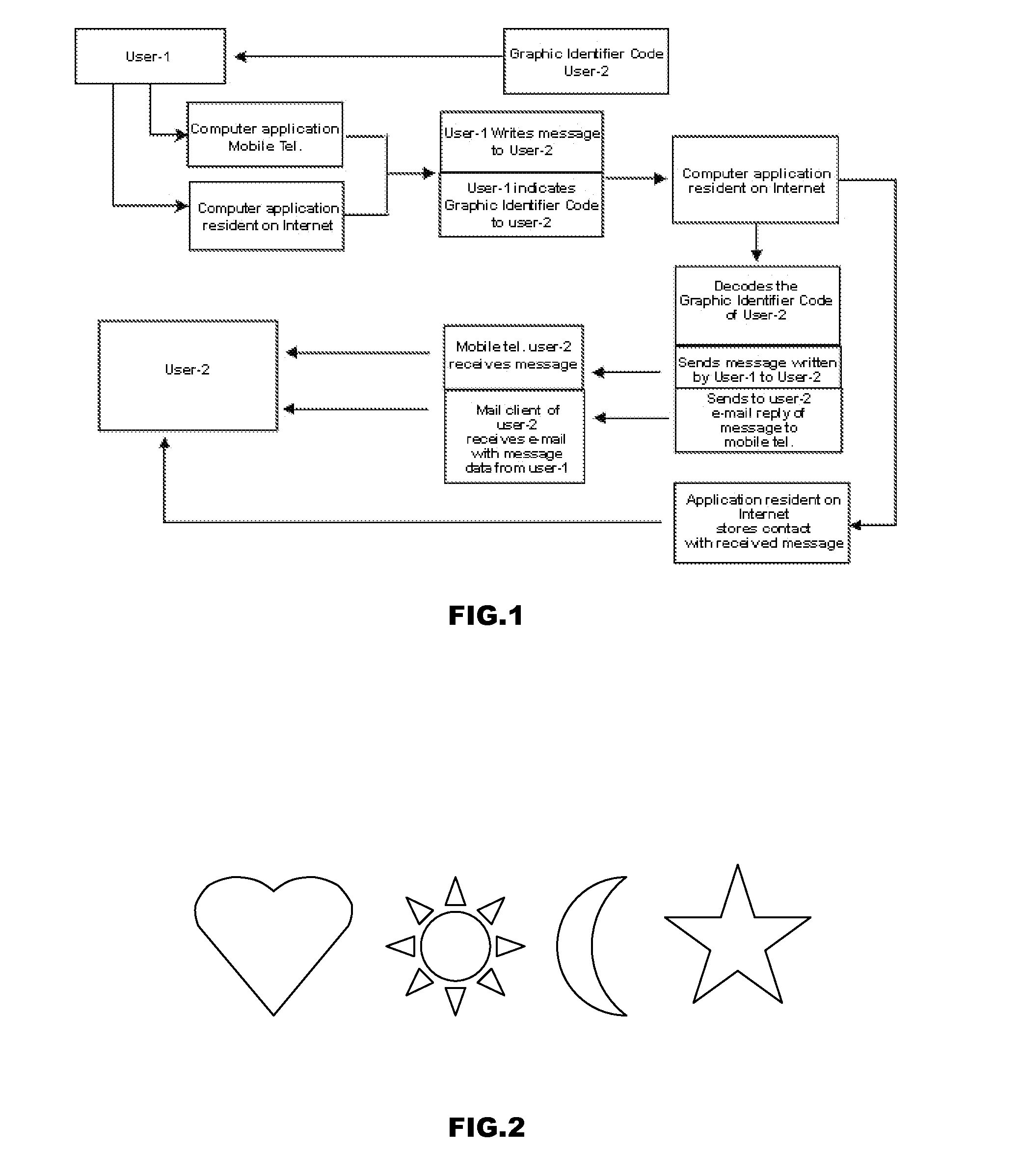
Method and System of Communication That Allow People Unknown to Each Other Who Have Visual Contact to Communicate by SMS or E-mail
InactiveUS20120108274A1Simple and effective and economicalObstacle to communicationWireless commuication servicesCommerceGraphicsPattern perception
Method and system of communication that allow people unknown to each other who have visual contact, to communicate by sms or e-mail based on the identification of system users through the perception of codes of registered users, formed from the combination of graphic symbols that follow uniquely identifying coding rules for each user within the system, by use of a computer application that decodes said user codes and allows the delivery of messages between said users, ensuring maximum discretion during communication, both towards the rest of the environment and towards the user with whom one wishes to establish contact.
Owner:ACEBO RUIZ AGUSTIN +1
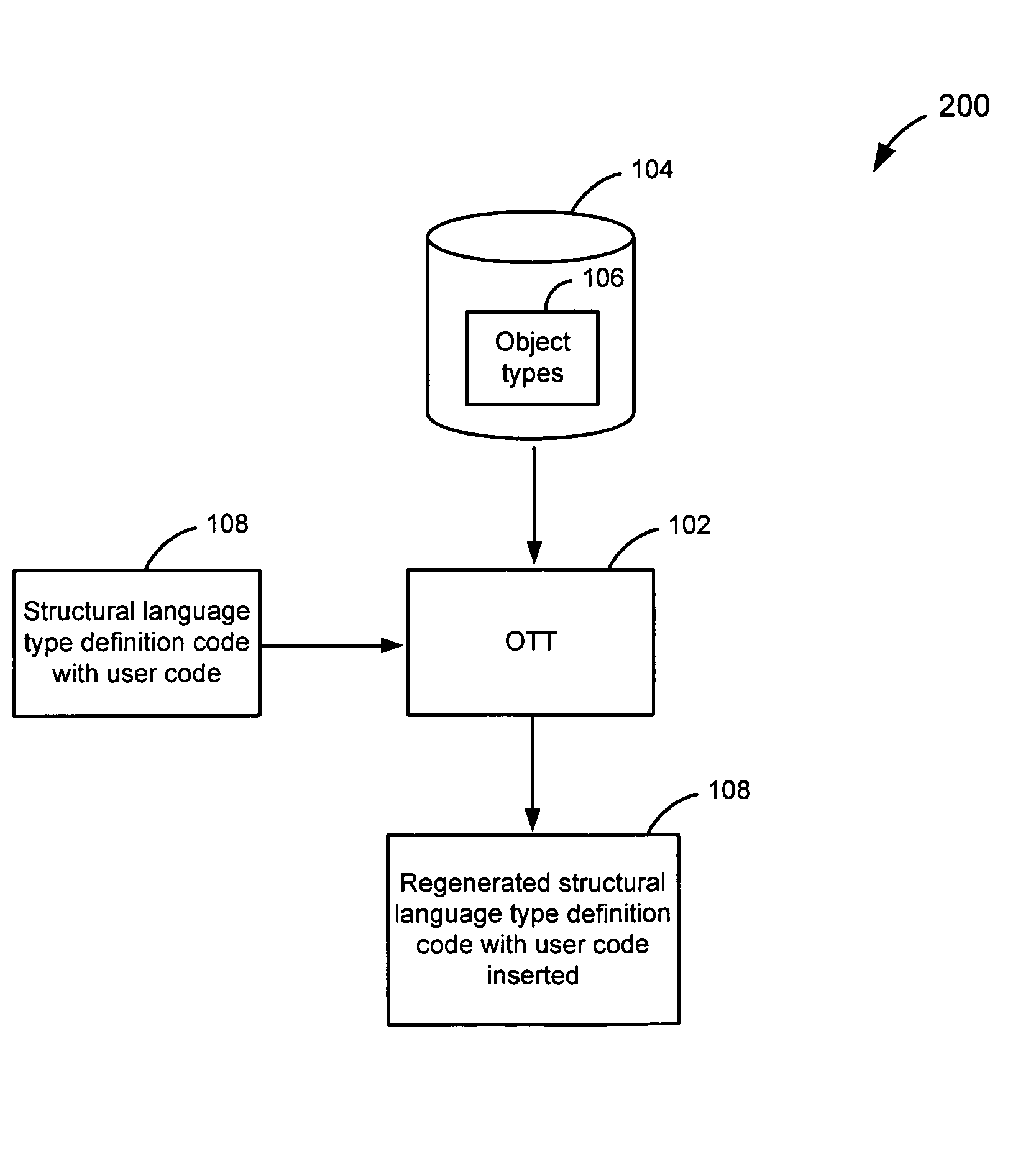
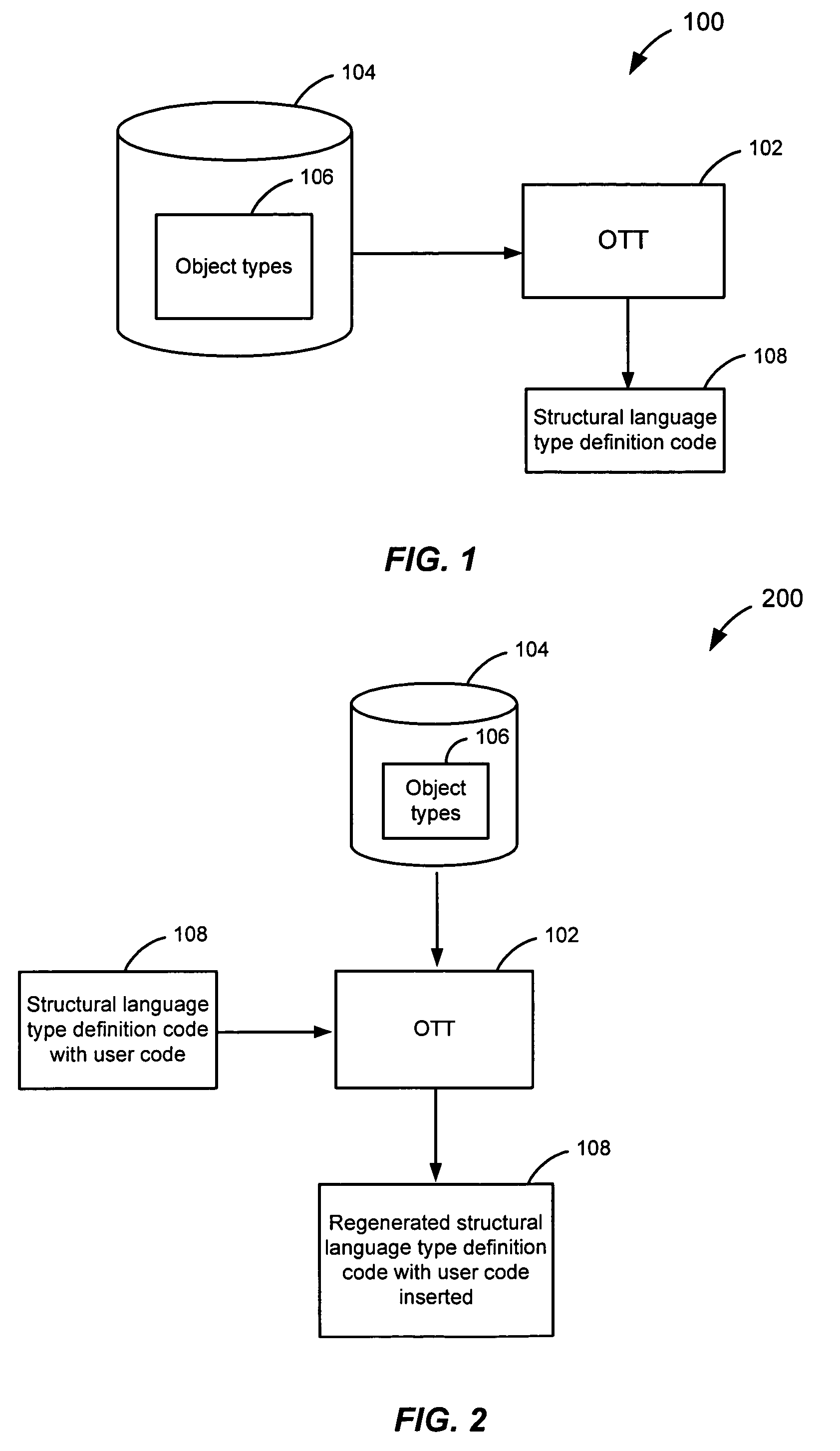
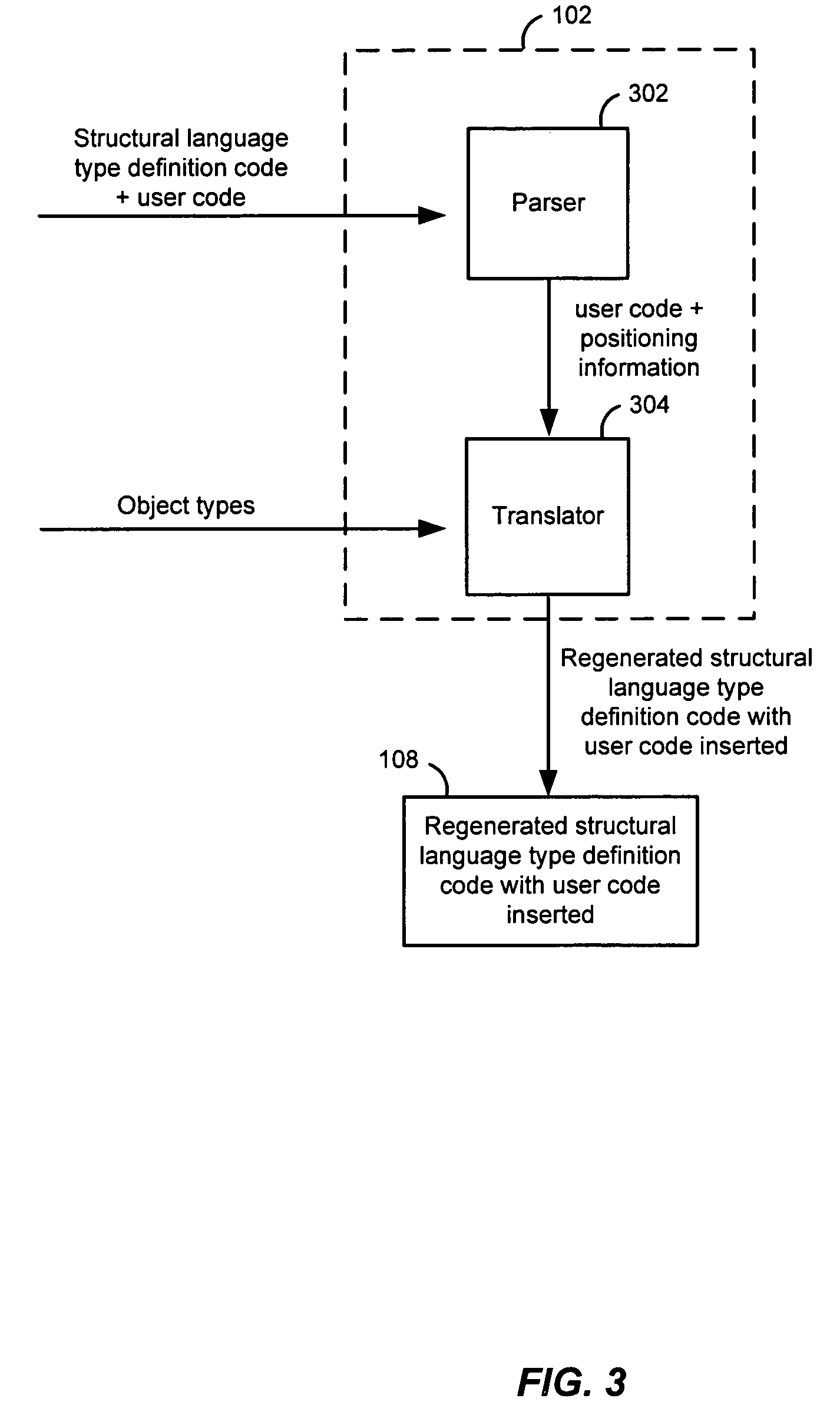
Preserving user code in OTT-generated classes
ActiveUS7401088B2Data processing applicationsDigital data information retrievalCode generationObject type
An object type translator (OTT) determines one or more database object types. The one or more database object types are mapped to a first structural language type definition code. After being generated, the user may add user code to the first structural language type definition code. During regeneration of these files, the first structural language type definition code is then parsed to determine the user code that has been added, based on the start and end markers that the user code segments have been marked with. OTT maps these user-code segments to the corresponding database types and keeps track of the mapping and the user code. When the OTT starts generating the second structural language code, the OTT determines a position where the user code should be inserted into the second structural language type definition code using that mapping. The user code is then inserted in the second structural language code in the position determined. Accordingly, the user code that was added is not lost when the structural language type definition code is regenerated from the one or more database object types.
Owner:ORACLE INT CORP
System and method for generating ultra wideband pulses
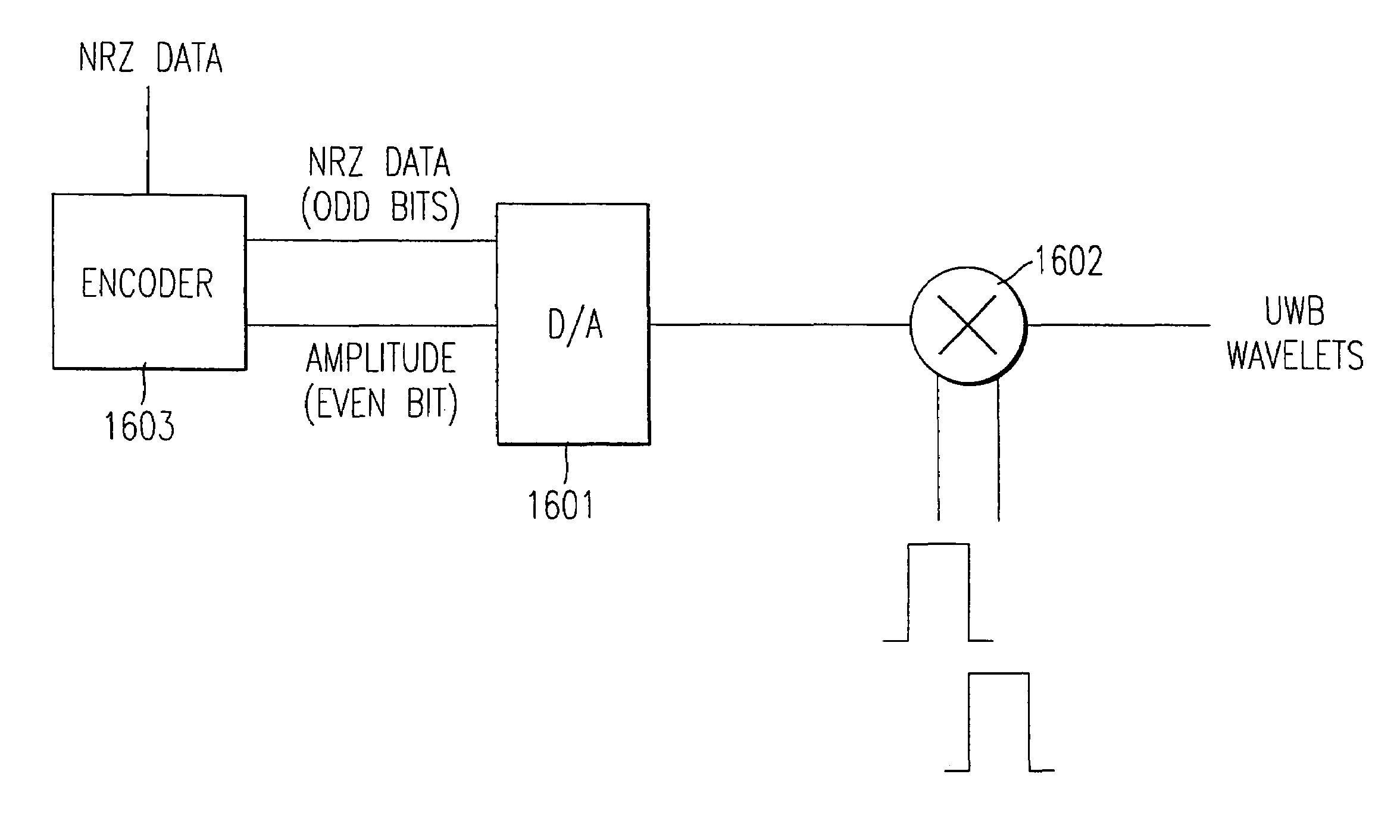
InactiveUS7010056B1Modulated carrier system with waveletsAmplitude-modulated carrier systemsUltra-widebandPeak value
An ultra-wide band (UWB) waveform generator and encoder for use in a UWB digital communication system. The UWB waveform is made up of a sequence of shaped wavelets. The waveform generator produces multi-amplitude, multi-phase wavelets that are time-constrained, zero mean, and can be orthogonal in phase, yet still have a −10 dB power spectral bandwidth that is larger than the frequency of the peak of the power spectrum In one embodiment, the wavelets are bi-phase wavelets. The encoder multiplies each data bit by an n-bit identifying code, (e.g., a user code), resulting in a group of wavelets corresponding to each data bit. The identifying codeword is passed onto the UWB waveform generator for generation of a UWB waveform that can be transmitted via an antenna.
Owner:NORTH STAR INNOVATIONS
Proximity sensor enhanced power management
ActiveUS7010710B2Accelerated programEnergy efficient ICTVolume/mass flow measurementPower modeProximity sensor
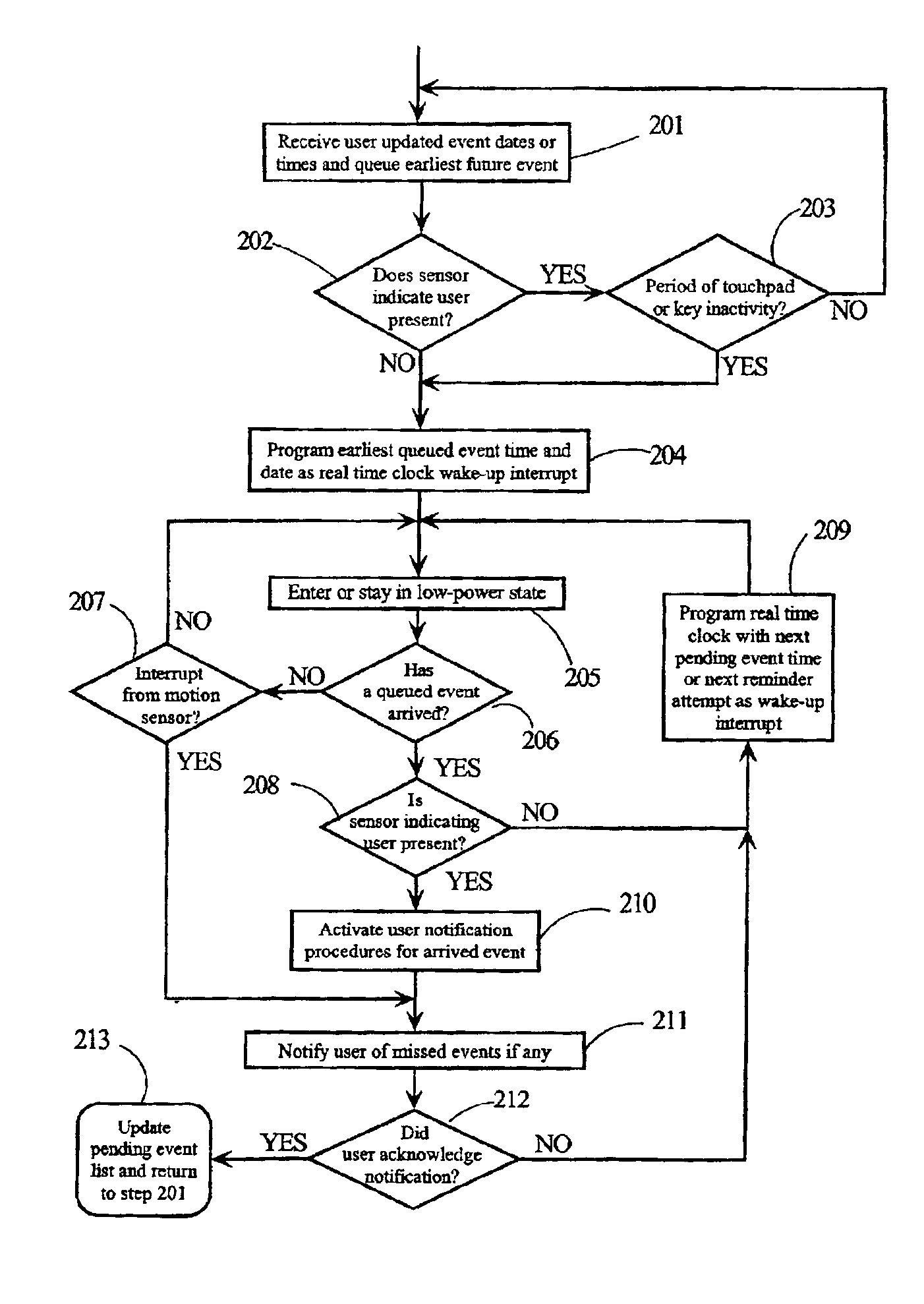
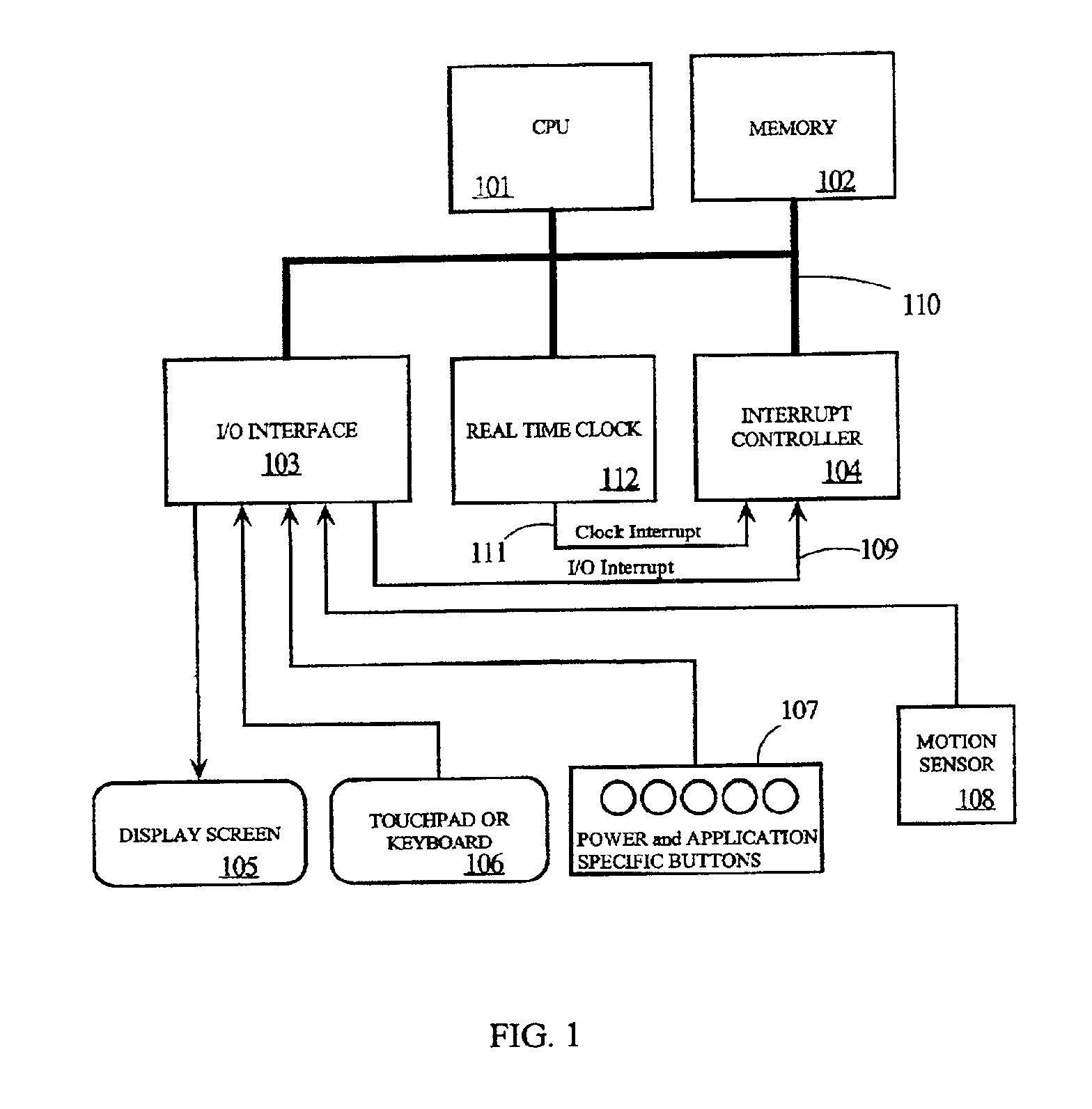
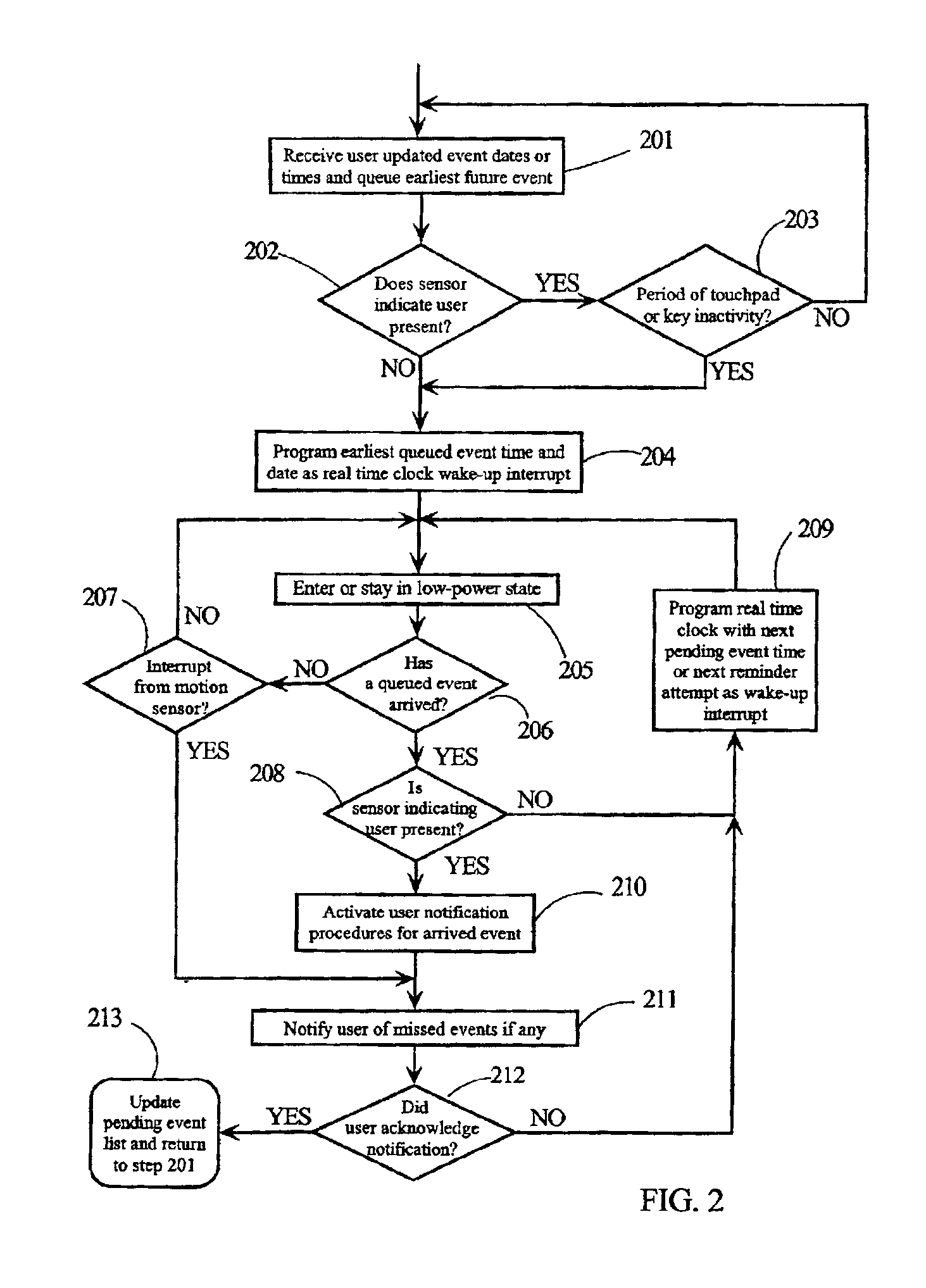
A computing device incorporates a user sensor to signal when a user is moving or within a specified proximity of the computing device. If the user is not present, the computing device will go into a low-power mode. A real-time clock is programmed to interrupt at user indicted event times and dates. If a queued event occurs, the computing device samples the user sensor and begins notification procedures if the user is present. If a queued event time occurs while the user is not present, then the computing device enters or stays in the low-power mode. If the user sensor indicates that the user is present, the computing device notifies the user of the pending event and any missed events. The computing device may require a user code before normal operation is activated following a transition to an indication that the user is present.
Owner:LENOVO GLOBAL TECH INT LTD
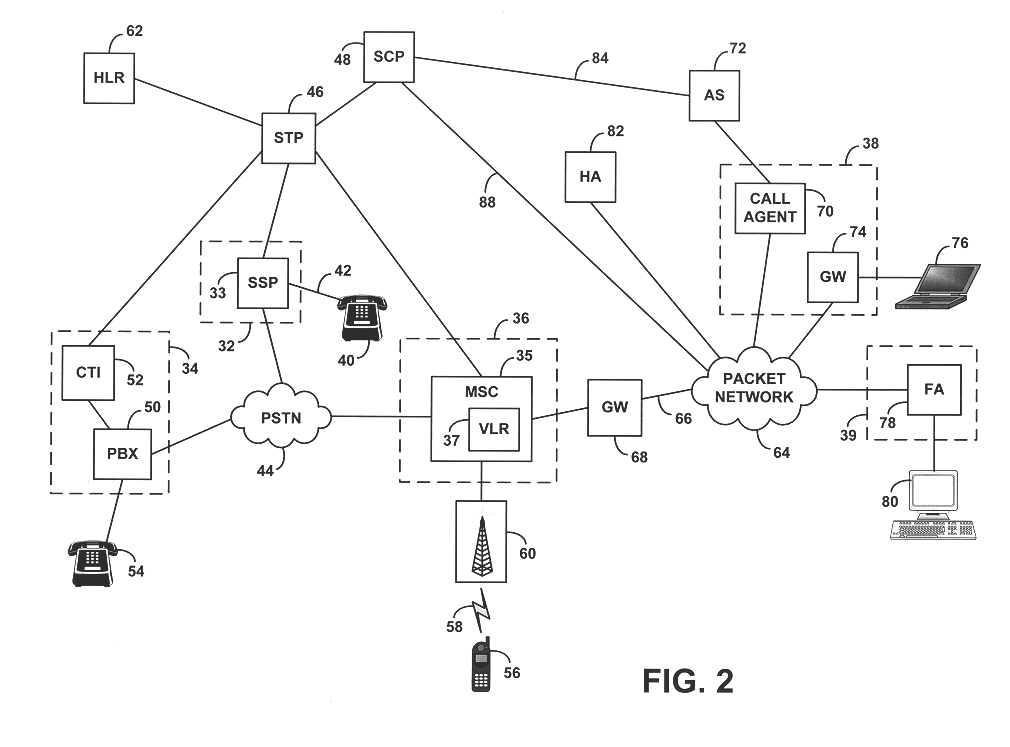
Method and apparatus for control of a subscriber identity module in a data communication system
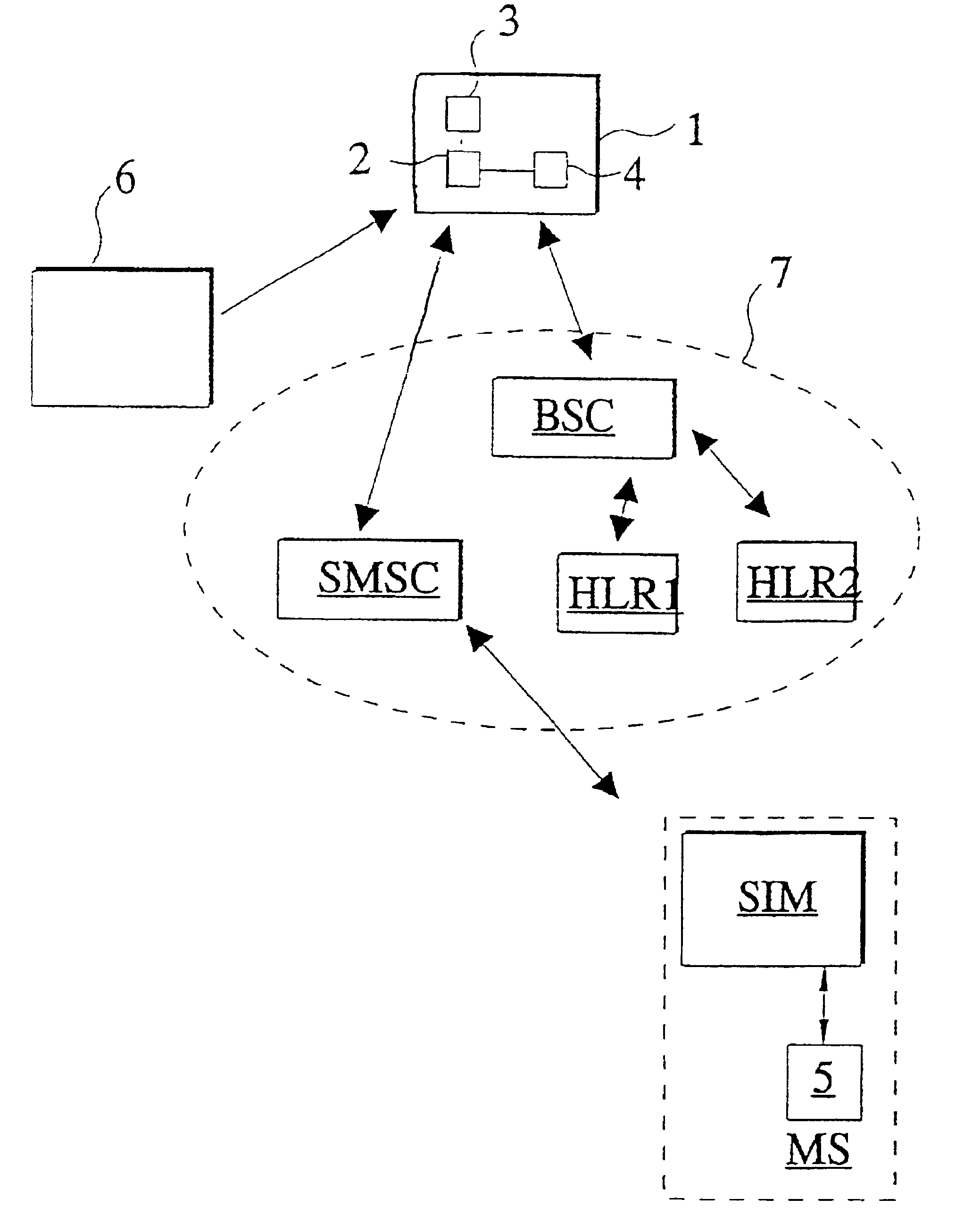
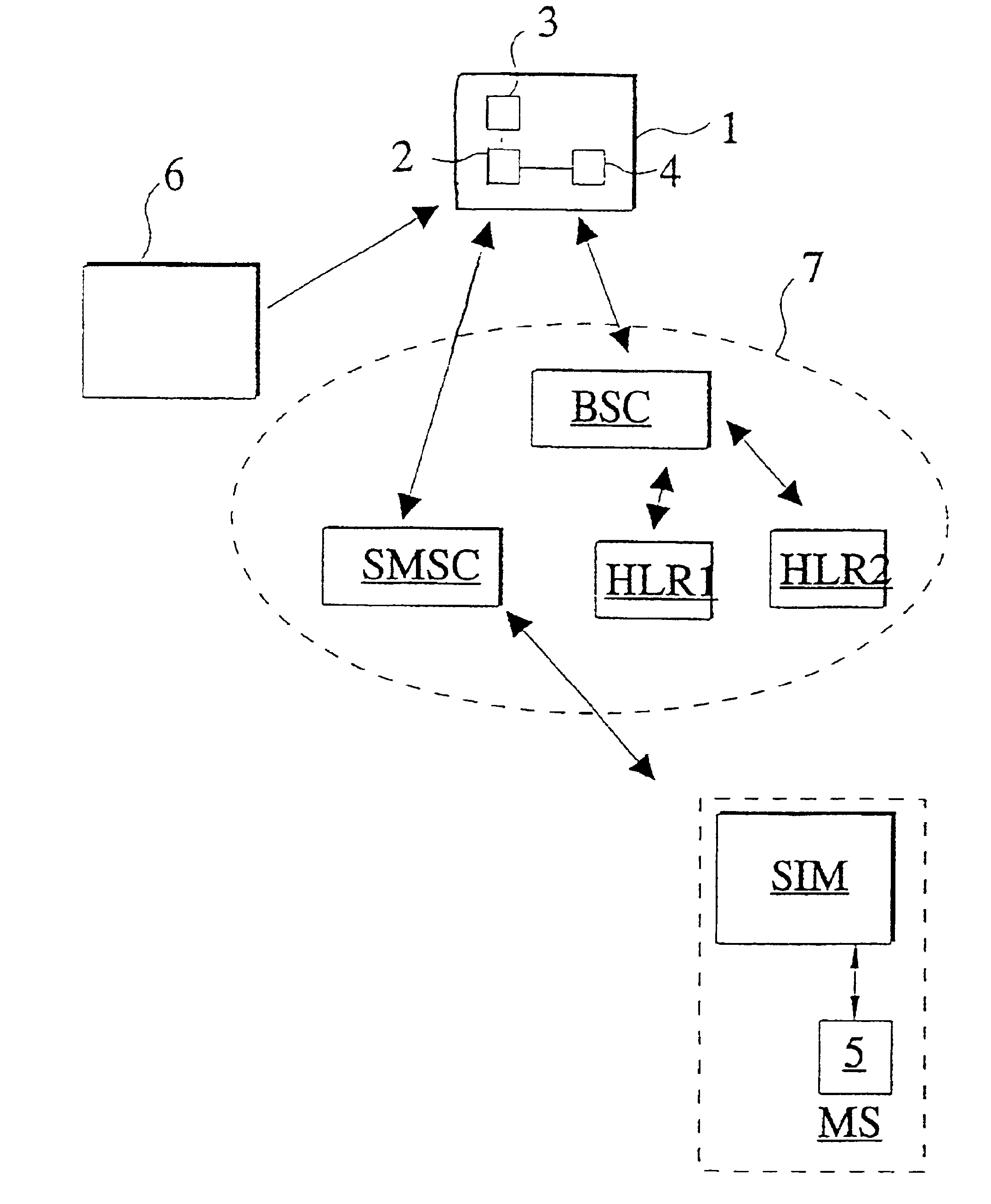
InactiveUS6934391B1Avoid logistical problemFaster customer serviceUser identity/authority verificationHardware monitoringTransport systemCommunications system
A method and apparatus for the control of a subscriber identity module (SIM) in a data communication system, preferably a mobile communication system. The data communication system includes first and second subscriber registers (HLR1, HLR2) for maintaining subscriber records defining a subscriber identity module registry, a short message transmission system (SMSC) for transmission of messages in the communication system, and a mobile station (MS) connected to the subscriber identity module (SIM) for use by a subscriber in effecting mobile communications through the data communication system. The subscriber identity module (SIM) stores therein data comprising a first subscriber code (IMSI1) and an encrypted code key (Ki) corresponding to a first subscription for the mobile station subscriber and associated with the subscriber identity module A record of data corresponding to the first subscription is created in the first subscriber register (HLR1) when the first subscription is opened, the record comprising a first subscription specific call number (MSISDNx), the encryption code key (Ki) and a subscriber identity code (IMSI1) for the mobile station subscriber. A second subscription for the mobile station subscriber and associated with the subscriber identity module (SIM) is opened; a record corresponding to the opened second subscription and comprising a second subscription-specific call number (MSISDN), a second subscriber identity code (IMSI1) and the encryption key (Ki) is created in the second subscriber register (HLR2); a message (SMS) is sent through the communication system directed to the first subscription and instructing that the data stored in the subscriber identity module be changed from data corresponding to the first subscription to data corresponding to the second subscription.
Owner:SONERA
Transmitting and receiving messages through a customizable communication channel and programming model
InactiveUS7200676B2Filing/rasping devicesMultiprogramming arrangementsComputer hardwareMessage passing
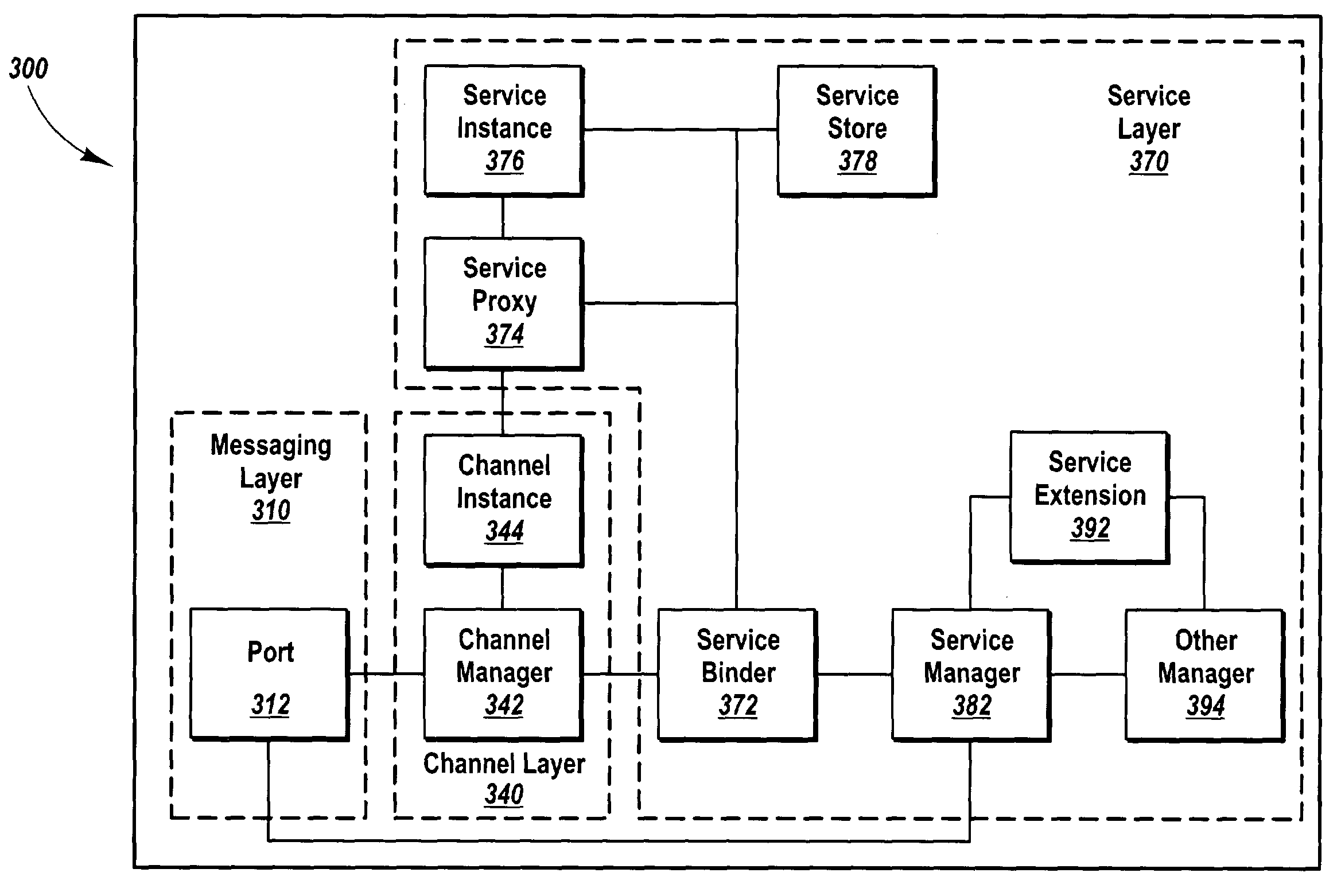
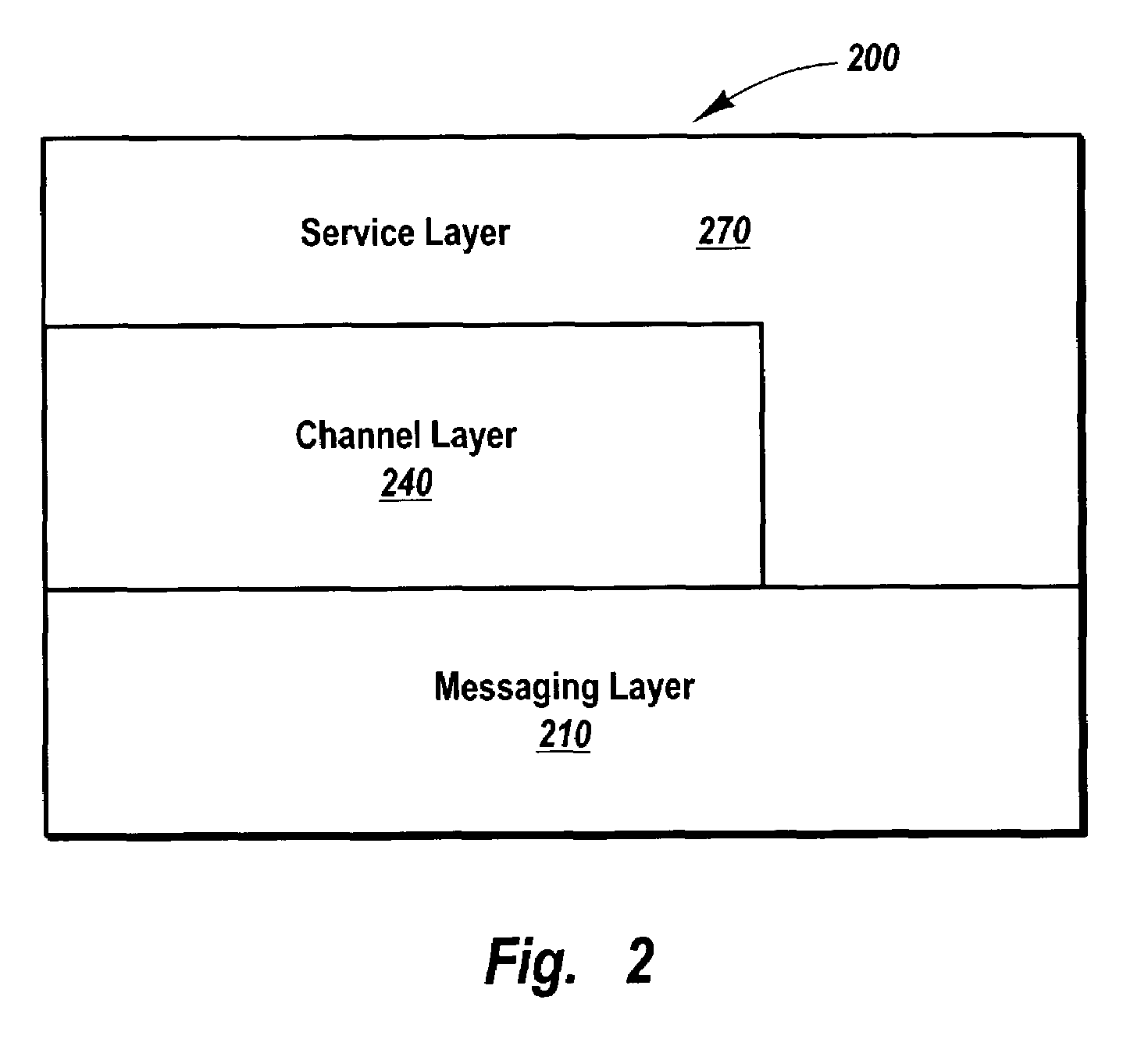
Methods, systems, and computer program products for abstracting processing layers within a messaging infrastructure so that changes or enhancements can be made to the infrastructure while retaining existing functionality. Message transport implementations are abstracted within a message layer, allowing other layers within the infrastructure to interact with messages in a more structured fashion, largely independent of message transport. Transport examples include named pipes, Transmission Control Protocol (TCP), HyperText Transfer Protocol (HTTP), Simple Mail Transfer Protocol (SMTP), etc. A channel layer above the message layer abstracts message exchange implementations, allowing other layers within the infrastructure to send and receive messages in a more structured fashion, largely independent of the message exchange semantics of a specific implementation. Message exchange examples include datagrams, dialogs, monologs, queues, and the like. Above the channel layer and message layer, a service layer abstracts the binding implementations that bind message exchange implementations to user code implementations.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for switching third party landing and third party network and service server
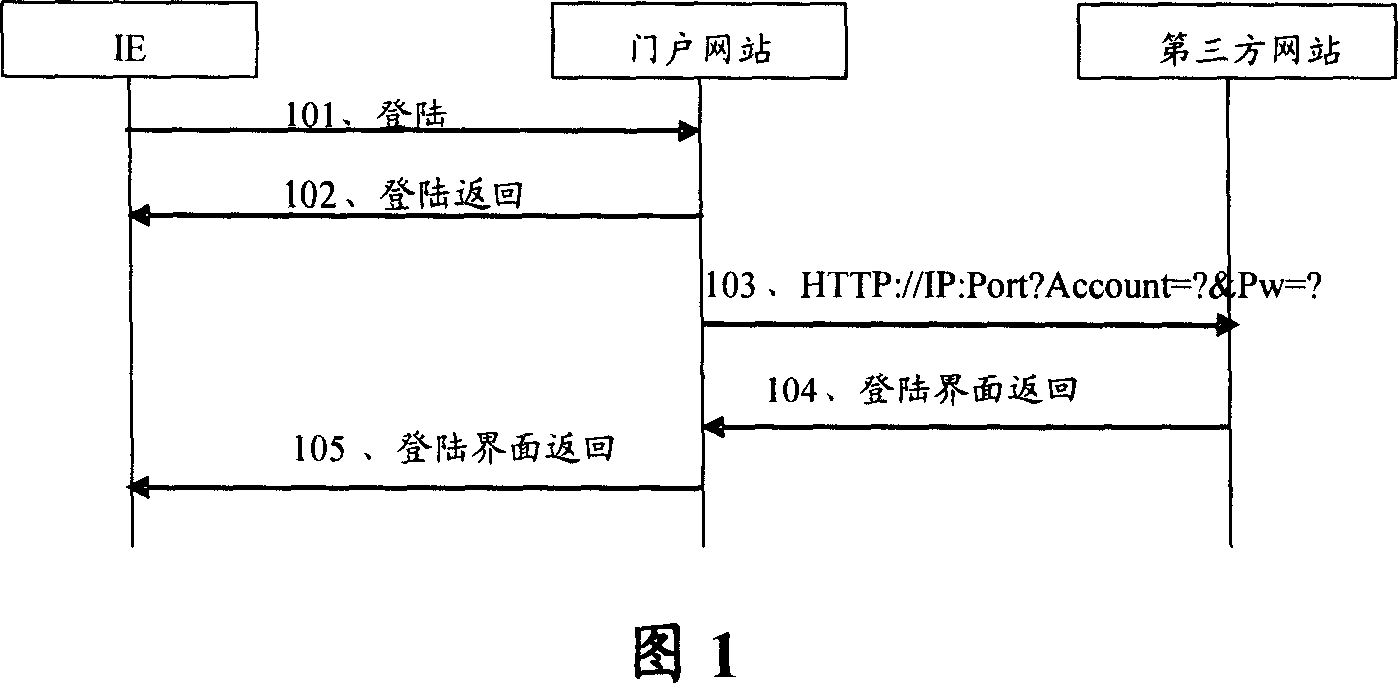
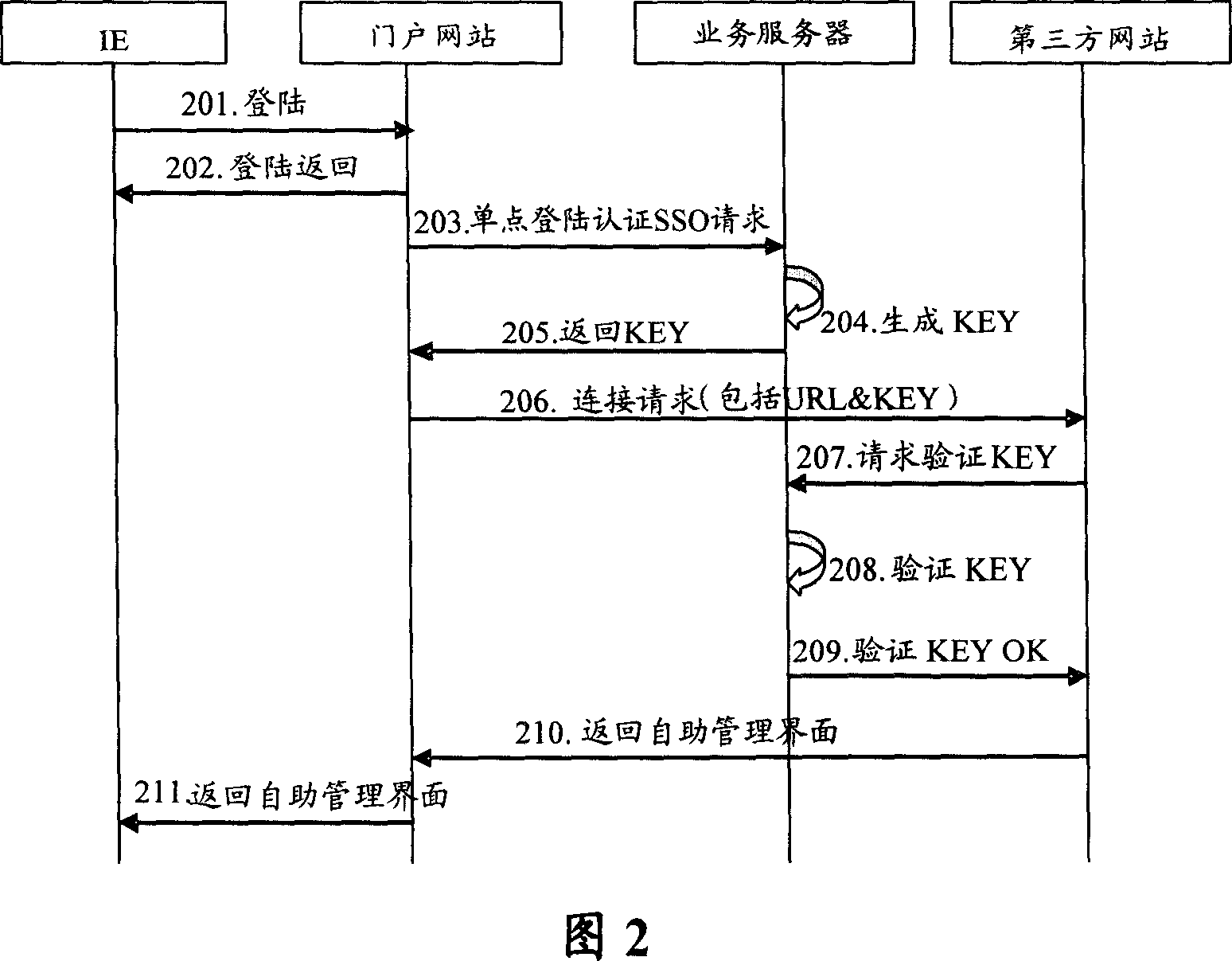
ActiveCN1946022AAvoid transmissionGuaranteed absolute securityUser identity/authority verificationThird partyWeb service
This invention provides a method for transferring third party landing based on IP network including: a door network station carries a ciphered KEY generated randomly by a service server to send a link request to a third party network station so as to avoid transmission of user ciphered codes and ensure absolute security of user codes, besides, since the third party network station calls back the Web server by copying the ciphered KEY to verify the cryptographic key so as to secure the absolute safety of shaking hands, since the door network station does not transfer user ciphered codes with the third party network station, which is not necessary to synchronize with the door station about codes, thus the requirement of complicated maintenance to synchronization on ciphered codes to the third party is reduced. This invention also provides a system for authenticating the transfer of third party landing based on the IP network and the third party network station and service servers.
Owner:HUAWEI TECH CO LTD
Network login system and method with face authentication
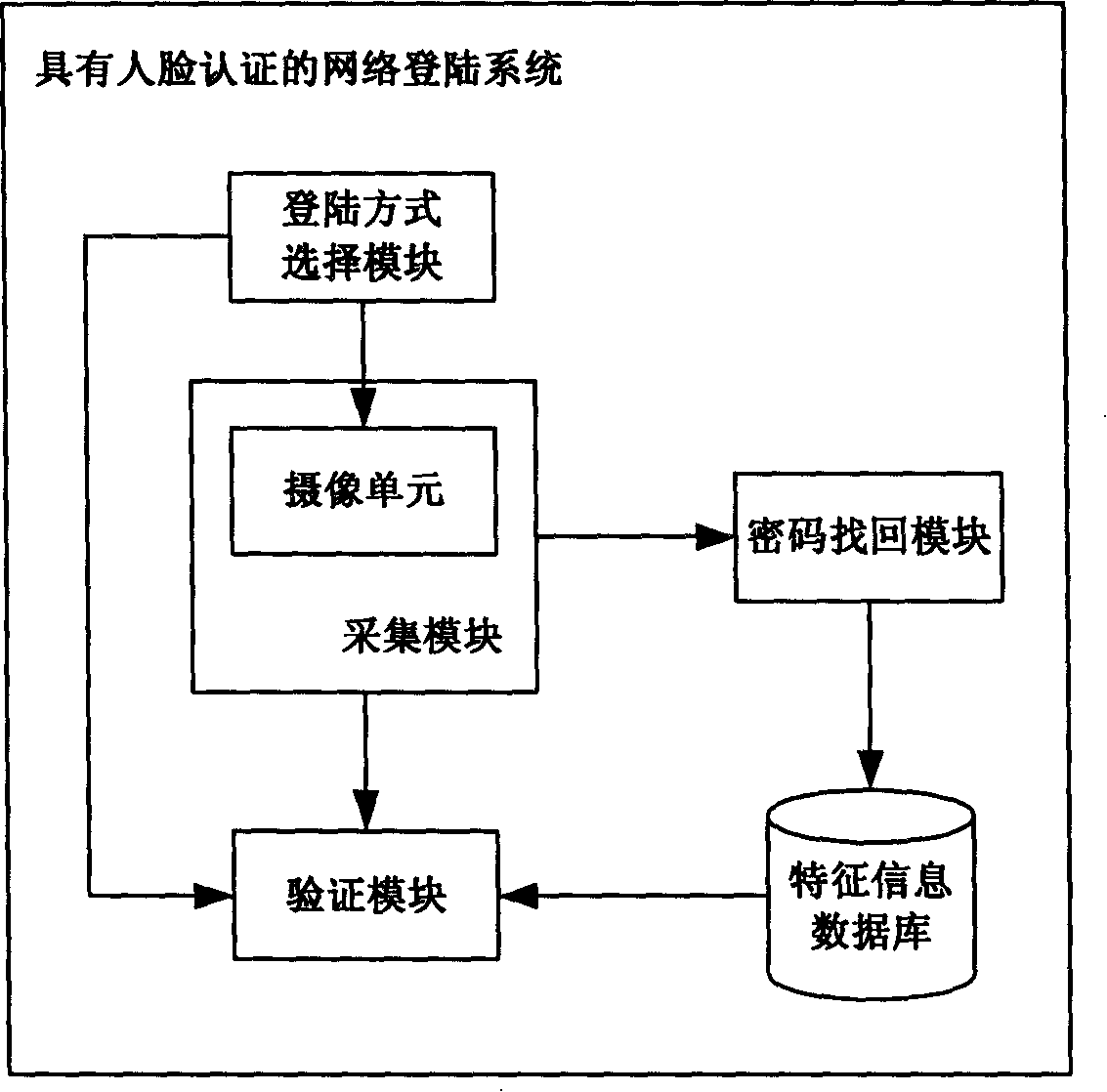
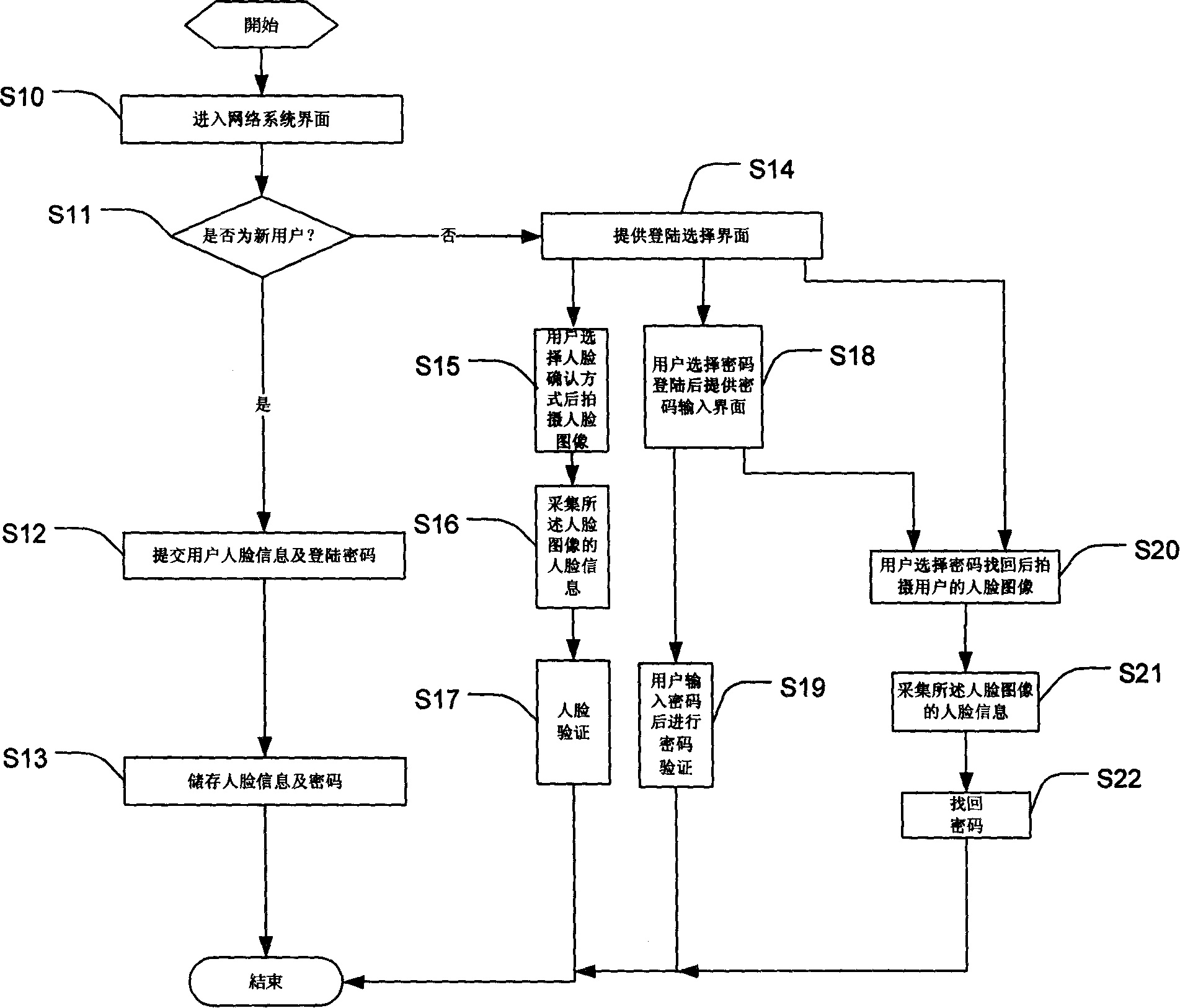
InactiveCN101174948ARealize the function of self-management of its login identityImprove securityUser identity/authority verificationCharacter and pattern recognitionUser codeComputer science
A network landing system with face identification and a landing method; the feature information which is submitted when a user registers on the network system and comprises the face information is memorized, when the user lands again, the corresponding validation is implemented according to the selected landing pattern, e.g. when user selects the pattern of face identification for landing, the face information of user is collected in real time to be compared with the one which is submitted when the user registers; in this way the real ID of the network user can be confirmed and the user code can be prevented from being stolen, the loss of the user ID can be prevented; at the same time, because the submitted face information in registration can be memorized locally, the network user can manage the landing ID, so the security of the user ID is promoted.
Owner:SHANGHAI ISVISION INTELLIGENT RECOGNITION TECH
Application program interface interception system and method
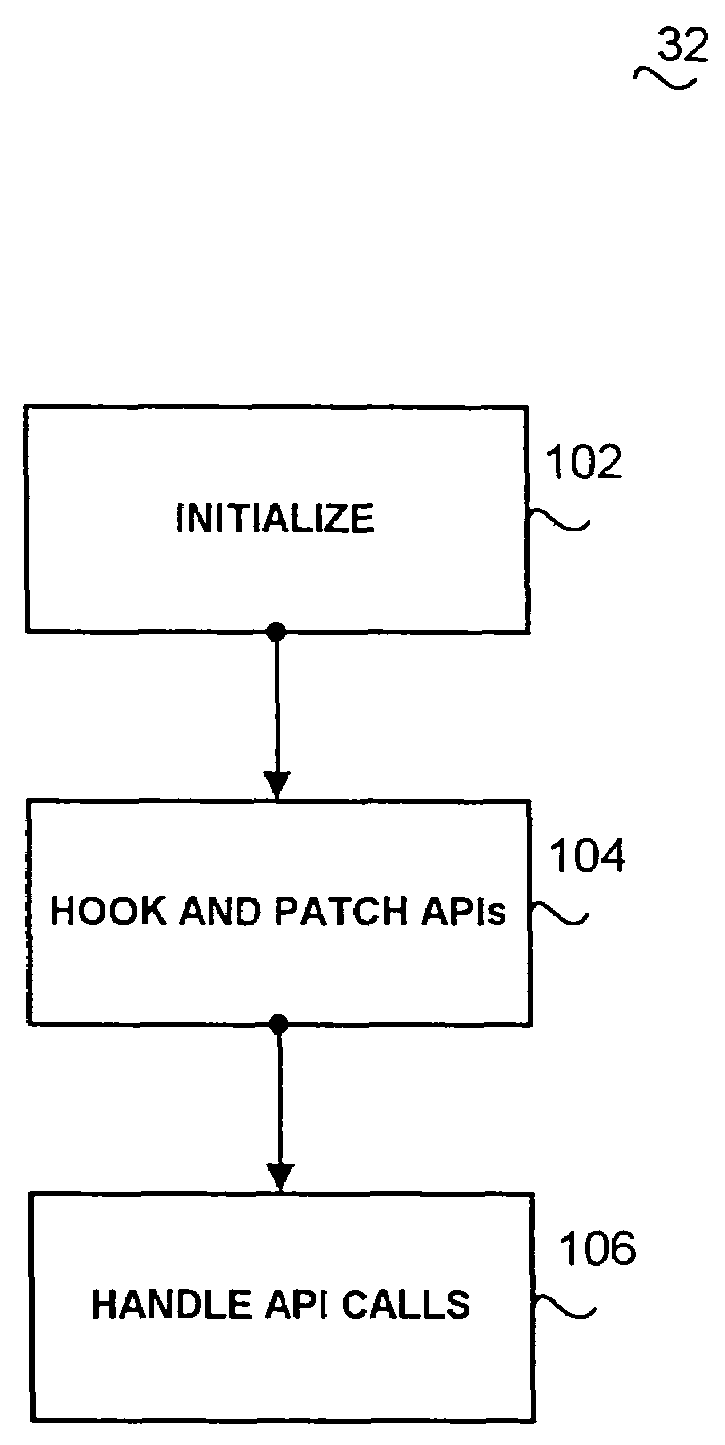
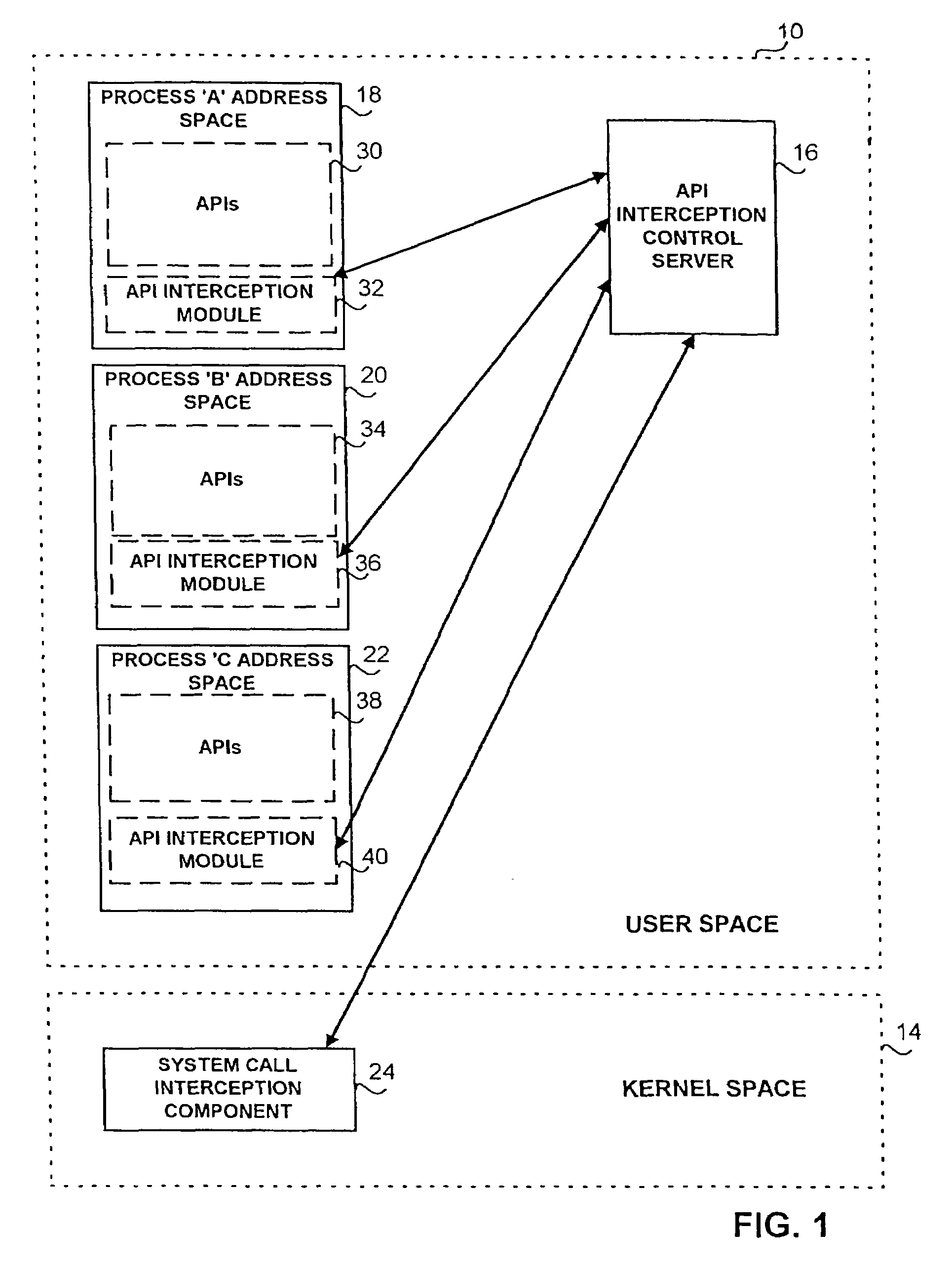
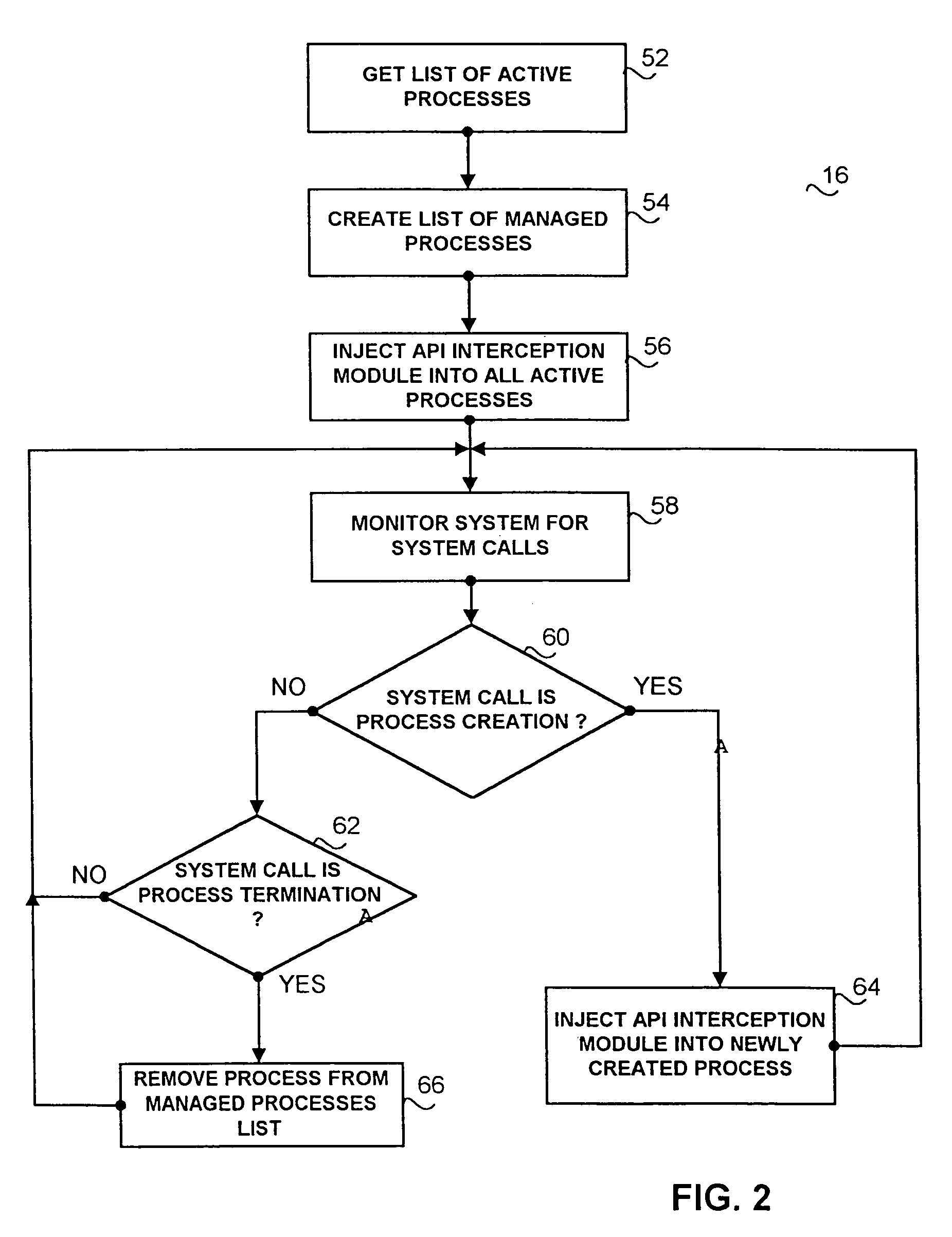
InactiveUS7213153B2Memory loss protectionUnauthorized memory use protectionOperational systemSystem call
A method of intercepting application program interface, including dynamic installation of associated software, within the user portion of an operating system. An API interception control server in conjunction with a system call interception module loads into all active process spaces an API interception module. An initializer module within the API interception module hooks and patches all API modules in the active process address space. When called by the application programs, the API routines' flow of execution, by virtue of their patched code, is re-directed into a user-supplied code in a pre-entry routine of the API interception module. The API routine might be completely by-passed or its input parameters might be filtered and changed by the user code. During the operation, the API routine is double-patched by the API interception module to ensure that all simultaneous calls to the API routine will re-direct its flow of control into the API interception module. A user-supplied code in a post-entry module of the API interception module might filter or change the return values of the API.
Owner:MCAFEE LLC
Method to enable user selection of segments in an instant messaging application for integration in other applications
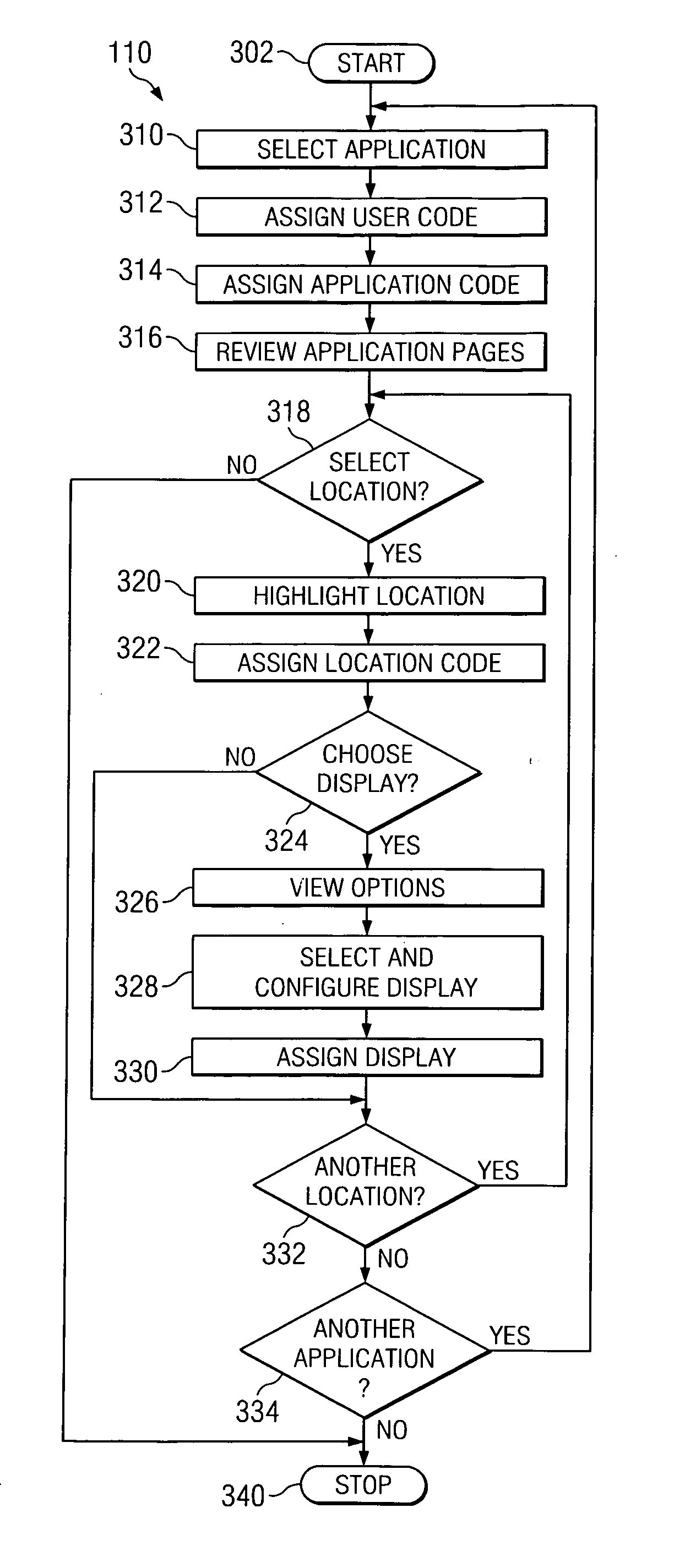
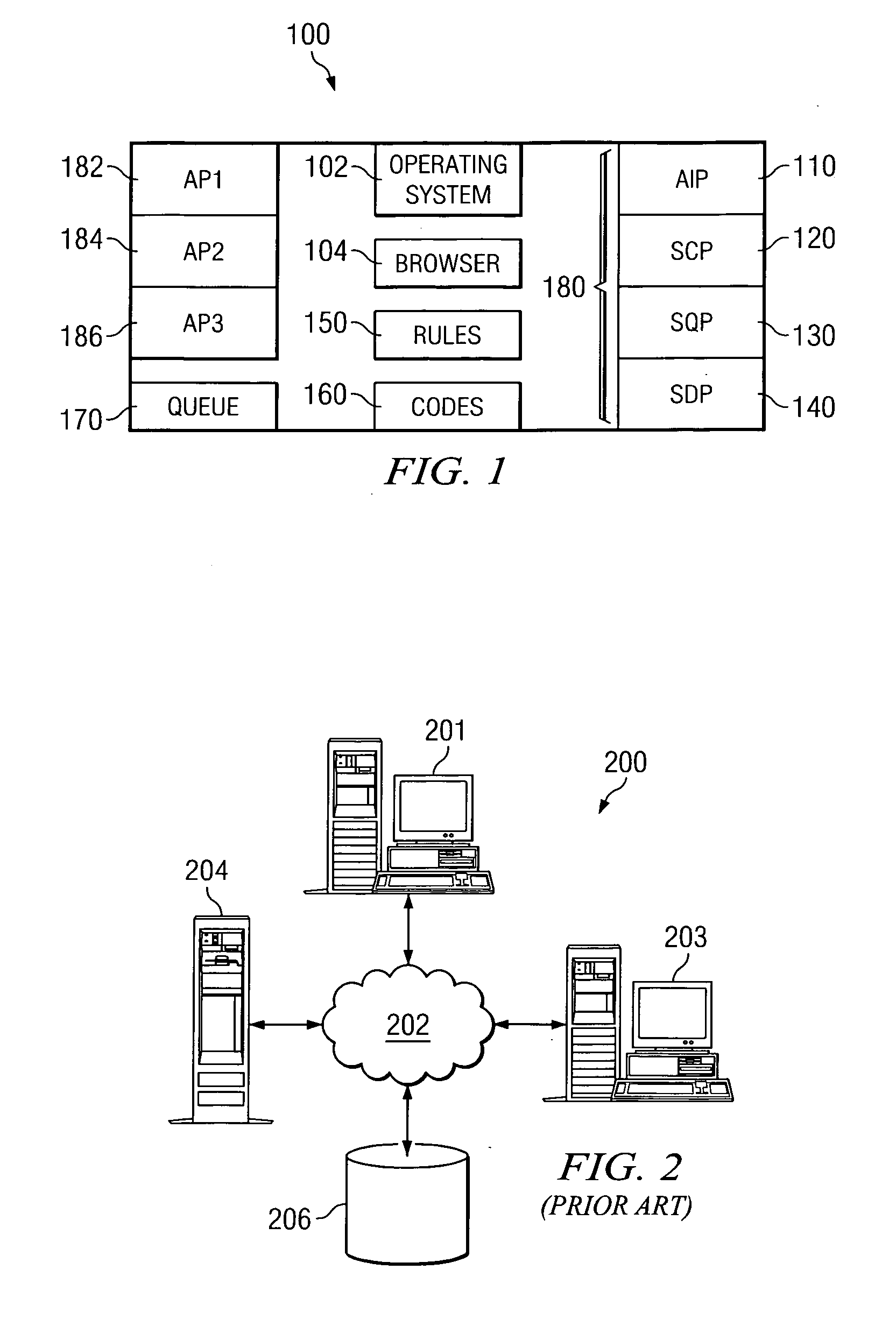
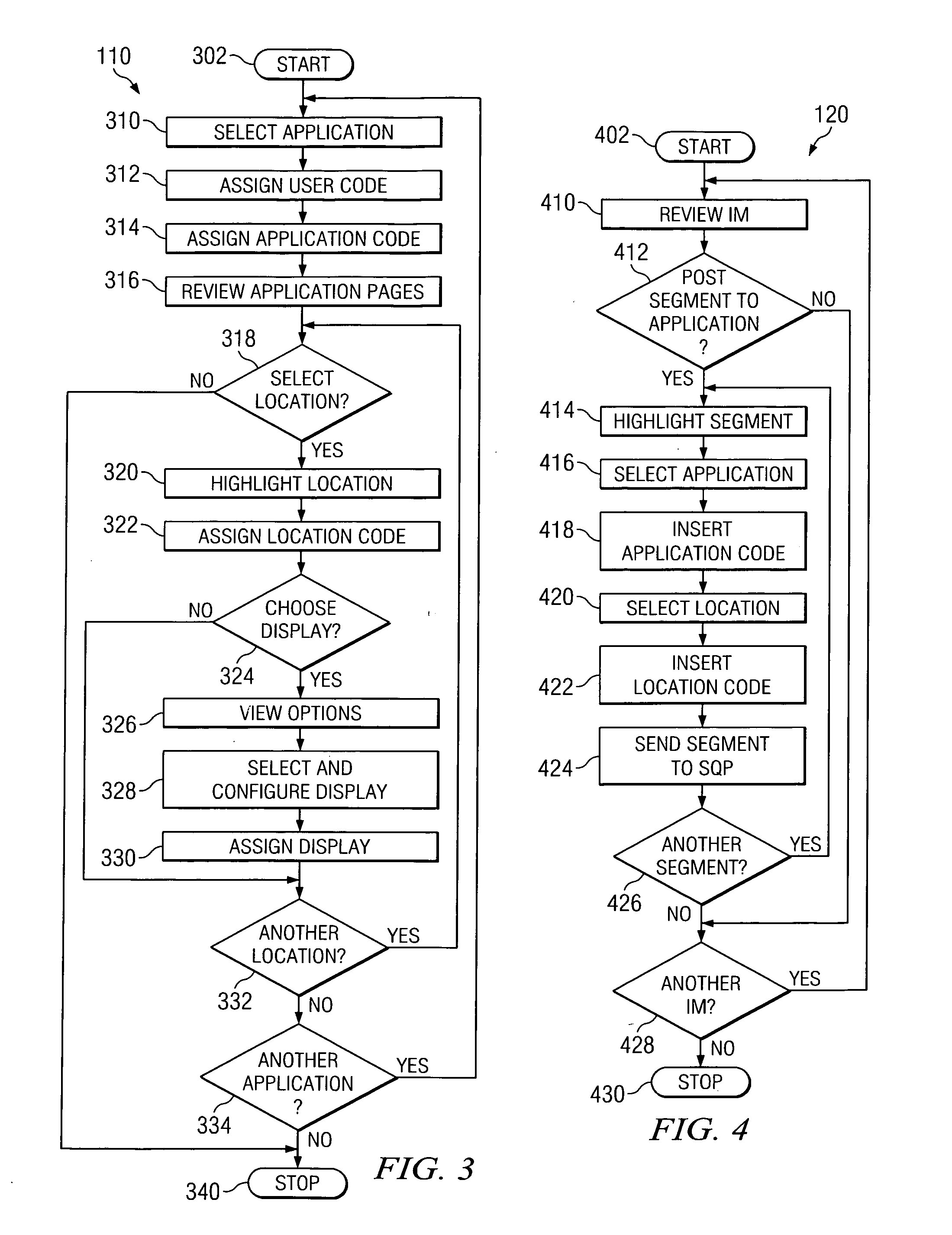
A Segment Interface Program (SIP) is disclosed that enables a user to choose locations in other applications to receive segments, and to mark segments for manual or automatic transmission to those applications. The SIP comprises an Application Interface Program (AIP), a Segment Creator Program (SCP), a Segment Queue Program (SQP), and a Segment Delivery Program (SDP). The SIP accesses a Rules database, a codes database, and a queue database. The AIP enables a user to select a location in an application and assign an application code and a location code to the location. The SCP enables a user to select a segment in a chat transcript, assign an application code and a location code to the segment, and send the segment to the SQP. The SQP receives the segment, assigns a queue number, and places the segment in a queue table. The SDP reads the user code, the application code and, when the application is active, sends the segment to the location in the application with the corresponding code. A single segment may be inserted into an application in multiple locations by creating additional codes for multiple instances of a location.
Owner:IBM CORP
Sandboxing technology for webruntime system
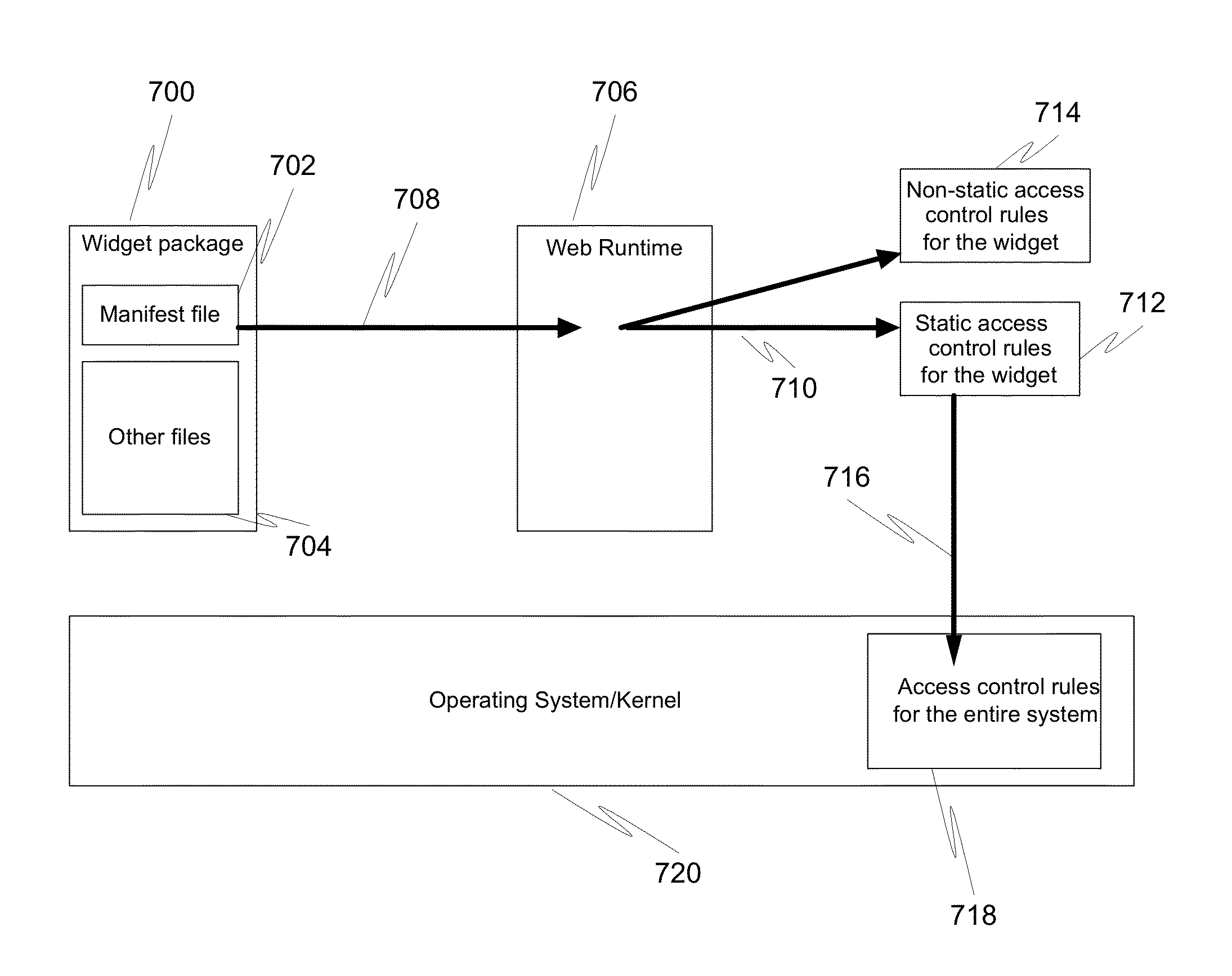
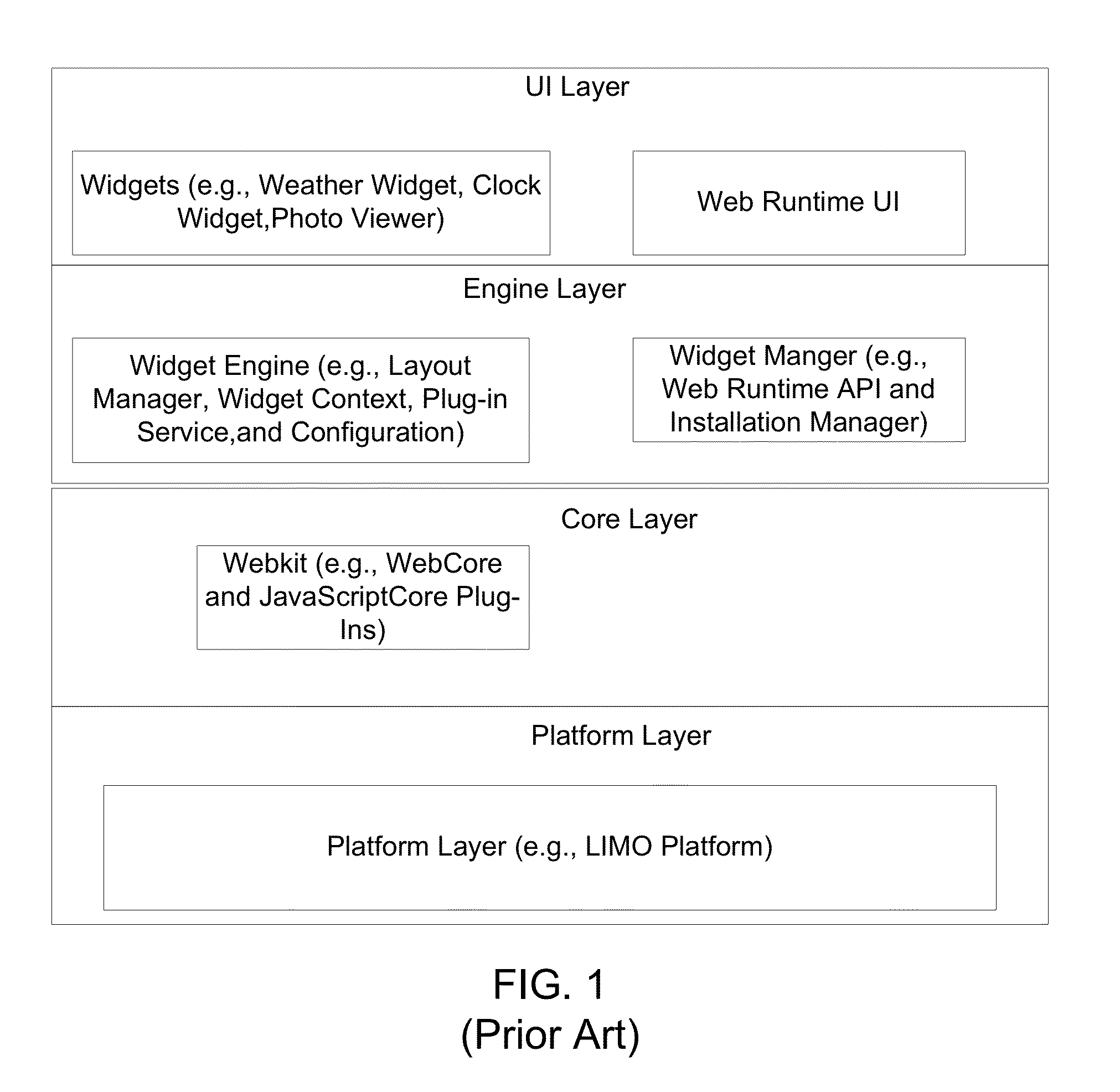
ActiveUS20130036448A1Improved widget securityPlatform integrity maintainanceProgram controlUser codeAccess control
In a first embodiment of the present invention, a method of providing security enforcements of widgets in a computer system having a processor and a memory is provided, comprising: extracting access control information from a widget process requesting a service, generating access control rules customized for the widget process, and providing the access control rules to a trusted portion of the computer system outside of the user code space of a Web Runtime (WRT) system; and for any static access control rule, delegating security checking of the widget process from the WRT system to the trusted portion of the computer system.
Owner:SAMSUNG ELECTRONICS CO LTD
Software integration testing method and system based on extensible markup language (XML) database
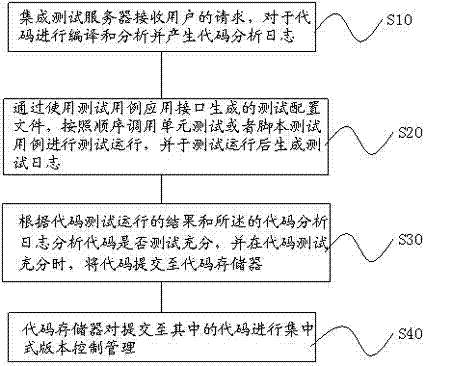
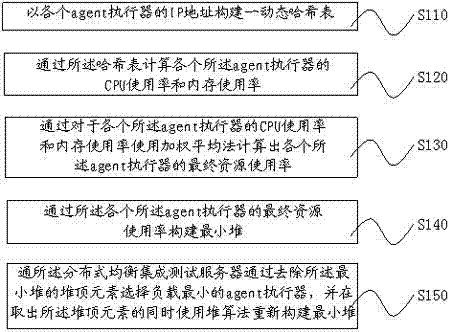
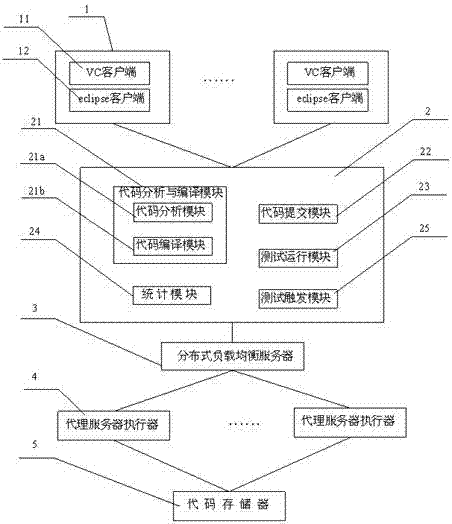
InactiveCN102880546AQuality improvementImprove accuracySoftware testing/debuggingSpecial data processing applicationsContinuous integrationIntegration testing
The invention provides a software integration testing method and a software integration testing system based on an extensible markup language (XML) database. An operation interface for extending a test case, a distributed load equalizer based on a minimum heap and Hash algorithm and code automatic compilation, analysis and submission functions are provided. A tester only needs to upload a compiled test case to a code memory, the operation interface which is provided by an integrated testing server of a testing tool is used for configuration, and new test case addition and continuous integration functions can be realized. Under the condition of addition or reduction of test resources, by dynamically constructing minimum heap and Hash, the distributed load equalizer can automatically meet requirements of new environment. By adoption of the code automatic compilation, analysis and submission functions, the submission quality of user codes is improved. Continuous integration in software is realized, the accuracy of code submission is improved, and the regression efficiency of test is improved. Moreover, by adoption of a distributed design idea, the problems about resource bottleneck of a testing machine and platform automatic selection are solved, and the utilization rate of resources is improved.
Owner:PEKING UNIV FOUNDER GRP CO LTD +2
Method and Arrangement for Secure Authentication
ActiveUS20090119759A1Digital data processing detailsUser identity/authority verificationData terminalComputer terminal
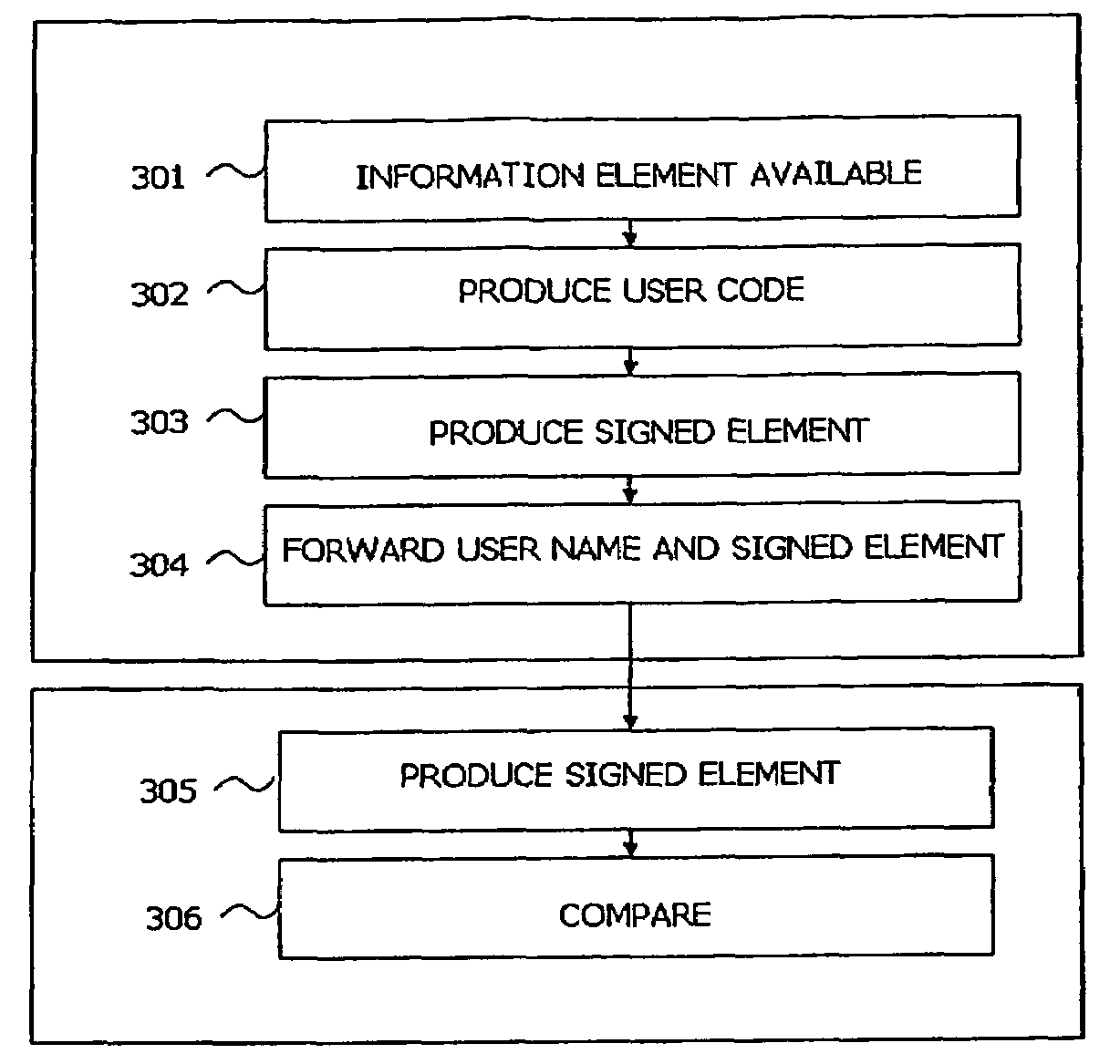
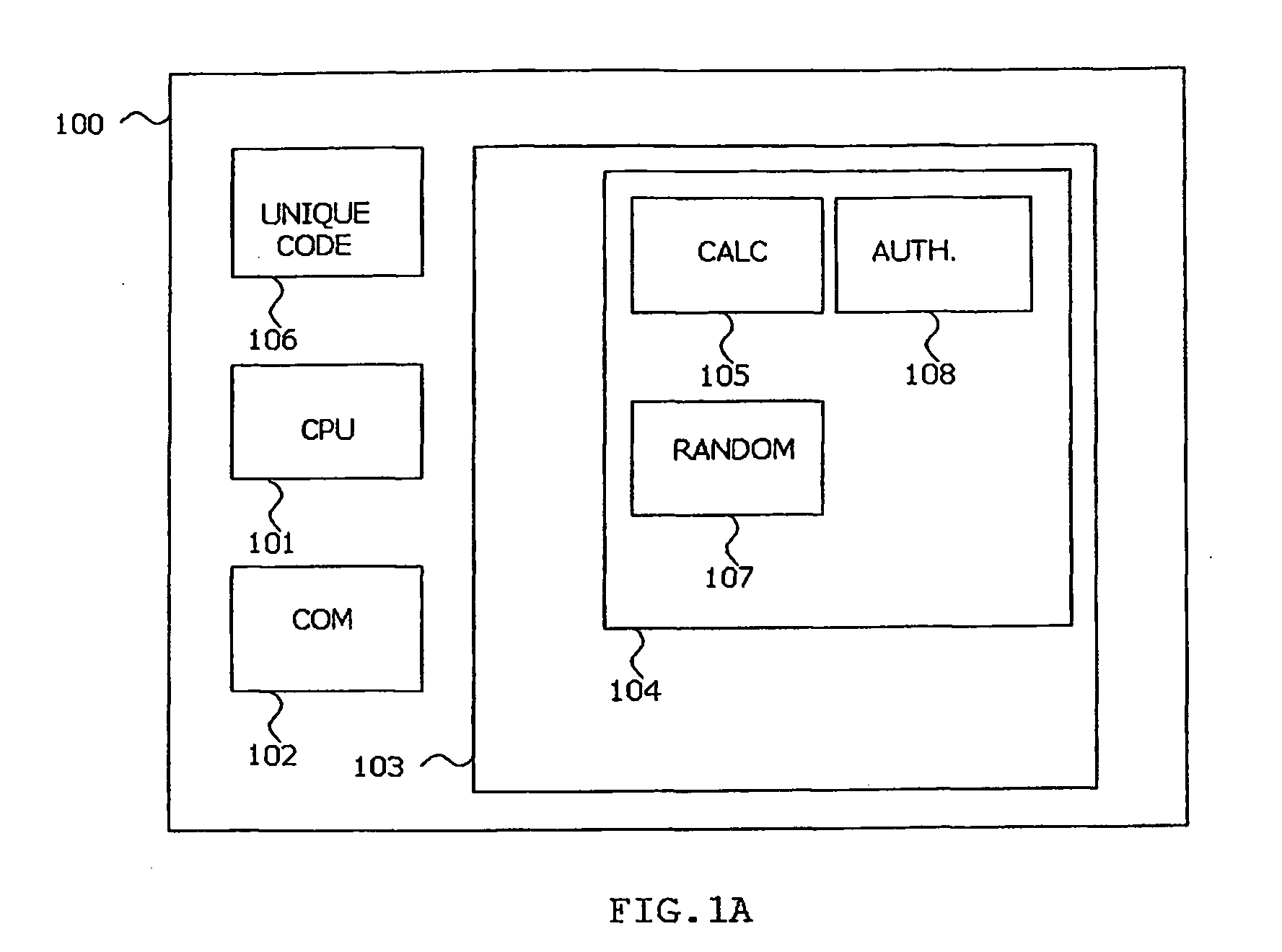
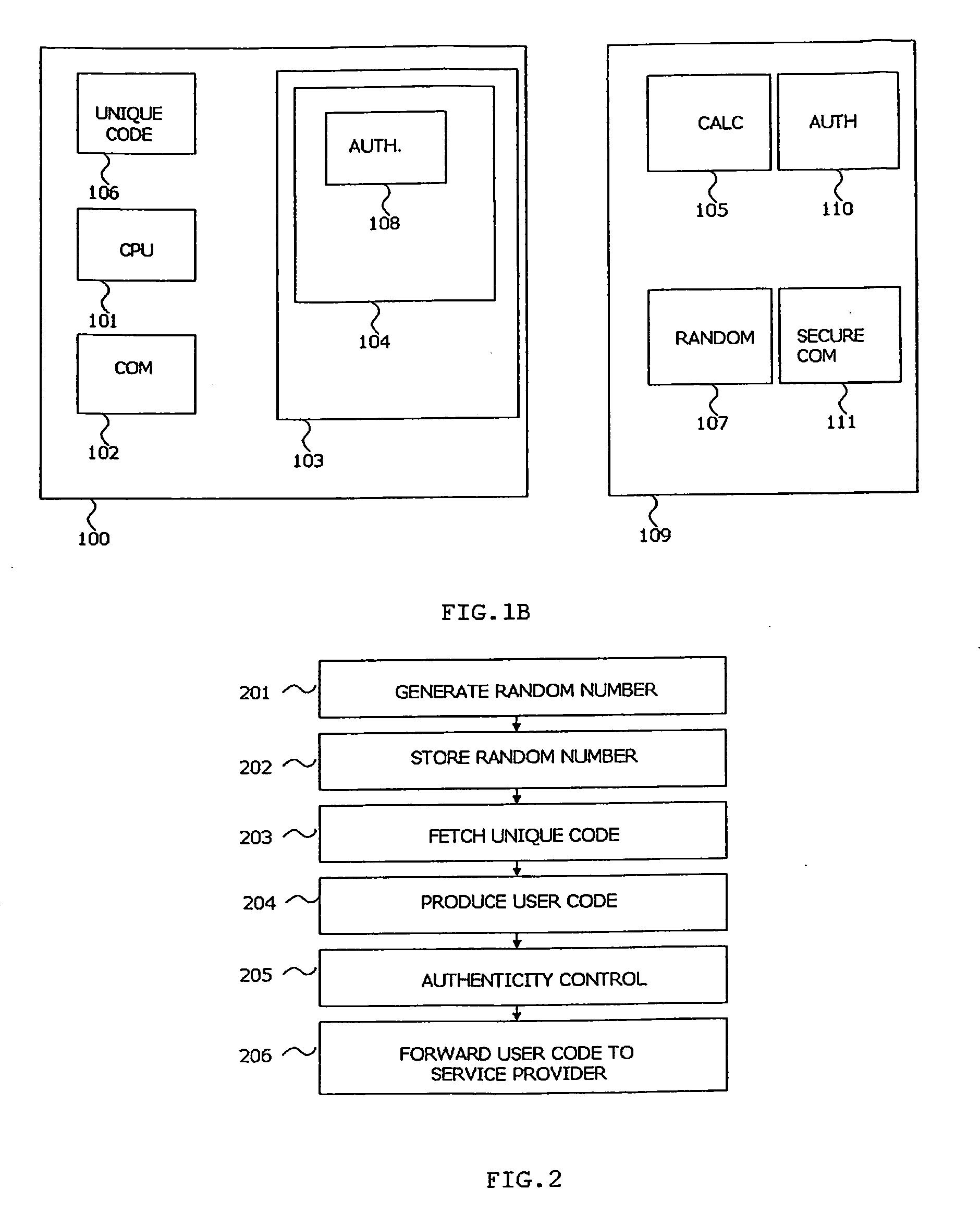
A method and arrangement for utilising a generally available personal data terminal as a secure and reliable authentication factor for user authentication is described. Also, a method for secure transfer of data between two parties, a user and a service provider, where the user generates a unique authentication factor adapted for user authentication (104), called a user code, and the service provider registering the user's user code as an authentication factor is disclosed. The method is useful for various security services involving a user and a service provider in electronic channels where service providers are faced with the challenges of authenticating the users of their services.
Owner:ENCAP AS
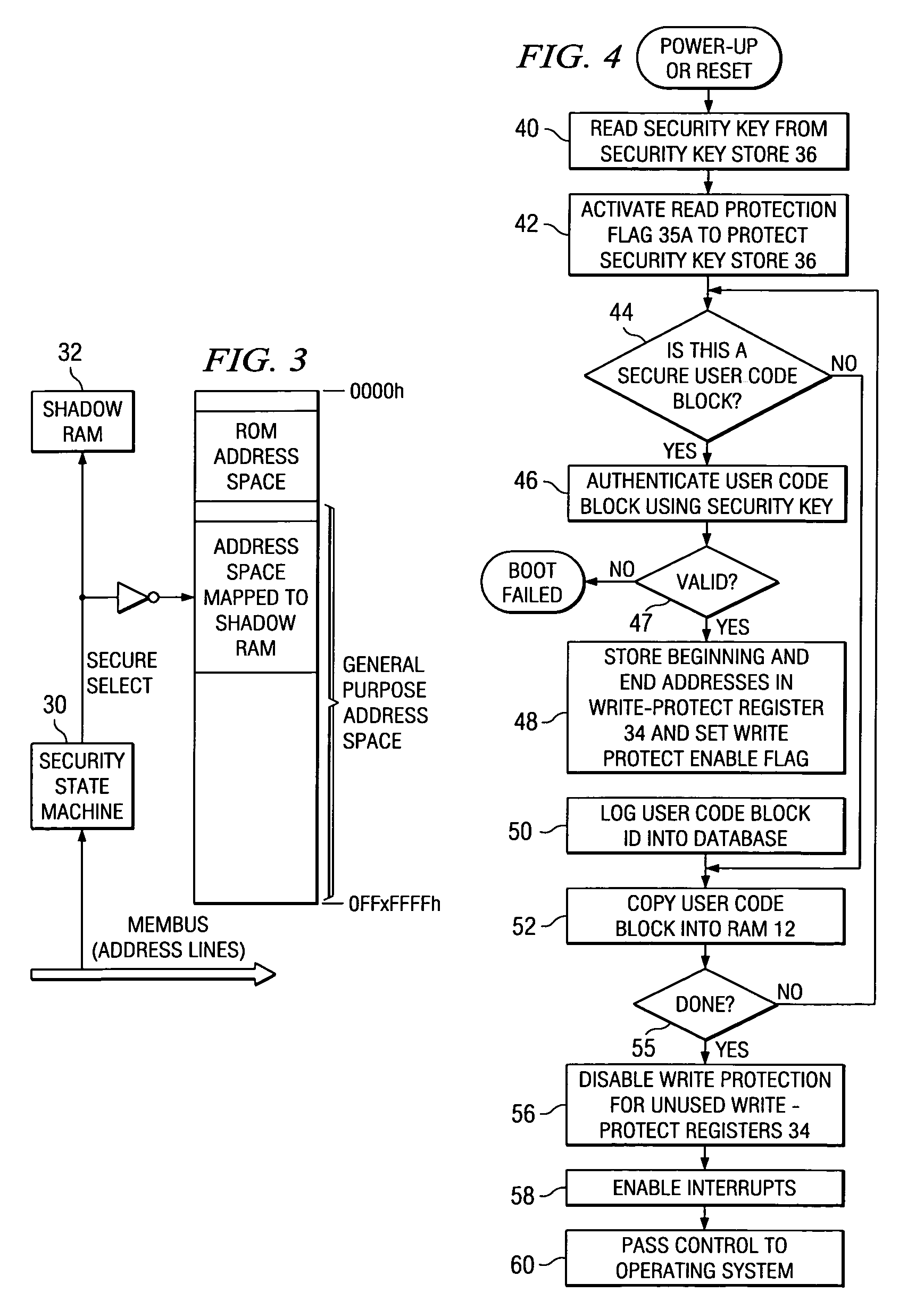
Implementation of a secure computing environment by using a secure bootloader, shadow memory, and protected memory
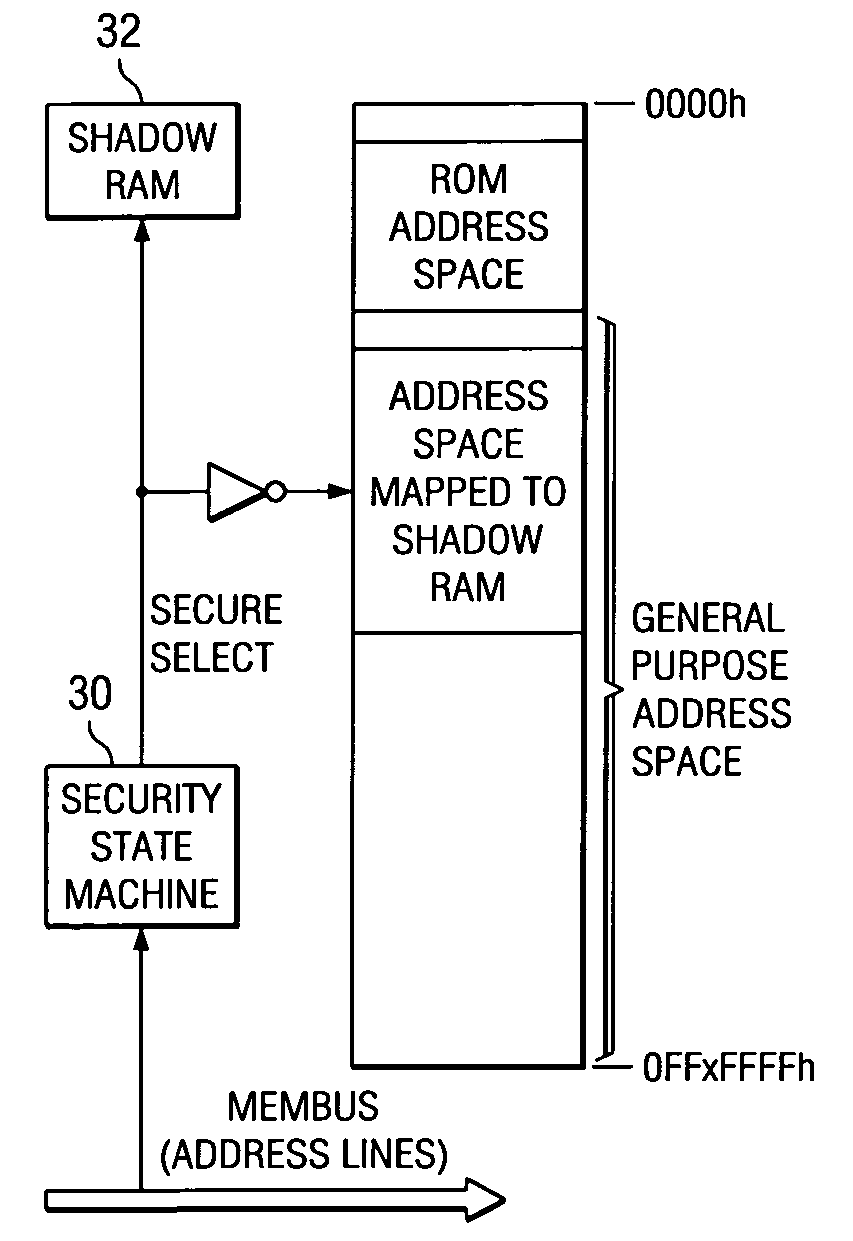
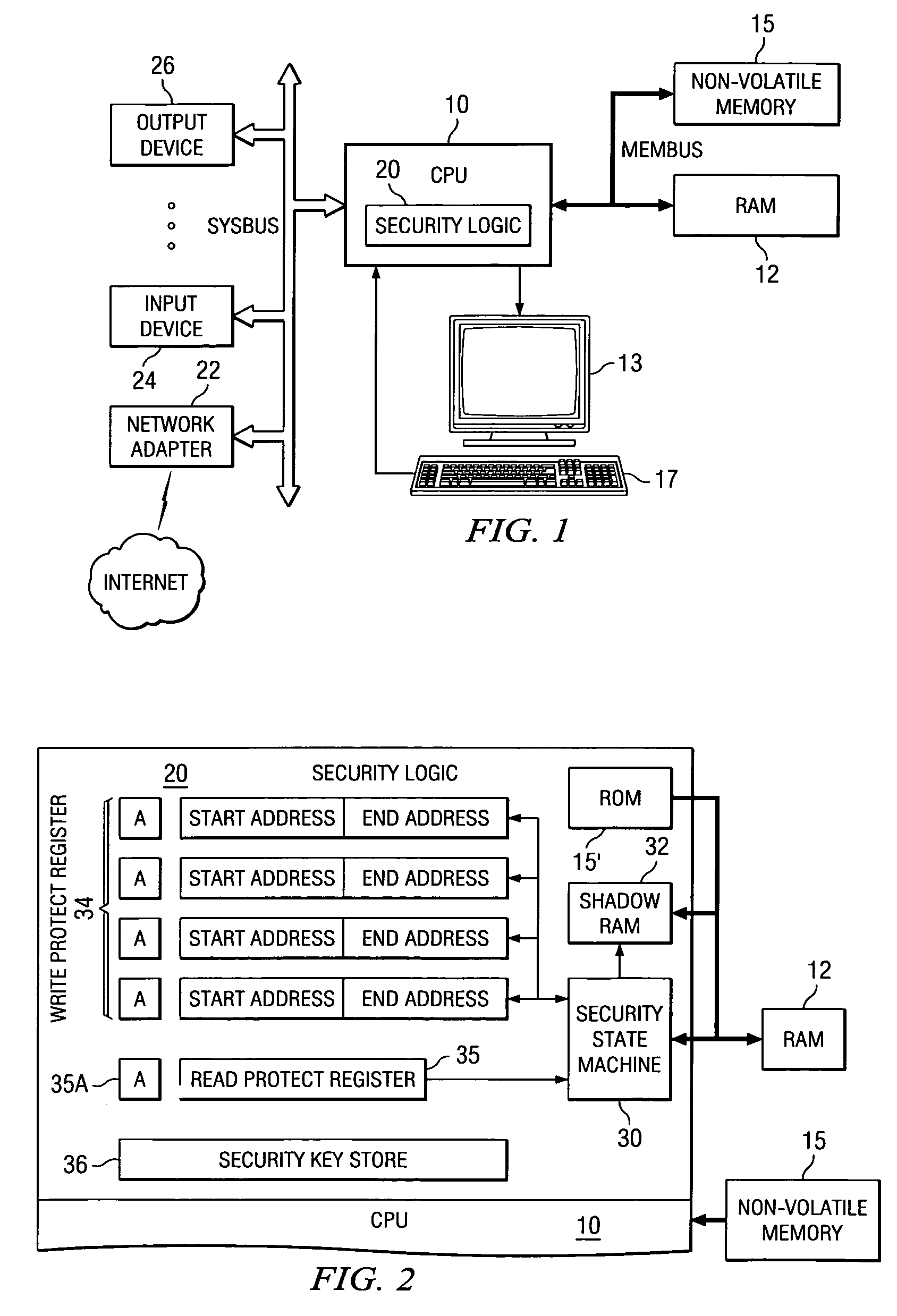
A computer system with a secure bootloading function is disclosed. Security logic (20) is implemented on-chip with a central processing unit (CPU) (10), and performs security functions following a system reset, such as upon power-up or a hardware or software reset. A security key value from a security key store (36), which is read-protected from subsequent read accesses, is used to authenticate each code block associated with secure applications. Write-protect registers (34) store the memory addresses of authenticated code blocks, so that these code blocks cannot be altered. A shadow memory (32) is provided on-chip with the CPU (10), to which access is granted for program instructions having a physical memory address within the memory address ranges stored in the write-protect registers (34), and thus usable by the secure applications. Successful authentication of the user code block ensures that the bootloaded code is not corrupt, prior to passing control to the operating system.
Owner:TEXAS INSTR INC
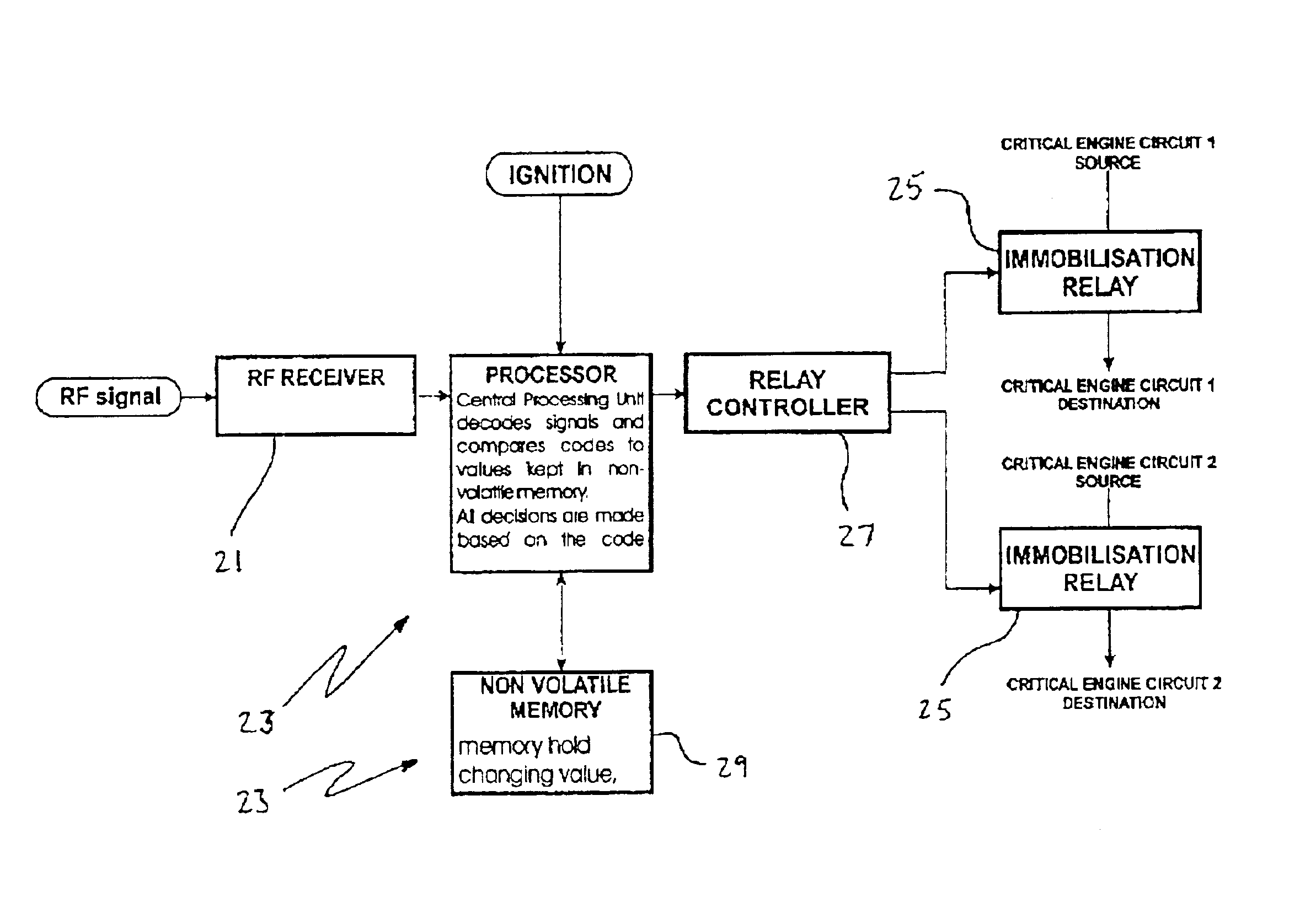
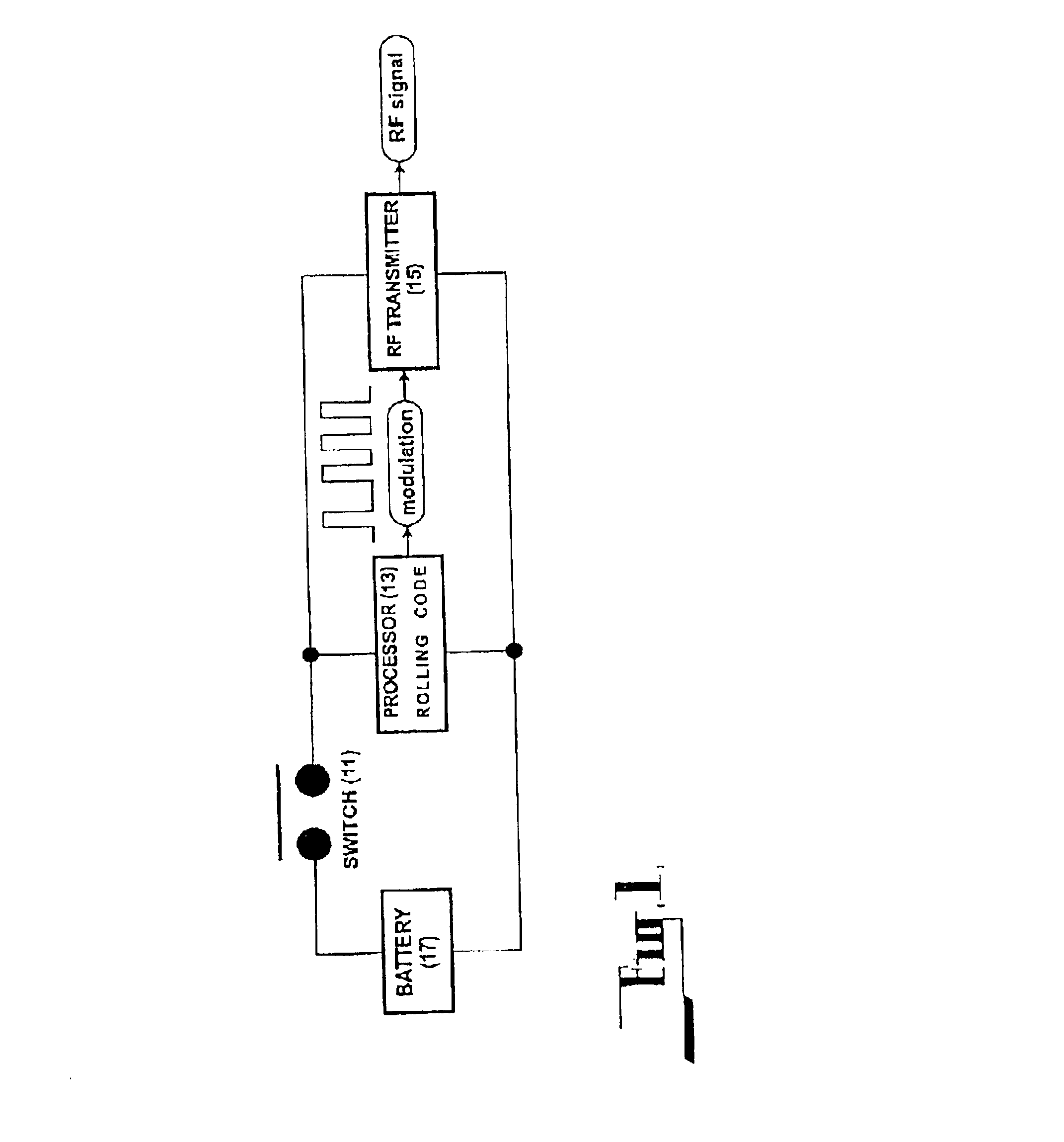
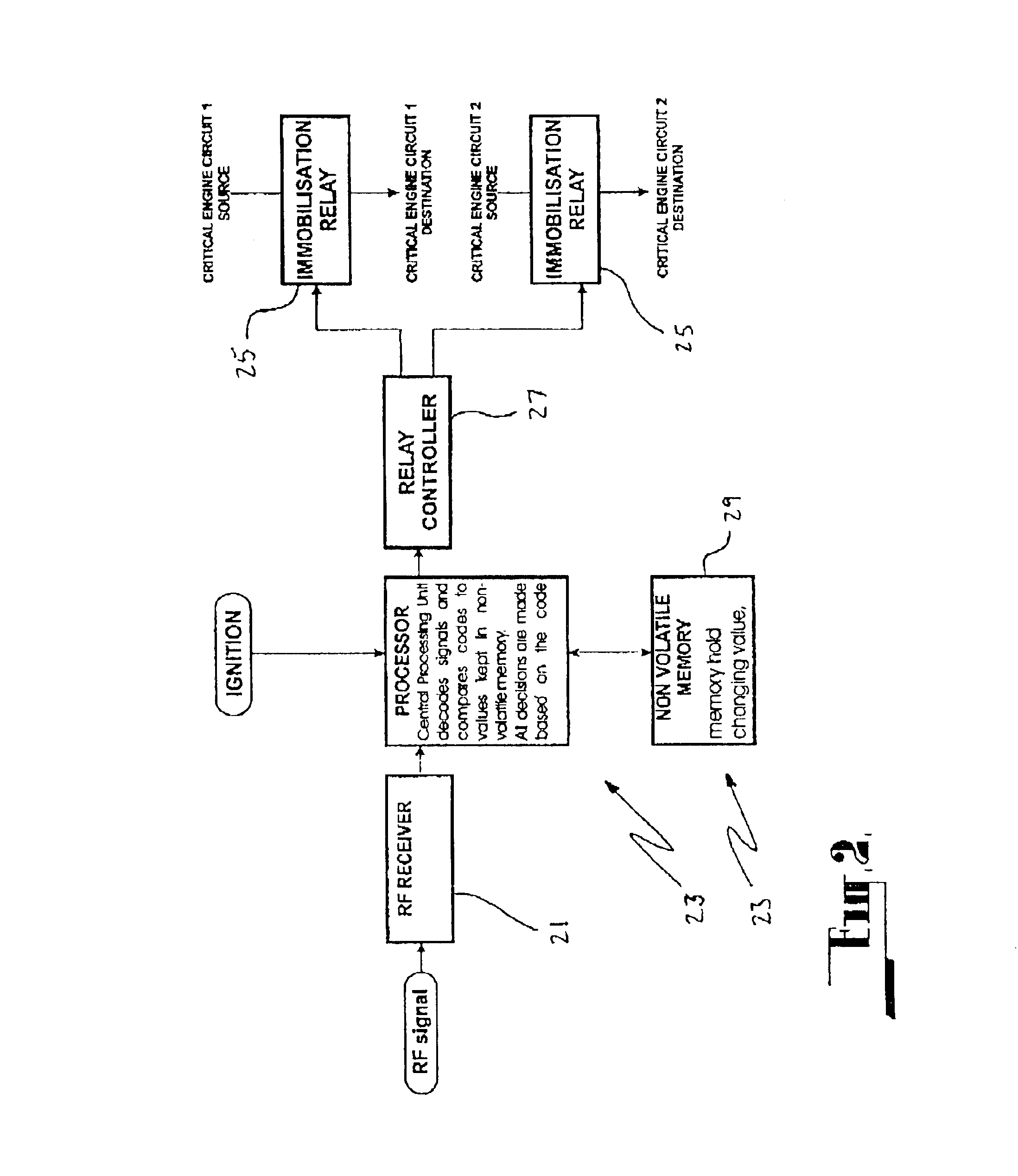
Vehicle immobiliser/alarm
InactiveUS6809636B2Save a lot of timeElectric signal transmission systemsAnti-theft cycle devicesHand heldUser code
A security system having security devices with hierarchical levels of access provided to coded keys which may be hand held transmitter units, is disclosed. The levels of access are master which is restricted to the manufacturer, seller and installer, supervisor which can be allocated to a site, and user which is usually specific to one security device only. The security devices can be programmed to be responsive to all of the supervisor coded keys and / or user coded keys, or a user coded key only. The security system can be used in a method of securing all vehicles at a car sales, where all of the vehicles can have their security devices programmed to be responsive to supervisor coded keys specific to the car sales site. When a vehicle is sold, its security device can be reprogrammed to be responsive to specific user coded keys only.
Owner:DYNAMCO
Test executive which provides heap validity checking and memory leak detection for user code modules
ActiveUS20060143537A1Improve executionImprove execution performanceError detection/correctionCode moduleTest execution
A system and method for automatically detecting heap corruption errors and memory leak errors caused by user-supplied code modules that are called by steps of a test executive sequence. The test executive sequence may first be created by including a plurality of test executive steps in the test executive sequence and configuring at least a subset of the steps to call user-supplied code modules. The test executive sequence may then be executed on a host computer under control of a test executive engine. For each step that calls a user-supplied code module, the test executive engine may perform certain actions to automatically detect whether the user-supplied code module causes a heap corruption error and / or automatically detect whether the user-supplied code module causes a memory leak error.
Owner:NATIONAL INSTRUMENTS
Method of customizing a user's browsing experience on a World-Wide-Web site
In accordance with a first aspect of the present invention, a method of customizing the browsing experience of a user of a Web site comprised of a plurality of Web pages is provided. Each Web page is indexed using at least one coding system. A user record for each user is maintained on the Web site, which contains personal information of the user coded in accordance with said coding system. The user's browsing experience on the site may thus be readily customized using the user's personal information via code comparison. In accordance with a second aspect of the present invention, a method of ensuring the privacy of the user's personal information is provided through use of a unique Universal Anonymous Identifier (UAI) assigned to each user by a third party registration authority.
Owner:PERSONALPATH SYST
Imaging system having preset processing parameters adapted to user preferences
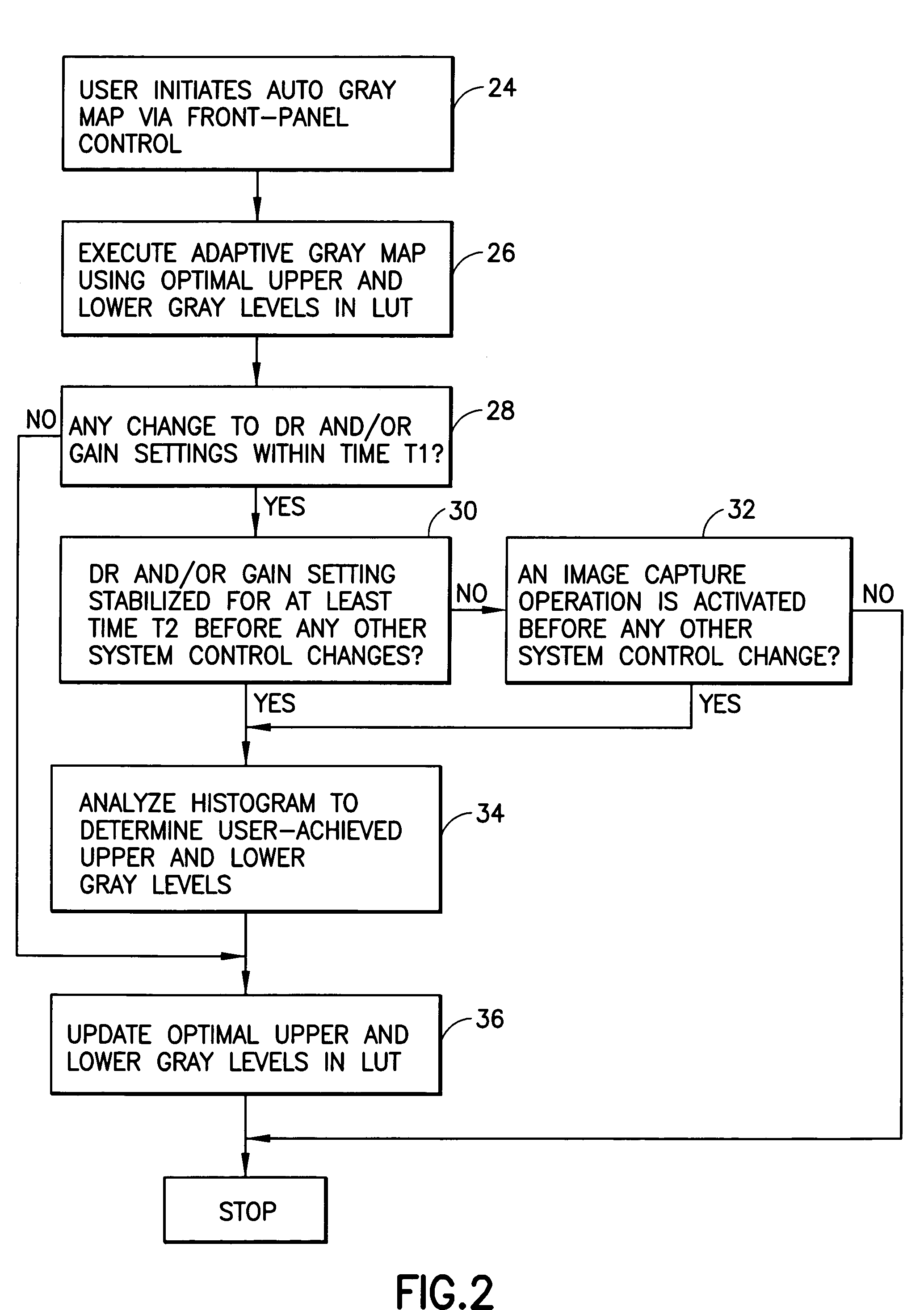
InactiveUS7062714B1Fast approachInput/output for user-computer interactionUltrasonic/sonic/infrasonic diagnosticsControl setImaging processing
An imaging system has a computer which monitors changes to any given front-panel control setting for a particular image processing parameter (e.g., dynamic range, transmit foci position, Doppler wall filter setting, etc.) as compared to its default or preset value. For each user ID (e.g., based on the system user's name or any user code) and each application type, if, over a number of exam cycles, the user is found to consistently adjust a particular control setting to values that deviate significantly from the preset value, the system computer will automatically adjust the preset value to, e.g., the average setting of that image processing parameter over the past N trials, where N is a predefined integer number.
Owner:GE MEDICAL SYST GLOBAL TECH CO LLC
Convenient and fast car sharing system and method for commute
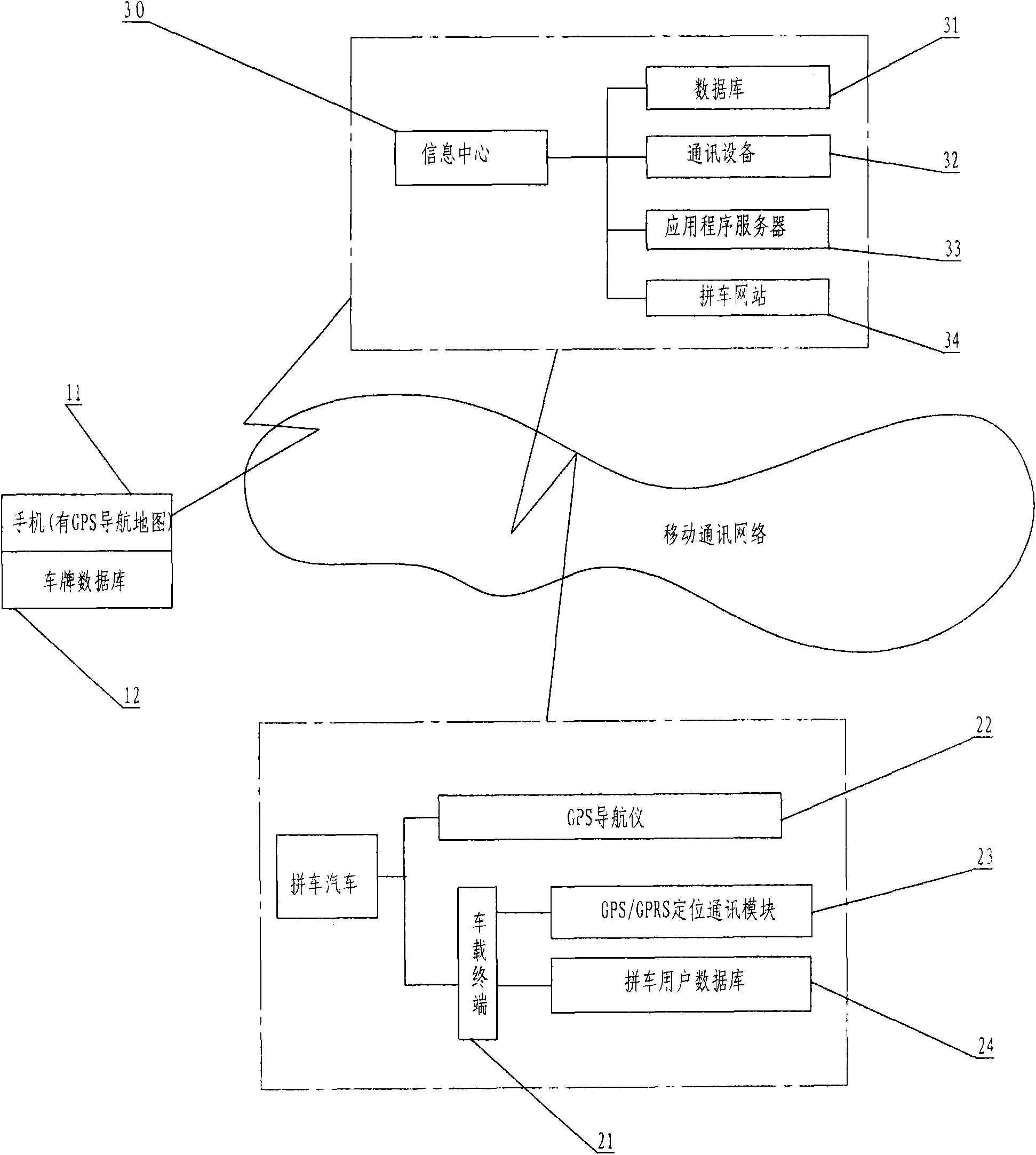
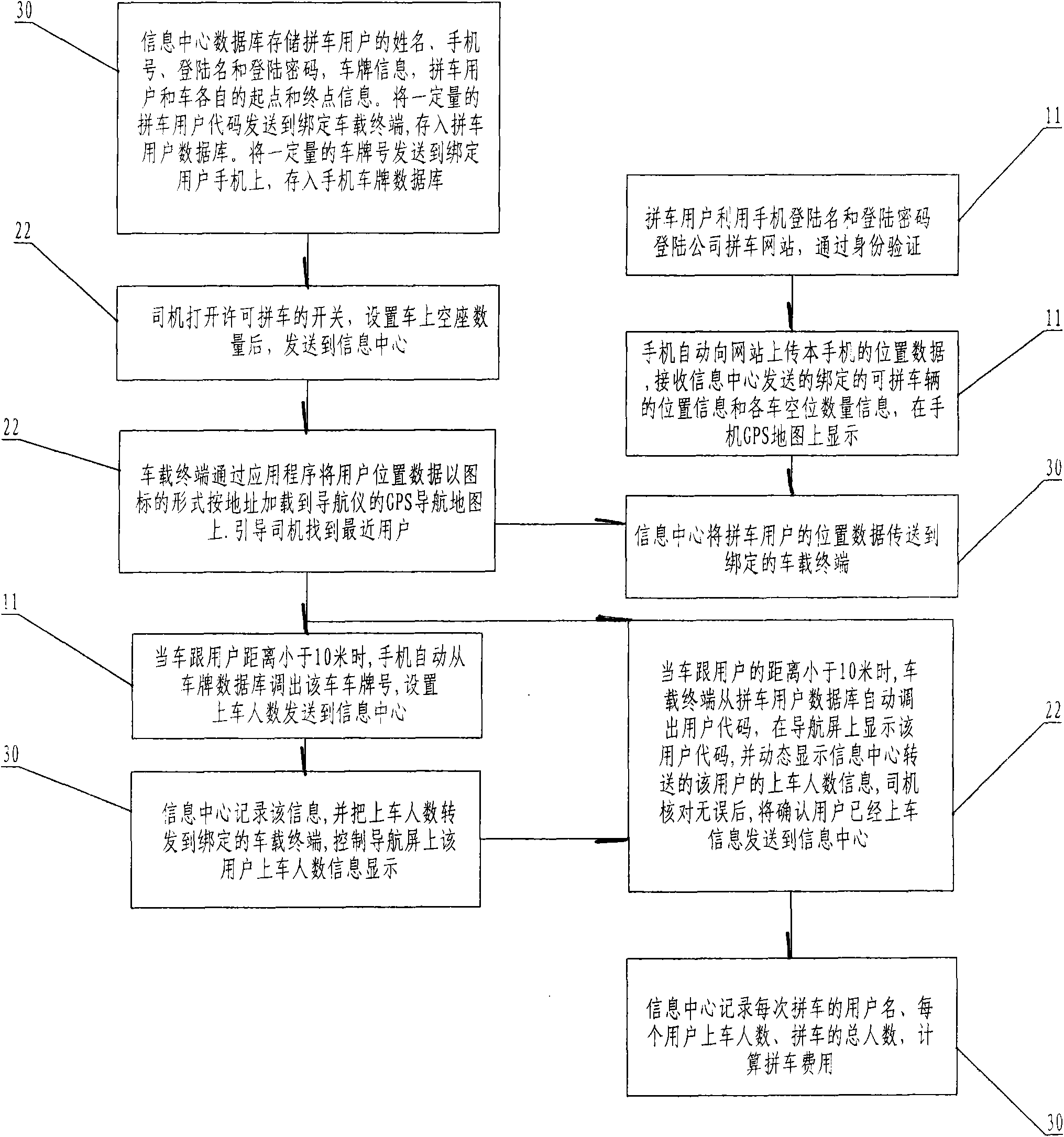
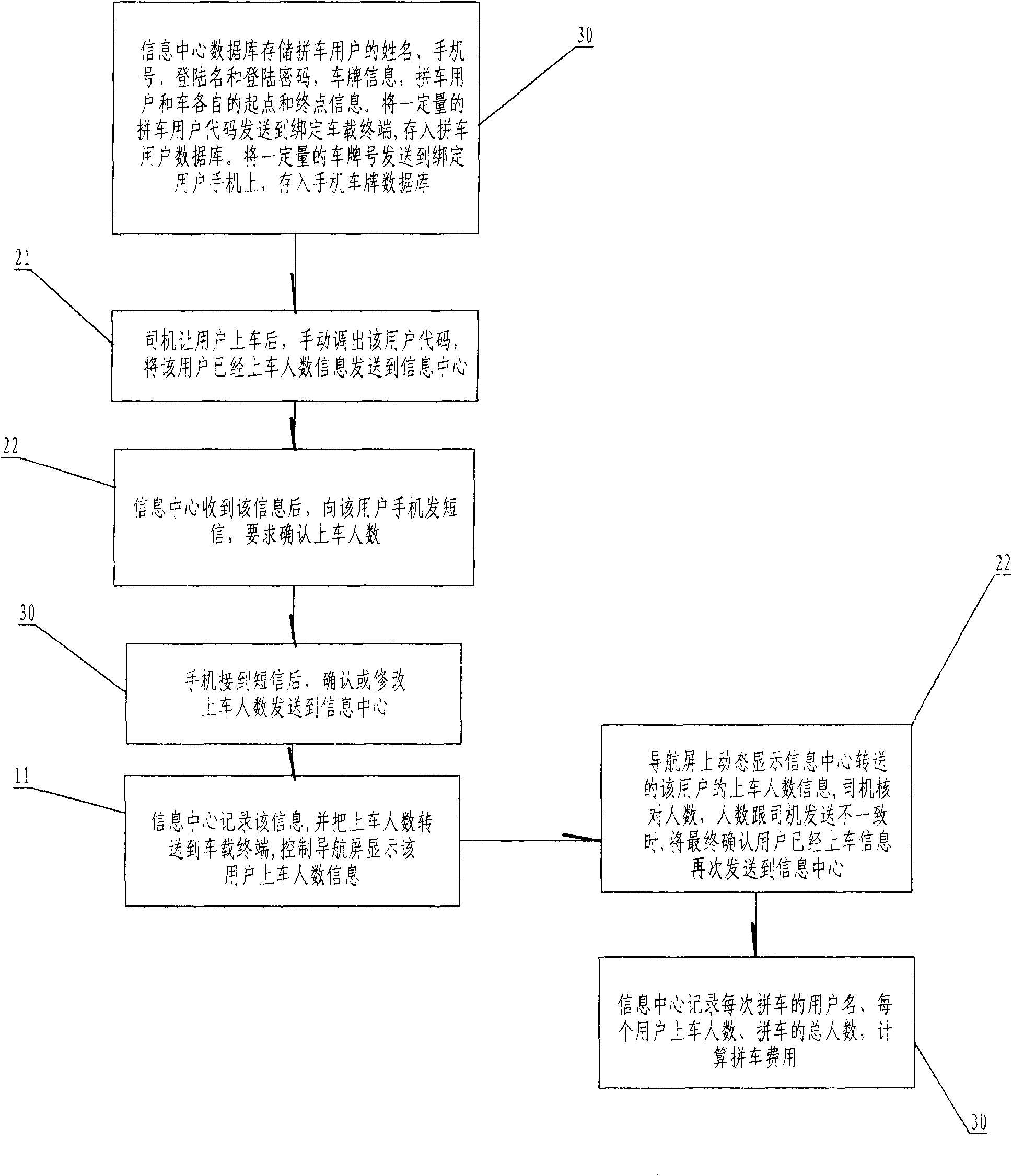
InactiveCN102592244AEnsure safetyLegal and reliableInstruments for road network navigationData processing applicationsCar sharingComputer terminal
The invention discloses a convenient and fast car sharing system and a convenient and fast car sharing method for commute. The system consists of a user mobile phone, a sharing car and an information center. A data communication passage and a management platform are built between a driver and a car sharing user by using the information center, the user mobile phone and a vehicle-mounted terminal, user codes and license plate numbers are utilized as major operation data for implementing the car sharing, and the convenient and free car sharing between the driver and the car sharing user is realized. The car sharing system and the method have the advantages that the safety, the reliability and the simplicity in the car sharing process can be ensured, and meanwhile, the calculation and the sharing of the car sharing cost are also simplified.
Owner:周军现
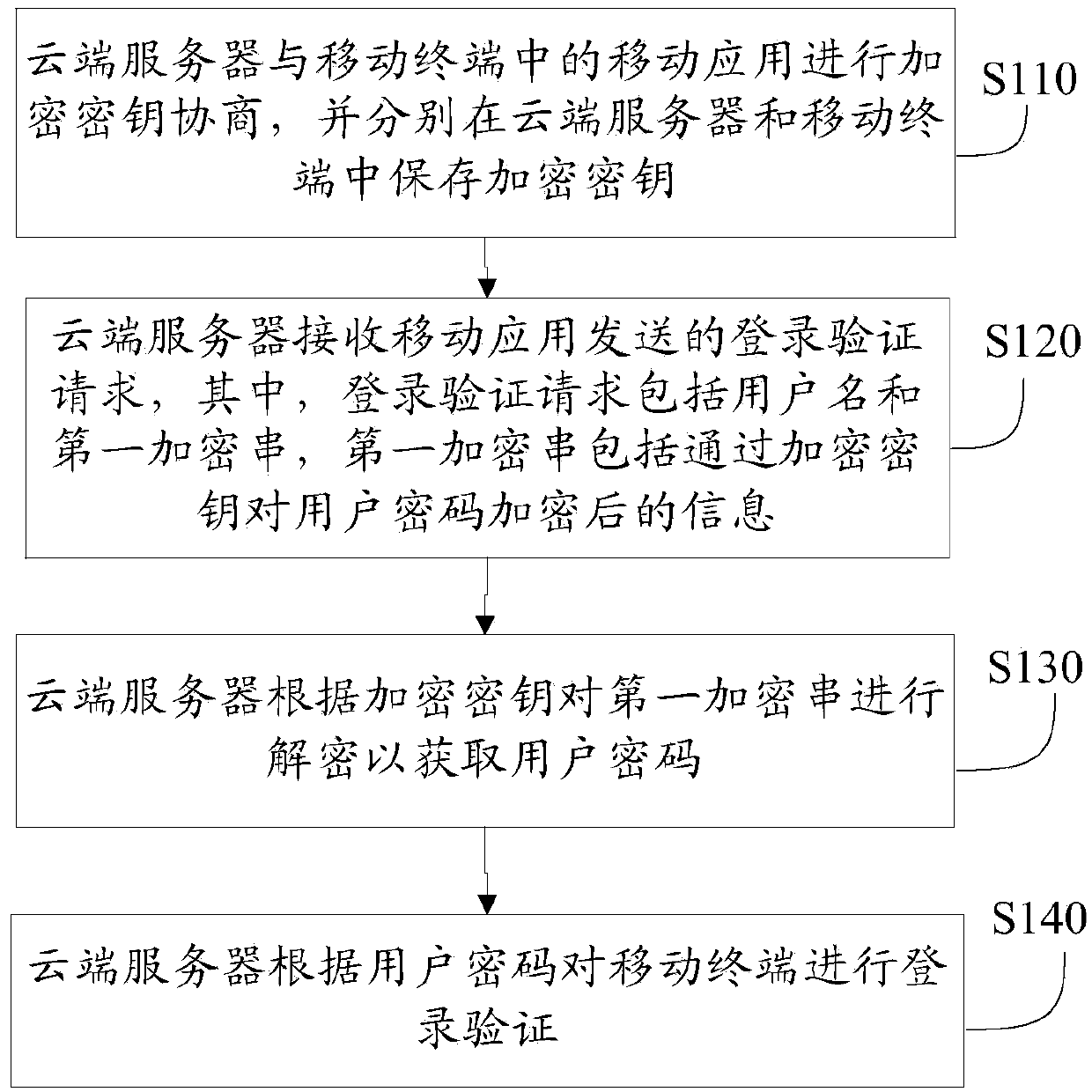
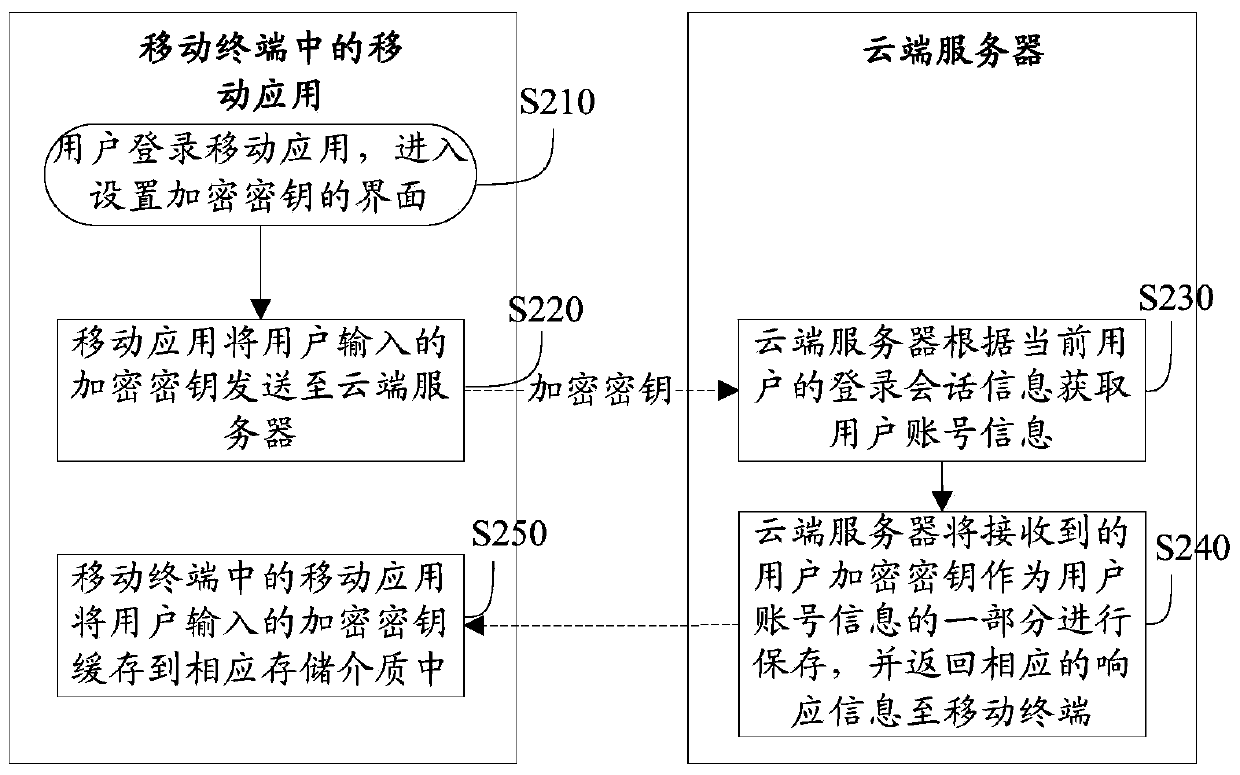
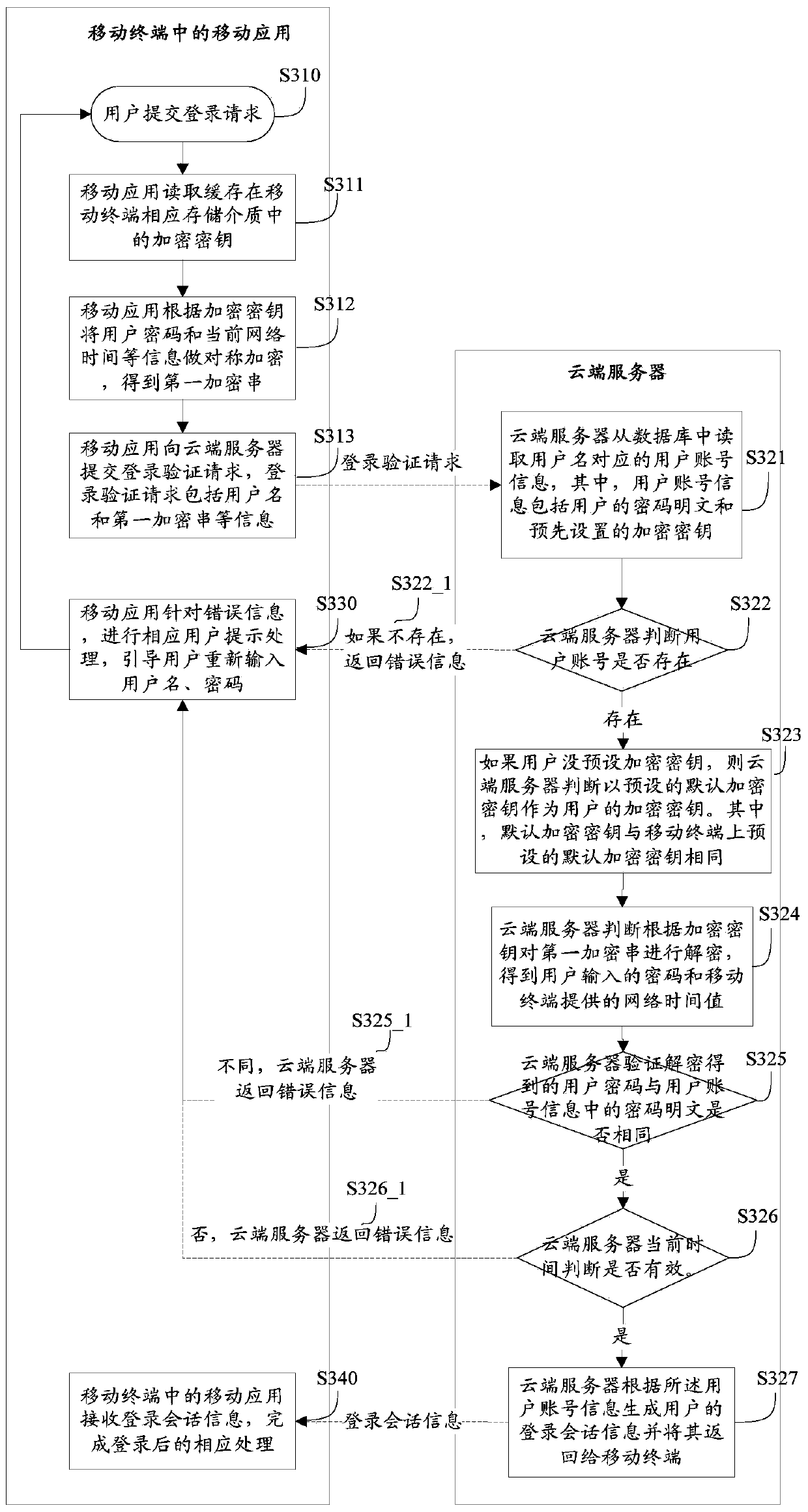
Safety logging method, system and device of mobile application
The invention provides a safety logging method of a mobile application. The safety logging method includes the following steps that the encryption key arrangement is performed on the mobile application in a cloud server and a mobile terminal, and an encryption key is stored in the cloud server and the mobile terminal respectively; the cloud server receives a logging verification request sent by the mobile application, wherein the logging verification request comprises a user name and a first encryption string, and the first encryption string comprises information obtained after a user code is encrypted through the encryption key; the cloud server decrypts the first encryption string according to the encryption key so as to obtain the user code; the cloud server performs logging verification on the mobile terminal according to the user code. According to the safety logging method of the mobile application, through the encryption key arrangement, safety of a logging system on the mobile application is ensured, and user privacy is protected. The invention further discloses a safety logging system and the cloud server for the mobile application.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
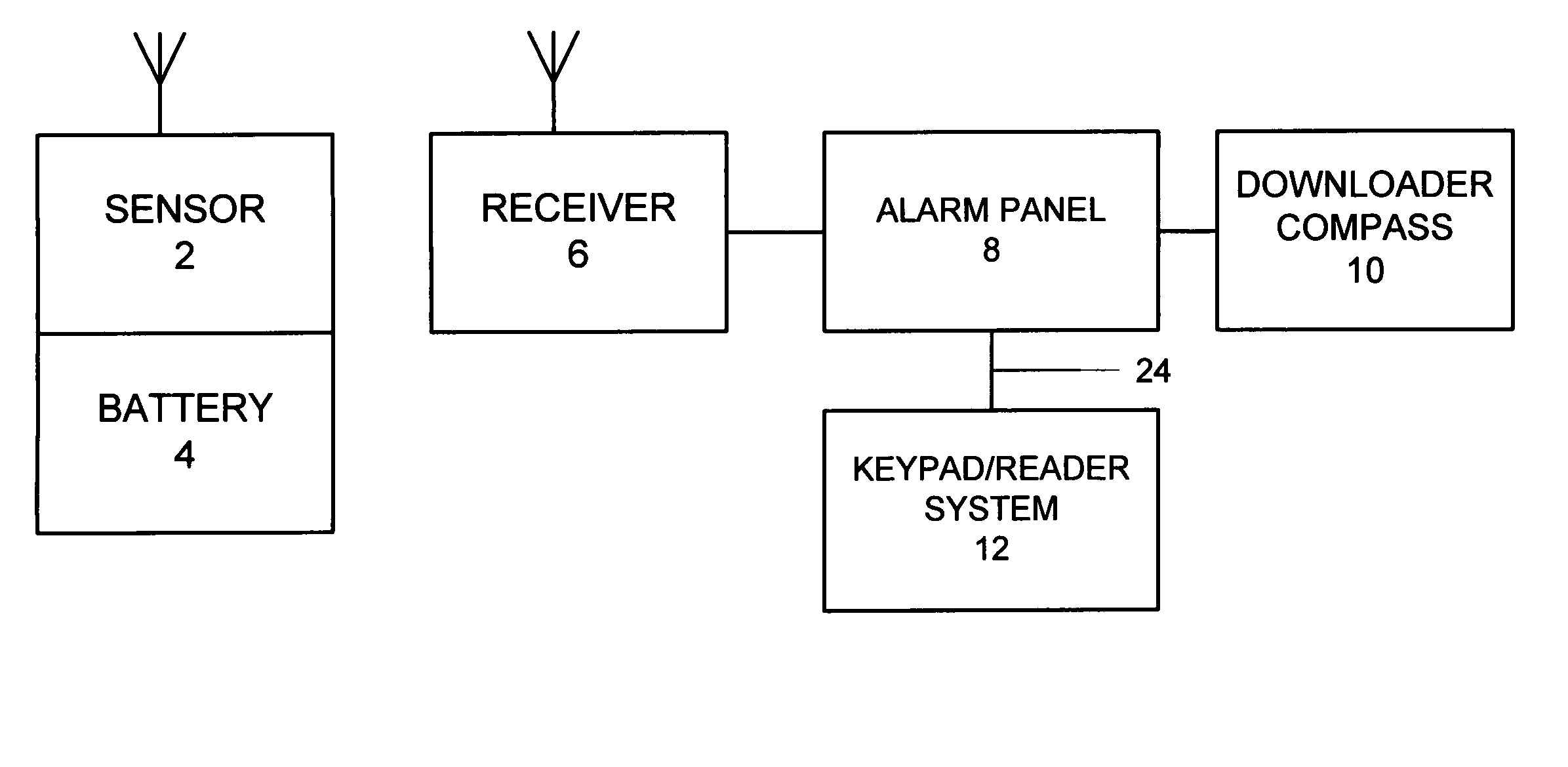
Security system access control and method
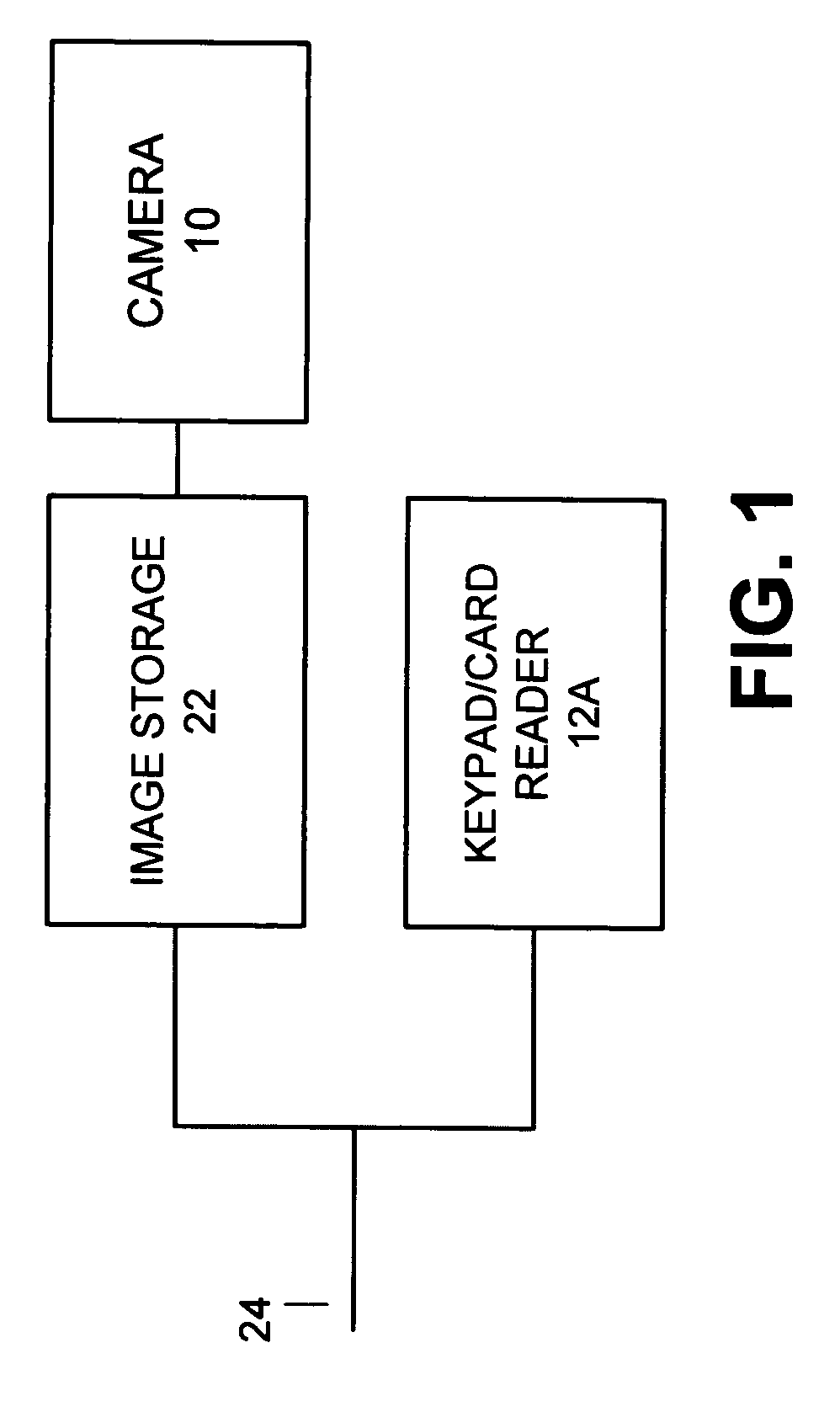
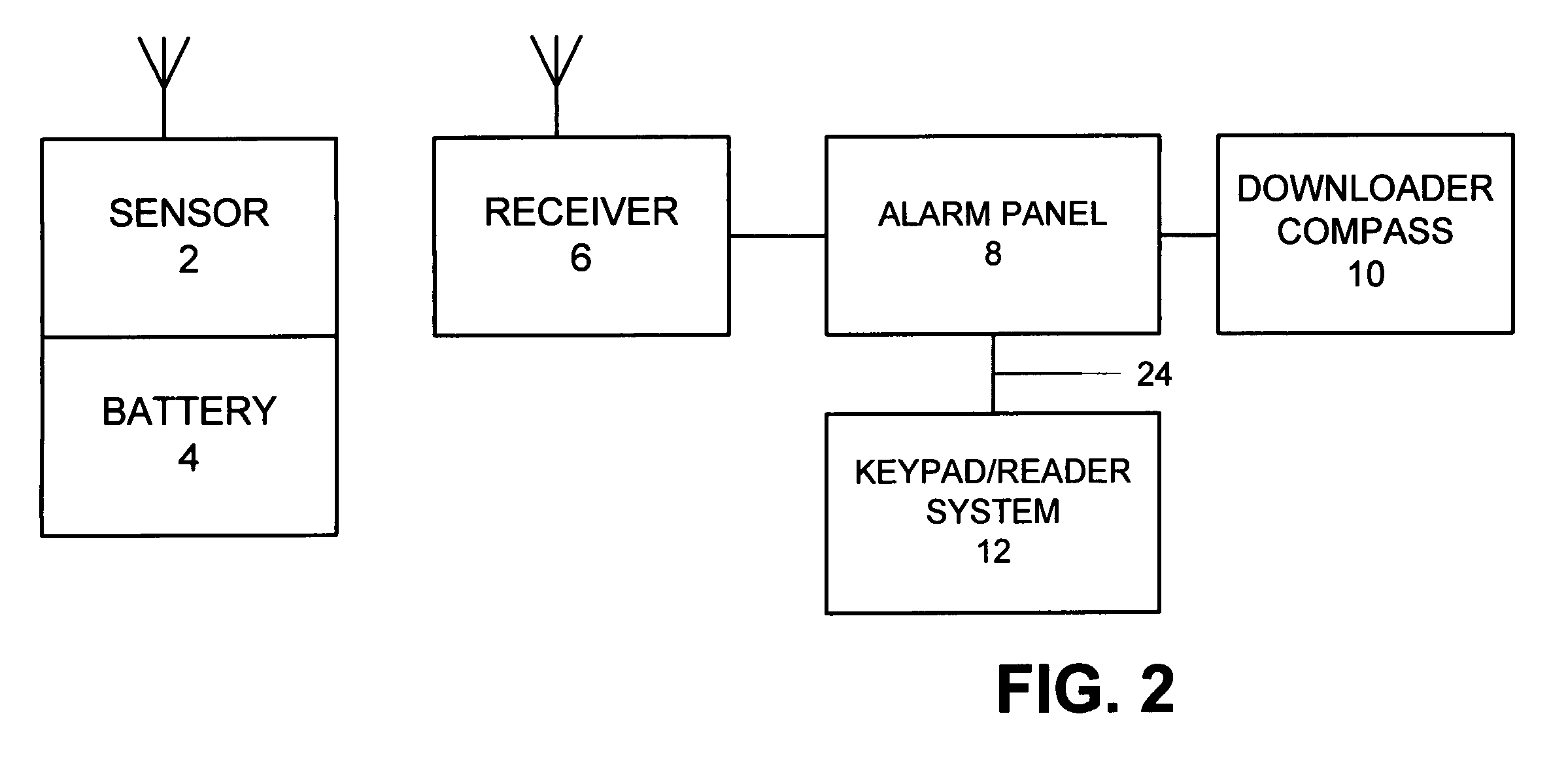
ActiveUS7397371B2Improve security levelImprove securityColor television detailsClosed circuit television systemsUser codeSecurity system
A security system which includes at least a first sensor, an alarm panel including a control system and programmable apparatus, a connection between the at least one sensor and set alarm panel, a keypad assembly including a camera, and a connection between the keypad assembly and the alarm panel. In various embodiments of the invention the camera includes a CMOS image sensor, the camera produces digital images, the camera tracks the user of the keypad assembly, the camera is remotely controllable from the alarm panel to focus on an object of interest, and / or the camera is remotely controllable from a central monitoring station to focus on an object of interest. In some cases the camera system is configured to take a picture in response to a specific user code entered by the user, take a picture in response to time of day when the input occurs, take a picture in response to invalid code entry and / or take a picture in response to an invalid card being presented. The invention also includes the method for providing enhanced security for protected premises which includes providing at least a first sensor, providing an alarm panel including a control system and programmable apparatus, providing a connection between the at least one sensor and the alarm panel, providing an input device including a camera, and initiating operation of the camera from the alarm panel.
Owner:HONEYWELL INT INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com