Method and system for switching third party landing and third party network and service server
A server and website technology, applied in the field of communication, can solve problems such as password synchronization, data destruction, and high third-party requirements, and achieve the effect of ensuring absolute security, avoiding transmission, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
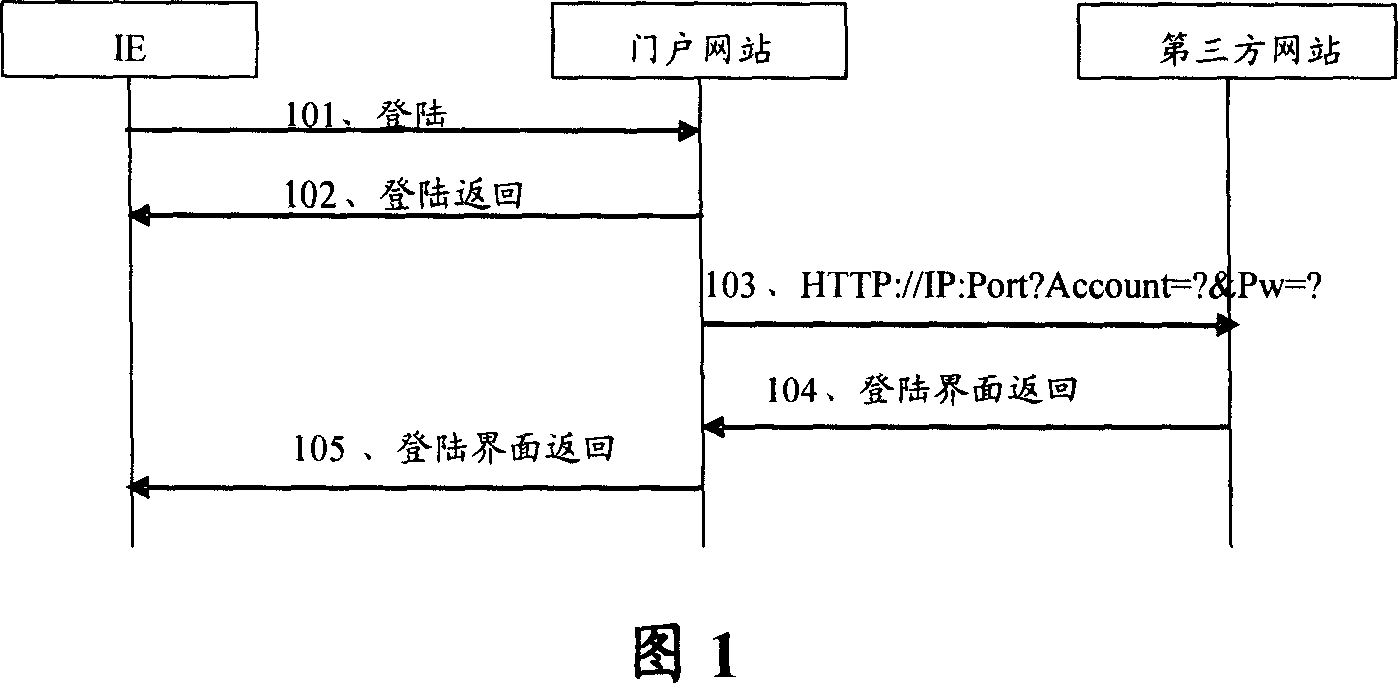
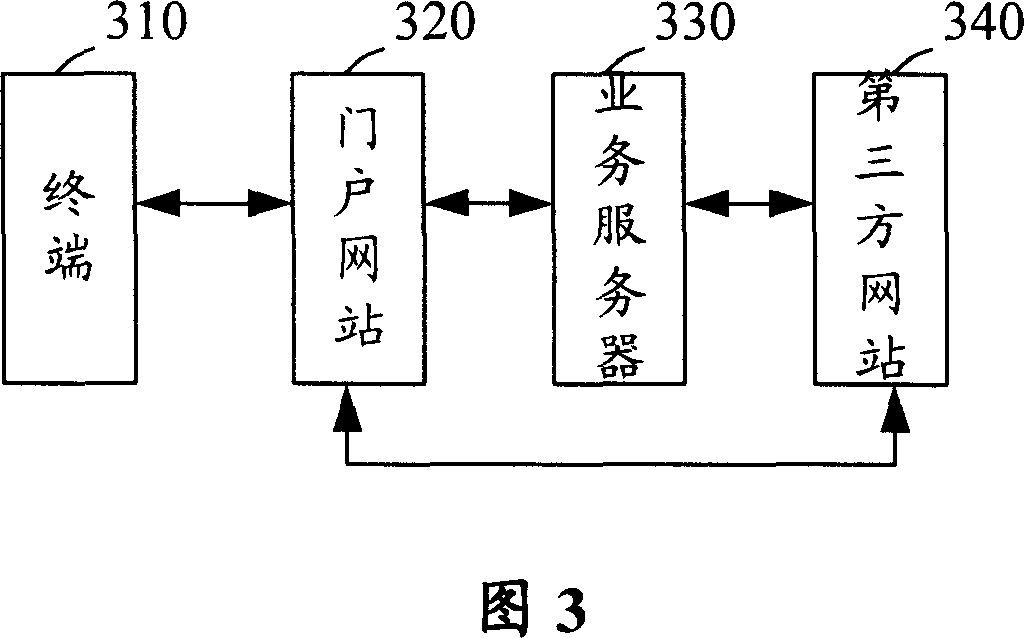
[0033] The basic idea of the present invention is: when the portal website transfers to a third-party website, it adopts the encrypted KEY randomly generated based on the service server instead of carrying the user's key, so that when the portal website is transferred to the third-party website, both To ensure the security of network transmission, but also to ensure the relationship of trust between the portal and third-party websites.
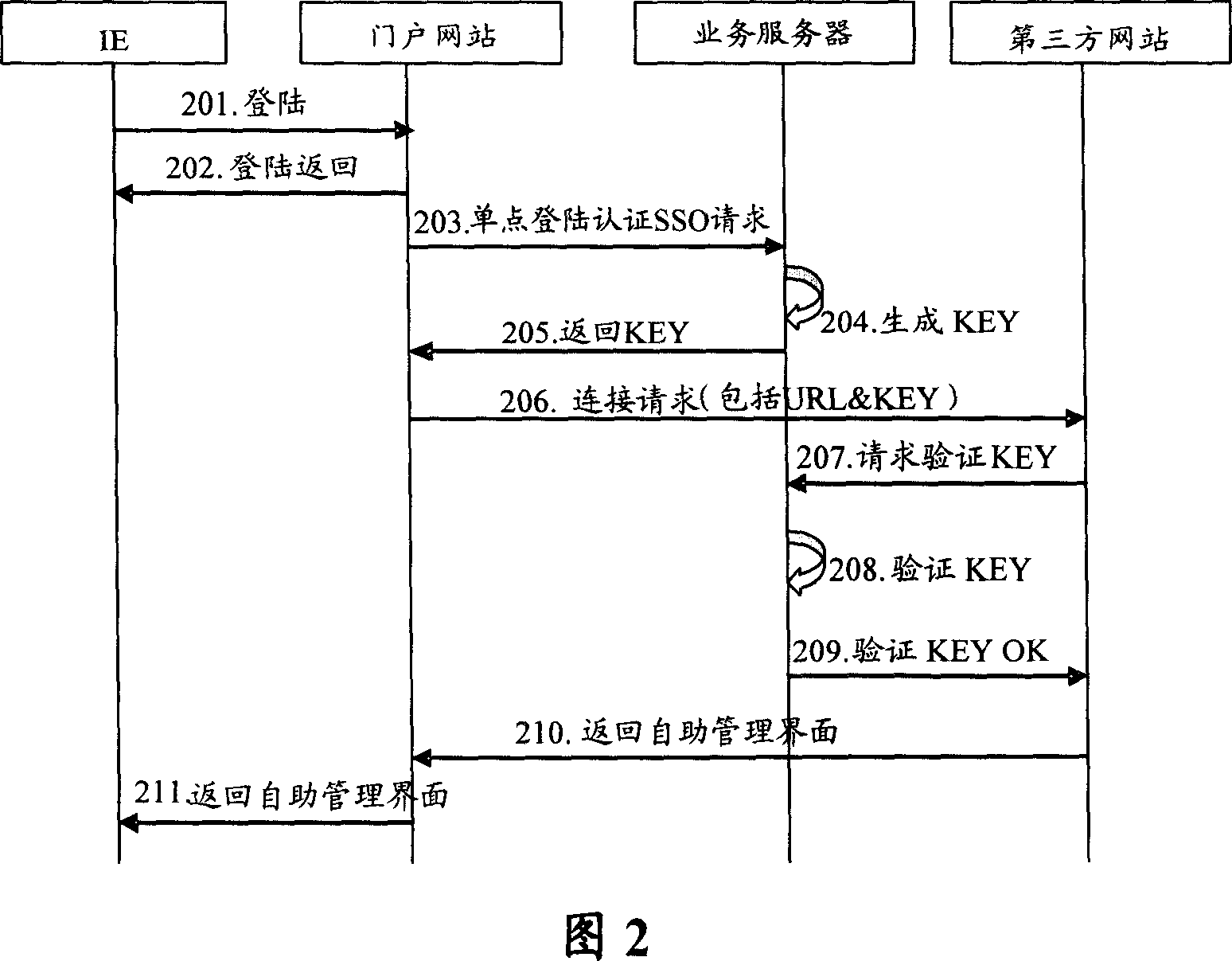
[0034] FIG. 2 is a schematic diagram of a process for realizing transfer of third-party login authentication based on an IP network according to an embodiment of the present invention.
[0035] Steps 201-202, log in and visit the portal website through IE, the user enters the personal registration account number and password to log in the portal website, and the portal website returns to the post-login interface after the verification is successful. Management interface for maintenance operations.
[0036] When the user manages personal inf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com