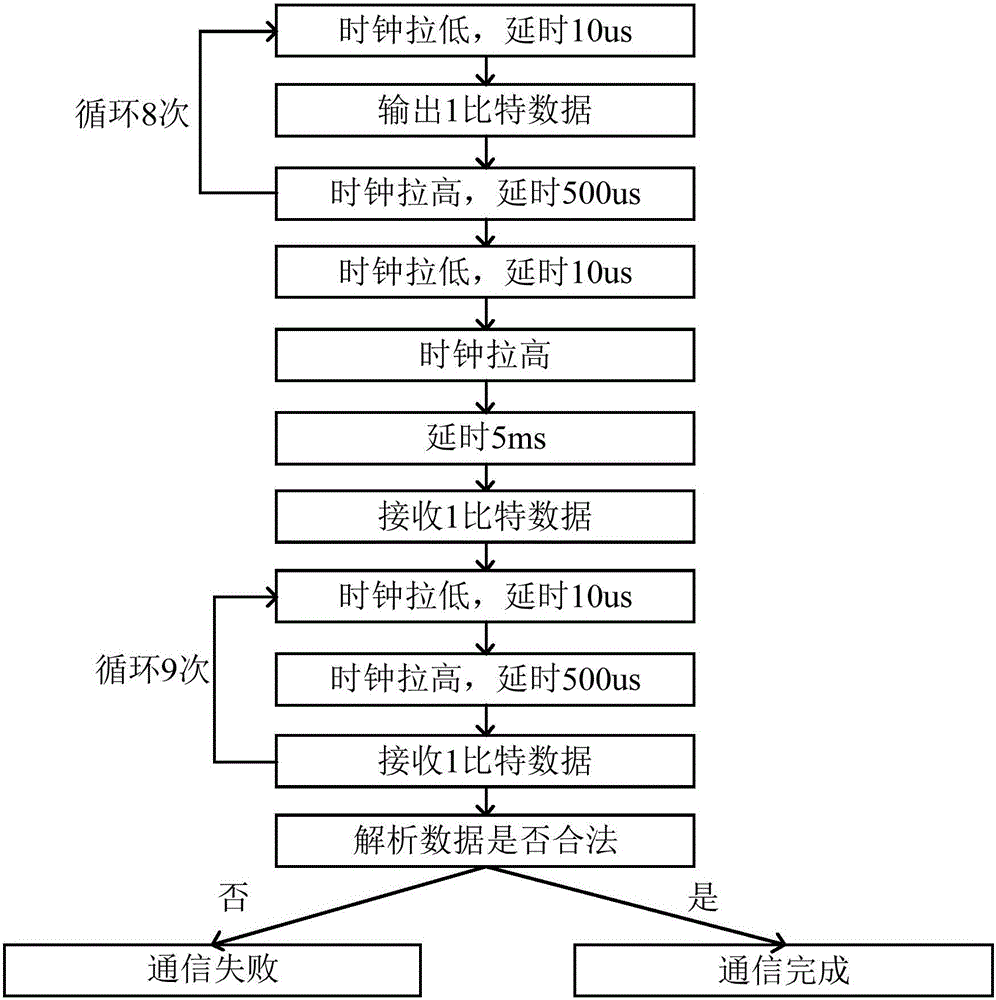
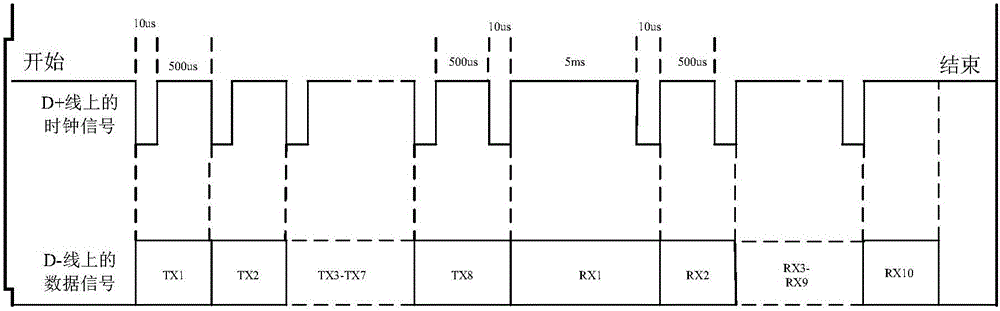
Patents
Literature
120 results about "Shaking hands" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
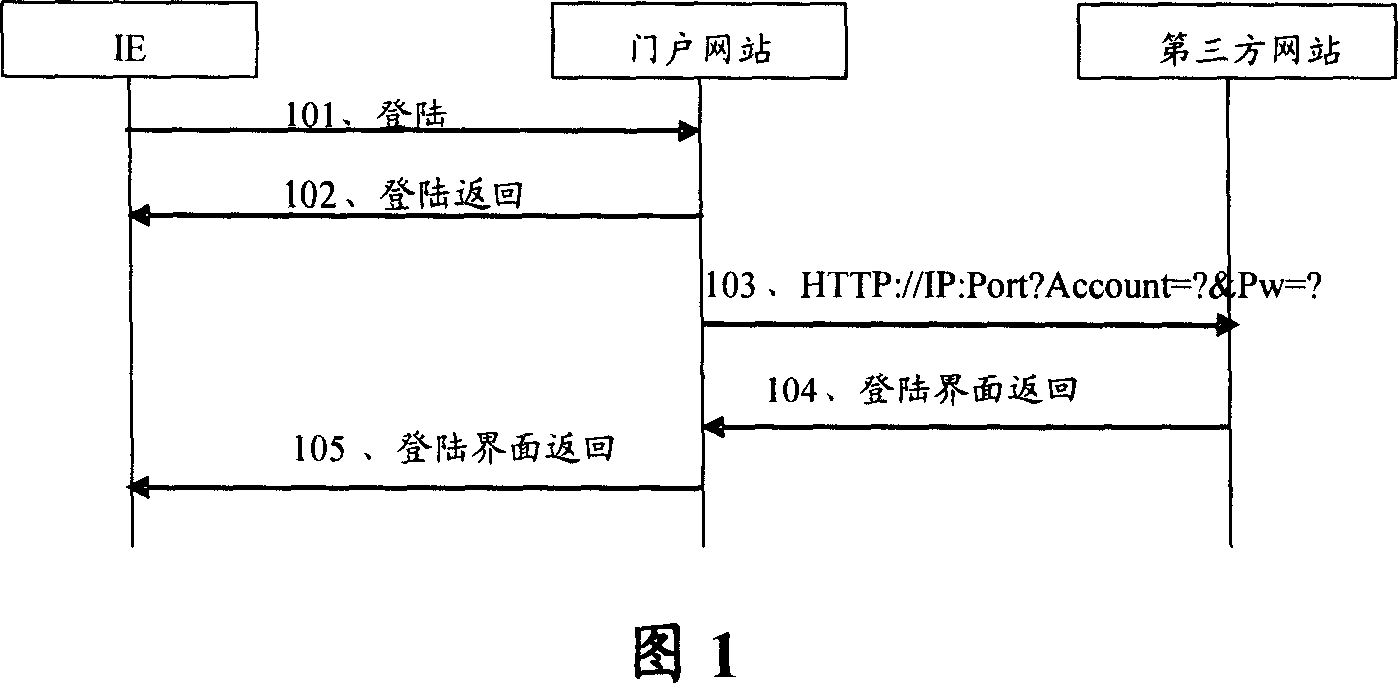
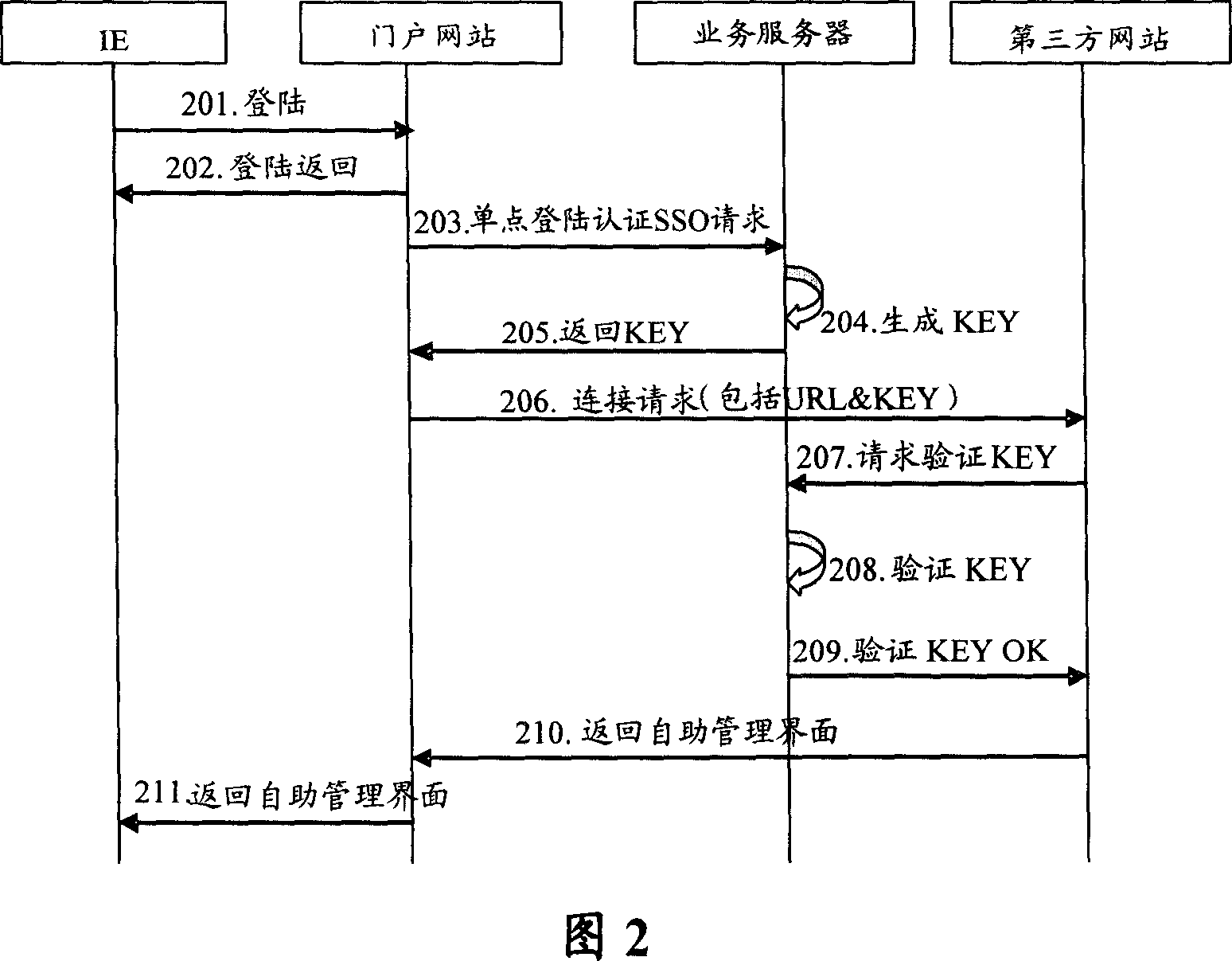
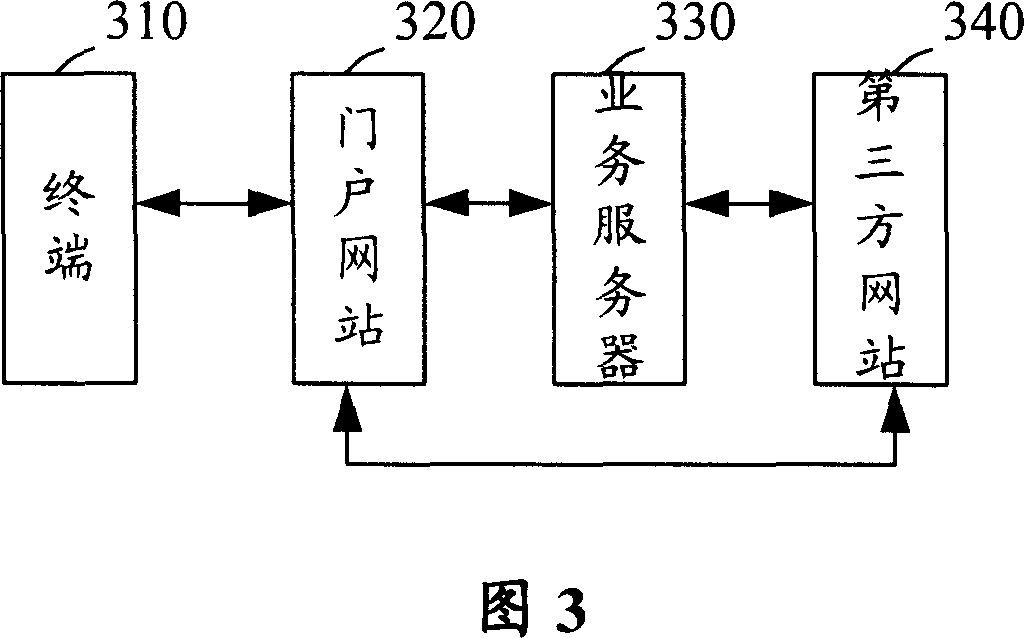
Method and system for switching third party landing and third party network and service server
ActiveCN1946022AAvoid transmissionGuaranteed absolute securityUser identity/authority verificationThird partyWeb service
This invention provides a method for transferring third party landing based on IP network including: a door network station carries a ciphered KEY generated randomly by a service server to send a link request to a third party network station so as to avoid transmission of user ciphered codes and ensure absolute security of user codes, besides, since the third party network station calls back the Web server by copying the ciphered KEY to verify the cryptographic key so as to secure the absolute safety of shaking hands, since the door network station does not transfer user ciphered codes with the third party network station, which is not necessary to synchronize with the door station about codes, thus the requirement of complicated maintenance to synchronization on ciphered codes to the third party is reduced. This invention also provides a system for authenticating the transfer of third party landing based on the IP network and the third party network station and service servers.
Owner:HUAWEI TECH CO LTD
Fight behavior detection method based on spatio-temporal interest point
ActiveCN103279737AHigh fighting behavior recognition rateEffective fighting behavior detectionImage analysisCharacter and pattern recognitionPattern recognitionHuman body
The invention discloses a fight behavior detection method based on a spatio-temporal interest point. The fight behavior detection method based on the spatio-temporal interest point comprises the following steps: firstly, detecting the spatio-temporal interest point of the current frame; then, segmenting to extract an effective spatio-temporal interest point set; analyzing the distribution of the effective spatio-temporal interest point set and the average displacement amount of the centroid of the effective spatio-temporal interest point set; according to the distribution of the effective spatio-temporal interest point set and the average displacement amount of the centroid of the effective spatio-temporal interest point set, regulating the fight level of the current scene; and outputting the state information ''fight'' or ''normal''. According to the fight behavior detection method based on the spatio-temporal interest point, which is disclosed by the invention, the human body movement in a video is described by the spatio-temporal interest point, and the human body interaction acute degree is detected by analyzing the distribution of the effective spatio-temporal interest point set and the average displacement amount of the centroid of the spatio-temporal interest point set so as to judge whether the fight behavior happens in the current monitoring scene. According to the fight behavior detection method based on the spatio-temporal interest point, the area with drastic movement in the current frame image can be accurately reflected, the fight behavior detection method is unlikely to be affected by the change of environment such as the change of illumination and has the advantages of high detection speed and better robustness, the fight behavior in the scene can be accurately and timely identified, normal behaviors of shaking hands and running and the like can be better distinguished, and the false alarm rate is effectively lowered.
Owner:SHANGHAI JIAO TONG UNIV
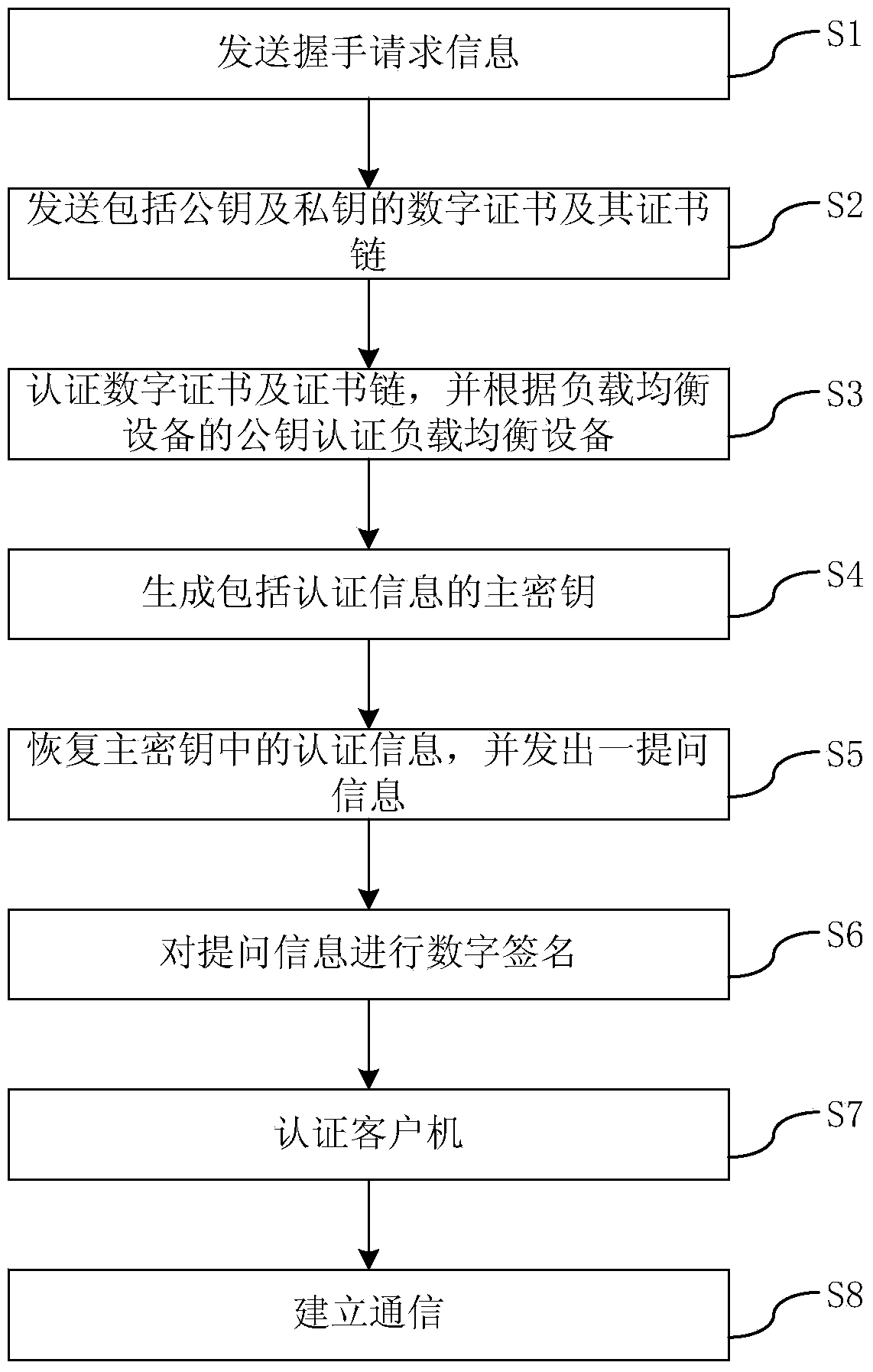
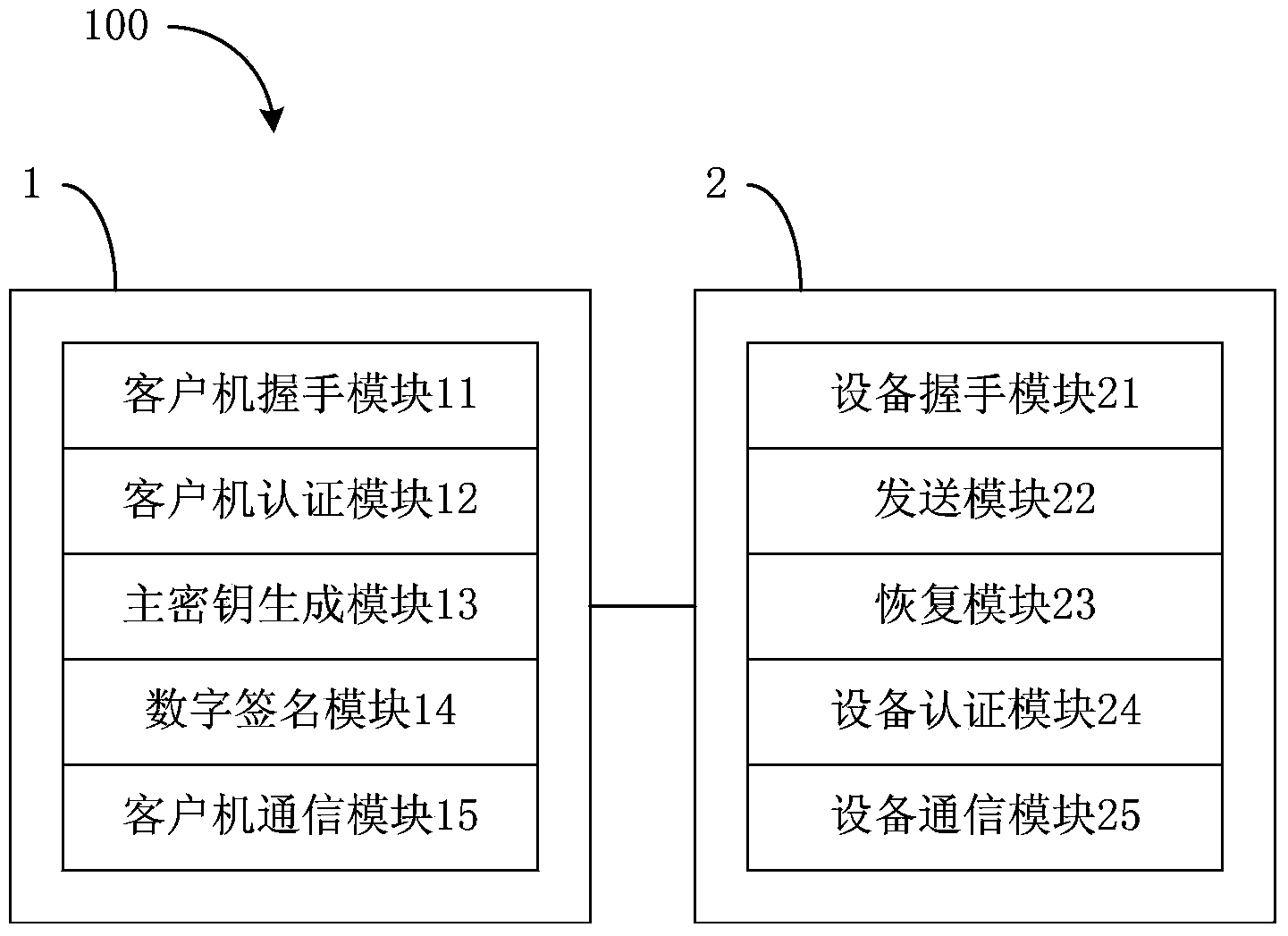
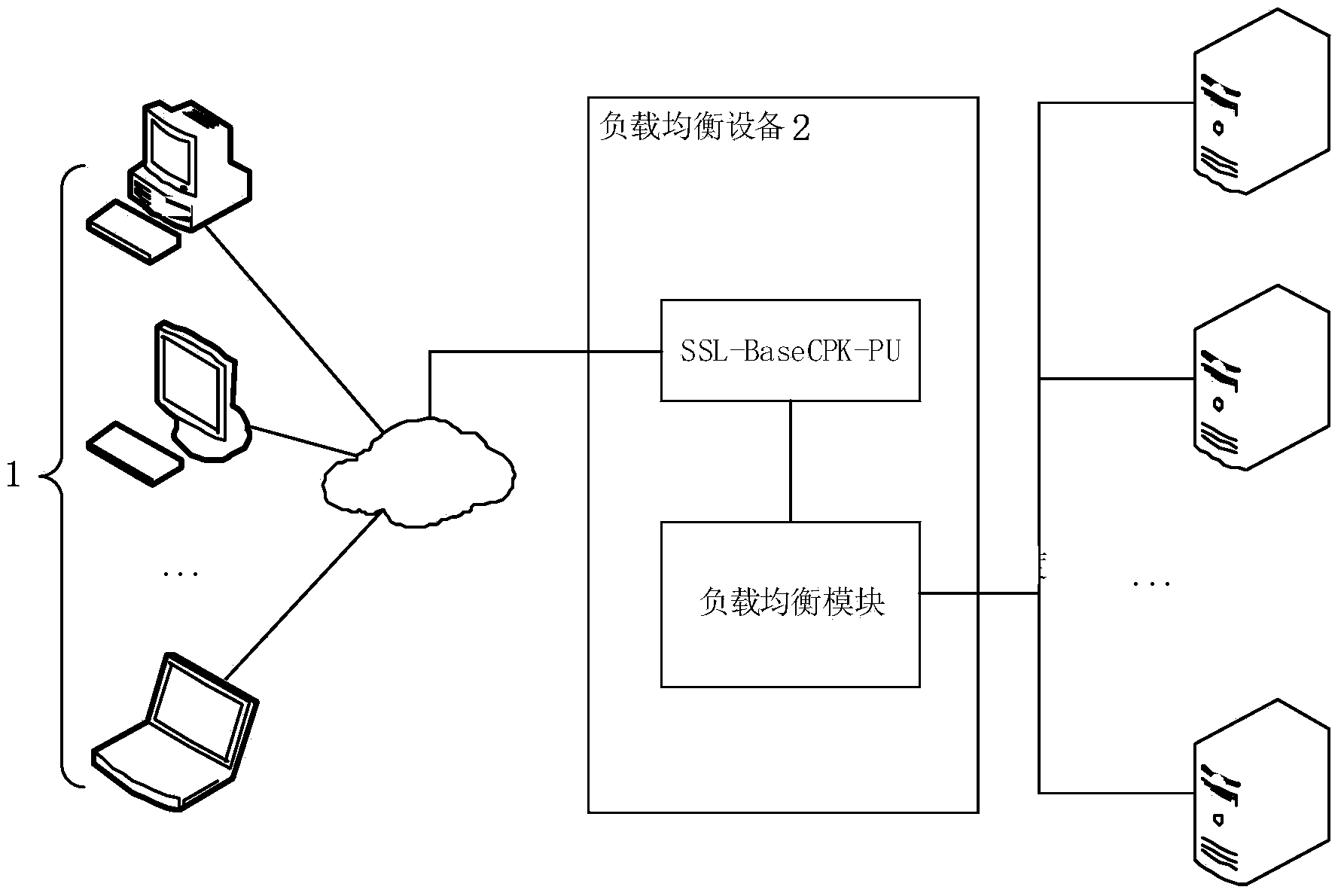
SSL-based method and system for establishing communication
ActiveCN104378374AImprove computing efficiencyIncrease flexibilitySecuring communicationKey sizeClient-side
The invention discloses an SSL-based method and system for establishing communication. The method comprises the steps that firstly a client and load balancing equipment are made to mutually shake hands in the SSL and then authenticate each other, and after authentication, the client establishes communication with the load balancing equipment. The method and system have the advantages that the SSL protocol is adopted to provide reliable and quick data communication for a client side and a server side; besides, the operation efficiency of the SSL is improved by designing a combined public key, the length of cryptographic keys under the same intensity is reduced, and the flexibility and the availability of a network are improved.
Owner:国家超级计算深圳中心(深圳云计算中心)
Hangover remedy and alcohol abatement composition
InactiveUS20050191395A1Easy to carryRelieve pressureHeavy metal active ingredientsFood preservationNausea sicknessFood additive
An anti-intoxication composition and method of making and using are provided for treating and preventing drinker's remorse and other toxic effects of excessive alcohol consumption by humans. The anti-intoxication composition is an acidic mixture containing sweeteners, flavoring agents, food additives and a processed mixture of metallic salts, sulfuric acid, ammonium sulfate and water. When the anti-intoxication composition is ingested, it promotes the beneficial metabolism of alcohol, primarily ethanol, in the body. The beneficial metabolism results in the conversion of alcohol to amino acids and eliminates the toxic reactions of a hangover, including, but not limited to, a pounding headache, nausea, dry mouth, shaking hands, hypersensitivity to bright lights and sounds.
Owner:TASKER PRODS IP HLDG CORP
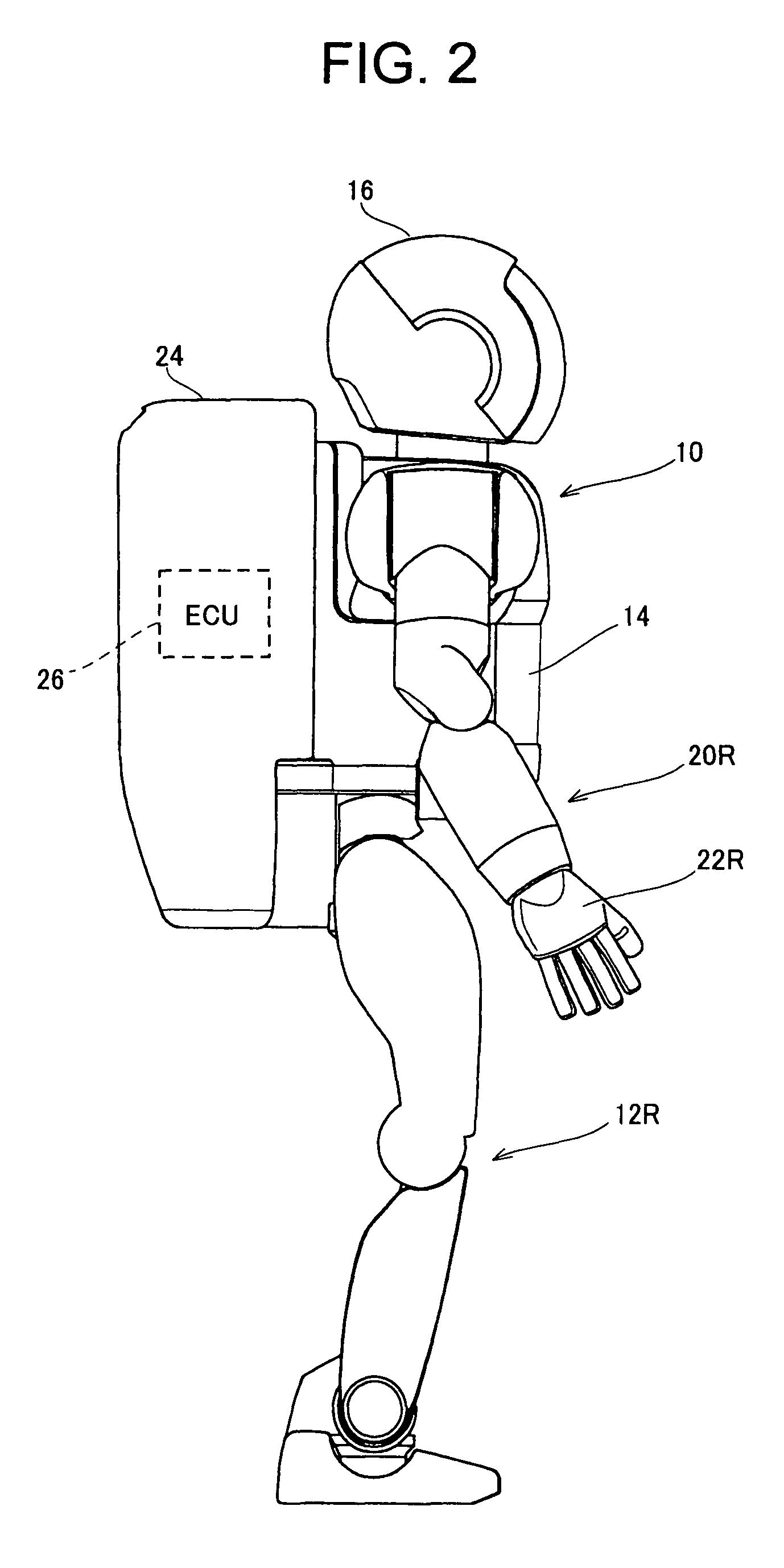
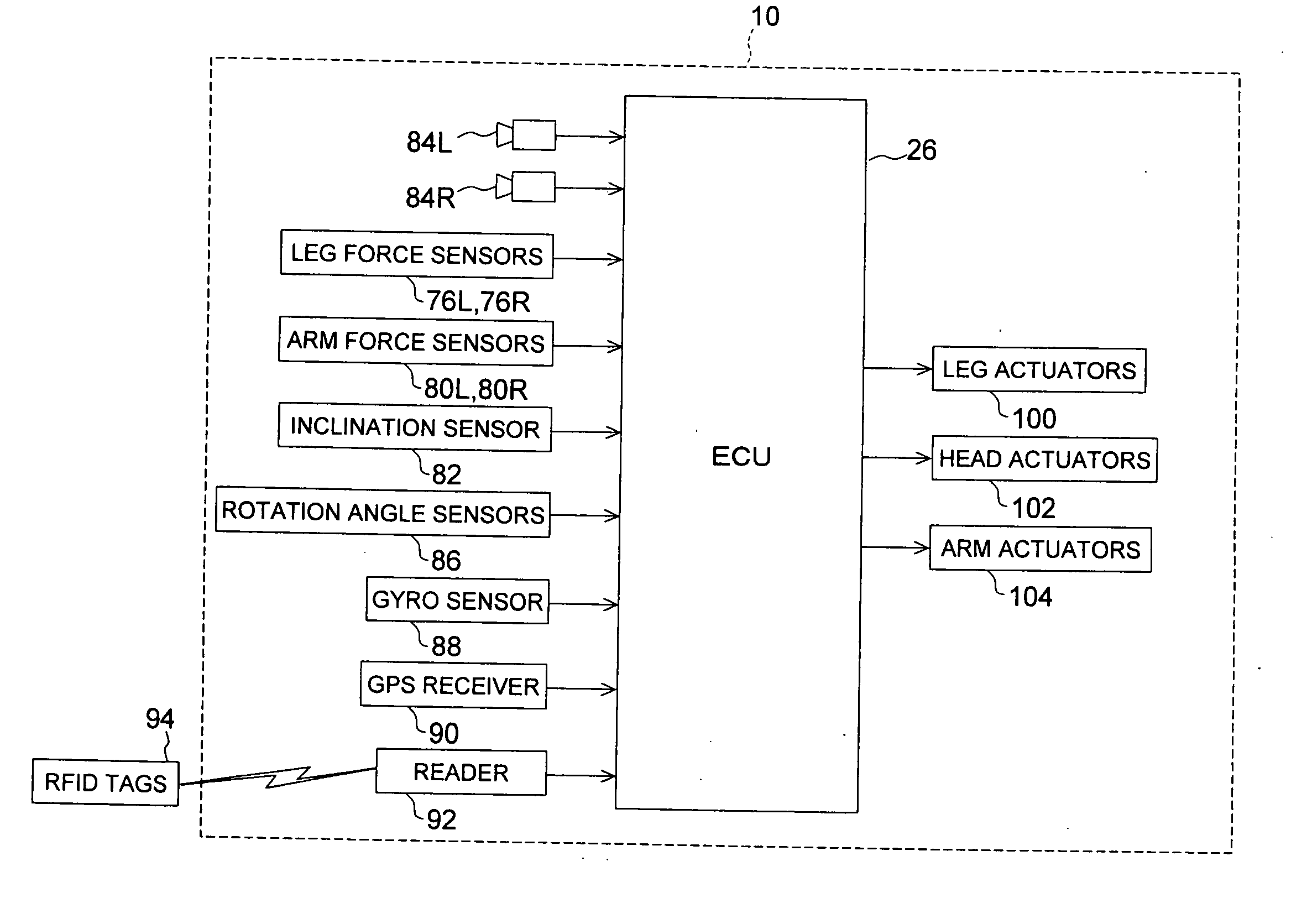
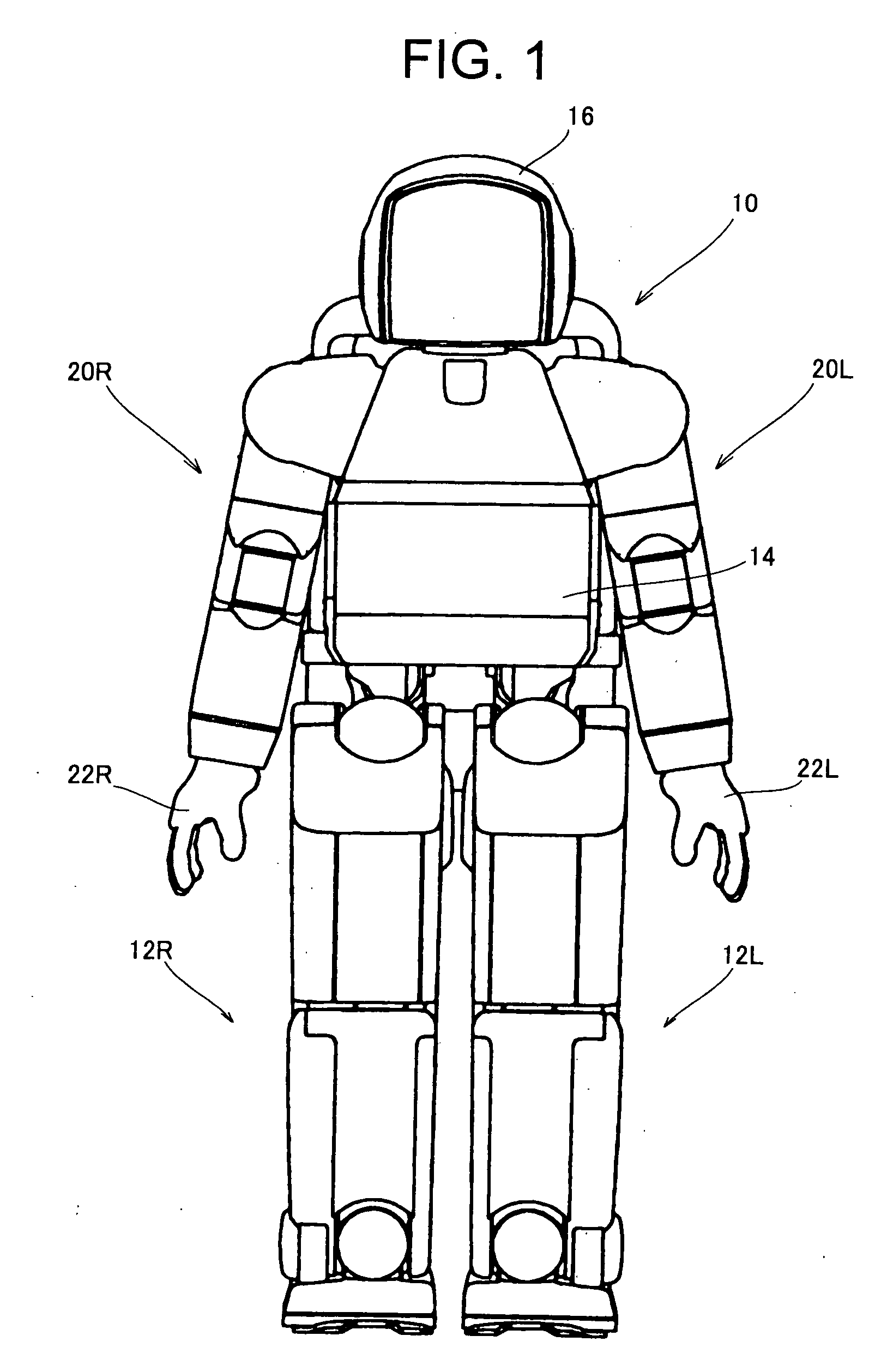
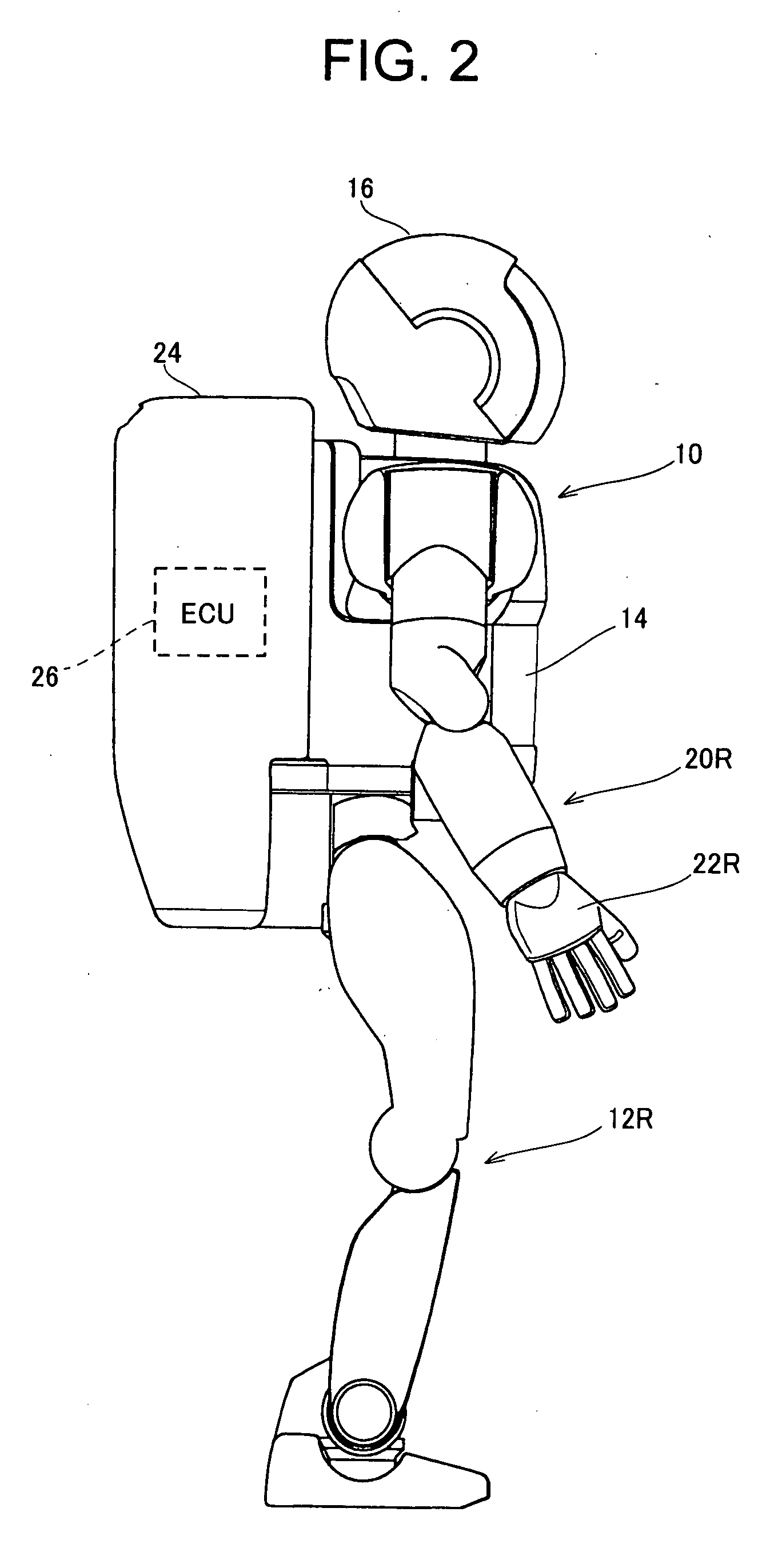
Handshake legged mobile robot control system
InactiveUS7877165B2Improve communication performancePostural stabilityProgramme-controlled manipulatorComputer controlMobile robot controlActuator
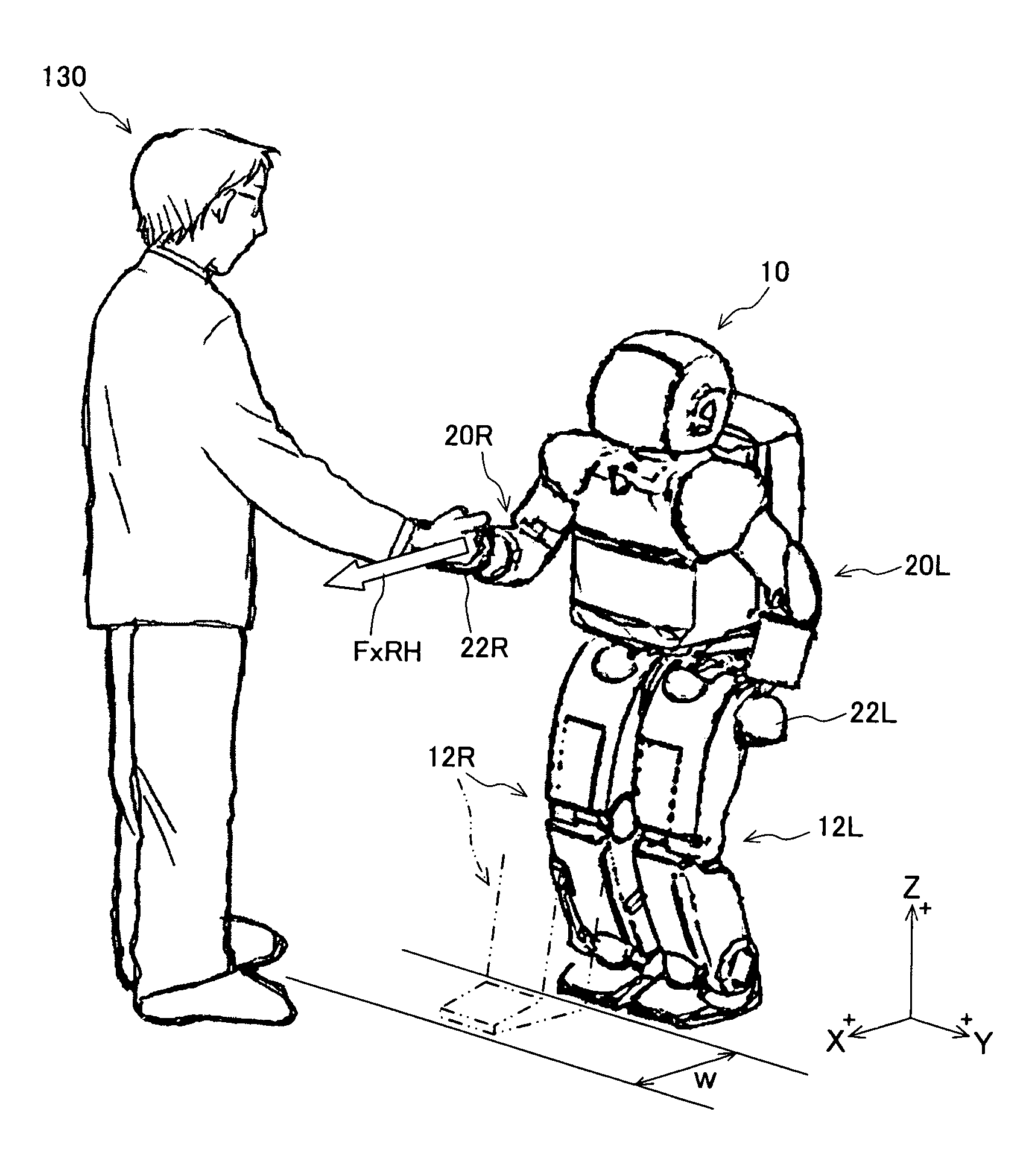
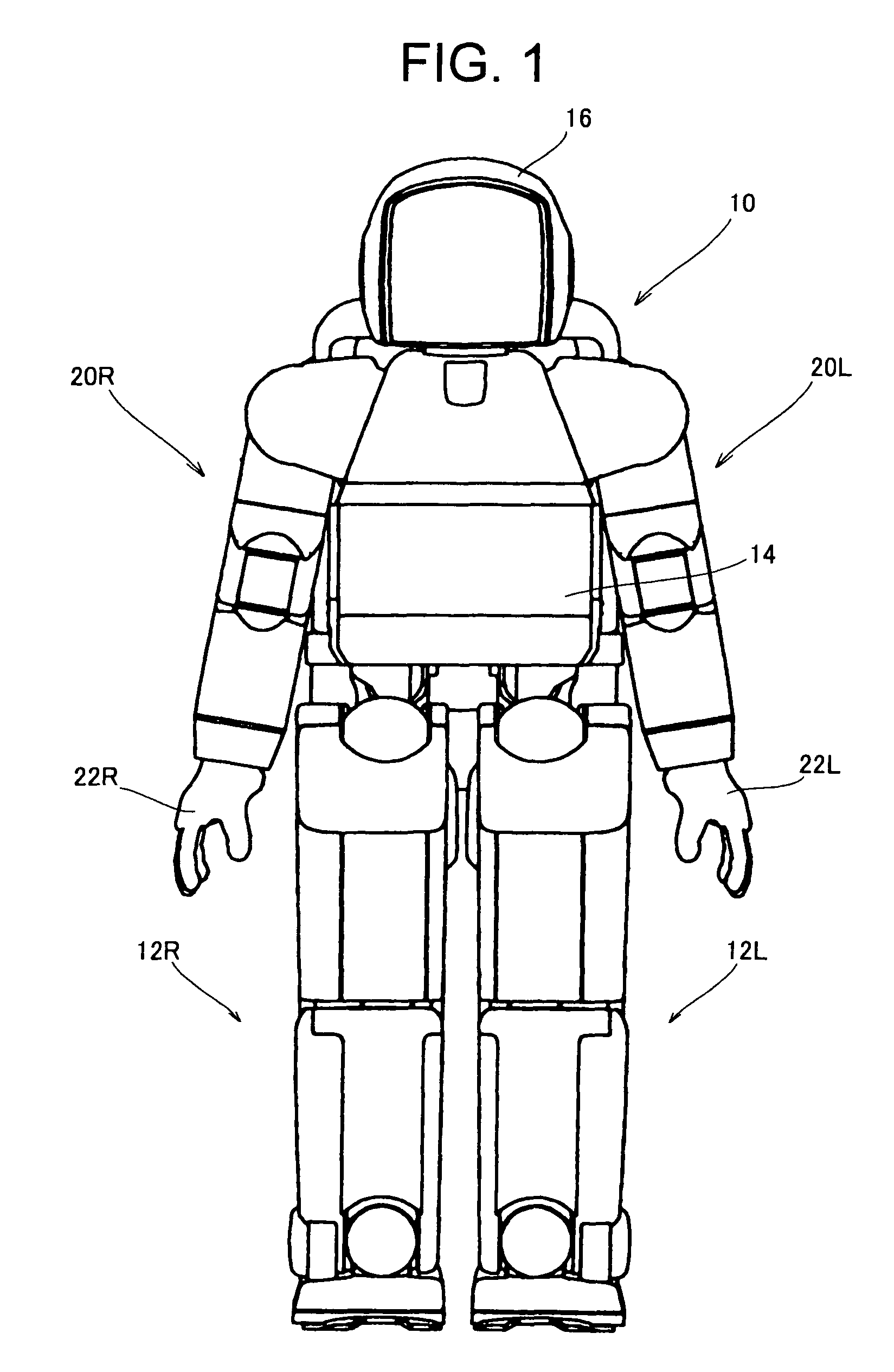
In a legged mobile robot control system having leg actuators each driving the individual legs and arm actuators each driving the individual arms, an external force acting on the right arm is detected, operation of the right arm actuators is controlled to produces a handshake posture, and operation of the leg actuators is controlled based on the detected external force acting on the right hand during handshaking, thereby improving communication capability by enabling it to shake hands with humans and to maintain a stable posture during the handshaking.
Owner:HONDA MOTOR CO LTD
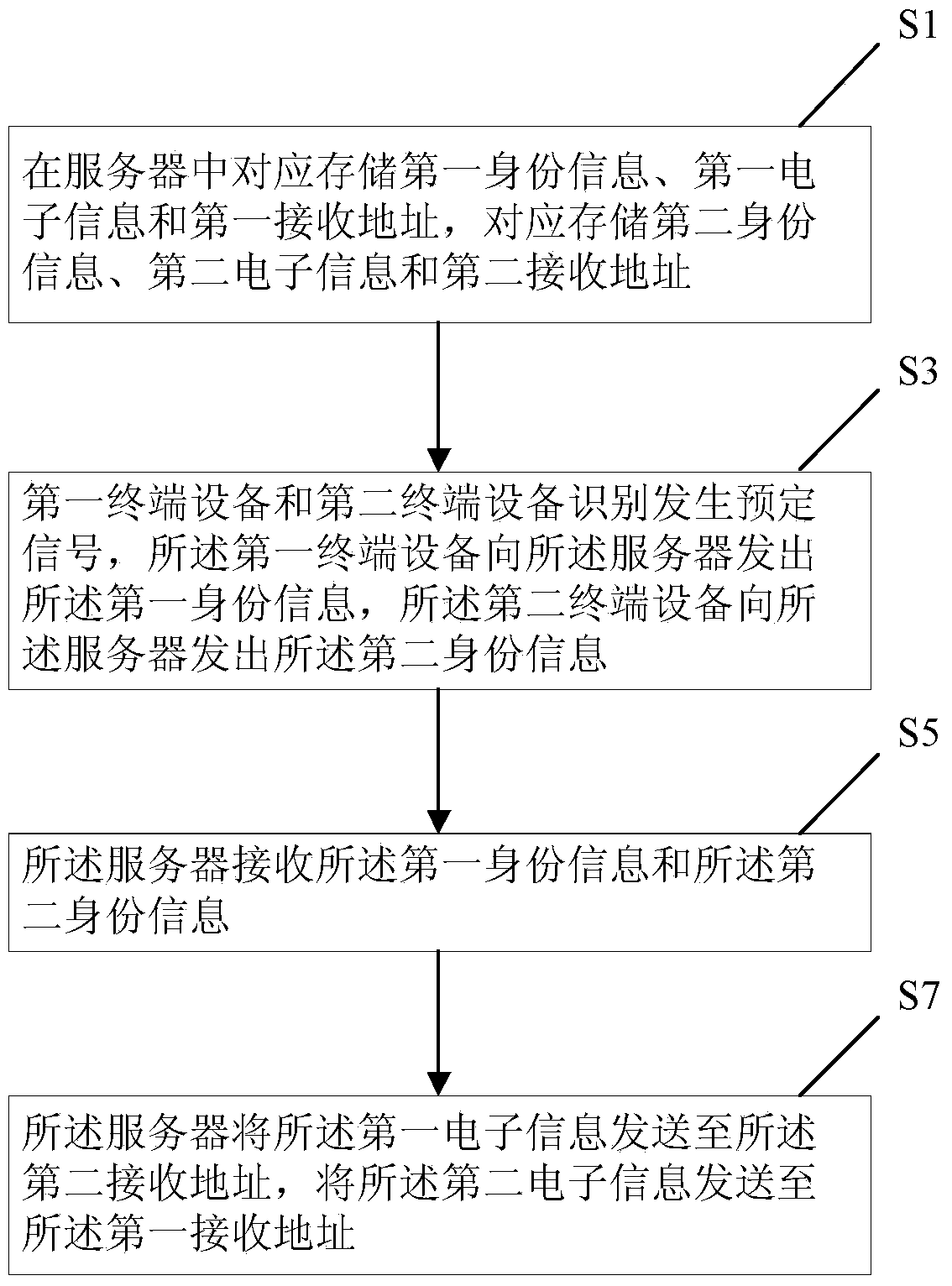
Method for exchanging electronic business cards and information by virtue of handshaking actions
The invention provides a method for exchanging electronic business cards and information by handshaking actions. The method comprises the following steps: correspondingly storing first identity information, first electronic information and a first receiving address in a server; correspondingly storing second identity information, second electronic information and a second receiving address; generating predetermined signals by virtue of first terminal equipment and second terminal equipment; sending the first identity information to the server by virtue of the first terminal equipment and sending the second identity information to the server by virtue of the second terminal equipment; receiving the first identity information and the second identity information by virtue of the server; sending the first electronic information to the second receiving address by virtue of the server; sending the second electronic information to the first receiving address by the server. By adopting the method, users can exchange the electronic information by shaking hands so as to bring great convenience to the users.
Owner:BEIJING UNIV OF POSTS & TELECOMM
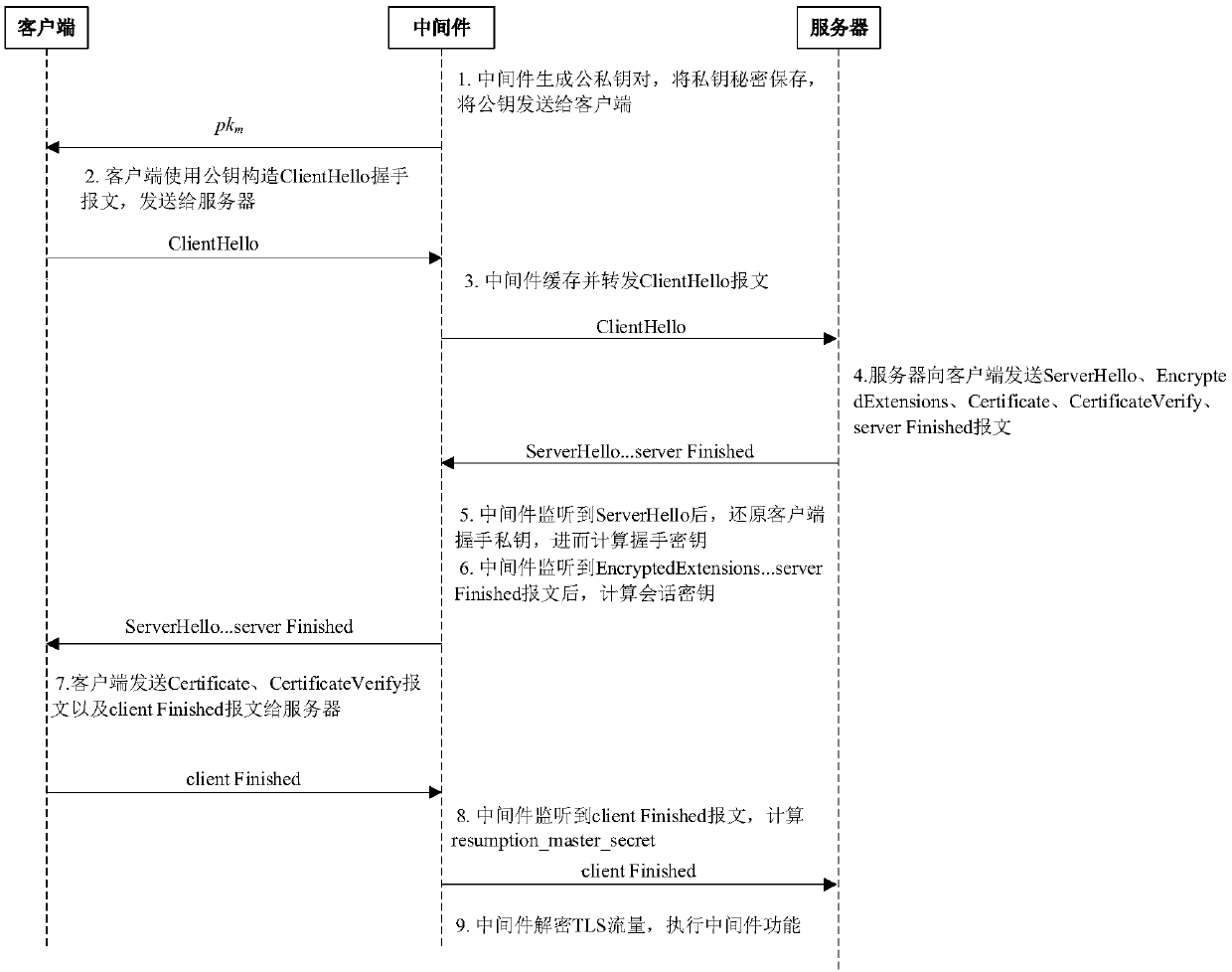
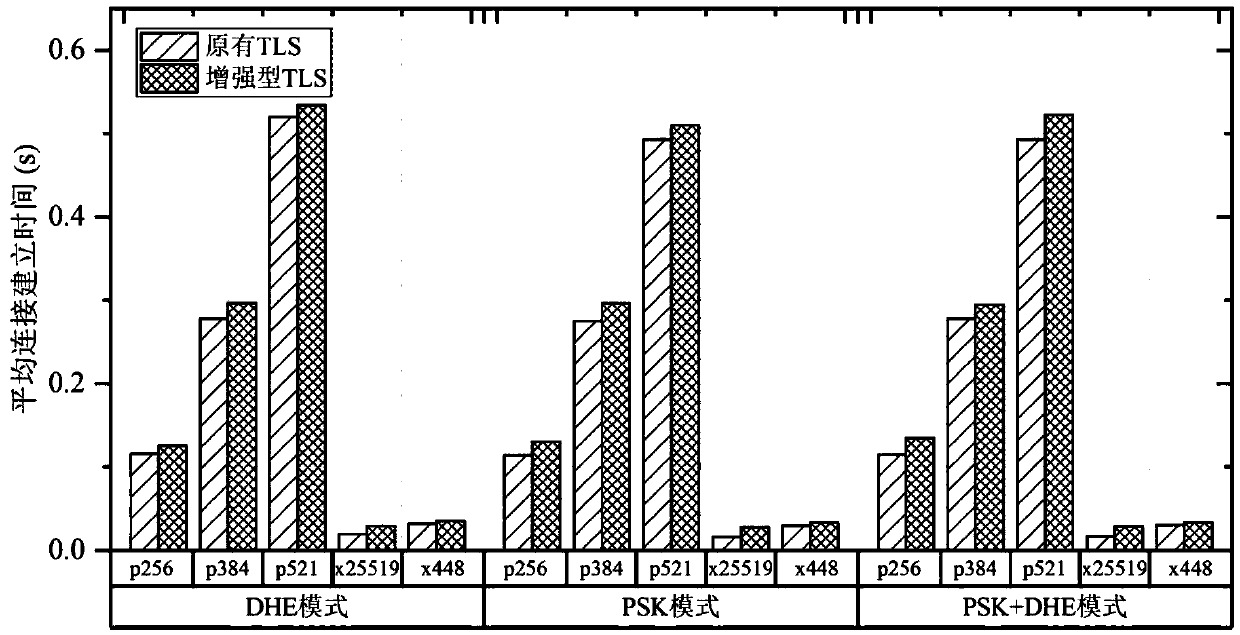
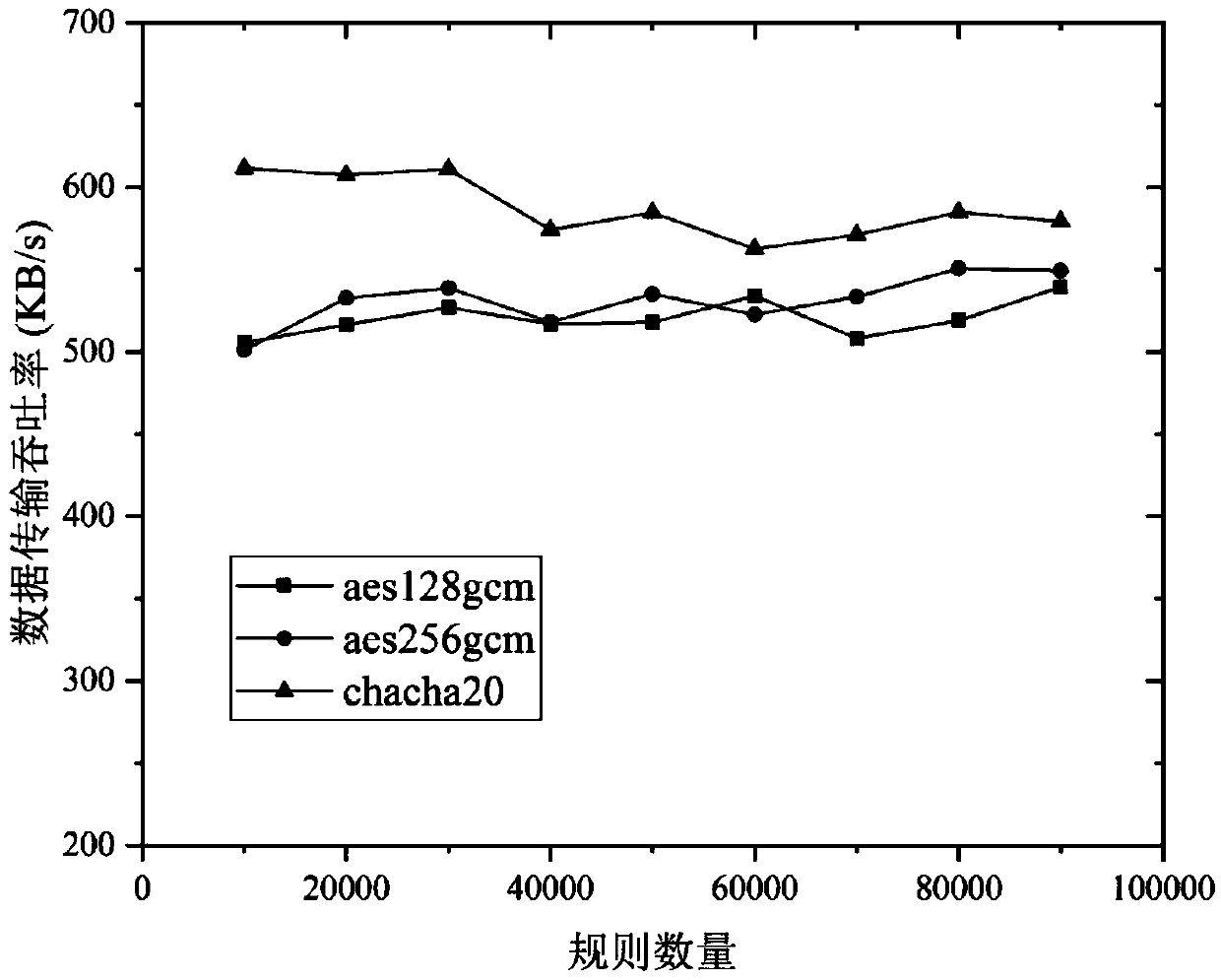
TLS protocol session key restoration method based on random number implicit negotiation
ActiveCN109600226AReduce computational overheadKey distribution for secure communicationPublic key for secure communicationPasswordRestoration method
Owner:NAT UNIV OF DEFENSE TECH
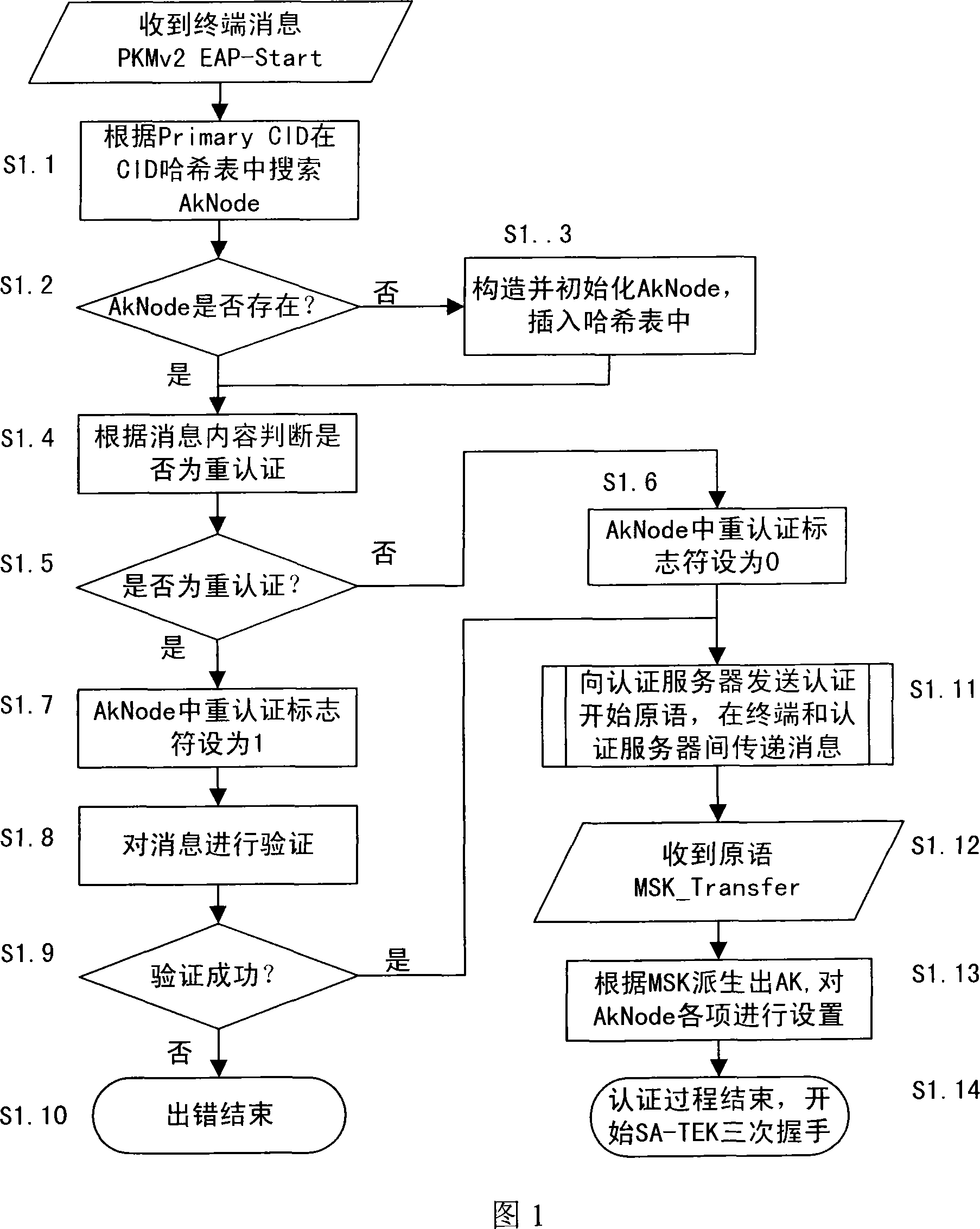
An organization structure and maintenance method of security context in media accessing control system
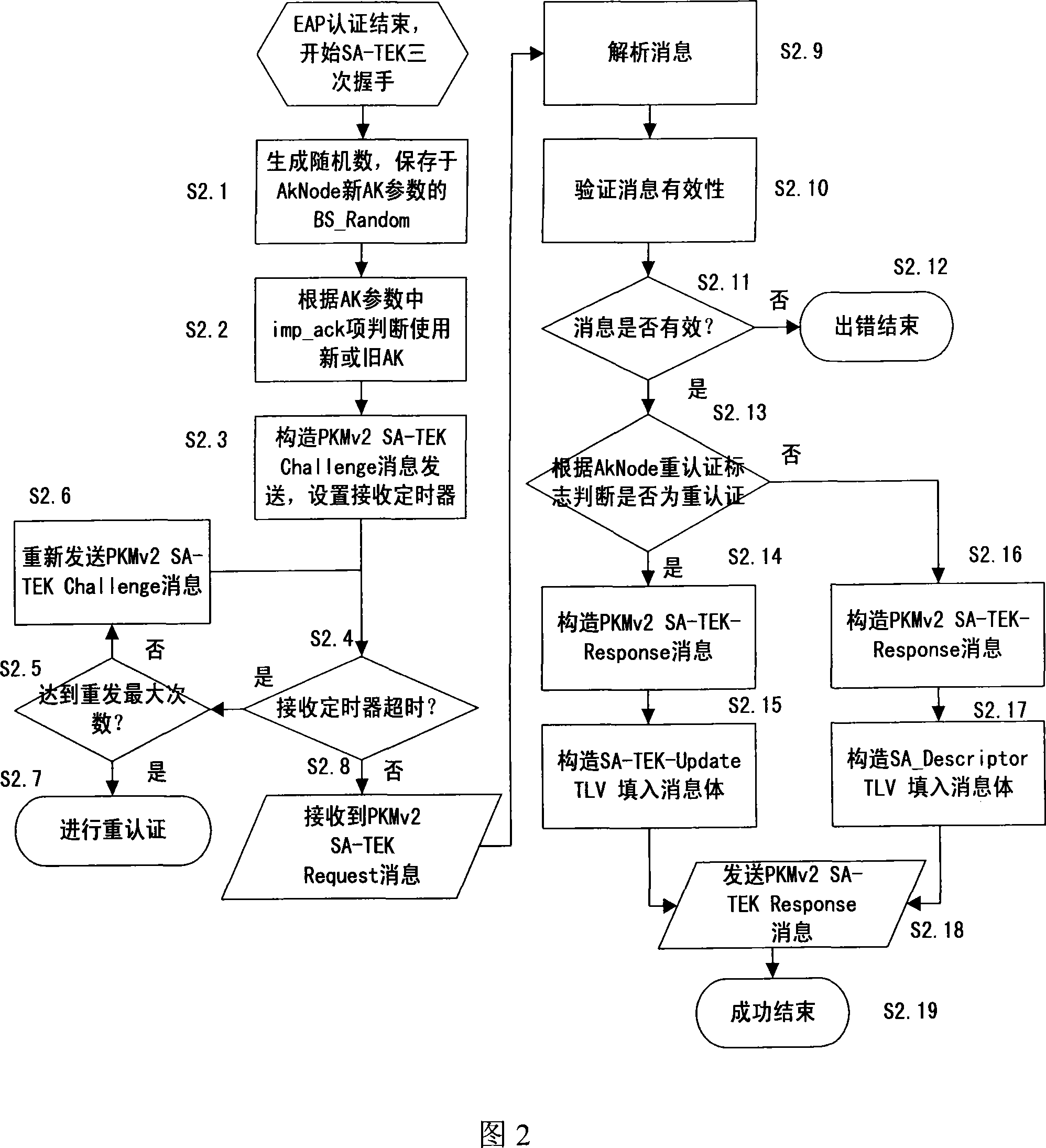
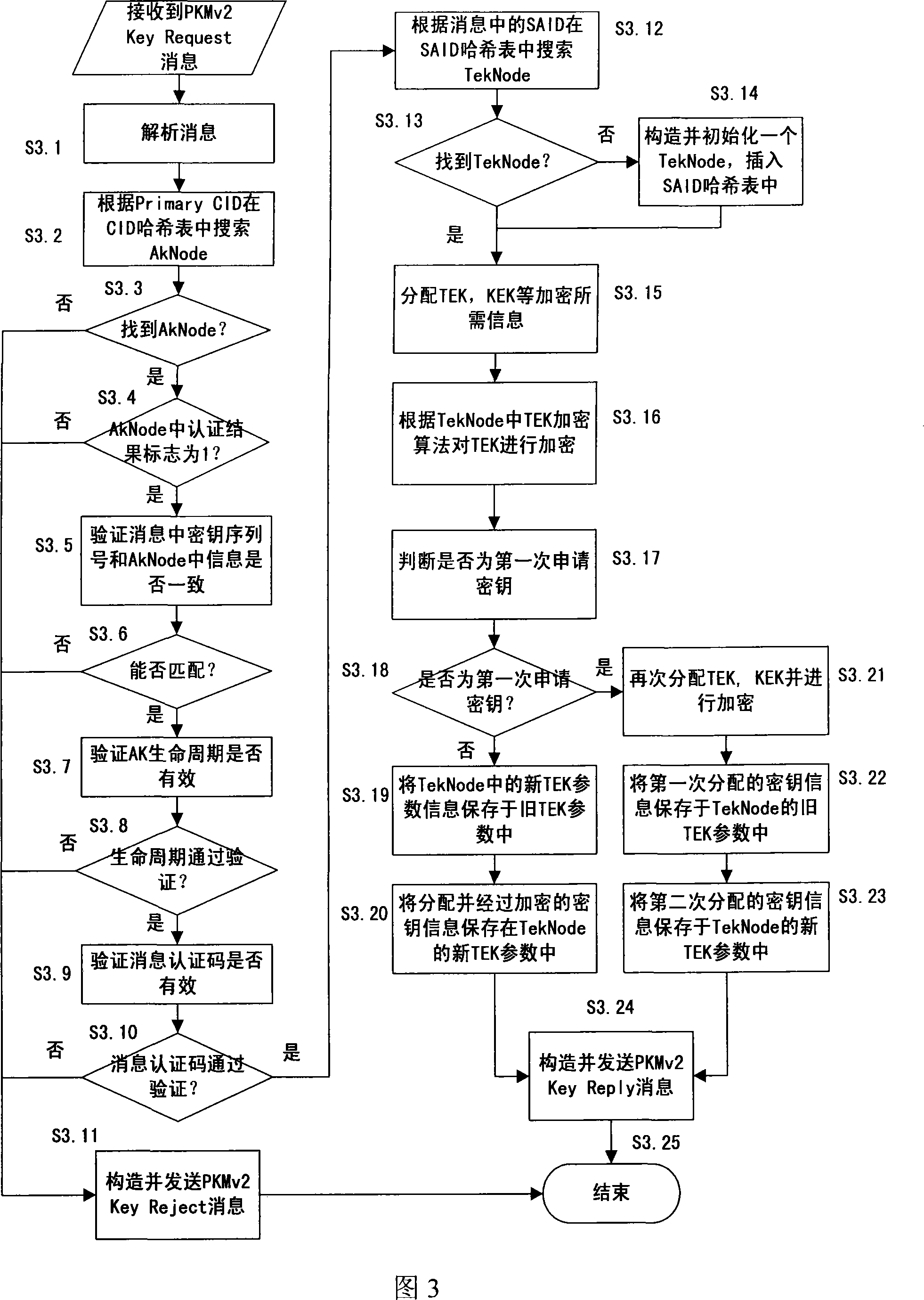
ActiveCN101217364AAchieve maintenanceImprove maintenance efficiencyKey distribution for secure communicationRadio/inductive link selection arrangementsService flowControl system
The invention discloses a safe context organizing structure and a maintaining method in broadband wireless metropolitan area network base station medium accessed to a control system. The organizing structure comprises a connection identifiers hashtable which is used for managing the context of authorization keys and a safety association identifying hashtable which is used for managing the context of communication secret keys. The maintaining method operates on the connection identifiers hashtable and the safety association identifying hashtable respectively when can authenticate the expandable authentication agreement to terminals, when in the process of safety association-communication encryption secret key shaking hands and when terminals distributes secret keys and create service flow. The invention can realize the organization and maintenance of safety context and high-speed searching. When terminals are in large number and the data amount is large, the maintaining efficiency of data can be improved to a large extent.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Optical interface speed auto-negotiation method and device
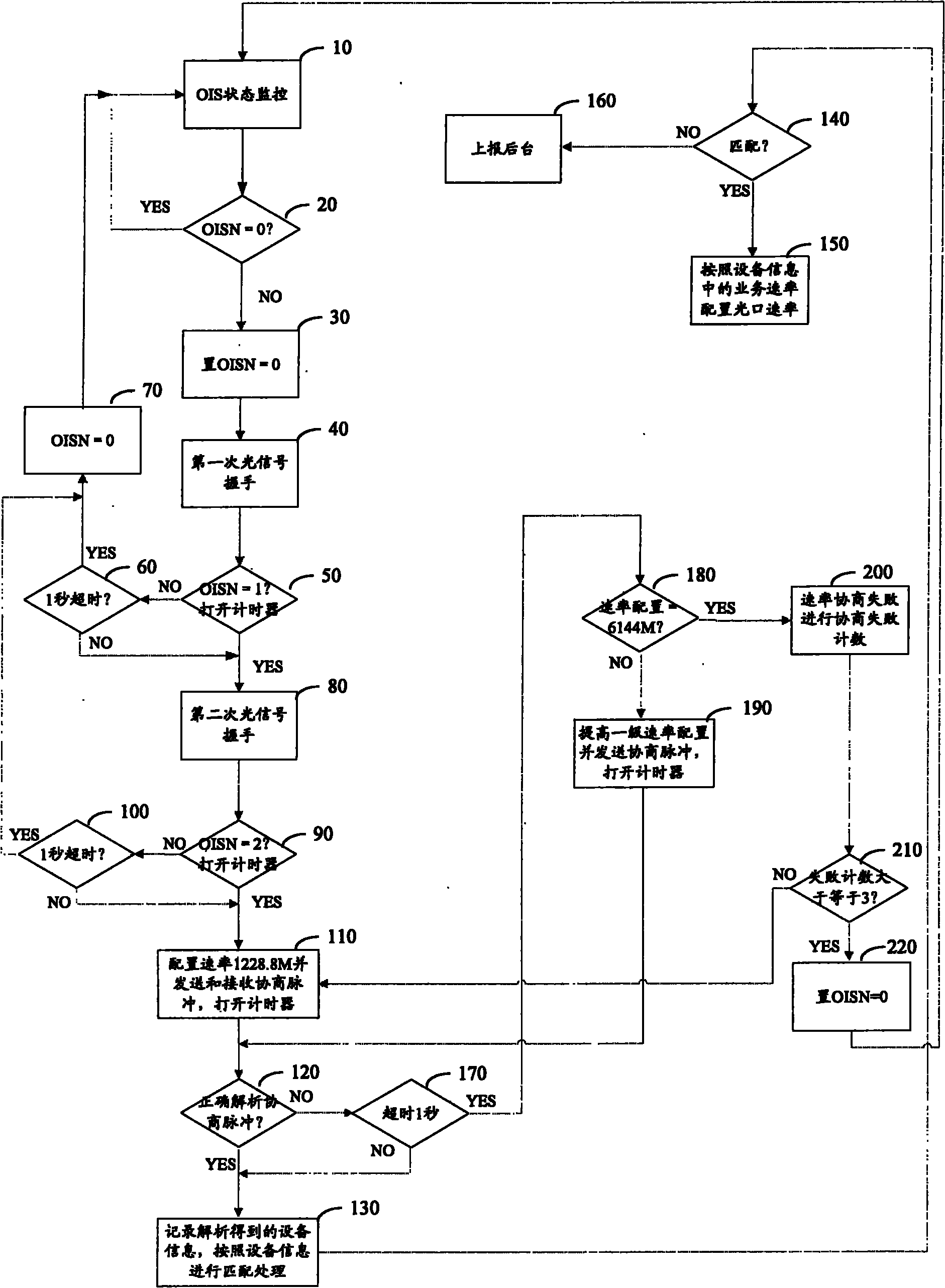
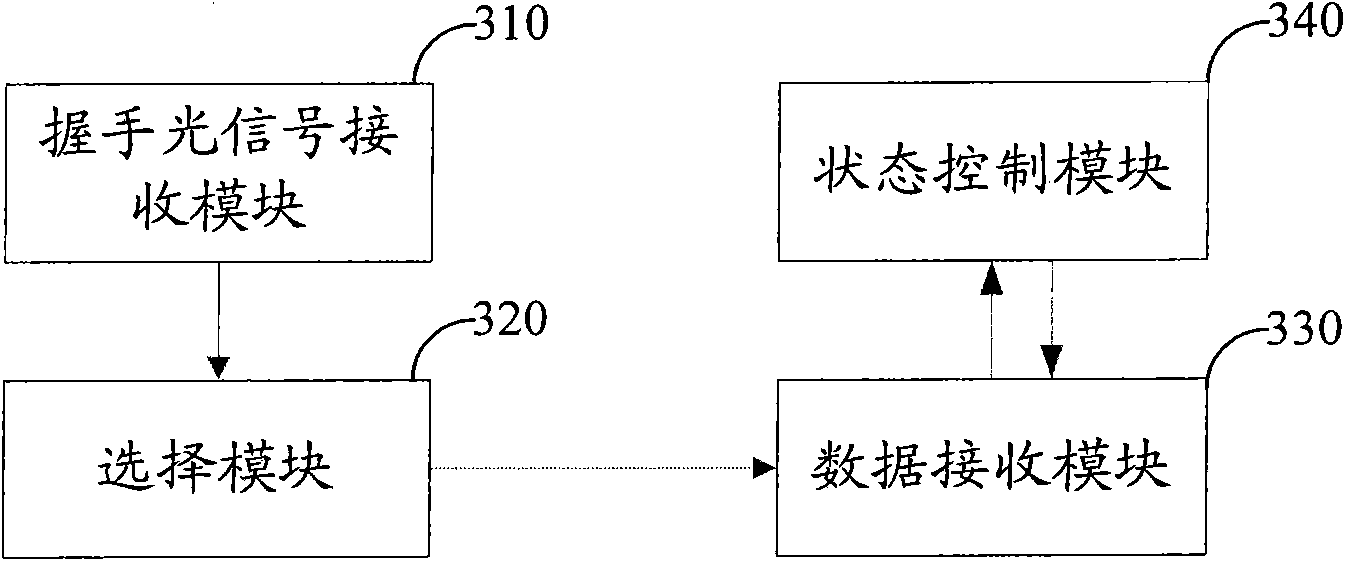
InactiveCN102340352AGood rate configuration flexibilityElectromagnetic transmissionWireless communicationEngineeringEquipment use
The invention relates to the field of optical transmission and particularly relates to an optical interface speed auto-negotiation method and a device. In the prior art, since the speed of one end of fixed when speed configuration is conducted to equipment using optical interfaces for mutual communication, the problem that system speed configuration flexibility is poor exists. The method comprises the steps that two ends shake hands through optical signals to conduct auto-negotiation synchronization, speed configuration is conducted according to a speed selected from multiple speeds, data is received according to the configured speed at the same time, the data transmitting speed of a transmitting end is equal to the configured speed, the received data is analyzed, whether the speed auto-negotiation is successful or not is judged according to an analysis result, and if the analysis result is that the received data is correct, the speed auto-negotiation is successful. By adopting the scheme, since the speed can be selected from the multiple speeds to actively conduct optical interface auto-negotiation, the system speed configuration flexibility is good.
Owner:ZTE CORP
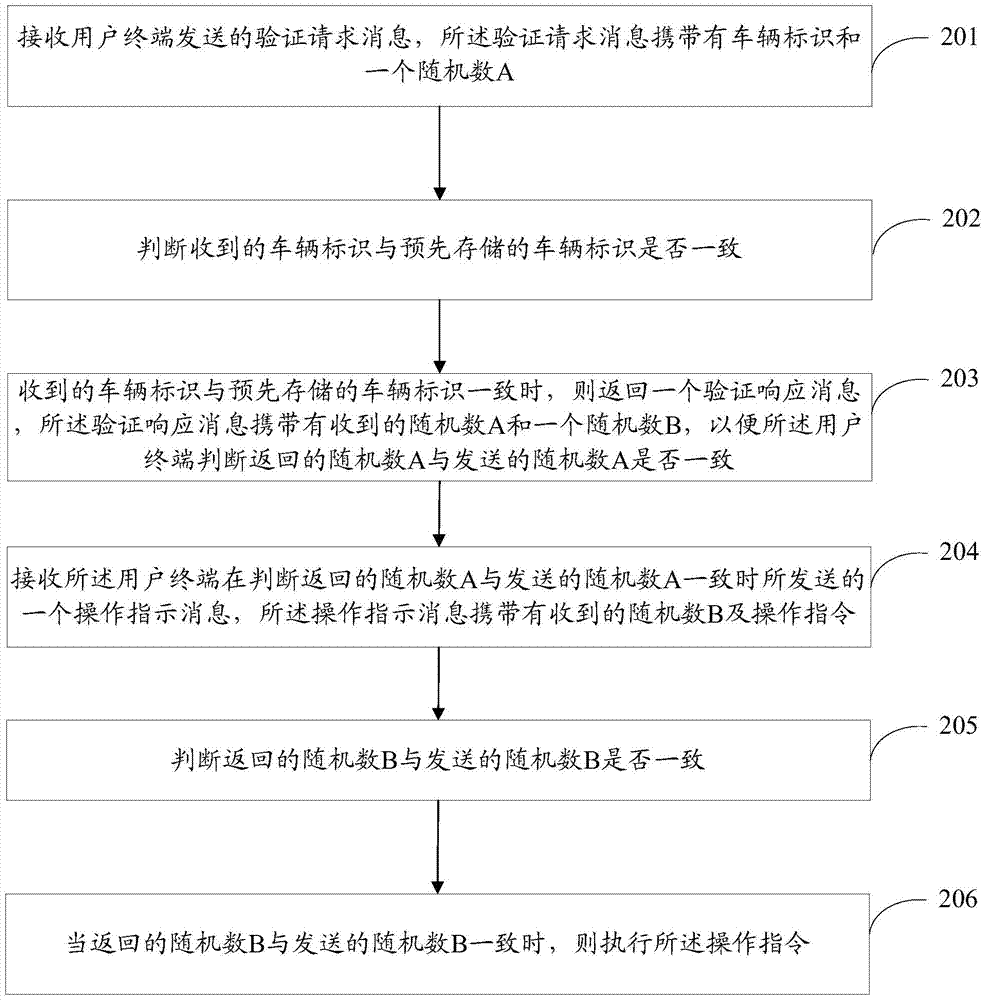
Remote control method of vehicle, user terminal and vehicle-mounted terminal
ActiveCN103617713AImprove securityAvoid crackingTransmission systemsUser identity/authority verificationRemote controlComputer terminal
The invention is applicable to the technical field of remote control and provides a remote control method of a vehicle, a user terminal and a vehicle-mounted terminal. The method comprises the following steps: sending a verification request message to the vehicle-mounted terminal, wherein the verification request message carries a vehicle mark and a random number A; receiving a verification respond message which is returned when the vehicle-mounted terminal judges that the received vehicle mark is the same as a vehicle mark pre-stored in the vehicle-mounted terminal, wherein the verification respond message carries a received random number A and a random number B; when the returned random number A is the same as the sent random number A, sending an operation indication message to the vehicle-mounted terminal, wherein the operation indication message carries a received random number B and an operation instruction; and executing the operation instruction when the vehicle-mounted terminal judges that the returned random number B is the same as the sent random number B. According to the user terminal and the vehicle-mounted terminal provided by the invention, interaction and verification of various messages can be carried out in a manner of shaking hands three times, so that the safety of remote control is improved greatly and the remote control is not easy to crack.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
Legged mobile robot control system
InactiveUS20060129278A1Improve communication performancePostural stabilityProgramme-controlled manipulatorComputer controlMobile robot controlEngineering
In a legged mobile robot control system having leg actuators each driving the individual legs and arm actuators each driving the individual arms, an external force acting on the right arm is detected, operation of the right arm actuators is controlled to produces a handshake posture, and operation of the leg actuators is controlled based on the detected external force acting on the right hand during handshaking, thereby improving communication capability by enabling it to shake hands with humans and to maintain a stable posture during the handshaking.
Owner:HONDA MOTOR CO LTD
Wireless module of network tester
InactiveCN102082613AAvoid troubleAvoid testing errorsTransmission monitoringWireless mesh networkTester device
The invention provides a wireless module of a network tester, comprising a wireless signal sending module, a wireless signal receiving module and a judgment module. The wireless fault test of the network tester is realized by handshaking of the network tester with a wireless network. The wireless module of the network tester can shake hands with multiple types of networks easily by wireless technologies such as Bluetooth, WIFI and the like, thus avoiding connection troubles of multiple types of network cables for the network tester, and effectively preventing test errors and fault misjudgment resulting from cable errors.
Owner:CHANGSHU HUAHAI ELECTRONICS
Fixing device of bronchoscope
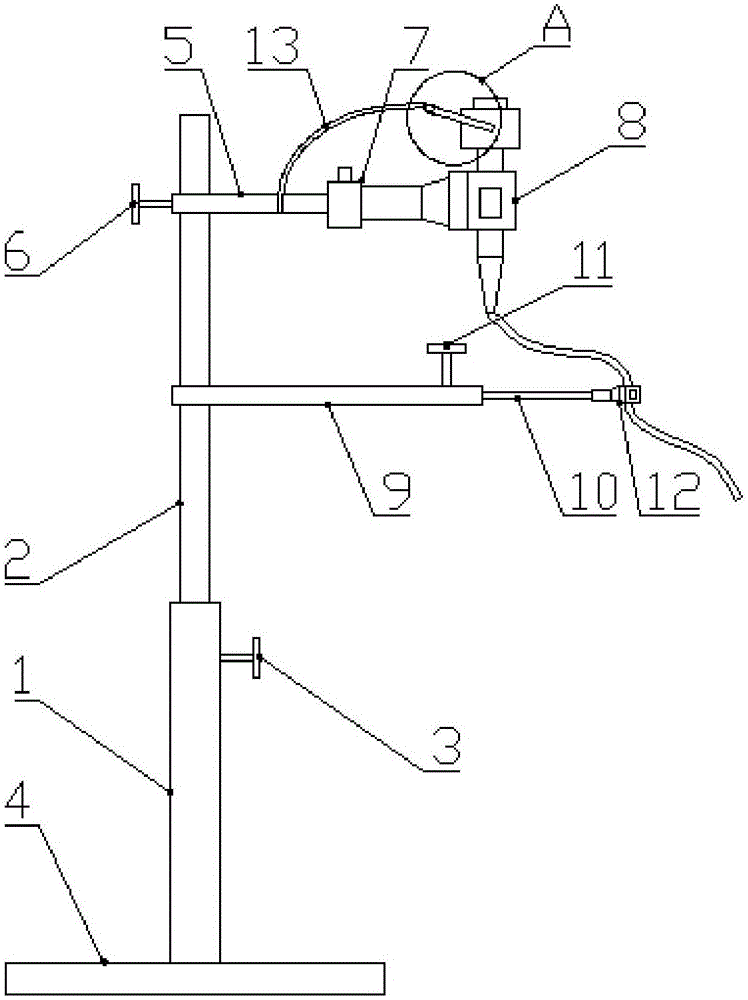
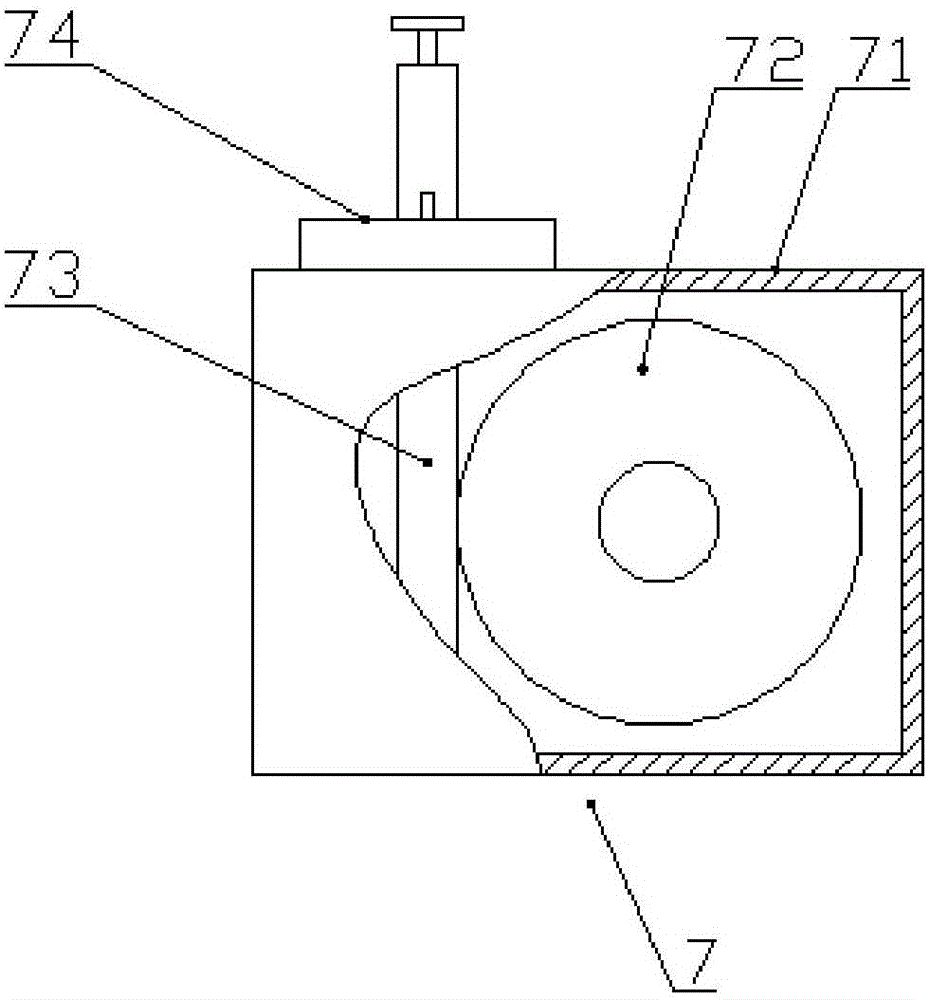
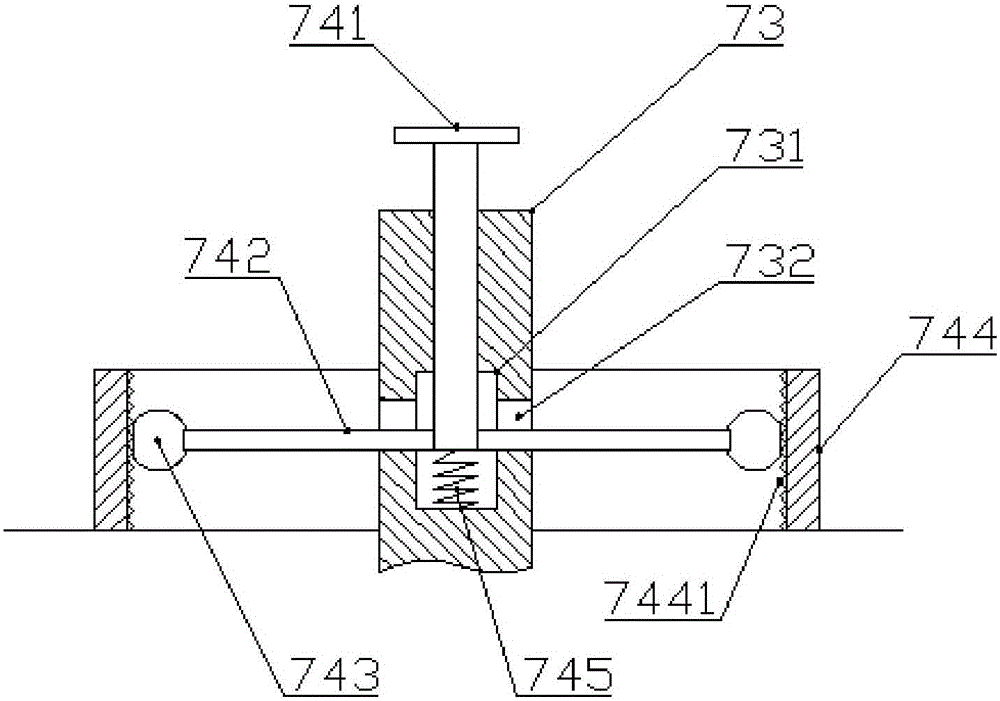
InactiveCN106344175AAvoid shaking handsAvoid Positioning EffectsSurgical instrument supportEngineeringShaking hands
The invention discloses a bronchoscope fixing device, which comprises a bracket arranged longitudinally, a base installed at the lower end of the bracket, and first and second support rods arranged transversely on the bracket, the free ends of the first and second support rods The first fixing jacket for fixing the operating part of the bronchoscope and the second fixing jacket for fixing the insertion part of the bronchoscope are respectively arranged on the first support rod, and the first fixing jacket is also provided on the first support rod to make the first fixing jacket in the longitudinal plane. Swing angle adjustment device. The device has a simple structure and is easy to operate. It can replace the hands to fix the operating part and the insertion part of the bronchoscope, avoiding hand tremors, inaccurate positioning, fatigue and other disadvantages caused by the operator's long-term holding, reducing operational risks and improving the success of disease diagnosis and treatment. Rate.
Owner:THE THIRD AFFILIATED HOSPITAL OF THIRD MILITARY MEDICAL UNIV OF PLA
Dual system detection method and system for rising of students
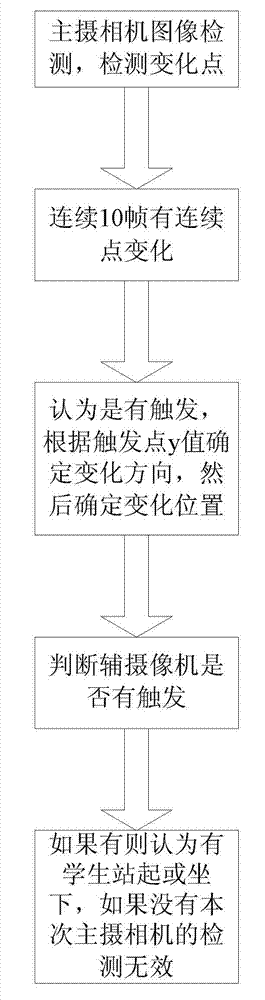
ActiveCN103686092ARemove misidentificationImprove accuracyClosed circuit television systemsComputer visionShaking hands
The method discloses a dual system detection method for rising of students. A main camera for locating images and au auxiliary camera for detecting height are combined to judge the rising of students. According to the dual system detection method and system for rising of students, the dual system detection method is adopted, so that misidentification to lowering heads, rising heads, shaking hands and the like can be effectively eliminated, and identification accuracy is greatly improved.
Owner:SZ REACH TECH
Ceramic tile seam beautifying automatic glue injection and edge pressing building decoration robot
InactiveCN108035522AEnsure safetySimplify workBuilding constructionsUltimate tensile strengthMaterials science
The invention relates to a ceramic tile seam beautifying automatic glue injection and edge pressing building decoration robot. The ceramic tile seam beautifying automatic glue injection and edge pressing building decoration robot comprises a gluing device and an edge pressing device, wherein the rear end of the gluing device is mounted at the front end of the edge pressing device. The ceramic tileseam beautifying automatic glue injection and edge pressing building decoration robot can solve the problems that, in traditional seam beautifying operation, workers need to inject glue and press edges through tools to result in complex processes; during seam beautifying agent application, the workers need to firstly place seam beautifying agent into a seam beautifying gun and then inject the seam beautifying agent into seams, seam beautifying agent fixation via the seam beautifying gun is instable, manual glue application possibly leads to glue applying deviation due to shaking hands, and manual lateral glue end cutting possibly leads to hand injury due to misoperation; during edge pressing, the workers need to forcefully press the edges of the seams with glue applied through edge pressing balls to result in limp and numb hands due to long-time hard work, long time consumption, high labor intensity, low efficiency and the like.
Owner:盛亚明
Wireless charging method and related device
ActiveCN110474437AHigh power transmission efficiencyImprove charging efficiencyCircuit arrangementsTerminal equipmentComputer terminal
The invention provides a wireless charging method and a related device. The method comprises the following steps of if a terminal device successfully shakes hands with an external charging device, making a first magnet work at first power, wherein the first magnet working at the first power is used for carrying out adsorption and counterpoint on the terminal device and the charging device, and a position of the charging device, which corresponds to the first magnet, is provided with a second magnet; and after the adsorption and counterpoint of the terminal device and the charging device, receiving electric energy transmitted by the charging device through a first charging coil so as to charge the terminal device. Through the adsorption and counterpoint of the first magnet on the terminal device and the second magnet on the charging device, a first charging coil on the terminal device is aligned with a second charging coil on the charging device so as to improve power transmission efficiency of the charging device to the terminal device and further increase charging efficiency of the terminal device.
Owner:VIVO MOBILE COMM CO LTD
Method for realizing communication between smart mobile phone chips and smart mobile phone
ActiveCN101931700AGuaranteed real-timeGuaranteed accuracySubstation equipmentData transmissionEmbedded system
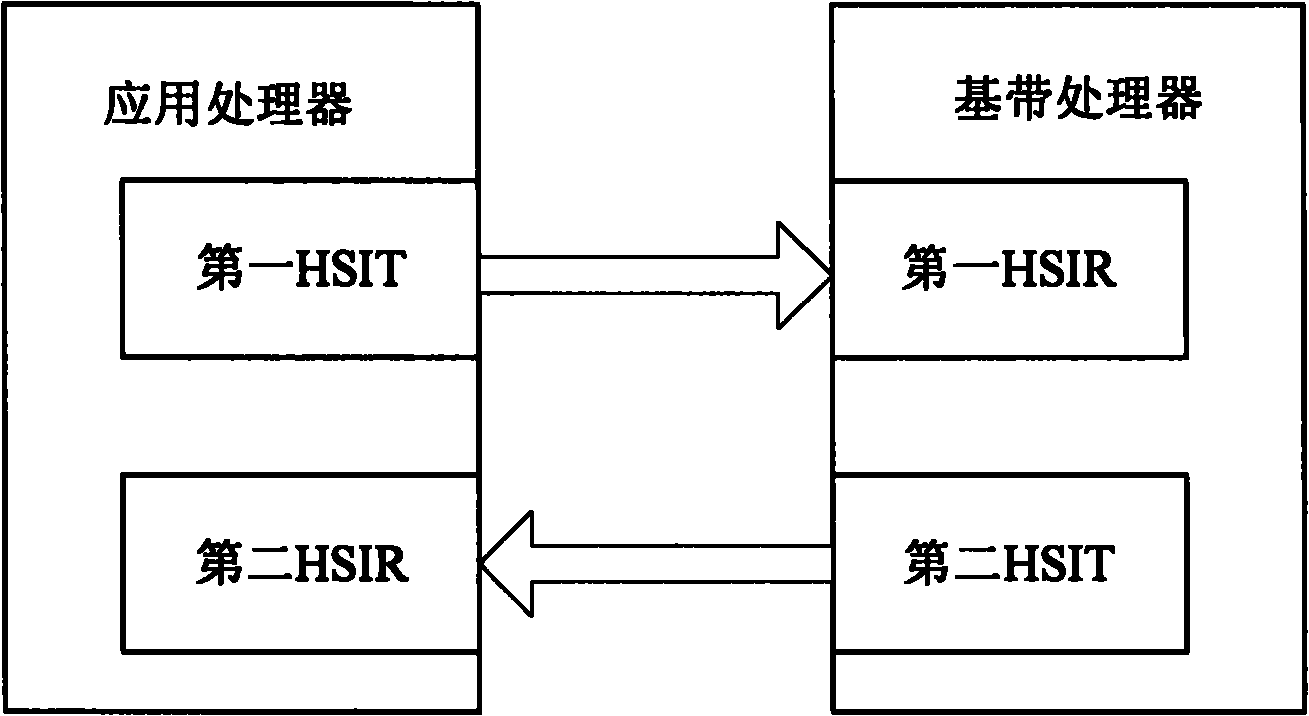
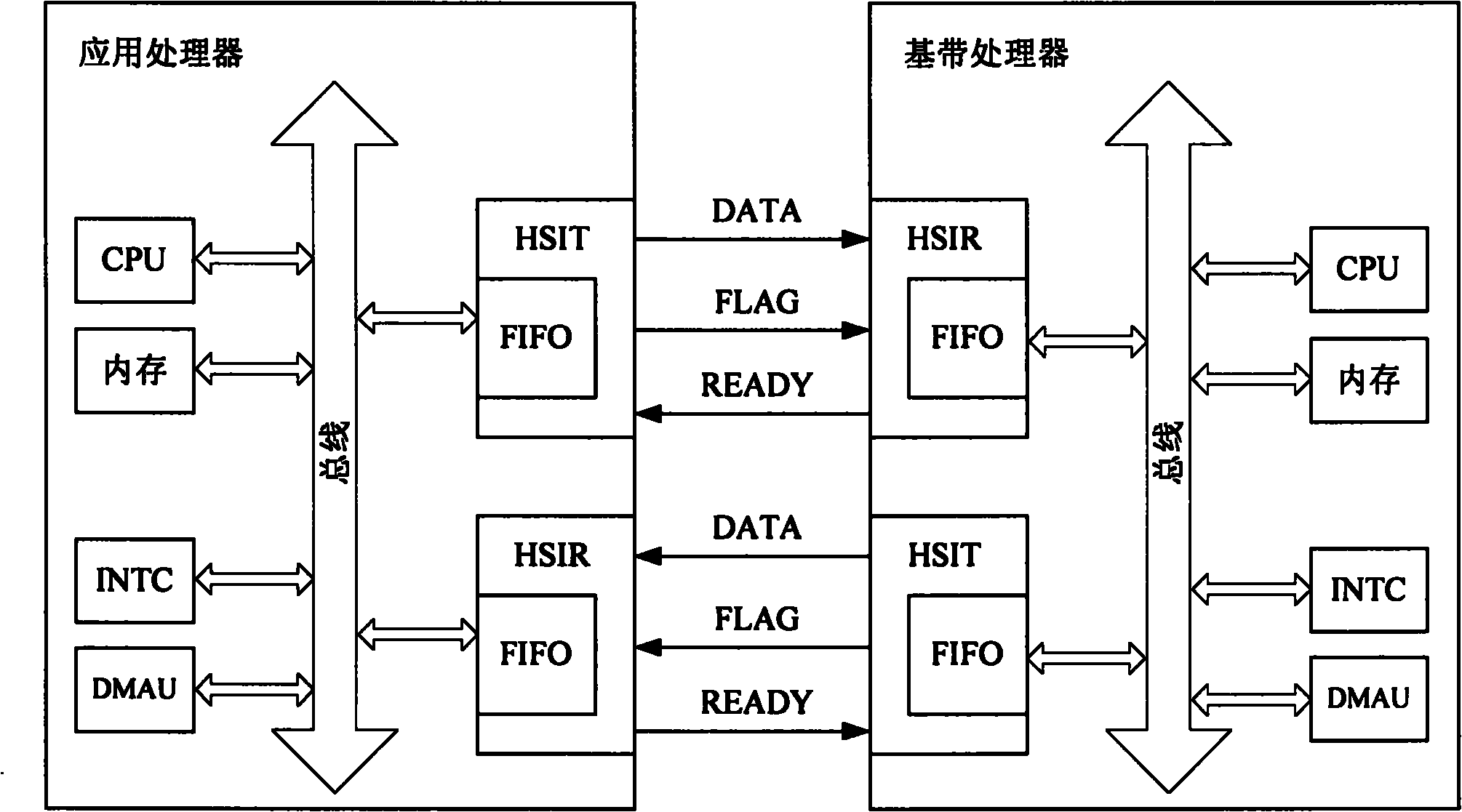
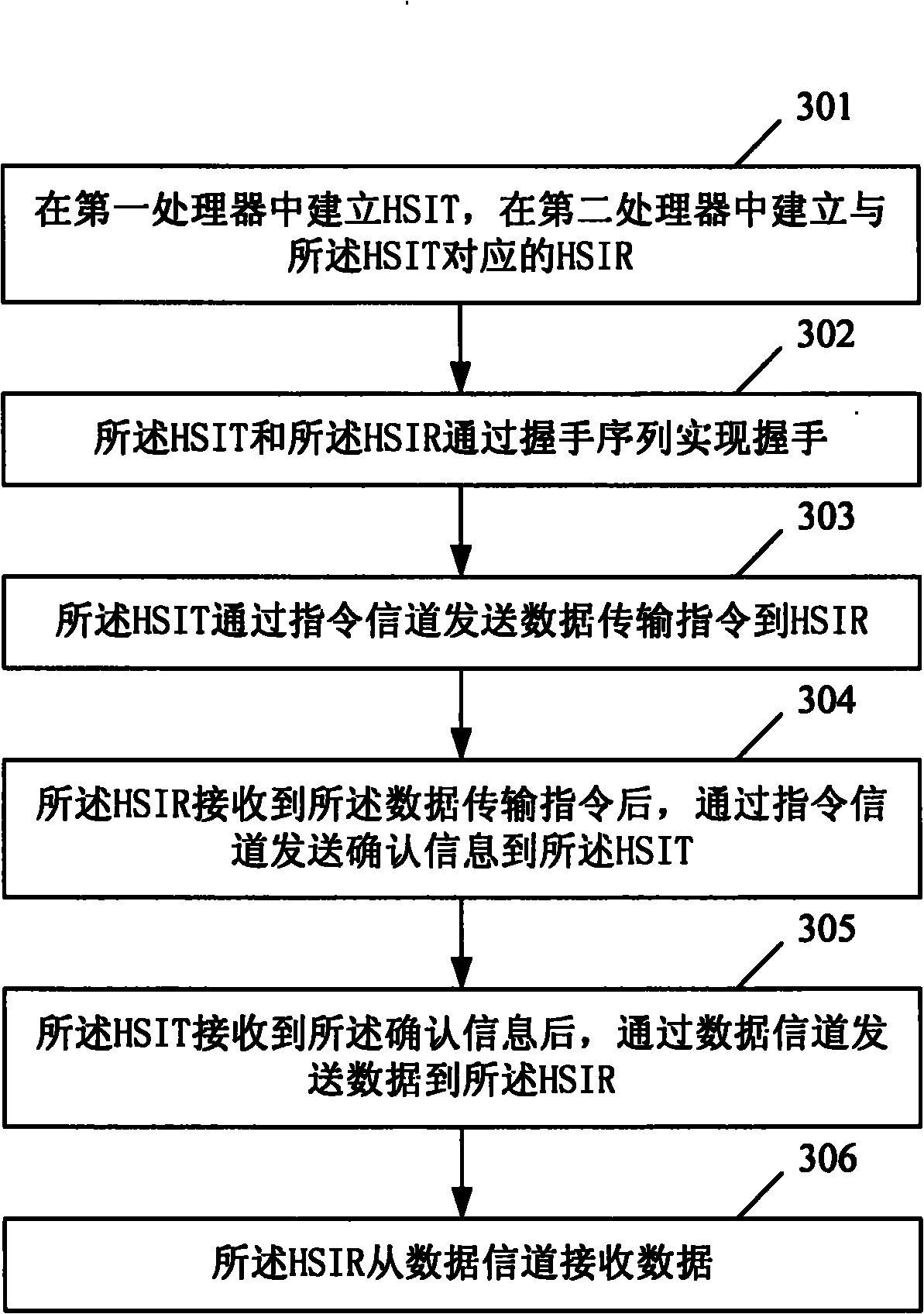
The invention provides a method for realizing the communication between smart mobile phone chips and a smart mobile phone. The smart mobile phone is configured with a first processor and a second processor. The method comprises that: an HSIT is established in the first processor and an HSIR in the second processor, wherein the HSIT and the HSIR shake hands through a handshaking sequence; the HSITsends a data transmission instruction to the HSIR through an instruction channel; the HSIR receives the data transmission instruction and transmits confirmation information to the HSIT through the instruction channel; the HSIT receives the confirmation information and transmits data to the HSIR through the data channel; and the HSIR receives the data from the data channel. In the invention, the communication between the smart mobile phone chips is realized on the basis of an HSI protocol, and the flexibility increase and complexity reduction and cost reduction of the communication between thesmart mobile phone chips are realized on the premise of ensuring the real-time and accuracy of the communication between the smart mobile phone chips.
Owner:ST ERICSSON SEMICON BEIJING
Party plate
A party plate composite for use at social gatherings and the like that serves as a plate for food as well as a holder for an eating utensil, a napkin, and a beverage container, to enable the user to hold all with one hand while leaving the other hand free to shake hands with others, or use a cell phone, to use the eating utensil or napkin, or to drink the beverage, the party plate composite comprising (a) a plate component for depositing food upon the upper surface thereof, and having an aperture depending through the upper and lower surfaces of the plate component, (b) a coupler component for disposition into the aperture and for attachment within the aperture, and (c) a beverage container holder component appropriately attached to the lower portion of the coupler component.
Owner:EVANS GREGORY A
Underwater acoustic environment monitoring wireless communication system and method
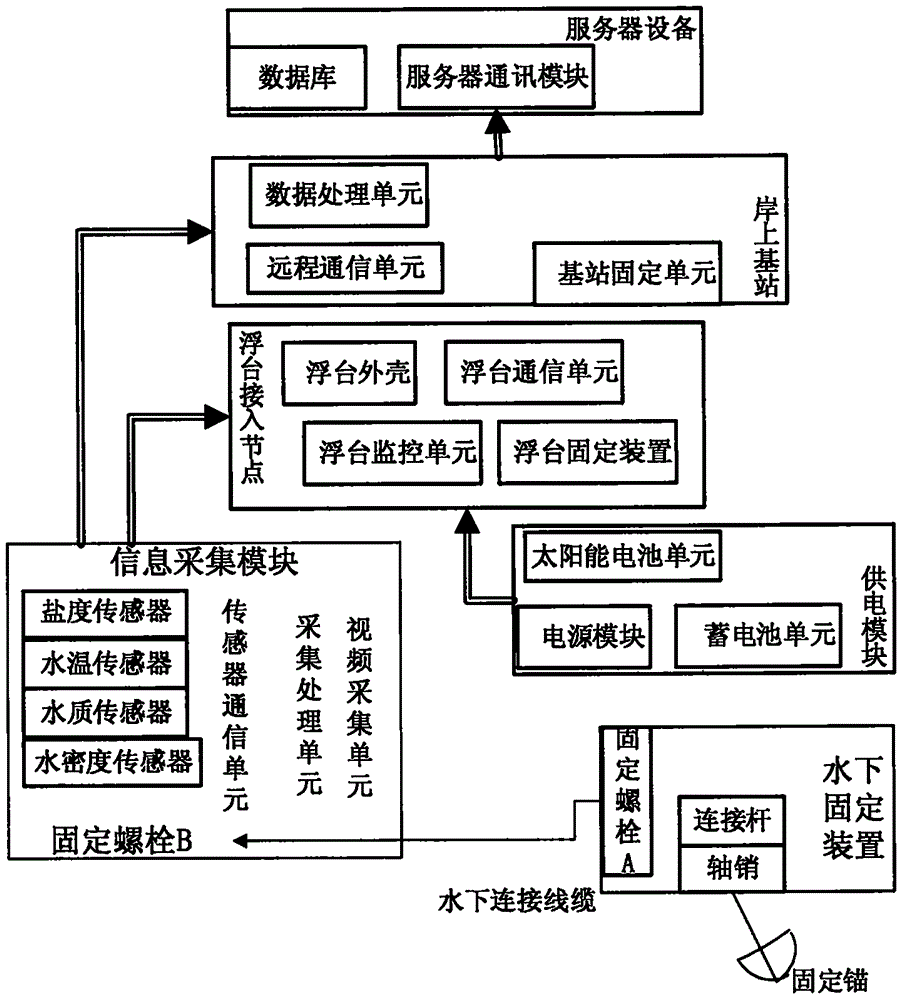
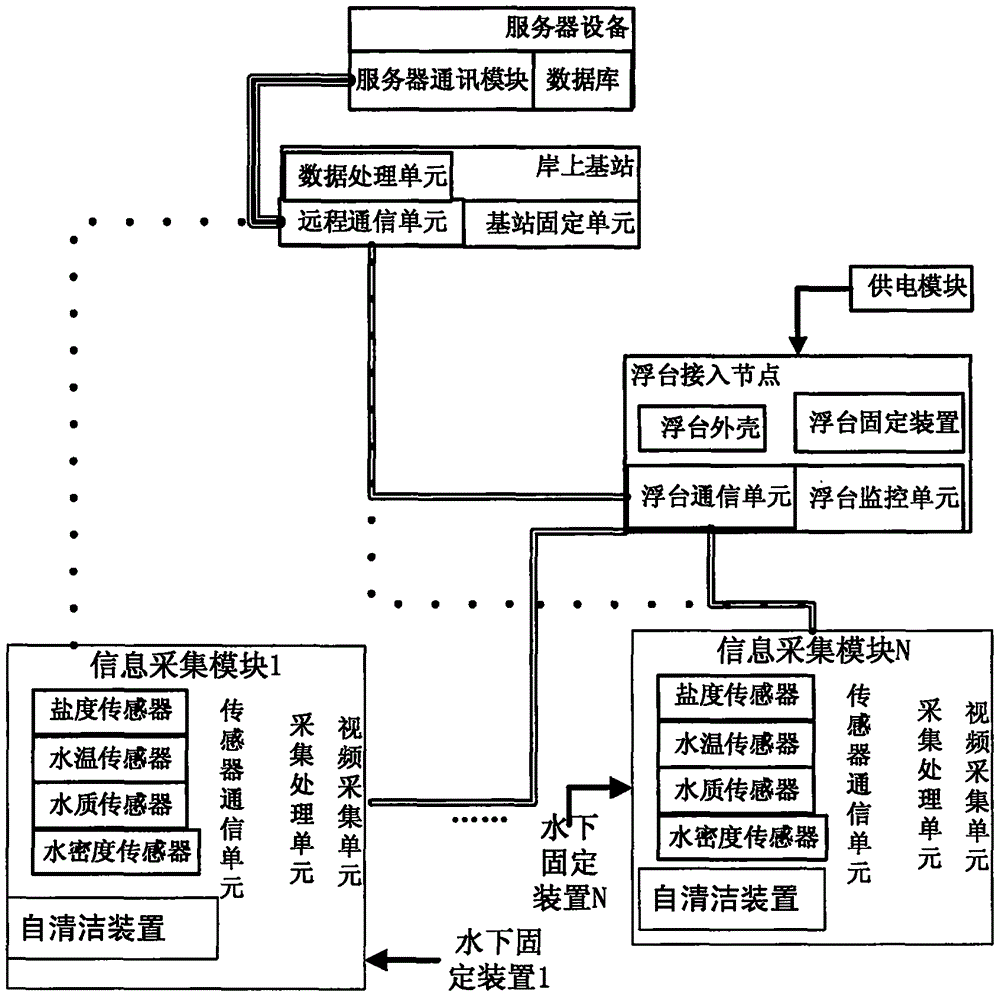
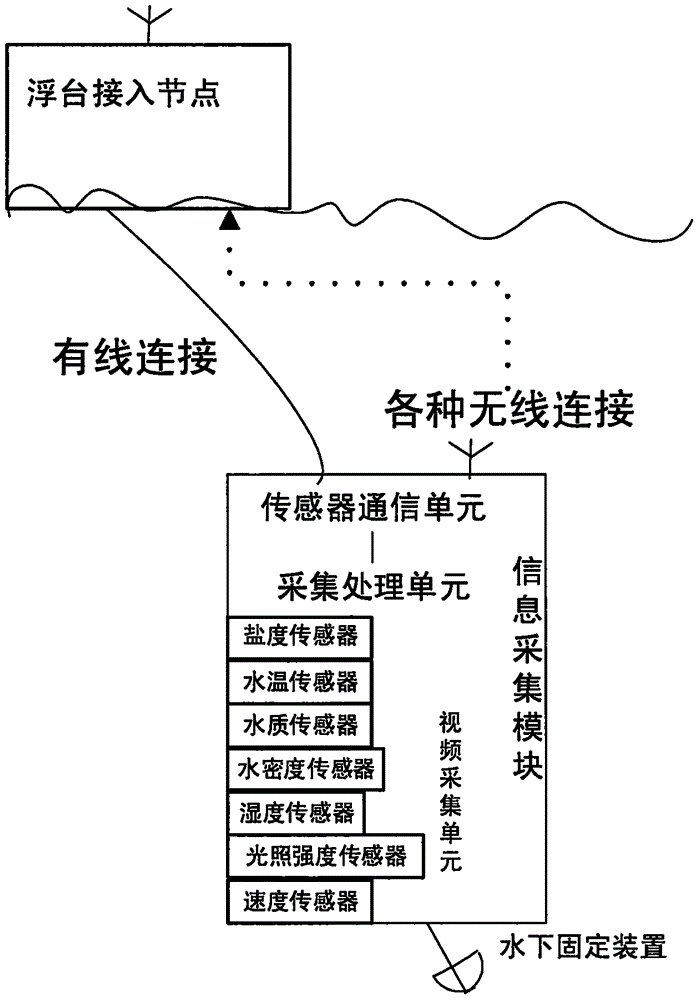
ActiveCN106197543AImprove effectivenessImprove reliabilityMeasurement devicesTransmission systemsTransmission technologyAnimal monitoring
The invention relates to an underwater acoustic environment monitoring wireless communication system and method, belonging to the technical field of water body animal monitoring, underwater acoustic environment and underwater monitoring. The system includes a floating platform access node, a shore base station, a power supply module, an information acquisition module, an underwater fixing device, and a server device. The method includes that 1) the modules in the underwater acoustic environment monitoring wireless communication system are connected and initialized; 2) the information acquisition module acquires the information and then sends the information to a sensor communication unit; 3) the sensor communication unit sends the information to the floating platform access node or the shore base station; 4) the shore base station feeds back the handshake information to a floating platform communication unit, and determines whether shaking hands with the sensor communication unit; and 5) the server device allows the shore base station to visit. The underwater acoustic environment monitoring wireless communication system and method integrate a variety of transmission technology, have the advantages of flexible realization and high information transmission efficiency, and can achieve continuous underwater acoustic environment monitoring.
Owner:NORTH BLASTING TECH
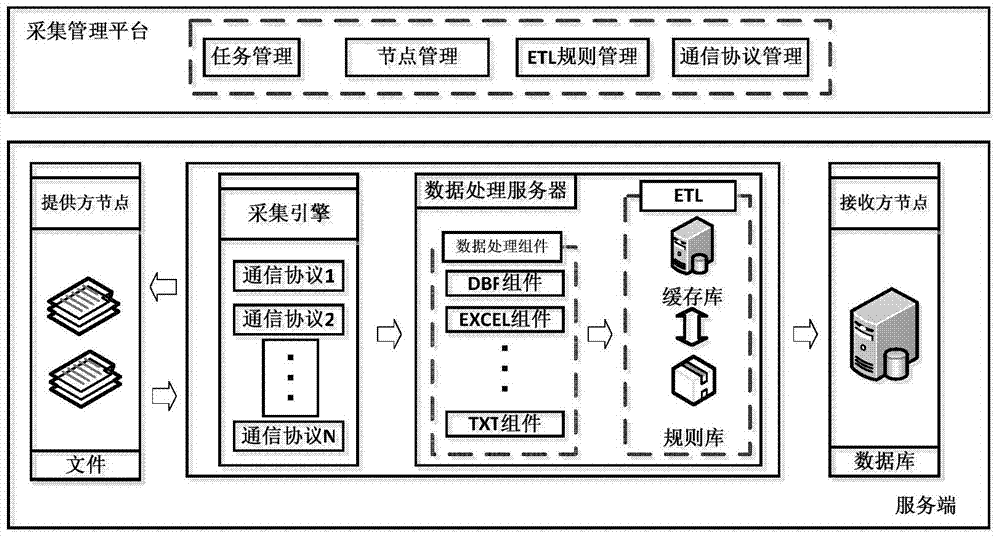
Many-to-many data acquisition system and acquisition method thereof
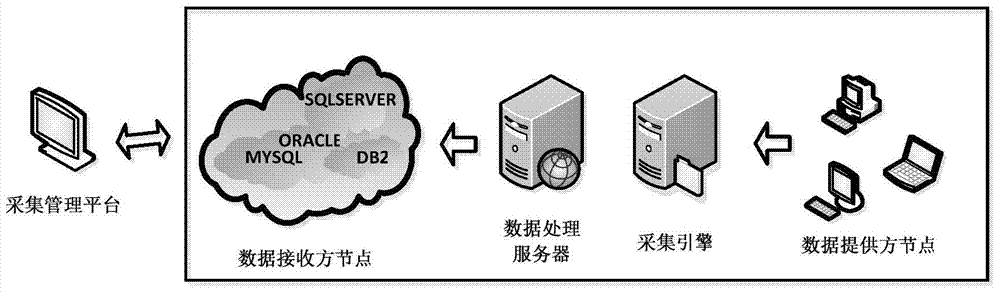
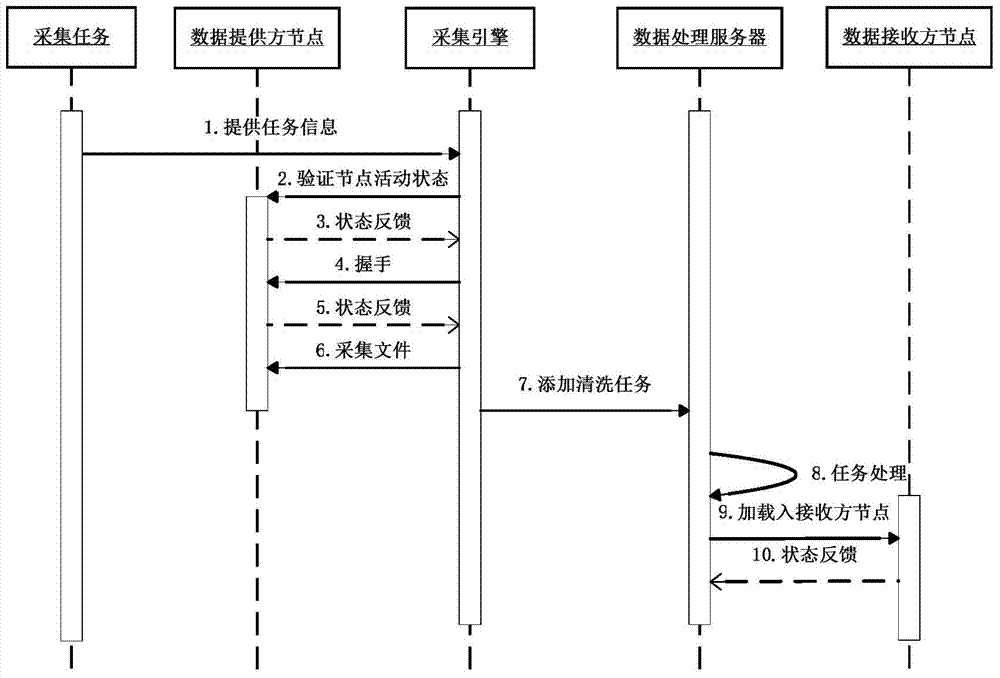
ActiveCN104504010AGuaranteed to be scalableRealize task process managementDatabase management systemsSpecial data processing applicationsRelational databaseData provider
The invention relates to the field of computer application technologies, in particular to a many-to-many data acquisition system and an acquisition method thereof. The system consists of an acquisition management platform, an acquisition engine and a data processing server, wherein the acquisition management platform is used for managing nodes, communication protocols, ETL (Extract-Transform-Load) rules and acquisition tasks; the acquisition engine supports a plurality of communication ways, and is used for shaking hands with a data provider node through a communication protocol, identifying the legitimacy of a provider, performing data acquisition, and informing the data processing server; the data processing server comprises a data cleaner and a plug-in data processing assembly. By adopting the many-to-many data acquisition system and the acquisition method thereof, a data acquisition flow is standardized, and an assembly interface is standardized; the many-to-many data acquisition system has the characteristics of high expandability, wide application range and the like, and can be applied to various systems of relational databases.
Owner:G CLOUD TECH
Secure communication method and terminal and cloud thereof
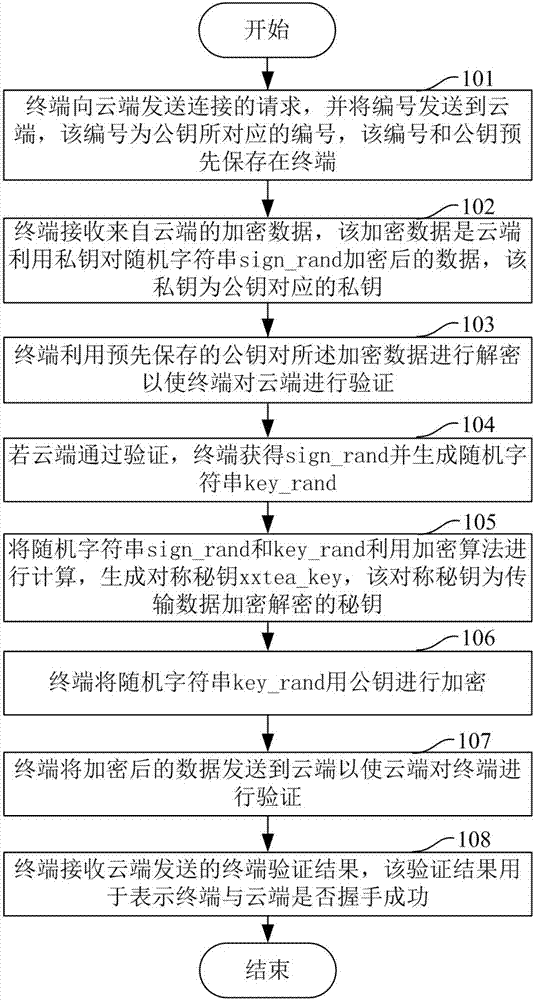
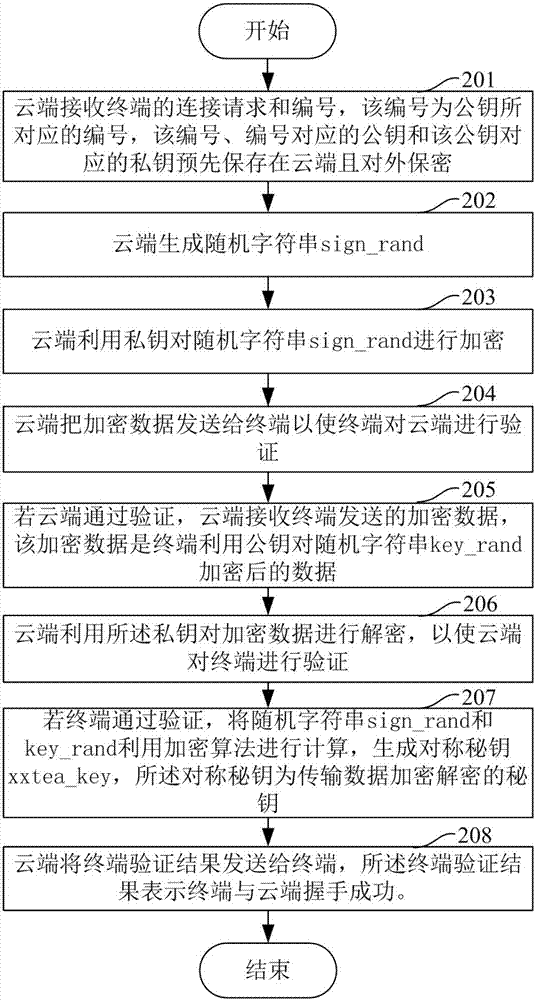
InactiveCN107483388AVerify legitimacySimplify the interaction processTransmissionSecure communicationEncryption decryption
The invention provides a secure communication method and a terminal and a cloud thereof. The method comprises the following steps: transmitting a connection request to the cloud by the terminal, and transmitting a number corresponding to a public key to the cloud; receiving encrypted data from the cloud by the terminal, wherein the encrypted data are obtained by using a private key to encrypt a random string sign-rand by the cloud; decrypting the encrypted data by using the public key by the terminal, so as to enable the terminal to verify the cloud; if the verification is passed, calculating the random string sign-rand obtained by the terminal and a random string key-rand generated by the terminal by using an encryption algorithm, and generating symmetric keys, wherein the symmetric keys are keys for encrypting and decrypting transmitted data; encrypting the random string key-rand by using the public key by the terminal; transmitting the encrypted data to the cloud by the terminal, so as to enable the cloud to verify the terminal; and receiving a terminal verification result sent by the cloud which is used for representing whether the terminal and the cloud shake hands successfully by the terminal. The method, the terminal and the cloud provided by the invention reduce the operation and maintenance cost and reduce the number of times of network interactions.
Owner:SHENZHEN SPOTMAU INFORMATION TECH CO LTD
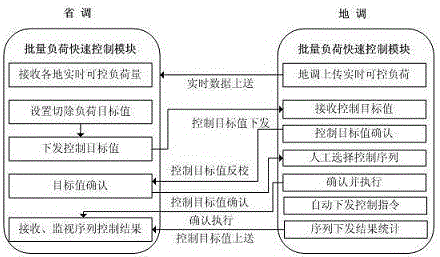
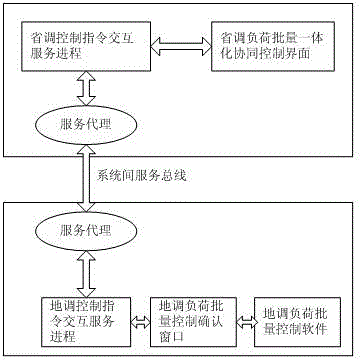
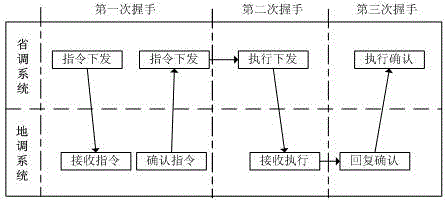
Provincially-locally integrated load batch cooperative control method and system
ActiveCN106786618ASafe and stable operationRealize one-button batch load control with saving adjustmentPower network operation systems integrationAc network voltage adjustmentSmart gridPower grid
The invention relates to a provincially-locally integrated load batch cooperative control method and a system. Based on a provincial-local intelligent power grid regulation and control isomorphic system, in case of an emergent accident, load that each region should provided is calculated through provincial regulation; a load cutting target value is issued to each region; the local regulation receives a control command to shake hands for three times with the provincial regulation; and load batch cutting is performed according to the load cutting target value. Thus, provincial regulation one-button type batch load control is achieved; in the case that when large power is deficient in the provincial power grid, rapid and batch control of load of each region is achieved; and safe and reliable operation of regional power grid is effectively ensured. According to the invention, by use of a cross system service bus, cooperative interaction of provincial-local load batch control information, rapid issuing of the control command and real-time feedback of the control result are achieved; safety and rapidness of batch load control between provinces and regions can be greatly improved; and safe and stable operation of the power grid in case of an emergency is ensured.
Owner:NARI TECH CO LTD +3
Complex dynamic routing analysis method for realizing telecommunication network based on intelligent routing simulation technique
The invention relates to a complex dynamic routing analysis method for realizing a telecommunication network based on the intelligent routing simulation technique. A BGP router is simulated by a software program at a monitoring host computer and is only used for monitoring all neighbors and does not forward BGP packets of the neighbors; the software router configures the neighbors at a front page; the router receives and analyzes the update information transmitted by the neighbors and writes the information into a local routing table and a database after shaking hands with the neighbors through open information, but does not broadcast the local routing table to the neighbors, so that the neighbors can not know the reachable destination network through a local software router, and the neighbors can not transmit a BGP protocol packet to the local software router for the forwarding service; and the software router adopts the steps for configuring monitoring neighbors: after a user edits the increase of neighbors, elimination of the neighbors and edition of the neighbor's information on the front page of the software router, the configuration of BGP neighbors is realized through TCP connection to transmit the BGP background of the monitoring host computer.
Owner:LINKAGE SYST INTEGRATION
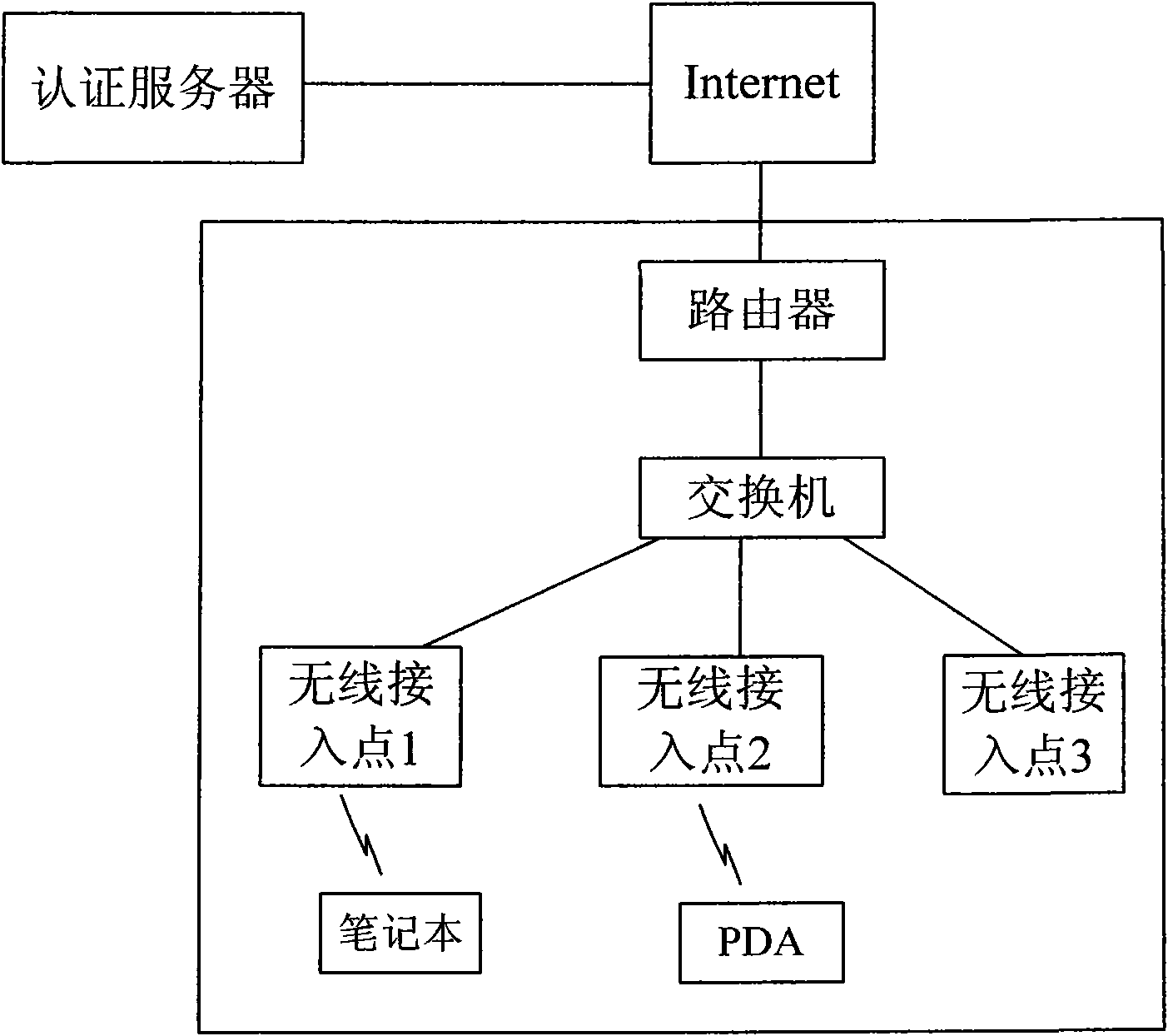
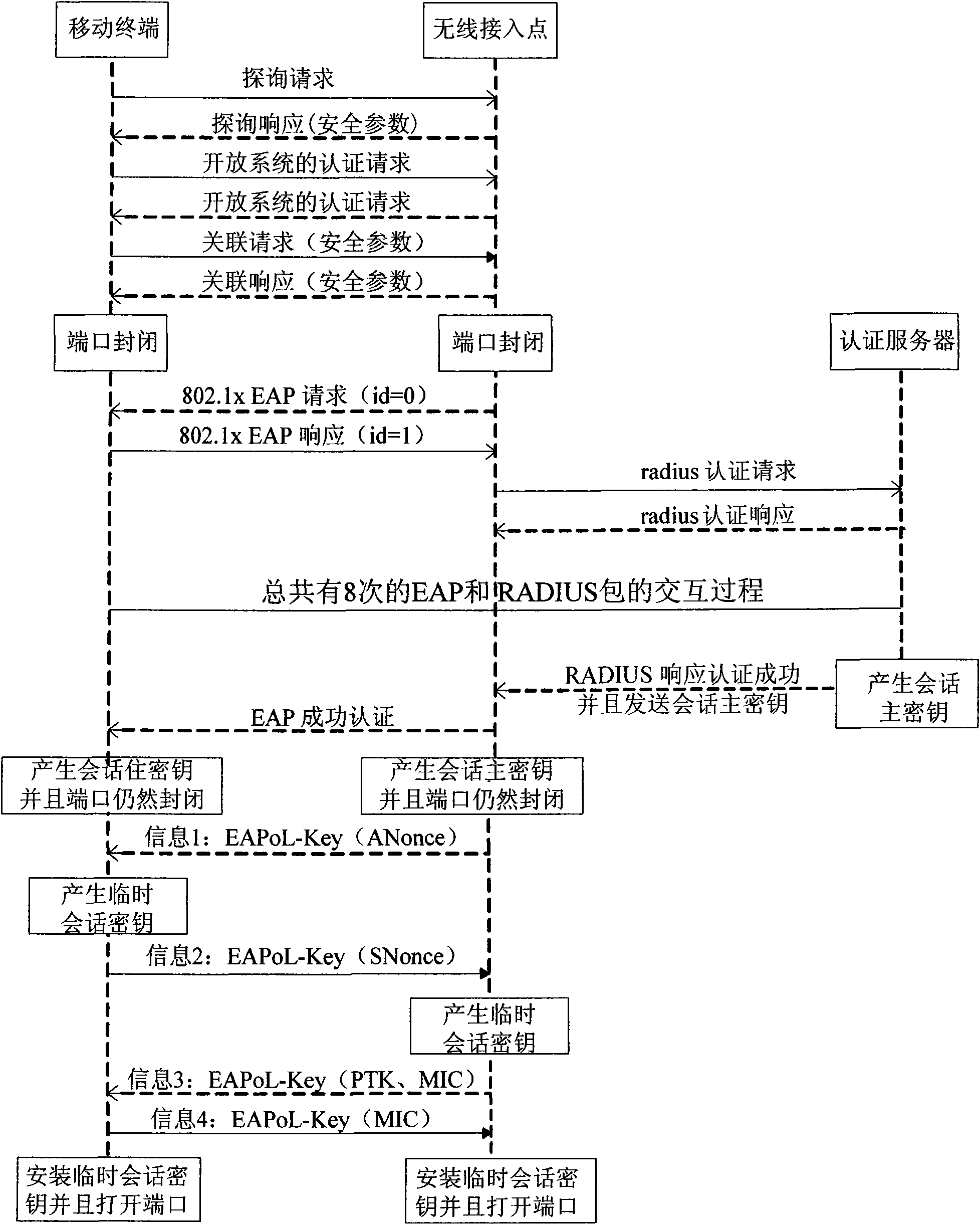
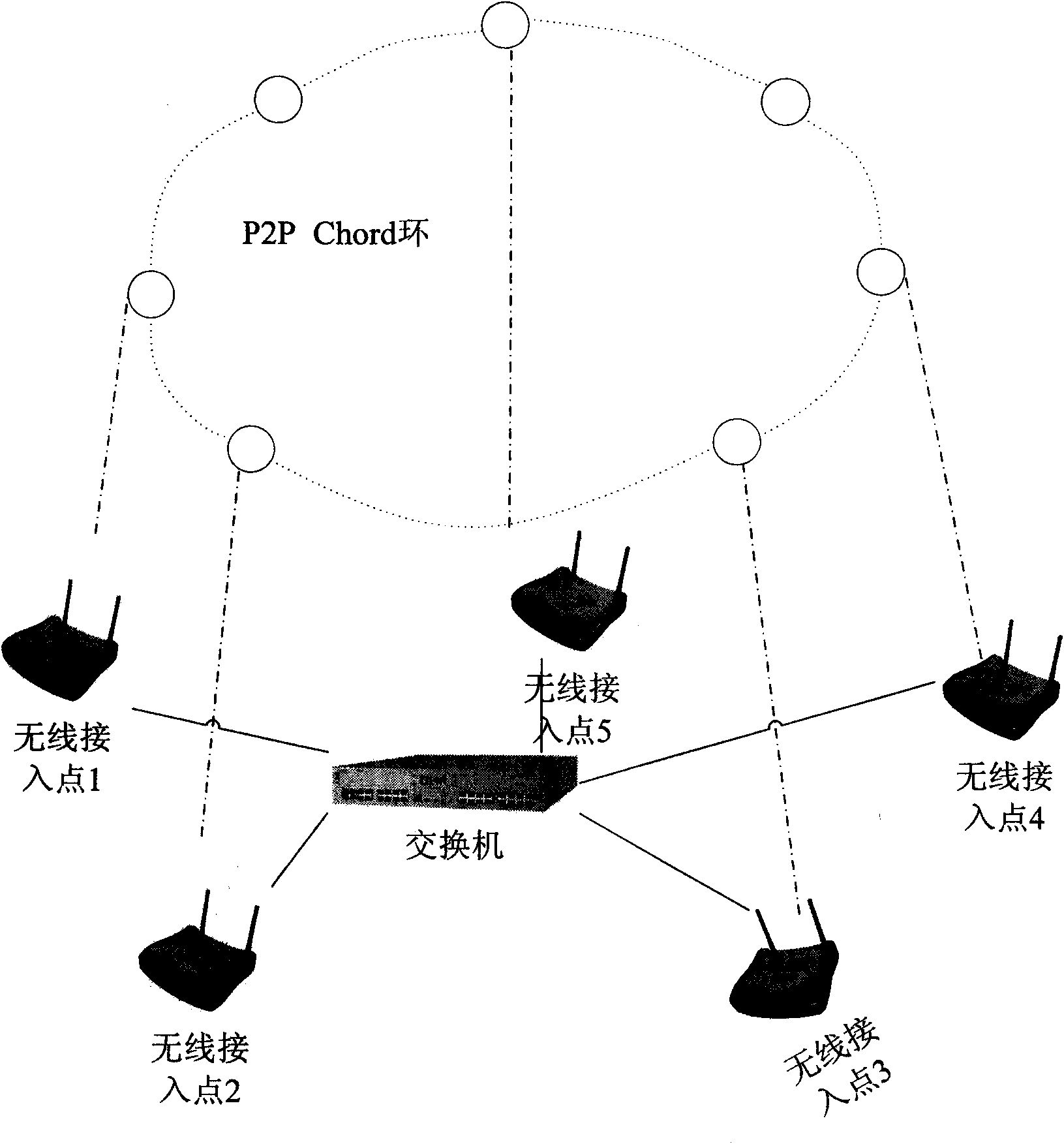
Method for realizing roaming authentication of mobile terminal in wireless local area network and access point
ActiveCN101902722AEnsure balanceInstant Routing RestorationSecurity arrangementNetwork data managementQuality of serviceRogue access point
The invention relates to a method for realizing roaming authentication of a mobile terminal in a wireless local area network and a wireless access point. The method comprises the following steps: an AP in the wireless local area network forms a Chord ring through a point-to-point Chord algorithm; the mobile terminal firstly accesses to the wireless local area network to complete the identity authentication through the AP; the AP generates a temporary session key through repeatedly shaking hands with the mobile terminal according to the session master key information distributed by a server tocomplete the authentication, and distributes the session mater key information to a corresponding AP in the Chord ring; and the mobile terminal roams and requests to access in another AP, the anotherAP acquires the session master key information from the AP stored with the master key information, and shakes hands with the mobile terminal repeatedly by utilizing the session master key informationto generate a temporary session key so as to complete the roaming authentication. The invention can reduce the changing-over delay of the mobile terminal, ensure the service quality of real-time communication, and reduce the burden of an authentication server so as to solve the problem of single fault point.
Owner:NANTONG WELL ELECTRIC MOTOR
Wireless charging method and related equipment
ActiveCN110571951AHigh power transmission efficiencyImprove charging efficiencyBatteries circuit arrangementsElectric powerTerminal equipmentEngineering
The invention provides a wireless charging method and related equipment. The method comprises the following steps that: under the condition that charging equipment successfully shakes hands with external terminal equipment, a driving assembly is controlled to drive a second magnet to move to a target position, a distance between the second magnet at the target position and a first magnet on the terminal equipment is smaller than a preset distance; at the target position, the second magnet is controlled to work with first power, and the second magnet working with the first power is used for theadsorption and alignment of the charging equipment and the terminal equipment; and after the charging equipment and the terminal equipment are adsorbed to each other and aligned with each other, thesecond charging coil of the charging equipment transmits electric energy to the first charging coil of the terminal equipment, so that the battery of the terminal equipment can be charged. Therefore,with the movable second magnet adpted, the charging equipment can charge terminal equipment of different types and sizes, and the types of the terminal equipment are effectively enriched.
Owner:VIVO MOBILE COMM CO LTD
Automatic centering device of belted layer of tyre building machine
InactiveCN102019703AQuality improvementRealize automatic correction functionTyresNarrow rangeEngineering
The invention discloses an automatic centering device of a belted layer of a tyre building machine. The automatic centering device comprises left and right guide plates arranged above a feeding rack, wherein the left guide plate is fixedly provided with a left splint; an automatic centering device is additionally arranged at a feeding head part close to a belt drum; shaking hand wheel causes a screw rod to rotate to push the right guide plate at one side to move; a synchronous belt is driven by the splint to cause a left guide roll to simultaneously move toward the opposite direction, so that the distance between two rows of rolls is close to the width of the belted layer; and a cylinder shaft extends out to push the guide plates to move within a narrow range. After the belt material contact the belt drum, a photoelectric sensor sends out an electrical signal to control the cylinder shaft to retract; and the left and right guide plates clamp and center materials, thereby achieving an automatic centering function. The center of the mechanism deviates from the center of the drum, a nut is screwed off, a bolt is regulated to cause the whole device to transversely move, and the nut is screwed down after the center is centered, thereby improving the quality of a molded tyre.
Owner:健伦精密机械(中国)有限公司
Wireless charging method and related equipment
ActiveCN110571952AHigh power transmission efficiencyImprove charging efficiencyBatteries circuit arrangementsElectric powerElectrical batteryTerminal equipment
The invention provides a wireless charging method and related equipment. The method comprises the following steps that: the electric quantity of terminal equipment is detected under the condition thatthe terminal equipment successfully shakes hands with external charging equipment; the target power of a first magnet is determined based on the electric quantity of the terminal equipment; the firstmagnet is controlled to work with target power, the first magnet working with the target power is used for the adsorption and alignment of the terminal equipment and the charging equipment, and a second magnet is arranged at a position, corresponding to the first magnet, of the charging equipment; and after the terminal equipment and the charging equipment are adsorbed to each other and aligned with each other, power is transmitted through a first charging coil, so that the charging equipment charges the battery of the terminal equipment. Therefore, the efficiency of the electric energy transmission of the charging equipment to the terminal equipment can be improved, and the charging efficiency of the terminal equipment is improved.
Owner:VIVO MOBILE COMM CO LTD
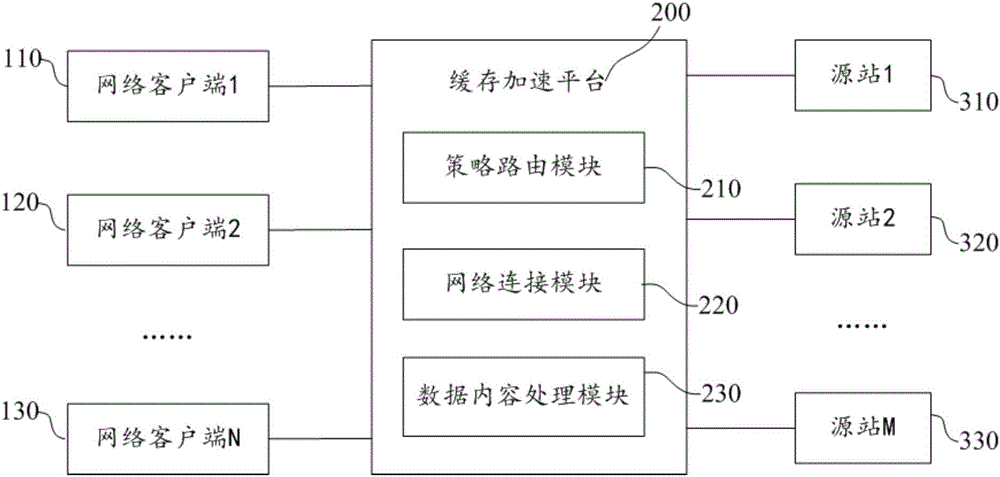
HTTP transparent proxy caching implementation method and system
InactiveCN107528908AImprove access speedAvoiding the Security Concerns of PhishingTransmissionSpecial data processing applicationsTTEthernetInternet content
The invention belongs to the technical field of network communication, and provides an HTTP transparent proxy caching implementation method and system in order to solve the technical problem that in the prior art, requests of netizens are guided to a non-source station IP address in the process of implementing Internet content caching acceleration. The method comprises the steps that 1, a network request uplinked by a network client is routed to a caching acceleration platform through a predetermined strategy, and a message downlinked to the network client is routed to the caching acceleration platform through a predetermined strategy; 2, when the network client is ready to initiate a TCP handshake connection with a host IP address of a to-be-accessed source station, the caching acceleration platform simulates the source station to achieve the TCP handshake connection with the network client; and 3, after the caching acceleration platform successfully shakes hands with the network client, the network client initiates an HTTP GET request message to the caching acceleration platform.
Owner:北京新流万联网络技术有限公司
Roller-replacing trolley
ActiveCN102492909AEasy to replaceReduce labor intensityHot-dipping/immersion processesHydraulic cylinderHydraulic pump
The invention provides a roller-replacing trolley. According to the invention, a roller comprises a shaft head and a roller notch; the roller-replacing trolley comprises a roller traction trolley, a traction motor, a motor transmission traction mechanism, a connection rod lifting mechanism, a rocker arm, a two-force rod, a support frame, a support block, a support rod, an electric control cabinetsupport, an electric control cabinet, a hydraulic pump station, a lifting guiding wheel, a walking transmission motor, a transmission shaft, a hydraulic cylinder, a wheel, a guiding rail, a roller-replacing sphere top hydraulic cylinder, a shaking hand wheel, a roller clamping plate, a positioning pin, a synchronizing shaft, a trailer wagon headstock and a sliding rail. The roller-replacing trolley provided by the invention brings great convenience for continuous zinc coating and the replacement of the roller in a degreasing section of an annealing line, the time for replacing the roller is reduced, the labor intensity of workers is lightened, and the production cost is reduced for a production line. The roller-replacing trolley is simple to operate, safe and reliable, shows humanity management of mechatronics and is inevitable equipment for a strip steel production line.
Owner:TANGSHAN CAOFEIDIAN DISTRICT SHOUYAN MACHINERY CO LTD
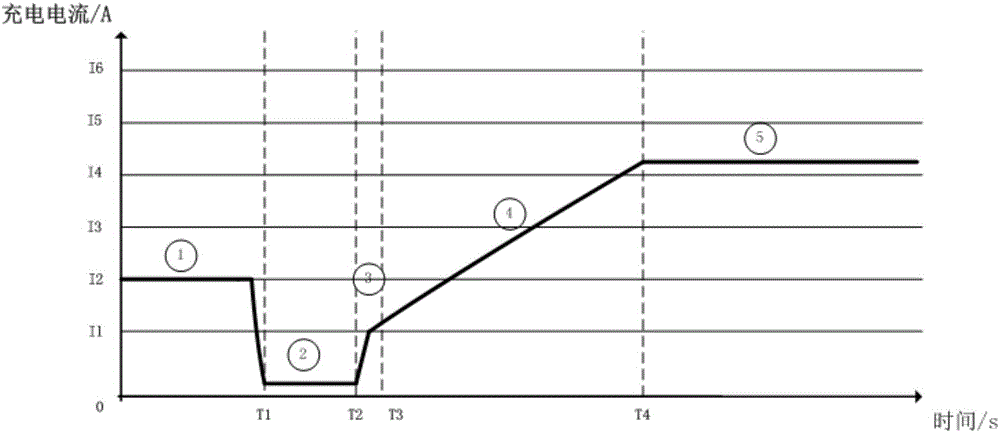
Quick charging method, mobile terminal and adapter
ActiveCN106537723AImprove securityCircuit authenticationCurrent supply arrangementsComputer terminalConstant current
In the embodiment of the invention, a mobile terminal identifies the type of an adapter and actively starts a quick charging request, so the mobile terminal can shake hands with the adapter so as to determine charging parameters; the adapter can use a segmented constant current mode to charge the battery of the mobile terminal, thus ensuring the quick charging process to be safe and reliable.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com