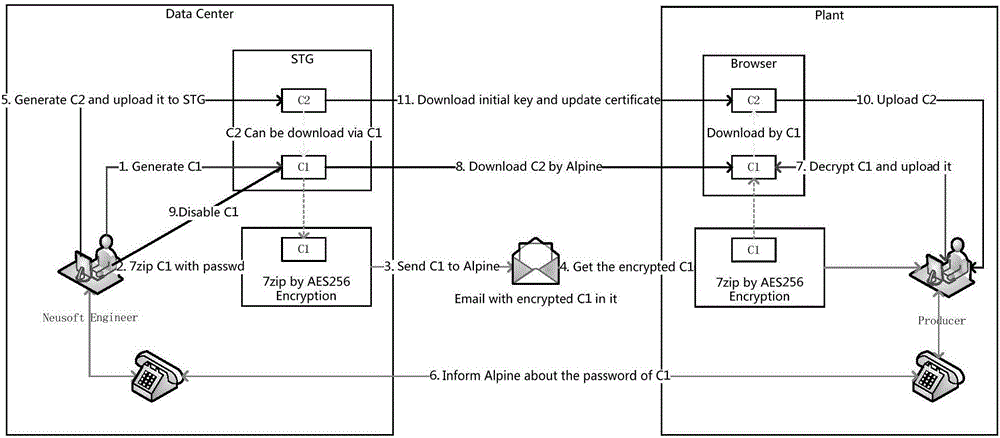
Patents
Literature
2264 results about "Handshake" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A handshake is a globally widespread, brief greeting or parting tradition in which two people grasp one of each other's like hands, in most cases accompanied by a brief up-and-down movement of the grasped hands. Handshakes are sometimes used to signify romantic relationships.
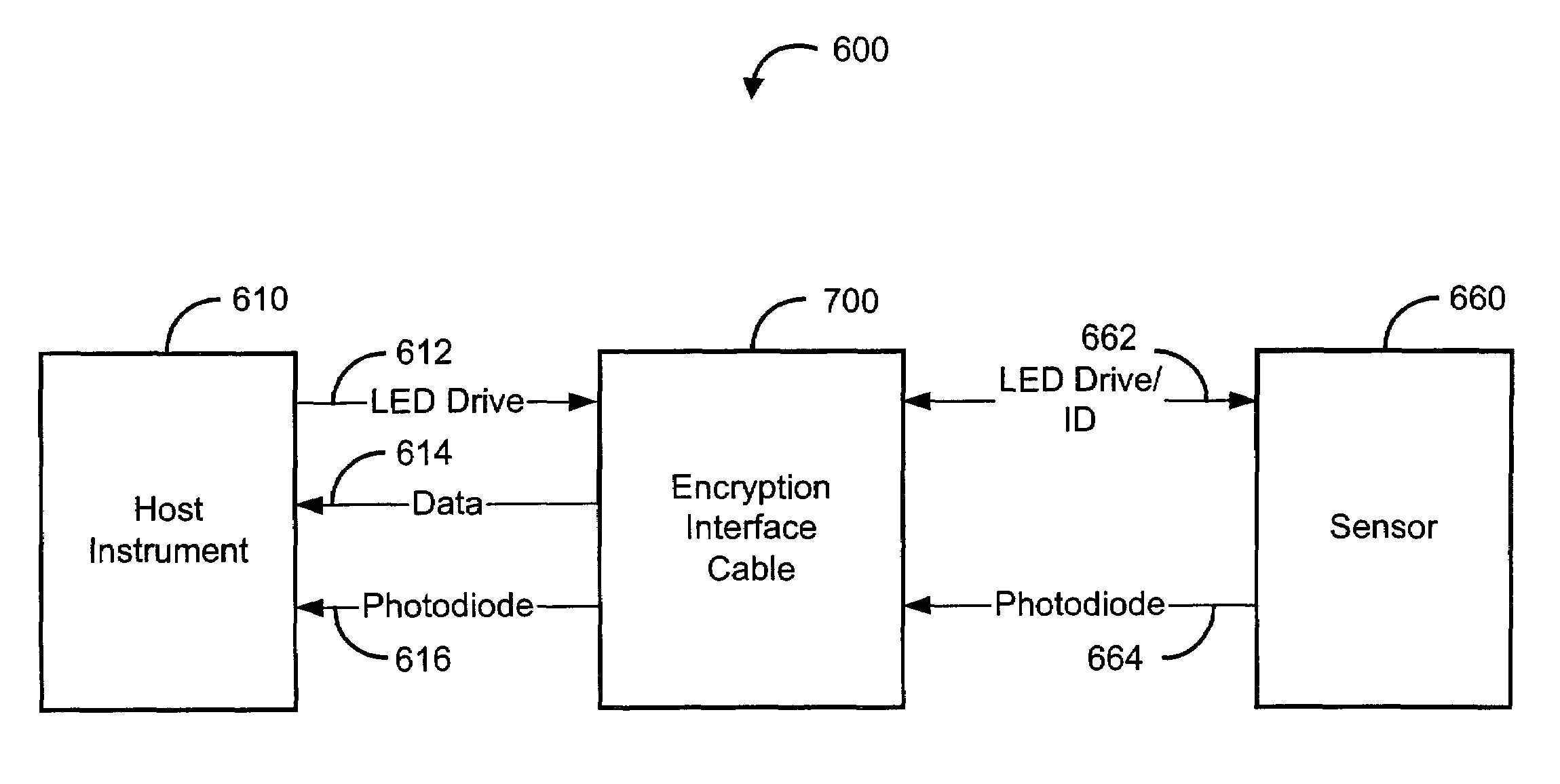
Interface cable
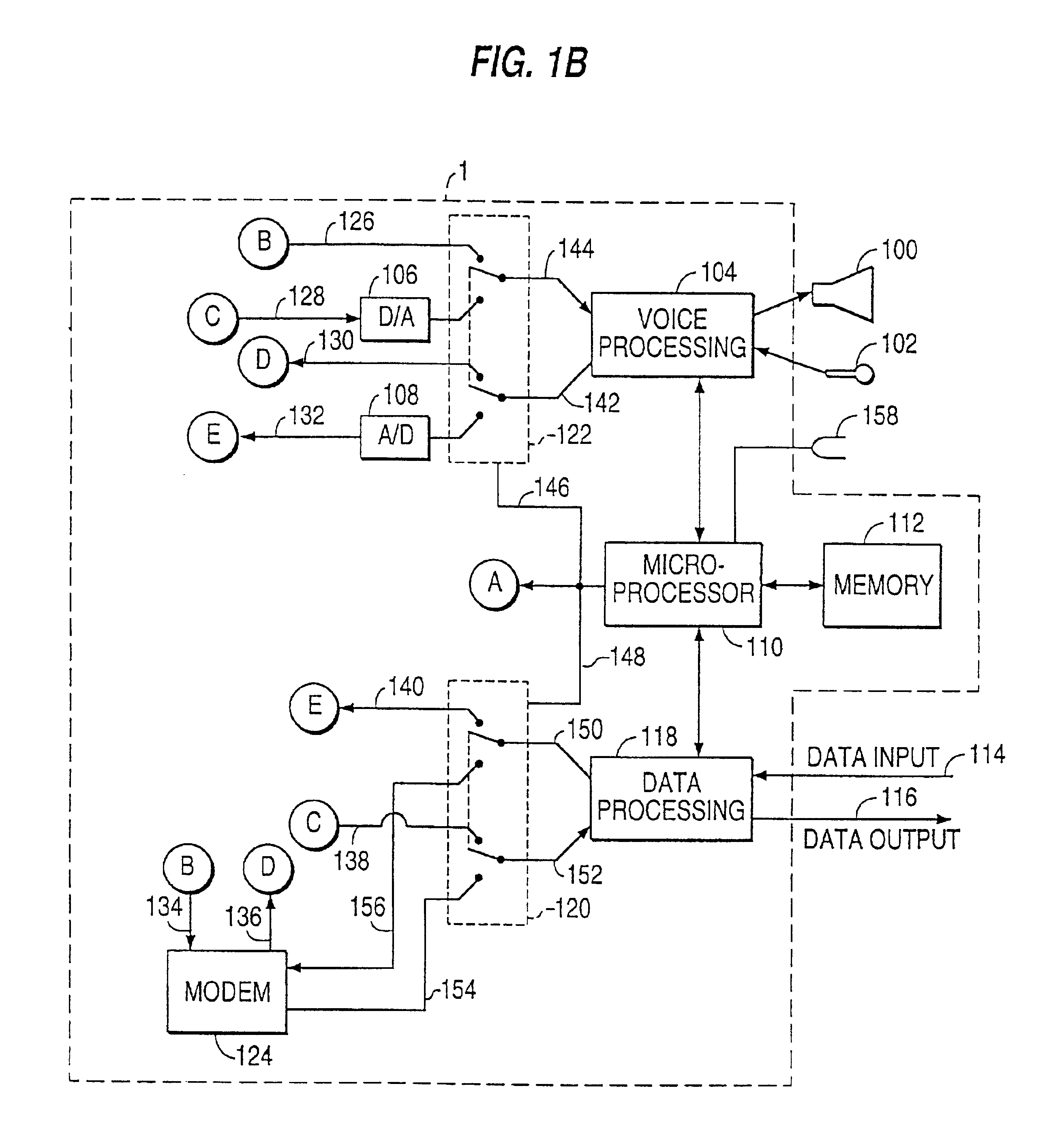
ActiveUS7509494B2Digital data processing detailsUser identity/authority verificationData signalEngineering
An interface cable is configured to connect a host instrument to a physiological sensor. The interface cable has an ID signal input from the sensor and a LED drive signal input from the host instrument sensor port. The interface cable also has a data signal output to the host instrument sensor port. The LED drive signal and the data signal provide an encrypted handshake to and from the host instrument. The handshake is responsive to the ID signal so as to enable normal operation of the host instrument and the sensor.
Owner:JPMORGAN CHASE BANK NA
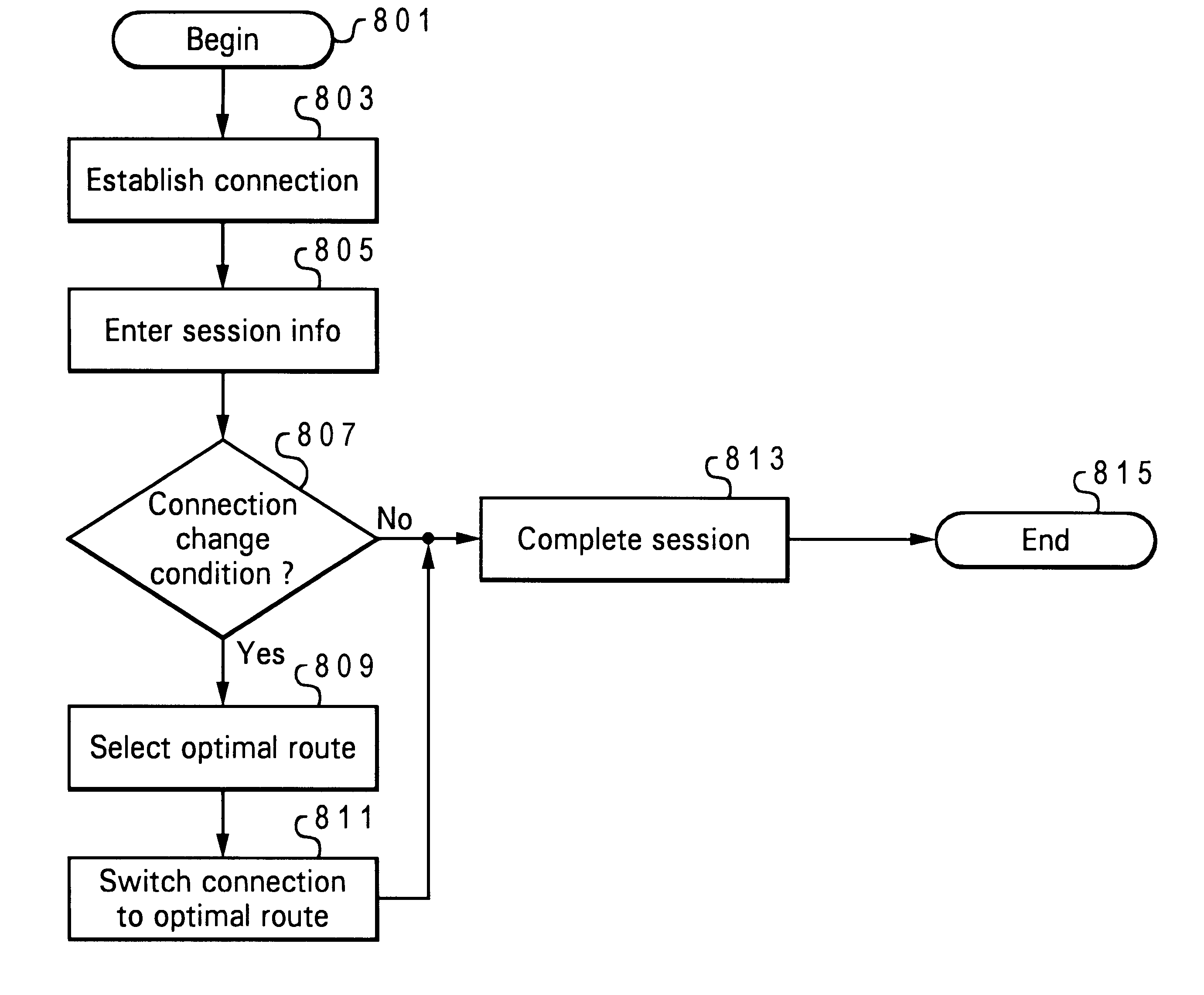
Dynamic, seamless switching of a network session from one connection route to another
InactiveUS6766373B1Multiple digital computer combinationsData switching networksClient-sideHandshake
A system for providing continuous connection between a client and a network during a session. The system comprises of a connection utility, which monitors a network session for an occurrence of a pre-defined event and / or condition. The system is particularly advantageous in scenarios where a session's connection is lost and the session has to be reconnected to the network. The system also finds applicability with several other types of events / conditions, including a connection break, a slow or congested connection or a change in the type of data being transmitted. When any one of the pre-defined events / conditions occur, the session is automatically routed from the present connection route to another connection route, and is completed on the other connection route. In order to complete the re-routing of the sessions, session information is cached on the client and the server. The session data is tagged with the original session ID. On the server, a special Client Key is stored for later retrieval, and on the client a special Server Key is stored. During the reconnect, the server uses its previously stored session data associated with the client key and previous session ID to regain a new session connection. The client uses its previously stored session data to regain its side of the connection and to pass the proper request over the wire to the server. This special "handshake" occurs at session reconnect time and allows the special session re-connection to occur. The re-routing of the session is completed with no noticeable loss in connection or session information. Thus, a substantially seamless switching of the session from the first connection route to the second connection route is implemented.
Owner:IBM CORP
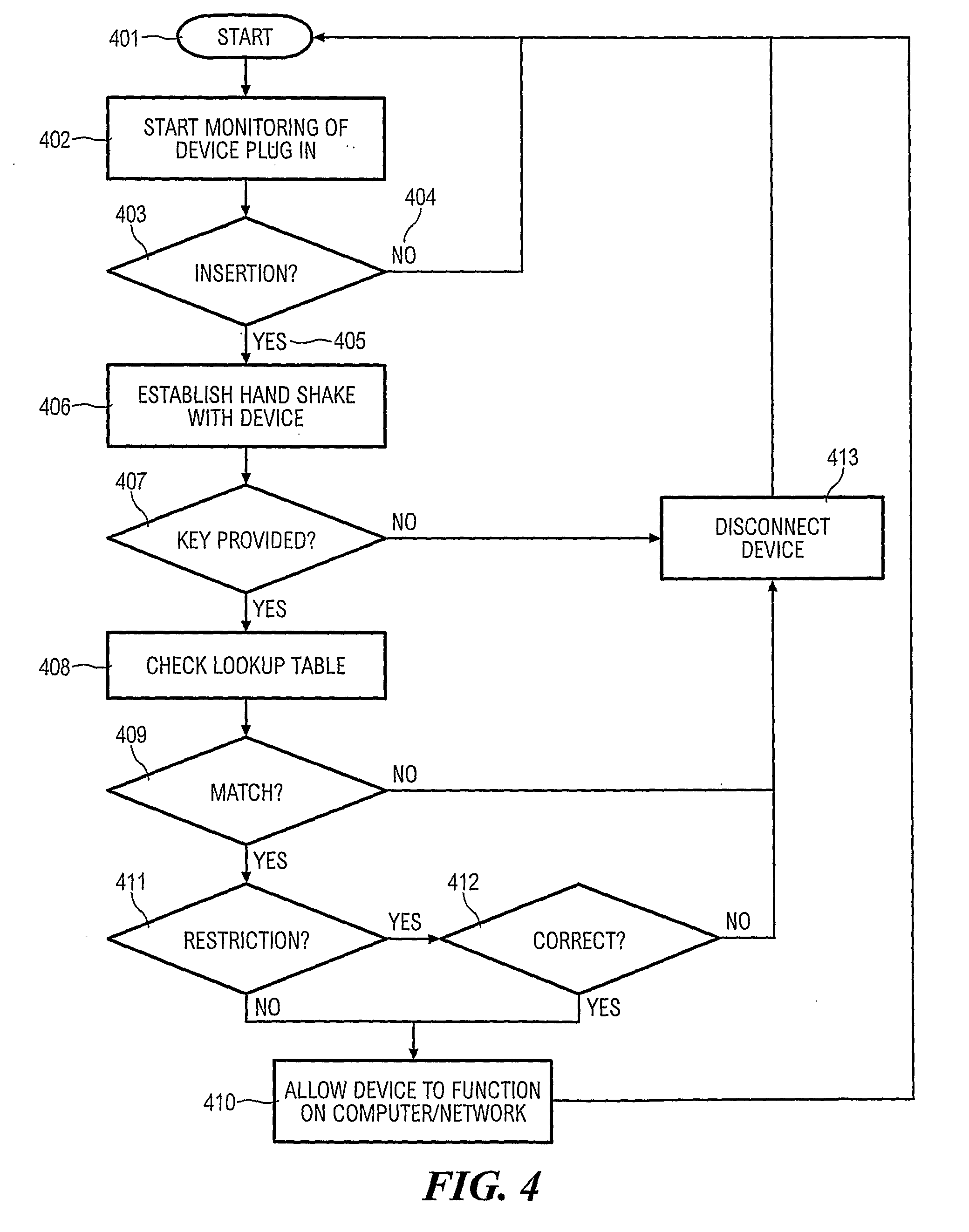
Method, apparatus and system for authentication of external storage devices
ActiveUS20100017546A1Key distribution for secure communicationMultiple keys/algorithms usageElectricityHandshake
A method for authentication of an external storage device (16) operatively connected to a port of a host computer (10) where the host computer (10) conducts a handshake with the external storage device (16) seeking an authentication key from the external storage device. The host computer (10) electrically disconnects the external storage device (16) from the host computer (10) if the authentication key is incorrect or not provided within a predetermined period. The host computer (10) allows access to the host computer (10) by the external storage device (16) if the authentication key is correct and provided within the predetermined period. Corresponding apparatus and systems are also disclosed.
Owner:TREK 2000 INT
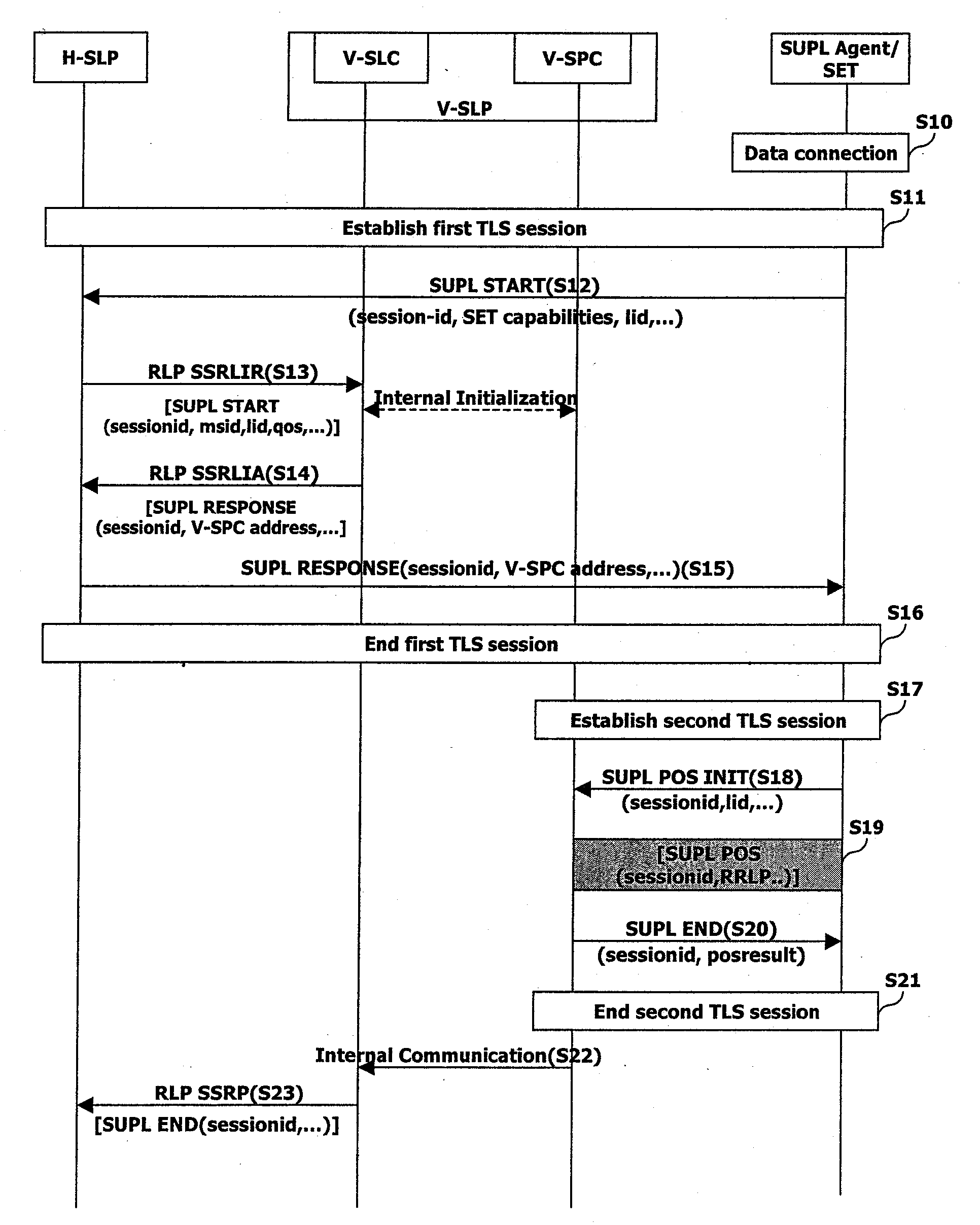
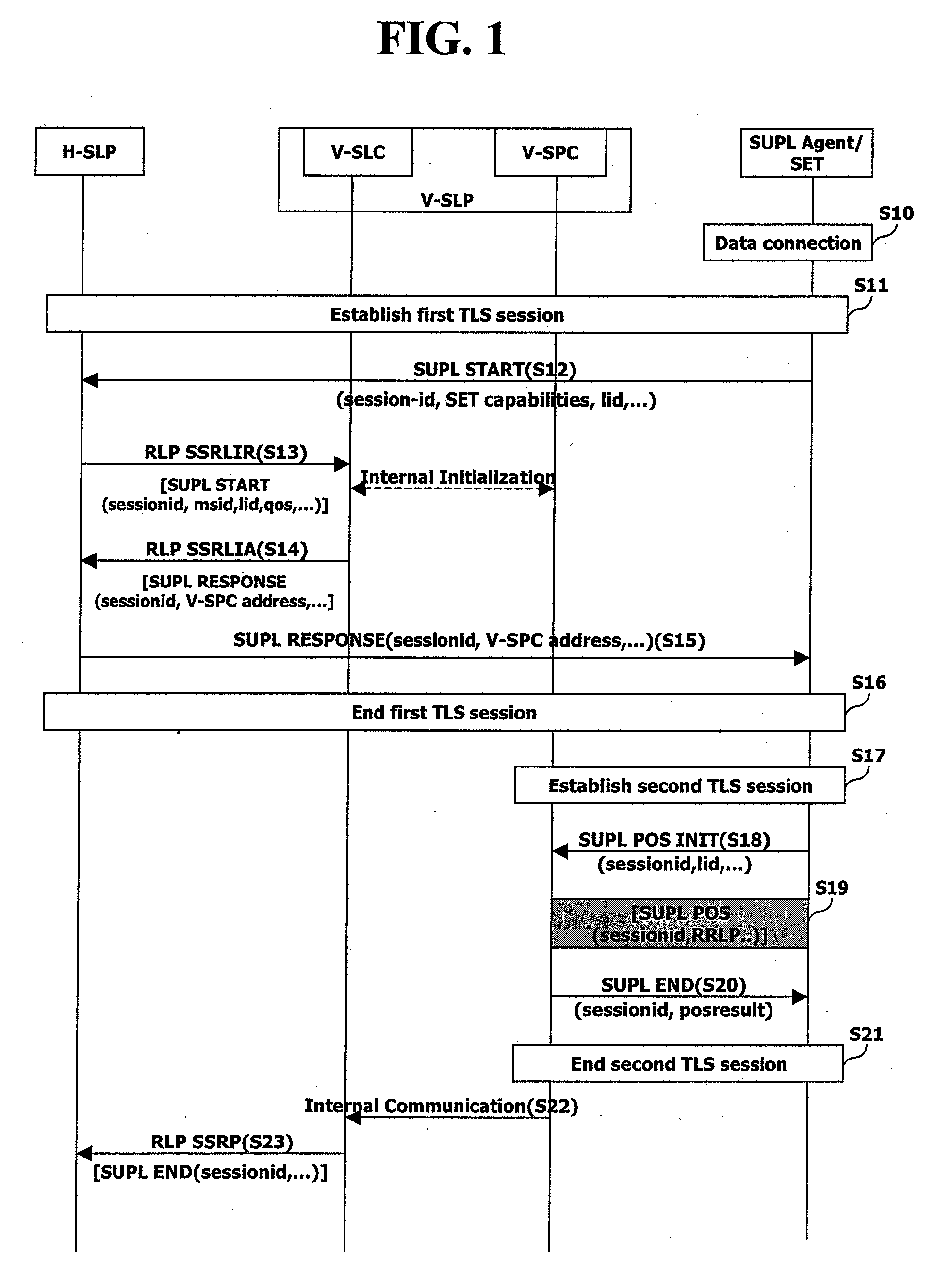
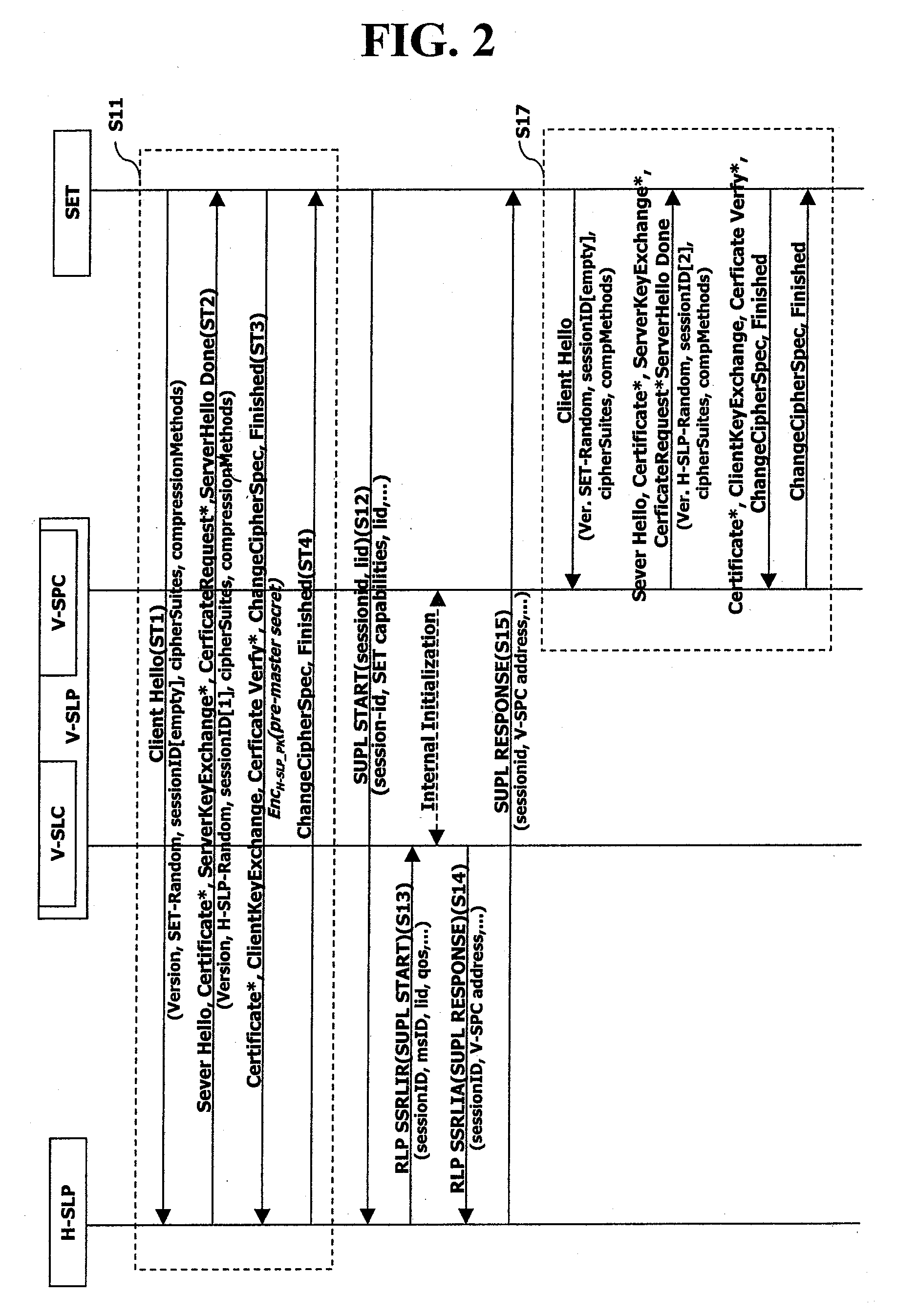
Tls Session Management Method In Supl-Based Positioning System
InactiveUS20080109650A1Improve efficiencyEncryption apparatus with shift registers/memoriesSecret communicationSession managementRoaming
Owner:LG ELECTRONICS INC
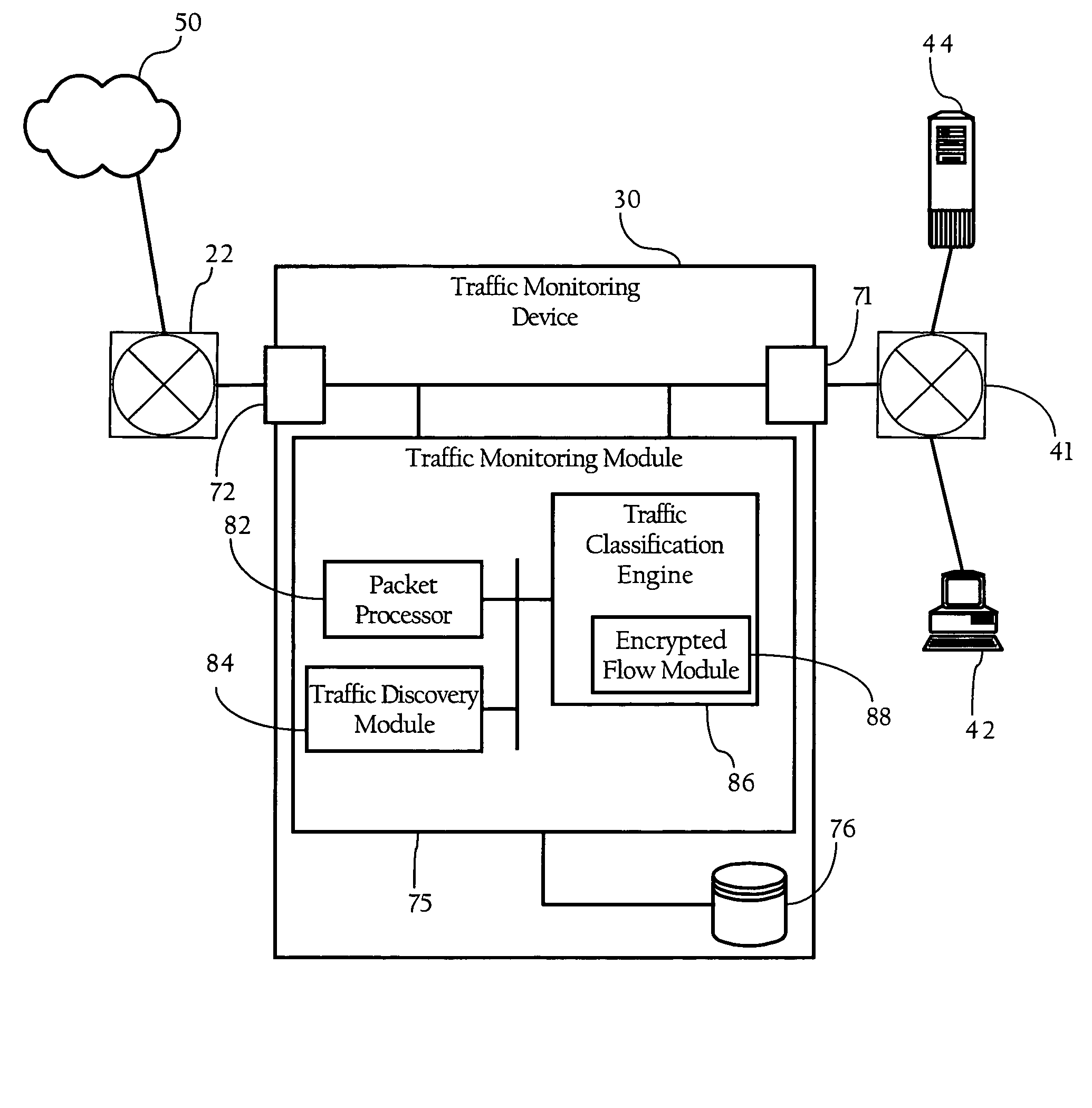
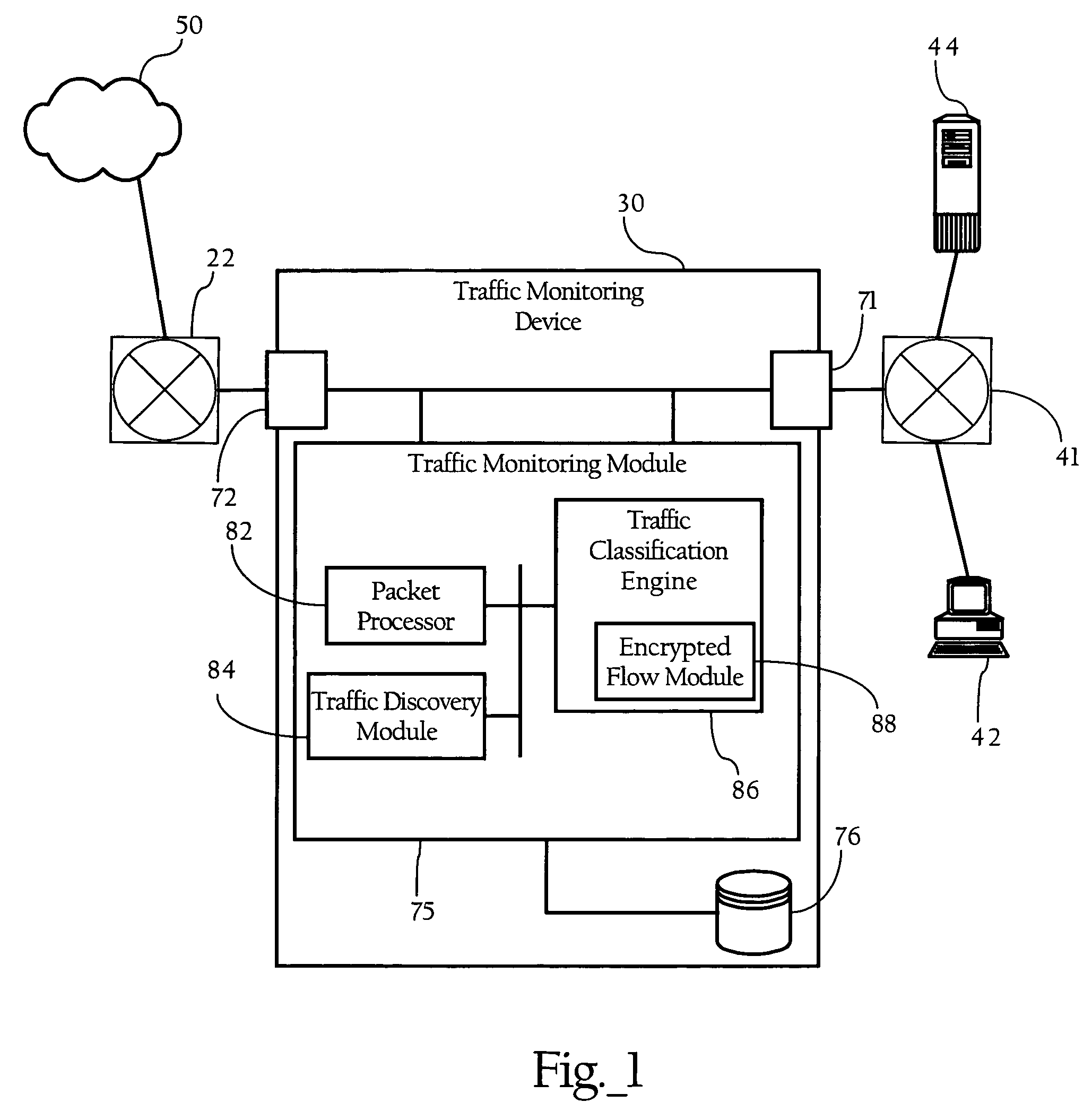
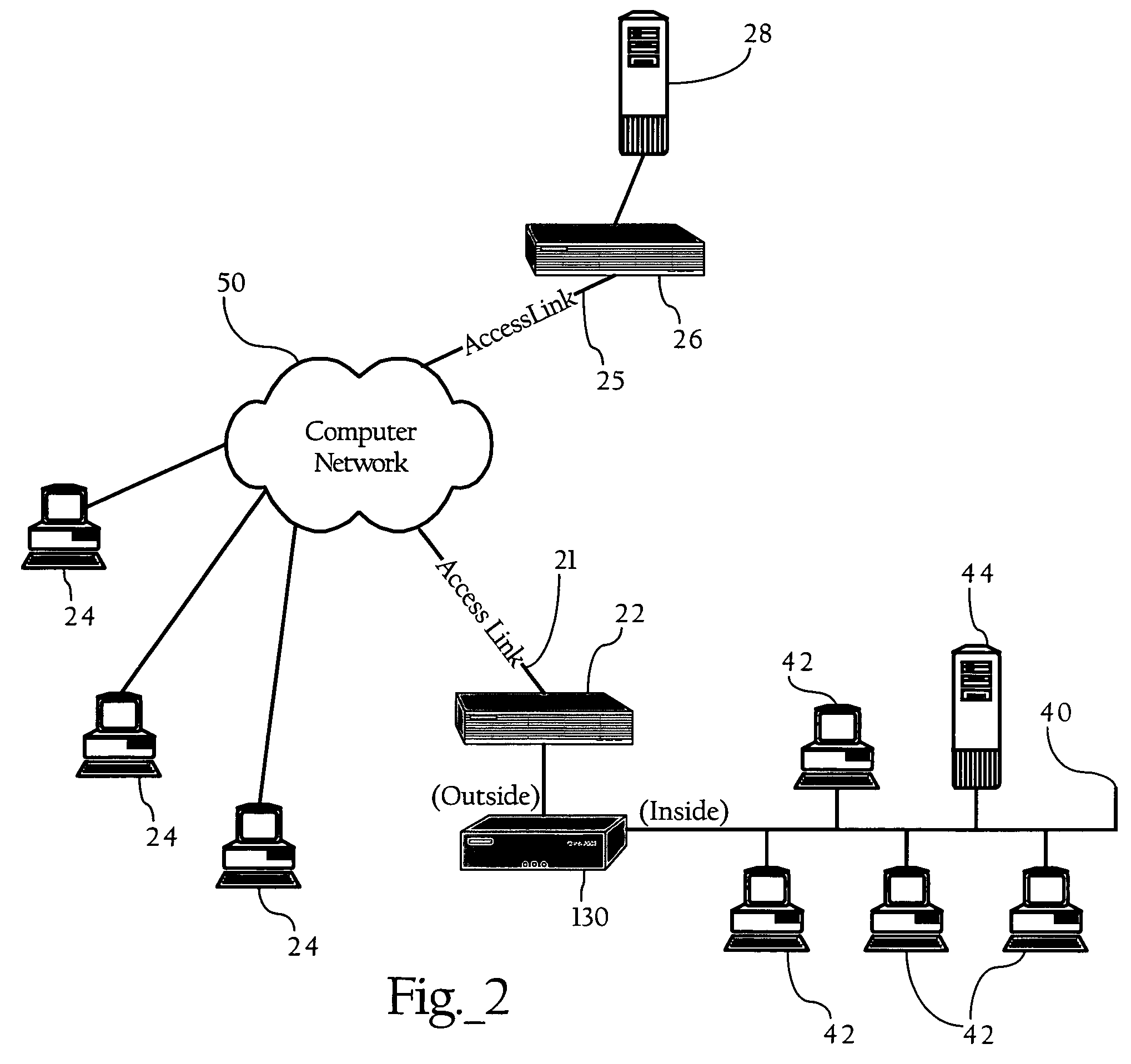
Examination of connection handshake to enhance classification of encrypted network traffic
ActiveUS7778194B1Easy to classifyError preventionFrequency-division multiplex detailsTraffic capacityEnd system
Methods, apparatuses and systems directed to the classification of encrypted network traffic. In one implementation, the present invention facilitates the classification of network traffic that has been encrypted according to a dynamically-created encryption mechanism involving a handshake between two end-systems, such as the SSL and TLS protocols. In one implementation, the present invention observes and analyzes attributes of the handshake between two nodes to enhance the classification of network traffic. In one embodiment, the enhanced classification mechanisms described herein operate seamlessly with other Layer 7 traffic classification mechanisms that operate on attributes of the packets themselves. Implementations of the present invention can be incorporated into a variety of network devices, such as traffic monitoring devices, packet capture devices, firewalls, and bandwidth management devices.
Owner:CA TECH INC
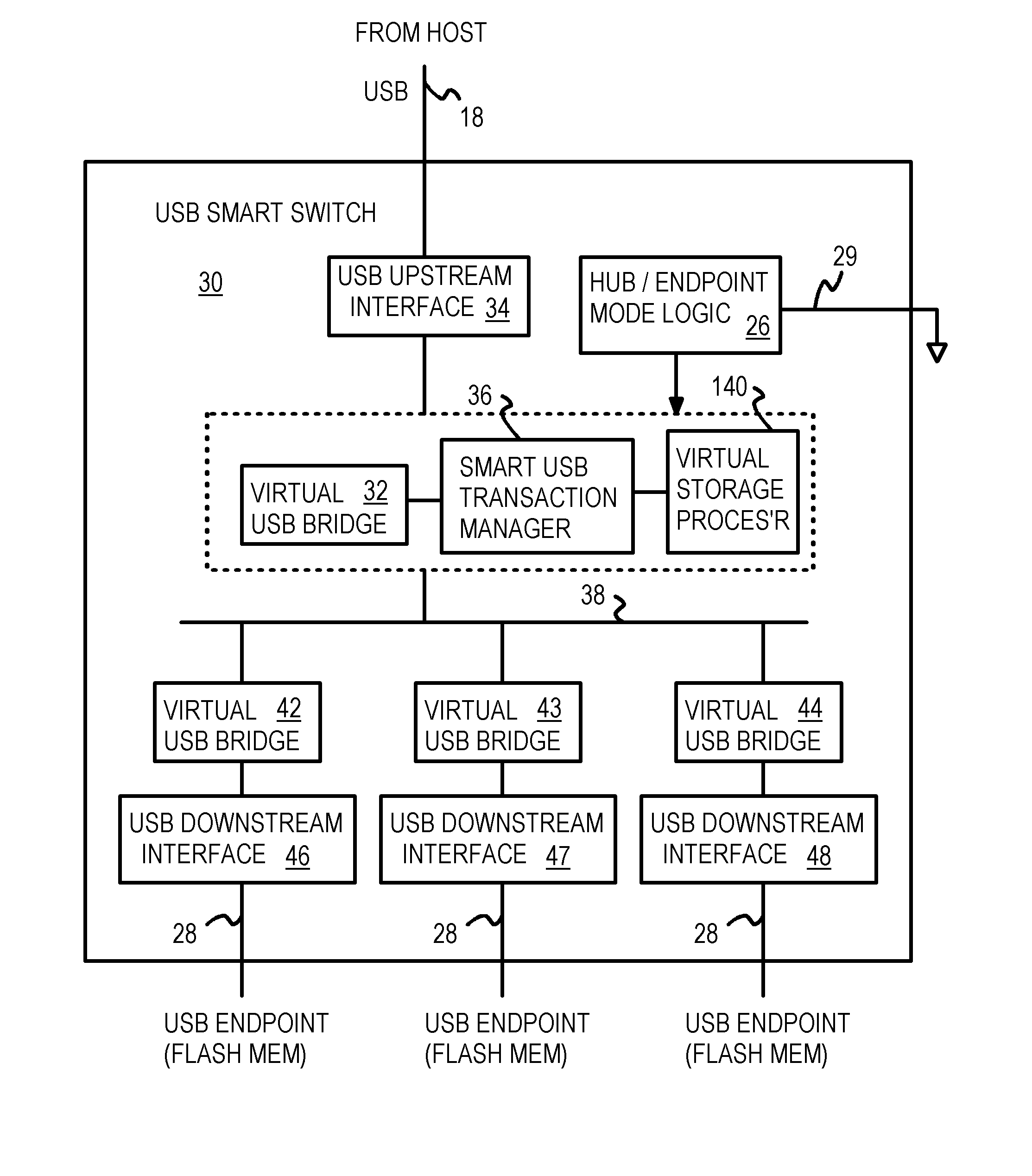
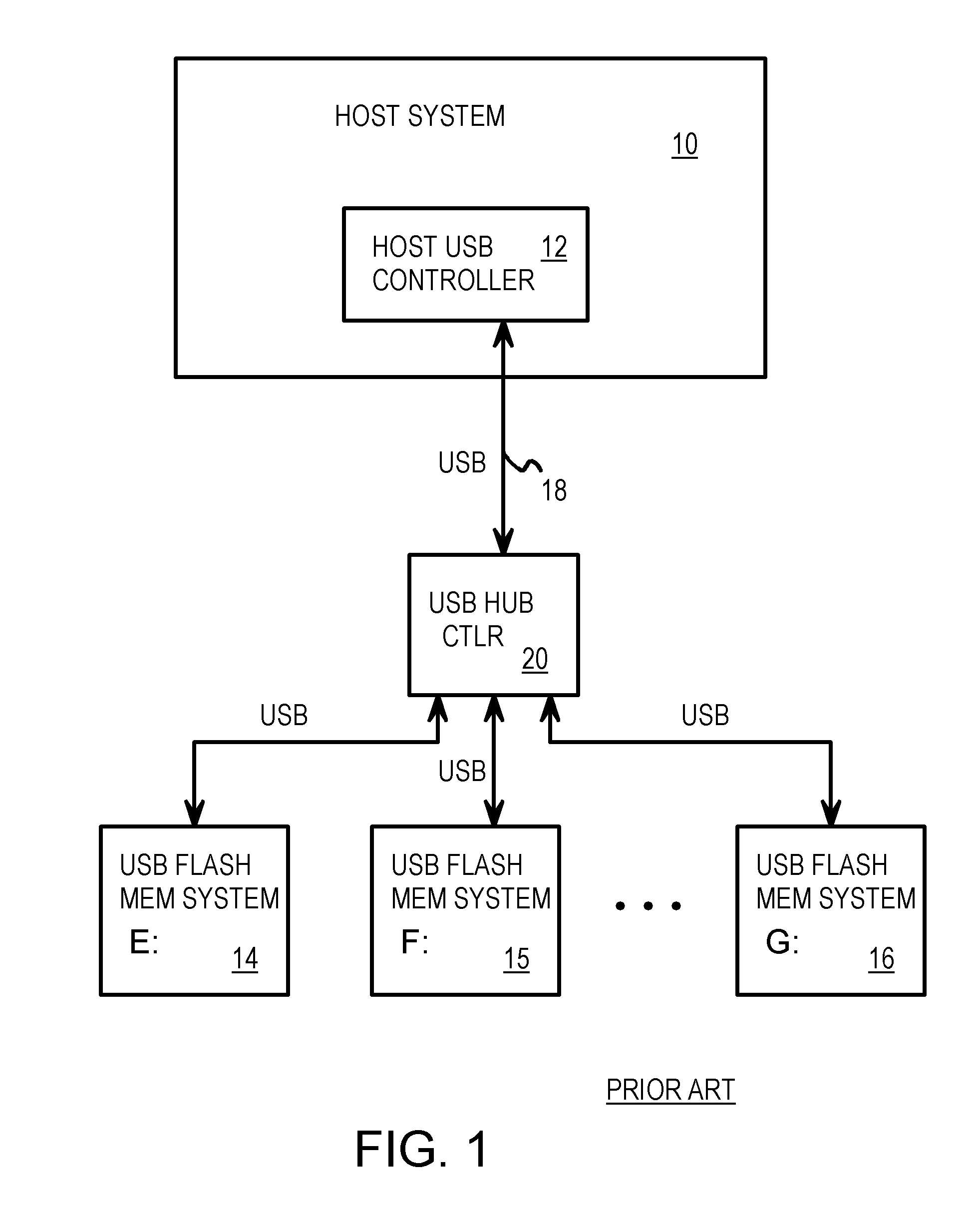
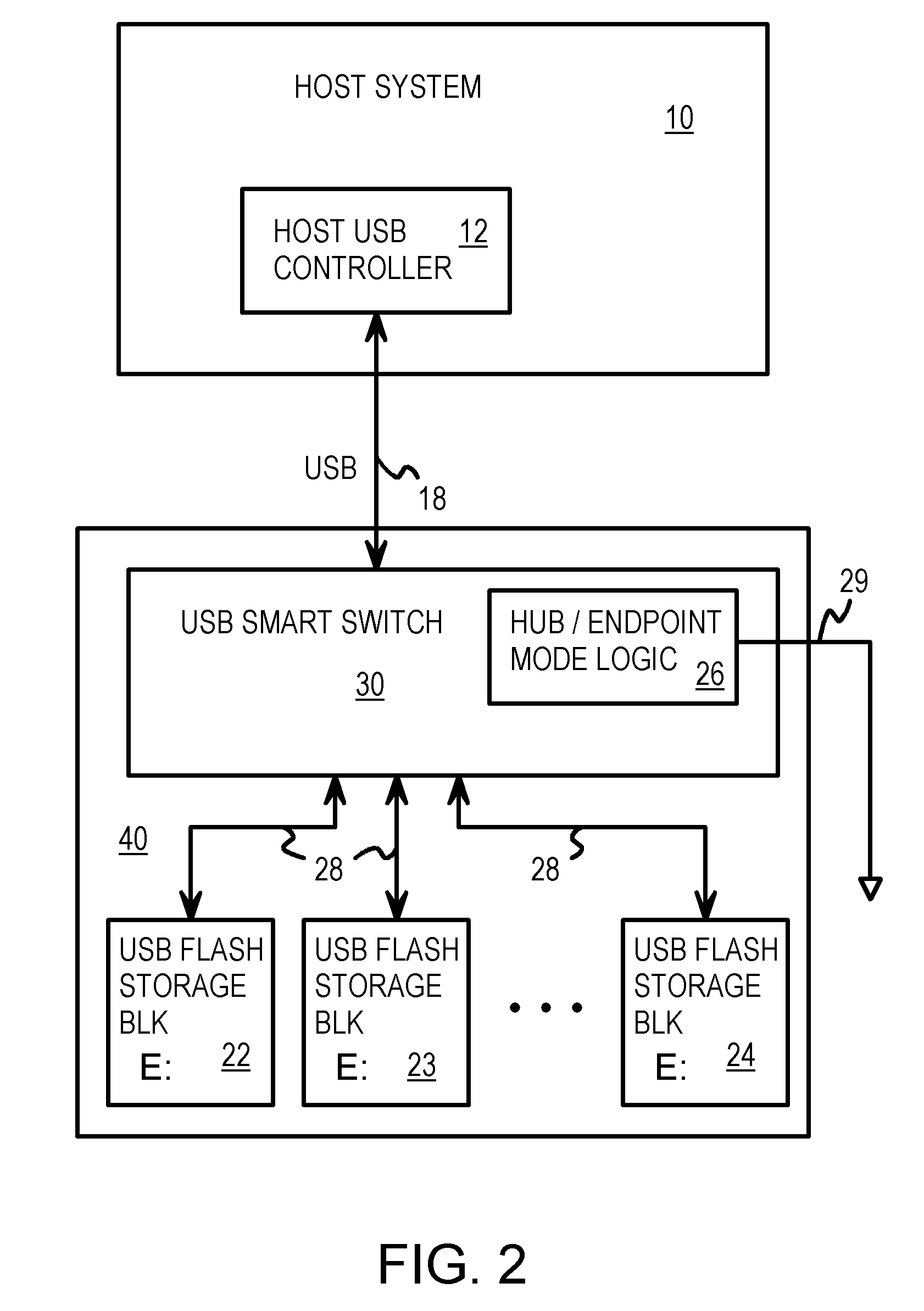
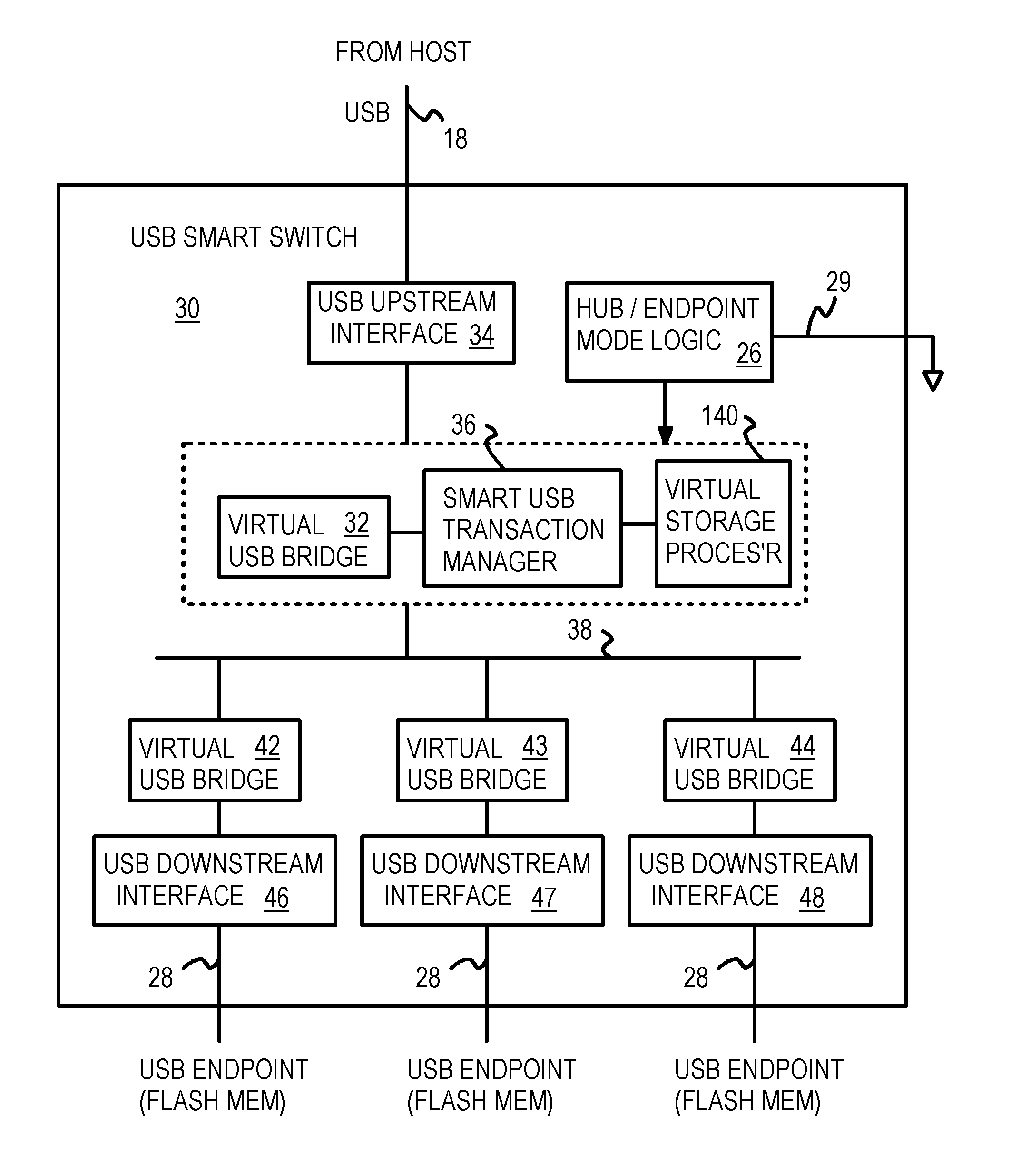
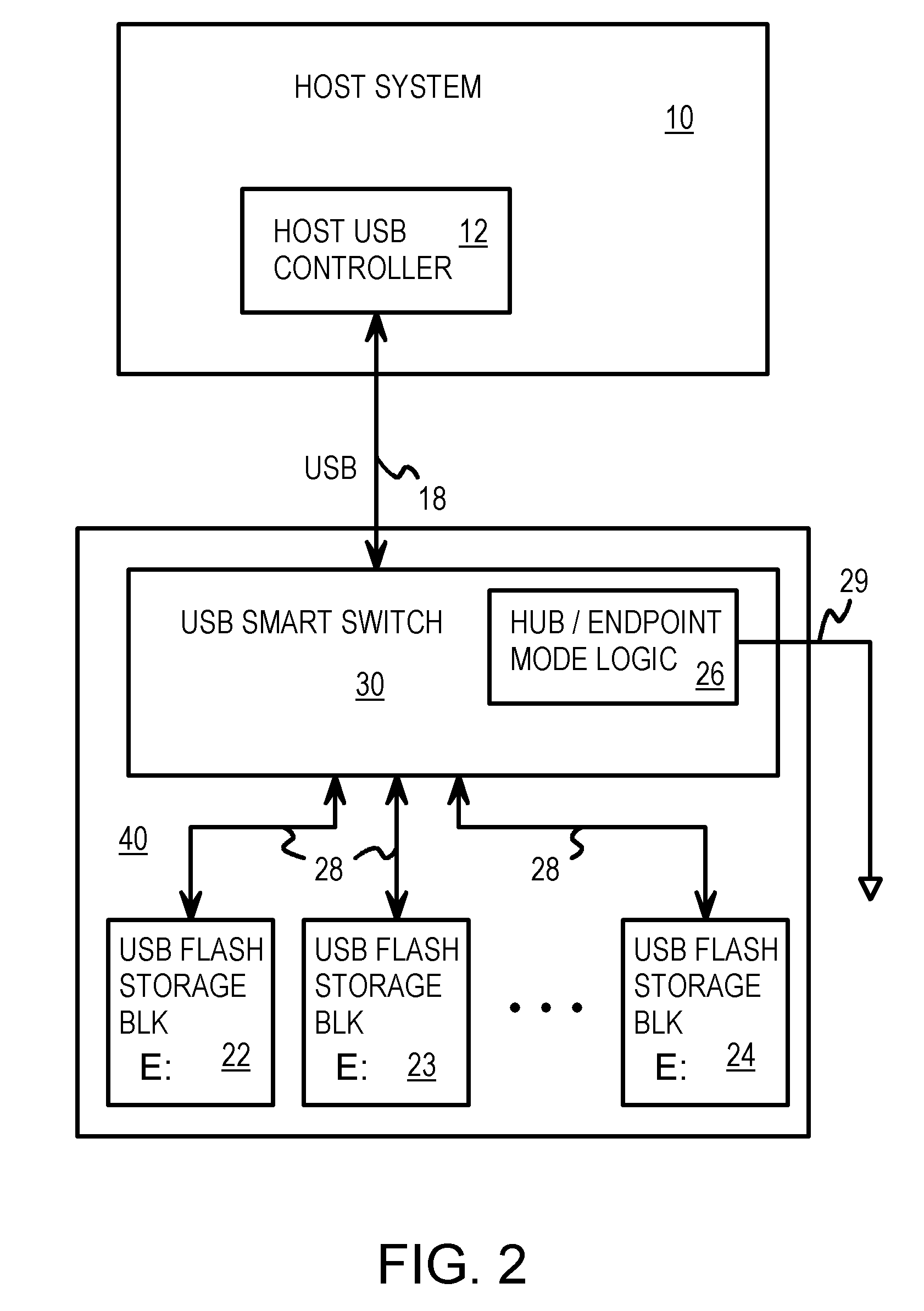
USB Smart Switch with Packet Re-Ordering for Interleaving among Multiple Flash-Memory Endpoints Aggregated as a Single Virtual USB Endpoint
A dual-mode Universal-Serial-Bus (USB) switch can operate in a normal hub mode to buffer transactions from a host to multiple USB flash storage blocks that are USB endpoints. When operating in a single-endpoint mode, the dual-mode USB switch intercepts packets from the host and responds to the host as a single USB endpoint. The USB switch aggregates all downstream USB flash storage blocks and reports a single pool of memory to the host as a single virtual USB memory. Adjacent transactions can be overlapped by packet re-ordering. A token packet that starts a following transaction is re-ordered to be sent to the USB flash storage blocks before the data and handshake packets that end a first transaction, allowing the second transaction to begin accessing the flash memory earlier. Data can be mirrored or striped across several USB flash storage blocks and parity can be added for error recovery.
Owner:SUPER TALENT TECH CORP
USB smart switch with packet re-ordering for interleaving among multiple flash-memory endpoints aggregated as a single virtual USB endpoint
A dual-mode Universal-Serial-Bus (USB) switch can operate in a normal hub mode to buffer transactions from a host to multiple USB flash storage blocks that are USB endpoints. When operating in a single-endpoint mode, the dual-mode USB switch intercepts packets from the host and responds to the host as a single USB endpoint. The USB switch aggregates all downstream USB flash storage blocks and reports a single pool of memory to the host as a single virtual USB memory. Adjacent transactions can be overlapped by packet re-ordering. A token packet that starts a following transaction is re-ordered to be sent to the USB flash storage blocks before the data and handshake packets that end a first transaction, allowing the second transaction to begin accessing the flash memory earlier. Data can be mirrored or striped across several USB flash storage blocks and parity can be added for error recovery.
Owner:SUPER TALENT TECH CORP
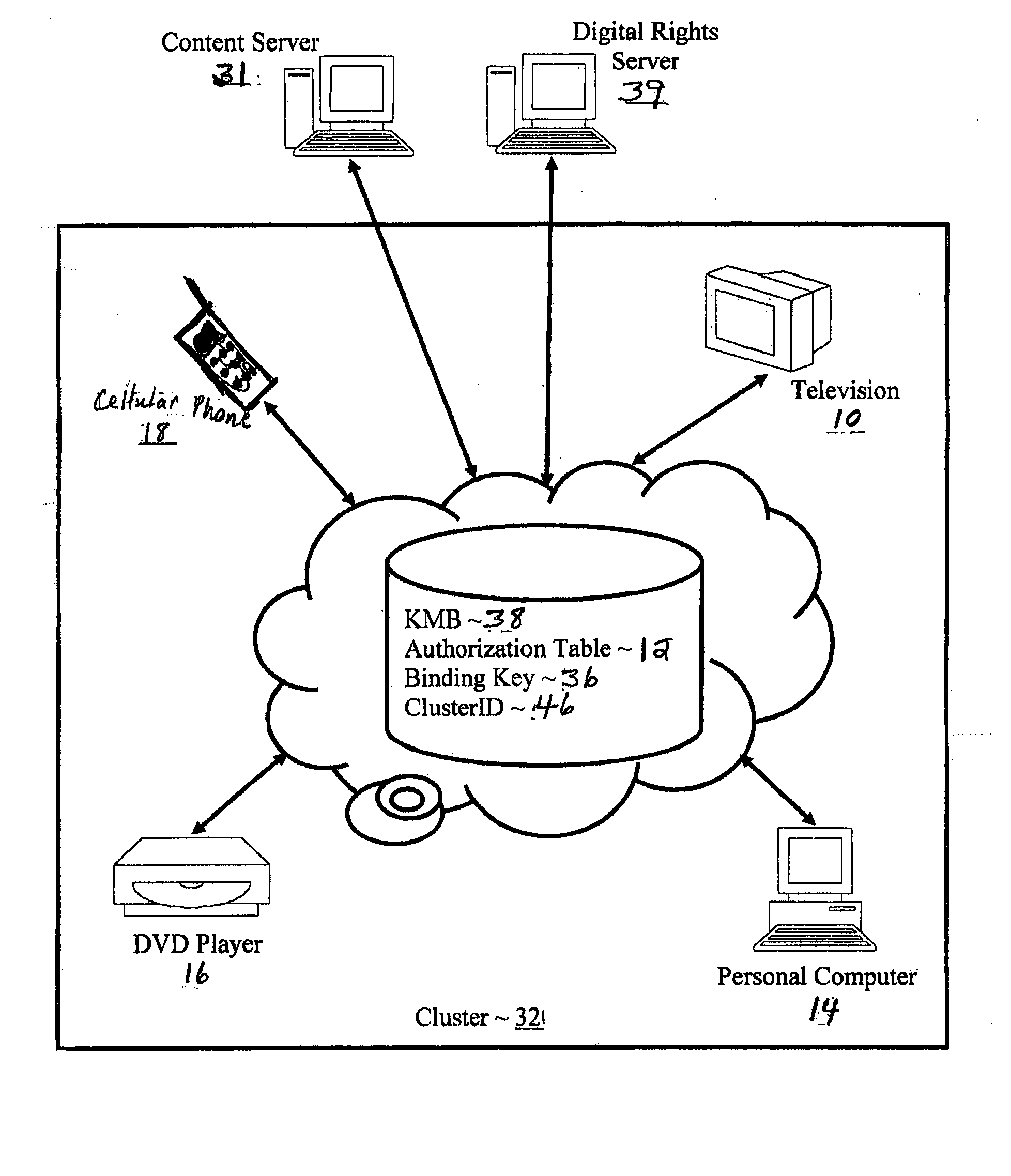
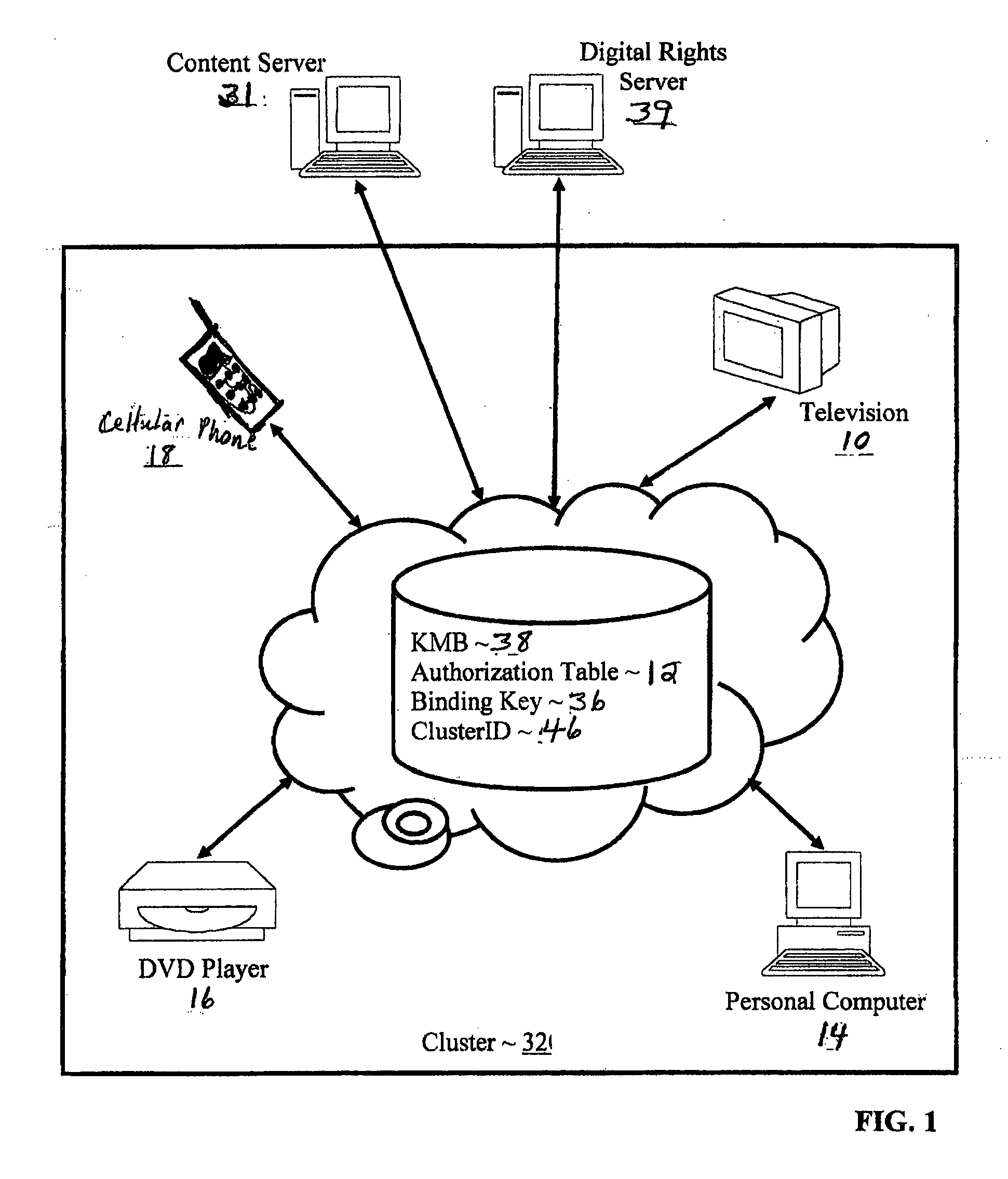
System and method for enforcing network cluster proximity requirements using a proxy
InactiveUS20060233372A1Satisfies requirementLimit deliverySecret communicationTransmissionSystems approachesNetsniff-ng
A system, method and computer program for enforcing network cluster proximity requirements using a proxy is useful in preventing unauthorized devices from receiving encrypted broadcast content intended for only authorized users within a network cluster. The current art allows users to remotely establish trust via a cryptographic handshake. This results in encrypted broadcast content being delivered to unauthorized devices. The present invention assures that encrypted broadcast content is delivered to only authorized devices, allowing authorized remote devices to receive encrypted broadcast content while preventing unauthorized remote devices from doing so. The present invention enforces network proximity requirements to authorized devices within a defined area by timing the cryptographic handshaking, and by authorizing device proxies within a geographic area for retransmitting to authorized remote devices outside said geographic area.
Owner:IBM CORP
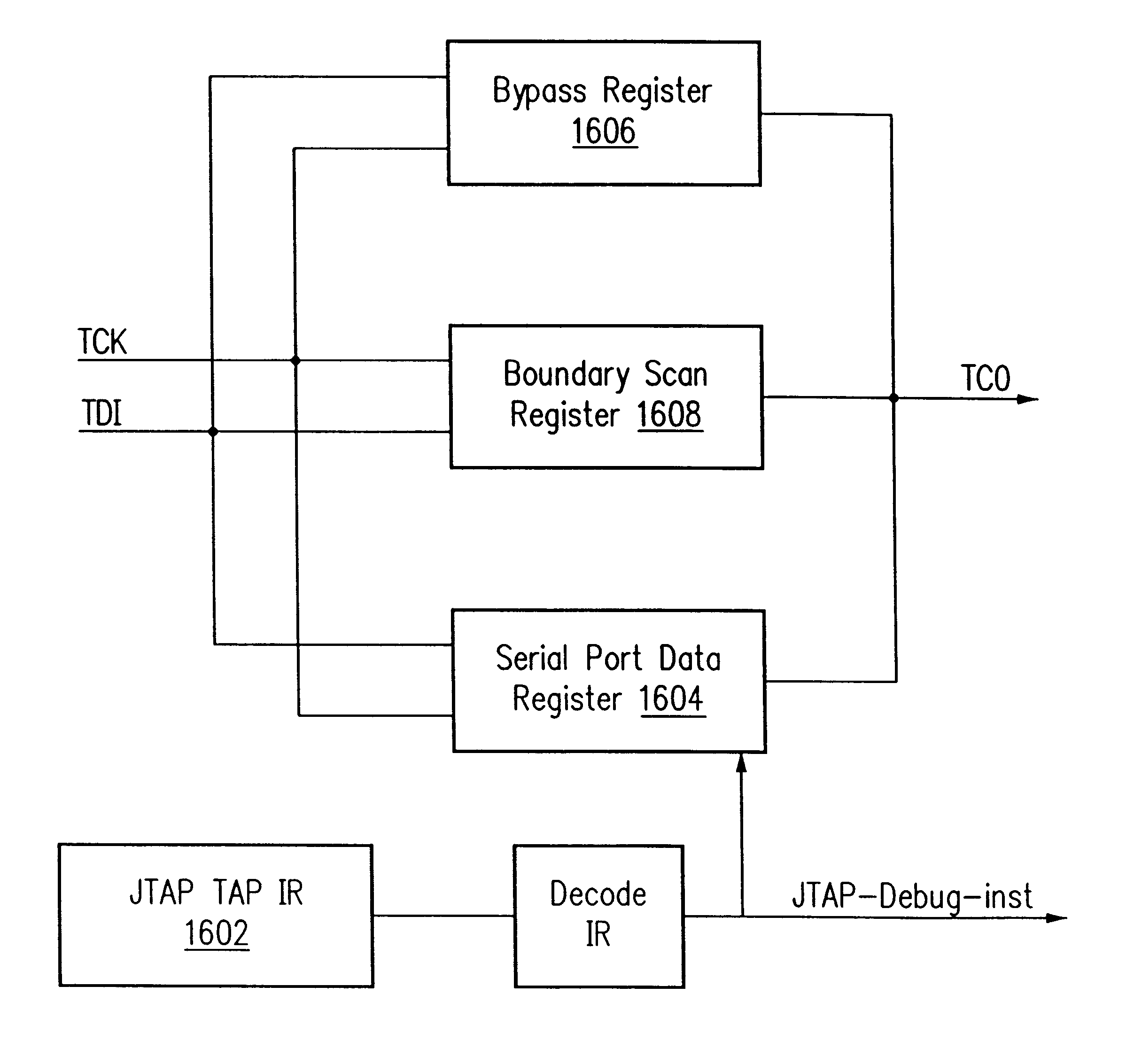
Debug interface including logic generating handshake signals between a processor, an input/output port, and a trace logic
A system for debugging a processor includes a debug interface including a handshake logic for communicating commands and data from a serial input / output port to a processor and to a trace control logic with a low delay. The handshake logic results in a low latency through the inclusion of a state machine that operates at the same speed as the processor. The state machine generates handshake signals to communicate among the serial input / output port, the processor, and the trace control logic.
Owner:ADVANCED MICRO DEVICES INC
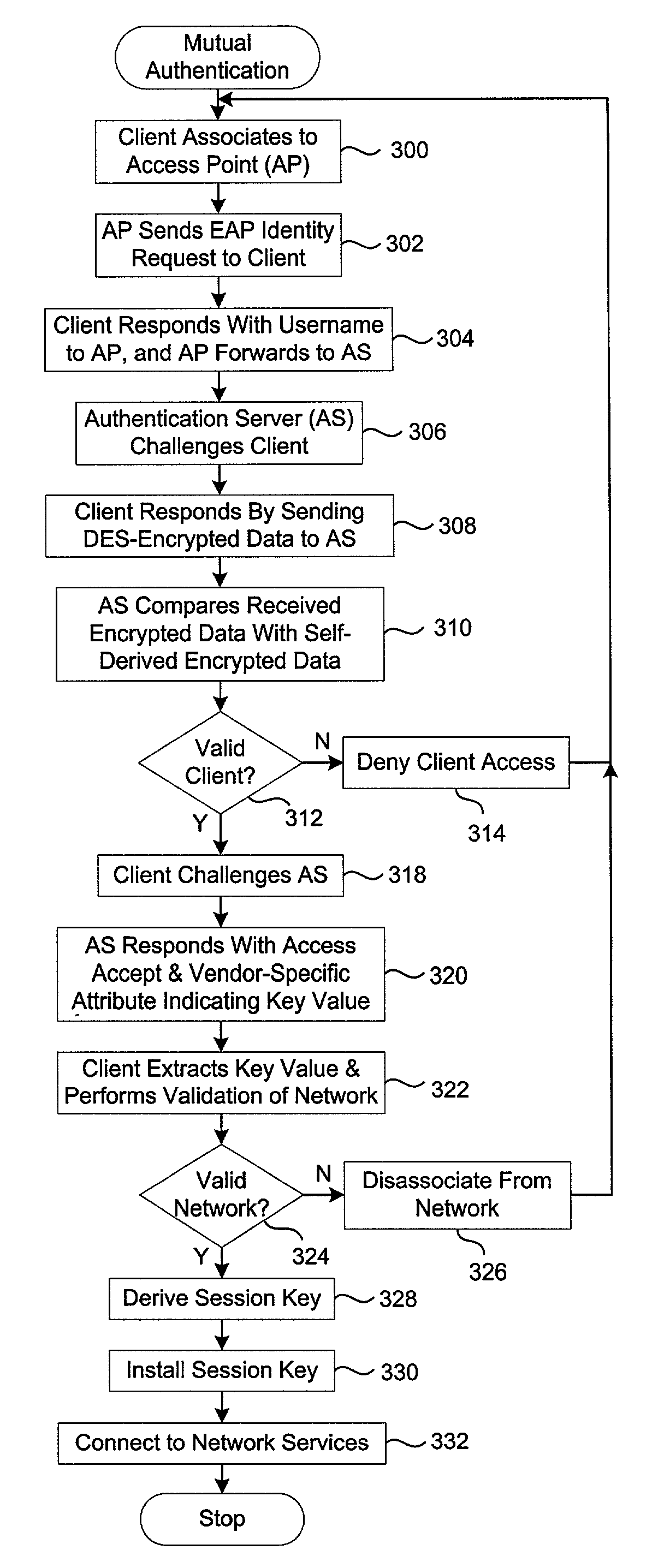
Wireless authentication protocol
ActiveUS6996714B1User identity/authority verificationNetwork topologiesWireless Application ProtocolClient-side
A wireless authentication protocol. Access to a network is managed by providing a challenge-handshake protocol within the Extensible Authentication Protocol for authentication between a client and the network.
Owner:CISCO TECH INC
Adaptive omni-modal radio apparatus and methods
InactiveUS6934558B1Easily and conveniently identifyIntense competitionMetering/charging/biilling arrangementsAccounting/billing servicesTransmission protocolTransceiver
A frequency and protocol agile wireless communication product, and chipset for forming the same, including a frequency agile transceiver, a digital interface circuit for interconnecting the radio transceiver with external devices, protocol agile operating circuit for operating the radio transceiver in accordance with one of the transmission protocols as determined by a protocol signal and an adaptive control circuit for accessing a selected wireless communication network and for generating the frequency control signal and the protocol control signal in response to a user defined criteria Among the possible user defined criteria would be (1) the cost of sending a data message, (2) the quality of transmission link (signal strength, interference actual or potential), (3) the potential for being bumped off of the system (is service provider at near full capacity), (4) the security of transmnission, (5) any special criteria which the user could variably program into his omni-modal wireless product based on the user's desires or (6) any one or more combinations of the above features that are preprogrammed, changed or overridden by the user. The disclosed invention allows wireless service providers to broadcast electronically as part of any “handshaking” procedure with a omni-modal wireless product information such as (1) rate information and (2) information regarding system operating characteristics such as percent of system capacity in use and / or likelihood of being dropped. The disclosed invention creates a user oriented source enrollment and billing service in the wireless data market by establishing uniform standard for “handshakes” to occur between cell service providers and omni-modal wireless products. In addition, the disclosed invention can be implemented on a standard chip or chipset including a radio transceiver specifically designed to be used in all types of omni-modal wireless products.
Owner:ANTON INNOVATIONS INC
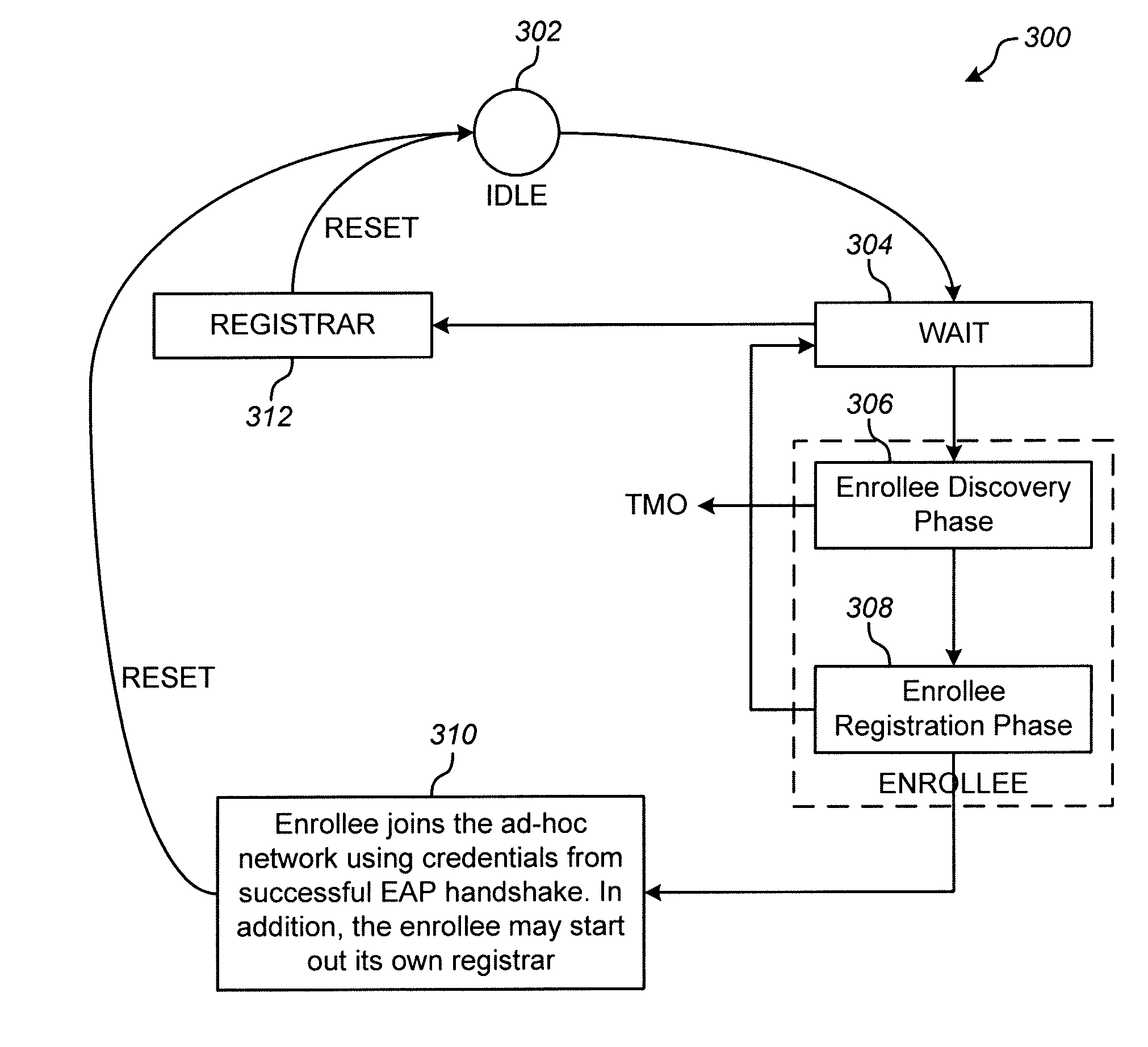
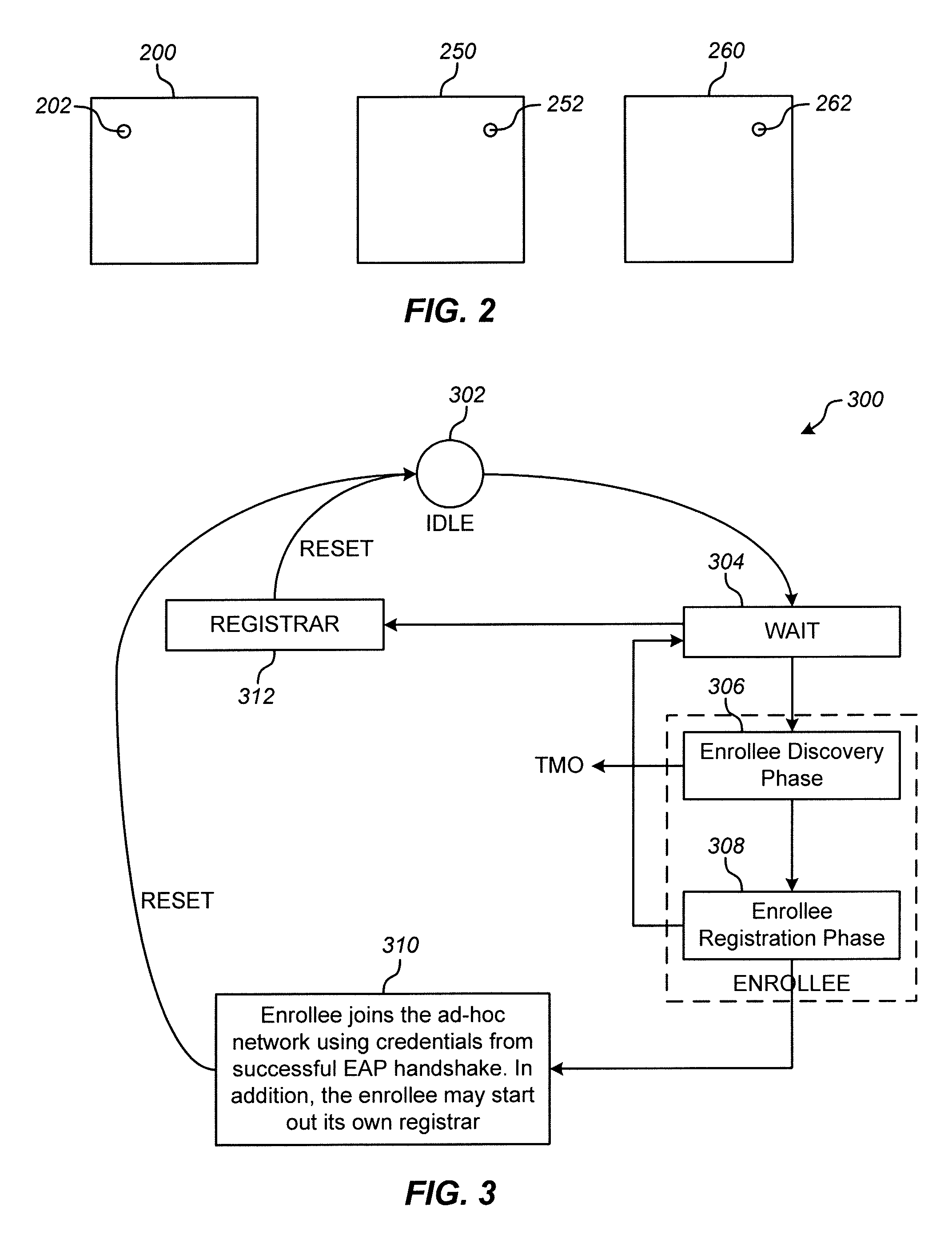
Establishment of ad-hoc networks between multiple devices
ActiveUS20080089300A1Improve usabilityReduce battery consumptionUnauthorised/fraudulent call preventionEavesdropping prevention circuitsAuthenticationWireless network
A method of configuring an ad-hoc wireless network between an authenticator and a plurality of wireless devices seeking authentication includes assigning a wireless device as the authenticator and receiving a first setup message transmitted from a first device seeking authentication to the authenticator and initiating a first handshake process between the authenticator and the first device seeking authentication. The method also includes receiving a second setup message transmitted from a second device seeking authentication to the authenticator. The second setup message is received by the authenticator prior to completion of the first handshake process. The method further includes initiating a second handshake process between the authenticator and the second device seeking authentication. The second handshake process is initiated prior to completion of the first handshake process. Moreover, the method includes completing the first handshake process and completing the second handshake process.
Owner:MARVELL ASIA PTE LTD
Enhanced association for access points
ActiveUS8126145B1Reduce the possibilitySmall rangeData switching by path configurationSecret communicationClient-sideHandshake
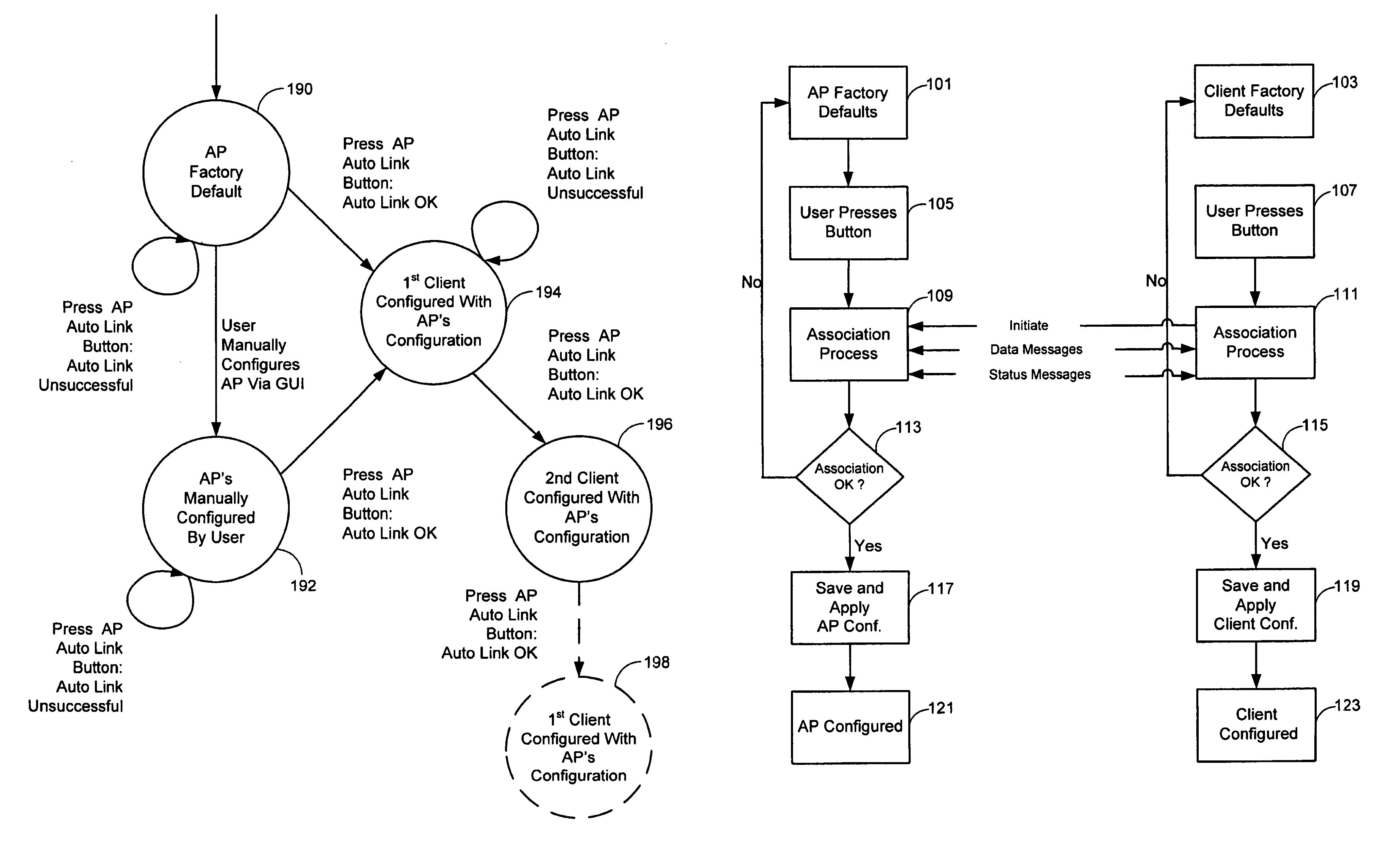
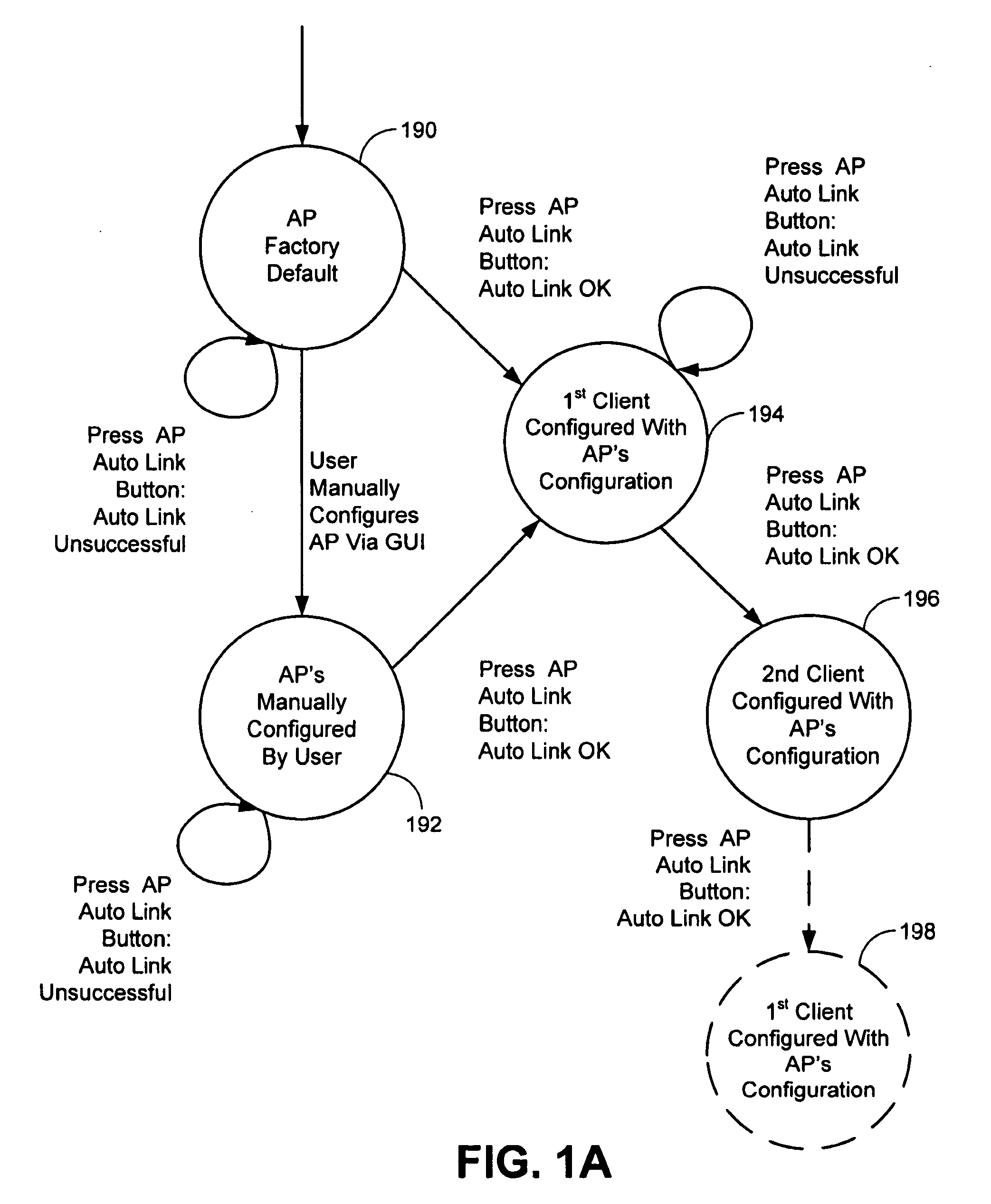
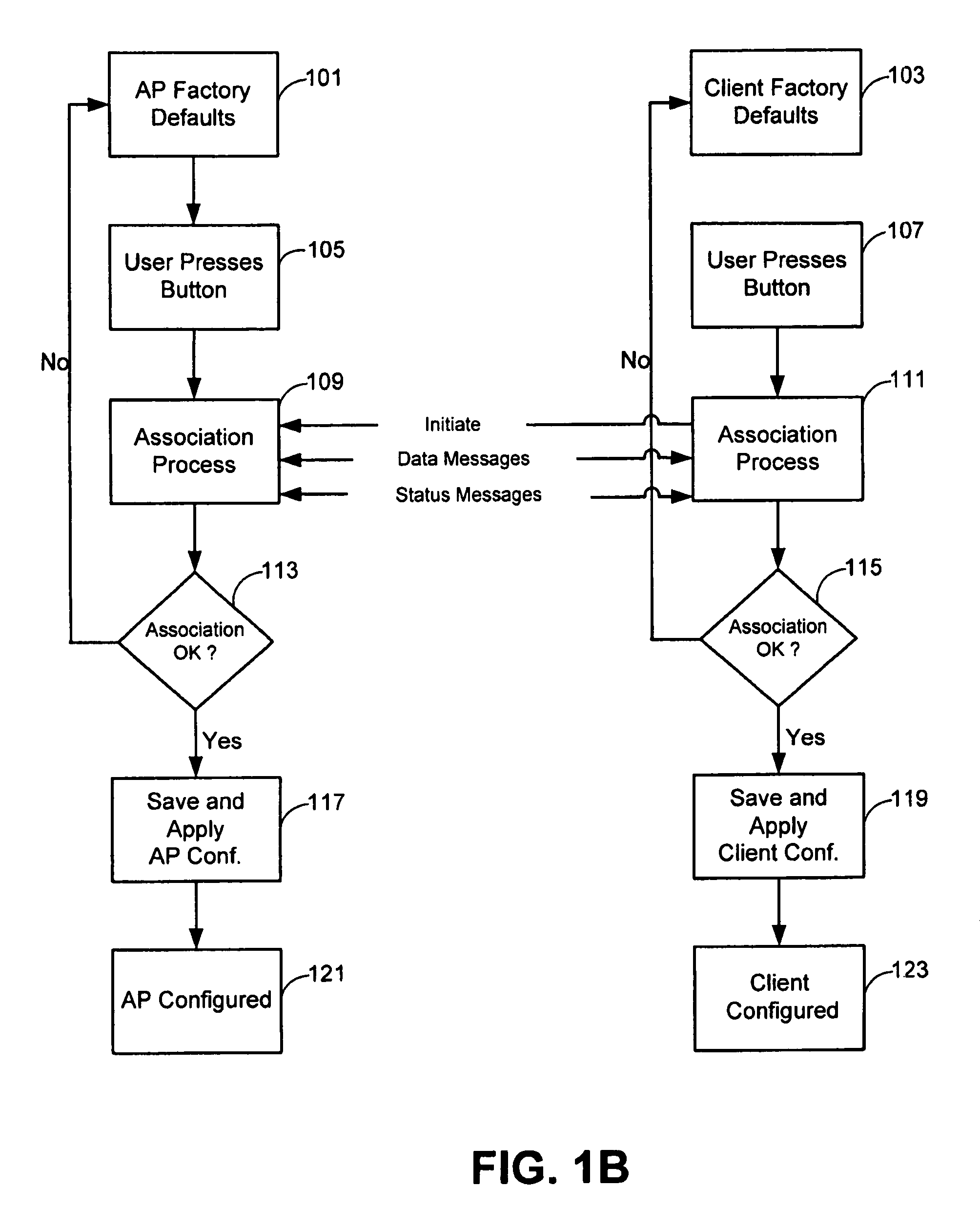
The invention relates to a method for associating a client with an access point using a security protocol. The method may include initiating a handshake and exchanging operational information between the access point and the client, establishing an encrypted operational key if the operational information is validated and entering an operational phase using the operational key and an unique service set identifier if valid.
Owner:MARVELL ASIA PTE LTD
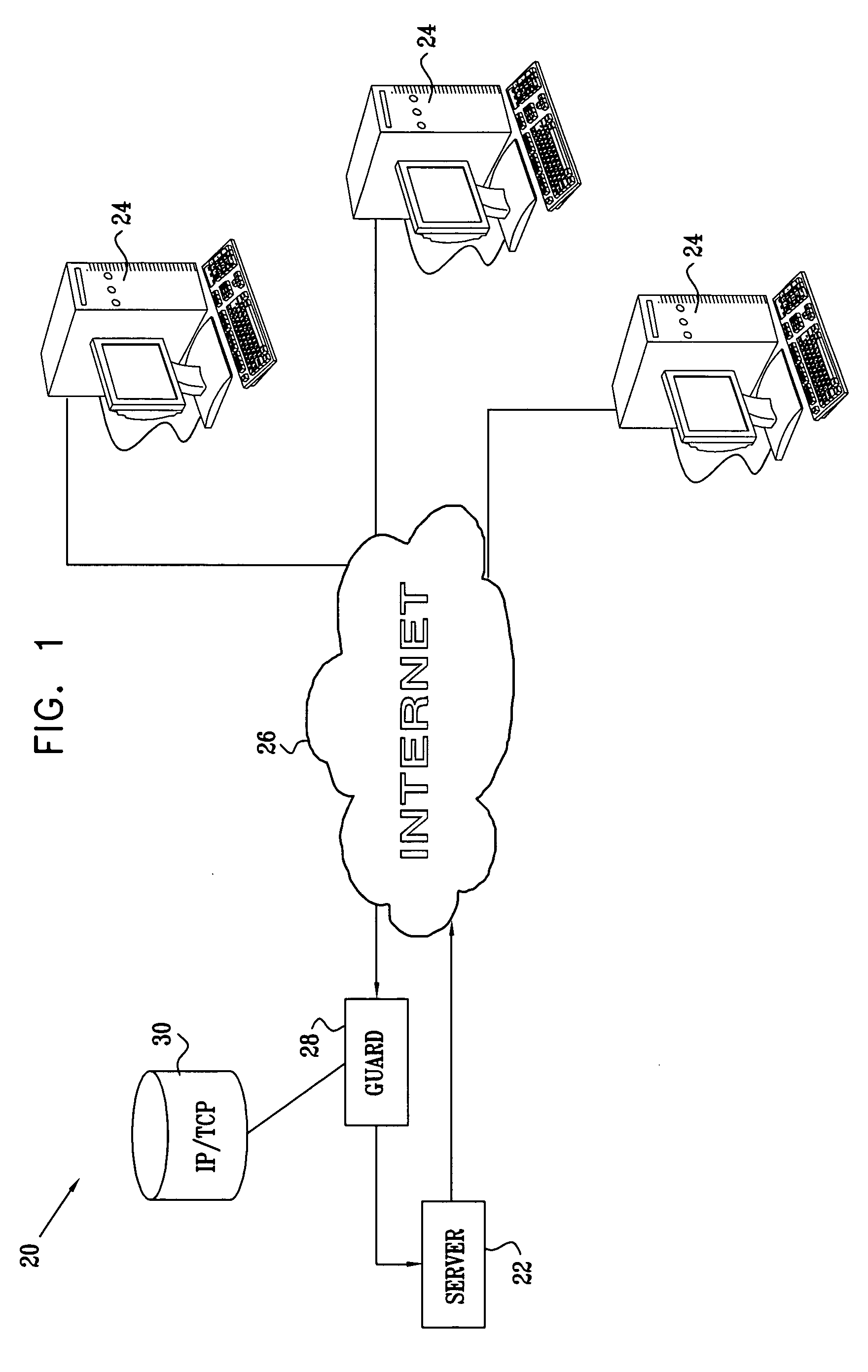
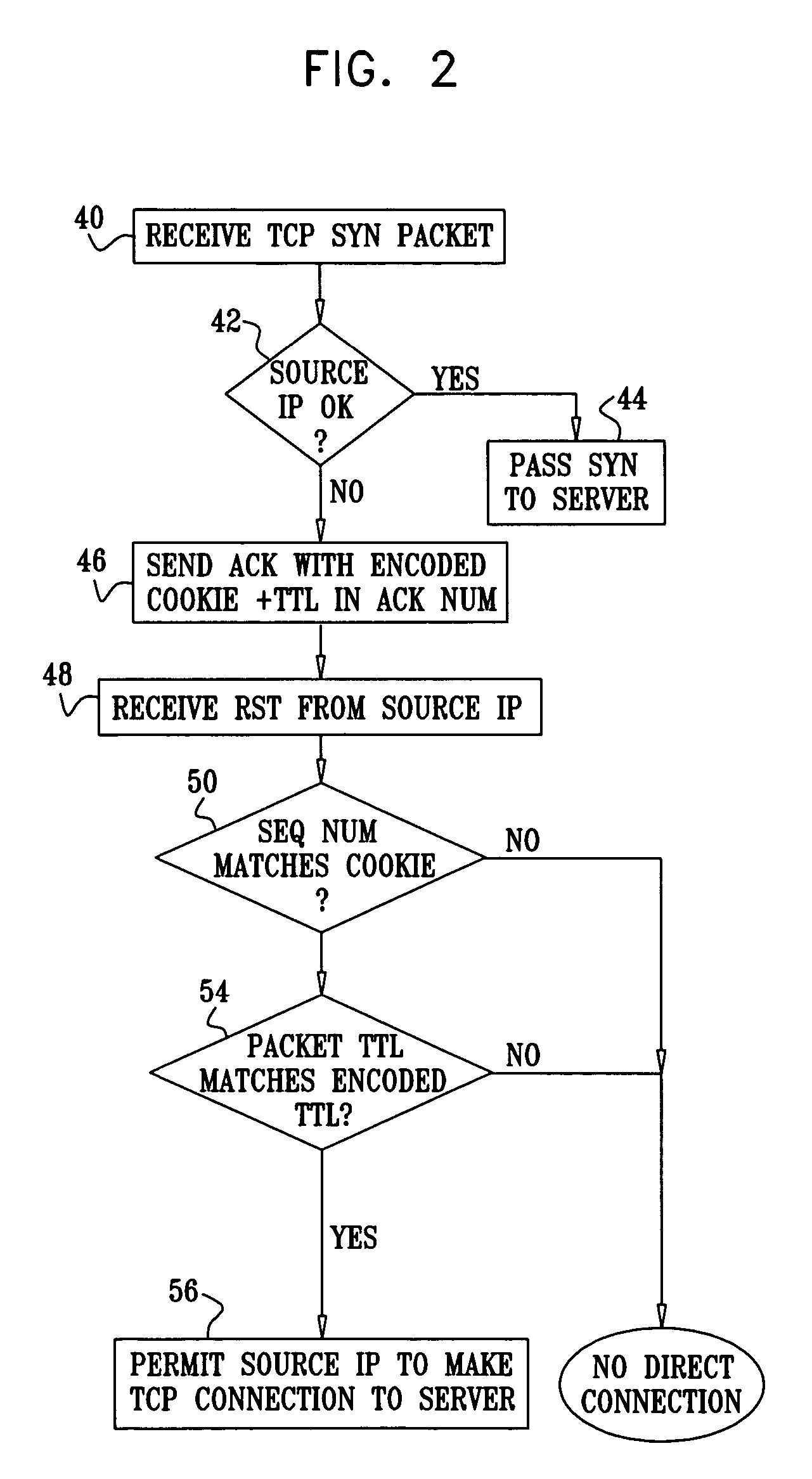
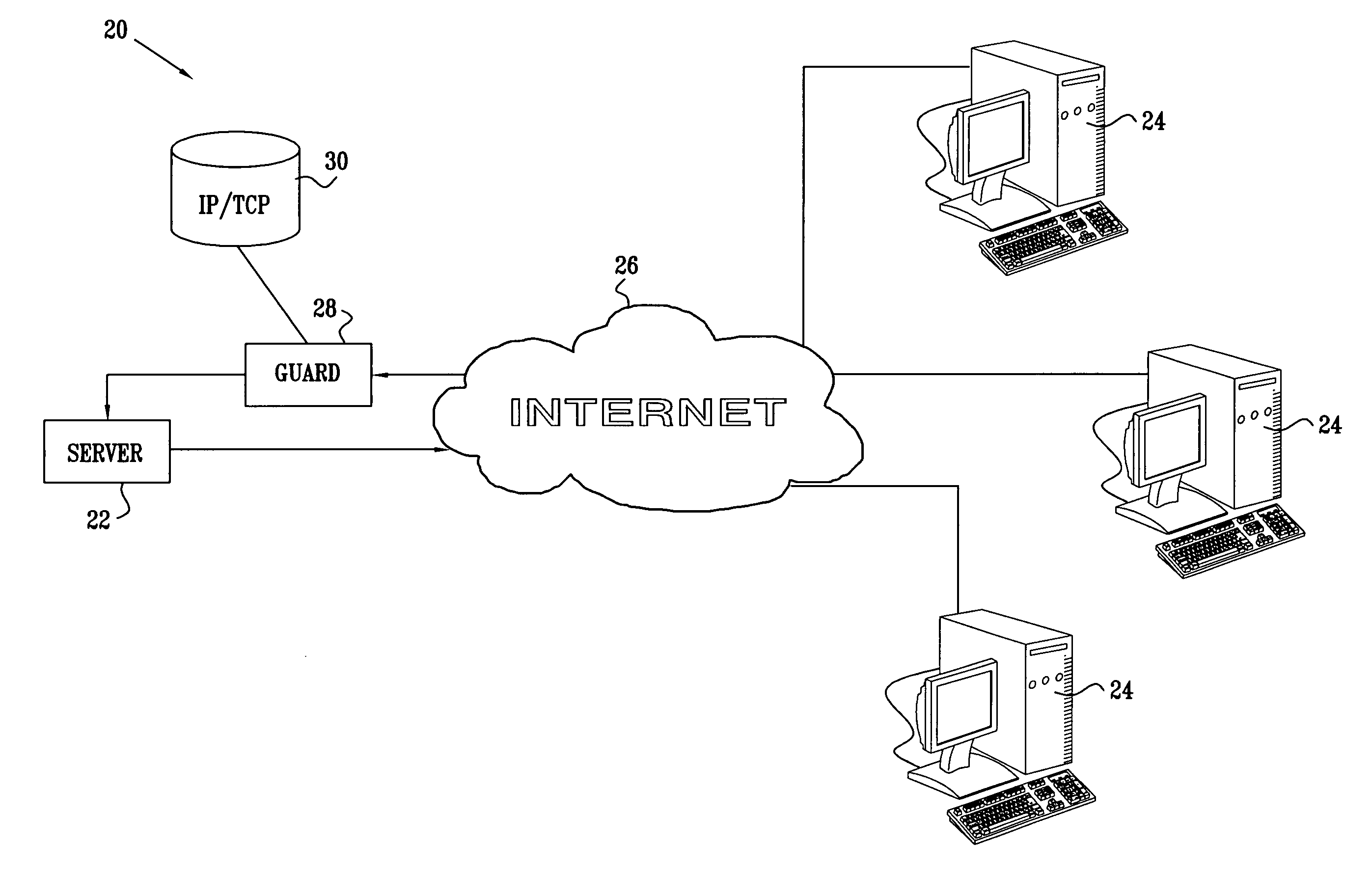
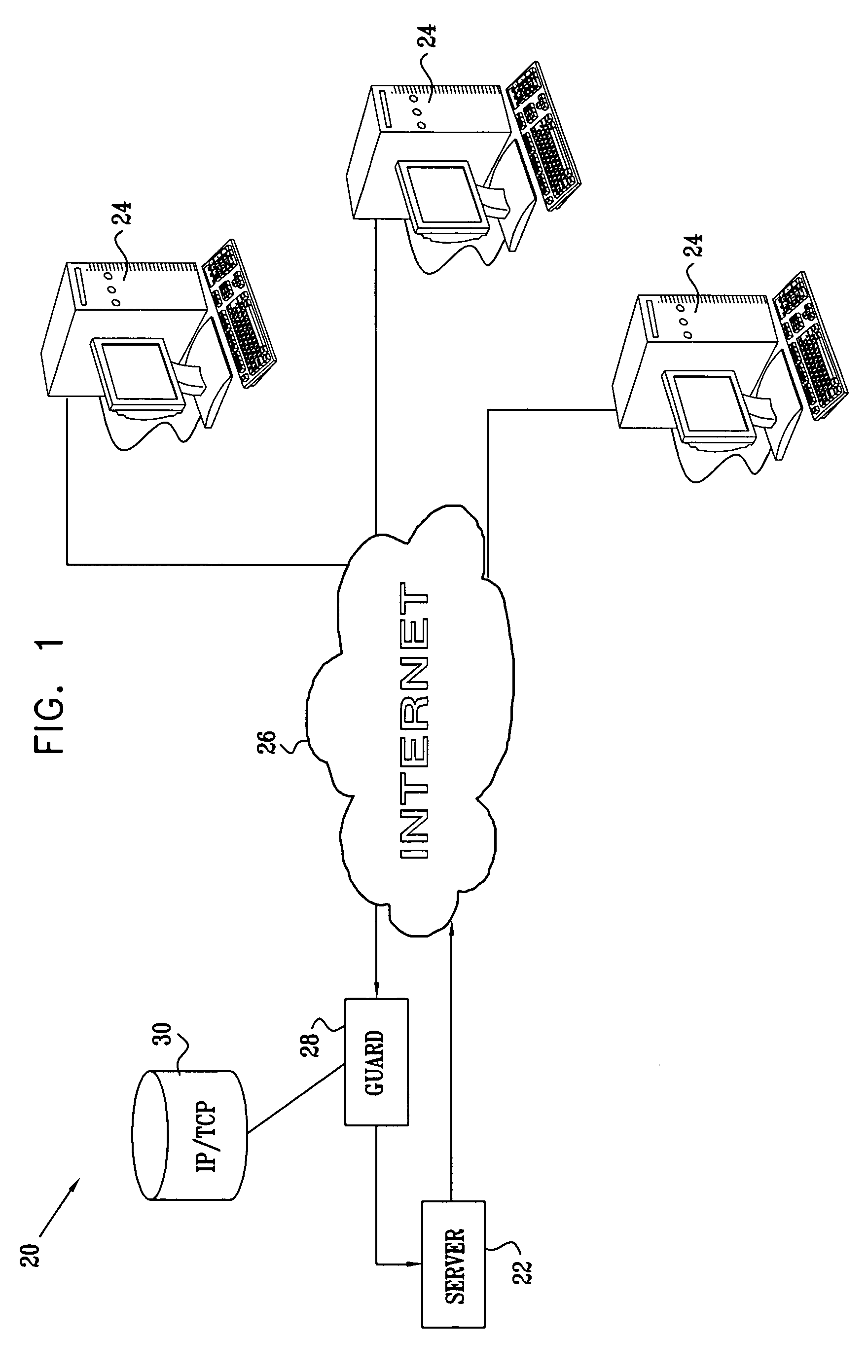
Using TCP to authenticate IP source addresses
ActiveUS20050021999A1Memory loss protectionError detection/correctionProtocol for Carrying Authentication for Network AccessHandshake
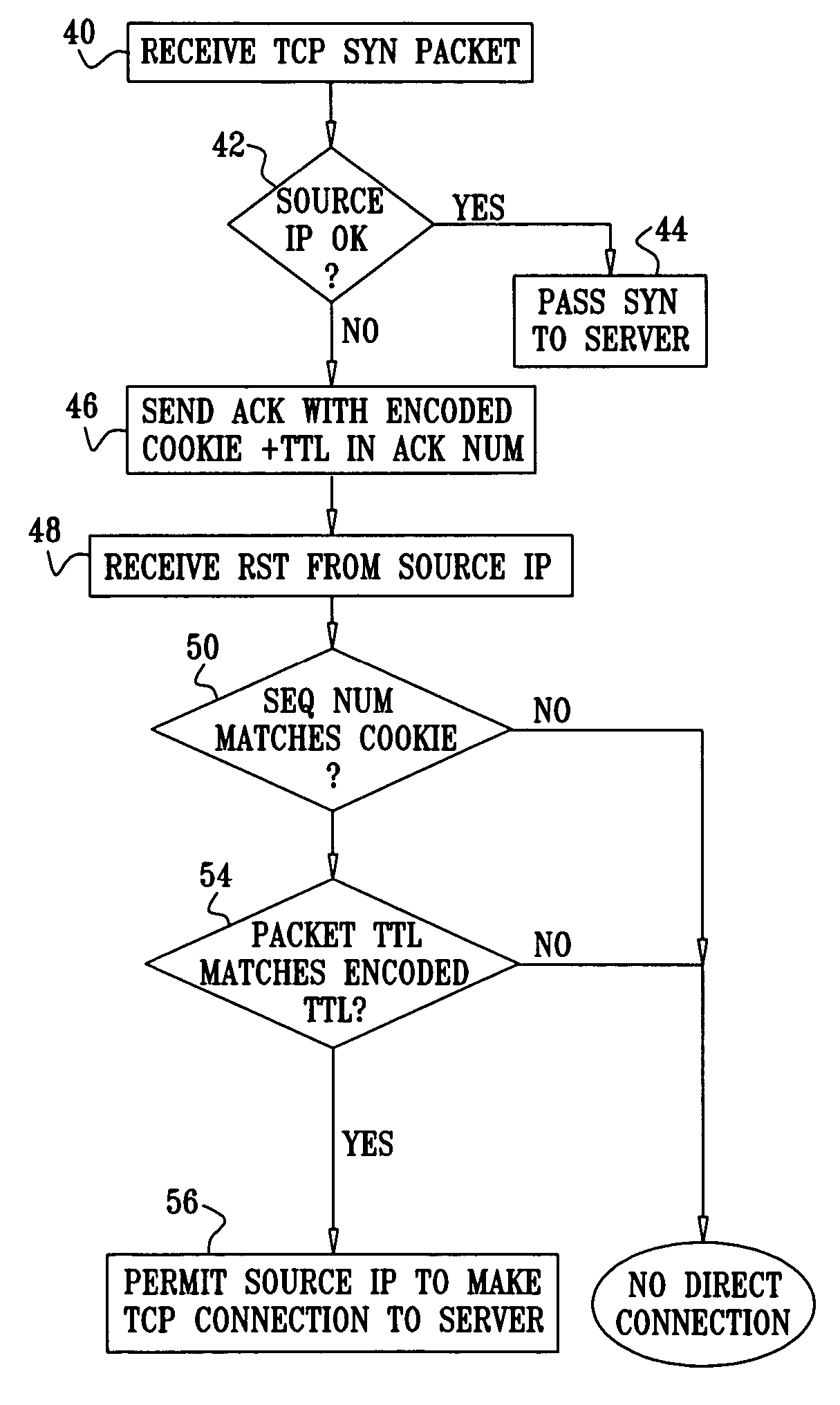
A method for authenticating communication traffic includes intercepting a request directed over a network from a source address to open a connection to a target computer in accordance with a handshake procedure specified by a predetermined communication protocol. A reply to the request that deviates from the specified handshake procedure is sent to the source address. A response from the source address to the reply is analyzed in order to make an assessment of legitimacy of the source address. Upon determining, based on the assessment, that the source address is legitimate, the target computer is permitted to complete the handshake procedure so as to open the connection with the source address.
Owner:CISCO TECH INC
Using TCP to authenticate IP source addresses
ActiveUS7979694B2Memory loss protectionError detection/correctionProtocol for Carrying Authentication for Network AccessHandshake
A method for authenticating communication traffic includes intercepting a request directed over a network from a source address to open a connection to a target computer in accordance with a handshake procedure specified by a predetermined communication protocol. A reply to the request that deviates from the specified handshake procedure is sent to the source address. A response from the source address to the reply is analyzed in order to make an assessment of legitimacy of the source address. Upon determining, based on the assessment, that the source address is legitimate, the target computer is permitted to complete the handshake procedure so as to open the connection with the source address.
Owner:CISCO TECH INC
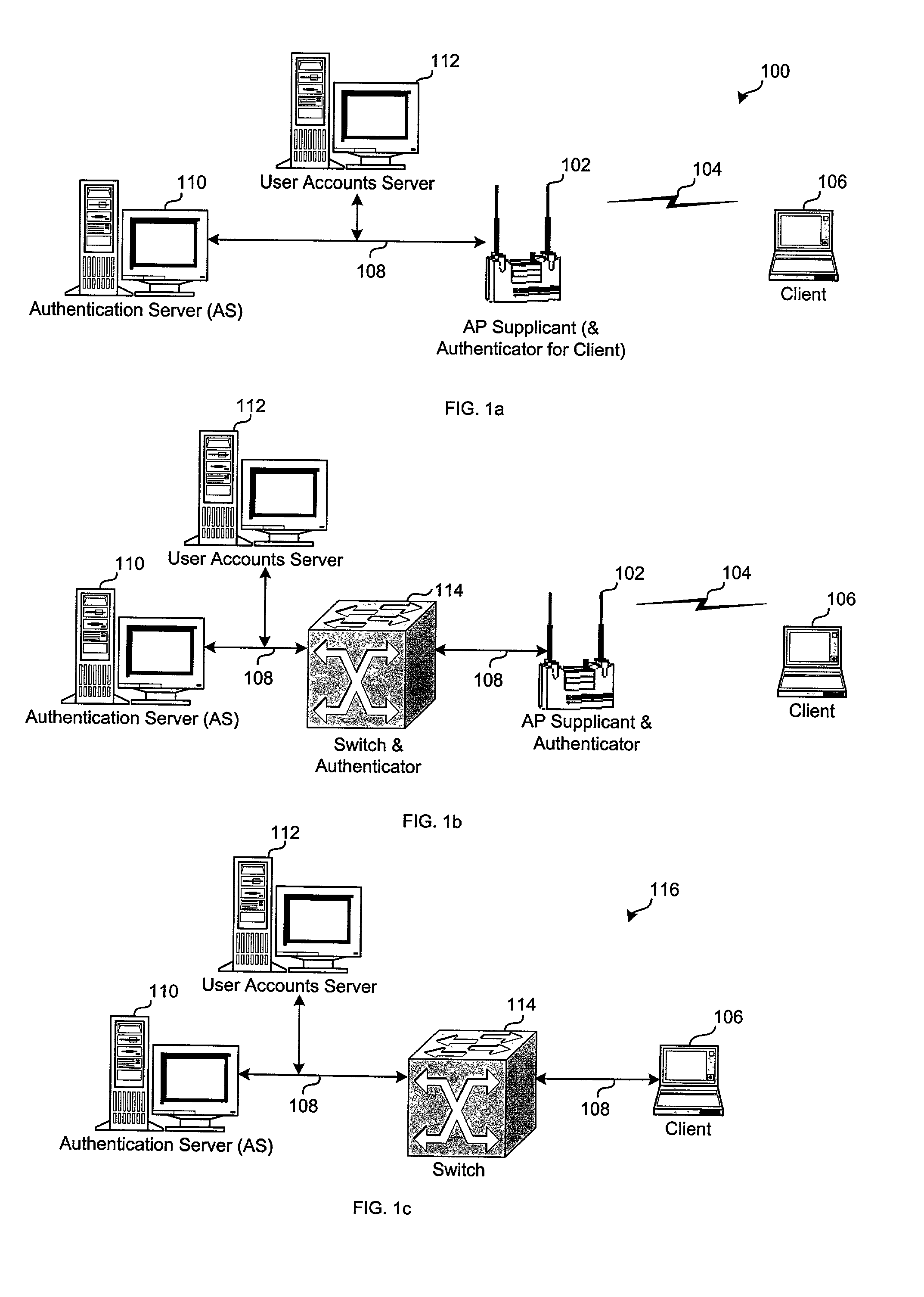
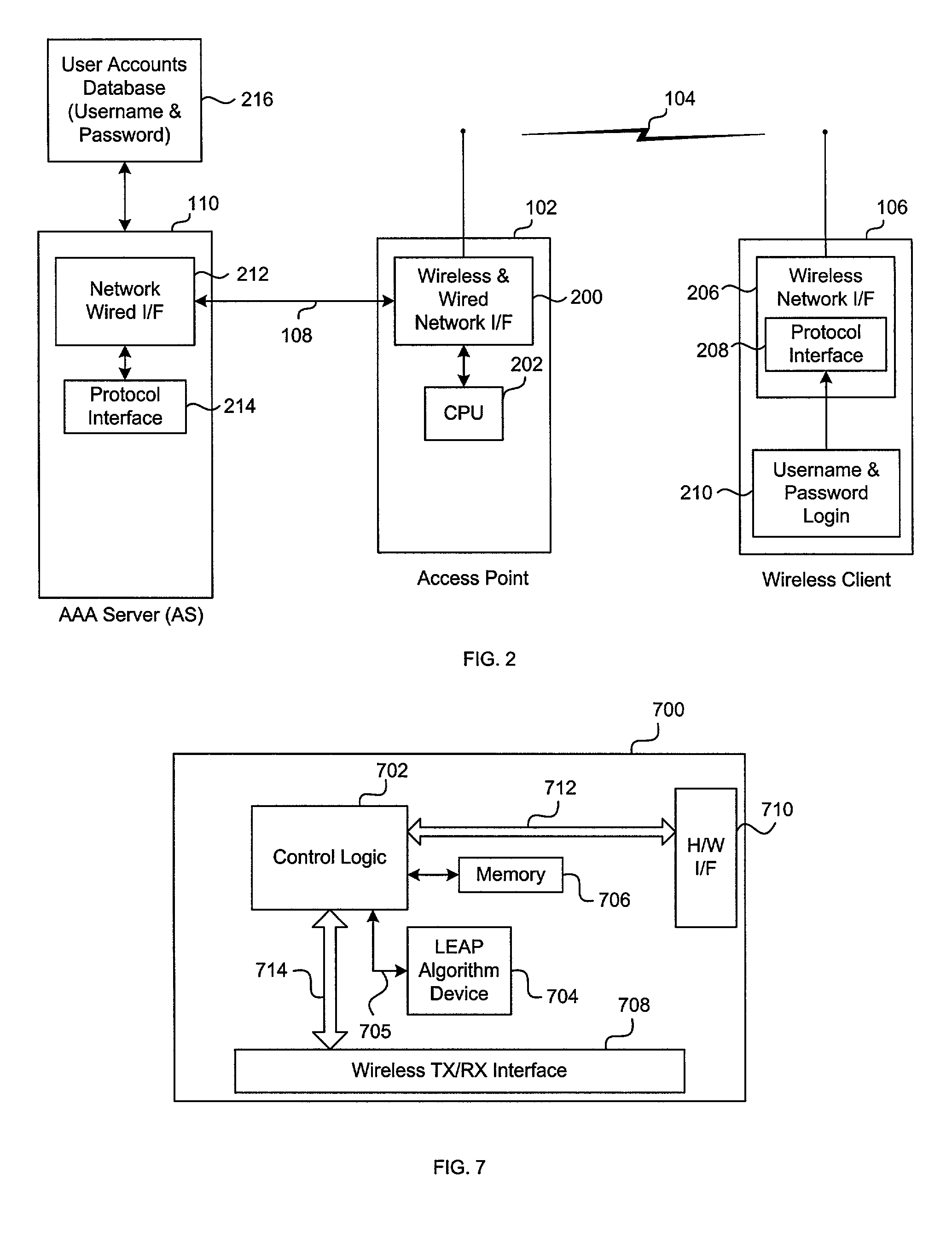
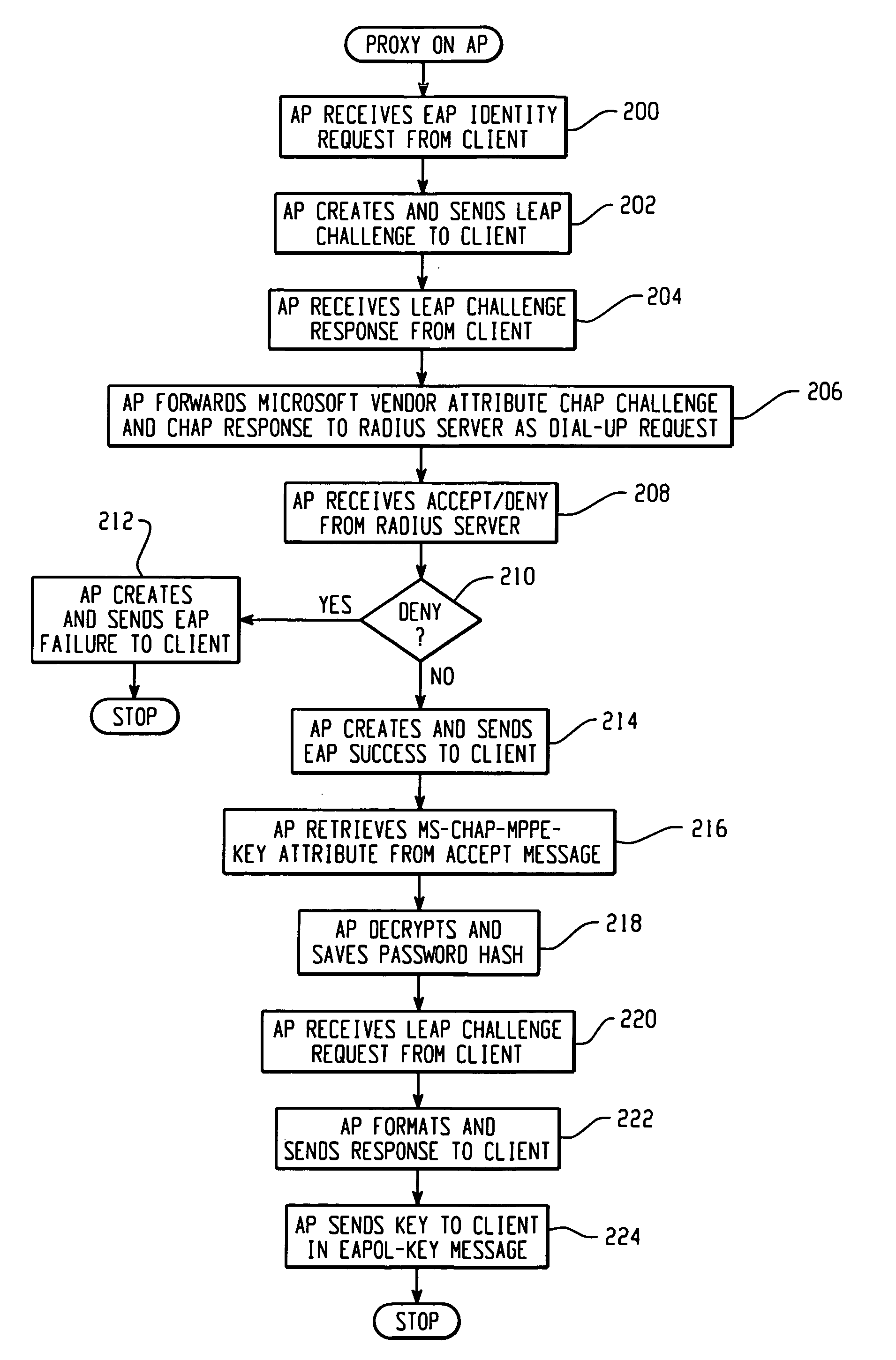
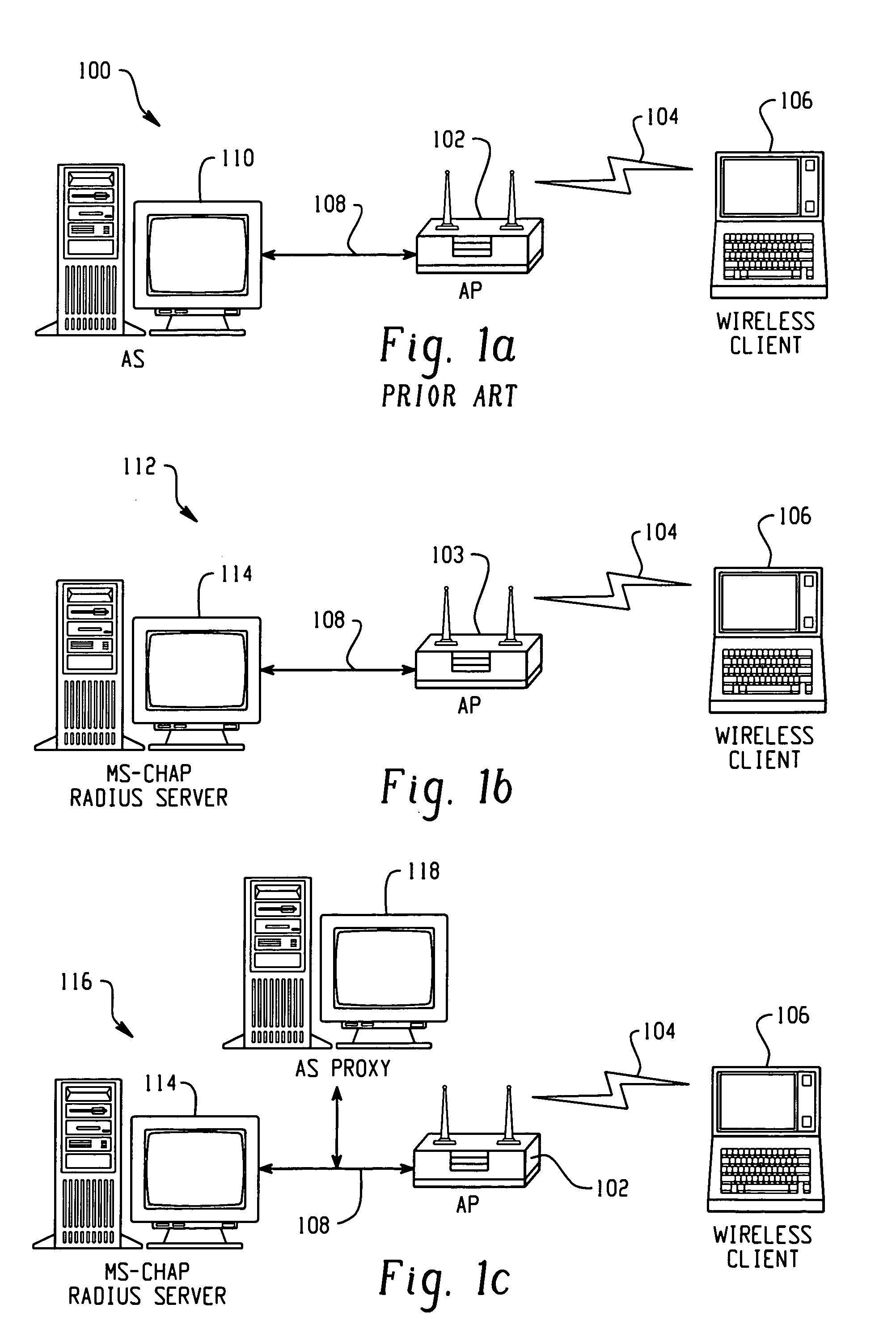
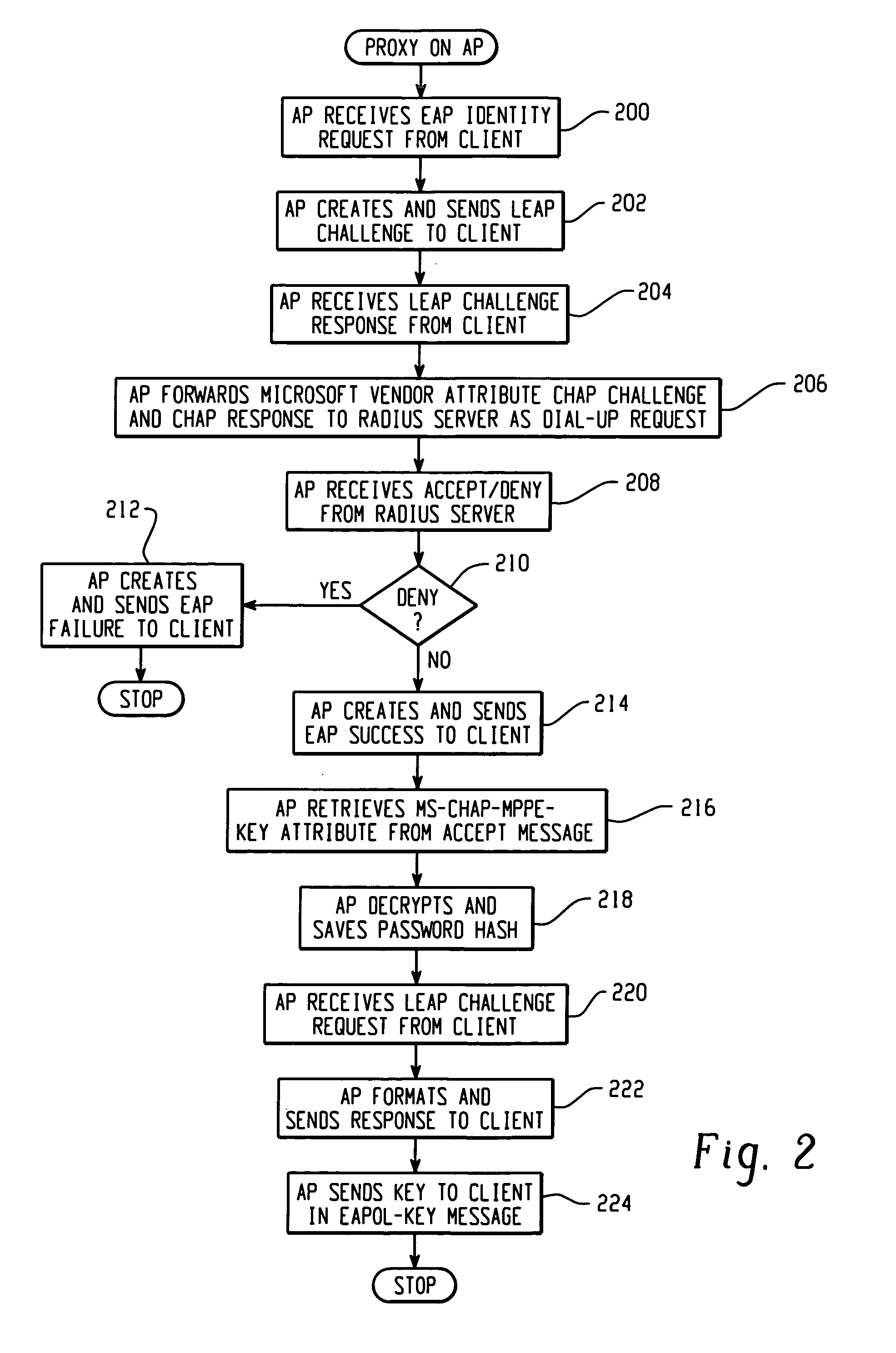
System and method of controlling access by a wireless client to a network that utilizes a challenge/handshake authentication protocol
Architecture for controlling access by a Light Extensible Authentication Protocol (LEAP)-compatible wireless client to a network that utilizes a challenge / handshake authentication protocol (CHAP). A proxy service is hosted on a network server disposed on the network, and accessed in response to receiving access information from the client. The access information is processed with the proxy service into CHAP-compatible access information, and forwarded to a CHAP-based access control server disposed on the network to determine whether to grant network access to the client.
Owner:CISCO TECH INC
Physical interaction dependent transactions
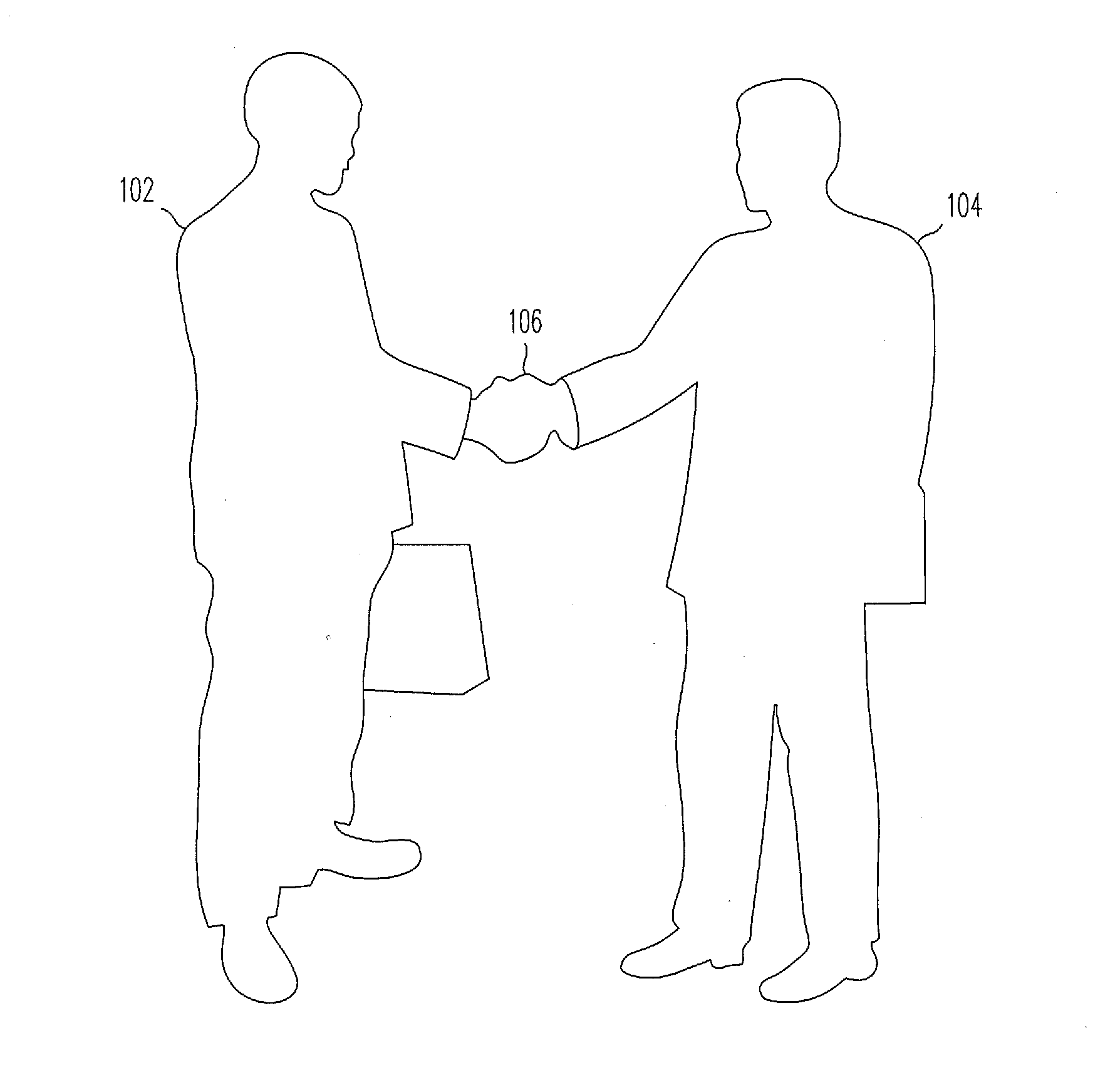
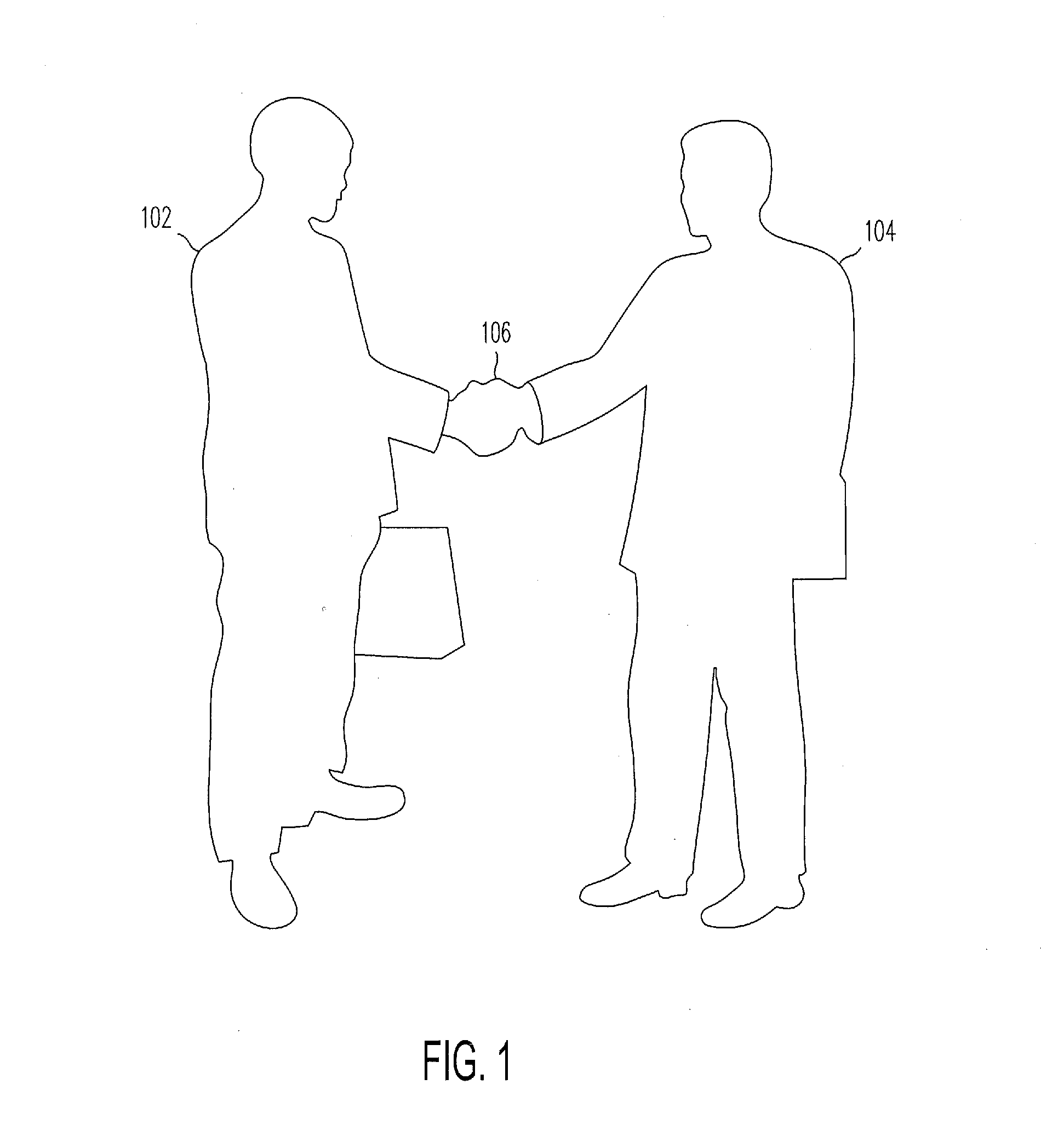
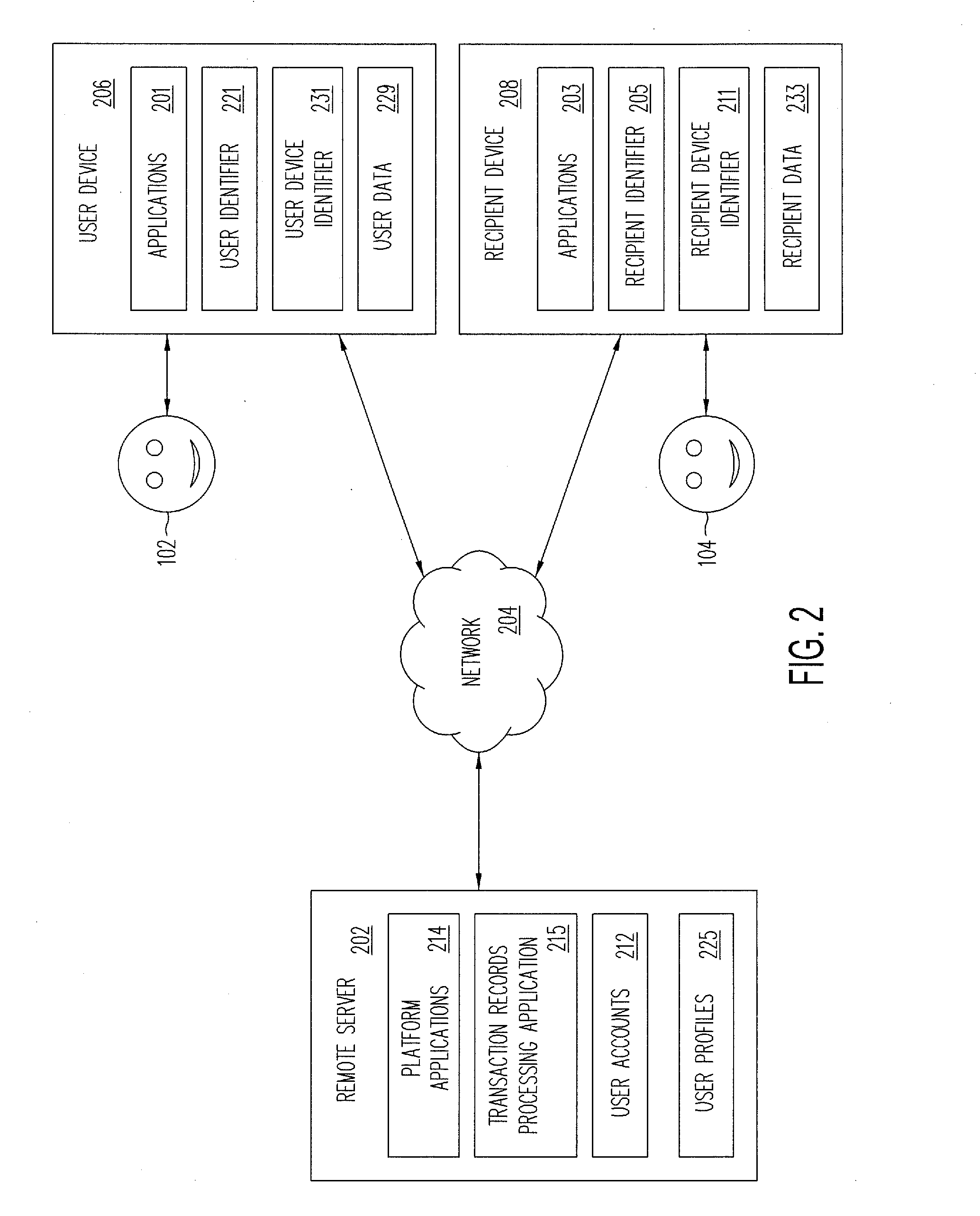
Systems and methods are provided according to one or more embodiments for conducting transactions based on actions or gestures such as physical interactions between users each having a user device. In that regard, gestures such as a handshake or other physical interactions between users may be detected to determine transaction details such as a payment amount or a value to be transferred from one user via a user device to a recipient via a recipient device. The amount or value may then be transferred based on one or more determinations including proximity between the user or the user device and the recipient or the recipient device, a specific action or gesture, voice commands, facial recognition, preset transfer instructions, a unique identifier, or other close-quarter determinations.
Owner:PAYPAL INC
Multiple user authentication for online console-based gaming
InactiveUS20020126846A1Key distribution for secure communicationData processing applicationsTicketInternet privacy
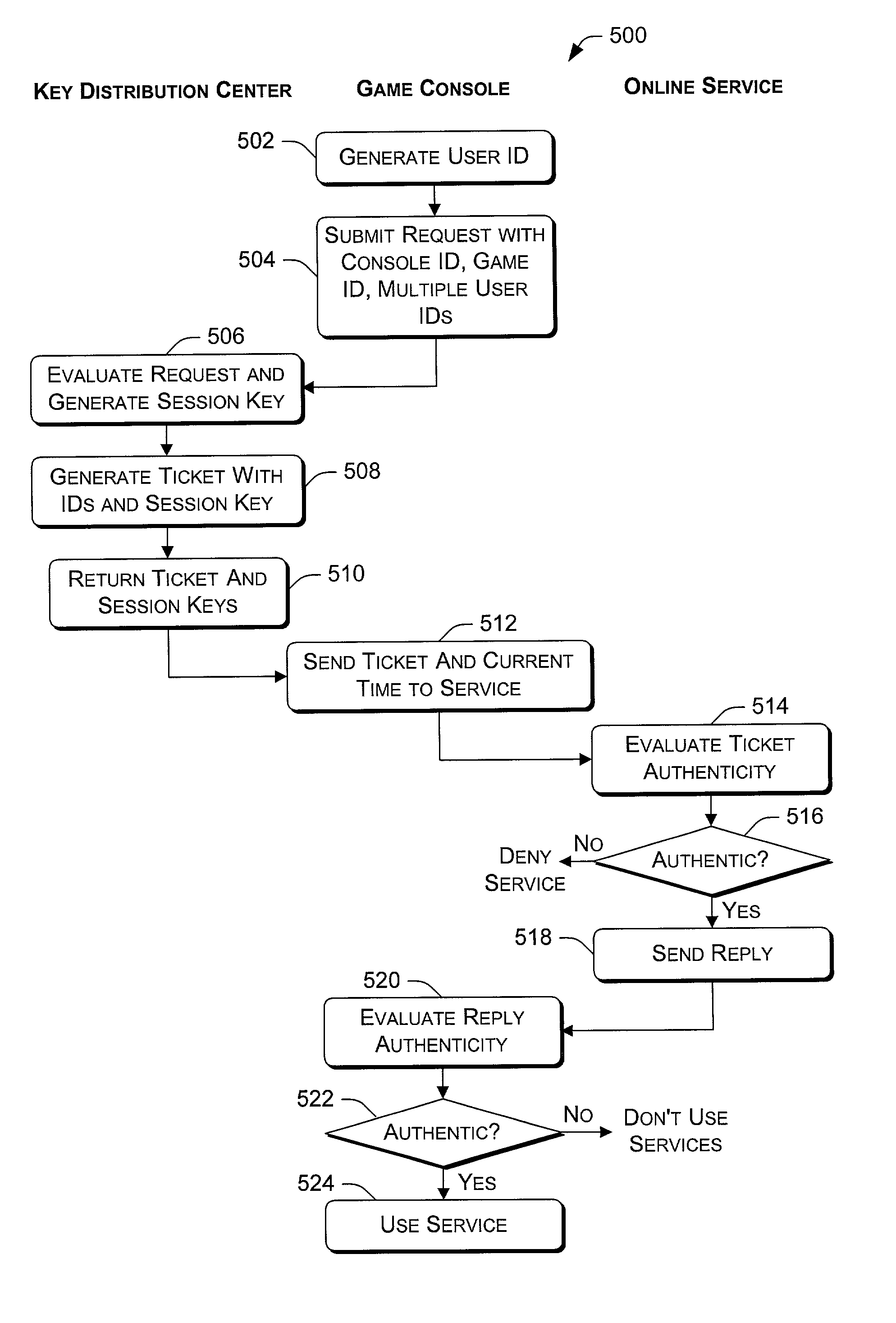
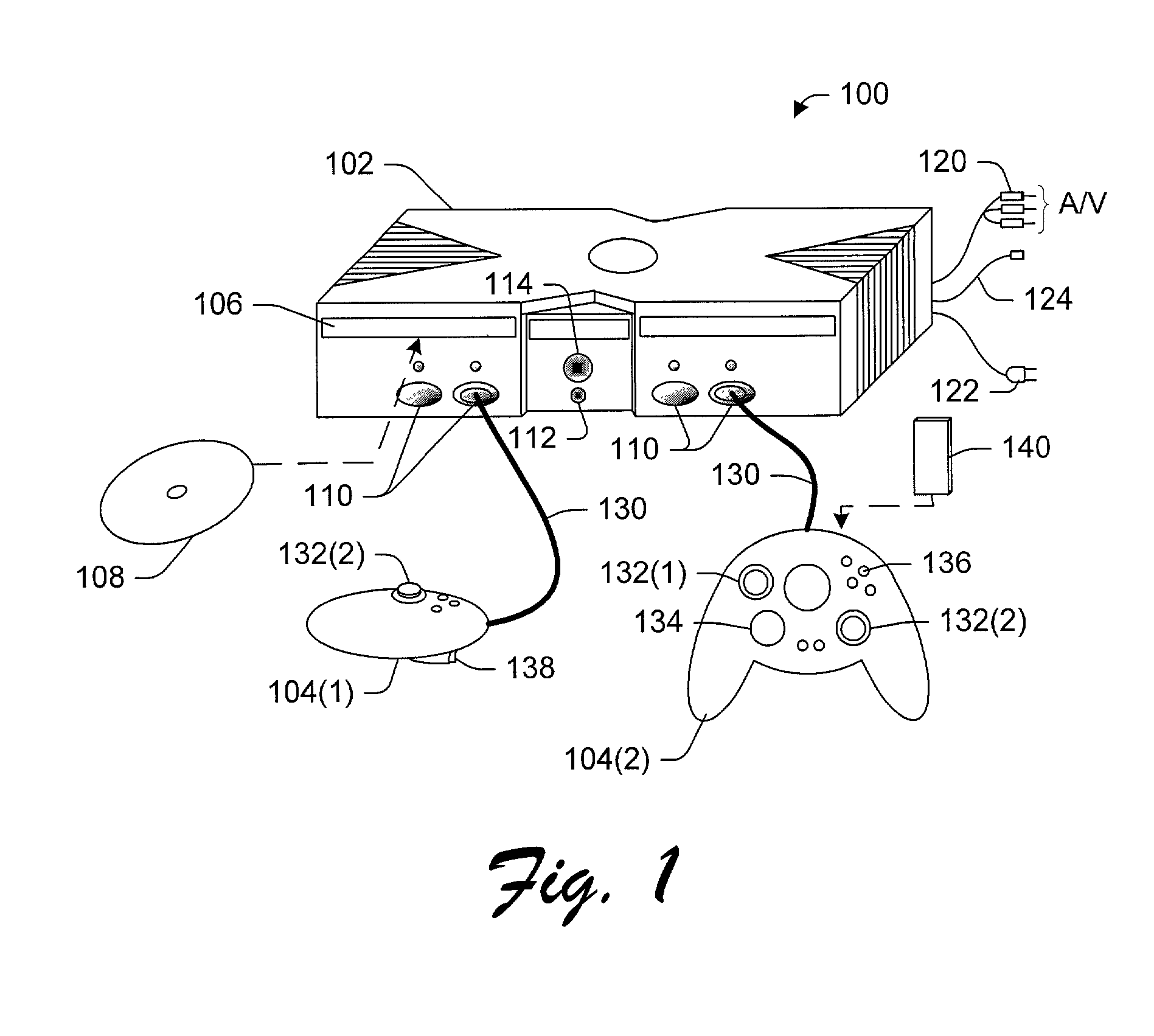
A console-based multi-user authentication process allows multiple users of a game console to be authenticated together in a single request / reply exchange with an authentication entity. The results of which is the possession of a single ticket that can be used to prove authenticity of multiple authentication principals to one or more online services. Also described is a handshake process that can be used to initially establish an authentication account for each game console, in which the account creation server can trust that a genuine game console is making the request.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for optimizing ssl handshake processing
ActiveUS20080046727A1Effective bufferEfficiently encryptDigital data processing detailsUser identity/authority verificationVia deviceClient-side
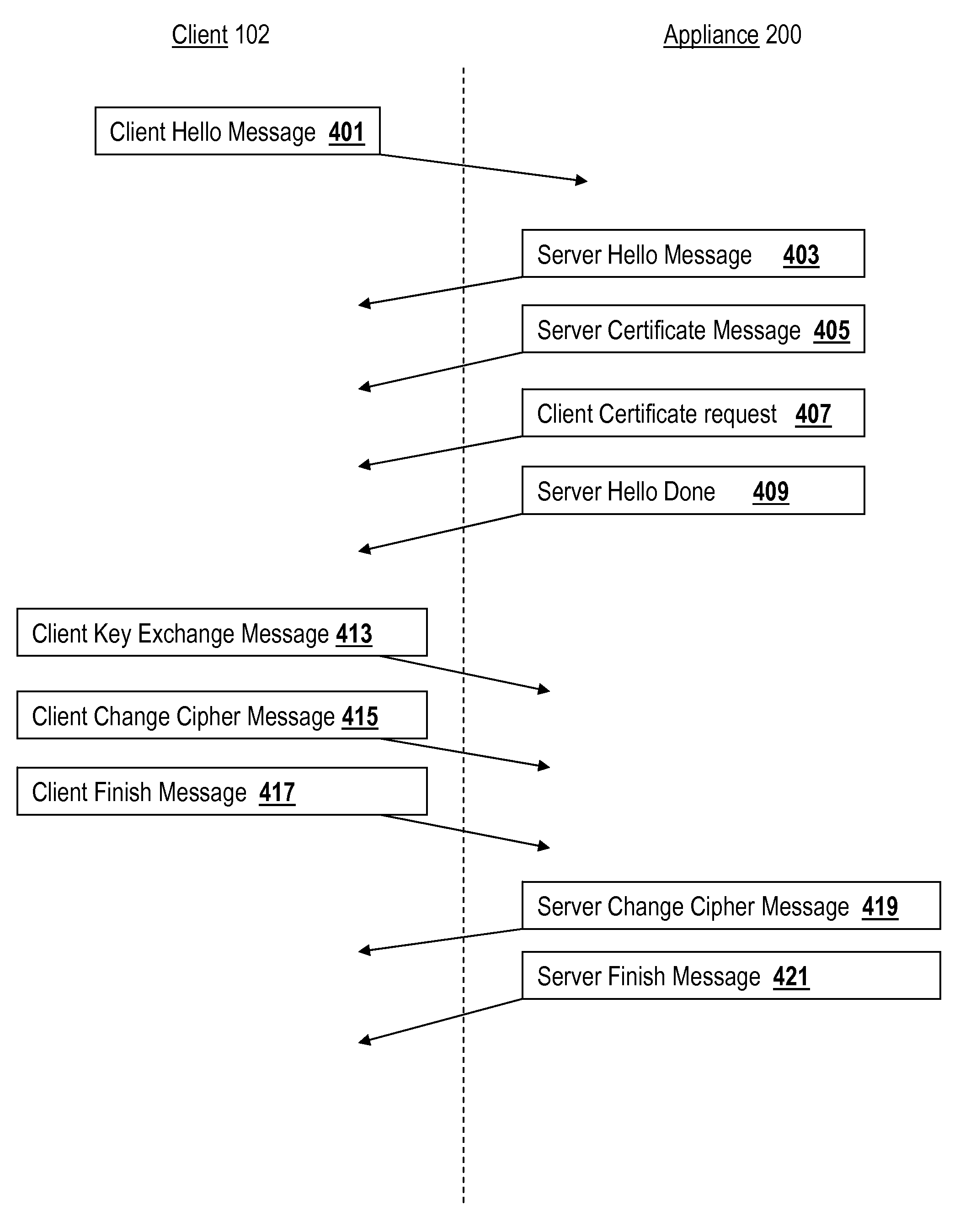
A method for buffering SSL handshake messages prior to computing a message digest for the SSL handshake includes: conducting, by an appliance with a client, an SSL handshake, the SSL handshake comprising a plurality of SSL handshake messages; storing, by the appliance, the plurality of SSL handshake messages; providing, by the appliance to a message digest computing device in response to receiving a client finish message corresponding to the SSL handshake, the plurality of SSL handshake messages; receiving, by the appliance from the message digest computing device, a message digest corresponding to the provided messages; determining by the appliance, the message digest matches a message digest included in the SSL client finish message; and completing, by the appliance with the client, the SSL handshake. Corresponding systems are also described.
Owner:CITRIX SYST INC
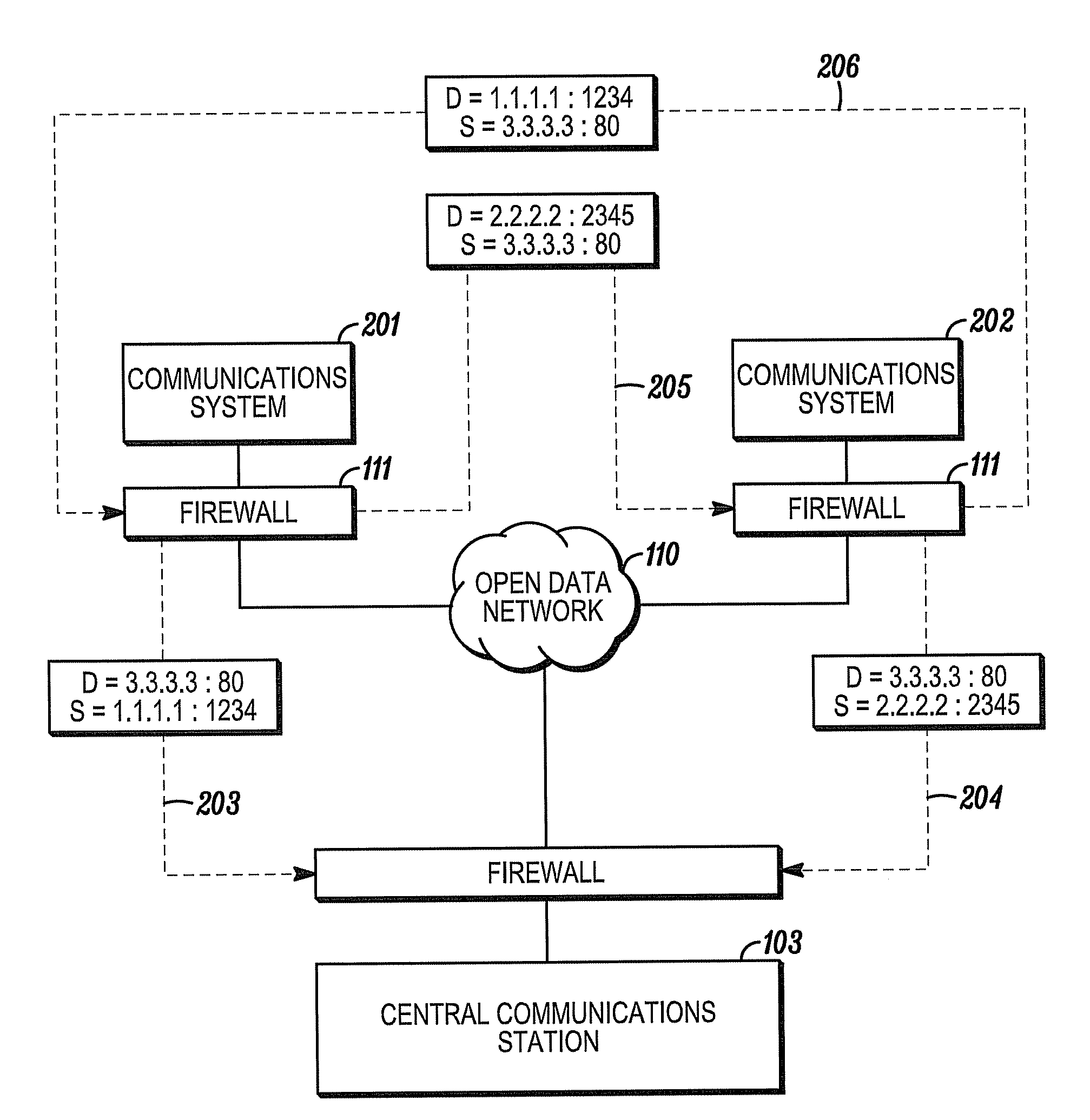
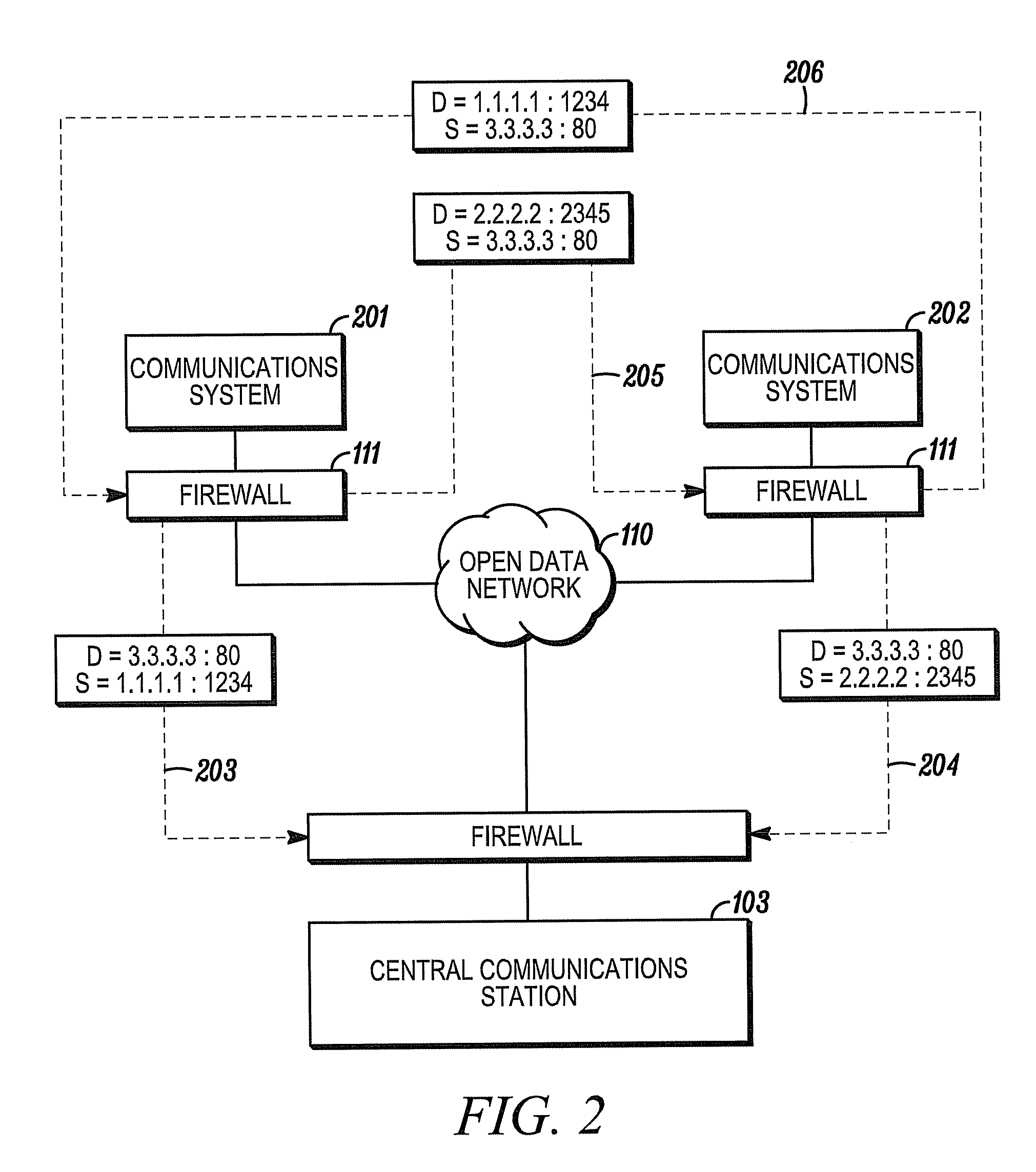
Method for permitting two parties to establish connectivity with both parties behind firewalls
ActiveUS7992199B1Multiple digital computer combinationsProgram controlCommunications systemExternal data
A communications scheme enables a central communications station to assist two communications systems located behind firewalls that prevent communication initiated from an external data network to establish direct communication with each other. In one embodiment, the systems separately establish communications with the central communications station and obtain from it the connection information (e.g., IP address, port, etc.) of the other. The systems then directly communicate with each other using the obtained connection information while pretending to be the central communications station. In another embodiment in which the firewalls include NAT devices that implement network address translation, the systems exchange connection information for establishing a new connection through the central communications station and then complete a three-way handshake with the assistance of the central communications station, thereby allowing the central communications station to remove itself from the communication.
Owner:ADEMCO INC
Multi-hazard alarm system using selectable power-level transmission and localization
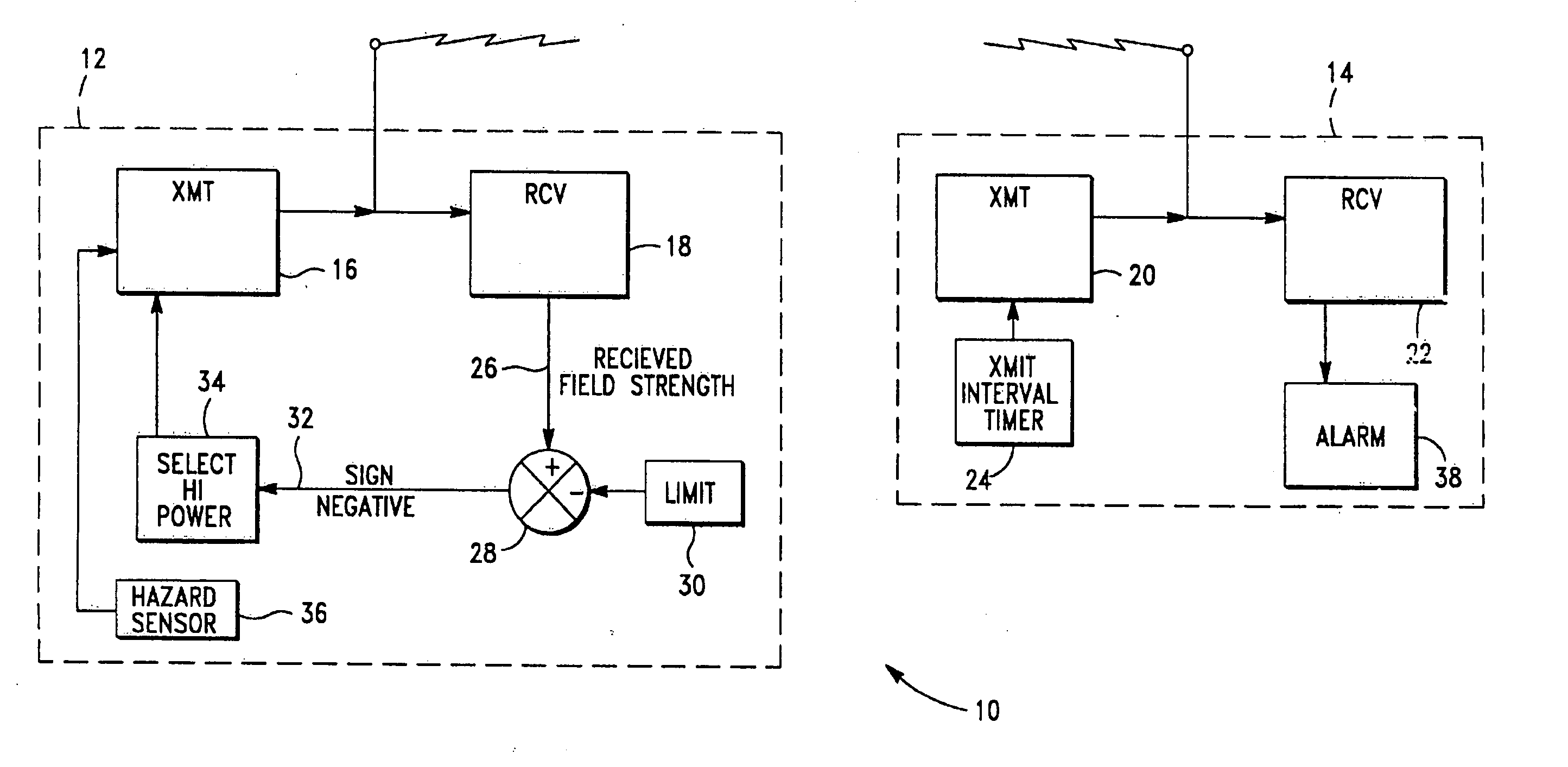
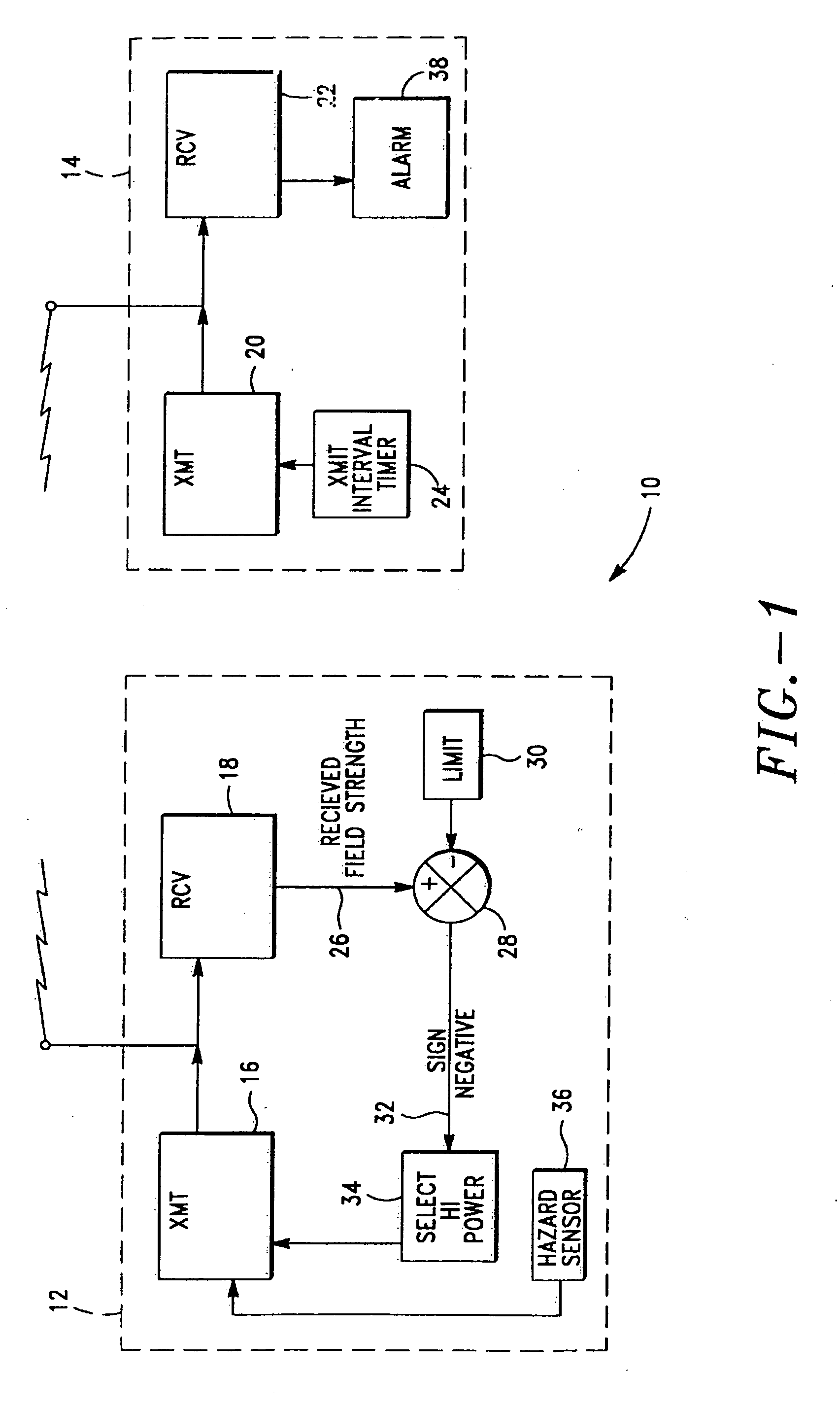
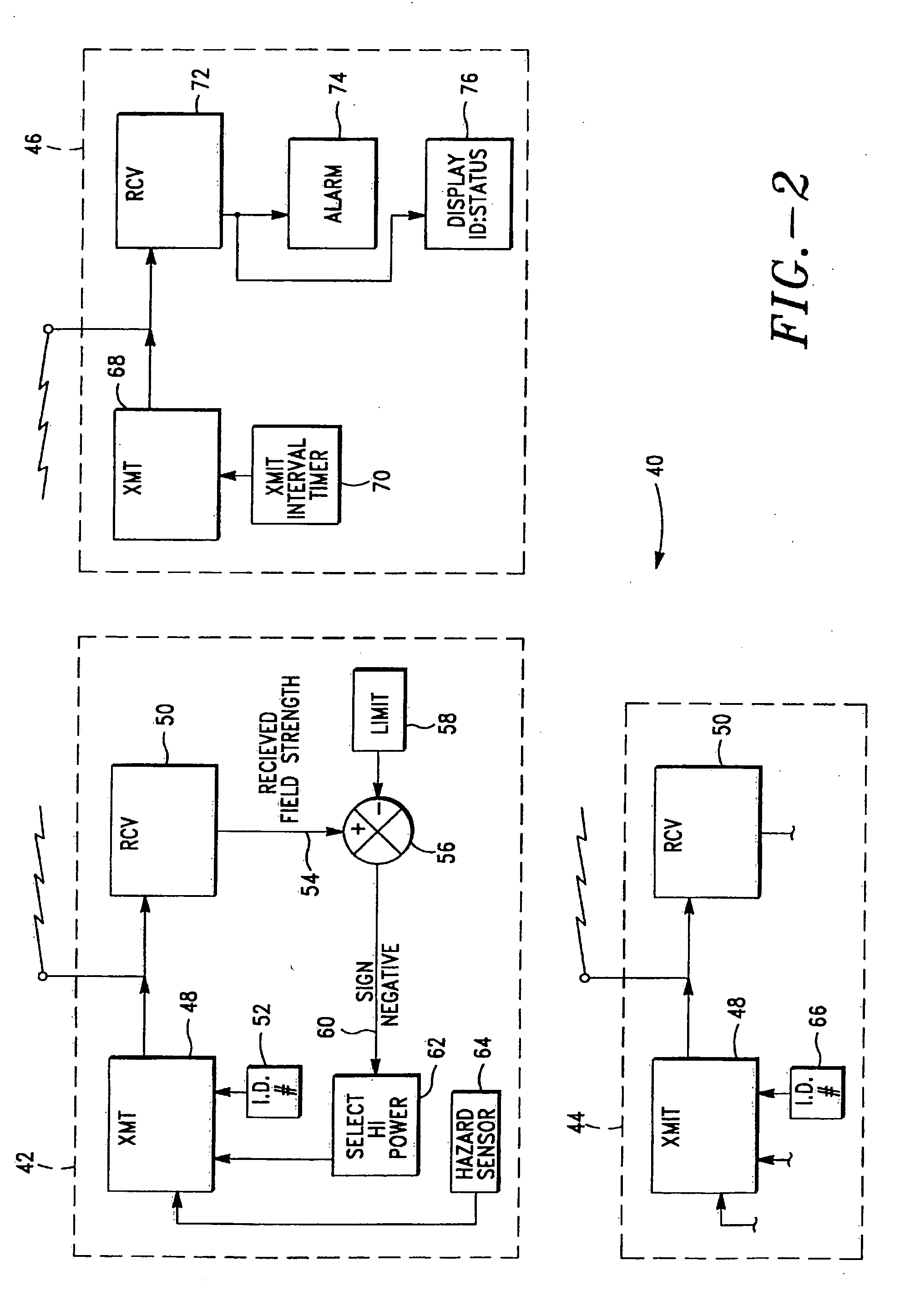
InactiveUS20070030156A1Prolong remote unit battery lifeAccurate and fast positioningEmergency connection handlingFrequency-division multiplex detailsMulti hazardEmergency situations
A personal alarm system includes a monitoring base station and one or more remote sensing units in two-way radio communication. An electronic handshake between the base station and each remote unit is used to assure system reliability. The remote units transmit at selectable power levels. In the absence of an emergency, a remote unit transmits at a power-conserving low power level. Received field strength is measured to determine whether a remote unit has moved beyond a predetermined distance from the base station. If the distance is exceeded, the remote unit transmits at a higher power level. The remote unit includes sensors for common hazards including water emersion, smoke, excessive heat, excessive carbon monoxide concentration, and electrical shock. The base station periodically polls the remote units and displays the status of the environmental sensors. The system is useful in child monitoring, for use with invalids, and with employees involved in activities which expose them to environmental risk. Alternative embodiments include a panic button on the remote unit for summoning help, and an audible beacon on the remote unit which can be activated from the base station and useful for locating strayed children. In another embodiment, the remote unit includes a Global Positioning System receiver providing location information for display by the base station.
Owner:CONVERSANT INTPROP MANAGEMENT INC
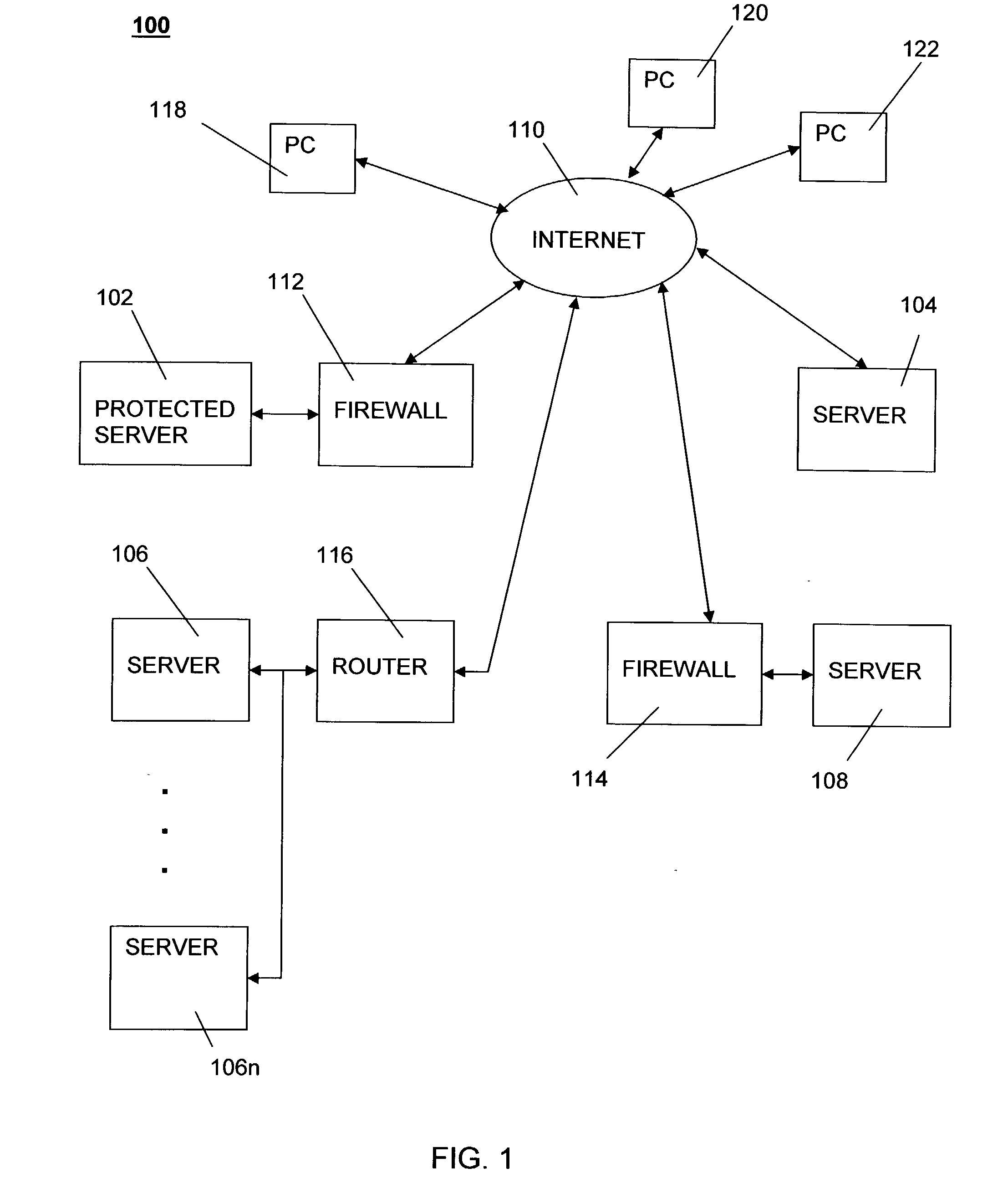
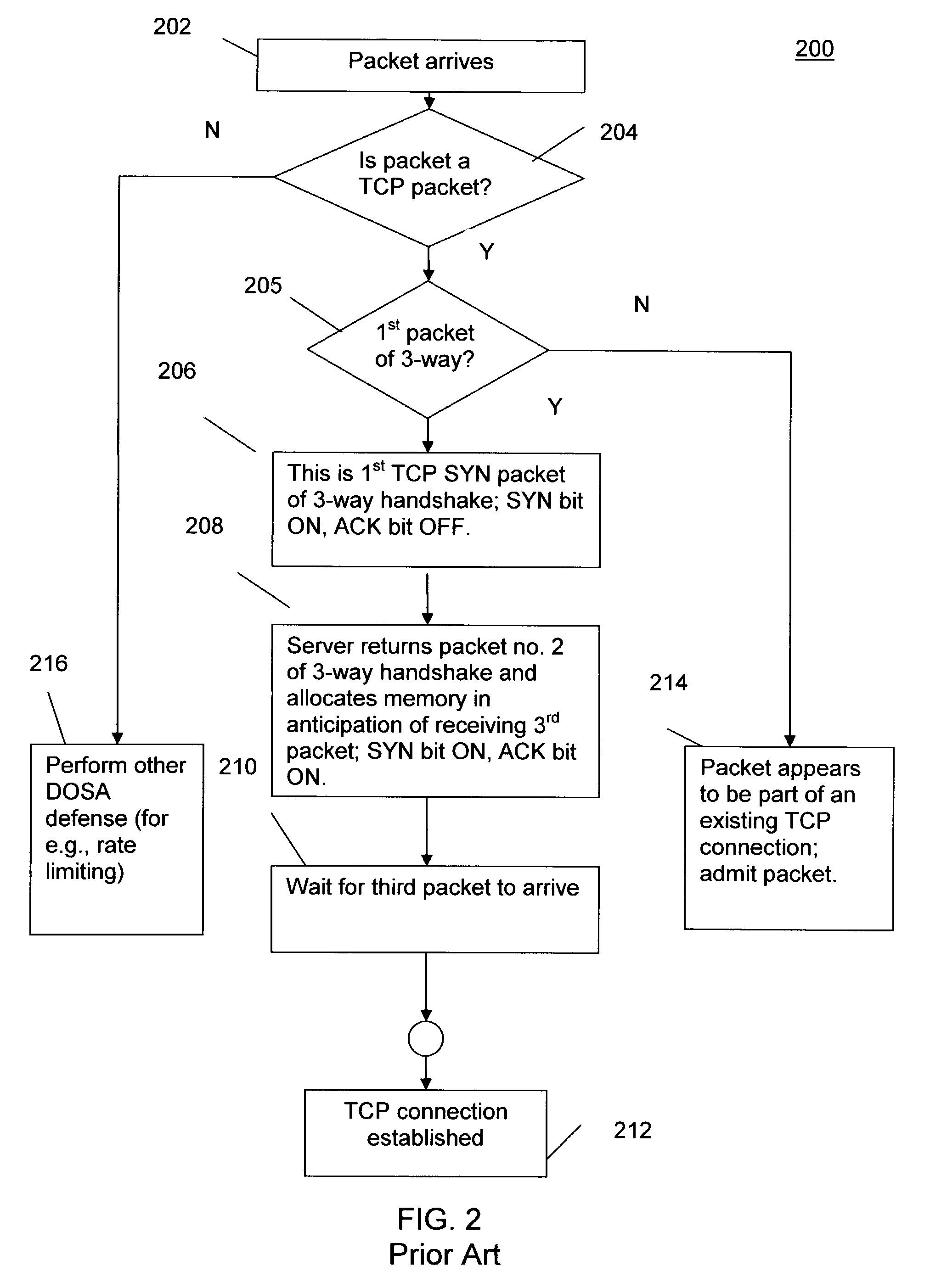
Protection against denial of service attacks
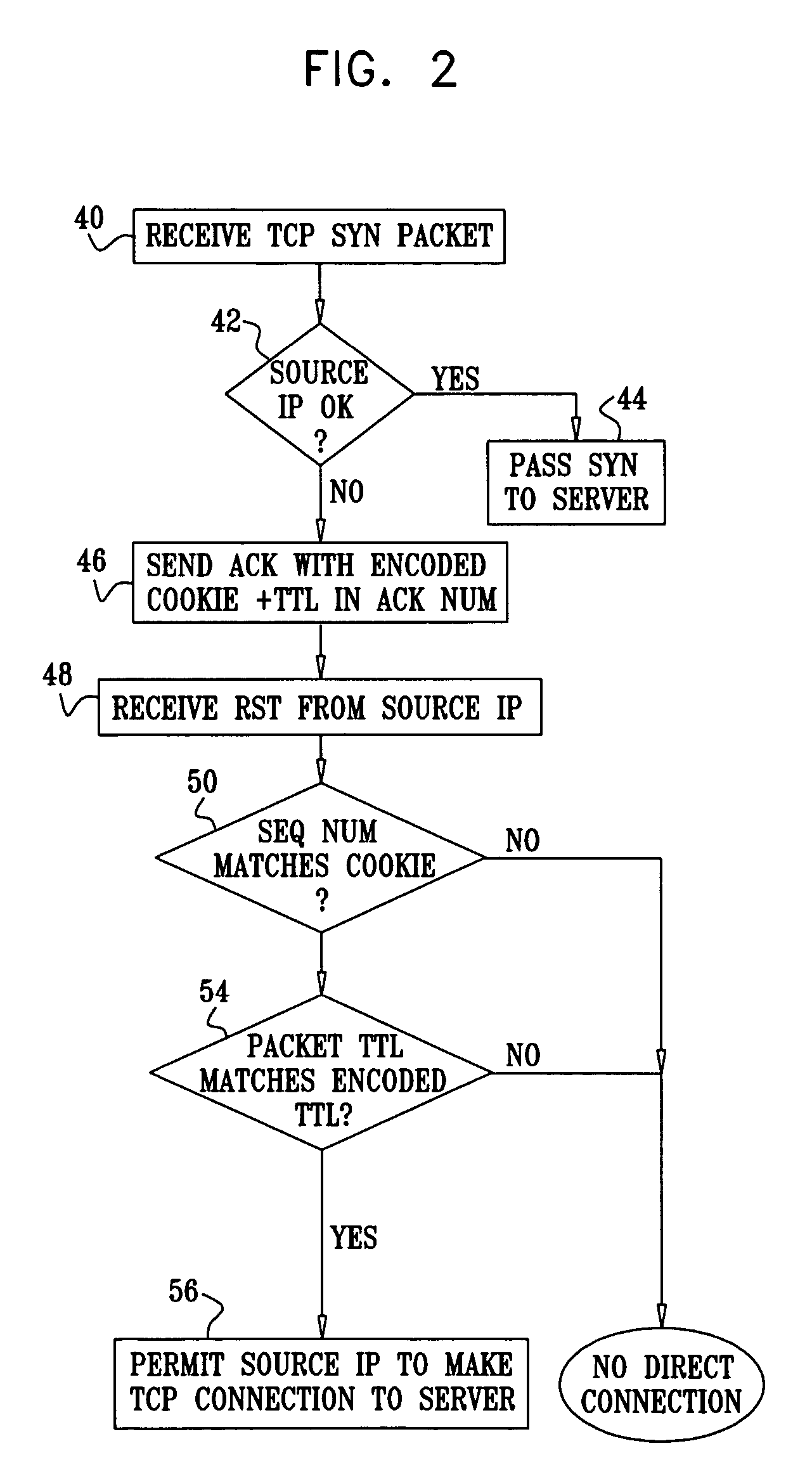
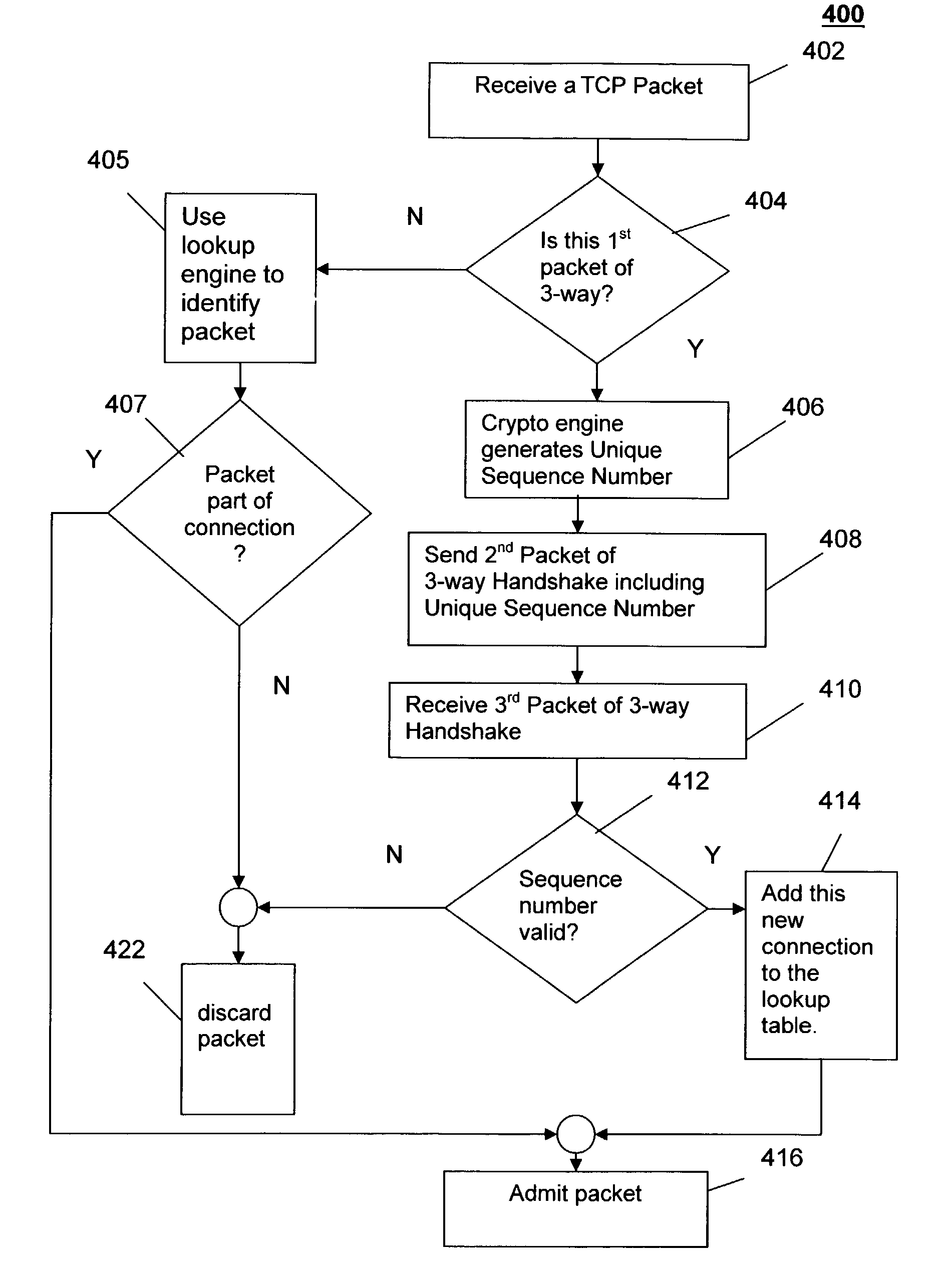
InactiveUS20040111635A1Memory loss protectionUnauthorized memory use protectionInformation processingClient-side
An information processing system for protecting against denial of service attacks comprises an interface (310) to receive and send packets, wherein the packets comprise at least one synchronization packet that is part of a handshake process for establishing the connection between the source client computer (118) and the target server computer (102); a crypto engine (306) adapted to create a unique sequence number for inclusion in a packet to be sent to a client (118) requesting establishment of a connection between a client (118) and server (102), wherein the crypto engine (306) is further adapted to validate unique sequence numbers in received synchronization packets that are part of a handshake process for establishing the connection between the source client (118) and the protected server (102); and a lookup table (304) for storing information defining established connections between the server (102) and clients so that arriving packets that purport to be part of an established connection can be validated by comparing information in the packet with entries in the table.
Owner:IBM CORP
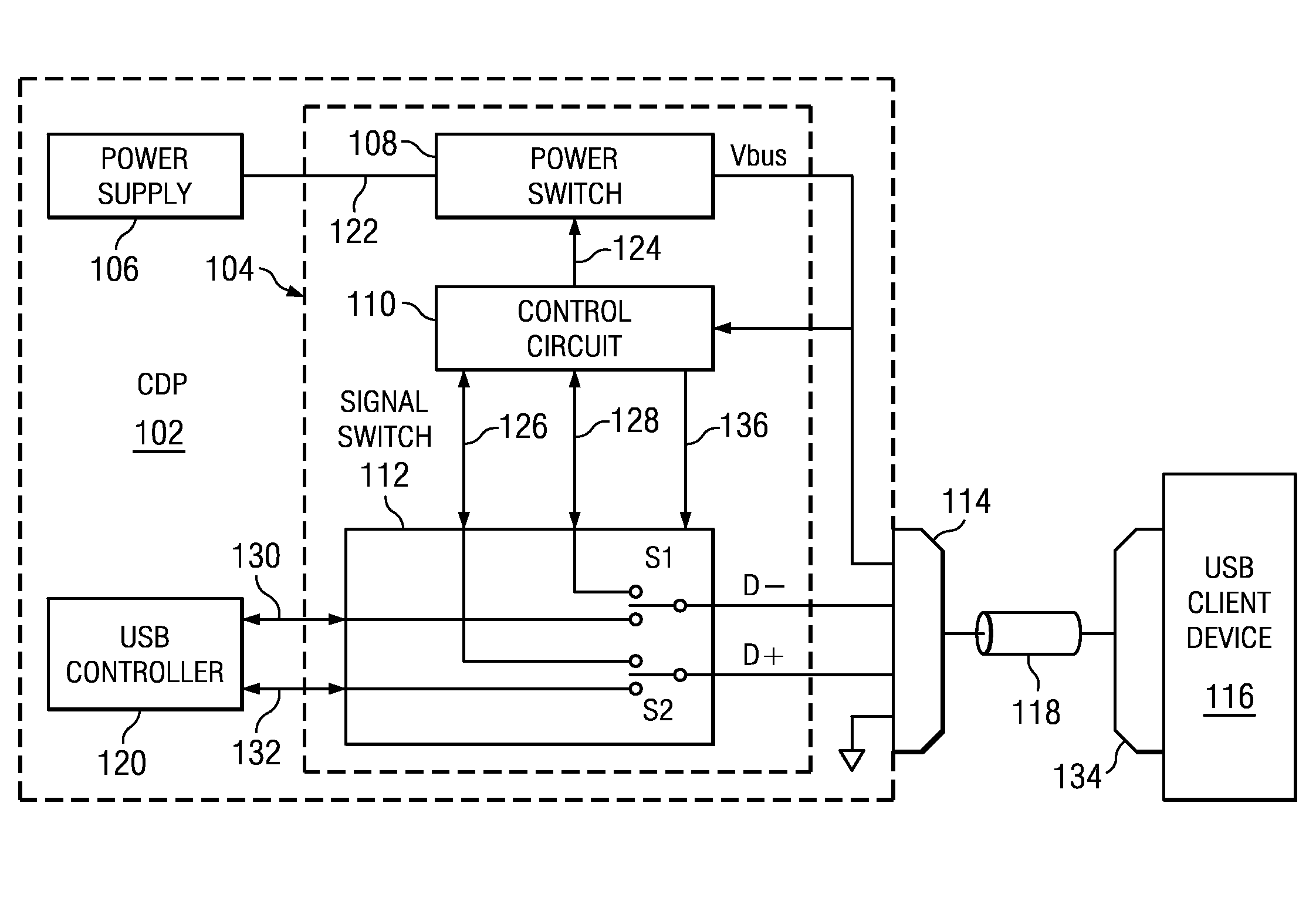
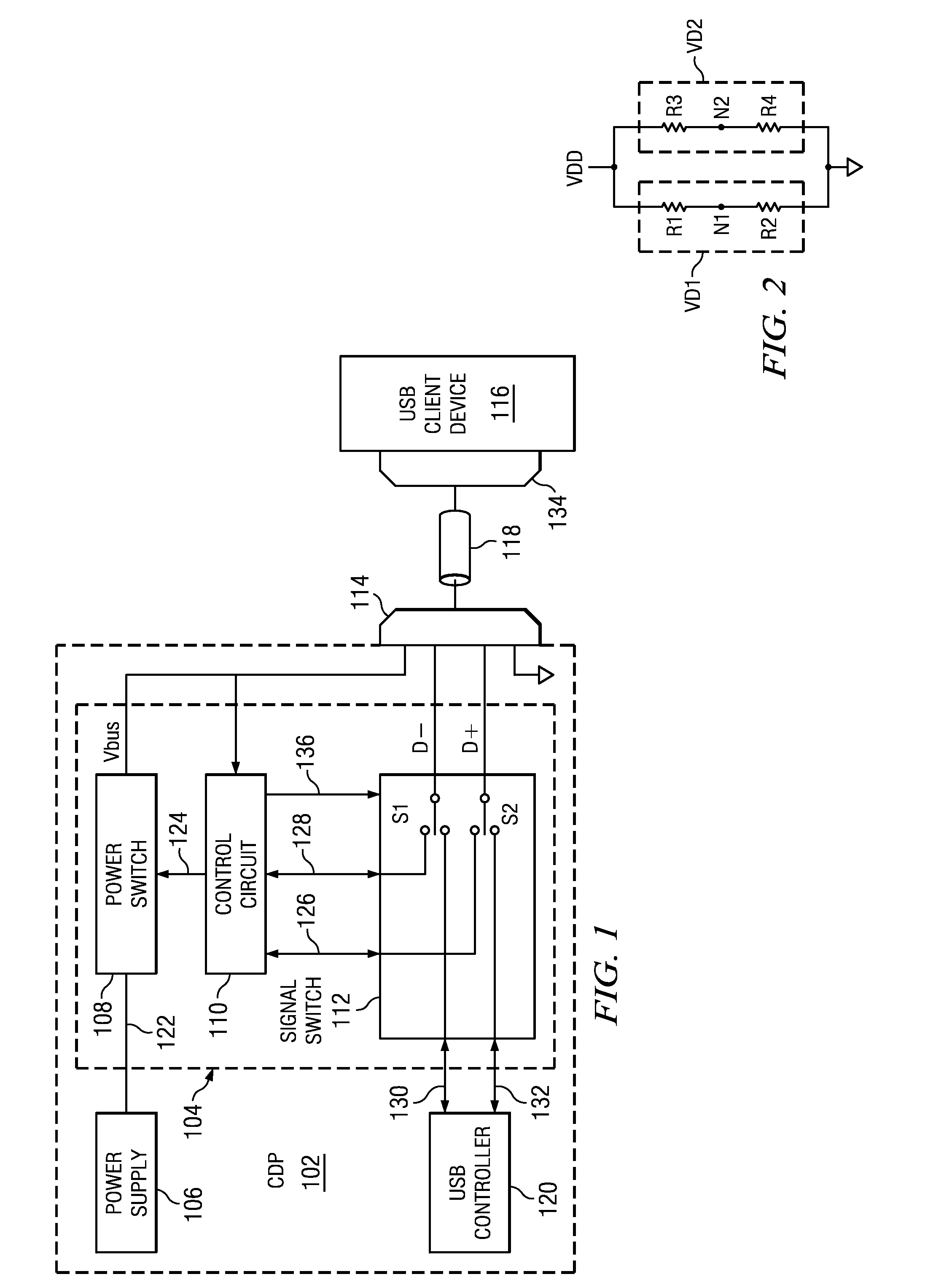
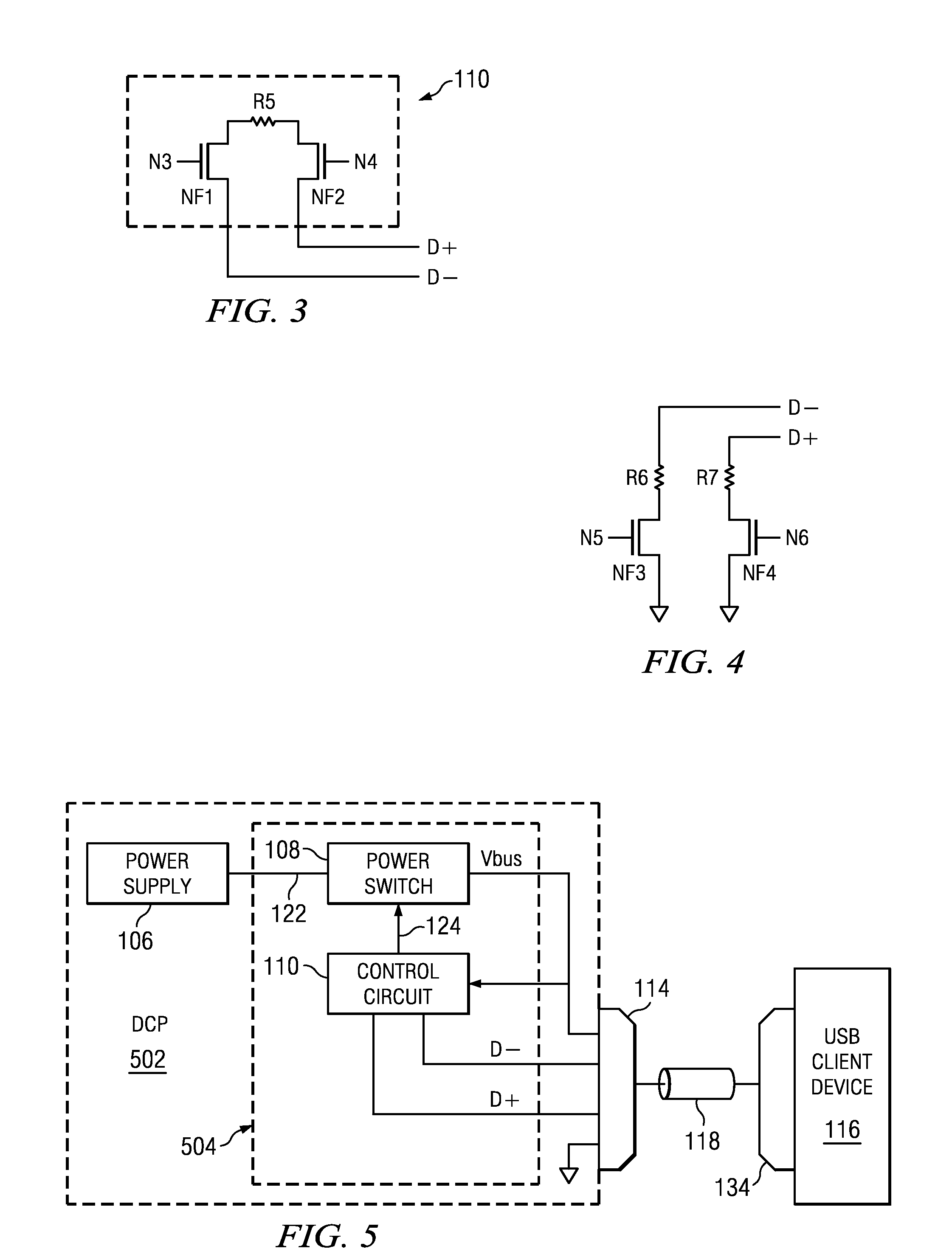
Auto-Detect Polling for Correct Handshake to USB Client
An embodiment of the invention provides a method for providing power to a USB client device and polling for a correct protocol. A USB host device provides power and a first part of a first handshake determined by a first protocol. The host then monitors the client for a second part of the first handshake. When the second part of the first handshake is detected by the host, the client recognizes that power may be applied according to the first protocol. When the second part of the first handshake is not presented by the client device, the host provides a first part of a second handshake according to a second protocol. When the second part of the second handshake is provided by the client, the host the client recognizes that power may be applied according to the second protocol.
Owner:TEXAS INSTR INC
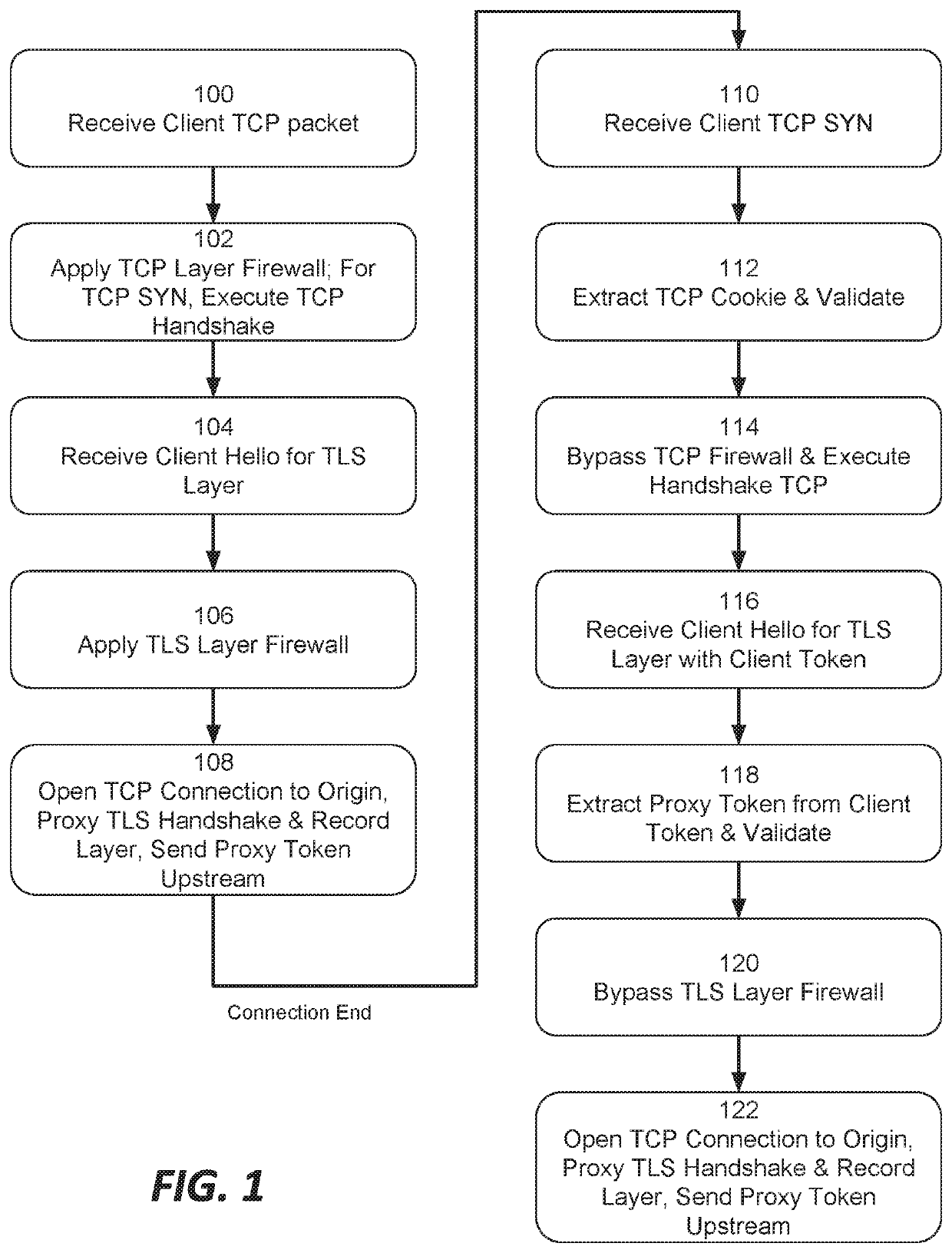
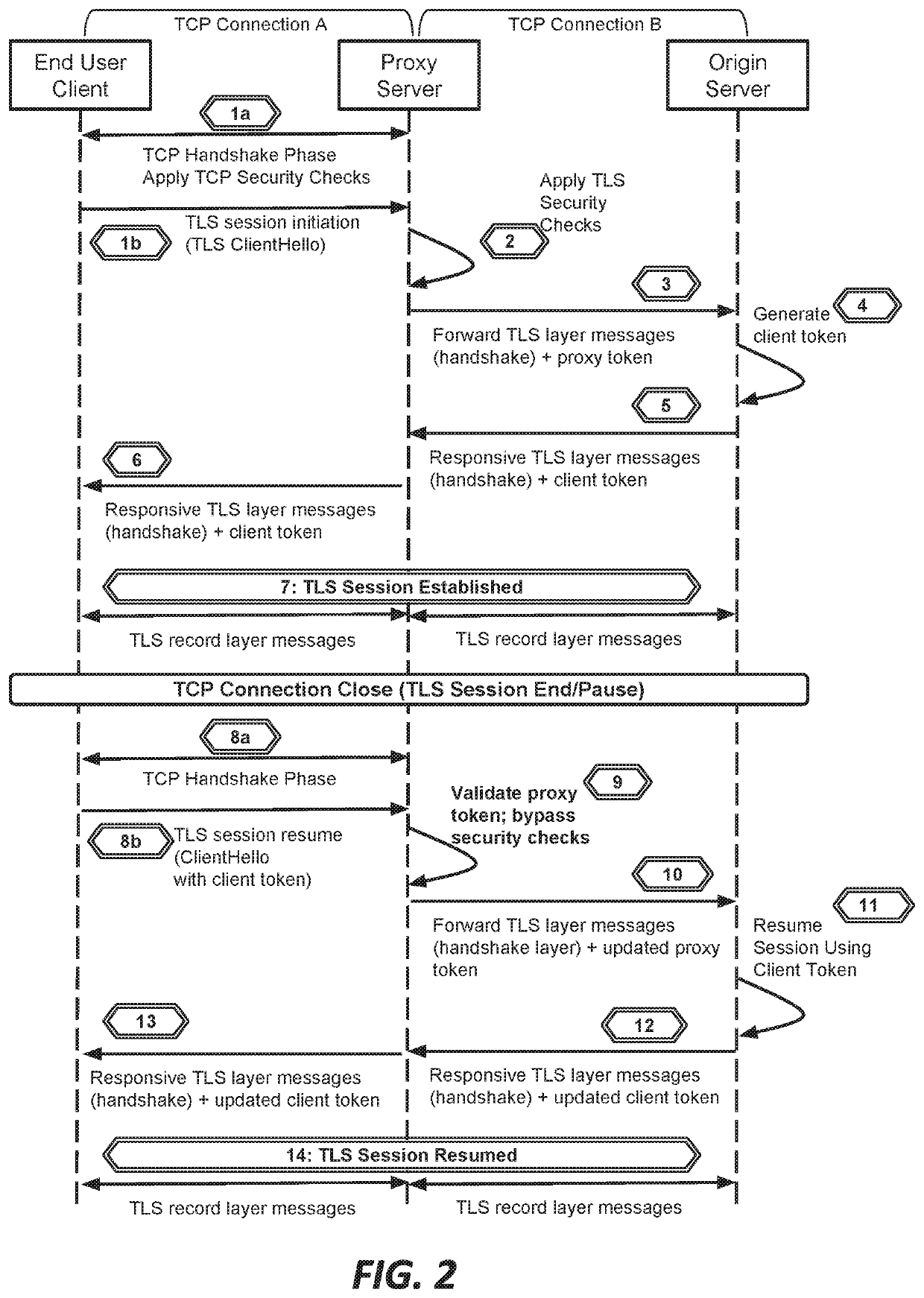
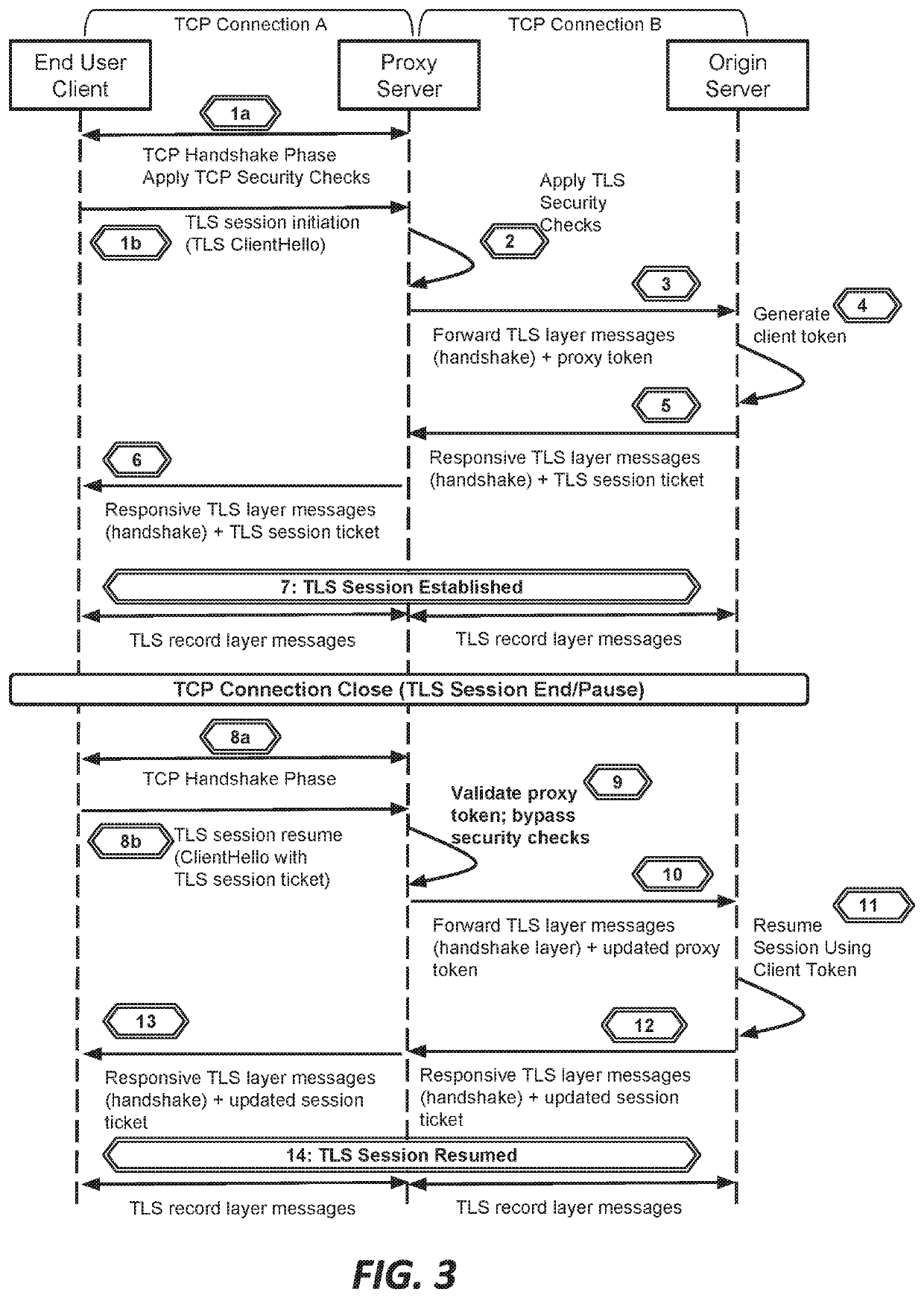
Systems and methods for proxying encrypted traffic to protect origin servers from internet threats
This document describes, among other things, systems and methods for more efficiently resuming a client-to-origin TLS session through a proxy layer that fronts the origin in order to provide network security services. At the time of an initial TLS handshake with an unknown client, for example, the proxy can perform a set of security checks. If the client passes the checks, the proxy can transmit a ‘proxy token’ upstream to the origin. The origin can incorporate this token into session state data which is passed back to and stored on the client, e.g., using a TLS session ticket extension field, pre-shared key extension field, or other field. On TLS session resumption, when the client sends the session state data, the proxy can recover its proxy token from the session state data, and upon successful validation, bypass security checks that it would otherwise perform against the client, thereby more efficiently handling known clients.
Owner:AKAMAI TECH INC
Method and apparatus for recording events
InactiveUS20080014947A1Data switching by path configurationRadio/inductive link selection arrangementsTelecommunicationsComputer science
A data collection method for collecting data describing at least one encounter of a mobile wireless device with at least one other wireless device, said method comprising: conducting a digital handshake between said mobile wireless device and said at least one other wireless device over a wireless link; and communicating a record of said encounter between said mobile wireless device and said other wireless device to a recording device.
Owner:CARNALL MURAT
Strong ssl proxy authentication with forced ssl renegotiation against a target server
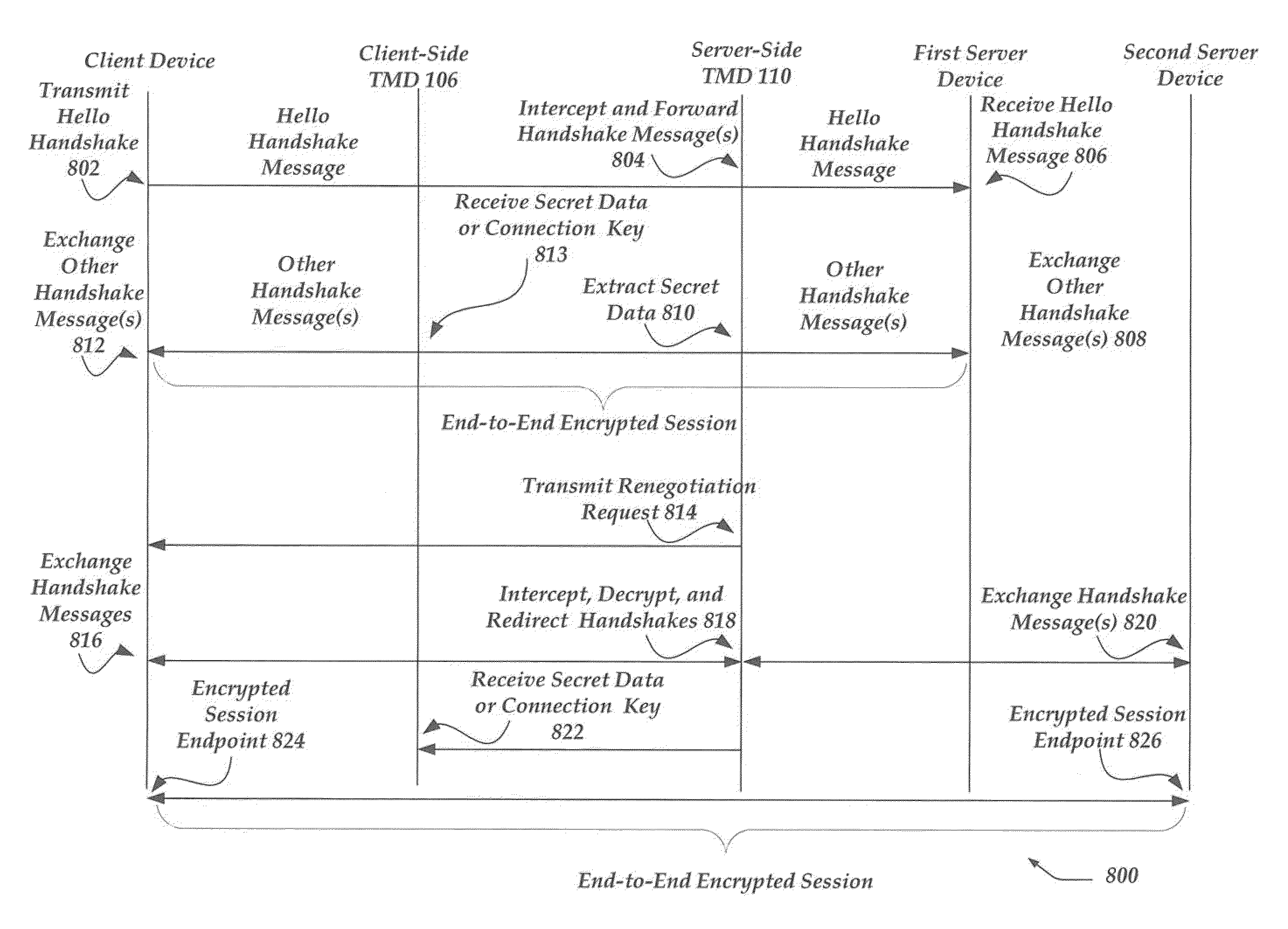
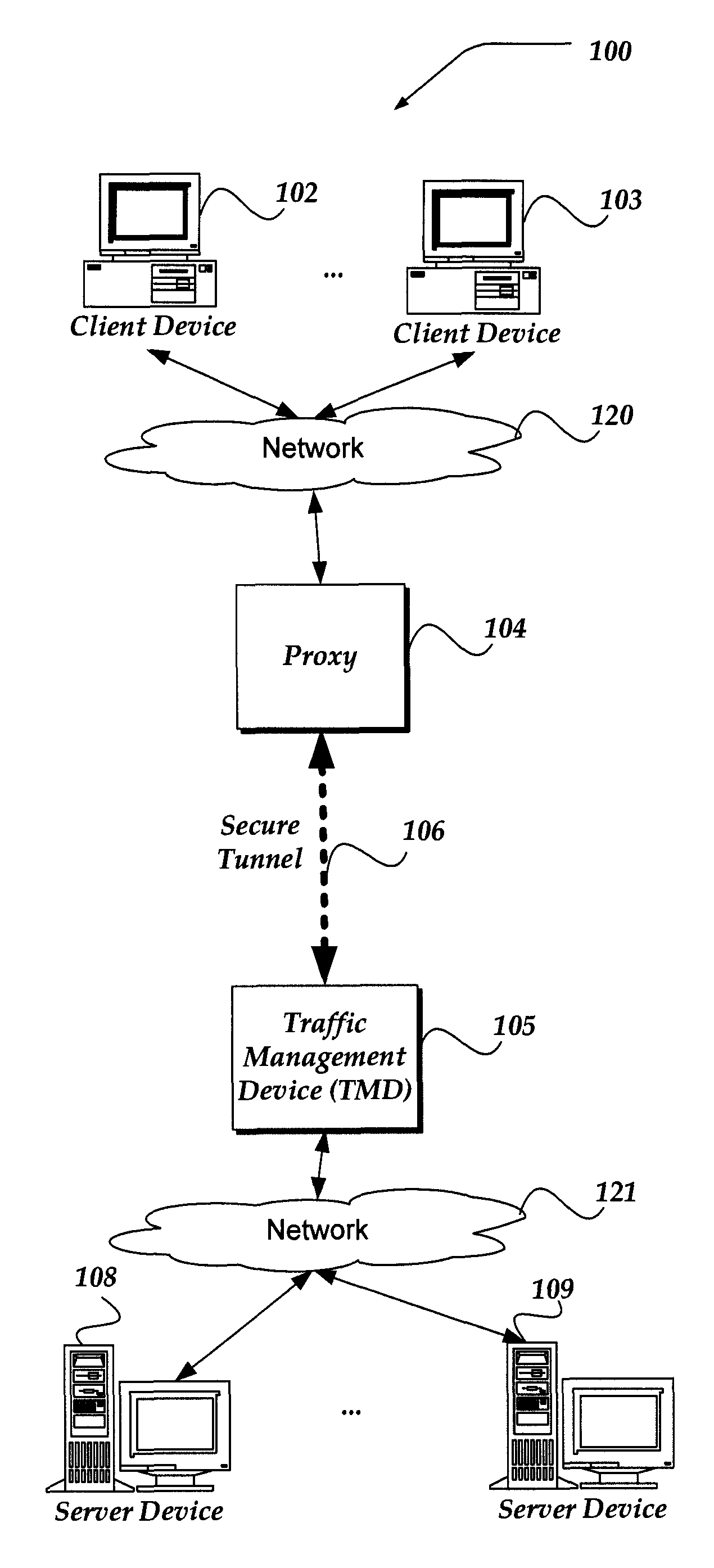
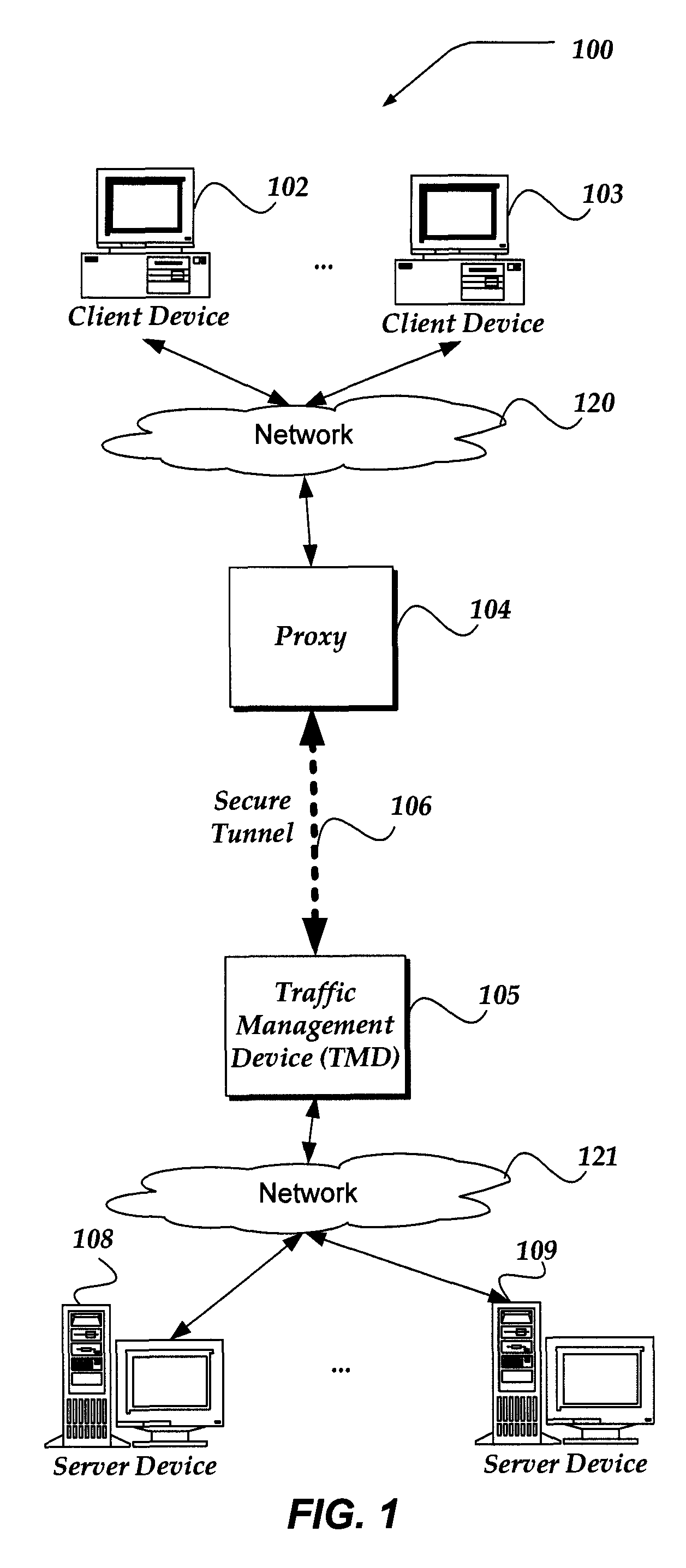
InactiveUS20110231651A1Computer security arrangementsSecuring communicationNetwork connectionClient-side
Embodiments are directed towards establishing an encrypted session between a client device and a target server device when the client device initiates network connections through a proxy device. In one embodiment, the client device initiates an encrypted session with the proxy device. Once the encrypted session is established, the client device communicates the address of the target server device to the proxy device. Then, the proxy device sends an encrypted session renegotiation message to the client device. The client device responds to the encrypted session renegotiation message by transmitting an encrypted session handshake message to the proxy device. The proxy device forwards the encrypted session handshake message to the target server device, and continues to forward handshake messages between the client device and the target server device, enabling the client device and the target server device to establish an encrypted session
Owner:F5 NETWORKS INC
Accessing SSL connection data by a third-party
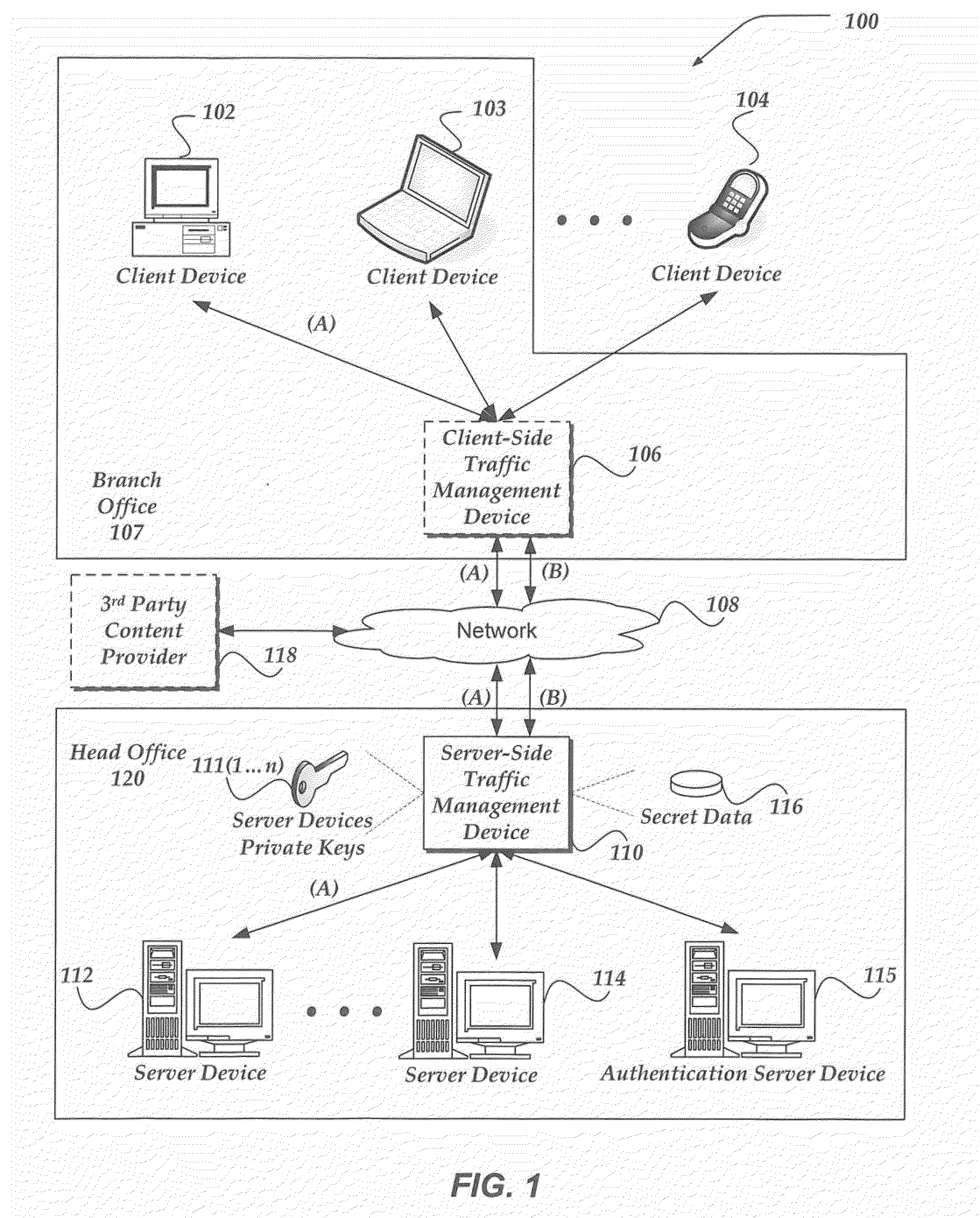
ActiveUS8782393B1Digital data processing detailsComputer security arrangementsThird partyClient-side
A method, system, and apparatus are directed towards enabling access to payload by a third-party sent over an SSL session. The third-party may be a proxy situated between a client and a server. SSL handshake messages are sent between the client and the server to establish the SSL connection. As the SSL handshake messages are routed through the proxy, the proxy may extract data. In addition, one of the client or the server may send another message within, or out-of-band to, the series of SSL handshake message directly to the proxy. The other SSL message may include secret data that the proxy may use to generate a session key for the SSL connection. With the session key, the proxy may receive SSL messages over the SSL connection, modify and / or transpose the payload within the received SSL messages, and / or terminate the SSL connection at the proxy.
Owner:F5 NETWORKS INC
Identity based efficient anonymous batch authentication method in IOV (Internet of Vehicles) environment
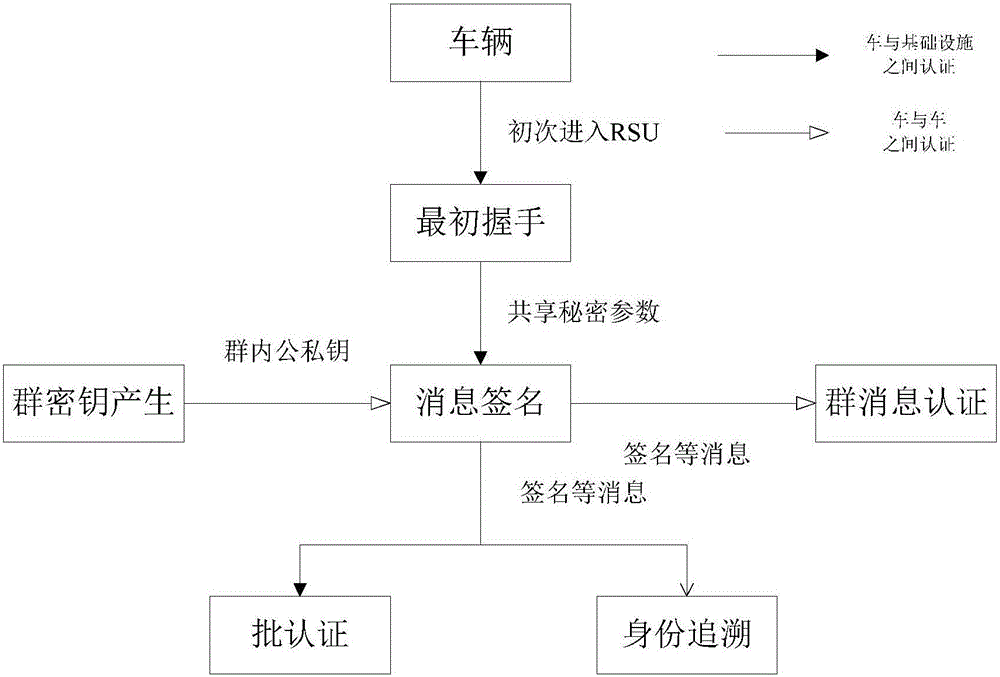
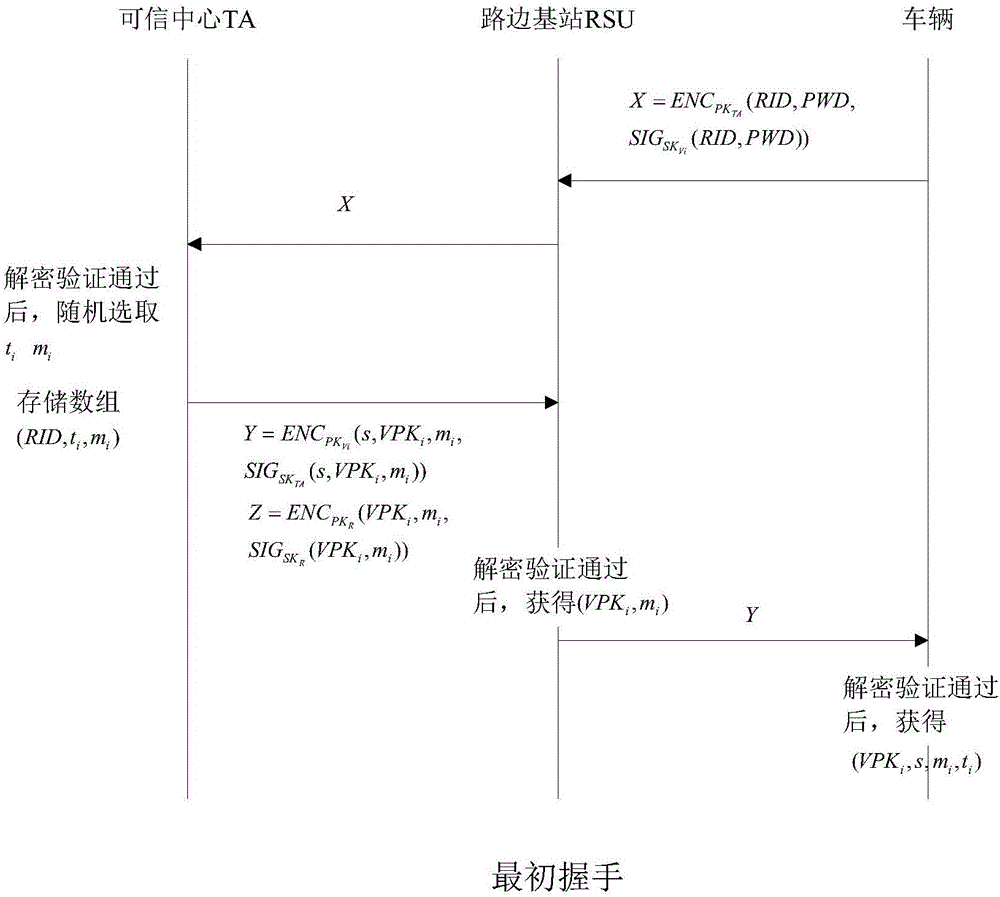
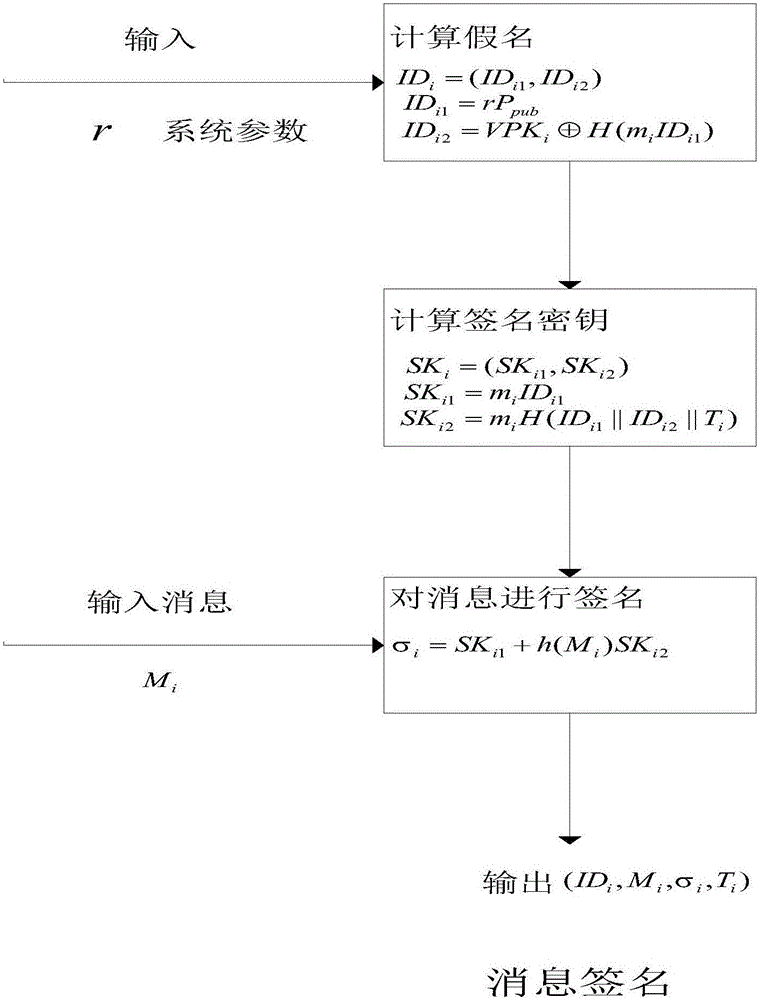
ActiveCN105847235AAchieve authenticationImprove securityUser identity/authority verificationTrusted authorityTamper resistance
The invention discloses an identity based efficient anonymous batch authentication method in an IOV (Internet of Vehicles) environment. The identity based efficient anonymous batch authentication method in the IOV environment comprises an initial handshake module, a message signature module, a batch authentication module, an identity tracing module, a group key generation module and a group message signature and authentication module. According to the identity based efficient anonymous batch authentication method in the IOV environment, authentication between vehicles and infrastructures and authentication between vehicles can be realized, no tamper-proofing device is depended, privacy protection is realized by utilizing a pseudonymous name, conditional privacy protection is realized as a TA (Trusted Authority) can trace the real identity of each vehicle if necessary, the efficiency is improved as batch authentication is adopted, and the authentication process is simple and efficient. The message signature process and the group message signature process are same, the operating cost is low, and a replay attack can be borne as a time stamp is added.
Owner:南京秉蔚信息科技有限公司
Base station-assisted mobile terminal equipment autonomously accessing method and device
ActiveCN101902822AGuaranteed reasonable useGuaranteed fast communicationWireless communicationAccess methodTerminal equipment
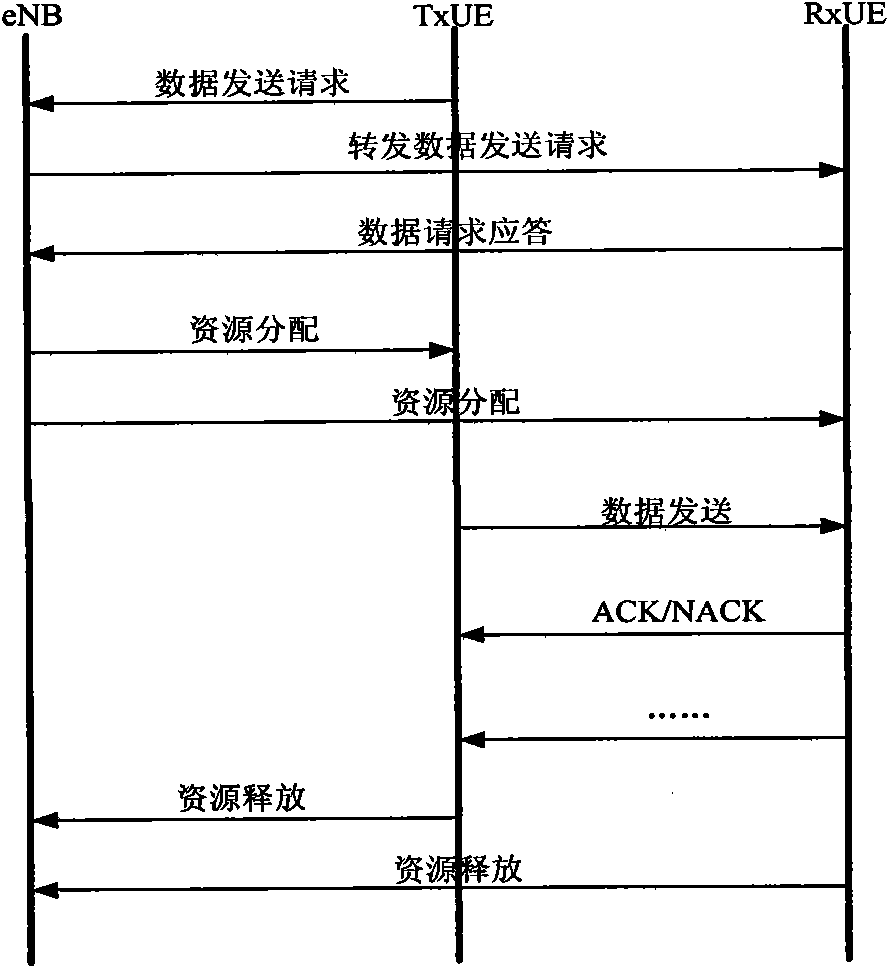
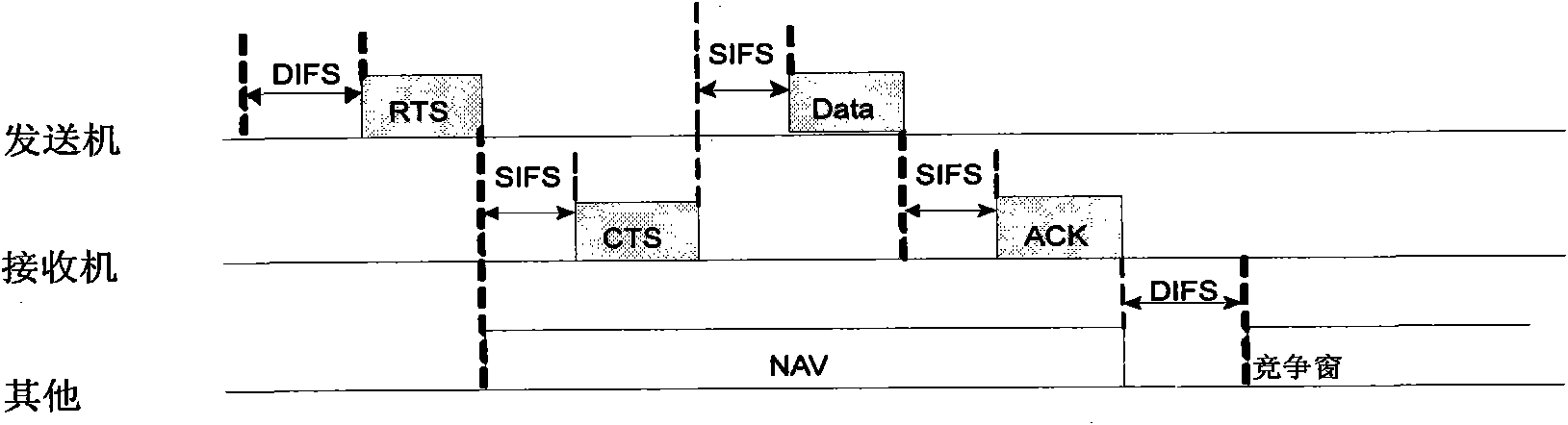
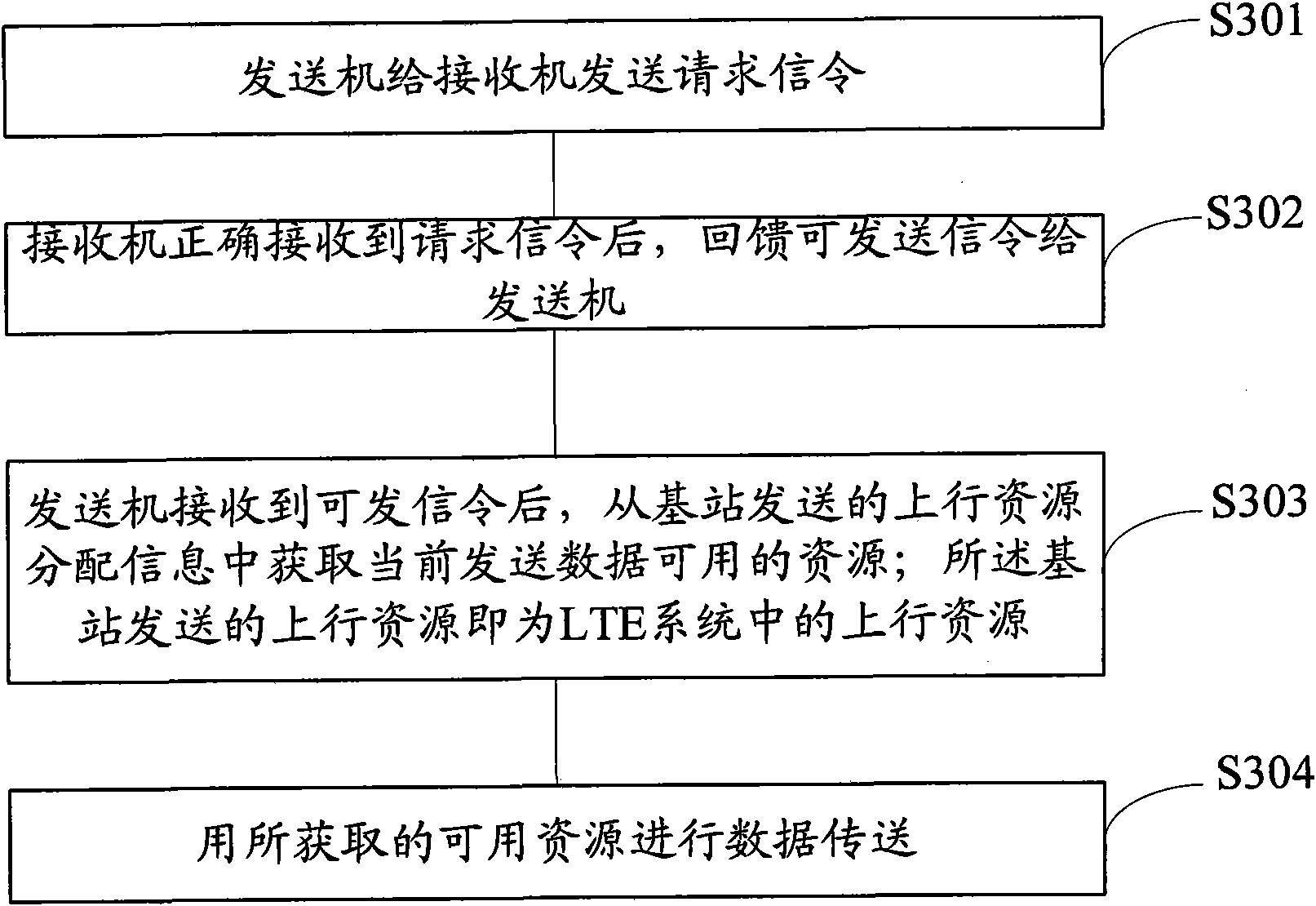
The invention provides a base station-assisted mobile terminal equipment autonomously accessing method and a base station-assisted mobile terminal equipment autonomously accessing device. The method comprises the following steps of: transmitting a request signaling to a receiver by using a transmitter, wherein the request signaling comprises the ID of the transmitter and the ID of the receiver; after the receiver receives the request signaling, feeding back a transmittable signaling to the receiver; after the receiver receives the transmittable signaling, acquiring available resource of current transmitting data from uplink resource distribution information transmitted from a base station of an LTE system; and performing data transmission by using the acquired available resource. Resourceis seized by means of handshake between terminals and is transmitted by adopting the same frequency and the same time slot as those of the LTE system, so that rapid communication between user terminals and reasonable utilization of the sources are ensured.
Owner:BEIJING JIAOTONG UNIV
Internet of Vehicles safety communication method, vehicle-mounted terminal, server and system
ActiveCN106453269AImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesTransmission protocolThe Internet
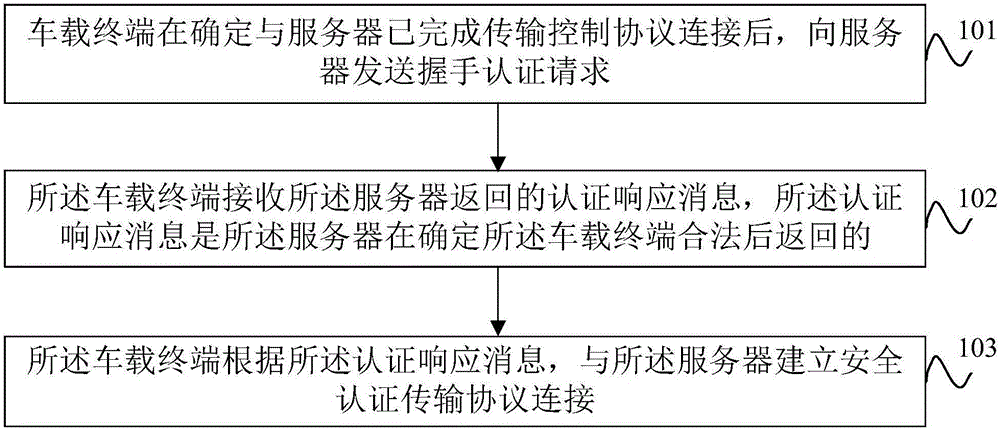
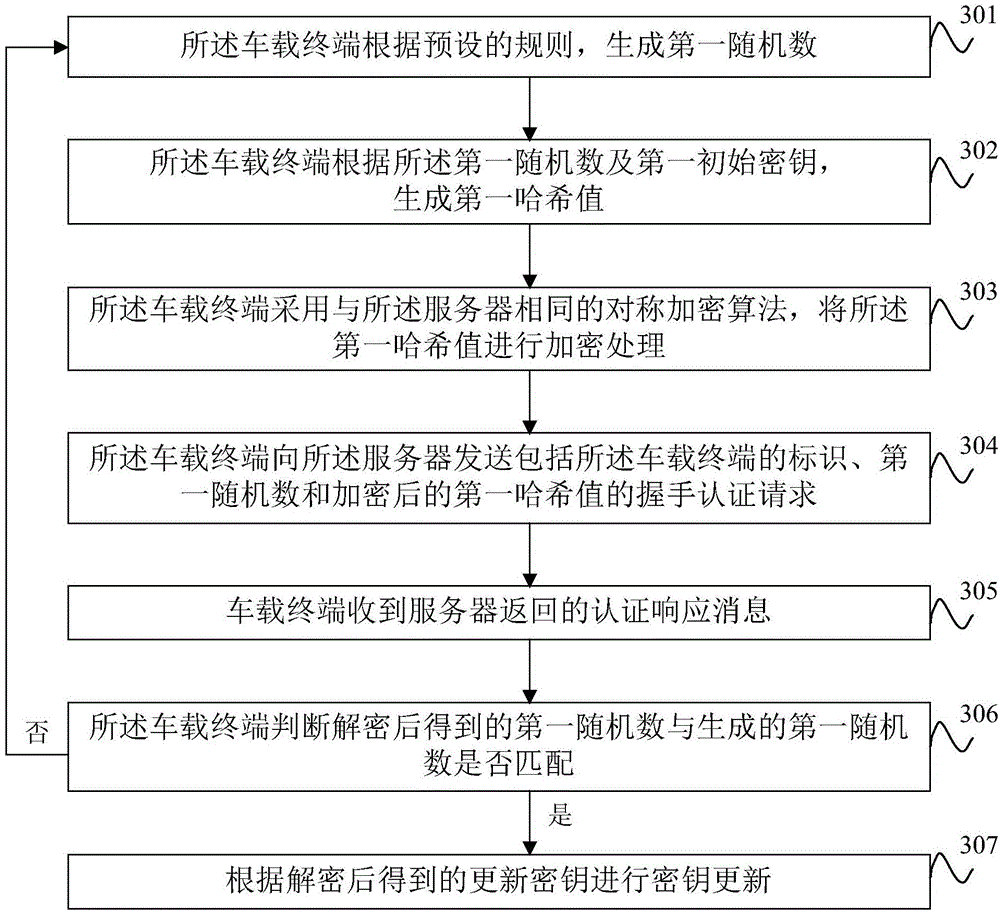
The application provides an Internet of Vehicles safety communication method, a vehicle-mounted terminal, a server and a system. The Internet of Vehicles safety communication method is characterized by comprising the following steps: the vehicle-mounted terminal sends a handshake authentication request to a server after determining that the transmission control protocol connection with the server has been finished, wherein the handshake authentication request comprises an identifier of the vehicle-mounted terminal and a first Hash value encrypted by use of a symmetrical encryption algorithm same as that adopted by the server; the vehicle-mounted terminal receives an authentication response message returned by the server, wherein the authentication response message is returned by the server after determining that the vehicle-mounted terminal is legal; and the vehicle-mounted terminal establishes a safety authentication transmission protocol connection with the server according to the authentication response message. A lightweight safety authentication transmission protocol is established between the vehicle-mounted terminal and the server by use of less resource, and the security of the data transmission between the vehicle-mounted terminal and the server is improved.
Owner:NEUSOFT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com