Patents
Literature
16825 results about "Manet routing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Abstract: Ad hoc On-demand Distance Vector routing (AODV) is a widely adopted network routing protocol for Mobile Ad hoc Network (MANET). The design of AODV, however, paid little attention to security considerations, hence resulting in the vulnerability of such MANET to the black hole attack.
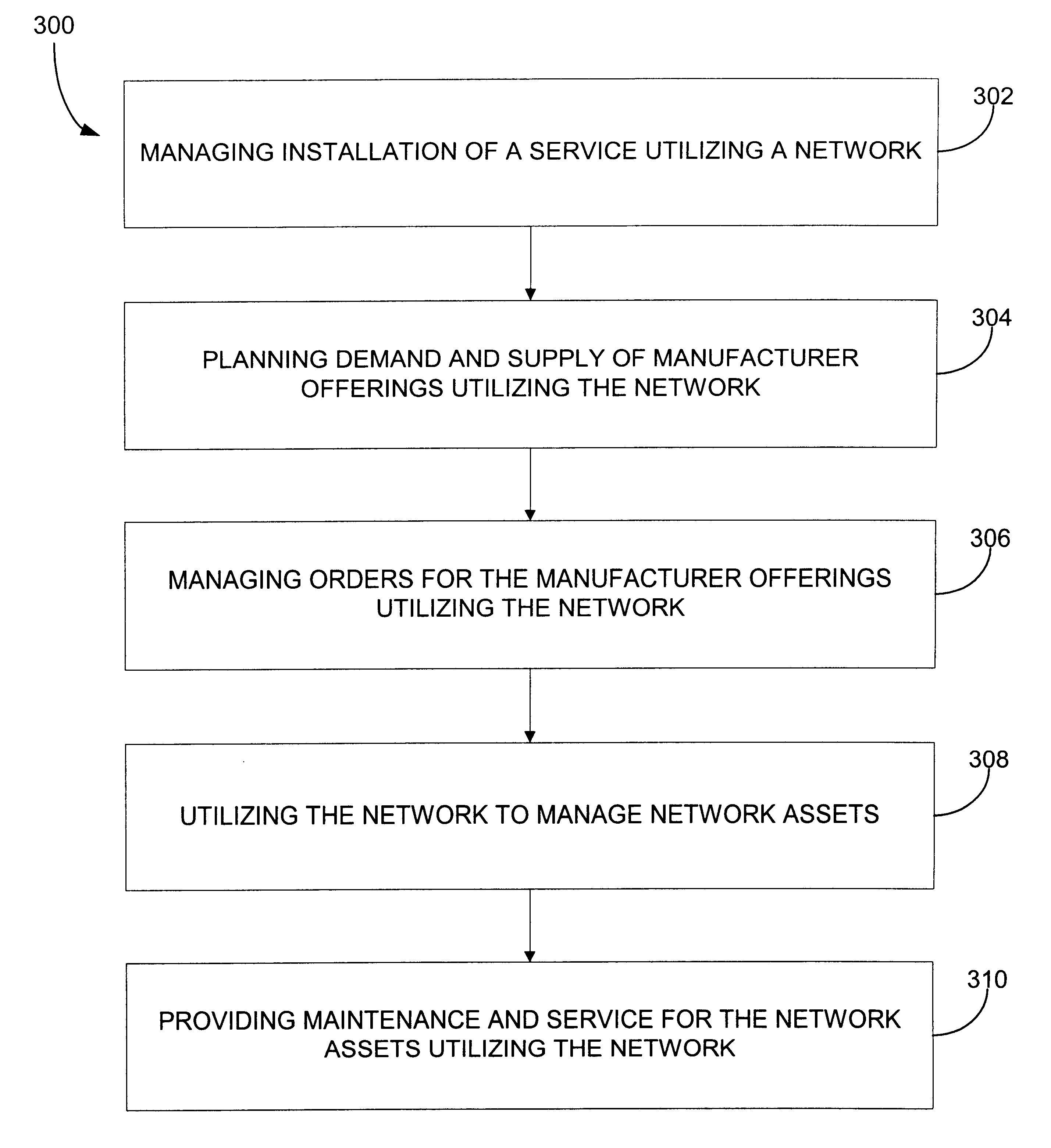
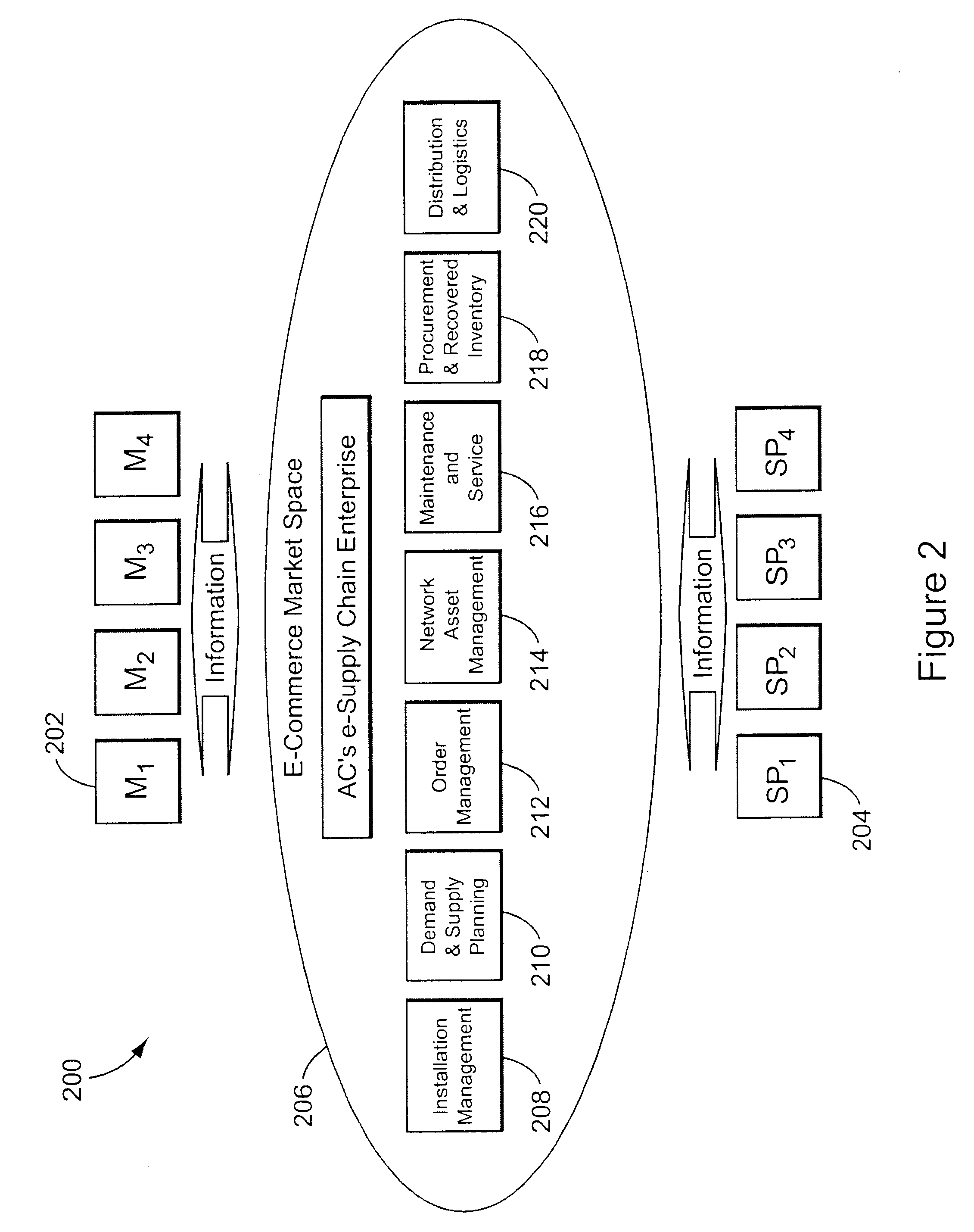
Providing collaborative installation management in a network-based supply chain environment
InactiveUS6606744B1Interconnection arrangementsSpecial service for subscribersWeb applicationService provision
A system, method and article of manufacture are provided for collaborative installation management in a network-based supply chain environment. According to an embodiment of the invention, telephone calls, data and other multimedia information are routed through a network system which includes transfer of information across the internet utilizing telephony routing information and internet protocol address information. The system includes integrated Internet Protocol (IP) telephony services allowing a user of a web application to communicate in an audio fashion in-band without having to pick up another telephone. Users can click a button and go to a call center through the network using IP telephony. The system invokes an IP telephony session simultaneously with the data session, and uses an active directory lookup whenever a user uses the system. Users include service providers and manufacturers utilizing the network-based supply chain environment.
Owner:ACCENTURE GLOBAL SERVICES LTD
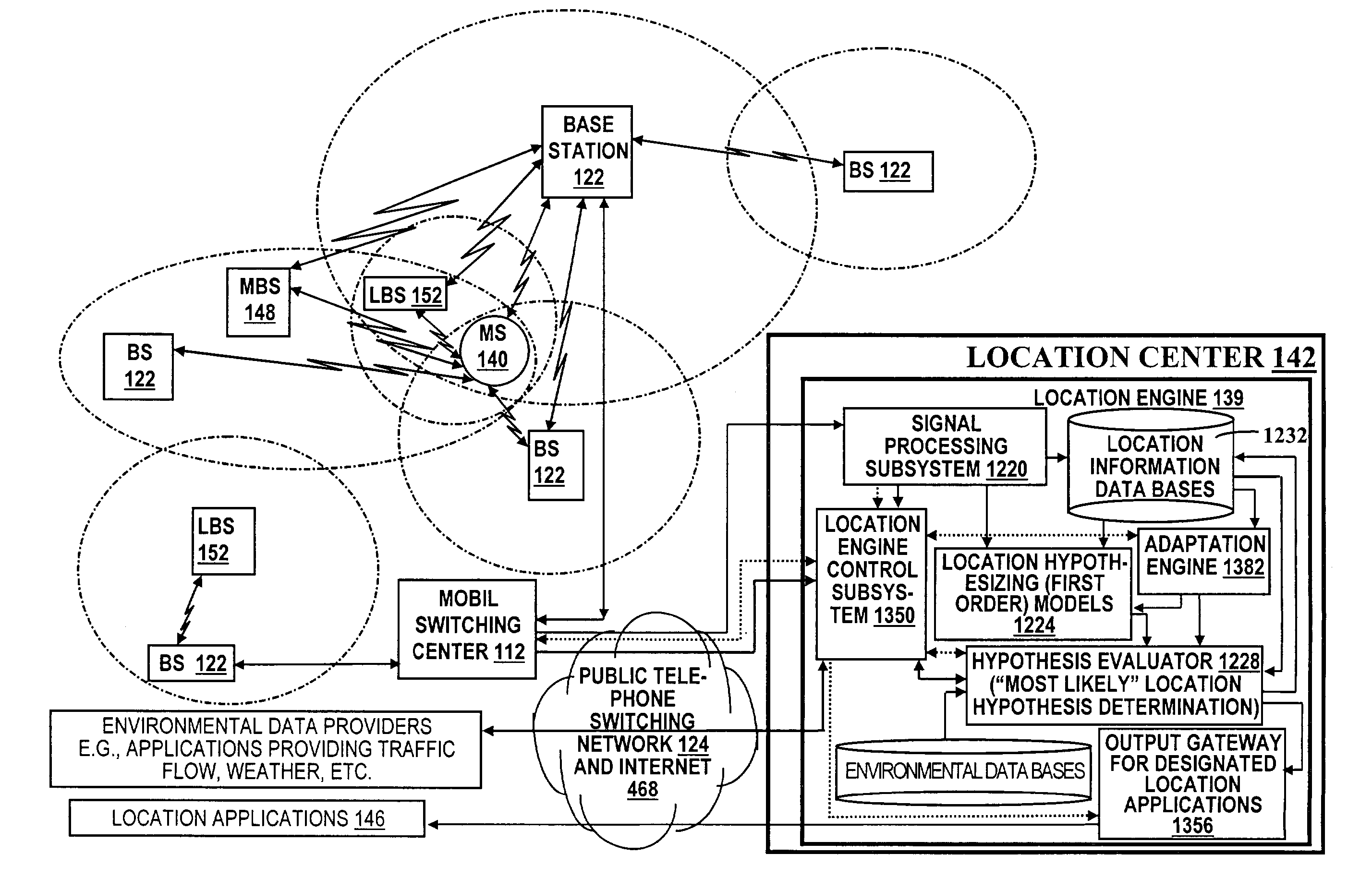
Applications for a wireless location gateway
InactiveUS20040198386A1Easy to implementEffectively and straightforwardly resolvedPosition fixationRadio/inductive link selection arrangementsTerrainInternet communication
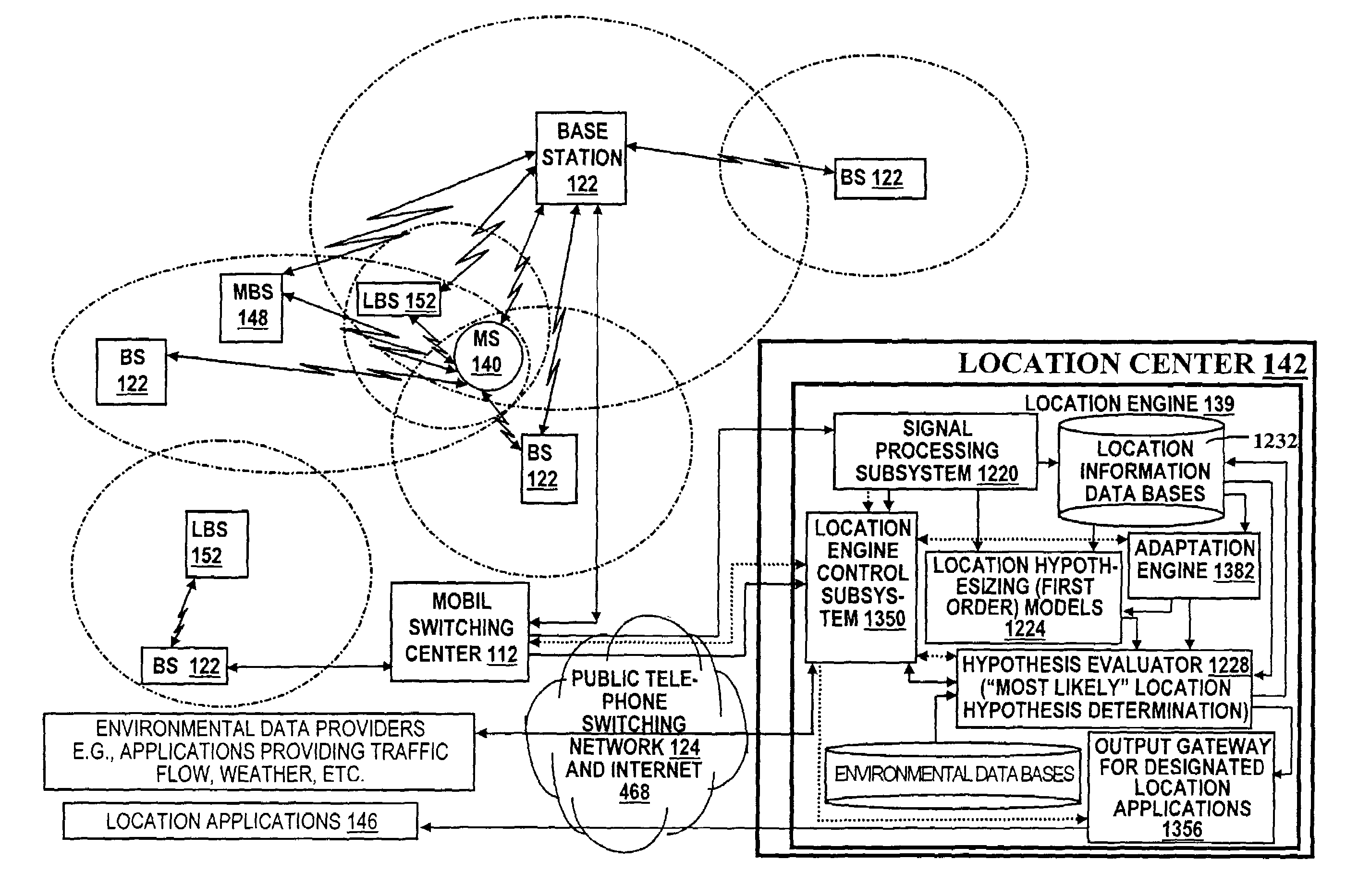
A location system is disclosed for commercial wireless telecommunication infrastructures. The system is an end-to-end solution having one or more location centers for outputting requested locations of commercially available handsets or mobile stations (MS) based on, e.g., CDMA, AMPS, NAMPS or TDMA communication standards, for processing both local MS location requests and more global MS location requests via, e.g., Internet communication between a distributed network of location centers. The system uses a plurality of MS locating technologies including those based on: (1) two-way TOA and TDOA; (2) pattern recognition; (3) distributed antenna provisioning; (5) GPS signals, (6) angle of arrival, (7) super resolution enhancements, and (8) supplemental information from various types of very low cost non-infrastructure base stations for communicating via a typical commercial wireless base station infrastructure or a public telephone switching network. Accordingly, the traditional MS location difficulties, such as multipath, poor location accuracy and poor coverage are alleviated via such technologies in combination with strategies for: (a) automatically adapting and calibrating system performance according to environmental and geographical changes; (b) automatically capturing location signal data for continual enhancement of a self-maintaining historical data base retaining predictive location signal data; (c) evaluating MS locations according to both heuristics and constraints related to, e.g., terrain, MS velocity and MS path extrapolation from tracking and (d) adjusting likely MS locations adaptively and statistically so that the system becomes progressively more comprehensive and accurate. Further, the system can be modularly configured for use in location signaling environments ranging from urban, dense urban, suburban, rural, mountain to low traffic or isolated roadways. Accordingly, the system is useful for 911 emergency calls, tracking, routing, people and animal location including applications for confinement to and exclusion from certain areas.
Owner:DUPRAY DENNIS J
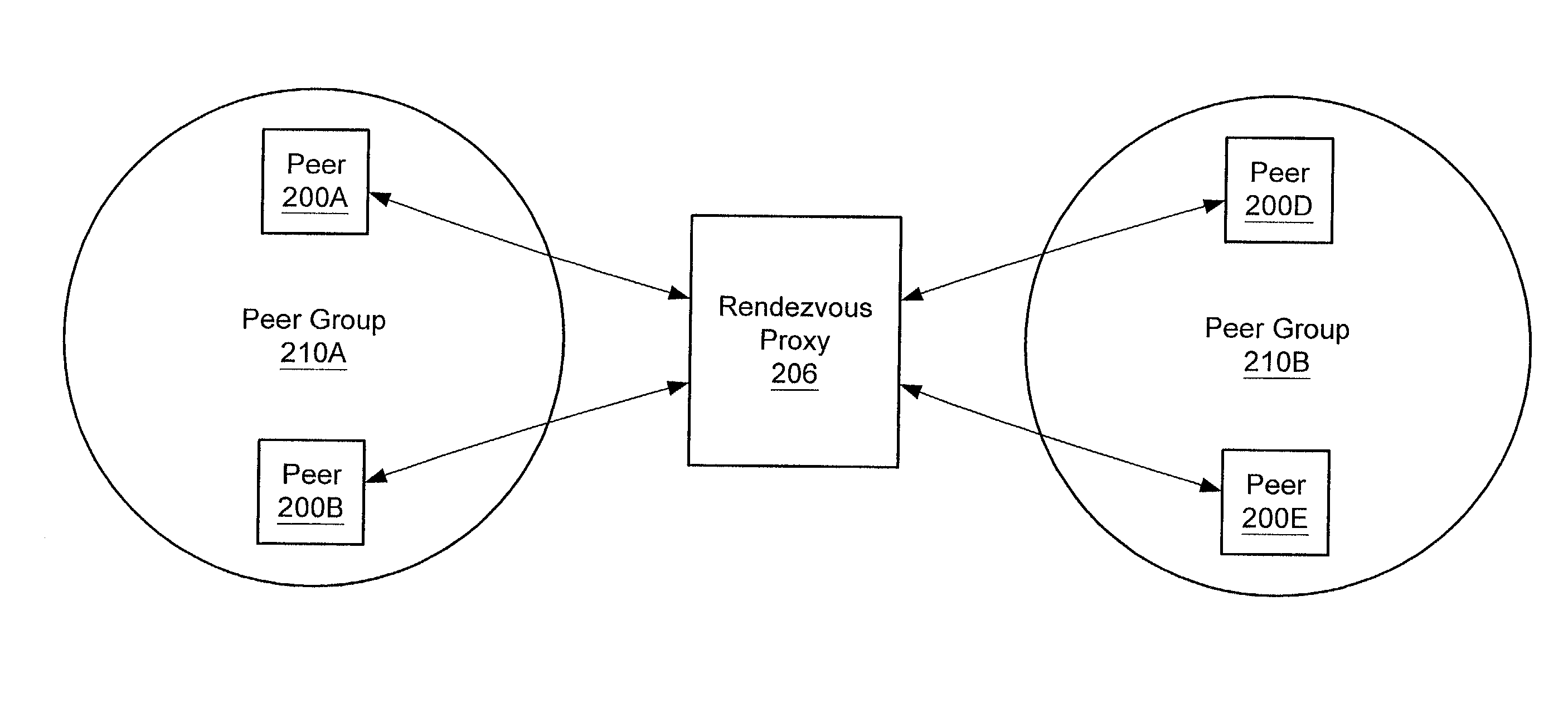
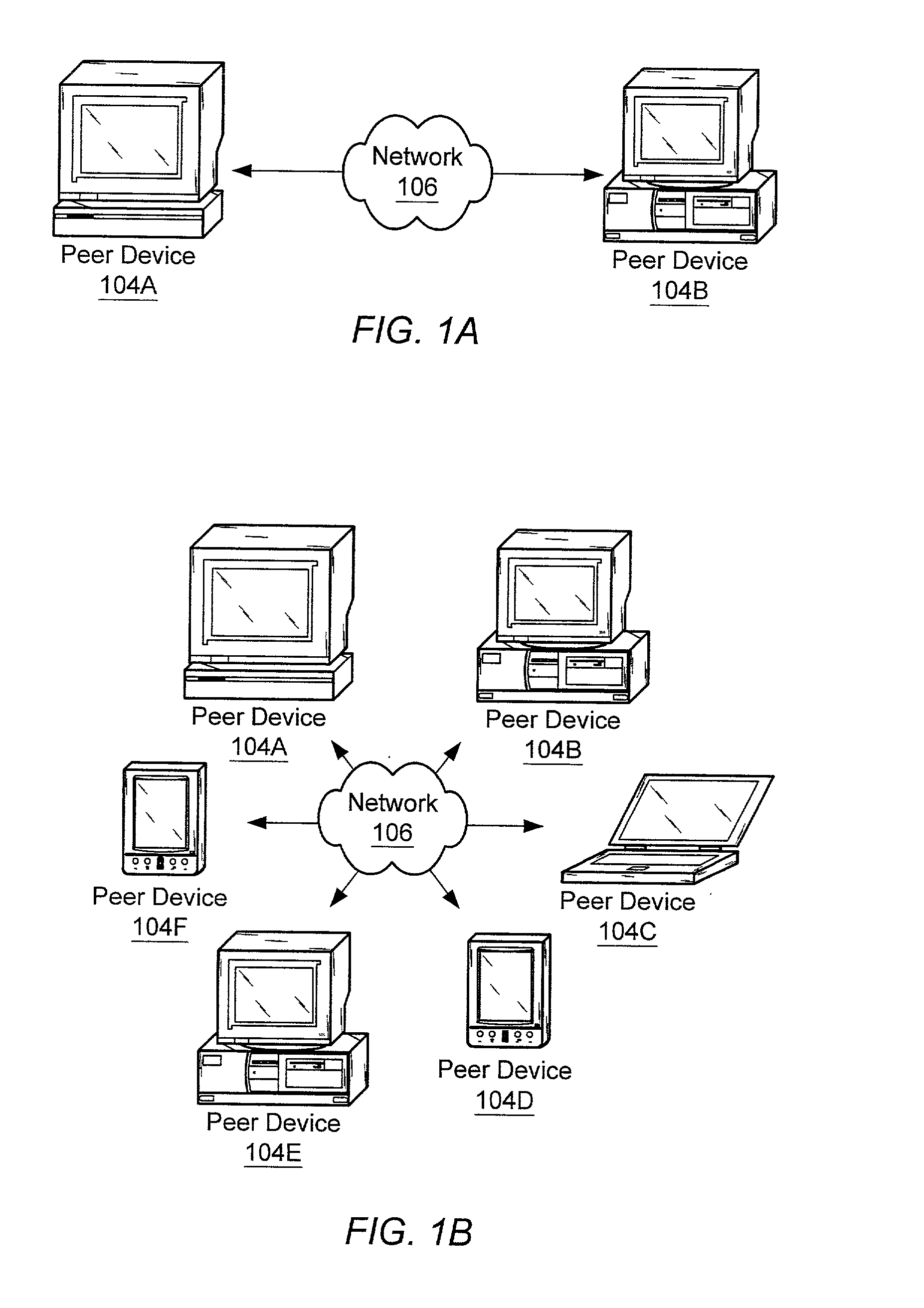
Relay peers for extending peer availability in a peer-to-peer networking environment
ActiveUS20020143855A1Multiprogramming arrangementsMultiple digital computer combinationsDistributed computingPeer-to-peer
A system and method for allowing peers to exchange messages with other peers independently of their network location in a peer-to-peer environment. Messages may be transparently routed, potentially traversing partitions (e.g. firewalls and NATs), and using different protocols to reach the destination peers. In one embodiment, any peer node may serve as a relay peer that allows peers inside a partition to have a presence outside the partition and provides a mechanism for peers outside partitions to discover and communicate with peers inside the partitions. In one embodiment, a relay peer may maintain information on routes to other peers and assist in relaying messages to other peers. In one embodiment, any peer may query a relay peer for route information. In one embodiment, messages may include routing information as part of their payloads.
Owner:ORACLE INT CORP
Interoperable systems and methods for peer-to-peer service orchestration
InactiveUS20050027871A1Facilitating commercial exchangeIncrease flexibilityWeb data indexingCryptography processingOperational systemWeb service
Systems and methods are described for performing policy-managed, peer-to-peer service orchestration in a manner that supports the formation of self-organizing service networks that enable rich media experiences. In one embodiment, services are distributed across peer-to-peer communicating nodes, and each node provides message routing and orchestration using a message pump and workflow collator. Distributed policy management of service interfaces helps to provide trust and security, supporting commercial exchange of value. Peer-to-peer messaging and workflow collation allow services to be dynamically created from a heterogeneous set of primitive services. The shared resources are services of many different types, using different service interface bindings beyond those typically supported in a web service deployments built on UDDI, SOAP, and WSDL. In a preferred embodiment, a media services framework is provided that enables nodes to find one another, interact, exchange value, and cooperate across tiers of networks from WANs to PANs.
Owner:INTERTRUST TECH CORP
On/off keying node-to-node messaging transceiver network with dynamic routing and configuring
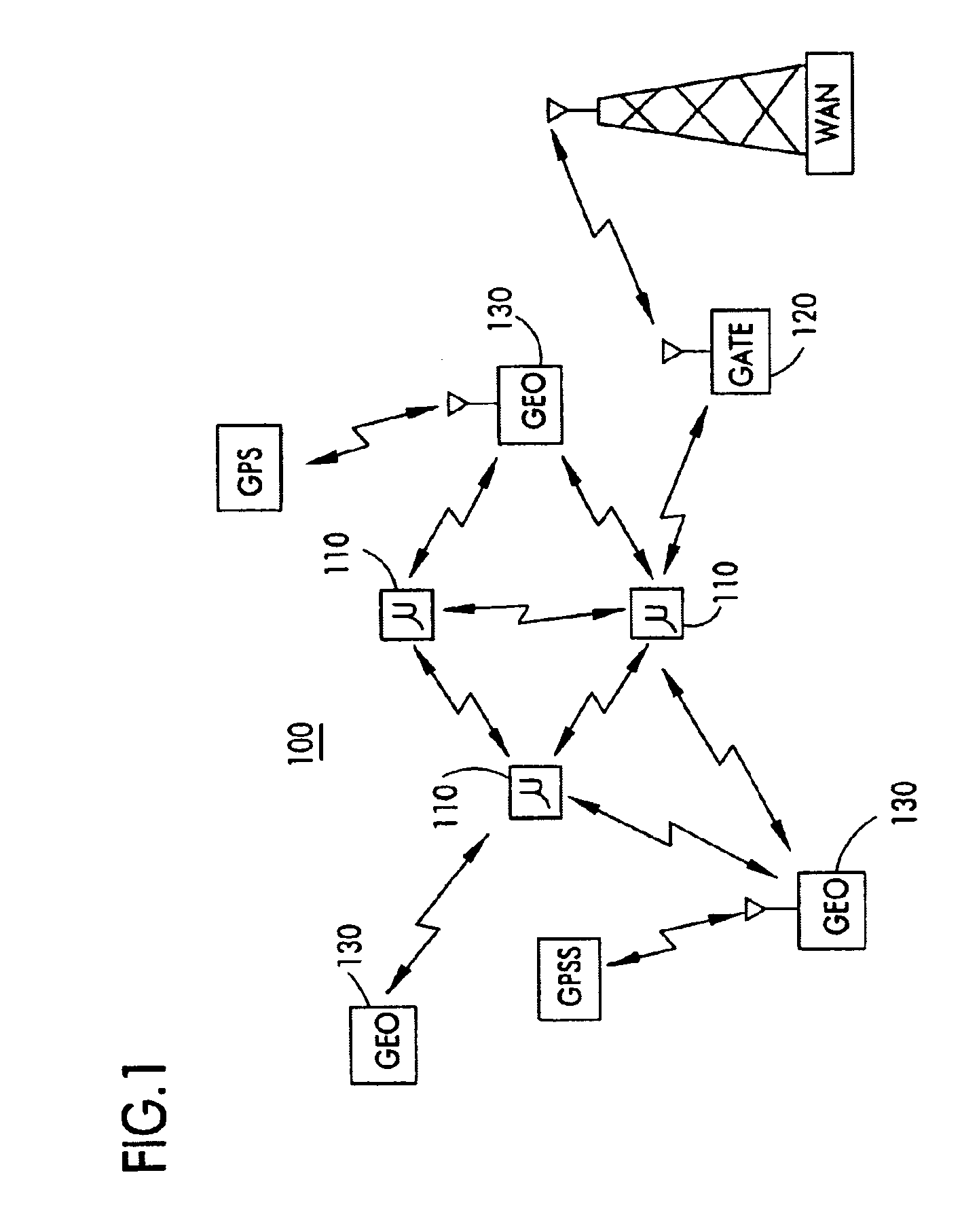
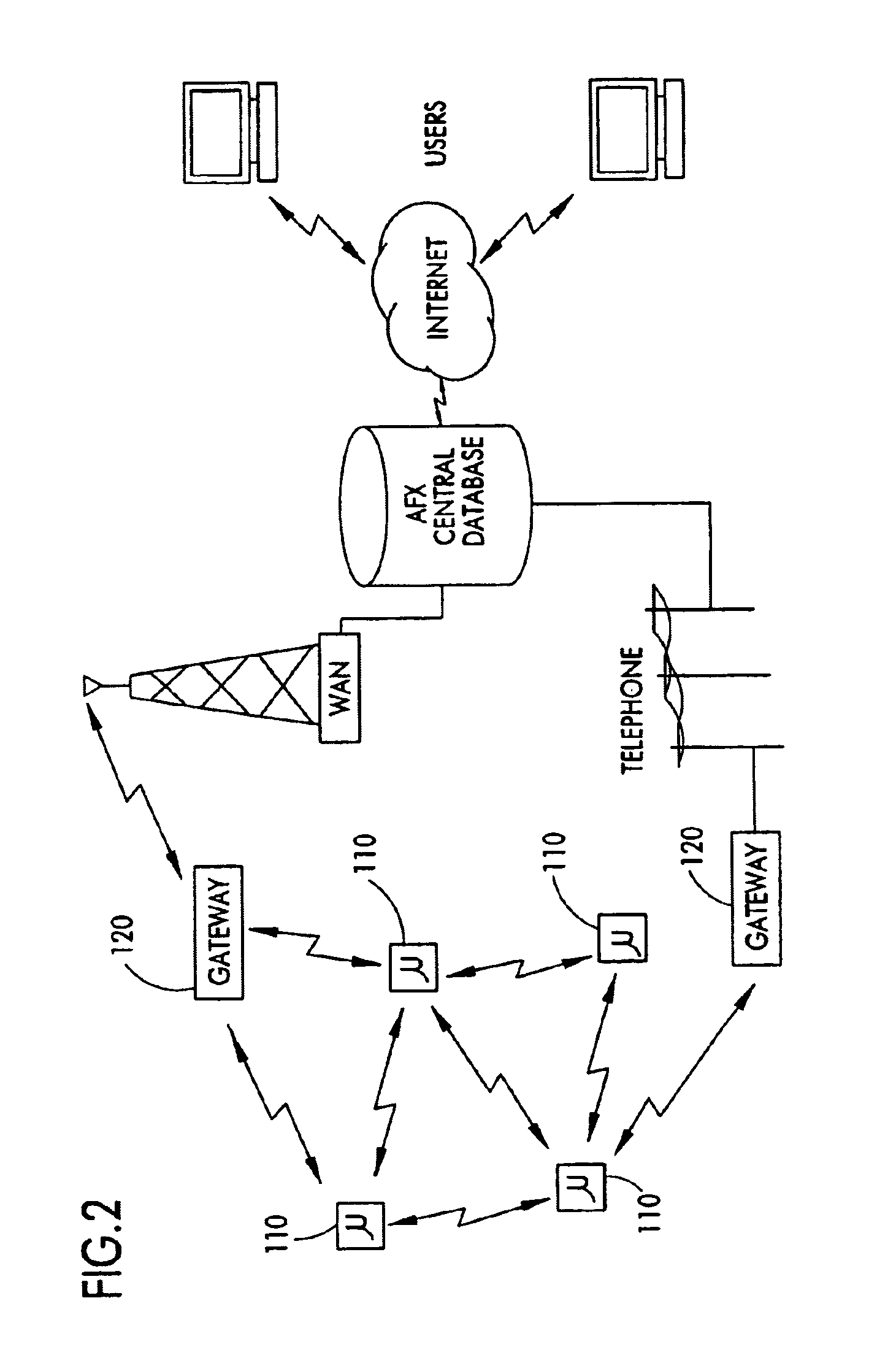
InactiveUS7027773B1Low costReduce trafficNear-field transmissionError preventionTransceiverAdaptive routing
The invention is a system operating on a reference frequency. The system comprises a plurality of at least three nodes. Each node hands off a message received from another node to a subsequent node. Each of the nodes comprises a transceiver receiving a message on the reference frequency from another node and transmitting the received message on the reference frequency to a subsequent node, and a controller controlling operation of the transceiver to receive the.. message transmitted by another node and to transmit the received message to a subsequent node.
Owner:AFX TECH GRP INT
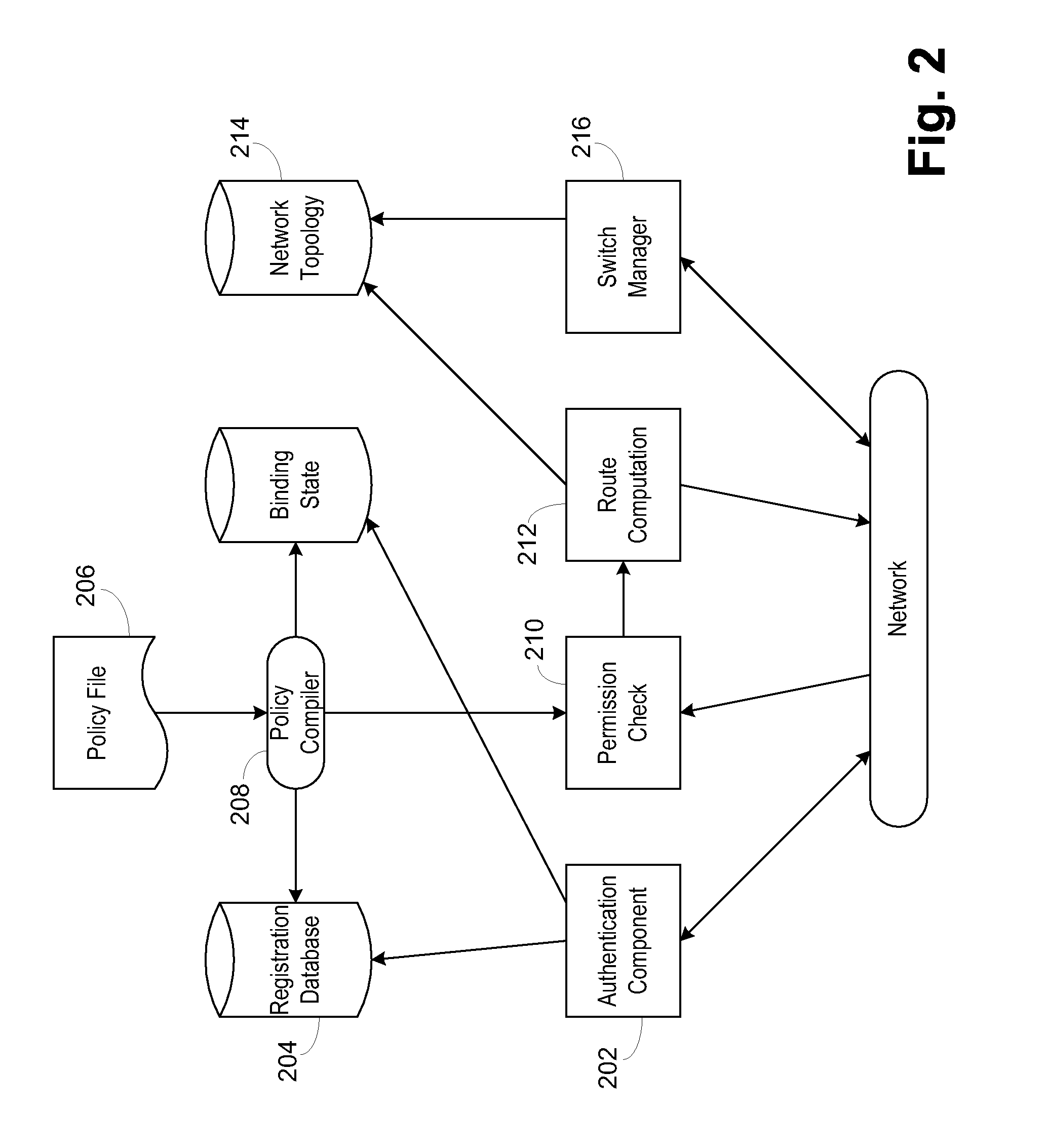
Secure network switching infrastructure
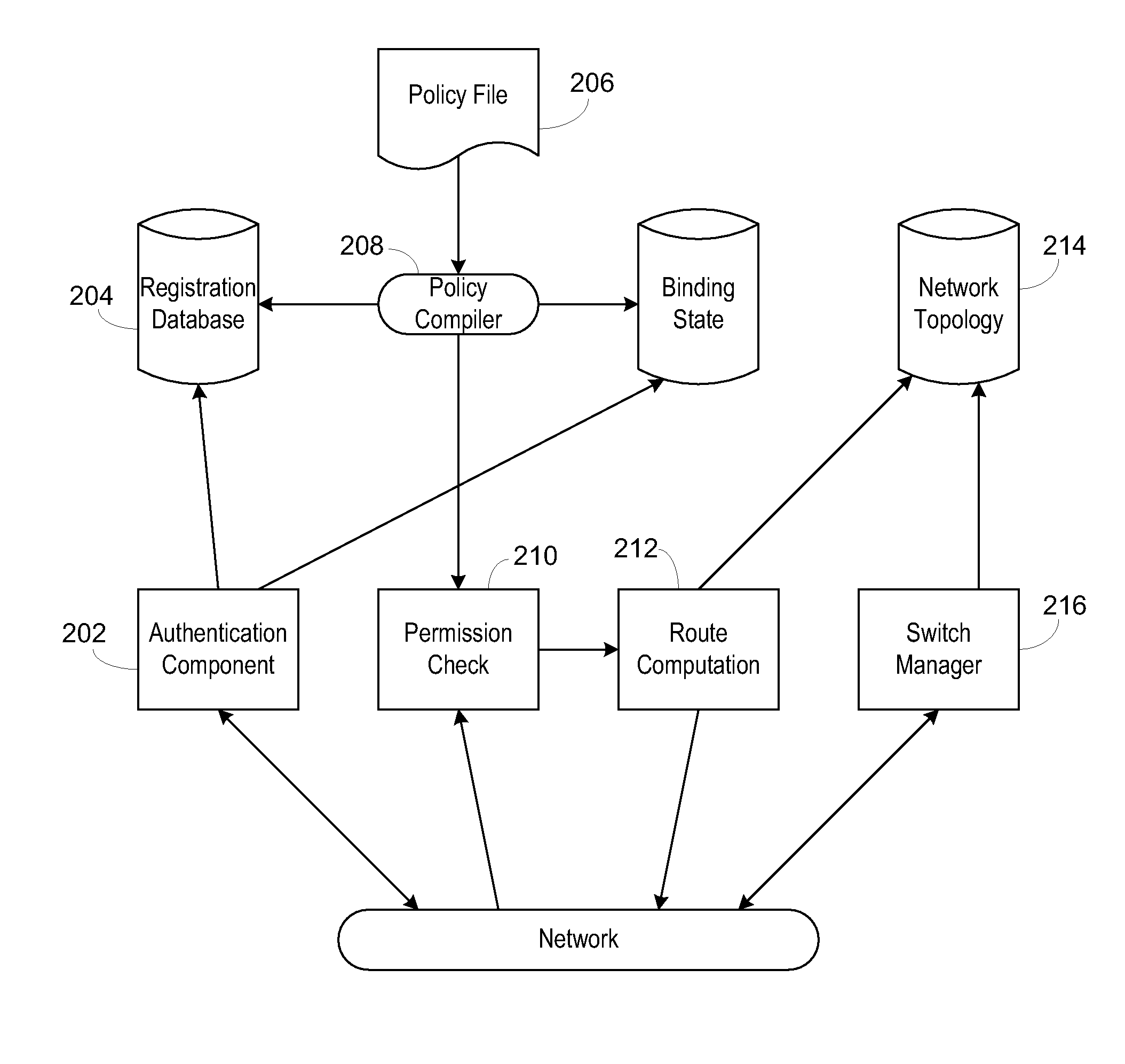
InactiveUS20080189769A1Reduces the trusted computing baseReduce overheadDigital data processing detailsUser identity/authority verificationNetwork packetNetwork control
Use of a centralized control architecture in a network. Policy declaration, routing computation, and permission checks are managed by a logically centralized controller. By default, hosts on the network can only route to the network controller. Hosts and users must first authenticate themselves with the controller before they can request access to the network resources. The controller uses the first packet of each flow for connection setup. When a packet arrives at the controller, the controller decides whether the flow represented by that packet should be allowed. The switches use a simple flow table to forward packets under the direction of the controller. When a packet arrives that is not in the flow table, it is forwarded to the controller, along with information about which port the packet arrived on. When a packet arrives that is in the flow table, it is forwarded according to the controller's directive.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
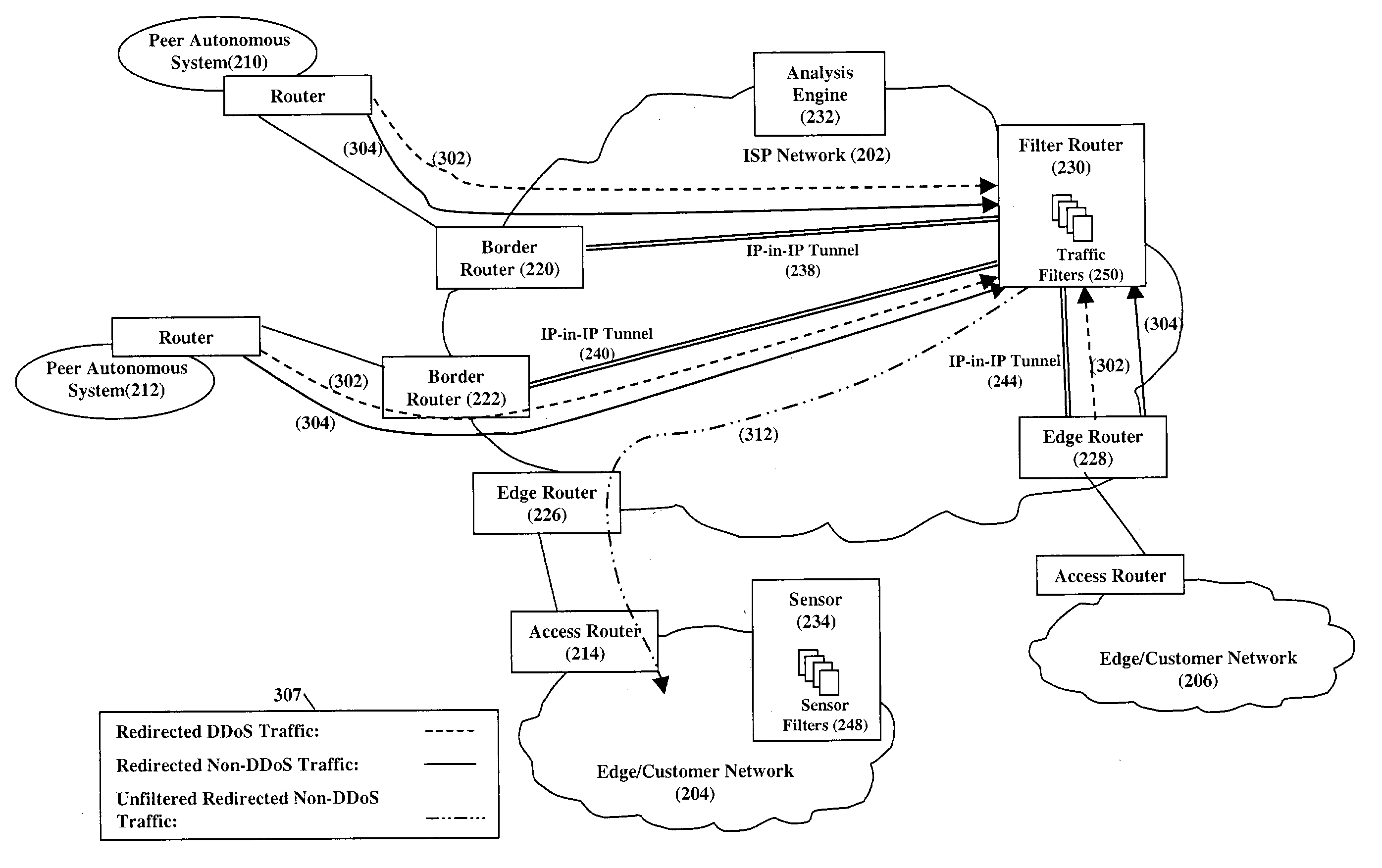
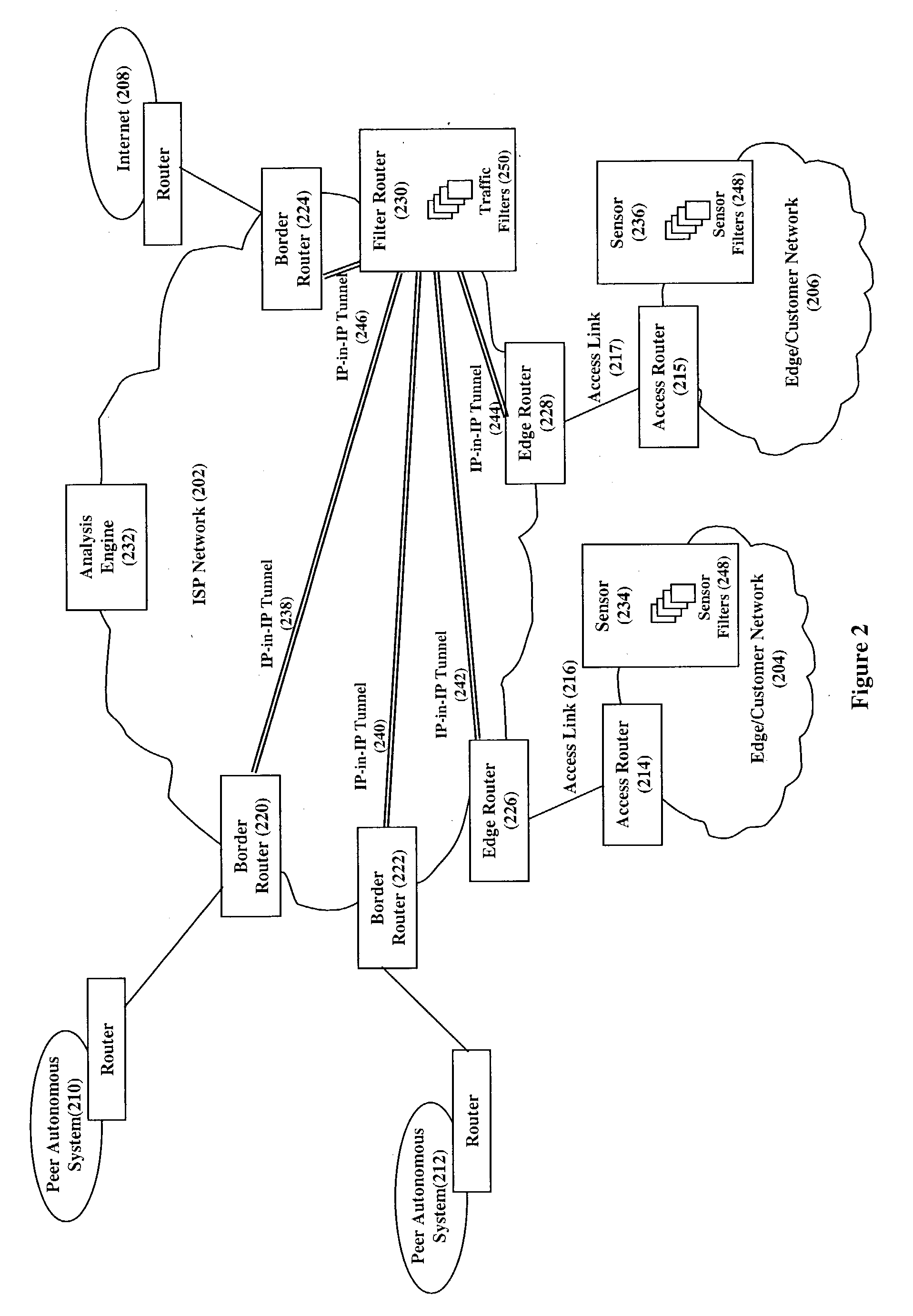
Mitigating denial of service attacks
InactiveUS20040148520A1Easily scaledMemory loss protectionUnauthorized memory use protectionThe InternetNetwork routing
Service attacks, such as denial of service and distributed denial of service attacks, of a customer network are detected and subsequently mitigated by the Internet Service Provider (ISP) that services the customer network. A sensor examines the traffic entering the customer network for attack traffic. When an attack is detected, the sensor notifies an analysis engine within the ISP network to mitigate the attack. The analysis engine configures a filter router to advertise new routing information to the border and edge routers of the ISP network. The new routing information instructs the border and edge routers to reroute attack traffic and non-attack traffic destined for the customer network to the filter router. At the filter router, the attack traffic and non-attack traffic are automatically filtered to remove the attack traffic. The non-attack traffic is passed back onto the ISP network for routing towards the customer network.
Owner:TELCORDIA TECHNOLOGIES INC
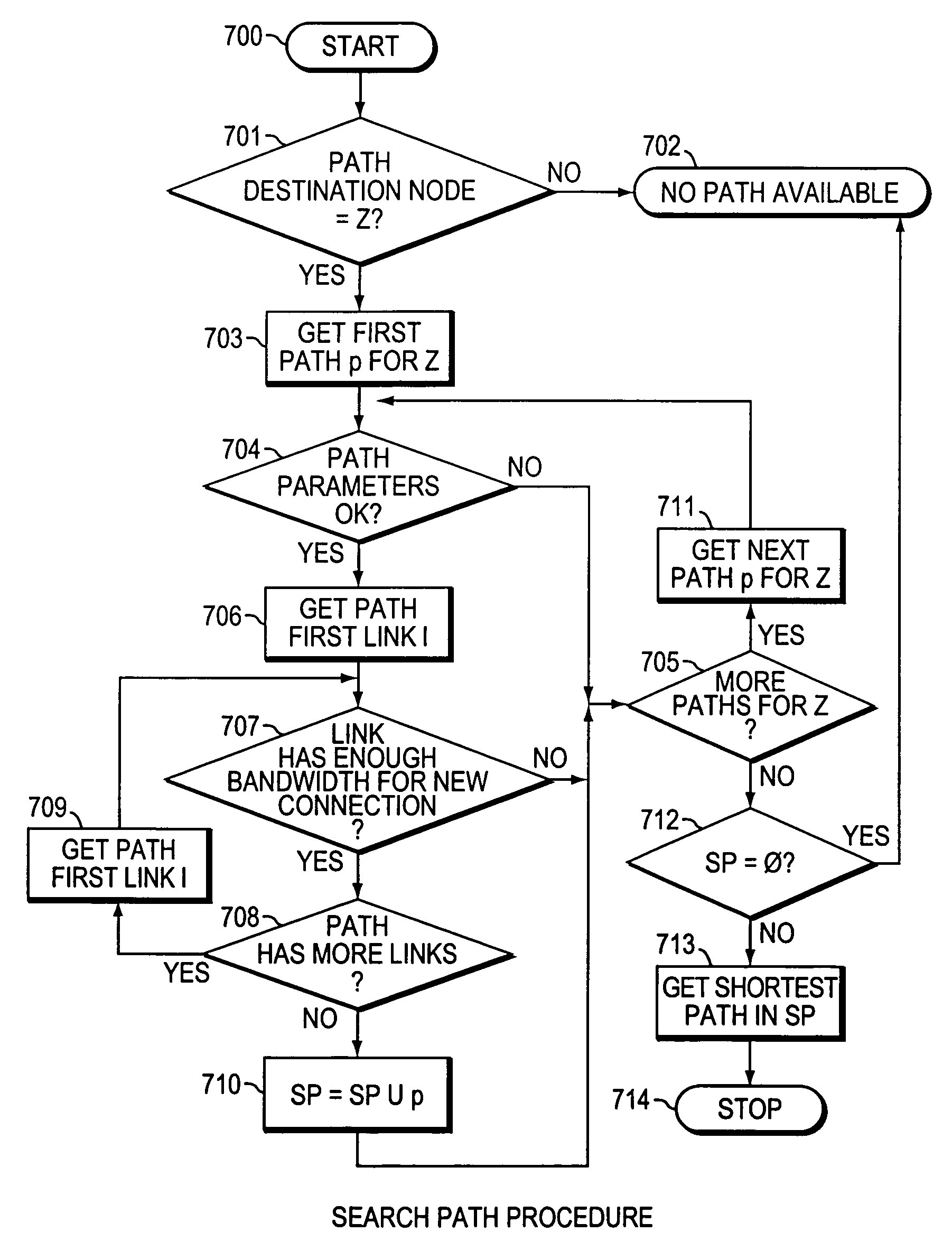
Method and system for minimizing the connection set up time in high speed packet switching networks
InactiveUS6934249B1Minimize delayMinimize in in to selectError preventionFrequency-division multiplex detailsTraffic capacityPacket switched
The present invention is directed to a high speed packet switching network and, in particular to a method and system for minimizing the time to establish a connection between an origin and a destination node. Due to high dynamicity of the traffic on transmission links, it is important to select a routing path according to a fully up-to-date information on all network resources. The simpler approach is to calculate a new path for each new connection request. This solution may be very time consuming because there are as many path selection operations as connection set up operations. On another hand, the calculation of paths based on an exhaustive exploration of the network topology, is a complex operation which may also take an inordinate amount of resources in large networks. Many of connections originated from a network node flow to the same destination network node. It is therefore possible to take a serious benefit in reusing the same already calculated paths for several connections towards the same node. The path calculated at the time the connection is requested is recorded in a Routing Database and updated each time a modification occurs in the network. Furthermore, alternate paths for supporting non-disruptive path switch on failure or preemption, and new paths towards potential destination nodes can be calculated and stored when the connection set up process is idle. These last operations are executed in background with a low processing priority and in absence of connection request.
Owner:CISCO TECH INC
Domain name routing
InactiveUS6119171AImprove service qualityEasy to useTime-division multiplexData switching by path configurationDomain nameComputer network
The present invention provides for a Domain Name Router (DNR) that uses domain names to route data sent to a destination on a network (e.g., a stub network). Each corporate entity or stub network can be assigned one or a small number of global addresses. Each of the hosts on the stub network can be assigned a global address. When a source entity sends data to a destination entity with a local address, the data is sent to the DNR using a global address. The source entity embeds the destination's domain name and its own domain name inside the data. The DNR extracts the destination's domain name from the data, translates that domain name to a local address and sends the data to the destination.
Owner:F POSZAT HU +1
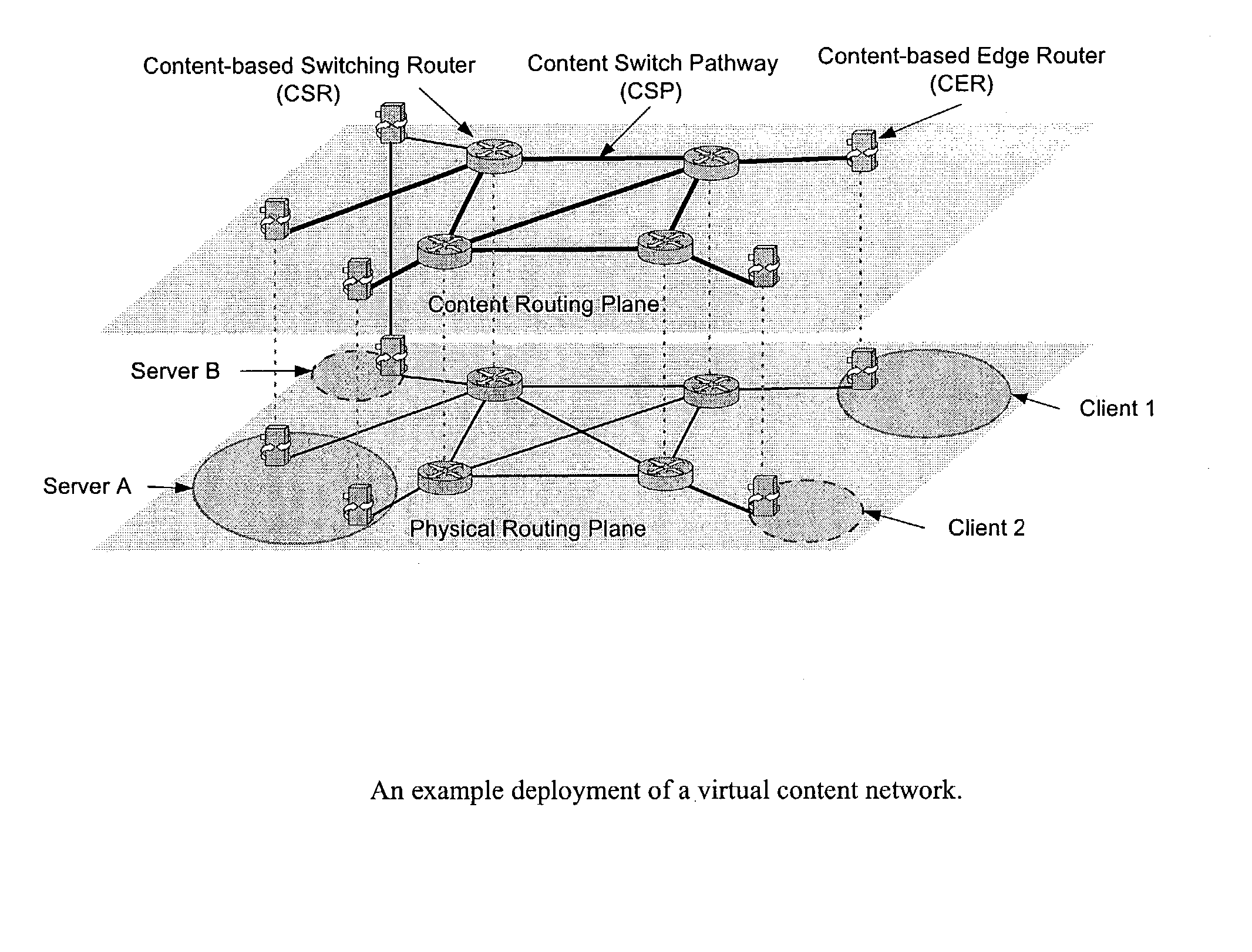
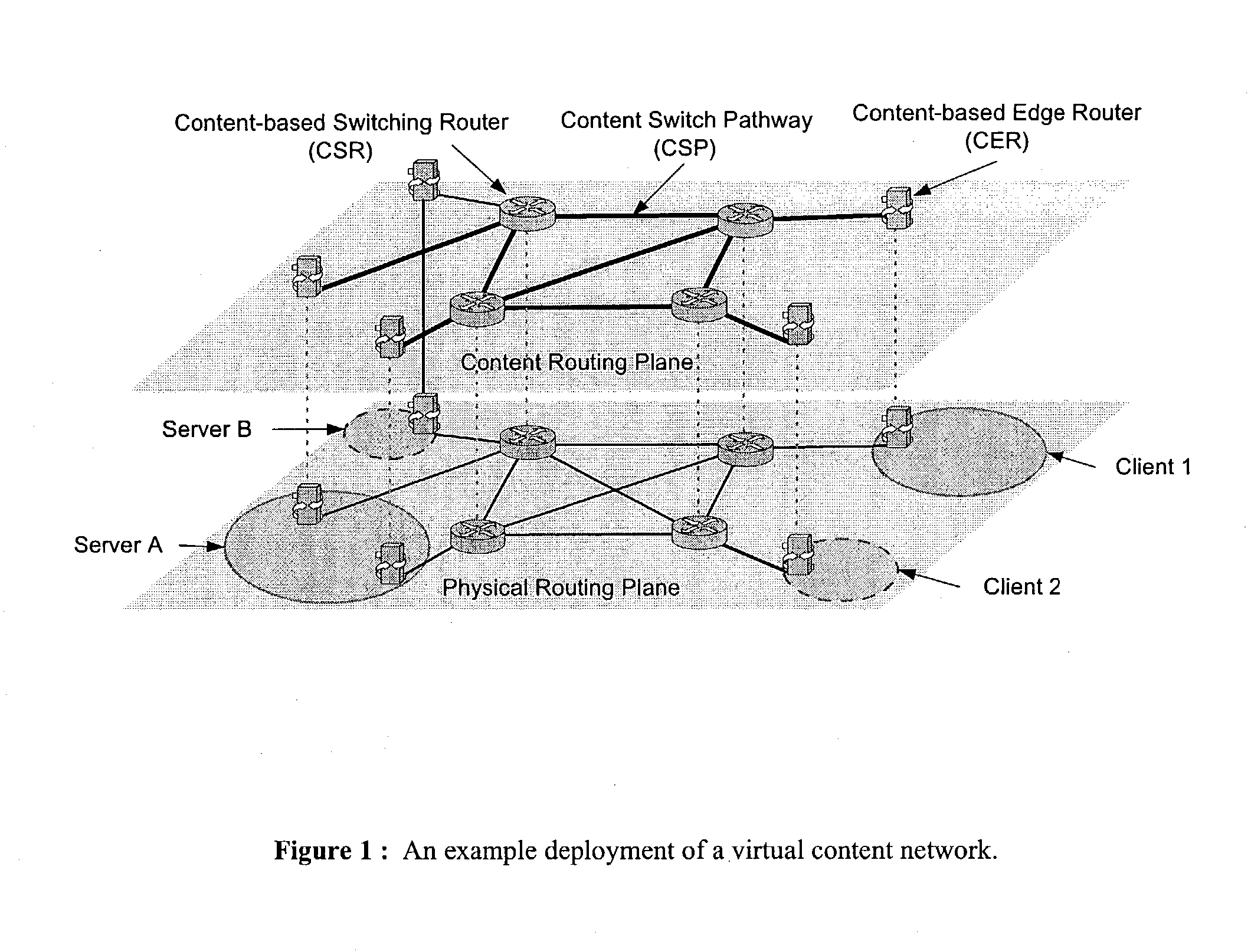
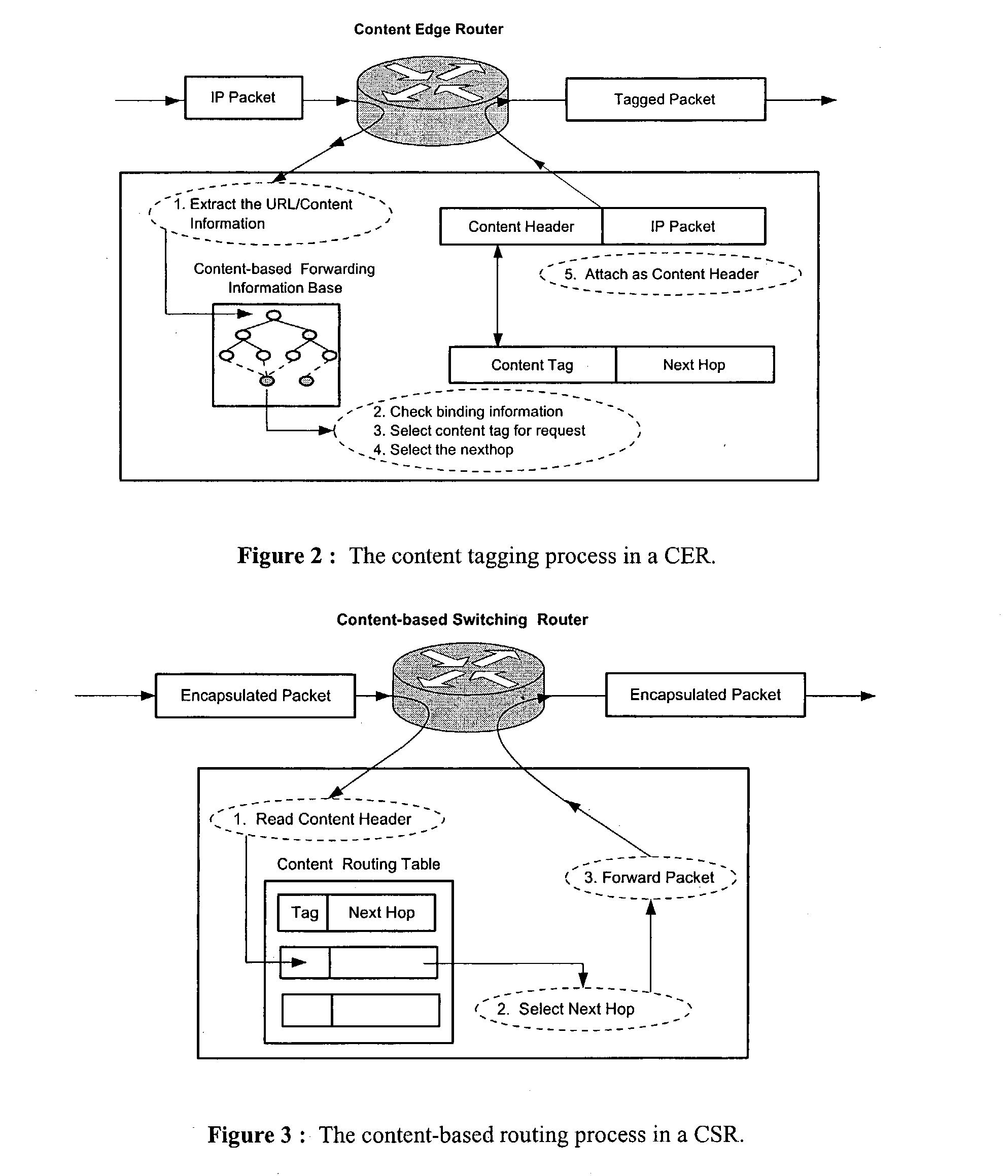
Wide-area content-based routing architecture
InactiveUS20030099237A1Easy to manageMaximum connectivityData switching by path configurationWide areaVirtualization
Content networking is an emerging technology, where the requests for content accesses are steered by "content routers" that examine not only the destinations but also content descriptors such as URLs and cookies. In the current deployments of content networking, "content routing" is mostly confined to selecting the most appropriate back-end server in virtualized web server clusters. This invention presents a novel content-based routing architecture that is suitable for global content networking. In this content-based routing architecture, a virtual overlay network called the "virtual content network" is superimposed over the physical network. The content network contains content routers as the nodes and "pathways" as links. The content-based routers at the edge of the content network may be either a gateway to the client domain or a gateway to the server domain whereas the interior ones correspond to the content switches dedicated for steering content requests and replies. The pathways are virtual paths along the physical network that connect the corresponding content routers. The invention is based on tagging content requests at the ingress points. The tags are designed to incorporate several different attributes of the content in the routing process. The path chosen for routing the request is the optimal path and is chosen from multiple paths leading to the replicas of the content.
Owner:TELECOMM RES LAB
Server load balancing using IP option field approach to identify route to selected server
InactiveUS20060233155A1Improve efficiencyData switching by path configurationRouting decisionField methods
A router for routing data from a client through load-balancing nodes to a selected load-balanced server among a plurality of servers in a network involves: receiving, at a last load balancing node associated with a selected server among the plurality of servers, a first packet of a server reply to a request from the client; storing identifiers of ingress interfaces on which the packet arrives, in a send path list for server load balancing, as the first packet of the server reply is routed from the last load balancing node to the client using hop-by-hop decisions; receiving subsequent packets of the client request; and forwarding the subsequent packets to the selected server only on a route that is defined by the send path list and without hop-by-hop routing decisions. Packet flows are routed from the same client to the same server without hop-by-hop routing decisions or repeated load-balancing decisions.
Owner:CISCO TECH INC
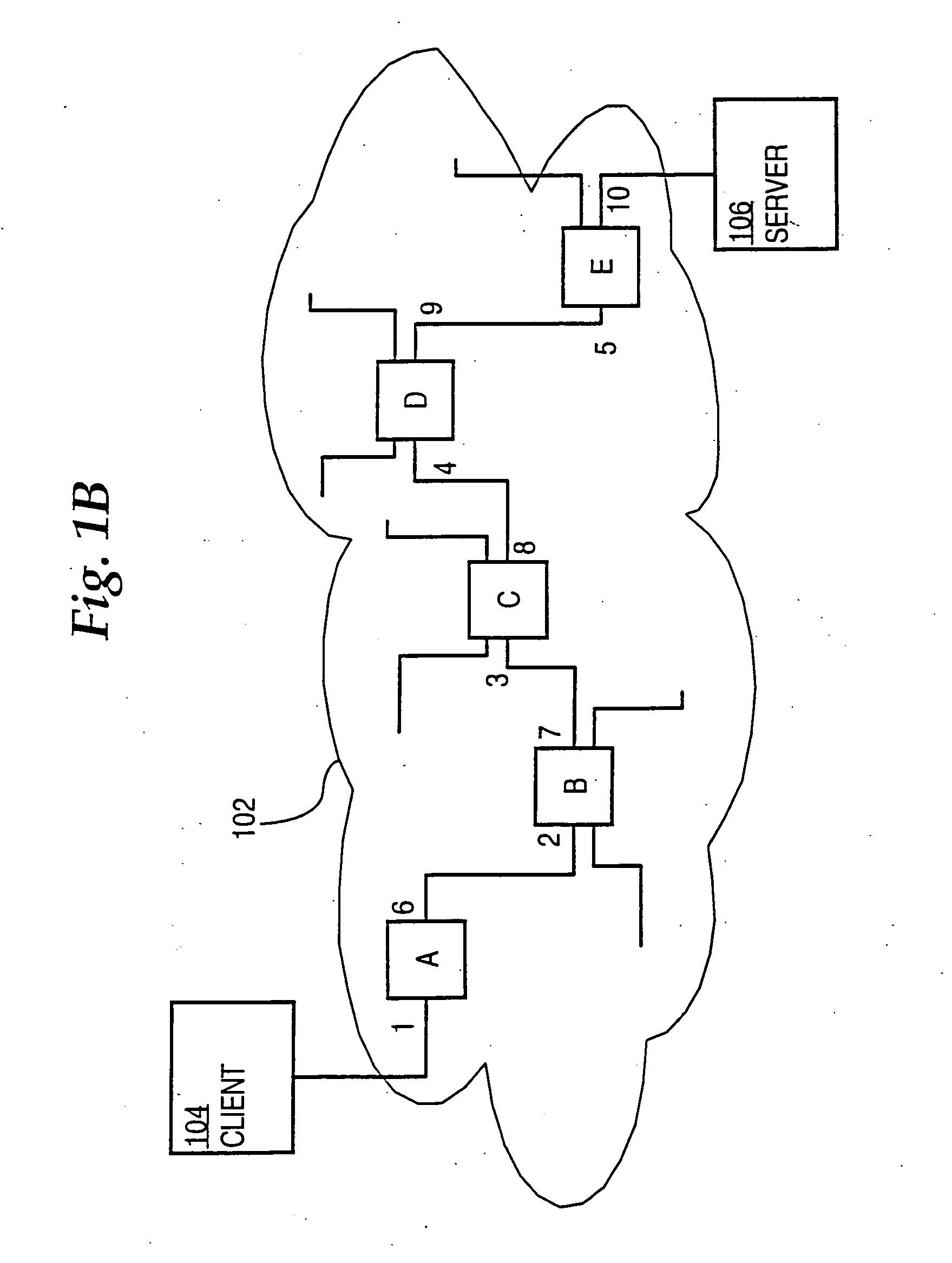
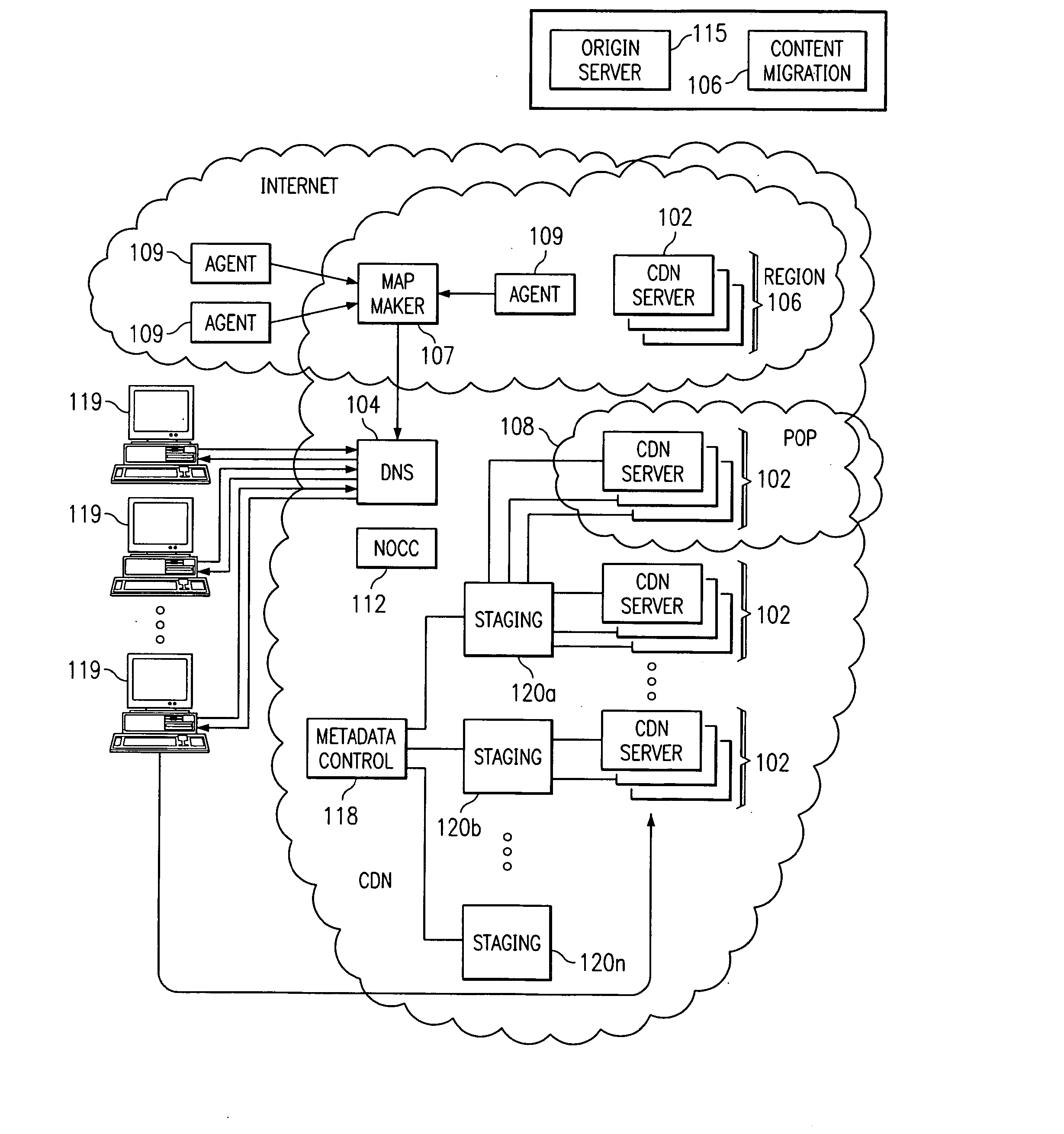
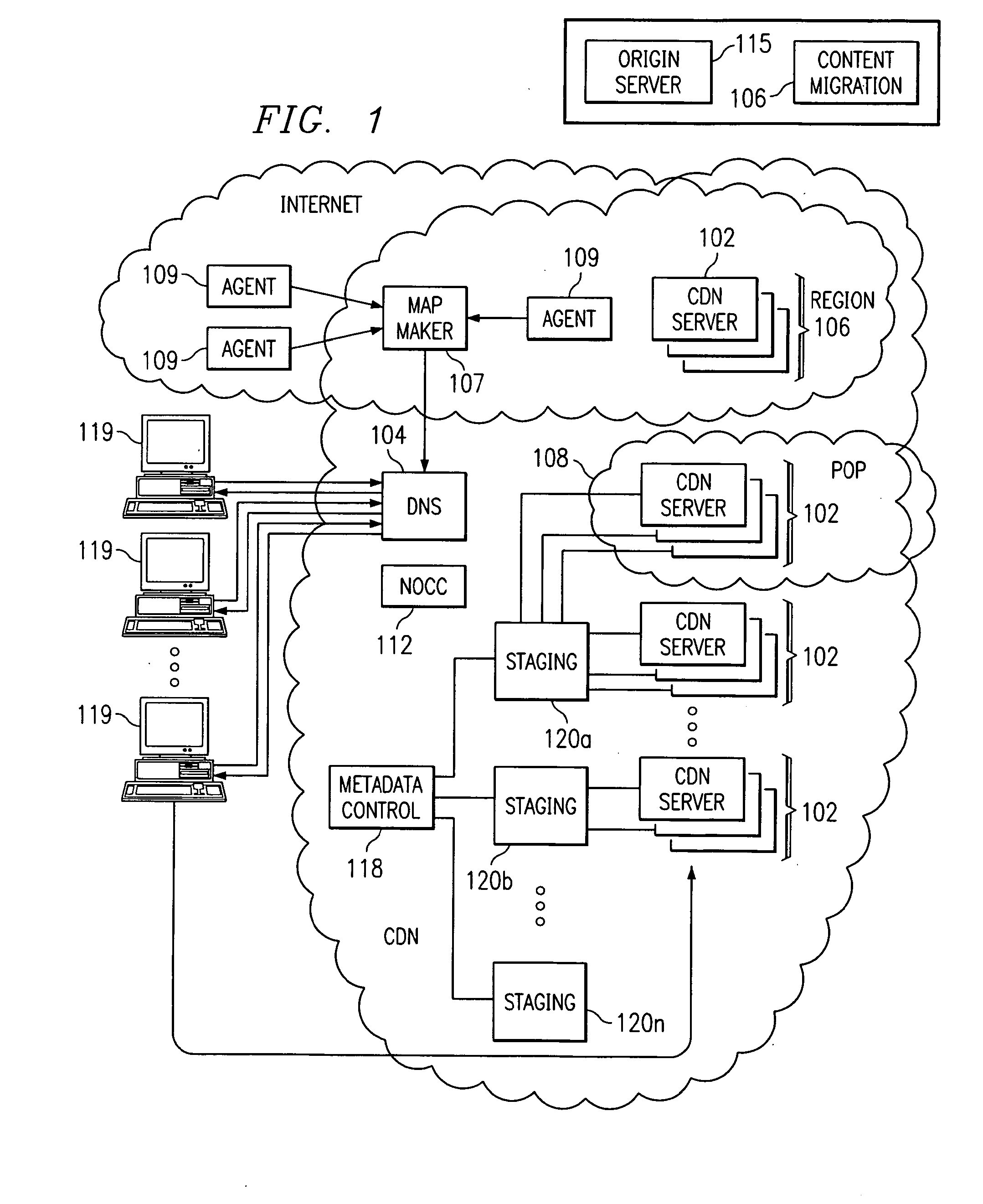
Optimal route selection in a content delivery network
InactiveUS20080008089A1Improve speed and reliabilityRetrieve content (cacheableError preventionTransmission systemsFile area networkPeer-to-peer
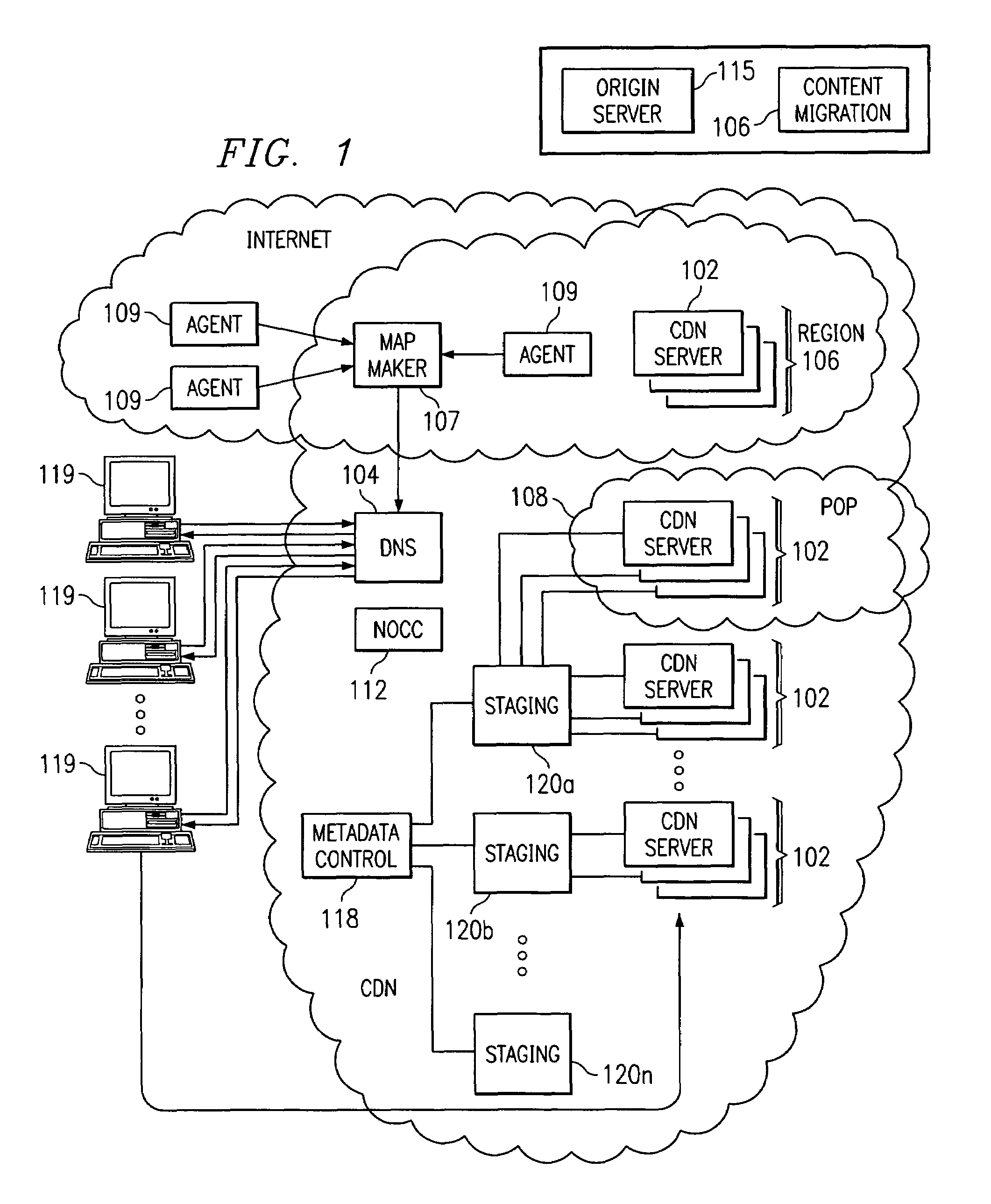
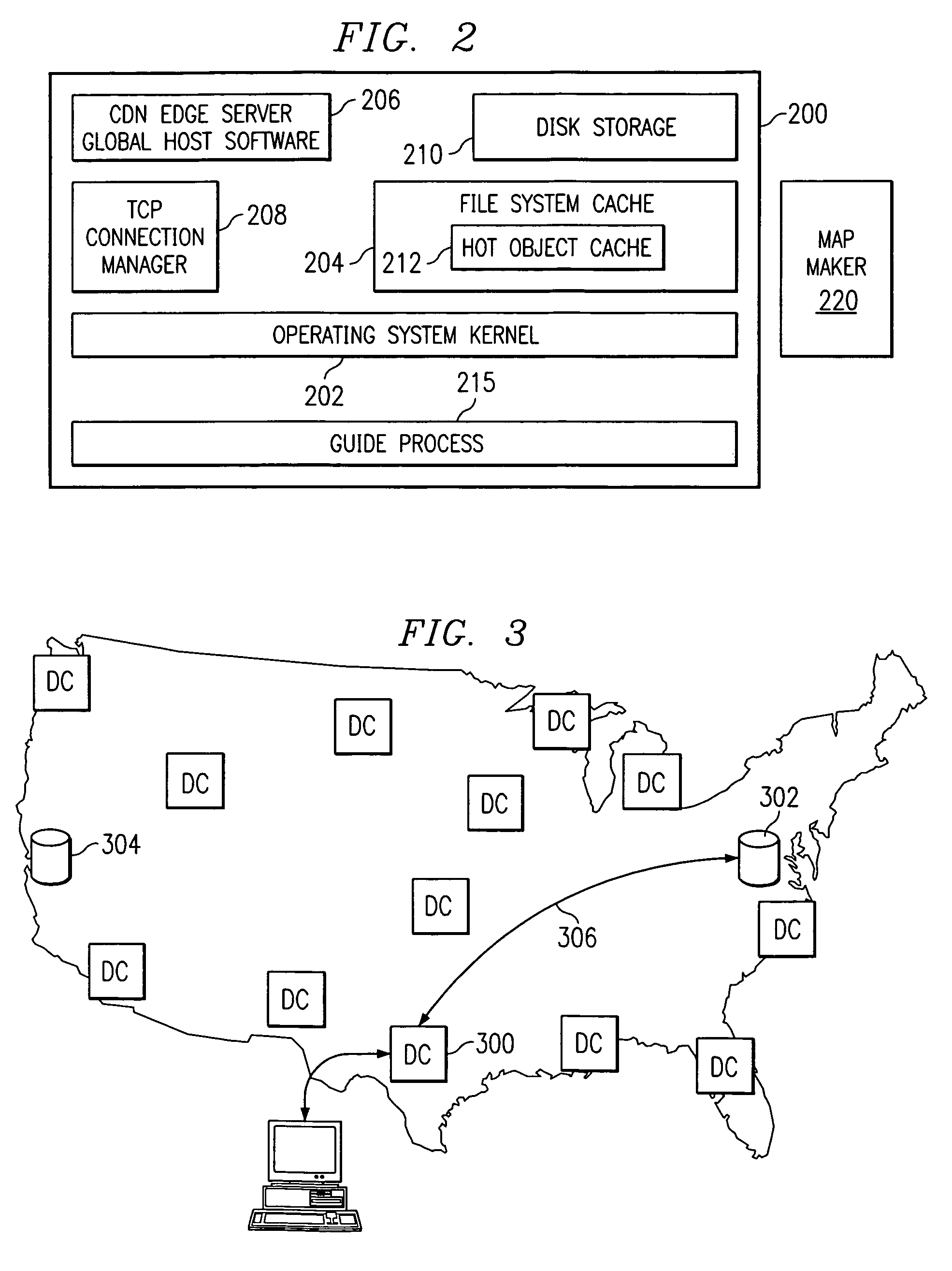
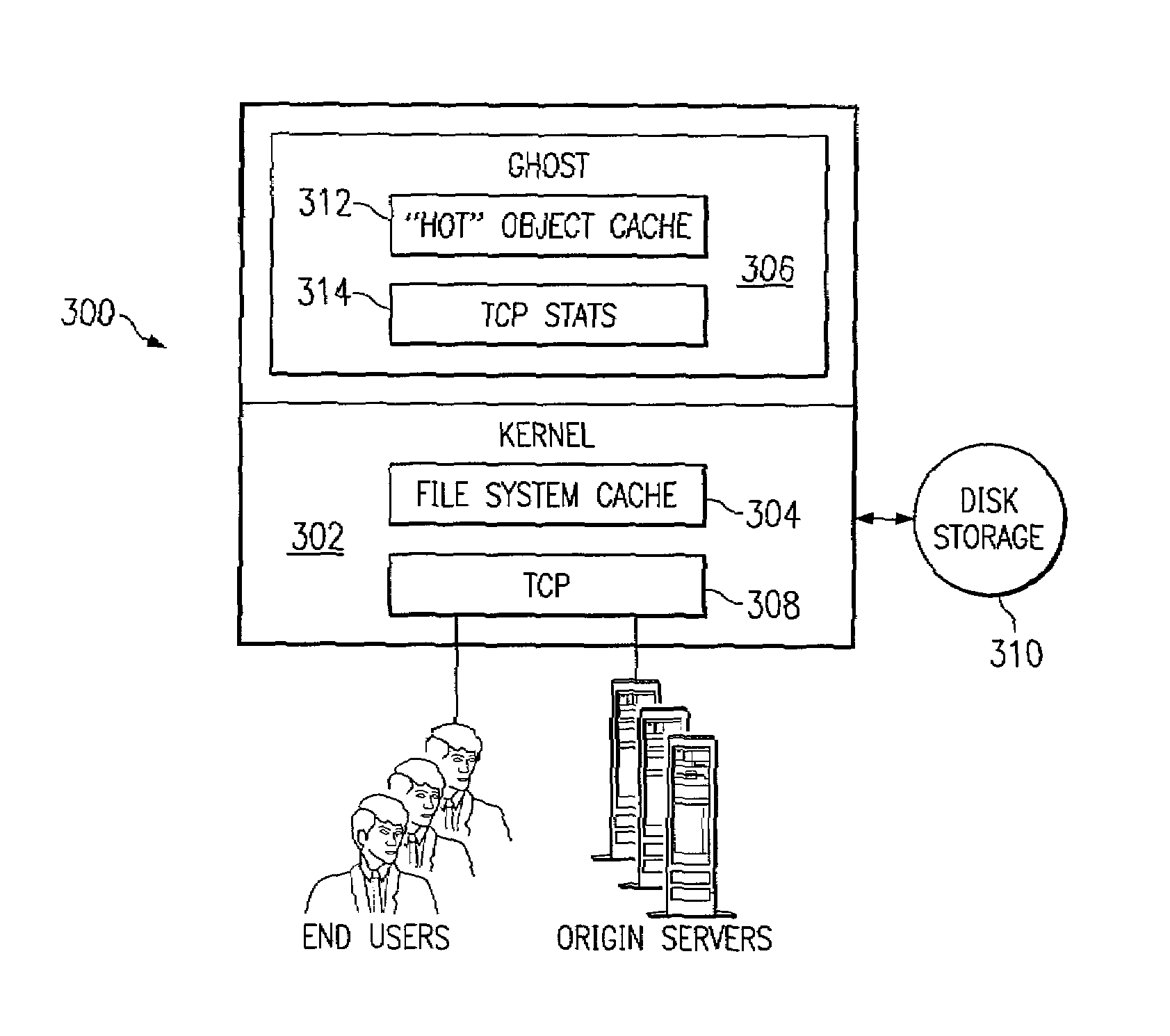
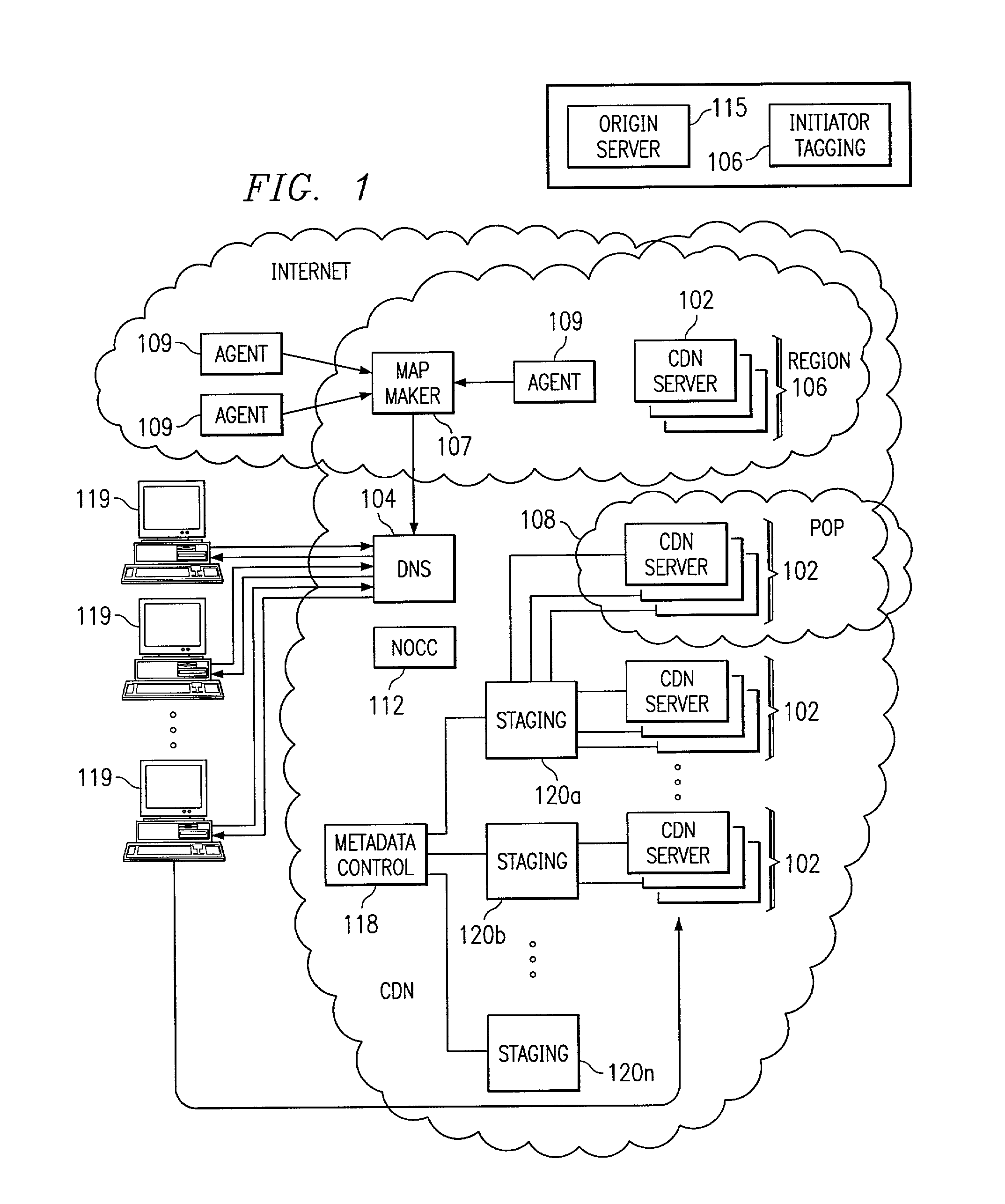
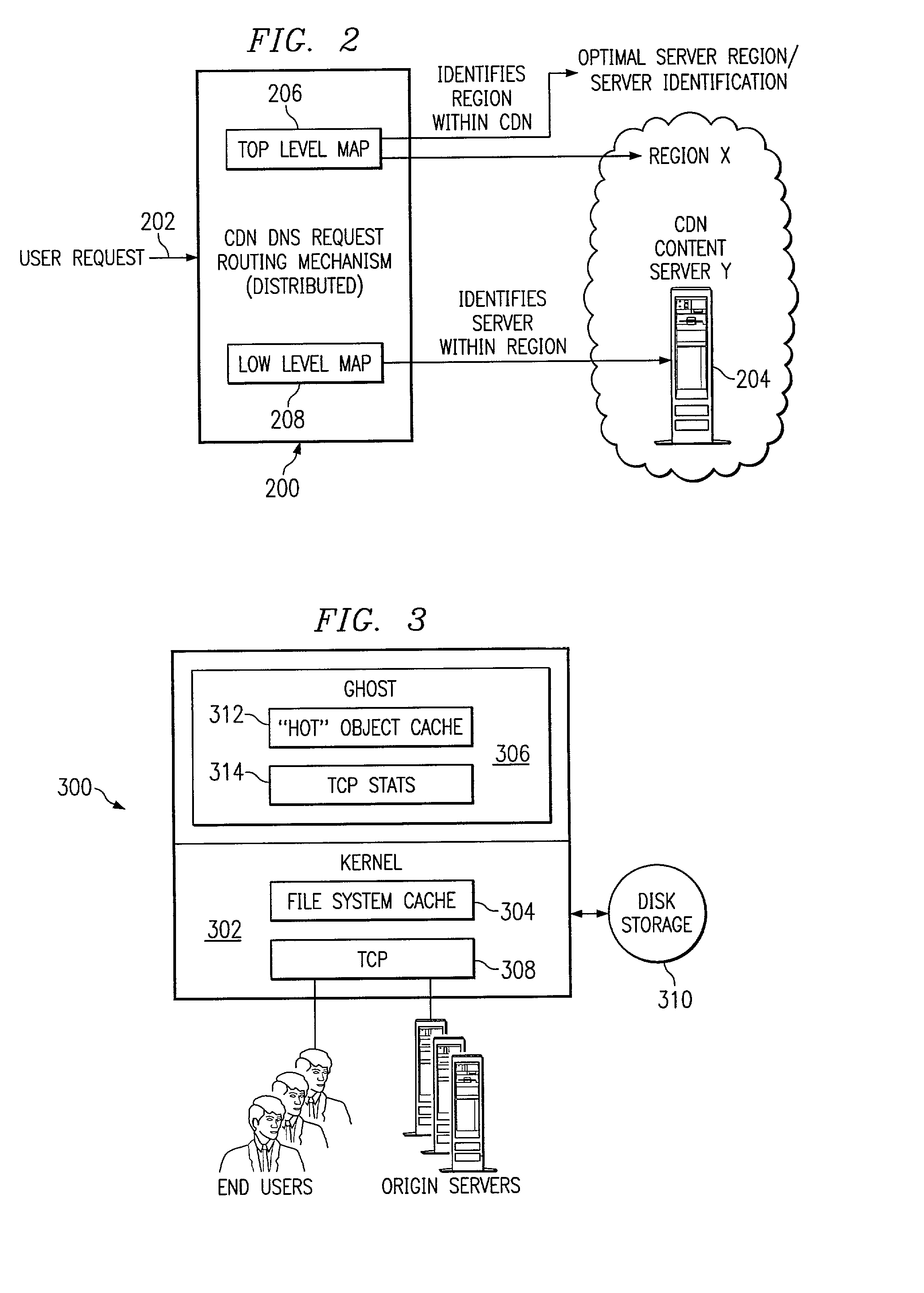
A routing mechanism, service or system operable in a distributed networking environment. One preferred environment is a content delivery network (CDN) wherein the present invention provides improved connectivity back to an origin server, especially for HTTP traffic. In a CDN, edge servers are typically organized into regions, with each region comprising a set of content servers that preferably operate in a peer-to-peer manner and share data across a common backbone such as a local area network (LAN). The inventive routing technique enables an edge server operating within a given CDN region to retrieve content (cacheable, non-cacheable and the like) from an origin server more efficiently by selectively routing through the CDN's own nodes, thereby avoiding network congestion and hot spots. The invention enables an edge server to fetch content from an origin server through an intermediate CDN server or, more generally, enables an edge server within a given first region to fetch content from the origin server through an intermediate CDN region.
Owner:AKAMAI TECH INC
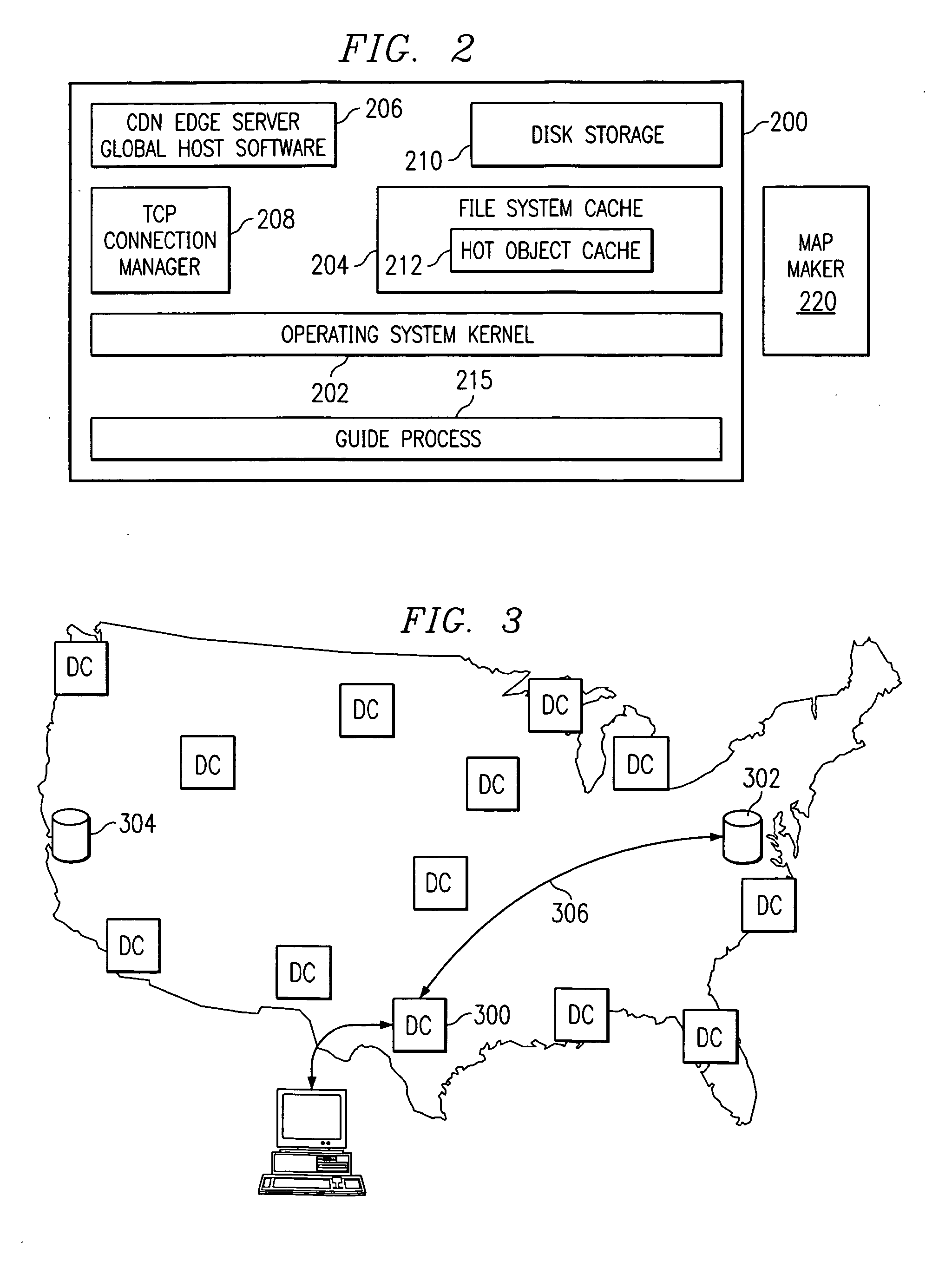
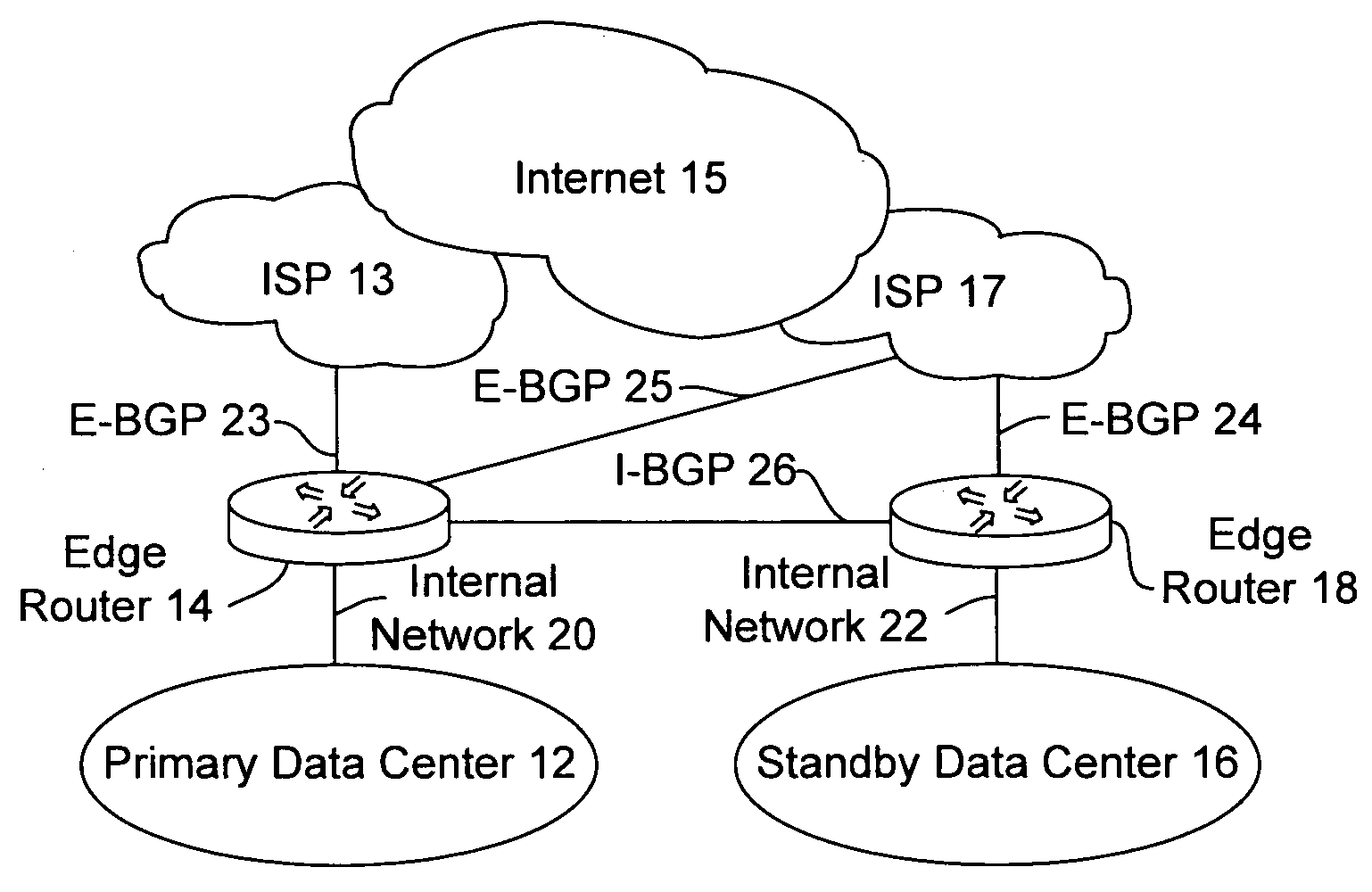
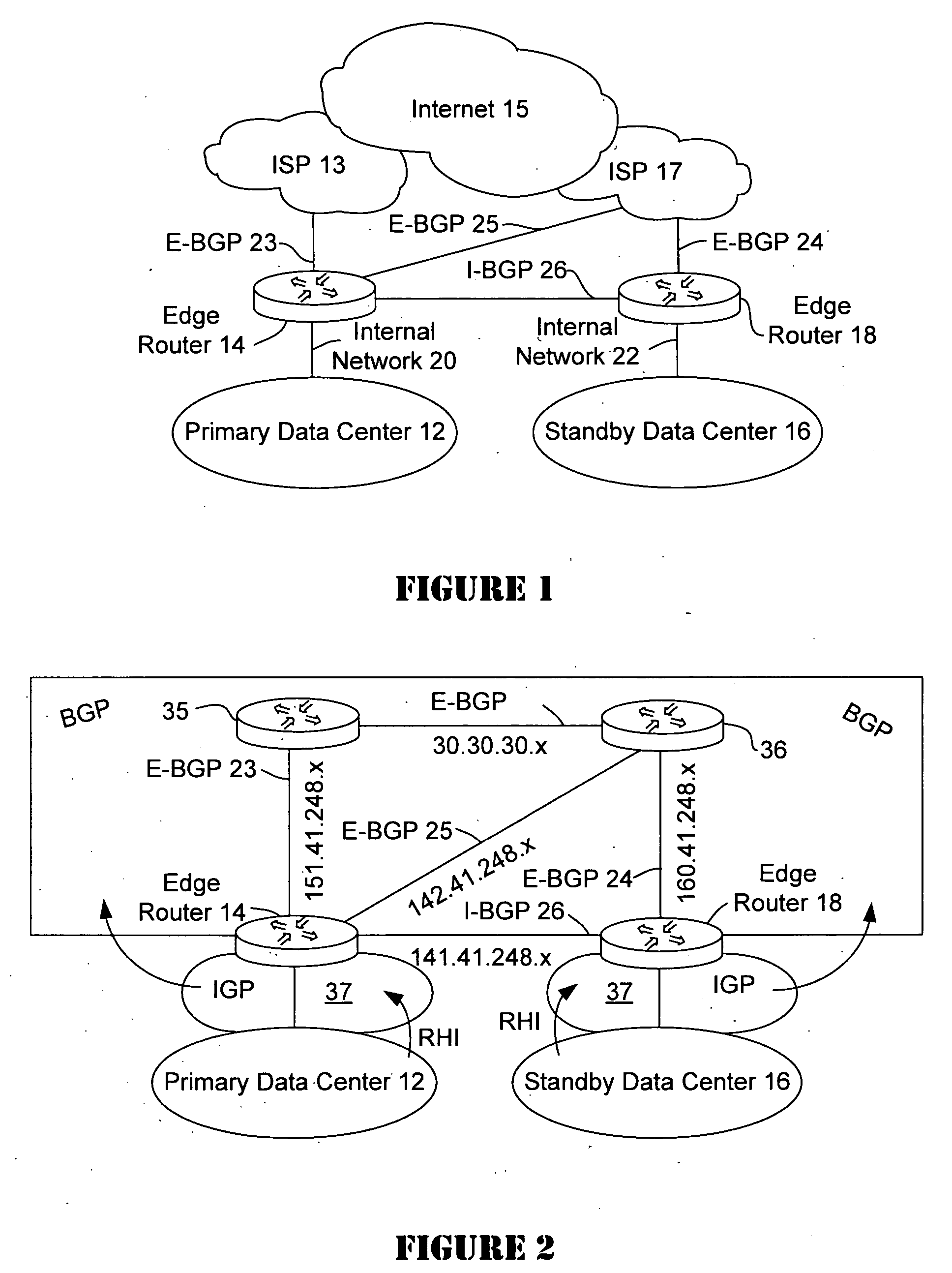
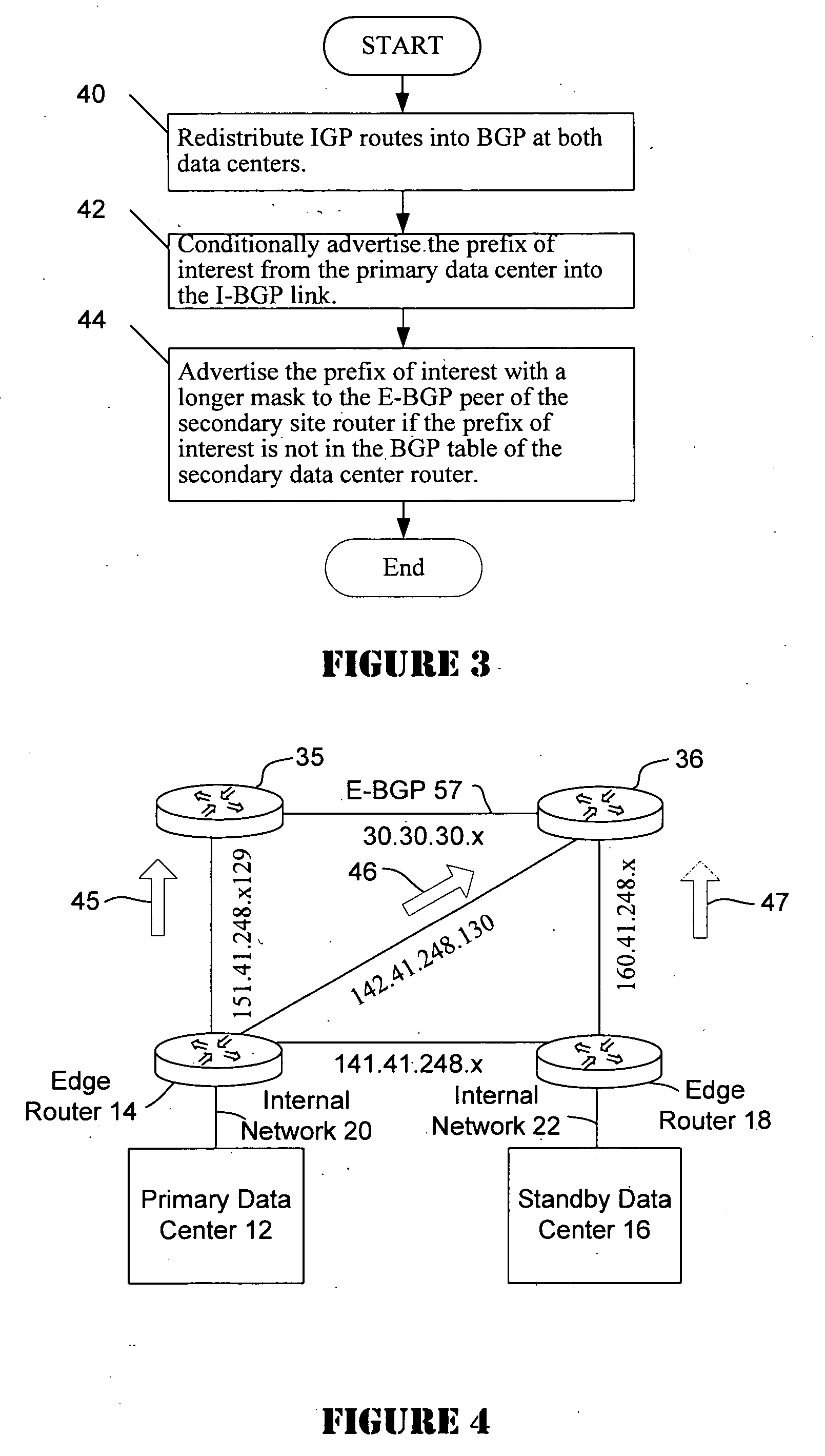
Disaster recovery for active-standby data center using route health and BGP
The present invention provides an active / standby data center that avoids the delay associated with a cached DNS entry to switch from the active data center to the standby data center. When the active data center becomes unavailable, the standby data center advertises the same address as the primary data center so the change over occurs quickly. When the IP address of the primary data center is no longer visible to the standby data center, the standby data center begins to advertise.
Owner:CISCO TECH INC
Geographic location using multiple location estimators
InactiveUS7298327B2Overcome inaccurate recognitionThe result is accurate and reliableDirection finders using radio wavesBeacon systems using radio wavesTerrainHeuristic
A location system is disclosed for commercial wireless telecommunication infrastructures. The system is an end-to-end solution having one or more location centers for outputting requested locations of commercially available handsets or mobile stations (MS) based on, e.g., CDMA, AMPS, NAMPS or TDMA communication standards, for processing both local MS location requests and more global MS location requests via, e.g., Internet communication between a distributed network of location centers. The system uses a plurality of MS locating technologies including those based on: (1) two-way TOA and TDOA; (2) pattern recognition; (3) distributed antenna provisioning; and (4) supplemental information from various types of very low cost non-infrastructure base stations for communicating via a typical commercial wireless base station infrastructure or a public telephone switching network. Accordingly, the traditional MS location difficulties, such as multipath, poor location accuracy and poor coverage are alleviated via such technologies in combination with strategies for: (a) automatically adapting and calibrating system performance according to environmental and geographical changes; (b) automatically capturing location signal data for continual enhancement of a self-maintaining historical data base retaining predictive location signal data; (c) evaluating MS locations according to both heuristics and constraints related to, e.g., terrain, MS velocity and MS path extrapolation from tracking and (d) adjusting likely MS locations adaptively and statistically so that the system becomes progressively more comprehensive and accurate. Further, the system can be modularly configured for use in location signaling environments ranging from urban, dense urban, suburban, rural, mountain to low traffic or isolated roadways. Accordingly, the system is useful for 911 emergency calls, tracking, routing, people and animal location including applications for confinement to and exclusion from certain areas.
Owner:TRACBEAM
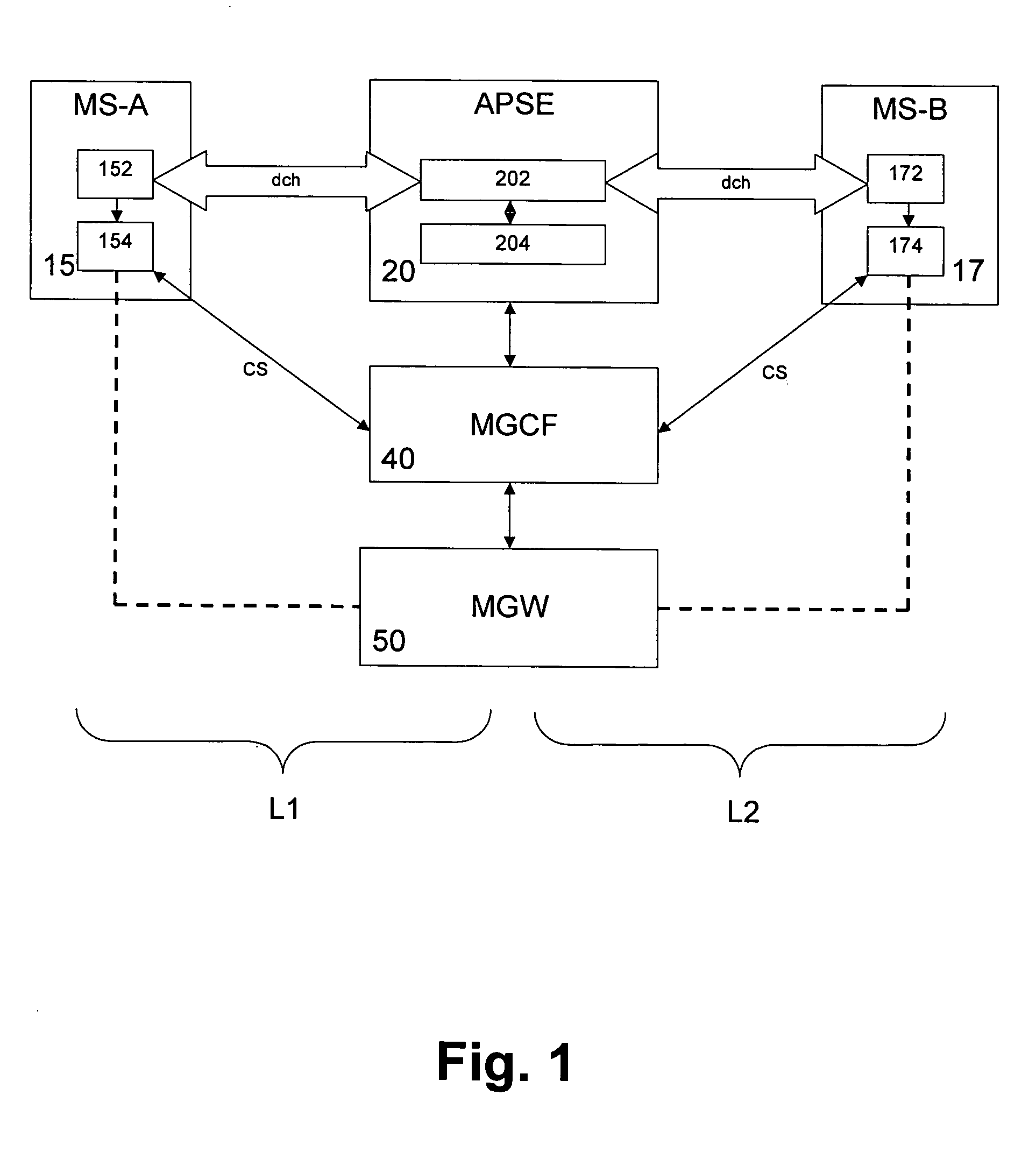
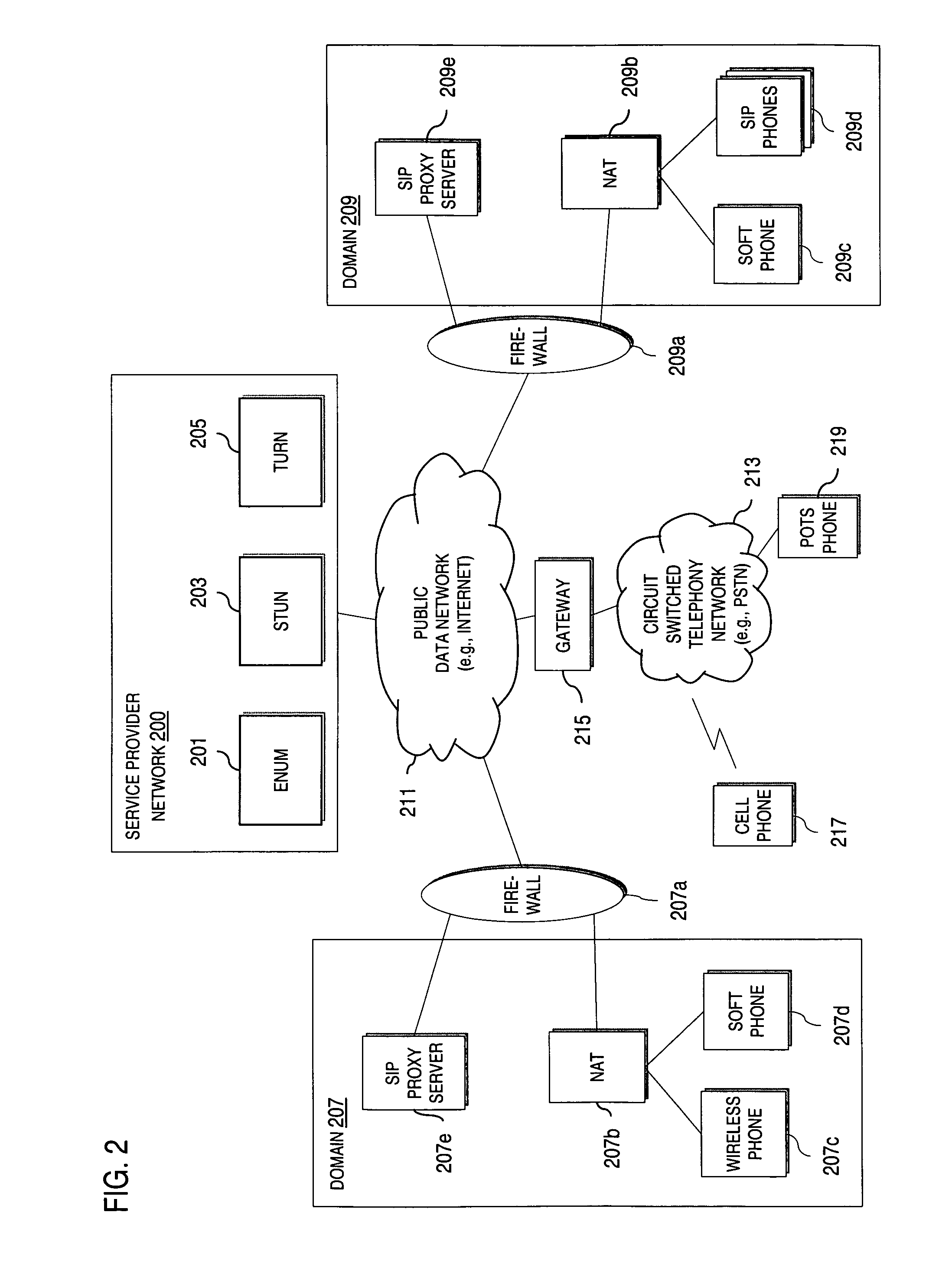
IP-based services for circuit-switched networks
ActiveUS20050058125A1Multiplex system selection arrangementsInterconnection arrangementsRadio access networkVoice over IP
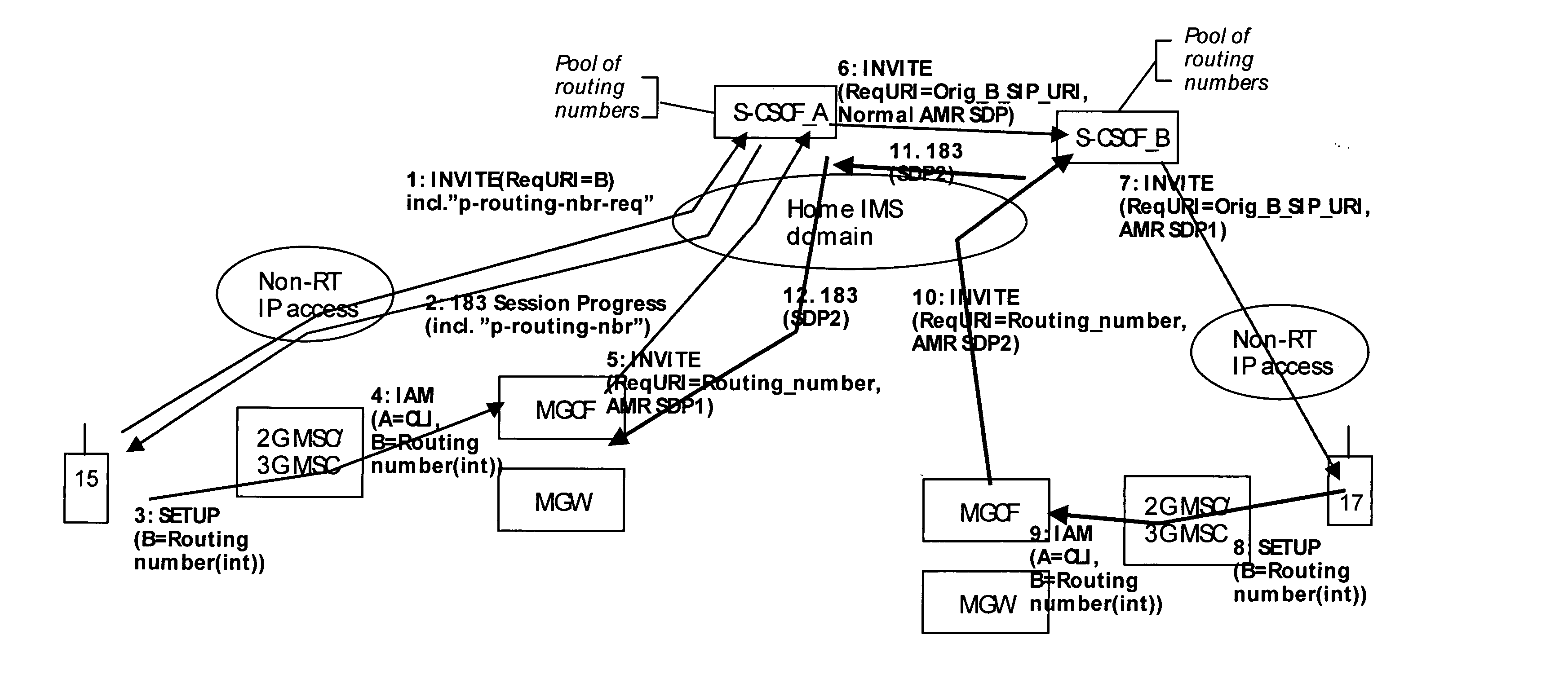
A mechanism for providing a connection from an IP-based network to a circuit-switched network, such as a GSM network is disclosed. A temporary routing number for the circuit-switched network, such as an E.164 number, is delivered to a user terminal, and a circuit-switched call leg is established from the user terminal to the IP-based network using the routing number. Thereby, IMS-services are provided for end users which are located in the radio access network not having sufficient QoS required for voice over IP. In the example of a conference call service, a request for a conference call may forwarded via a data channel or data path to an application server which provides that conference call service. The application server then selects a conference routing number and returns the routing number to the conference host terminal via the data channel. Using the received conference routing number, the conference host terminal can then set up a circuit-switched connection as a call leg of the conference call.
Owner:NOKIA TECHNOLOGLES OY
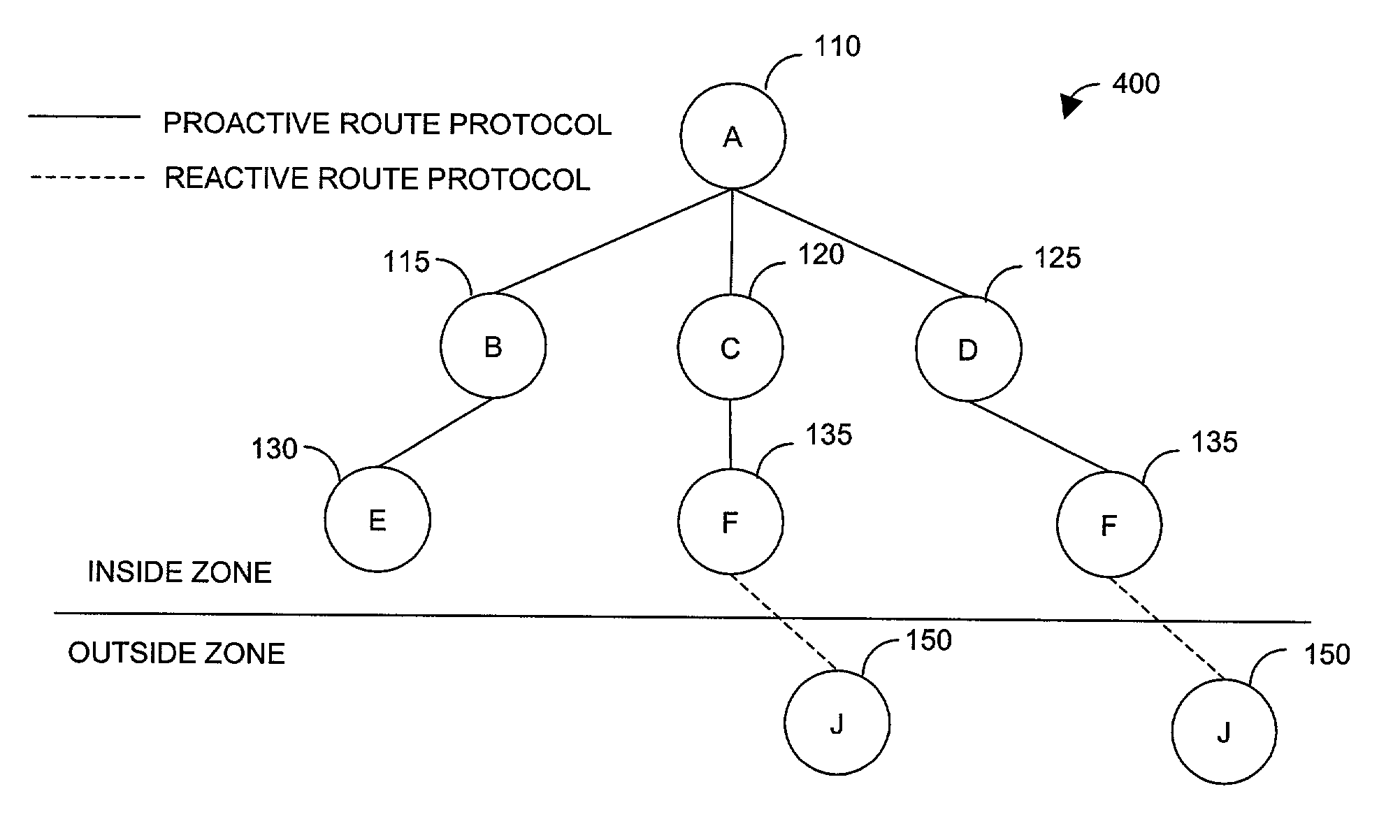
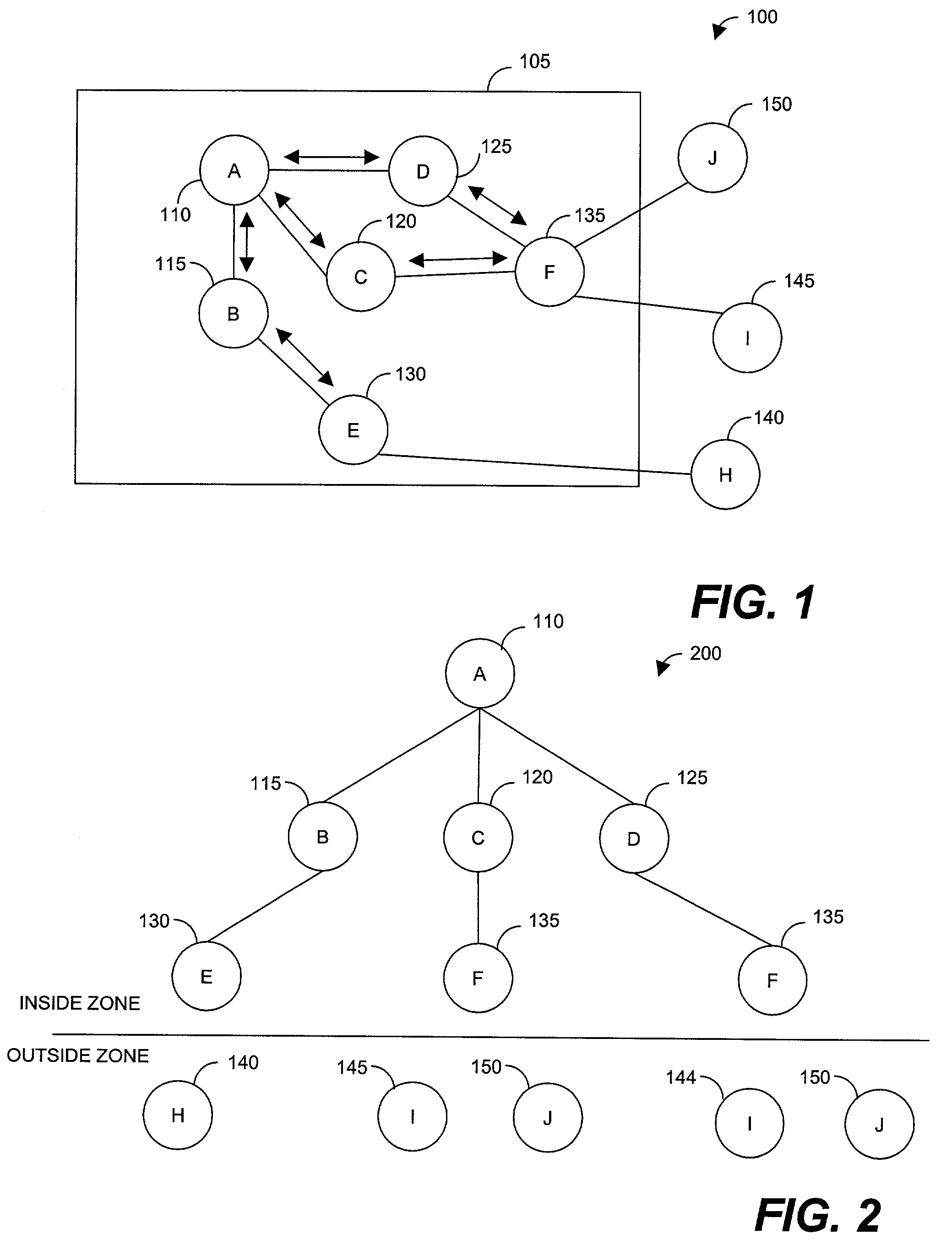
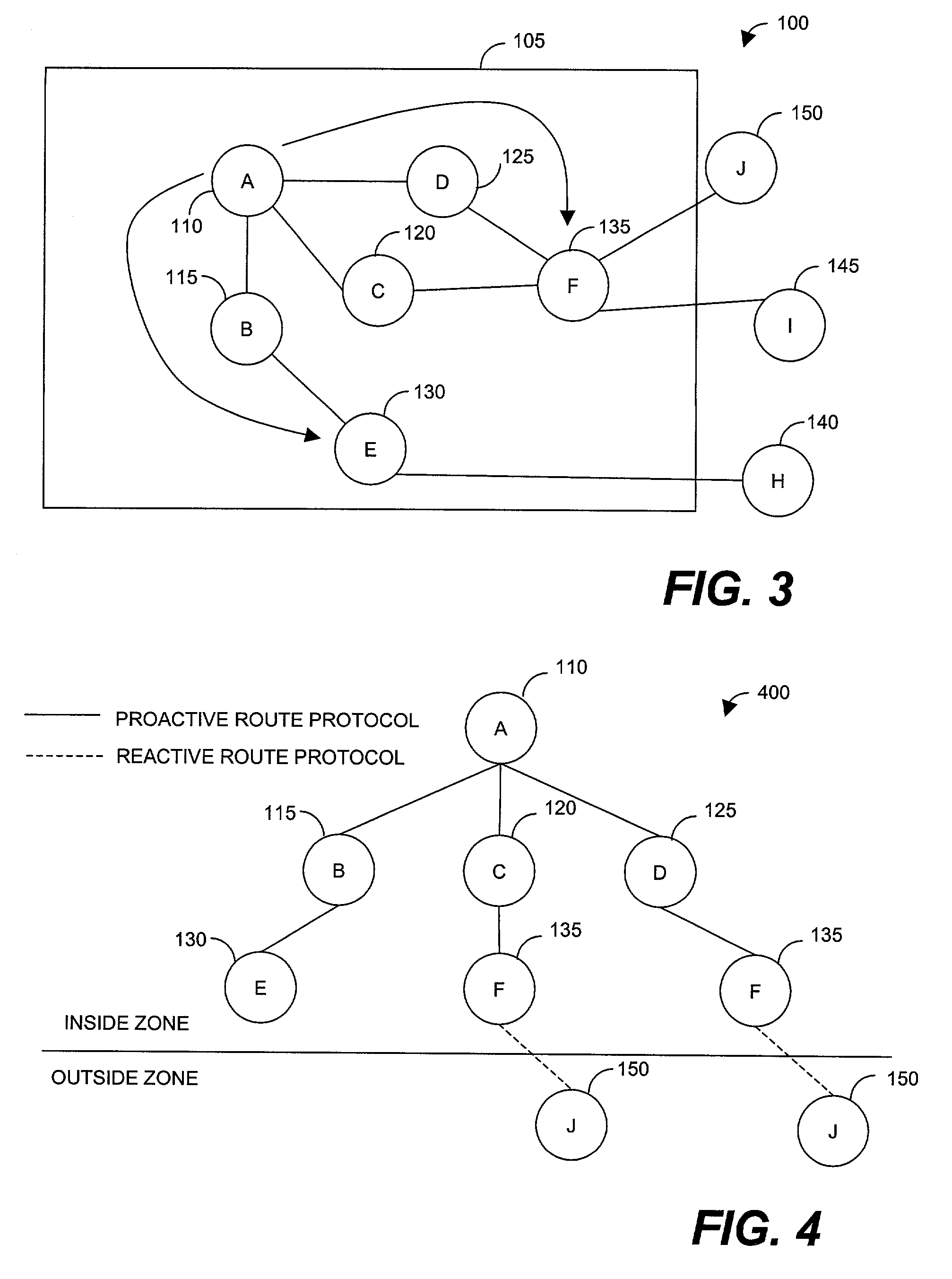
Wireless routing protocol for ad-hoc networks
InactiveUS7177295B1Quality of serviceNetwork topologiesTime-division multiplexTelecommunications linkCommunication link
Method for selecting a route within a wireless ad-hoc routing protocol using a QoS metric. The method begins by dynamically defining a routing zone that encompasses at least two of the network nodes. A communications link is established between the source node and a destination node. If the destination node is within the routing zone of the source node, the route is determined by a proactive routing protocol. If, however, the destination node is outside the routing zone, the route is determined using a reactive routing protocol. A QoS metric for each route is calculated by combining the individual QoS metrics for each hop within the particular route. Finally, the route with the best QoS metric is selected to use as the communications link between the source node and the destination node.
Owner:SCI RES
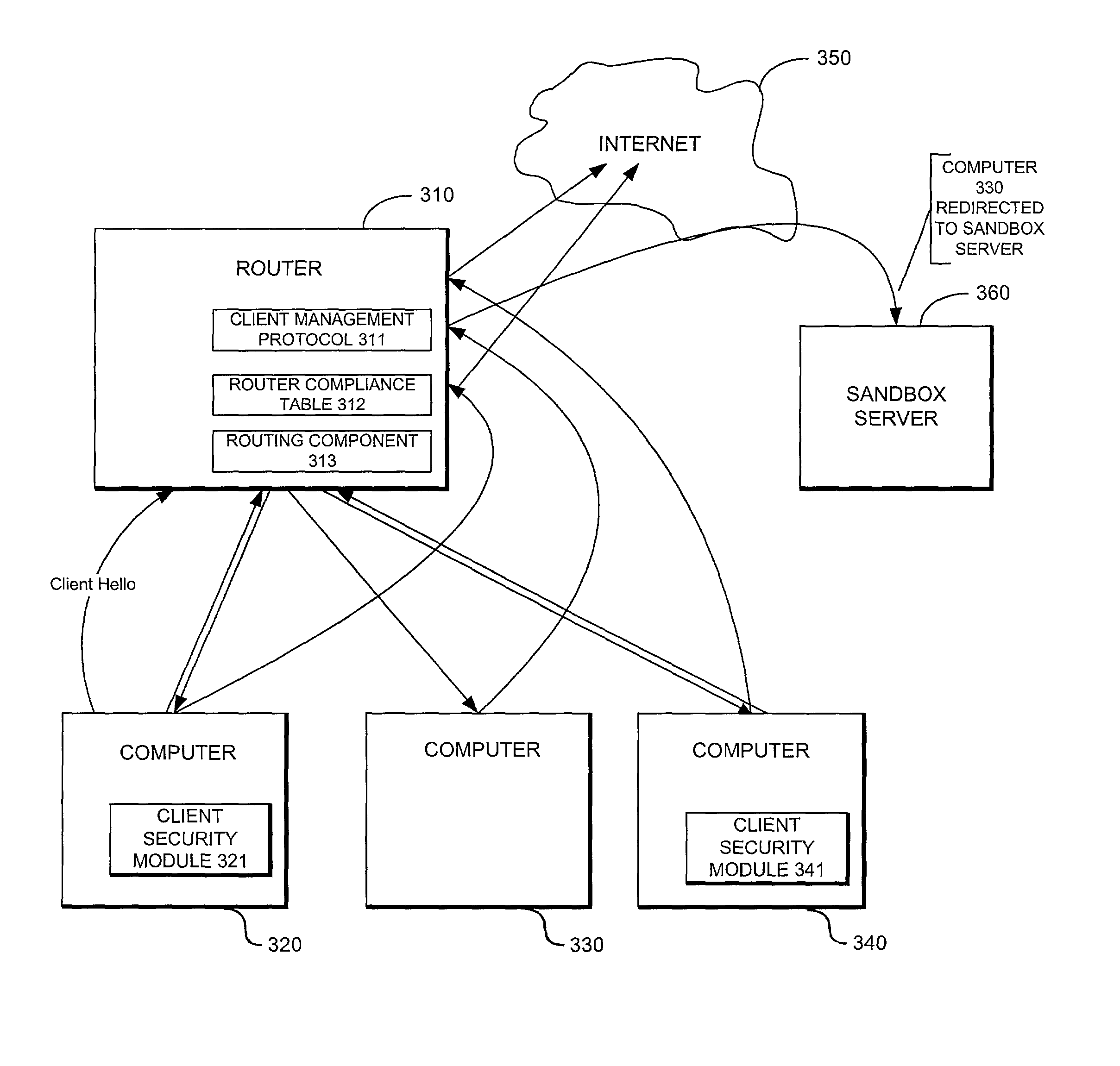
System providing internet access management with router-based policy enforcement
ActiveUS20030055962A1Multiple digital computer combinationsTransmissionInternet accessApplication software
A computing environment with methods for monitoring access to an open network such as the Internet, is described. The system includes one or more client computers, each operating applications (e.g., Netscape Navigator or Microsoft Internet Explorer) requiring access to an open network, such as a WAN or the Internet, and a router or other equipment that serves a routing function (e.g., a cable modem) for the client computers. A centralized security enforcement module on the router maintains access rules for the client computers and verifies the existence and proper operation of a client-based security module on each client computer. The router-side security module periodically sends out a router challenge via Internet broadcast to the local computers on the network. If the client-side security module is installed and properly operating, the client-side security module responds to the router challenge. The responses received by the router-side security module are maintained in a table. Each time the router receives a request from a client computer to connect to the Internet, the router-side security module reviews the table and analyzes whether or not the computer requesting a connection to the Internet properly responded to the most recent router challenge. If it determines that the computer has properly responded to the router challenge, then it permits the computer to connect to the Internet. If a computer has not properly responded or if a computer has not answered the router challenge, then the computer is not allowed to connect to the Internet as requested.
Owner:CHECK POINT SOFTWARE TECH INC
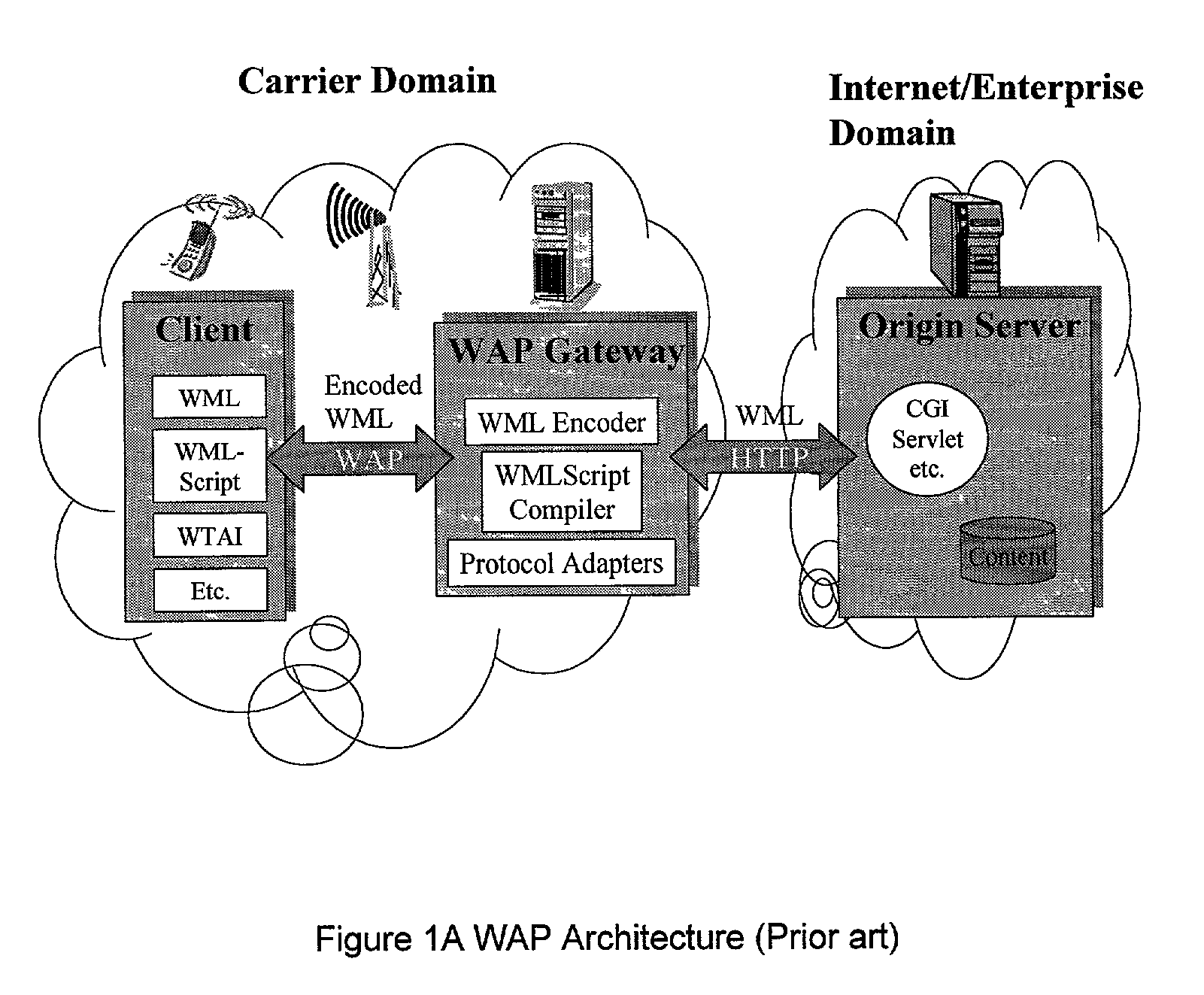
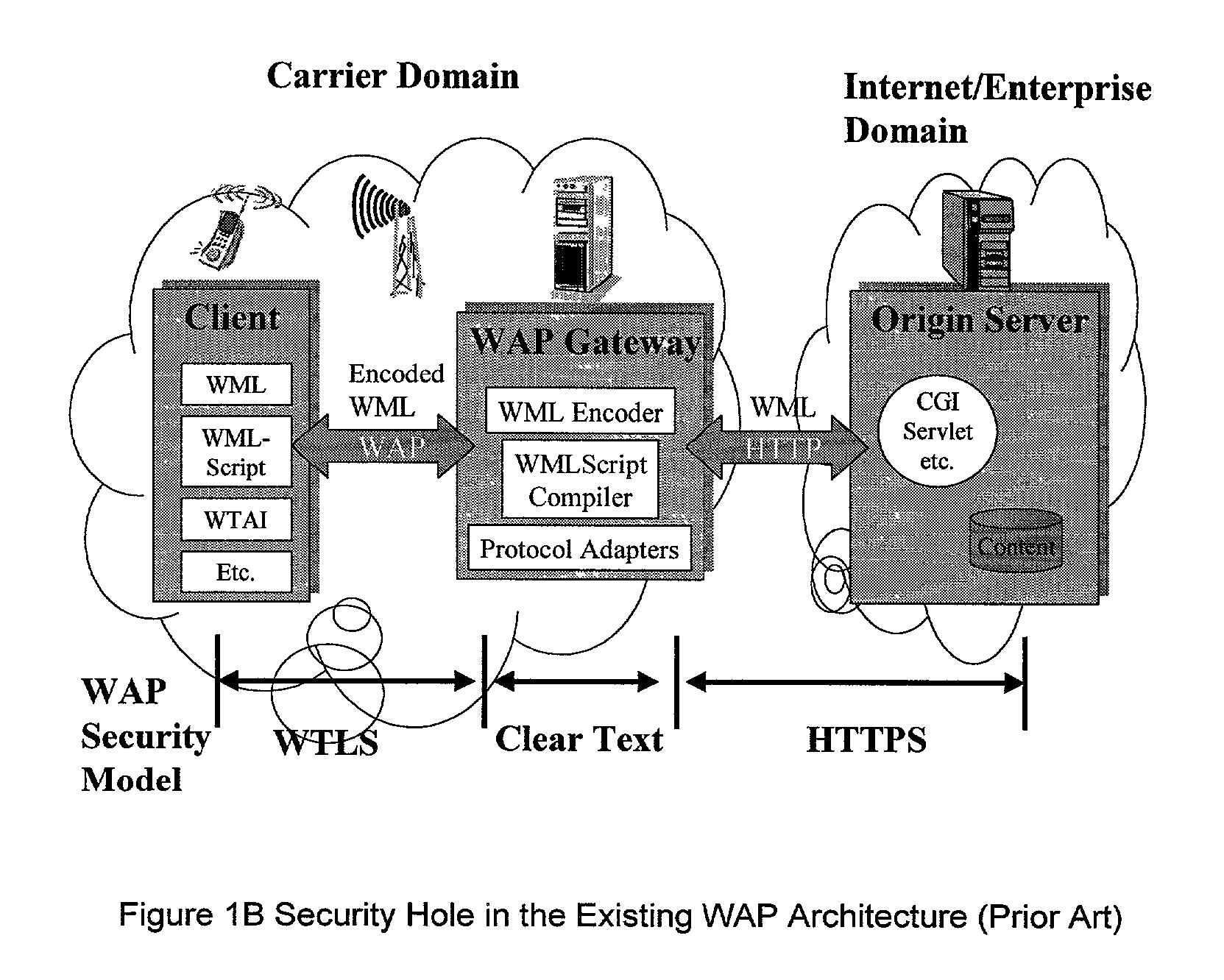
Method and apparatus for providing service selection, redirection and managing of subscriber access to multiple WAP (Wireless Application Protocol) gateways simultaneously
ActiveUS7039037B2Time-division multiplexData switching by path configurationCyber operationsComputer network
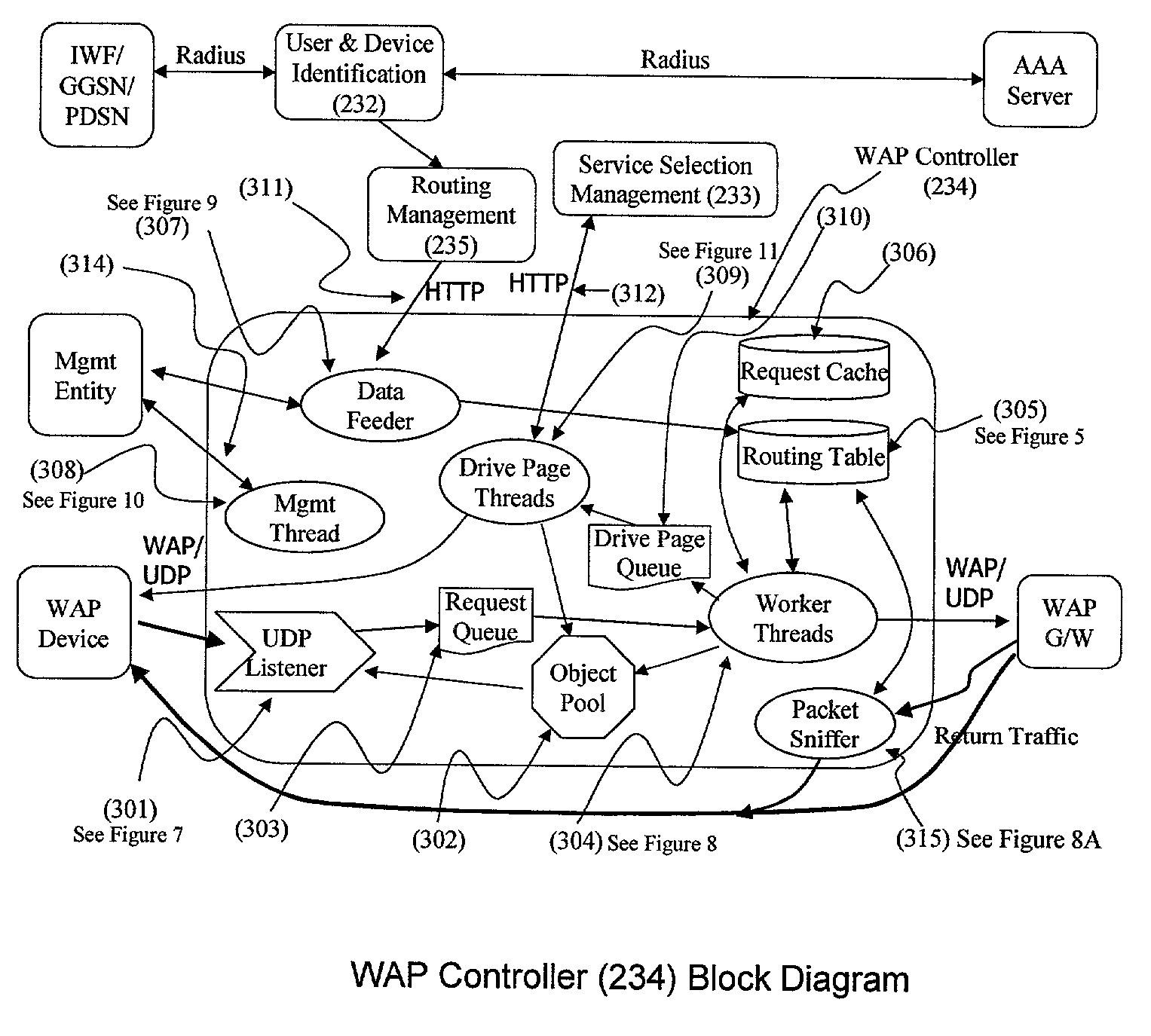
A method (FIG. 5) and apparatus (FIG. 3) to provide control and policy enforcement of WAP (Wireless Application Protocol) services in a wireless data networks is taught herein. WAP traffic is inspected with efficient algorithms to intercept un-registered WAP access and intercept dynamic change of user service selection. The intercepted WAP requests are modified with value-added parameters (such as QoS and subscriber identifiers) as per user and service provider agreement and table data. A series of strategies are described to blend wireless intelligence, user preference and service subscription, network operator requirements and service provider or enterprise preferences into routing and drive page generation. The means to dynamically provision users' service choices to wireless network elements are also presented without having to break the session within the system. This enables innovative data services such as pay-per-use, smart routing, and enterprise secured WAP services unlike any current conventional system.
Owner:MAVENIR SYST INC
Optimal route selection in a content delivery network
ActiveUS7274658B2Improve speed and reliabilityRetrieve content (cacheableError preventionTransmission systemsFile area networkPeer-to-peer
A routing mechanism, service or system operable in a distributed networking environment. One preferred environment is a content delivery network (CDN) wherein the present invention provides improved connectivity back to an origin server, especially for HTTP traffic. In a CDN, edge servers are typically organized into regions, with each region comprising a set of content servers that preferably operate in a peer-to-peer manner and share data across a common backbone such as a local area network (LAN). The inventive routing technique enables an edge server operating within a given CDN region to retrieve content (cacheable, non-cacheable and the like) from an origin server more efficiently by selectively routing through the CDN's own nodes, thereby avoiding network congestion and hot spots. The invention enables an edge server to fetch content from an origin server through an intermediate CDN server or, more generally, enables an edge server within a given first region to fetch content from the origin server through an intermediate CDN region. As used herein, this routing through an intermediate server, node or region is sometimes referred to as “tunneling.”
Owner:AKAMAI TECH INC
Router and methods using network addresses for virtualization
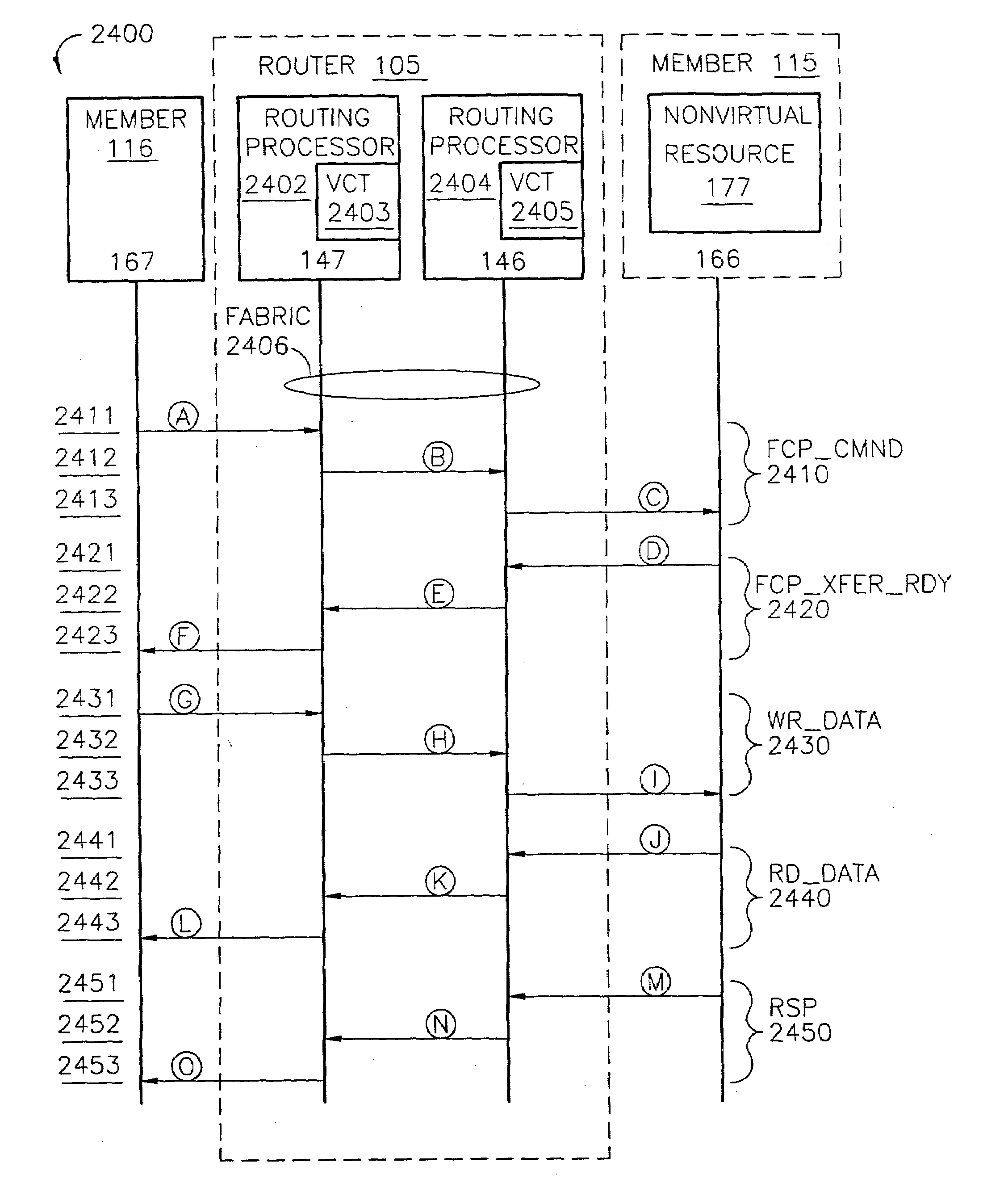
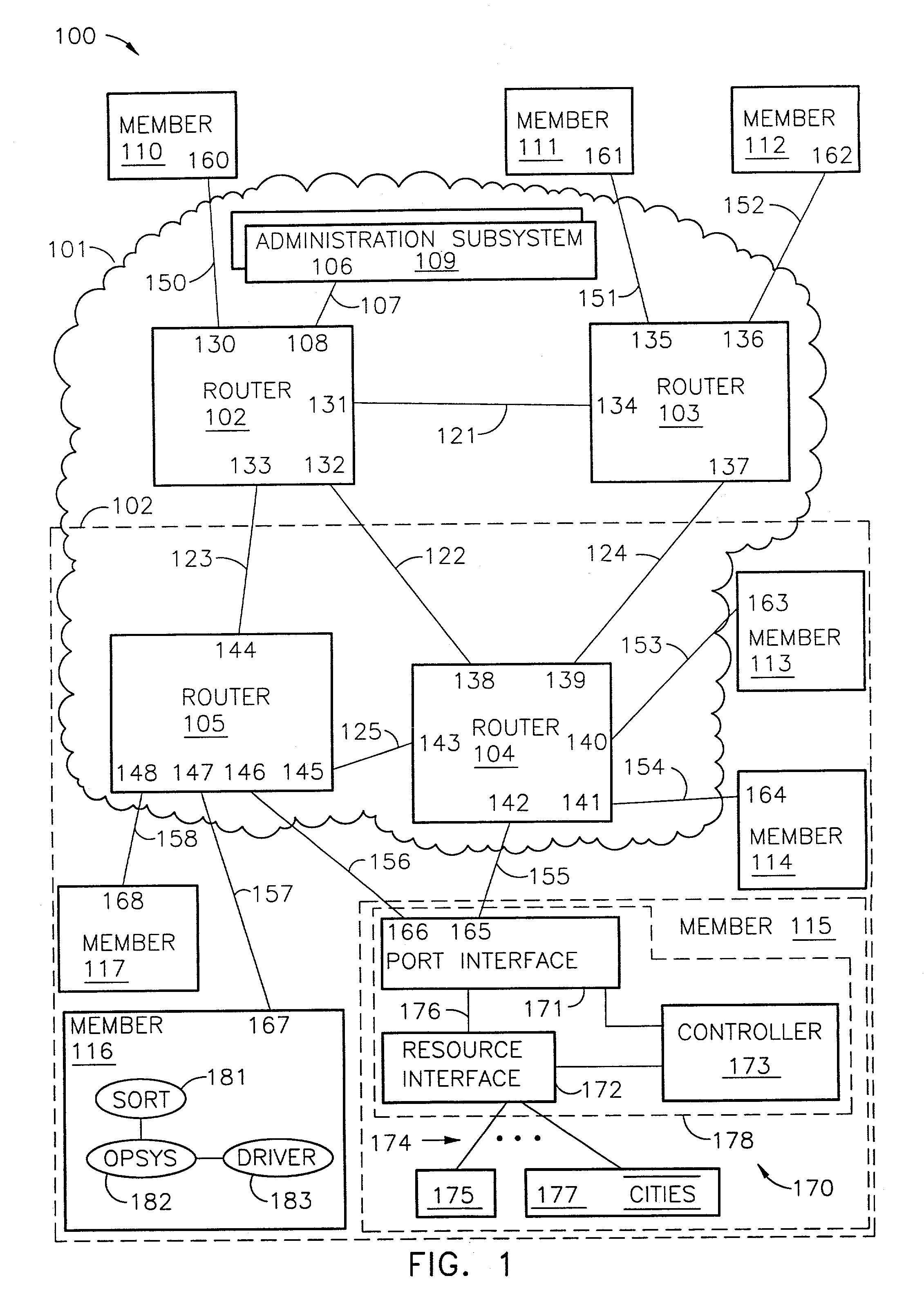
ActiveUS7200144B2Easy to operateImprove efficiency and reliabilityData switching by path configurationQuality of serviceDeficit round robin
A router for use in a network includes a scalable architecture and performs methods for implementing quality of service on a logical unit behind a network port; and for implementing storage virtualization. The architecture includes a managing processor, a supervising processor; and a plurality of routing processors coupled to a fabric. The managing processor has an in-band link to a routing processor. A routing processor receives a frame from the network, determines by parsing the frame, the protocol and logical unit number, and routes the frame to a queue according to a traffic class associated with the logical unit number in routing information prepared for the processors. An arbitration scheme empties the queue in accordance with a deficit round robin technique. If a routing processor detects the frame's destination is a virtual entity, and so is part of a virtual transaction, the router conducts a nonvirtual transaction in concert with the virtual transaction. The nonvirtual transaction accomplishes the intent of the virtual transaction but operates on an actual network port, for example, a storage device.
Owner:MARVELL ASIA PTE LTD
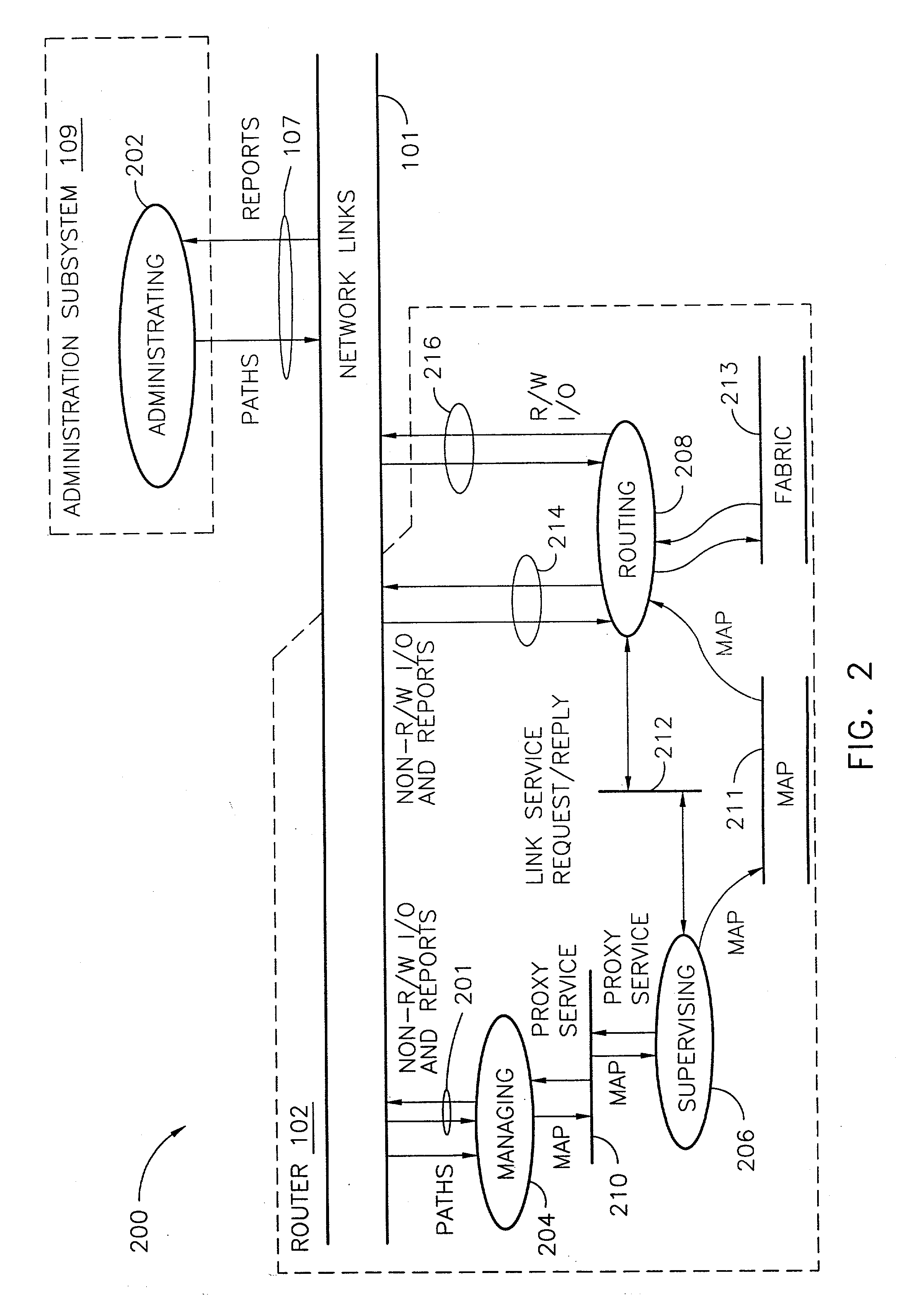
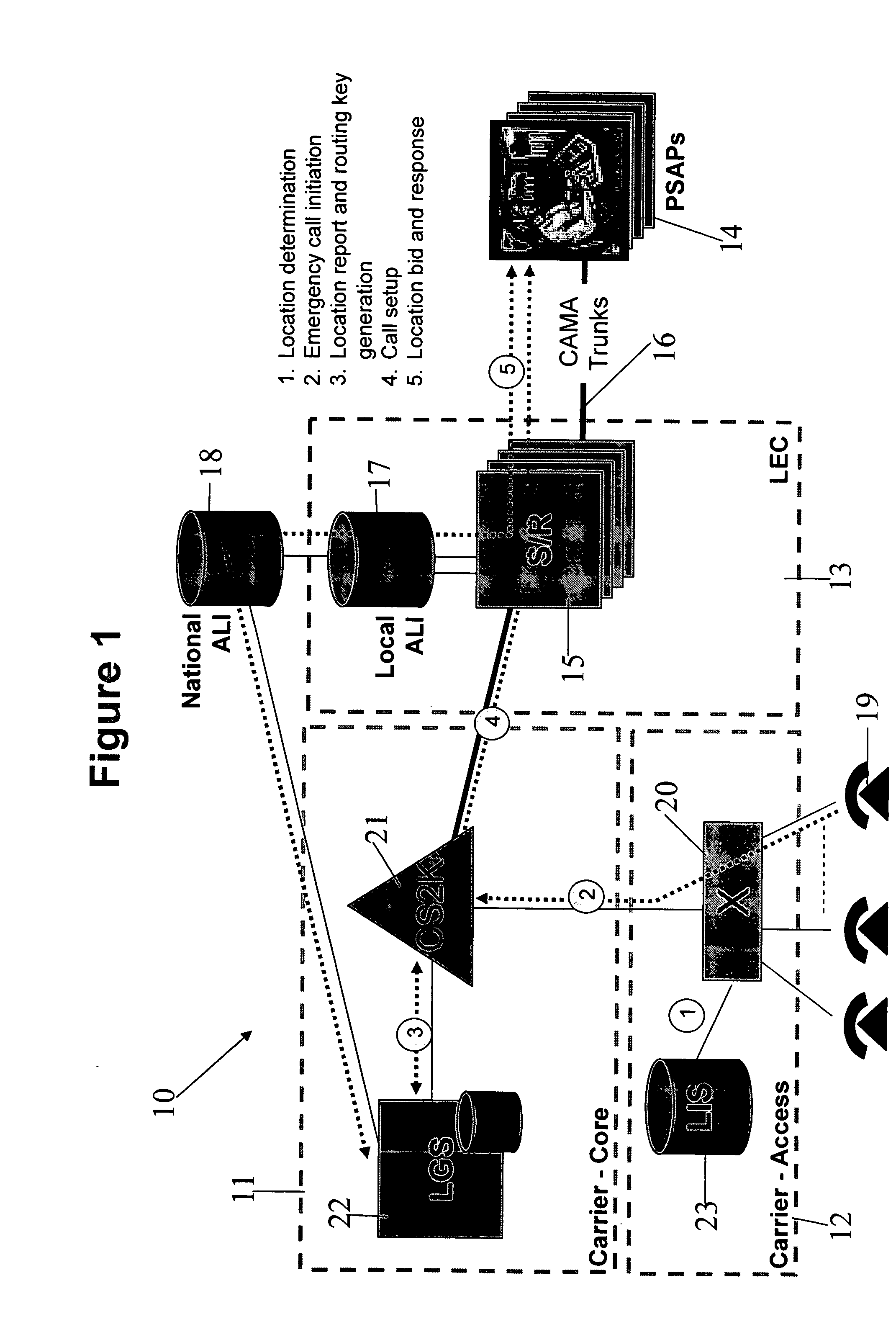
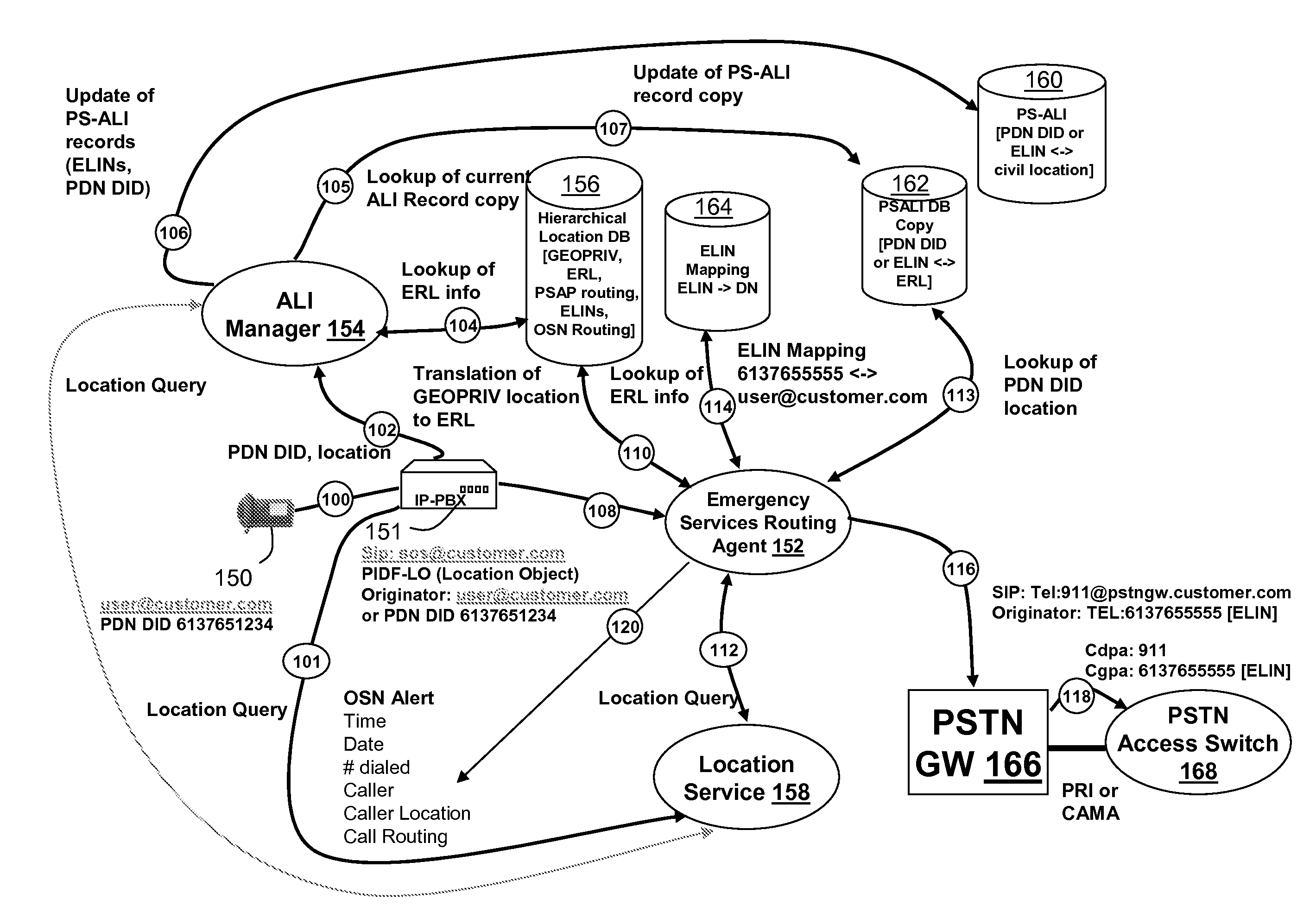
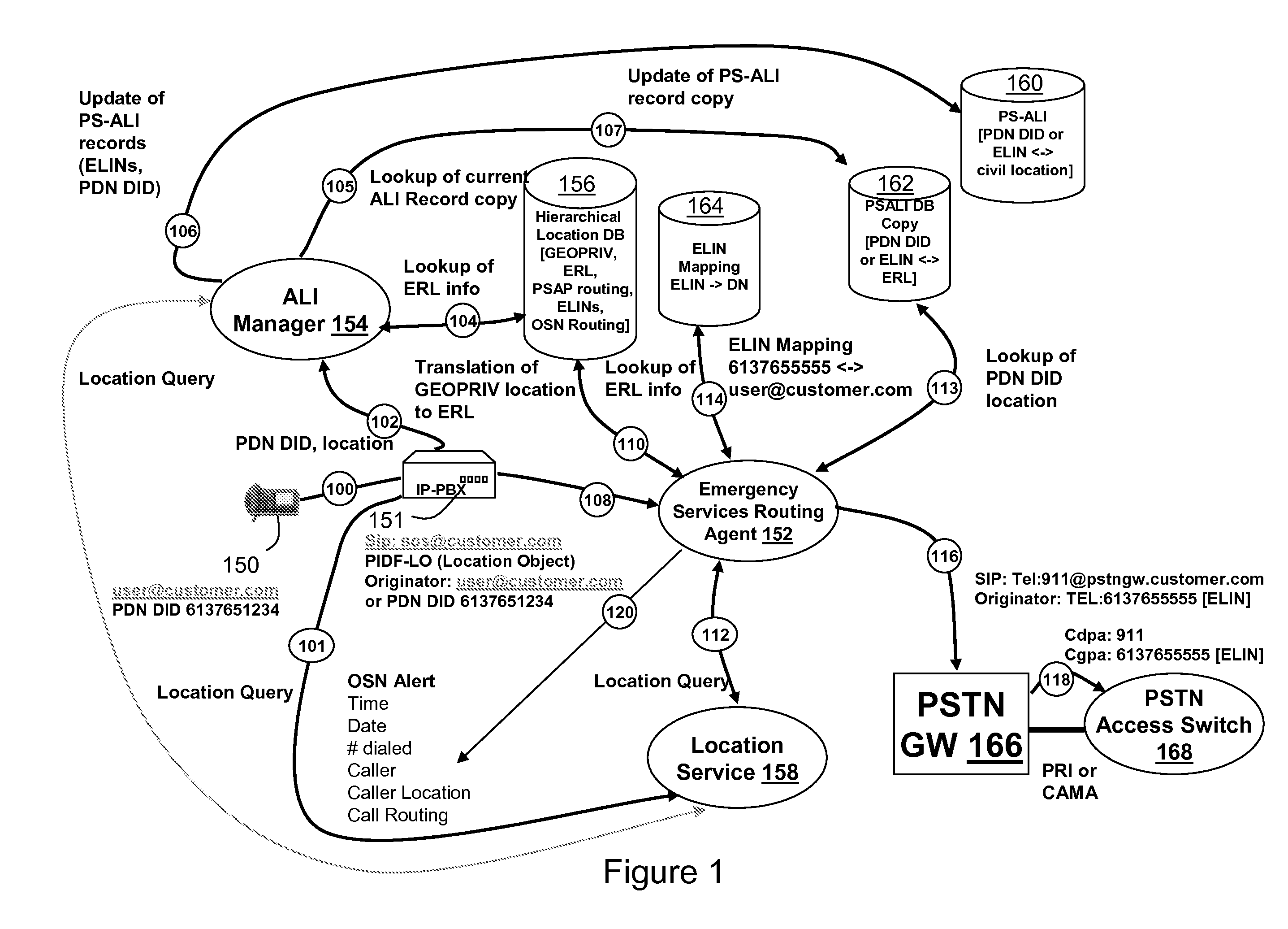
Determining the geographical location from which an emergency call originates in a packet-based communications network
ActiveUS20050190892A1Reduce needLow costSpecial service for subscribersNetwork connectionsCommunications systemSpeech sound
In order that emergency service vehicles can be dispatched to the correct destination promptly, accurate information about the location of the caller is needed. Another problem concerns routing emergency calls to the correct destination. For emergency calls a universal code is used such as 911 in North America and 112 in Europe. This universal code cannot be used to identify the destination of the call. These problems are particularly acute for nomadic communications systems such as voice over internet protocol communications networks. That is because user terminals change network location. These problems are solved by enabling the geographical location of the emergency caller to be determined by entities within a packet-based network without the need for modification of existing emergency services network infrastructure.
Owner:AVAYA INC
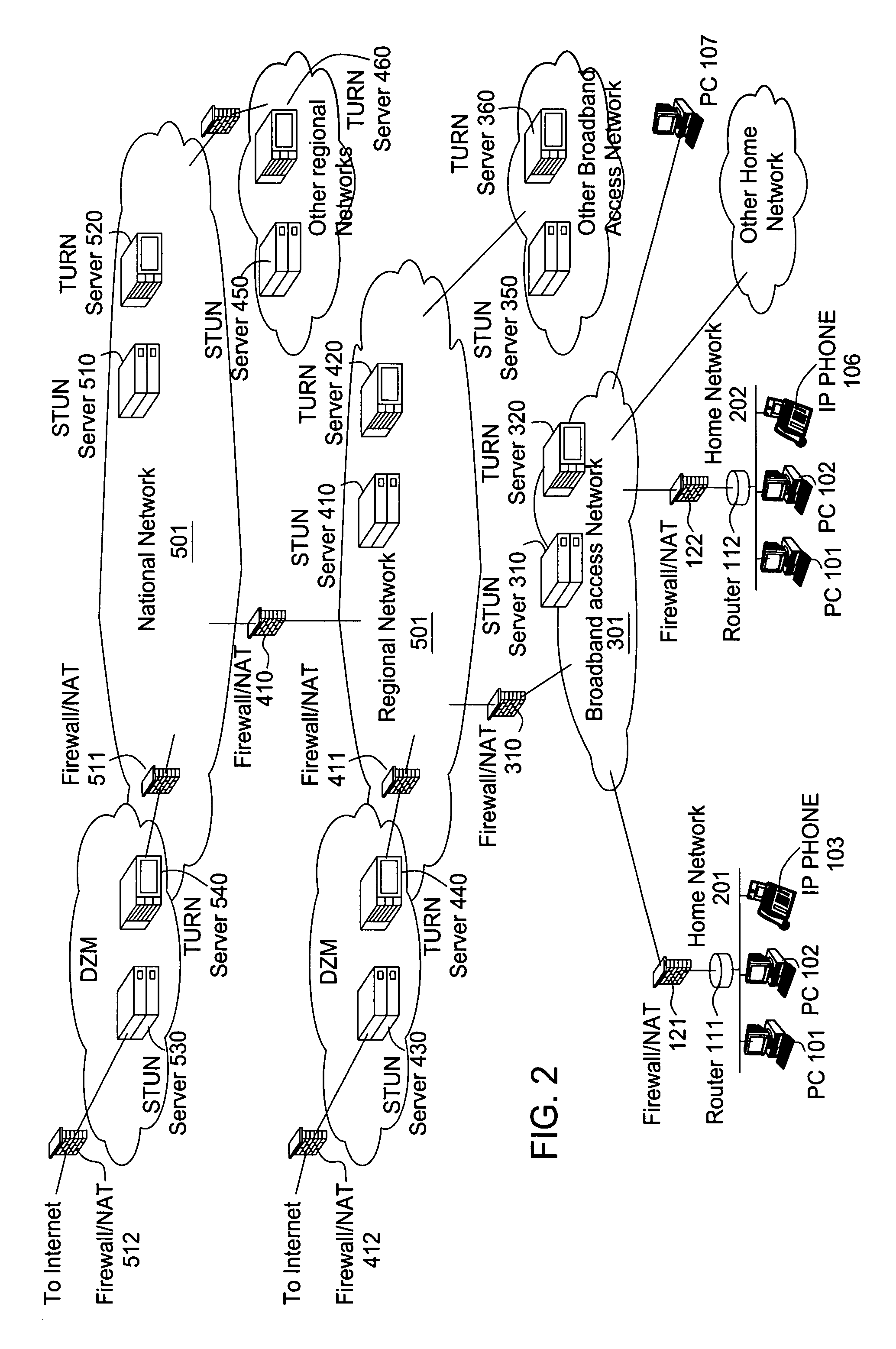
System and method to provide routing control of information over data networks
InactiveUS7222190B2Cost-effective useAccurate measurementError preventionTransmission systemsTraffic capacityData traffic
A system and a method for controlling routing of data over multiple networks. Accordingly, network users can define specific flow polices to ensure that a particular flow of data traffic maintains an acceptable level of performance, such as in terms of latency, loss, jitter, or an acceptable level usage that includes cost and bandwidth management across multiple networks.
Owner:INTERNAP HLDG LLC
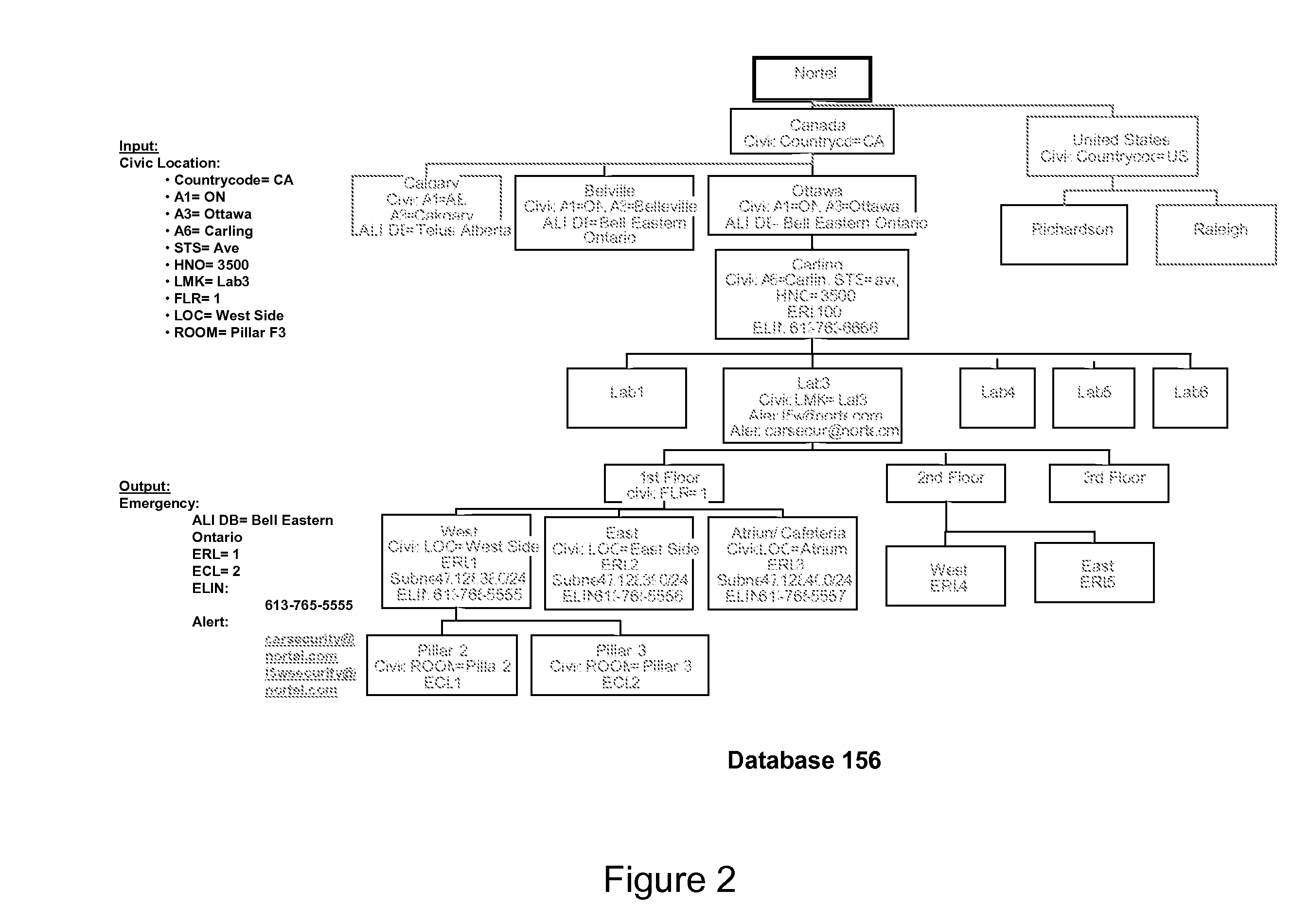
Adaption of emergency calls to the emergency services network based on caller location
ActiveUS20080037715A1Highly integratedEasy to carryTelephonic communicationComputer scienceEmergency situations
The invention includes a technique for integrating emergency calling for VoIP users with legacy emergency services to facilitate adapting to the evolving emergency services network and the services that are available in a given location. Generic location information provided by (or determined for) VoIP emergency callers, typically in civic or geodetic formats, is translated into Emergency Response Locations (ERLs) defining an area, such as an area within an enterprise premises, in which the caller is located. The translated location information is conveyed to the Public Safety Answering Point (PSAP) with the emergency call in for form of the ANI (Automatic Number Identification) or calling line identification number. An appropriate route / gateway is then selected to be used to reach the PSAP appropriate for the caller's location, and an emergency call notification to the appropriate local emergency response personnel is generated within the enterprise based on the caller's location.
Owner:AVAYA INC
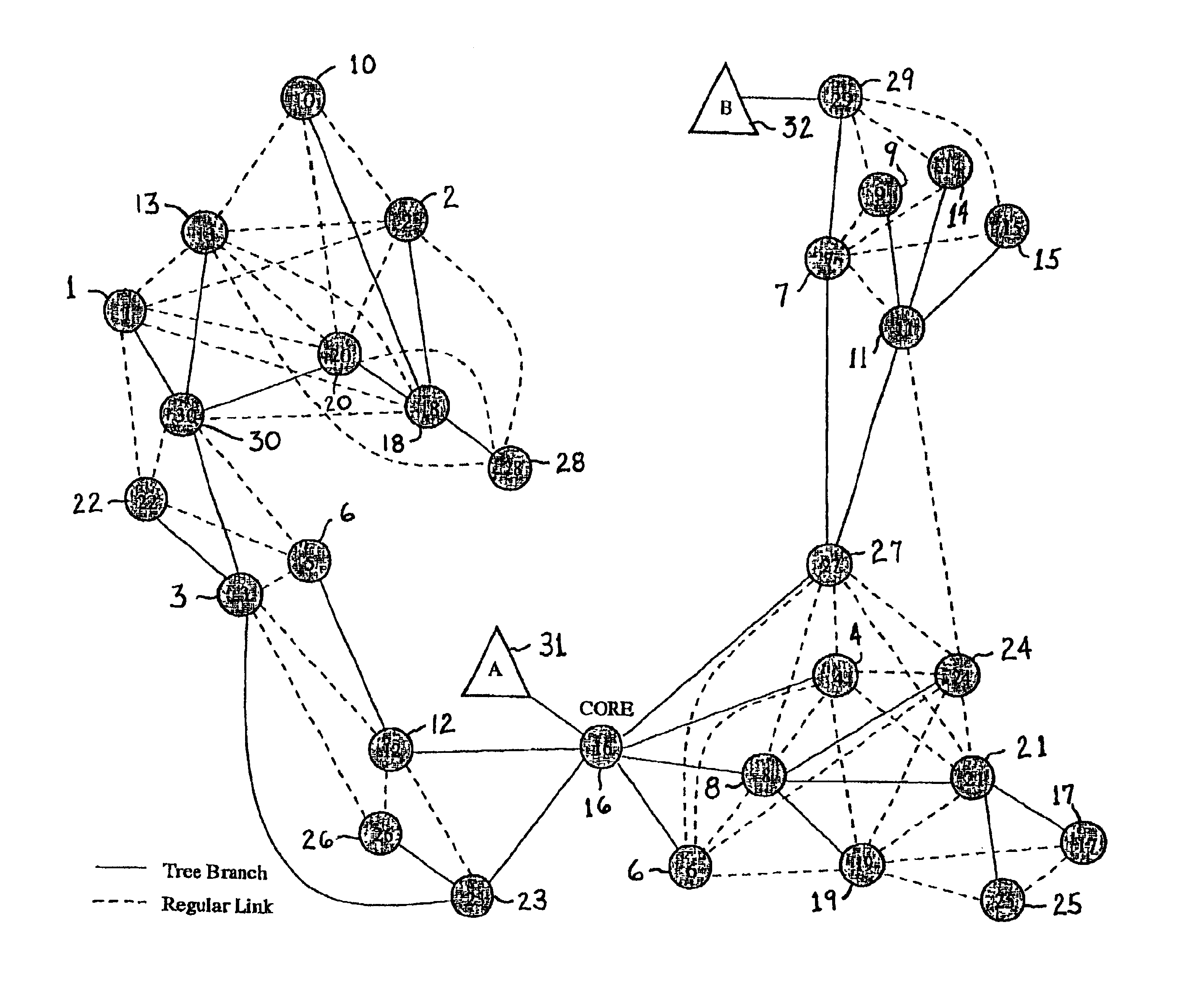
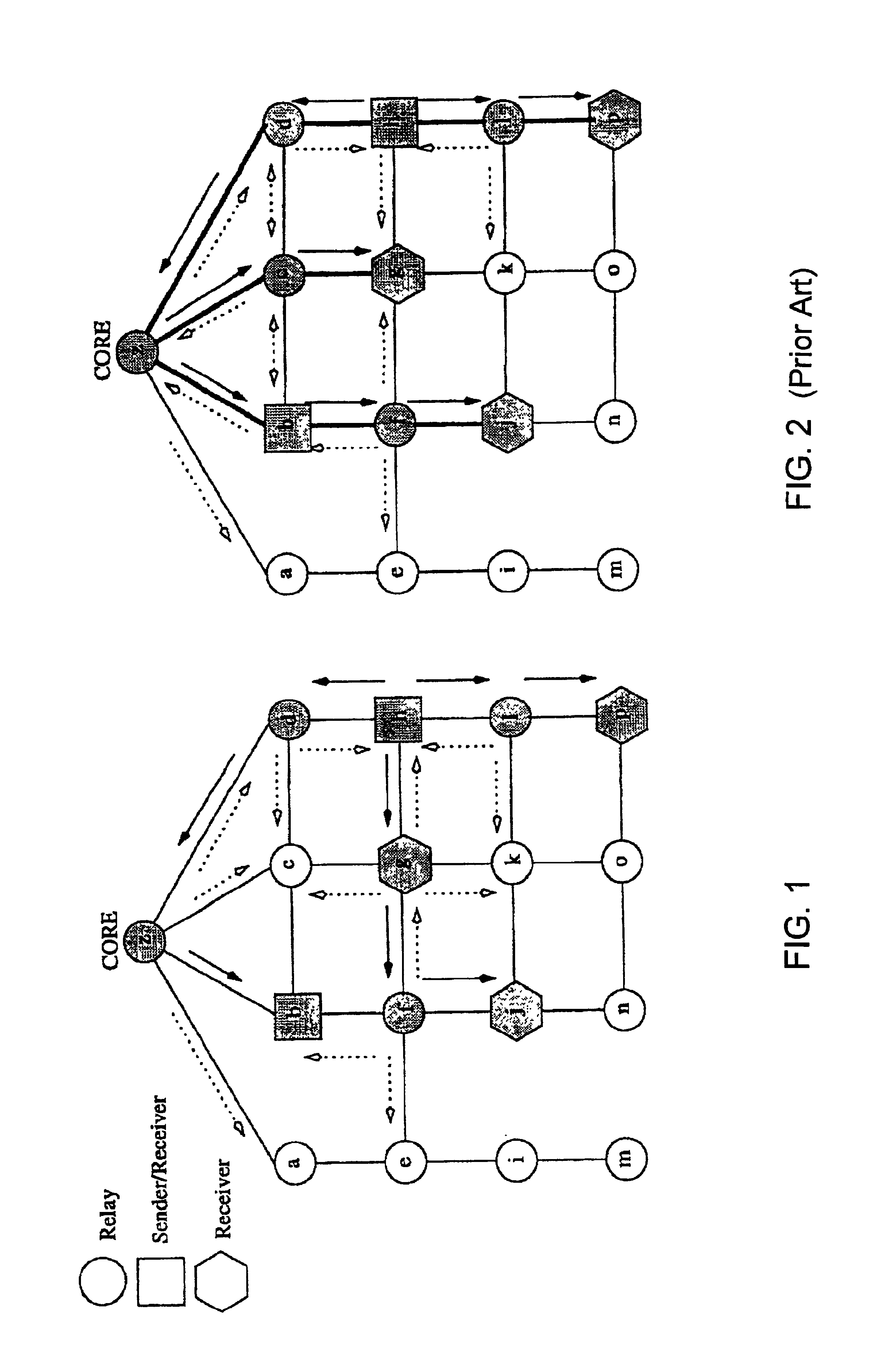
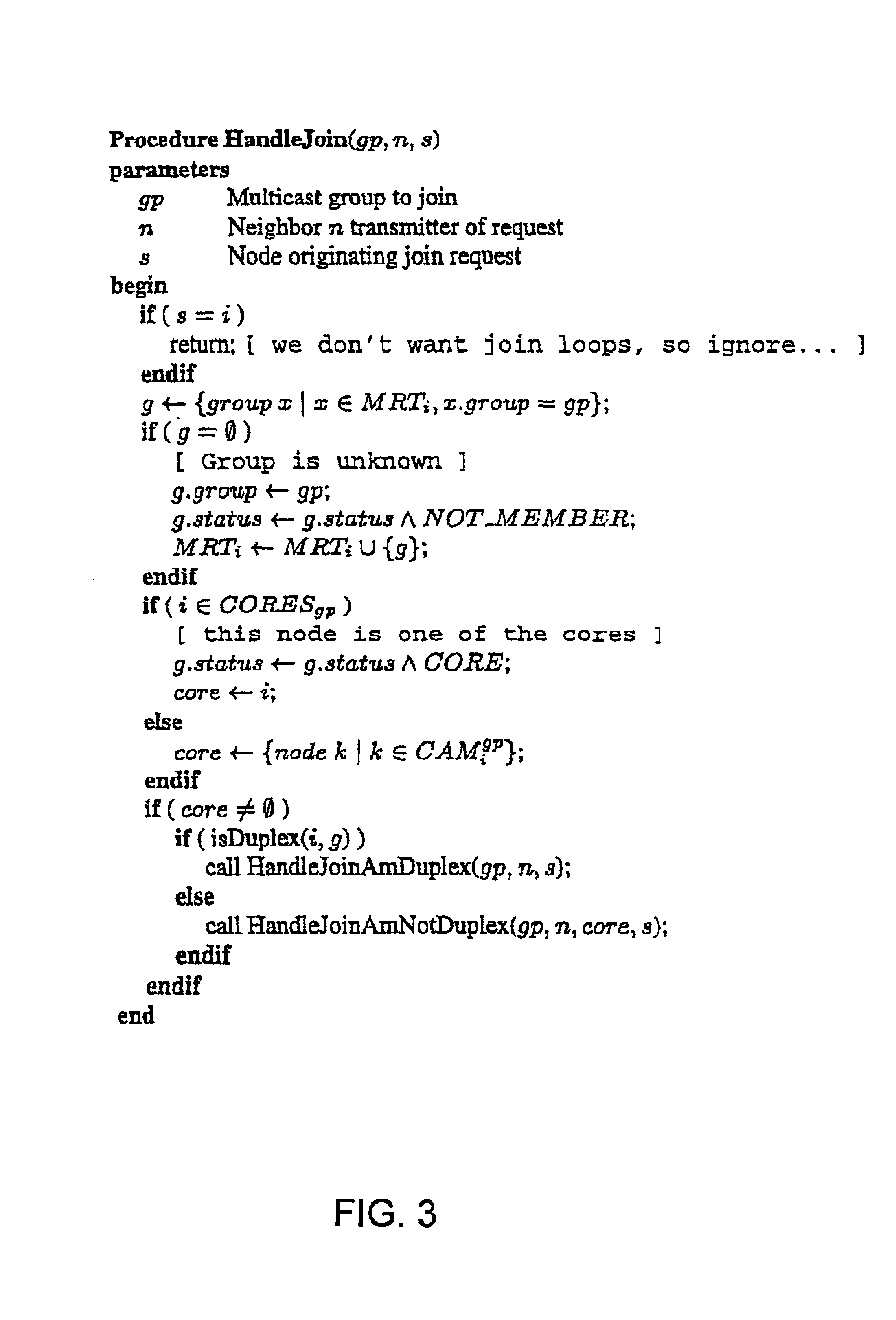
Core assisted mesh protocol for multicast routing in ad-hoc Networks
InactiveUS6917985B2Enrich connectivityStay connectedSpecial service provision for substationError preventionIP multicastBroadcasting
A method of providing multicast routing for use in ad hoc broadcast networks, such as wireless and mobile networks. The method is described within a protocol referred to as core-assisted mesh protocol, or CAMP. The method departs from traditional tree-structured multicast protocols and utilizes multicast meshes in which the network need not be flooded with control or data packets to establish routing paths. Each router configured for CAMP is capable of accepting unique packets arriving from any neighbor in the mesh, wherein packets are forwarded along reverse shortest paths to the receiver. Multiple cores may be defined for a group wherein the loss of a single core does not prevent packet flow. Routers for sender-only hosts are allowed to join the multicast mesh in simplex mode, and in certain cases may join without the sending of a join request.
Owner:RGT UNIV OF CALIFORNIA
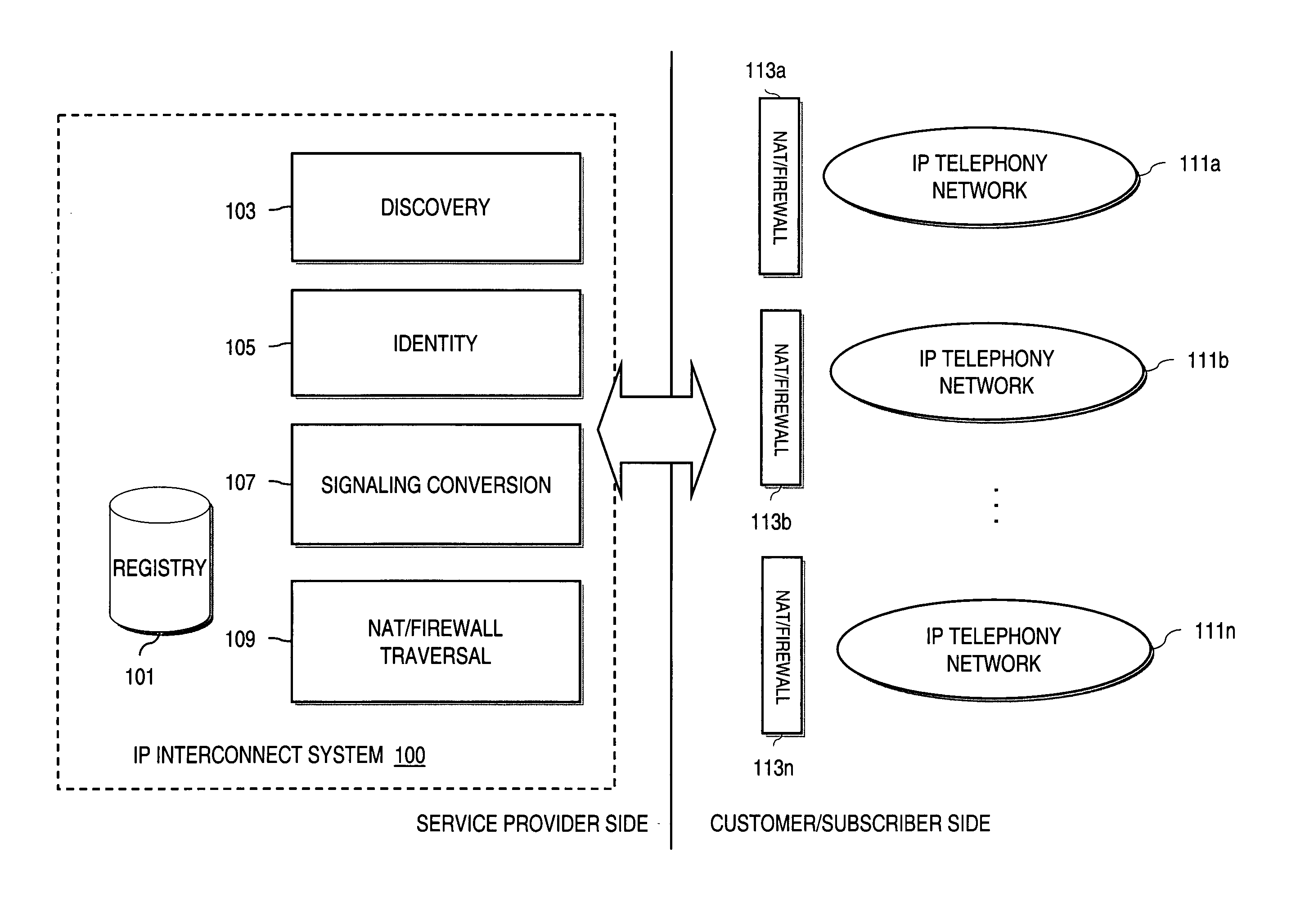
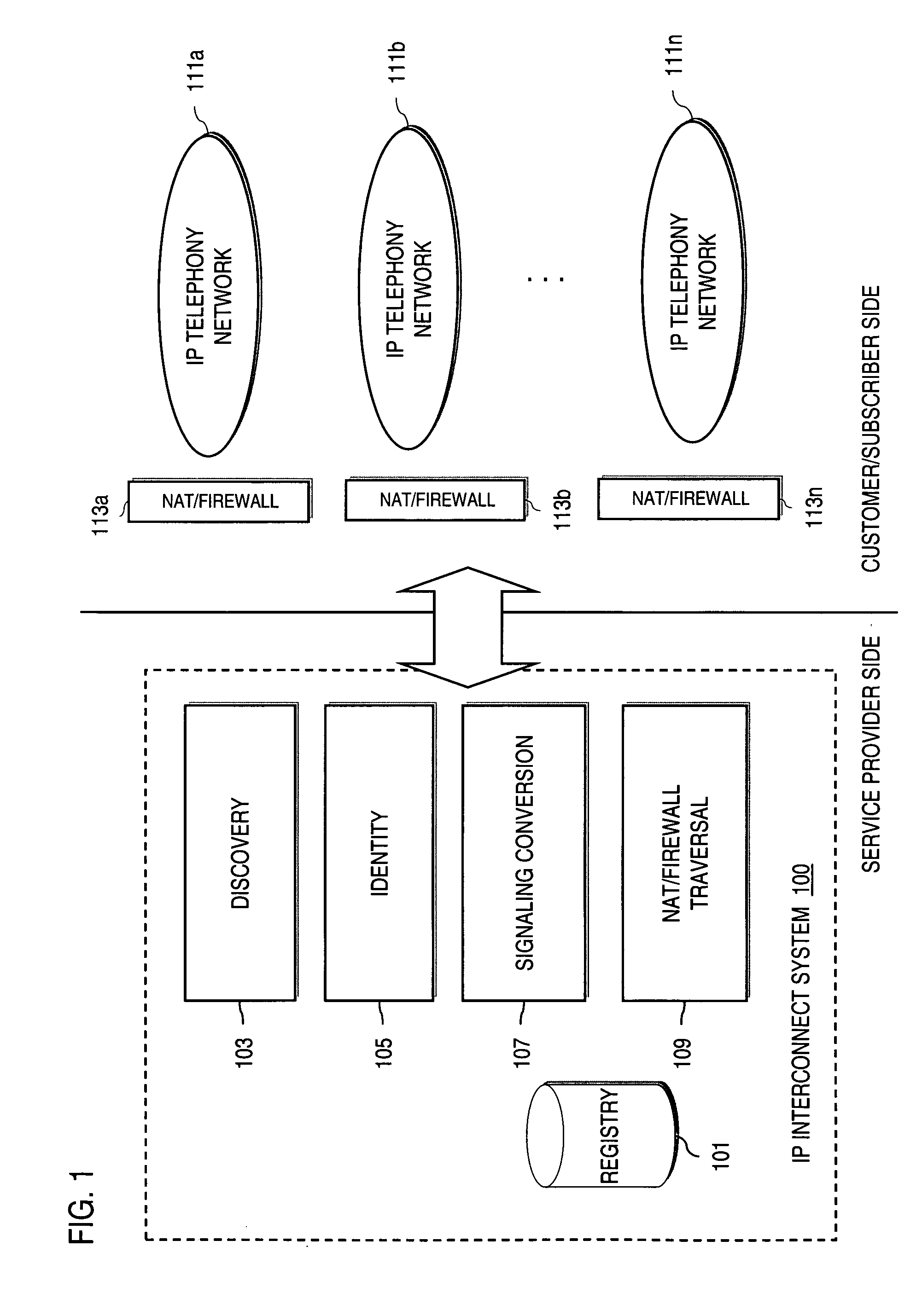
Method and system for providing voice over IP managed services utilizing a centralized data store
ActiveUS20070036143A1Interconnection arrangementsData switching by path configurationVoice over IPData memory
An approach provides interdomain traversal to support packetized voice transmissions. A centralized data store, maintained by a service provider, stores one or more user identifiers and an associated directory number. The centralized data store also stores routing information including one or more communication paths corresponding to the user identifier, wherein the routing information includes a data path or a circuit-switched path for establishing a call to the user. In response to a request for establishing the call to the directory number, the data store retrieves the routing information for use to establish the call.
Owner:VERIZON PATENT & LICENSING INC
Integrated customer web station for web based call management
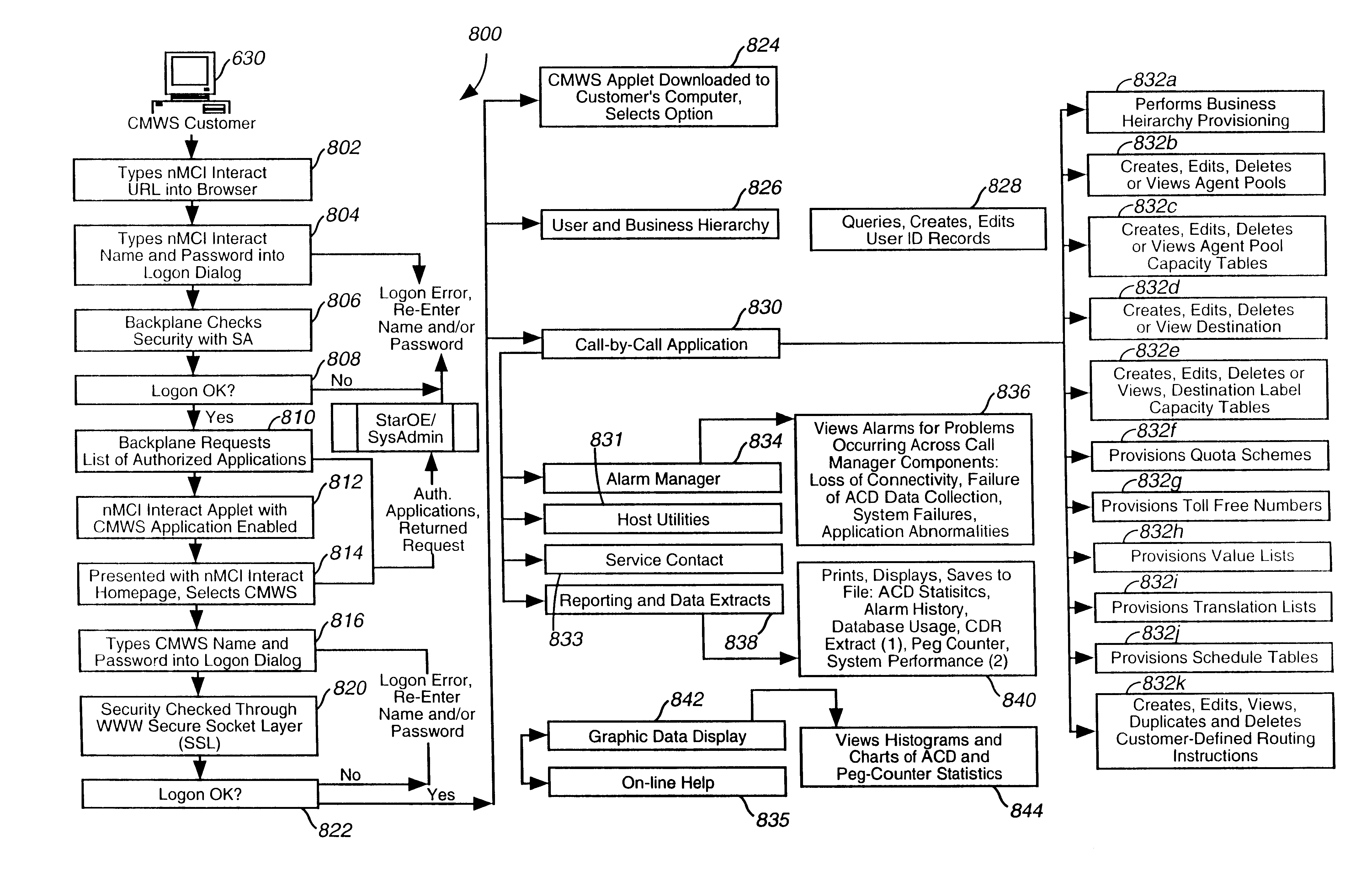
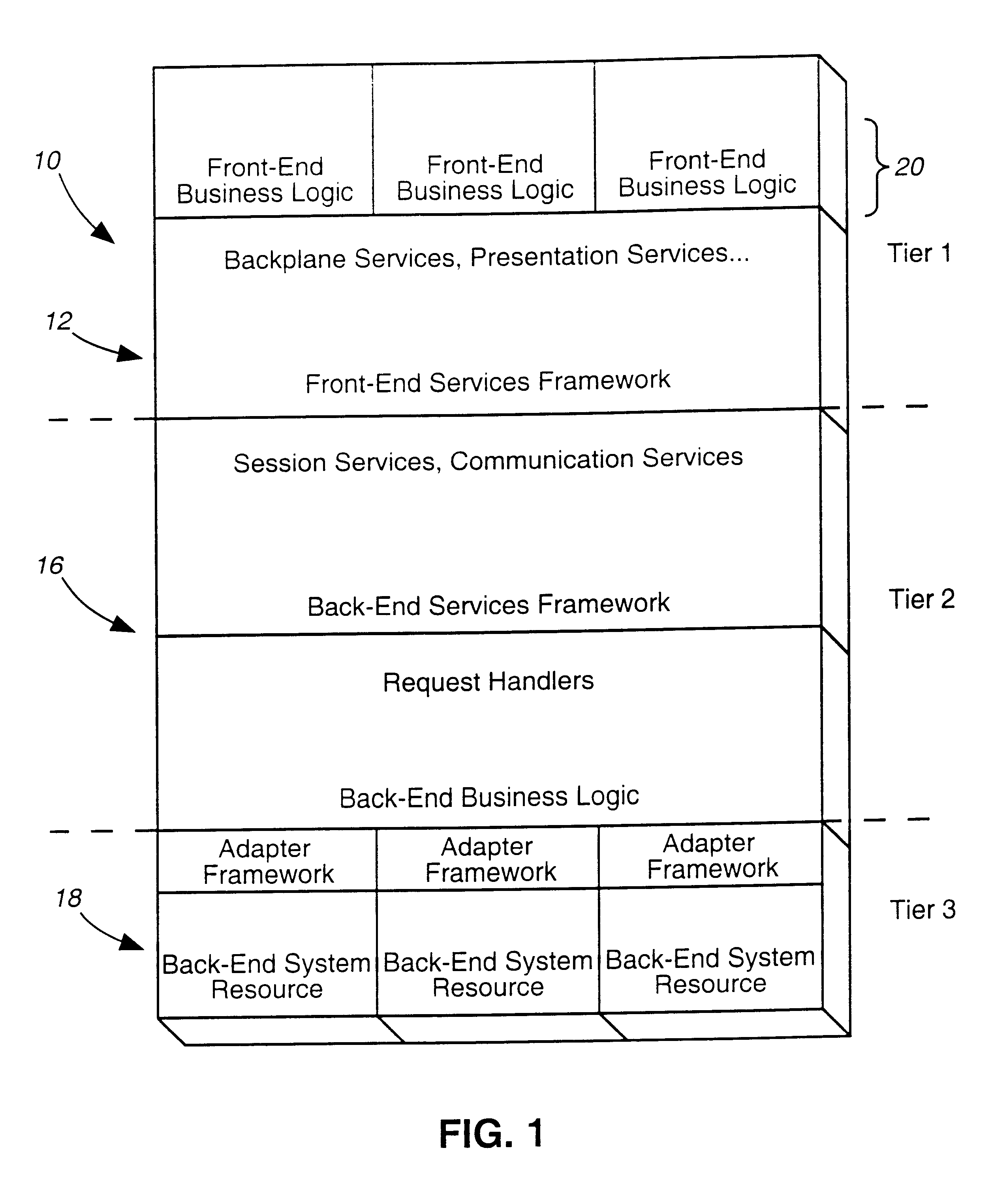
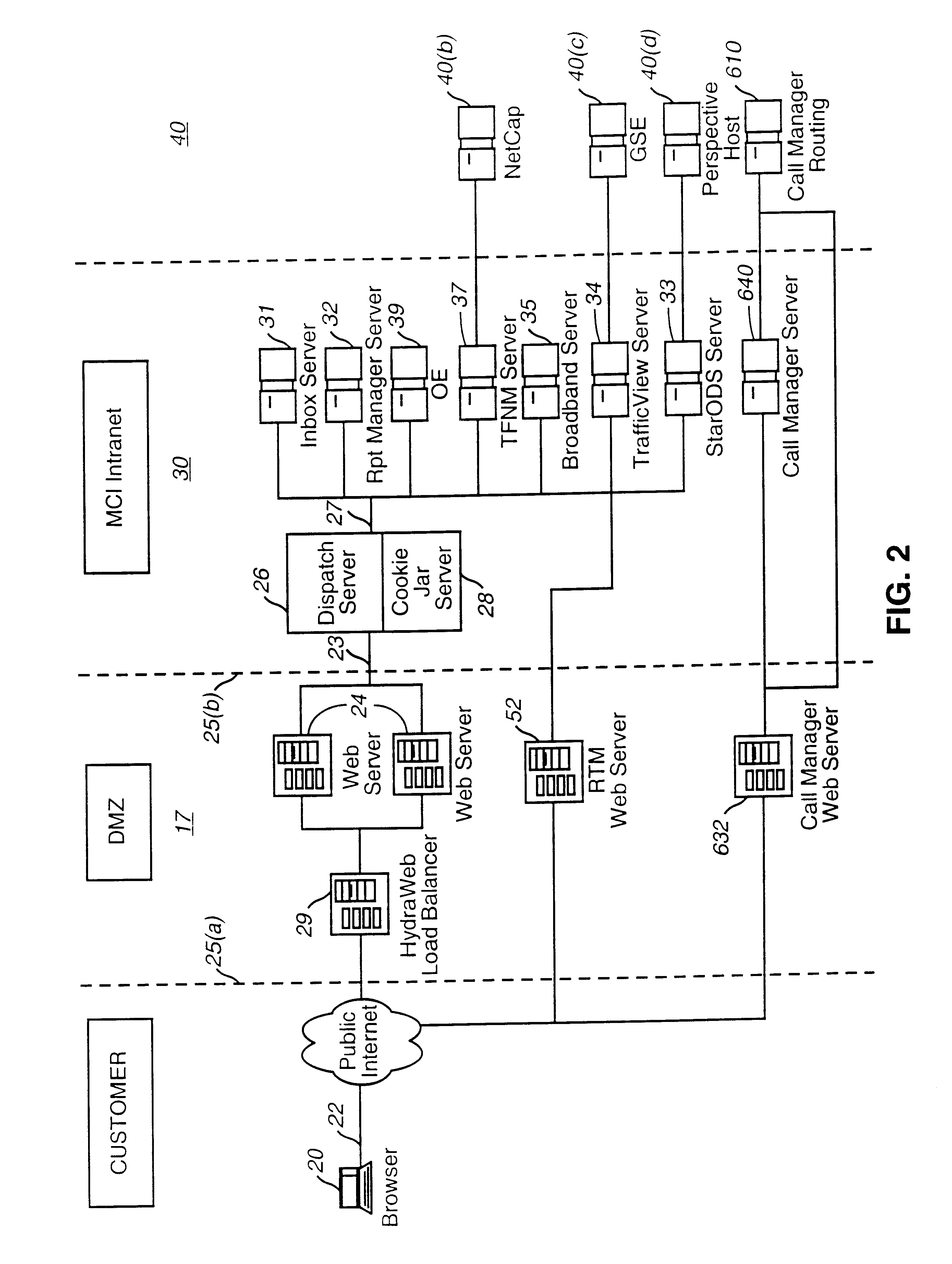
A Web-based call routing management workstation application which allows authorized customers to control toll free routing and monitor call center status. An architecture including one or more web servers located in a firewalled demilitarized zone (DMZ) as communications medium between the customer workstations at the customer sites and the enterprise back-end applications providing the call routing management services, provides a secure infrastructure for accessing the enterprise applications via the otherwise insecure public Internet. The present invention enables creation and management of call by call routing rules by a customer with a workstation having an Internet access and a supported Web browser. The customized rules may be tested and / or debugged via the Web-enabled workstation, using a debugger / tester which runs the routing rules under a simulated environment. In addition, customers may provision hierarchies for their business; create, modify or delete agent pools; manipulate capacity tables; and define quota schemes, value lists and schedule tables, all at the customer site via the Web-enabled workstation. The present invention also enables the customers to view near real-time displays of call center ACD statistics and peg counts based on routing rules, as well as, run provisioning and statistical reports on provisioning and statistical data and also to extract the data for further analysis. Additionally, the present invention supports foreign language and branding features on a graphical user interface. An infrastructure is provided which enables secure initiation, acquisition, and presentation of the call manager functionalities to customers from any computer workstation having a web browser and located anywhere in the world.
Owner:VERIZON PATENT & LICENSING INC
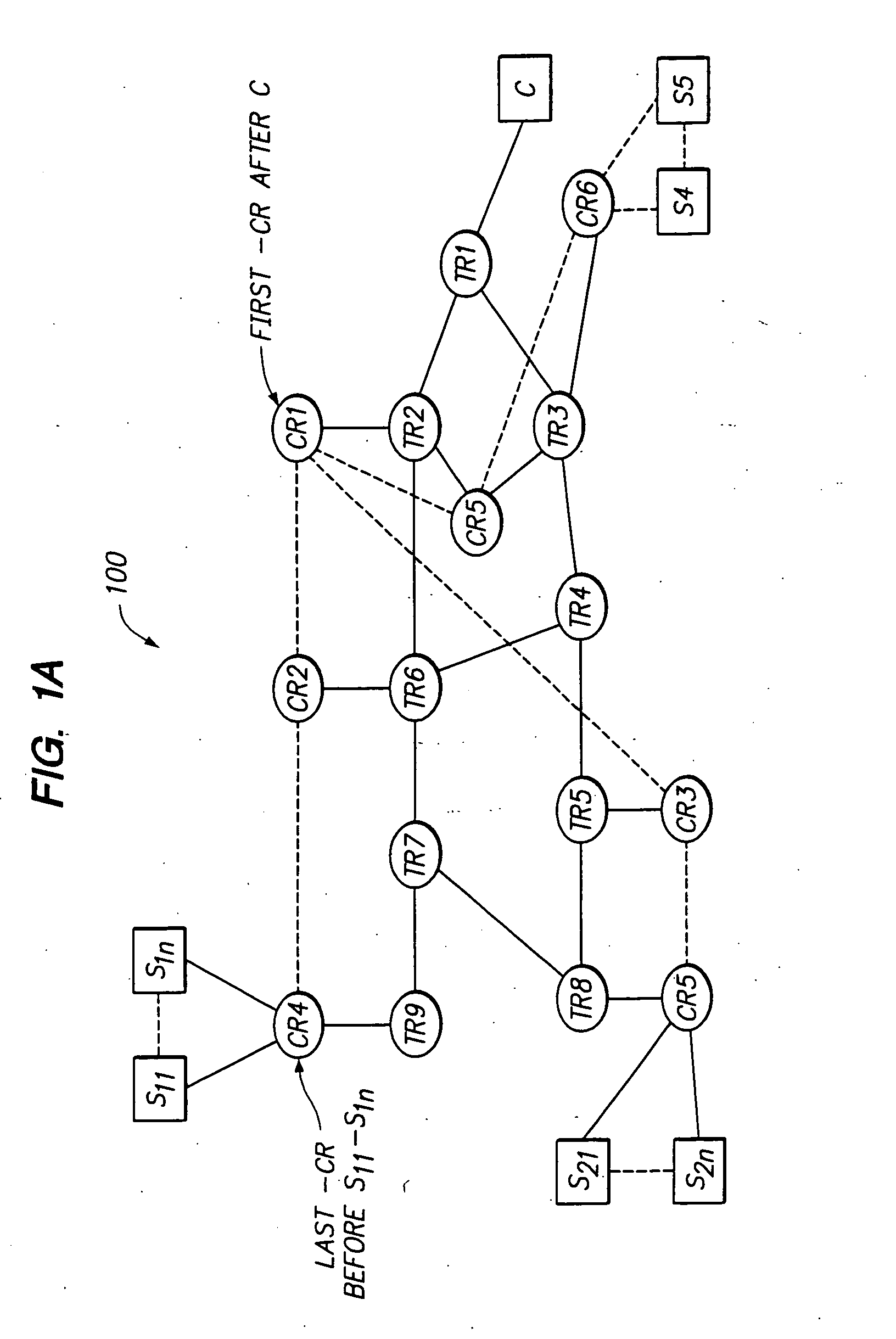
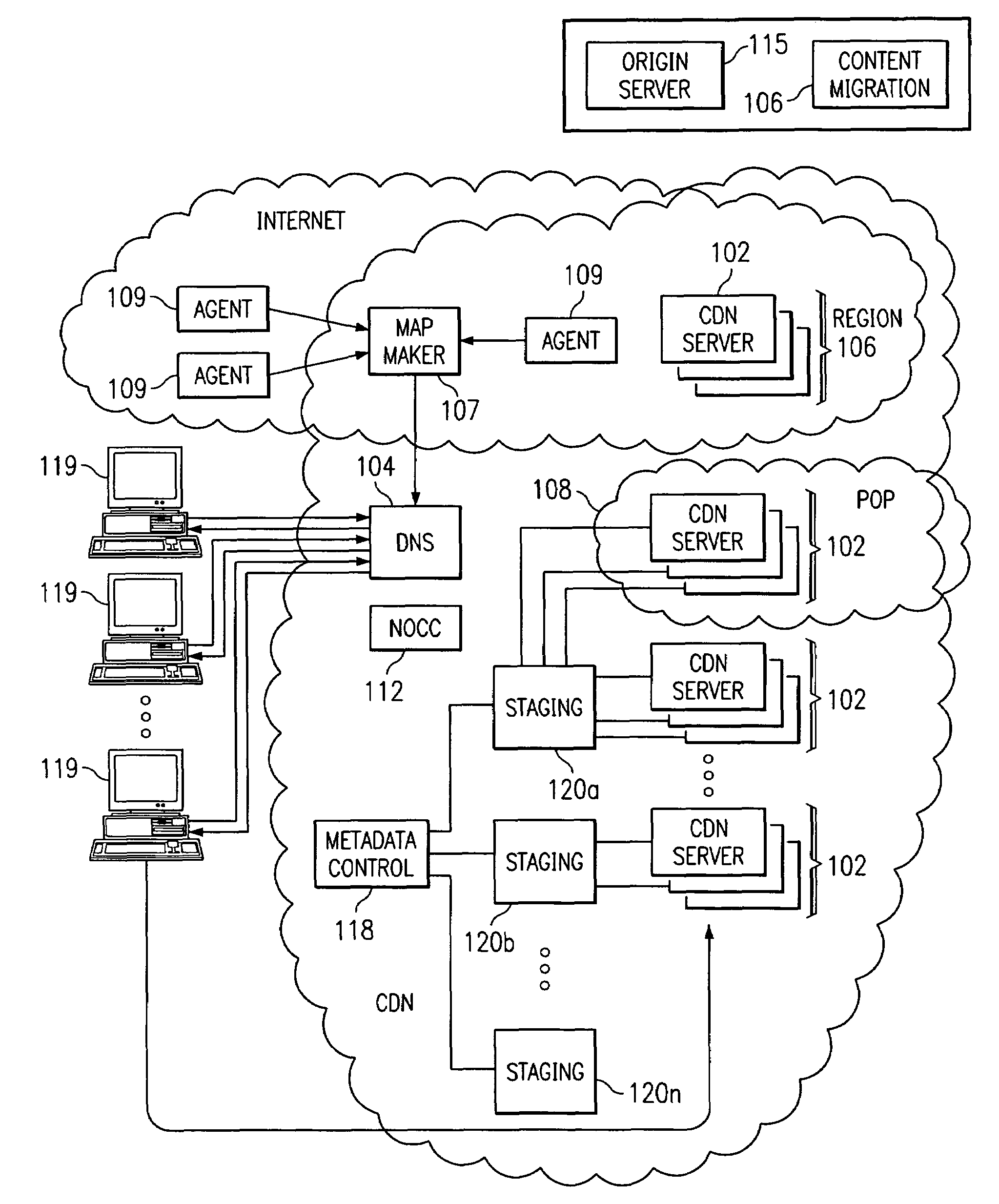
Content delivery network map generation using passive measurement data
ActiveUS7007089B2Easy mappingImprove subsequent routingDigital computer detailsData switching networksGeneration processRouting decision
A routing method operative in a content delivery network (CDN) where the CDN includes a request routing mechanism for routing clients to subsets of edge servers within the CDN. According to the routing method, TCP connection data statistics are collected are edge servers located within a CDN region. The TCP connection data statistics are collected as connections are established between requesting clients and the CDN region and requests are serviced by those edge servers. Periodically, e.g., daily, the connection data statistics are provdied from the edge servers in a region back to the request routing mechanism. The TCP connection data statistics are then used by the request routing mechanism in subsequent routing decisions and, in particular, in the map generation processes. Thus, for example, the TCP connection data may be used to determine whether a given quality of service is being obtained by routing requesting clients to the CDN region. If not, the request routing mechanism generates a map that directs requesting clients away from the CDN region for a given time period or until the quality of service improves.
Owner:AKAMAI TECH INC
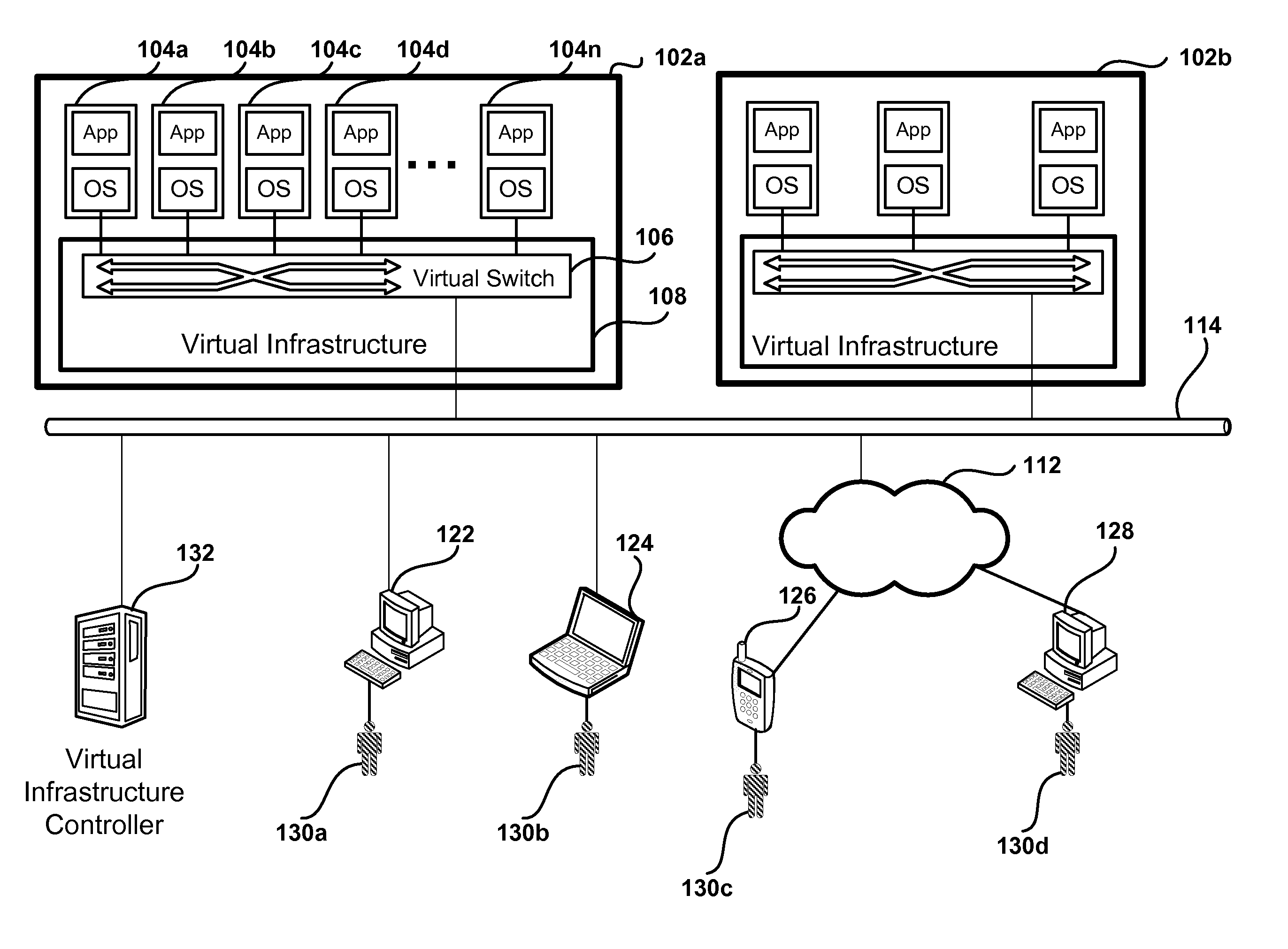
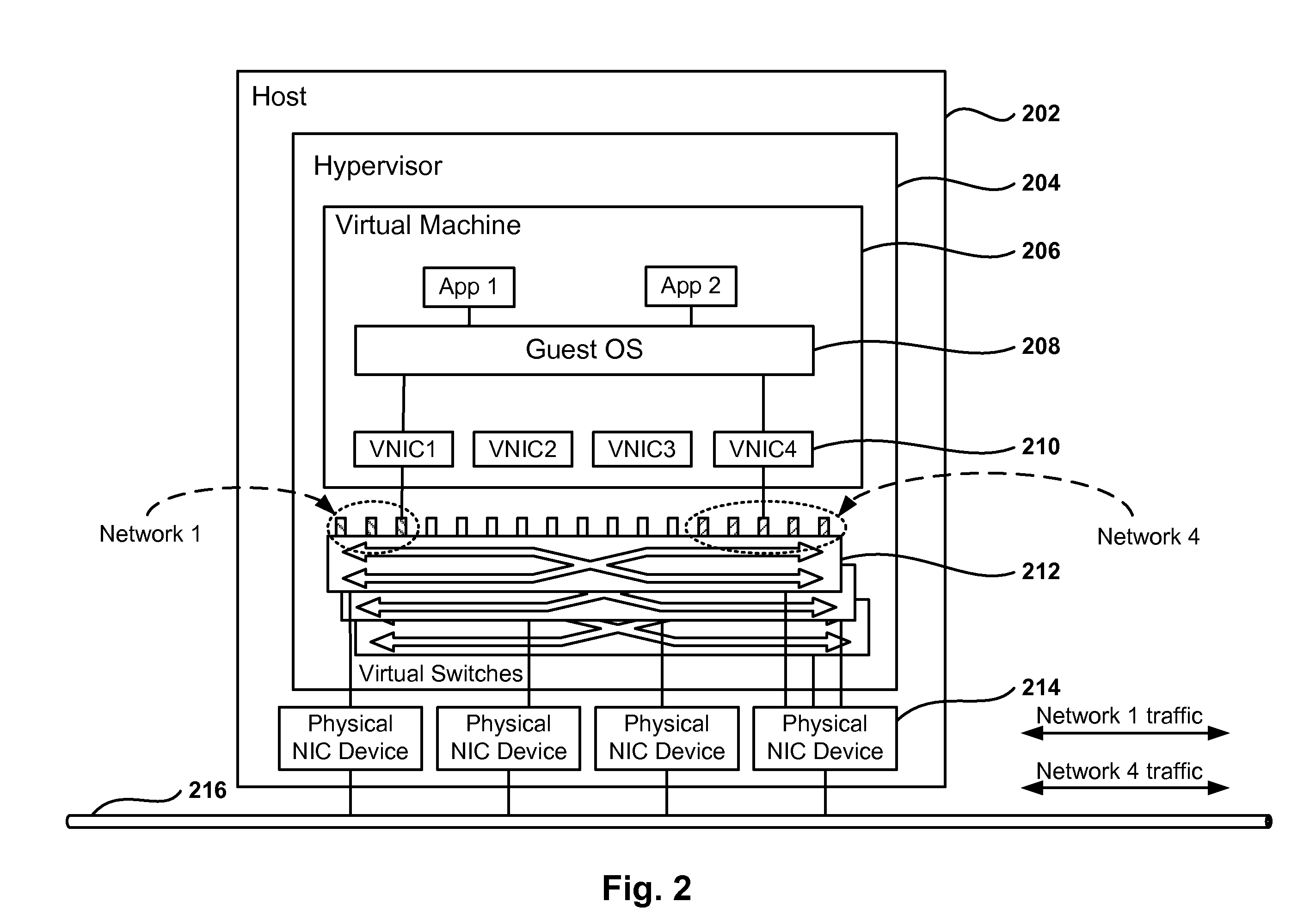
Private Allocated Networks Over Shared Communications Infrastructure
Methods and systems for implementing private allocated networks in a virtual infrastructure are presented. One method operation creates virtual switches in one or more hosts in the virtual infrastructure. Each port in the virtual switches is associated with a private allocated network (PAN) from a group of possible PANs. In one embodiment, one or more PANs share the same physical media for data transmission. The intranet traffic within each PAN is not visible to nodes that are not connected to the each PAN. In another operation, the method defines addressing mode tables for the intranet traffic within each PAN. The entries in the addressing mode tables define addressing functions for routing the intranet traffic between the virtual switches, and different types of addressing functions are supported by the virtual switches.
Owner:NICIRA
Method for optimal path selection in traversal of packets through network address translators
InactiveUS20050259637A1Reduce administrative overheadFast convergenceMultiplex system selection arrangementsError preventionNetwork addressNetwork address translation
Reduction of administrative overhead in maintaining network information, rapid convergence on an optimal routing path through the data network, and utilization of only required network resources are realized by a novel method for establishing a call path between network users. The method is based upon deployment of a network information server that stores network topology information and that is addressable by each end user. In this method, the network information server receives a request to establish a call path. The request identifies at least the calling party. In response to the request, the network information server determines a network traversal between the calling party and a root network wherein the network traversal includes call path information about the sub-networks between the calling party and the root network. The request for establishing a call path can also identify the called party. Based on the calling and called party identification, the network information server also determines a second network traversal between the called party and the root network. The second network traversal is sent to either the calling party or the called party or to both the calling and called parties. The server can determine an intersection of the traversals and send the intersection information to the parties. The intersection information is known as a merge point and represents an optimal call path between the parties.
Owner:ALCATEL-LUCENT USA INC
Methods and apparatus for improved 911 support for VoIP service
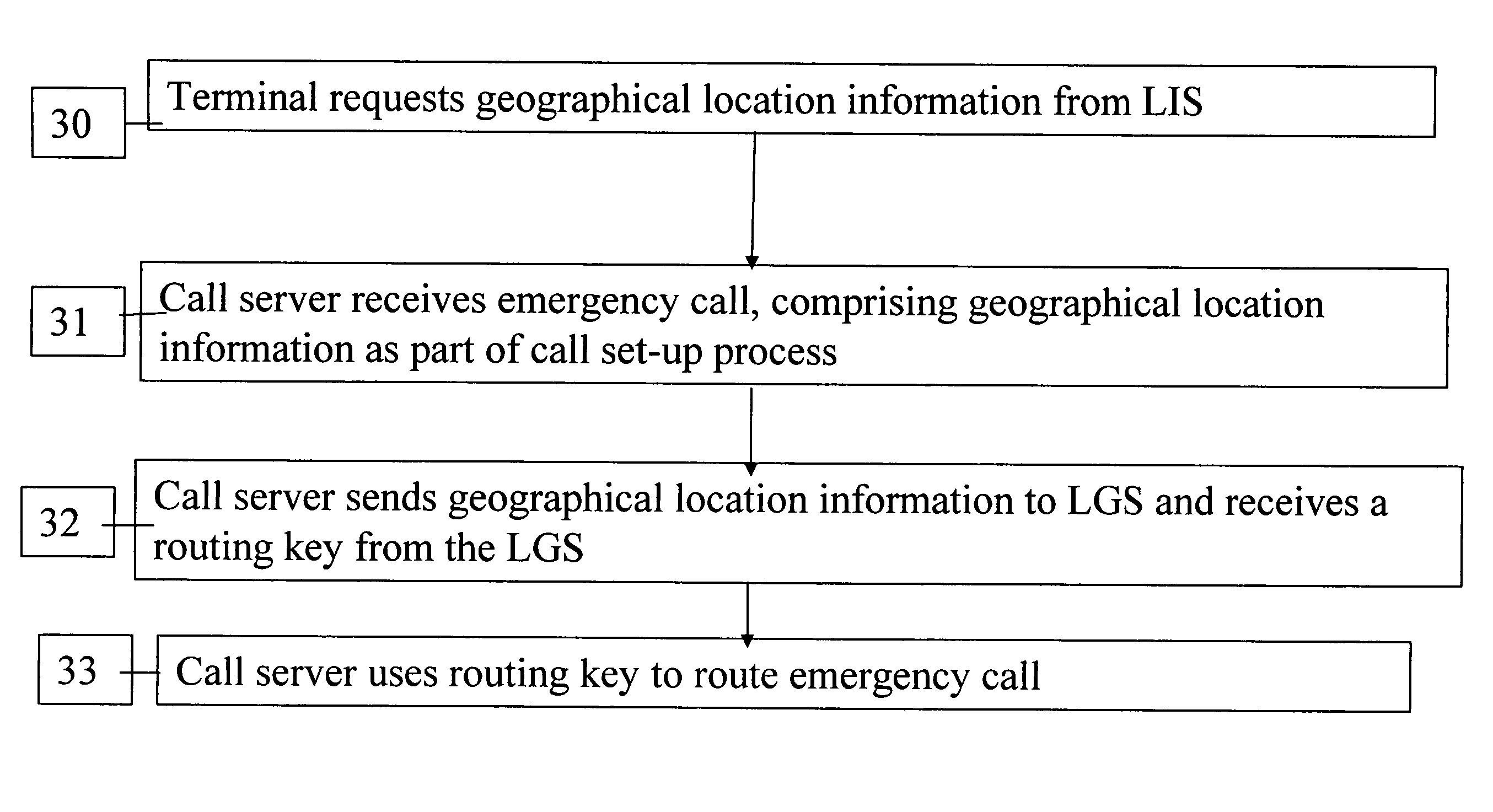
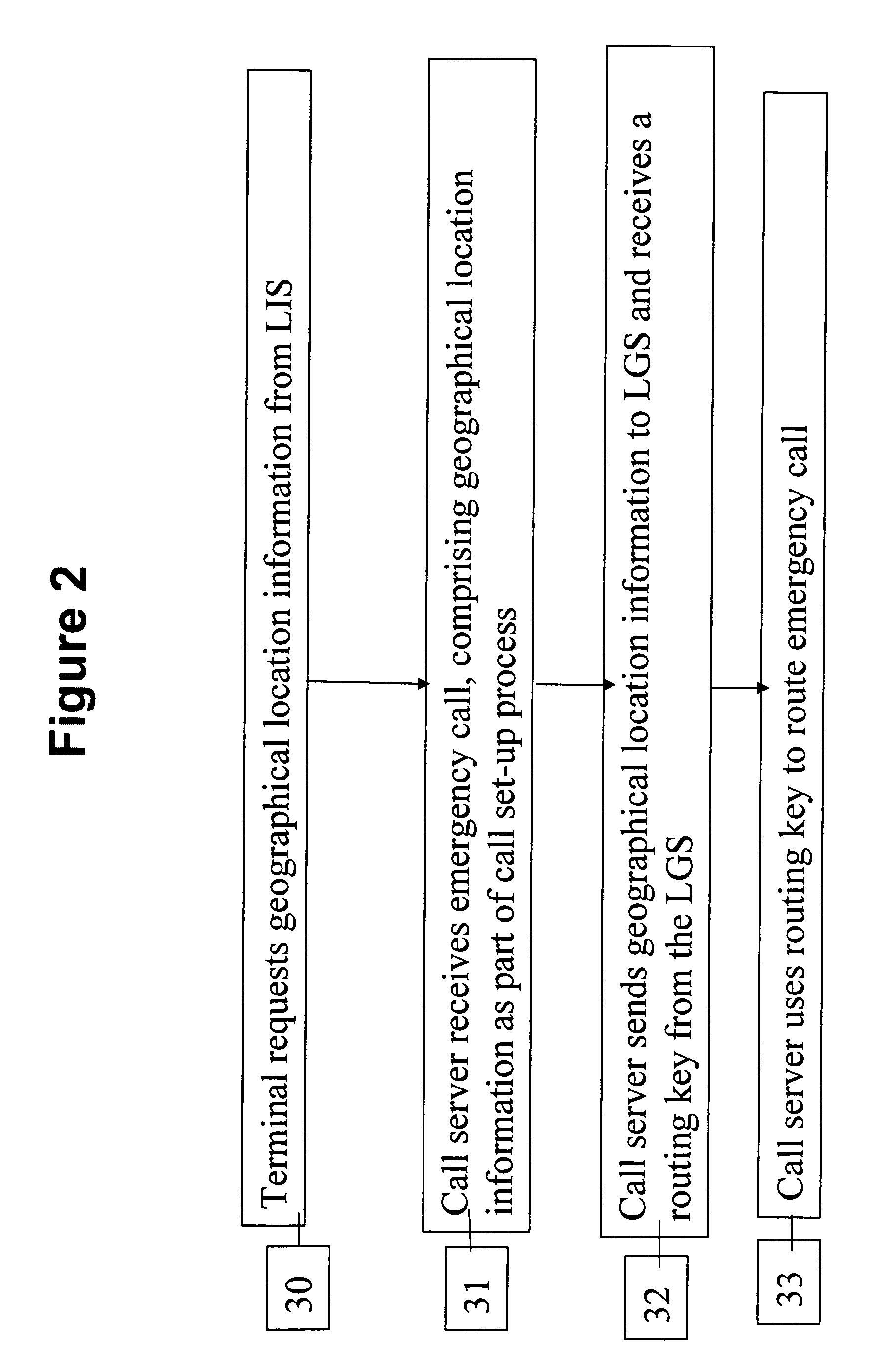
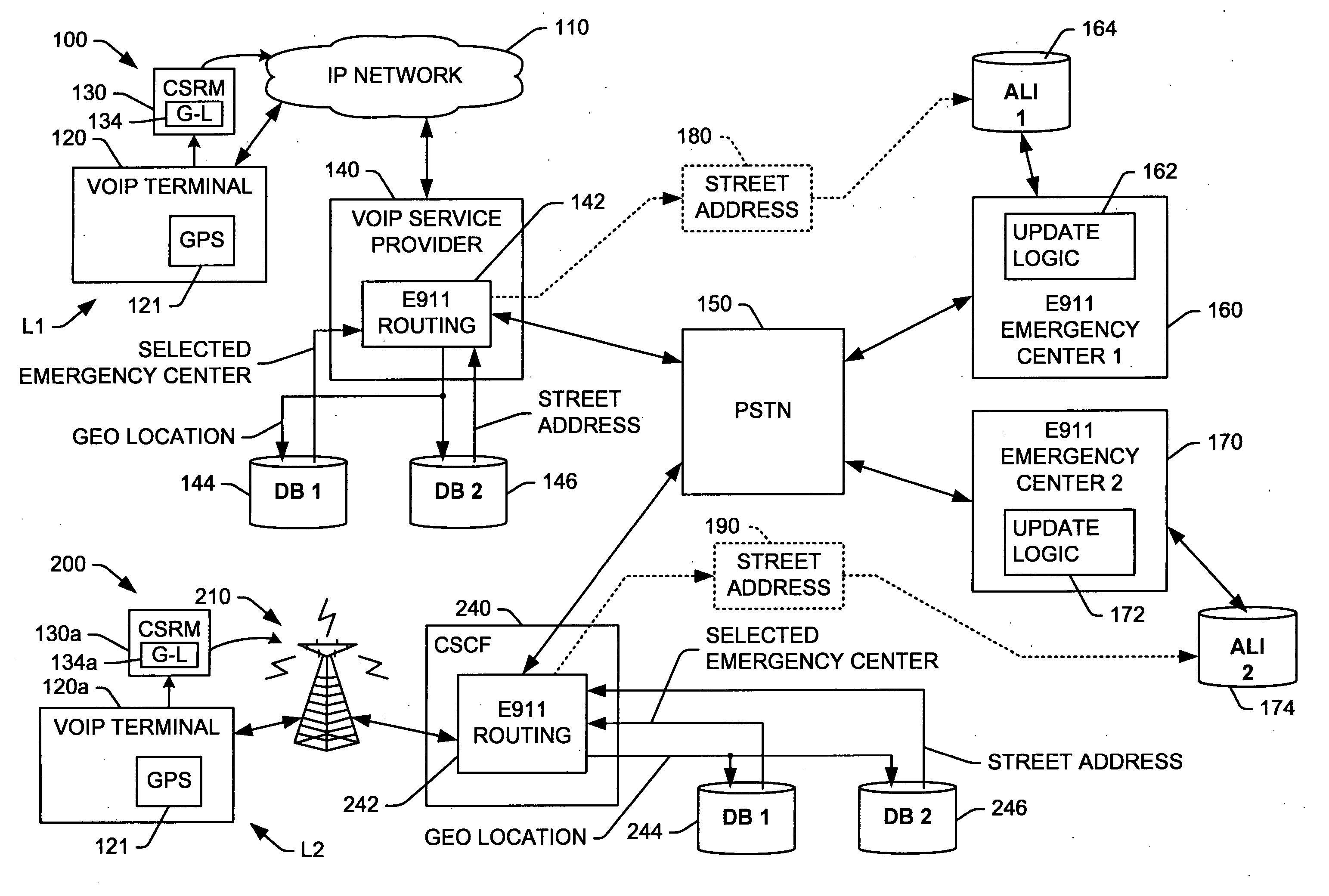
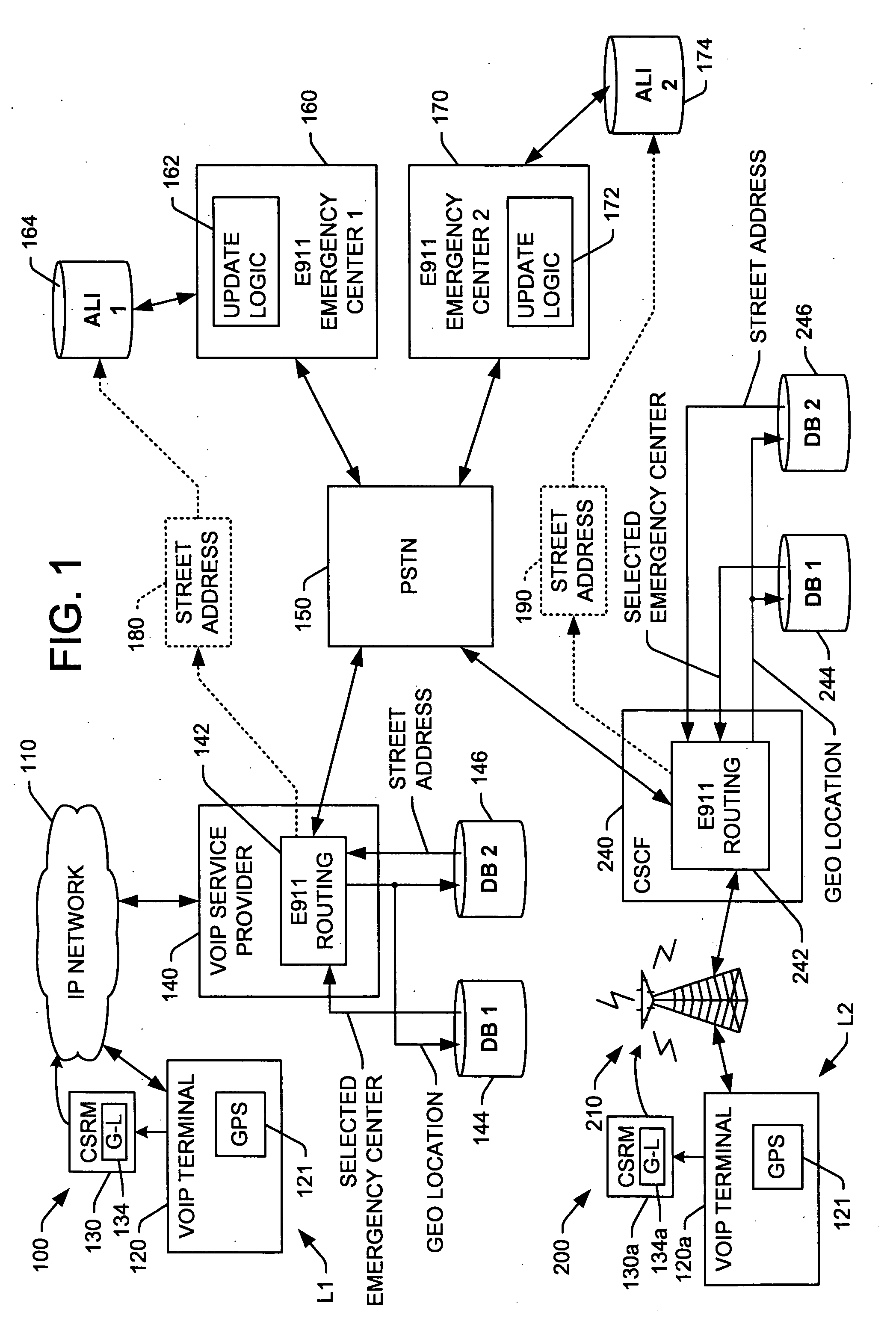
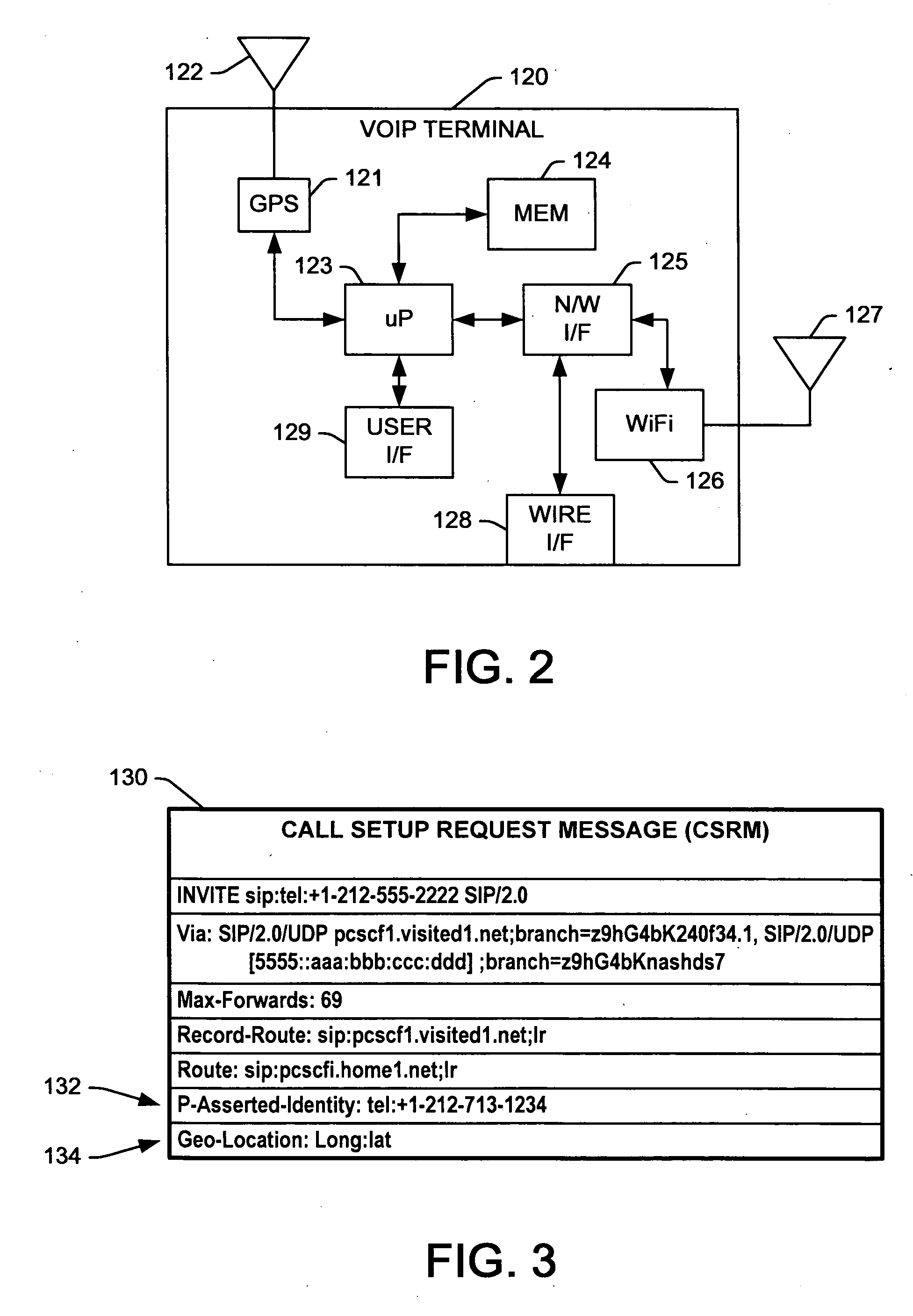
InactiveUS20060293024A1Emergency connection handlingConnection managementTerminal equipmentComputer science
Systems and methods are presented for routing 911 or other emergency calls from VoIP terminal equipment, wherein the terminal includes GPS or other means to obtain geographic location information for the current location when a 911 call is initiated, and the terminal includes the geographic location information in a call setup request message to the service provider. Routing logic receives the set request and uses the geographic information to search one or more databases to identify the proper emergency service center to which the call is routed, and also the street address corresponding to the caller's current location. The emergency call is then routed to the selected service center, where the call may be delivered with the street address or the street address information is updated in an ALI database of the 911 system by the routing logic before or during call delivery to ensure the emergency service operator or dispatcher knows where to direct emergency services.
Owner:LUCENT TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com