Patents
Literature
517 results about "Cyber operations" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Cyber Operations is an interdisciplinary major that covers the entire scope of cyberspace and related operations, both technical and non-technical. As such, the Cyber Operations major provides a basic foundation in computer architecture, programming, data structures, networks, internet, database systems,...
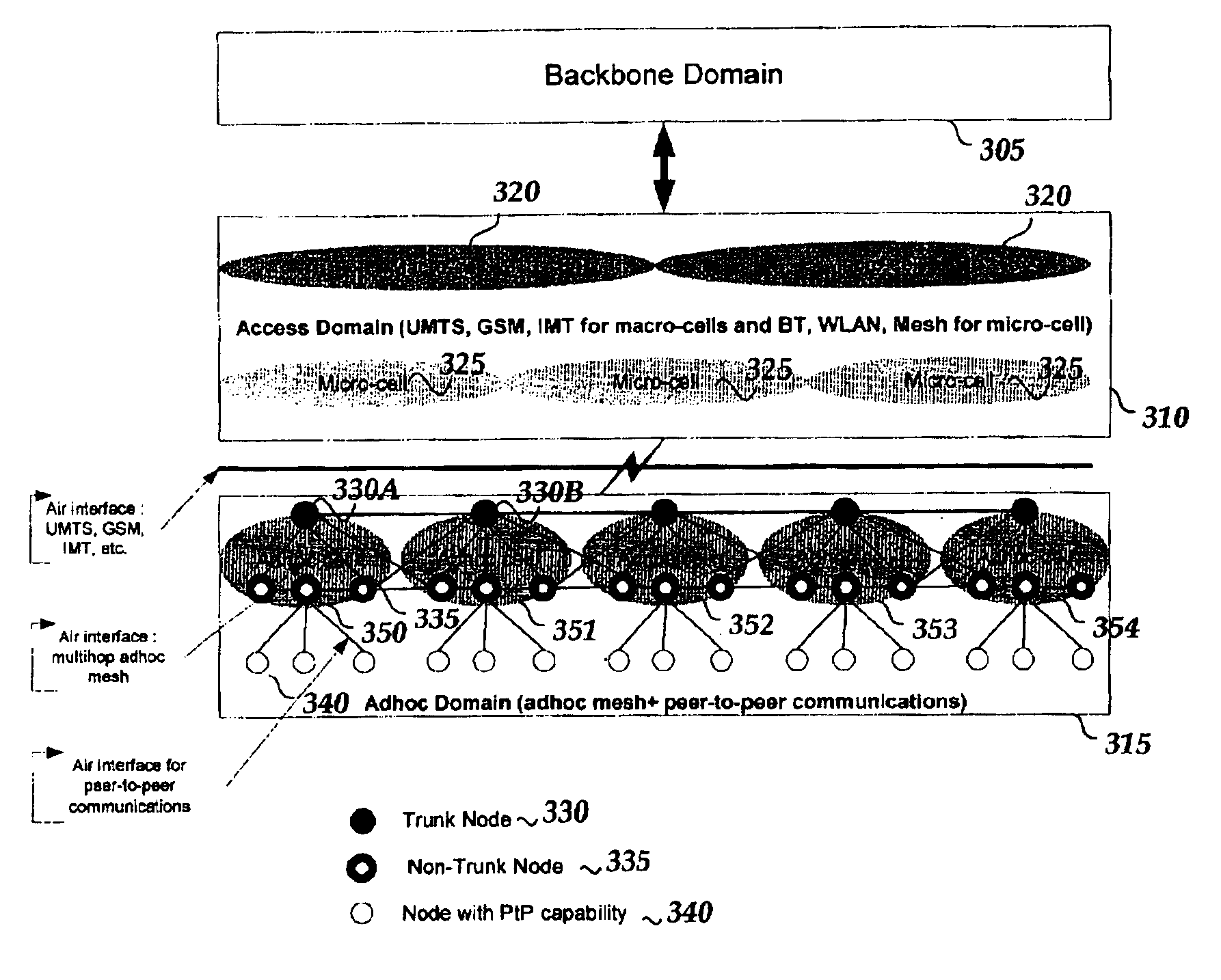
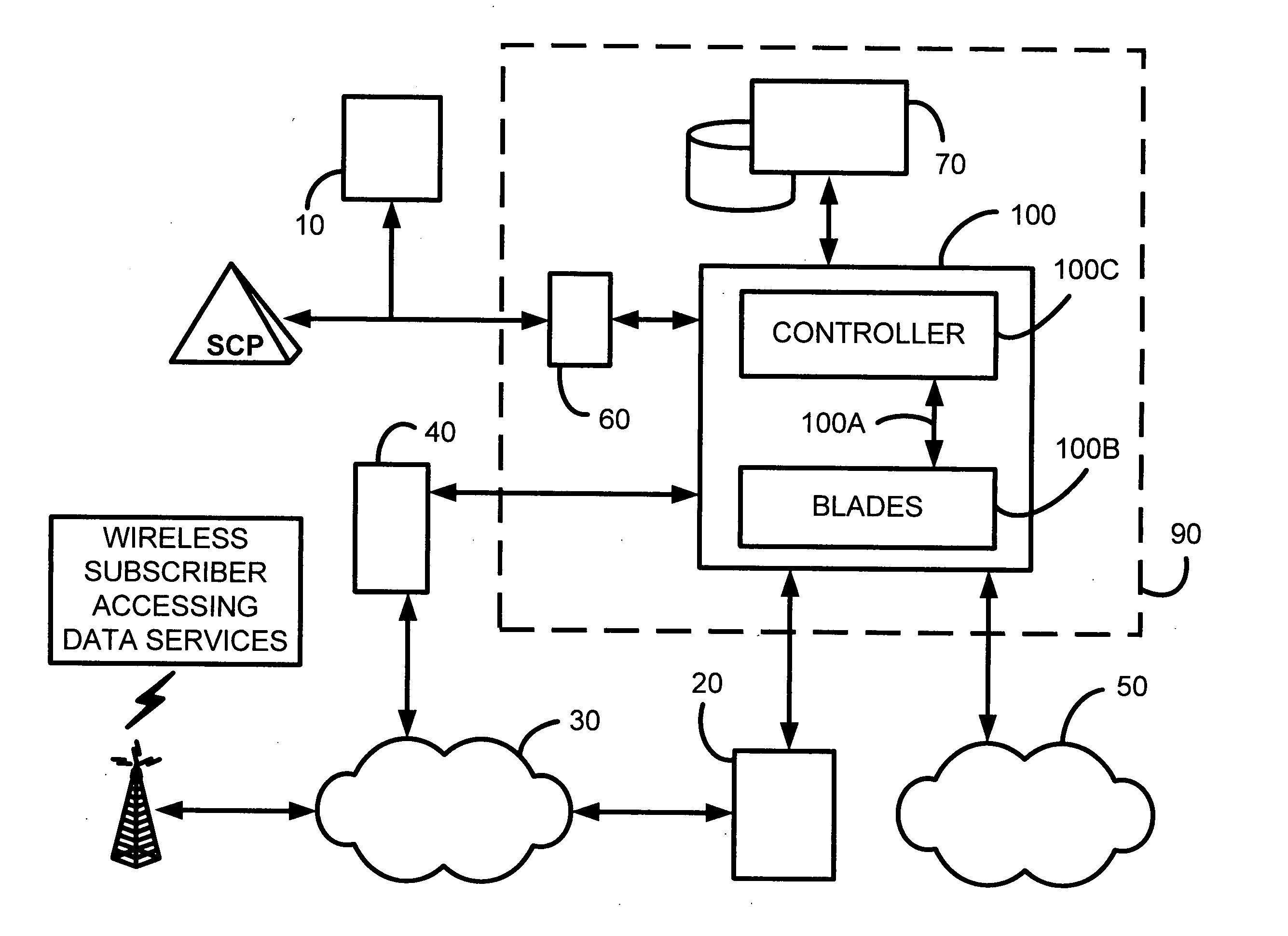
Mobile mesh Ad-Hoc networking
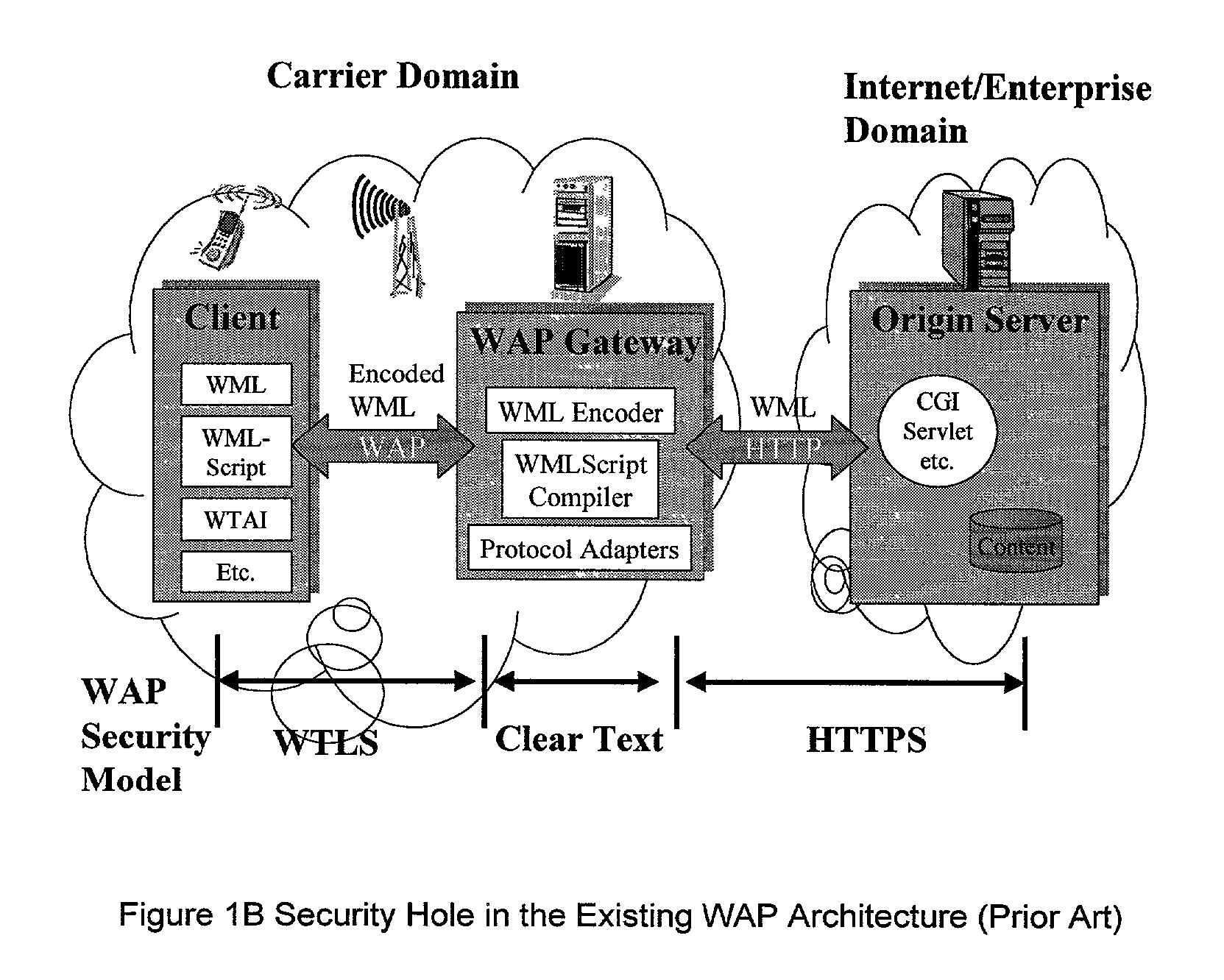
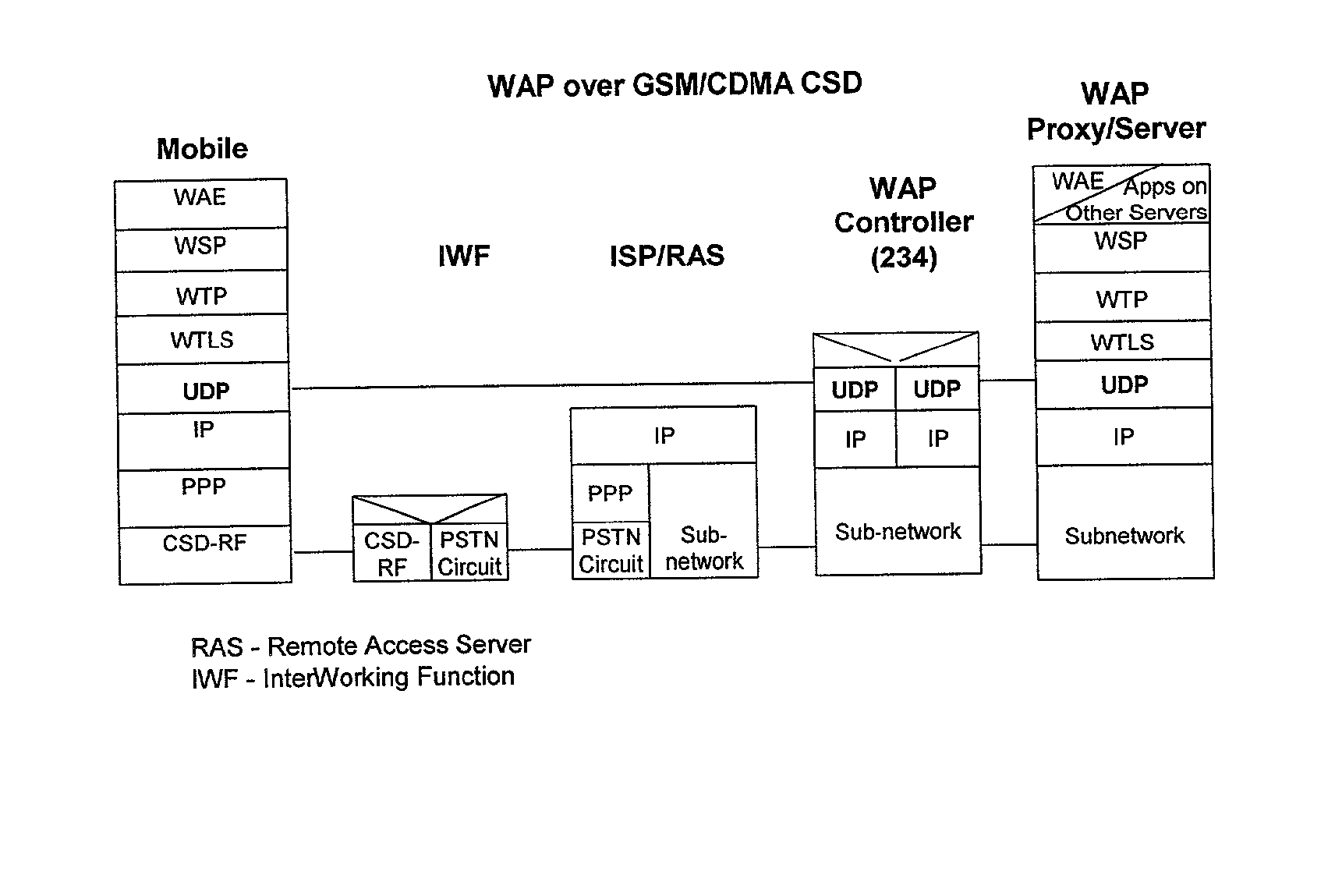
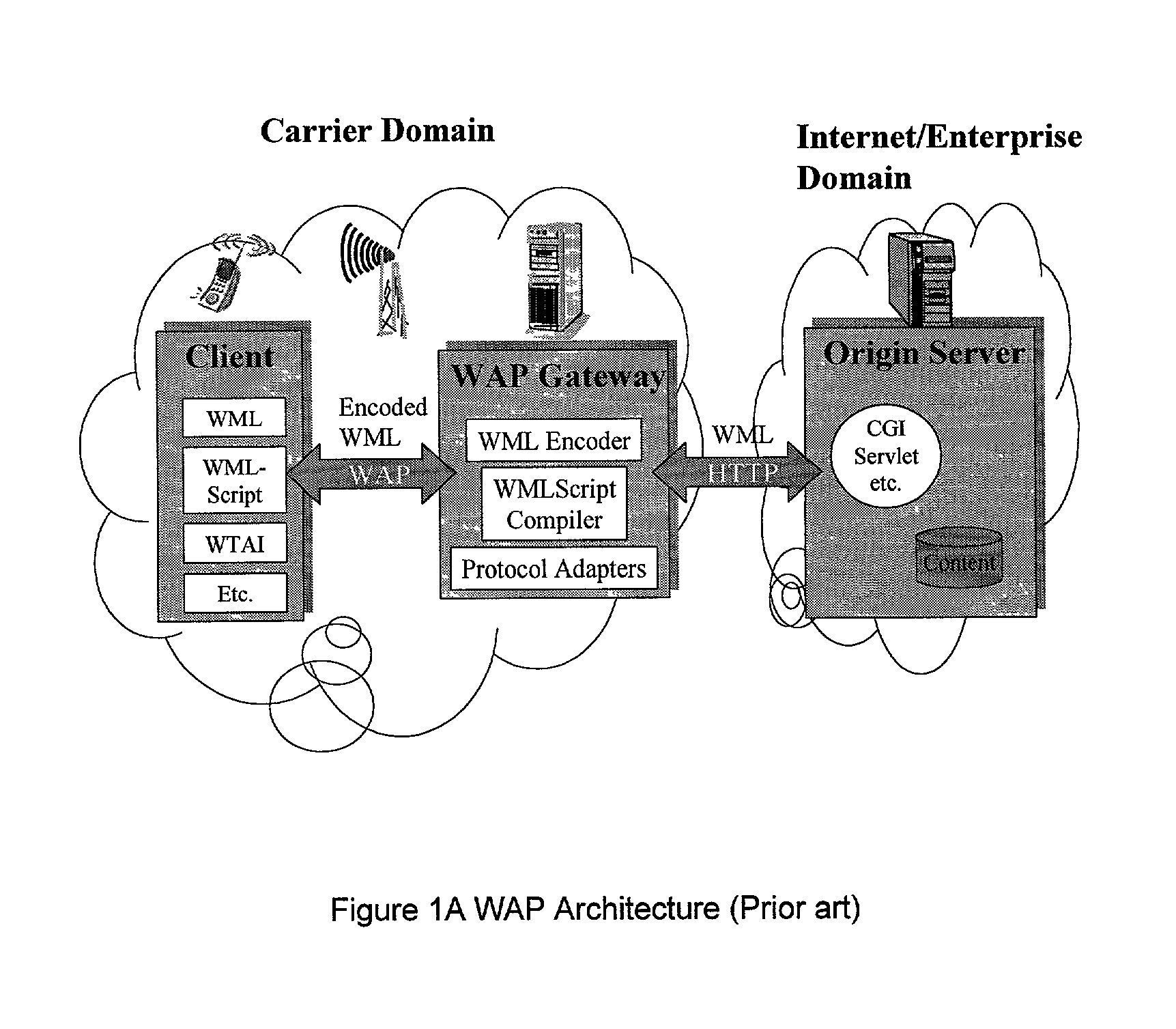
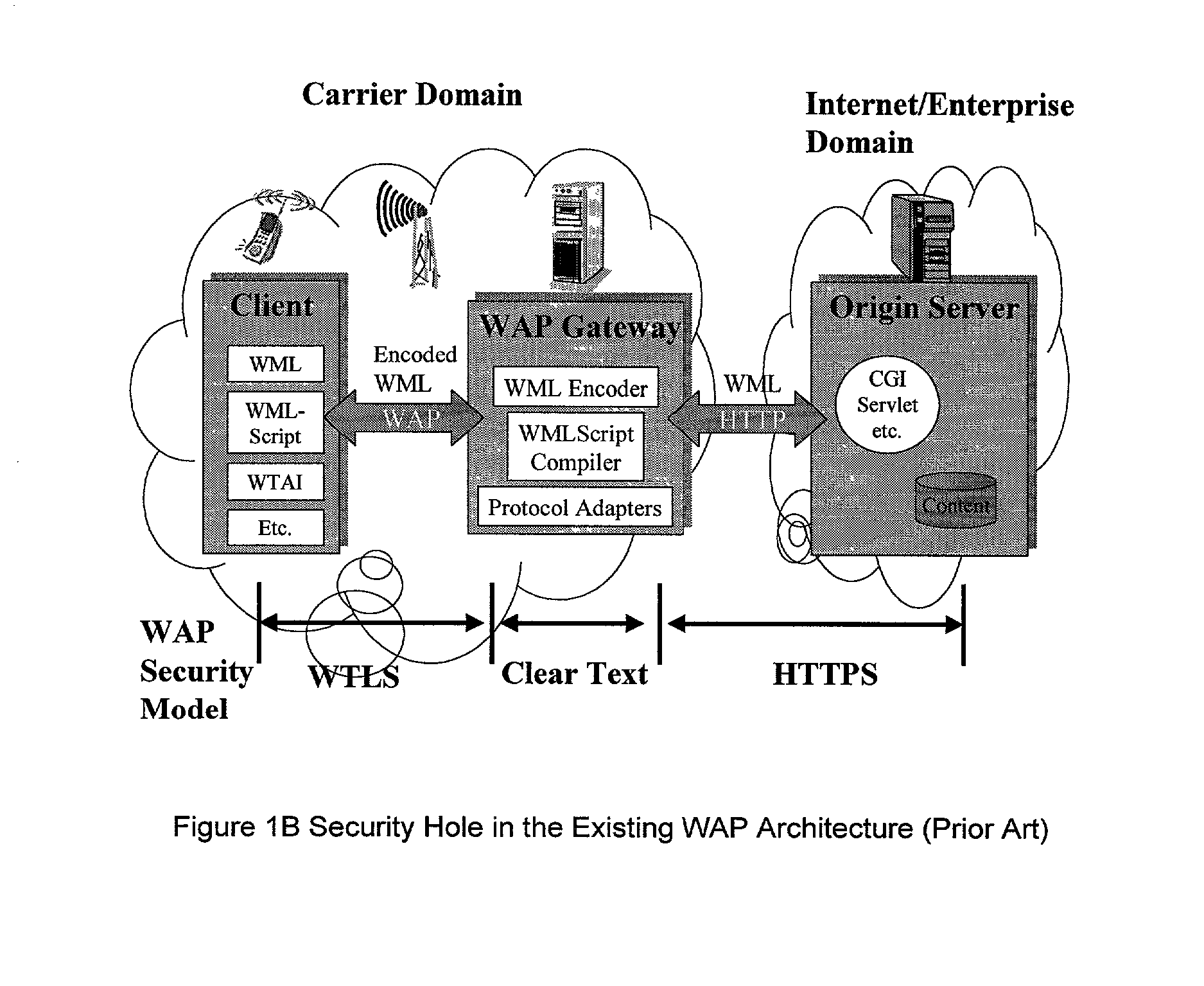
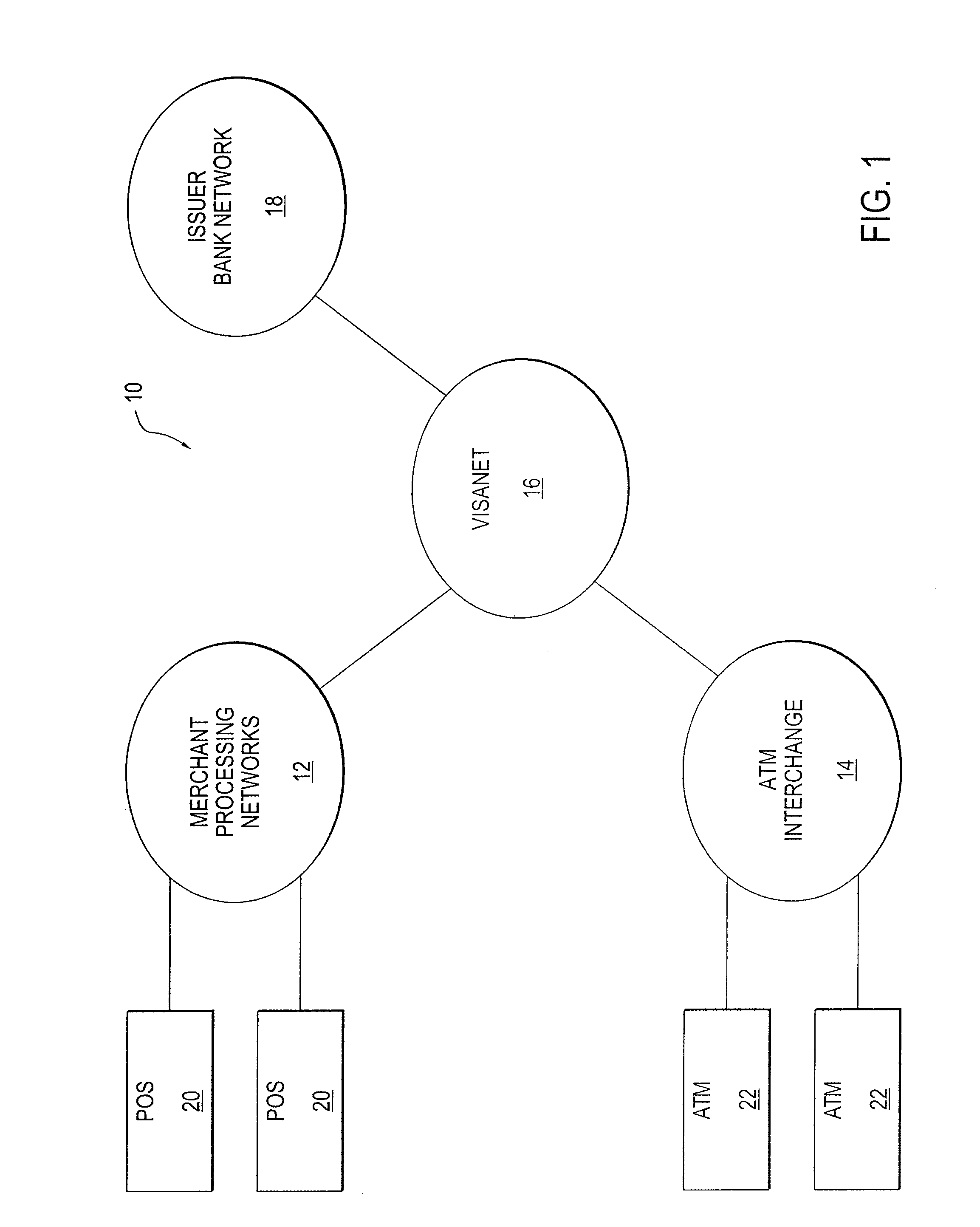
InactiveUS6879574B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsCyber operationsAccess network
An architectural solution in which standalone ad-hoc network cells are used as an extension of the backbone infrastructure in terms of network architecture or / and its service capabilities is provided. These Ad-Hoc networks will integrate to the Internet via cellular and other access networks. This integration brings new possibilities to network operators and ISP's. In its extended architecture, it is envisaged that the mobility issues are handled by utilizing the IP mobility capabilities, taking into account the mobile mesh Ad-Hoc specific requirements.
Owner:NOKIA TECHNOLOGLES OY
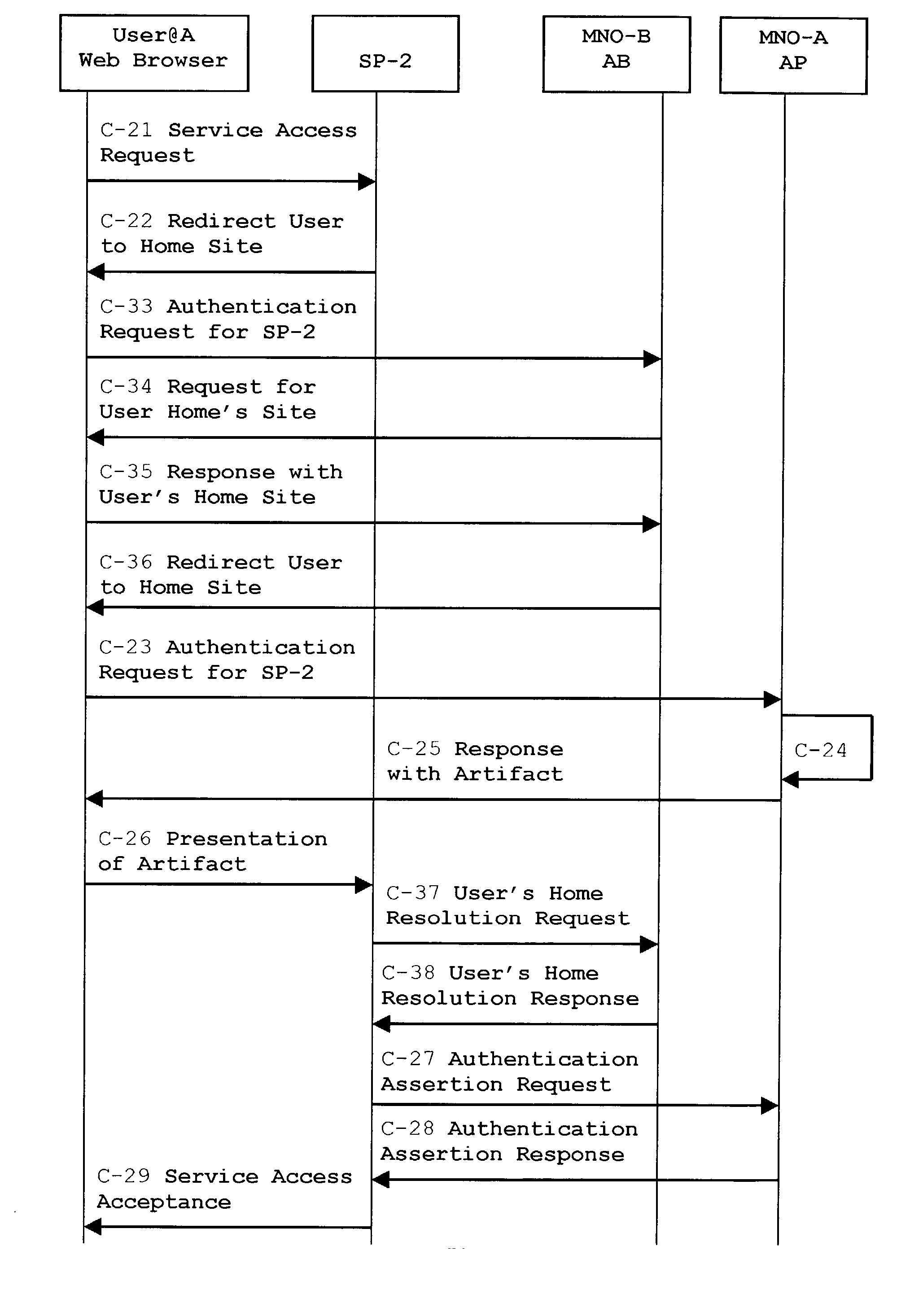
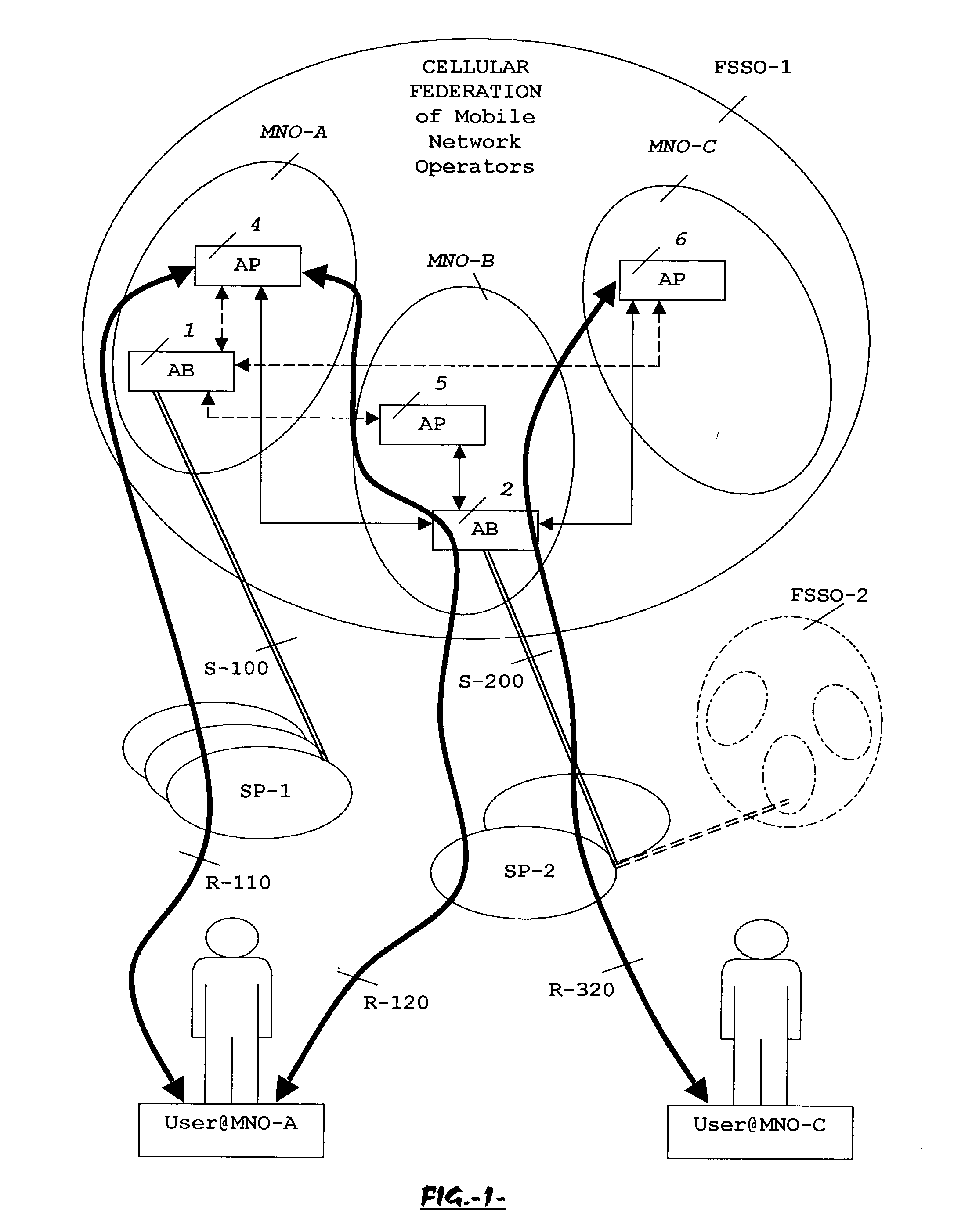
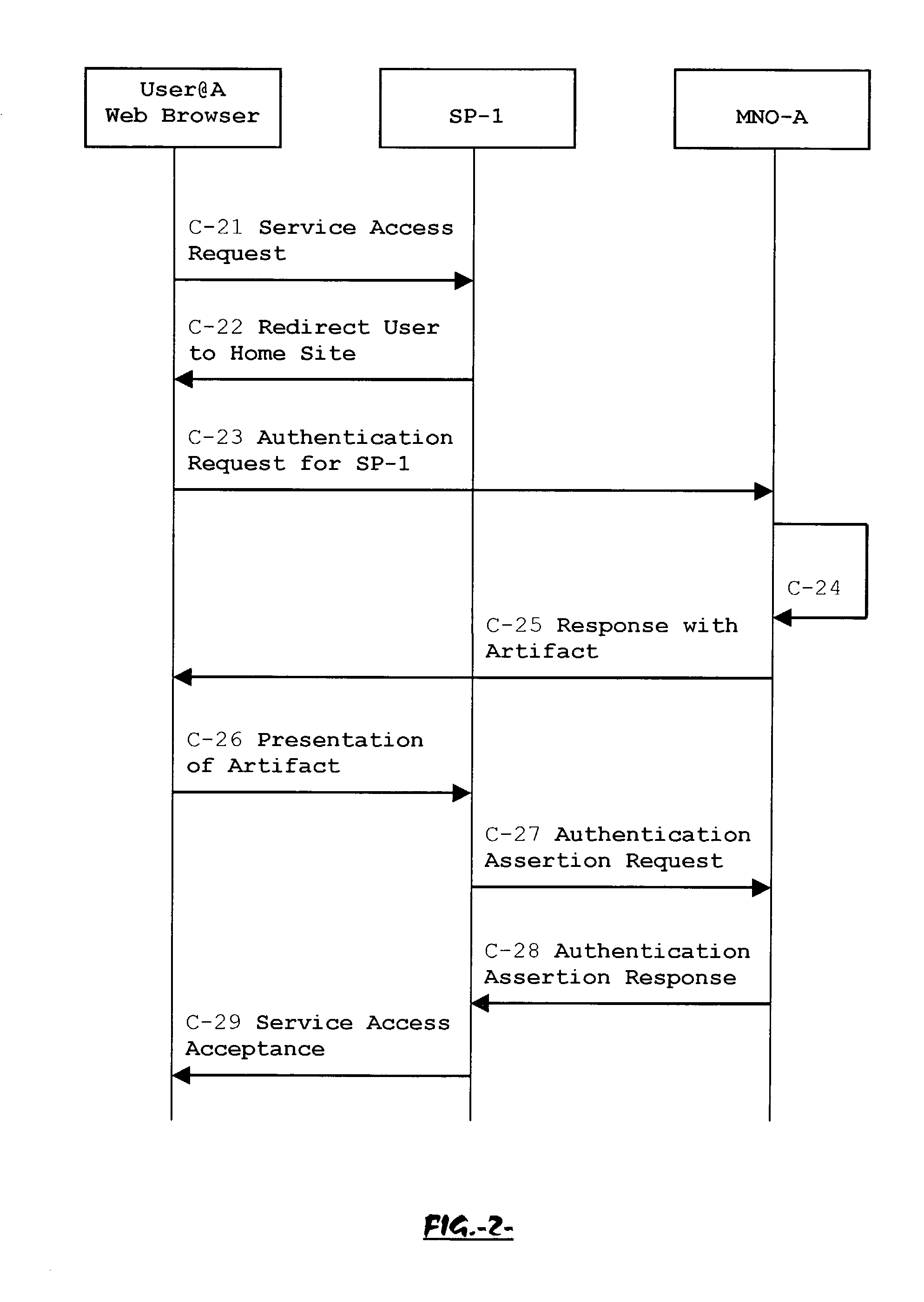
System, method and apparatus for federated single sign-on services
ActiveUS20030163733A1Unauthorised/fraudulent call preventionDigital data processing detailsCyber operationsService domain
The advent of new and sophisticated web services provided by Service Providers to users, services that individually require authentication of user and authorization of access, brings the needs for a new service to facilitate such authentication and access, a service referred to as Single Sign-On (SSO). The basic principle behind SSO is that users are authenticated once at a particular level, and then access all their subscribed services accepting that level of authentication. The present invention provides a system, method and apparatus wherein a cellular Federation of mobile network operators becomes an SSO authentication authority for subscribers of this Federation accessing Service Providers having such agreement with a mobile network operator of the Federation. In accordance with this invention, mobile network operators can leverage their operator-subscriber trust relationship in order to act as SSO authentication authority for those subscribers accessing Service Providers in a service domain other than the mobile network domain.
Owner:TELEFON AB LM ERICSSON (PUBL)
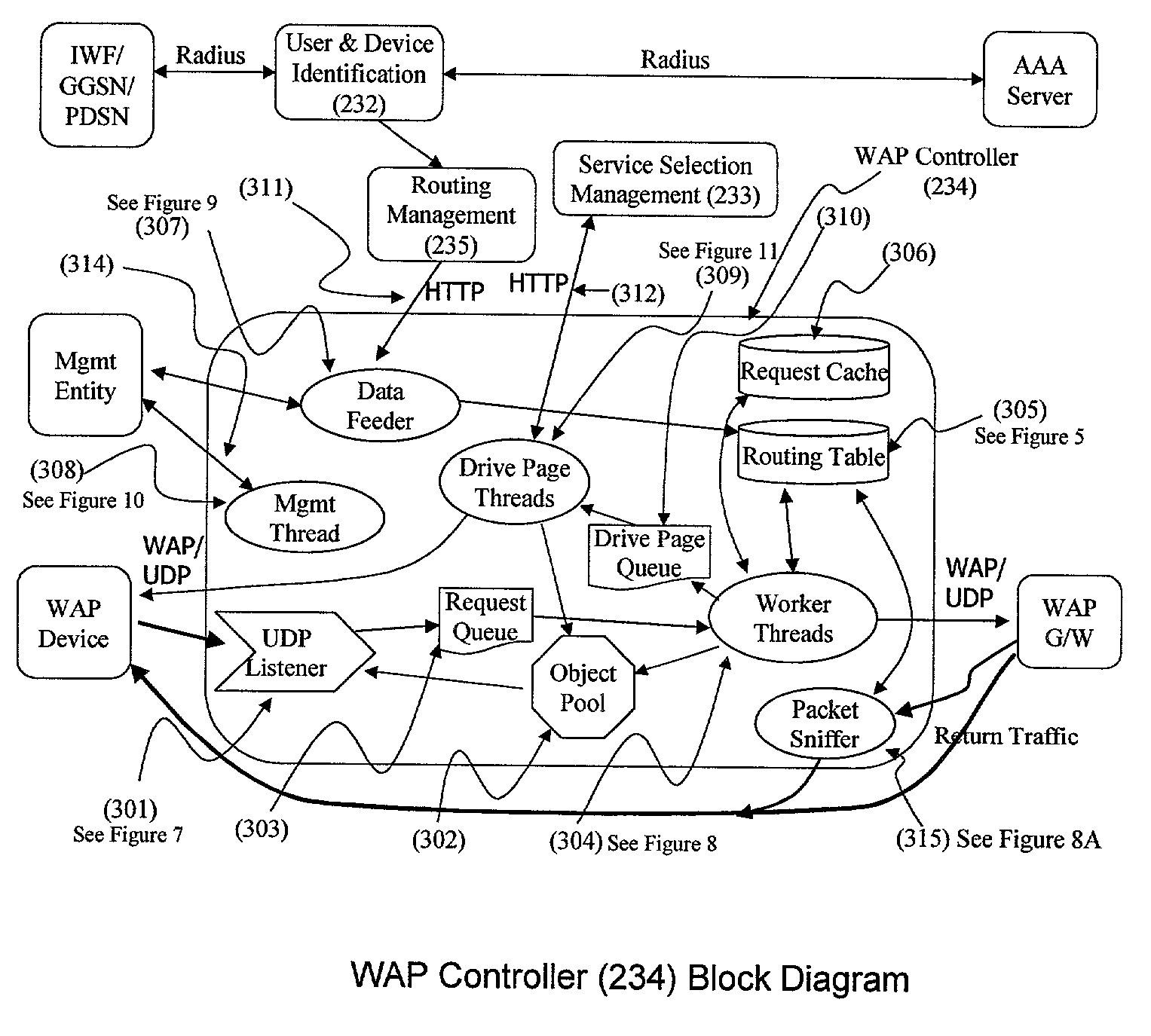
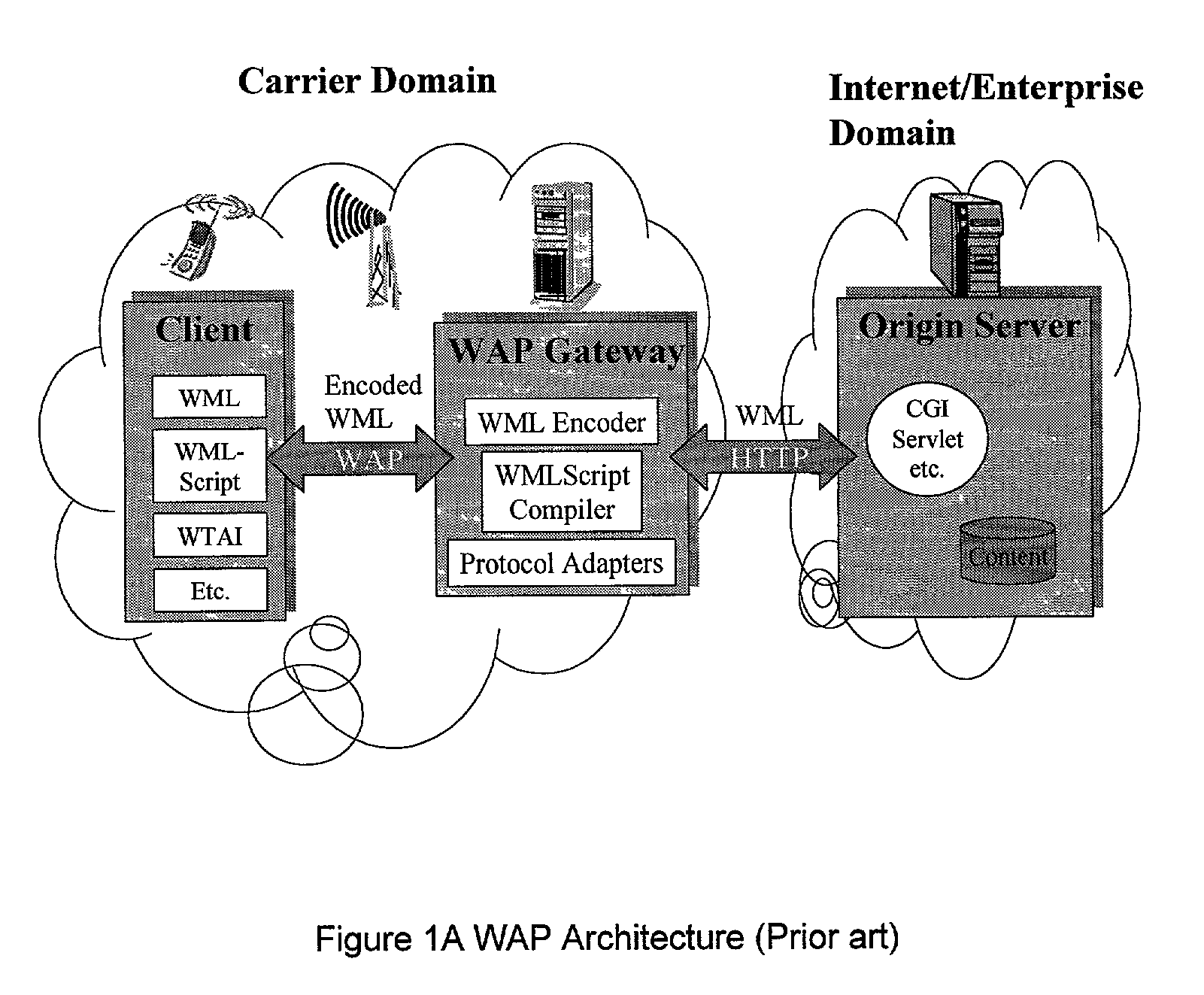
Method and apparatus for providing service selection, redirection and managing of subscriber access to multiple WAP (Wireless Application Protocol) gateways simultaneously
ActiveUS7039037B2Time-division multiplexData switching by path configurationCyber operationsComputer network
A method (FIG. 5) and apparatus (FIG. 3) to provide control and policy enforcement of WAP (Wireless Application Protocol) services in a wireless data networks is taught herein. WAP traffic is inspected with efficient algorithms to intercept un-registered WAP access and intercept dynamic change of user service selection. The intercepted WAP requests are modified with value-added parameters (such as QoS and subscriber identifiers) as per user and service provider agreement and table data. A series of strategies are described to blend wireless intelligence, user preference and service subscription, network operator requirements and service provider or enterprise preferences into routing and drive page generation. The means to dynamically provision users' service choices to wireless network elements are also presented without having to break the session within the system. This enables innovative data services such as pay-per-use, smart routing, and enterprise secured WAP services unlike any current conventional system.
Owner:MAVENIR SYST INC
Method and apparatus for providing service selection, redirection and managing of subscriber access to multiple WAP (Wireless Application Protecol) geteways simultaneously
ActiveUS20030035409A1Time-division multiplexData switching by path configurationCyber operationsTraffic capacity
A method (FIG. 5) and apparatus (FIG. 3) to provide control and policy enforcement of WAP (Wireless Application Protocol) services in a wireless data networks is taught herein. WAP traffic is inspected with efficient algorithms to intercept un-registered WAP access and intercept dynamic change of user service selection. The intercepted WAP requests are modified with value-added parameters (such as QoS and subscriber identifiers) as per user and service provider agreement and table data. A series of strategies are described to blend wireless intelligence, user preference and service subscription, network operator requirements and service provider or enterprise preferences into routing and drive page generation. The means to dynamically provision users' service choices to wireless network elements are also presented without having to break the session within the system. This enables innovative data services such as pay-per-use, smart routing, and enterprise secured WAP services unlike any current conventional system.
Owner:MAVENIR SYSTEMS
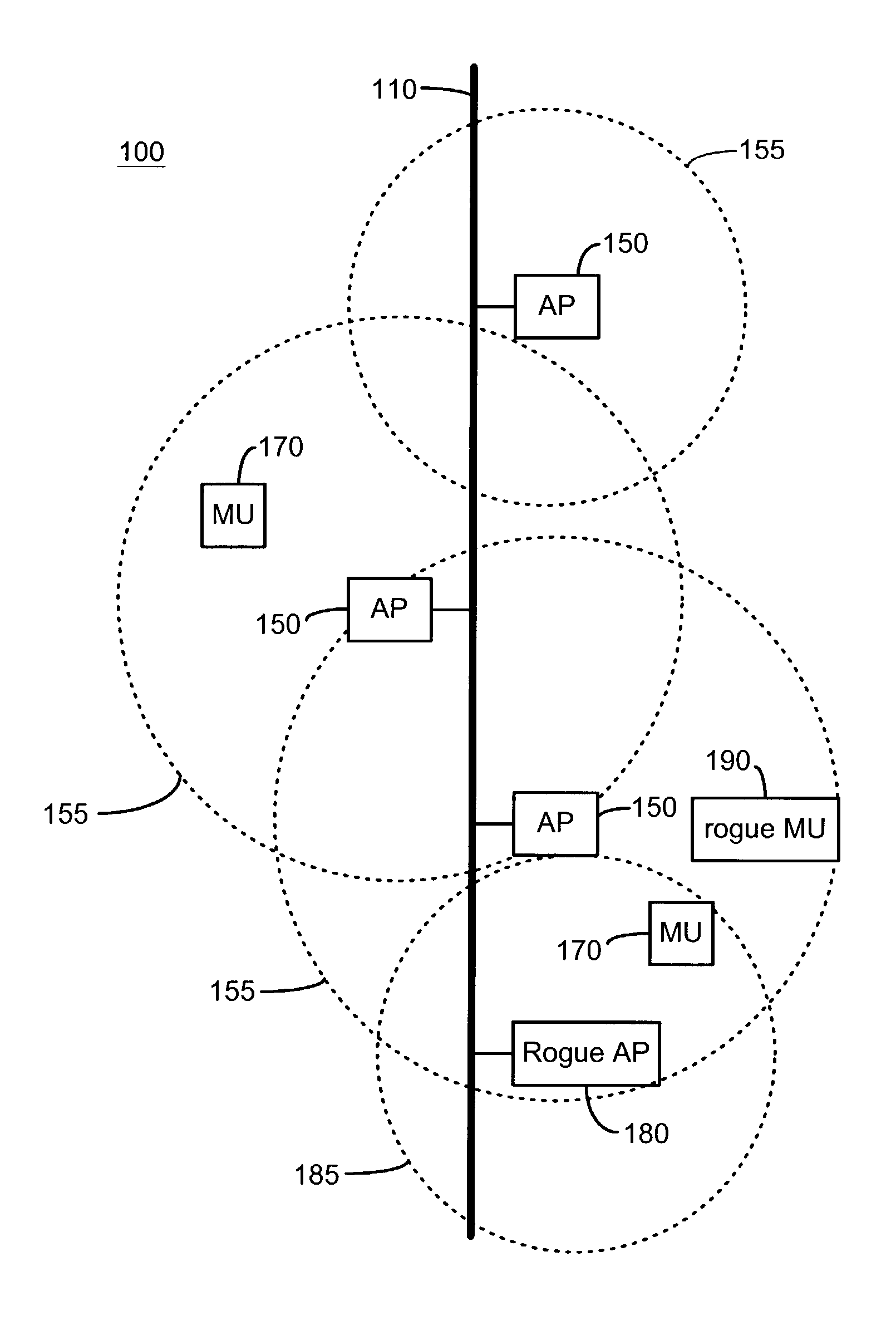
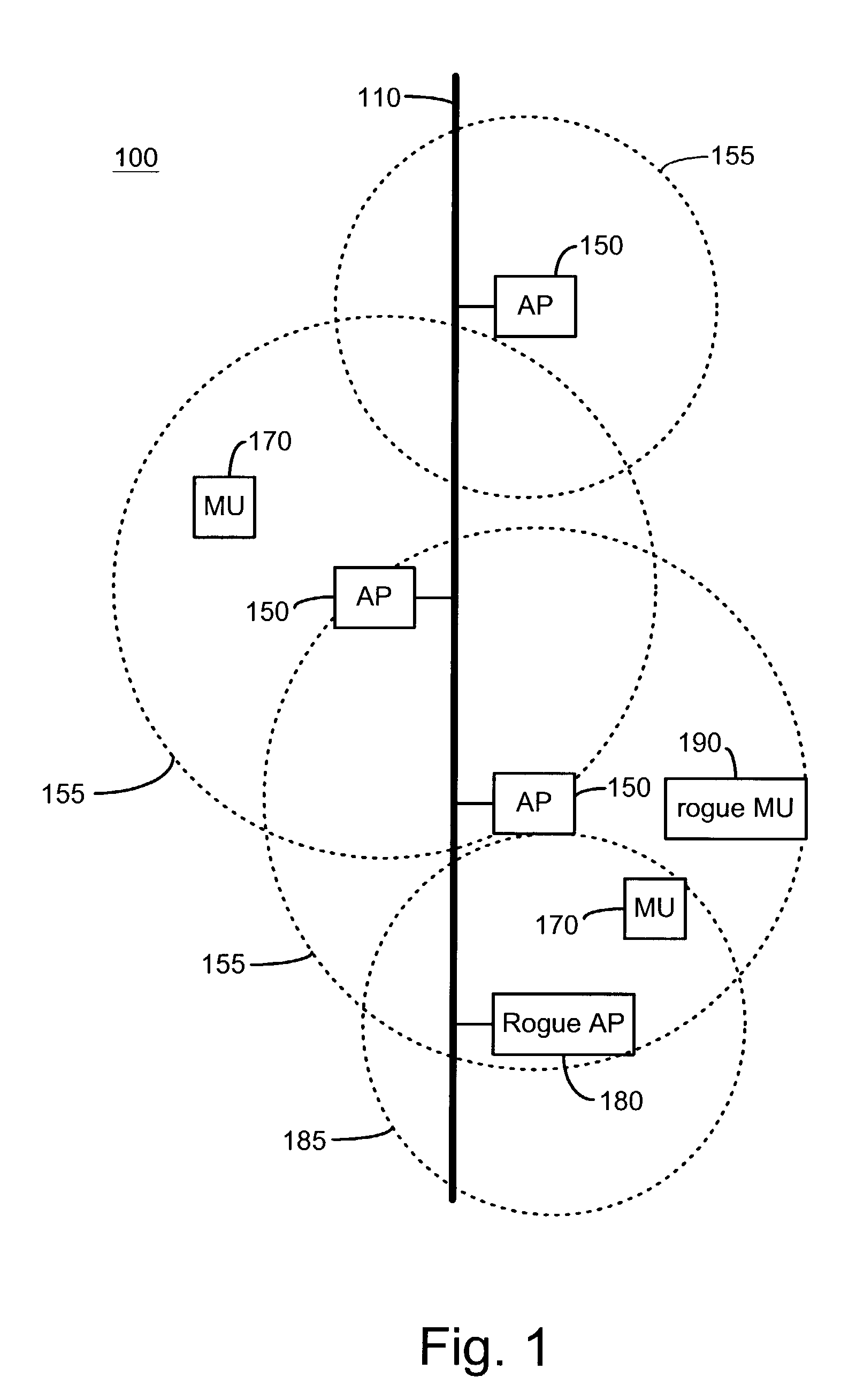
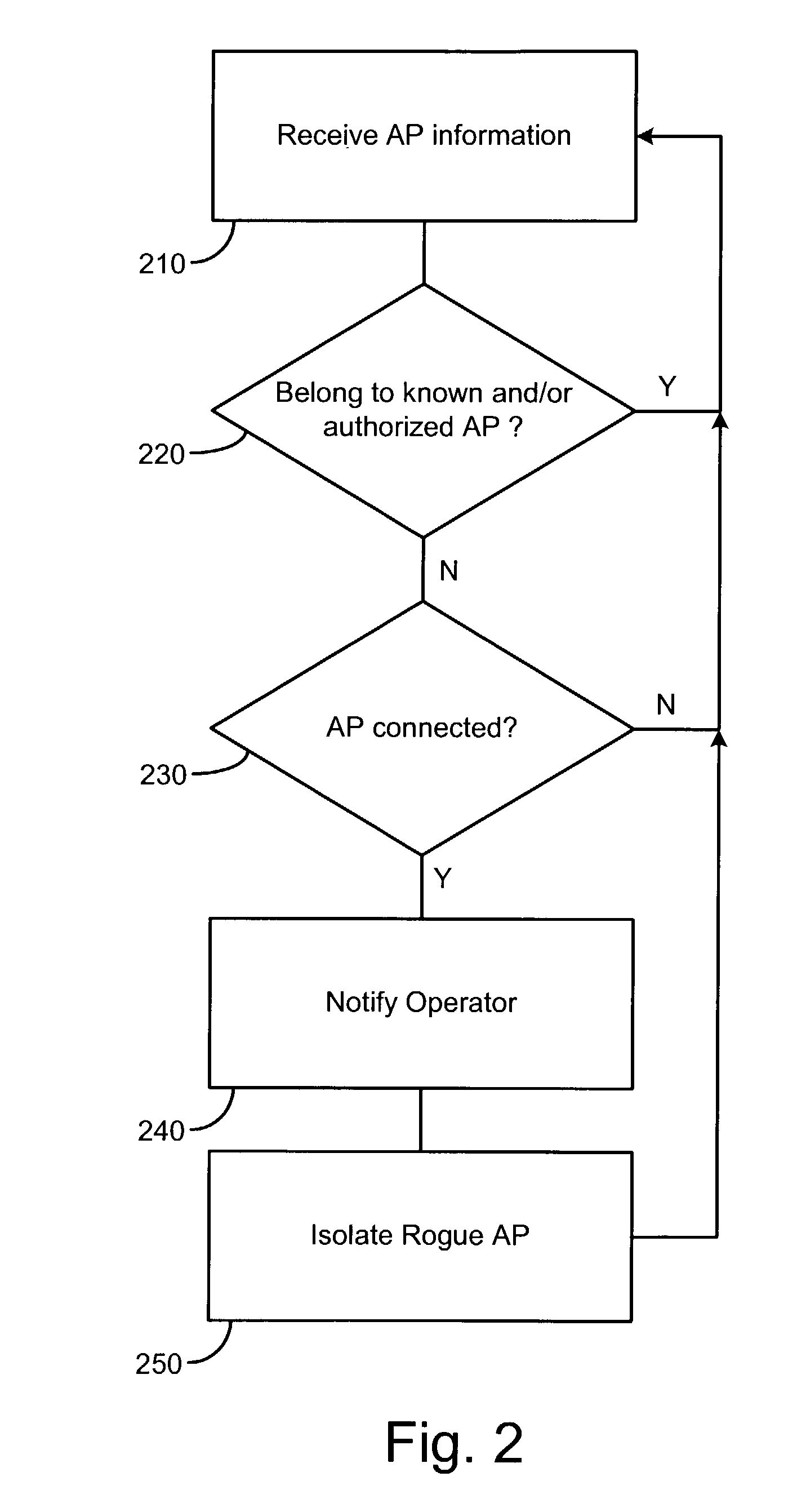
System and method for detecting unauthorized wireless access points
InactiveUS7965842B2Data switching by path configurationSecret communicationCyber operationsInternet privacy
Unauthorized wireless access points are detected by configuring authorized access points and mobile units to listen to all wireless traffic in its cell and report all detected wireless devices to a monitor. The monitor checks the reported devices against a list of authorized network devices. If the reported wireless device is not an authorized device, the monitor determines if the reported device is connected to the network. If the reported device is connected to the network and is not an authorized device, the monitor alerts the network operator or network manager of a rogue device connected to the network and attempts to locate and isolate the rogue device.
Owner:IVANTI INC
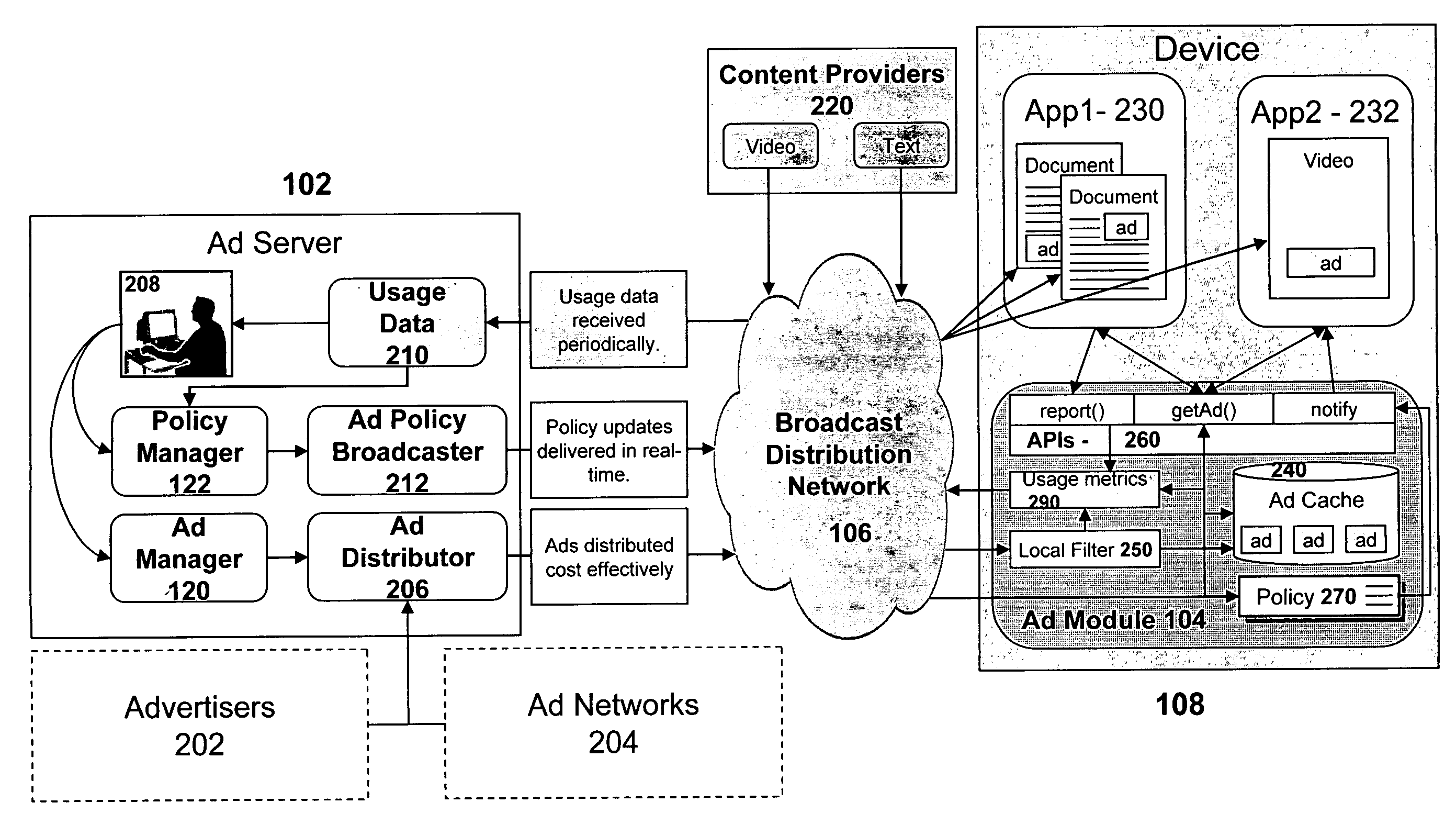
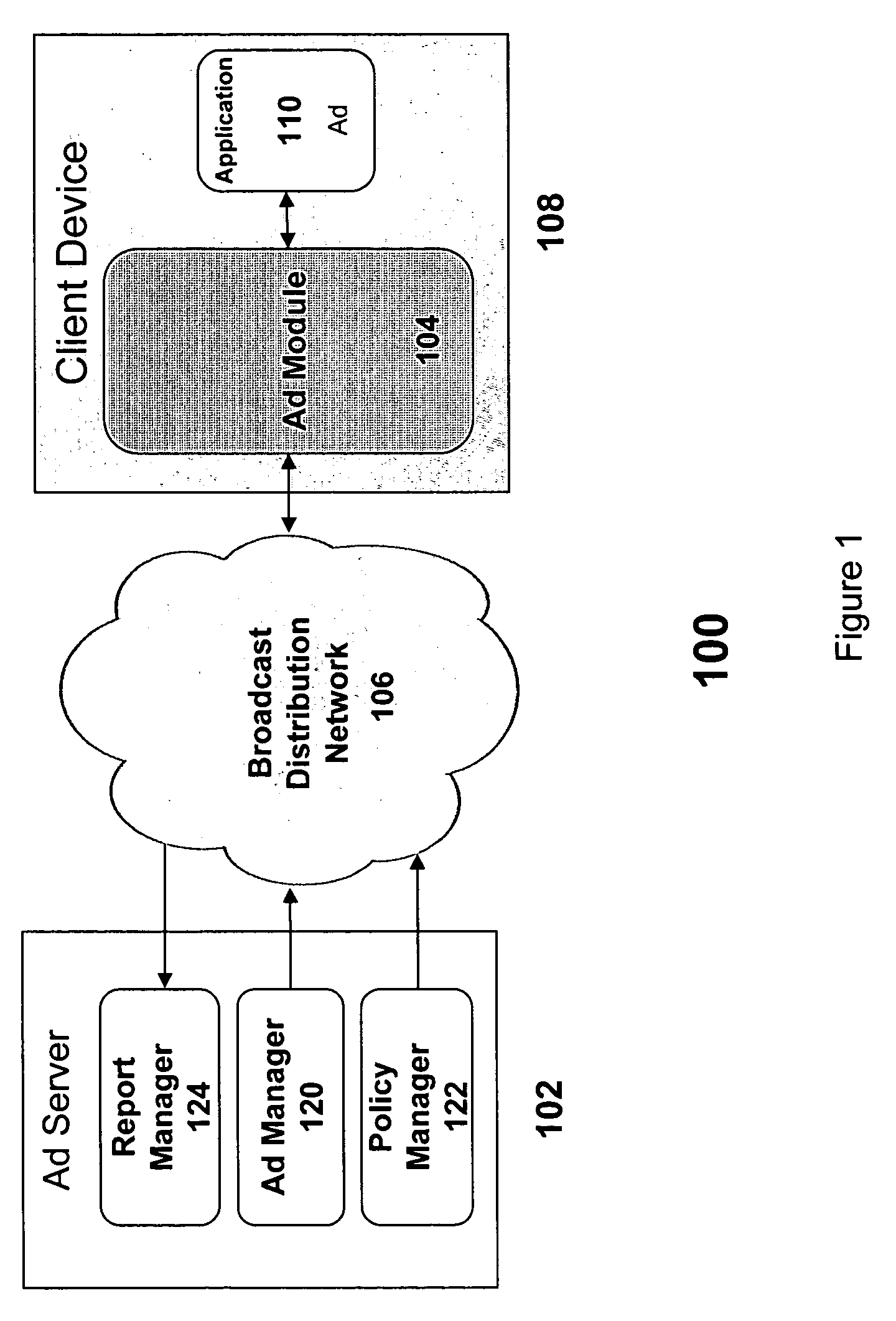
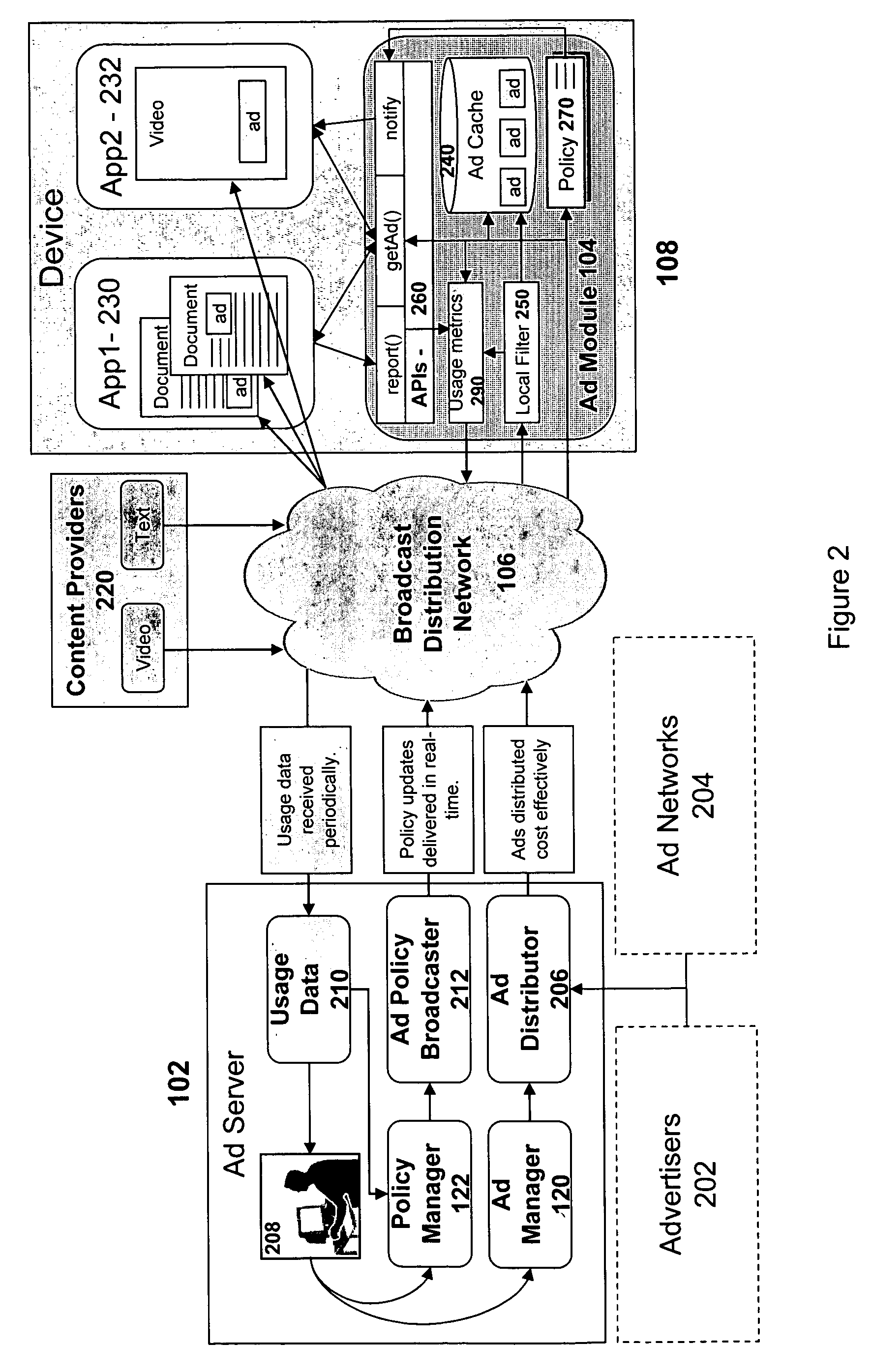
Distribution and display of advertising for devices in a network
InactiveUS20080098420A1Good choiceElectrical cable transmission adaptationMarketingCyber operationsClient-side
A system and associated apparatus and methods for the distribution, selection and display of advertising content for devices operating in a network. The devices need not initiate a point-to-point communication with an ad server to provide the ability to filter received advertising content and enable the display of advertisements that are targeted to a device's user. The invention enables a service provider or network operator to control the policy used to specify the selection, timing, and display of an advertisement stored in a cache of a client device. A modification to the policy can be broadcast and implemented in real-time by the device. Advertisements stored in the cache may be filtered both by the service provider or network operator and by the device itself so as to provide the best selection of ads tailored to the user of the device. The device implements cache management processes to determine how best to maintain the advertisements of greatest relevance to the user of the device. The invention also provides mechanisms for the reporting of statistics that can be used for billing purposes and to better filter the selection of advertisements cached at each device.
Owner:ROUNDBOX
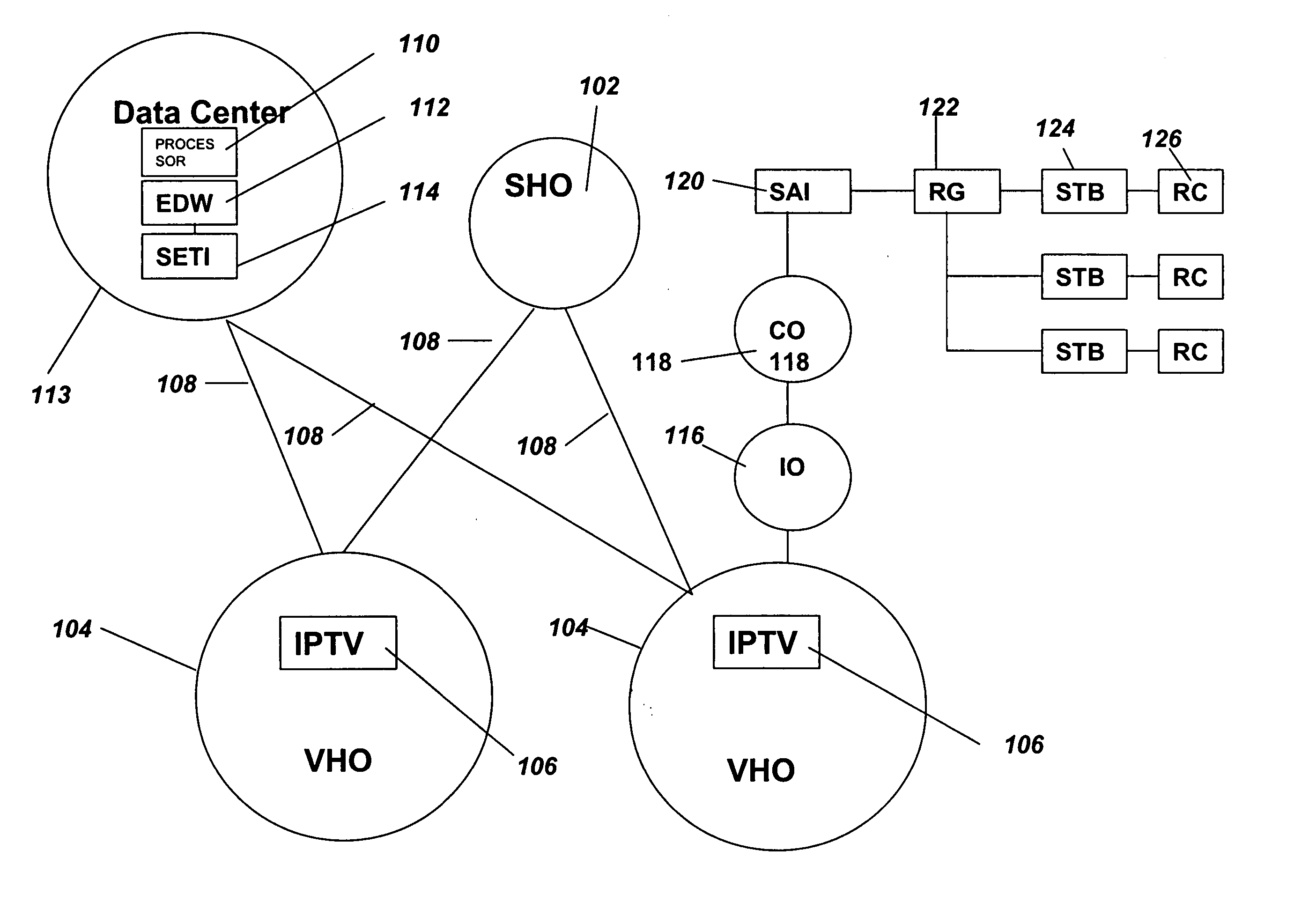
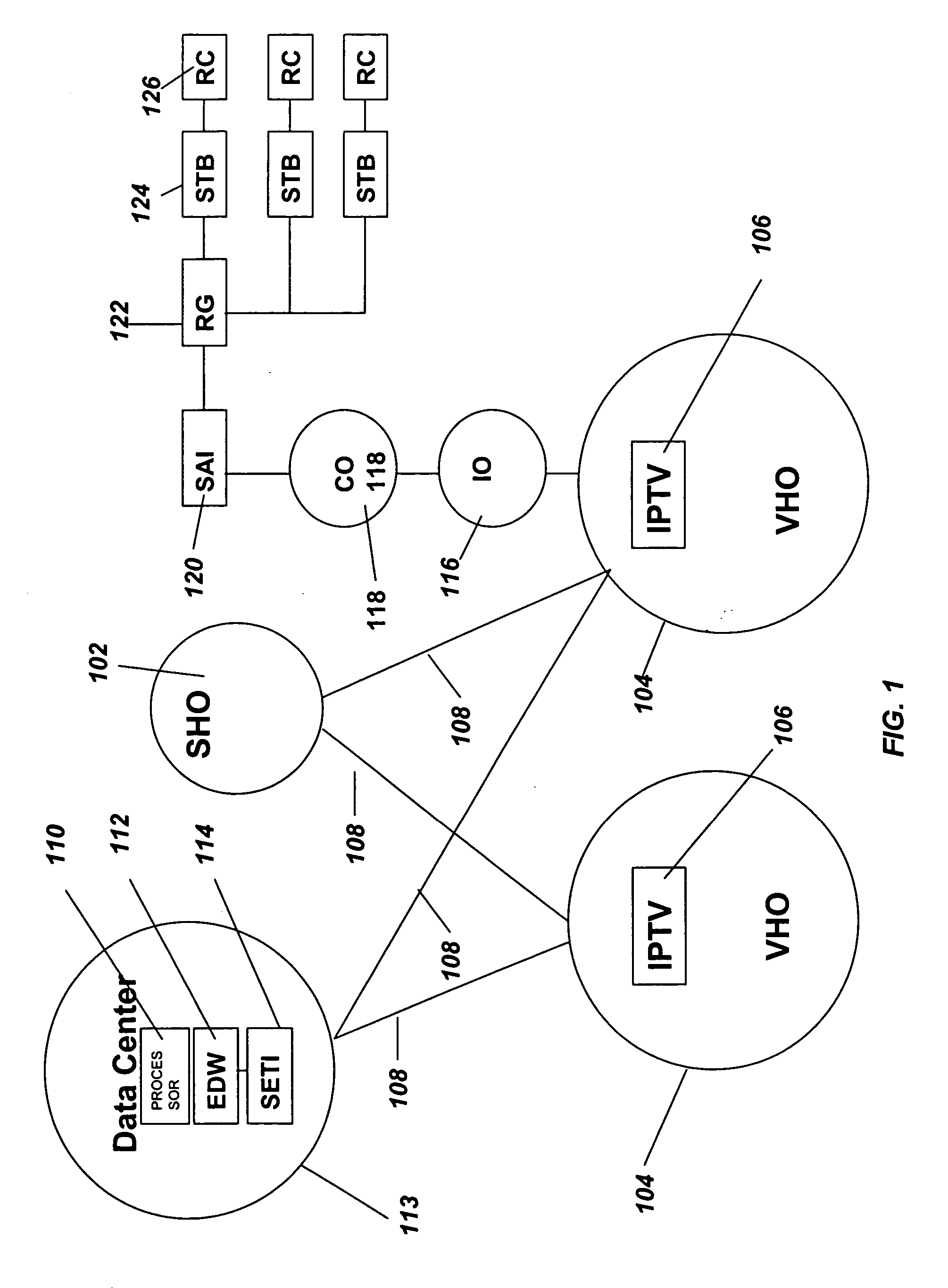
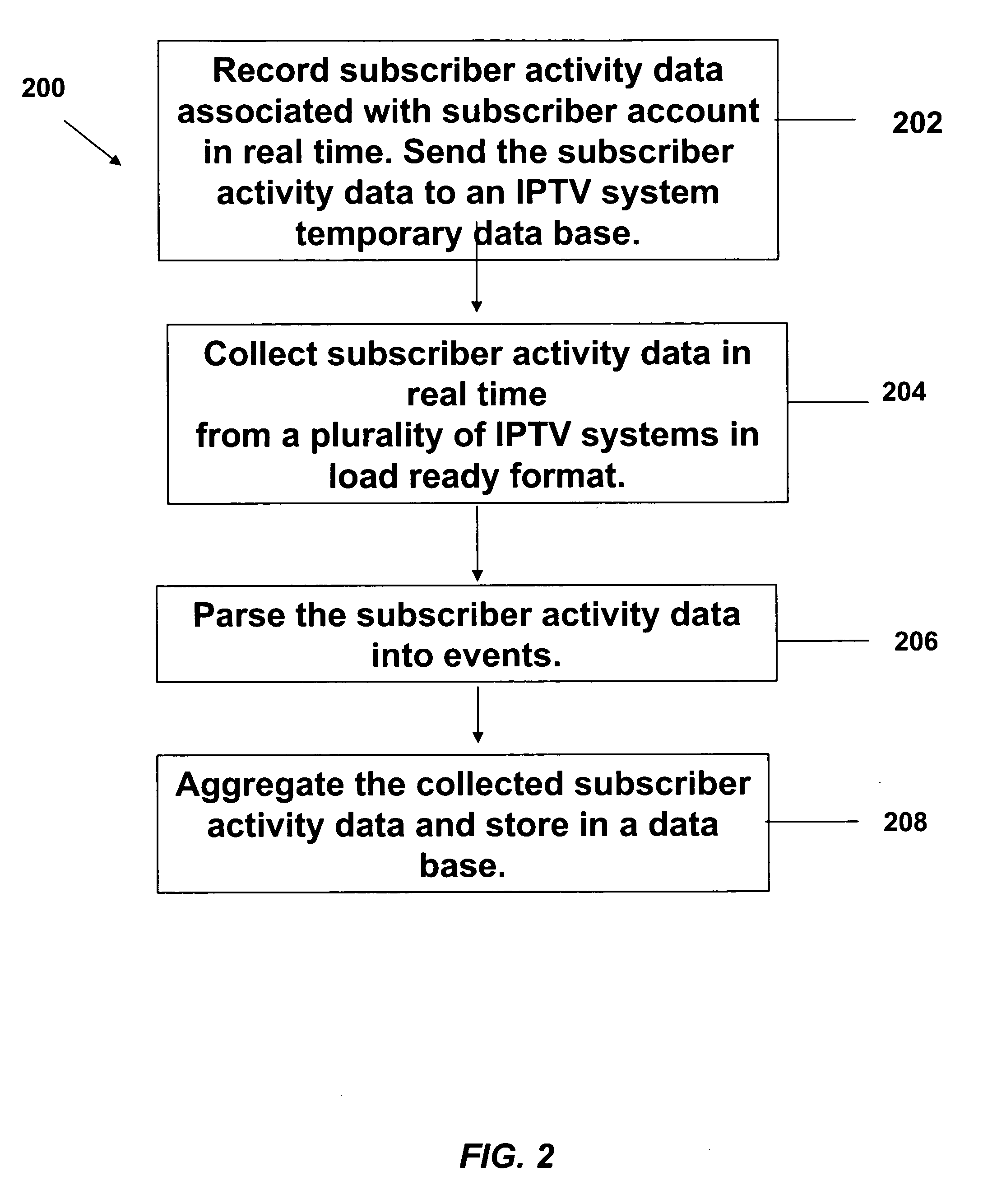
Data collection and analysis for internet protocol television subscriber activity
InactiveUS20070074258A1Easy to understandTwo-way working systemsSelective content distributionCyber operationsSummary data
A method and apparatus are provided that interact with an IPTV product deployed in a communication network. The method and apparatus of the present invention collects subscriber activity data, such as channel changes generated by the subscriber while watching video or TV in an IPTV system. The system and method of the present invention collects, parses and processes this consumer activity data. The method and apparatus of the present invention collects and aggregates the IPTV consumer activity data from multiple IPTV consumer activity data collection systems. The aggregated data, collected over a national or global basis can then be used to generate metrics. The metrics are then analyzed by business rules to generate marketing data reports that can be used as an strategic analysis tool for communication network operators, content providers and advertisers to determine consumer usage of the IPTV systems and viewing of programming and advertising.
Owner:SBC KNOWLEDGE VENTURES LP
Method for implementing an intelligent content rating middleware platform and gateway system
InactiveUS20050135264A1Highly scalable, manageable and reliableMetering/charging/biilling arrangementsError preventionCyber operationsMiddleware
The method for implementing an Intelligent Content Rating middleware platform and gateway system disclosed herewith provides telecommunications carriers and network operators with the ability to define routing and actions based on HTTP / SIP based content and subscriber context through a powerful, extensible Layer 4-7 switching fabric technology. The invention mediates communications between applications and networks for IP packet flows, personal messaging, location-based services and billing. Furthermore, it enables advanced context-sensitive dialogue scenarios with the wireless subscriber such as, but not limited to, Advice-of-Charge dialogues. The art permits telecommunications network operators and like entities to introduce real-time rating of data services for both prepaid and post-paid subscribers. Further advances in the art include the validation of digital signatures, combined with authentication and non-repudiation techniques to ensure subscriber privacy remains protected.
Owner:REDKNEE INC
Method of making secure on-line financial transactions
InactiveUS20080046362A1Shorten the timeConvenient transactionFinancePayment circuitsCyber operationsThe Internet
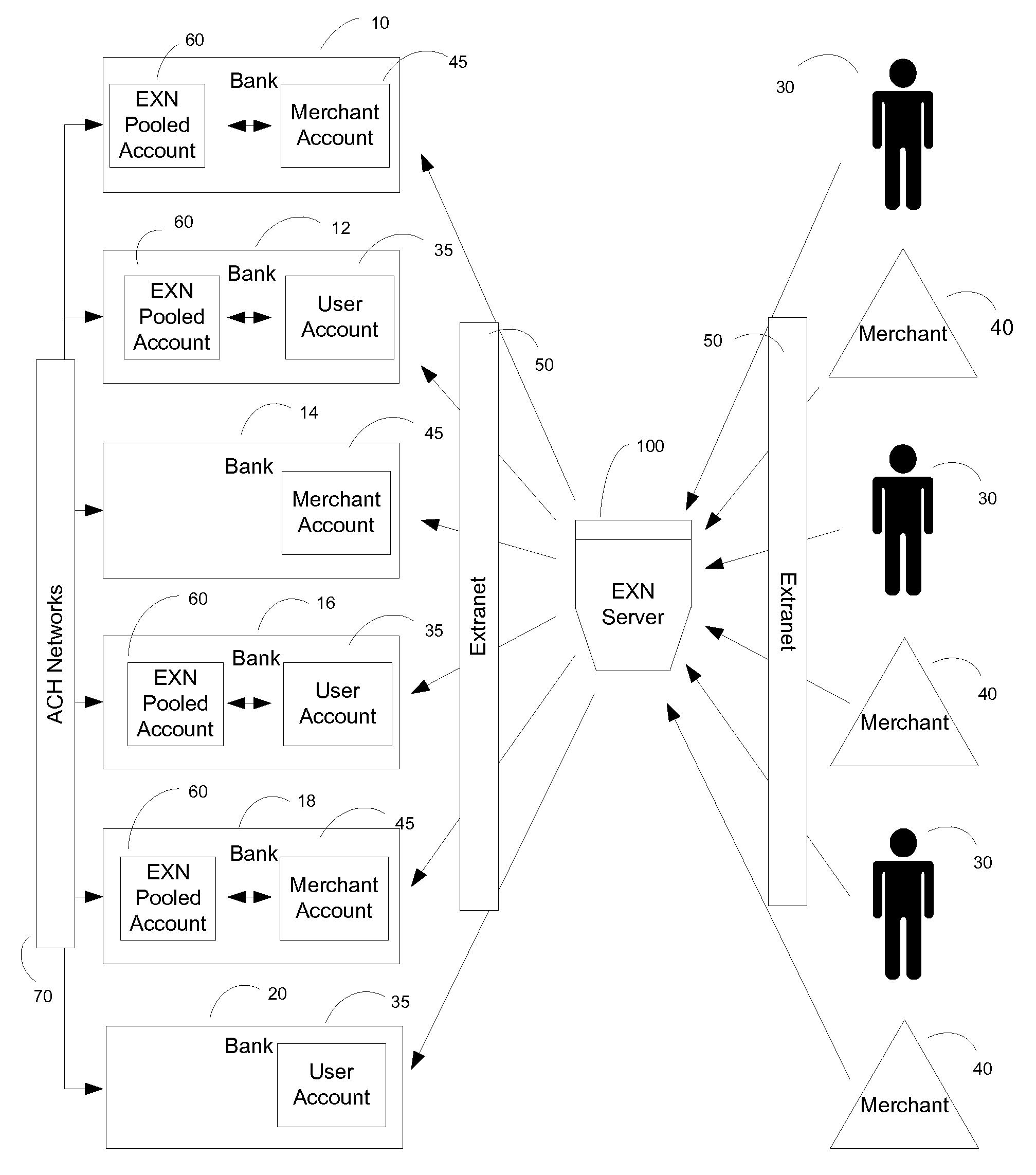
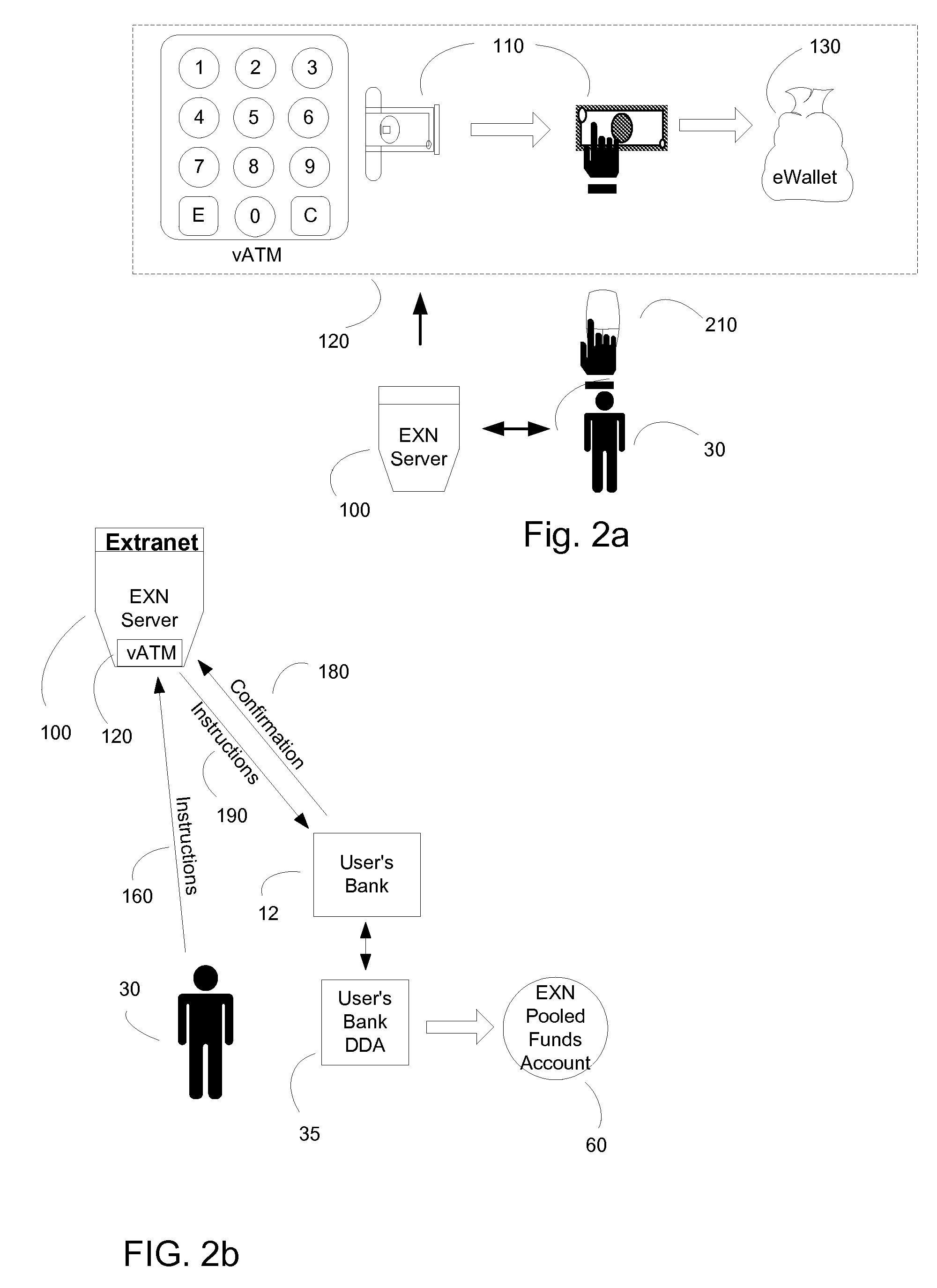
A method of providing secure financial transactions using the internet creates virtual currency that is used to settle monetary obligations amongst authorized purchasers, merchants, and other financial operators. The network operator maintains available funds in pooled fund accounts at various financial institutions, and uses those funds to purchase and sell virtual currency that may then be used on-line. Actual monetary transfers take place between pooled accounts using traditional automated clearing house (ACH) networks, pursuant to instructions provided to financial institutions by the network operator. User authentication and authorization are provided through a dual registration process, and a user's identity may be authenticated using a physical medium or a PIN. Instructions may be given remotely to the network operator through cellular telephones and PDAs.
Owner:EASTERLY FRANK
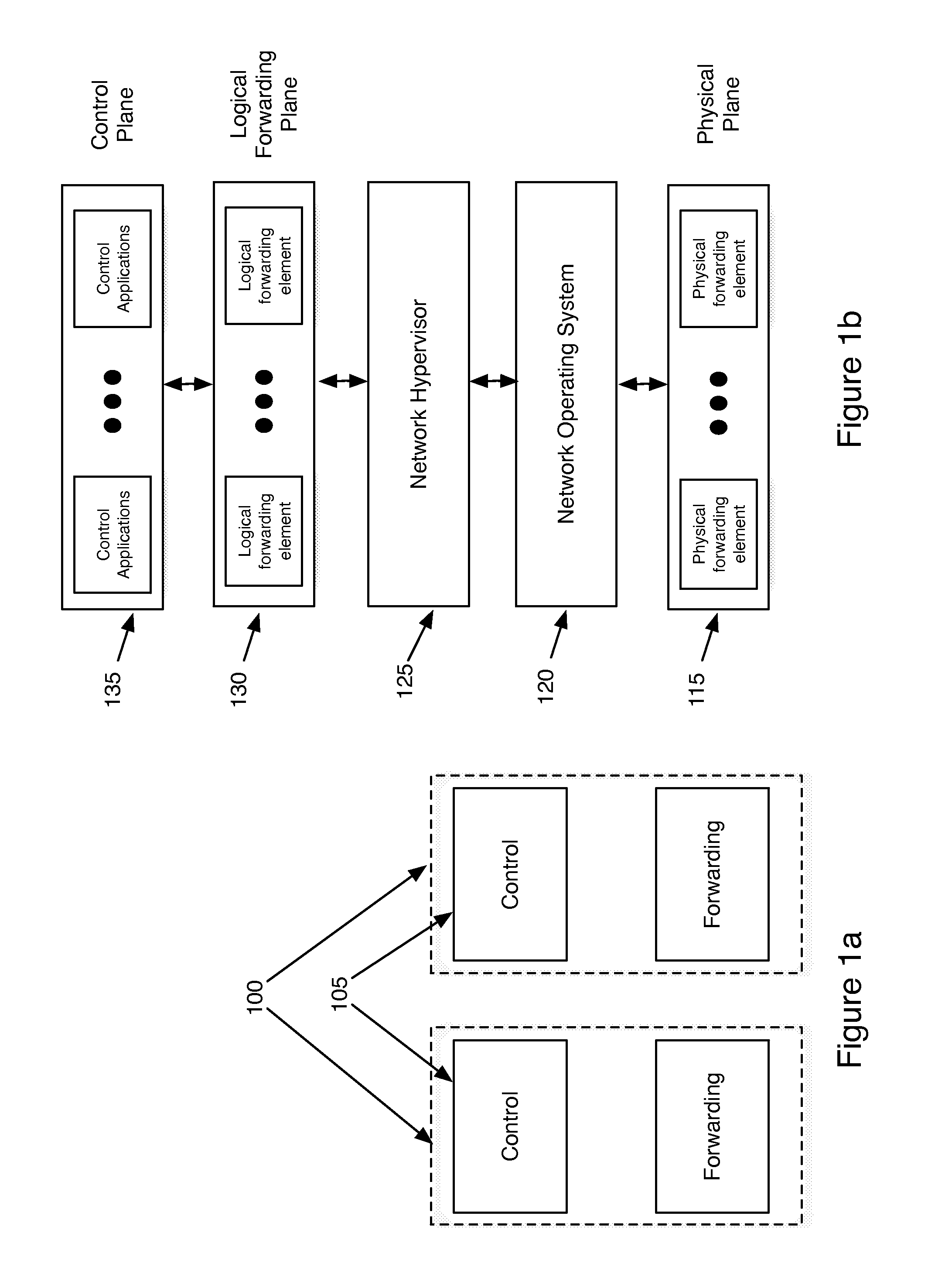
Network virtualization
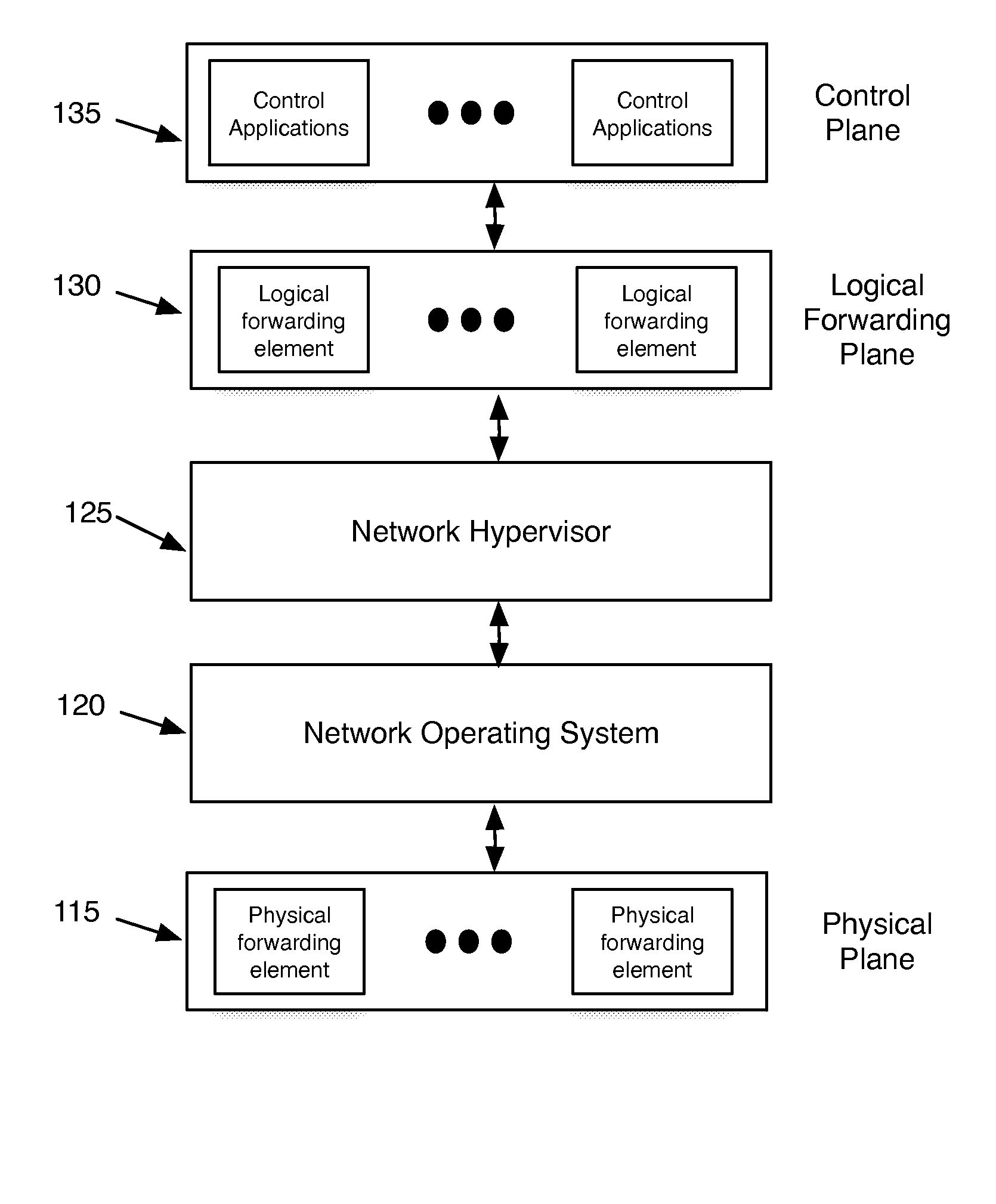
ActiveUS20130060940A1Fault responseMultiple digital computer combinationsCyber operationsNetworking hardware
Some embodiments of the invention provide a robust scaling-out of network functionality by providing a software layer, called the network hypervisor, that sits between the network forwarding functions (i.e., the forwarding plane) and the network control interfaces (i.e., the control plane). The network hypervisor of some embodiments provides a logical abstraction of the network's forwarding functionality, so that network operators make their control decisions in terms of this abstraction, independent of the details of the underlying networking hardware. The network hypervisor of some embodiments may then “compile” commands placed against this abstraction into configurations of the underlying hardware. Accordingly, in some embodiments, there are two design challenges: (1) the choice of the network abstraction, and (2) the technology needed to compile the logical “abstract” controls into low-level configurations.
Owner:NICIRA
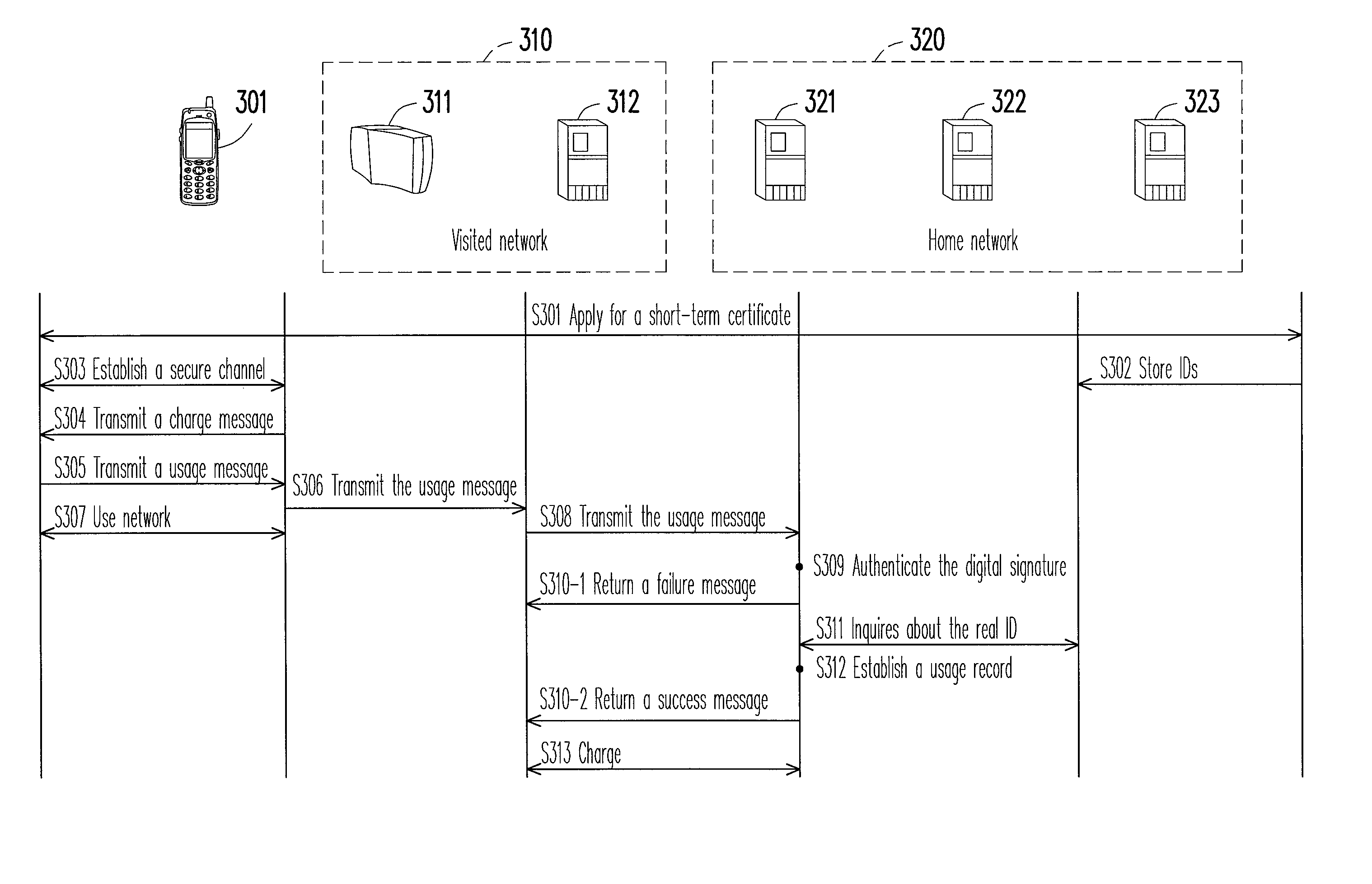
Method and system for managing network identity
A method and a system for managing network identity are provided. The method and the system realize a management mechanism of temporary identification (ID) and real ID, which simultaneously achieves functionalities such as anonymity, accounting, and authorization. A short-term certificate and a corresponding public / private key pair are used to protect a temporary ID usable for accounting. This protection prevents the temporary ID from theft. The user generates a digital signature in the reply to a charge schedule statement from the visited network. This procedure is incorporated into an existing authentication framework based on Transport Layer Security (TLS) in order to provide an undeniable payment mechanism. The payment mechanism is applicable in an environment of multiple network operators and reduces the difficulty of integrating network operators. The method and the system do not have to consult a certificate revocation list (CRL) for authentication and thus are able to shorten authentication time.
Owner:IND TECH RES INST
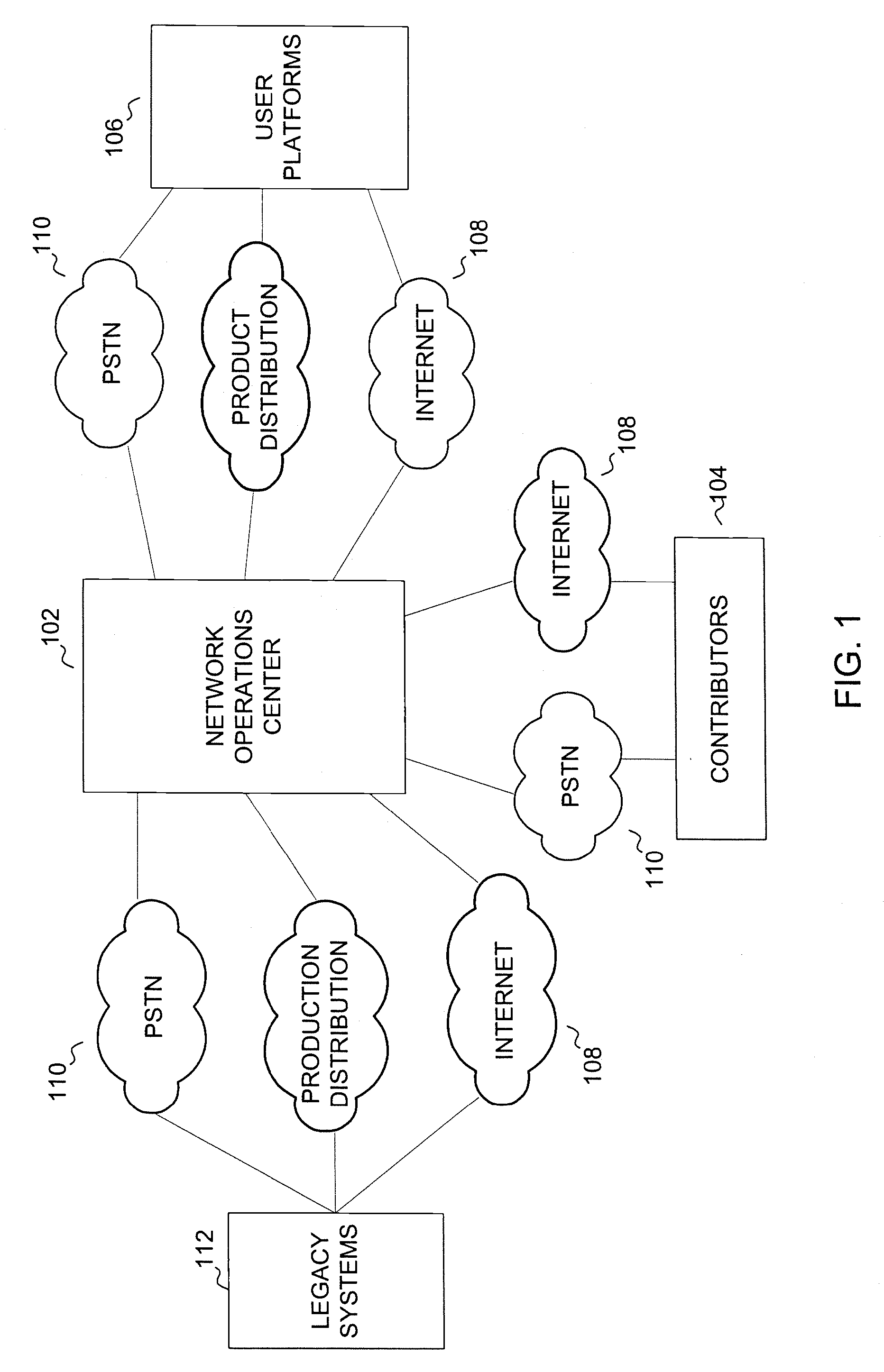
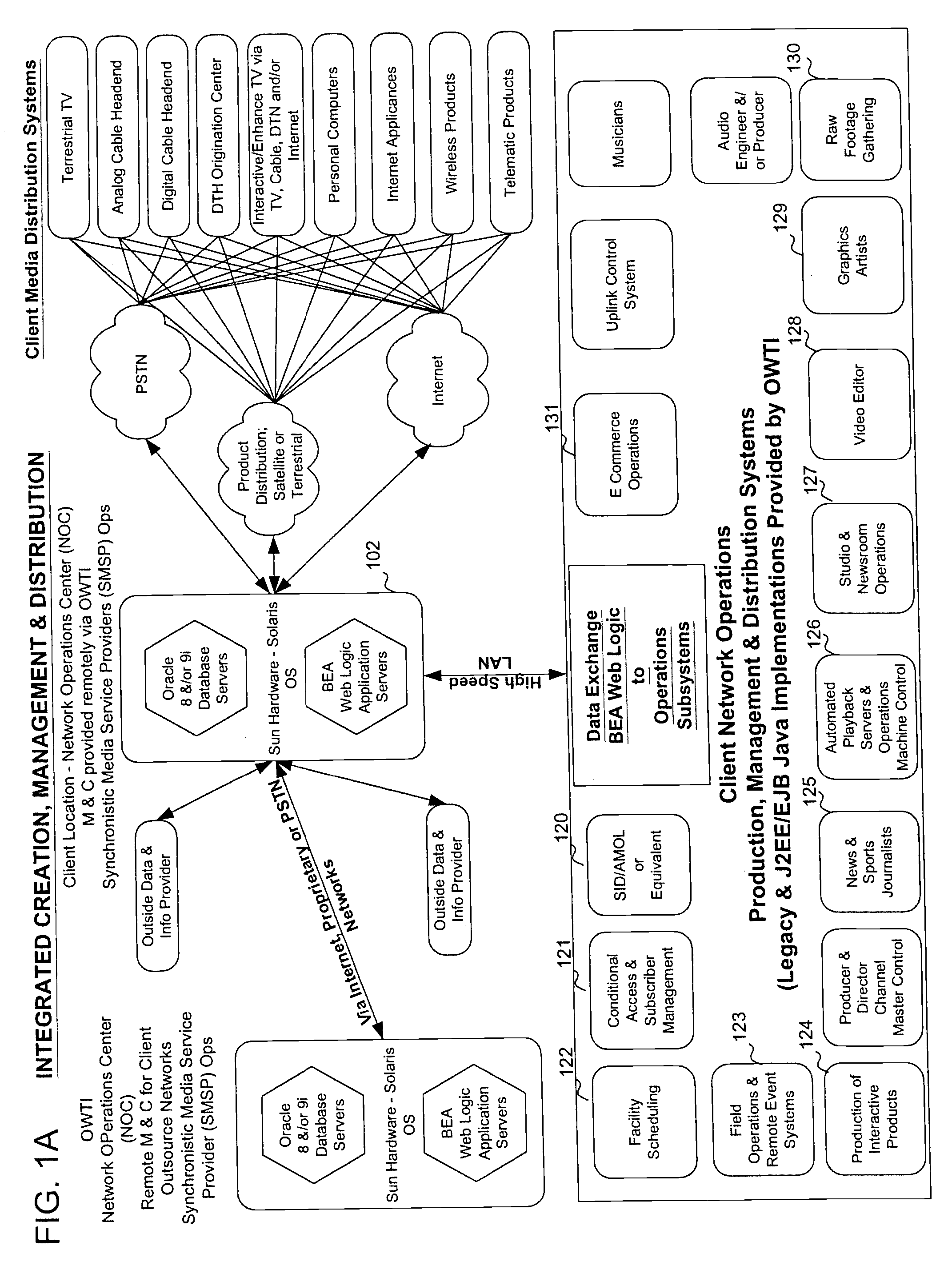
System and method for collaborative, peer-to-peer creation, management & synchronous, multi-platform distribution of profile-specified media objects
InactiveUS7207057B1Improve scalabilityAnalogue secracy/subscription systemsTransmissionCyber operationsLegacy system
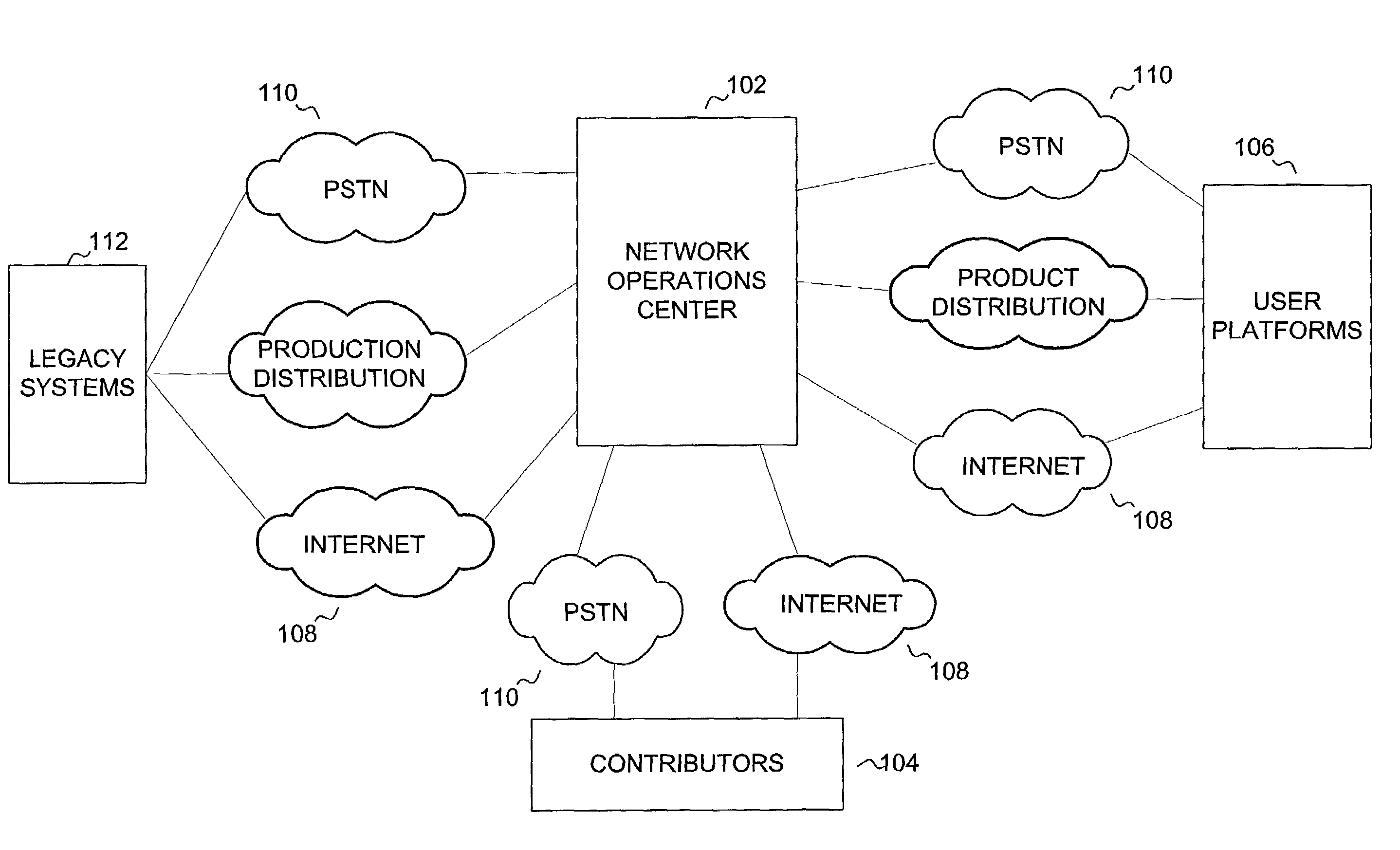
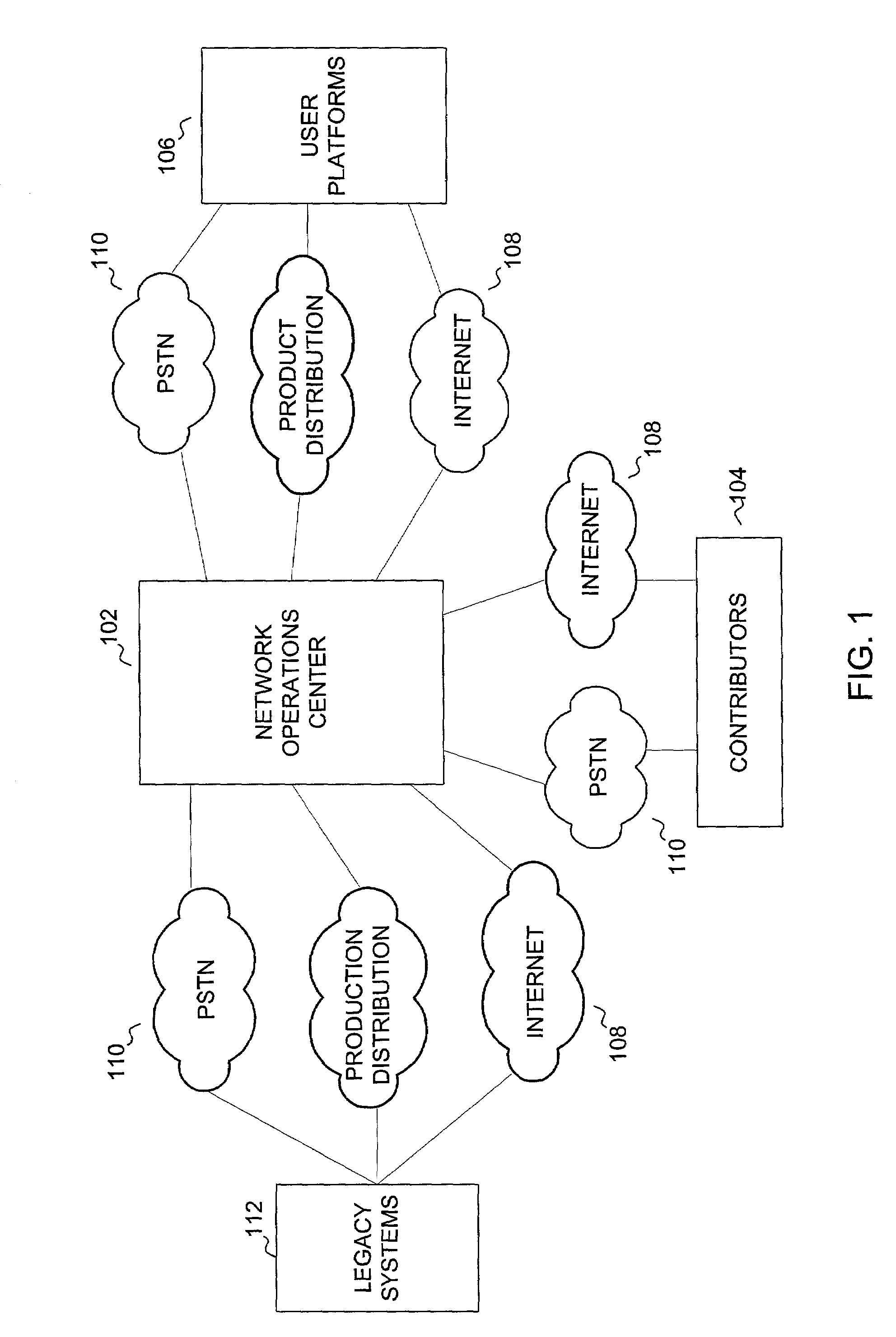
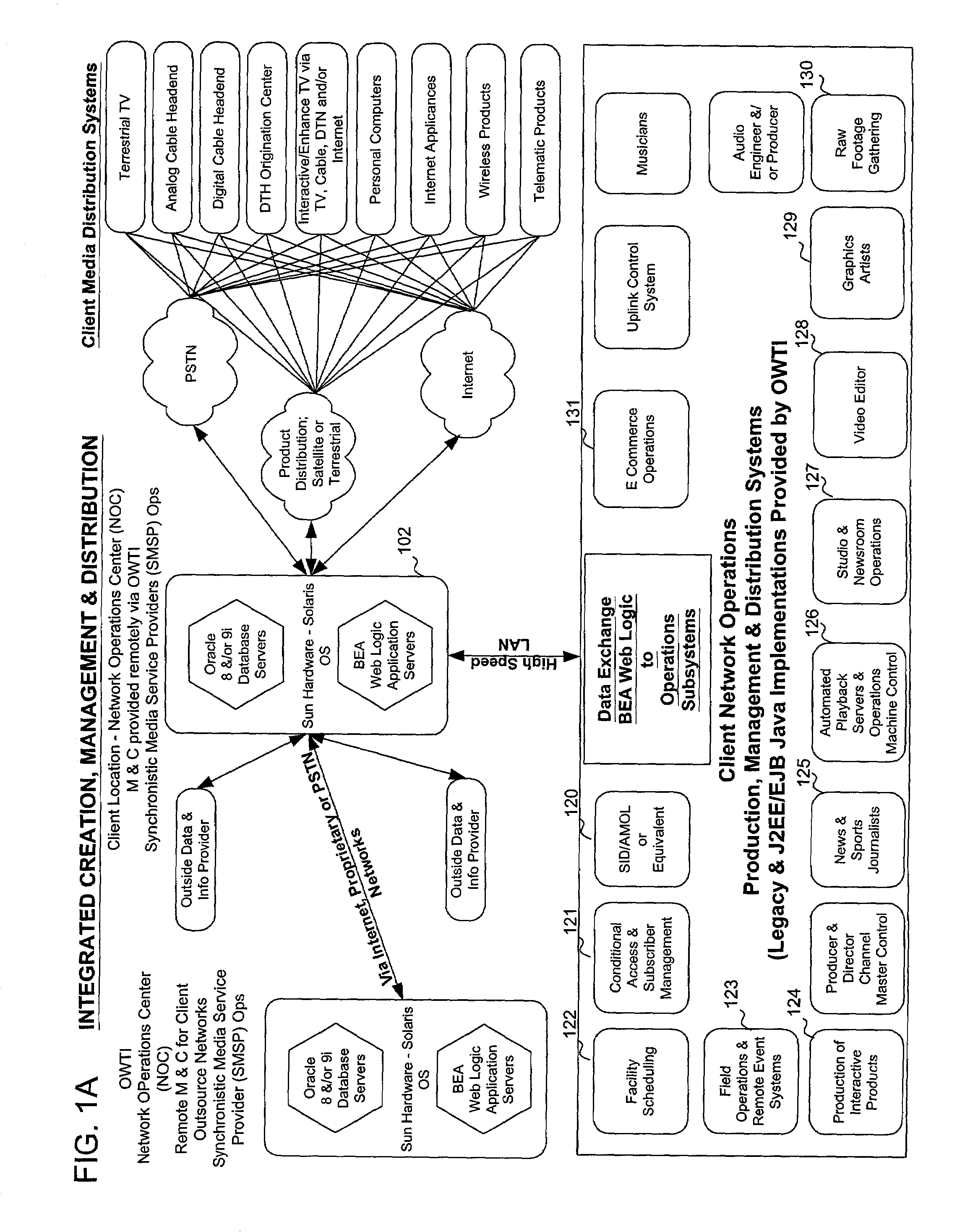
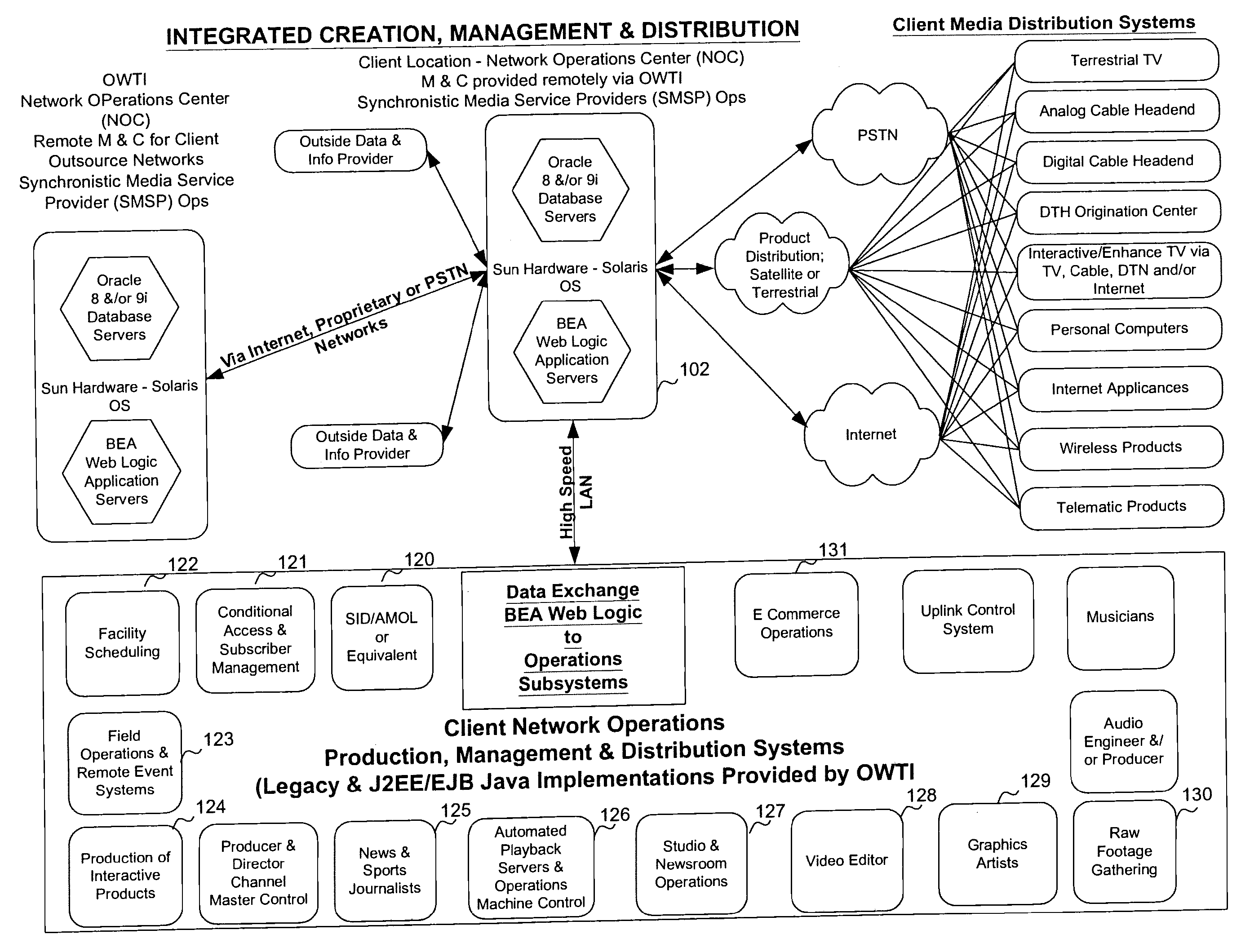
In a television programming management system, contributors access television programming functionality of legacy systems using a web-based interface provided by a network operations center. The network operations center is a best-of-breed J2EE-based implementation that provides a middleware interface to legacy systems. Using the interface provided by the network operations center, contributors can access any functionality required to create and distribute television programming. The present invention provides security features though a classifier. Use of playlists allows synchronization of created objects. Television programming can be performed by users and contributors.
Owner:ROWE LYNN T
Security state vector for mobile network platform
ActiveUS20050254654A1Minimal amountMemory loss protectionError detection/correctionRolloverCyber operations
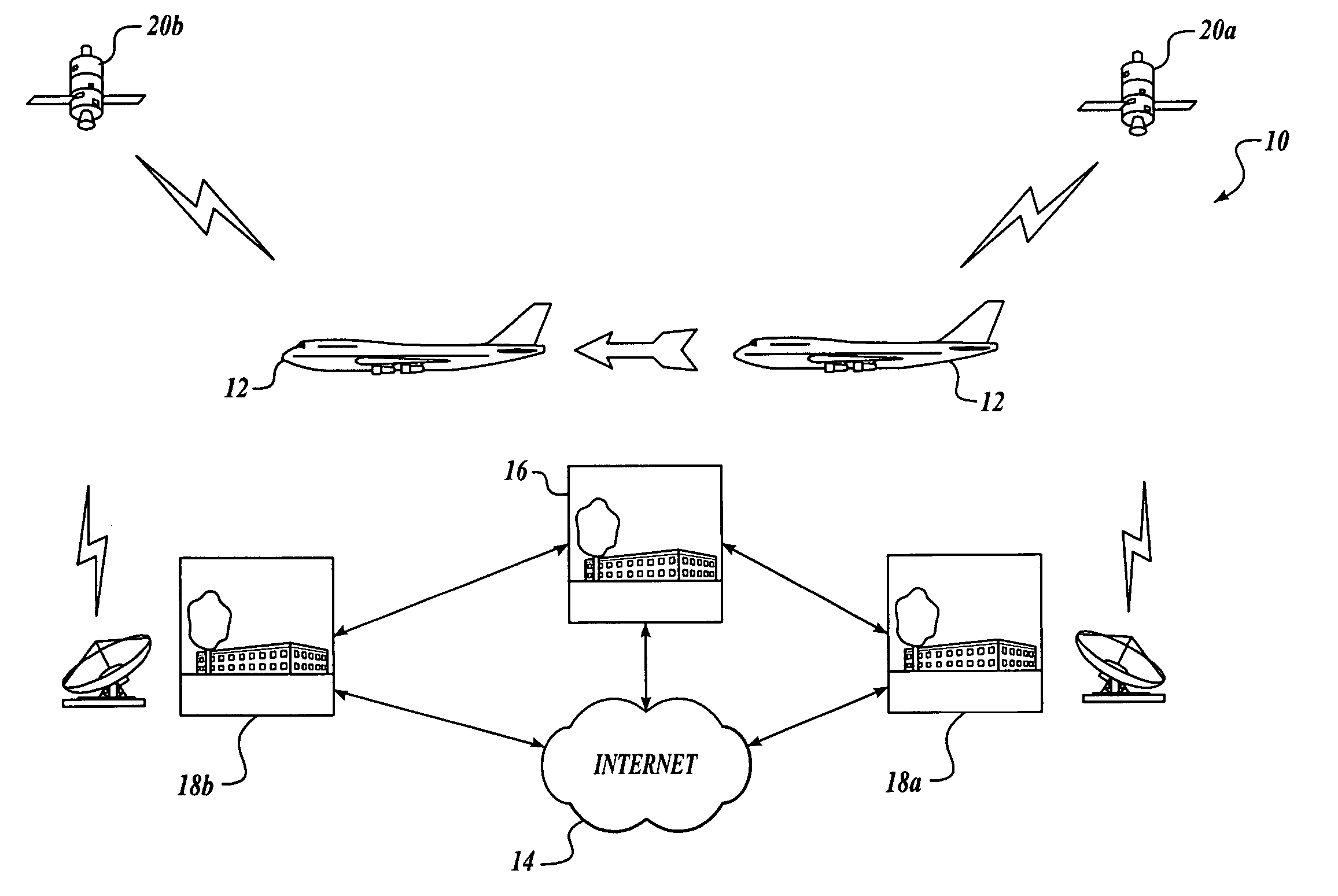
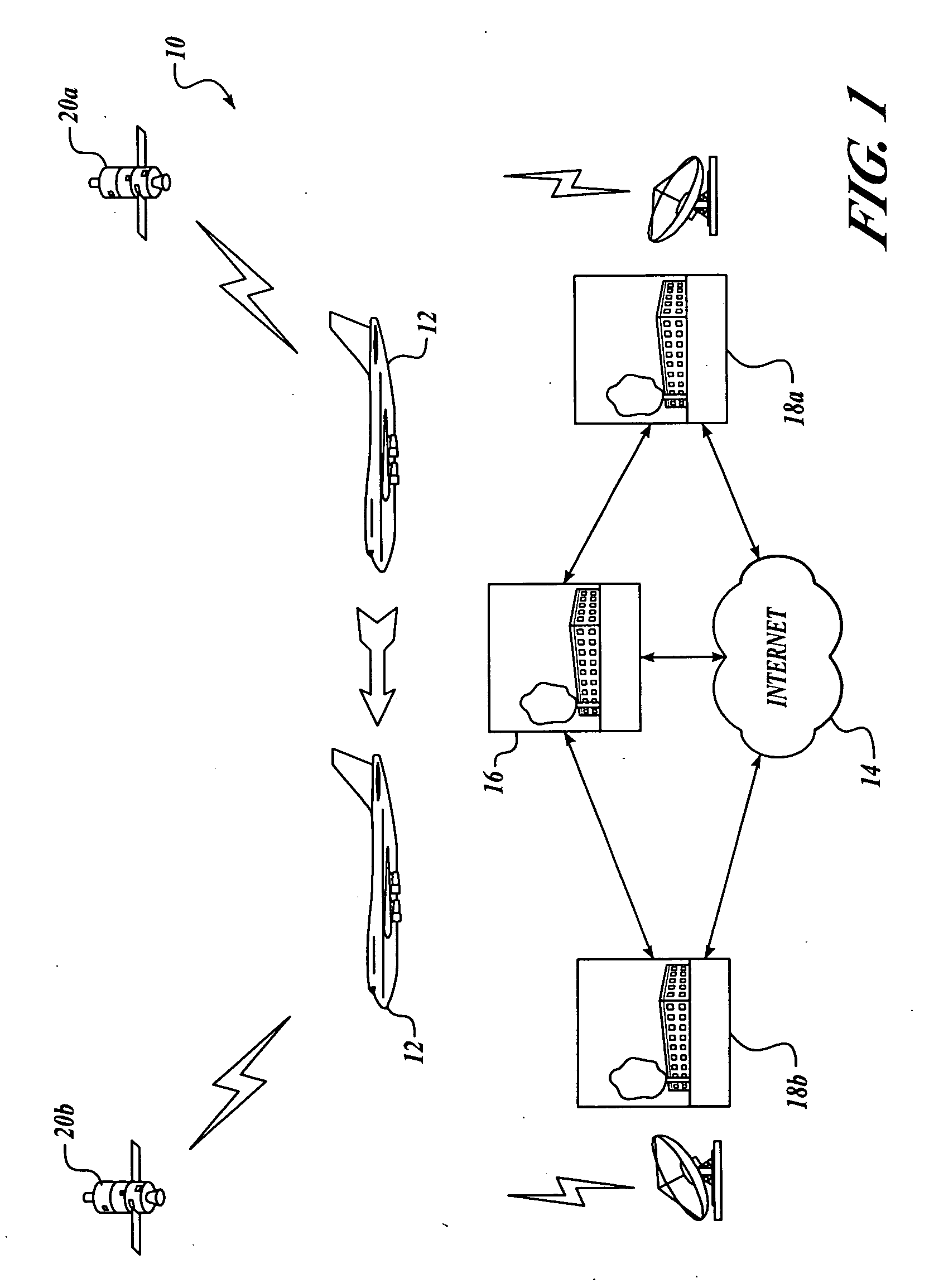
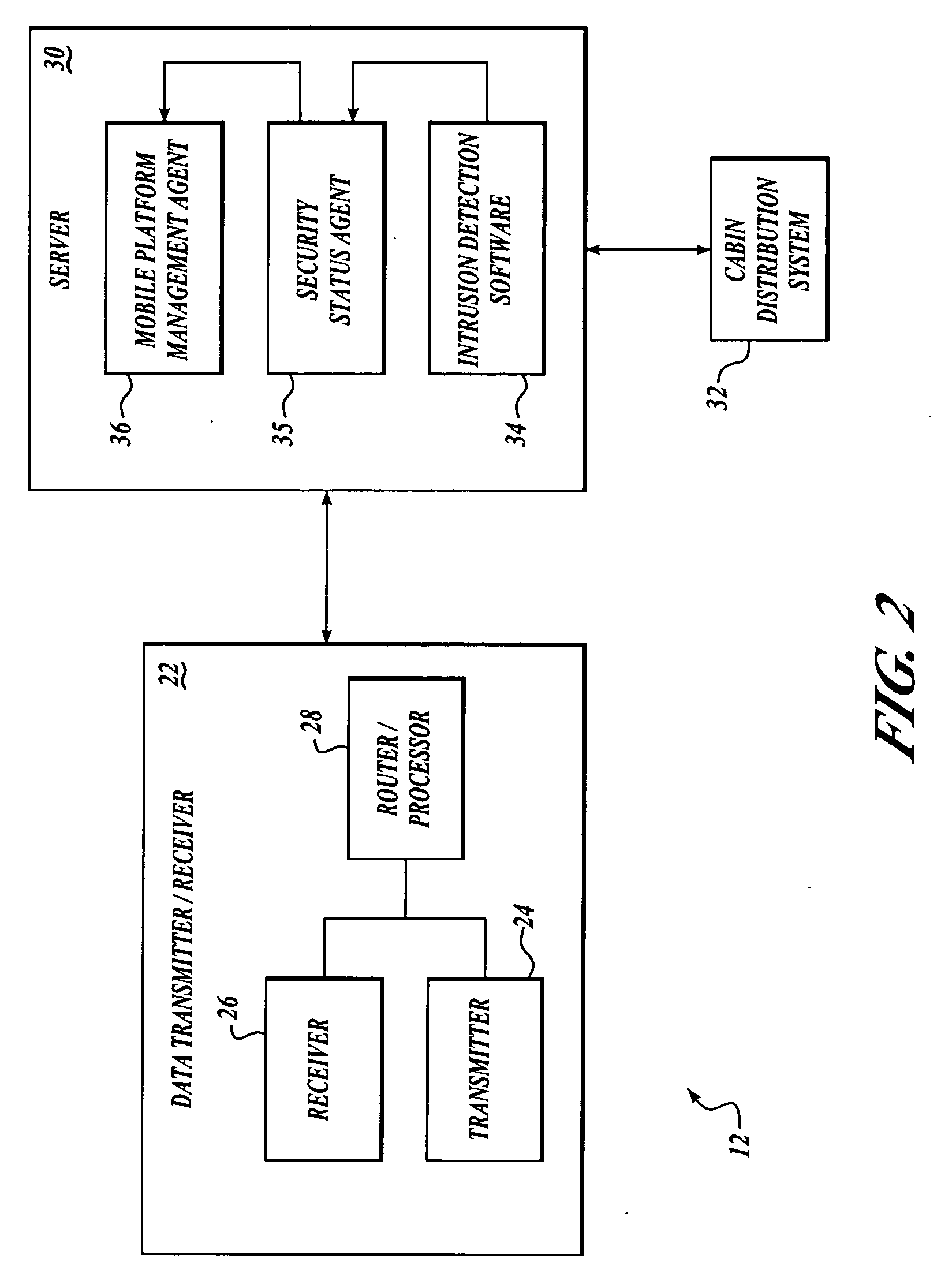
State of security in a mobile communications network is communicated. Data regarding nature and severity of security events onboard at least one mobile platform is generated and processed. A message that includes the processed data is generated and transmitted periodically. The processed data makes up a security state vector that includes the number of security events detected since power-up of the mobile platform node, sum of highest severity security events since power-up or counter rollover, sum of the second highest severity security events detected since power-up or counter rollover, sum of the third highest severity security events detected since power-up or counter rollover, highest security event classification, second-highest security event classification, and third-highest security event classification. The processed data may be used in a network operations center to prioritize mobile platforms from which logged data should be retrieved for further investigation and monitoring.
Owner:THE BOEING CO
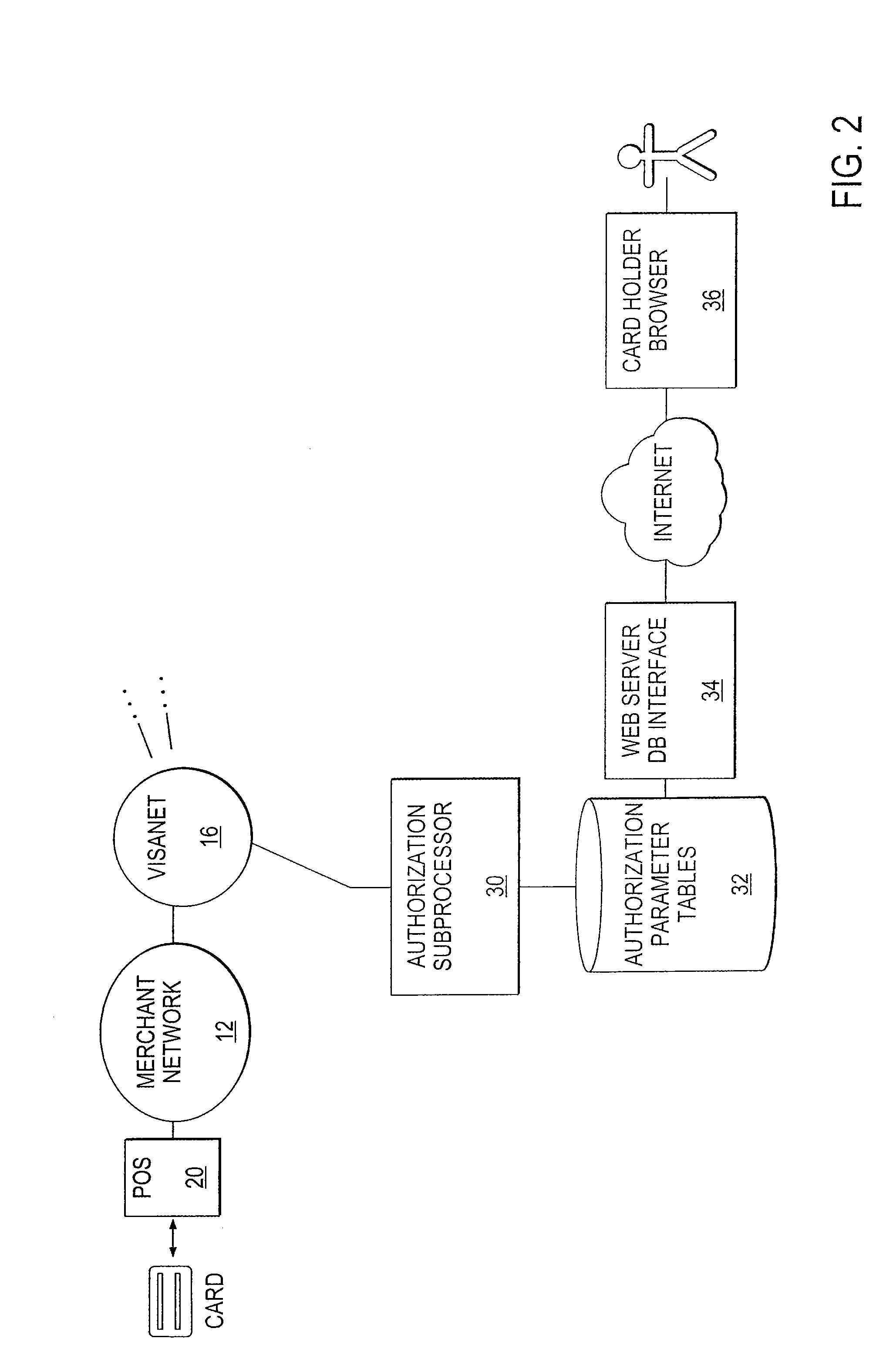
System for personal authorization control for card transactions
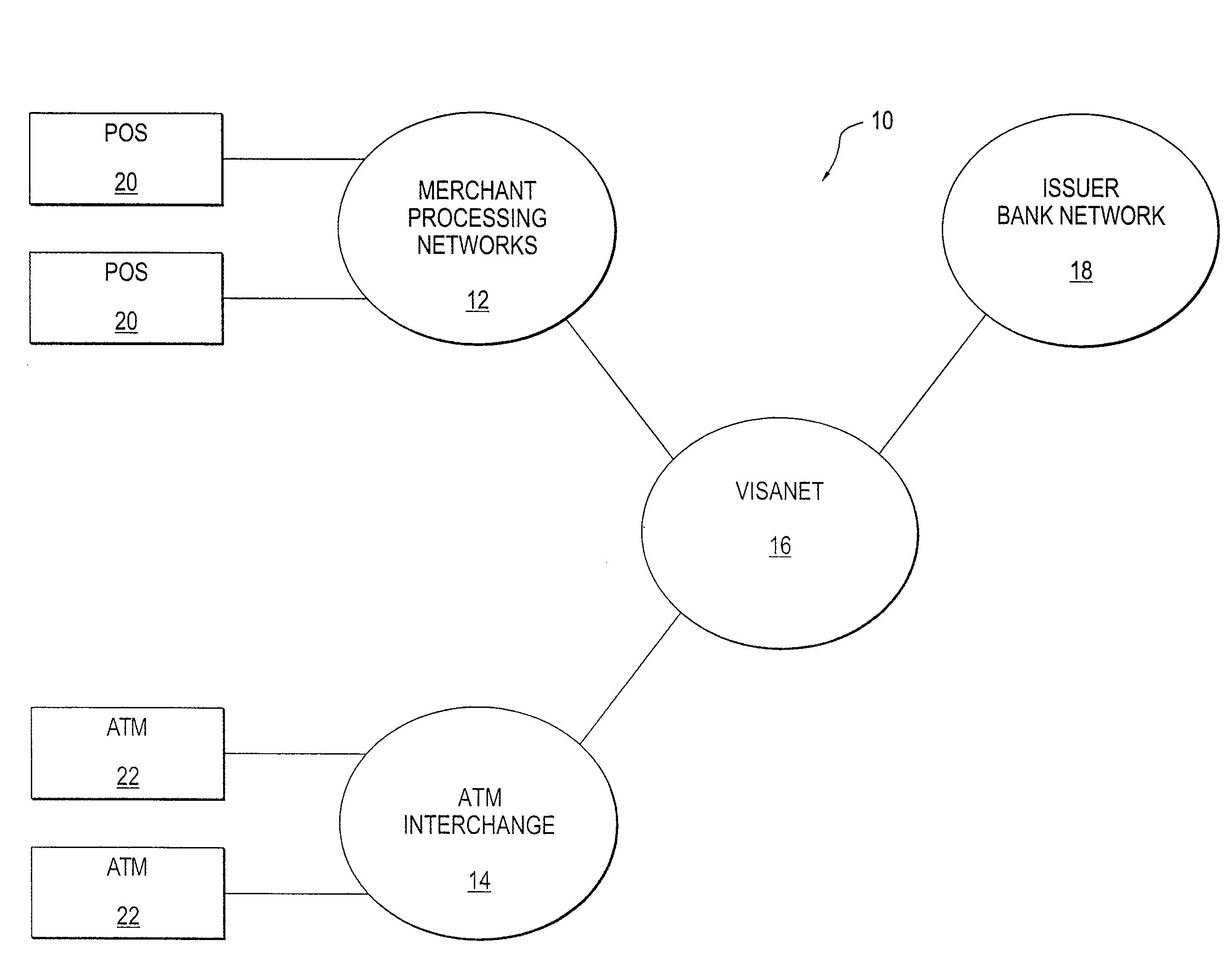
ActiveUS7389275B2Buying/selling/leasing transactionsPayment circuitsCyber operationsInternet privacy
An authorization system allows for cardholder-provided parameters to a personal authorization subsystem. The parameters can be selected by the cardholder to limit the authorizations that would otherwise be granted on the card. The parameters can indicate limits by frequency, dollar amount, merchant, geographic location, time of day, combinations thereof, or the like. Authorization for a given transaction, even where authorized by an issuer and a network operator, might be denied based on self-constraints set by the cardholder. In some variations, messages are sent to the cardholder based on constraints set by the cardholder and transactions might be approved and messaged, or denied and messaged.
Owner:VISA USA INC (US)
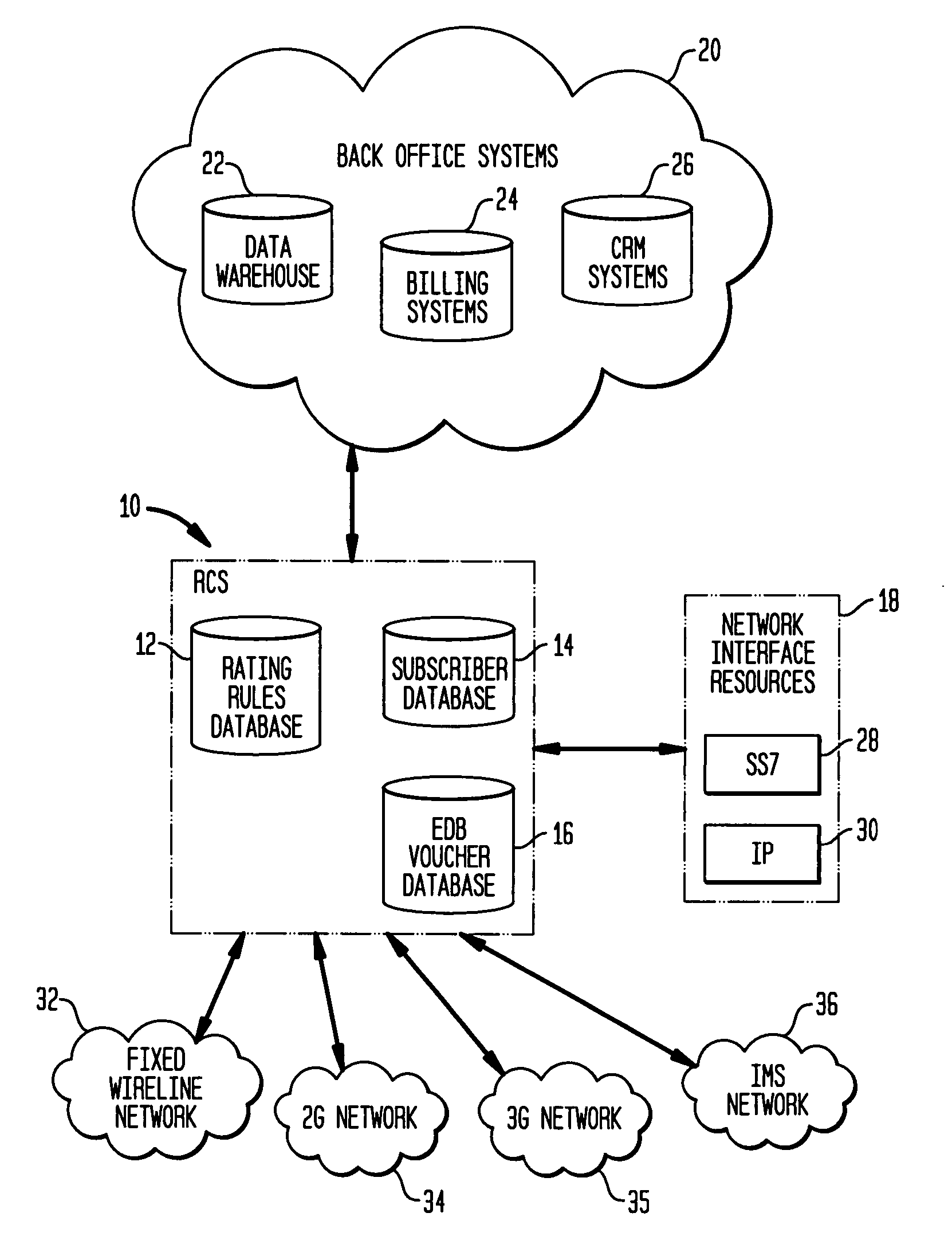
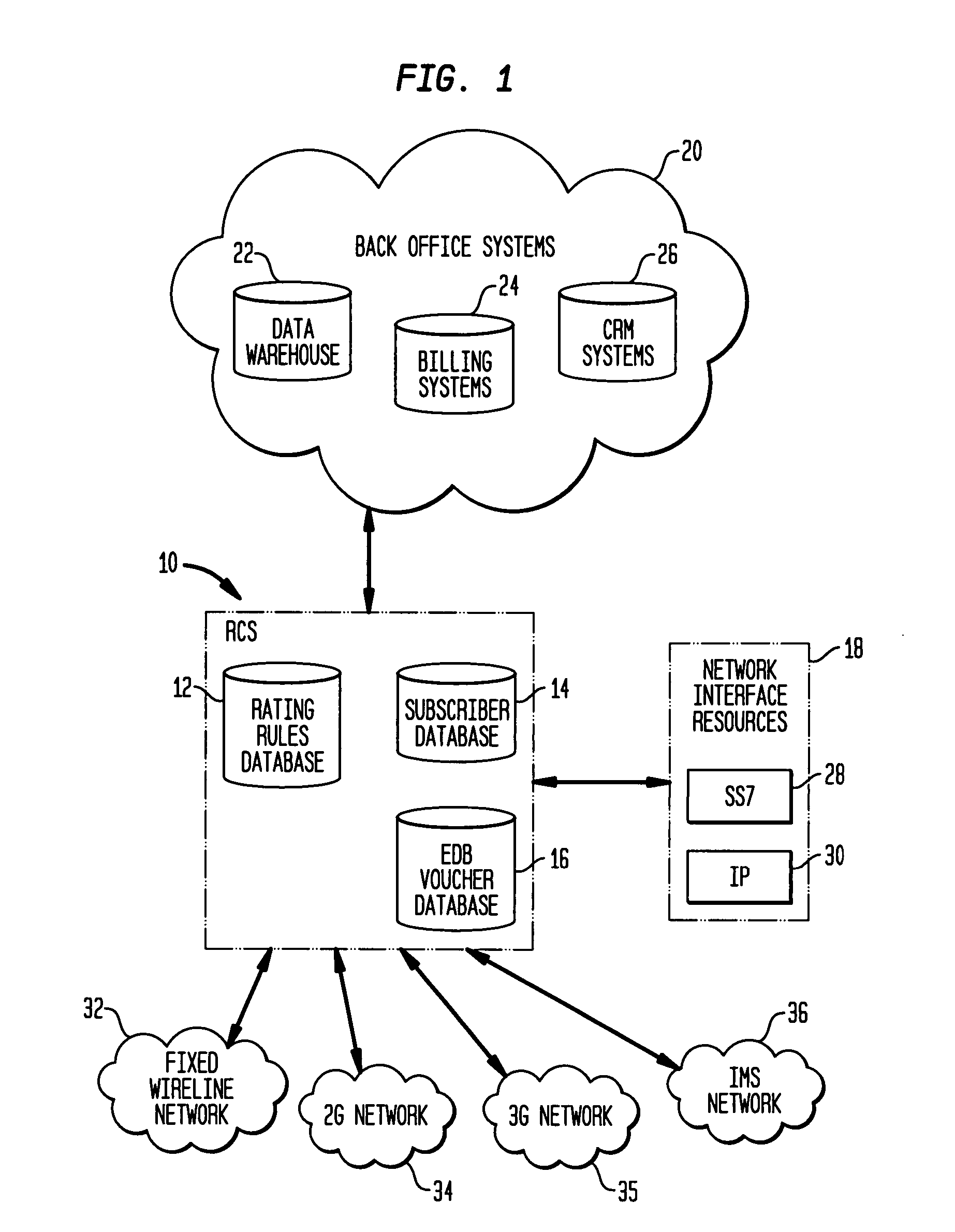
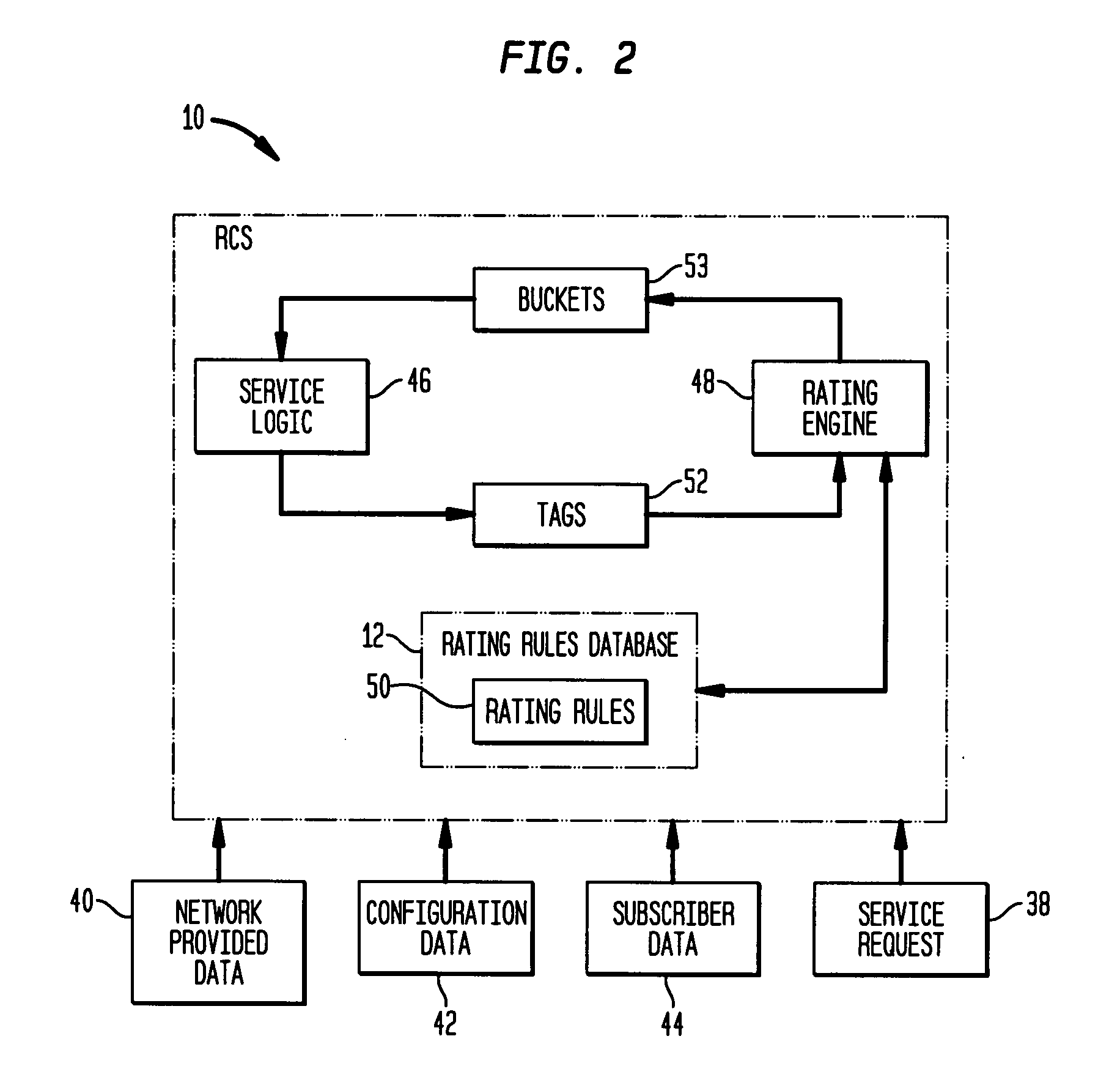
Flexible rating rules and calender rules implemented in a real-time charging system for a telecommunications network
ActiveUS20080014904A1Complete banking machinesSpecial service for subscribersReal-time chargingCyber operations
By coupling a rating engine with call processing, rating rules are generated that enable a flexible interface between call process and call rating without necessitating that fixed data be passed between them. The real time charging system (RCS) provides a process that creates a generic entity, called a bucket, and uses it to keep track of account information and / or to count types of usage. The bucket allows an operator to define accounts and usage counters and how they are used as part of the rating rules. Use of these buckets is defined in rating rules, thus turning control over subscriber account and usage counters to the network operator. Further, the RCS provides a calendar option for limiting times during which calls to general telephone numbers can be made or received.
Owner:INTELLECTUAL VENTURES II
Method and device for quality measuring of streaming media services
InactiveUS20140201330A1Easy to mergeLow costMultiple digital computer combinationsTransmissionMass parameterQuality measurement
Method and probe device for quality measuring in IP streaming of audio, video, or a synchronized mix of both, performing:receiving a streaming media flow at a user's end,measuring at least one network parameter which indicates QoS and / or QoE,extracting frames from the streaming at the user's end,analyzing the frames at the user's end by searching for determined errors and delivering at least a quality parameter defined by certain results of said searching;correlating each measured network parameter and each delivered quality parameter at the user's end and returning the results to the IP network operator though a control and configuration interface.The operator uses the control and configuration interface to configure at the user's end how to perform the correlation between the parameters, taking into account in said correlation the user's preferences described by an ontology.
Owner:TELEFONICA SA
System and method for communicating using bandwidth on demand
ActiveUS8787873B1Increase data rateEfficient combinationNetwork traffic/resource managementTelephonic communicationCyber operationsQuality of service
A system and method for dynamically changing the quality of service (QoS) for a subscriber of a cellular radio system. Bandwidth-on-Demand (BoD) enables the subscriber to dynamically switch to higher bandwidth and to enable a higher throughput. This may be for a limited time or amount of data, for example. The initiation may be by the subscriber, carrier, sponsor, or automatically by an application. The QoS increase may be dynamically priced in a kind of auction. The wireless device may contact the policy servers of a multiple network operator (MNO), which in turn contacts the Authentication, Authorization and Accounting (AAA) server in the MNO's core network. The policy server contacts the scheduler on the serving basestation which then determines whether to allocate more resources (i.e. bandwidth in the form of subcarriers, resource blocks, resource elements, timeslots) to the subscriber. The initiation may start a timer or data counter.
Owner:RPX CORP
System and method for collaborative, peer-to-peer creation, management & synchronous, multi-platform distribution of profile-specified media objects
InactiveUS20070271587A1Improve scalabilityTwo-way working systemsTransmissionCyber operationsNetwork operations center
In a television programming management system, contributors access television programming functionality of legacy systems using a web-based interface provided by a network operations center. The network operations center is a best-of-breed J2EE-based implementation that provides a middleware interface to legacy systems. Using the interface provided by the network operations center, contributors can access any functionality required to create and distribute television programming. The present invention provides security features through a classifier. User of playlists allows synchronization of created objects. Television programming can be performed by users and contributors.
Owner:ROWE LYNN T
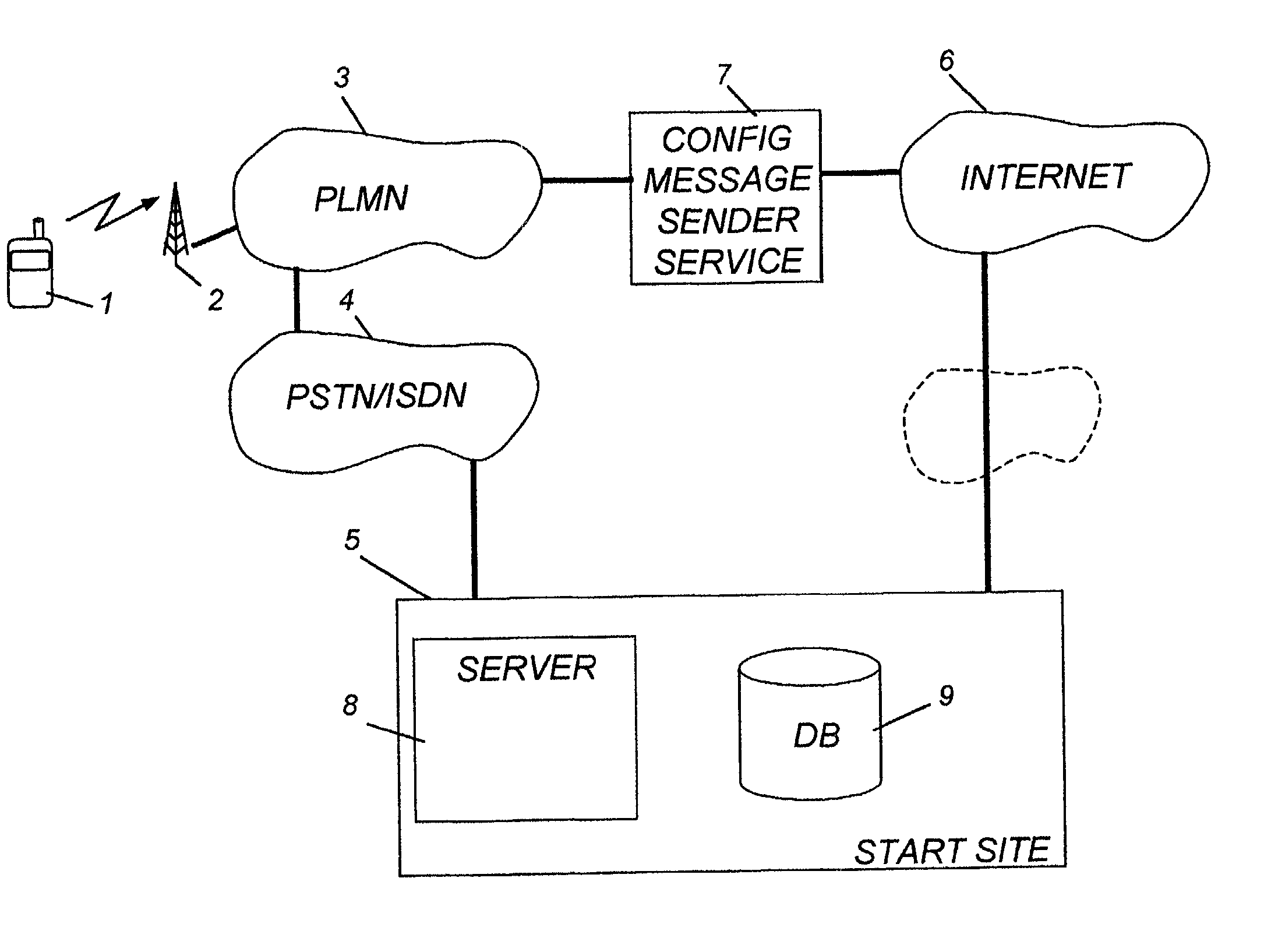
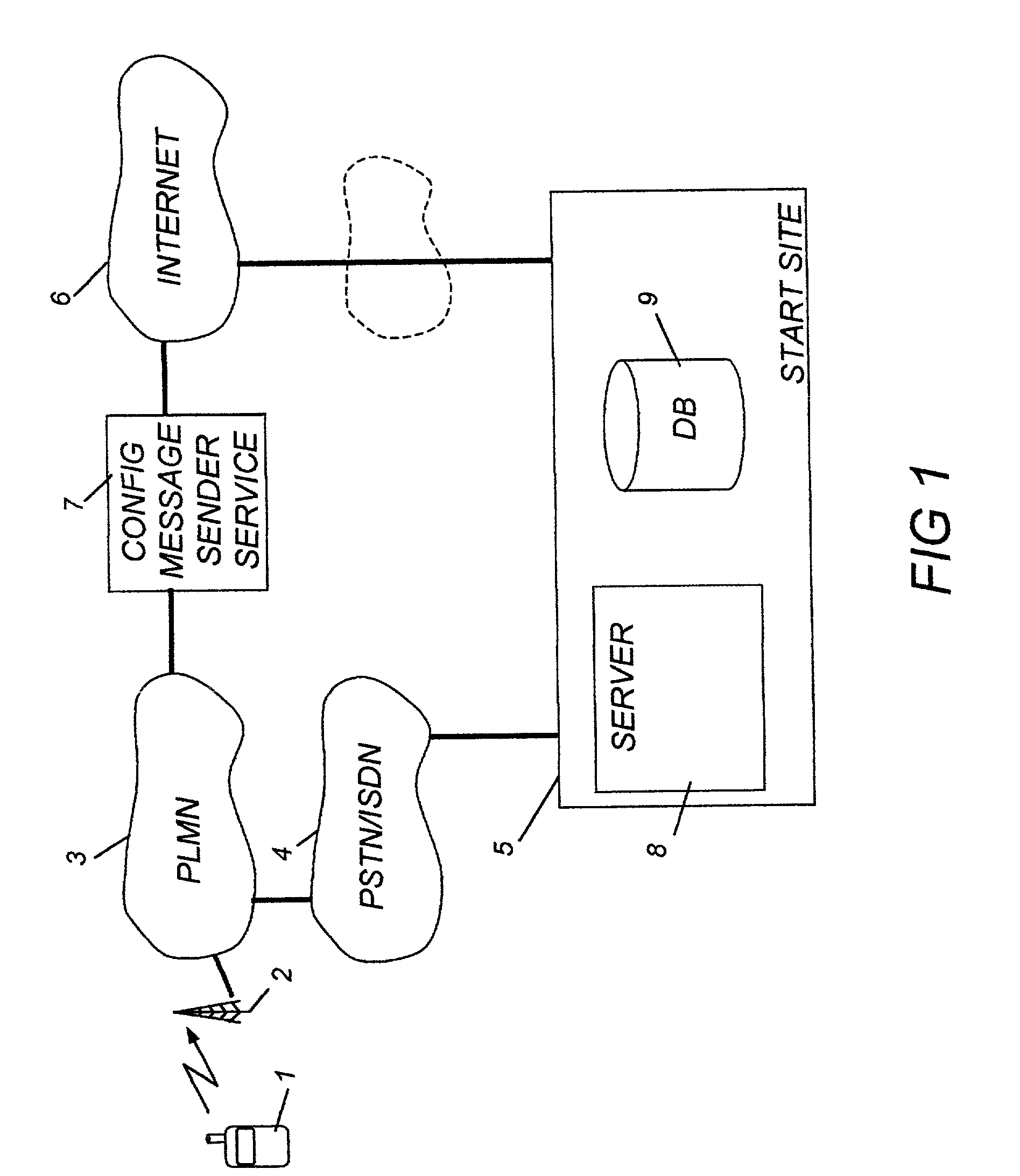
Method and arrangement for configuring a mobile telephone
InactiveUS20020078185A1Simple processIncrease profitTelephone data network interconnectionsSpecial service for subscribersReceiptPersonalization
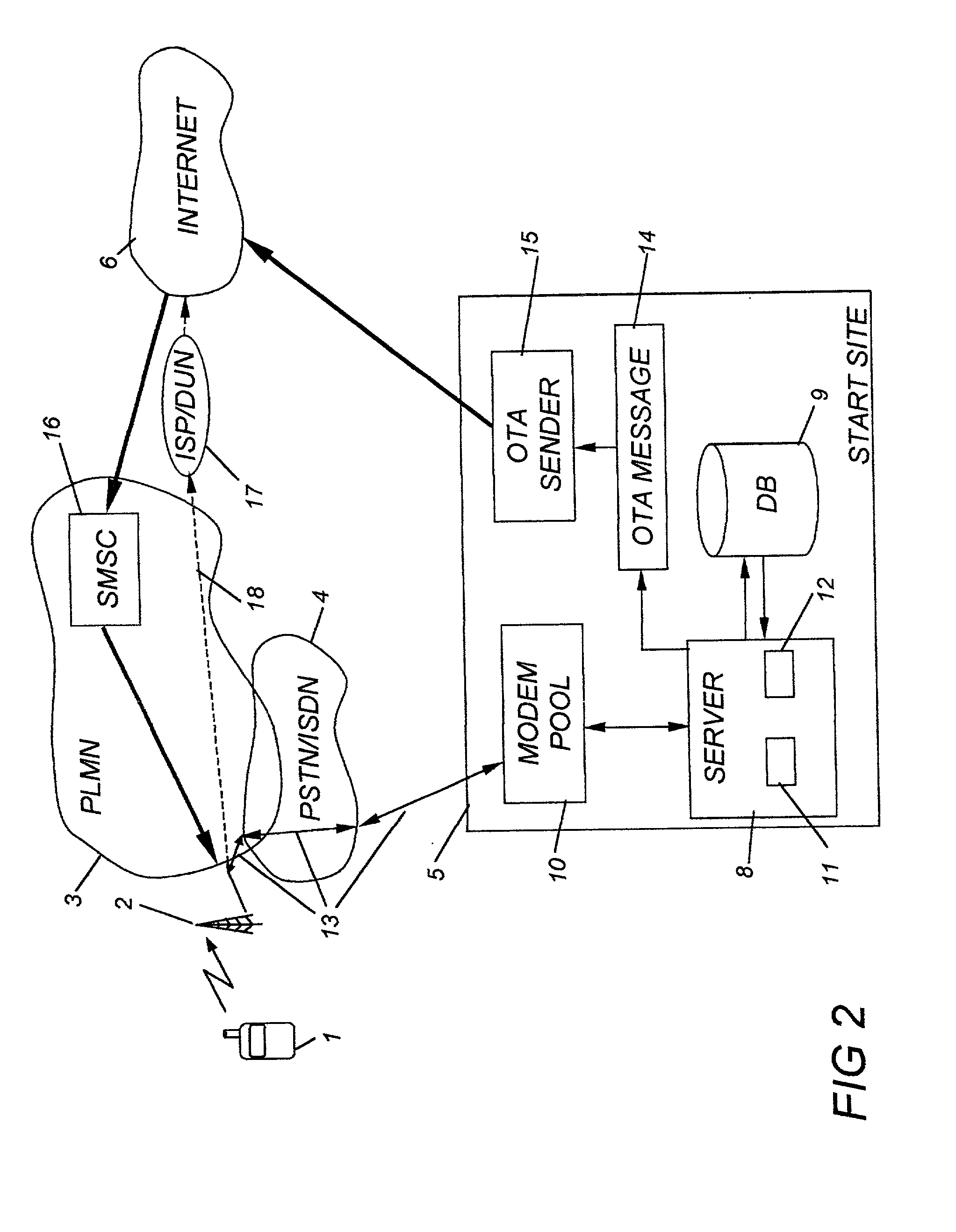
The invention relates to a method and a start site (5) for configuring a mobile telephone (1) for access to digital communication services. The invention also relates to a mobile telephone which on delivery from the shelf is pre-configured with a telephone number that goes to the start site. The start site comprises a server (8) and a data base (9). When the start site receives a call from a subscriber it requests the subscriber, by presenting text pages in the mobile's display, to select network operator and e-mail provider. Configuration data relating to access of the selected operator's digital services, and to the selected e-mail provider's services, including personalized information, are fetched from the data base and are placed in a configuration message which is transmitted to the mobile telephone. Upon receipt of the configuration message the mobile performs an automatic configuration process. Wap enabled telephones and SMS or OTA configuration messages may be used.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method and apparatus for steering idle mobile stations
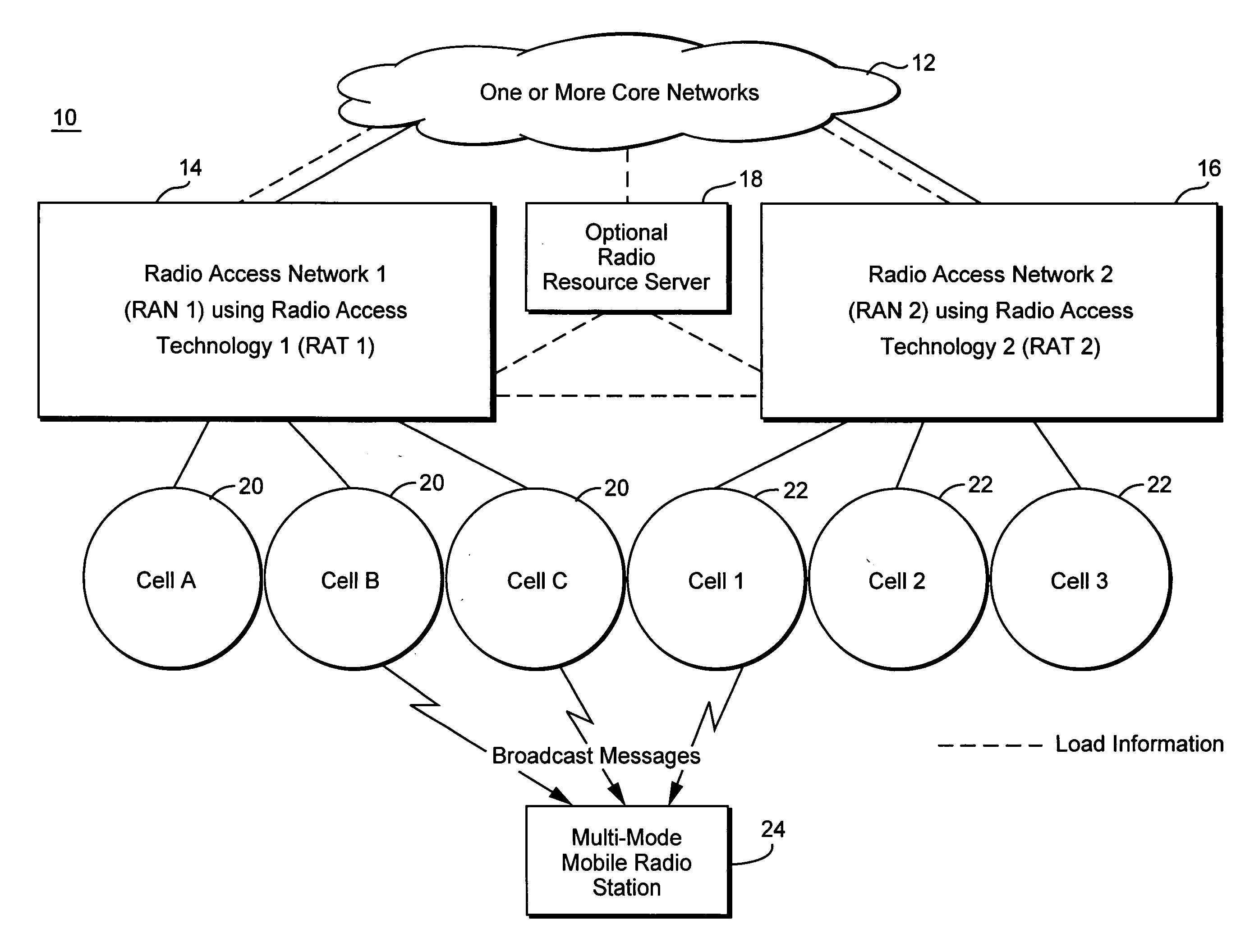
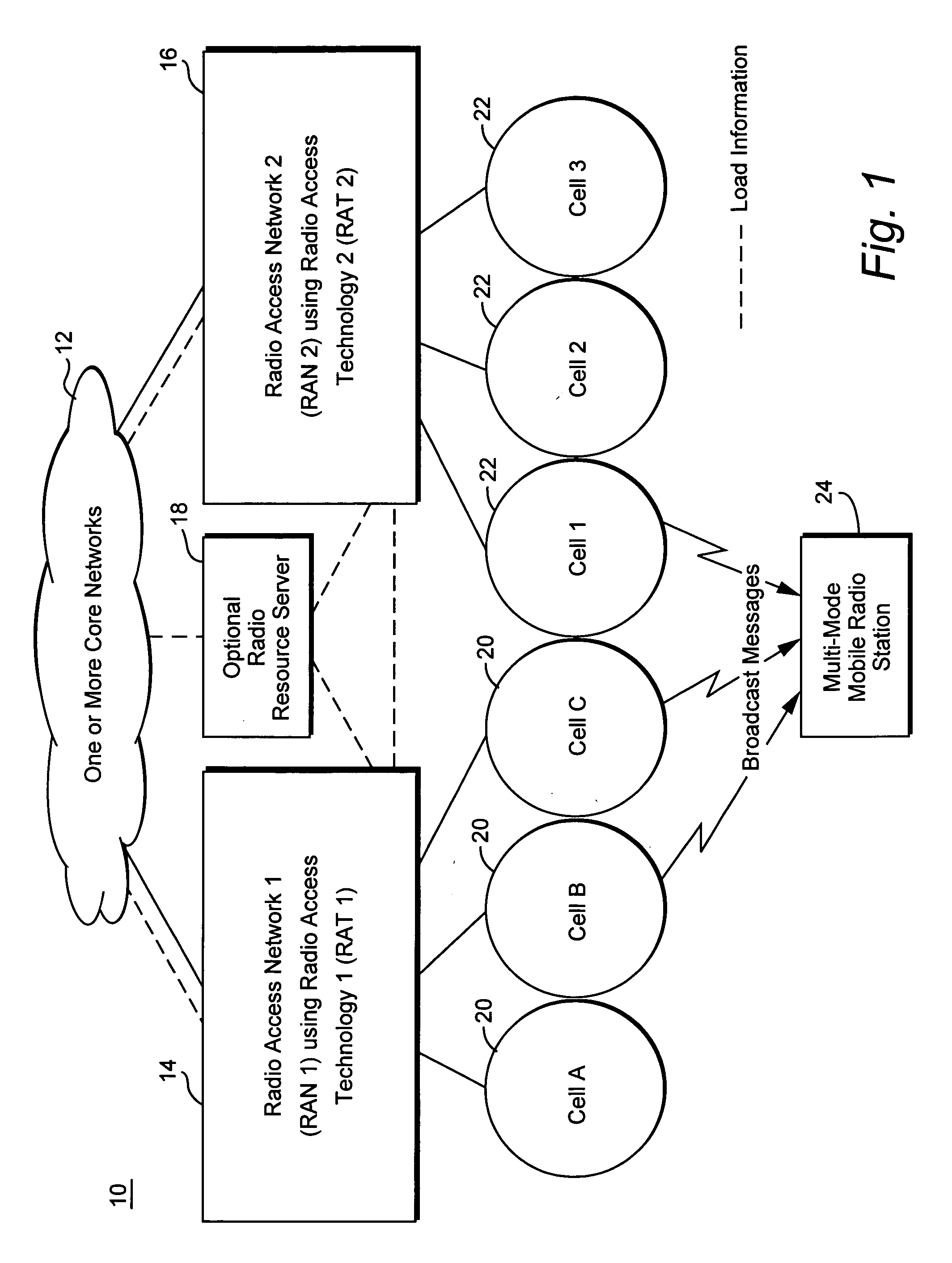
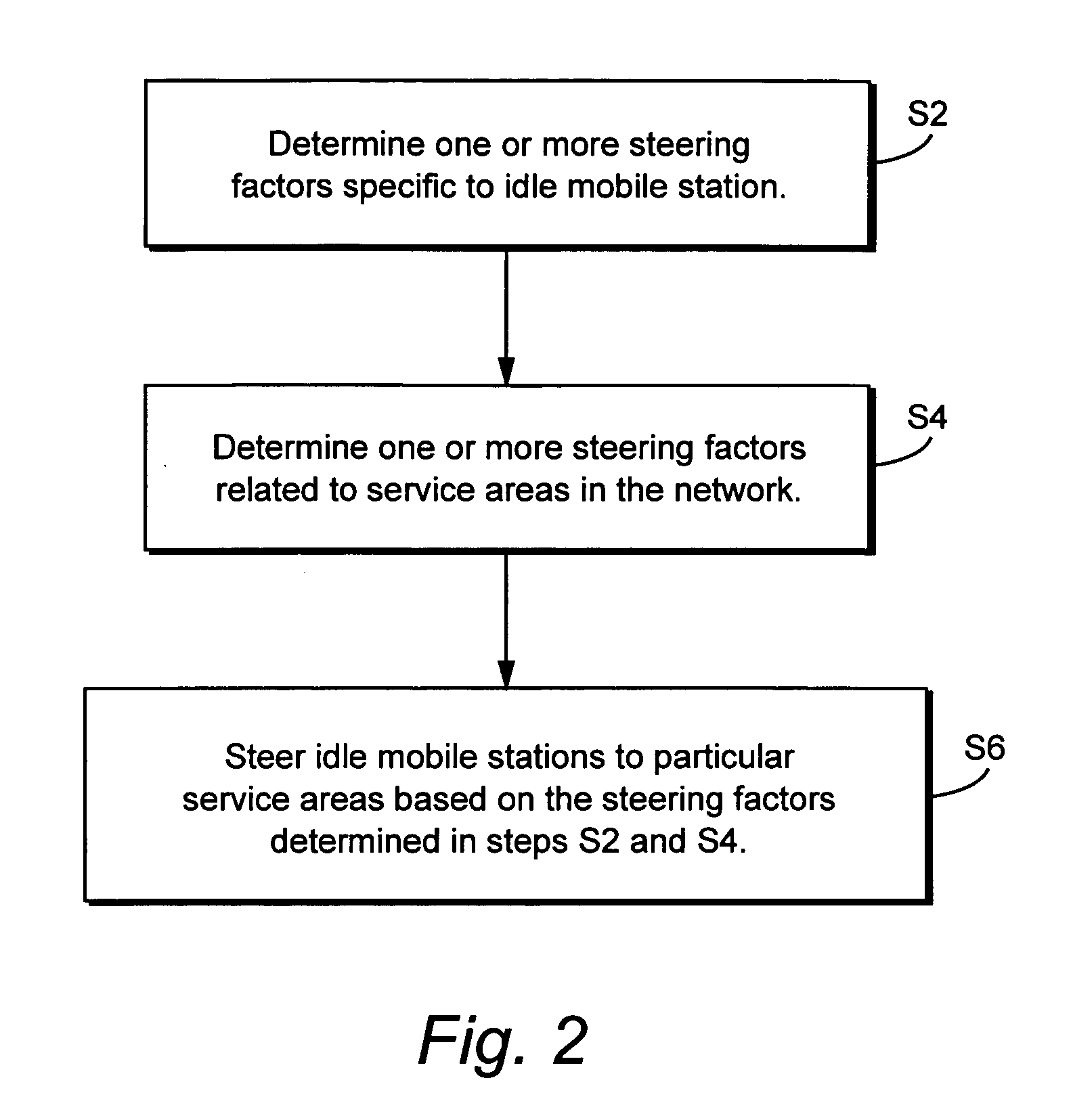
InactiveUS20060128392A1Simple processSimple mechanismNetwork traffic/resource managementAssess restrictionCyber operationsTelecommunications
Idle mobile stations are steered to a particular cell or service area to accommodate subscriber preferences or restrictions, subscription services, or network operator preferences or restrictions and / or to accomplish load redistribution or other network management functions. Multiple idle mobile station steering factors are considered. Steering may be accomplished using a variety of techniques such as rejecting registration attempts in certain cells and accepting those attempts in others and adjusting cell broadcast parameters.
Owner:TELEFON AB LM ERICSSON (PUBL)
Cluster server intelligent dispatching method and system
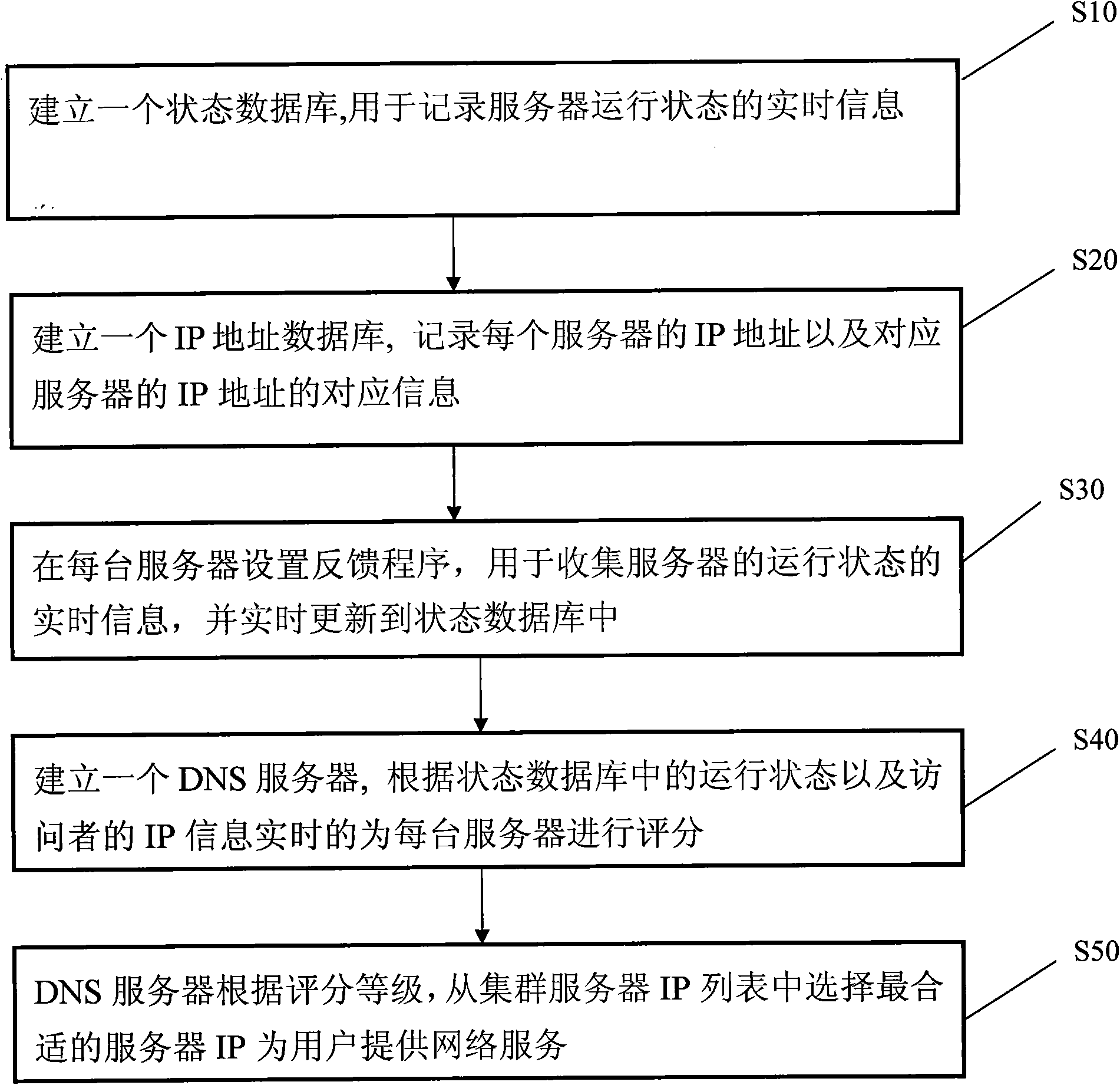
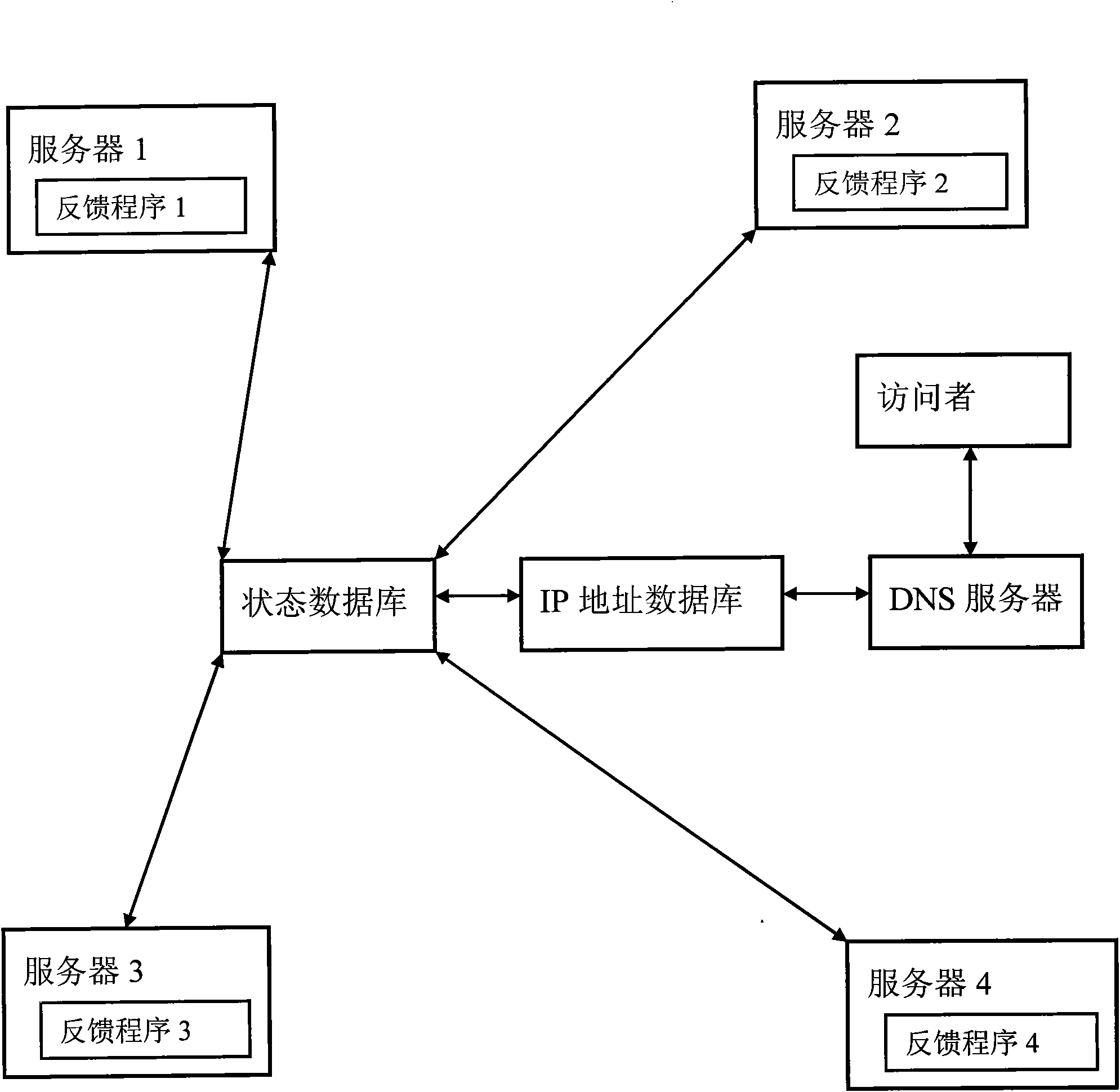
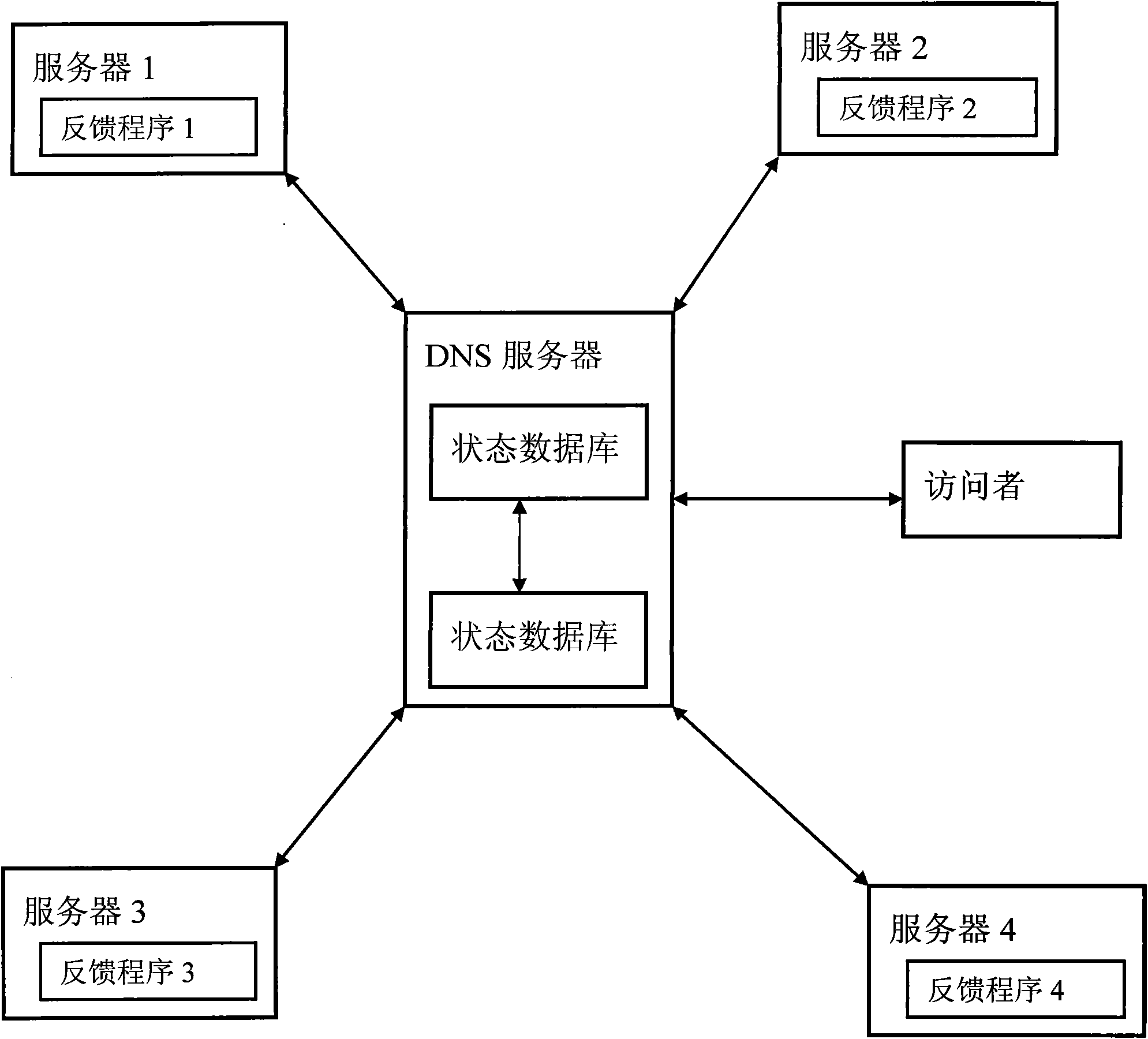
The invention relates to cluster server intelligent dispatching method and system. The cluster server intelligent dispatching system comprises a group of cluster servers, a state database, an IP (Internet Protocol) address database and a DNS (Domain Name Server) server, wherein the group of cluster servers are respectively provided with a feedback program used for collecting the real-time information of the operating states of the servers; the state database is connected with the group of cluster servers and used for recording the real-time information of the operating states of the servers according to the real-time information of the operating states of the servers, wherein the real-time information is collected by the feedback programs; the IP address database is connected with the state database and used for recording the IP address of each server, the geographic position of the IP address of the corresponding server and the information of network operators; and the DNS server is connected with the IP address database, used for distributing same domain names to the cluster servers providing same services, scoring each server in real time according to the operating states inside the state database and the IP information of accessors to obtain the scoring grades of the servers and providing network services for users by selecting an optimum server IP.
Owner:SHENZHEN TEMOBI SCI &TECH
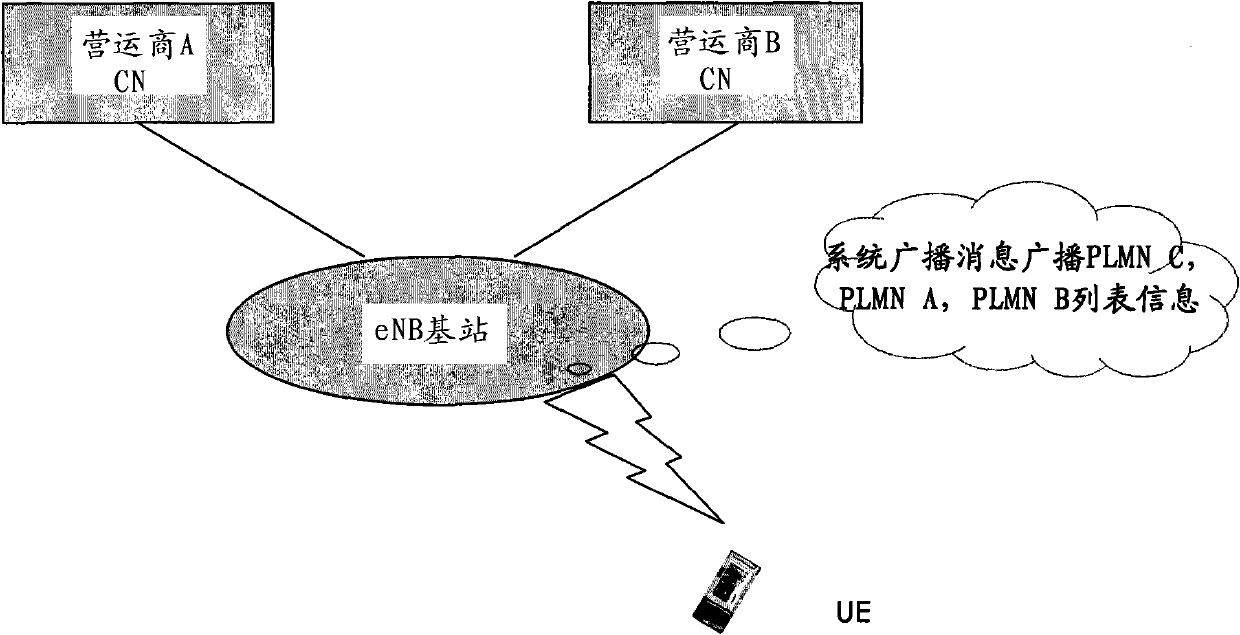
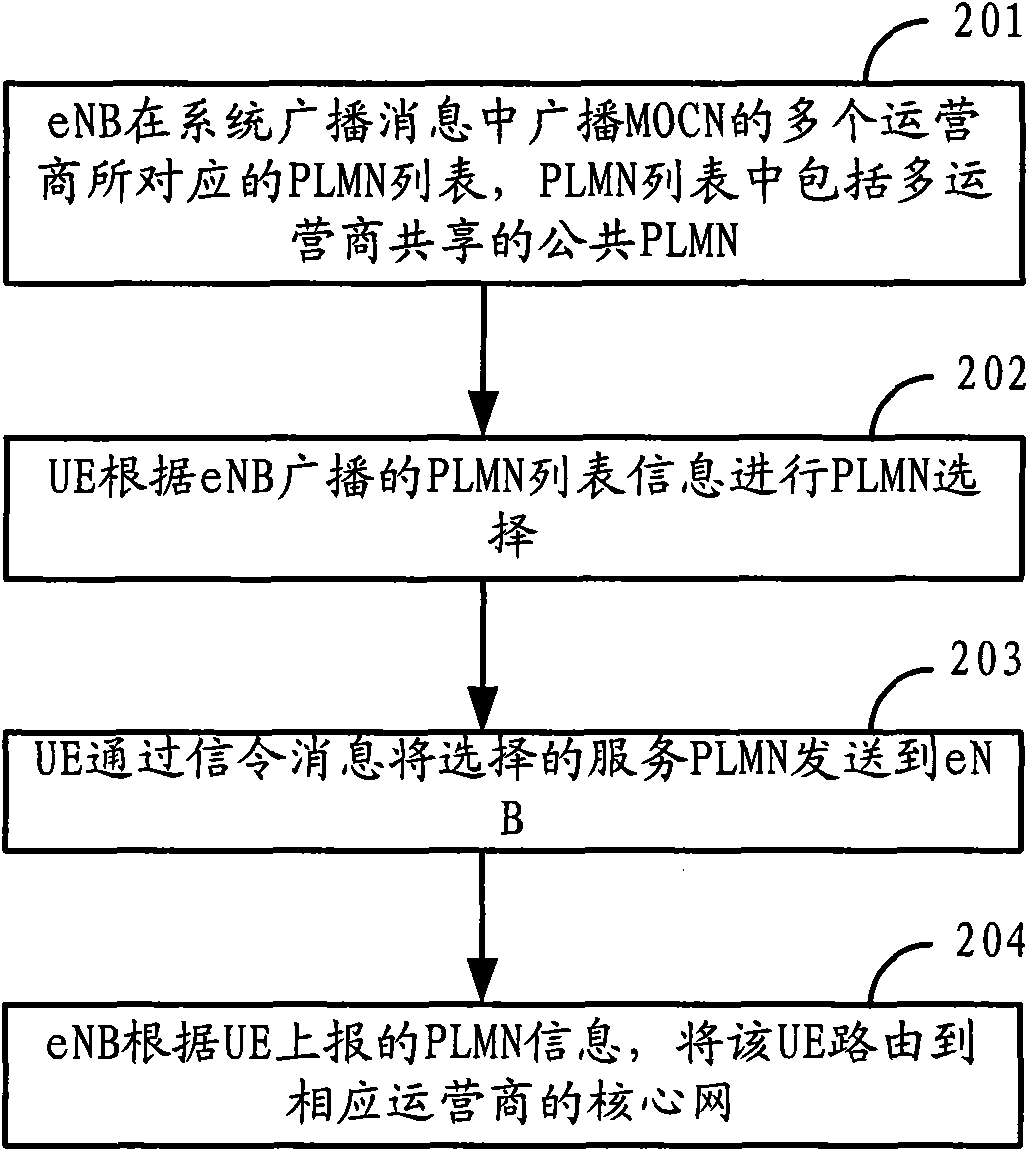
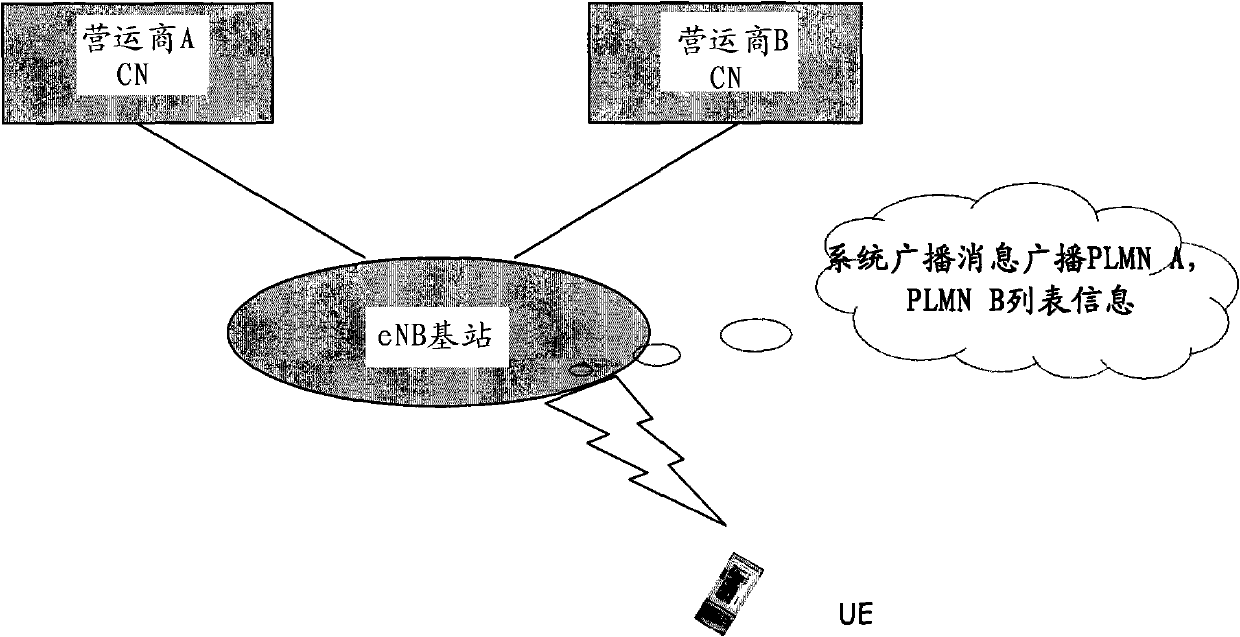
Method, device and system for sharing network
The invention relates to a wireless communication technology and discloses a method, device and system for shearing a network. The method comprises the following steps: broadcasting a system message which includes a plurality of PLMN (public land mobile networks) corresponding to a plurality of operators and reflects the priority relationship among the plurality of the PLMN in a multi-operator core network (MOCN) cell; receiving the PLMN which is sent by user equipment (UE) and selected according to the system message; and routing the UE to a core network which corresponds to the selected PLMN according to the PLMN selected by the UE. Through the technical scheme provided by the embodiment of the invention, the network selection for the roaming UE can be controlled and the balance of interests of roaming users among operators of the shared network can be further realized.
Owner:HUAWEI TECH CO LTD
Servers and Methods for Controlling Group Management
InactiveUS20070220005A1Enhanced advantageSpecial service provision for substationNetwork topologiesCommunications systemUser privacy
The present invention addresses the management of user groups, user contact lists, and user access lists in a telecom-communication system whereby a user access to a group and list management server for creating, deleting or modifying a group, contact list and access list in terms of group policies and members. User groups, user contact lists, and user access lists are operated without any validation other than being syntactically correct, and without taking into consideration the users access capabilities, the users privacy, and even the user existence. In particular, the telecommunication system may comprise a number of networks operated by different network operators where the users hold subscriptions. The present invention offers a new interface between a group management server and a subscriber server of a network operator where the users hold their subscriptions, so that user policies in the subscriber server govern operations on groups, contact lists and access lists.
Owner:TELEFON AB LM ERICSSON (PUBL)
Means and method for controlling service progression between different domains
InactiveUS20070117548A1Special service for subscribersDigital data authenticationThird partyCyber operations
At present, the existing mechanisms for authorising a user of a service network operator to access a service provided by a third party service provider are valid for most of the existing services based on a request and an answer, but for transactional services, those where a service delivery implies several transactions, the existing techniques present serious limitations for the operators to fully control the progression of services. To overcome this limitation, the invention provides means and methods to control the progression of a service, service which requires a plurality of transactions, at a first domain where the service has been authorised while the user is using said service provided by a second domain, as well as a verification mechanism for verifying the use of the service between the service network operator and the service provider.
Owner:TELEFON AB LM ERICSSON (PUBL)
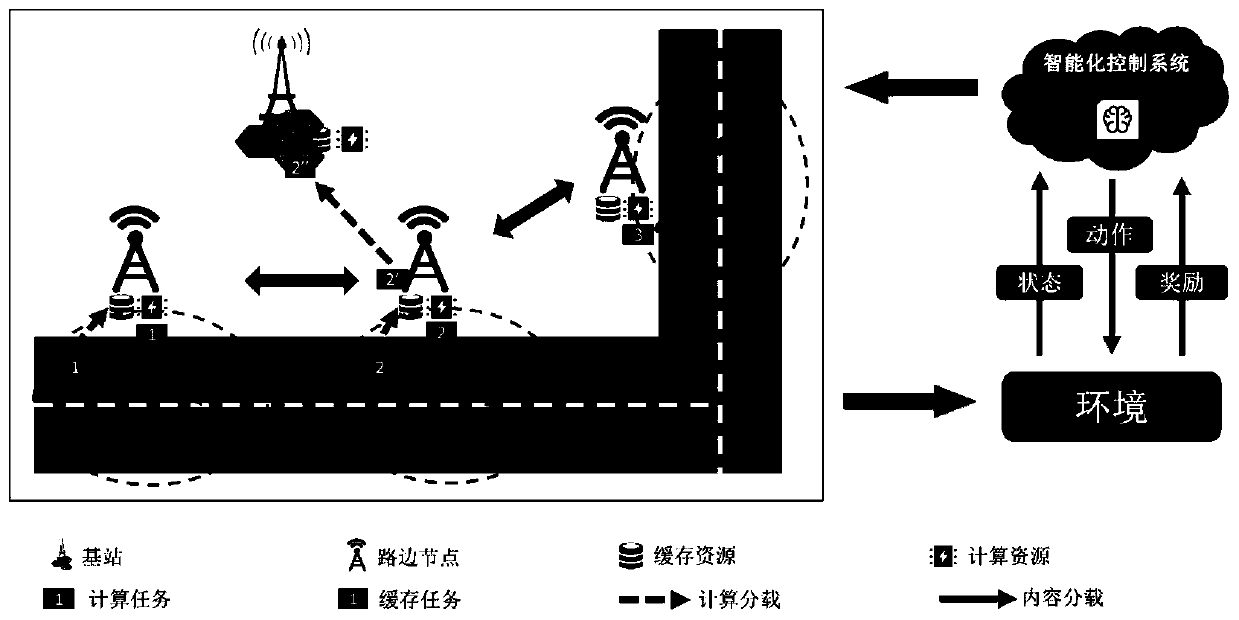
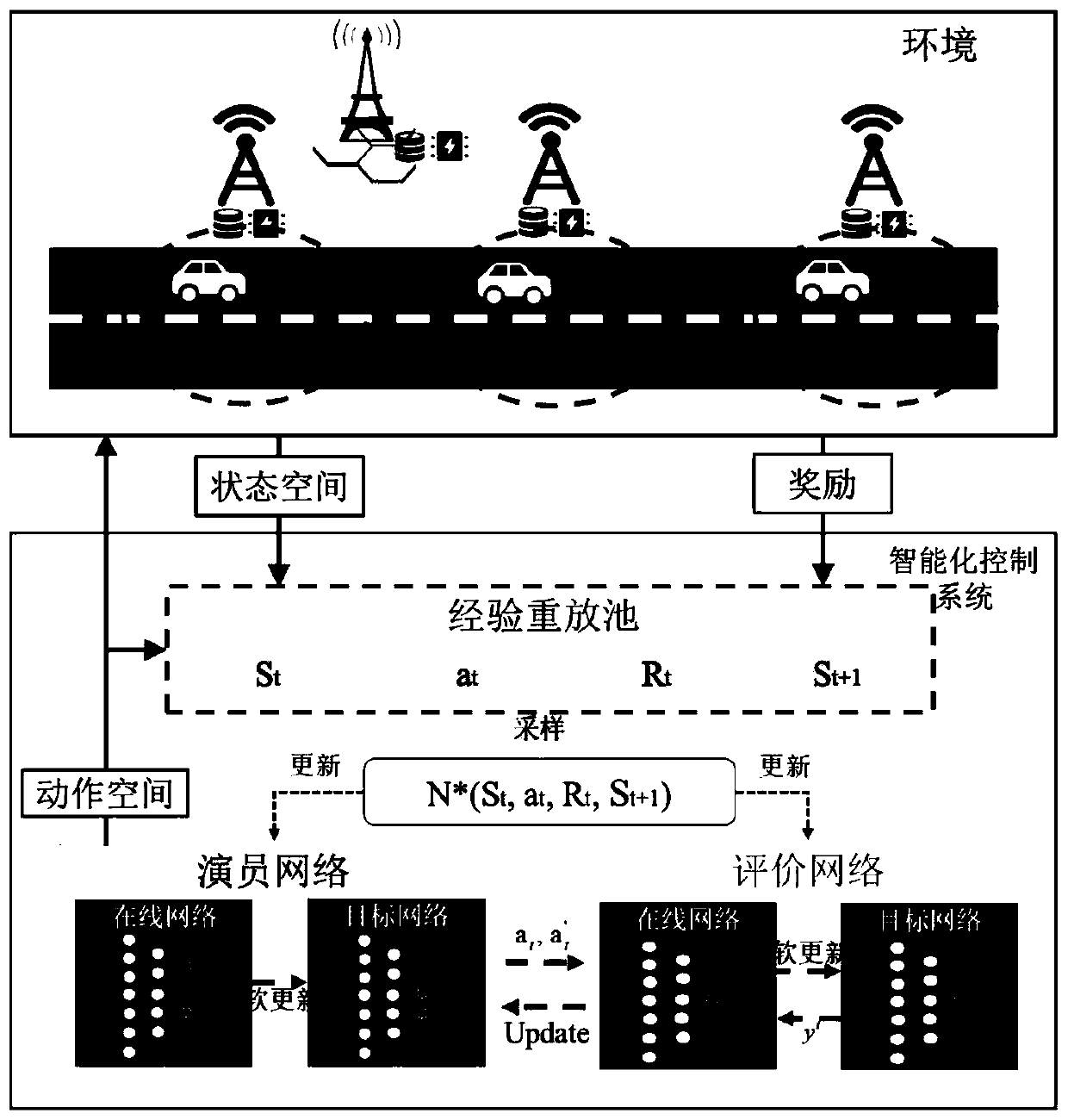
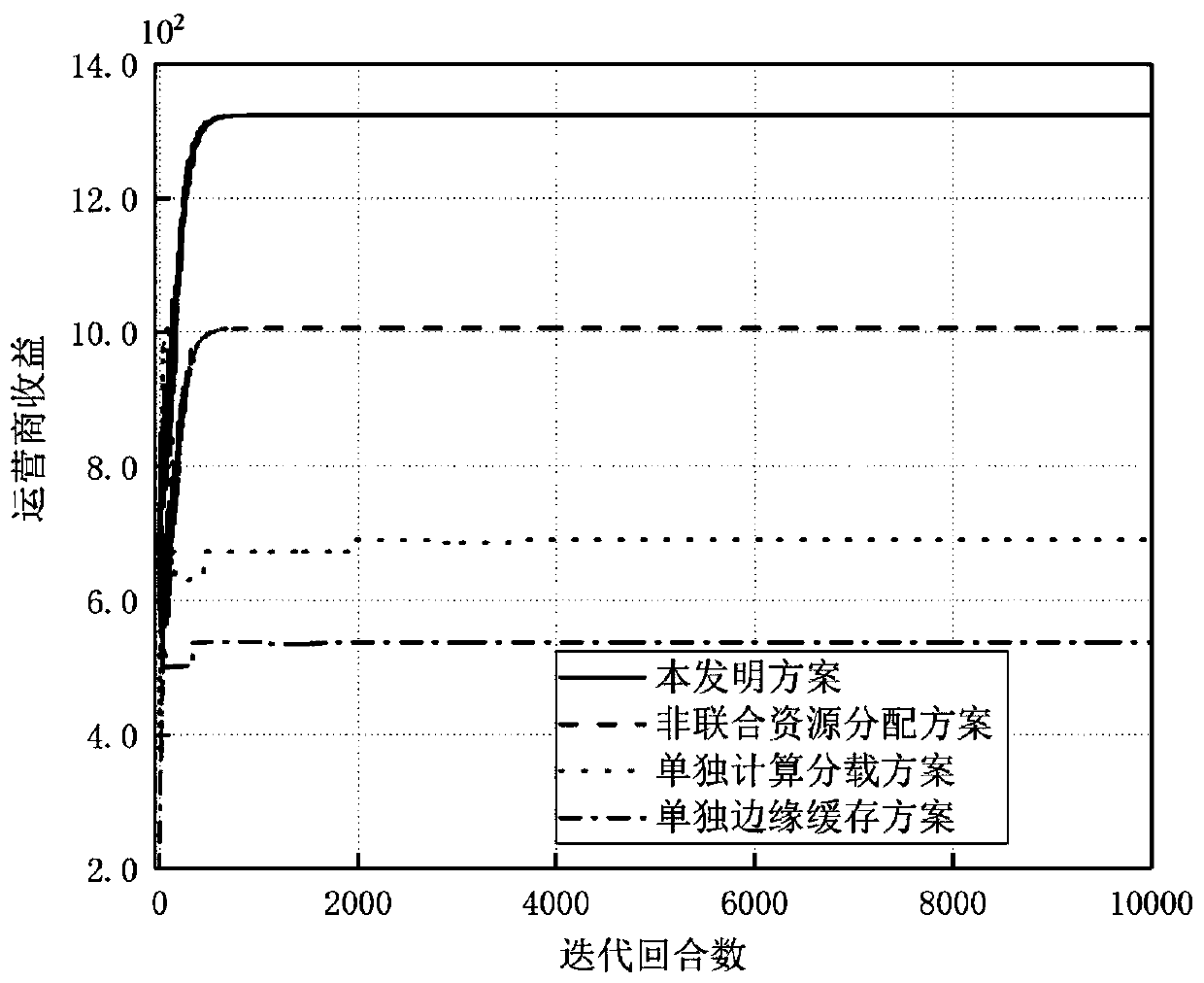
Intelligent resource allocation method in Internet of Vehicles
ActiveCN110213796AProfit maximizationNetwork traffic/resource managementNeural architecturesApplications of artificial intelligenceThe Internet
The invention discloses an intelligent resource allocation method in the Internet of Vehicles, which applies an artificial intelligence algorithm to solve the problem of resource allocation in a vehicle network so as to maximize the revenue of a network operator. Specifically, the method comprises: establishing a base station-roadside node combined vehicle edge calculation and cache resource scheduling framework to distribute requested resources for vehicles; establishing a network operator revenue function in combination with the operator revenue and the user experience quality to evaluate the resource distribution problem, and establishing a joint optimization problem to maximize the network operator revenue; solving the joint optimization problem through deep reinforcement learning, obtaining an intelligent task scheduling and resource distribution scheme, arranging the obtained scheme in an intelligent control system, and performing intelligent scheduling and arrangement on vehiclerequests and server resources. According to the intelligent resource distribution method in the Internet of Vehicles, the revenue of a network operator can be maximized while the user experience is considered, and a new idea and angle are provided for practical application of artificial intelligence.
Owner:DALIAN UNIV OF TECH
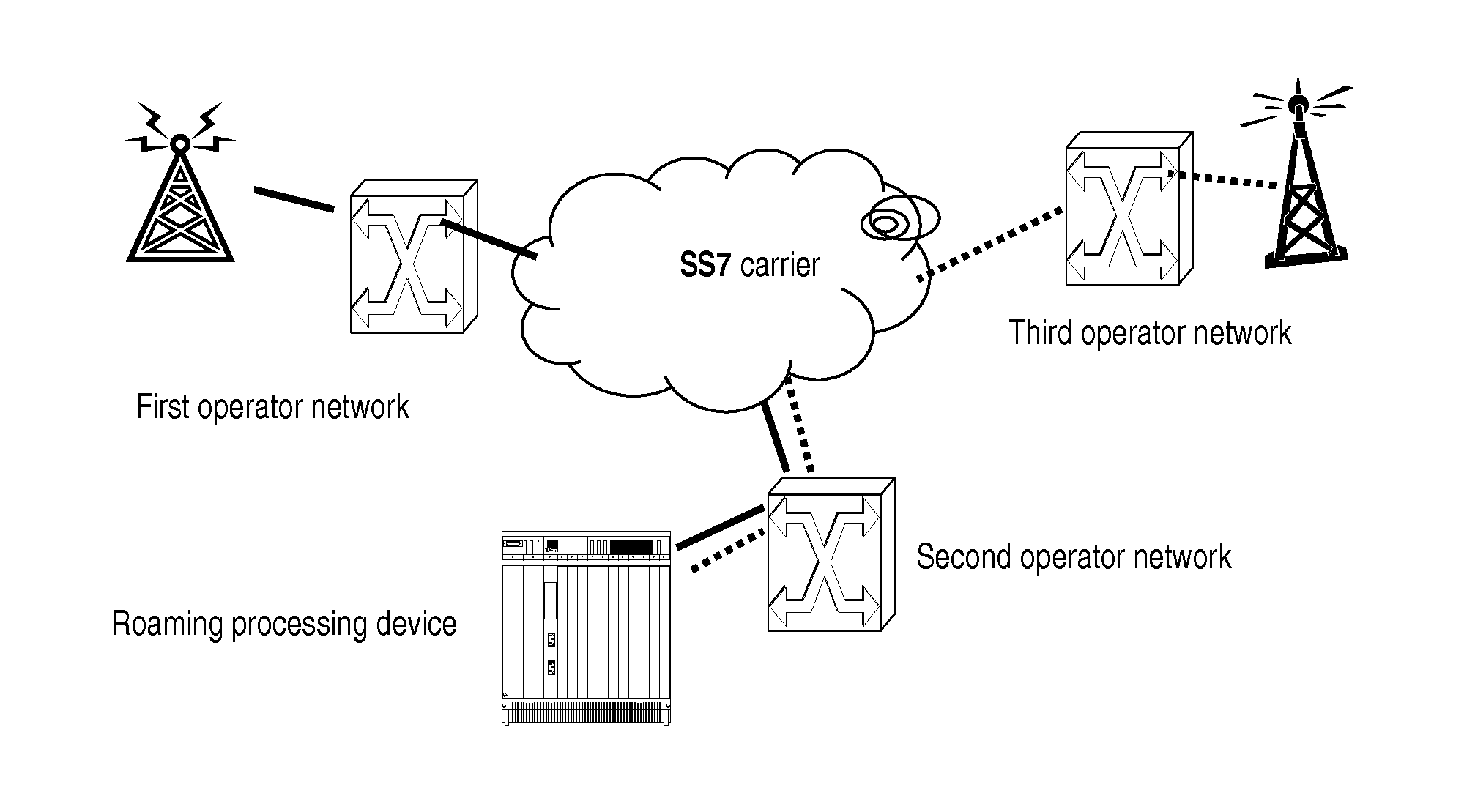
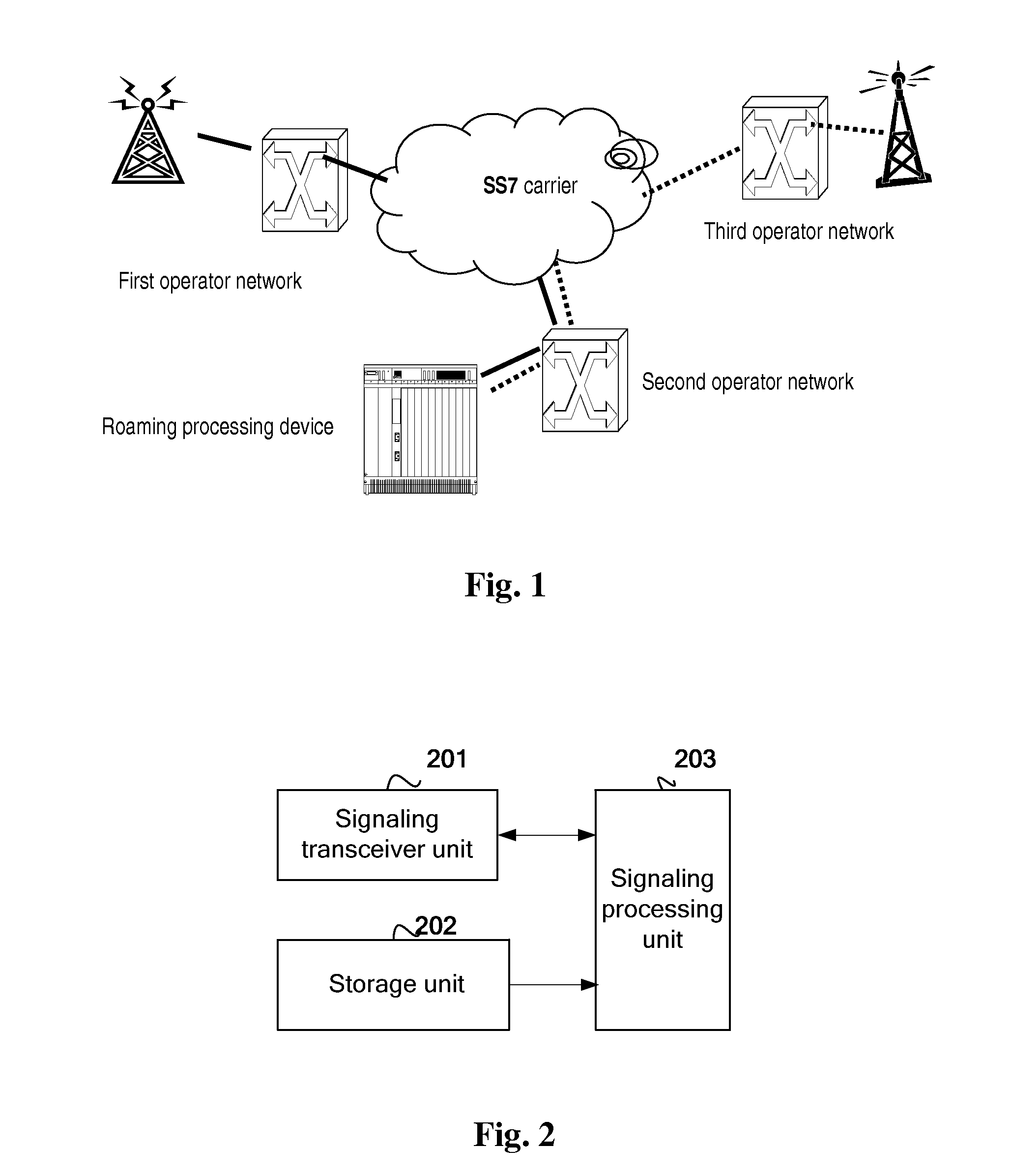
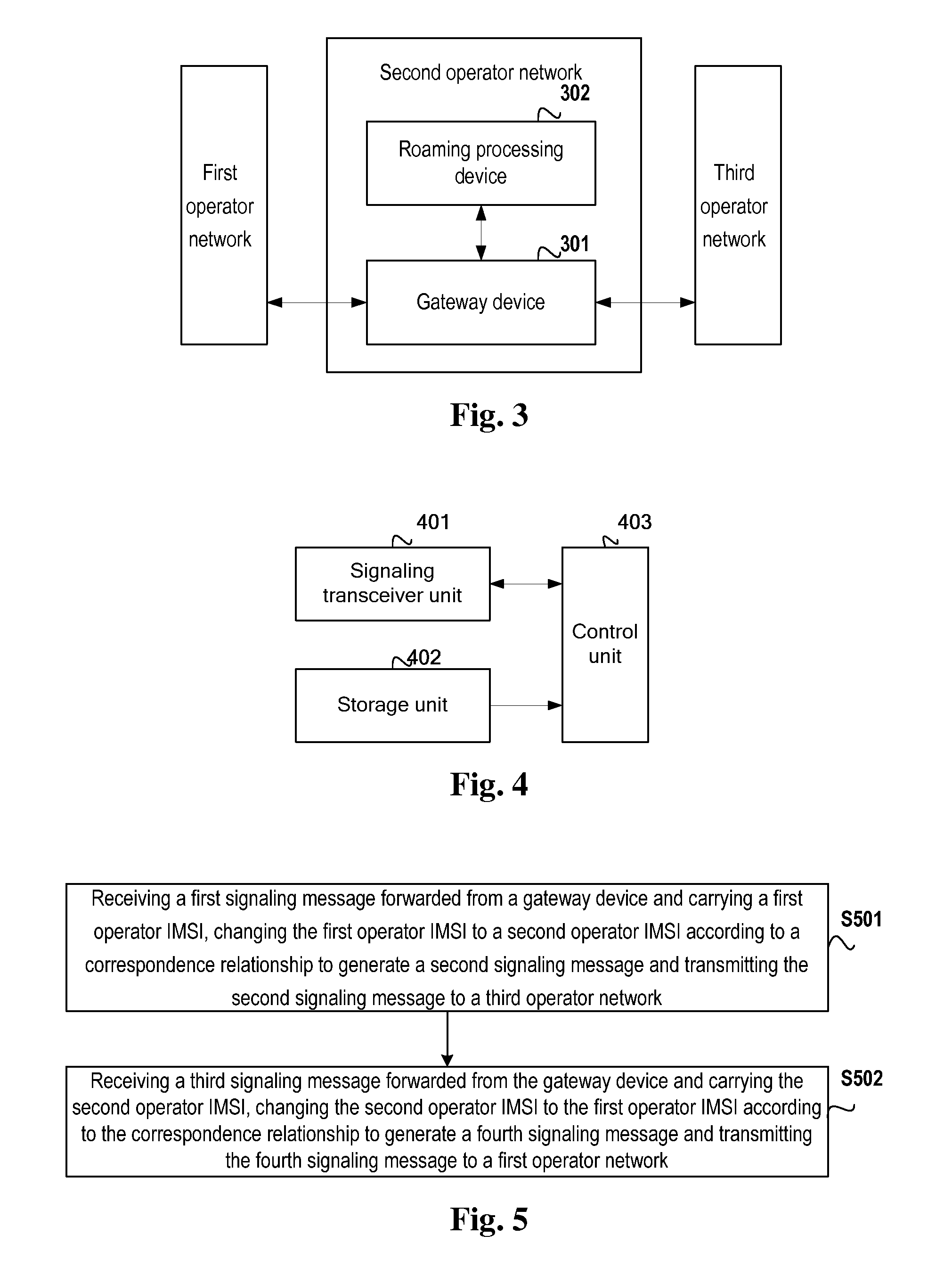
Method, roaming processing device and communication system for implementing international roaming
ActiveUS20110007726A1Spread fastWireless commuication servicesData switching networksCyber operationsCommunications system
There are disclosed an international roaming method, a roaming processing device and a communication system for international roaming of an international roaming subscriber of a first operator in a third operator network. When the international roaming subscriber of the first operator provided with a first operator IMSI and a second operator IMSI. roams in the third operator network, the roaming processing device of a second operator modifies a first signaling message from a first operator network and carrying the first operator IMSI to a second signaling message carrying the second operator IMSI and transmits the second signaling message to the third operator network. and modifies a third signaling message from the third operator network and carrying the second operator IMSI to a fourth signaling message carrying the first operator IMSI and transmits the fourth signaling message to the first operator network. There is also disclosed a gateway device.
Owner:CHINA MOBILE COMM GRP CO LTD
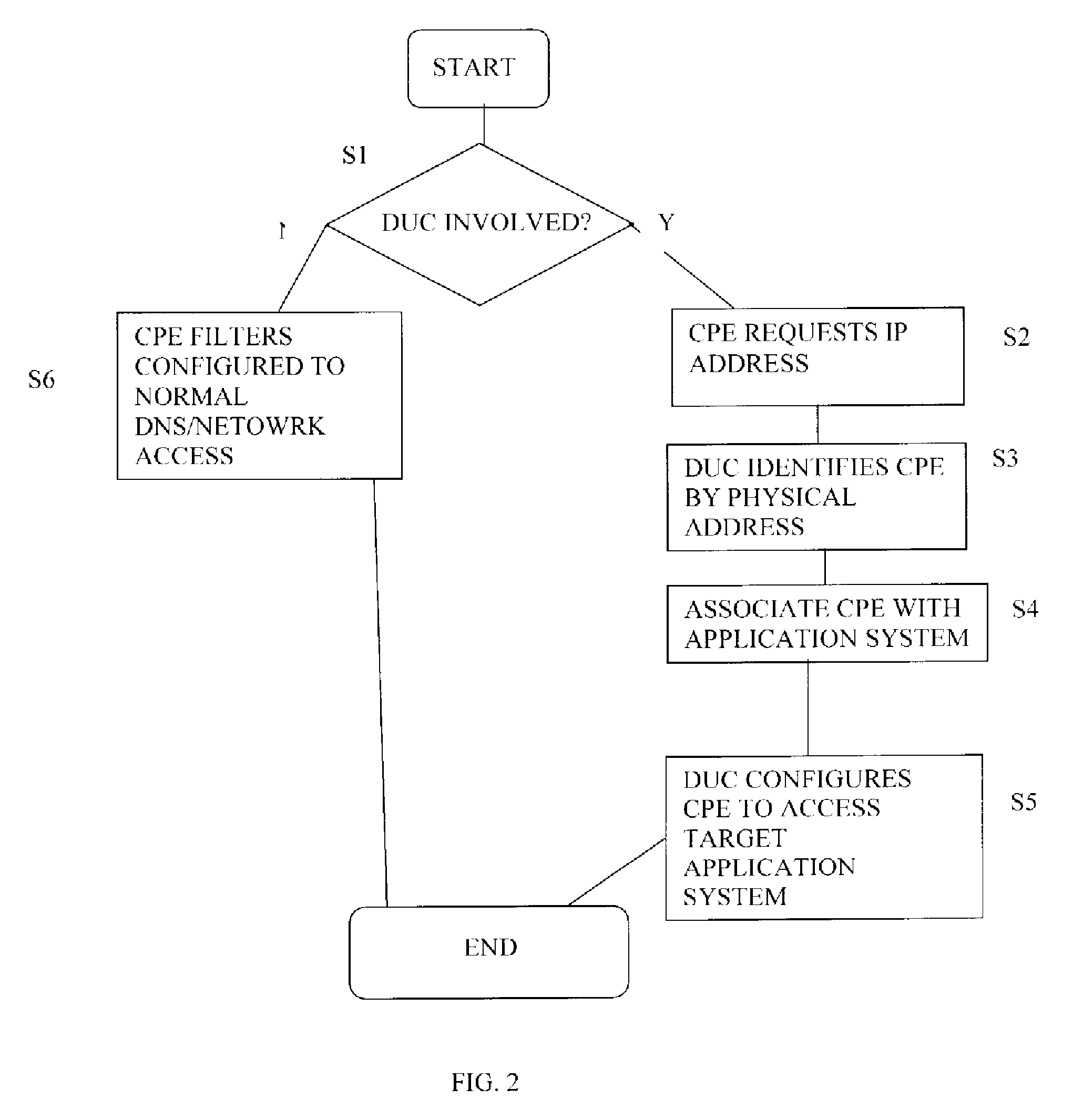
A process for dynamic user control on always-on IP network
A system and method for permitting an operator of a terminal device to switch from a first network to a second network without requiring a rebooting or resetting of the communication protocol system is disclosed. More specifically, filters present at the customer premise equipment (CPE) are configured to as to permit or block access to the respect first and second networks in response to configuration and setting information provided from a dynamic user control system and apparatus (DUCS). As a result, IP traffic is blocked or permitted in accordance with information from DUCS, so as to permit seamless switching between networks under conditions as warranted by a network operator.
Owner:NEXT GENERATION BROADBAND
Network brokering system
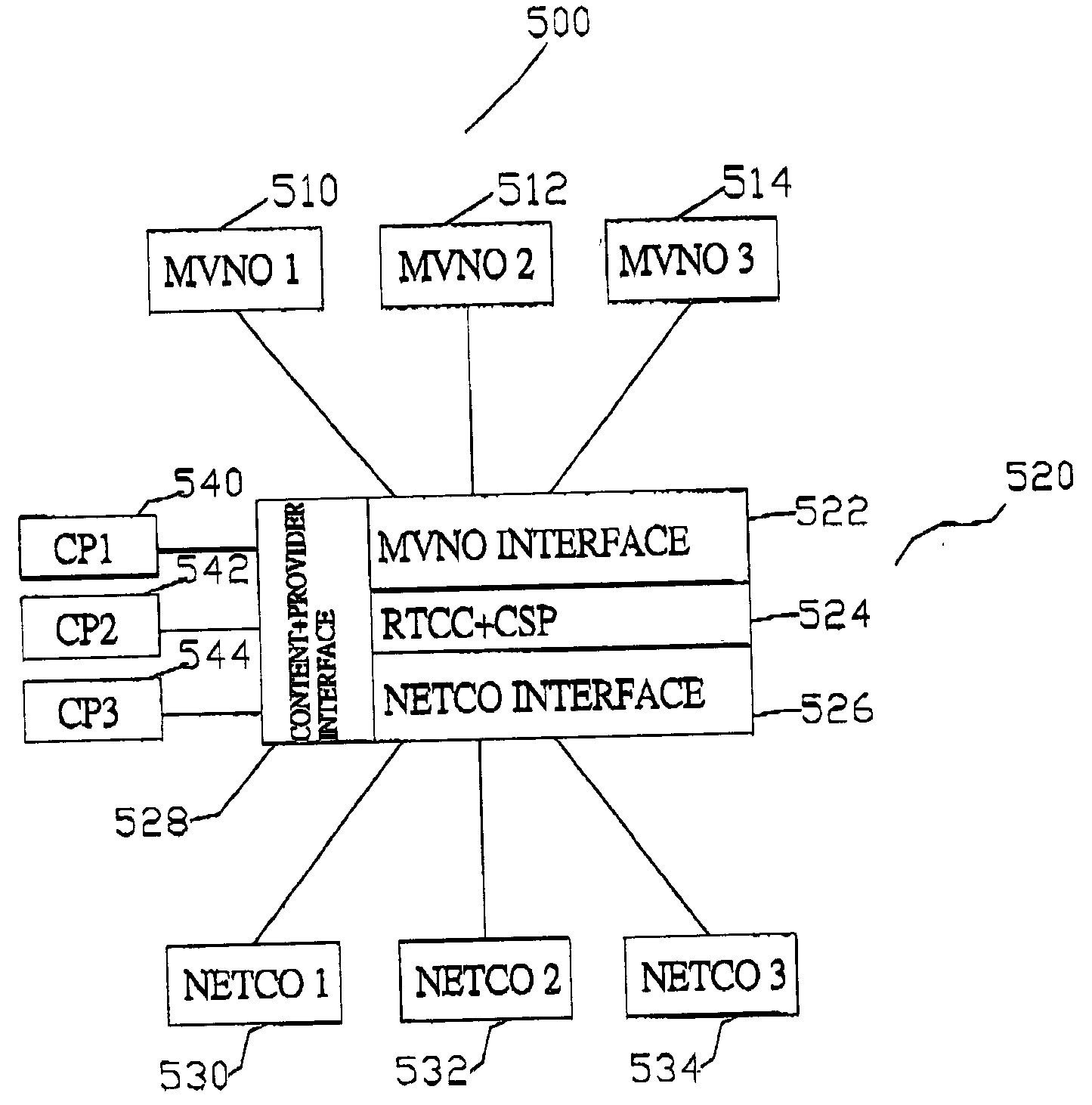
InactiveUS20050074014A1Increase valueMetering/charging/biilling arrangementsData switching by path configurationPaymentCyber operations
A network and network services brokering system between network companies and mobile virtual network operators which provides efficient billing systems in order to provide improved network services to subscribers. The network brokering system comprises a virtual network operator who provides network services to subscribers, a network company who provides usage of their physical networks to the virtual network operator, and a network broker who interfaces between the network company and virtual network operator. Additionally, the network broker provides interfacing between virtual network operators and independent content providers. The network broker further comprises a real-time call control and common service platform for real-time controlling of call, billing, and payment information. Using the real-time call control and common service platform allows complex billing such as partial pre-paid and partial post-paid payment schemes. Through the services of the network broker, the virtual network operator has usage of the network company's networks.
Owner:FAR EASTONE TELECOMM
System and method for brokering the sale of internet advertisement inventory
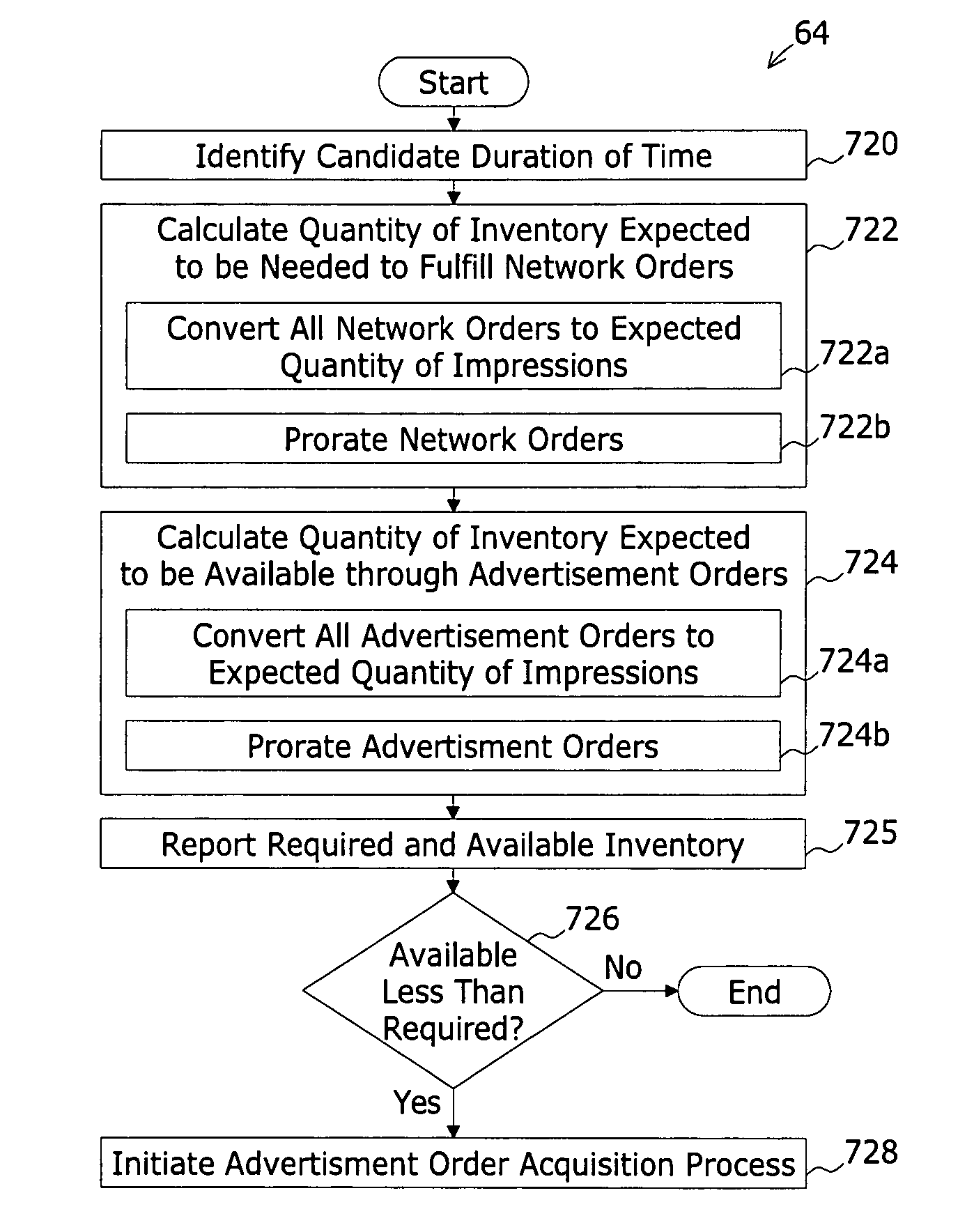
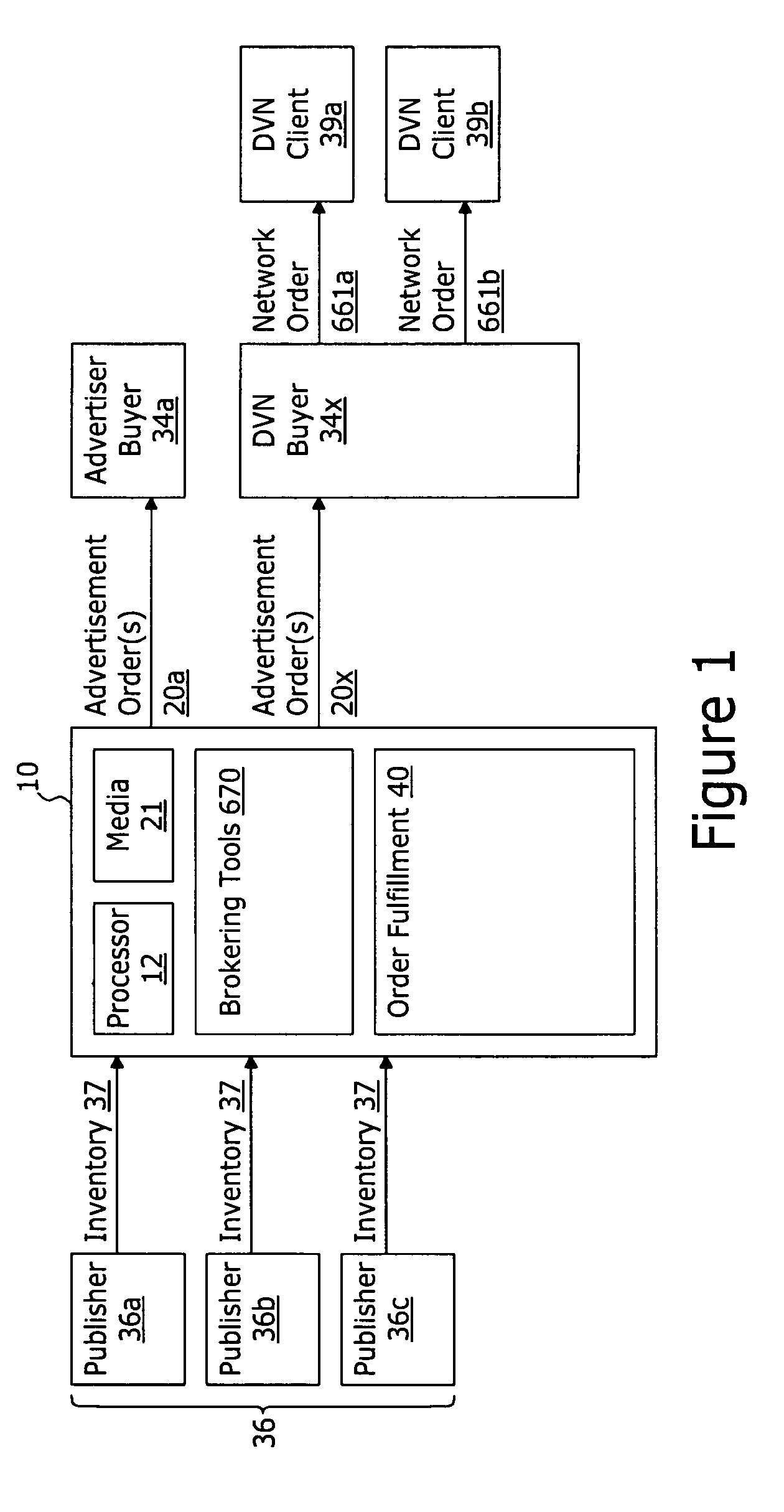
A dynamic vertical network management system is adapted to broker, between each publisher of a group of publishers and each advertiser of a group of advertisers, the sale of at least a portion of the each publisher's inventory of advertisement impressions. At least a portion of the advertisers are clients of a dynamic vertical network operator (DVN) with the DVN purchasing inventory from the publisher and utilizing such purchased inventory to fulfill advertising orders placed by the client with the DVN (network orders). A publisher data store stores, for each publisher of the group of publishers, a group of segmented ad placements. Each segmented ad placement comprises: i) a placement ID identifying an advertisement placement region within a web page; and ii) at least one distinguishing traffic attribute parameter. An advertisement-order data store stores, for each segmented ad placement, a group of advertisement orders. Upon receiving an ad request from an end user system rendering the web page, an order delivery system: i) determines the selected ad placement, ii) determines an open order for the selected ad placement meeting selection criteria, and iii) if such order is a DVN order: a) determines a client network order meeting network order criteria, and b) delivers ad content associate with the selected network order.
Owner:INFINEON TECH AG +2
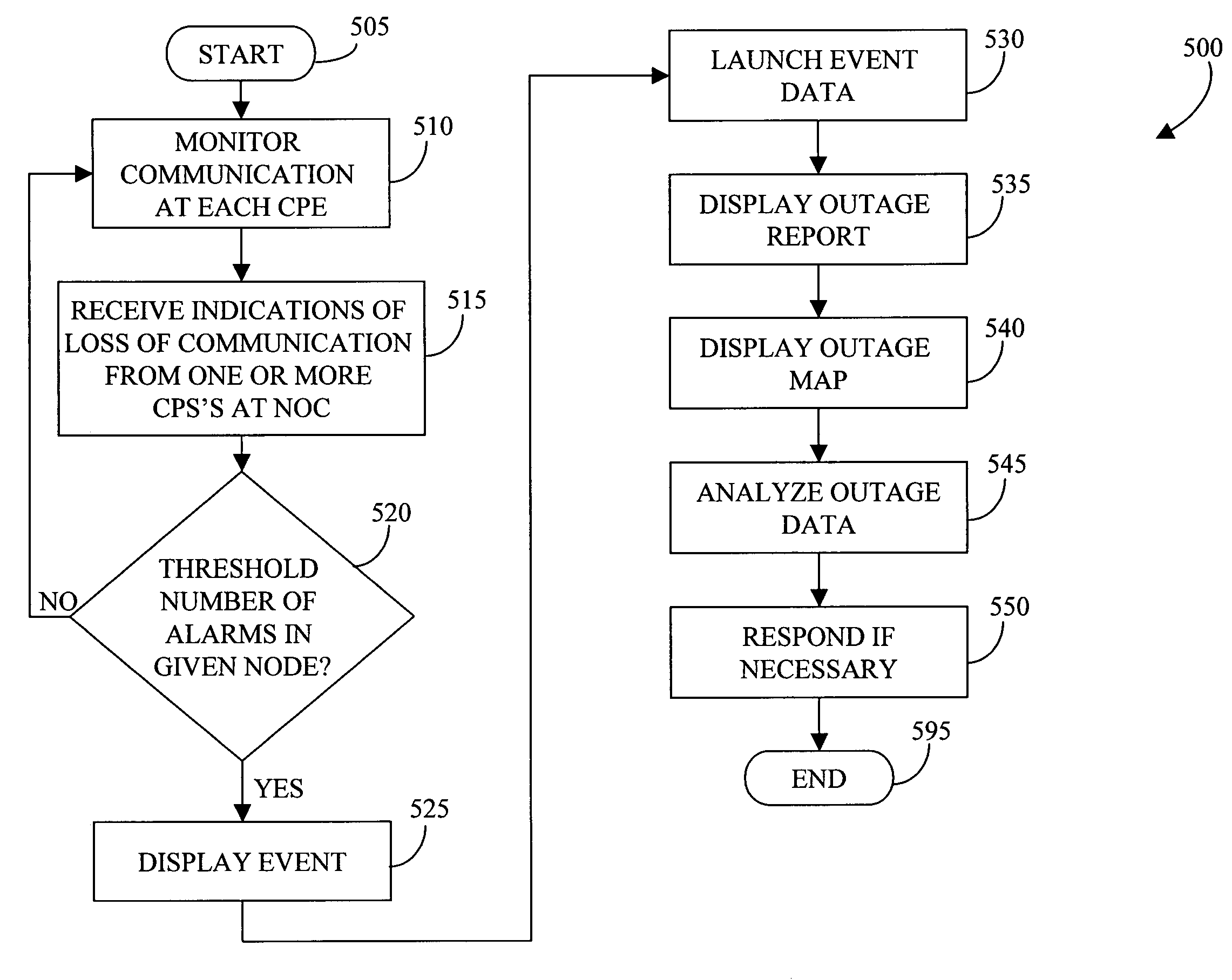
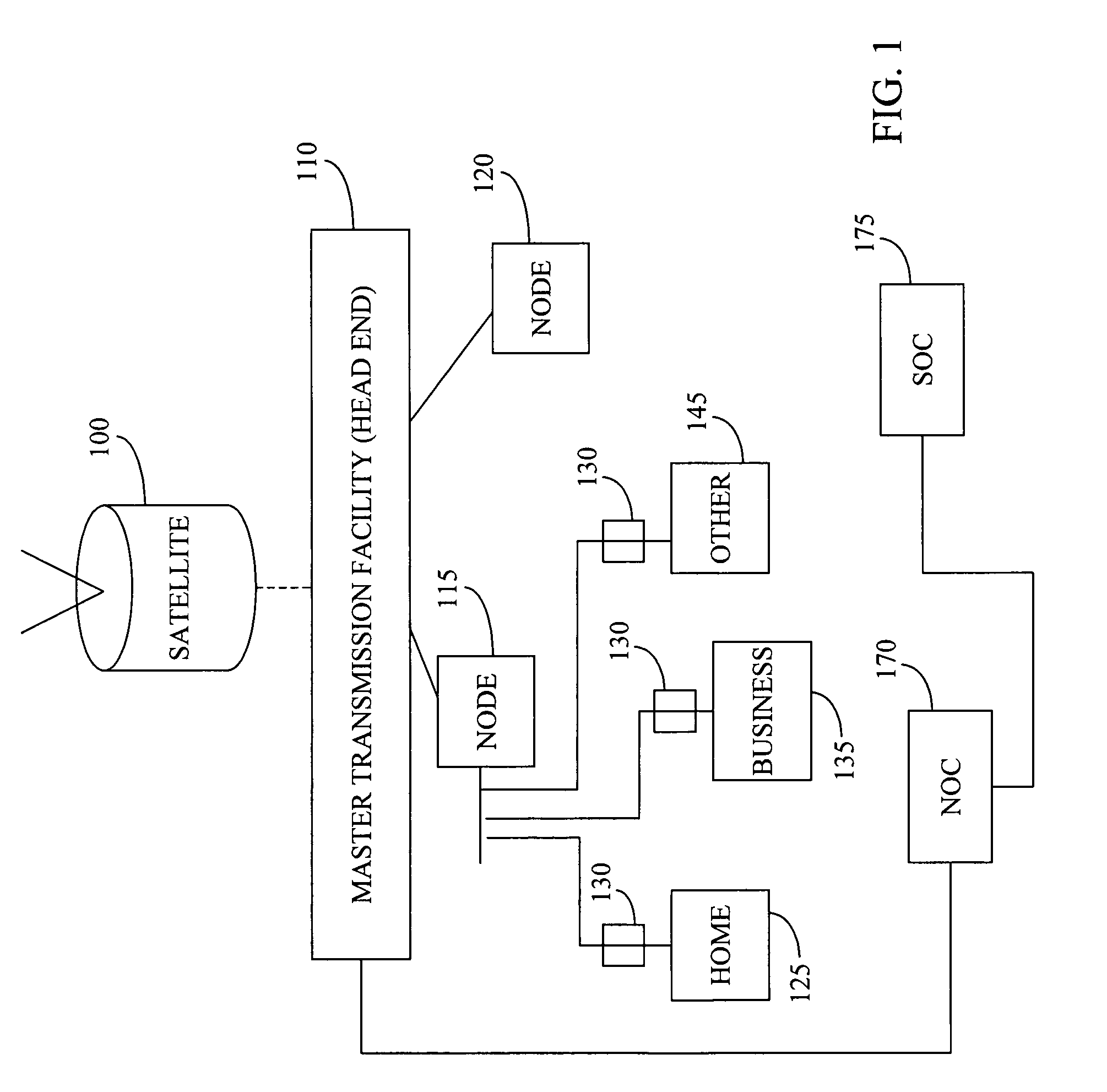
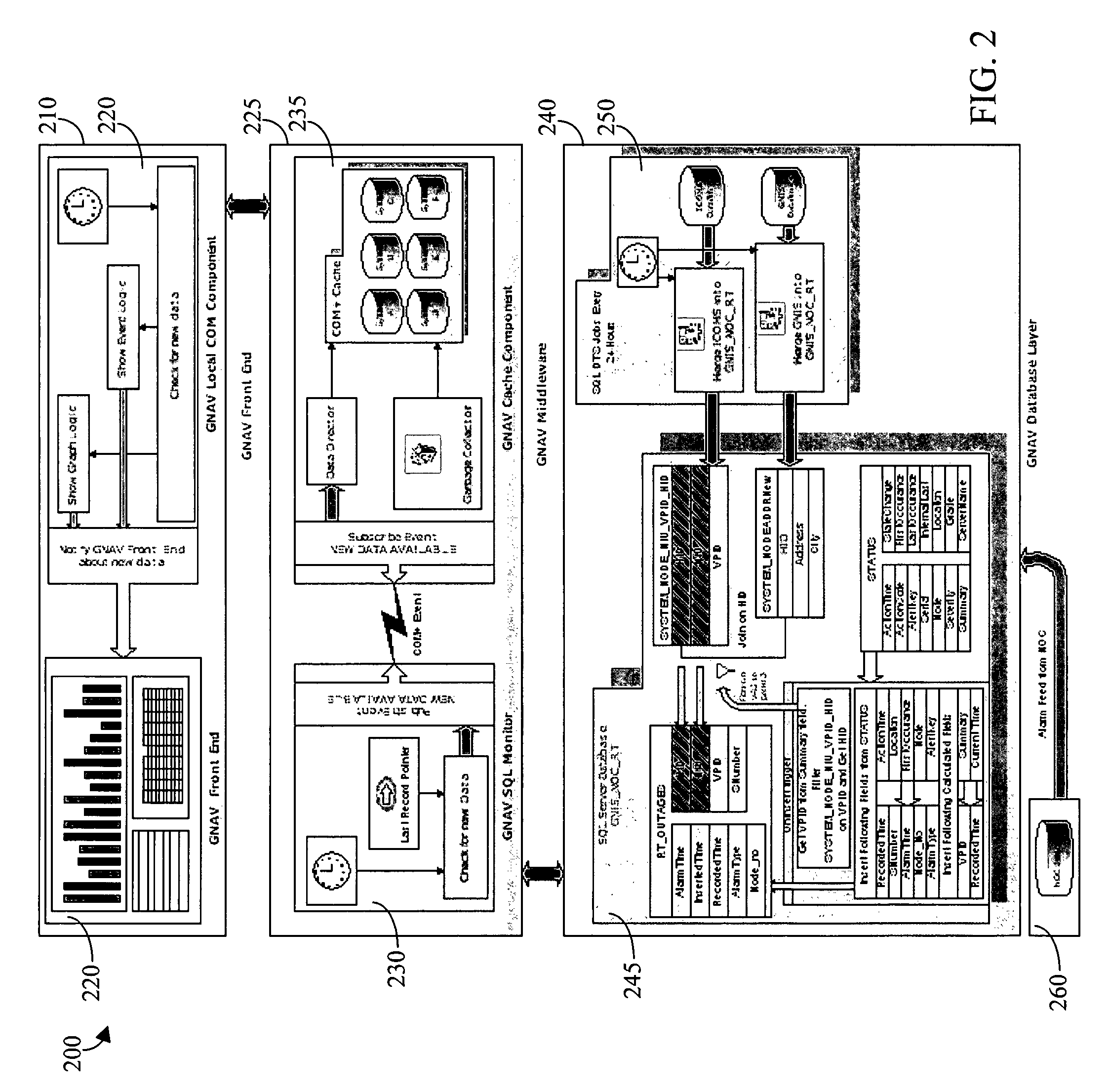
Geographical network alarm viewer
Methods and systems provide a geographical network alarm viewer (GNAV) application that receives, tracks, aggregates, reports, and maps data associated with cable telephony services outages occurring in a cable services network. The GNAV application integrates network map data and identification information associated with customer locations, equipment, and associated network alarm data from a network operations center. All customer location addresses associated with individual network alarms are located and mapped on a geographical network map. Because the alarms are received, tracked, aggregated, reported, and mapped in real-time, service personnel may respond to network outages in a more efficient manner, and service technicians and service vehicles may be directed to repair service outages based on more accurate location and service outage timing data.
Owner:COX COMMUNICATIONS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com