Patents
Literature
6094results about "Fault response" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
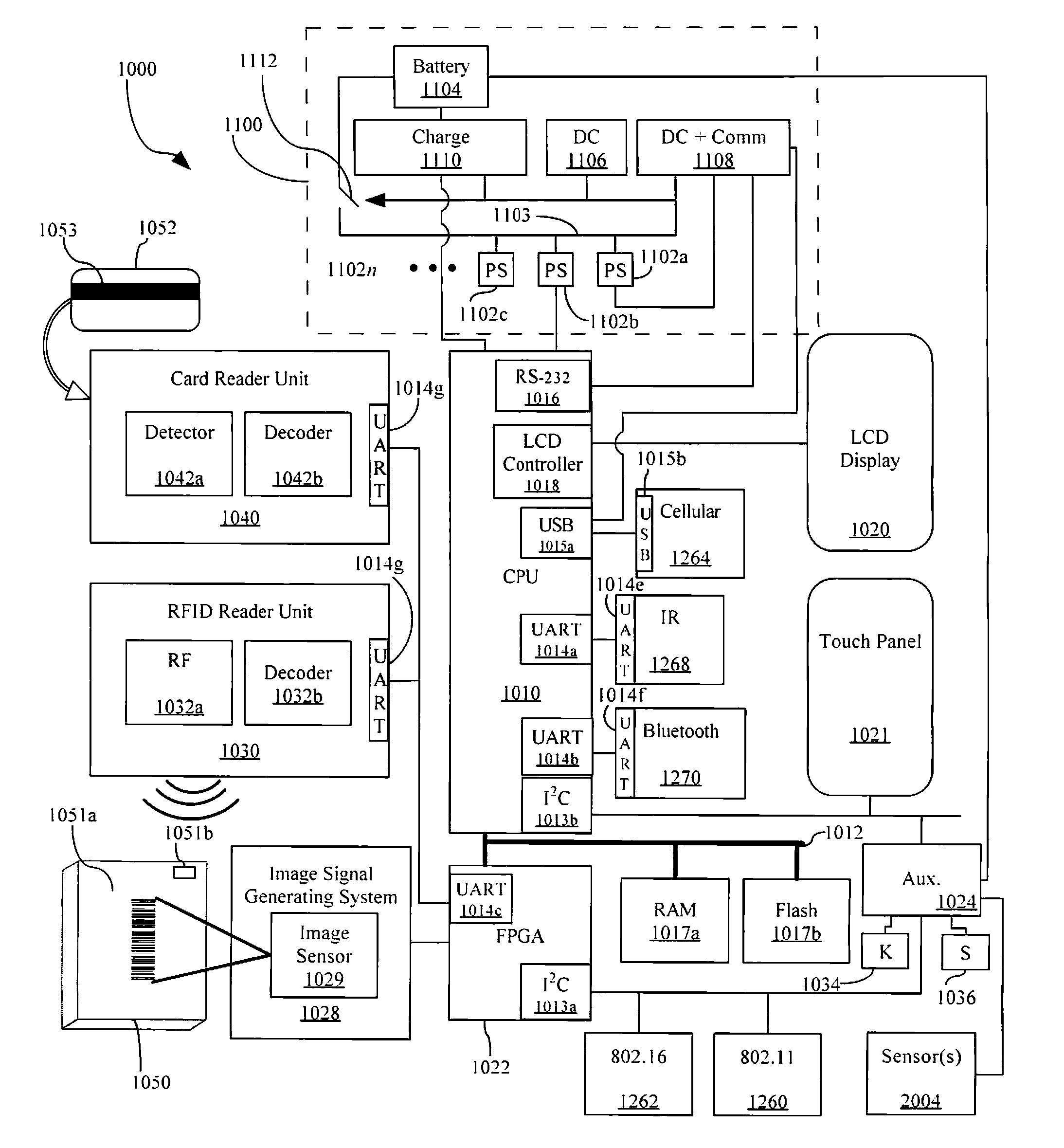
Apparatus and methods for monitoring one or more portable data terminals
Owner:HAND HELD PRODS
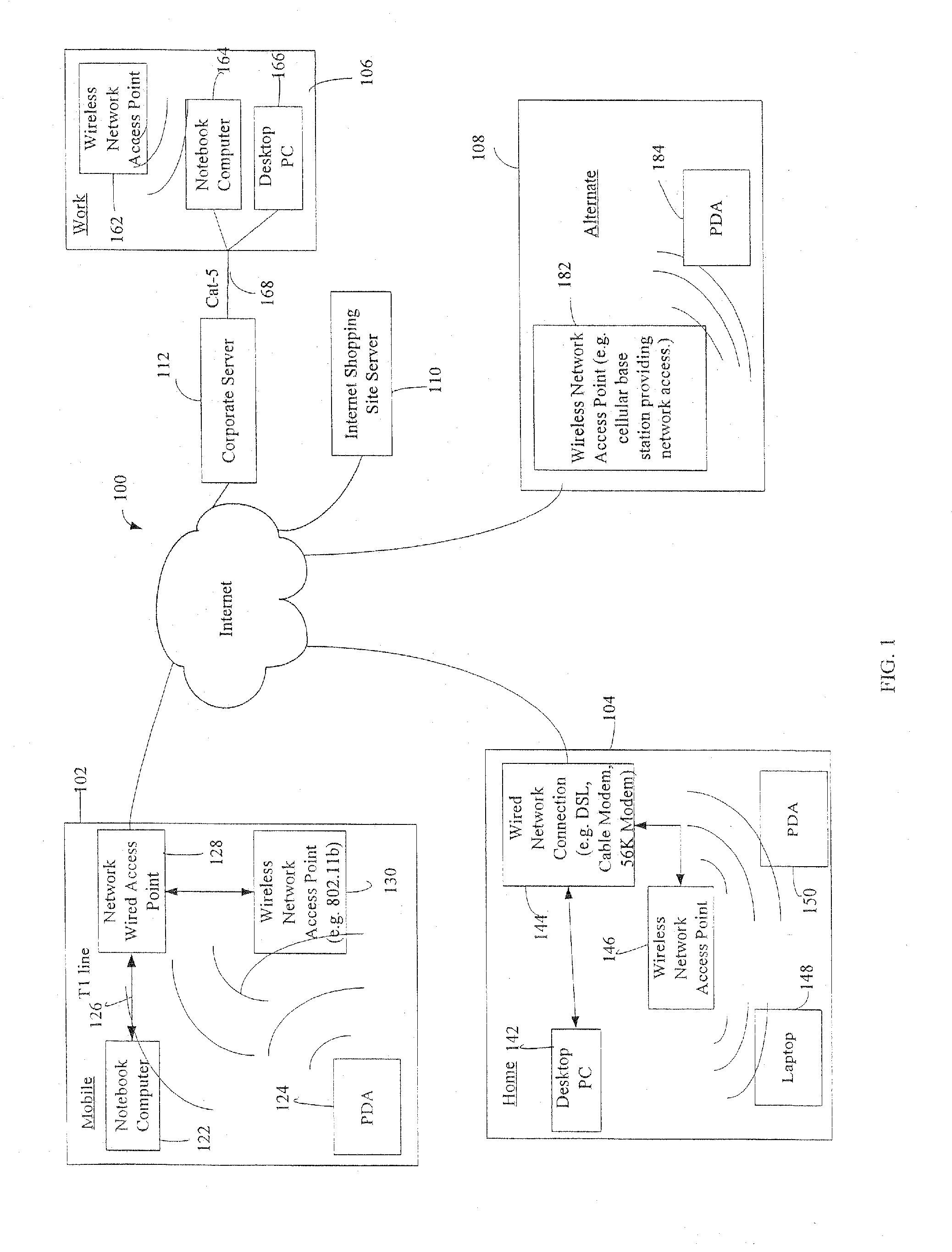
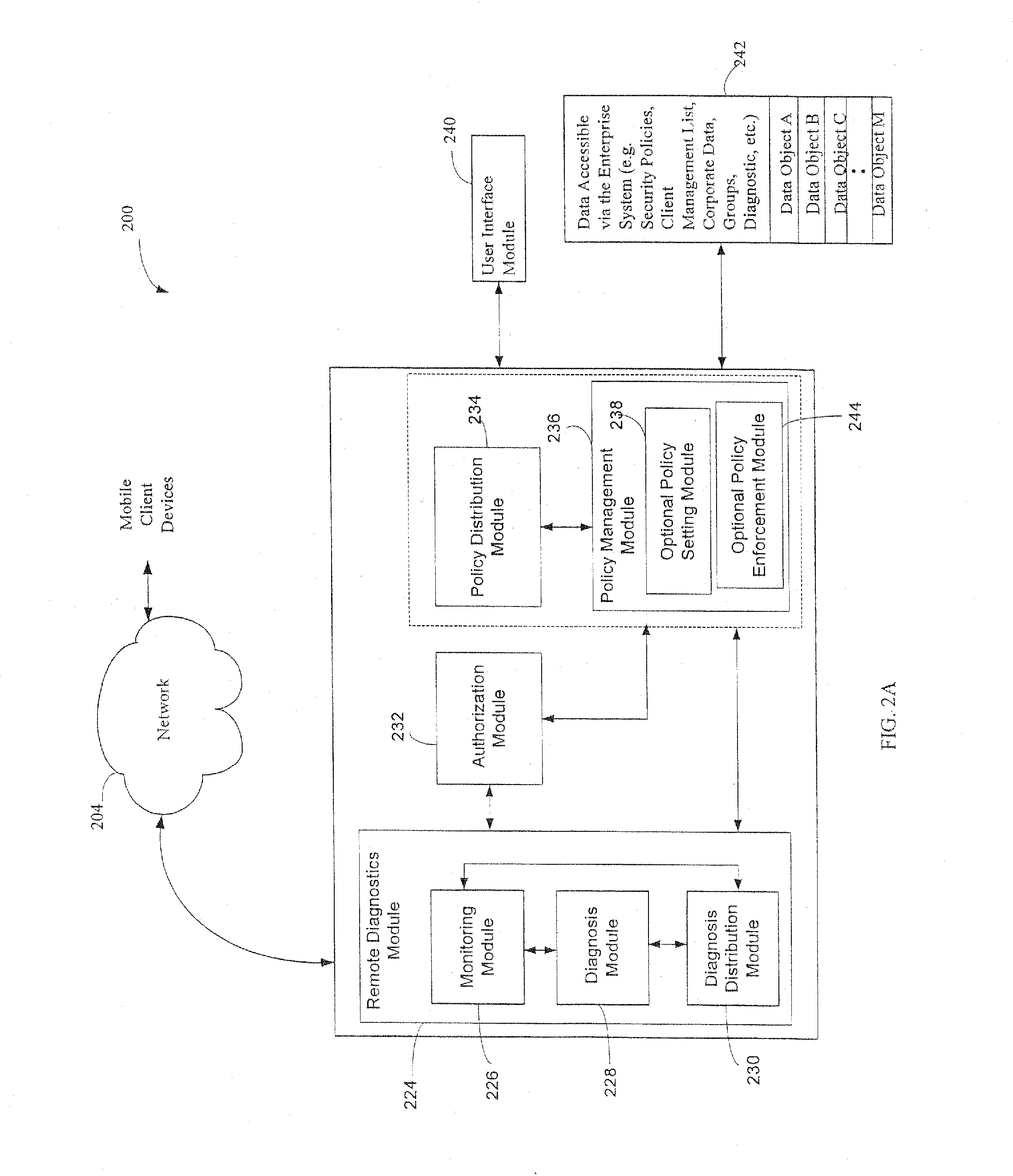
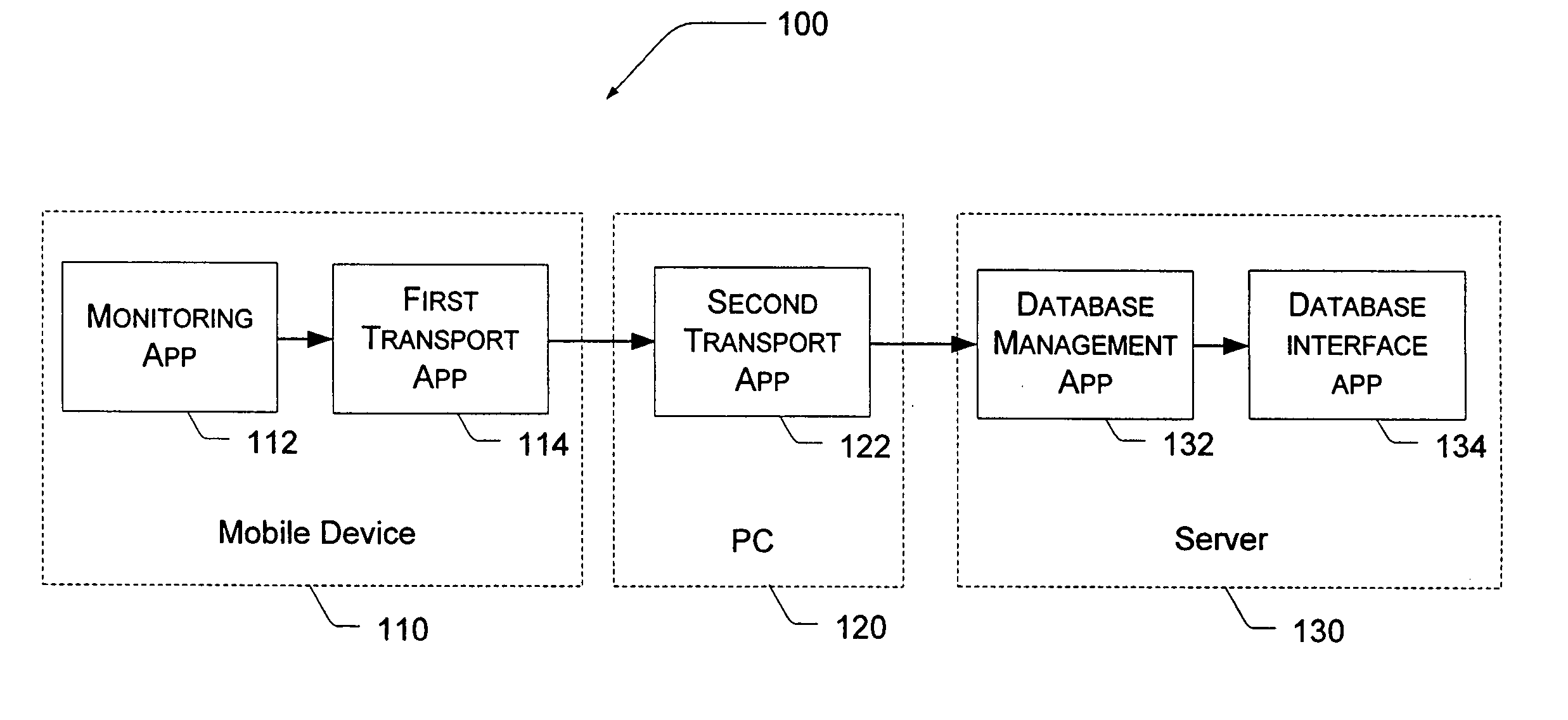
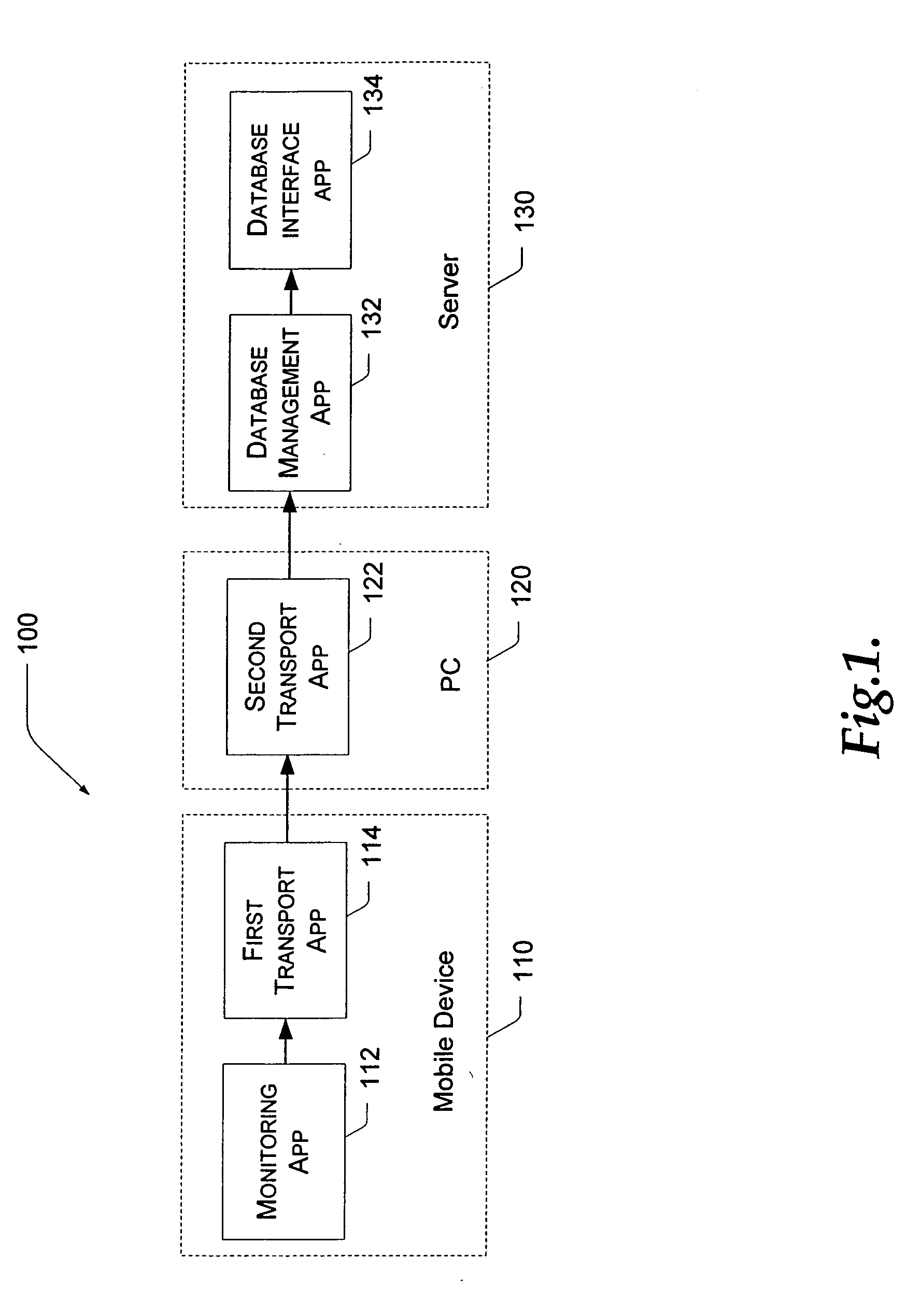
Administration of protection of data accessible by a mobile device
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
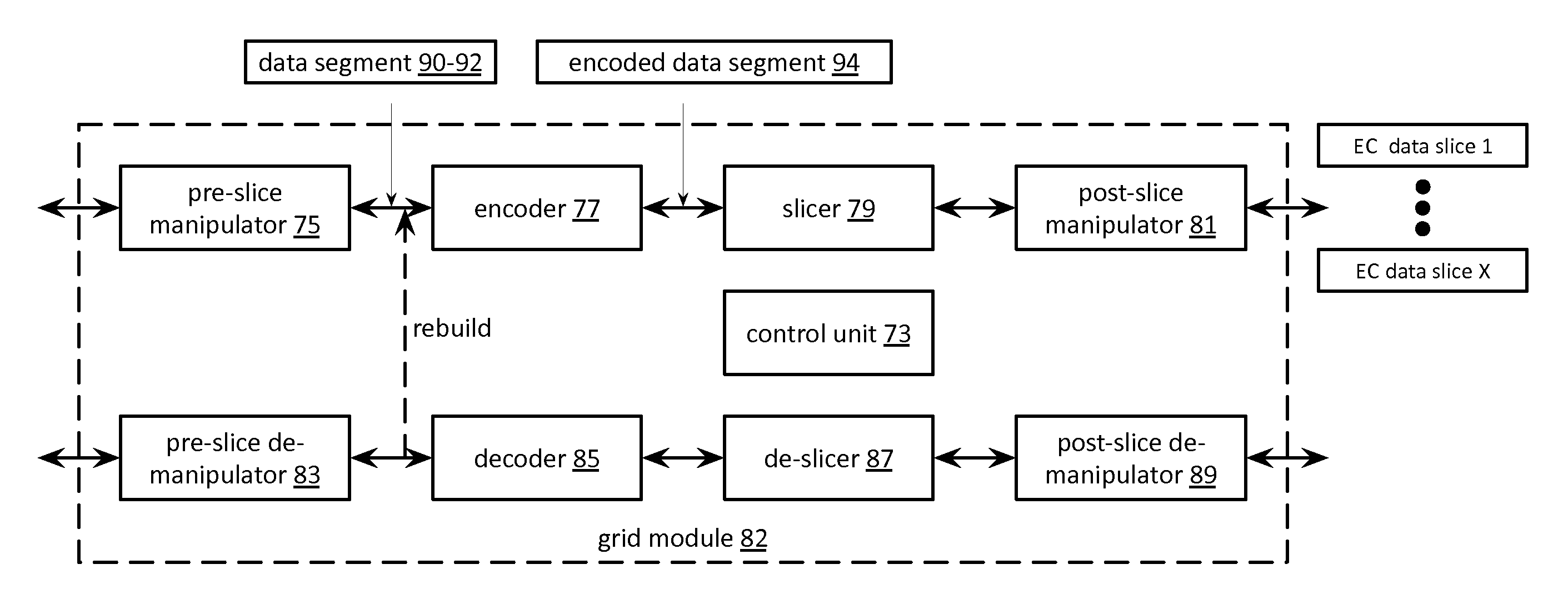
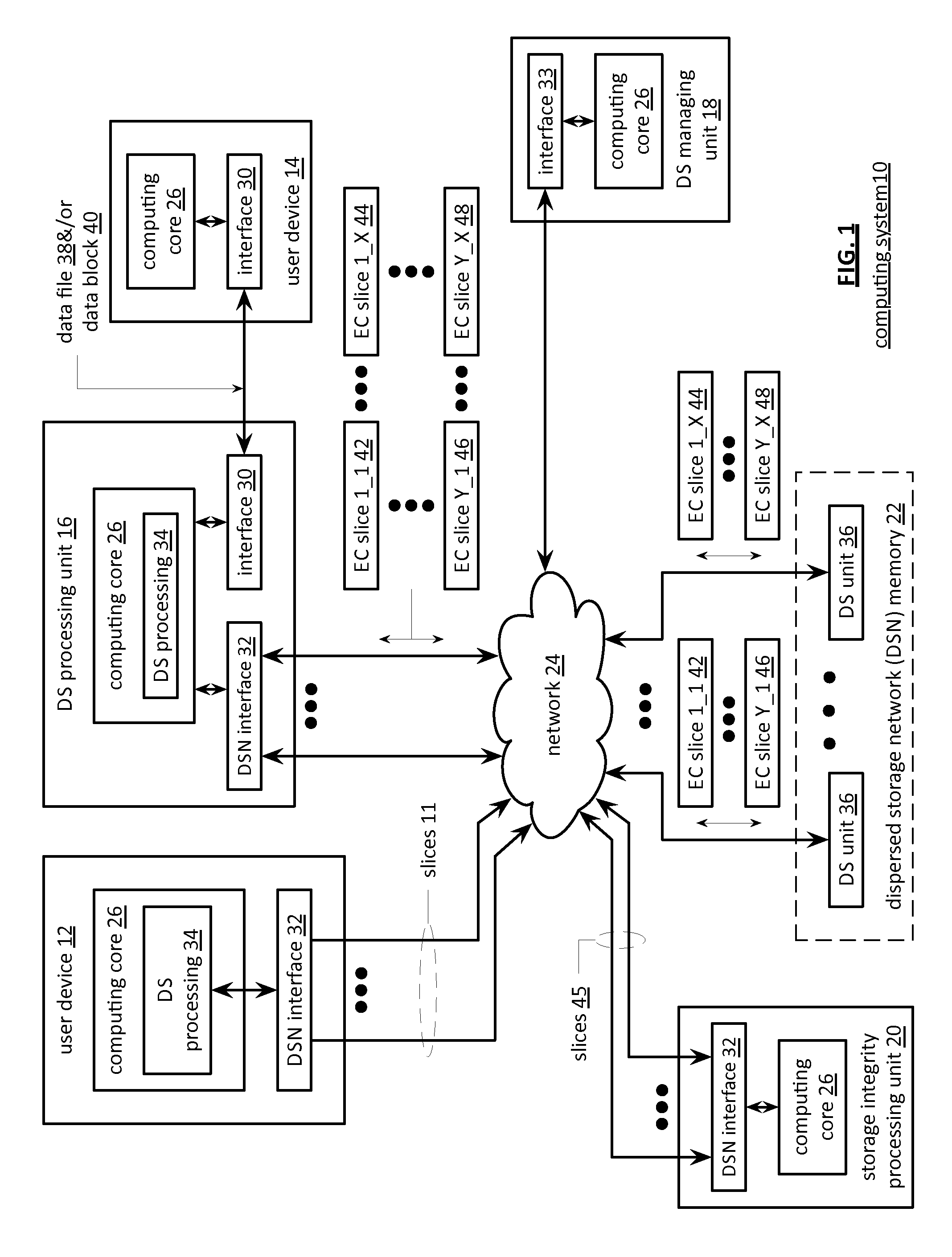
Identifying an error cause within a dispersed storage network
A method begins by a dispersed storage (DS) processing module selecting two or more correlated error messages of a plurality of error messages. The method continues with the DS processing module identifying two or more collection of records corresponding to the selected two or more correlated error messages such that a collection of records includes an event record including information regarding an event, a first record including information regarding a dispersed storage (DS) processing module processing an event request to produce a plurality of sub-event requests, and a plurality of records including information regarding a plurality of DS units processing the plurality of sub-event requests. The method continues with the DS processing module identifying a correlation cause of one or more errors corresponding to the two or more correlated error messages based on the two or more collections of records.
Owner:PURE STORAGE
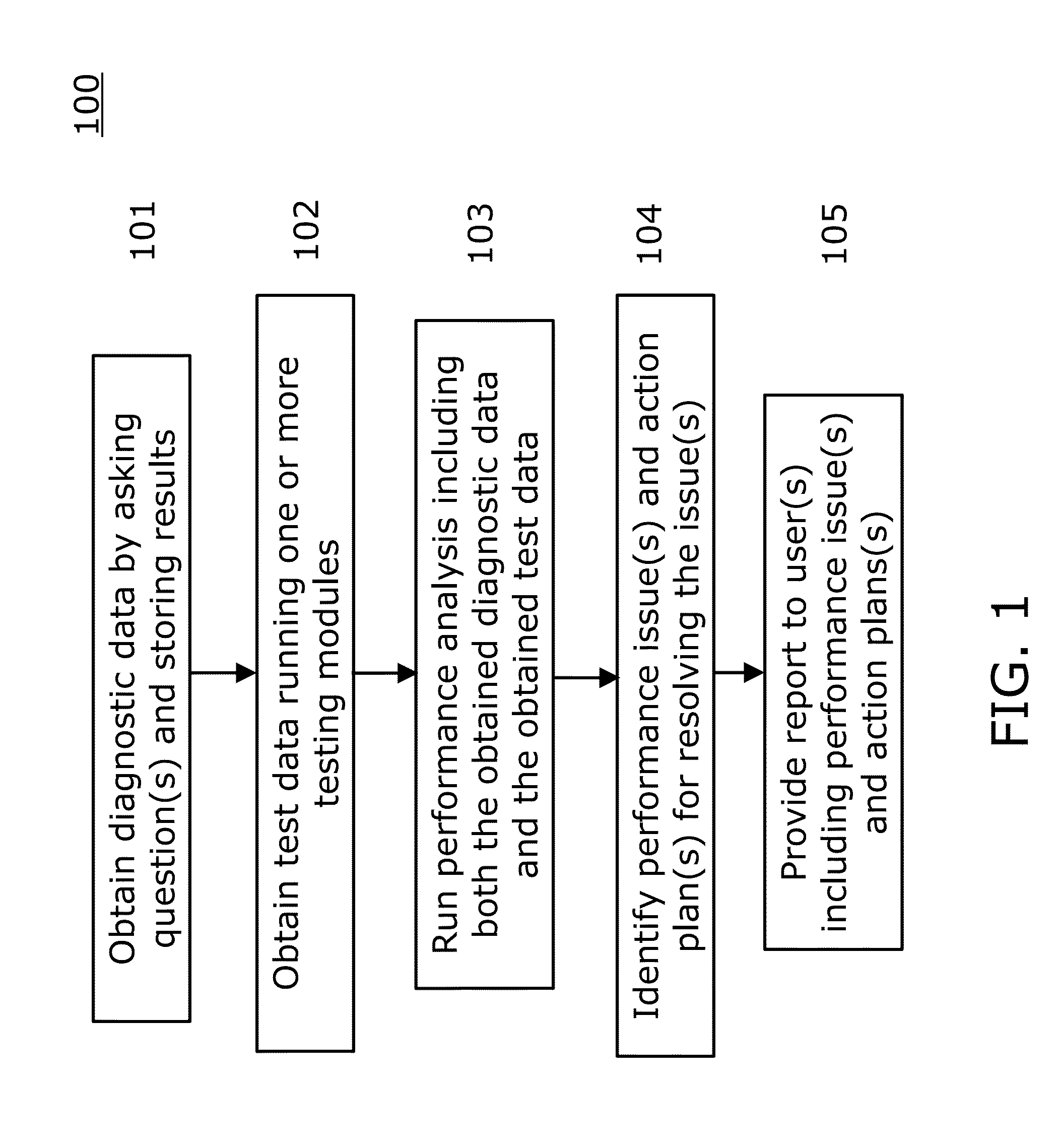
SAN Performance Analysis Tool
The present invention is directed to a method and information handling system (IHS) for improving system performance in a storage area network. An embodiment of the present invention begins by obtaining diagnostic data for the storage area network by asking a user one or more questions and storing results to the one or more questions. Next, test data is obtained by running one or more testing modules on at least one component of the storage area network. A performance analysis of the storage area network is executed, including the obtained diagnostic data and the obtained test data. Then, one or more performance issues and one or more action plans for resolution are identified based upon the analysis. Finally, a report to one or more users is provided including the one or more identified performance issues and the one or more action plans.
Owner:DELL PROD LP
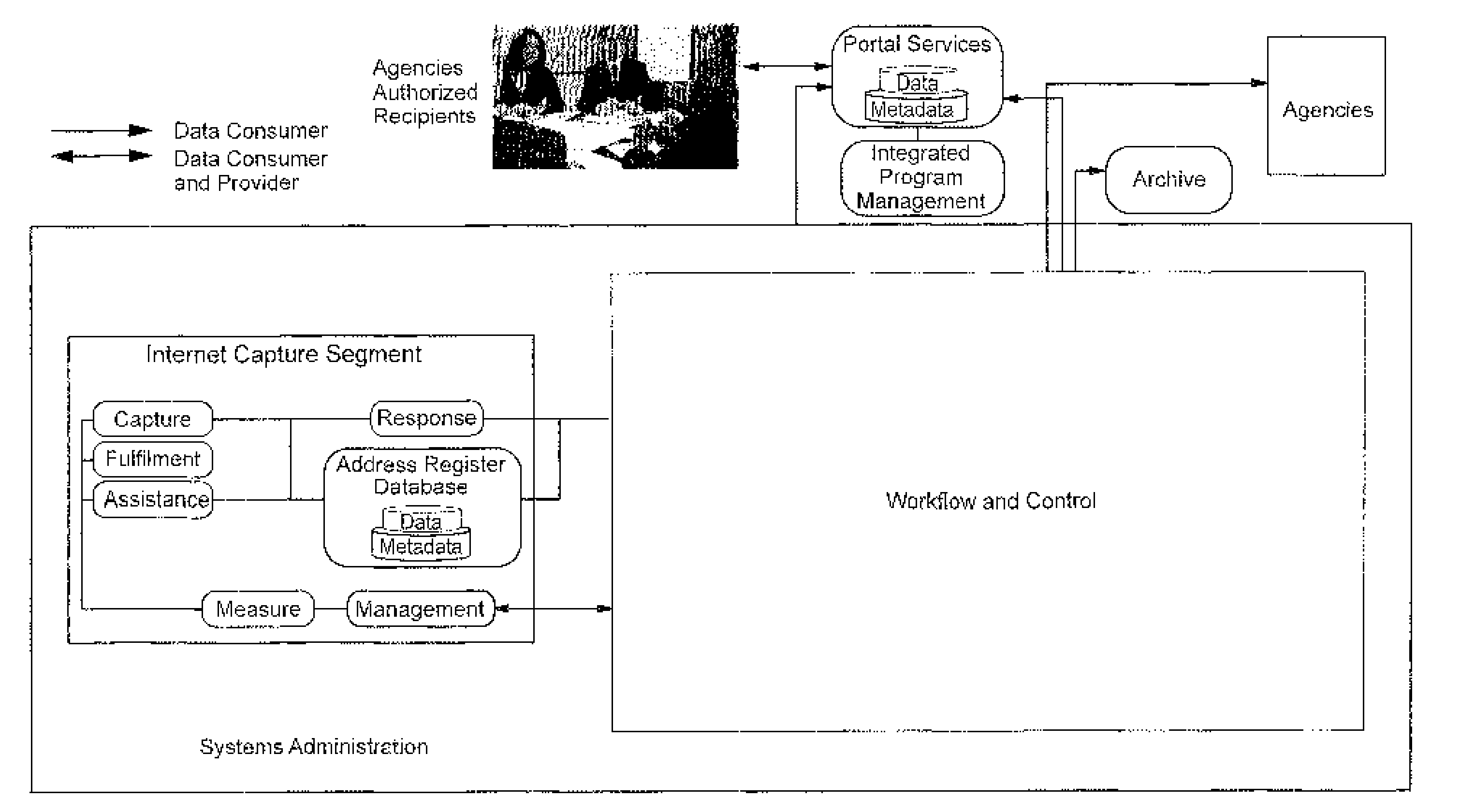
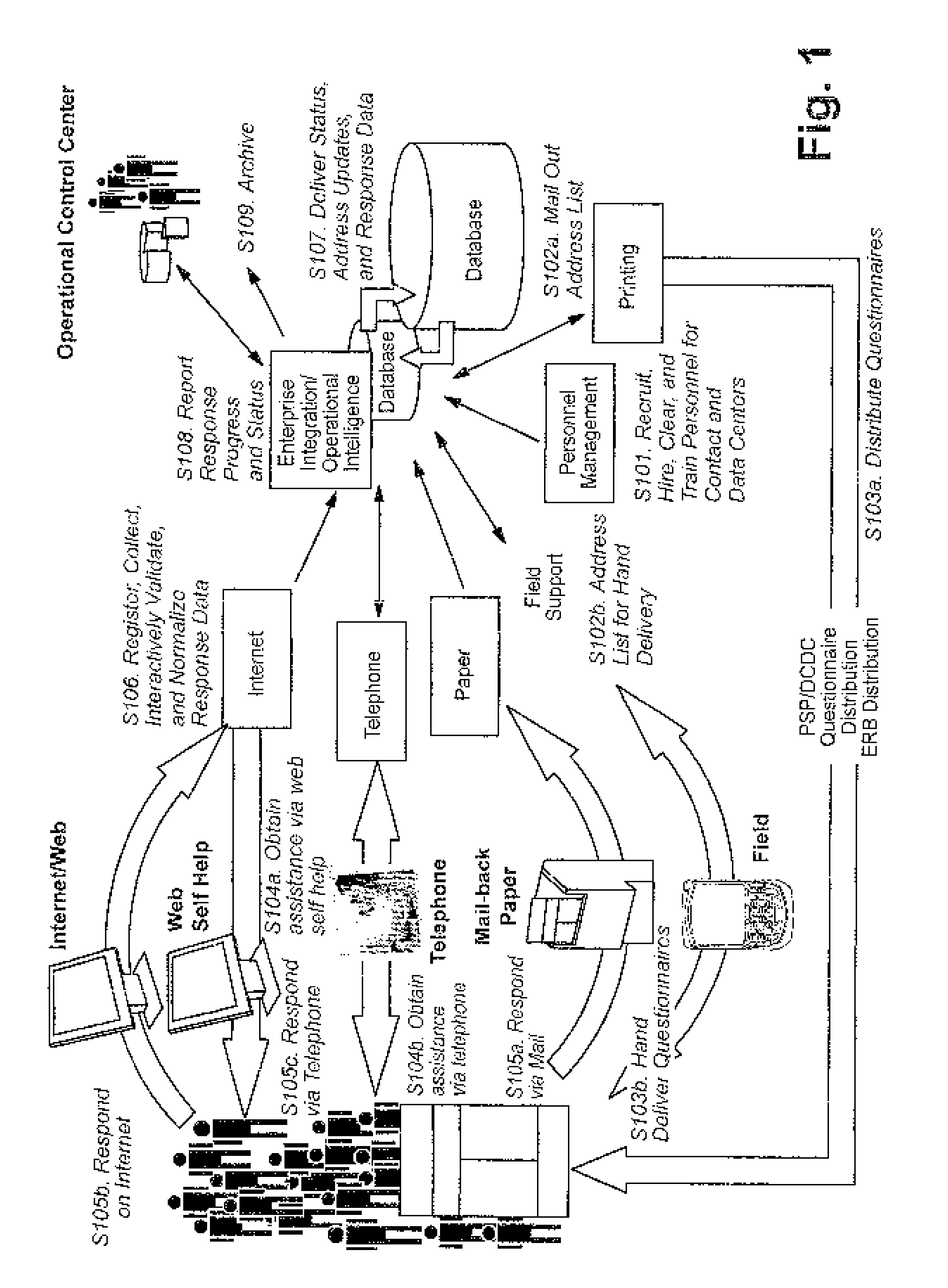
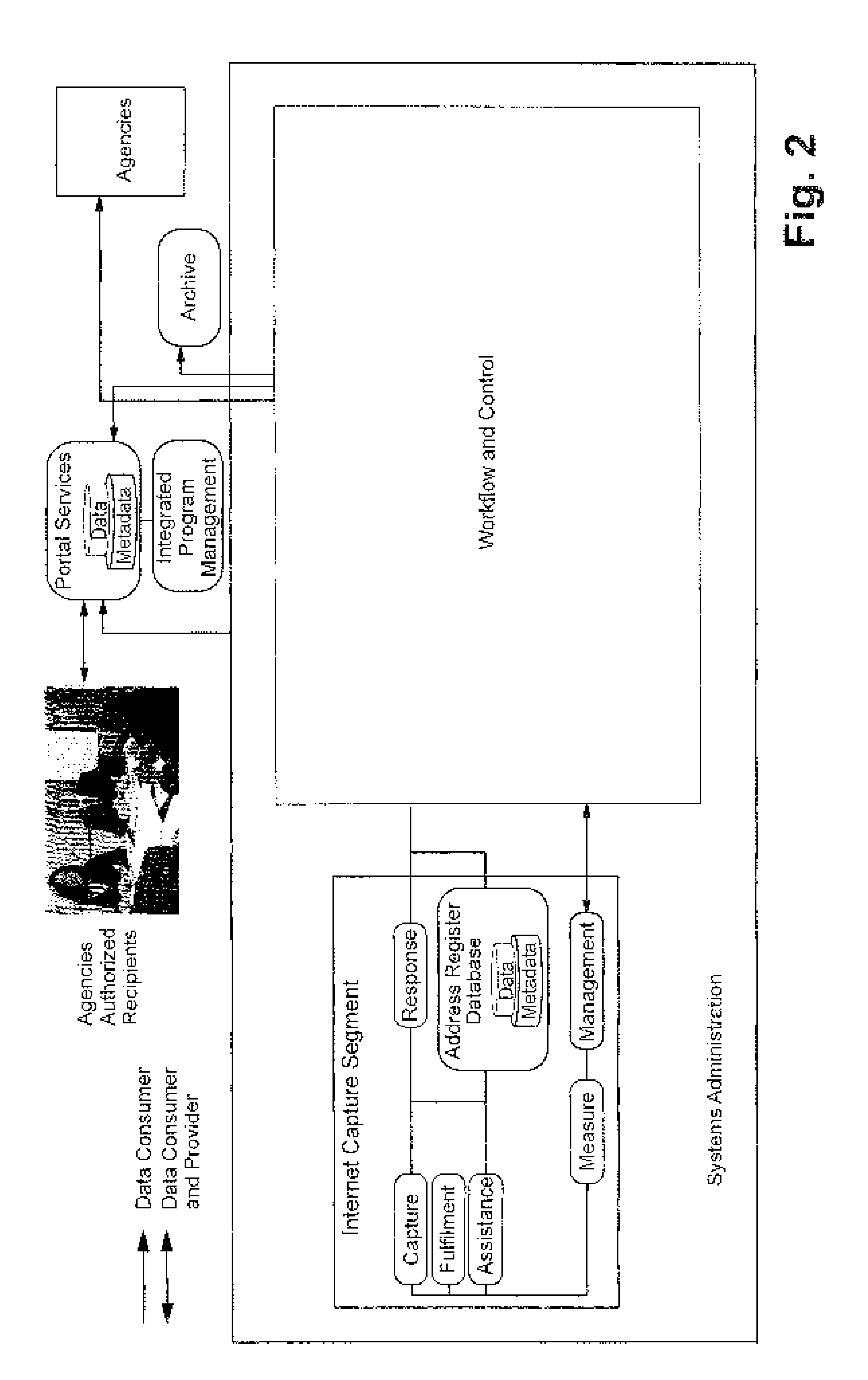
Dynamically generated web surveys for use with census activities, and assocated methods
InactiveUS20100281313A1Improve economyFoster just societyInput/output for user-computer interactionFault responseLook and feelApplication software
Certain example embodiments disclosed herein relate to online survey systems and / or methods. In certain example embodiments, the questions to be asked are substantially insulated from an application that asks the questions. This abstraction may be accomplished in certain example embodiments by dynamically generating a computer-accessible (e.g., web-based) survey from one or more definition files. For example, a survey may be defined via a response definition file and a user interface definition file, thereby enabling the definition files to be read and the survey to be presented with the appropriate questions, validations, and transformations being specified by the response definition file, and with the look and feel being specified by the user interface definition file. Answers to questions may be persisted for a respondent in a storage location remote from the respondent. Such online surveys systems and / or methods may be suitable for census-related activities.
Owner:LOCKHEED MARTIN CORP
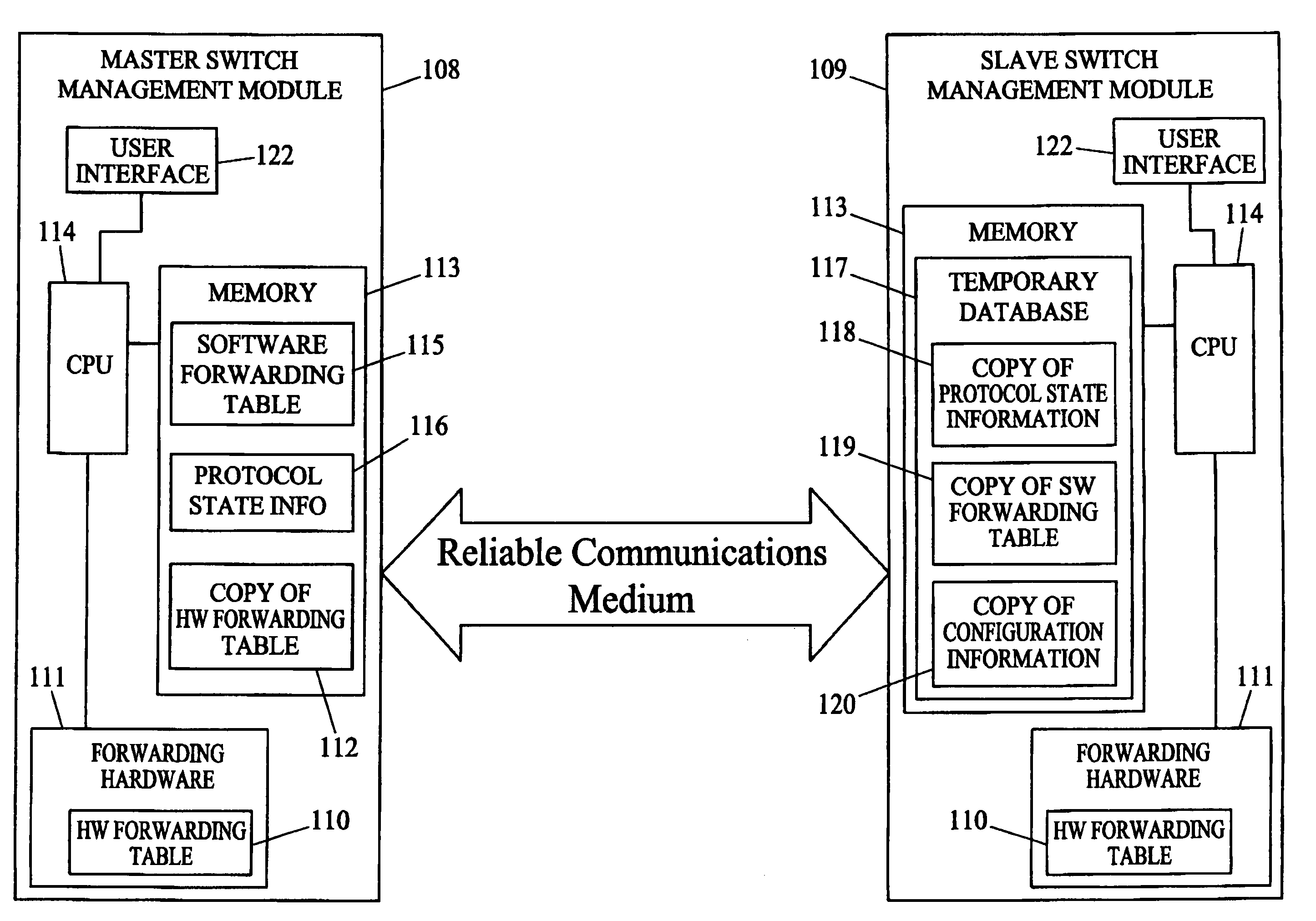
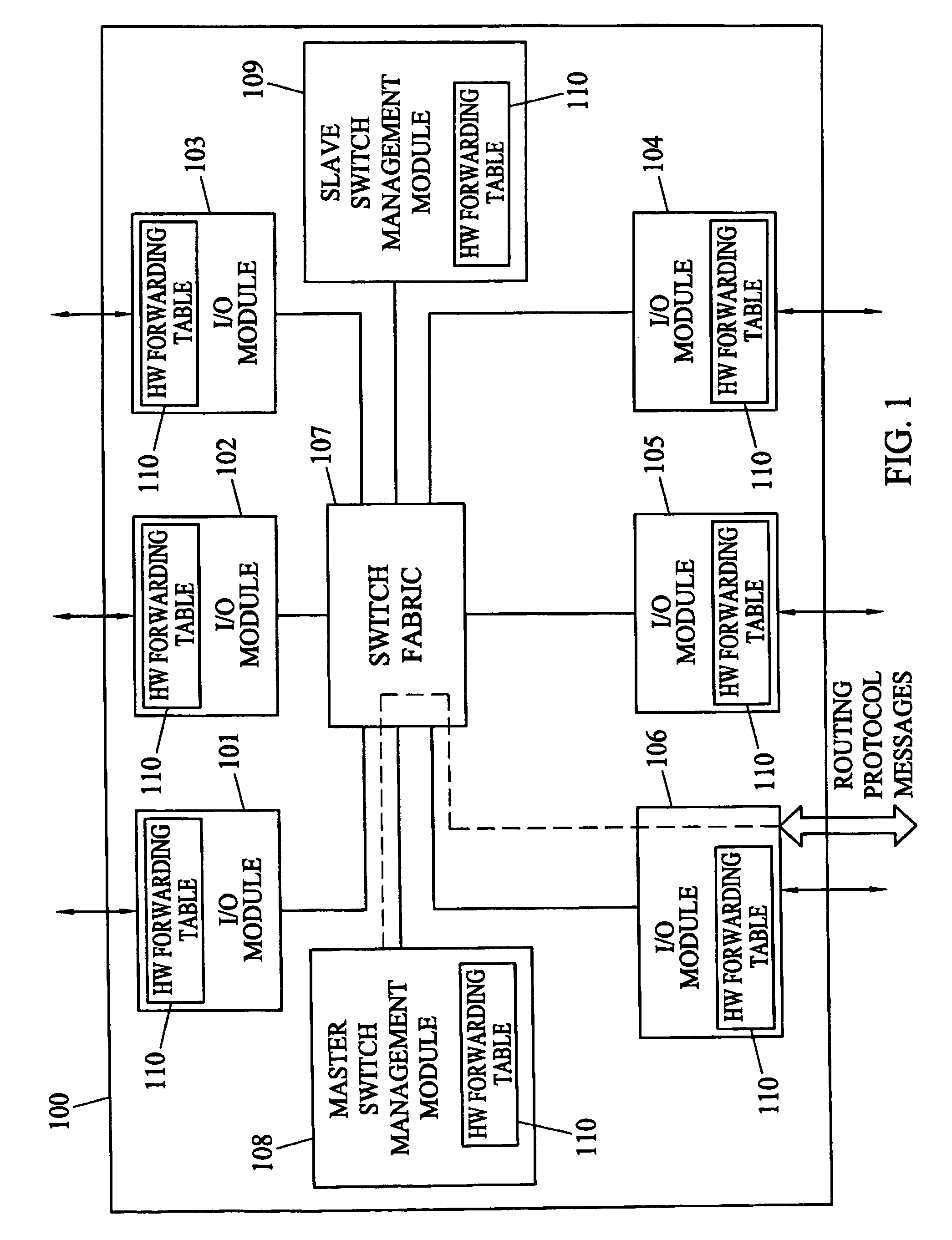
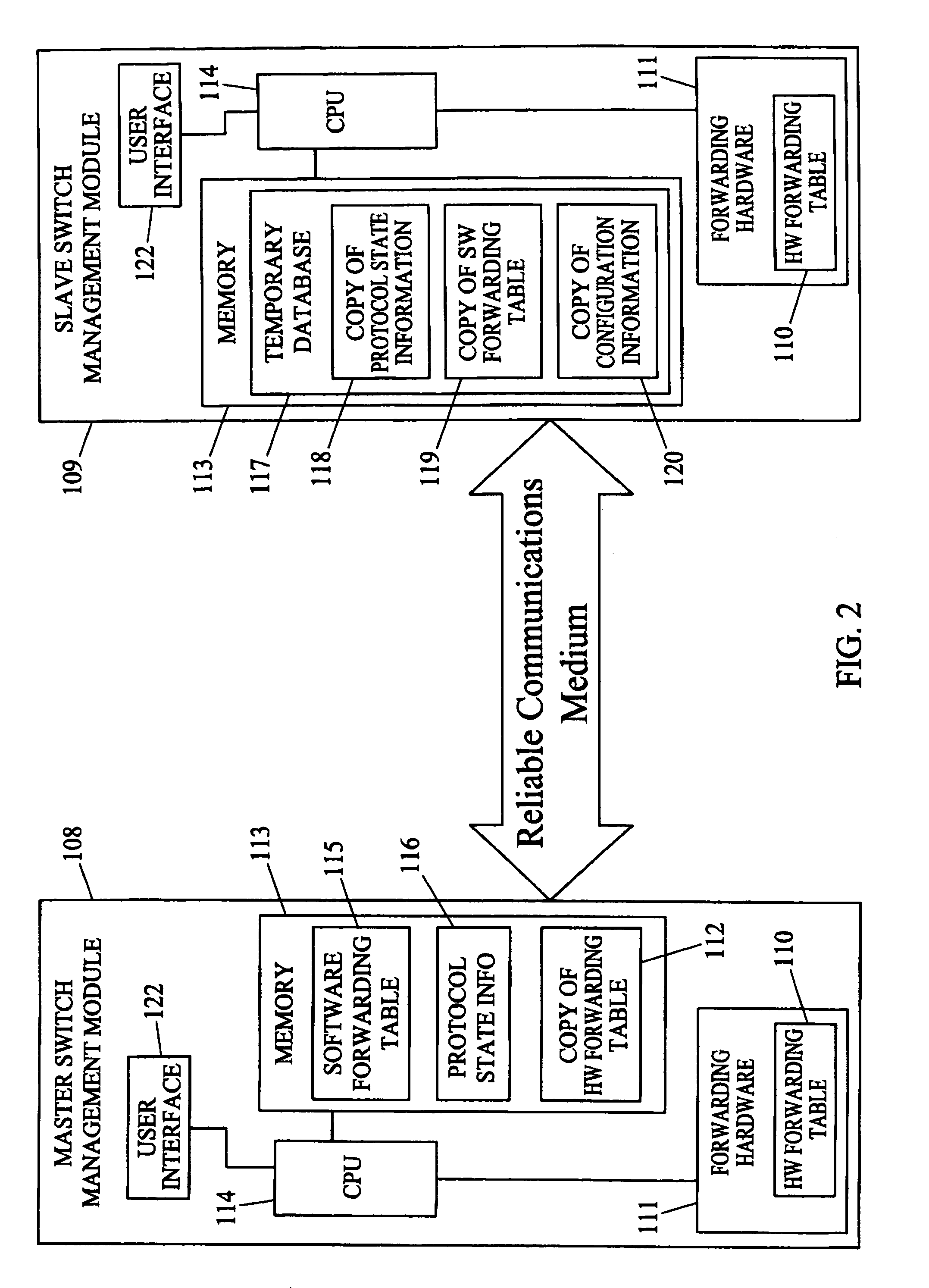
Methods and systems for hitless switch management module failover and upgrade
Methods and systems for hitless switch management module failover and upgrade are disclosed. According to one method, a master switch management module participates in network protocols and performs packet forwarding operations. The master switch management module distributes protocol state and packet forwarding information to the slave switch management module. The slave switch management module continuously monitors the operational state of the master switch management module. In response to detecting failure of the master switch management module or a forced failover initiated by the user interface on the master switch management module, the slave switch management module begins network protocol operation in the master mode in a state where the master switch management module last operated correctly.
Owner:EXTREME NETWORKS INC
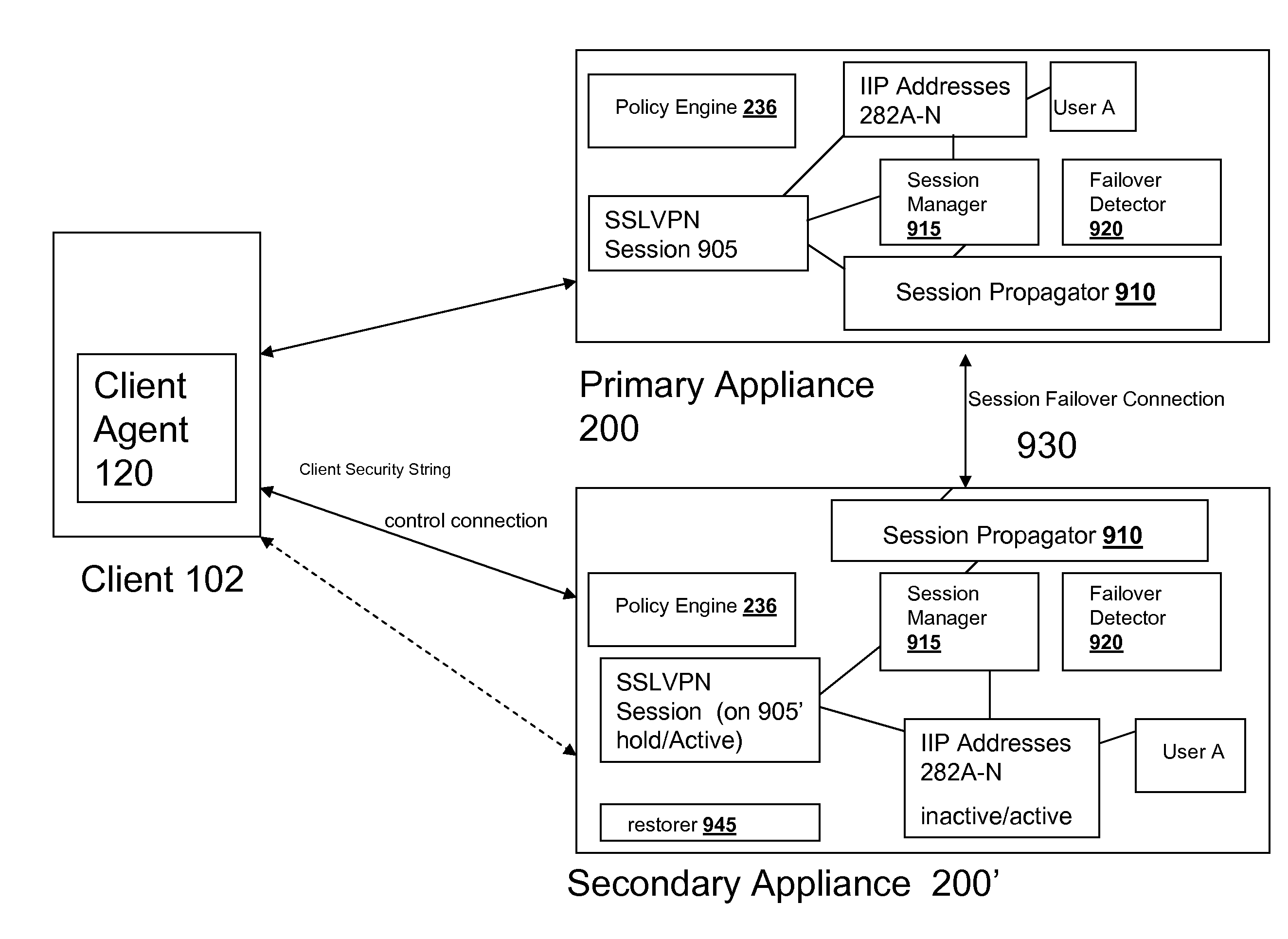
Systems and Methods for Providing IIP Address Stickiness in an SSL VPN Session Failover Environment
The SSL VPN session failover solution of the appliance and / or client agent described herein provides an environment for handling IP address assignment and end point re-authorization upon failover. The appliances may be deployed to provide a session failover environment in which a second appliance is a backup to a first appliance when a failover condition is detected, such as failure in operation of the first appliance. The backup appliance takes over responsibility for SSL VPN sessions provided by the first appliance. In the failover environment, the first appliance propagates SSL VPN session information including user IP address assignment and end point authorization information to the backup appliance. The backup appliance maintains this information. Upon detection of failover of the first appliance, the backup appliance activates the transferred SSL VPN session and maintains the user assigned IP addresses. The backup appliance may also re-authorize the client for the transferred SSL VPN session.
Owner:CITRIX SYST INC
System and method for a redundant communication channel via storage area network back-end
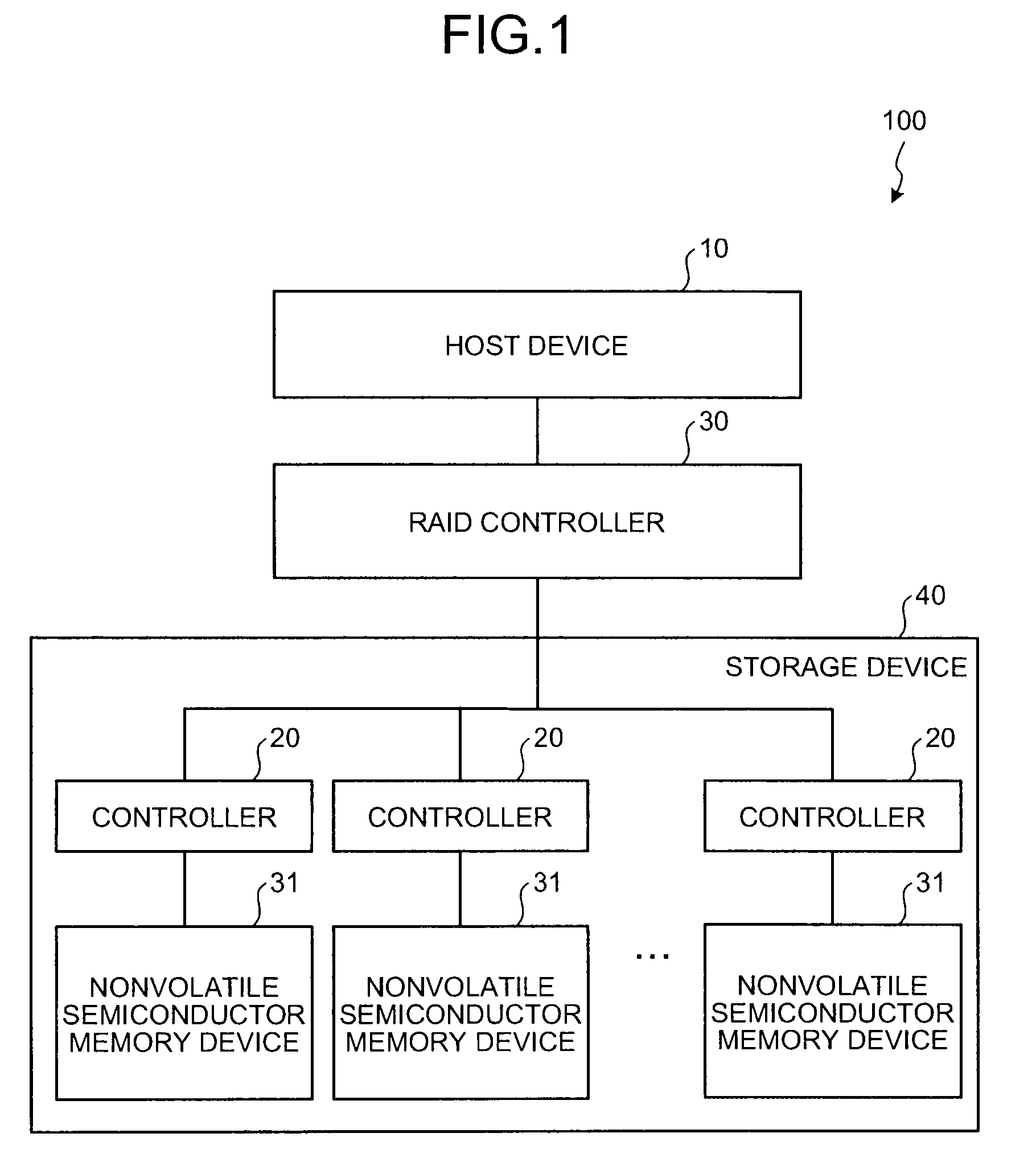
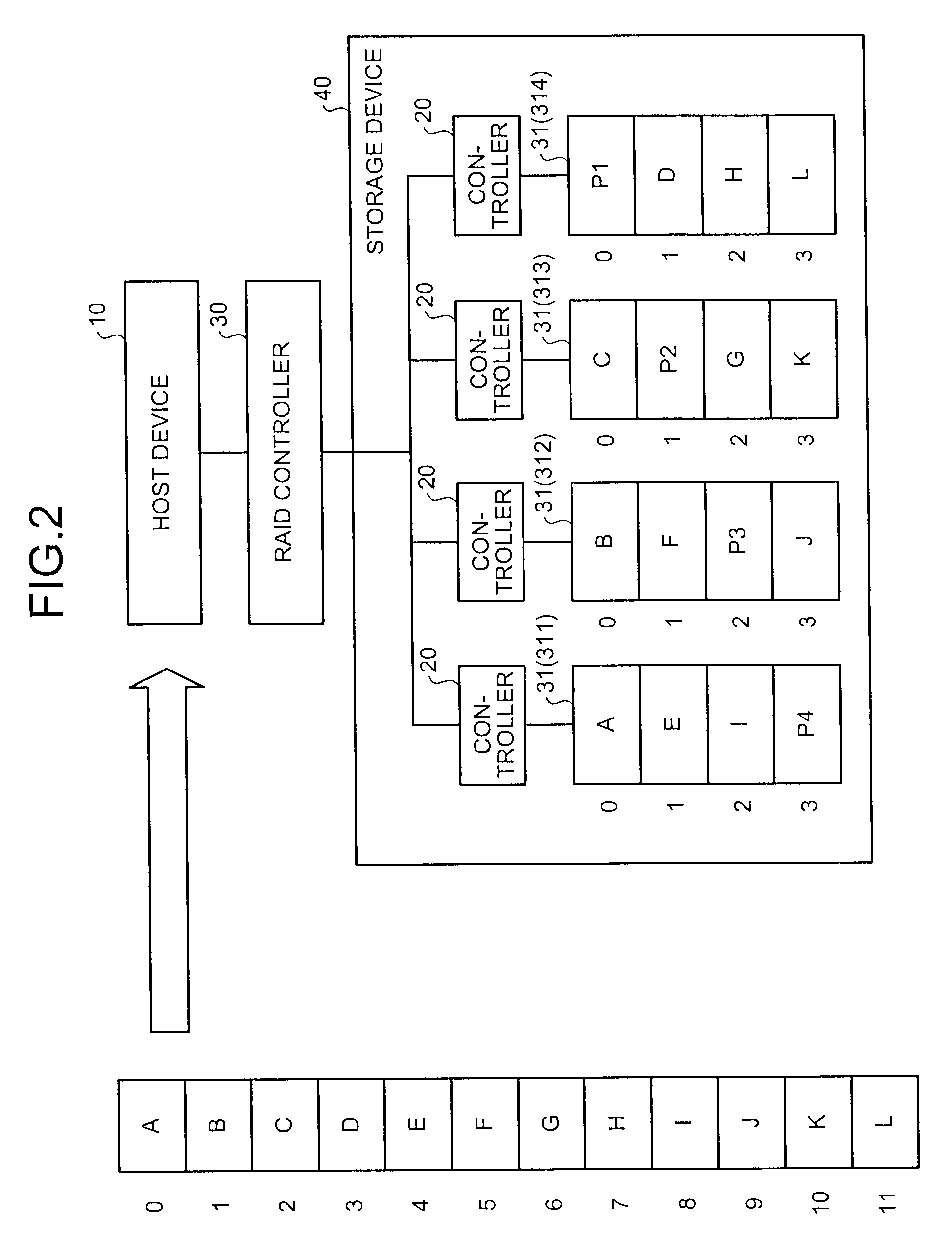
InactiveUS6883065B1Redundancy and robustness in systemInput/output to record carriersFault responseFailoverRAID
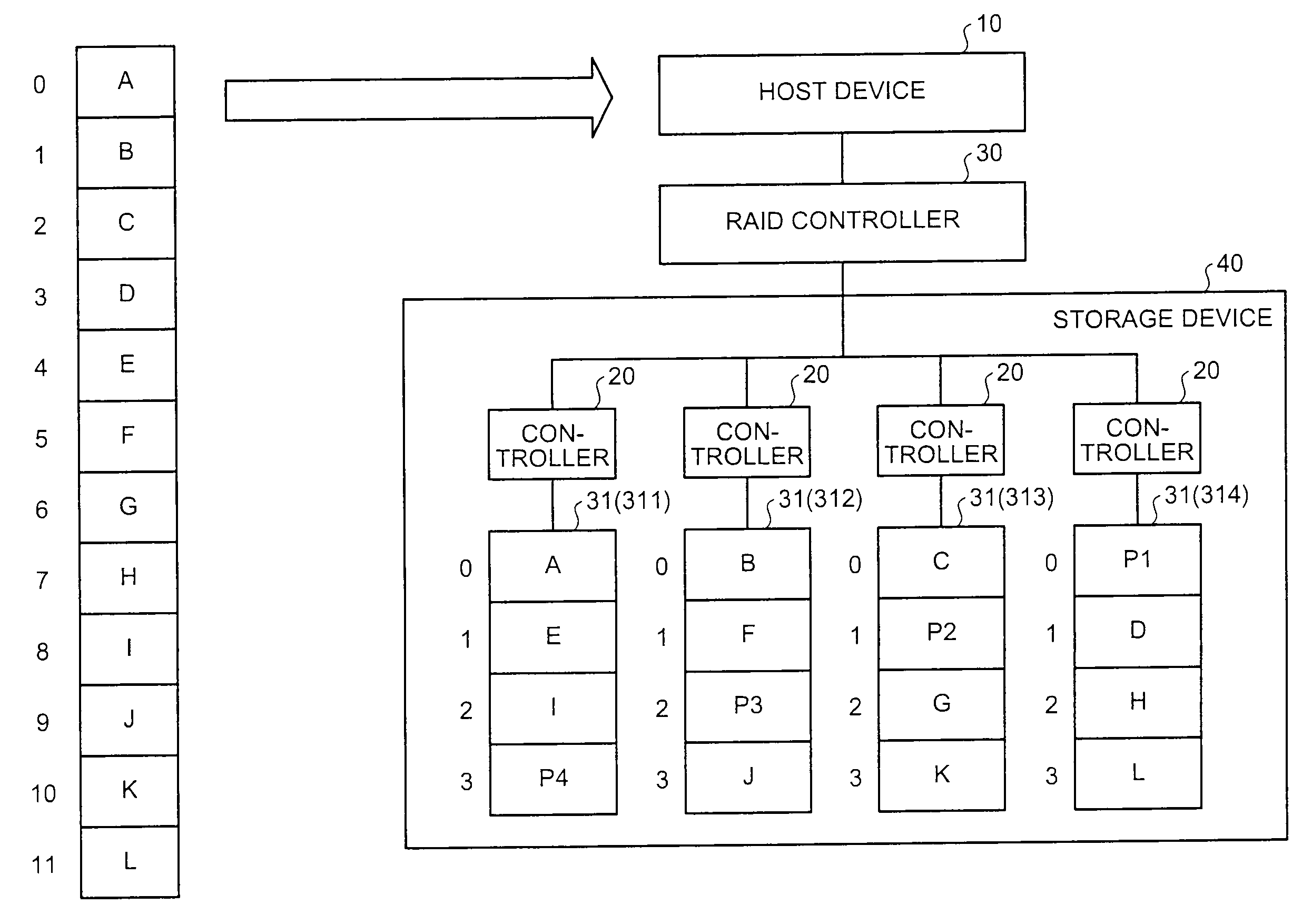
A fiber channel storage area network (SAN) provides virtualized storage space for a number of servers to a number of virtual disks implemented on various virtual redundant array of inexpensive disks (RAID) devices striped across a plurality of physical disk drives. The SAN includes plural controllers and communication paths to allow for fail-safe and fail-over operation. The plural controllers can be loosely-coupled to provide n-way redundancy and have more than one independent channel for communicating with one another. In particular, respective portions from each of the back-end physical disk drives within the SAN are used as one of these alternative communication channels to pass messages between controllers. Such an alternative communications channel provides even further redundancy and robustness in the system.
Owner:INNOVATIONS IN MEMORY LLC
Systems, Methods, and Computer Program Products for Instant Recovery of Image Level Backups
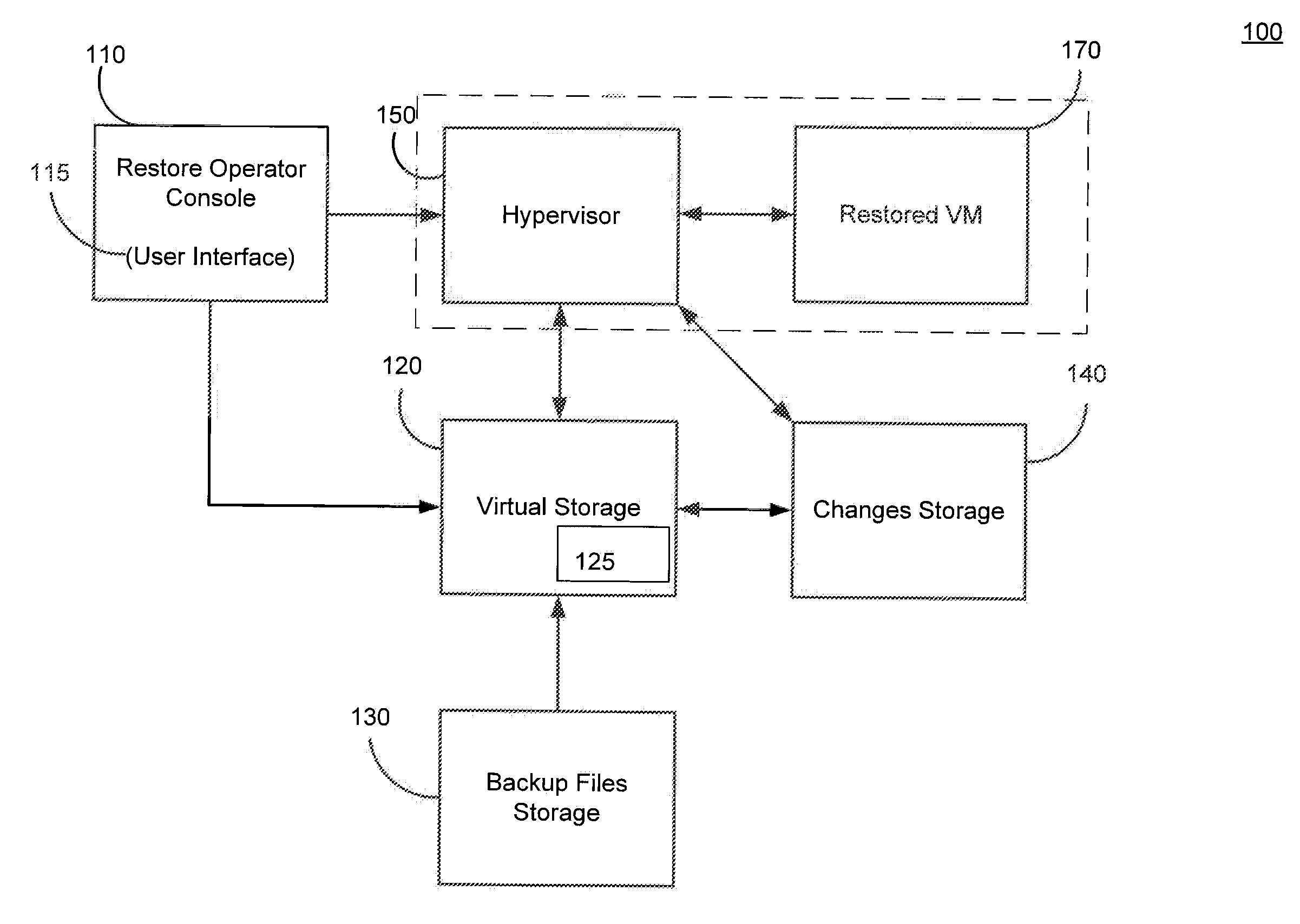
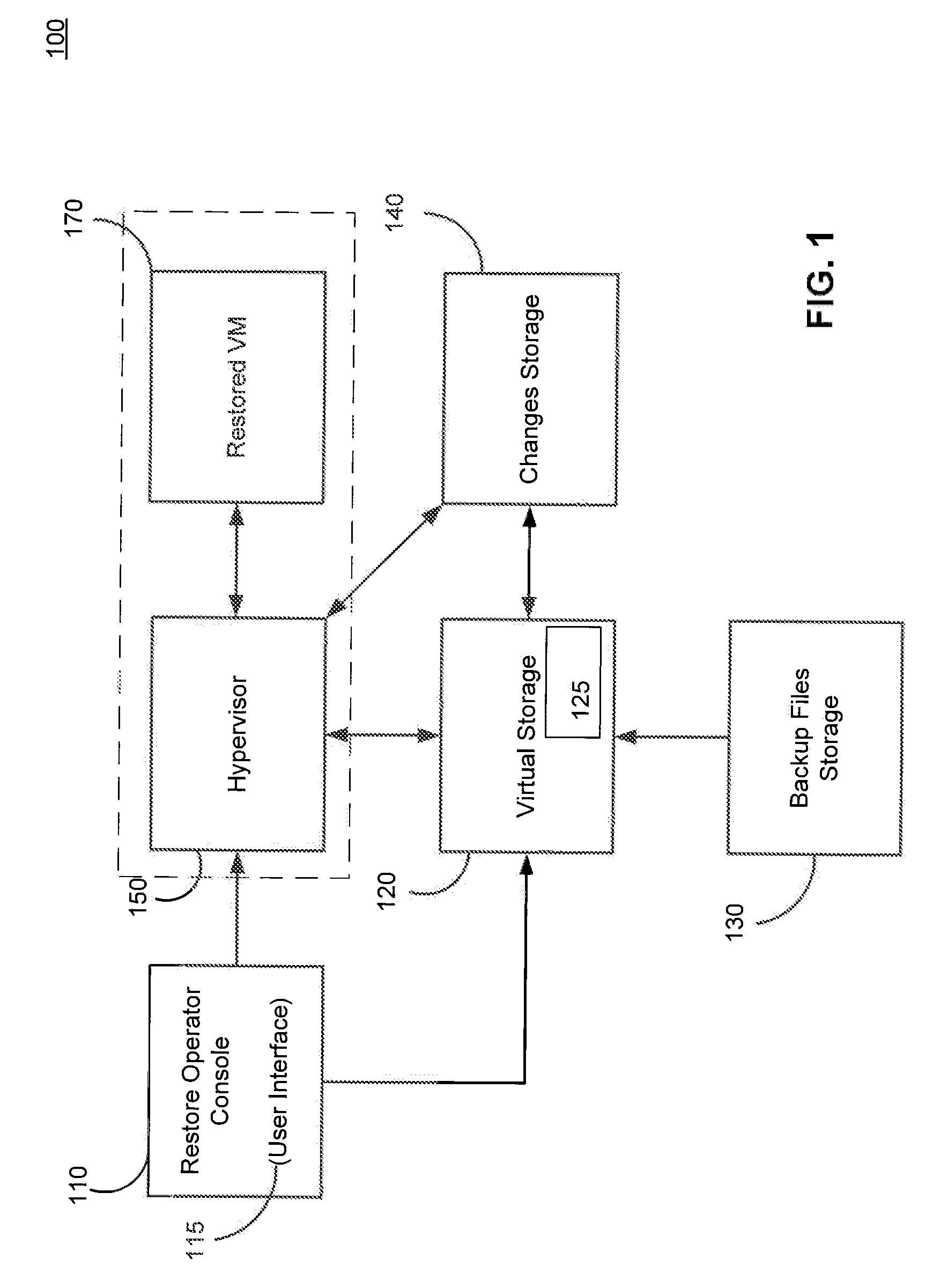
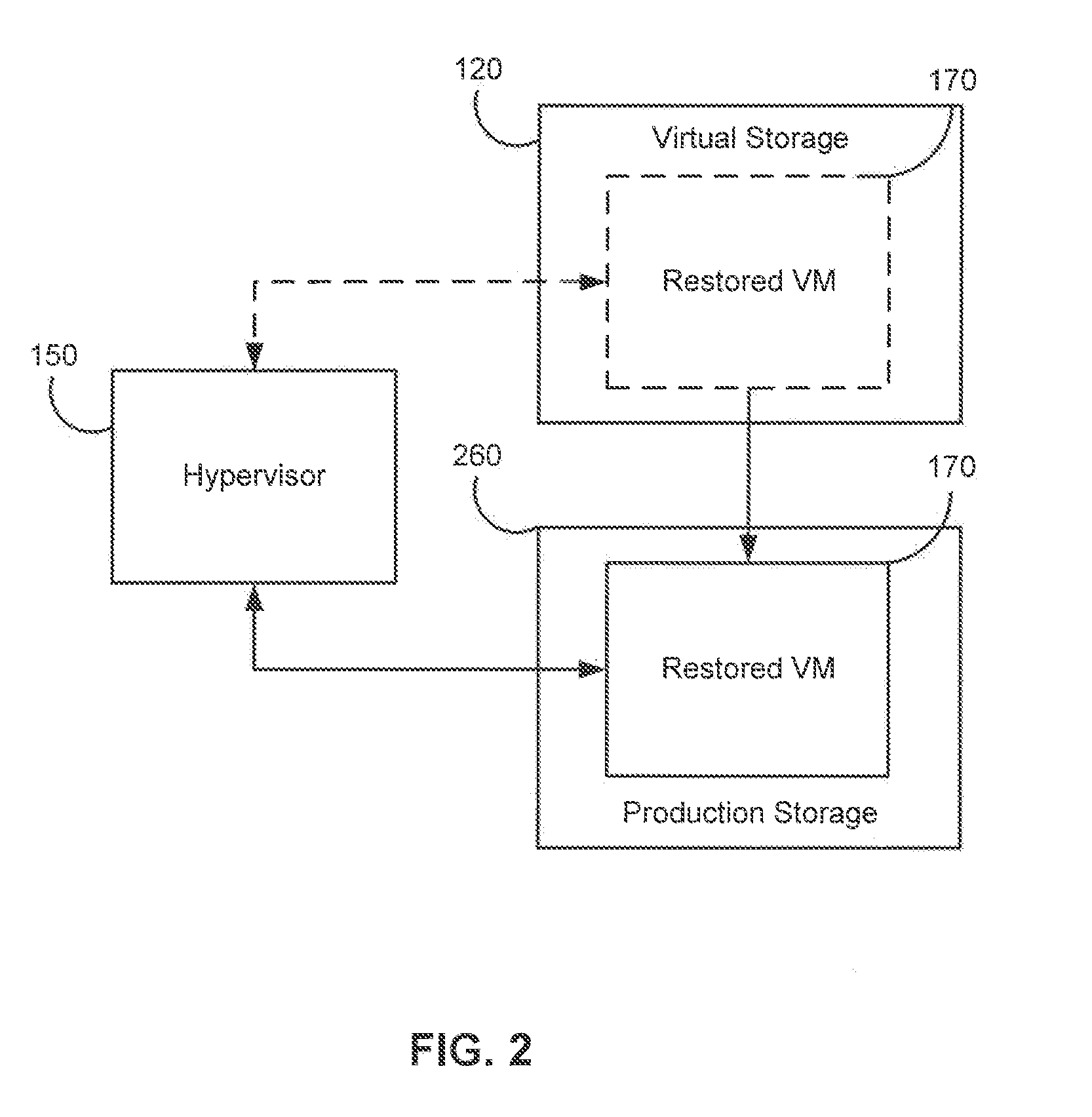
ActiveUS20120017114A1Fault responseSoftware simulation/interpretation/emulationOperational systemDowntime
Systems, methods, and computer program products are provided for instant recovery of a virtual machine (VM) from a compressed image level backup without fully extracting the image level backup file's contents to production storage. The method receives restore parameters and initializes a virtual storage. The method attaches the virtual storage to a hypervisor configured to launch a recovered VM. The method stores virtual disk data changes inflicted by a running operating system (OS), applications, and users in a changes storage. The method provides the ability to migrate the actual VM disk state (taking into account changed disk data blocks accumulated in changes storage) so as to prevent data loss resulting from the VM running during the recovery and accessing virtual storage, to production storage without downtime. In embodiments, the method displays receives restore parameters in an interactive interface and delivers the recovery results via an automated message, such as an email message.
Owner:VEEAM SOFTWARE GROUP GMBH
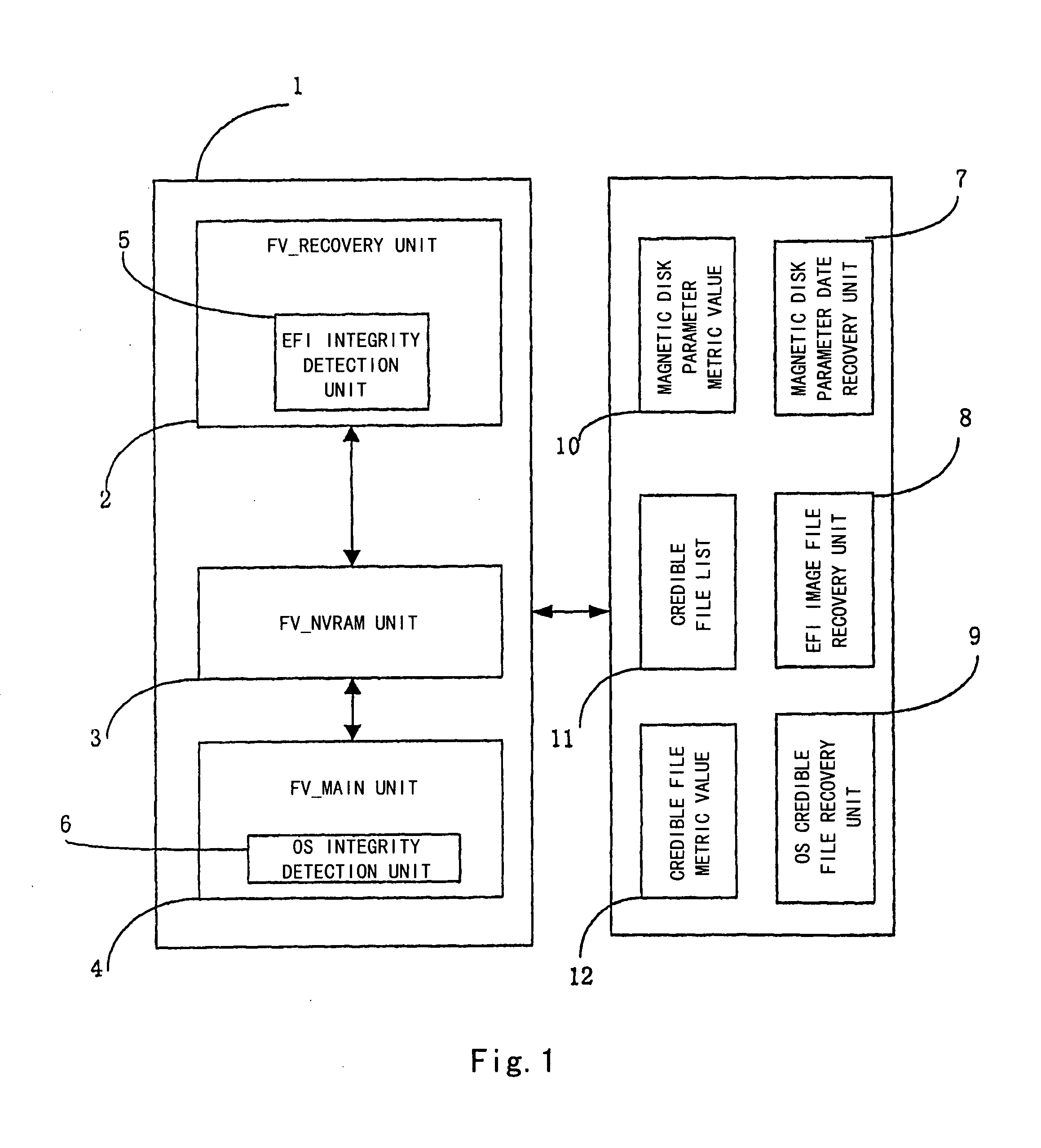
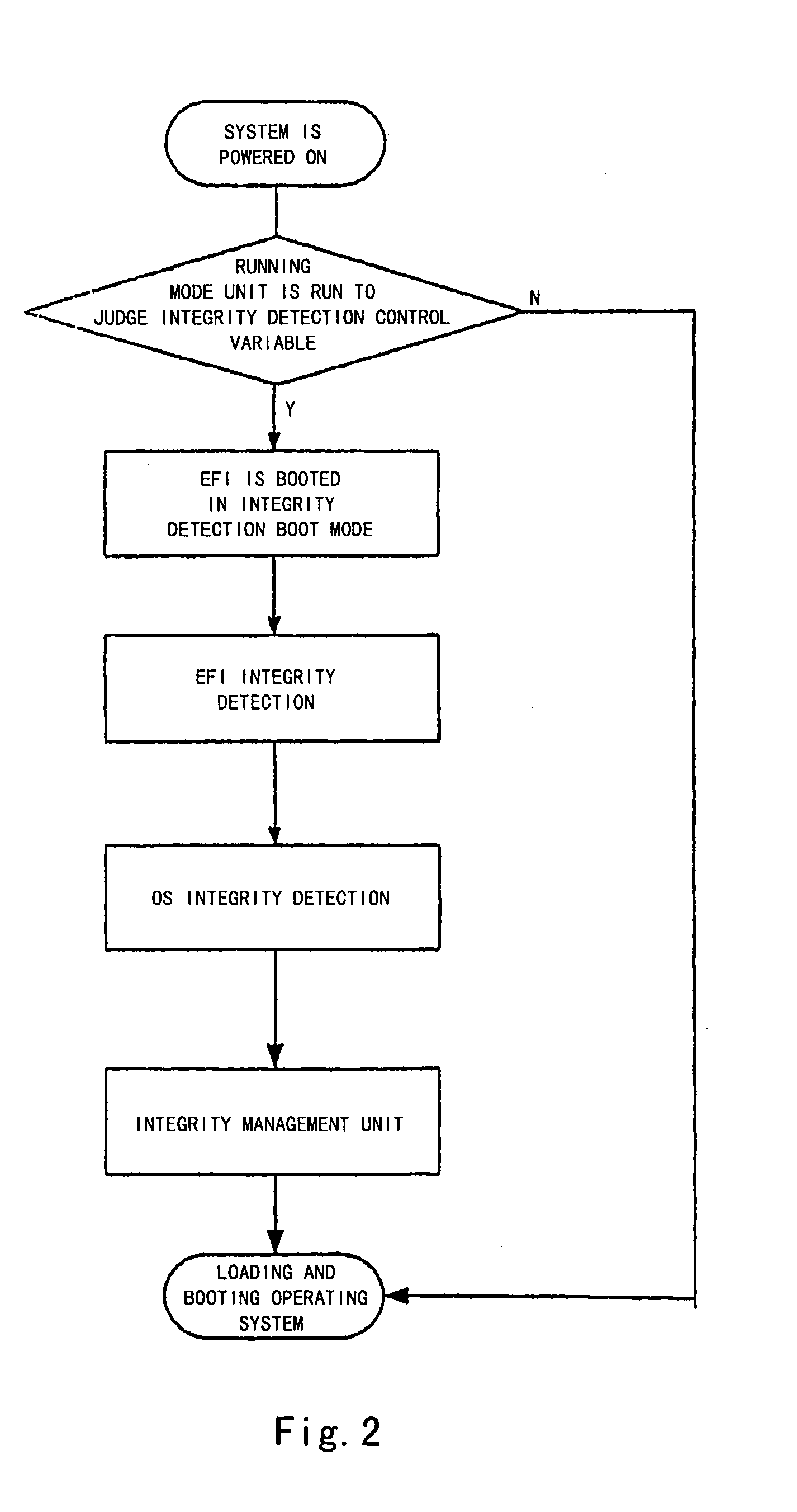
Computer System and Method for Performing Integrity Detection on the Same
InactiveUS20090300415A1Ensure consistencyEnsures strictnessFault responseDigital data processing detailsOperational systemComputerized system
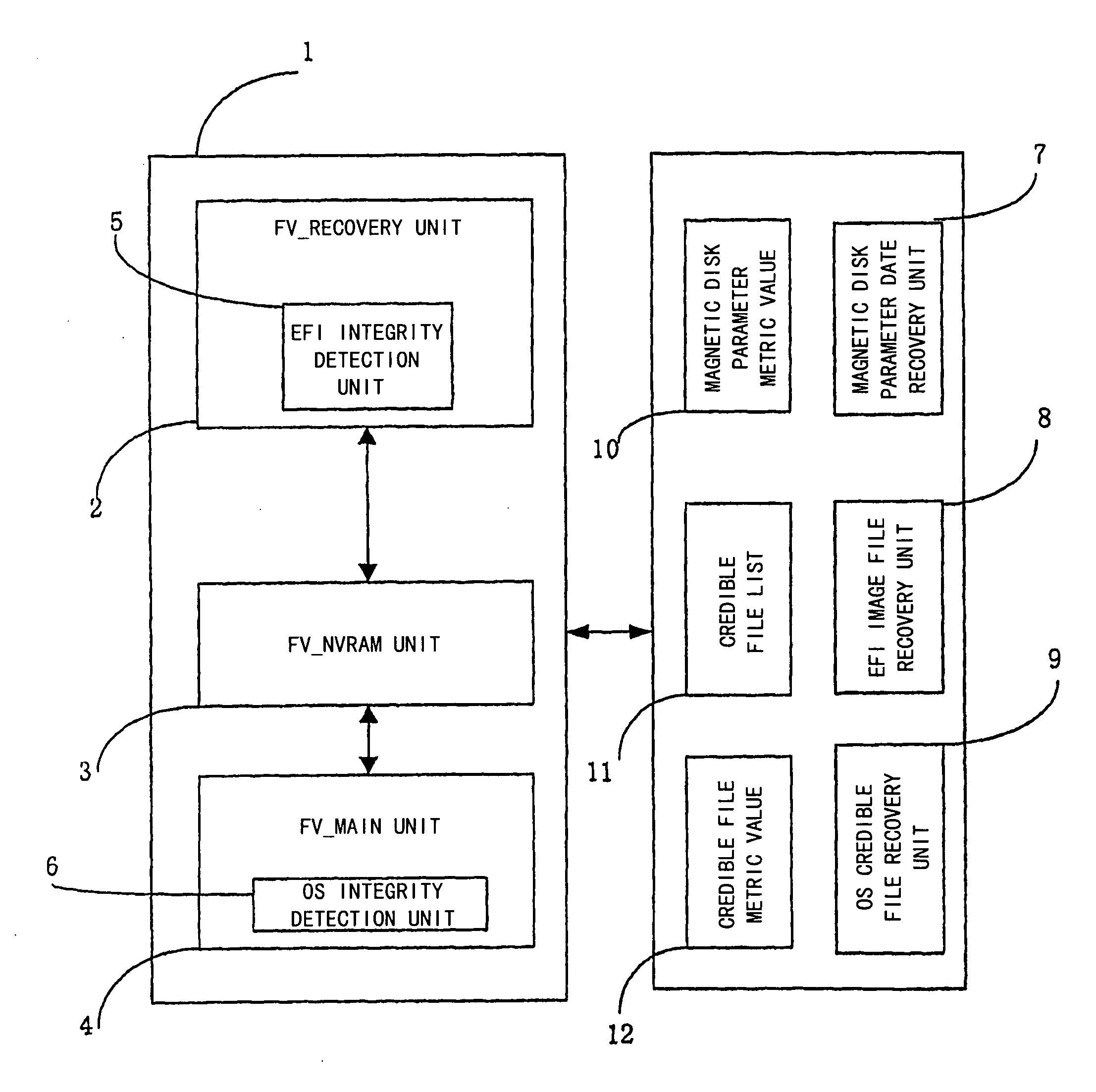
The present invention proposes a computer system and a method capable of performing integrity detection, comprising: a running mode unit which comprises an integrity detection boot variable to determine whether or not to initiate an integrity detection boot mode by judging said running mode unit; an EFI integrity detection unit (5), which is used for performing an integrity detection on EFI image codes in the integrity detection boot mode, and comprises an integrity metric value for being compared with an EFI integrity calculated value generated after the EFI integrity detection unit performs the integrity detection on the EFI image codes, to determine the integrity of the EFI image codes; an operating system integrity detection unit (6); and an integrity management unit. The present invention is based on the EFI BIOS to perform the integrity detection on the operating system during the pre-boot stage, having better reliability and security.
Owner:LENOVO (BEIJING) CO LTD
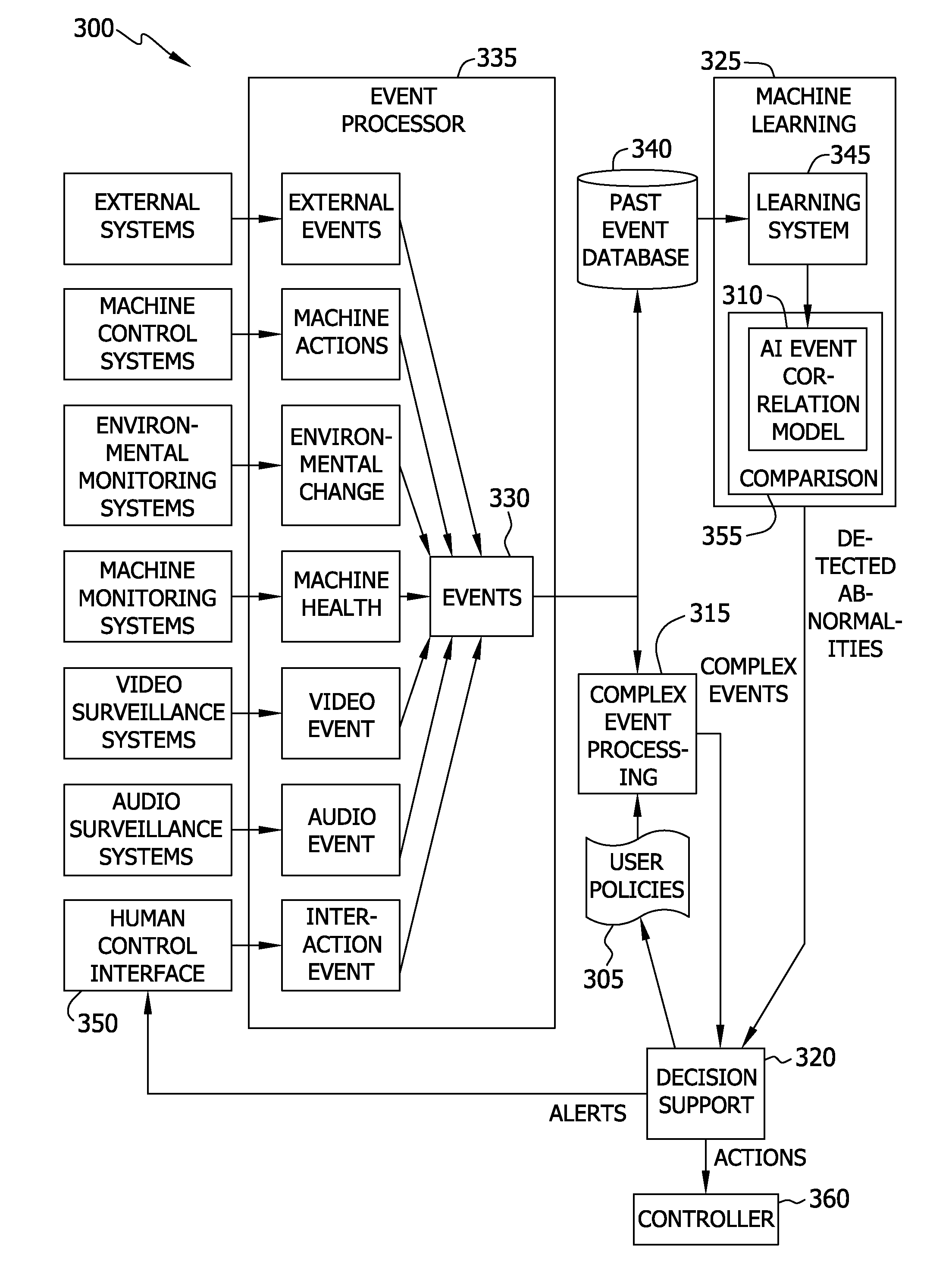
Methods and systems for use in identifying abnormal behavior in a control system
Methods and apparatus for use in identifying abnormal behavior in a control system. Operating events associated with a control system are received, and an actual behavior of the control system is determined based on the received operating events. The actual behavior is compared to expected behavior to determine whether the actual behavior differs from the expected behavior. The expected behavior includes a correlation between a plurality of operating events associated with the control system. The expected behavior is updated based on an indication of whether the actual behavior is abnormal from a user.
Owner:THE BOEING CO
Systems and methods for detailed error reporting in data storage systems
ActiveUS8713357B1Efficient discoveryEasy to understandInput/output to record carriersFault responseData operationsData access
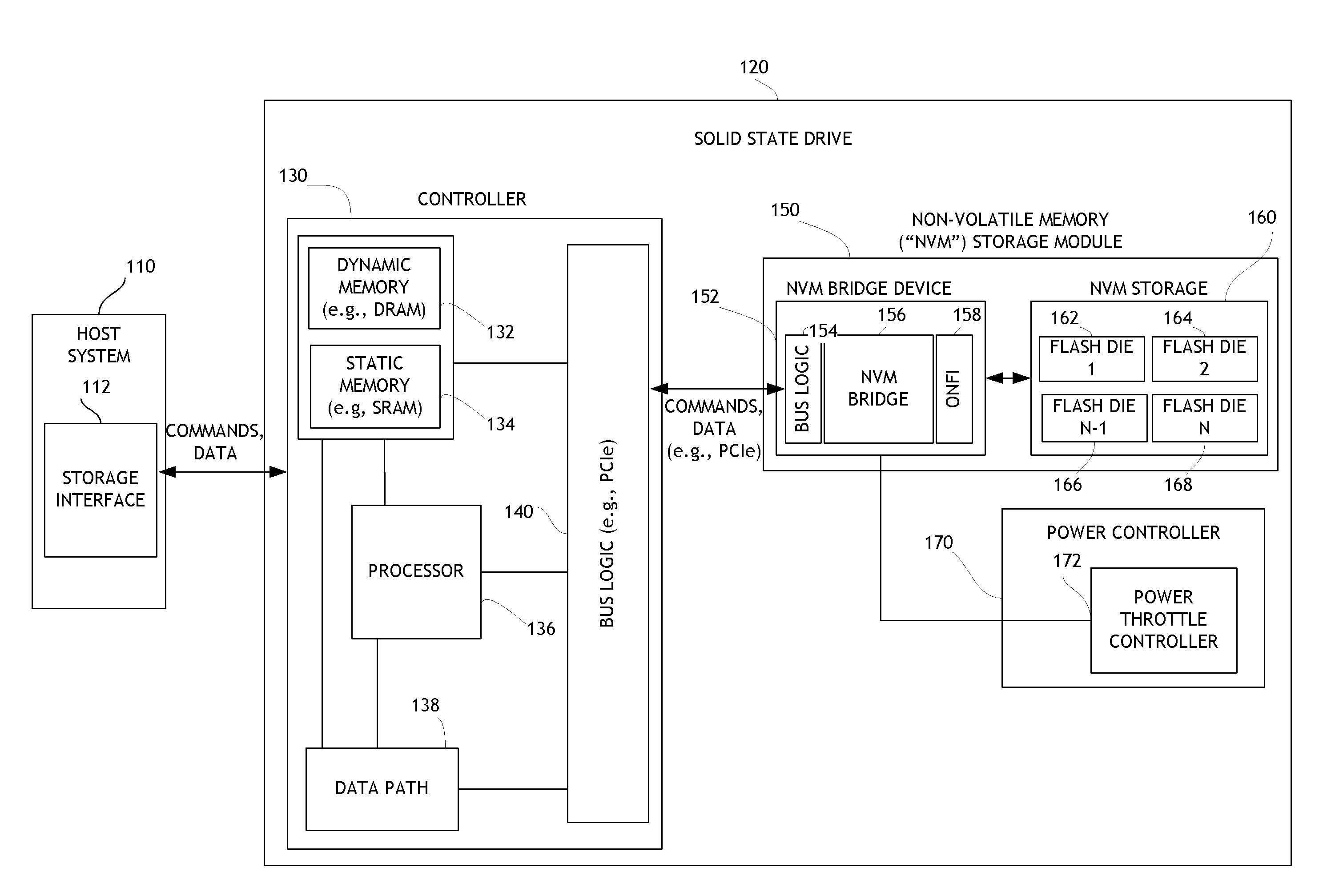
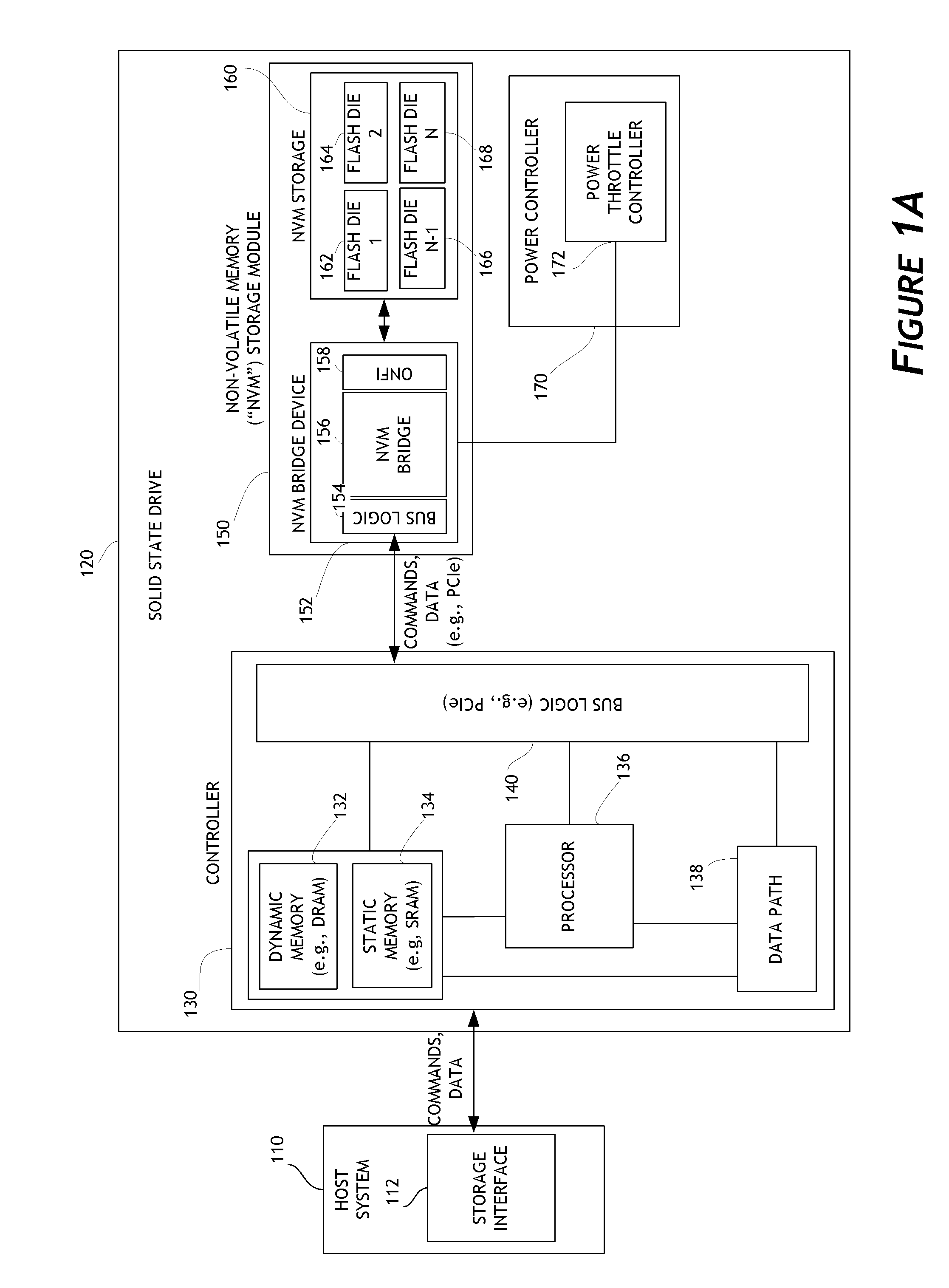
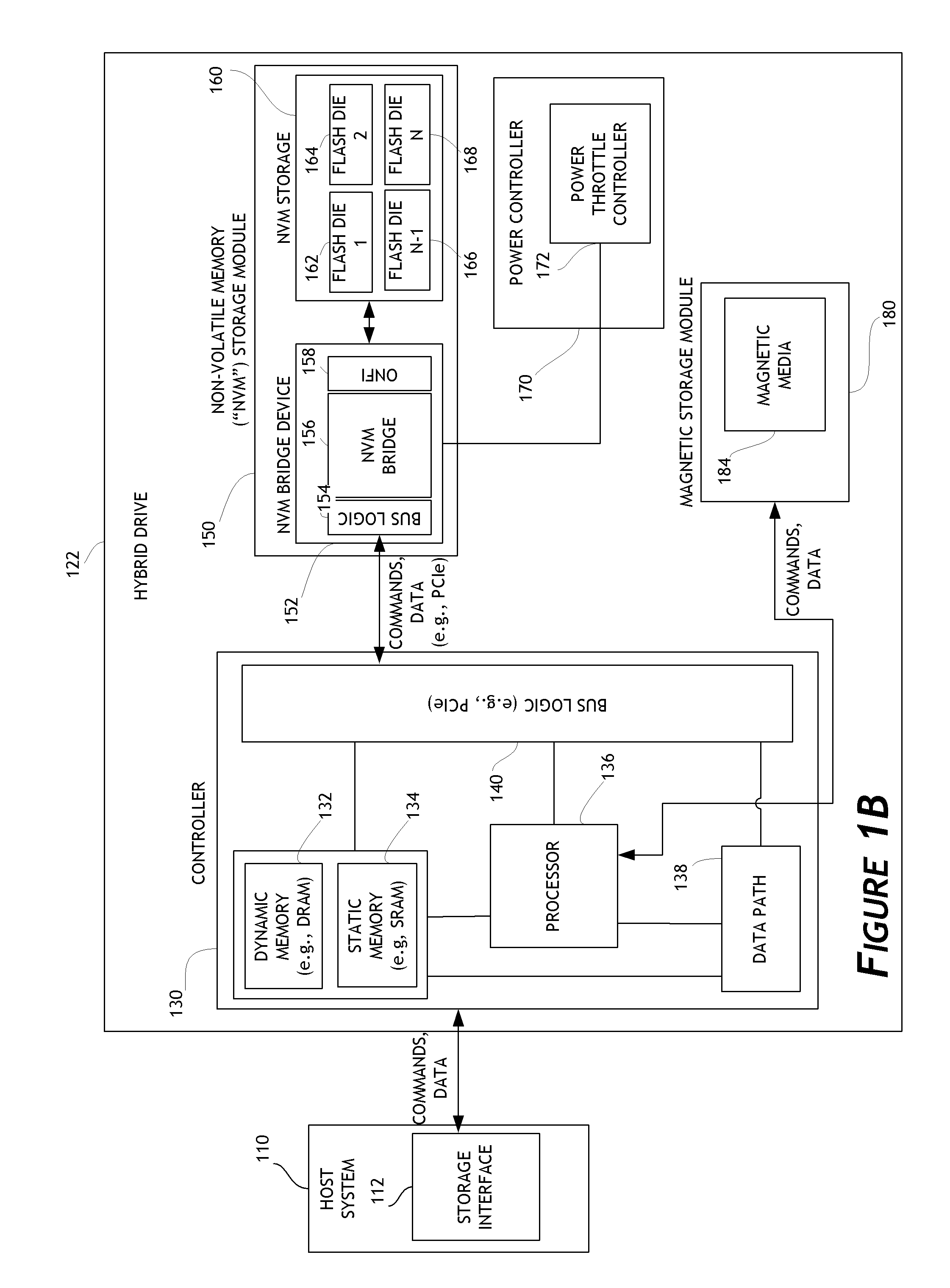
Embodiments of the invention are directed to providing detailed error reporting of data operations performed on a NVM storage device. In one embodiment, a controller interfaces with a NVM storage device including NVM storage coupled with a bridge. In one embodiment, the controller is provided physical, page-level access to the NVM via the bridge, and the bridge provides detailed error reporting of the data operations that the bridge performs on the NVM on behalf of the controller. For example, the bridge may provide page level reporting indicating which page(s) failed during a read operation. Detailed error reporting allows the controller to better understand the failures that occurred in a data access operation in the NVM. It also enables the controller to manage the flash media at the physical page / block level. In one embodiment, detailed error reporting also enables the return of discontinuous ranges of data with the error portions removed.
Owner:WESTERN DIGITAL TECH INC
System and method for managing information technology models in an intelligent workload management system
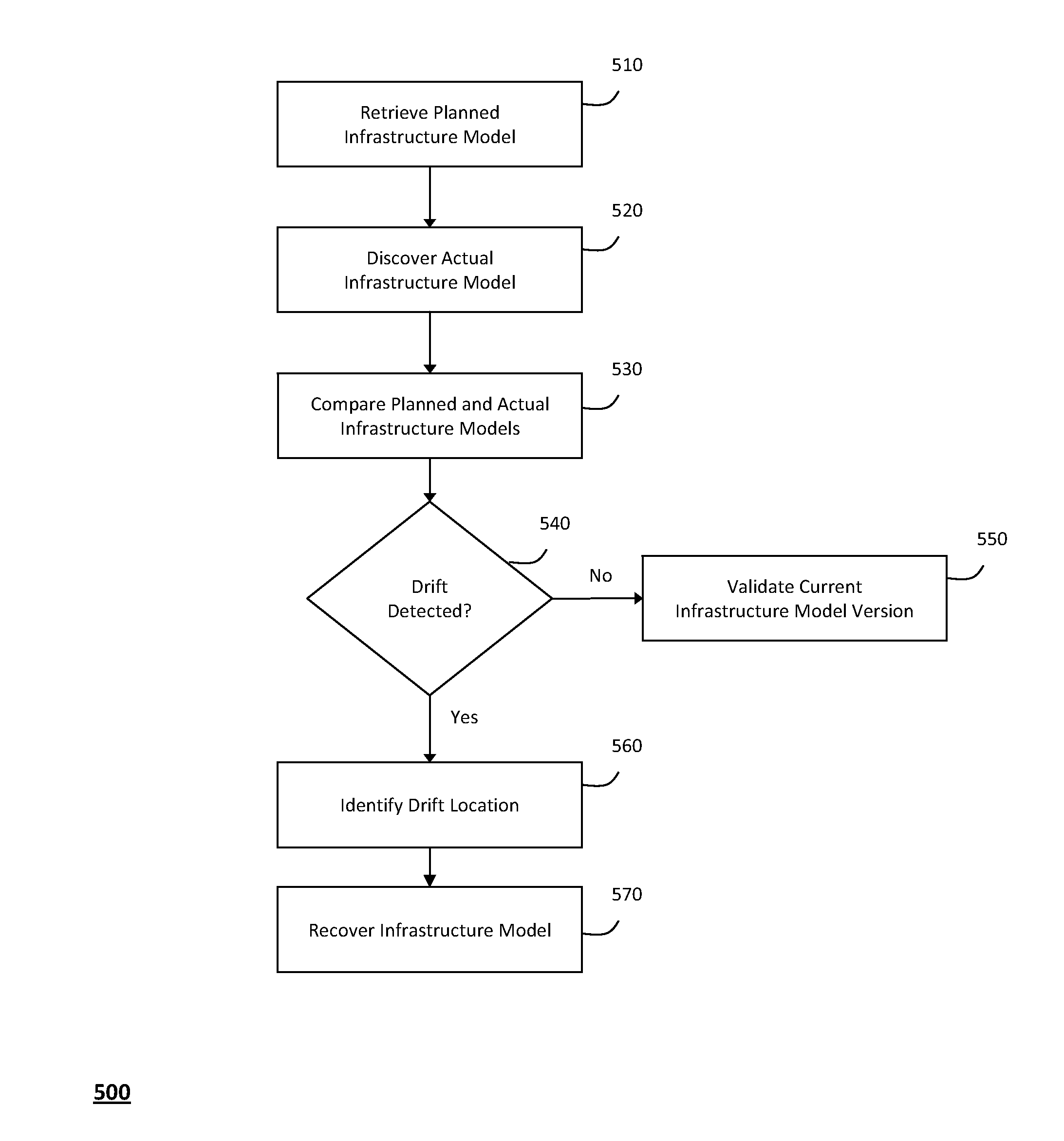
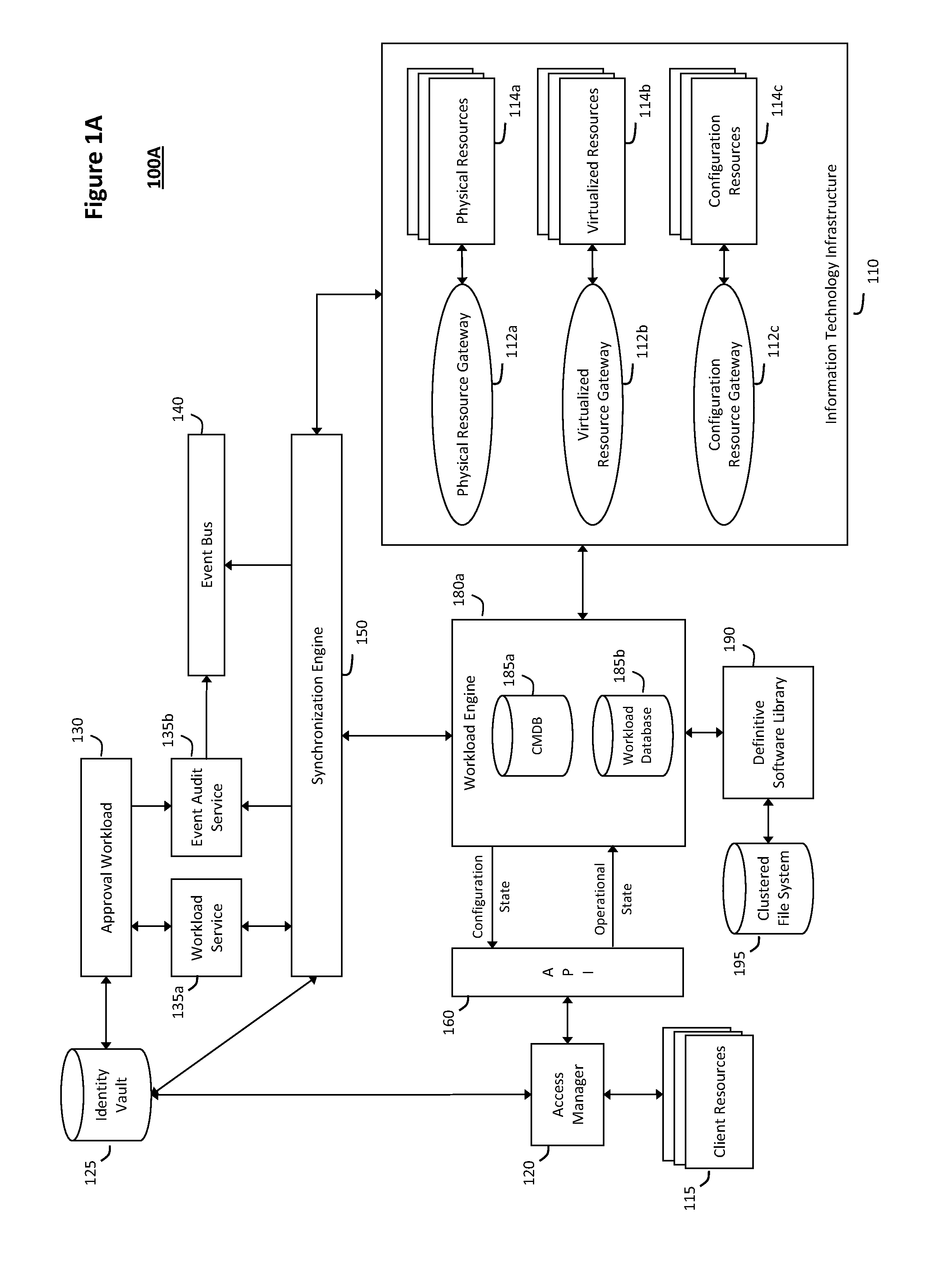
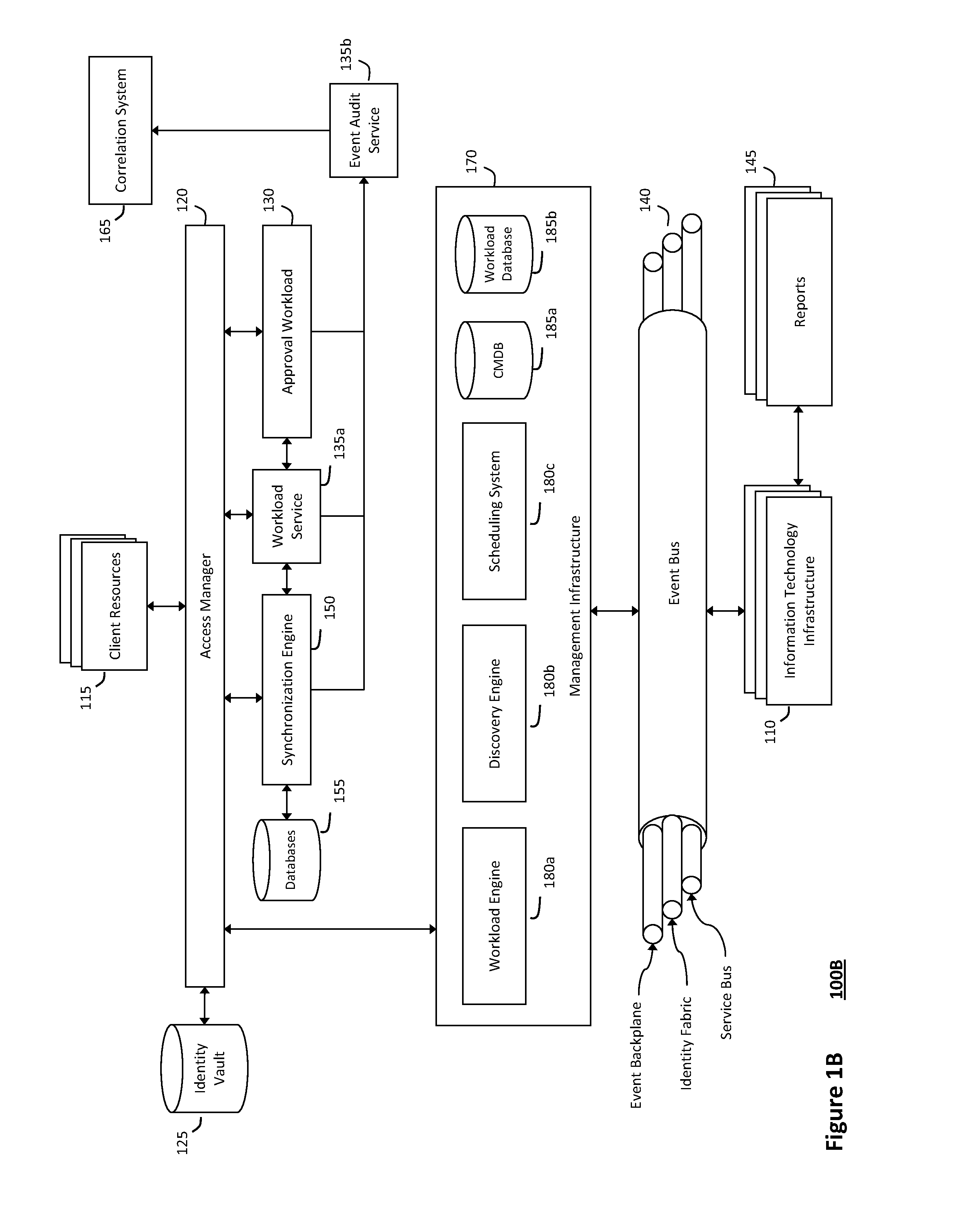
ActiveUS20110126047A1Free computational resourceAgile and flexible managementFault responseDigital computer detailsPlanned changeService-oriented architecture
The system and method described herein for managing information technology models in an intelligent workload management system may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads. In particular, the management threads may converge information for managing planned changes and recovery processes for version-controlled snapshots of the information technology models. For example, a discovery engine may enrich models of an infrastructure with identity information obtained from an identity vault and the infrastructure itself, and a management infrastructure may then manage planned changes to the infrastructure model. In particular, the management infrastructure may construct implementation plans that coordinate interaction between managed entities to implement the planned changes, and may further detect drifts between operational states and planned states for the infrastructure models.
Owner:MICRO FOCUS SOFTWARE INC
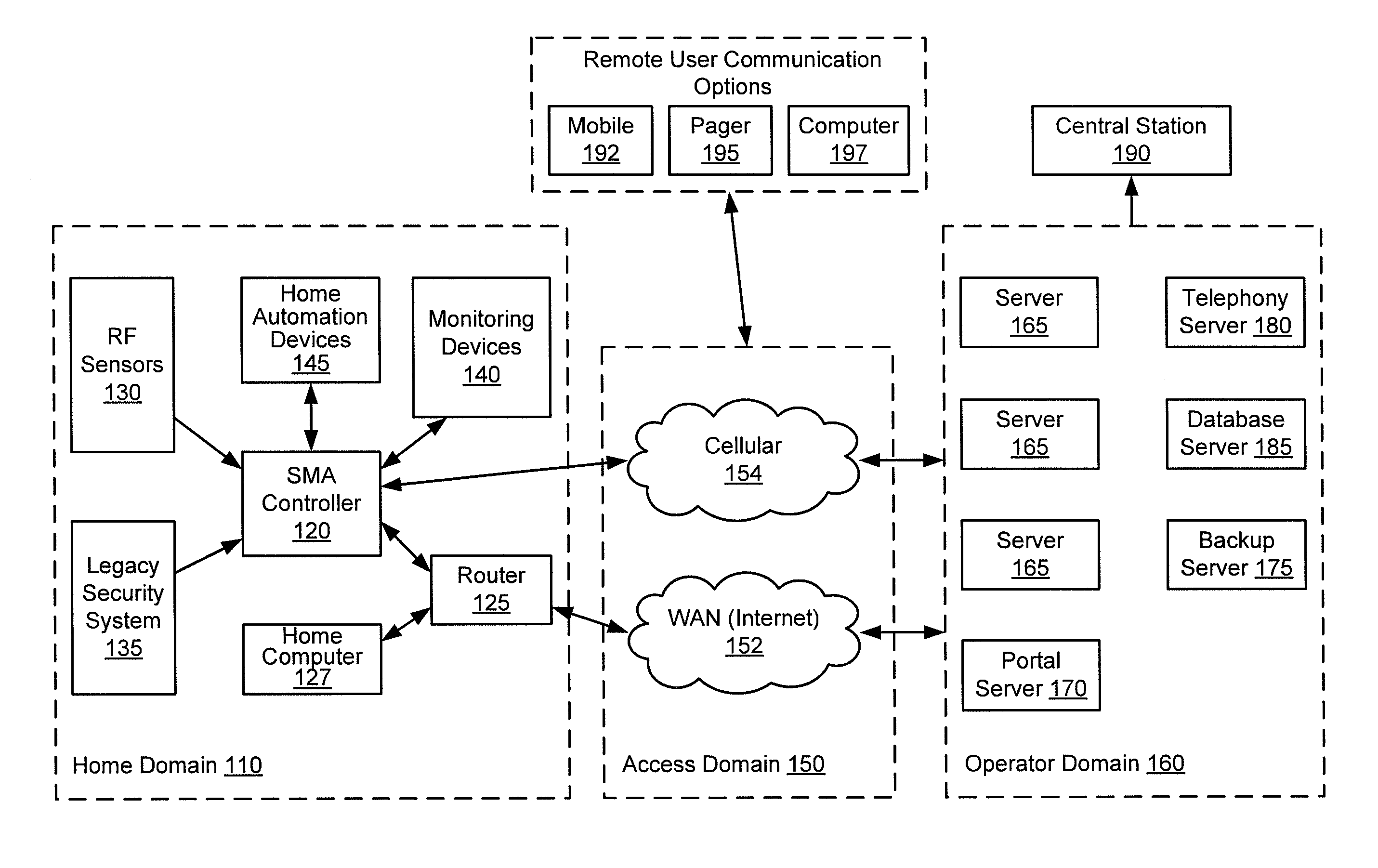
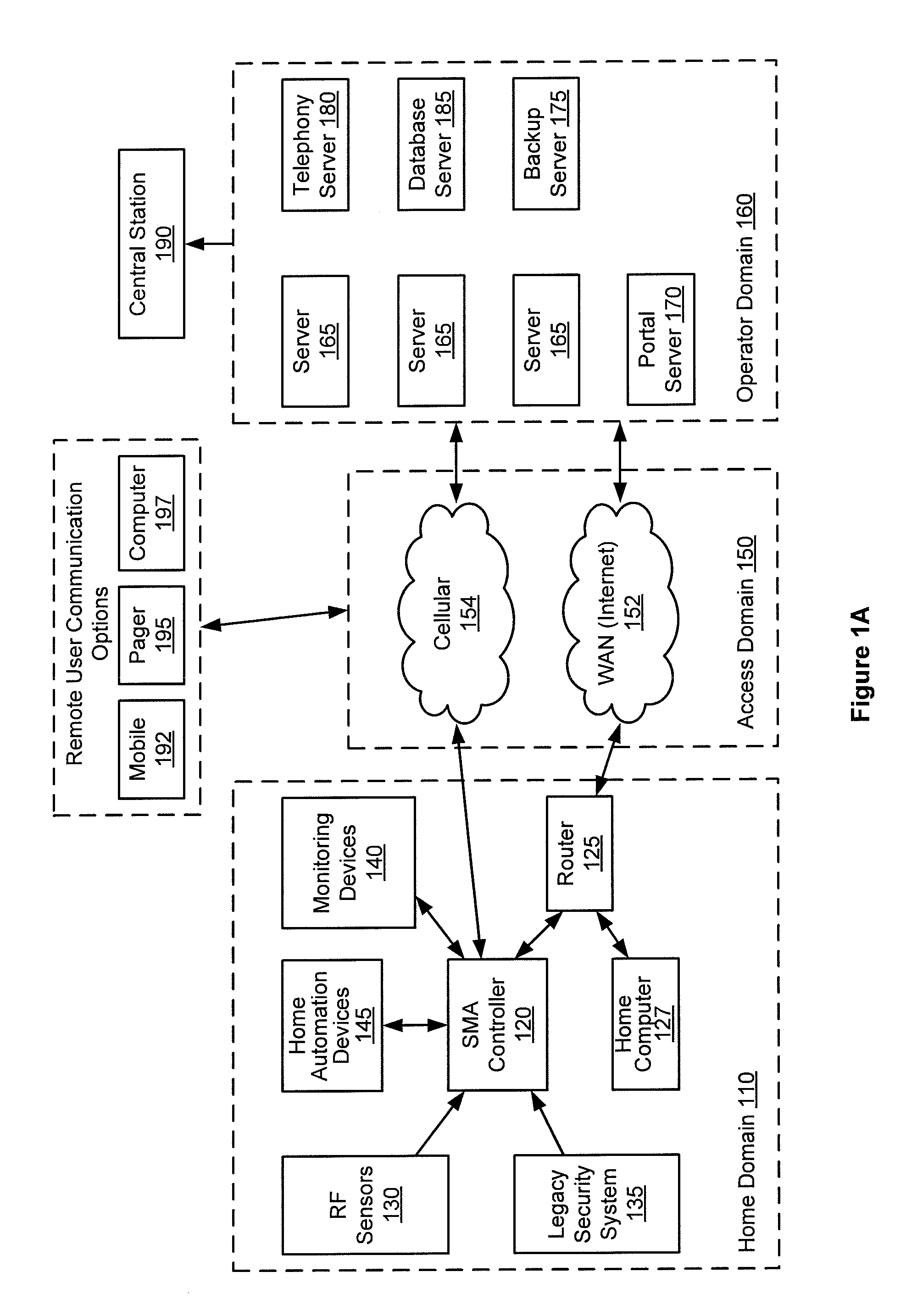
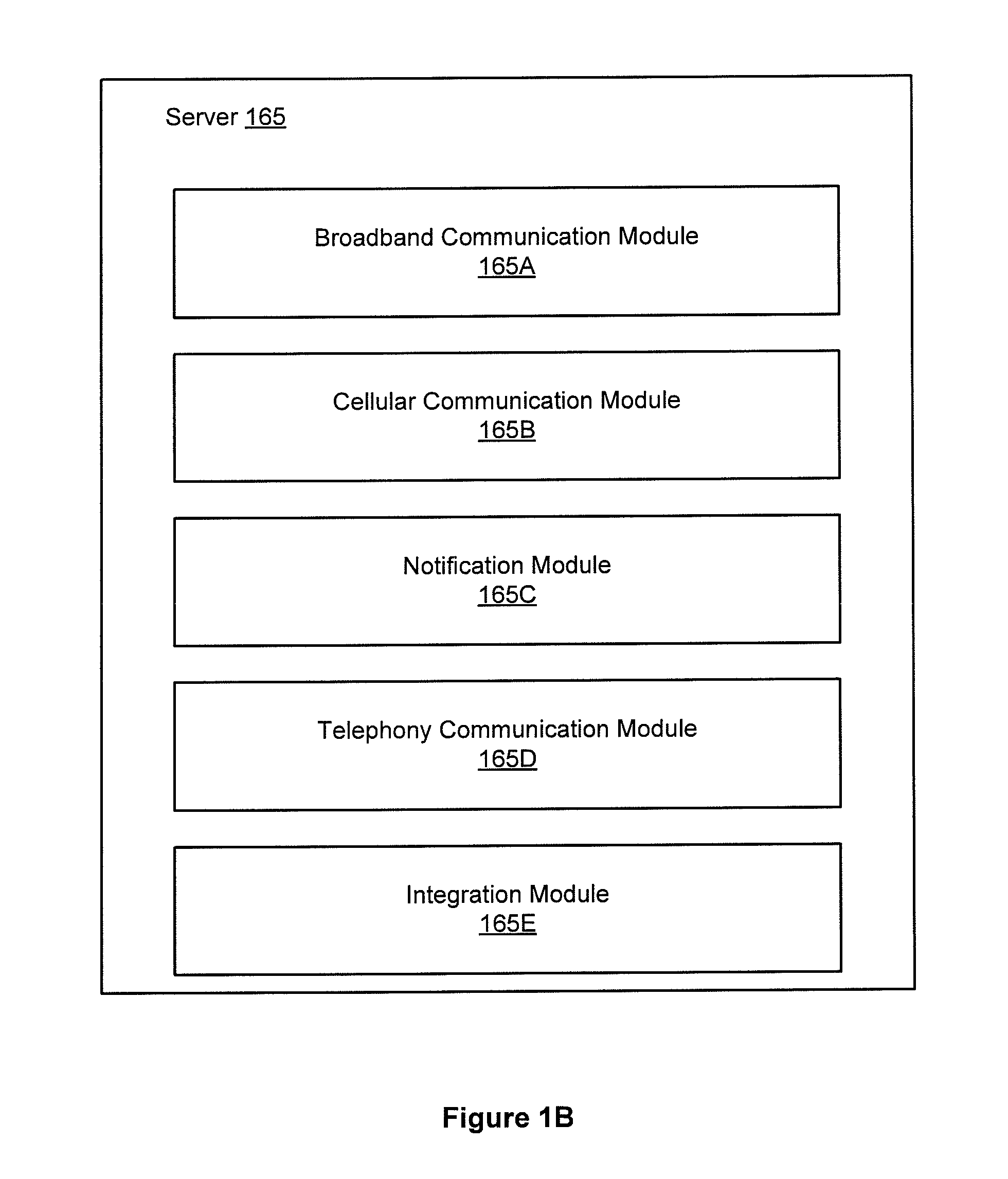
Server-based notification of alarm event subsequent to communication failure with armed security system
A server-based environment for reporting a status of a security, monitoring and automation controller is provided. Detecting cessation of an always-on persistent network connection between the SMA controller and the server is also provided. Reporting the cessation of the network connection to an end user and defined others is further provided. A further aspect provides for automatically reporting an alarm event to a central station, the end user, and others, in the event the cessation of the network connection occurs while the SMA controller is armed and after a zone fault event, and not receiving a disarm notification prior to expiration of a preset entry delay.
Owner:ICONTROL NETWORKS
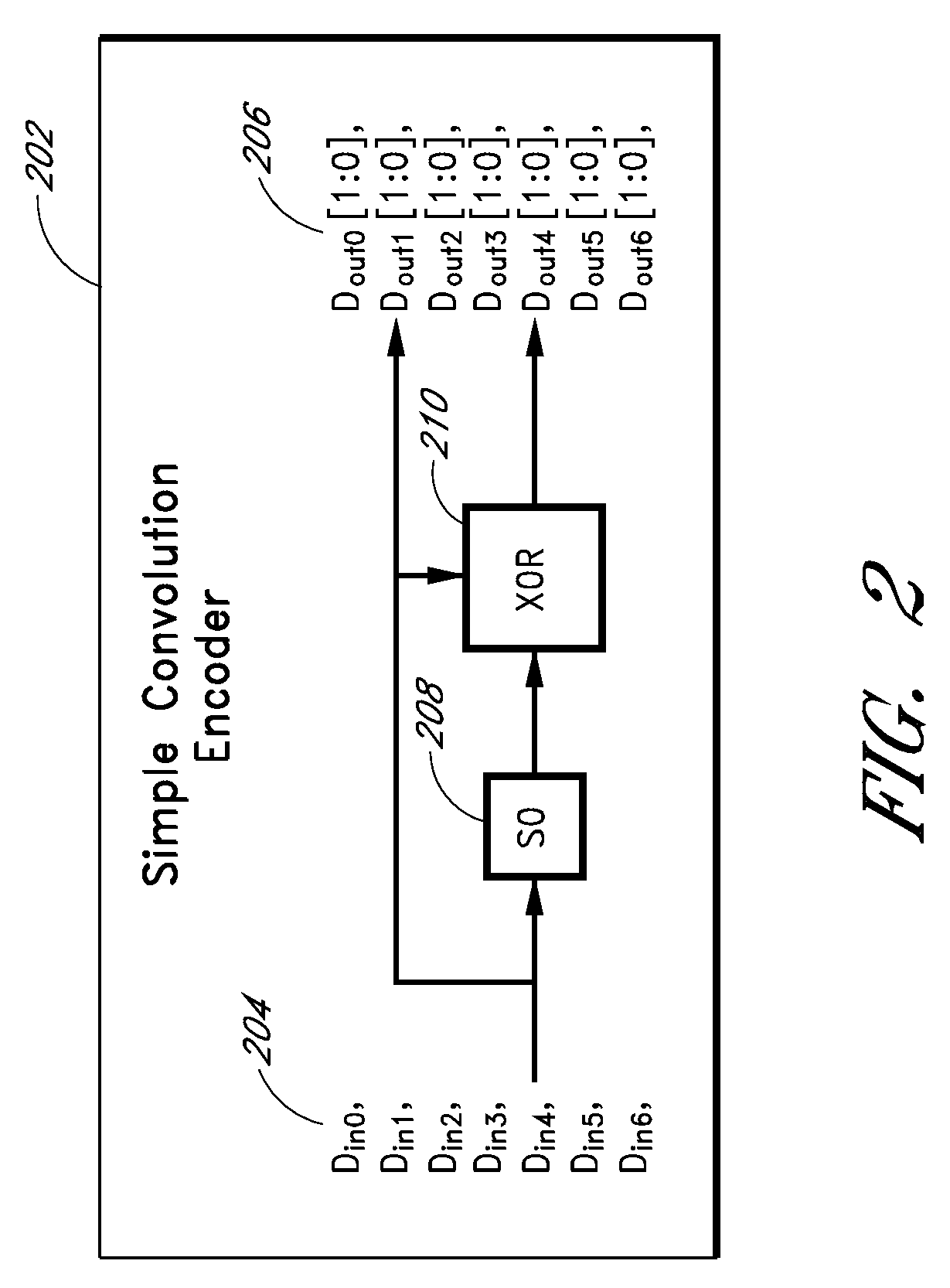
Error recovery storage along a nand-flash string
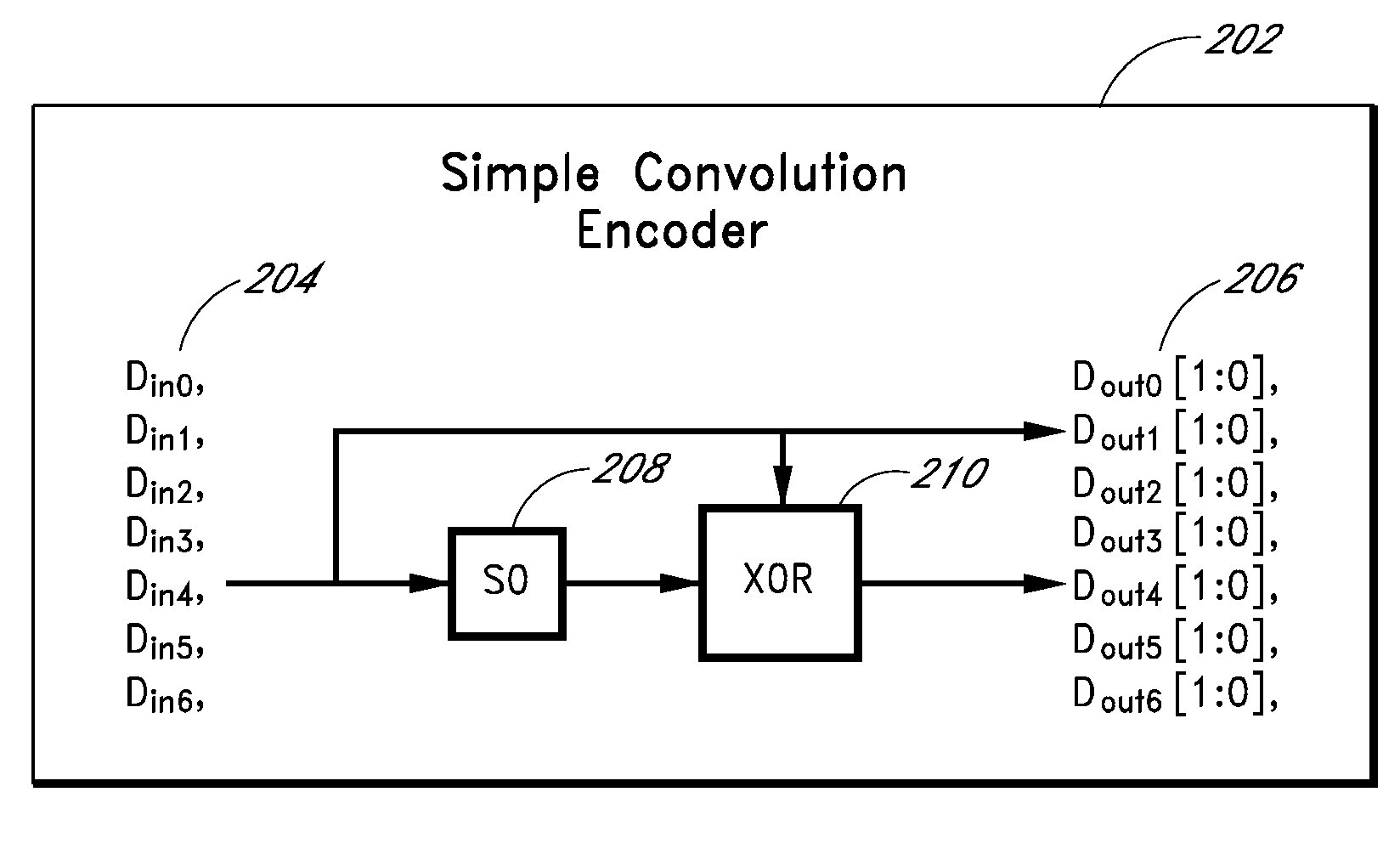
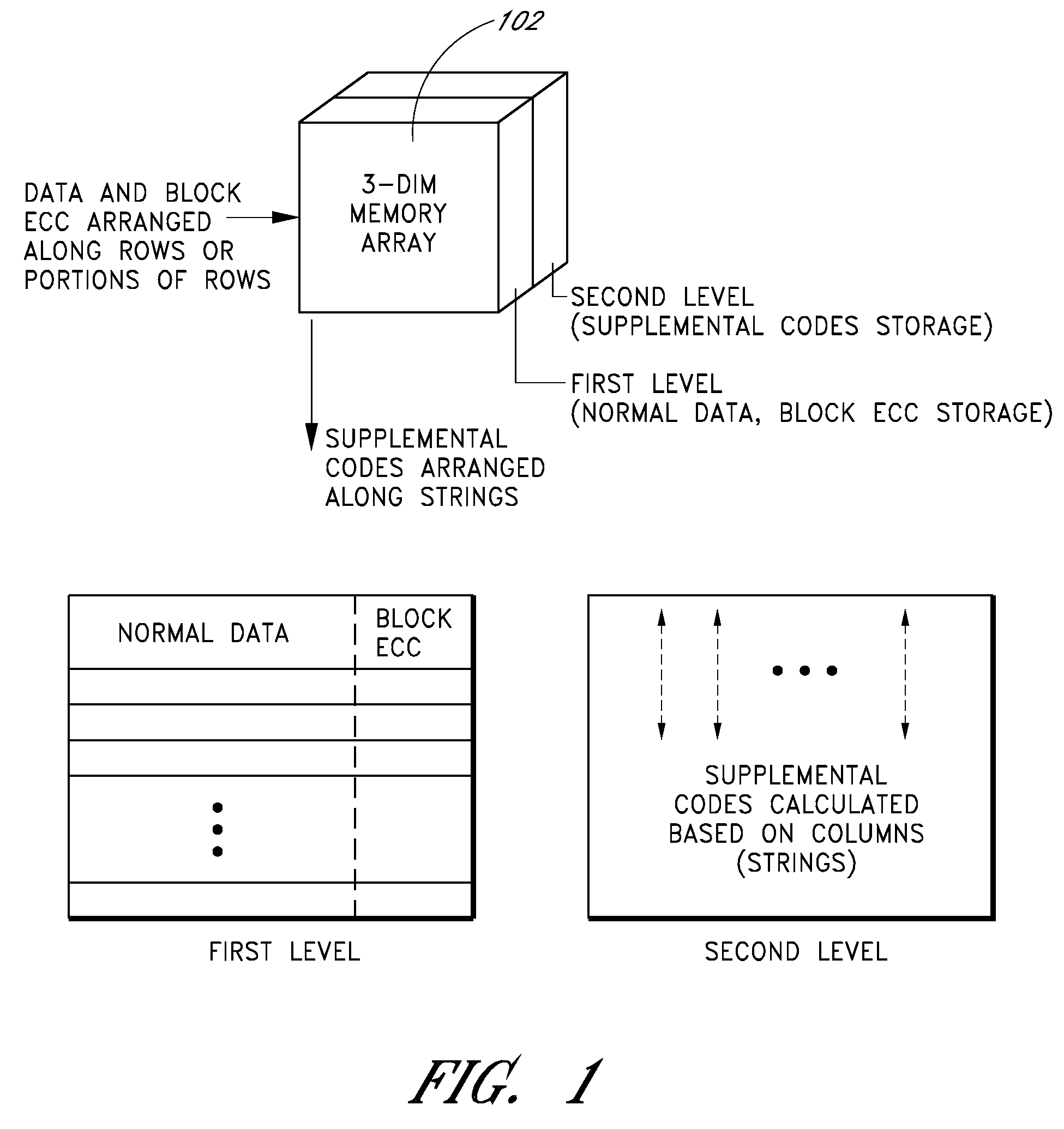
ActiveUS20090013233A1Error prevention/detection by using return channelError correction/detection using convolutional codesConvolutional codeData storing
Apparatus and methods store error recovery data in different dimensions of a memory array. For example, in one dimension, block error correction codes (ECC) are used, and in another dimension, supplemental error correction codes, such as convolutional codes, are used. By using separate dimensions, the likelihood that a defect affects both error recovery techniques is lessened, thereby increasing the probability that error recovery can be performed successfully. In one example, block error correction codes are used for data stored along rows, and this data is stored in one level of multiple-level cells of the array. Supplemental error correction codes are used for data stored along columns, such as along the cells of a string, and the supplemental error correction codes are stored in a different level than the error correction codes.
Owner:MICRON TECH INC
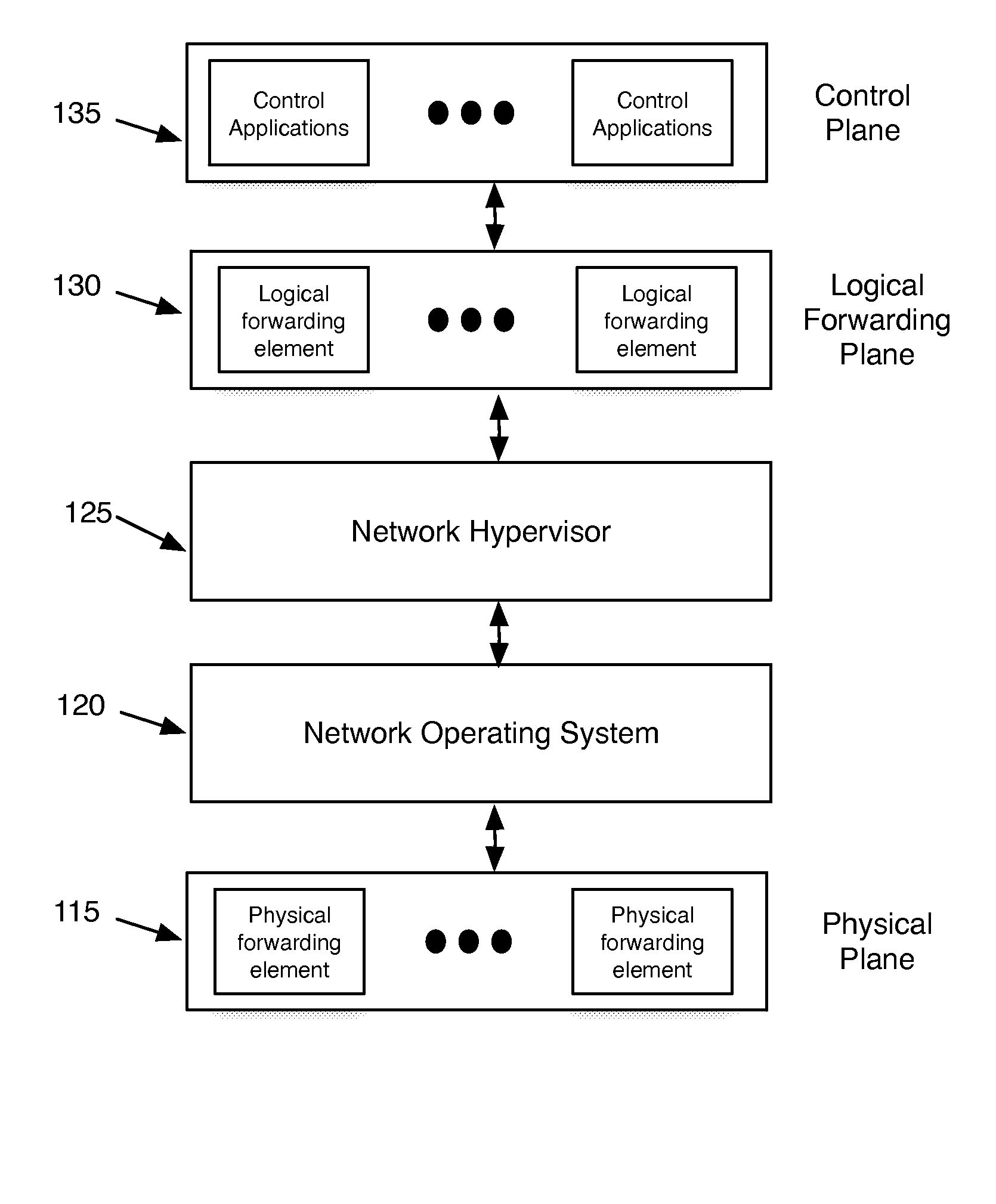
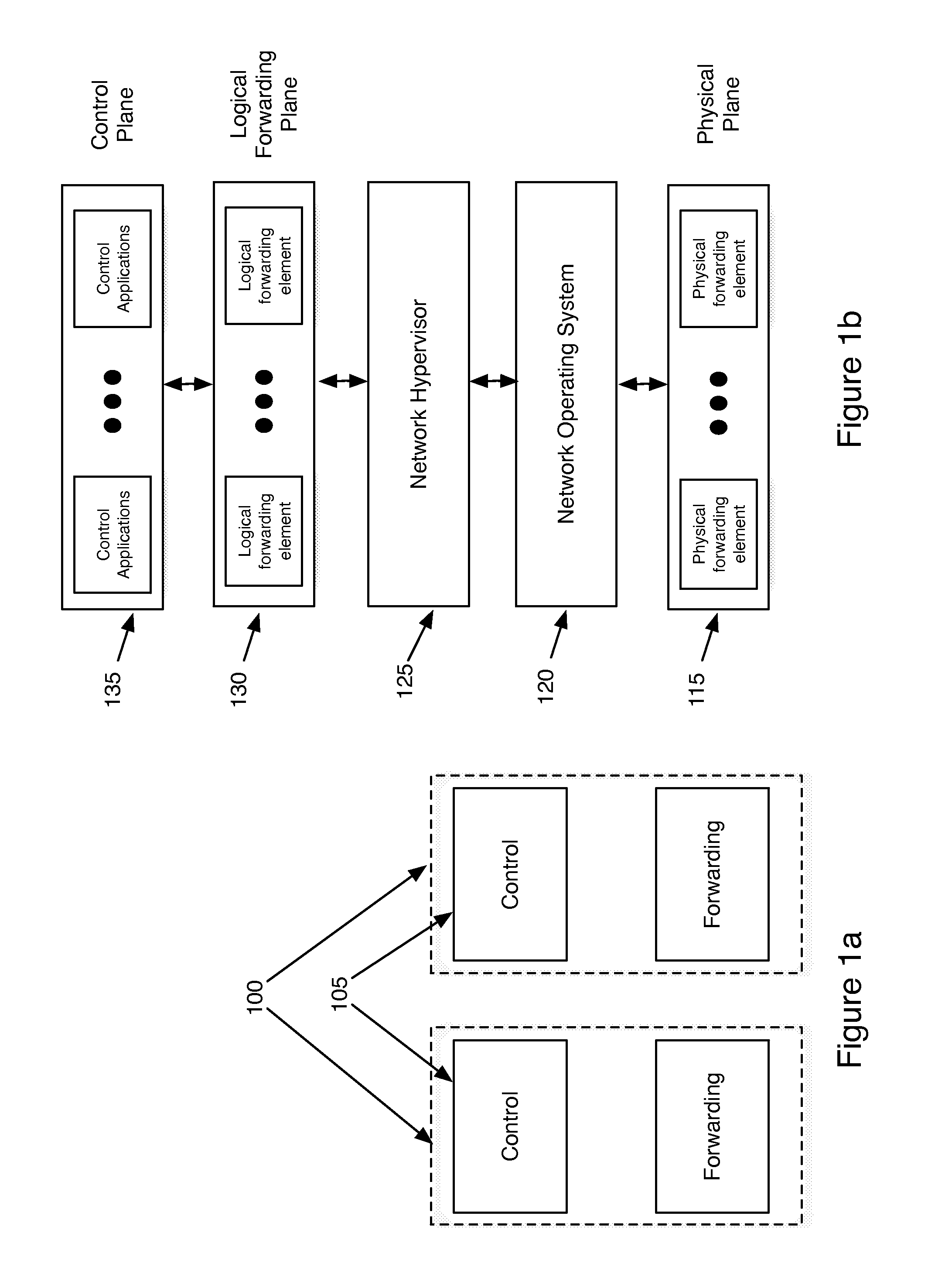
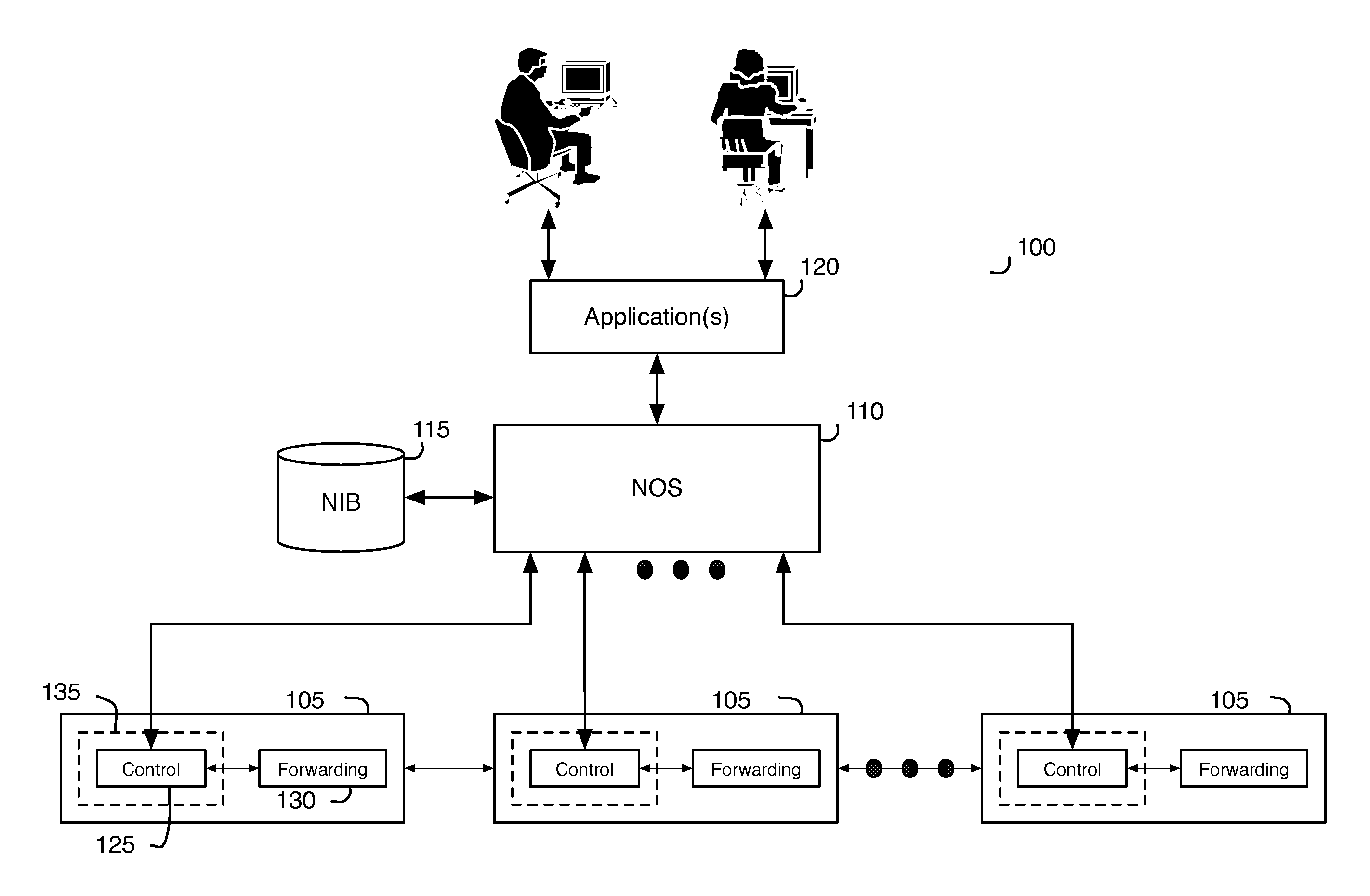
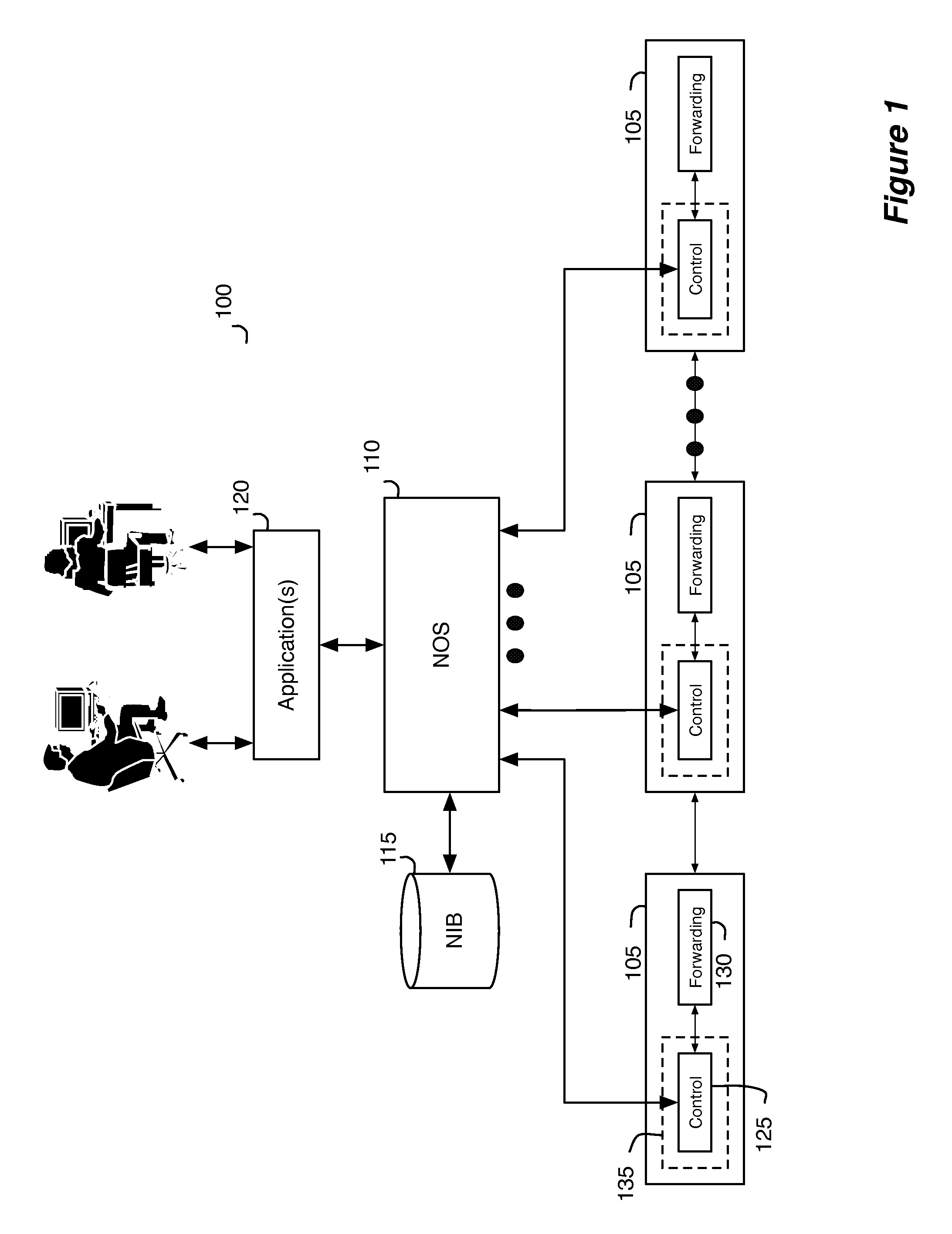
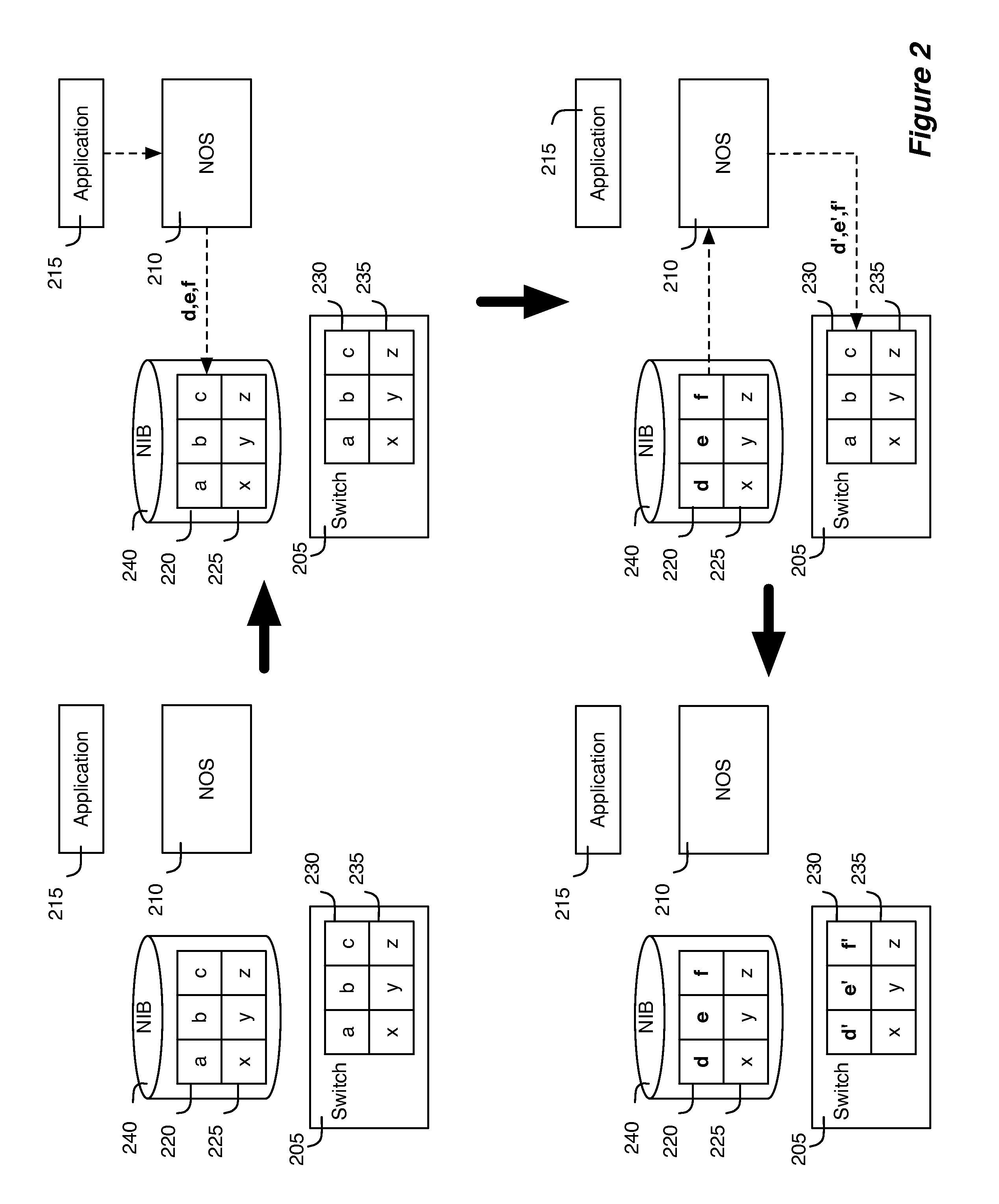
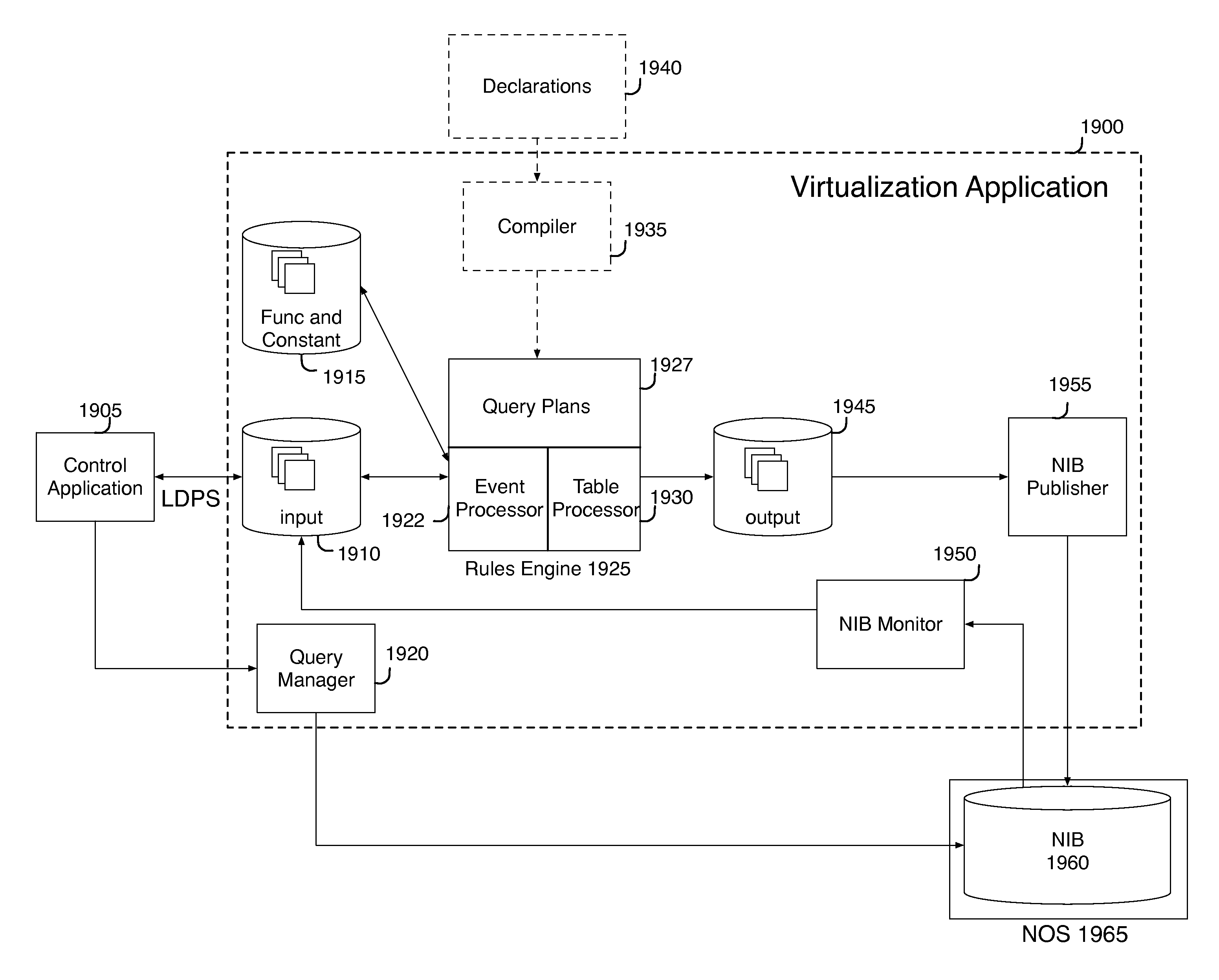
Network virtualization
ActiveUS20130060940A1Fault responseMultiple digital computer combinationsCyber operationsNetworking hardware
Some embodiments of the invention provide a robust scaling-out of network functionality by providing a software layer, called the network hypervisor, that sits between the network forwarding functions (i.e., the forwarding plane) and the network control interfaces (i.e., the control plane). The network hypervisor of some embodiments provides a logical abstraction of the network's forwarding functionality, so that network operators make their control decisions in terms of this abstraction, independent of the details of the underlying networking hardware. The network hypervisor of some embodiments may then “compile” commands placed against this abstraction into configurations of the underlying hardware. Accordingly, in some embodiments, there are two design challenges: (1) the choice of the network abstraction, and (2) the technology needed to compile the logical “abstract” controls into low-level configurations.
Owner:NICIRA
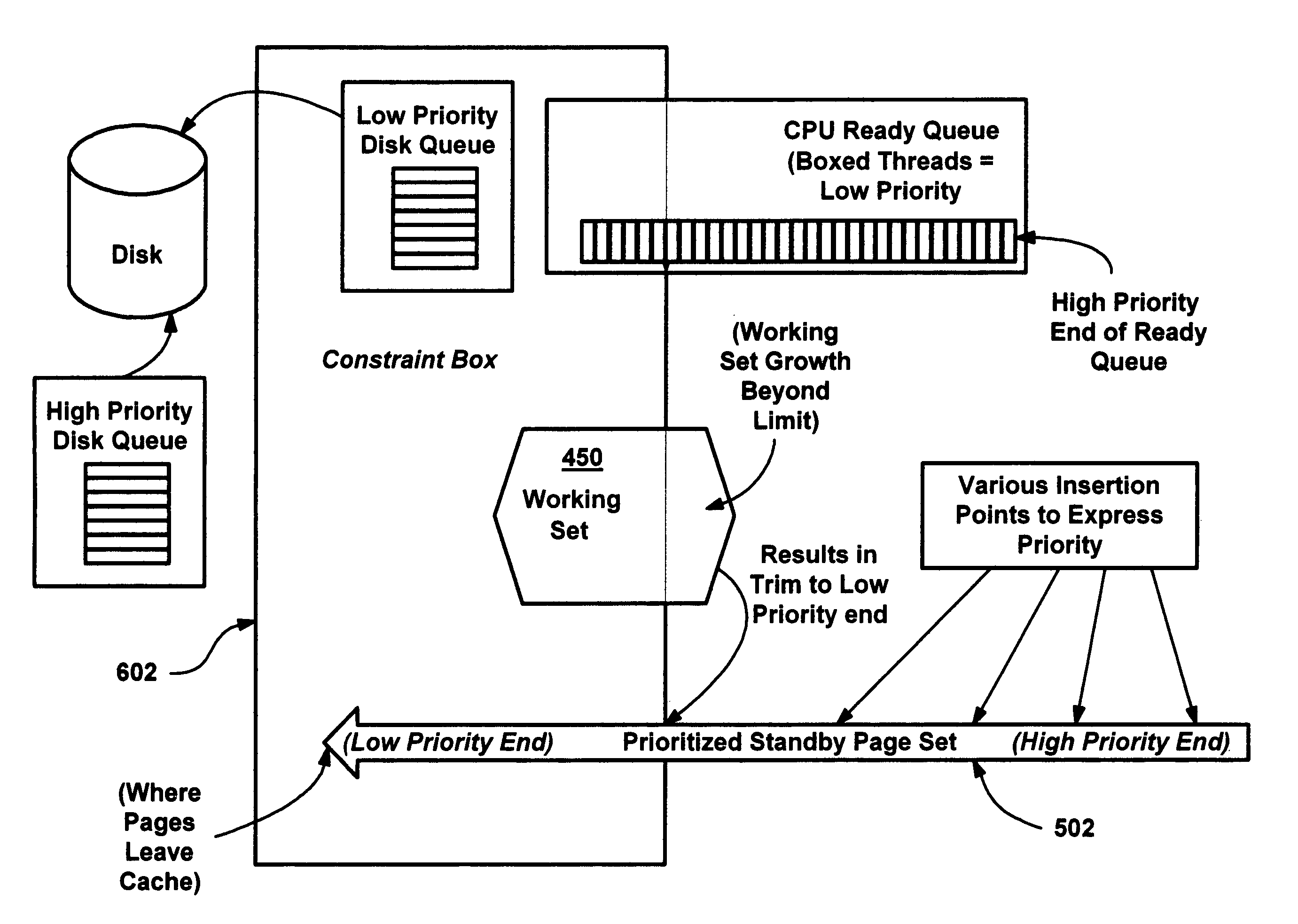
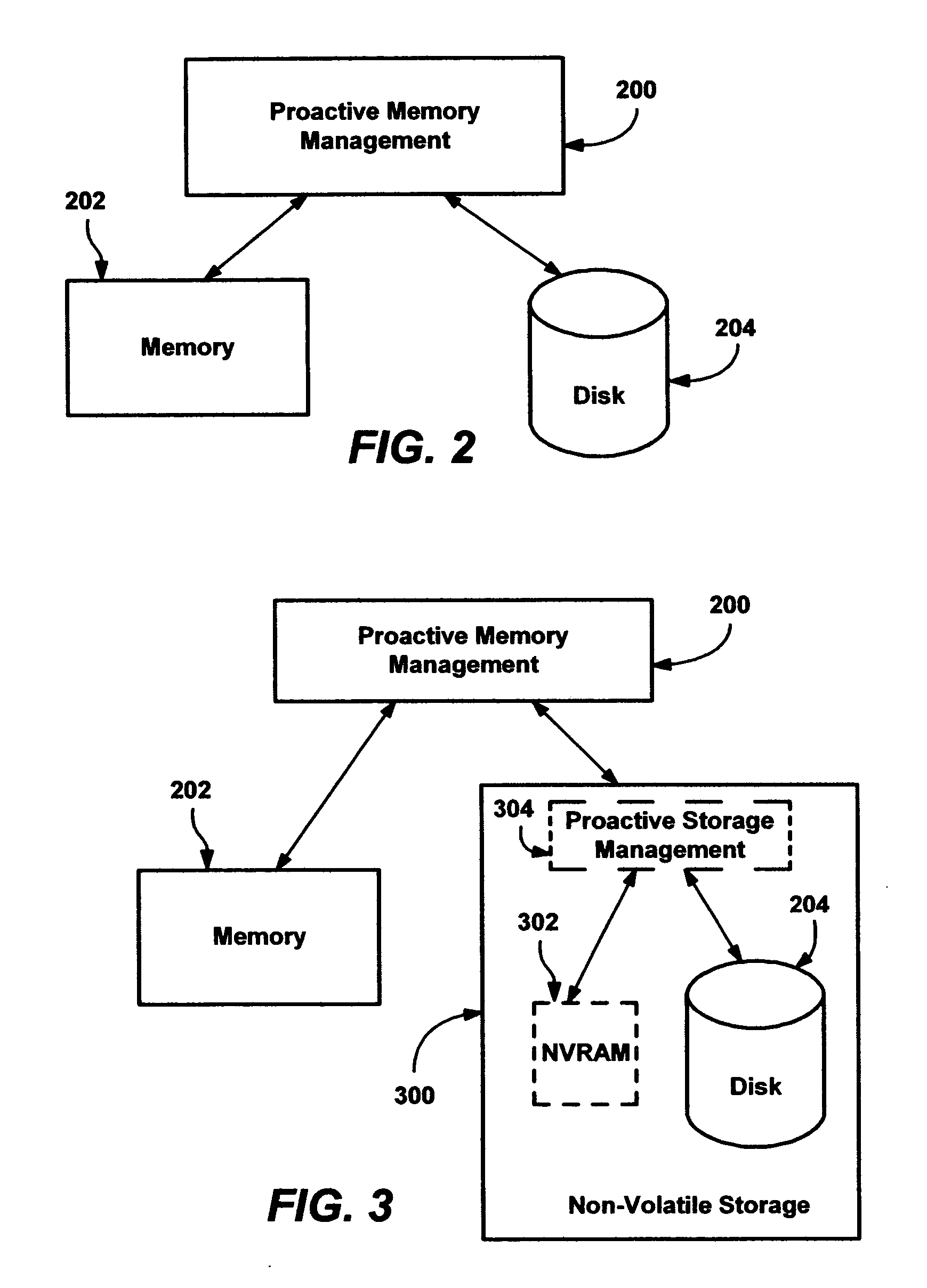
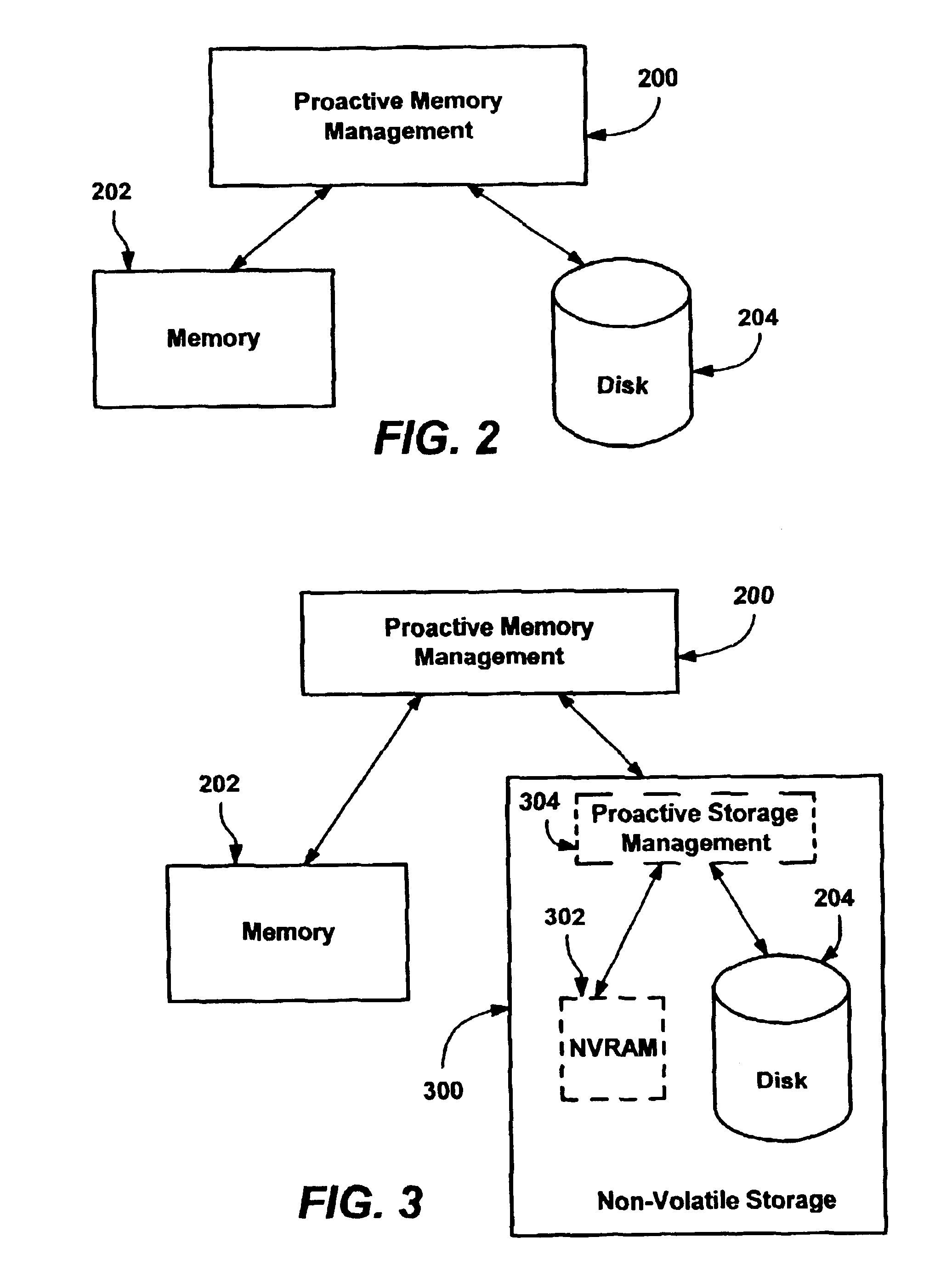
Methods and mechanisms for proactive memory management
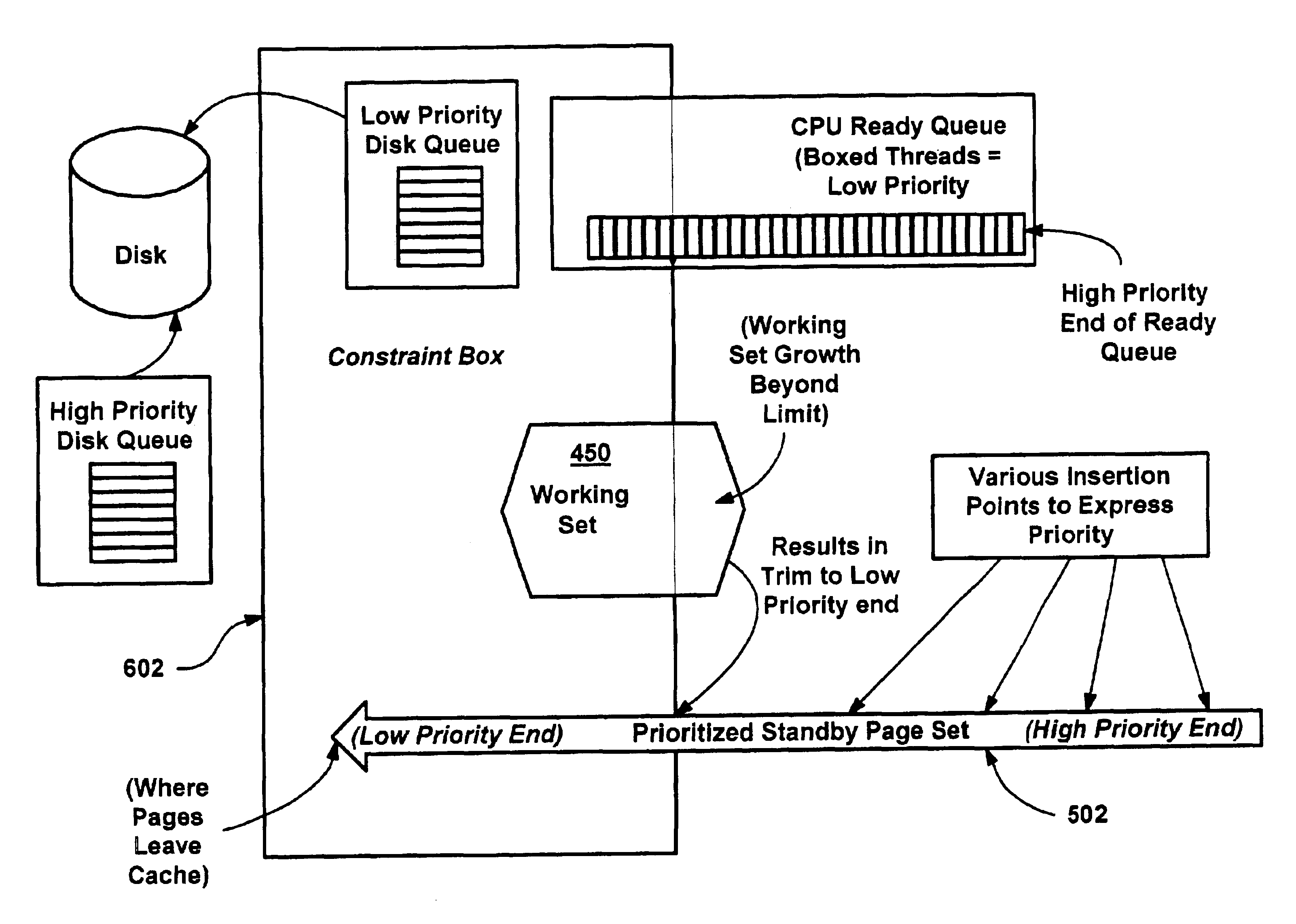
InactiveUS20050228964A1Reduces or eliminates on-demand disk transfer operationsReduces or eliminates I/O bottlenecksInput/output to record carriersFault responseSelf-tuningTerm memory
A proactive, resilient and self-tuning memory management system and method that result in actual and perceived performance improvements in memory management, by loading and maintaining data that is likely to be needed into memory, before the data is actually needed. The system includes mechanisms directed towards historical memory usage monitoring, memory usage analysis, refreshing memory with highly-valued (e.g., highly utilized) pages, I / O pre-fetching efficiency, and aggressive disk management. Based on the memory usage information, pages are prioritized with relative values, and mechanisms work to pre-fetch and / or maintain the more valuable pages in memory. Pages are pre-fetched and maintained in a prioritized standby page set that includes a number of subsets, by which more valuable pages remain in memory over less valuable pages. Valuable data that is paged out may be automatically brought back, in a resilient manner. Benefits include significantly reducing or even eliminating disk I / O due to memory page faults.
Owner:MICROSOFT TECH LICENSING LLC
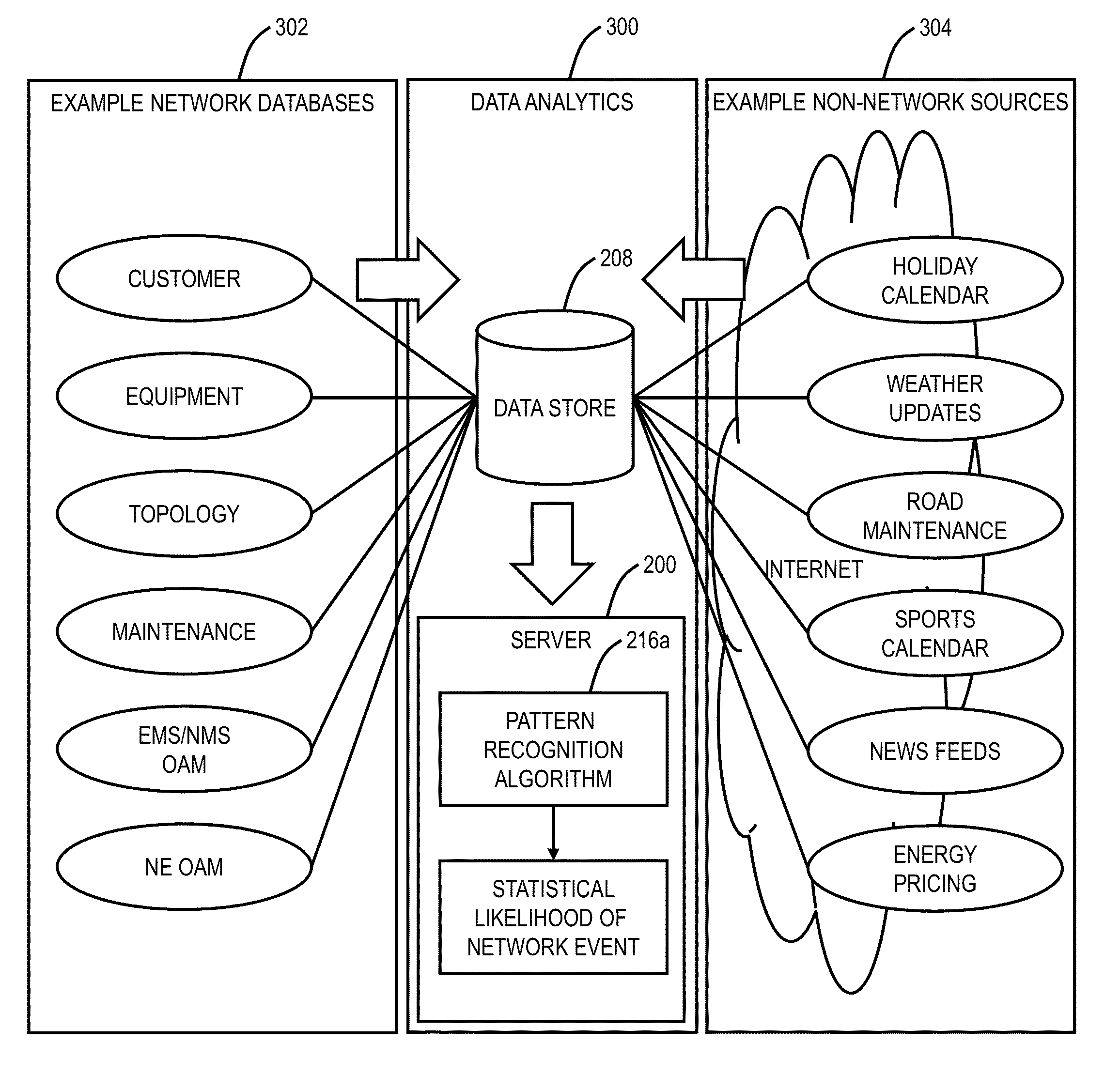
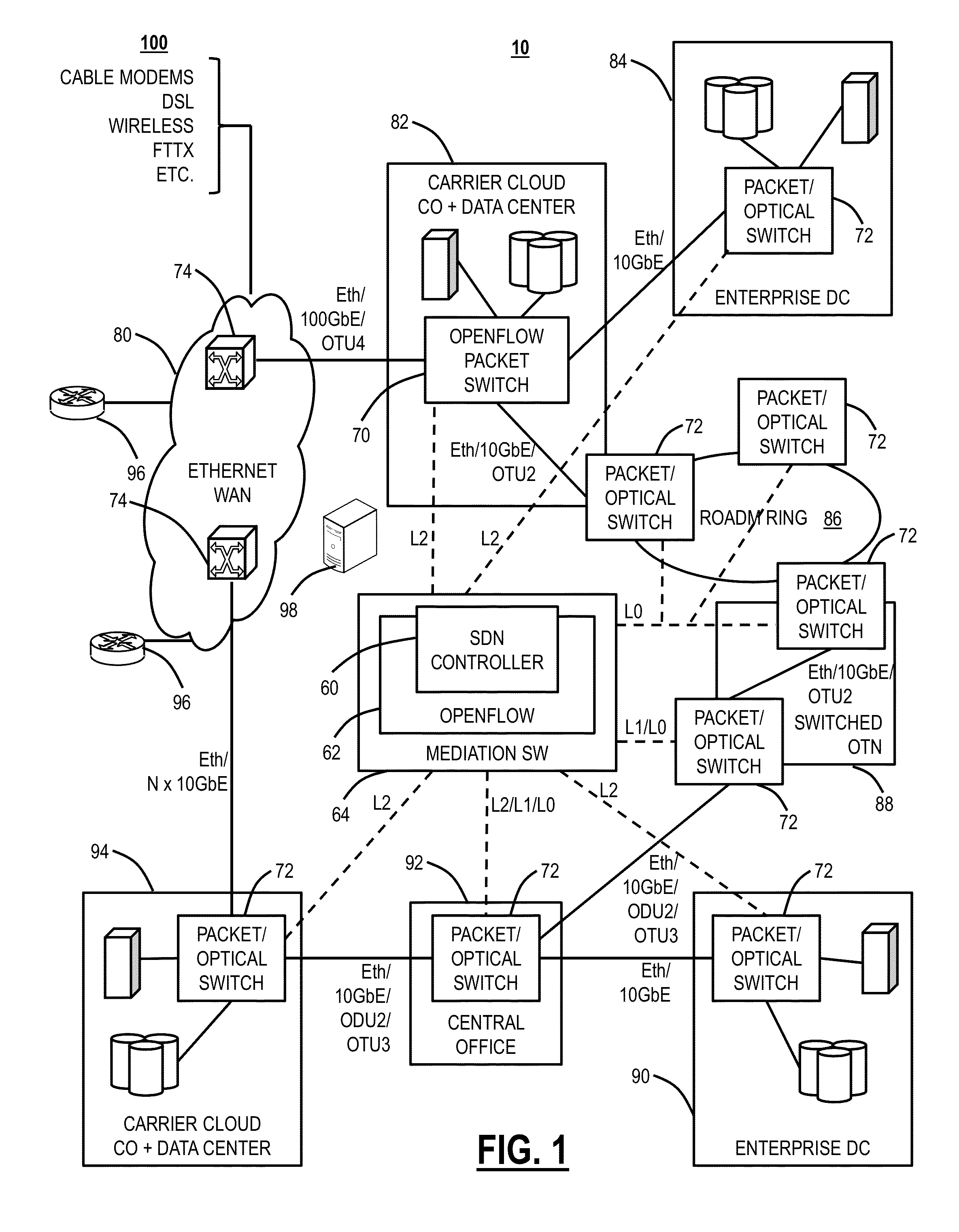
Proactive operations, administration, and maintenance systems and methods in networks using data analytics
A computer-implemented method, a system, and a network include receiving network data from a network and non-network sourced data from one or more external sources relative to the network; performing data mining on the network data and the non-network sourced data; developing a predictive analytics model based on the data mining; and performing predictive analytics on the network data and the non-network sourced data using the predictive analytics model to detect likely future failures in the network. The network can include a Software Defined Network (SDN) operating at any of Layers 0, 1, 2 and / or 3.
Owner:INNOVATION ASSET COLLECTIVE
Methods and mechanisms for proactive memory management
InactiveUS6910106B2Raise priorityIncrease profitInput/output to record carriersFault responseSelf-tuningPaging
A proactive, resilient and self-tuning memory management system and method that result in actual and perceived performance improvements in memory management, by loading and maintaining data that is likely to be needed into memory, before the data is actually needed. The system includes mechanisms directed towards historical memory usage monitoring, memory usage analysis, refreshing memory with highly-valued (e.g., highly utilized) pages, I / O pre-fetching efficiency, and aggressive disk management. Based on the memory usage information, pages are prioritized with relative values, and mechanisms work to pre-fetch and / or maintain the more valuable pages in memory. Pages are pre-fetched and maintained in a prioritized standby page set that includes a number of subsets, by which more valuable pages remain in memory over less valuable pages. Valuable data that is paged out may be automatically brought back, in a resilient manner. Benefits include significantly reducing or even eliminating disk I / O due to memory page faults.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for maintaining a workload service level on a converged platform
ActiveUS20130311989A1Fault responseSoftware simulation/interpretation/emulationService-level agreementComputerized system
A management server is provided in a computer system having one or more hosts, one or more storage systems and one or more switches, the hosts having a plurality of virtual machines, each virtual machine being defined according to a service level agreement. The management server is operable to manage the virtual machines and resources associated with the virtual machines; receive a notification of an event from a node in the computer system; determine if the event affects a service level agreement for any of the virtual machines defined in the computer system, the service level agreements listing required attributes for the corresponding virtual machines; allocate a new resource for a virtual machine whose service level agreement is affected by the event; and move the virtual machine whose service level agreement is affected by the event to the newly allocated resource.
Owner:HITACHI LTD
Network relay device for relaying data in a network and control method for the same
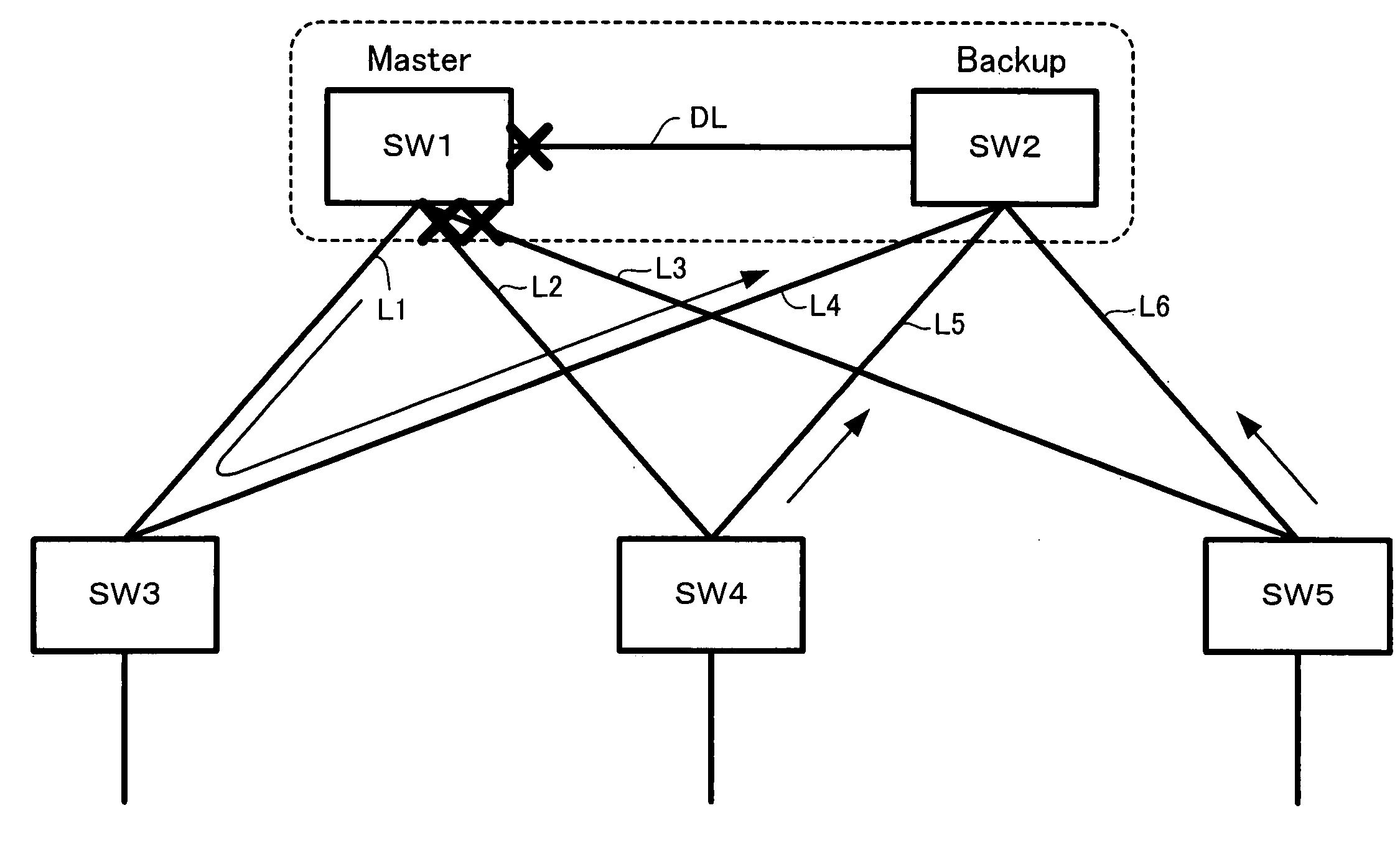
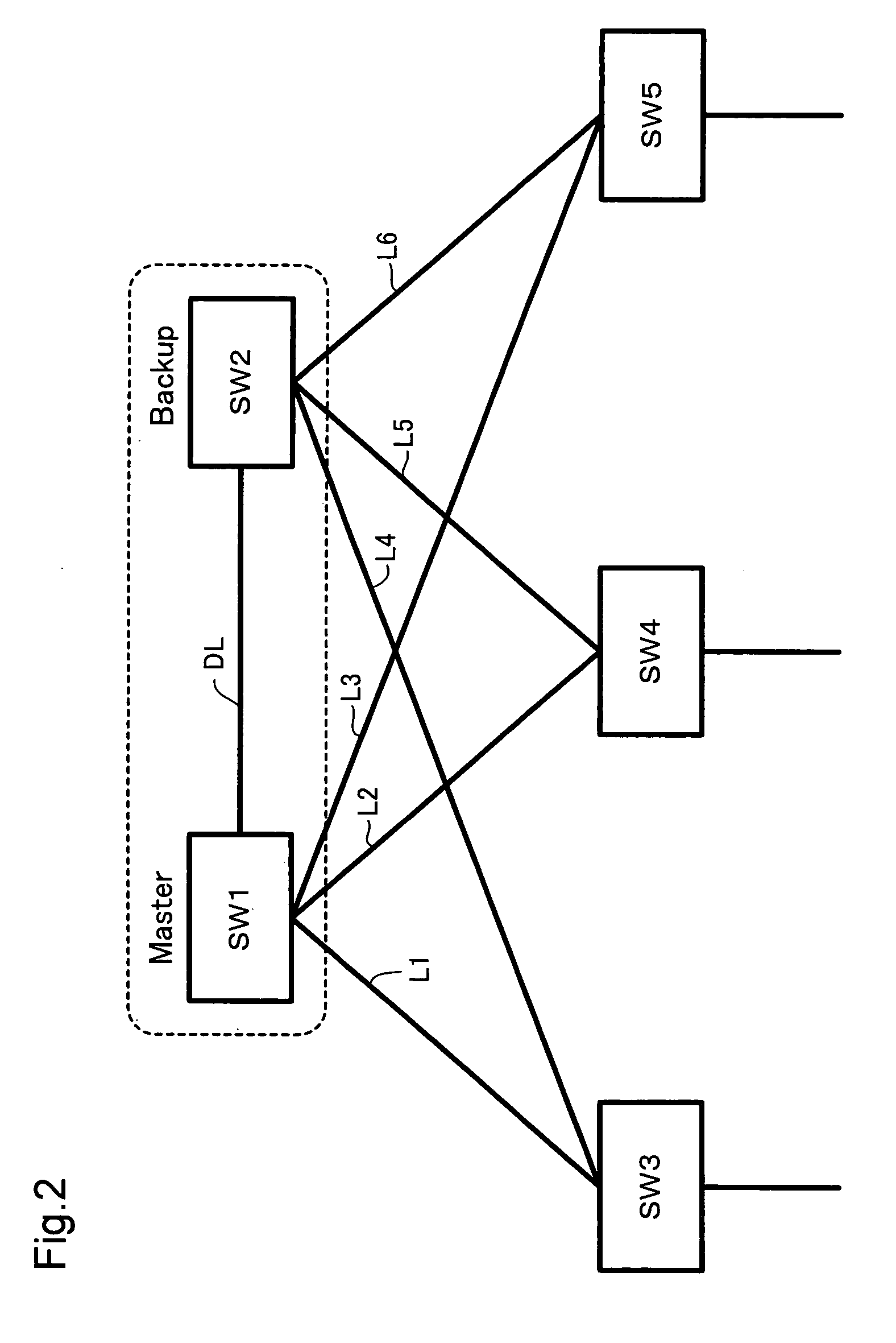
In the case of detection of failure on a direct link interconnecting Master and Backup upstream switches, a control module of the Master upstream switch sends a partial failure message representing the occurrence of partial failure in the Master upstream switch via any of multiple lines connected to multiple ports of the Master upstream switch to the Backup upstream switch. Upon reception of the partial failure message from the Master upstream switch, a control module of the Backup upstream switch identifies partial failure occurring in the Master upstream switch and keeps the Backup operating status of the Backup upstream switch. Upon no reception of the partial failure message from the Master upstream switch, on the other hand, the control module of the Backup upstream switch identifies total failure occurring in the Master upstream switch and switches over the operating status of the Backup upstream switch from Backup to Master. In the event of failure occurring in the Master upstream switch, this arrangement effectively prevents unintentional interruption of data communication but ensures normal data communication in a network without causing the double-master state and the control loop in the network.
Owner:ALAXALA NETWORKS
Data control apparatus, storage system, and computer program product
InactiveUS20100005228A1Memory architecture accessing/allocationFault responseSemiconductor memoryComputer program
Owner:TOSHIBA MEMORY CORP
Routing bandwidth guaranteed paths with local restoration in label switched networks
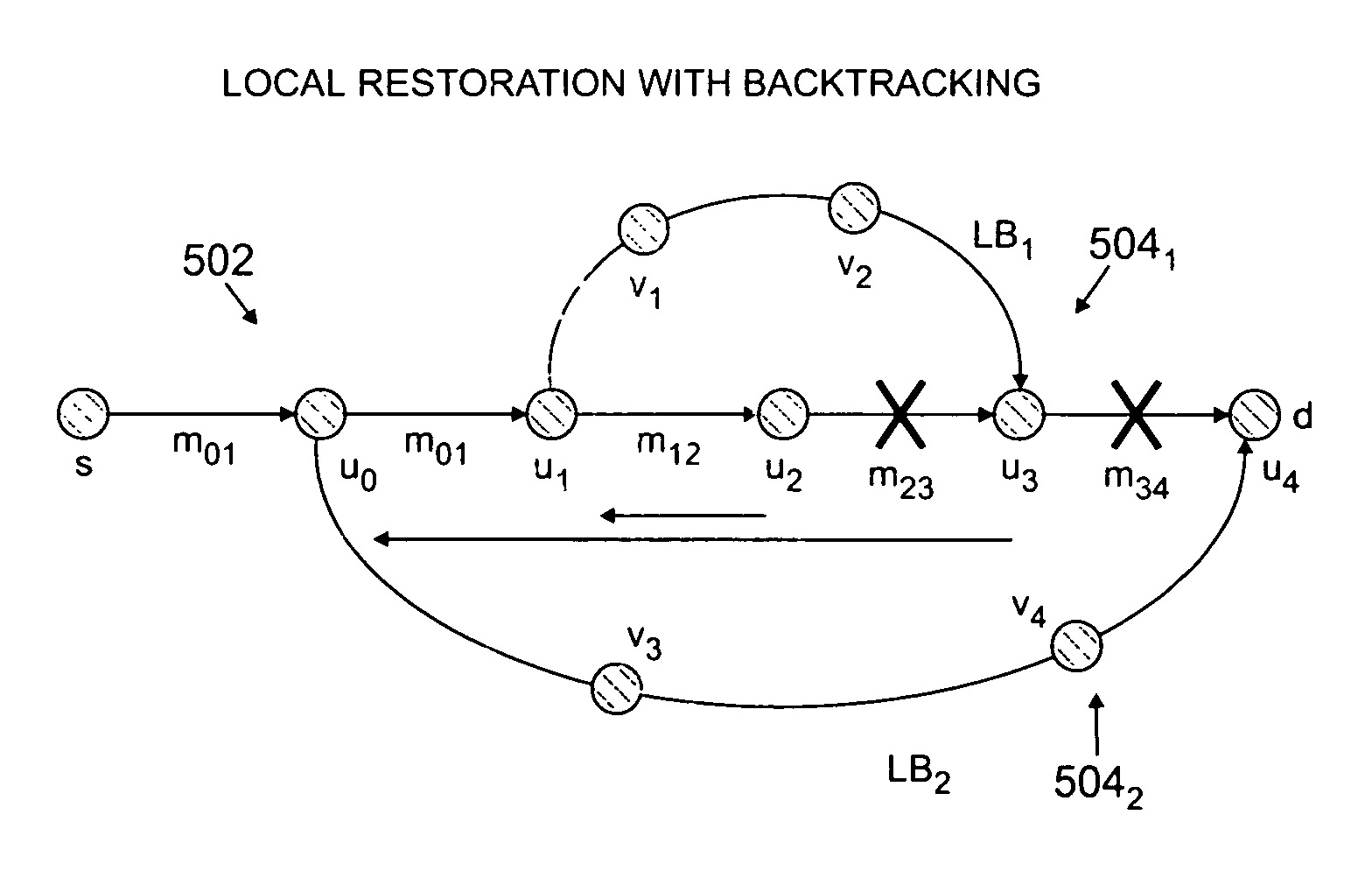
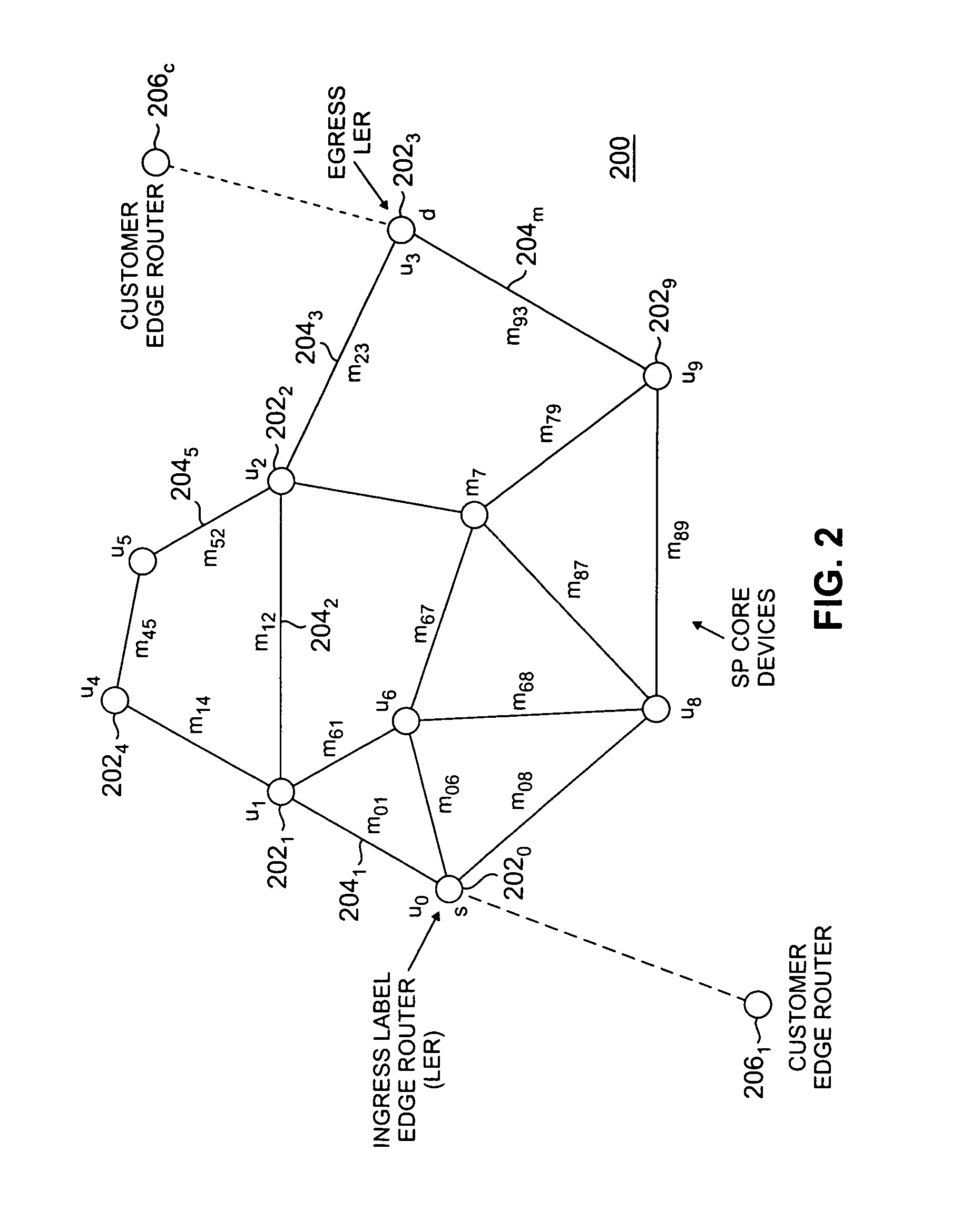
ActiveUS8675493B2Free excess bandwidthMinimize bandwidth usageError preventionFrequency-division multiplex detailsPath costLabel switching
A method of providing at least one restoration path for a primary routing path in a network. The method includes receiving a customer connection request to route information. Costs are assigned for the primary routing path, and the primary routing path is computed based upon the primary routing path costs. A backtracking distance over the primary routing path is determined, and costs for at least one restoration path are assigned. The at least one restoration path may then be computed based upon the at least one restoration path costs.
Owner:WSOU INVESTMENTS LLC
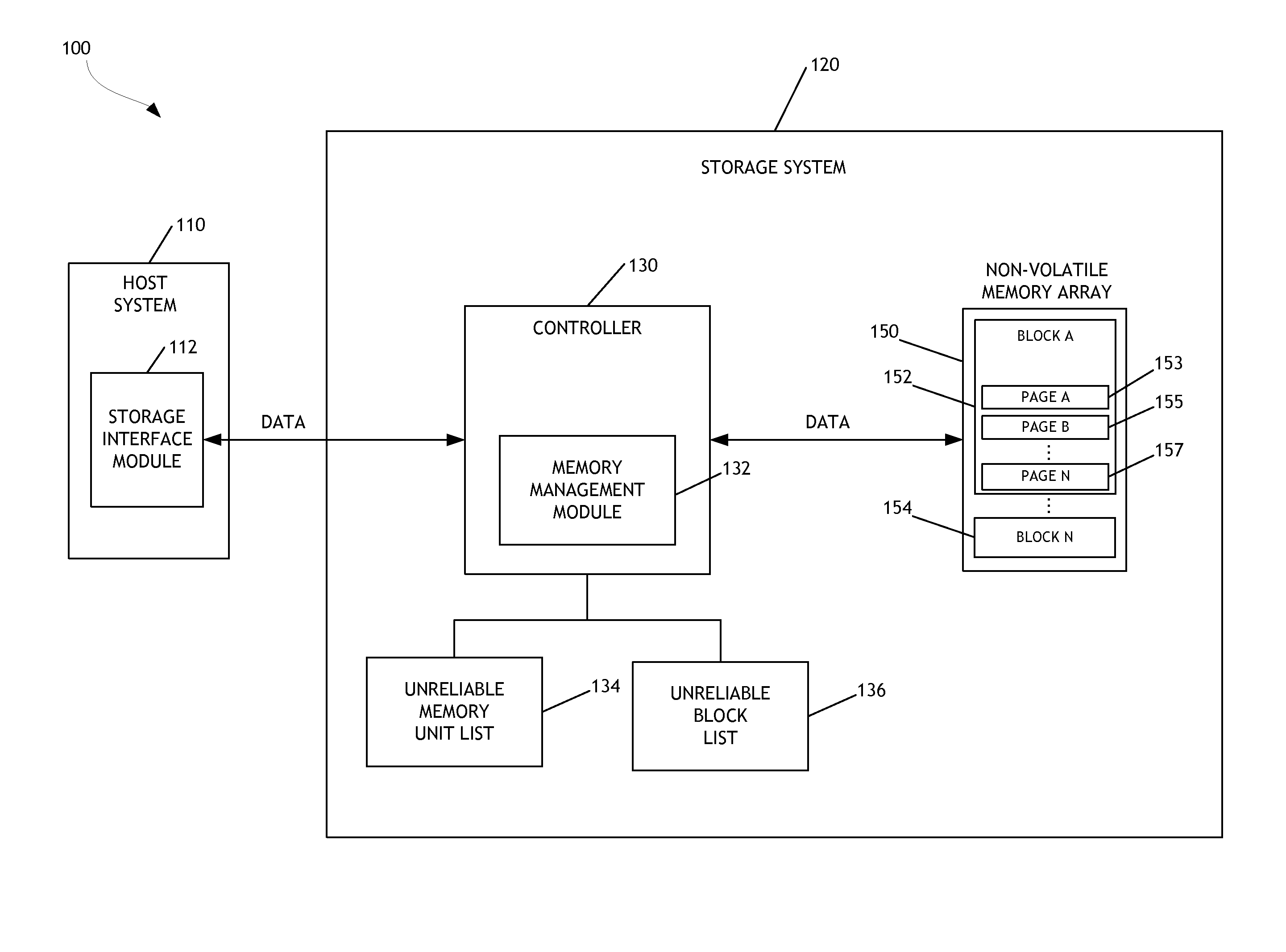
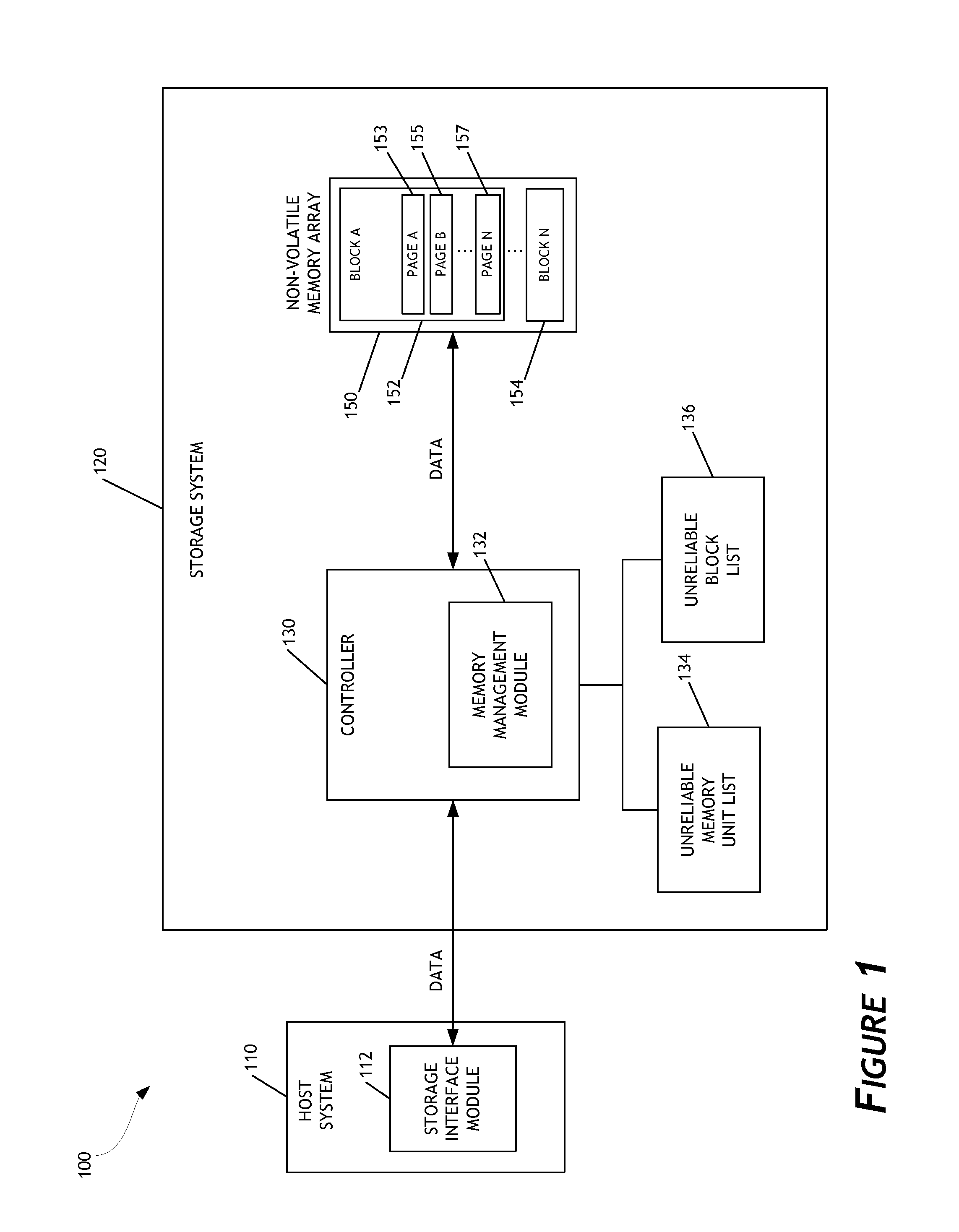
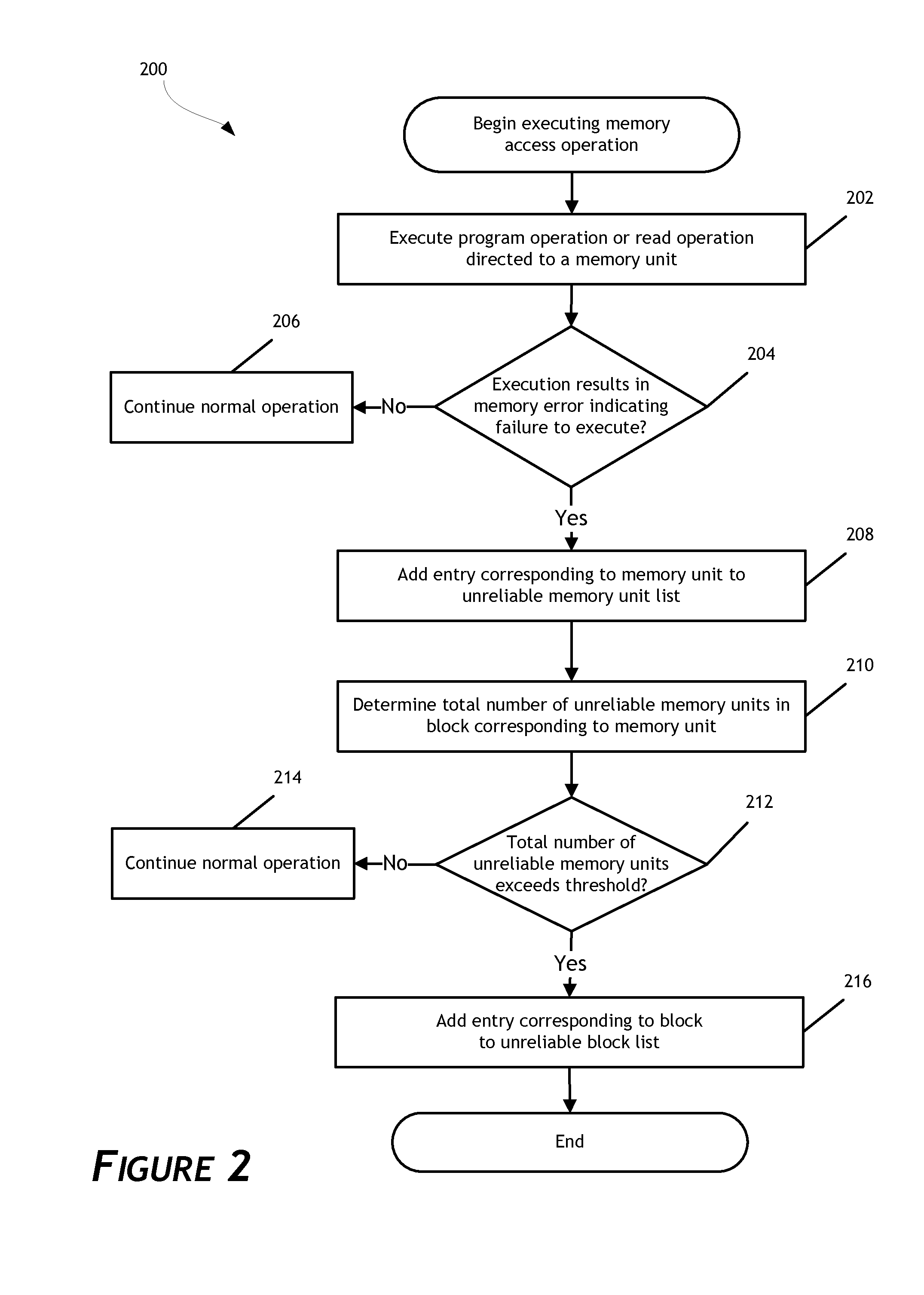
Managing unreliable memory in data storage systems
A data storage system configured to manage unreliable memory units is disclosed. In one embodiment, the data storage system maintains an unreliable memory unit list designating memory units in a non-volatile memory array as reliable or unreliable. The unreliable memory unit list facilitates management of unreliable memory at a granularity level finer than the granularity of a block of memory. The data storage system can add entries to the unreliable memory unit list as unreliable memory units are discovered. Further, the data storage system can continue to perform memory access operations directed to reliable memory units in blocks containing other memory units determined to be unreliable. As a result, the operational life of the data storage system is extended.
Owner:WESTERN DIGITAL TECH INC
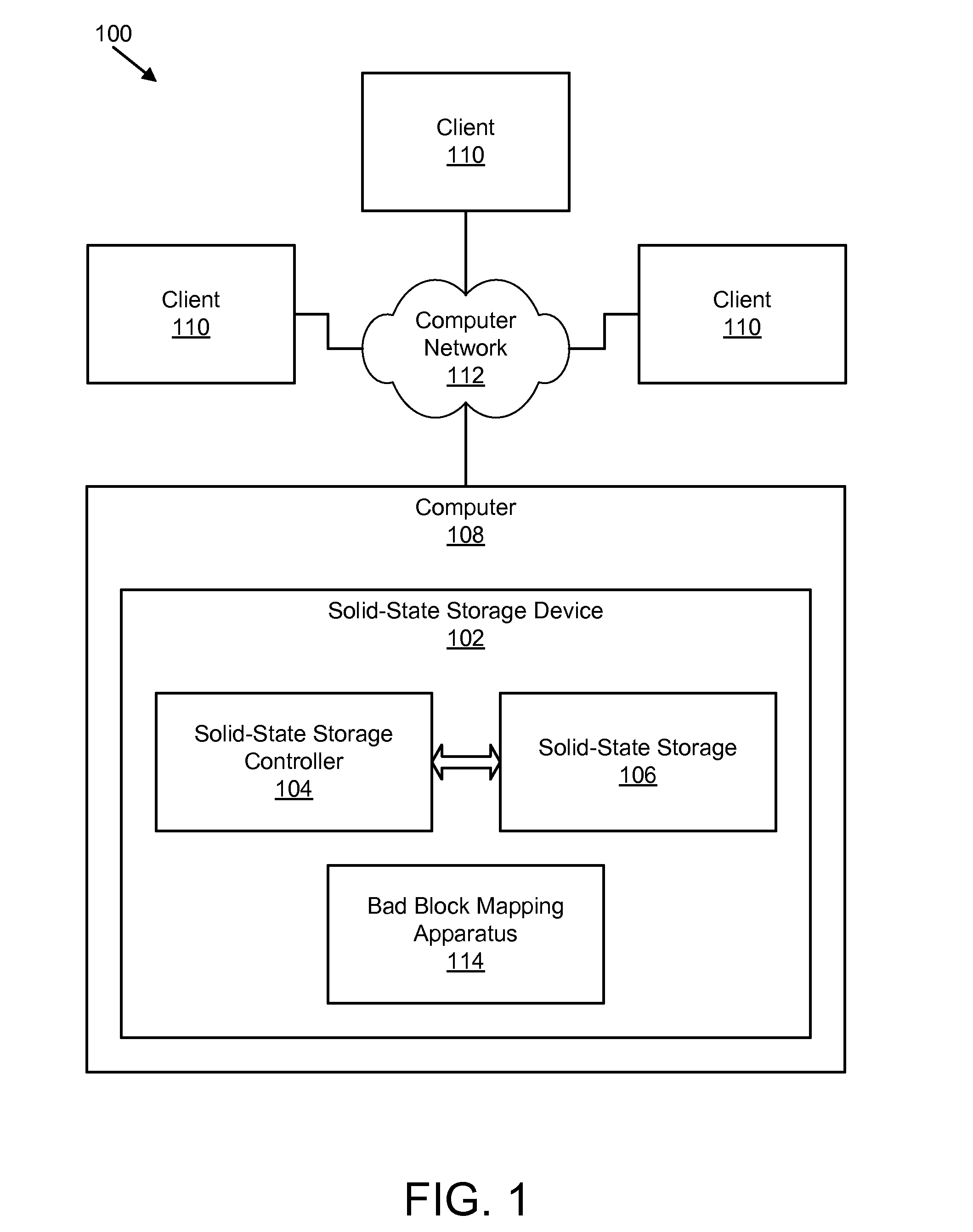
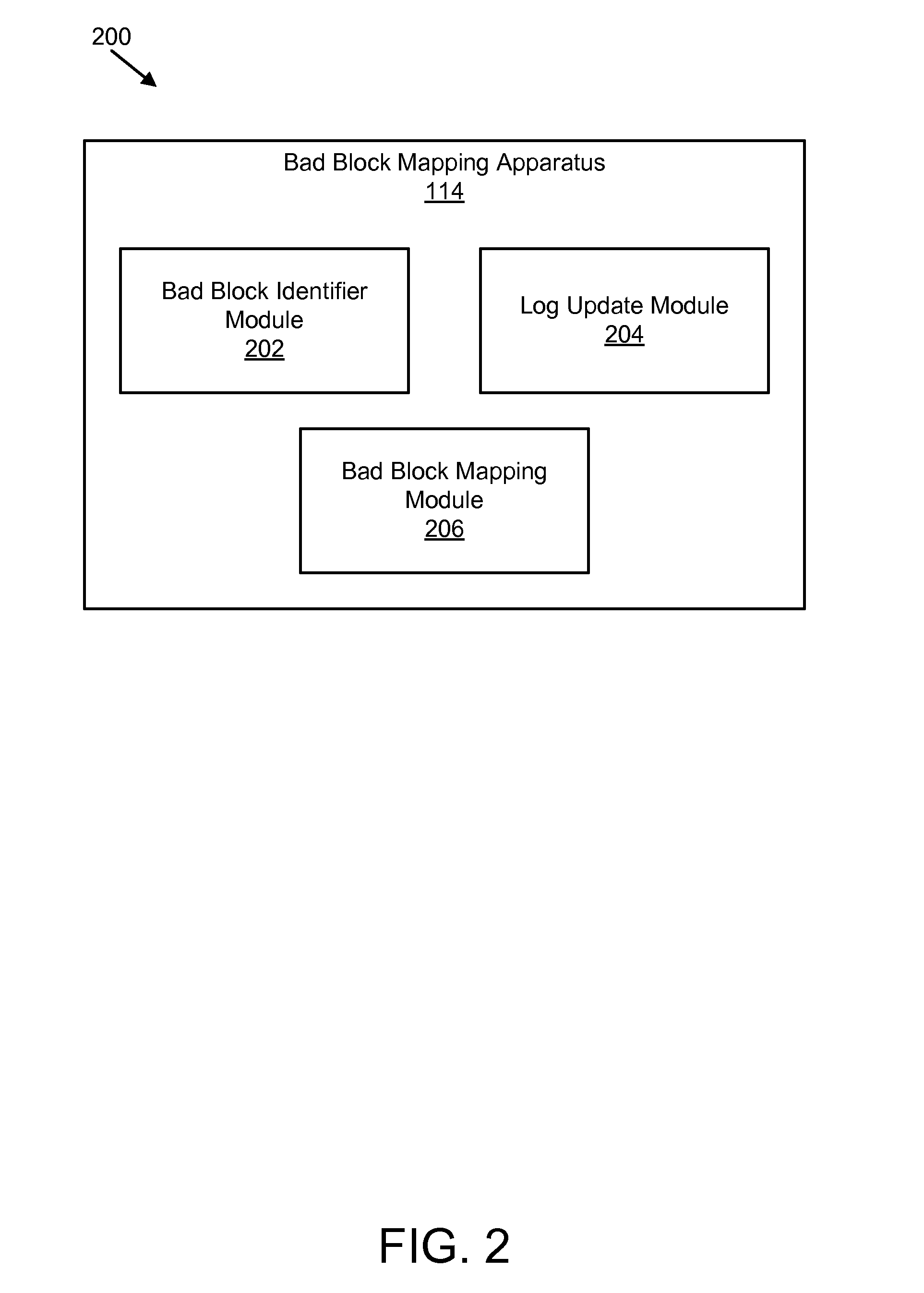
Apparatus, system, and method for bad block remapping
ActiveUS20090282301A1Improve reliabilityAvoid managementMemory architecture accessing/allocationError preventionSolid-state storageParallel computing
An apparatus, system, and method are disclosed for bad block remapping. A bad block identifier module identifies one or more data blocks on a solid-state storage element as bad blocks. A log update module writes at least a location of each bad block identified by the bad block identifier module into each of two or more redundant bad block logs. A bad block mapping module accesses at least one bad block log during a start-up operation to create in memory a bad block map. The bad block map includes a mapping between the bad block locations in the bad block log and a corresponding location of a replacement block for each bad block location. Data is stored in each replacement block instead of the corresponding bad block. The bad block mapping module creates the bad block map using one of a replacement block location and a bad block mapping algorithm.
Owner:SANDISK TECH LLC
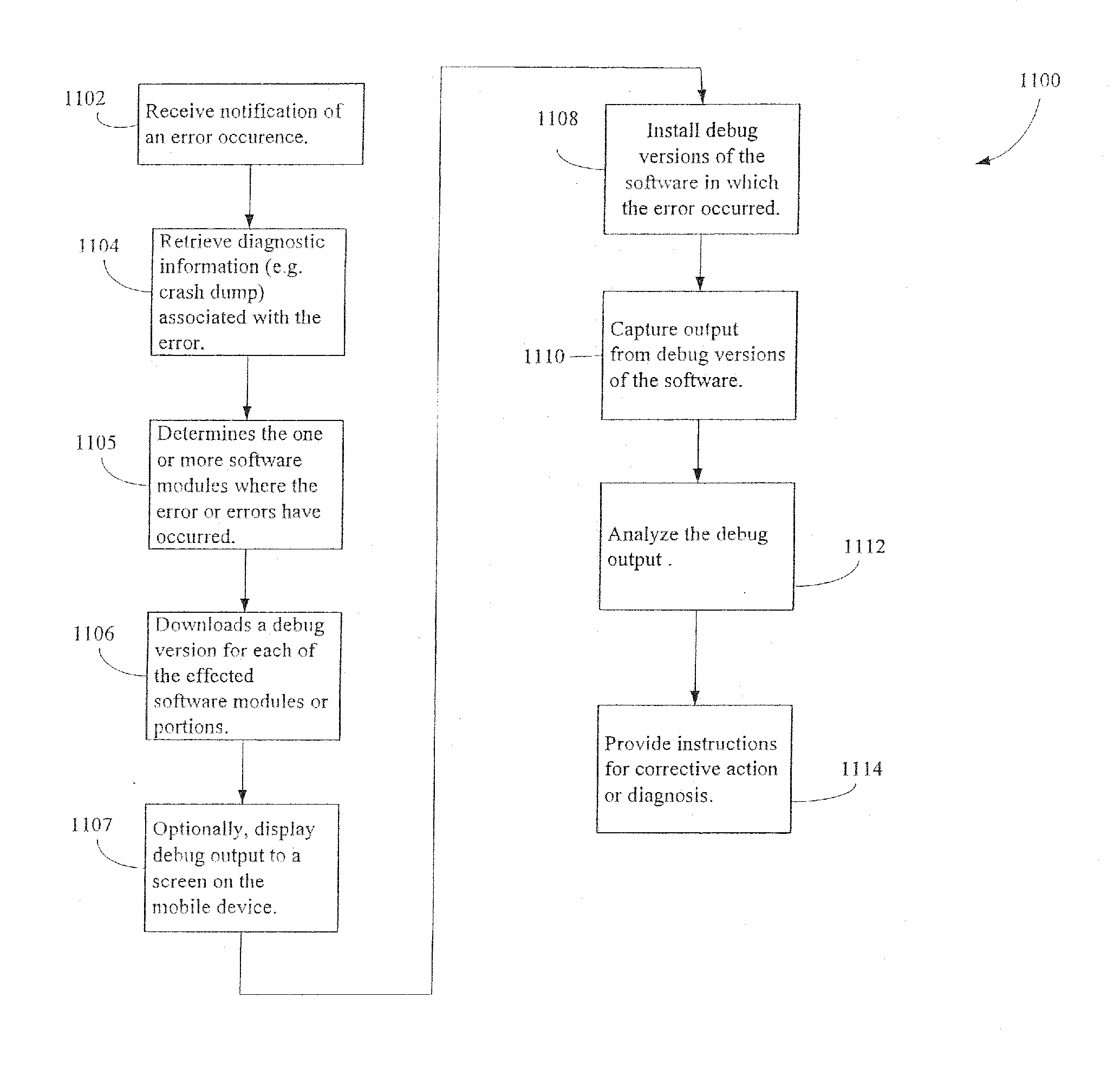
System and method for gathering and automatically processing user and debug data for mobile devices
InactiveUS20050193036A1Better products to market more quicklyManage the constraint of storage space on the device and the bandwidth limitationsFault responseHardware monitoringData miningMobile device
A system and method for tracking user patterns, getting debug information from retail devices in use, and gathering data automatically into a central location where it is processed automatically. Information pertaining to the state of the system at the time a failure occurred on a mobile device is accessible by a developer in a disconnected mode. In addition, usage patterns are ascertainable from the data gathered.
Owner:MICROSOFT TECH LICENSING LLC
Network virtualization apparatus and method with a table mapping engine
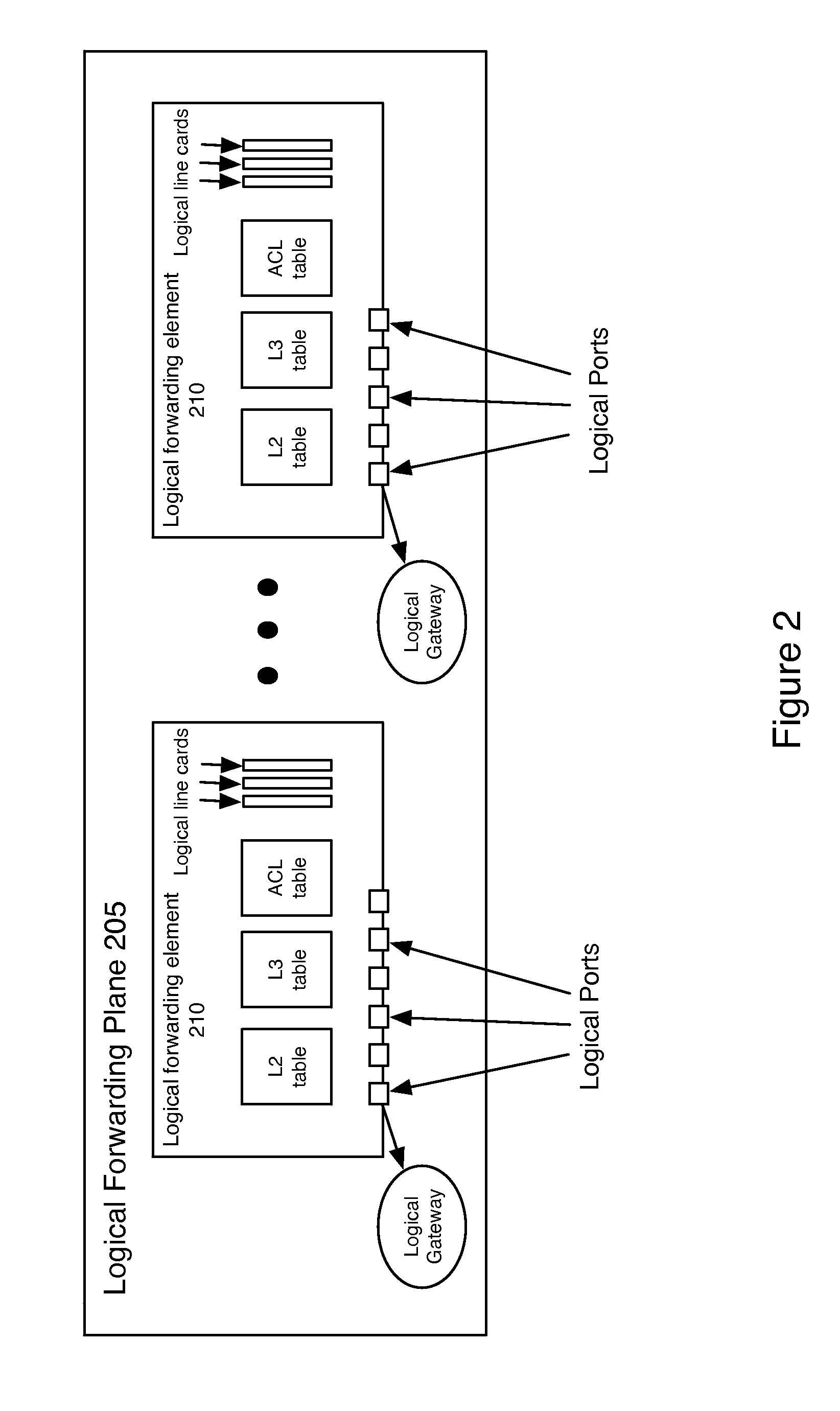
ActiveUS20130058215A1Error preventionTransmission systemsNetwork virtualizationDistributed computing
Some embodiments provide a virtualizer for managing a plurality of managed switching elements that forward data through a network. The virtualizer comprises a first set of tables for storing input logical forwarding plane data and a second set of tables for storing output physical control plane data. It also includes a table mapping engine for mapping the input logical forwarding plane data in the first set of tables to output physical control plane data in the second set of tables by performing a set of database join operations on the input logical forwarding plane data in the first set of tables. In some embodiments, the physical control plane data is subsequently translated into physical forwarding behaviors that direct the forwarding of data by the managed switching elements.
Owner:NICIRA
Capturing system error messages
The present invention provides a method and apparatus for capturing system error messages. The method includes accessing information associated with an error. The method further includes identifying a category associated with the error based upon the accessed information and accessing at least one pre-determined attribute in the accessed information based upon the identified category.
Owner:ORACLE INT CORP
Dynamic stream interleaving and sub-stream based delivery
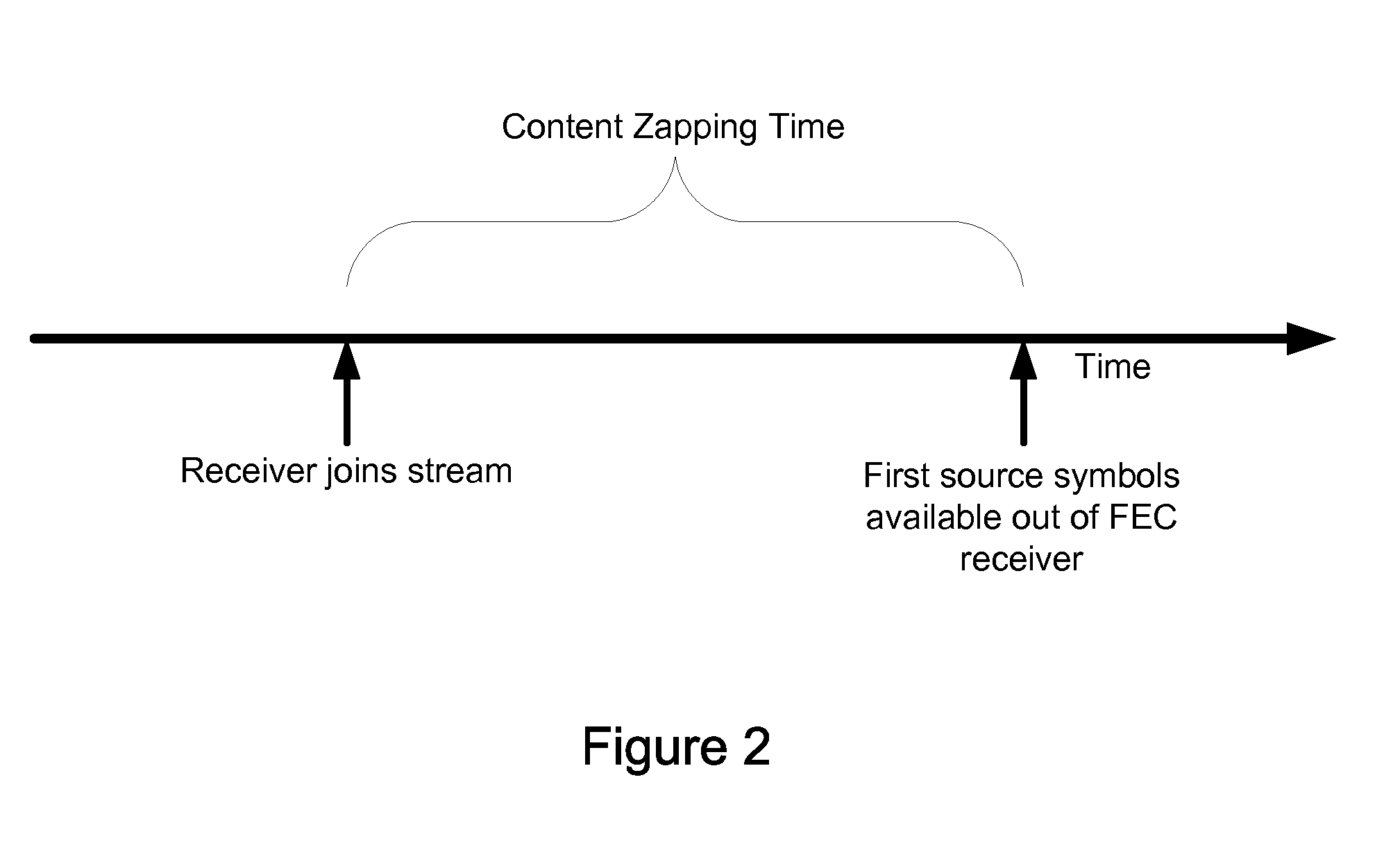
ActiveUS20080256418A1Convenient amountLoss of protectionFault responseCode conversionPacket lossCommunications system
A communications system can provide methods of dynamically interleaving streams, including methods for dynamically introducing greater amounts of interleaving as a stream is transmitted independently of any source block structure to spread out losses or errors in the channel over a much larger period of time within the original stream than if interleaving were not introduced, provide superior protection against packet loss or packet corruption when used with FEC coding, provide superior protection against network jitter, and allow content zapping time and the content transition time to be reduced to a minimum and minimal content transition times. Streams may be partitioned into sub-streams, delivering the sub-streams to receivers along different paths through a network and receiving concurrently different sub-streams at a receiver sent from potentially different servers. When used in conjunction with FEC encoding, the methods include delivering portions of an encoding of each source block from potentially different servers.
Owner:QUALCOMM INC
Network virtualization apparatus and method with a table mapping engine
Some embodiments provide a virtualizer for managing a plurality of managed switching elements that forward data through a network. The virtualizer comprises a first set of tables for storing input logical forwarding plane data and a second set of tables for storing output physical control plane data. It also includes a table mapping engine for mapping the input logical forwarding plane data in the first set of tables to output physical control plane data in the second set of tables by performing a set of database join operations on the input logical forwarding plane data in the first set of tables. In some embodiments, the physical control plane data is subsequently translated into physical forwarding behaviors that direct the forwarding of data by the managed switching elements.
Owner:NICIRA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com