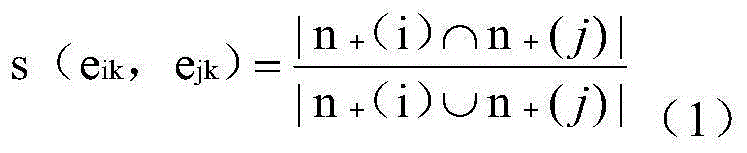Patents
Literature
485results about How to "Efficient discovery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
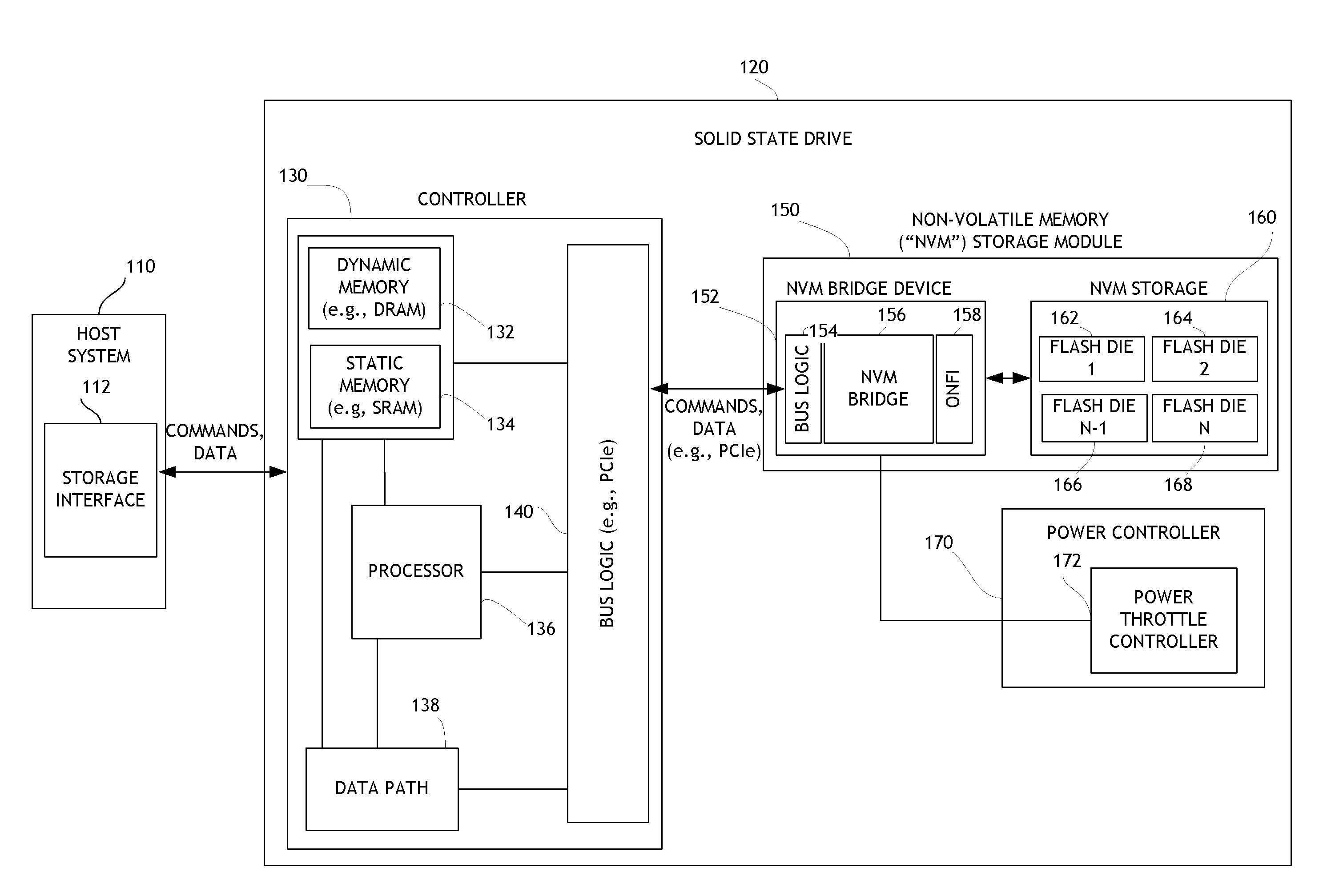
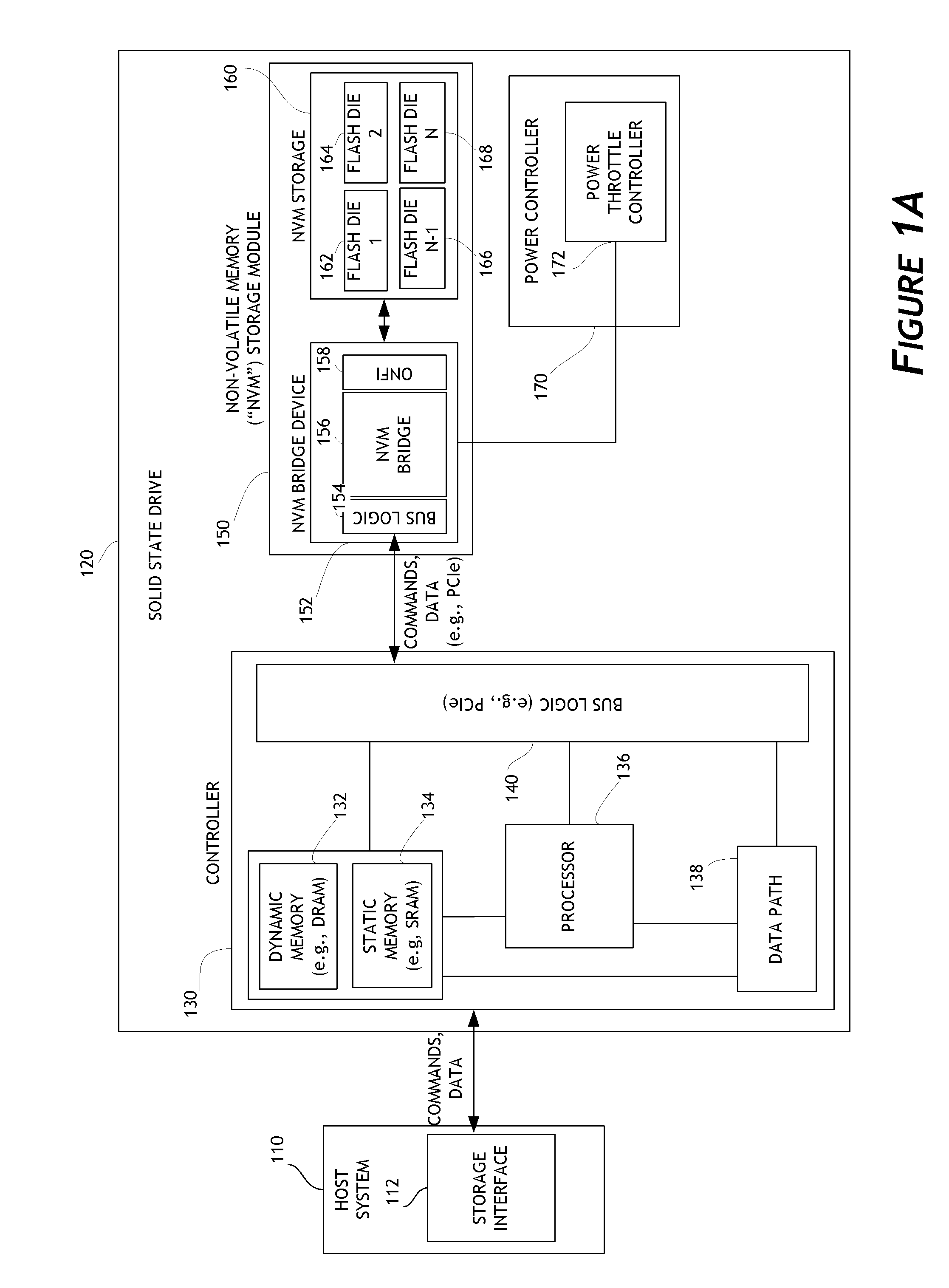
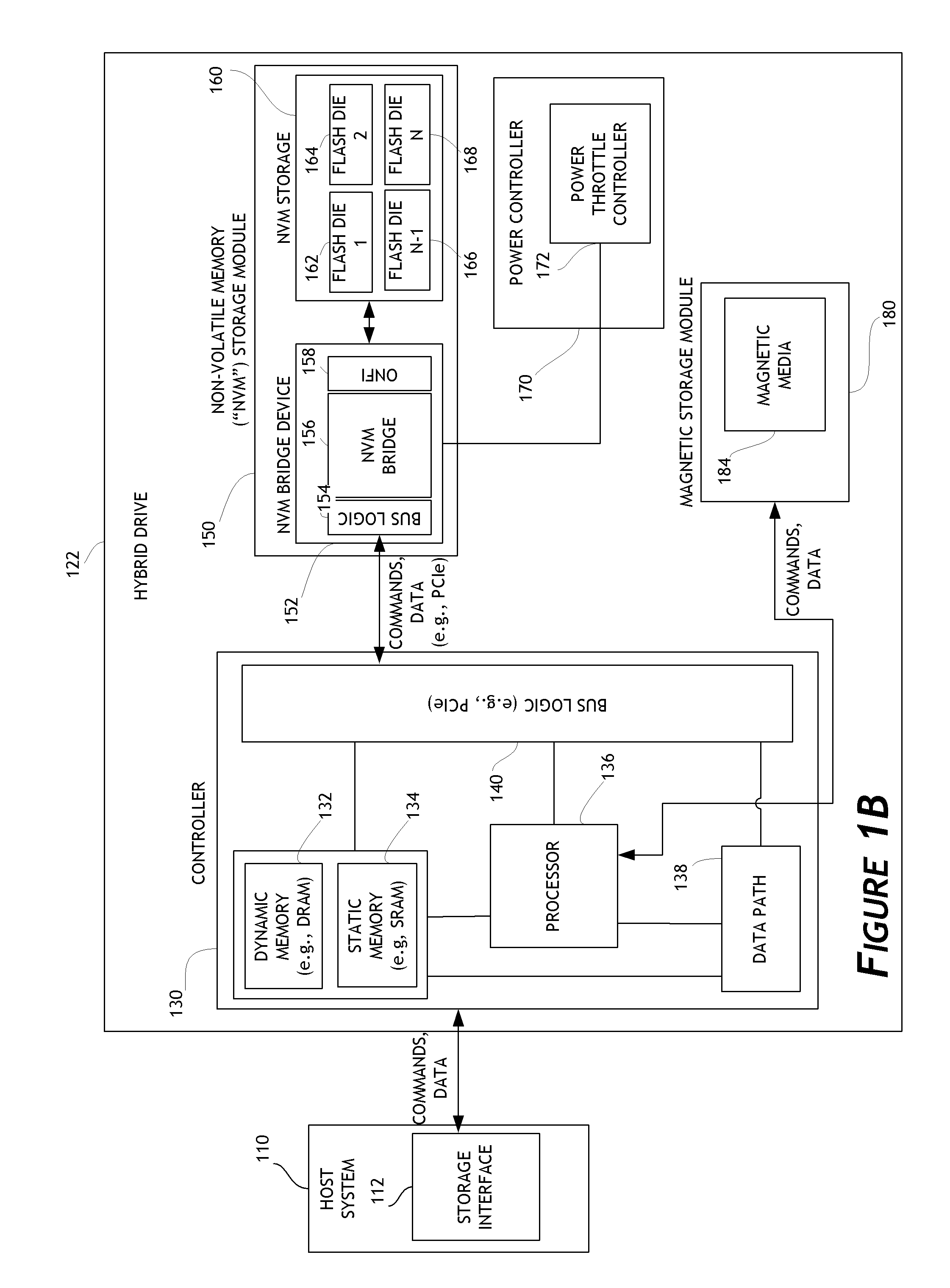
Systems and methods for detailed error reporting in data storage systems
ActiveUS8713357B1Efficient discoveryEasy to understandInput/output to record carriersFault responseData operationsData access
Embodiments of the invention are directed to providing detailed error reporting of data operations performed on a NVM storage device. In one embodiment, a controller interfaces with a NVM storage device including NVM storage coupled with a bridge. In one embodiment, the controller is provided physical, page-level access to the NVM via the bridge, and the bridge provides detailed error reporting of the data operations that the bridge performs on the NVM on behalf of the controller. For example, the bridge may provide page level reporting indicating which page(s) failed during a read operation. Detailed error reporting allows the controller to better understand the failures that occurred in a data access operation in the NVM. It also enables the controller to manage the flash media at the physical page / block level. In one embodiment, detailed error reporting also enables the return of discontinuous ranges of data with the error portions removed.
Owner:WESTERN DIGITAL TECH INC
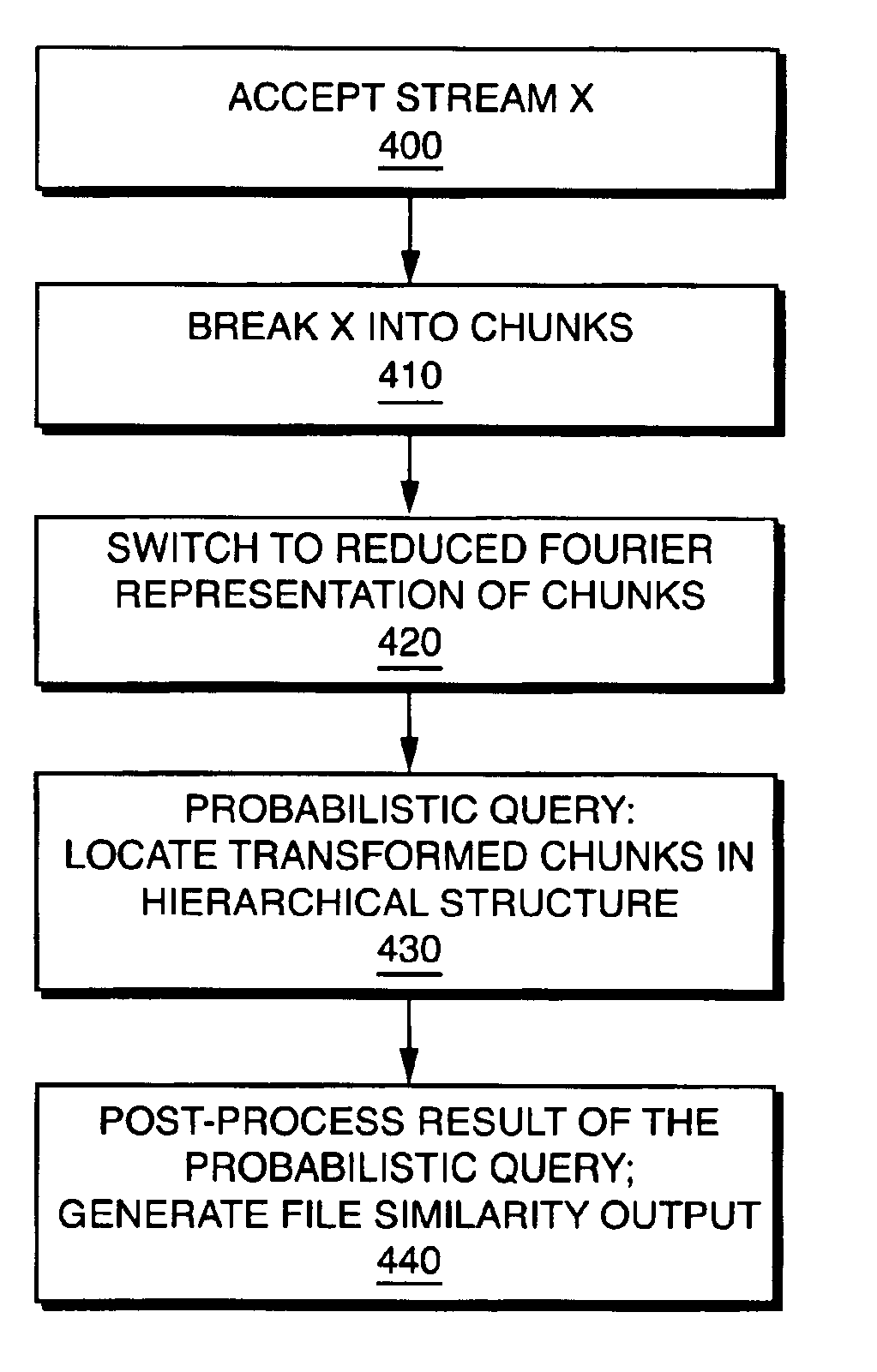
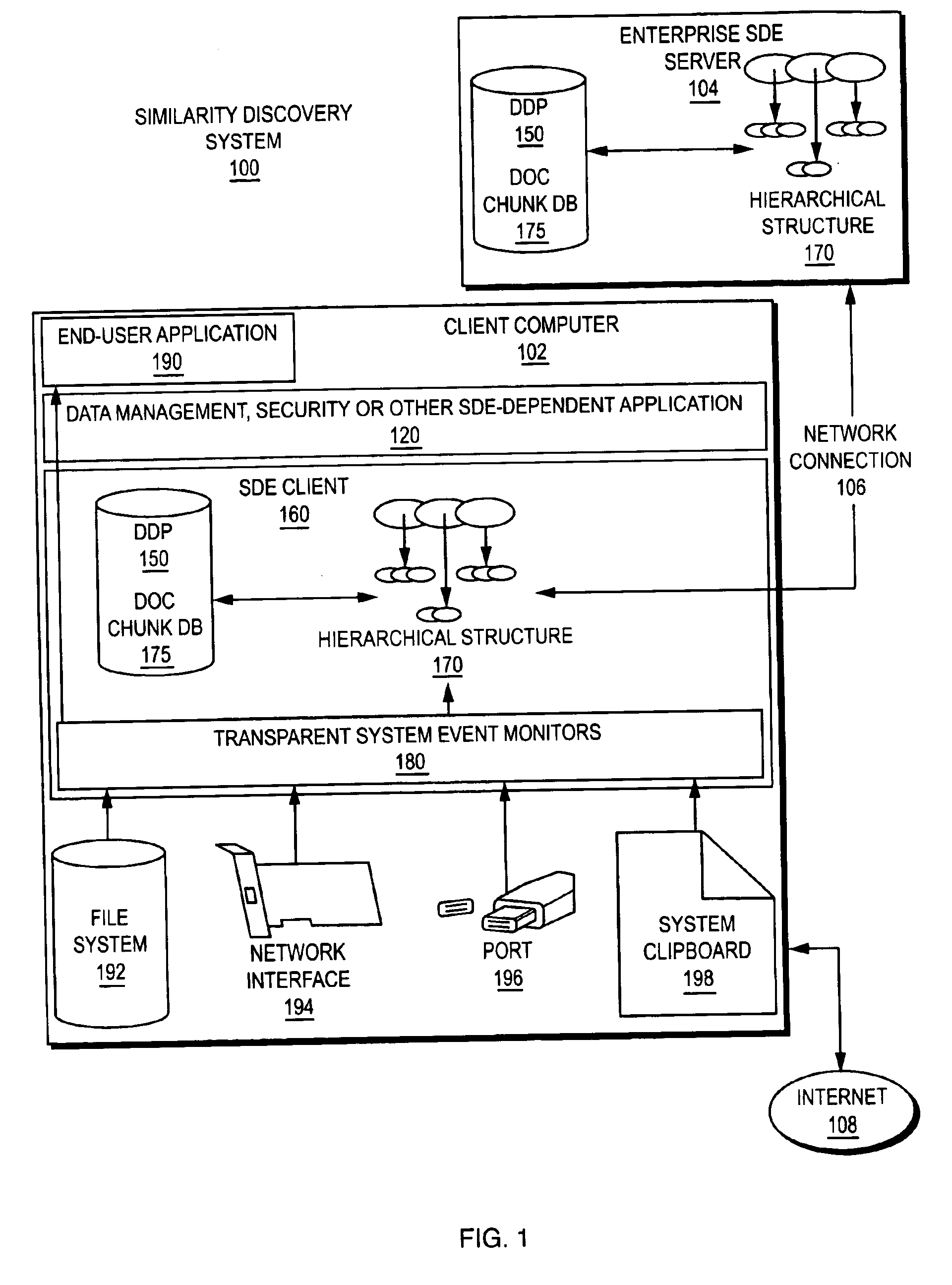
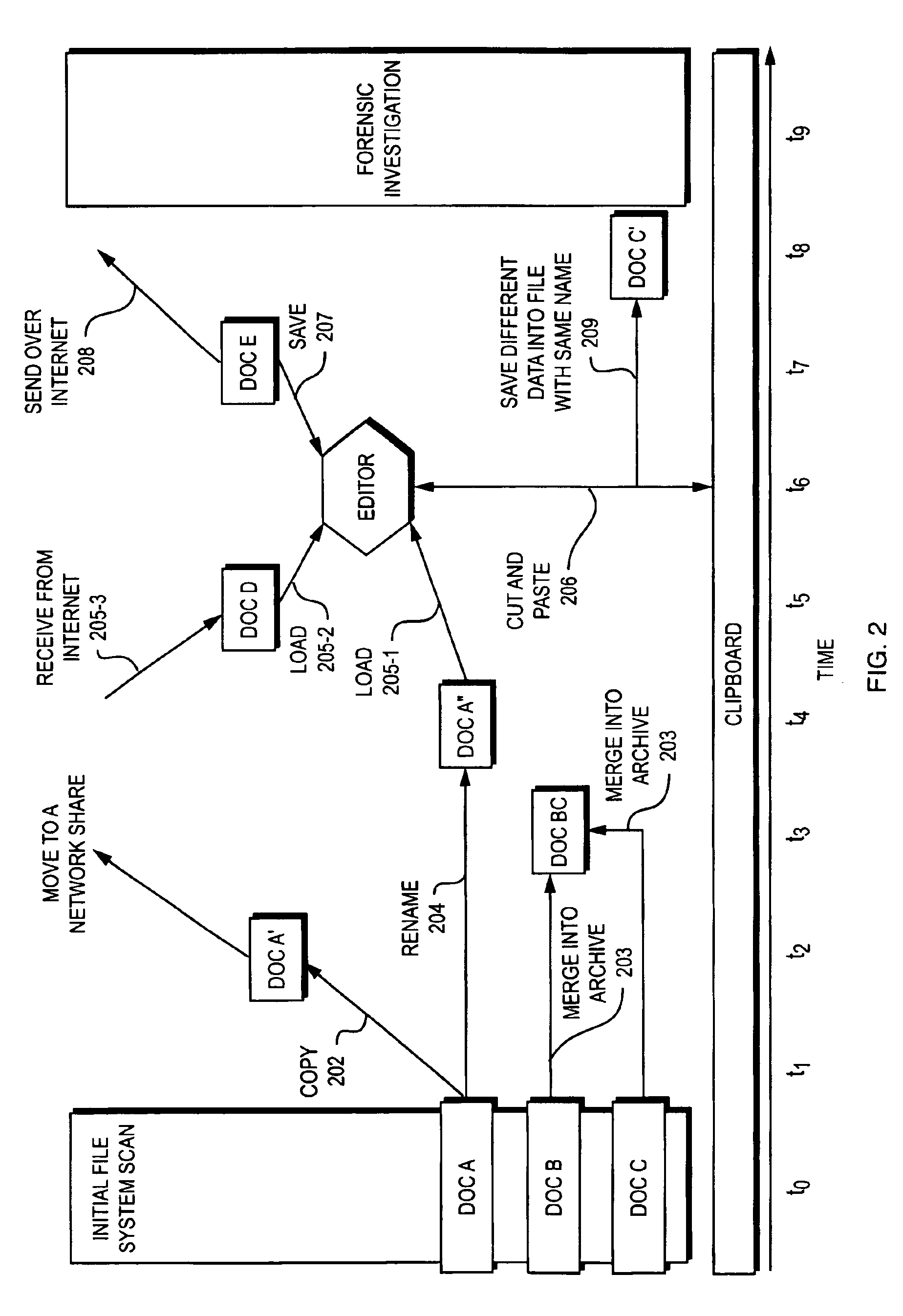
Identifying similarities within large collections of unstructured data
ActiveUS6947933B2Improper accessImproper distributionData processing applicationsDigital data processing detailsData processing systemUnstructured data
A technique for determining when documents stored in digital format in a data processing system are similar. A method compares a sparse representation of two or more documents by breaking the documents into “chunks” of data of predefined sizes. Selected subsets of the chunks are determined as being representative of data in the documents and coefficients are developed to represent such chunks. Coefficients are then combined into coefficient clusters containing coefficients that are similar according to a predetermined similarity metric. The degree of similarity between documents is then evaluated by counting clusters into which chunks of similar documents fall.
Owner:DIGITAL GUARDIAN LLC
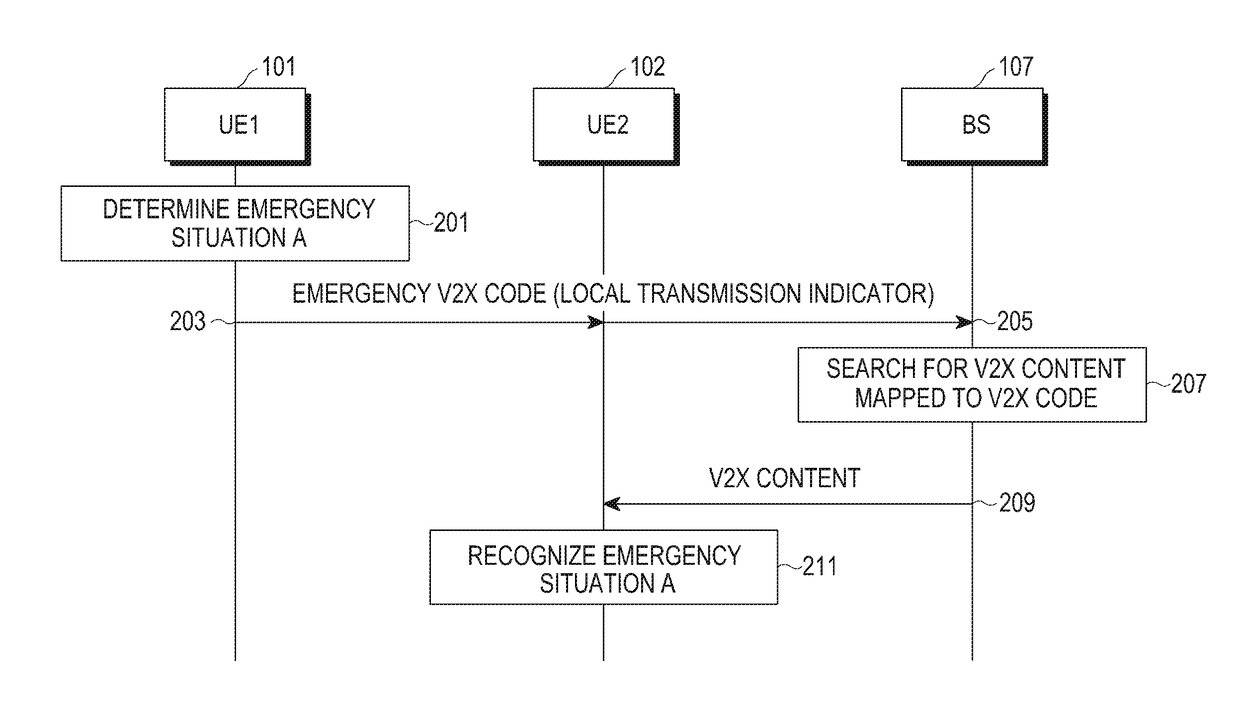
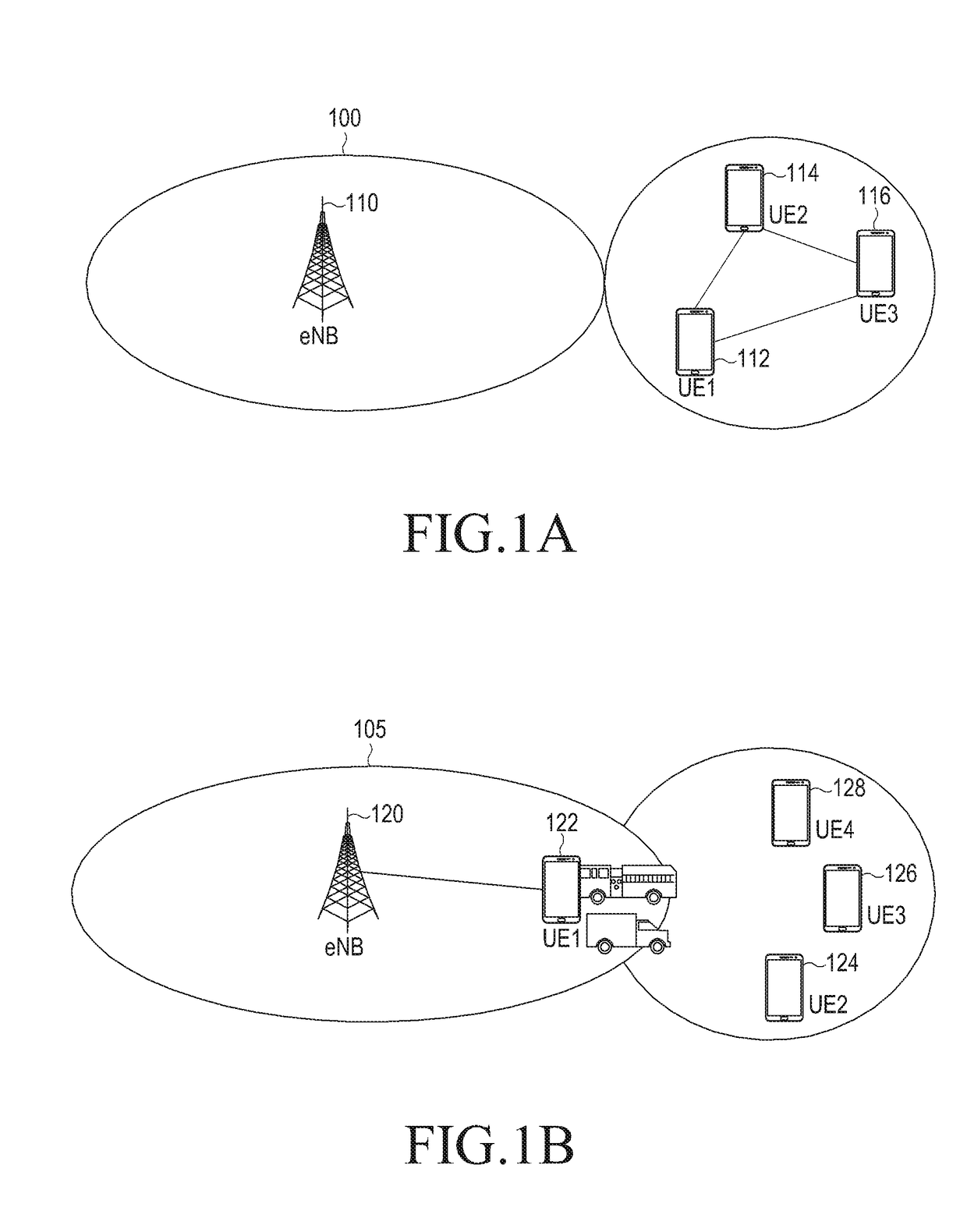
Method and device for inter-device communication
ActiveUS20180035276A1Efficient discoveryAssess restrictionConnection managementData transmissionInternet of Things
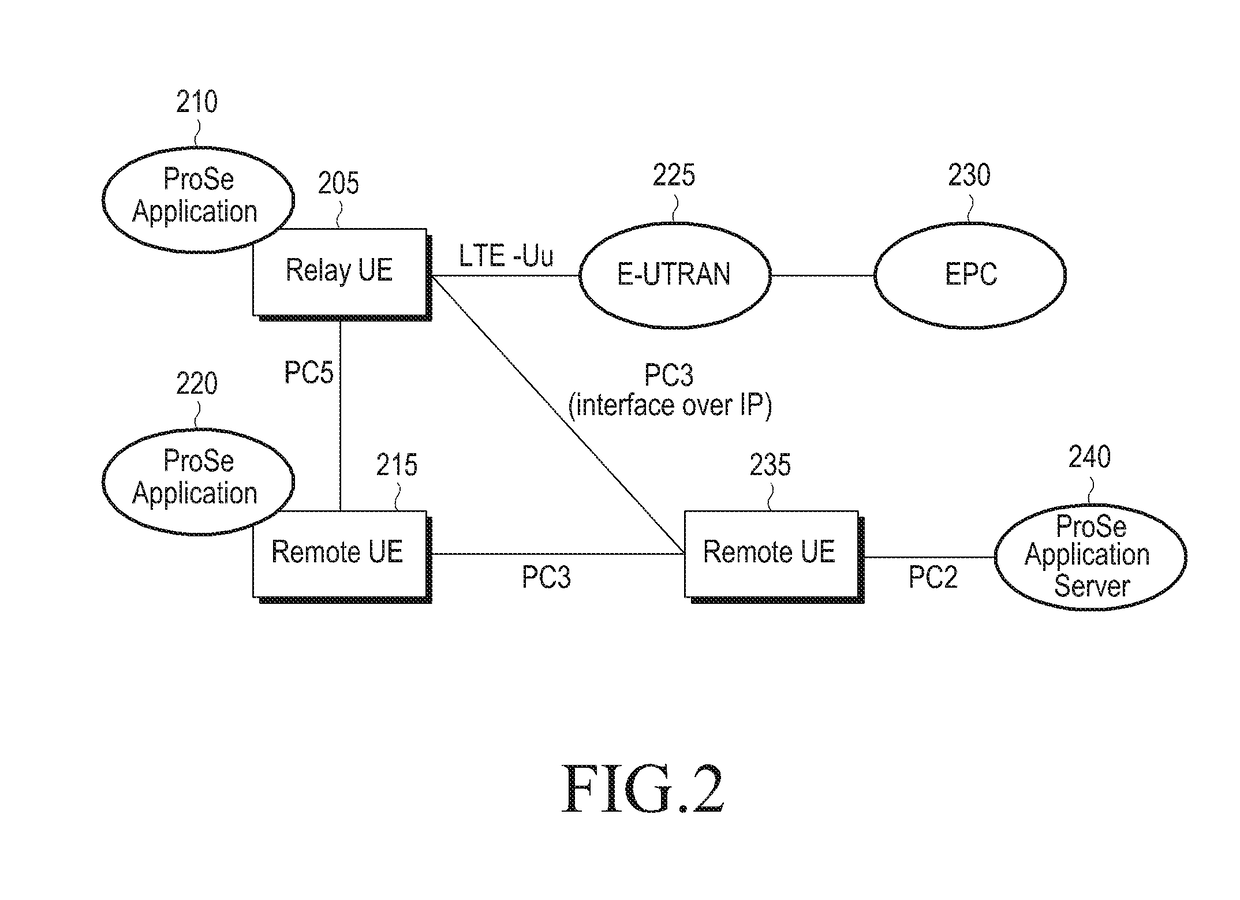
The present disclosure relates to a 5G or pre-5G communication system to be provided in order to support a higher data transmission rate following 4G communication systems such as LTE. Disclosed are a method and device for improving device searching in a D2D communication system supporting direct communication between devices. The method comprises the steps of: generating a search signal including search information; selecting a transmission resource to transmit the search signal; transmitting the search signal through the selected transmission resource; and when a request signal requesting additional information on the search from a counterpart device that has received the search signal is received, transmitting a confirmation signal including the requested additional information to the counterpart device. The present disclosure relates to a communication technique and system which combine a 5G communication system, for supporting a higher data transmission rate following 4G systems, with IoT technology.
Owner:SAMSUNG ELECTRONICS CO LTD
Theme word vector and network structure-based theme keyword extraction method
ActiveCN108052593AEfficient discoveryThe result is accurateCharacter and pattern recognitionSpecial data processing applicationsNetwork structureDocumentation
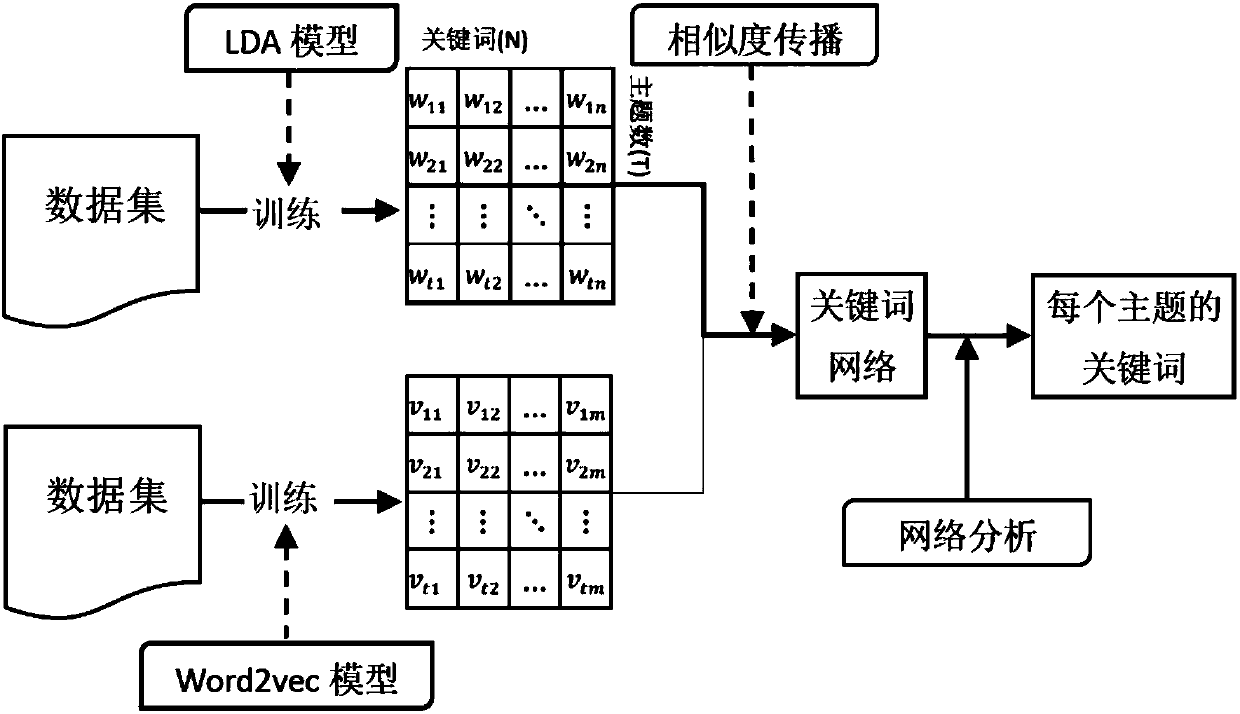
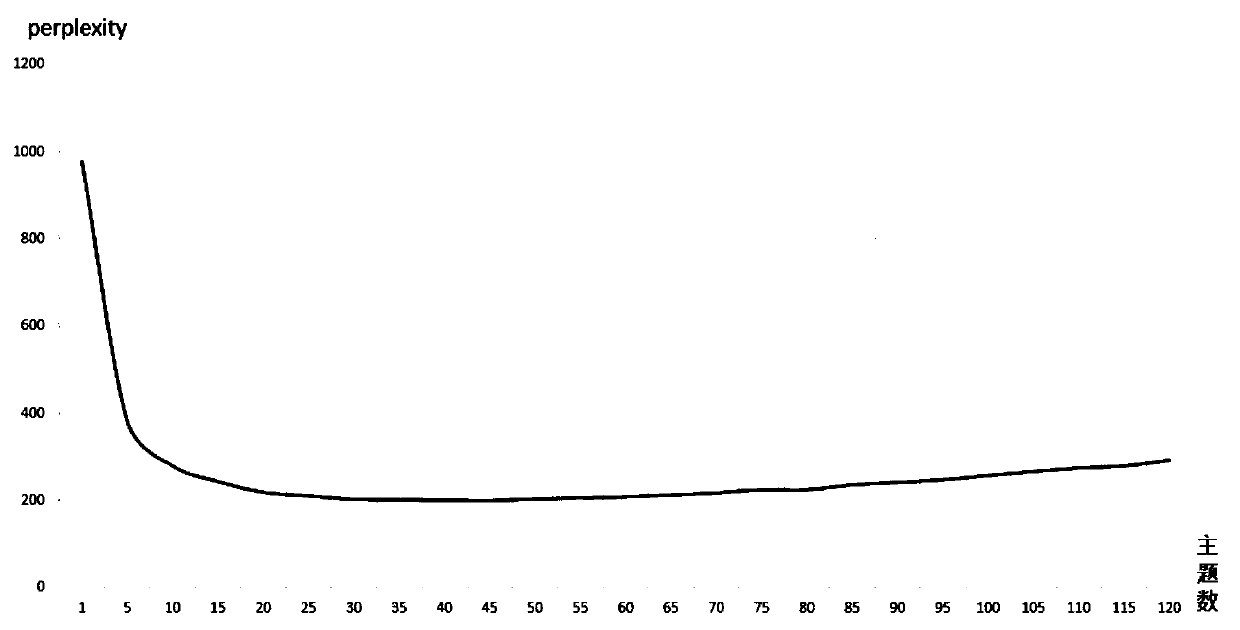
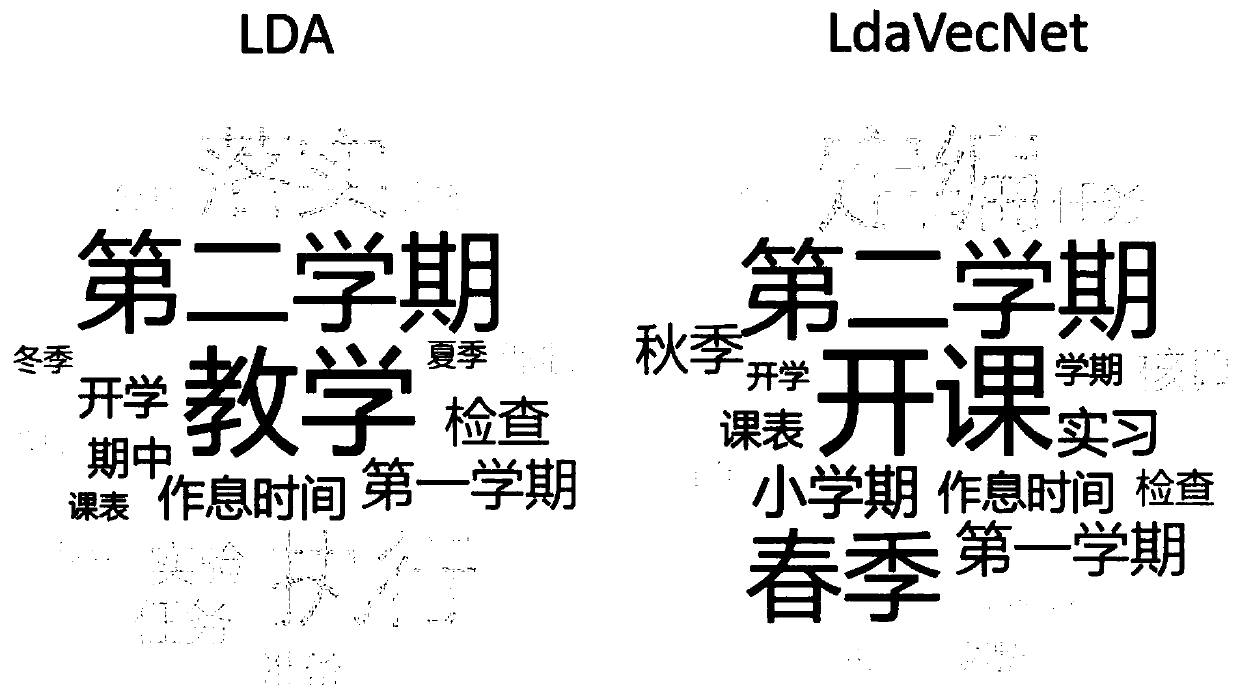
The invention discloses a theme word vector and network structure-based theme keyword extraction method, and particularly relates to the technical field of extracting keywords from texts. The theme word vector and network structure-based theme keyword extraction method comprises the following steps of: carrying out theme clustering on a text corpus on the basis of an LDA theme model, and obtaining100 keywords, relevancies of which with each theme are top 100 in the theme; expressing each word in the text corpus as a word vector by utilizing word2vec, obtaining a semantic similarity between every two words through calculation, and respectively calculating 5 words, semantic similarities of which with each keyword in the keywords are top 5, wherein the keywords and the words, the semantic similarities of which with each keyword are top 5 form a new keyword set; and constructing a keyword network and obtaining the top 20 words in each set to serve as keywords of the theme. According to the method, keywords which have relatively high word frequencies in documents can be extracted, and keywords which have relatively word frequencies and are strongly associated with themes can be effectively discovered.
Owner:SHANDONG UNIV OF SCI & TECH
Multifunctional intelligent insole and gait similarity detection method
ActiveCN104082905AImprove adaptabilityImprove acceleration performanceInsolesDiagnostic recording/measuringTerminal equipmentLarge Calorie
The invention relates to the technical field of articles for daily use, in particular to a multifunctional intelligent insole and a gait similarity detection method. The multifunctional intelligent insole is convenient to use, light, convenient to carry, flexible to use and multifunctional, and has a series of functions of weighing, step counting, distance measuring, calorie consumption measuring, lostness prevention, warning while people fall off and wireless data transmission. According to the method, step postures and coordination of a detected object are judged mainly by analyzing triaxial accelerated speed, triaxial angular speed and pressure information of three positions of feet when the detected object moves, accordingly incorrect or abnormal gaits can be effectively found and corrected, and the insole has important application value for dancing lovers, babies learning to walk and patients walking for rehabilitation. Meanwhile, the gait detection method can be matched with an intelligent system for use, and test results can be presented to users visually through an intelligent terminal device.
Owner:杭州华亭科技有限公司
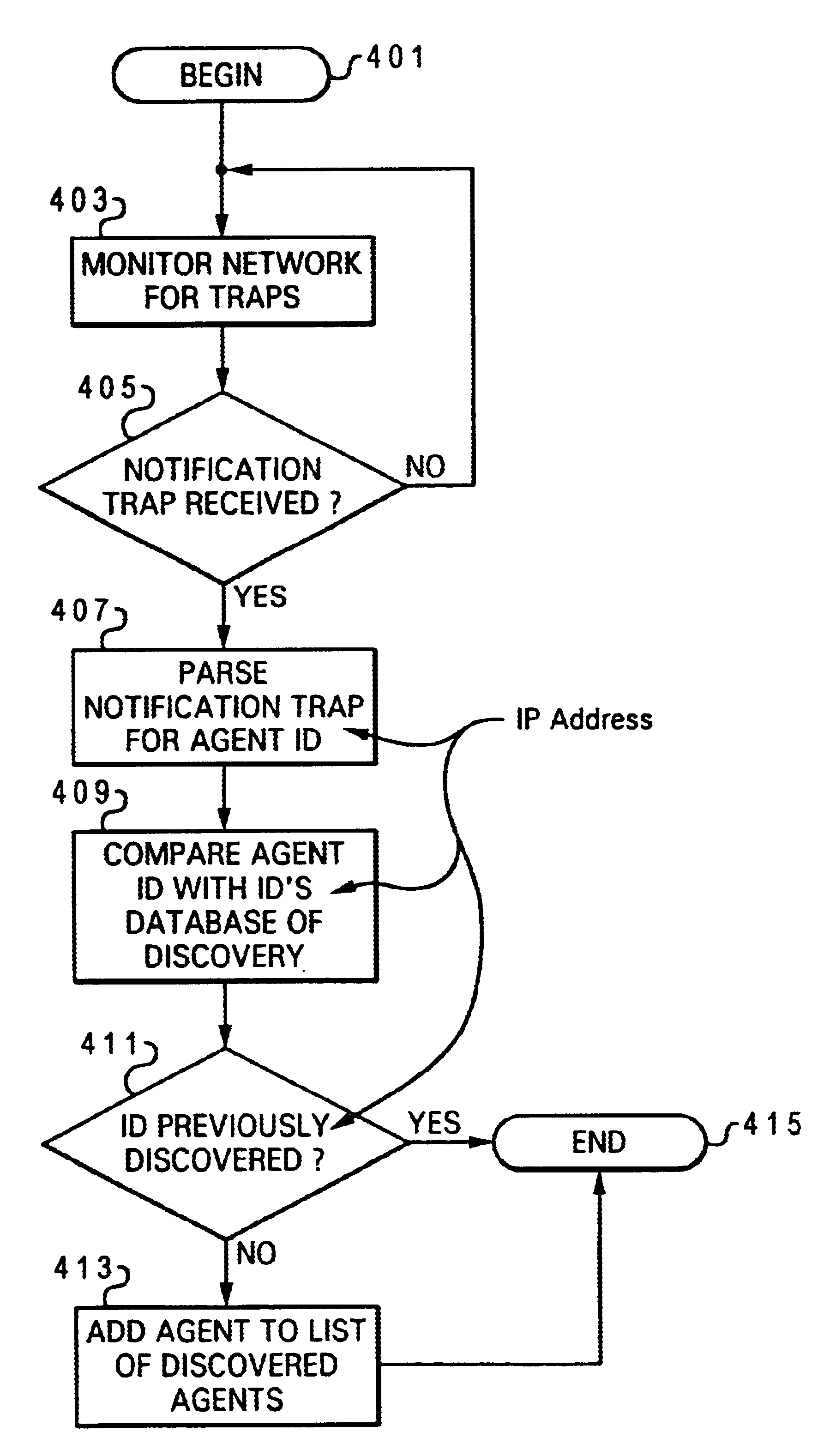
Notification method that guarantees a system manager discovers an SNMP agent
InactiveUS6633909B1Simple methodEfficient discoveryMultiple digital computer combinationsData switching networksIp addressNetwork management
A method for a guaranteeing a network manager discovers SNMP agents on a communications network. Each SNMP agent transmits a trap to the network manager. The trap contains the network manager's IP address and the SNMP agent's identifying information, including its IP address. When the trap is received at the network manager, it is parsed for the agent identifying information, which is compared against a list of previously identified / discovered agents. If the agent identifying information is not found, i.e., if the agent is a newly discovered agent, the network manager adds the agent to the list of discovered agents. The agent is then registered / stored in the discovered agents file. When the trap does not include sufficient identifying information, the network manager sends a query to the agent to extract additional identifying information. The system manager is thus able to discover all connected agents without broadcasting a query message.< / PTEXT>
Owner:GOOGLE LLC
Safe log analyzing method and system
InactiveCN101399658AEfficient discoveryRealize detectionSecuring communicationInformation processingSerial pattern
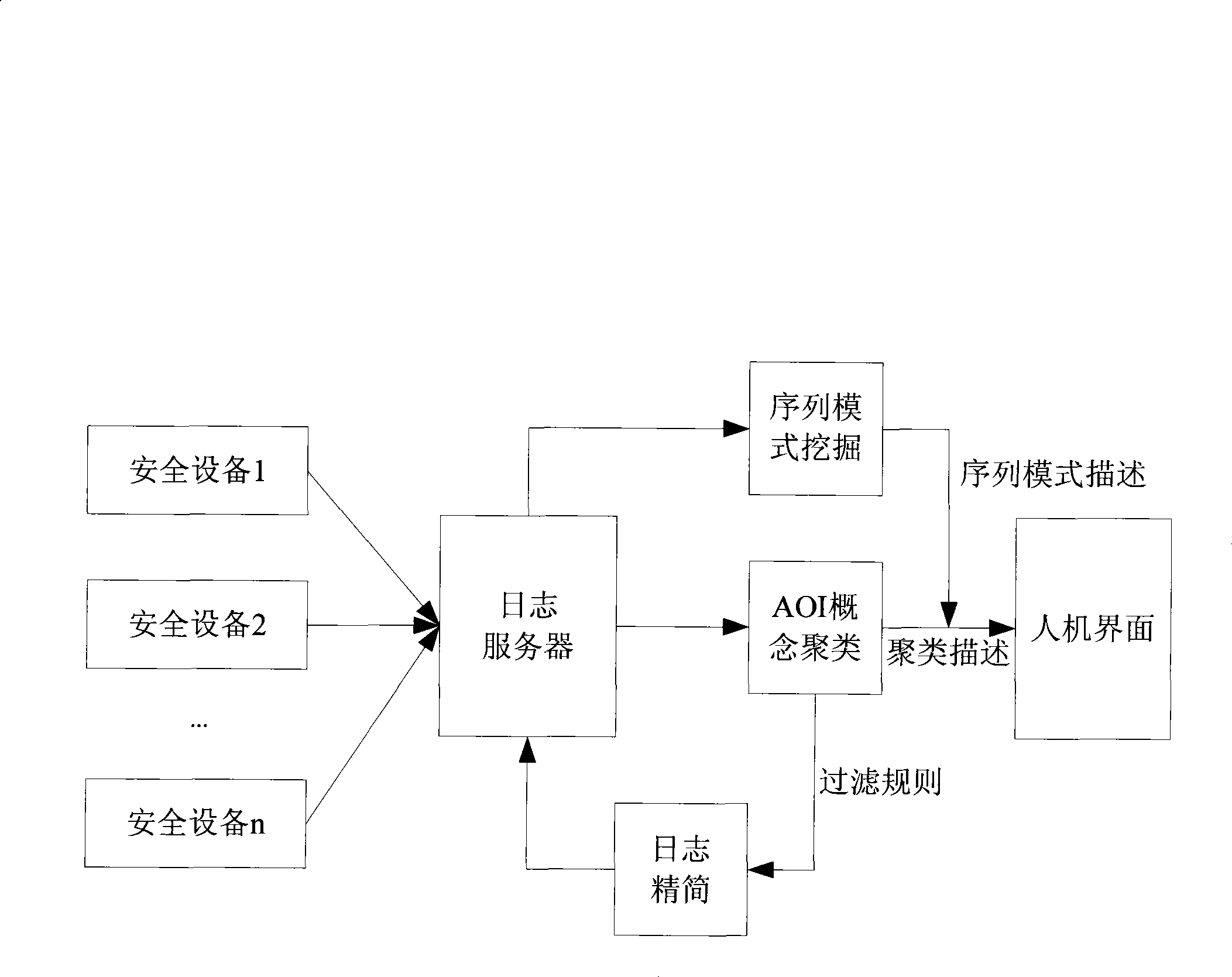
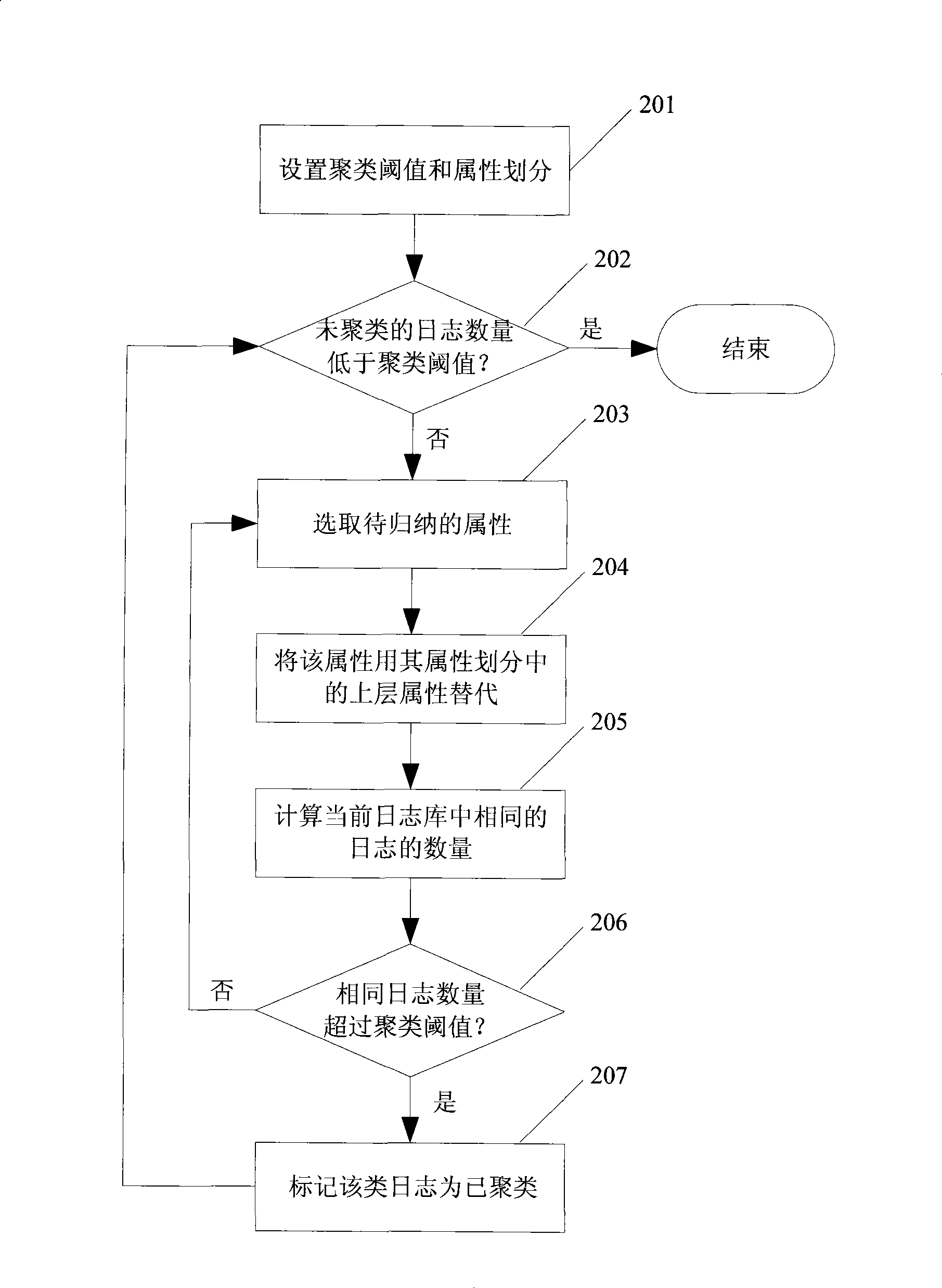
The invention discloses a method for analyzing a security log and a system thereof, which realizes filtration of invalid logs and misreported logs in mass logs, and discovers large-scale network security events and common attack sequences. The method comprises the following steps: the mass logs are subject to cluster analysis by the attribute-oriented inductive algorithm so as to generate class description of each class of log after clustering; an administrator sets filtration regulations according to the clustered class description, unrelated and misreported logs are removed from the current log base so as to simplify the mass logs; Internet Worms, distributed denial of service attacks and other large-scale network security events characteristics are extracted; the simplified log is subject to sequential pattern mining to find attack behavior sequence description commonly used by attackers to be finally submitted to the administrator. The system comprises a clustering analysis module, a filtration module and a sequential pattern mining module. The method and the system can be applied to information processing of the mass logs of security products.
Owner:BEIJING VENUS INFORMATION TECH
Android application vulnerability detection method and Android application vulnerability detection system
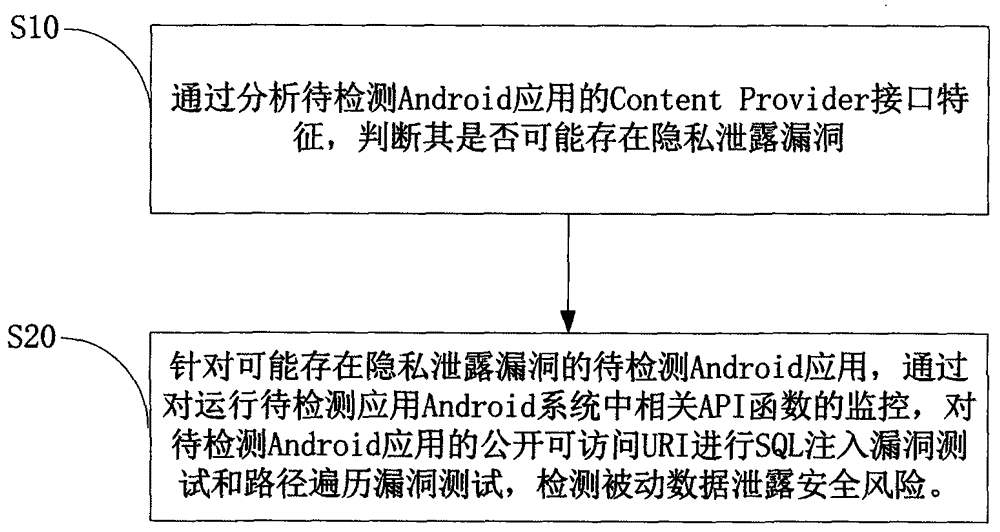
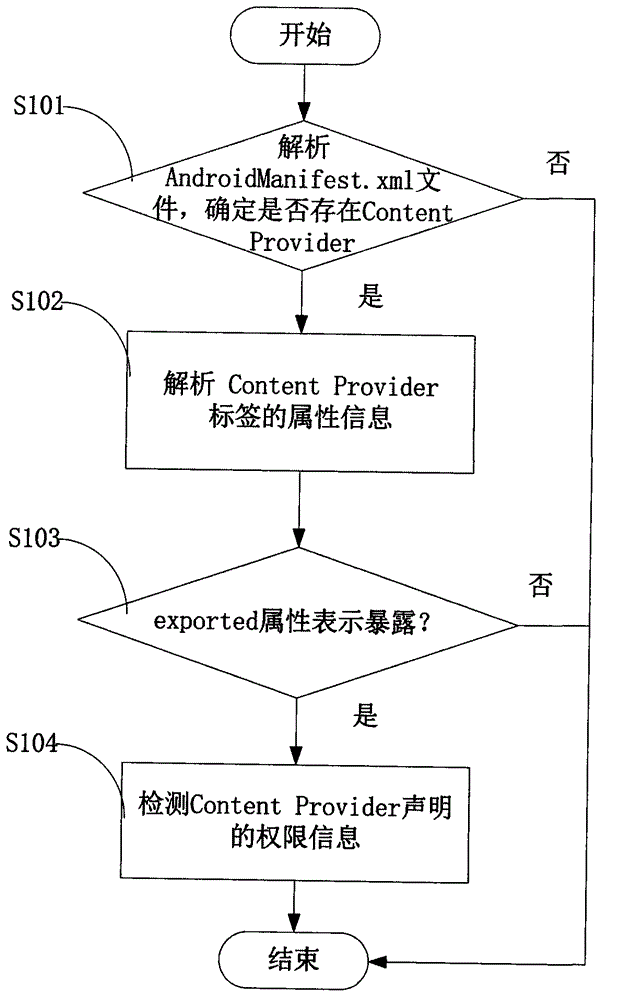
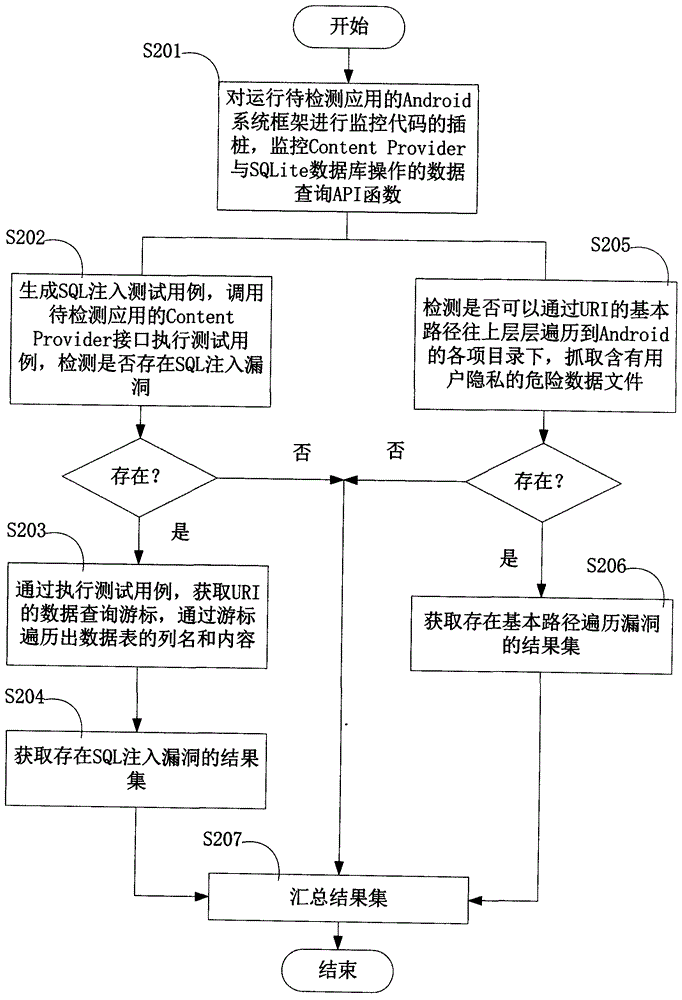
InactiveCN103984900AAvoid false positivesEfficient discoveryPlatform integrity maintainanceSQL injectionUniform resource identifier
The invention provides an Android application vulnerability detection method which comprises the following steps: 1, judging whether a privacy leakage vulnerability possibly exists or not by virtue of analyzing Content Provider interface characteristics of a to-be-detected Android application; 2, if the privacy leakage vulnerability possibly exists, performing an SQL (Structured Query Lanaguge) injection vulnerability test and a path traversal vulnerability test on a public accessible URI (Uniform Resource Identifier) of the to-be-detected Android application which possibly has the privacy leakage vulnerability by virtue of monitoring a related API (Application Program Interface) function in an Android system, and then detecting passive data leakage safety risks. The invention also provides an Android application vulnerability detection system. The method and the system can be used for rapidly discovering privacy leakage and data pollution vulnerabilities possibly existing in the Android application, avoiding misdeclaration, and providing a powerful support for discovering the privacy leakage and data pollution vulnerabilities in the Android application on a large scale.
Owner:南京赛宁信息技术有限公司 +1
Method for automatically screening abnormal electricity consumption user
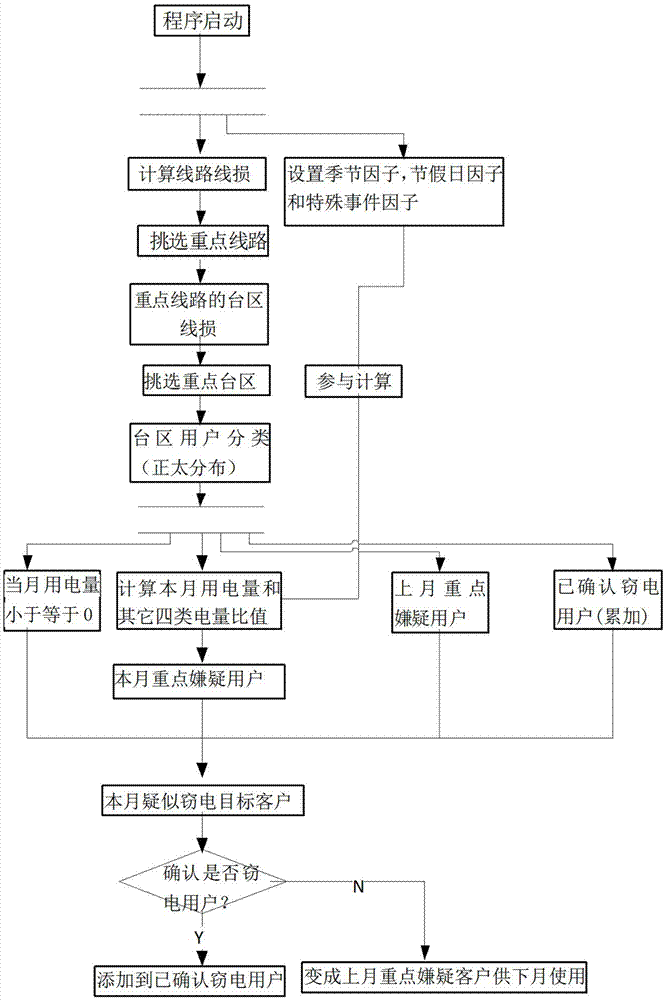
InactiveCN103488867AReduce electricity disputesEfficient discoverySpecial data processing applicationsElectricityScreening method
The invention belongs to the technical field of intelligent electric energy meters and provides a method for automatically screening an abnormal electricity consumption user. The method comprises the following steps of calculating line loss; acquiring a focus distribution area according to the line loss, wherein the focus distribution area is a distribution area of which the line loss is greater than a set threshold value; processing current electricity consumption data and historic electricity consumption data of users in the focus distribution area to obtain suspected electricity larceny users. User data are classified through normal distribution and are respectively calculated according to the classified users, and the suspected electricity larceny users can be quickly and accurately found according to special event factors, holiday factors, seasonal factors and the like. According to the method, by mining electricity consumption data, the abnormal electricity consumption user can be timely found, electricity consumption disputes are reduced, an electricity larceny behavior is effectively found, and a normal electricity consumption order is maintained. Parameters such as user classification coefficients and the seasonal factors can be finely adjusted according to an actual operating effect after user classification and calculation are completed in a calculation process so as to achieve an accurate analysis effect.
Owner:SHENZHEN TECHRISE ELECTRONICS
Suspected target analyzing system and method by video investigation
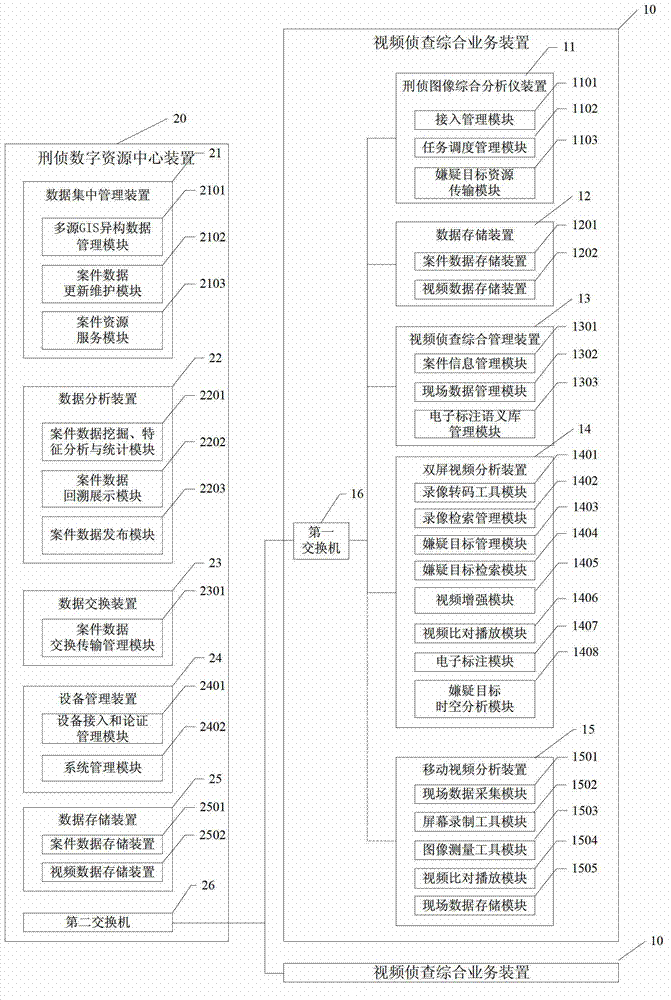
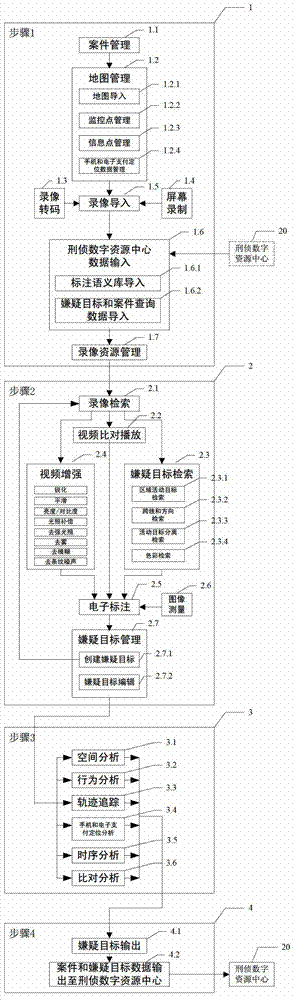
ActiveCN102819578AImprove playbackAvoid latency effectsImage analysisSpecial data processing applicationsPattern recognitionTarget analysis
The invention discloses a suspected target analyzing system and a method by a video investigation, belonging to the field of a criminal investigation video analysis. The system comprises a video investigation comprehensive business device and a criminal investigation digital resource center device which are connected to each other through an exchanger. By using the system, the case field information is structured, various monitoring video formats are transcoded to an uniform format; each frame image of a fuzzy video including a suspected target is enhanced to form a video enhanced segment; a suspected target video segment is obtained through the suspected target index with zero loss and low false drop rate; the unified semantic electronic mark is carried out on the suspected target video segment; the suspected target is found, screened and tracked by performing the space analysis, action analysis, trajectory tracking, positioning trace analysis of telephone and electronic payments, time sequence analysis, feature contrasting and analysis; furthermore, the system and the method can be widely applied to the video investigation and case solution.
Owner:WUHAN DAQIAN INFORMATION TECH
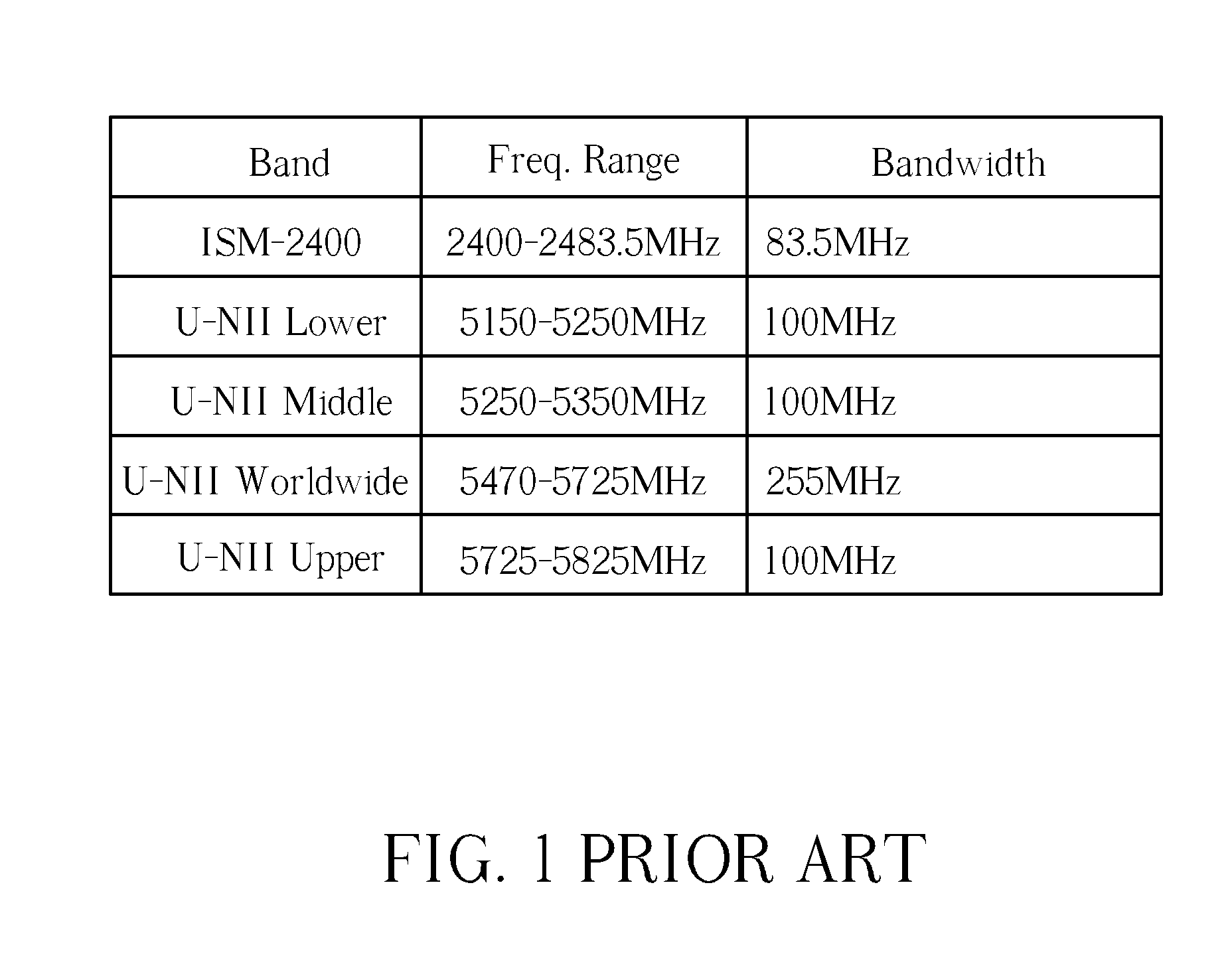
Methods of optimizing scanning parameters for a plurality of channels in a wireless band
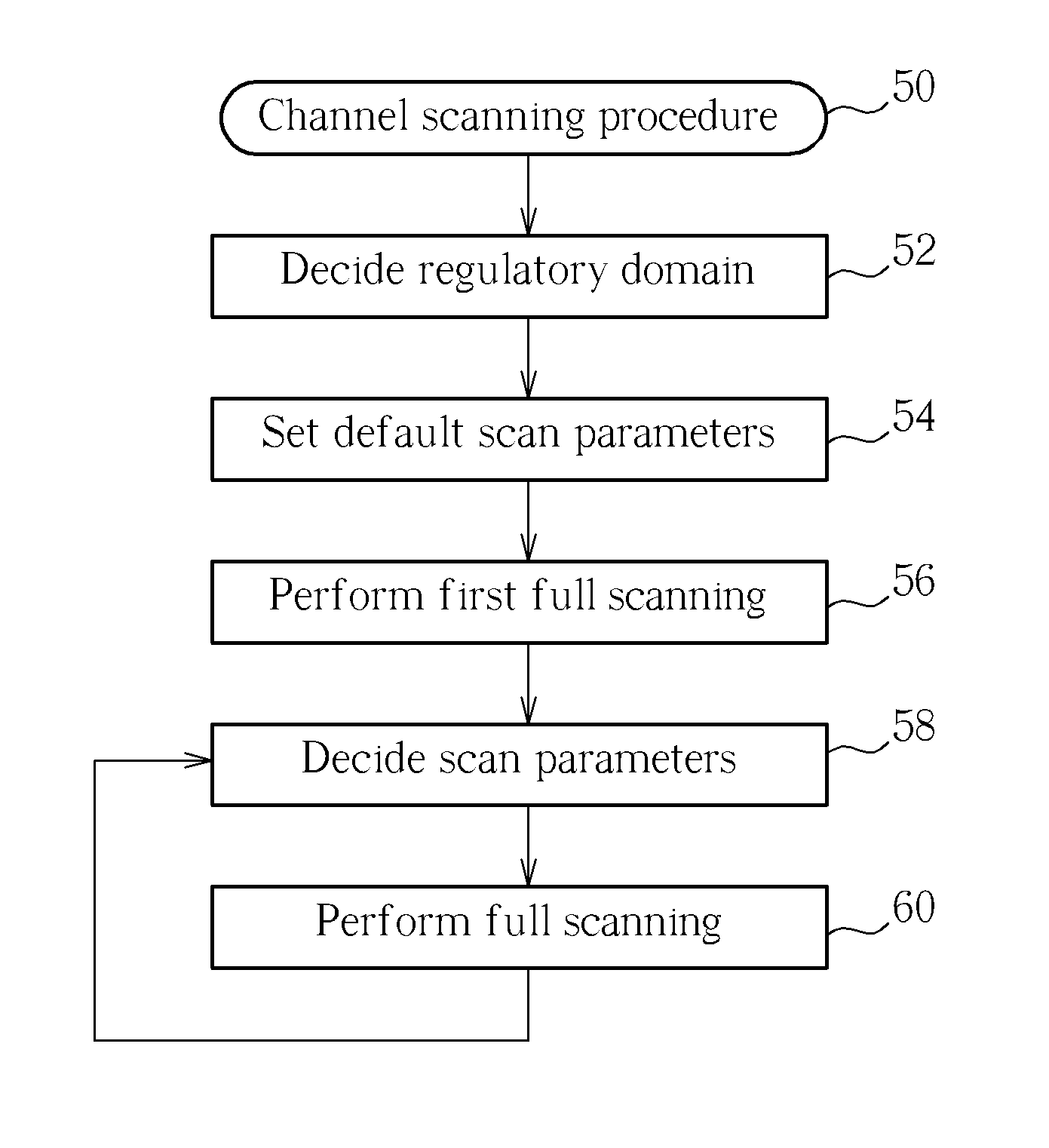
ActiveUS20130039181A1Efficient scanningEfficient discoveryError preventionFrequency-division multiplex detailsFrequency bandVIT signals
A method of optimizing scanning parameters for a plurality of channels in a wireless band includes identifying channels in the plurality of channels as overlapping channels and identifying channels in the plurality of channels as non-overlapping channels, wherein each of the non-overlapping channels transmits and receives signals at frequencies that do not overlap frequencies of other non-overlapping channels. Then scanning parameters for each channel are optimized in order to assign the scanning parameters to be normal scanning parameters or extended scanning parameters, the extended scanning parameters indicating longer scanning times used for scanning channels than that of the normal scanning parameters. Next each overlapping channel is scanned with a networked electronic device using the normal scanning parameters. The method also includes scanning each non-overlapping channel with the networked electronic device using the extended scanning parameters.
Owner:AMTRAN TECH
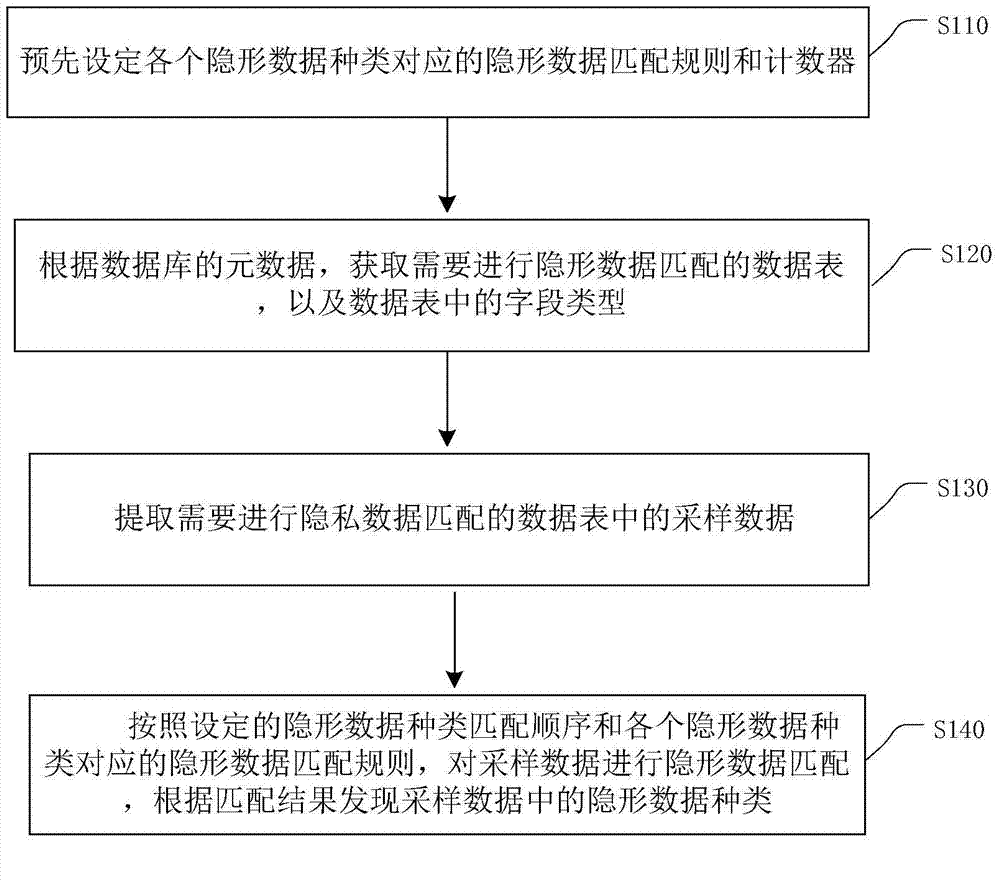
Method for finding and sorting private data in data table
ActiveCN104731976AAutomatic discoveryEfficient discoverySpecial data processing applicationsLicense numberEmail address
The embodiment of the invention provides a method for finding and sorting private data in a data table. The method mainly comprises the steps that private data analysis rules corresponding to all private data types are preset; sampling data are extracted from the data table; private data analysis is conducted on the sampling data according to the set analysis sequence of the private data types and the private data analysis rules corresponding to all the private data types, 10 kinds of private data types are found in the sampling data according to the analysis result, wherein the private data types include ID card numbers, zip codes, business license numbers, organization codes, identification numbers of taxpayers, e-mail addresses, company names, phone numbers, Chinese names and addresses. Key data in the data table of an enterprise application database are efficiently found out and sorted, workload can be greatly lightened, and work time can be greatly shortened.
Owner:MASSIVE CLOUD BEIJING DATA TECH
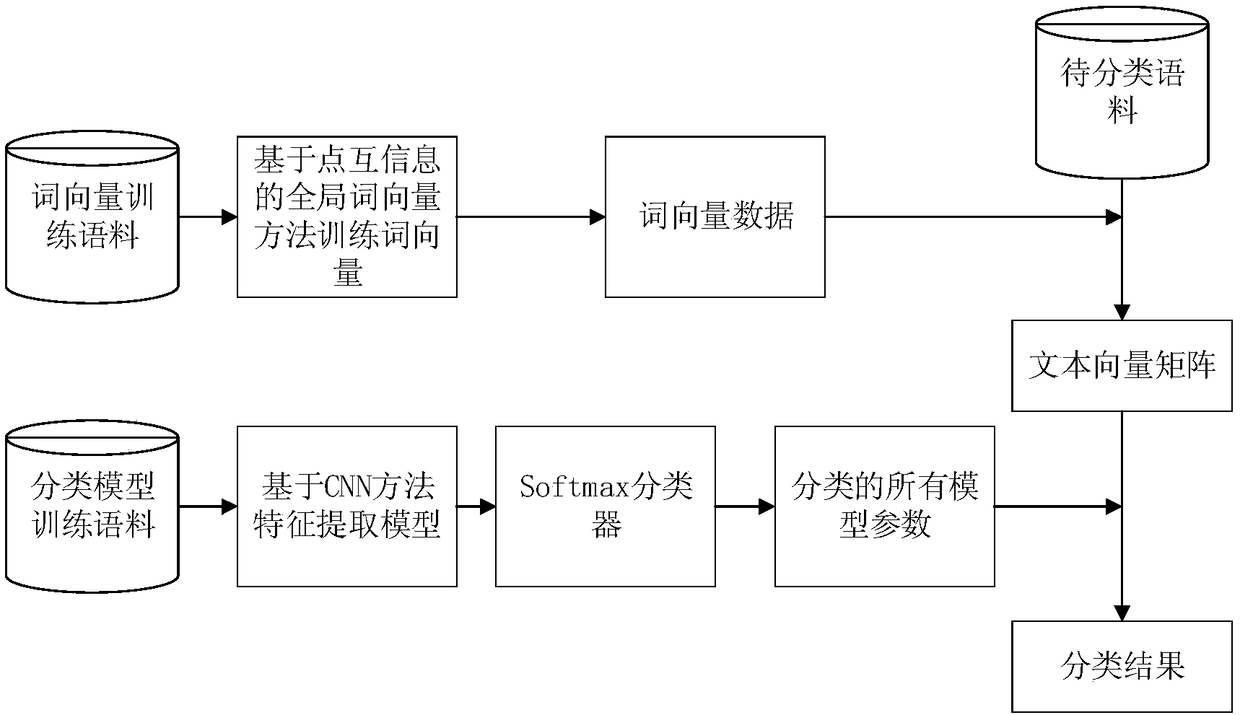
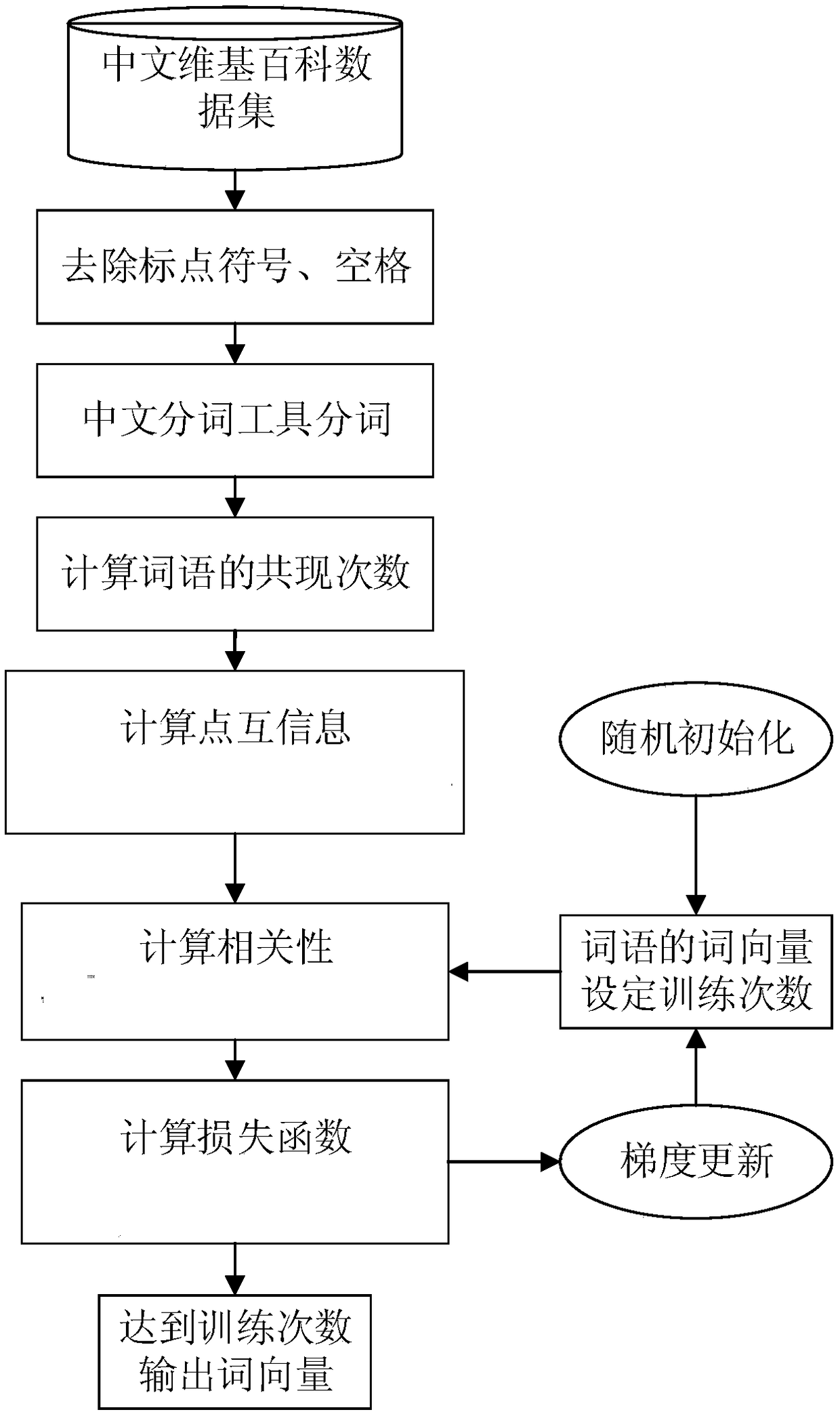
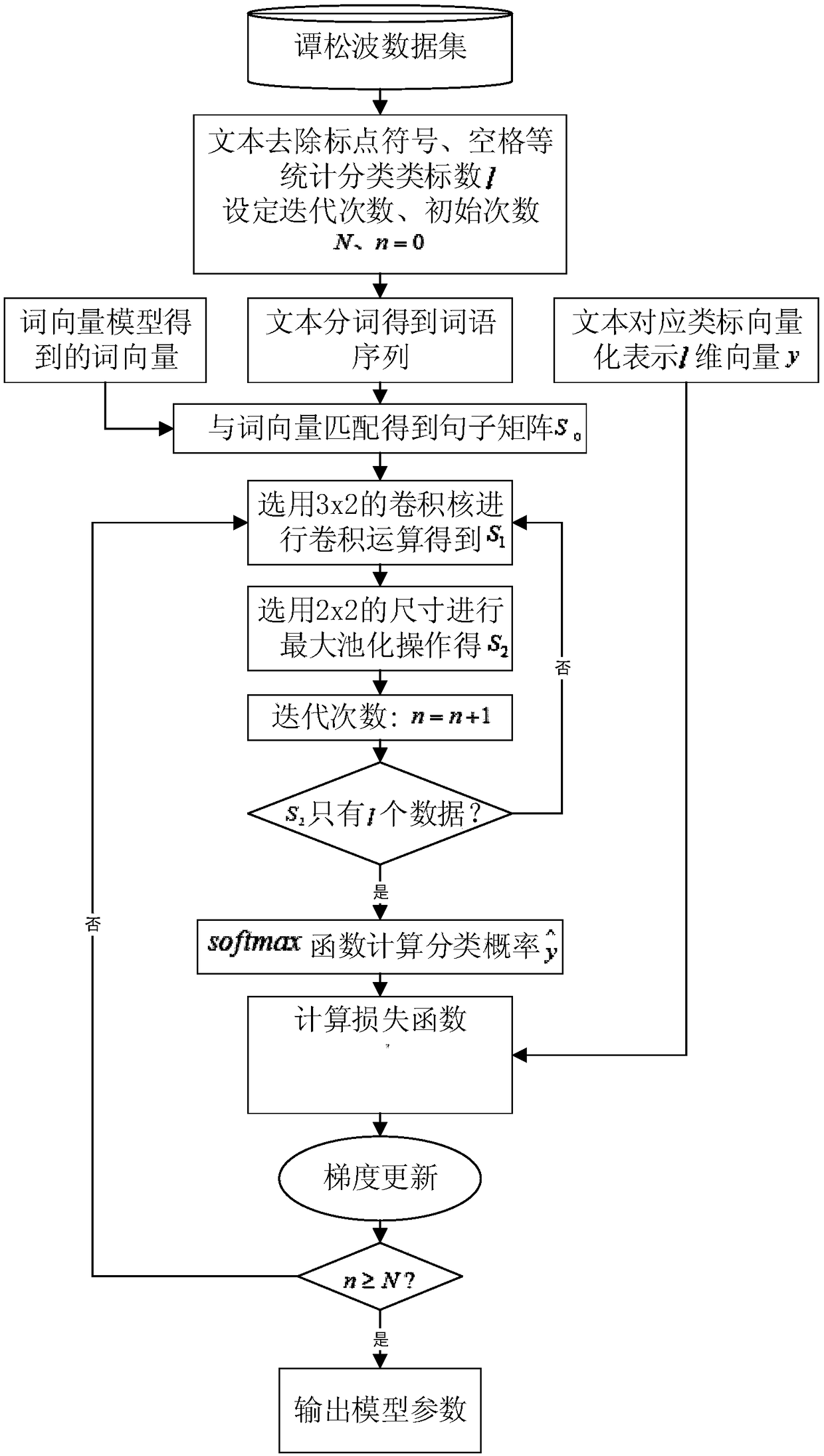
Word vector model based on point mutual information and text classification method based on CNN
ActiveCN109189925AImprove the objective functionExact objective functionCharacter and pattern recognitionNeural architecturesFeature extractionText categorization
The invention discloses a word vector model based on point mutual information and a text classification method based on CNN. The method comprises the following steps: (1) training a word vector modelthrough a global word vector method based on point mutual information; (2) determining a word vector matrix of the text according to the trained word vector model; (3) extracting features from word vector matrix by CNN and training classification model; (4) extracting input text features according to the trained word vector model and CNN feature extraction model; (5) according to the text featuresextracted from CNN feature extraction model, calculating the mapping distance between text and preset categories by softmax and the cross entropy method, wherein the nearest one is the correspondingcategory of text. This method overcomes the shortcomings of Glove word vector in the semantic capture and statistical co-occurrence matrix, reduces the training complexity of the model, can accuratelymine the text classification features, is suitable for text classification in various fields, and has great practical value.
Owner:NANJING SILICON INTELLIGENCE TECH CO LTD
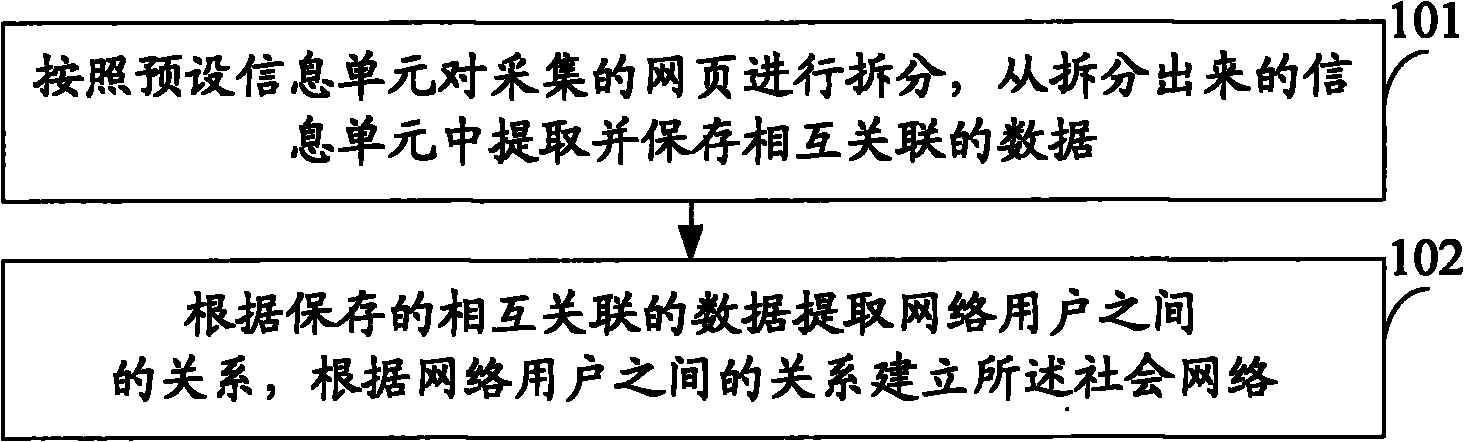
Method and system for establishing social network and method and system for mining network community
InactiveCN101887441AEfficient discoverySpecial data processing applicationsInformation dispersalModularity
The embodiment of the invention discloses a method and a system for establishing a social network and a method and a system for mining a network community. The method for mining the network community comprises the following steps of: calculating the node intensity of each node in the social network, wherein the node intensity of a certain node is the weight sum of all sides connected with the node; expanding the current community according to the modularity of the current community by using an initial node selected according to node intensity as the basis until the modularity of the current community is maximized, namely the community with the maximized modularity is the community to be mined. The method can effectively discover a user cluster or a user community with certain characteristics, and can provide more valuable services, such as information spreading, service recommendation and friend recommendation and the like based on the user cluster or community with different characteristics.
Owner:HUAWEI TECH CO LTD
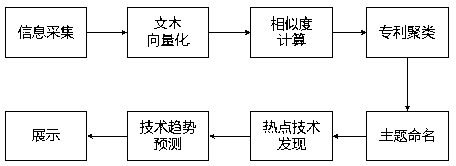
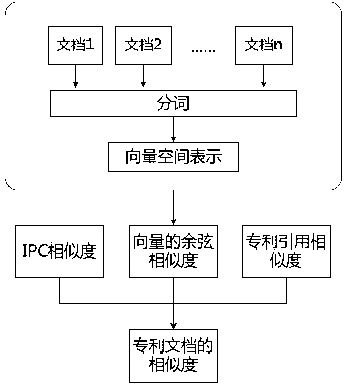
Patent hotspot discovery and trend analysis method
ActiveCN103164540ASolve the problem of low similaritySimple resultSpecial data processing applicationsCurve fittingDegree of similarity
The invention discloses a patent hotspot discovery and trend analysis method. During the discovery process of patent hotspots, firstly, word classification is carried out, similarity among patent documents is calculated, and the patent documents are classified according to the similarity; then phrases of each cluster are combined so that results are more concise and visual; then hotspot techniques are discovered through the hotspot calculation method, and the hotpot degree of each hotspot technique is analyzed; and lastly, curve fitting is carried out according to historical data, a current technical life cycle of one technique is judged by means of a logistic regression curve, and development conditions and potential research value of the technique are further analyzed. Meanwhile, effective trend analysis is carried out on the hotspot techniques, and a development trend of each technique is presented. According to the patent hotspot discovery and trend analysis method, effective information can be discovered from a large amount of precious patent data, and wide practicality and high market value are achieved.
Owner:WUHAN UNIV
Temperature sensor self-testing device and method
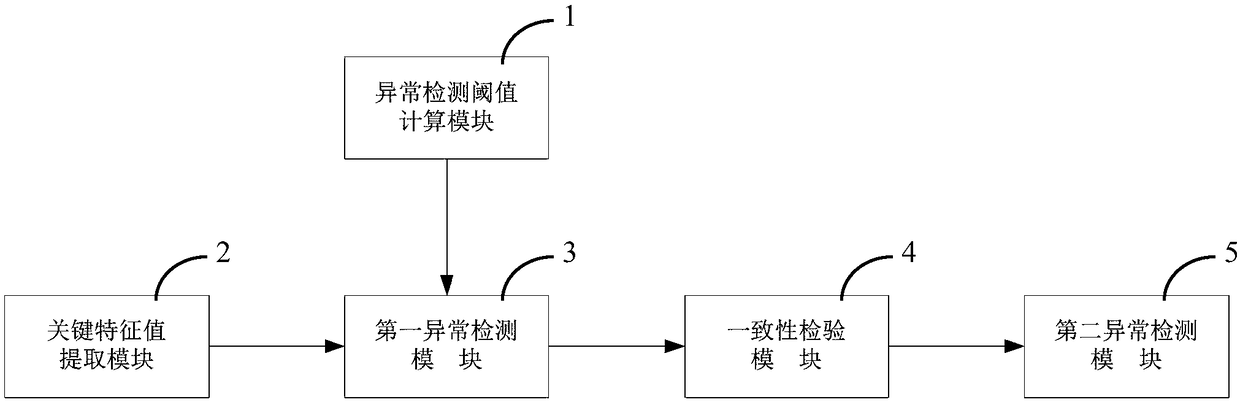
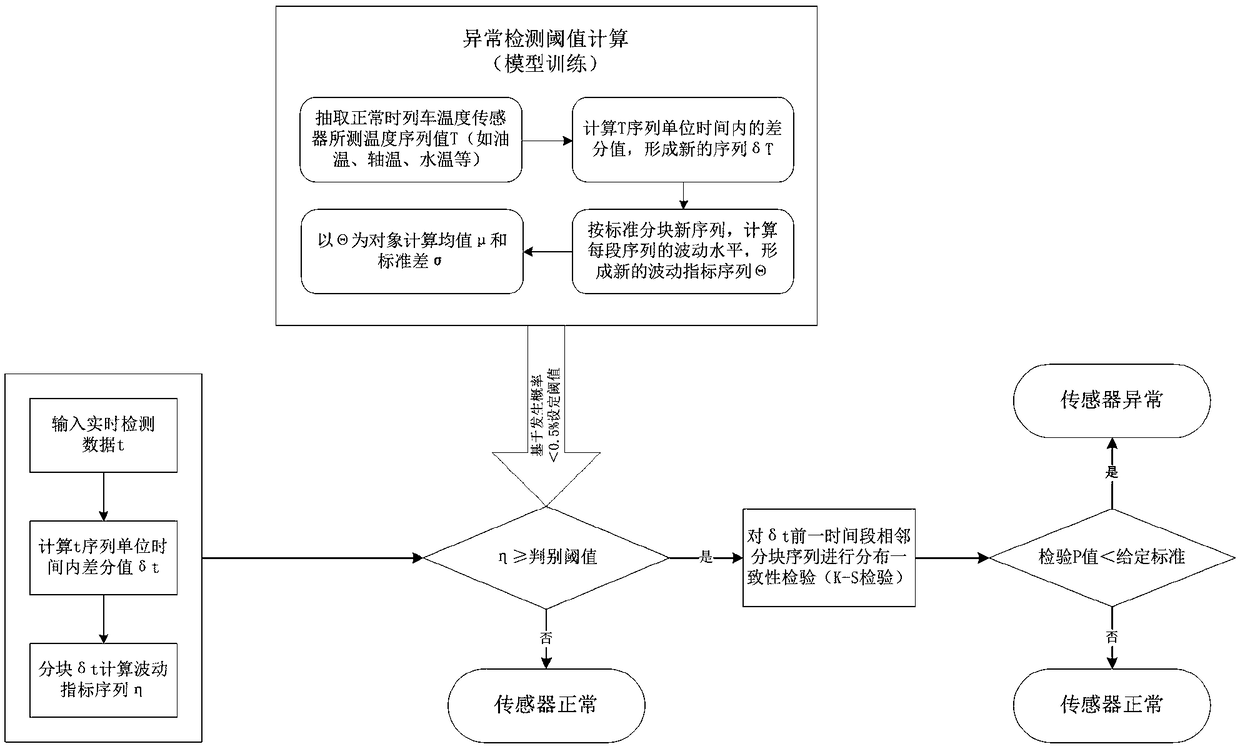
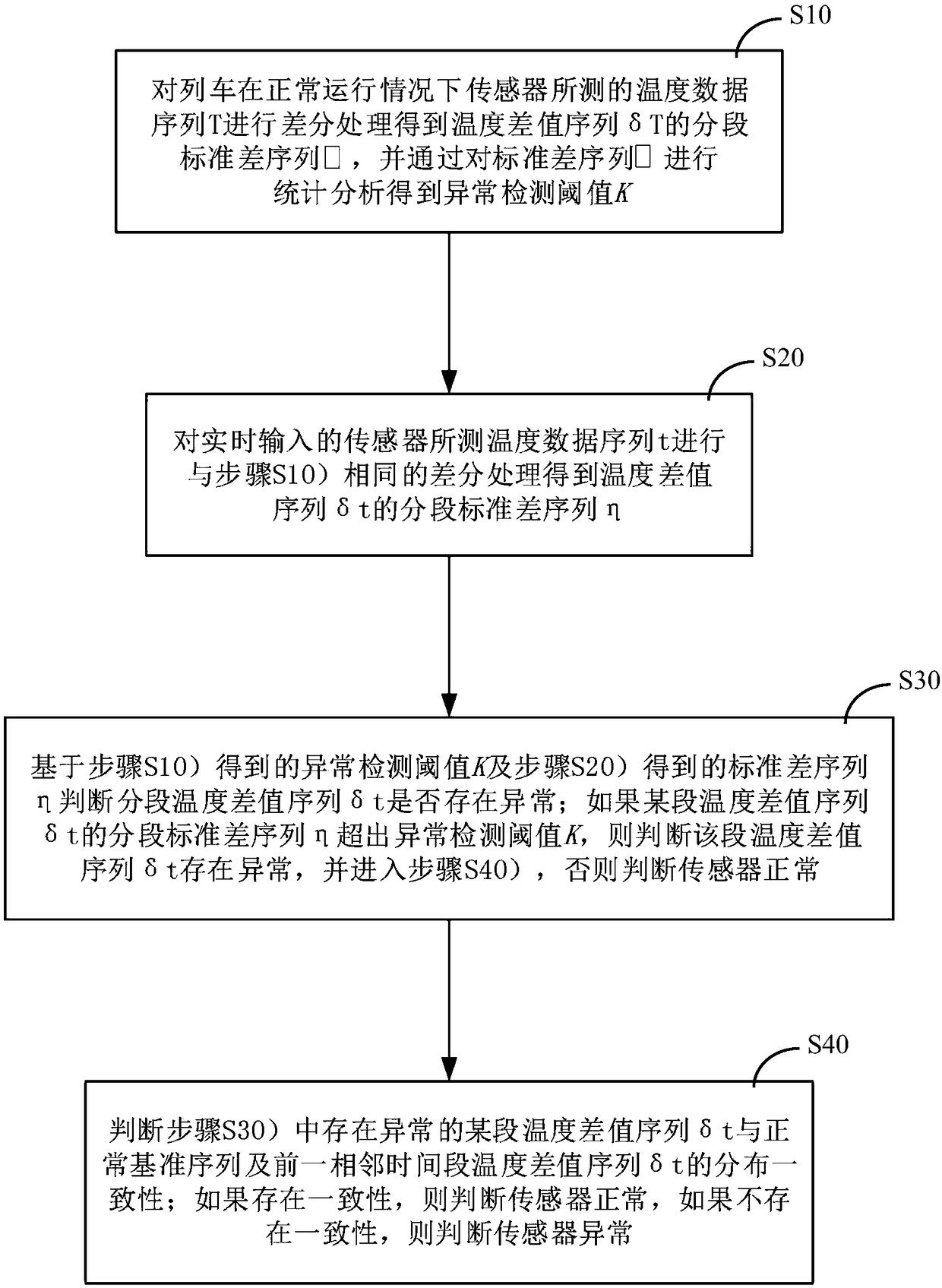
ActiveCN109186813AEfficient discoveryDirect discoveryThermometer testing/calibrationStatistical analysisAnomaly detection
The invention provides a temperature sensor self-testing device and method. The method comprises the following steps: performing differential processing on a temperature data sequence of a train undernormal conditions to obtain a segmented standard deviation sequence, and performing statistical analysis on the standard deviation sequence to obtain an abnormality detection threshold; performing differential processing on a real-time input temperature data sequence to obtain segmented standard deviation sequence; judging whether the segmented standard deviation sequence is abnormal based on thethreshold and the standard deviation sequence; if a certain segment of segmented standard deviation sequence is greater than or equal to the threshold, judging that the segment of temperature deviation sequence is abnormal, and entering the next step, otherwise, indicating that the sensor is normal; judging the distribution consistency between the abnormal certain segment of temperature deviationsequence, a normal reference sequence and the previous adjacent time period of temperature deviation sequence; if the consistency is present, judging that the sensor is normal, otherwise, judging that the sensor is abnormal. By adoption of the temperature sensor self-testing device and method provided by the invention, the technical problems that fast and effect self-testing cannot be performedon the temperature sensor in the prior art, and the safe and efficient running of the train cannot be guaranteed are solved.
Owner:ZHUZHOU CSR TIMES ELECTRIC CO LTD
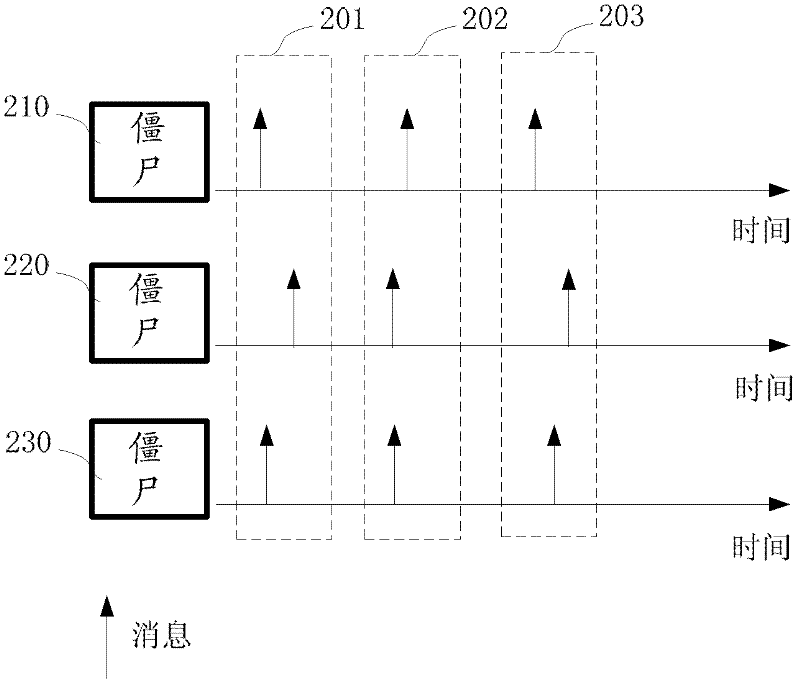
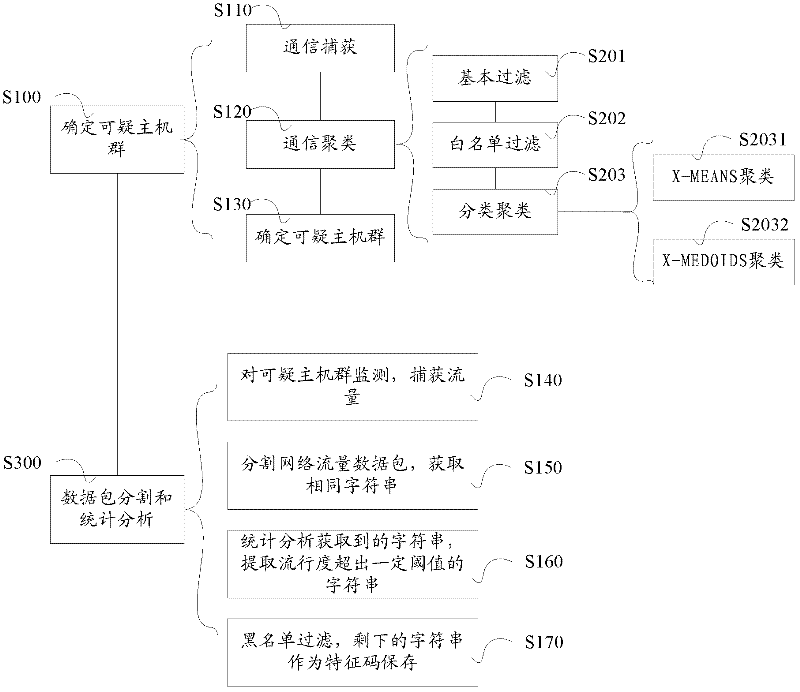
Feature code generation method and detection method of mobile botnet
InactiveCN102333313AReal-time discoveryEfficient discoveryTransmissionSecurity arrangementAlgorithmStatistical analysis
The invention provides a method for generating feature codes of a mobile botnet. The method comprises the following steps: capturing network flow of a suspicious host group; partitioning a network flow data packet based on contents, and obtaining identical character strings; carrying out statistical analysis on the identical character strings, calculating the popularity of the character strings, and extracting the character strings the popularity of which exceeds a certain threshold value; and filtering the character strings the popularity of which exceeds a certain threshold value, excluding the common character strings, and taking the residual character strings as the feature codes. The invention further provides a method for detecting the mobile botnet by the generated feature codes. The method comprises the following steps of: capturing network flow of a host group to be detected, wherein, the network flow is a data packet, the data packet is provided with a packet header and an effective load, and the packet header and the effective load are a series of character strings; matching the character strings by virtue of the feature codes; determining the successfully matched flow as a bot program for a mobile phone, and recording information; and discharging the unsuccessfully matched flow.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
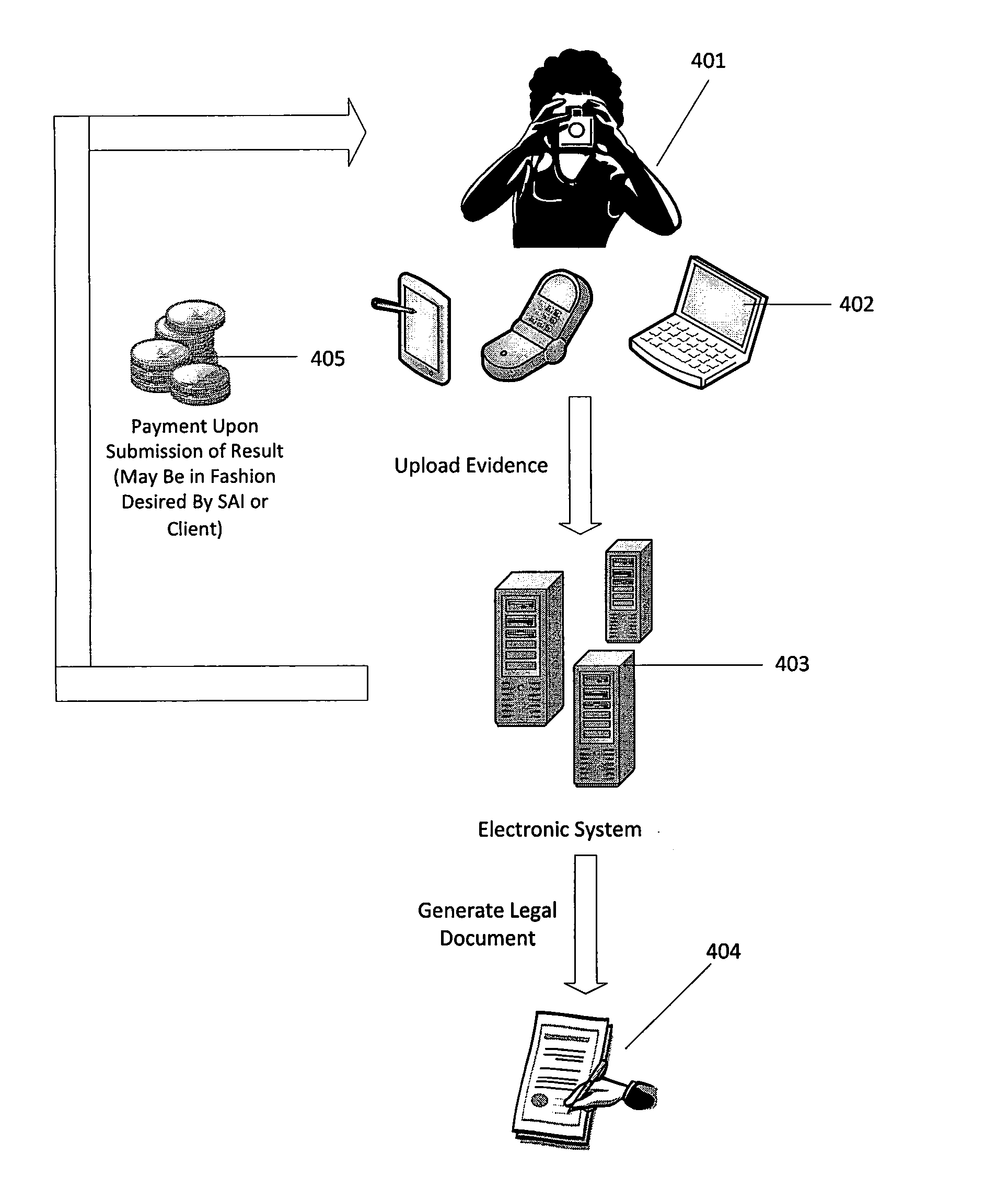
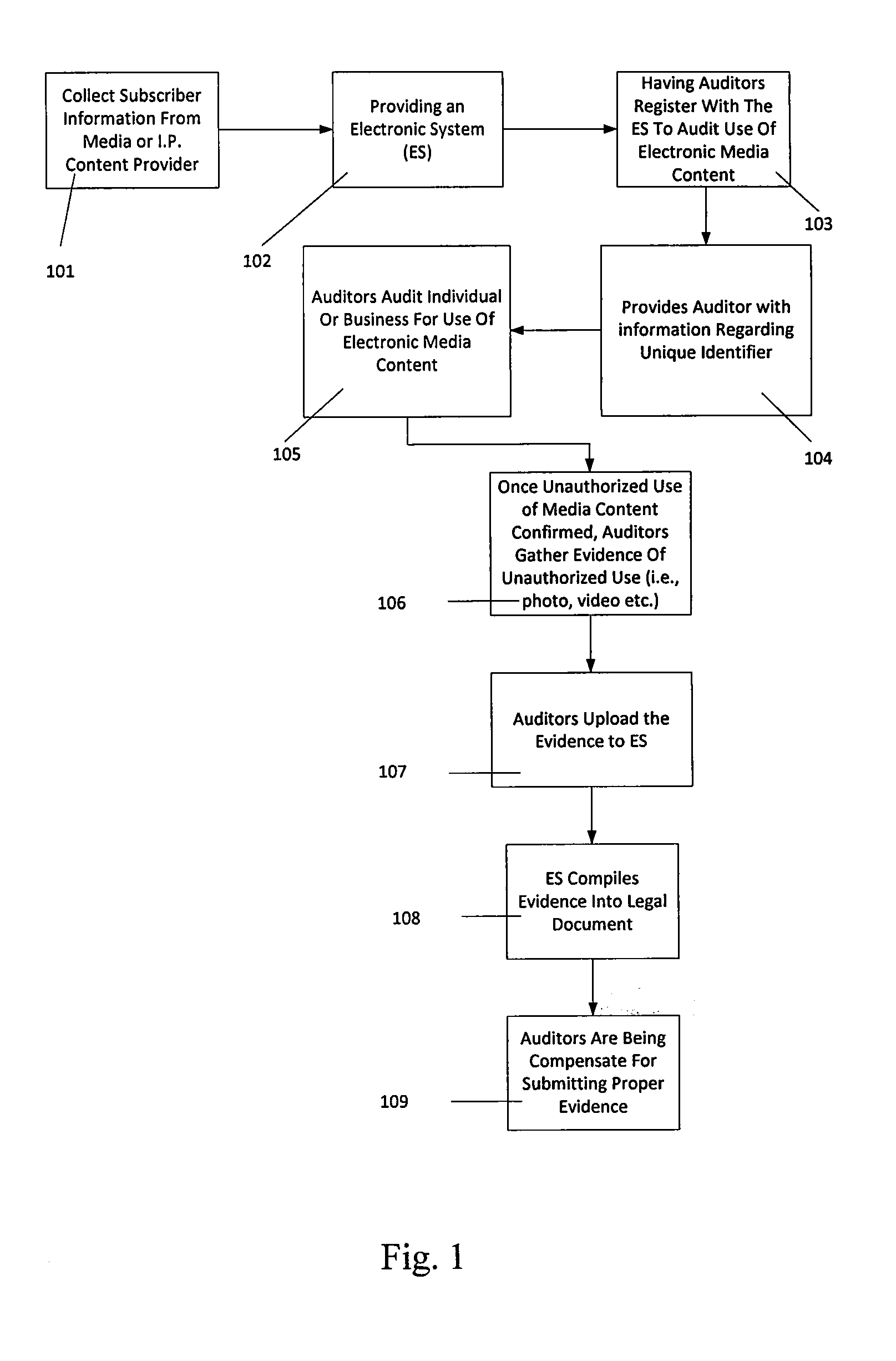
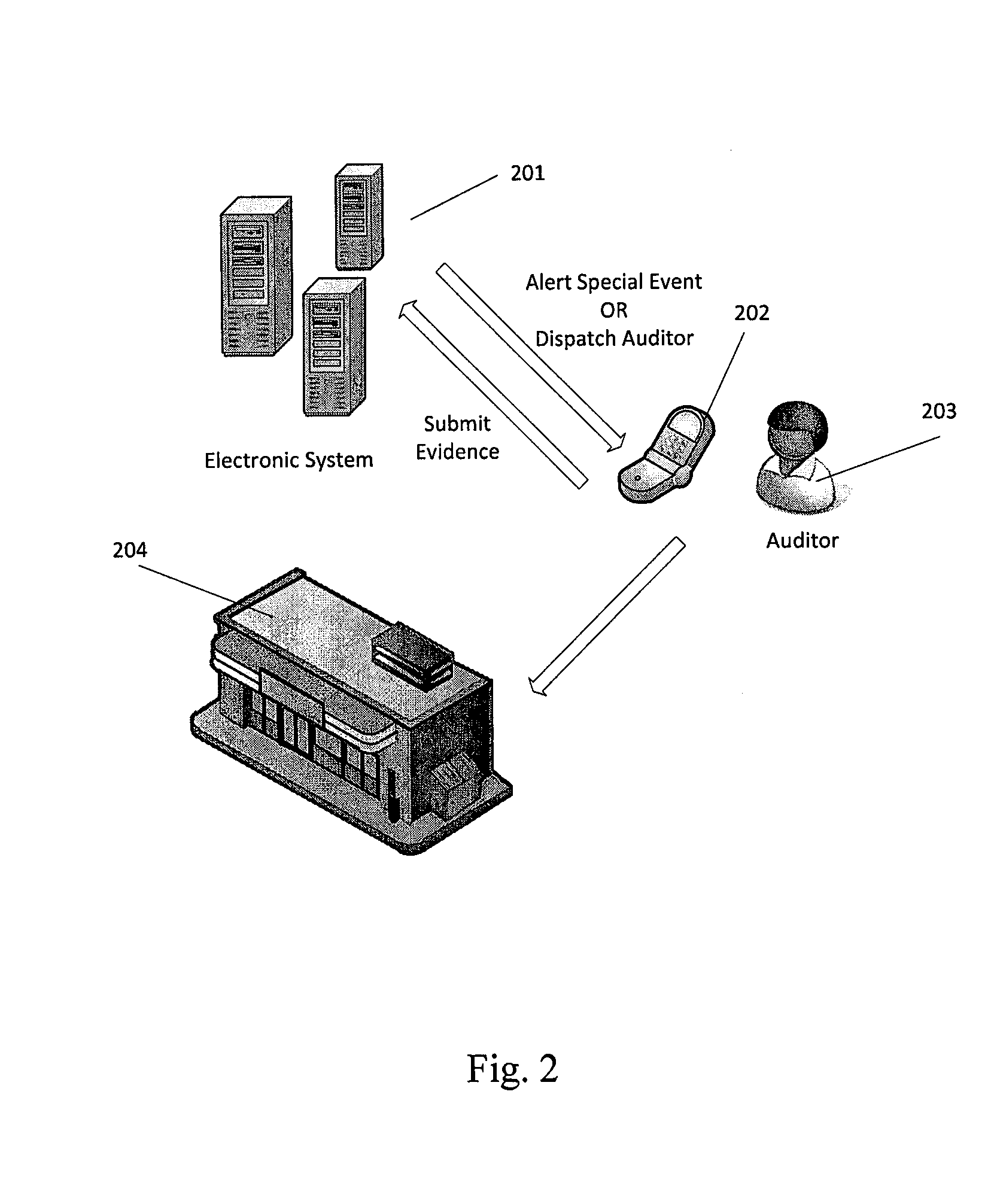
Methods and systems for detecting, verifying, preventing and correcting or resolving unauthorized use of electronic media content
ActiveUS20140283123A1Efficient discoveryUnauthorized useData processing applicationsDigital data processing detailsElectronic systemsIntellectual property
A method of detecting, verifying, preventing and correcting or resolving unauthorized use of electronic media content. In one embodiment, the method comprises providing an electronic system that allows auditors to register to audit the use of electronic media content, providing the auditors with information through the electronic system regarding a unique identifier that identifies one or more items of electronic media content, owners of electronic media content or other intellectual property or users who have subscribed to the use of electronic media content, obtaining information from auditors through the electronic system regarding unauthorized use of the electronic media content and verifying that the information received from auditors is complete.
Owner:LONSTEIN WAYNE D +1
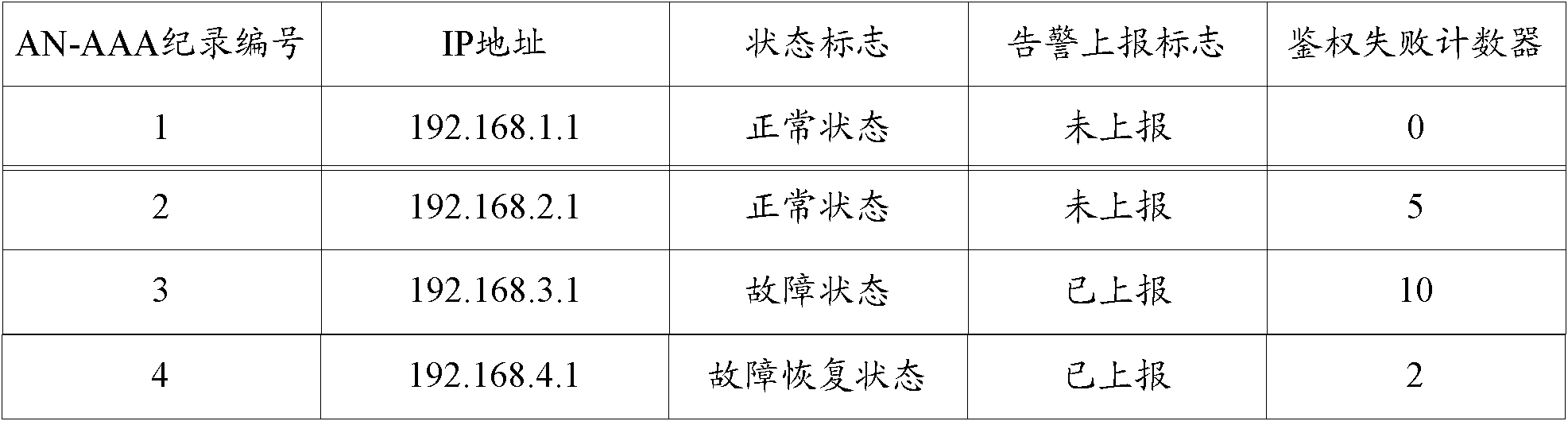
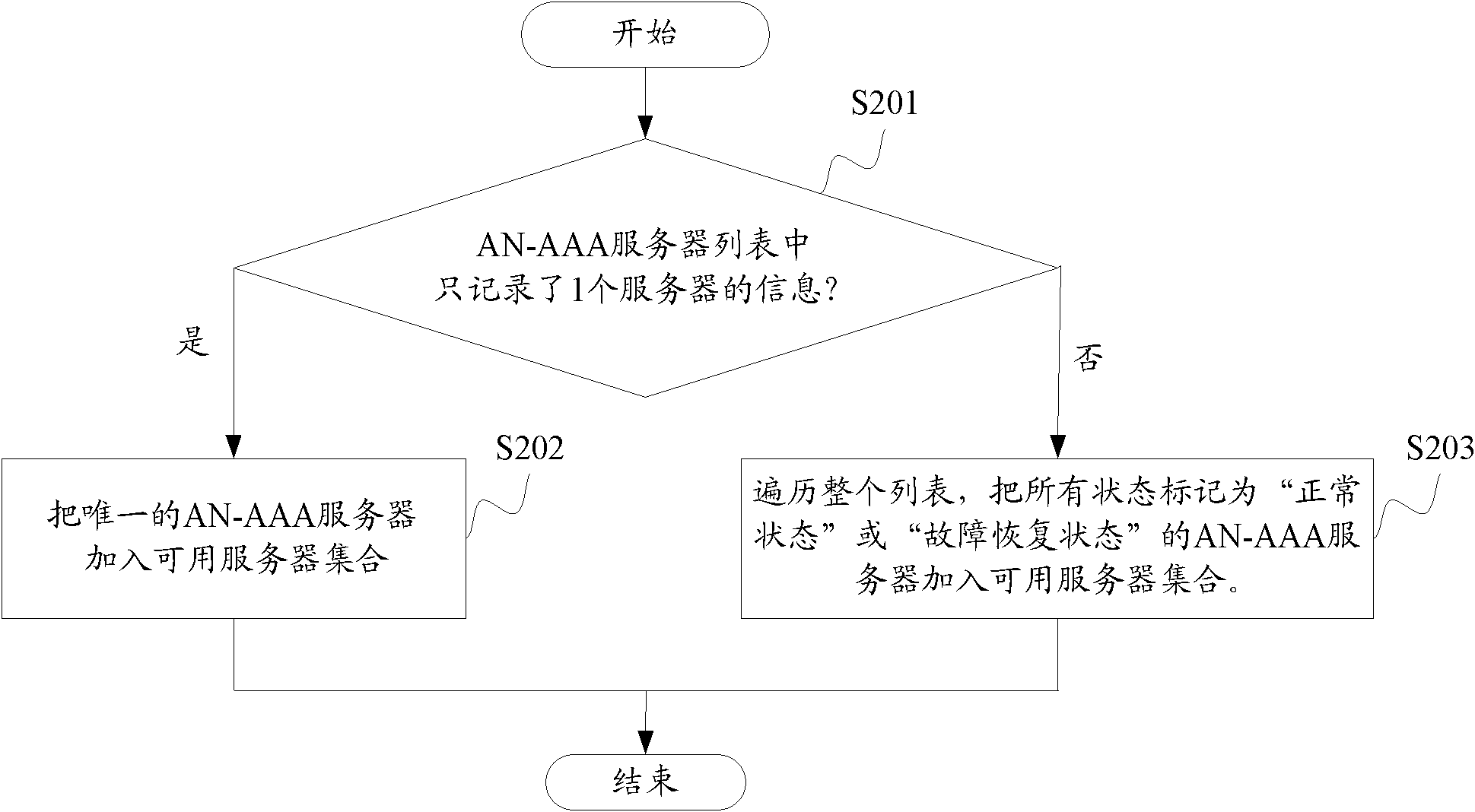
Method and device for detecting server state
ActiveCN102075380AAvoid misjudgmentFailure is timely and effectiveData switching networksTimerNormal state
The invention discloses a method and a device for detecting a server state, which are used for realizing the server state detection by using actual services, making the detected server state more accurate on the premise of effectively determining the server state in time and avoiding misjudgment caused by link flash. The server state detecting method provided by the invention comprises the following steps of: determining a server in the normal state to which the current authentication request message is required to send, sending the authentication request to the server, starting a failure detection timer corresponding to the server when the authentication request fails, and counting the times of continuous failure of the authentication request sent to the server through an authentication request failure counter corresponding to the server, wherein the authentication request failure counter is reset when a response message fed back by the server is received; and the server state is upgraded into the failure state when the failure detection timer is overtime and the counting value of the authentication request failure counter exceeds the preset first threshold value.
Owner:ZTE CORP
Personalized discovery of services
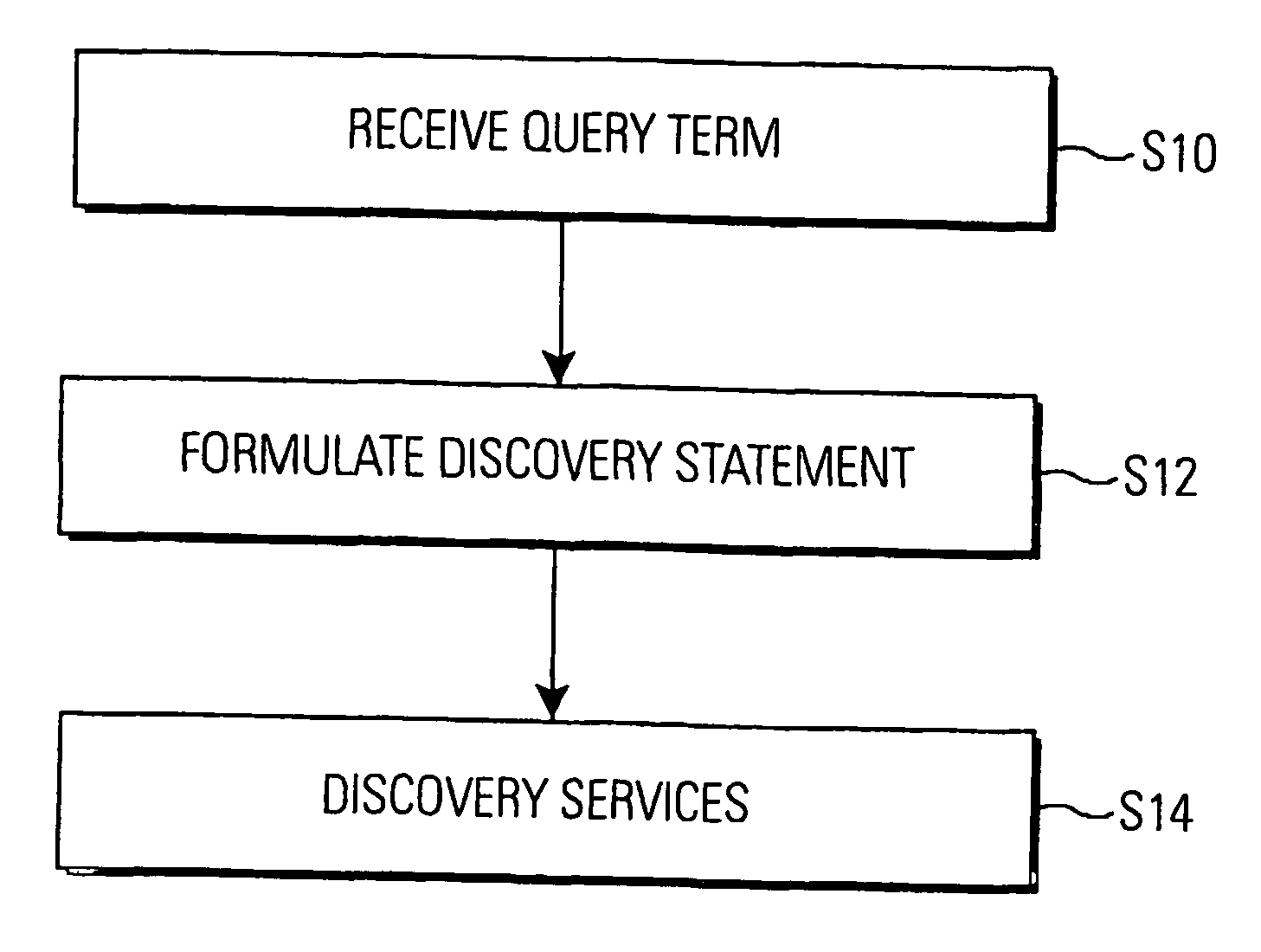
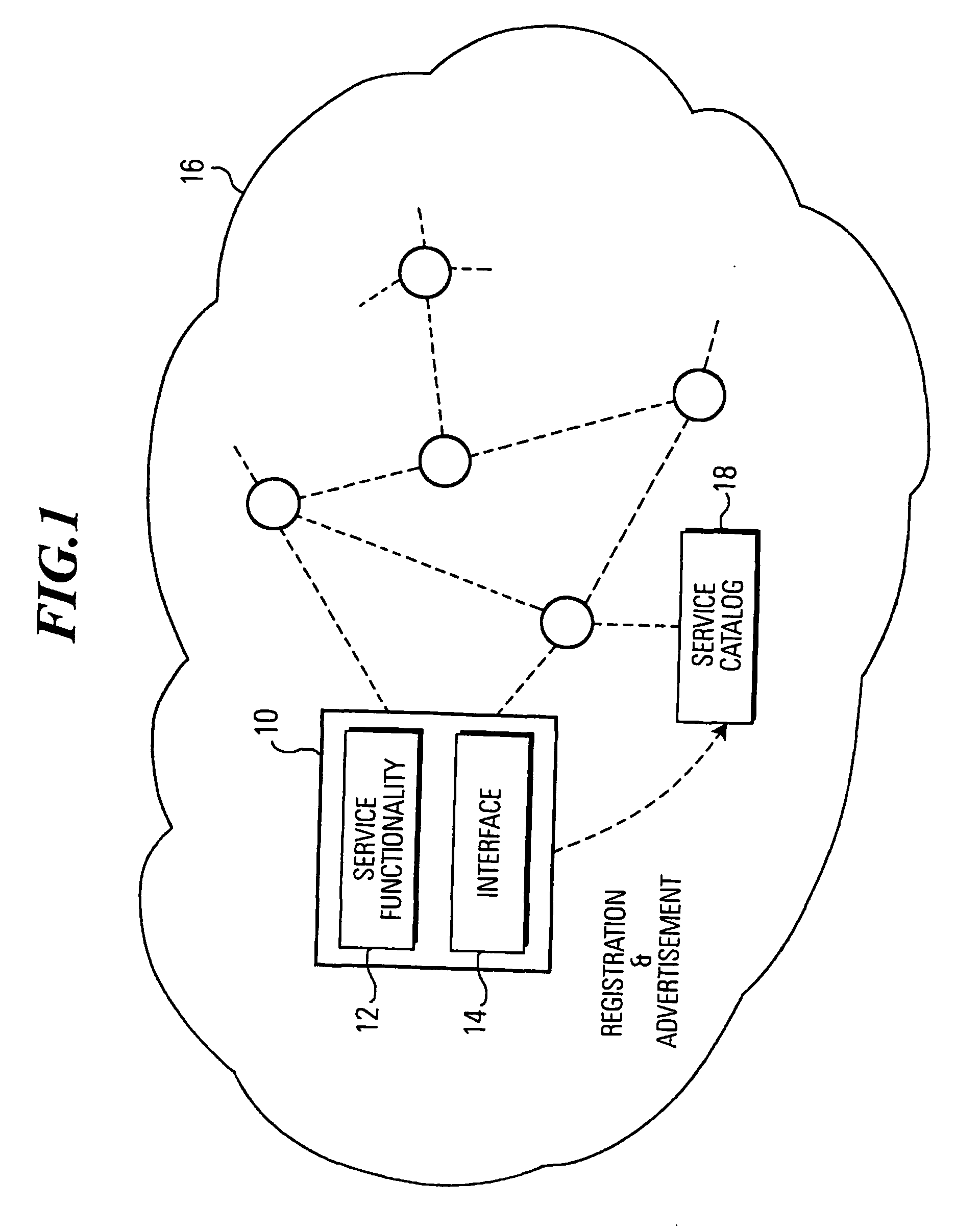
InactiveUS20070033261A1Enhanced interactionReduce in quantityMultiple digital computer combinationsWebsite content managementPersonalizationCommunications system
A method of discovering at least one service being advertised in a communication system using at least one service ontology describing service characteristics with service attributes supports user-centered and personalized discovery of services. A discovery statement is formulated as a function of the query term and services with service attributes matching the discovery statement are discovered using the structure implied by the service ontology.
Owner:NTT DOCOMO INC
Device for preventing myopia and cervical spondylosis
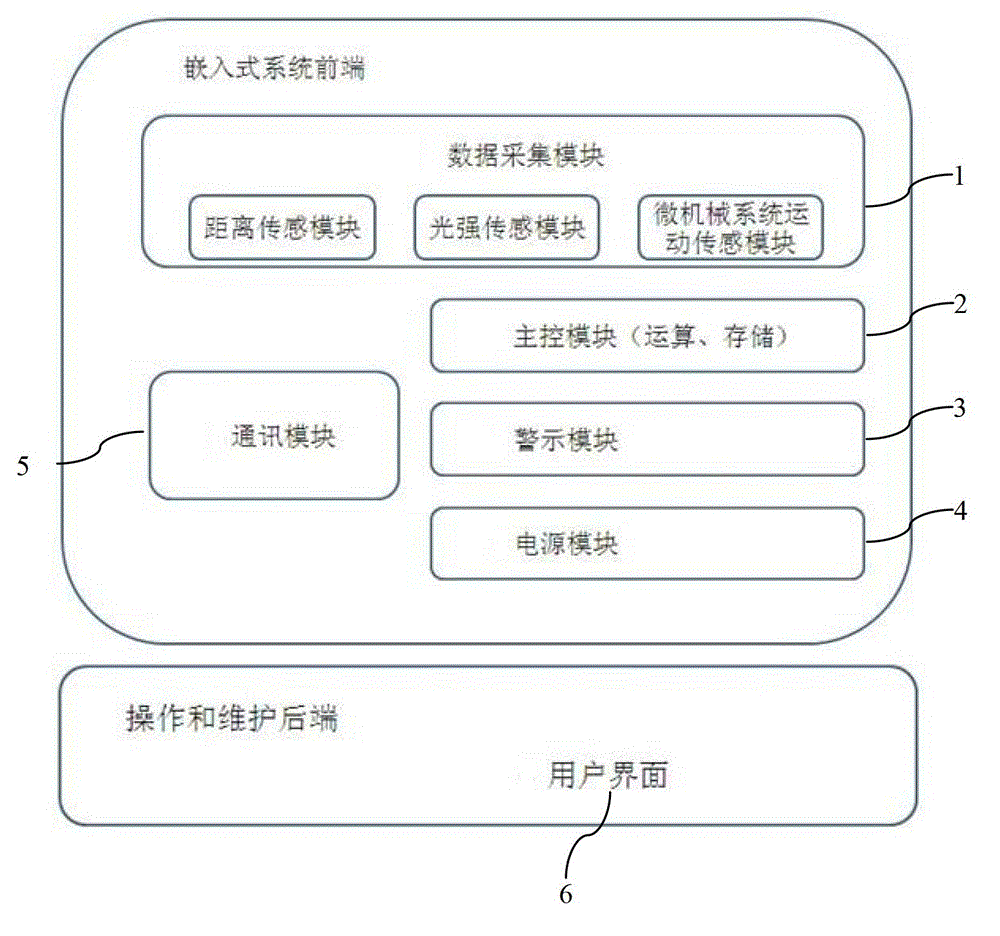
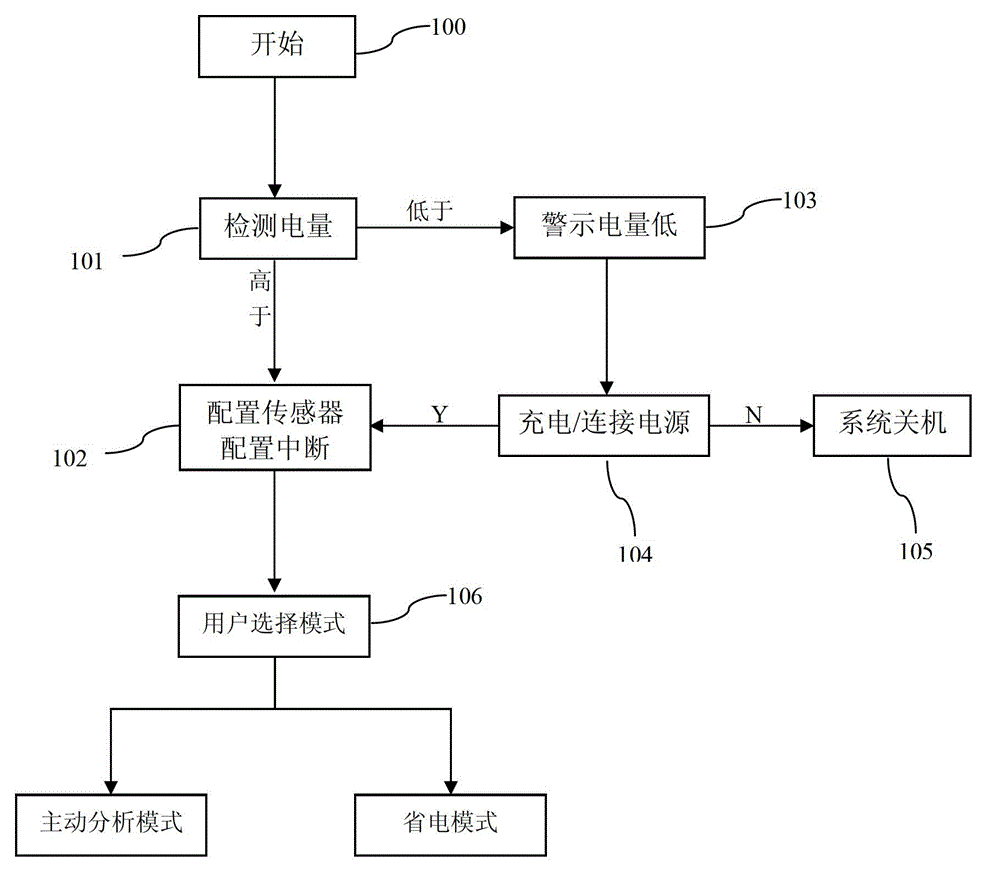
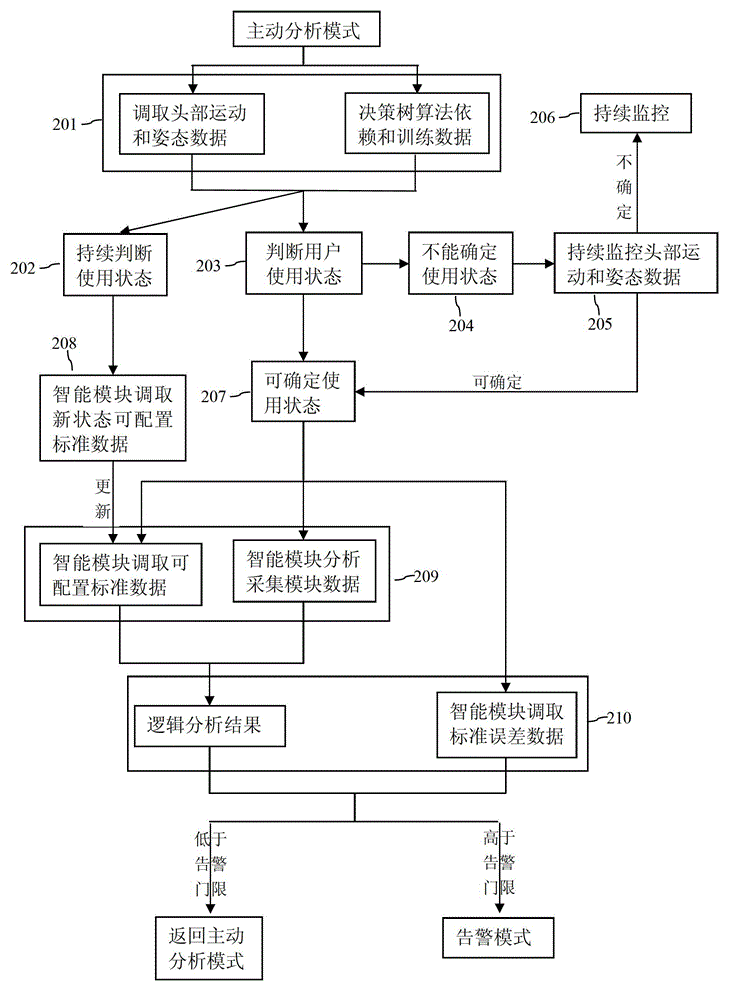
InactiveCN102973276APrevent myopiaPrevent cervical spondylosisMedical automated diagnosisDiagnostic recording/measuringCervical spondylosisComputer module
The invention discloses a device for preventing myopia and cervical spondylosis, which comprises a data acquisition module (1), a main control module (2), a warning module (3) and a power module (4), wherein the data acquisition module (1) is connected with the main control module (2); the main control module (2) is connected with the warning module (3); the power module (4) is used for supplying power and managing charging for the device; each module receives and sends data or instructions through a data bus; and the main control module (2) determines the using state of a user by processing the data acquired by the acquisition module and the dependence and training data of a posture and motion decision tree algorithm. The device determines whether to give a warning or not by performing logic operation on different configurable standard data and the acquired data in different using states. The device not only can judge the using state of the user, but also adjusts the standard parameter for warning according to different using state of the user, so that the false warning rate is low; and in addition, the device can further realize different functions according to the choice of the user so as to be wide in application range.
Owner:毛毅翔
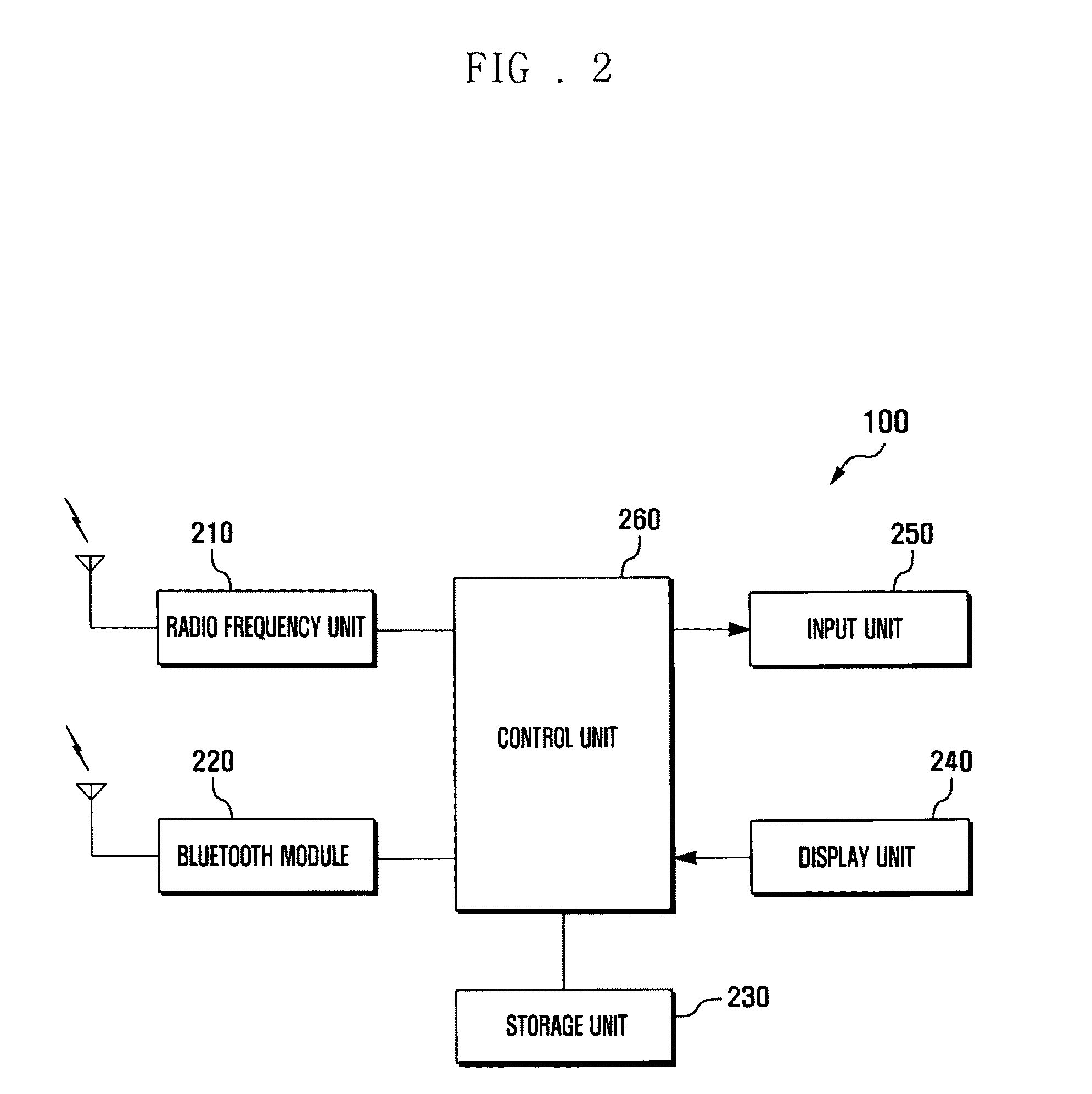
Method for searching and connecting bluetooth devices and apparatus using the same
ActiveUS20100190440A1Efficient discoveryEffective blockingNetwork topologiesDevices with bluetooth interfacesBluetoothDevice name
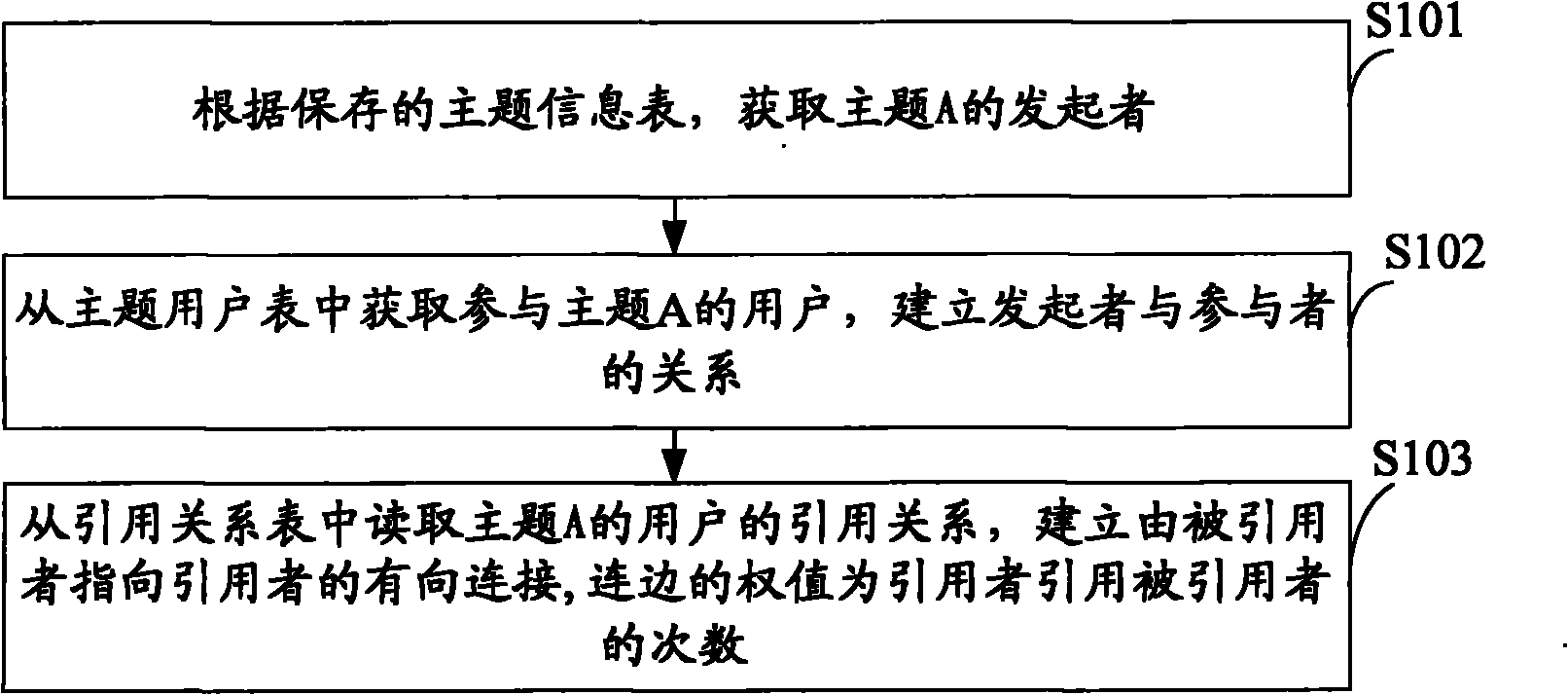
A Bluetooth master device is capable of performing search and connection method for Bluetooth devices. The Bluetooth master device receives device information from at least one Bluetooth device in response to a Bluetooth device search request made by a user. A responding Bluetooth device that is capable of providing a Bluetooth service in a preset service list is selected. The Bluetooth master device sends a name request signal to the selected Bluetooth device and displays a device name received from the selected Bluetooth device.
Owner:SAMSUNG ELECTRONICS CO LTD
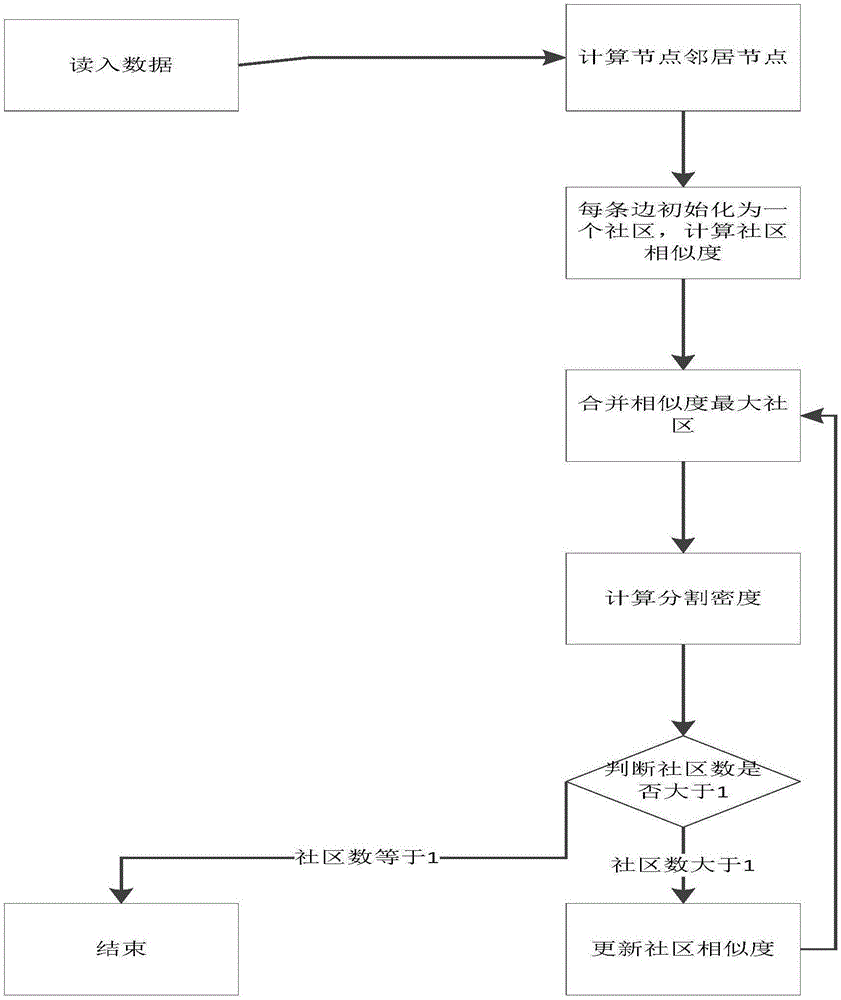
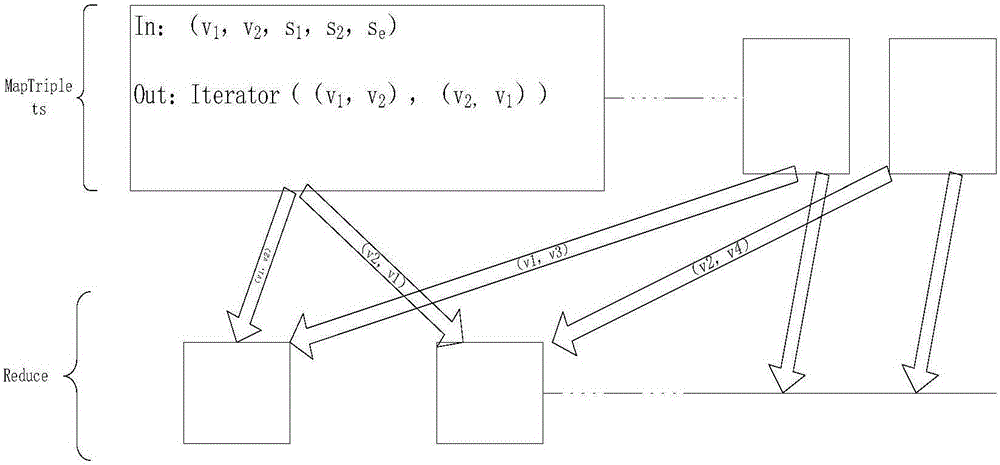
Overlapping community parallel discovery method of memory iteration on basis of spark platform
InactiveCN105069039ASolve Computational BottlenecksHigh speedWebsite content managementSpecial data processing applicationsNODALAlgorithm
The invention discloses an overlapping community parallel discovery method of memory iteration on the basis of a spark platform. The method comprises the following steps of: reading original community network data via GraphX on a calculation cluster configured with spark environment, and building a graph instance; parallelly calculating a neighbor node set of each vertex in the graph instance through the GraphX, and using the neighbor node set as the attribute of each vertex in the graph instance; initializing each edge of the graph instance as one community, and calculating the similarity between every two edges with a common vertex in the graph instance according to the neighbor node sets of the graph instance; finding two communities with the maximum similarity, and merging the two communities into one new community; updating the community similarity set; using a division density formula to calculate the division quality of the community division in the current time; judging whether the current community number is greater than 1 or equal to 1; and obtaining the community division with the highest division quality if the current community number is equal to 1.
Owner:SHANDONG UNIV +1
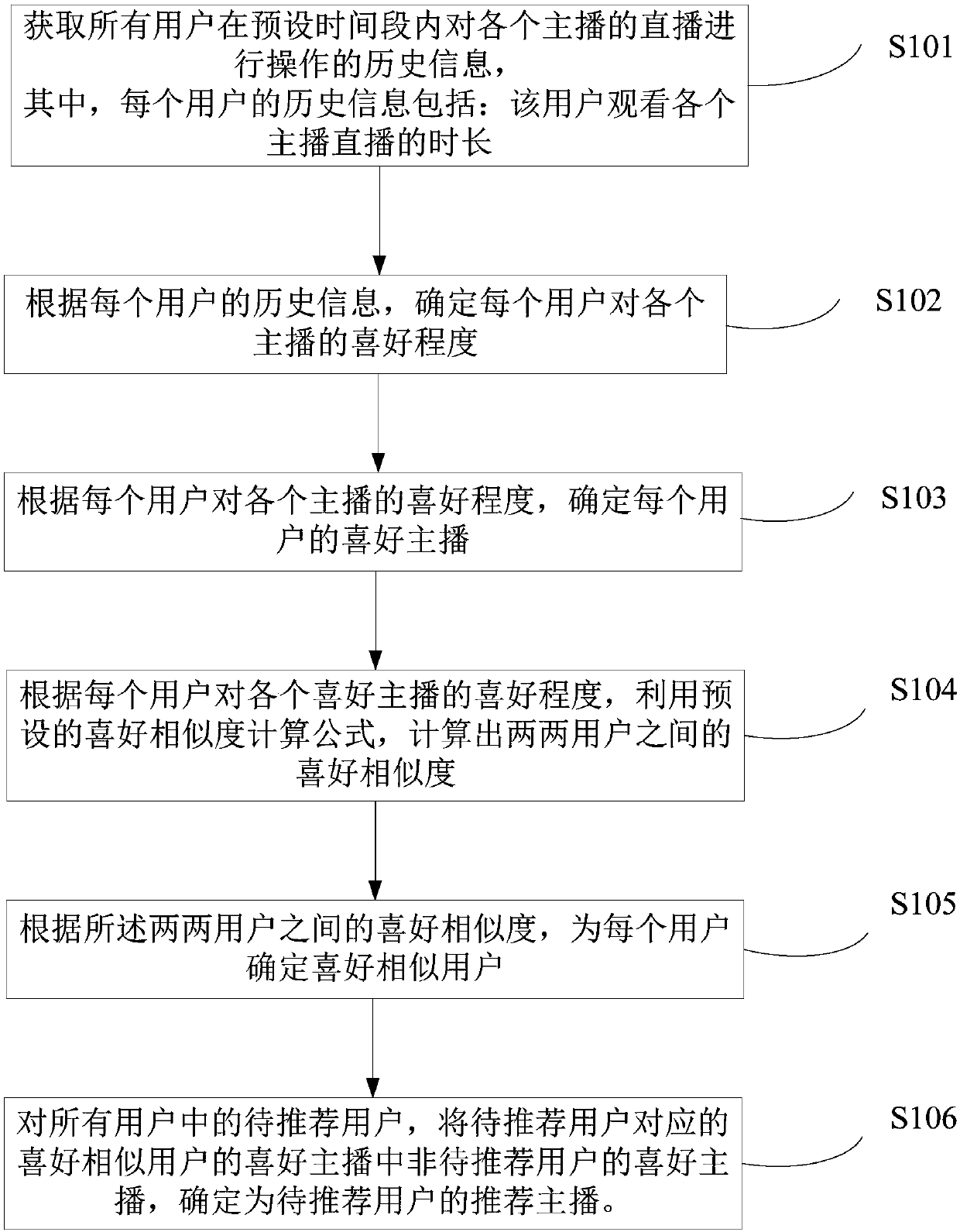
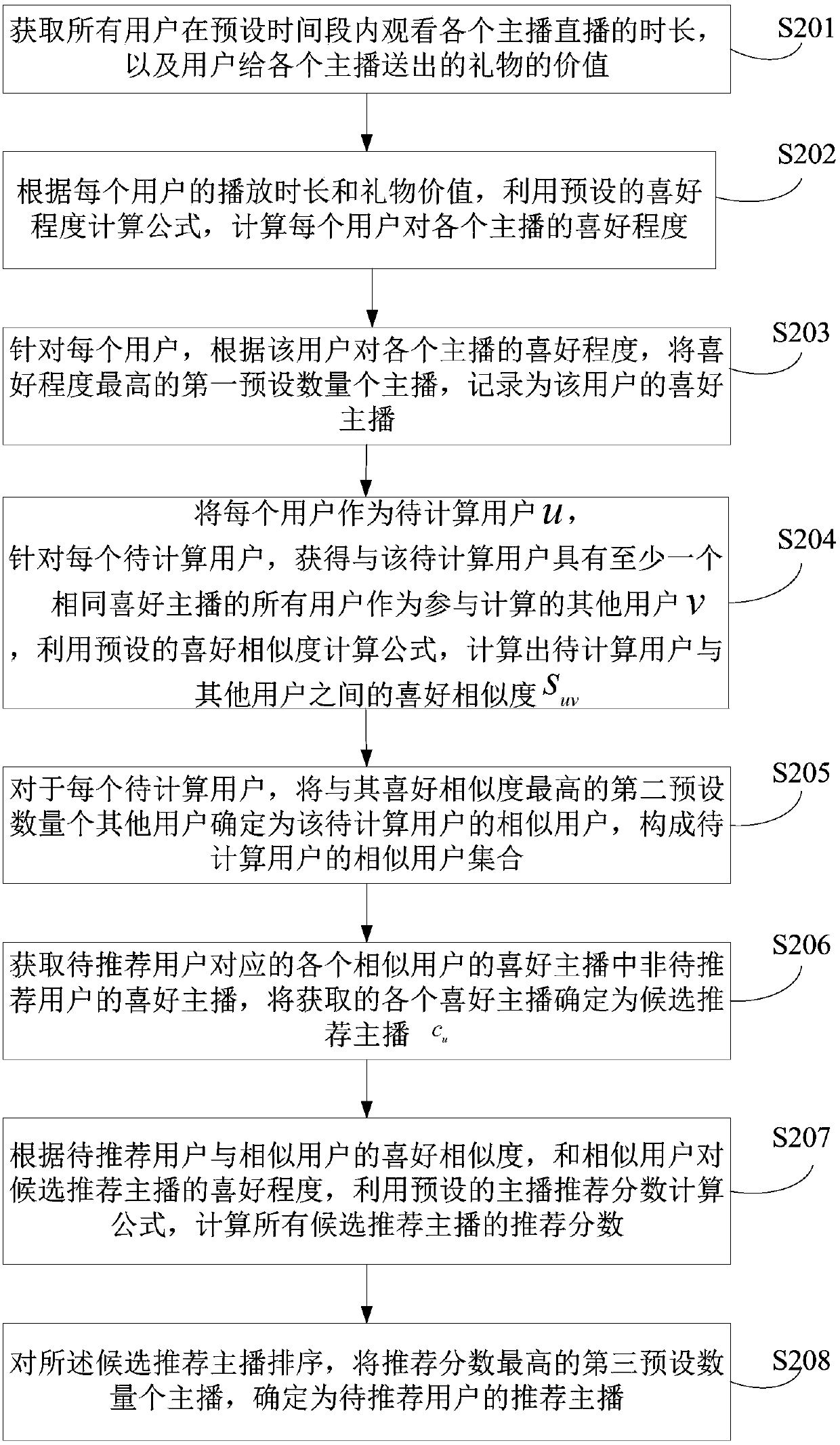
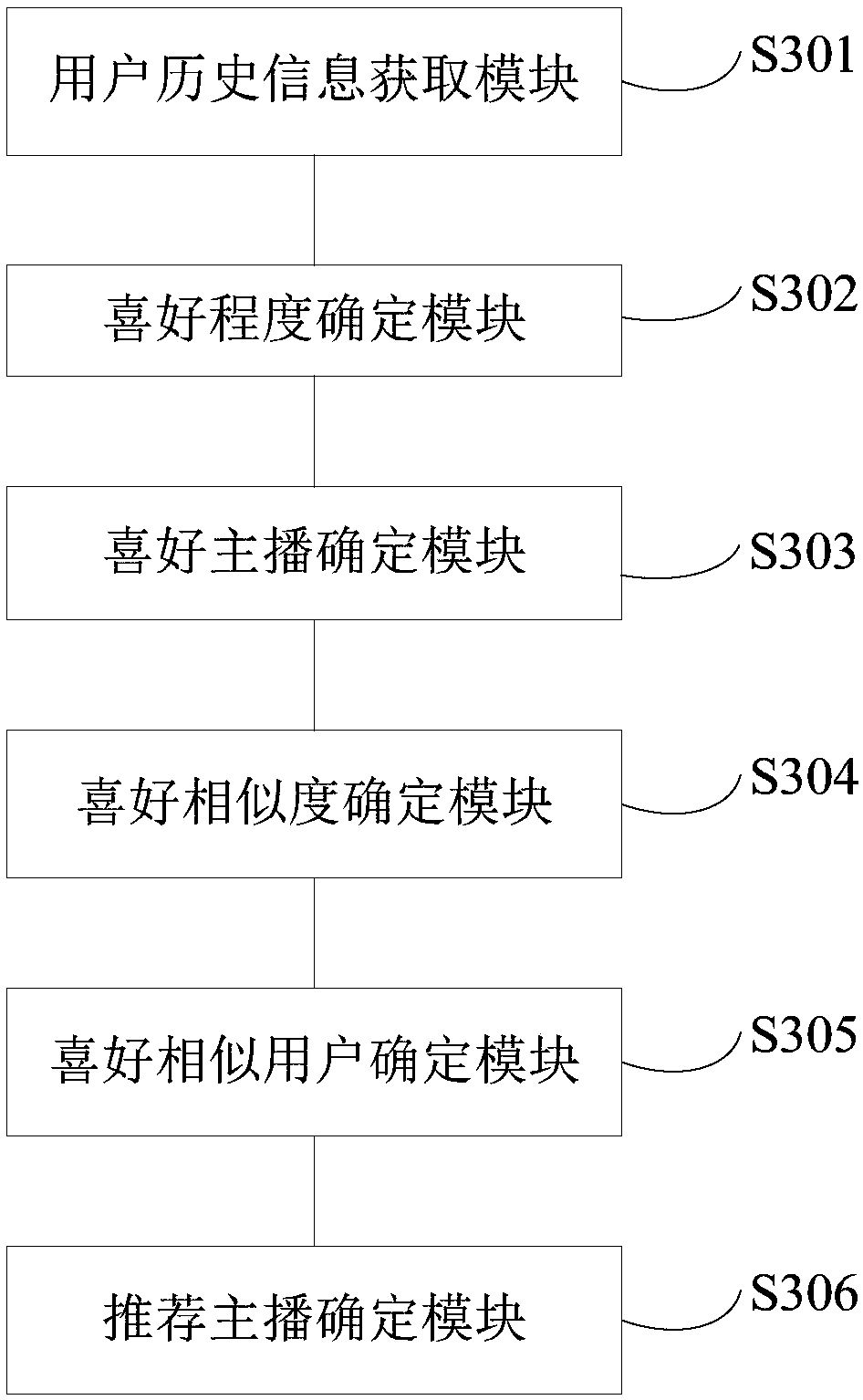
Personalized anchor recommendation method and apparatus, and electronic device
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
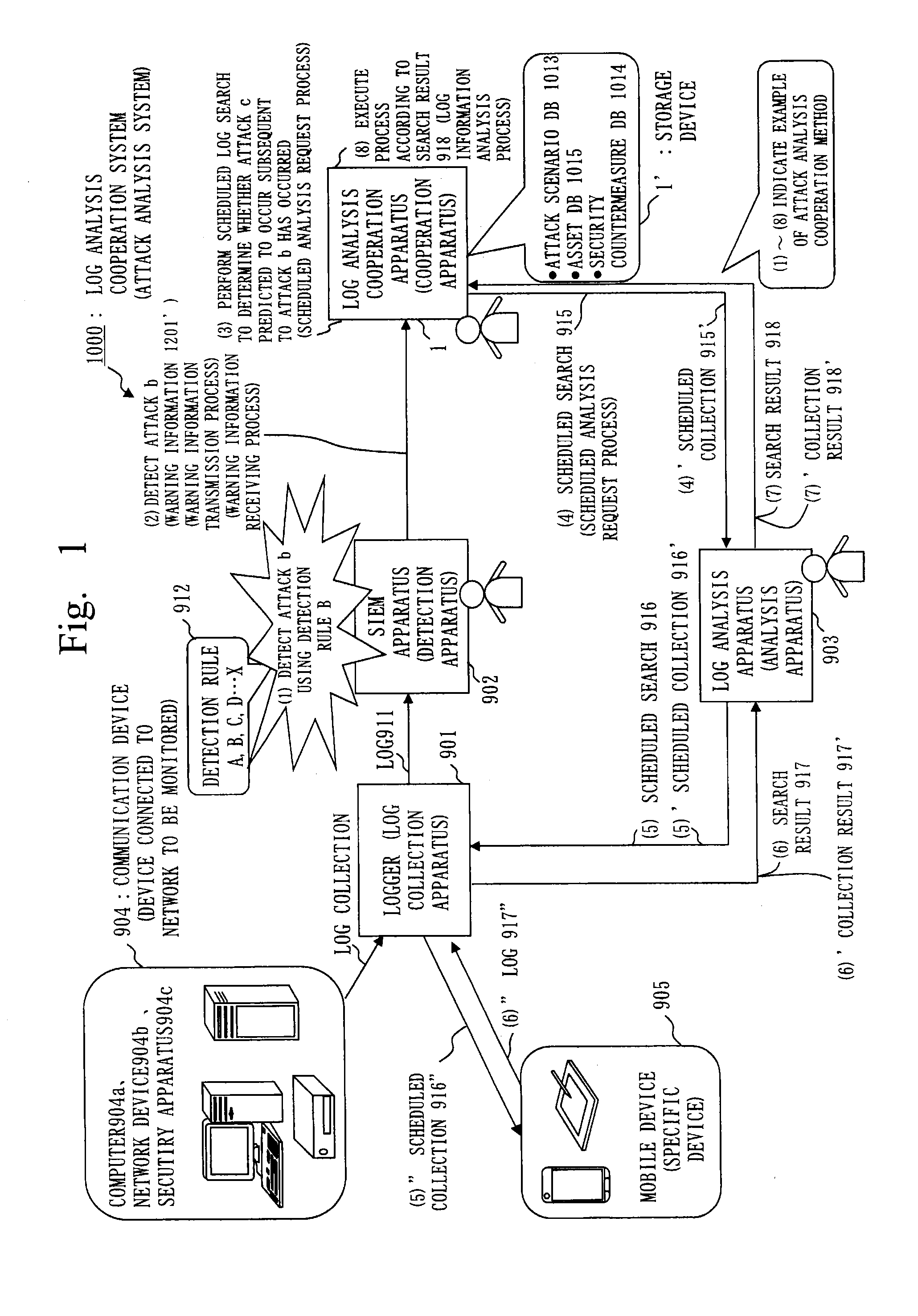
Attack analysis system, cooperation apparatus, attack analysis cooperation method, and program
ActiveUS20150256554A1Efficient discoveryMemory loss protectionUnauthorized memory use protectionAttack analysisData mining
In a log analysis cooperation system including a logger that collects a log of a communication device and stores the log in a storage device, a SIEM apparatus that detects an attack, and a log analysis apparatus that analyzes the log collected by the logger, a log analysis cooperation apparatus stores an attack scenario in a storage device, receives from the SIEM apparatus warning information including information on the detected attack, computes a predicted occurrence time of an attack predicted to occur subsequent to the detected attack based on the warning information and the attack scenario, and transmits to the log analysis apparatus a scheduled search to search the log at predicted occurrence time computed. The log analysis apparatus transmits a scheduled search to the logger to search the log at the predicted occurrence time.
Owner:MITSUBISHI ELECTRIC CORP
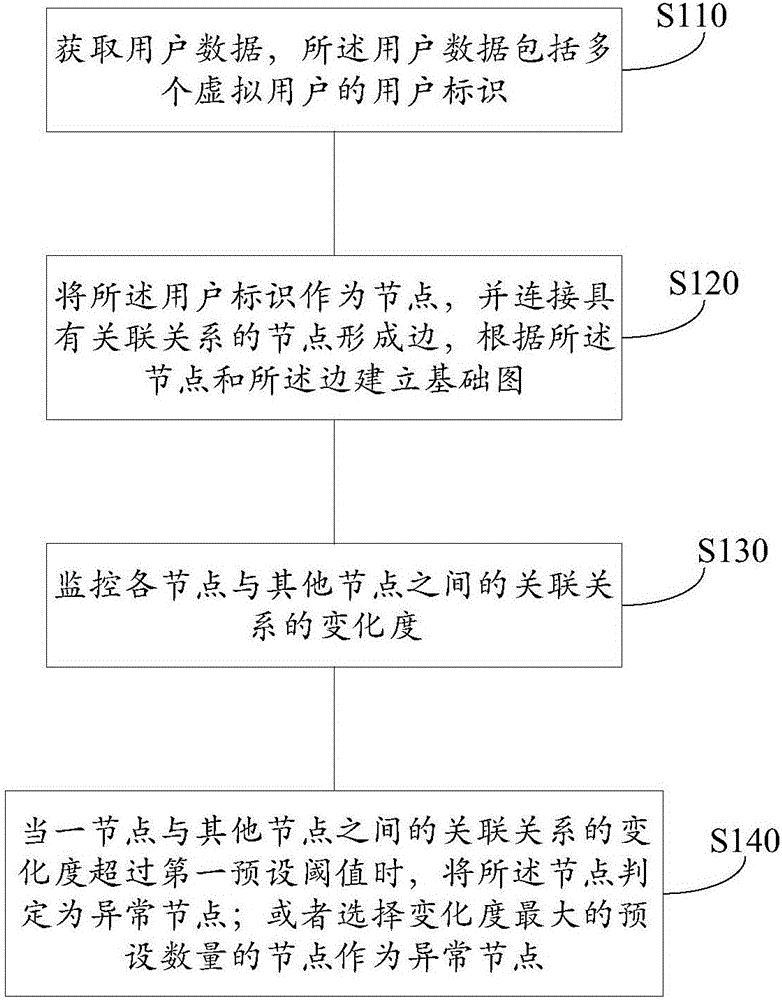
Method and device for monitoring change of node and auxiliarily identifying blacklist as well as electronic device
ActiveCN106850346AMonitor changesMonitor abnormally changed nodesFinanceData switching networksVirtual userComputer science
Owner:JINGDONG TECH HLDG CO LTD
Smart city heterogeneous data sharing method based on meta model
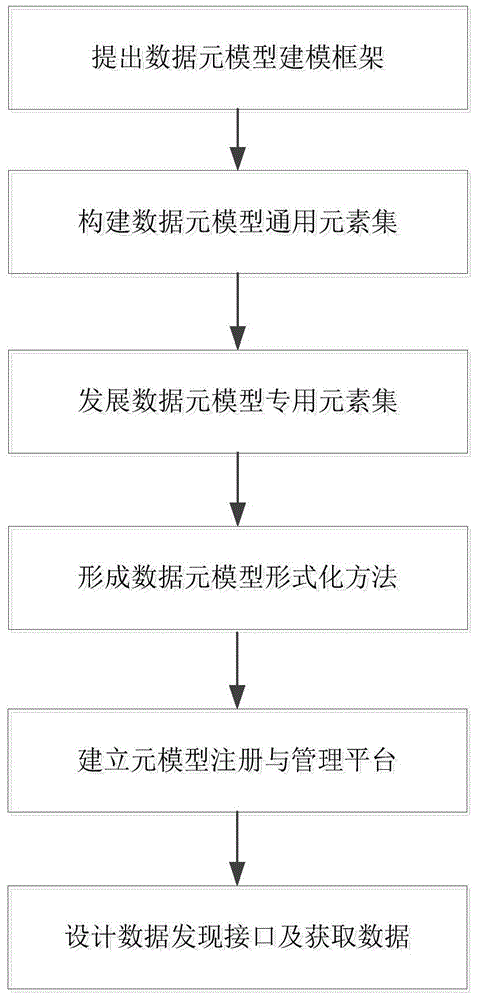
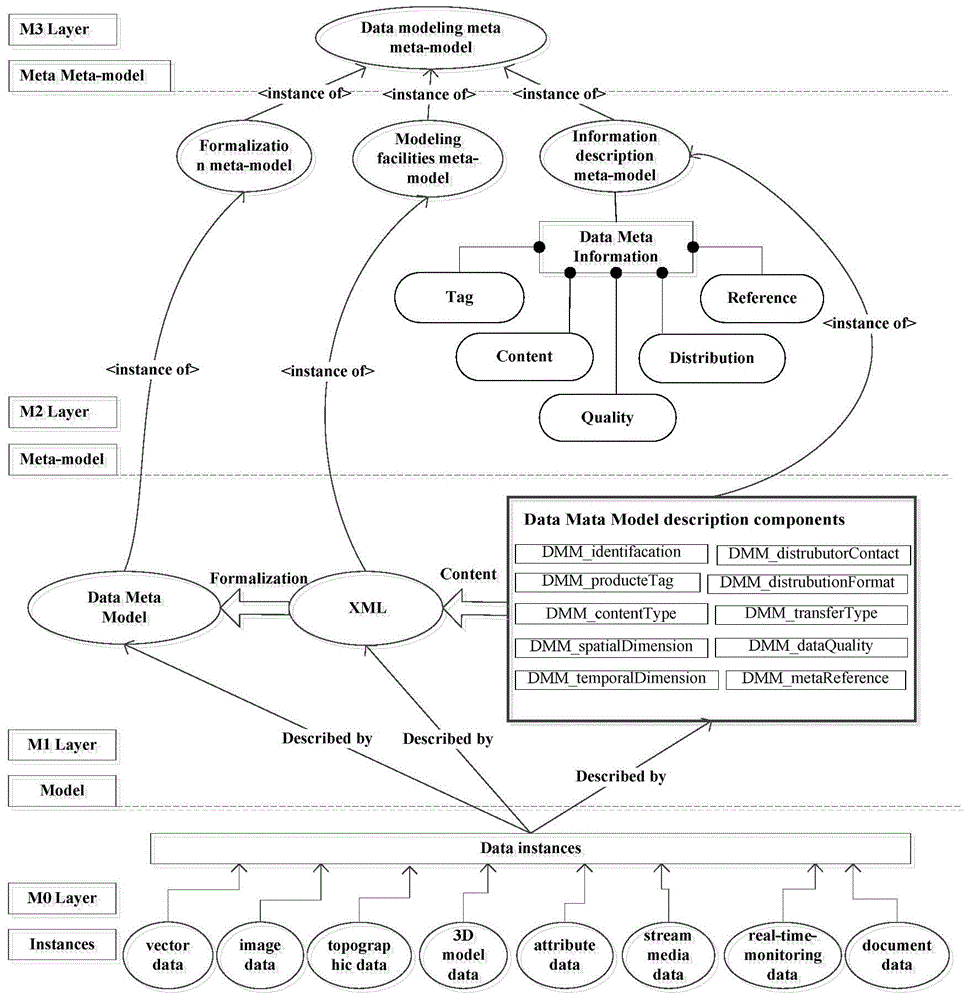
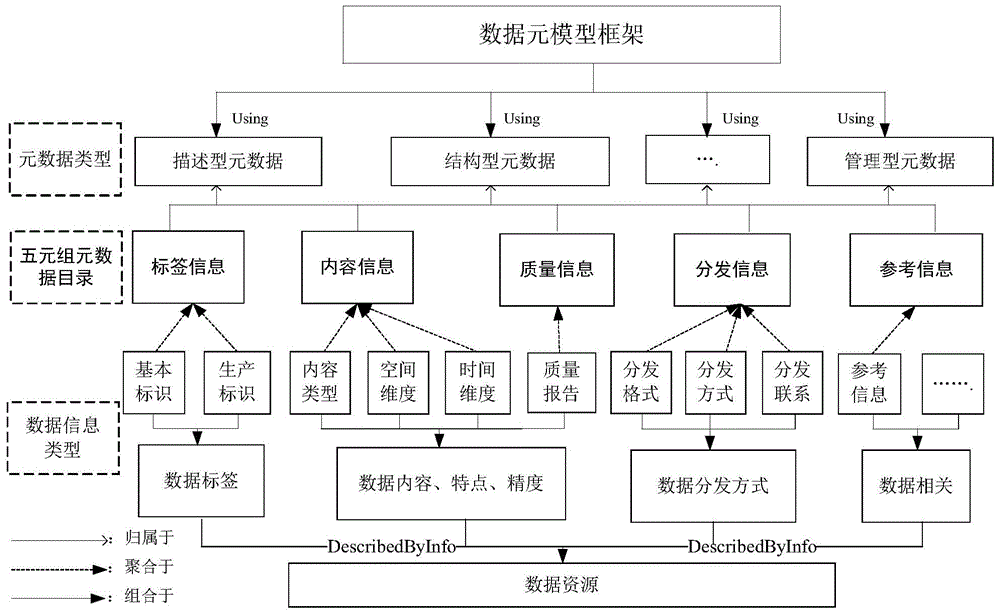
ActiveCN104462244AAchieving a unified and comprehensive descriptionEasy to shareDatabase management systemsSpecial data processing applicationsIntelligent cityMetamodeling
The invention discloses a smart city heterogeneous data sharing method based on a meta model. The smart city heterogeneous data sharing method based on the meta model comprises the first step of establishing a city data meta model modeling frame according to the MOF meta modeling theory, the second step of establishing a city data meta model universal element set according to city data characteristics and description requirements, the third step of developing a data meta model special element set according to city data basic classification and a special element set expansion mode, the fourth step of forming a meta model universal element set and special element set formalization method on the basis of XML template modeling, the fifth step of achieving network directory services and data services and establishing an open city data meta model registering and managing platform, and the sixth step of designing a city data fine granularity discovery interface and obtaining data according to practical application requirements of users. According to the smart city heterogeneous data sharing method based on the meta model, an open and standard city heterogeneous data sharing solution is provided for users, support is provided for city heterogeneous data online access, follow-up processing and collaborative application, and the method is efficient, practical and reliable during city heterogeneous data sharing.
Owner:WUHAN UNIV
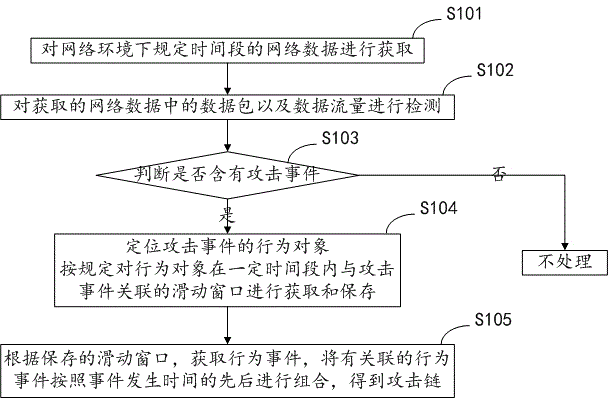
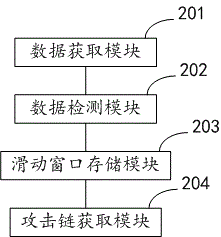
Attack chain obtaining method and system in network environment
The invention brings forward an attack chain obtaining method and system in a network environment. According to a specified time period, network data is obtained, whether the obtained network data includes an attack event is detected, if the attack event is included, active window data associated with the attack event within a period before and after the time when the attack event takes place is obtained and stored at an attack end or a victim end, according to the active window data, an attack chain is obtained, furthermore, denoising processing is also performed on the obtained attack chain, a high-threat event attack chain is obtained, and according to an event taking place taking place at the earliest time in the attack chain, an attack source is traced back. The method and system provided by the invention make up for the technical defect of difficult restoration of an attack chain due to single-point detection frequently employed in conventional network threat detection technologies.
Owner:HARBIN ANTIY TECH
Method for discovering transmission control protocol/Internet protocol (TCP/IP) network private access equipment
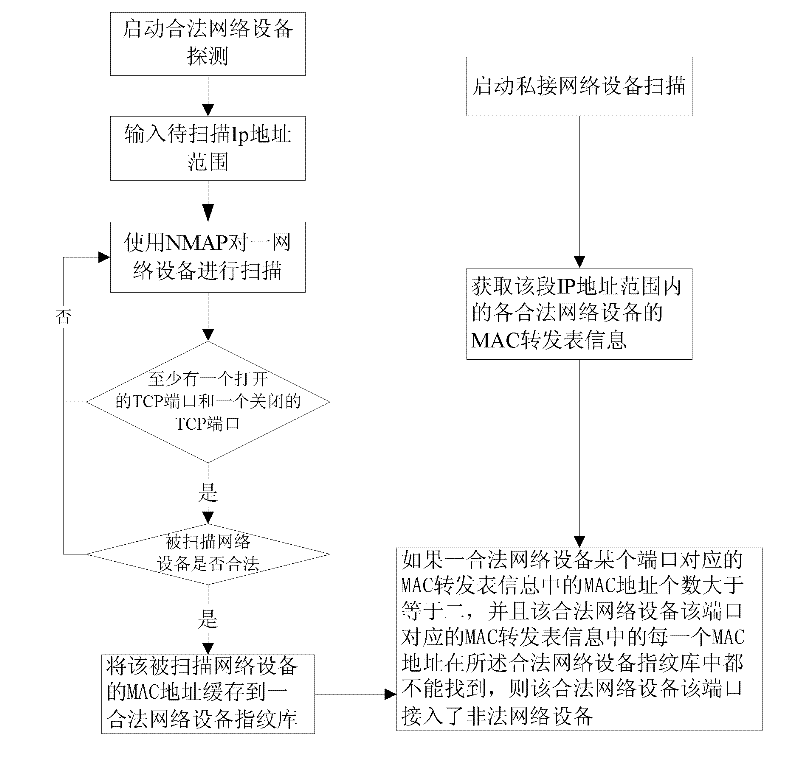
ActiveCN102684897AEasy to findEfficient discoveryData switching networksIp addressMedia access control
The invention discloses a method for discovering transmission control protocol / Internet protocol (TCP / IP) network private access equipment. The method comprises the following steps of: establishing a legal network equipment fingerprint database within an IP address range, wherein the legal network equipment fingerprint database records media access control (MAC) addresses of all legal network equipment within the IP address range; acquiring the MAC forwarding table information of each piece of legal network equipment within the IP address range; and if the number of MAC addresses in MAC forwarding table information corresponding to a certain port of a piece of legal network equipment is more than or equal to 2, and each MAC address in the MAC forwarding table information corresponding to the port of the legal network equipment cannot be found from the legal network equipment fingerprint database, illegal network equipment accesses the port of the legal network equipment. According to the method for discovering the TCP / IP network private access equipment, network private access equipment in a TCP / IP network can be quickly discovered.
Owner:SHANGHAI BAOSIGHT SOFTWARE CO LTD
Police unmanned aerial vehicle big data acquisition system and crime spatial database construction method
InactiveCN105095451AEfficient discoveryFacilitate correlation analysisClosed circuit television systemsSpecial data processing applicationsData acquisitionSimulation
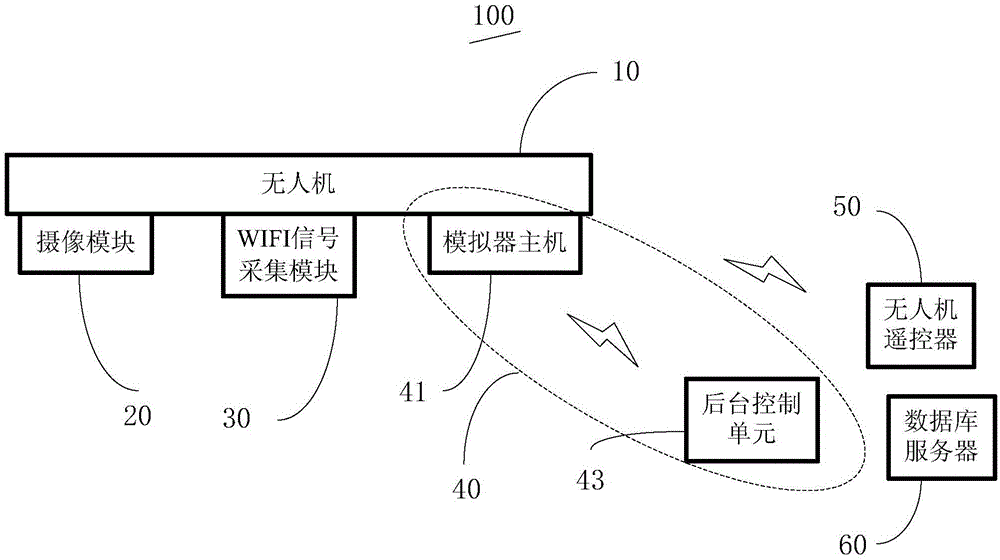
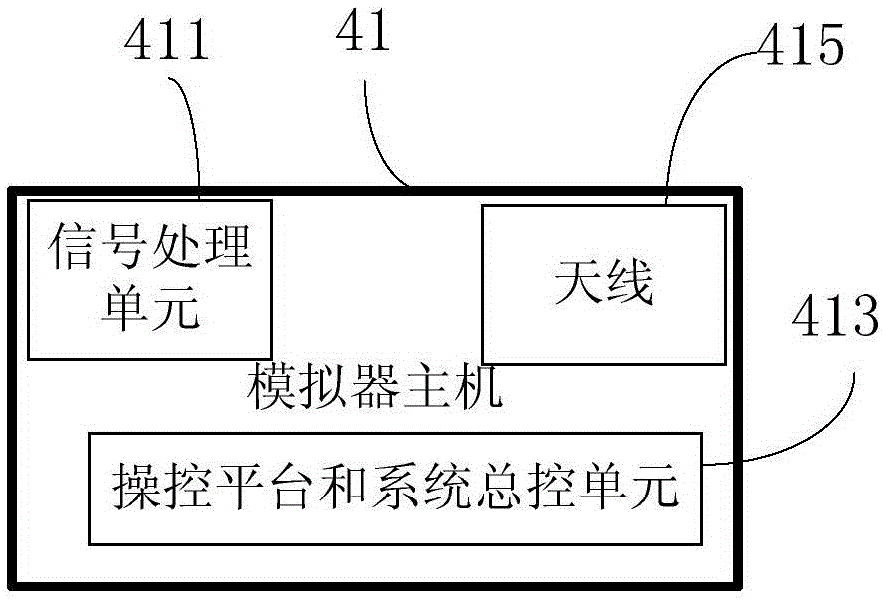
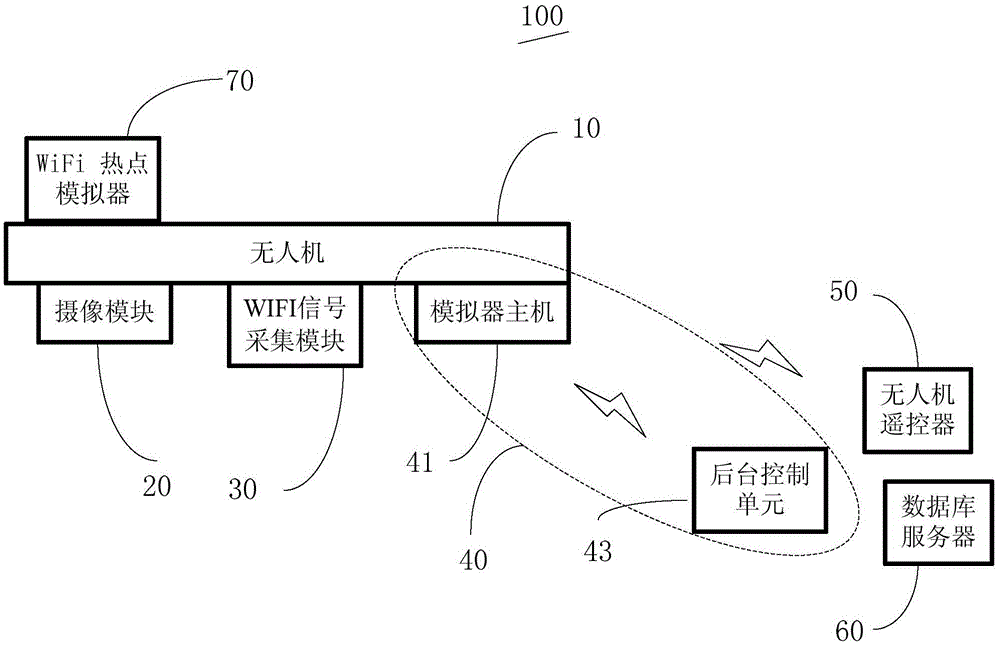
The invention provides a police unmanned aerial vehicle big data acquisition system, comprising an unmanned aerial vehicle, a camera module used to obtain video information, a WIFI signal acquisition module, a base station simulator used to search phone cards and position information, an unmanned aerial vehicle remote controller, and a database server. The base station simulator comprises a simulator host, and a background control unit. The camera module, the WIFI signal acquisition module, and the simulator host are installed on the unmanned aerial vehicle. The simulator host is dynamically connected with the background control unit through WIFI, and transmits data in real time. The police unmanned aerial vehicle big data acquisition system uses the unmanned aerial vehicle, the camera module, the WIFI signal acquisition module, and the base station simulator module to give full play to three-dimensional spatial motion capability, so as to obtain videos, networks, and mobile phones and other multisource information from higher positions, more flexible angles, closer distances, and in a more hidden method. The invention also provides a crime spatial database construction method.
Owner:SHENZHEN INST OF ADVANCED TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com