Patents
Literature
2030 results about "Detection threshold" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Detection threshold. The point at which the software determines the beginning and the end of the peak will shift depending on the threshold. The threshold should be set as low as possible. If it is set too low, the software will interpret baseline noise as peaks.
Method and system for determining spectrum availability within a network
InactiveUS7564816B2Shorten the overall cycleHigh transmission powerTransmission monitoringWireless commuication servicesSpectrum availabilityFrequency spectrum
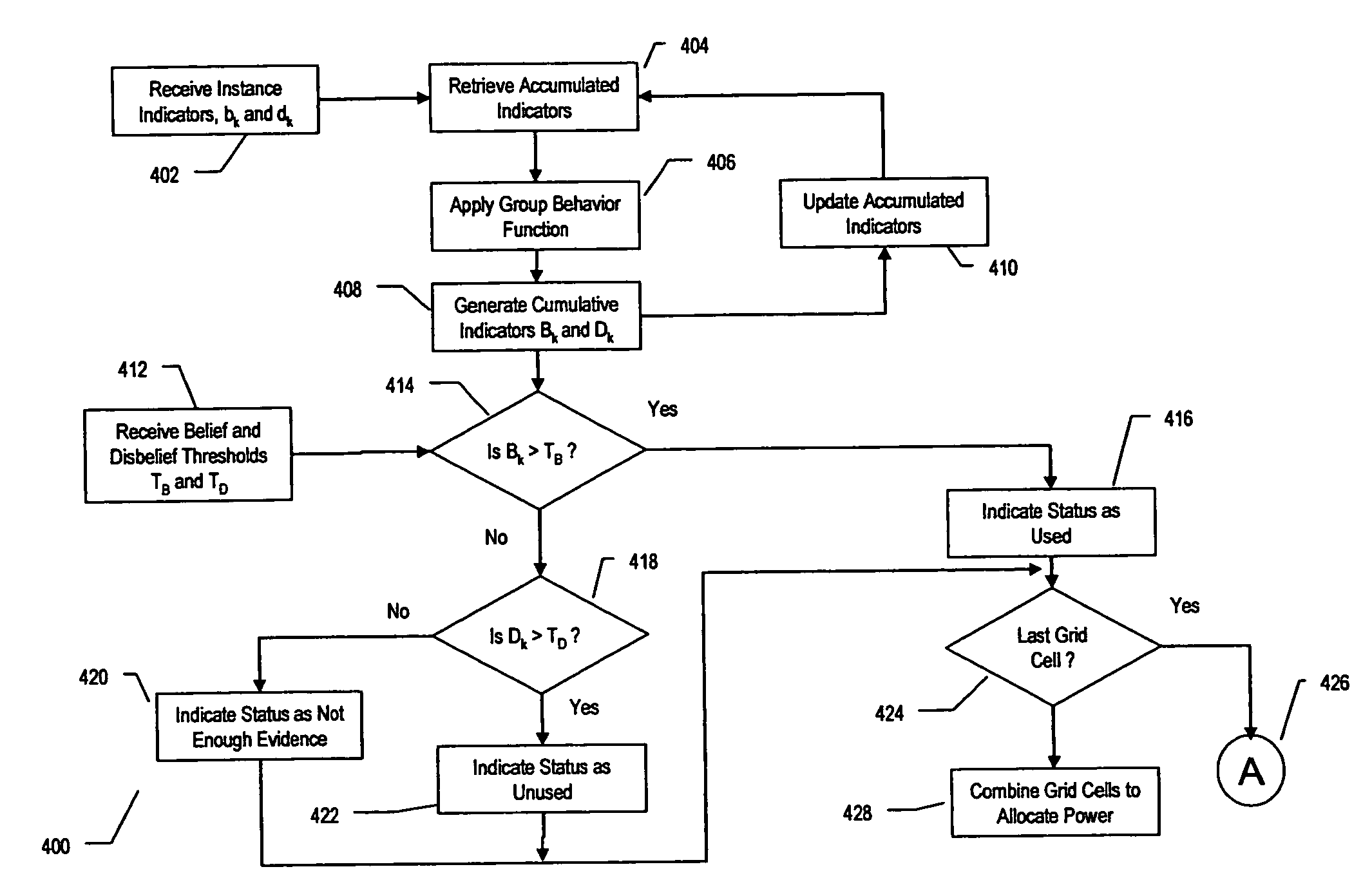
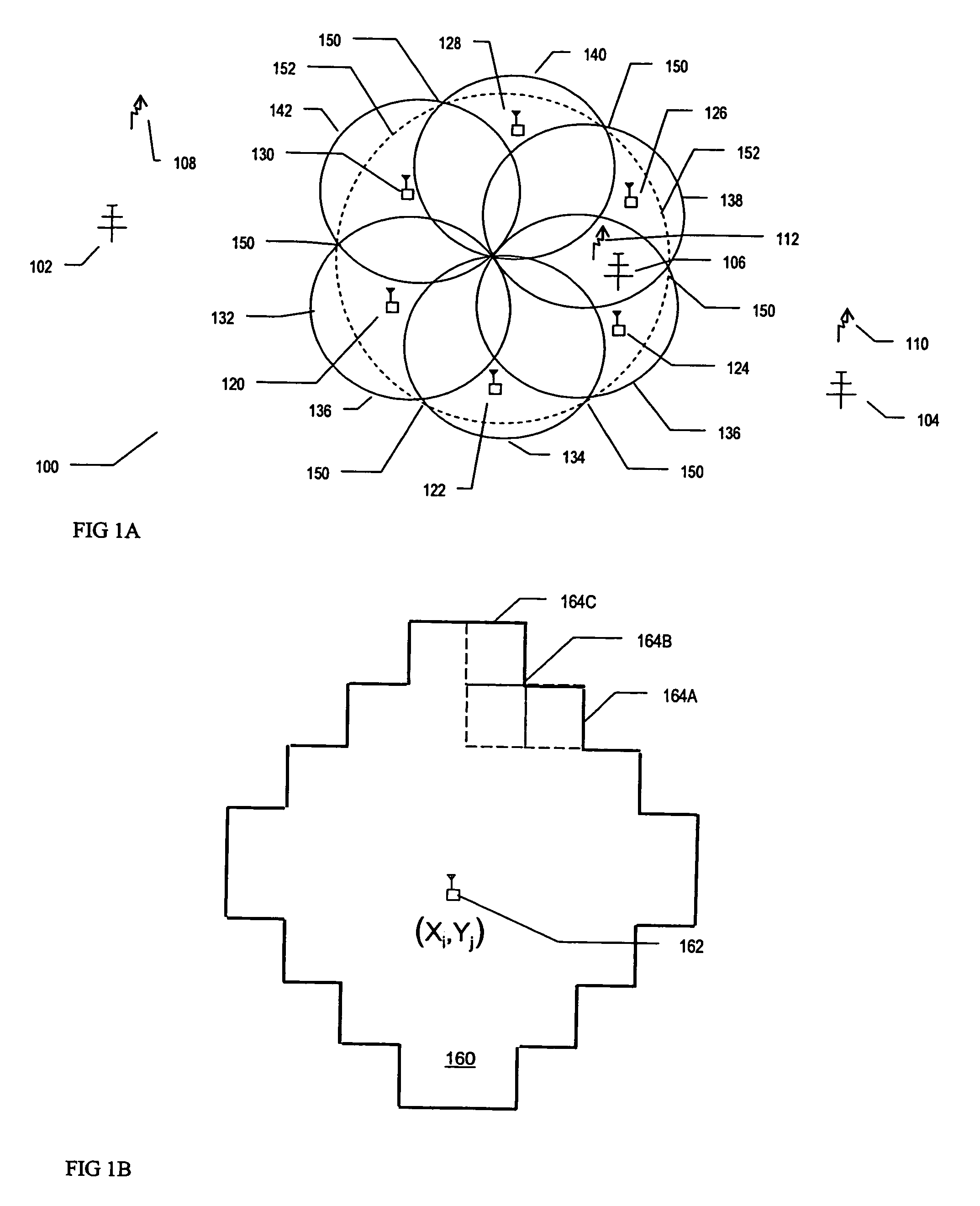
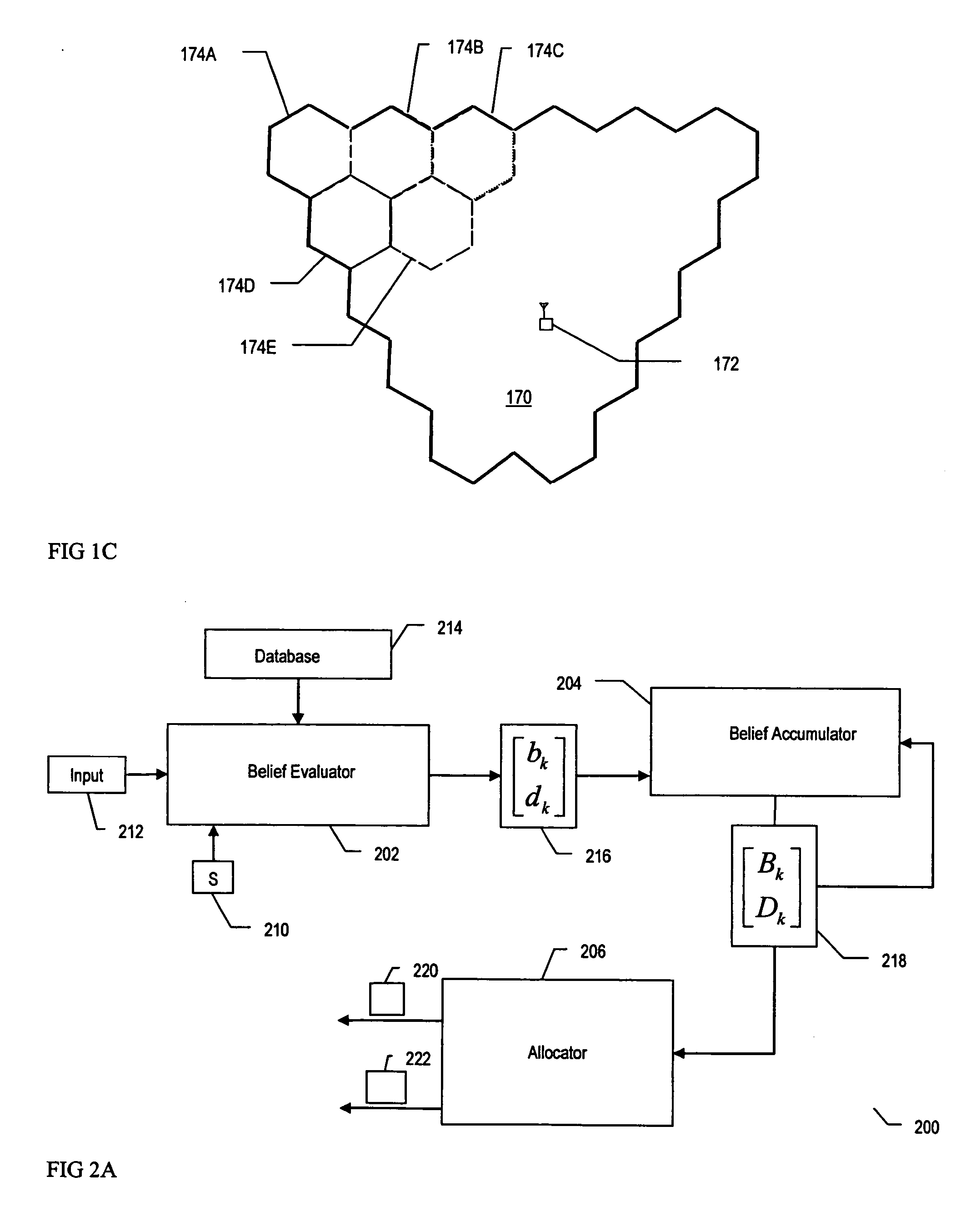
A method and transceiver for determining spectrum availability within a give area is disclosed. The given area includes cells in a grid. A belief evaluator receives a measurement from a signal and assigns an instantaneous belief indicator, an instantaneous disbelief indicator and an instantaneous ignorance indicator based on a detection threshold and the power level of the measurement. The indicators quantify the probability of a presence of a transmitter within the grid cell. A belief accumulator uses the instantaneous indicators along with accumulated belief, disbelief and ignorance indicators from previous measurements to determine cumulative belief, disbelief and ignorance indicators. The accumulated belief, disbelief and ignorance indicators are the results of previous measurements and belief / disbelief / ignorance determinations for the grid cell. An allocator indicates the status of the grid cell and whether a spectrum is available. If a spectrum is available, then the grid cell is added to other available cells within the area to generate the spectrum hole.
Owner:SHARED SPECTRUM
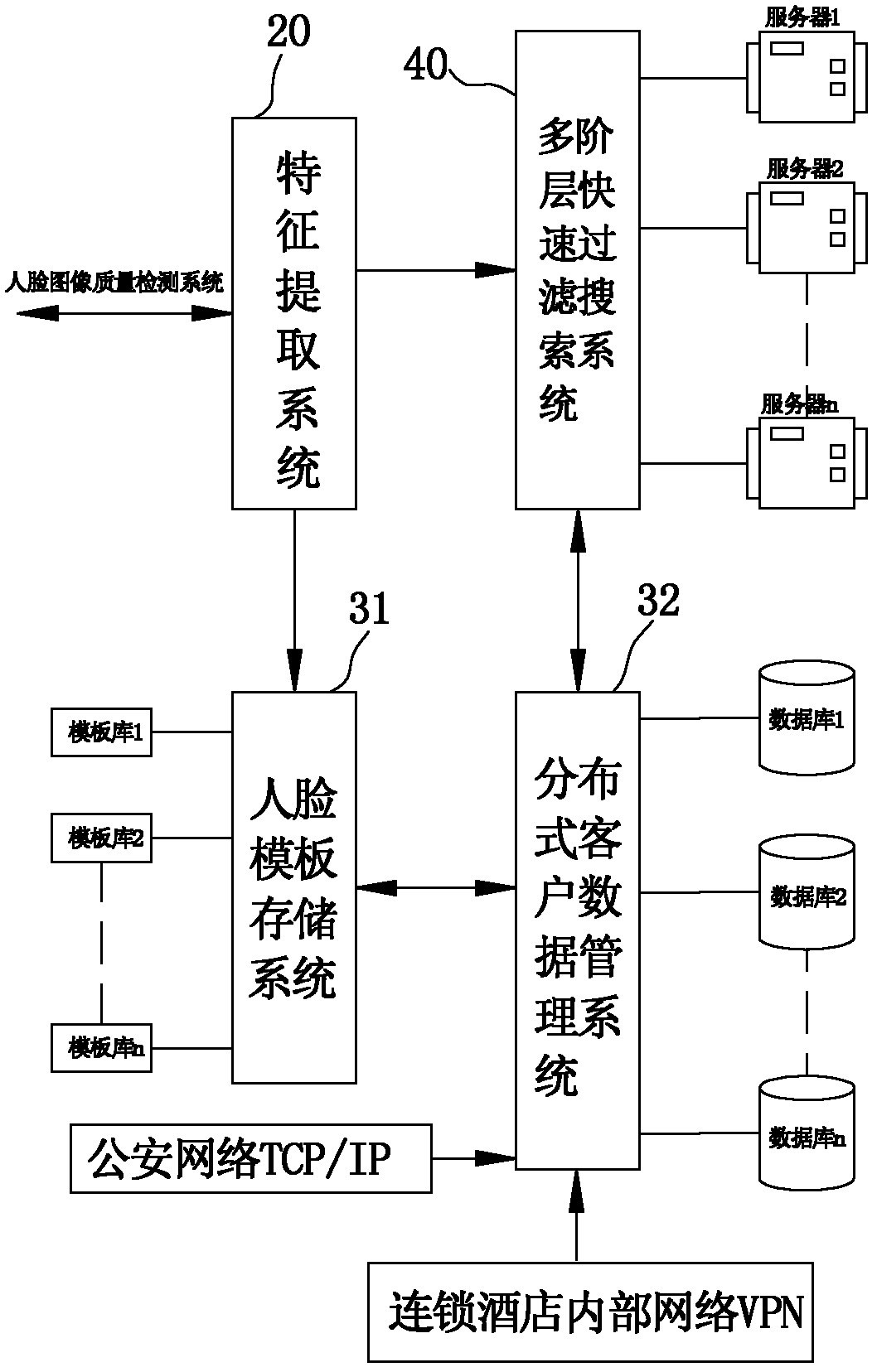
Intelligent safety monitoring system and method based on multilevel filtering face recognition
InactiveCN102201061AImprove recognition accuracyImprove search efficiencyCharacter and pattern recognitionSpecial data processing applicationsFace detectionPattern recognition
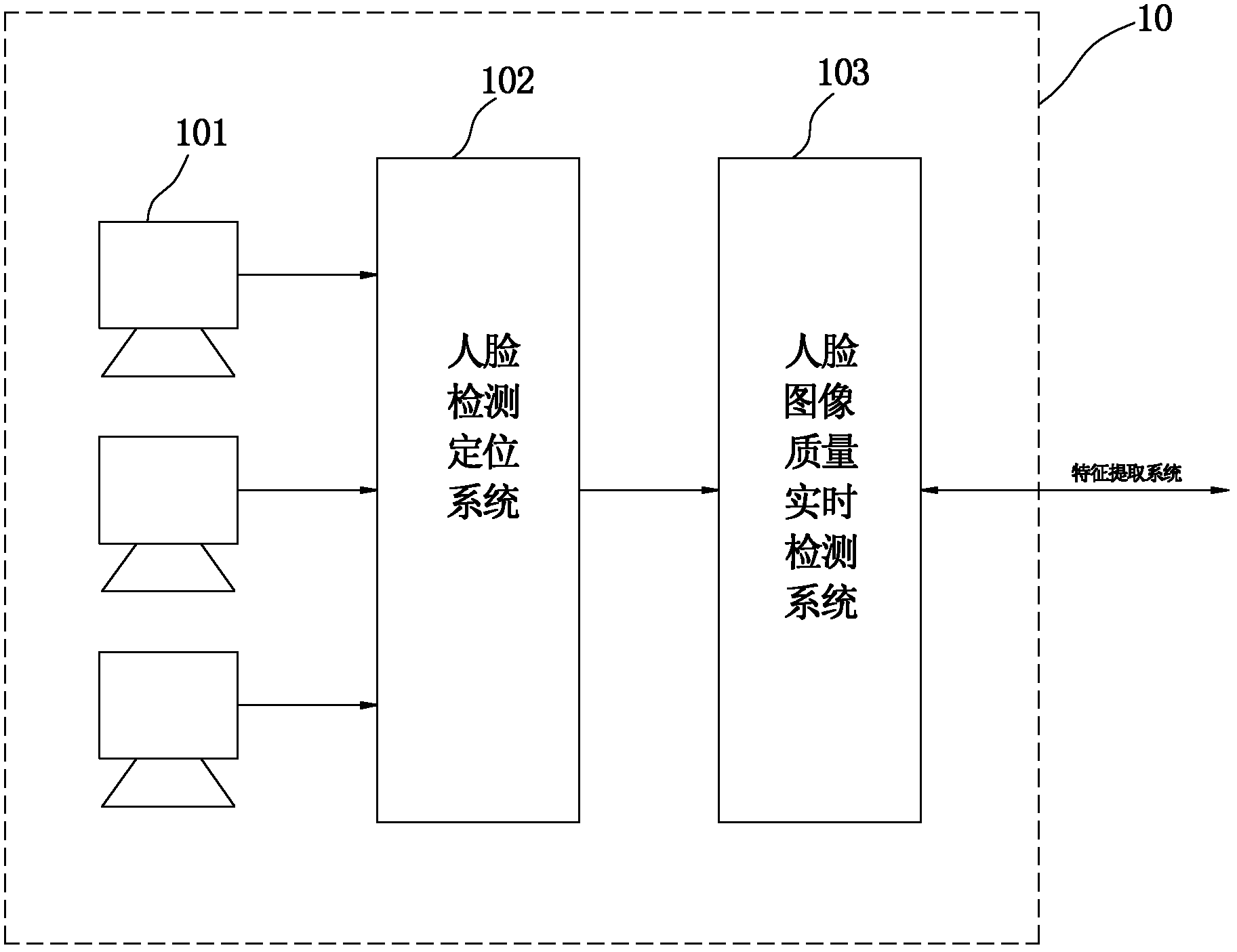
The invention discloses a method based on multilevel filtering face recognition. The method comprises the following steps of: collecting a face image of a detected man through an image collection system on a user terminal; automatically detecting and partitioning an exact position of a face from the collected face image by a face detection and positioning system, and performing intelligent indication and image quality real-time monitoring on a face image collection process through an automatic and real-time face image quality detection system; extracting characteristic points from the face image of the user terminal according to an image quality detection threshold value, and generating corresponding target face templates; and performing real-time comparison on a face to be recognized which is detected by a client and a known face database based on a multilevel filter searching algorithm through a background server, finding out the face template having the highest matching score, judging according to a preset threshold value of the system and determining identity information of the shot man in real time. The invention also provides an intelligent identity recognition and safety monitoring system based on a multilevel face filtering and searching technology with high reliability and flexibility.
Owner:CHANGZHOU RUICHI ELECTRONICS TECH
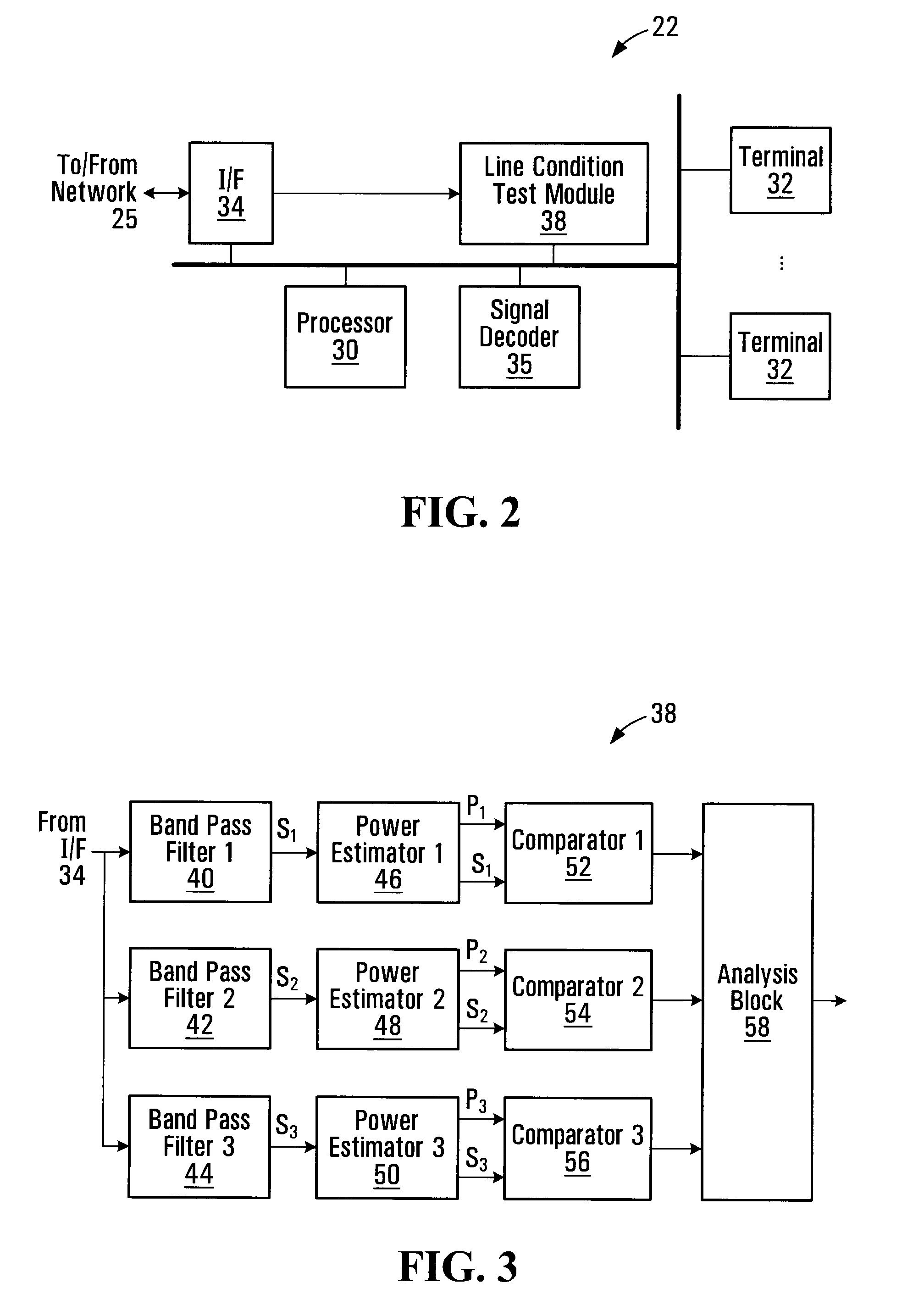
Alarm monitoring telecommunications line condition detection and automatic calibration
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
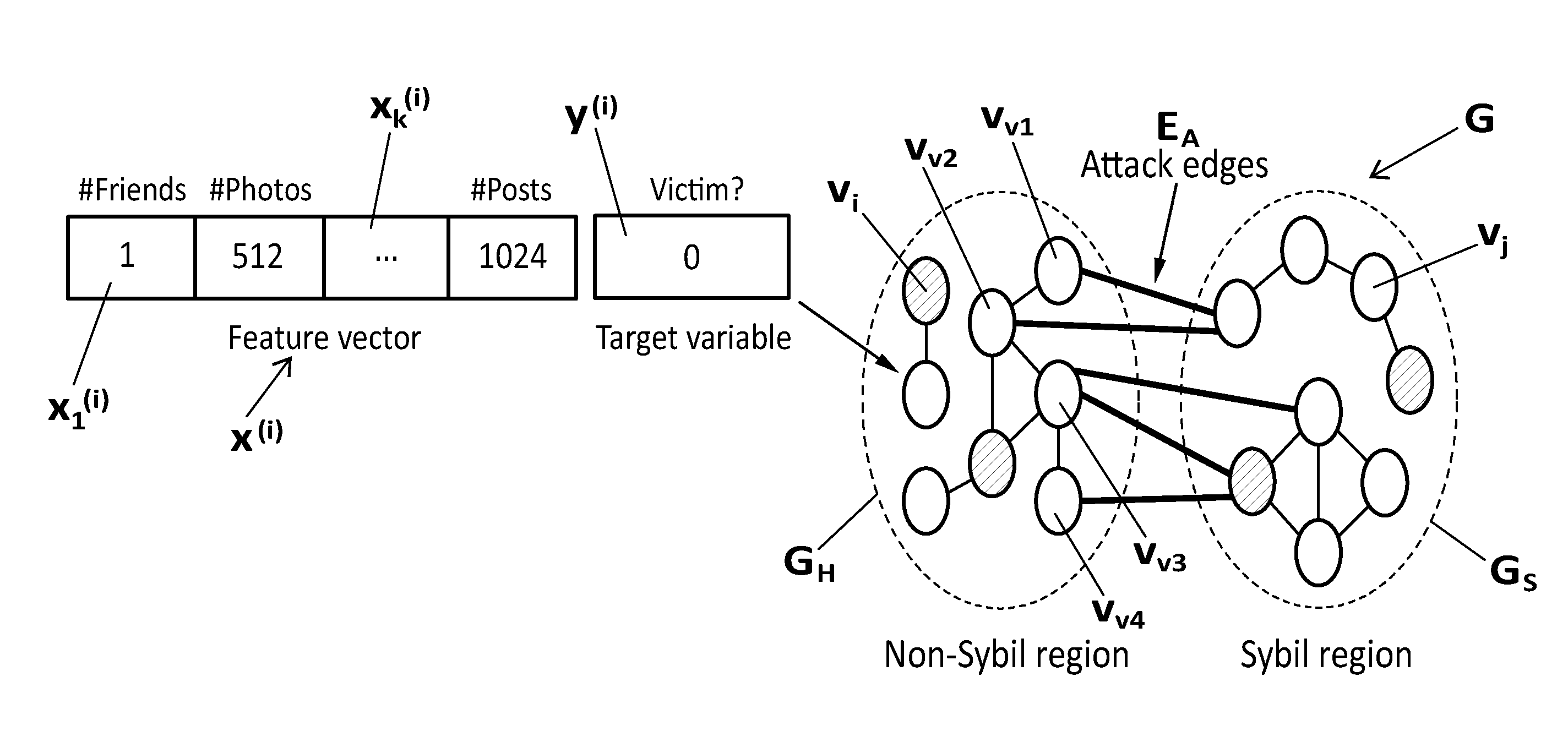
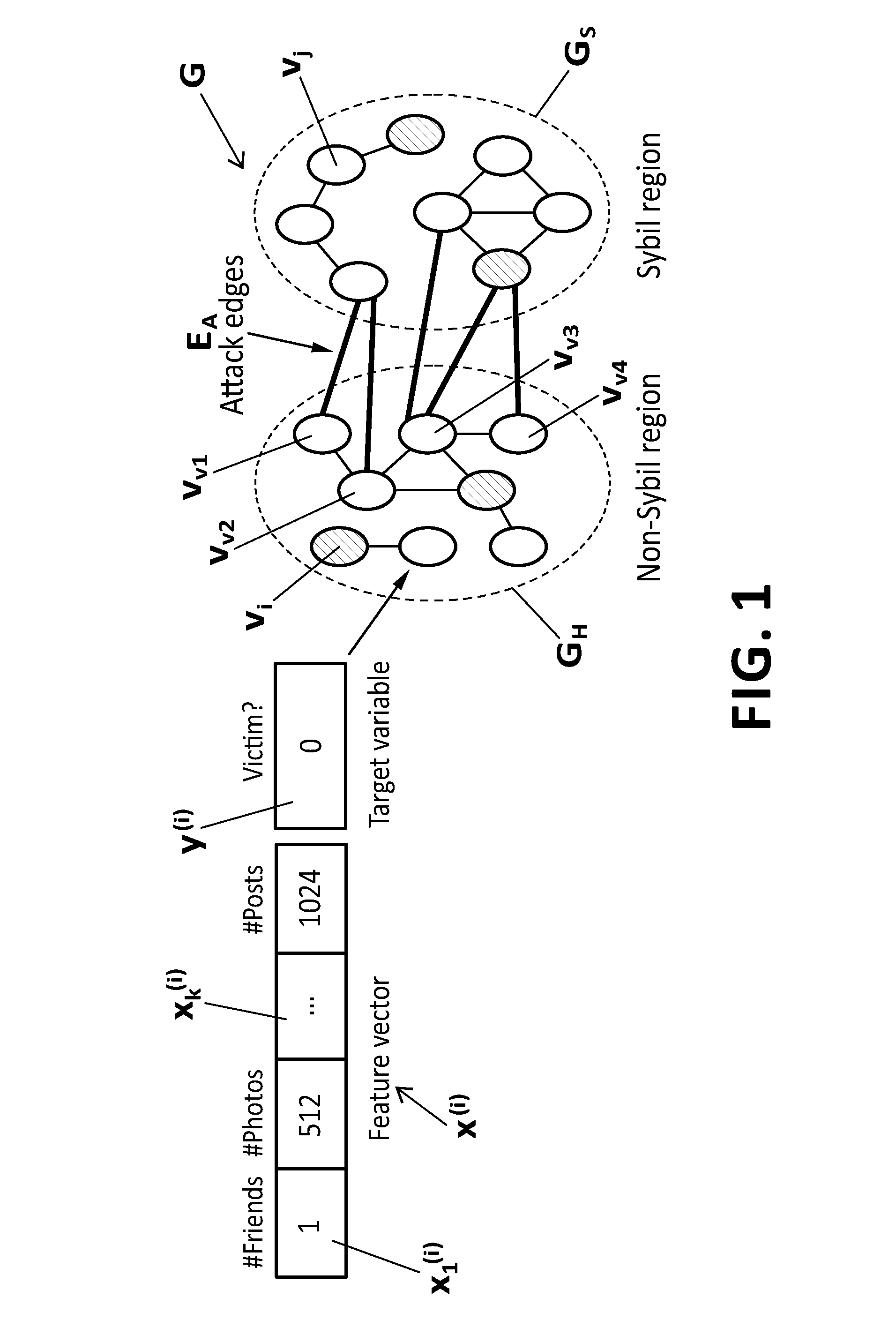
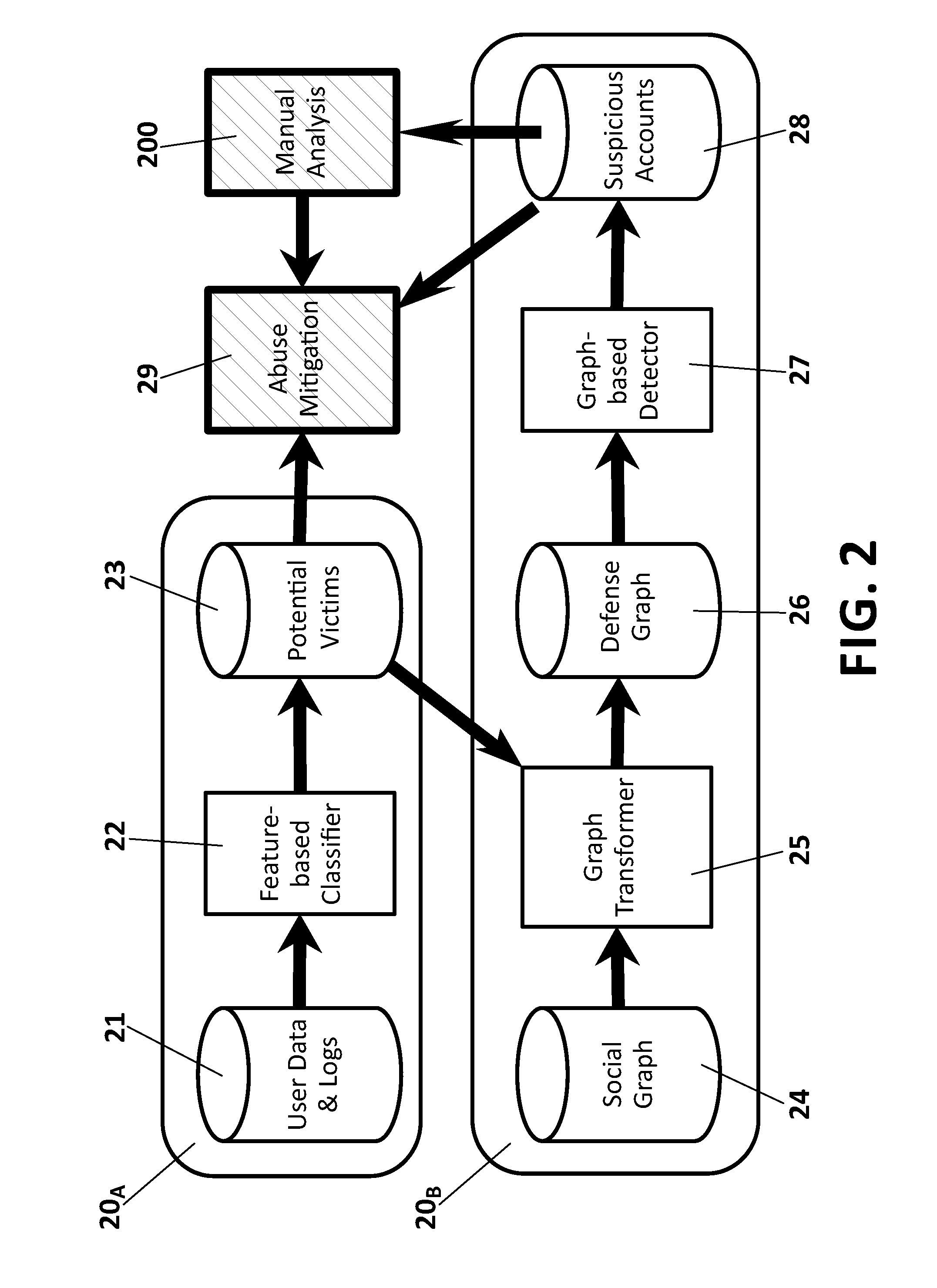
Method and system for predicting victim users and detecting fake user accounts in online social networks
InactiveUS20150188941A1Proactive mitigationPrevented being annoyedMemory loss protectionError detection/correctionAlgorithmTransformer
A system and method for predicting victims and detecting fake accounts in OSNs, comprising: a feature-based classifier for predicting victims by classifying, with a classification probability, a target variable of each user in the OSN social graph; a graph-transformer for transforming the social graph into a defense graph by reassigning edge weights to incorporate victim predictions using the classification probability, a graph-based detector for detecting fake users by computing through the power iteration method a probability of a random walk to land on each node in the defense graph after 0(log n) steps, assigning to each node a rank value equal to a node's landing probability normalized by the node degree, sorting the nodes by their rank value and estimating a detection threshold such that each node whose rank value is smaller than the detection threshold is flagged as representing a fake account.
Owner:TELEFONICA DIGITAL ESPANA
Method and apparatus for laser-based remote methane leak detection
ActiveUS7075653B1Promotes user comfortEasy to identifyDetection of fluid at leakage pointRadiation pyrometryMoving averageSpectroscopy
A method and apparatus for remote laser-based detection of gas at levels exceeding natural background levels preferably utilizing wavelength modulated tunable diode laser absorption spectroscopy. In a preferred embodiment, background gas and noise are estimated using statistical moving average and variance calculations. Gas concentration length measurements resulting from the spectroscopy are preferably compared in real-time or near-real-time to the sum of the background and noise estimates and an alarm limit to detect gas presence of concern. Gas levels exceeding this detection threshold are preferably indicated by a prolonged output tone with a pitch indicative of the magnitude of the gas measurement, and gas levels below the detection threshold are preferably indicated by silence.
Owner:HEATH CONSULTANTS
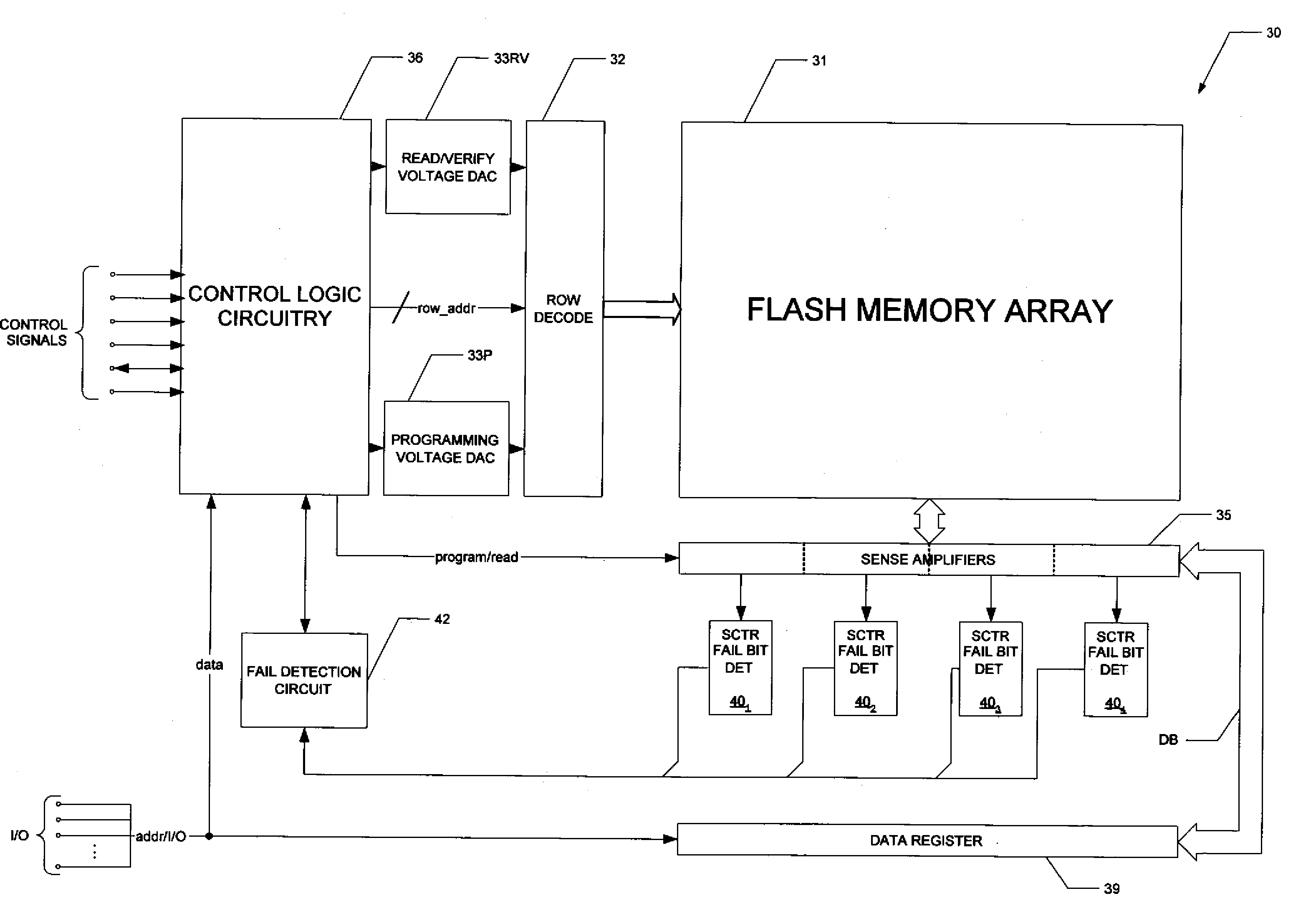
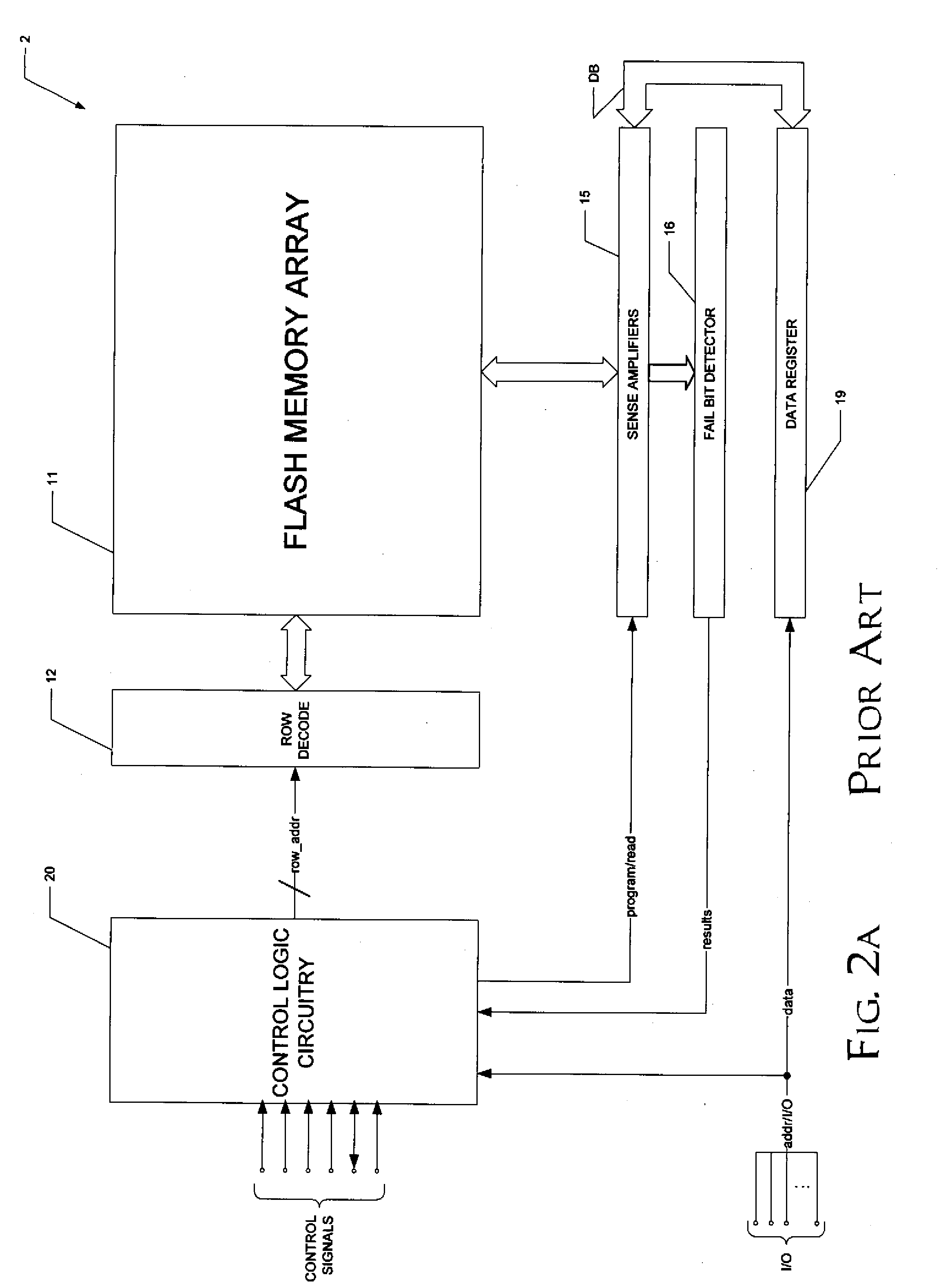
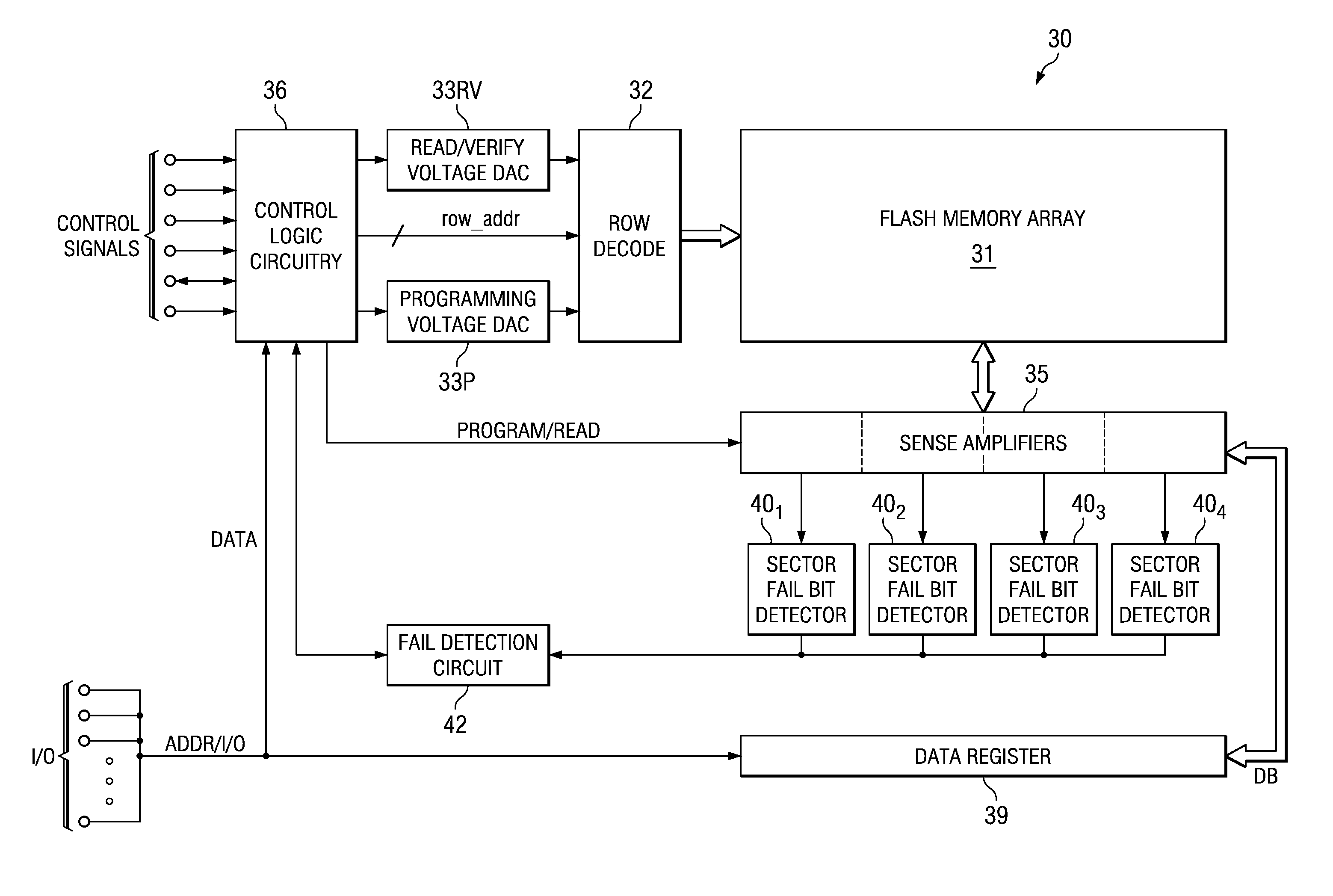
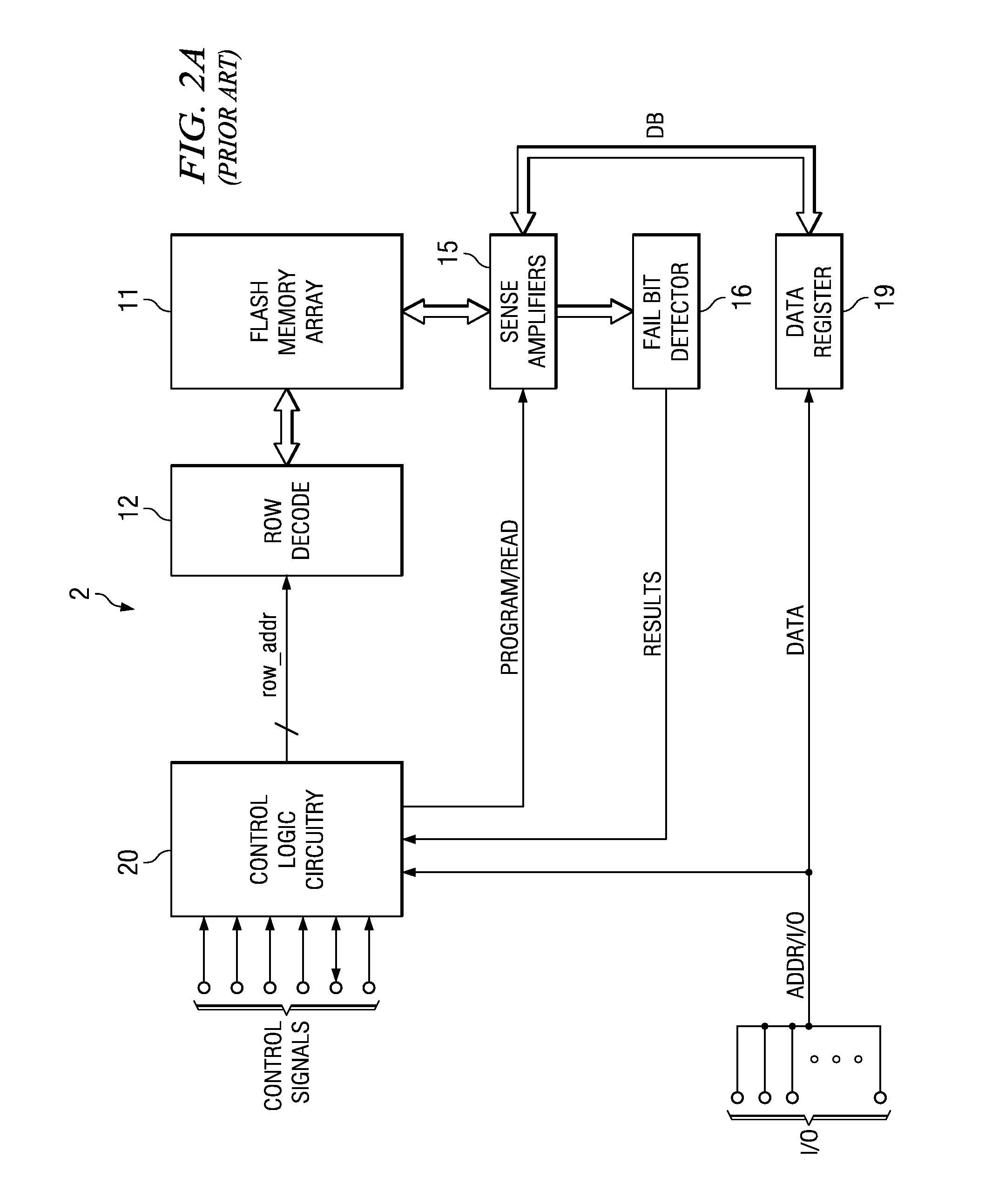
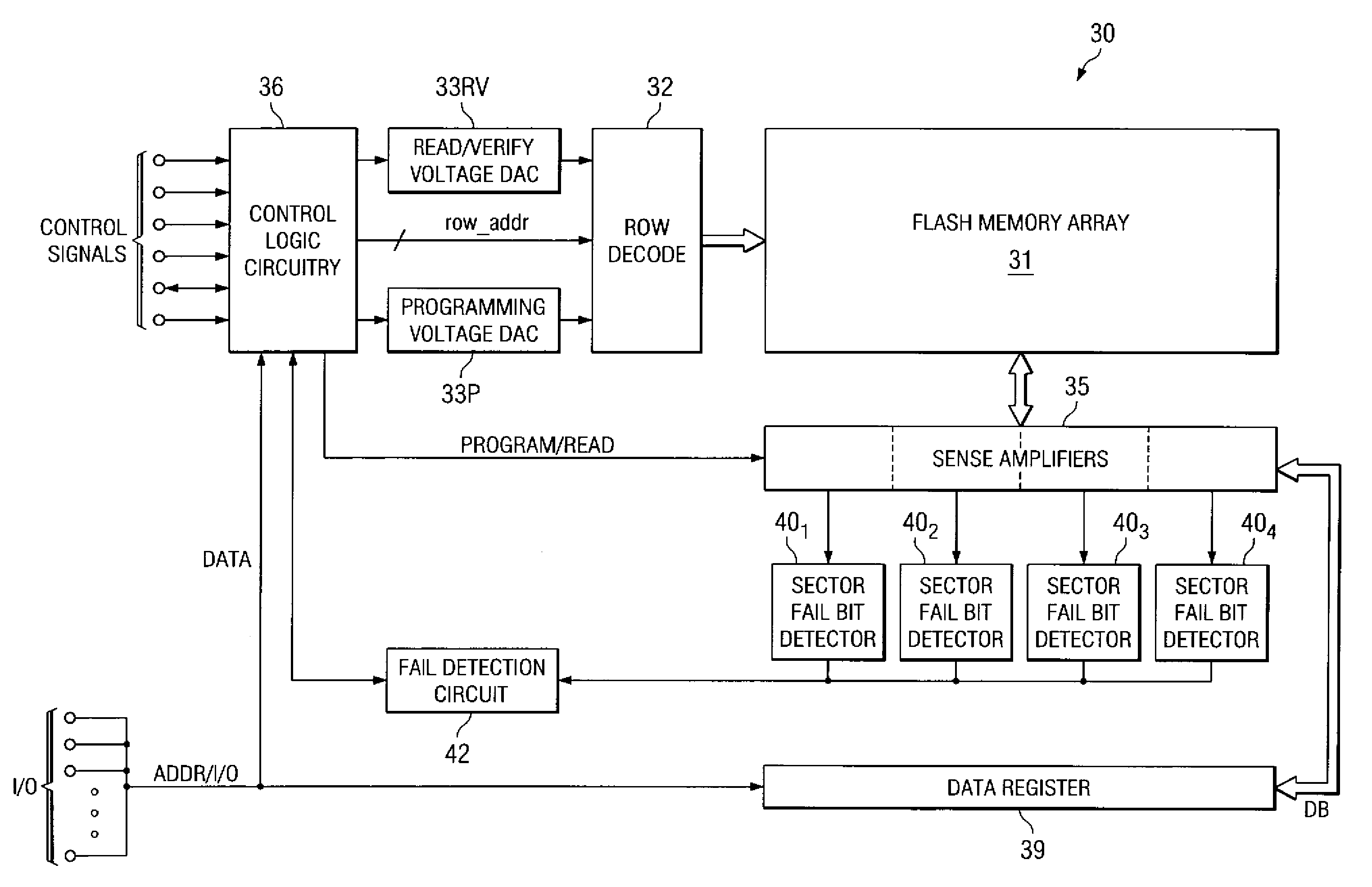
Partial Page Fail Bit Detection in Flash Memory Devices
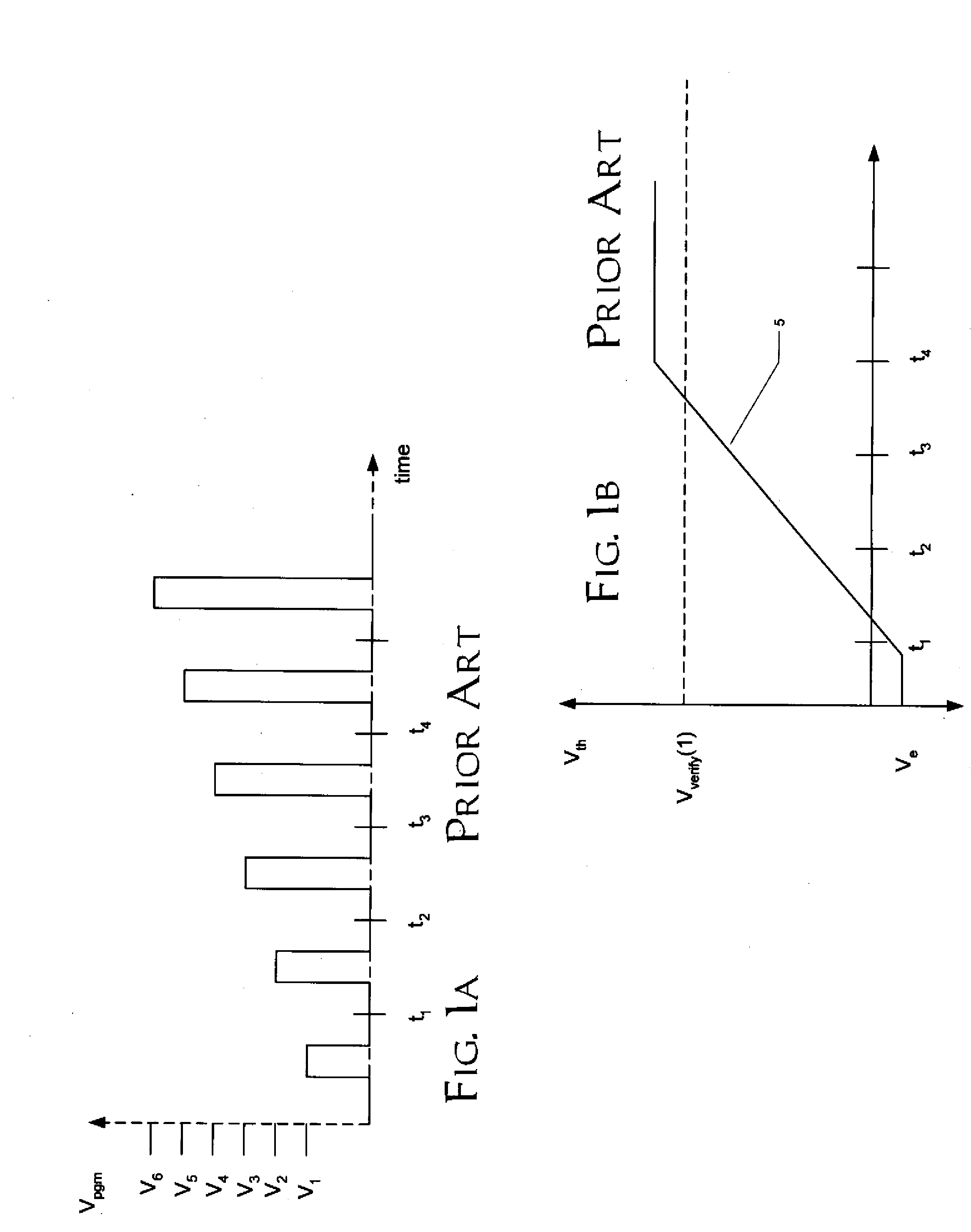
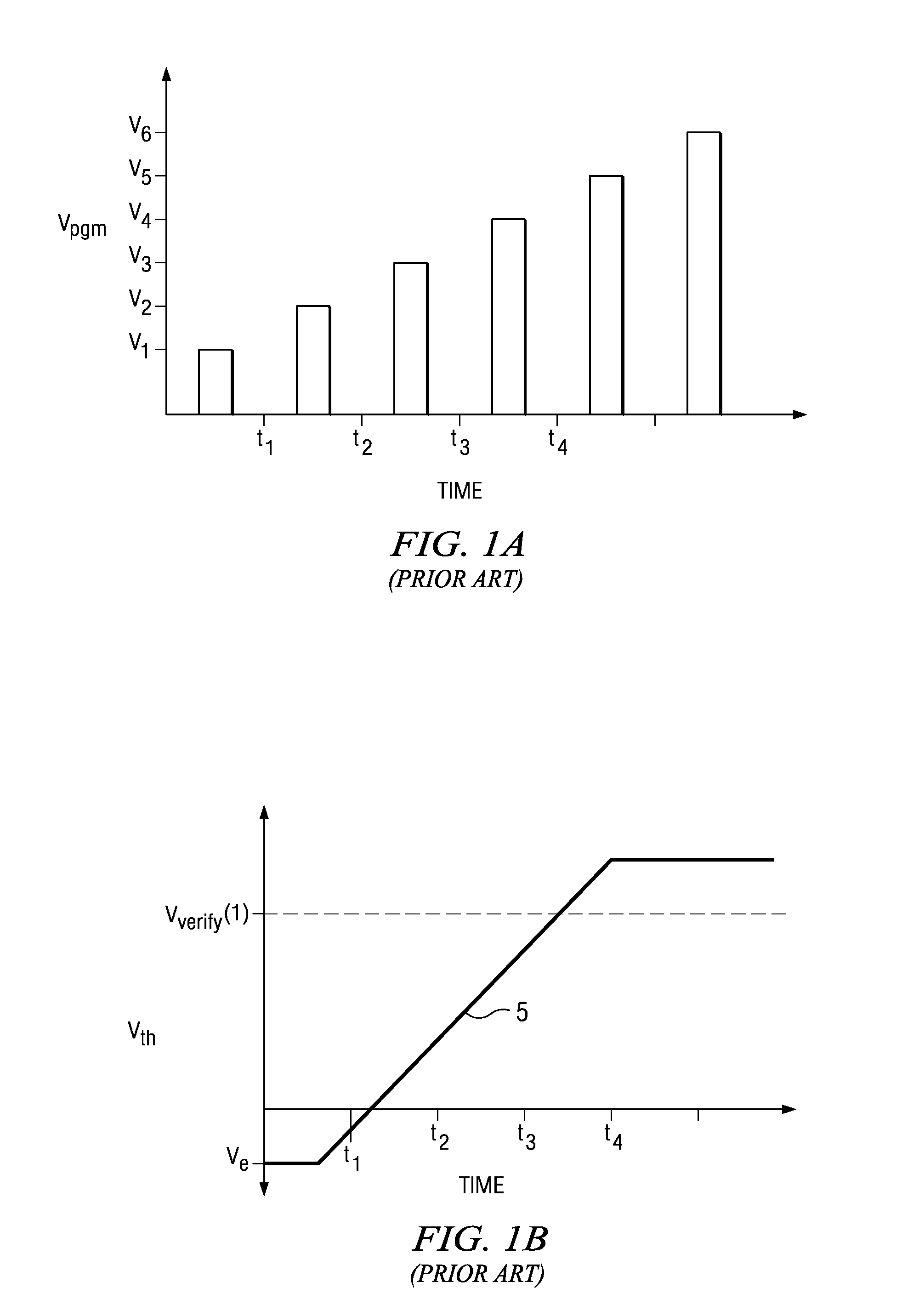
ActiveUS20080002468A1Improve efficiencyEarly terminationError detection/correctionRead-only memoriesDetection thresholdError correction coding
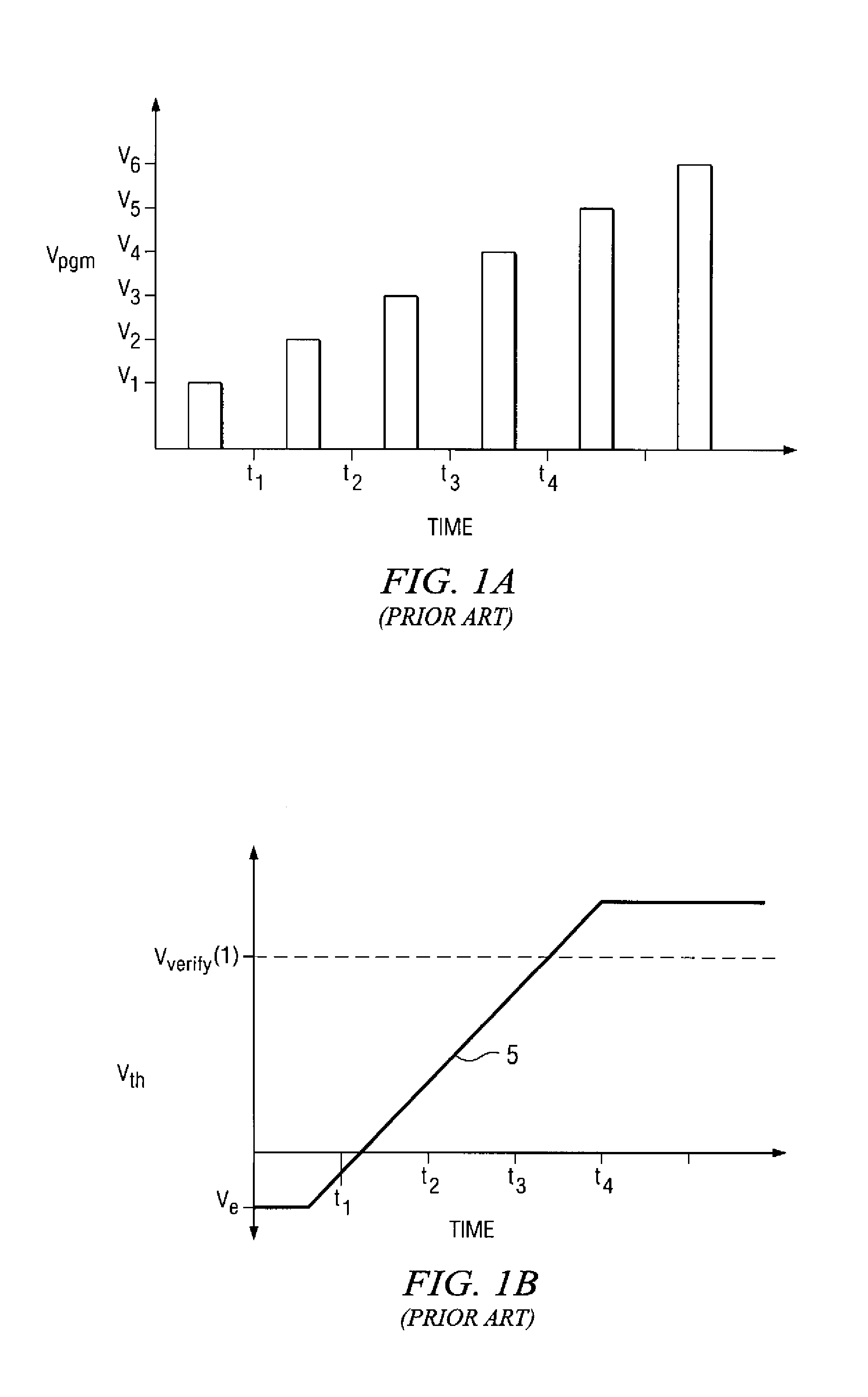
A flash memory device, and a method of operating the same, is disclosed. The array of the flash memory device is arranged in pages of memory cells, each page having memory cells associated into groups of memory cells within the page for purposes of fail bit detection in program verification. For example, these groups may correspond to sectors within the page. In a programming operation, the verify process determines whether each group of memory cells within the page has fewer than a selected ignore bit limit for the sector. If not, additional programming is required for the insufficiently programmed cells in the page. By applying a fail bit detection threshold for each of multiple groups within the page, the efficiency of error correction coding in the flash memory is improved. A similar verify and fail bit detection approach may be used in erase and soft programming operations.
Owner:SANDISK TECH LLC
Method of partial page fail bit detection in flash memory devices
ActiveUS7304893B1Improve efficiencyEarly terminationRead-only memoriesDigital storageDetection thresholdCorrection code
A flash memory device, and a method of operating the same, is disclosed. The array of the flash memory device is arranged in pages of memory cells, each page having memory cells associated into groups of memory cells within the page for purposes of fail bit detection in program verification. For example, these groups may correspond to sectors within the page. In a programming operation, the verify process determines whether each group of memory cells within the page has fewer than a selected ignore bit limit for the sector. If not, additional programming is required for the insufficiently programmed cells in the page. By applying a fail bit detection threshold for each of multiple groups within the page, the efficiency of error correction coding in the flash memory is improved. A similar verify and fail bit detection approach may be used in erase and soft programming operations.
Owner:SANDISK TECH LLC
Fragrance compositions
The present invention relates to a composition comprising:(a) a fragrance oil wherein the fragrance oil comprises:(i) greater than about 50%, by weight of the fragrance oil, of perfume raw materials with high odour impact perfume raw materials which have an odour detection threshold of less than, or equal to, about 50 parts per billion;(ii) less than about 5%, by weight of the fragrance oil, of top note perfume raw materials wherein the top note perfume raw materials have a boiling point of less than about 250° C. at 1 atmosphere pressure(b) an entrapment material which is selected from the group consisting of polymers;capsules, microcapsules, and nanocapsules; liposomes; pro-perfumes; film formers; absorbents; cyclic oligosaccharides and mixtures thereof.(c) greater than about 50%, by weight, of a volatile solvent.The present invention provides compositions wherein the fragrance character remains detectable for greater than about 2 hours, preferably greater than about 4 hours, more preferably greater than about 6 hours, after the composition has been applied to the substrate.
Owner:PROCTER & GAMBLE CO
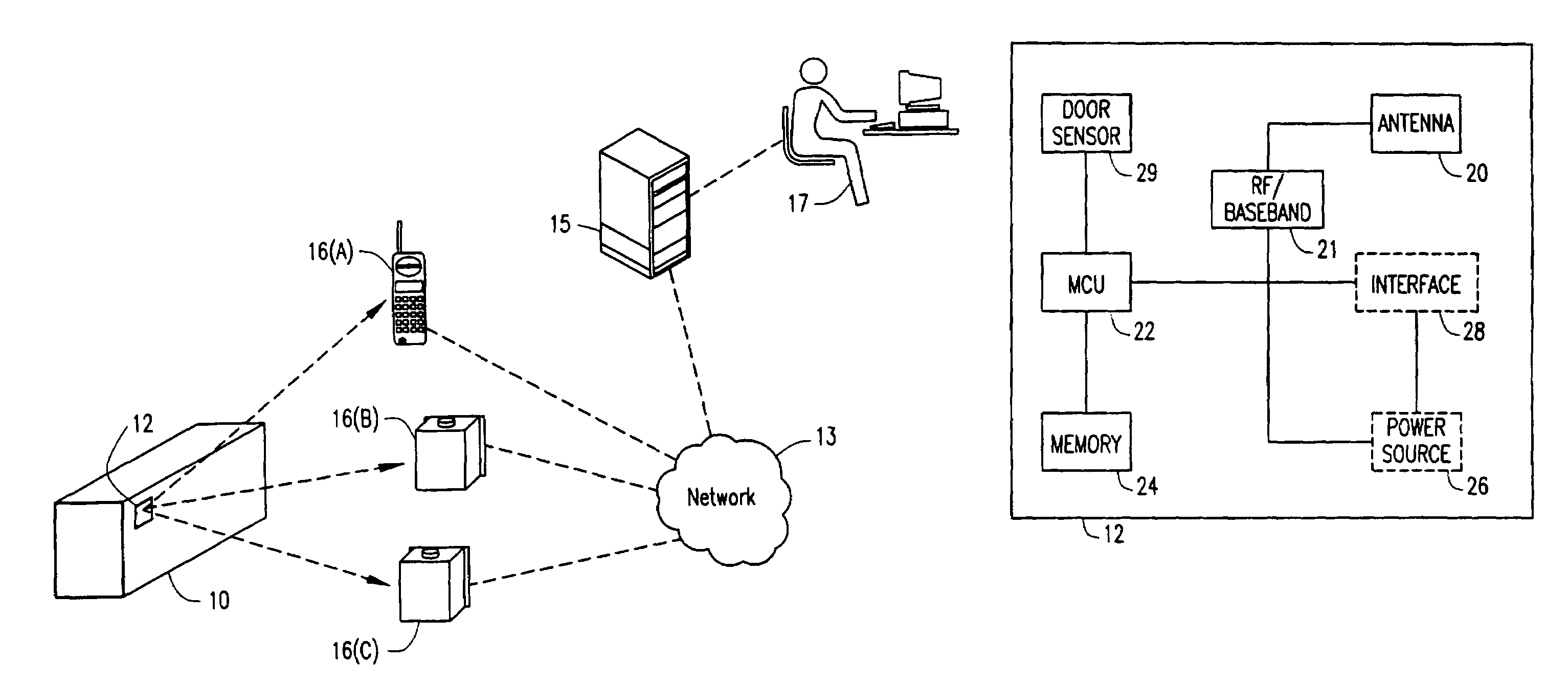
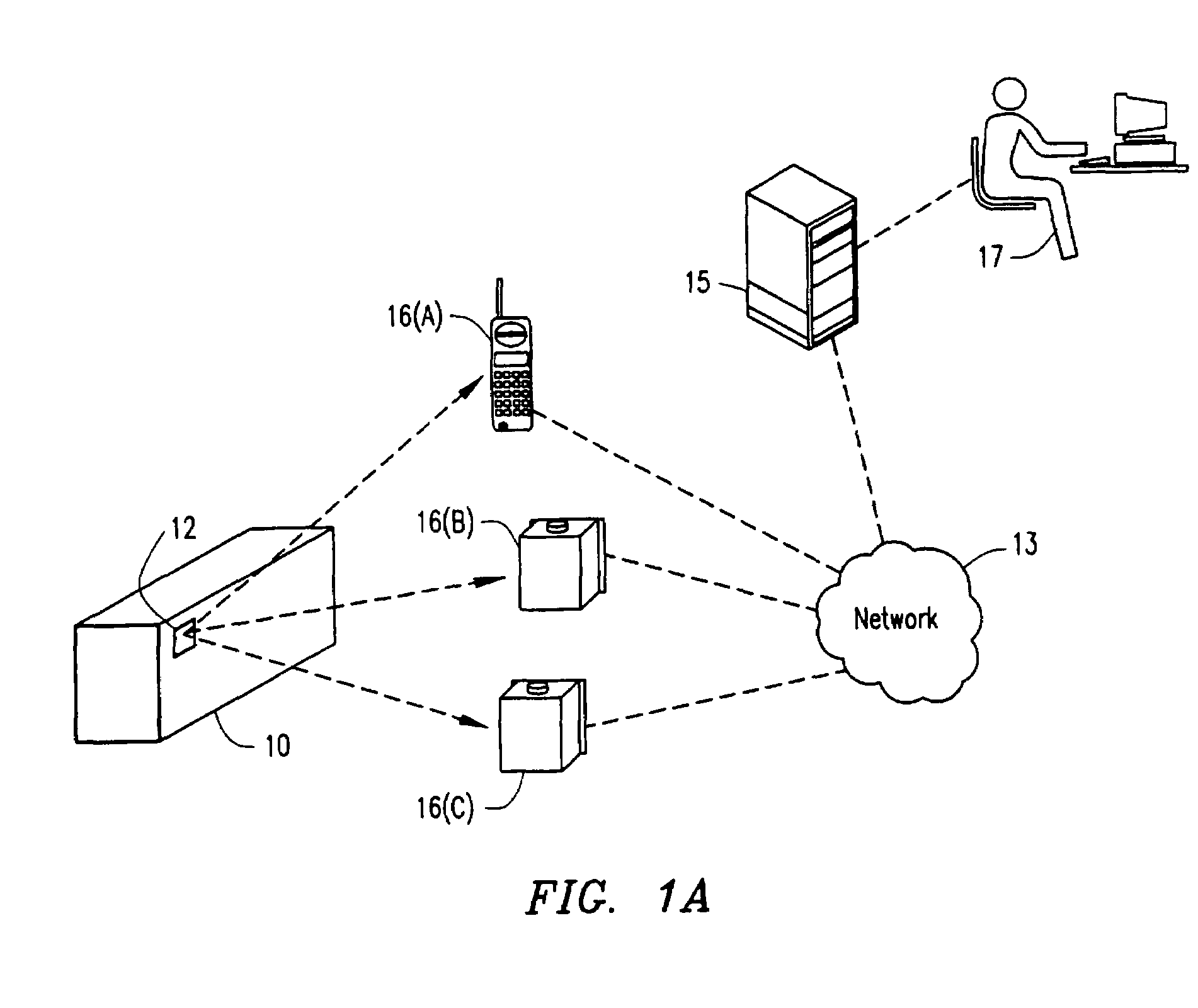
Method and system for monitoring containers to maintain the security thereof
A container and contents monitoring system includes a device, a reader, a server, and a software backbone. The device communicates with the reader in order to determine the security of the container to which the device is attached. The reader transmits the information from the device to the server. The sensor senses a distance or an angle value between a door of the container and a frame of the container and the sensed value is then transmitted to the device. The device obtains a baseline value that is related to a calculated mean value. The device also obtains a detection threshold. The device determines if a security condition has occurred based on the sensed value and the detection threshold.
Owner:COMMERCEGUARD
Adjustment of radio detection level for request signals based observed false detection
ActiveUS20110110240A1Improve balanceError preventionTransmission systemsTelecommunicationsRadio channel
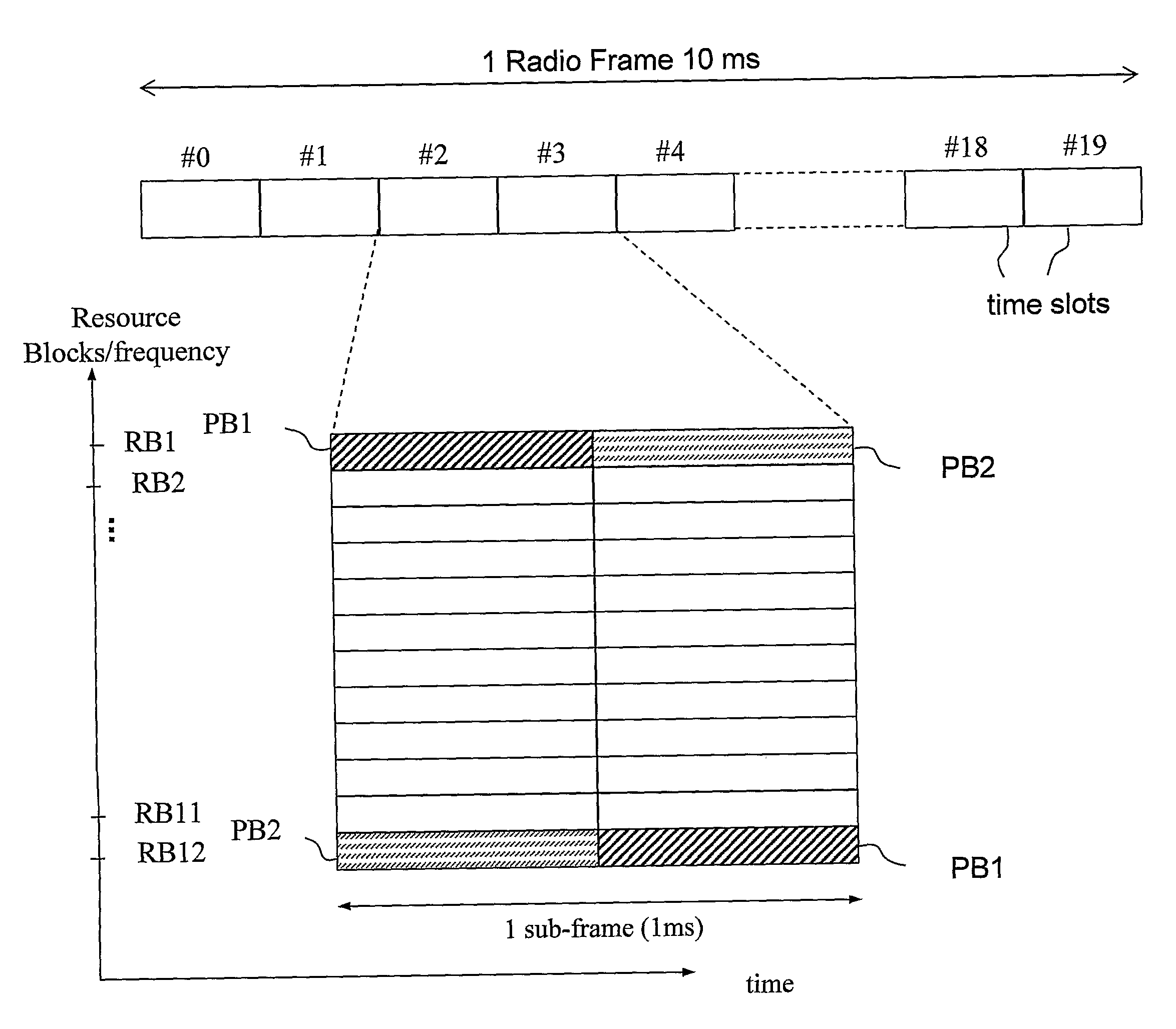
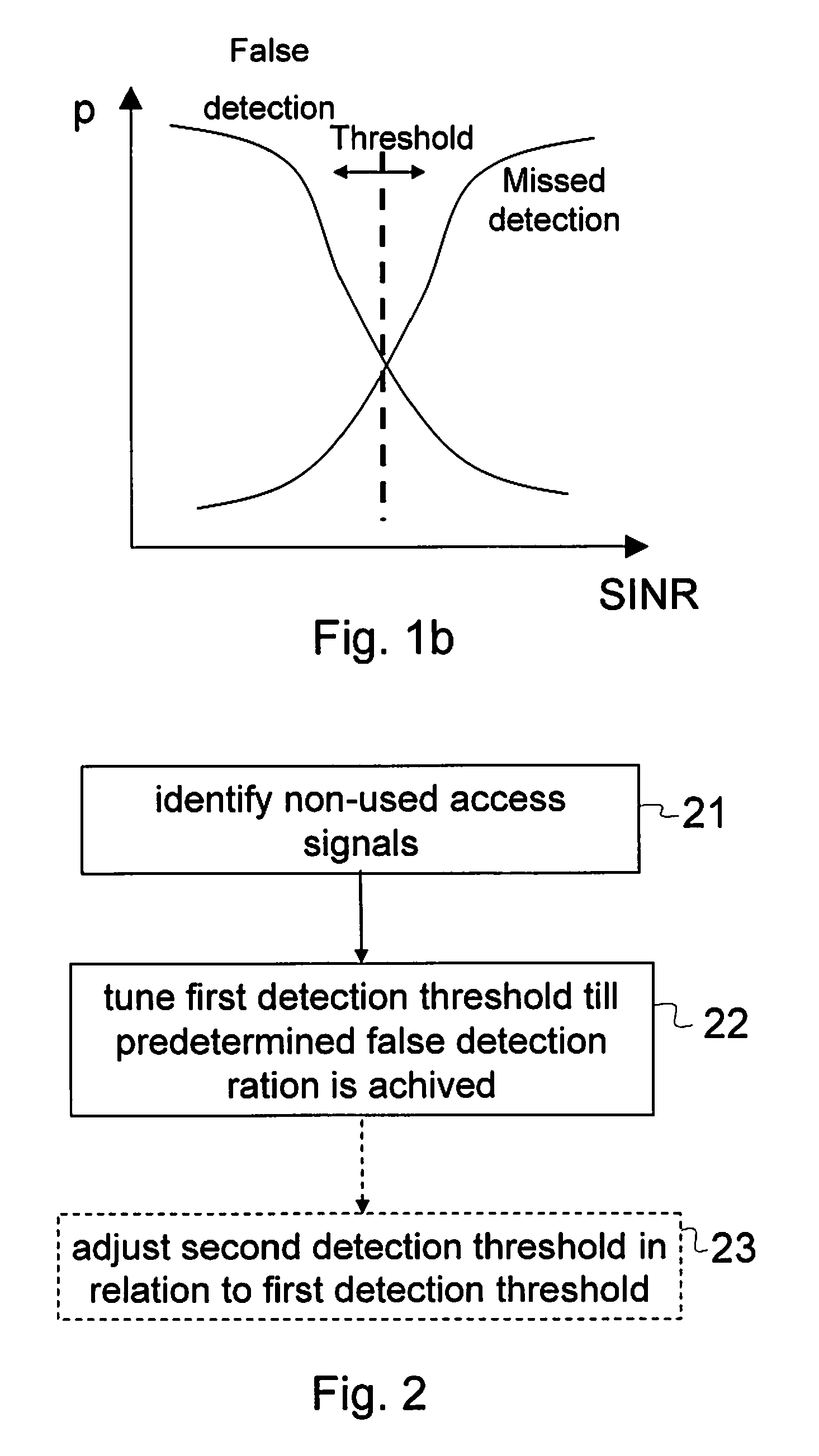
The present invention relates to receiving access signals from a plurality of terminals over a radio channel and in particular to determining a detection threshold level on the radio channel. A detection threshold level should balance the risk of missed detections to the risk of false detections. A problem in finding an equilibrium threshold is the radio environment, with noise and interference, change and then also the radio false detections or missed detections change. According to the present invention some access signals can be identified as being not assigned and therefore not being in use, and any detection of a non-used signal is identified as a false detection. By monitoring the ratio of false detections vs. correct detections the threshold level for detection is tuned into an equilibrium level, and that is adapted to the changing radio environments. In addition the detection threshold level for access signals detection threshold for data and / or control signalling may be adjusted in relation to the access signal threshold level.
Owner:TELEFON AB LM ERICSSON (PUBL)
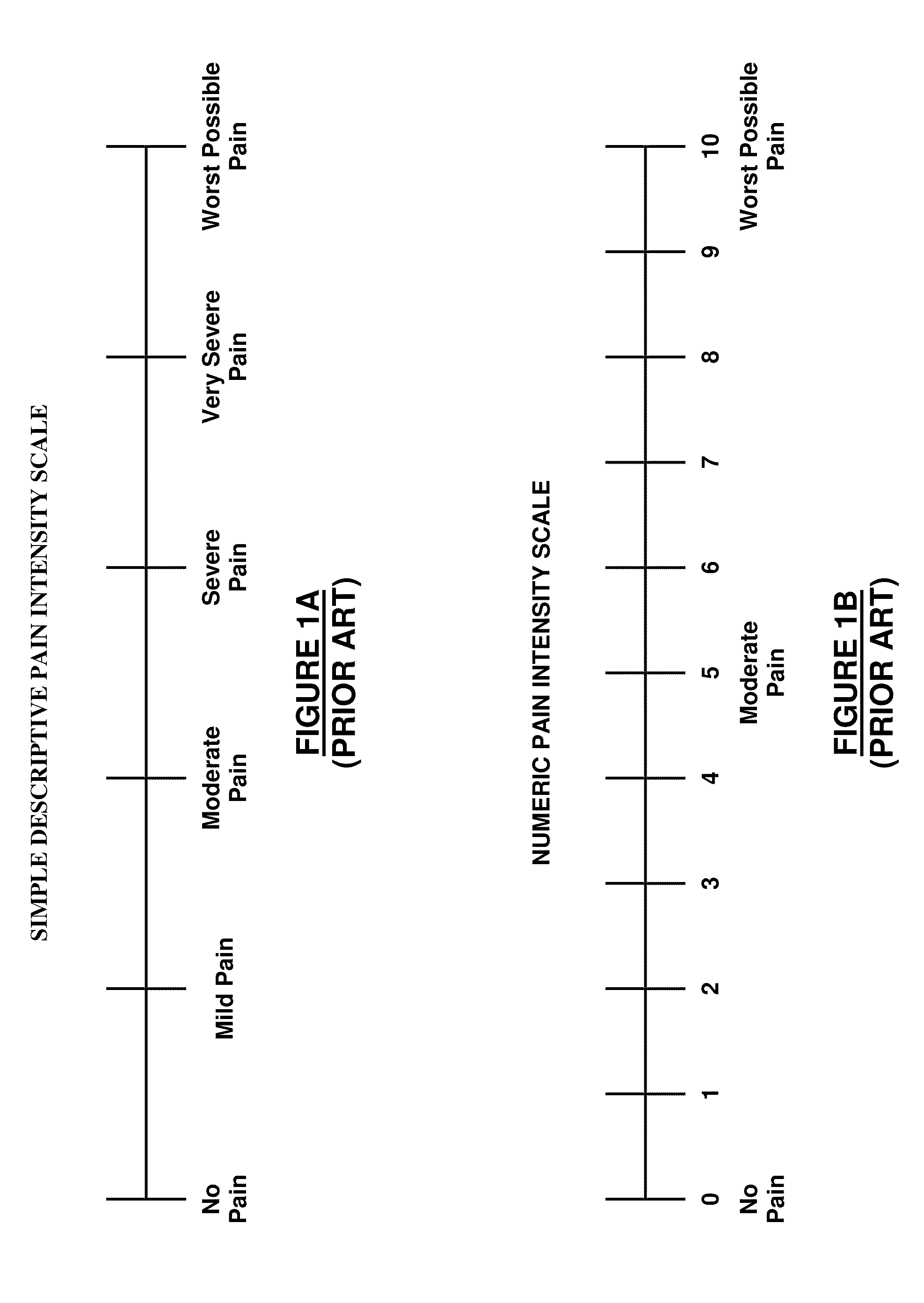
Apparatus and method for human algometry
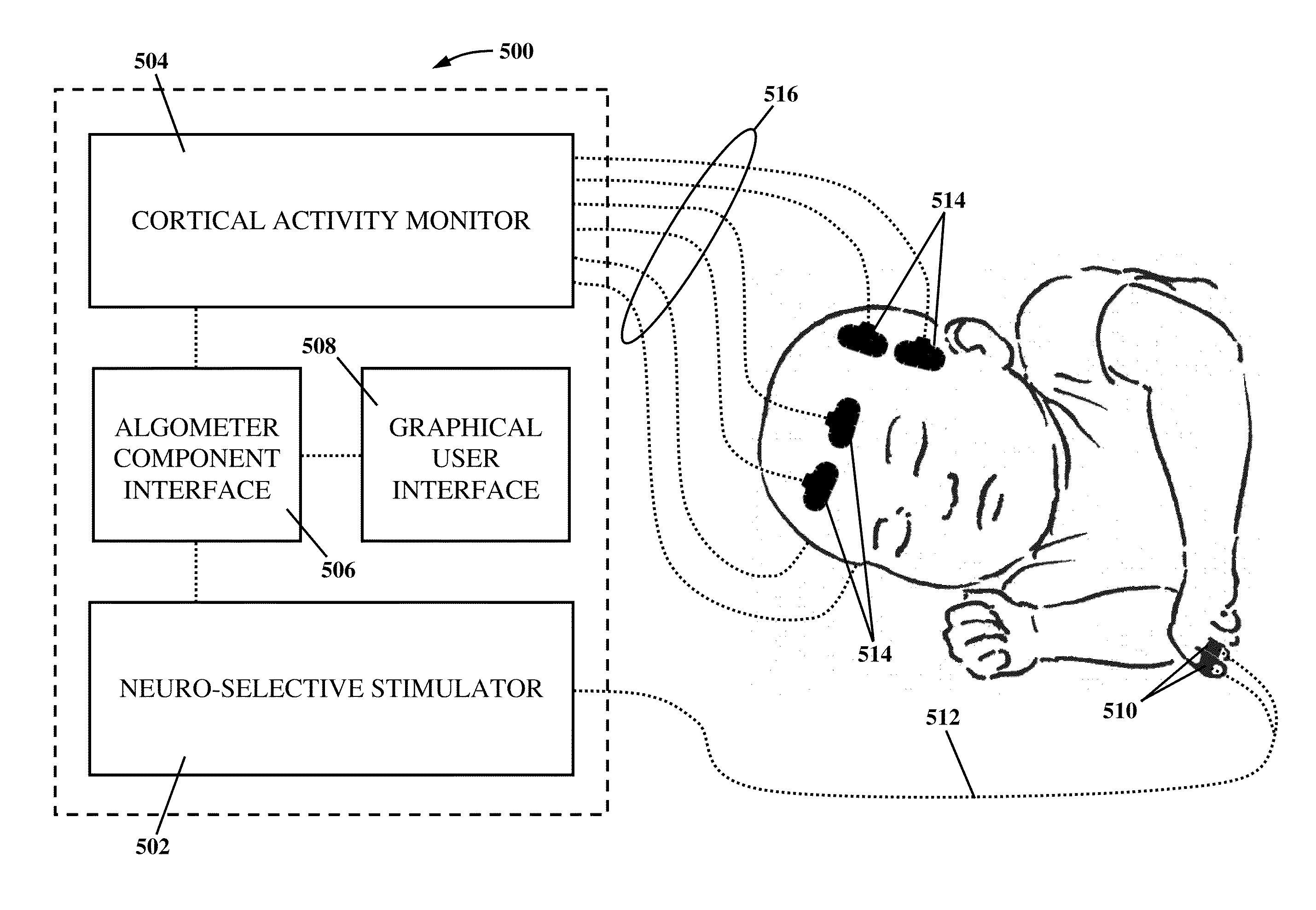
An apparatus and method for performing human algometry are disclosed. They include a stimulator configured to apply electrical stimulation of variable intensity to an area of a patient's body, a monitoring device configured to measure a. level of cortical activity in one or more regions of the patient's brain, and a microprocessor connected to the stimulator and the monitoring device that is configured to correlate the intensity of the electrical stimulation with the level of activity in the one or more regions of the patient's brain and to determine at least one of a measurement of pain intensity, a measurement of a sensory detection threshold (SDT), a measurement of a drug's analgesic impact, an indication of an onset of tolerance to a drug, an indication of an onset of analgesic-induced hyperalgesia, an indication of conditions of allodynia, a measurement of dose-response characteristics of pain management drugs, and a characterization of a pain condition.
Owner:CHILDRENS NAT MEDICAL CENT
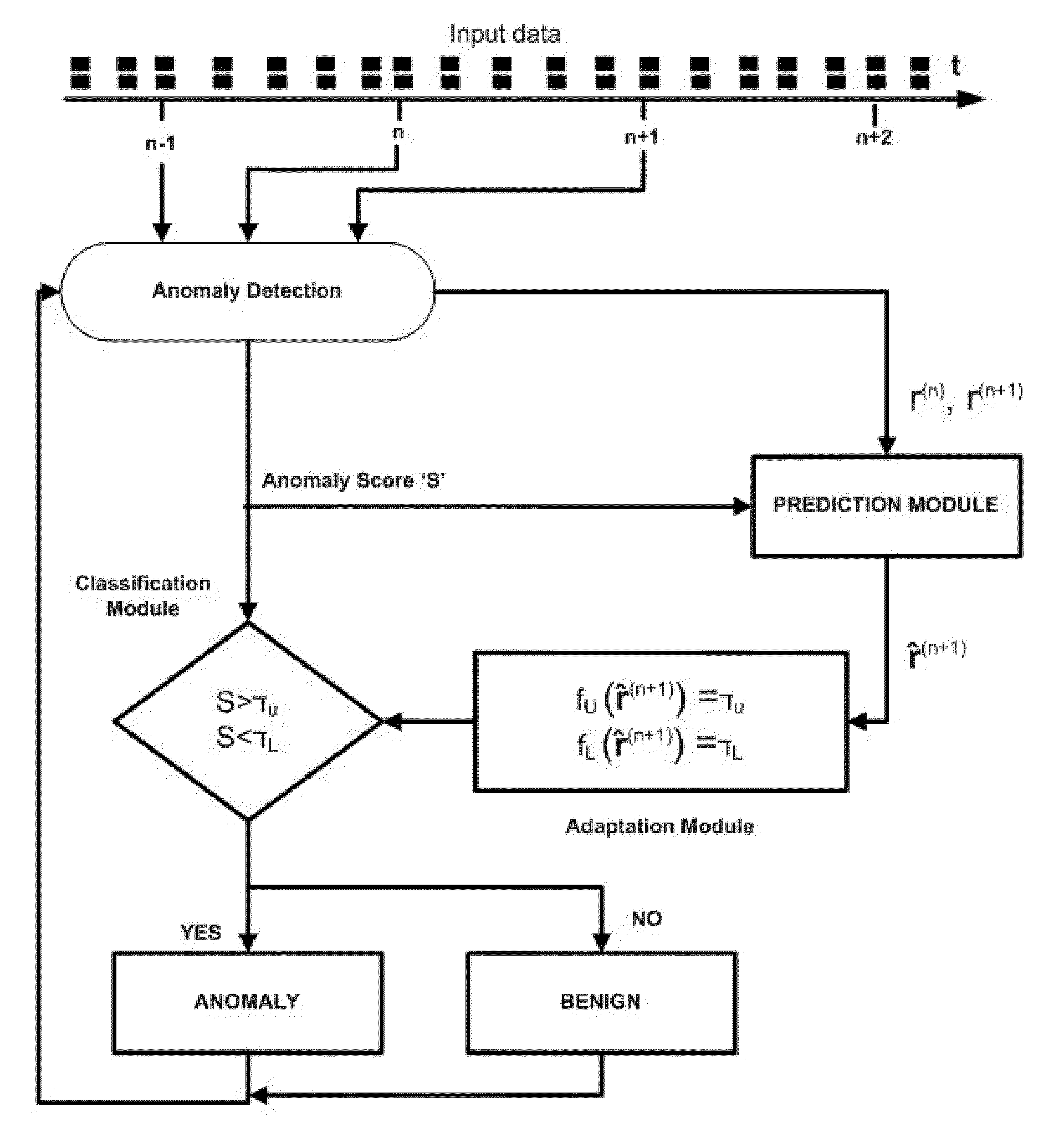
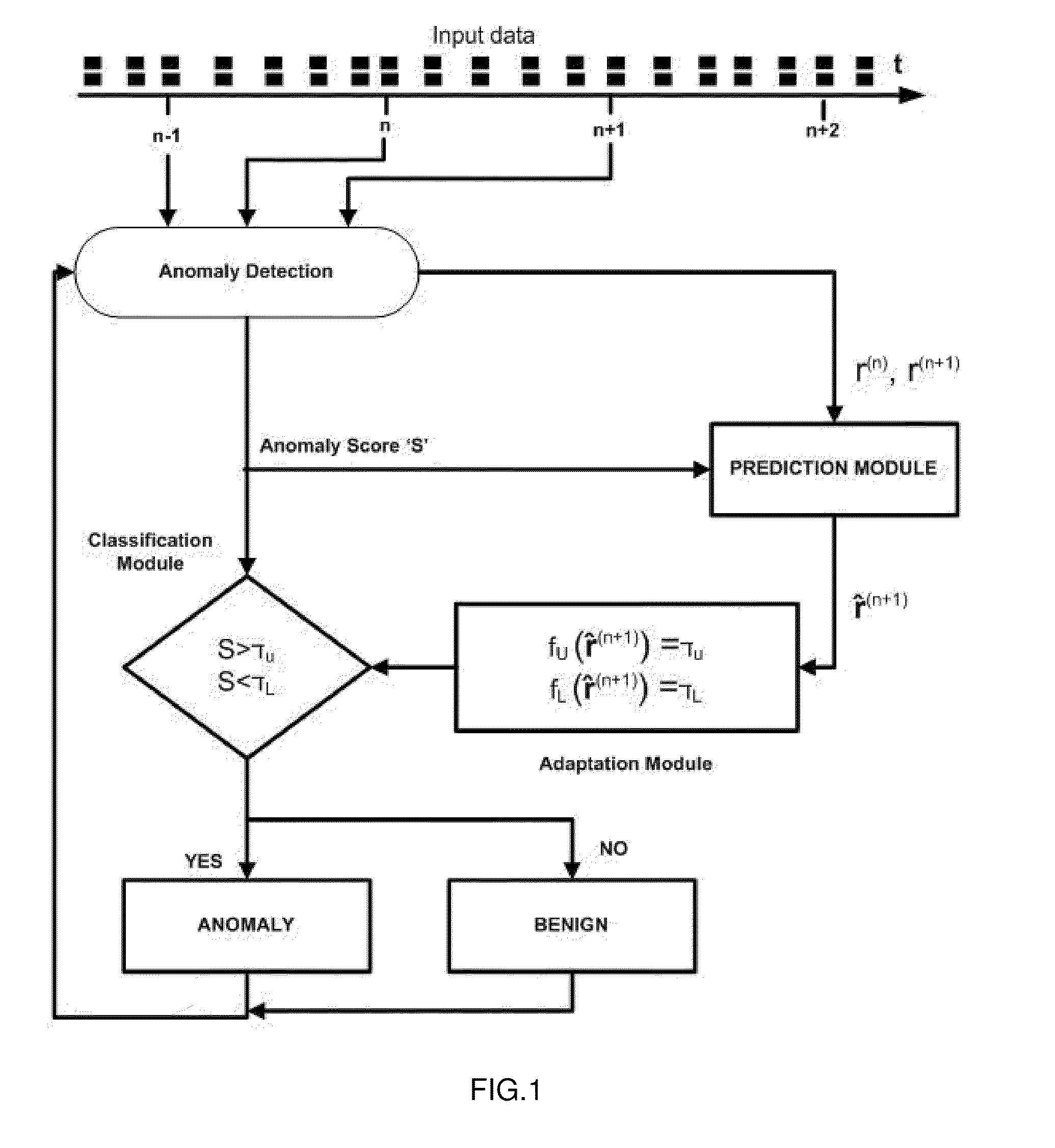
Method and system for adaptive anomaly-based intrusion detection
InactiveUS20110185422A1Convenient and accuratePoint becomes highMemory loss protectionError detection/correctionTime correlationNetwork behavior
The input characteristics of a real-time IDS change continuously with time therefore setting a rigid (time and behavior invariant) classification threshold limits the accuracy that the IDS can potentially achieve. A generic threshold tuning method and system is proposed which can adaptively tune the detection threshold of a real-time IDS in accordance with varying host and network behavior. The method and system perform statistical and information-theoretic analyses of network and host-based IDSs' anomaly based intrusions to reveal a consistent time correlation structure between benign activity periods which is used to predict future anomaly scores and to adapt an IDS' detection threshold accordingly.
Owner:THE SCHOOL OF ELECTRICAL ENG & COMP SCI SEECS NAT UNIV OF SCI & TECH NUST
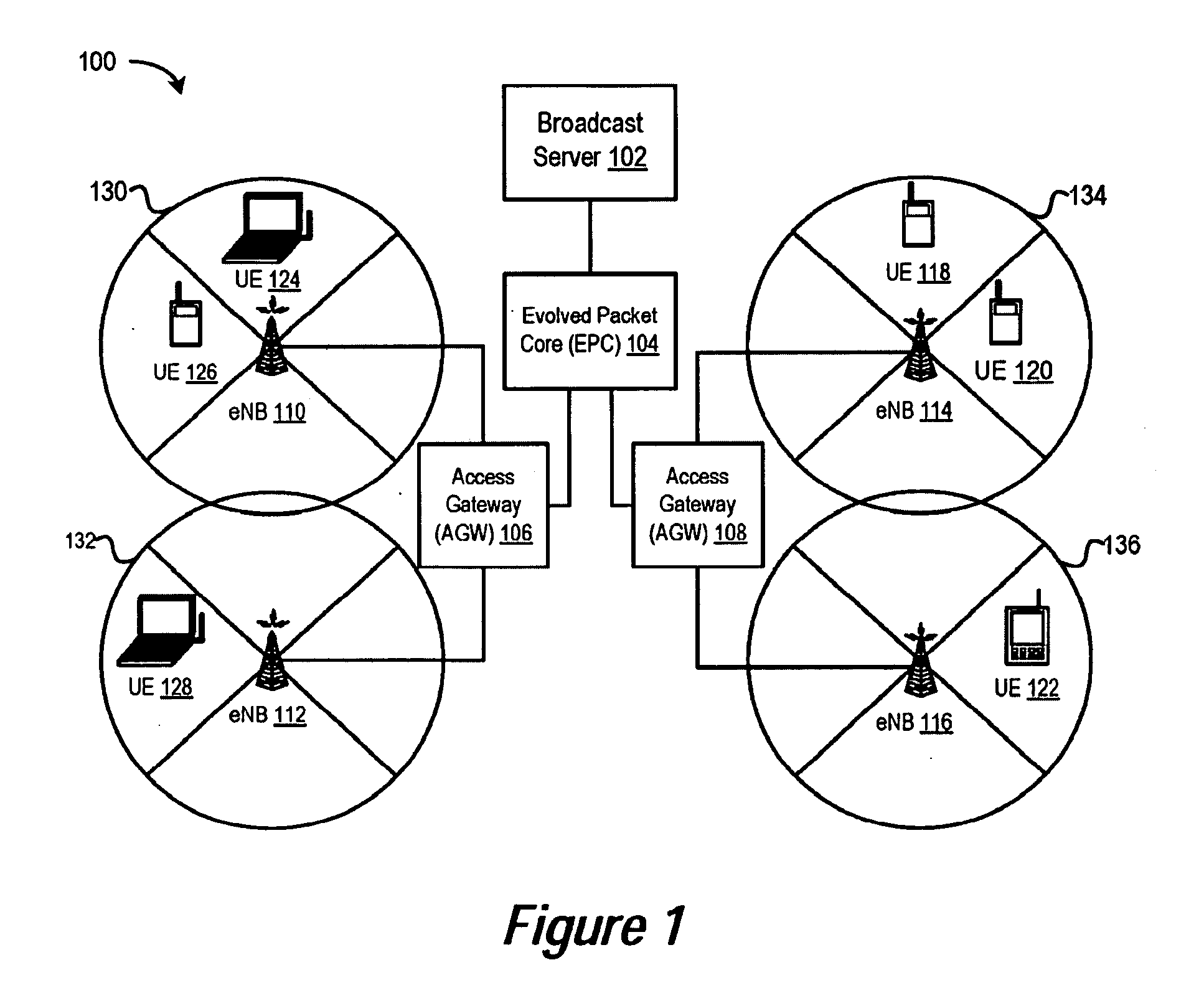
Video service buffer management in a mobile rate control enabled network
InactiveUS7895629B1Network traffic/resource managementGHz frequency transmissionDetection thresholdFrame rate
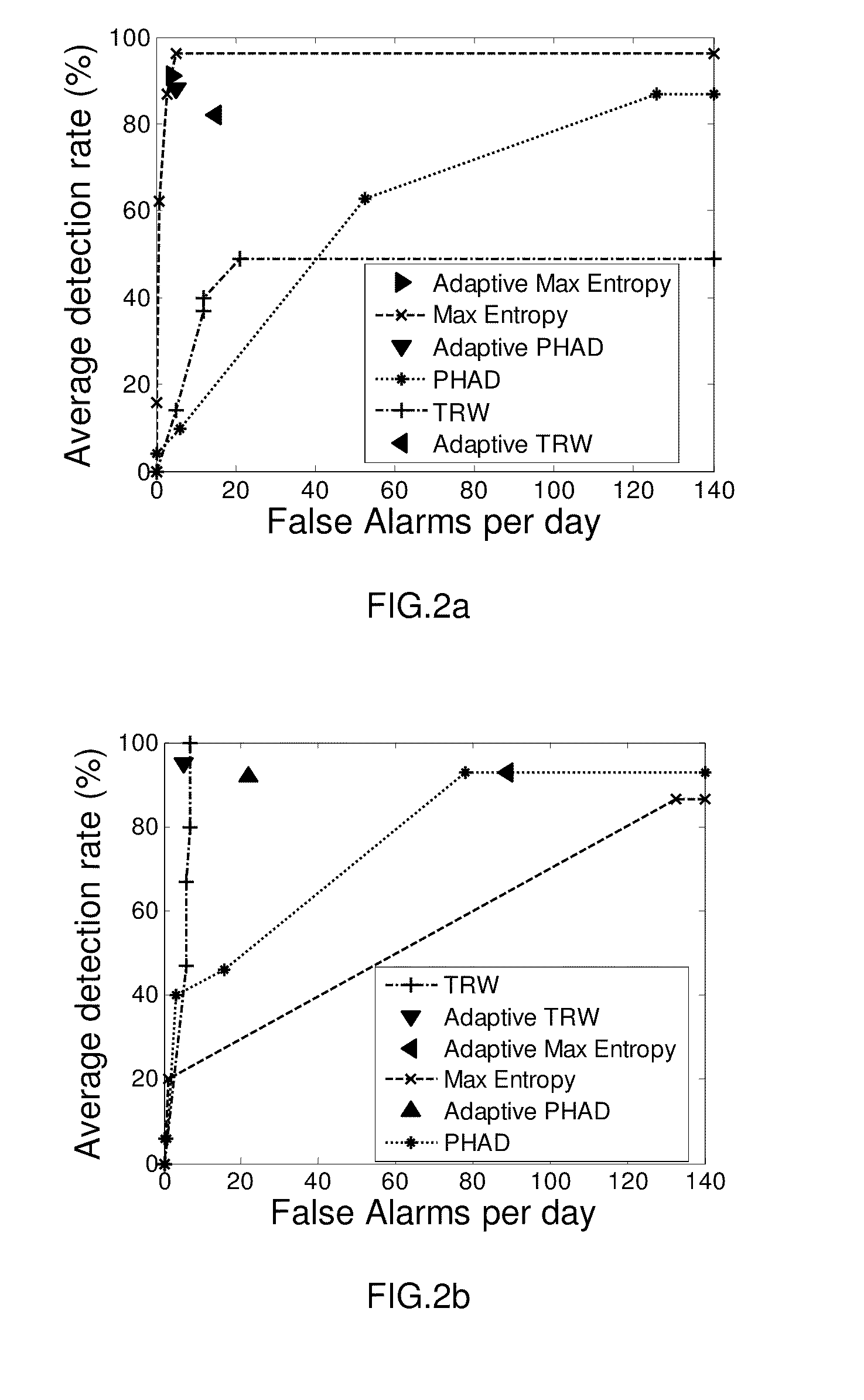
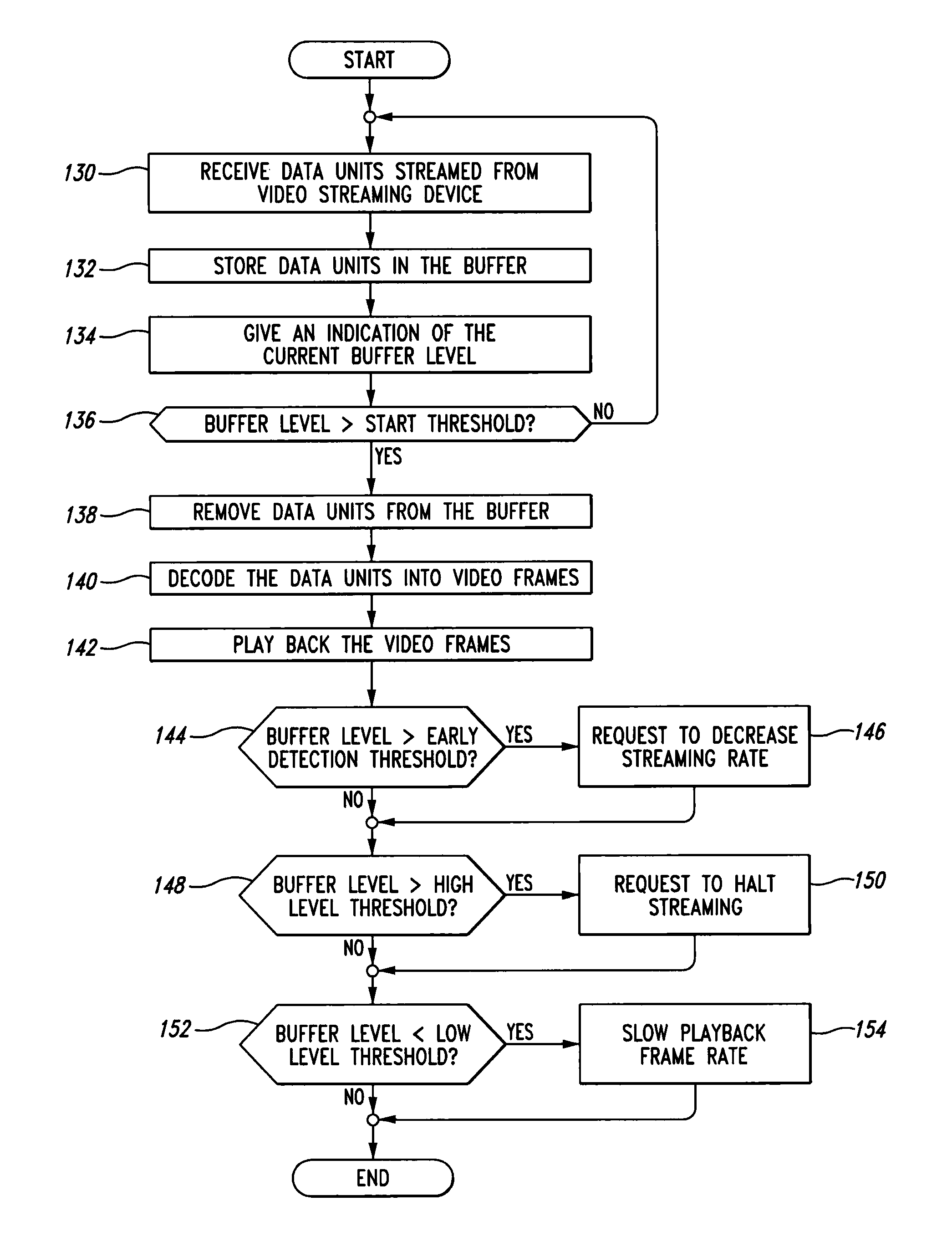
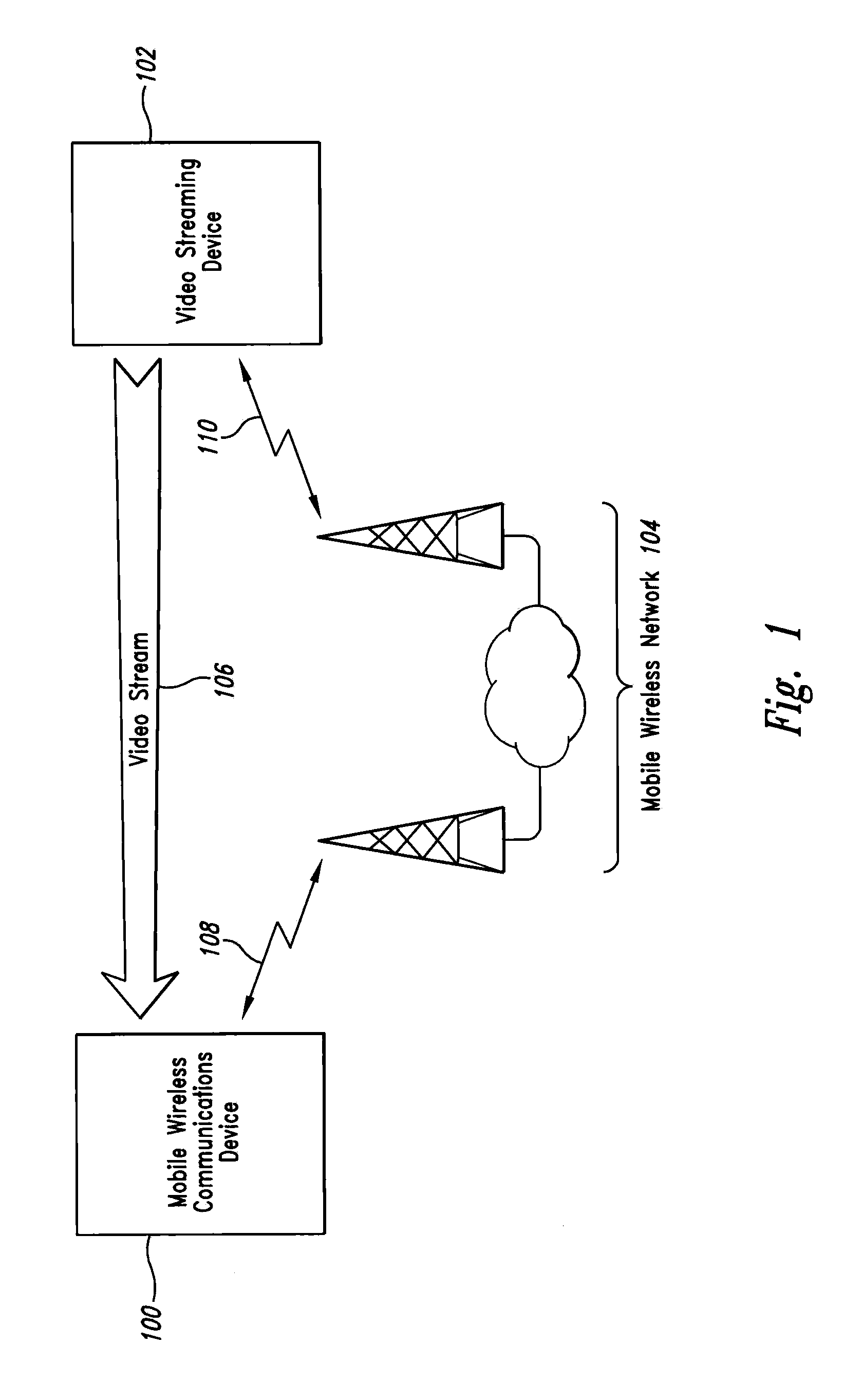
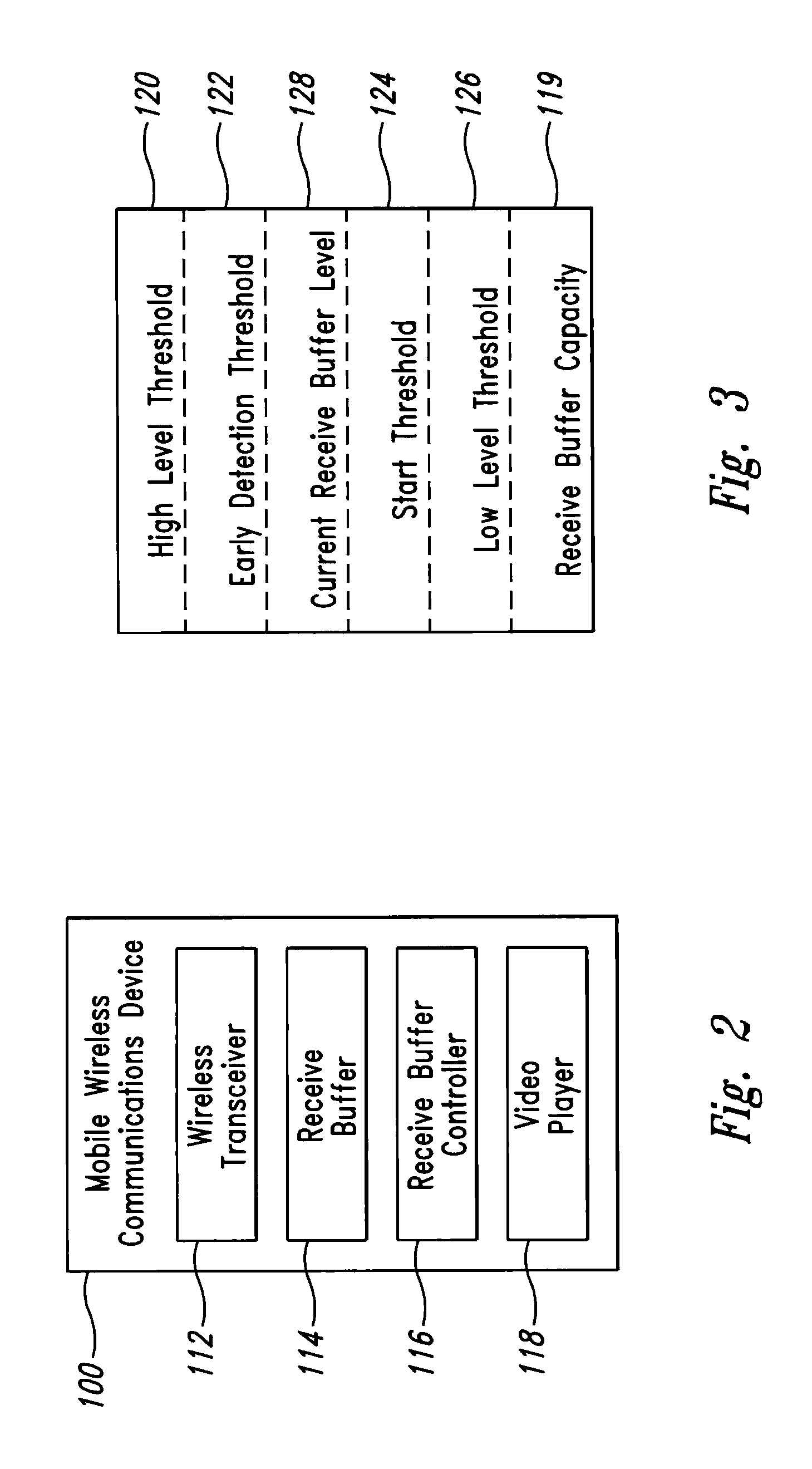
A system for a mobile wireless device to receive and display a video stream while preventing overflow or starvation of its receive buffer by requesting changes to the video streaming or encoding rates and by controlling the video playback frame rate. The current receive buffer level is used to make comparisons with several thresholds, the results of which are used to trigger actions. If the current receive buffer level has risen above a start level, then playback of the video can begin. If the current receive buffer level rises above an early detection threshold, then the video streaming device is requested to slow its streaming rate. If the current receive buffer level rises above a high level threshold, then the video streaming device is requested to stop streaming the video. If the current receive buffer level drops below a low level threshold, then the playback frame rate is slowed.
Owner:AT&T MOBILITY II LLC
Signal detection in cognitive radio systems
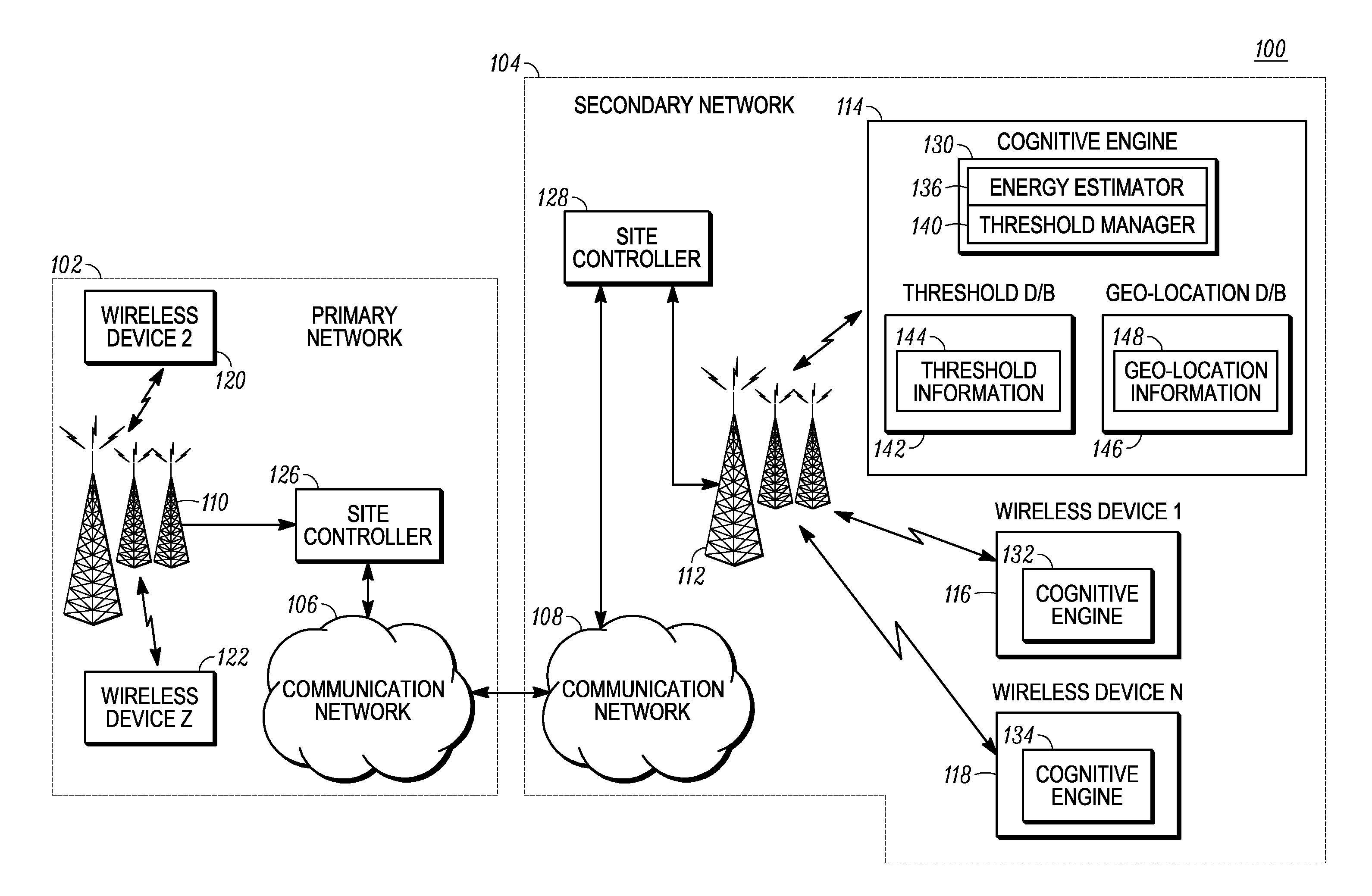
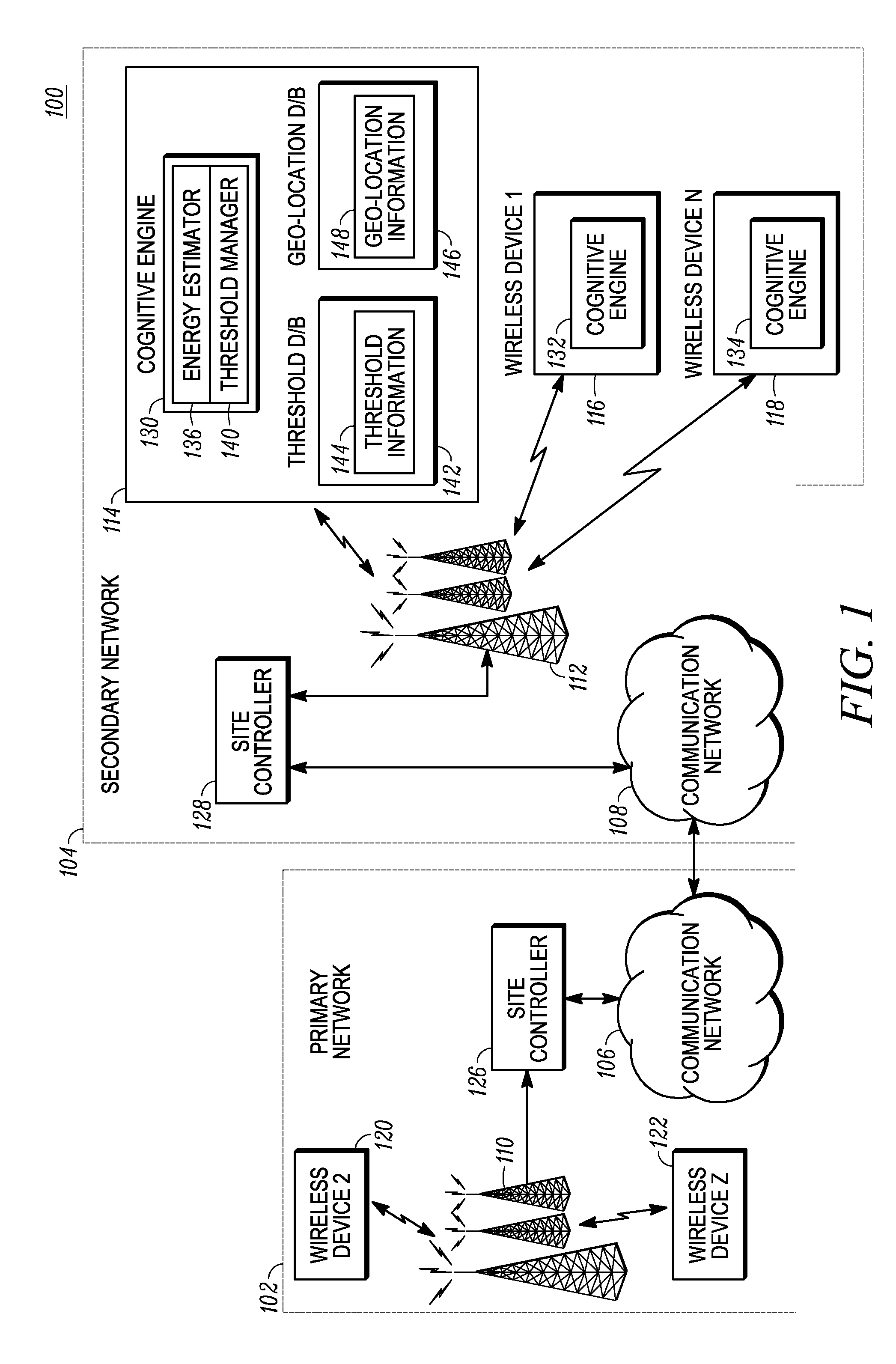
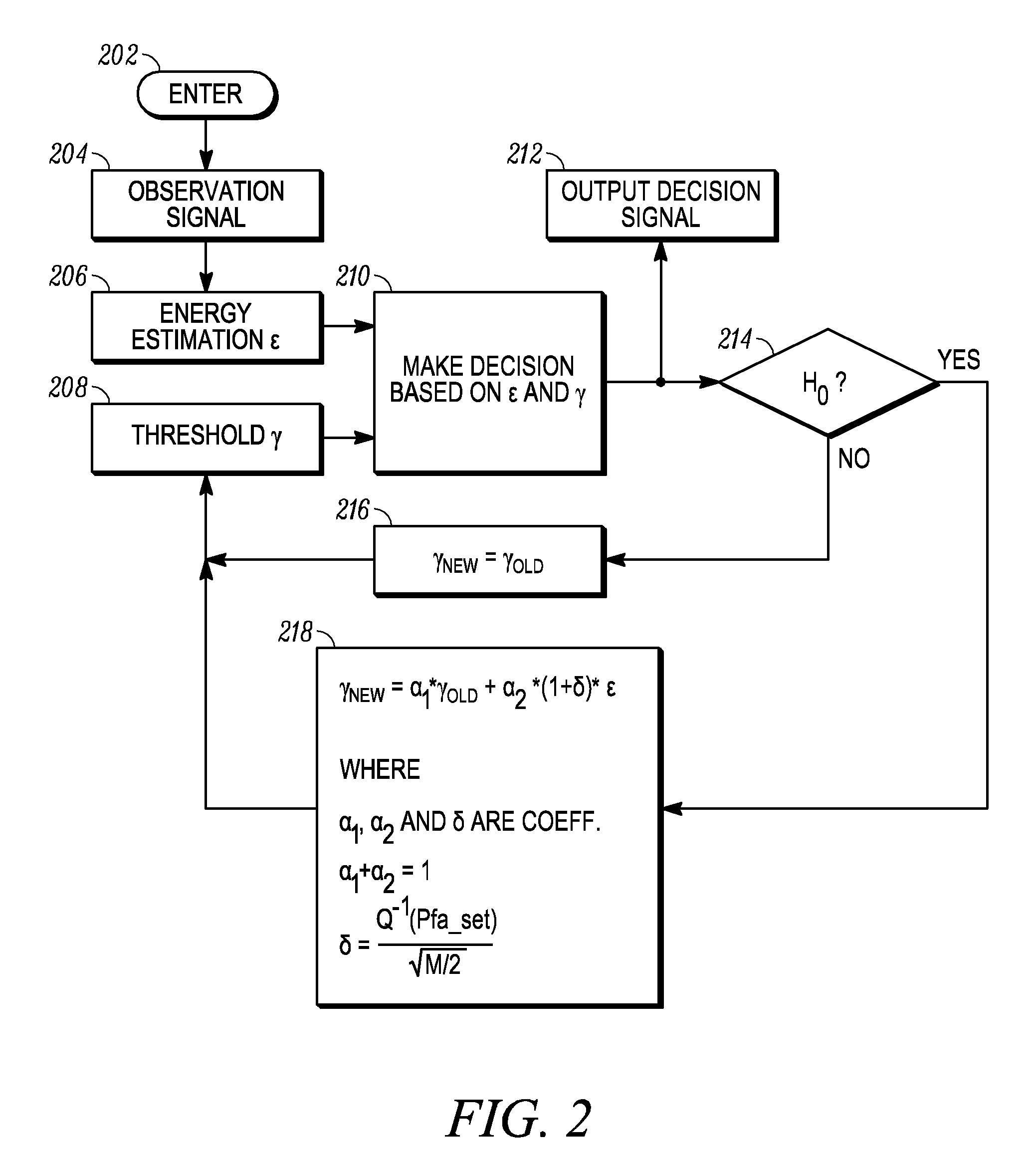
ActiveUS20100081387A1Efficient use ofTransmission monitoringLine-transmission monitoring/testingEnergy estimationComputer science
A cognitive radio wireless device (114) dynamically manages signal detection in a cognitive radio system (100). Spectrum sensing is performed for a first sensing frame on at least one communication channel. At least one observed signal is received (204) on the at least one communication channel. A detection decision (210) is performed to determine if the observed signal is noise or an active signal associated with an active user. The detection decision (210) is performed by comparing observed signal energy estimation with a current detection threshold. The current detection threshold can be an arbitrarily defined threshold or a detection threshold based on a previous detection decision for a sensing frame immediately prior to the first sensing frame.
Owner:MOTOROLA SOLUTIONS INC
Detection method for accidental precursor access
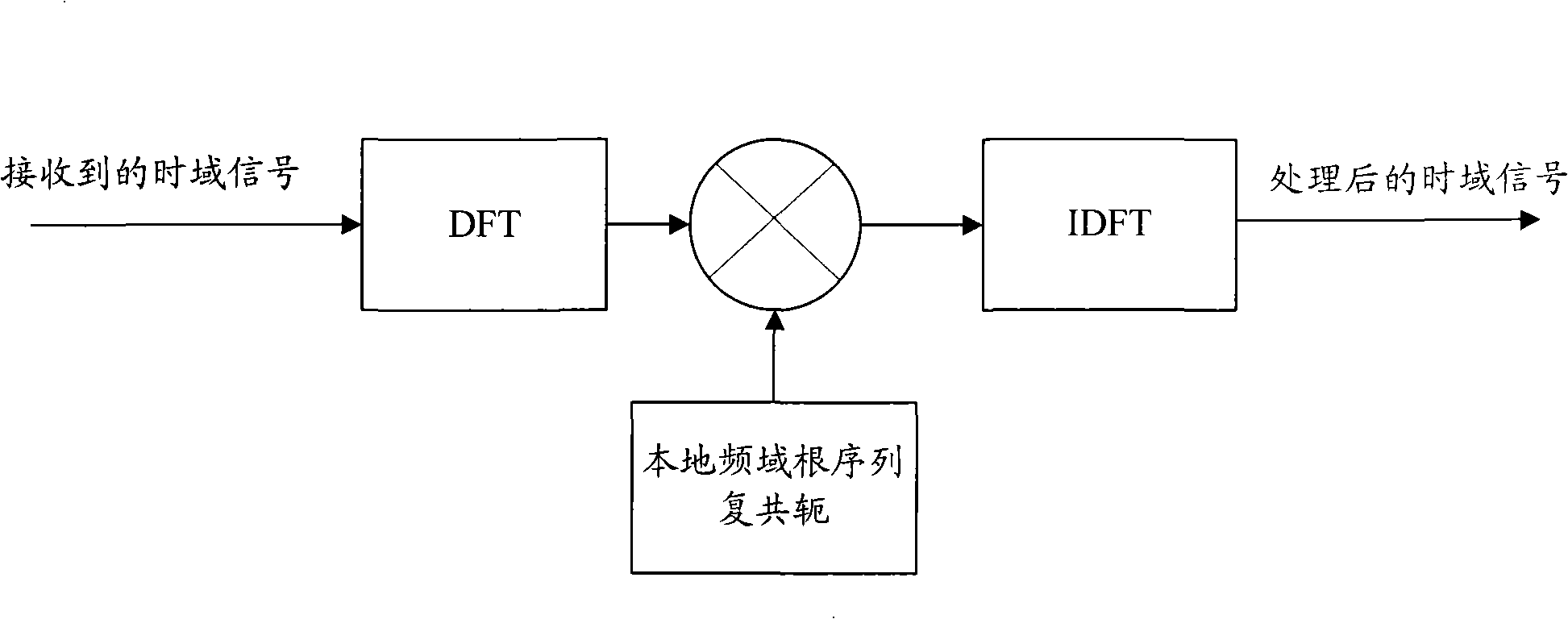
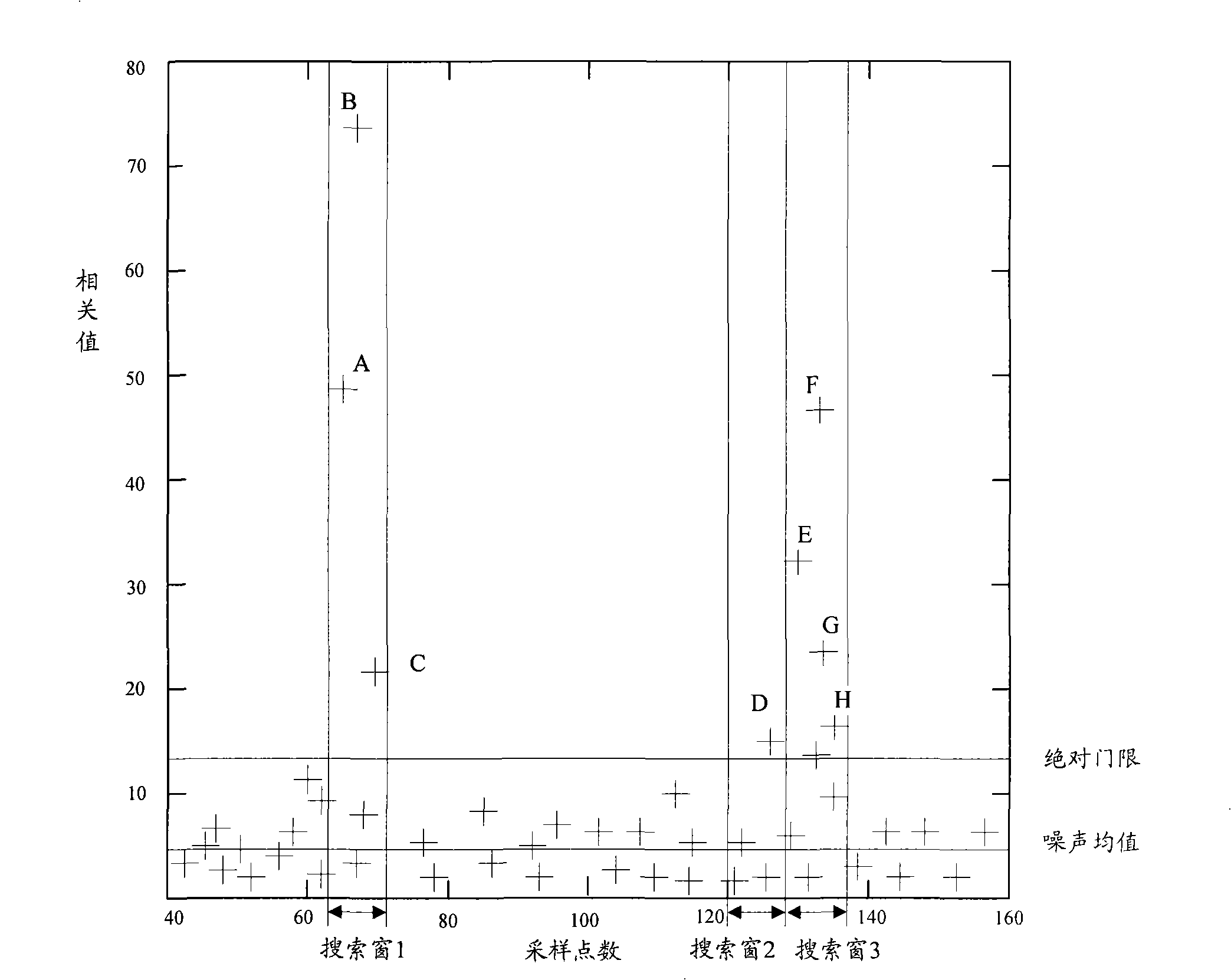
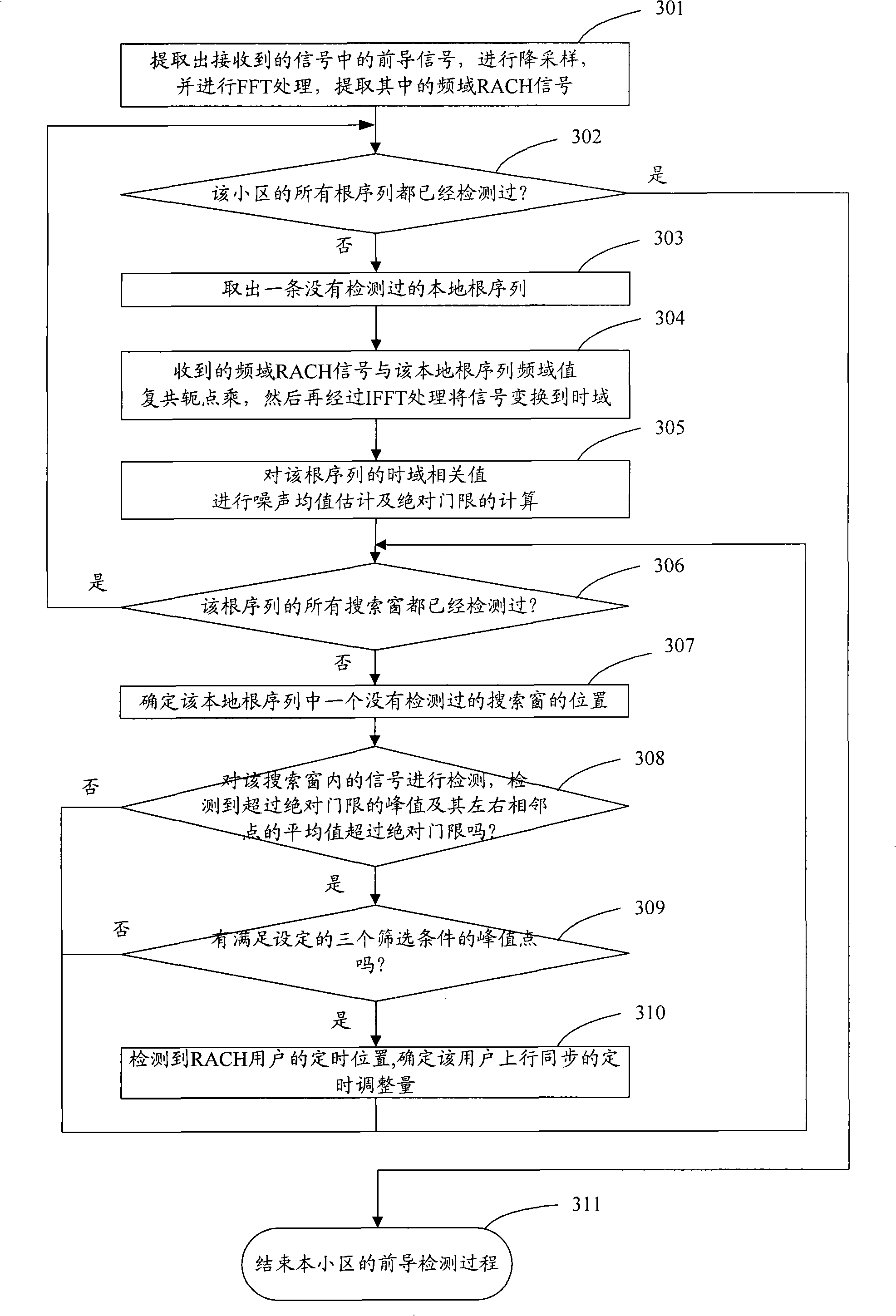
ActiveCN101295999AReduce computationReduce the difficulty of data processingModulated-carrier systemsWireless communicationTime domainAbsolute threshold
The invention discloses a method for detecting a random access leader. After a random access channel (RACH) signal is treated with the simplified time domain-related operation, noise mean estimation is carried out to each root sequence; an absolute threshold is then detected according to a signal obtained by the noise estimation and signals in a search window are detected; the signals which exceed the detection threshold are screened and then a timing position can be determined in a fast and accurate way so as to provide reliable uplink timing adjustment information to a mobile terminal, guarantee the accuracy of the uplink synchronization and effectively eliminate the timing error due to the over-sampling and reduce the false alarm in the detection.
Owner:ZTE CORP
Automatic threshold selection method for improving the detection of a wireless signal
ActiveUS20050181731A1Easy to detectInfluence is negligiblePower managementTransmission noise suppressionSignal qualityWireless transmission
System and method for improving the detection performance of a wirelessly transmitted signal. A preferred embodiment comprises specifying a desired response for missed channel detection and false alarm probabilities for a plurality of signal qualities and determining if a channel detection threshold is based on missed channel detection or false alarm probabilities for the plurality of signal qualities. A signal quality estimate of a channel can be inferred from a signal quality measurement of a second channel, wherein the channel and the second channel are sourced by a single transmitter. The channel detection threshold can be adjusted based upon the previously determined required response and the signal quality estimate of the channel.
Owner:TEXAS INSTR INC
Video analysis based abnormal behavior detection method and system
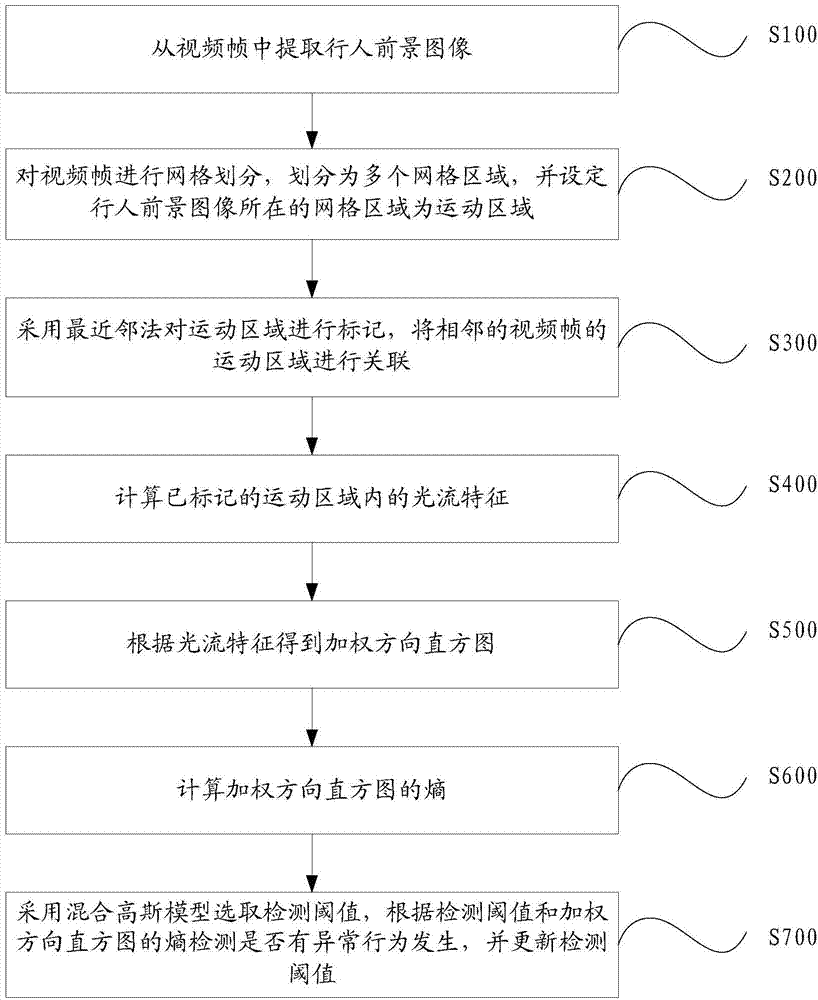
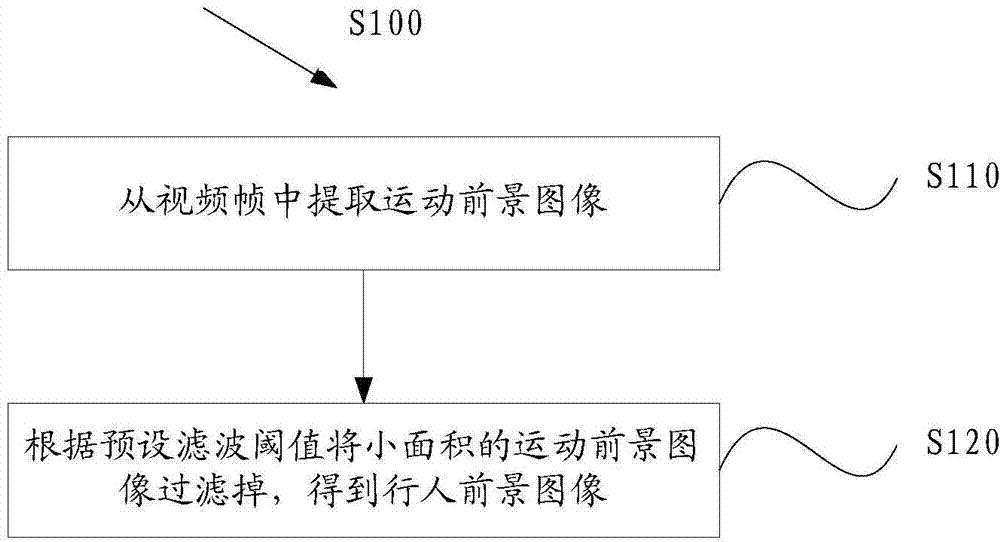
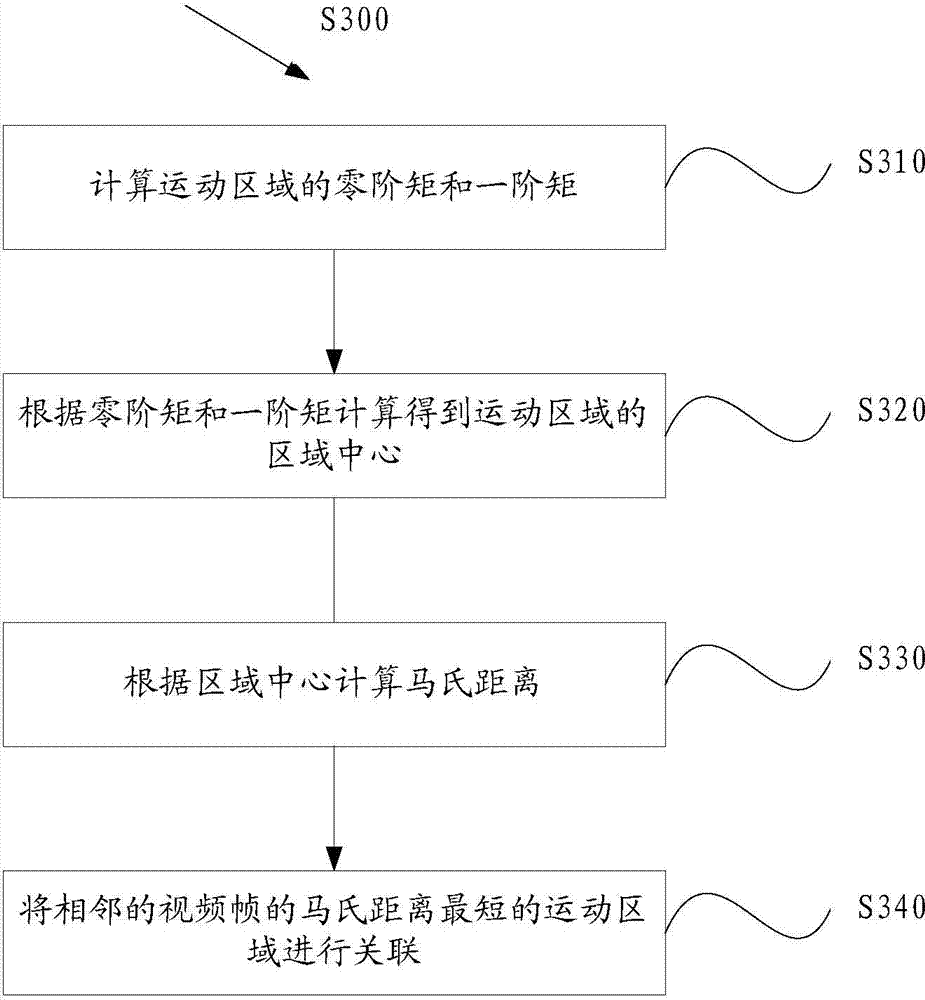
ActiveCN104123544AReduce workloadEndanger public safetyCharacter and pattern recognitionAnomalous behaviorNear neighbor
The invention provides a video analysis based abnormal behavior detection method and system. The video analysis based abnormal behavior detection method comprises the following steps of extracting pedestrian foreground images from video frames; performing mesh generation on the video frames to divide the video frames into a plurality of mesh areas and setting the mesh areas in which the pedestrian foreground images are arranged to be movement areas; marking the movement areas through a nearest neighbor method and correlating the movement areas of the adjacent video frames; calculating light stream characteristics of the marked movement areas; obtaining a weighting direction histogram according to the light stream characteristics; calculating entropy of the weighting direction histogram; selecting a detection threshold value through a Gaussian mixture model, detecting whether an abnormal behavior is generated or not according to the detection threshold value and the entropy of the weighting direction histogram and updating the detection threshold value. The nested state machine based deduction process control method can automatically detect the abnormal behavior in a video scene, avoid the abnormal behavior disturbing the public plate order and endangering the public security and personal safety, reduce personnel workload and avoid potential risks caused by leak detection and error detection.
Owner:CRSC COMM & INFORMATION GRP CO LTD
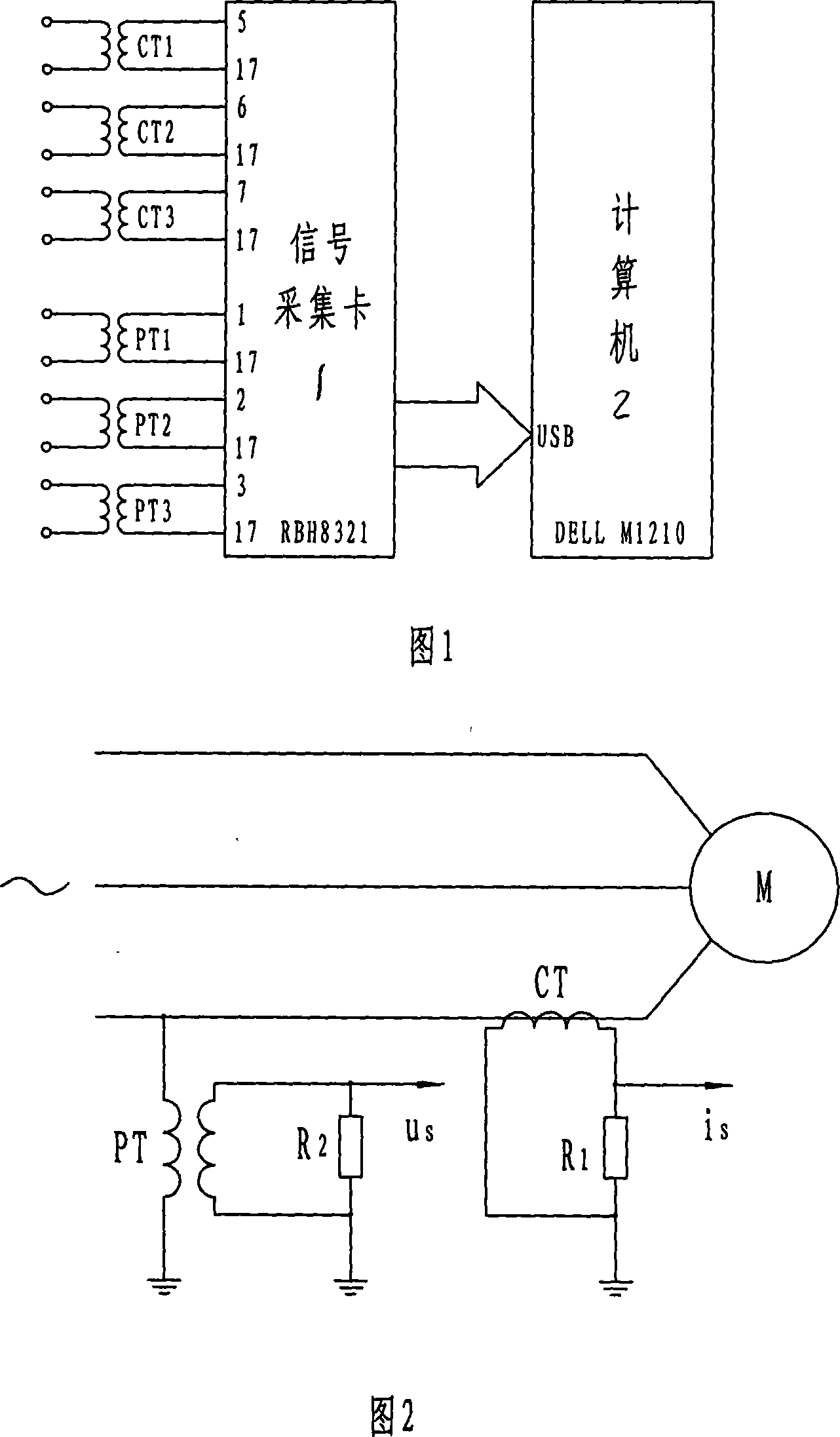
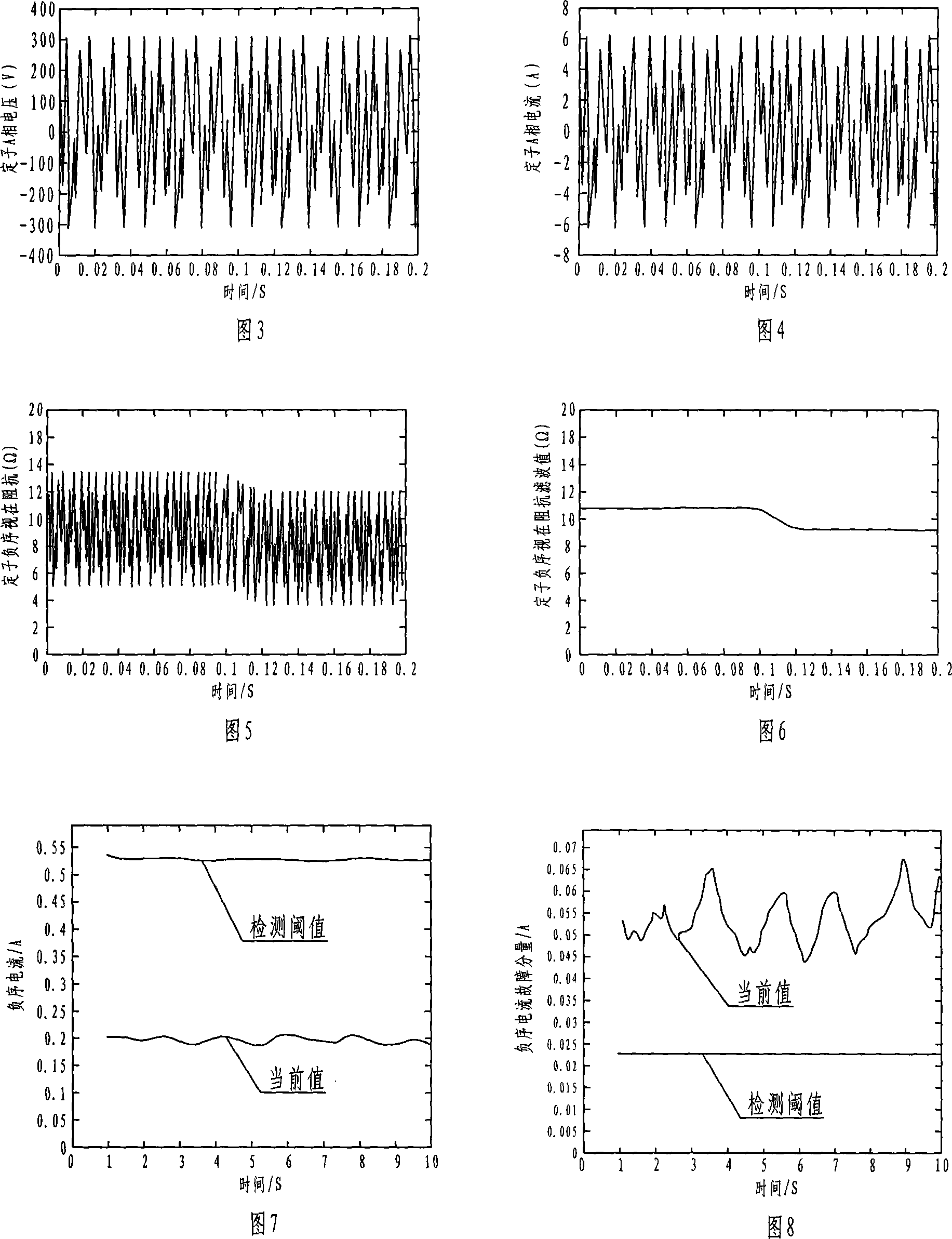
Asynchronous motor stator winding inter-turn short circuit failure on-line detecting method and device
InactiveCN101025434AGuaranteed safe operationAvoid adverse effects of fault detectionDynamo-electric machine testingStator voltageInduction motor
The invention relates to a online testing process for shorted fault of asynchronous motor's stator winding, which is belong to Detecting Technology. It was designed to solve the detecting problem of stator winding. The project is that it figures out the voltage and current of negative sequence and positive sequence of the stator winding by collecting three-phase stator voltage, instantaneous-current signal. Then using of normal motor sample reference document estimated the filter value of the stator negative sequence, figured out the stator negative sequence current fault component. And then base on the threshold of the stator negative sequence current fault component educe failure exponent. Finally according to the index judge whether to exist short circuit failure or not. This invention also gave corresponding detection device. Not only can high sensitivity, high reliability and on-line measurement asynchronous motor stator windings at the beginning of the early short circuit fault, but also can judge short circuit phase. This can effectively ensure the asynchronous motor operating safely.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Snore detecting method and apparatus
InactiveUS20030066529A1Improve detection accuracyRespiratorsOperating means/releasing devices for valvesSupporting systemIntensive care medicine
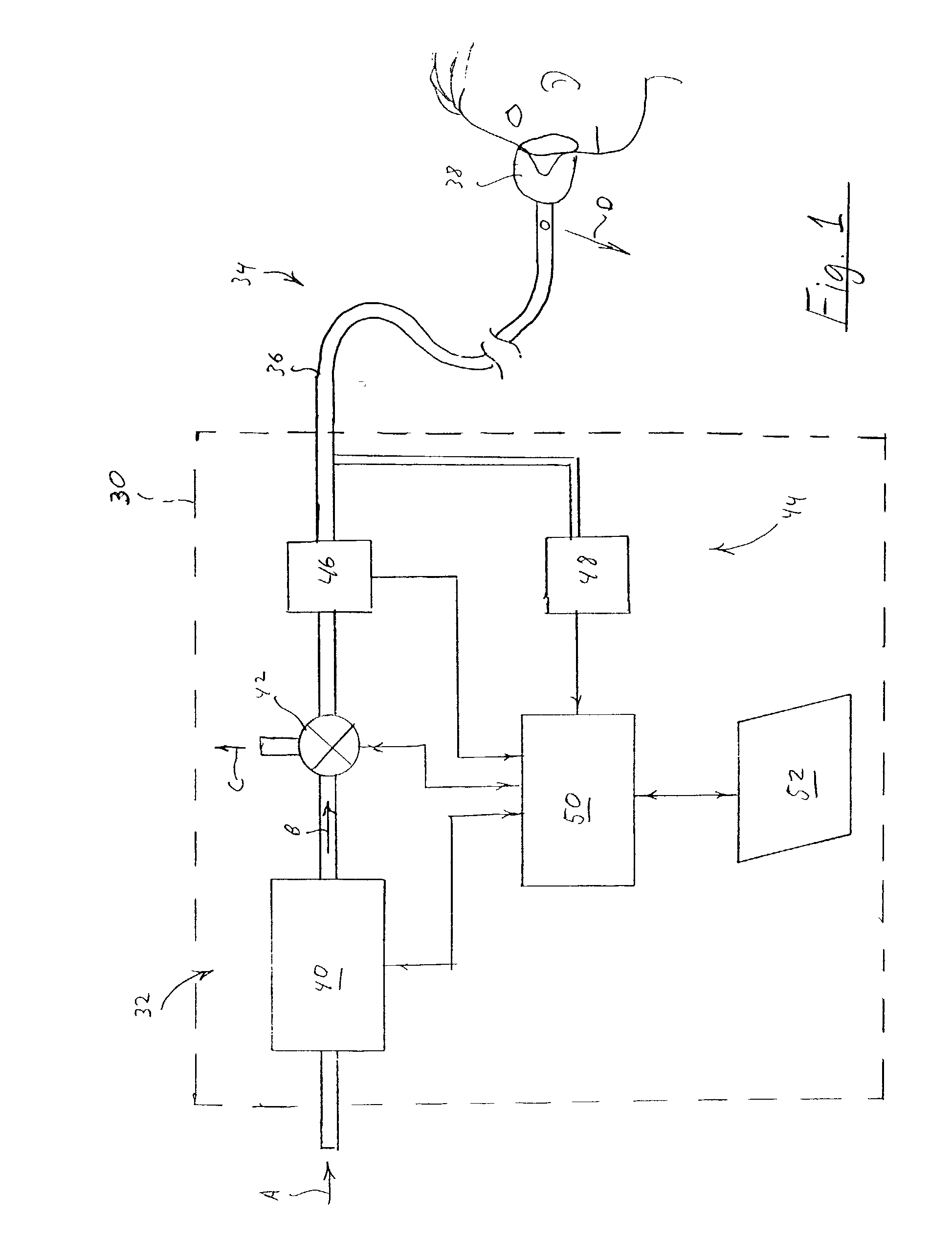
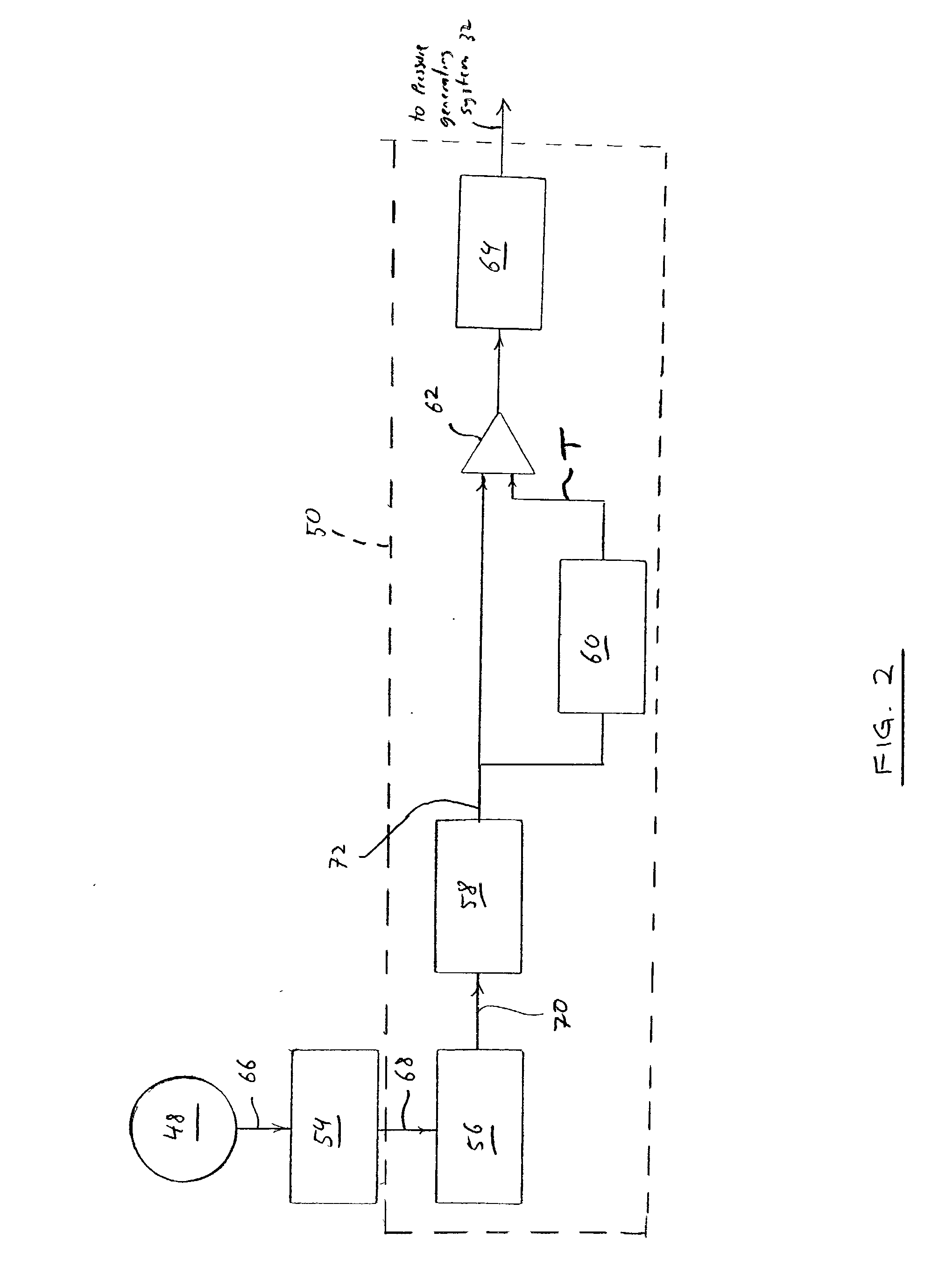
Method and apparatus for detecting disordered breathing in a patient and, in particular, to a method and apparatus for detecting patient snoring and / or for dynamically determining a snore detection threshold, and to a pressure support system and method of providing pressure support that uses this unique snore detection and / or snore detection dynamic adjustment technique to control the pressure provided to at patient.
Owner:RIC INVESTMENTS LLC
Management of ARQ Detection Threshold in Communication Networks
ActiveUS20100042881A1Error prevention/detection by using return channelTransmission systemsQuality of serviceTransmitted power
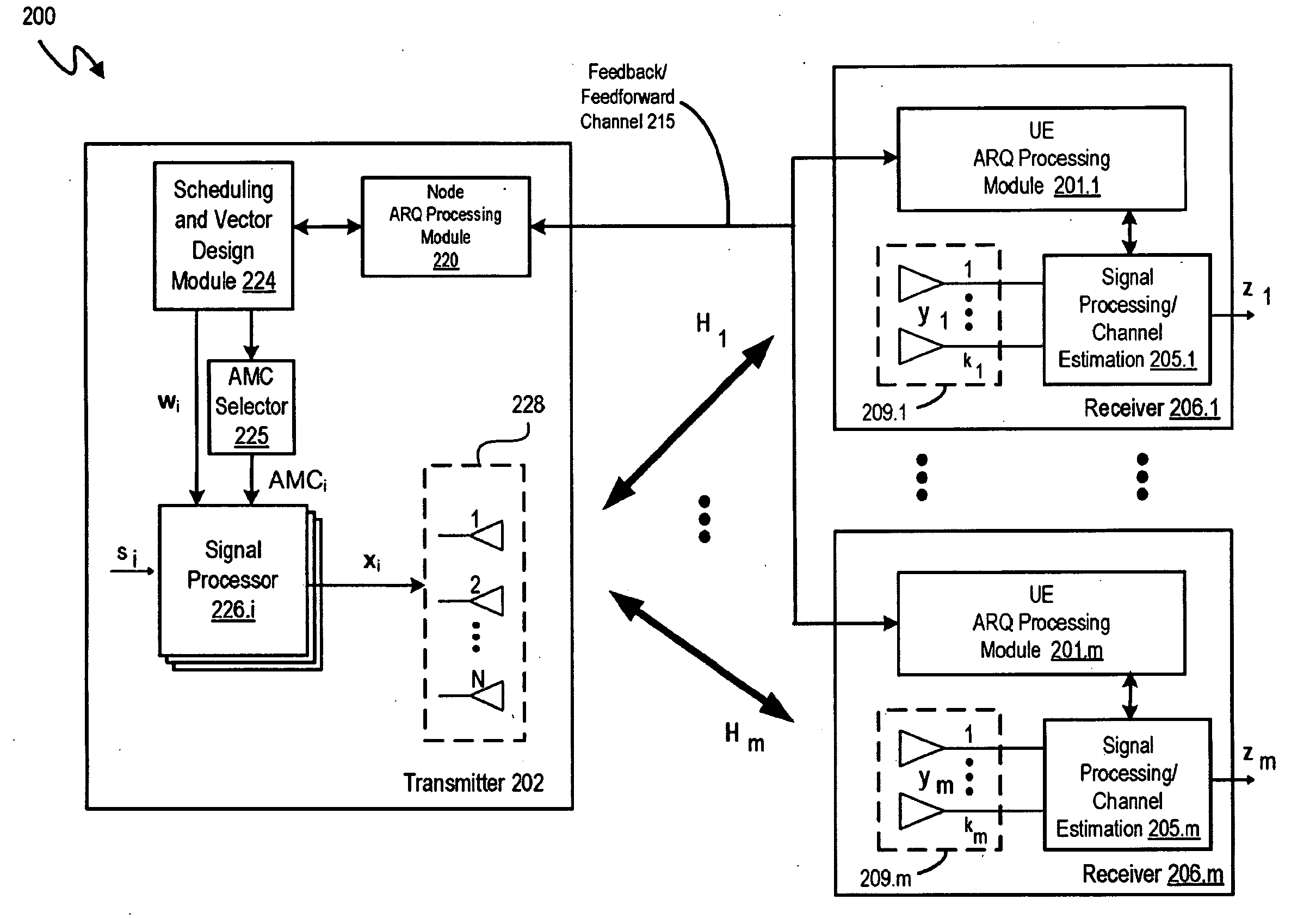
Embodiments of a system and methodology are disclosed for enabling a network to manage threshold values provided to UEs for use in decoding ACK-NAK signals. In various embodiments described herein, a base station signals an actual fixed threshold value in a semi-static manner for use by UEs to decode ACK / NAK signals. In these embodiments, the threshold value is part of a semi-static but UE-specific threshold value. This allows the base station to accommodate varying UE geometries, and optimize power savings for ACK-NAK transmissions. Embodiments of the invention also allow the base station to enforce a desired quality of service (QoS) without excessive power variations across ACK / NAK which are limited by the transmit power dynamic range.
Owner:APPLE INC
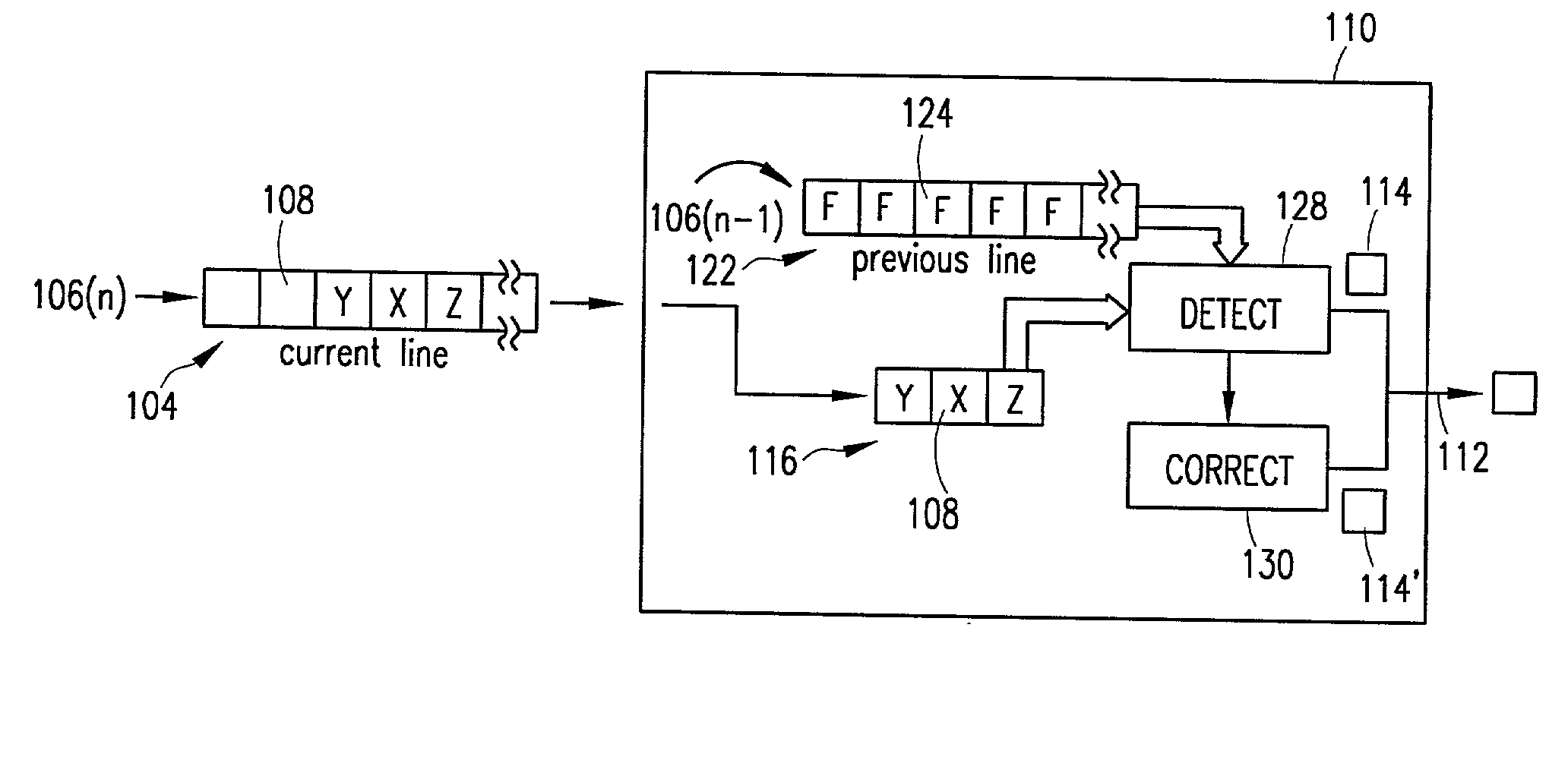
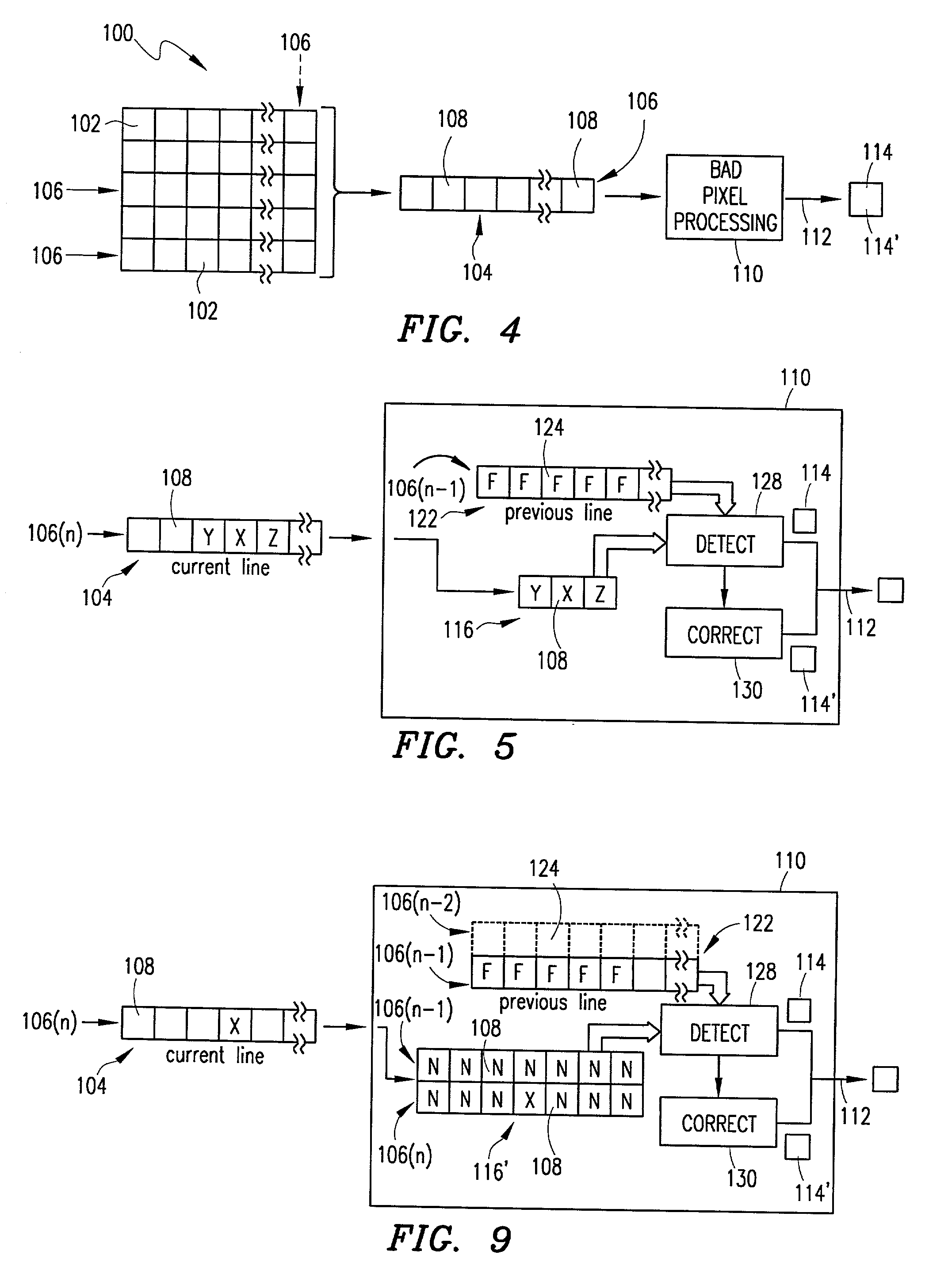
Bad pixel detection and correction in an image sensing device
InactiveUS20030001078A1Television system detailsSolid-state devicesCorrection algorithmPhotovoltaic detectors
A sensor includes an array of photodetectors each generating an output signal of pixel data indicative of incident light intensity. This pixel data is read out from the array one line at a time and stored in a line buffer. A bad pixel processor includes a first buffer that stores pixel data obtained from the line buffer for a certain pixel in a currently read out line and pixel signal light data for pixels adjacent to the certain pixel. An included second buffer stores features that are indicative of whether the pixels in a previously read out line were identified as bad pixels. Using the information in the first and second buffers, the processor identifies whether the certain pixel is a bad pixel. In one operation, the processor precludes any finding of the certain pixel as being a bad pixel if the features in the second buffer indicate that a pixel in the previous line that is adjacent to the certain pixel in the current line was identified as a bad pixel. In another operation, the processor applies a variable detection threshold against the certain pixel, with the value of that threshold being set higher if the features in the second buffer indicate that a pixel in the previous line that is adjacent to the certain pixel in the current line was identified as a bad pixel. When a bad pixel is detected, a correction algorithm is executed to replace the pixel data for the bad pixel with data that more accurately represents, estimates or approximates the intensity of the light that is incident on the photodetector.
Owner:OVONYX MEMORY TECH LLC
Device for monitoring the integrity of information delivered by a hybrid ins/gnss system
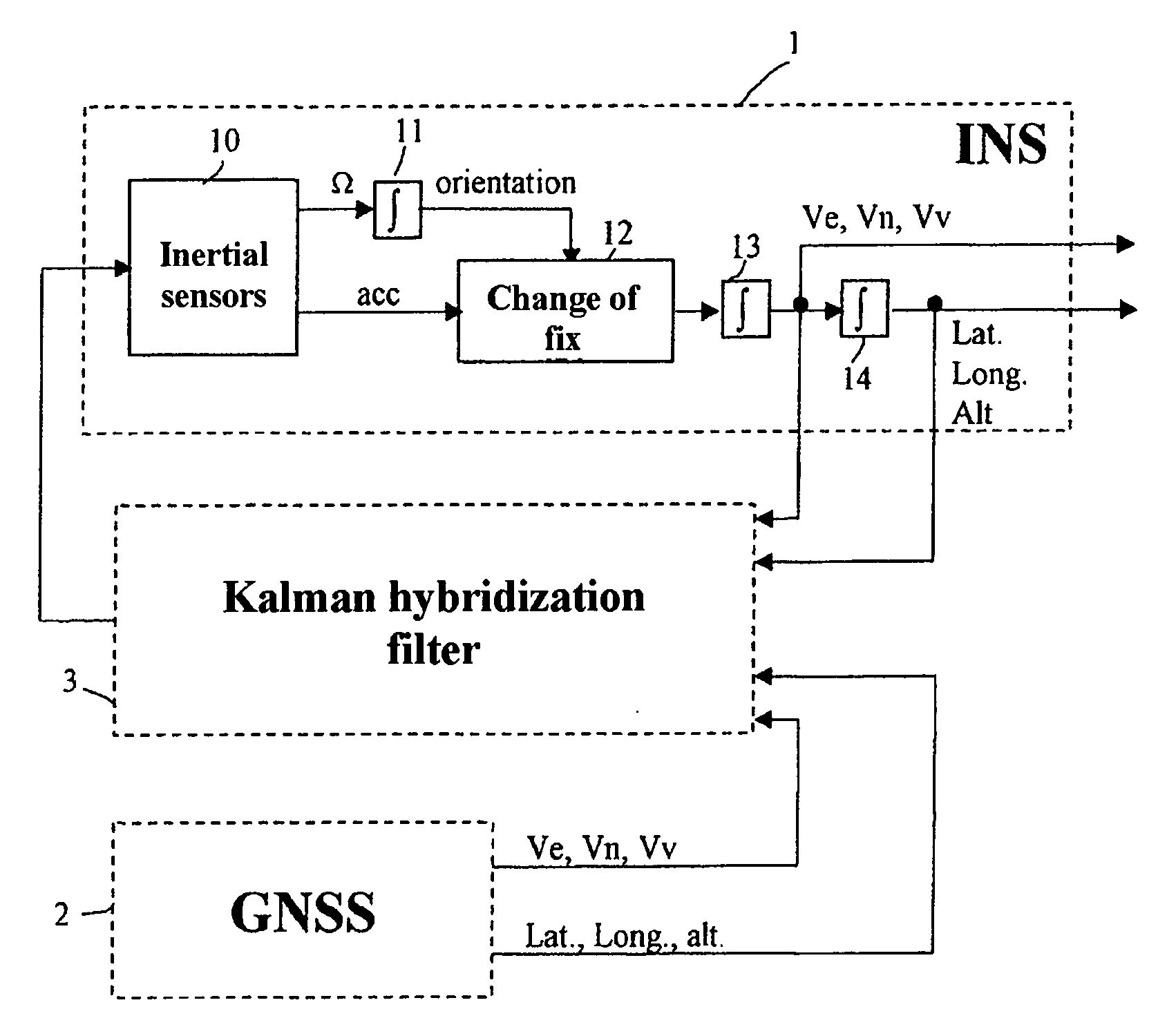
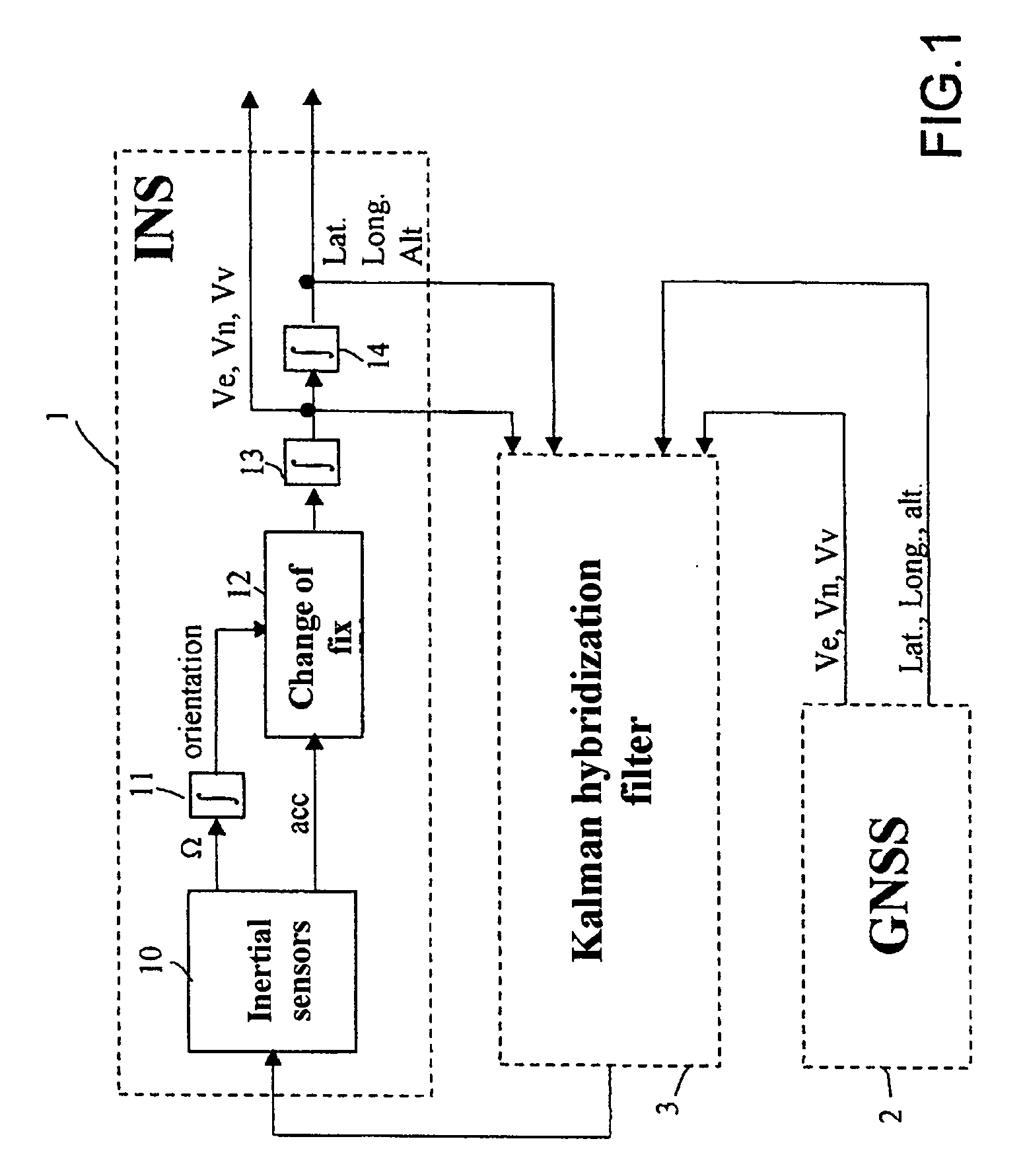
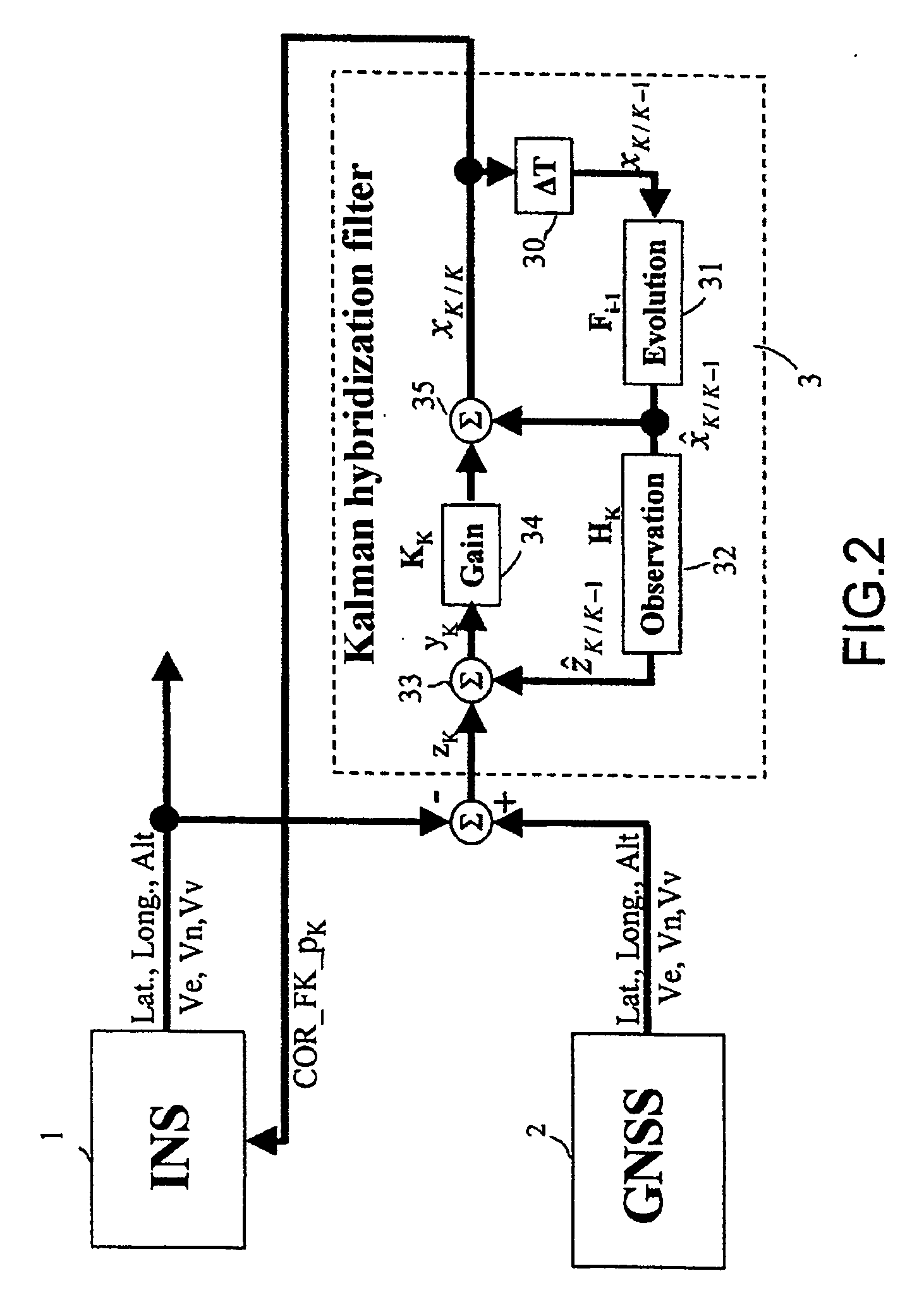
InactiveUS20070156338A1Navigation by speed/acceleration measurementsPosition fixationHybrid systemDetector circuits
The device is for monitoring the integrity of the position and speed information supplied by a hybrid system comprising an inertial unit INS readjusted using a GNSS satellite positioning receiver by means of a Kalman hybridization filter using a readjustment gain K and an evolution matrix F. It includes a satellite problem-detector circuit comprising a bank of predictor / estimator filters which uses the gain K and the evolution matrix F of the Kalman hybridization filter, each filter observing the deviation between the positioning point obtained from the N visible satellites, in the form of geographic coordinates, delivered by the GNSS receiver and one of the positioning points P(N−1) / i, also in the form of geographic coordinates, delivered by this same GNSS receiver, obtained by using N−1 of the N visible satellites for resolution, and test circuits comparing the states of the predictor / estimator filters with their variances and detecting a satellite failure when a test is positive, the deviation found being greater than a detection threshold.
Owner:THALES SA
Partial page fail bit detection in flash memory devices
ActiveUS7355892B2Improve efficiencyEarly terminationError detection/correctionRead-only memoriesDetection thresholdCorrection code
Owner:SANDISK TECH LLC
Cage type asynchronous motor rotor strip-broken failure detecting method
InactiveCN101025430AEliminate asymmetryEliminate air gap eccentricityDynamo-electric machine testingInduction motorDetection threshold
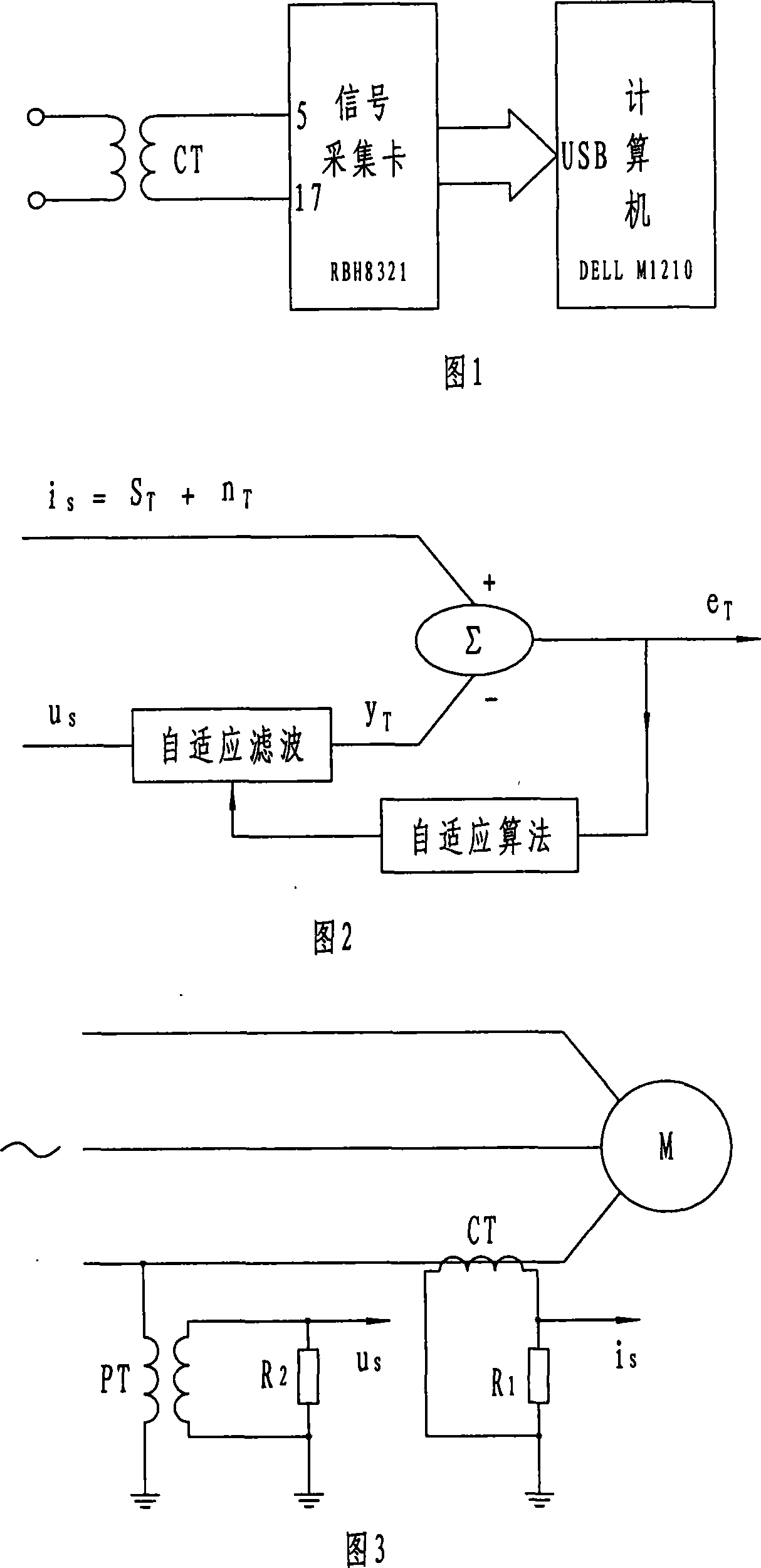
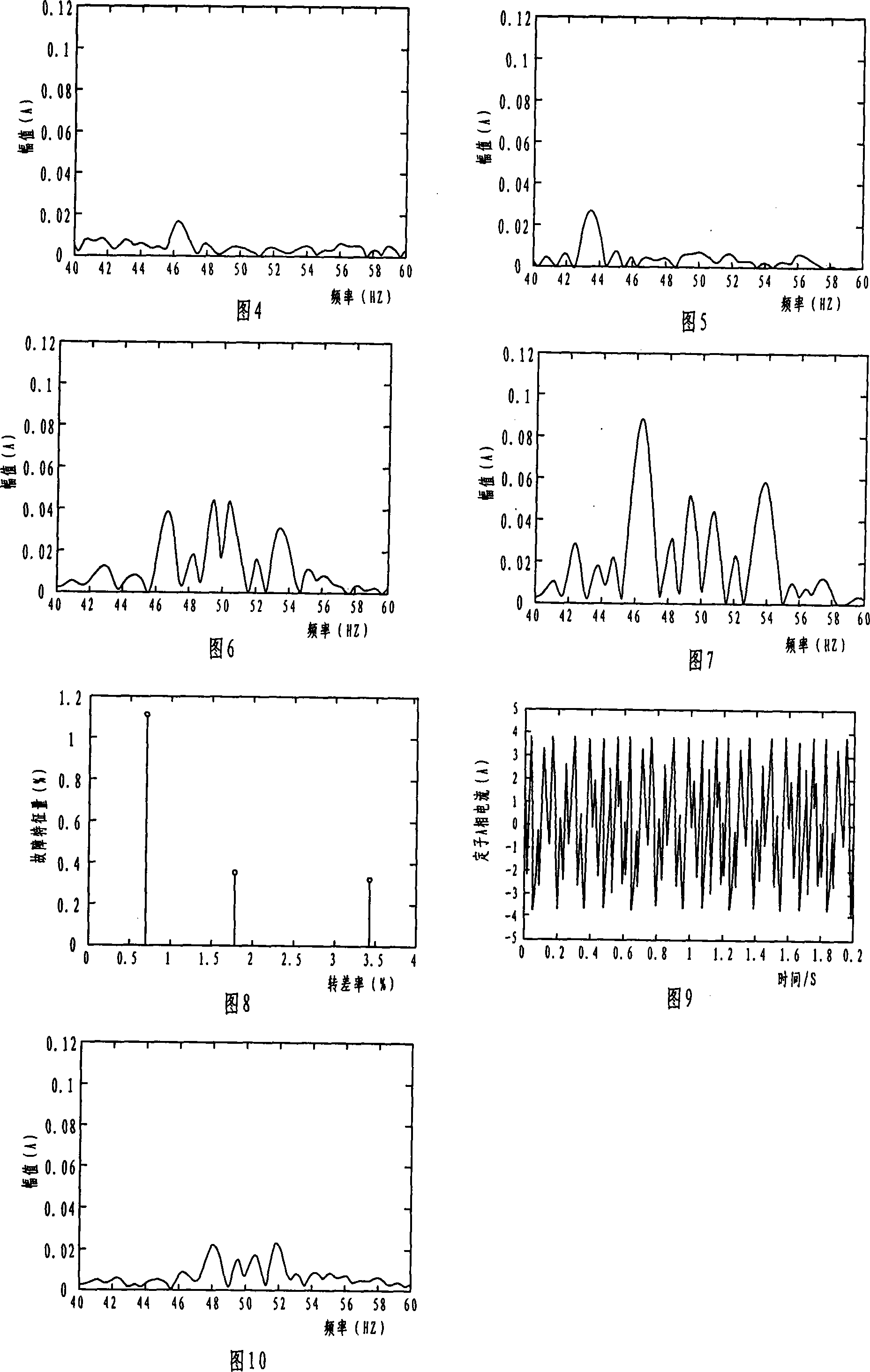
This invention is a methods and devices for detecting the fault of a cage rotor, which belongs to testing technology and for the settlement of broken rotor on the early detection of fault issue. Its technical program: through the acquisition of the stator transient current (is) continuously to do Fourier transform, receiving fundamental wave namely reference signal uS. Do adaptive filtering based the reference signal uS and the frequency f1 for the stator current transient signal. And then filter the output signal eT to do continuous the Fourier transform, identified (1 +- 2s) f1-frequency component and the amplitude of the fundamental components ratio as a failure features, the final determining fault index depending on fault detection threshold index and judge of Broken Bars, This invention can high sensitivity, high reliability and on-line detect the early induction motor of Broken Bars.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
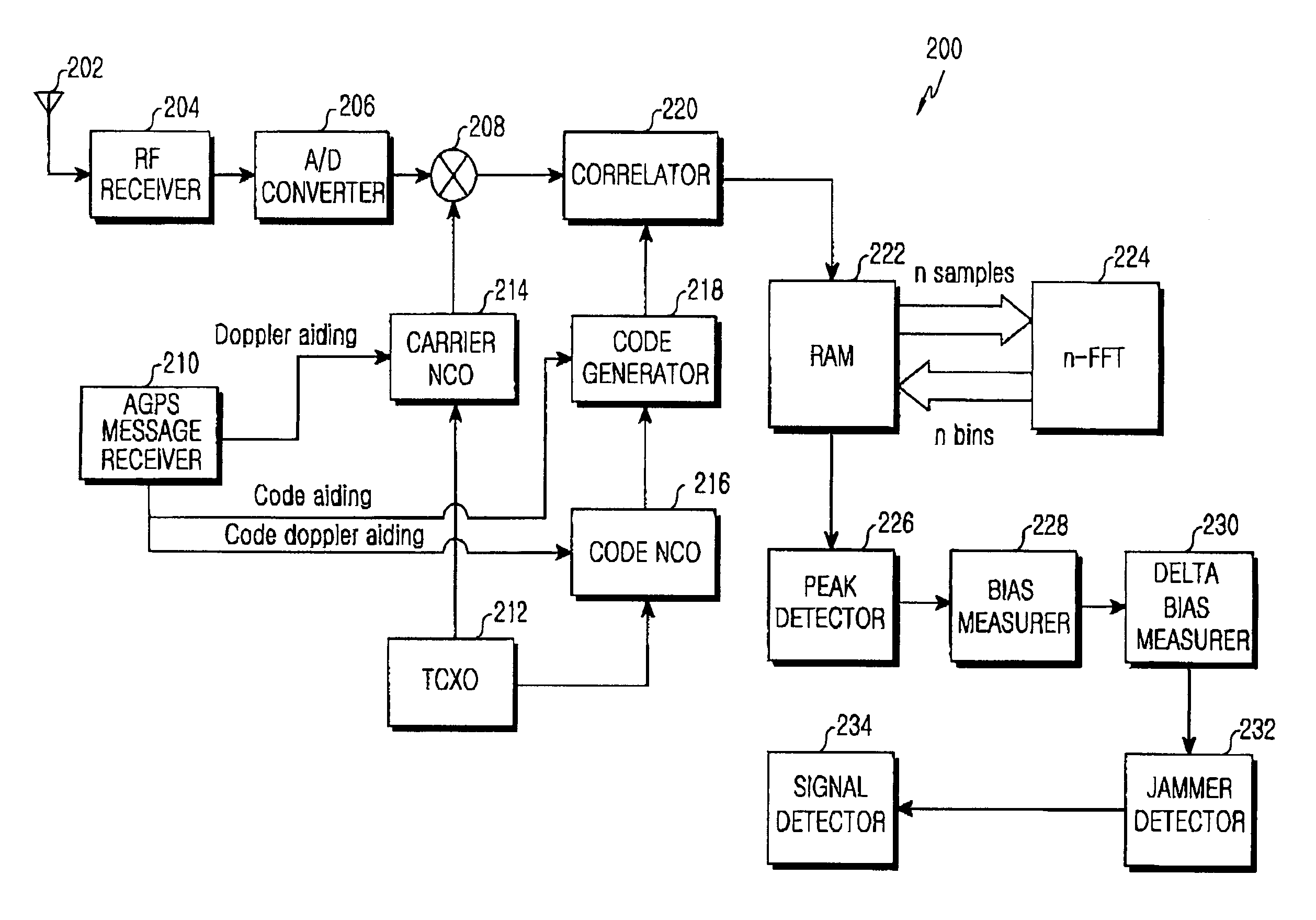
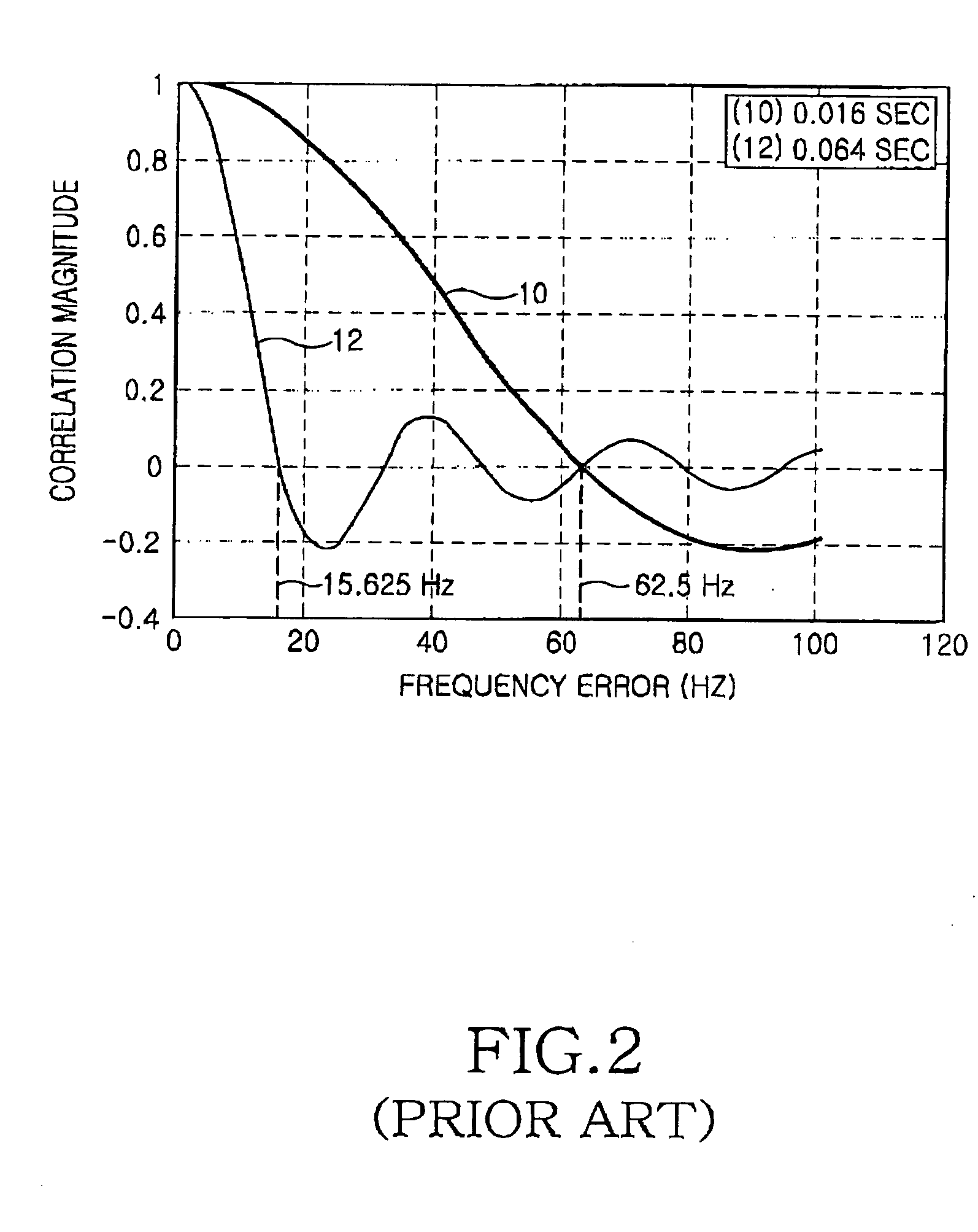
GPS receiver and method for detecting a jammer signal using fast fourier transform
InactiveUS20050285781A1Sufficient energyImprove receiver sensitivityPosition fixationBeacon systemsPeak valueFrequency offset
A global positioning system (GPS) receiver and method are provided for detecting a jammer signal using fast Fourier transform (FFT). A correlator correlates GPS signals received from GPS satellites with codes based on a plurality of carrier frequency signals having predetermined frequency offsets therebetween, and computes n correlated samples associated with each of the GPS satellites. A memory stores the n correlated samples associated with each of the GPS satellites and n FFT bins corresponding thereto. A FFT processor transforms the n correlated samples read from the memory using n-point FFT to obtain the n FFT bins, and transfers the n FFT bins to the memory. A peak detector detects largest peaks exceeding a lowered detection threshold from the FFT bins associated with each of the GPS satellites. A jammer detection unit makes a determination as to whether a peak relatively far away from other peaks is present among the largest peaks, and detects a signal of a peak far away from other peaks.
Owner:SAMSUNG ELECTRONICS CO LTD
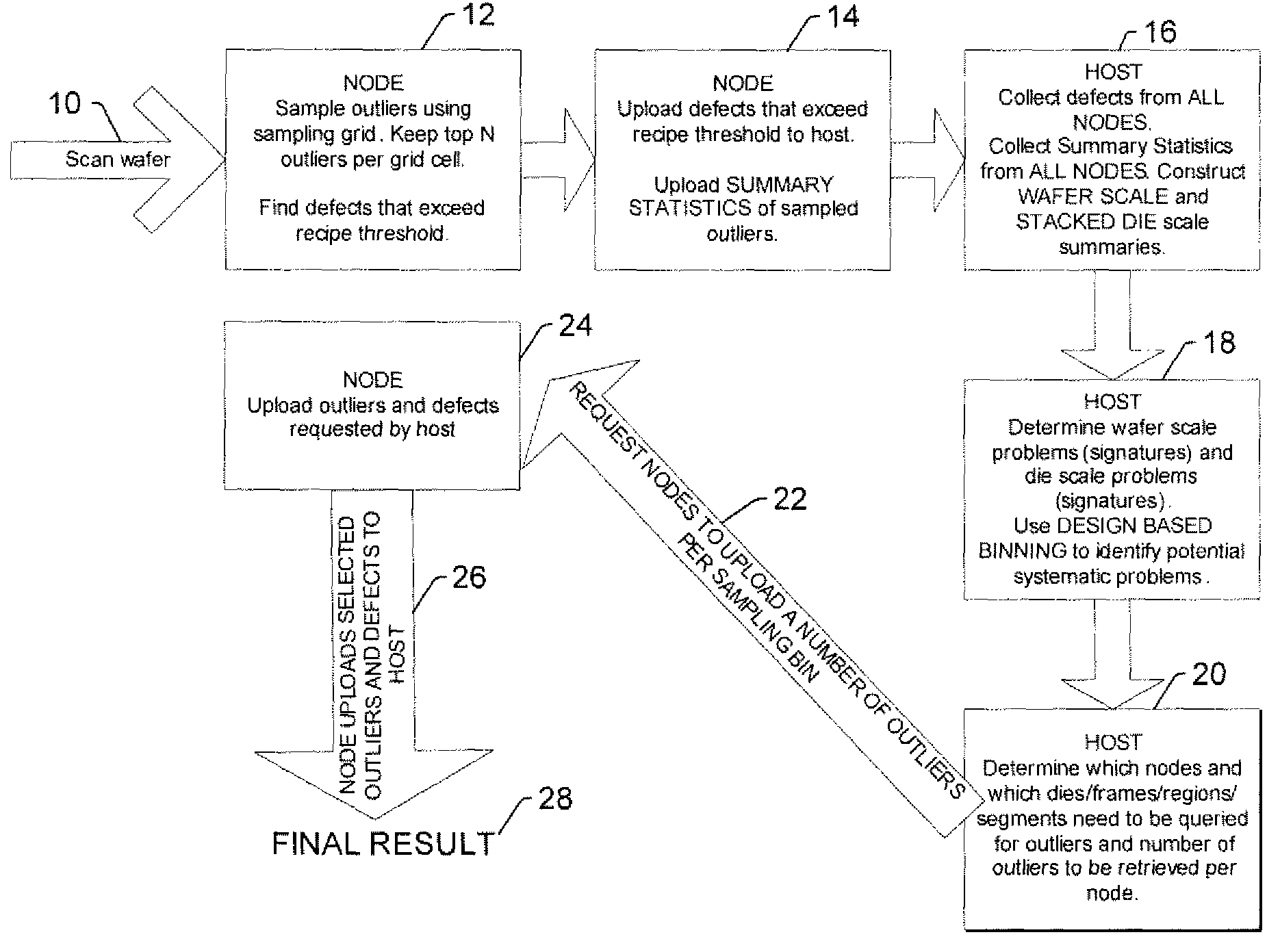
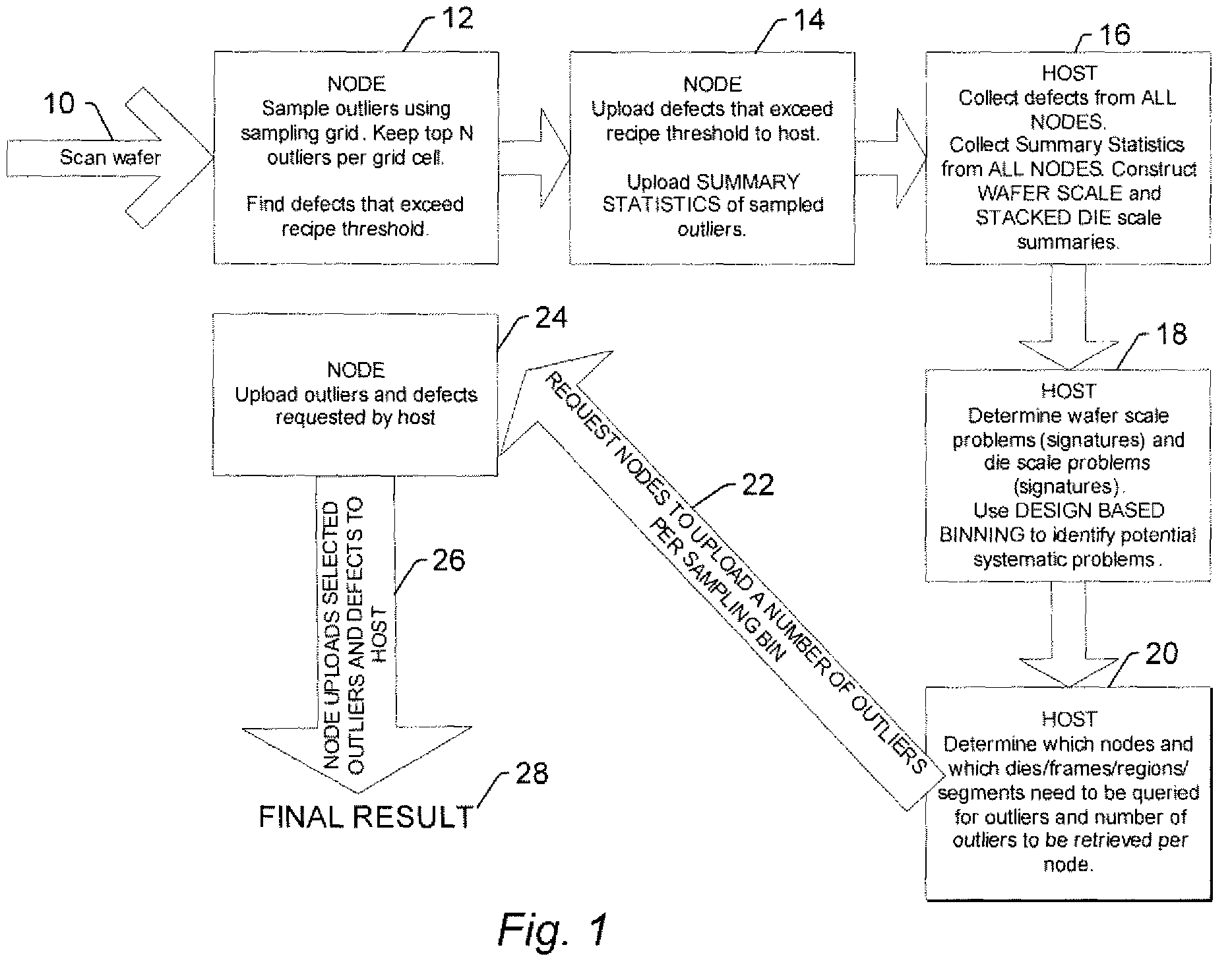
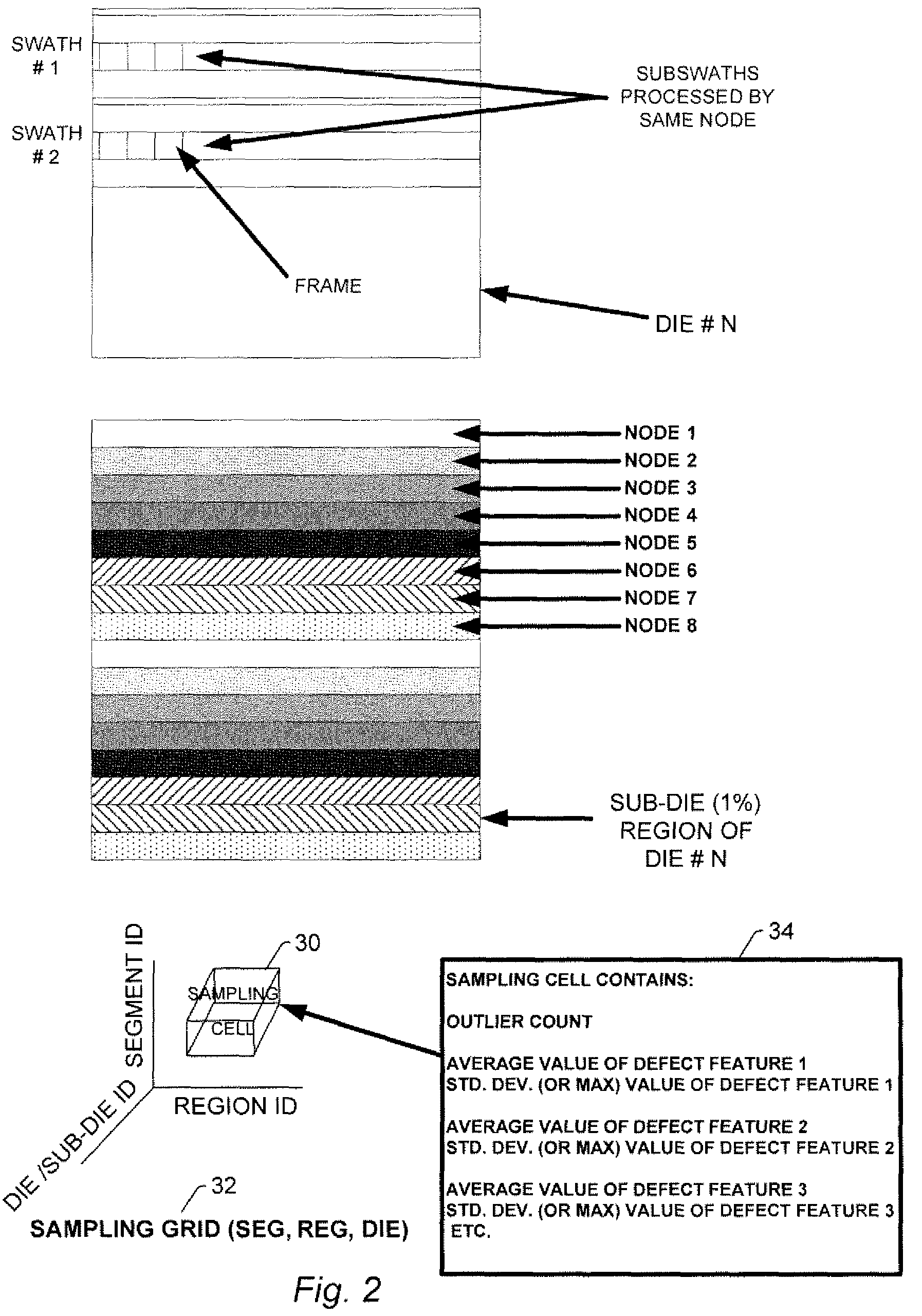
Systems and methods for detecting defects on a wafer and generating inspection results for the wafer
ActiveUS7756658B2Programme controlSemiconductor/solid-state device testing/measurementOutlierDetection threshold
Systems and methods for detecting defects on a wafer and generating inspection results for the wafer are provided. One method includes detecting defects on a wafer by comparing output generated by scanning of the wafer performed by an inspection system to one or more defect detection thresholds. The method also includes sampling outliers in the output by selecting the output having the highest values from bins defined based on one or more predetermined criteria. In addition, the method includes selecting a portion of the sampled outliers based on wafer-level analysis of the sampled outliers. The method further includes generating inspection results for the wafer by combining information about the selected portion of the sampled outliers with information about the defects detected using the one or more defect detection thresholds.
Owner:KLA CORP
Segmentation combination-based adaptive constant false alarm rate target detection method for SAR image
InactiveCN101975940AEasy to detectSmall amount of calculationImage analysisRadio wave reradiation/reflectionPattern recognitionReference window
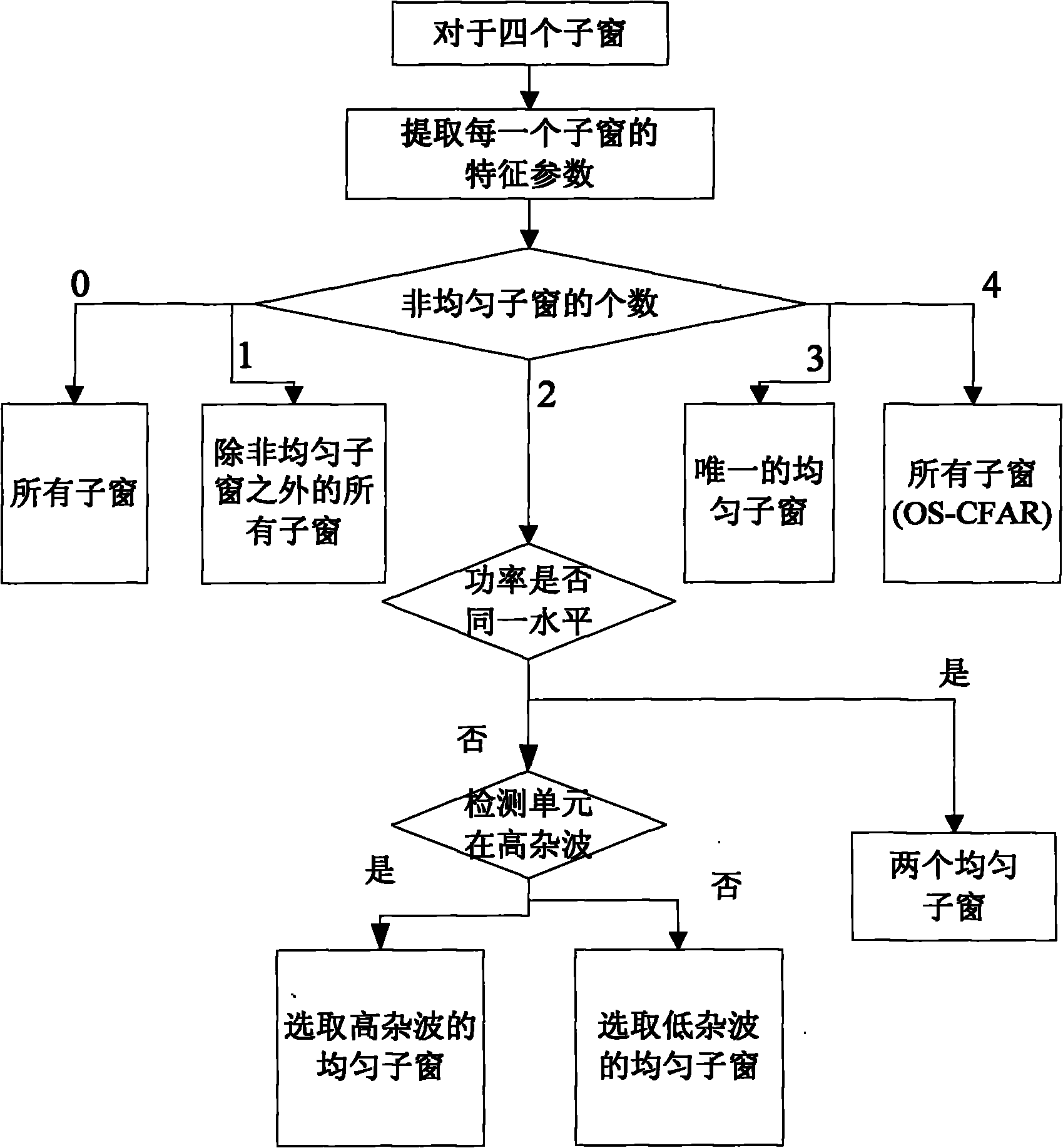
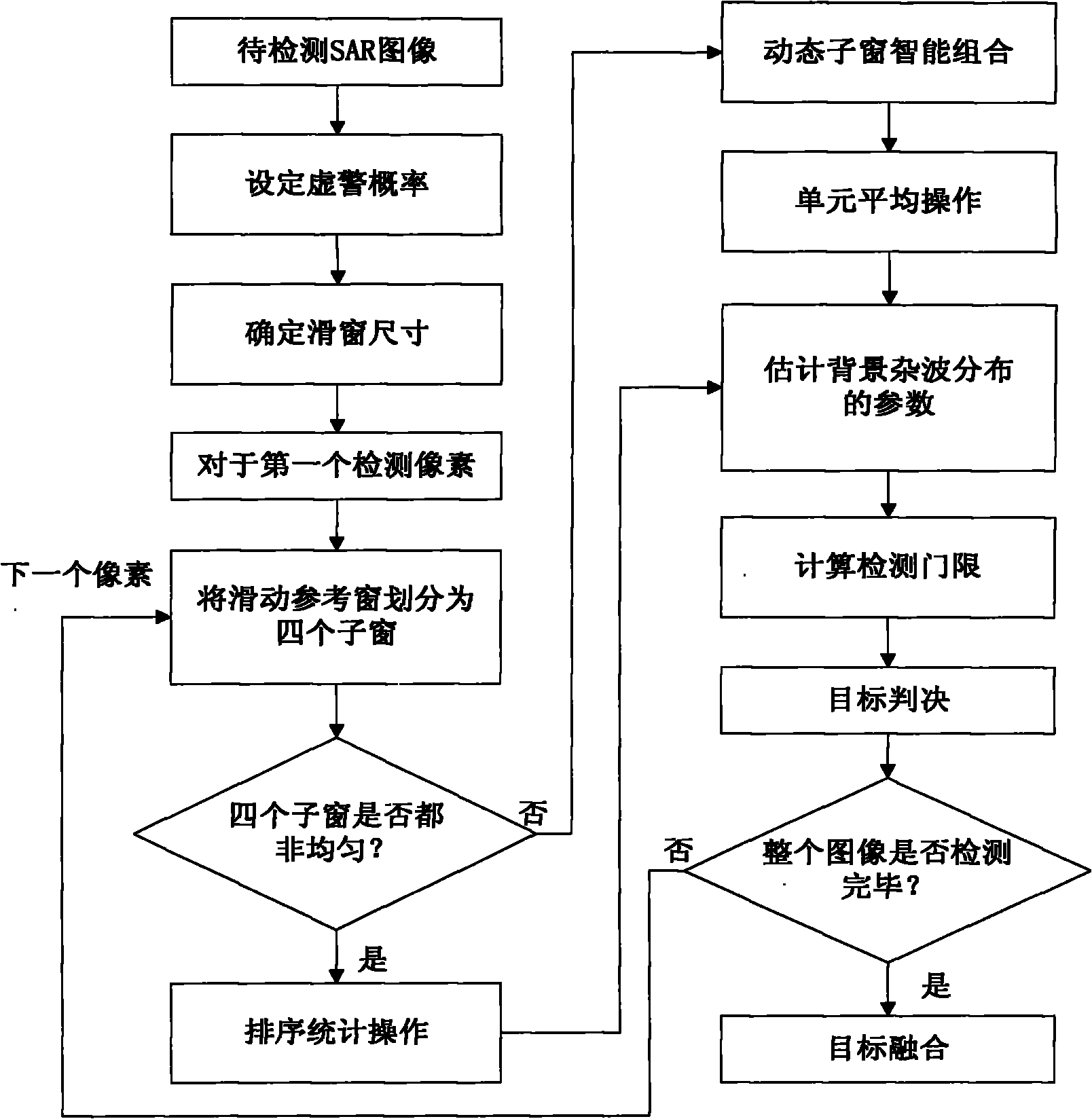
The invention discloses a segmentation combination-based adaptive constant false alarm rate target detection method for an SAR (synthetic aperture radar) image, and belongs to the technical field of synthetic aperture radars. The method comprises the following steps of: dividing a reference window into four sub windows, extracting uniformity statistics of the four sub windows and judging whether the sub windows are uniform; obtaining parameters for estimating background clutter models by adopting corresponding sub window combination strategies according to the non-uniform number, and then obtaining a detection threshold value by using a false alarm probability and a relationship between the clutter models; and comparing the pixel value of a current detection unit with the detection threshold value, judging whether a target exists, detecting the whole SAR image to be detected by adopting a running water form, and performing target fusion operation on the detected SAR image. According to the scheme, the method has low calculation quantity and simple operation, solves the problems of low detection probability, high false alarm rate and the like when the environment is complex and changeable and multiple targets are adjacent under high-resolution large scenes in the prior art, obviously improves the detection effect, and can keep good detection performance under various complex detection environments.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
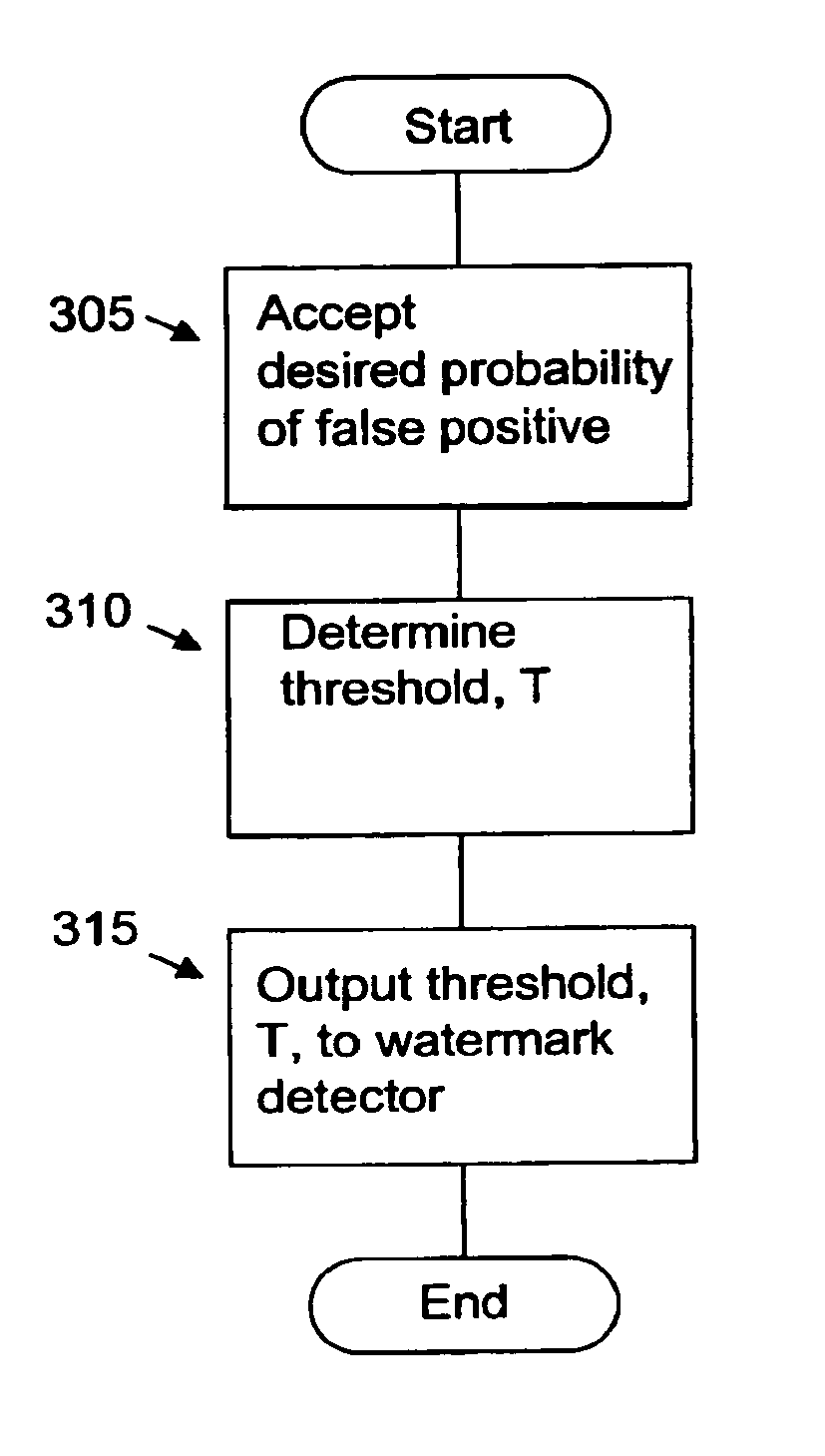
Method and apparatus for setting a detection threshold given a desired false probability
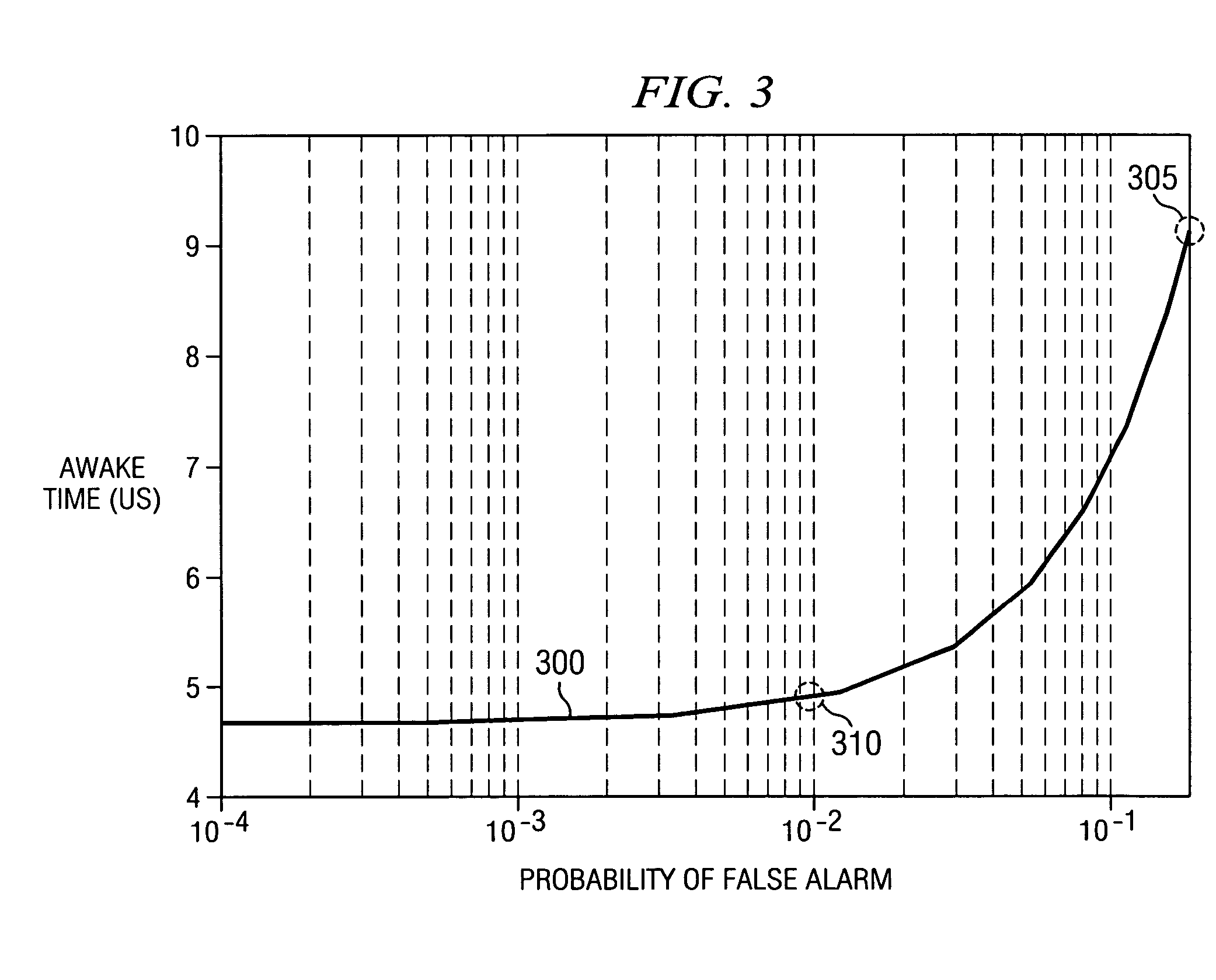
Owner:MAGNOLIA LICENSING LLC
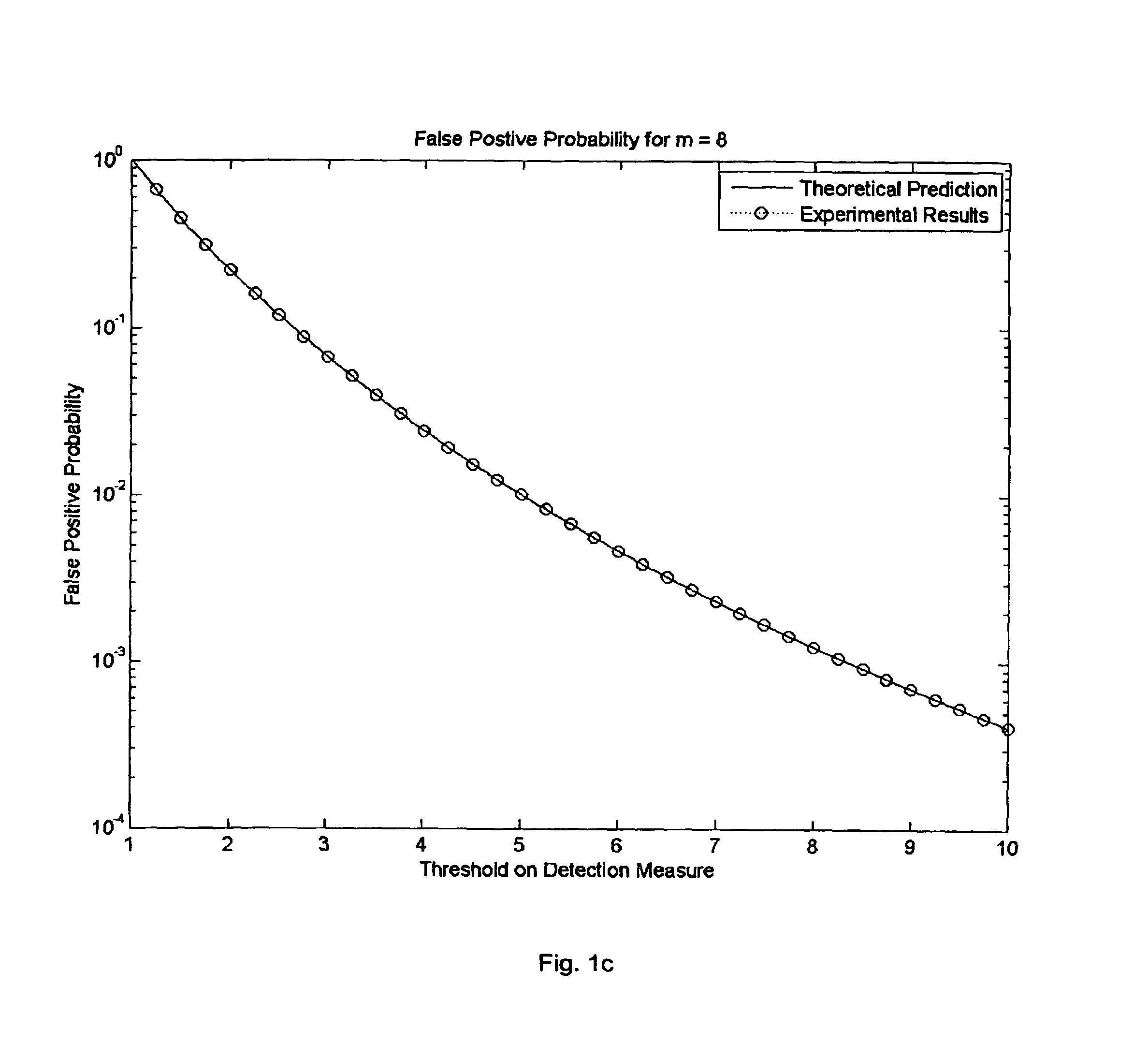
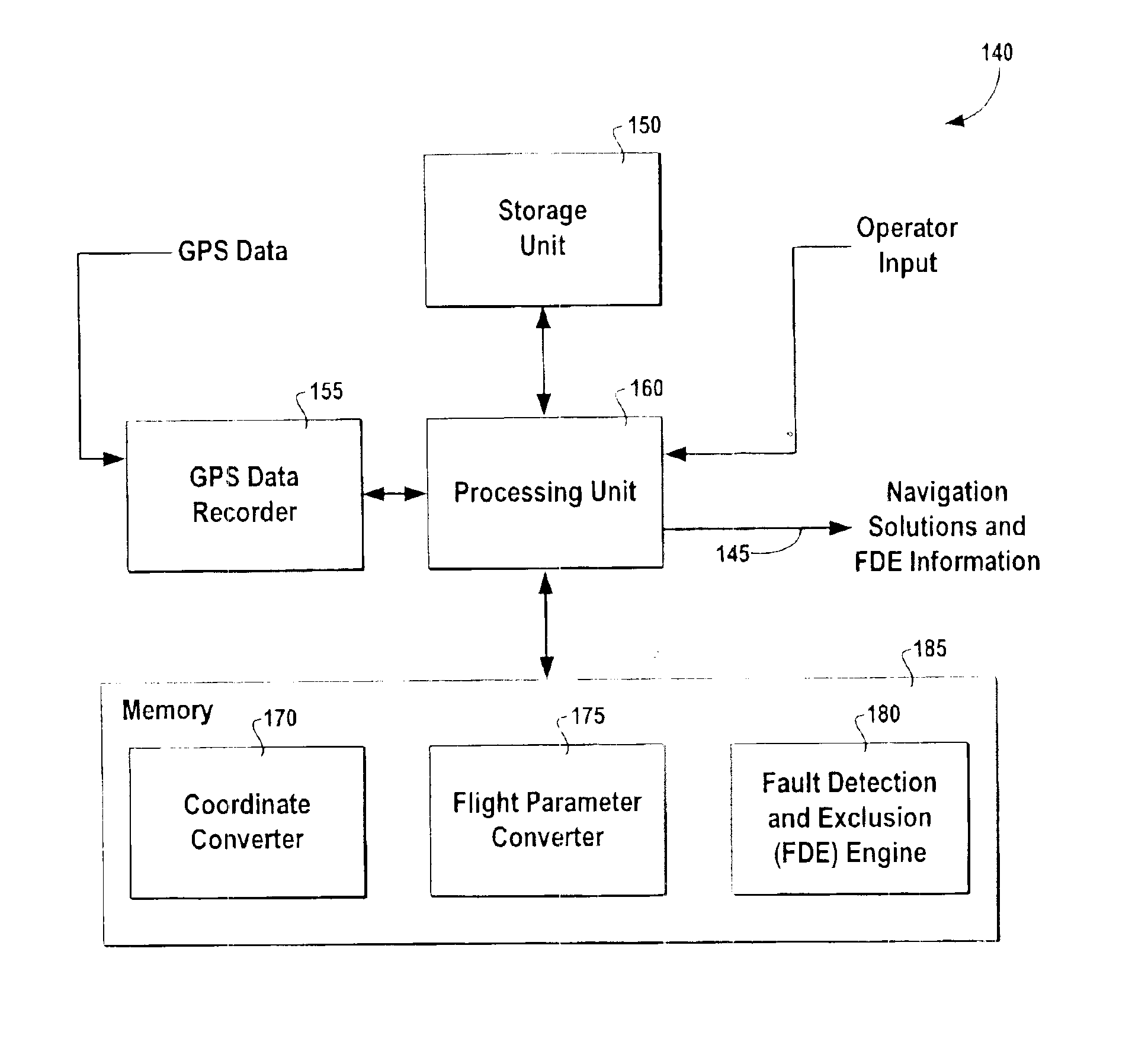
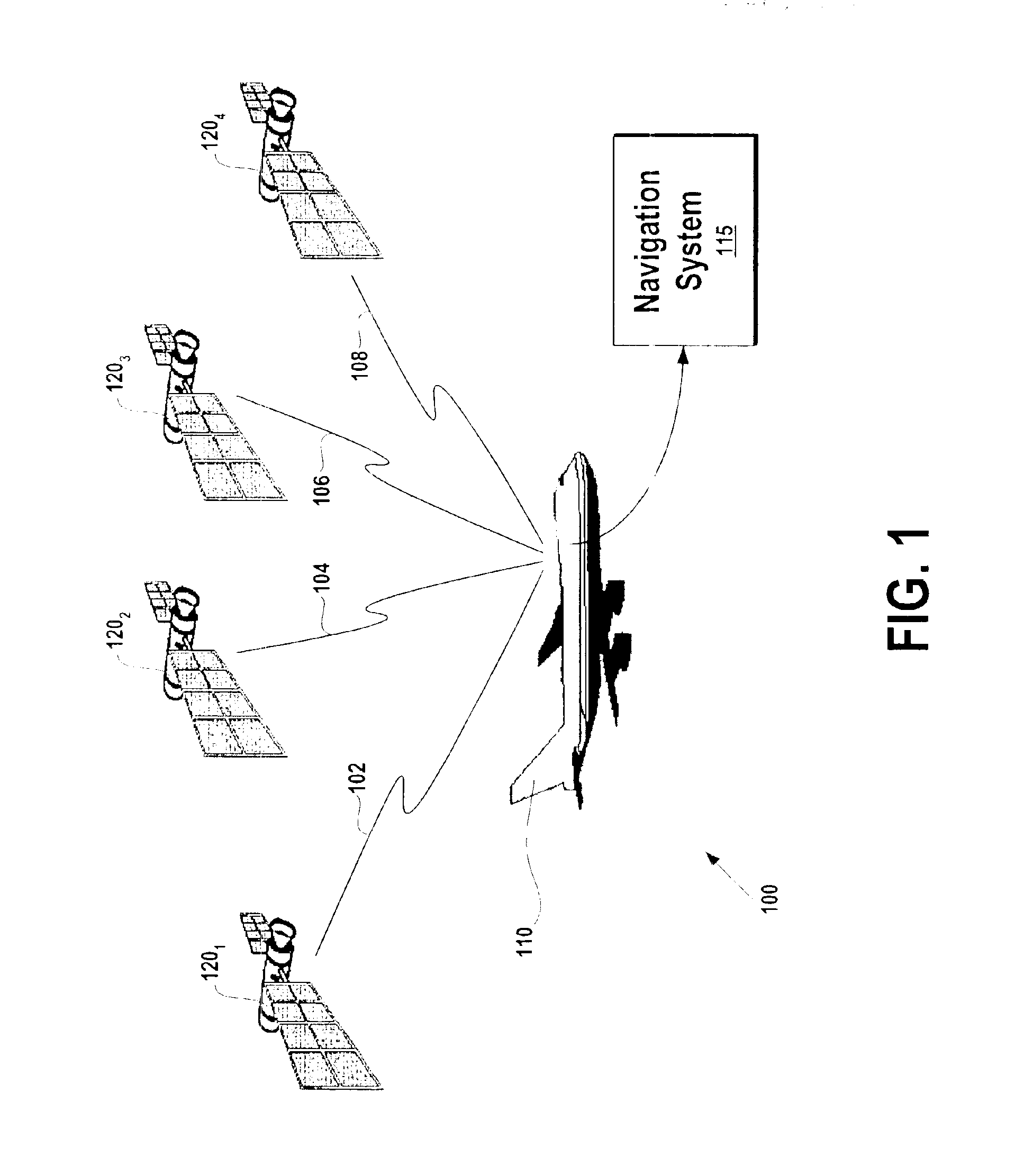
Systems and methods for fault detection and exclusion in navigational systems
InactiveUS6856905B2Increase flexibilityIncreases the likelihood of quickly and successfully identifyingPosition fixationNavigation instrumentsNavigation systemPosition error
The Fault Detection and Exclusion (FDE) system for use in navigational systems that rely upon multiple ranging signals, such as GPS satellites, uses an FDE algorithm to detect, as soon as possible, whether a fault exists in a signal associated with one or more of the GPS satellites. The system makes this determination by comparing a computed residual error with a first fault detection threshold. After determining that the computed residual error has exceeded the first, relatively low, fault detection threshold, the system transmits a signal to one or more external systems indicating that one or more signals associated with the various GPS satellites may be faulty. The system then monitors horizontal estimated position error (HUL) until this value has met or exceeded a relatively high fault isolation threshold value. The system then attempts to isolate and exclude the faulty satellite from the current navigational solution.
Owner:GARMIN AT
Method of adjusting the working range of a multi-analyte assay
InactiveUS20060177873A1Reduce available analyte concentrationHinder availabilityBiological testingSpecial data processing applicationsHigh concentrationMulti analyte
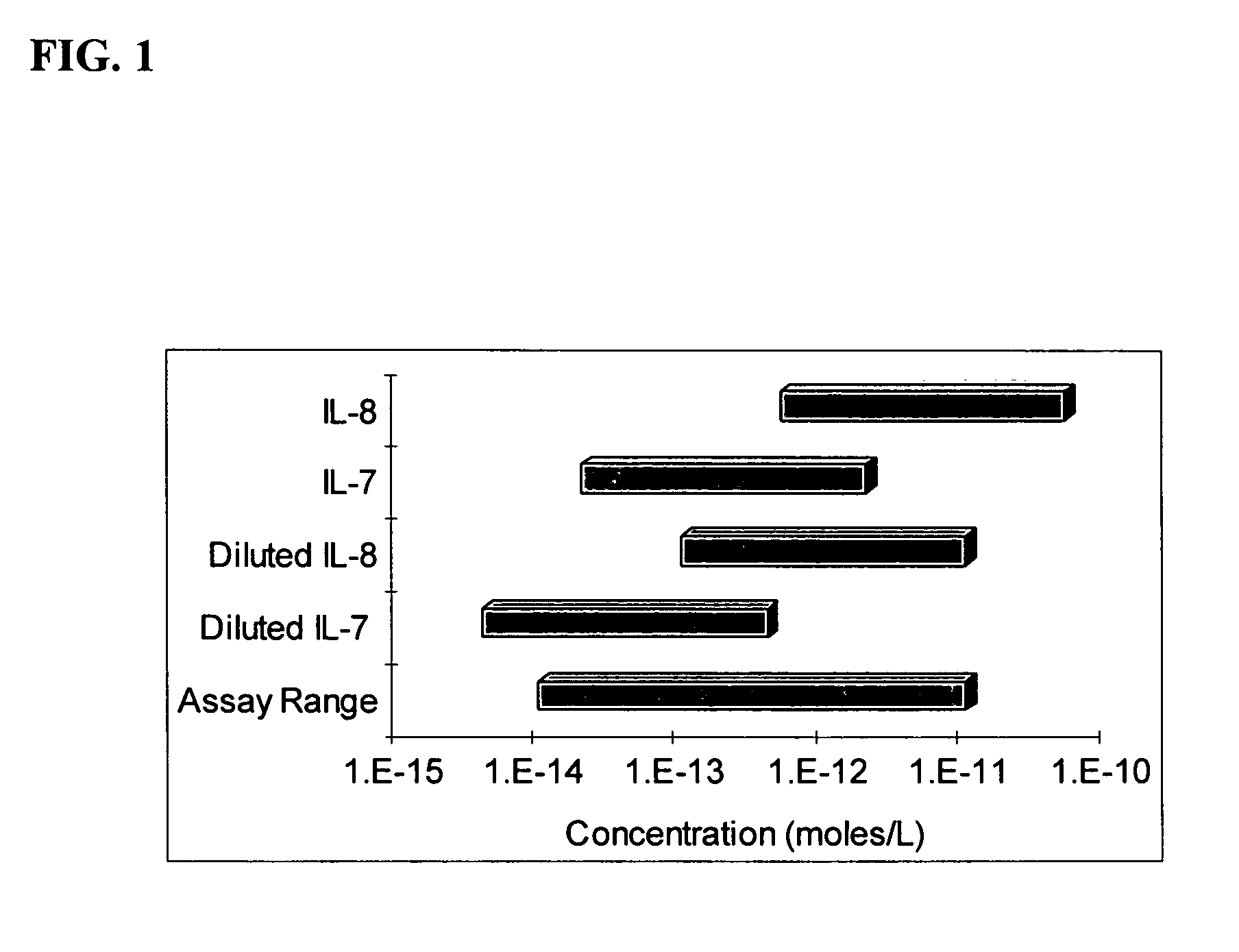
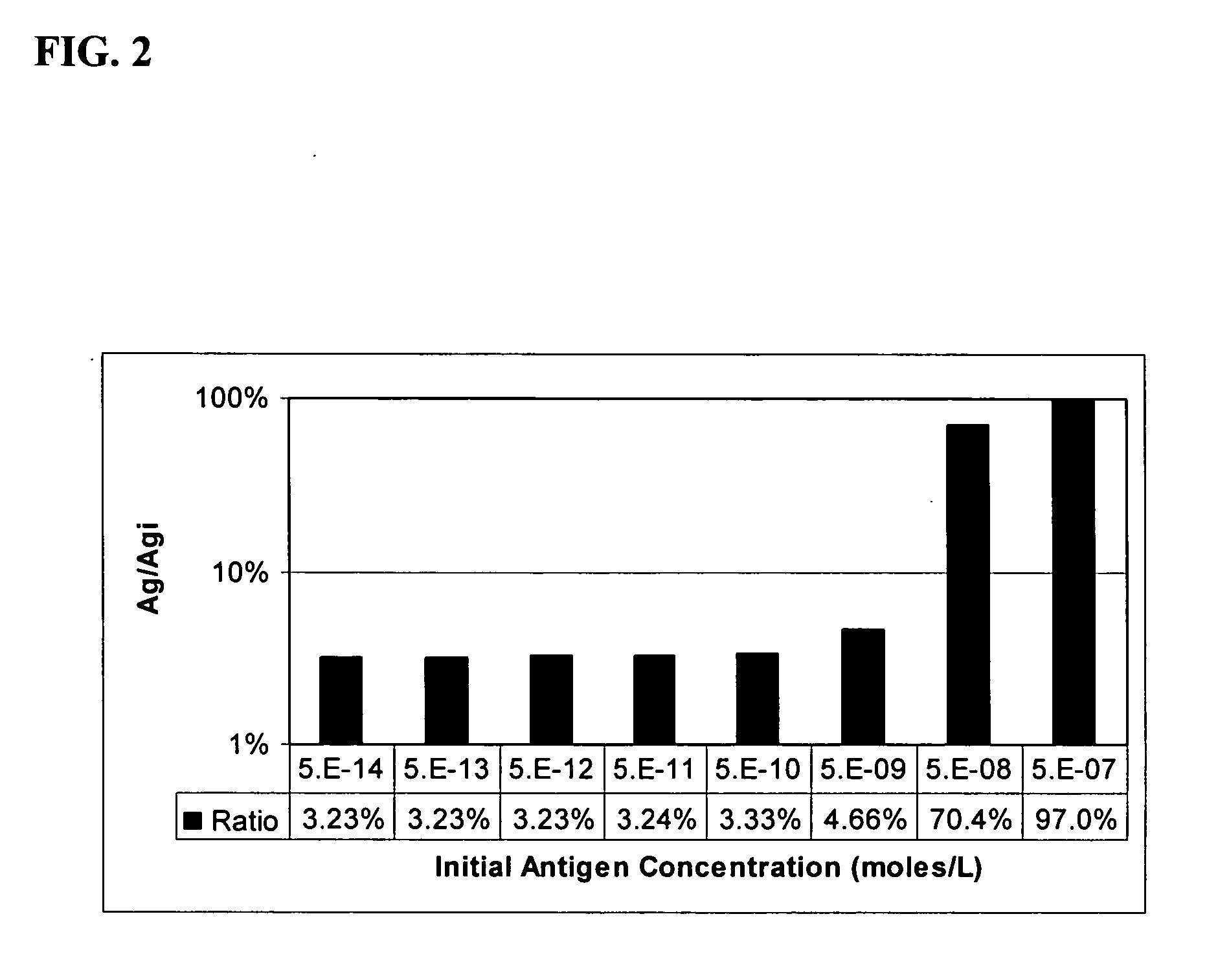
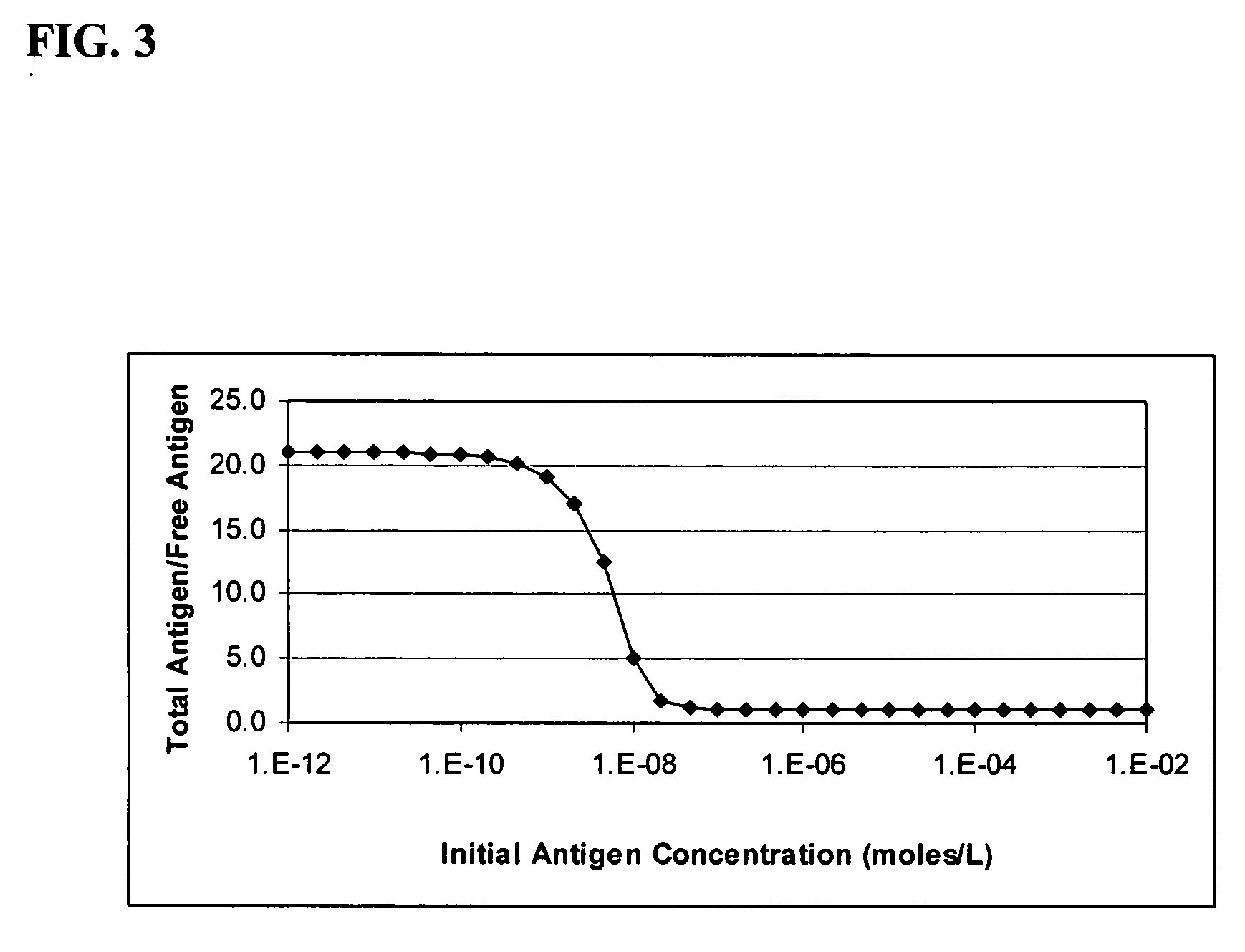
The invention features a method of adjusting the concentration of at least one but not all of a plurality of analytes in a fluid sample to match a known working range of detection of an analyte assay system, where each of the plurality of analytes may or may not be present within an expected initial concentration range having a high end and a low end, and at least one analyte has a high end expected concentration range that exceeds the high end of the working range of the assay system. The expected concentration of the high concentration analyte is adjusted by a proportional scaling constant, α, so that the high end of the adjusted expected concentration range is less than or equal to the high end of the working range, without adjusting the expected concentration range of at least one other of the plurality of analytes. Adjustment is preferably accomplished by adding to the solution phase of the assay one or more scaling agents, each scaling agent binding with specificity to an analyte and thereby preventing it from being detected by the assay system, e.g., by competing with binding to immobilized capture agent. This scaling method contrasts with prior methods, in which a concentration of available analyte is offset by a fixed amount to adjust the detectable threshold of the assay. Here, the amount of scaling agent is proportional to a scaling coefficient, and the scaling agent is present in the solution phase of the assay at high concentrations relative to analyte. Due to the equilibrium conditions established by the laws of mass transfer, the amount of free analyte remaining in solution in the presence of scaling agent is predictable and finite, and can be measured as a quantitative indicator of the initial concentration of the analyte in the sample.
Owner:COURTAGEN LIFE SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com