Feature code generation method and detection method of mobile botnet
A botnet and feature code technology, applied in the field of mobile botnet feature code generation and mobile botnet detection, can solve the problems of no research on mobile botnet detection and little research on mobile botnet defense, and achieve false positives low rate effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
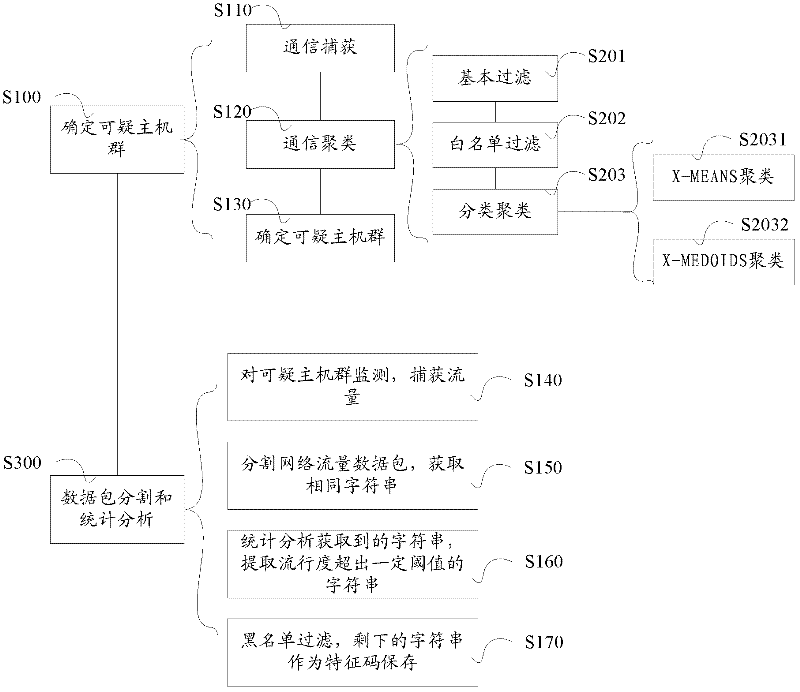
[0027] In order to make the purpose, technical solution and advantages of the present invention clearer, the method for detecting mobile botnets provided in the embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
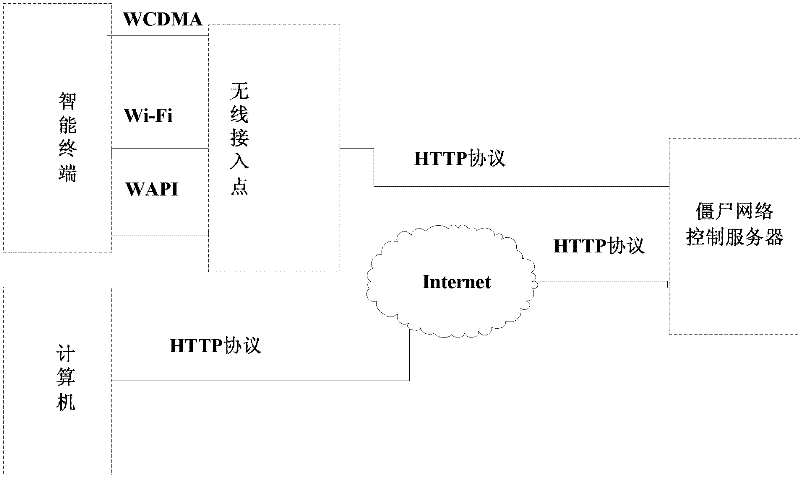
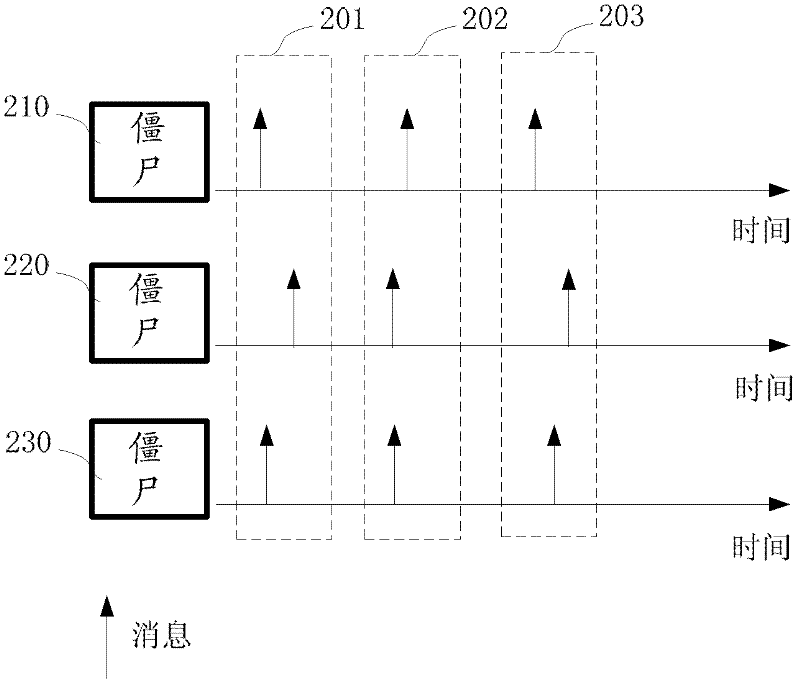
[0028] In order to detect a botnet, it is first necessary to understand the characteristics of the botnet. The inventors have found through long-term research that the botnet has the following characteristics: since the response behavior of the bot to the command and control has been determined during programming, the behavior of the bot in the same botnet has similarity in time and space. Among them, the spatio-temporal similarity means that a large number of bots often show coordination when maintaining connections, sending and receiving con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com