Patents
Literature
580 results about "Electronic media" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Electronic media are media that use electronics or electromechanical audience to access the content. This is in contrast to static media (mainly print media), which today are most often created electronically, but do not require electronics to be accessed by the end user in the printed form. The primary electronic media sources familiar to the general public are video recordings, audio recordings, multimedia presentations, slide presentations, CD-ROM and online content. Most new media are in the form of digital media. However, electronic media may be in either analogue electronics data or digital electronic data format.
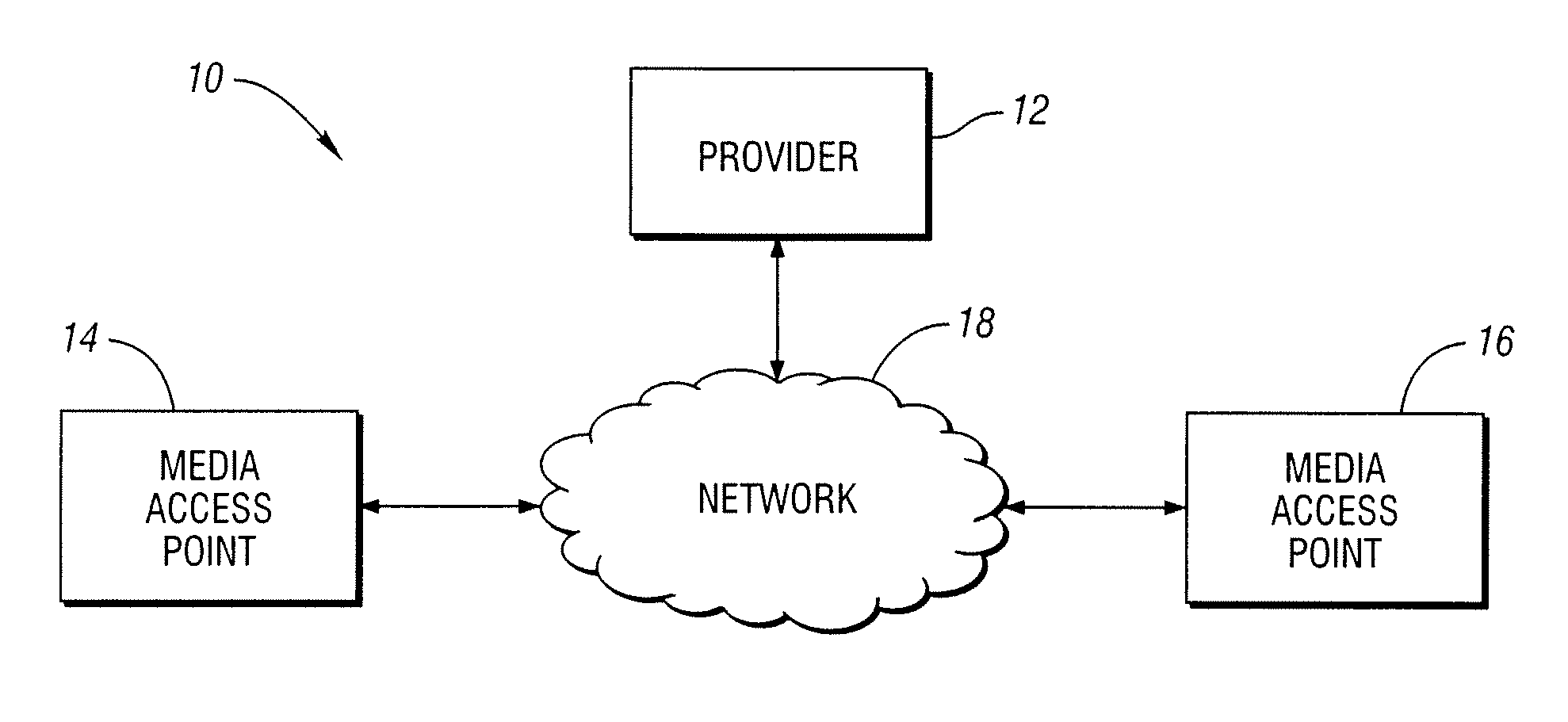
Electronic music/media distribution system
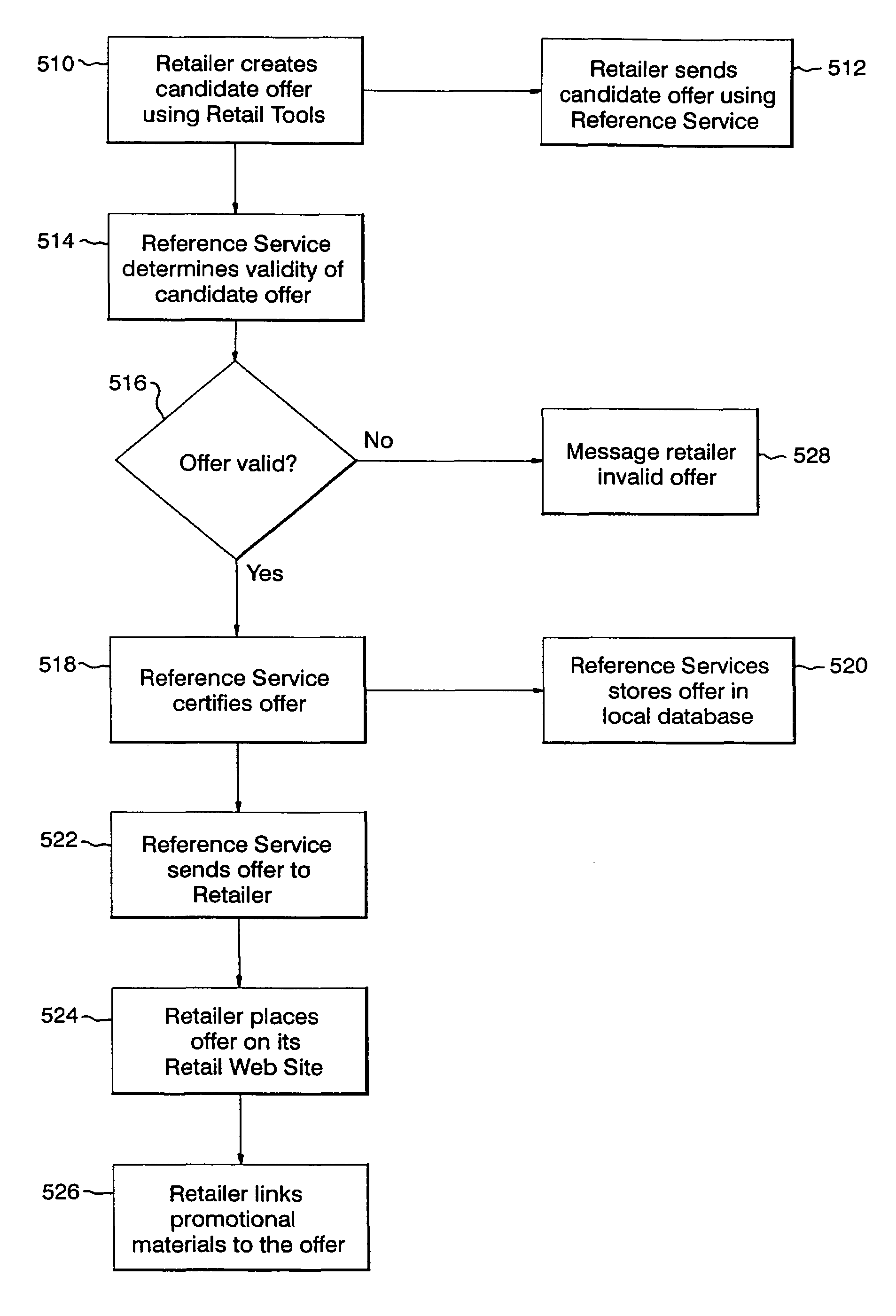
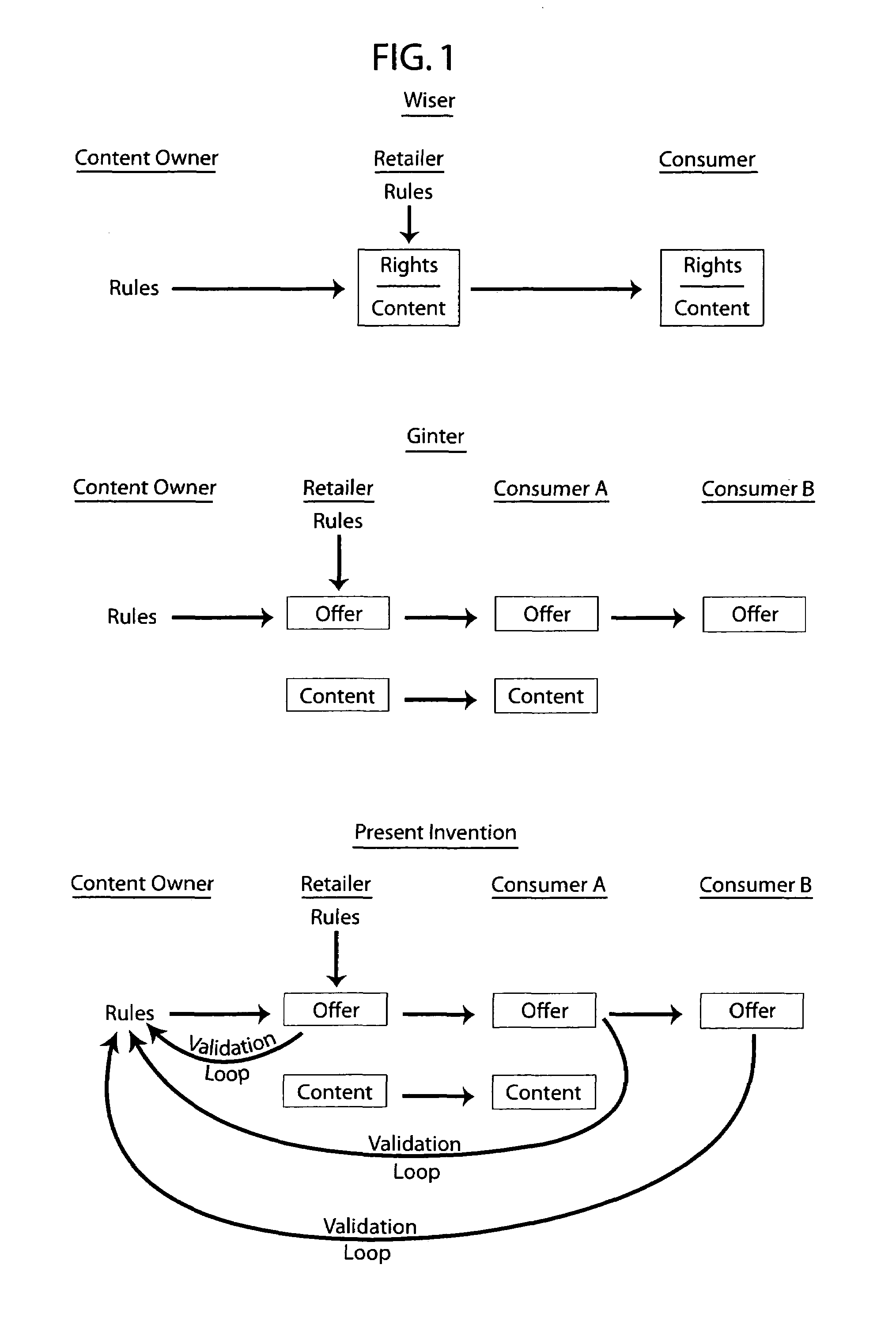
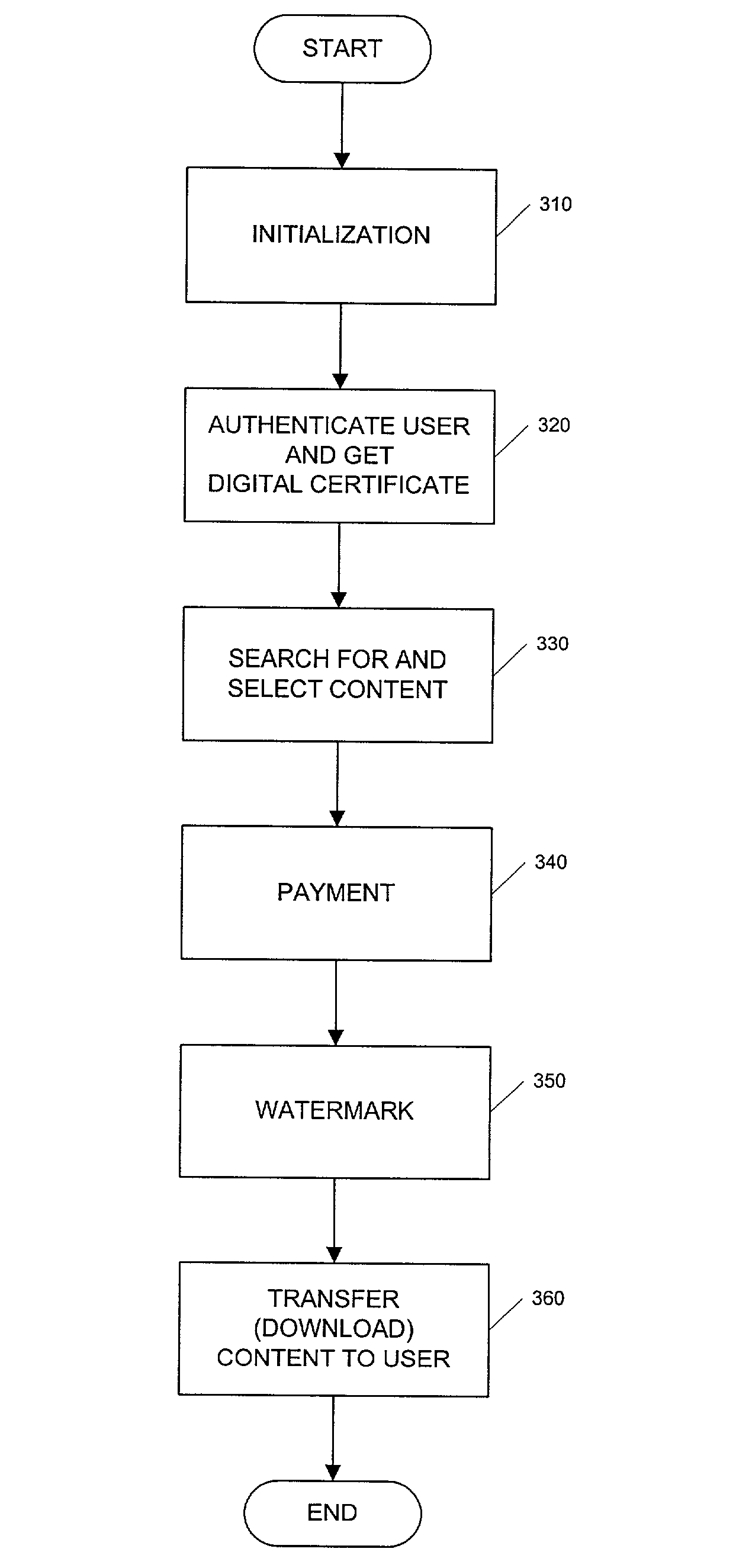
InactiveUS7209892B1Optimize allocationFacilitates continued control over the musical content sentCommerceProgram/content distribution protectionElectronic contractsIntellectual property
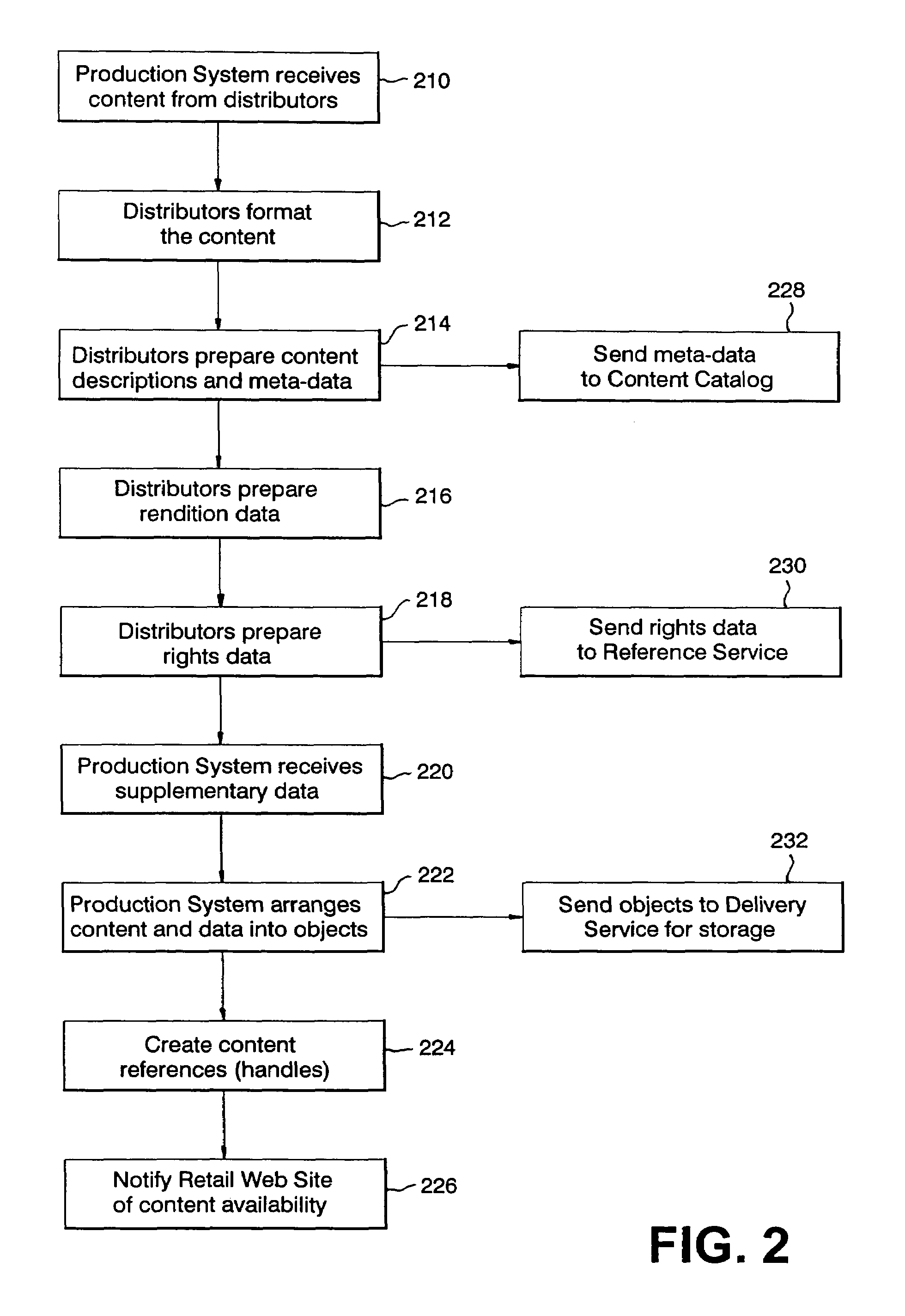
An electronic media distribution system which facilitates the distribution of media to consumers over a network, such as the Internet, while achieving commercial business objectives and protecting the intellectual property rights associated with the media being distributed. The system provides the infrastructure and support for various market participants to engage in buying, selling, finding and distributing music. The system provides an interface for consumers to locate, access and receive musical content over the Internet. The system facilitates continued control over the musical content sent to consumers by dynamically enforcing retailer agreements and restrictions governing the purchase, use, and distribution of the content. The system also provides a service to retailers and distributors in assisting with the management of sales and distribution of music over the Internet. Specifically, the system certifies and distributes retail offers for the content where the offers are dynamically updated by electronic contracts between the retailers and distributors of the music.
Owner:UNIVERSAL MUSIC GROUP
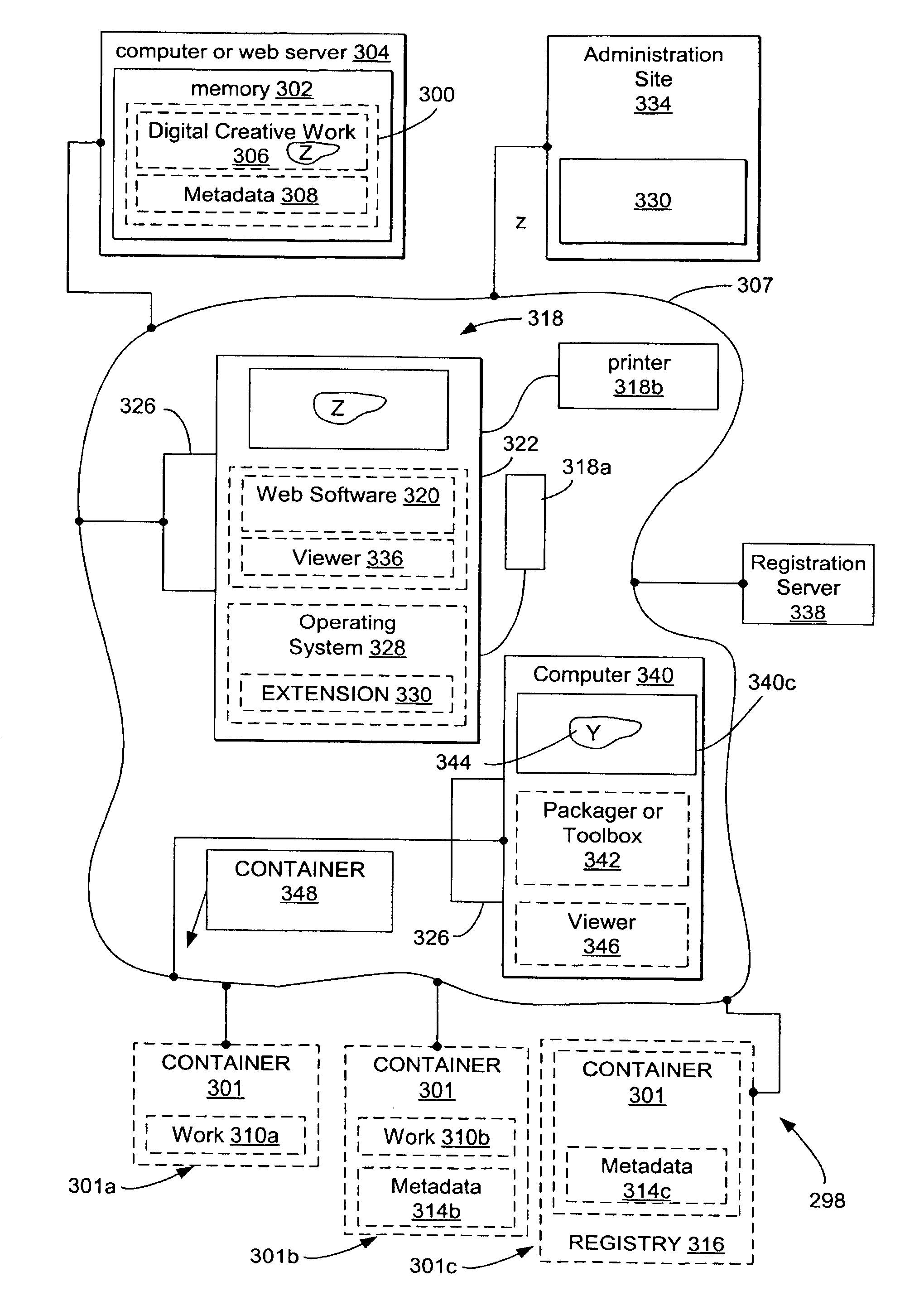
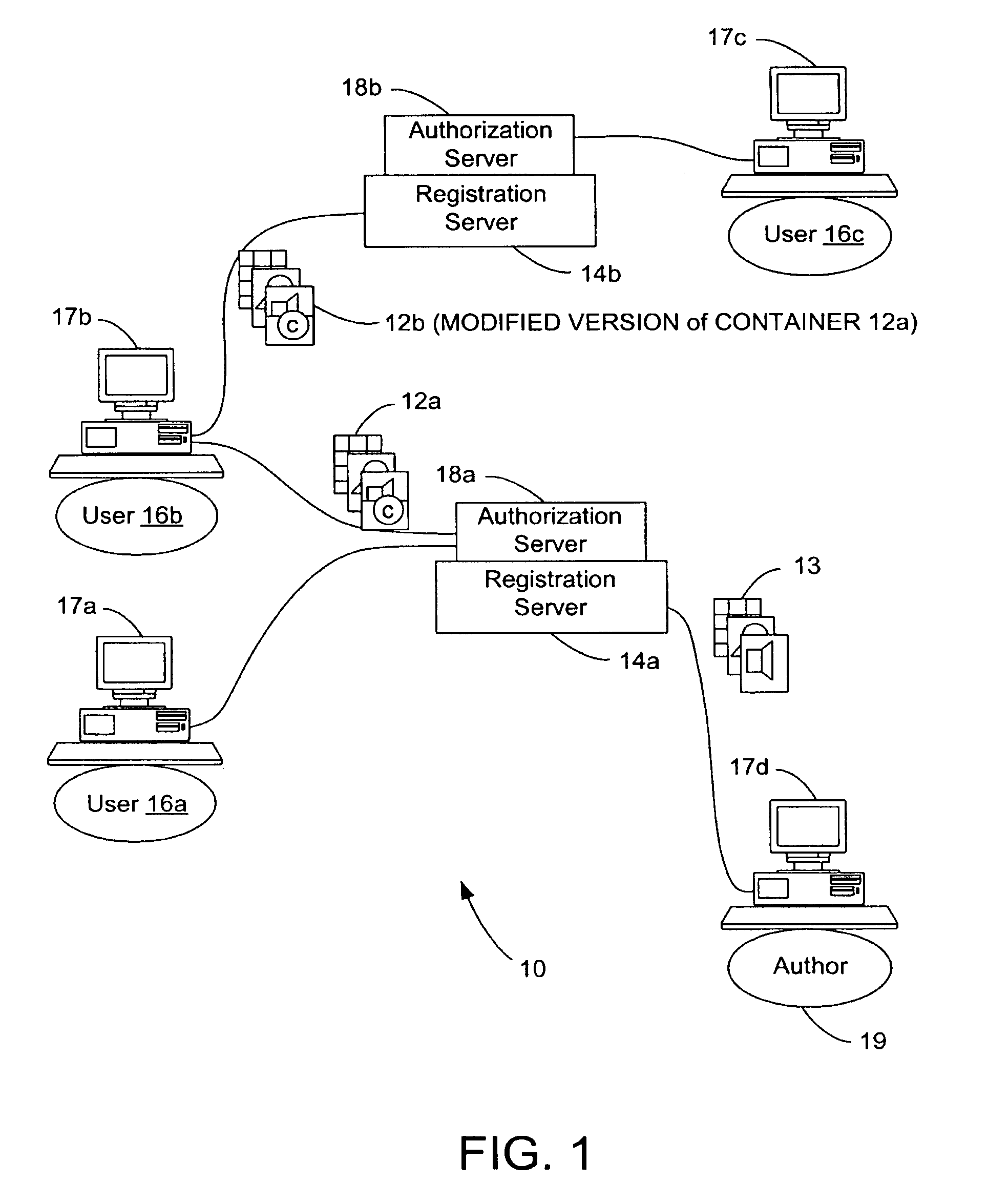
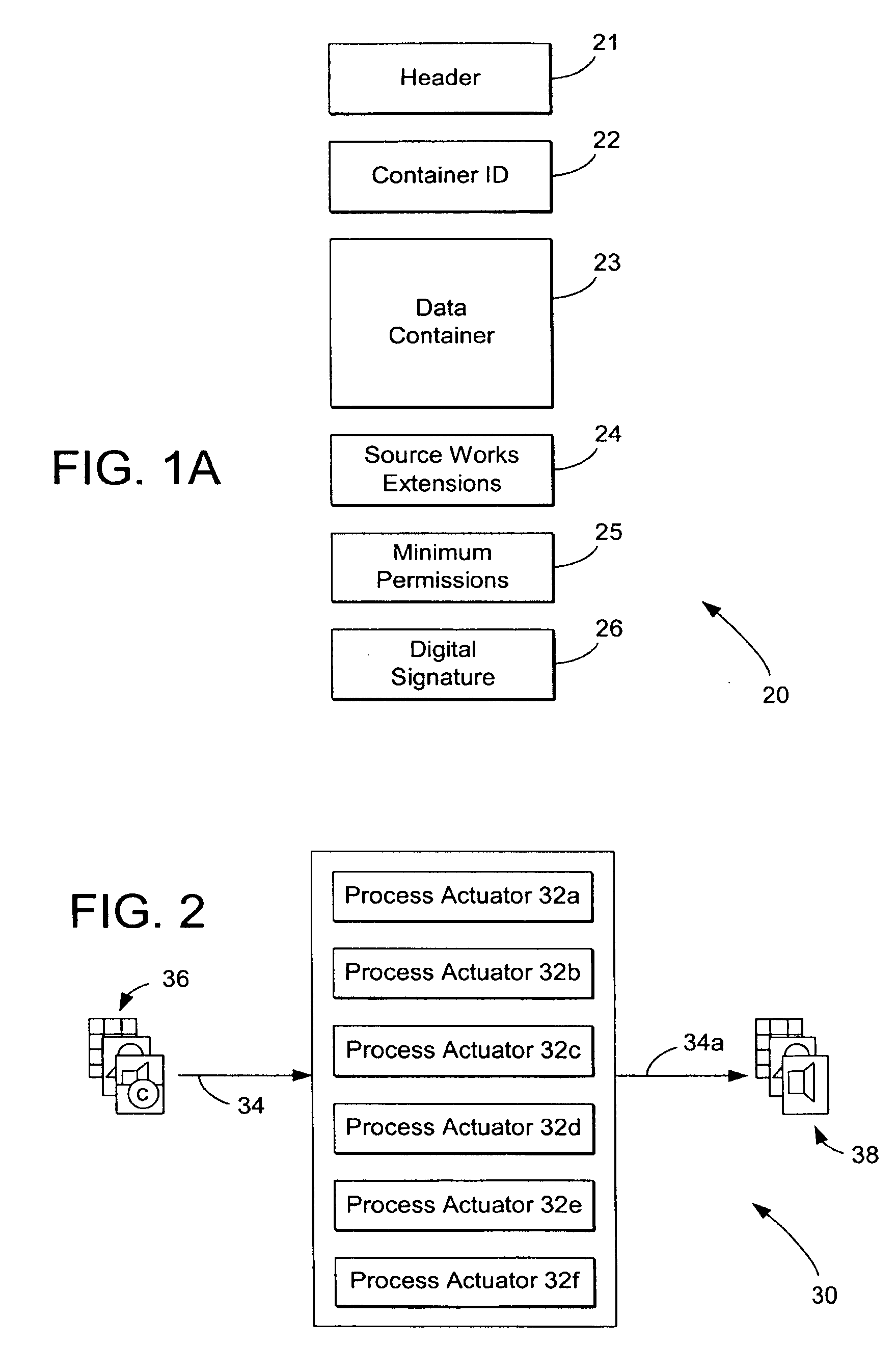
System and methods for managing digital creative works
InactiveUS7047241B1Improve network efficiencyEliminate needKey distribution for secure communicationData processing applicationsData setDigital signature
Digital Creative Works such as copyrighted electronic media are packaged in a secure electronic format, or CONTAINER, and registered on associated registration server, which serves to provide on-line licensing and copyright management for that Work. Users are connected to the registration server through a computer network or the Internet to enable data transfers and to transact licenses to utilize the media. Packaged electronic media are typically created by an author or derivative user of the work. Once the packaged media is registered on the server, the media is made available for limited use and possible license through an authorization server. This limited use is specified within the minimum permissions data set assigned to each packaged media. Without a license, users are typically permitted to view the packaged media—through a system which unpackages the media—but cannot save, print or otherwise transfer the media without obtaining auxiliary permissions to do so from the authorization server. The electronic media is authenticated through digital signatures and optional encryption.
Owner:DIGIMARC CORP
Network-based content distribution system
InactiveUS20090037388A1Maximize potential return-on-investmentMinimal burdenDigital data processing detailsUser identity/authority verificationContent distributionPublic network
Owner:VERIMATRIX INC
Method and apparatus for accessing electronic data via a familiar printed medium
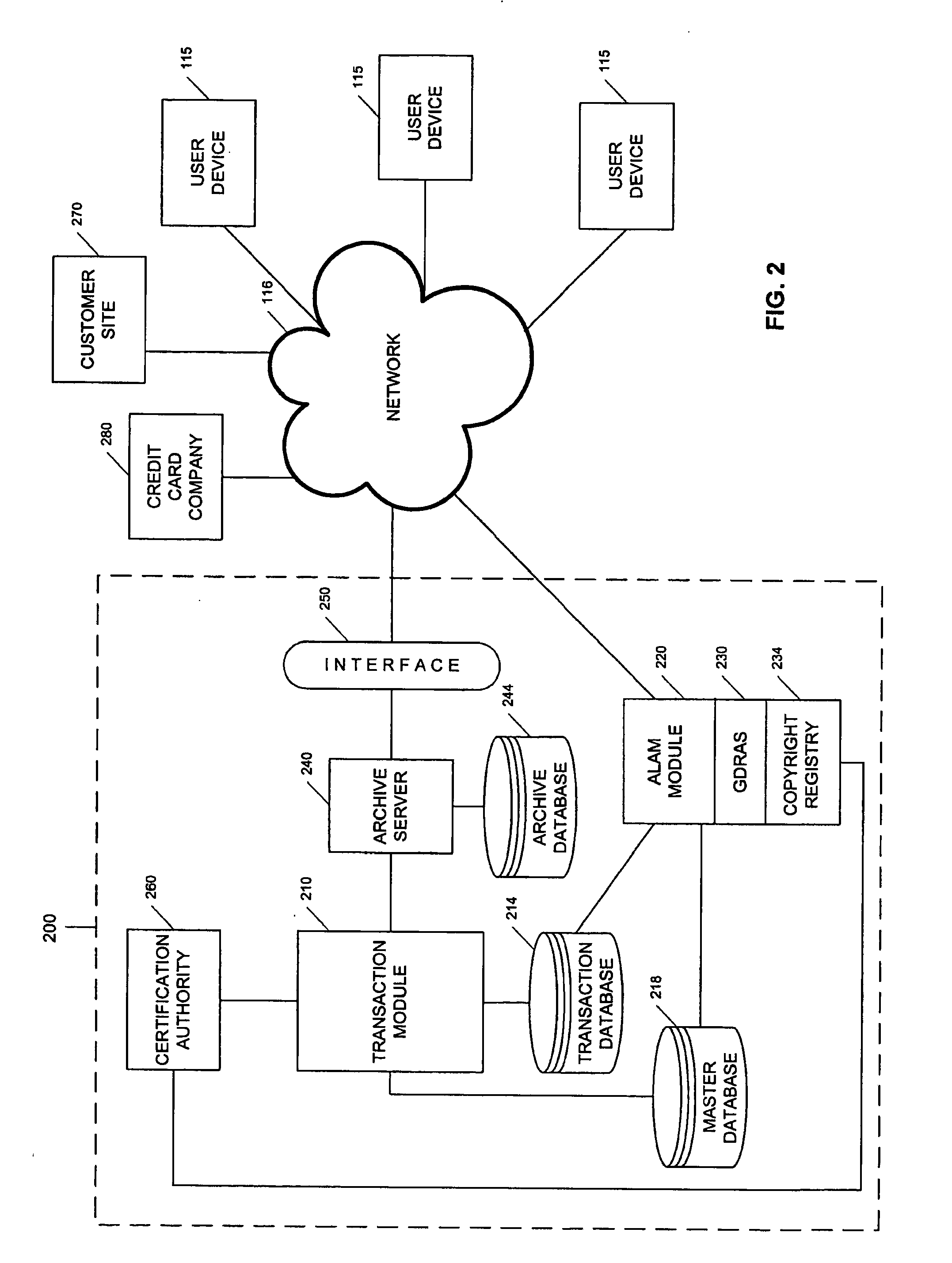
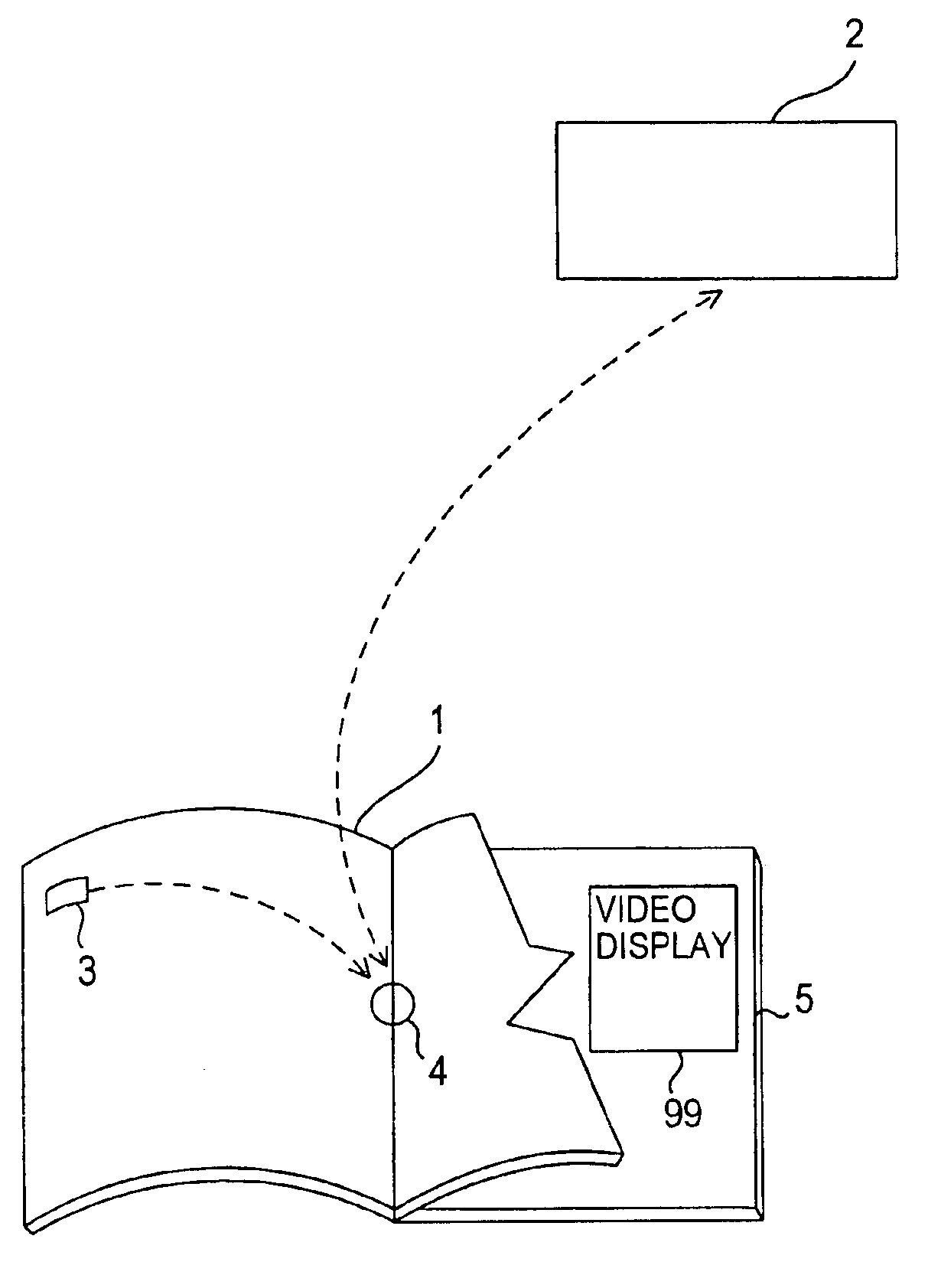
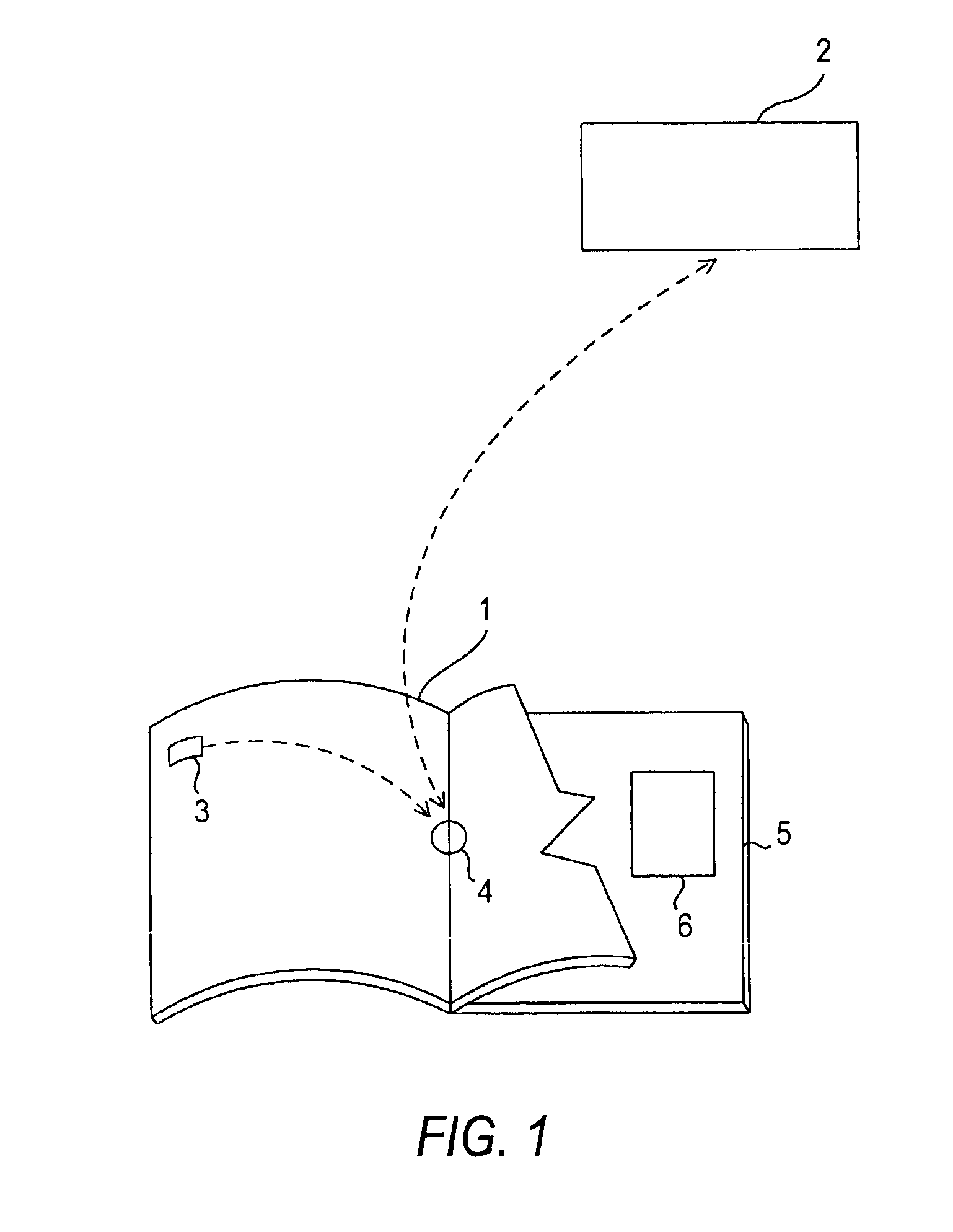
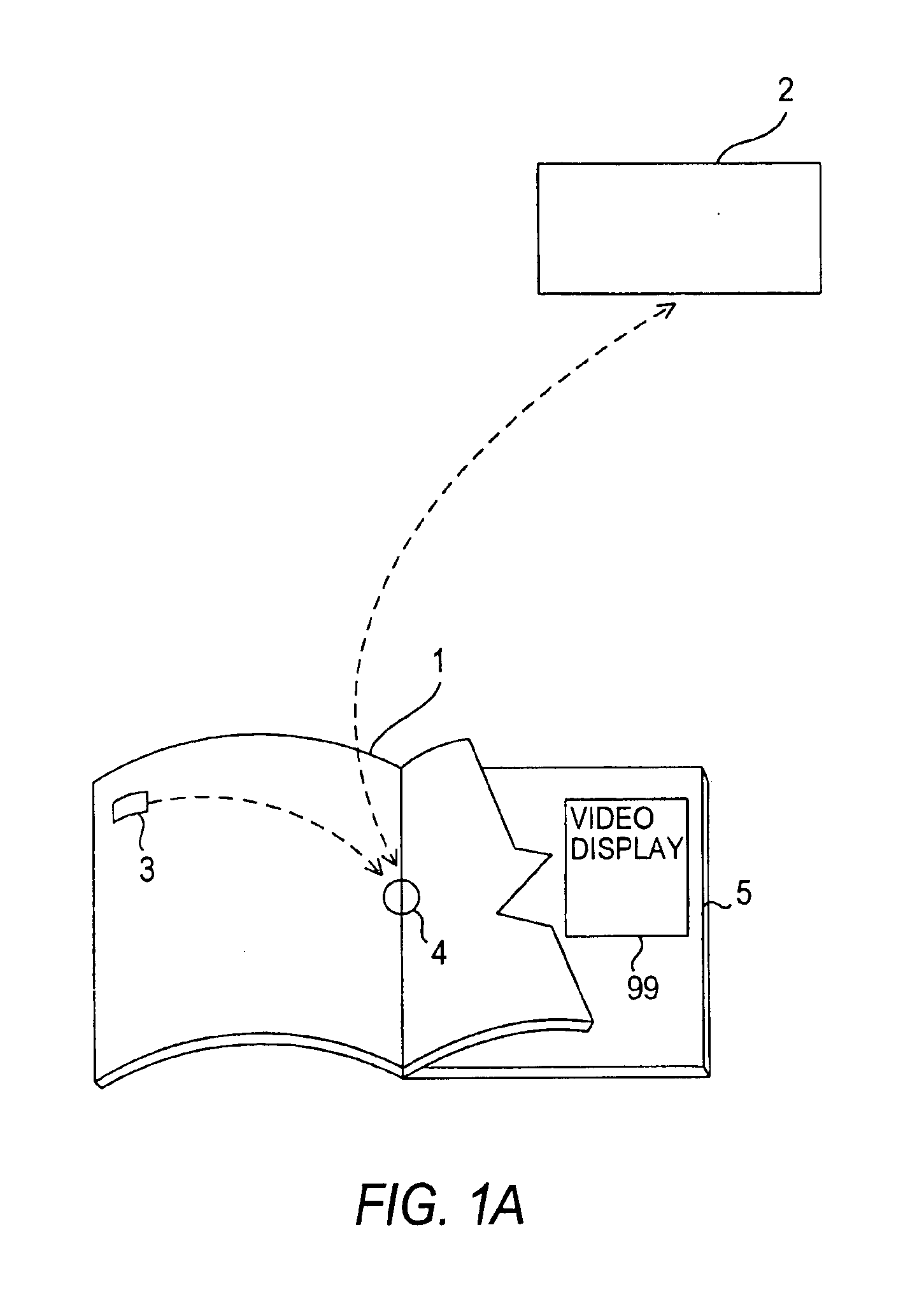
InactiveUS6866196B1Low costTelevision system detailsAnalogue secracy/subscription systemsOutput deviceComputer memory
Owner:MARSHALL FEATURE RECOGNITION
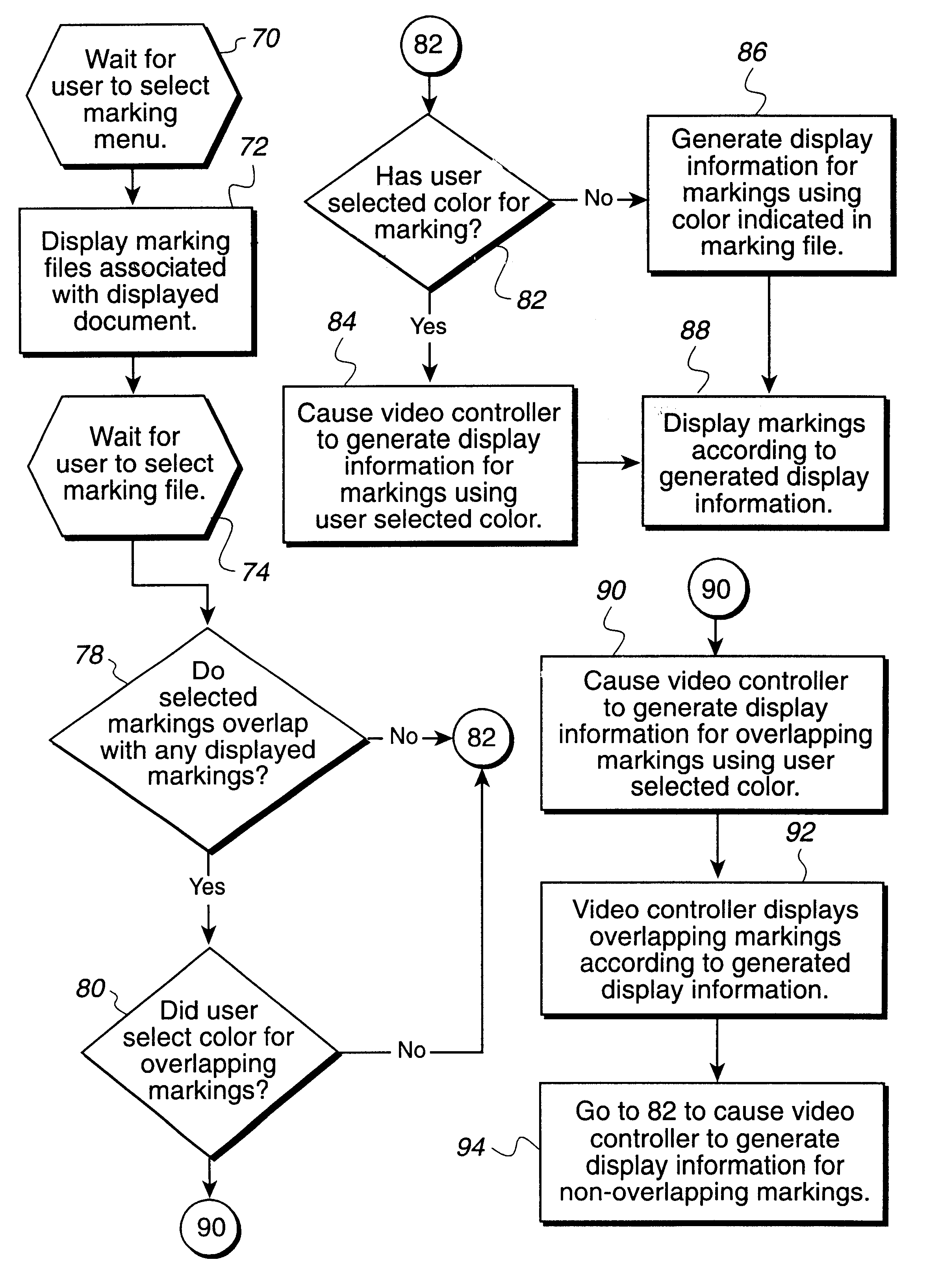
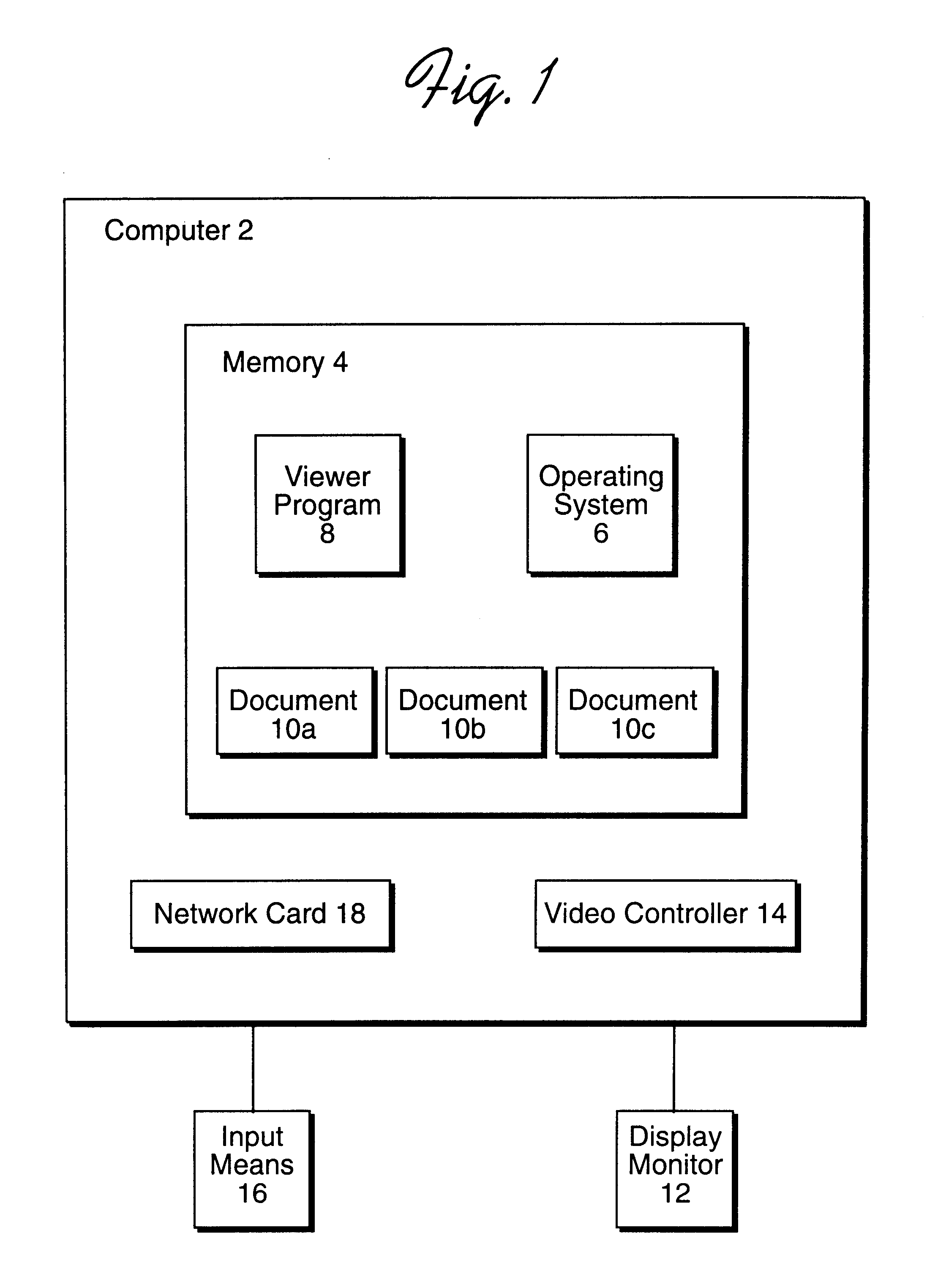
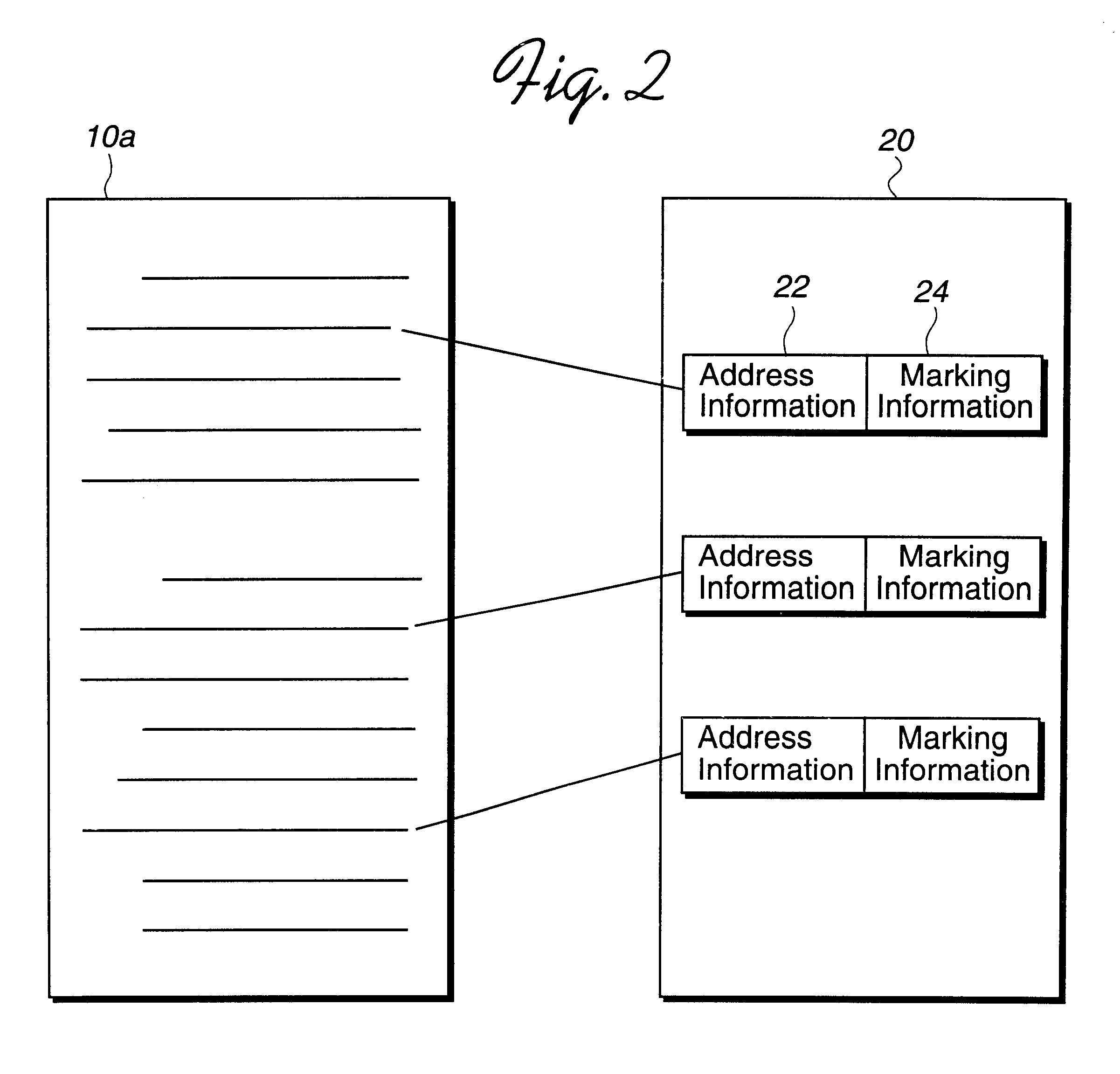
Method, system, and program for storing and retrieving markings for display to an electronic media file
InactiveUS6551357B1Digital computer detailsCathode-ray tube indicatorsGraphicsGraphical user interface
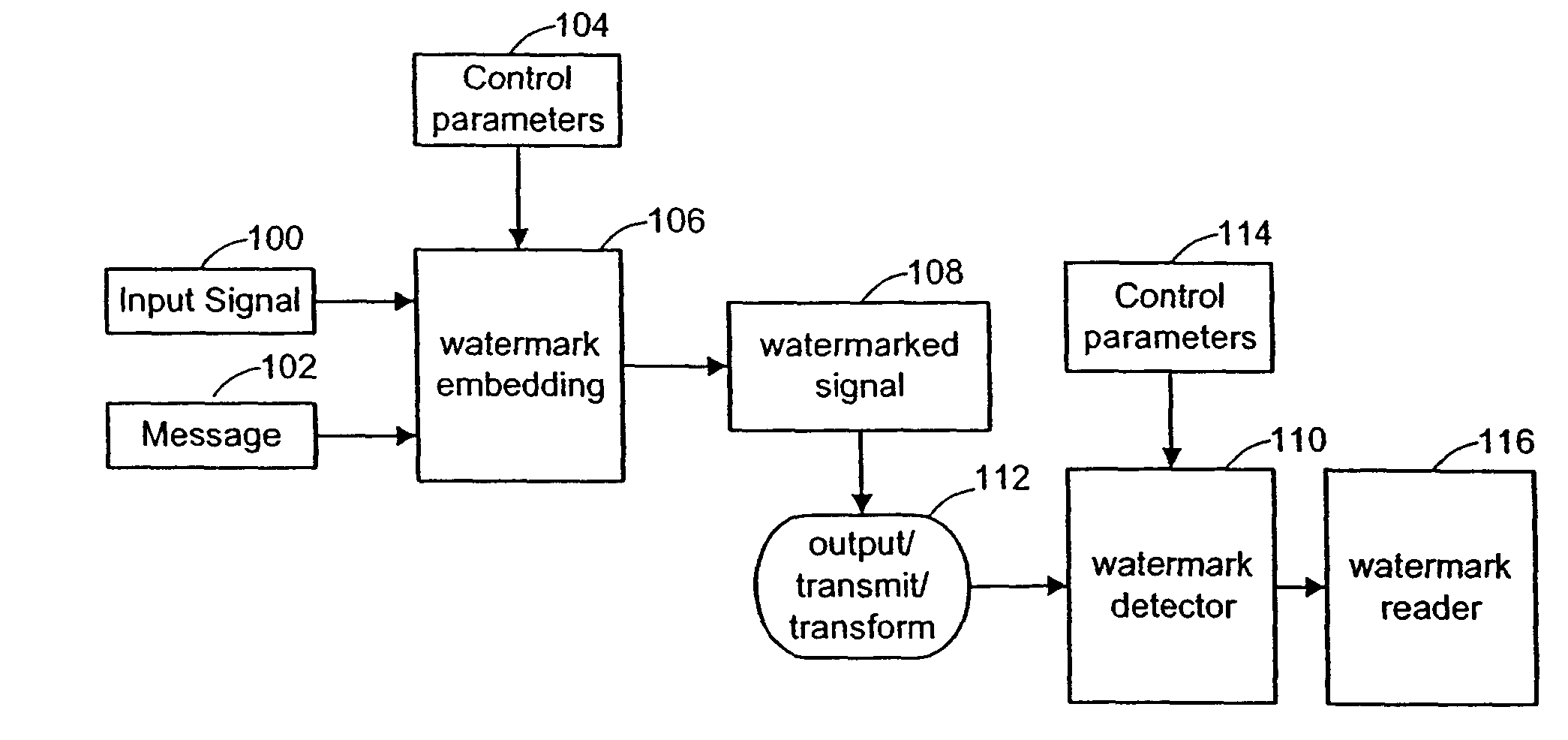
Disclosed is a method, system, and program for displaying markings to electronic media, such as text, images, video clips, audio clips, etc., in an electronic media file. A marking file includes markings and address information indicating locations of electronic media in the electronic media file to which the markings apply. The marking file is created by receiving marking input entered into a graphical user interface (GUI) window displaying the electronic media on a monitor attached to the computer. The marking file is then stored as a separate file from the electronic media file. The electronic media file and marking file are processed to display the markings indicated in the marking file superimposed on the electronic media from the electronic media file on the monitor.
Owner:IBM CORP
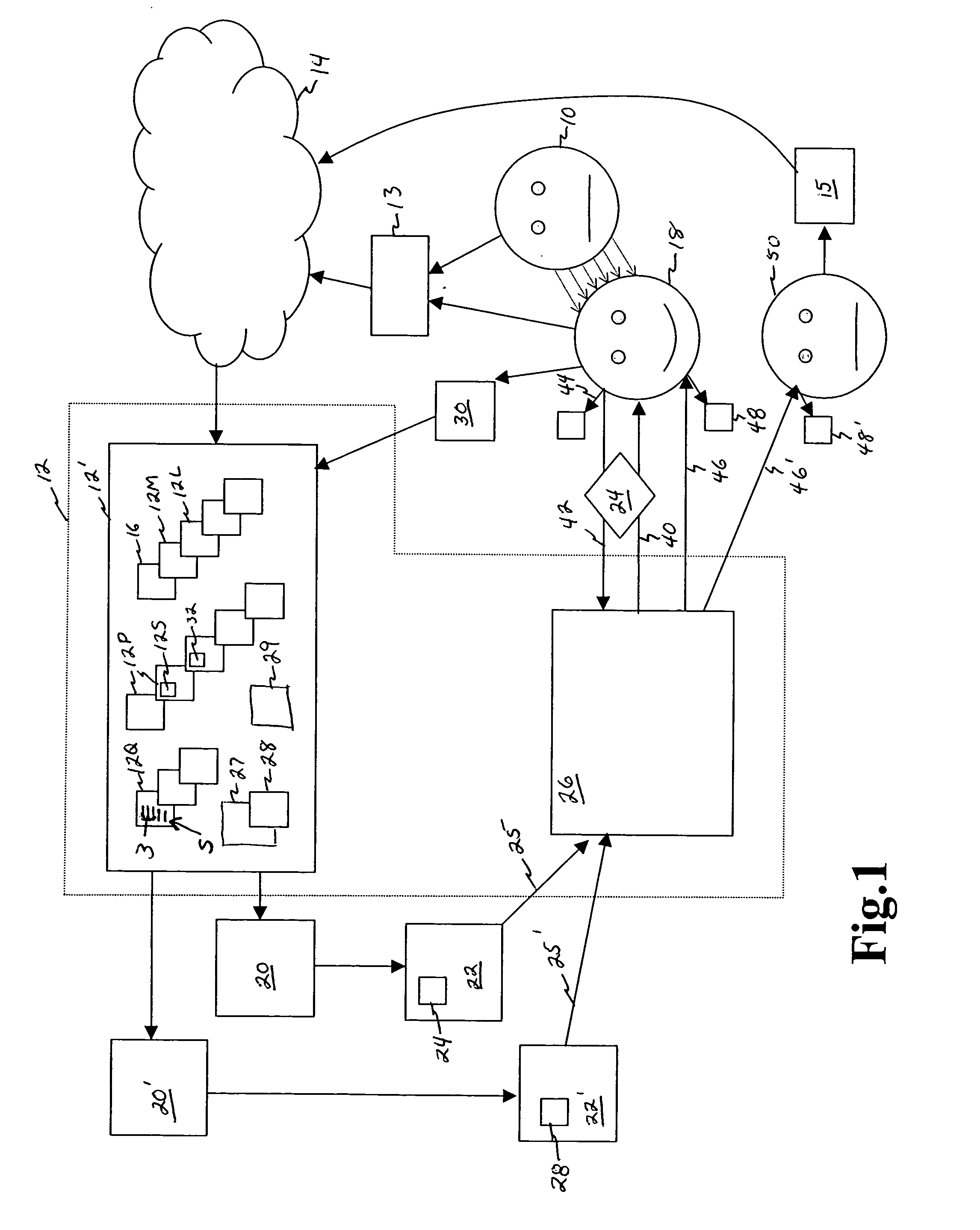
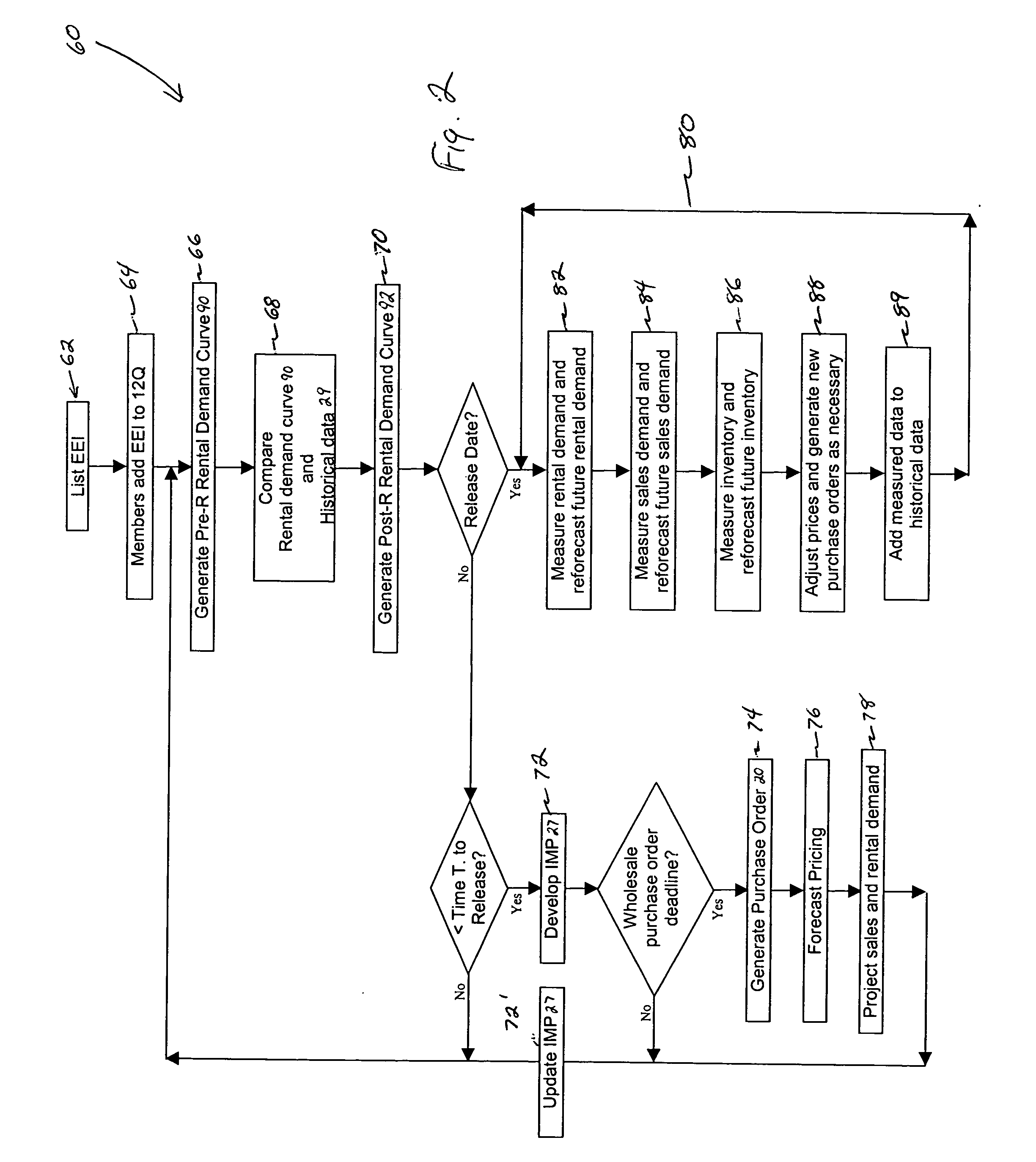
Method and apparatus for managing demand and inventory
InactiveUS20040068451A1Increase salesDecrease stockSpecial data processing applicationsMarketingComputer scienceInventory level
The present invention is directed to a method and system for managing the inventory level of, and the distribution of, electronic media rental units, including but not limited to videogame discs, musical compact disks, or movie VCD / DVDs. More specifically, preferred embodiments of the present invention forecasts future rental and sales demand for a given electronic media, such as a videogame, prior to the release of that electronic media to the general public. The forecast is based on the pre-release demand of the electronic media in that the future rental and sales demand is estimated from the rental and sales demand of previously released electronic media having similar pre-release demand. Furthermore, the preferred embodiments of the present invention allows registered members of a rental user group to keep rented units of the electronic media for a purchase price, which is dynamically controlled to minimize rental shortage and maximize profits.
Owner:GAMEFLY
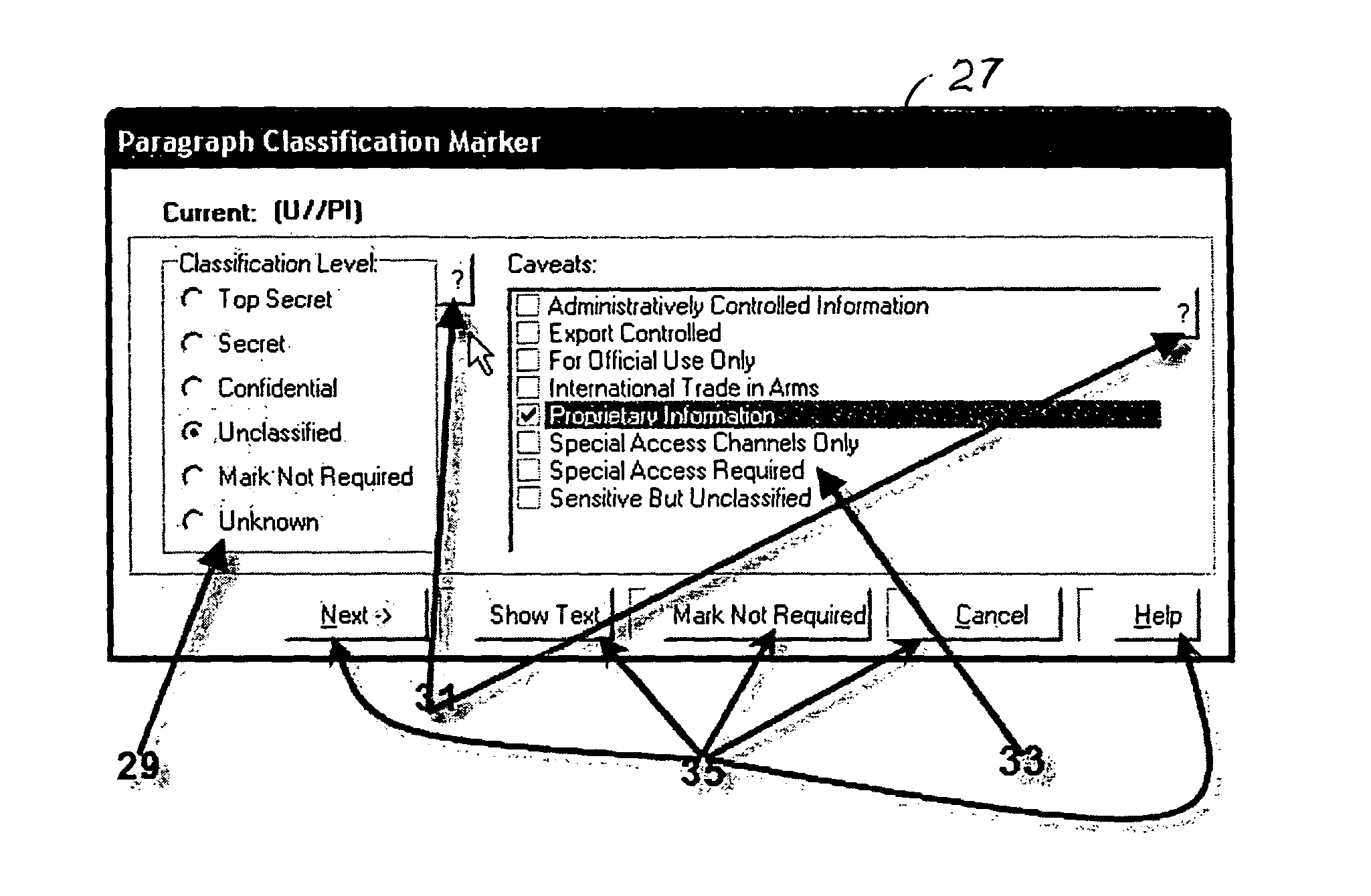
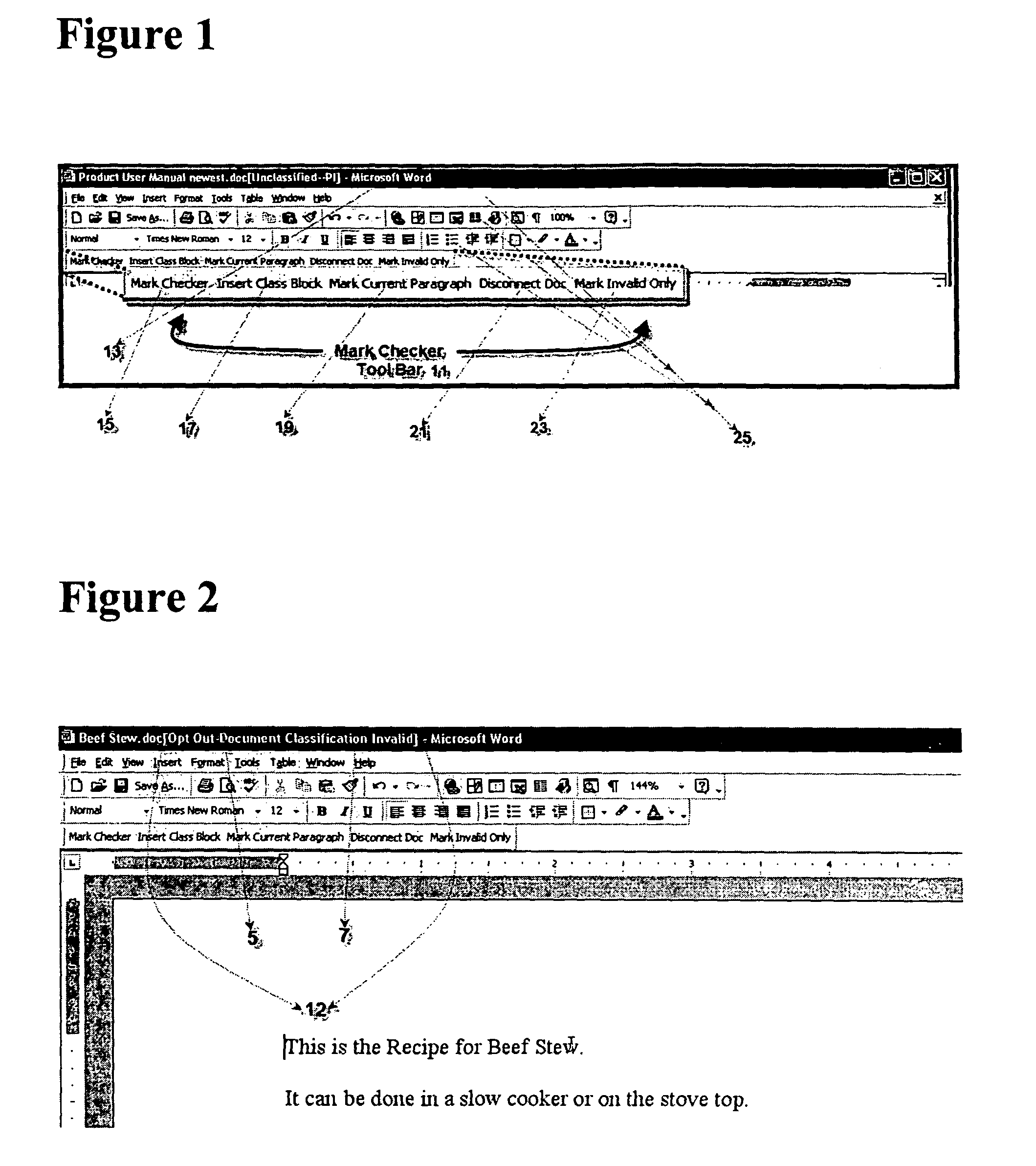
Method for providing customized and automated security assistance, a document marking regime, and central tracking and control for sensitive or classified documents in electronic format
ActiveUS7958147B1Guarantee capacityPositive determinationDigital data information retrievalDigital data processing detailsOff the shelfDocumentation procedure
A software engine runs in a compatible mode with off-the-shelf word processors, e-mail programs and presentation development software and other document development software. The software engine is used for the security classification of sensitive or national security classified information in electronic and resultant hard copy document formats. The software engine ensures that the individual considers all informational portions of a document, that appropriate document marks are employed, that document marks in their electronic format are persistent and that all necessary information, such as classification guides, standards and security regulations, provided by the organization to classify information is at hand and immediately available. In addition to the document sensitivity or classification determination and marking support, the software engine tracks and controls documents and the electronic media storing documents. It also provides warnings and alarms, ad hoc document security analysis and reporting capability to system security administrators with respect to document or network events or captured information that may be indicative of risk to the information requiring protection. The software also provides the ability for an organization to centrally establish and control a security classification or sensitivity marking hierarchy for automated security classification support.
Owner:TURNER JAMES LUKE +1
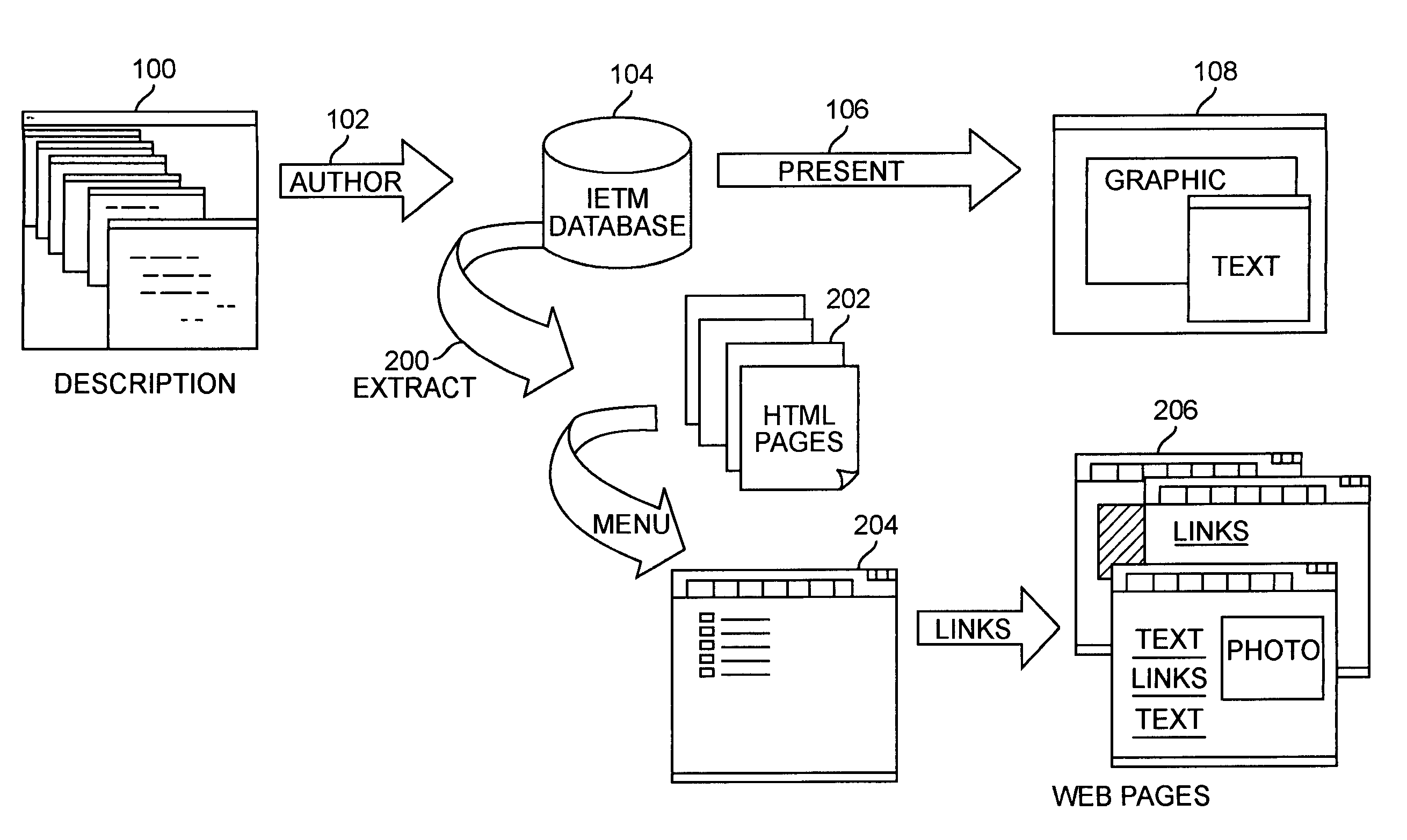
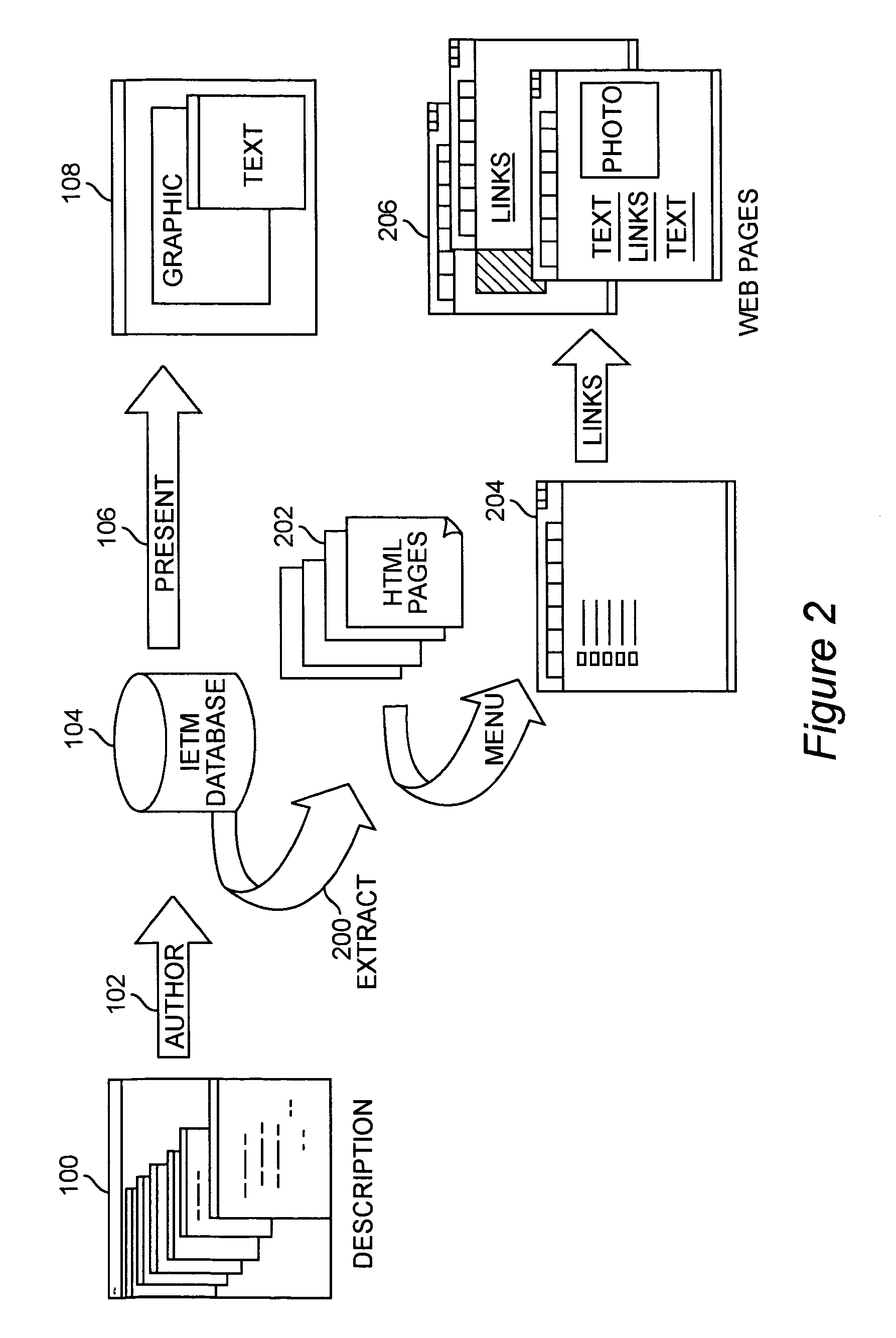
System and method for interactive electronic media extraction for web page generation
InactiveUS6961897B1Efficient updateExtend the life cycleDigital computer detailsNatural language data processingData warehouseRelational database
A system and method for parsing an electronic media database structure to produce tagged data that preserves the content, links, and electronic media structure. In particular, HyperText Markup Language (HTML) data is generated as an Interactive Electronic Technical Manual (IETM) (home page) linked into a relative structure of Web pages to support IETM deployment. An extraction process assesses the functionality associated with each node designated for presentation and builds a virtual Web, based on attributes stored in the IETM database. A series of Web pages with links that hierarchically presents IETM data at run time is produced. The method supports a data warehousing strategy that converts any data type eligible within the relational database. This expands support across multiple types of technical and engineering data. The preferred implementation utilizes a relative addressed pure HTML solution viewable in standard Web browsers. This open system implementation is cross platform and infrastructure independent, requiring no special server software. Retaining the hierarchical structure dictated by the relational database in HTML output enhances the supportability and maintainability of the Web implementation. Updates to this Web implementation can be incrementally applied within the hierarchy (small sections of data) or the entire logical sections of Web data.
Owner:LOCKHEED MARTIN CORP
Network-based content distribution system
InactiveUS7426750B2Maximize potential return-on-investmentMinimal burdenDigital data processing detailsUser identity/authority verificationContent distributionPublic network
A method and system for transferring electronic media information over a public network in such a way as to provide safeguards for inappropriate distribution of copyright or otherwise protected materials are described. The media information is transparently watermarked with a unique ID, such as one generated from X.509 Digital Certificate and public-key cryptography public / private key pairs, such that the information can be identified as belonging to a particular individual. A system and method for monitoring the movement of such watermarked files, positively identifying people who have inappropriately distributed copyright materials over a public network without permission, and taking appropriate enforcement action against such people.
Owner:VERIMATRIX INC
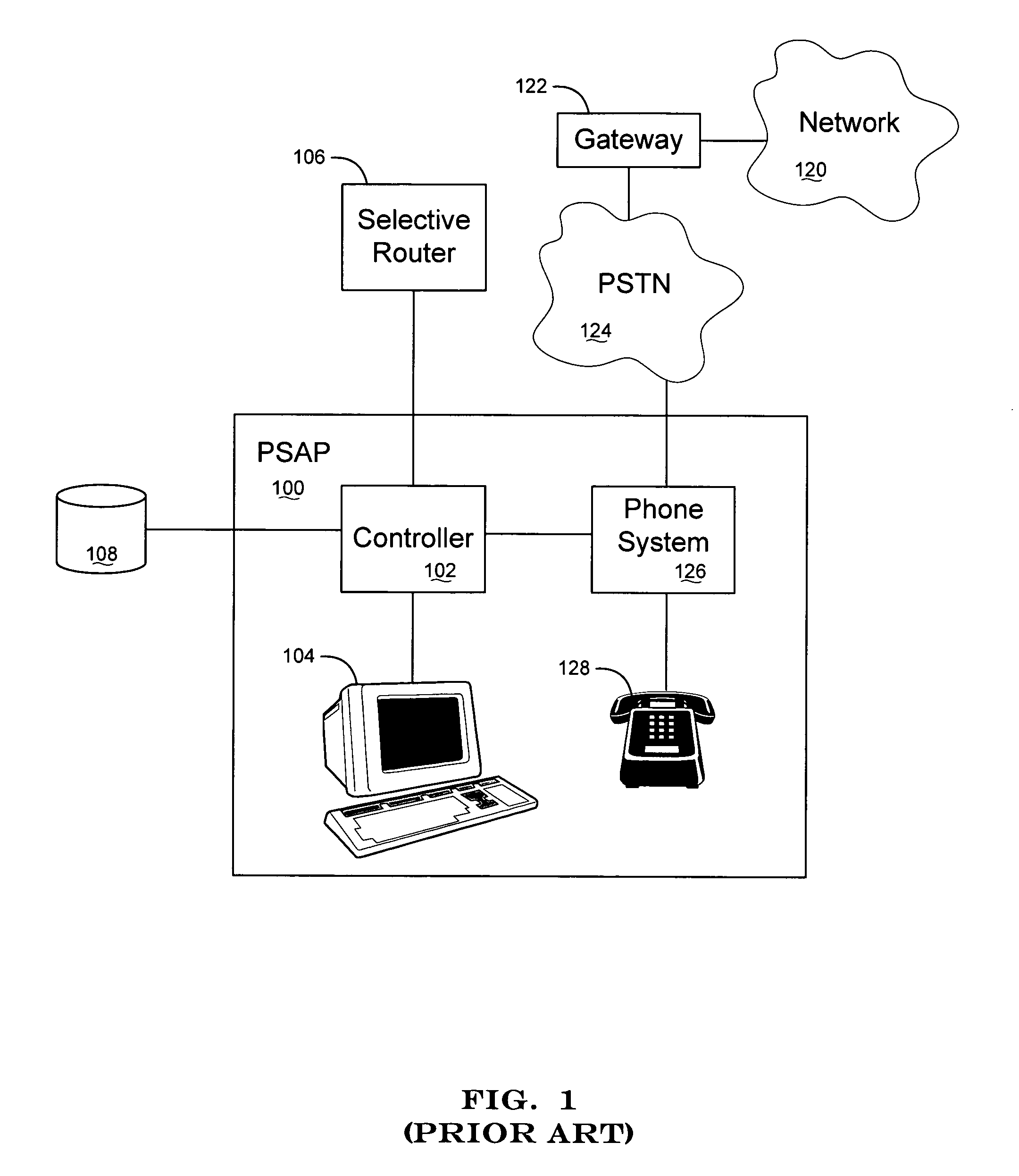
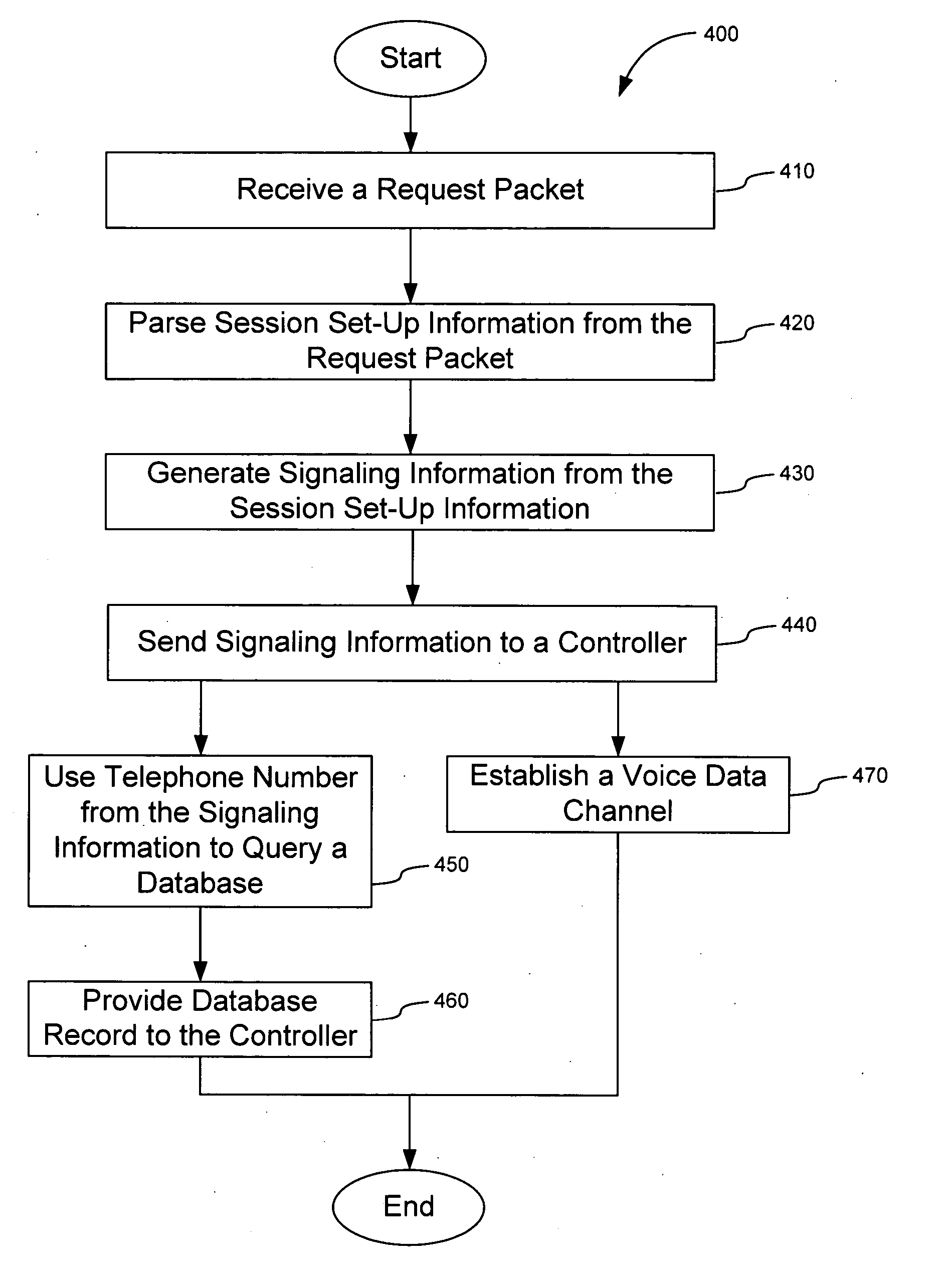
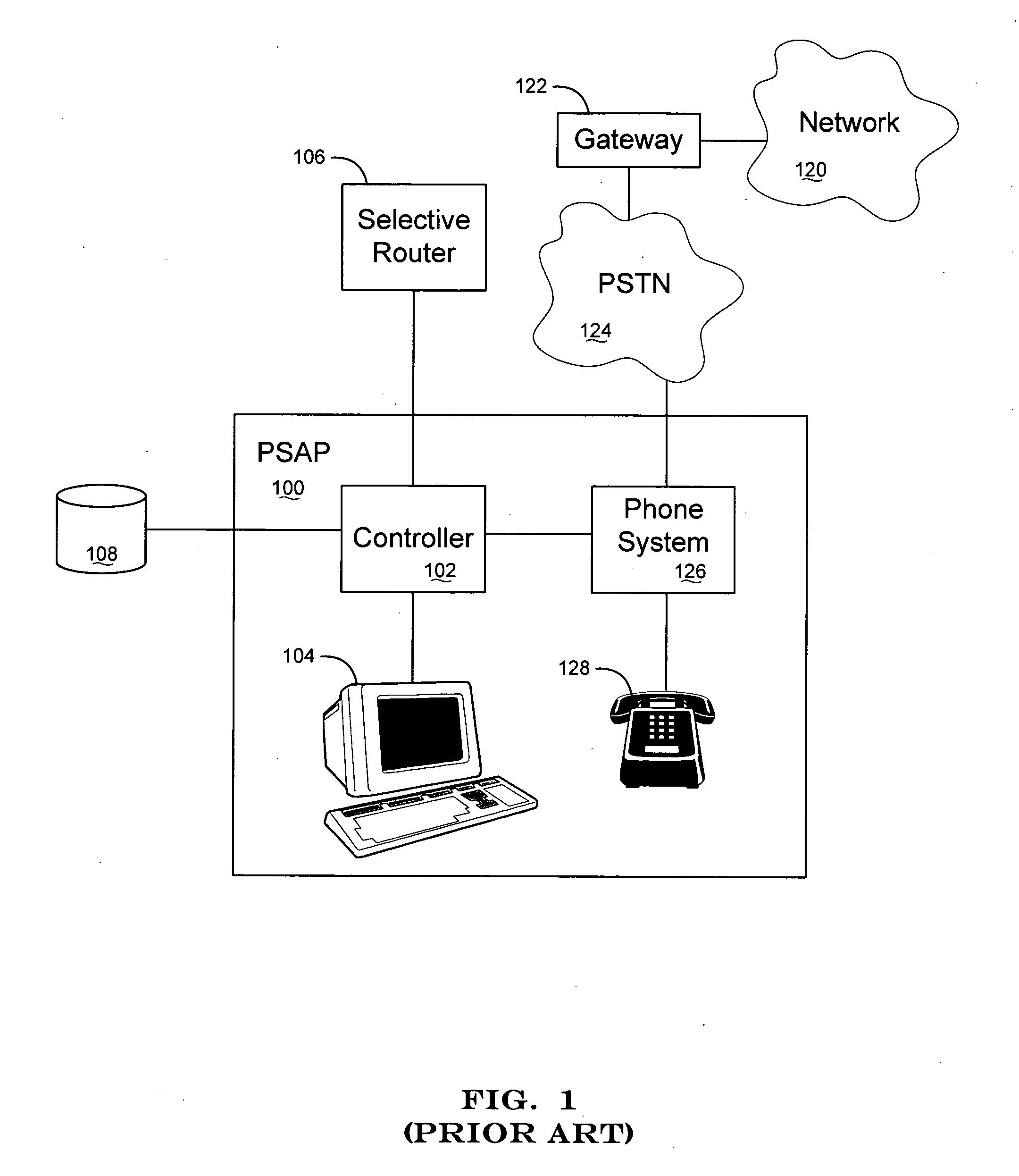
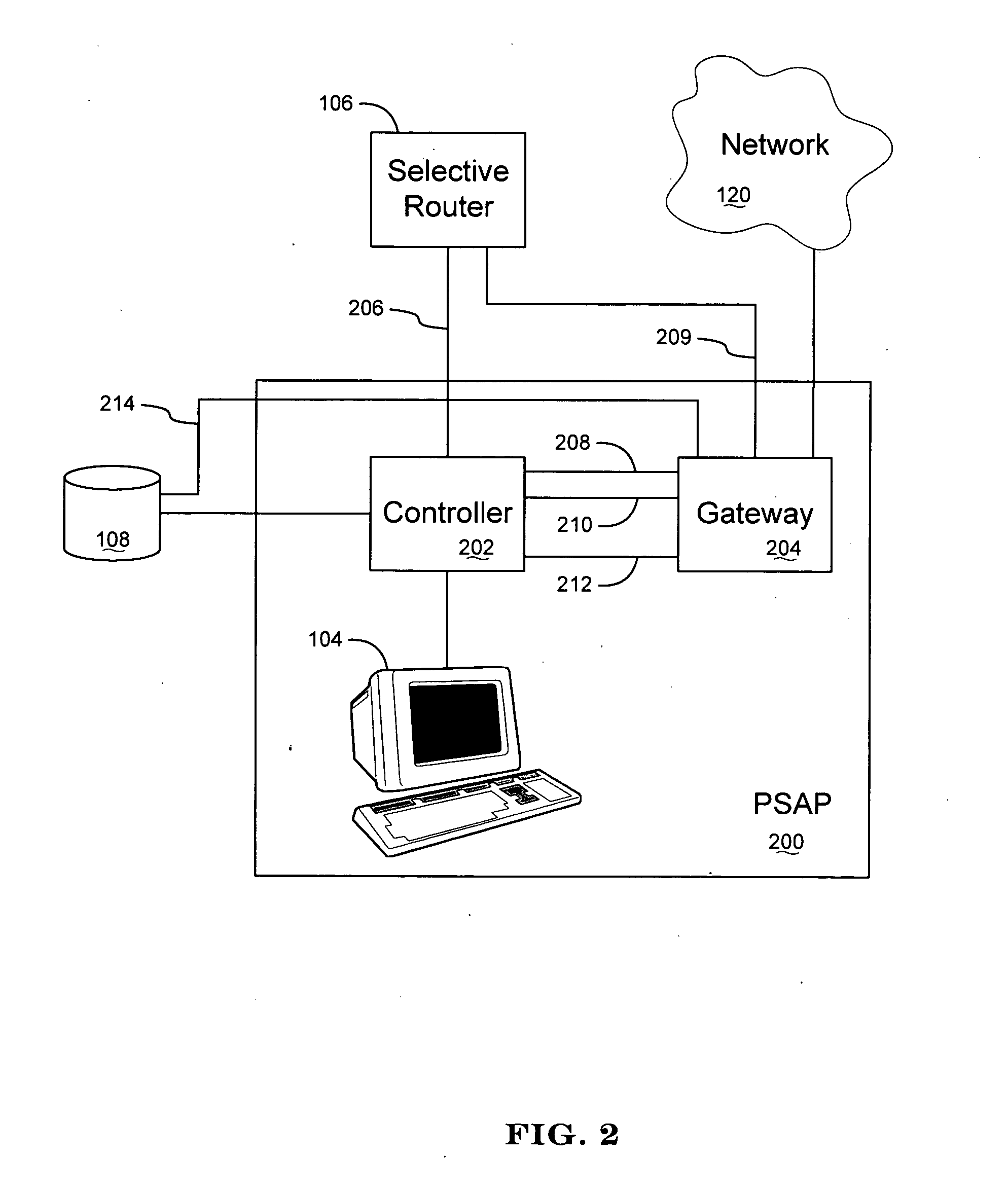
Apparatus and method for interfacing packet-based phone services with emergency call centers
InactiveUS7369530B2Telephonic communicationData switching by path configurationLogical frameworkComputer science
Owner:KEAGY SCOTT
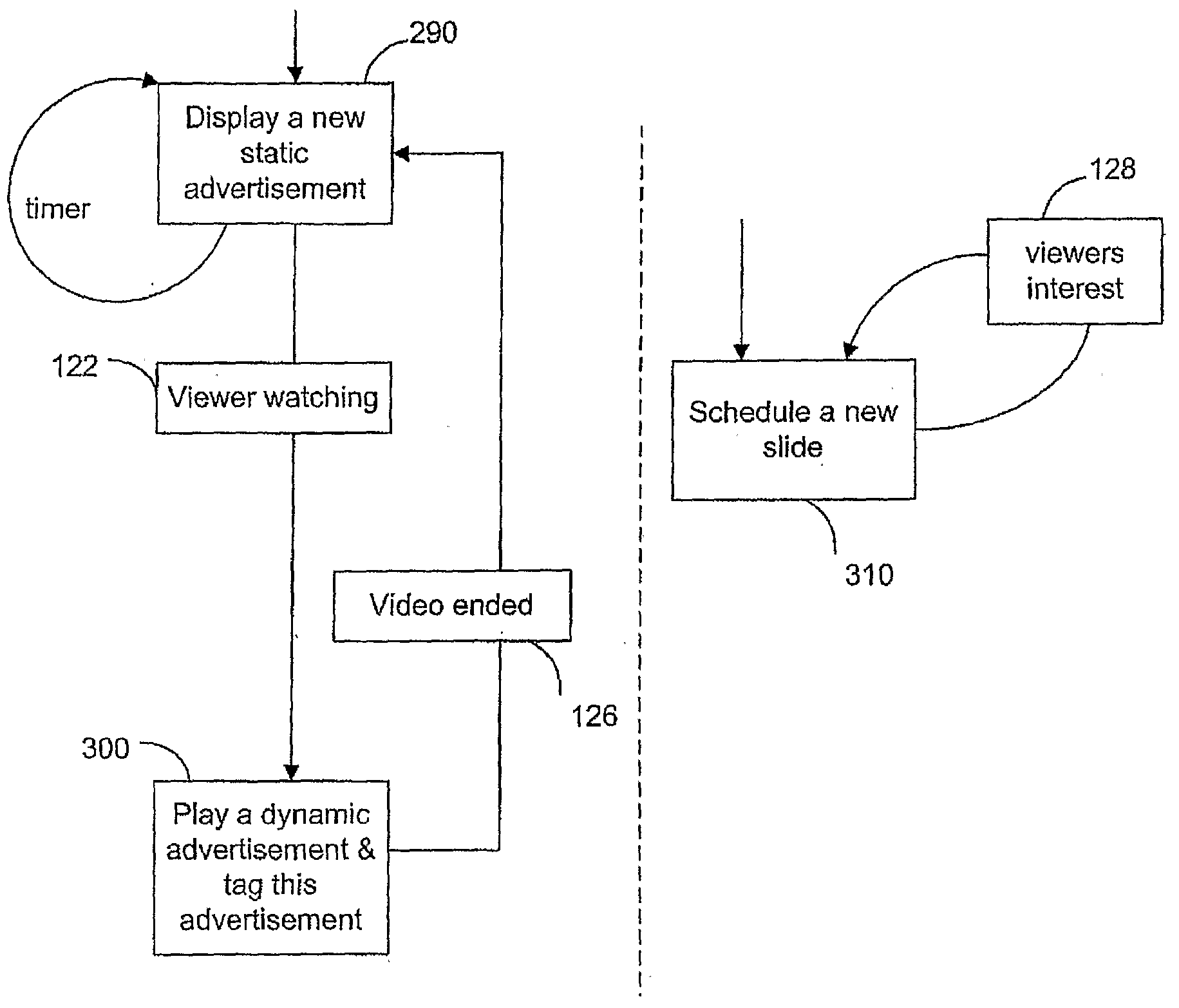
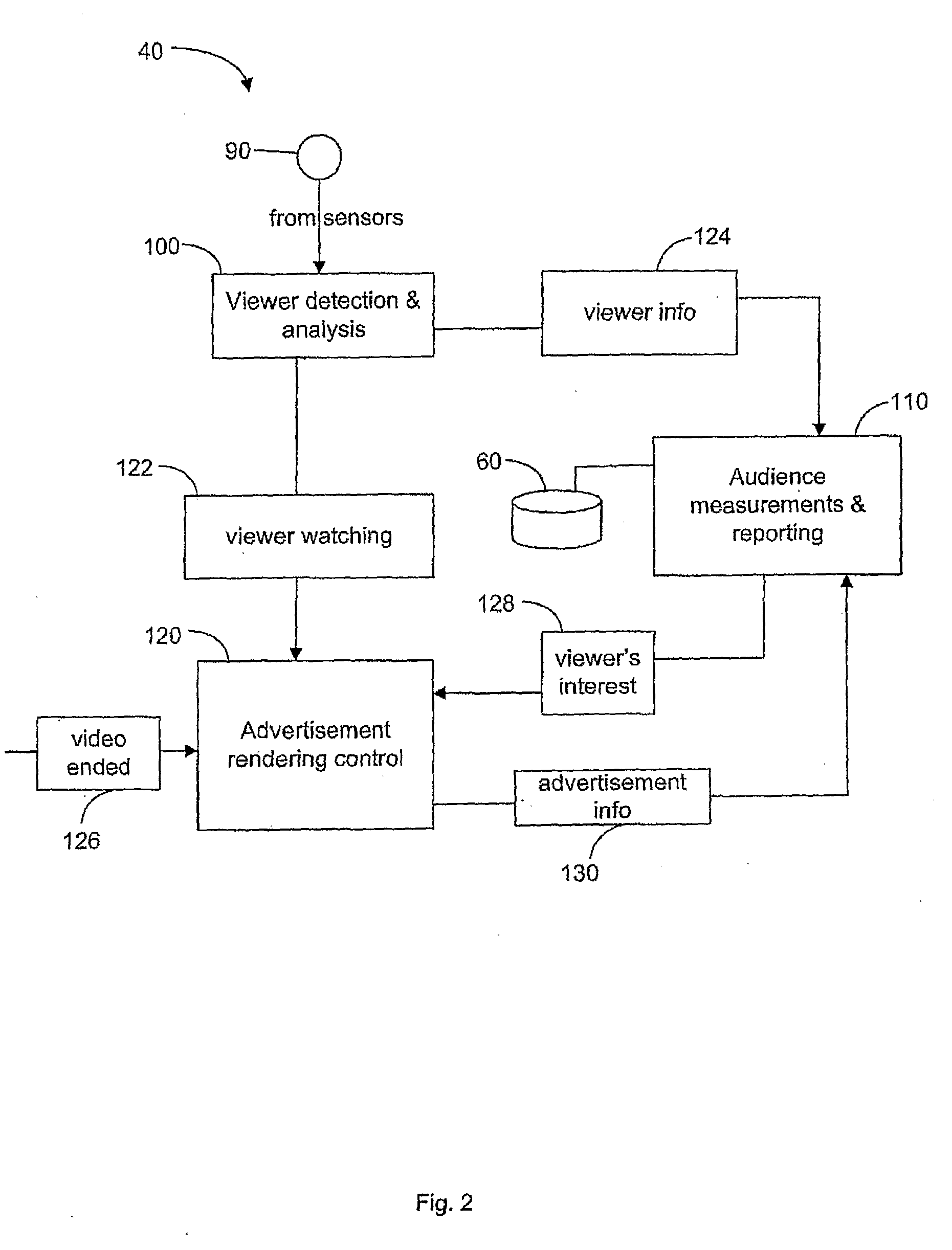
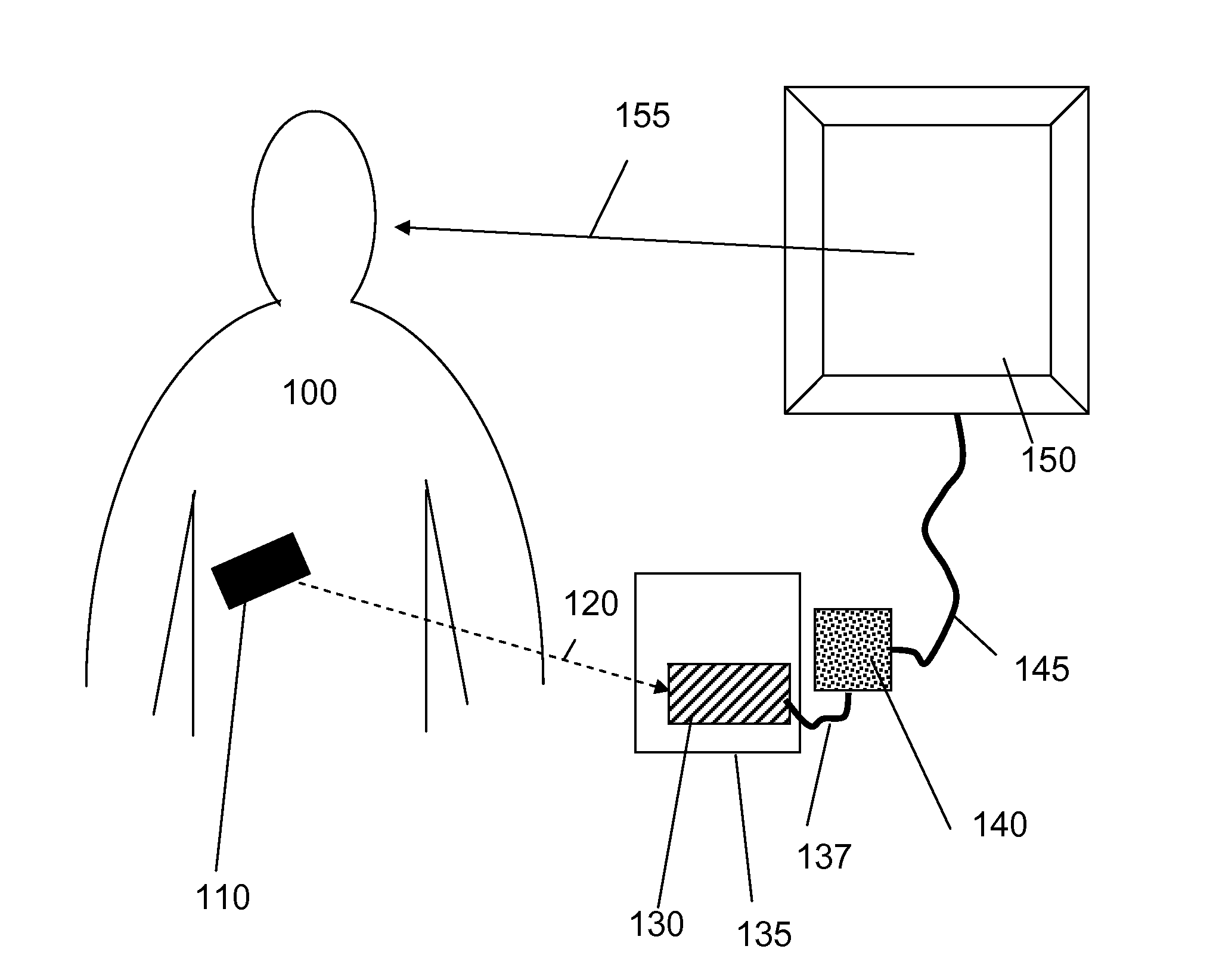
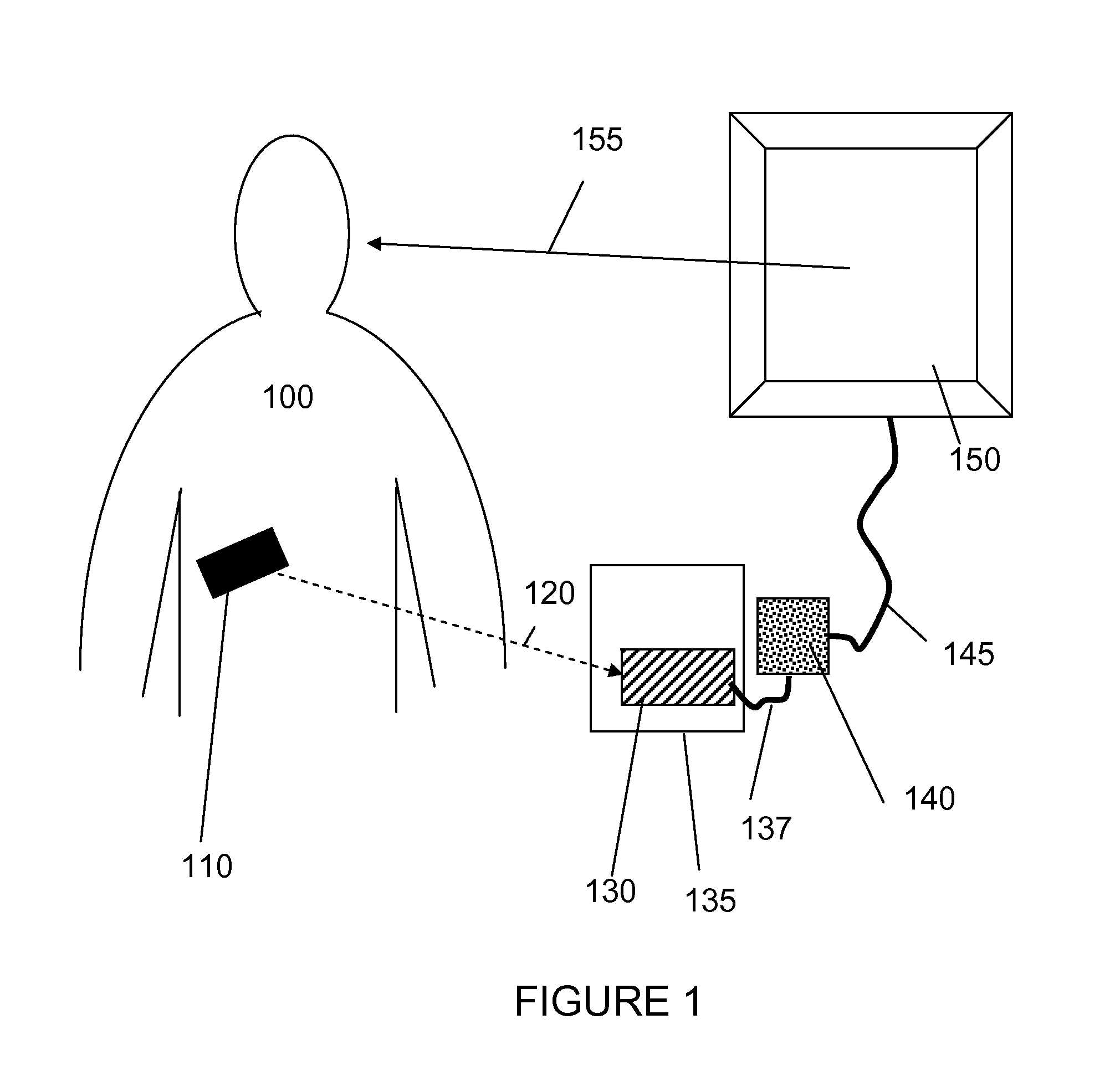
Electronic media system
ActiveUS20090177528A1Stay focusedReduce delaysAnalogue secracy/subscription systemsCharacter and pattern recognitionInformation display systemsDisplay device
The invention is a digital information display system (10), comprised of an electronically controlled display (20), usually used to display advertising, A video camera (30) is used to detect one or more viewers in the audience who are paying attention (100) to the display (20), and if so which part of the display (30). Based on which part of the display has the viewers attention, the advertising displayed is adjusted in real-time and based on the viewer analysis to promote continued attention from the viewer. It is an advantage of the invention that the display is able to continuously present relevant advertising content, and with reduced delay, to an audience by using its passive observation and analysis capabilities.
Owner:NAT ICT AUSTRALIA
Method and system for preventing unauthorized reproduction of electronic media
ActiveUS20060021057A1Digital data processing detailsAnalogue secracy/subscription systemsProcess identificationWorld Wide Web
A method for selectively controlling access to electronic media disposed on a media storage device according to one embodiment is described. The method comprises creating a first list comprising a plurality of process identification values. Each of the plurality of process identification values of the first list is associated with a software application that is accessing the media disposed upon the media storage device. The method further includes creating a second list comprising a second plurality of process identification values. Each of the second plurality of process identification values is associated with a software application that is storing data. The method further includes determining that a particular software application is creating an unauthorized copy of the media disposed upon the media storage device. The method further includes preventing the particular software application from storing a usable copy of said electronic media.
Owner:MEDIA RIGHTS TECH
System utilizing physiological monitoring and electronic media for health improvement
InactiveUS20110230732A1SensorsMeasuring/recording heart/pulse ratePhysiological monitoringPhysiological computing
The present invention generally relates to the use of physiological monitoring to enable an individualized response, e.g. feedback, recommendations, rewards or guidance to be presented to the individual within the context of electronic media. Specifically, the response is preferably based upon measured physiological data obtained while the individual is not directly involved with the electronic media and is preferably delivered in the context of an electronic game or interactive social activity program.
Owner:PHILOMETRON
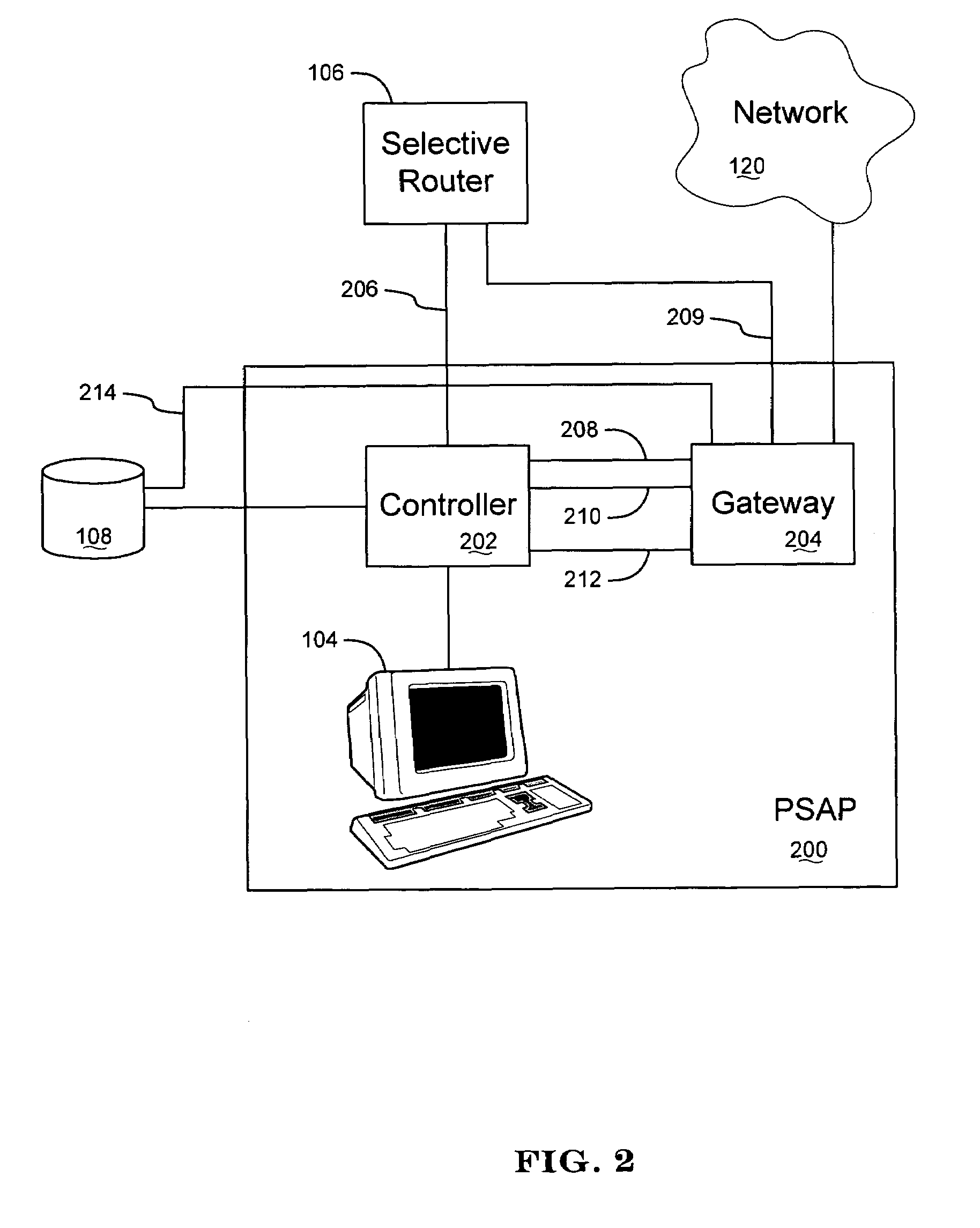
Apparatus and method for interfacing packet-based phone services with emergency call centers
InactiveUS20050174991A1Telephonic communicationData switching by path configurationLogical frameworkComputer science
A gateway is provided for interfacing packet-based phone services with controllers of emergency call centers. For each type of electronic medium to be interfaced, the gateway comprises a specific I / O interface and a specific module such as a protocol stack. The gateway also comprises an auxiliary information gateway application that integrates the I / O interfaces and modules into a logical framework that enables inter-working therebetween. A controller that includes the functionality of the gateway device is also provided. Methods for enabling emergency calls, and more generally for enabling a multi-media session, are also provided.
Owner:KEAGY SCOTT
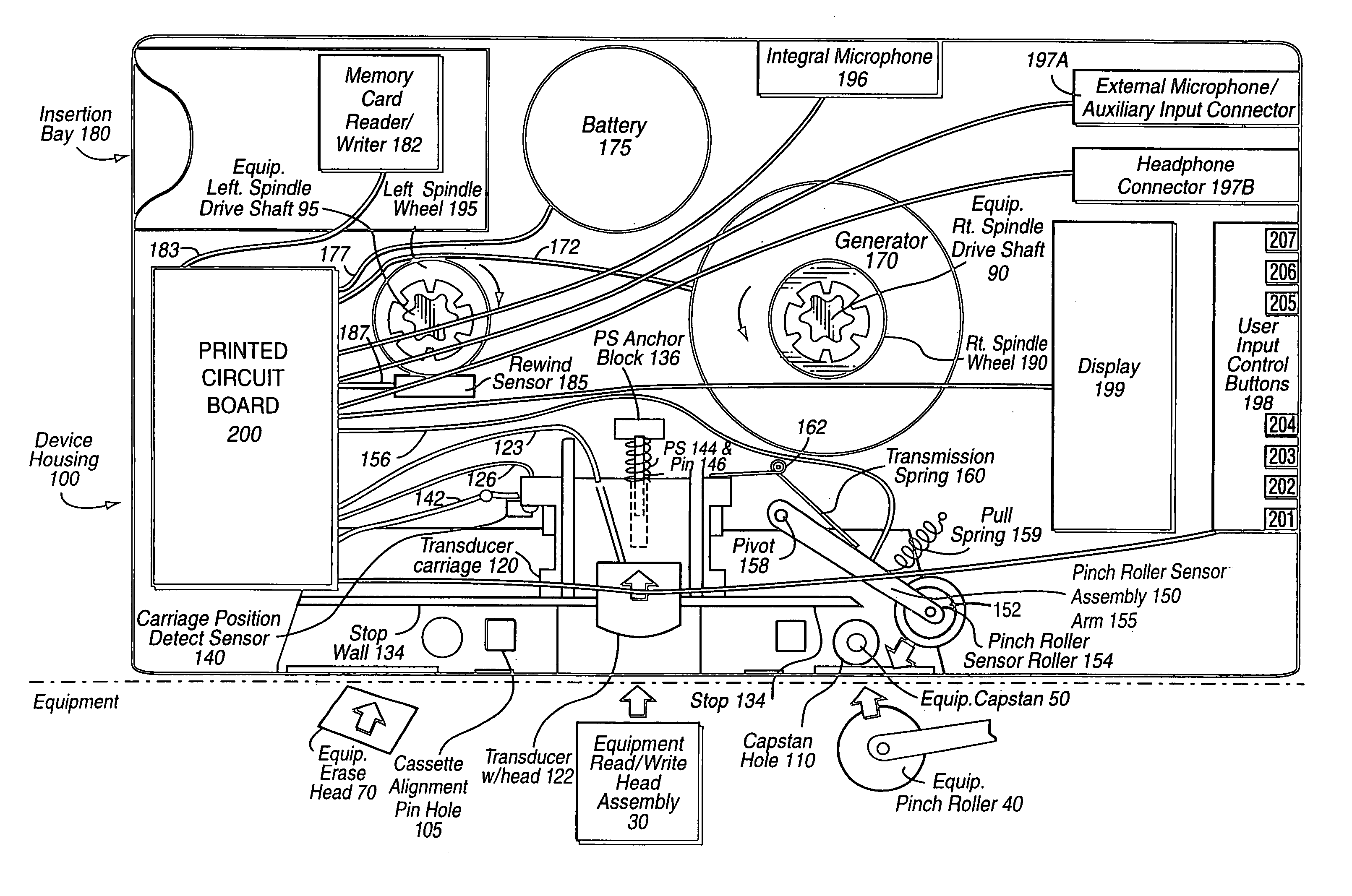
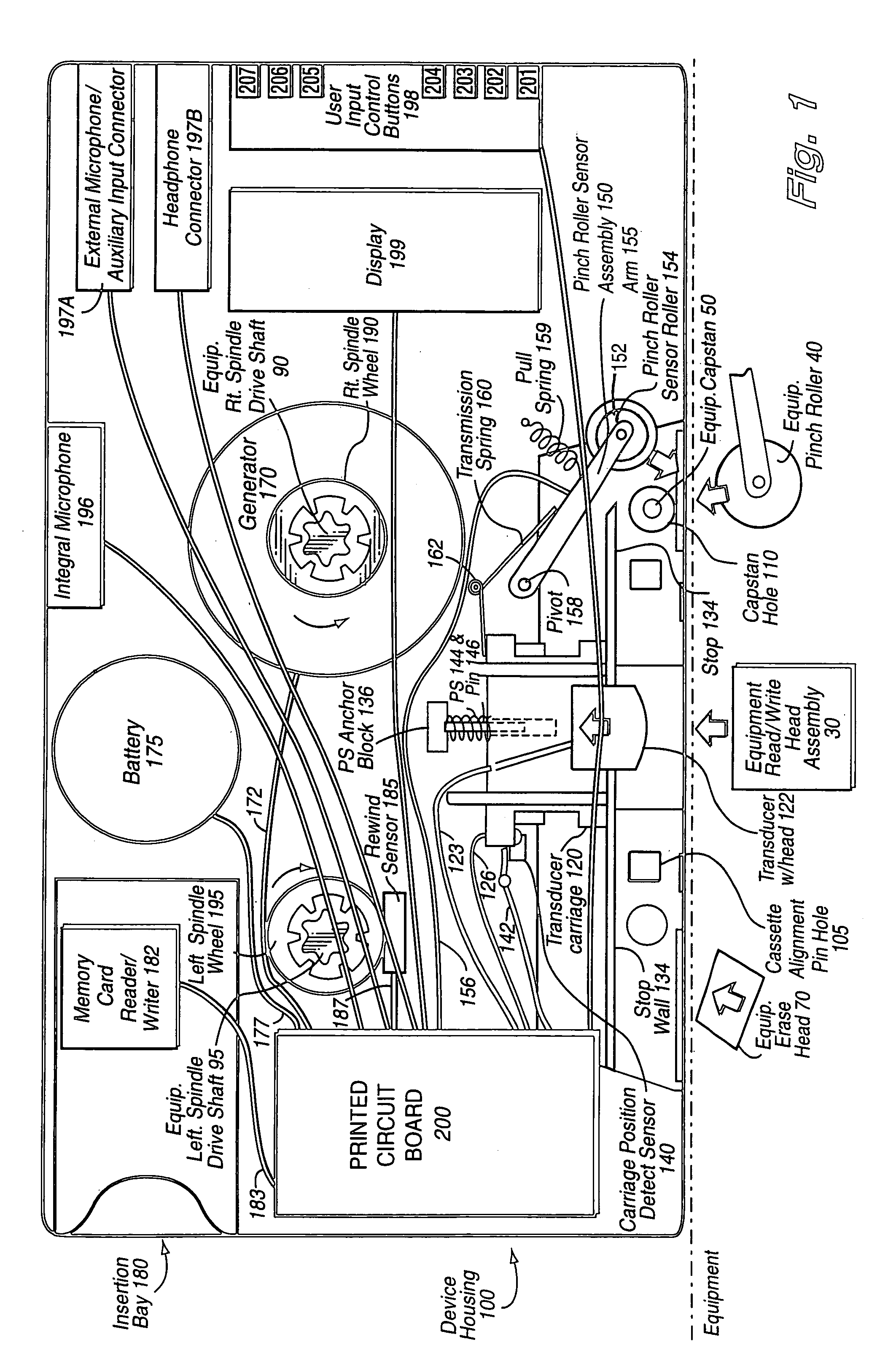
Audio cassette emulator
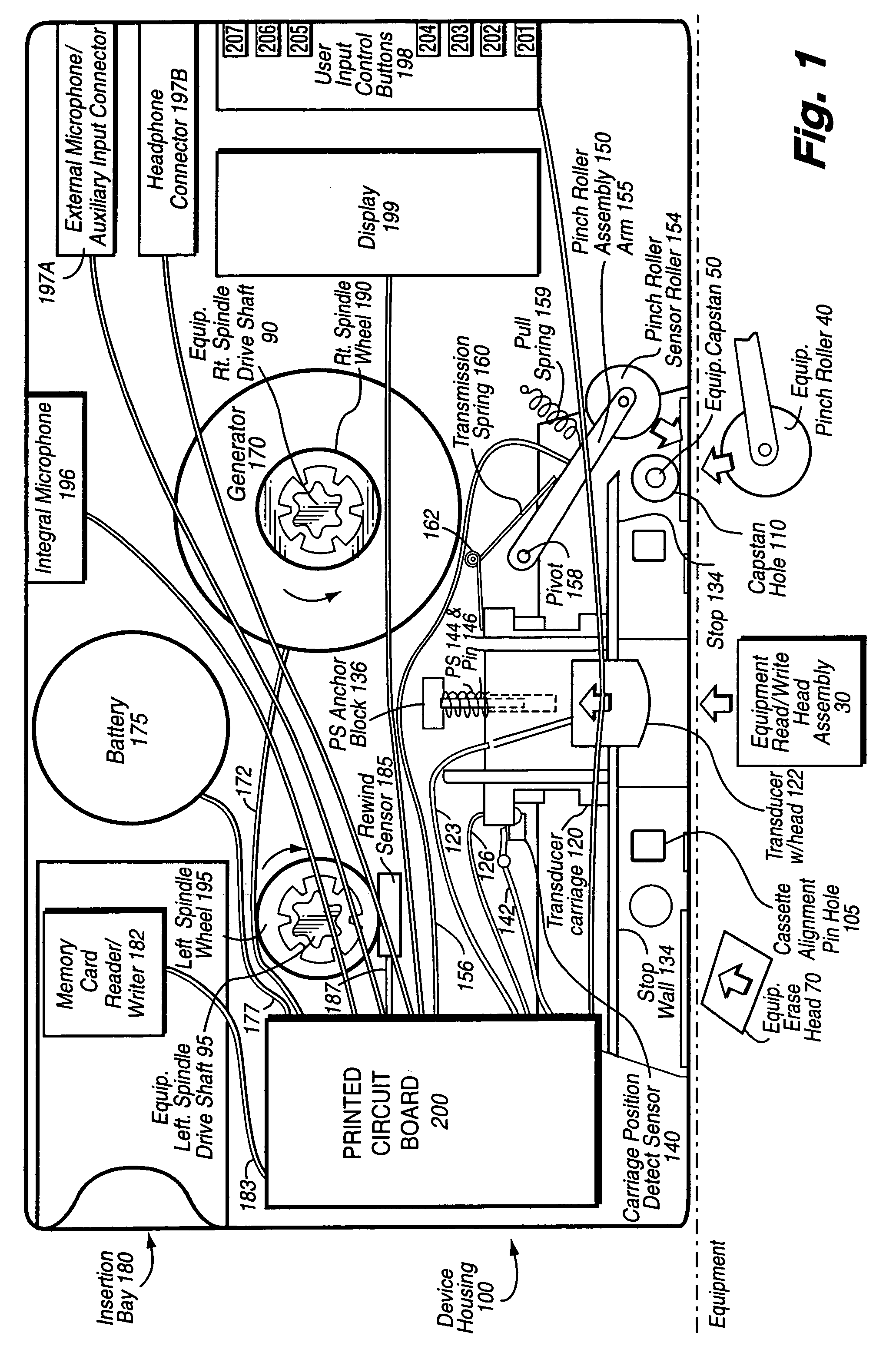
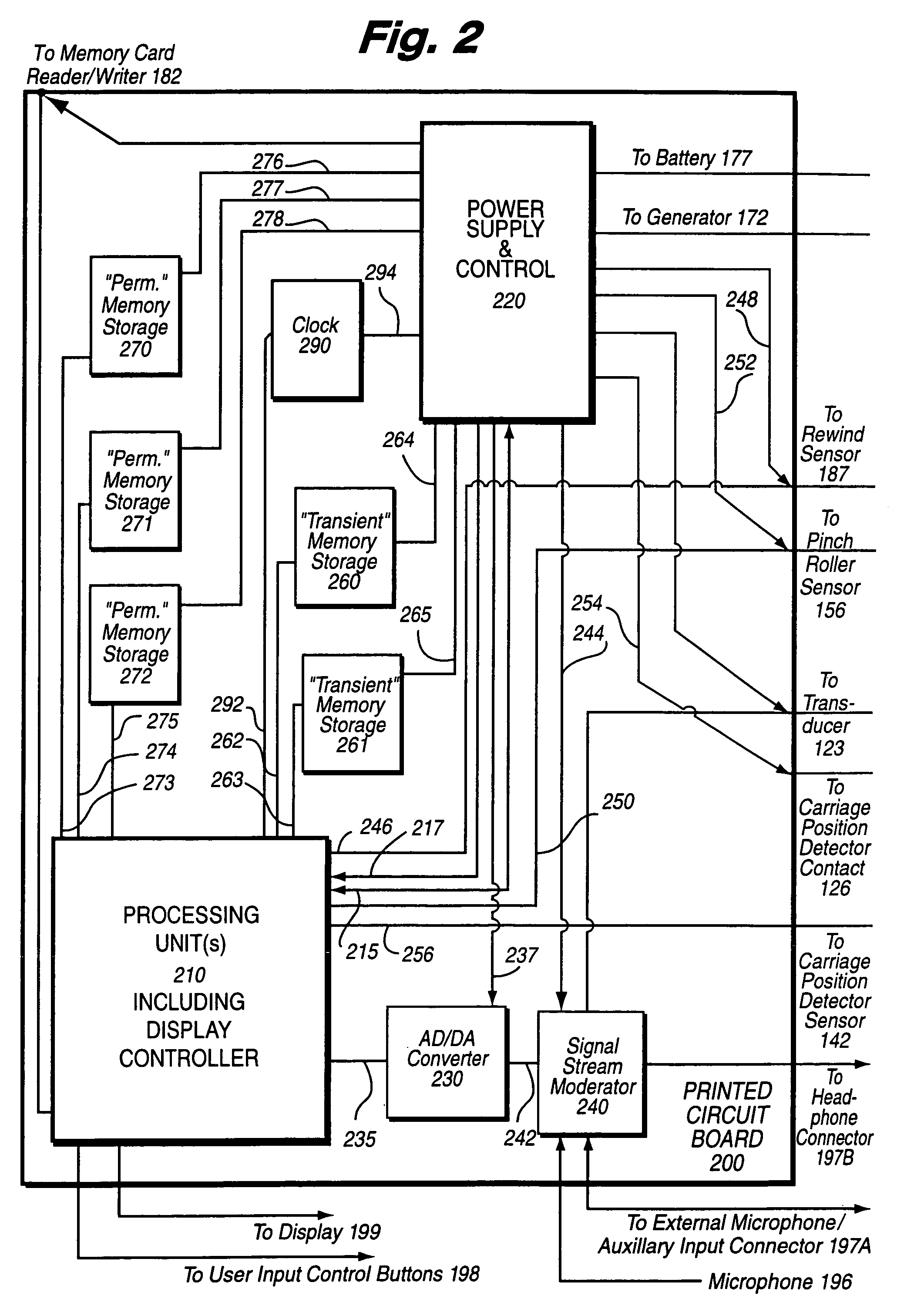
InactiveUS6941180B1Saving positionSaving stateApparatus for flat record carriersRecord information storageThe InternetMultiple sensor
A device of the same general physical size and shape as a standard audio cassette tape, but which accepts digital information from any of a variety of sources—including for example: Internet transmission, a digital computer, or memory cards (especially digital memory cards)—and plays this digital information through any, for example, standard audio tape cassette player. The device operates by converting the digital representation of the sound into magnetic signals which are presented to the read / write head of the cassette player equipment. The device allows the user of the cassette player to regulate the audio playback using conventional equipment controls such as: START, STOP, REWIND, FAST REWIND, FORWARD, FAST FORWARD, etc. In one exemplary implementation, the device has the same general physical dimensions of a standard audio cassette; at least one digital processor; and a slot into which electronic media such as, for example, memory cards, smart cards having a processor and a memory embodied thereon and other memory media may be inserted. Converter circuitry converts data stored in digital memory to an analog signal which is magnetically coupled to the read head of the equipment. Numerous sensors detect changes in at least one of the tape equipment mechanisms in the audio cassette emulator.
Owner:FISCHER ADDISON M
Authentication of physical and electronic media objects using digital watermarks
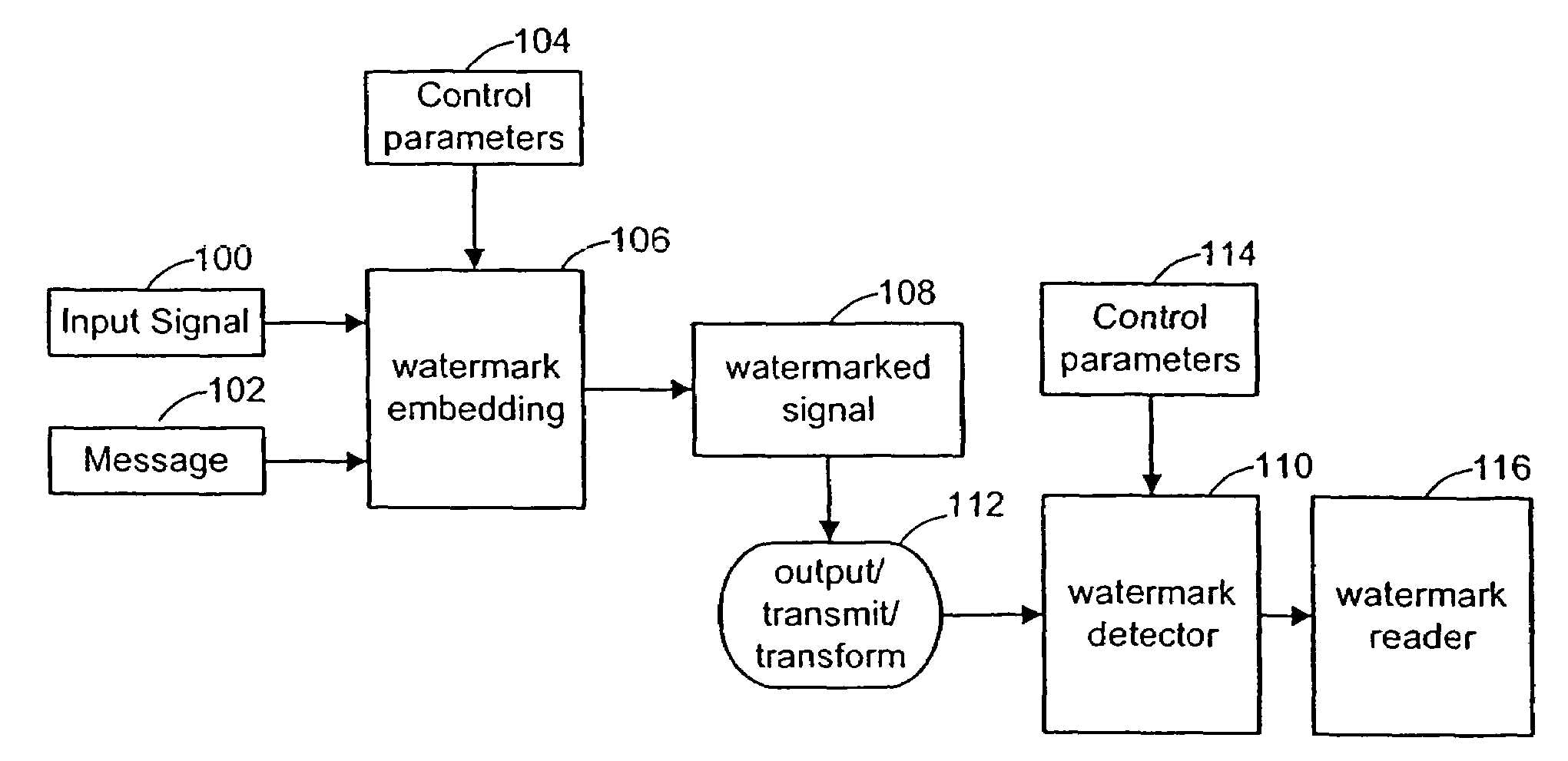
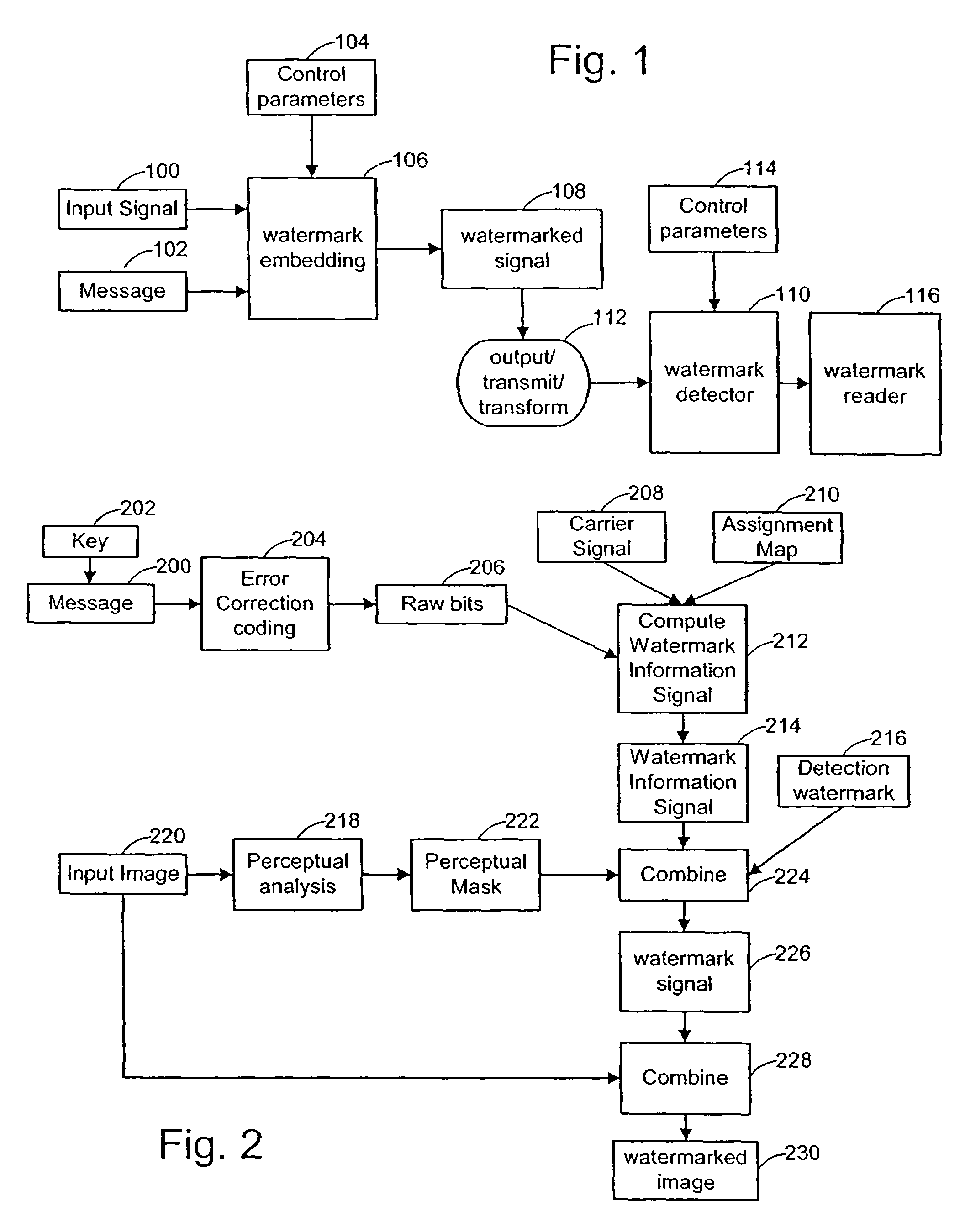
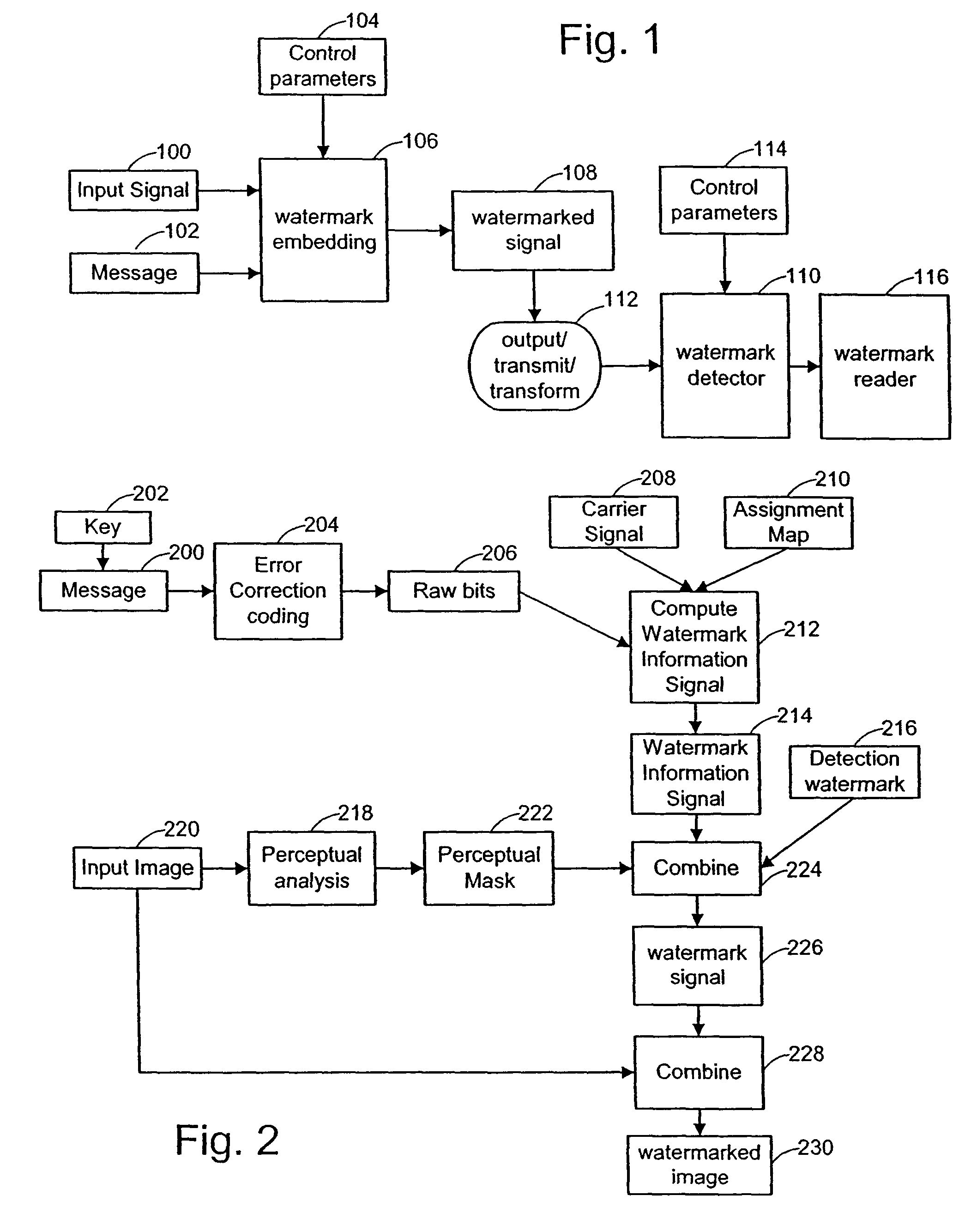
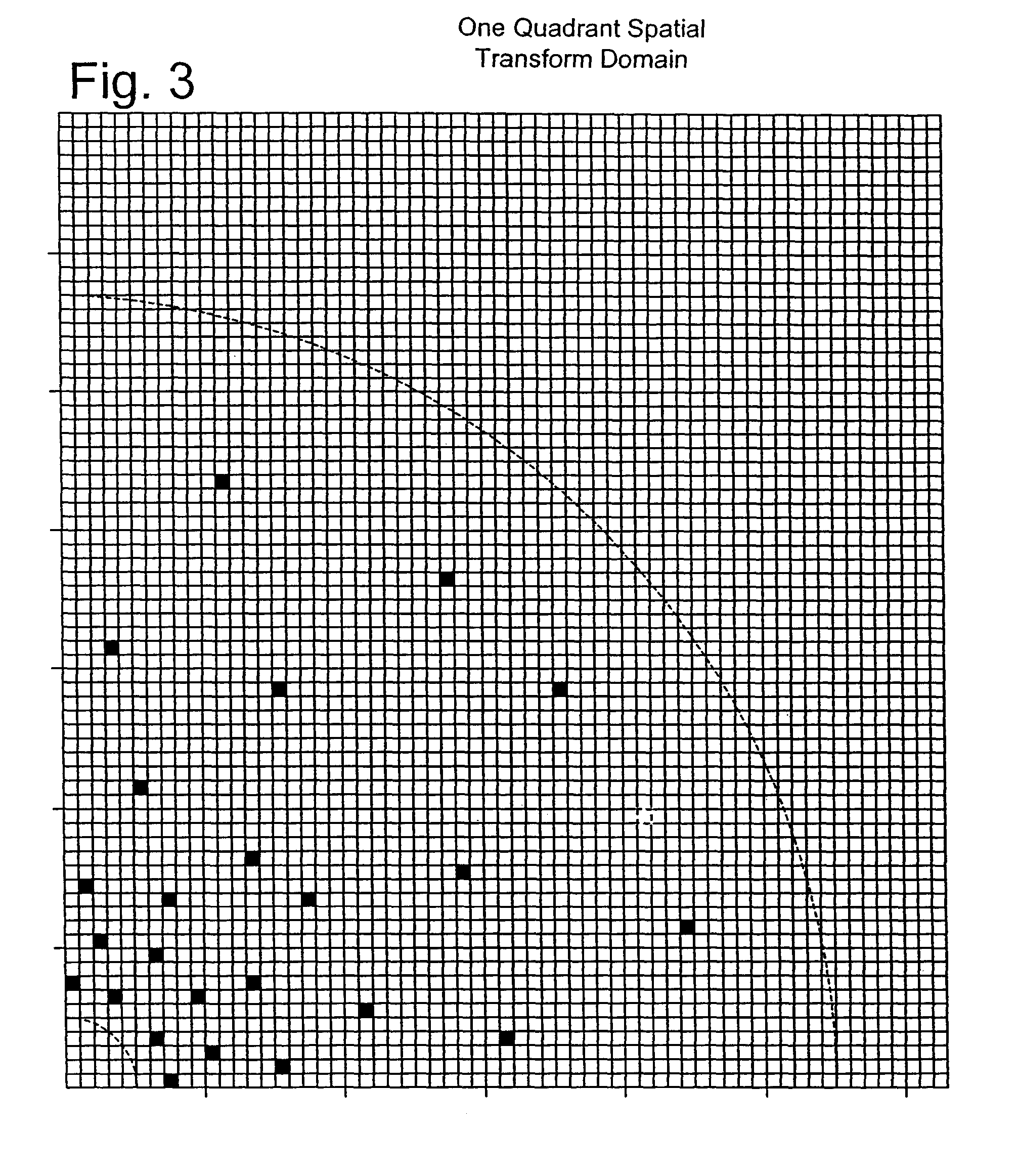
Digital watermark methods for encoding auxiliary data into a host signal are used to authenticate physical and electronic objects. One such method computes a content specific message dependent on the host signal, encodes the content specific message into a watermark signal, and embeds the watermark in the host signal such that the watermark signal is substantially imperceptible in the host signal. One specific implementation embeds data representing salient features of the host signal into the watermark. For example, for photo IDs, the method embeds the spatial location of salient features of the photo into the watermark. Another implementation computes a semi-sensitive hash of the host signal, such as a low pass filtering of the signal, and embeds the hash into the watermark. The watermark signal may be content dependent by making the watermark key dependent on some attribute of the signal in which the watermark is embedded. Another approach is to make the watermark key dependent on a user or an attribute of the user. Yet another approach is to use multiple watermark components and multiple watermark detection stages that help identify and screen out invalid watermark signals. Another digital watermarking method for authenticating a media object transforms a media signal to a frequency domain comprising an array of frequency coefficients. It selects a first set of frequency coefficients, and alters the selected first set of frequency coefficients so that values of the coefficients in the set correspond to a pattern. The pattern of the media signal is authenticated by comparing a pattern of the values of the frequency coefficients in the set with an expected pattern.
Owner:DIGIMARC CORP
Method and apparatus for graphically representing information stored in electronic media
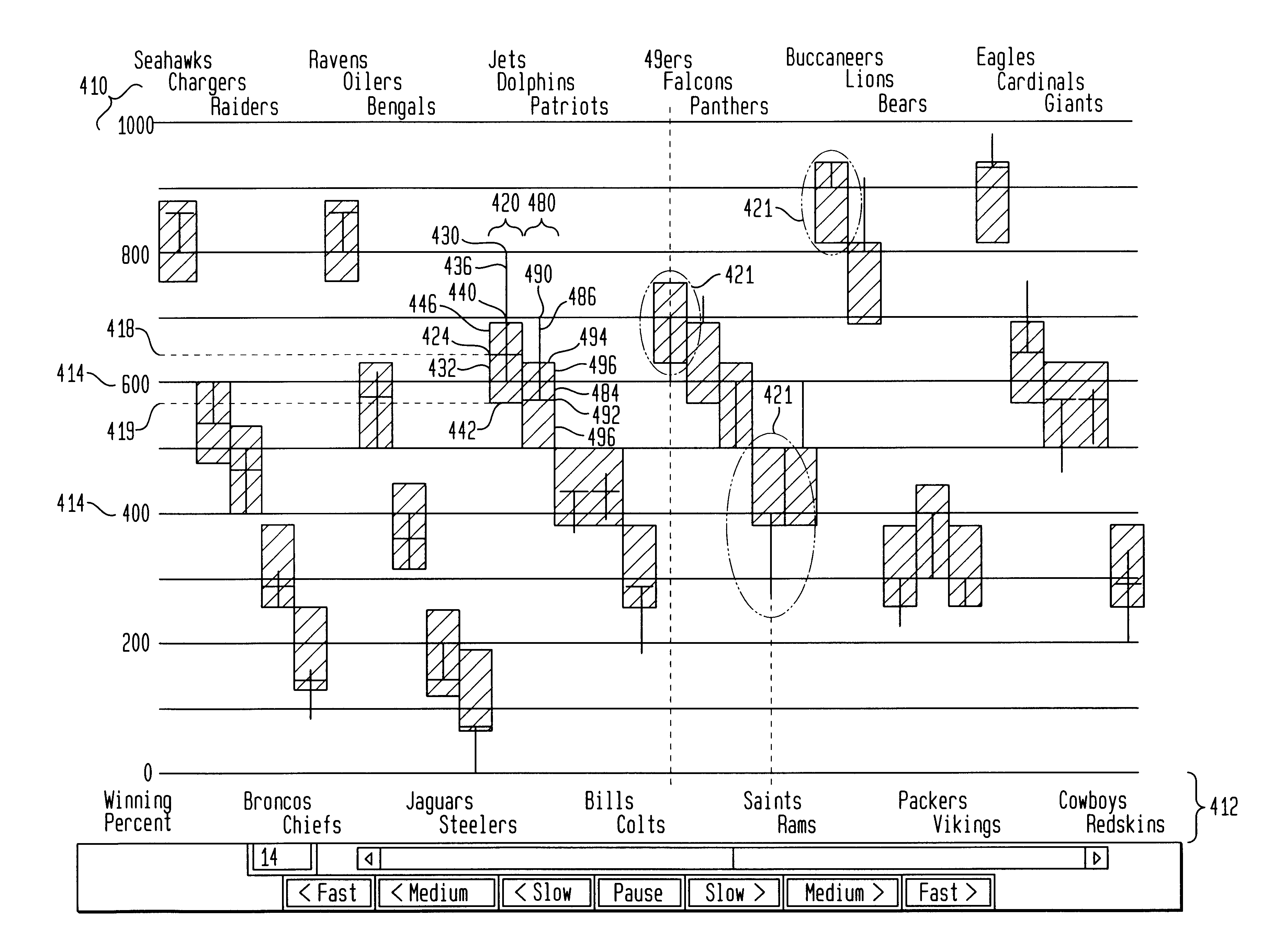
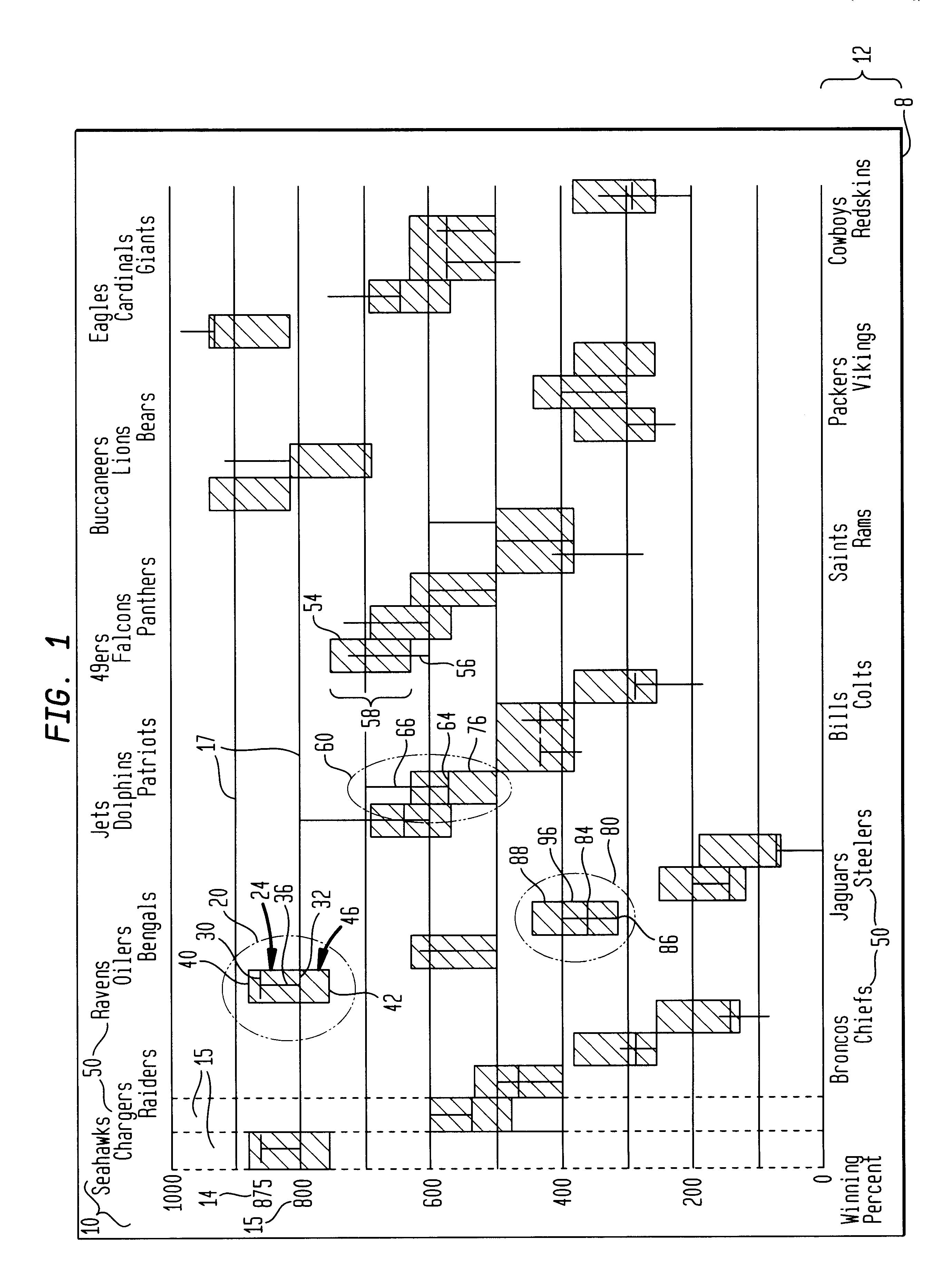
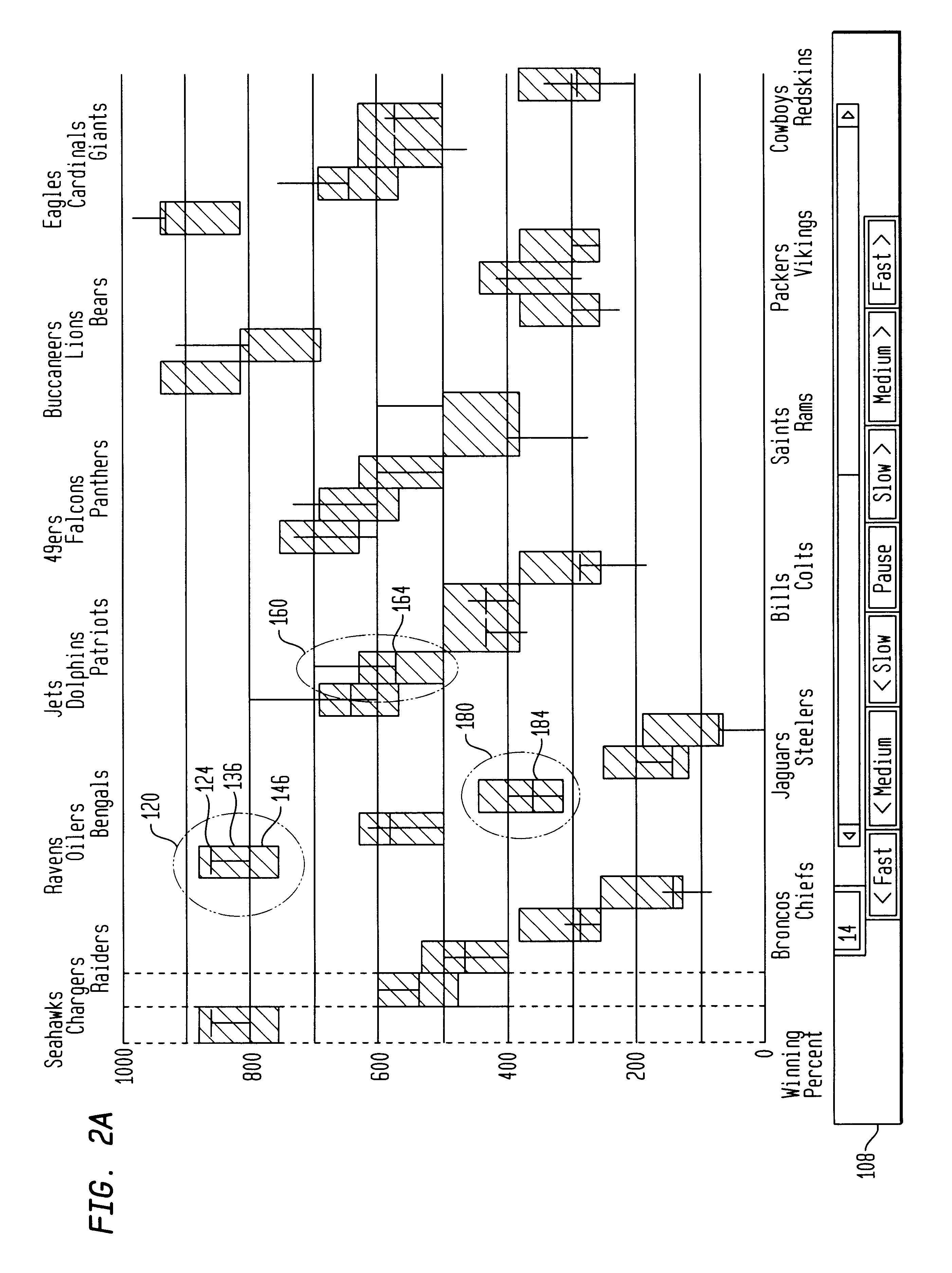
InactiveUS6211873B1Suppress mutationEasy to displayOther databases browsing/visualisationSpecial data processing applicationsGraphicsDisplay device
Apparatus and methods for displaying dynamic electronic data are provided for a computer-based display system. The apparatus includes a display, a frame within the display for displaying the data and a measure along a first frame axis for indicating a value of the displayed data. Entity display areas, each containing one entity defined by five data points, are displayed within the frame in non-overlapping, fixed positions along a second frame axis. The five data points include: a current data point, represented by a marker and indicting a current value of the entity in the display, first and second end data points of a first data range relating to the entity, represented by a first range marker, and first and second end data points of a second data range relating to the entity, represented by a second range marker. A label associated with the entities is also displayed in a fixed position with respect to the entity display areas. In one method of the invention, the dynamic data is displayed in sequential frames wherein the current marker and first and second range markers move dynamically within the entity display area to reflect the changing data related to each entity.
Owner:MOYER TODD
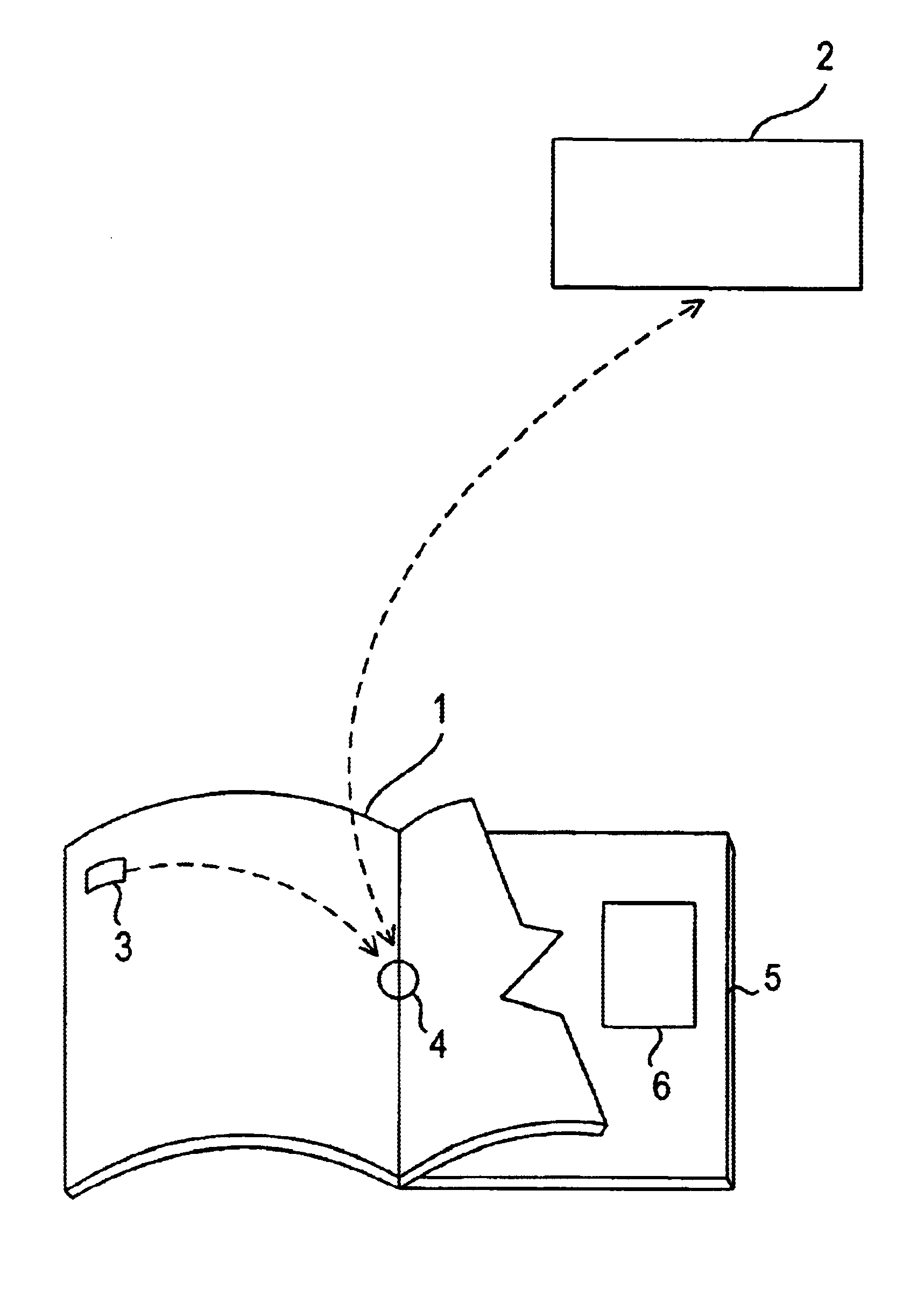
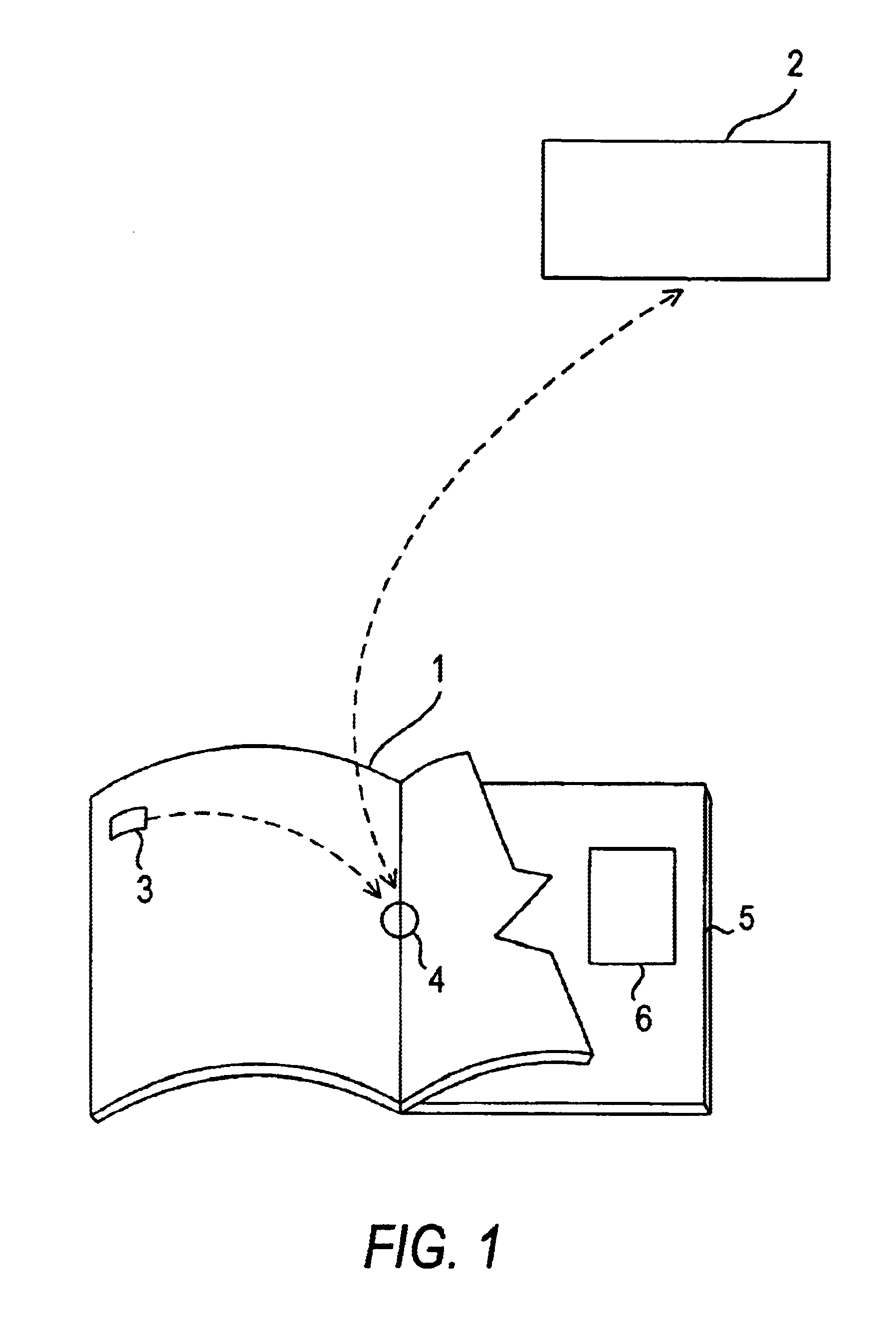
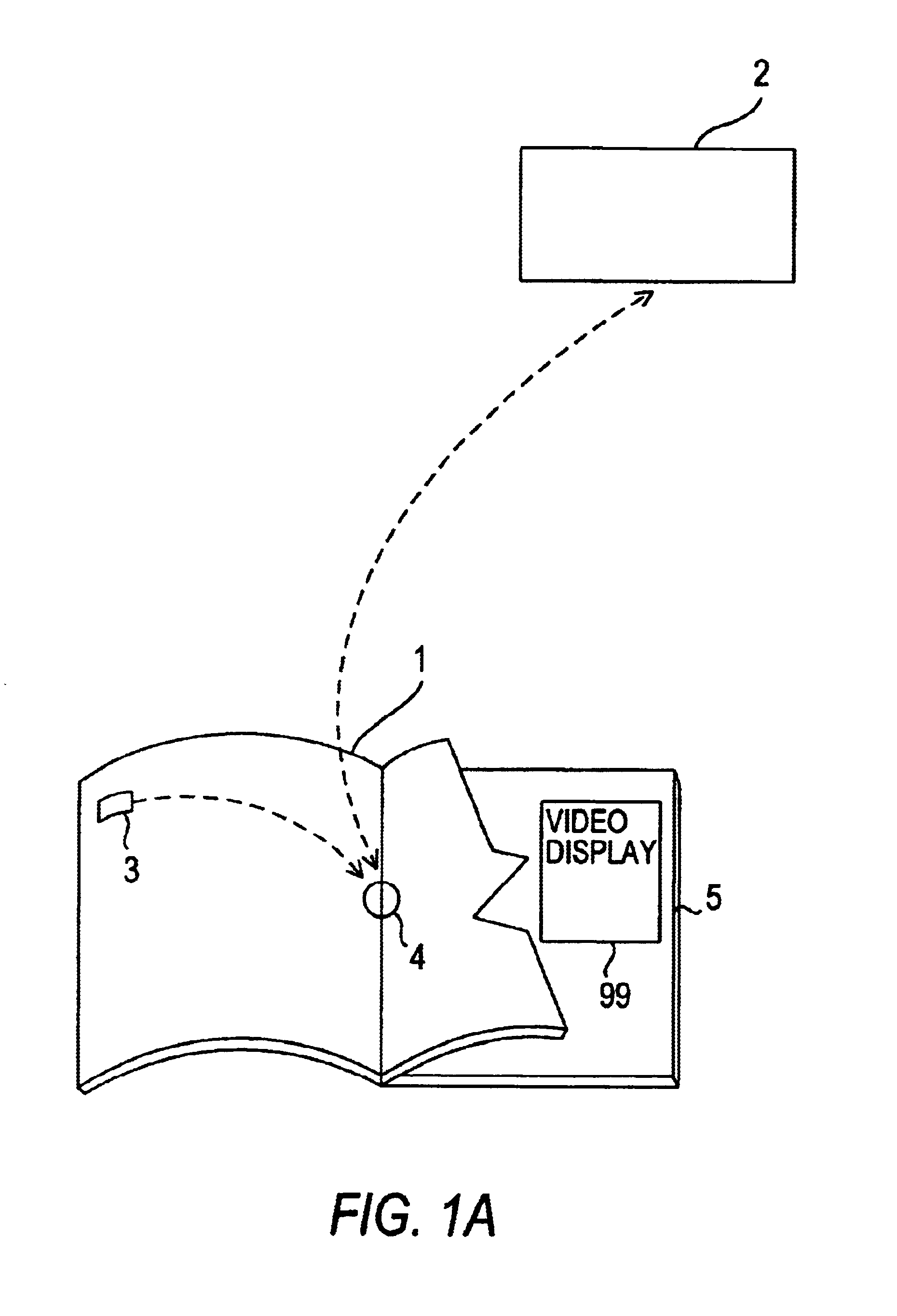
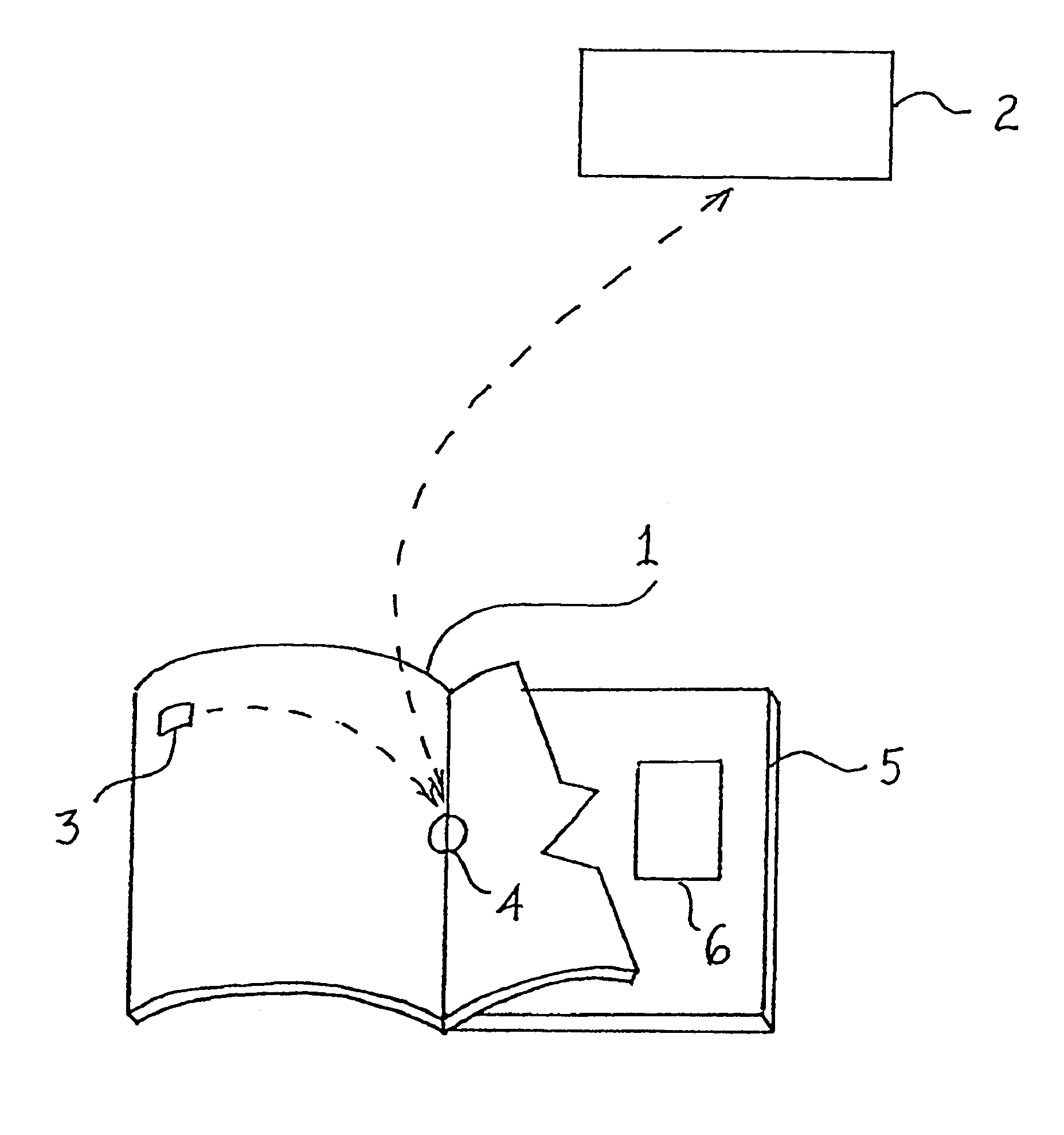
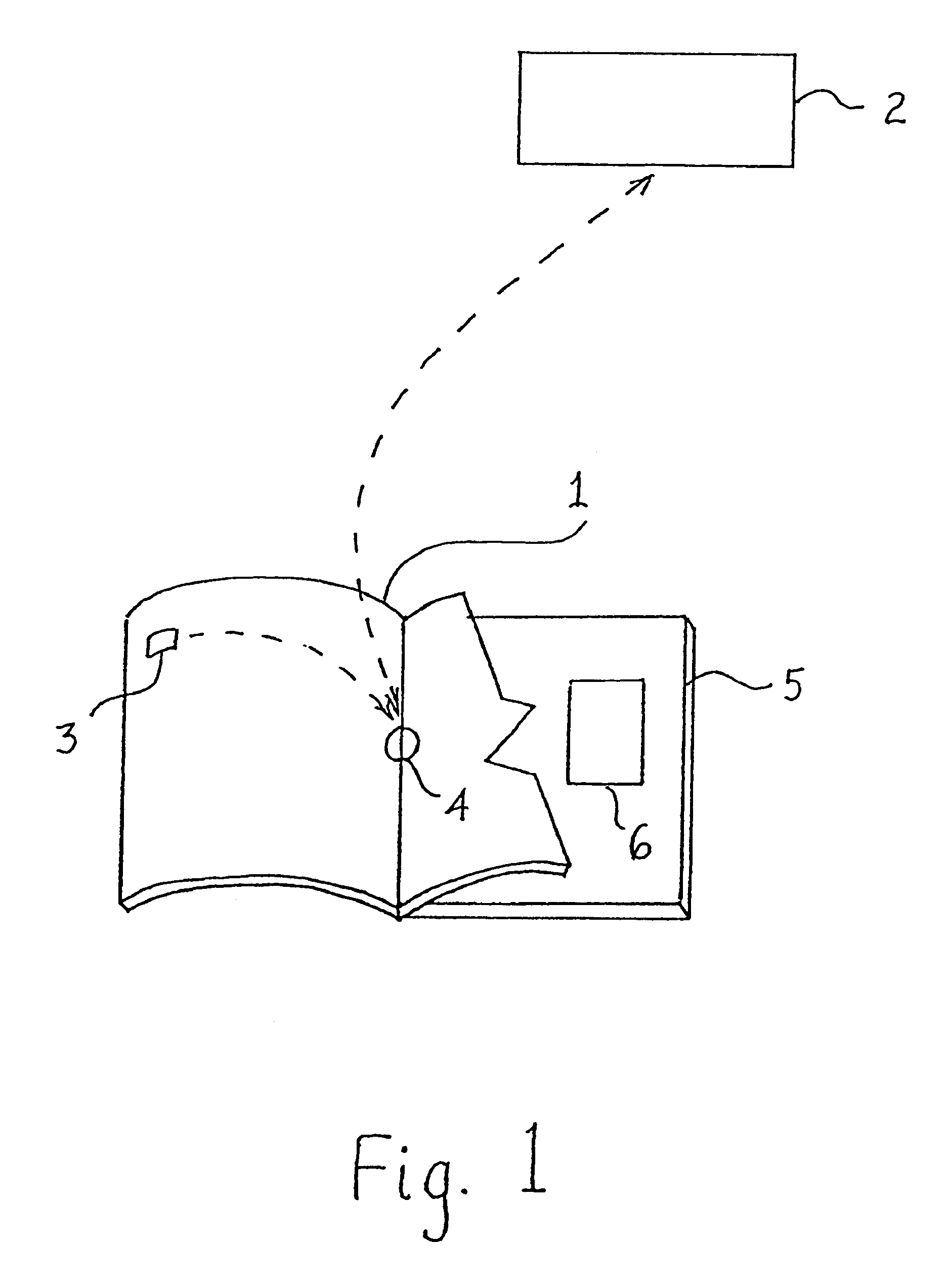
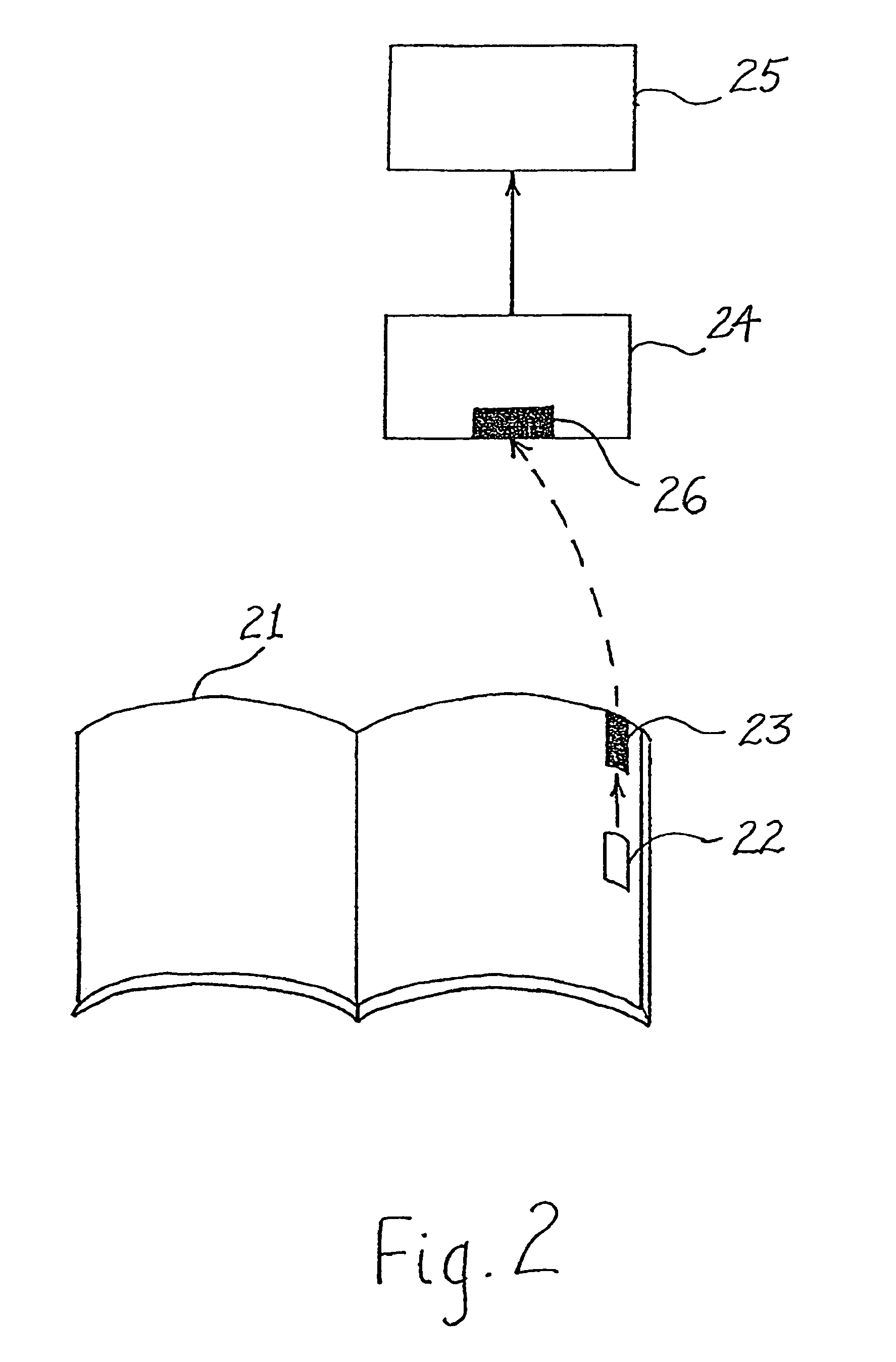
Method and apparatus for accessing electronic data via a familiar printed medium
InactiveUS6843411B2Low costTelevision system detailsAnalogue secracy/subscription systemsOutput deviceComputer memory
The disclosed methods and apparatus relate generally to the electronics media industry, such as cable television (CATV), home shopping services, on-line computer services and computer memory applications. These methods and apparatus allow a user to access and make use of electronic media input and output devices by reference to and / or utilization of standard printed matter, such as magazines, textbooks, or any other printed matter that can be correlated to electronic media.
Owner:MARSHALL FEATURE RECOGNITION
Universal system interface
InactiveUS20070038434A1Complete transparency to the userEfficient solutionDigital data processing detailsVehicle componentsEmbedded systemUser interface
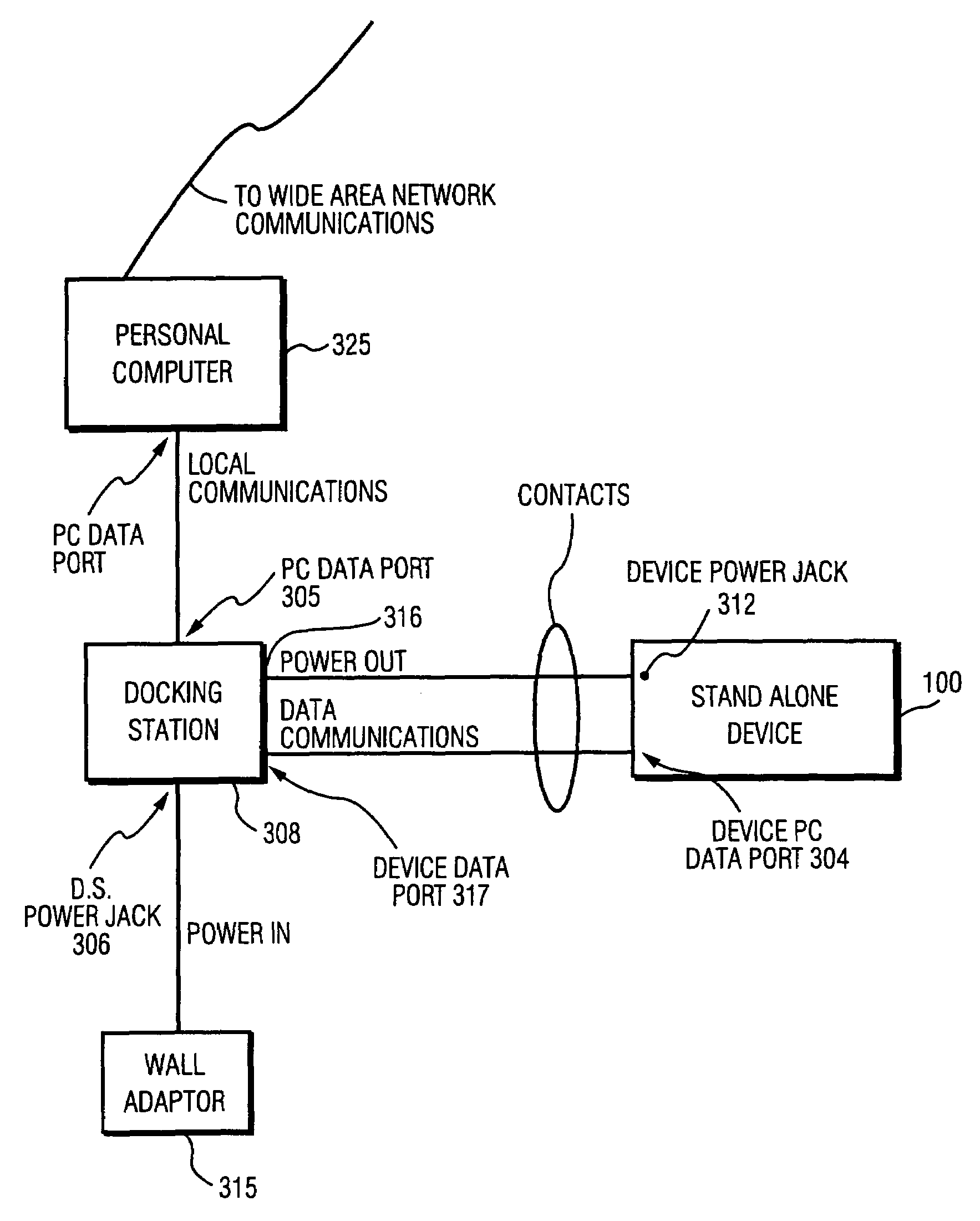
A vehicular system including a vehicle mounted electronic device including user and device interfaces, an electronic media storage device including user and device physical interfaces and a signal processor. In combination the signal processor is operationally situated between the vehicle mounted electronic device and the electronic media storage device. The devices are interconnected and the vehicle mounted electronic device is configured to display at least a portion of the electronic media storage device user interface data and emulate a portion of the electronic media storage device functionality.
Owner:CVETKO JONATAN
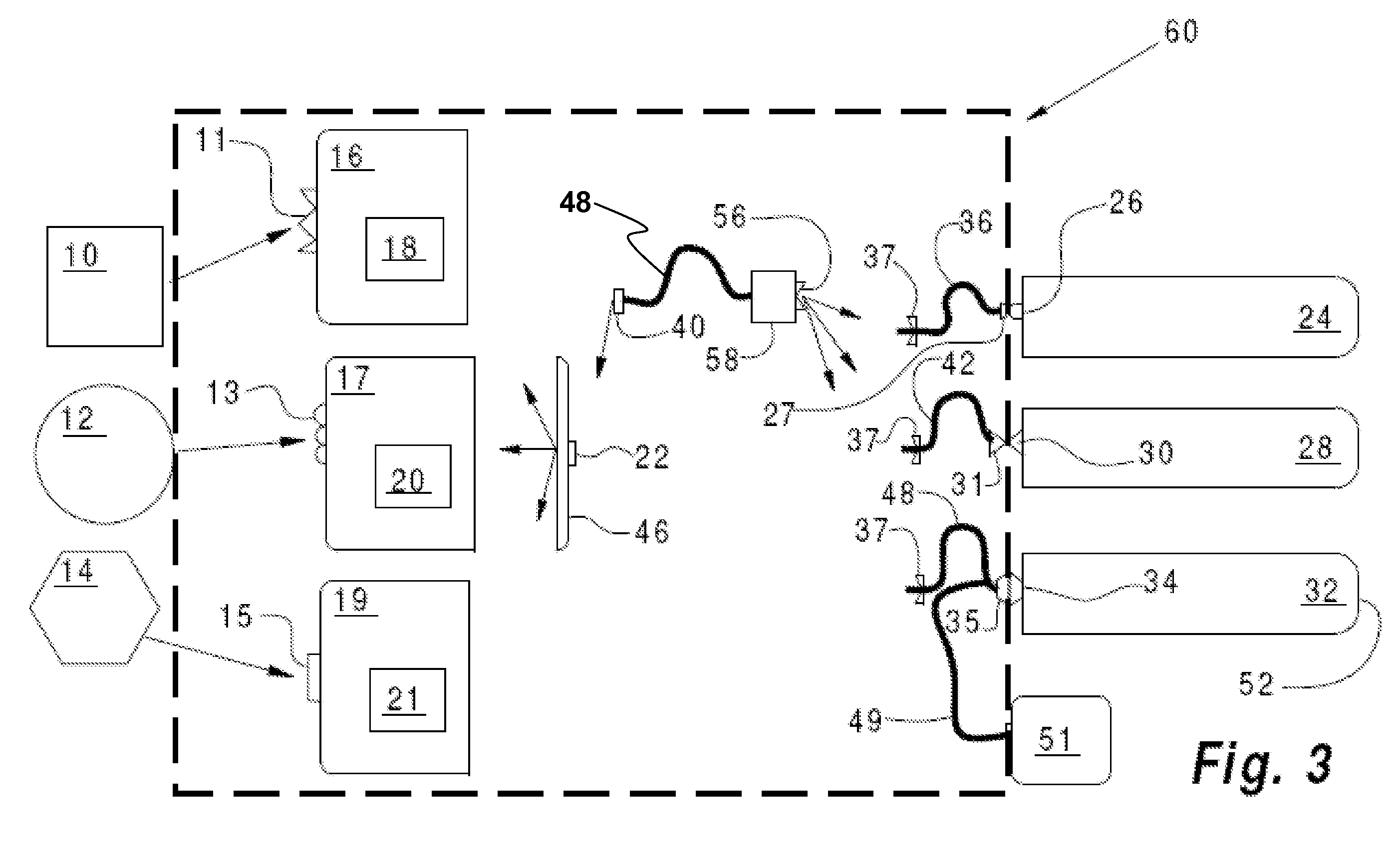
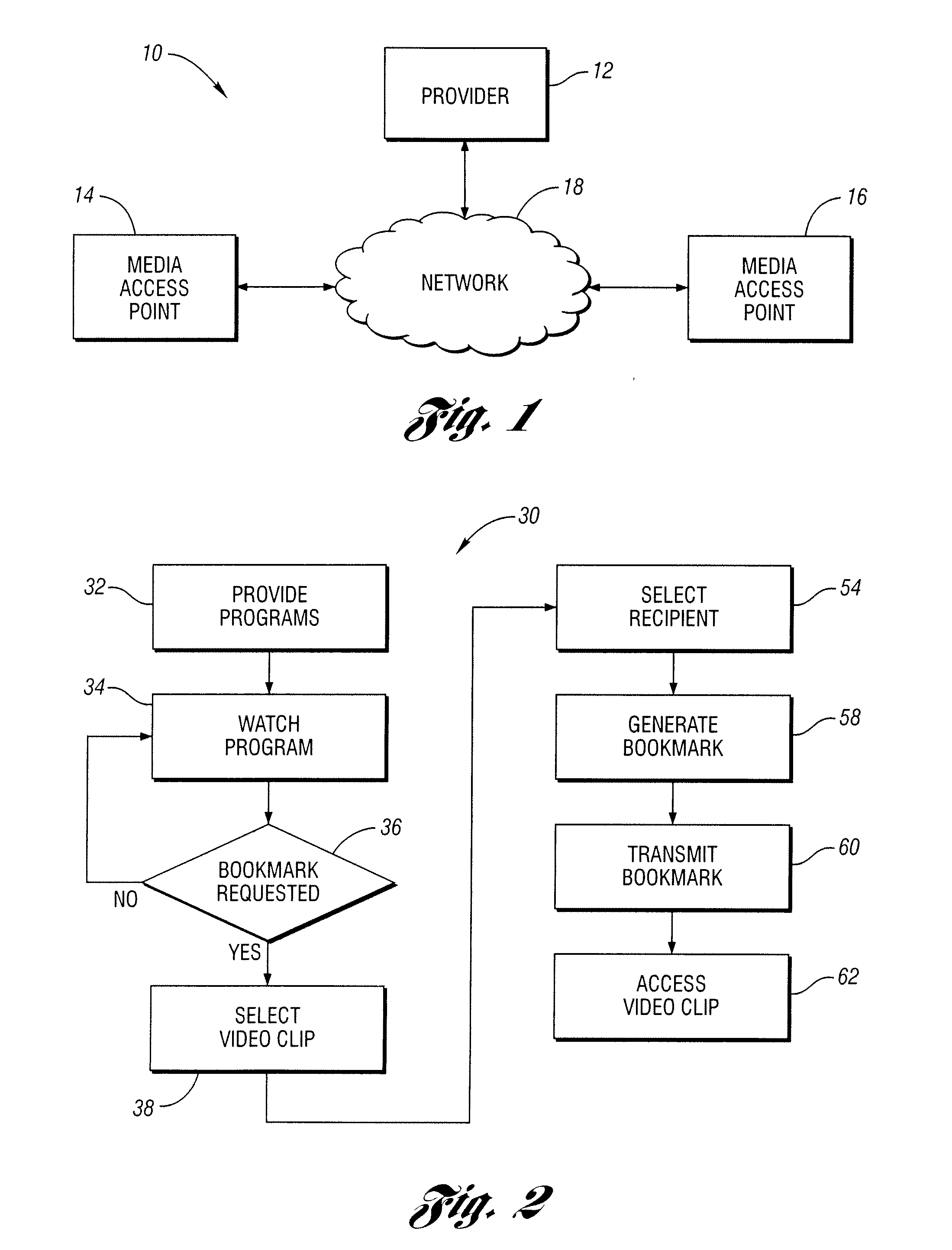
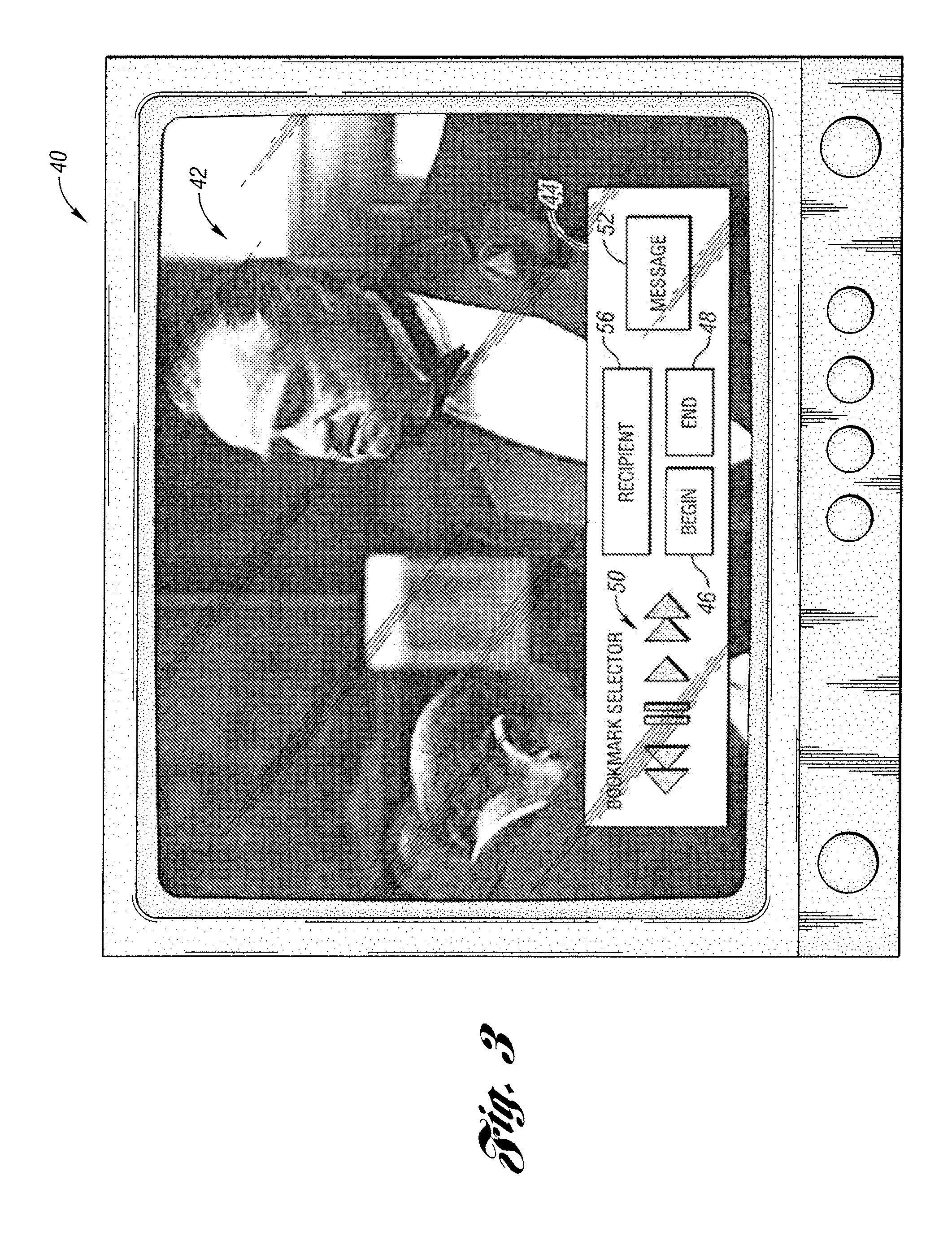
Media content sharing
ActiveUS20090049118A1Television system detailsMultimedia data retrievalContent sharingElectronic media
A media content sharing concept wherein users are able to share highlights or other portions of content with friends. The concept may be used in any number of environments where electronic media, such as but not limited to audio, video, and multi-media, is transferable between a number of users. Bookmarks or other features may be used to facilitate accessing the video clips for subsequent viewing.
Owner:CABLE TELEVISION LAB
Electronic-monetary system
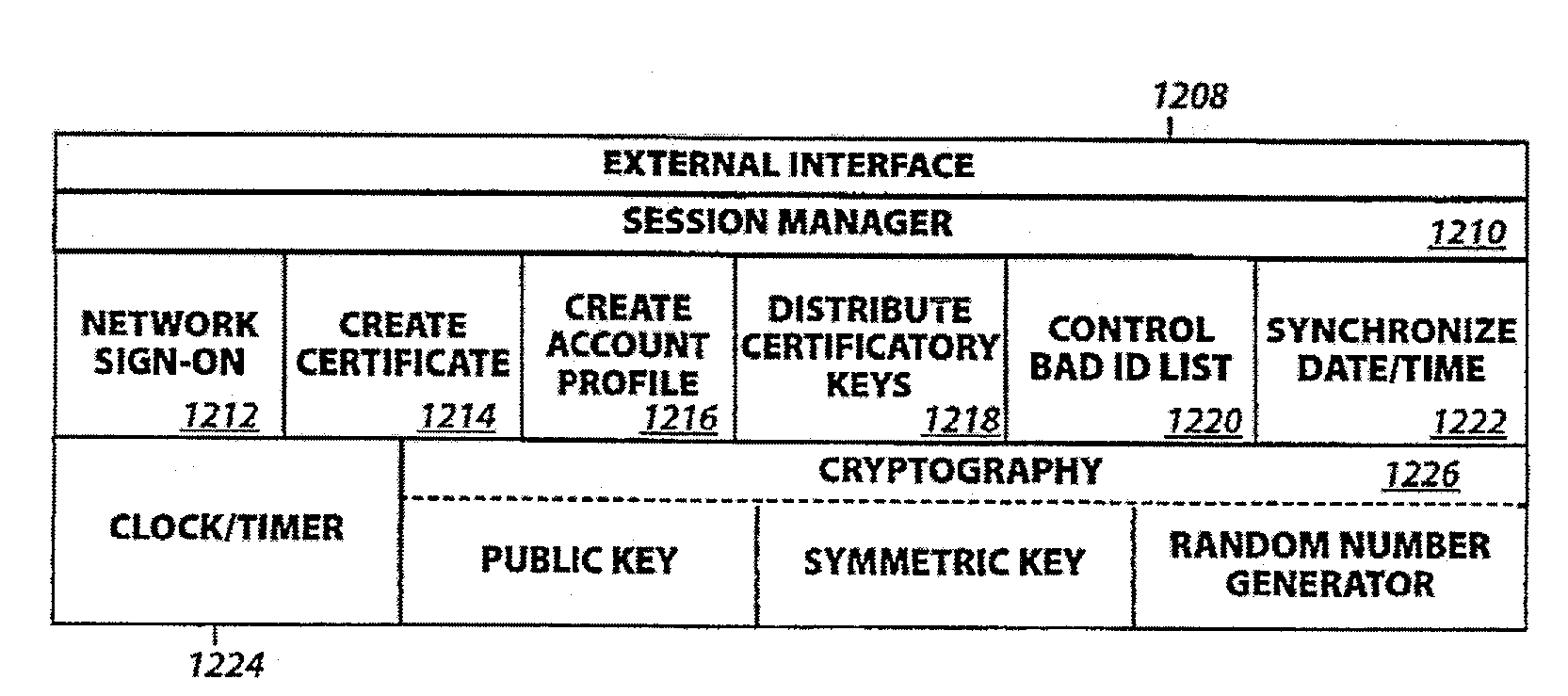
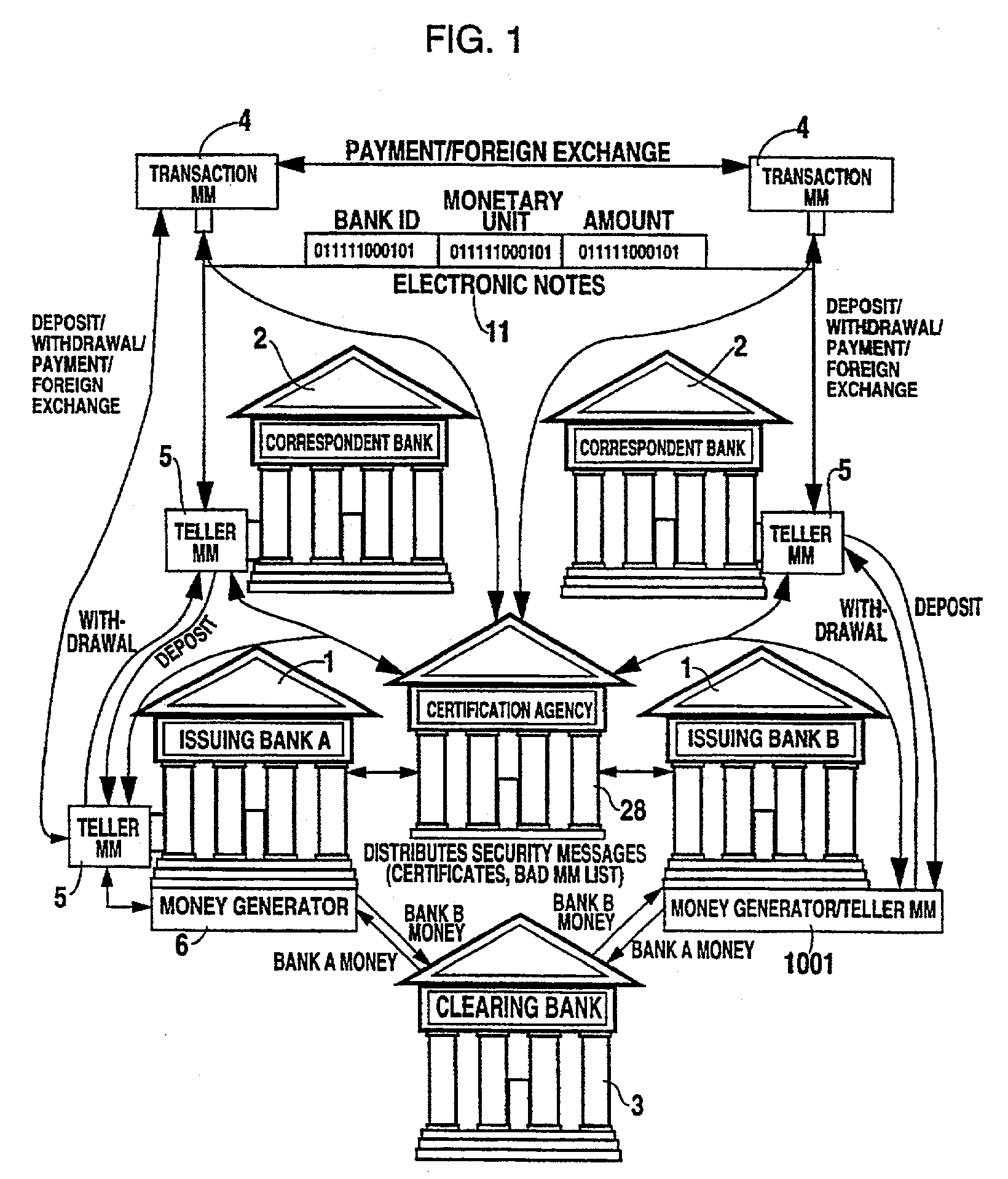
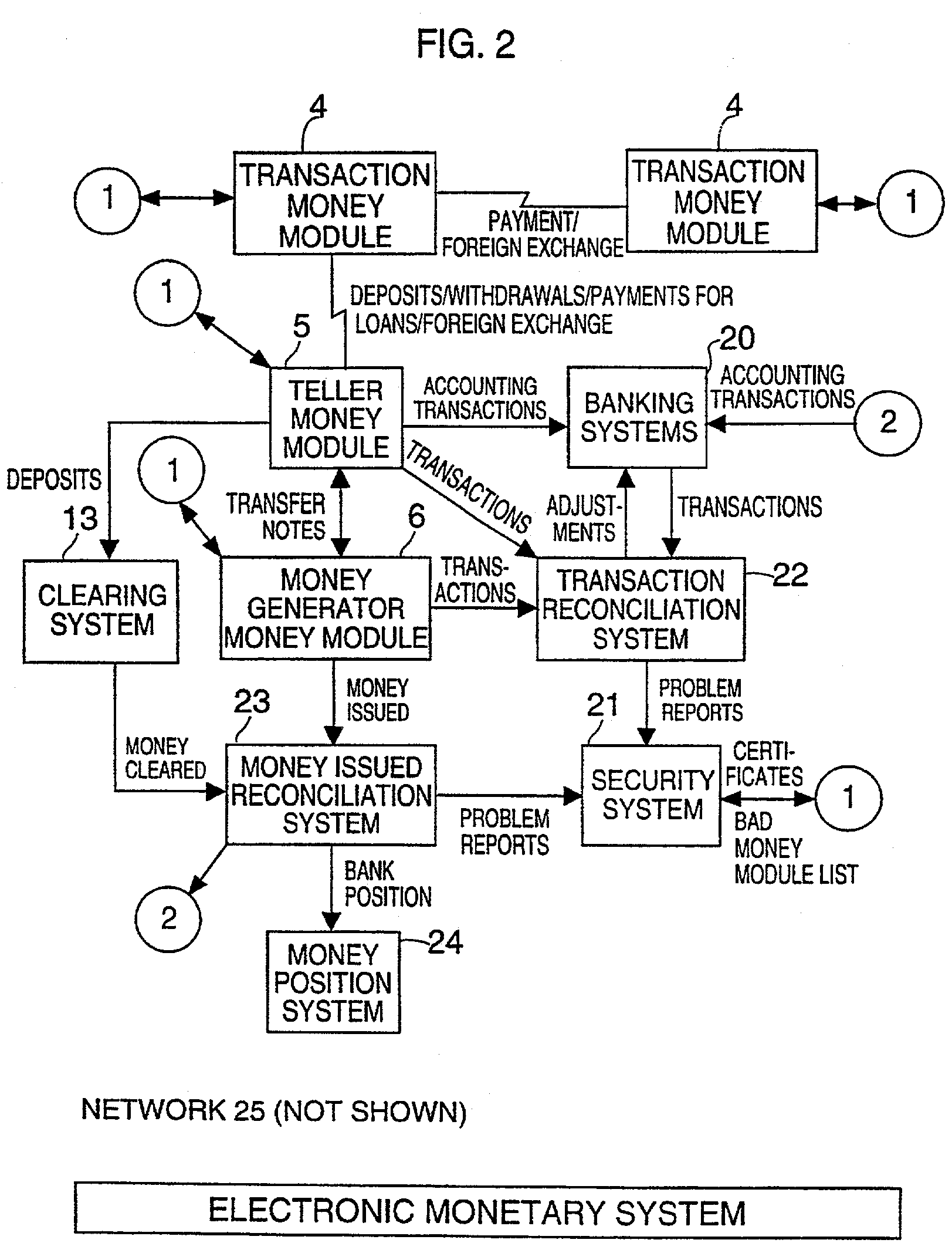
An improved monetary system using electronic media to exchange economic value securely and reliably is disclosed. The system provides a complete monetary system having electronic money that is interchangeable with conventional paper money. Also disclosed is a system for open electronic commerce having a customer trusted agent securely communicating with a first money module, and a merchant trusted agent securely communicating with a second money module. Both trusted agents are capable of establishing a first cryptographically secure session, and both money modules are capable of establishing a second cryptographically secure session. The merchant trusted agent transfers electronic merchandise to the customer trusted agent, and the first money module transfers electronic money to the second money module. The money modules inform their trusted agents of the successful completion of payment, and the customer may use the purchased electronic merchandise.
Owner:CITIBANK
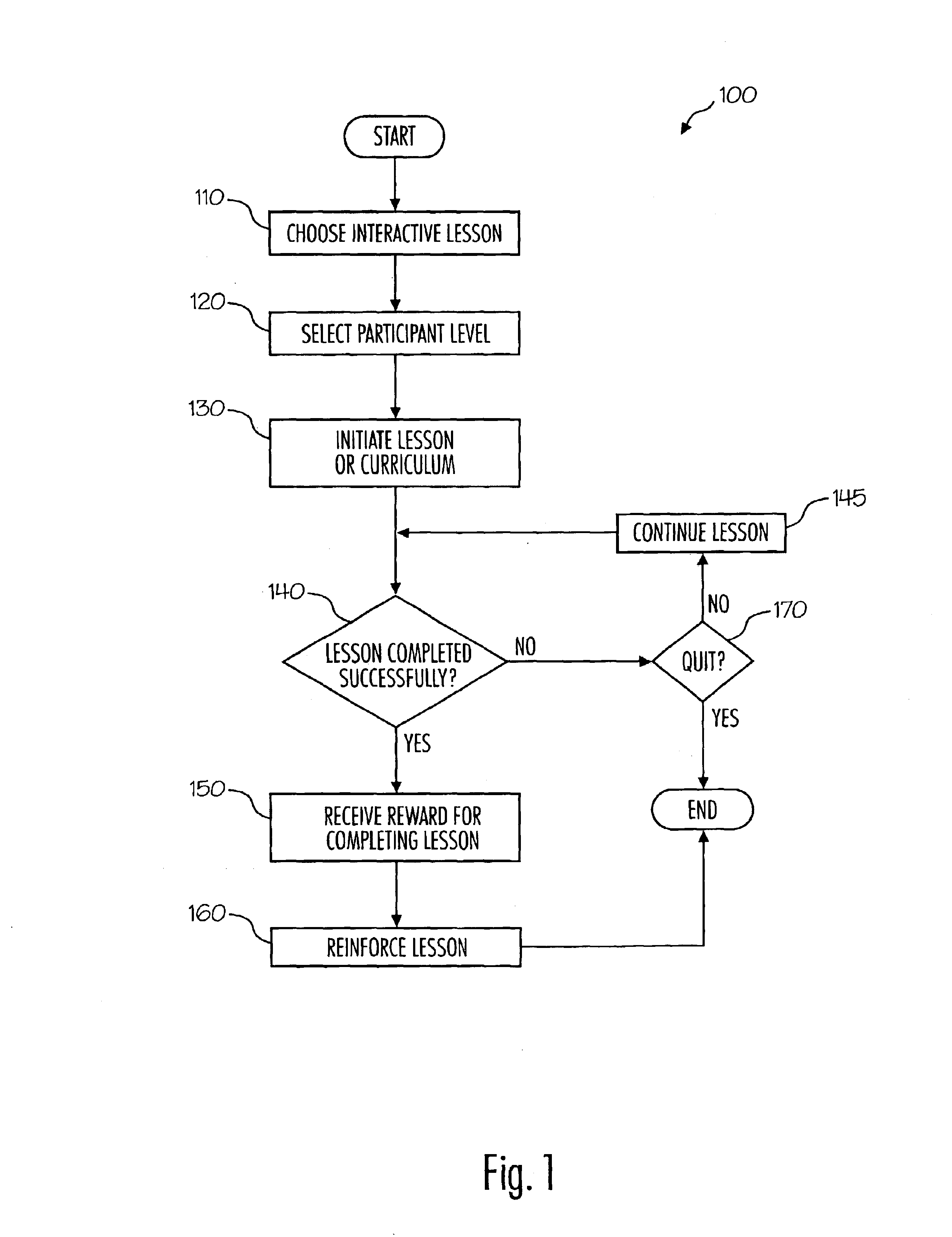
Interactive games for teaching financial principles
InactiveUS6890179B2Enhances student attentionEnhances recollectionData processing applicationsVideo gamesThe InternetGame play
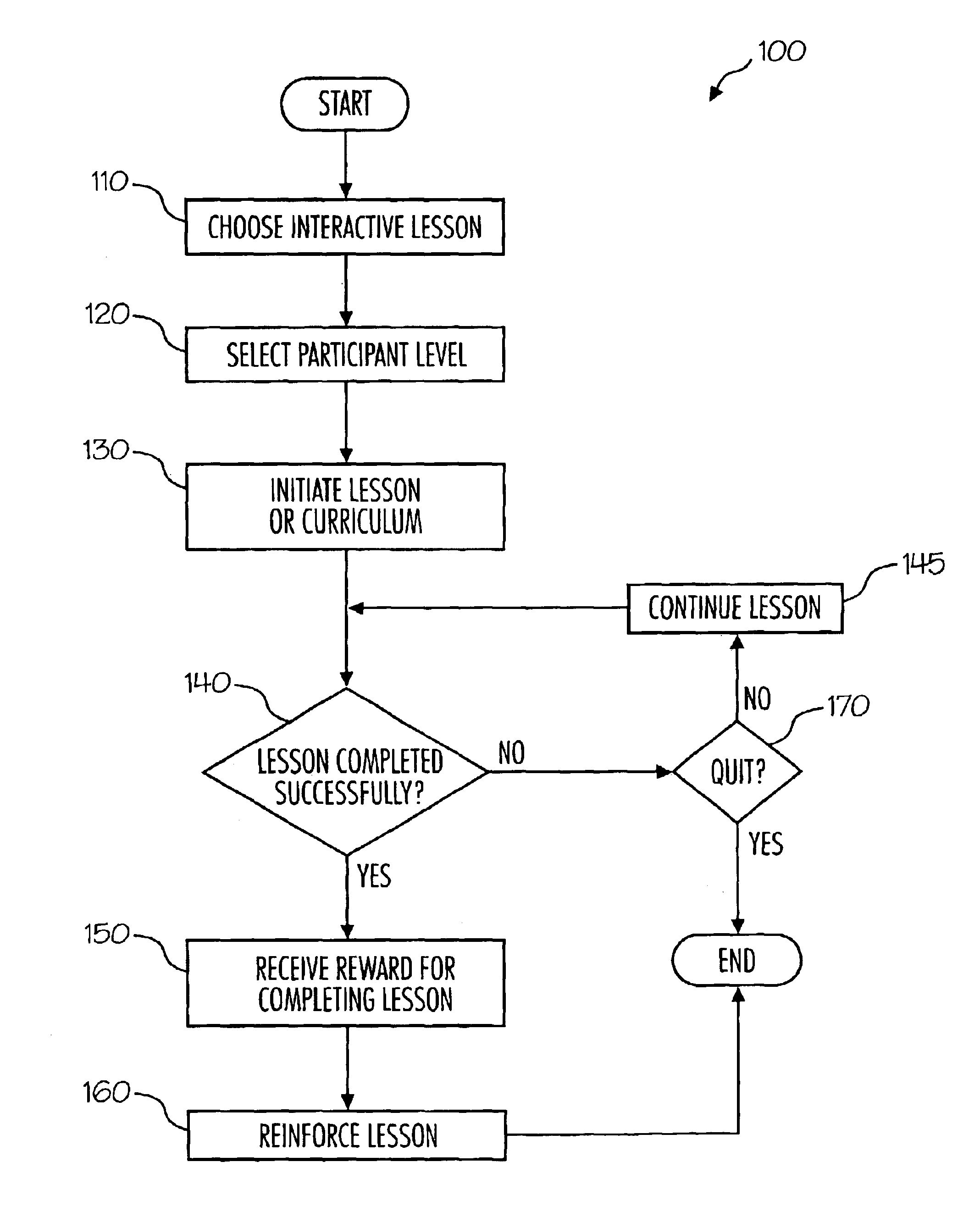
Electronic media for teaching others financial principles includes an interactive game that includes a financial lesson. The interactive game may be remotely accessed by users via a network such as the Internet. In certain embodiments the interactive game includes (i) a lesson portion; (ii) a game play portion; and, optionally, (iii) a lesson reinforcement portion. In other embodiments the interactive game includes one or more rewards for successfully completing each interactive game. Such rewards may include a certificate of achievement and / or access to an otherwise inaccessible game.
Owner:CASHFLOW TECH
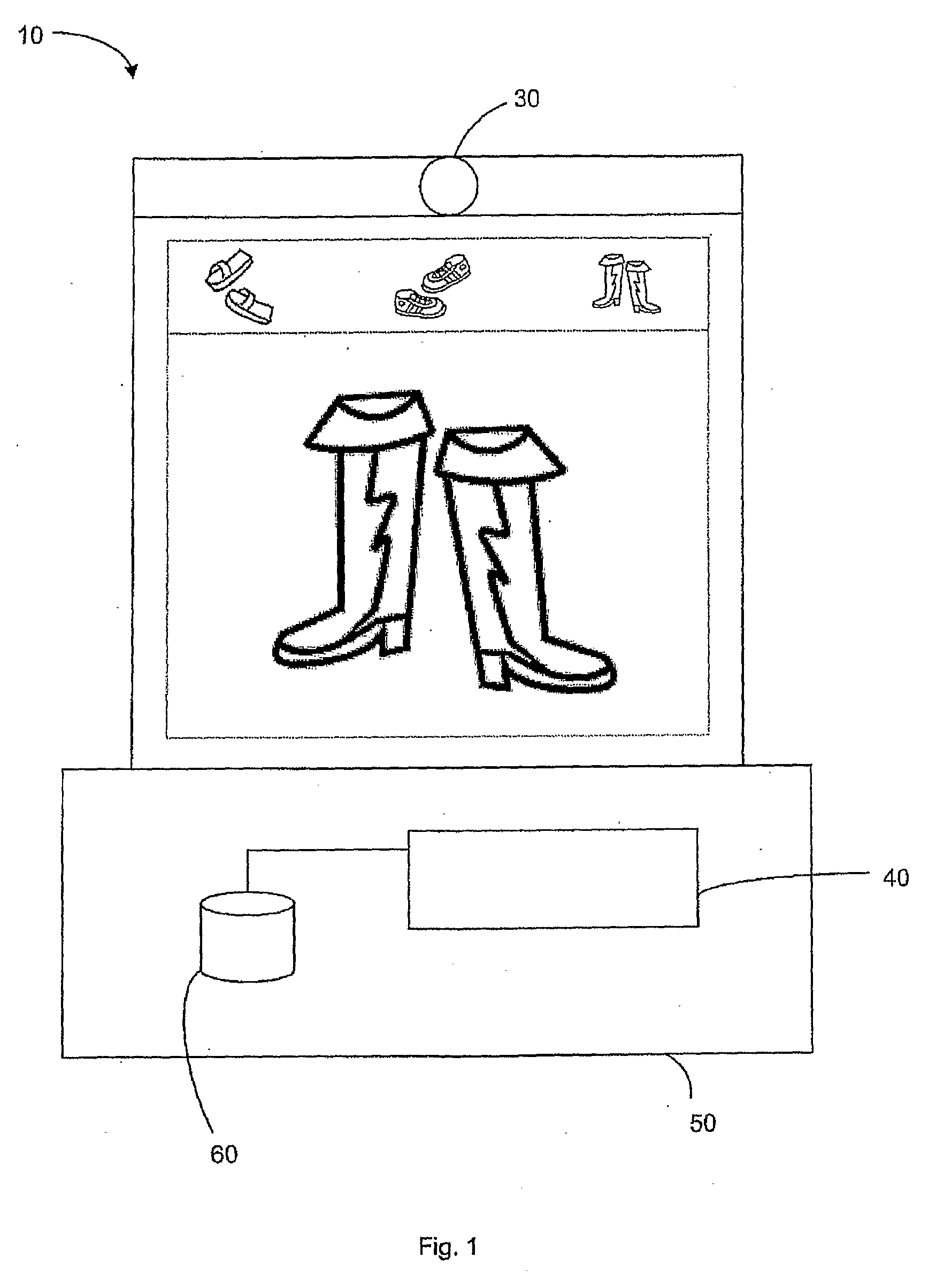
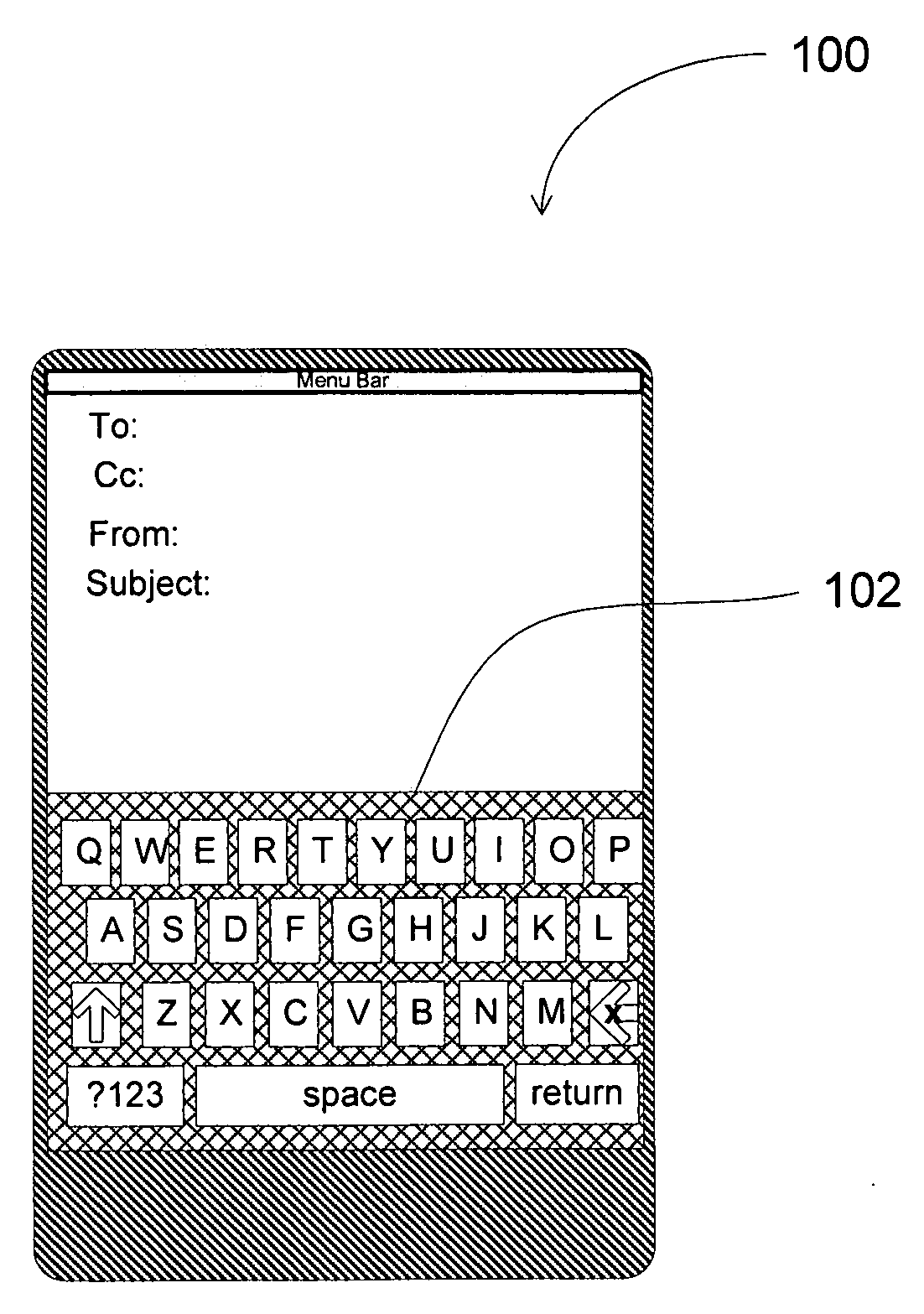
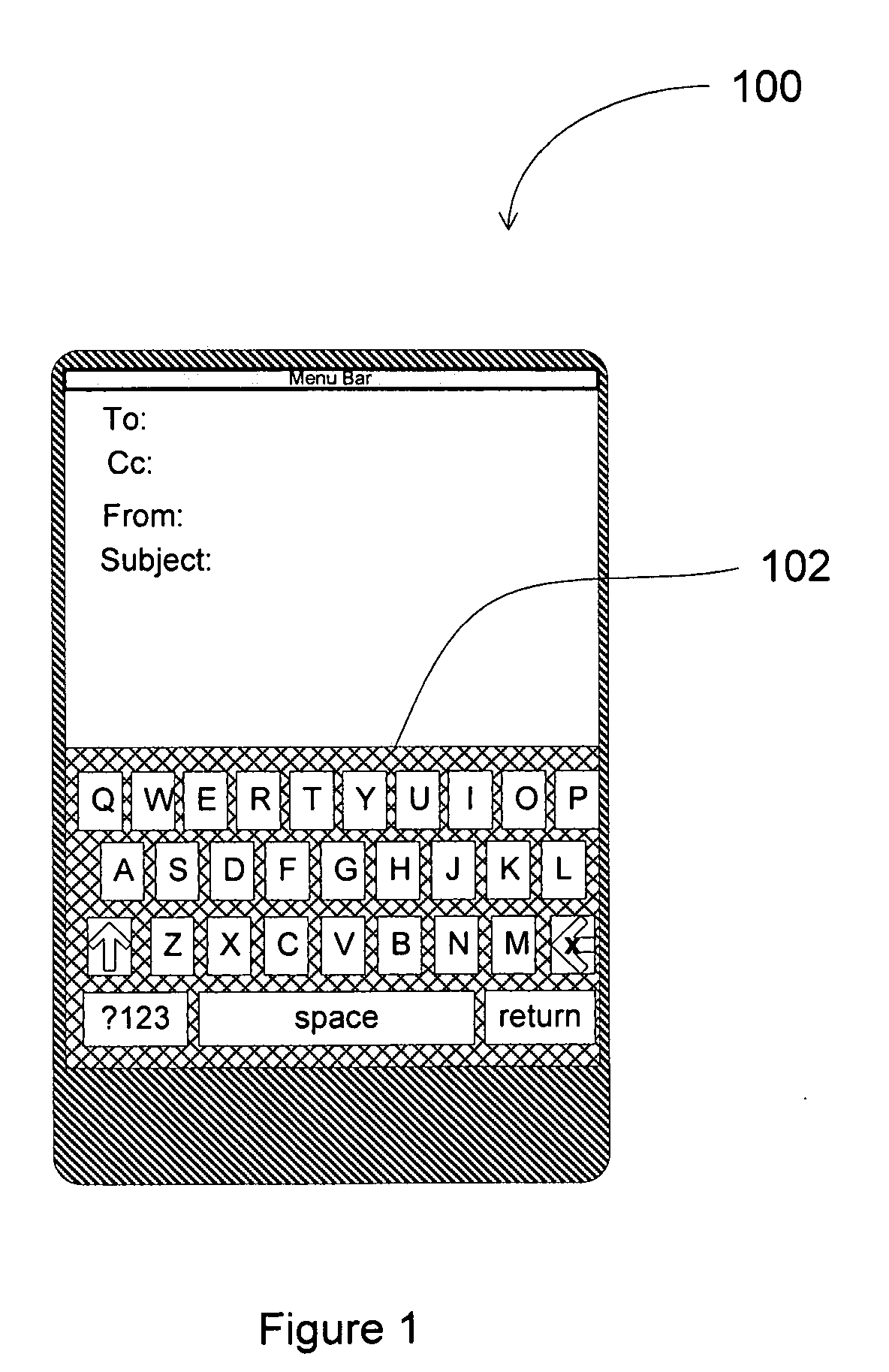
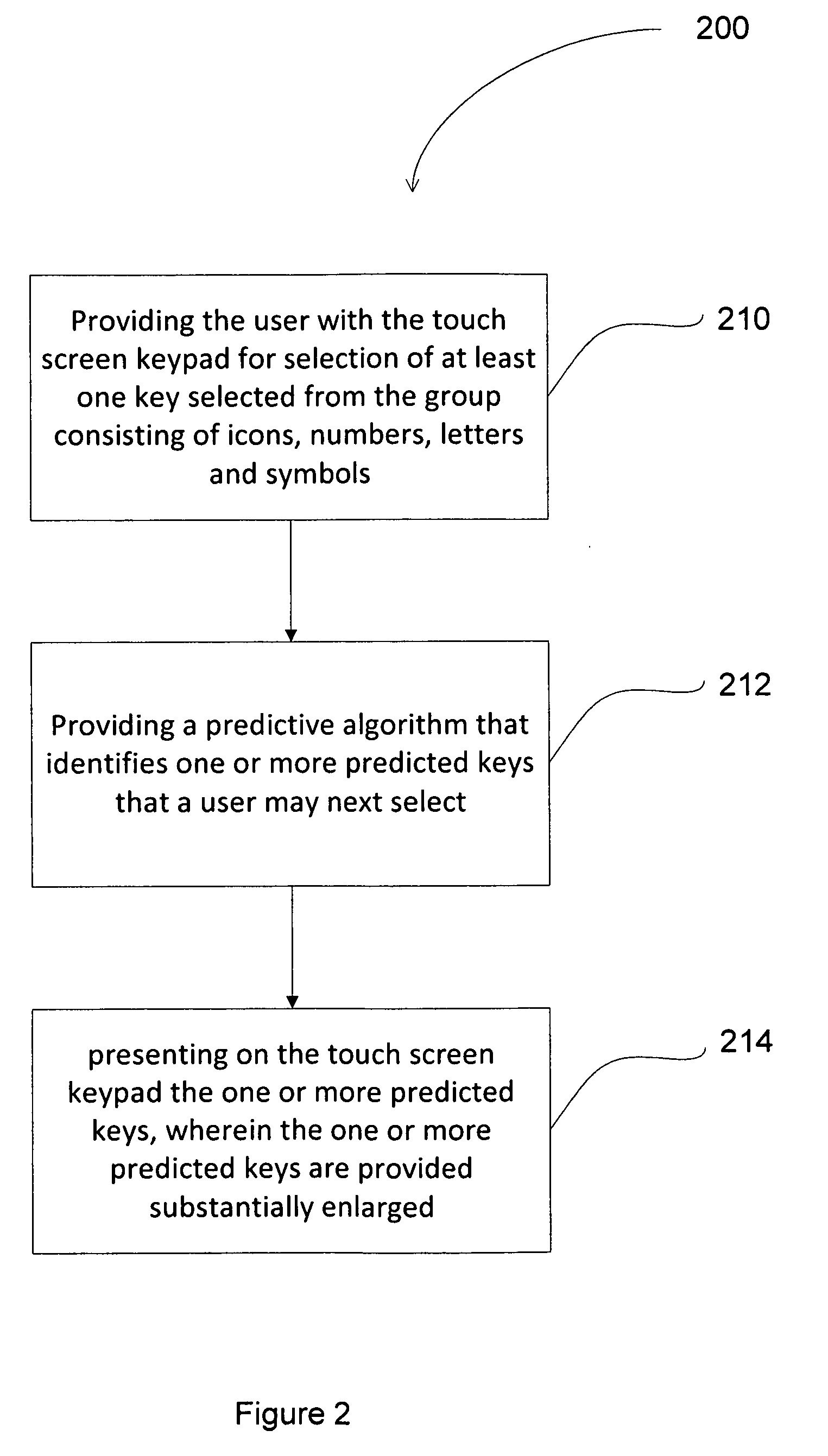
System, method and computer readable media for enabling a user to quickly identify and select a key on a touch screen keypad by easing key selection
InactiveUS20100265181A1Improve efficiencyReduce workloadInput/output for user-computer interactionCathode-ray tube indicatorsDisplay deviceTouchscreen
In the embodiments of the present invention, a system, method and computer useable medium are introduced that increase the efficiency in which a user can interface, through keys prediction, with a system that includes a touch screen display, a computer usable medium; having a computer readable instructions for controlling a computer, a computer processor, and a predictive algorithm. This method provides the user with the ability to quickly identify and select, through the enhanced keys prediction, and display the keys of the cell phone or electronic media. The keys include but are not limited to, icons, numbers, symbols and their combinations. In addition, the computer processor and the predictive algorithm, using the keys that are inputted through the touch screen or keypad, anticipate the icons, numbers and symbols necessary to complete the interface request resulting in increase user efficiency.
Owner:SHORE MICHAEL W
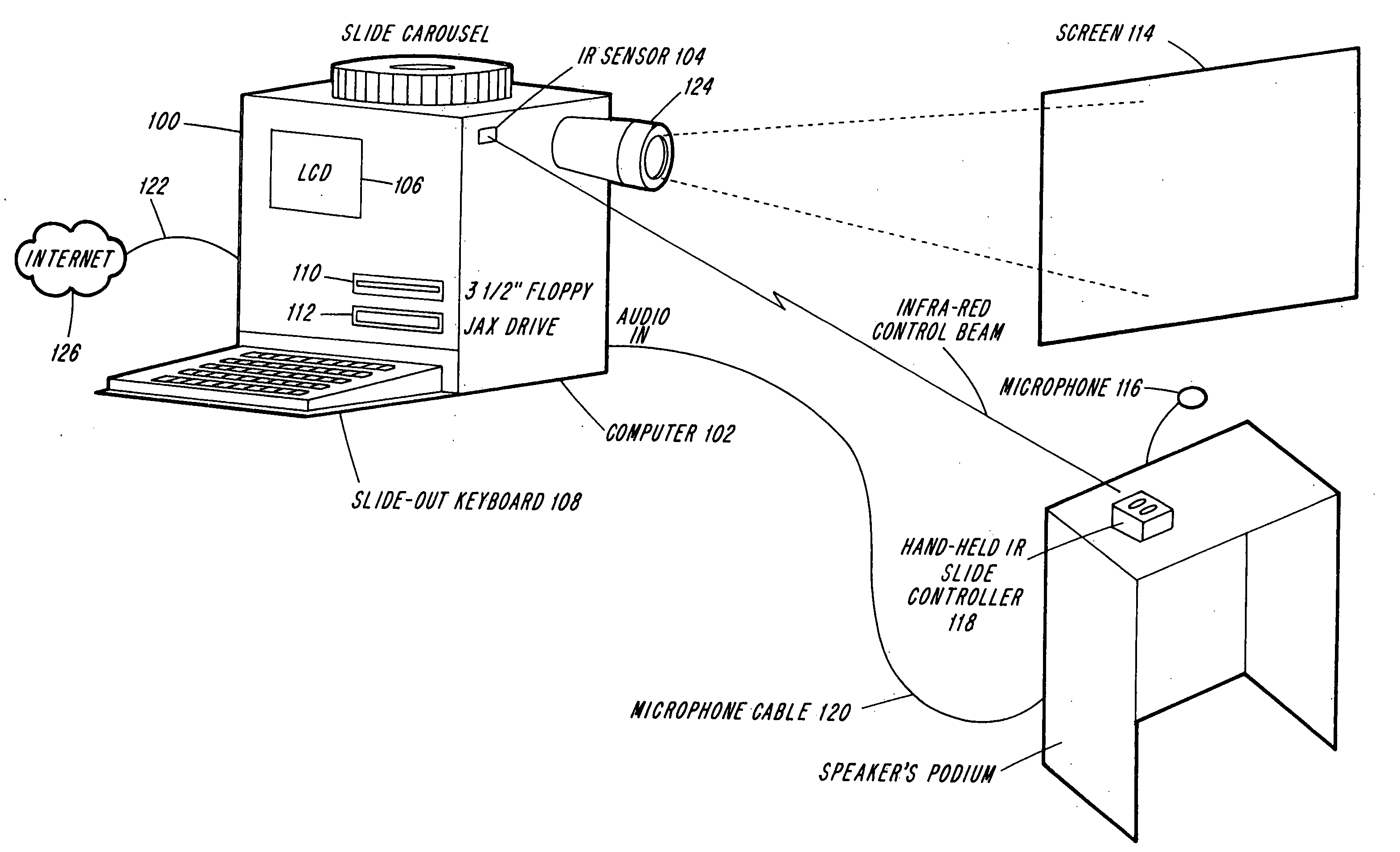
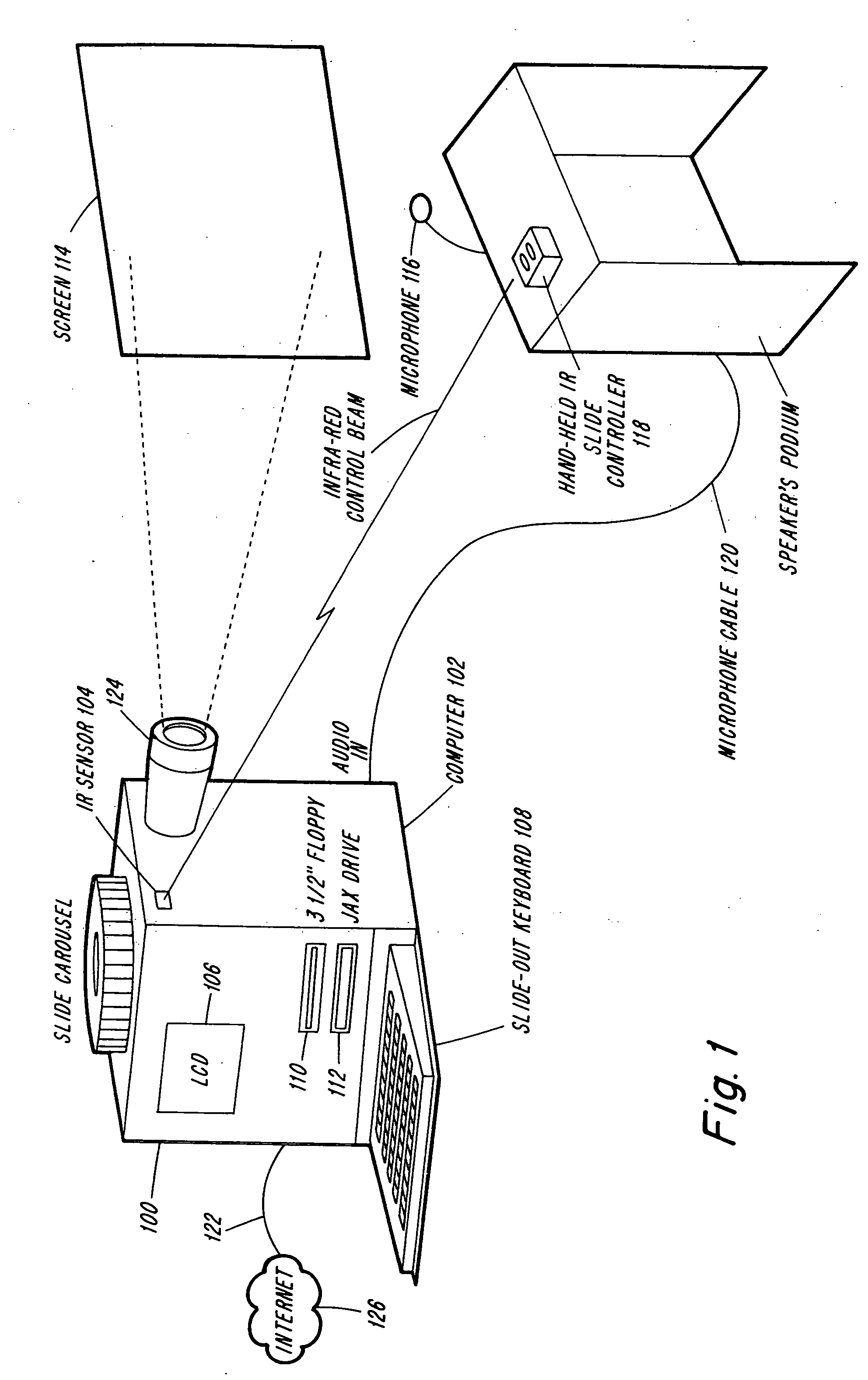
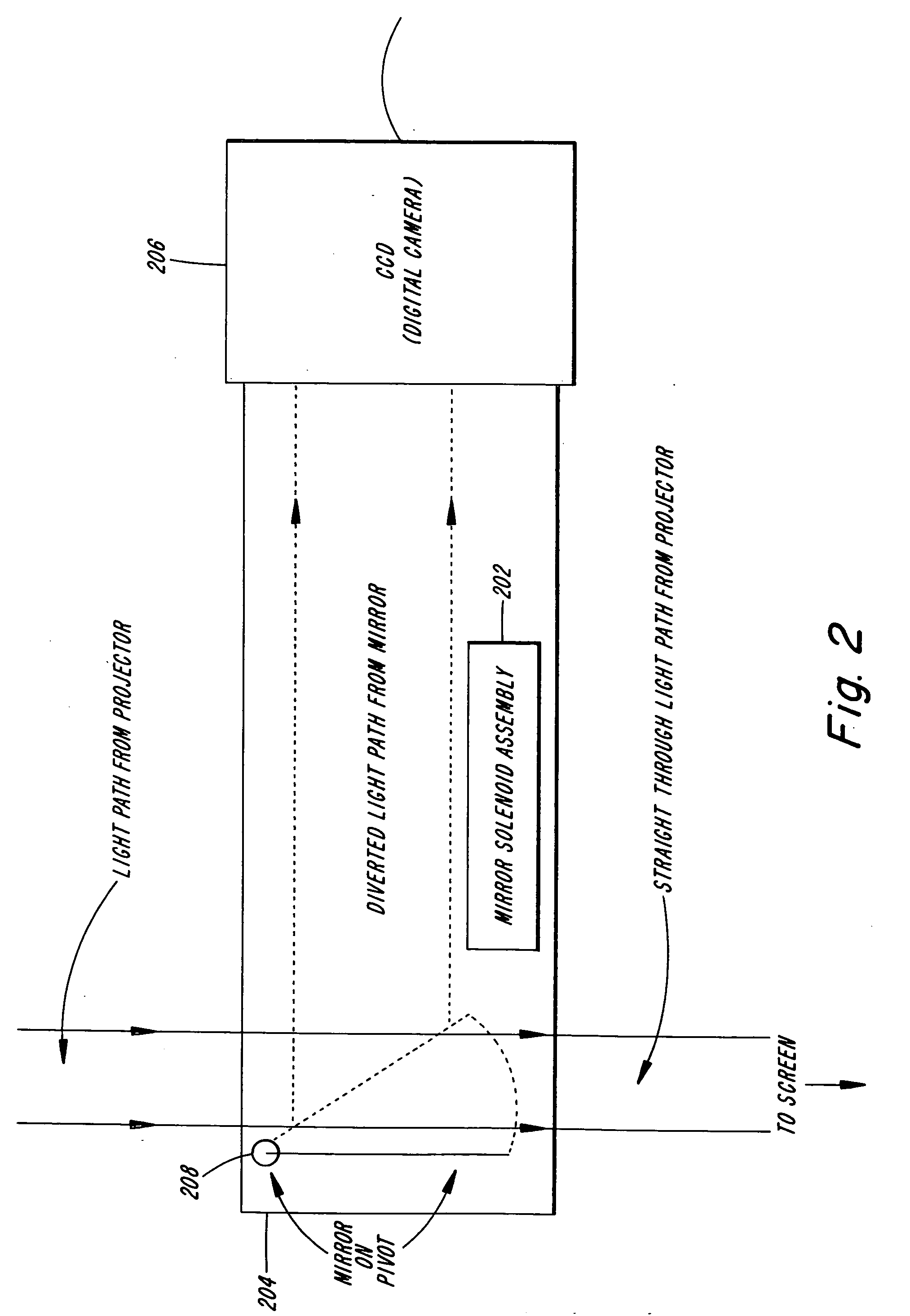
Enhanced capture, management and distribution of live presentations
InactiveUS20070033528A1Efficient managementQuick conversionTelevision system detailsWeb data retrievalComputer graphics (images)Engineering
Techniques are provided for converting live presentations into electronic media and managing captured media assets for distribution. An exemplary system includes capture devices that capture media assets of live presentations comprising a session, including image data of sequentially presented visual aids accompanying the live presentations and audio data. Each capture device has an interface for real-time image data marking of the image data for identification of individual images and session marking of the image data for demarcation of individual presentations of the session. A centralized device processes the captured media assets and automatically divides the captured media assets into discrete files associated with the individual presentations based on the session markings. An administrative tool manages the processed media assets to produce modified presentations and enables modification of the visual aid images identified by the image data markings. A production device formats the modified presentations for distribution on distribution media.
Owner:ECHO 360 CONTINUING EDUCATION LLC
Authentication of physical and electronic media objects using digital watermarks
InactiveUS7822225B2Character and pattern recognitionImage data processing detailsComputer hardwareDigital watermarking
A content watermarking method derives a watermark key from data representing content. In one particular method, a plural symbol message is algorithmically transformed in dependence on the derived watermark key. In another arrangement, the key specifies how or where the message is embedded in the content. A variety of other features and arrangements are also detailed.
Owner:DIGIMARC CORP
Audio cassette emulator with cryptographic media distribution control
InactiveUS7436957B1Saving positionSaving stateKey distribution for secure communicationDigital data processing detailsDistribution controlThe Internet
A device of the same general physical size and shape as a standard audio cassette tape, but which accepts digital information from any of a variety of sources—including for example: Internet transmission, a digital computer, or memory cards (especially digital memory cards)—and plays this digital information through any, for example, standard audio tape cassette player. The device operates by converting the digital representation of the sound into magnetic signals which are presented to the read / write head of the cassette player equipment. The device allows the user of the cassette player to regulate the audio playback using conventional equipment controls such as: START, STOP, REWIND, FAST REWIND, FORWARD, FAST FORWARD, etc. The device has the same general physical dimensions of a standard audio cassette; at least one digital processor; and a slot into which electronic media such as, for example, memory cards, smart cards having a processor and a memory embodied thereon and other memory media may be inserted. Numerous sensors detect changes in at least one of the tape equipment mechanisms in the audio cassette emulator. Various cryptographic techniques are described for protecting the unauthorized distribution of audio information.
Owner:FISCHER ADDISON M
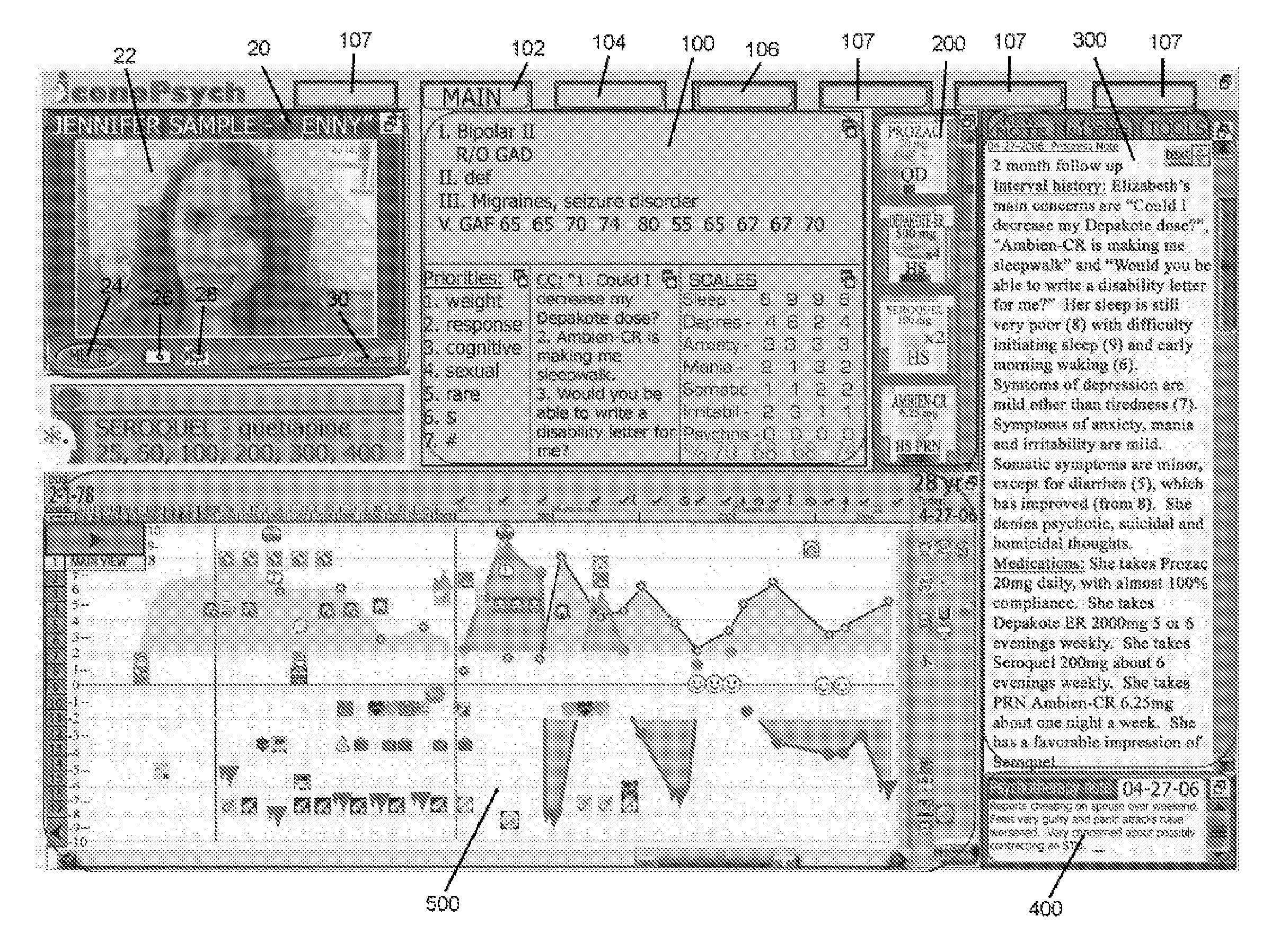
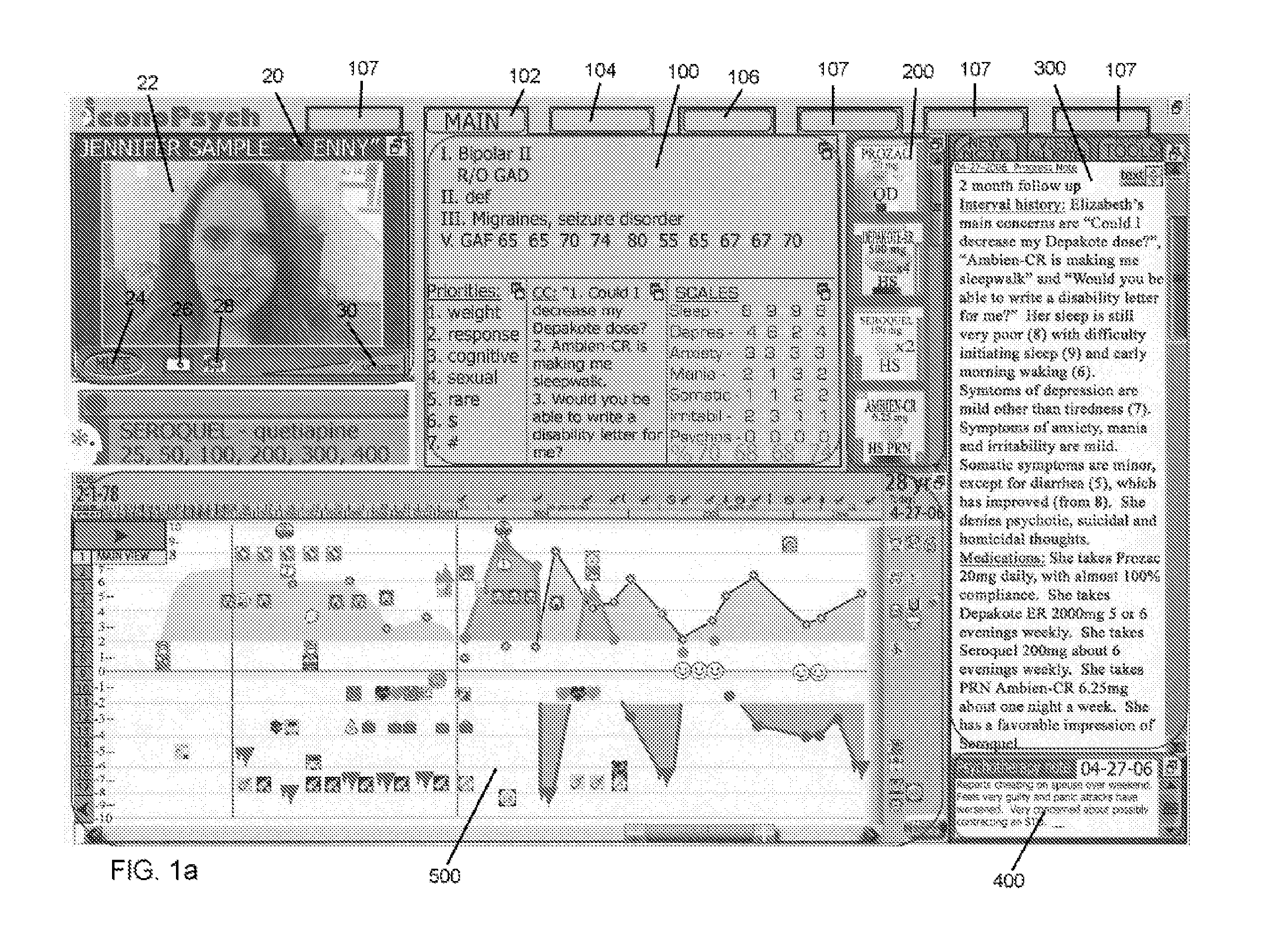
System for Integrated Teleconference and Improved Electronic Medical Record with Iconic Dashboard
InactiveUS20080243548A1Easy fashionComputer-assisted medical data acquisitionOffice automationDashboardMedical record
A method for conveying complex or large amounts of data to a user in a readily understandable fashion. The method includes providing a computerized graphical user interface for displaying information to a user of the method, providing a reference database containing data pertaining to a field of endeavor engaged in by a user of the method, the reference database being stored on an electronic medium in communication with the computerized graphical user interface, streamlining by an automated process the data contained in the reference database such that at least a portion of the data is identified as being that which is pertinent to a problem being addressed by the user, displaying with the computerized graphical user interface at least a portion of the data identified as being that which is pertinent to a problem being addressed by the user, and displaying to the user with the computerized graphical user interface a graphical timeline illustrating a history of the problem being addressed by the user.
Owner:ICONIC HEALTH
Method and apparatus for accessing electronic data via a familiar printed medium
InactiveUS7232057B2Low costCharacter and pattern recognitionBuying/selling/leasing transactionsOutput deviceComputer memory
The disclosed methods and apparatus relate generally to the electronics media industry, such as cable television (CATV), home shopping services, on-line computer services and computer memory applications. These methods and apparatus allow a user to access and make use of electronic media input and output devices by reference to and / or utilization of standard printed matter, such as magazines, textbooks, or any other printed matter that can be correlated to electronic media.
Owner:MARSHALL FEATURE RECOGNITION
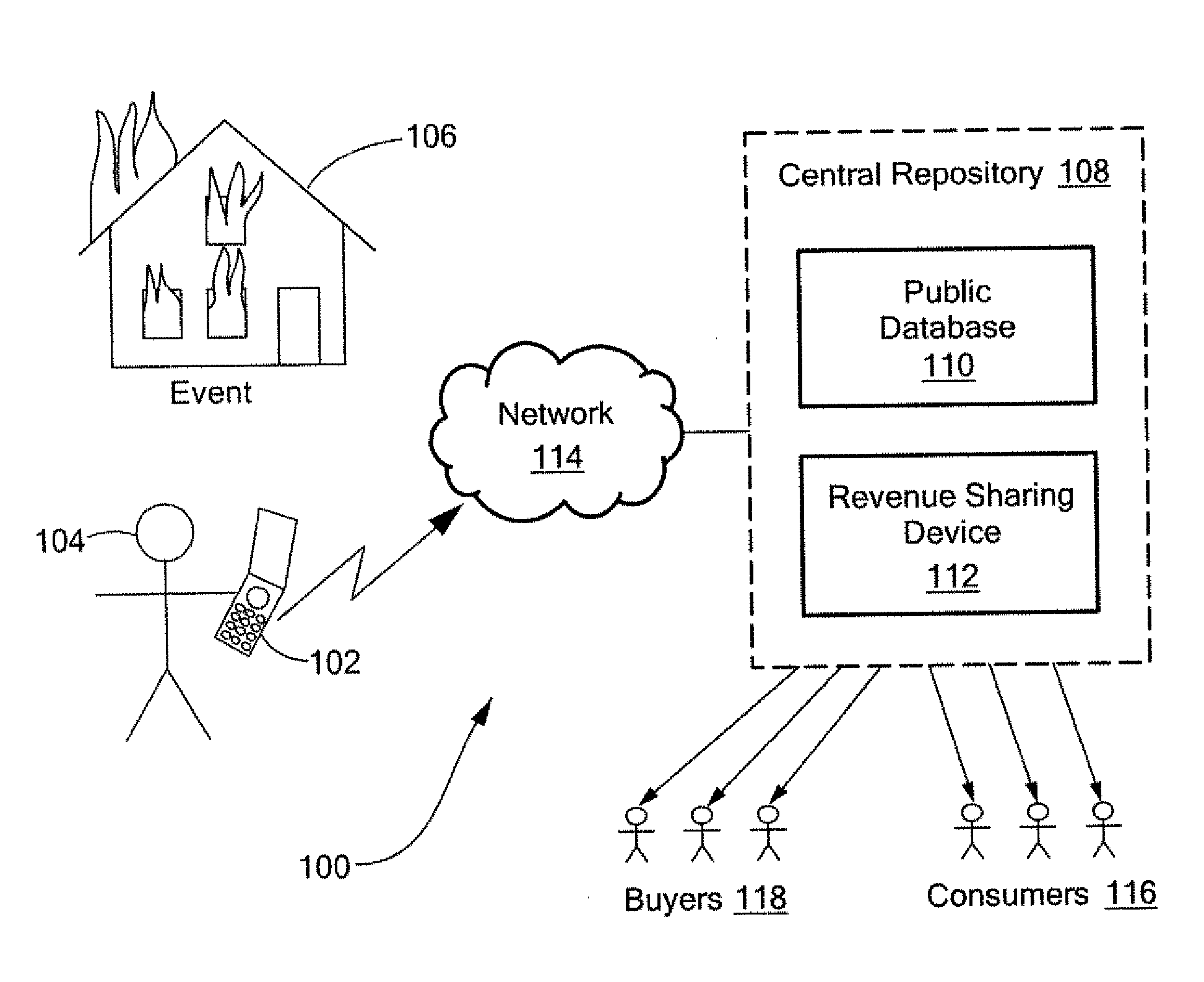
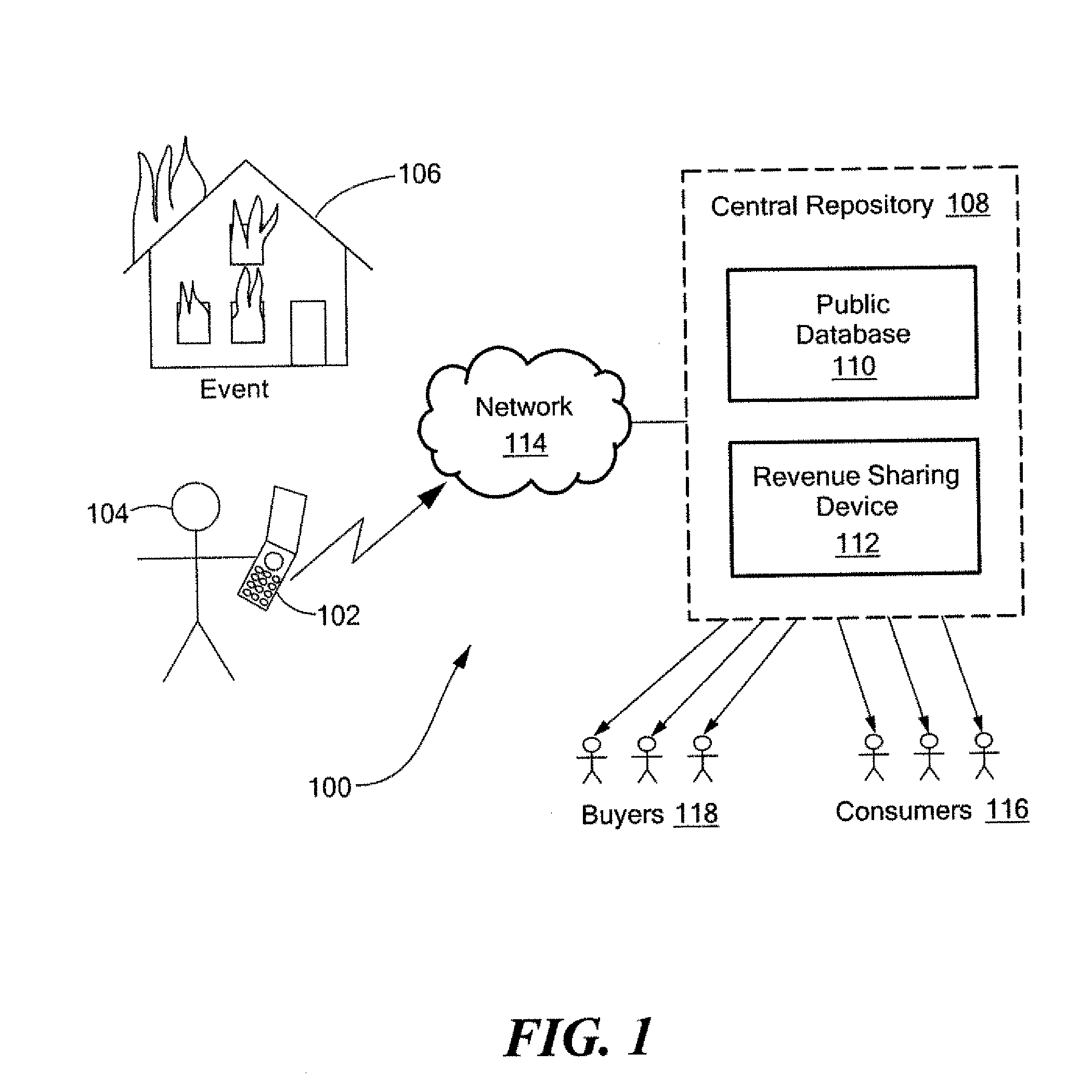
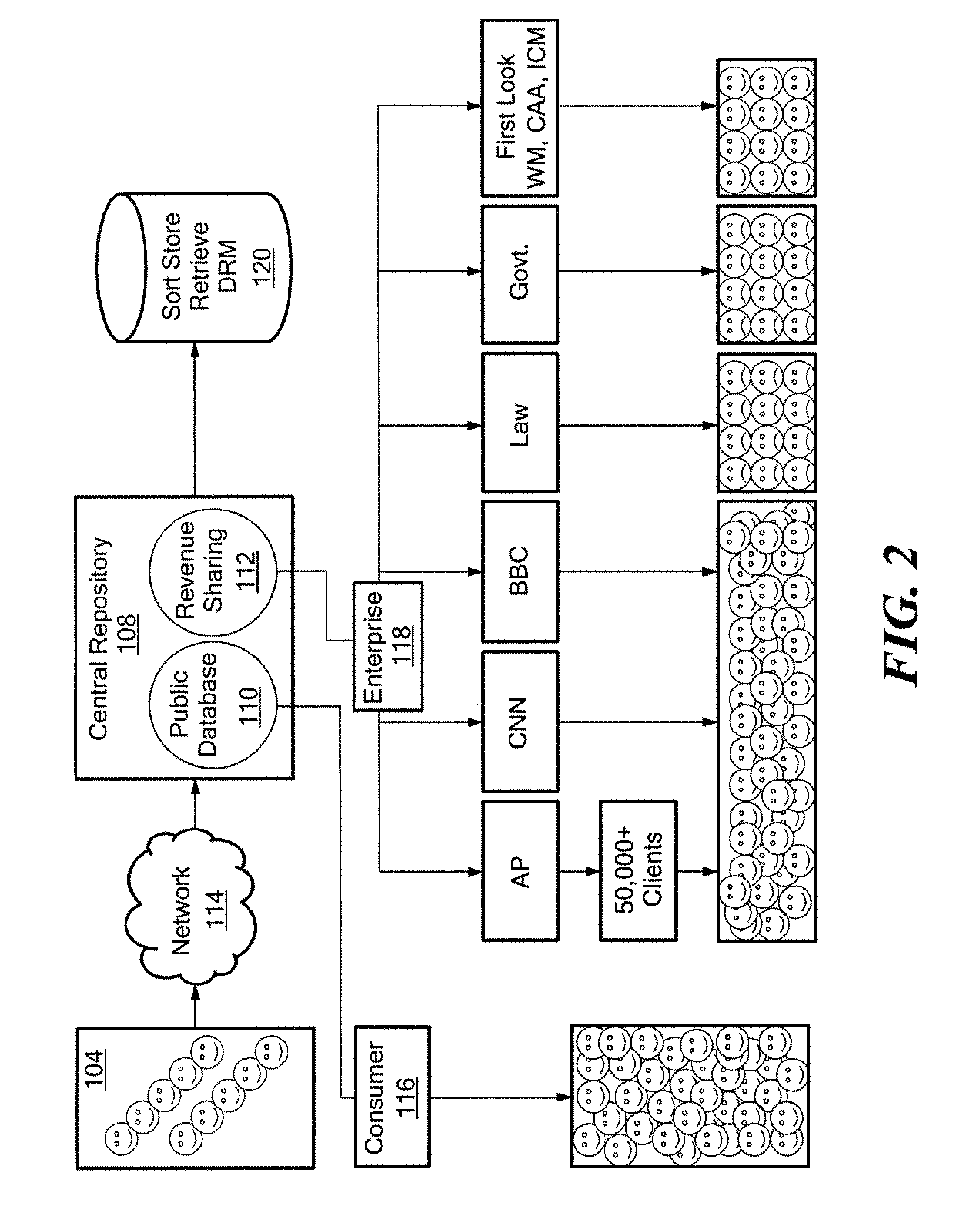
Method and system for on-line content acquisition and distribution
InactiveUS20090044235A1Two-way working systemsBuying/selling/leasing transactionsThird partyMobile telephony
A method and system for capturing and distributing electronic media content over a communications network. One or more subscribers capture media about a specific event with the use of a media capture device such as the camera of a mobile phone. The subscriber contacts a central repository and transmits the media content to the repository where the content can be stored, indexed and categorized. The content can be made available to one or more interested third party subscribers such as, for example, news agencies seeking information about the event. A bidding system can be implemented to allow the agency with the highest bid to receive access to the desired content. In return, the subscriber that submitted the content can receive compensation for the submitted content.
Owner:ENGAGEMENT MEDIA TECH
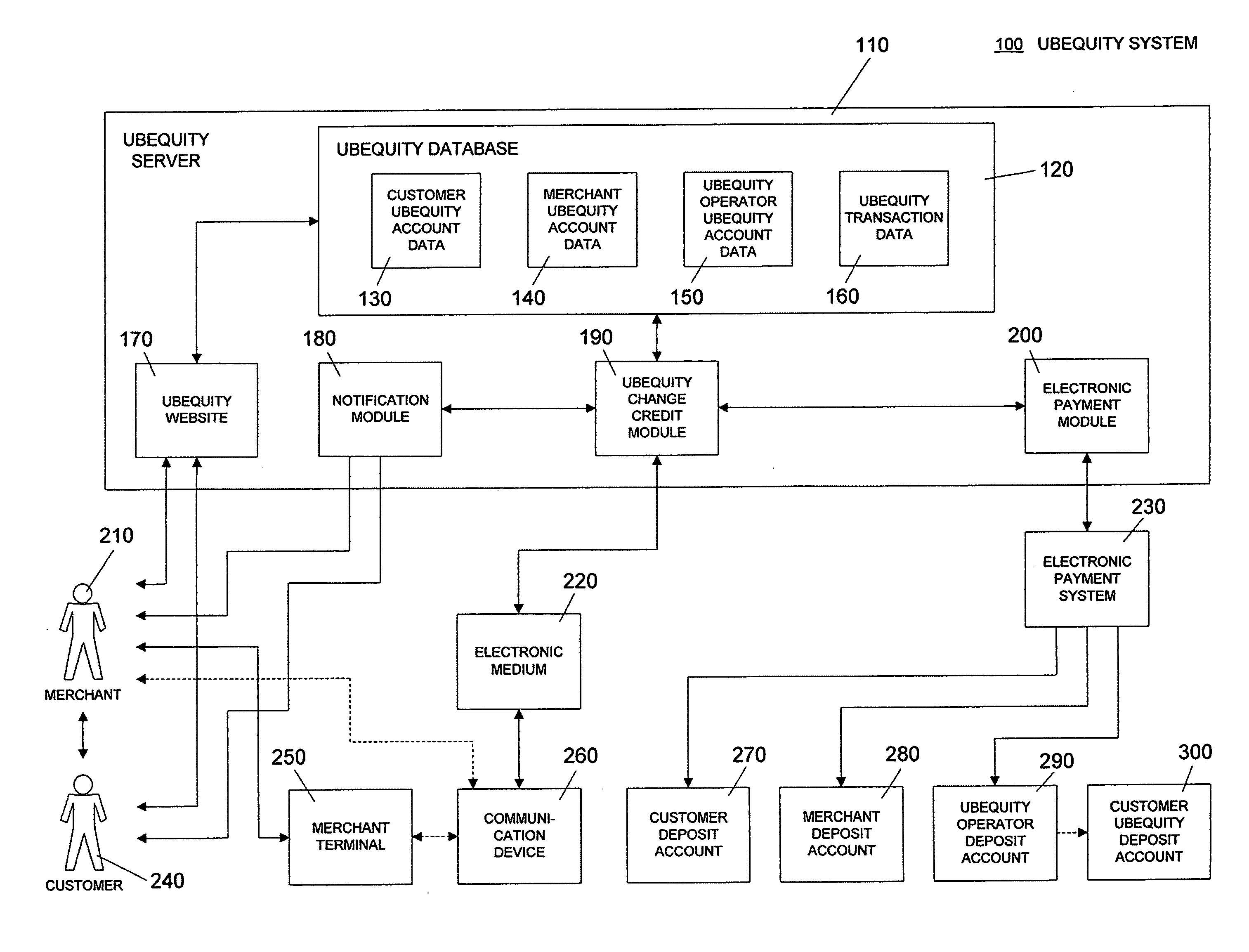
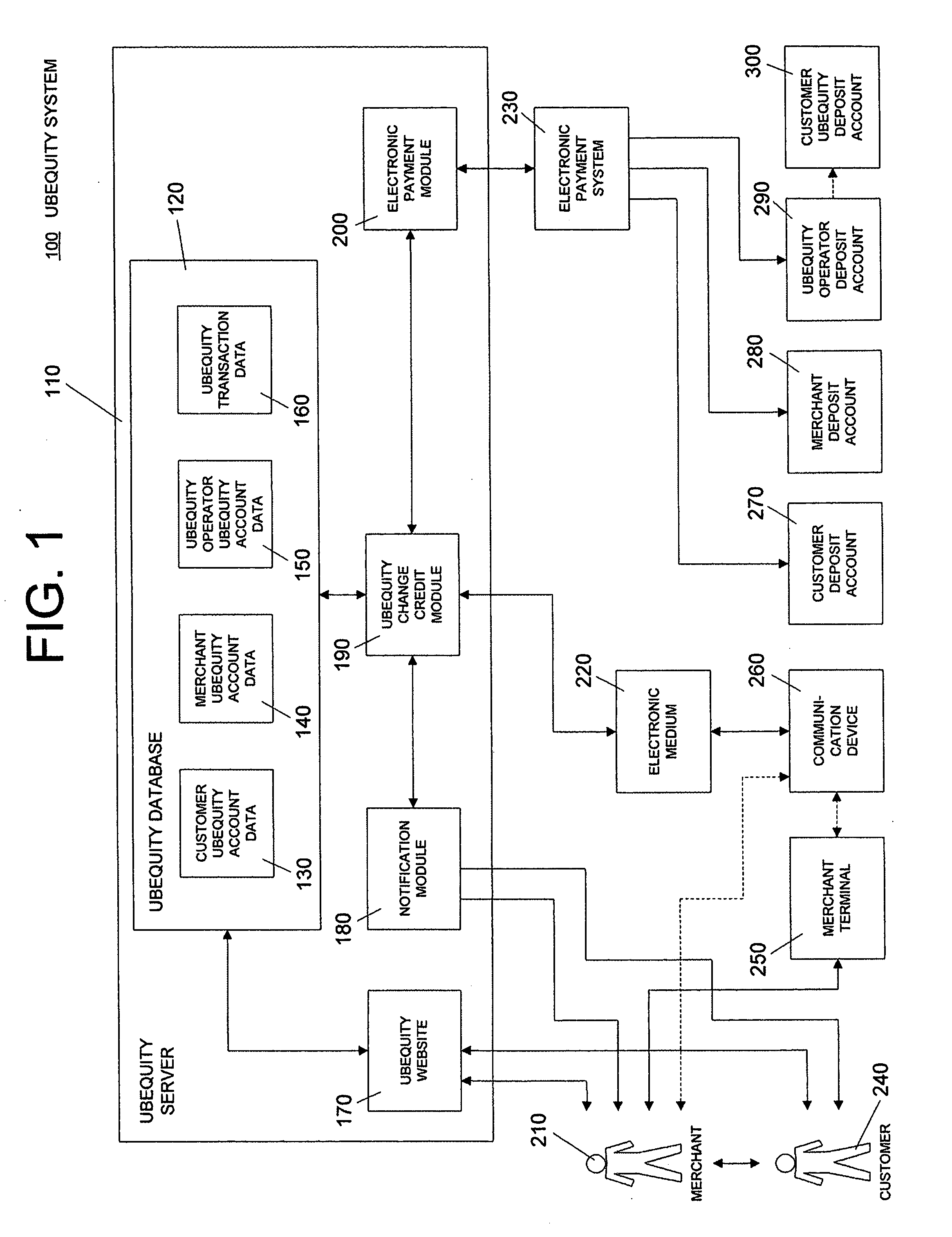
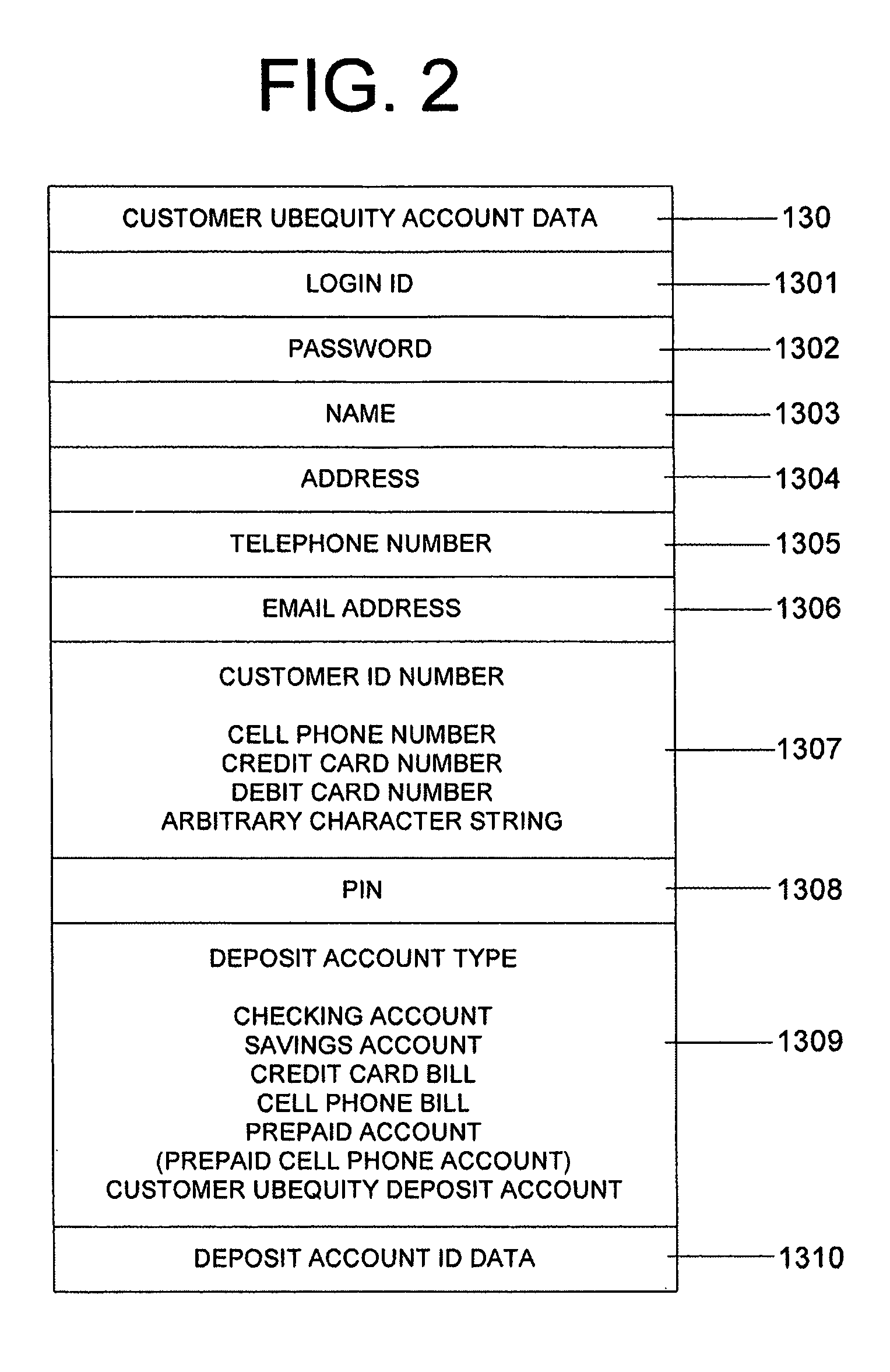
System and method of reducing or eliminating change in cash transaction by crediting at least part of change to buyer's account over electronic medium
InactiveUS20070156579A1Efficient reductionEliminate effectiveFinancePayment architectureDatabaseCommunication device
A method of reducing or eliminating change in a cash transaction includes receiving a cash payment for an article or a service from a buyer; and crediting at least part of change from the cash payment due the buyer to an account of the buyer over an electronic medium. A system of reducing or eliminating change in a cash transaction includes a merchant terminal that processes a cash payment received from a buyer for an article or a service; a communication device that sends a message over an electronic medium specifying that at least part of change from the cash payment is to be credited to an account of the buyer; and a change credit apparatus that credits the at least part of the change to the buyer's account.
Owner:UBEQUITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com