Patents
Literature
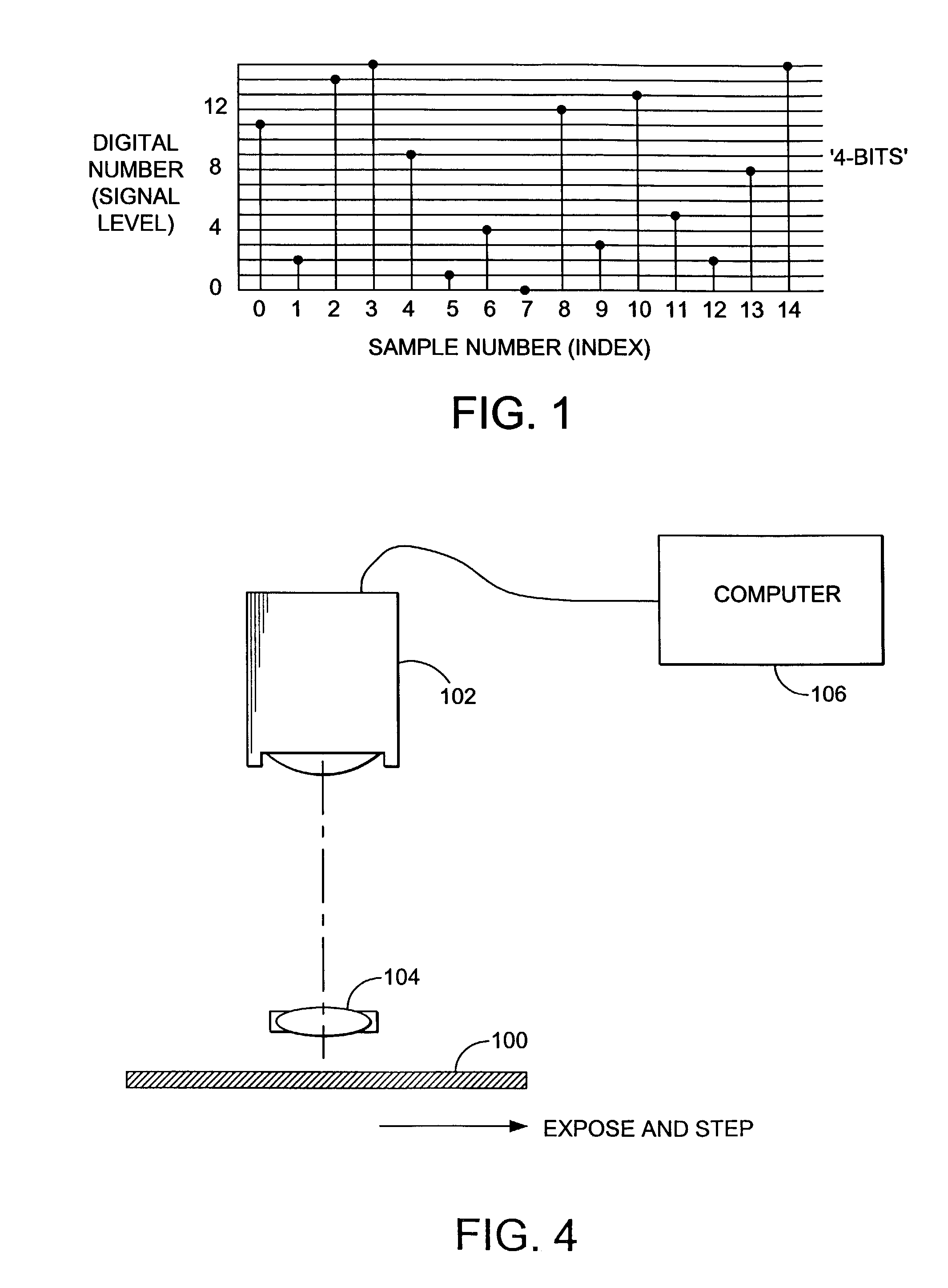
533 results about "Document security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
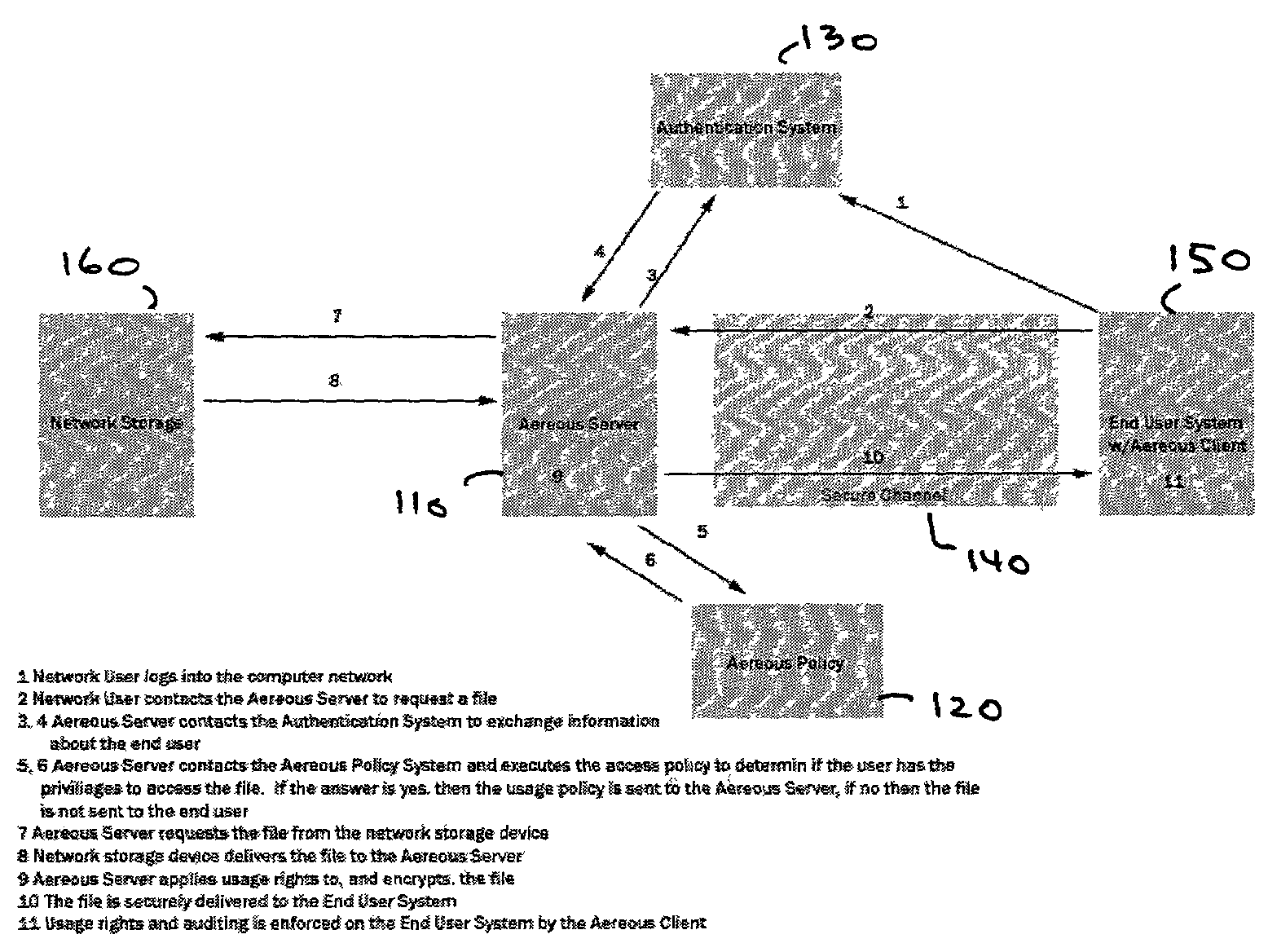
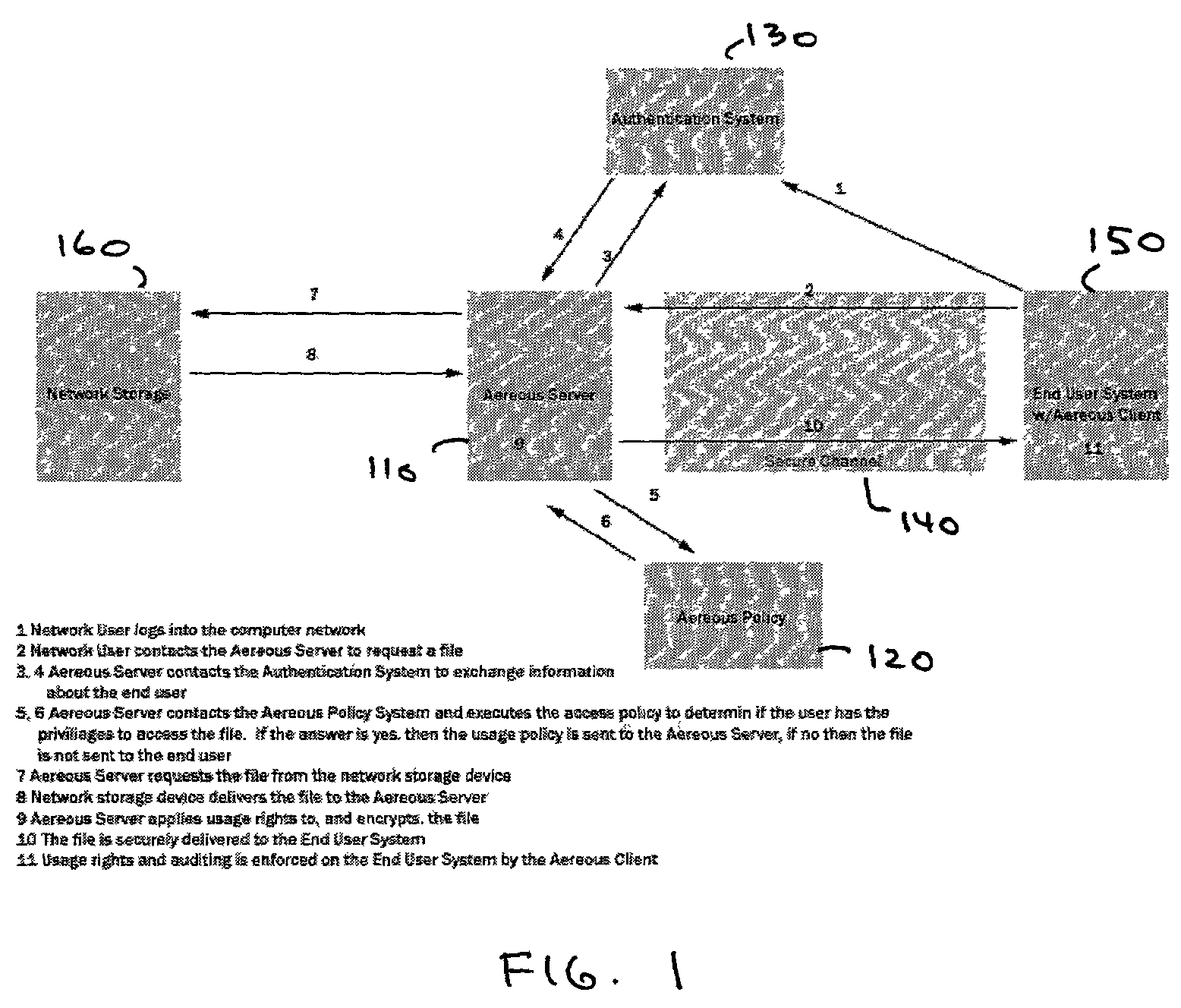
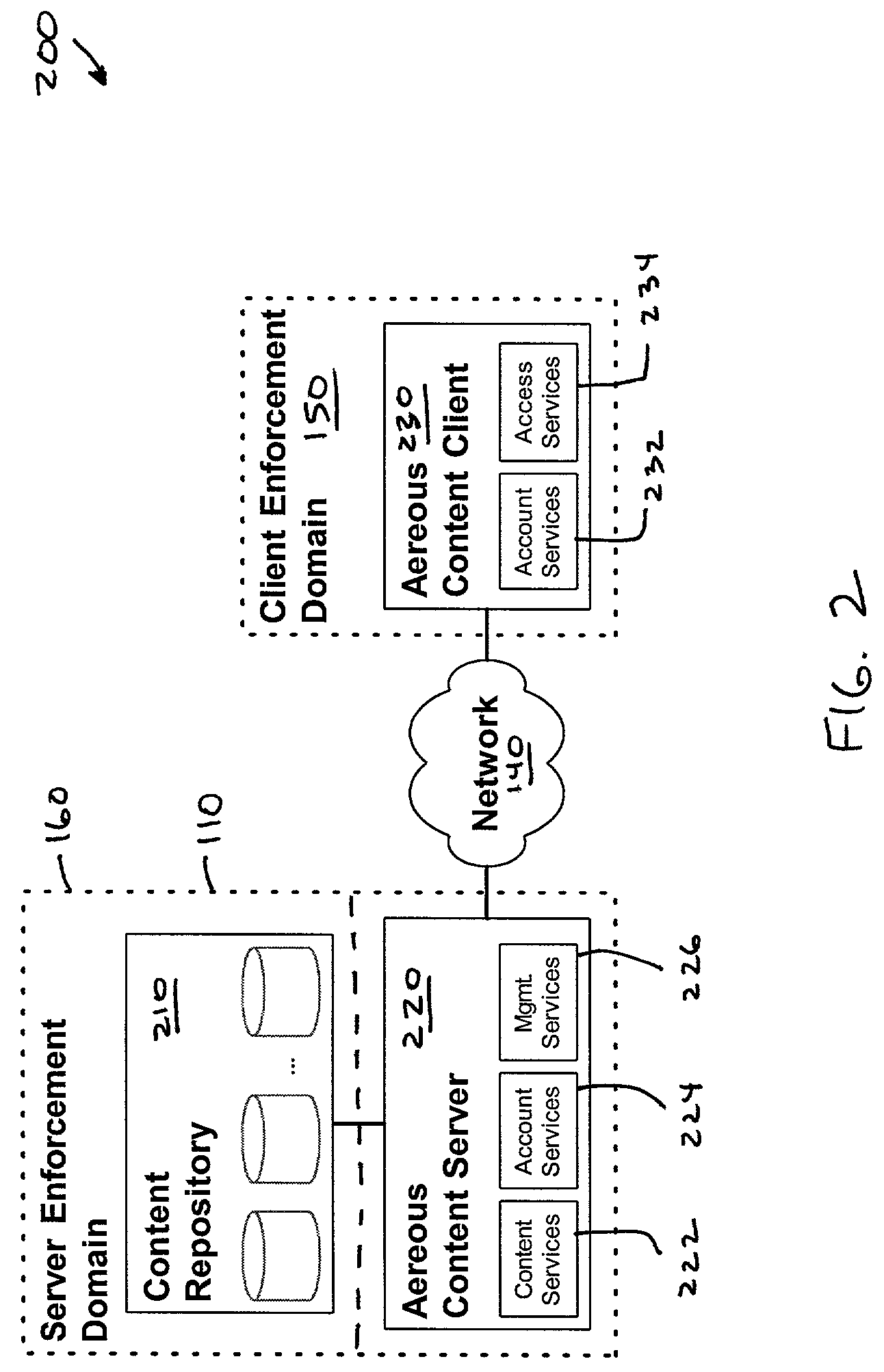
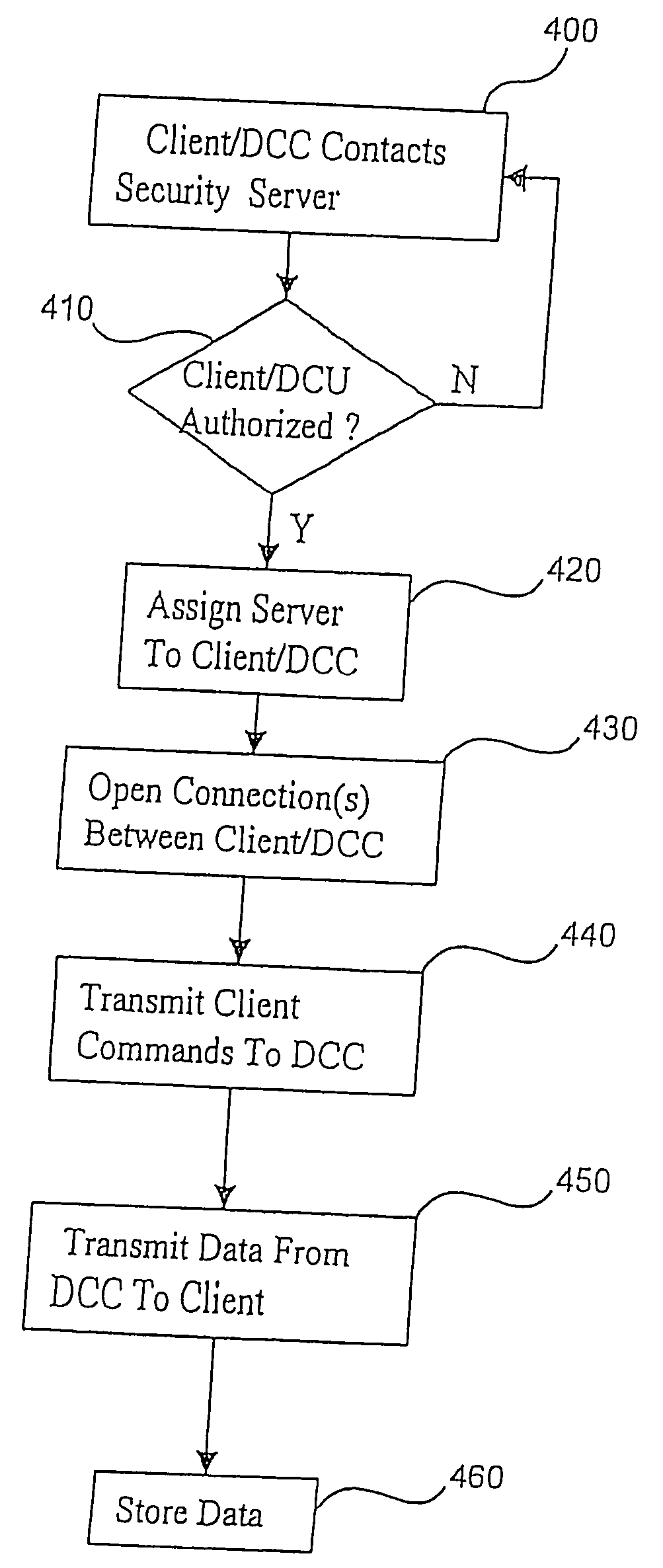
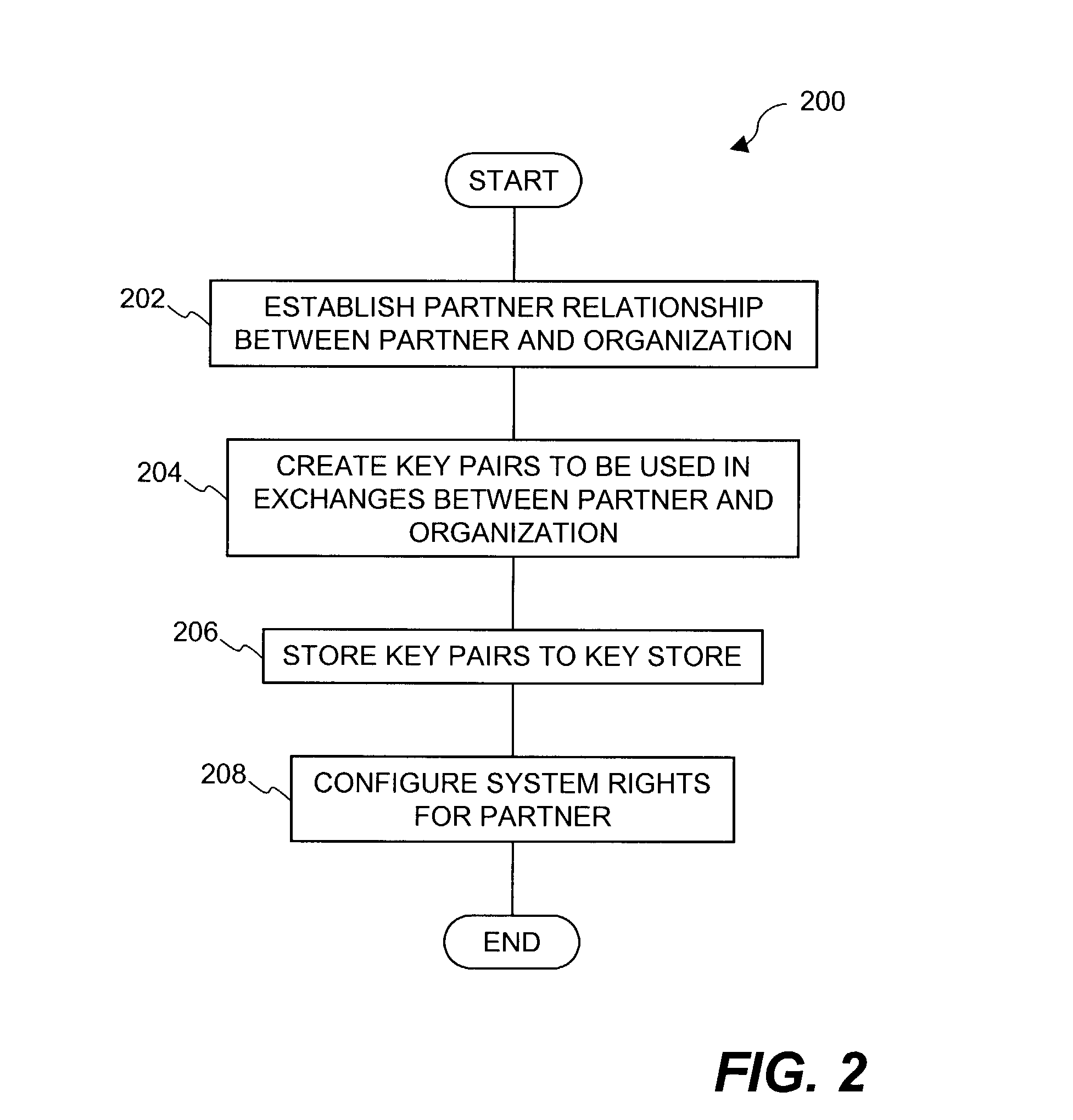
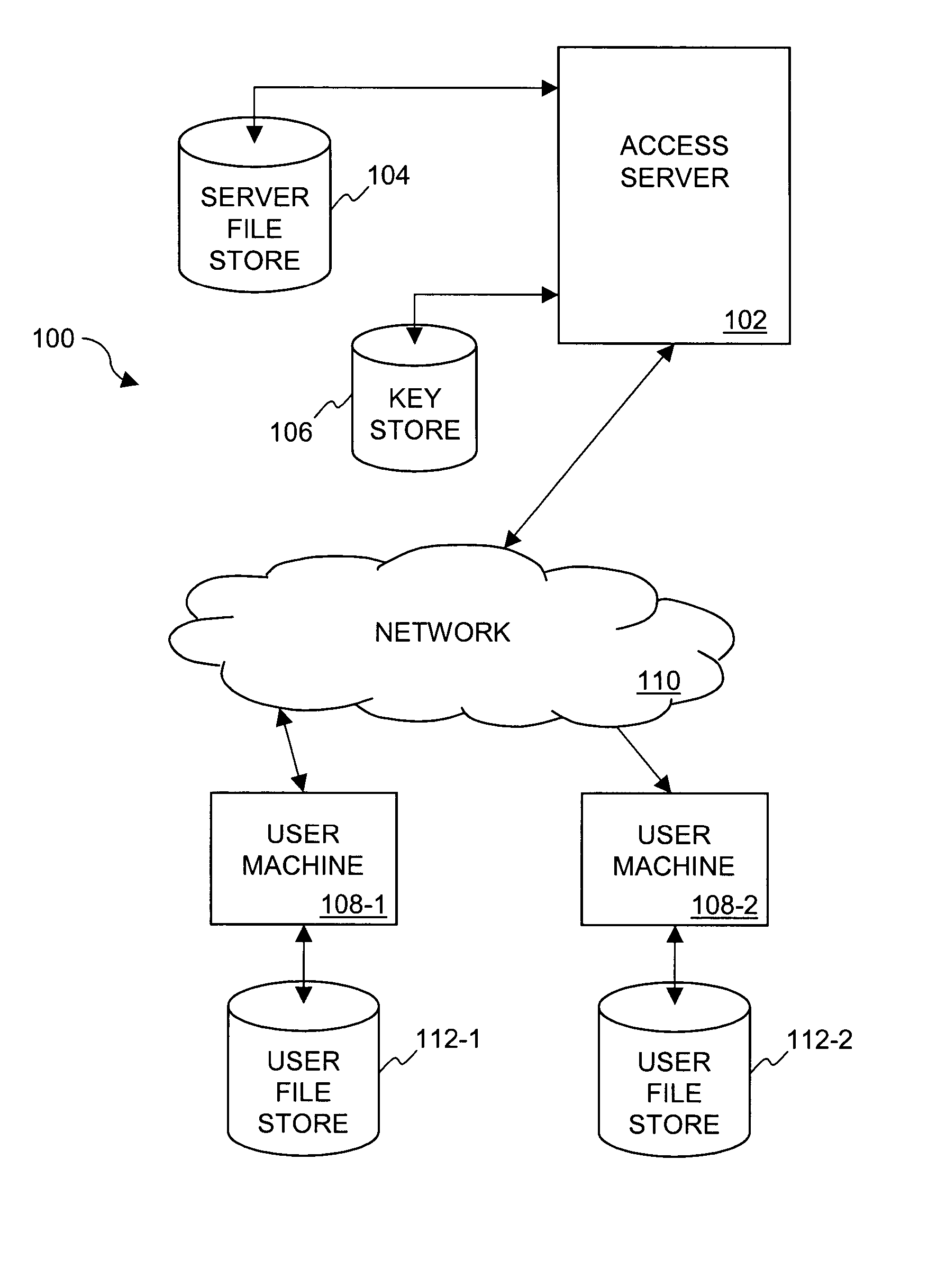
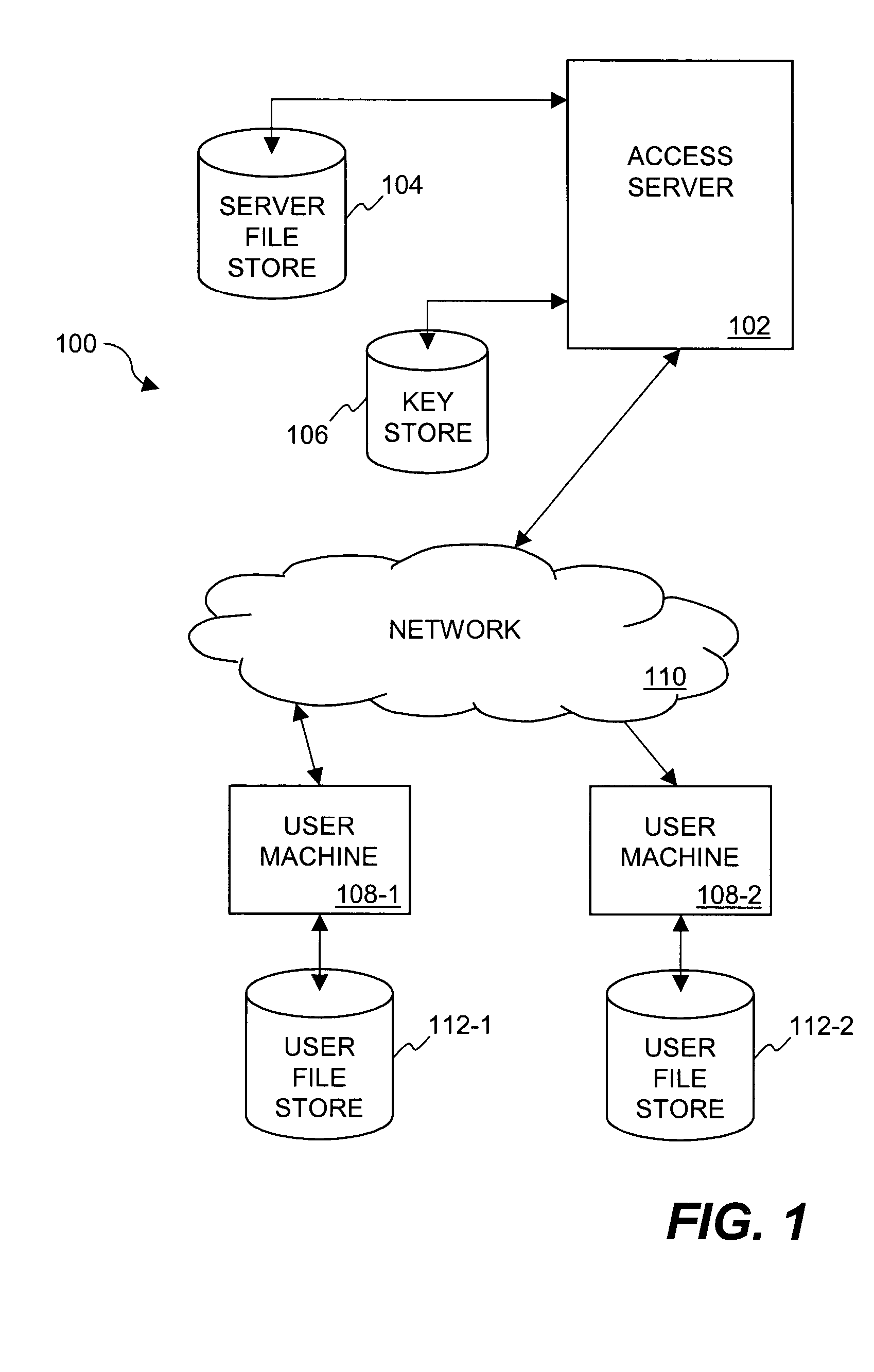
Dynamic file access control and management
InactiveUS7660902B2Improve securitySelectively accessedComputer security arrangementsMultiple digital computer combinationsDistributed File SystemFile system
A dynamic file access control and management system and method in accordance with the present invention may be a proxy file management system that includes one or more file system proxy servers that provide selective access and usage management to files available from one or more file systems or sources. The present invention may embody a secure transport protocol that tunnels distributed file systems, application independent usage controls connected to files on end-user computers, dynamically merging secondary content to a requested file, and applying bandwidth management to any of the foregoing. Embodied in the various implementations of the present invention is enhanced file security. Preferably, the proxy file management system is transparent to an end-user. A dynamic content management system may also be included that selectively adds content to requested files.
Owner:EMC IP HLDG CO LLC
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS20050149481A1Reduce bandwidth requirementsDigital data processing detailsMultiple digital computer combinationsData accessRemote computer
Applications, systems and methods for efficiently accessing and controlling data of devices among multiple computers over a network. Peer-to-peer exchanges of data between private computers is made possible while providing seamless, firewall-compliant connectivity. Such functionality is available even among private users over a public network, and even when multiple firewalls must be passed through. A firewall compliant connection may be established between a local computer and at least one remote computer; at least one file on a storage device associated with one of the computers is selected, and securely sent to at least one other computer over the secure connections. Computers may be connected over a wide area network with or without a connection server, with or without a VPN.
Owner:WESTERN DIGITAL TECH INC
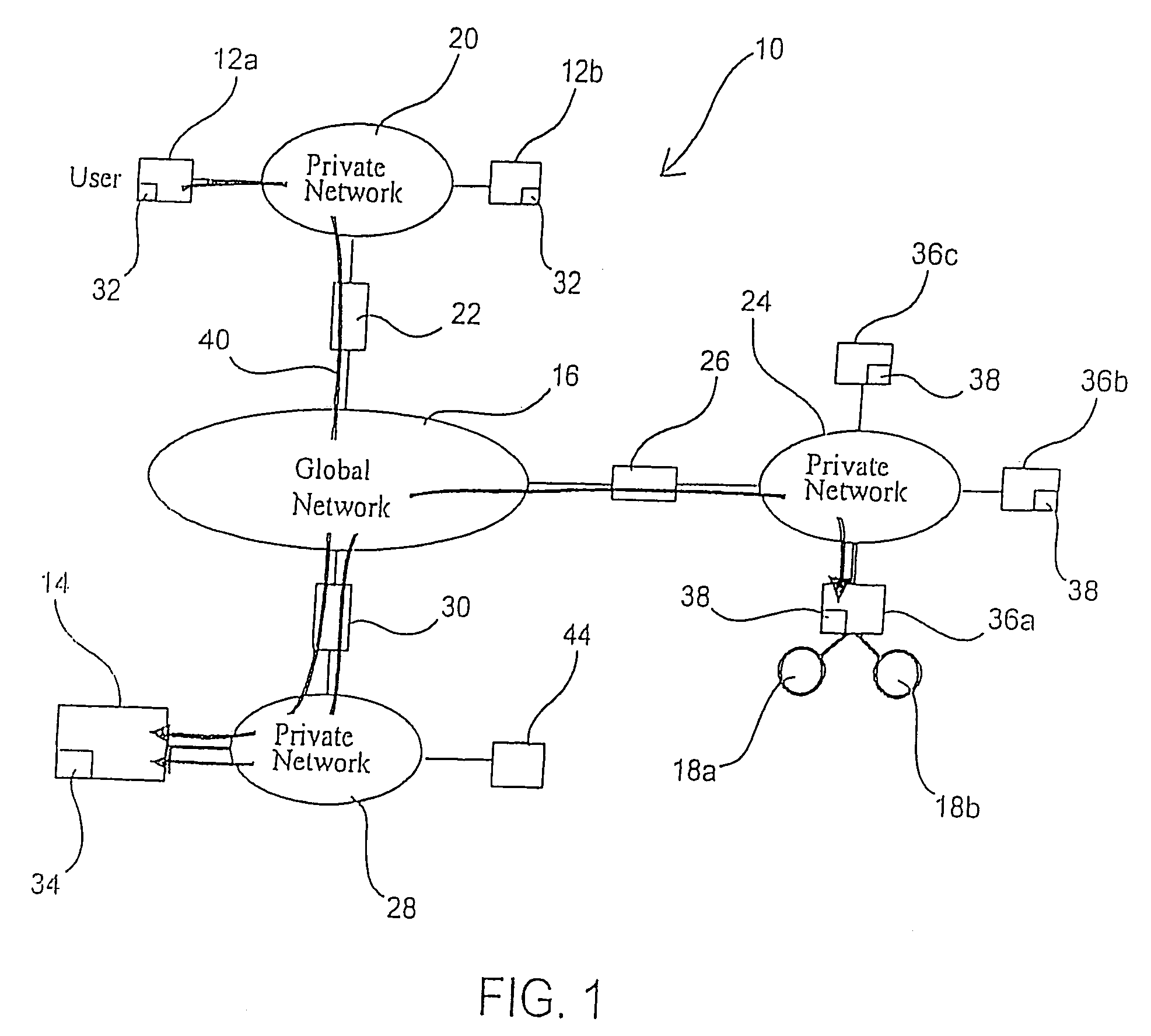
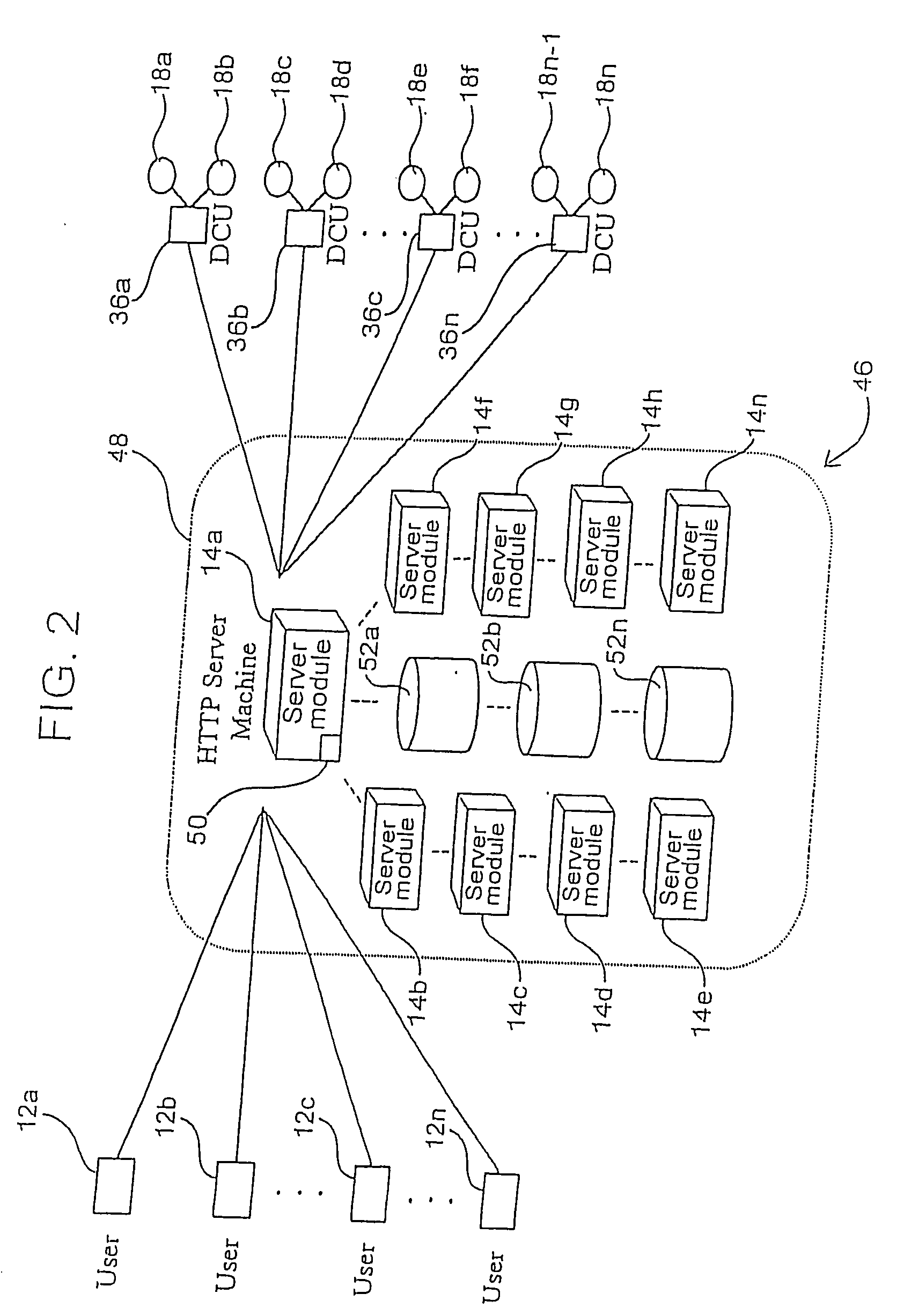
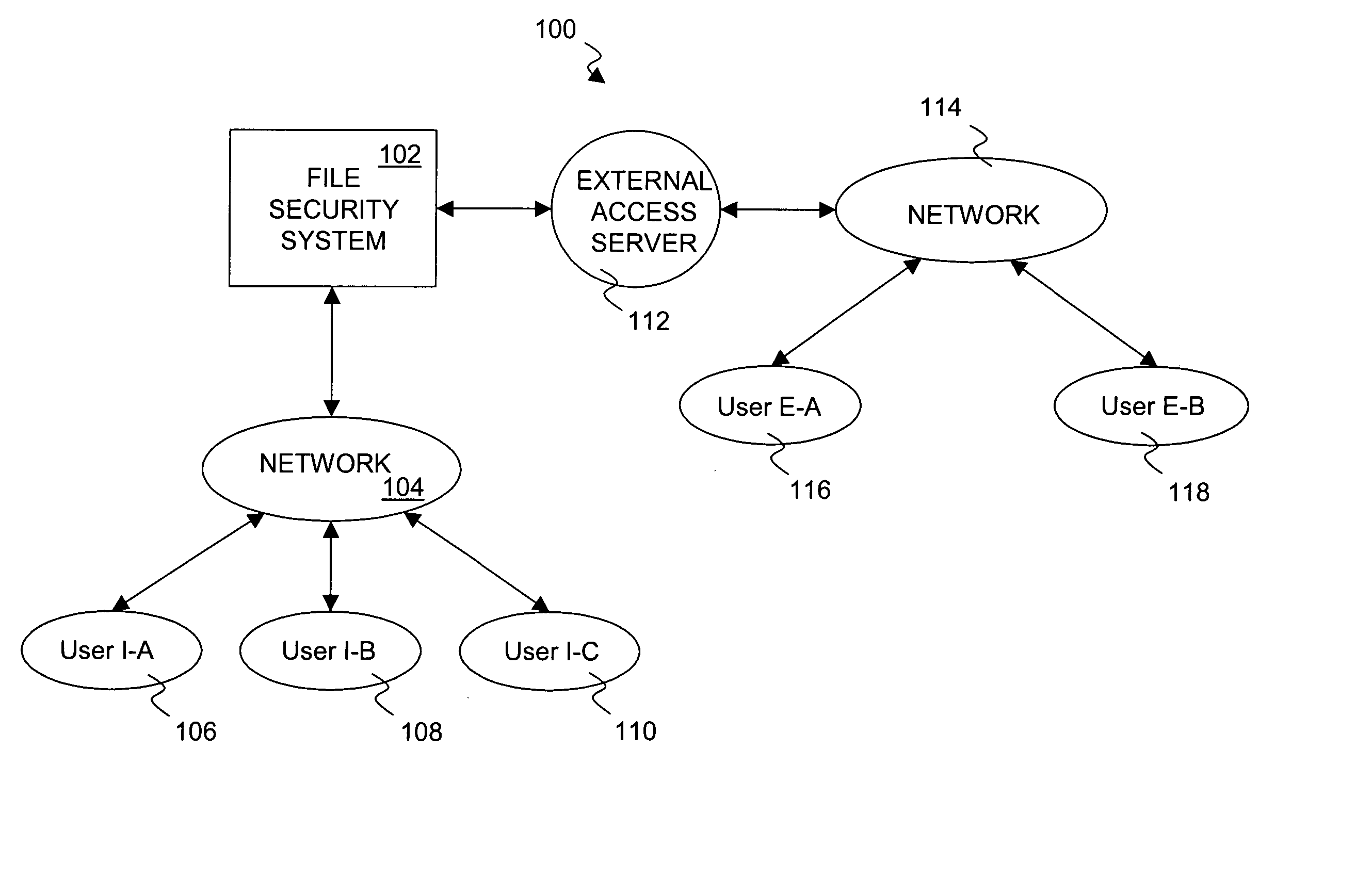
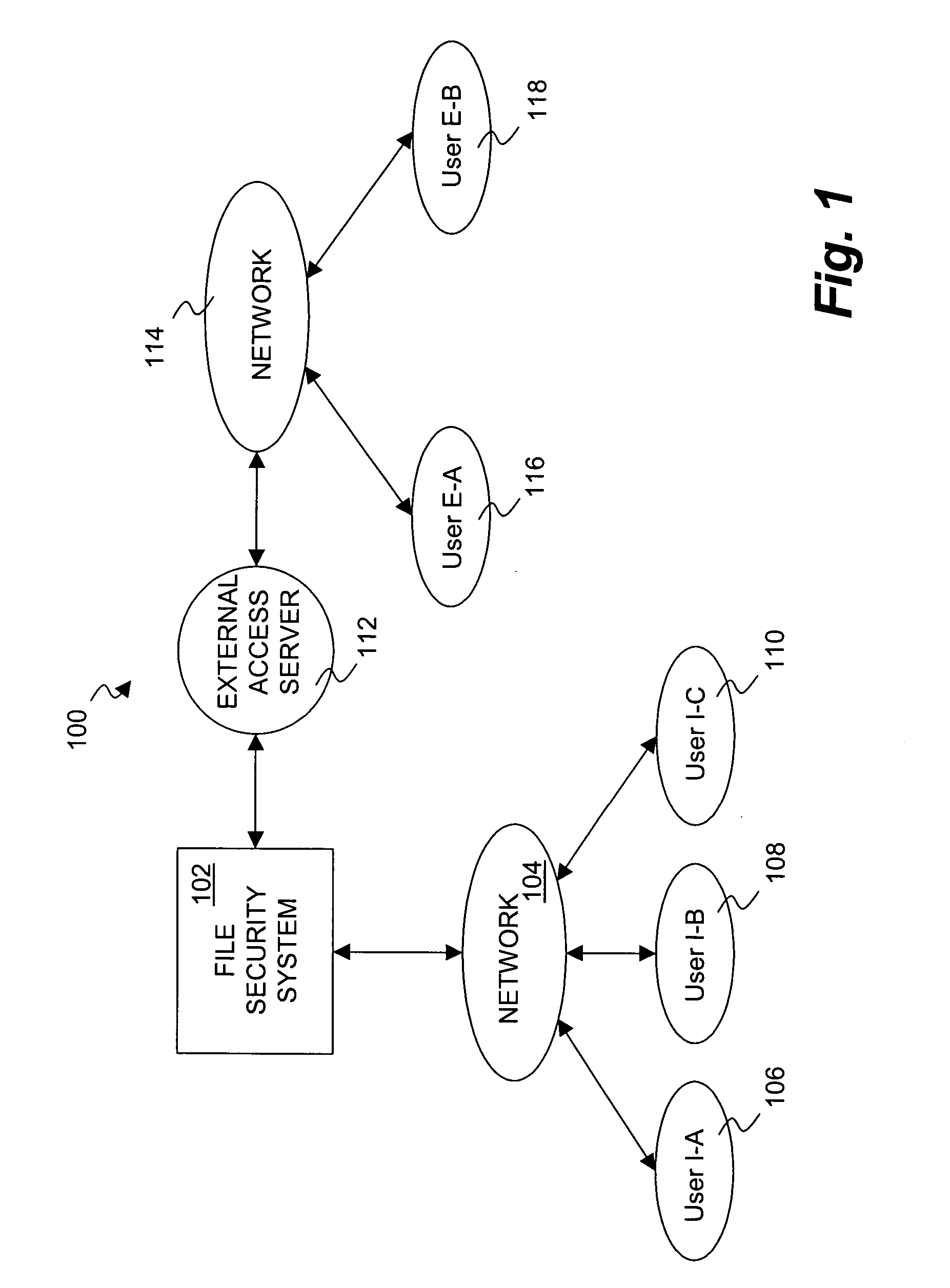
Document security system that permits external users to gain access to secured files
ActiveUS8176334B2Minimal amountLimited accessDigital data processing detailsUser identity/authority verificationUser PrivilegeInternal documentation
An improved system and approaches for exchanging secured files (e.g., documents) between internal users of an organization and external users are disclosed. A file security system of the organization operates to protect the files of the organization and thus prevents or limits external users from accessing internal documents. Although the external users are unaffiliated with the organization (i.e., not employees or contractors), the external users often have working relationships with internal users. These working relationships (also referred to herein as partner relationships) often present the need for file (document) exchange. According to one aspect, external users having working relationships with internal users are able to be given limited user privileges within the file security system, such that restricted file (document) exchange is permitted between such internal and external users.
Owner:INTELLECTUAL VENTURES I LLC
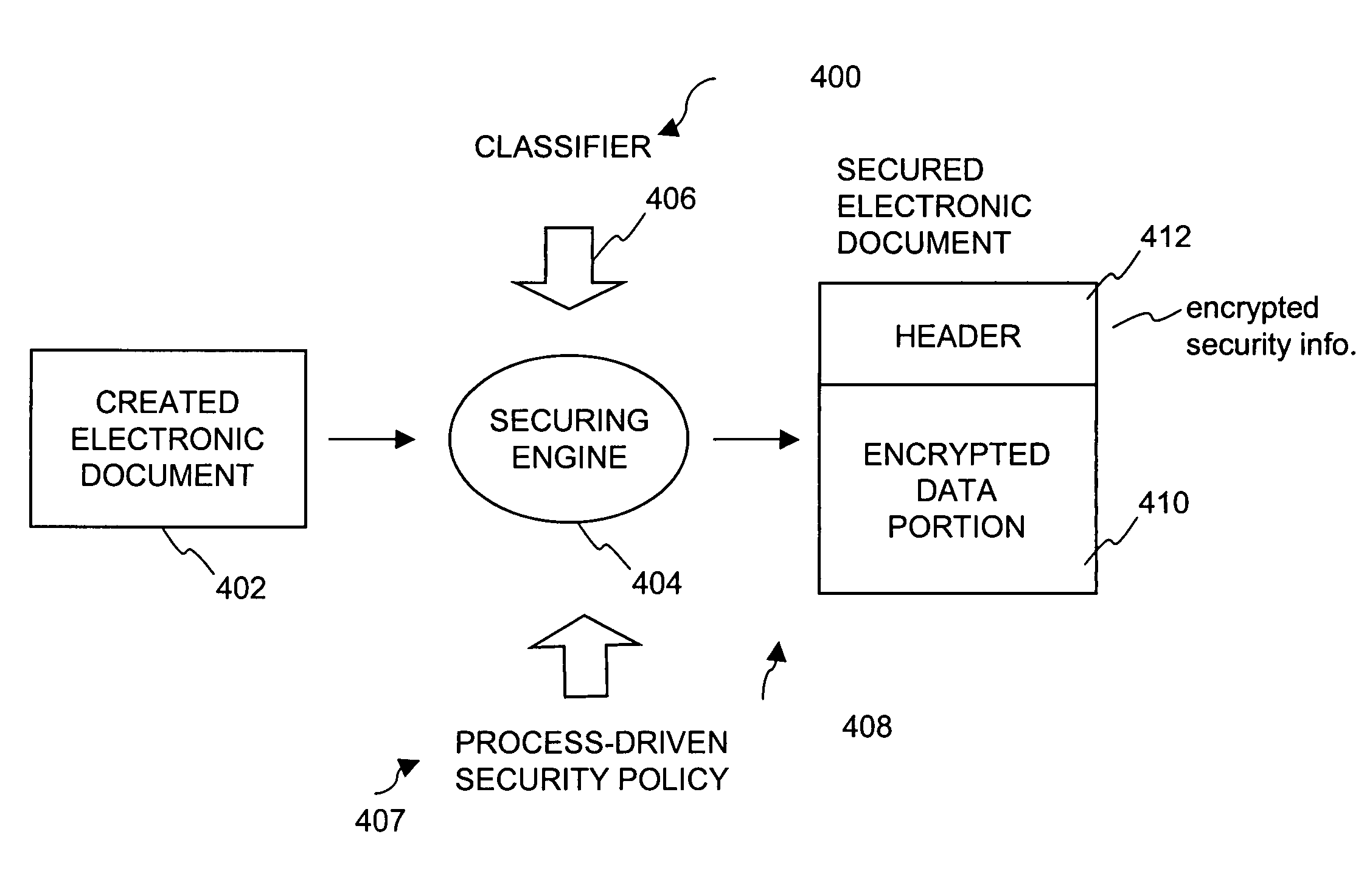
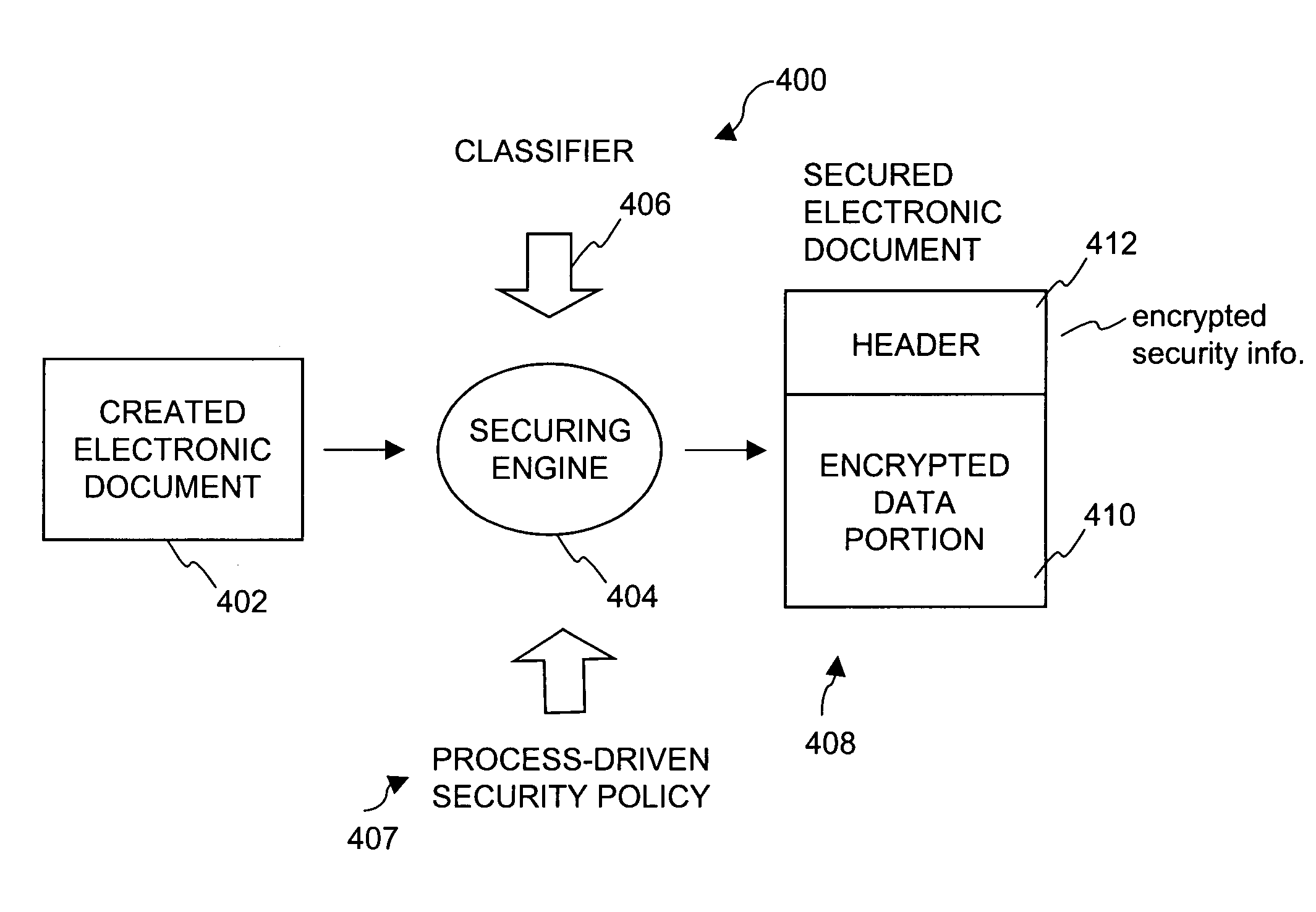
Method and system for securing digital assets using process-driven security policies
ActiveUS7703140B2More burdensomeGood flexibilityKey distribution for secure communicationPublic key for secure communicationSecurity policySecurity system
Techniques for dynamically altering security criteria used in a file security system are disclosed. The security criteria pertains to keys (or ciphers) used by the file security system to encrypt electronic files to be secured or to decrypt electronic files already secured. The security criteria can, among other things, include keys that are required to gain access to electronic files. Here, the keys can be changed automatically as electronic files transition between different states of a process-driven security policy. The dynamic alteration of security criteria enhances the flexibility and robustness of the security system. In other words, access restrictions on electronic files can be dependent on the state of the process-driven security policy.
Owner:INTELLECTUAL VENTURES I LLC
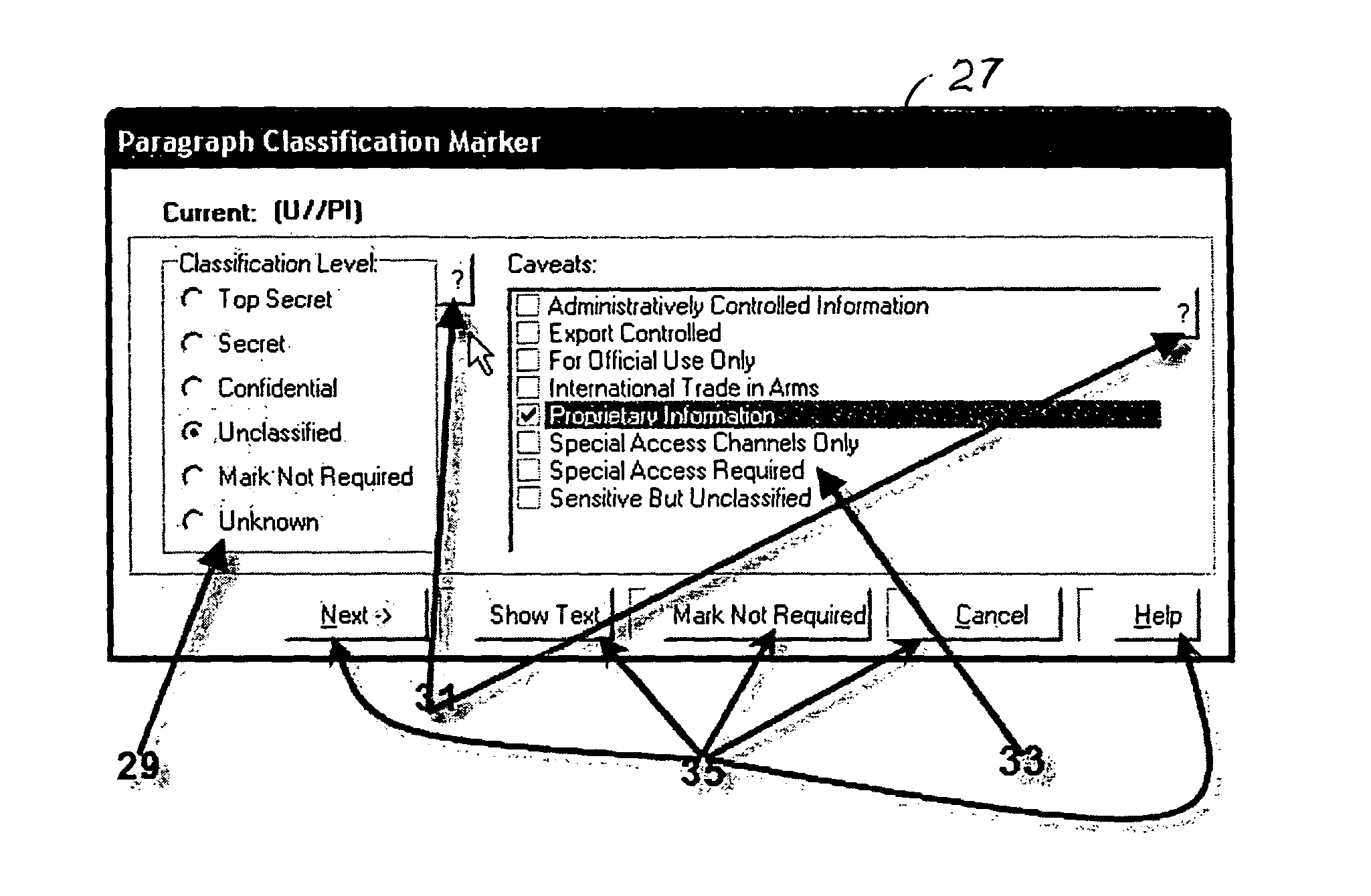
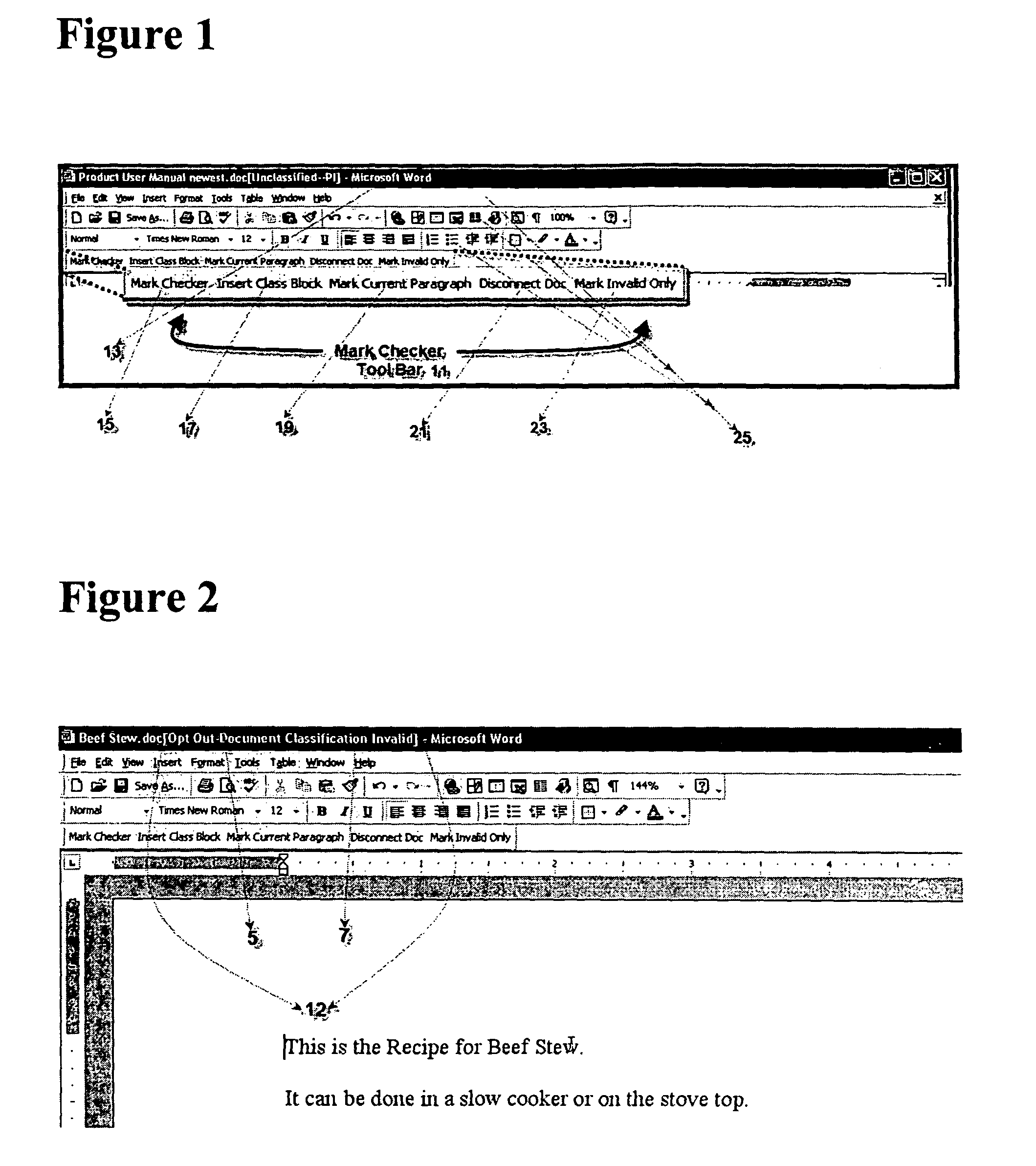
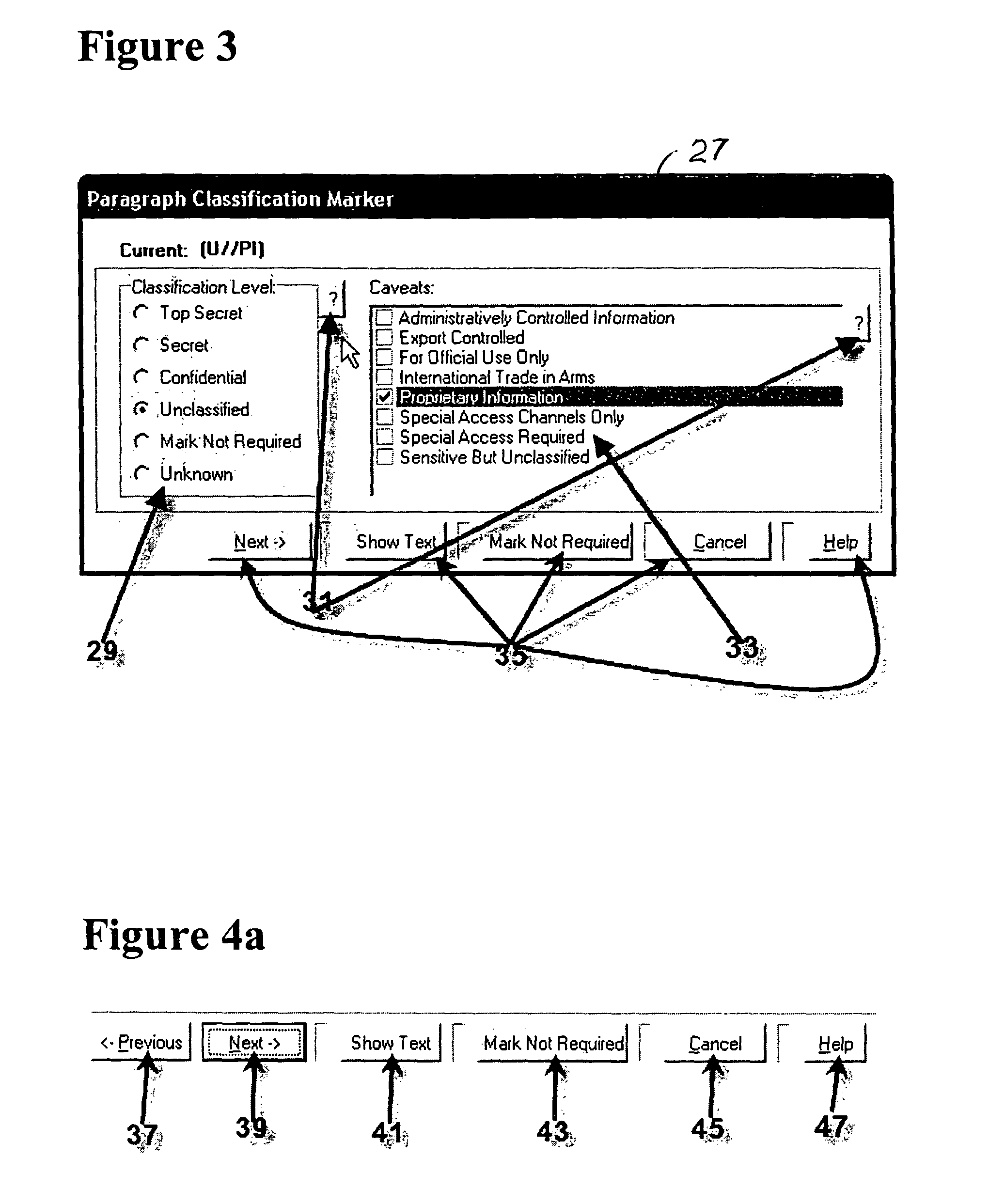
Method for providing customized and automated security assistance, a document marking regime, and central tracking and control for sensitive or classified documents in electronic format
ActiveUS7958147B1Guarantee capacityPositive determinationDigital data information retrievalDigital data processing detailsOff the shelfDocumentation procedure
A software engine runs in a compatible mode with off-the-shelf word processors, e-mail programs and presentation development software and other document development software. The software engine is used for the security classification of sensitive or national security classified information in electronic and resultant hard copy document formats. The software engine ensures that the individual considers all informational portions of a document, that appropriate document marks are employed, that document marks in their electronic format are persistent and that all necessary information, such as classification guides, standards and security regulations, provided by the organization to classify information is at hand and immediately available. In addition to the document sensitivity or classification determination and marking support, the software engine tracks and controls documents and the electronic media storing documents. It also provides warnings and alarms, ad hoc document security analysis and reporting capability to system security administrators with respect to document or network events or captured information that may be indicative of risk to the information requiring protection. The software also provides the ability for an organization to centrally establish and control a security classification or sensitivity marking hierarchy for automated security classification support.
Owner:TURNER JAMES LUKE +1
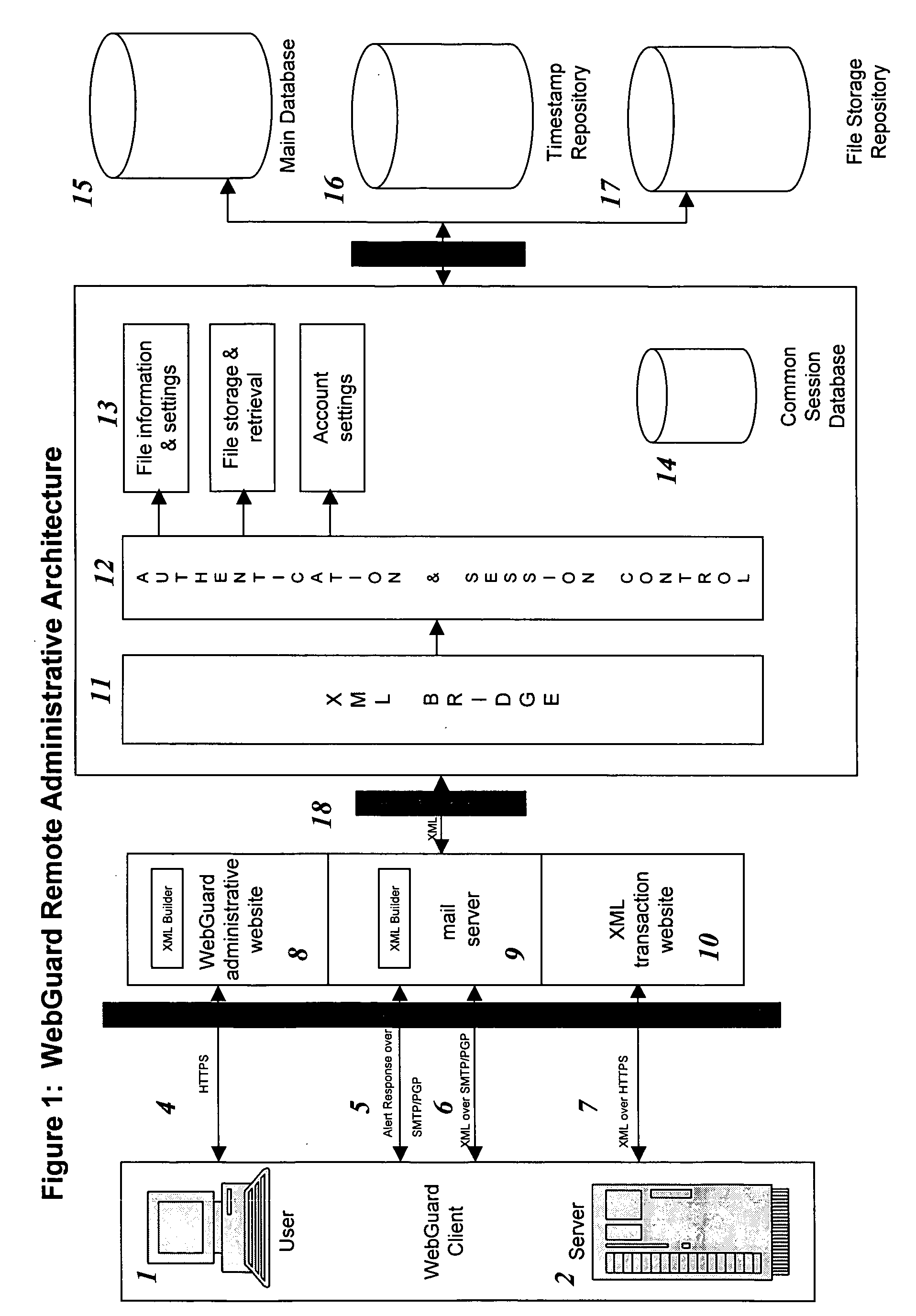
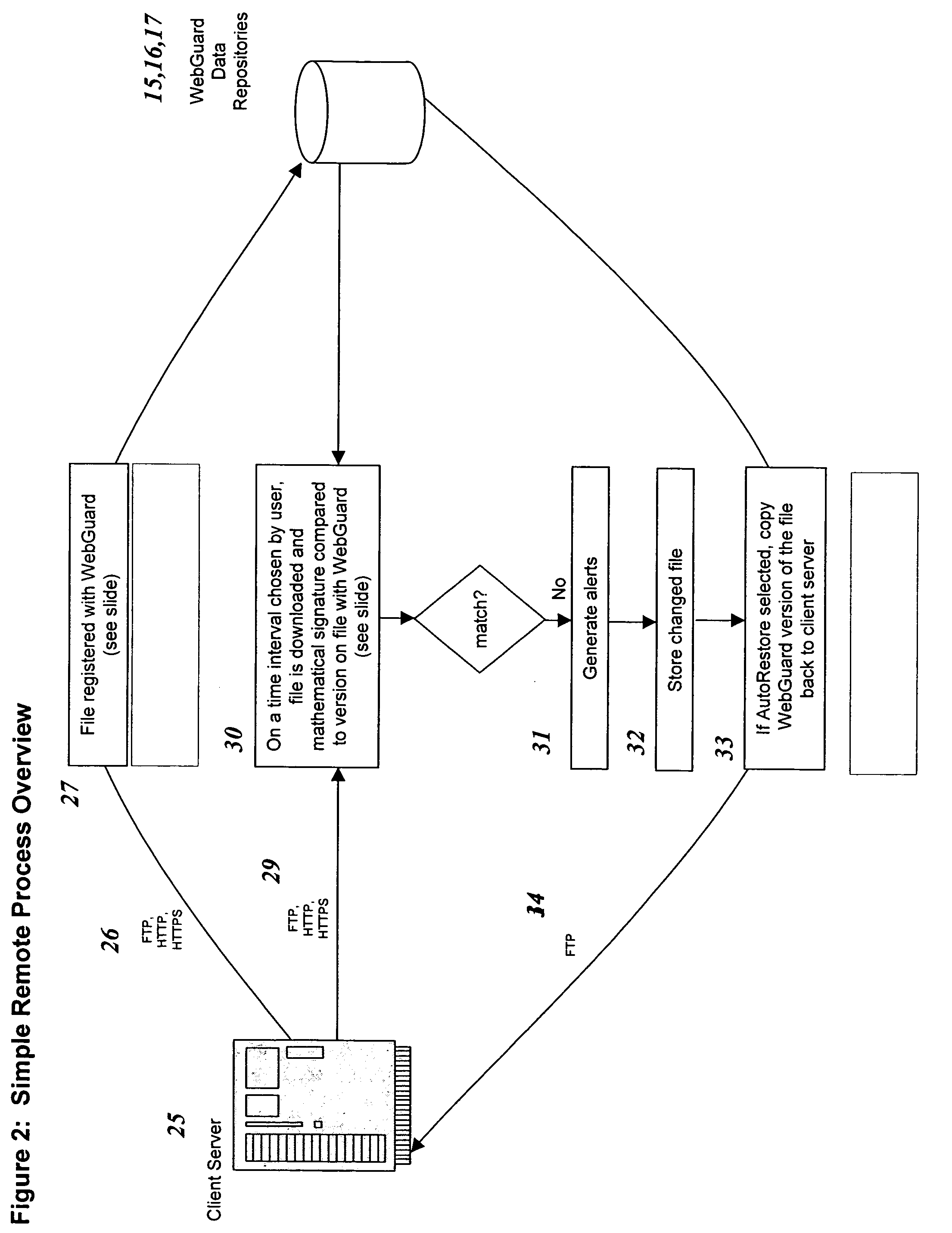
Remote web site security system
InactiveUS20050114658A1Digital data processing detailsUnauthorized memory use protectionWeb siteDatabase
The invention is a method for monitoring a file in a file security system, including providing a first file representation of a file in which the file is disposed at a first location and first processing the first file representation to provide first signals in accordance with the first file representation. The first signals are stored in a central repository disposed at a second location wherein the second location is remote from the first location. A second file representation of the file is provided wherein the file is disposed at a third location remote from the second location. Second processing of the second file representation is performed to provide second signals in accordance with the second file representation. The first signals are accessed from the central repository and the first signals are compared with the second signals. A status of the file is determined in accordance with the comparing.
Owner:SHORE VENTURE GROUP
Authentication of identification documents
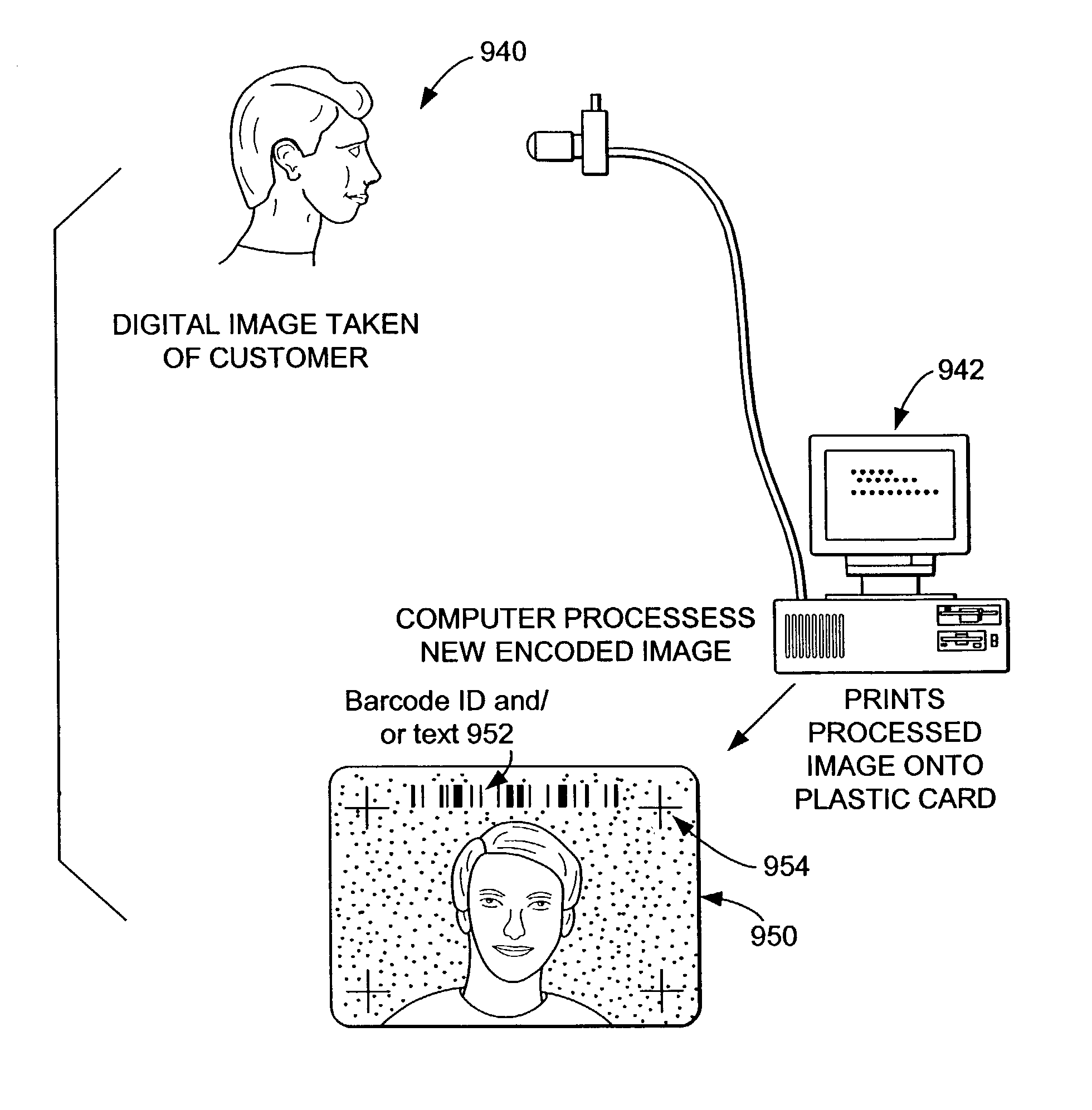
InactiveUS7016516B2Commercial value is not compromisedMaximization of identification signal energyTelevision system detailsDigital data processing detailsDocumentationComputer science
Security of photographic identification documents is enhanced by providing machine-readable information that may be correlated to other information pertaining to the individual represented by the image, such other information being, for example, printed on the document adjacent to the photograph.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
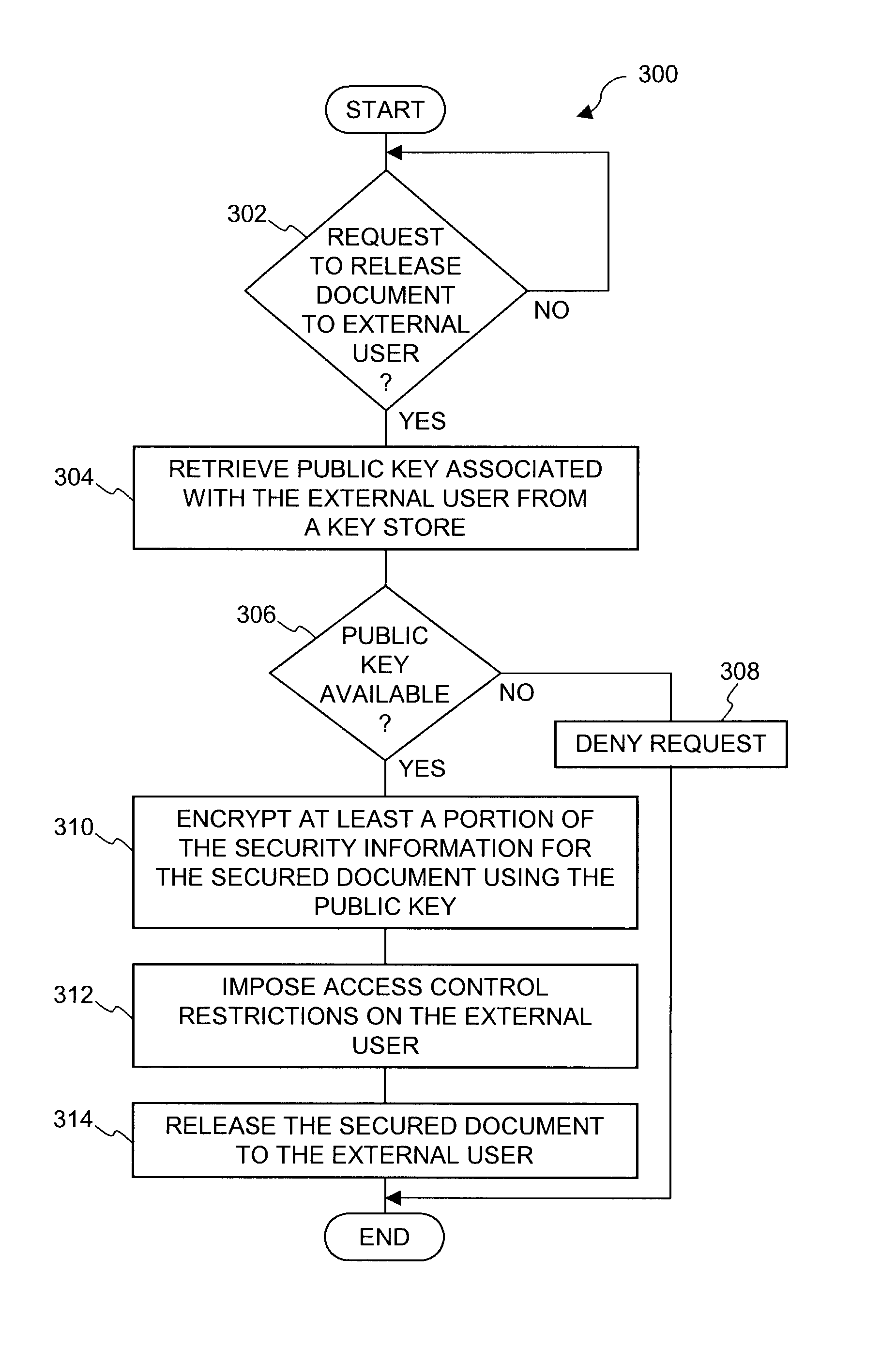
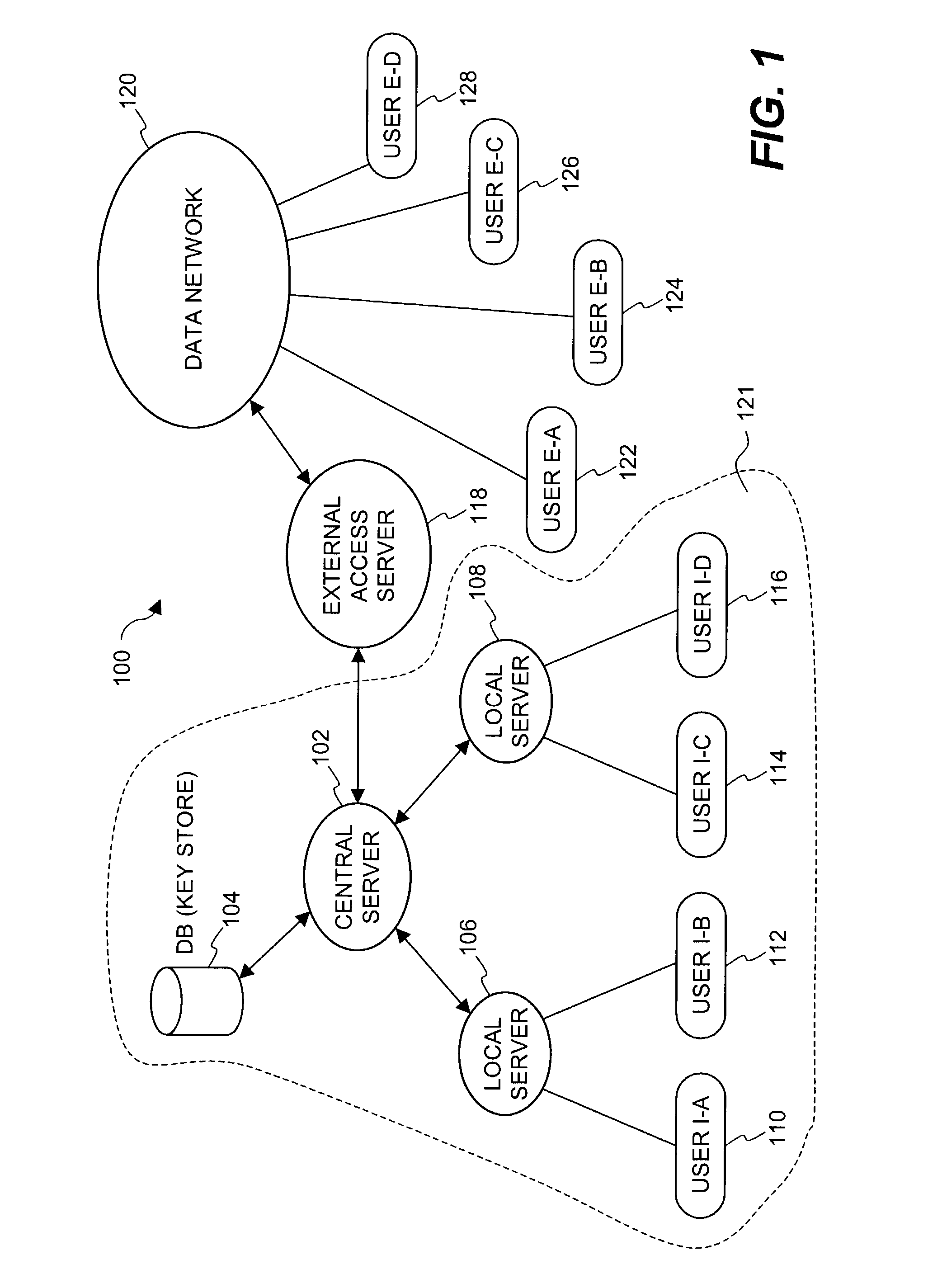
Document Security Management System
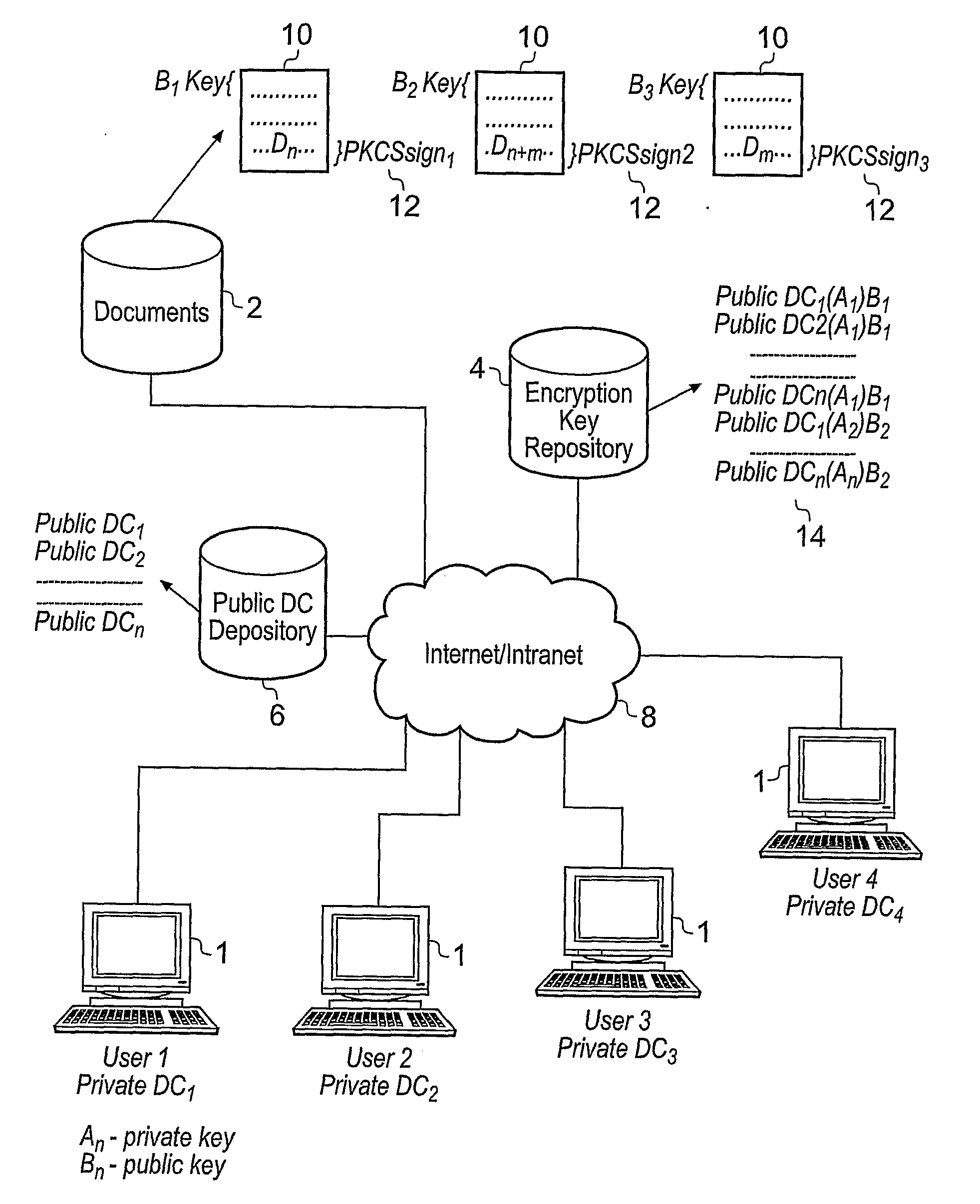
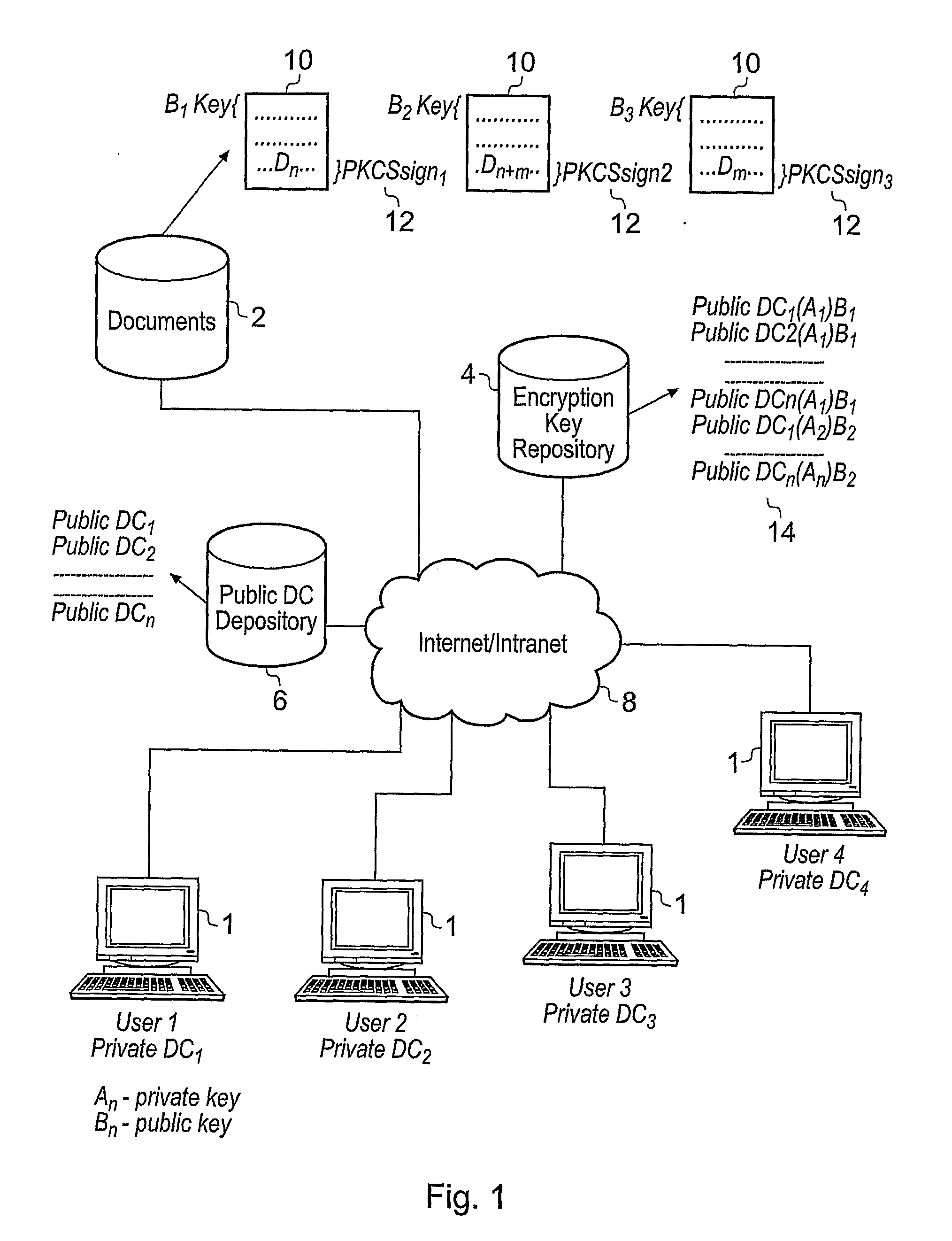
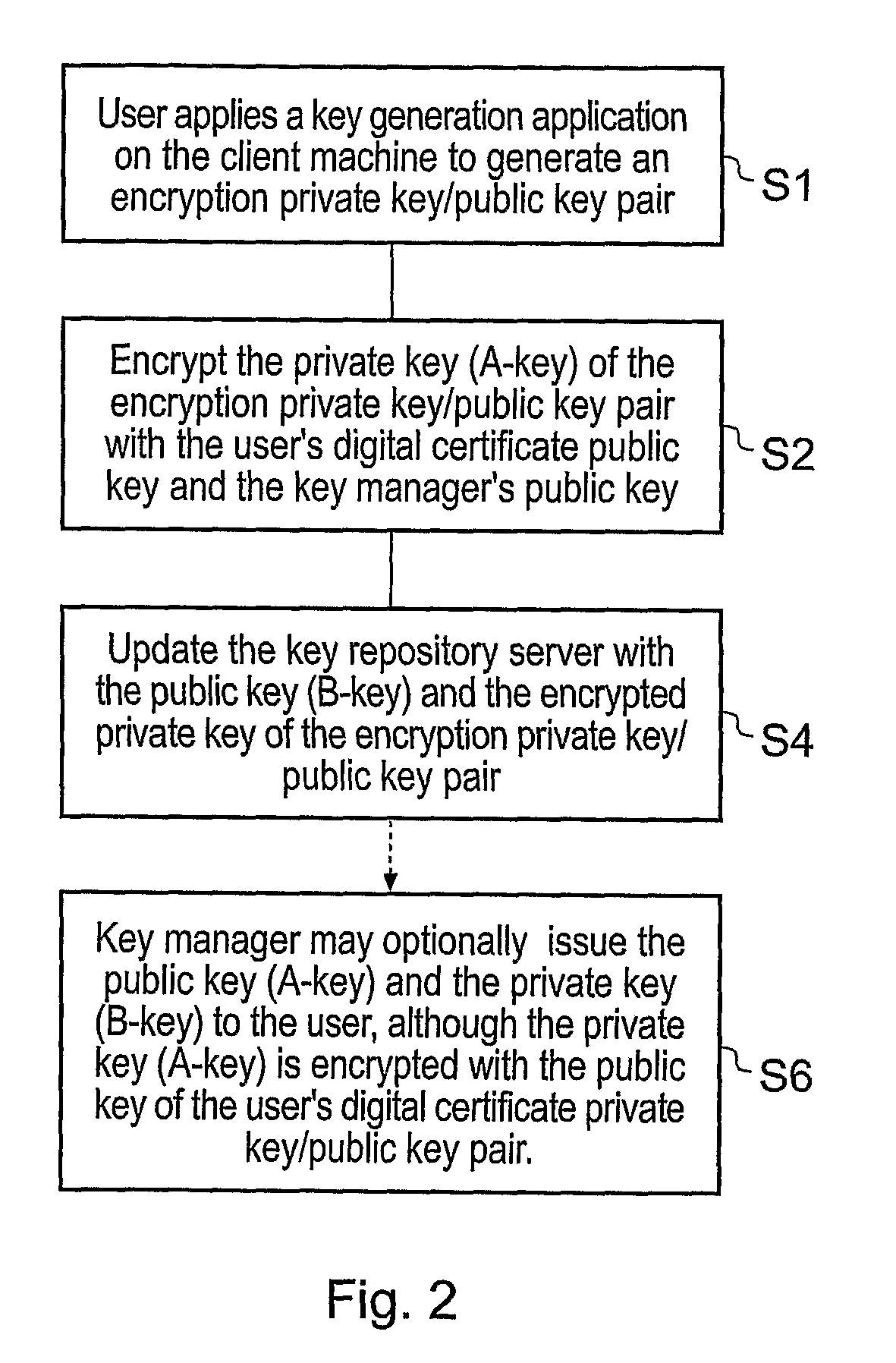
InactiveUS20100217987A1Maintain securityImprove securityUser identity/authority verificationUnauthorized memory use protectionData fileComputer terminal
A document security management system for securely managing documents for users. The document management system comprises a document repository providing a facility for storing data files representing the documents. A key repository stores a public key of one or more encryption key pairs, each of the encryption key pairs being associated with one of the documents stored in the document repository. Each document stored in the document repository is encrypted with the public key of the encryption key pair associated with the document. A plurality of client terminals are operable to store and to retrieve the documents from the documentary repository for processing by a user. Each user is in possession of a digital certificate comprising a certificate key pair. The key repository includes the private key of the encryption key pair encrypted with the public key of the certificate key pair associated with the user. The client terminal is operable with the private key of the certificate key pair in possession of a user. The client terminal is operable to decrypt the private key of the encryption key pair using the private key of the certificate key pair of a user, and to retrieve the encrypted document from the document repository and to decrypt the document using the decrypted private key of the encryption key pair. Thus, in accordance with the present invention a two tier arrangement of private key / public key pairs is provided with a first private key / public key pair called the encryption key pair being associated with each of the documents and a second digital certificate private key / public key pair called a certificate key pair being associated with the users. A document management system according to the present invention is therefore provided with an improvement in security with respect to document management and document management security.
Owner:SHEVADE RAVINDRA WAMAN
Digital authentication with analog documents
InactiveUS7043052B2Easy to recordEfficient and reliableTelevision system detailsDigital data processing detailsPhoto imageAuthentication
Owner:DIGIMARC CORP
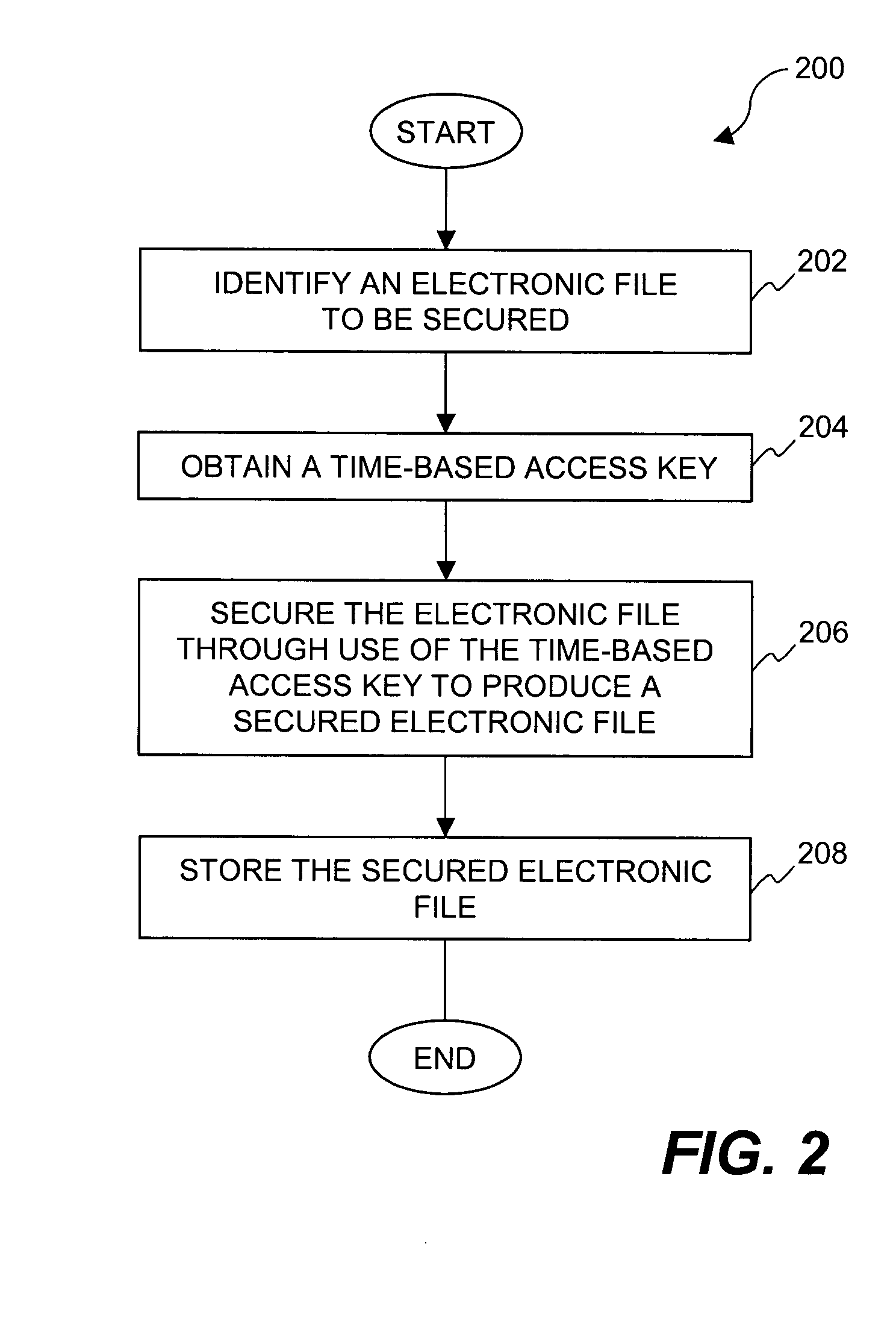
Method and system for securing digital assets using time-based security criteria
InactiveUS20050071657A1Key distribution for secure communicationUser identity/authority verificationSecurity systemSafety standards
Techniques for utilizing time-based security criteria in a file security system are disclosed. At least a portion of the security criteria can have a time associated therewith (i.e., time-based security criteria) that serves as a time-based restriction on the ability to gain access to electronic files. If the time-based restriction is not satisfied, then the associated security criteria is not made available and thus access to a secured electronic file is prevented. In other words, access restrictions on electronic files can be dependent on the time at which access to the electronic files is attempted. The security criteria can pertain to keys (or ciphers) used by the file security system to secure (e.g., encrypt) electronic files to be secured, or to unsecure (e.g., decrypt) electronic files already secured.
Owner:GUARDIAN DATA STORAGE
Web based data collaboration tool
A web based data collaboration tool includes a dynamic international collaborative environment in which system partners, including customers, technology partners and suppliers, can exchange information between one another in a truly collaborative environment. The web based data collaboration tool includes unique “fine grain” security at both the document and sub-document level. This allows one source document to be shared between the system partners, including partners from different companies and those located in different countries, based upon an individual document / sub-document security profile. Further, the web based data collaboration tool includes a secure “Sandbox” for peer-to-peer sharing of sensitive documents and electronically incorporates a business area export representative (BAER) approval process that includes the required retention of International Traffic in Arms Regulations (ITAR) documents making the web based data collaboration tool fully ITAR compliant.
Owner:UNITED TECH CORP
Document security management for repeatedly reproduced hardcopy and electronic documents
InactiveUS20050171914A1Digital data protectionSecret communicationElectronic documentImage formation
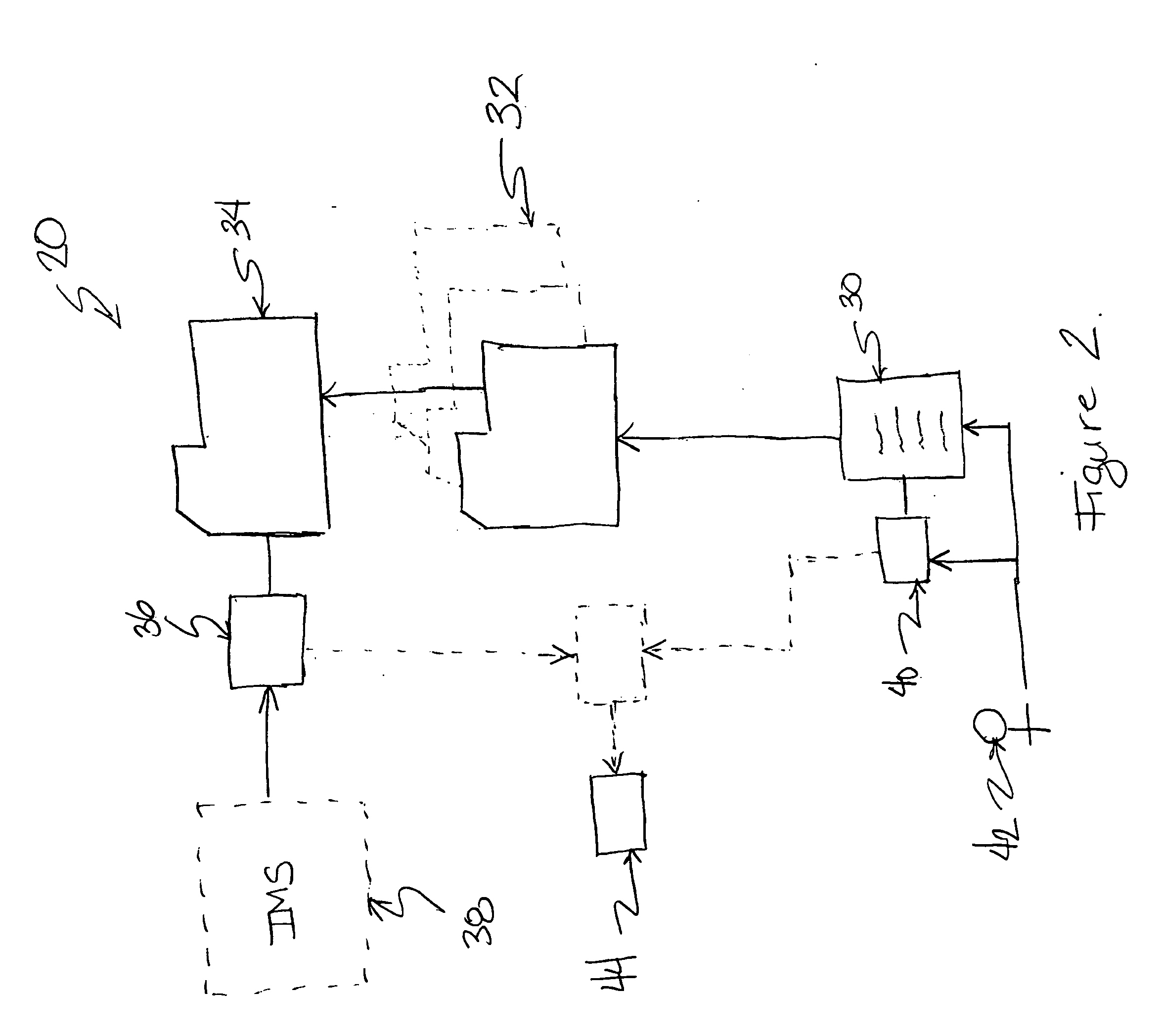
In a document security management method for controlling document security across multiple domains, a domain ID is extracted from a document to be processed at an image forming and reproducing apparatus placed in a first domain. Then, it is determined at a first security server of the first domain whether the document to be processed is controlled in the first domain, based on the extracted domain ID. If the document to be processed is not controlled in the first domain, location information about a second domain that controls the document to be processed is acquired. Then, the image forming and reproducing apparatus accesses a second security server provided in the second domain to confirm permissibility of the processing of the document.
Owner:RICOH KK
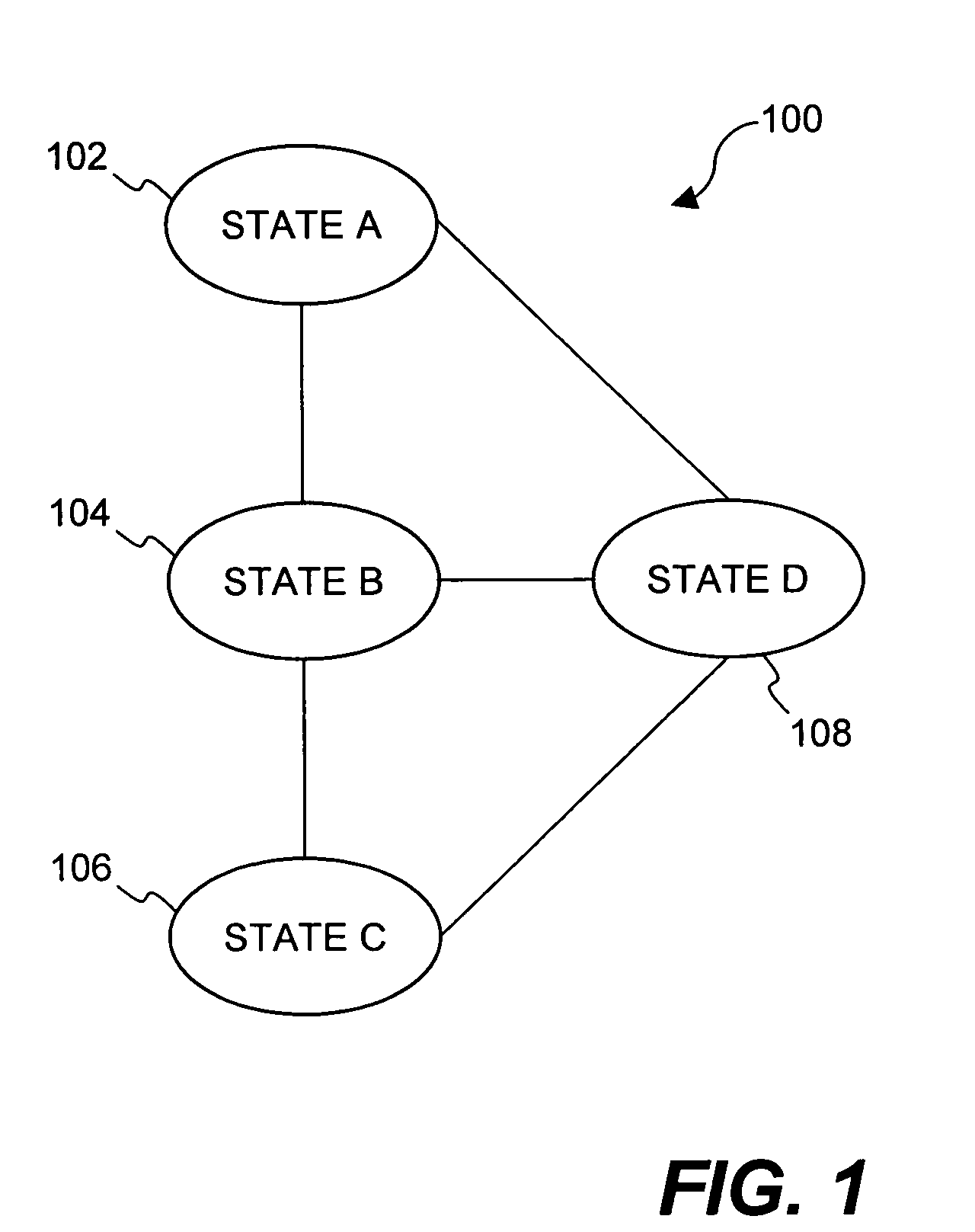
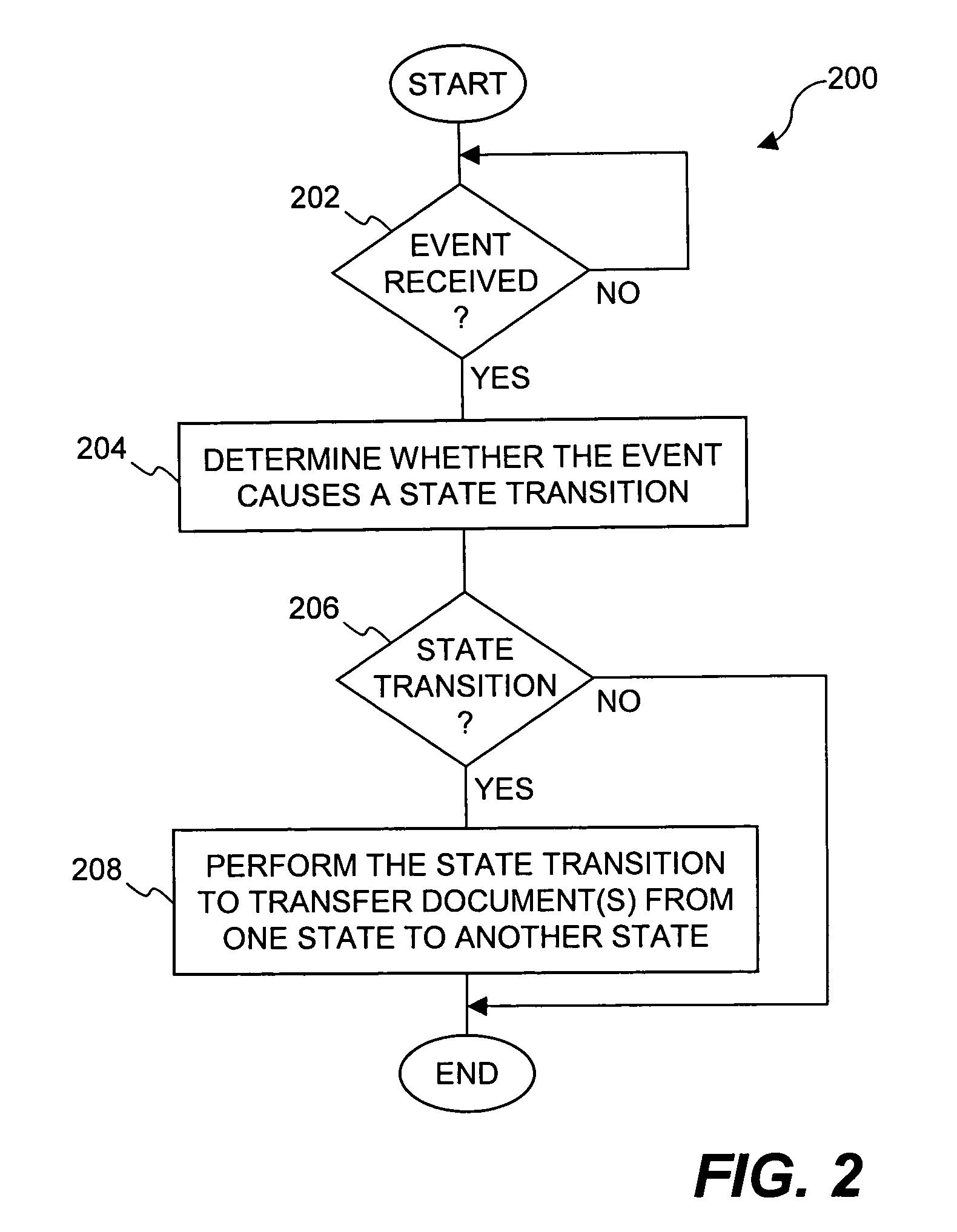
Method and apparatus for transitioning between states of security policies used to secure electronic documents
ActiveUS20050071275A1More burdensomeGood flexibilityKey distribution for secure communicationDigital data processing detailsElectronic documentSecurity policy
Techniques for dynamically altering security criteria used in a file security system are disclosed. The security criteria pertains to keys (or ciphers) used by the file security system to encrypt electronic files to be secured or to decrypt electronic files already secured. The security criteria can, among other things, include keys that are required to gain access to electronic files. Here, the keys can be changed automatically as electronic files transition between different states of a process-driven security policy. The dynamic alteration of security criteria enhances the flexibility and robustness of the security system. In other words, access restrictions on electronic files can be dependent on the state of the process-driven security policy and enforced in conjunction with one or more cryptographic methods.
Owner:INTELLECTUAL VENTURES I LLC
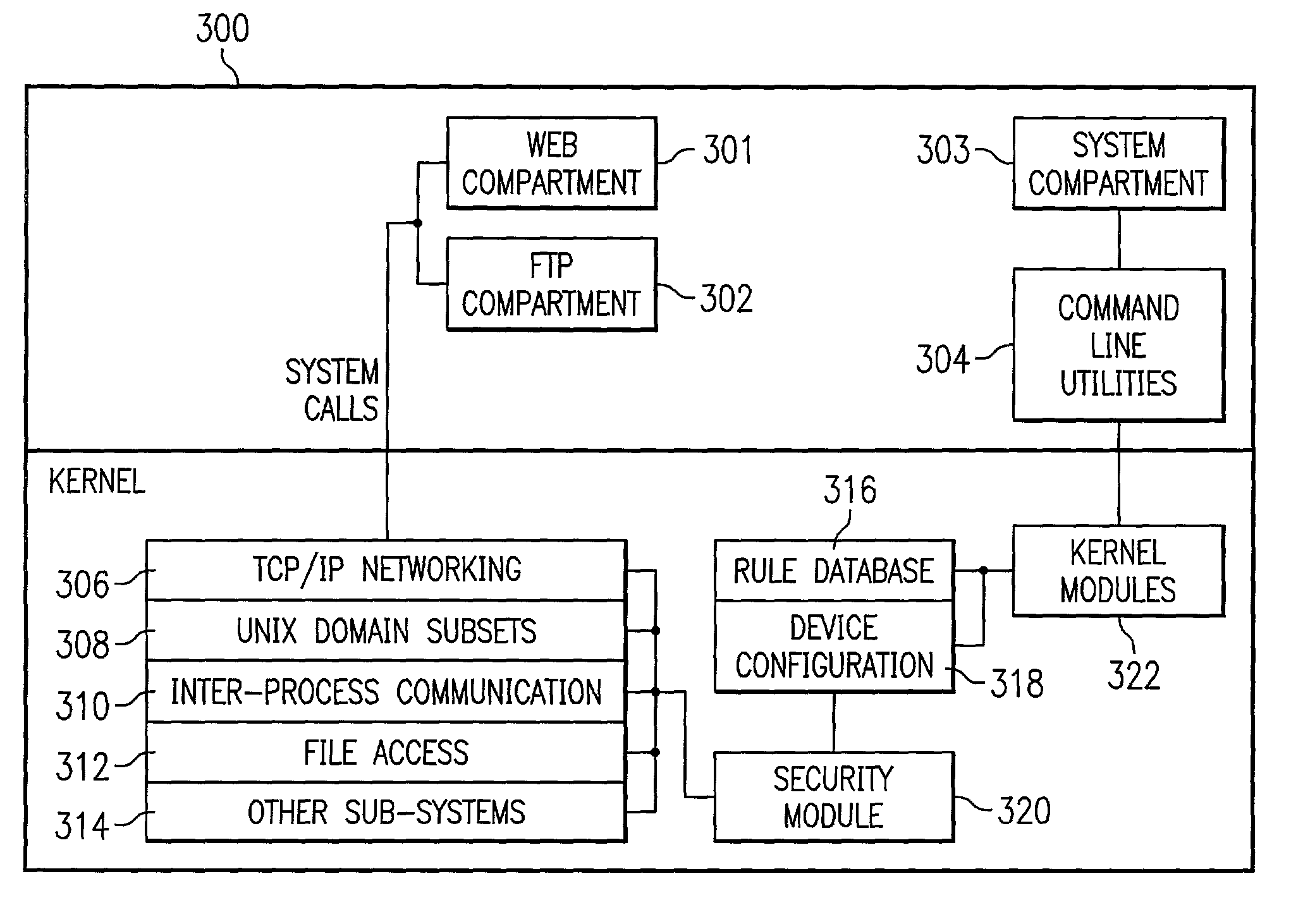
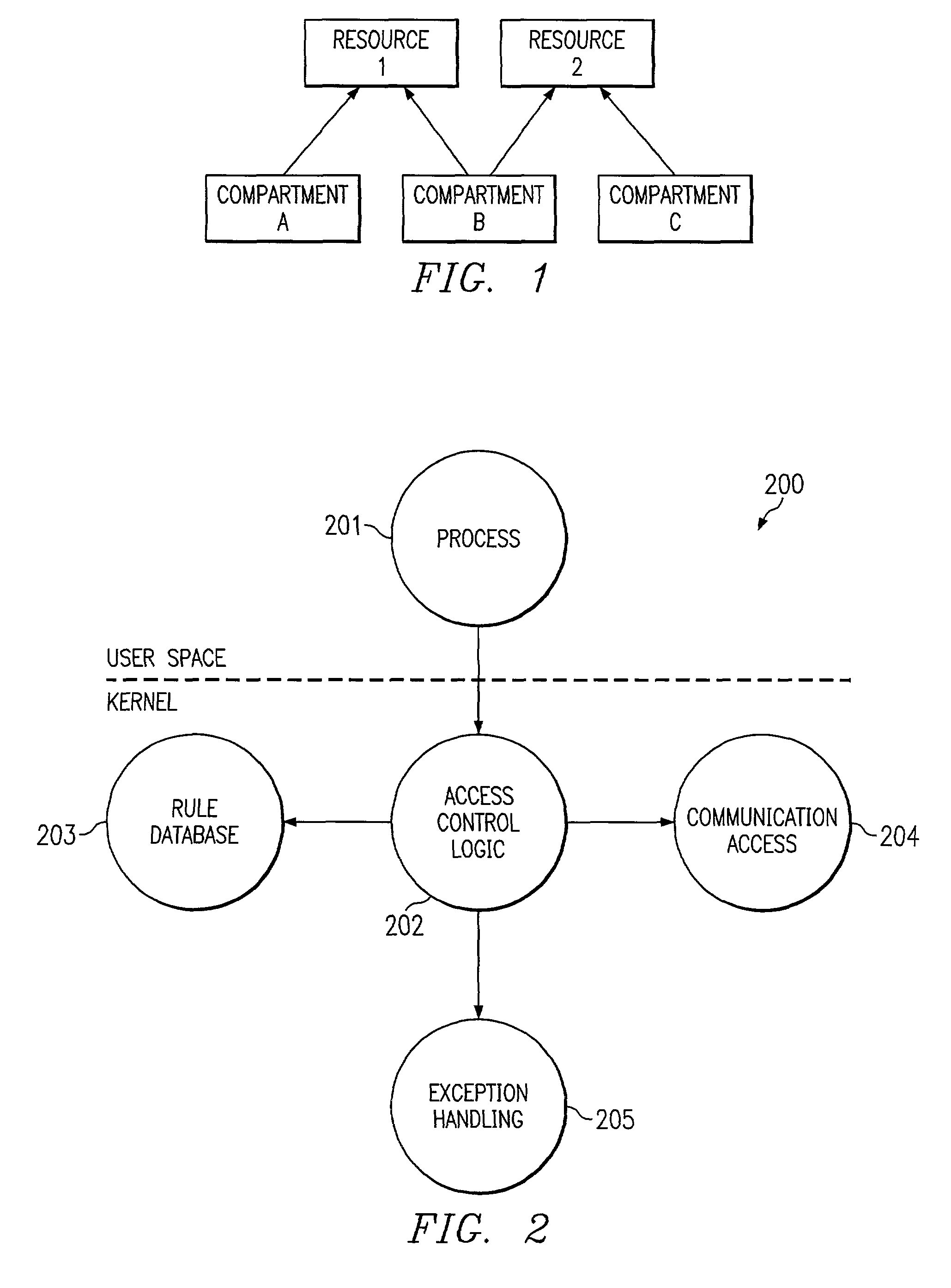
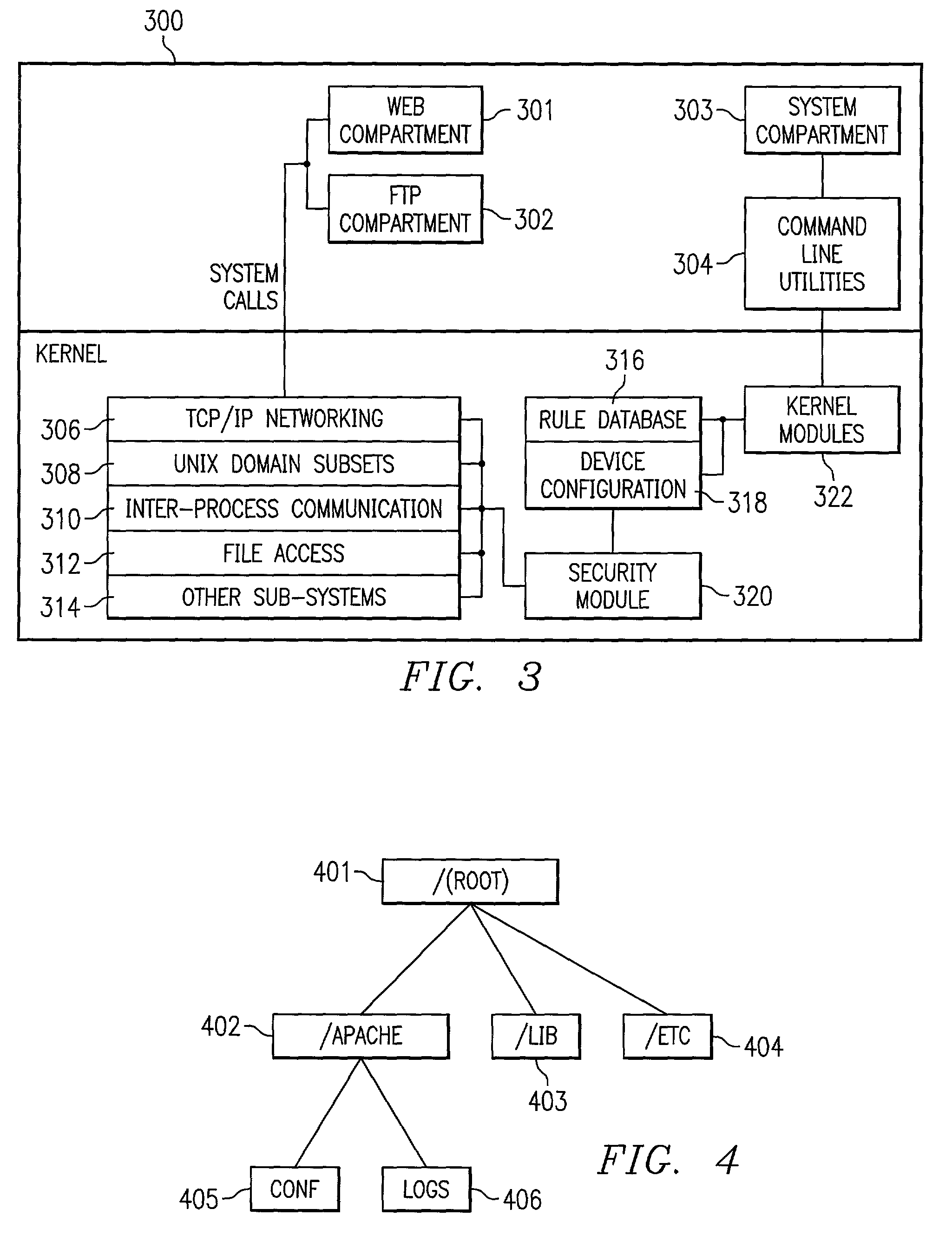
System and method for file system mandatory access control
InactiveUS7962950B2Digital data processing detailsAnalogue secracy/subscription systemsOperational systemFile system
In one embodiment, the present invention is related to a computer system including compartments implemented on an operating system. A database contains access rules with the access rules defining which compartments are authorized to access particular file resources. A kernel module receives a system call to access a file from a user space application belonging to a compartment. A security module determines whether the user space application is authorized to access the file utilizing access rules stored in the database.
Owner:MICRO FOCUS LLC
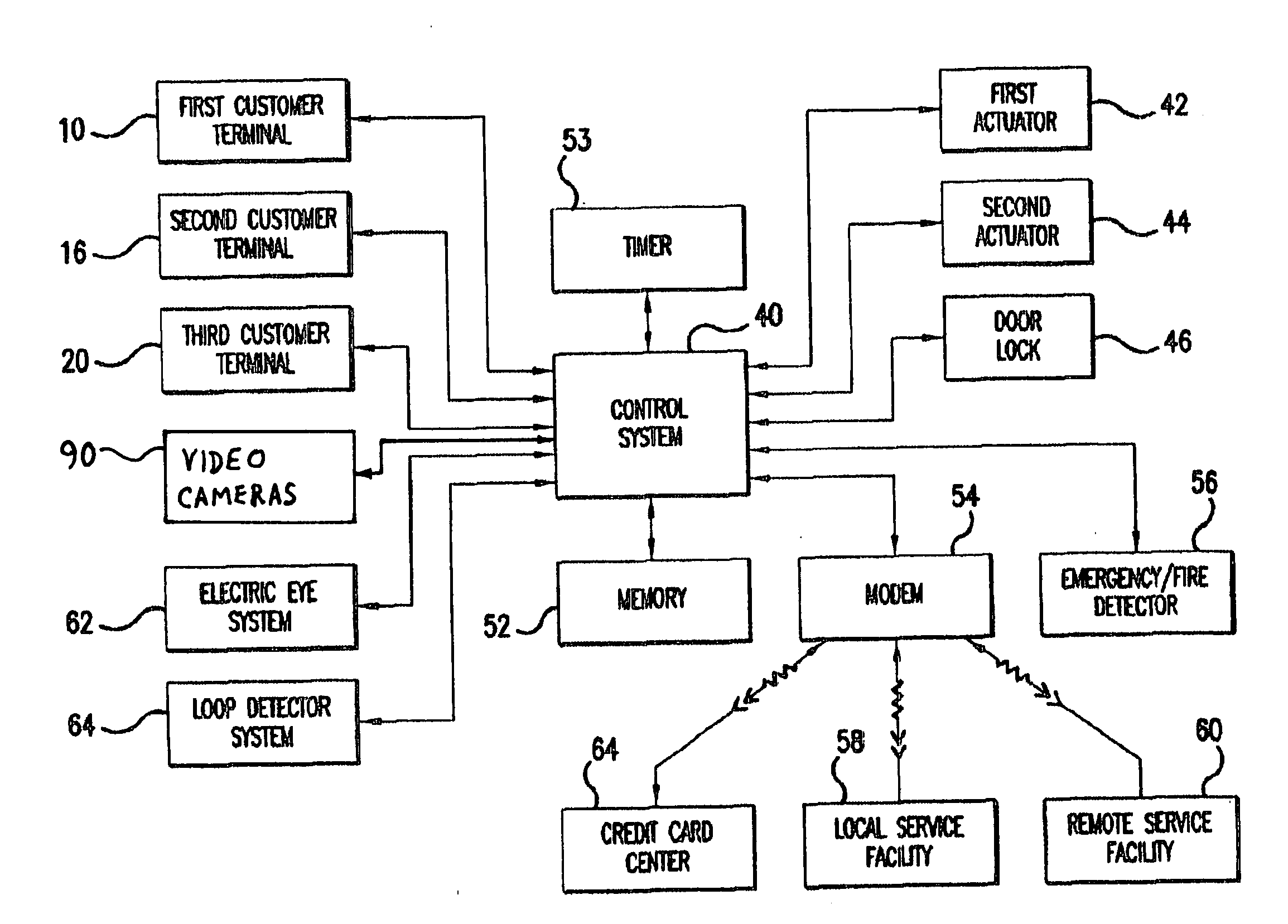
Management and control system for a designated functional space having at least one portal
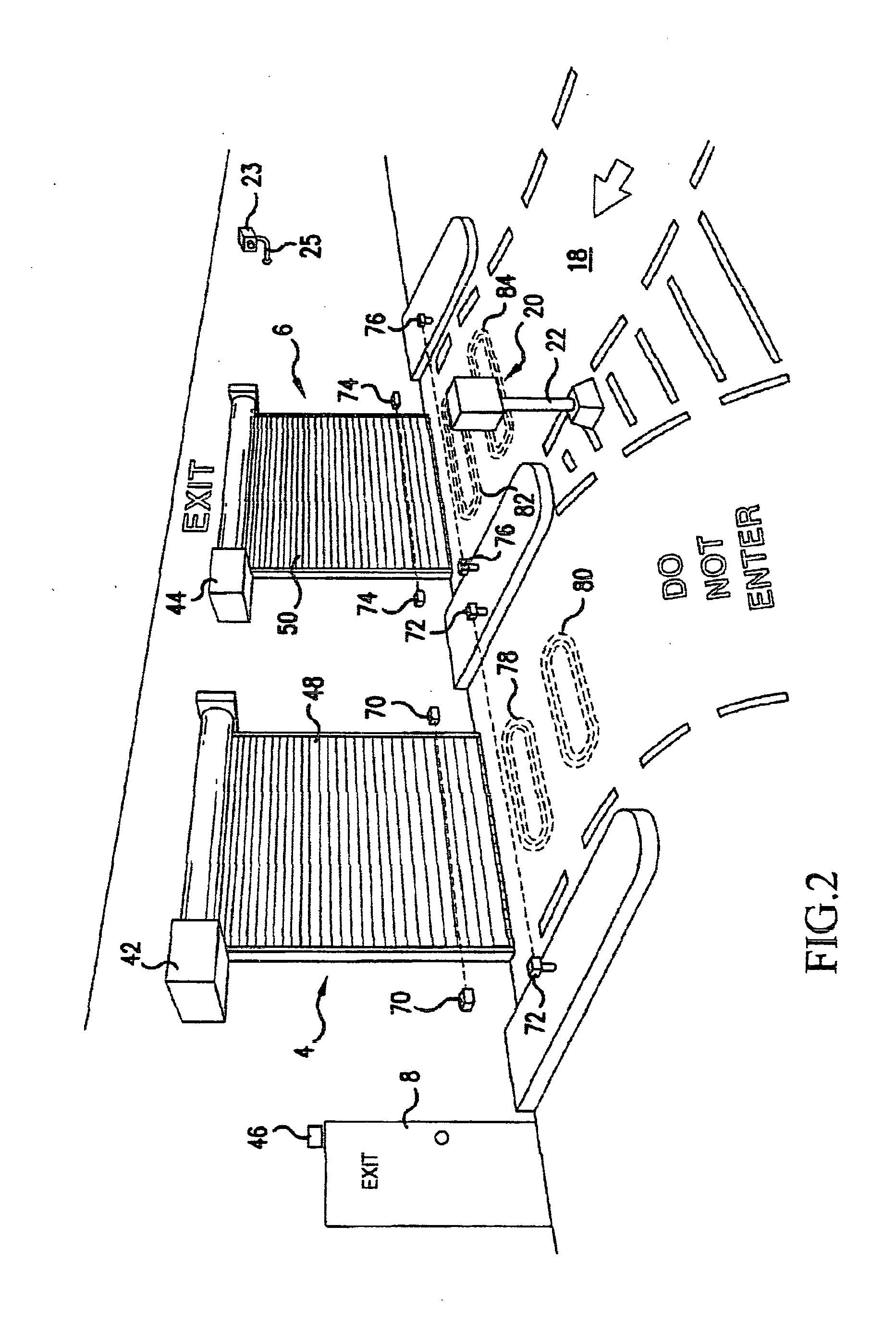
InactiveUS20110313893A1Accurate assessmentEliminate human errorTicket-issuing apparatusDigital data processing detailsDocumentation procedureCard reader
A control and management system for defined areas such as loading docks, fire stations, and other designated defined areas, employs a card reader, vehicle sensing loop detectors and electric eyes, entrance door sensors and operators, truck securement devices, cameras, a control system with memory, and a wireless connection or internet / intranet connection, is provided to produce event log documentation. The event information is readily accessible by management or supervisory personnel, to see all of the recorded information concerning a specified event. Thus, an event can be readily reconstructed after the fact, using all available sensors and other information relevant to a manager or supervisor. This aids in locating lost packages, documents security procedures, preventing or detecting thefts and vandalism, and for other purposes. An alert can be issued whenever an abnormal or unauthorized event occurs during operations. A QR code reader can be provided for a cell phone with picture-taking capability, which communicates with the system to enable a person carrying the cell phone to scan QR codes at specified locations or on specified items or vehicles.
Owner:WEIK III MARTIN HERMAN
Systems and method for secure delivery of files to authorized recipients
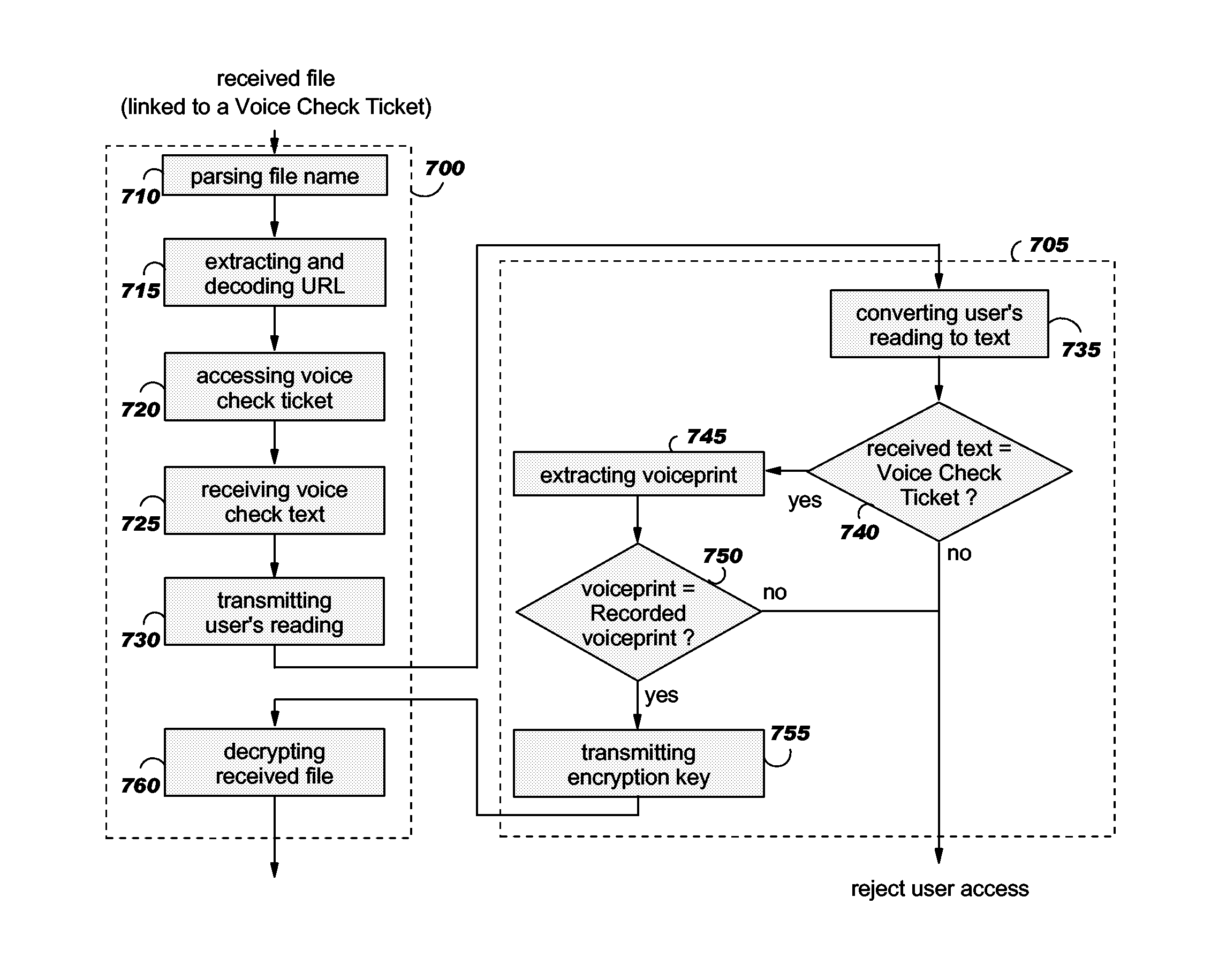
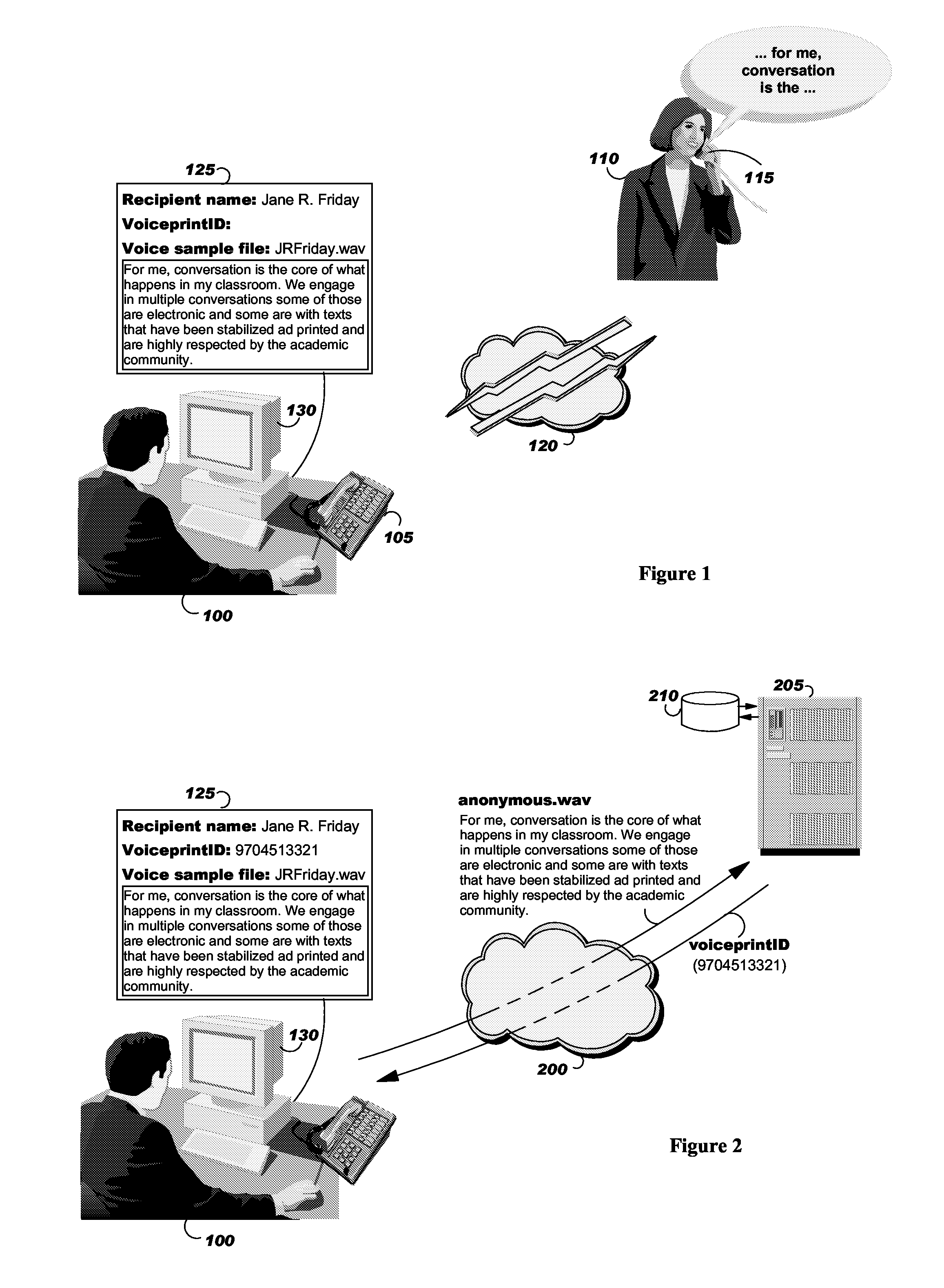
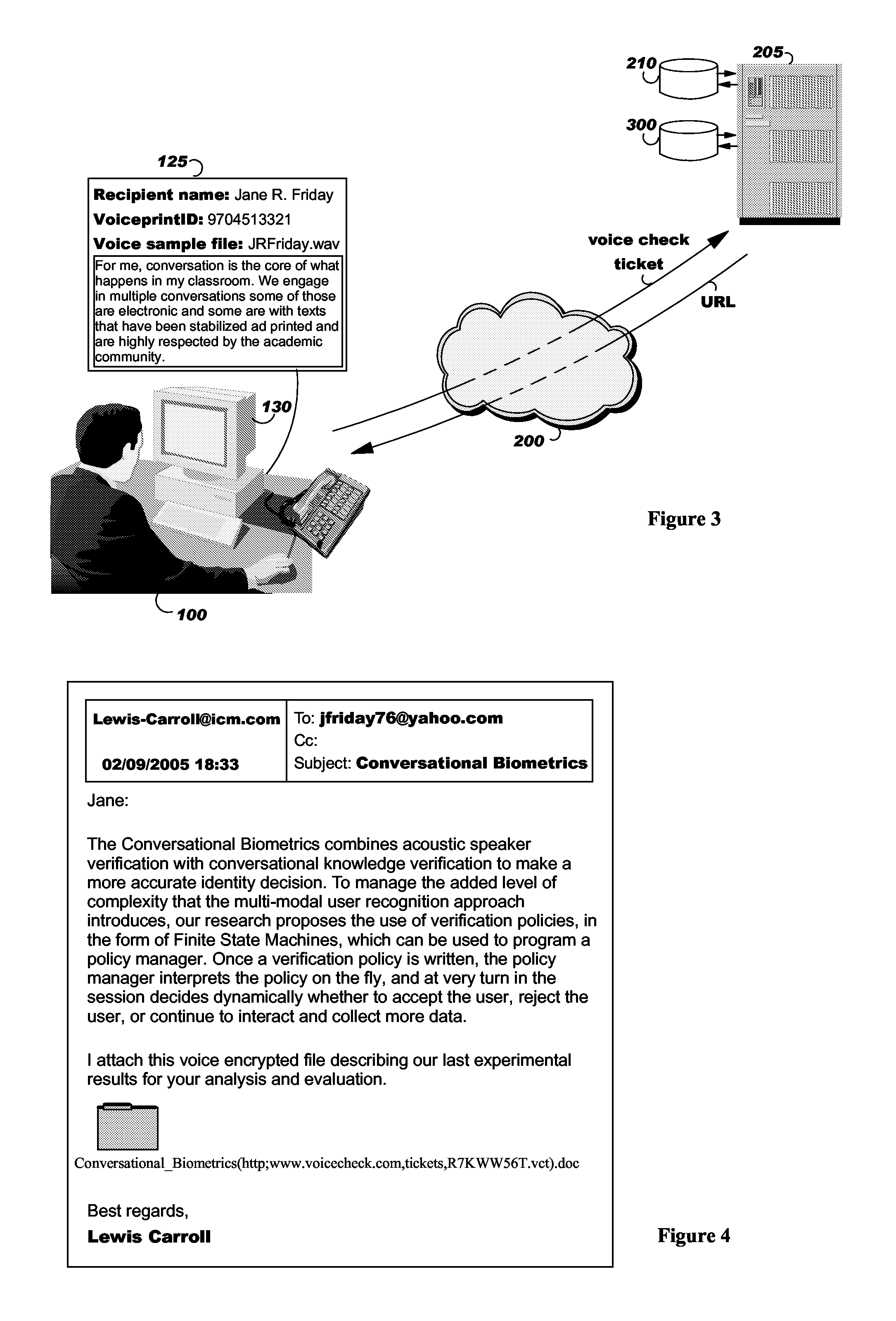
ActiveUS20100281254A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationUniform resource locatorAutomatic speech
By asking the recipient of an encrypted received file to read aloud a check text, retrieved from a network server, that address, or URL, is encoded within the file name of the encrypted received file, the system of the invention automatically verifies the identity of the recipient, confirms that the file has been received by the intended recipient, and then decrypts the file. The utterances of text spoken by the recipient are processed by means of an automatic speech recognition component. The system determines whether the spoken text corresponds to the check text presented to the reader, in which case the system applies an automatic speaker recognition algorithm to determine whether the person reciting the check text has voice characteristics matching those of the intended recipient based on a previous enrollment of the intended recipient's voice to the system. When the system confirms the identity of the recipient, the decryption key is transmitted and the encrypted received file is automatically decrypted and displayed to the recipient. In a preferred embodiment, the system records and marks with a time-stamp the recipient's reciting of the voice check text, so that it can later be compared to the intended recipient's voice if the recipient repudiates reception.
Owner:KYNDRYL INC
Method and system for validating timestamps
ActiveUS20050138383A1Minimizing per-transmission network overheadHigh time accuracyUser identity/authority verificationDigital computer detailsTime rangeTimestamp
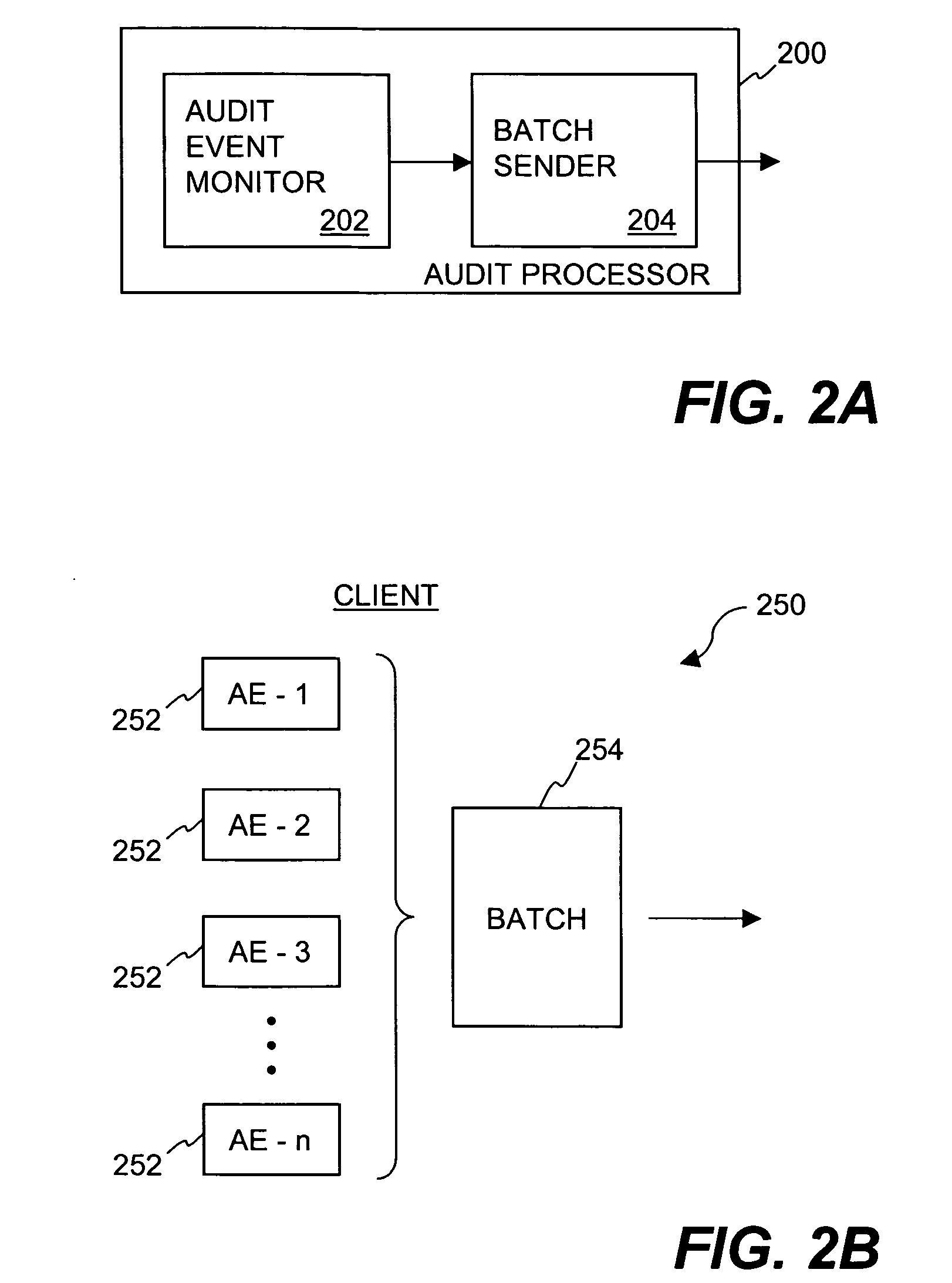
Improved techniques for validating timestamps used in a client-server environment are disclosed. A client can associate client-provided timestamps with events that occur at the client. The client can then send event information as well as the timestamps to a server. Preferably, the event information and timestamps are sent in a batch pertaining to a plurality of events that have occurred at the client. The server, which has greater time accuracy, can then validate the client-provided timestamps. The server can also modify the client-provided timestamps so as to improve accuracy of the timestamps. Once modified, the timestamps can pertain to a range (e.g., window) of time during which the associated events can be known to have reliably occurred. In one embodiment, the client-server environment is a distributed file security system in which the events and event information pertain to audit files. The distributed file security system provides efficient and reliable techniques to ensure accuracy of client-provided timestamps.
Owner:INTELLECTUAL VENTURES I LLC
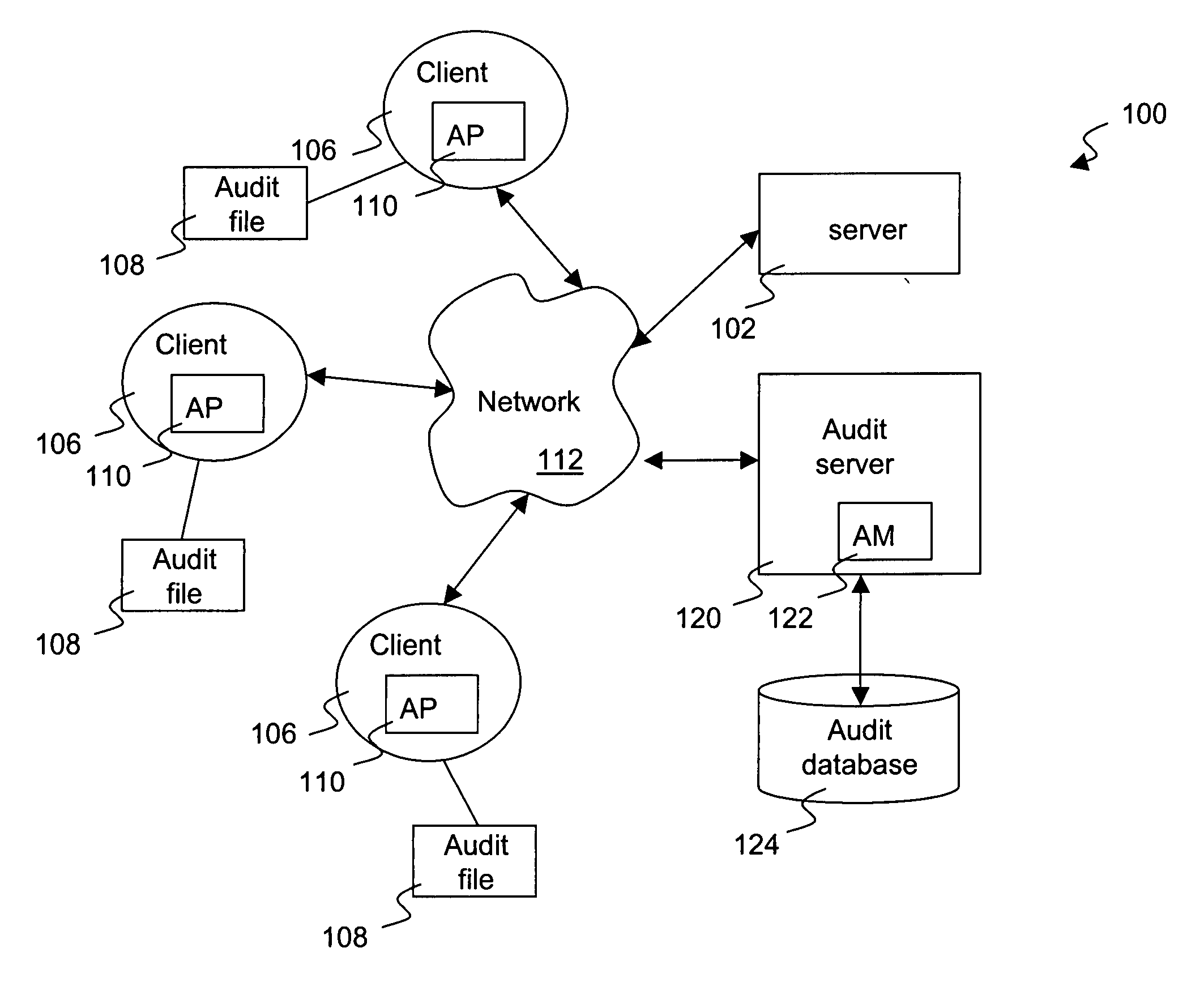
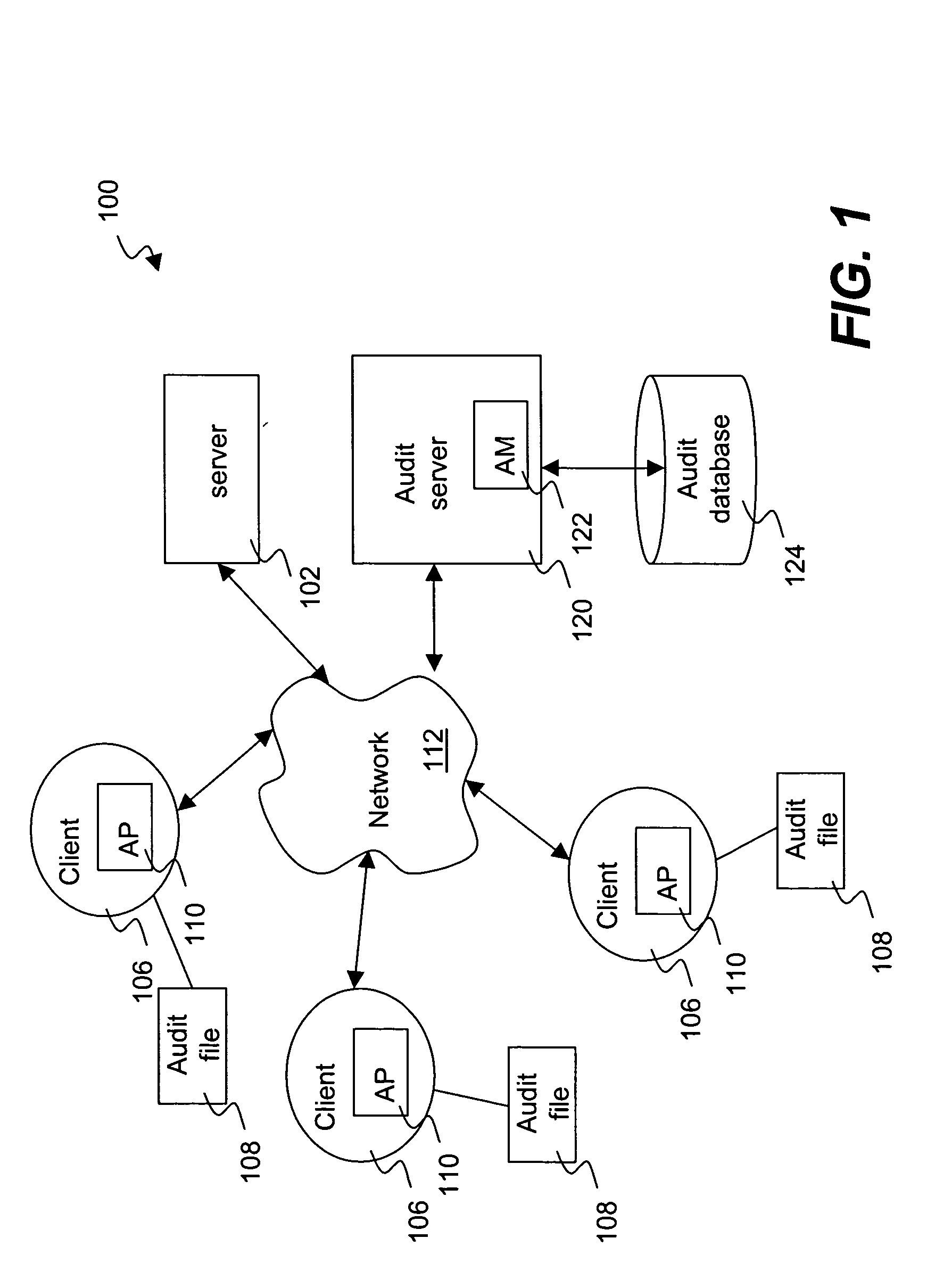
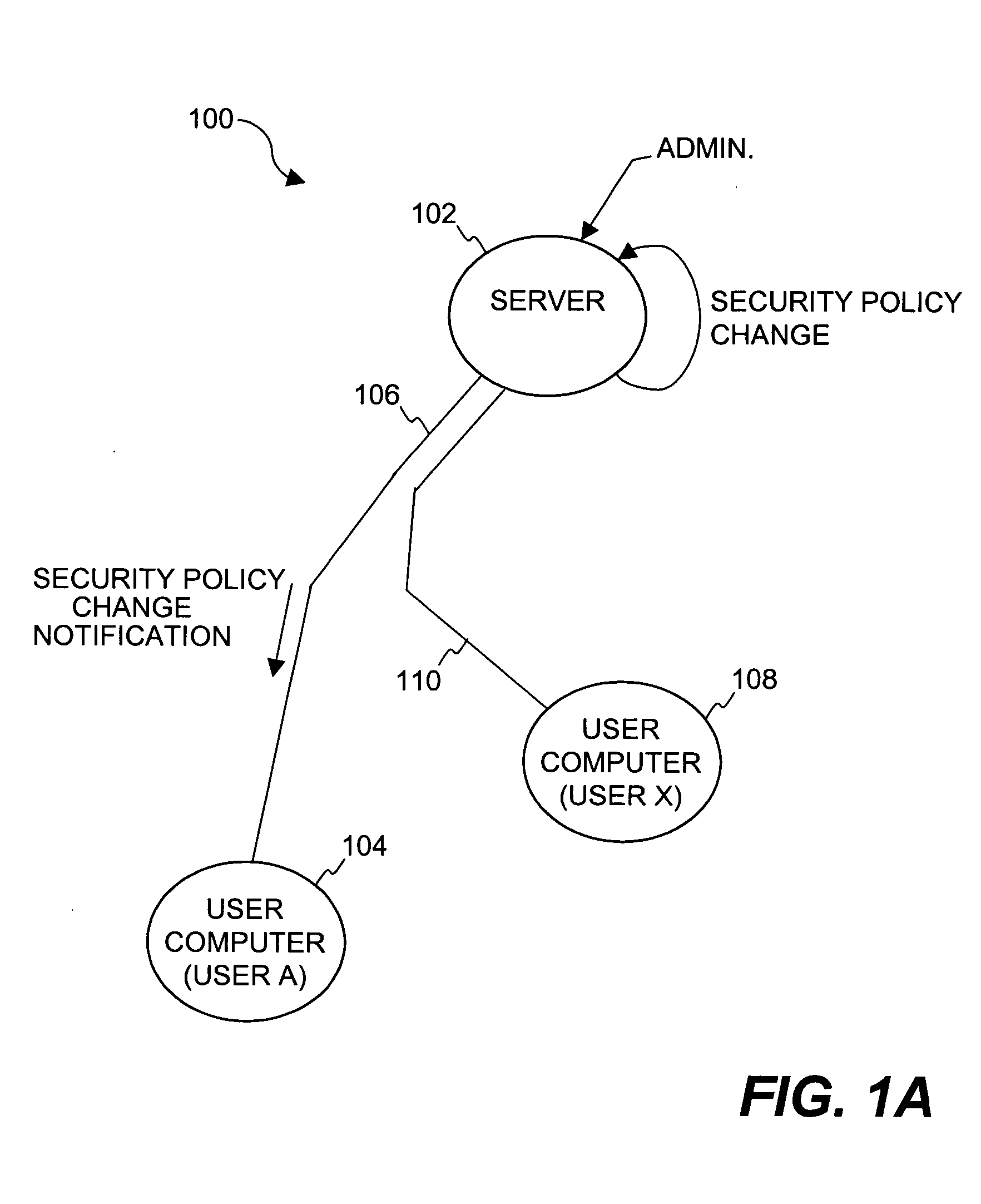
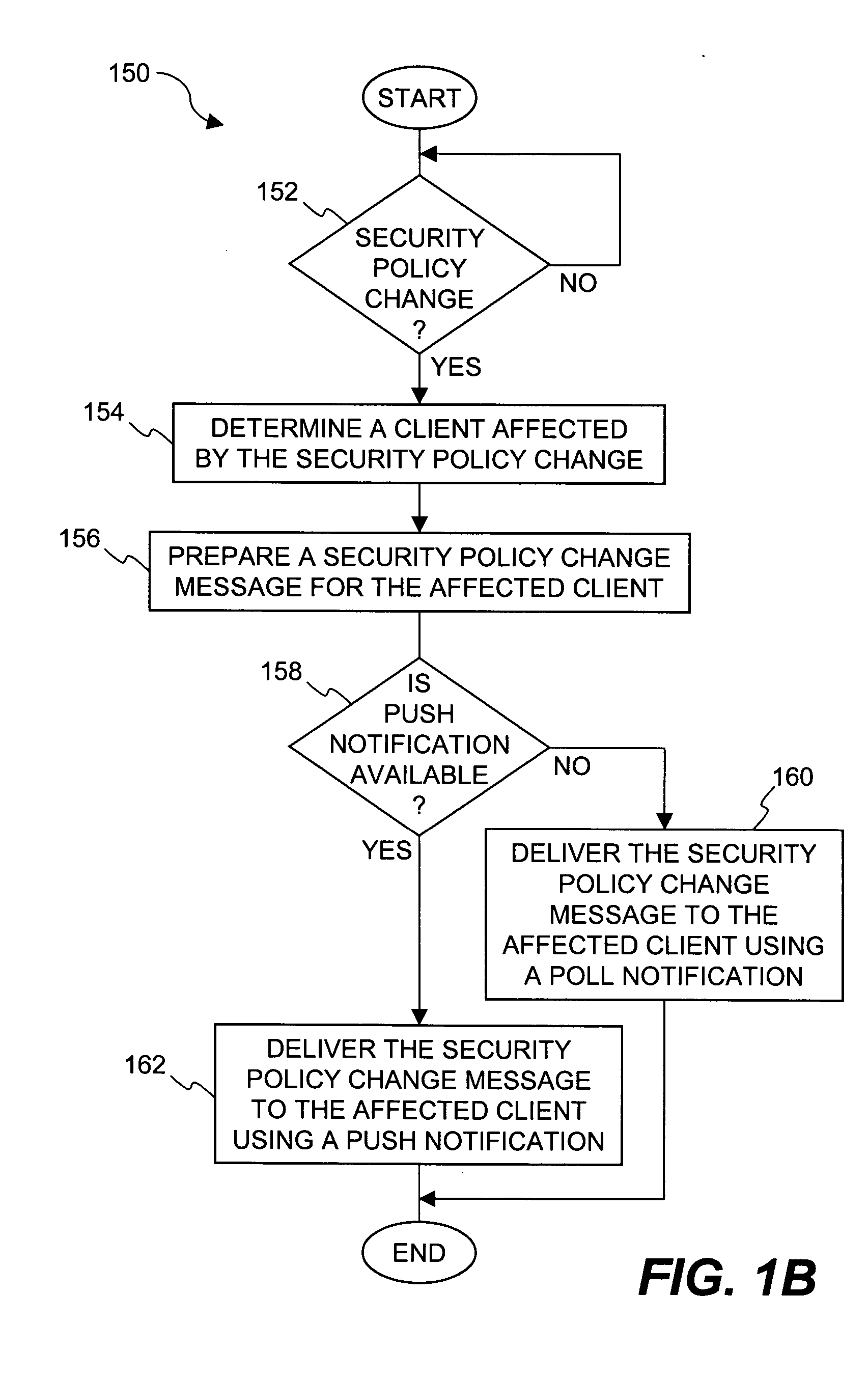
Method and system for distribution of notifications in file security systems
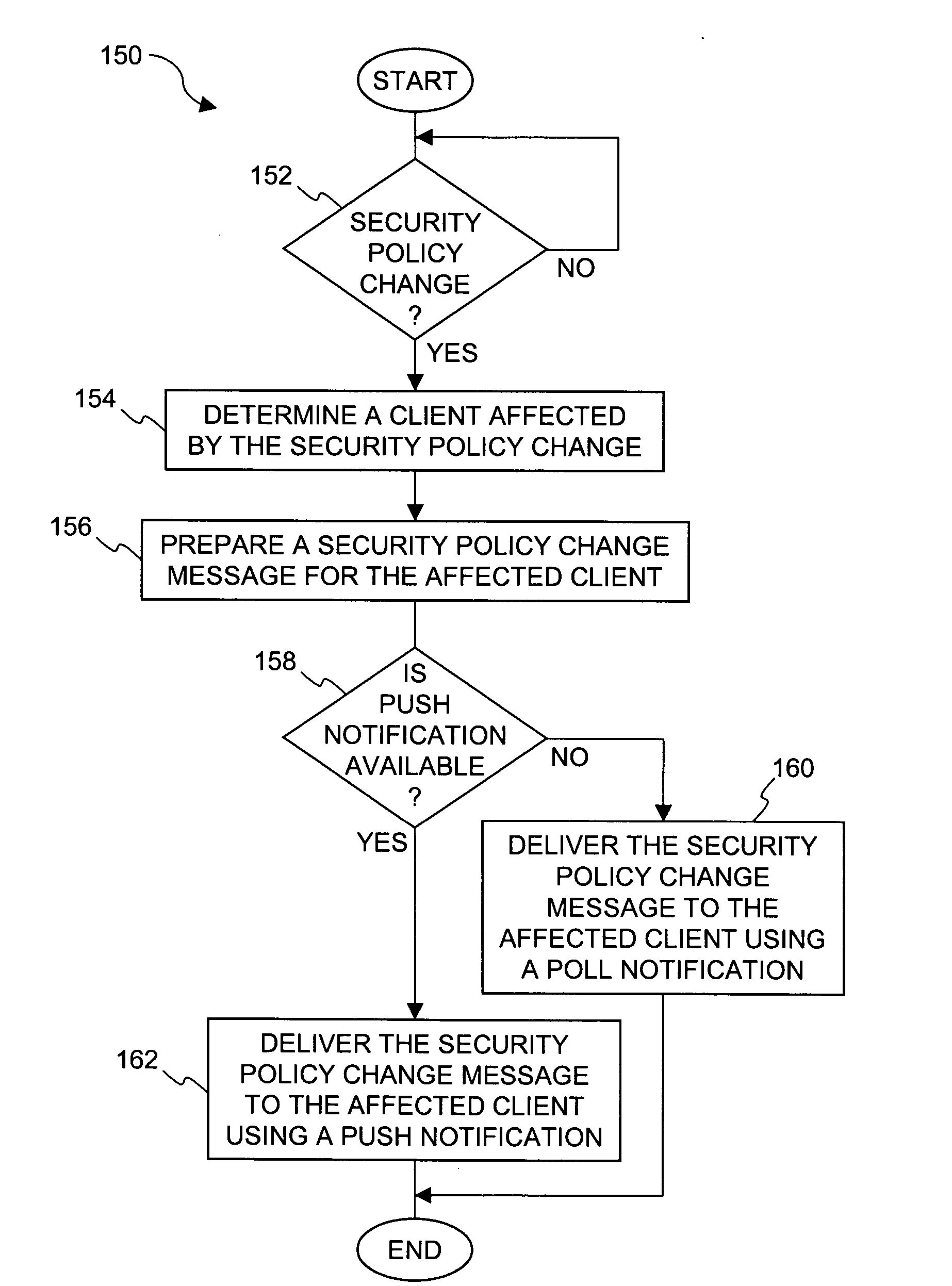
Improved approaches for providing notifications in a distributed file security system are disclosed. The file security system includes a file security server that manages file security for a plurality of clients. When security criteria (e.g., security policies or rules) change at the file security system, typically the clients need to be notified so that they operate in accordance with the correct security criteria. The security criteria impacts whether a particular client (or its user) are able to access certain files being protected by the file security system. A client can be notified in different ways depending on network characteristics. In one embodiment, an appropriate way to perform notifications between the file security server and clients can be automatically determined, thus advantageously minimizing user impact and allowing the system to transparently adapt to different networks.
Owner:INTELLECTUAL VENTURES I LLC
Method and system for proxy approval of security changes for a file security system
InactiveUS20050086531A1Avoid bottlenecksDigital data processing detailsUnauthorized memory use protectionSecurity systemDocument security
A system and method for providing a file security system with an approval process to implement security changes are disclosed. The approval process can be substantially automated as well as configurable and / or flexible. The approval process can make use of a set of approvers that can approve or deny a security change. Different security changes can require the approval of different approvers. The approvers can also be arranged into groups of approvers, and such groups can make use of a hierarchical arrangement.
Owner:INTELLECTUAL VENTURES I LLC
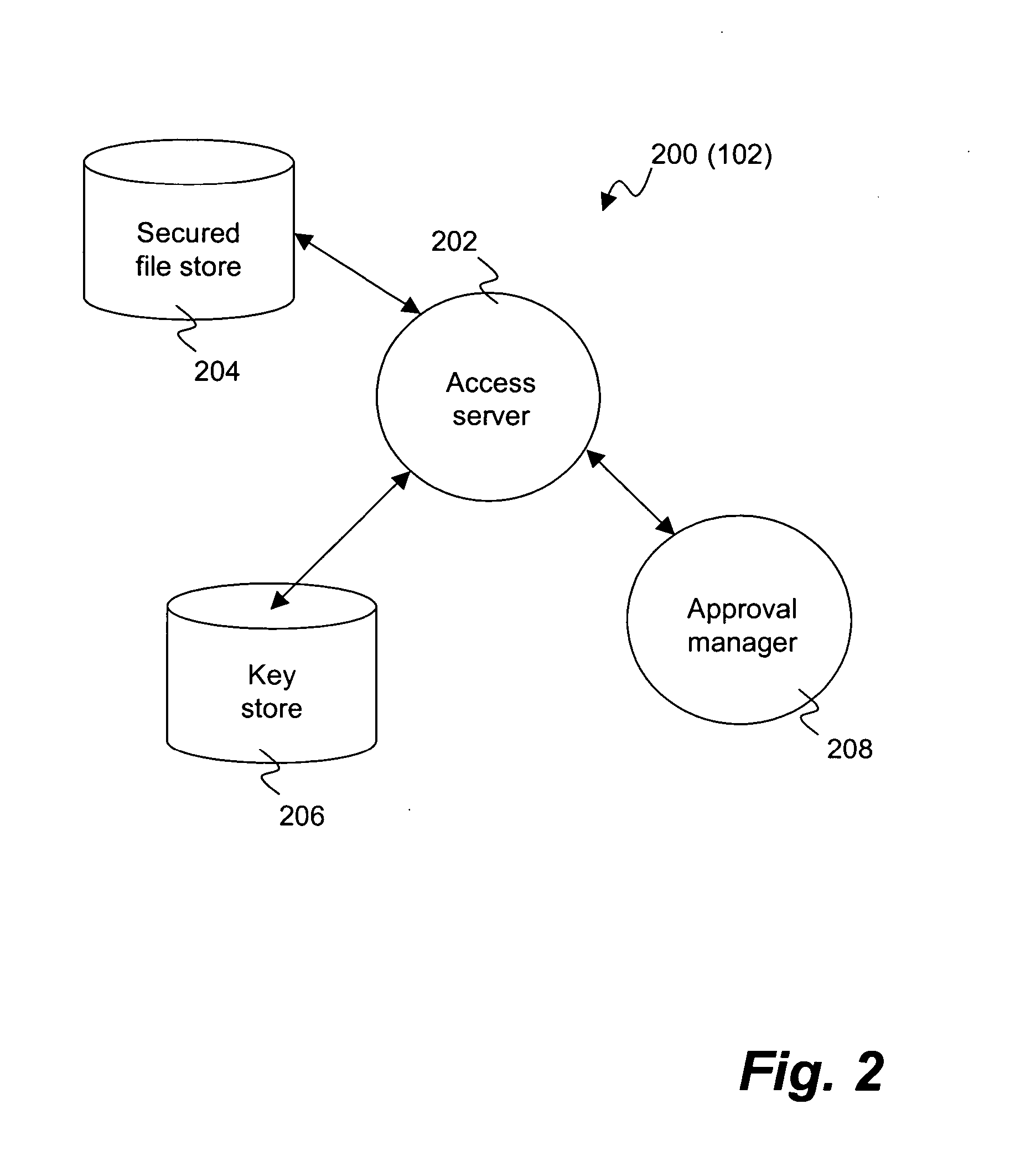
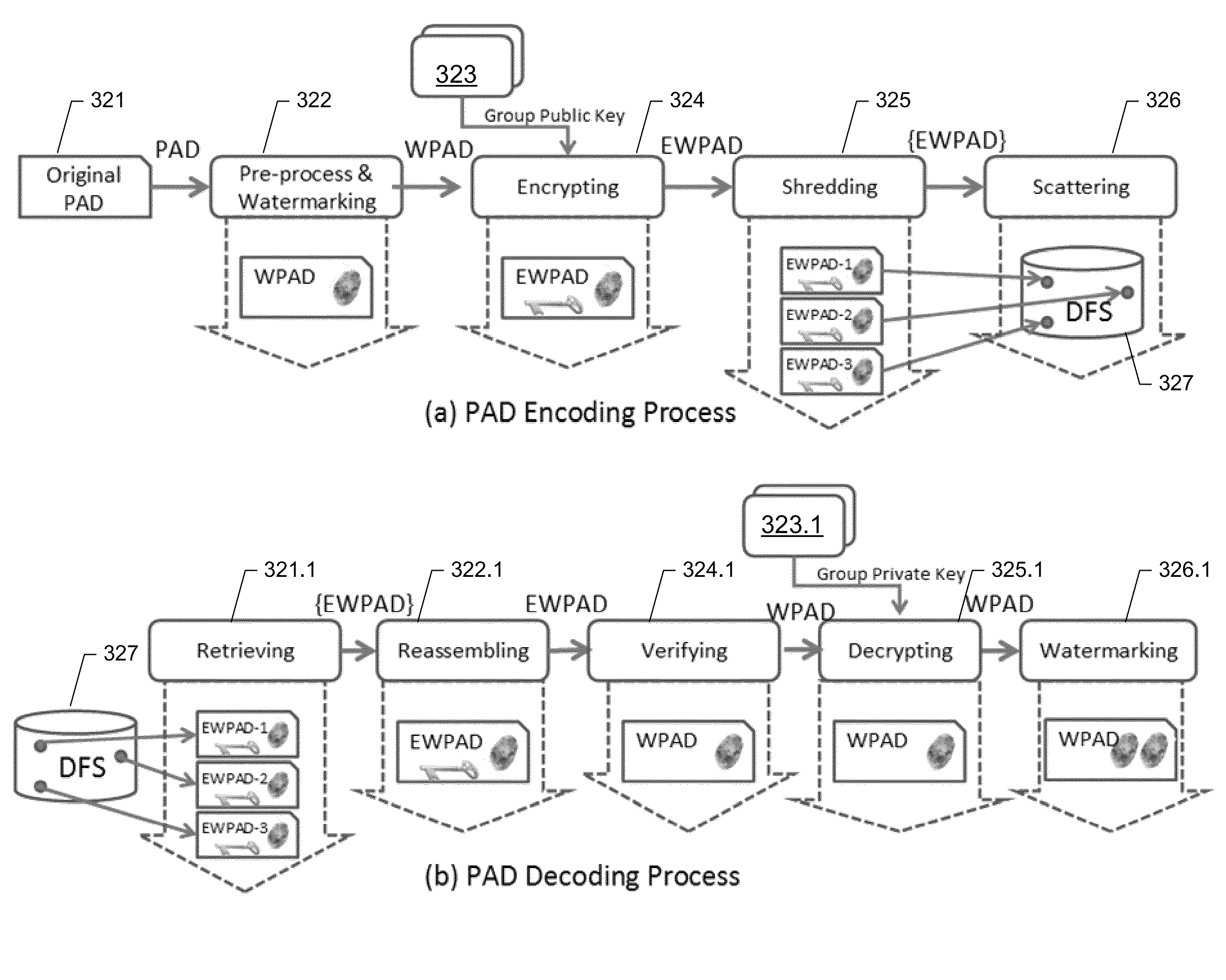
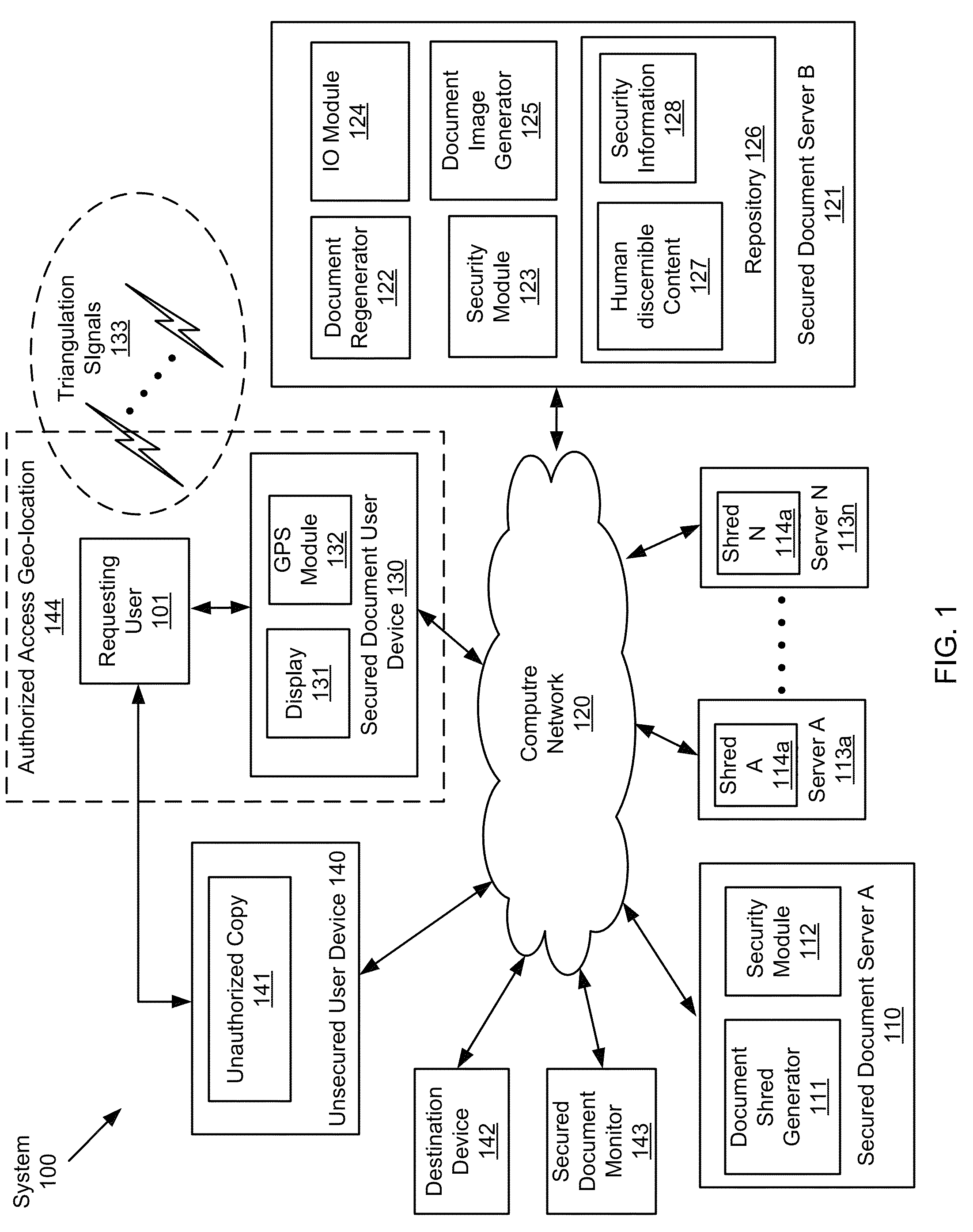
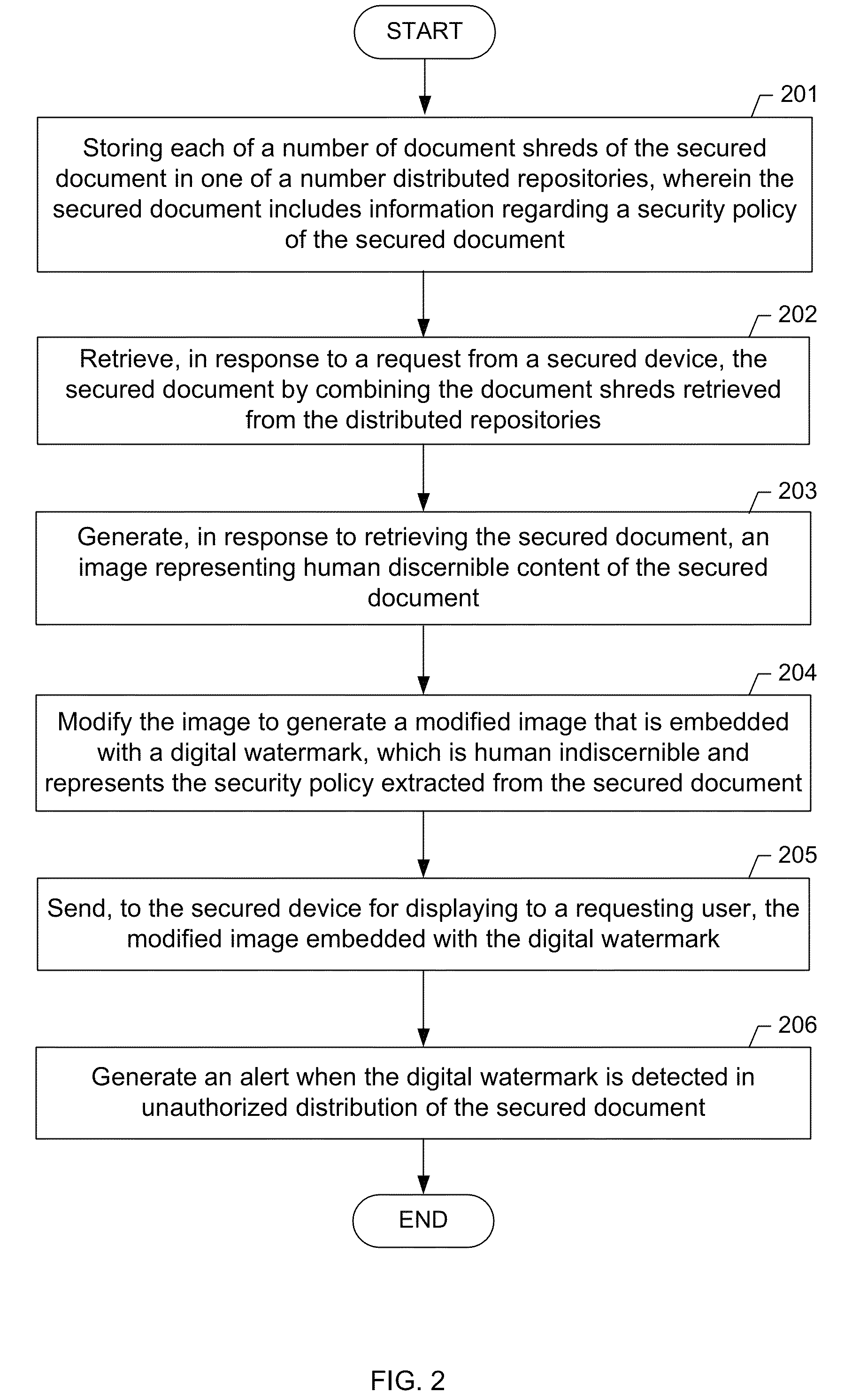
Document security
ActiveUS8677132B1User identity/authority verificationDigital data protectionDocumentation procedureHere document
A method for managing a secured document. The method includes storing and retrieving the secured document based on hybrid fragmentation and replication scheme to provide user viewing of the secured document by (a) generating an image representing human discernible content of the secured document, (b) modifying the image to generate a modified image that is embedded with a digital watermark, where the digital water mark is human indiscernible and represents a security policy extracted from the secured document, and (c) sending, to a secured device for displaying to the requesting user, the modified image embedded with the digital watermark.
Owner:THE BOEING CO
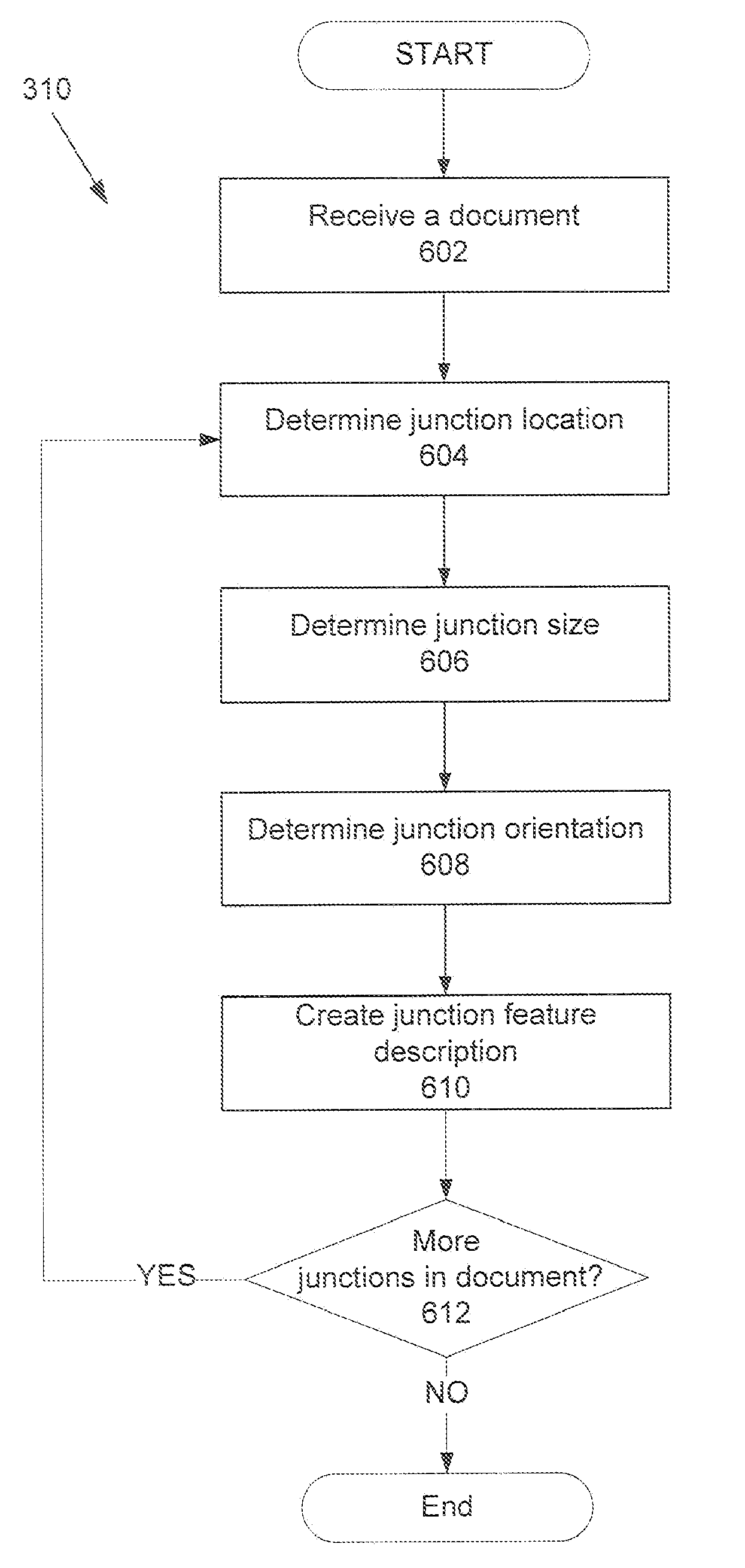
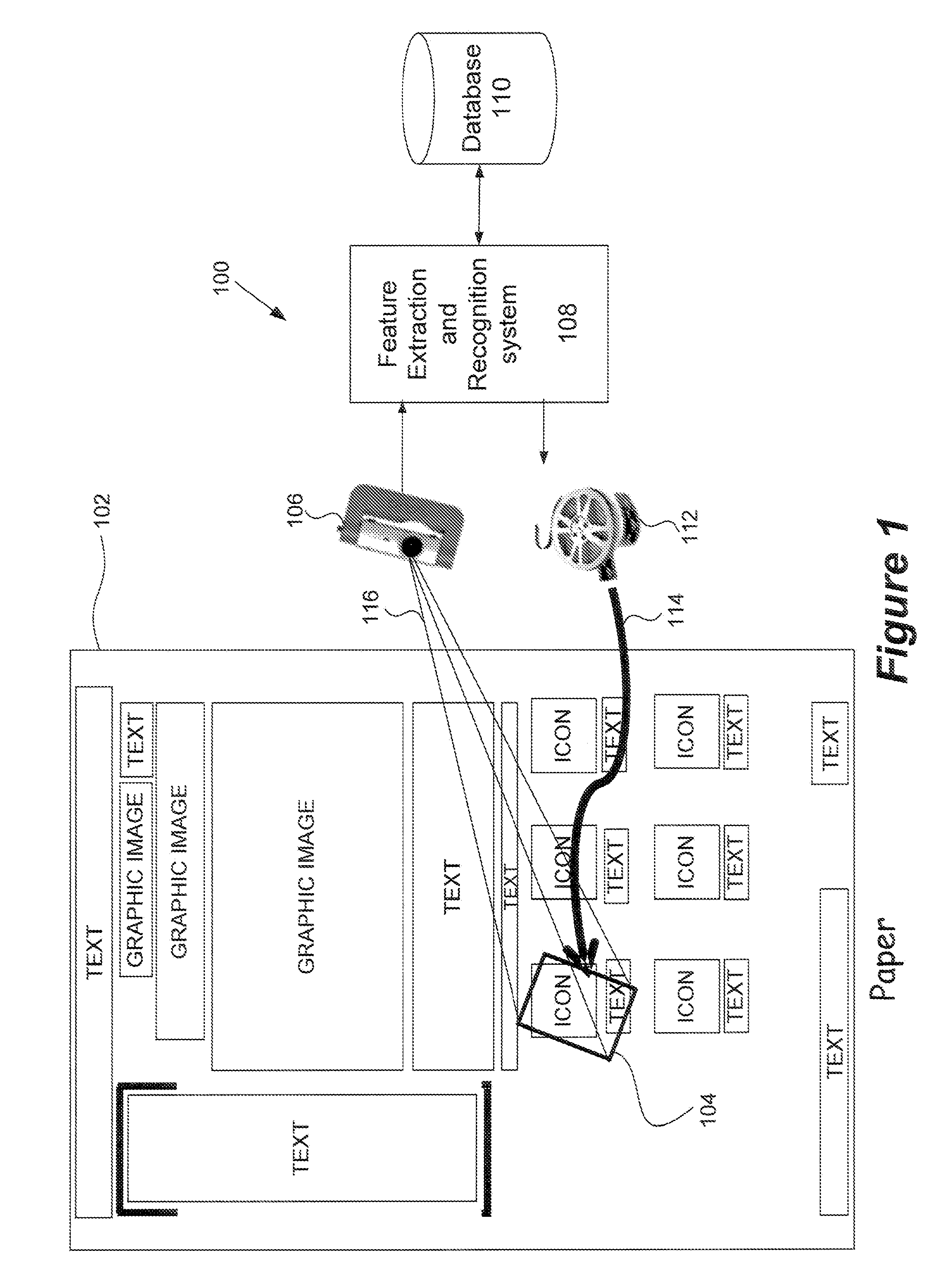
Invisible Junction Feature Recognition For Document Security or Annotation
ActiveUS20090016615A1Overcome deficienciesCharacter and pattern recognitionDigital data protectionElectronic documentFeature extraction
The present invention uses invisible junctions which are a set of local features unique to every page of the electronic document to match the captured image to a part of an electronic document. The present invention includes: an image capture device, a feature extraction and recognition system and database. When an electronic document is printed, the feature extraction and recognition system captures an image of the document page. The features in the captured image are then extracted, indexed and stored in the database. Given a query image, the features in the query image are extracted and compared against those stored in the database to identify the query image. The feature extraction and recognition system of the present invention is integrated into a multifunction peripheral. This allows the feature extraction and recognition system to be used in conjunction with other modules to provide security and annotation applications.
Owner:RICOH KK
Imaging apparatus, imaging system, security management apparatus, and security management system
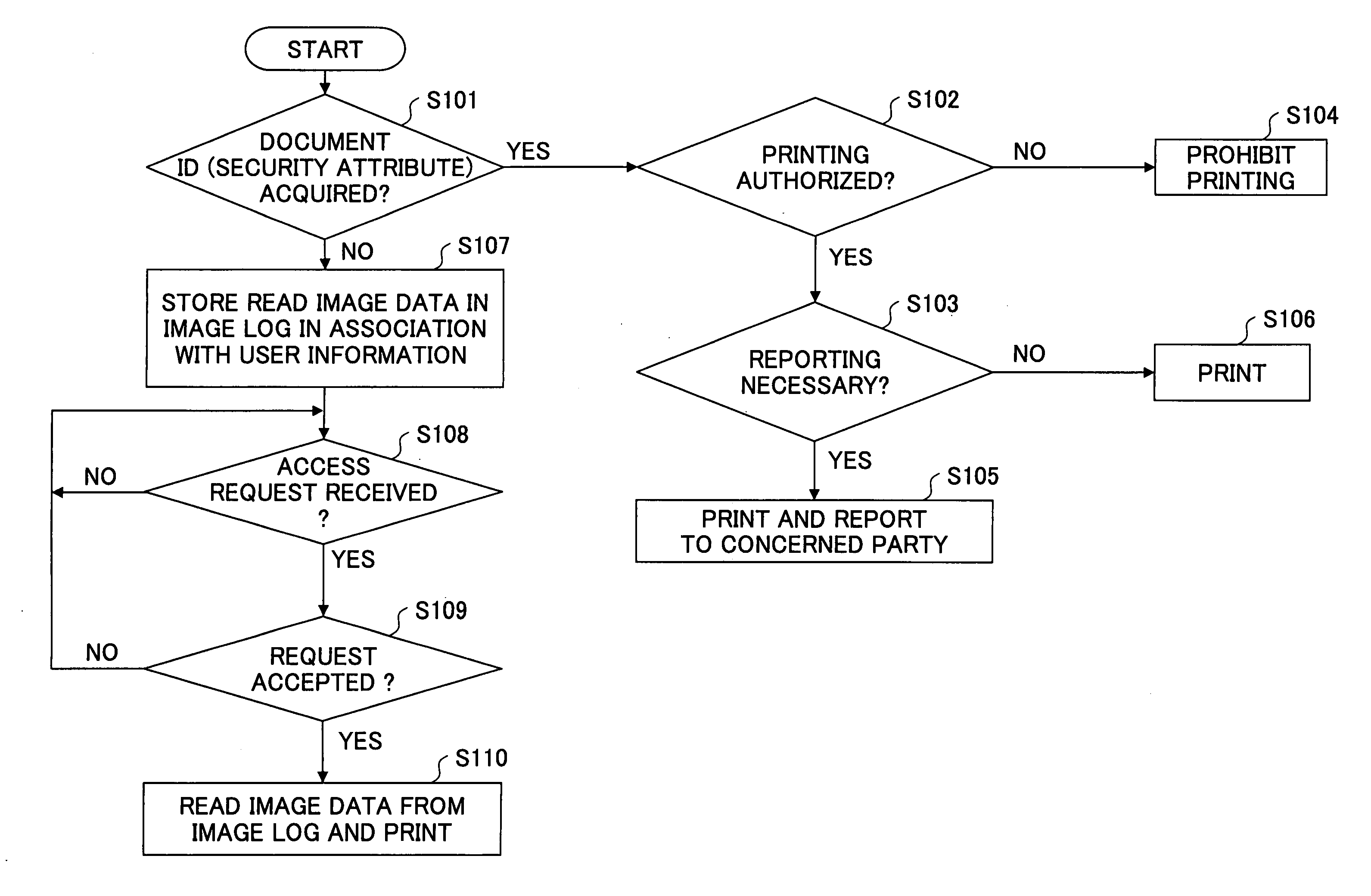
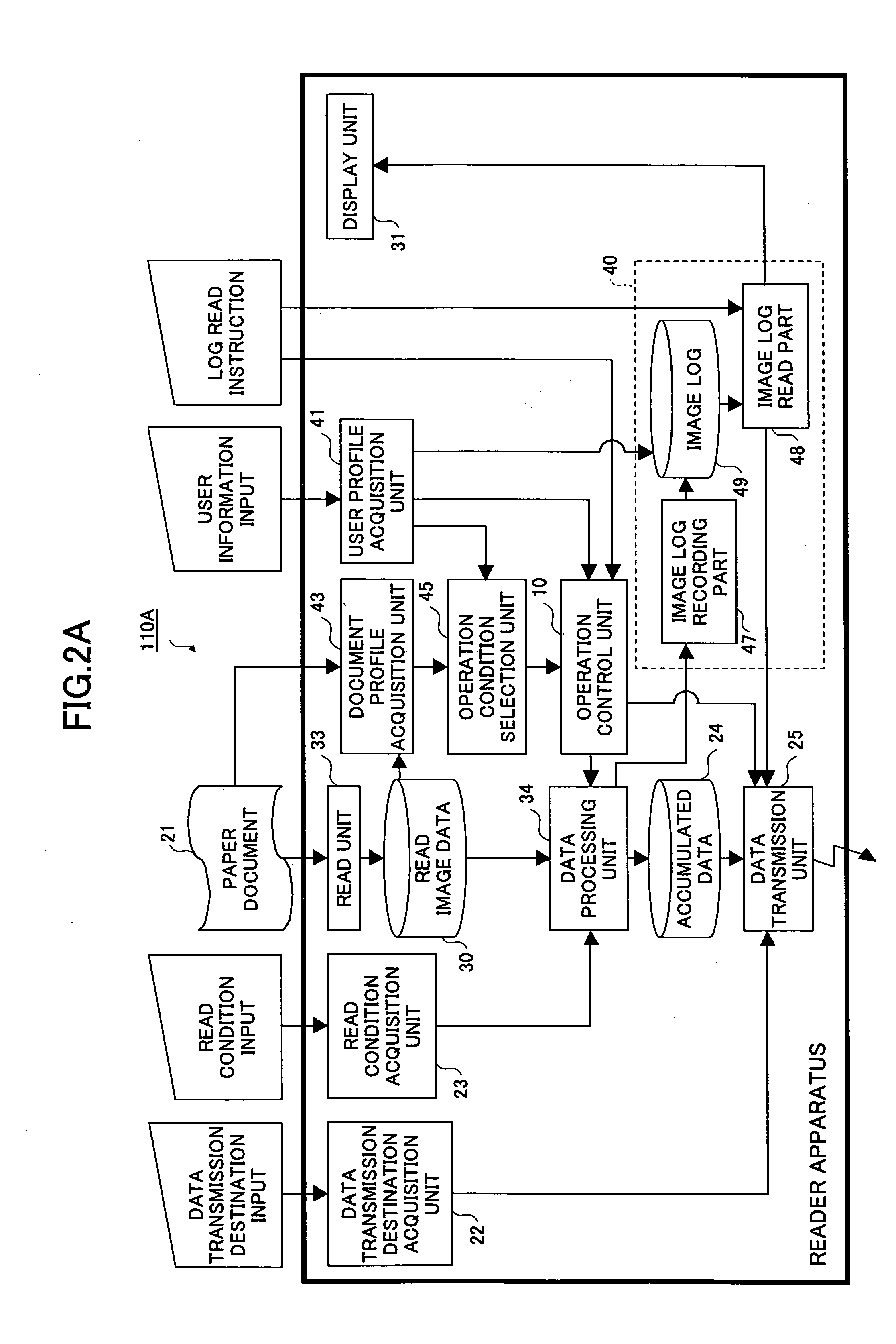
InactiveUS20050144469A1User identity/authority verificationUnauthorized memory use protectionSafety management systemsPaper document
An imaging apparatus is provided that is capable of maintaining document security control even in a case where document ID information cannot be identified from a physical document that is subject to an imaging operation. The imaging apparatus includes a read unit for reading image data from a physical document in response to an imaging request from a user, a user information acquisition unit for acquiring user information including a security attribute of the user, a document information acquisition unit for acquiring document information including a security attribute of the physical document, an operating condition selection unit for determining whether to authorize outputting of the image data read from the physical document based on the user information and the document information by referring to a predetermined rule, and a log management unit for storing the image data in association with the user information without allowing the image data to be output when the document information is not acquired at the document information acquisition unit.
Owner:RICOH KK
Security document and security element for a security document
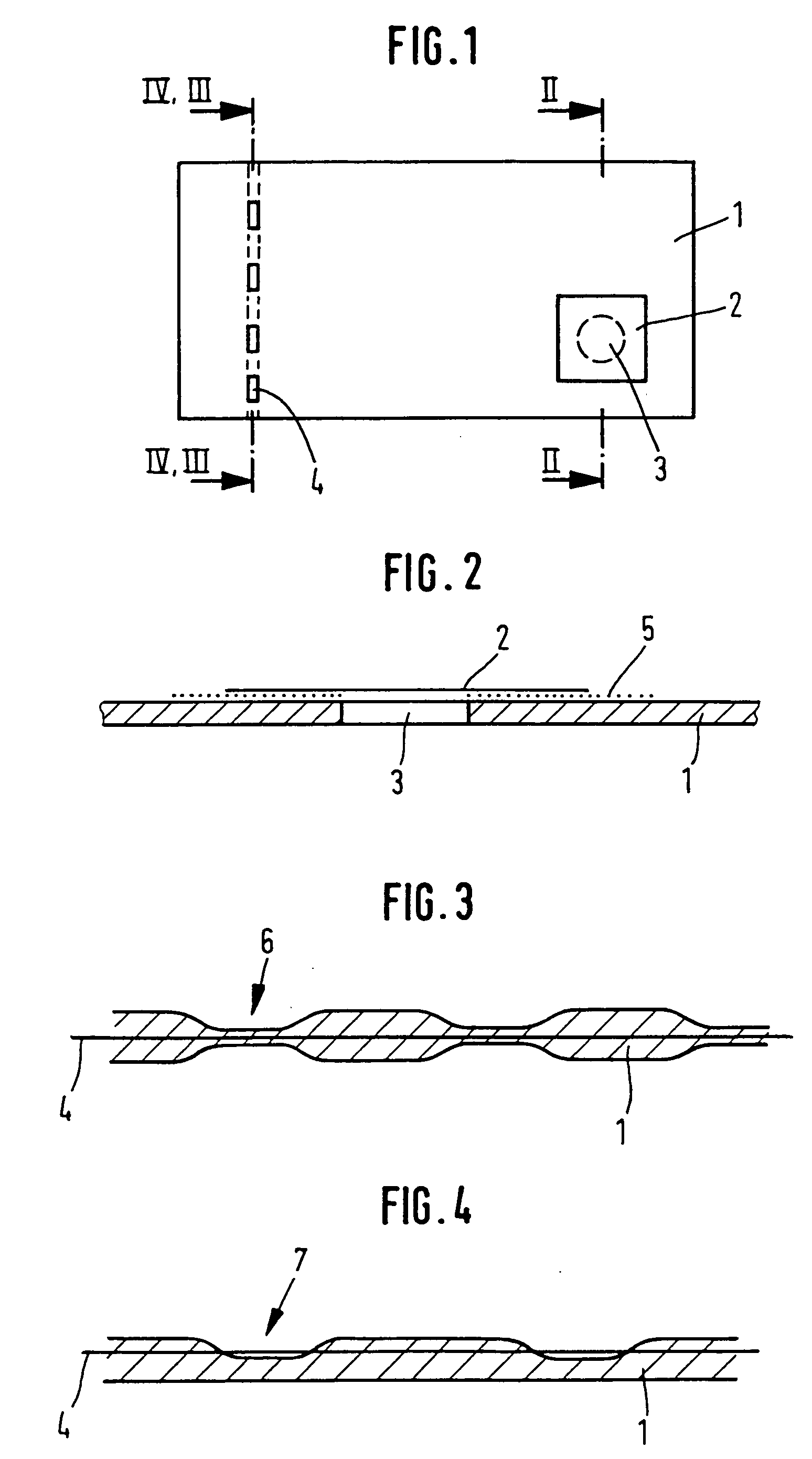
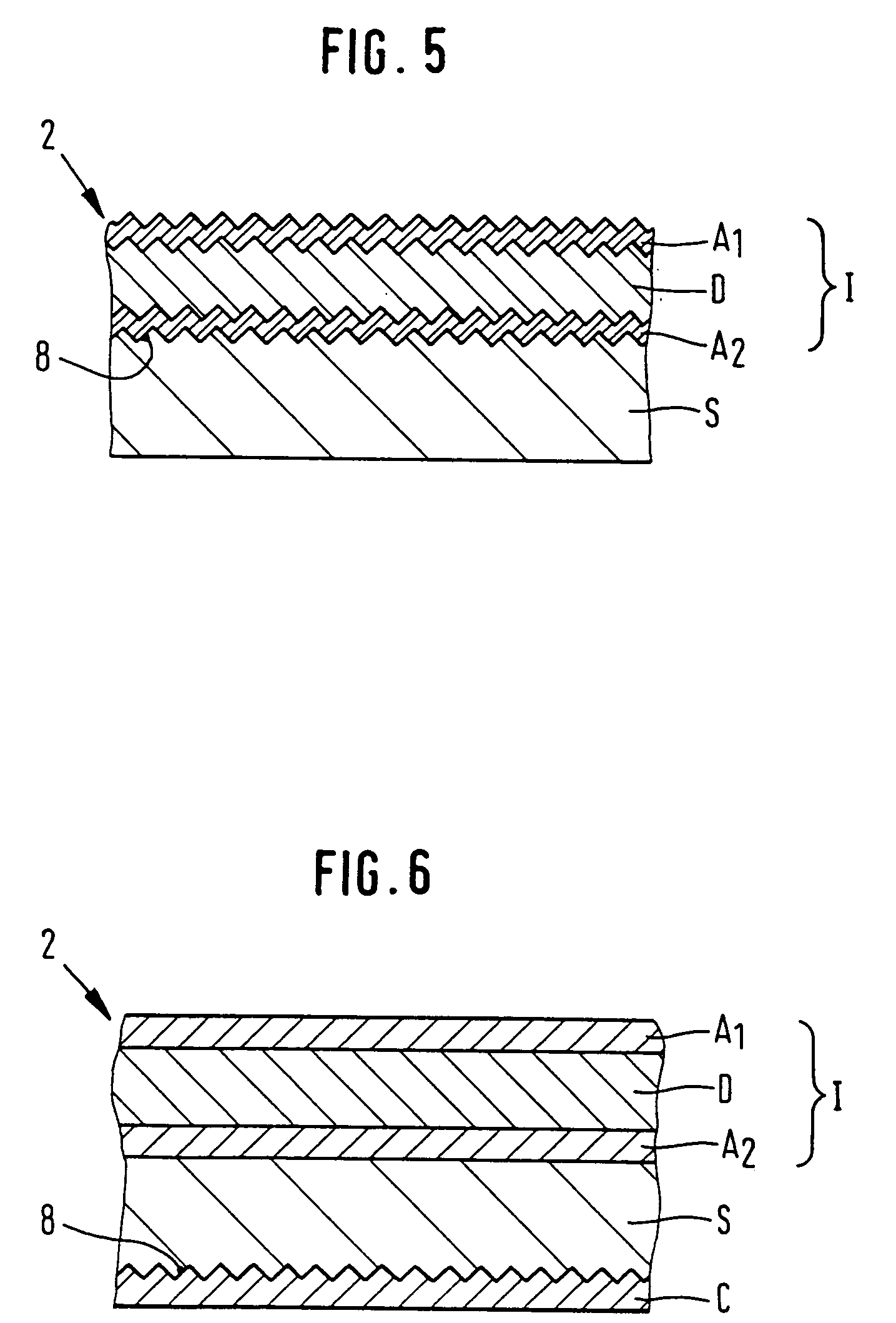
ActiveUS20050151368A1Improve protectionBetter visibleOther printing matterLayered productsColor shiftDocument preparation
Security element 2, 4 to be embedded in or applied to a security document so that it is visually recognizable from both sides of security document 1 is of multilayer construction and includes interference element I with a color shift effect and diffraction structures 8. Depending on the arrangement of the layers and existing diffraction structures 8 on transparent substrate S the color shift effect and / or the diffractive effects are perceptible from one or both sides of security element 2, 4. The security element is suitable in particular as two-sided windowed thread 4 and as label or transfer element 2 over hole 3.
Owner:GIESECKE & DEVRIENT CURRENCY TECHNOLOGY GMBH
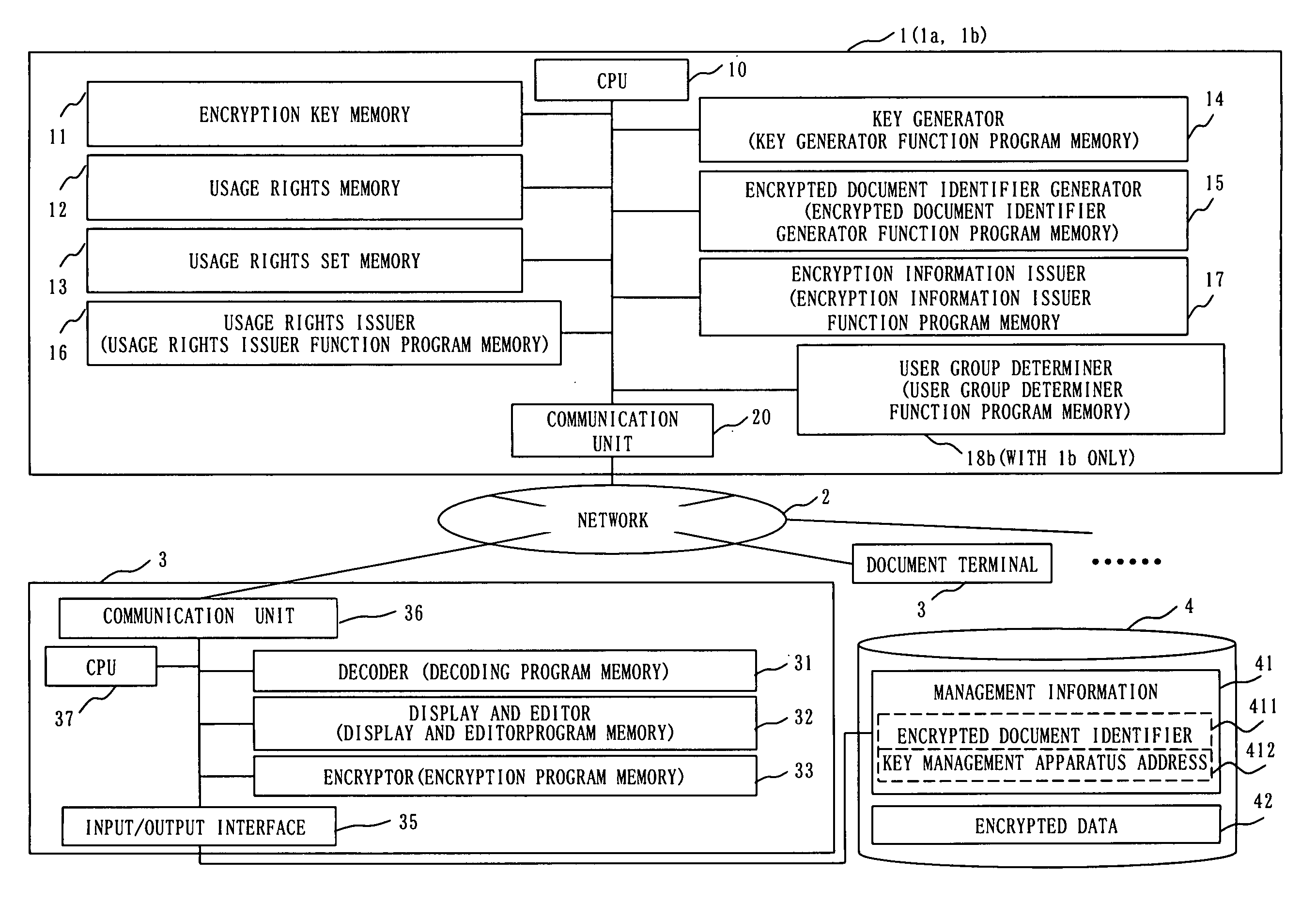
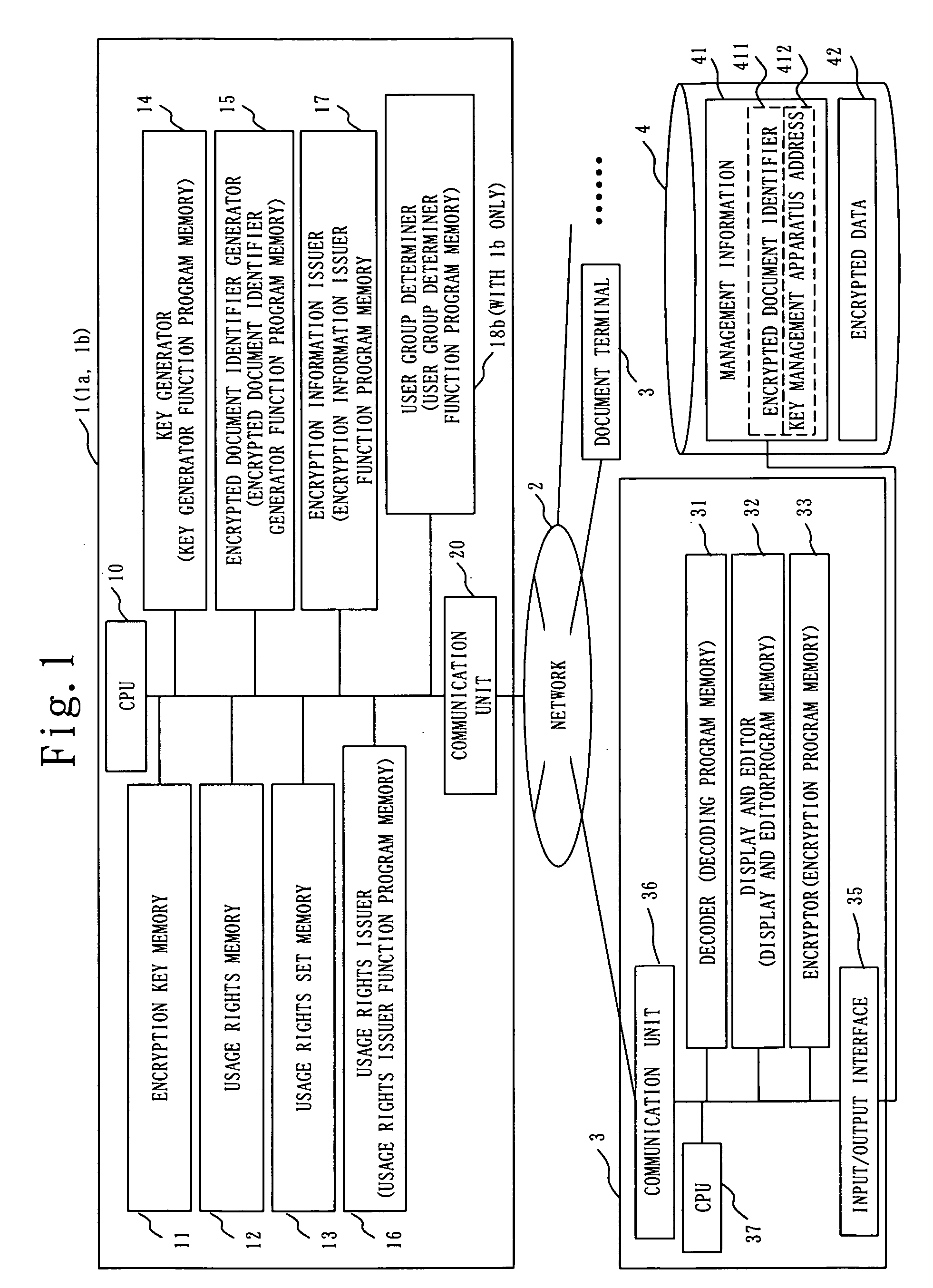
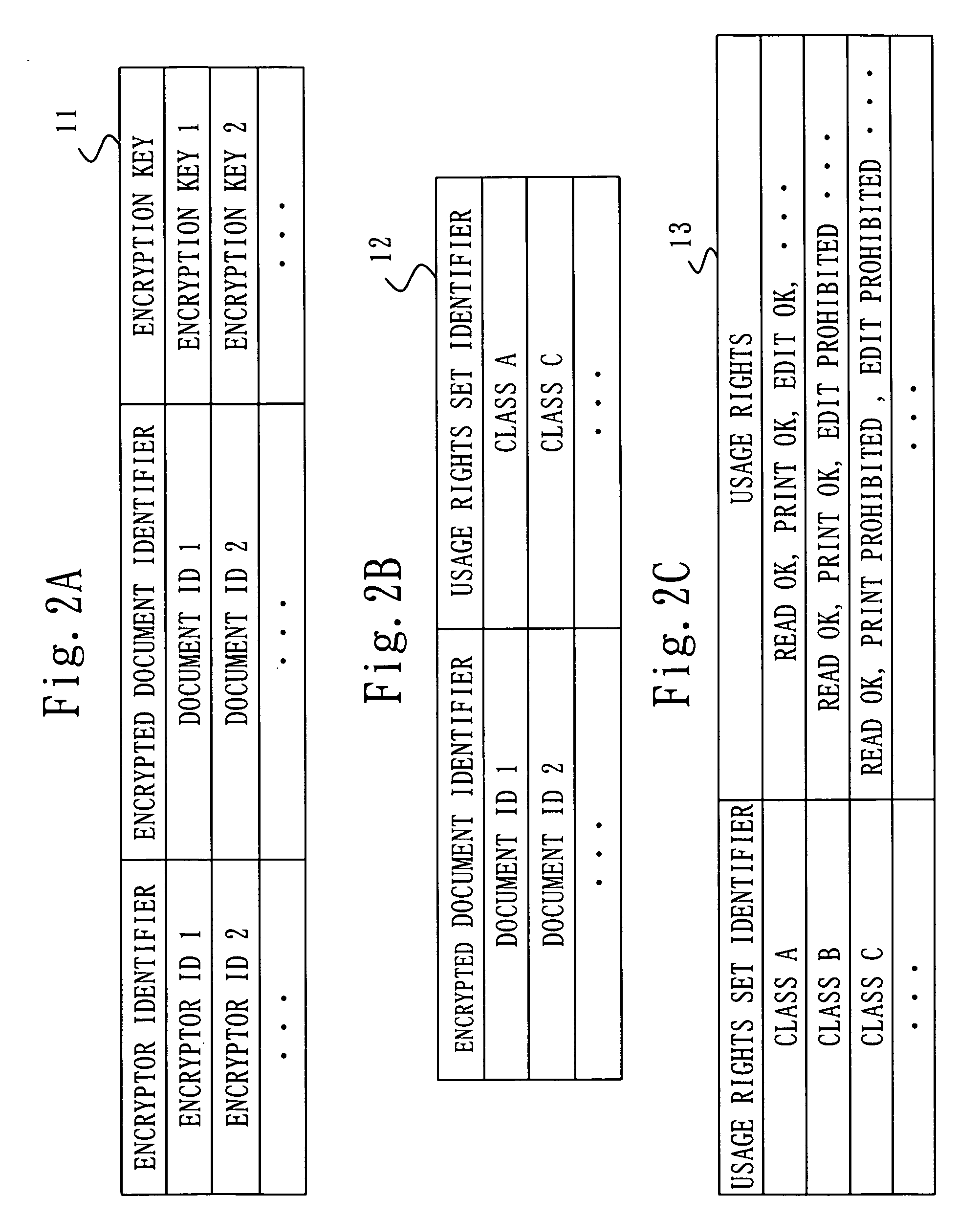
Key management apparatus, document security and editing system, and key management method
InactiveUS20060047977A1Easy to manageEfficient use ofUnauthorized memory use protectionHardware monitoringDocument IdentifierDocumentation
An objective is to provide a key management apparatus in a document security and editing system that controls and manages the usage rights of a document, allows a user with usage rights to read and edit freely according to user qualification, and manages the usage rights in compliance with document management rules established by an organization. The key management apparatus includes an encryption key memory 11 that stores an encrypted document identifier of an encrypted document and an encryption key of the encrypted document; a usage rights set memory 13b that stores the encrypted document identifier and usage rights; a user group determiner 18b that determines the usage rights of a user; a usage rights issuer 16 that receives a read request using the encrypted document identifier, refers to the encryption key memory and the usage rights set memory, and sends the usage rights and the encryption key of the encrypted document; and an encryption information issuer 17 that receives an edit request, refers to the encryption key memory and the usage rights set memory, instructs to generate an identifier of a document to be encrypted and a encryption key of the document to be encrypted, and sends the generated identifier and the generated encryption key.
Owner:MITSUBISHI ELECTRIC CORP
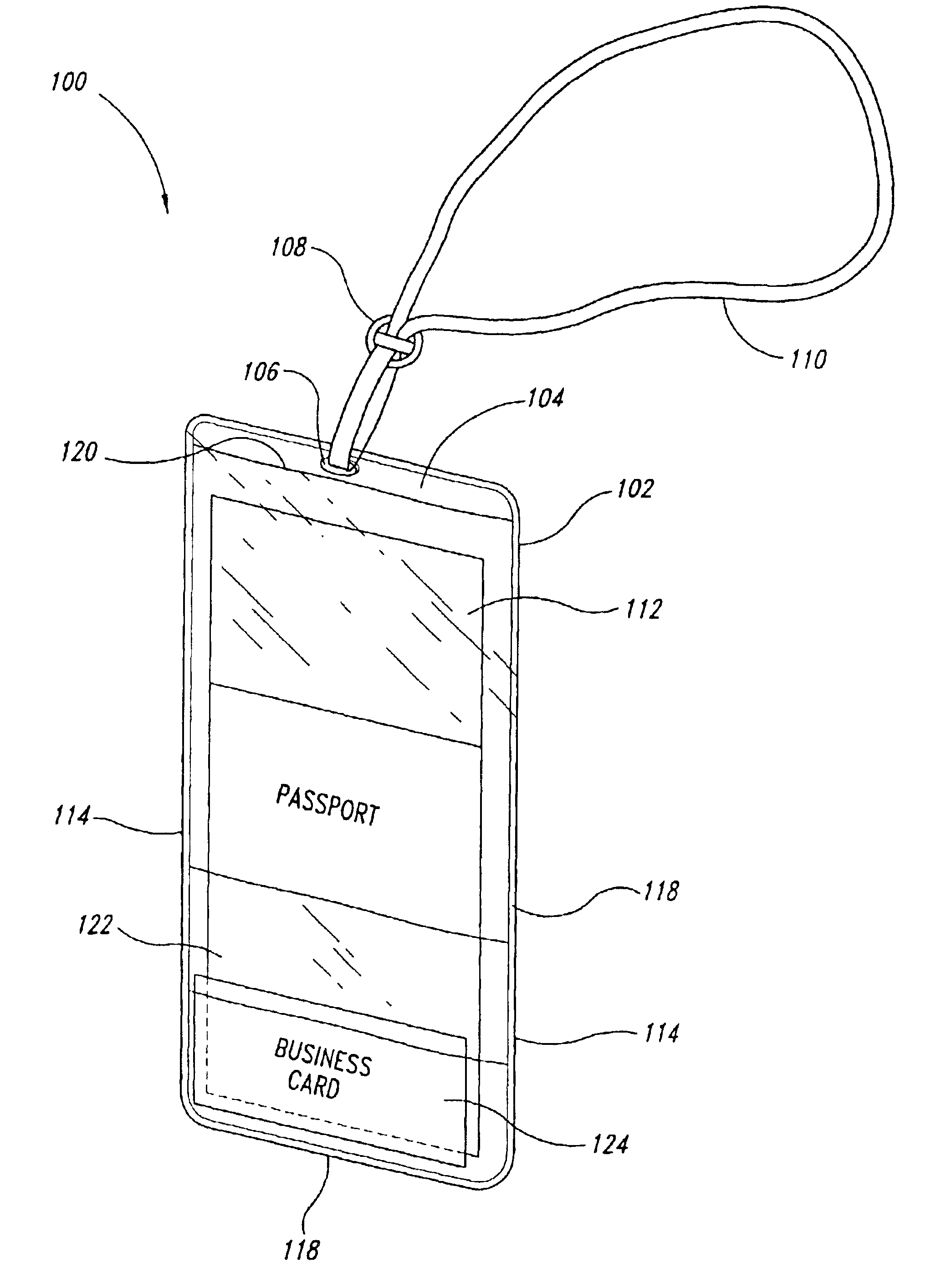
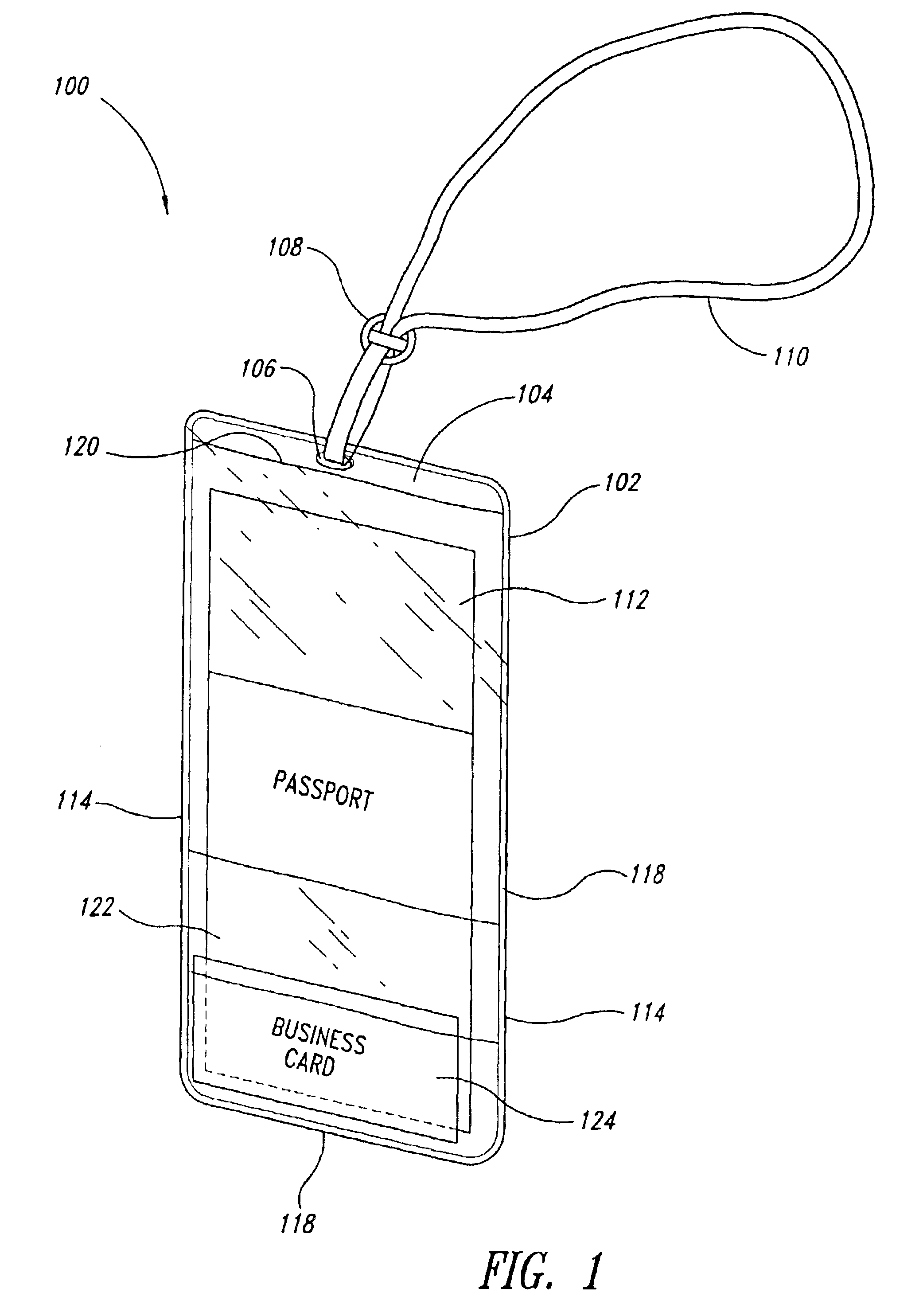
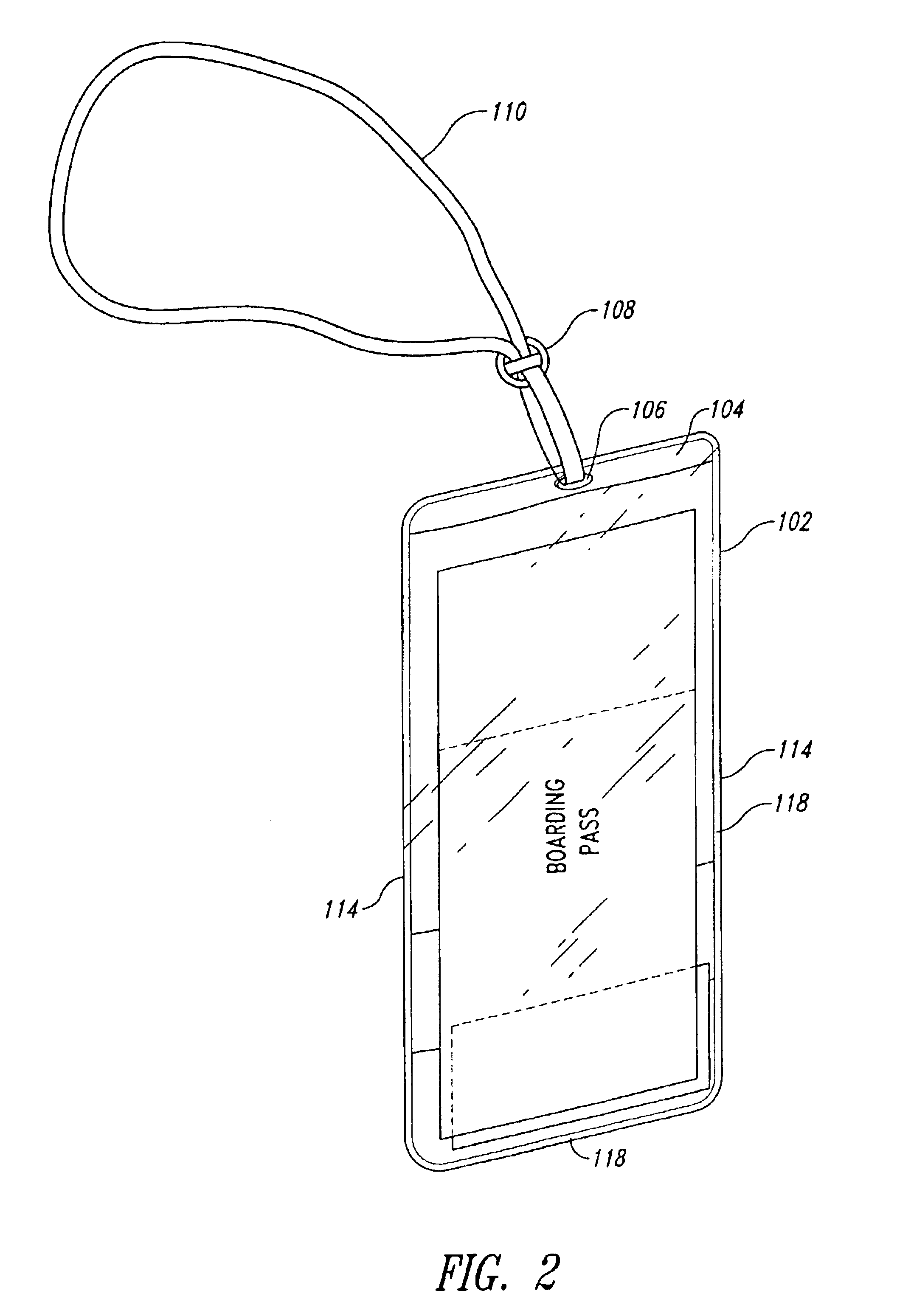
Holder for displaying travel related documents
Owner:HARTGREGORY GRP THE
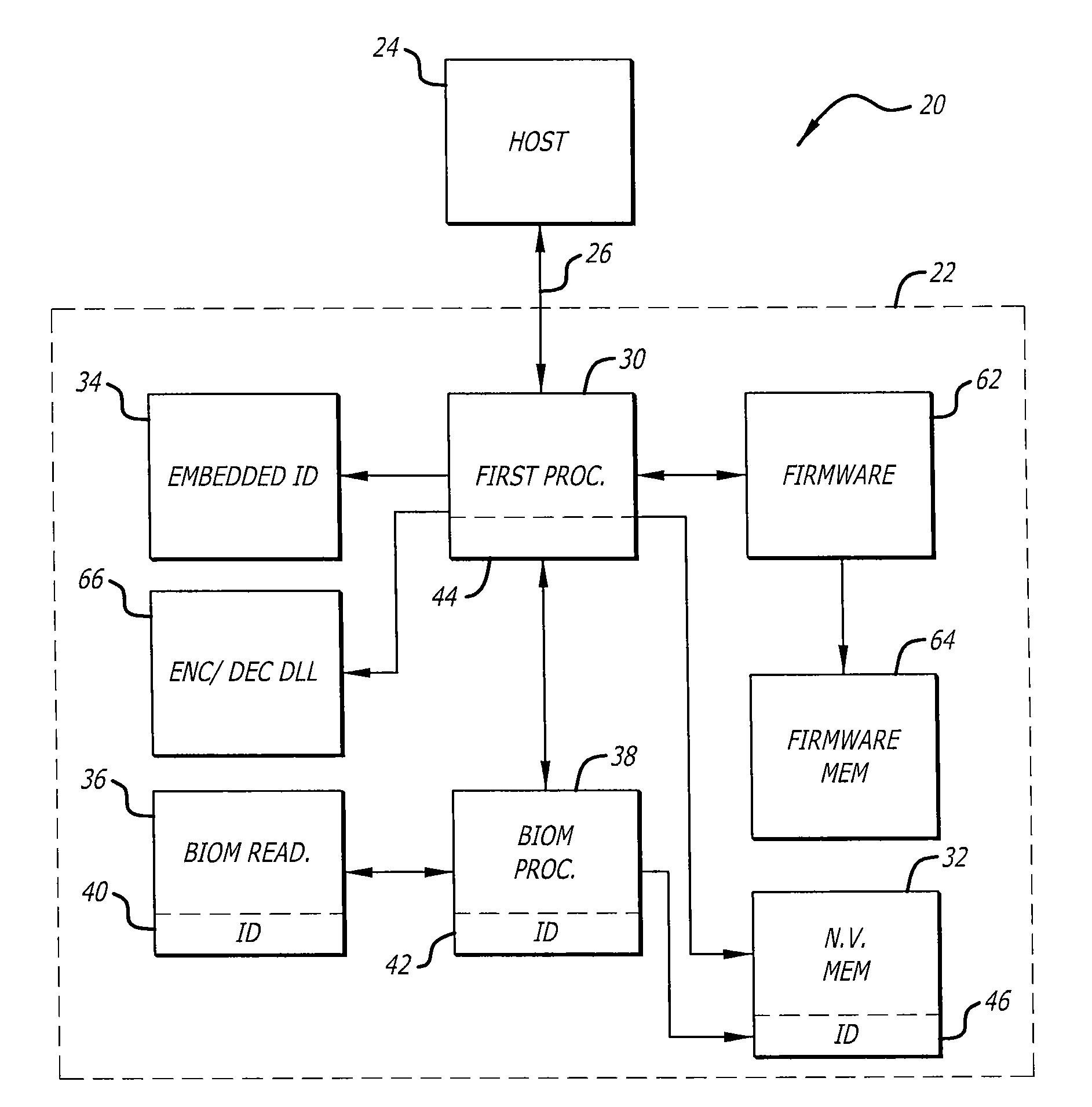
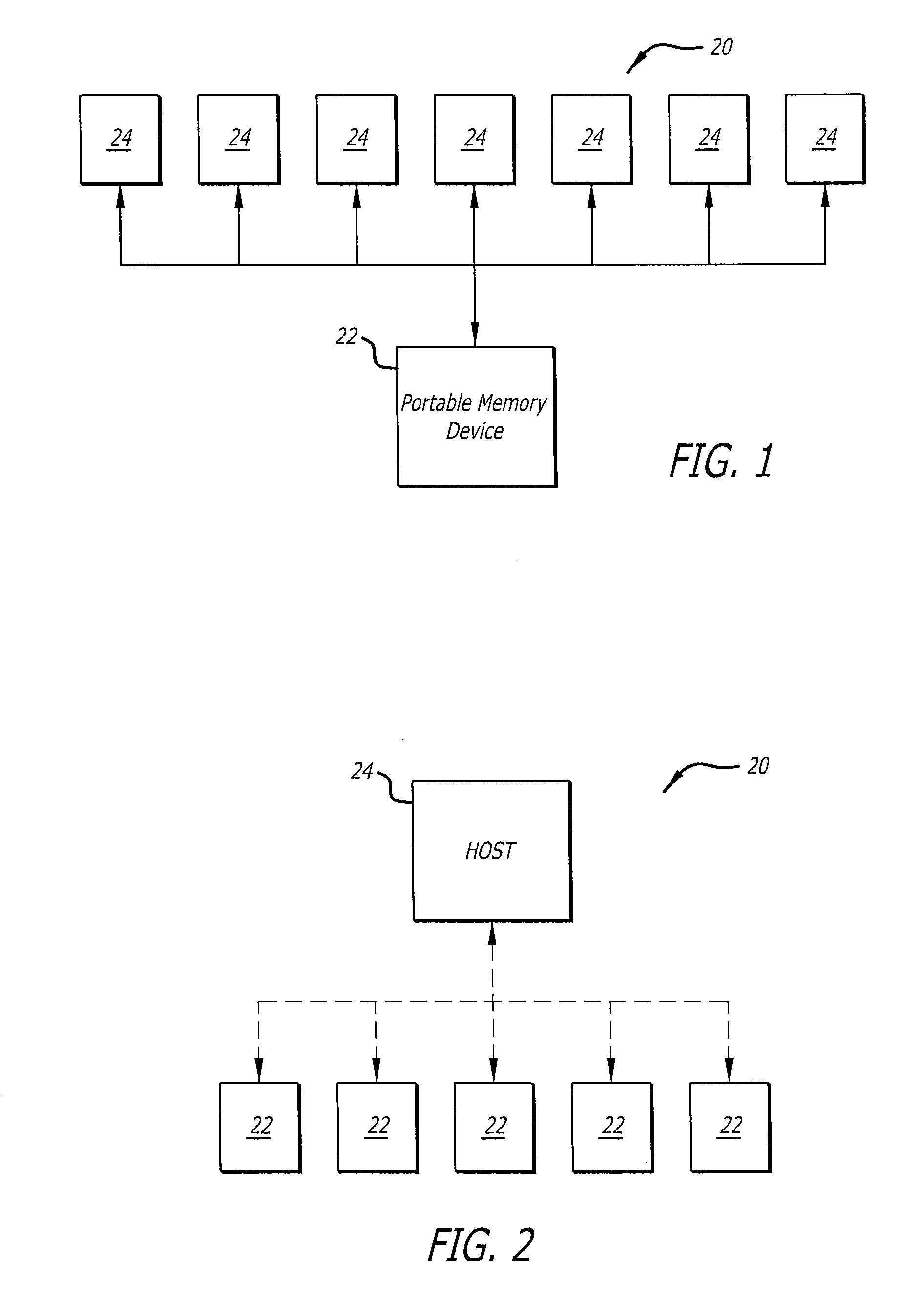
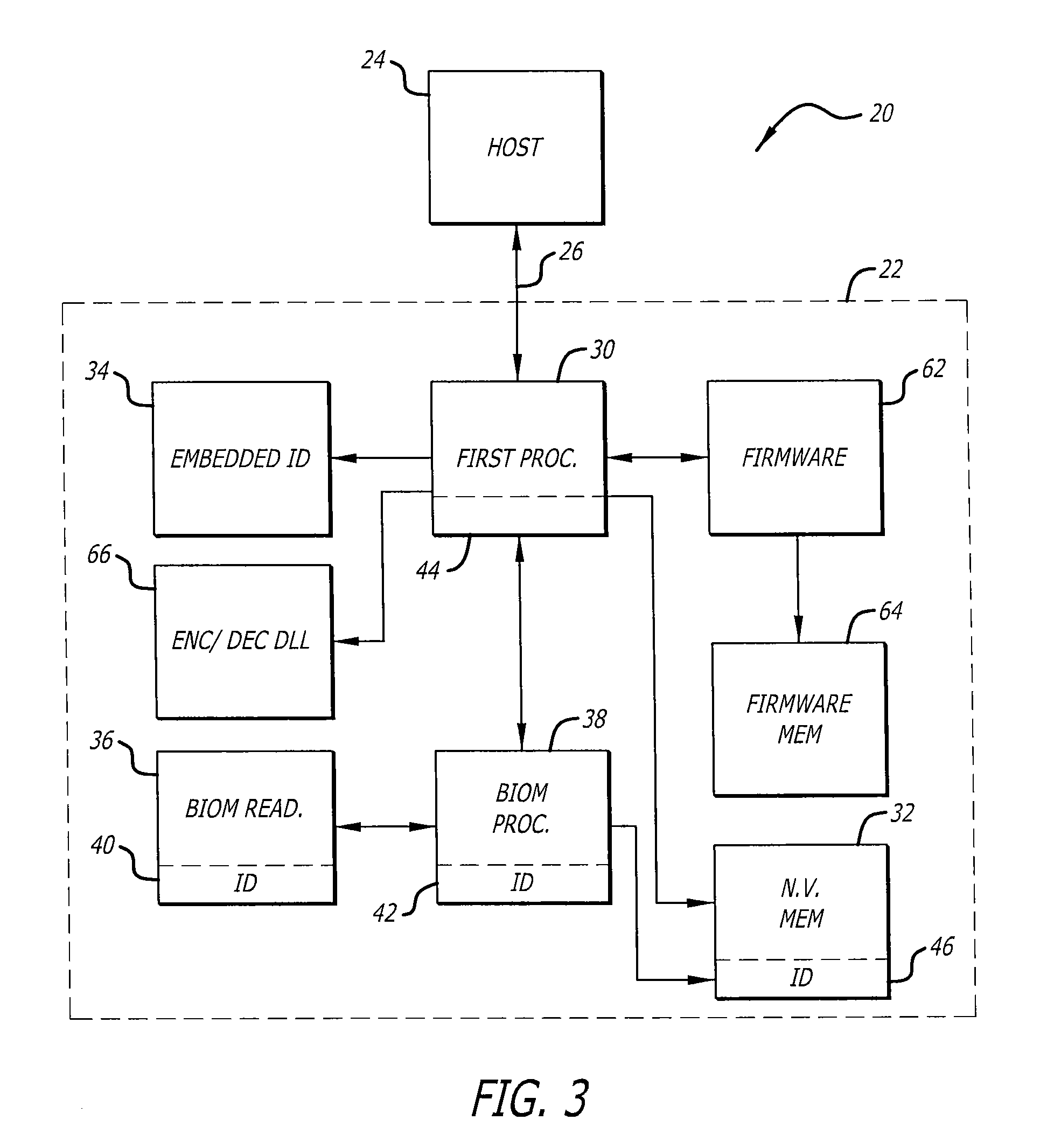
Secure portable data transport & storage system
InactiveUS20090327743A1Digital data processing detailsUnauthorized memory use protectionFile allocationHash function
A portable data transport device that provides security to data stored therein, and is configured to communicate data with a host computer for securing and transporting data. The portable data transport device includes a first processor and a biometric identification system. Upon successful biometric identification of an enrolled user, the first processor permits mounting of the data transport device to a host computer. However, prior to the commencement of read / write operations, cross-checking of stored identification codes of components of the portable data transport device occurs, including the use of a hash function. If any identifier does not match, no read / write data operations are permitted. The portable data transport device includes a file security program that includes a DLL encryption / decryption program having a self-check feature. Upon self check, if any changes were made to the encryption / decryption program, no read / write operations are permitted. The portable data transport device permits the selection of multiple files for encryption together into a single data container pack file and to store that data container pack file. The file security program permits an enrolled user at a host computer to assign only a password to a data container pack file. If a user at a host computer enters an incorrect password a predetermined number of times, portable data transport device processor will erase all data in any volatile memory it is using and will lock itself in a non-operational configuration.
Owner:PHOTONIC DATA SECURITY
Encoding message data in a cover contone image via halftone dot orientation
ActiveUS20100060942A1Error detection processOther printing matterImage watermarkingProbit modelPresent method
What is disclosed is a novel system and method for encoding / decoding data in a cover contone image via halftone dot orientation modulation. Arrays of halftone threshold values are used to determine a desired orientation, e.g. 0 / 90°±45° for a given single data value of the original message to be embedded. Message data is embedded as a function of halftone dot orientation. Detection modeling of the print-scan process enables the determination of dot orientation from the image scan via statistically motivated image moments. A probabilistic model of the print-scan channel conditions received moments on input orientation. Density values of the received moments are used to determine dot orientation for each halftone cell. The embedded data is retrieved based on the determined orientations. The present method is applicable to areas of data embedding, document security, and the like.
Owner:UNIVERSITY OF ROCHESTER +1
Method for protecting and managing retention of data on worm media
InactiveUS20060123232A1Digital data information retrievalSpecial data processing applicationsRetention periodData retention
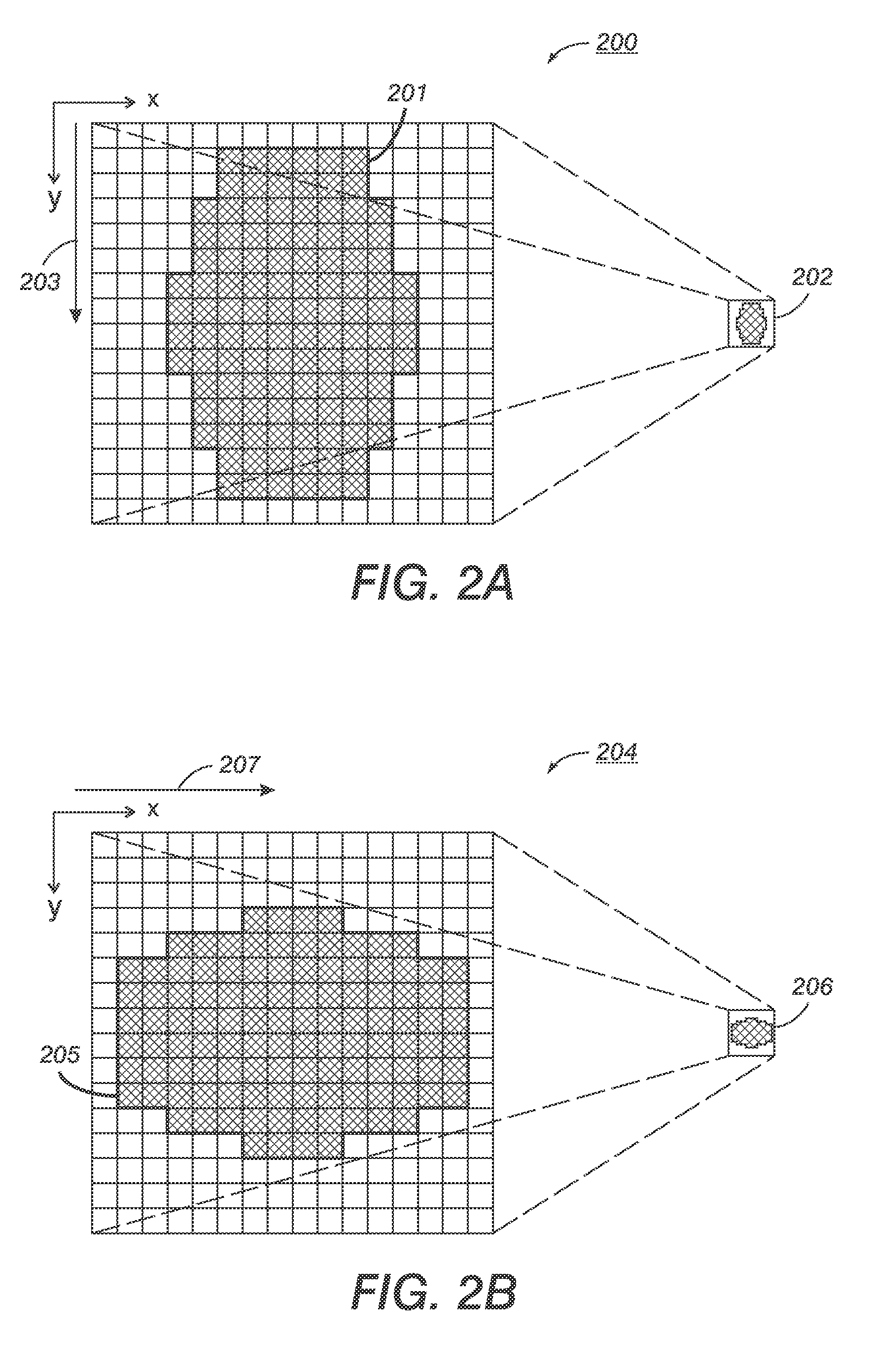
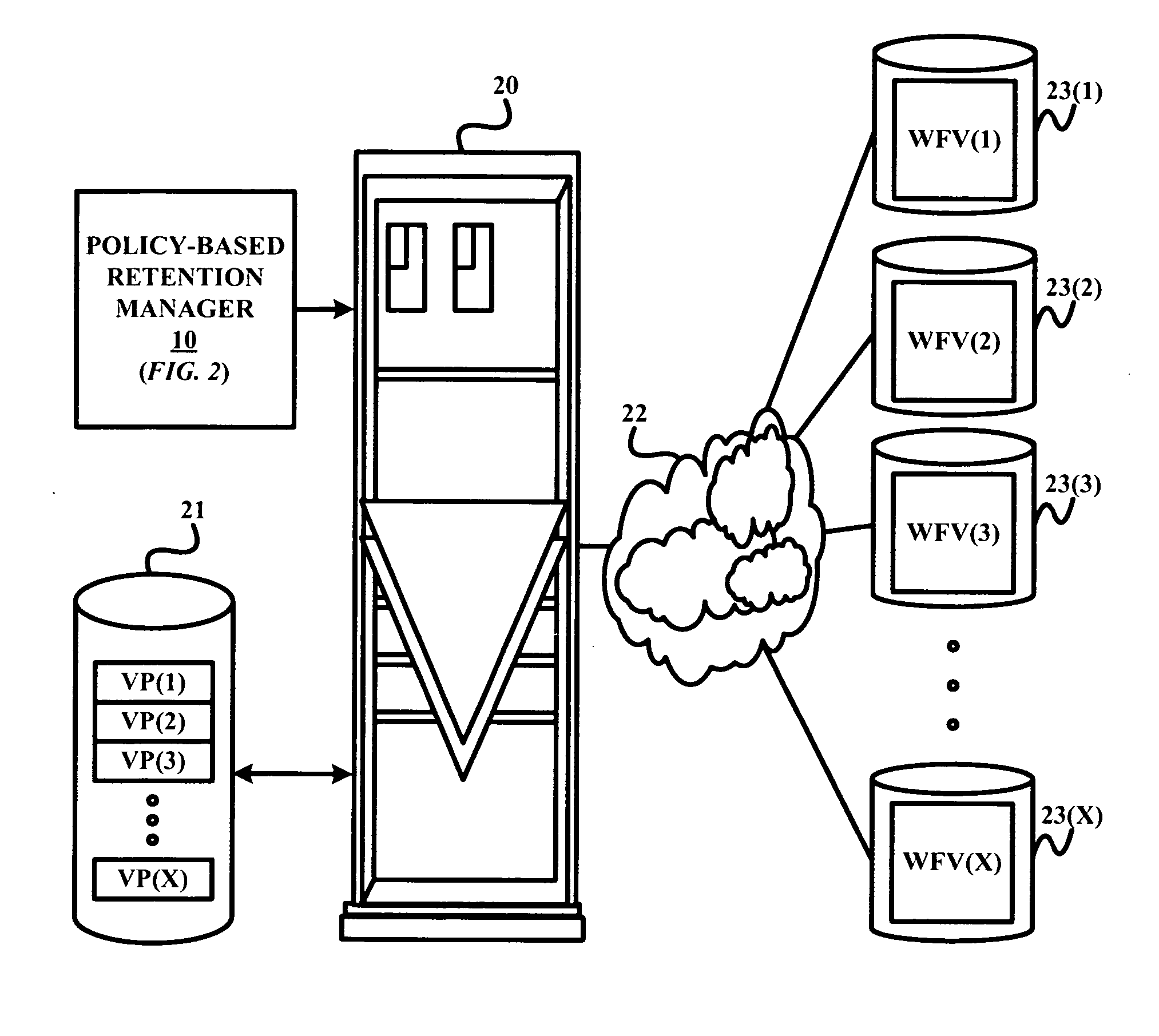
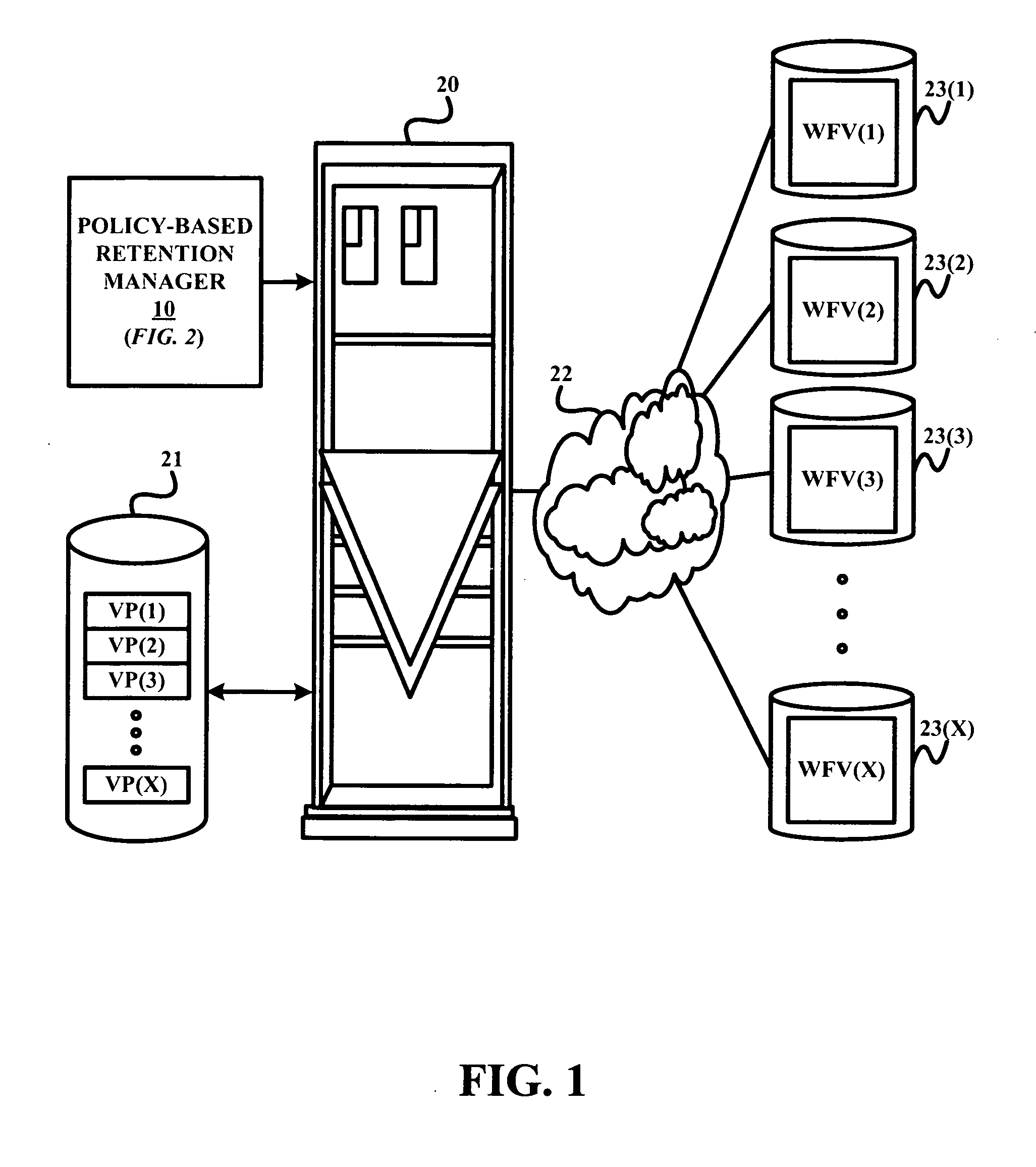
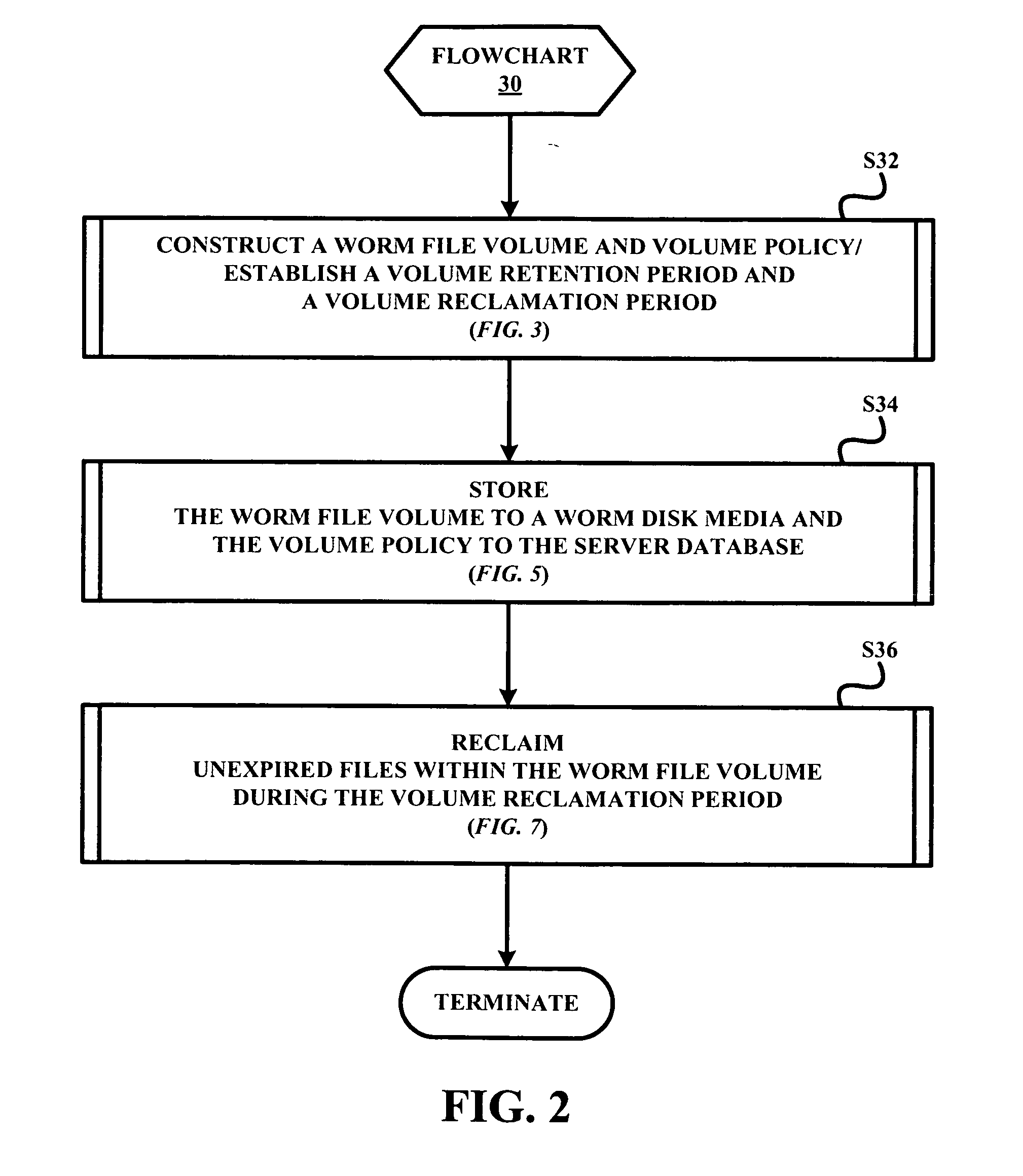
A policy-based retention manager provides protection and management of files in a WORM file volume. The protection of the files is accomplished by the manager establishing a volume retention period for securely storing the files within the WORM file volume on a WORM media (e.g., a WORM disk media) based on a file retention end date of each file within the WORM file volume, and securely storing the WORM file volume on the WORM media during the volume retention period. The management of the files is accomplished by the manager establishing a volume reclamation period for reclaiming unexpired files within the WORM file volume prior to an expiration of the volume retention period, and reclaiming each unexpired file within the WORM file volume from the WORM media during the volume reclamation period.
Owner:IBM CORP
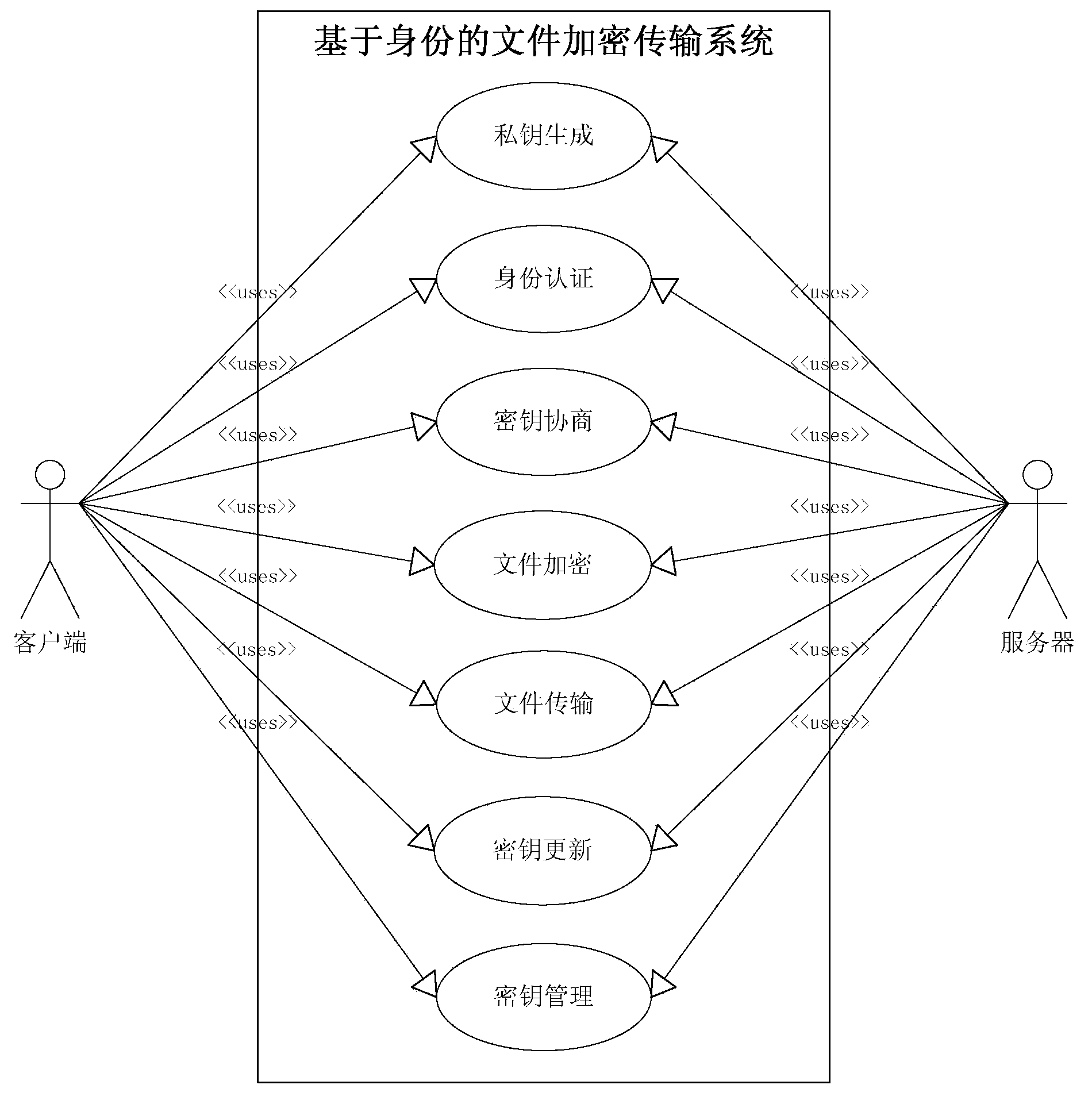
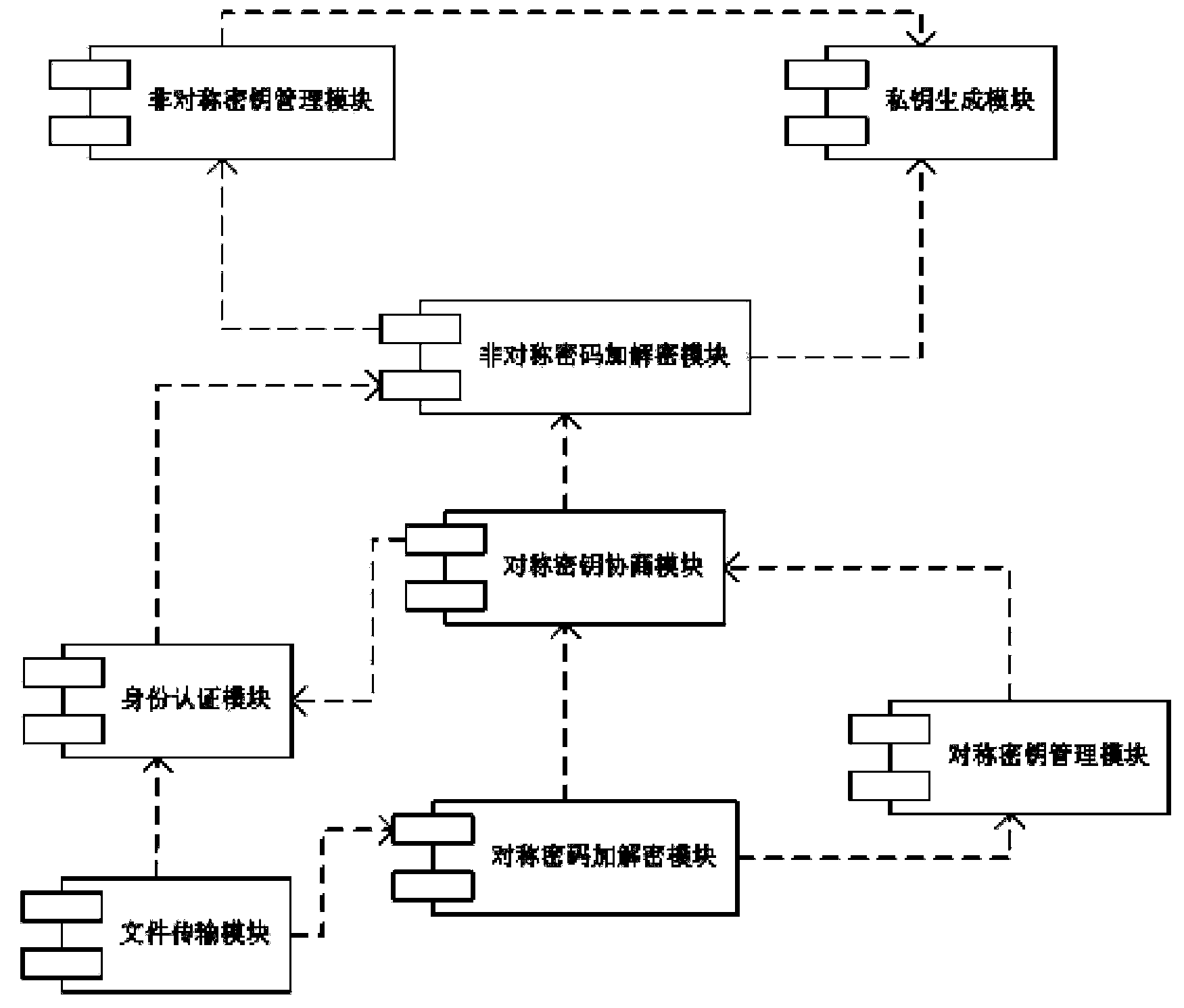
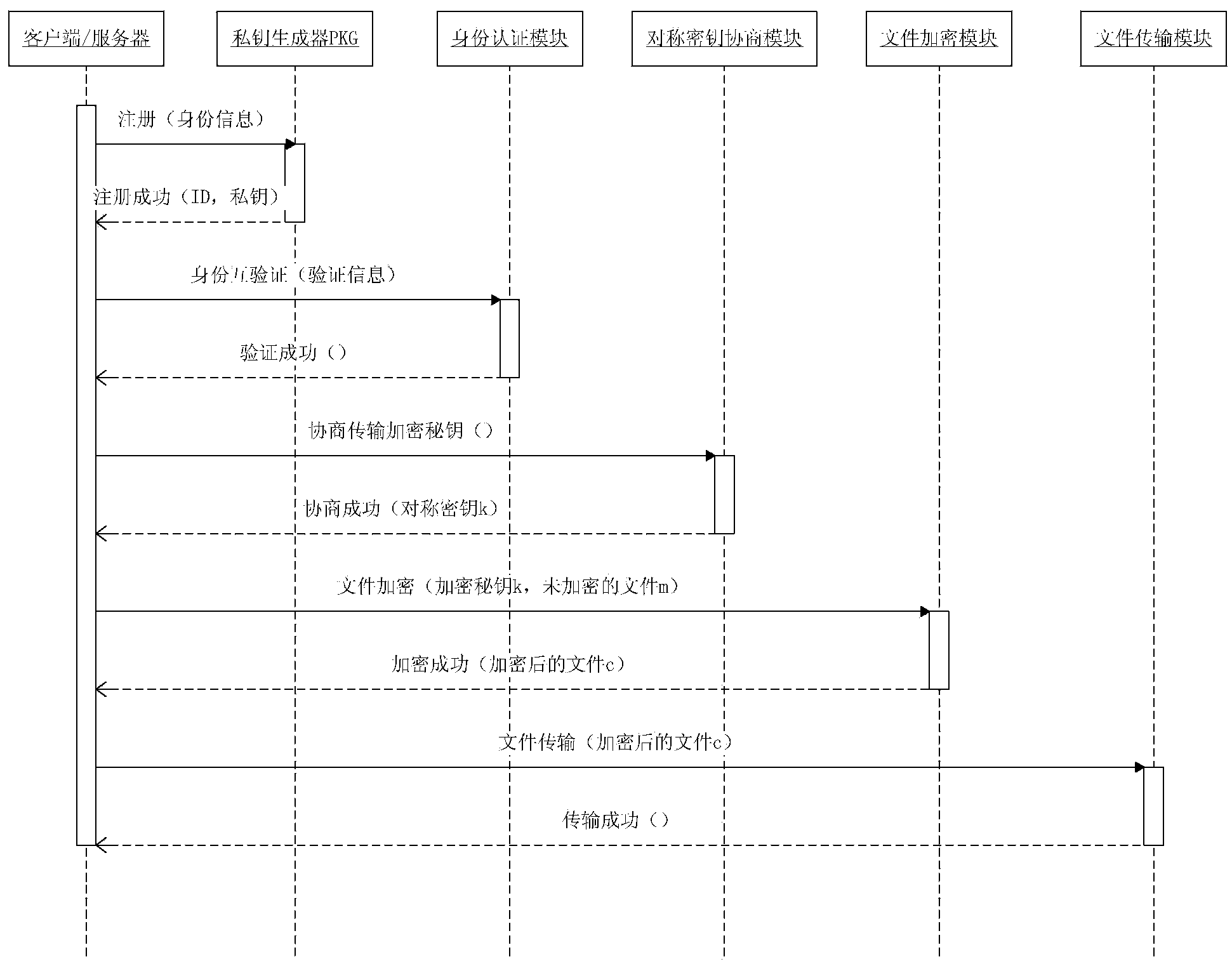
Identity-based file encryption transmission method
ActiveCN103354498AResist attackDelayed decryptionUser identity/authority verificationClient-sideEncryption
The invention discloses an identity-based file encryption transmission method which is applicable to a system of client / server architecture based on FTP. The method, based on identity based encryption algorithm, comprises the following steps: generation of public keys and private keys of a client and a server; identity authentication; negotiation of a symmetric key; transmission of encrypted files and secret key update and management. The identity based encryption (IBE) algorithm is used in the identity-based method, so that users can communicate safely and signature of each person is authenticated without exchanging the public keys and the private keys; besides, the file safety transmission method is low in cost, flexible in form, high in efficiency and good in safety.
Owner:北京创世泰克科技股份有限公司
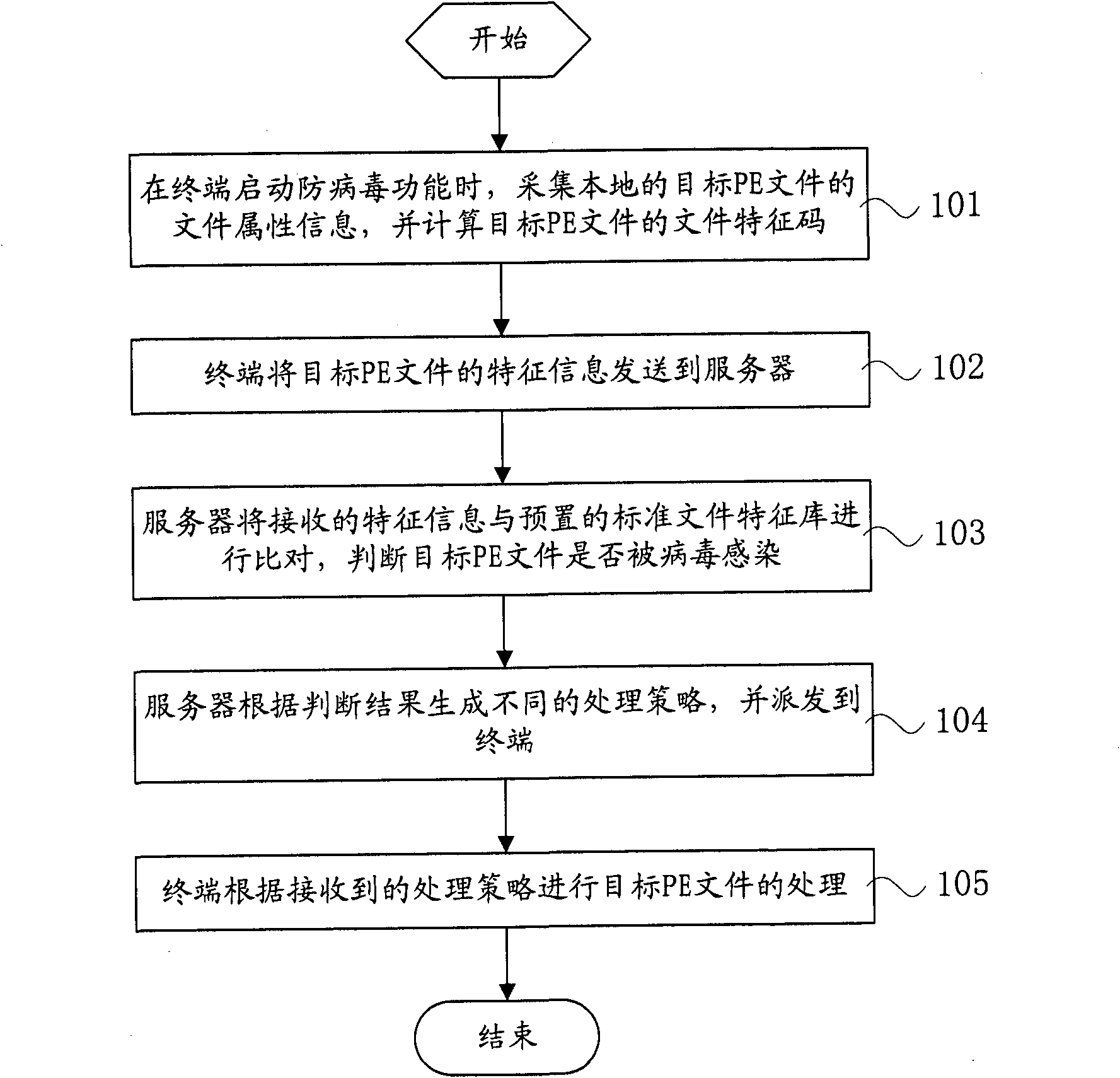
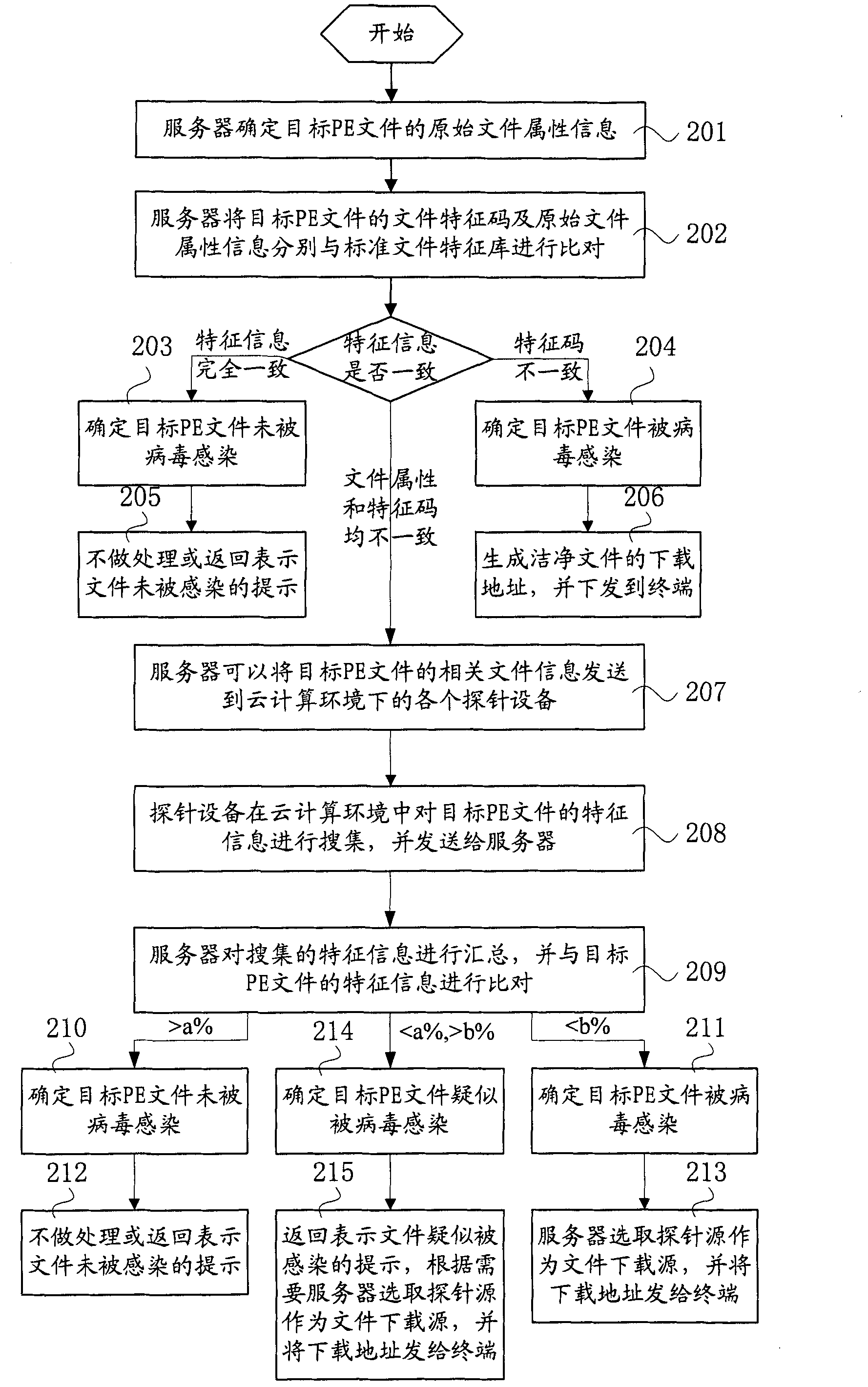
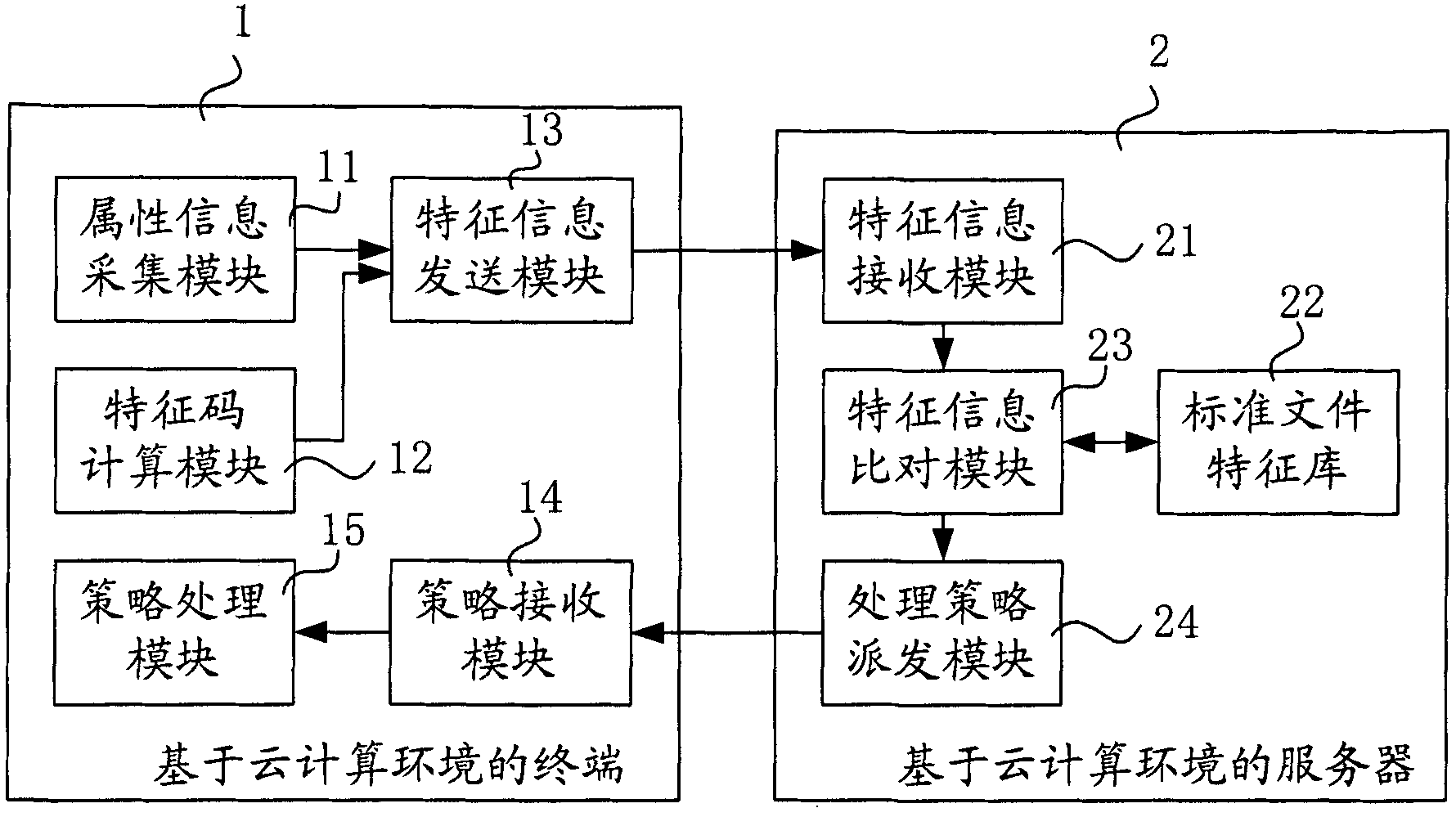
Secure file processing method, equipment and system
The invention relates to a secure file processing method. The secure file processing method comprises the following steps: a terminal collects file attribute information of a local target PE (portable execute) file when the terminal starts the anti-virus function, and calculates a file feature code of the target PE file; the terminal transmits the feature information of the target PE file to a server; the server compares the received feature information with a preset standard file feature library to determine whether the target PE file is infected by virus, generates different processing strategies according to the determination result, and transmits the processing strategies to the terminal; and the terminal processes the target PE file according to the received processing strategies. The invention also relates to a secure file processing system, a terminal, a server and probe equipment. According to the invention, the method can clean file-type viruses and repair the infected files based on the cloud computing environment without frequently upgrading the virus feature library, can clean unknown viruses and repair the infected files, and has the advantage of less user terminal resource occupied.
Owner:CHINA TELECOM CORP LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com