Patents
Literature
1563results about How to "Maintain security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Remote document serving
InactiveUS6763501B1Maintaining data securityBetter fault-toleranceData processing applicationsSpecial data processing applicationsDocument preparationApplication software
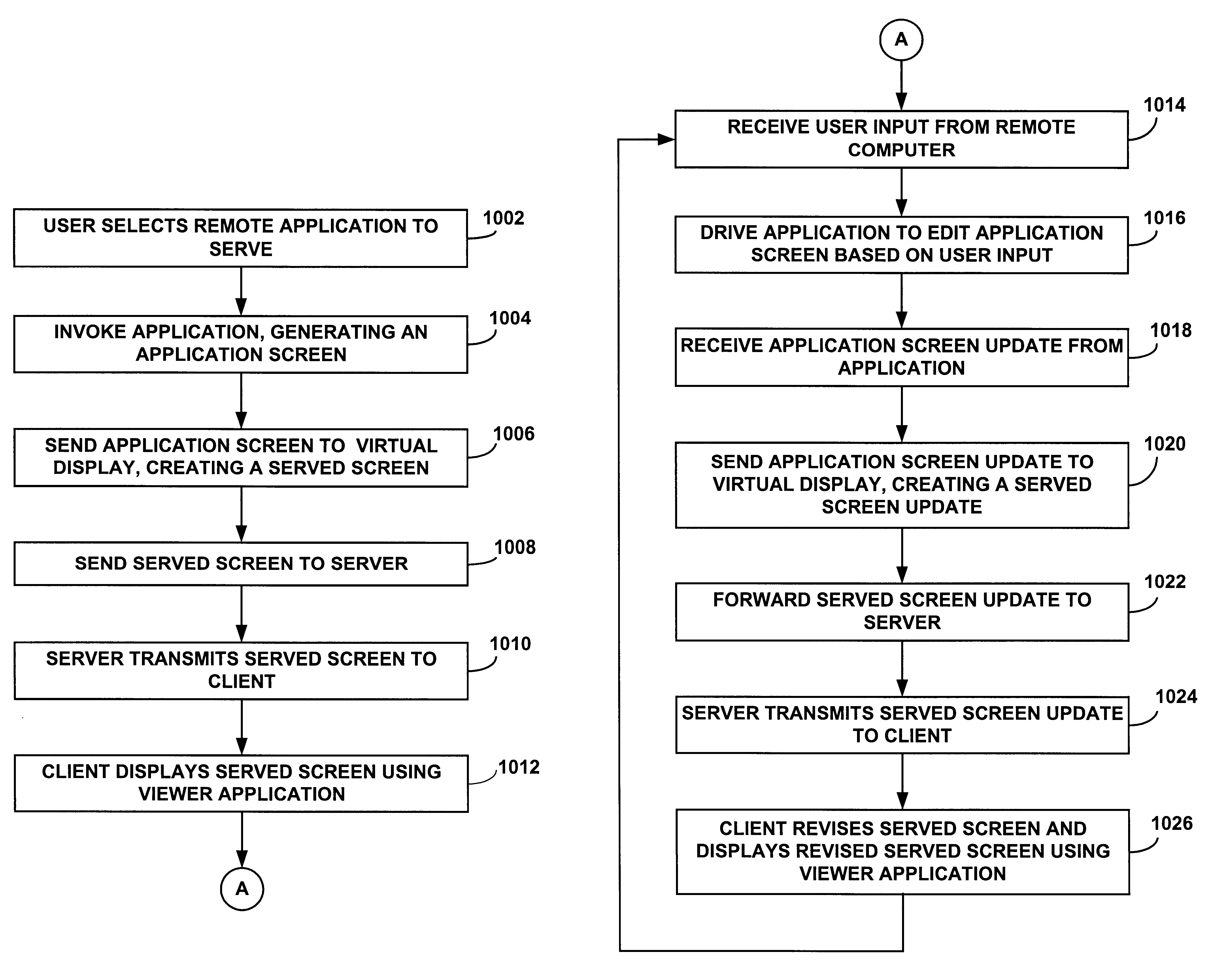
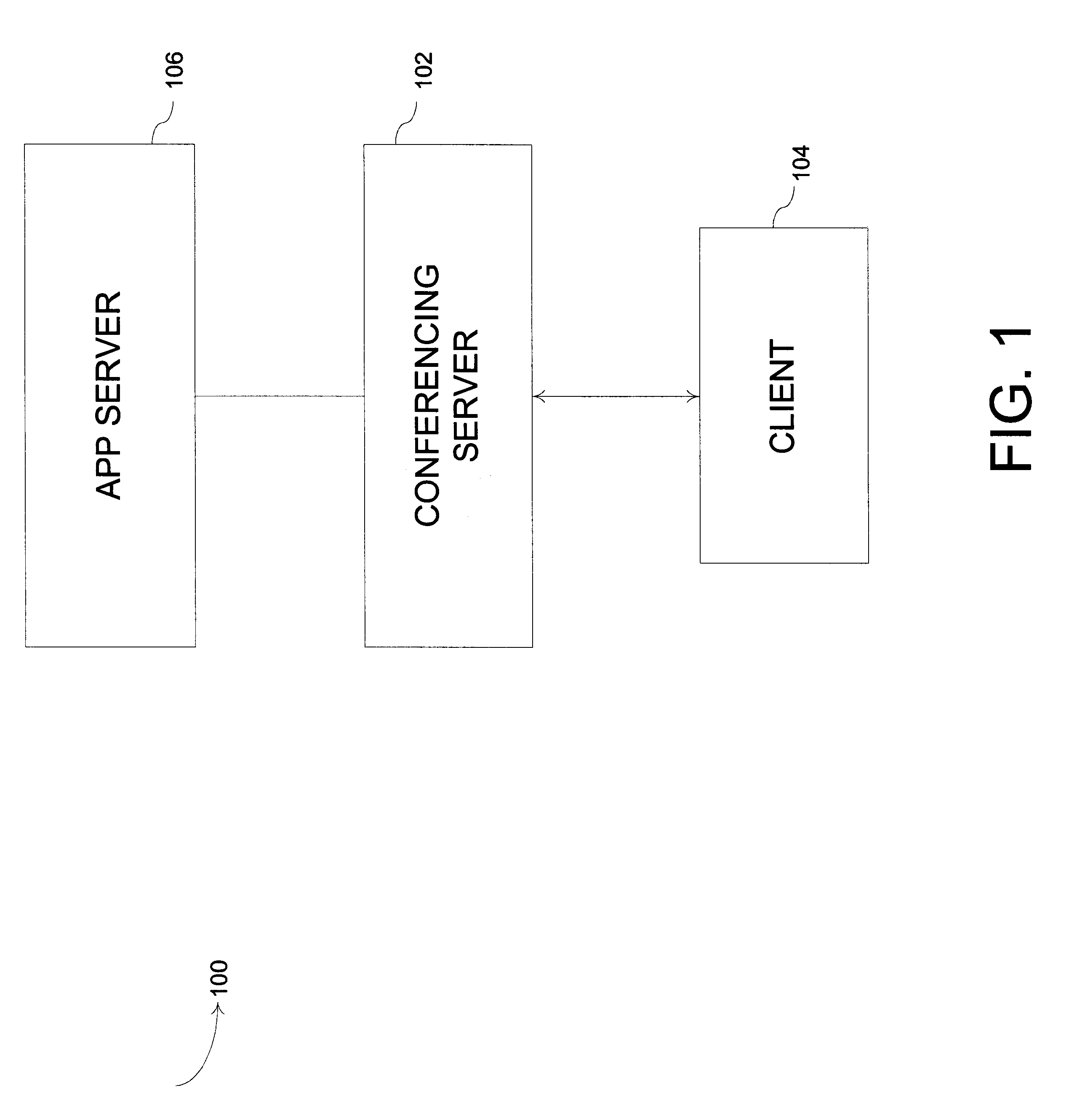
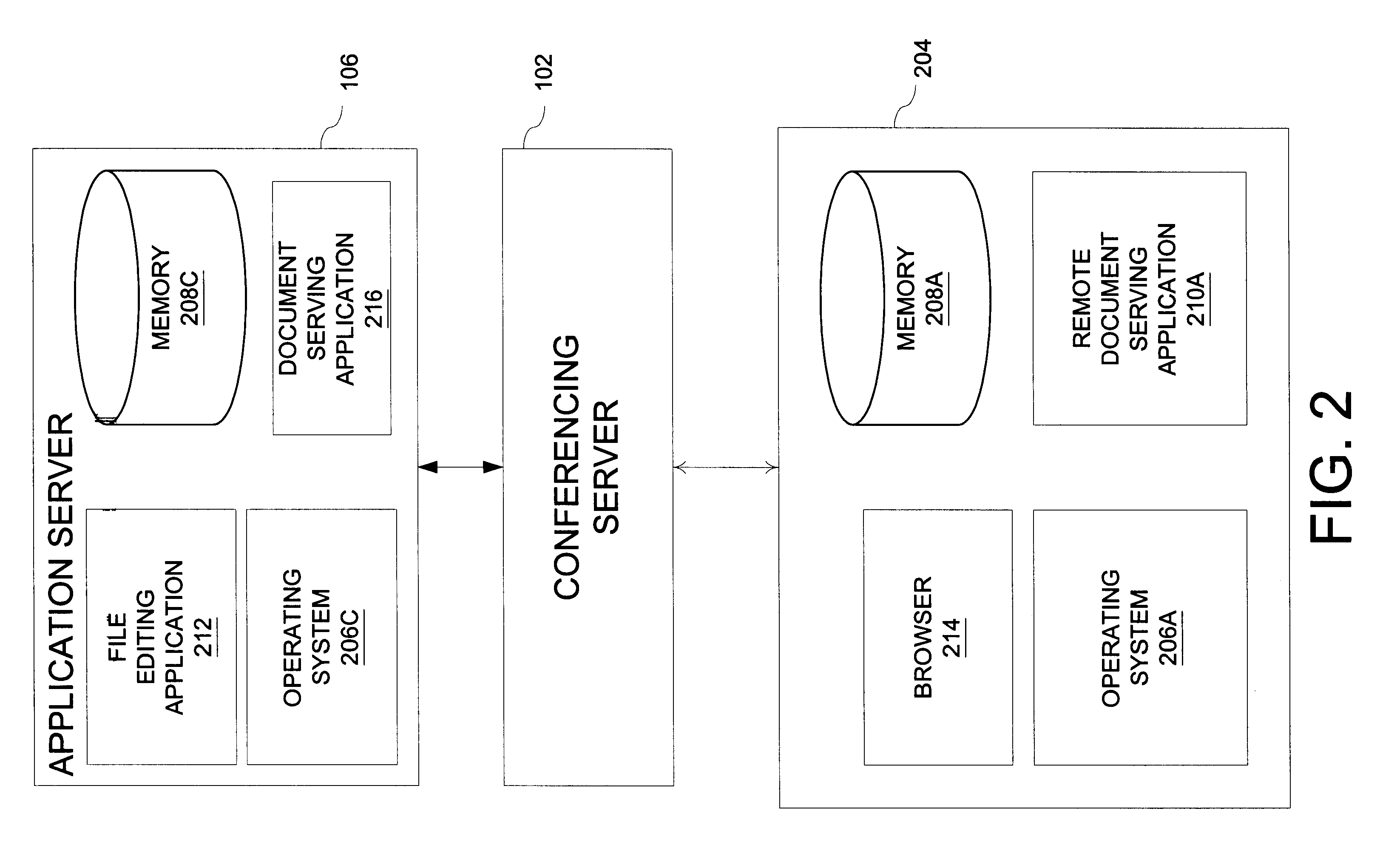
An apparatus, method, and computer program product for instant remote document serving. In one implementation, referred to as "remote document serving," a remote file is converted to a "served document" which is distributed to a member of a data conference for review. In another implementation, referred to as "remote application serving," the "owner" of a remote document views the screens created by a remote application associated with the document. The owner can view the screens and interact with the remote application.
Owner:CISCO TECH INC
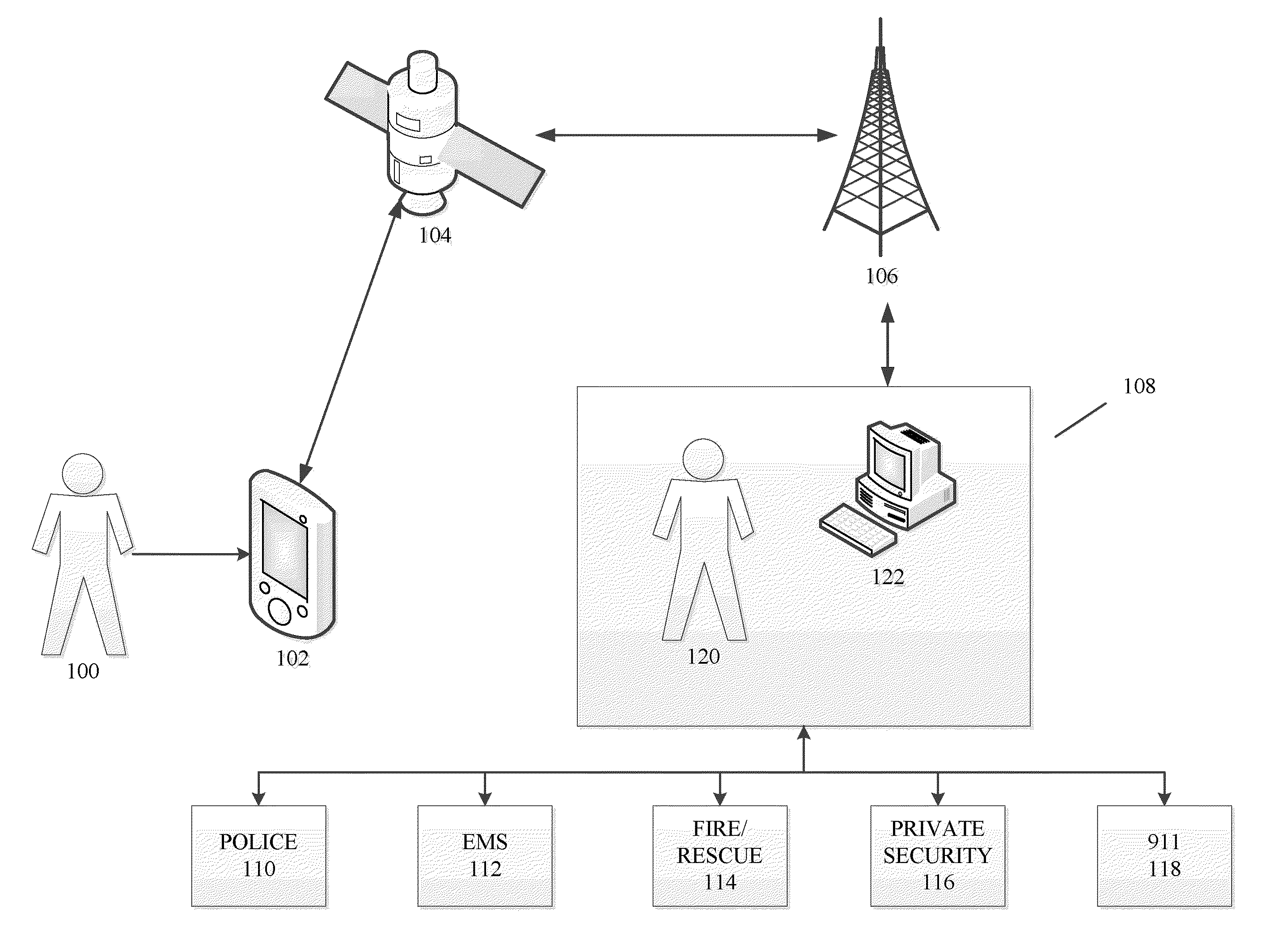
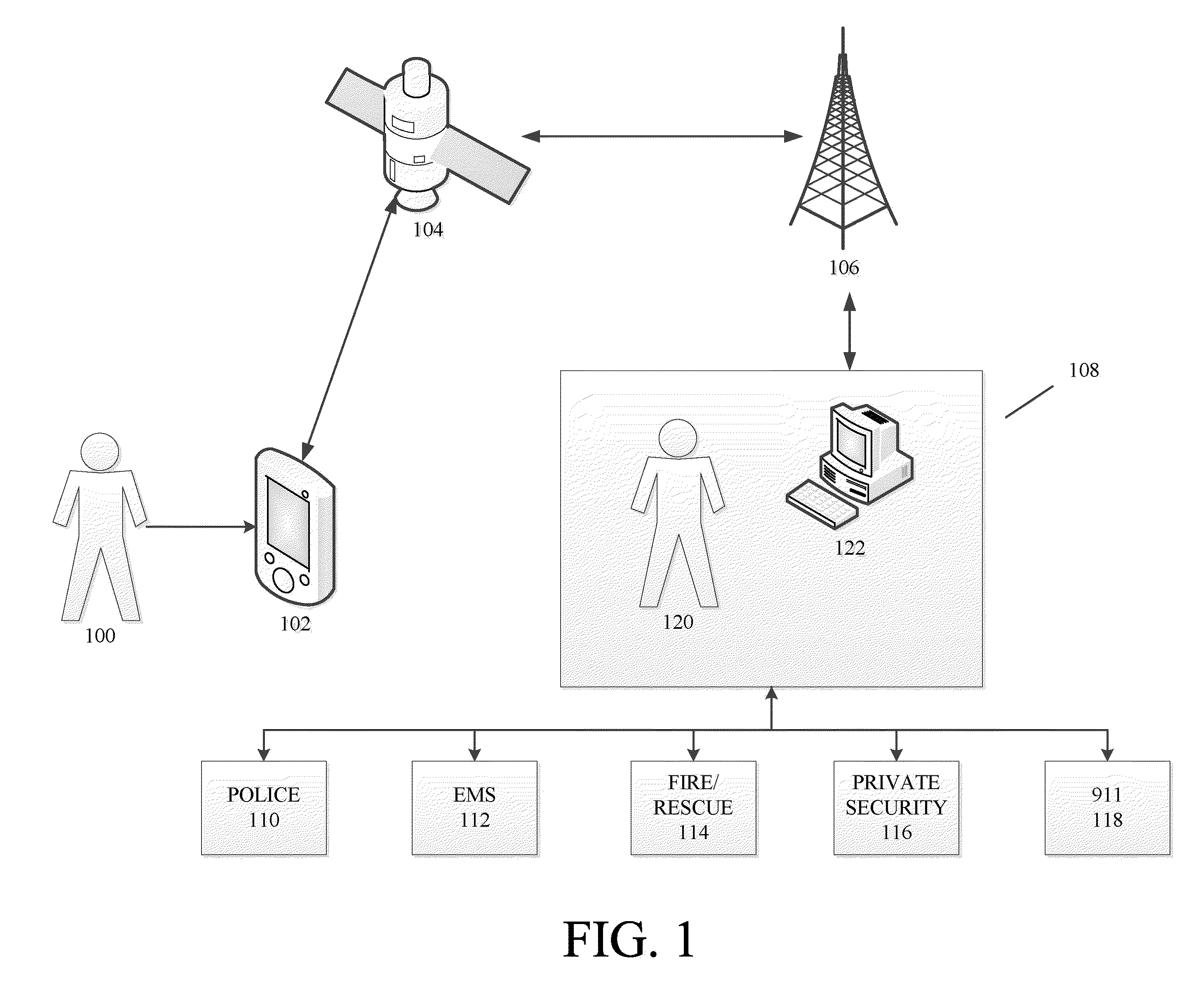
Methods and systems for requesting the aid of security volunteers using a security network
InactiveUS20140118140A1Reduce morbidityMaintain awarenessAlarmsElectric signalling detailsDividing attentionMobile device
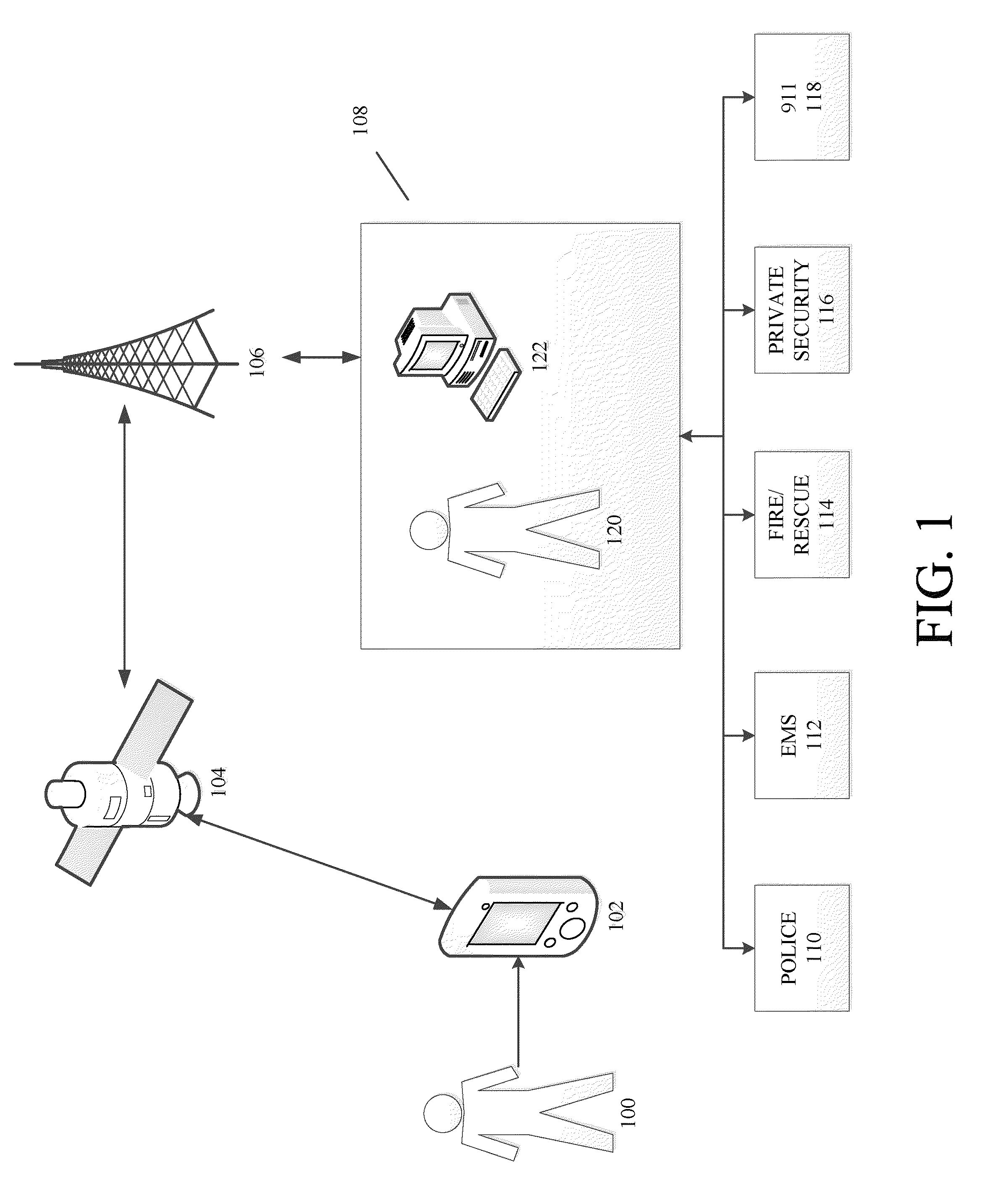
The disclosure generally relates to providing a network of security volunteers who can opt-in to provide security services and / or a physical presence to deter, distract, delay, or prevent a potentially threatening situation. Security volunteers can receive alerts from a central monitoring center regarding nearby distress signals sent from a victim's device, and can then proceed to the location of the victim. Security volunteers can view their location and the location of the victim on a map on their mobile devices, as well as communicate with a victim's device, the central monitoring center, and other security volunteers who are responding to the scene.
Owner:AMIS DAVID
Data access control apparatus for limiting data access in accordance with user attribute
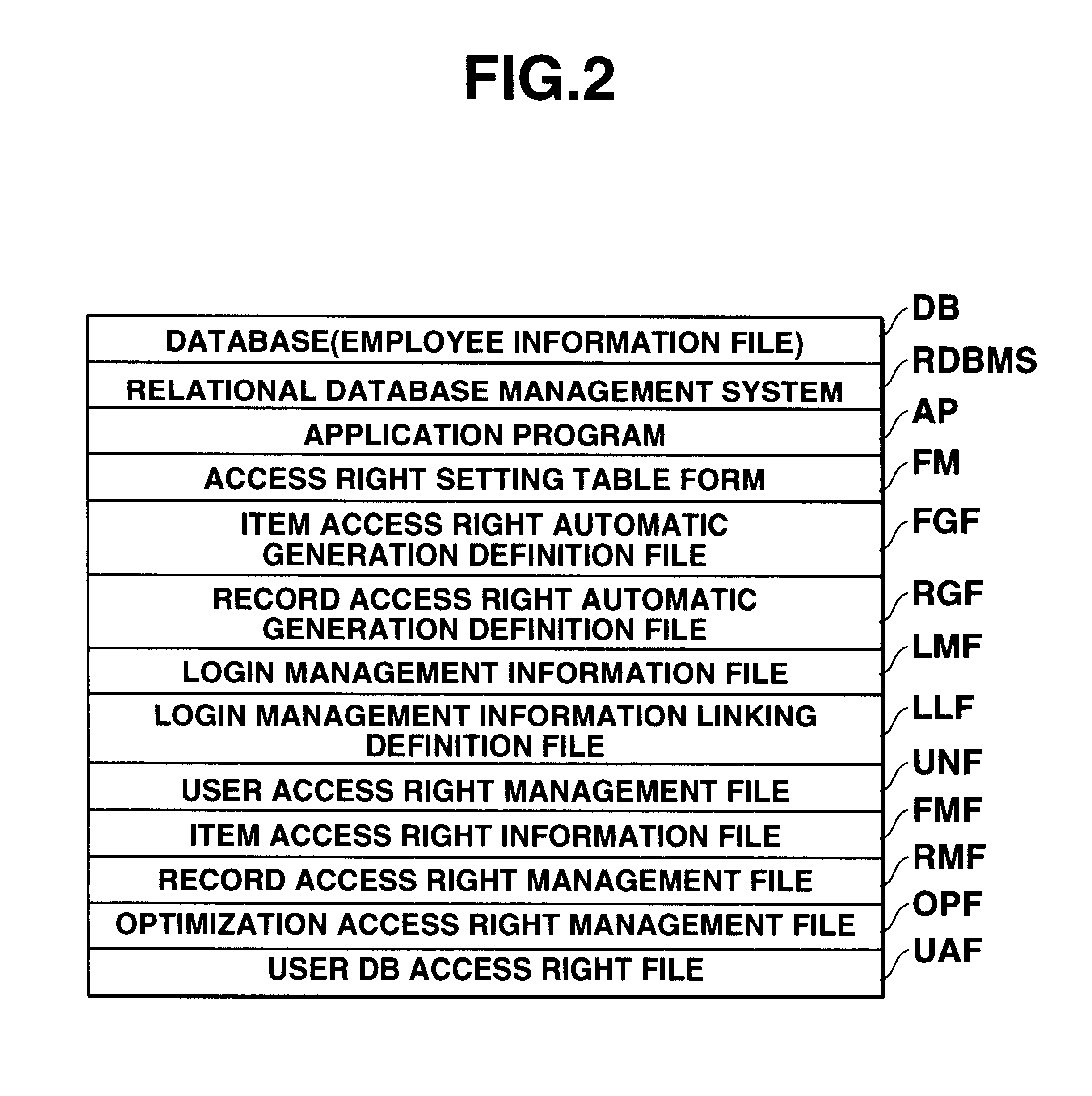
InactiveUS6275825B1Reduce loadPrevent setting errorsData processing applicationsDigital data processing detailsData access controlRights management
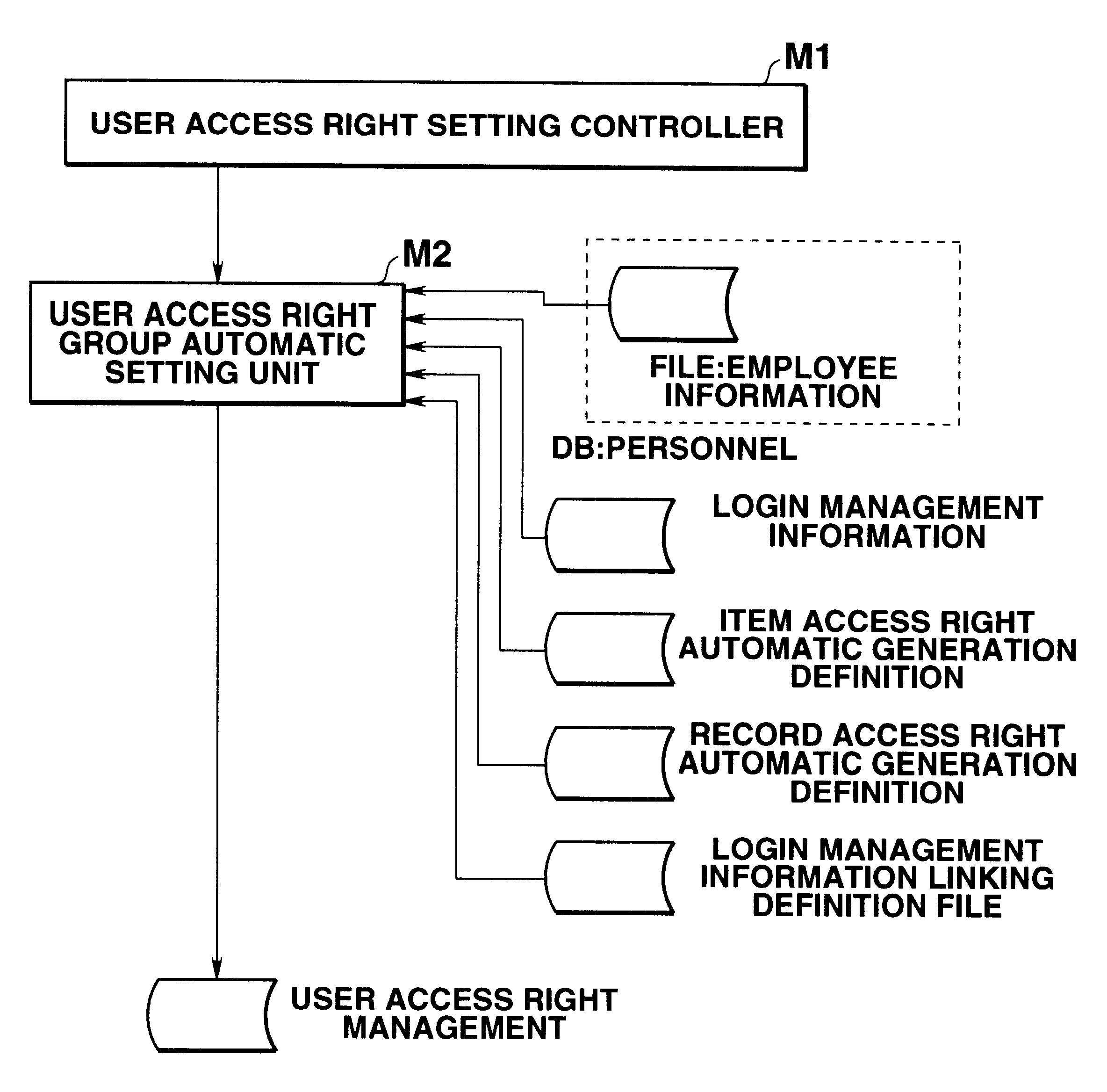
This invention provides a data access control apparatus arranged to automatically set access right information limiting data access, in accordance with a user attribute when a user accesses a database. In setting, for a plurality of users, access right information corresponding to each user, the load on an operator can be reduced, and access right information setting errors can be prevented. An automatic setting unit reads out information from a login management information file and an employee information file on the basis of definition information of a definition files to automatically generate a user access right management file which stores a login ID, an item access right, and a record access right group code for each user. When a login ID is input in accessing the employee information file, a setting controller refers to the management file to determine a user group to which the user belongs and an access enabled / disabled state of the data on the basis of the access right made to correspond to this user group.
Owner:CASIO COMPUTER CO LTD
Methods and systems for threat assessment, safety management, and monitoring of individuals and groups
InactiveUS20110046920A1Improve security levelReduce morbidityError detection/correctionMultiple digital computer combinationsComputer scienceSecurity management
The disclosure generally relates to methods and systems anticipating a potentially threatening or dangerous incident, and providing varying levels of response to a user. In an exemplary embodiment, the present invention provides varying levels of assistance to a user prior to, during, and after a threatening incident occurs. By providing assistance prior to a threatening incident occurring, the system may be able to thwart potential attacks, bodily harm, robberies, break-ins, and other criminal or dangerous activity. The assistance can be, for example, in the form of deterrents, alerting first responders to go to the scene, sending security personnel to the scene, remotely monitoring the scene, remotely interacting with the scene, providing information and advice to the user.
Owner:STRIDER
Communication apparatus and method using human body as medium
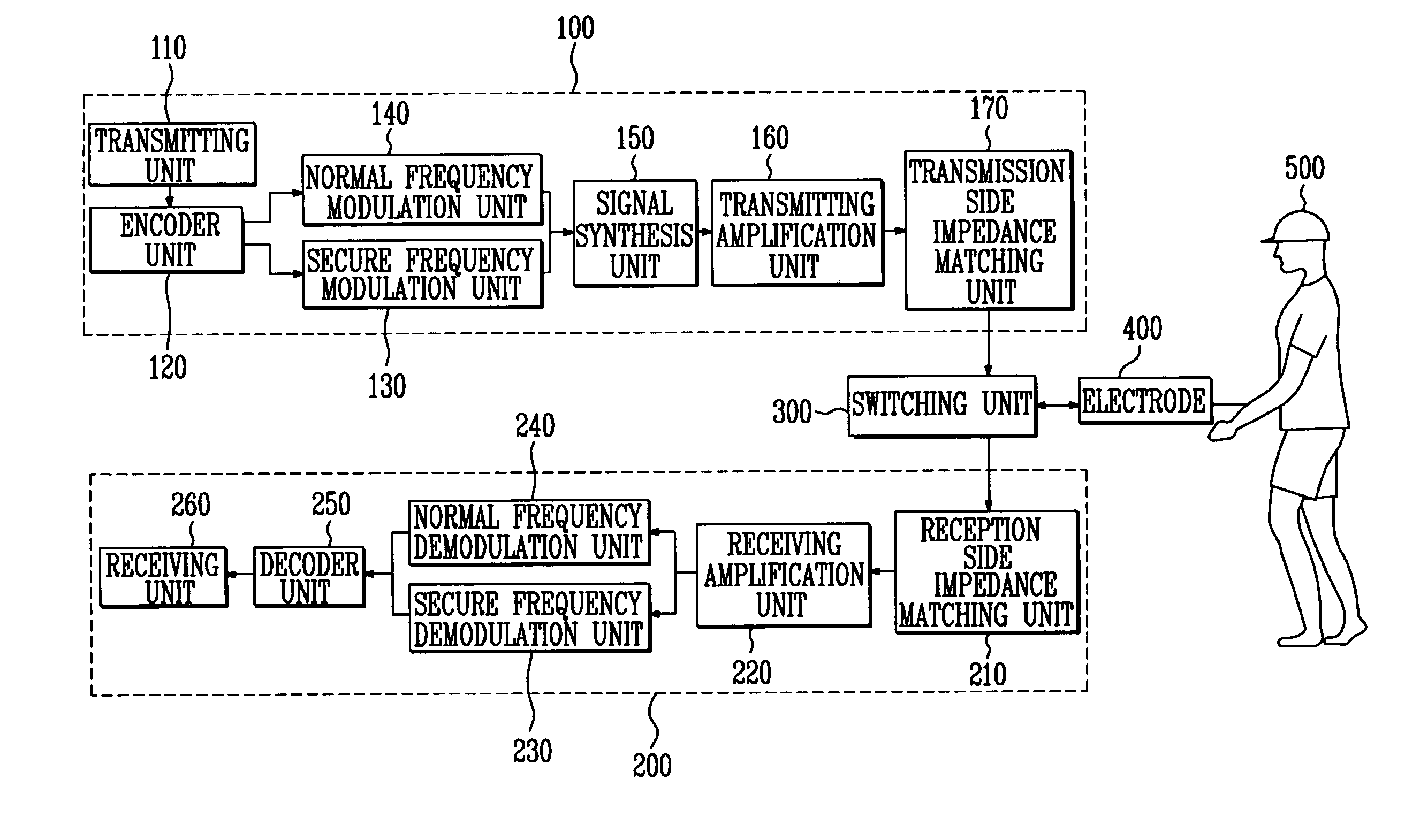
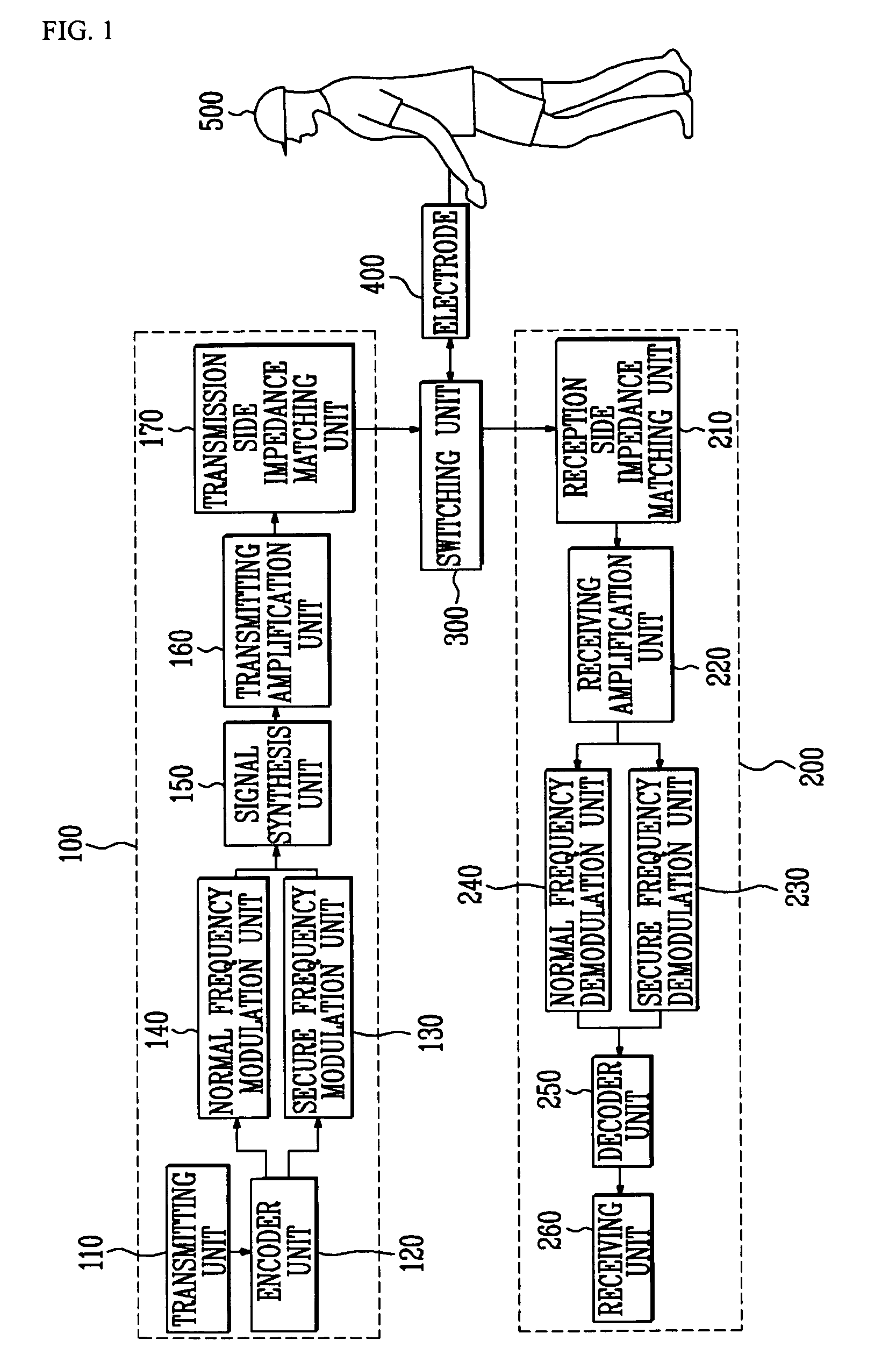
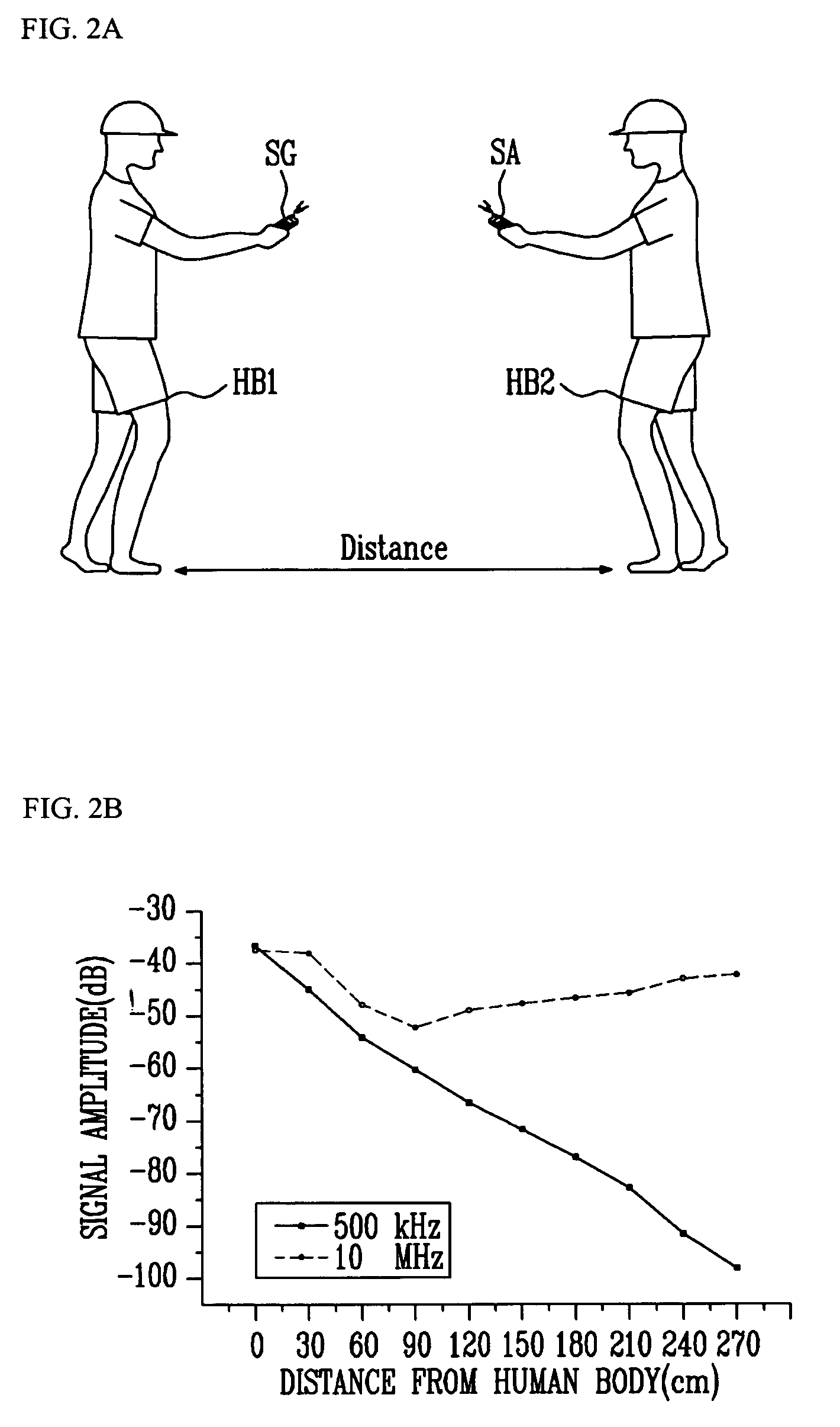
ActiveUS7171177B2Improve data transfer rateMaintain securityUnauthorised/fraudulent call preventionEavesdropping prevention circuitsHuman bodyData signal
Provided is to a communication apparatus and method using a human body as a medium, in which secure / normal data signals are transmitted / received to the inside and outside of a human body respectively, through at least two different frequency channels classified according to a predetermined reference value, to thereby efficiently use a frequency based on a physical characteristic of a channel and increase a data transmission rate while maintaining security.
Owner:ELECTRONICS & TELECOMM RES INST
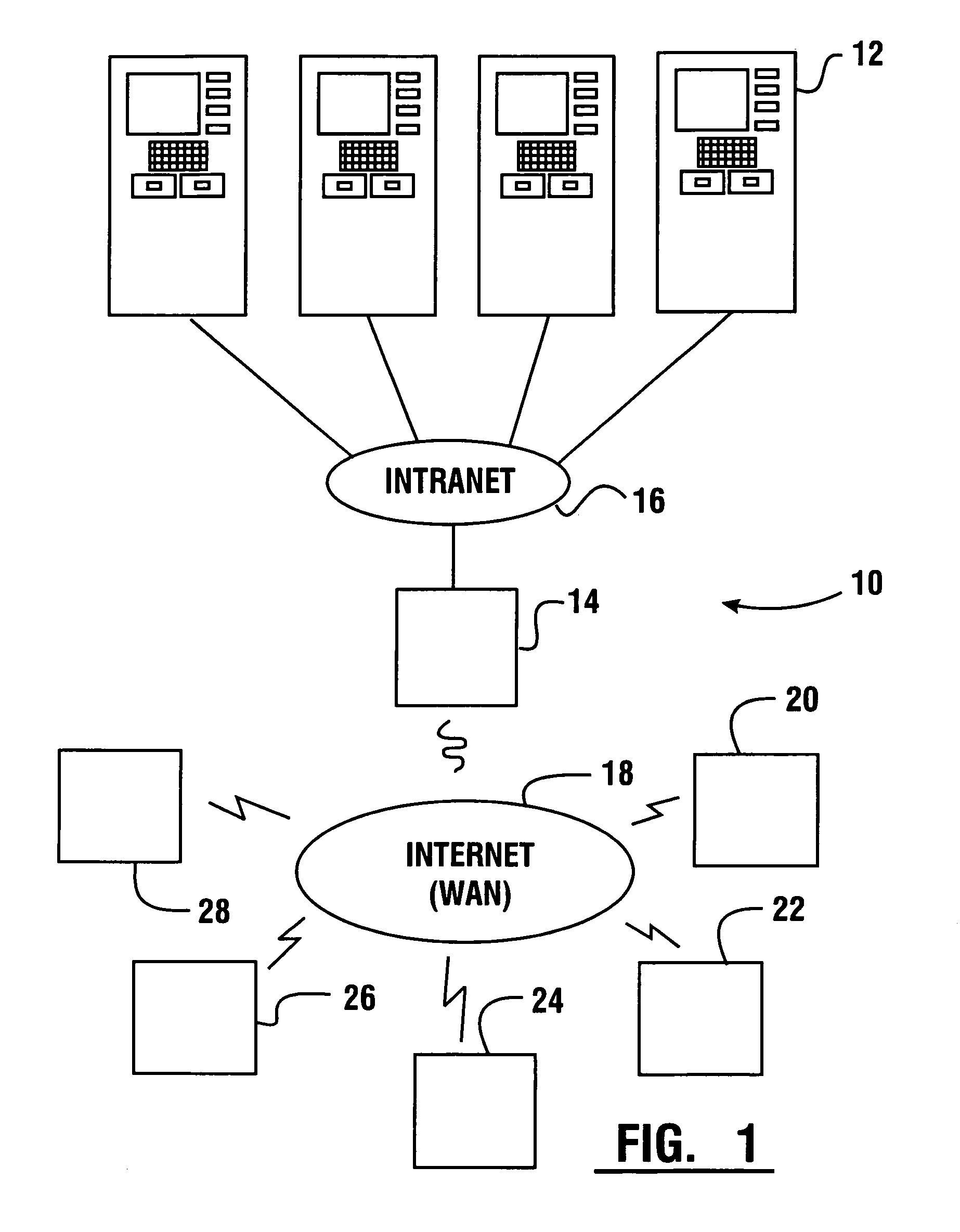
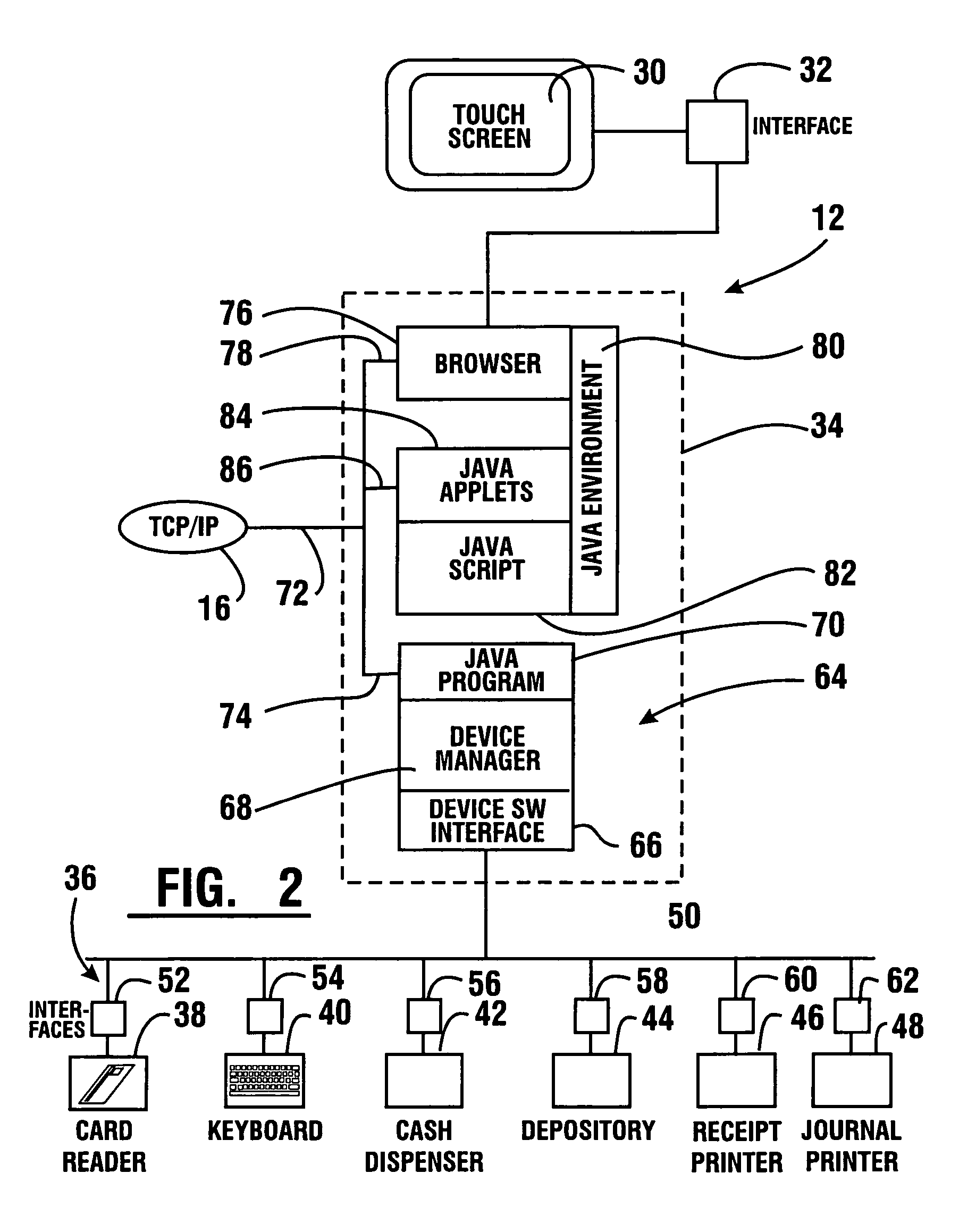
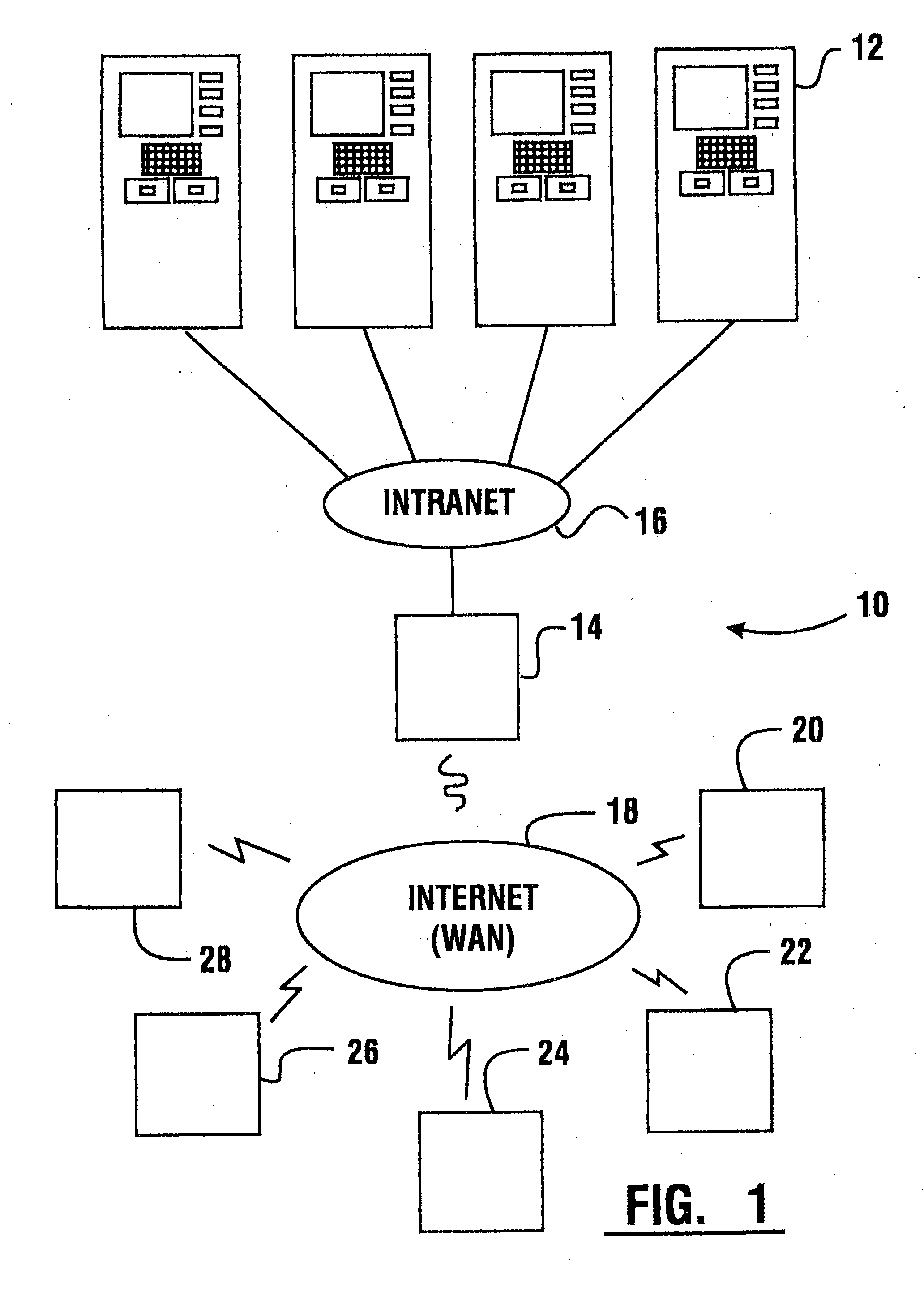
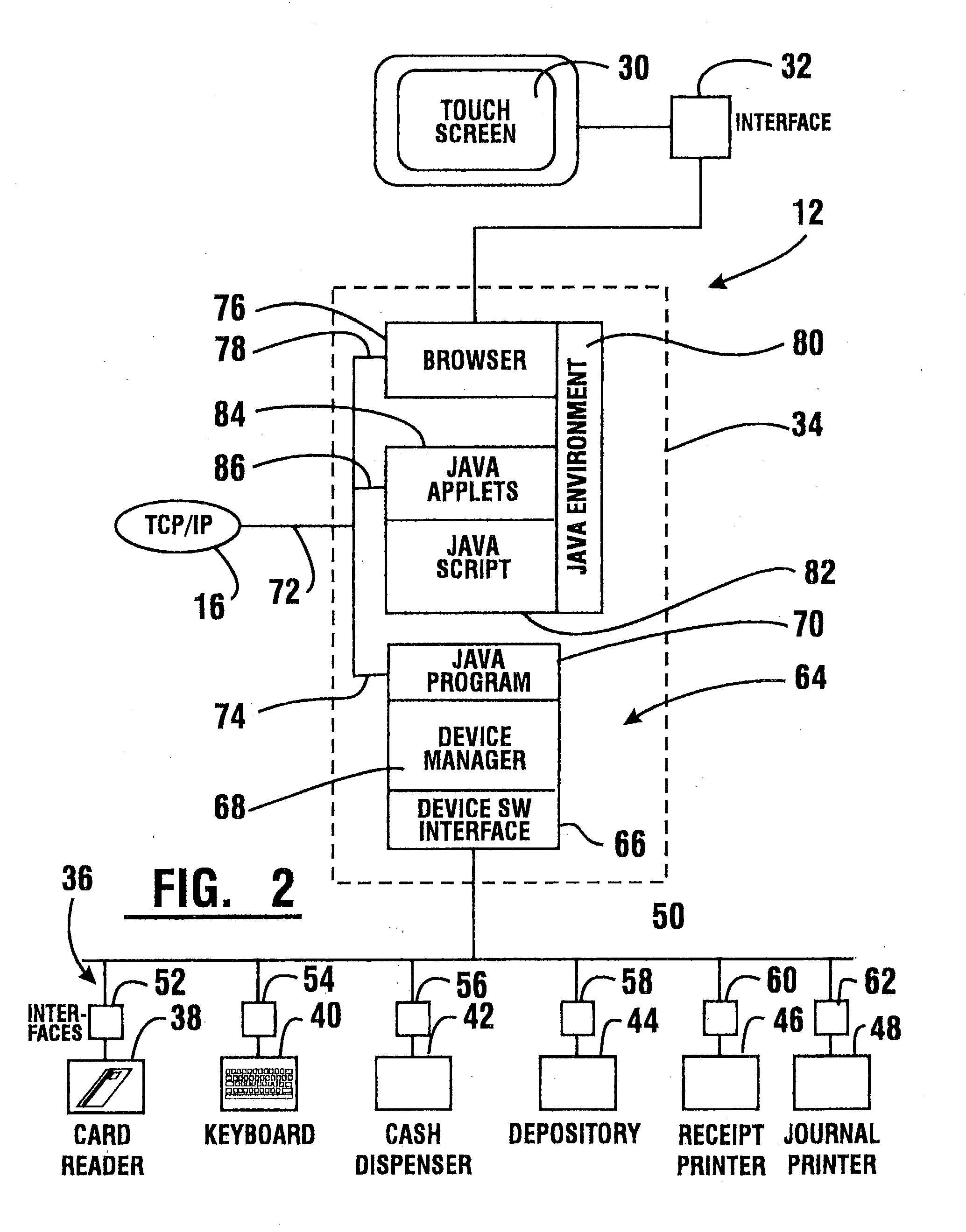
Cash dispensing automated banking machine system and communication method
InactiveUS7606767B1Easy to operateMaintain securityFinancePayment architectureApplication serverMachining system
A method of operating an automated banking machine is provided. The method comprises sending a configuration XML message to an ATM from an application server, wherein the configuration XML data includes configuration data targeted to the ATM. The method also includes sending with the application server an application XML message to the ATM, wherein the application XML message includes application data. In addition, the method includes mapping the application data to at least one corresponding resource on the ATM responsive to the configuration data. In addition, the method includes performing a banking transaction using the at least one resource on the ATM responsive to the application XML message.
Owner:DIEBOLD NIXDORF
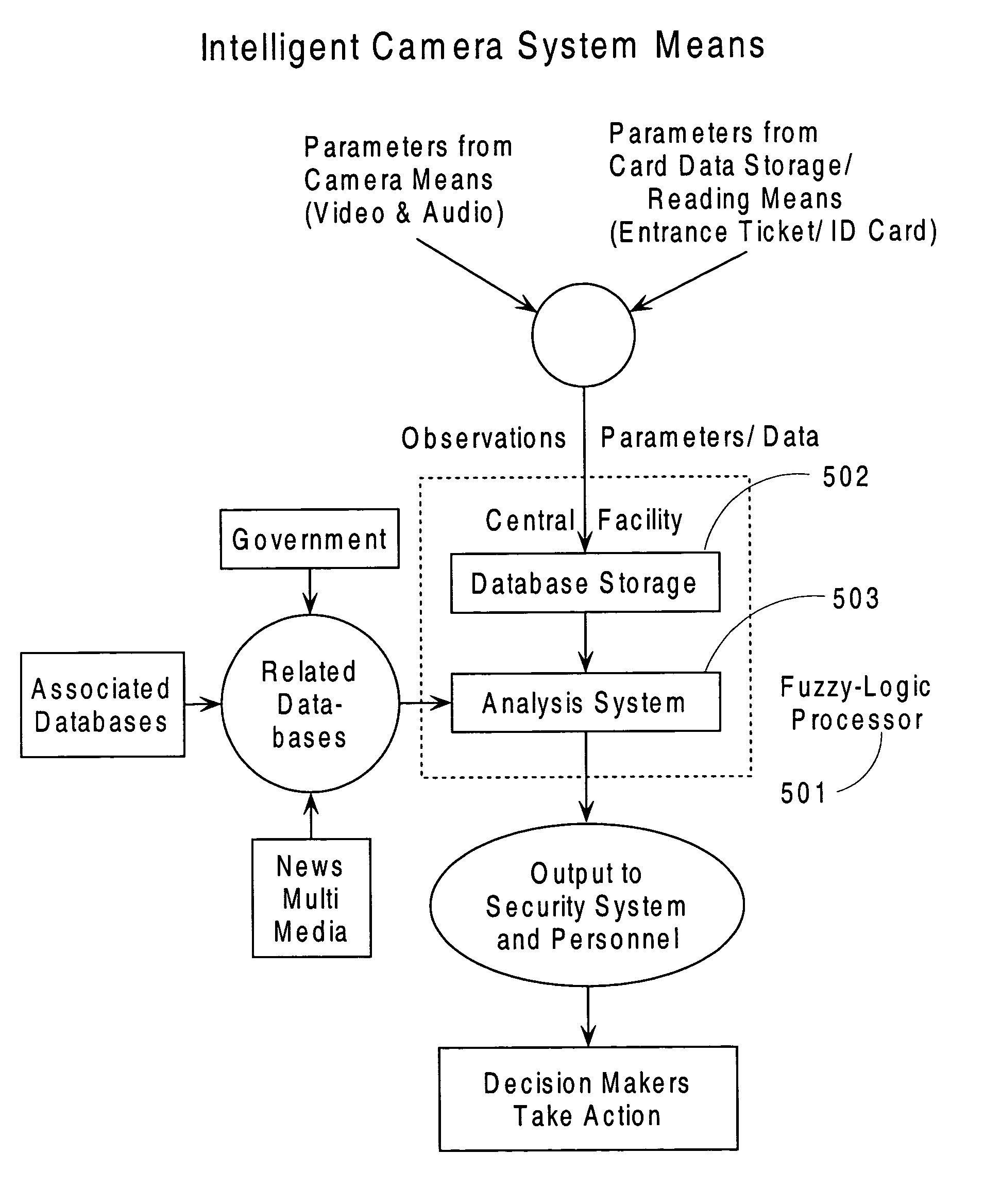
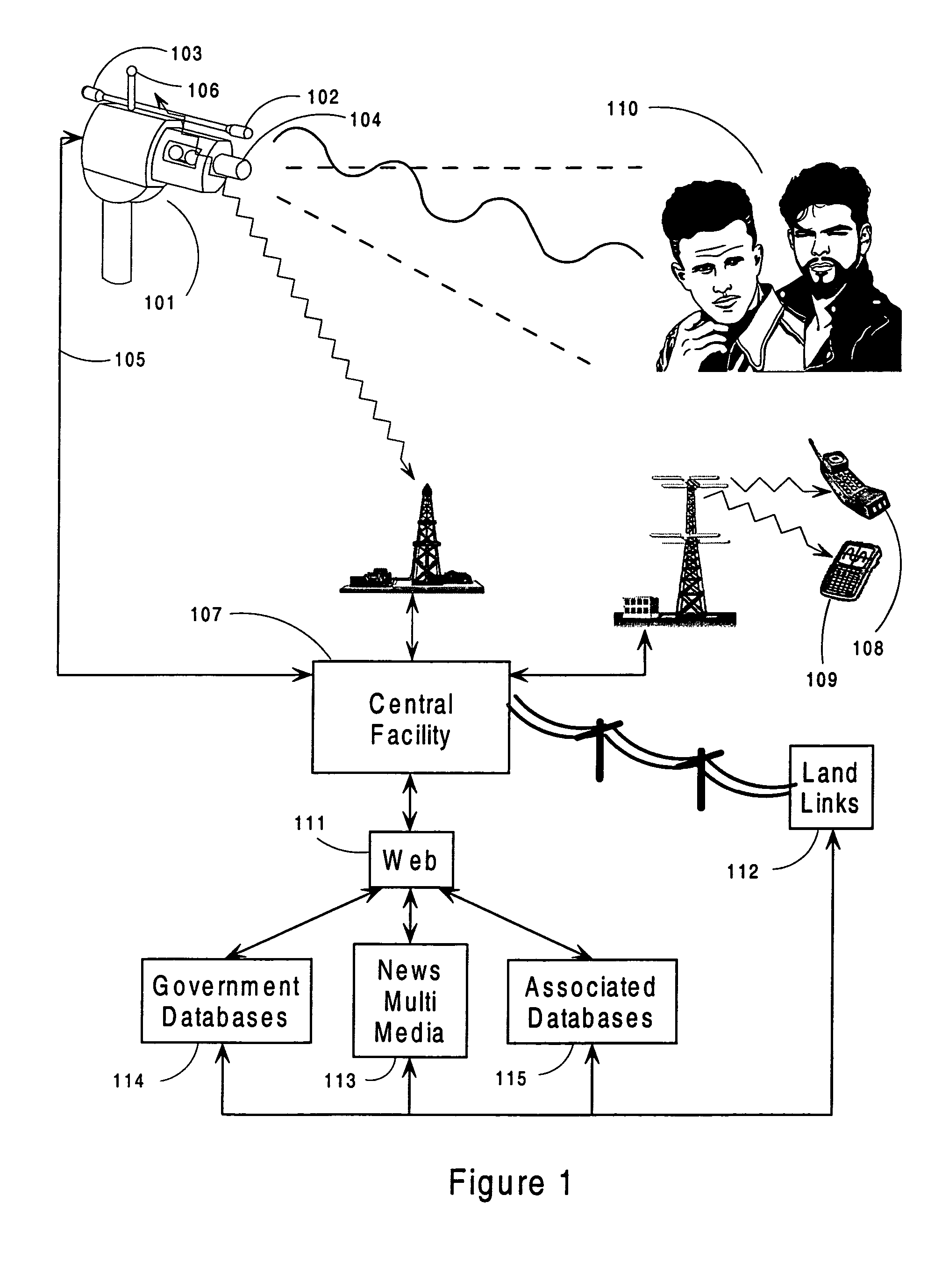
Voice, lip-reading, face and emotion stress analysis, fuzzy logic intelligent camera system
InactiveUS20060028556A1Improve abilitiesMaintain integrityTelevision system detailsColor television detailsPattern recognitionCrowds
Revealed is an intelligent camera security monitoring, fuzzy logic analyses and information reporting system that includes video / audio camera, integrated local controller, interfaced plurality of sensors, and input / output means, that collects and analyses data and information observations from a viewed scene and communicates these to a central controller. The central controller with fuzzy logic processor receives, stores these observations, conducts a plurality of computer analyses techniques and technologies including face, voice, lip reading, emotion, movement, pattern recognition and stress analysis to determine responses and potential threat of / by a person, crowd, animal, action, activity or thing. This invention recognizes possible terrorists, criminals, enraged or dangerous persons and also can identify a person's level of intoxication or impairment by alcohol or drugs via a new “Visual Response Measure”. The invention provides an intelligent tool to assist security systems and personnel, improving capability to record, display and share information and maintain security.
Owner:STRESSCAM OPERATIONS & SYST
Universal, Biometric, Self-Authenticating Identity Computer Having Multiple Communication Ports
InactiveUS20080148059A1Maintain securityLimited accessUser identity/authority verificationPayment architectureSmart cardCard reader
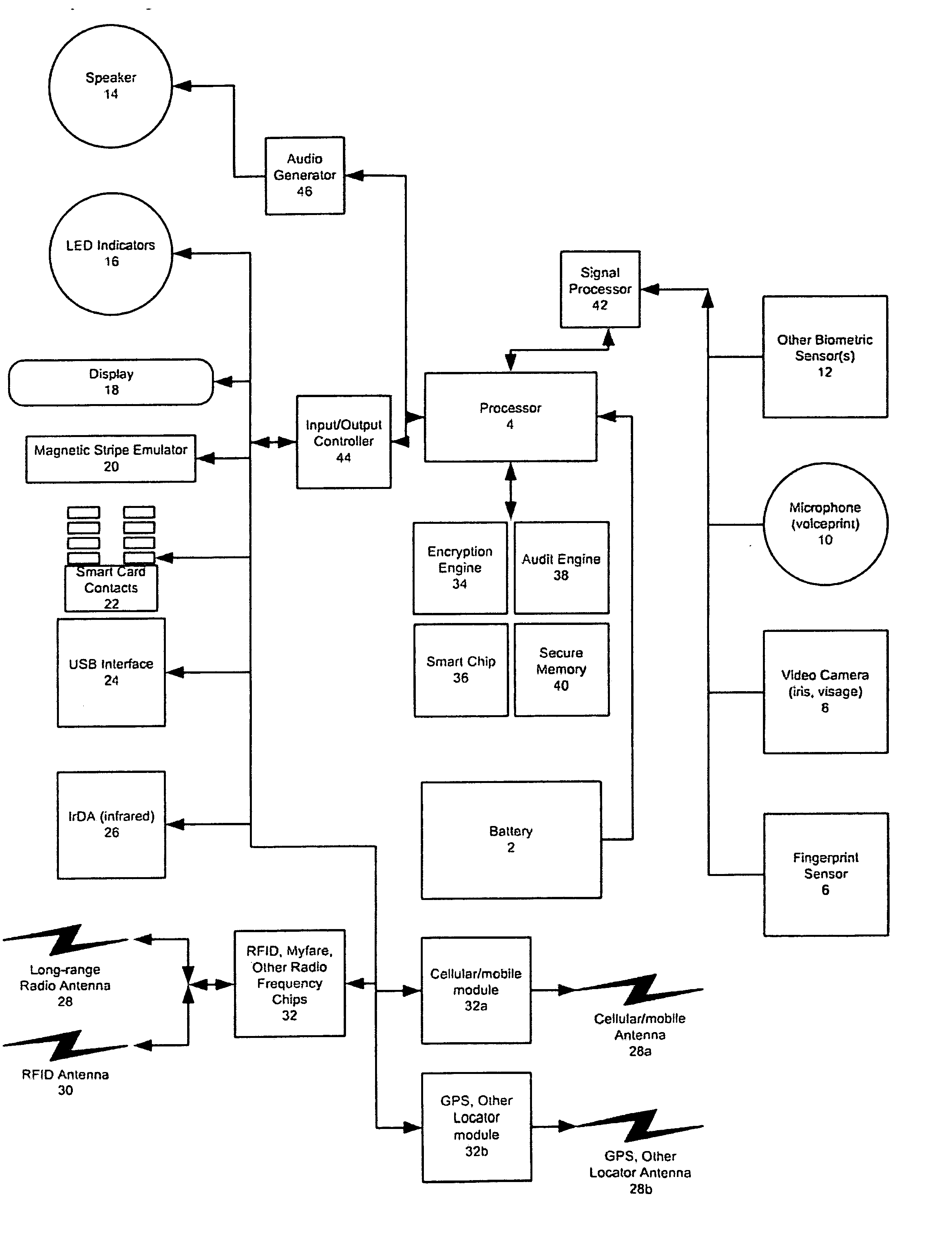
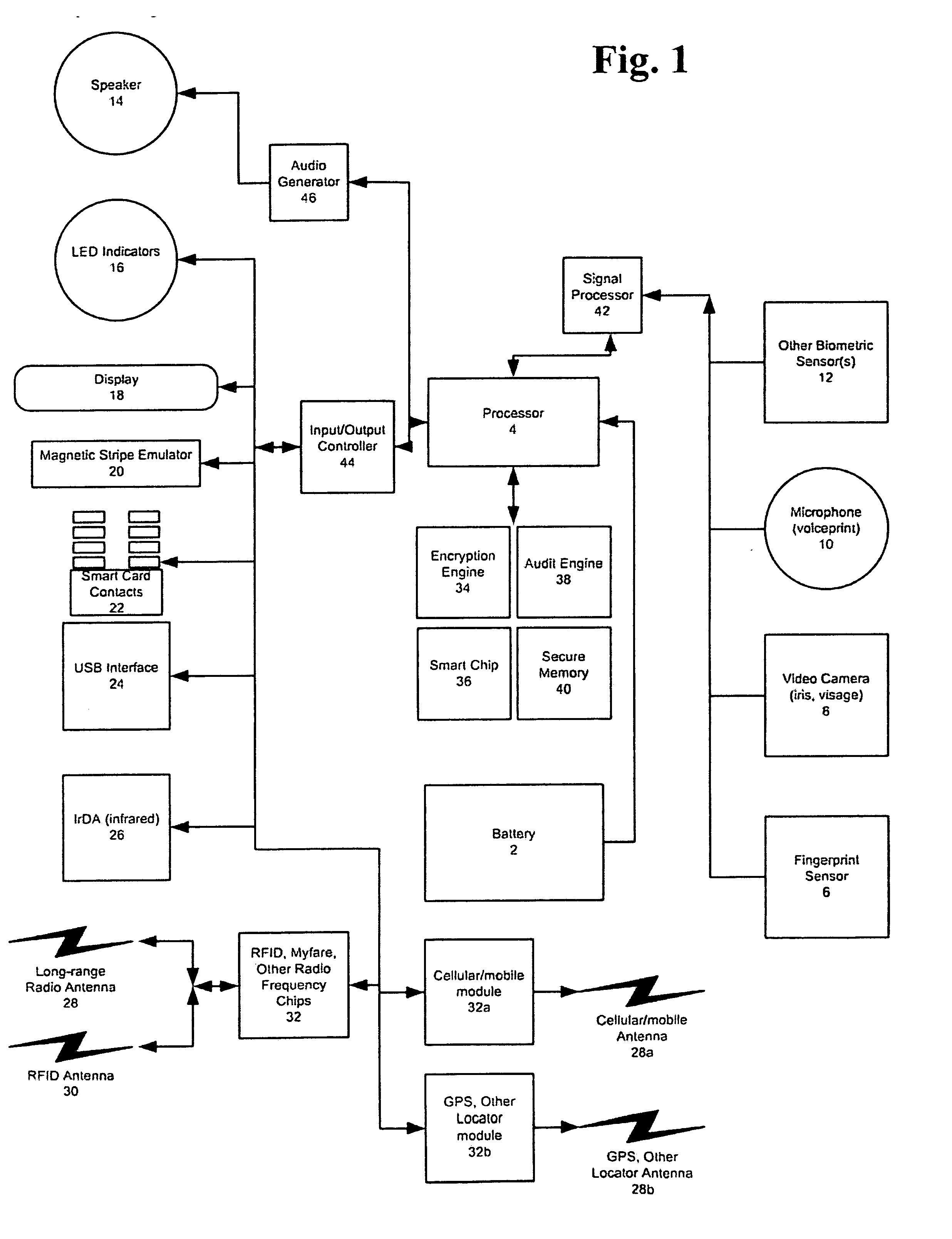
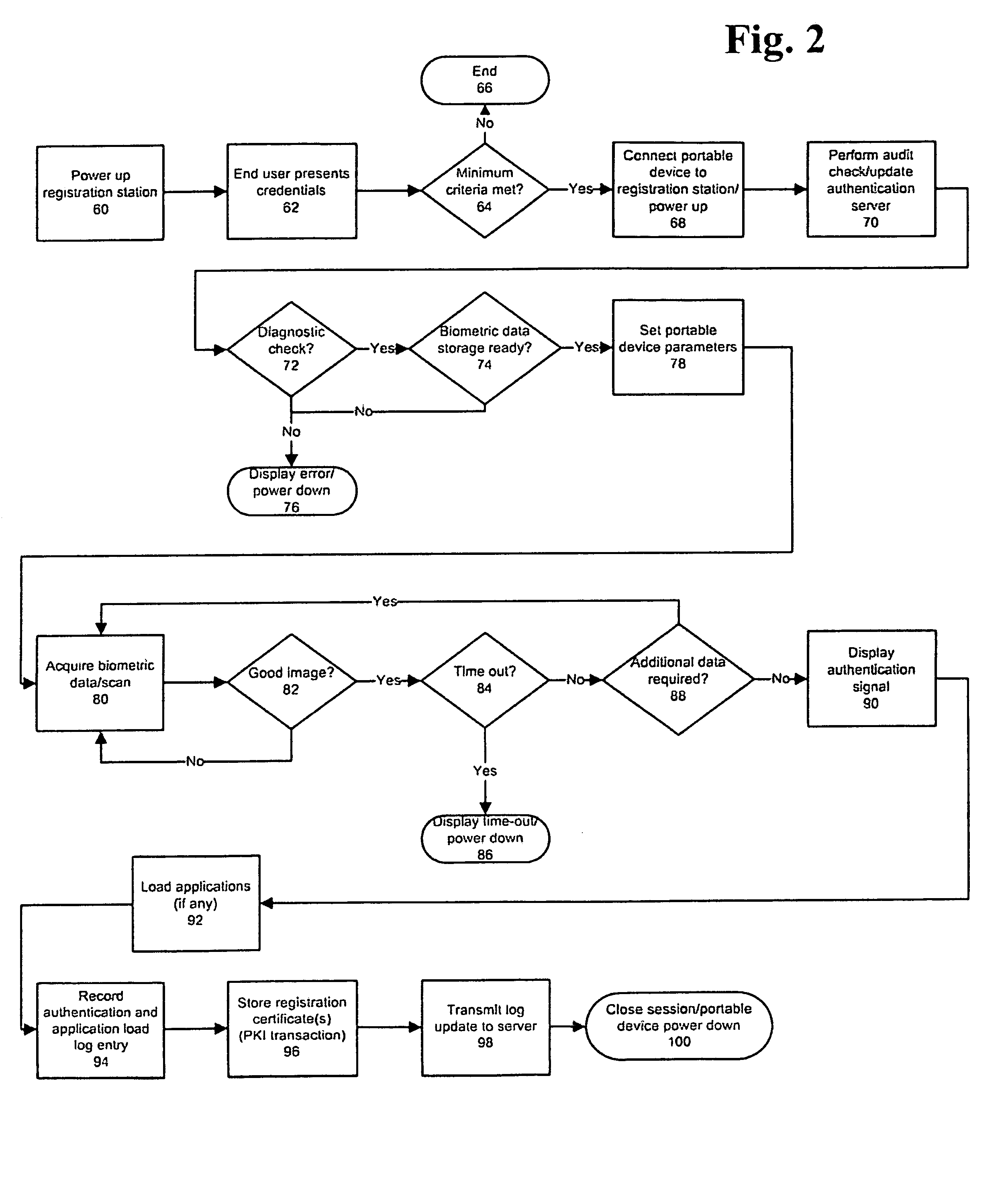
An improved device for use in authorizing transactions, supplying information and performing applications is provided by the present invention, effectively implementing a secured individual and portable Public Key Infrastructure (PKI) terminal. The device uses a local processor and secure data storage in conjunction with a variety of sensors to perform authentication processes that establish an individuals identity and provide authority to perform a desired transaction. The sensors allow the device to directly scan biometric identifying information from an individual. A card swipe interface and a proximity antenna are provided to facilitate communication between the device and remote interface devices such as magnetic swipe card readers, smart card readers, infrared communications ports and proximity and long range radio scanners. In addition, the local processor, memory, display and user inputs allow the device to run applications such as those performed by a traditional computer, gaming device, personal data assistant and smart phone.
Owner:SHAPIRO MICHAEL F
Force feedback devices using fluid braking
InactiveUS7113166B1High strengthLow costInput/output for user-computer interactionCathode-ray tube indicatorsInherent safetyFluid viscosity
A haptic feedback device including a fluid viscosity-controlled brake that outputs high forces to the device user at low cost while maintaining inherent safety. An interface device includes a manipulandum physically contacted by the user. A sensor senses a position of the manipulandum and outputs a sensor signal. The interface device also includes a brake including a field-controlled fluid having a viscosity that can be controlled by controlling an electric current in a coil, where a resistive force or drag on the manipulandum is controlled by controlling the fluid's viscosity. The fluid can be an electrorheological fluid controlled by an electric field or a magnetorheological fluid controlled by a magnetic field. In one preferred embodiment, the resistive force is controlled by adjusting a degree of contact of the brake with the manipulandum based on the fluid's viscosity. Disclosed embodiments include fishing devices, bicycle simulators, and control knobs.
Owner:IMMERSION CORPORATION
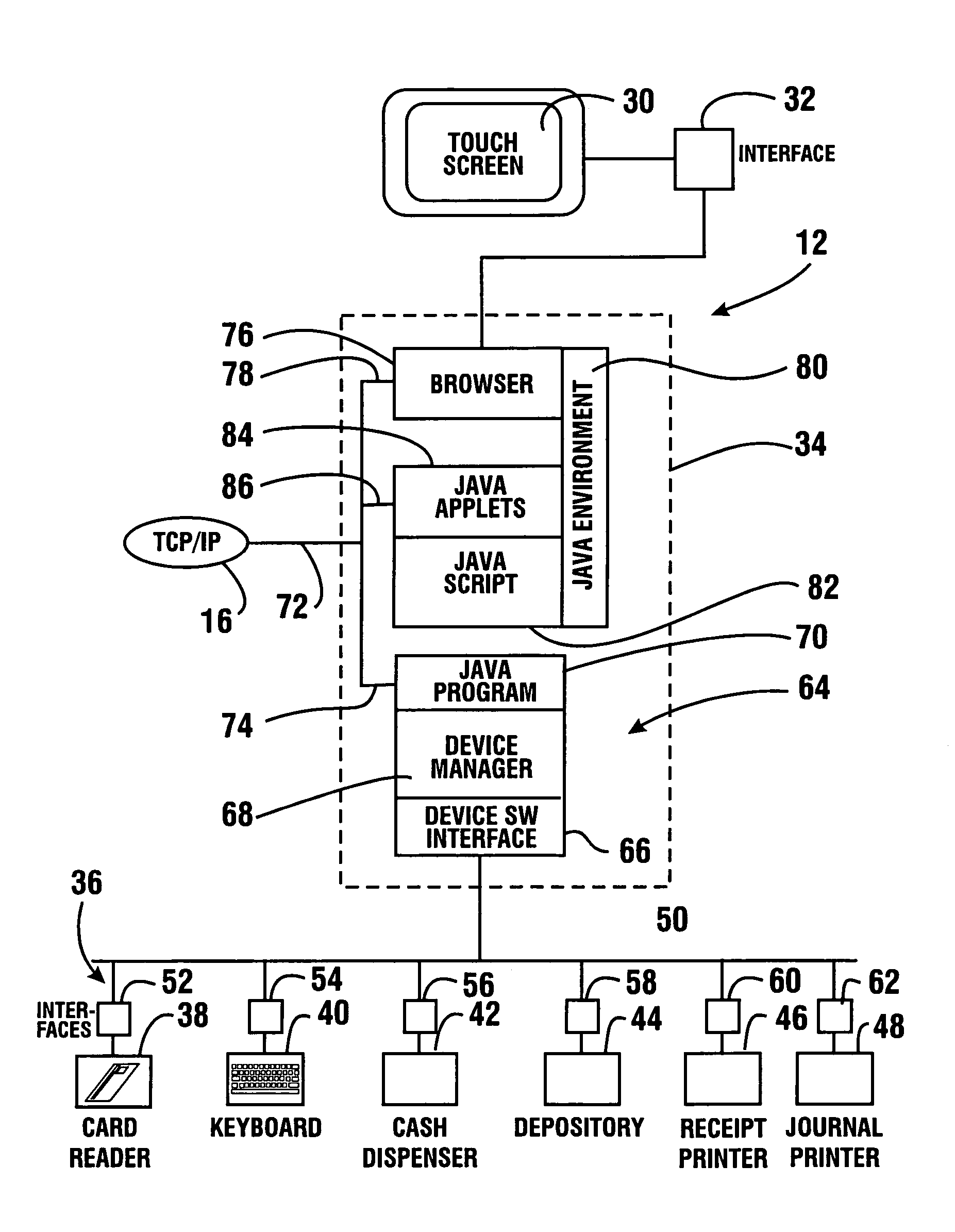
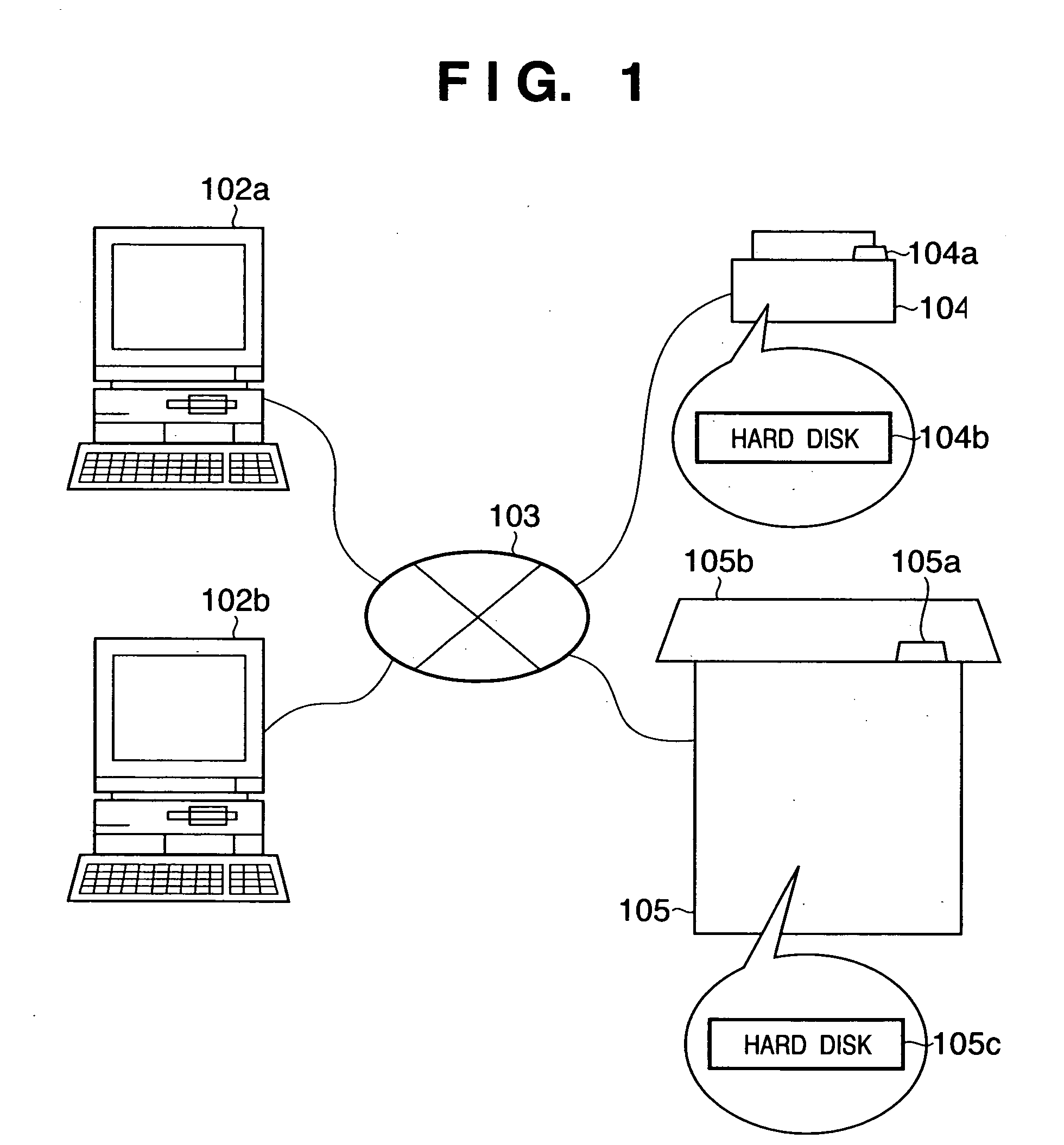
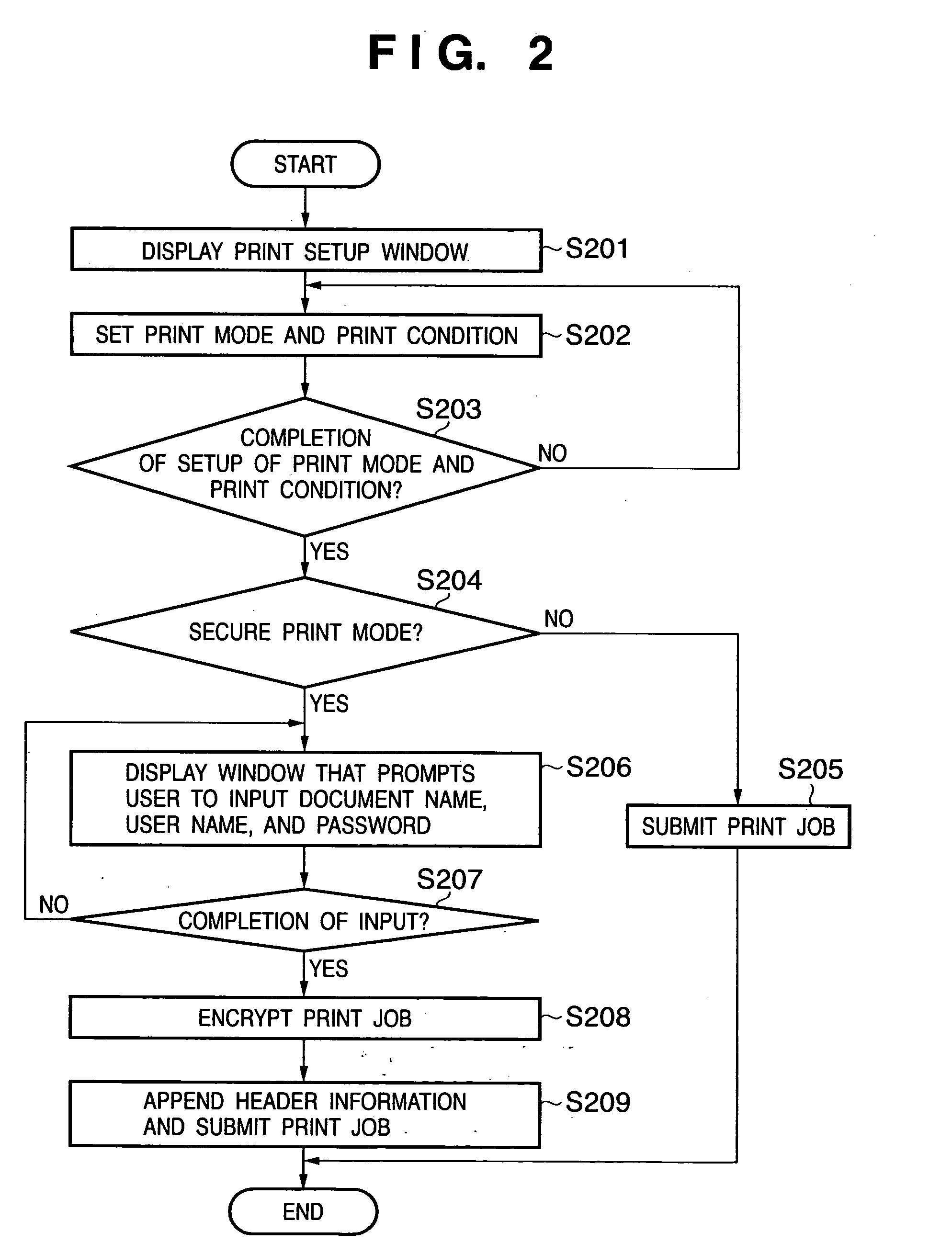
Print apparatus, print system, print method, job processing method, storage medium, and program
InactiveUS20050100378A1Maintain securityImprove securityDigital data processing detailsUser identity/authority verificationComputer scienceAuthentication
In order to maintain high security of a job that requires a high security level even after a print interrupt factor has been removed, and to achieve both the effect of maintaining high security of a job that requires a high security level even after the print process is interrupted, and the effect of improving the productivity of jobs other than a job of this type, when a print apparatus which can process a plurality of print jobs including a print job of a first type and that of a second type restarts a print operation of a print job, which is interrupted in the print apparatus, and when the print job is a print of the first type, the print apparatus is controlled to execute an authentication process, and then allowed to restart the print operation of the print job. When the print apparatus restarts a print operation of a print job, which is interrupted in the print apparatus, and when the print job is a print of the second type, the print apparatus is allowed to restart the print operation of the print job without executing the authentication process.
Owner:CANON KK
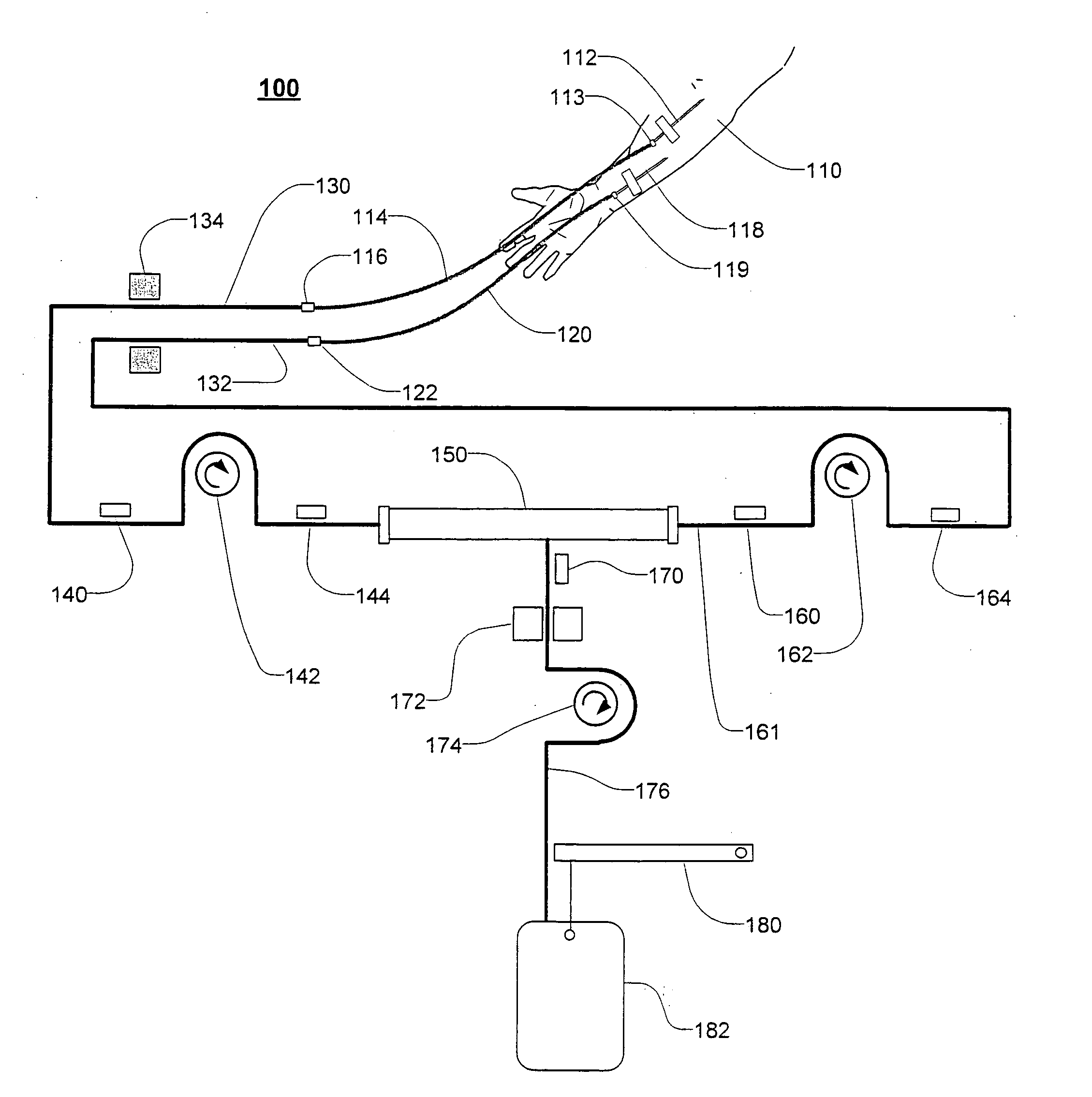
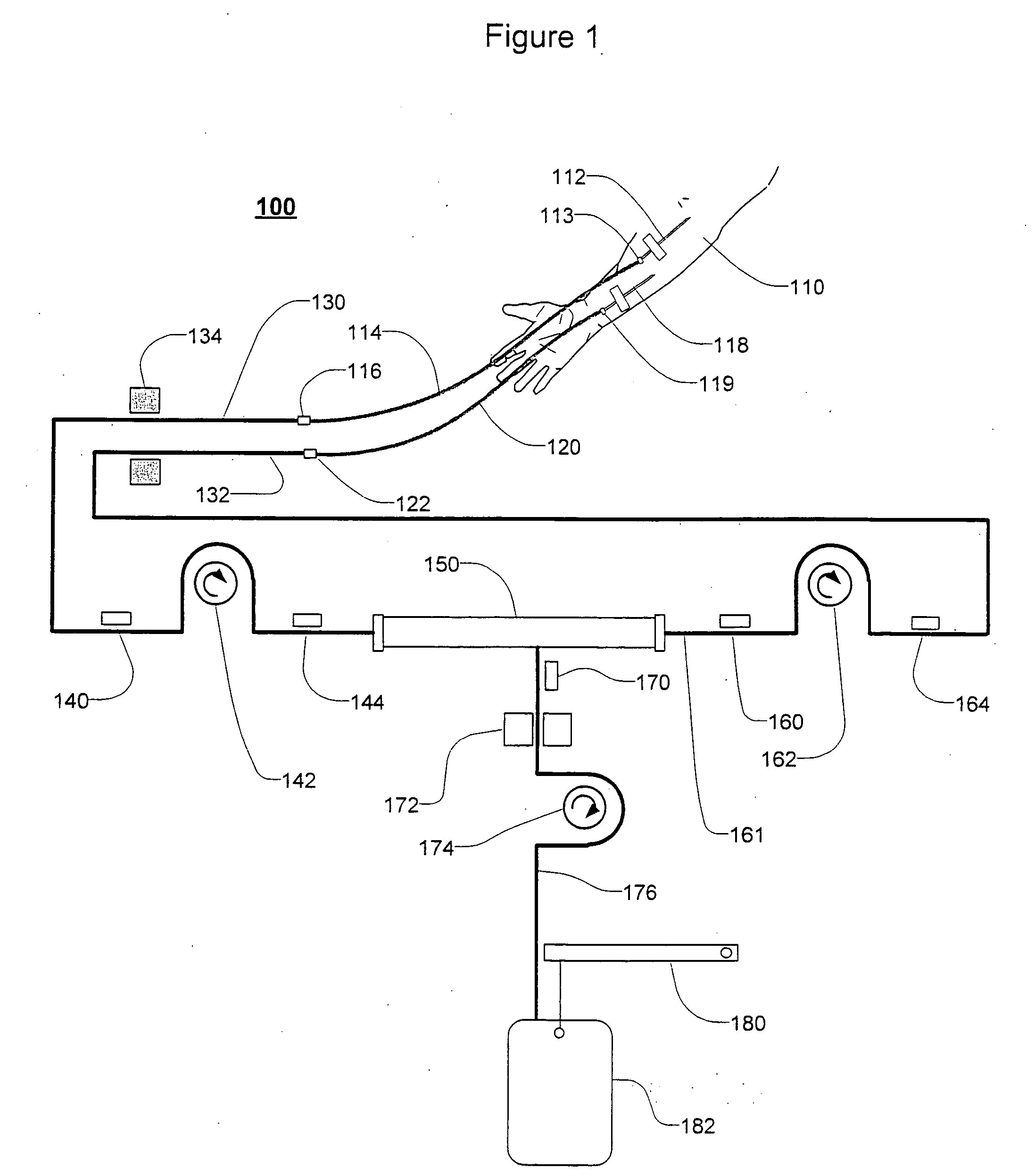
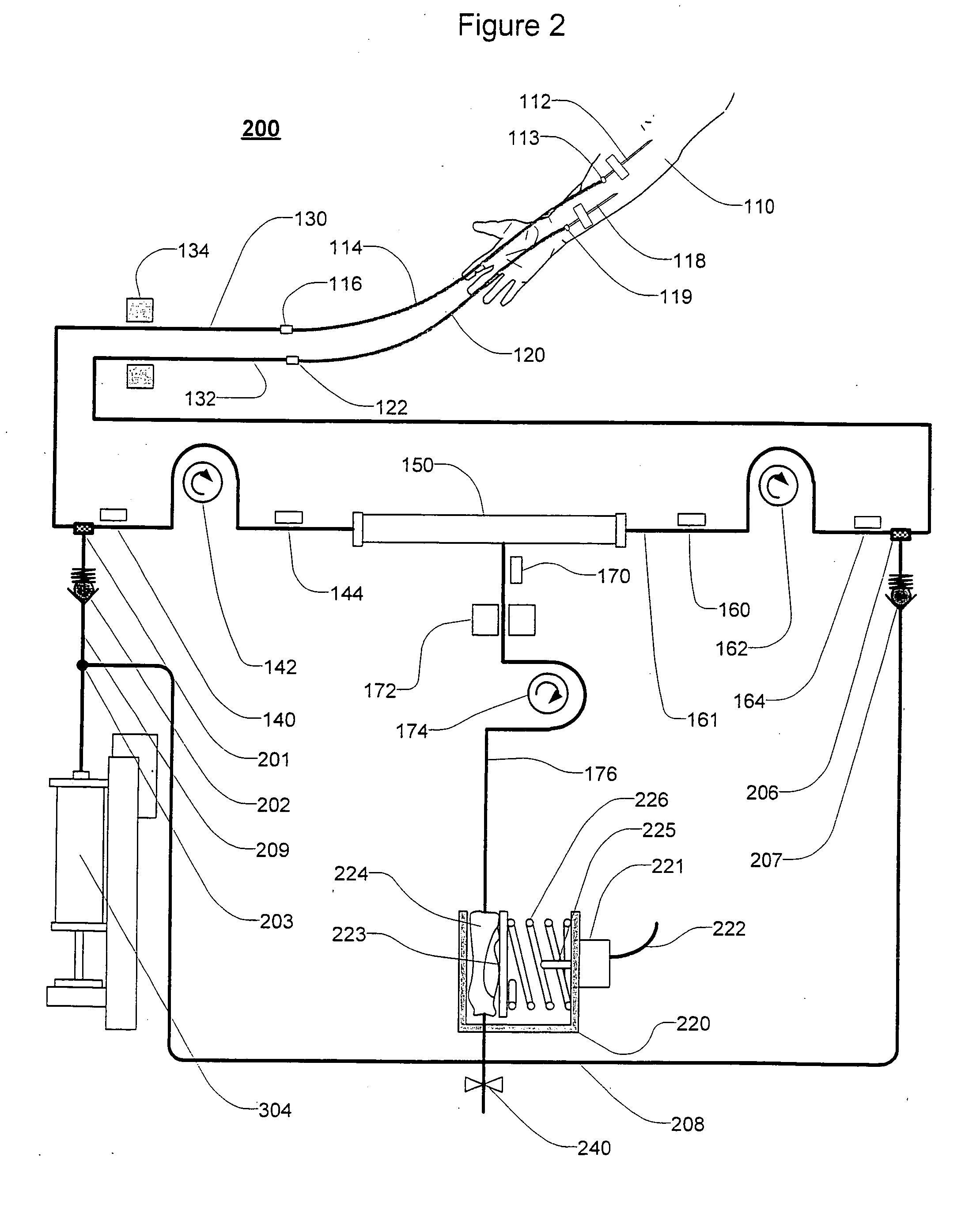
Extracorporeal blood treatment and system having reversible blood pumps
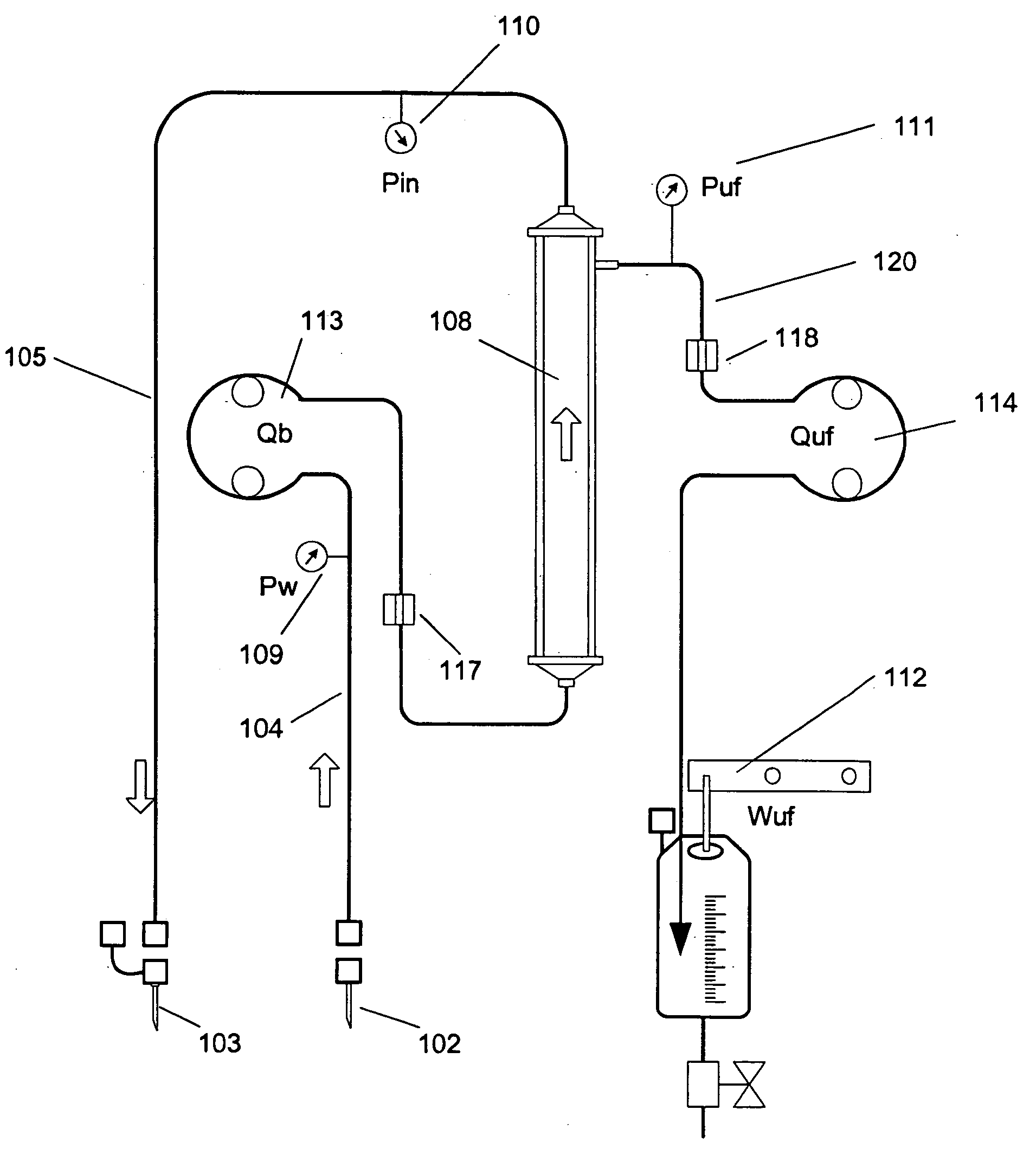
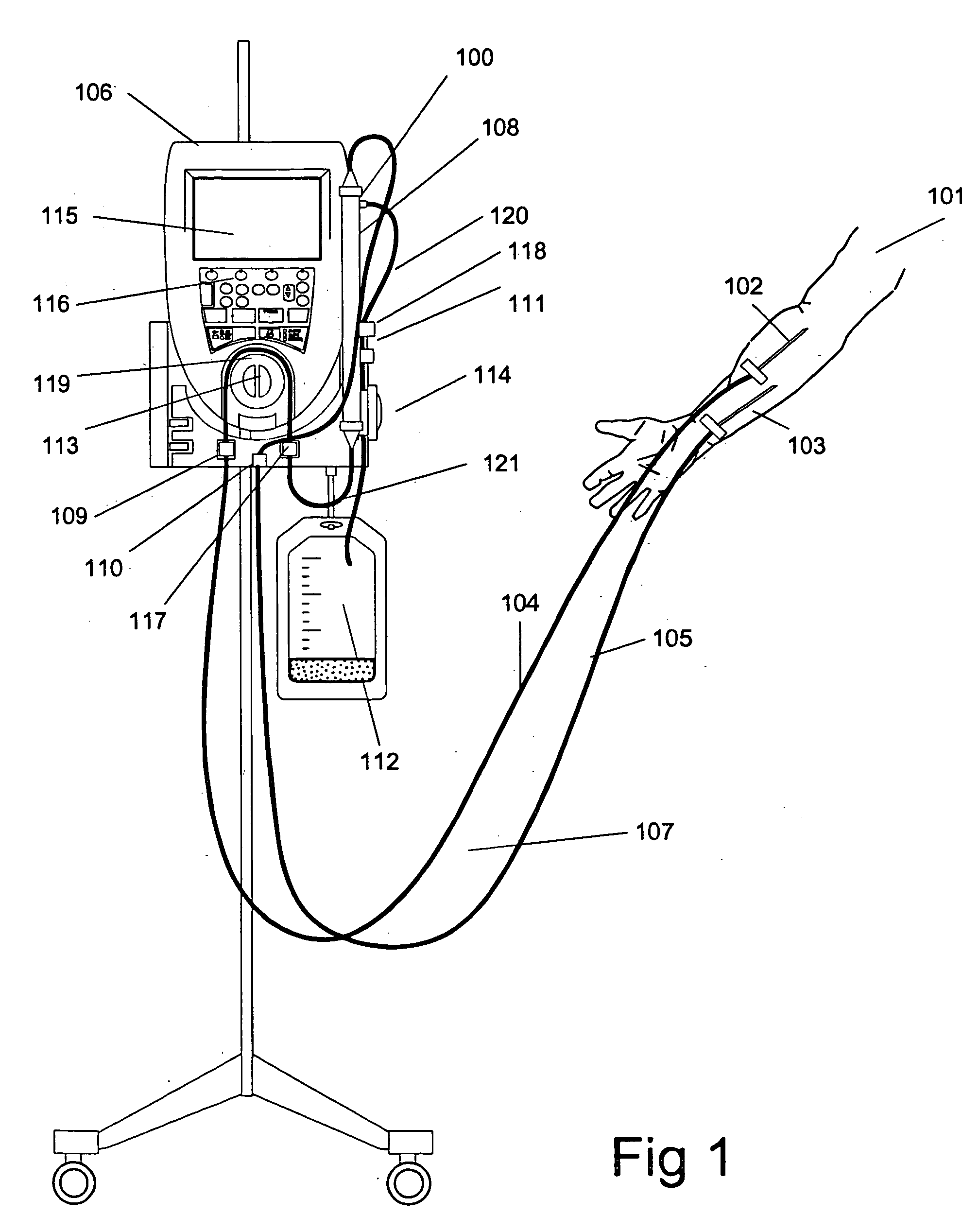
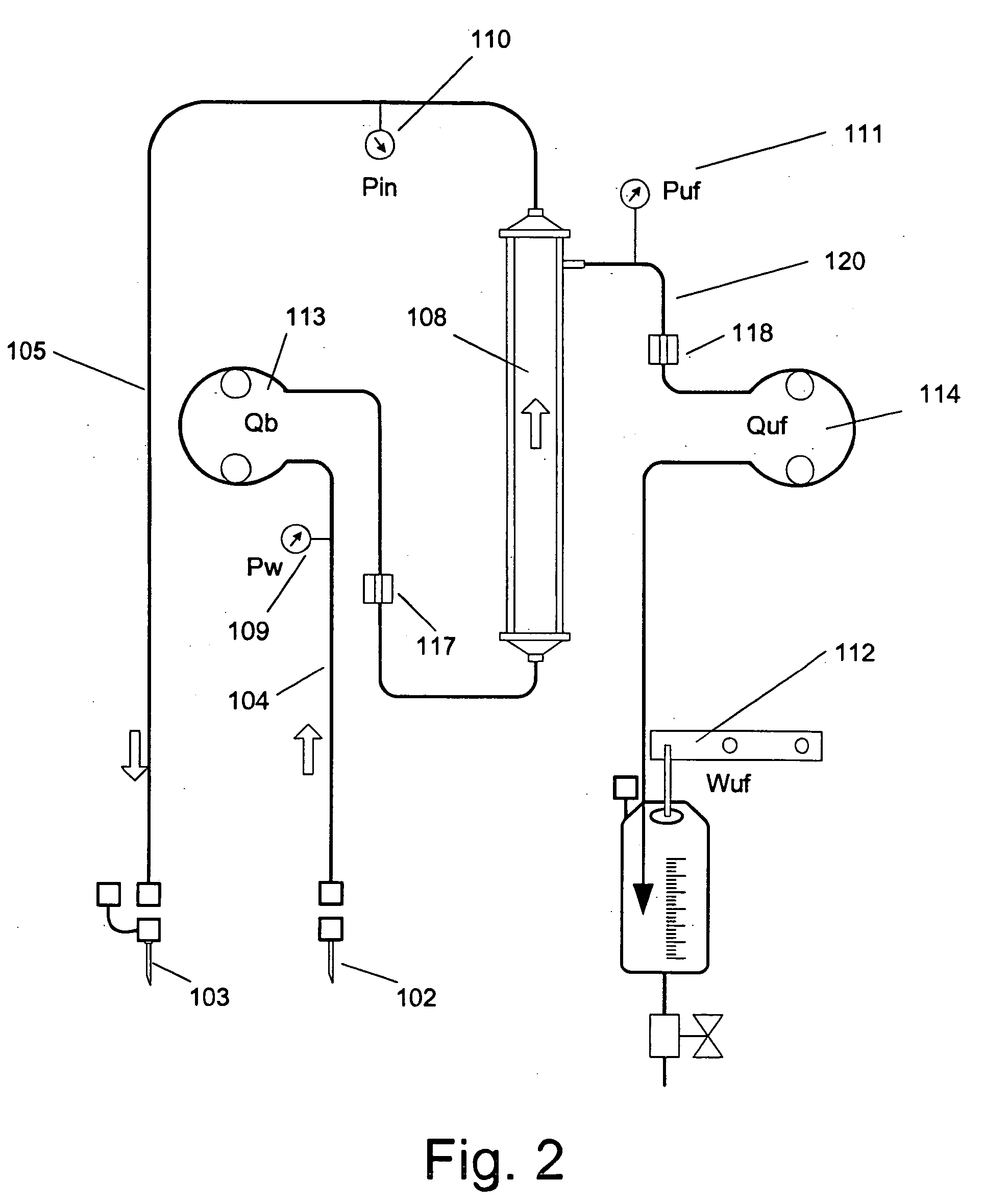
InactiveUS20060122552A1Increase blood flowKeep for a long timeSolvent extractionOther blood circulation devicesTreatment systemBlood vessel
An extracorporeal blood treatment system including: a blood circuit having a first blood passage coupled at a first end to a first end of a blood treatment device and a second blood passage coupled at a first end to a second end of the treatment device, wherein the first and second blood passages each have a second end adapted to be coupled to a vascular system of a human patient; a first blood pump connectable to the first blood passage and a second blood pump connectable to the second blood passage, wherein said first and second blood pumps are adapted to move blood through the first and second blood passages in a first direction and in a reverse direction, and a pump controller operatively connected to the first and second blood pumps, said controller operates the blood pumps to cyclically move blood through the first and second blood passages in the first direction and the reverse direction.
Owner:GAMBRO LUNDIA AB
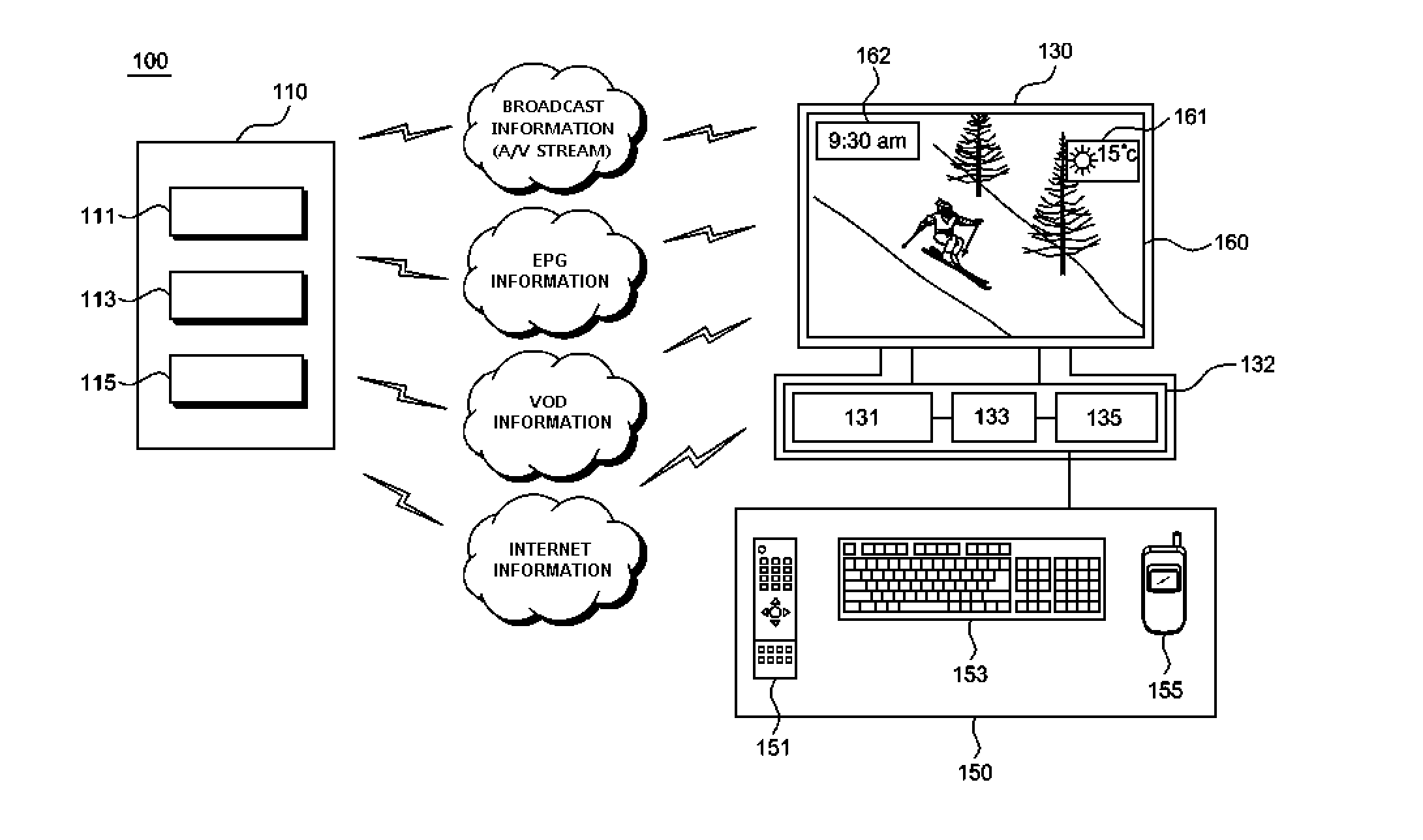
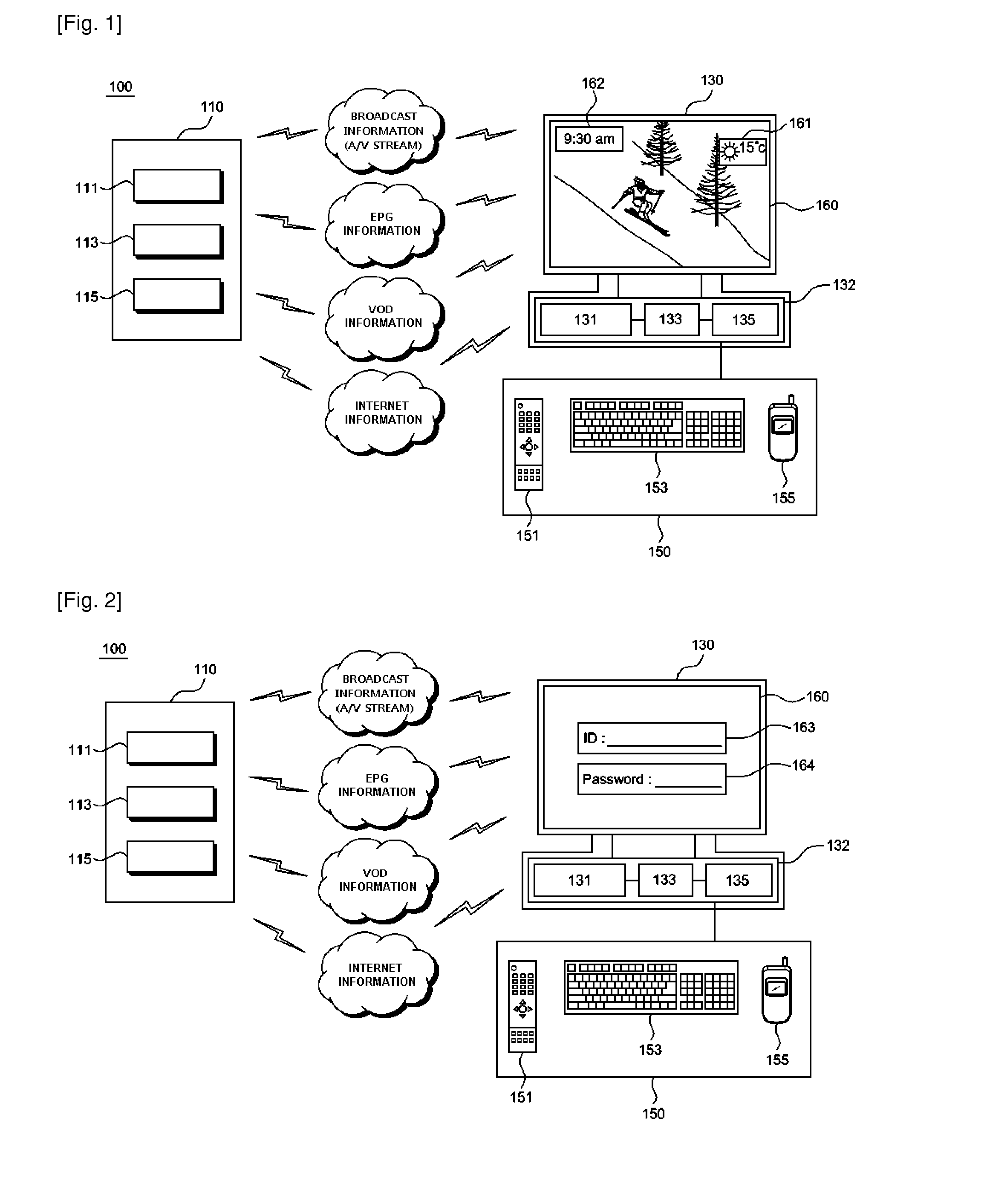
Digital broadcast widget system
InactiveUS20100229197A1Convenient to useMaintain securityTelevision system detailsColor television detailsBroadcast domainProcess information
Provided is a digital broadcast (digital TV) widget system. The digital broadcast widget system includes: a transmitter for providing widget information for generating a widget and for providing one or more of broadcast information (A / V stream), EPG information, VOD information and Internet information for digital broadcast; a receiver for displaying the widget on a TV screen by processing the broadcast information (A / V stream), the EPG information, the VOD information, the Internet information and the widget information; and a user input unit for enabling a user to input to the receiver information responding to the widget. The receiver includes an application platform which having a browser for processing information provided from the transmitter or the user input unit and for generating the widget corresponding to the widget information, based on the broadcast information (A / V stream), the EPG information, the VOD information, the Internet information, and device information of the receiver.
Owner:PXD
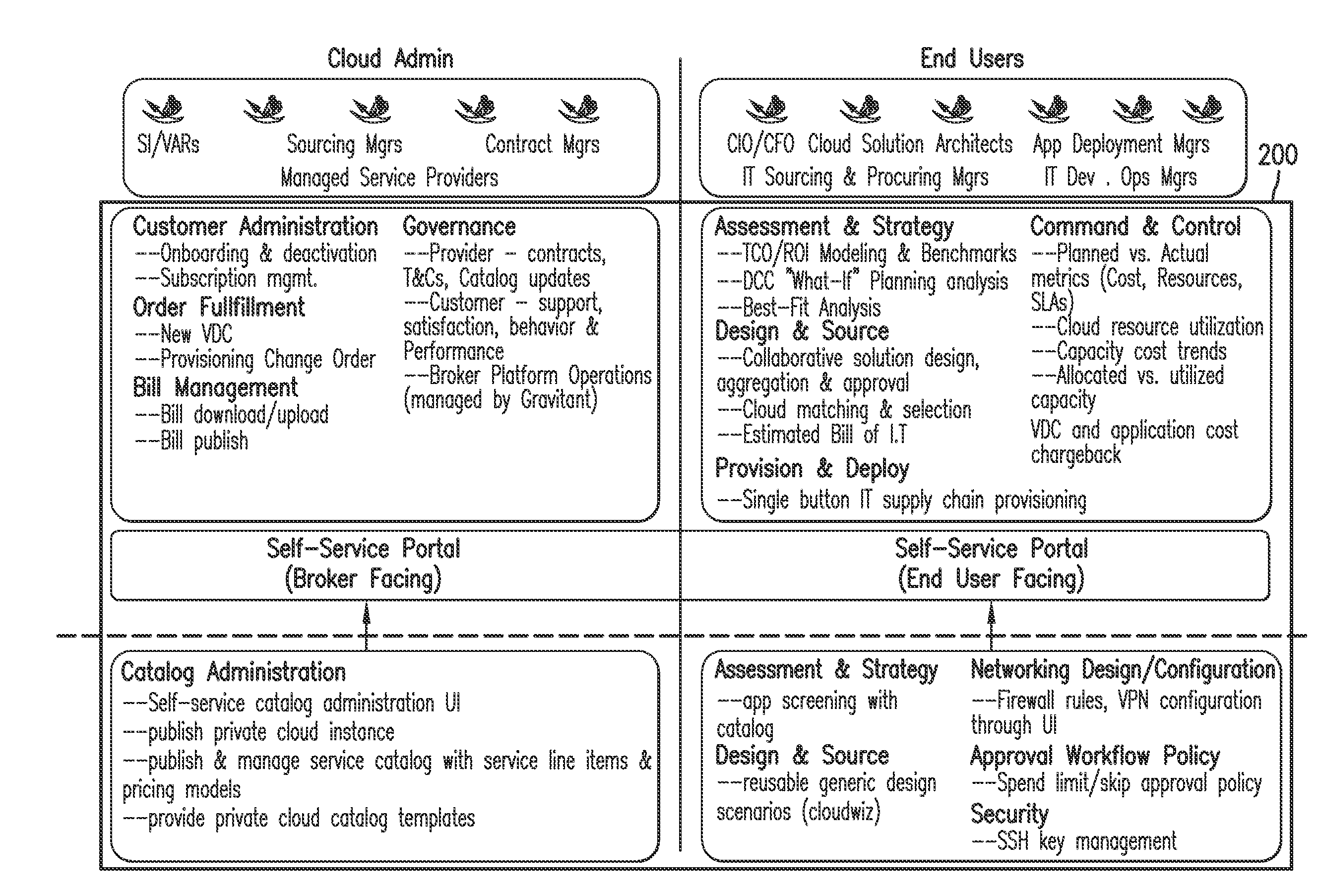
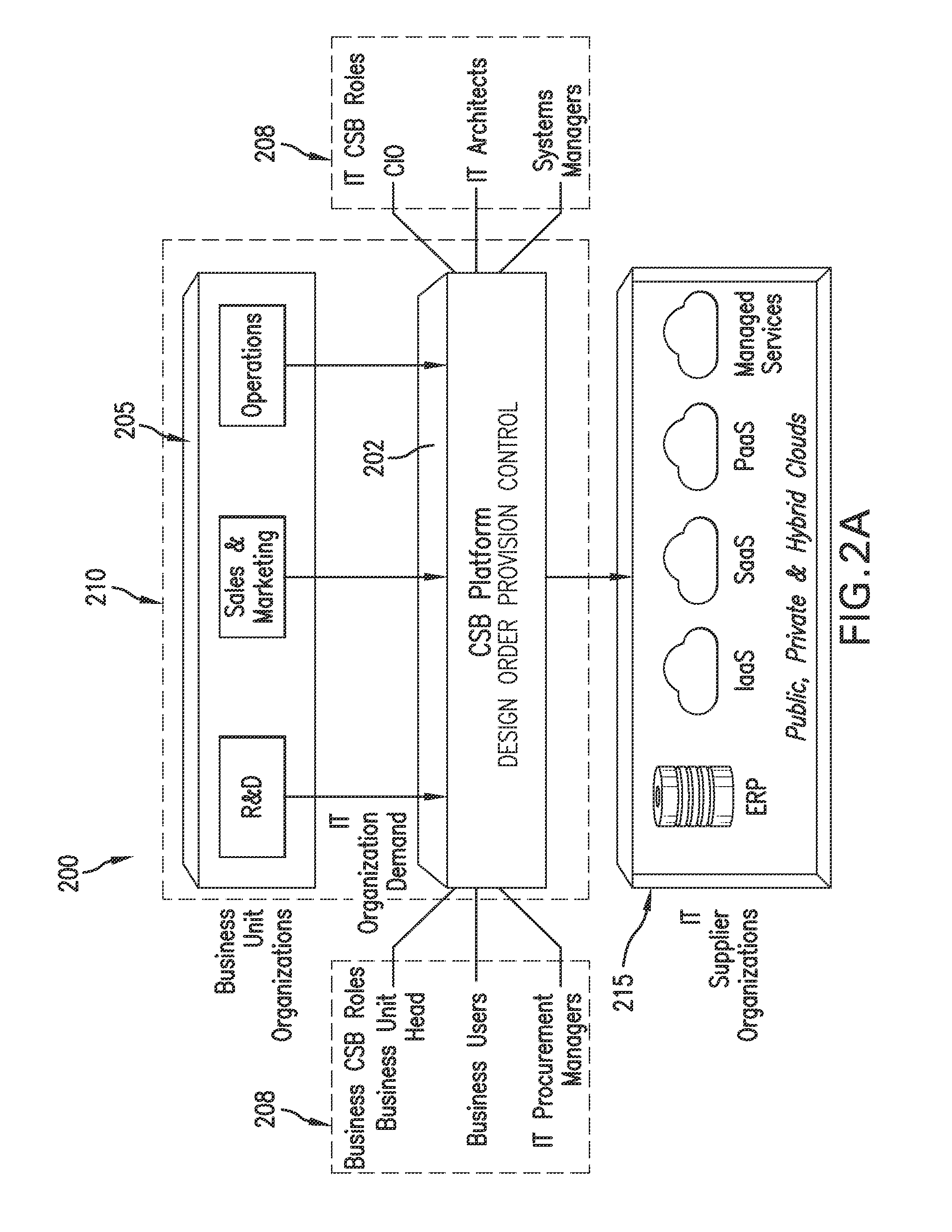
Fulfillment of cloud service orders
ActiveUS20160065417A1Efficient and effectiveMaintain securityResource allocationFinanceAuto-configurationWorkflow
A fulfillment bridge orchestrates various types of fulfillment that fall generally into three categories of fulfillment: CSB platform based automated provisioning; external automated provisioning; and manual workflow provisioning. External automated provisioning is implemented through fulfillment agents. The fulfillment agents can implements self-registration for allowing the fulfillment bridge to understand the capabilities of the fulfillment agent. Examples of such capabilities include, but are not limited to, supported actions and input / output parameters. Adapters of the fulfillment bridge interface with the fulfillment agents and fulfillment scripts that are independently operated with respect to the CSB platform can be use to interface with the fulfillment adapters.
Owner:HCL TECH LTD
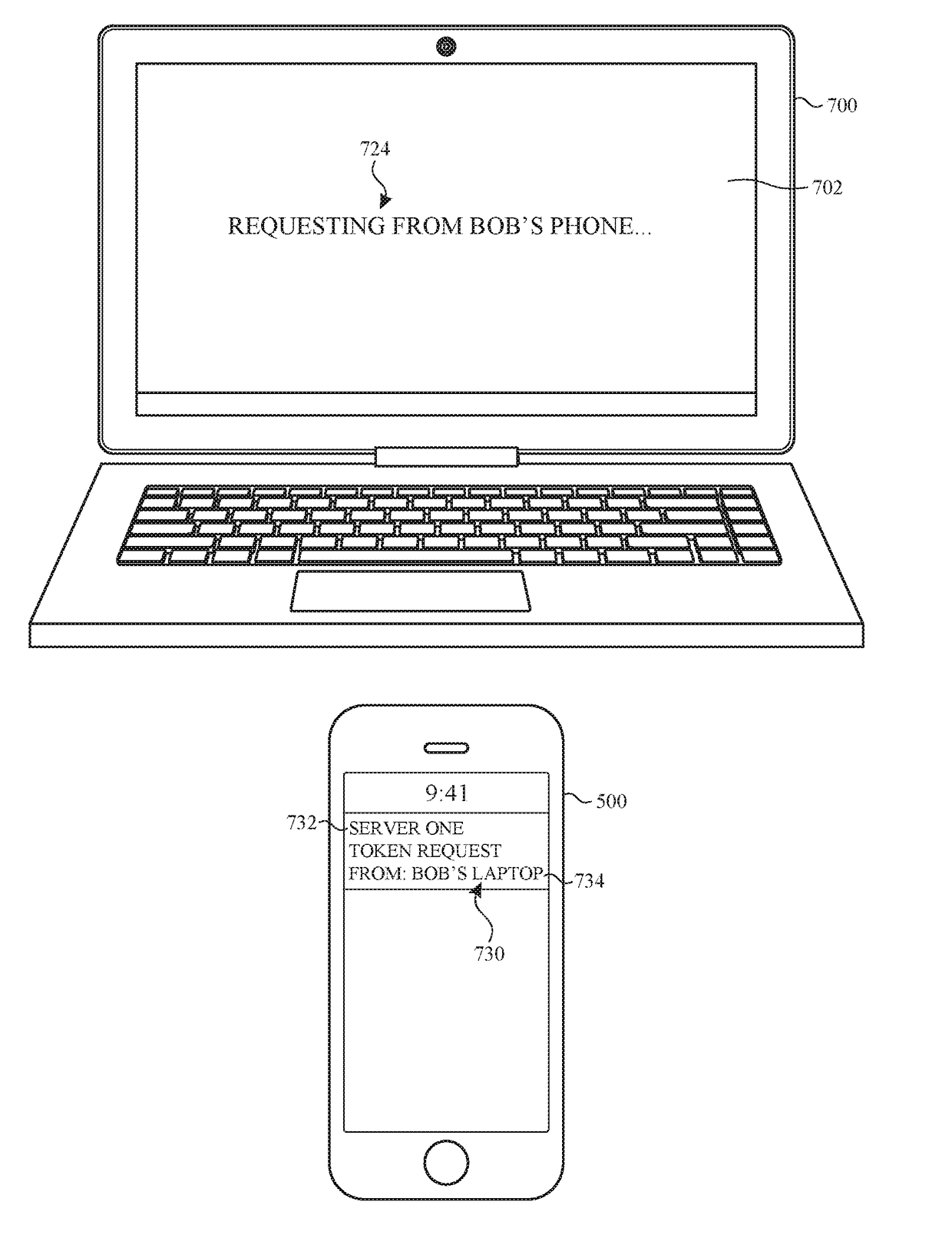
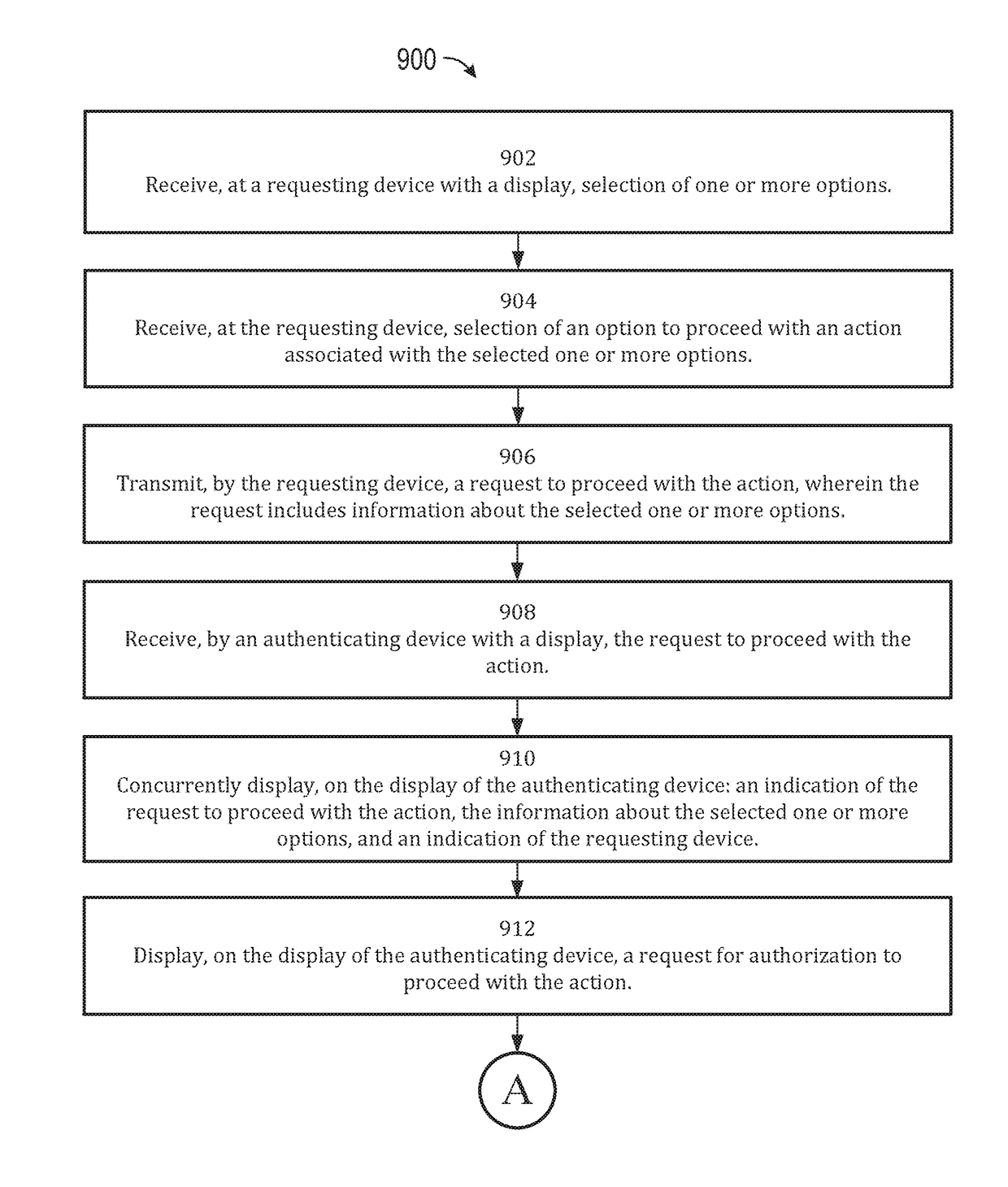
User interface for a device requesting remote authorization
ActiveUS20170339151A1Faster and efficient methodImprove effectivenessUser identity/authority verificationPayment architectureComputer hardwareNetwork connection
The present disclosure generally relates to techniques for managing a remote authorization to proceed with an action, such as creating a secure network connection. In some examples, a requesting device receives selection of one or more options. The requesting device transmits a request to proceed with an action to an authenticating device. The authenticating device concurrently displays an indication of the request to proceed with the action, information about the selected one or more options, and an indication of the requesting device. The authenticating device receives authorization to proceed with the action and transmits a response to the requesting device regarding the request to proceed with the action.
Owner:APPLE INC
Safety razor with pivot point shift from center to guard-bar under applied load
Owner:EDGEWELL PERSONAL CARE BRANDS LLC
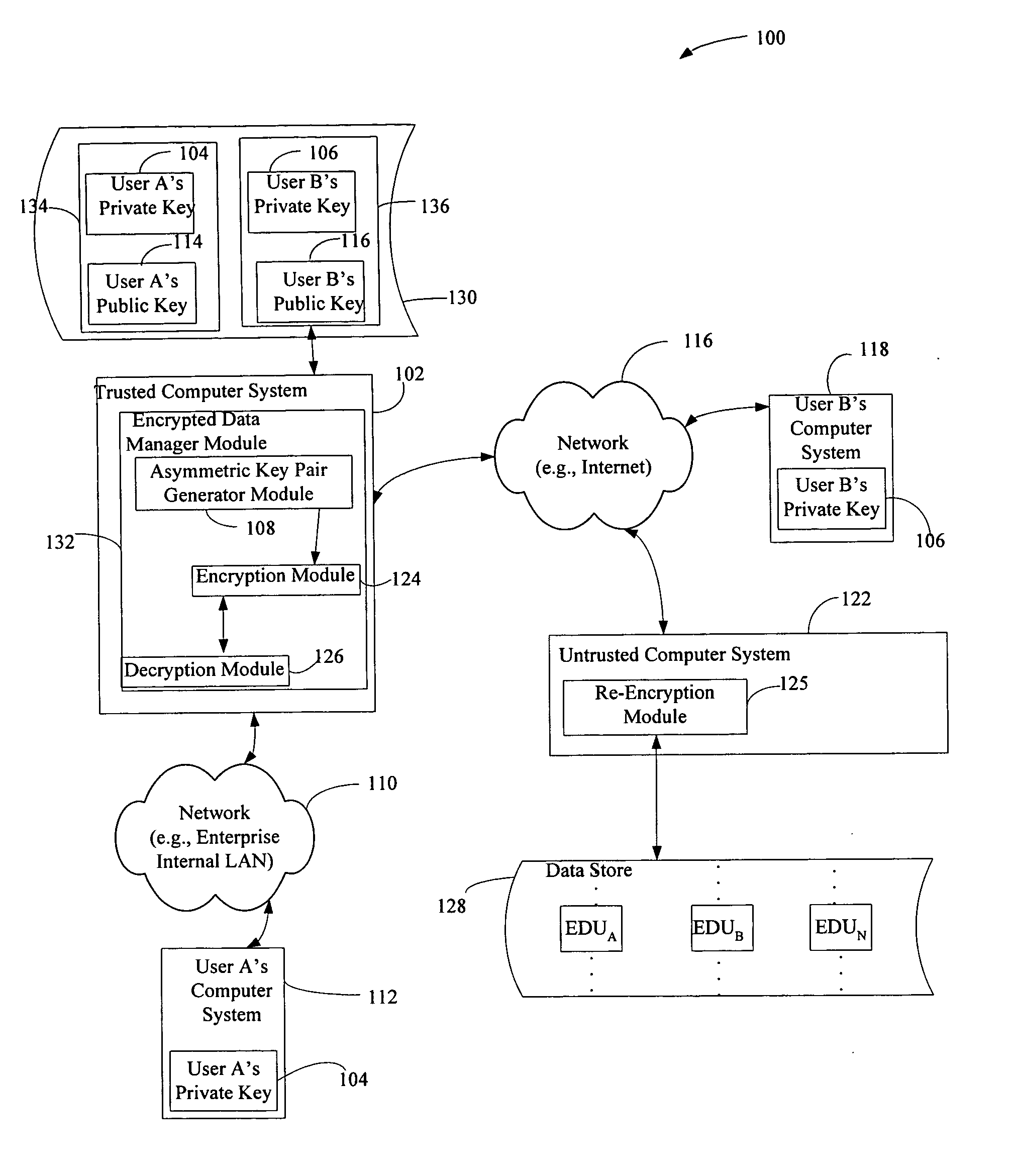
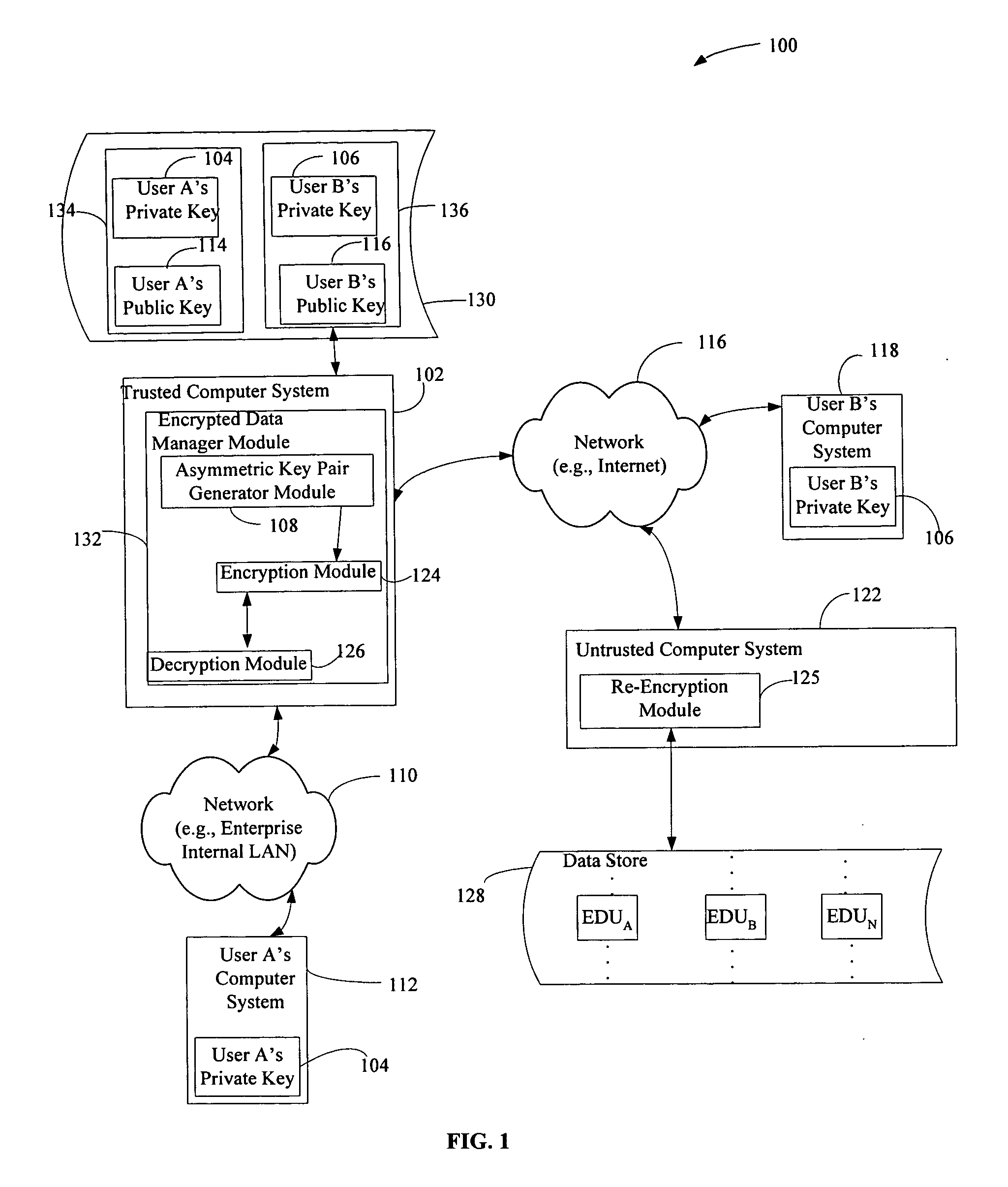
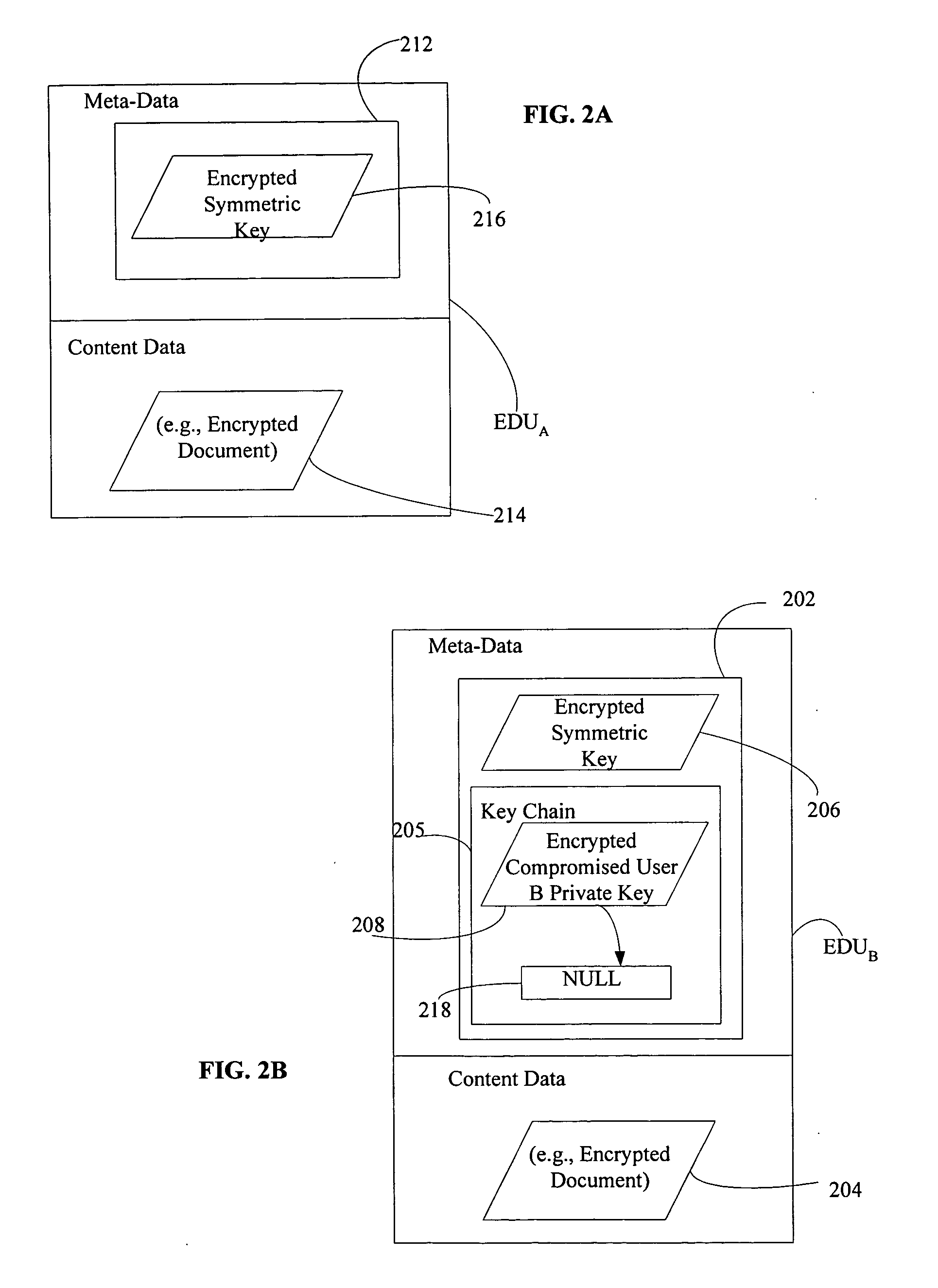
Off-loading data re-encryption in encrypted data management systems
InactiveUS20060093150A1Maintain securityKey distribution for secure communicationPublic key for secure communicationInternet privacyData management
Described is a solution for maintaining the security of encrypted data despite a compromised private key by using a re-encryption process that does not require decryption of the encrypted data. The compromised private key is re-encrypted using a new public key as is the encrypted symmetric key which the compromised private key can decrypt. When a decrypted version of the encrypted data is requested, the private key corresponding to the new public key decrypts both the encrypted version of the compromised private key and the re-encrypted version of the symmetric key resulting in the unencrypted compromised private key and the previously encrypted version of the symmetric key, which when decrypted using the compromised private key decrypts the encrypted data. The unencrypted symmetric key can then be encrypted using the new public key any encrypted compromised private key can be deleted.
Owner:HEWLETT PACKARD DEV CO LP
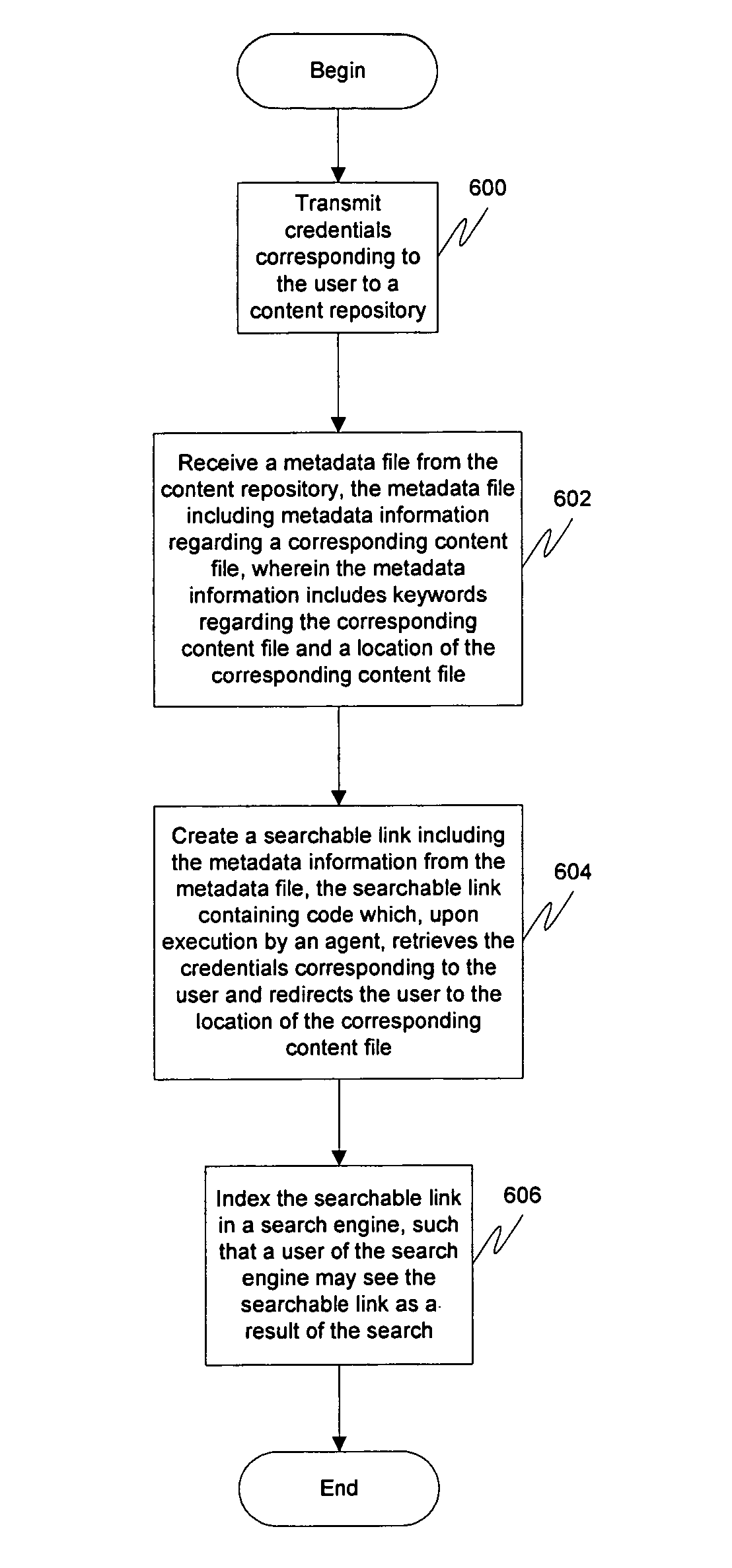
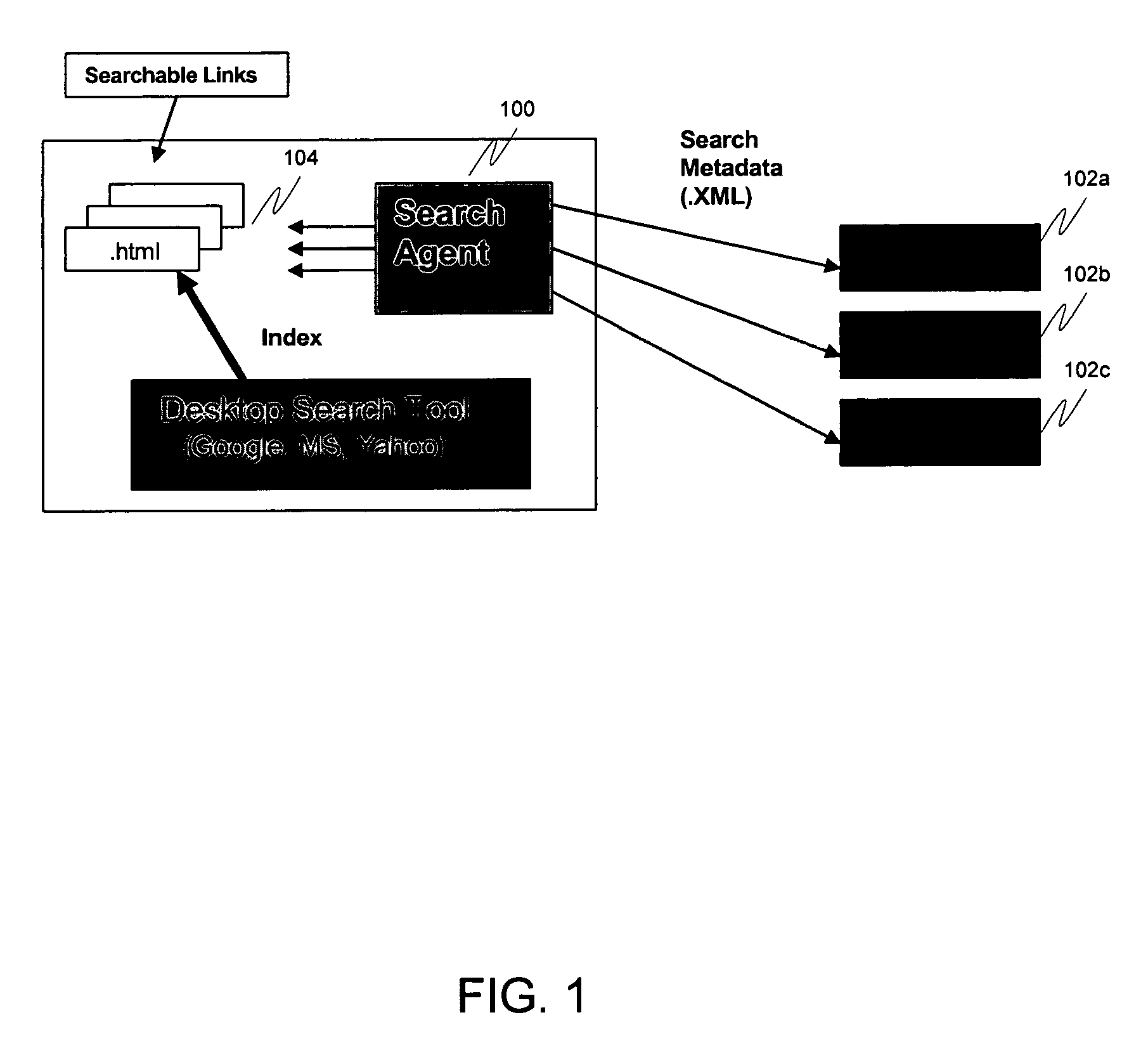
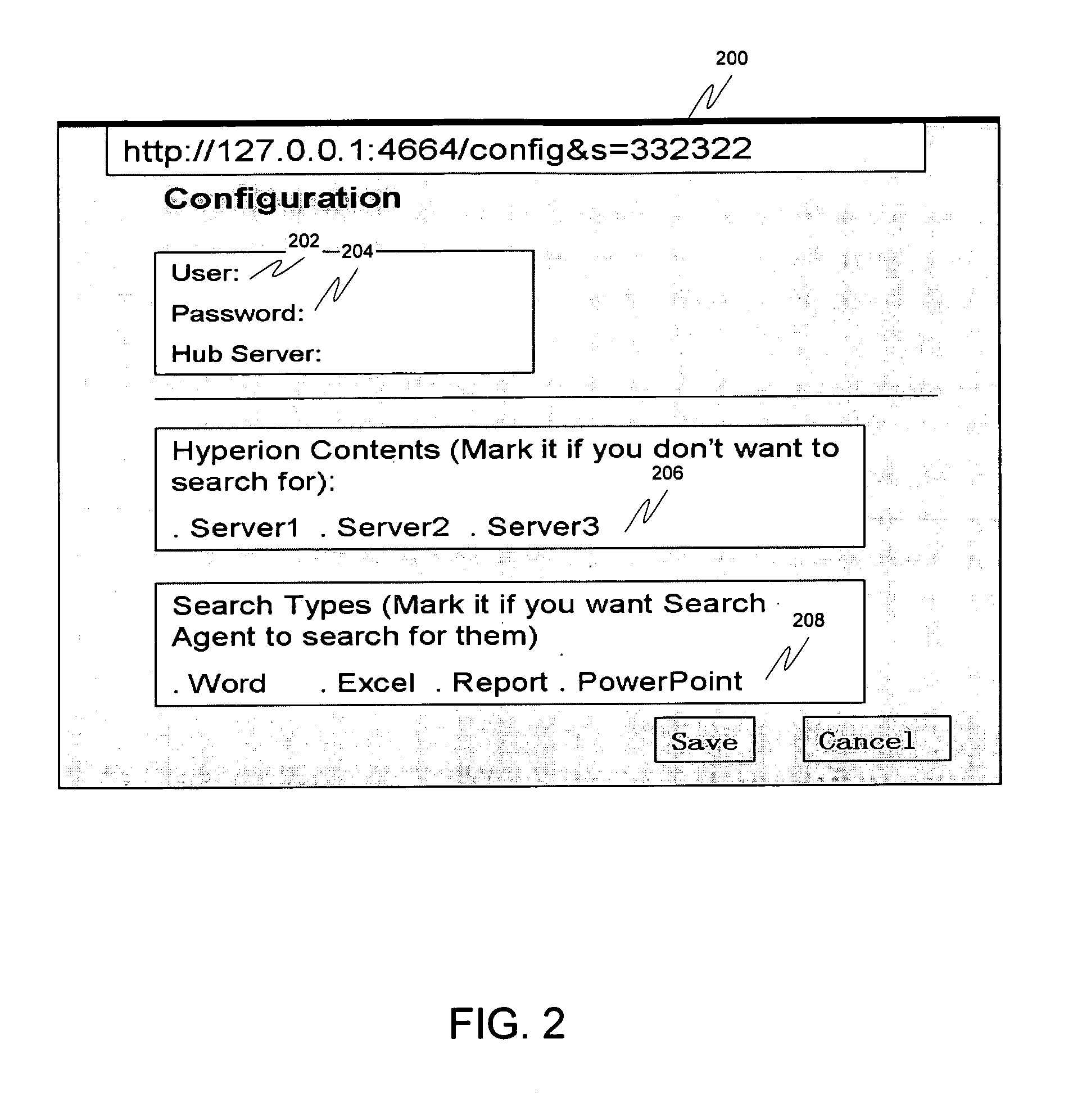
Enterprise content search through searchable links
ActiveUS8027976B1Maintain securityDigital data processing detailsSpecial data processing applicationsSearch problemLocal memories
A solution is provided that allows end users to search documents in multiple remote content repositories in an enterprise environment, while maintaining security of those documents. Additionally, end users are able to search for a document without knowing which server or directory it is stored under. This is accomplished by installing a search agent on the end user's machine. The search engine collects the metadata of authorized documents located in different repositories via a web protocol (such as Hypertext Transfer Protocol, or HTTP) and stores them in the user's local memory as “searchable links”. This solves the enterprise content search problem through the creation of searchable links of remote content objects in an end user's local machine while allowing emerging desktop-search technology to index them.
Owner:ORACLE INT CORP
Methods and systems for threat assessment, safety management, and monitoring of individuals and groups
InactiveUS8630820B2Reduce morbidityMaintain awarenessTelephonic communicationNuclear monitoringComputer scienceIndividual person
Owner:STRIDER
System and methods for implementing network traffic management for virtual and physical machines
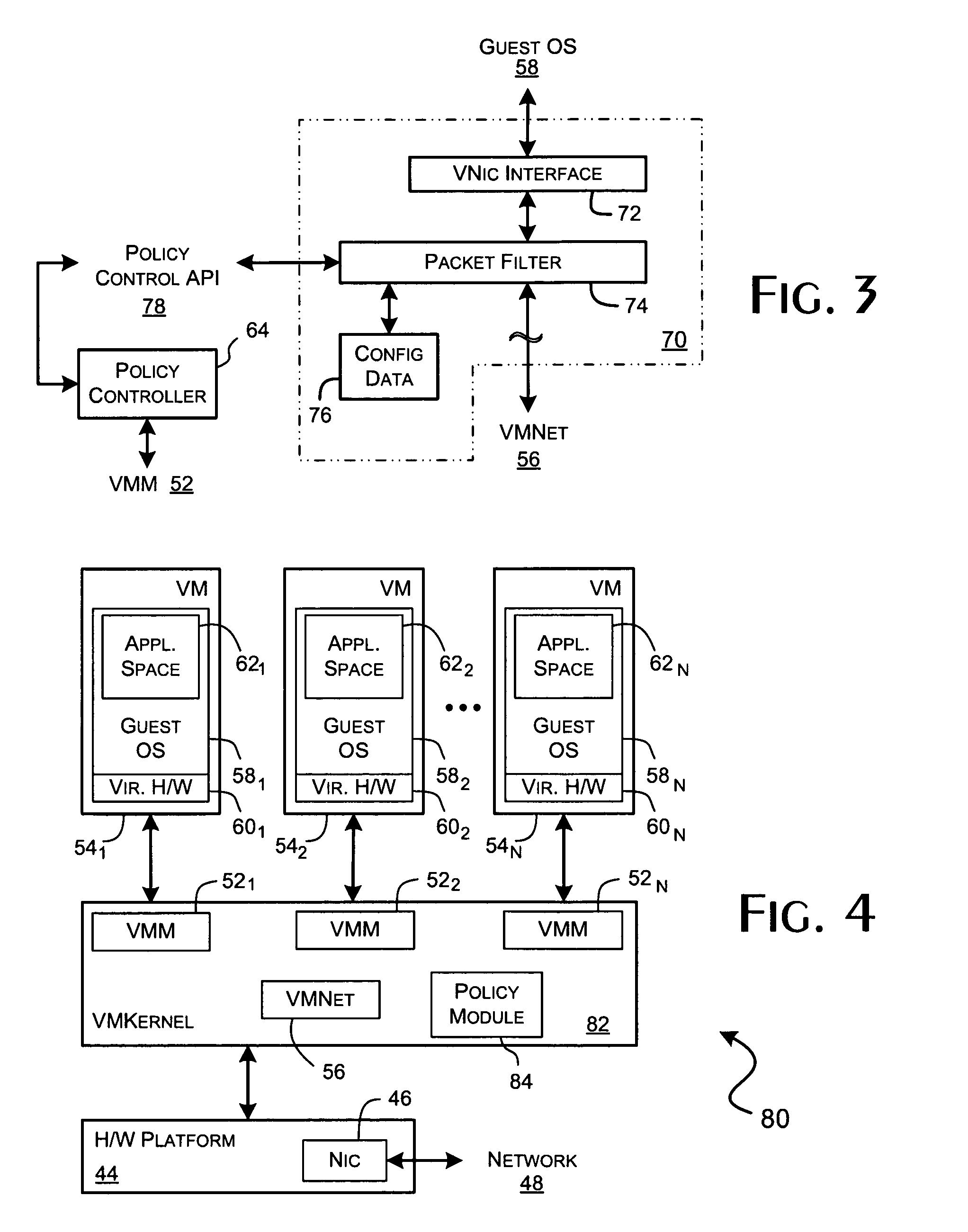
ActiveUS8166474B1Ensure safetyEasy to useDigital computer detailsSoftware simulation/interpretation/emulationVirtualizationTraffic capacity
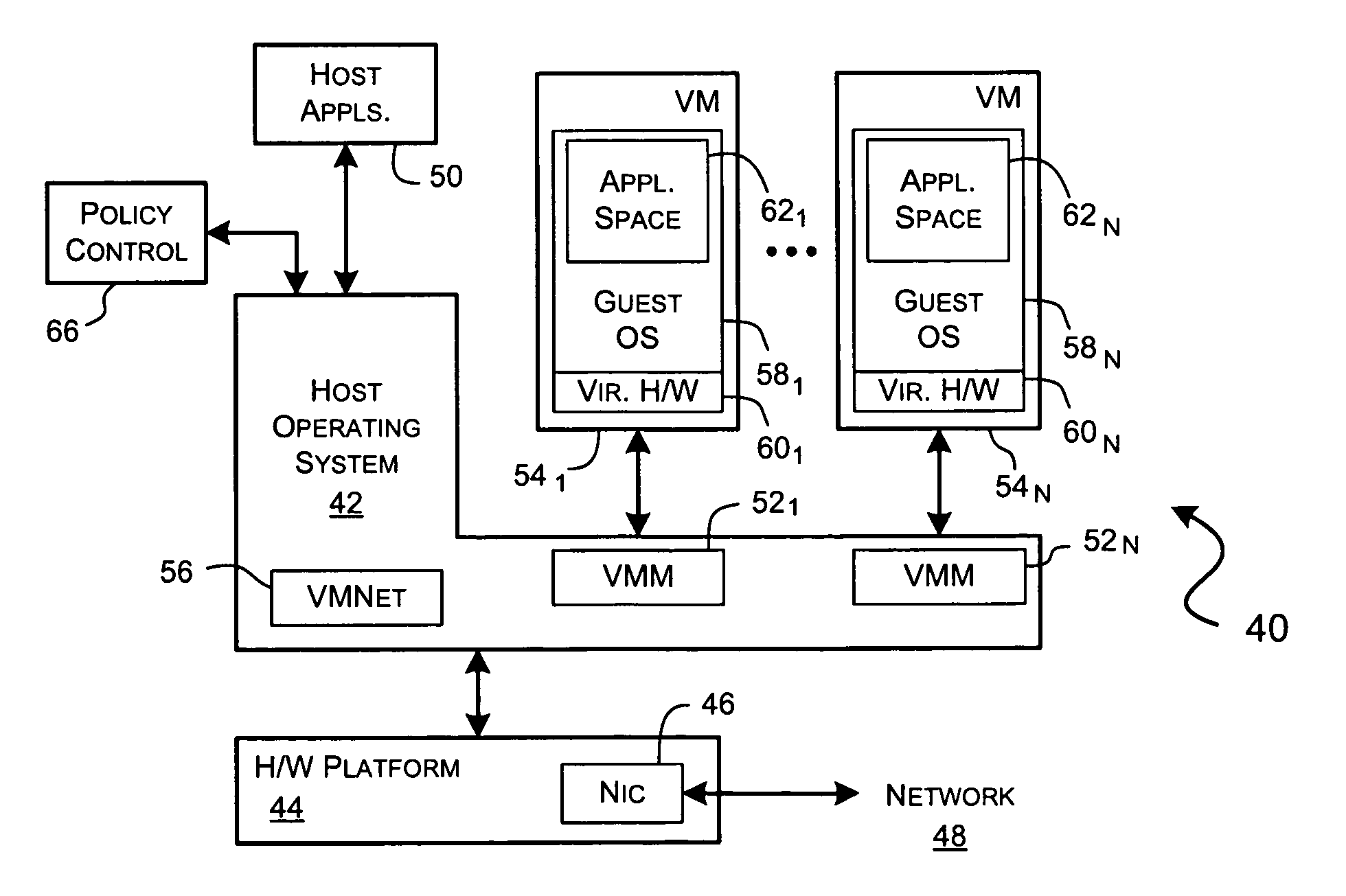
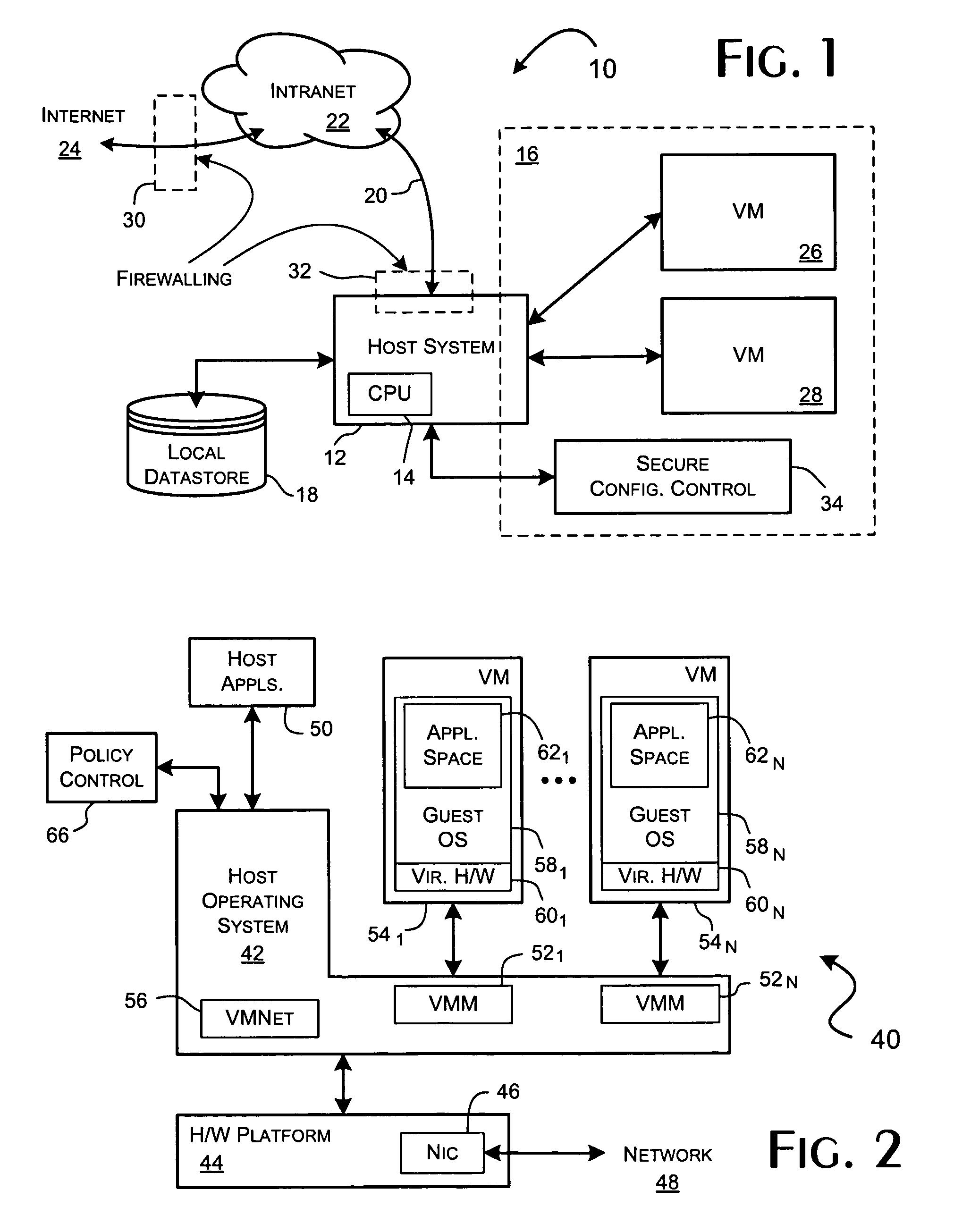
A virtualization framework provides security between multiple virtual machines with respect to network communications between the virtual machines and between the virtual machines and a physical network coupled to the underlying physical computer platform. The virtualization framework includes a network interface controller driver that provides an interface to the platform network interface controller and supports execution of a plurality of virtual machines. Each virtual machine includes a virtual network interface controller that provides a network communications path between the virtual machines and to the network interface controller driver. Each virtual network interface controller further contains a programmable network packet filter that controls the selective transfer of network packets with respect to a corresponding virtual machine.
Owner:VMWARE INC
Cryosurgical fluid supply
InactiveUS20020010460A1Inhibit hyperplasiaMaintain securityOperating means/releasing devices for valvesDomestic cooling apparatusMedicineRoom temperature
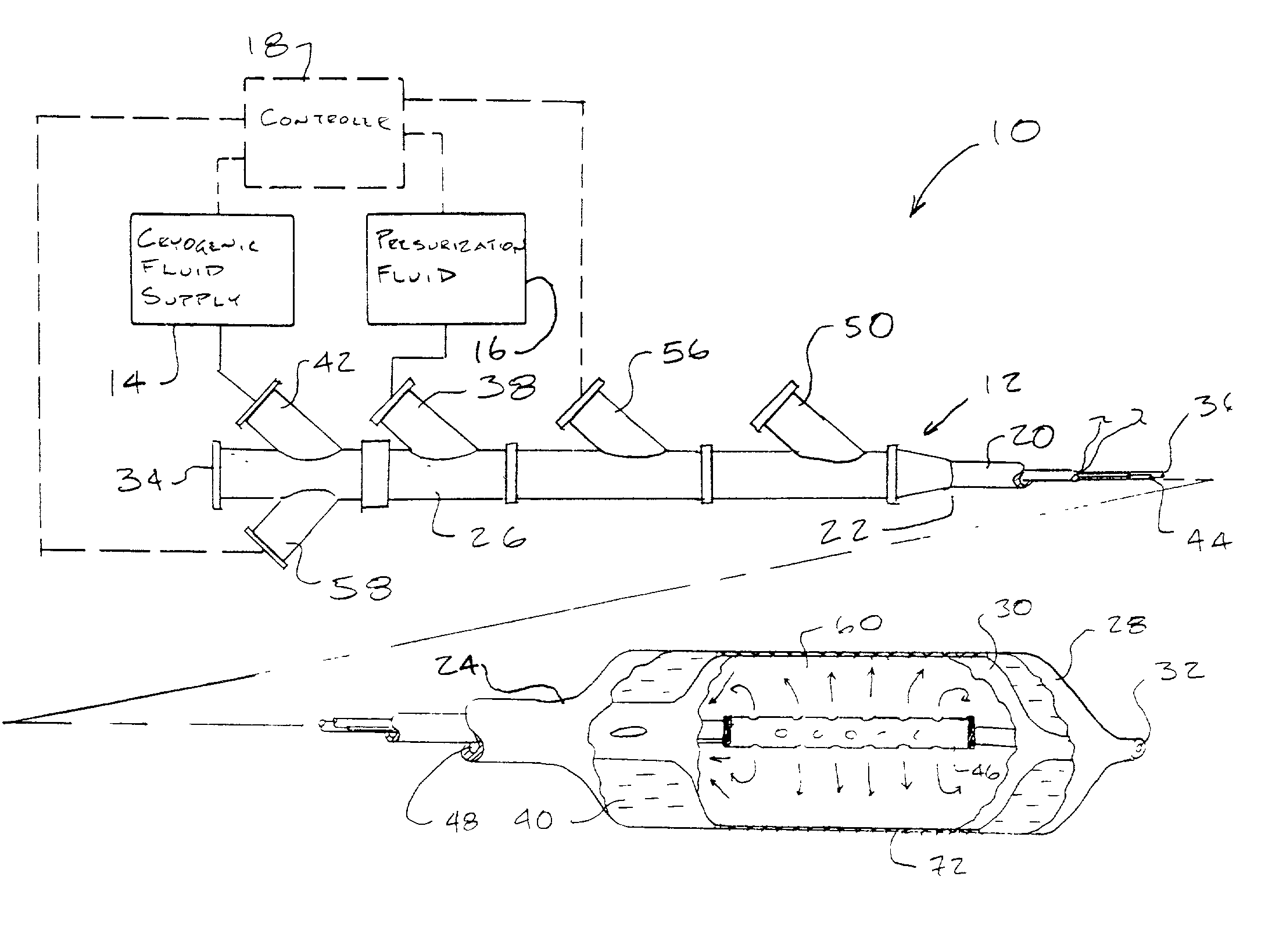
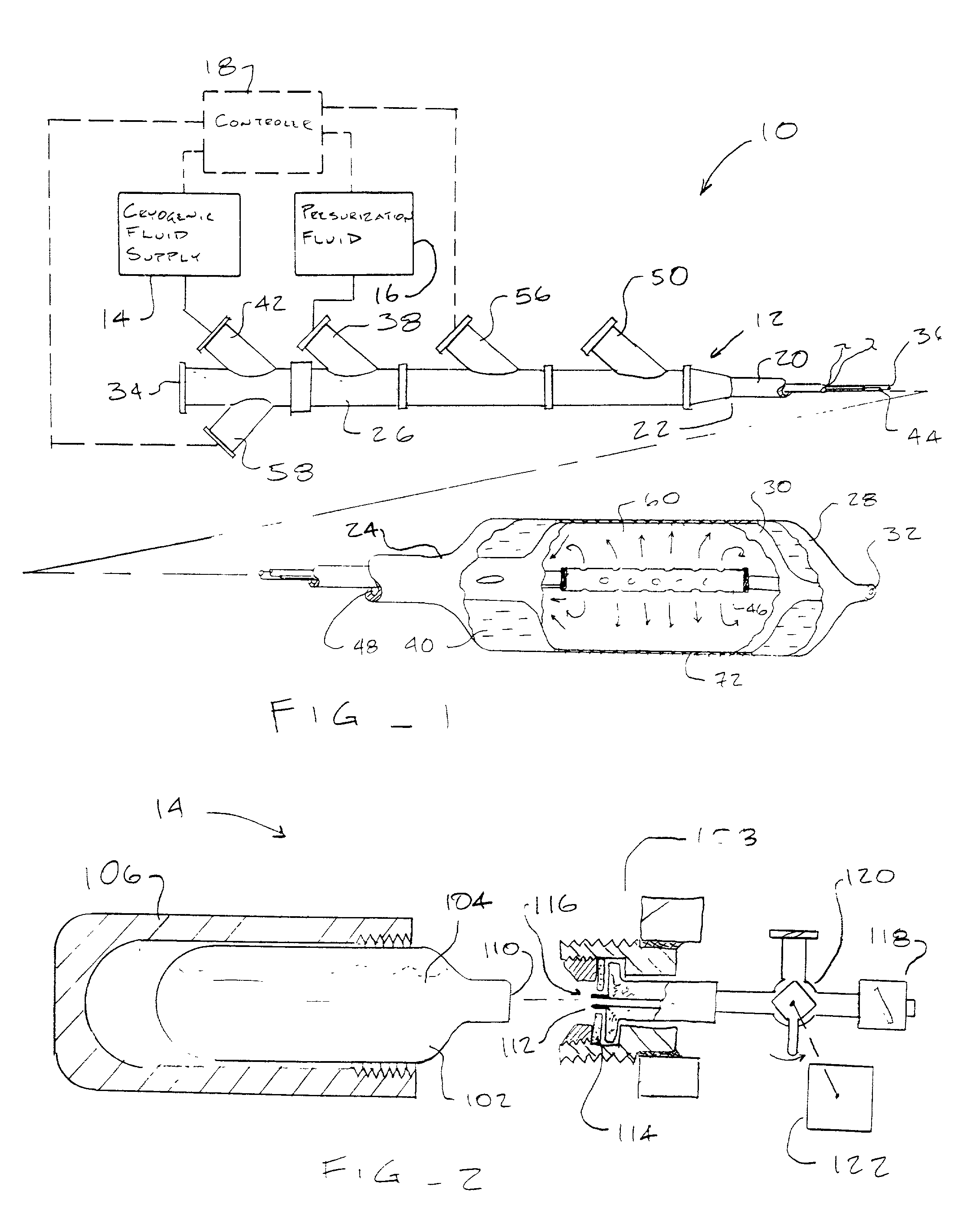
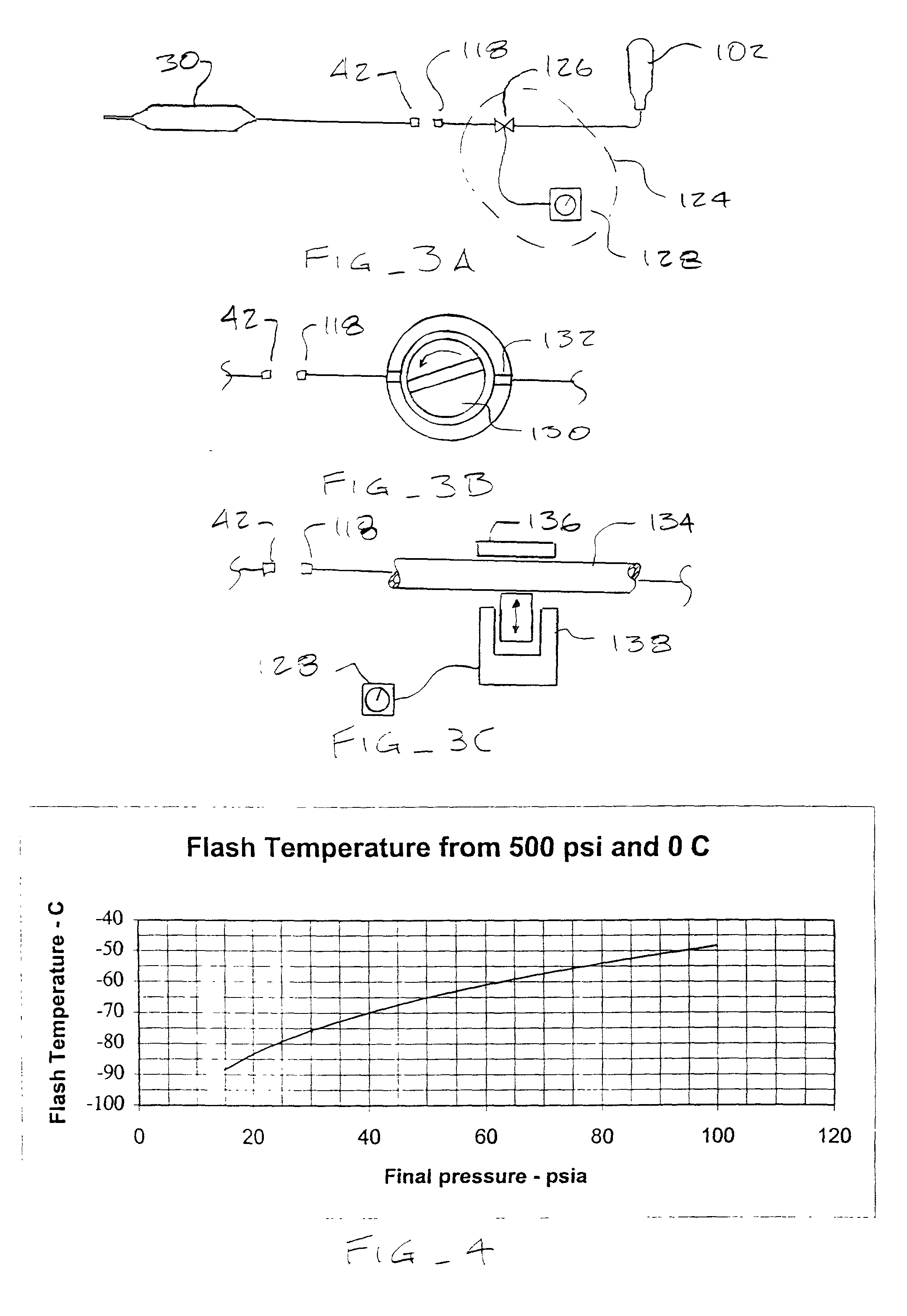
Improved systems, devices, and methods for delivering cryogenic cooling fluid to cryosurgical probes such as cryosurgical endovascular balloon catheters take advantage of the transients during the initiation and termination of cryogenic fluid flow to moderate the treatment temperatures of tissues engaged by the probe. A flow limiting element along a cryogenic fluid path intermittently interrupts the flow of cooling fluid, often cycling both the fluid flow and treatment temperature. This can maintain the tissue treatment temperature within a predetermined range which is above the treatment temperature provided by a steady flow of cryogenic fluid. In another aspect, room temperature single-use cooling fluid cartridges are filled with a sufficient quantity of cryosurgical fluid to effect a desired endovascular cryosurgical treatment.
Owner:BOSTON SCI SCIMED INC
System and method for a directory secured user account
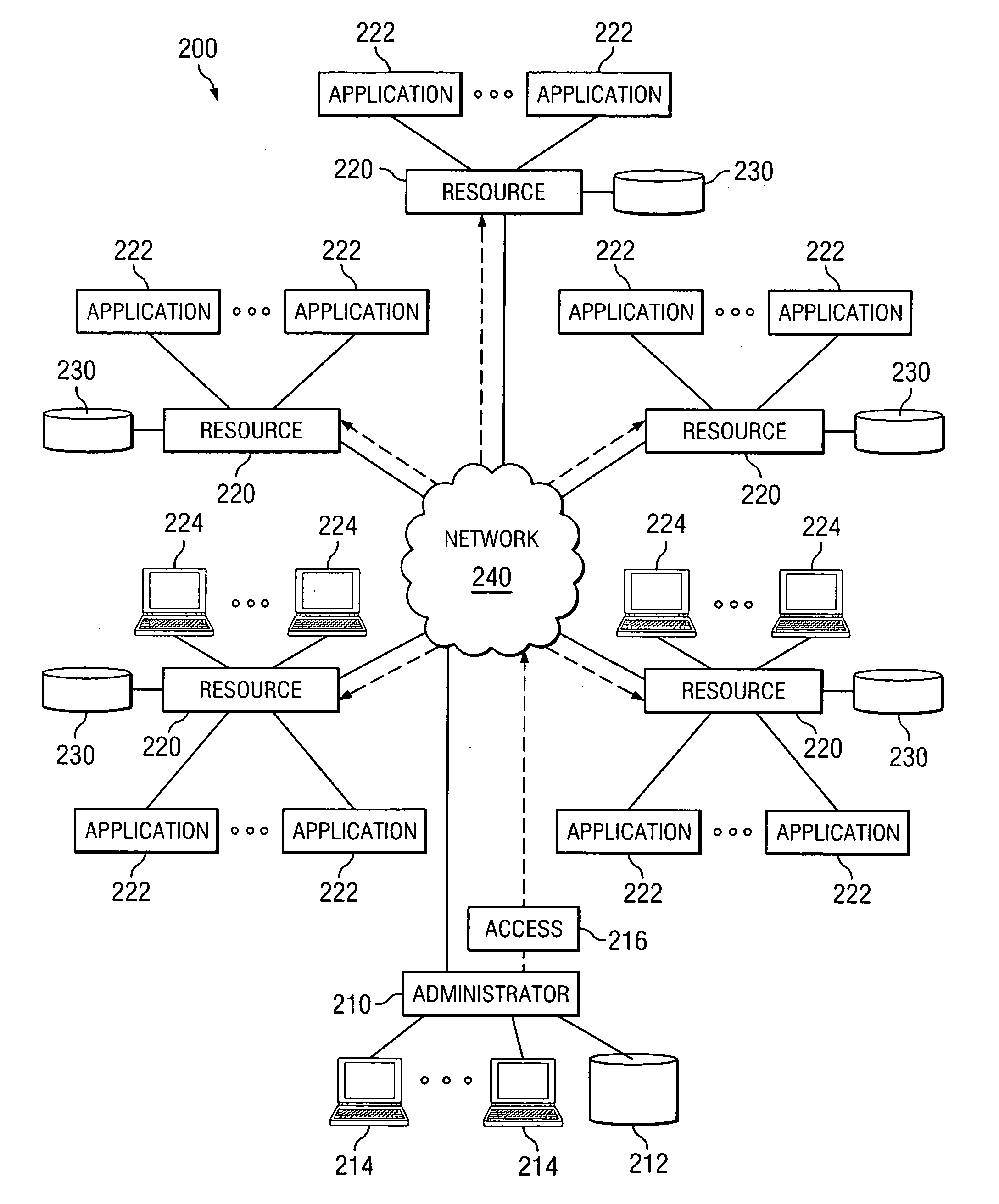
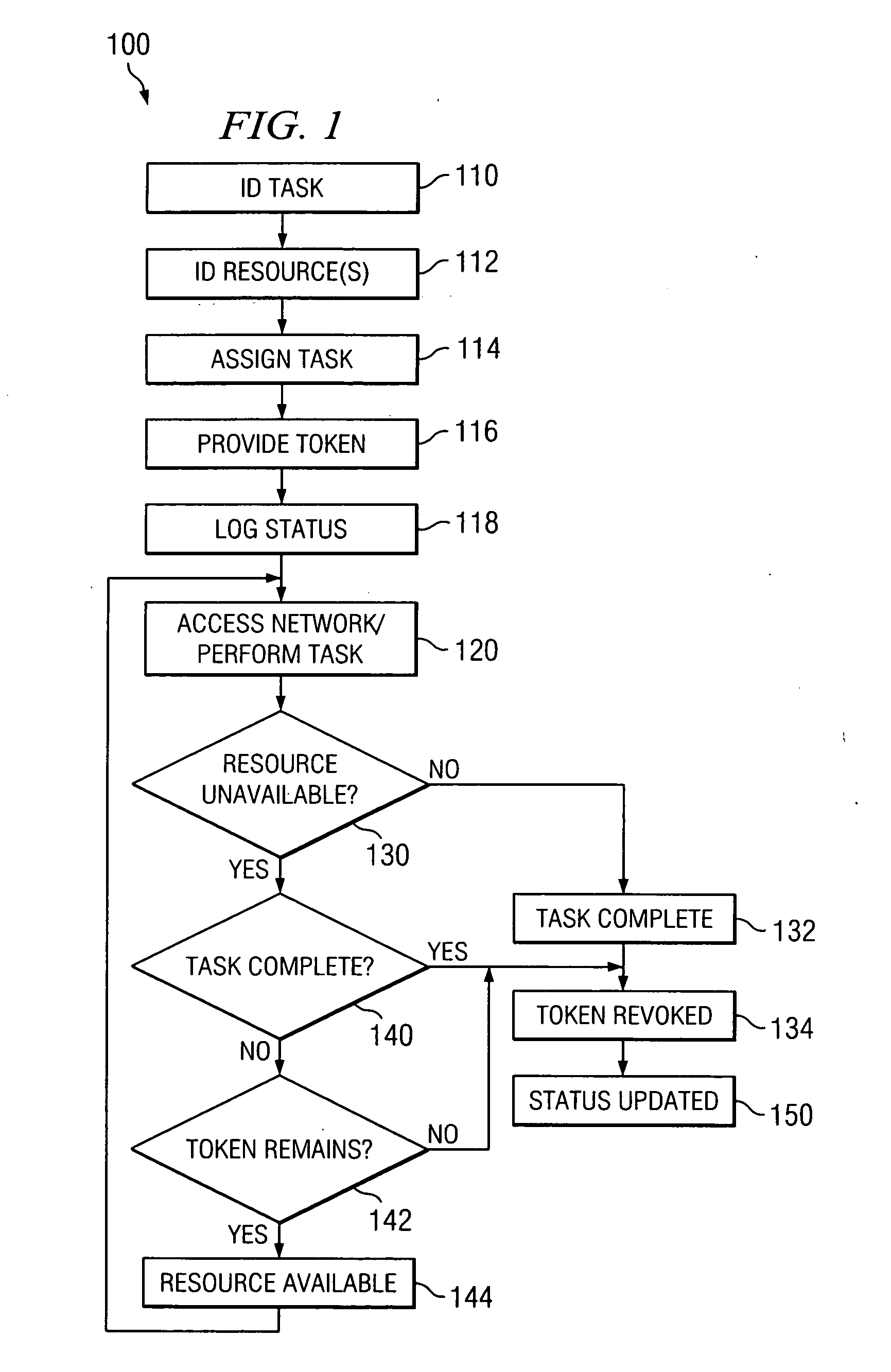
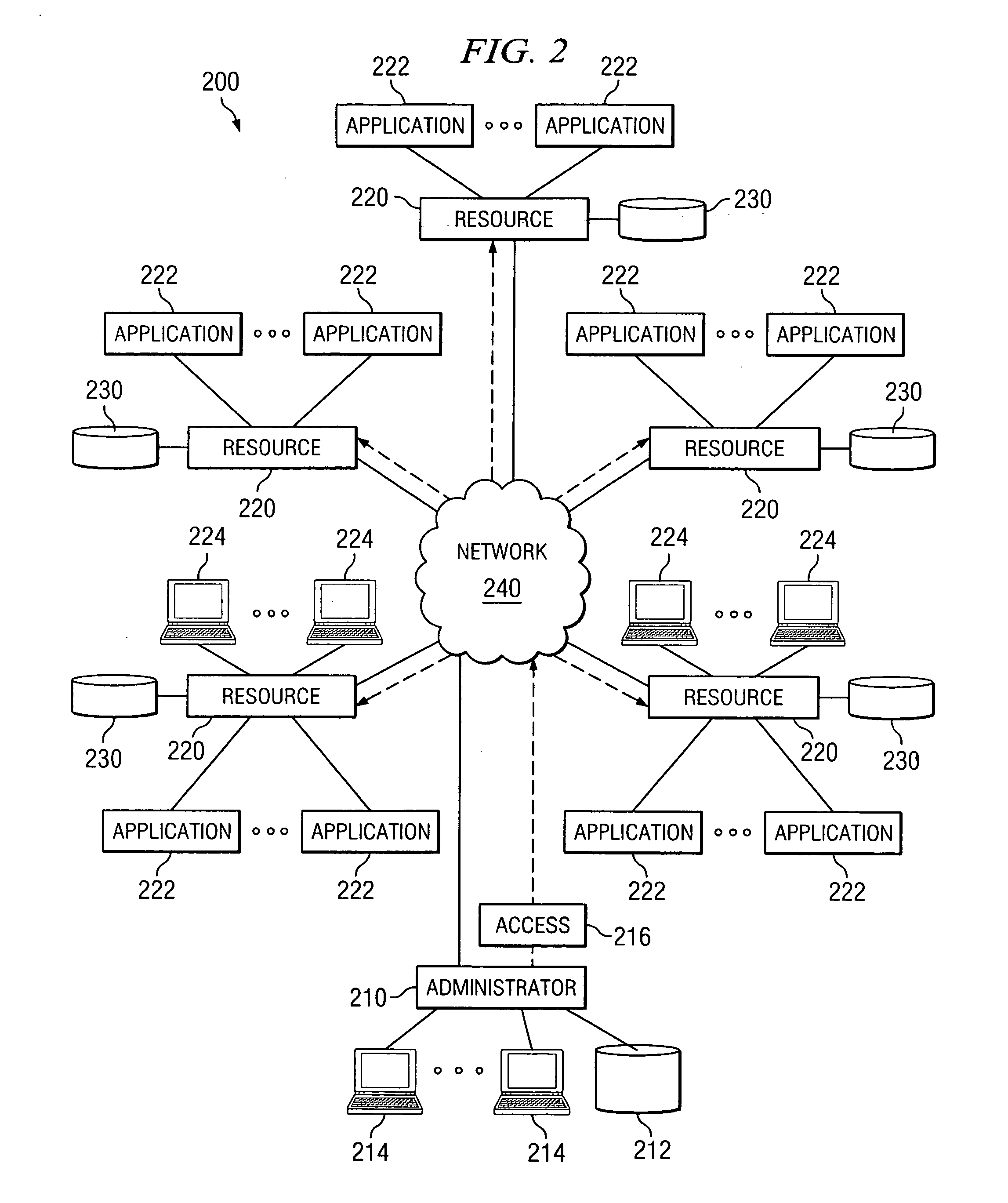
InactiveUS20050160276A1Access be reduced eliminatedDisadvantages can be reduced eliminatedComputer security arrangementsSecret communicationComputer networkAccess token
A system and method for providing network access includes identifying an available network resource, providing an access token to the available network resource, tracking the access token, and terminating the access token.
Owner:CAPITAL ONE FINANCIAL
Application service provider and automated transaction machine system and method
InactiveUS20030120597A1Easy to operateMaintain securityPayment architectureBuying/selling/leasing transactionsApplication service providerMachining system
An application service provider (ASP) and automated transaction machine method and system is provided. The method includes providing a plurality of individually accessible server side ATM applications through at least one ASP server. The method further includes enabling a plurality of ATMs to selectively access each server side ATM application through communication with the at least one ASP server. The method also includes performing services for the ATMs with the at least one ASP server responsive to the plurality of server side ATM applications.
Owner:DIEBOLD SELF SERVICE SYST DIV OF DIEBOLD NIXDORF INC
Voice, lip-reading, face and emotion stress analysis, fuzzy logic intelligent camera system
InactiveUS7999857B2Improve abilitiesMaintain integrityTelevision system detailsColor television detailsPattern recognitionCrowds
Revealed is an intelligent camera security monitoring, fuzzy logic analyses and information reporting system that includes video / audio camera, integrated local controller, interfaced plurality of sensors, and input / output means, that collects and analyses data and information observations from a viewed scene and communicates these to a central controller. The central controller with fuzzy logic processor receives, stores these observations, conducts a plurality of computer analyses techniques and technologies including face, voice, lip reading, emotion, movement, pattern recognition and stress analysis to determine responses and potential threat of / by a person, crowd, animal, action, activity or thing. This invention recognizes possible terrorists, criminals, enraged or dangerous persons and also can identify a person's level of intoxication or impairment by alcohol or drugs via a new “Visual Response Measure”. The invention provides an intelligent tool to assist security systems and personnel, improving capability to record, display and share information and maintain security.
Owner:STRESSCAM OPERATIONS & SYST
Method and apparatus for blood withdrawal and infusion using a pressure controller
InactiveUS20050230313A1Decreased blood flowIncrease heightSolvent extractionOther blood circulation devicesVeinTotal occlusion
A method and apparatus for controlling blood withdrawal and infusion flow rate with the use of a pressure controller. The pressure controller uses pressure targets based upon occlusion limits that are calculated as a function of flow. The controller has the ability to switch from controlling withdrawal pressure to controlling infusion pressure based upon the detection of an occlusion. The controller distinguishes between partial and total occlusions of the withdrawal vein providing blood access. Depending on the nature of occlusion, the controller limits or temporarily reverses blood flow and, thus, prevents withdrawal vessel collapse or reverses blood flow to quickly infuse blood into the vessel without participation from operator.
Owner:GAMBRO LUNDIA AB
User interface for a device requesting remote authorization
ActiveUS9847999B2Faster and efficient methodReduce cognitive loadUser identity/authority verificationPayment architectureComputer hardwareNetwork connection
The present disclosure generally relates to techniques for managing a remote authorization to proceed with an action, such as creating a secure network connection. In some examples, a requesting device receives selection of one or more options. The requesting device transmits a request to proceed with an action to an authenticating device. The authenticating device concurrently displays an indication of the request to proceed with the action, information about the selected one or more options, and an indication of the requesting device. The authenticating device receives authorization to proceed with the action and transmits a response to the requesting device regarding the request to proceed with the action.
Owner:APPLE INC
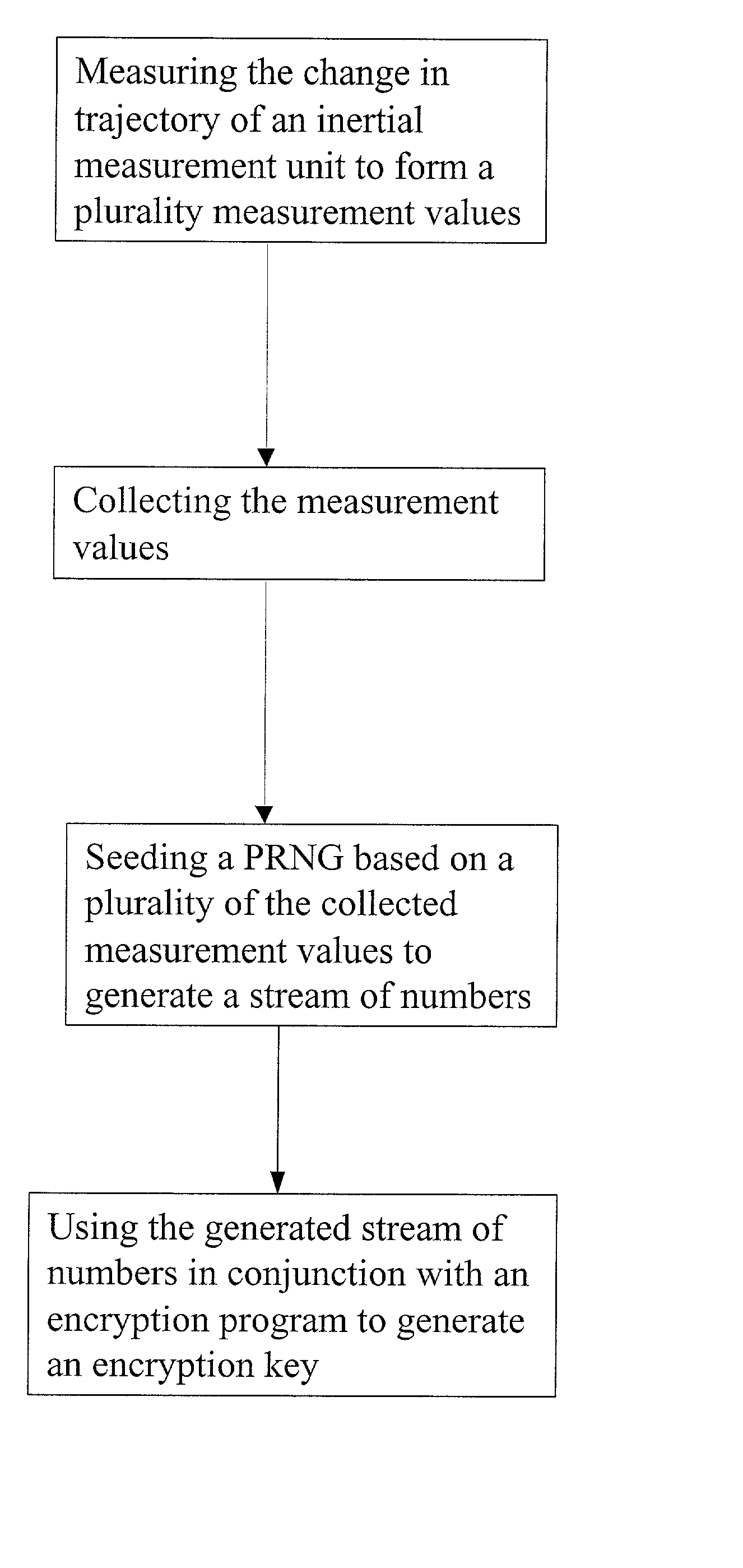
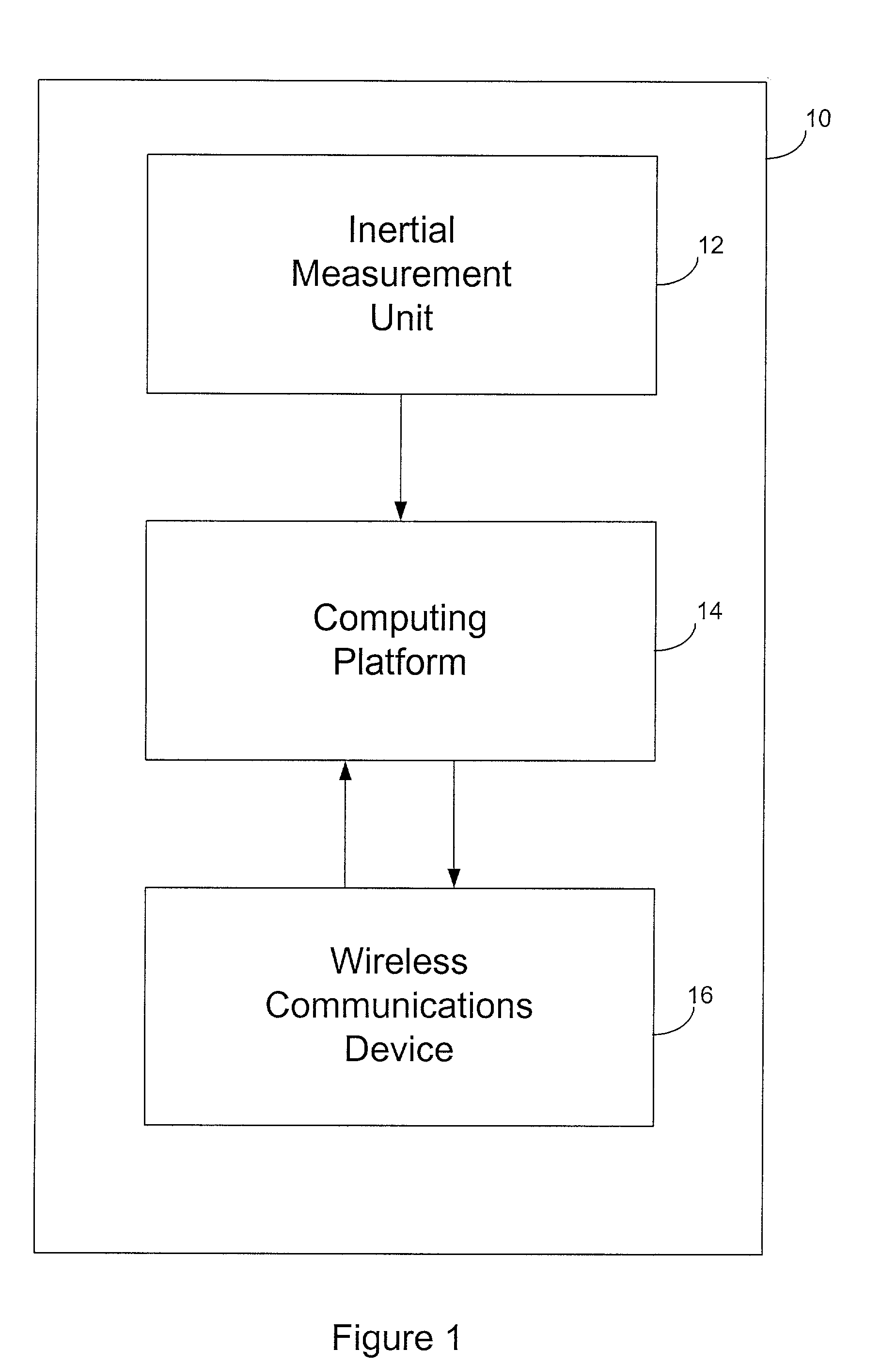
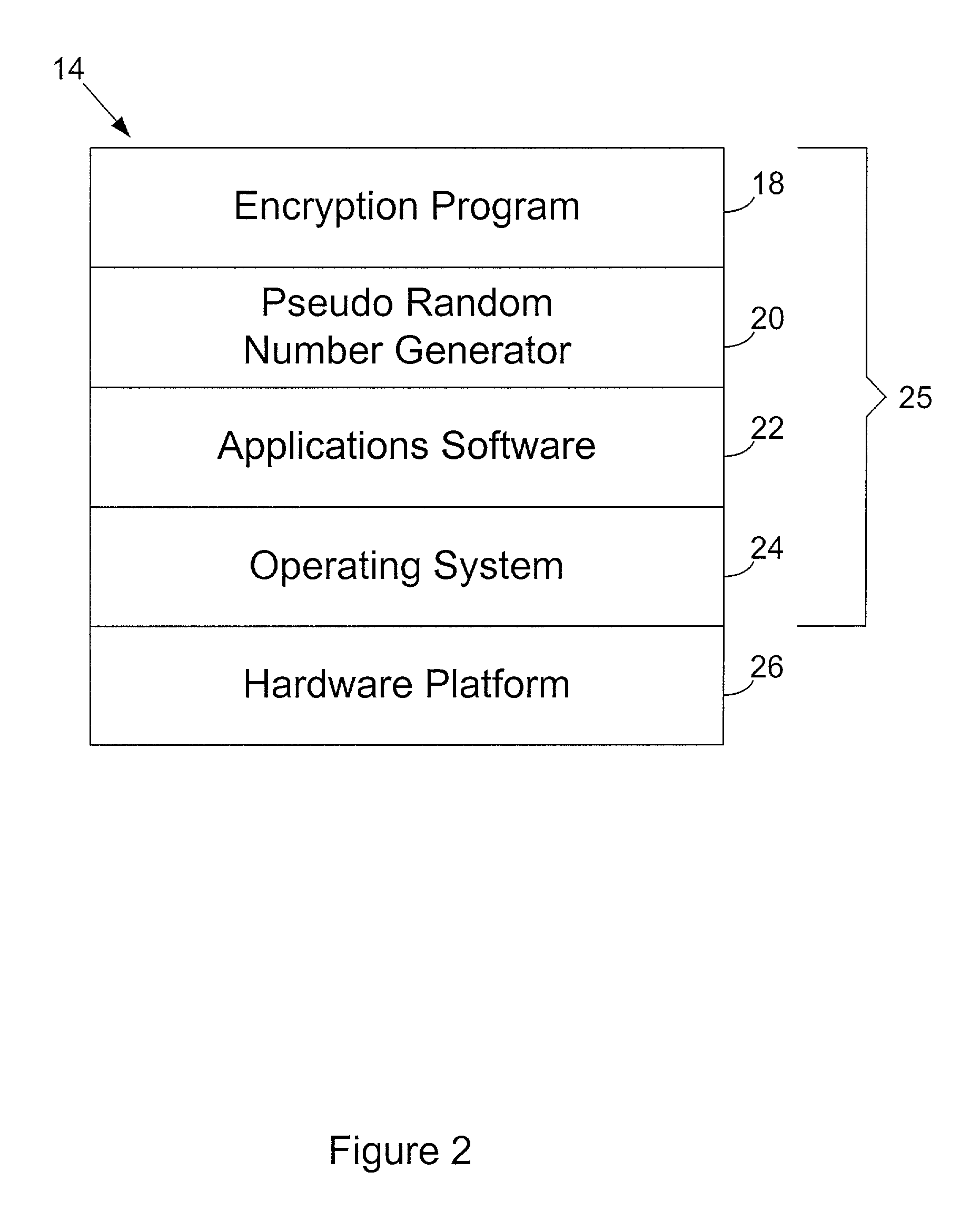
Entropy sources for encryption key generation
InactiveUS20020131592A1Maintain securityNecessary computer processing powerMechanically effected encryptionSecret communicationCryptographic key generationNumber generator
Inertial measurement units are subject to drift and noise characteristics that are normally distributed. While that drift and noise is problematic for inertial navigation, it is ideal for encryption key generation. The measurement values from an inertial measurement unit are random on several levels and can be used to effectively seed a pseudo random number generator for encryption key generation.
Owner:AIRBIQUITY INC
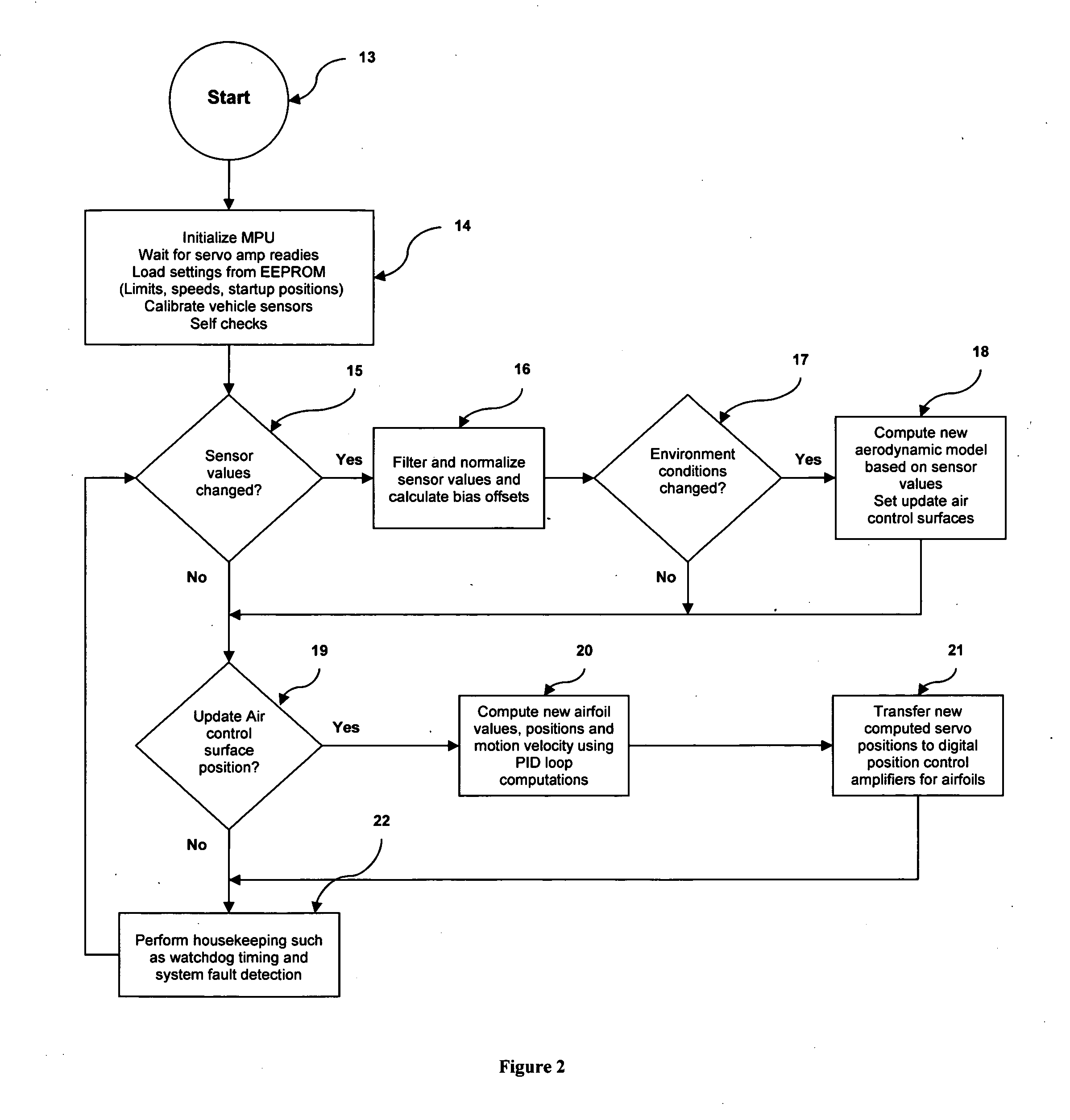
Fuel efficient dynamic air dam system
InactiveUS20070257512A1Improve fuel efficiencyMaintain securityVehicle seatsWindowsAerodynamic dragDifferential pressure
Active, aerodynamic controller that describes a method for dynamically controlling airflow using computer controlled movable air dams and airfoils on motor vehicles. It is well known that motor vehicles generally have a great deal of aerodynamic friction also known as drag. Fuel efficiency is greatly affected by a vehicle's aerodynamic drag. Aerodynamic drag is caused by both induced drag and parasitic drag. Parasite drag is somewhat fixed by the overall design and shape of a vehicle. Parasite drag is caused primarily by the laminar flow of air over the smooth surfaces of the vehicle's hood, roof, windows, side mirrors and door panels. Induced drag is much more variable and is primarily created by the differential pressure effects of air flowing over, under and around a vehicle, as well as the relative airflow caused by both ground effect and atmospheric air density and wind. This invention serves to actively minimize the effects of induced drag thus reducing the amount of fuel used by vehicles fitted with this invention.
Owner:ANDERSON SCOTT
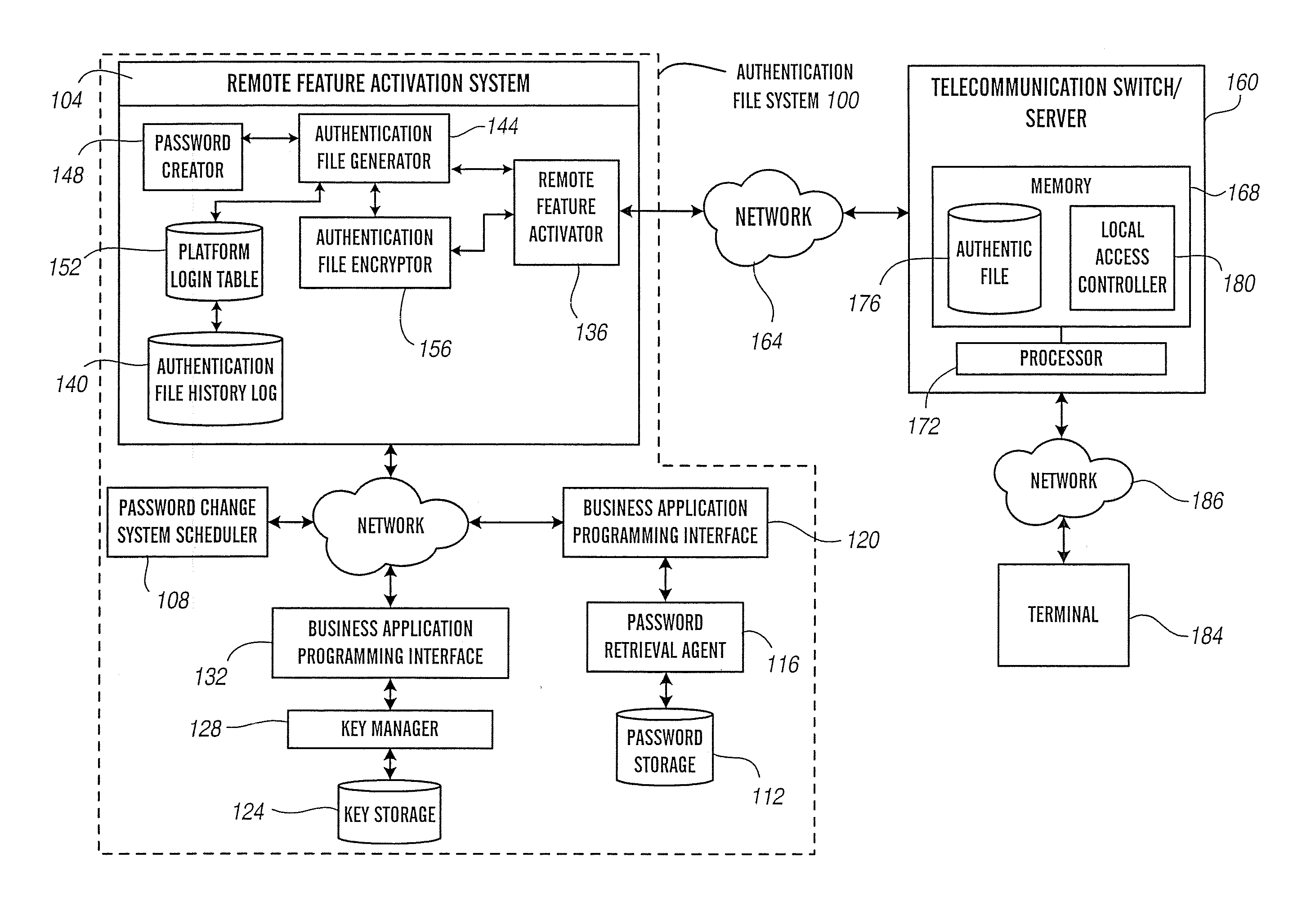
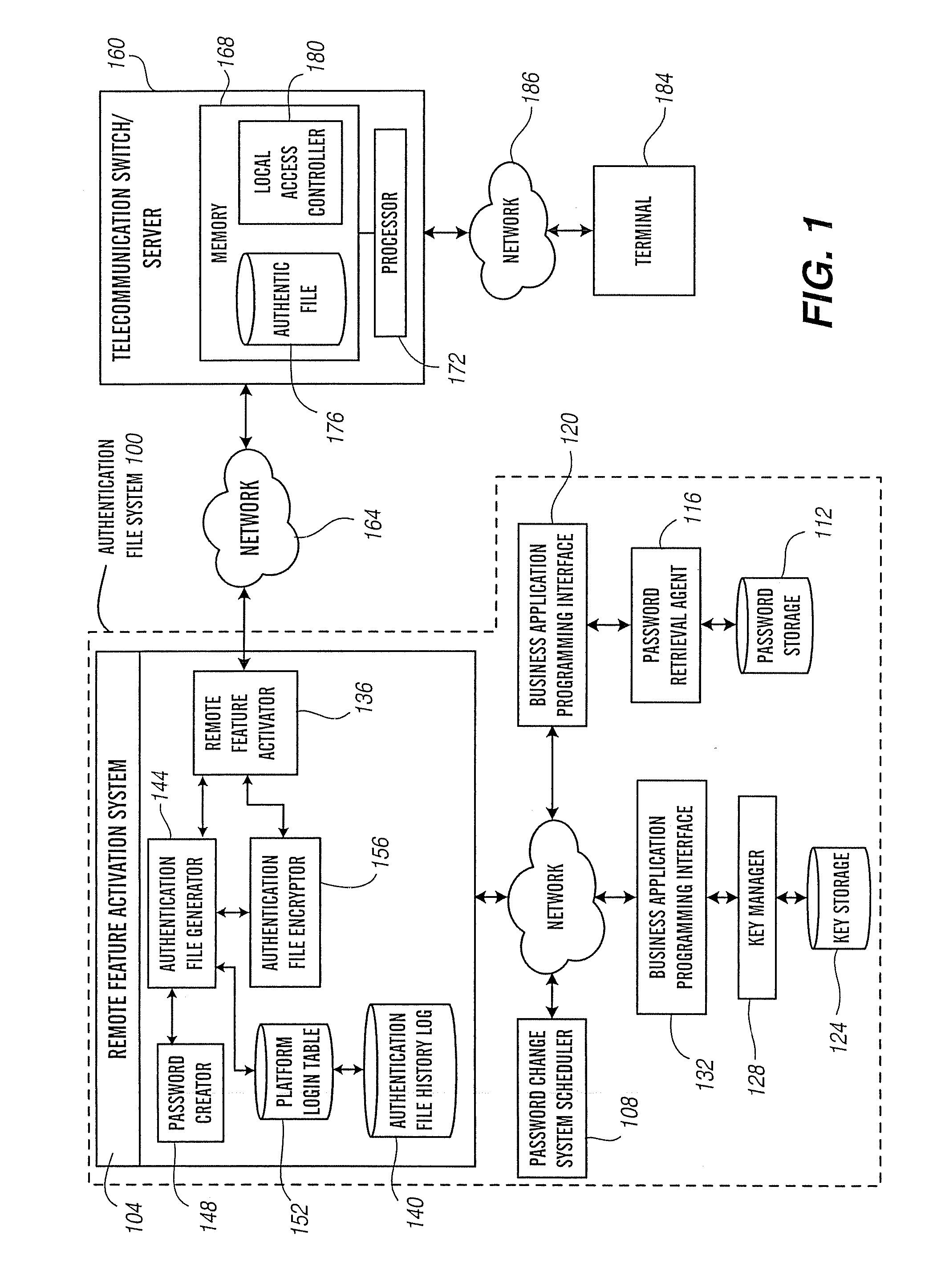
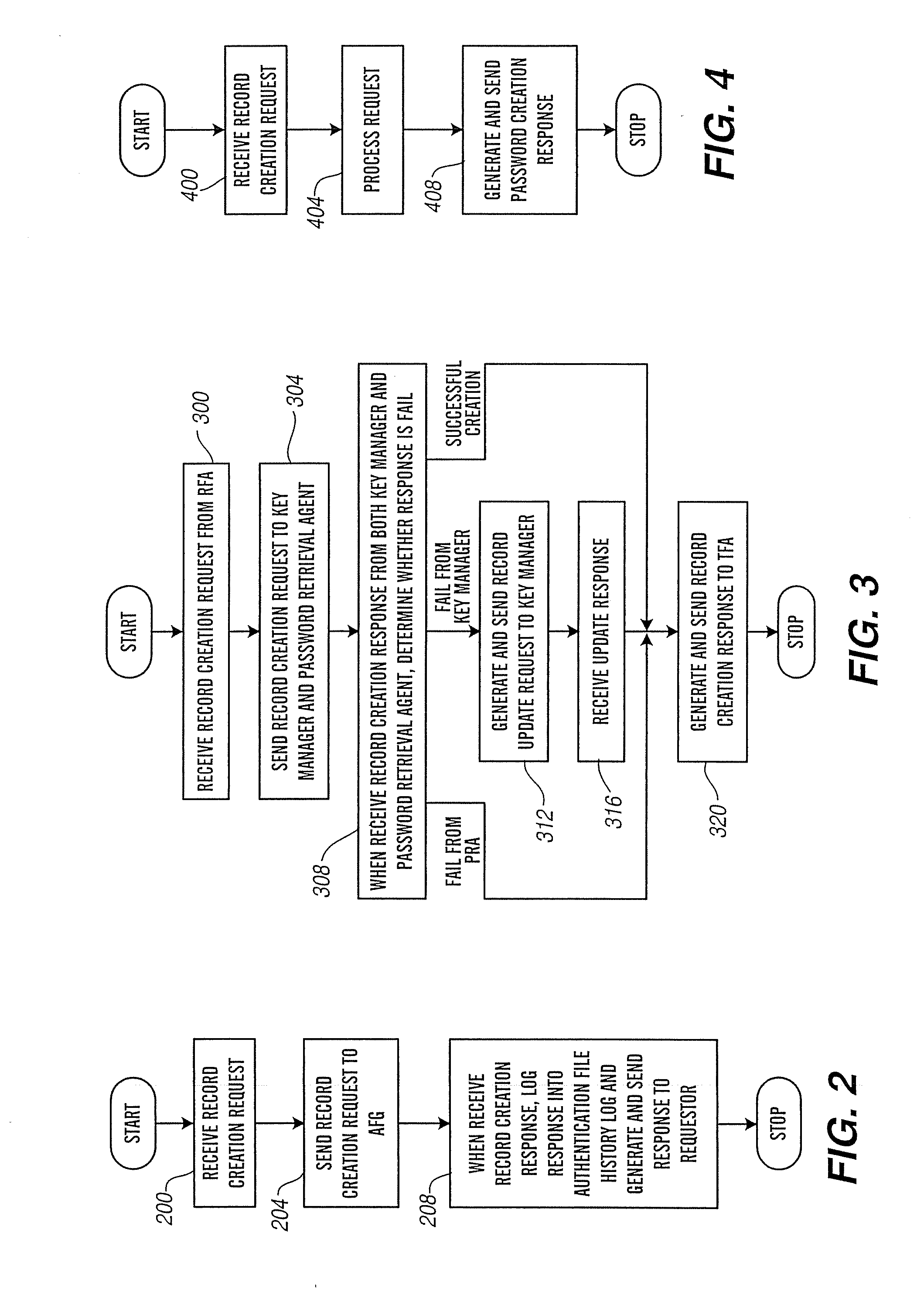
Remote feature activation authentication file system
ActiveUS20070094710A1Limited use privilegeMaintaining meaningful level of securityKey distribution for secure communicationDigital data processing detailsFile systemBiological activation
Owner:AVAYA TECH LLC
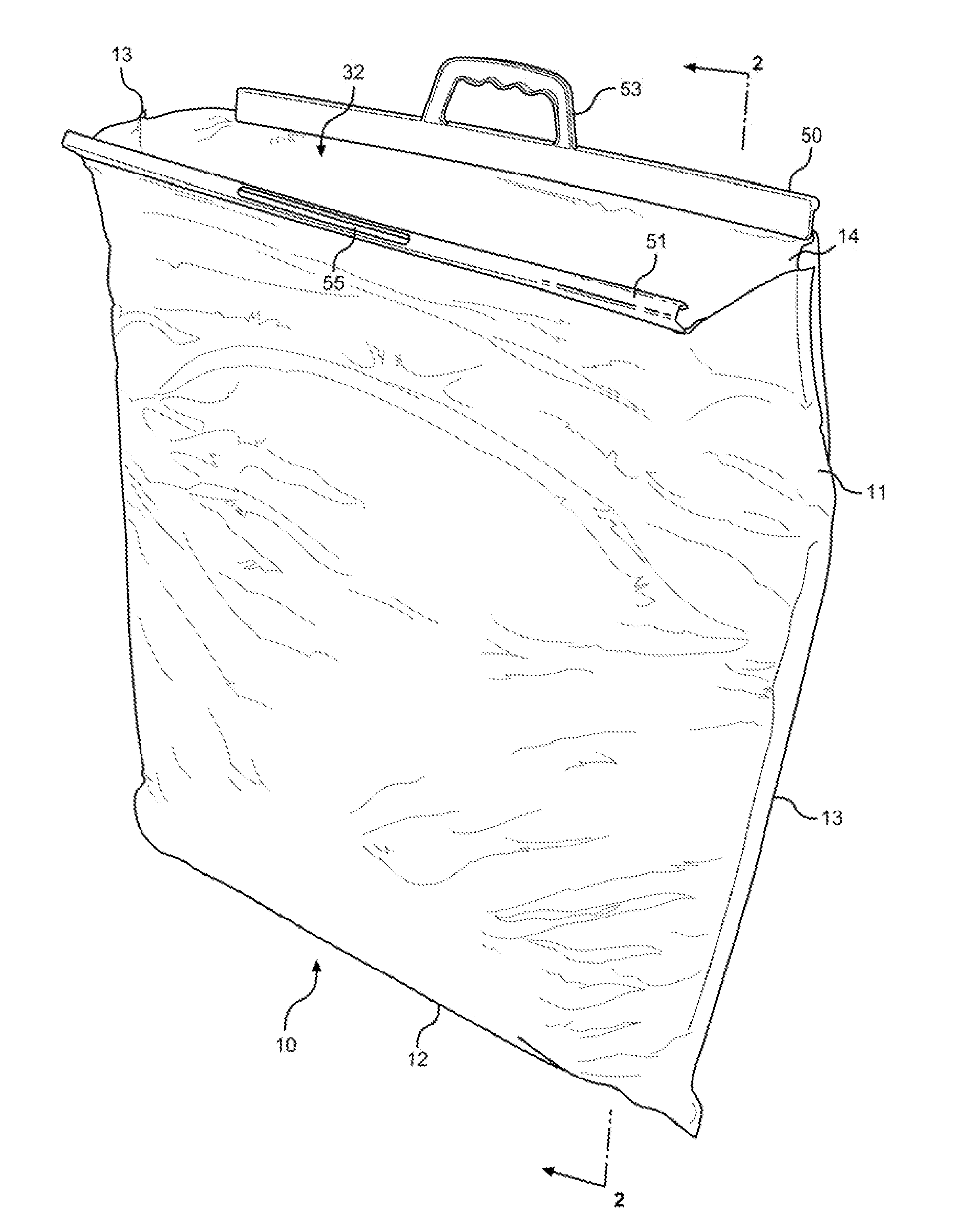
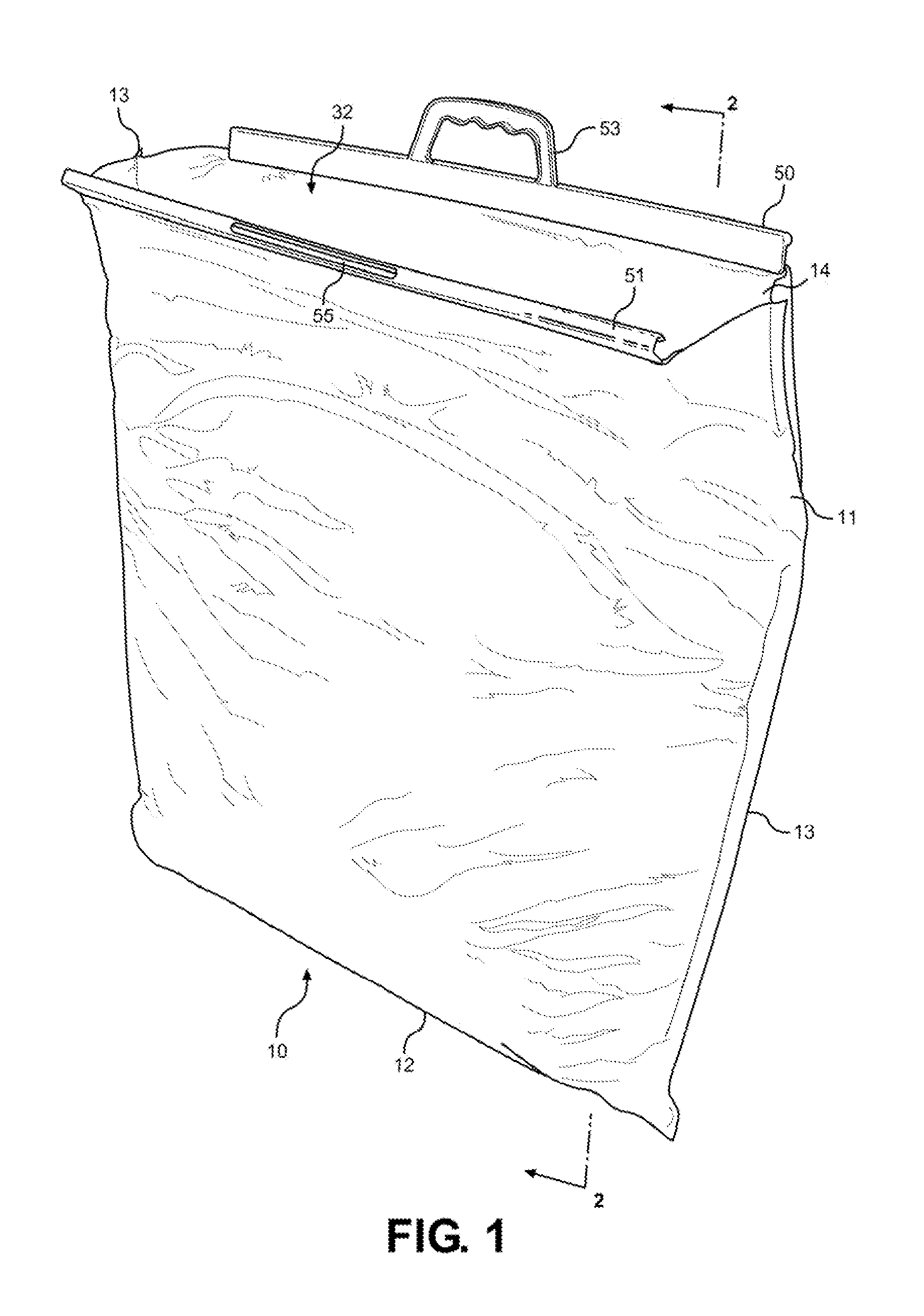
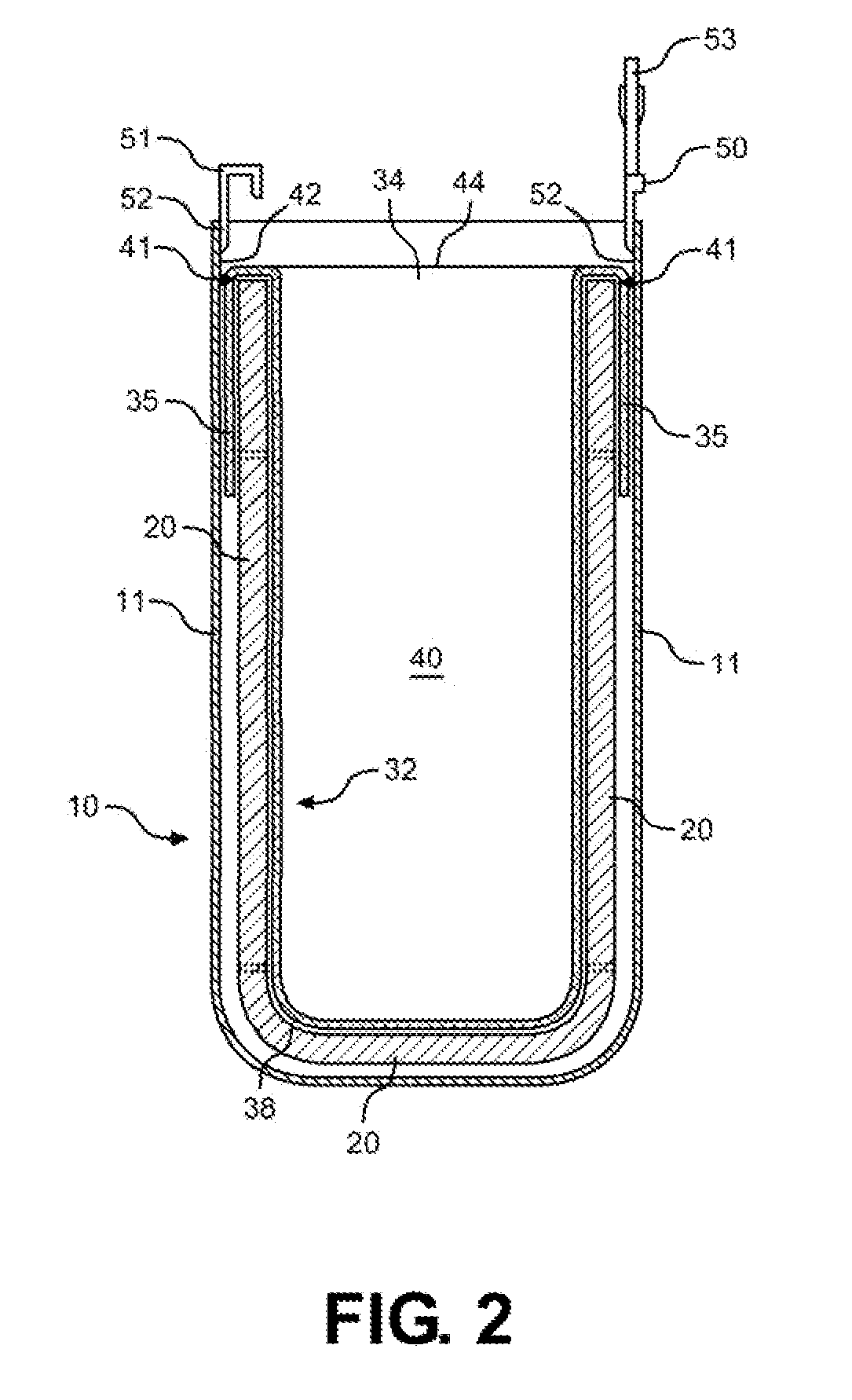
Insulated shipping bags
ActiveUS20160060017A1Increase temperatureMaintain securityDomestic cooling apparatusLighting and heating apparatusBiomedical engineeringPaper sheet
Owner:COLDKEEPERS INC
System and method for secure communication
ActiveUS20060230461A1Validity is limitedEliminates outdated trust indicatingDigital data processing detailsPublic key for secure communicationSecure communicationInternet privacy
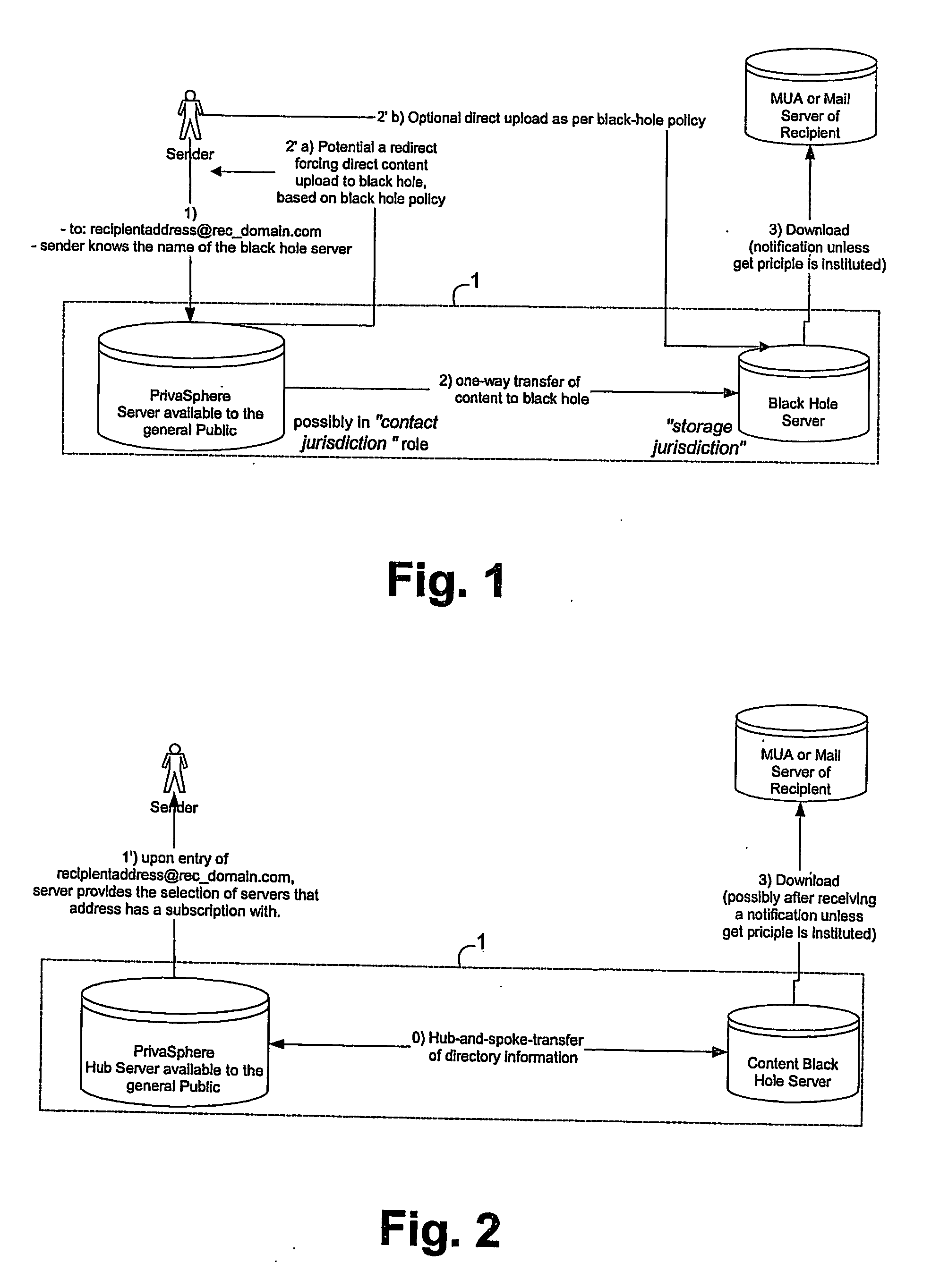
A system (1) for secure communication comprises a secure electronic messaging server (11) which is accessible by the public and a database (12) for storing data of messaging users. The data comprise the tracking of trust establishing out-of-band verification and the monitoring of the trust relations derived thereof, messaging user-based instructions related to the handling of incoming mails, wherein the instructions comprise information related to an at least one security level chosen by the messaging user. The system (1) comprises means to automatically handle in- and outgoing mails according to these instructions. This system (1) allows transmitting messages privately and securely with minimum prerequisites for its users. The inventive system (1) allows a secure transmitting of messages between a sender (S) and a recipient (R), wherein only one of the two parties is a messaging user.
Owner:PRIVASPHERE AG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com