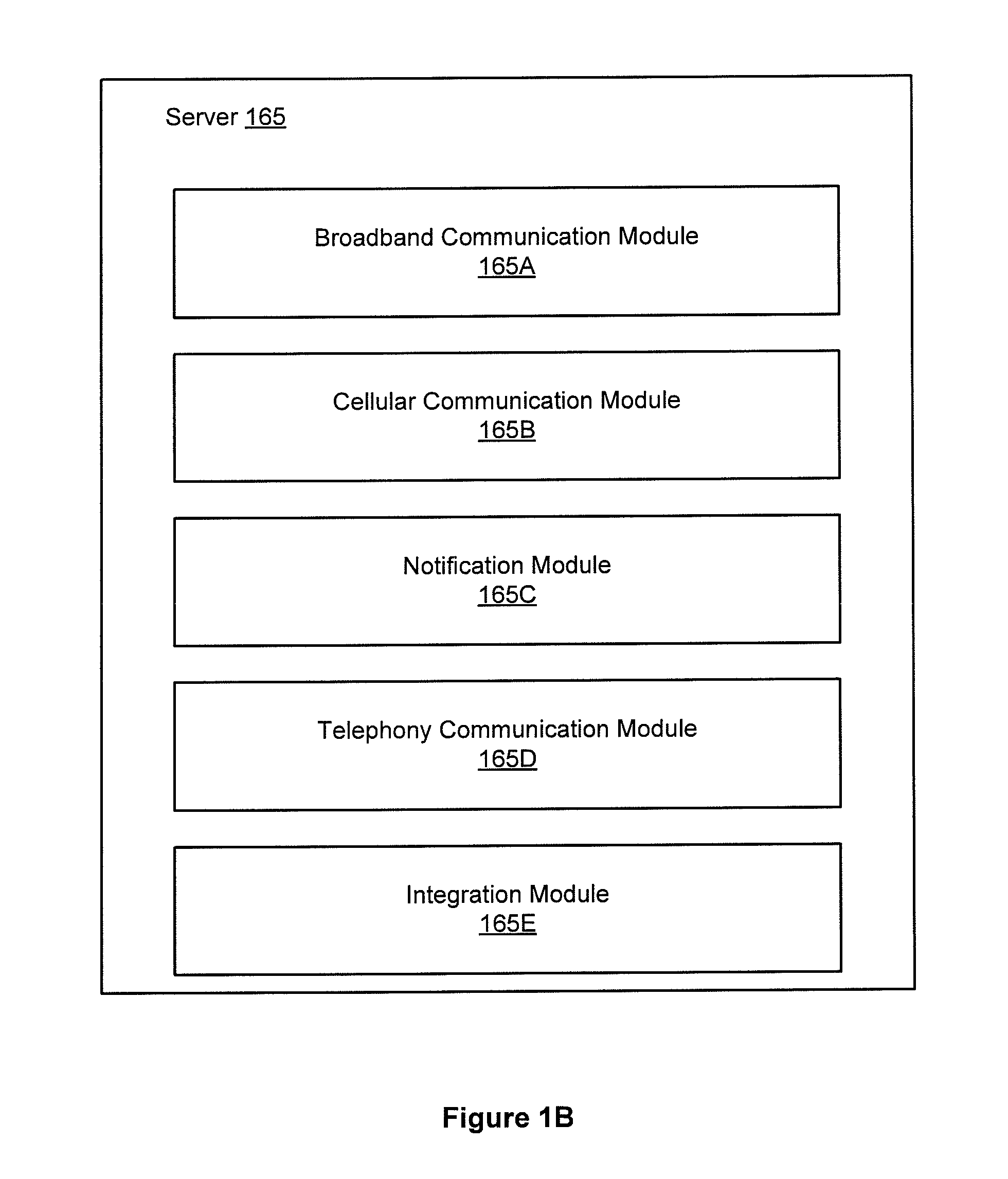
Patents
Literature
4559 results about "Security monitoring" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
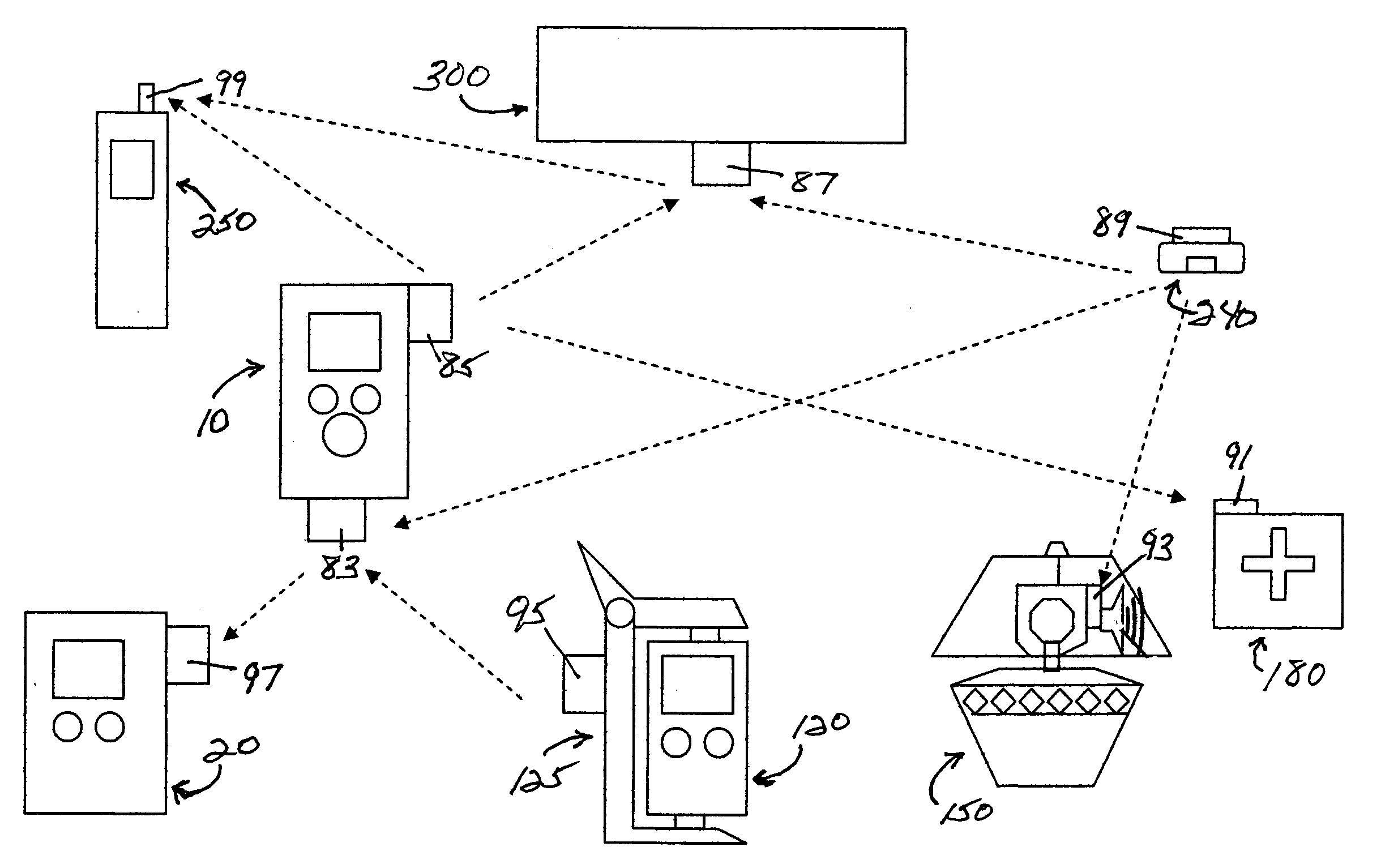
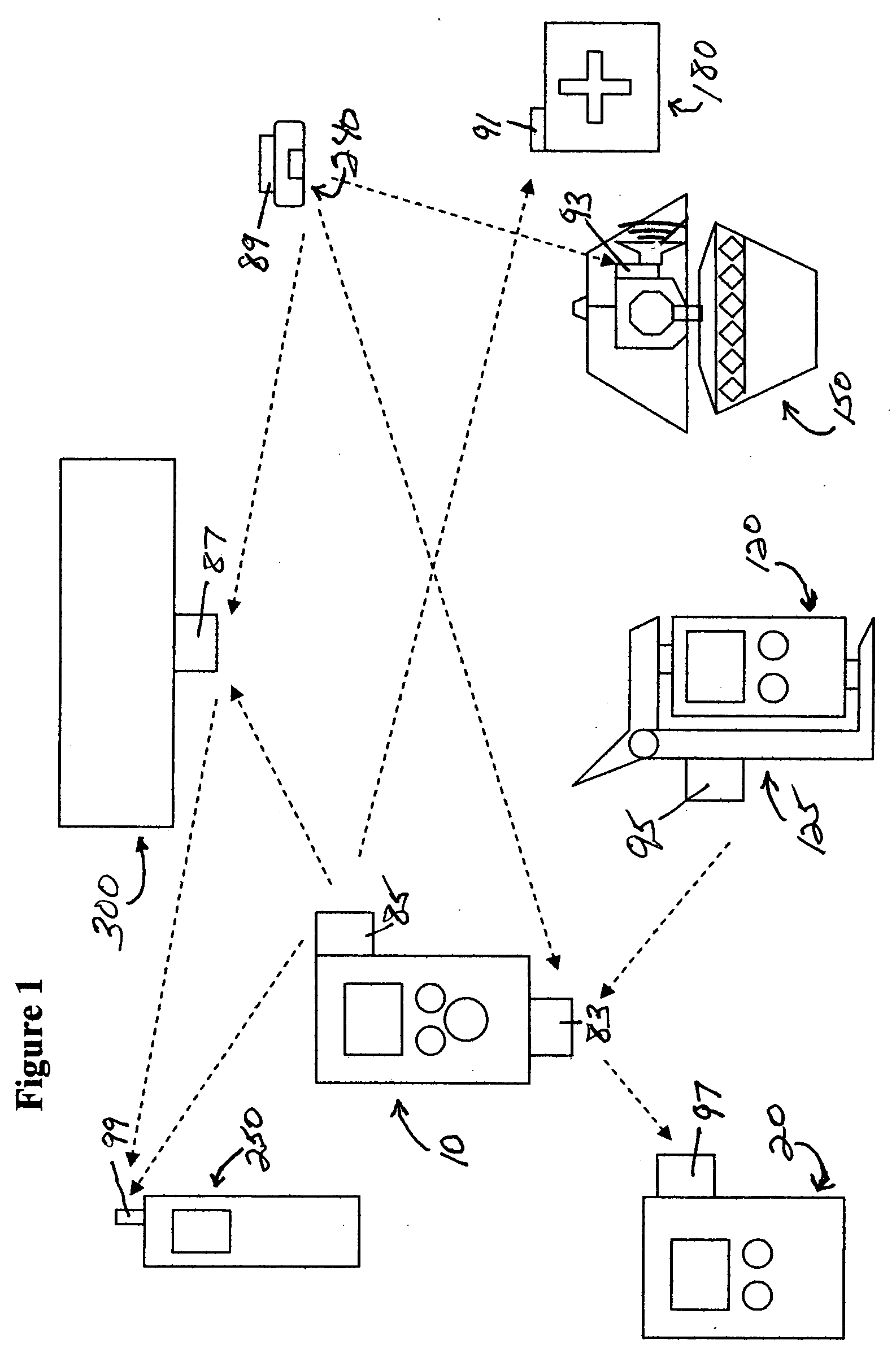
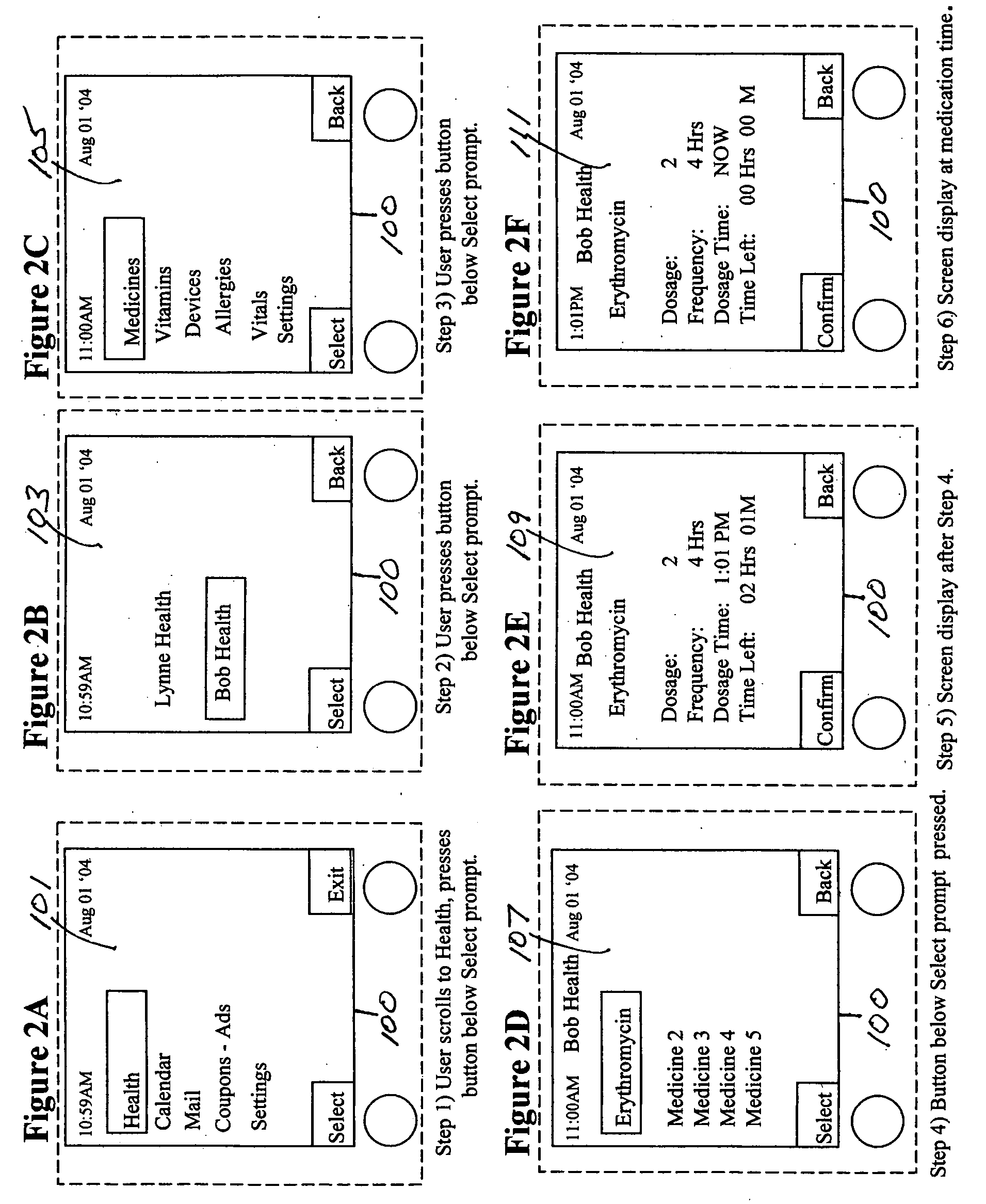
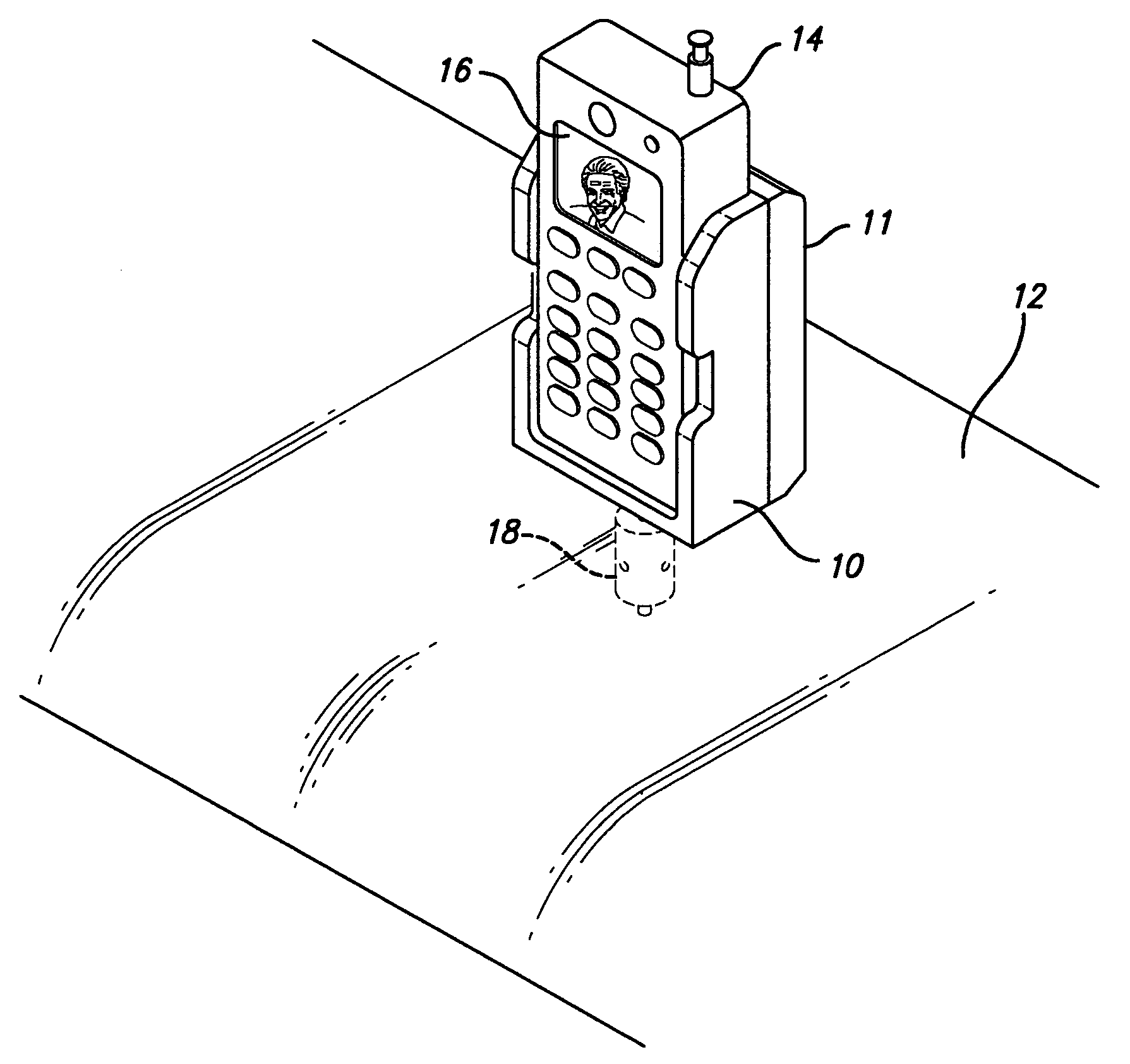
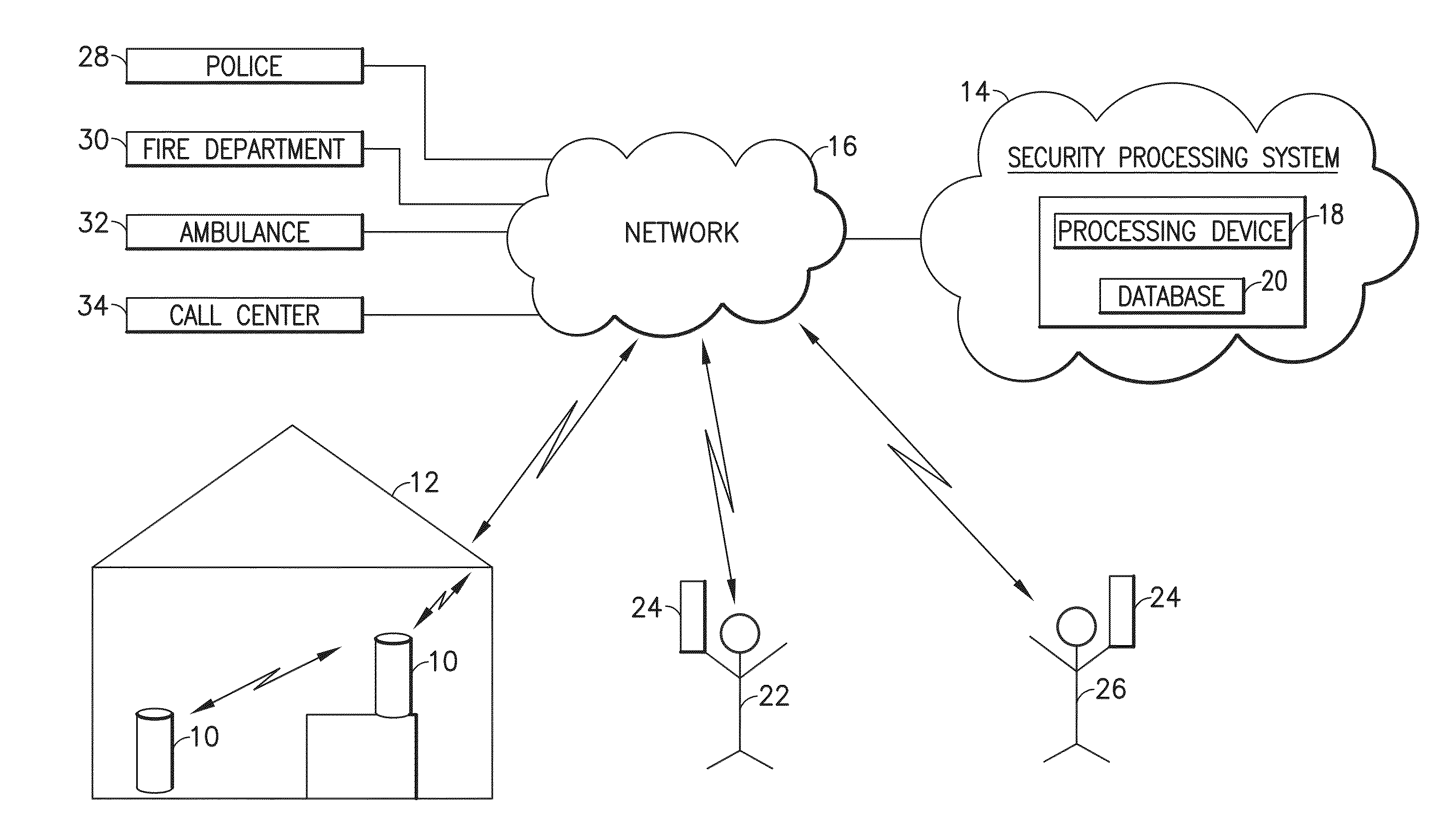
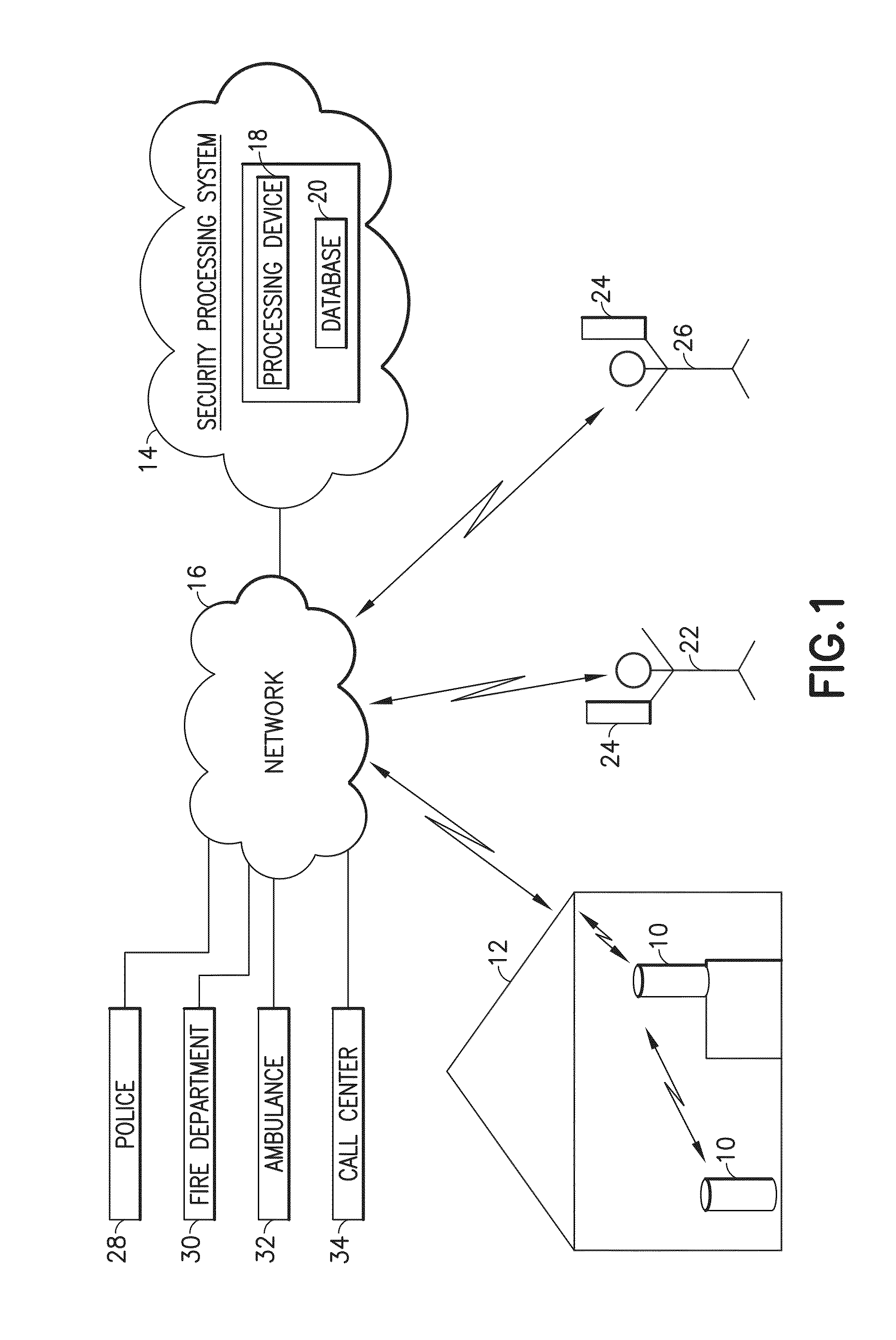
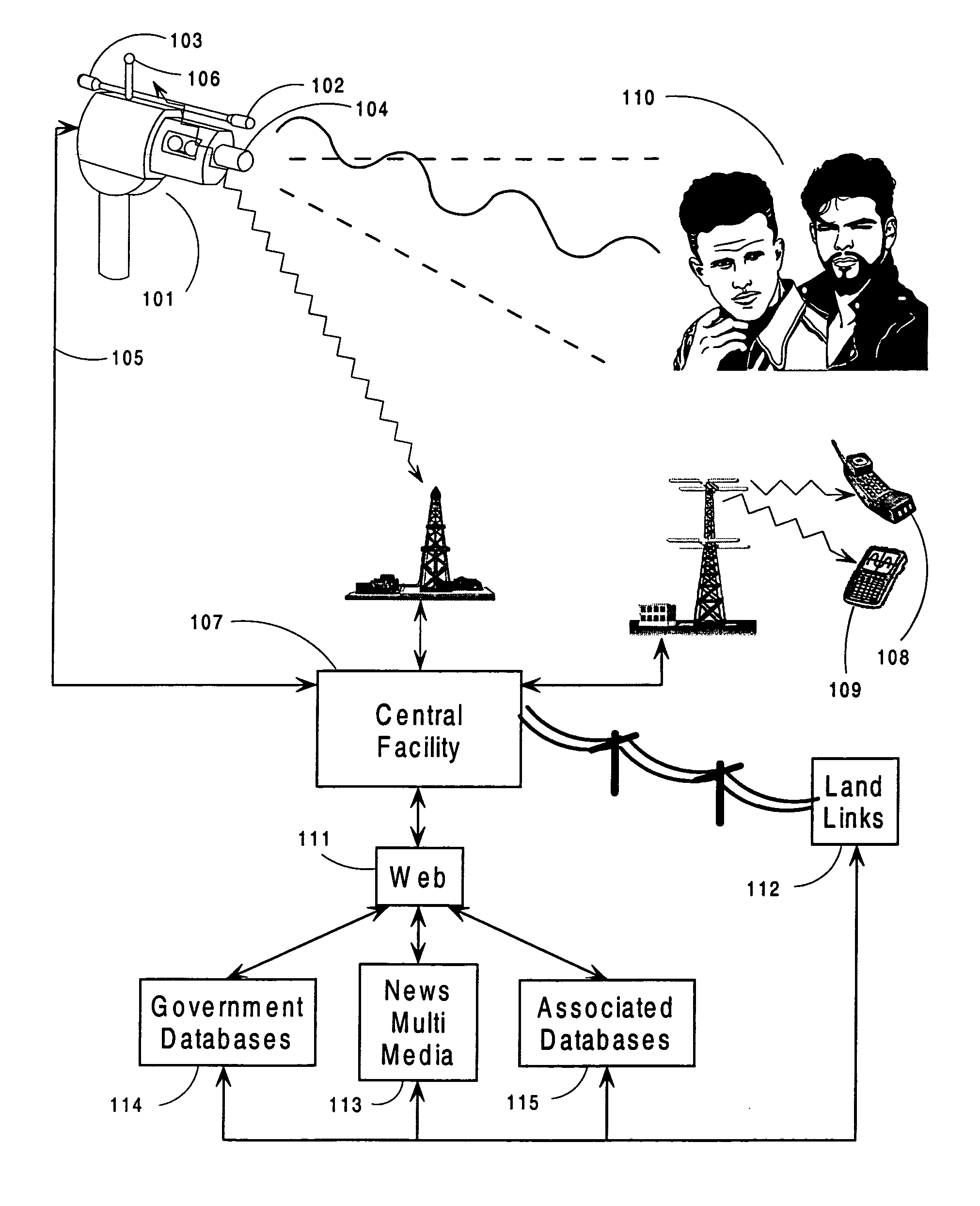
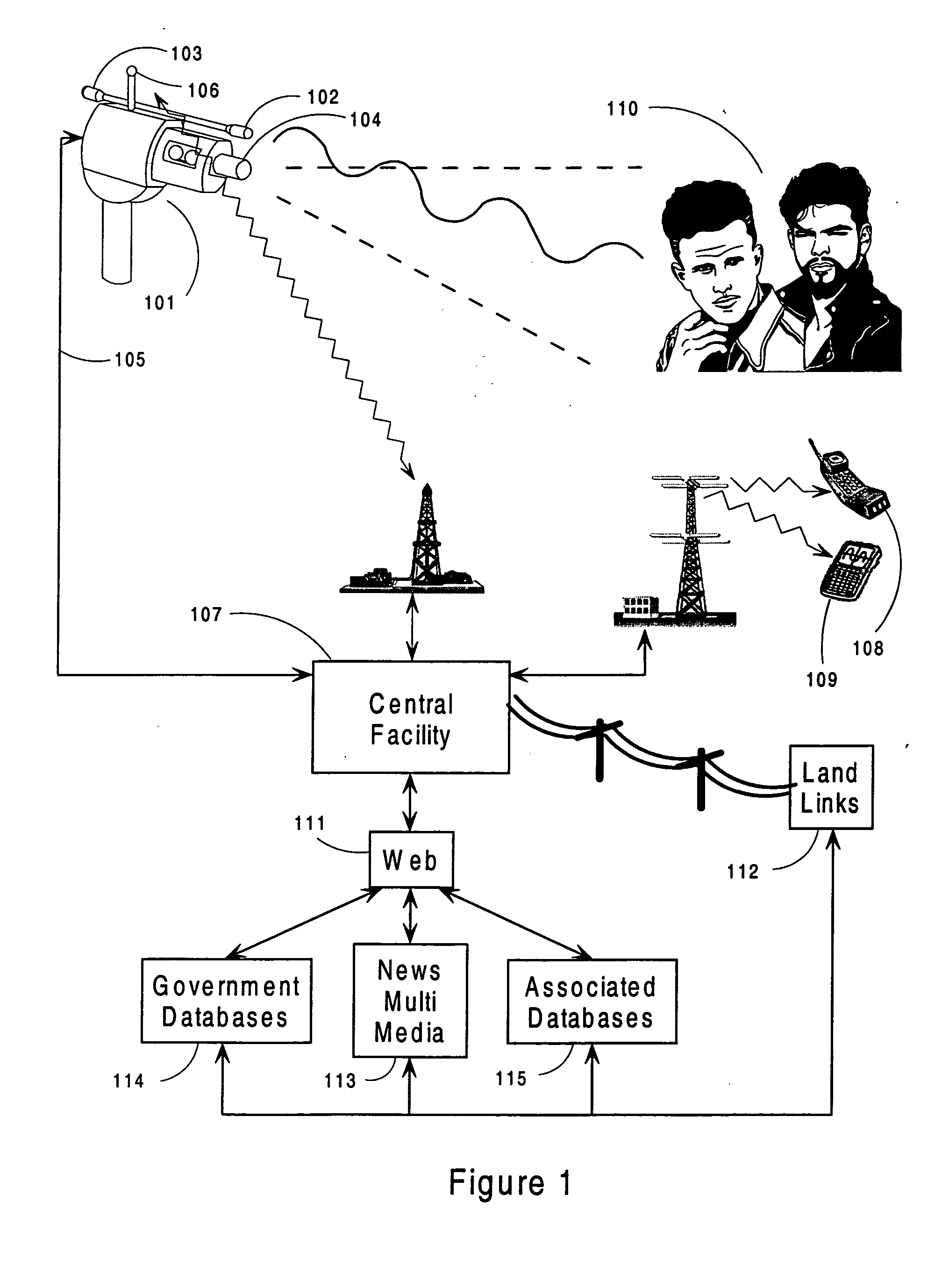
Medication & health, environmental, and security monitoring, alert, intervention, information and network system with associated and supporting apparatuses
InactiveUS20060154642A1Facilitate user and/or occupant well beingExtended stayDispersed particle filtrationDrug and medicationsNetworked systemHealth administration
Systems and apparatuses include devices, biosensors, environmental sensors, security related sensors, networked products, communications processors and components, alert and information components, processors, and software to support: 1) facilitating medication regimen and patient / user health administration, dosage control, tracking, compliance, information inquiry and presentation, reminder and notification; 2) providing monitoring, information, ordering, and intervention; 3) presenting the option of leveraging the preventative care, alert and notification components with other components to facilitate user or occupant well being, along with living, work area and dwelling environmental or security safety; and 4) enhancing the dwelling, living or work area with products that may be networked to support the widespread acceptance of these systems and apparatuses. The systems include a) processing, centralizing and communicating device commands and / or programs, e.g. a multifunctional device controller; b) device administration; c) patient / user information; d) dwelling environmental safety; e) security breach information; f) centralized and remote apparatus and system activations through primary component or at least one backup.
Owner:INSIGNIO TECH
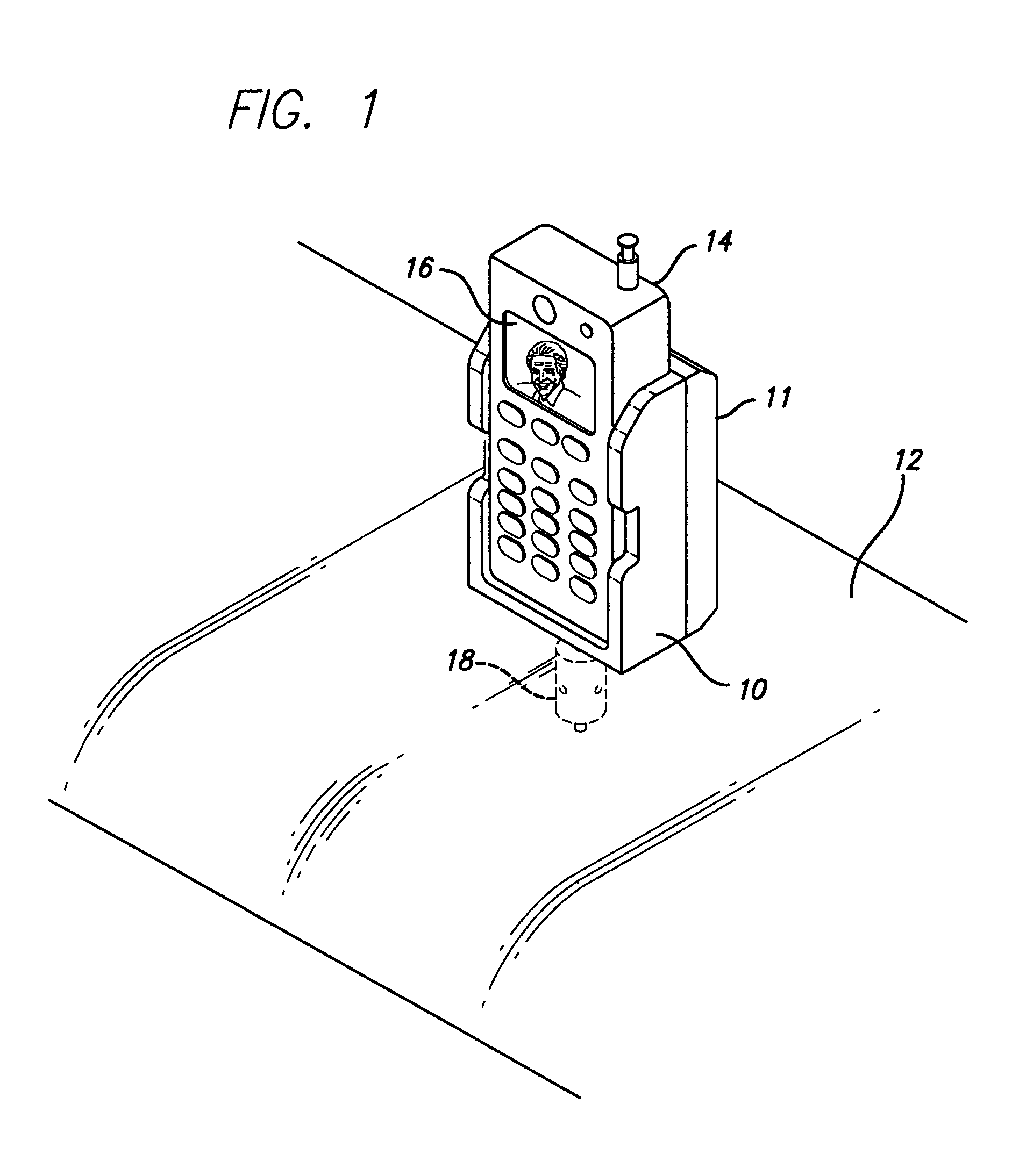
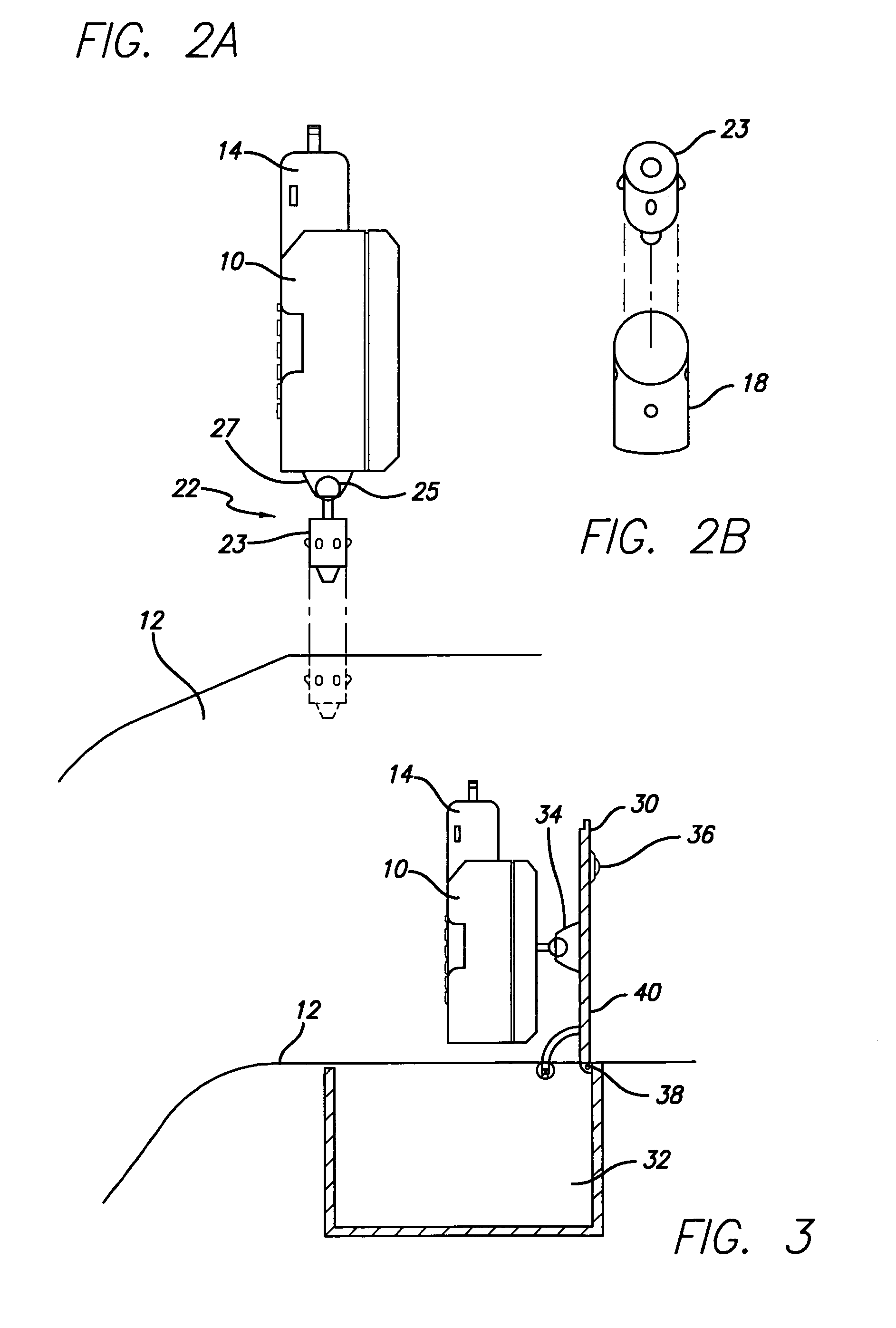
Cellular phone holder with charger mounted to vehicle dashboard
In a vehicle, means of mounting a cell phone on the vehicle dashboard with minimal wiring and external connections, using manufacturer power connections made available on the dashboard. The mounting means is either an after market accessory addition to the vehicle or a option available at the time of purchase to render easy and convenient mounting of the cell phone without loose wires and providing proper positioning of a video camera built into the cell phone. The cell phone is positioned for viewing either through the windshield or backward onto the occupants enabling monitoring accidents between vehicles, the result of an accident on the occupants of the vehicle or for security monitoring of the trespassers within the vehicle. This is accomplished by mounting the camera at the dashboard. Another advantage is to improve the power output of the cell phone by positioning the antenna (part of the hand held cell phone device) near the windshield.
Owner:KIM KI IL
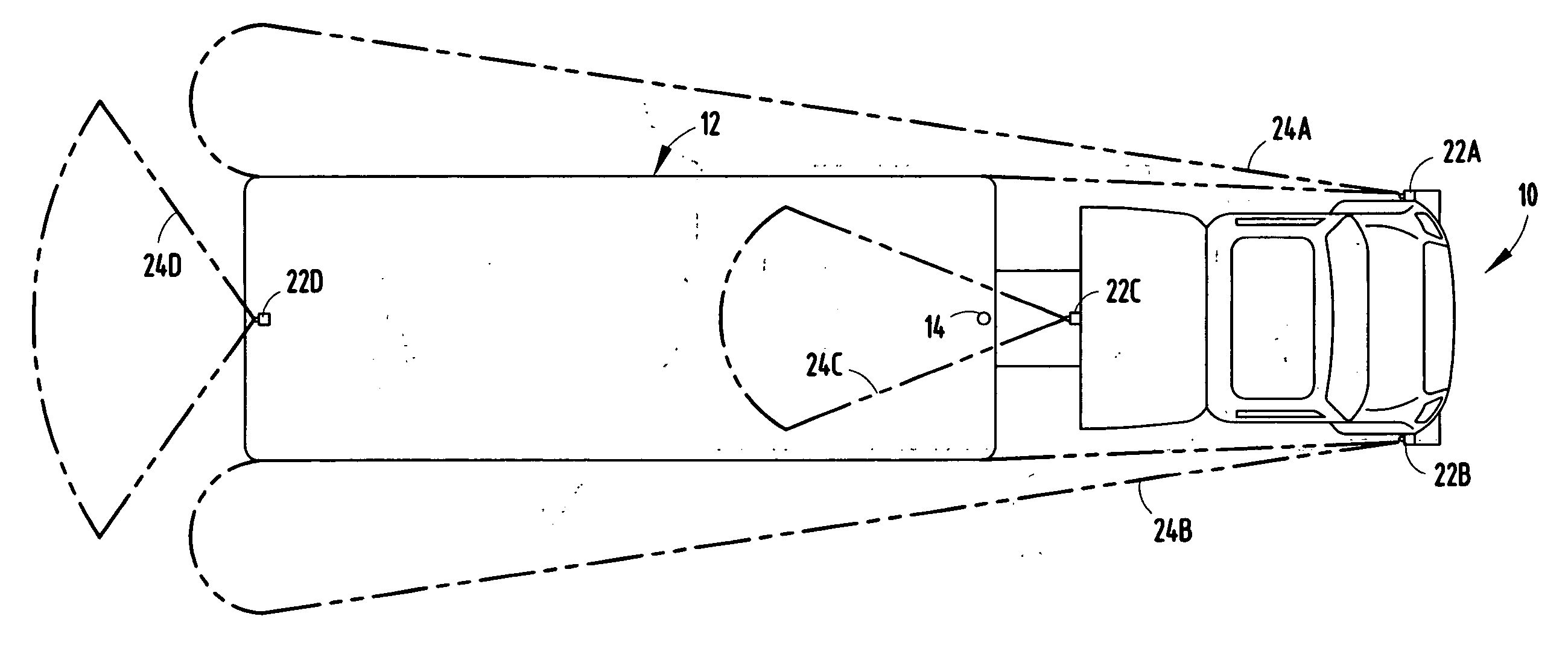
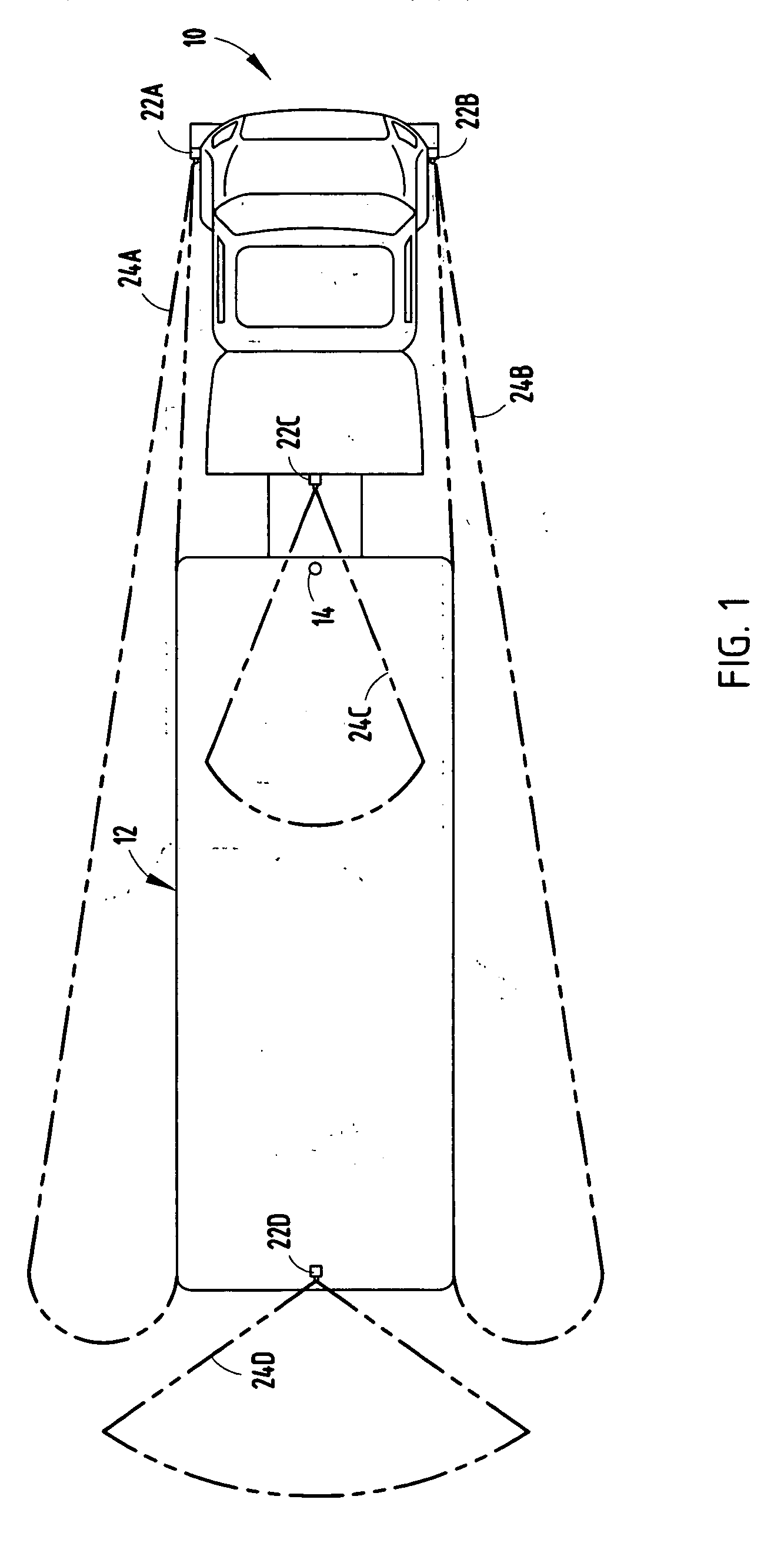
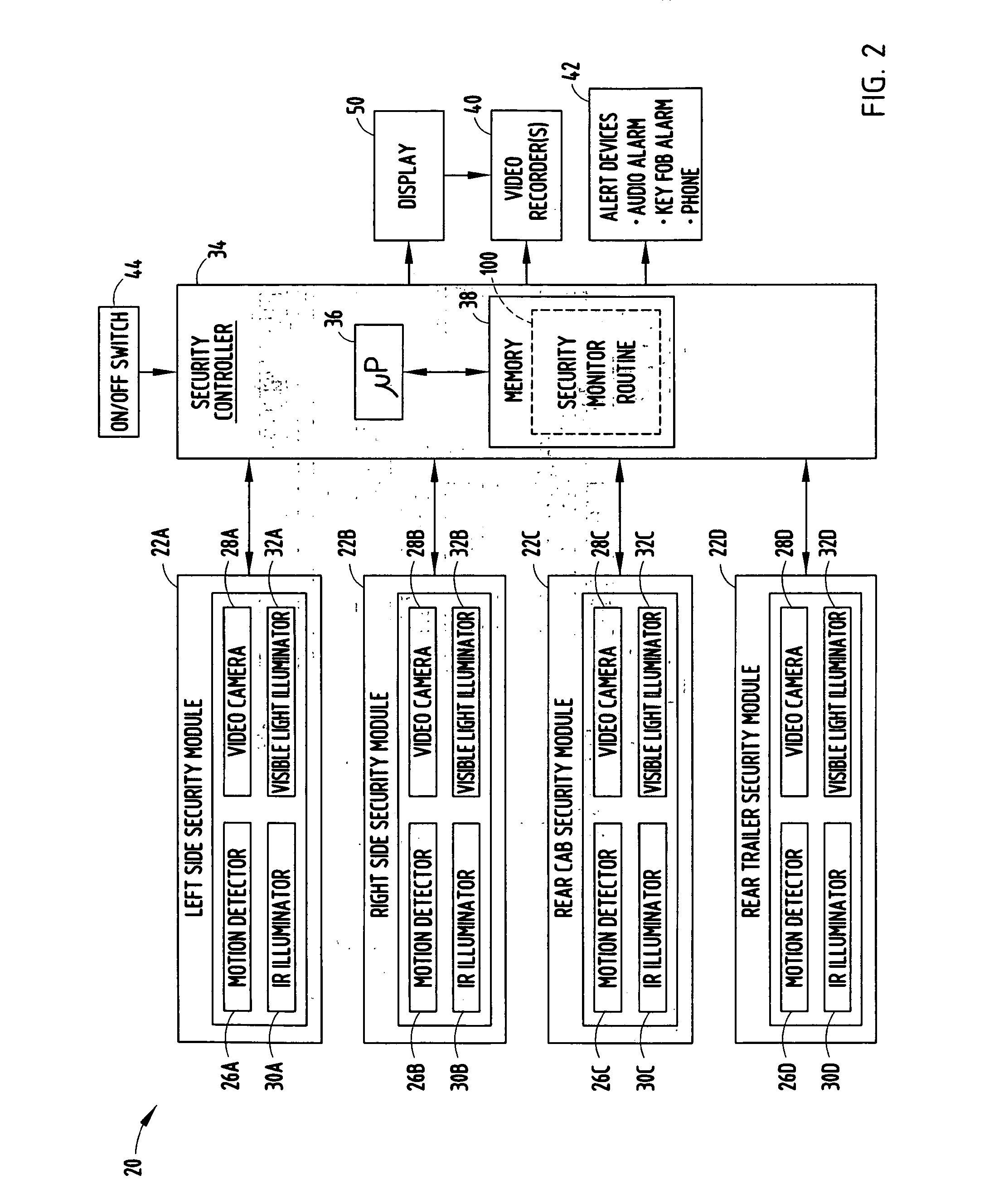
Vehicle security monitor system and method
InactiveUS20060250501A1Prevent and minimize theftImprove securityAnti-theft devicesColor television detailsMotion detectorDisplay device
A vehicle security monitoring system and method is provided for monitoring the security in detection zones near a vehicle. The system includes motion detectors positioned to detect motion of an object within security zones of a vehicle and cameras positioned to generate video images of the security zones. A display located onboard the vehicle displays images generated by a camera when the camera is activated. A controller controls activation of the camera and presentation of images on the display. The controller activates the camera and controls the display to output images captured by the camera when a moving object is detected IN THE security zone.
Owner:DELPHI TECH INC
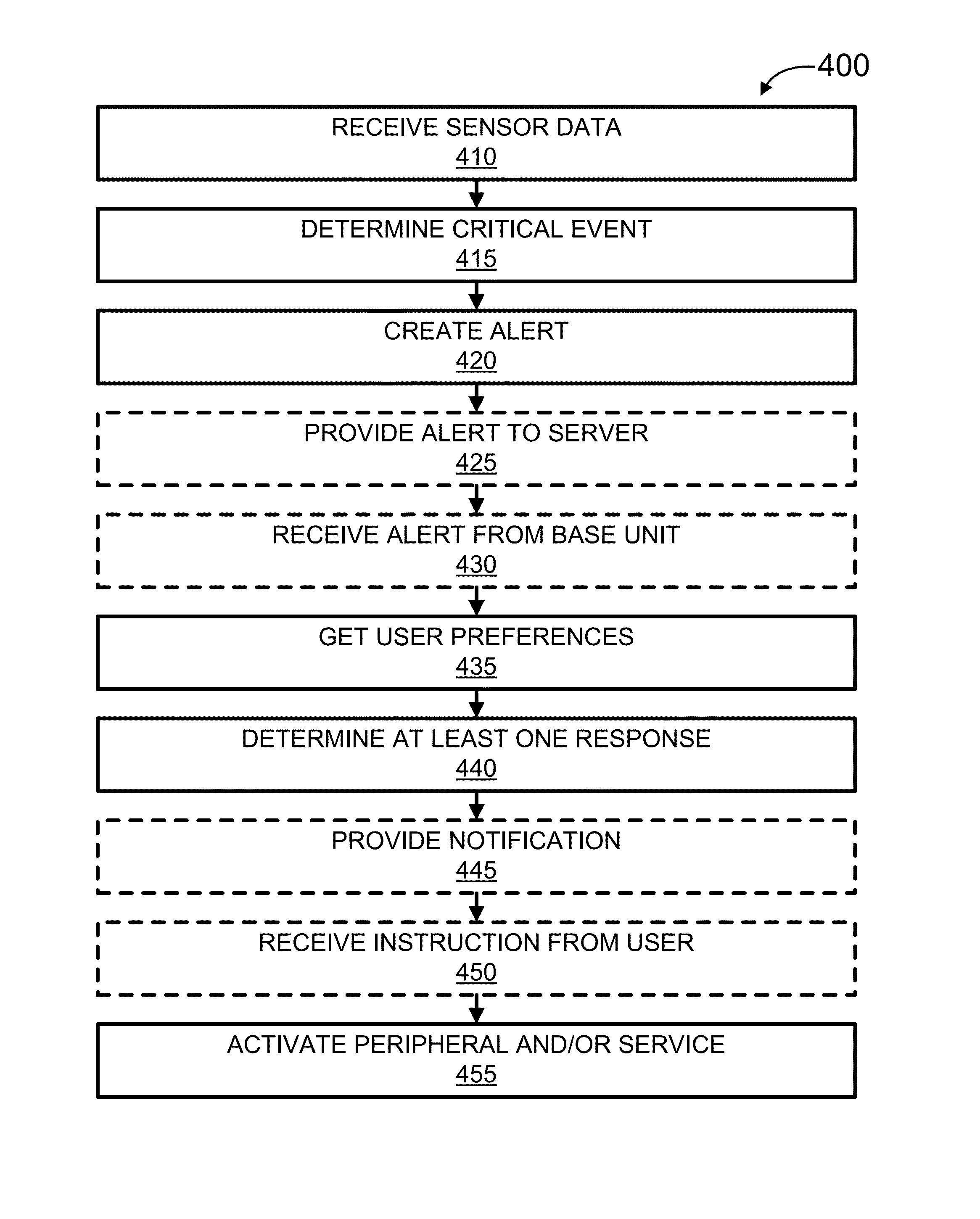
Security Monitoring and Control
ActiveUS20150339912A1Burglar alarm mechanical actuationControl systemStructure of Management Information
Systems, methods, and software for monitoring and controlling a security system for a structure are provided herein. An exemplary method may include receiving sensor data from at least one first peripheral, the sensor data associated with at least one of activity inside and activity outside of a structure; determining a critical event based in part on the sensor data; creating an alert based in part on the critical event; getting user preferences associated with at least one of a user and a base unit; determining a response based in part on the alert and user preferences; and activating at least one of a second peripheral and a service based in part on the response.
Owner:OOMA
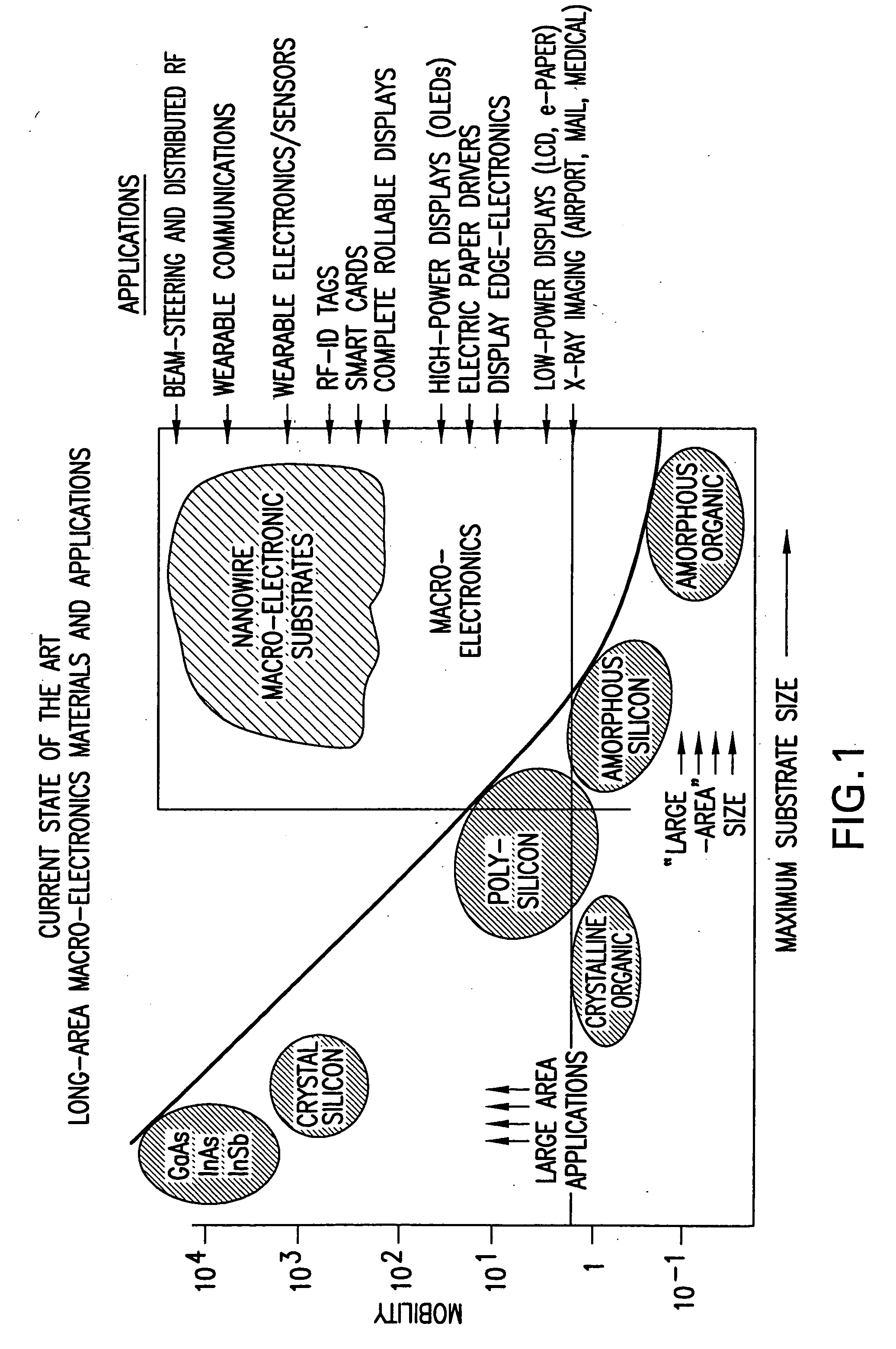
Applications of nano-enabled large area macroelectronic substrates incorporating nanowires and nanowire composites
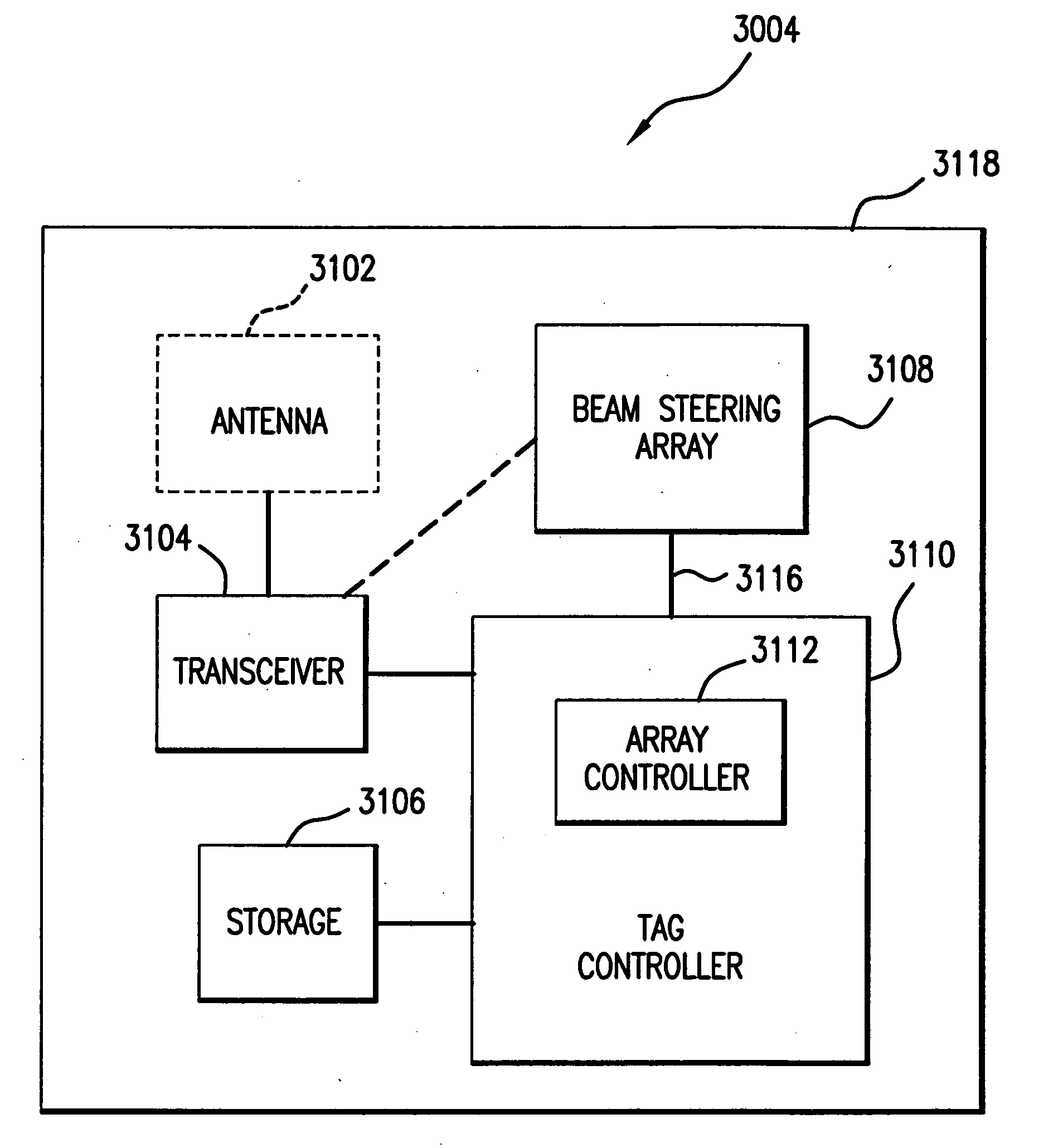
Macroelectronic substrate materials incorporating nanowires are described. These are used to provide underlying electronic elements (e.g., transistors and the like) for a variety of different applications. Methods for making the macroelectronic substrate materials are disclosed. One application is for transmission an reception of RF signals in small, lightweight sensors. Such sensors can be configured in a distributed sensor network to provide security monitoring. Furthermore, a method and apparatus for a radio frequency identification (RFID) tag is described. The RFID tag includes an antenna and a beam-steering array. The beam-steering array includes a plurality of tunable elements. A method and apparatus for an acoustic cancellation device and for an adjustable phase shifter that are enabled by nanowires are also described.
Owner:ONED MATERIAL INC
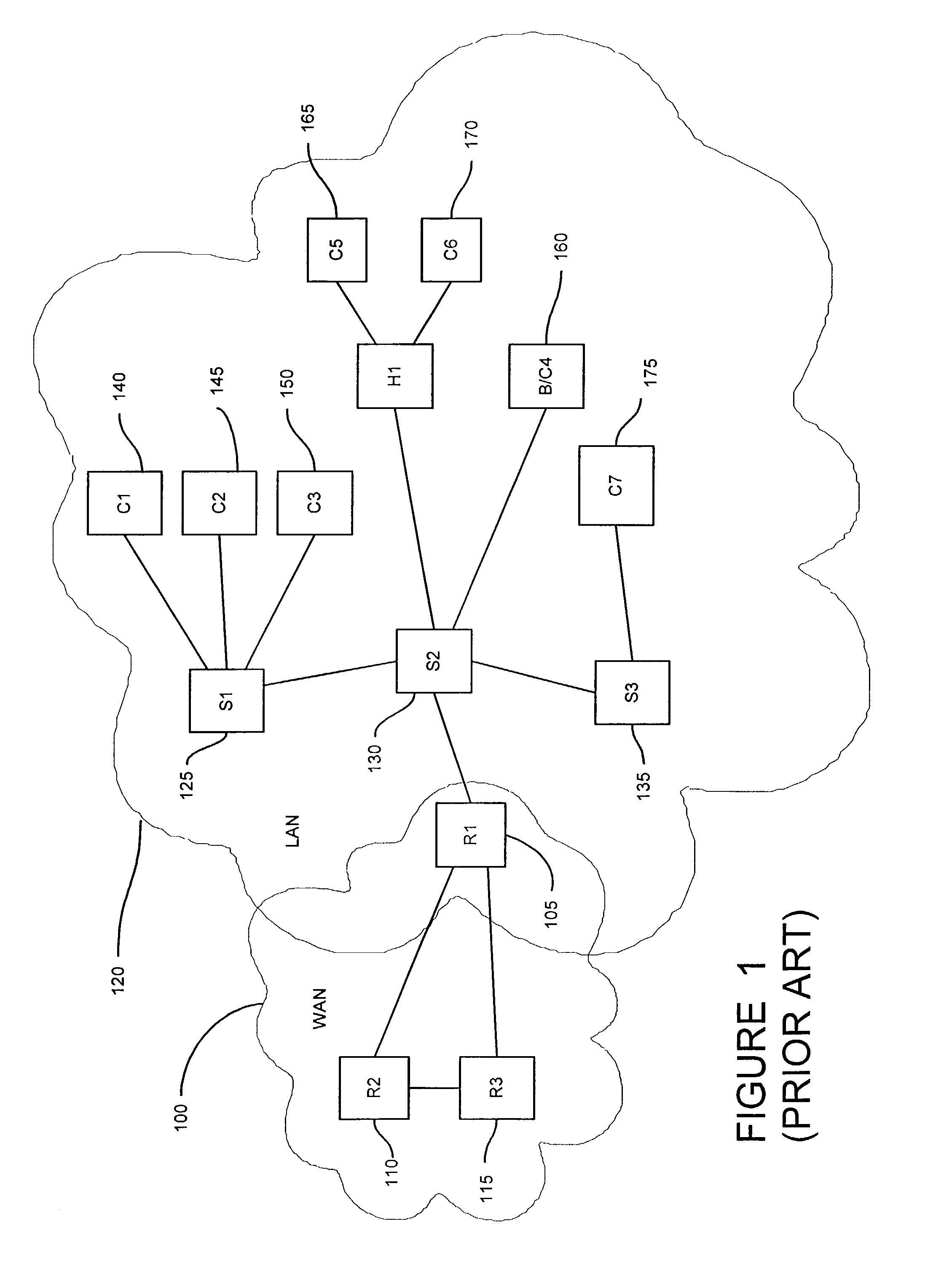
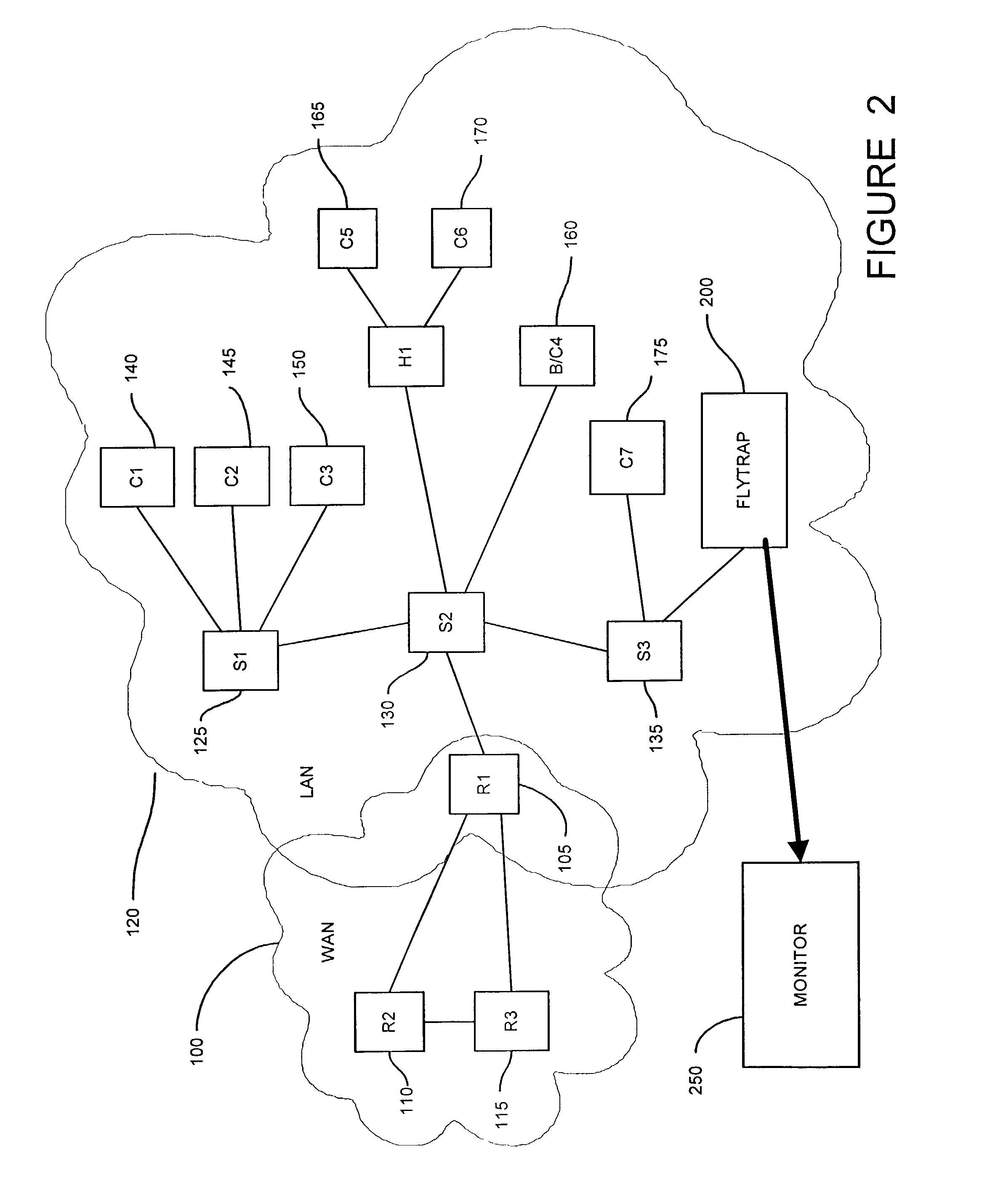
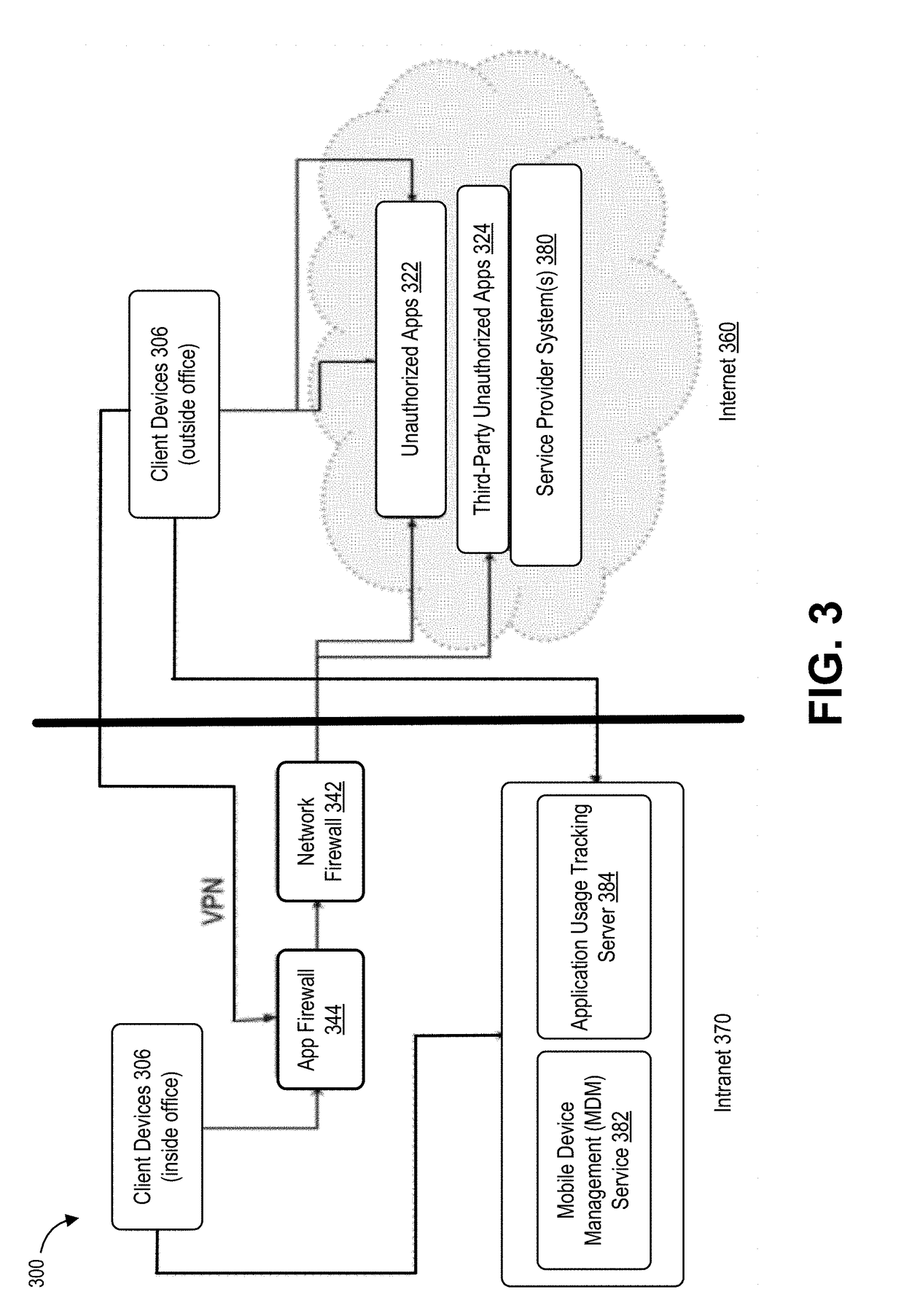
Method and apparatus for capturing and filtering datagrams for network security monitoring
ActiveUS7467408B1Improve network securityReduce network trafficMemory loss protectionUnauthorized memory use protectionTraffic capacitySecurity monitoring
A method and system for security monitoring in a computer network has a packet sink with filtering and data analysis capabilities. The packet sink is a default destination for data packets having an address unrecognized by the network routers. At the packet sink, the packets are filtered and statistical summaries about the data traffic are created. The packet sink then forwards the data to a monitor, the information content depending on the level of traffic in the network.
Owner:CISCO TECH INC
Entertainment device configured for interactive detection and security vigilant monitoring in communication with a control server
InactiveUS20070256105A1Facilitate transmission and receptionClosed circuit television systemsBurglar alarmSensor arrayEngineering
Home security detectors configured with the control components of the home comprising interactive detectors enhanced to support location-awareness and home occupant-awareness and functionality. The system includes at least one motion sensor configured with communication devices operatively arranged to transmit information about any motion of occupants in the various sections of the home as part of the information about the occupancy of the home during an emergency. At least one sensor is provided in various rooms of a home each sensing a state of the home. A central communication device is coupled, wired or wirelessly, directly or indirectly, to each home sensor configured to transmit the state of the home. The number of occupants in the home are determined by at least one body heat sensor and at least one heartbeat sensor each configured with the interactive detectors to detect the presence of emergency and home occupants and to know the present situations such as their heartbeats, such that the number of occupants and their locations are determinable from the number of detected body heat and their security and safety conditions are determinable by their heartbeats. The detection method includes the steps of sensing a state of the home and transmitting the state of the home to at least a server. Images of the home are captured by at least a camera means configured with at least a MOS and / or CMOS based active sensor array for producing real-time images and stored in the server for wireless retrieval. The images ideally include at least an intruder of the home. The server is configured with a central processor for enabling controlling security vigilance monitoring and for enabling rapid distribution of detection data, voice, and other detection signals within the monitoring environment. The system establishes a network which includes configuring home audio / visual devices, media destination means such as televisions, monitors, PDAs, notepads, notebooks, MP3, wireless stereo, cell phones etc for the detection means. The control server supports video / audio servings, telephony, messaging, file sharing, internetworking, and security monitoring and allows home occupants to access and control the home network environment from any location within a controlled residential, commercial / industrial and / or non-residential, commercial / industrial environment with at least a computer means such as a cell phone.
Owner:COSTA VERDI SERIES 63 OF ALLIED SECURITY TRUST I
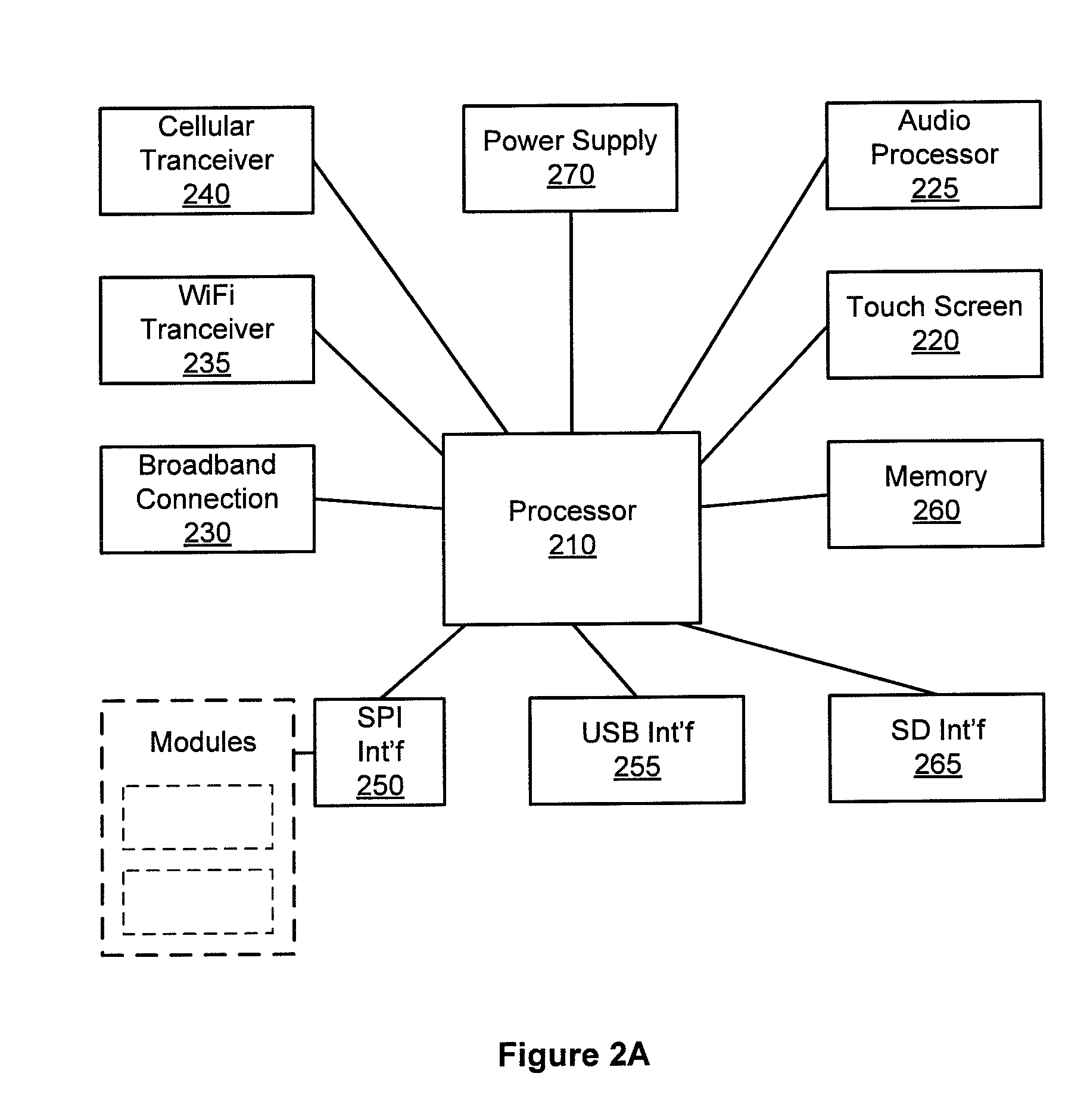
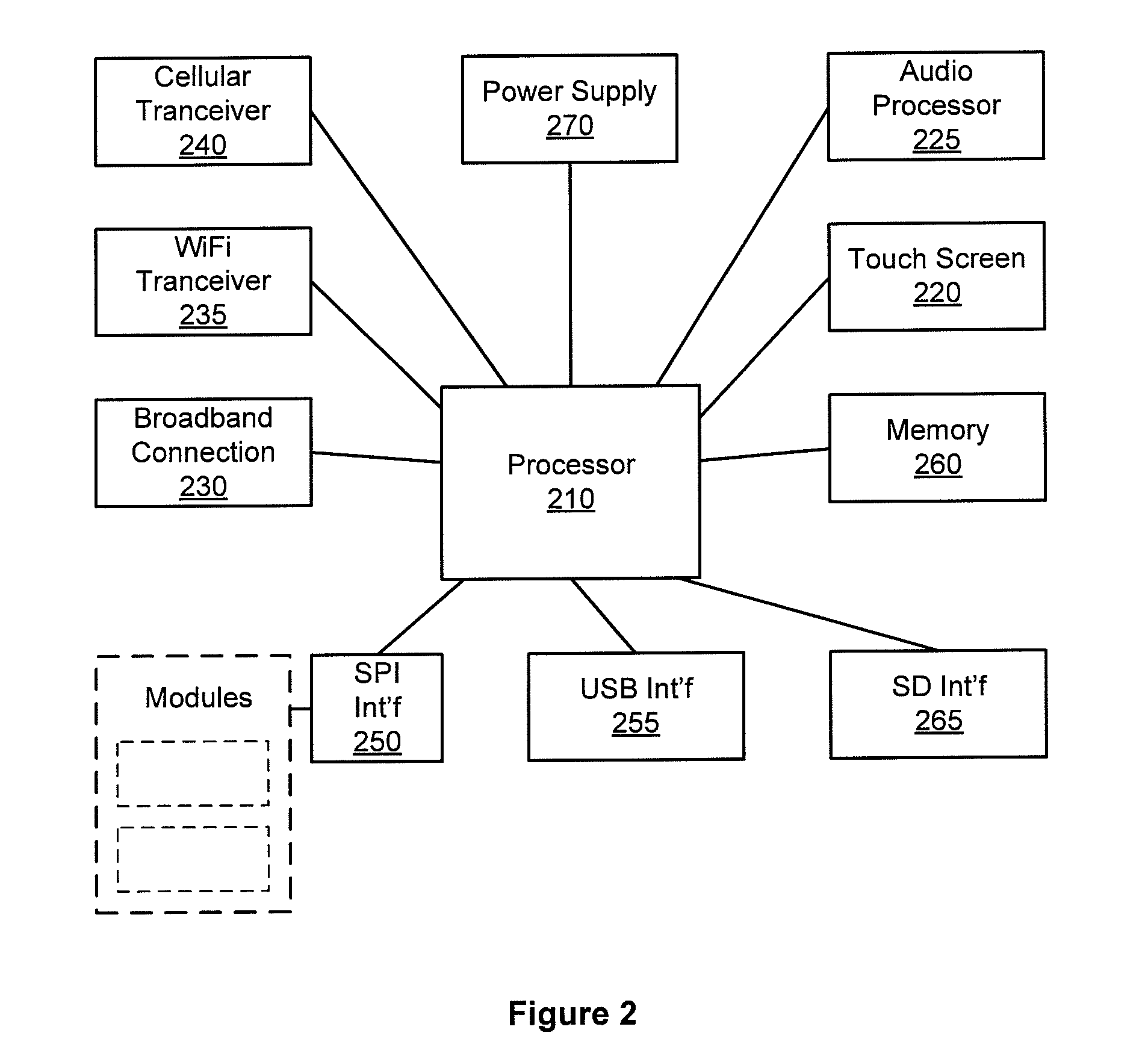
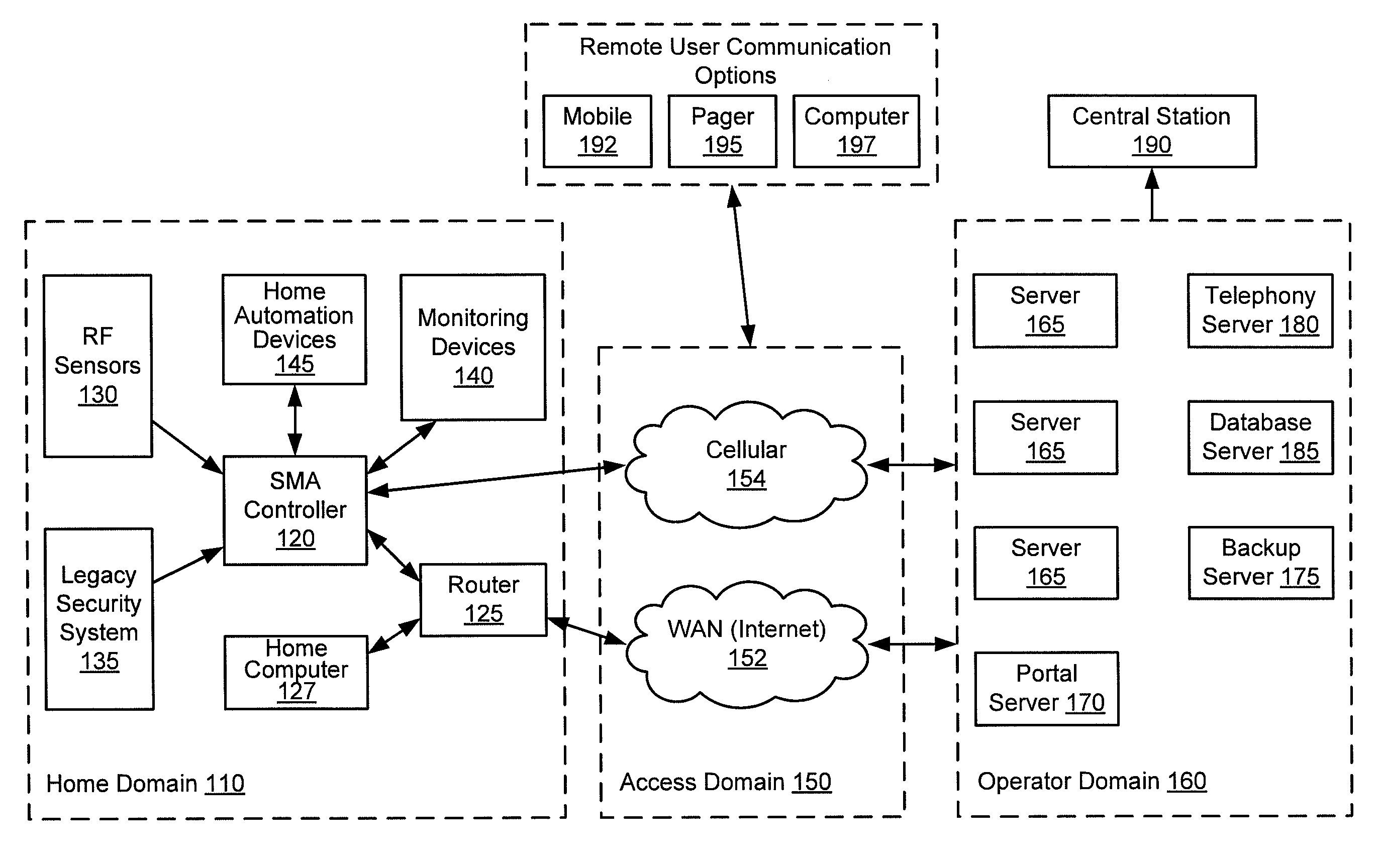
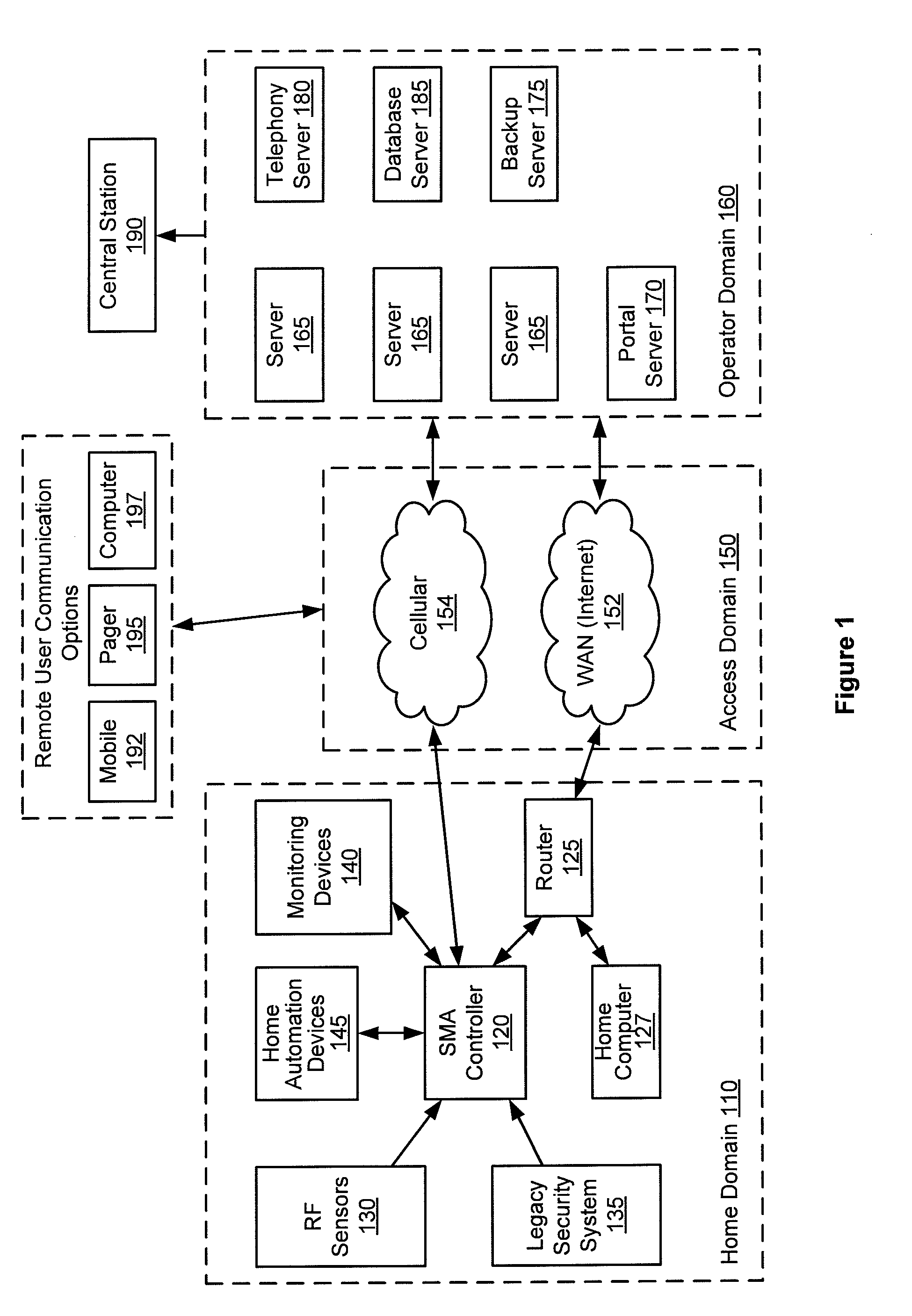
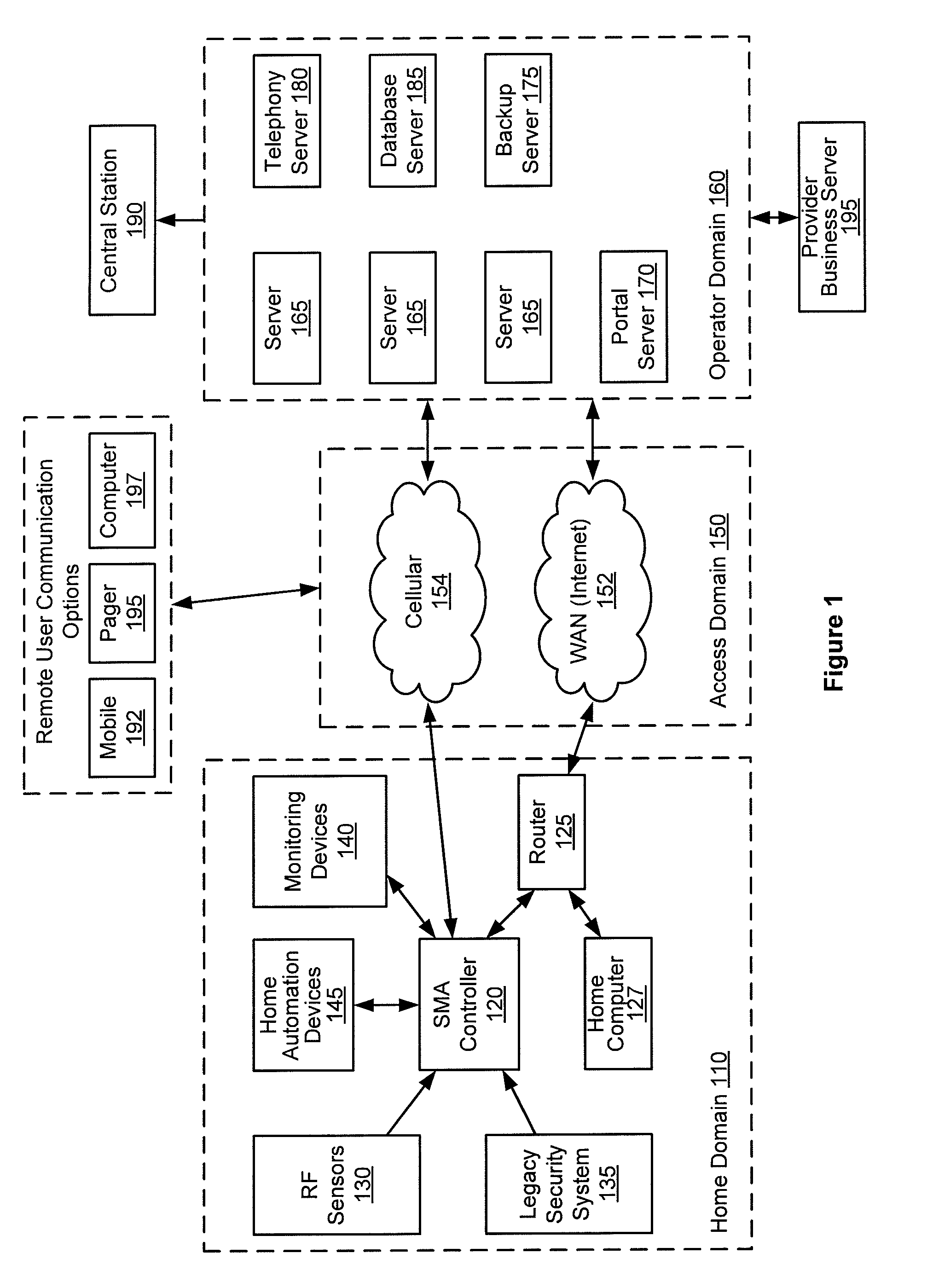
Configurable controller and interface for home sma, phone and multimedia
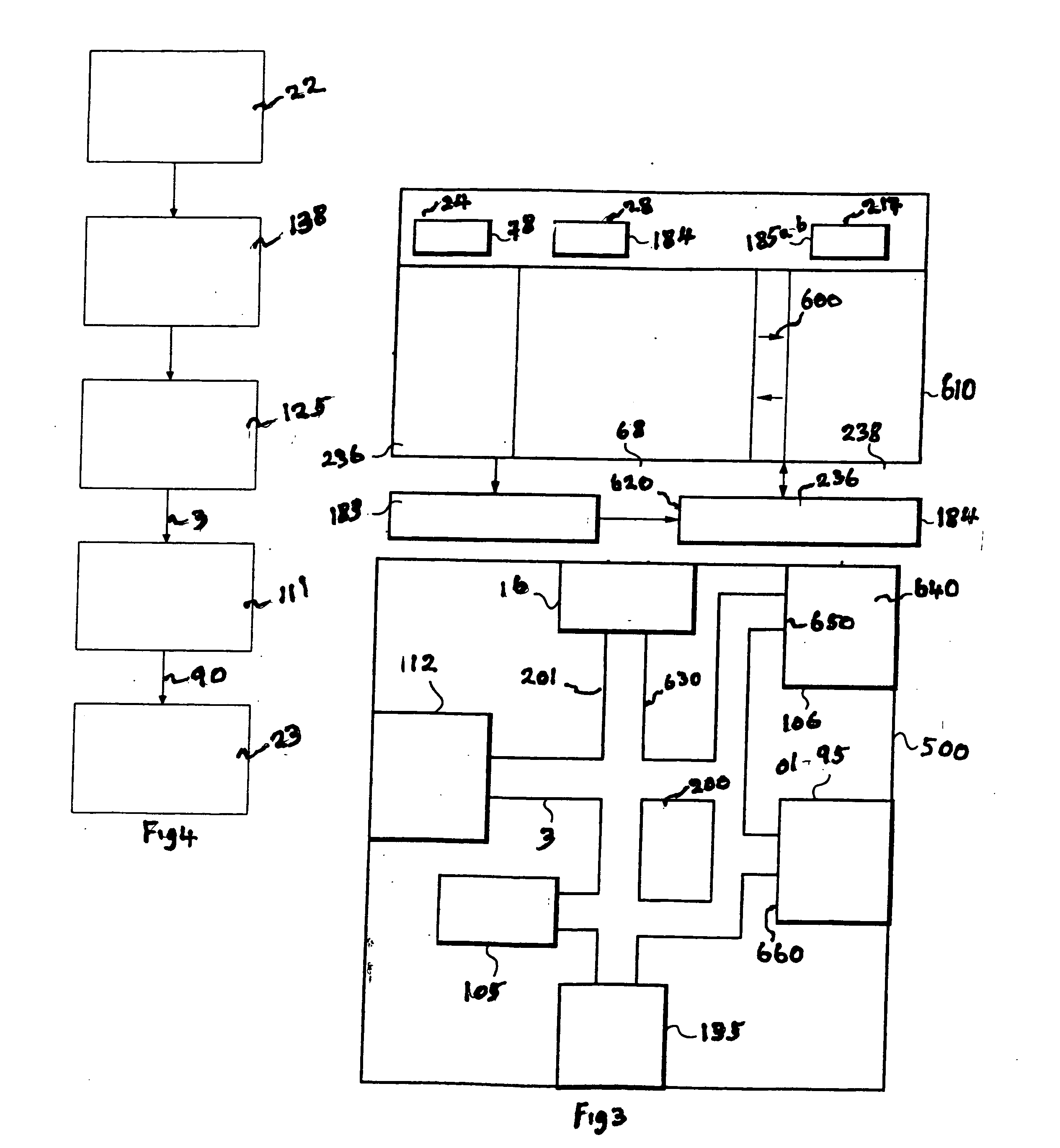
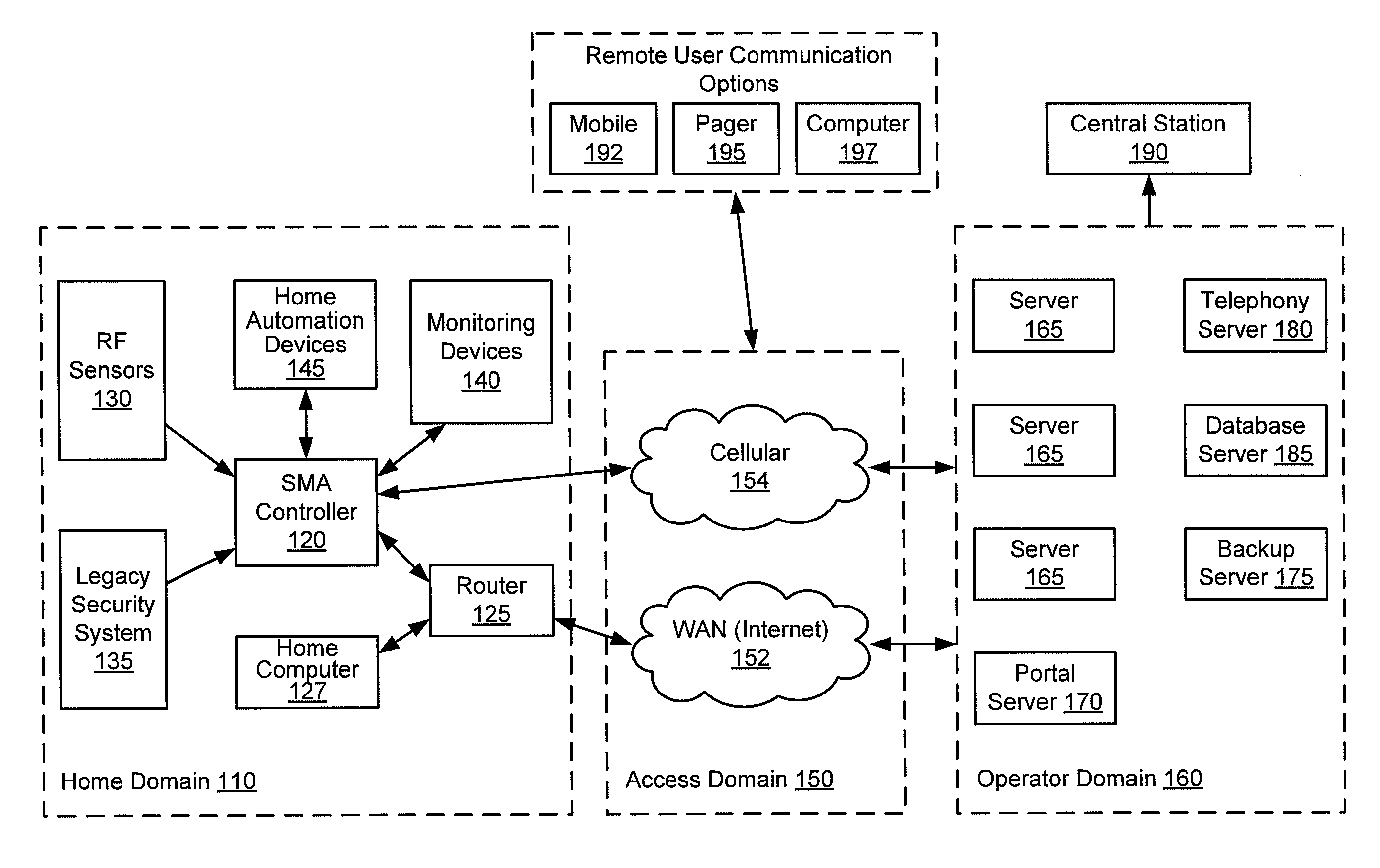
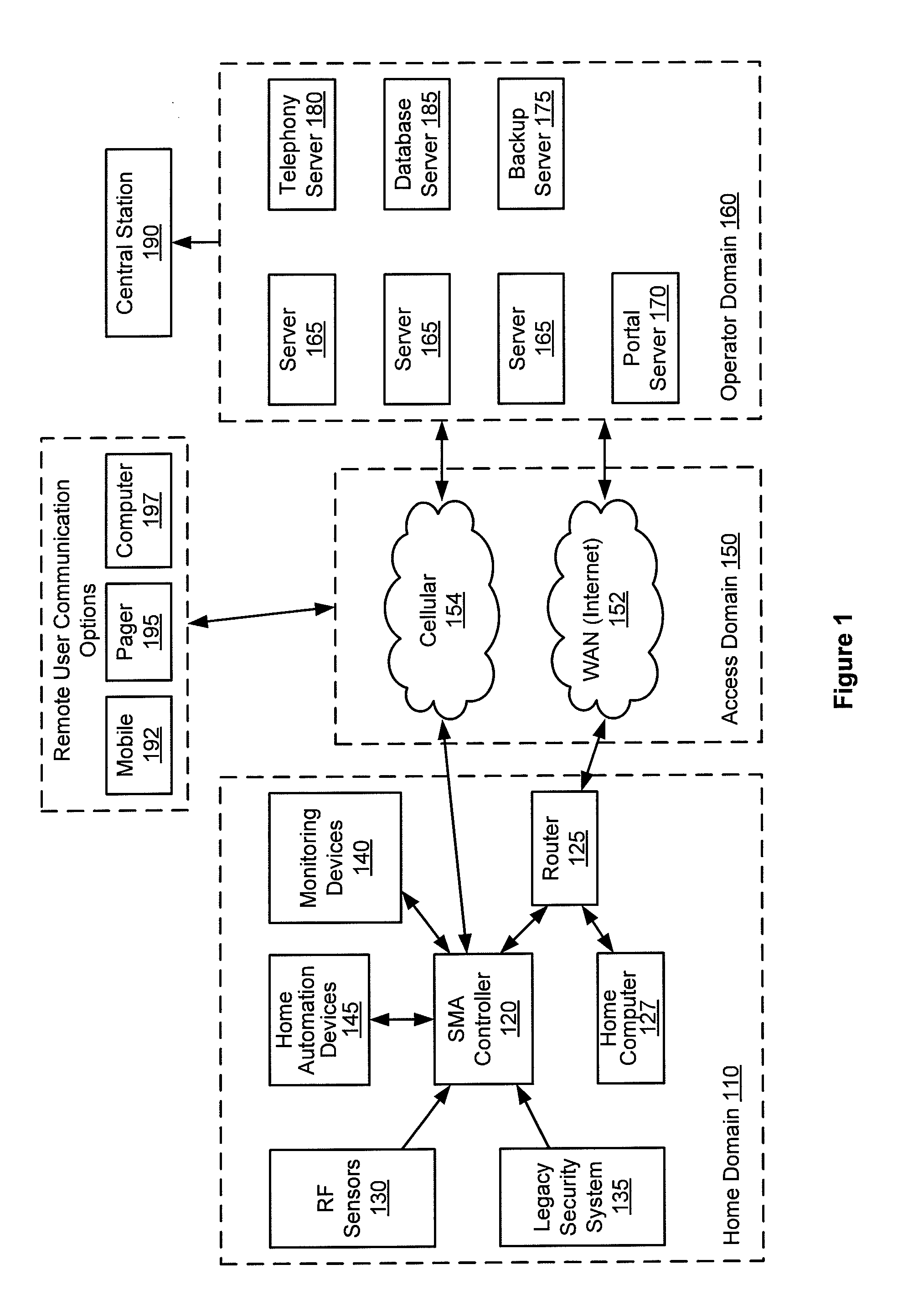
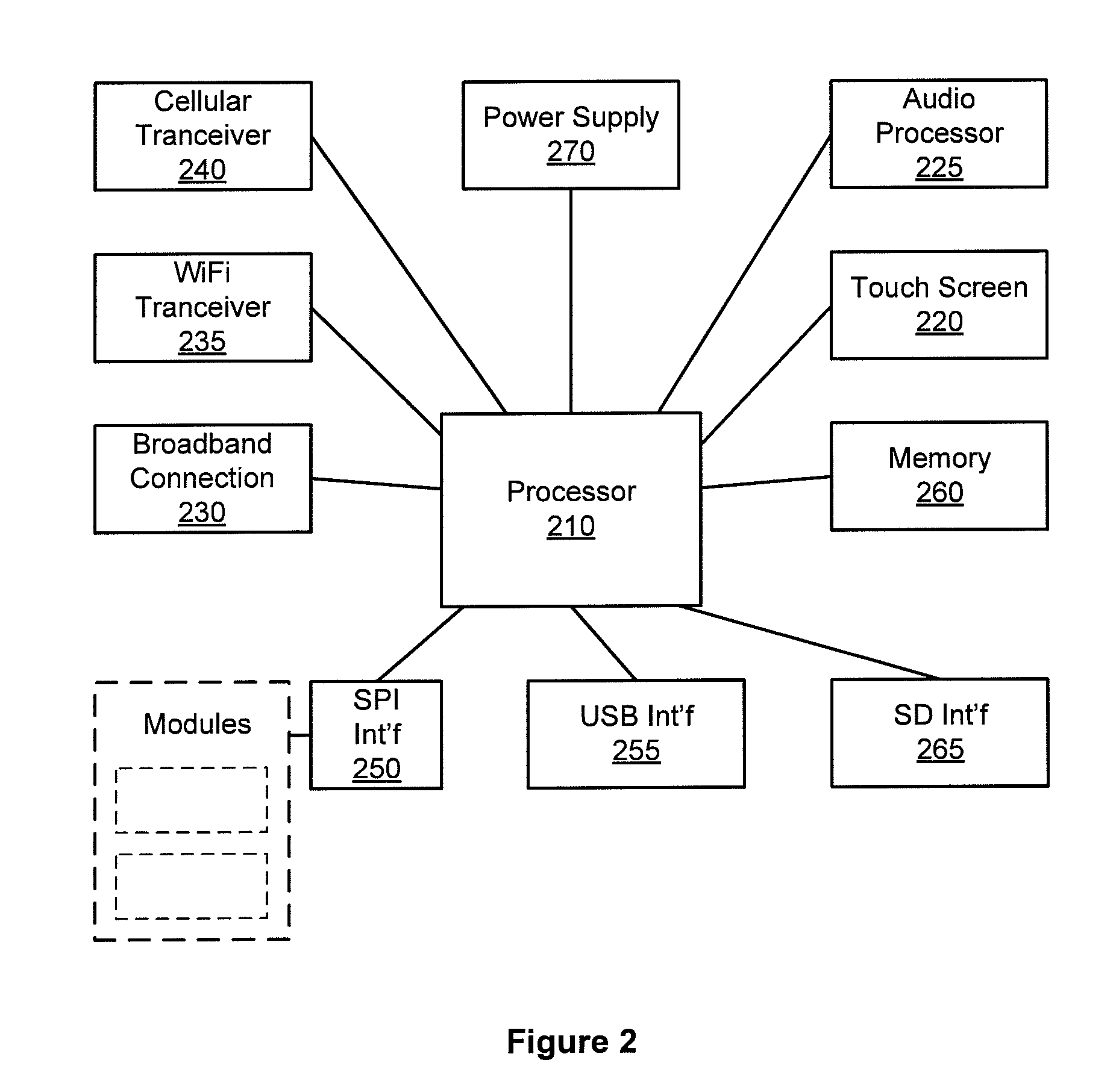
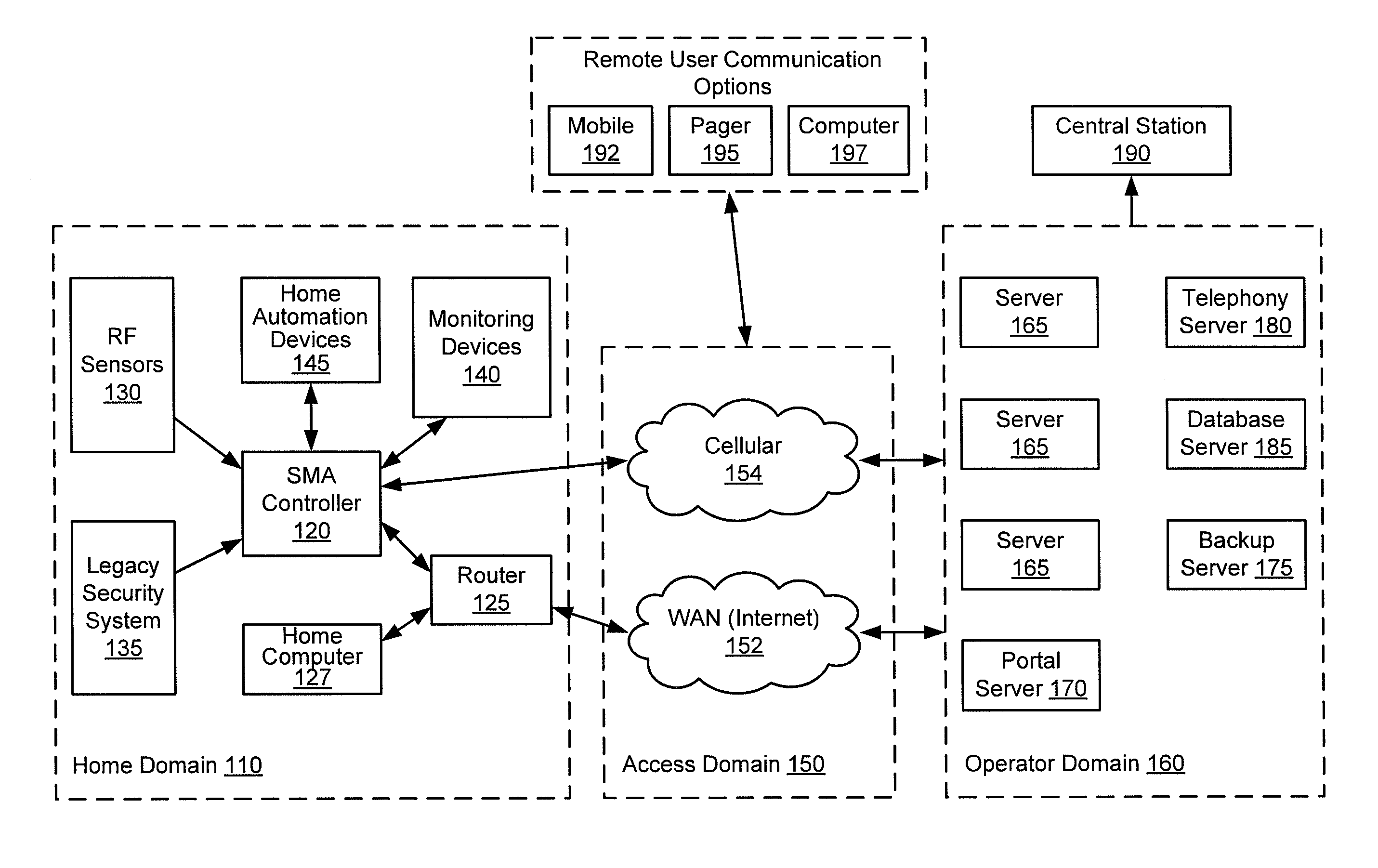
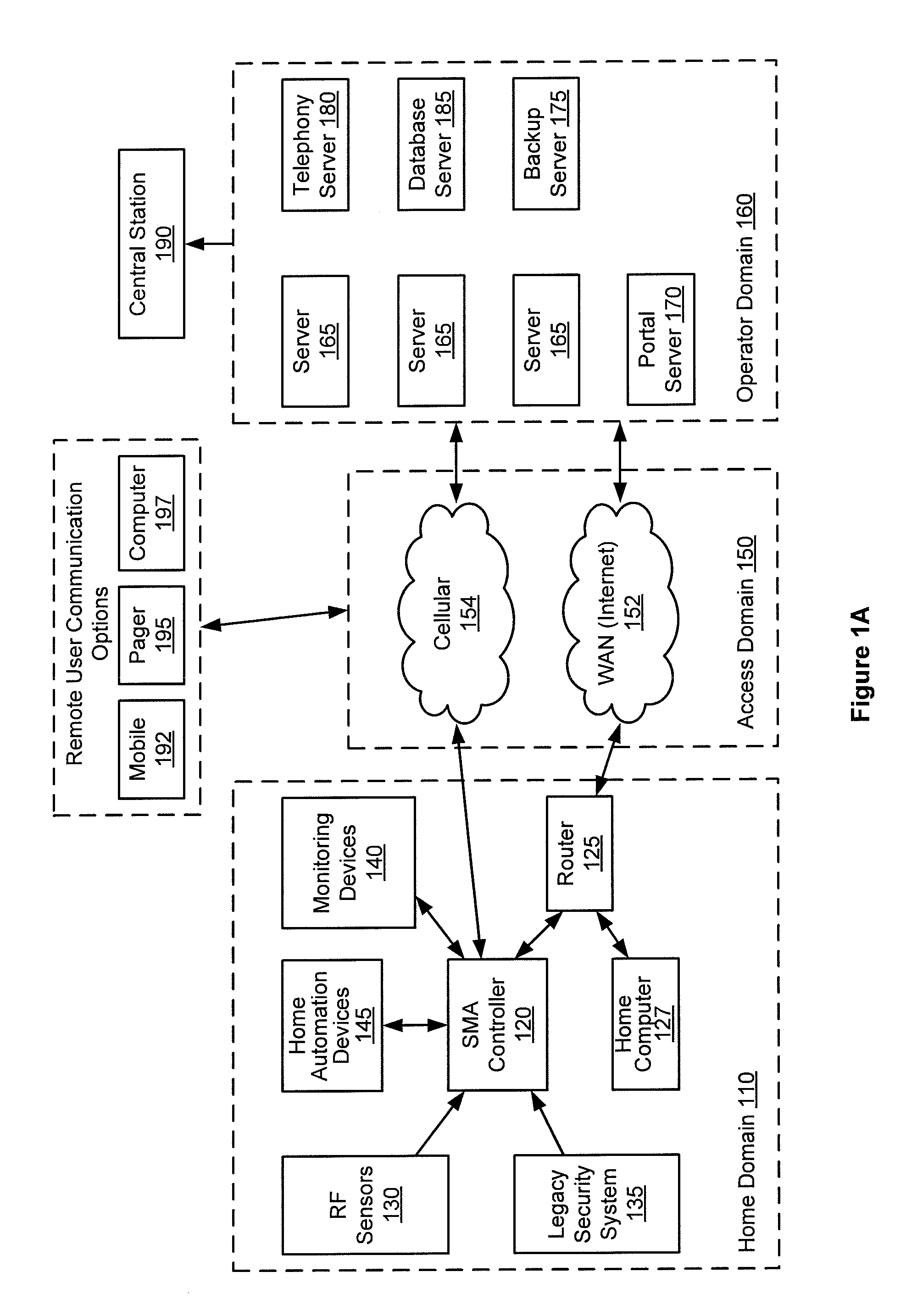
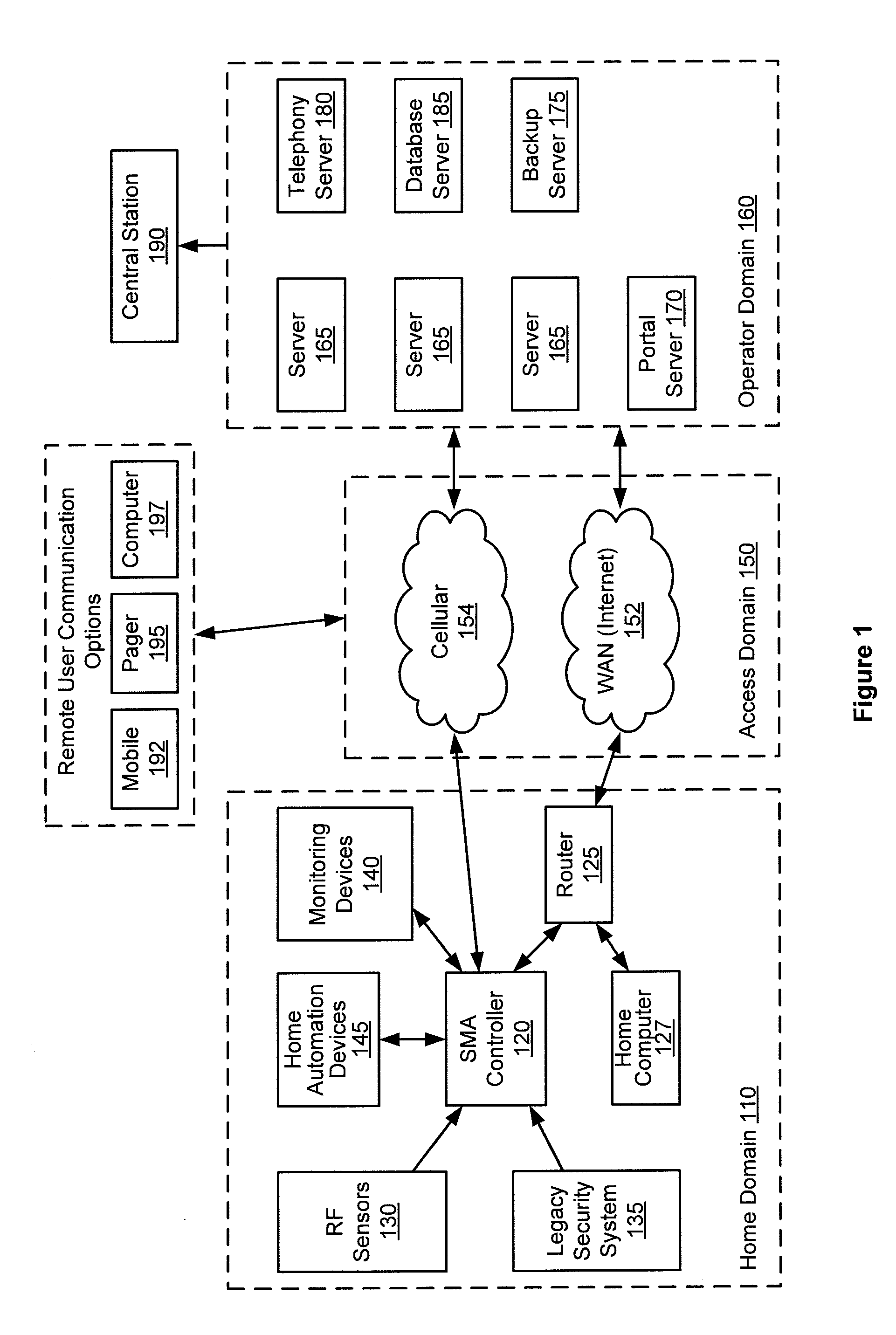
A single platform for controller functionality for each of security, monitoring and automation, as well as providing a capacity to function as a bidirectional Internet gateway, is provided. Embodiments of the present invention provide such functionality by virtue of a configurable architecture that enables a user to adapt the system for the user's specific needs. Embodiments of the present invention further provide for remote access to the configurable controller, thereby providing for remote monitoring of the state of a dwelling and for remote control of home automation.
Owner:ICN ACQUISITION LLC
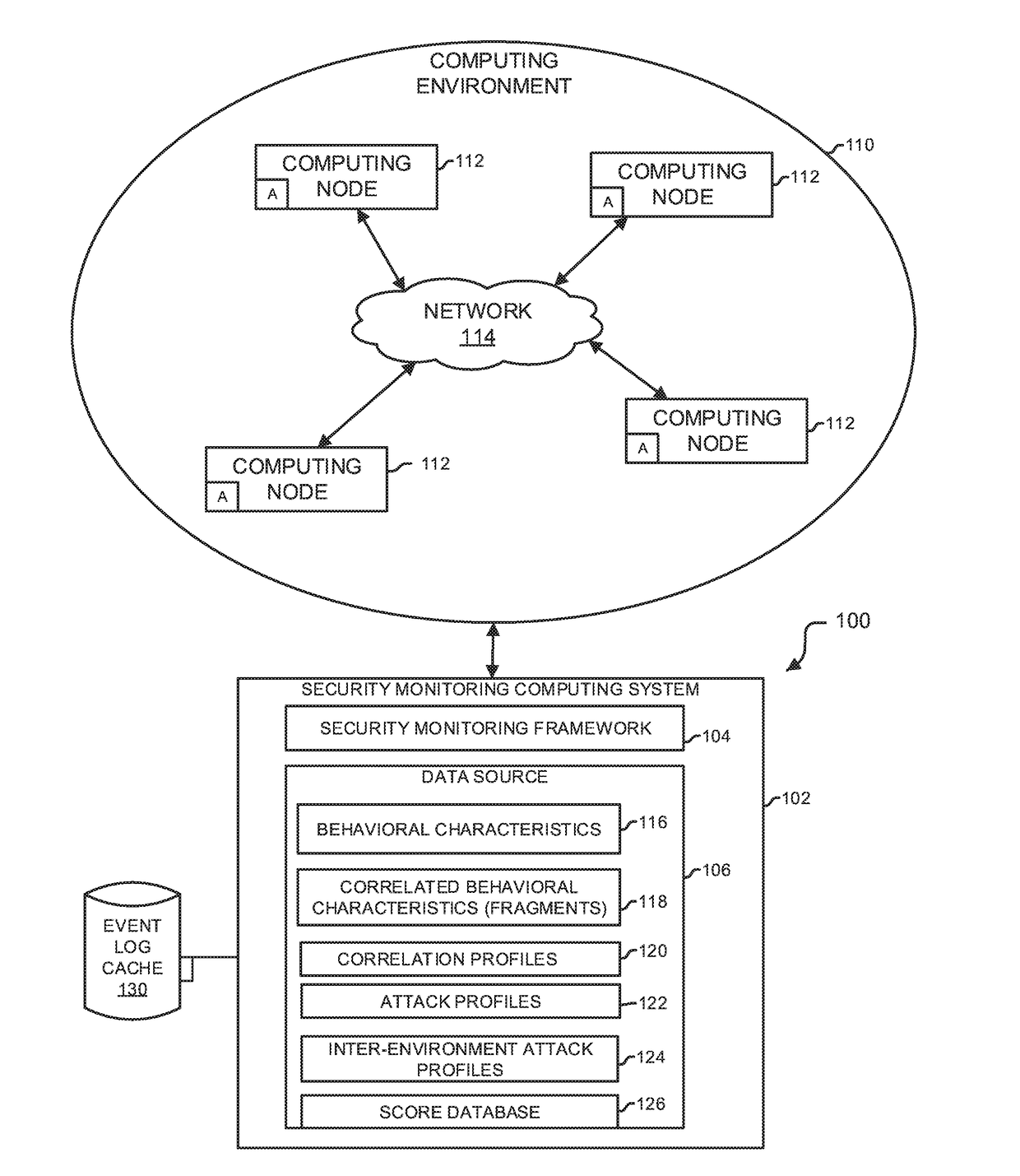
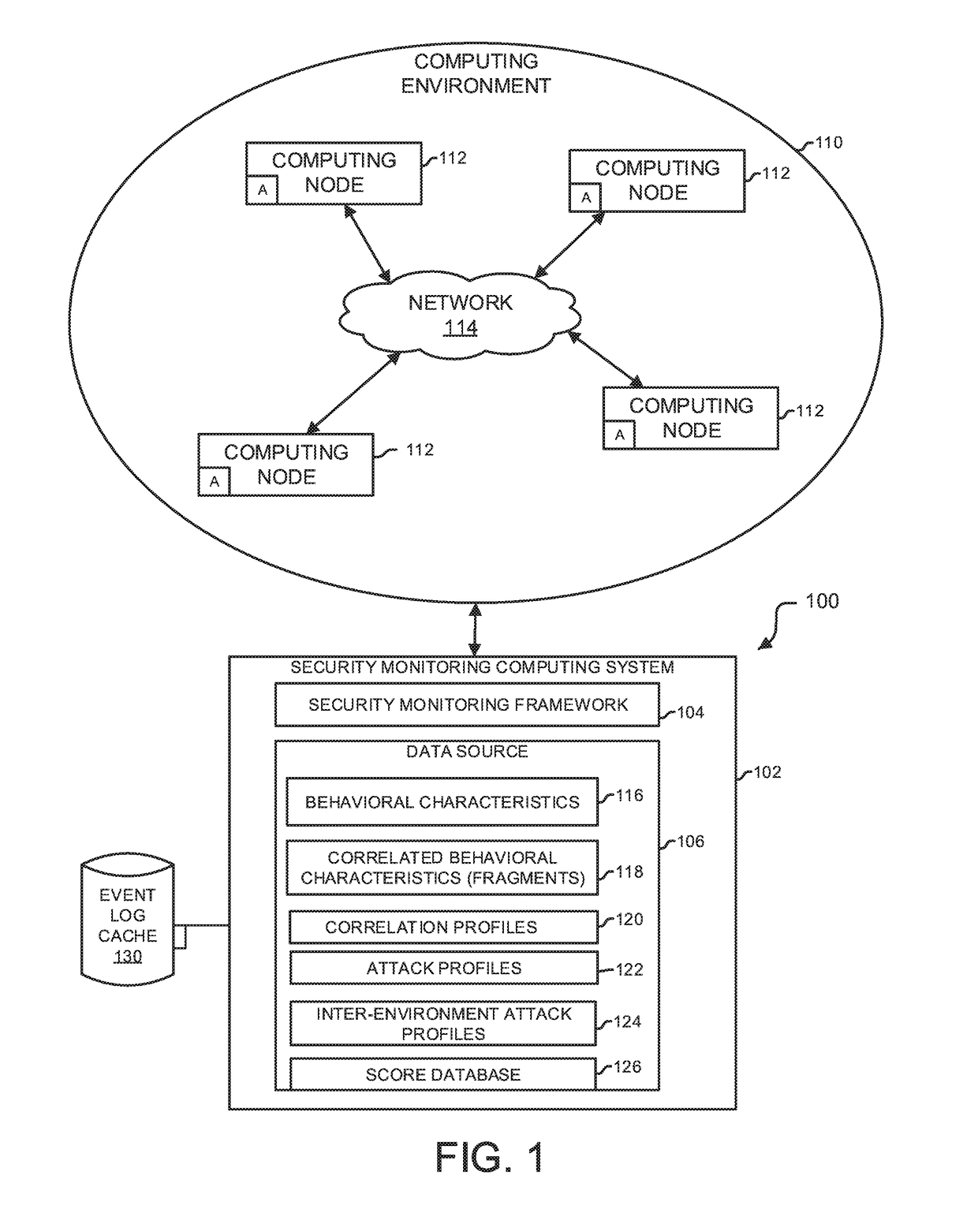
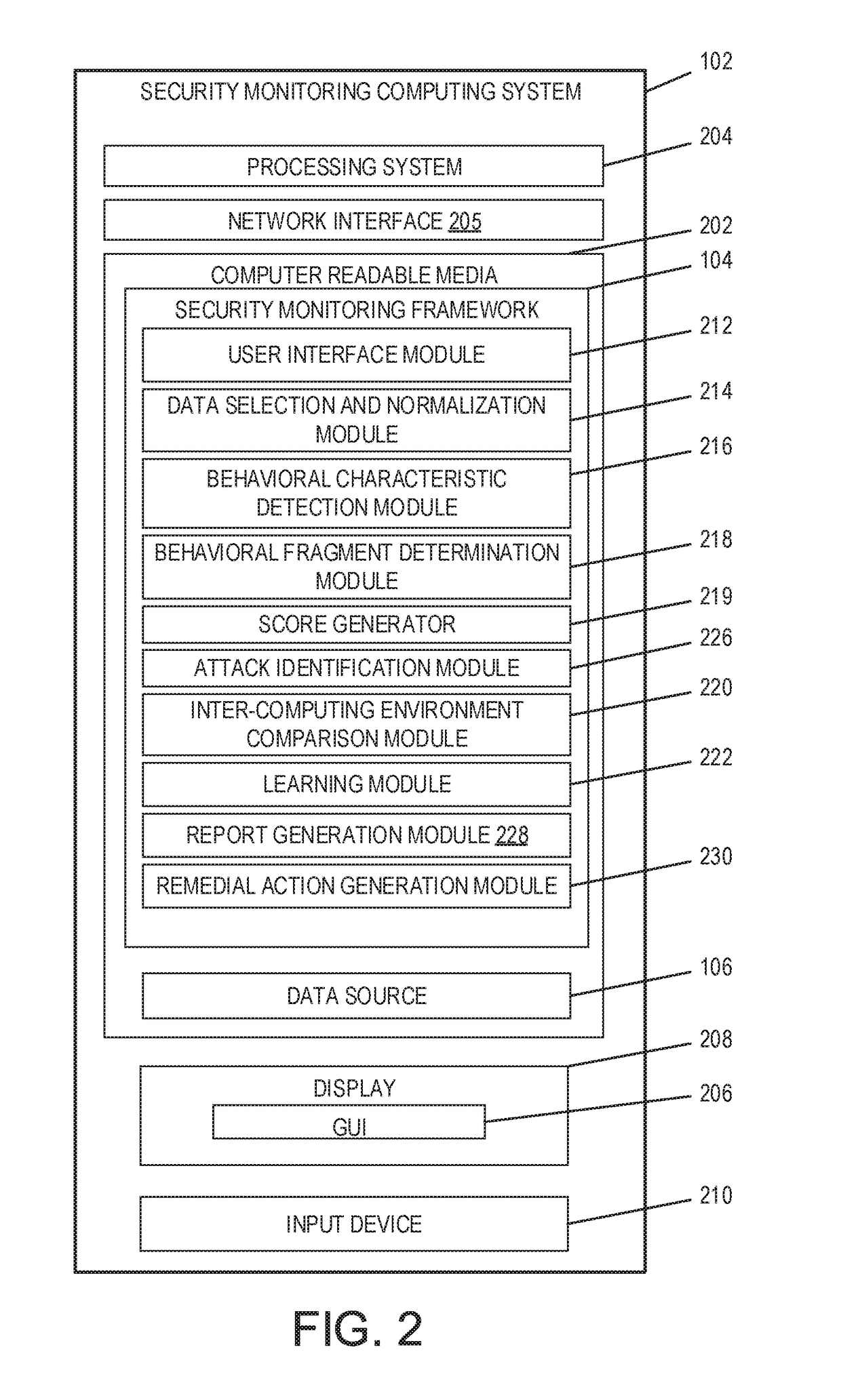
Analytics-based security monitoring system and method
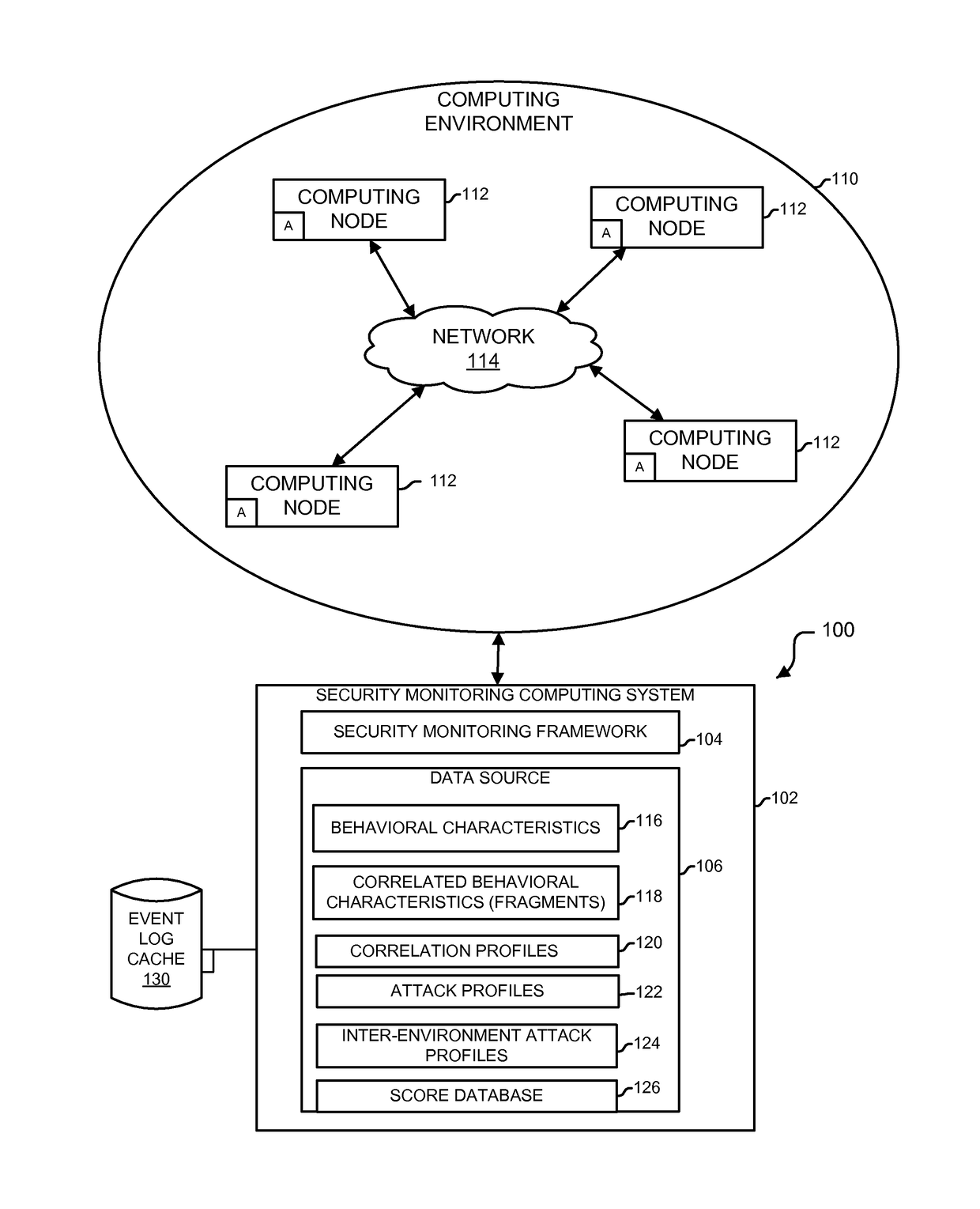
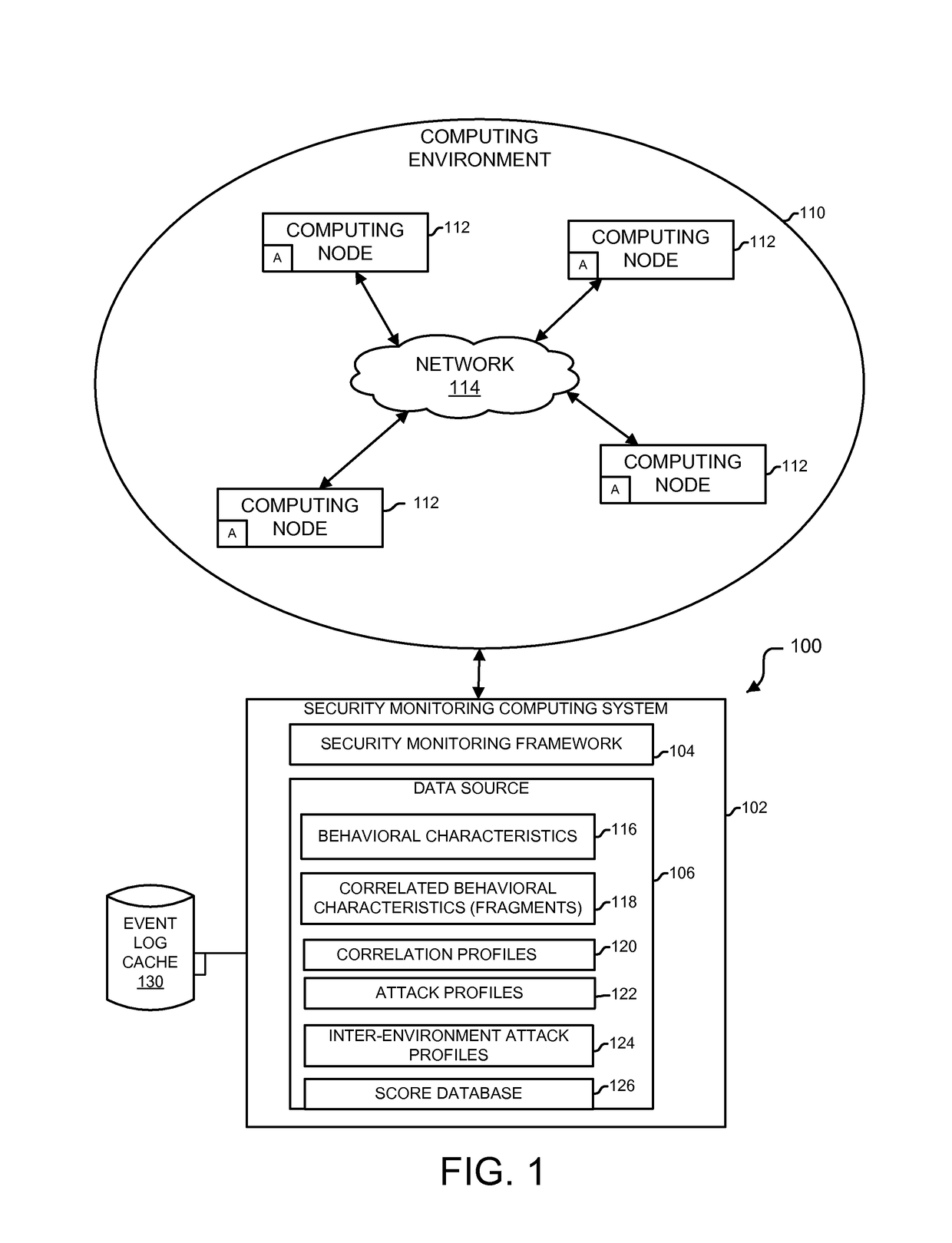
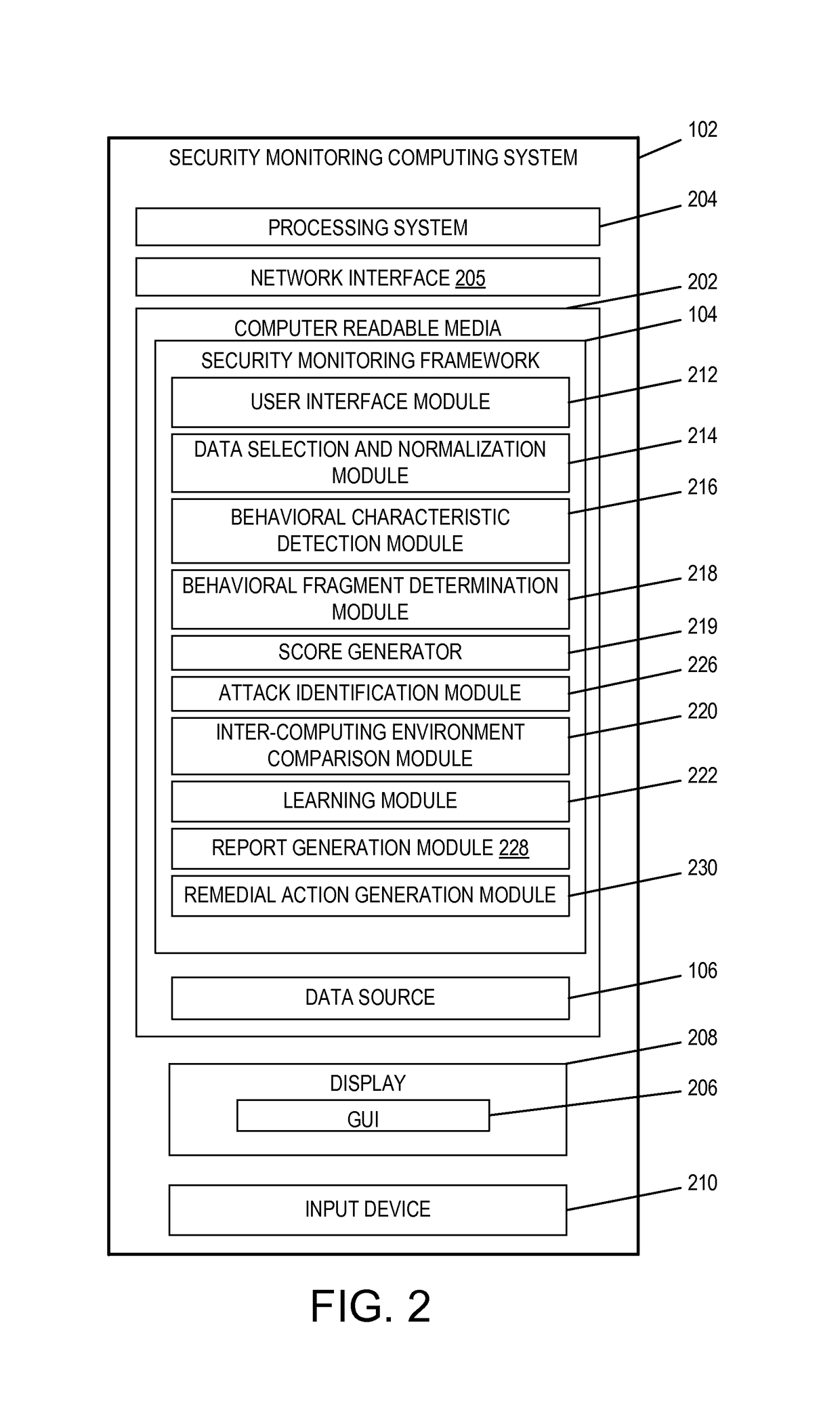
ActiveUS9654485B1Reduce size (quantity)Easy to analyzeMemory loss protectionError detection/correctionRemedial actionSecurity monitoring
An analytics-based security monitoring system includes instructions that may be executed by a computing system to receive data in the form of event logs from one or more network devices transferred through a computing environment, detect a plurality of behavioral characteristics from the received event logs, identify behavioral fragments composed of related behavioral characteristics, and identify an attack by correlating the behavioral fragments against patterns of known malicious attacks. The analytics-based security monitoring system may then perform a learning process to enhance further detection of attacks and perform one or more remedial actions when an attack is identified.
Owner:MANDIANT +1
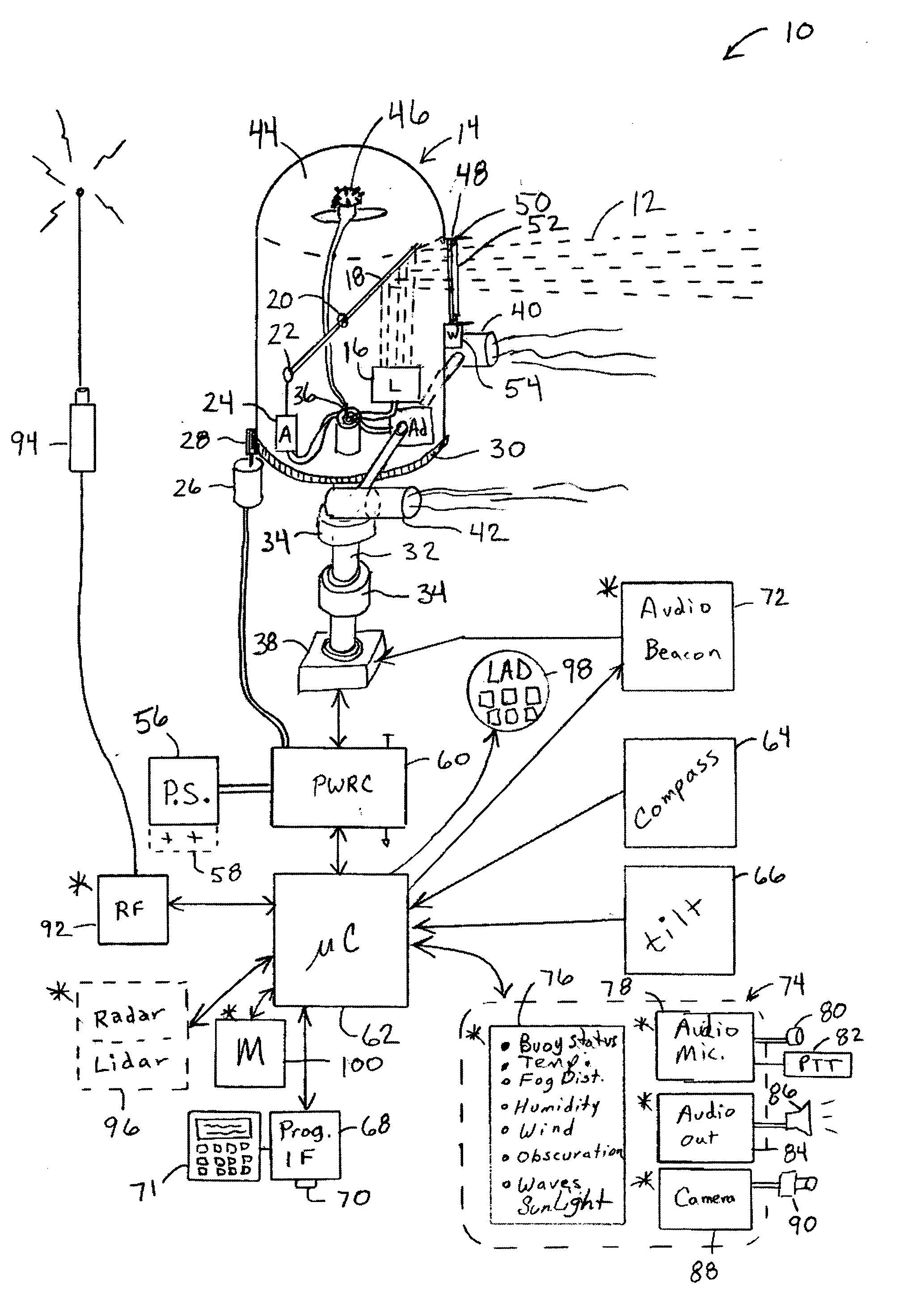
Transportation signaling device
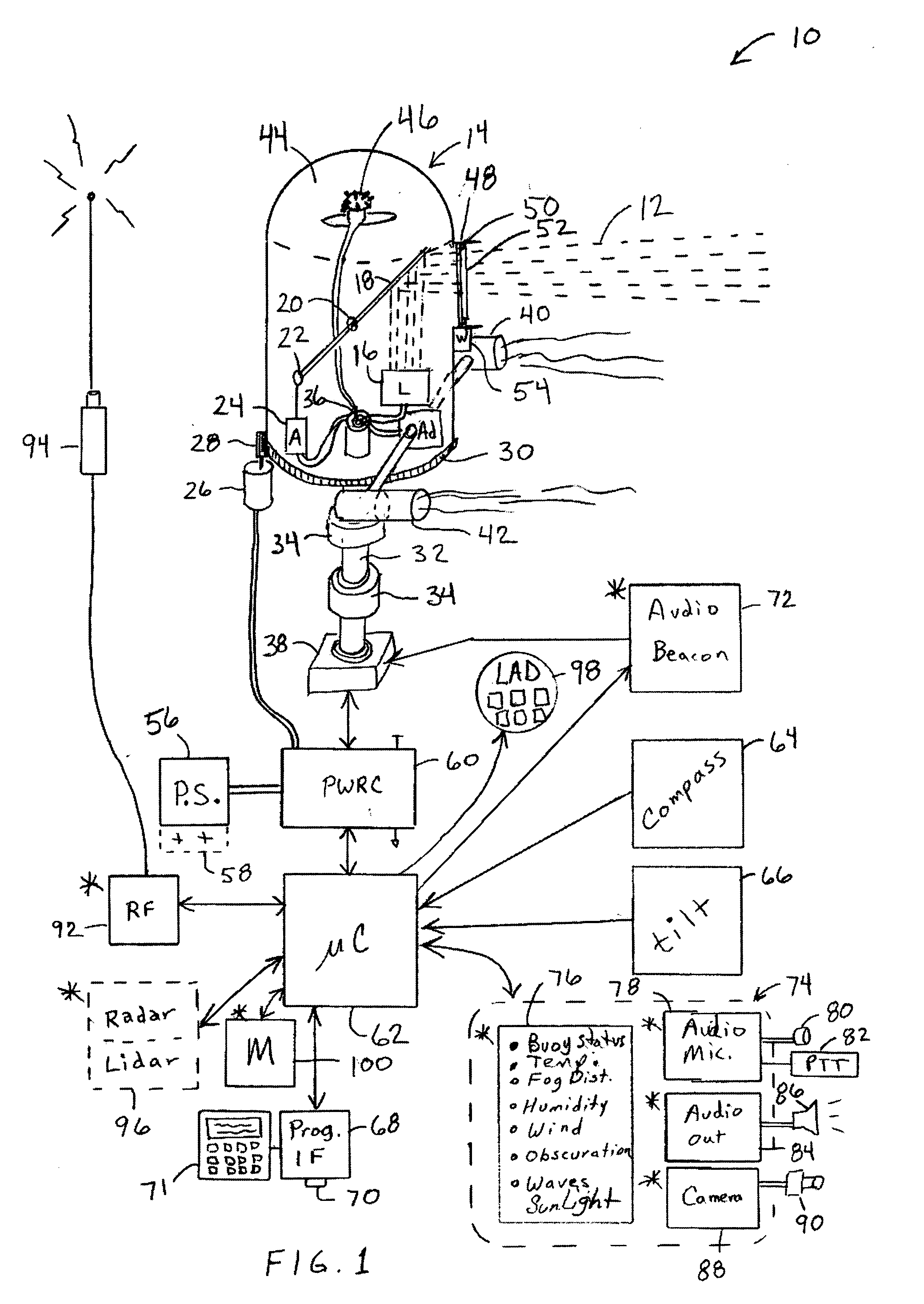
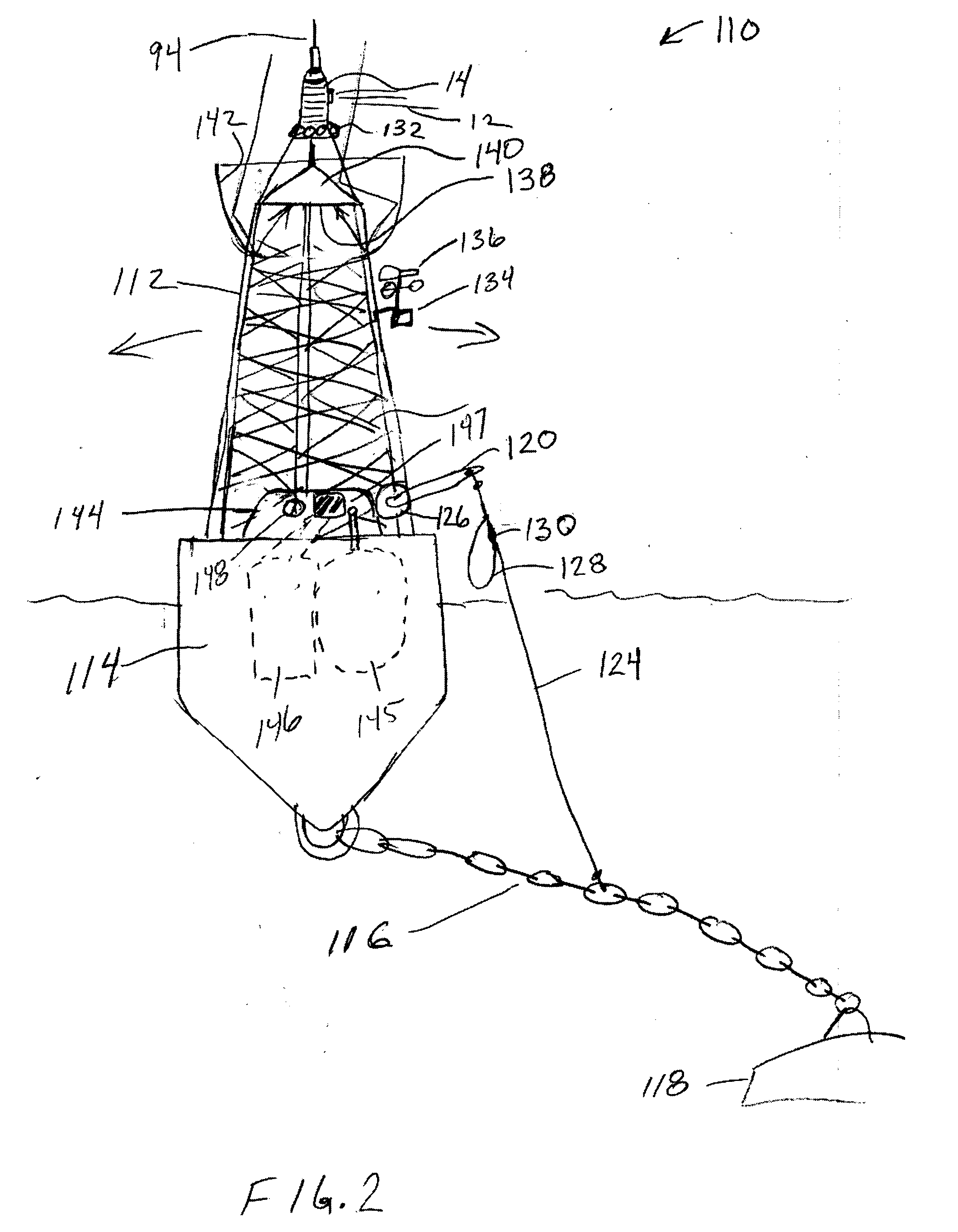
An apparatus for generating buoy light signals using a collimated light source. The system provides for communication of system conditions and ambient conditions, and can provide homeland security monitoring. The system senses motion of the buoy and compensates the direction of lighting, and optionally acoustics, being generated out over a body of water. Numerous other transportation related embodiments are described including devices for providing user comfort when flying, automotive signaling, auto parking control, sports bottles, visors, and lures.
Owner:RAST RODGER H
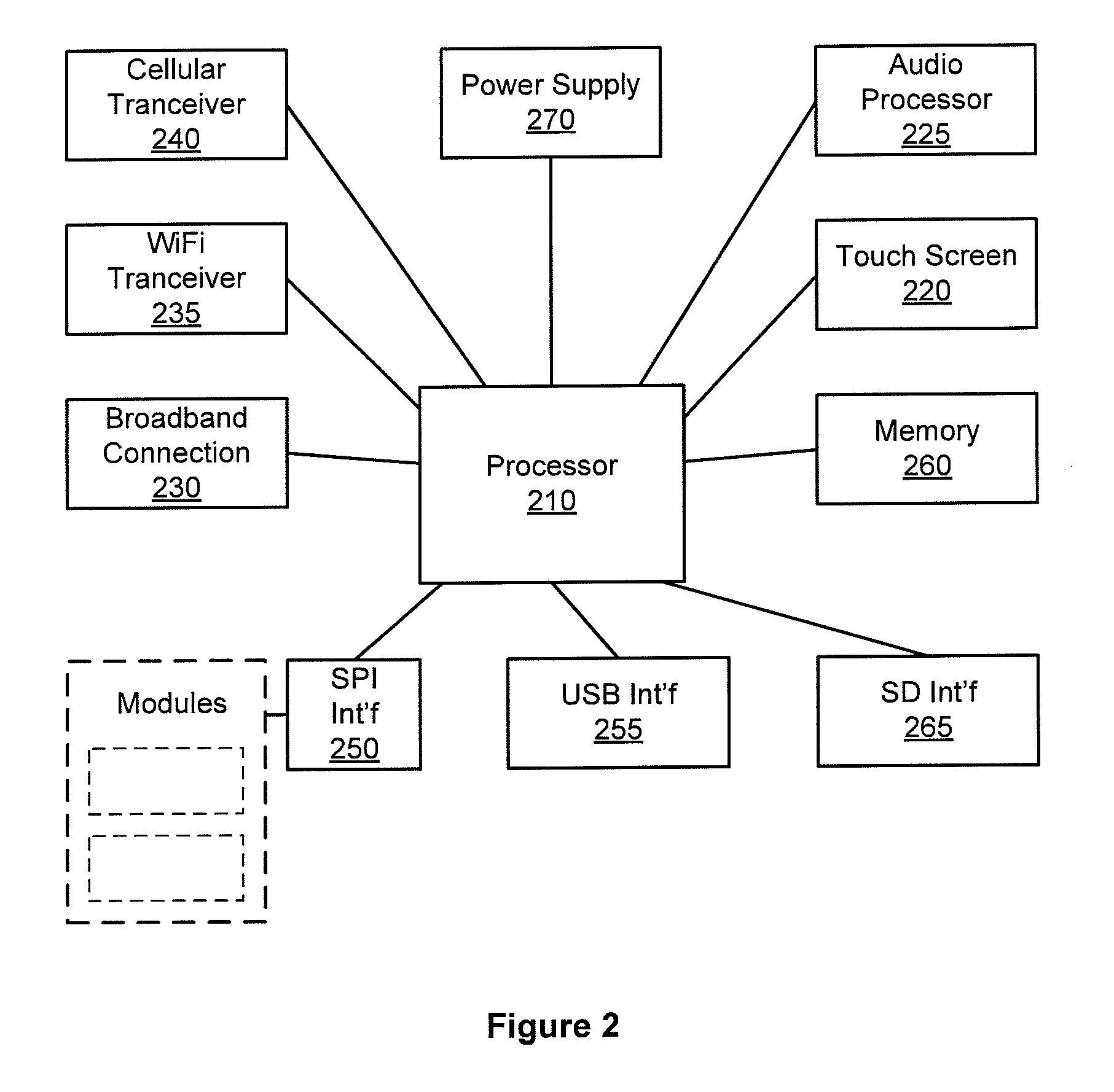
Hardware configurable security, monitoring and automation controller having modular communication protocol interfaces
A single platform for controller functionality for each of security, monitoring and automation, as well as providing a capacity to function as a bidirectional Internet gateway, is provided. Embodiments of the present invention provide such functionality by virtue of a configurable architecture that enables a user to adapt the system for the user's specific needs. Embodiments of the present invention further provide such functionality by providing for installation of removable, modular communication adapters for communication with a variety of devices external to the security, monitoring and automation controller.
Owner:ICONTROL NETWORKS
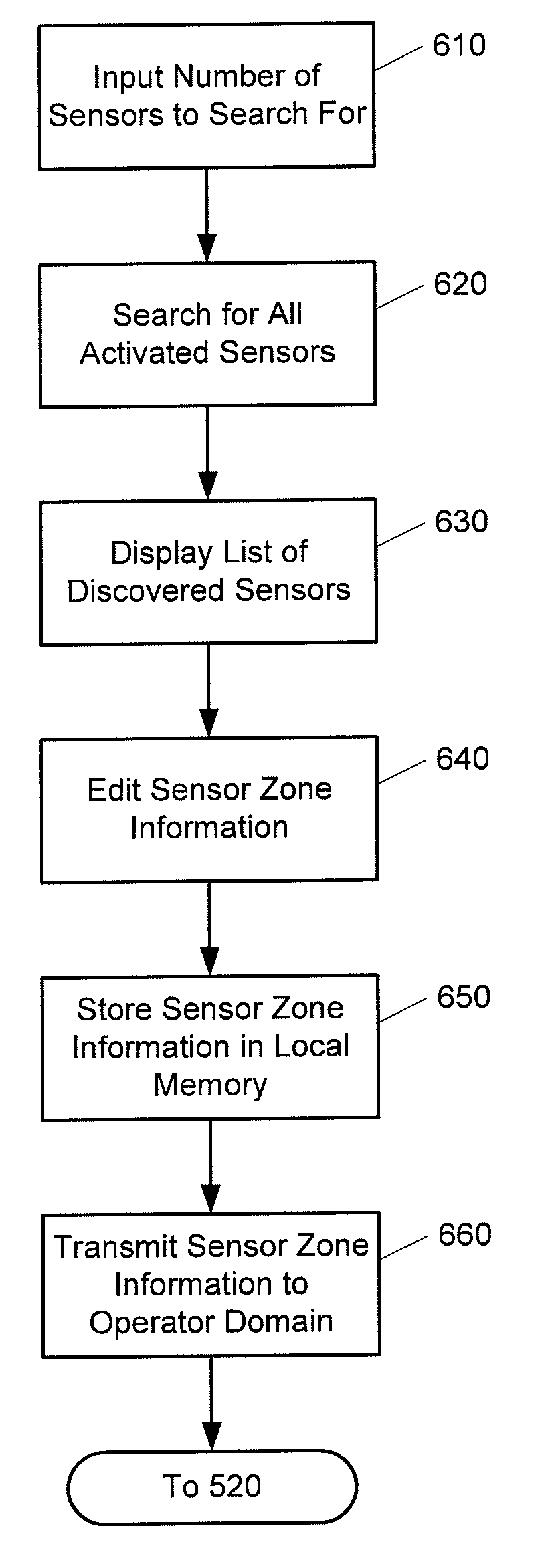
Method, system and apparatus for activation of a home security, monitoring and automation controller using remotely stored configuration data
Embodiments of the present invention provide a single platform that provides controller functionality for each of security, monitoring and automation, as well as providing a capacity to function as a bidirectional Internet gateway. Embodiments of the present invention provide such functionality by virtue of a configurable architecture that enables a user to adapt the system for the user's specific needs. Embodiments of the present invention further provide for a software-based installation workflow to activate and provision the controller and associated sensors and network. Embodiments of the present invention also provide for downloading of previously-stored configuration data to the controller from a remote server, and for activation and provisioning of the controller from the previously-stored configuration data.
Owner:ICONTROL NETWORKS
System and methods for notifying a community of security events
ActiveUS20140313032A1Clear pictureDecreasing false alarmProgramme controlThermometer detailsSecurity monitoringOperational safety
A method of operating a security monitoring system comprises defining a group of people to receive a notification of an event taking place at a location associated with any member of the group, by a system, determining that a security event has at least potentially taken place that the members of the group need to be notified of, by the system, and notifying the members of the group of the event, via a network. Notifications of the at least potential security event may be provided to a first party of the at least potential security event and members of the group may be notified if the first party does not respond to the notification within a predetermined period of time. A system is also disclosed.
Owner:WRV II LP
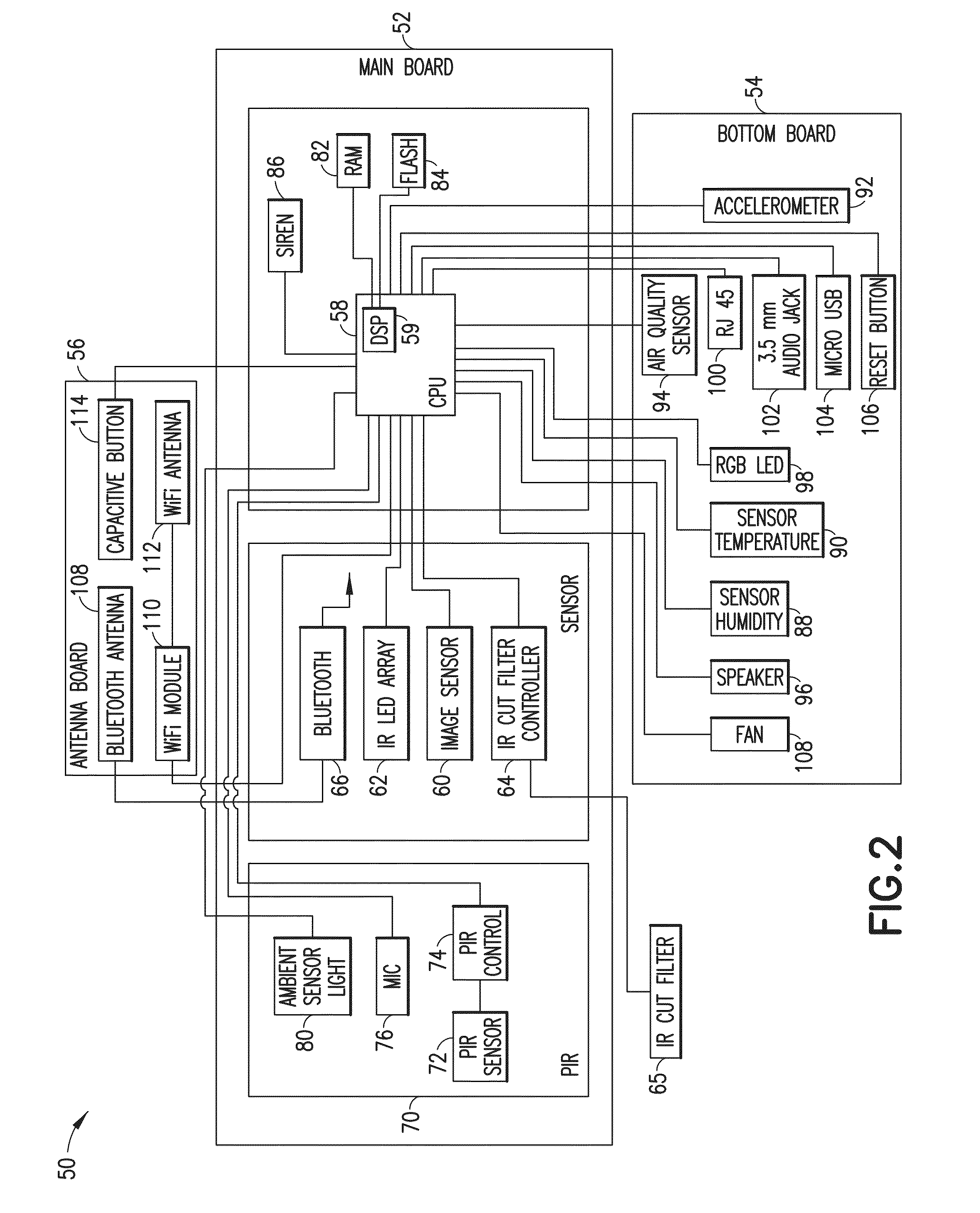
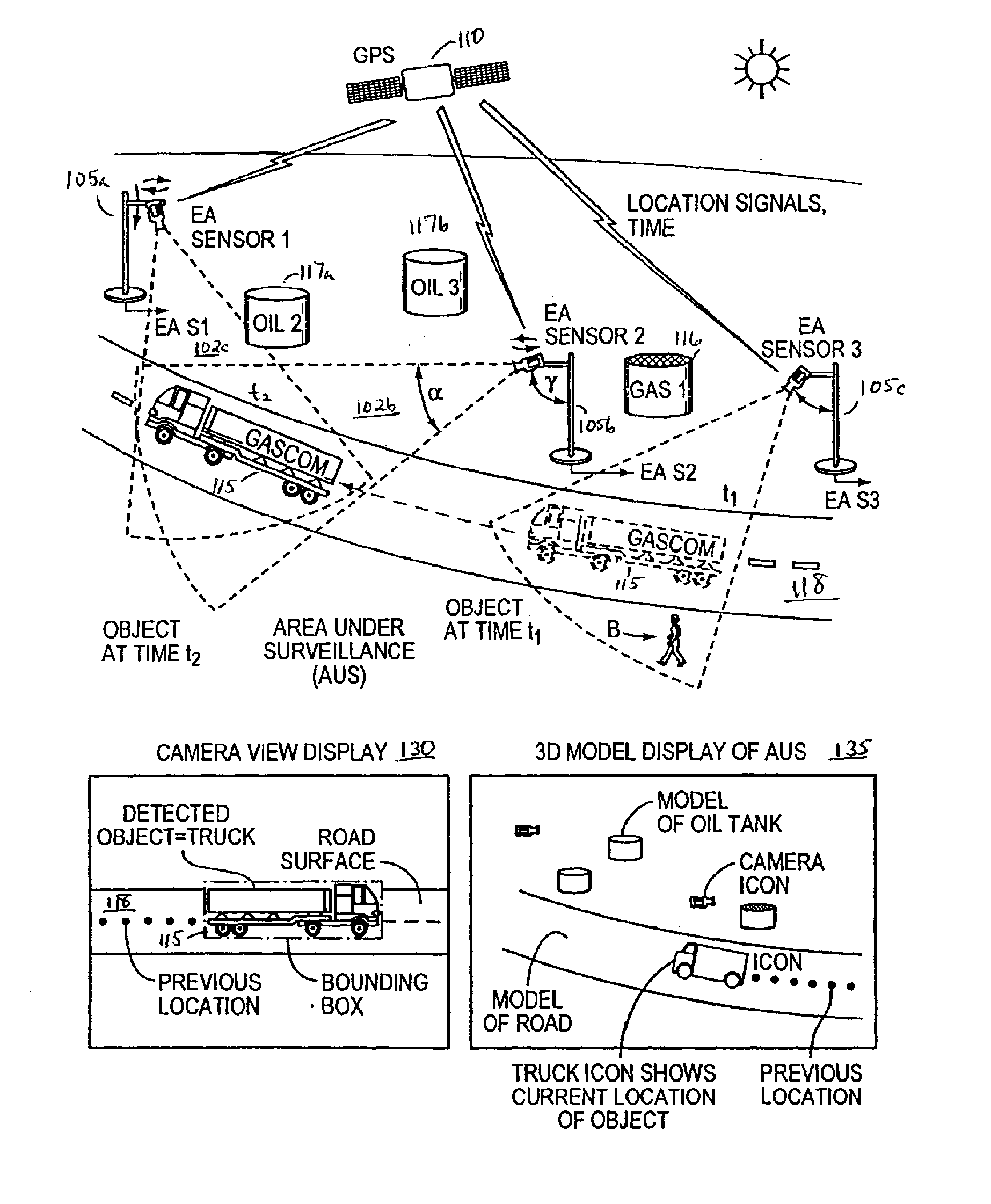
Environmentally aware, intelligent surveillance device
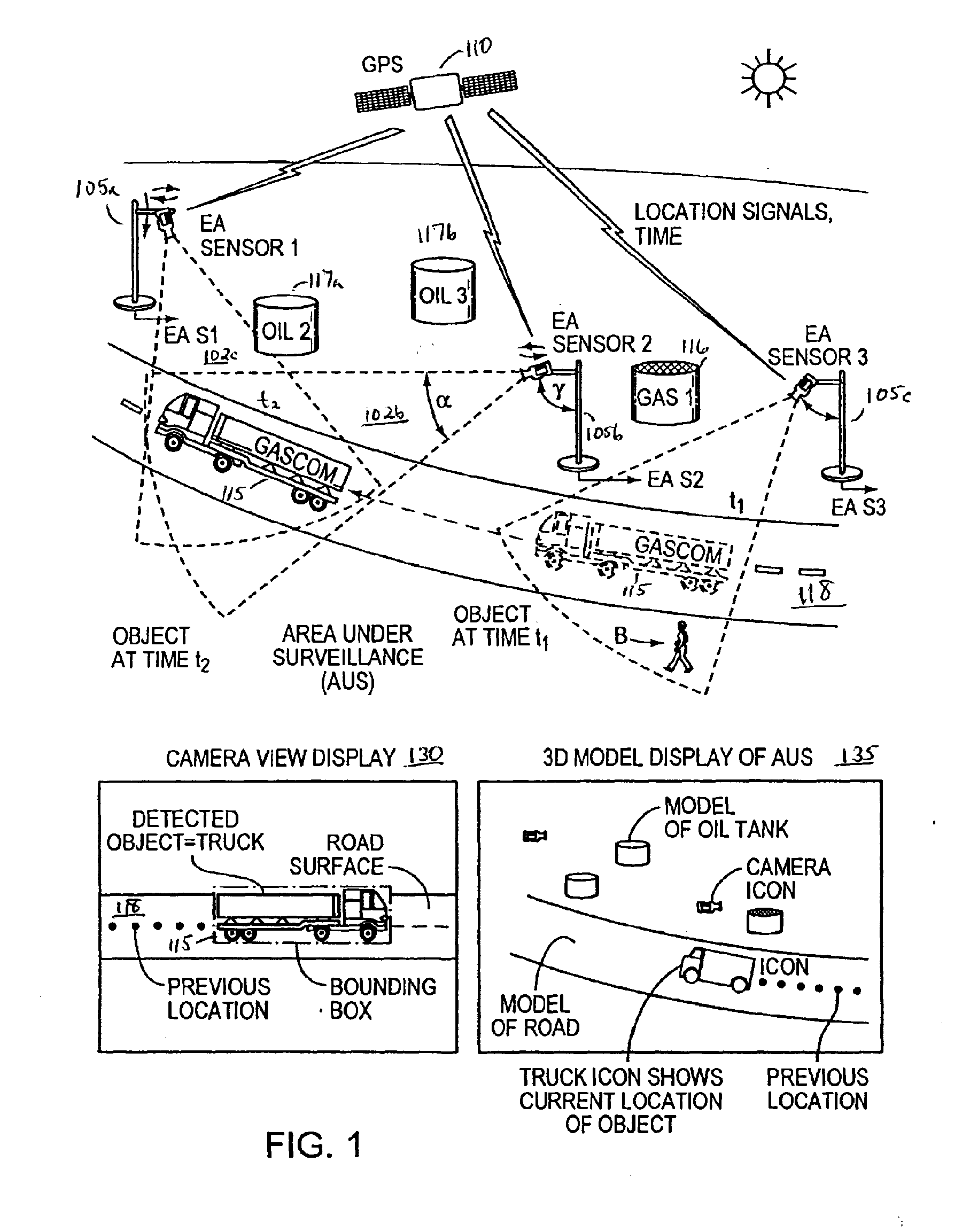
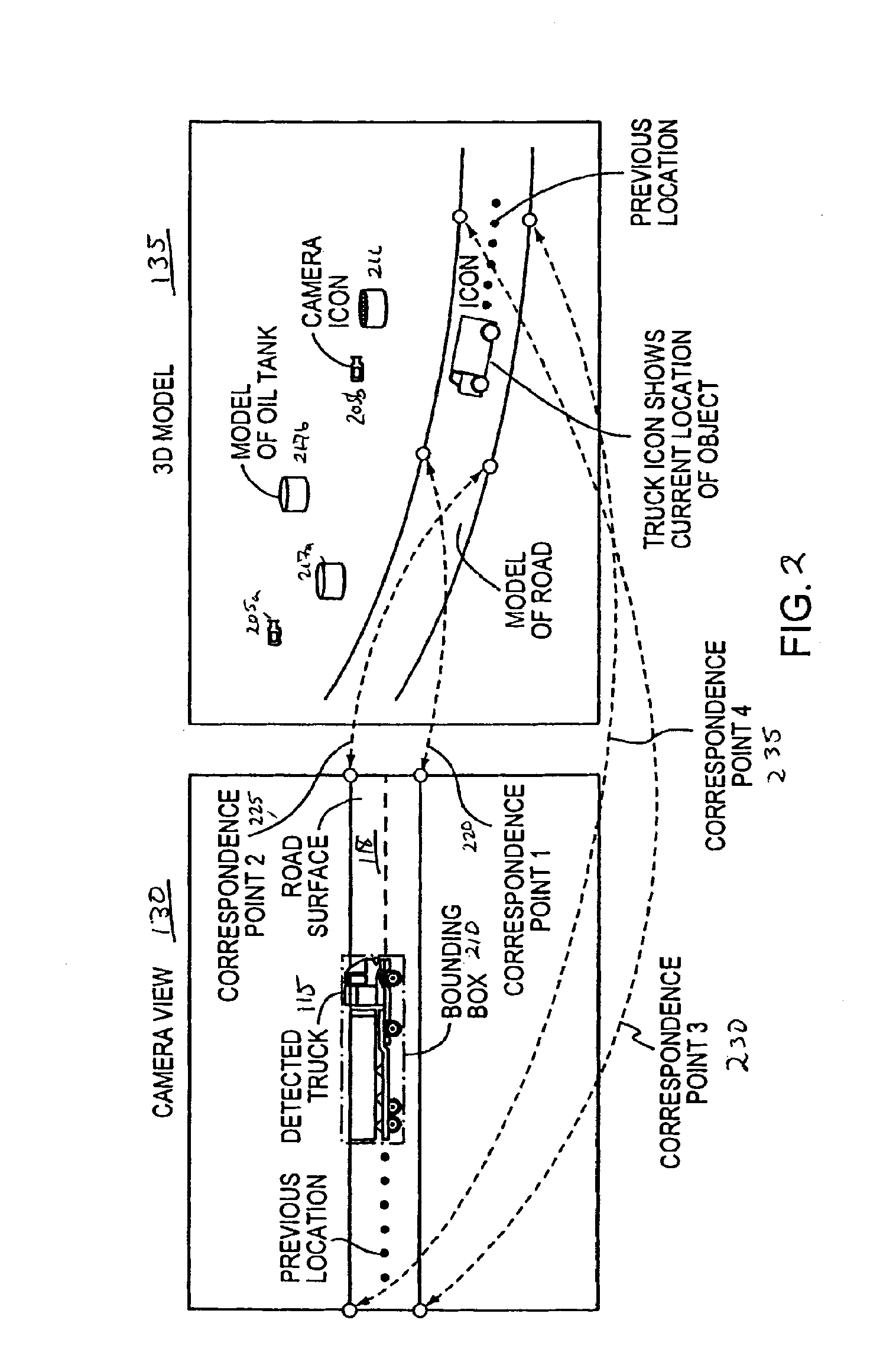
The present invention relates to methods and systems for the remote monitoring and sensing of a remote deployable, stand-alone, environmentally aware surveillance sensor device or unit that is capable of self-determining its location and orientation relative to a real world, 3D environment, detect conditions or events within the sensor's range of detection within that environment, and provide event information indicative of detected conditions or events including their location relative to the 3D real world environment as well as the raw sensor data feed to an external utilization system such as a security monitoring system. The exemplary sensor unit obtains position information from a position information source, orientation information from an orientation information source and time information, thereafter the unit processes the sensor feed to detect objects and types of objects, and provides event information or information output to an external utilization system such as a security monitoring system.
Owner:SIEMENS SWITZERLAND
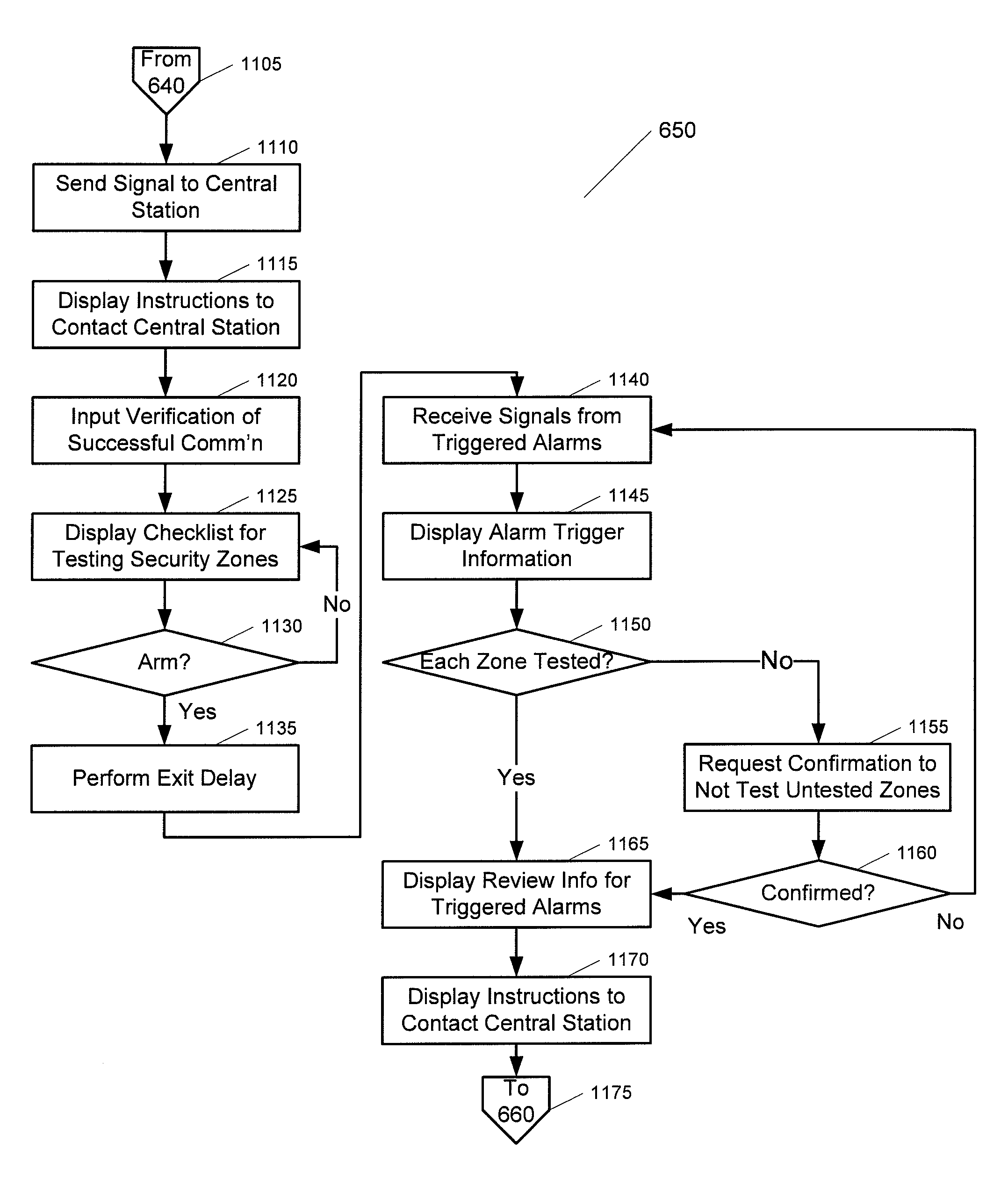
Server-based notification of alarm event subsequent to communication failure with armed security system
A server-based environment for reporting a status of a security, monitoring and automation controller is provided. Detecting cessation of an always-on persistent network connection between the SMA controller and the server is also provided. Reporting the cessation of the network connection to an end user and defined others is further provided. A further aspect provides for automatically reporting an alarm event to a central station, the end user, and others, in the event the cessation of the network connection occurs while the SMA controller is armed and after a zone fault event, and not receiving a disarm notification prior to expiration of a preset entry delay.
Owner:ICONTROL NETWORKS
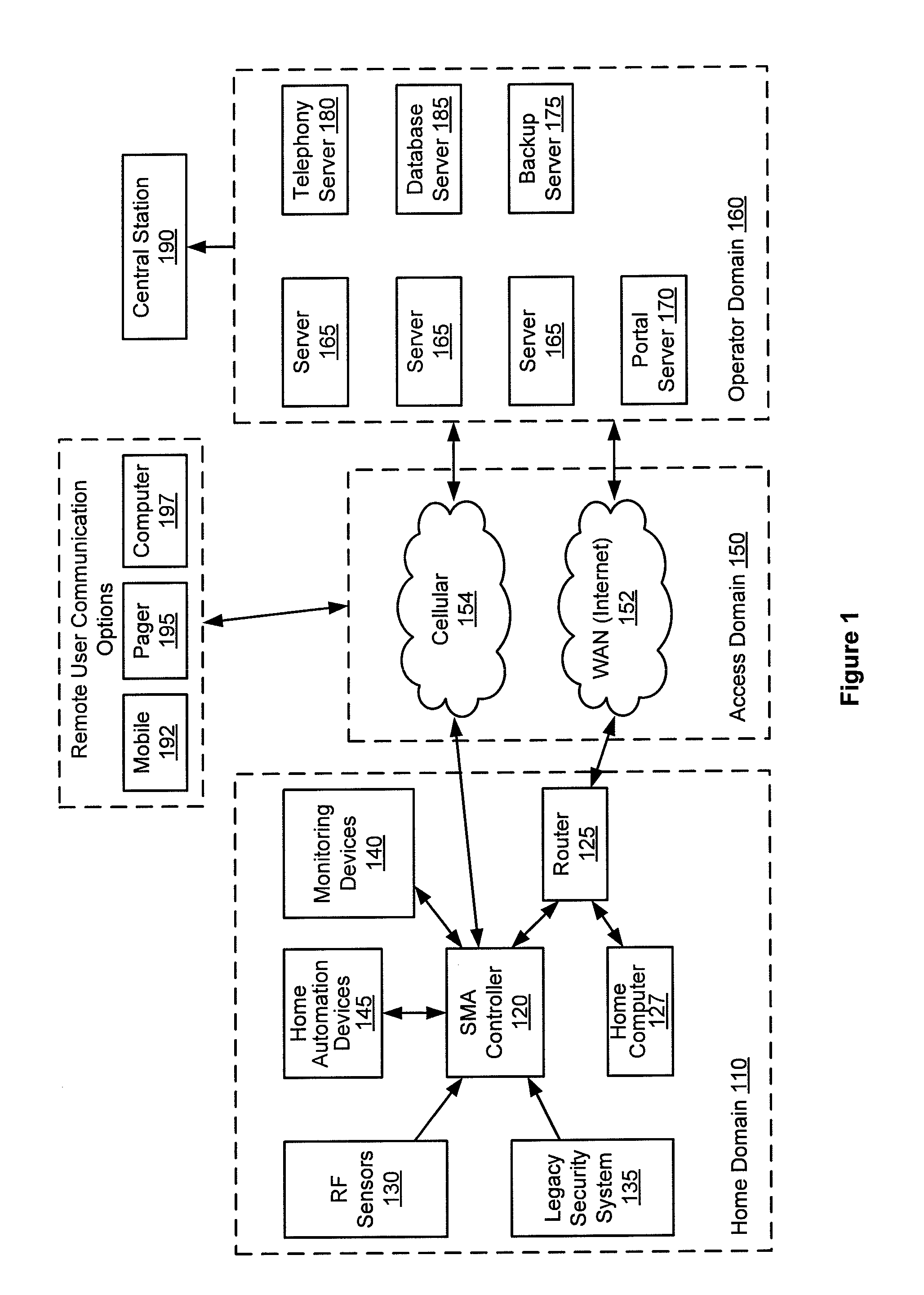
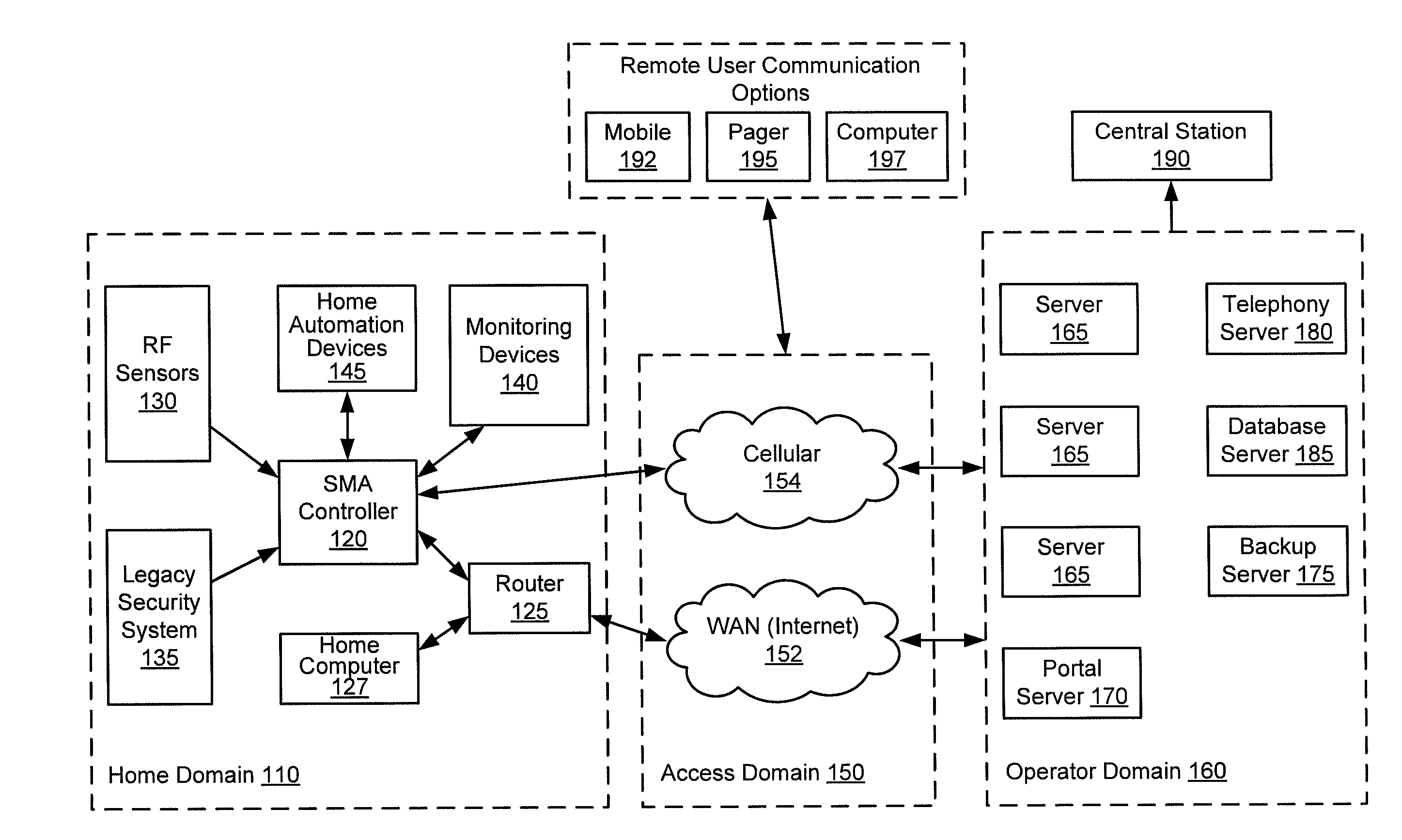
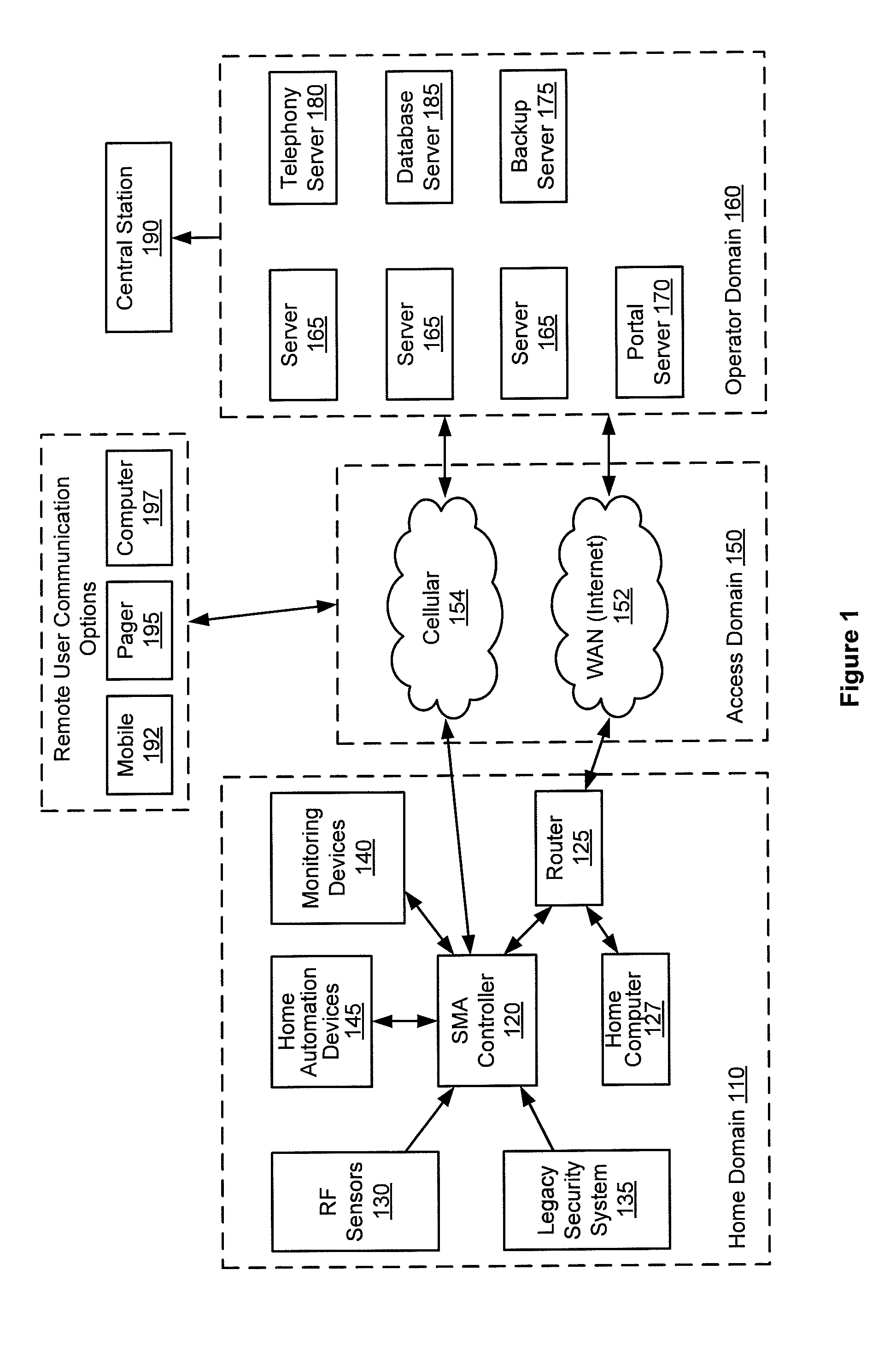
Remotely monitored and controlled building automation system
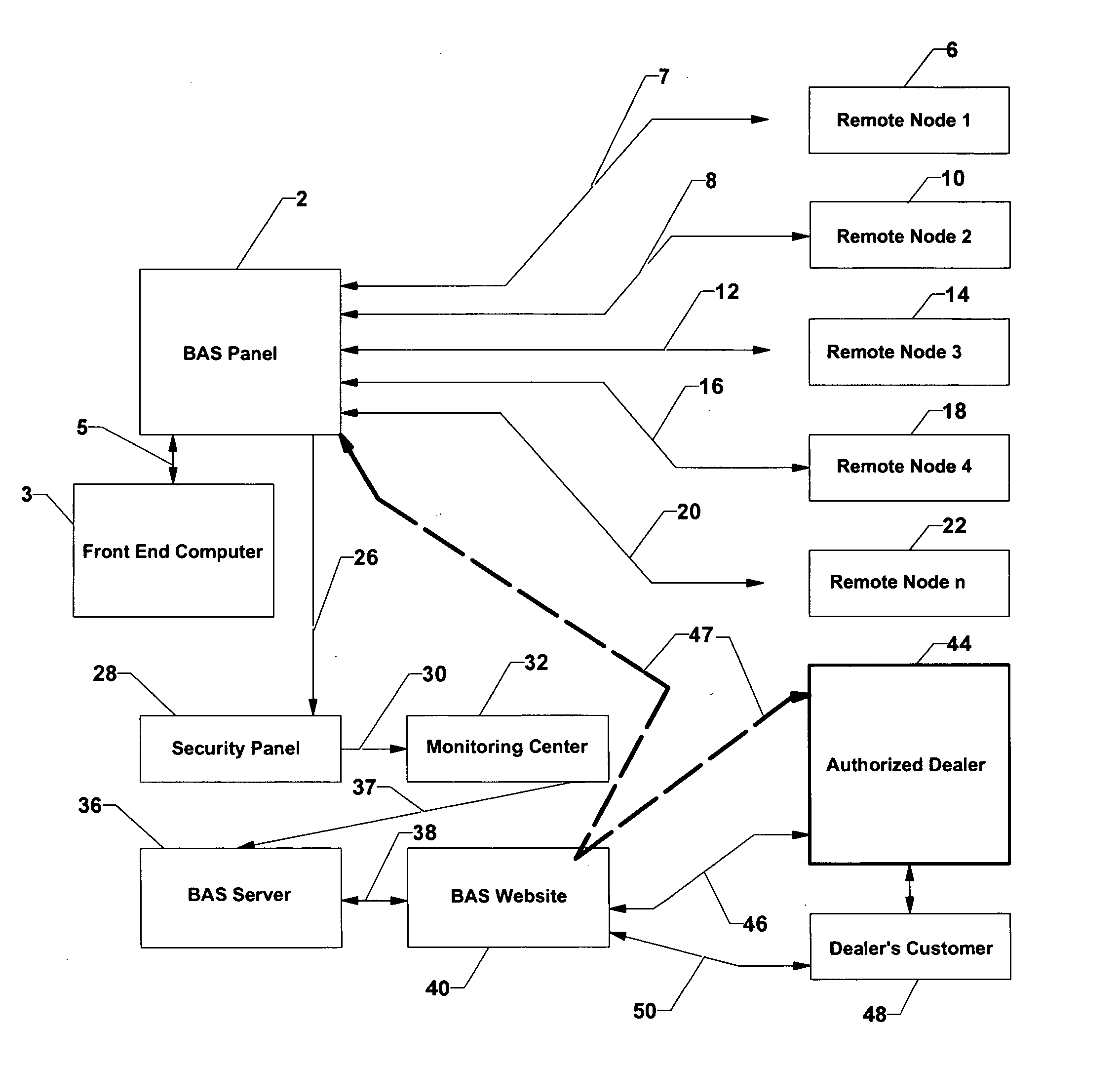
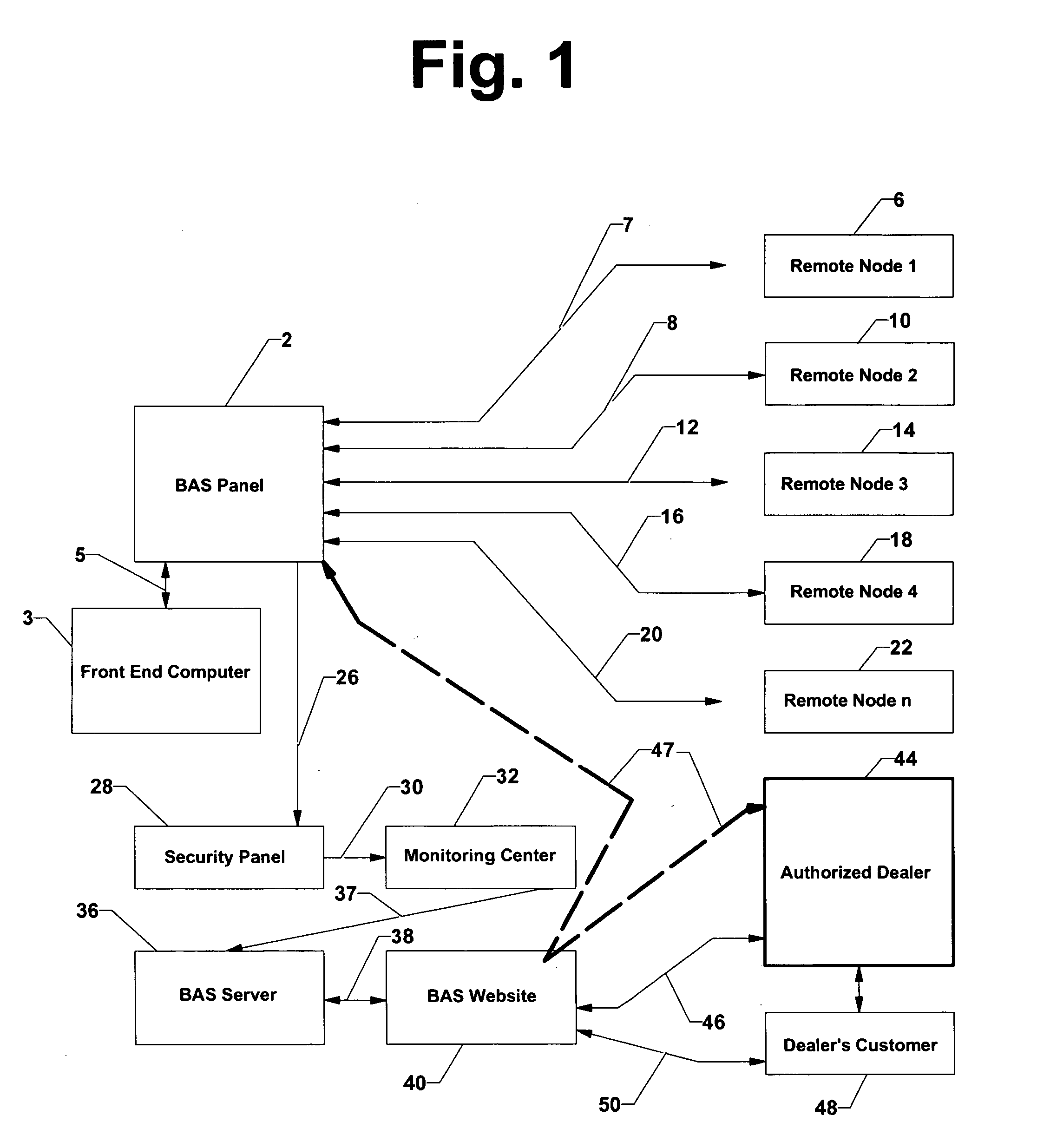
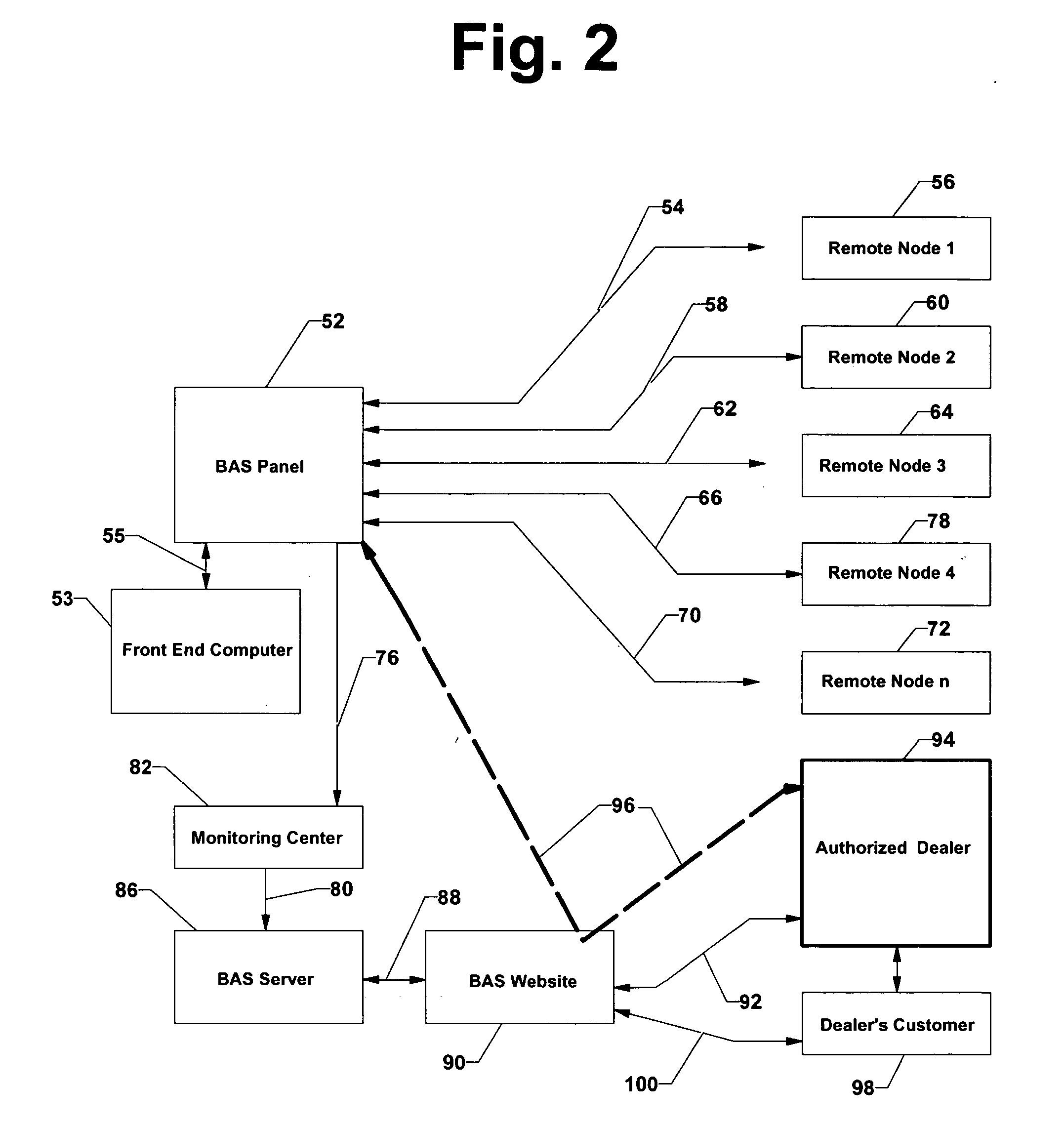
InactiveUS20050200474A1Improve build efficiencyEfficient use ofFrequency-division multiplex detailsTemperatue controlEngineeringSecurity monitoring
A remotely monitored and controlled building automation system is disclosed providing efficient offsite use of BAS personnel to monitor and control such systems while utilizing relatively inexpensive alarm monitoring services to advice of system emergencies. In a first preferred embodiment, the building automation system transmits a simplified BAS / energy alarm (including only building identity information) via a specially adapted and configured local security panel to an offsite monitoring center. Thereafter, the alarm is re-transmitted to a BAS web server and on to a BAS website. The BAS website provides notification of the energy alarm to trained BAS technicians located at a remote dealer and enables such personnel, via the website to maintain two-way communication with the building automation system from which the alarm originated. Such personnel are thereby enabled to fully analyze and properly respond to the circumstances which resulted in the alarm. In a second preferred embodiment, the building automation system transmits the simplified BAS alarm directly to a security monitoring center. A BAS controller is disclosed, especially configured and adapted to generate an “energy alarm” upon reception of sensor data indicating the existence of conditions beyond programmed parameters and to provide two way communication of detailed BAS data between the controller and an offsite location. In addition, an especially configured and adapted security panel is disclosed, including a specially coded sensor position, whereby reception of a simplified BAS alarm by the security panel is recognized and re-transmitted to a monitoring center as an energy alarm.
Owner:GLOBAL GATE TECH
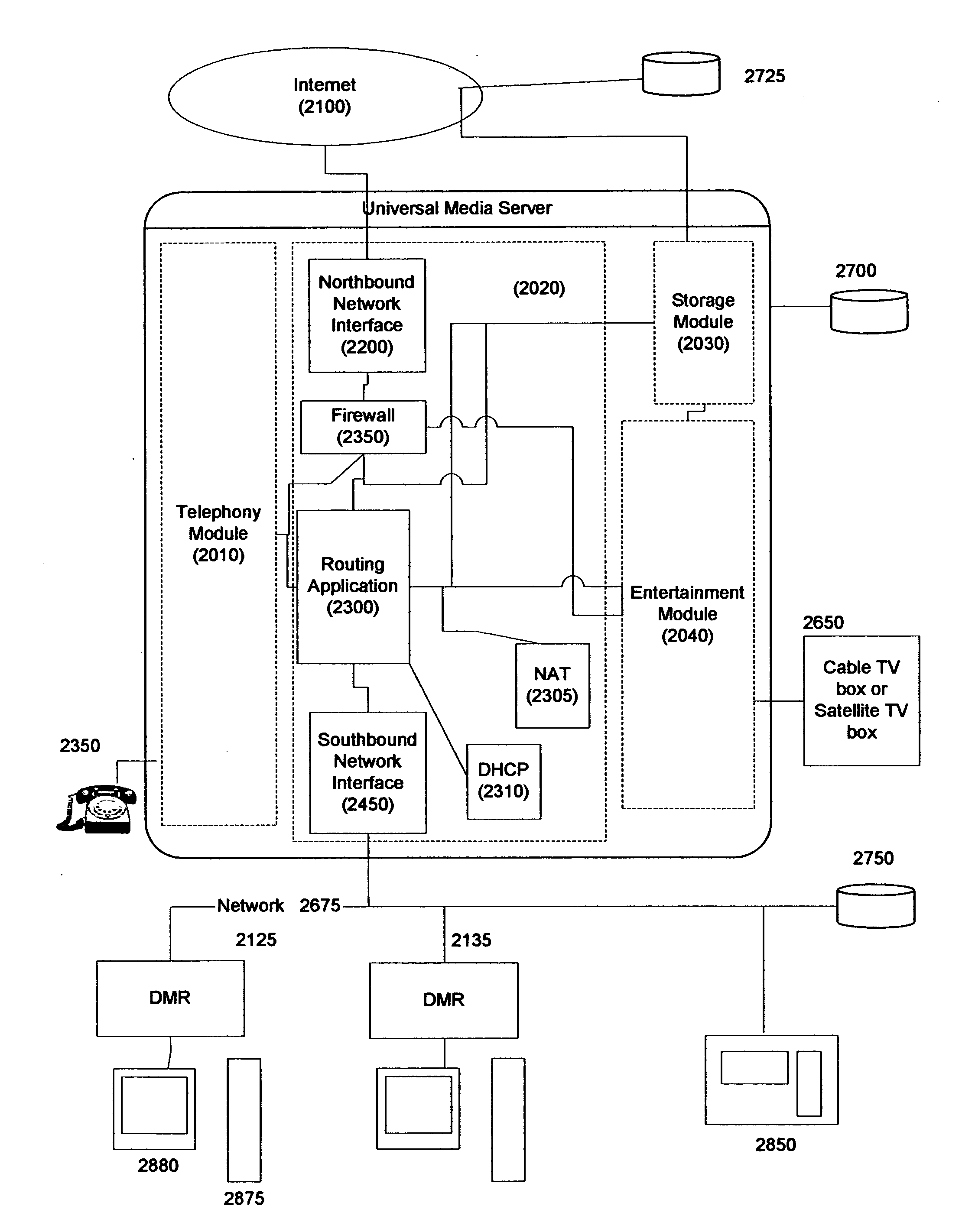
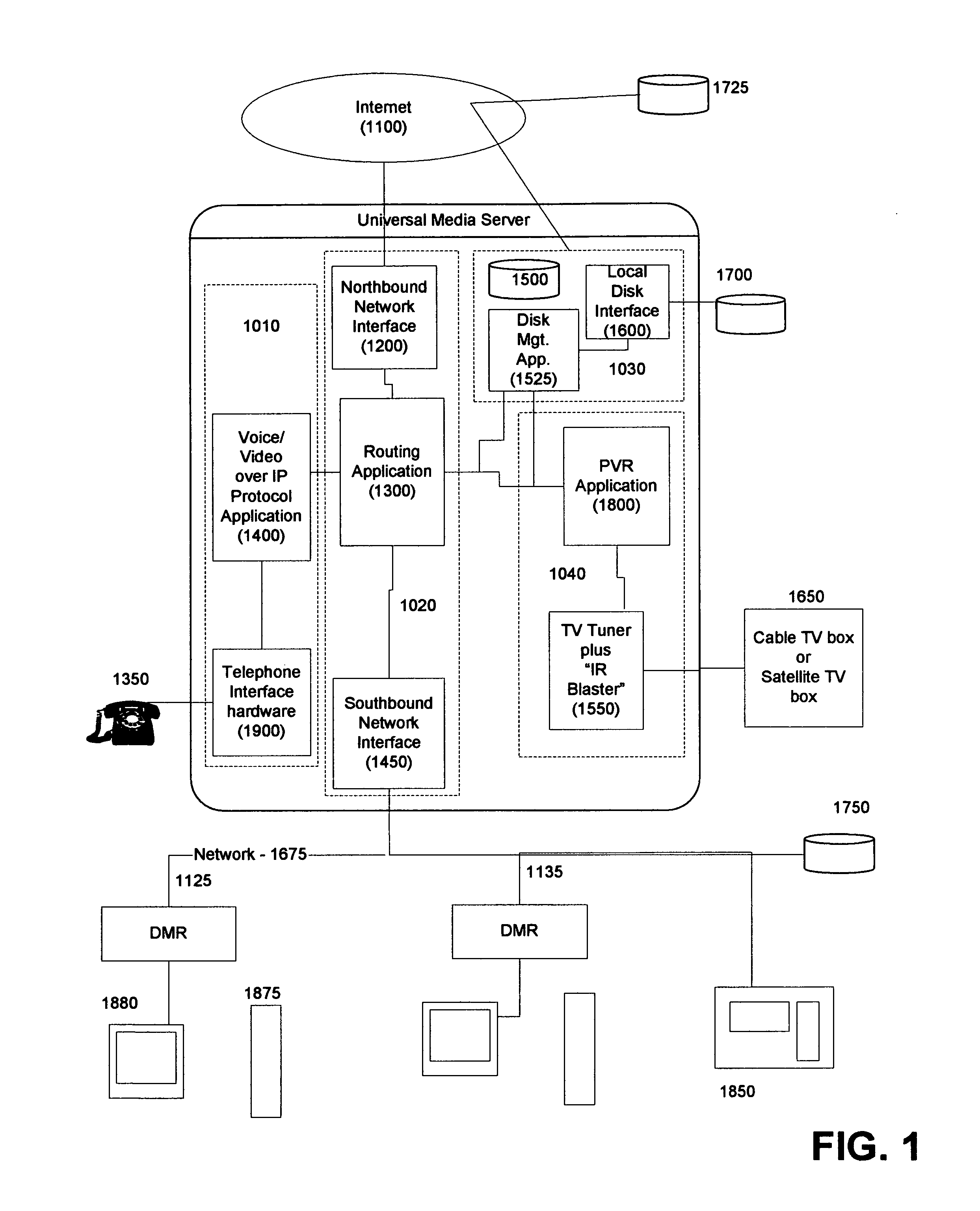
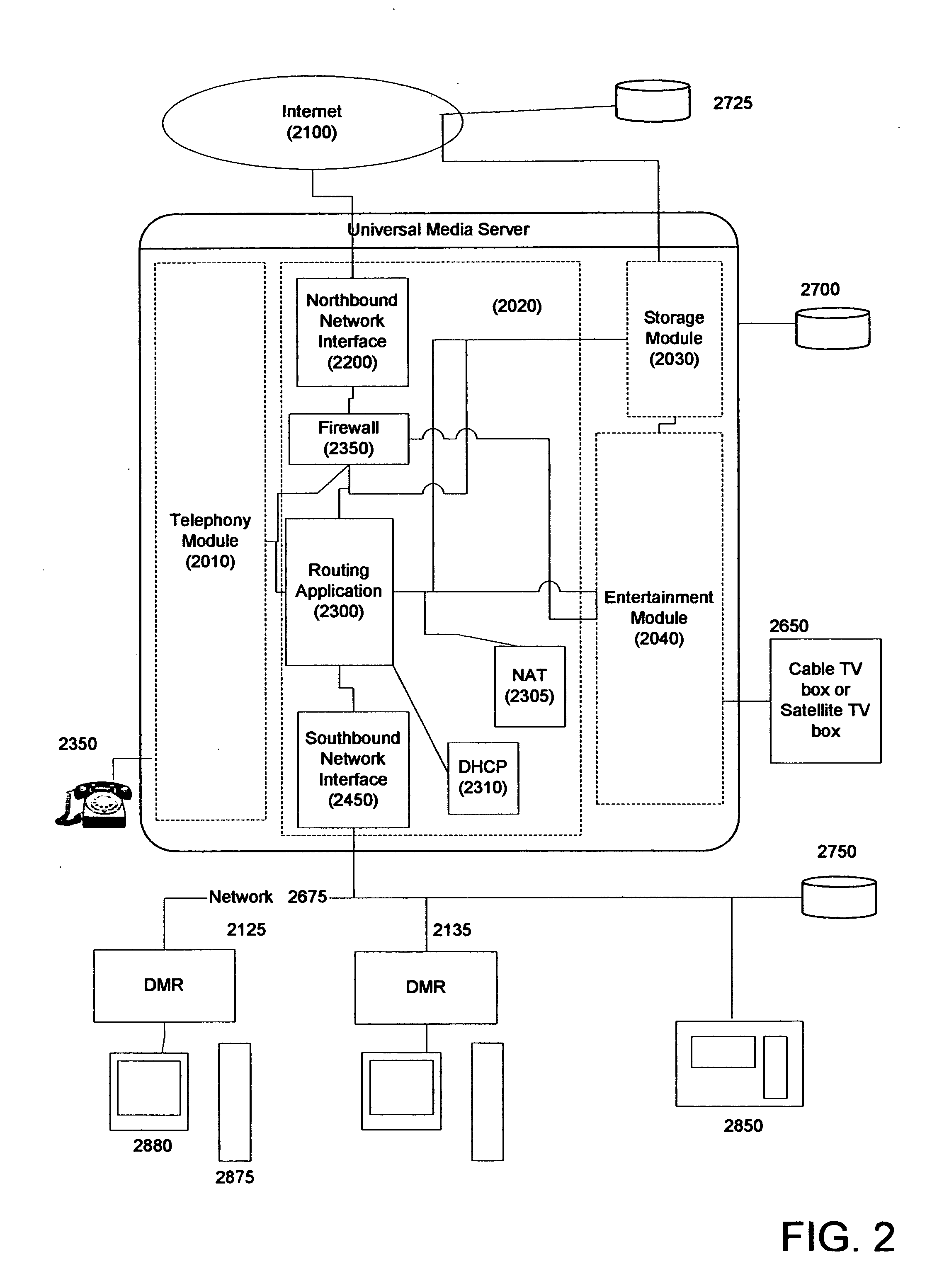
Systems and methods for a universal media server with integrated networking and telephony
InactiveUS20050216949A1Reliable retentionLow costTelevision system detailsPulse modulation television signal transmissionMedia serverSecurity monitoring
Systems and methods for creating a Universal Media Server (UMS) and associated Digital Media Renders (DMRs) are disclosed. This system provides functions such as in-home wired or wireless network for media distribution with PVR functions from a distributed archive while at the same time including functions such as an answering machine, voice recorder, voice over IP gateway, firewall, NAT, DHCP, and security monitoring. A variety of advanced features and functions are also disclosed.
Owner:CANDELORA RAY +2
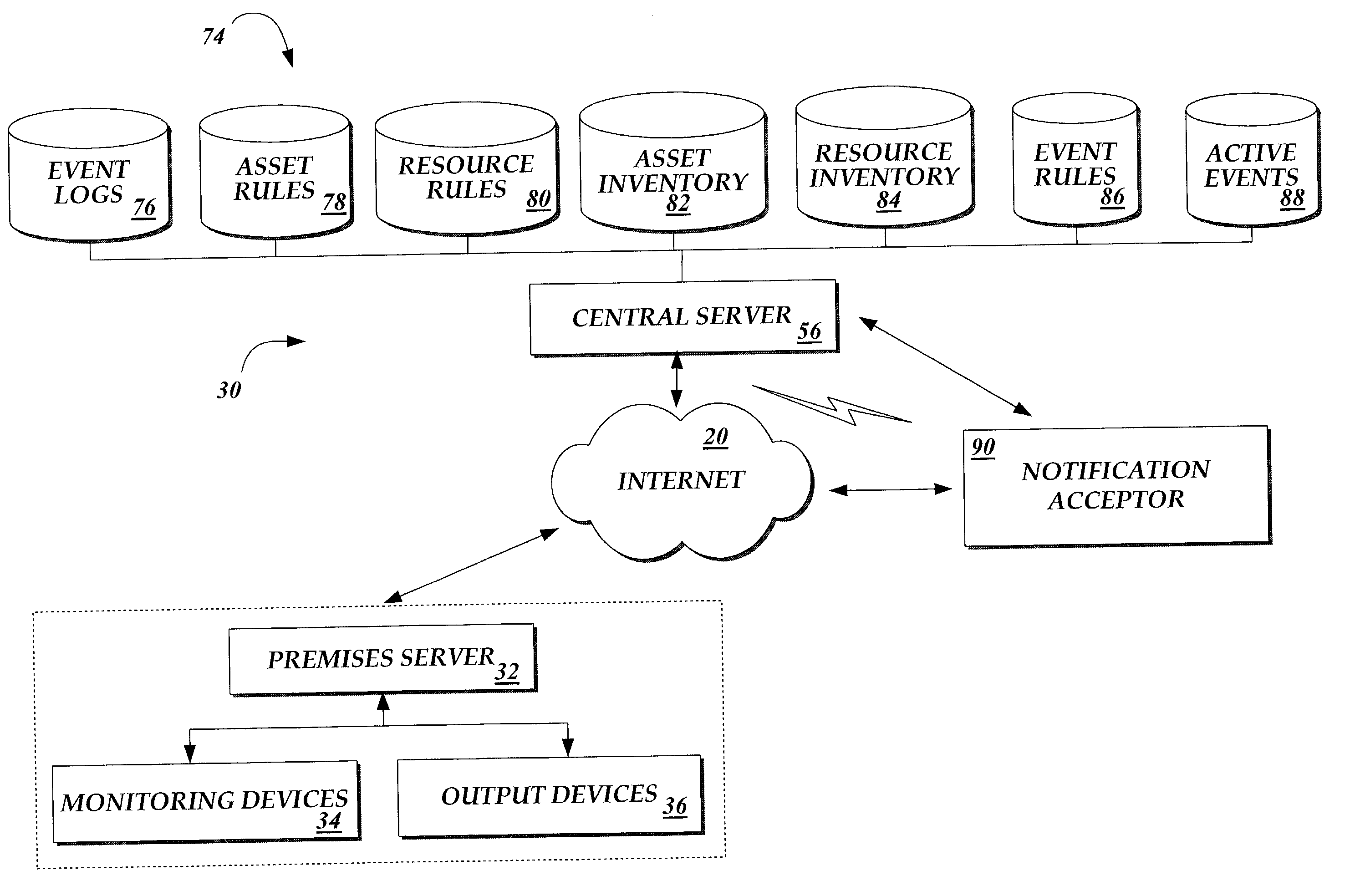
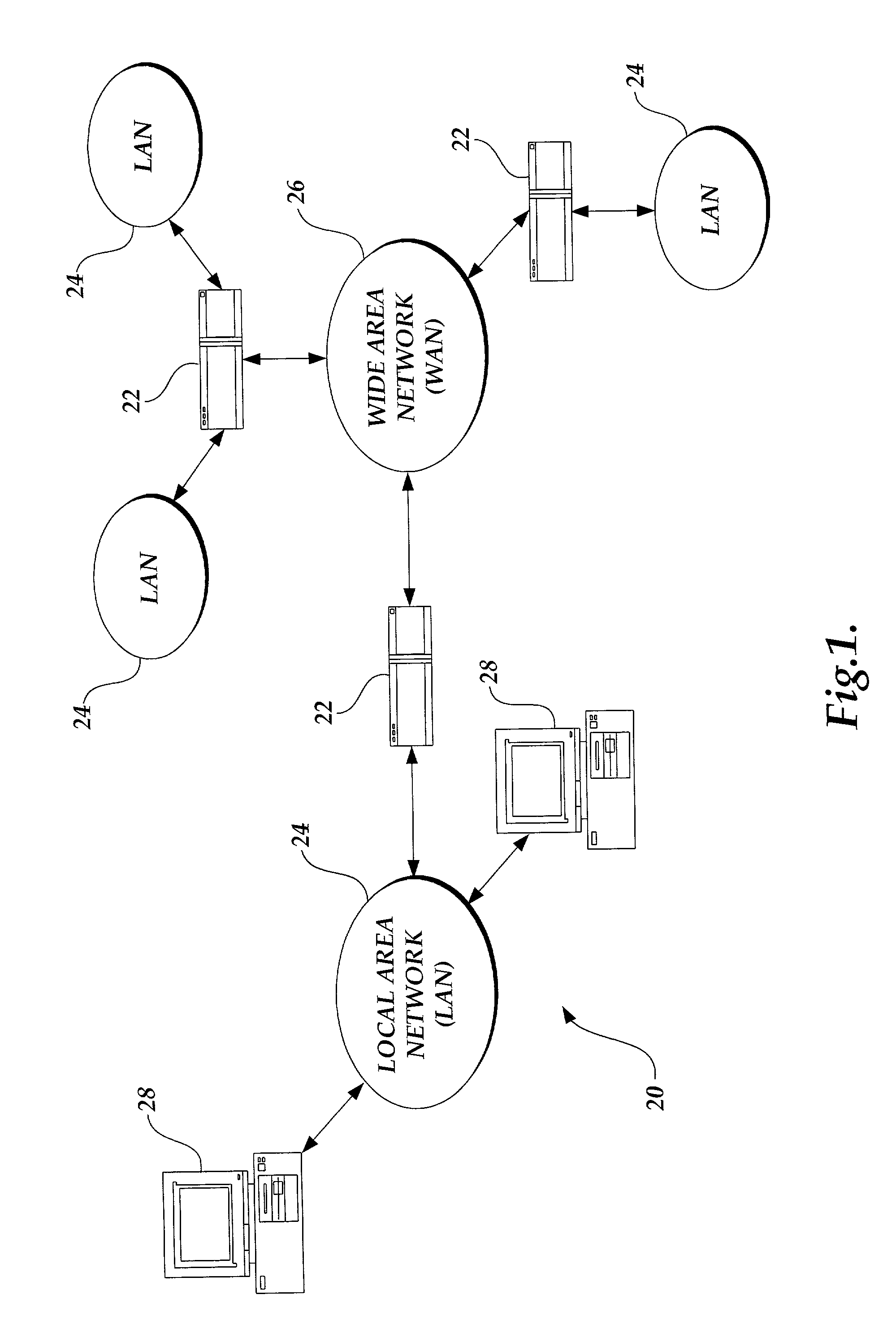
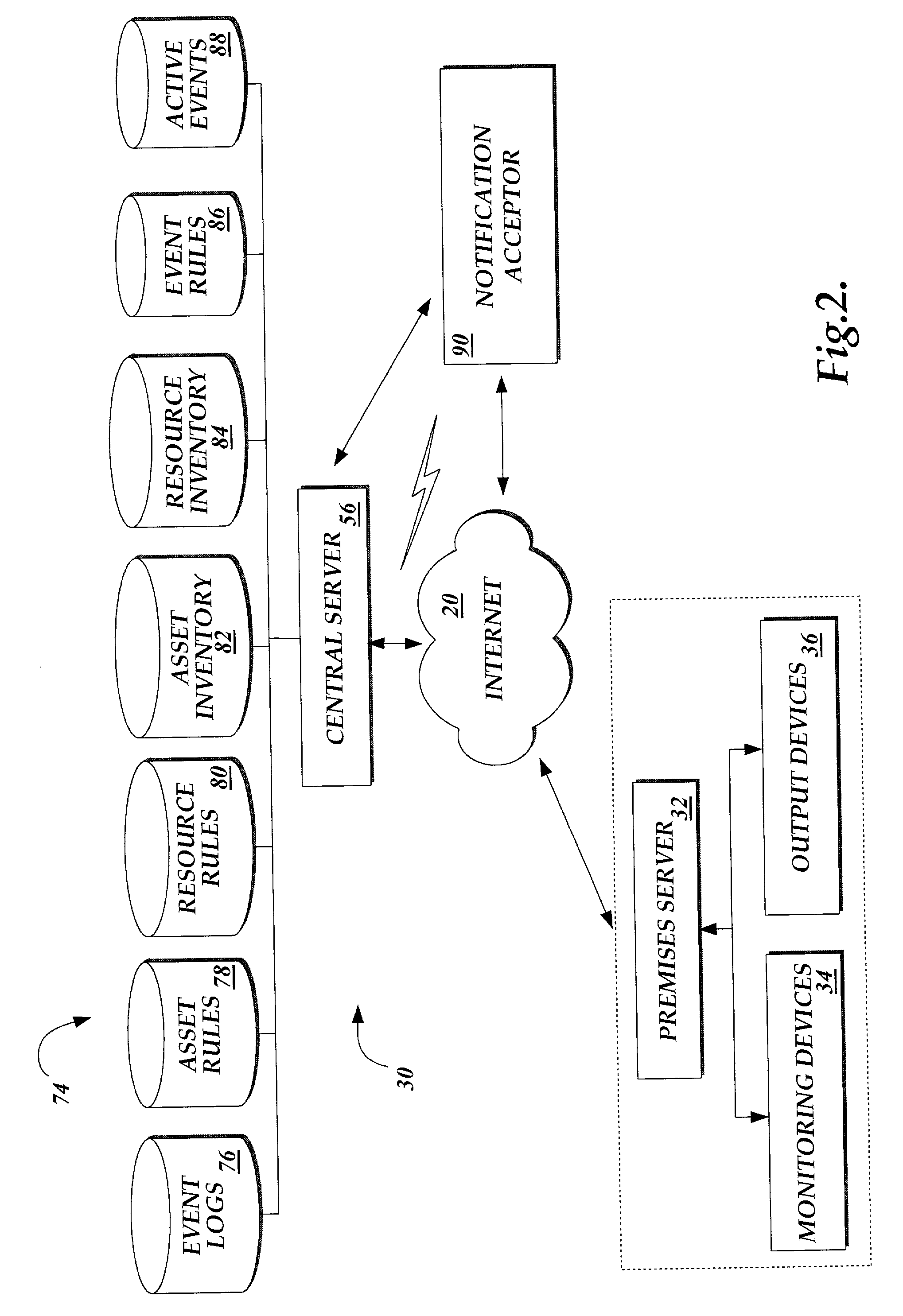
System and method for providing configurable security monitoring utilizing an integrated information system
InactiveUS7627665B2Multiple digital computer combinationsData switching networksGlobal information systemMonitor equipment
A system and method for implementing an integrated information system are provided. A premises server is in communication with a variety of information sources that produce monitoring data for a premises. The premises server collects, presents, and transmits the monitoring device data to a central server capable of processing data from multiple premises servers. The central server receives the data and traverses one or more logical rule sets to determine whether the inputted data violates the rules. Based on an evaluation of the rules, the central server generates outputs in the form of communication to one or more authorized users via a variety of communication mediums and devices and / or the instigation of a variety of acts corresponding to the evaluation of the rules.
Owner:VIVINT INC
Controller and interface for home security, monitoring and automation having customizable audio alerts for sma events
A single platform for controller functionality for each of security, monitoring and automation, as well as providing a capacity to function as a bidirectional Internet gateway, is provided. Embodiments of the present invention provide such functionality by virtue of a configurable architecture that enables a user to adapt the system for the user's specific needs. Such configurability includes associating selected audio event tones with selected events associated with sensors and zones coupled to the system.
Owner:ICONTROL NETWORKS
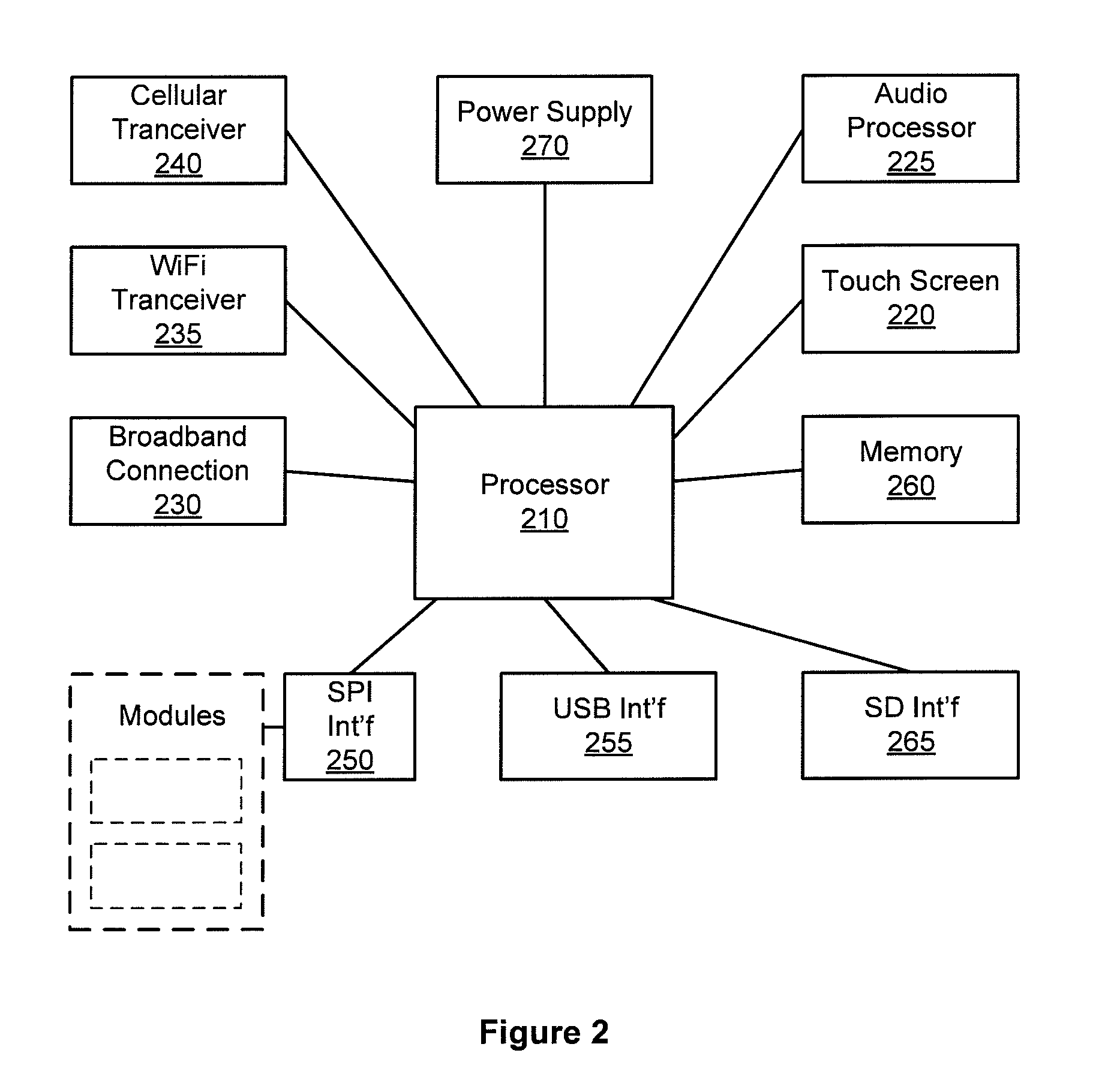
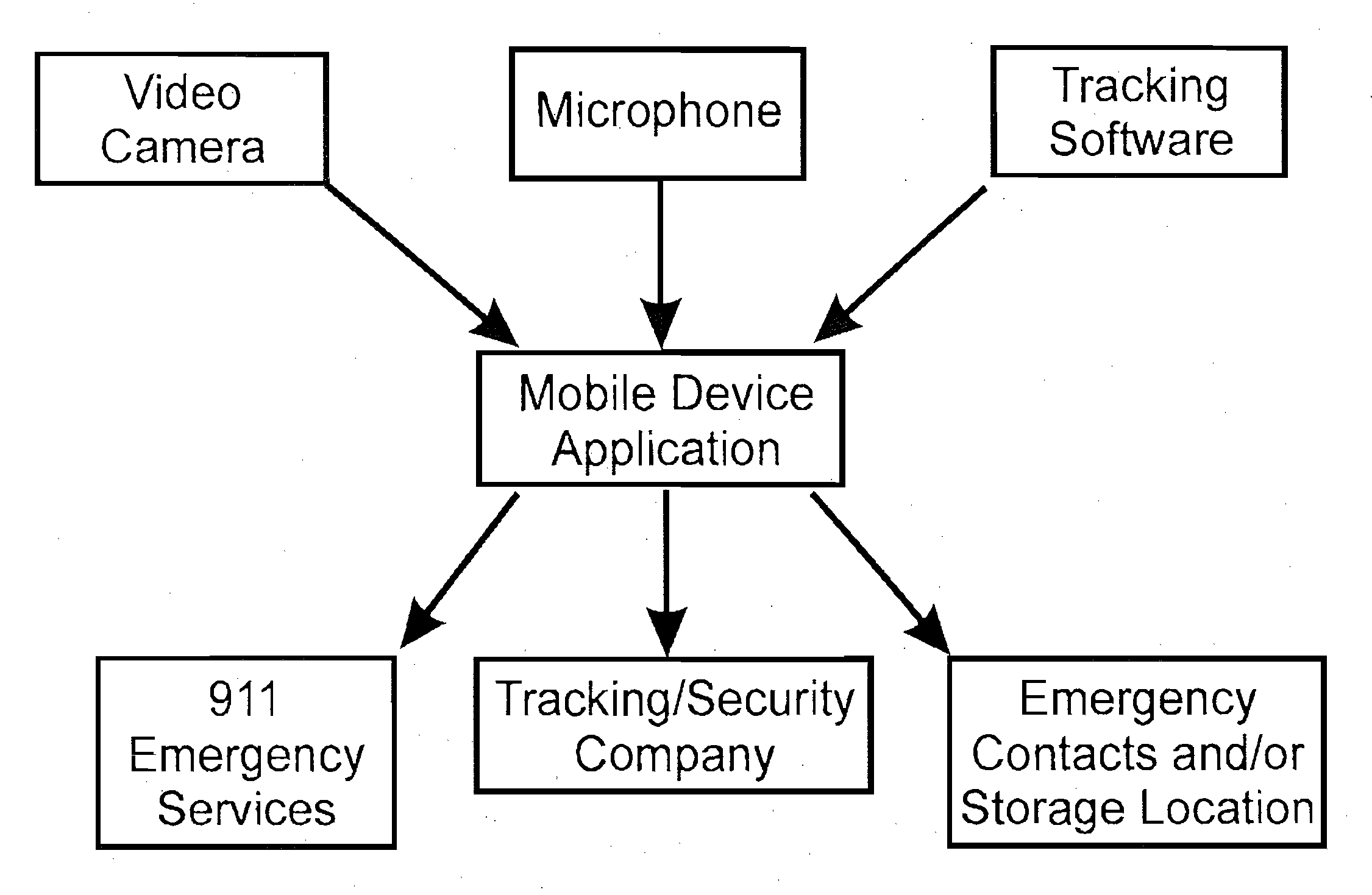
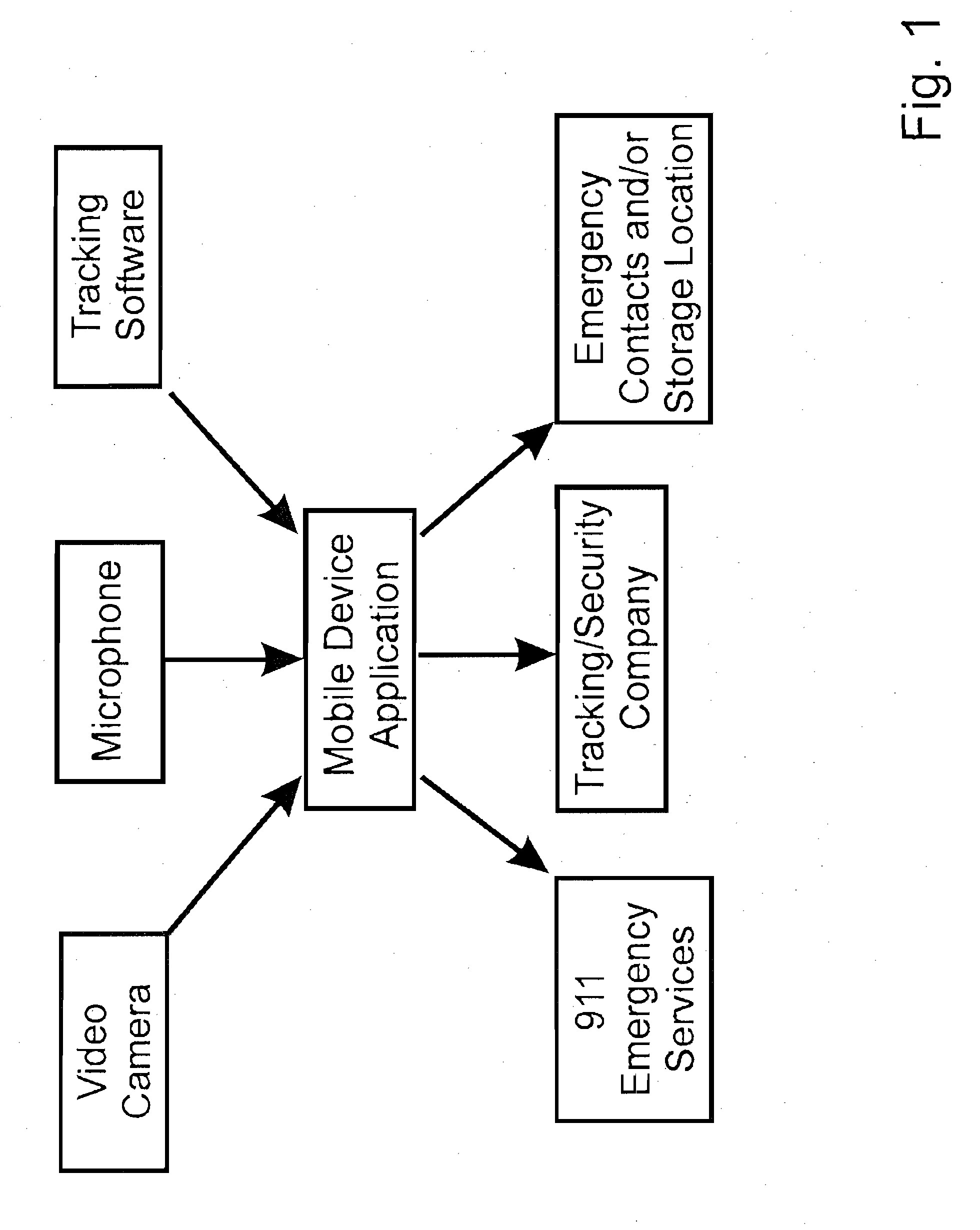
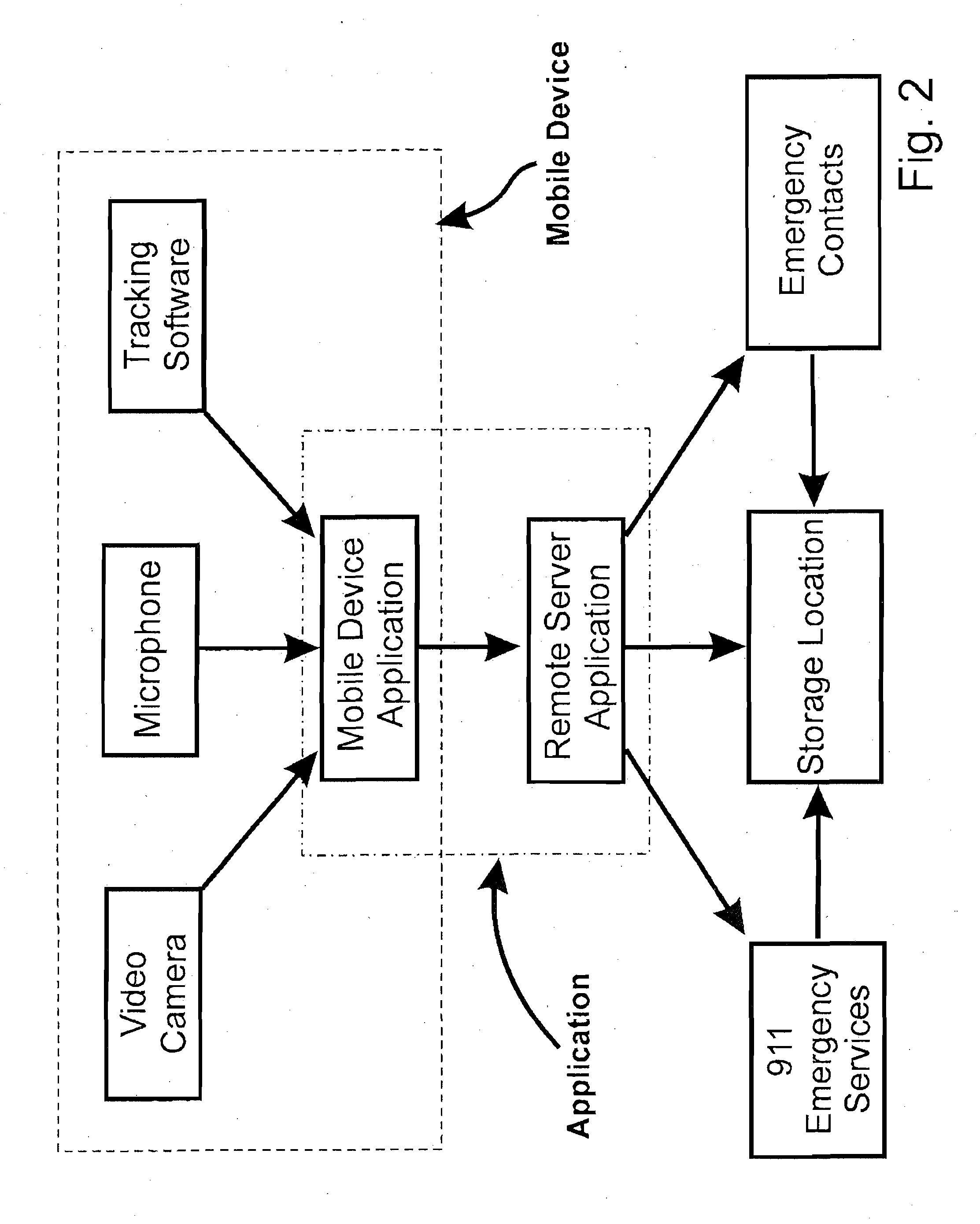
Notification and Tracking System for Mobile Devices
InactiveUS20130040600A1Devices with GPS signal receiverSubstation equipmentDigital imageBiological activation
An notification and tracking system for a mobile device. The system includes a mobile device application that is adapted to be stored in memory on the mobile device. The application, upon activation, determines the GPS coordinates of the mobile device, records digital images over a period of time, sends a preset message from the mobile device to at least one recipient, preferably an emergency responder, such as a security monitoring station, and sends the GPS coordinates and the digital images. The coordinates and images may be sent to a remote server for storage and which can be accessed by the emergency responder. The coordinates and images are periodically updated and sent while the program is activated.
Owner:EMERGENSEE
Method, system and apparatus for activation of a home security, monitoring and automation controller
Embodiments of the present invention provide a single platform that provides controller functionality for each of security, monitoring and automation, as well as providing a capacity to function as a bidirectional Internet gateway. Embodiments of the present invention provide such functionality by virtue of a configurable architecture that enables a user to adapt the system for the user's specific needs. Embodiments of the present invention further provide for a software-based installation workflow to activate and provision the controller and associated sensors and network.
Owner:ICONTROL NETWORKS
Method, system and apparatus for automated inventory reporting of security, monitoring and automation hardware and software at customer premises
A single platform for controller functionality for each of security, monitoring and automation, as well as providing a capacity to function as a bidirectional Internet gateway, is provided. Embodiments of the present invention provide such functionality by virtue of a configurable architecture that enables a user to adapt the system for the user's specific needs. Embodiments of the present invention further provide for remote access to the configurable controller, thereby providing for remote monitoring of the state of a dwelling and for remote control of home automation. Embodiments of the present invention further provide for reporting to a provider those sensors and other hardware used by the configurable architecture, enabling the provider to track inventory of such items.
Owner:ICONTROL NETWORKS
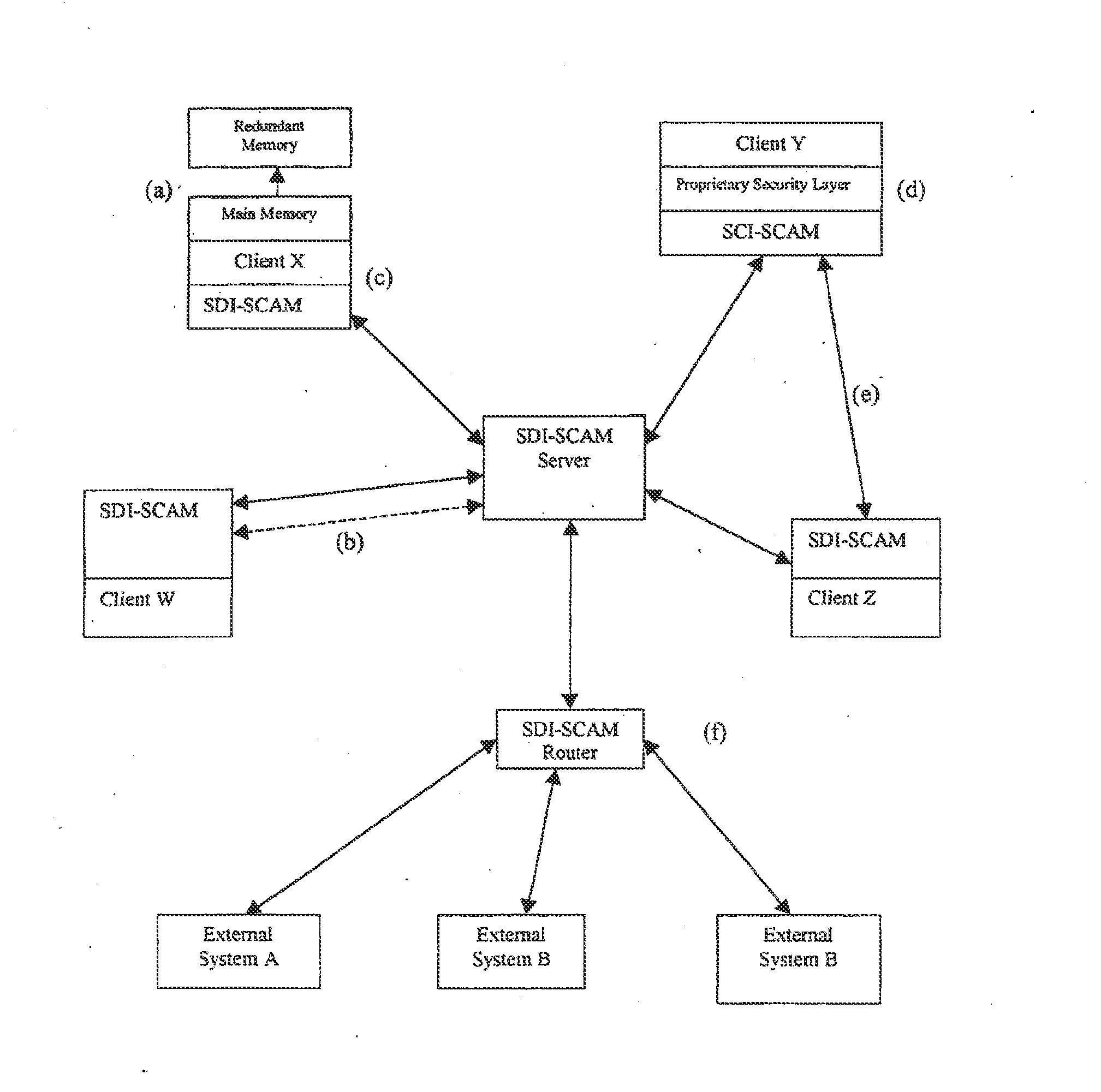
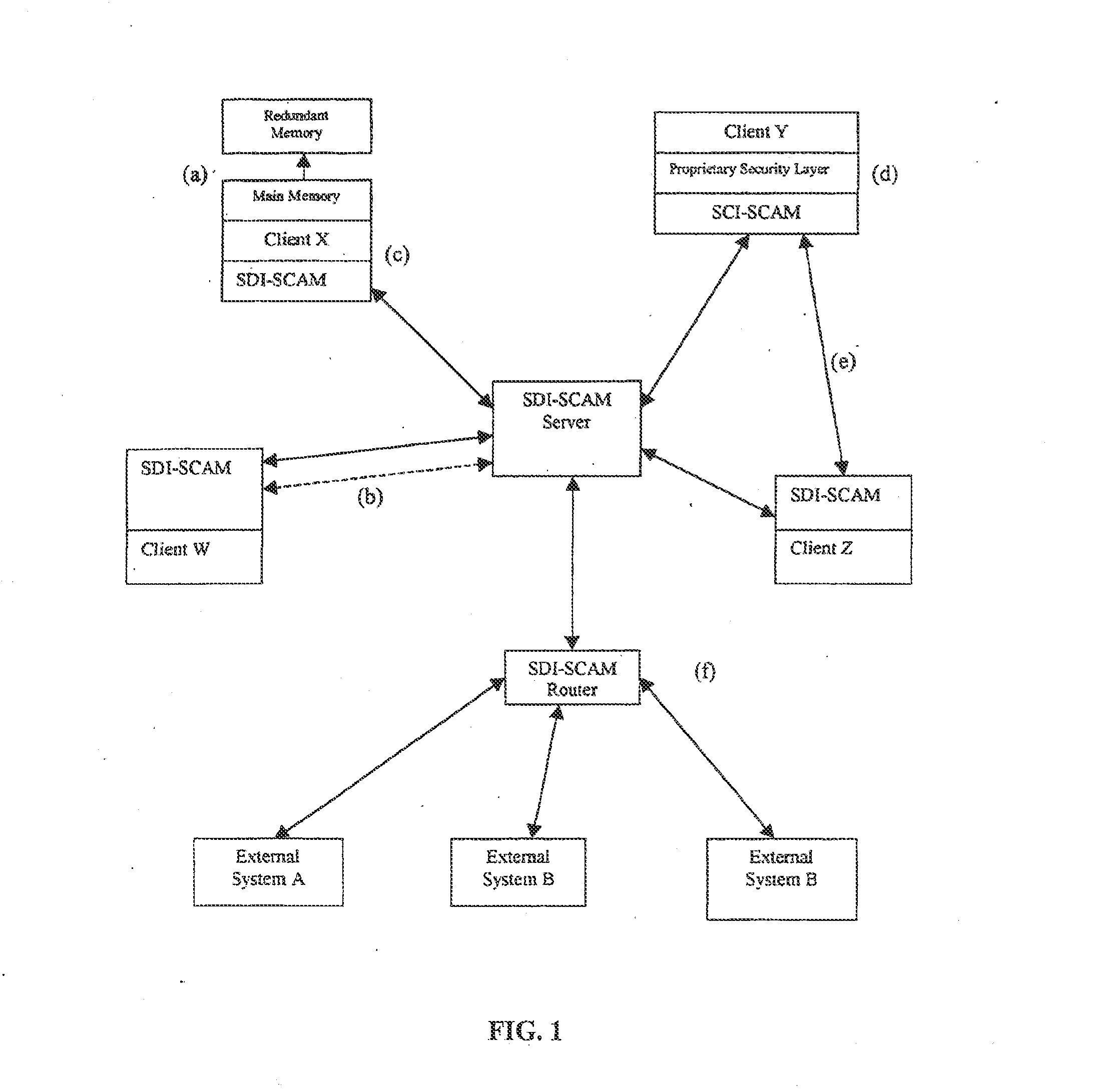
Distributed agent based model for security monitoring and response
ActiveUS20140237599A1Quick checkHigh and uniform level of securityMemory loss protectionError detection/correctionCountermeasureAgent-based model
An architecture is provided for a widely distributed security system (SDI-SCAM) that protects computers at individual client locations, but which constantly pools and analyzes information gathered from machines across a network in order to quickly detect patterns consistent with intrusion or attack, singular or coordinated. When a novel method of attack has been detected, the system distributes warnings and potential countermeasures to each individual machine on the network. Such a warning may potentially include a probability distribution of the likelihood of an intrusion or attack as well as the relative probabilistic likelihood that such potential intrusion possesses certain characteristics or typologies or even strategic objectives in order to best recommend and / or distribute to each machine the most befitting countermeasure(s) given all presently known particular data and associated predicted probabilistic information regarding the prospective intrusion or attack. If any systems are adversely affected, methods for repairing the damage are shared and redistributed throughout the network.
Owner:INVENTSHIP LLC
Voice, lip-reading, face and emotion stress analysis, fuzzy logic intelligent camera system
InactiveUS20060028556A1Improve abilitiesMaintain integrityTelevision system detailsColor television detailsPattern recognitionCrowds
Revealed is an intelligent camera security monitoring, fuzzy logic analyses and information reporting system that includes video / audio camera, integrated local controller, interfaced plurality of sensors, and input / output means, that collects and analyses data and information observations from a viewed scene and communicates these to a central controller. The central controller with fuzzy logic processor receives, stores these observations, conducts a plurality of computer analyses techniques and technologies including face, voice, lip reading, emotion, movement, pattern recognition and stress analysis to determine responses and potential threat of / by a person, crowd, animal, action, activity or thing. This invention recognizes possible terrorists, criminals, enraged or dangerous persons and also can identify a person's level of intoxication or impairment by alcohol or drugs via a new “Visual Response Measure”. The invention provides an intelligent tool to assist security systems and personnel, improving capability to record, display and share information and maintain security.
Owner:STRESSCAM OPERATIONS & SYST
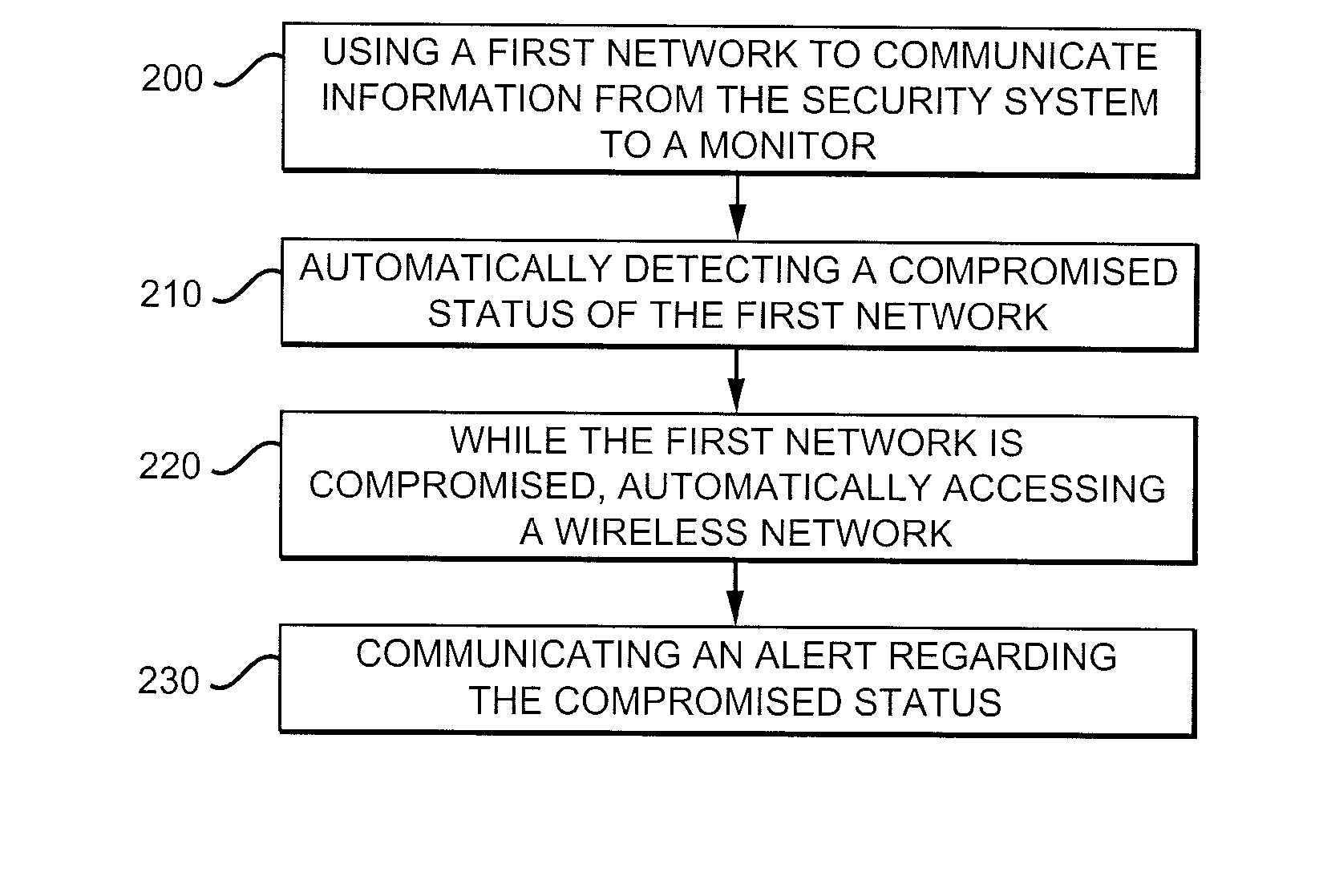
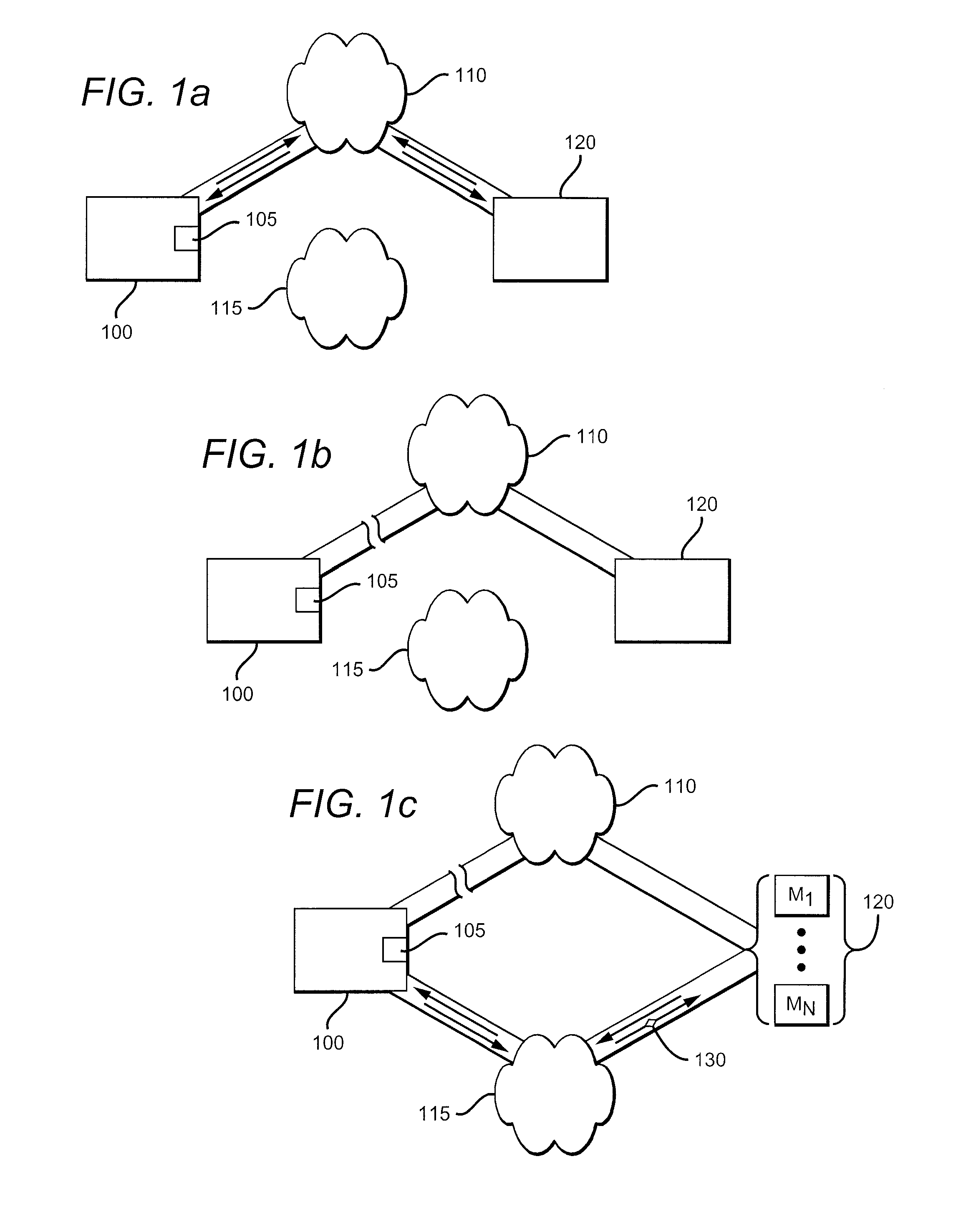
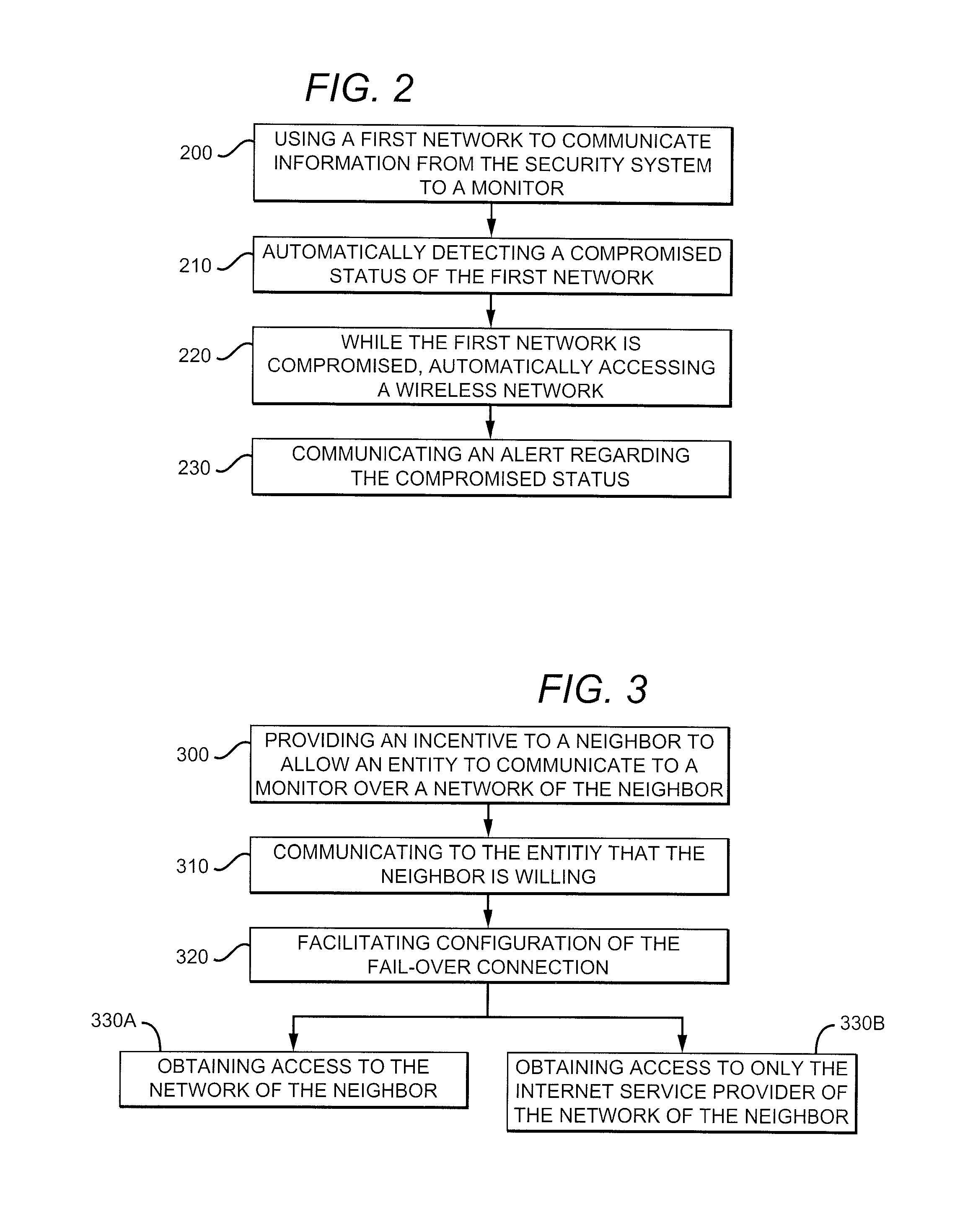
Sharing of a Neighboring Wireless Network
A security system can detect if a first network is compromised and automatically access a second network to communicate an alert to a monitor. The second network could be a wireless network of a neighbor. An incentive could be provided to the neighbor to allow the security system to access the neighbor's network and communicate an alert to at least one monitor. The monitor could include an emergency responder, a security monitoring service, and a cellular telephone of an entity of the security system.
Owner:DEI HLDG
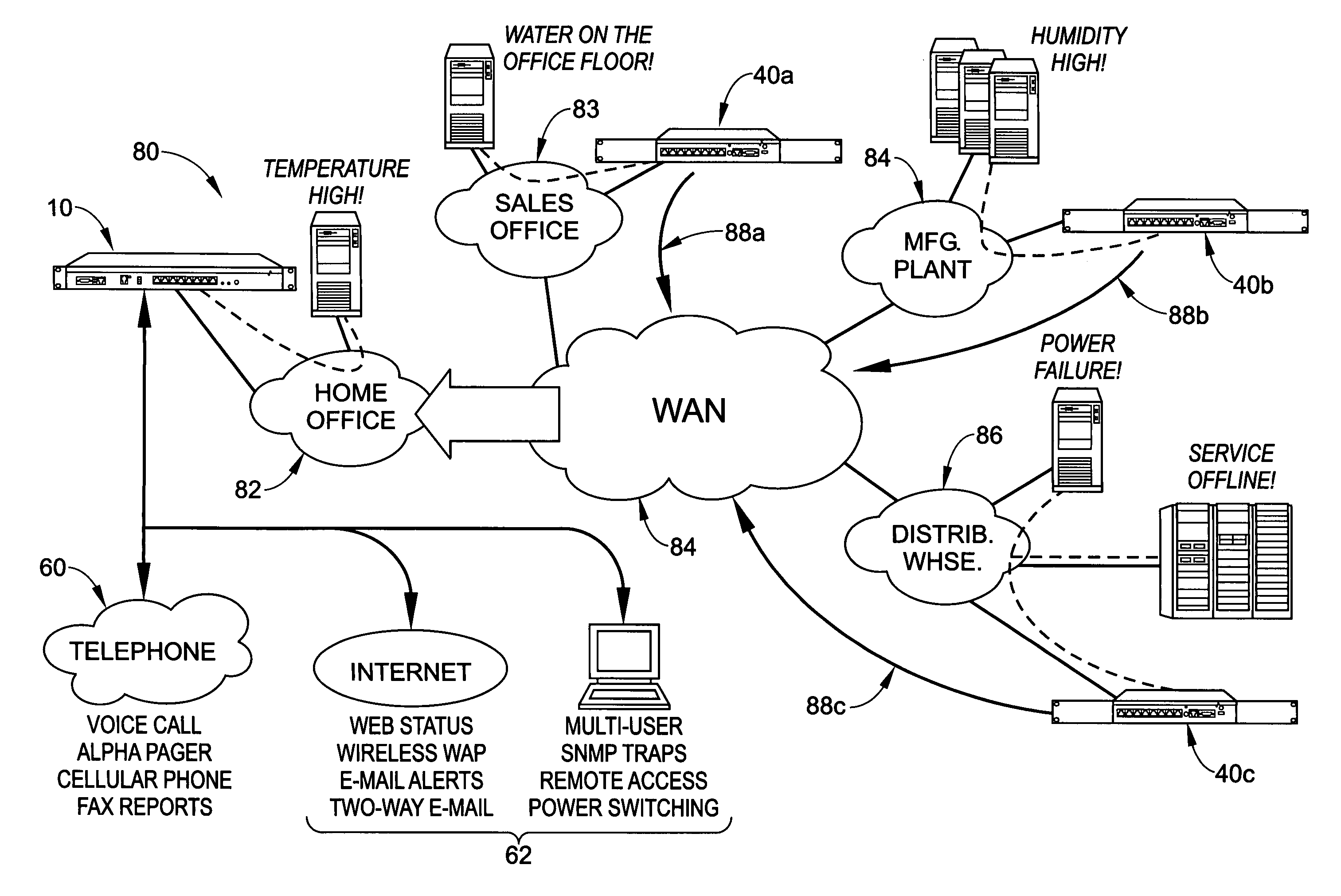
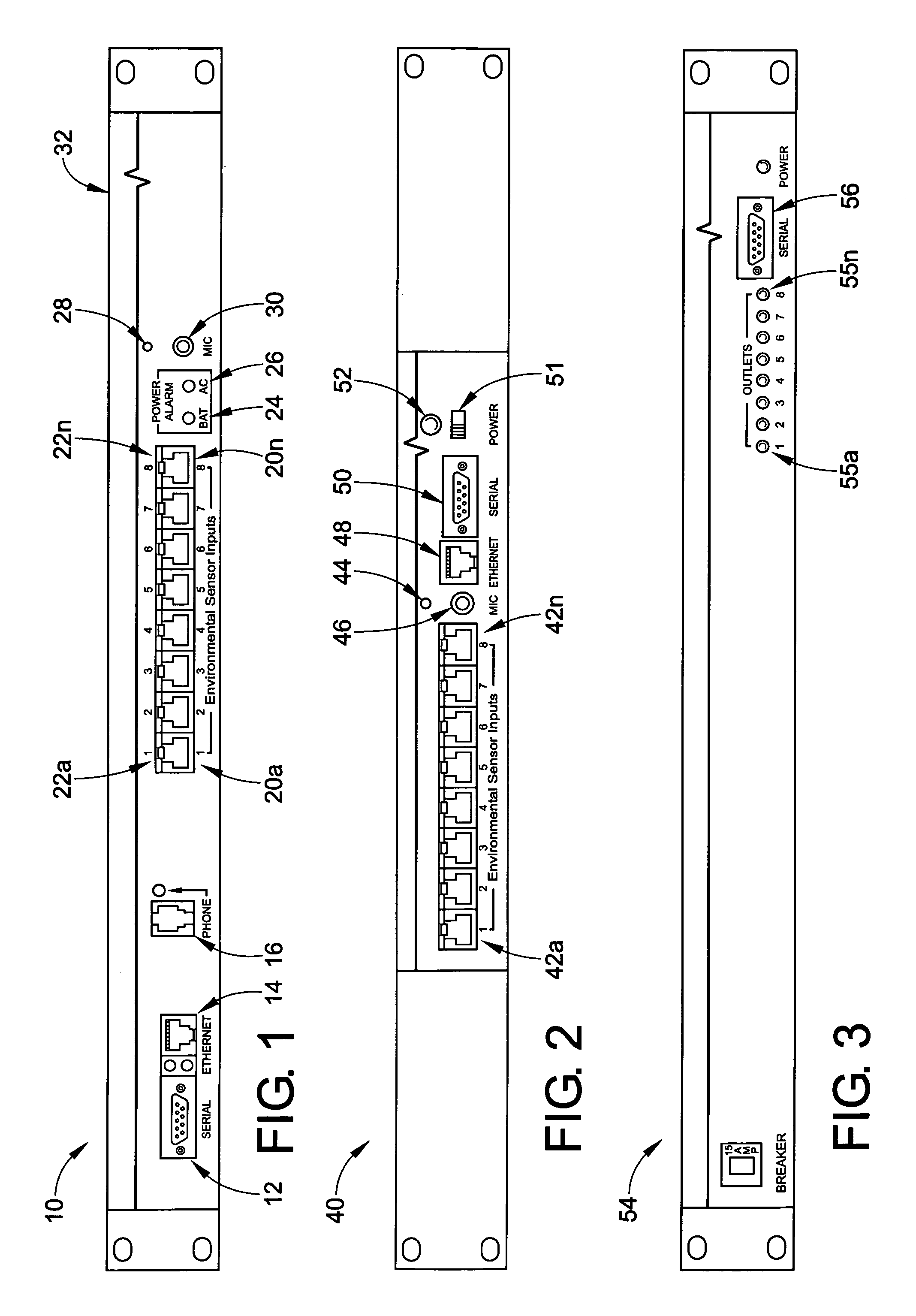
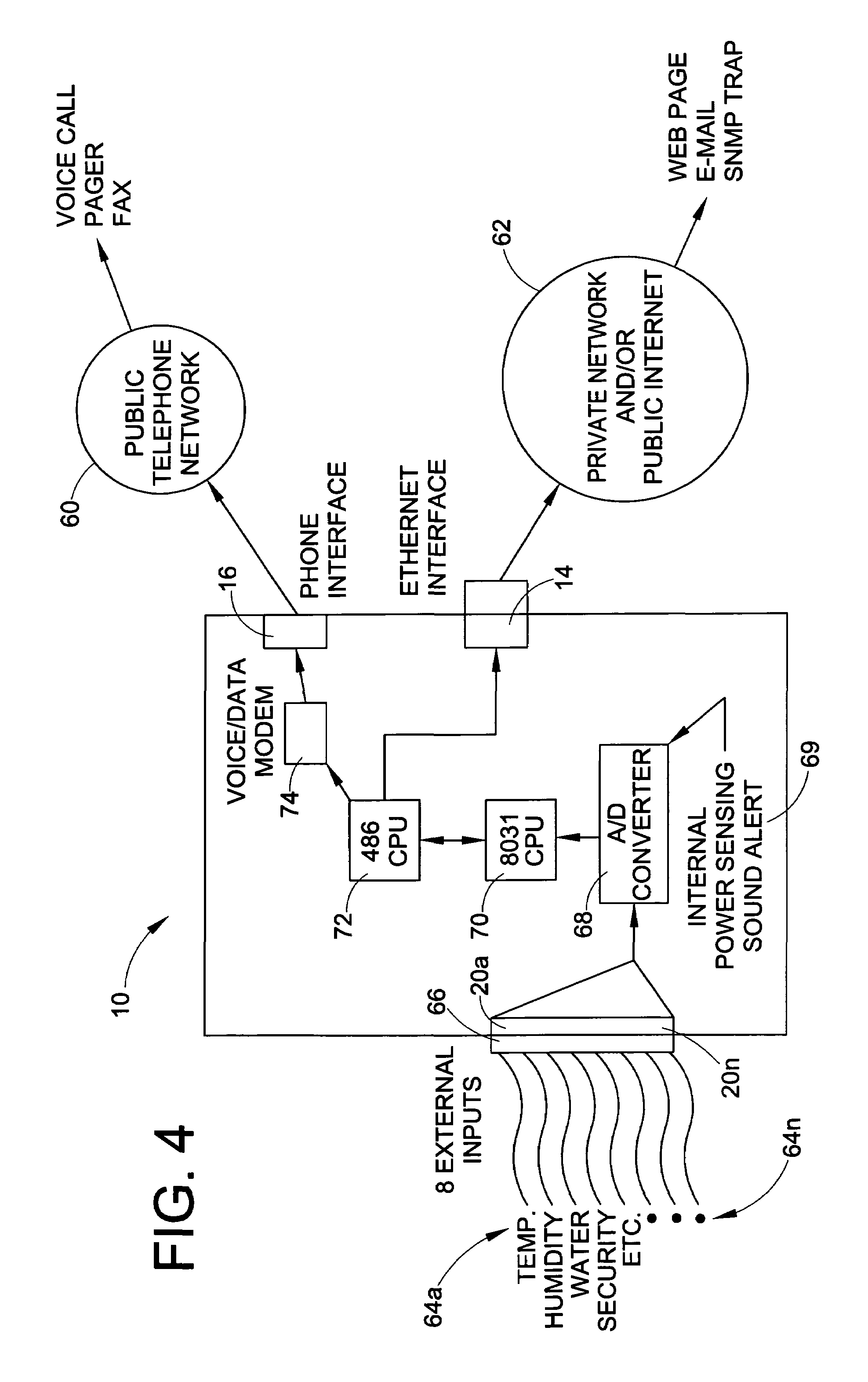
Environmental and security monitoring system with flexible alarm notification and status capability
A monitoring system includes a host having a plurality of sensor inputs for connection to sensors. A converter is designed to receive input signals from the sensor input and to convert the input signals from the sensors into digital signals. A processing system is configured to receive the digital signals and to generate alarm signals in response to selected ones of the received digital signals. An internally integrated voice / data modem is in operative association with the processing system. A phone connector is placed in operative association with the voice / data modem, to act as a port for transmission of the alarms to an external telephone network. A network connector is in operative association with the processing system and is designed to receive data in the form of alarms from the processing system and to act as a port for transmission of the alarm data to data network. The alarms are deliverable over phone lines as voice alarms, pager alarms and fax alarms, and are deliverable over a public or private network as e-mail alarms, SNMP trap alarms, and web page alarms. Remote status inquiries may be made via voice call and two-way e-mail operations.
Owner:PHONETICS
Analytic-based security with learning adaptability
ActiveUS10104102B1High attackReliable identificationMachine learningTransmissionRemedial actionSecurity monitoring
An analytics-based security monitoring system is adapted to receive data, such as in the form of event logs, from one or more network devices transferred through a computing environment, detect a plurality of behavioral characteristics from the received event logs, identify behavioral fragments composed of related behavioral characteristics, and identify an attack by correlating the behavioral fragments against patterns of known malicious attacks. The analytics-based security monitoring system may then perform a learning process to enhance further detection of attacks and perform one or more remedial actions when an attack is identified.
Owner:FIREEYE SECURITY HLDG US LLC +1
Video Motion Detection Method and Alert Management
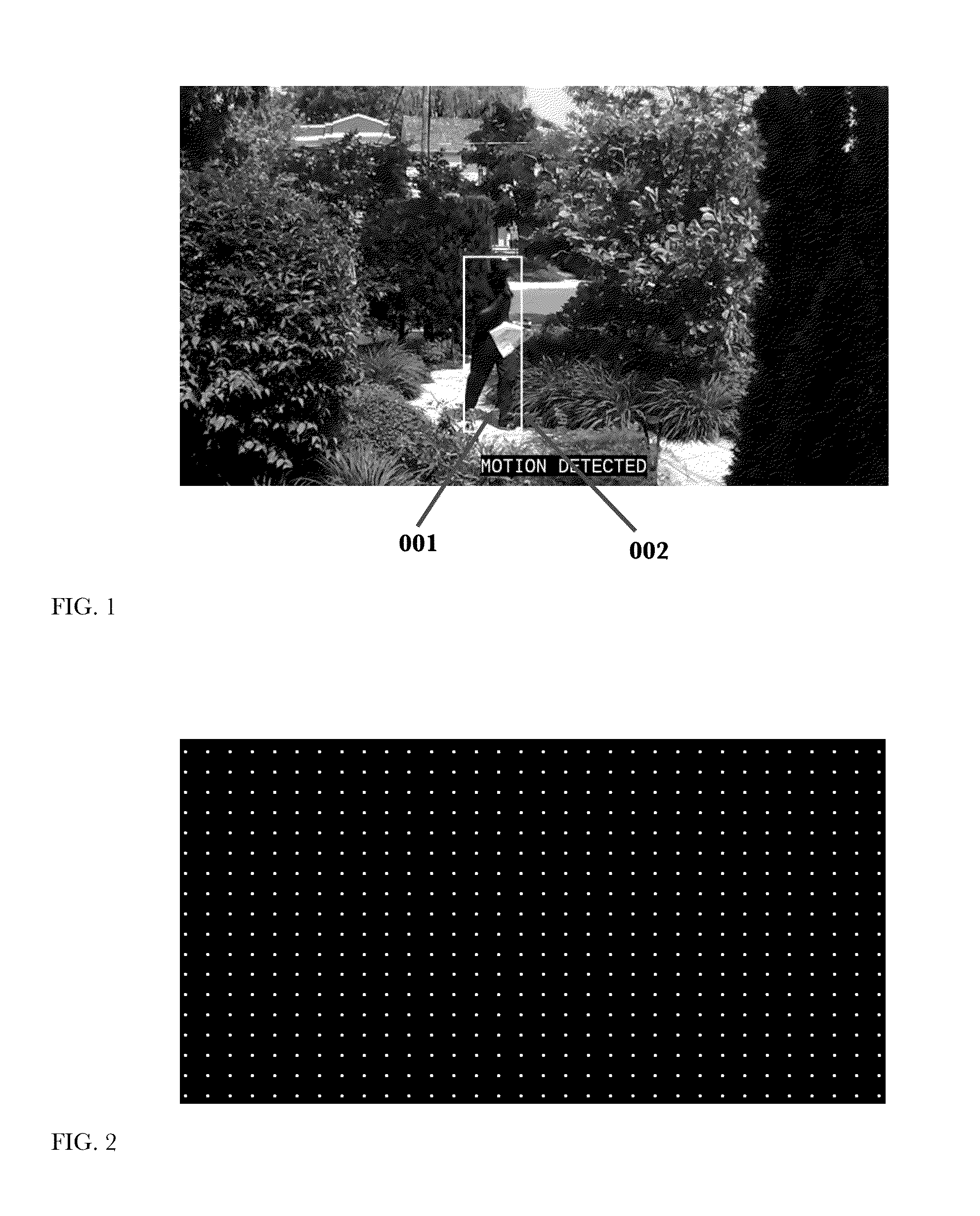
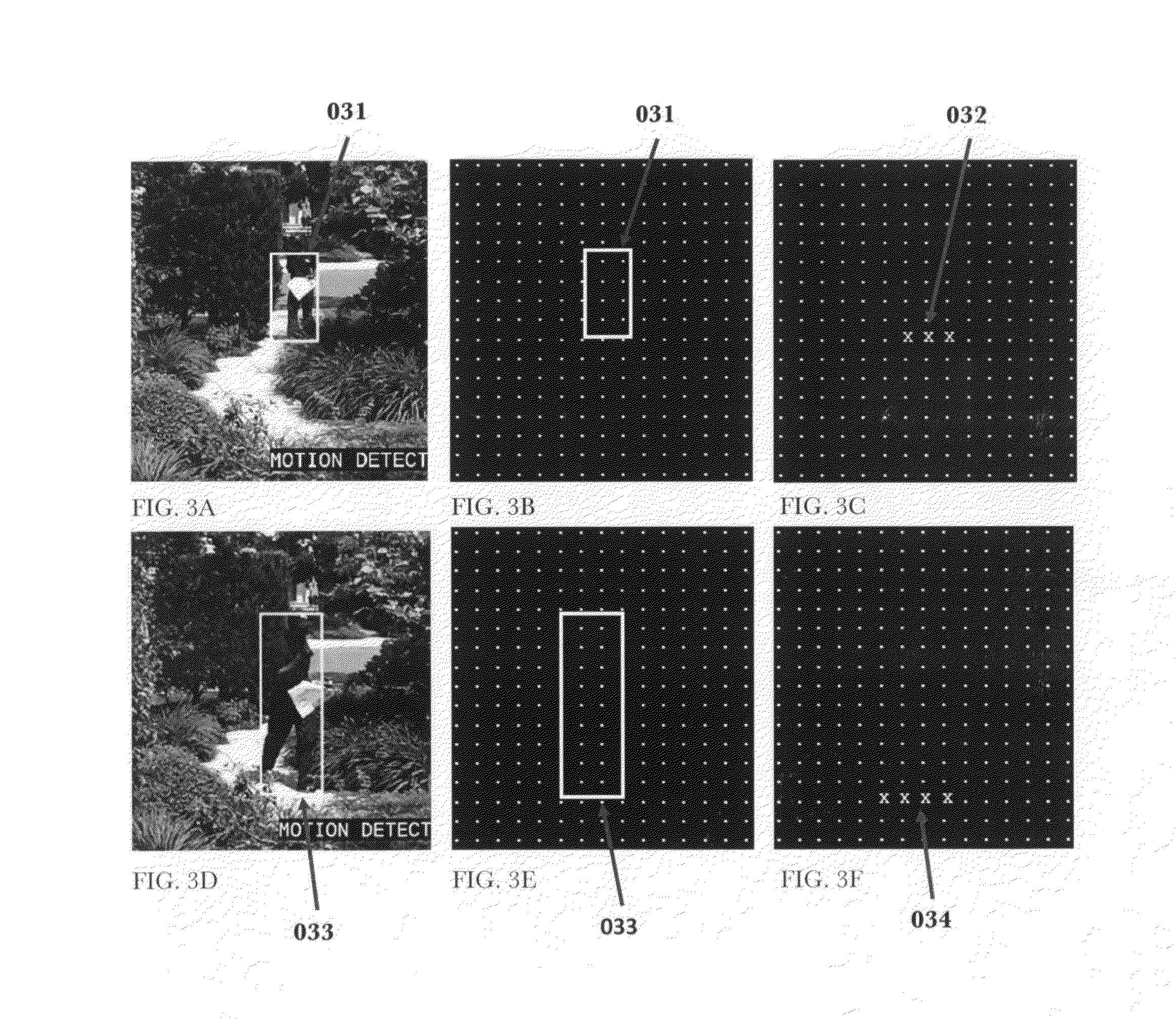
InactiveUS20160042621A1Reduce in quantityImprove abilitiesImage enhancementTelevision system detailsMathematical modelComputer graphics (images)
This invention describes a method and apparatus for security monitoring with a video camera. A mathematical model consisting of an array of cells, or learning map, is used to describe the motion of any object(s) detected by the camera. When an object(s) is detected, its positional location(s) for a period of time, or motion event, is recorded in a learning map. This learning map is then compared to a reference learning map where the camera determines whether to alert the user or not that an object of interest was detected. After viewing the video of the motion event, the user provides feedback that impacts how the reference learning map is updated by information in the motion event learning map. Through this user feedback mechanism, the camera learns to more accurately determine whether or not to alert the user about future motion events, thus reducing the number of false alarms.
Owner:HOGG WILLIAM DAYLESFORD +1
Cloud based security monitoring using unsupervised pattern recognition and deep learning
Provided are systems and methods for a cloud security system that learns patterns of user behavior and uses the patterns to detect anomalous behavior in a network. Techniques discussed herein include obtaining activity data from a service provider system. The activity data describes actions performed during use of a cloud service over a period of time. A pattern corresponding to a series of actions performed over a subset of time can be identified. The pattern can be added a model associated with the cloud service. The model represents usage of the cloud service by the one or more users. Additional activity data can be obtained from the service provider system. Using the model, a set of actions can be identified in the additional activity data that do not correspond to the model. The set of actions and an indicator that identifies the set of actions as anomalous can be output.
Owner:ORACLE INT CORP
Homeland intelligence systems technology "h-list" and battlefield apparatus
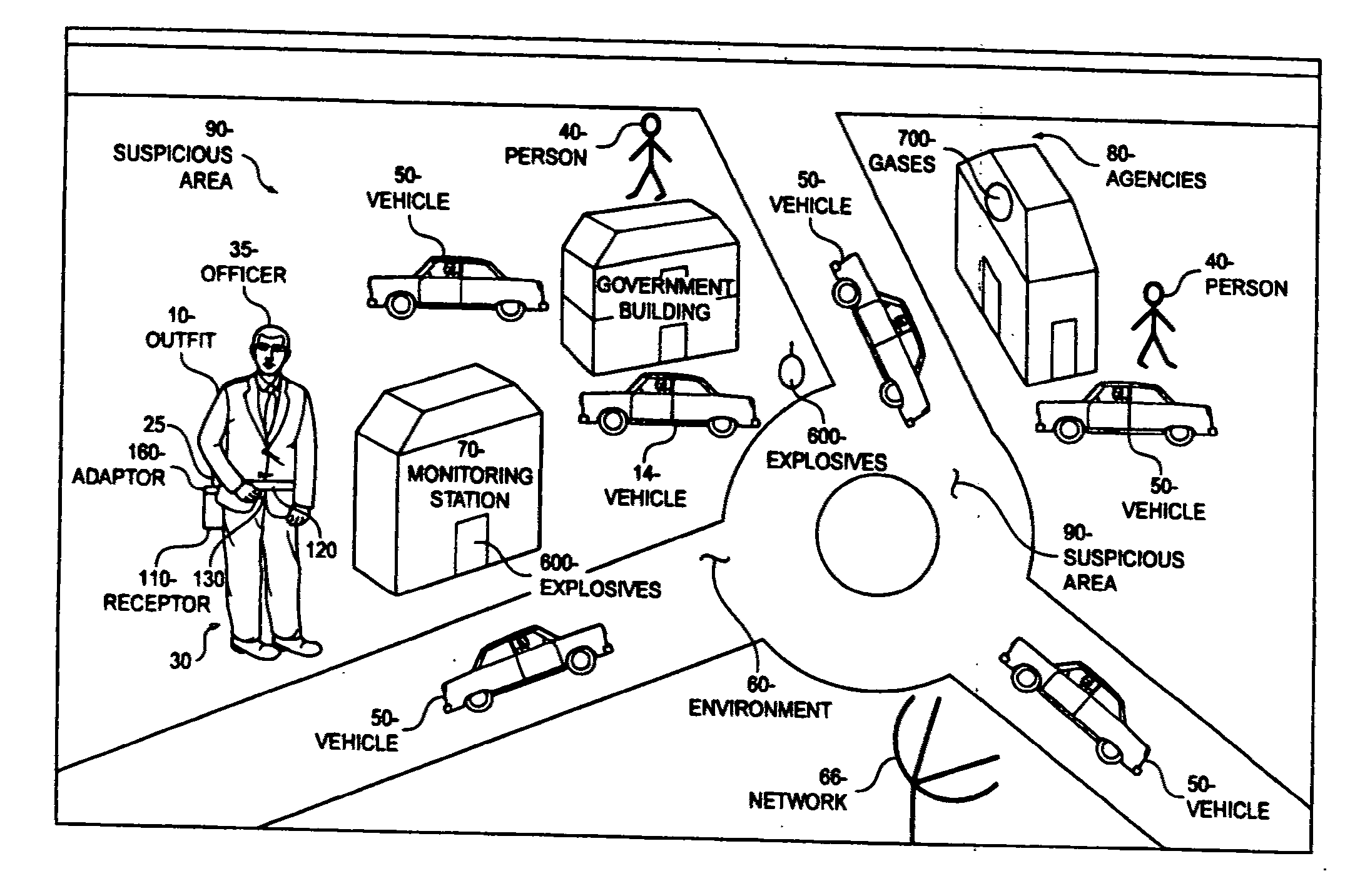
InactiveUS20120176237A1Improve adhesionMaintain good propertiesDiagnostic recording/measuringCamouflage devicesEngineeringSecurity monitoring
Homeland Intelligence Systems Technology “H-LIST” and battlefield apparatus comprises nano-sensors embedded in a silicon substrate and etched / fused in a micro-fibered material. The silicon substrate is alloyed with miniaturized steel responsive to weapons, preventing bullet penetration and providing effective detection platform on an outfit. The outfit is operable for monitoring suspicious terrorist activities and for tracking biological and chemical gases, and explosives, including weapons of mass destruction and physiological conditions of personnel. Disclosed embodiments provide wearable detection apparatus comprising plurality sensors on an outfit configured to be worn by military personnel, an officer, a security officer, a bus driver, hostesses, Doctors, civil establishment hospital patients and the like, for protection and for sensing deadly gases, explosives, and physiological conditions in a defined area. A receptor is operatively configured and worn proximate to the outfit responsive to detection signals. The receptor is communicatively connected to the sensors and operable for receiving / analyzing detection signal communications wirelessly indicative of the presence of a sensed agent, whereby detected signals are transported wirelessly to a central security monitoring station, providing communications to first responders. The communications could be reachable to backup security personnel or agents, prompting them to respond to the vicinity of the detection. The sensors are multifunctional and coded to recognize wavelike pattern of gases and explosives traveling through the wave. Embodiments provide the outfit and the receptor being operable to process the portion of the detection signal to determine the detection type and / or whether there is a concealed object by conducting a test in which a first characteristic of a first dielectric constant associated with a person is determined, and a second characteristic of a second dielectric constant associated with the concealed object and or weapons of mass destruction is determined to expedite data transmission and communication to first responders.
Owner:TABE JOSEPH AKWO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com