Patents
Literature
7284 results about "Modem device" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
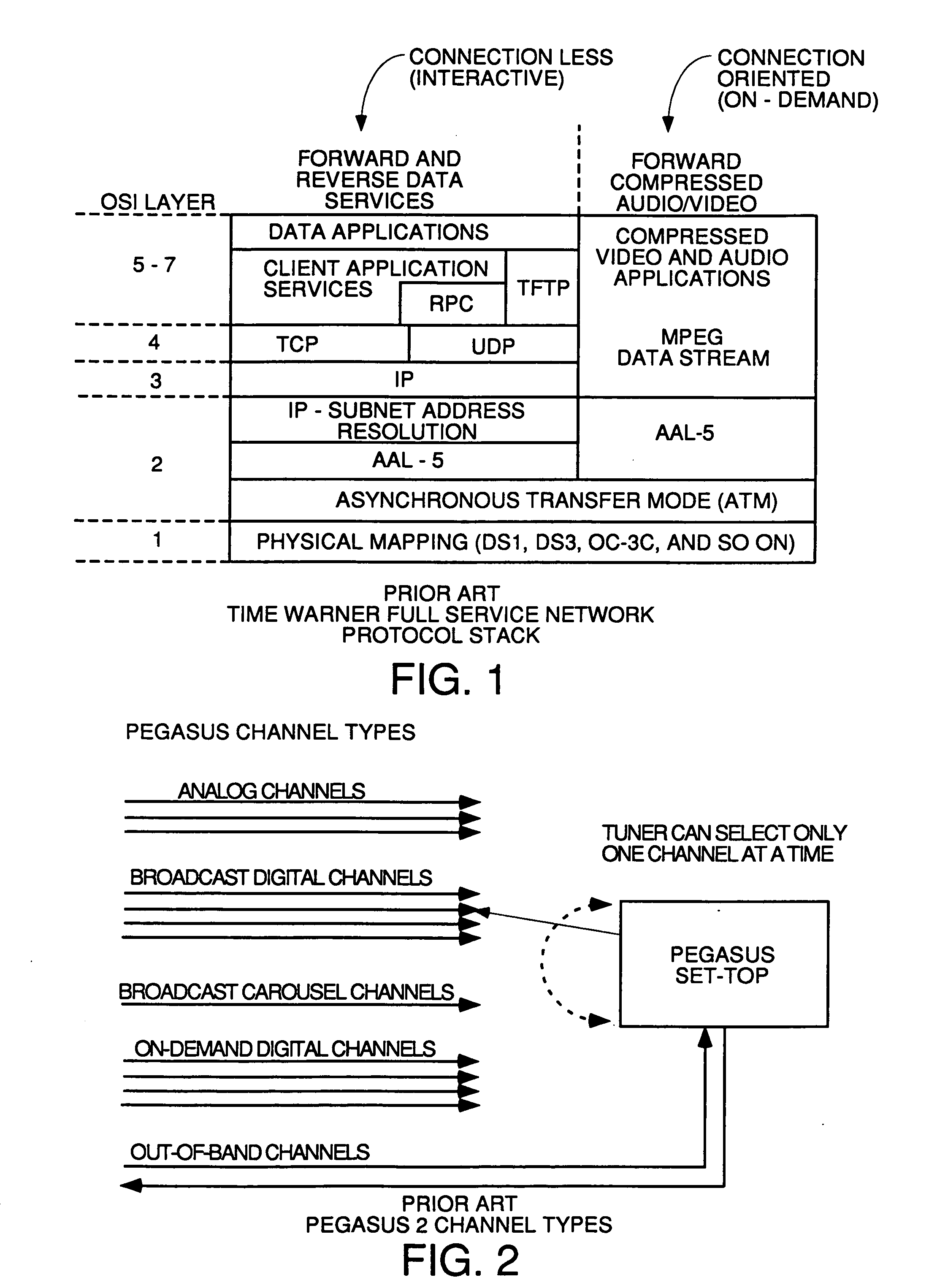
A modem (modulator–demodulator) is a network hardware device that modulates one or more carrier wave signals to encode digital information for transmission and demodulates signals to decode the transmitted information. The goal is to produce a signal that can be transmitted easily and decoded to reproduce the original digital data.
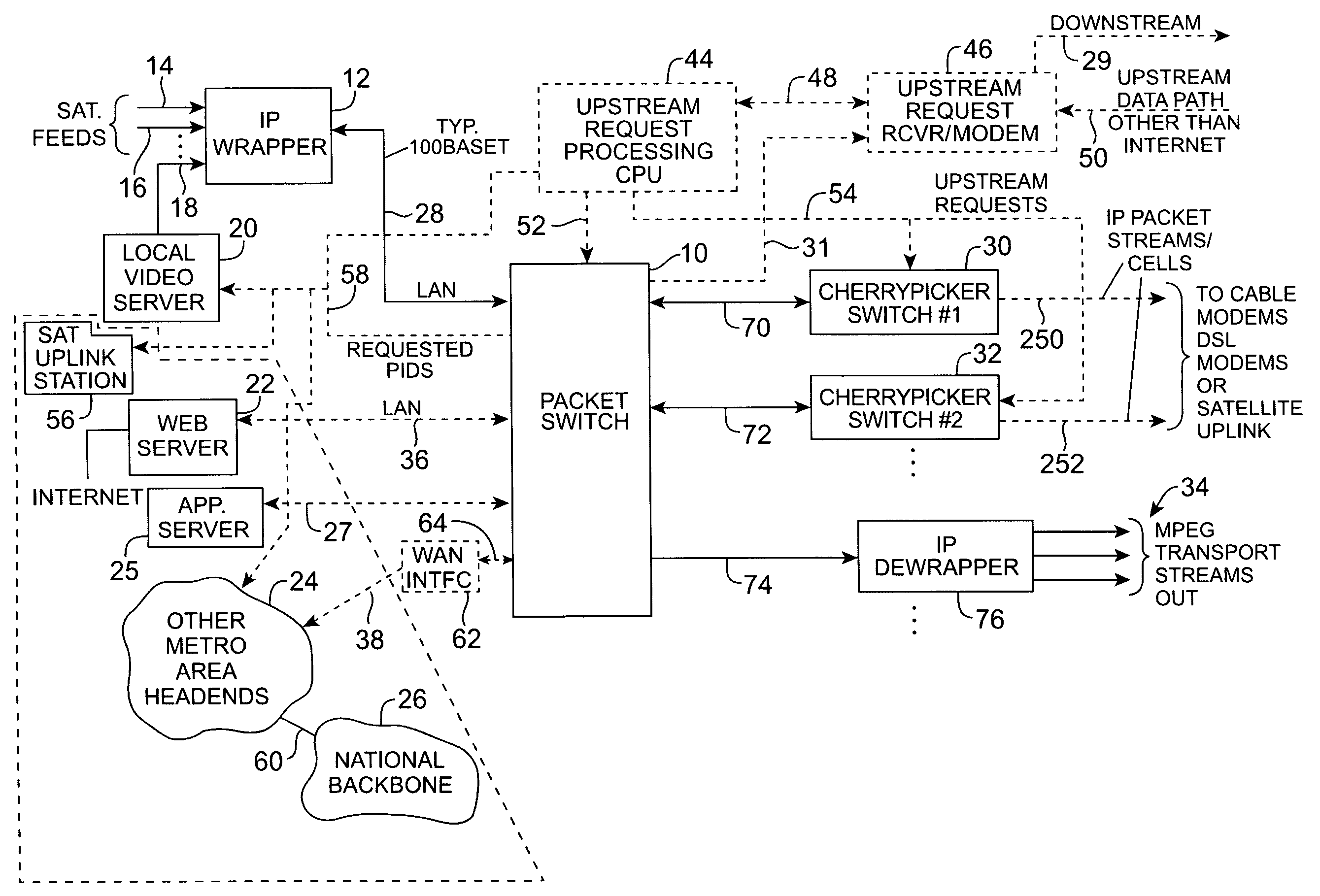
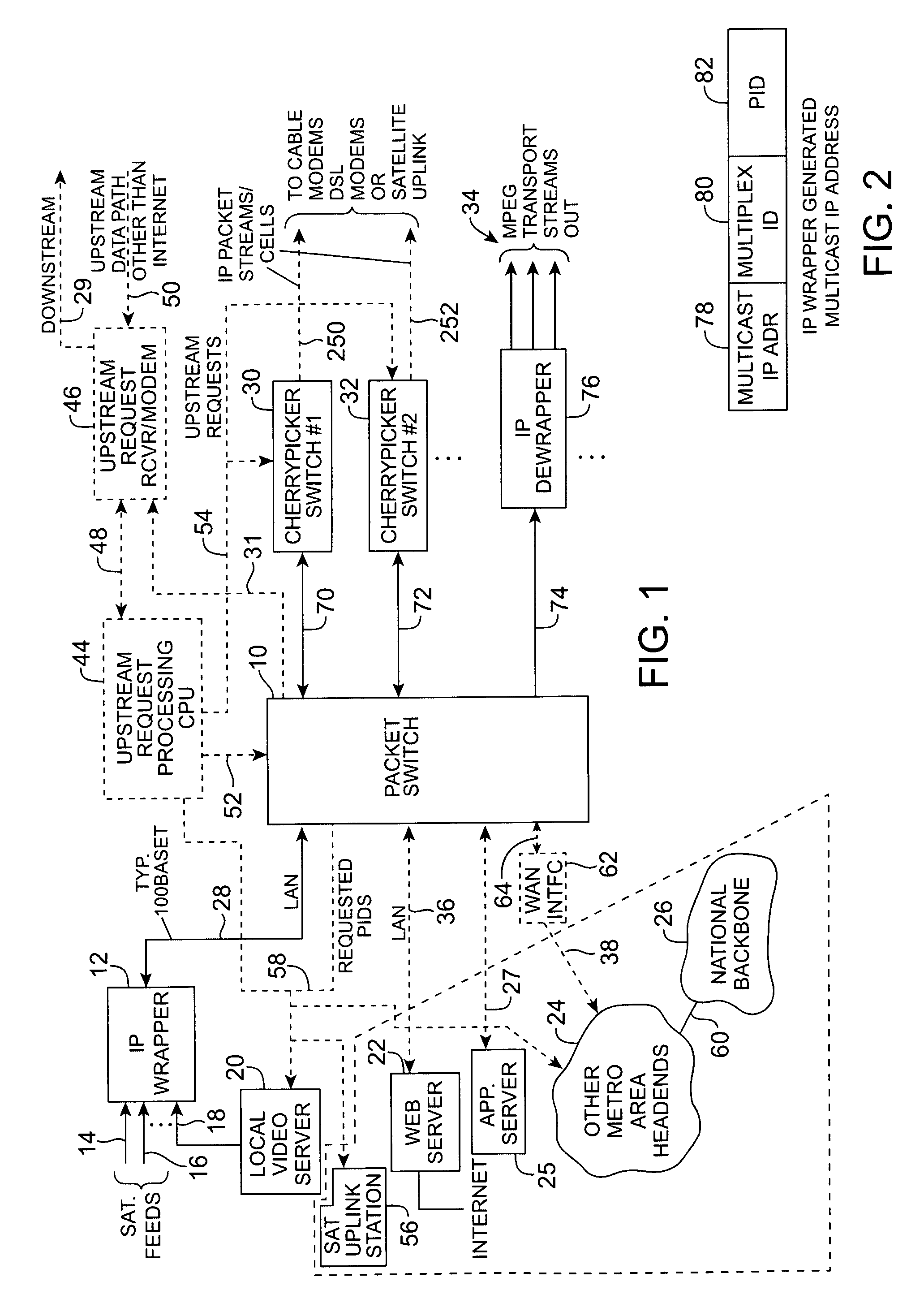
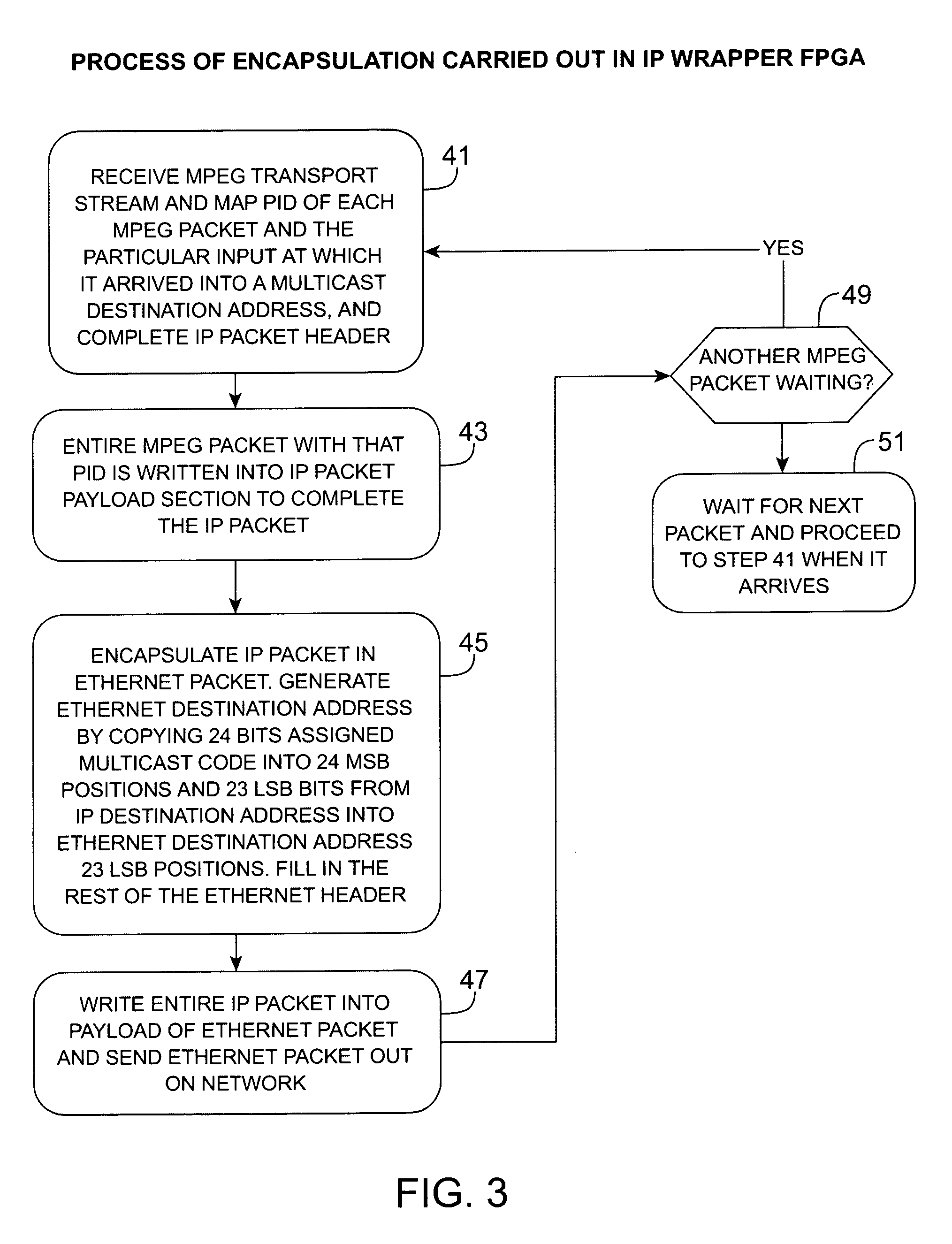
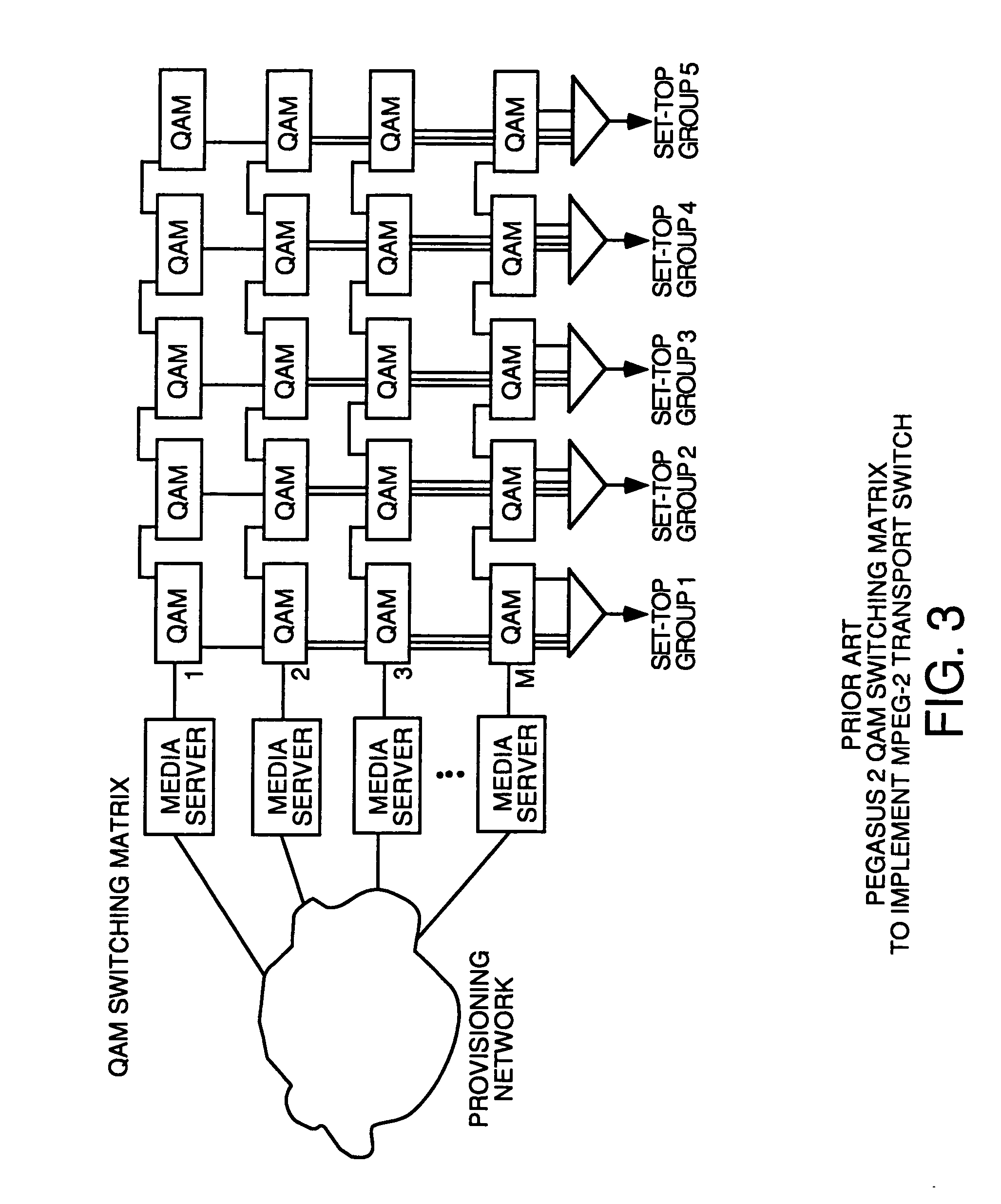
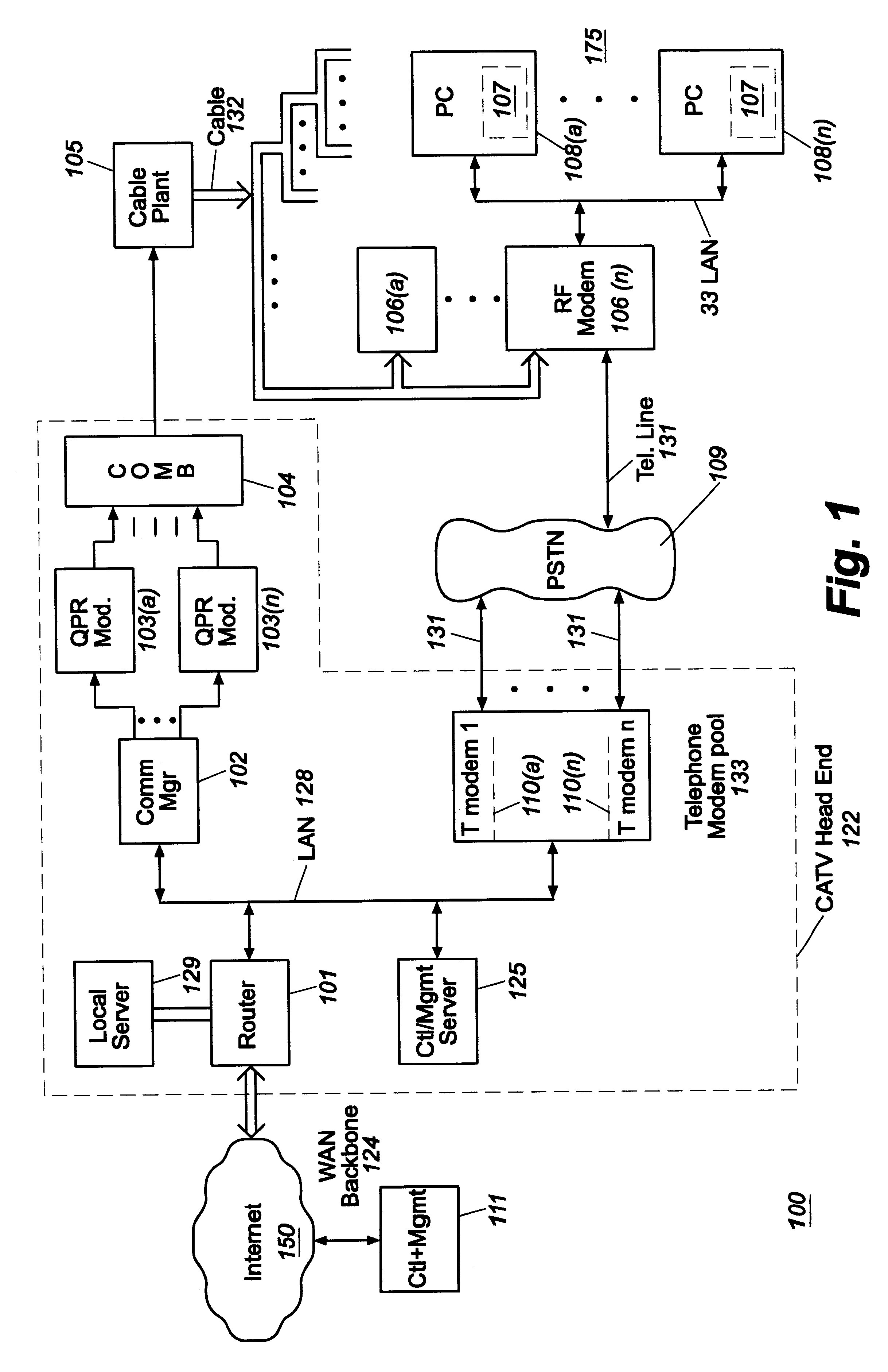
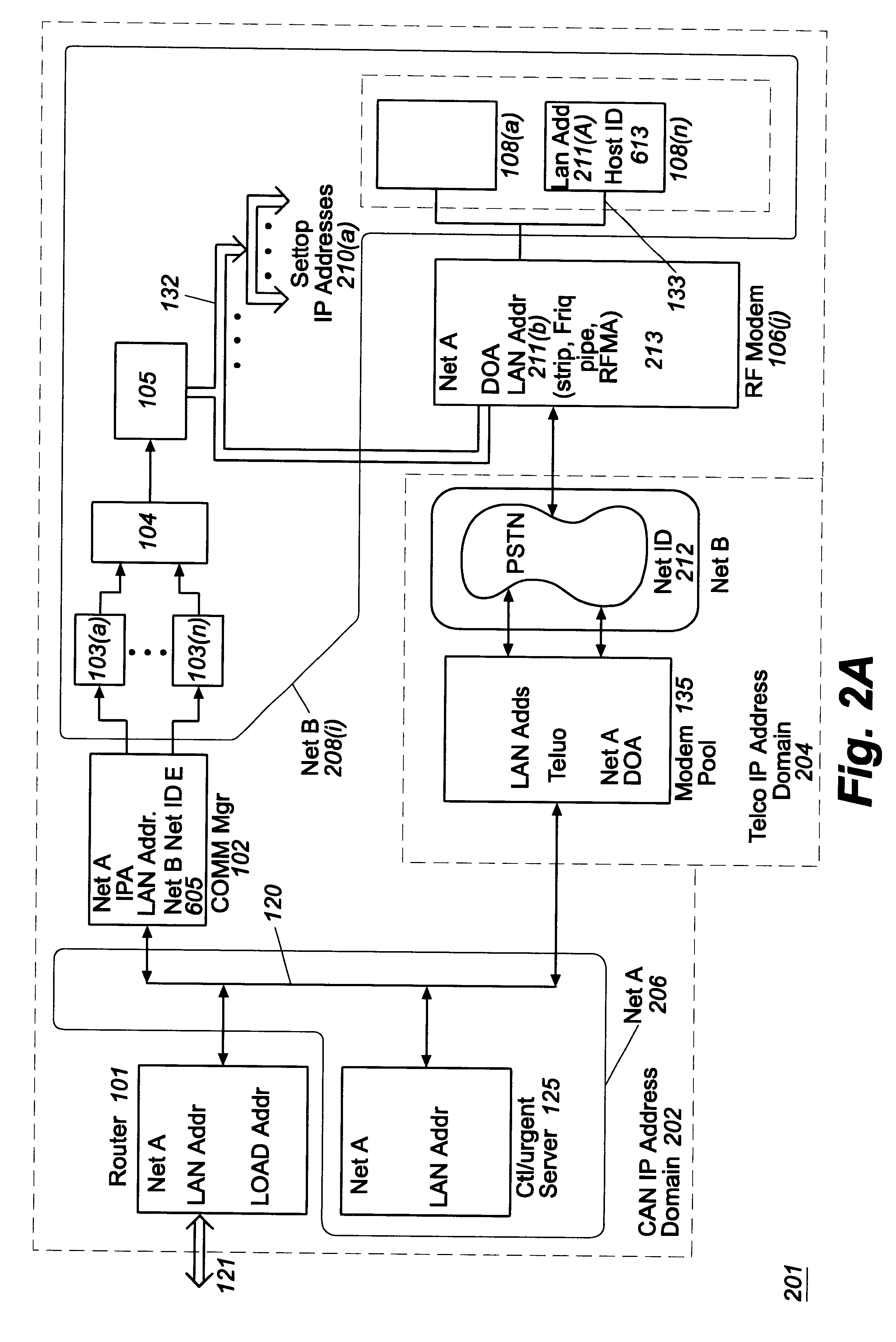
Headend cherrypicker multiplexer with switched front end
InactiveUS7039048B1Low costEasily scaledBroadband local area networksTime-division multiplexMPEG transport streamModem device
A headend or central office or satellite uplink facility for receiving upstream video-on-demand requests and MPEG transport streams containing video program data and packetizing said video data into TCP / IP or UDP / IP packets and LAN packets and routing them through a switch to one or more cherrypicker multiplexers. Each cherrypicker multiplexer receives LAN packets, depacketizes the MPEG data, partially or fully decompresses the data and recompresses the data to another smaller bandwidth, and repacketizes the data into MPEG packets or TCP / IP or UDP / IP packets. The repacketized TCP / IP or UDP / IP packets are transmitted directly to the customer as TCP / IP or UDP / IP packet data. MPEG packets generated by the cherrypicker multiplexer are, optionally, encapsulated in LAN packets addressed to an IP dewrapper circuit. There, they are depacketized back to MPEG packets and transmitted to the appropriate transmitter or modem for transmitting to a customer. Internet data and data from application servers, referred to as iData, can also be transmitted to customers through the cherrypicker multiplexers or a downstream modem, and upstream iData can be received through the modem.
Owner:GOOGLE TECH HLDG LLC
Systems, devices, agents and methods for monitoring and automatic reboot and restoration of computers, local area networks, wireless access points, modems and other hardware
ActiveUS20090013210A1Data switching networksRedundant operation error correctionDomain nameFully qualified domain name
An embodiment of the invention is a client on a local area network that periodically and automatically evaluates its physical connectivity with the local area network, exercises local-network services such as DHCP, and verifies Internet connectivity and function by pinging one or more numerically specified IP addresses and by pinging one or more IP addresses specified by an FQDN (Fully Qualified Domain Name) known to the assigned DNS servers. An embodiment of the invention may include a plurality of client elements monitoring one or more networks. Functionality according to embodiments of the invention can send notices, automatically initiate action, and otherwise assist in, among other things, remote monitoring and administration of networks, and particularly wireless networks.
Owner:SAND HLDG LLC
Rental/car-share vehicle access and management system and method
ActiveUS20130317693A1Reduce the time required for installationImprove reliabilityVehicle testingTicket-issuing apparatusMobile appsTablet computer
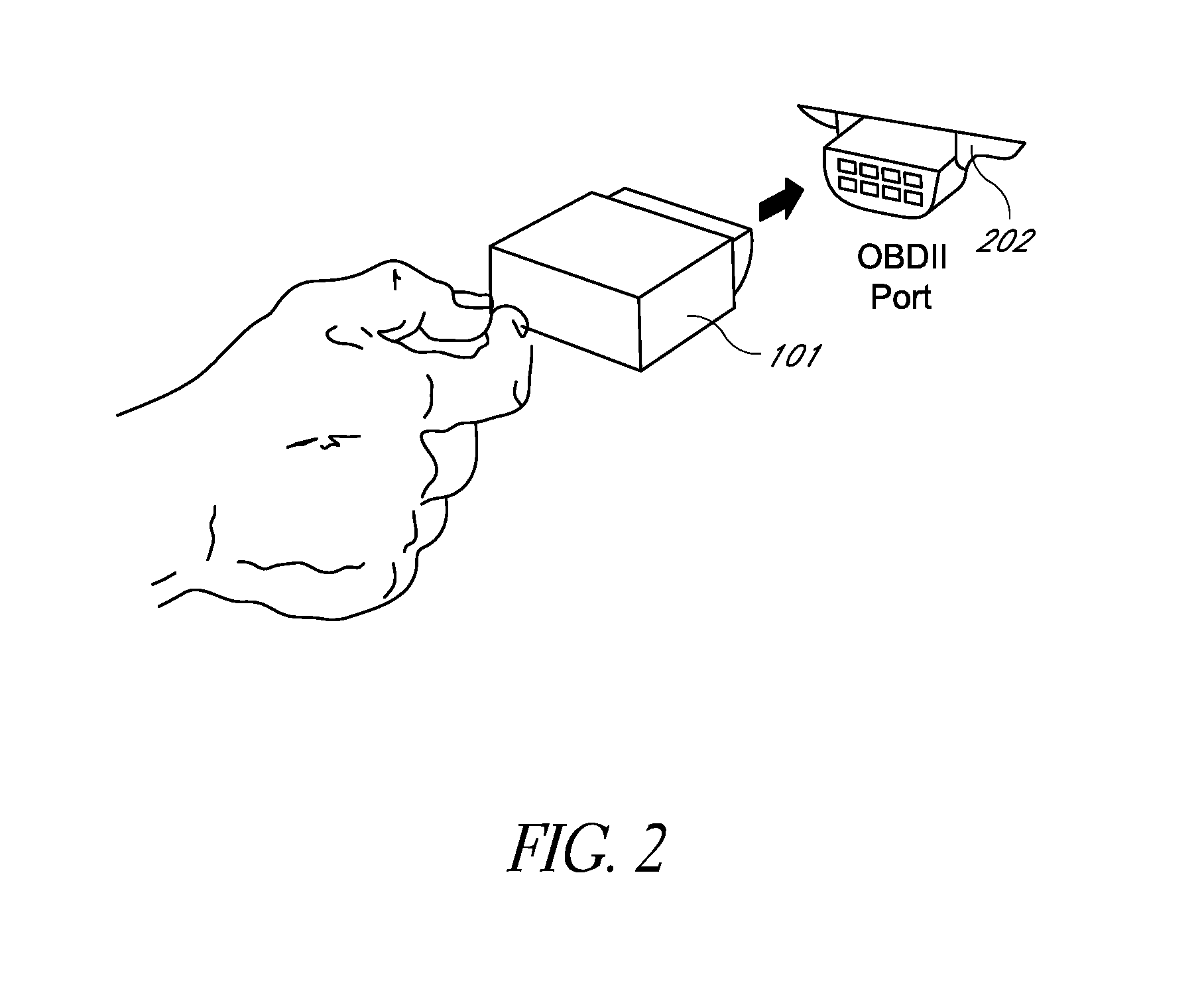
A rental / car-share (RCS) vehicle access and management system and method, in some embodiments, utilizes barcodes, QR codes (or NFC / RFID), GPS, and a mobile app coupled with a wireless network to enable customers to bypass the reservation desk and pickup and drop off reserved RCS vehicles using a mobile phone, tablet or laptop. The QR code, RFID, or NFC communication with the mobile application allows for identification of the vehicle by a mobile application, which, if authorized, can access the vehicle via a temporary access code issued by remote servers. The remote servers and / or mobile application communicates with a control module that plugs into the on-board diagnostics module of the rental / car-share (RCS) vehicle and includes a host processing unit with a processor, an accelerometer, data storage, a GPS with internal GPS antenna; a wireless modem with internal antenna, and CAN bus transceivers connected with the processor, and a USB programmable interface.
Owner:ENTERPRISE HOLDINGS
Programmable and expandable building automation and control system
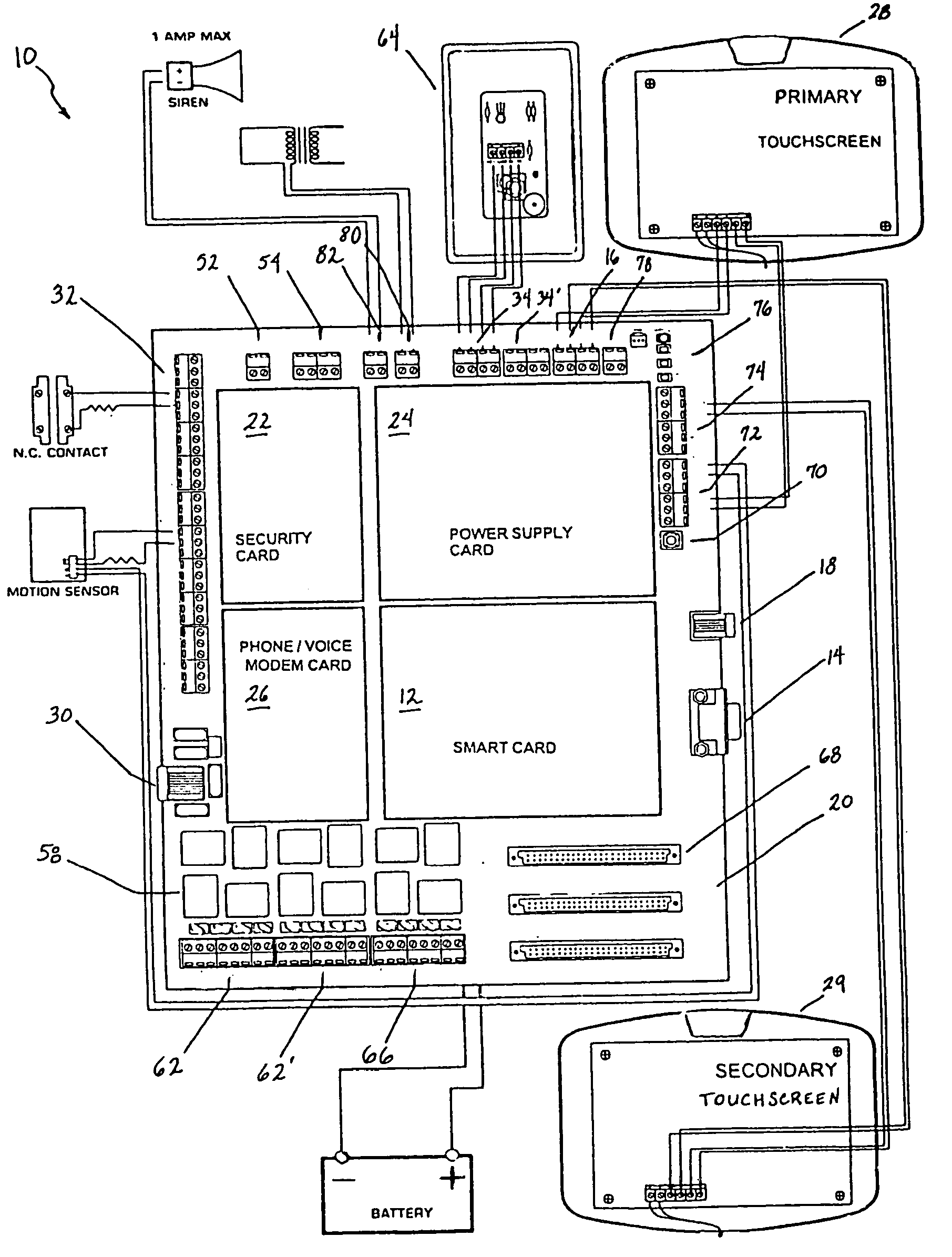
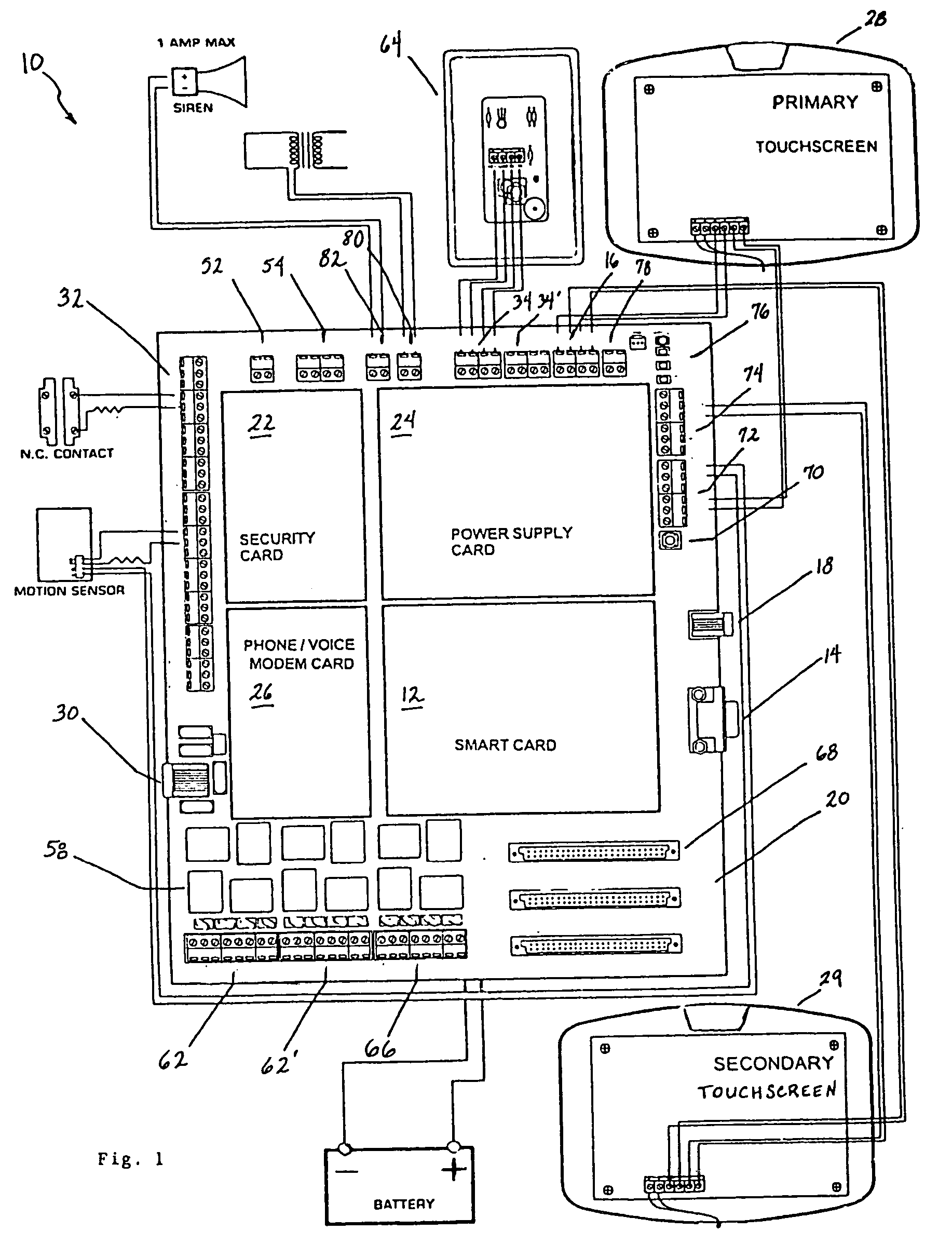
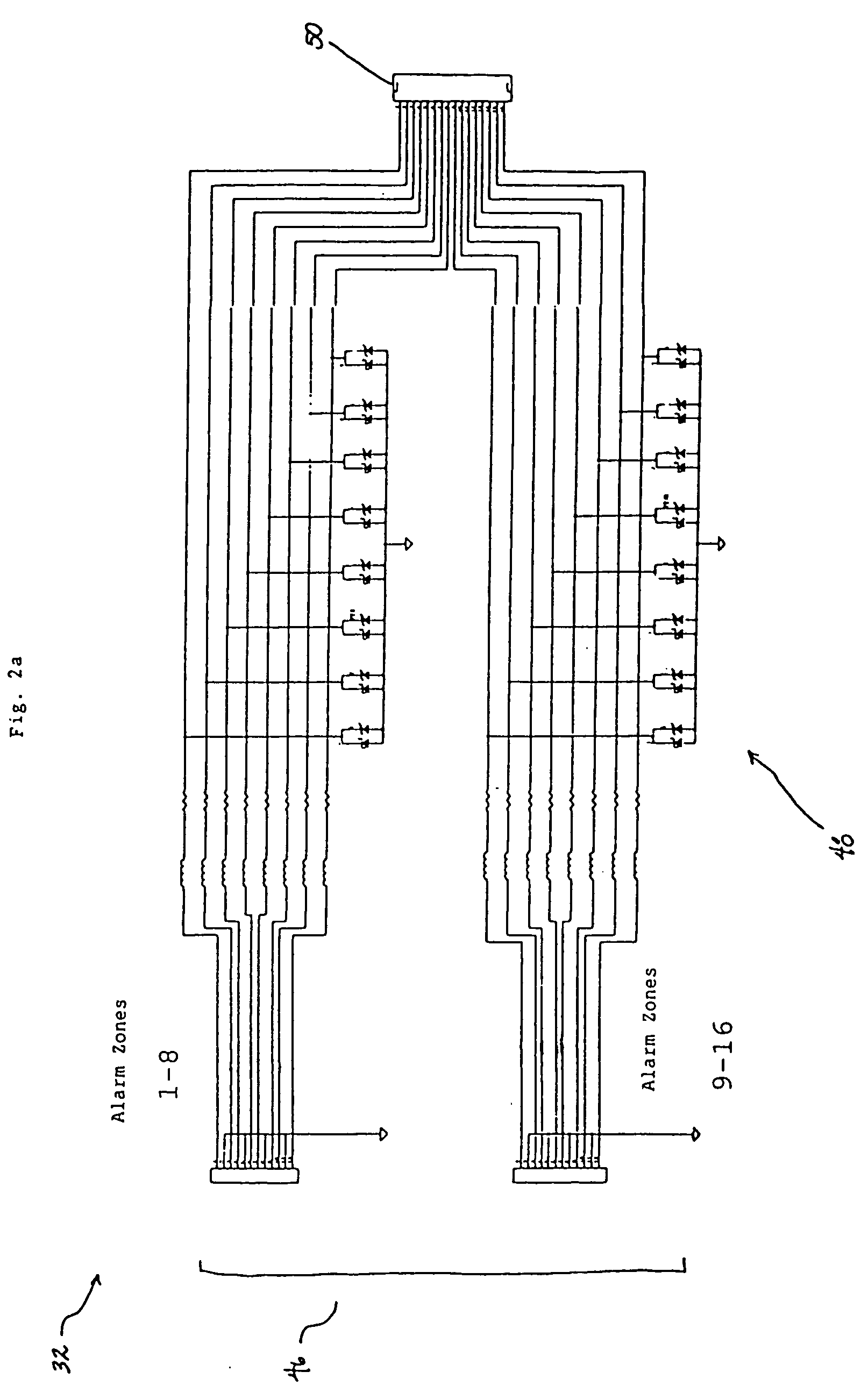
InactiveUS20050090915A1Readily modified and expanded and repairedReduces warranty and support costProgramme controlSampled-variable control systemsModem deviceSmart card
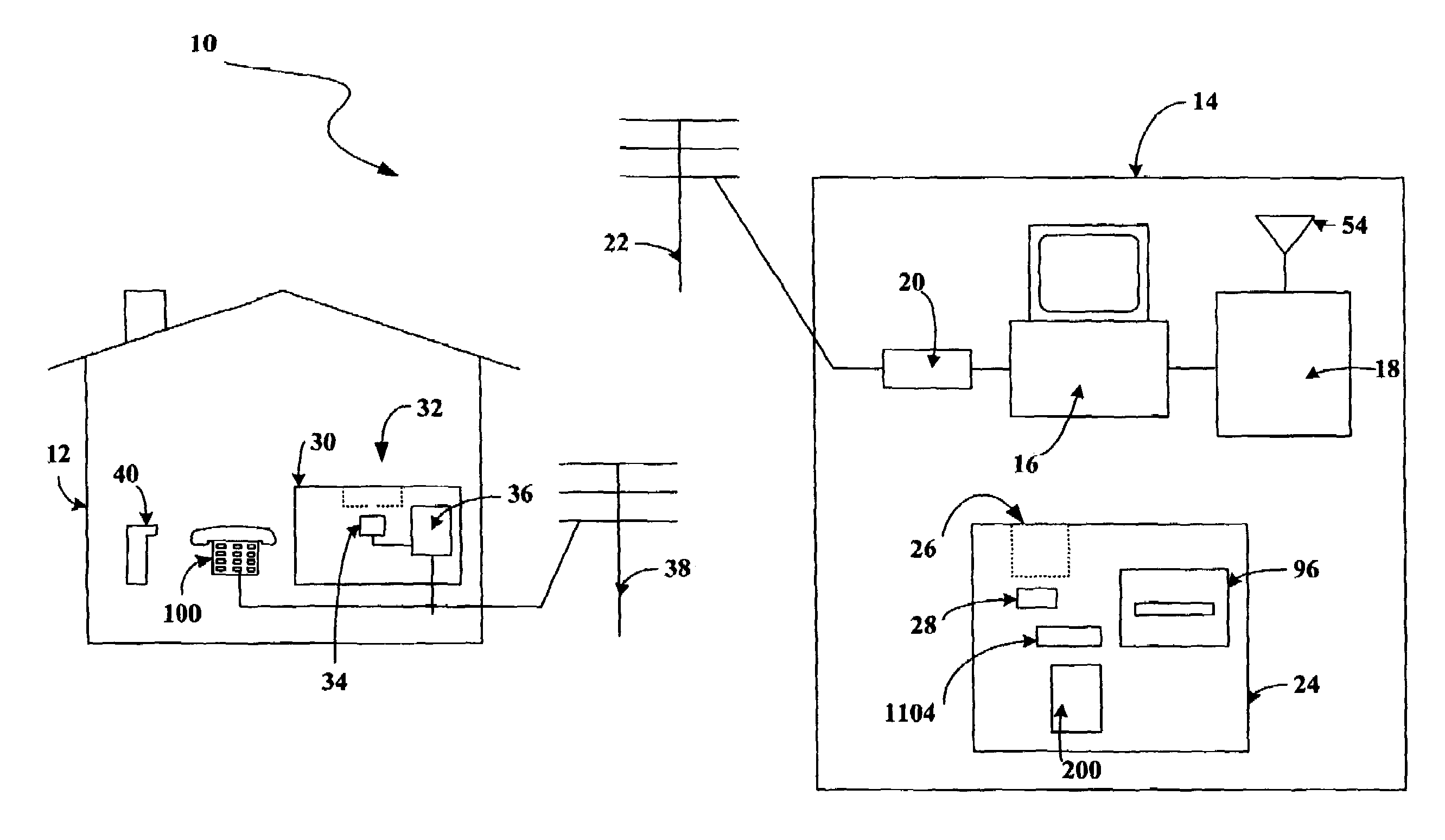
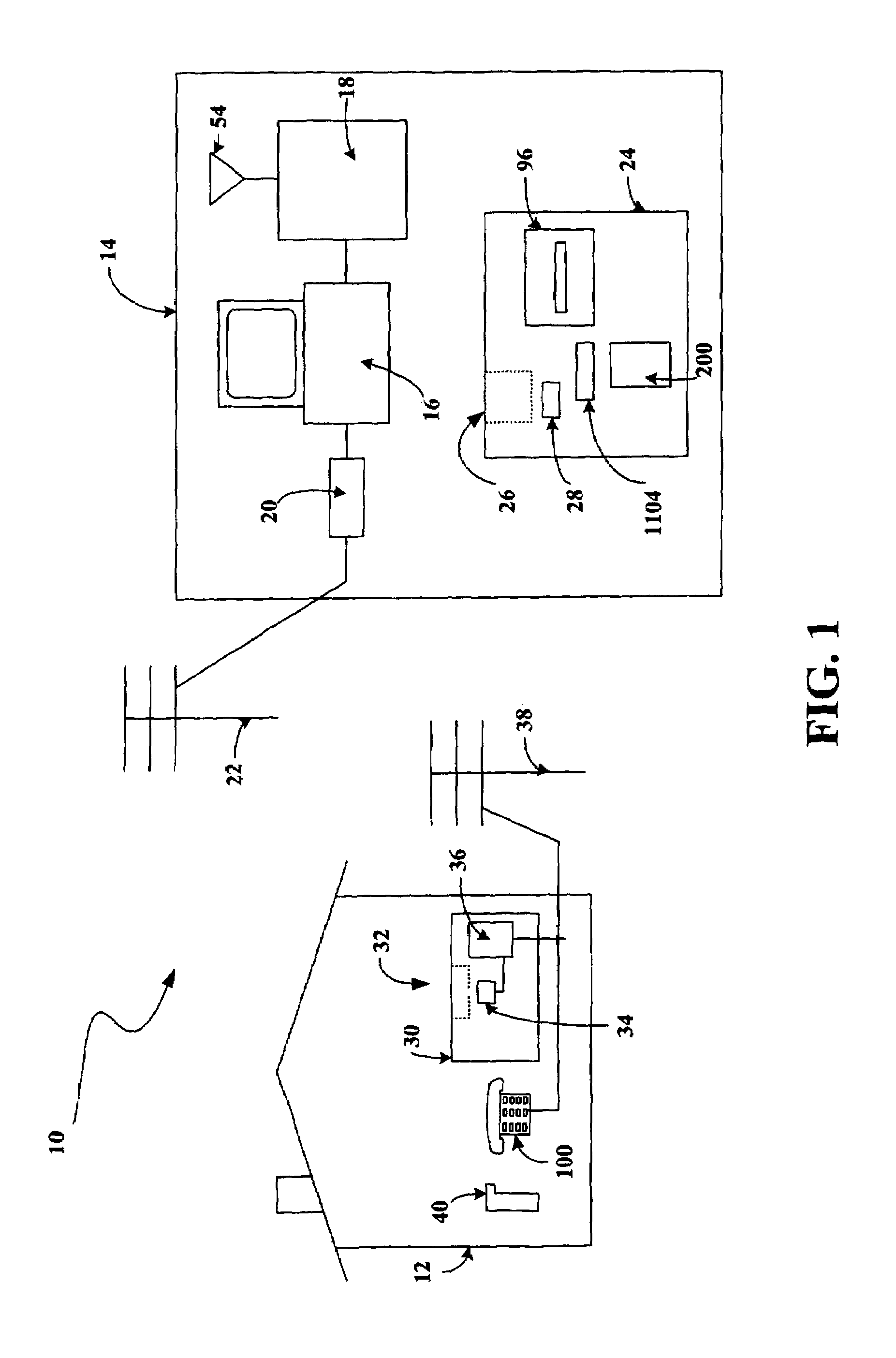
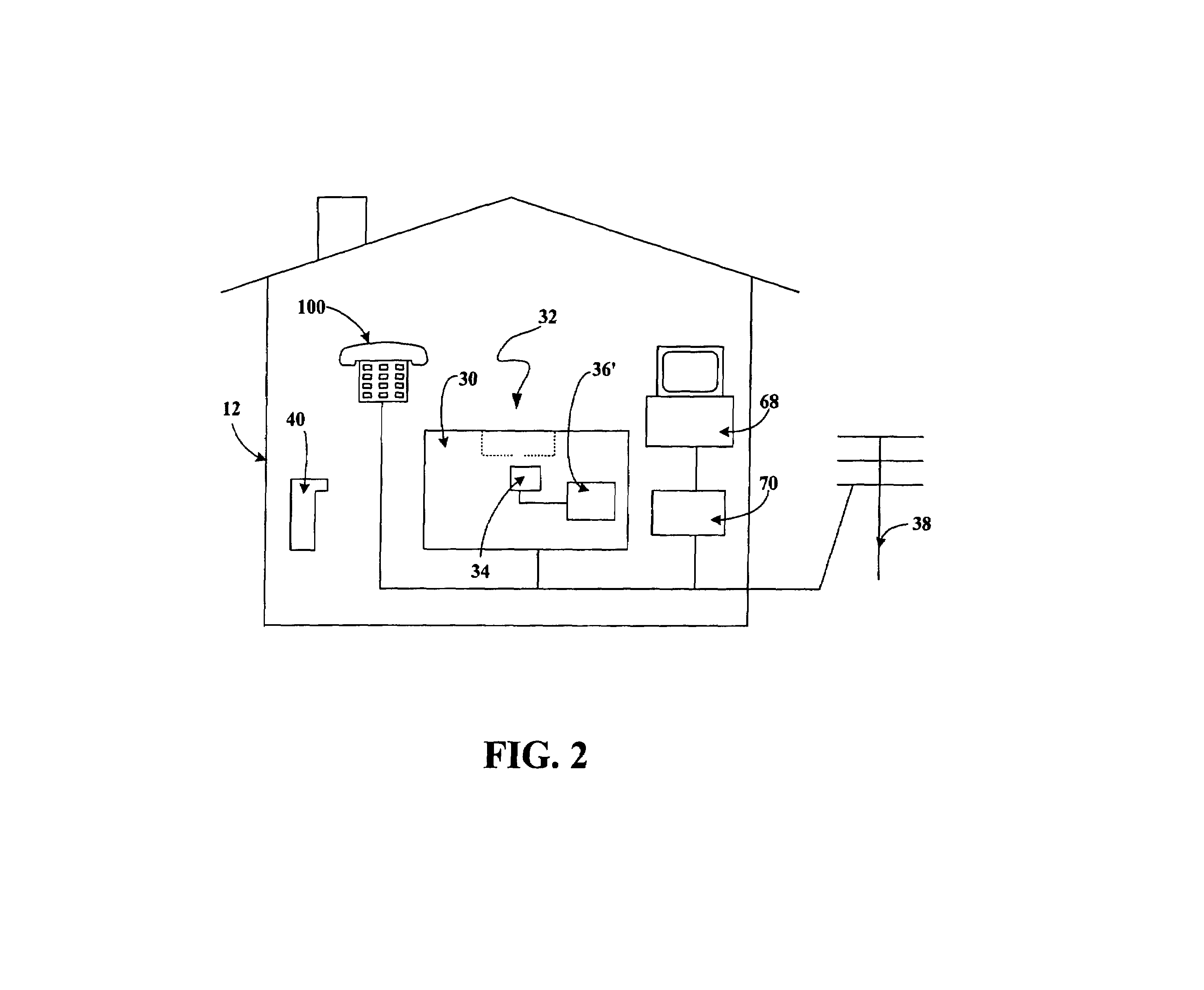
A programmable and expandable building automation and control system 10. A system platform supports interchangeable smart card 12, security card 22, power supply card 24, telephone / voice / modem card 26, HVAC relay control 62, auxiliary relay control 66, power 80, telephone interface 30, sensor analog inputs 32, smoke detector interface 54, siren / strobe output 82, tamper loop 52, protected peripheral power supply 72, switched peripheral power supply 74, PLC communication protocol interface 18, RS 232 communication interface 14, RS 485 communication interface 16, touchscreen user interface 28, and “smart” key interface 34 via “smart” key 104. In addition to touchscreen and smart key interface, user-interface with system 10 is accommodated via telephone, personal computer or personal digital assistant, or through infrared or radio frequency transmission.
Owner:SMART SYST TECH
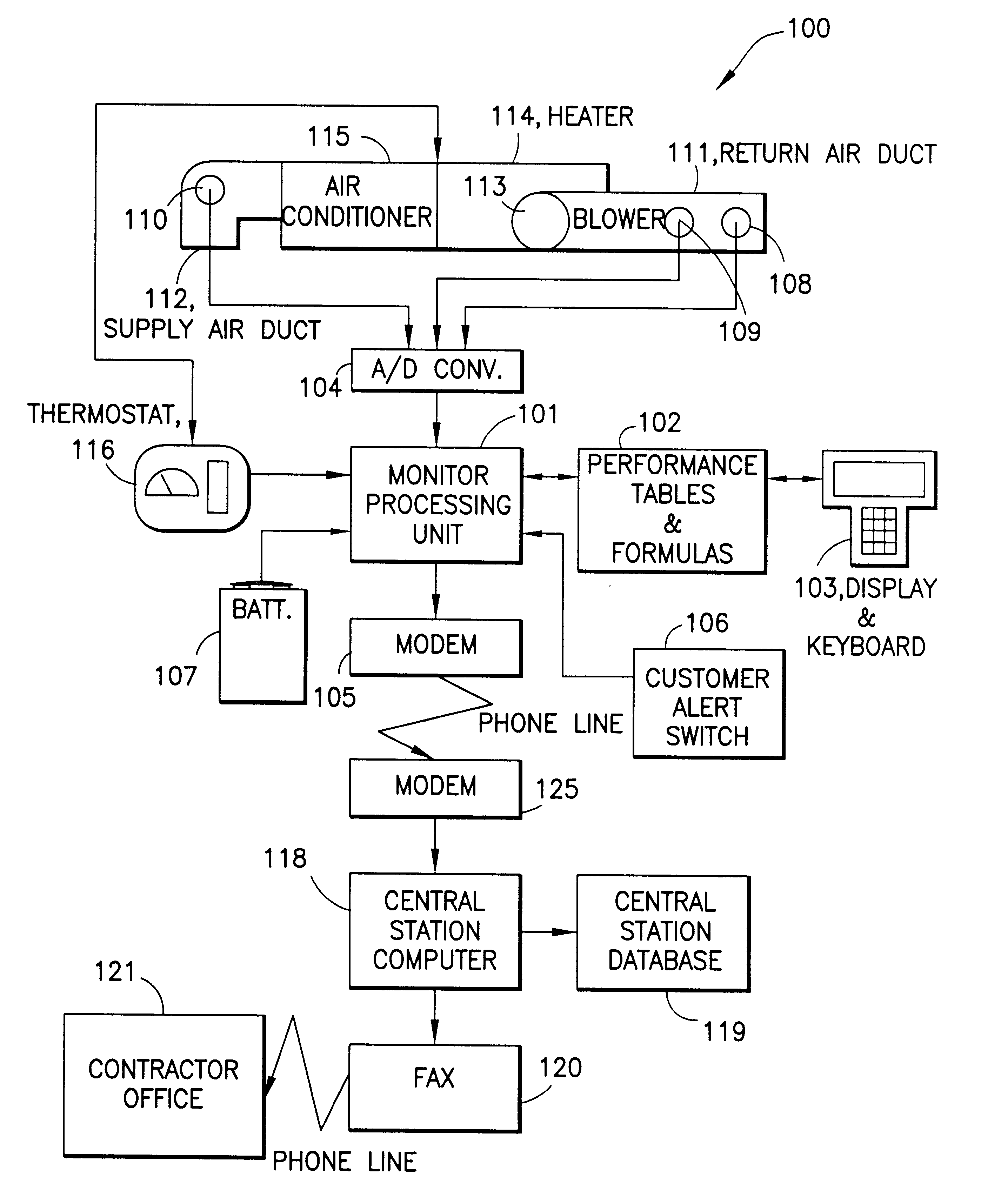
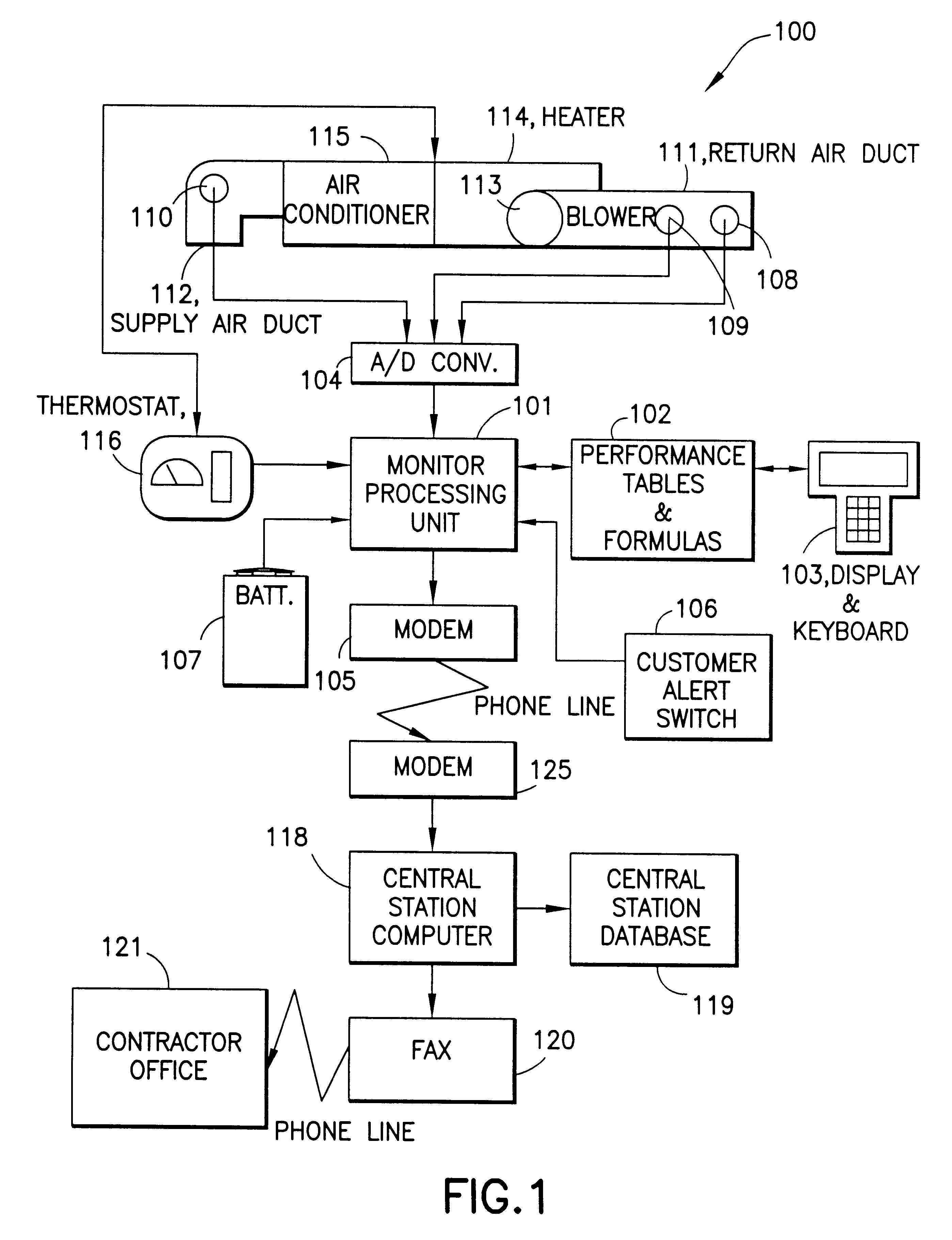
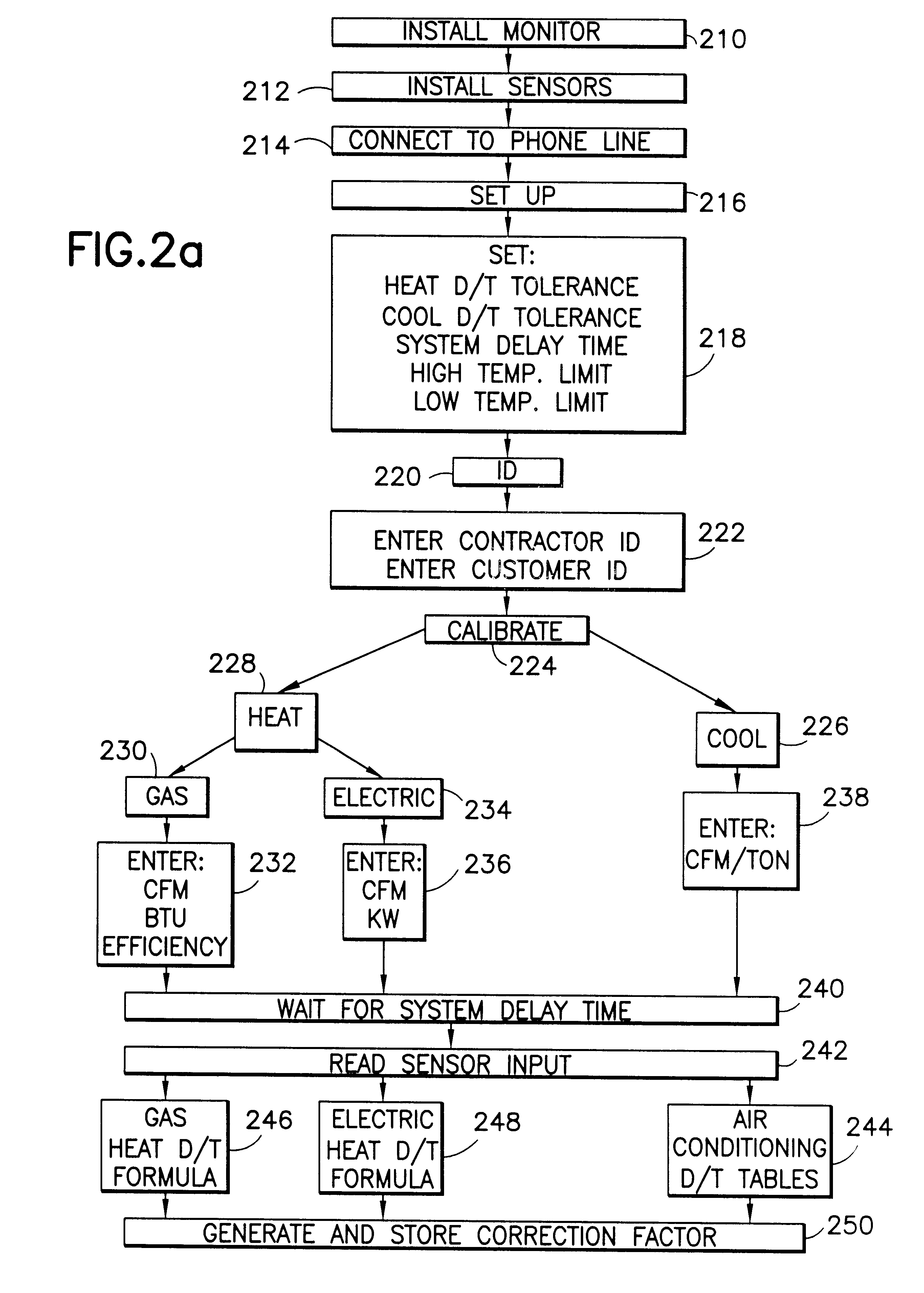
HVAC remote monitoring system
InactiveUS6385510B1Save moneyOvercome problemsSampled-variable control systemsMechanical apparatusModem deviceMonitoring system
An electronic HVAC monitoring computer continuously monitors the general condition and efficiency of an HVAC system and notifies a central station computer via modem link or other signal transmission means, when the general condition or efficiency of the HVAC system falls below certain industry standard values by a pre-set amount.
Owner:HOOG KLAUS D +1
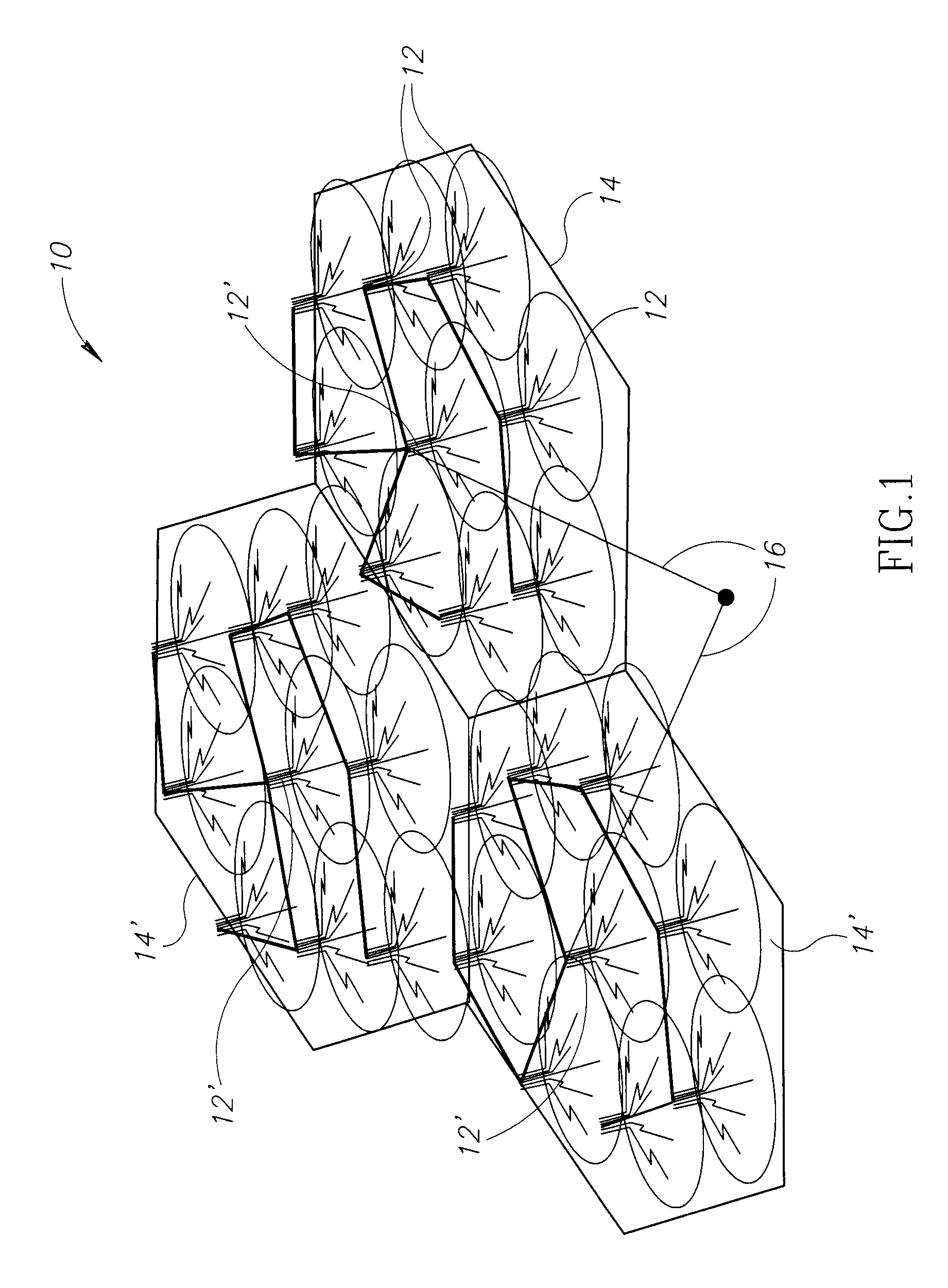
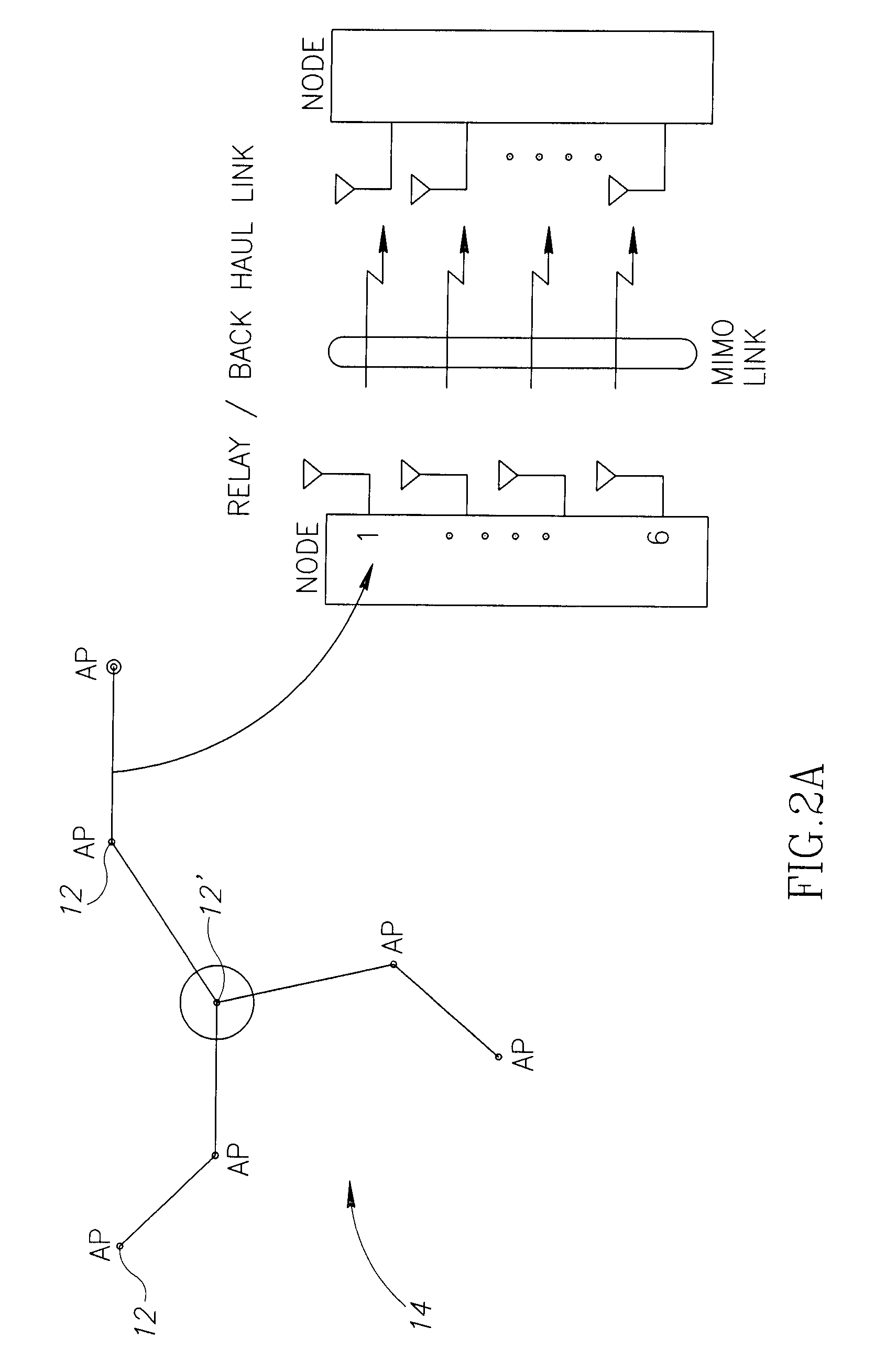
WiMAX ACCESS POINT NETWORK WITH BACKHAUL TECHNOLOGY
ActiveUS20080090575A1Low costLarge capacityPower managementNetwork traffic/resource managementTransceiverModem device
A WiMAX network and communication method, the network including a plurality of WiMAX nodes deployed in micro or pico cells for providing access service to a plurality of mobile subscribers, a plurality of these nodes being arranged in a cluster, one of the nodes in each cluster being a feeder node coupled to a core network, the modes in each cluster being couple for multi-hop transmission to the feeder node. According to a preferred embodiment, each node includes a transceiver with associated modem, an antenna arrangement coupled to the modem and arranged for multiple concurrent transmissions, and a MAC controller for controlling the transceiver, modem and antenna arrangement for providing both access and backhaul communication.
Owner:QUALCOMM INC
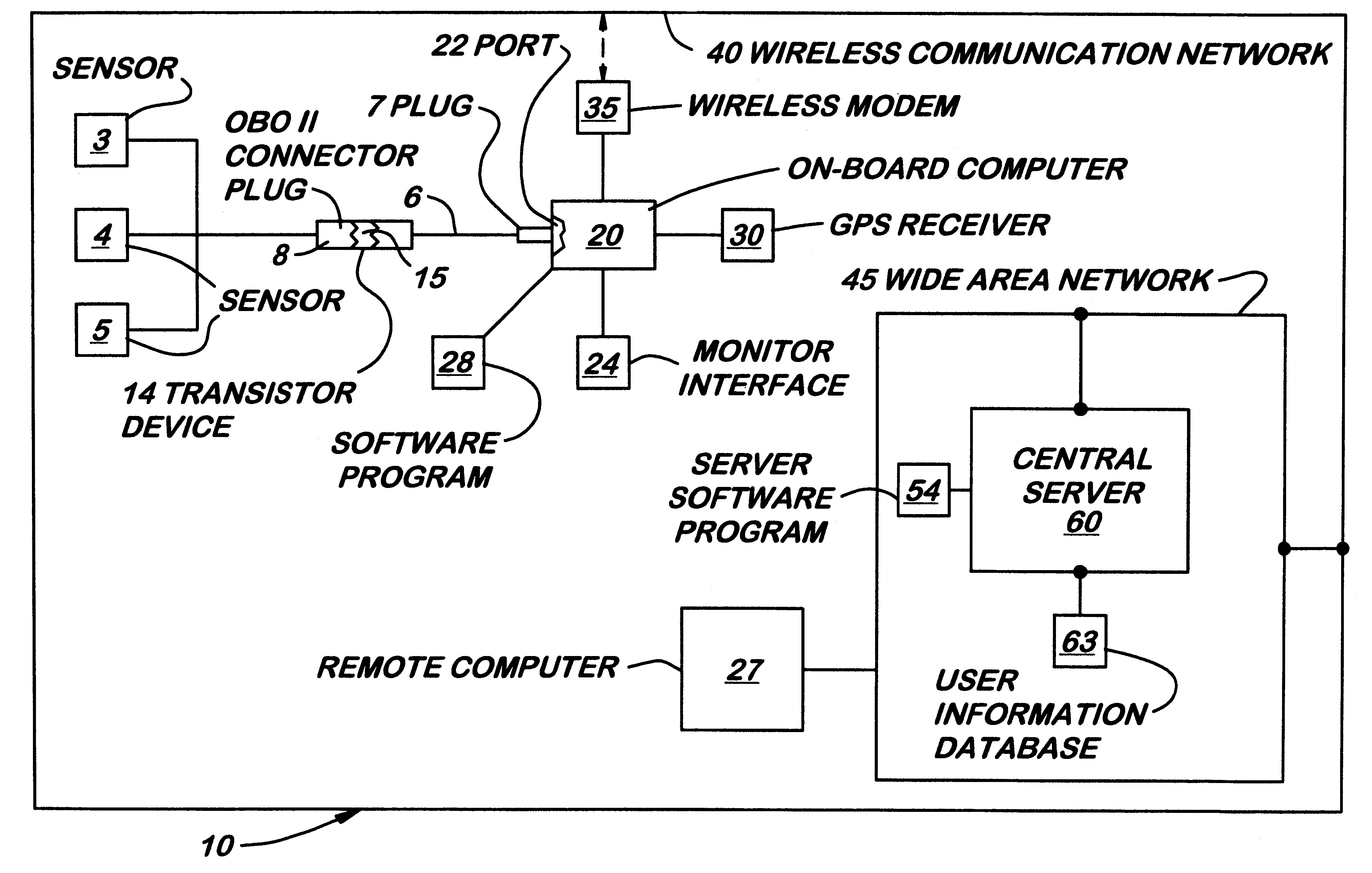
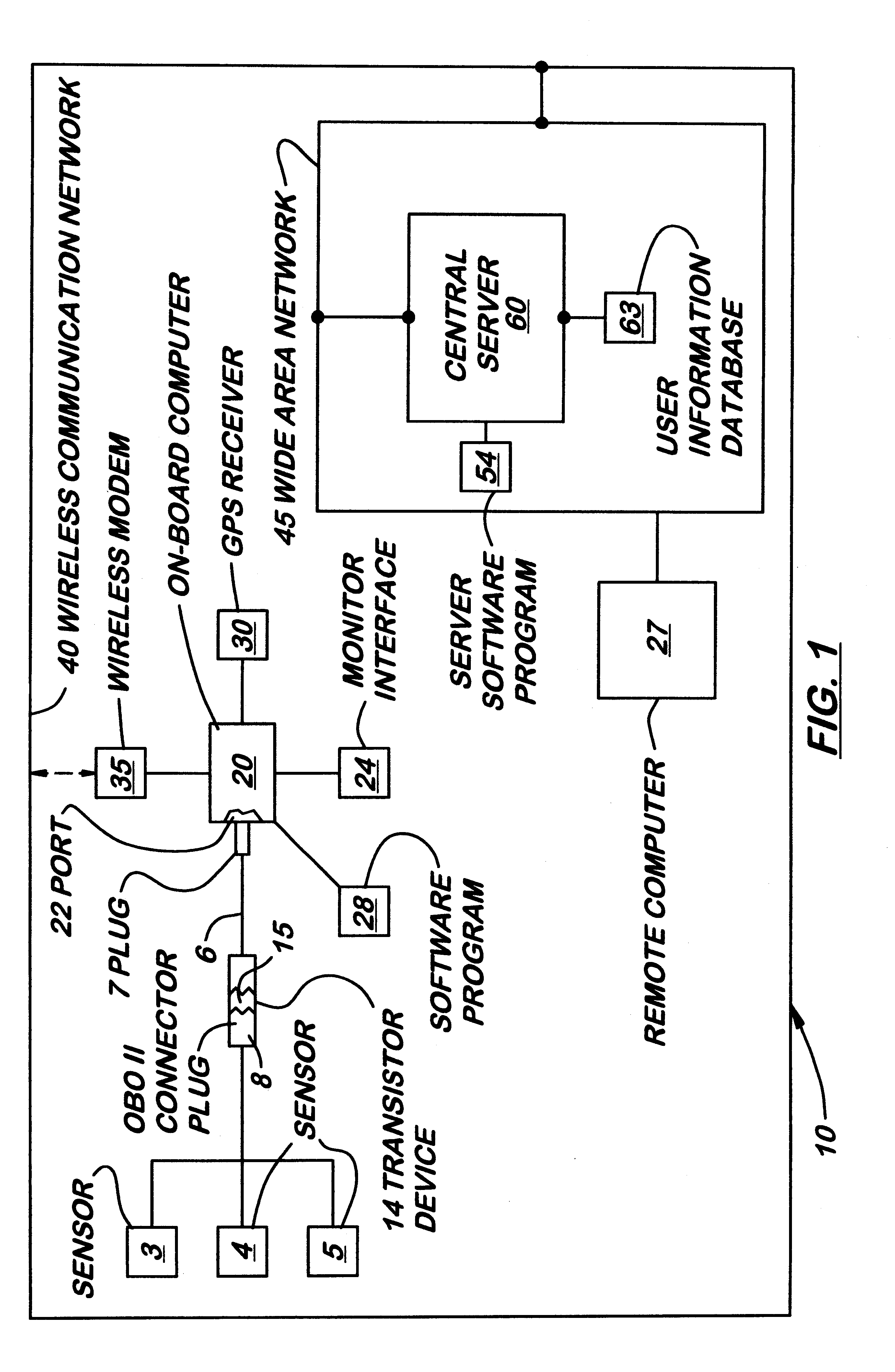
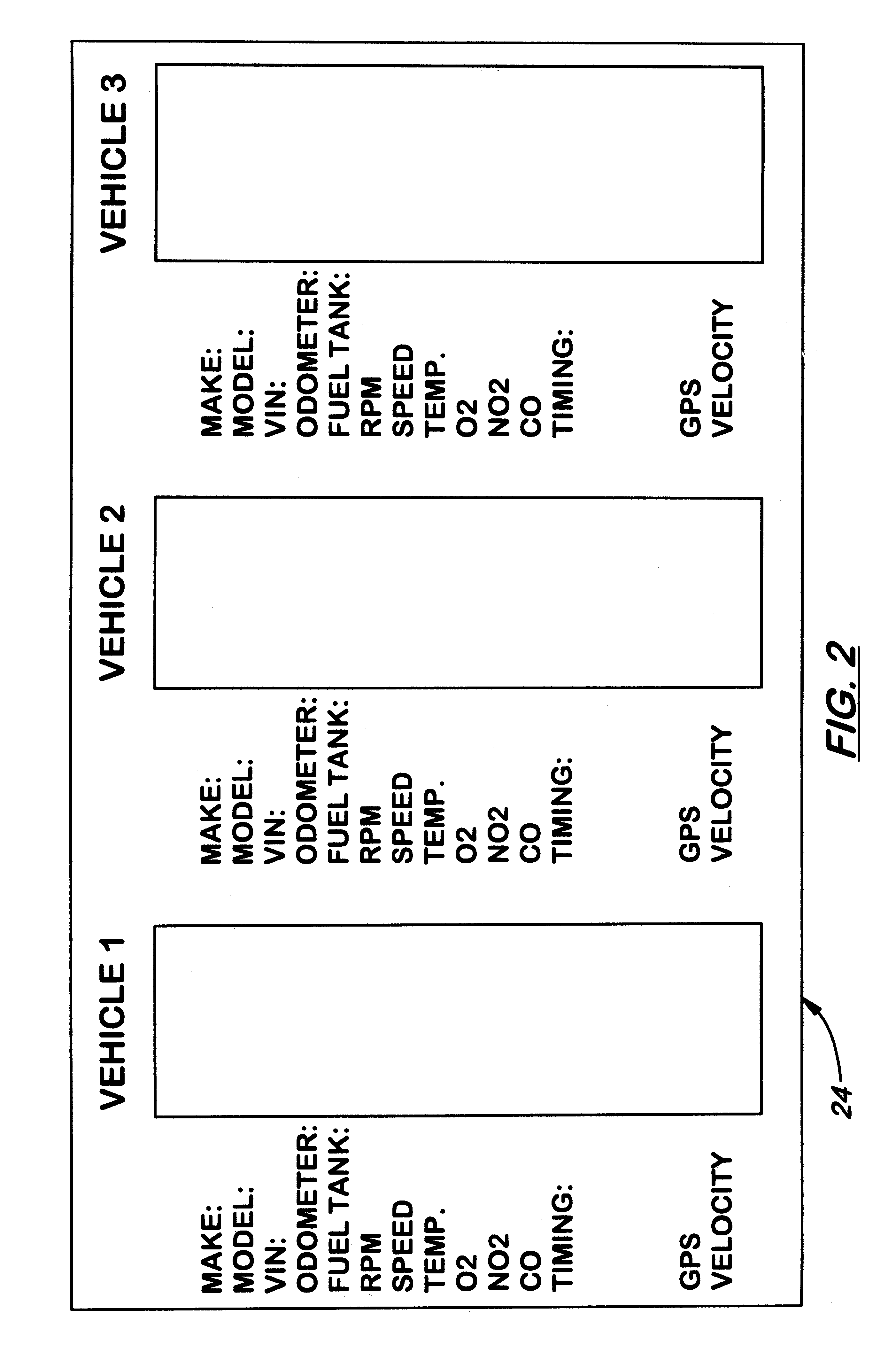
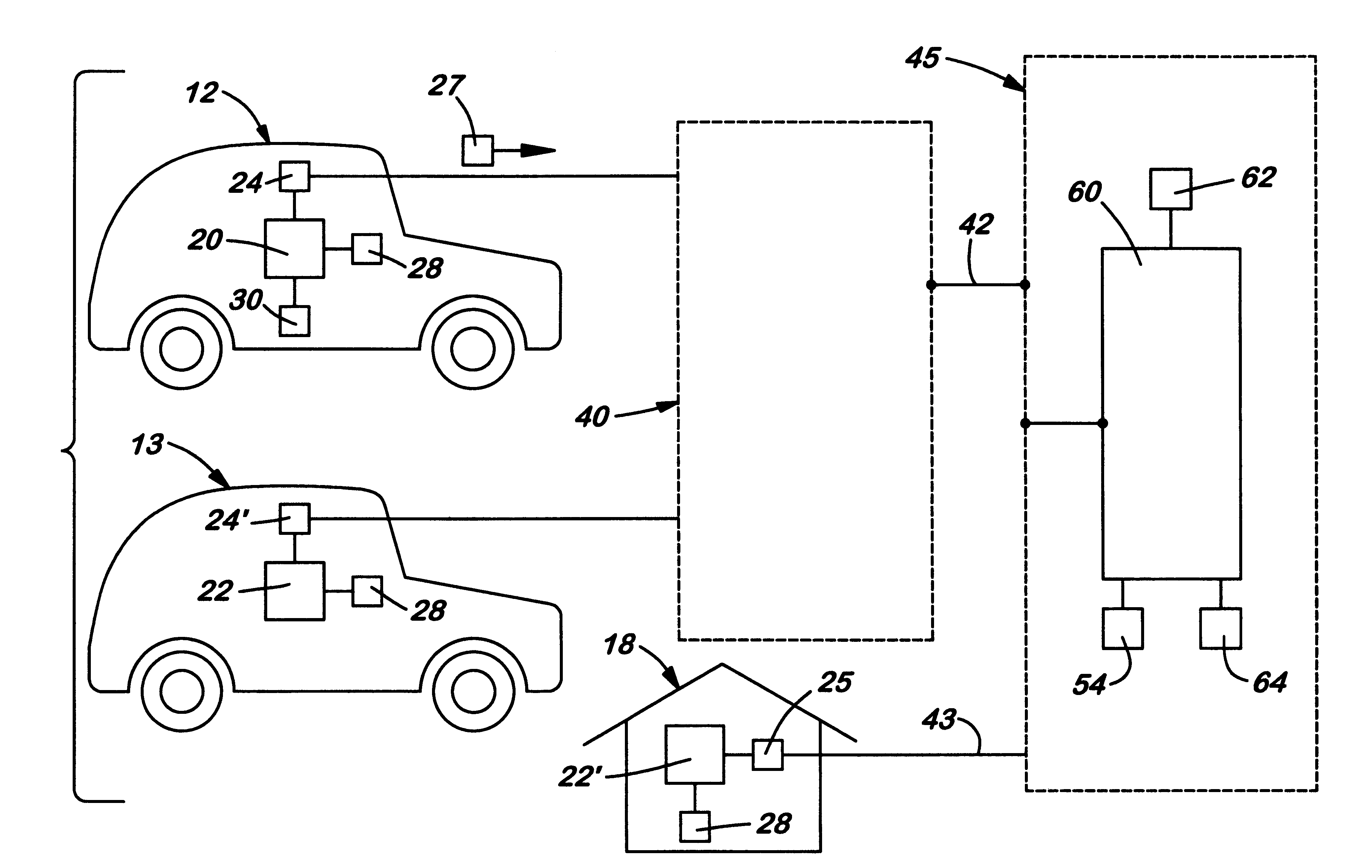
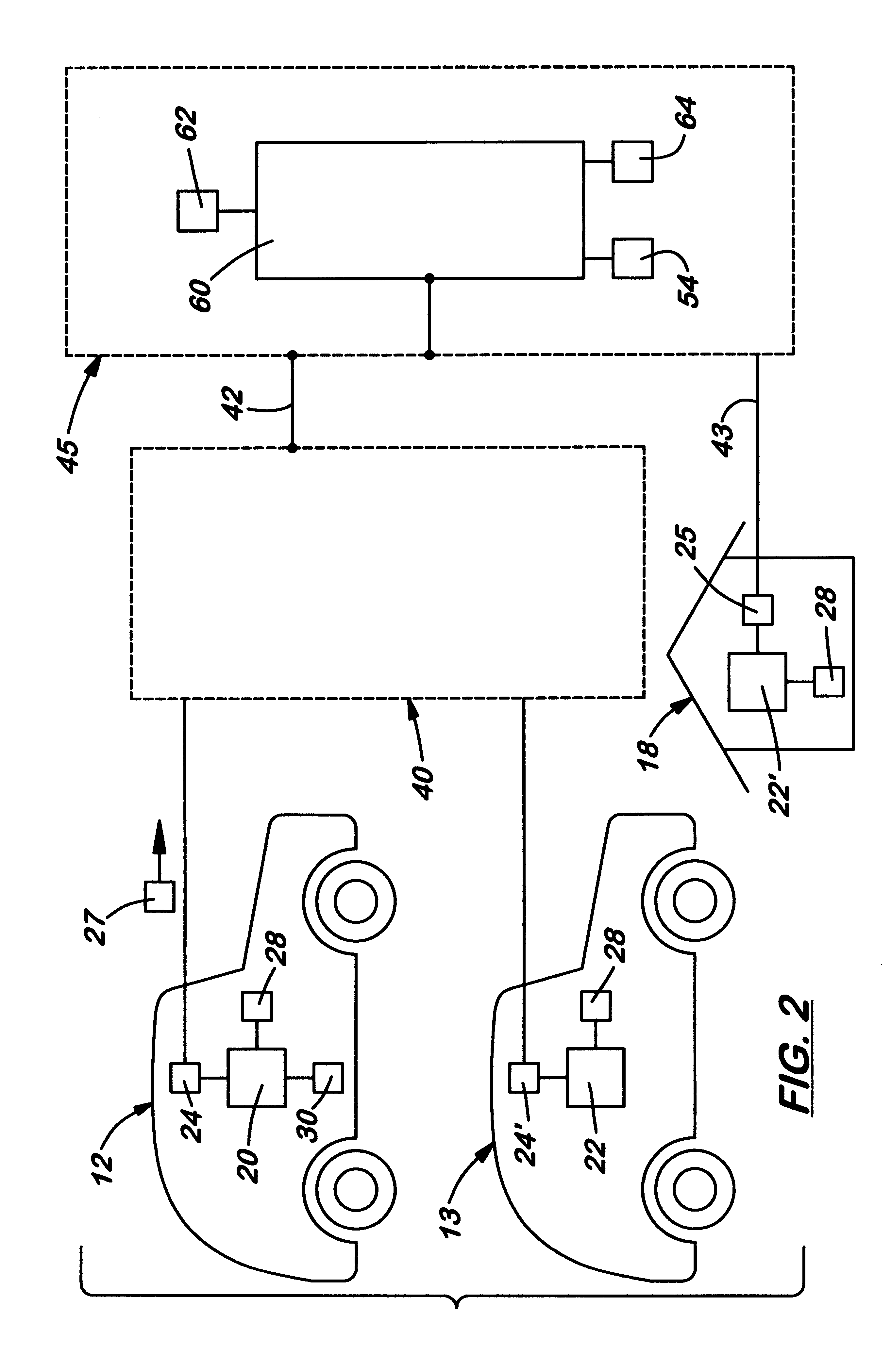
System for transmitting and displaying multiple, motor vehicle information
InactiveUS6295492B1Vehicle testingRegistering/indicating working of vehiclesMobile vehicleSystems design
A system for transmitting, collecting and displaying diagnostic and operational information from one or more motor vehicles to a central server connected to a wide area network. The system is designed to be used with an existing on-board diagnostic system found in most motor vehicles manufactured today. The system includes a translator device capable of translating the codes from an on-board diagnostic connector into computer readable files such as ASCII files. The translator device may be connected to an on-board computer that includes a wireless modem capable of connecting to a wireless communication network and eventually to a wide area network. A central server is connected to the wide area network which receives and stores information from the on-board computer. Authorized users may connect to central server via the wide area network and request information therefrom regarding selected motor vehicles. All of the information may be presented in a single interface.
Owner:VERIZON PATENT & LICENSING INC
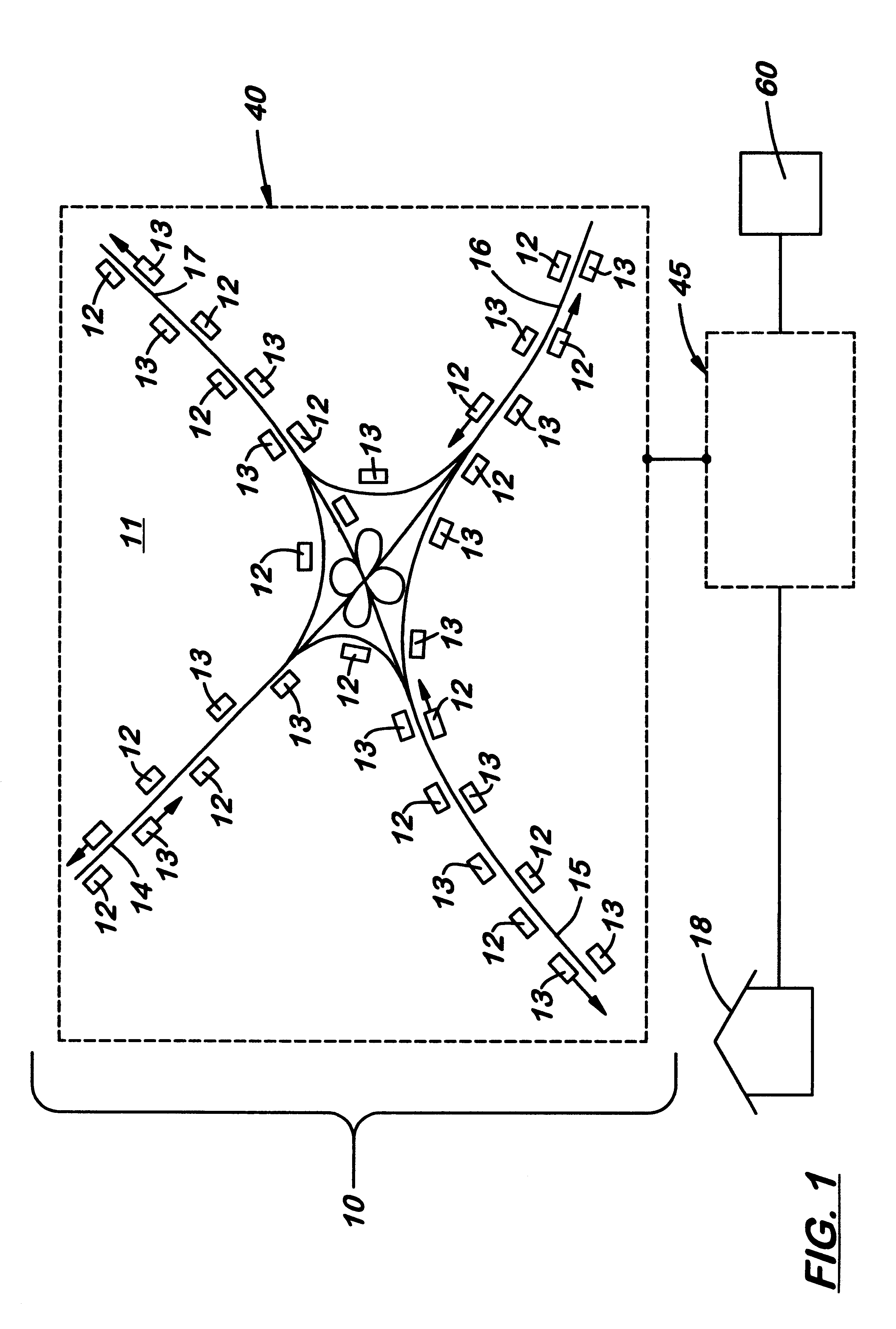
Instantaneous traffic monitoring system
InactiveUS6236933B1Less congestedControlling traffic signalsAnalogue computers for vehiclesModem deviceEngineering
A system for instantaneously monitoring traffic congestion including a plurality of monitoring electronic devices located in motor vehicles traveling on roadways in a selected region. Each monitoring electronic device is coupled to a GPS receiver that provides physical location to a wireless modem capable of connecting to a wireless communication network. The system also includes a central computer connected to a wide area network that is able of continuously downloading physical location information from a plurality of monitoring electronic devices also connected to the wide area network. The central computer uses a traffic monitoring software program and a mapping database containing roadway information for a region and the movement information from the monitoring electronic devices to create a continuously updated traffic congestion database. Authorized users of the system are able to log onto the central computer to a portion of the database that contains specific traffic flow and congestion information. Using the system, users are also able to obtain estimated times of arrival for a specific trip, and recommendations on alternative route information. The system can also take into consideration current or anticipated events that may affect traffic congestion.
Owner:INFOMOVE COM
Personal shopping system
The present invention relates to a personal shopping system for combined use in both the home of a user and a shopping establishment. The system includes a host computer which is coupled to a host modem and, optionally, to at least one wireless multi-access point. The portable terminal can be used in both the shopping establishment and the home of the user. It is configured to read bar codes associated with items related to shopping, and includes a memory, a bar code reader, a wireless transceiver, and a data interface. The data interface of the terminal communicates with a data interface of the shopping establishment kiosk cradle or directly with the shopping establishment's communications network.
Owner:SYMBOL TECH LLC
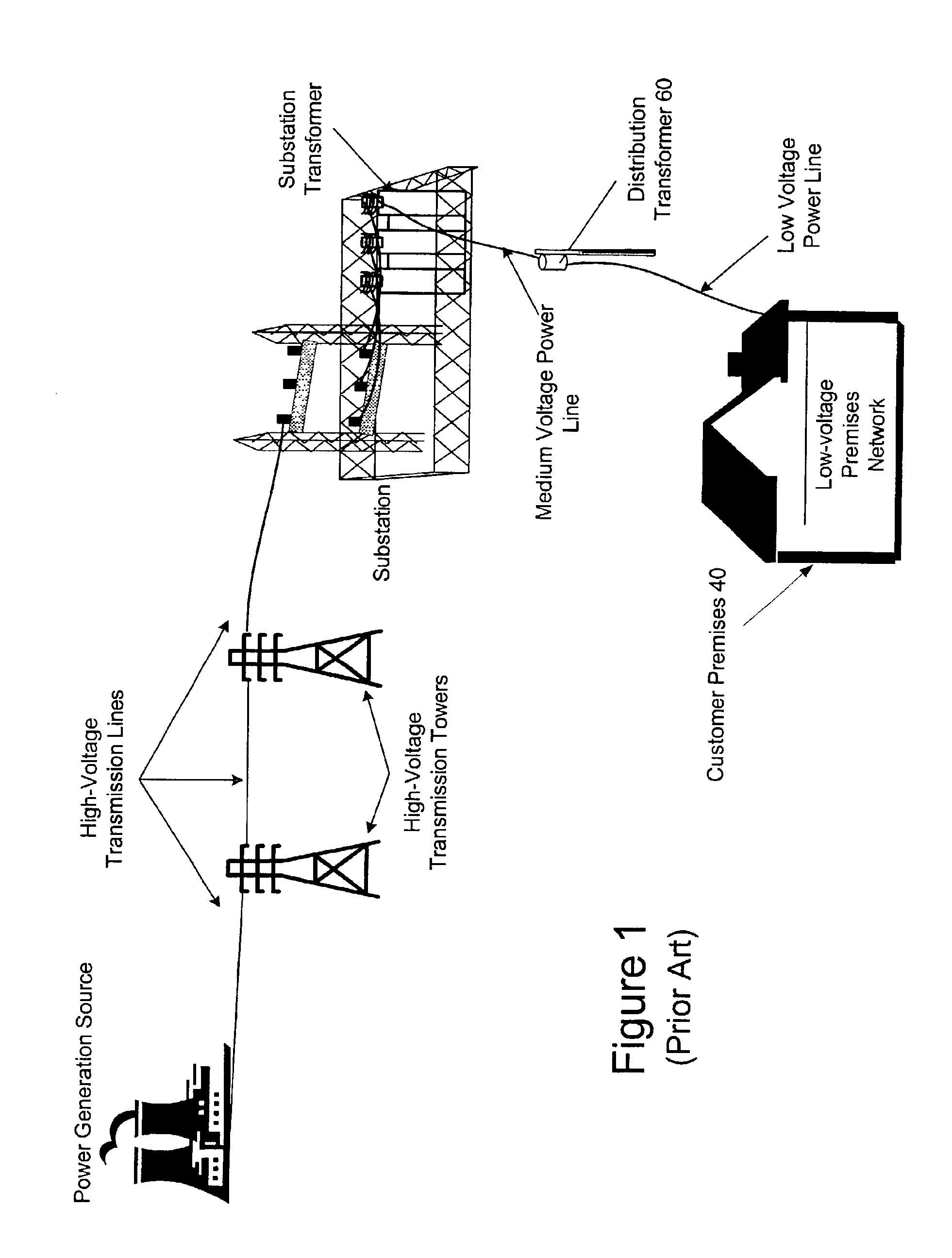
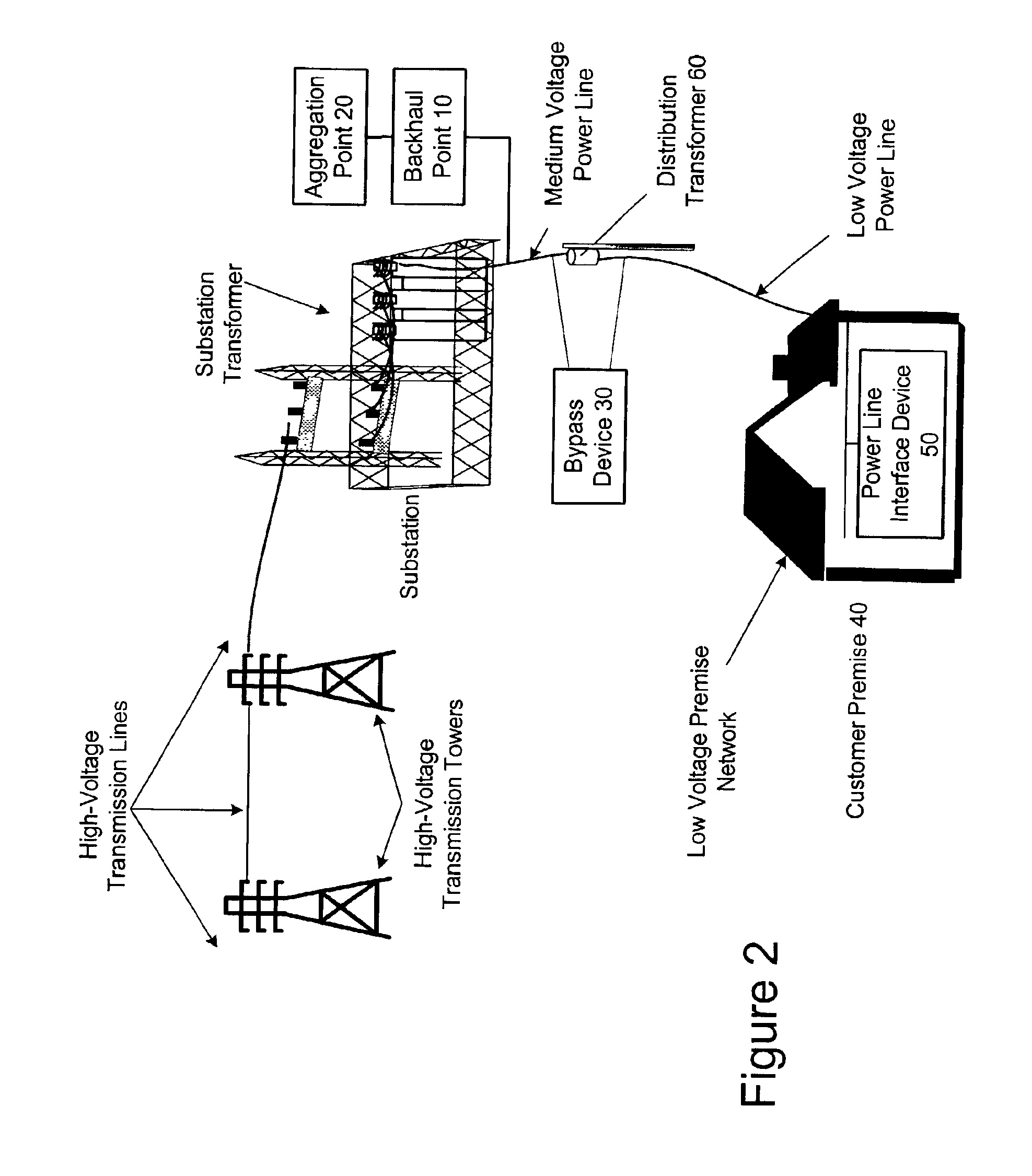
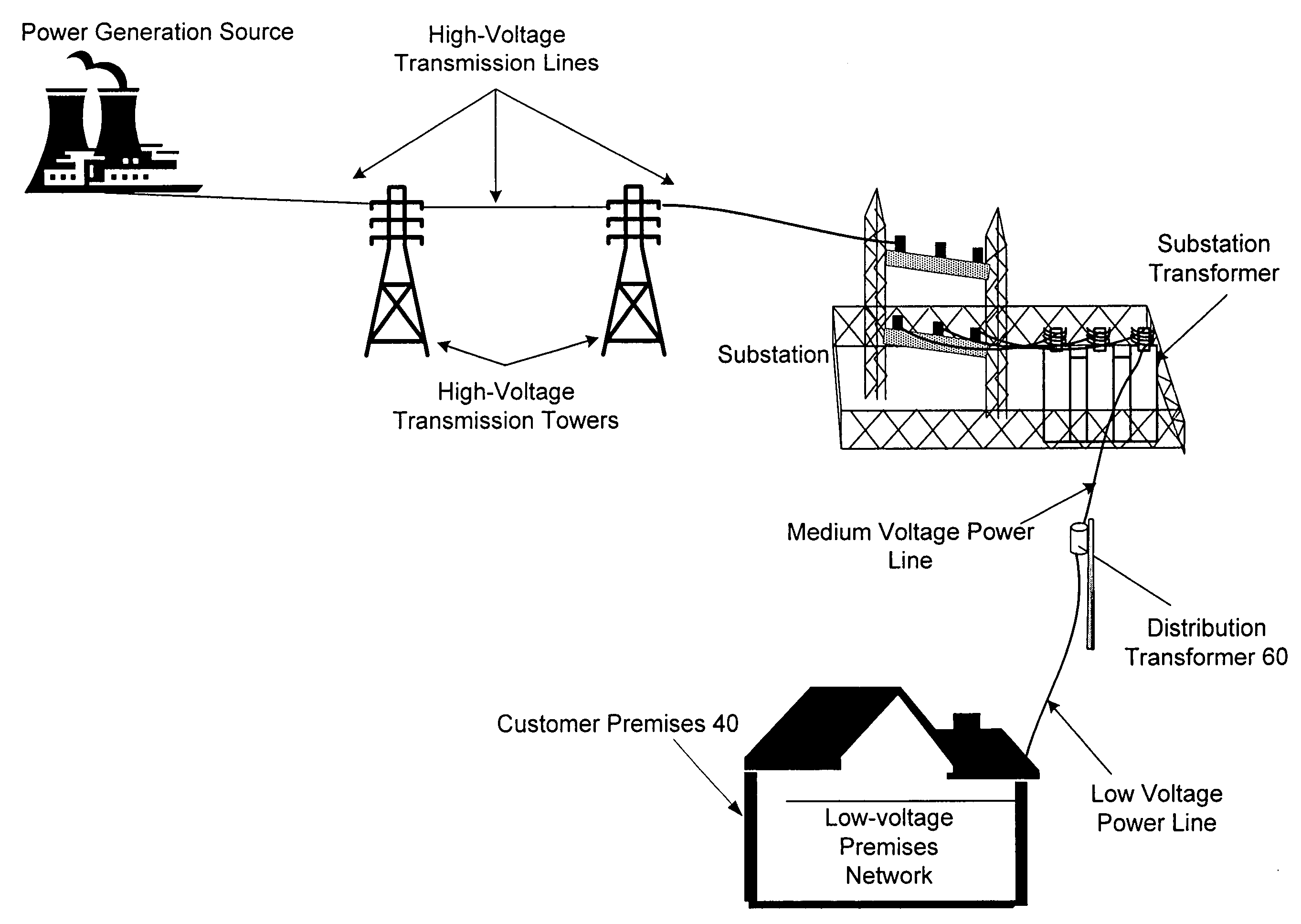
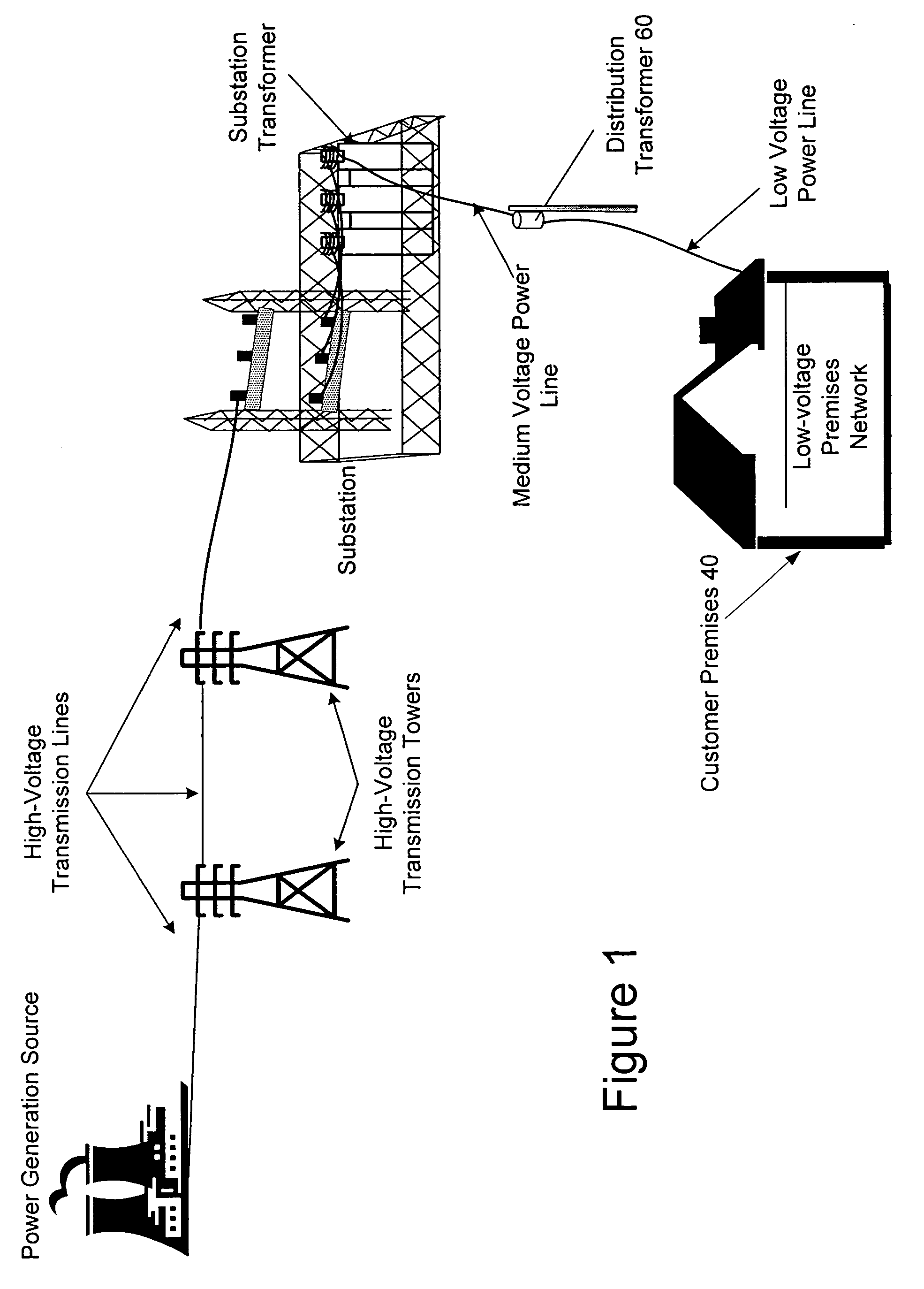
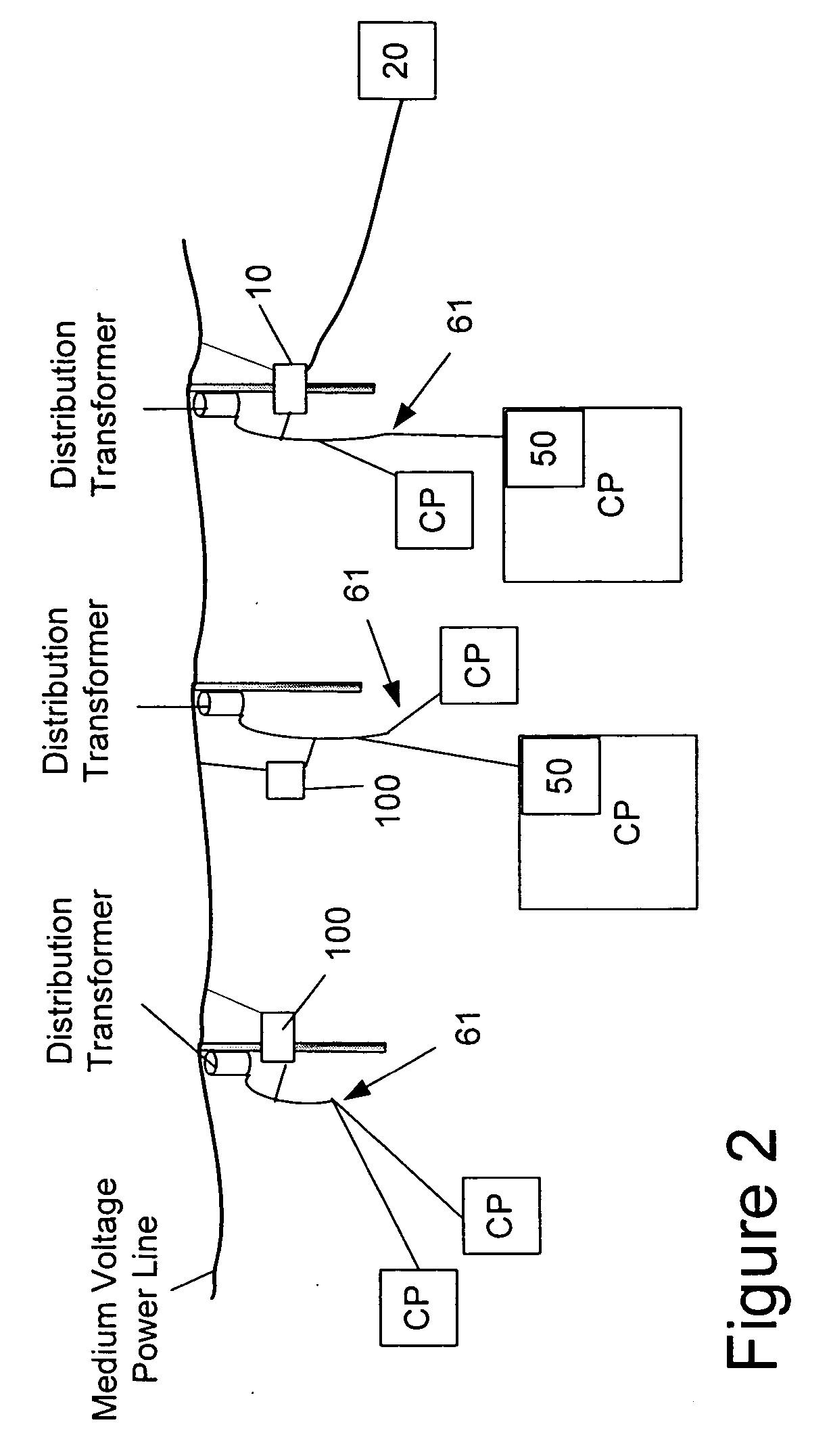
Power line communication system and method of using the same
InactiveUS6965302B2Electric signal transmission systemsWireless systems/telephoneCommunications systemWireless transceiver
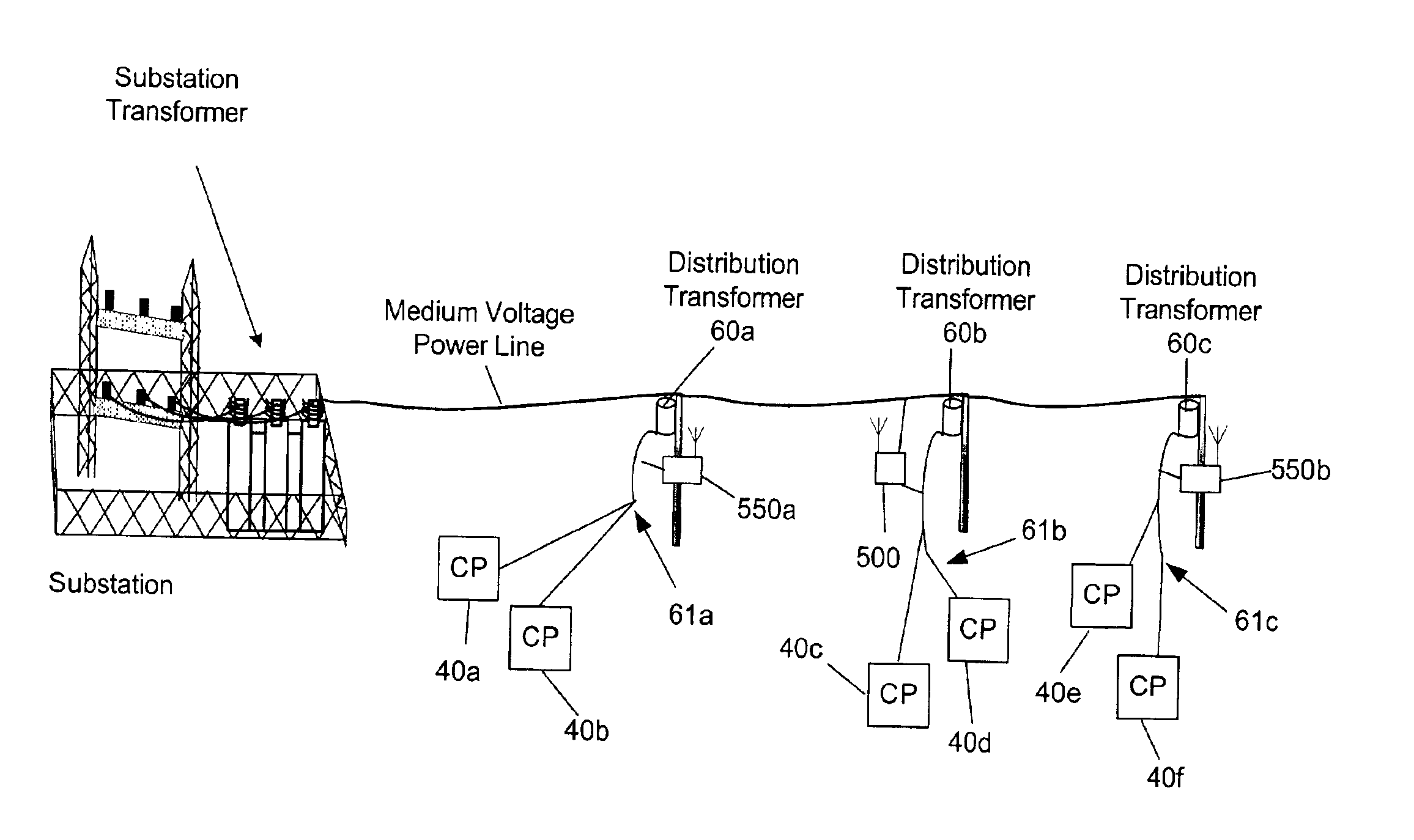
The communication system of one embodiment is for communicating data through a power distribution system having a medium voltage power line and low voltage power line and comprises a first device comprising a first wireless transceiver, a first modem in communication with the first wireless transceiver and the medium voltage power line. The system may also comprise a second device comprising a second wireless transceiver in wireless communication with the first wireless transceiver; and a second modem in communication with the second wireless transceiver and the low voltage power line.
Owner:CURRENT TECH
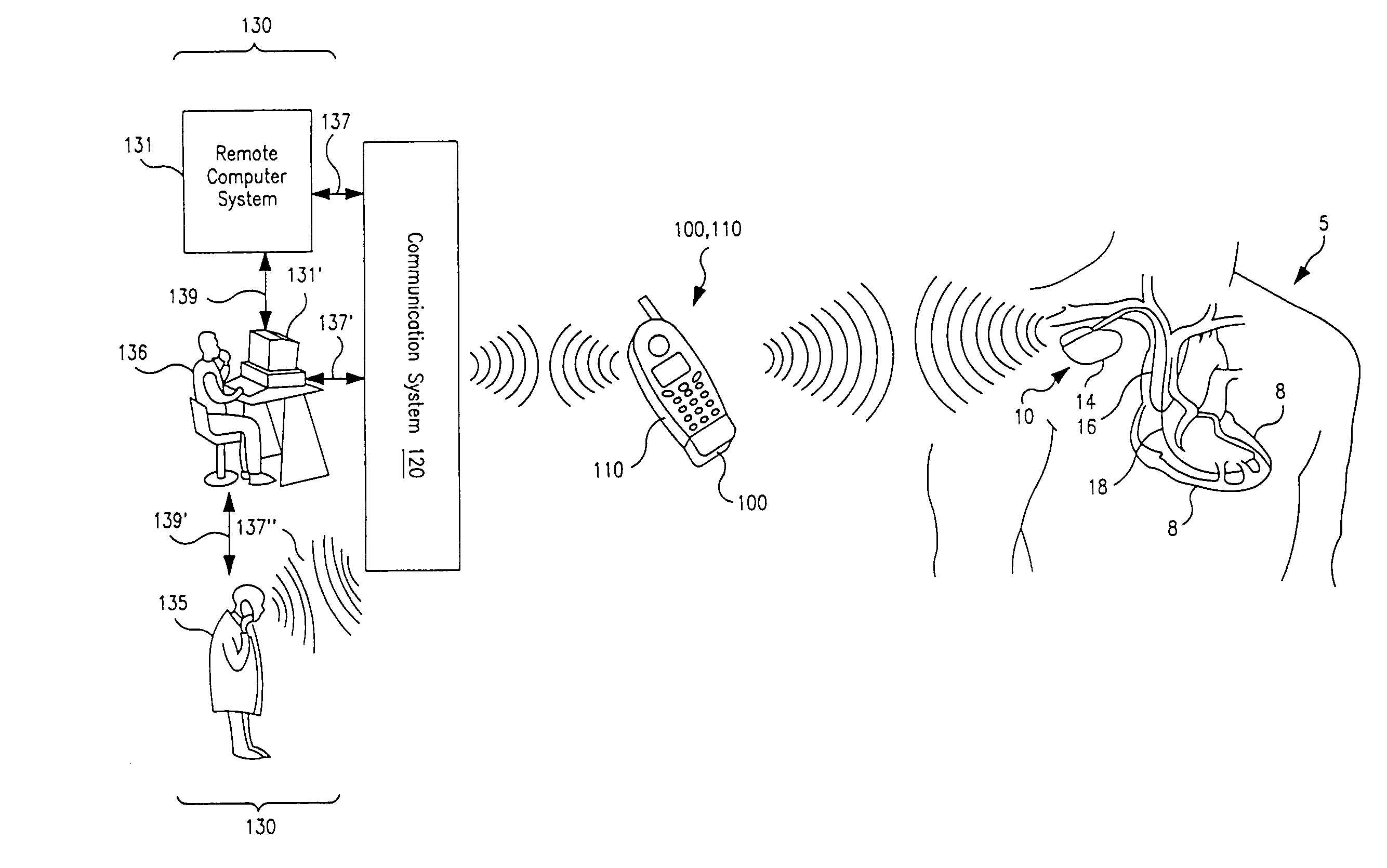
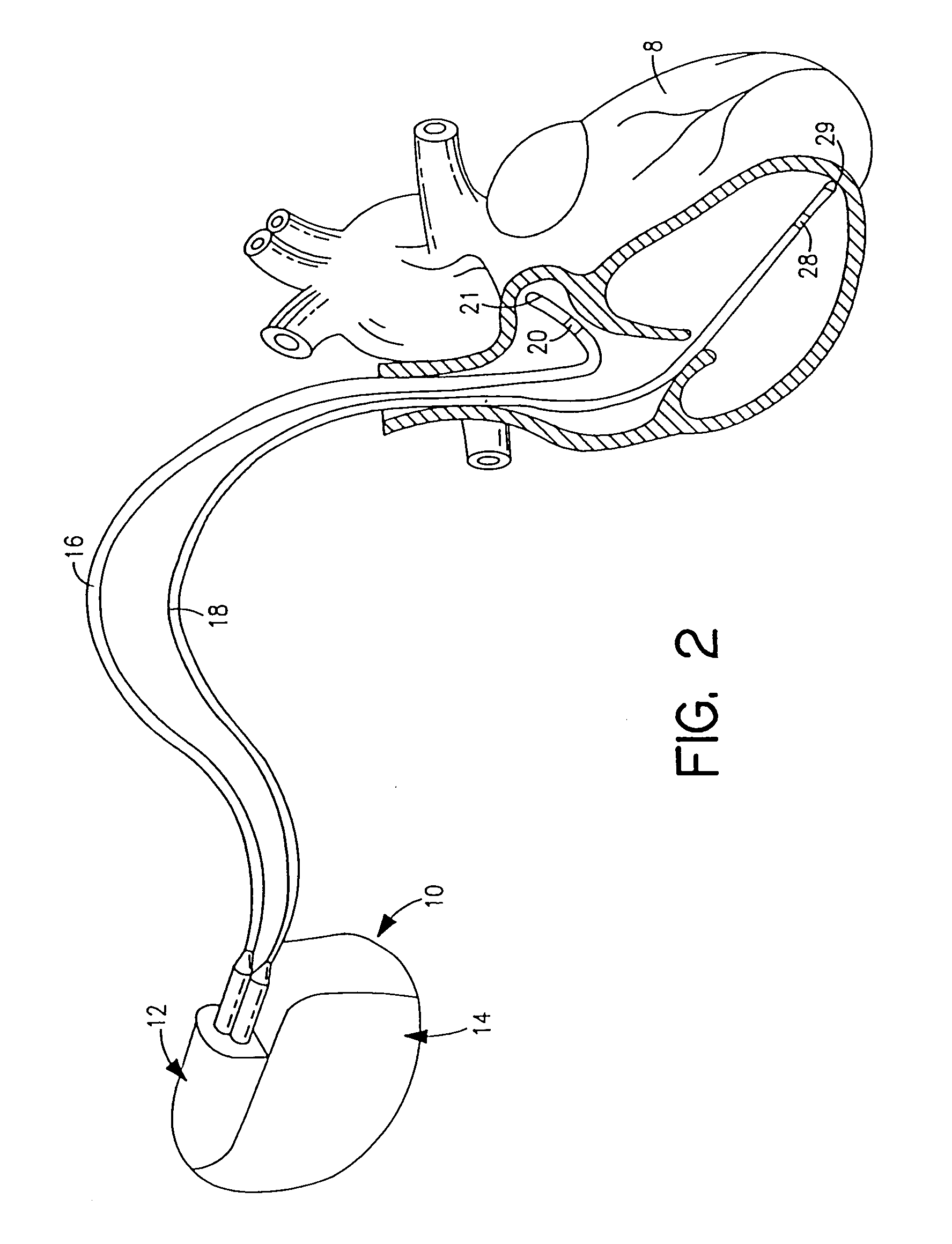
System and method for remote programming of an implantable medical device
InactiveUS7181505B2Significant compatibilitySignificant scalabilityElectrotherapyLocal control/monitoringModem deviceThe Internet
A method and corresponding system for updating or installing new software loaded into the memory of an implantable medical device(IMD) implanted within a body of a patient is described. The updated or new software may be installed in the memory of the IMD without the patient having to travel to a clinic or hospital, and may be effected by employing modem telecommunication and Internet techniques in conjunction with a remote computer system.
Owner:BELLTOWER ASSOC
Communications system for providing broadband communications using a medium voltage cable of a power system
InactiveUS6885674B2High frequencyModulated-carrier systemsTransmission path divisionModem deviceCommunications system
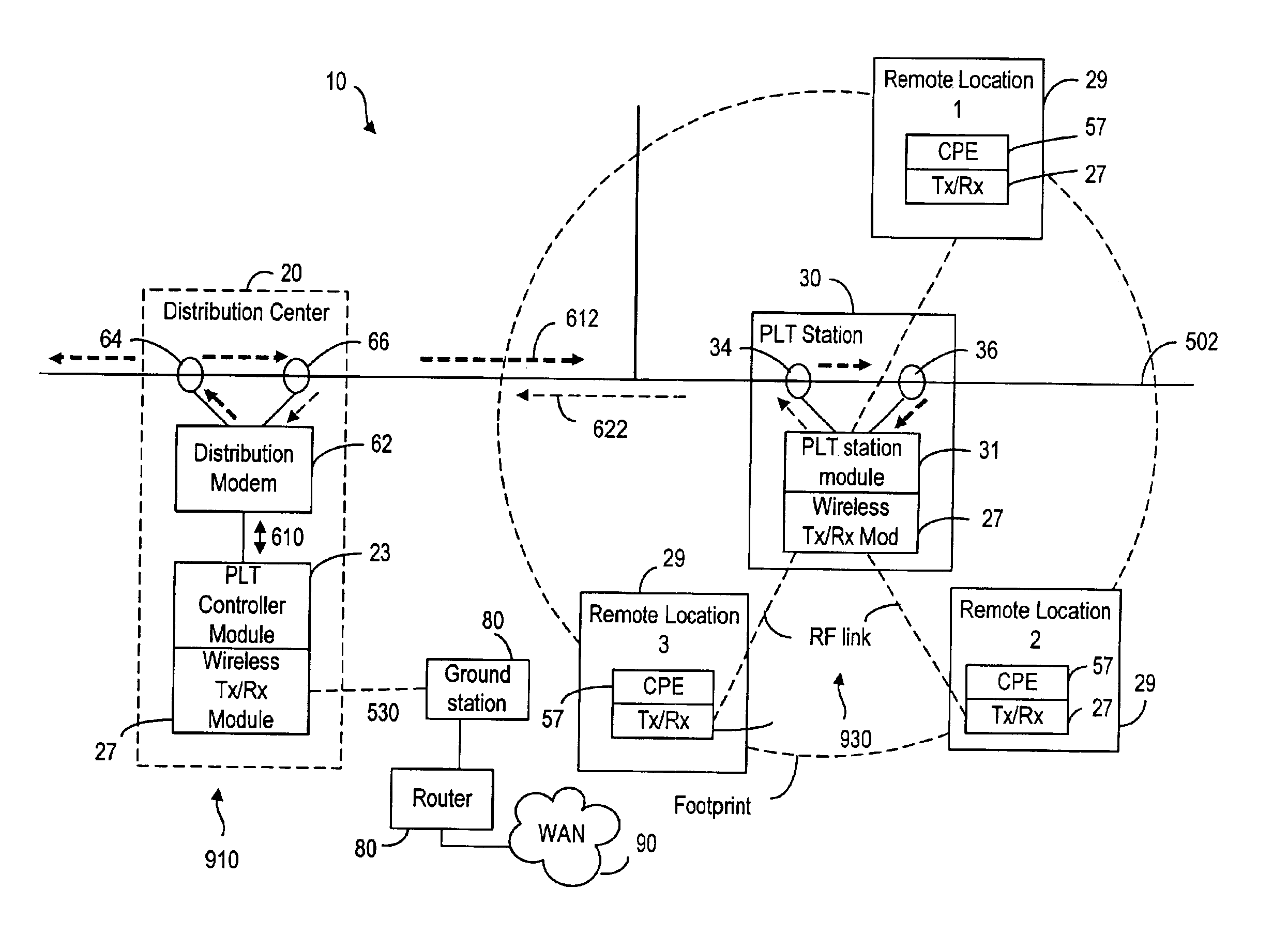
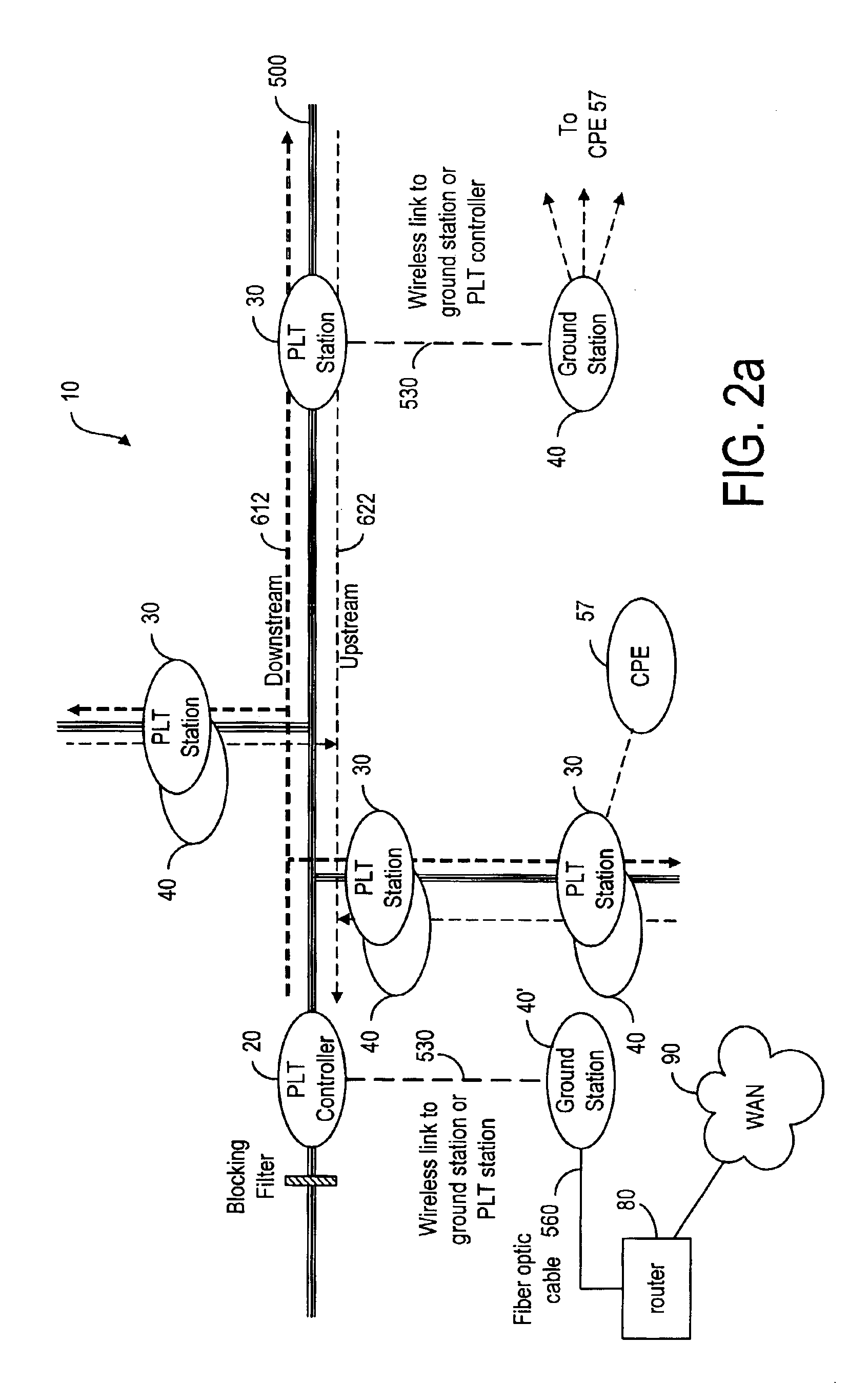
A broadband service communication system using an MV cable for conveying RF signals in a network segment, which includes a distribution center (PLT controller) and a plurality of power line telecommunication (PLT) stations. The PLT controller has a distribution modem for conveying downstream and upstream RF signals to and from the PLT stations through the MV cable via couplers. Each PLT station has a modem for conveying the downstream and upstream RF signals via couplers and for conveying media signals to one or more customer premises equipment (CPE) via, e.g. wireless links. The PLT controller controls each PLT station regarding upstream communications transfer of all downstream communications and also controls. The PLT controller can be connected via a router to a WAN to convey media signals to and from the WAN. Repeaters and interlinks are used to join multiple network segments.
Owner:AMPERION
Thin DOCSIS in-band management for interactive HFC service delivery
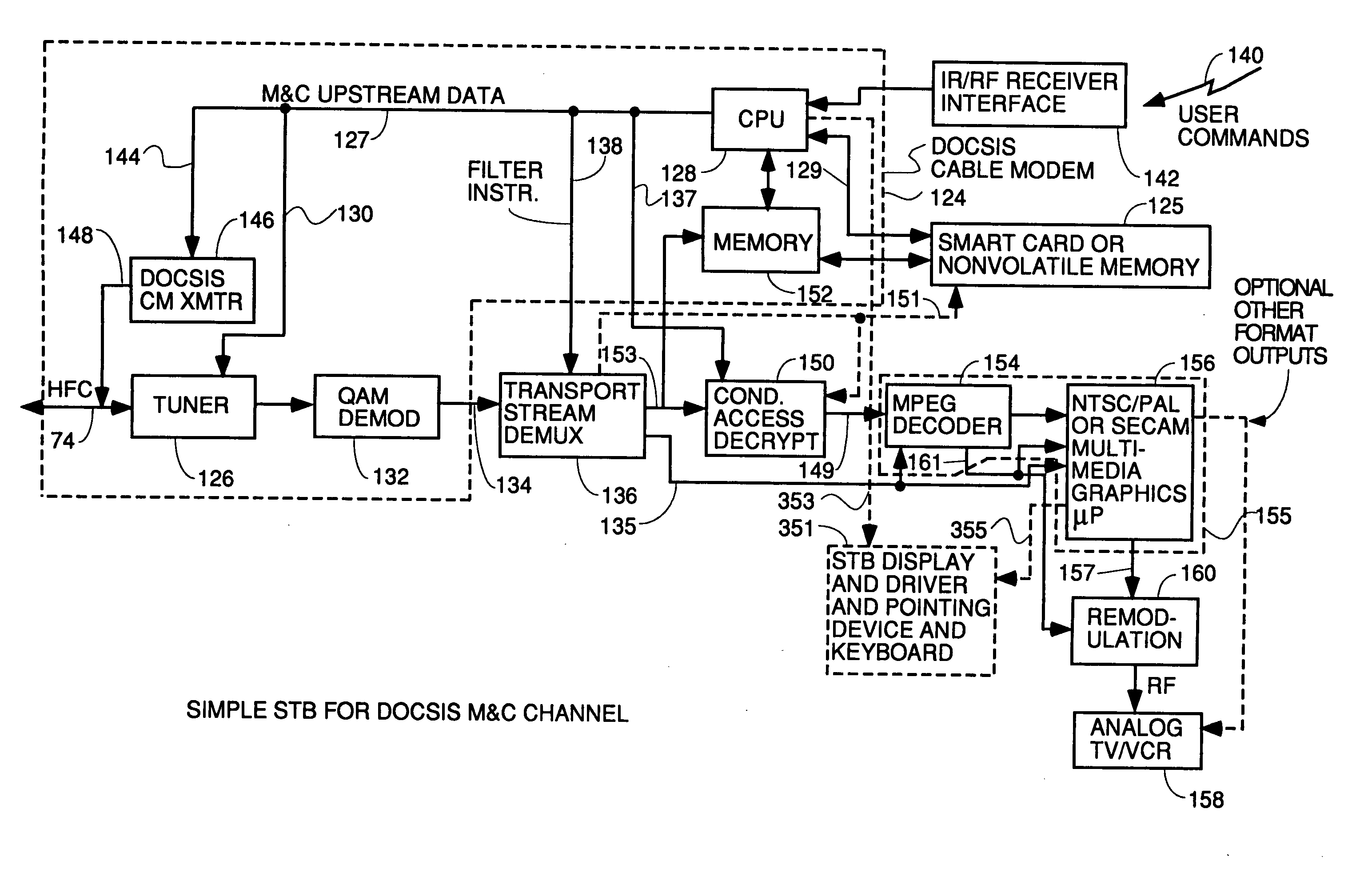
InactiveUS20040181800A1Simple processLess-expensive to buildAnalogue secracy/subscription systemsTwo-way working systemsModem deviceConditional access
Circuitry and processes carried out thereby are disclosed for implementing simple single tuner set top box decoders which do not require a separate tuner for an out of band management and control channel. Removable smart card conditional access circuitry and replaceable modules having decoding circuitry for different compression schemes and encoding circuitry for different format television circuits is disclosed. An embodiment with a single tuner and a full DOCSIS compatible modem which can interface to personal computers, etc. is also disclosed to make the set top box a simple, inexpensive home gateway is also disclosed.
Owner:TERAYON COMM SYST
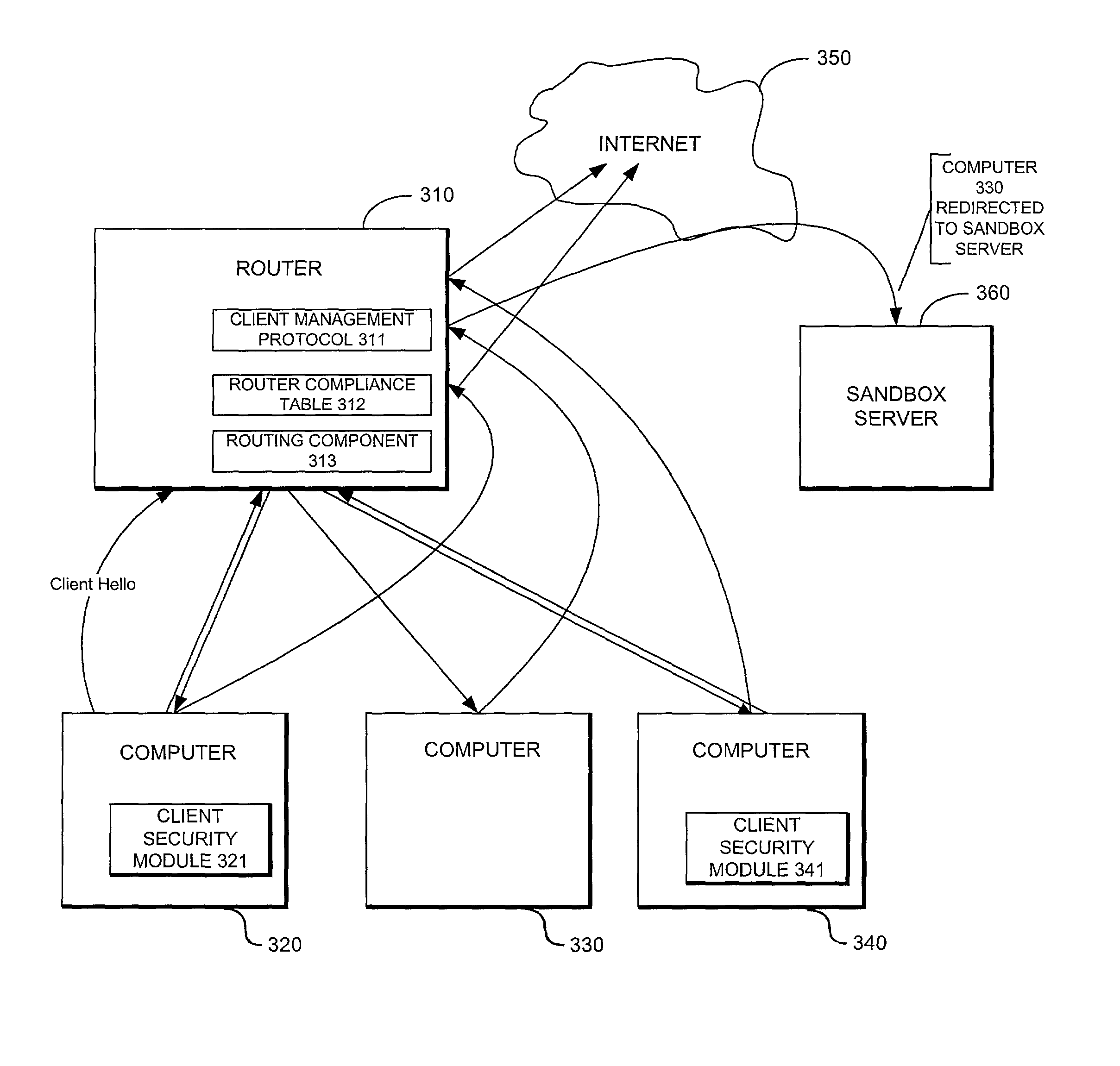
System providing internet access management with router-based policy enforcement
ActiveUS20030055962A1Multiple digital computer combinationsTransmissionInternet accessApplication software
A computing environment with methods for monitoring access to an open network such as the Internet, is described. The system includes one or more client computers, each operating applications (e.g., Netscape Navigator or Microsoft Internet Explorer) requiring access to an open network, such as a WAN or the Internet, and a router or other equipment that serves a routing function (e.g., a cable modem) for the client computers. A centralized security enforcement module on the router maintains access rules for the client computers and verifies the existence and proper operation of a client-based security module on each client computer. The router-side security module periodically sends out a router challenge via Internet broadcast to the local computers on the network. If the client-side security module is installed and properly operating, the client-side security module responds to the router challenge. The responses received by the router-side security module are maintained in a table. Each time the router receives a request from a client computer to connect to the Internet, the router-side security module reviews the table and analyzes whether or not the computer requesting a connection to the Internet properly responded to the most recent router challenge. If it determines that the computer has properly responded to the router challenge, then it permits the computer to connect to the Internet. If a computer has not properly responded or if a computer has not answered the router challenge, then the computer is not allowed to connect to the Internet as requested.
Owner:CHECK POINT SOFTWARE TECH INC
Mobile broadband wireless access point network with wireless backhaul
ActiveUS7620370B2Low costLarge capacityPower managementNetwork traffic/resource managementTransceiverModem device
A WiMAX network and communication method, the network including a plurality of WiMAX nodes deployed in micro or pico cells for providing access service to a plurality of mobile subscribers, a plurality of these nodes being arranged in a cluster, one of the nodes in each cluster being a feeder node coupled to a core network, the nodes in each cluster being coupled for multi-hop transmission to the feeder node. According to a preferred embodiment, each node includes a transceiver with associated modem, an antenna arrangement coupled to the modem and arranged for multiple concurrent transmissions, and a MAC controller for controlling the transceiver, modem and antenna arrangement for providing both access and backhaul communication.
Owner:QUALCOMM INC
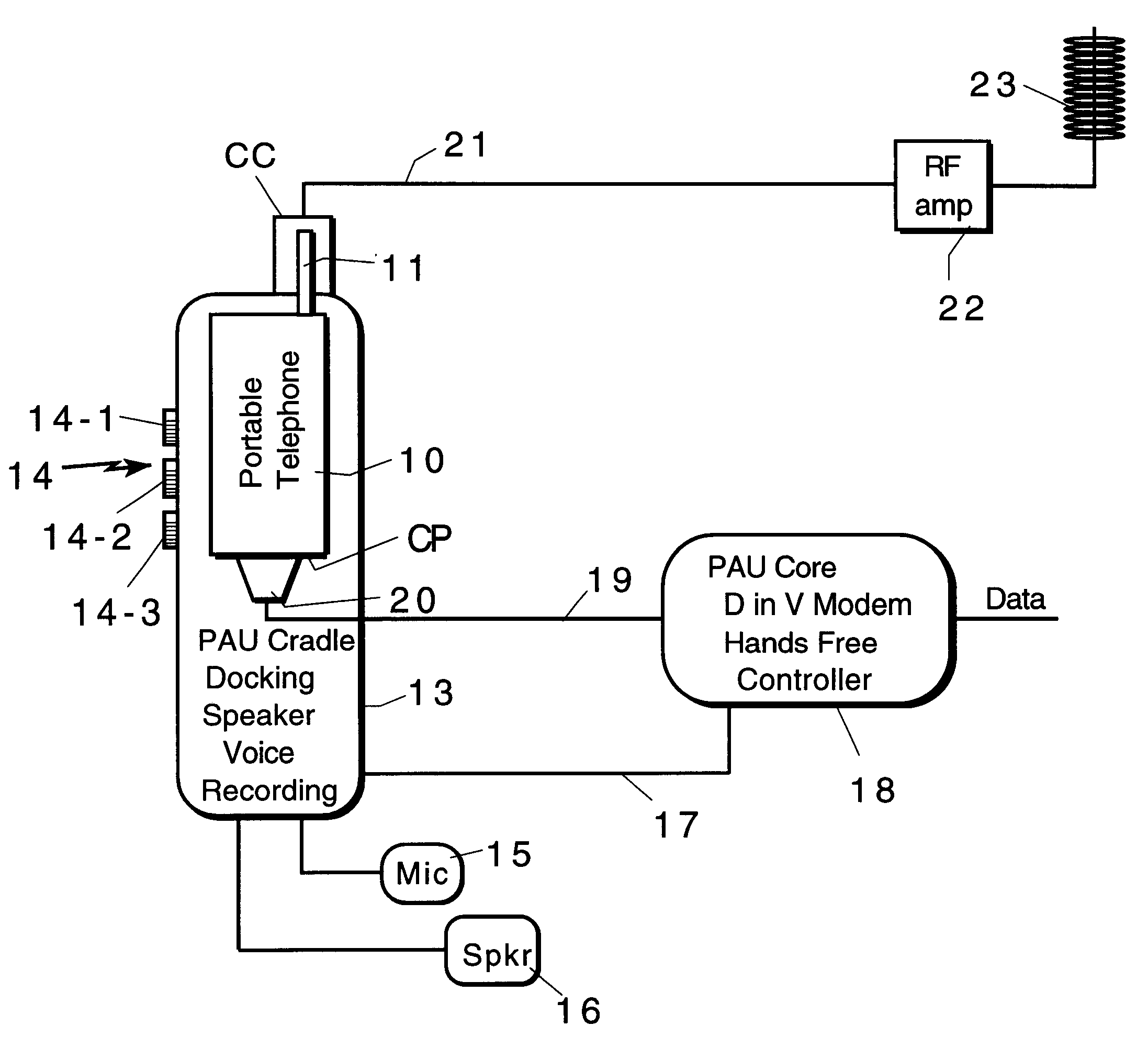
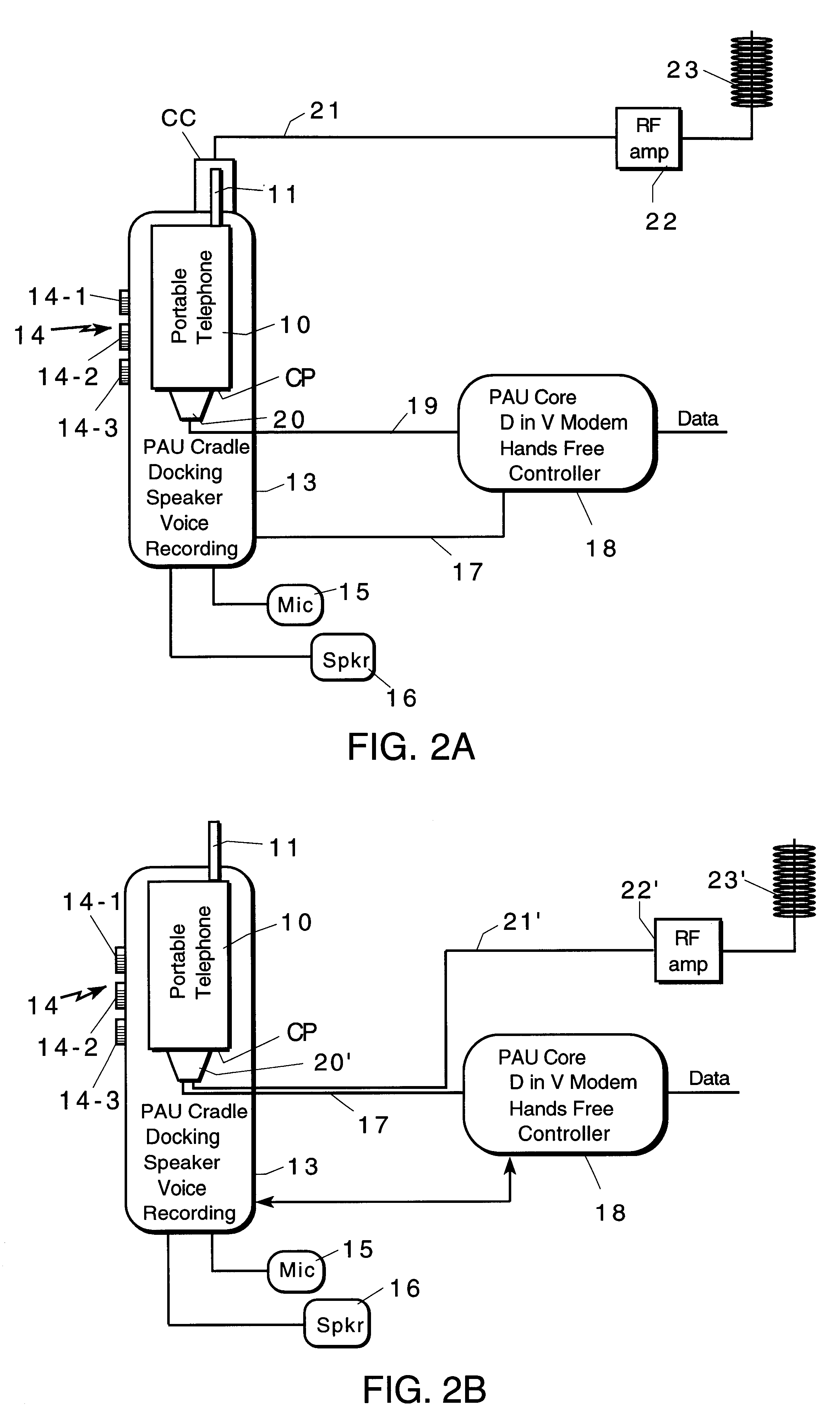
System for providing a simultaneous data and voice channel within a single channel of a portable cellular telephone to provide position-enhanced cellular services (PECS)
InactiveUS6226529B1Frequency-division multiplex detailsSubstation speech amplifiersDriver/operatorModem device
Owner:HARRIS CORP
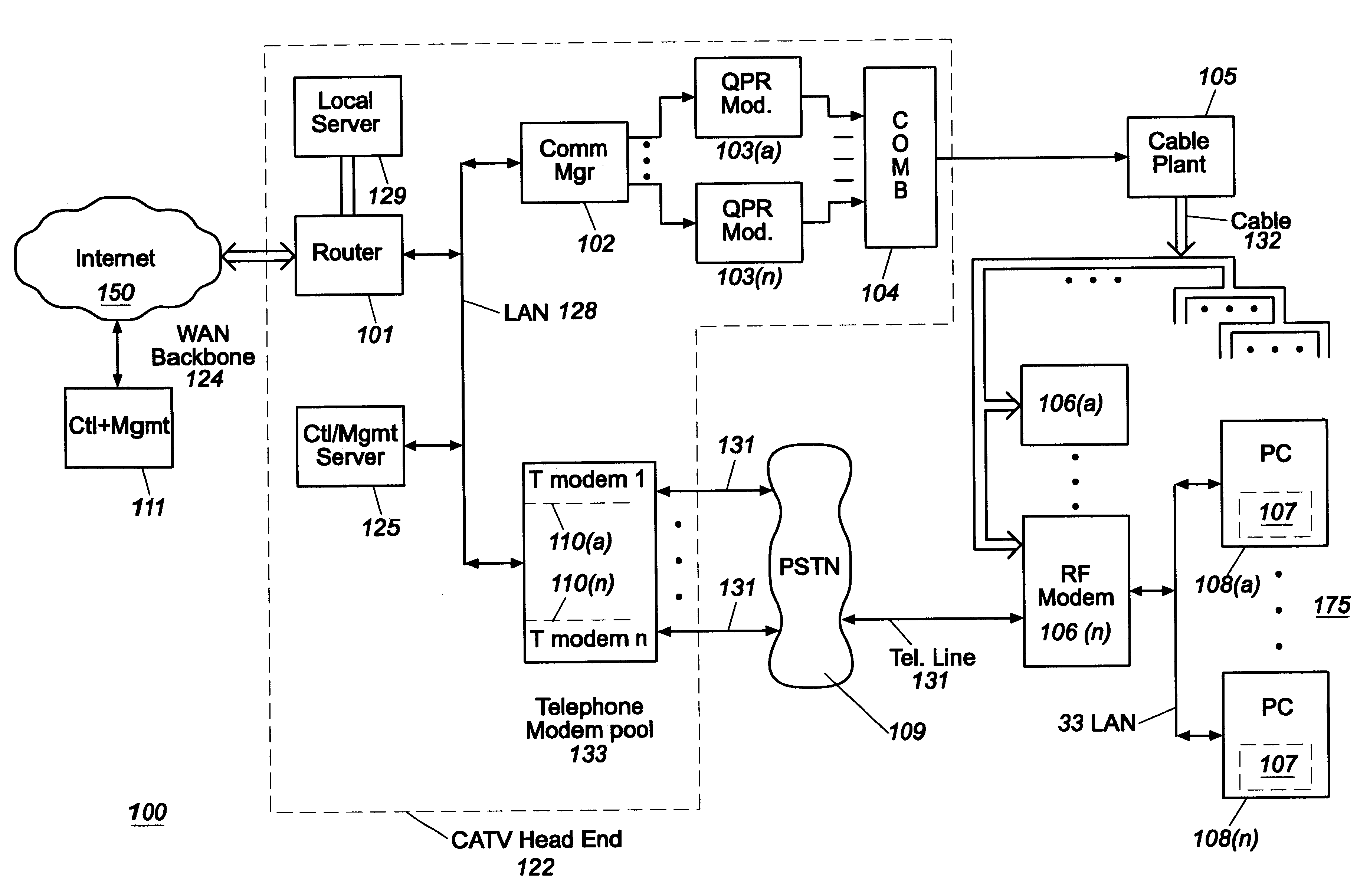
Cable modem map display for network management of a cable data delivery system
InactiveUS6272150B1Broadband local area networksBroadcast-related systemsTransport systemModem device
Apparatus for recording and collecting the installed location of cable modems in a cable data network comprises a network manager for maintaining and collecting cable modem location information. Components of the network manager maintains a software agent that manages a database of modem installation and status information. Responsive to a manager request, the component software agent provides the installation and status information to the network manager. The information is displayed as a map which can show the topology of the cable modem's location in the network with respect to other modems and other components of the network.
Owner:CISCO TECH INC
System and method for carrying a wireless based signal over wiring
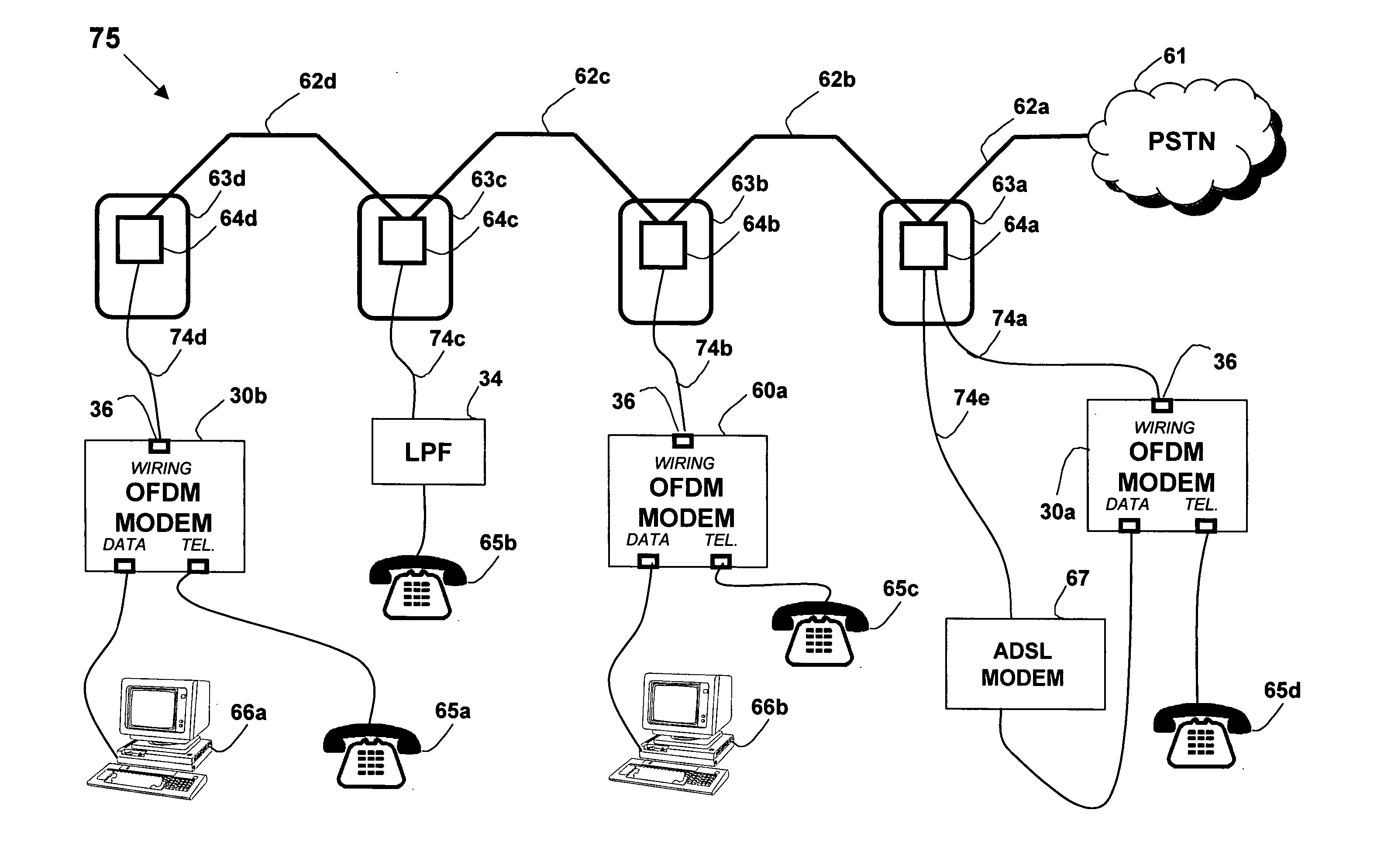
InactiveUS20050249245A1Power distribution line transmissionFrequency-division multiplexData connectionModem device
A device, network and method wherein a standard wireless modem is coupled to wiring for carrying a wireless baseband signal that may be OFDM based, and may be directly generated by the wireless IF modem, or extracted from the modem RF signal. The wiring may be a building utility wiring, such as telephone, AC power or CATV wiring. The baseband signal is carried simultaneously with the utility service signal over the utility wiring using Frequency Division Multiplexing. The device may be enclosed with a data unit, a standalone dedicated enclosure, within an outlet or as a plug-in outlet adapter. Data units may couple the device by a wiring port such as standard data connector, or via wireless connection. The device may be locally powered or via a power signal carried over the wiring. This abstract is not intended to limit or construe the scope of the claims.
Owner:CORNING OPTICAL COMM WIRELESS
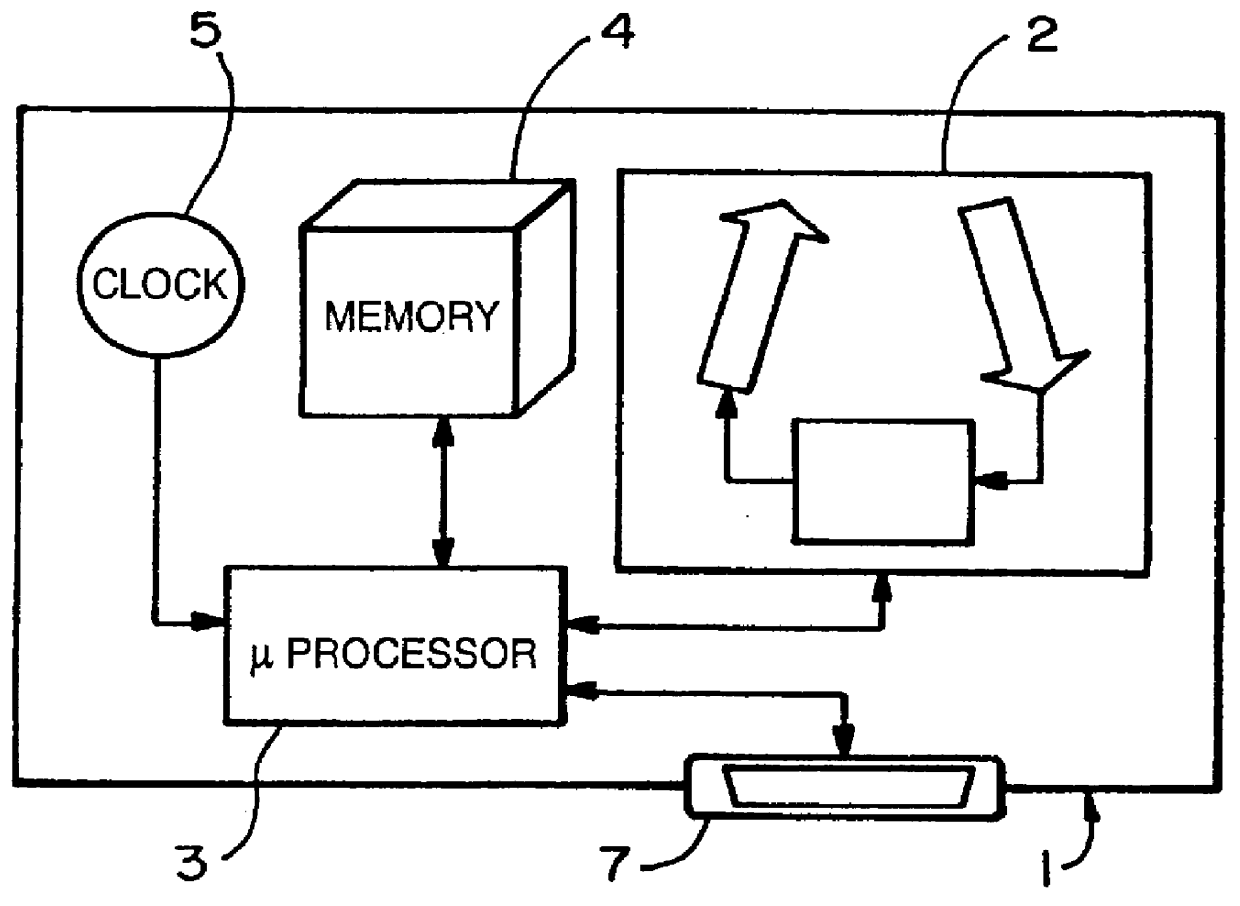
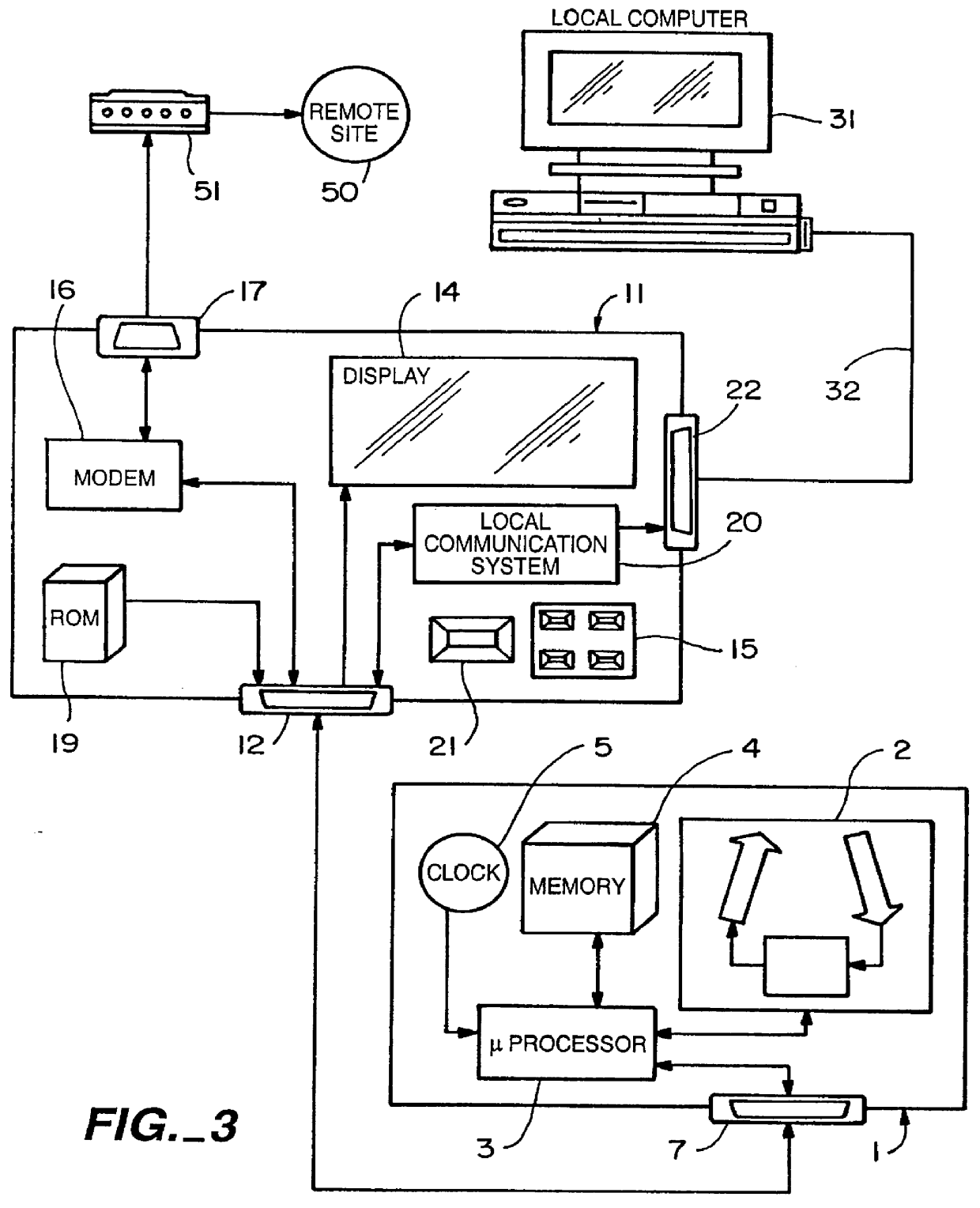
Analyte concentration information collection and communication system
A monitoring system which collects patient physiological date is designed specifically for communication with a communication module which facilitates data transfer from the monitoring system to a remote site. The communication module has data input mechanisms to facilitate setting parameters of the monitoring system and / or the communication module. The communication module is provided with a modem member which is used to communicate with the remote site and an optional data exchange module which is designed to communicate the same information with a local computer system. The remote site may be a bulletin board system or internet site where the monitoring information can be stored by the patient using the monitoring system by patient identification or name and include monitoring readings, time and date stamp, conditions such as meal times, exercise times and therapy amounts and their associated date and time.
Owner:ROCHE DIABETES CARE INC
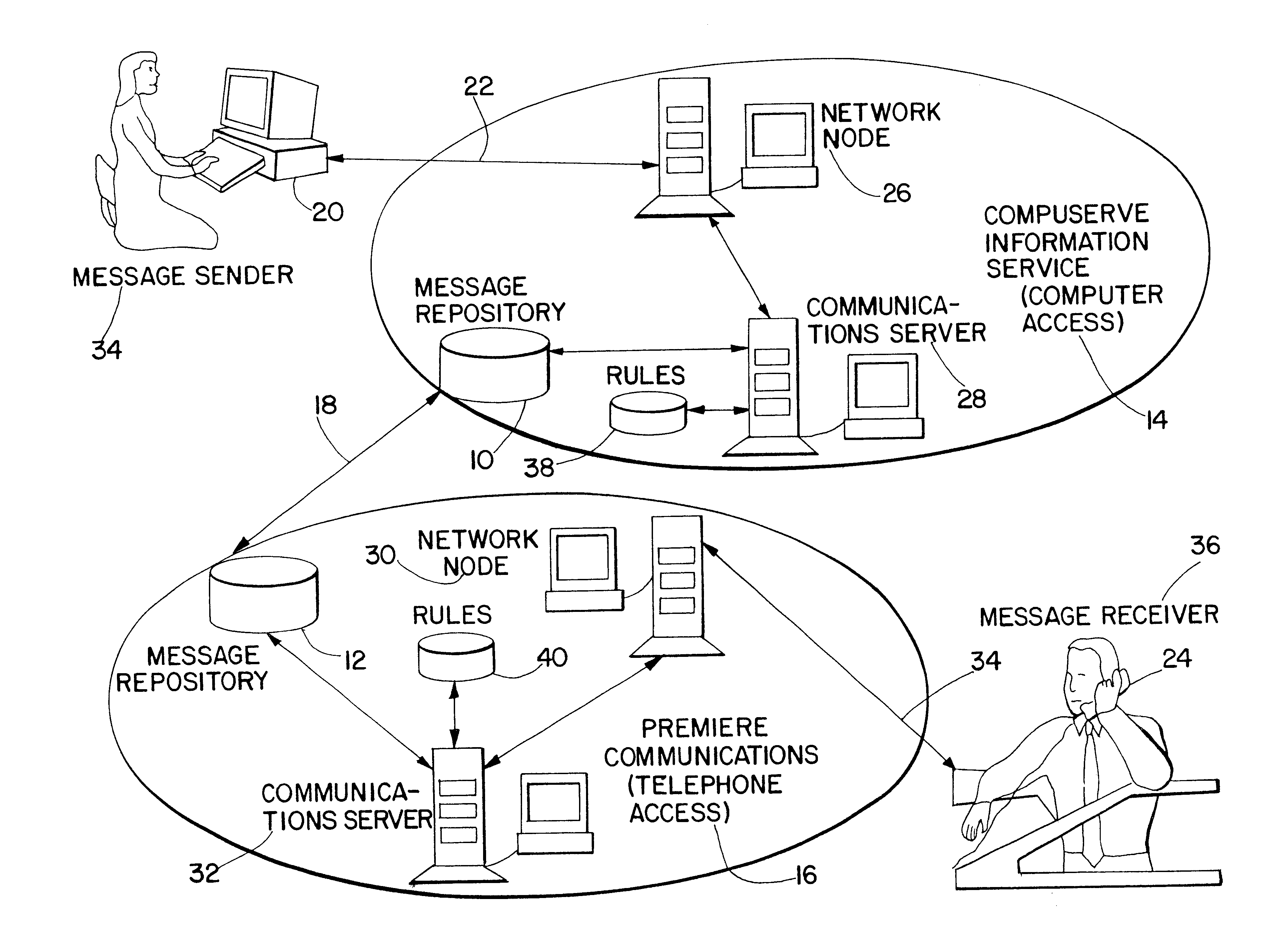
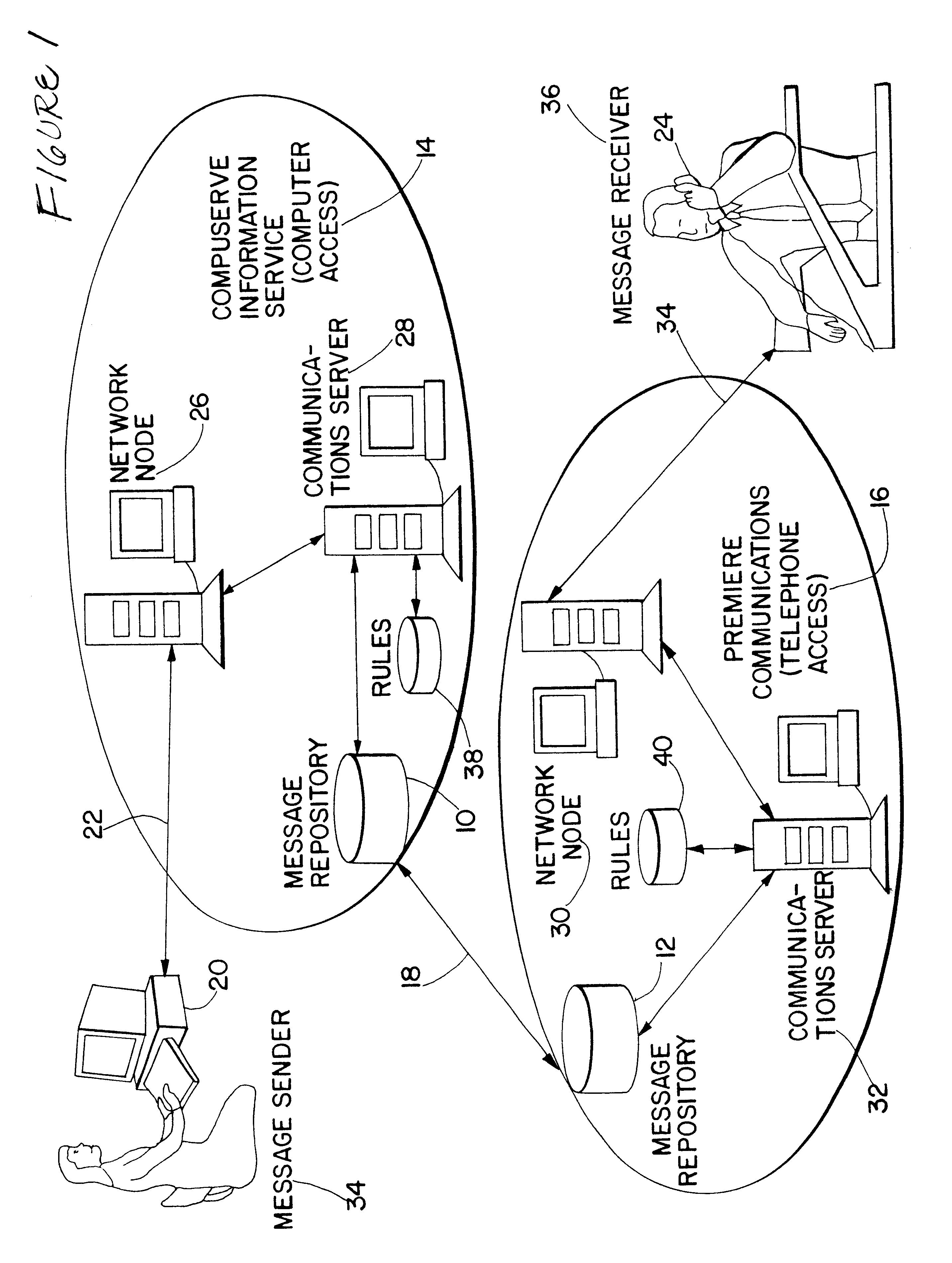
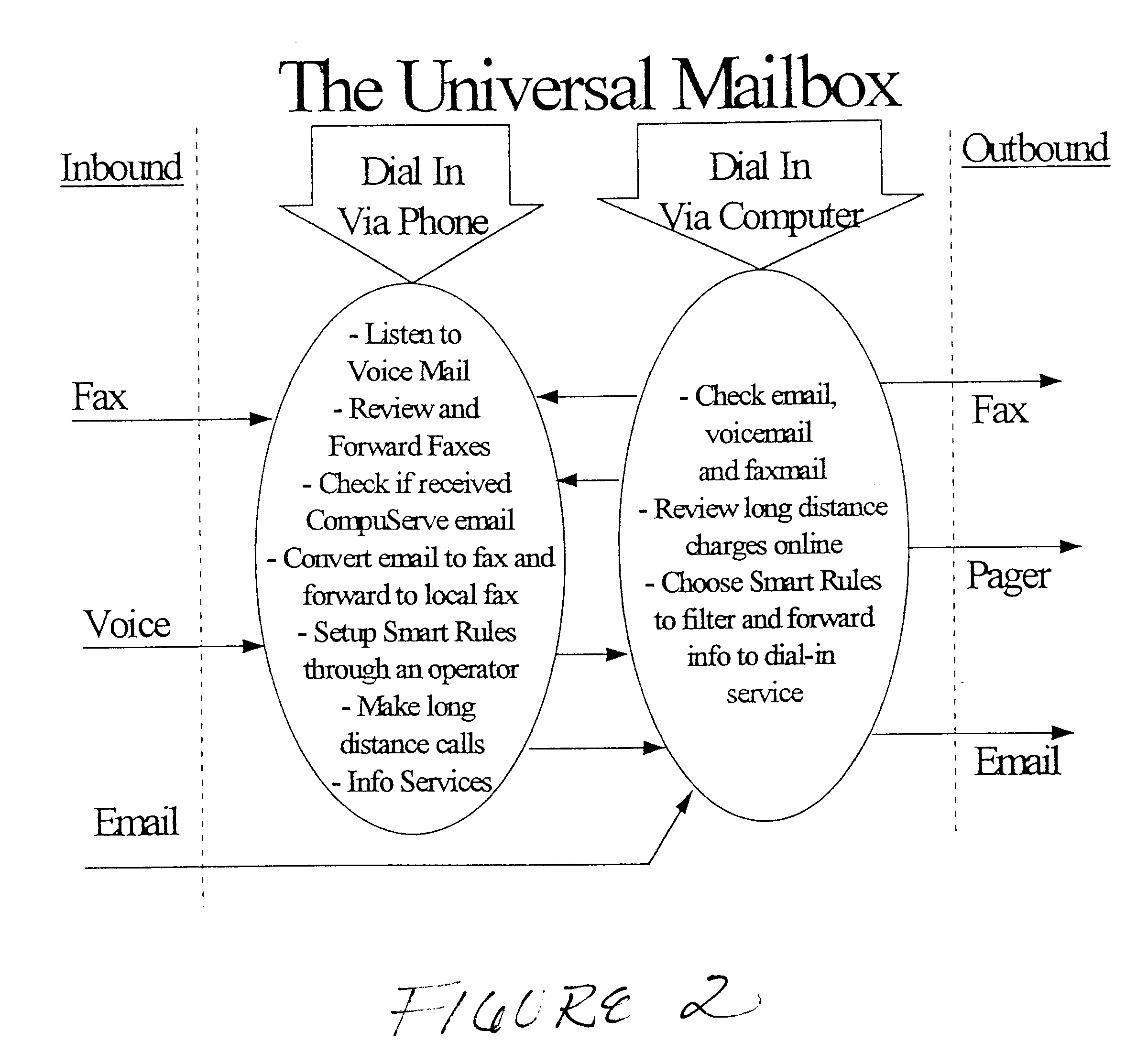
System for integrated electronic communications
InactiveUS6633630B1Special service for subscribersData switching networksModem deviceElectronic communication
A system is disclosed for integrating electronic mail, voice mail, and fax mail in a universal mailbox. Message receivers may access their messages with a telephone or a computer regardless of the communication medium used by the message sender. Using a telephone, message receivers may playback voice mail, redirect fax mail, and "listen" to e-mail through a text-to-speech conversion process. Using a computer and modem, message receivers may playback voice mail, view fax mail, and read e-mail by accessing the universal mailbox via connection software. Message senders and receivers may choose from a variety of filter and forward options that allow them to manage their communications via the universal mailbox. Forwarding and conversion of messages is performed automatically. The options are used to define a set of rules to be applied to inbound and outbound messages so that messages are sent and received in accordance with the preferences of the senders and receivers.
Owner:CRANBERRY PROPERTIES
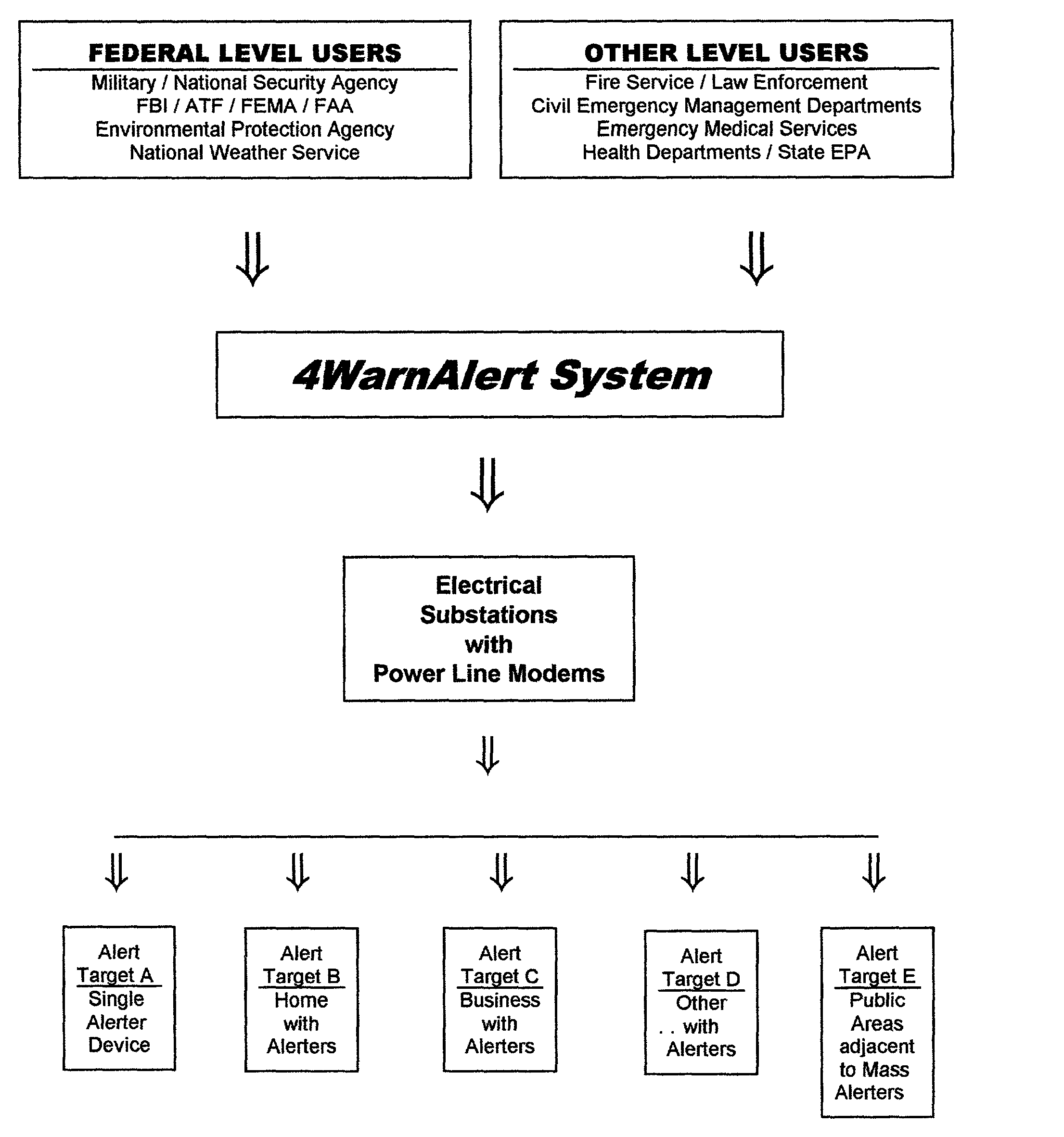
Civil defense alert system and method using power line communication
InactiveUS20020024424A1Special service provision for substationFrequency-division multiplex detailsModem deviceNetworked system
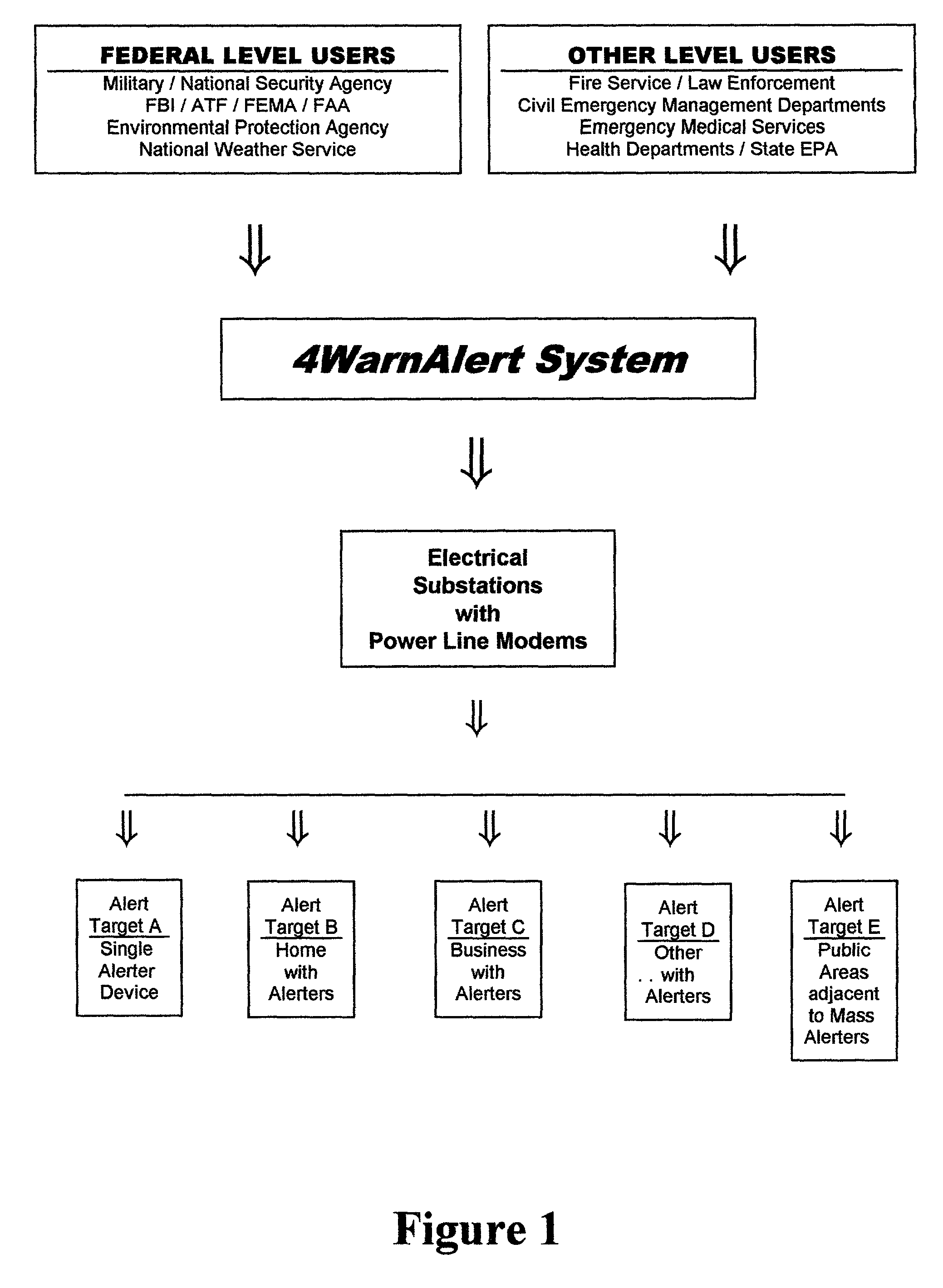
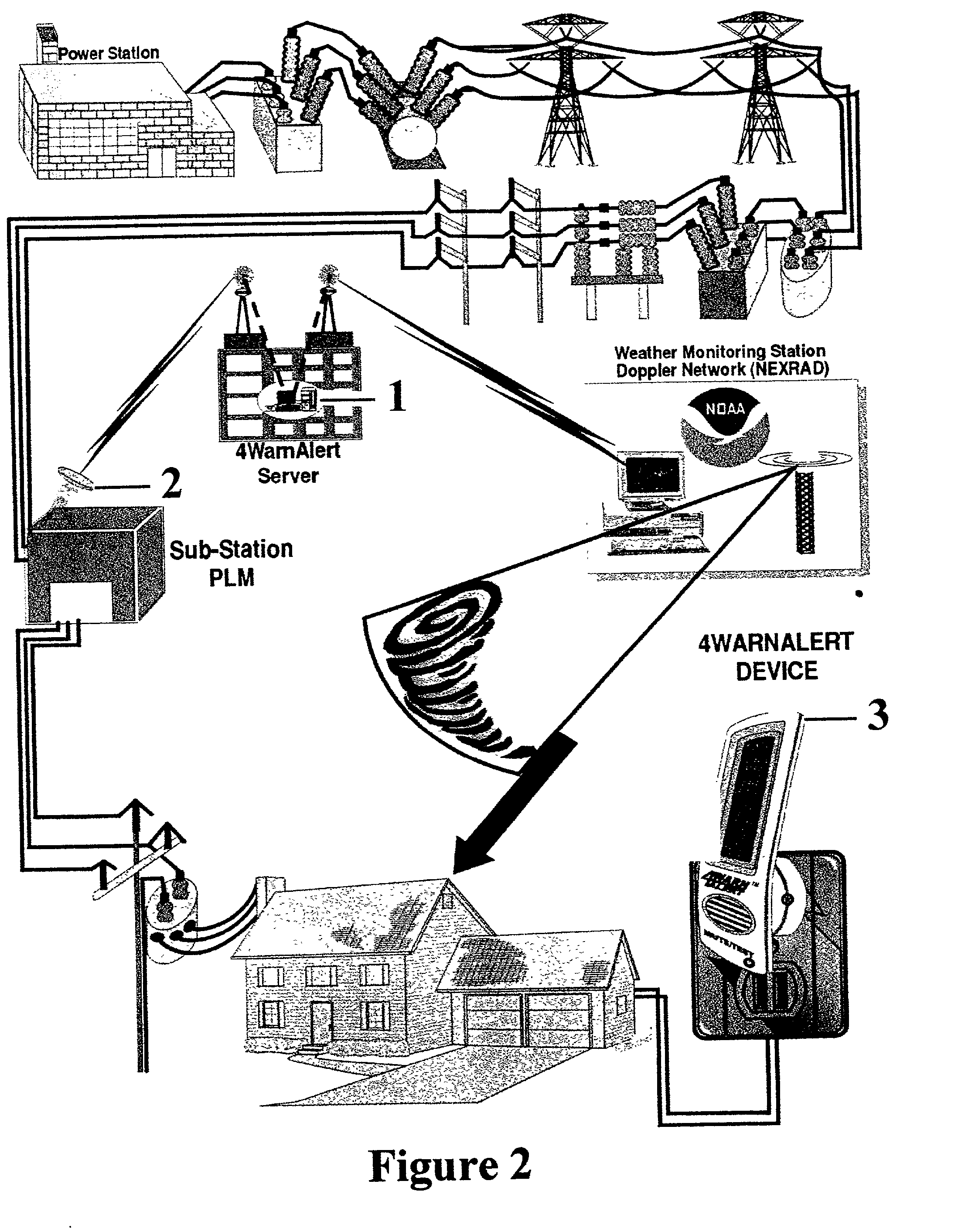
This invention pertains to the use of power line communication in a civil defense alerting system. The idea encapsulates the use of existing technology both in power line communication via a power line modem and network data transfer and applies it to an area to which it has never before been applied. Substantial improvement to both is developed through this invention as the prior art had never included or addressed the need for and ability to communicate over the power lines when no electrical power was flowing from the utility. The invention demonstrates that through a communications network it is possible for a system user to activate a single warning alerter device or a multitude of warning alerter devices that are connected to a standard power distribution network. Overall, this invention provides governmental users a more comprehensive and more fail-safe method and process f warning the public of risks, potentially hazardous situations, and safety instructions to minimize the loss of life and injury.
Owner:BURNS T D +1
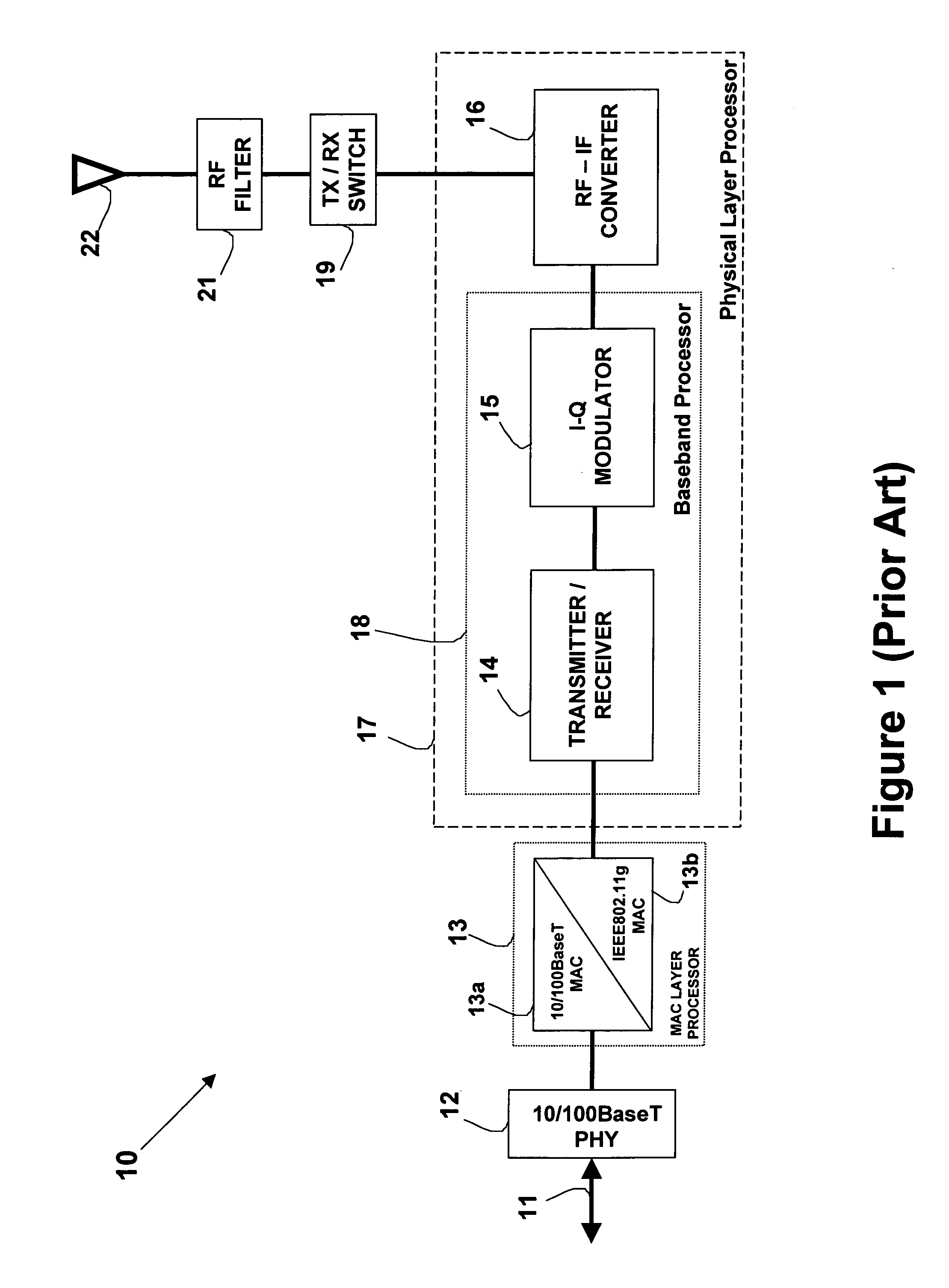
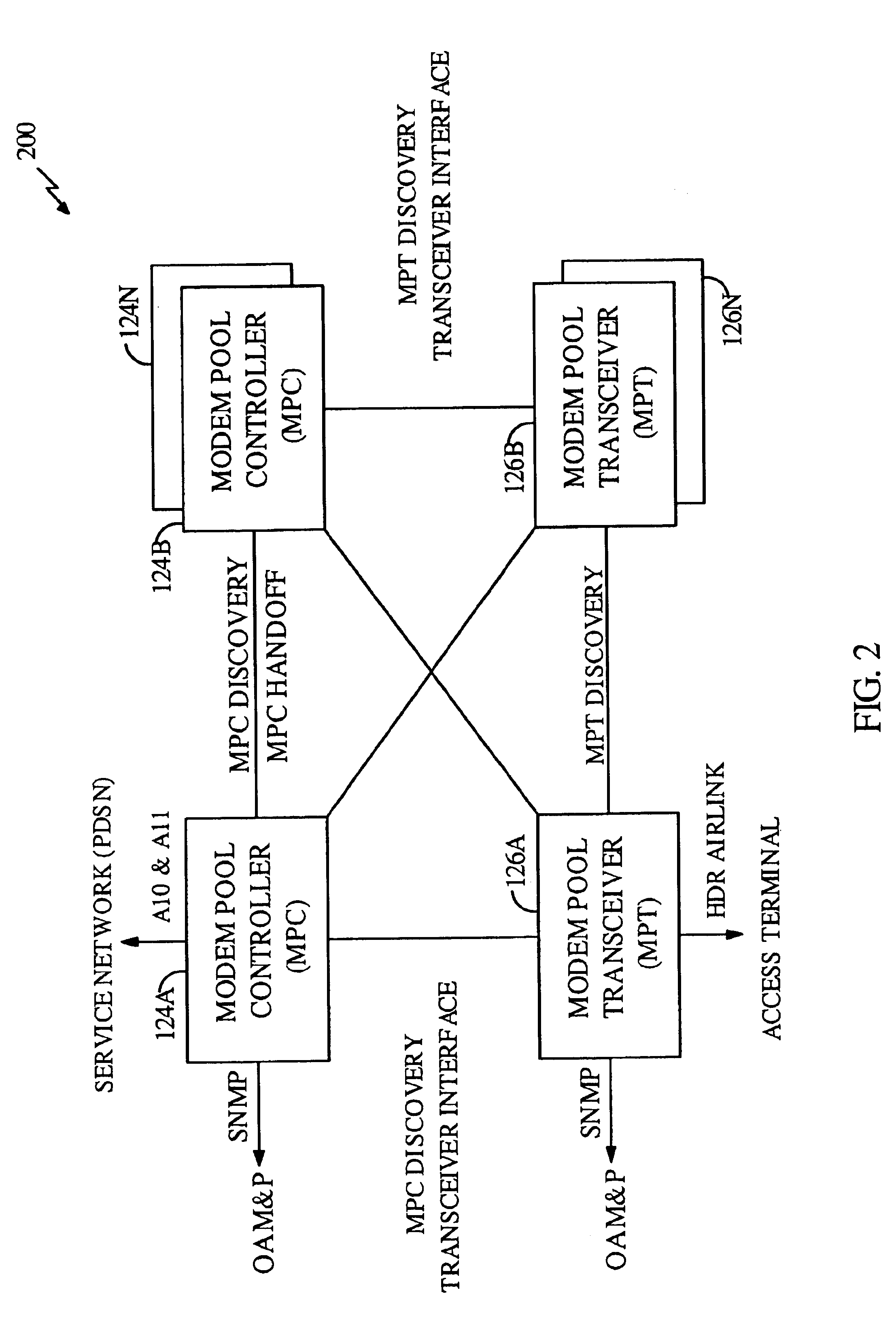
High data rate wireless packet data communications system
InactiveUS6894994B1Easy to deployEasy to upgradeError prevention/detection by using return channelNetwork topologiesTransceiverModem device
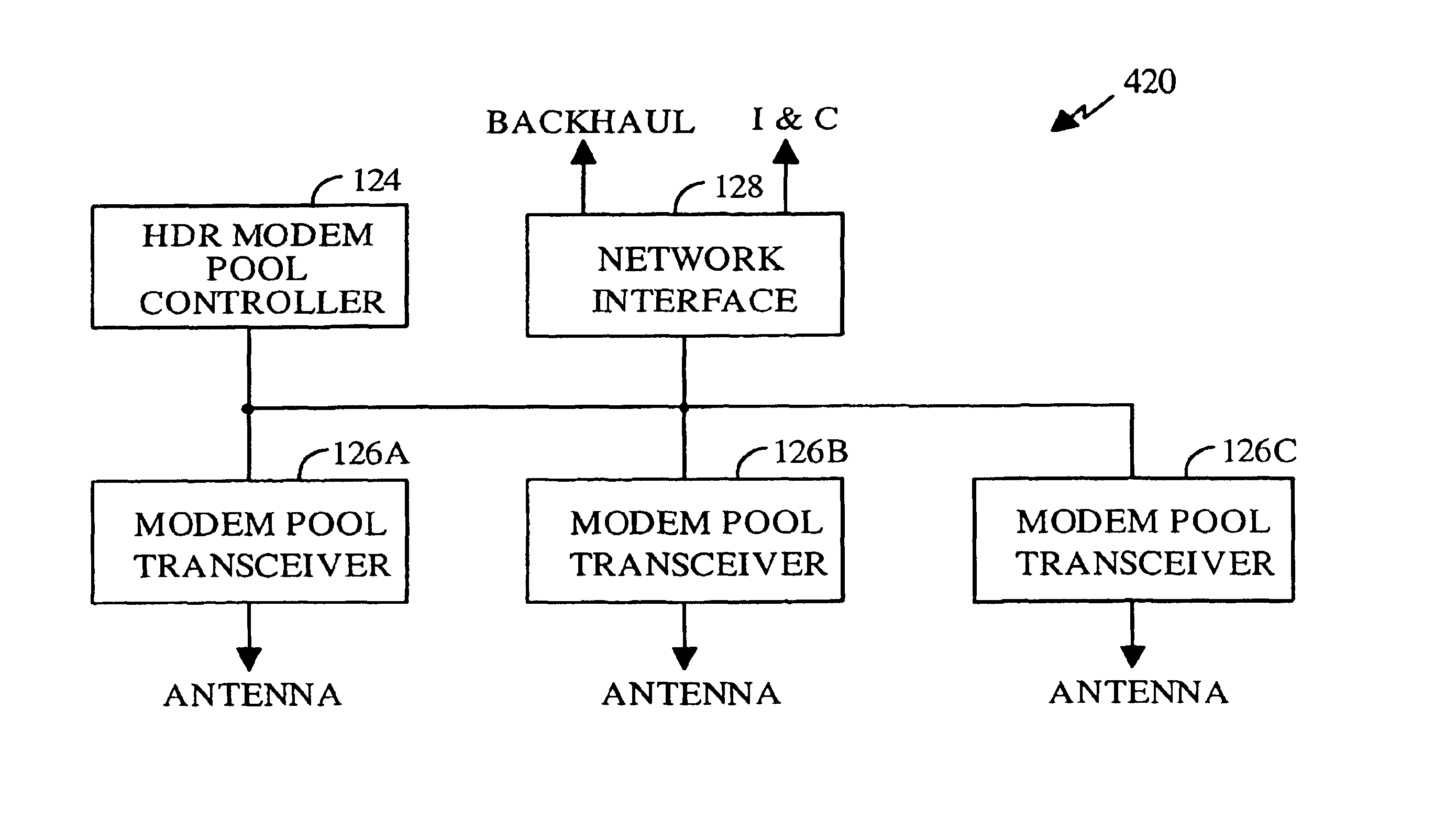
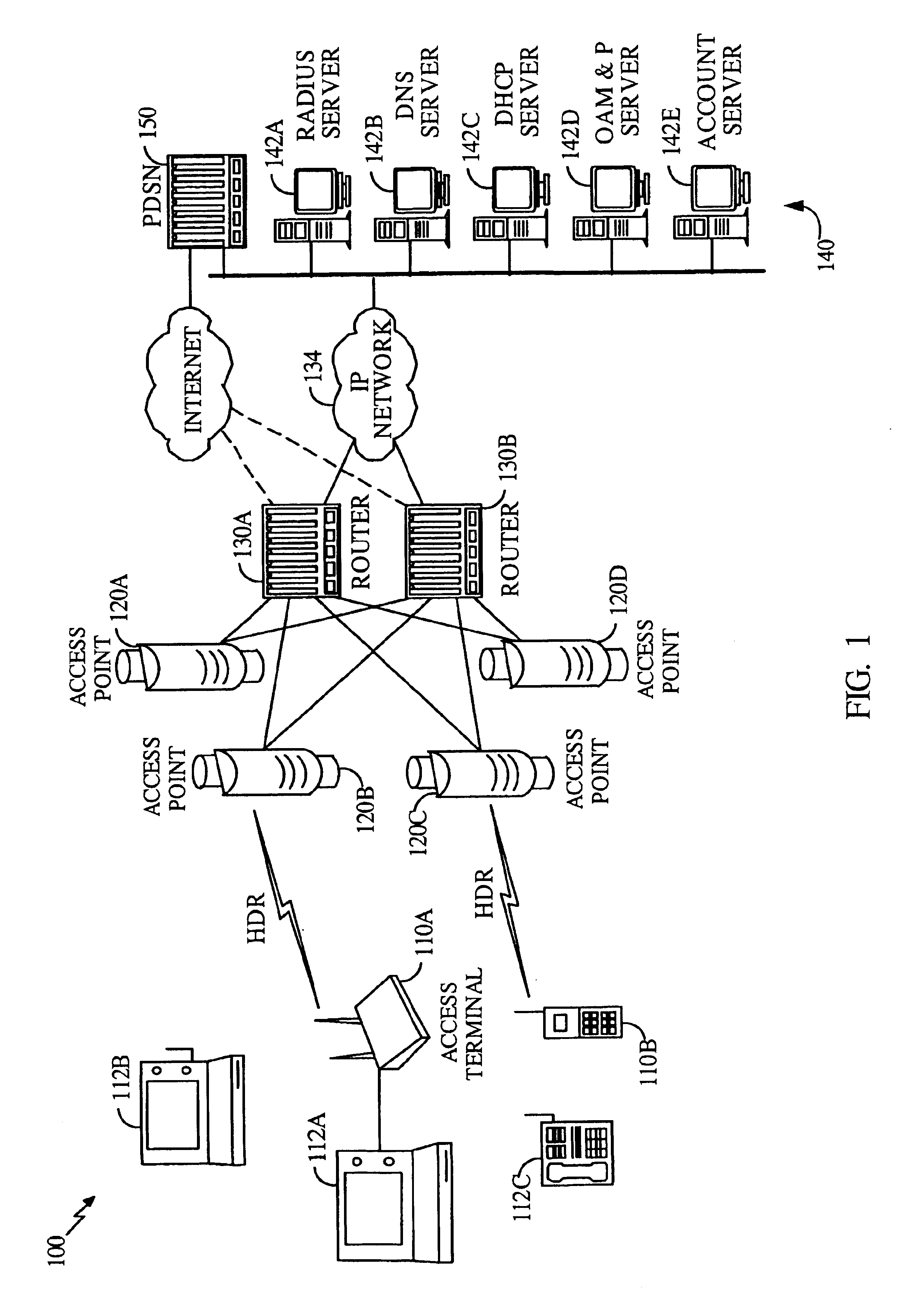
A wireless packet data communications system that includes a number of modem pool transceivers (MPTs), one or more modem pool controllers (MPCs), and one or more servers. Each MPT receives and processes data packets to generate a modulated signal (e.g., a CDMA spread spectrum signal) suitable for transmission over a terrestrial communications link. Each MPC provides call related processing for one or more MPTs. The servers couple to the MPTs and MPCs via an Internet Protocol (IP) back-bone and provide management of the communications system. The IP back-bone further interconnects the MPTs with one or more data networks and includes a number of routers that route data packets between the data networks and the MPTs. Each MPT can couple to two or more routers for redundancy. Each MPT is operated as an element in an IP network and is associated with an IP address that identifies the MPT. One to three MPTs can be deployed at each cell site to provide wireless data service coverage for up to three sectors at the cell site. The MPCs can either be centralized and coupled to the MPTs via the IP back-bone or distributed about the communications system.
Owner:QUALCOMM INC
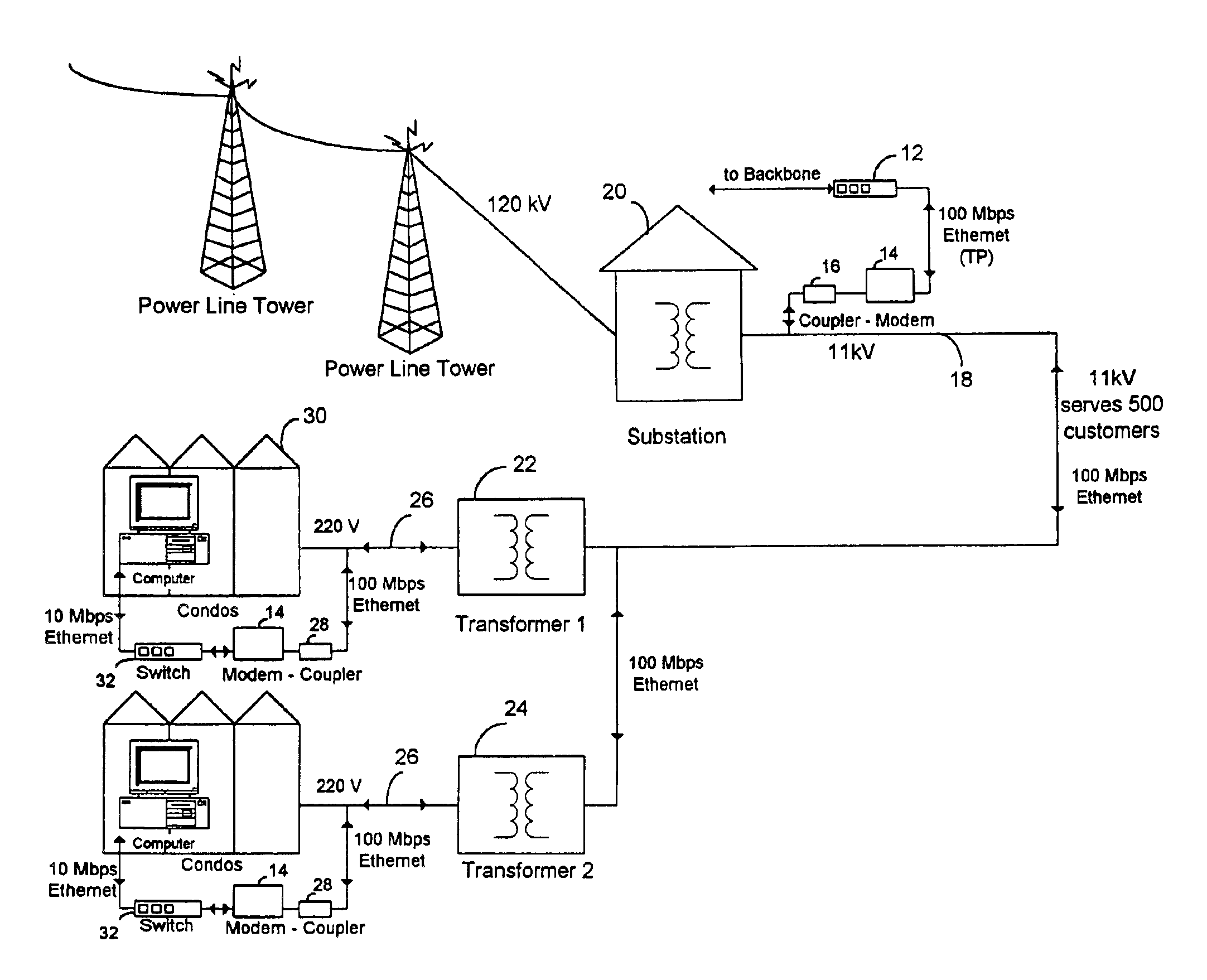
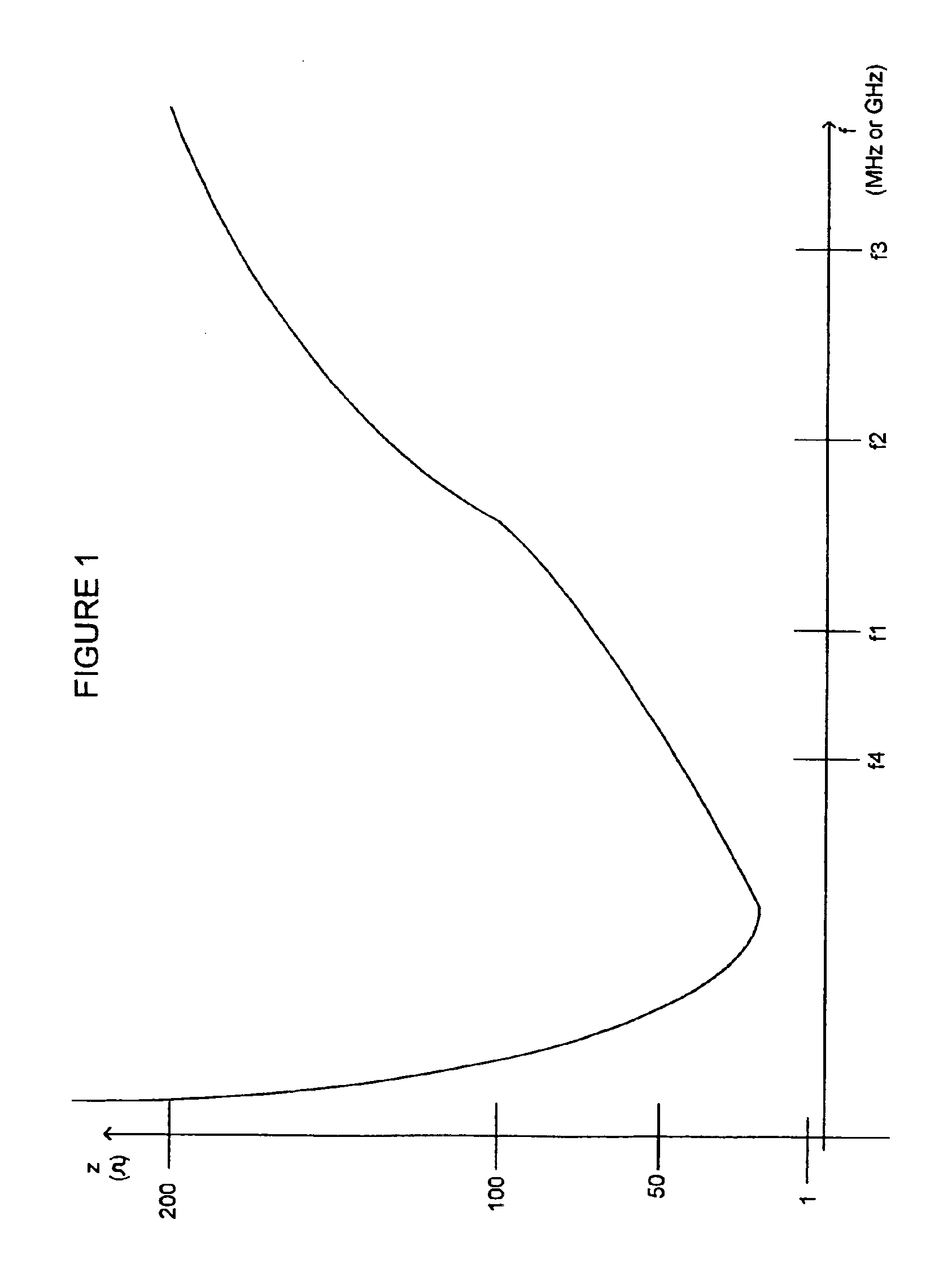
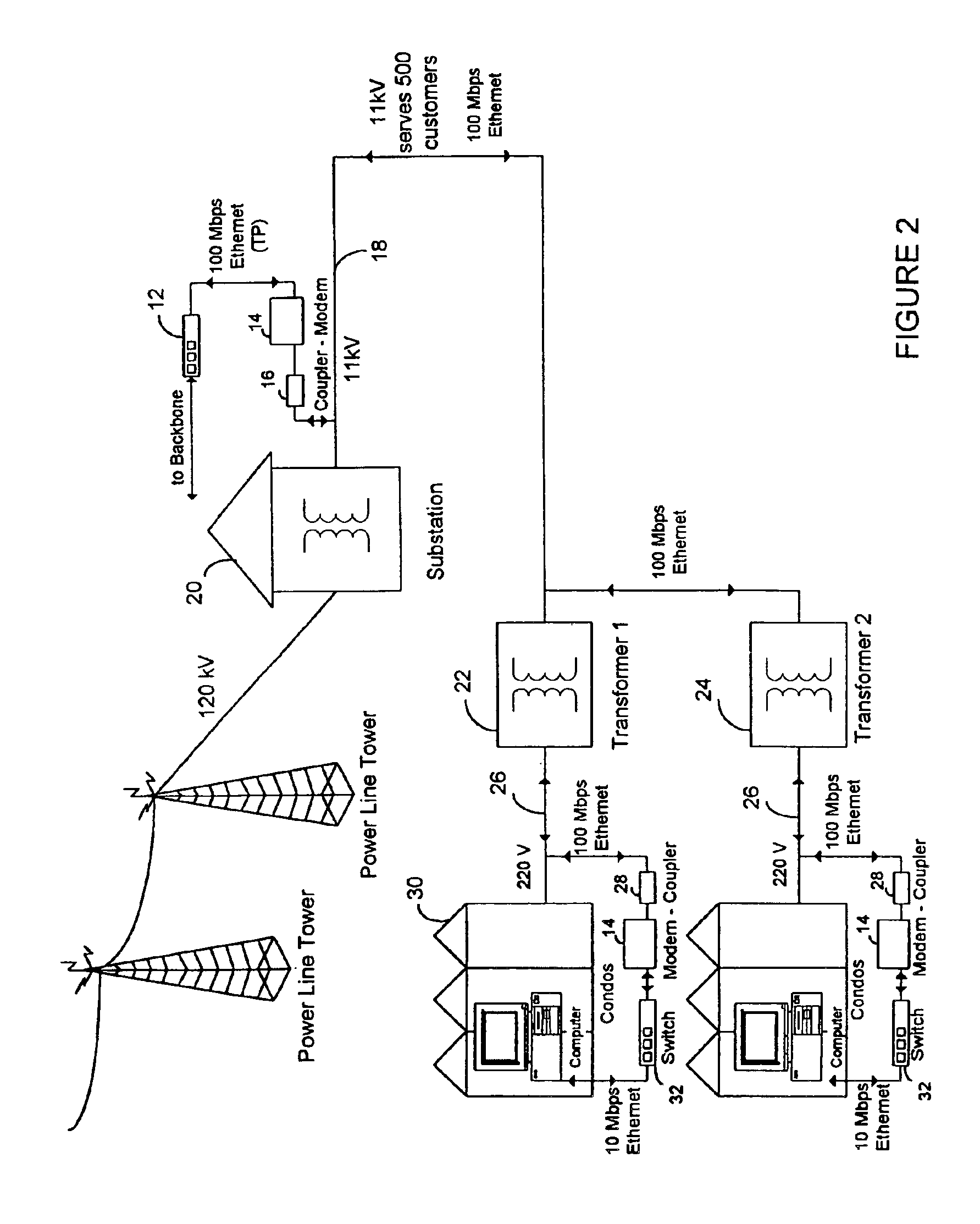
High frequency network multiplexed communications over various lines using multiple modulated carrier frequencies
InactiveUS6922135B2Substantial phase distortionMultiple-port networksPowerline communication systemsCapacitanceModem device
An apparatus is provided for high frequency multiplexed electrical line communication for cable TV, telephone, internet, security and other control applications over the mid and low voltage power lines and directly through the transformers. The apparatus includes a transmitter, a receiver, a modem, a multiplexer and multiple couplers at each of two or more locations along an electrical line. The couplers have capacitive circuits serially connected with an air-core or dielectric-core transformer. The capacitive circuits resonate with the transformer at a preselected frequency. The coupler eliminates noise and is matched to the characteristic impedance of the line at the preselected frequency, which linearizes communication on the line and allows high speed data and voice communication over long distances. Multiple modulators and demodulators are used to produce multiple modulated carrier frequencies.
Owner:SATIUS
Power line communication rate limiting system and method
InactiveUS20070002771A1Rate limiting quality of service (QoS) controlError preventionTransmission systemsQuality of serviceRate limiting
A power line communications device that may provide rate limiting and quality of service control is provided. The device may include a first modem in communication with one or more user devices via a low voltage power line subnet and a second modem communicatively coupled to a second communications medium. The device also may include a controller in communication with the first and second modems and a computer readable medium encoded with instructions to control the operation of the controller. The controller may rate limit data to and / or from a destination and / or source based one or more parameters such as the destination address, the source address, the type of data, temporal parameters, and other criteria. In addition, the controller may implement QoS for data and transmit QoS parameters to power line modems to allow the power line modems to perform QoS.
Owner:CURRENT TECH
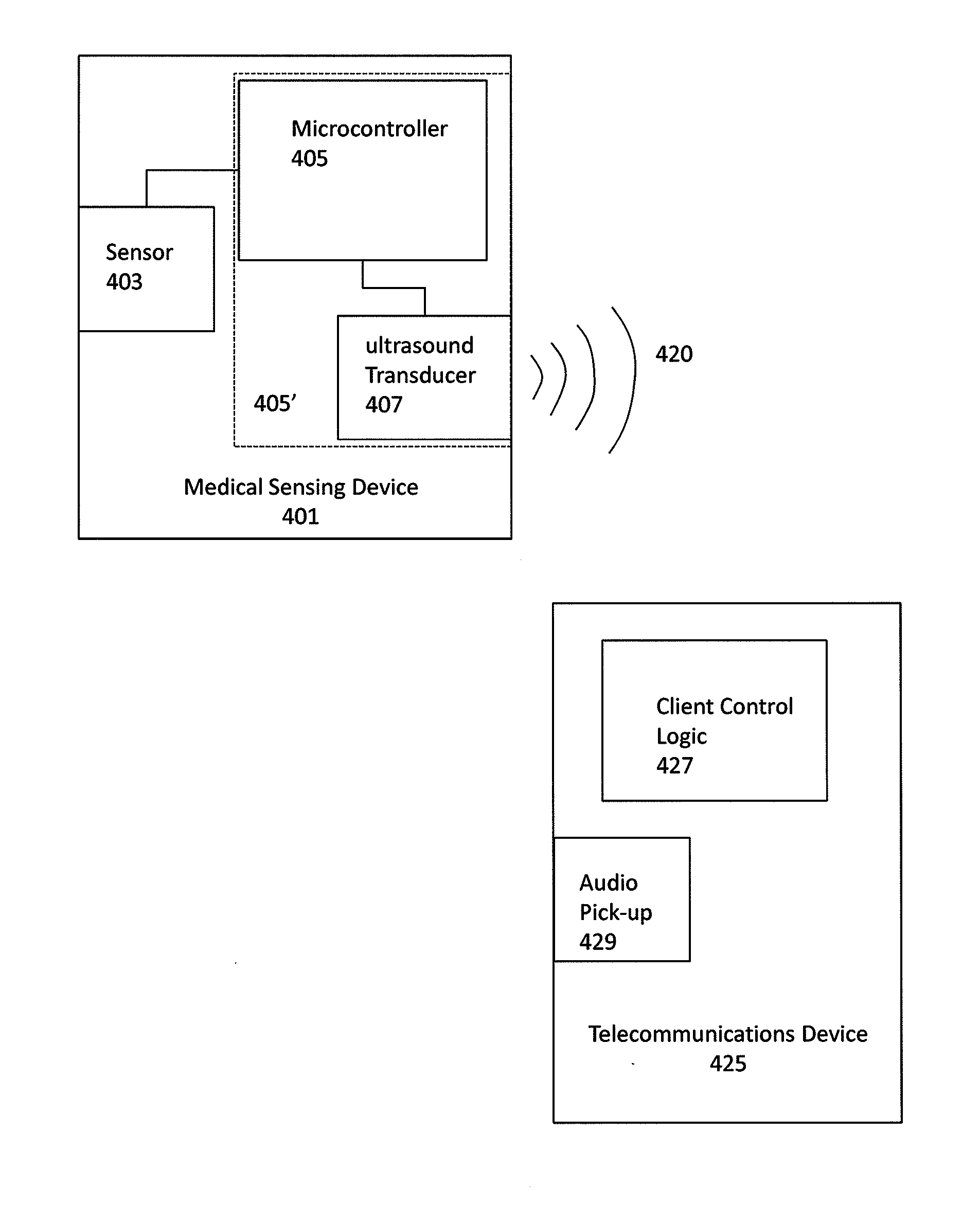
Ultrasonic digital communication of biological parameters
Medical sensing devices and systems that transmit digital data from a first device via an ultrasonic digital modem to a receiver such as a smartphone. Methods of transmitting digital biological data by ultrasound are also described.
Owner:ALIVECOR
Portable electronic terminal and data processing system
InactiveUS7171378B2Improve securityImprove programmabilityCredit registering devices actuationBuying/selling/leasing transactionsWireless transceiverModem device
The present invention relates to a personal shopping system for combined use in both the home of a user and a shopping establishment. The system includes a host computer which is coupled to a host modem and, optionally, to at least one wireless multi-access point. At least one shopping establishment kiosk cradle is employed to interface with a portable terminal which is also part of the system. The portable terminal can be used in both the shopping establishment and the home of the user. It is configured to read bar codes associated with items related to shopping, and includes a memory, a bar code reader, a wireless transceiver, and a data interface. The data interface of the terminal communicates with a data interface of the shopping establishment kiosk cradle. A home cradle for the portable terminal is also provided and is adapted to remain in the home of the user. It includes a home portable terminal-receiving station and a home data interface to communicate with the data interface of the portable terminal. A home data transfer circuit is also included to permit data exchange between the home data interface and the modem coupled to the host computer.
Owner:SYMBOL TECH INC
High data rate ethernet transport facility over digital subscriber lines
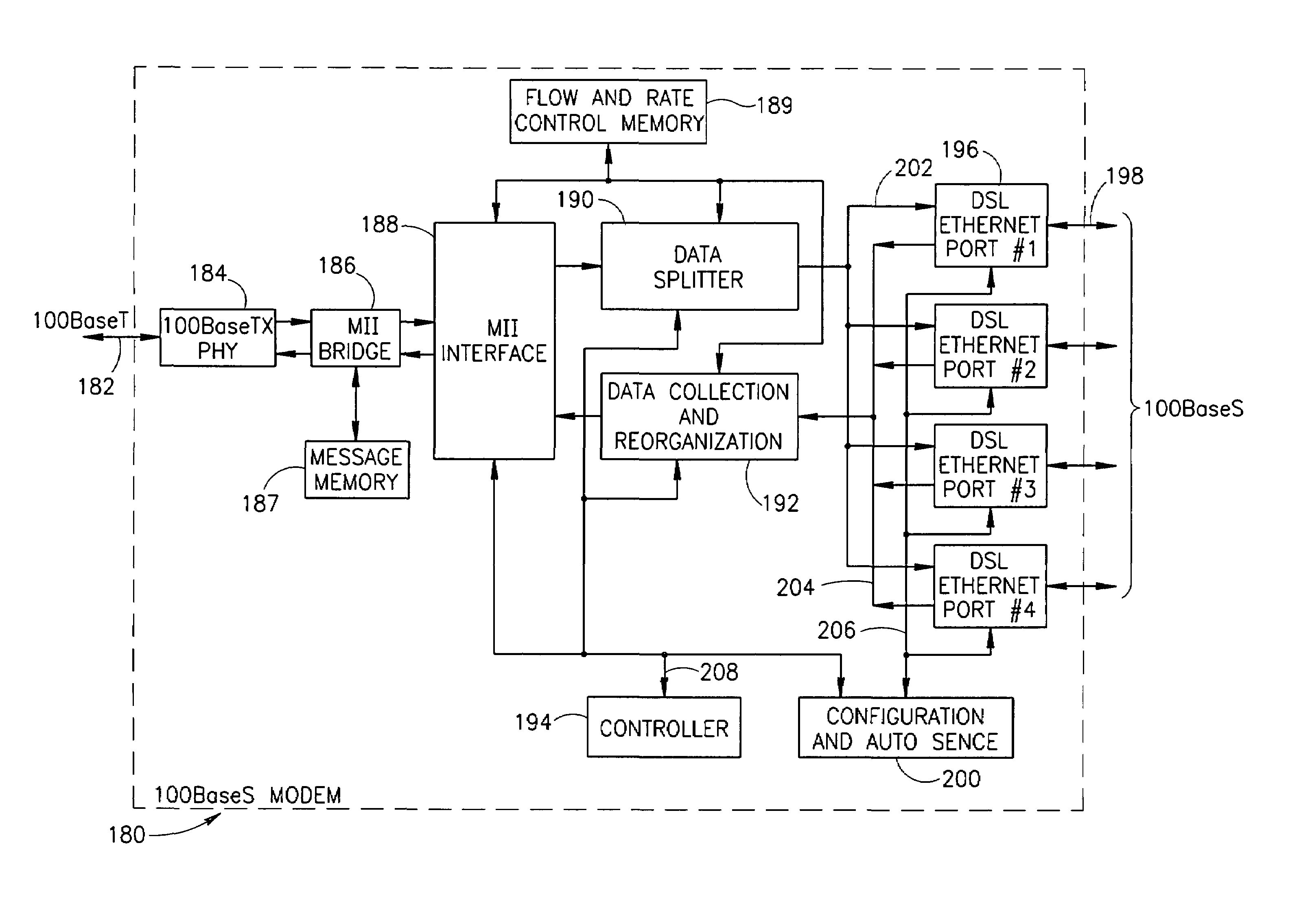
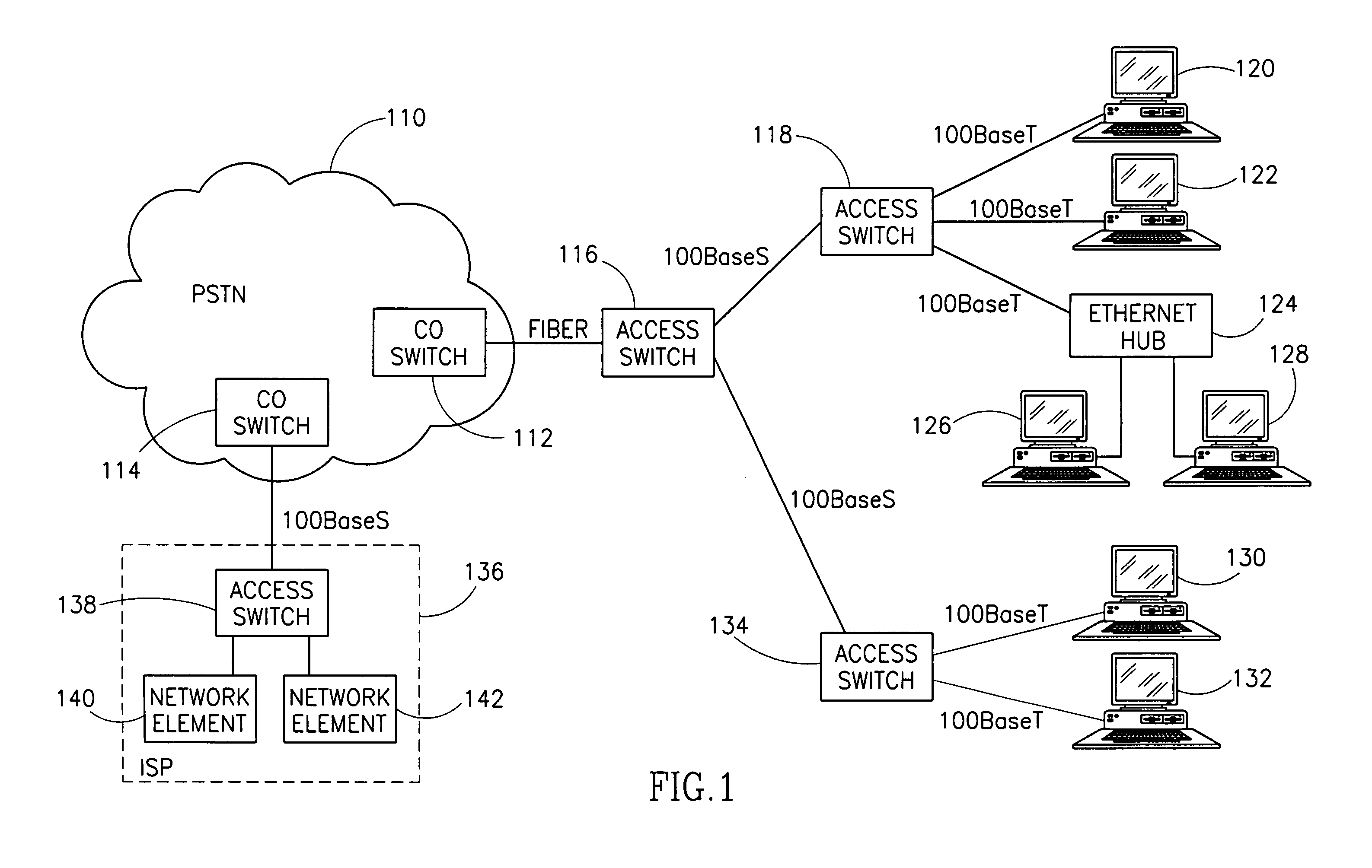
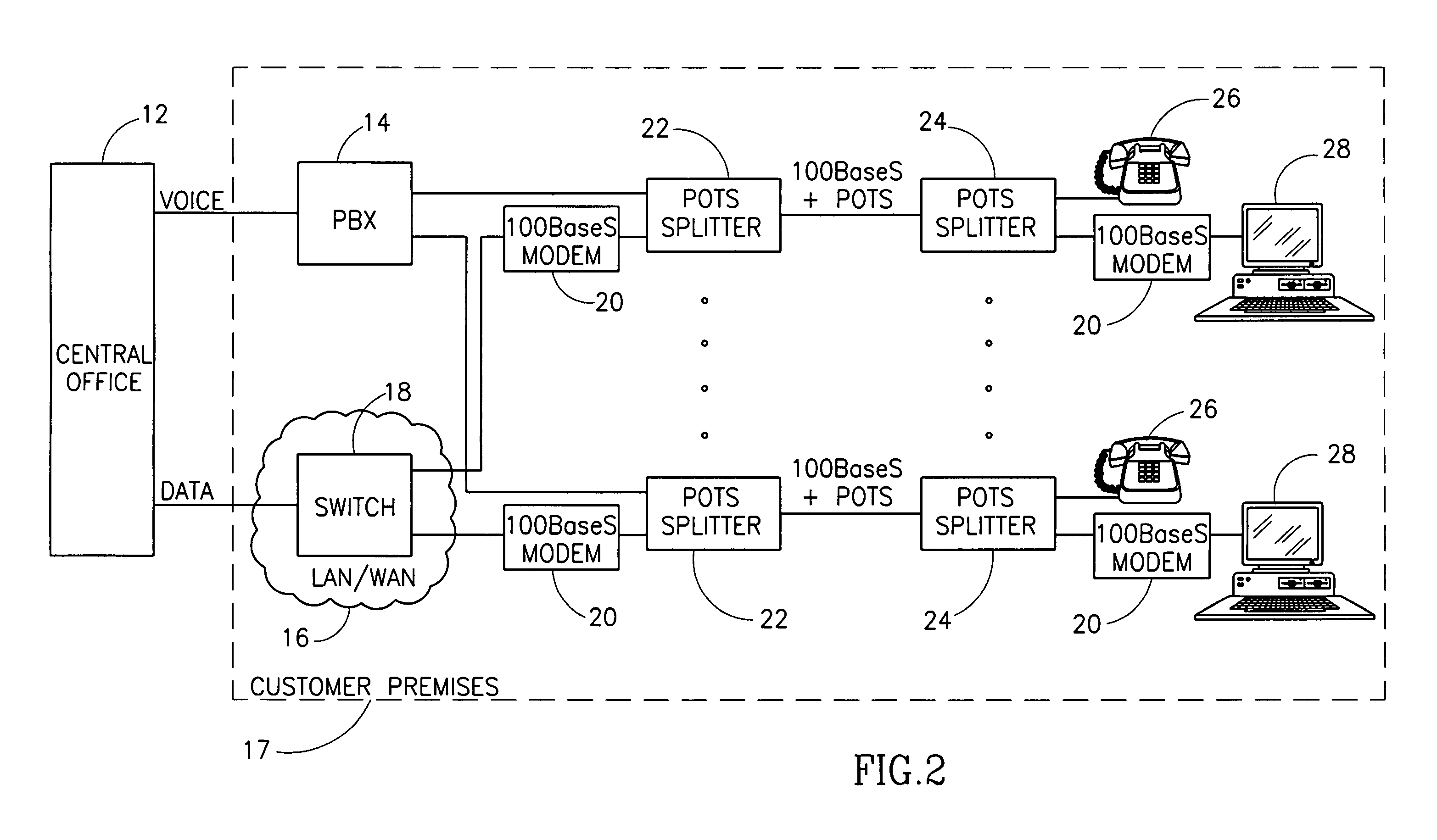
InactiveUS7054376B1Simple and cost-effectiveIncrease transfer speedMultiple-port networksError preventionTransport systemModem device
A facility transport system for transporting high speed Ethernet data over digital subscriber lines. The system, referred to as 100BaseS, is capable of transmitting 100 Mbps Ethernet over existing copper infrastructure up to distances of approximately 400 meters. The system achieves bit rates from 25 to 100 Mbps in increments of 25 Mbps with each 25 Mbps increment utilizing a separate copper wire pair. Each pair used provides a bidirectional 25 Mbps link with four copper wire pair connections providing 4×25 Mbps downstream channels and 4×25 Mbps upstream channels. The system utilizes framing circuitry to adapt the 100BaseT input data signal to up to four separate output signals. A DSL Ethernet Port card couples the modem to each twisted pair used. Each DSL Ethernet Port card comprises modem transmitter and receiver circuitry for sending and receiving 100BaseS signals onto twisted pair wires. The system utilizes QAM in combination with frequency division multiplexing (FDM) to separate downstream channels from upstream channels and to separate both the downstream and the upstream channels from POTS and ISDN signals.
Owner:LANTIQ BET GMBH & CO KG
INTERRELATED WiFi AND USB PROTOCOLS AND OTHER APPLICATION FRAMEWORK PROCESSES, CIRCUITS AND SYSTEMS
ActiveUS20110188391A1Avoid collisionEnergy efficient ICTError preventionModem deviceData transmission
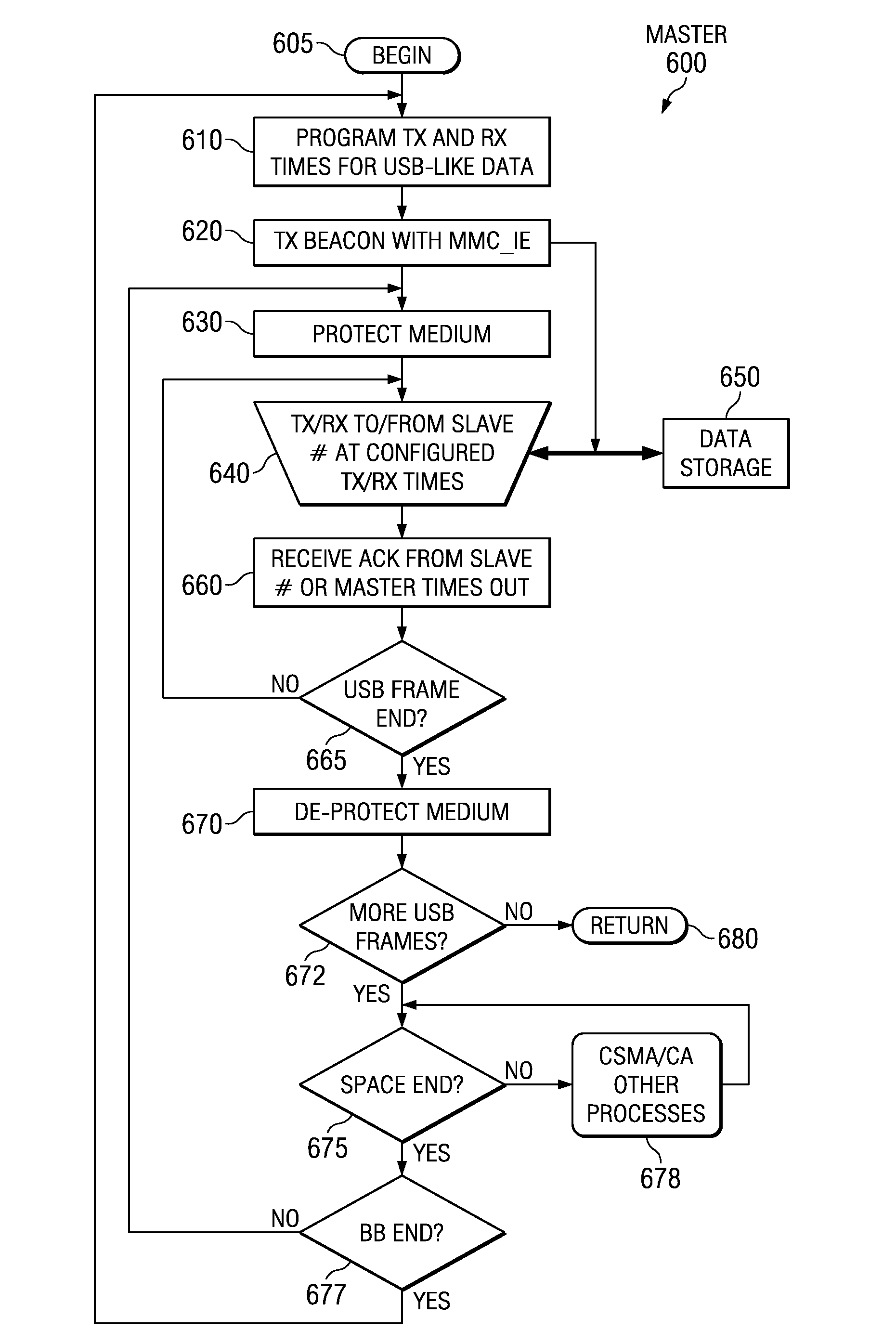
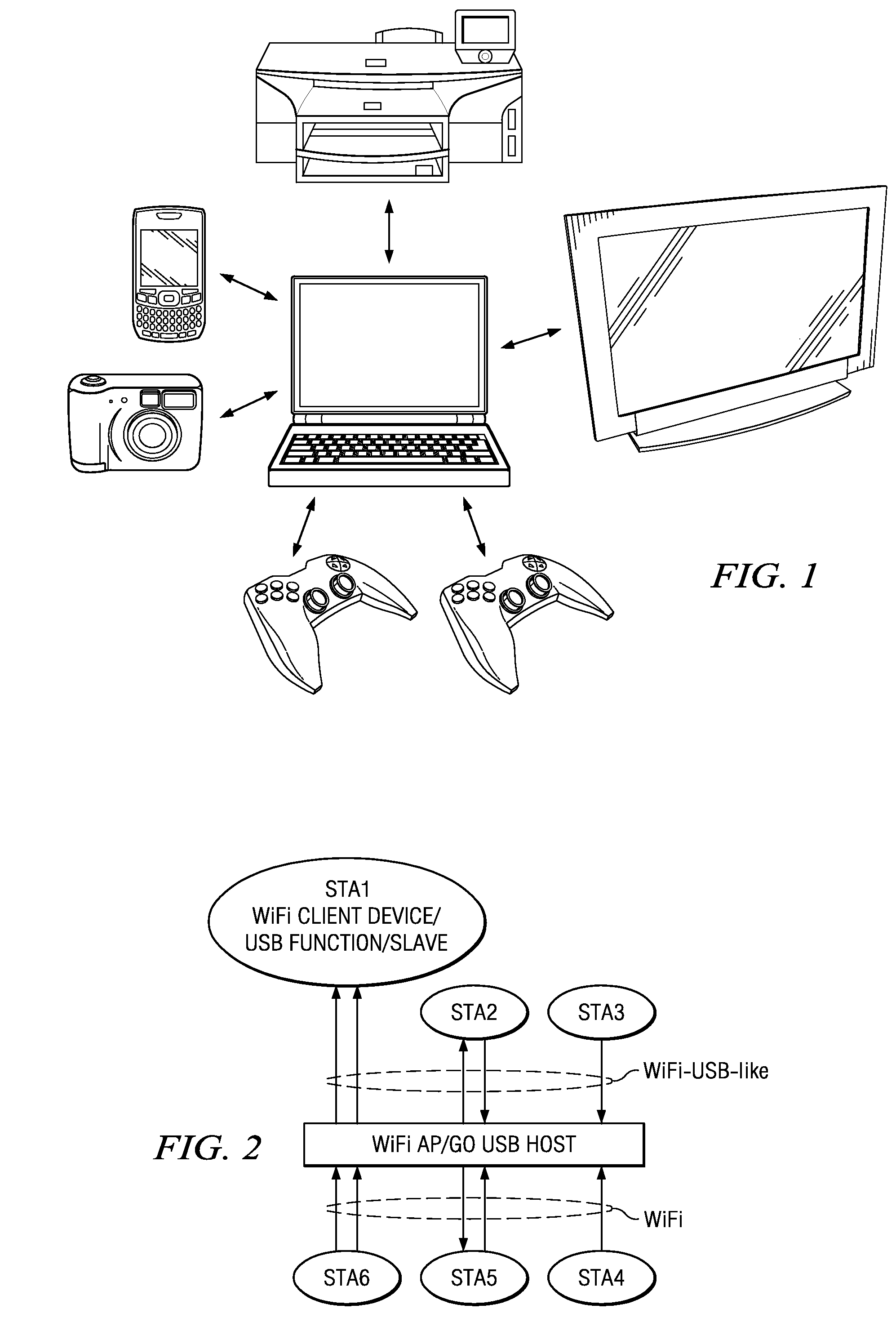
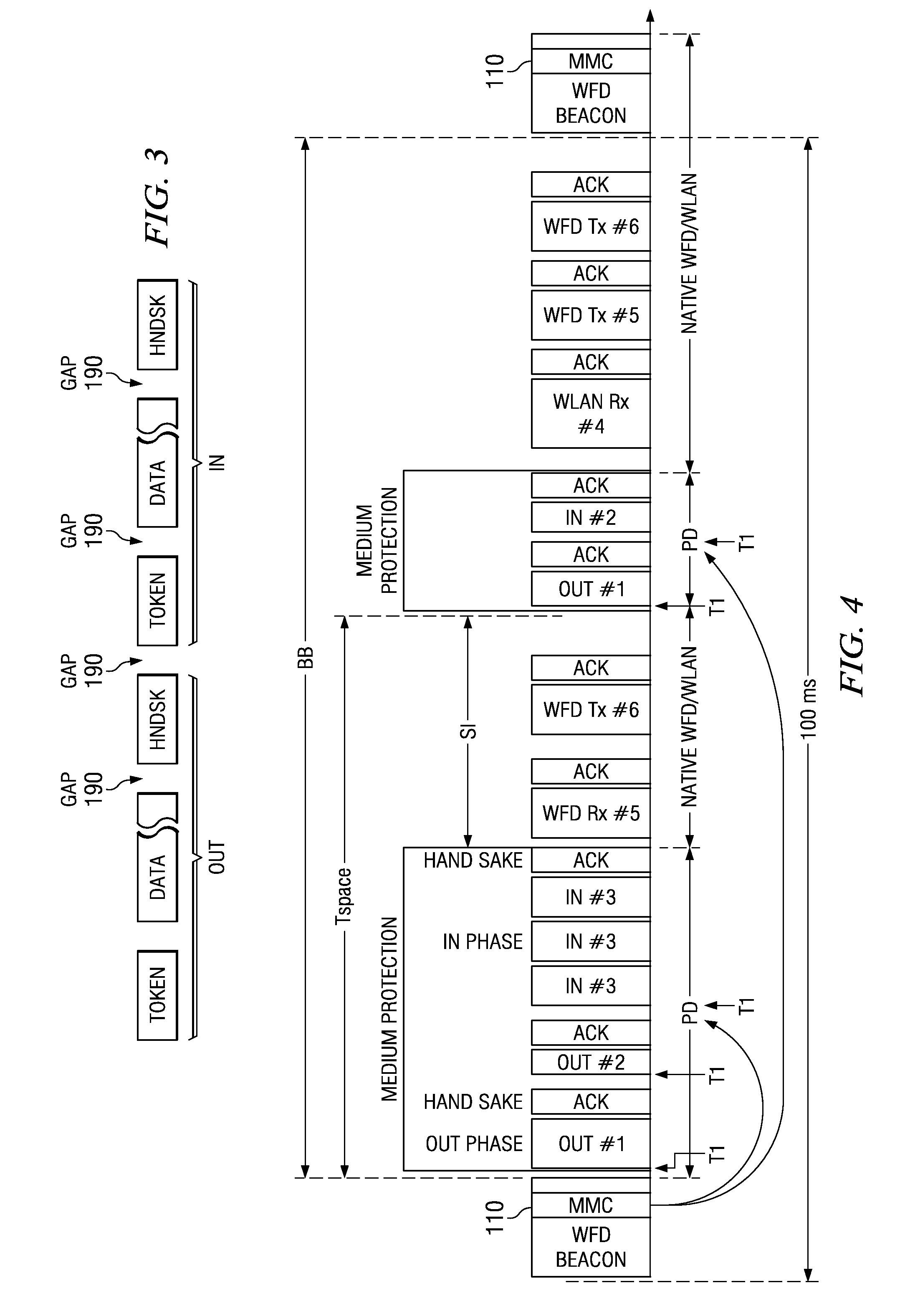
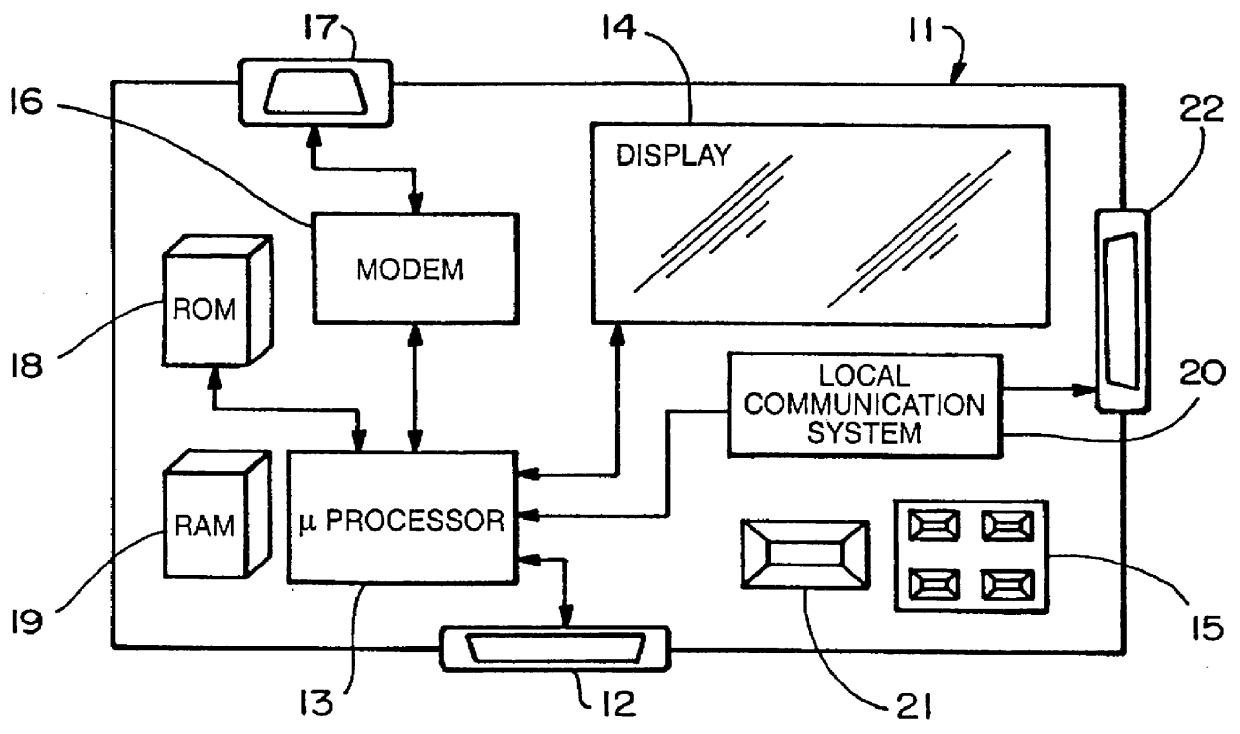
A master electronic circuit (300) includes a storage (324) representing a wireless collision avoidance networking process (332) involving collision avoidance overhead and combined with a schedulable process (345) including a serial data transfer process and a scheduler, a wireless modem (350) operable to transmit and receive wireless signals for the networking process (332), and a processor (320) coupled with the storage (324) and with the wireless modem (350) and operable to execute the scheduler to establish and transmit a schedule (110) for plural serial data transfers involving the processor (320) and distinct station identifications, and to execute the serial data transfers inside the wireless networking process and according to the schedule so as to avoid at least some of the collision avoidance overhead. Other electronic circuits, processes of making and using, and systems are disclosed.
Owner:TEXAS INSTR INC
Analyte concentration information collection and communication system
InactiveUS6134504AReduce system costIncrease transfer speedData processing applicationsLocal control/monitoringModem deviceExercise time
A monitoring system which collects patient physiological date is designed specifically for communication with a communication module which facilitates data transfer from the monitoring system to a remote site. The communication module has data input mechanisms to facilitate setting parameters of the monitoring system and / or the communication module. The communication module is provided with a modem member which is used to communicate with the remote site and an optional data exchange module which is designed to communicate the same information with a local computer system. The remote site may be a bulletin board system or internet site where the monitoring information can be stored by the patient using the monitoring system by patient identification or name and include monitoring readings, time and date stamp, conditions such as meal times, exercise times and therapy amounts and their associated date and time.
Owner:AMIRA MEDICAL +1
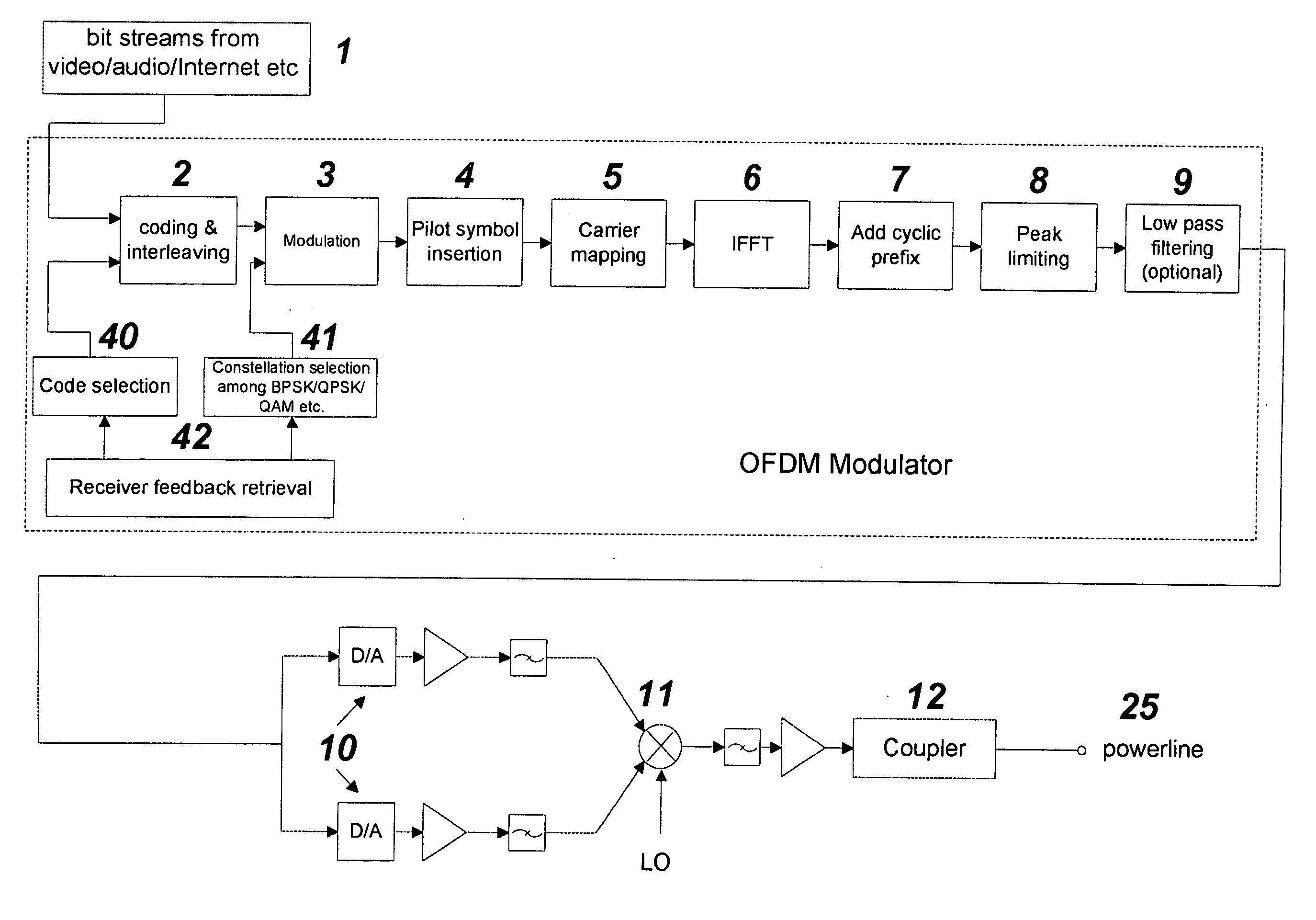
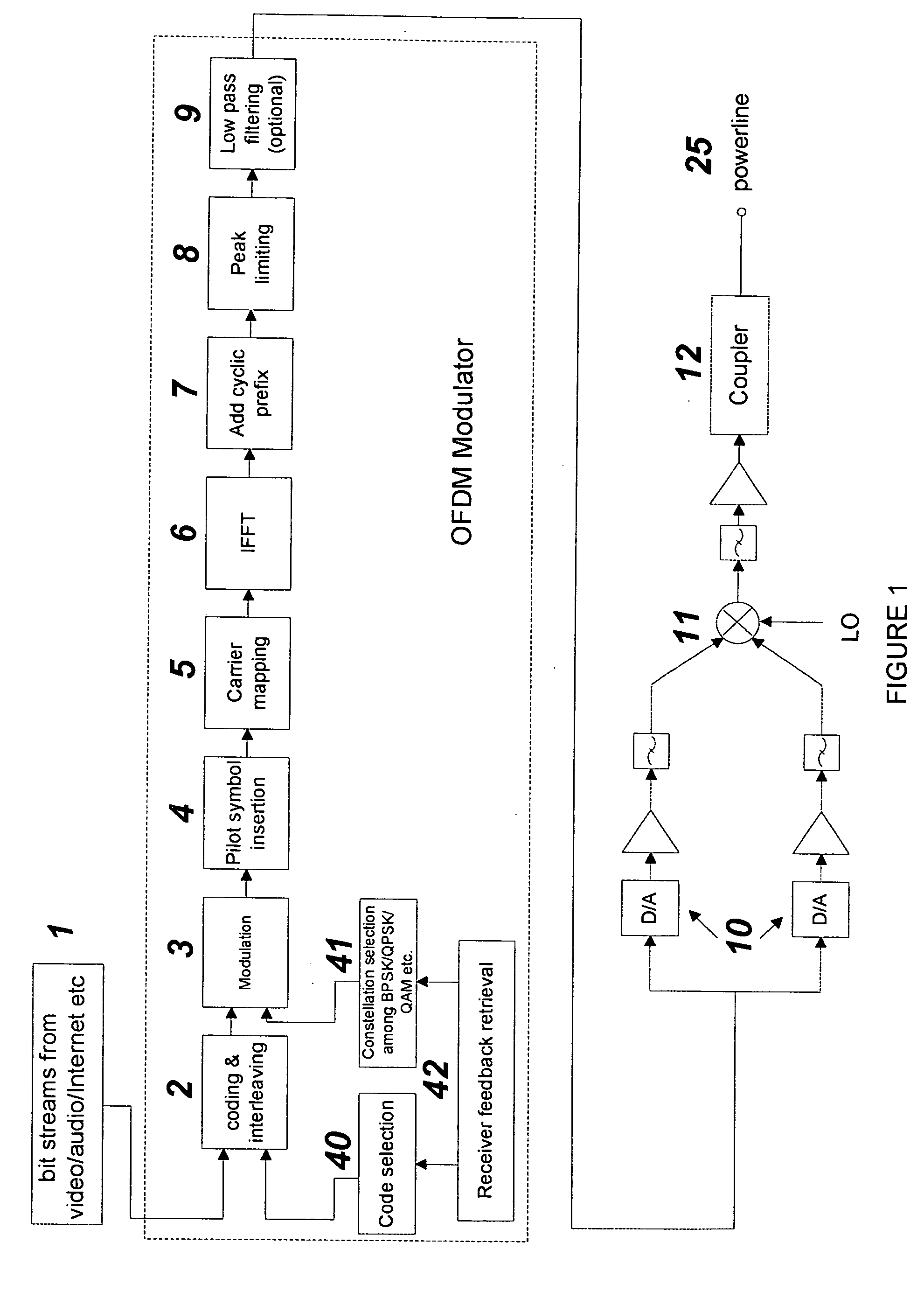
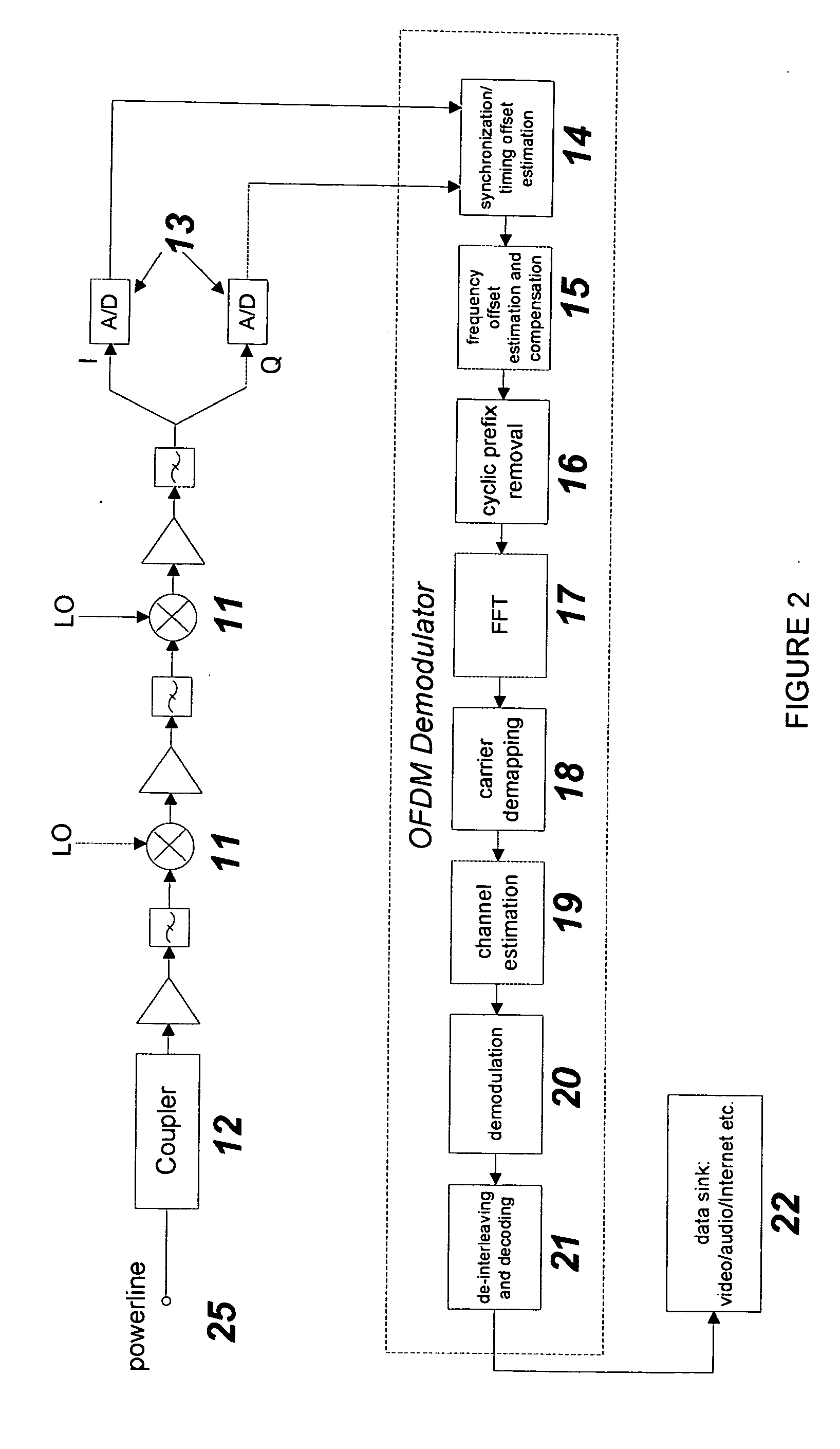
Frequency modulated OFDM over various communication media
ActiveUS20050169401A1Transmission/receiving by adding signal to waveFrequency-division multiplex detailsModem deviceEngineering
The present invention provides an FM Orthogonal Frequency Division Multiplexing (OFDM) modulation process that enable high-speed data communications over any transmission media and networks. The process is implemented with a modem device modulator and demodulator that provides communication with several other modem devices along any communication media that uses an FM OFDM modulation technique, a physical transmission medium such as power lines, or wireless (air), or cable, or twisted pairs communication media.
Owner:SATIUS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com