Patents
Literature
2629 results about "Network segment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
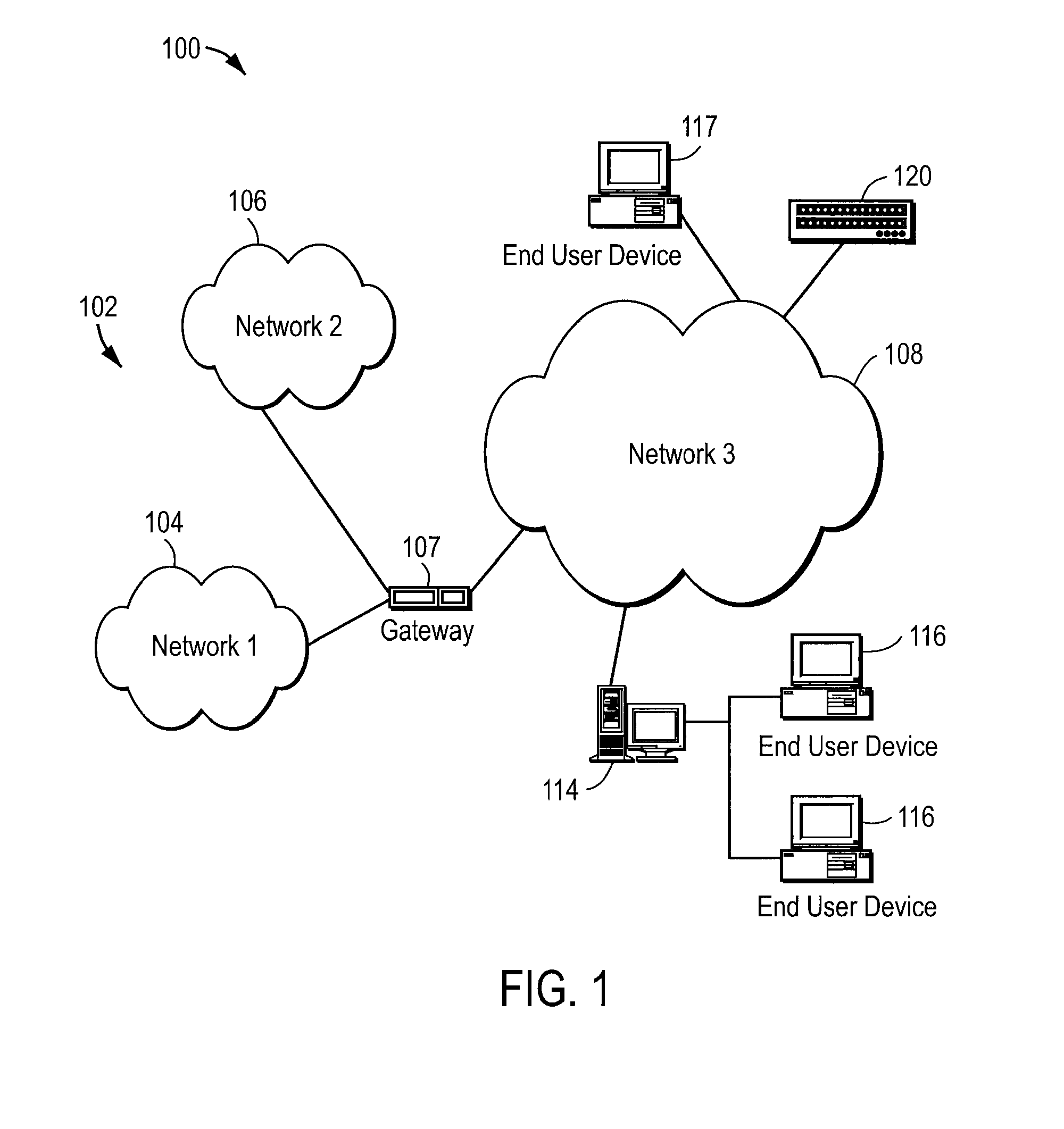
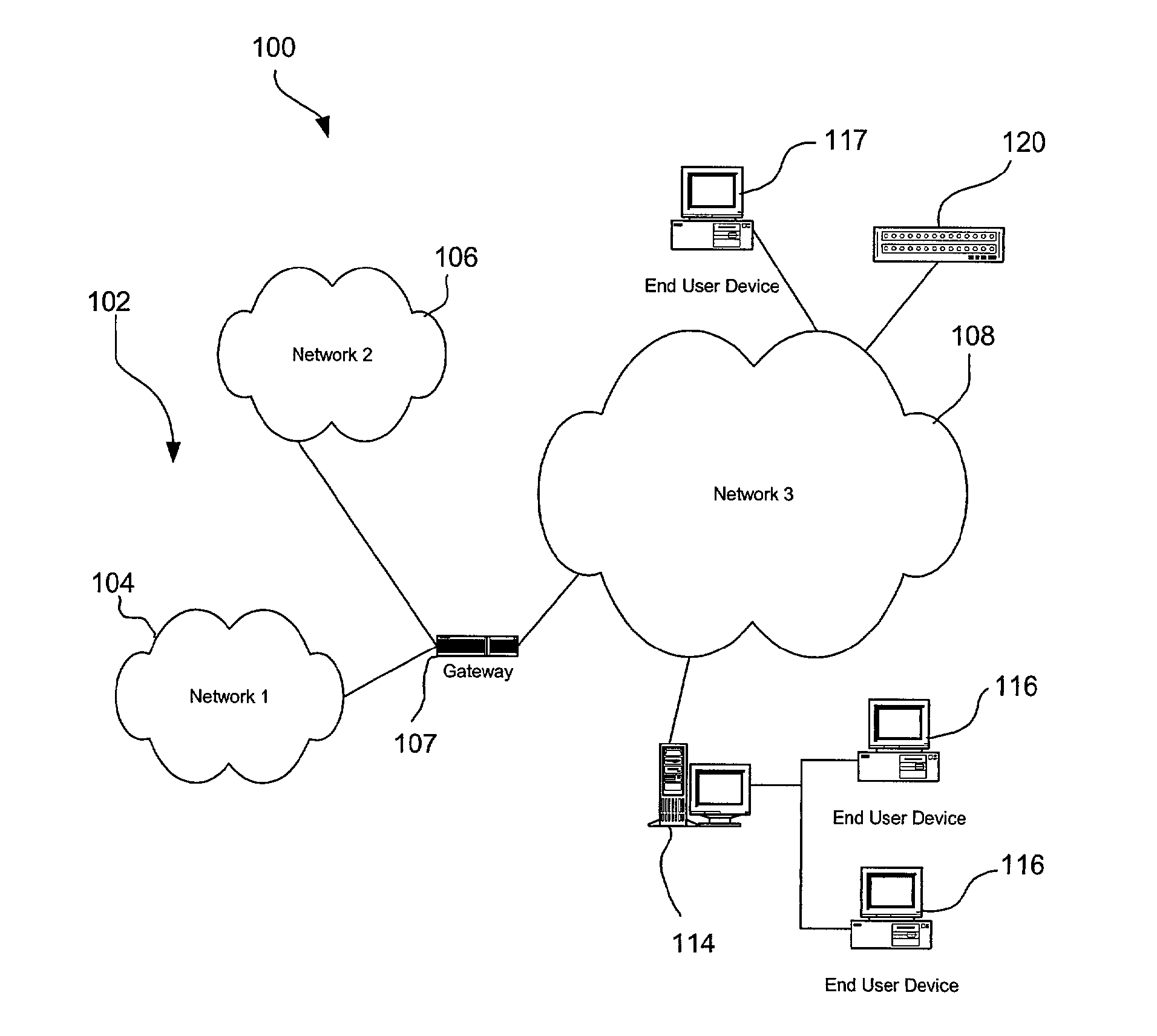
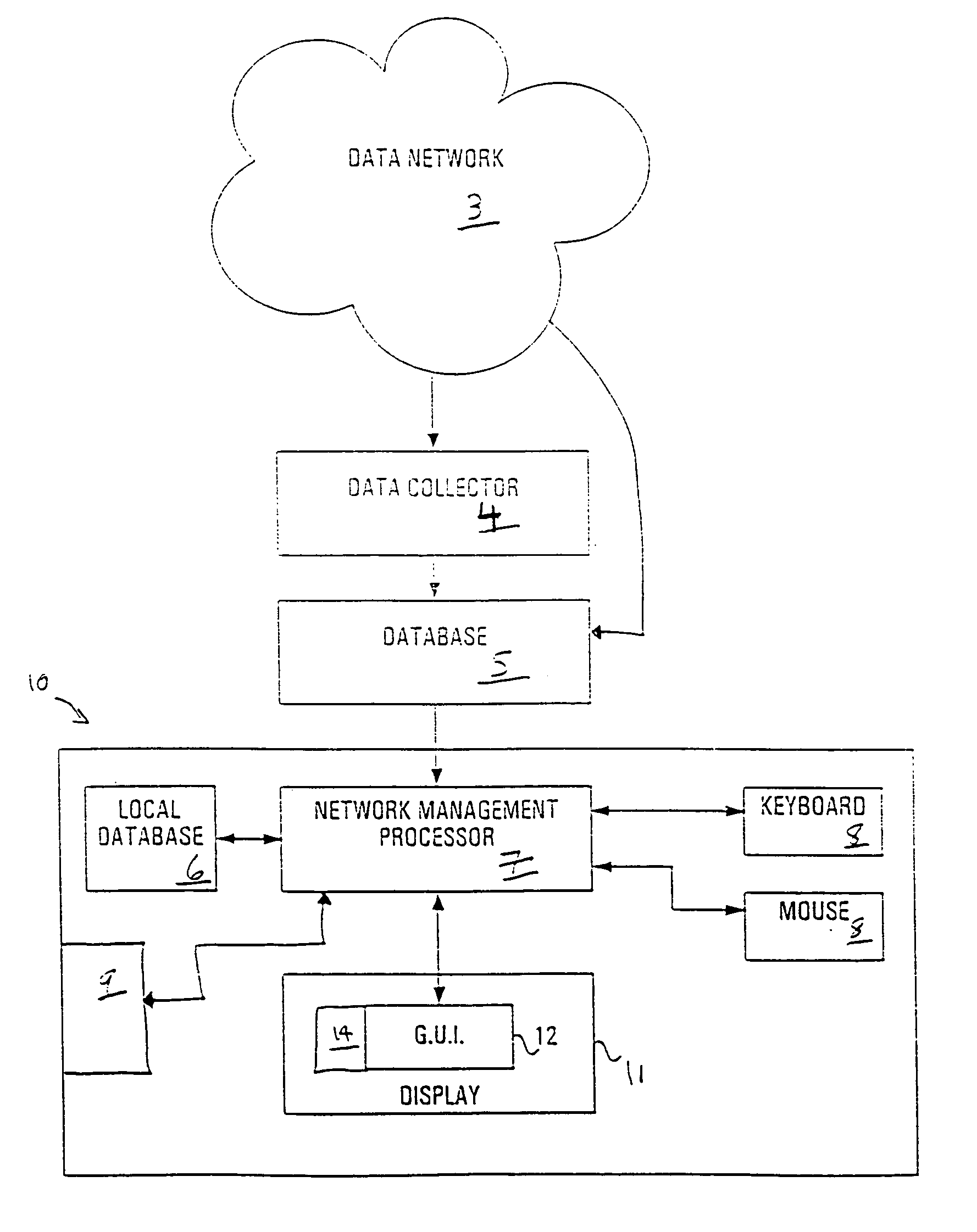
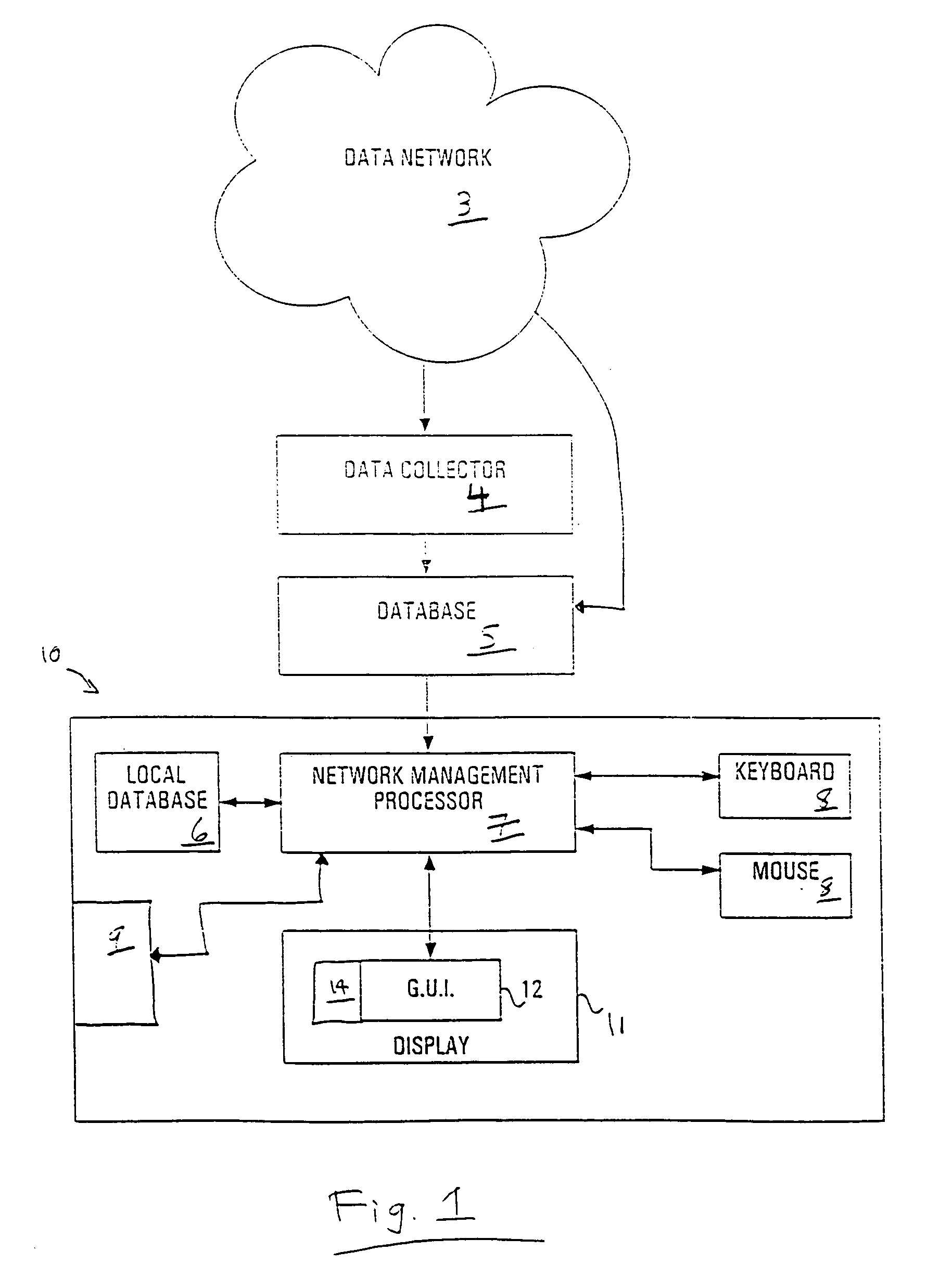
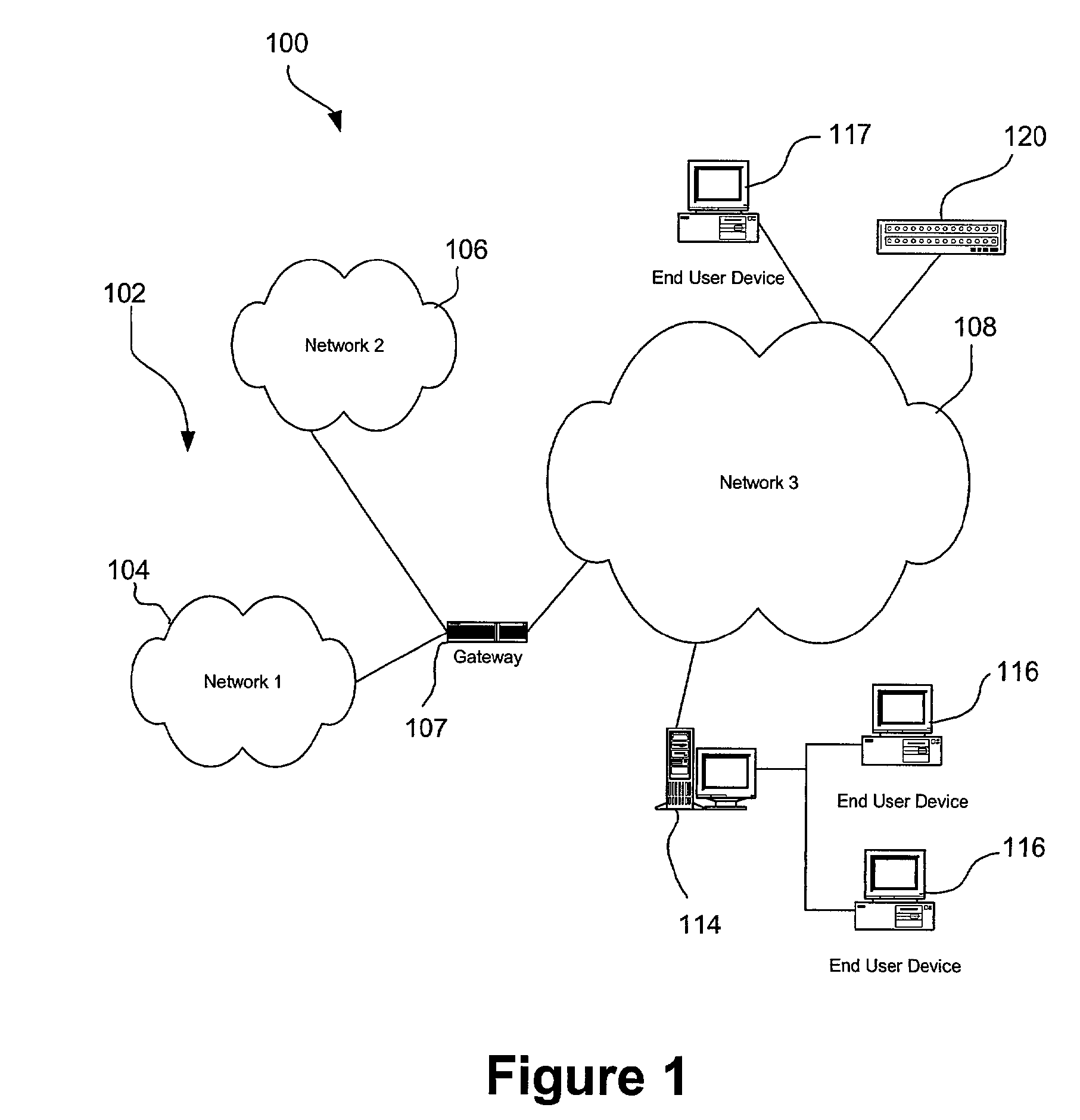
A network segment is a portion of a computer network. The nature and extent of a segment depends on the nature of the network and the device or devices used to interconnect end stations.
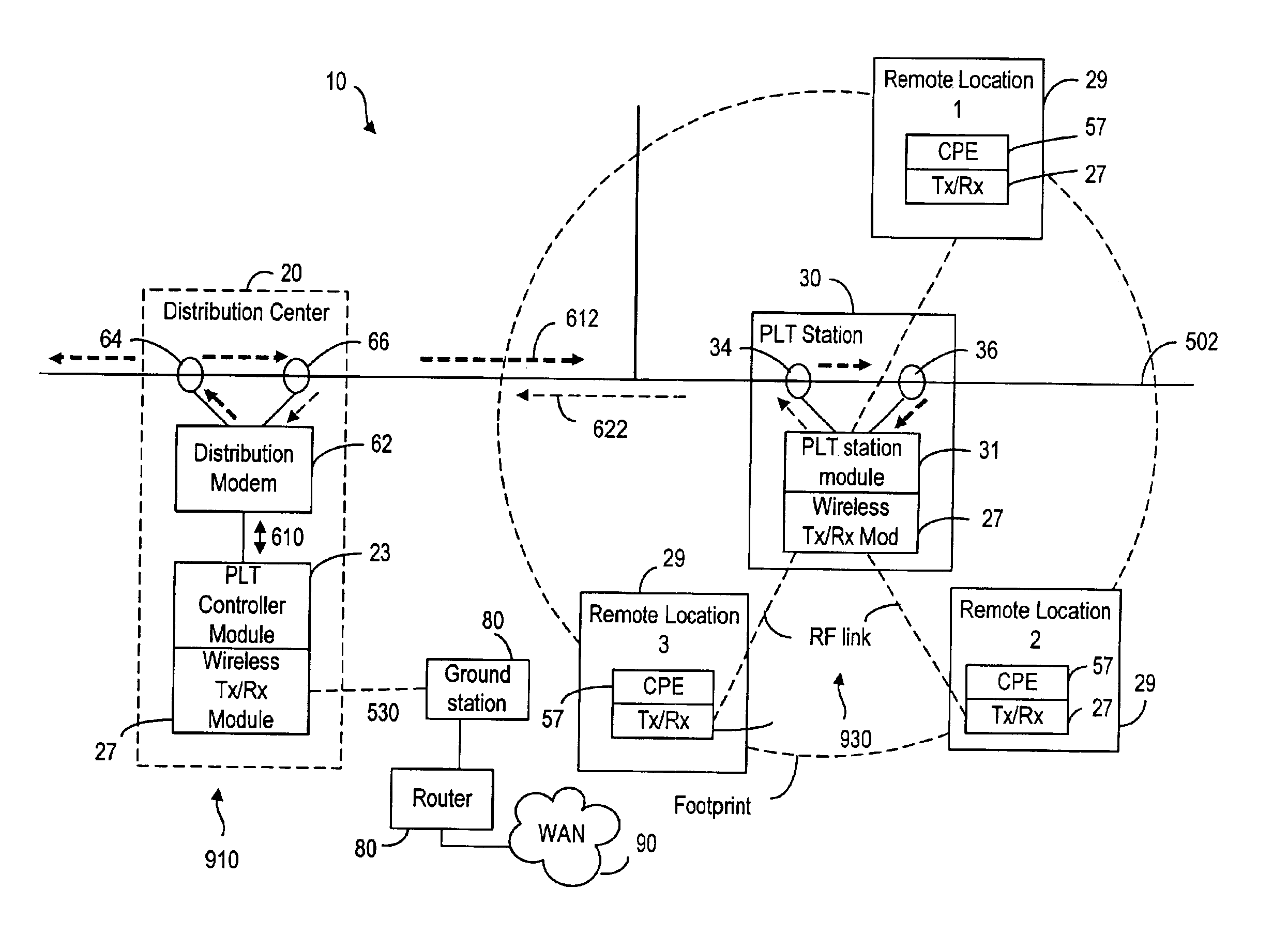
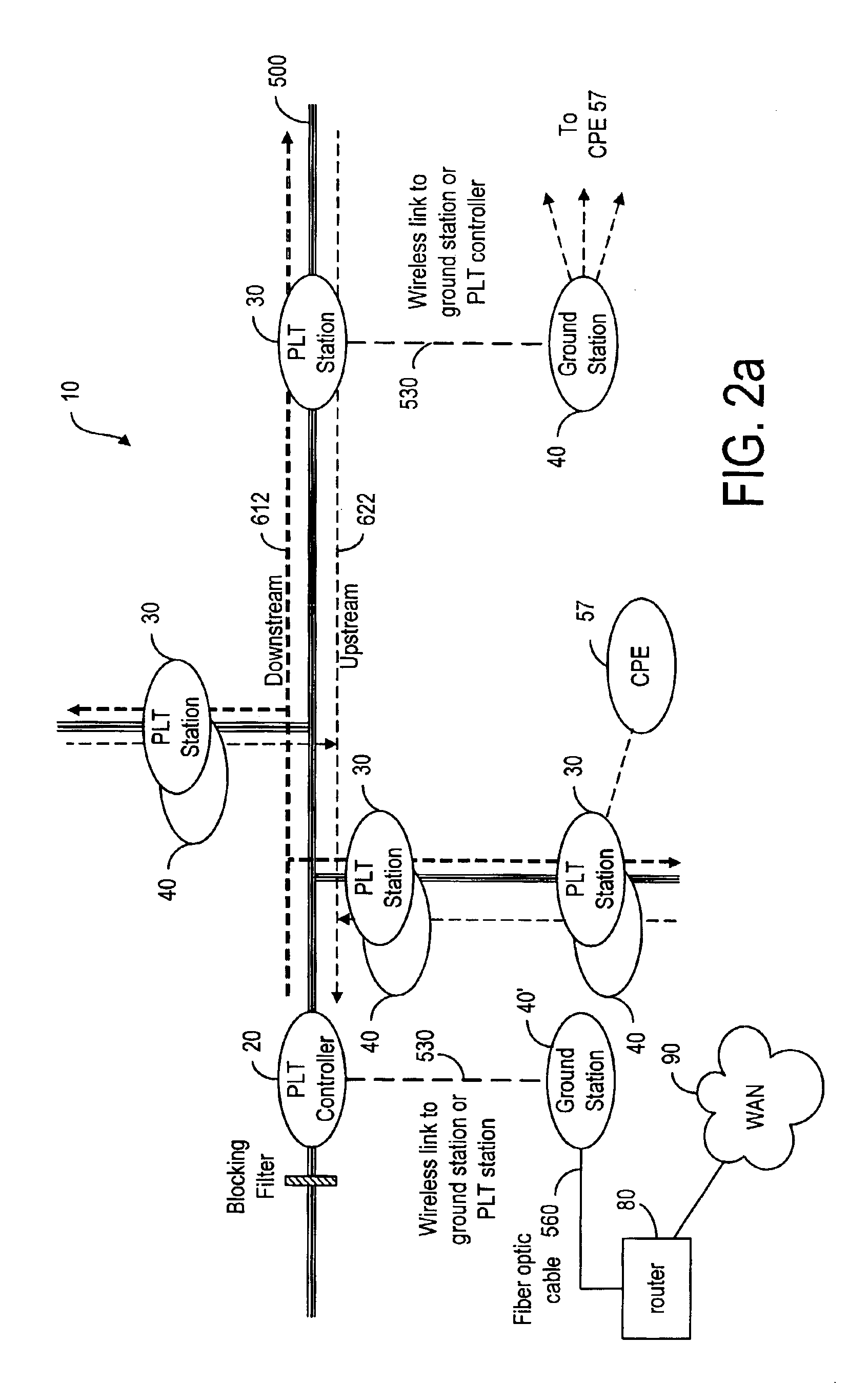
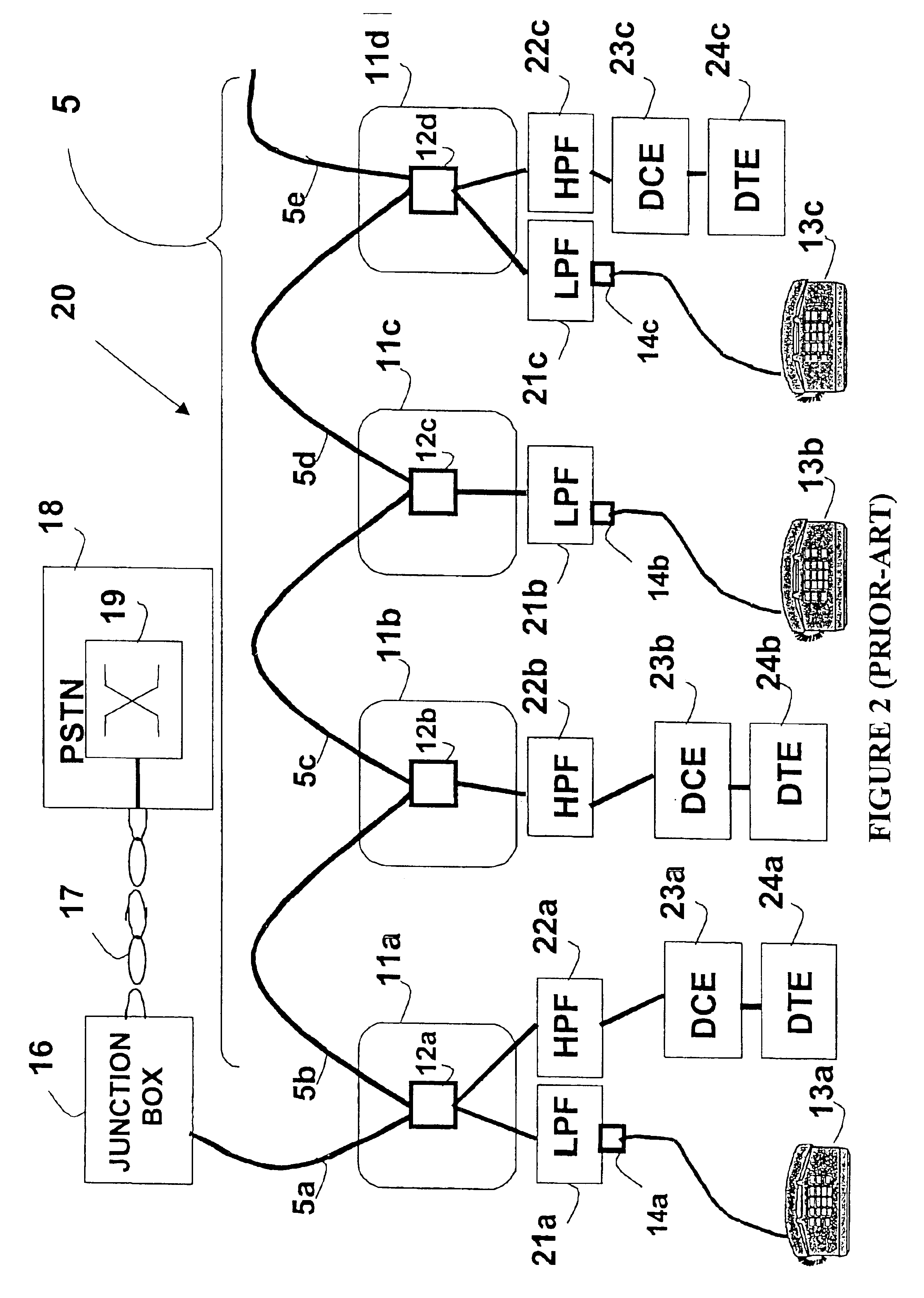
Communications system for providing broadband communications using a medium voltage cable of a power system
InactiveUS6885674B2High frequencyModulated-carrier systemsTransmission path divisionModem deviceCommunications system
A broadband service communication system using an MV cable for conveying RF signals in a network segment, which includes a distribution center (PLT controller) and a plurality of power line telecommunication (PLT) stations. The PLT controller has a distribution modem for conveying downstream and upstream RF signals to and from the PLT stations through the MV cable via couplers. Each PLT station has a modem for conveying the downstream and upstream RF signals via couplers and for conveying media signals to one or more customer premises equipment (CPE) via, e.g. wireless links. The PLT controller controls each PLT station regarding upstream communications transfer of all downstream communications and also controls. The PLT controller can be connected via a router to a WAN to convey media signals to and from the WAN. Repeaters and interlinks are used to join multiple network segments.
Owner:AMPERION
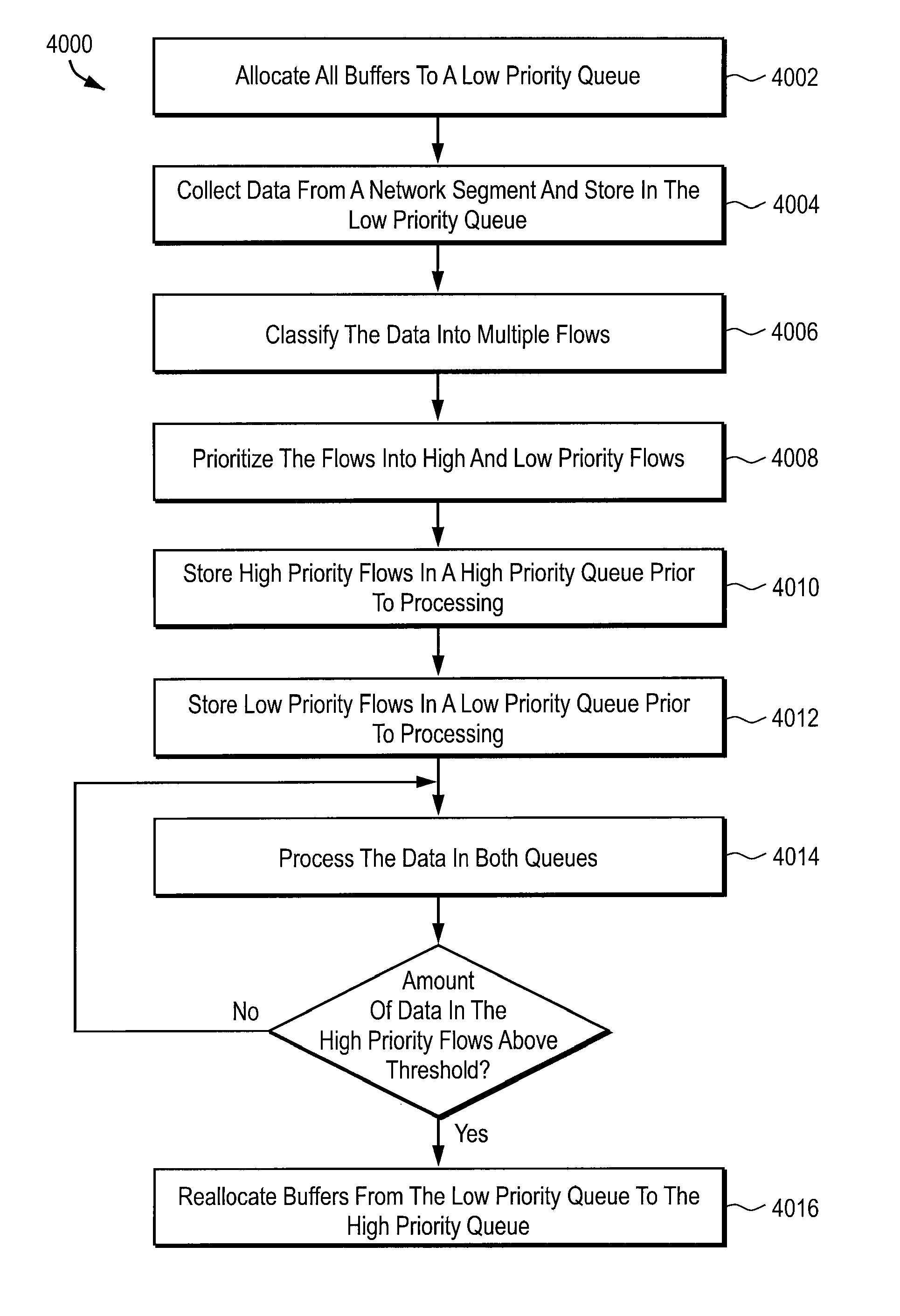
Media module apparatus and method for use in a network monitoring environment
InactiveUS7299277B1Avoid data lossReduce probabilityError preventionTransmission systemsApplication softwareMaster processor
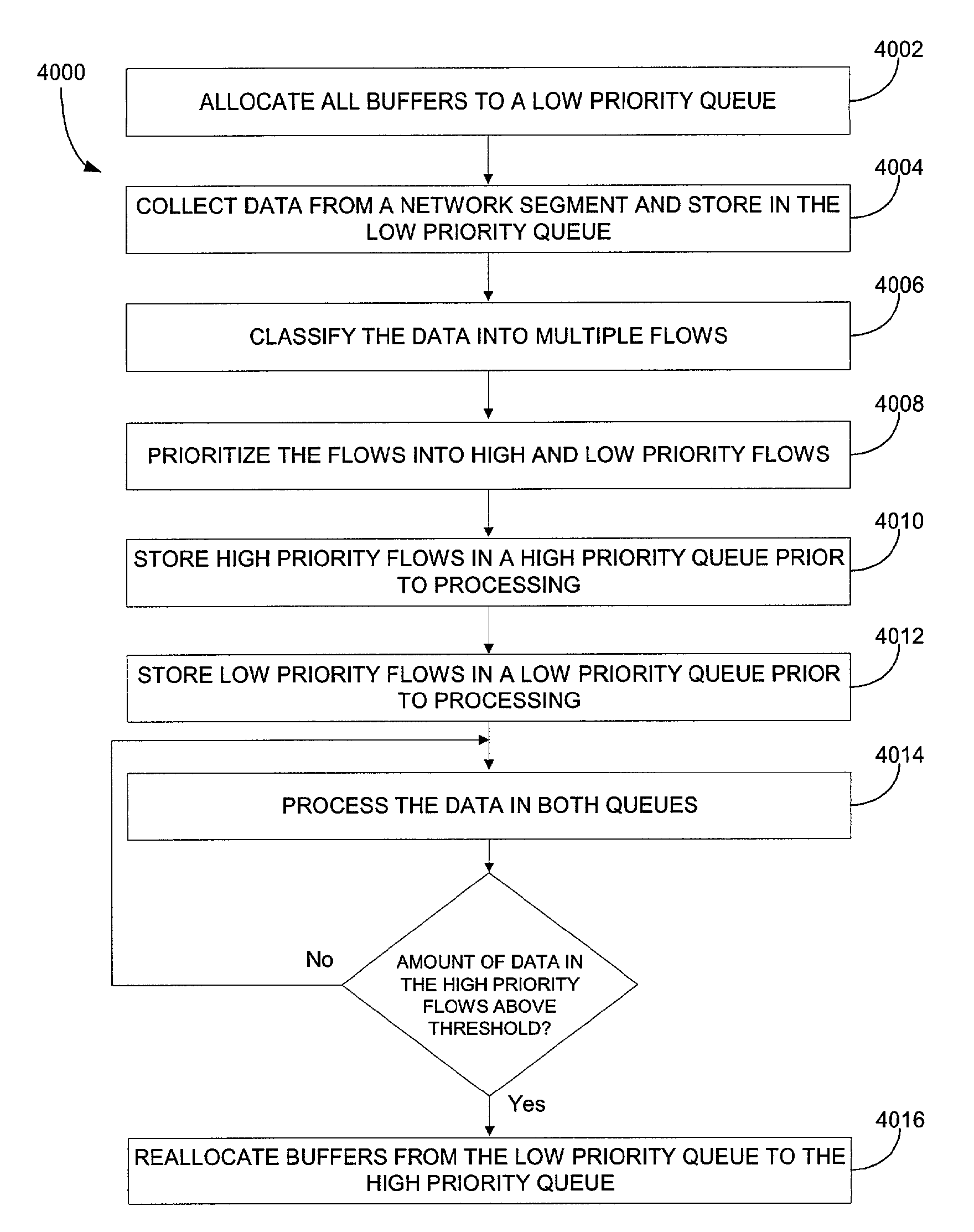
A probe apparatus, method and computer program product for application monitoring are provided. A data collection module collects data from a network segment. A flow processor coupled to the data collection module classifies the collected data into a plurality of flows. A capture system coupled to the flow processor filters and buffers the collected data. A main processor processes the filtered data.
Owner:NETWORK GENERAL TECH
Network combining wired and non-wired segments
InactiveUS6842459B1Substations coupling interface circuitsFrequency-division multiplexResidenceOperating energy
A local area network within a residence or other building, including both wired and non-wired segments. The wired segments are based on new or existing wires in the building, wherein access to the wires is provided by means of outlets, such as a telephone system, electrical power distribution system, or cable television wiring system. The non-wired segments are based on communication using propagated waves such as radio, sound, or light (e.g. infrared). The wired and non-wired segments interface in the outlet, using a module which serves as mediator between the segments. The module can be integrated into the outlet, partially housed in the outlet, or attached externally to the outlet. Such a network allows for integrated communication of data units connected by wires and data units connected without wires.
Owner:CONVERSANT INTPROP MANAGEMENT INC
Methods and apparatus for monitoring local network traffic on local network segments and resolving detected security and network management problems occurring on those segments
InactiveUS20050060535A1Small sizeImprove search capabilitiesSecuring communicationElectric digital data processingData connectionData pack
A system for providing network security through manipulating data connections and connection attempts over a data-packet-network between at least two network nodes is provided. The system includes a system host machine, a first software application residing on the host machine for detecting and monitoring connection activity, a data store for storing connection related data, and a second software application for emulating one or more end nodes of the connections or connection attempts. In a preferred embodiment the system uses the detection software to detect one or more pre-defined states associated with a particular connection or connection attempt including states associated with data content transferred there over and performs at least one packet generation and insertion action triggered by the detected state or states, the packet or packets emulating one or more end nodes of the connection or connection attempt to cause preemption or resolution of the detected state or states.
Owner:PRAEMIO TECH
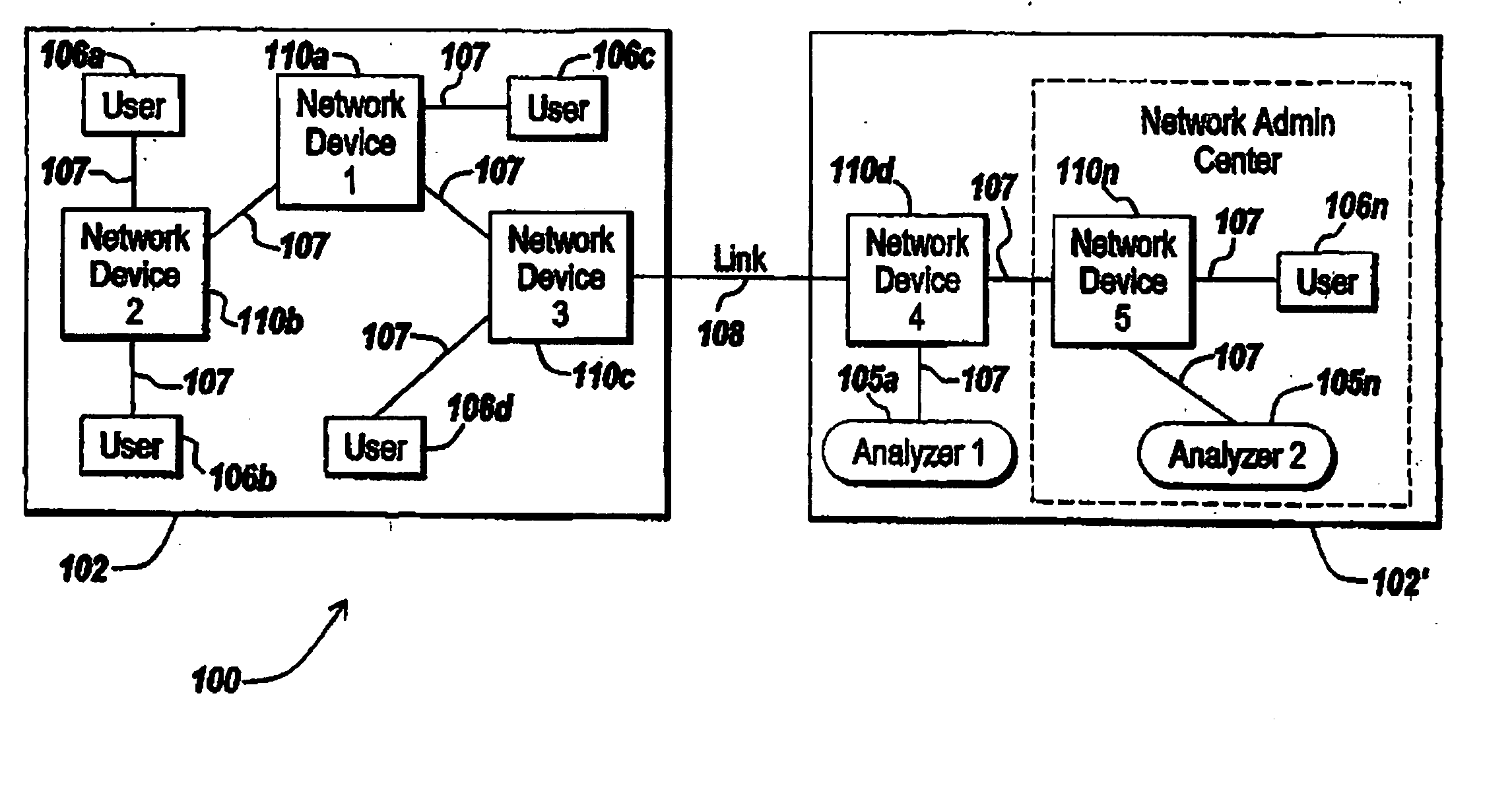
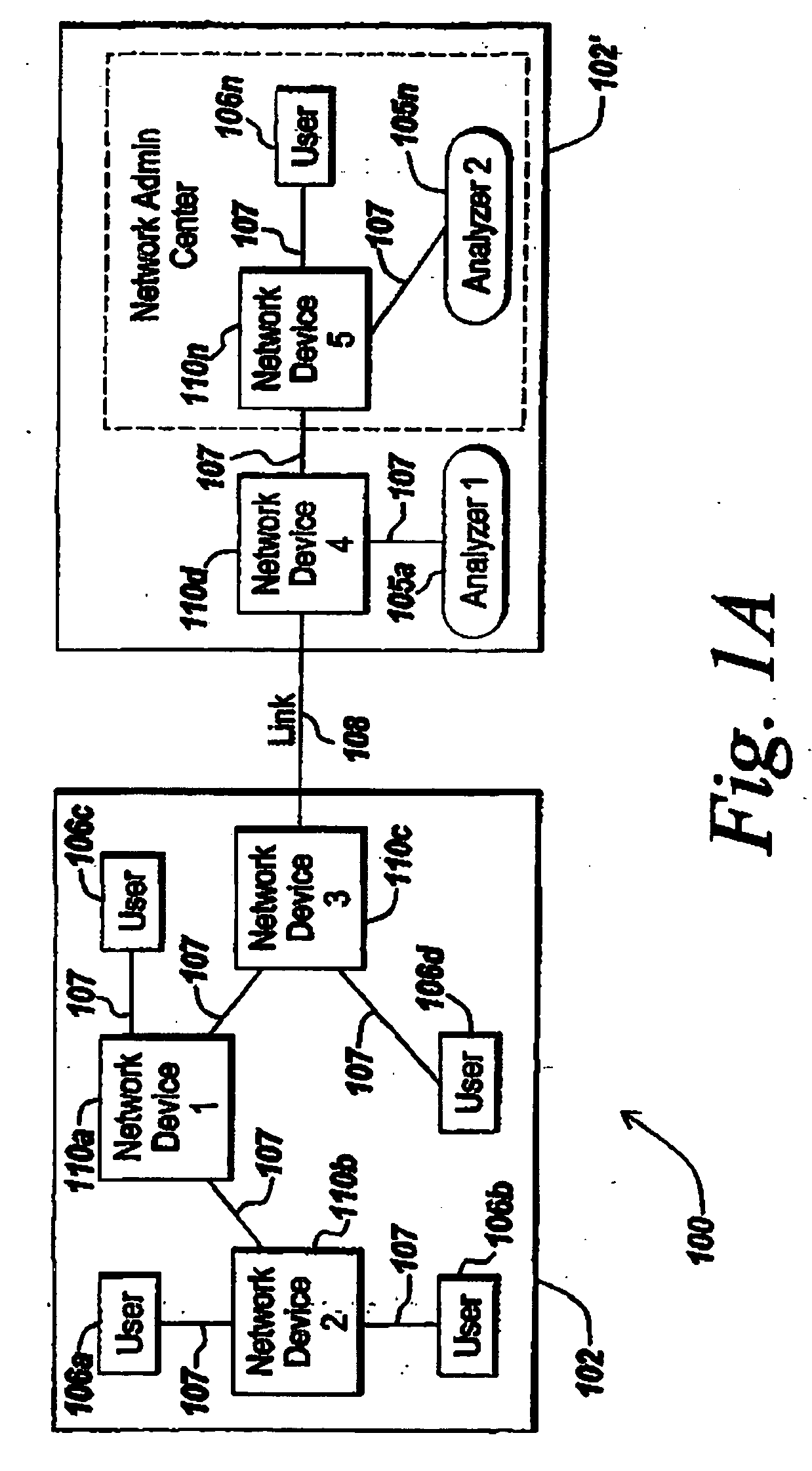
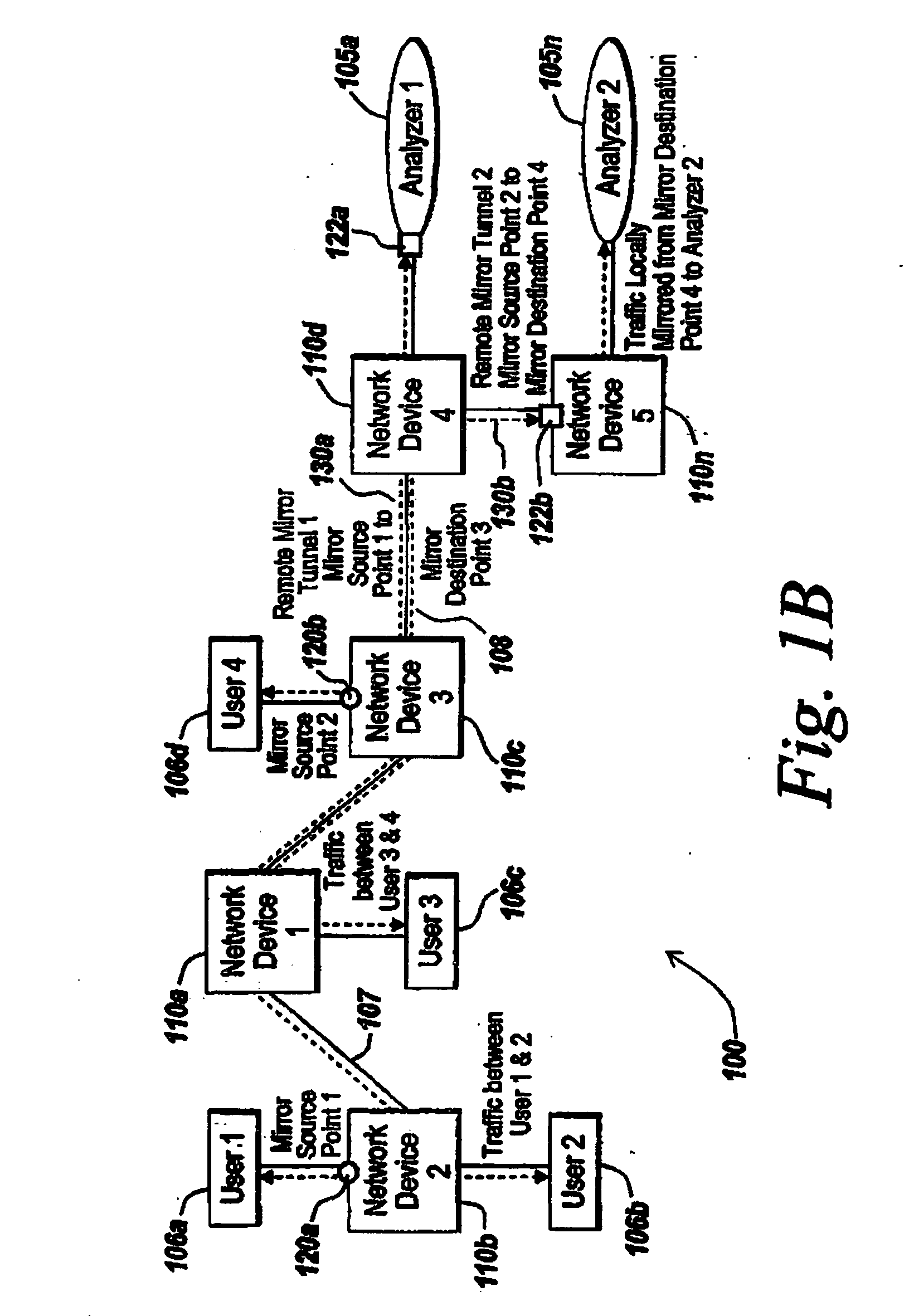
System, method and apparatus for traffic mirror setup, service and security in communication networks
ActiveUS20060059163A1Data switching networksSpecial data processing applicationsInternet networkPrivate network
The present invention provides method and systems for dynamically mirroring network traffic. The mirroring of network traffic may comprise data that may be considered of particular interest. The network traffic may be mirrored by a mirror service portal from a mirror sender, referred to as a mirror source, to a mirror receiver, referred to as a mirror destination, locally or remotely over various network segments, such as private and public networks and the Internet. The network traffic may be mirrored to locations not involved in the network communications being mirrored. The present invention provides various techniques for dynamically mirroring data contained in the network traffic from a mirror source to a mirror destination.
Owner:EXTREME NETWORKS INC
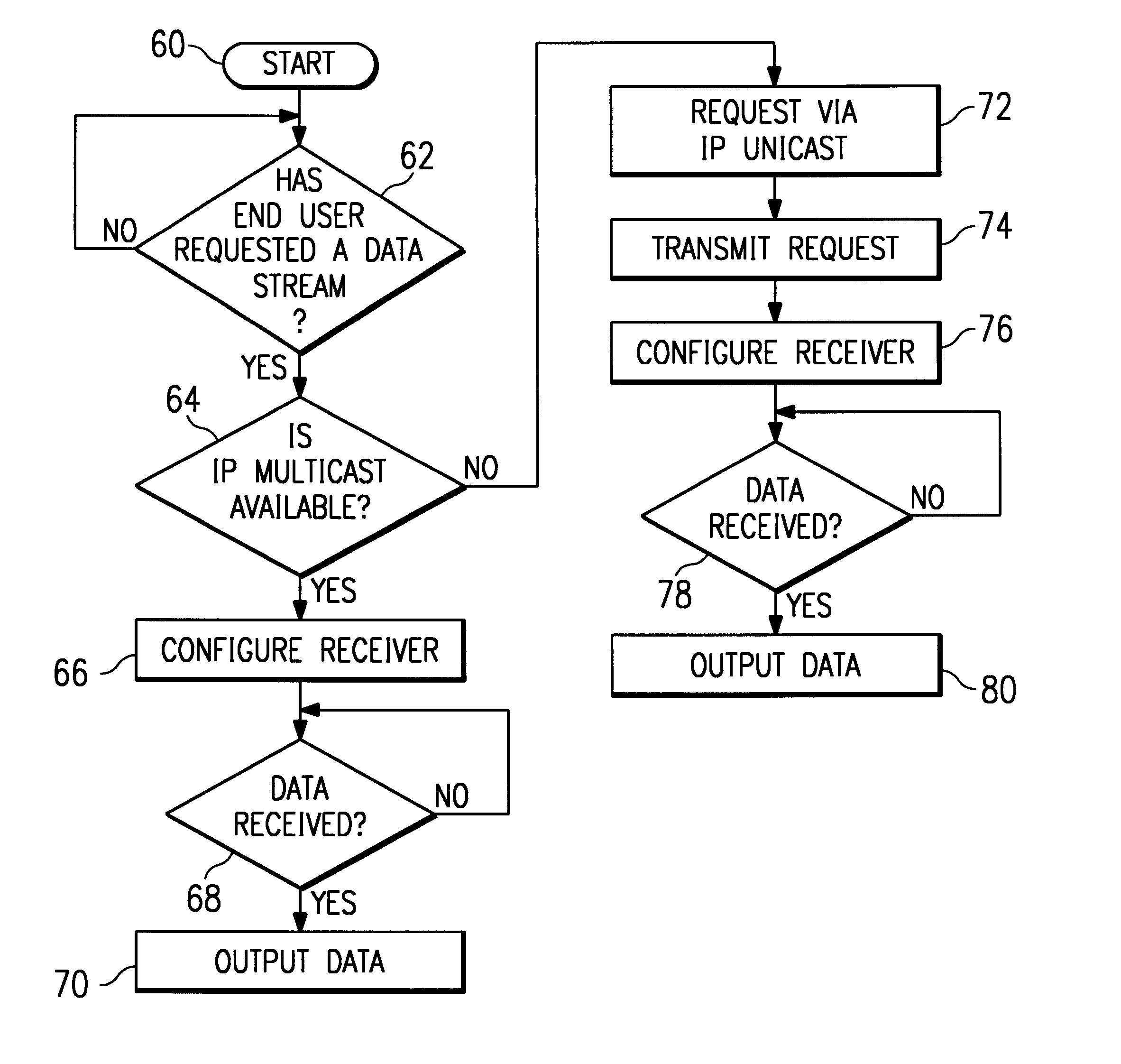
Selective tunneling of streaming data
InactiveUS6189039B1Spread the wordImprove bandwidth utilizationSpecial service provision for substationMultiple digital computer combinationsStreaming dataData stream
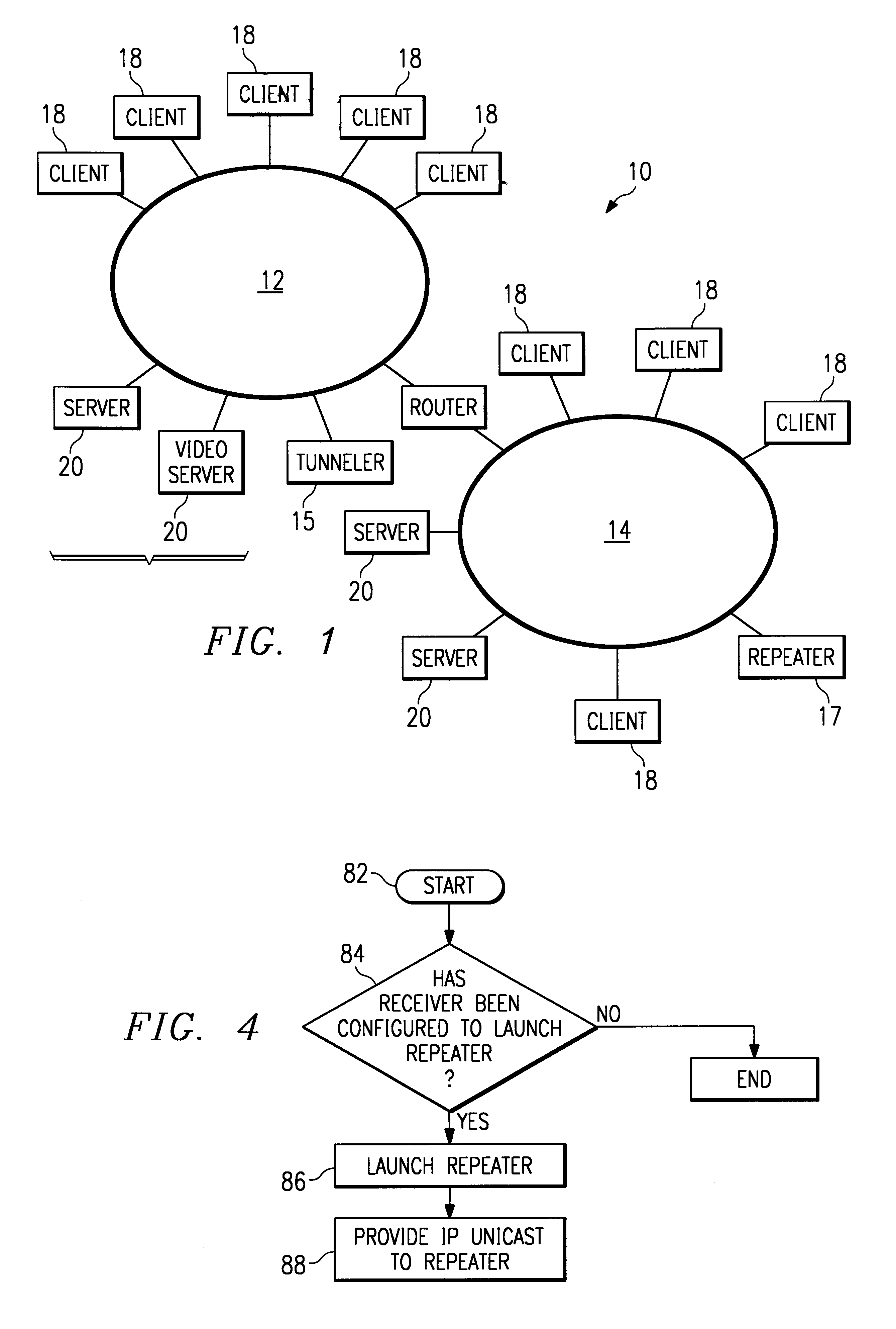
A method and system for "selective" tunneling of streaming data from a server to a client in a computer network having one or more network segments. The server has a tunneler utility, and the client has a receiver utility. The receiver utility first attempts to detect if a given data stream is available via IP multicast on the network segment supporting the client. If not, then the receiver utility issues a request for a IP unicast stream. This request is serviced by the tunneler utility. The tunneler utility re-broadcasts the IP multicast feed using IP unicast to send the data stream directly to the requesting user and / or to a repeater utility. The receiver utility then receives and processes the data stream for output to the end user. Alternatively, the receiver application, or a network administrator, launches the repeater utility, which then converts the IP unicast stream back to IP multicast format for re-broadcast over the network segment to other clients.
Owner:LEVEL 3 COMM LLC
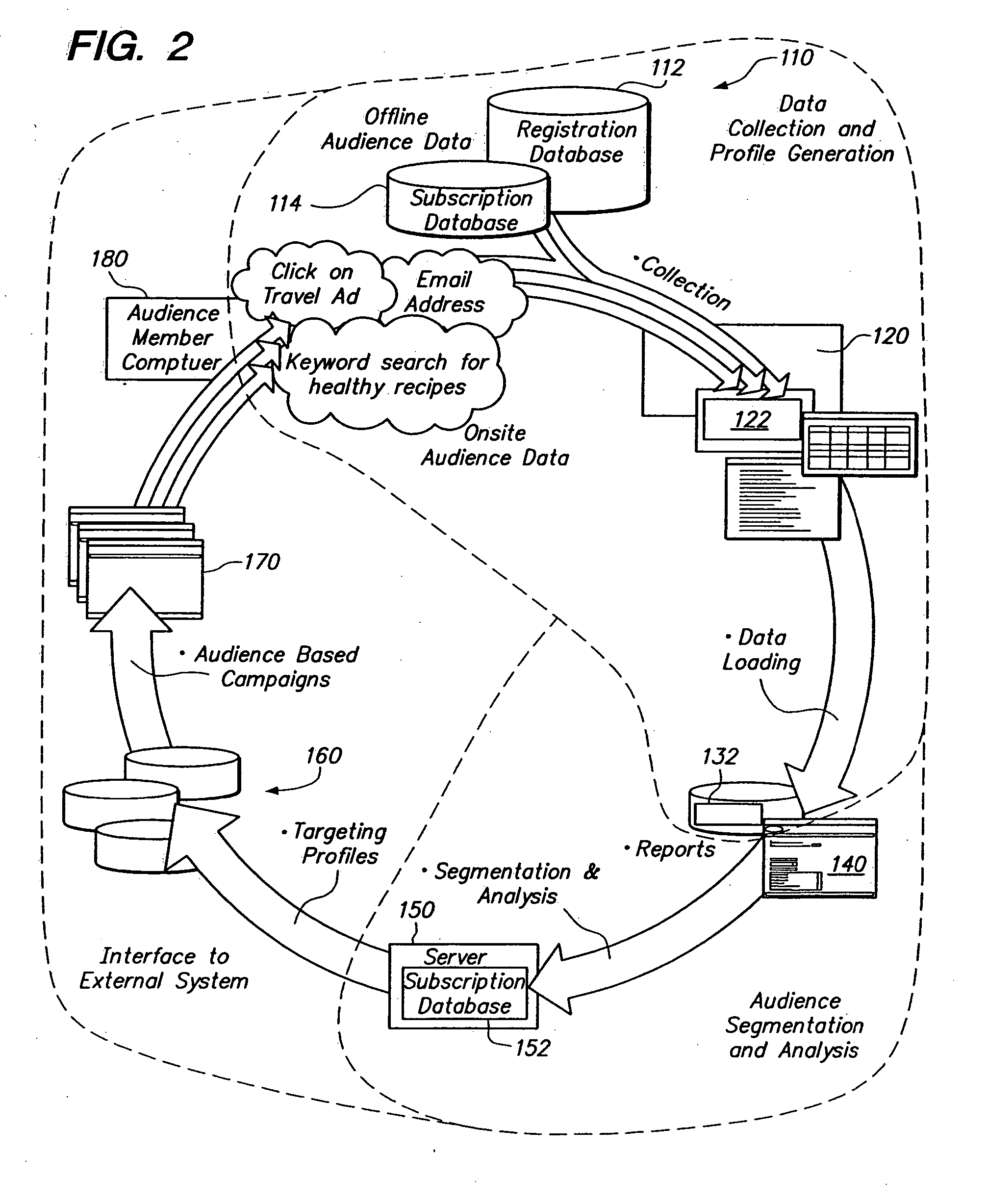
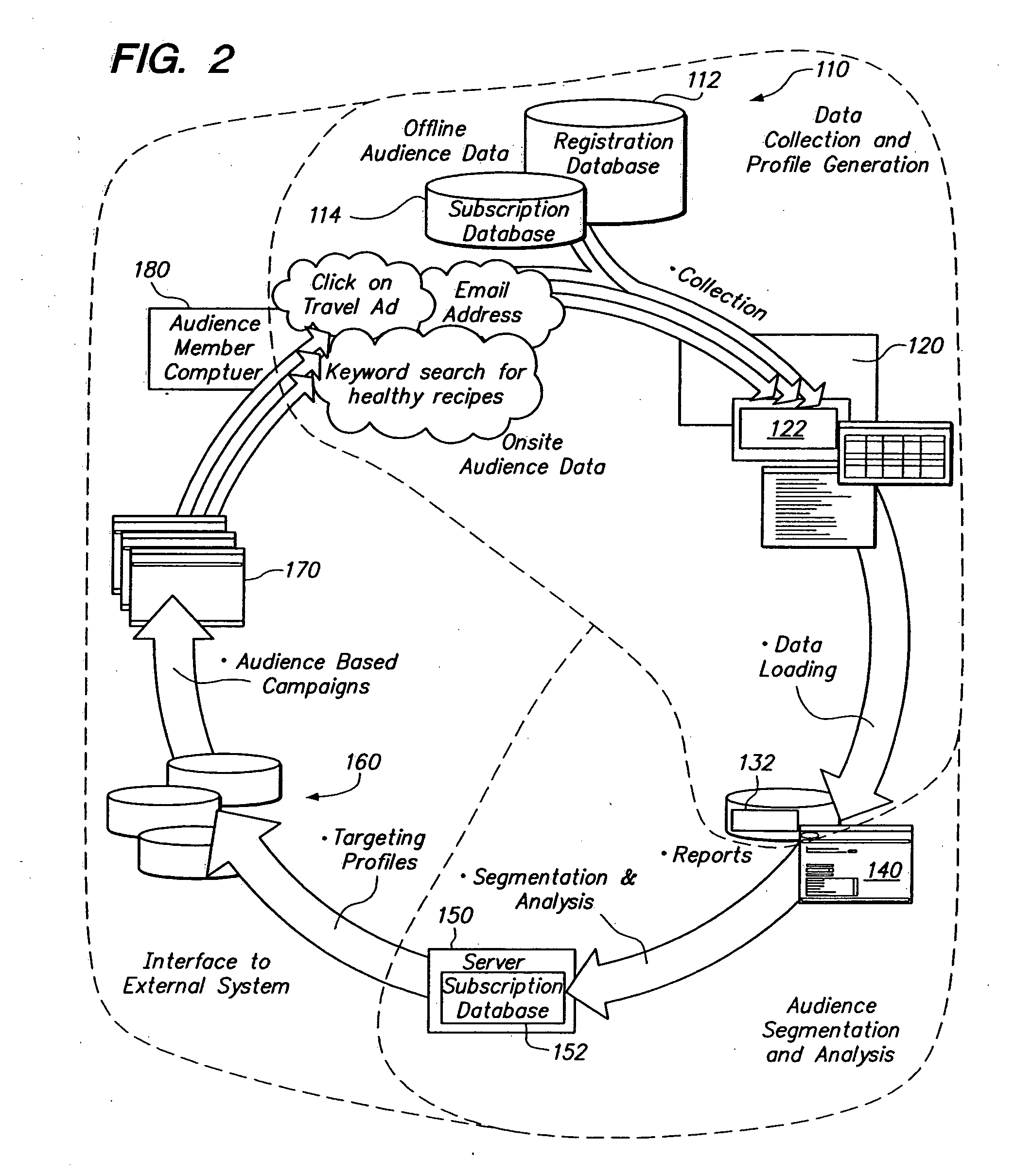
Network for matching an audience with deliverable content
ActiveUS20050166233A1Television system detailsBroadcast systems characterised by addressed receiversDistributed computingNetwork segment
Owner:YAHOO AD TECH LLC
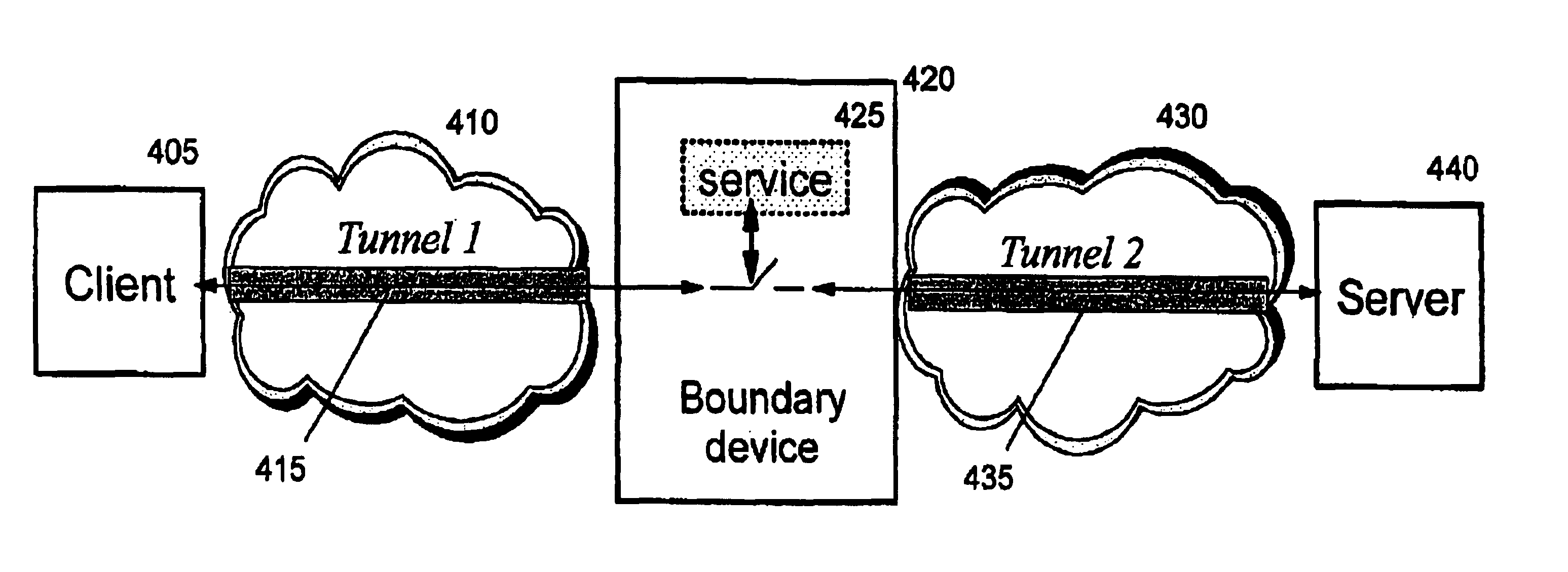
Establishing consistent, end-to-end protection for a user datagram
A method, system, and computer program product for providing consistent, end-to-end protection within a computer network for user datagrams (i.e. packets) traveling through the network. The network may comprise network segments that are conventionally assumed to be secure (such as those found in a corporate intranet) as well as network segments in non-secure networks (such as the public Internet or corporate extranets). Because security breaches may in fact happen in any network segment when datagrams are unprotected, the present invention discloses a technique for protecting datagrams throughout the entire network path by establishing cascaded tunnels. The datagrams may be exposed in cleartext at the endpoints of each tunnel, thereby enabling security gateways to perform services that require content inspection (such as network address translation, access control and authorization, and so forth). The preferred embodiment is used with the “IPSec” (Internet Protocol Security Protocol) and “IKE” (Internet Key Exchange) protocols, thus providing a standards-based solution.
Owner:IBM CORP
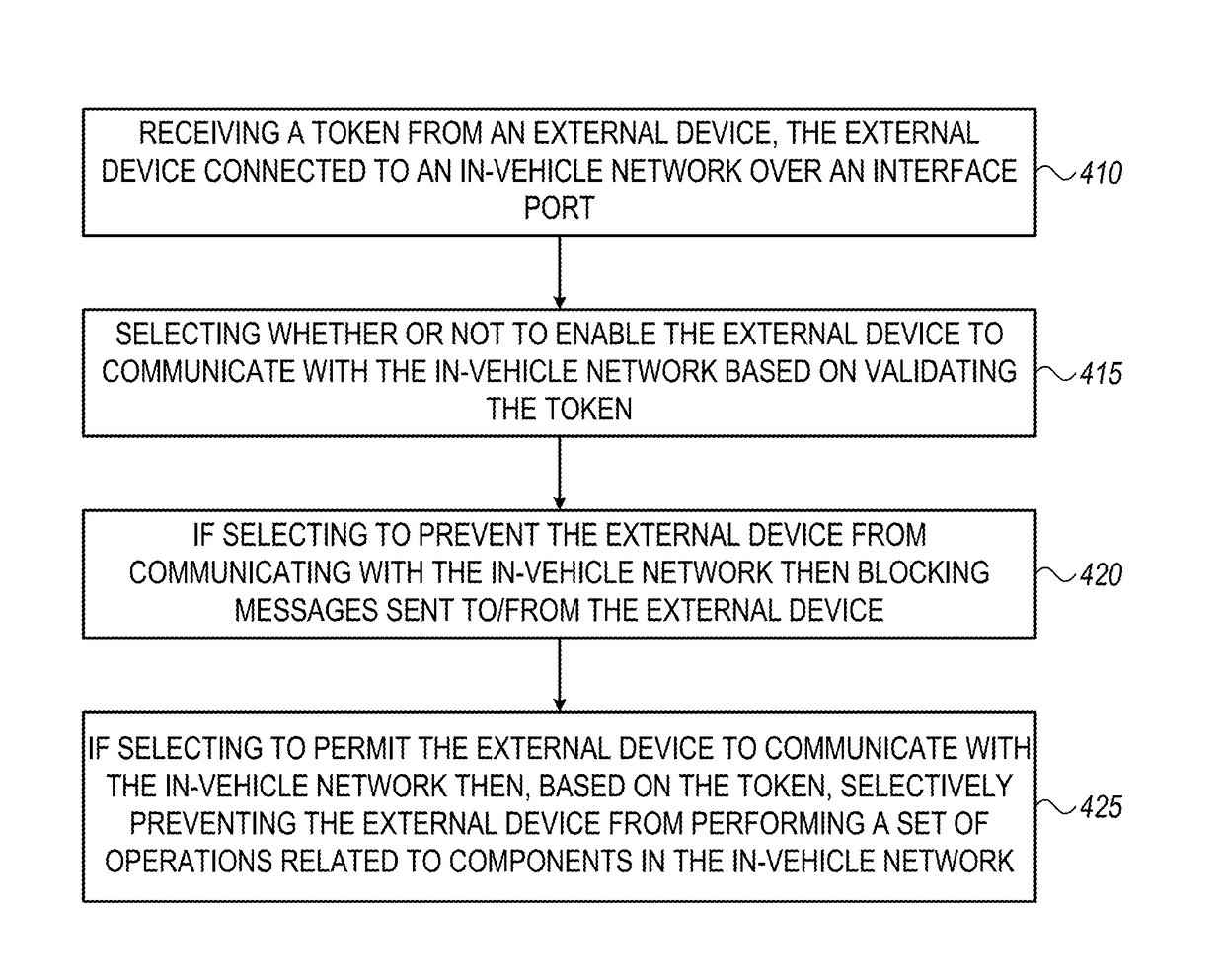
System and method for controlling access to an in-vehicle communication network
ActiveUS20170093866A1Memory architecture accessing/allocationDigital data authenticationIn vehiclePeripheral
A system or method may include an in-vehicle network including an interface port for connecting an external device to the in-vehicle network; and a security unit connected to the in-vehicle network, the security unit adapted to enable an external device to communicate with the in-vehicle network, over the interface port, based on a security token received from the external device. A system or method may, based on a token, prevent an external device from at least one of: communicating with a selected set of components on in an in-vehicle network, communicating with a selected set of network segments in the in-vehicle network and performing a selected set of operations.
Owner:ARGUS CYBER SECURITY LTD
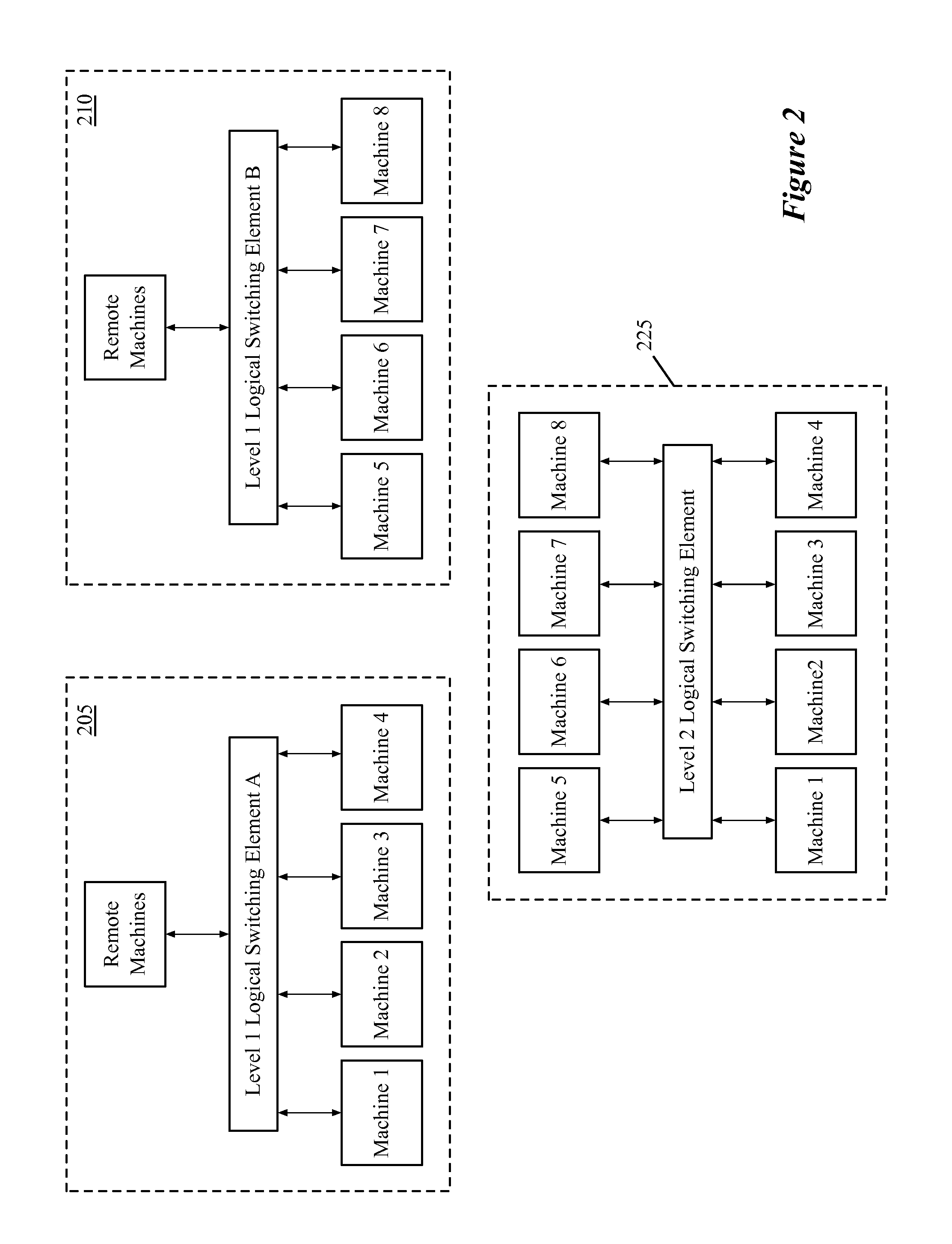
Generating flows for managed interconnection switches
ActiveUS20130044764A1Efficient use ofData switching by path configurationNetwork connectionsVirtualizationNetwork control
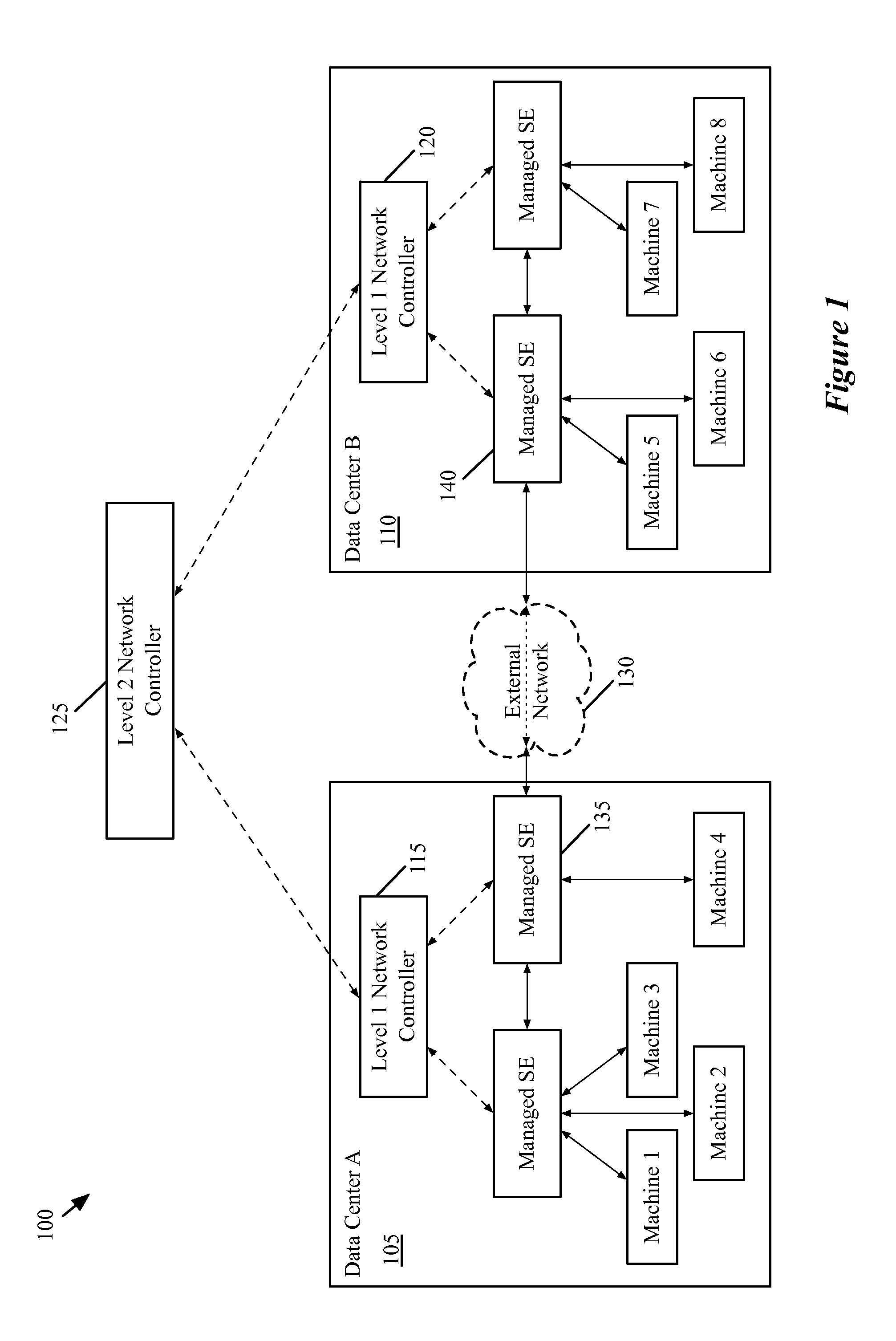
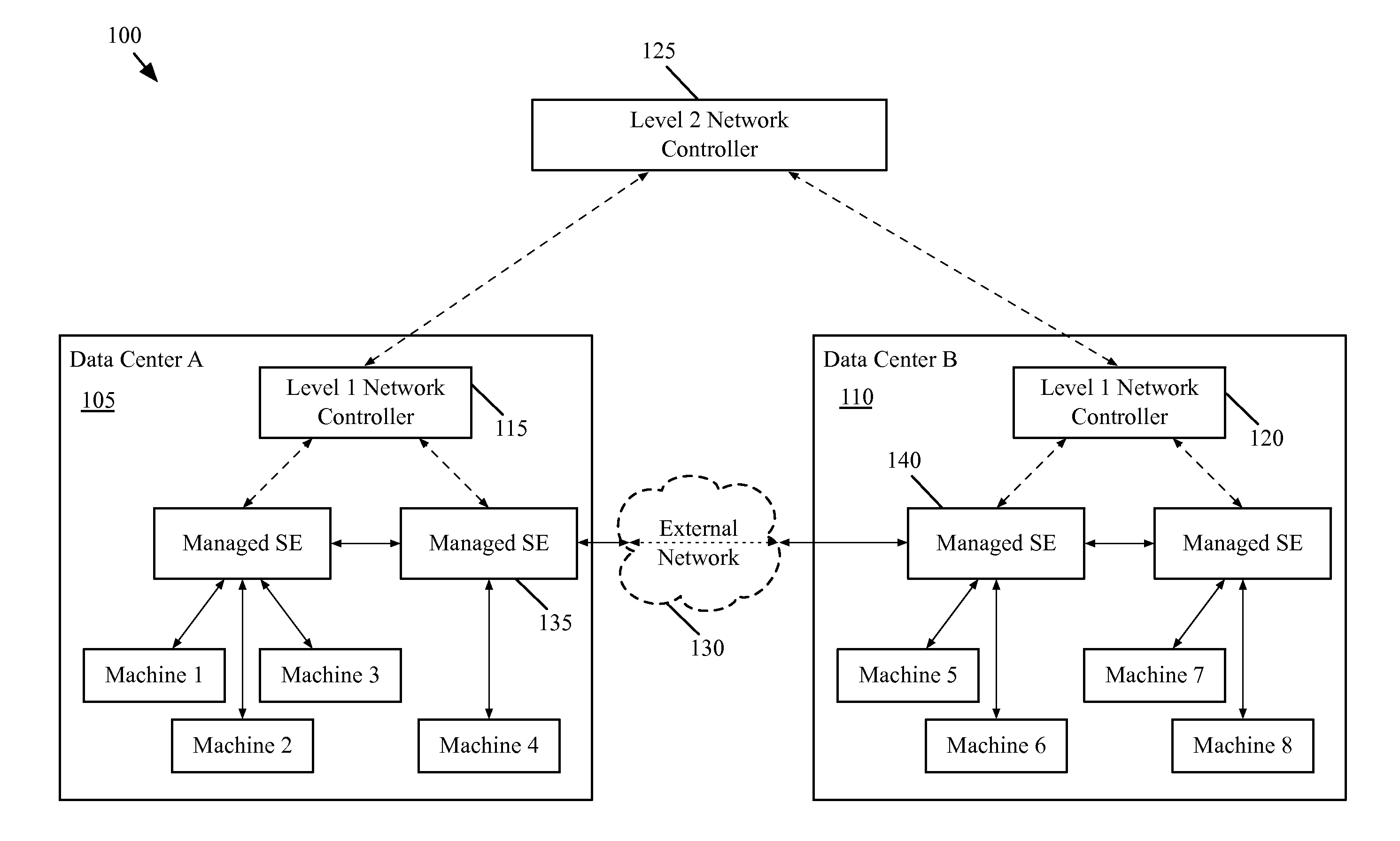
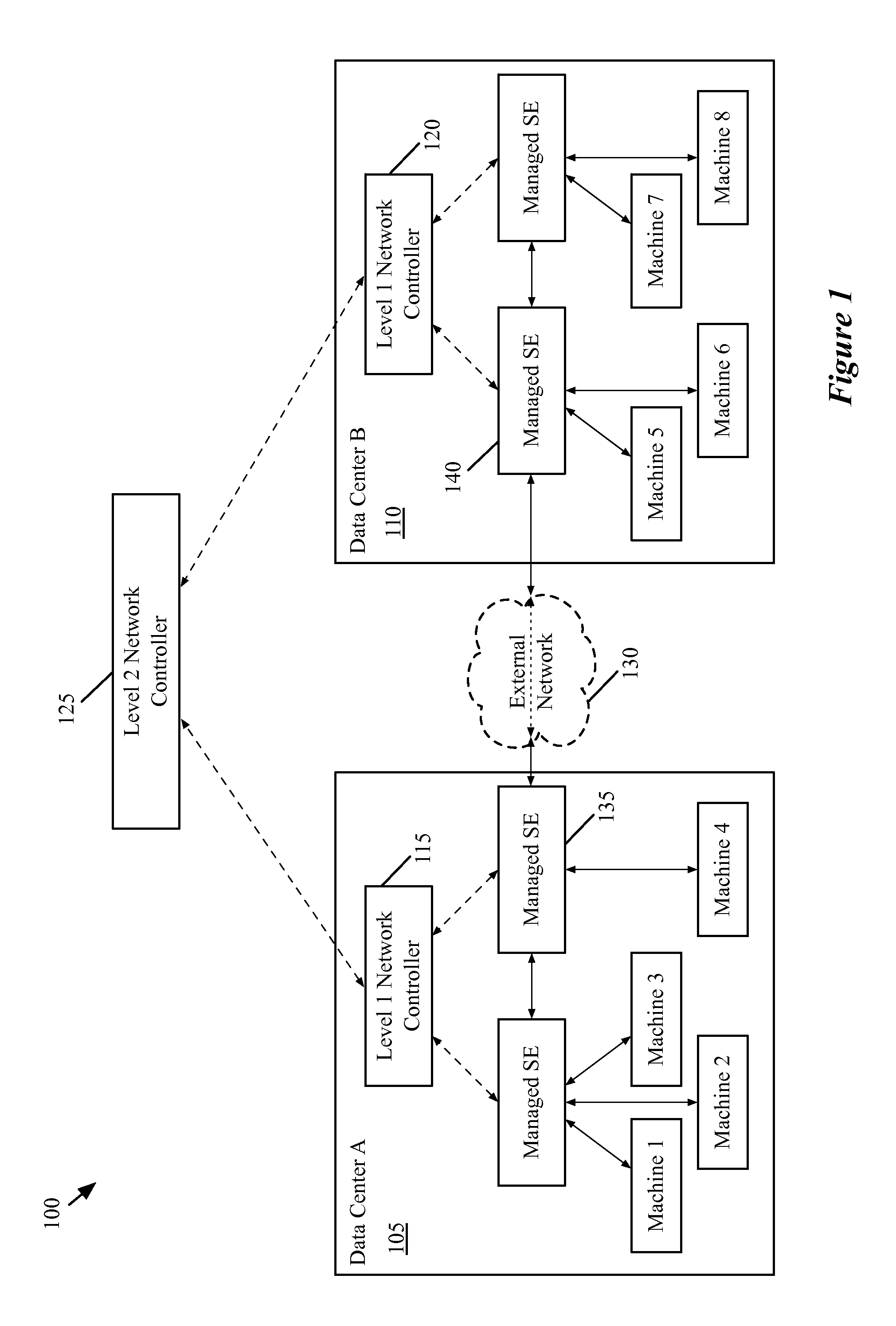
A network controller for managing a set of interconnection switching elements that connect segmented networks to a shared physical interconnection network. The network controller includes i) an interface for receiving a logical control plane definition of a logical switching element that couples to a set of network segments at different segmented networks; ii) a control application for translating the logical control plane definition of the logical switching element into a first set of flow entries in a logical forwarding plane; and iii) a virtualization application for translating the first set of flow entries into a second set of flow entries in a physical control plane. The flow entries in the physical control plane are for subsequent conversion by the managed interconnection switching elements into a third set of flow entries in a physical forwarding plane that directs the forwarding of network data by the managed interconnection switching elements.
Owner:NICIRA
Audience matching network with performance factoring and revenue allocation
ActiveUS20050165644A1Total revenue maximizationAdvertisementsTransmissionData harvestingNetwork segment
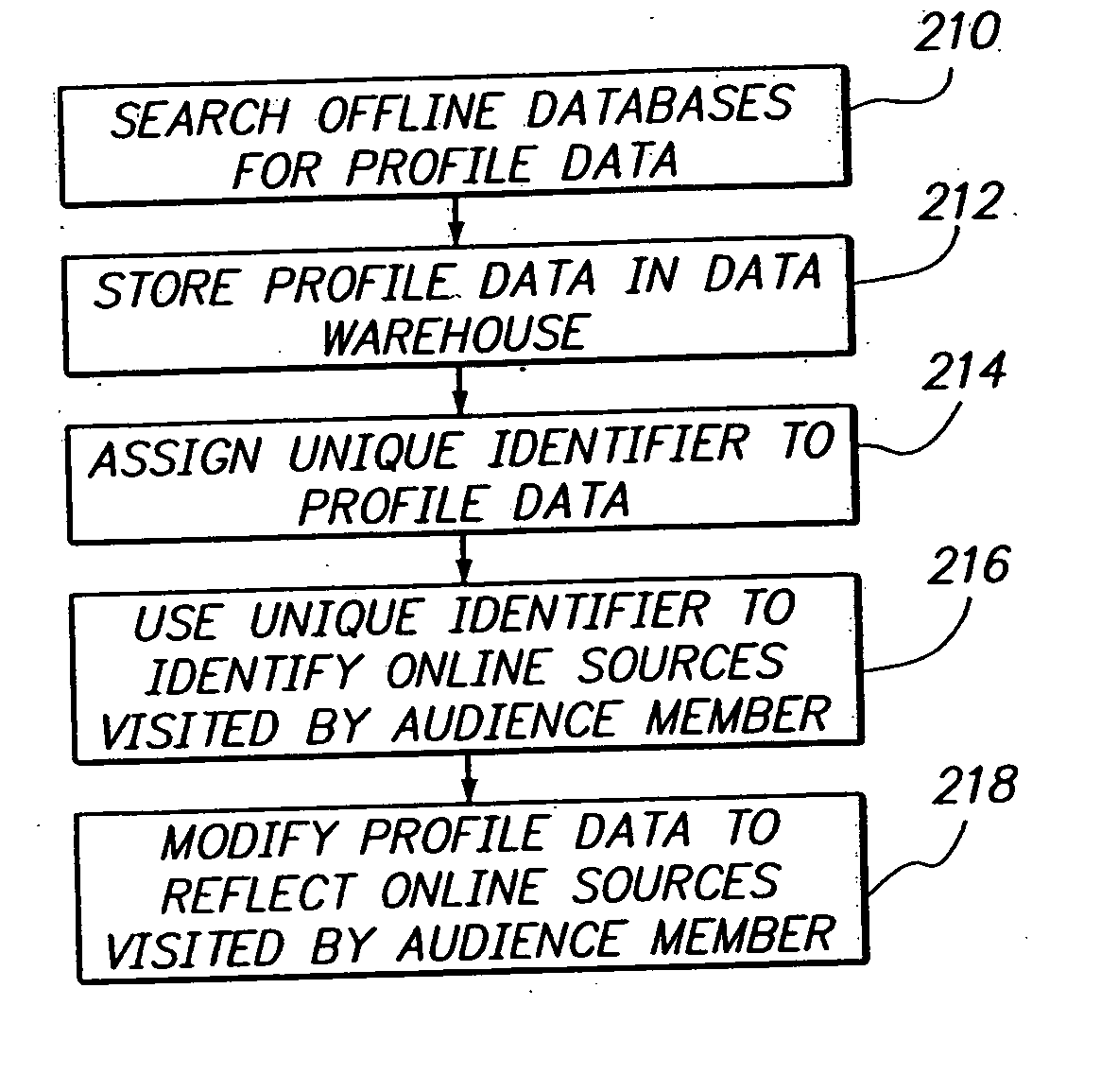
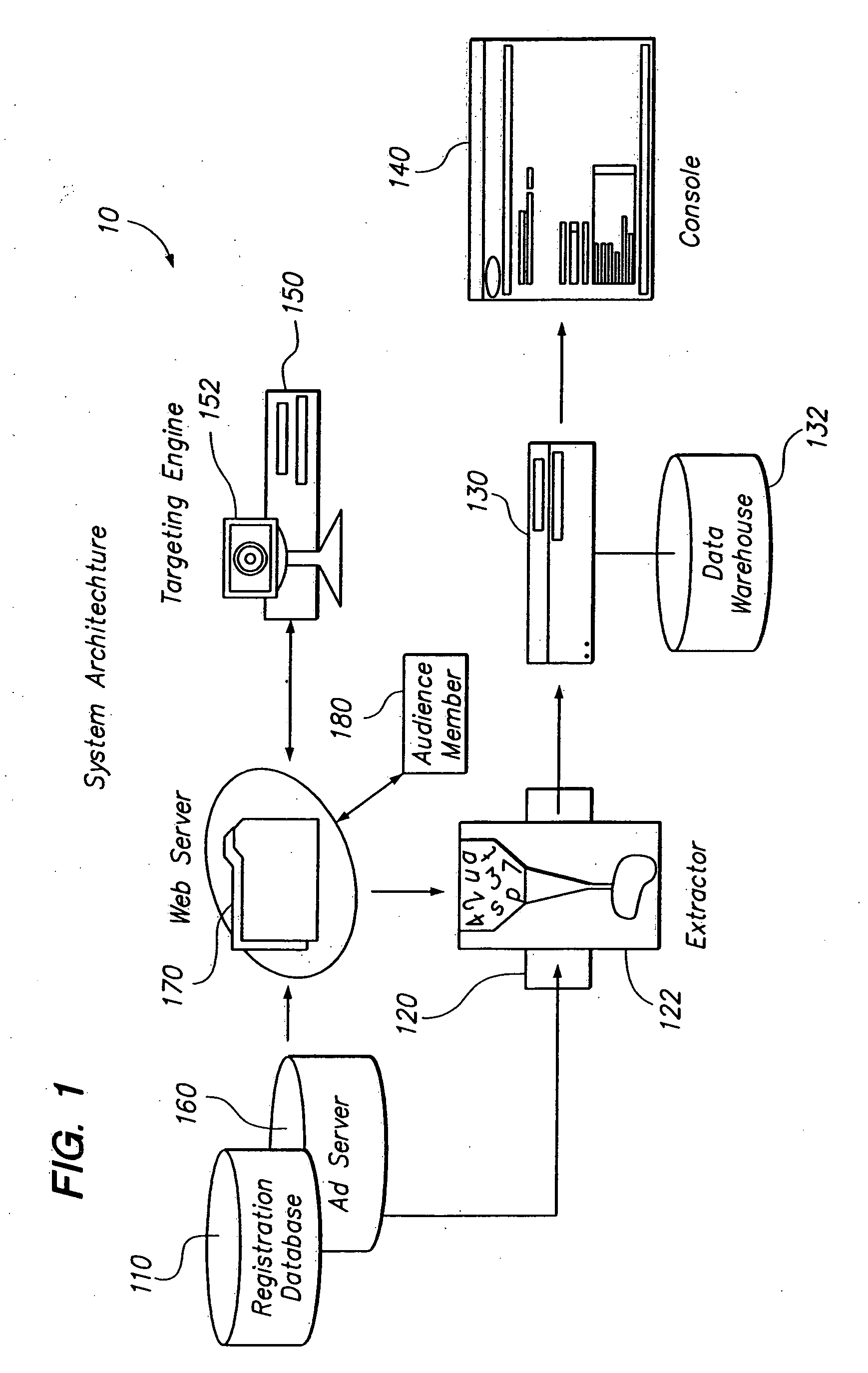
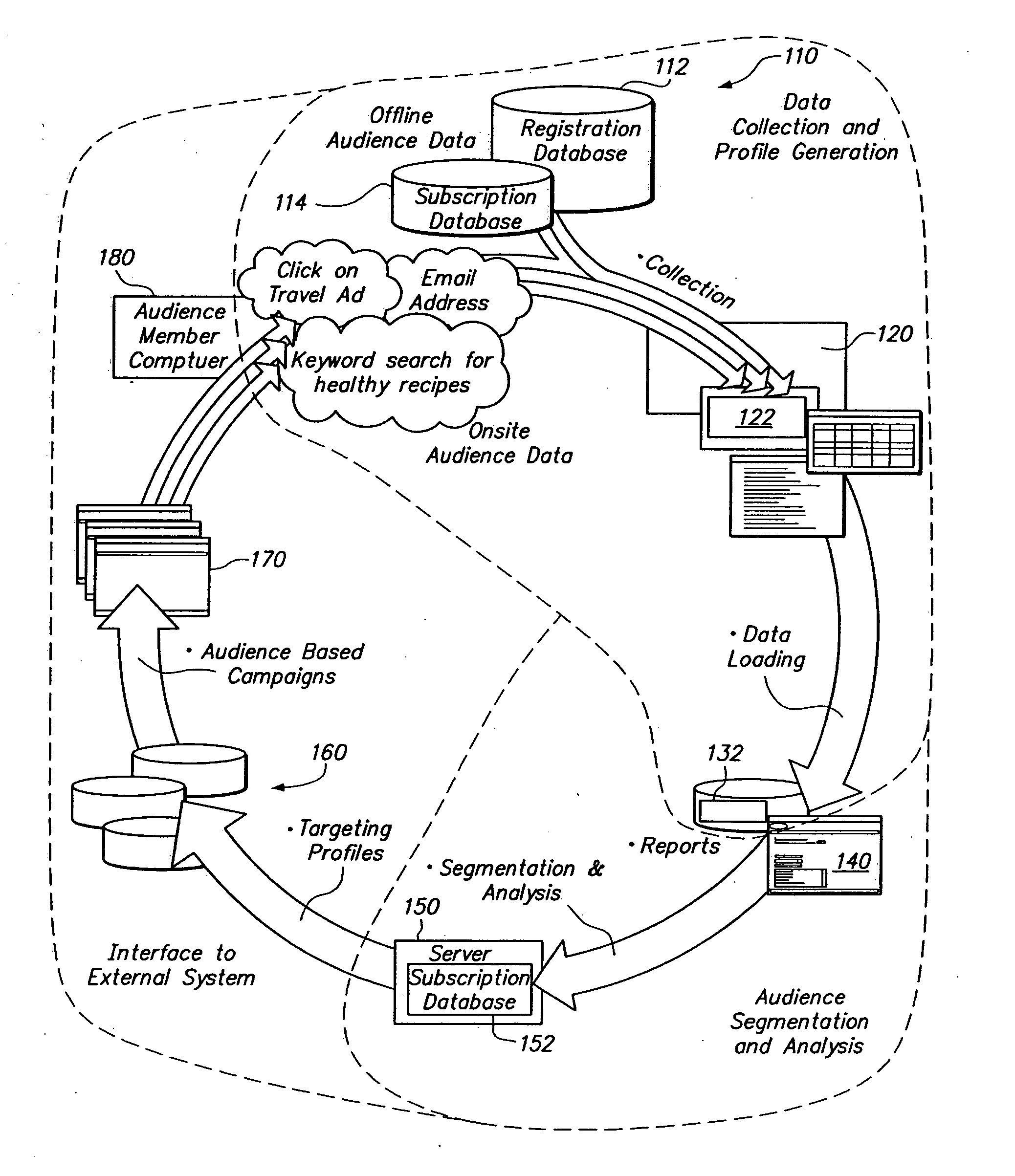
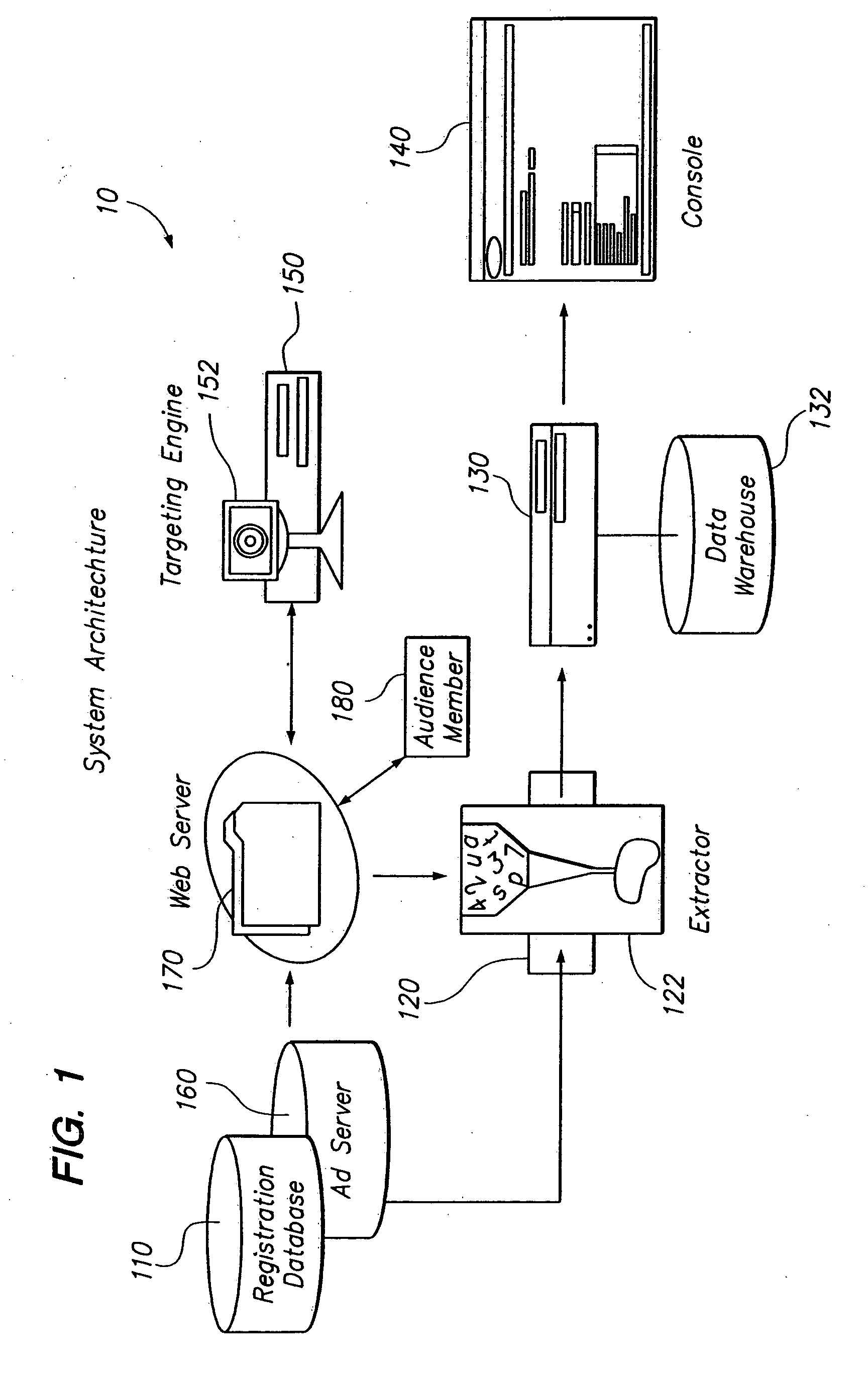
Performance based delivery of content to an audience member. A network of audience member information collection domains provide information about audience members. A profiled audience member may belong to a network segment. Delivery of an advertisement to the profiled audience member is accommodated based upon membership in the network segment and performance criteria. The performance criteria may be configured to benefit a publisher, such as by maximizing revenue. Allocating revenue based upon the collection of data used to target audience members is also provided.
Owner:YAHOO AD TECH LLC
Multi-Segment Network Application Monitoring and Correlation Architecture
InactiveUS20100091676A1Improve performanceError preventionTransmission systemsApplication serverAnalysis data
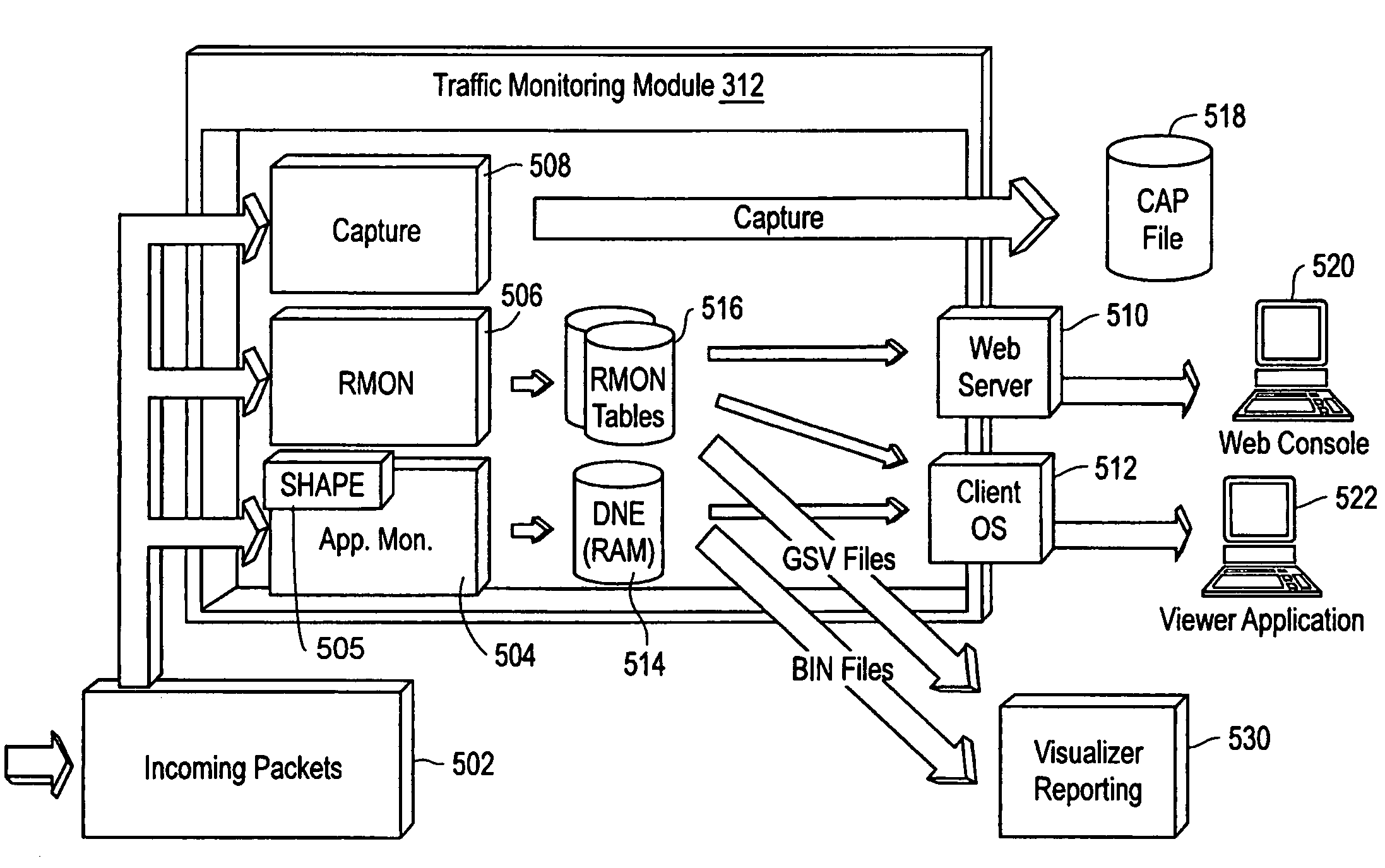
A system, method and computer program product are provided for network and network application monitoring. Accordingly, one or more media modules are each coupled to an associated network segment. In the case of network application monitoring, each media module is coupled to a network segment on which a network application is running. Each media module monitors and collects data relating to traffic on the associated network segment corresponding to the network application, wherein each media module is tailored for network analysis. An application server module is coupled to the at least one media module and receives the data and analyzes the data for helping to improve the performance of the network and / or network application.
Owner:NETWORK GENERAL TECH
HyperLock technique for high-speed network data monitoring
In one embodiment, a network architecture includes a plurality of application monitoring modules for monitoring network traffic data in a plurality of network segments. Network monitoring modules include a staging area that receives network traffic data from a packet capture and analysis engine and an indexing area that stores the data in meta-flow tuples with associated measures divided into time interval buckets. Index tables store dimension-based sorted pointers to the storage locations in the data buckets. HyperLock queries collect time aggregated results for measure based operators with respect to a queried dimension. For each value of the queried dimension, the time interval buckets are traversed compiling a partial result that is finally stored in a stack as the time aggregated value. The stored sorted pointers are used to determine the starting location in each bucket with respect to the next value of the queried dimension.
Owner:NETSCOUT SYSTEMS
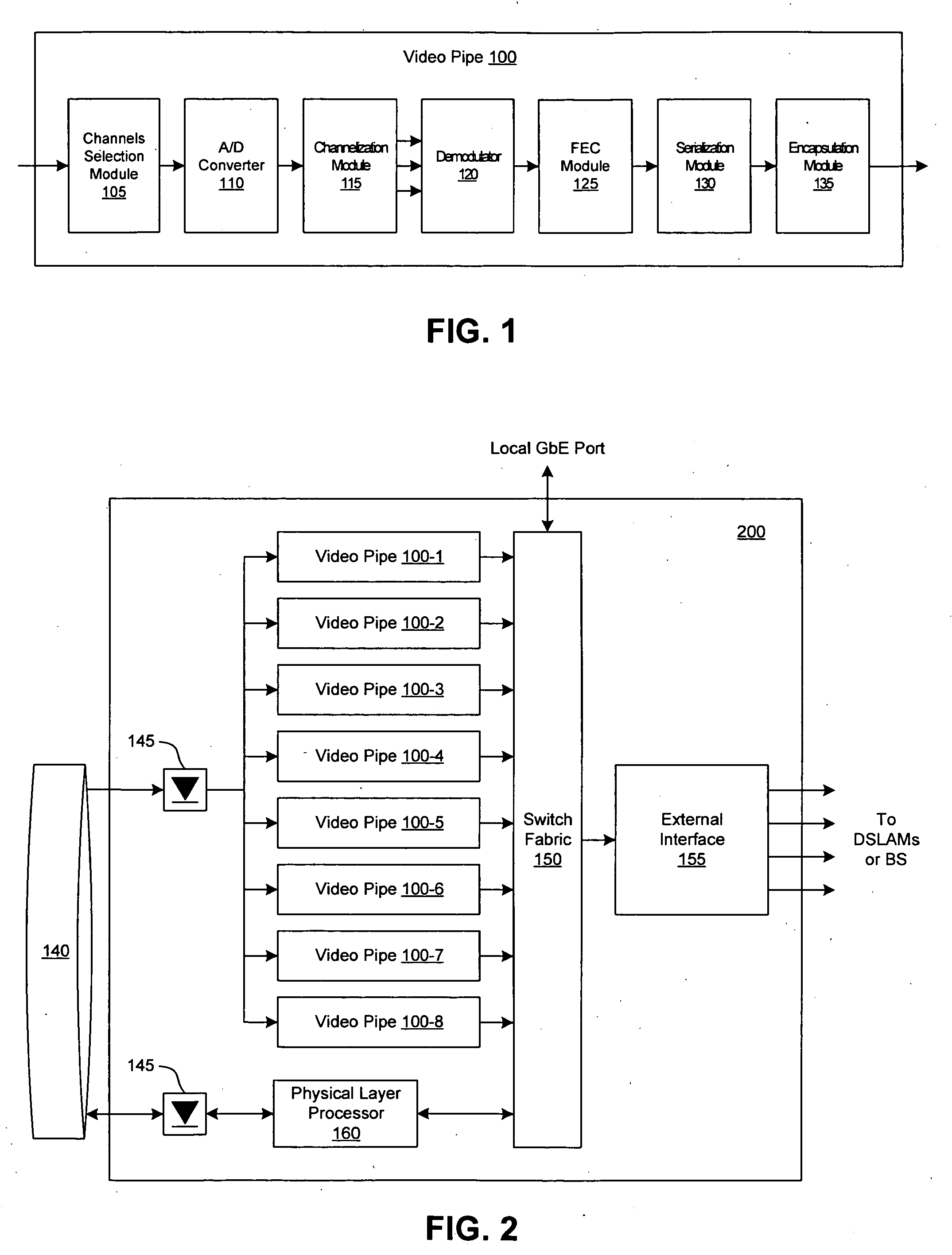
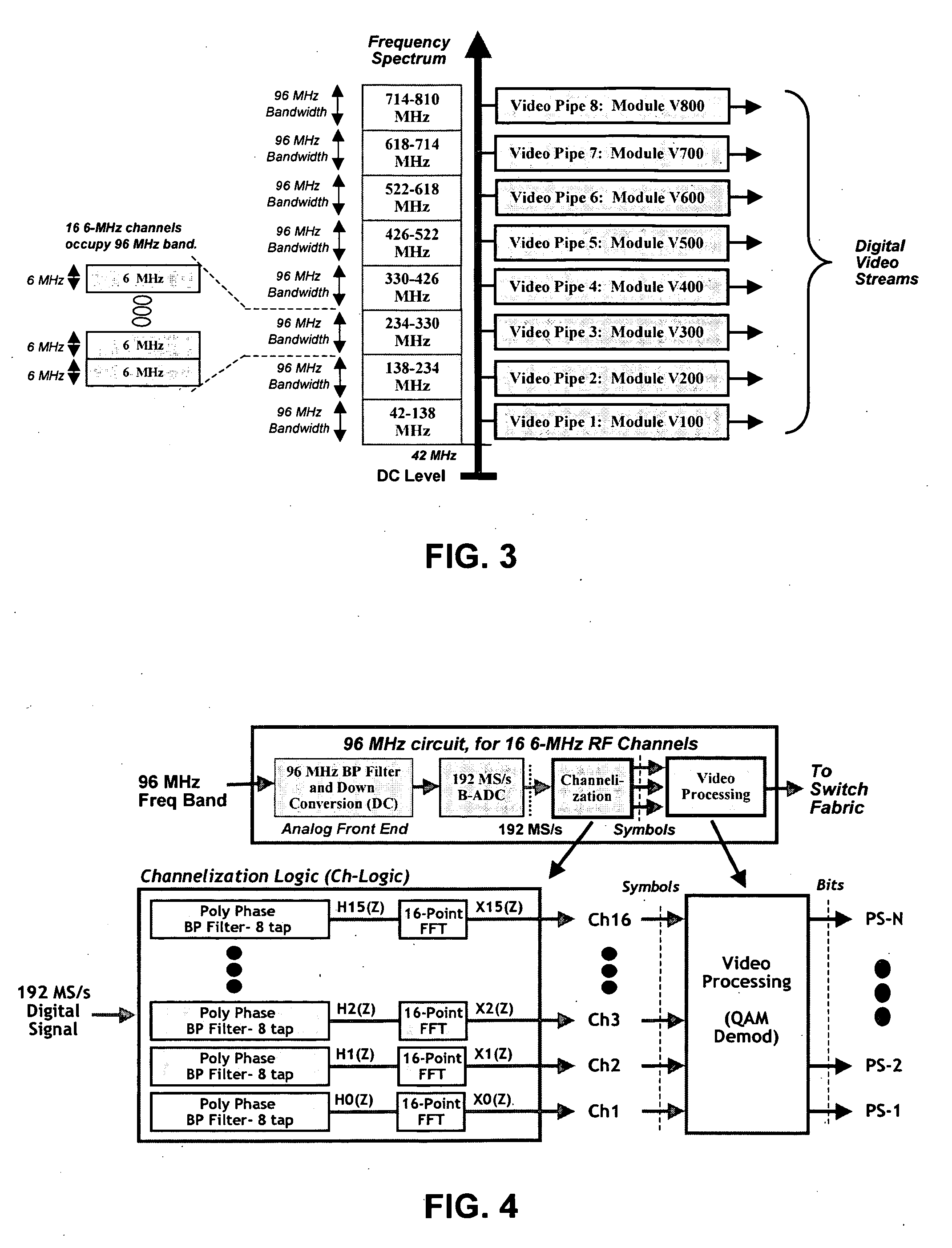
Bulk tuning of frequency-modulated video signals
InactiveUS20050289623A1Analogue secracy/subscription systemsTwo-way working systemsFiberMarket place
A video processing engine terminates frequency-modulated video signals transported over the so-called third mile (the network segment from the head-end to the access network) for delivery to an end user. In various network architectures, these signals are received at a central office (CO), for the telephone companies; at a fiber node (FN), for MSOs; or at a satellite dish, for satellite networks. By terminating these signals appropriately, high-quality video service can be delivered efficiently to customers over the last mile. Systems and methods for processing these video streams as well as various network architectures that allow the network providers to offer cost effective video services to the mass market are described.
Owner:MIDANI MOWAFFAK +2
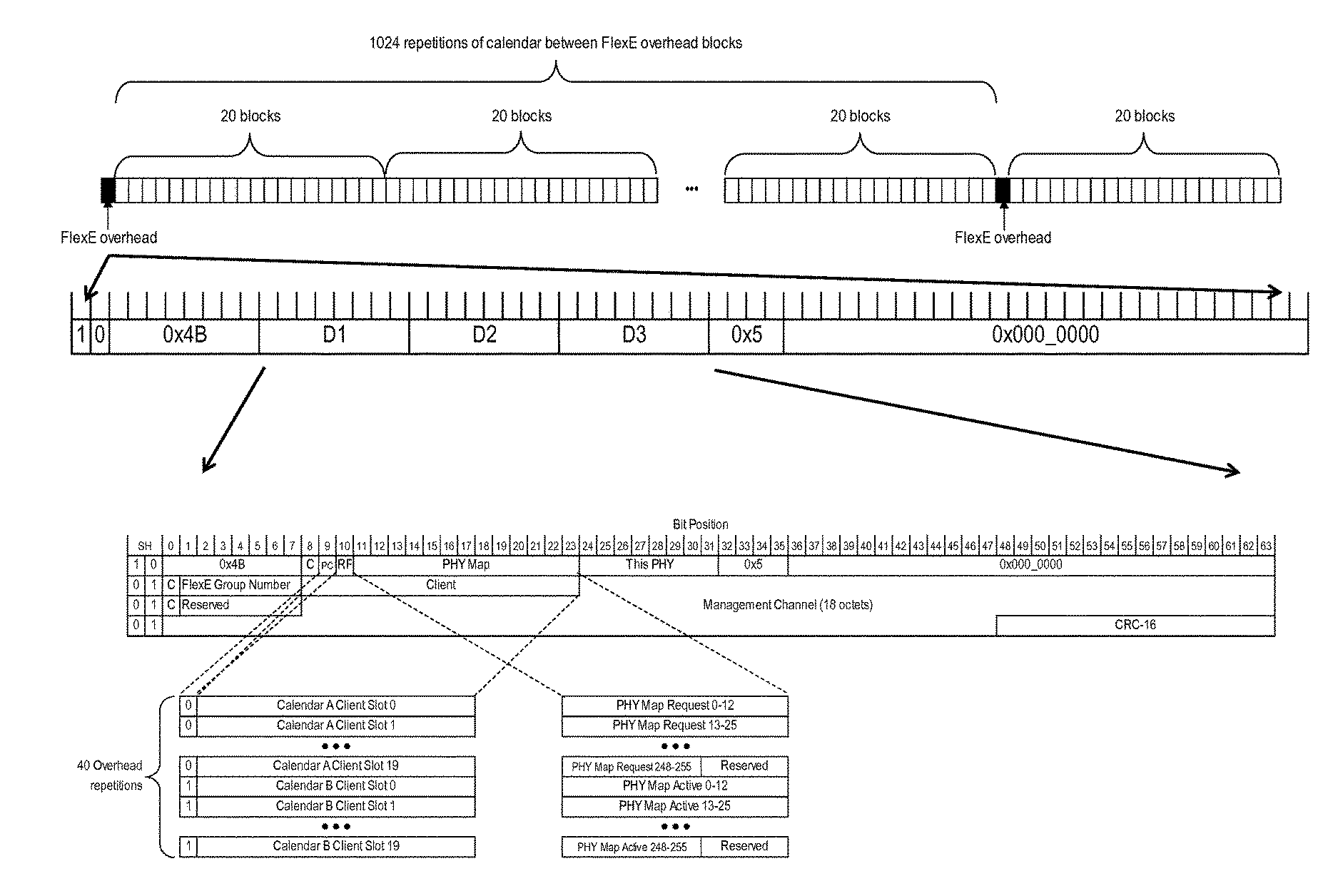
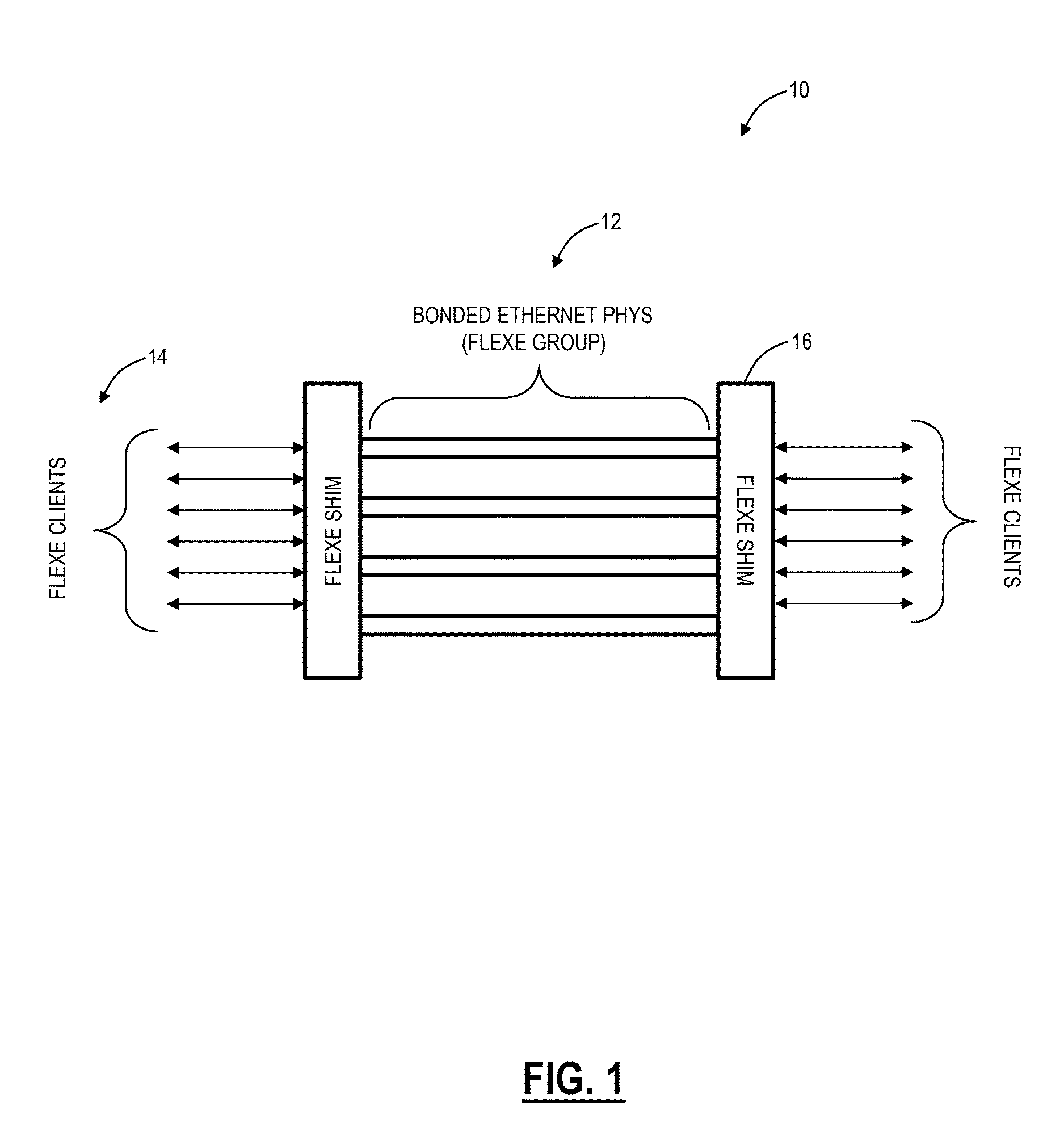
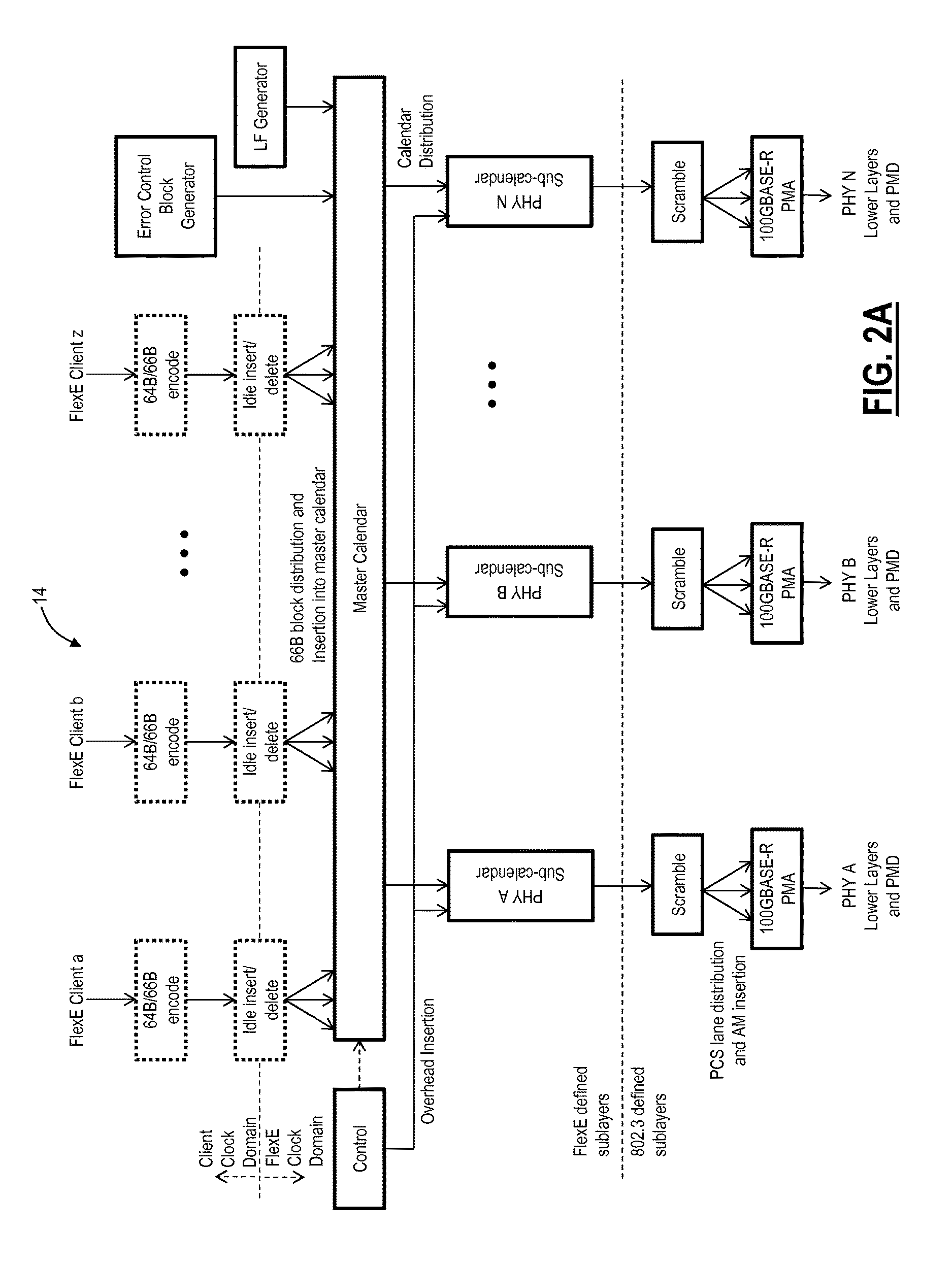
Flexible ethernet operations, administration, and maintenance systems and methods
A node configured to support a Flexible Ethernet (FlexE) client service in a network includes circuitry configured to receive a FlexE client; and circuitry configured to at least one of monitor and update one or more Operations, Administration, and Maintenance (OAM) fields in FlexE overhead, wherein the OAM fields cover a single client path along many network segments (sections) for the FlexE client. A method, implemented in a node, for supporting a Flexible Ethernet (FlexE) client service in a network includes receiving a FlexE client; and at least one of monitoring and updating one or more Operations, Administration, and Maintenance (OAM) fields in FlexE overhead, wherein the OAM fields cover a single client path along many network segments (sections) for the FlexE client.
Owner:CIENA
Method and apparatus for characterizing an end-to-end path of a packet-based network
Owner:APPARENT NETWORKS INC
Routing loop detecting method and system based on SDN
ActiveCN105721297AImprove detection efficiencyImprove detection accuracyData switching networksTheoretical computer scienceStructure of Management Information
The invention discloses a routing loop detecting method based on a SDN. The routing loop detecting method comprises the following steps of: obtaining routing table information and routing event information of each node in a network in real time; constructing a real-time topological structure of the network according to the obtained routing table information and routing event information; constructing a multi-routing-form prefix tree matched with the longest prefix by adopting a hierarchical compression method according to the real-time topological structure, and storing a forwarding subnet segment in the routing table of each node; generating a routing next-hop table for each subnet node in the prefix tree in the subnet segment, in which the loop is necessary to judge, and traversing each subnet node of the prefix tree to generate a node forwarding figure; and judging whether the routing loop exists or not according to the node forwarding figure. The invention further discloses a routing loop detecting system based on the SDN. By means of the routing loop detecting method and system based on the SDN, the routing loop detection efficiency and accuracy are increased; and simultaneously, the storage space and the calculation time are reduced.
Owner:BEIJING CHINA POWER INFORMATION TECH +4
Method and apparatus for transportation of data over a managed wireless network using unique communication protocol
InactiveUS6587441B1Multiplex system selection arrangementsError prevention/detection by using return channelWireless controlWireless mesh network
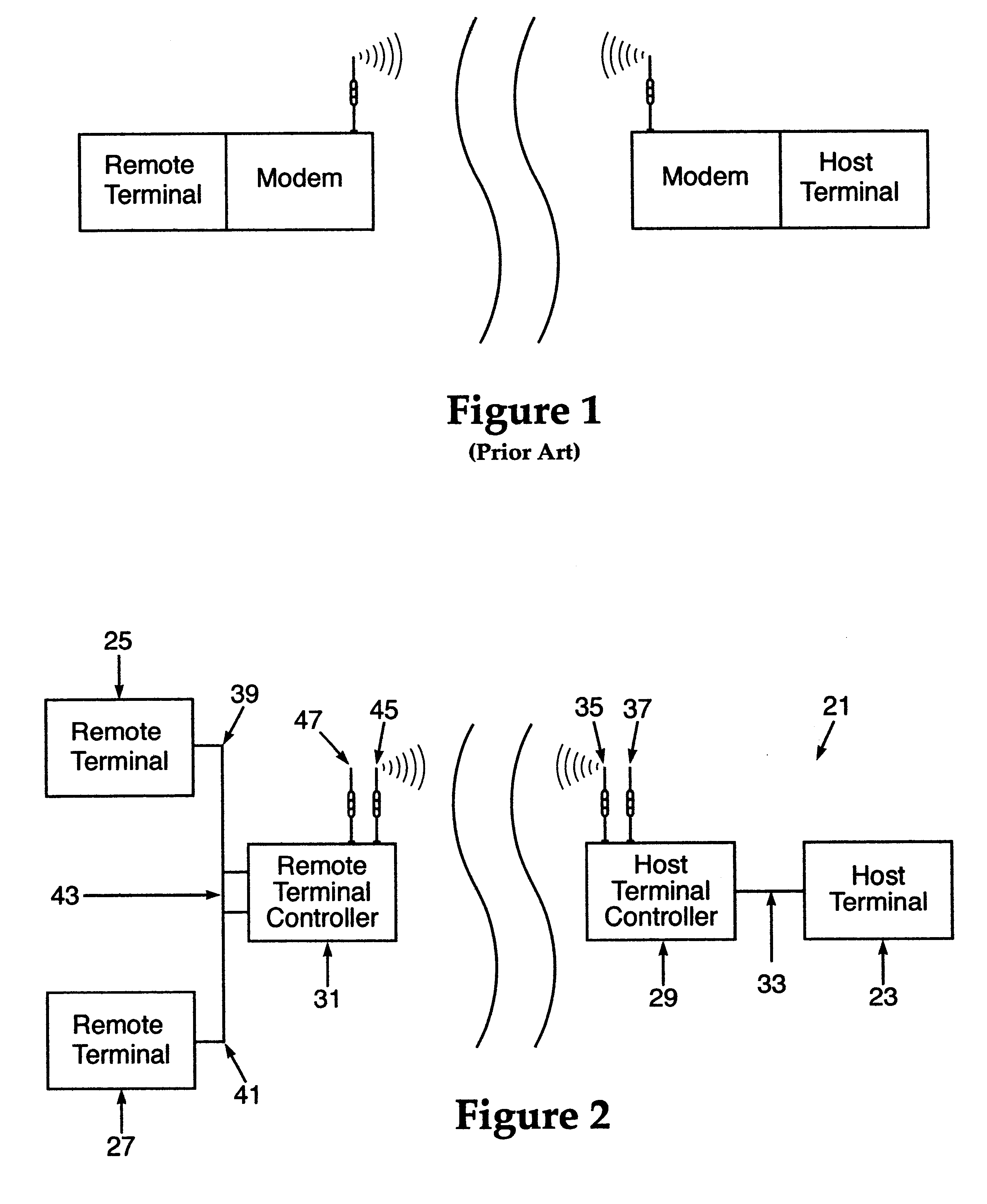
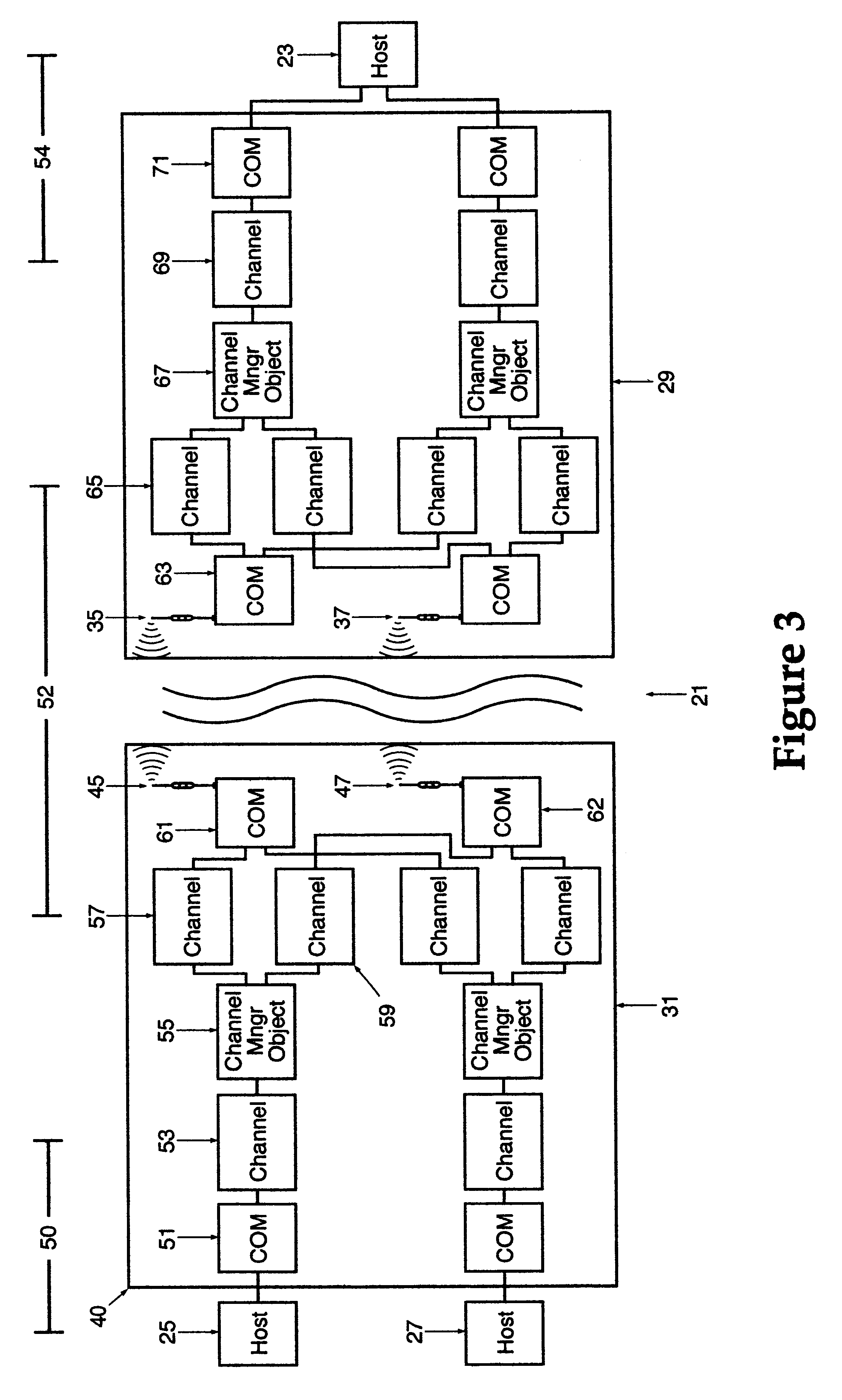
A wireless, redundant, secure, real-time, network for a proprietary interactive data transfer system having a remote terminal and a host data center, such as an automated teller banking system, is disclosed. Controllers for the remote terminal and the host data center receive the proprietary language messages and packetize and encrypt the messages for sending over the best wireless carrier among the plurality of wireless carriers the controllers are connected to. The wireless control protocol monitors the communications to provide for selection of the most reliable communication carrier for any part of a transmission. Each network segment of the signal path has at least one state-controlled gate which reports the status of that signal path. Real time transmission and acknowledgment of securely packetized messages on wireless communications carriers via an object oriented coding control application provides for reliable datagram transfer independent of the reliability of any one signal path.
Owner:MAYFAIR WIRELESS
Methods and apparatus for performing handoffs in a multi-carrier wireless communications system
ActiveUS7212821B2Minimize service disruptionMinimize disruptionTime-division multiplexRadio/inductive link selection arrangementsCommunications systemNetwork link
A mobile communications device initiates a handoff from its current base station (BS) sector network attachment point to a new BS sector. The mobile sends a handoff request over its current wireless link to the current BS sector, which forwards the request to the new BS sector, e.g., via a network link. The new BS sector processes the request assigning dedicated resources, e.g., an identifier and dedicated uplink segments. Information identifying the allocated resources is conveyed from the new BS sector via the current BS sector to the mobile. The mobile determines the time of the allocated dedicated segments based upon a received beacon signal from the new BS sector with known timing relationships to dedicated segments. The mobile breaks the original wireless link just prior to the time of the first assigned dedicated segment. The mobile communicates information on the assigned dedicated segments to perform registration operations, e.g., timing synchronization and power control, establishing a new wireless link.
Owner:QUALCOMM INC
Decoupling functionality related to providing a transparent local area network segment service
ActiveUS7577143B1Simple configurationData switching by path configurationTransport networkNetwork segment
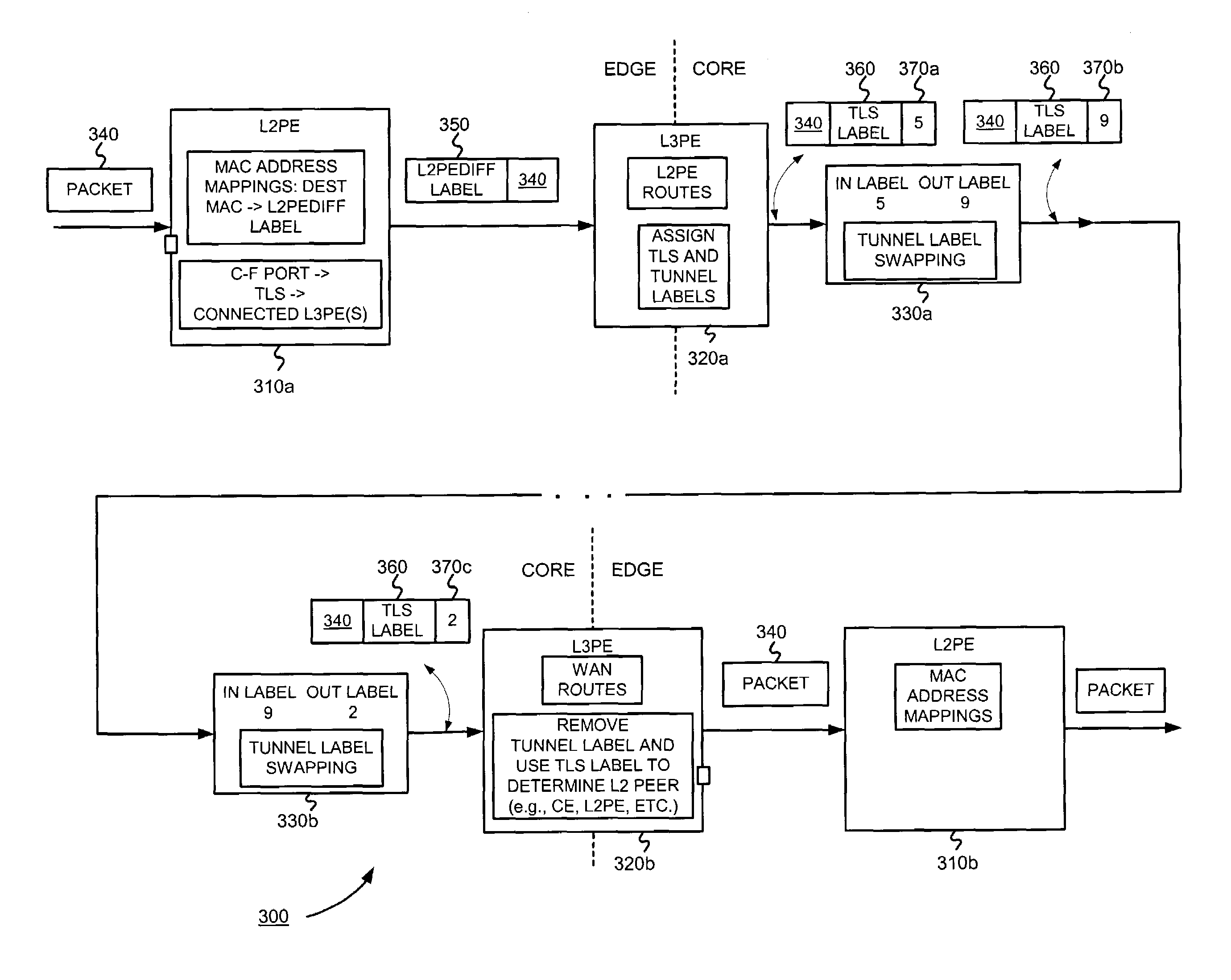
A transport LAN segment service is provided over a transport network. Responsibilities for configuring, provisioning and forwarding over a transport LAN segment are divided between layer 2 and 3 service provider edge devices, where the layer 3 edge device handles discovery and tunneling responsibilities, the layer 2 edge device handles learning and flooding responsibilities, and information can be exchanged between the layer 2 and 3 edge devices. Configuration is simplified by advertising TLS-label information, layer 2 address learning, and flooding when the needed configuration information has not yet been learned or discovered.
Owner:JUMIPER NETWORKS INC
Method and system for visually representing network configurations
InactiveUS6941359B1Assisted navigationImprove efficiencyMultiple digital computer combinationsData switching networksGraphicsNetwork management
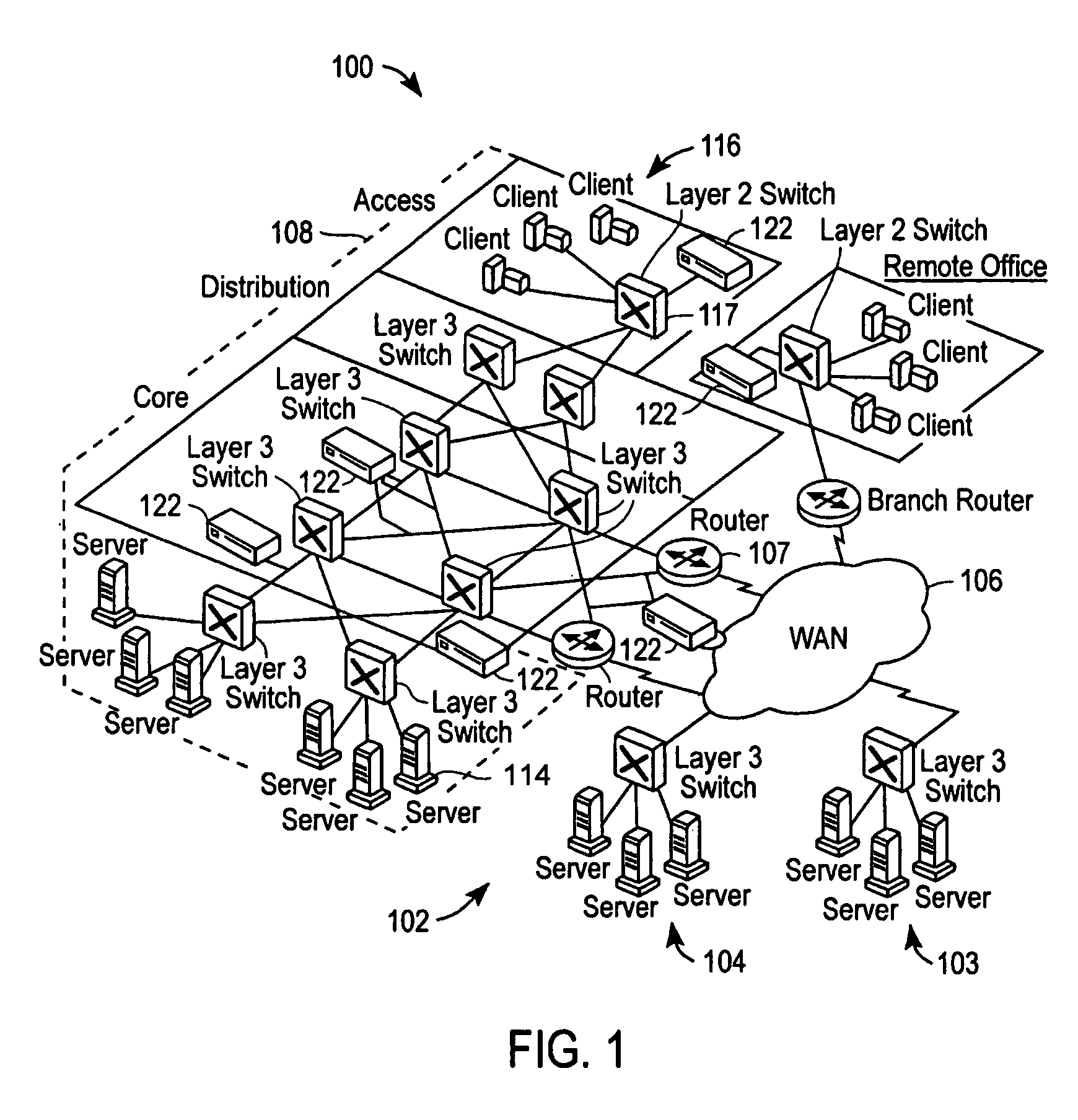
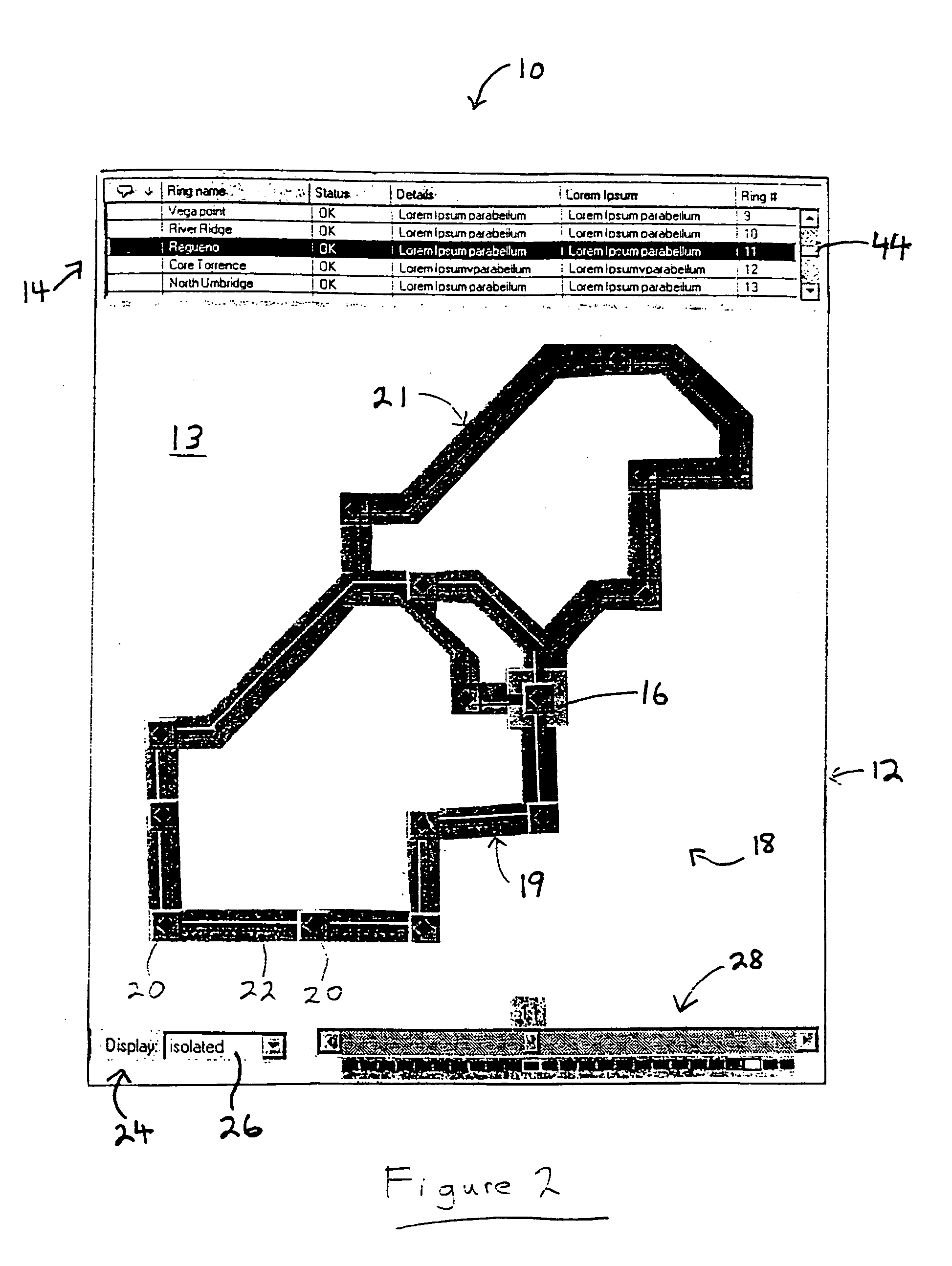
A visualization method for a hub network configuration allows exploration of a chosen network by way of a graphical display interface (GUI), wherein multiple distinct network segments such as lines or rings are shown attached to a common node or centralized hub. The technique combines a graphical view of the segments controlled by a segment selector. The selector is coupled to a series of display indicators and a list of the attached rings contained in the network. The list can contain descriptive elements of the segments, or can provide links to such detail. A mutually exclusive selection of the attached segments is enabled using either the selector or the list of attached segments. For each segment selected, the display indicators can show the currently displayed segments on the GUI, help to highlight on the GUI a selected attached segment and provide an indication of attached segments that are related in function to the selected segment. Selected and remaining segments of the network are displayed in various shadings or colours, which enables a Network Manager or other user of the system and method to easily distinguish and consider these aspects alternatively. In the graphical view, attached segments can be displayed in stacked, overlaid, or isolated formats. The segments can consist of rings, lines, stars, bars, and chains.
Owner:CIENA
Local discovery of mobile network services
InactiveUS20070286100A1Special service provision for substationMultiplex system selection arrangementsNetwork agentService information
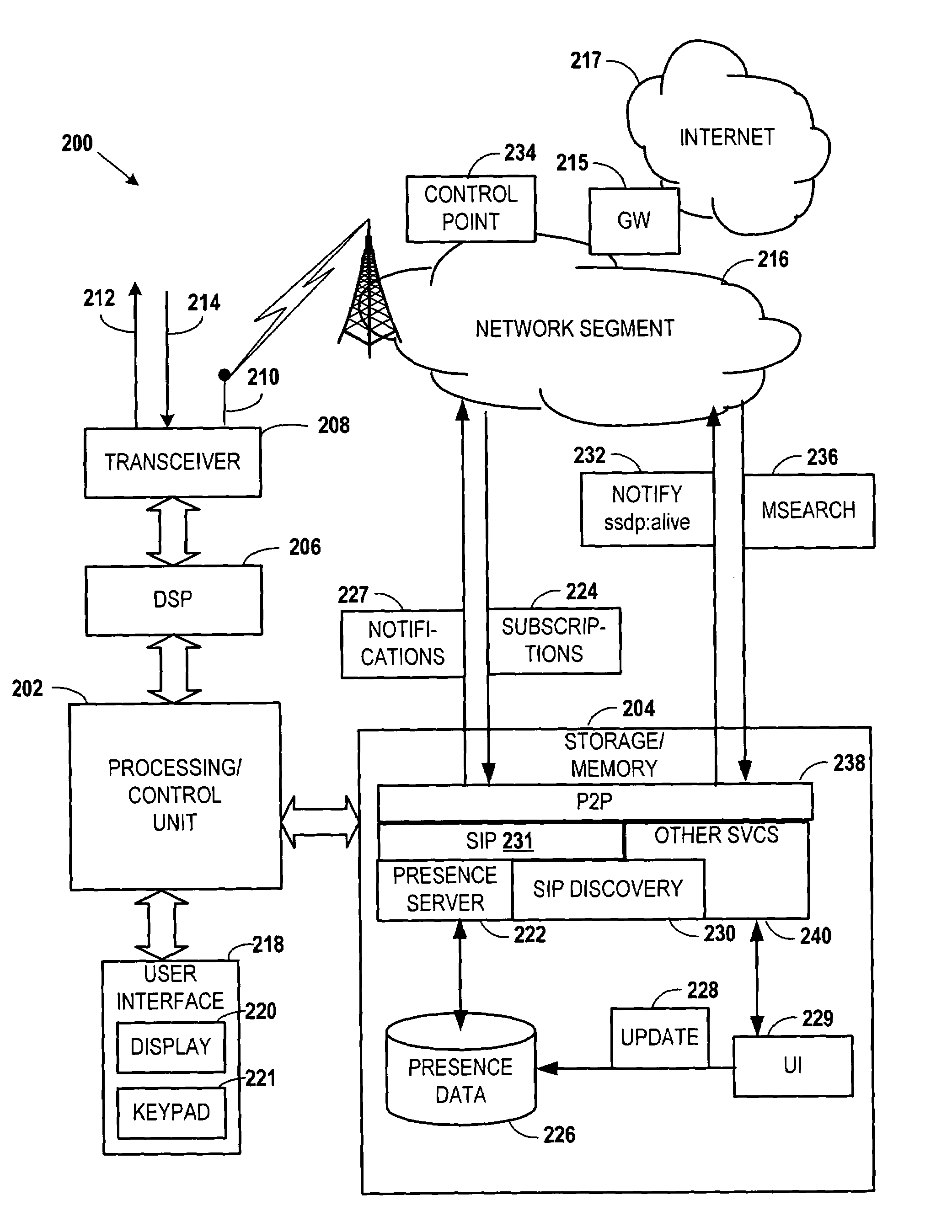
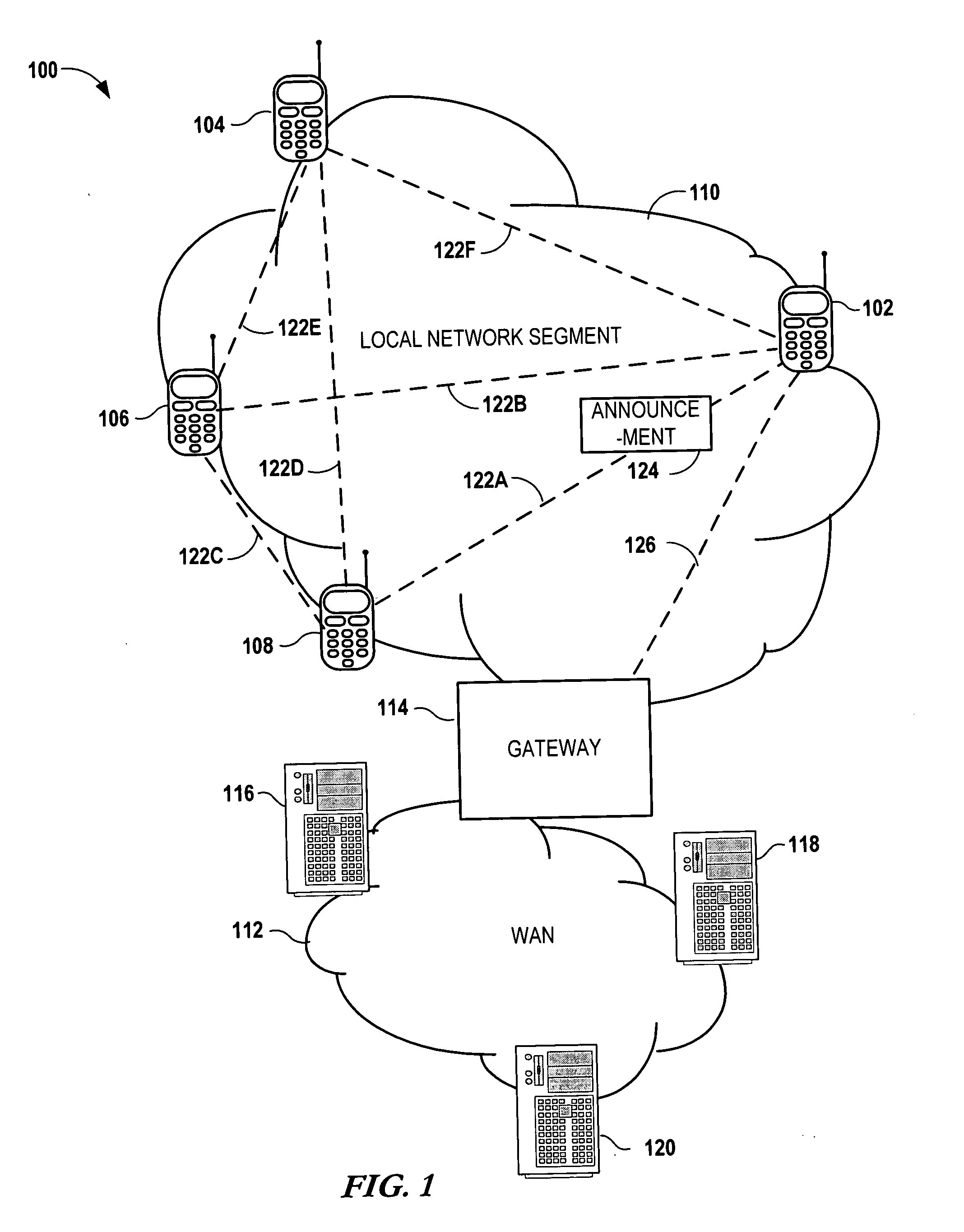
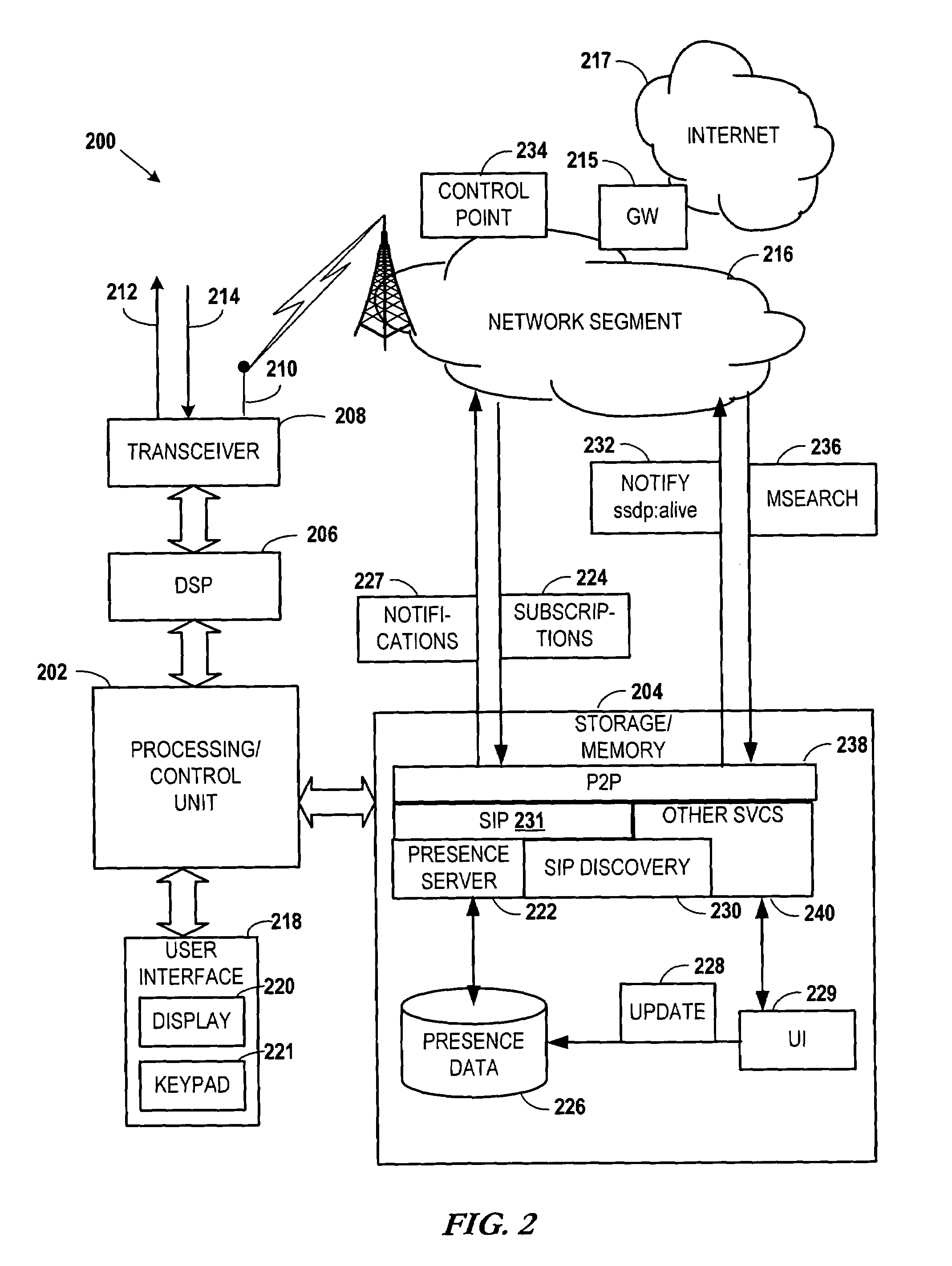
Local discovery of mobile network services involves coupling a communications device to a local network segment of a mobile data network. An announcement is sent from the communication device and / or a network entity (such as a network proxy) describing a service available via the respective devices. The announcement is receivable by any device on the local network segment. A request is received at the device for a detailed description of the service information in response to the announcement. A description of the service is sent from the communications device to the originator of the request in response to the request, and the service is established between the originator and the communication device and / or network entity in response to the sending of the description of the service
Owner:NOKIA CORP
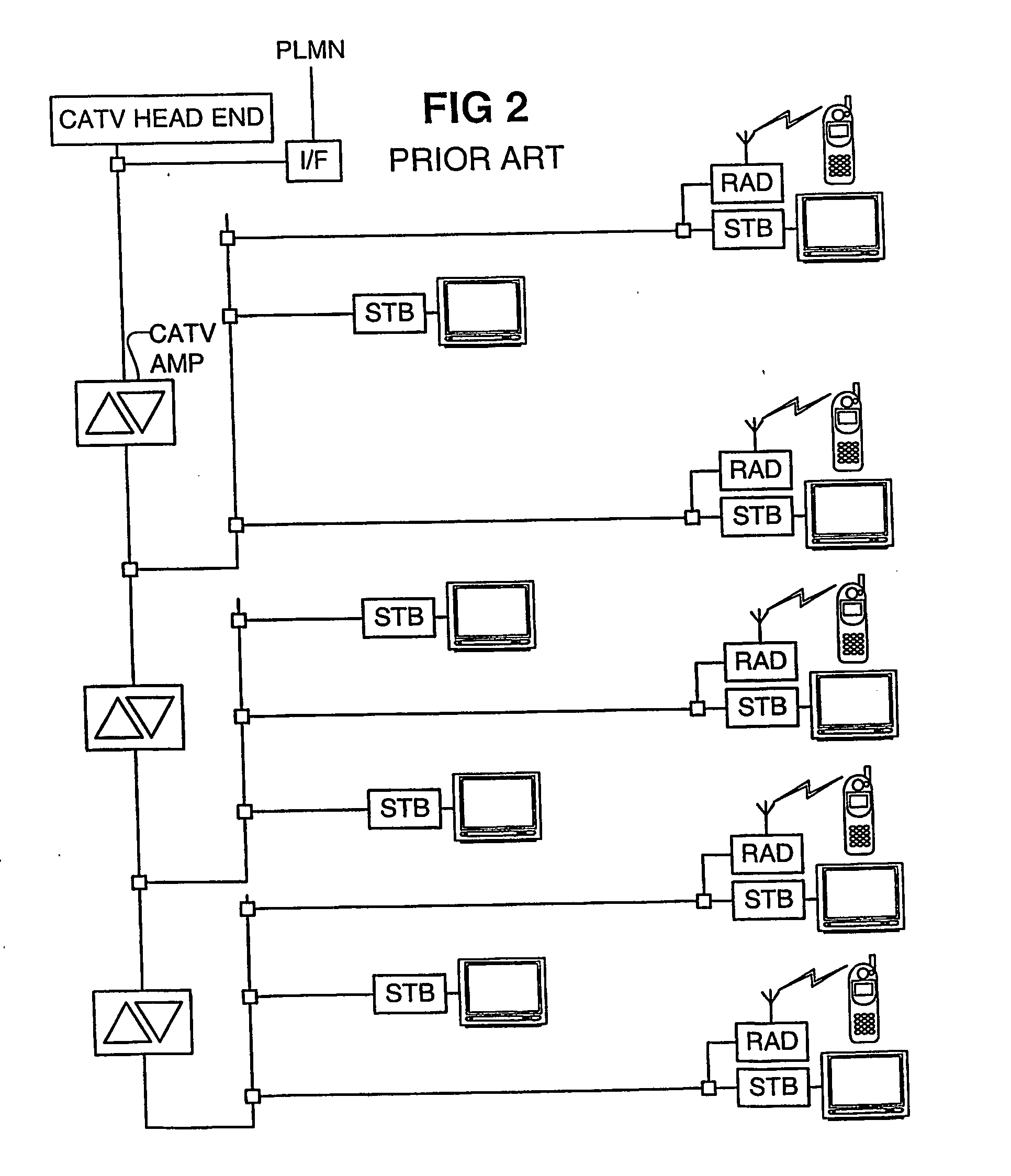
Wireless provider monitoring of catv segment
InactiveUS20050144647A1Reduce disadvantagesSmall cell sizeAccounting/billing servicesInformation formatAudio power amplifierInformation support
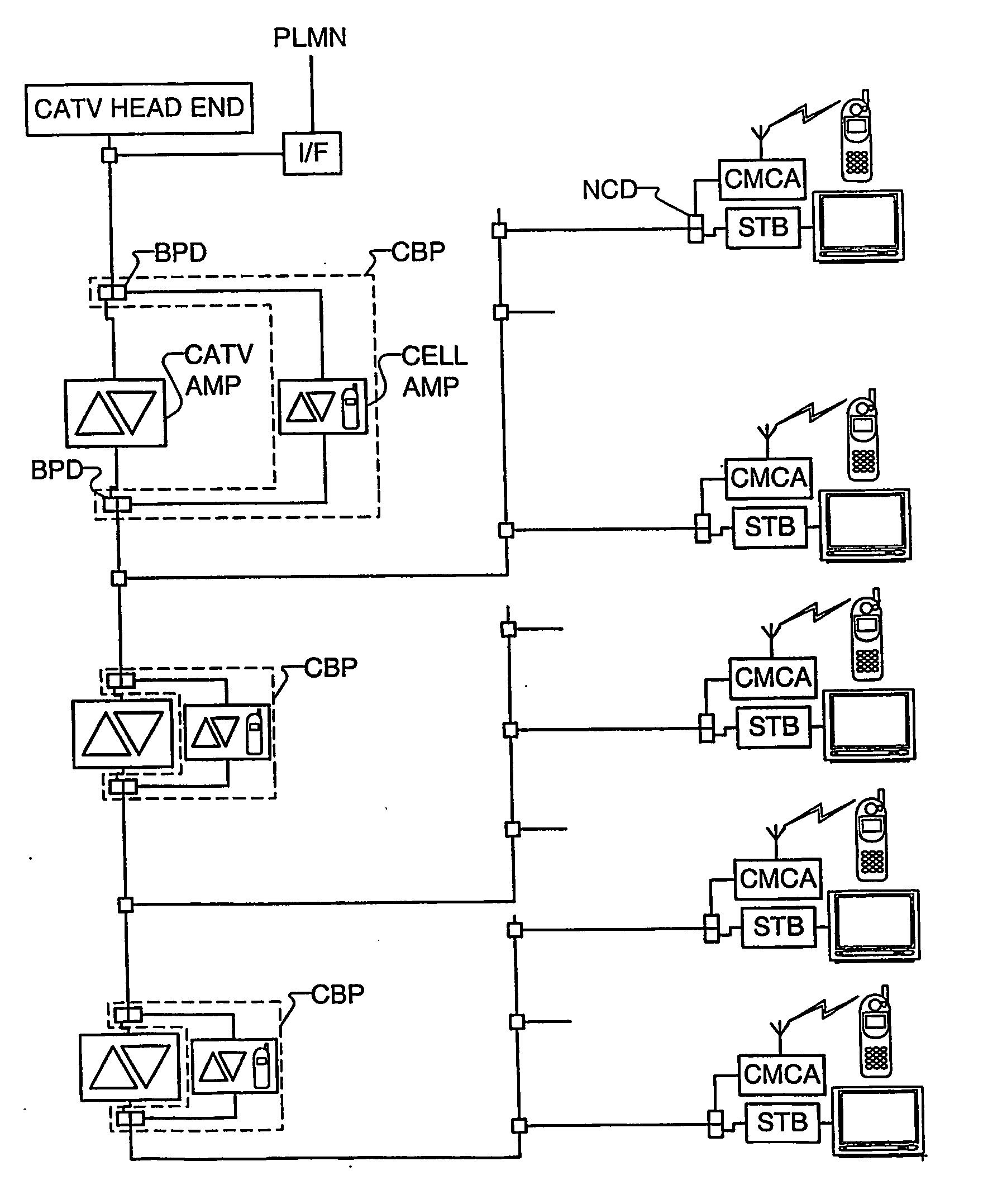
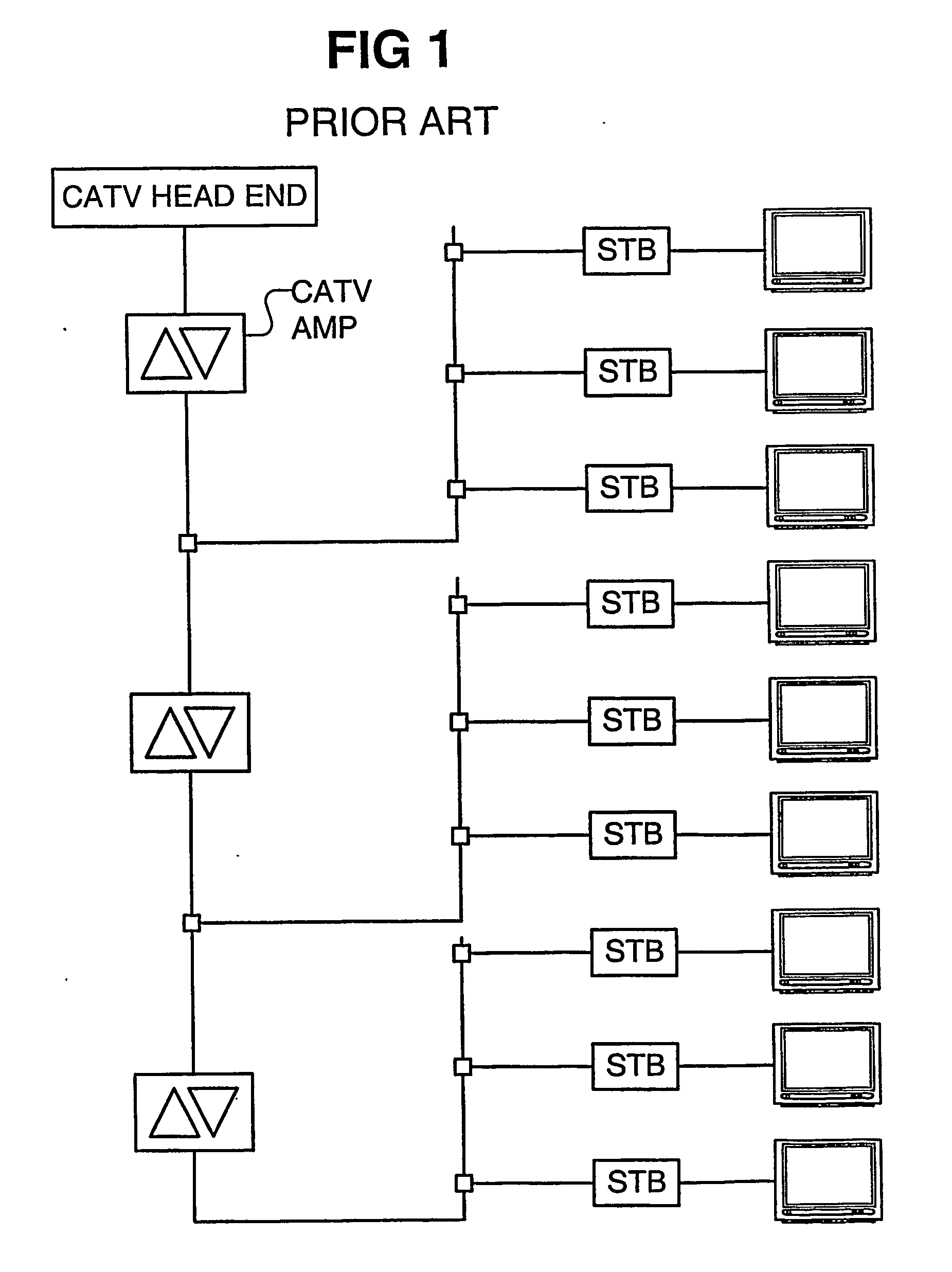
A monitor enabled amplifier in the CATV segment of a wireless network includes a cellular interface communicating with a network control center to provide status information pertaining to the CATV network. A monitor enabled cable Mount cellular antenna with a twin mode cellular interface provide status and location correlation information to the network control center. The location correlation information supports an emergency response system and differential billing.
Owner:ZUSN MORDECHAI +3
System and method for behavior-based firewall modeling
InactiveUS7610621B2Easy constructionMultiple digital computer combinationsProgram controlClient-sideTraffic flow
One embodiment of the present invention creates a model of the traffic through a network firewall and uses that model to dynamically manipulate the network firewall based on human intervention or based on the automatic invocations of processes and protocols that implement firewall policy. Another embodiment of the invention creates a model of the physical and virtual network interfaces that a firewall system controls and presents abstracted entities representing both the interface abstractions and the processing nodes (network segments or network client devices) to and through which network traffic flows.
Owner:RPX CORP
System and method for traversing metadata across multiple network domains at various layers of the protocol stack
InactiveUS20050122979A1Data processing applicationsData switching by path configurationProtocol stackNetwork segment
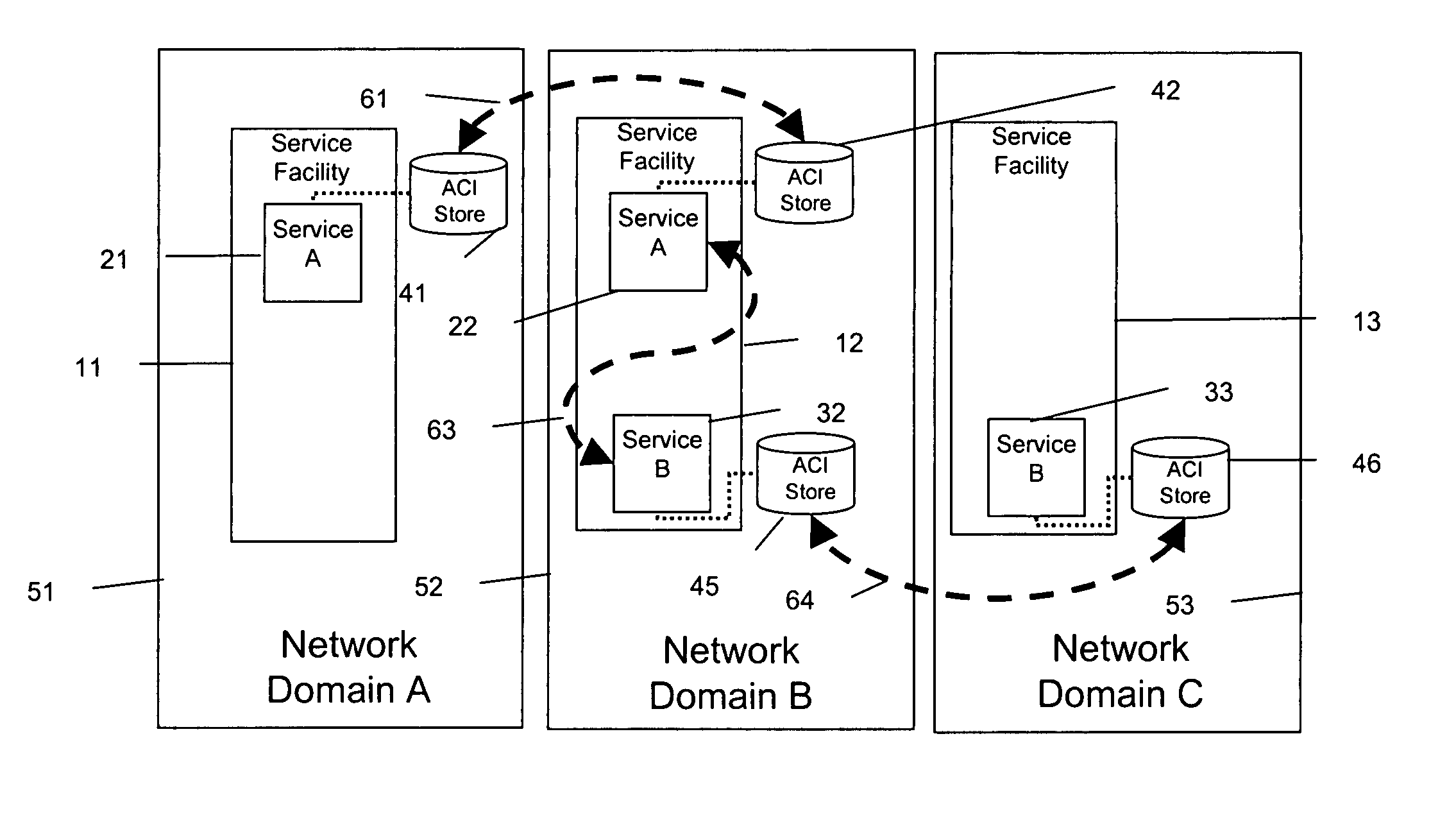
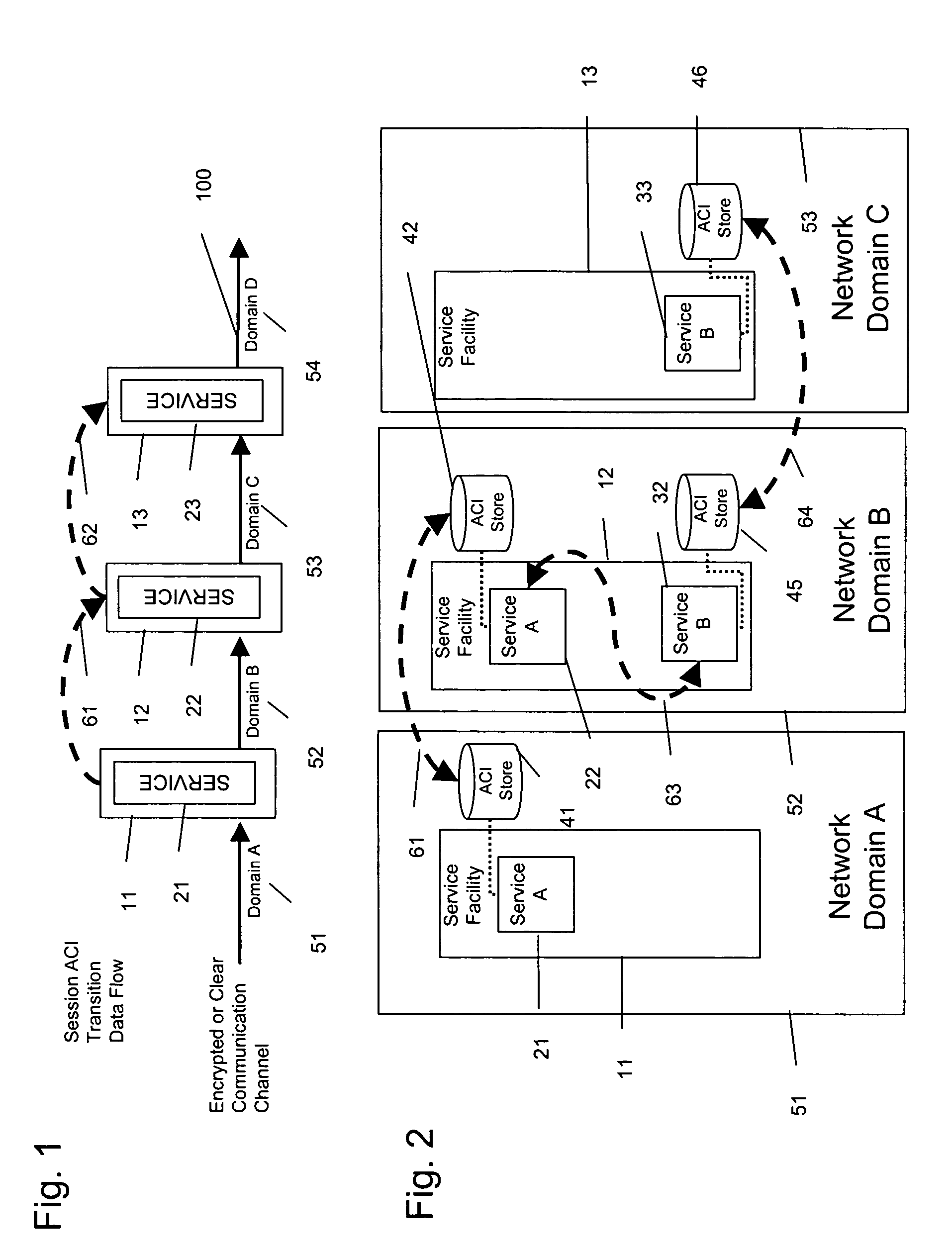
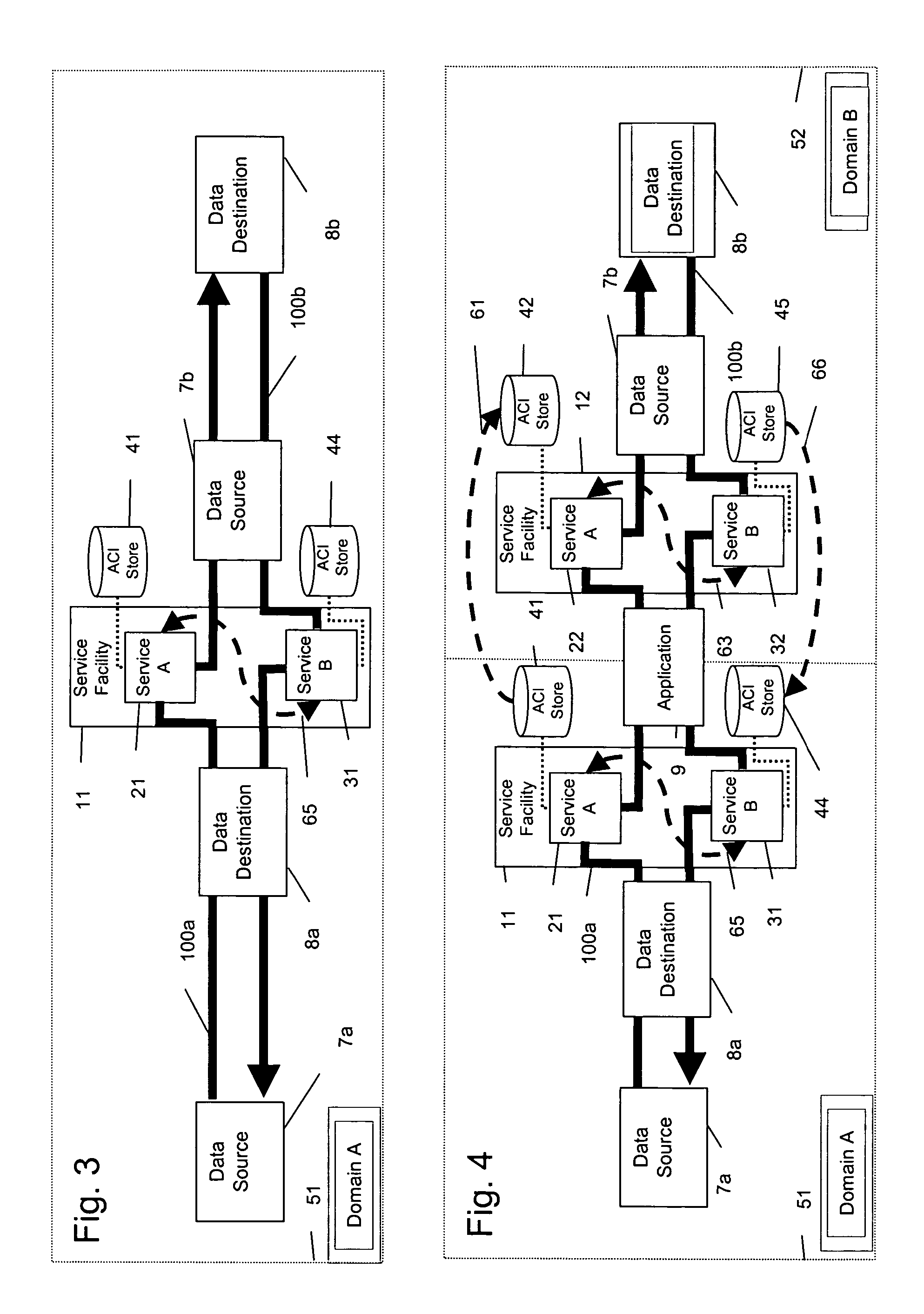
An inter-networking system and method that provides for access control identifier (ACI) metadata utilization for the life of a session even on unknown networks being traversed, allowing for ACI metadata utilization, reutilization, and modification in both the send and receive paths (bi-directional), and allowing for metadata transport over network segments requiring that ACIs be embedded at different layers of the communications stack.
Owner:CRYPTEK INC
Multi-segment network application monitoring and correlation architecture
InactiveUS8185651B2Improve performanceMultiple digital computer combinationsData switching networksTraffic capacityAnalysis data
Owner:NETWORK GENERAL TECH
Packet processing in managed interconnection switching elements
ActiveUS20130044751A1Efficient use ofData switching by path configurationNetwork connectionsInterconnectionComputer science
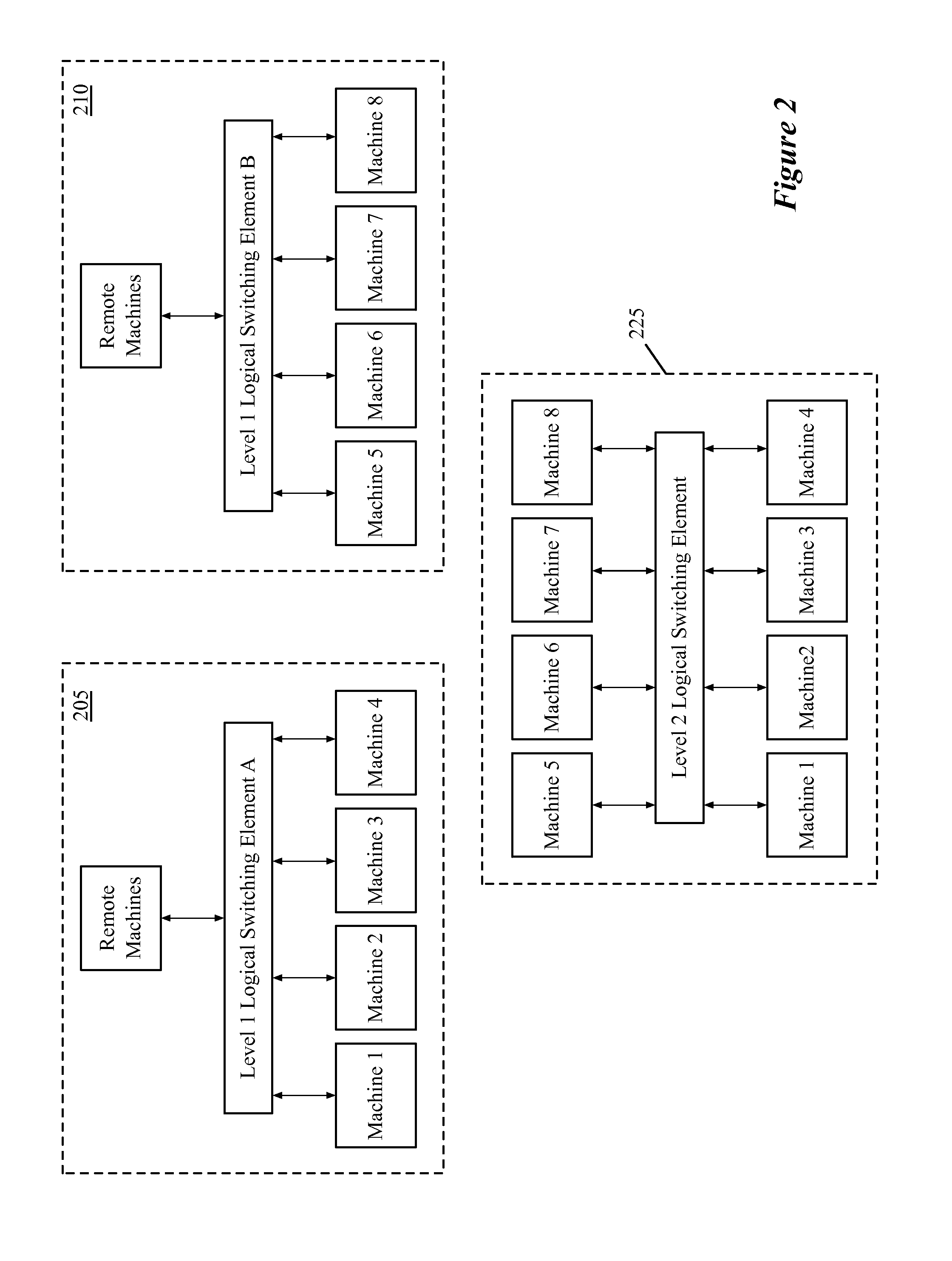
Some embodiments provide a novel method for forwarding a packet at a first managed interconnection switching element in a managed network of interconnection switching elements. The method receives a packet from a source machine on a first network segment in a first network. The packet identifies a destination machine located on a second network segment in a second, different network. The method removes a context tag that identifies the first network segment. The method uses the identification of the first network segment to determine a logical switching element that connects at least the first and second network segments. The method encapsulates the packet with a logical context identifier that identifies a logical port of the logical switching element. The logical port corresponds to the second network segment. The method transmits the twice-encapsulated packet towards a second managed interconnection switching element at the second network.
Owner:NICIRA
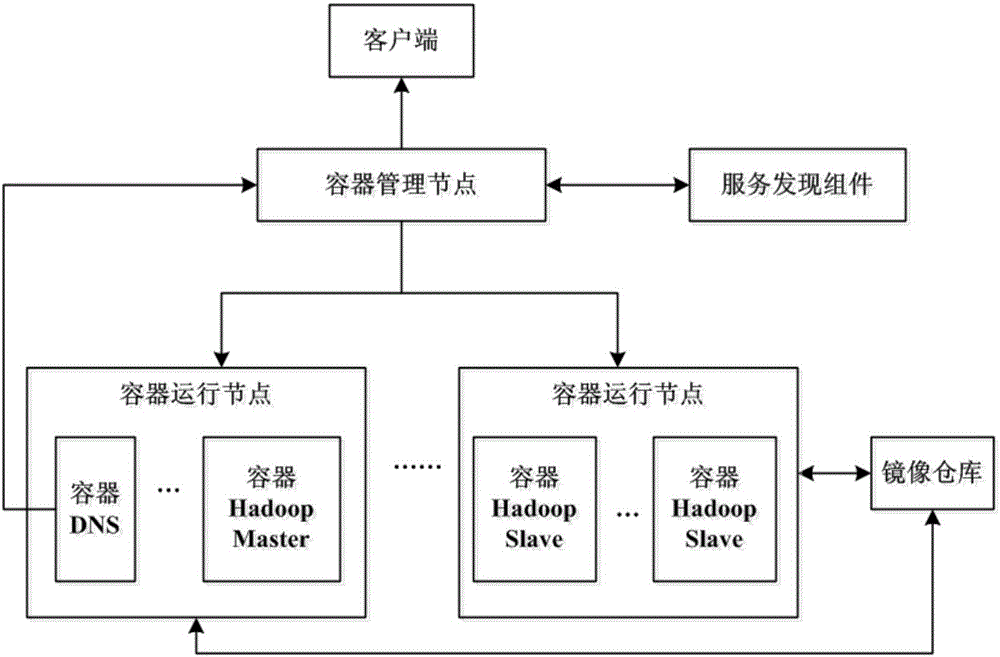
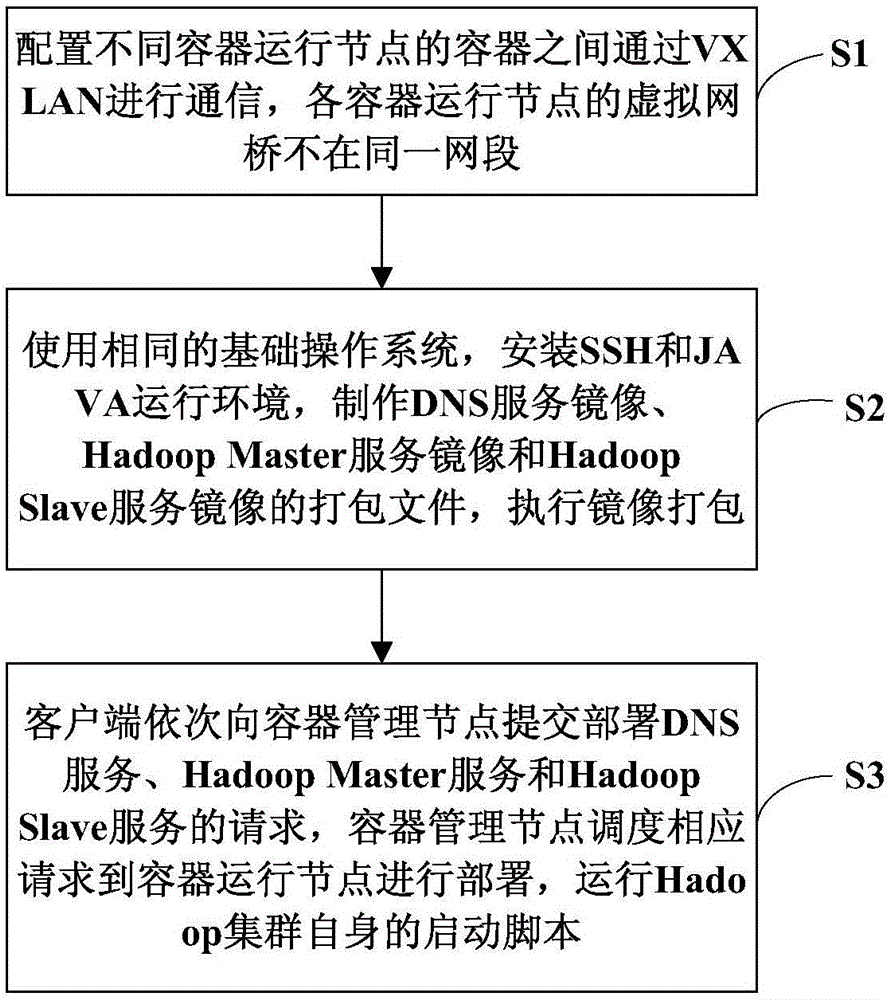
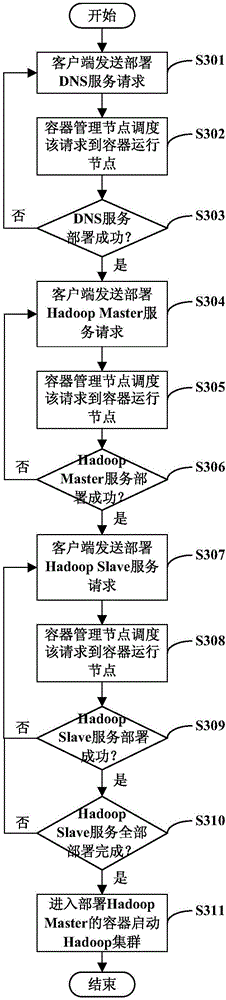
Hadoop cluster system and Hadoop cluster rapid establishment method based on container technology
InactiveCN106790483AQuickly deploy and go onlineRapid deploymentNetworks interconnectionCluster systemsClient-side
The invention discloses a Hadoop cluster system and Hadoop cluster rapid establishment method based on a container technology and relates to the technical field of big data and cloud computing. The method comprises the steps of configuring that containers between different container operation nodes communicate through a VXLAN, and configuring that virtual network bridges of the container operation nodes are not located in the same network segment; installing SSH and JAVA operating environments, producing packaging files of a DNS service mirror image, a Hadoop master service mirror image and hadoop slave service mirror images, packaging the mirror images, and transmitting the packaged mirror images to a mirror image warehouse for storage; and submitting requests for deploying three pieces of services to a container management node in sequence by a user through a client, scheduling the corresponding requests to the container operating nodes for deployment by the container management node, and registering the corresponding service. According to the system and the method, a Hadoop cluster can be deployed rapidly, the condition that the number of servers is insufficient is solved, and the availability of a Hadoop container cluster deployed on a Docker platform is improved.
Owner:WUHAN POST & TELECOMM RES INST CO LTD
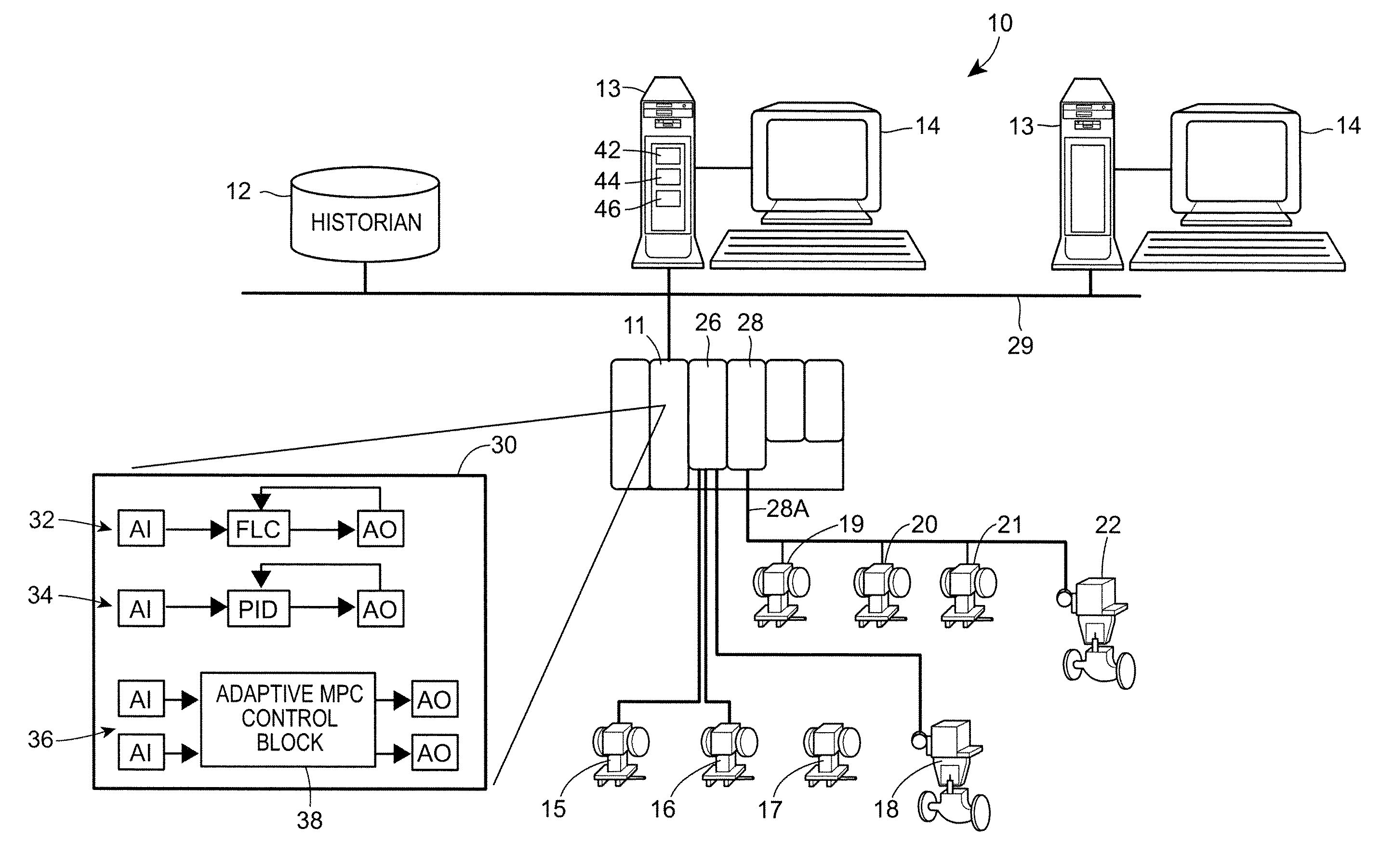
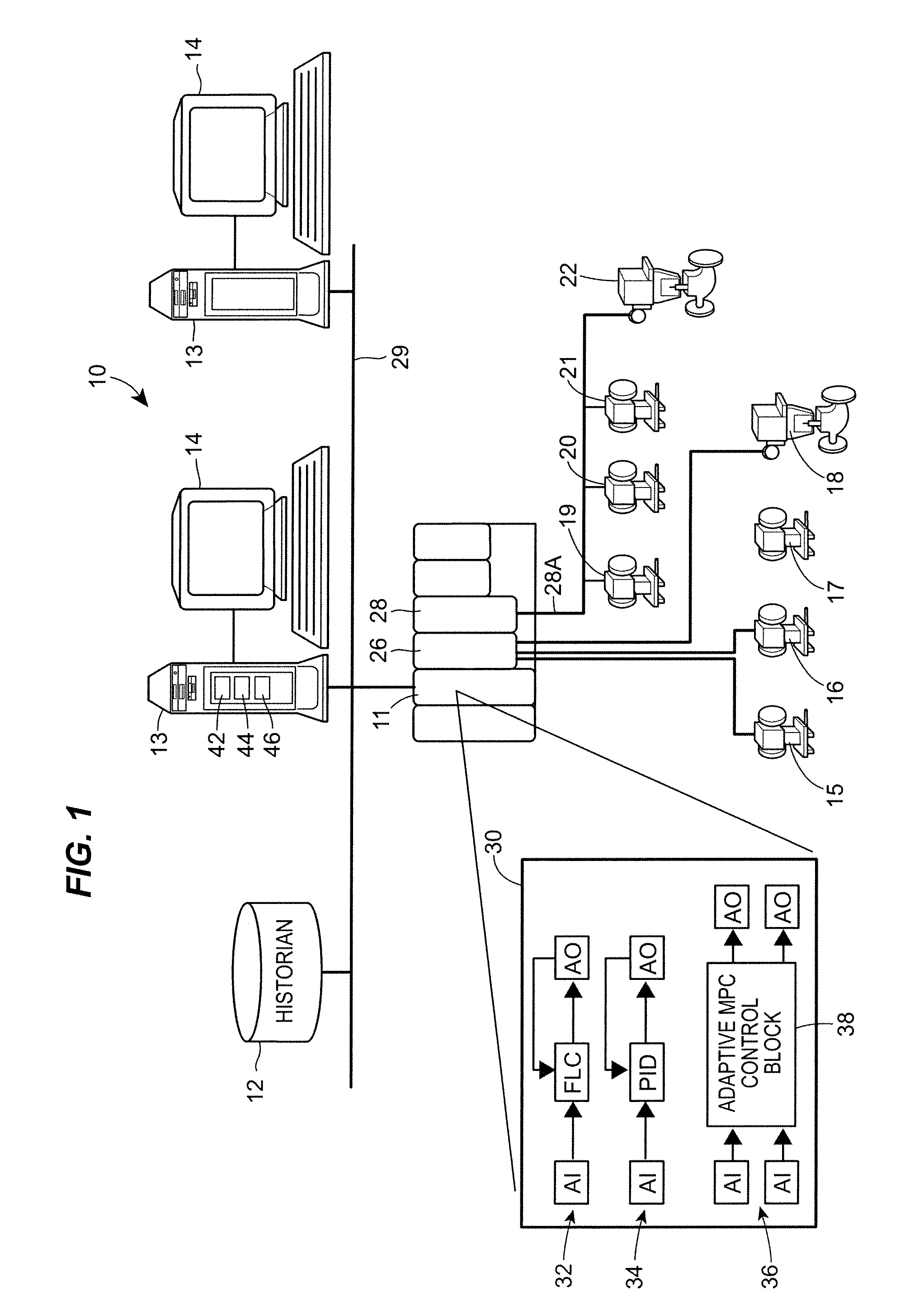
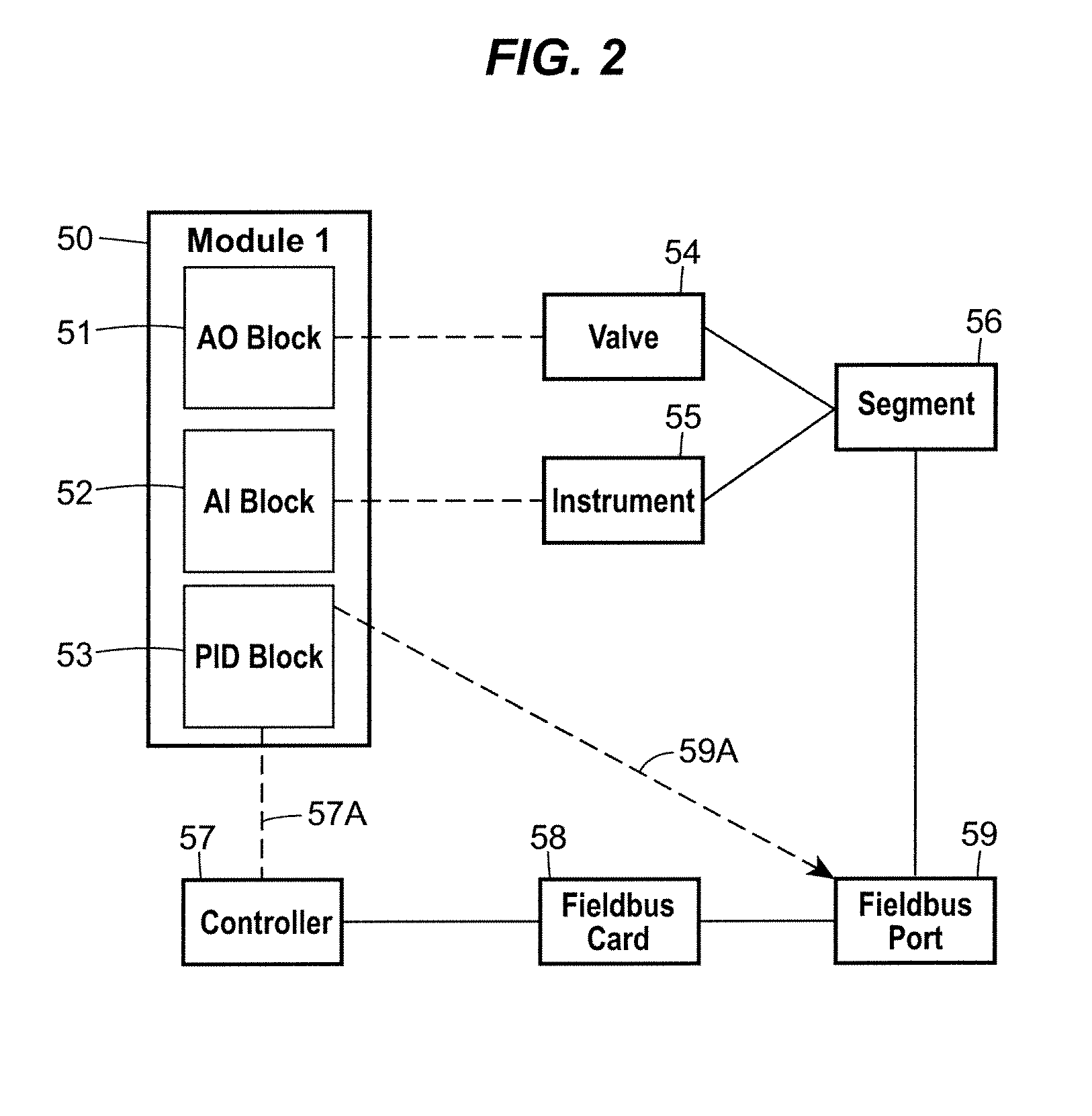
Automatic Configuration of Synchronous Block Execution for Control Modules Run in Fieldbus Networks
ActiveUS20080249641A1Easy and optimal useFaster rateComputer controlSimulator controlProcess control networkAuto-configuration
A method or apparatus automatically configures a control module for synchronous execution on a Fieldbus segment of a process control network by determining if all of the critical function blocks of a particular control module can be assigned to FOUNDATION® Fieldbus field devices or to the I / O device associated with a particular Fieldbus segment. If so, the method or apparatus automatically assigns the function blocks of the control module, which would otherwise be scheduled to execute in a controller, to the I / O device for the Fieldbus segment. This technique enables all of the critical or necessary function blocks within the control module to execute in one macrocycle of the Fieldbus segment, thereby executing synchronously on a Fieldbus segment. This operation, in turn, increases the overall execution rate of the control module with respect to control modules that have function blocks split between a controller and field devices on a Fieldbus segment, which has been the traditional manner of configuring control modules implemented using devices on a Fieldbus segment.
Owner:FISHER-ROSEMOUNT SYST INC
Virtual tunnel network router
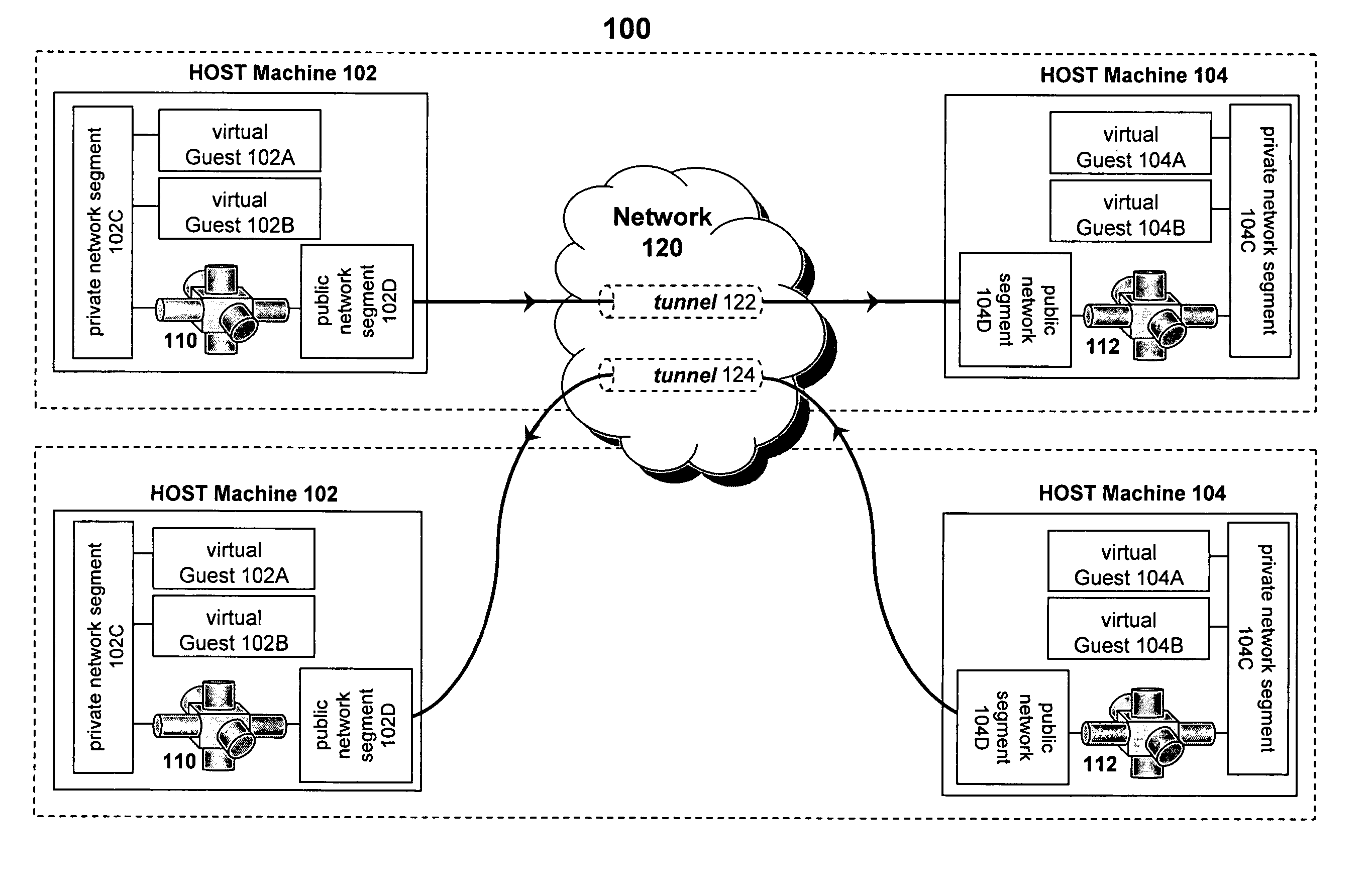
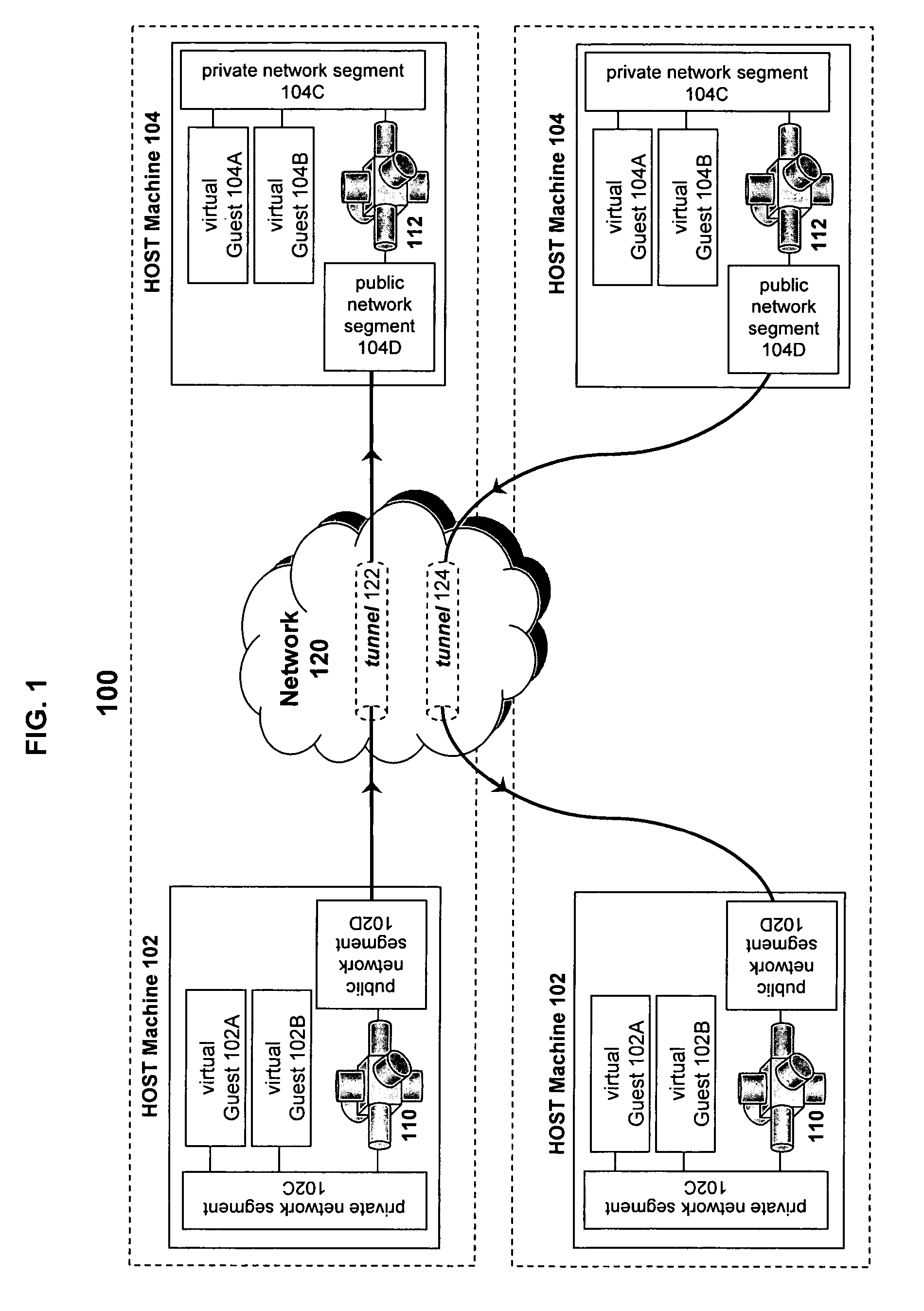
ActiveUS20070130366A1Facilitate communicationDigital computer detailsData switching networksVirtualizationPrivate network
A virtual host computer is presented that includes a virtualization software platform, at least one virtual machine executed by the virtualization software platform, a private network segment configured to prevent communications with at least one external computer, a public network segment configured to facilitate communications with the at least one external computer, and a virtual routing module that is executed as a virtual image by the virtualization software platform. The virtual routing module is configured to communicate with the at least one virtual machine via the private network segment, communicate with the public network segment, and execute a tunneling layer to form a private virtual network segment between the at least one virtual machine and the at least one external computer.
Owner:CA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com