Patents
Literature
678results about How to "Avoid data loss" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
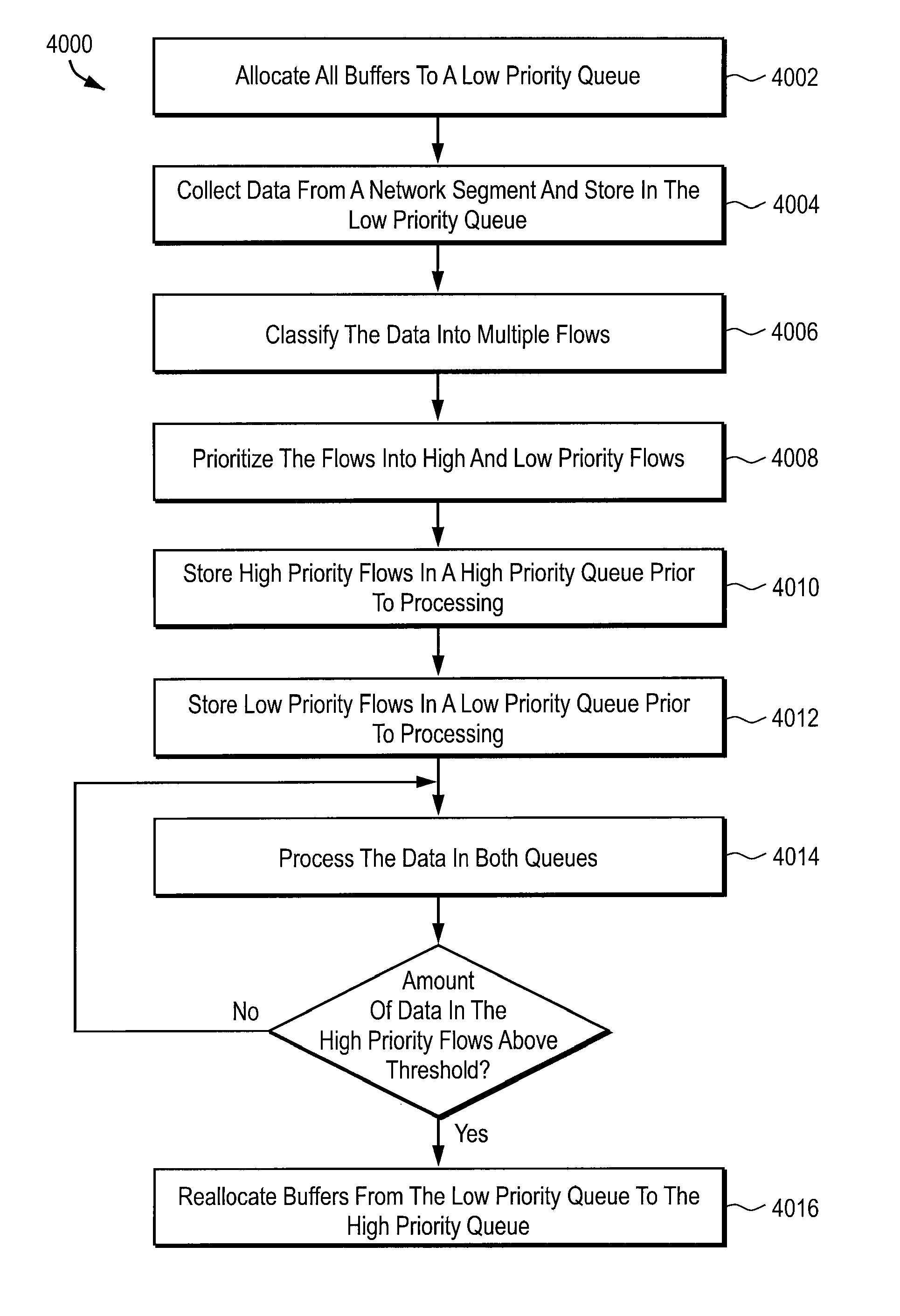
Media module apparatus and method for use in a network monitoring environment
InactiveUS7299277B1Avoid data lossReduce probabilityError preventionTransmission systemsApplication softwareMaster processor
A probe apparatus, method and computer program product for application monitoring are provided. A data collection module collects data from a network segment. A flow processor coupled to the data collection module classifies the collected data into a plurality of flows. A capture system coupled to the flow processor filters and buffers the collected data. A main processor processes the filtered data.
Owner:NETWORK GENERAL TECH
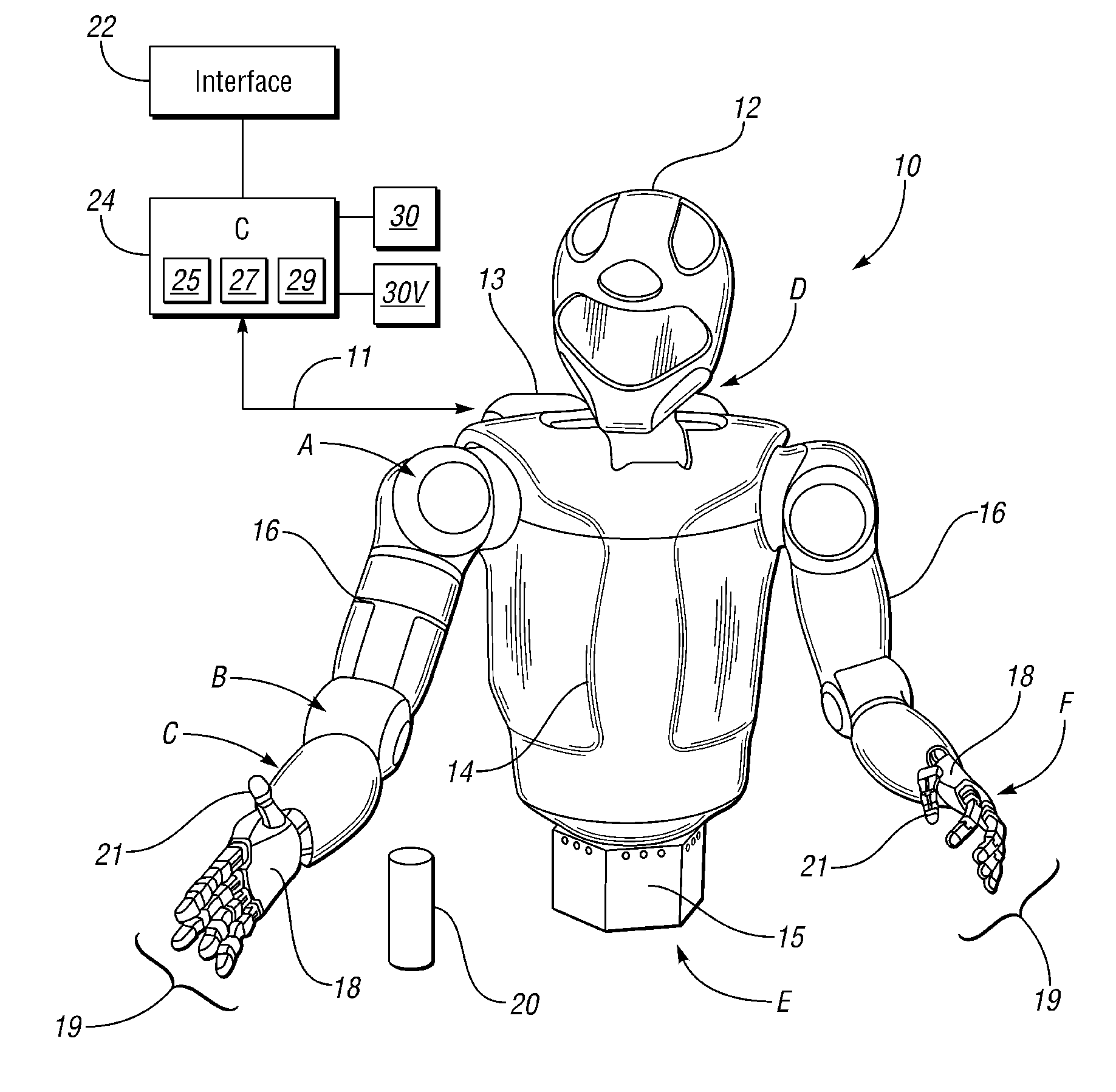
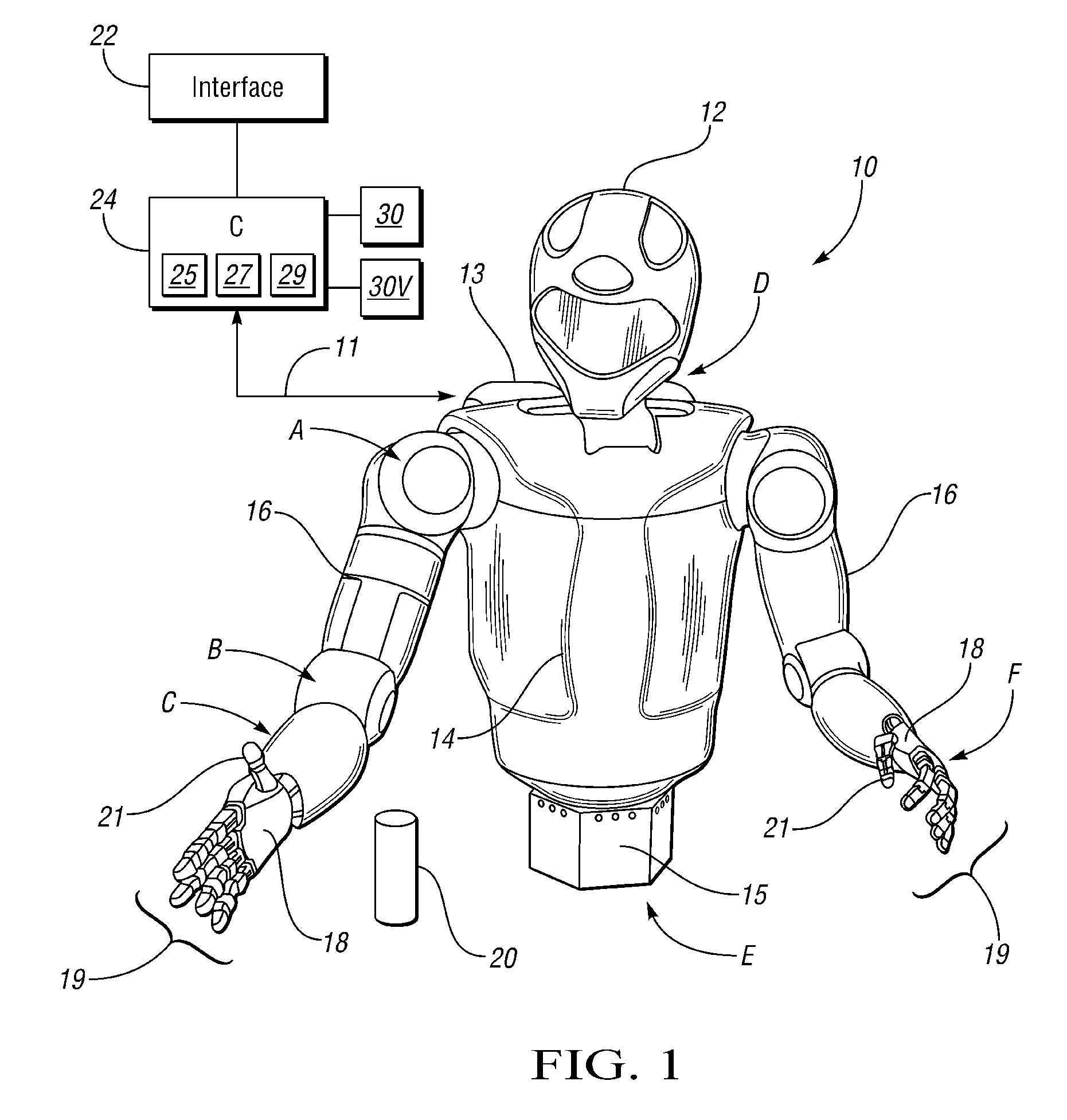
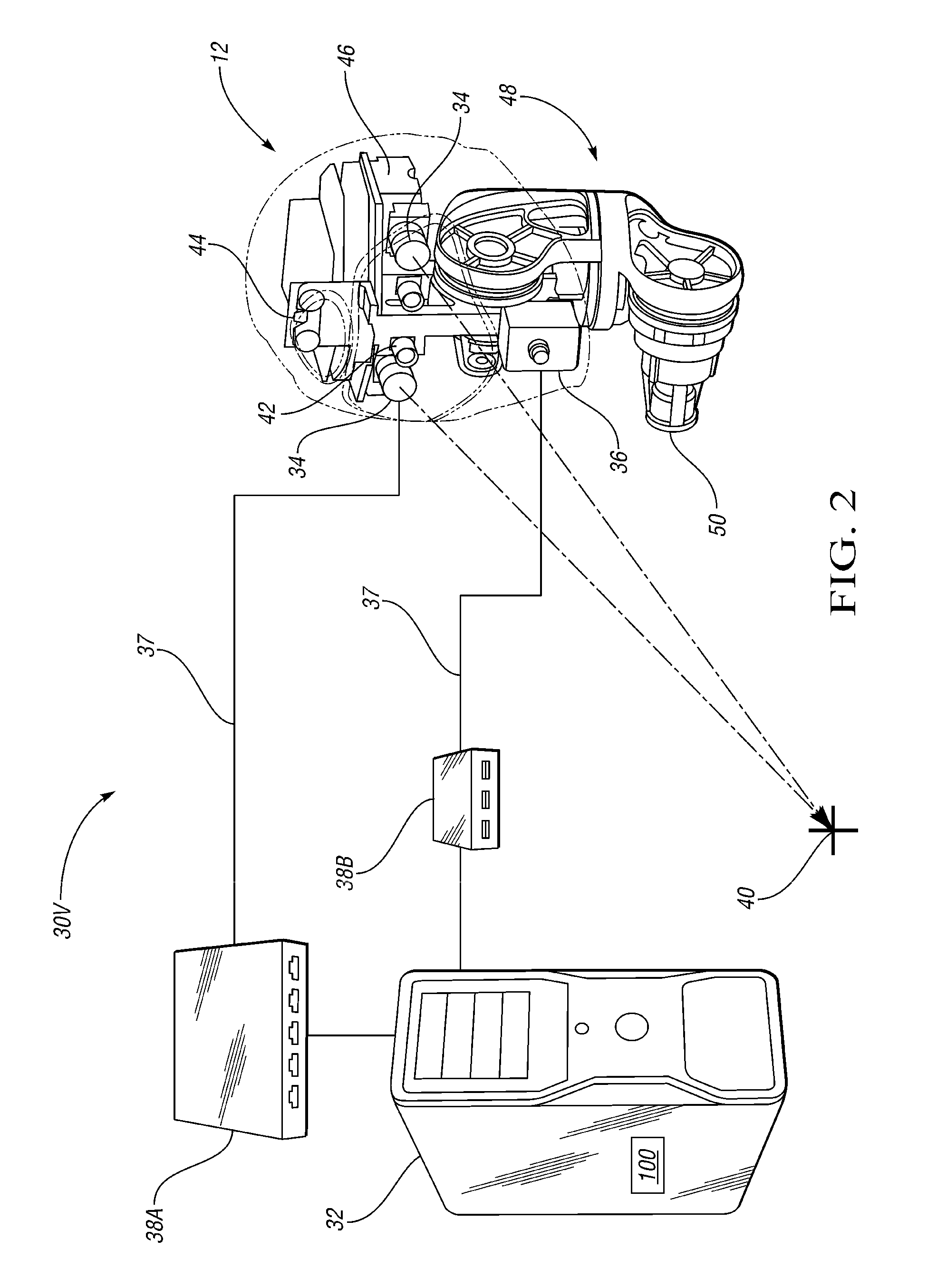
Visual perception system and method for a humanoid robot
ActiveUS20110071675A1Luminance is optimizedAvoid data lossImage enhancementTelevision system detailsRobotic systemsHumanoid robot nao
A robotic system includes a humanoid robot with robotic joints each moveable using an actuator(s), and a distributed controller for controlling the movement of each of the robotic joints. The controller includes a visual perception module (VPM) for visually identifying and tracking an object in the field of view of the robot under threshold lighting conditions. The VPM includes optical devices for collecting an image of the object, a positional extraction device, and a host machine having an algorithm for processing the image and positional information. The algorithm visually identifies and tracks the object, and automatically adapts an exposure time of the optical devices to prevent feature data loss of the image under the threshold lighting conditions. A method of identifying and tracking the object includes collecting the image, extracting positional information of the object, and automatically adapting the exposure time to thereby prevent feature data loss of the image.
Owner:GM GLOBAL TECH OPERATIONS LLC
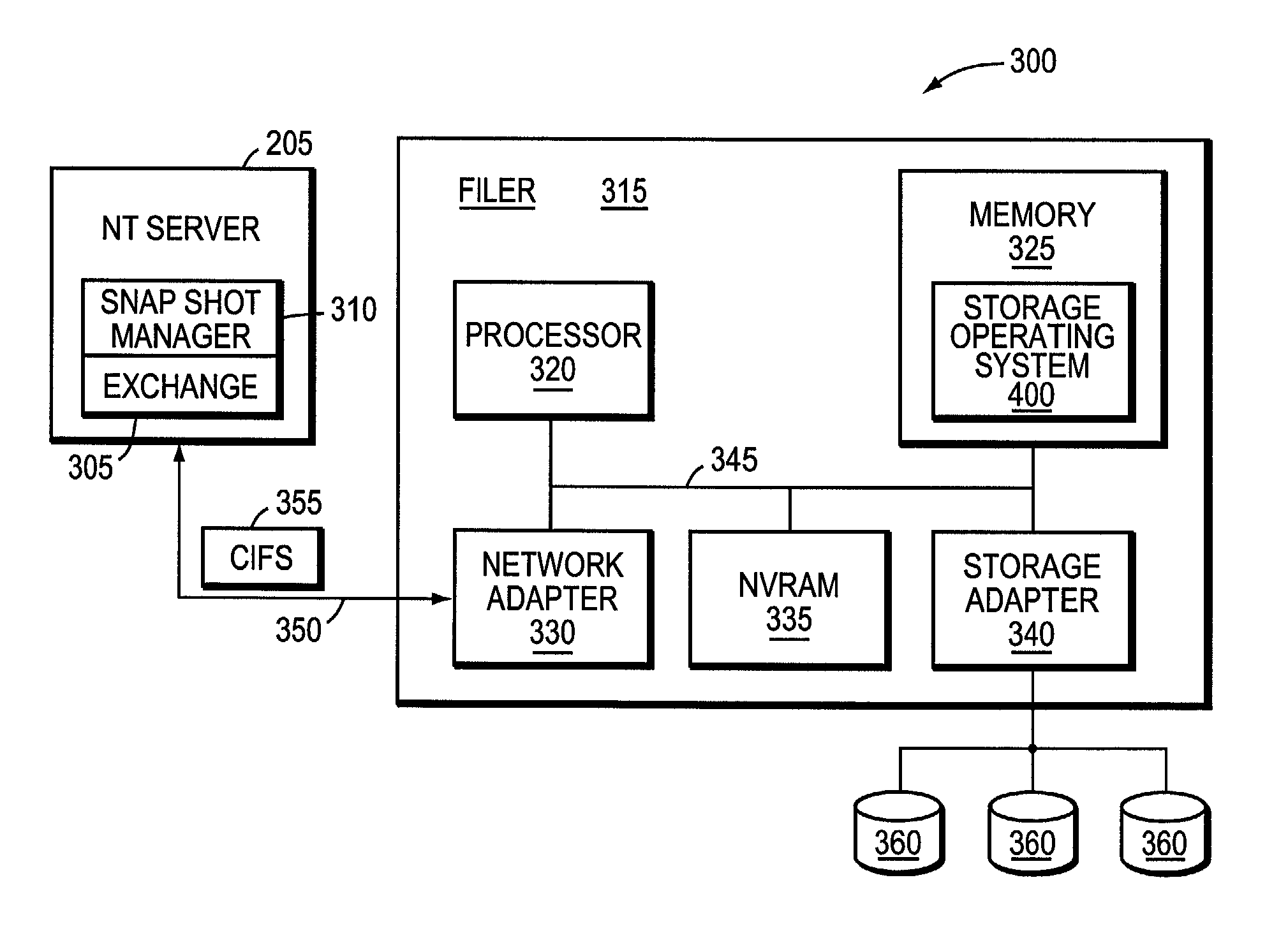
System and method for creating a point-in-time restoration of a database file
InactiveUS7373364B1Overcome disadvantagesAvoid data lossData processing applicationsError detection/correctionFile systemDatabase file
The present invention provides a method for generating a point-in-time restoration of database files and associated log files by utilizing a snapshot feature of the file system storing the files. At regular intervals, snapshots, which produce read-only copies of the files, are taken along with backups of the associated log files. To restore to a given point-in-time, the snapshot and stored log files are transferred to the active file system. In a second embodiment, all log files associated with snapshots taken after the selected snapshot are also restored.
Owner:NETWORK APPLIANCE INC
Protecting Information Using Policies and Encryption
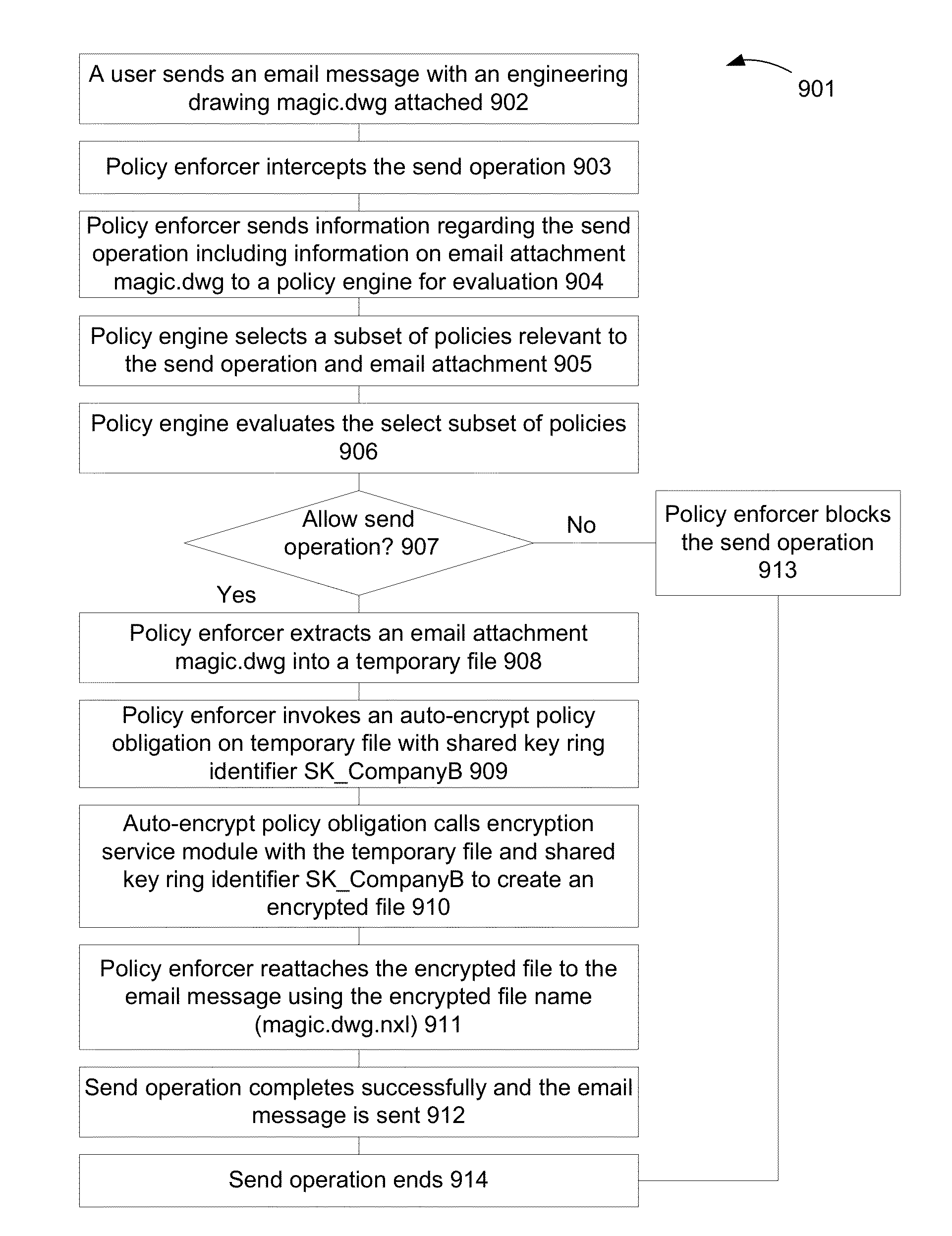
ActiveUS20130097421A1Ensure confidentialityAvoid data lossDigital data protectionSecuring communicationDocumentation procedureConfidentiality
A technique and system protects documents at rest and in motion using declarative policies and encryption. Encryption in the system is provided transparently and can work in conjunction with policy enforcers installed at a system. A system can protect information or documents from: (i) insider theft; (ii) ensure confidentiality; and (iii) prevent data loss, while enabling collaboration both inside and outside of a company.
Owner:NEXTLABS
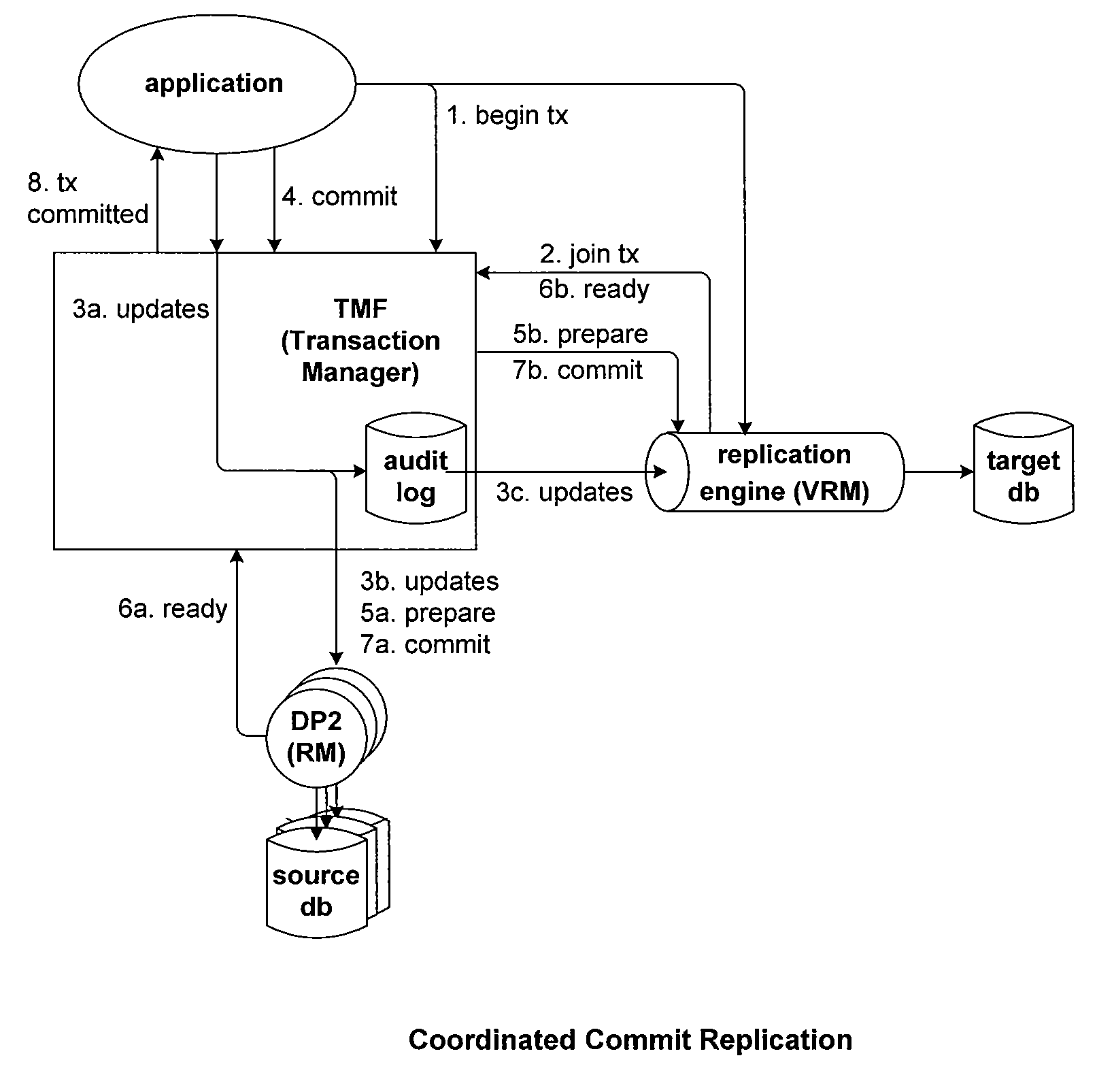
Mixed mode synchronous and asynchronous replication system
ActiveUS8301593B2Reduce stepsAvoid data lossDigital data processing detailsError detection/correctionAsynchronous communicationApplication software
A replication system that includes an asynchronous replication mode and a synchronous replication mode replicates data associated with a plurality of transactions. The replication system includes one or more target nodes connected via communication media in a topology. Each target node includes a database and a plurality of appliers allocated thereto. Each transaction has one or more transaction steps or operations. A first set of transaction steps or operations are allocated to the plurality of appliers on an object-by-object basis when the replication system operates in asynchronous replication mode. A second set of transaction steps or operations are allocated to the plurality of appliers on a transaction-by-transaction basis when the replication system operates in synchronous replication mode. The replication system further includes one or more originating nodes, and the requests for the first and second sets of transaction steps or operations to execute on an originating node can be initiated during the same time period.
Owner:RPX CORP
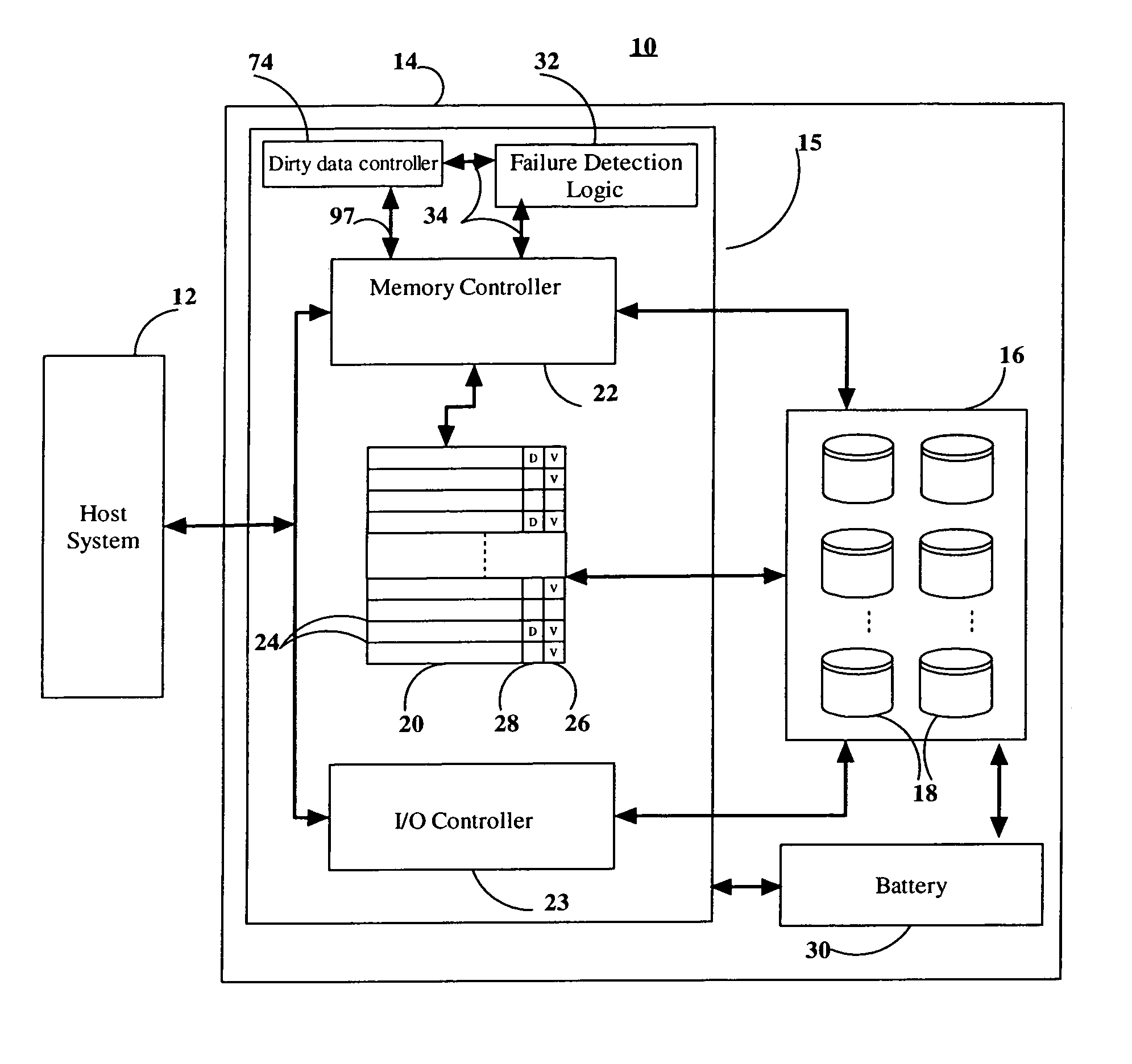
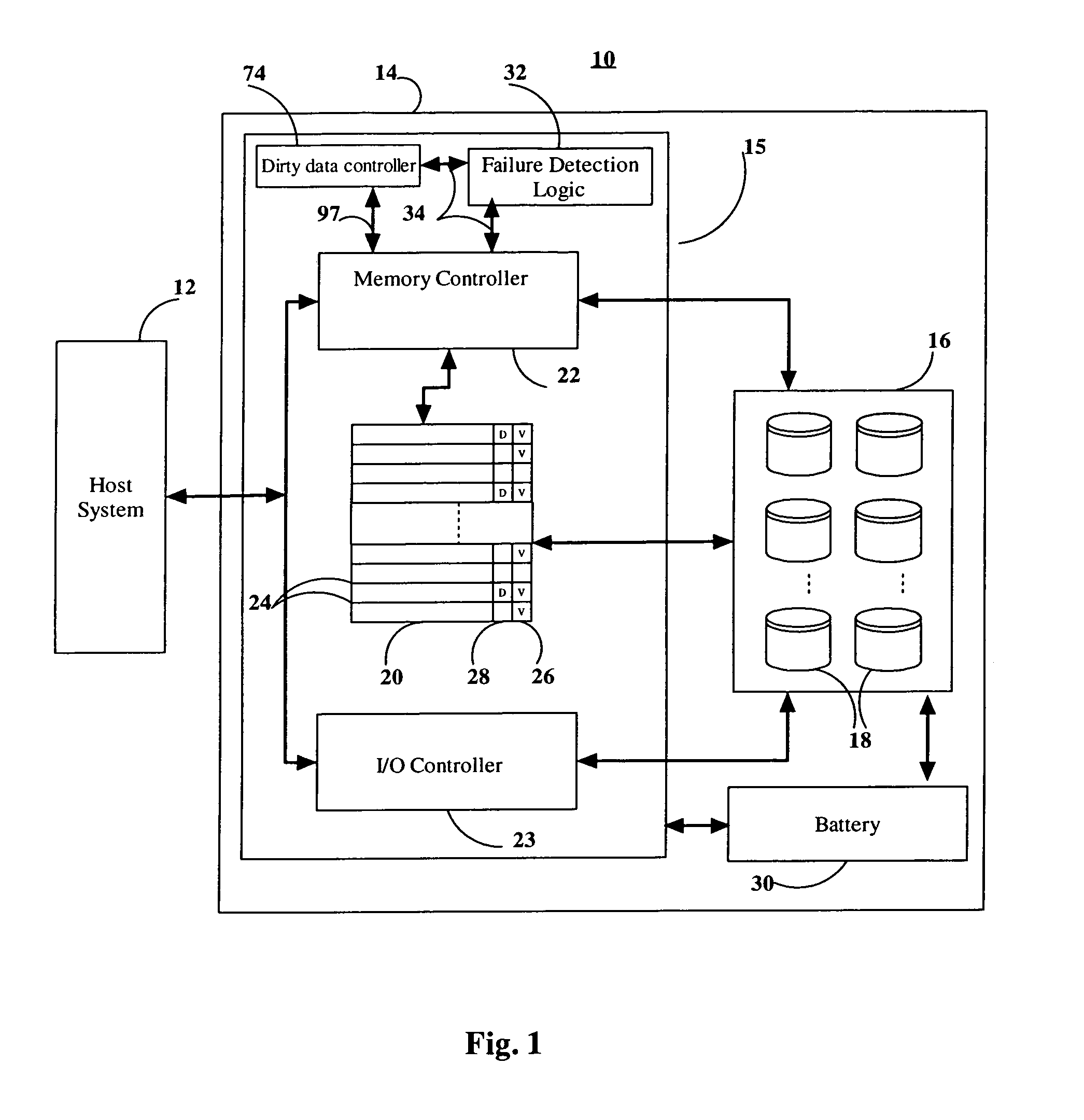
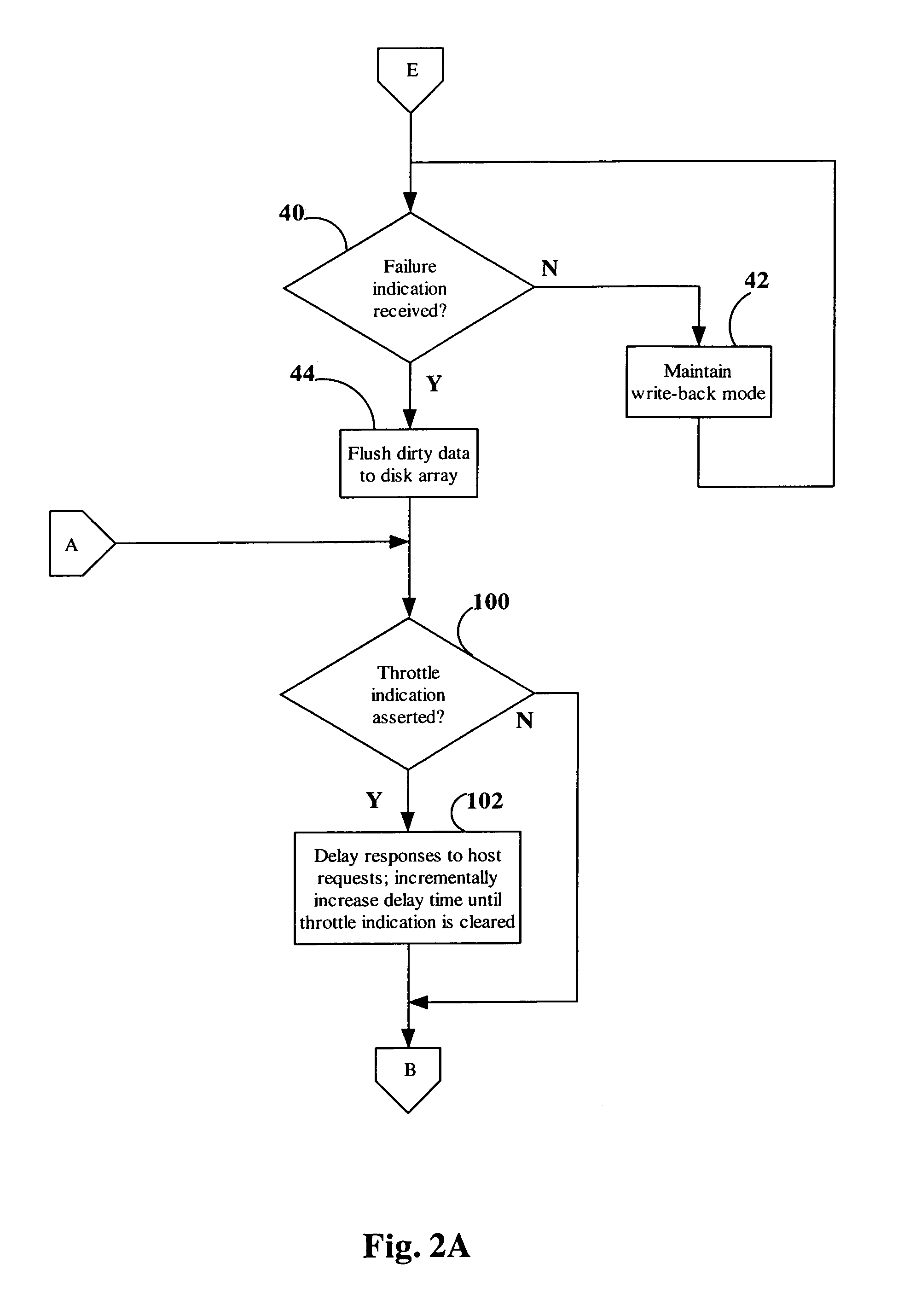
Data storage cache system shutdown scheme
ActiveUS7062675B1Not be preventPrevent dataError detection/correctionMemory systemsDirty dataOperating system
In a storage system including a write-back cache, dirty data can be flushed from the cache while a controller continues to service host I / O requests. A controller is capable of flushing all the dirty data in the cache to a storage device in response to an indication to do so, such as an indication of impending failure. The controller is further capable of responding to I / O requests from the host during the flushing of the dirty data. In particular, the controller is capable of responding to write requests from the host system by storing data on the storage device during the flushing of the dirty data.
Owner:EMC IP HLDG CO LLC
Method and device for data forwarding
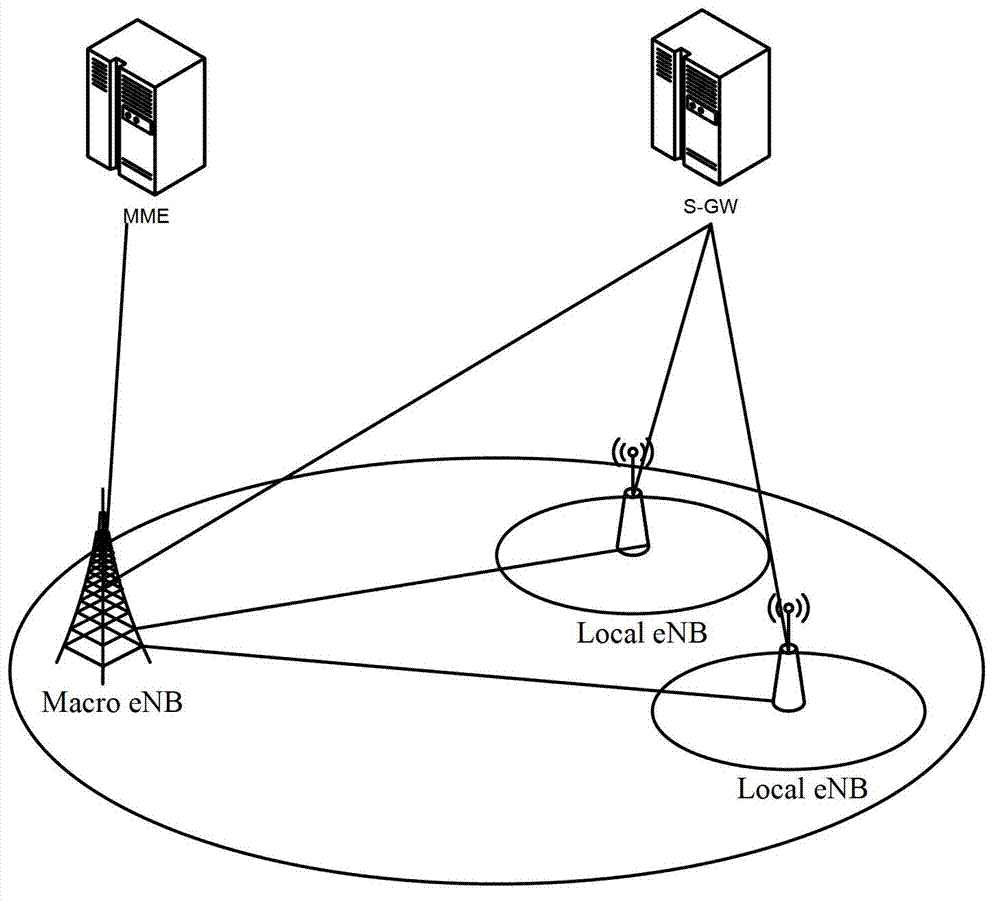
ActiveCN102833802AReduce communication interruptionsAvoid data lossTransmissionWireless communicationMacro base stationsRouting control plane
The invention discloses a method and a device for data forwarding and aims at solving the problem of communication outrage risk when UE (user equipment) is switched in an existing hierarchical network. The method includes: a source macro base station obtains serial number sending state information of uplink and downlink PDCP (packet data convergence protocol) data packet of a local base station currently accessed by the UE, wherein a control plane of the UE is connected with the macro base station, and a user plane is connected to the local base station; and the macro base station sends the serial number sending state information to a target base station of the UE to be switched, and the target base station establishes connection with the user plane of the UE according to serial number sending state data.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Data reconciliation between a computer and a mobile data collection terminal
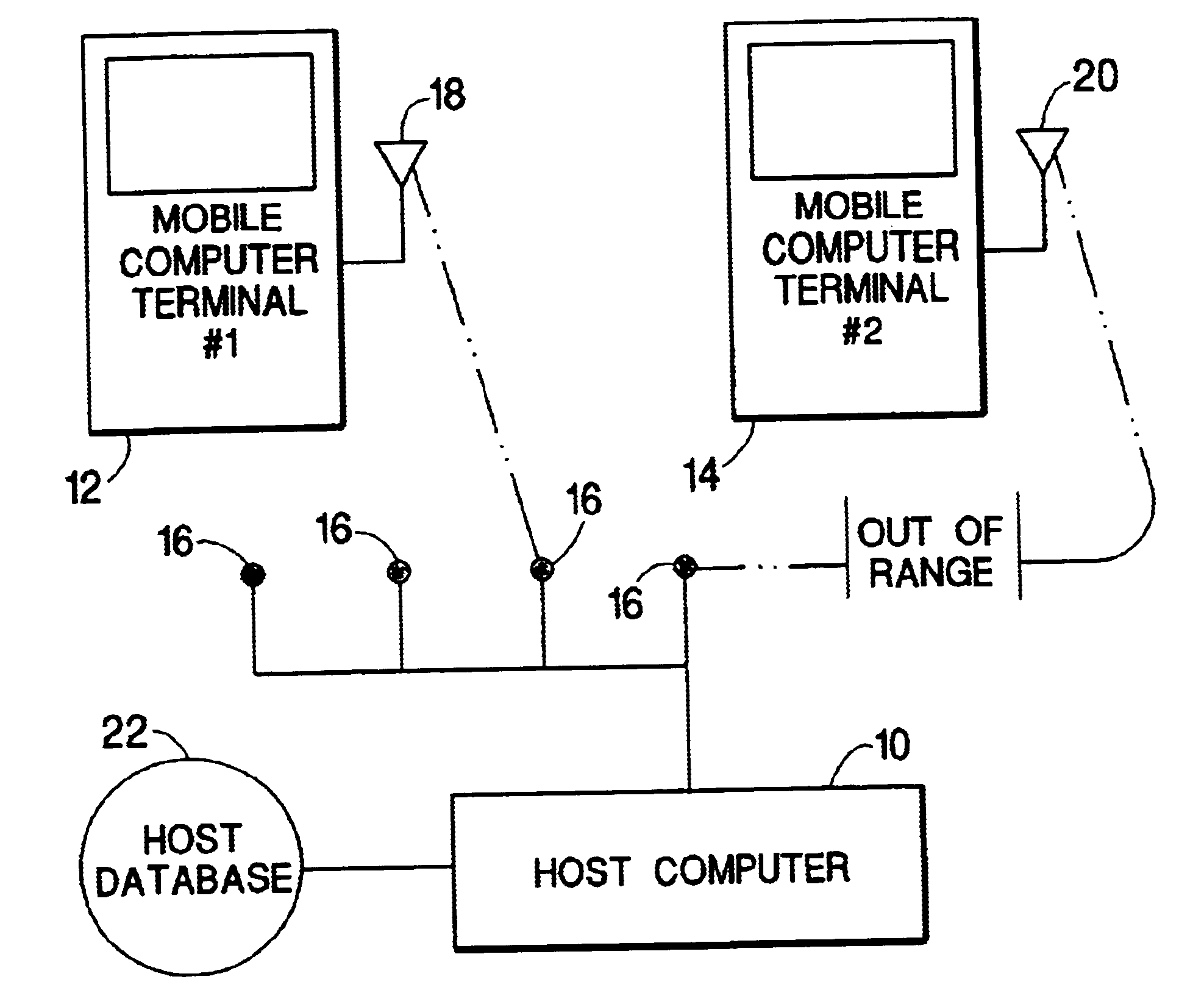
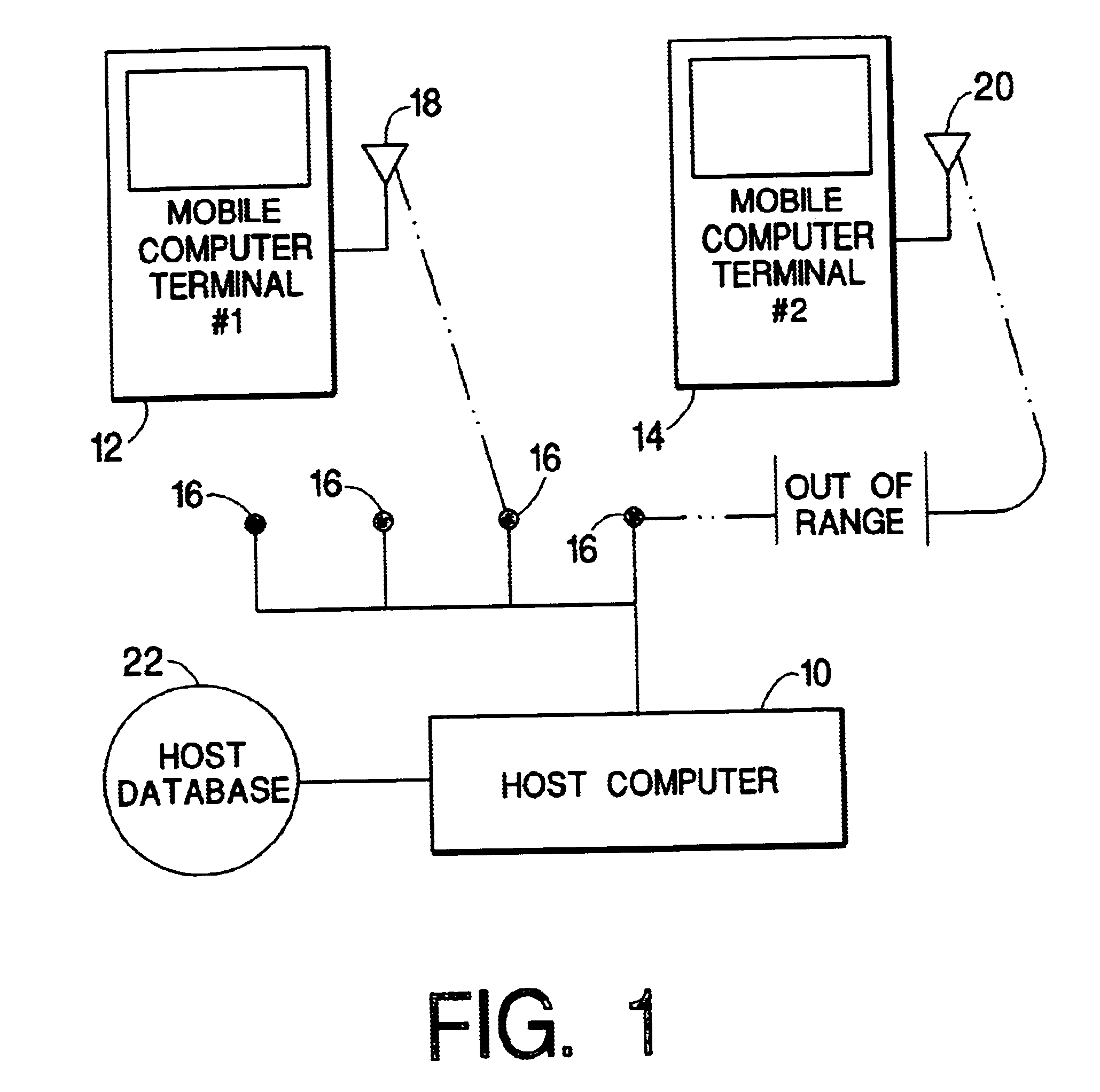
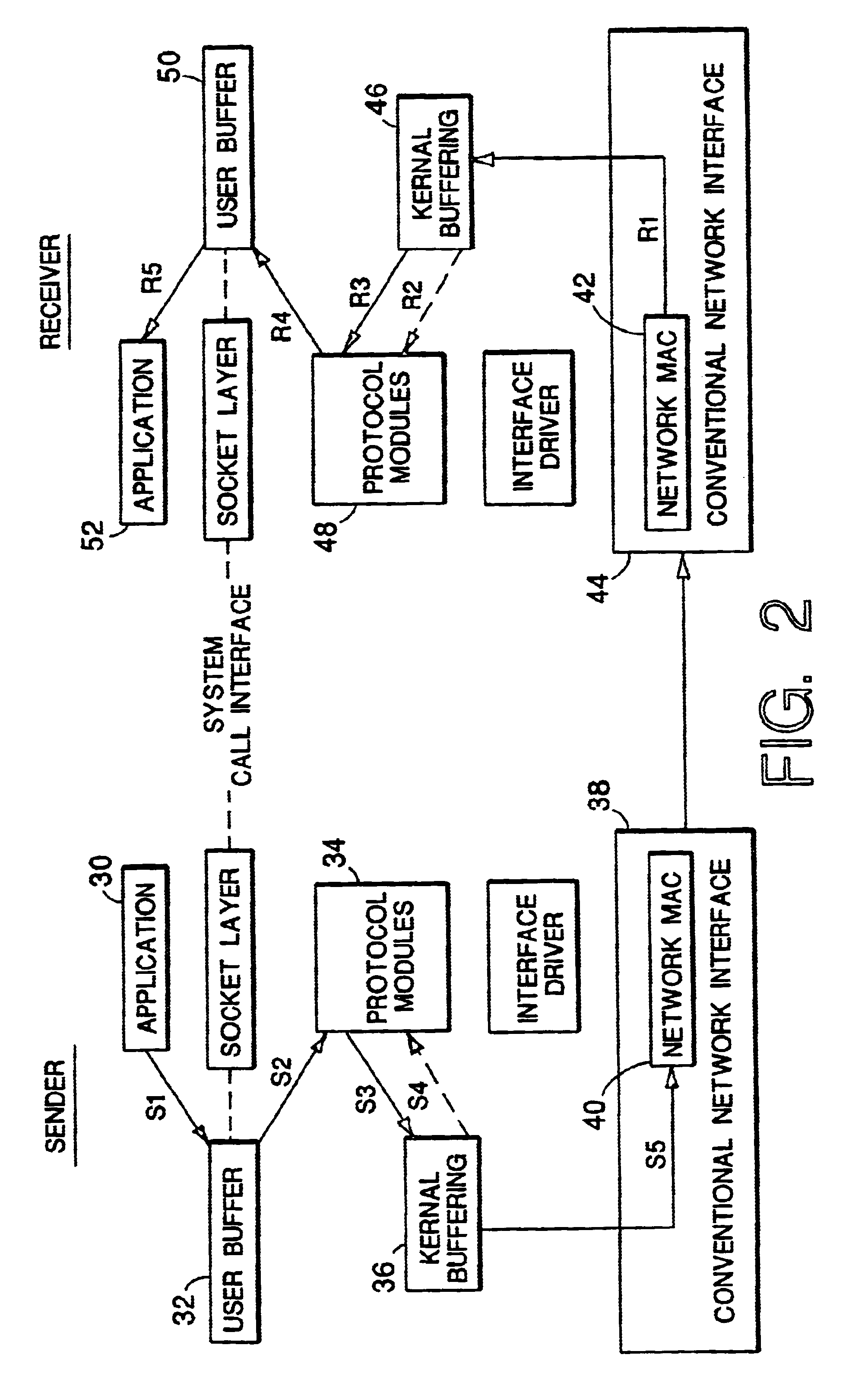
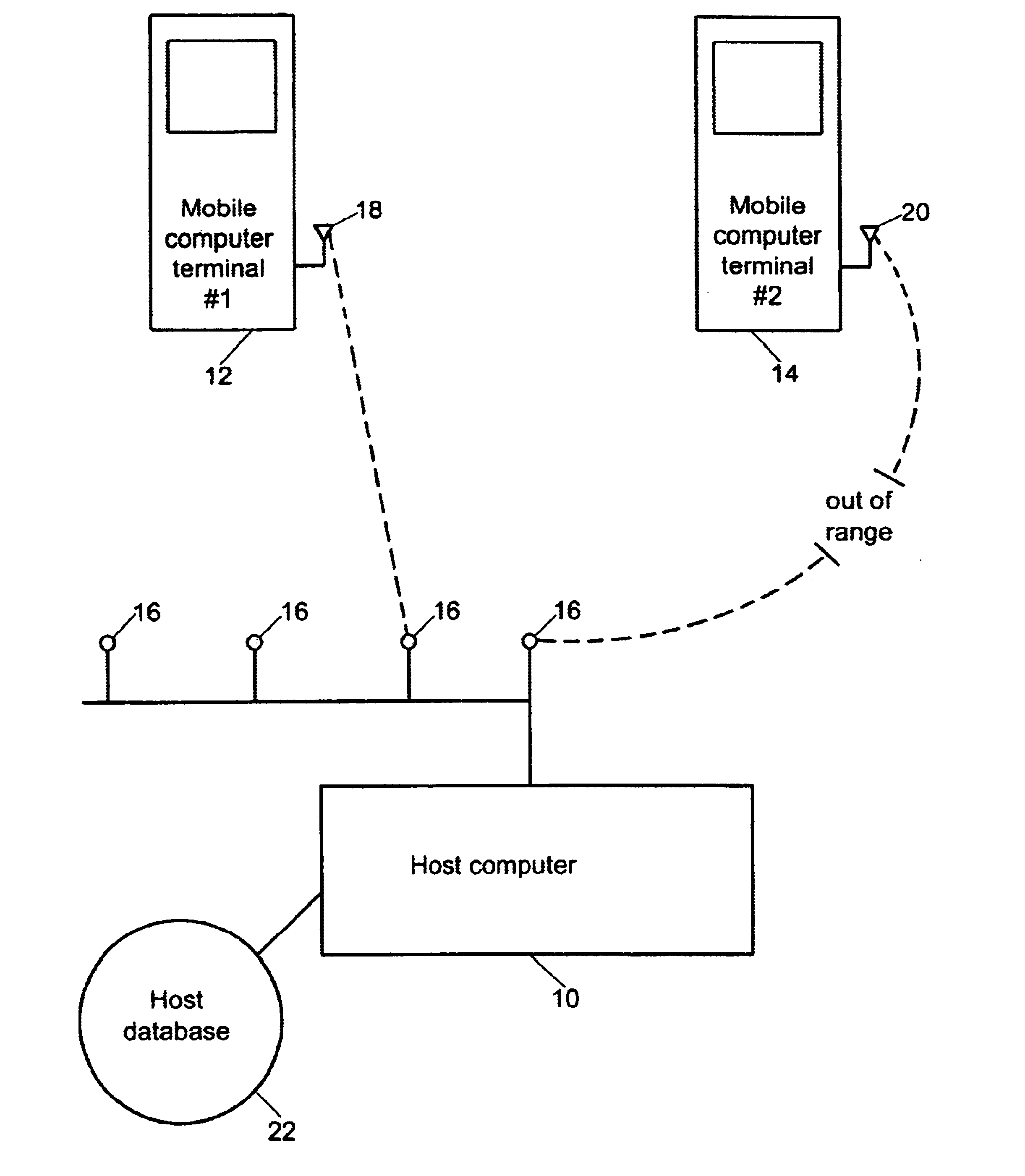
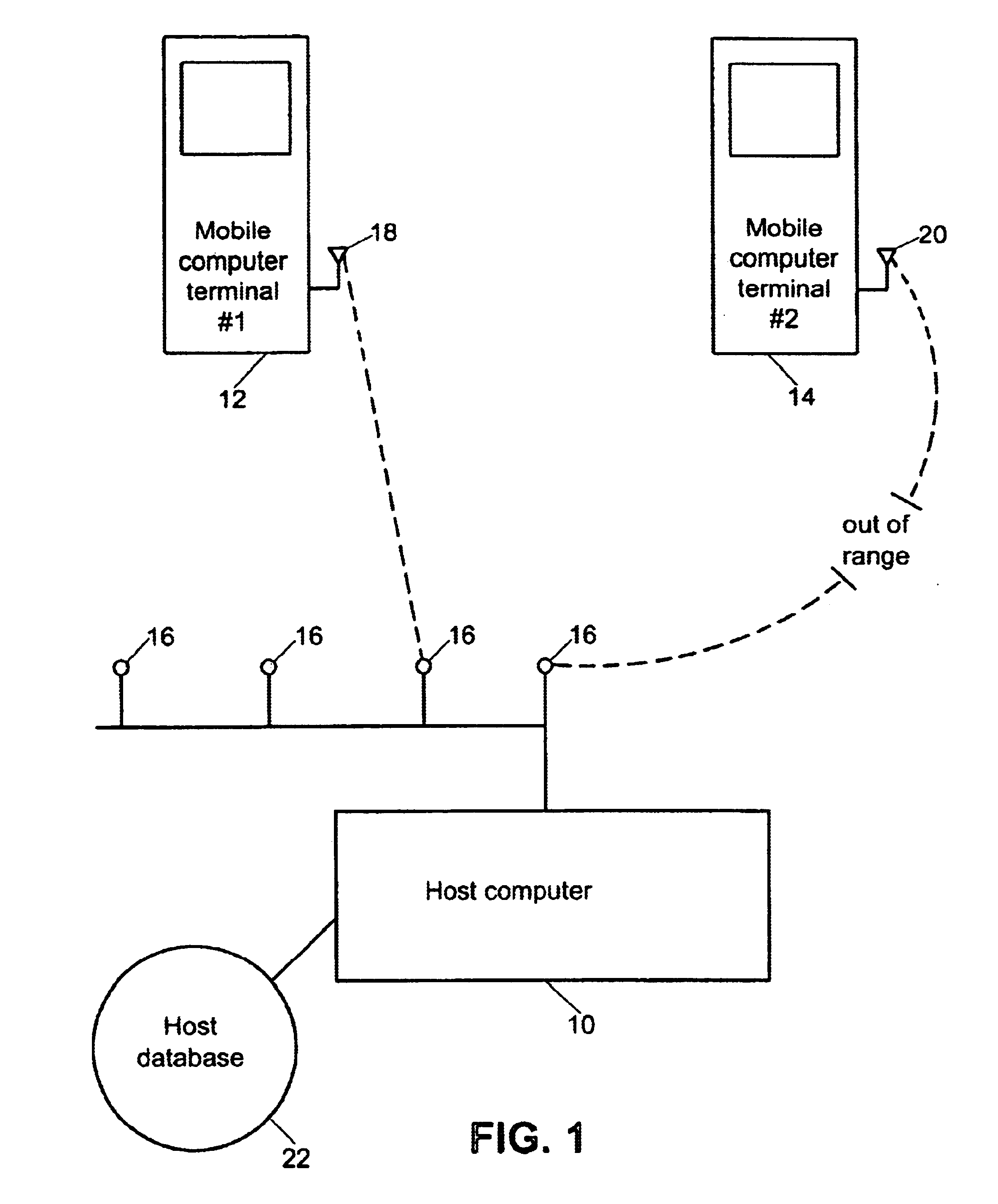
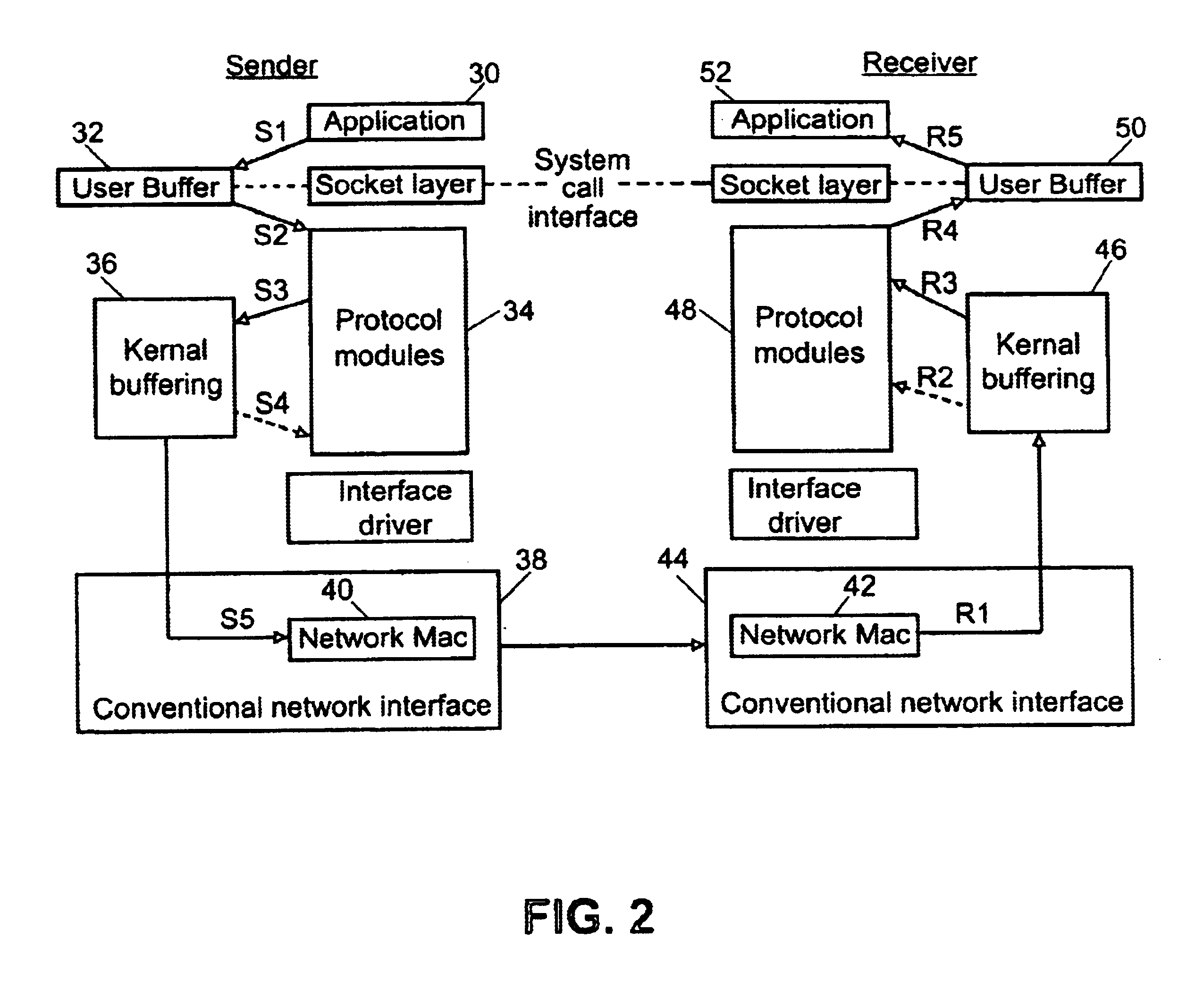
InactiveUS6694366B1Easy to handleAvoid data lossMultiple digital computer combinationsTransmissionData conversionMobile computing
A method for communication between a host computer and at least one mobile computer terminal which provides an efficient way of running a computer network where the at least one mobile computer terminal operates at a remote site, has selectable operating characteristics, and is connected to the host computer through a wireless communications network, and wherein the host computer executes an application program in which data is entered from the at least one mobile computer terminal and processed by the application program, the method comprising the steps of: configuring the operating characteristics of the mobile computer terminal to correspond to data field characteristics required by the application program running on the host computer; utilizing the at least one mobile computer terminal to automatically acquire data at the remote site in response to a data acquisition program running on the at least one mobile computer terminal; transforming the acquired data into a data structure in the mobile computer terminal in accordance with said data field characteristics required by the application program running on the host computer; and transferring said data structure to the host computer over the wireless communications network. The method also provides for a way to ensure that the application program running on the host computer handles data received from the at least one mobile computer terminals when one of the mobile computer terminals goes out of range of the wireless network, comprising the steps of: establishing communications and association between a first of the at least one mobile computer terminals and a first access point on a local network; determining in said first of the at least one mobile computer terminals, that communications between said first of the at least one mobile computer terminals and all other access points have been impeded and switching to batch mode to continue data collection.
Owner:SYMBOL TECH LLC
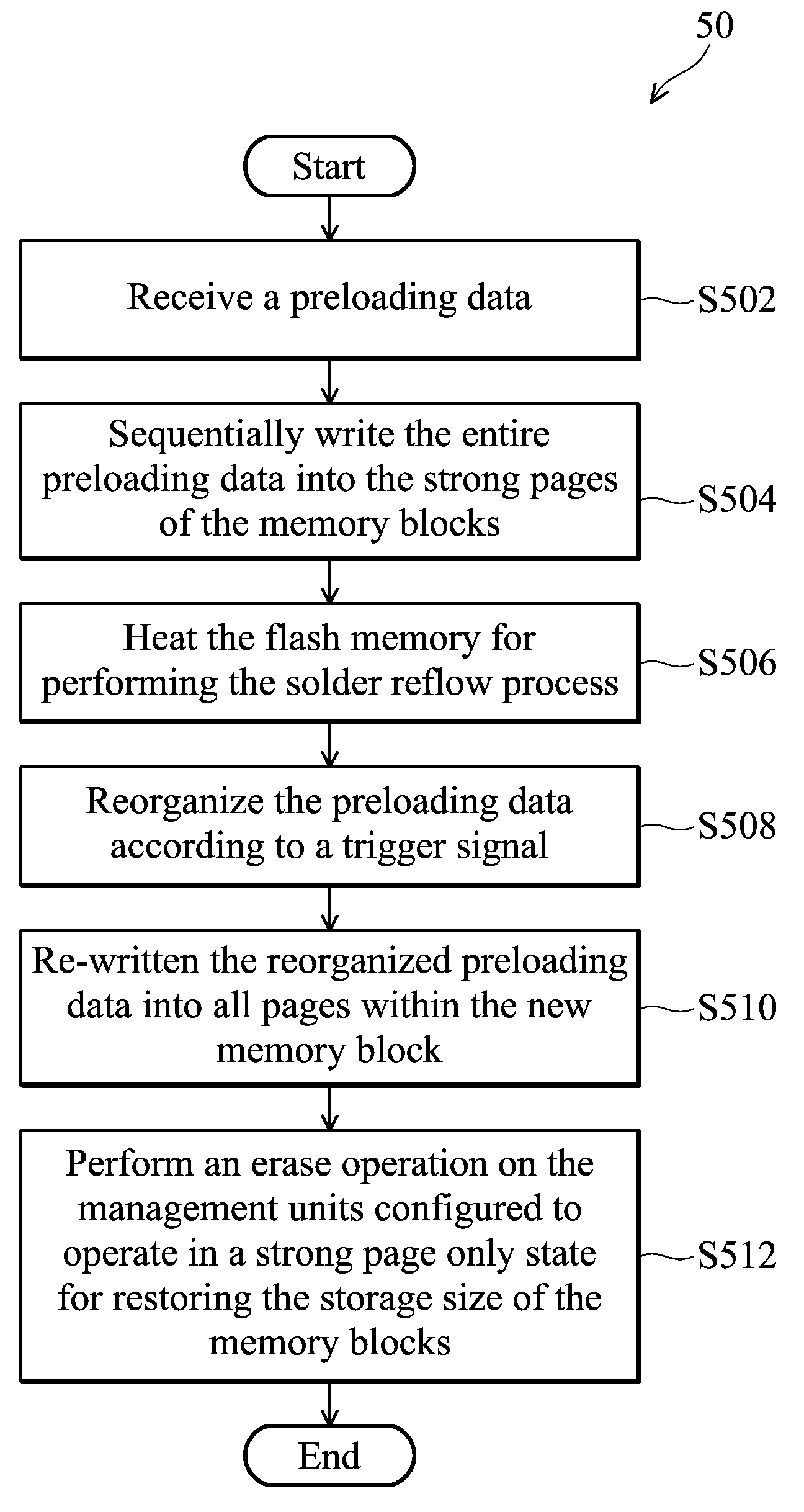
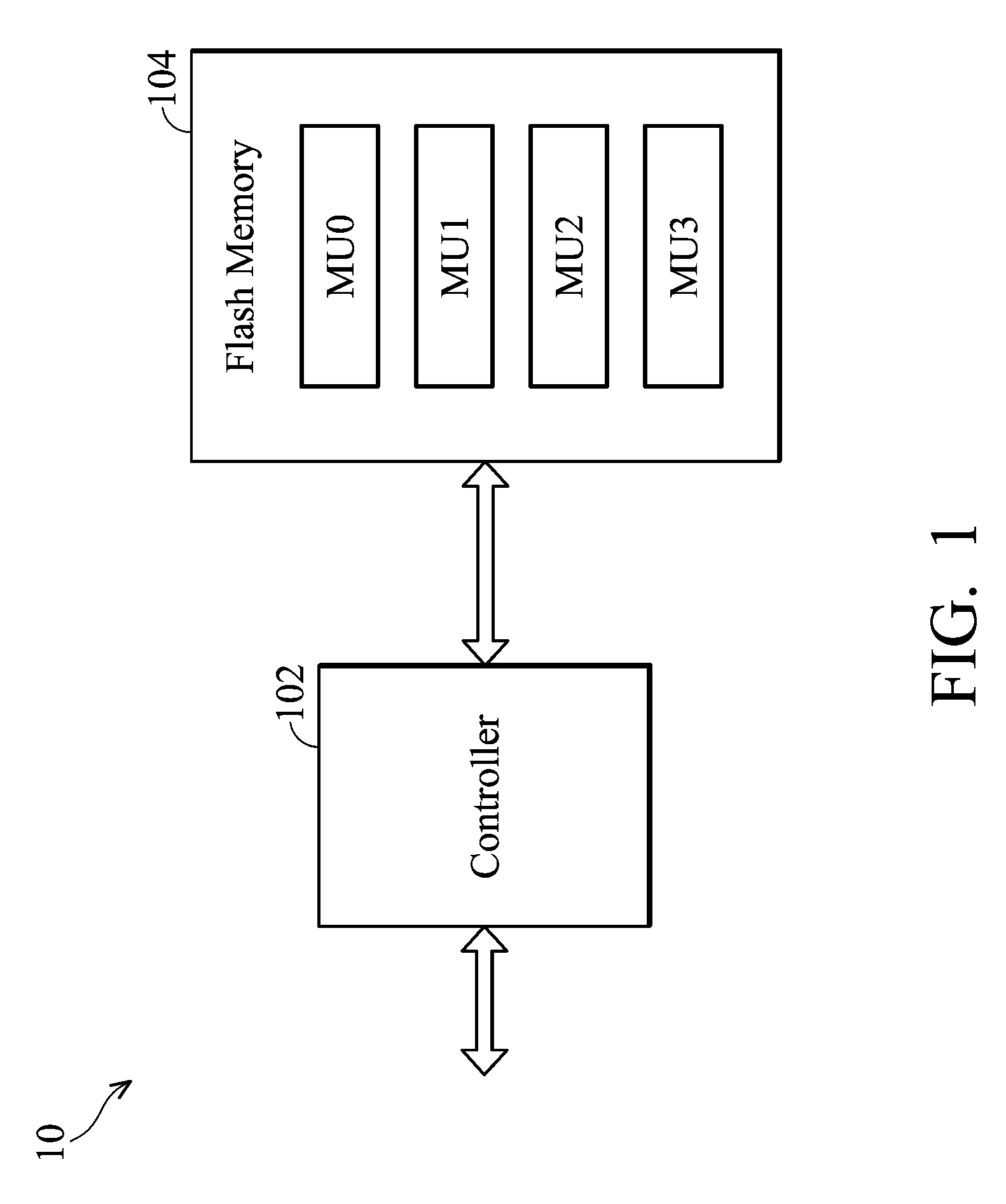
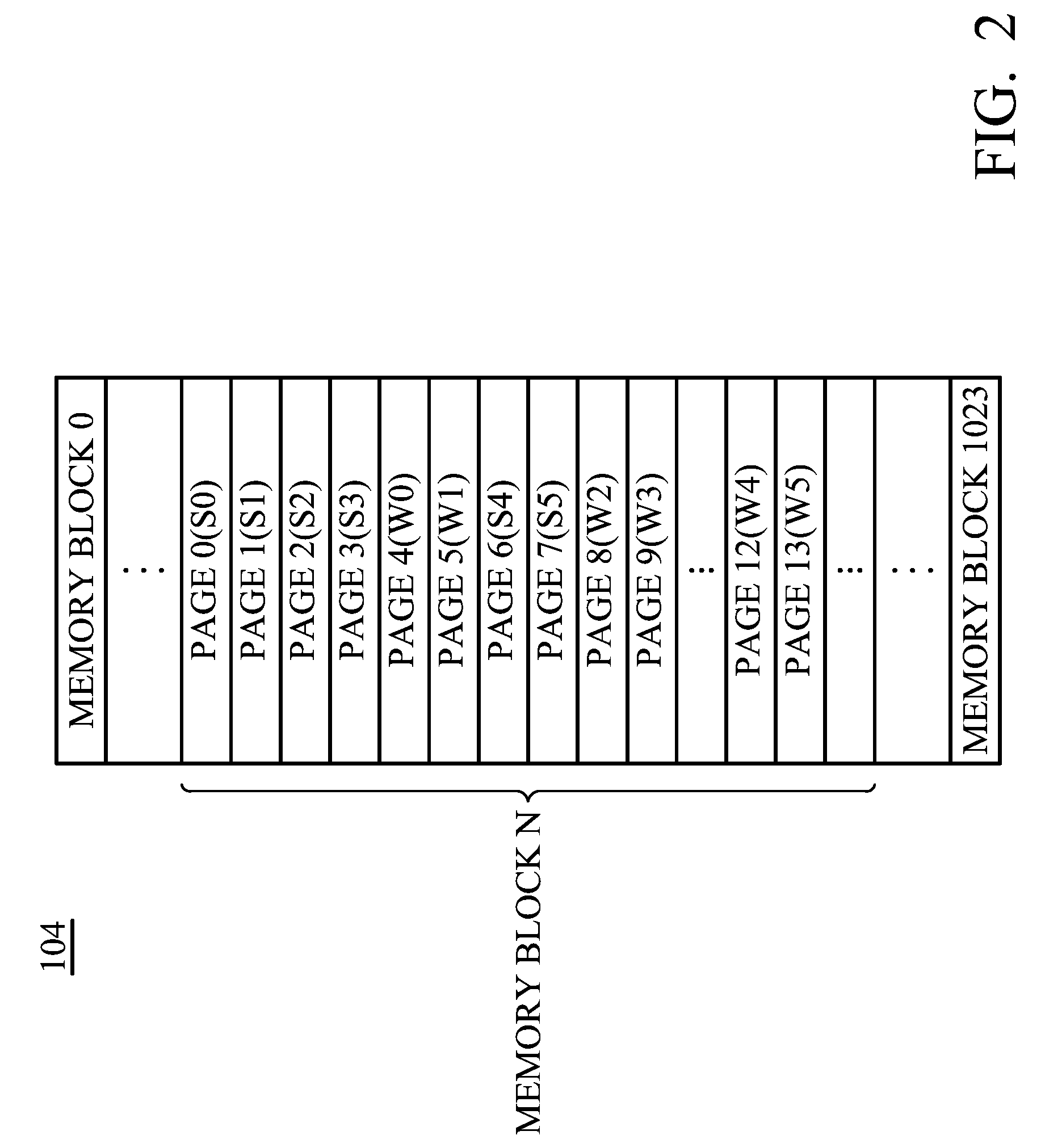
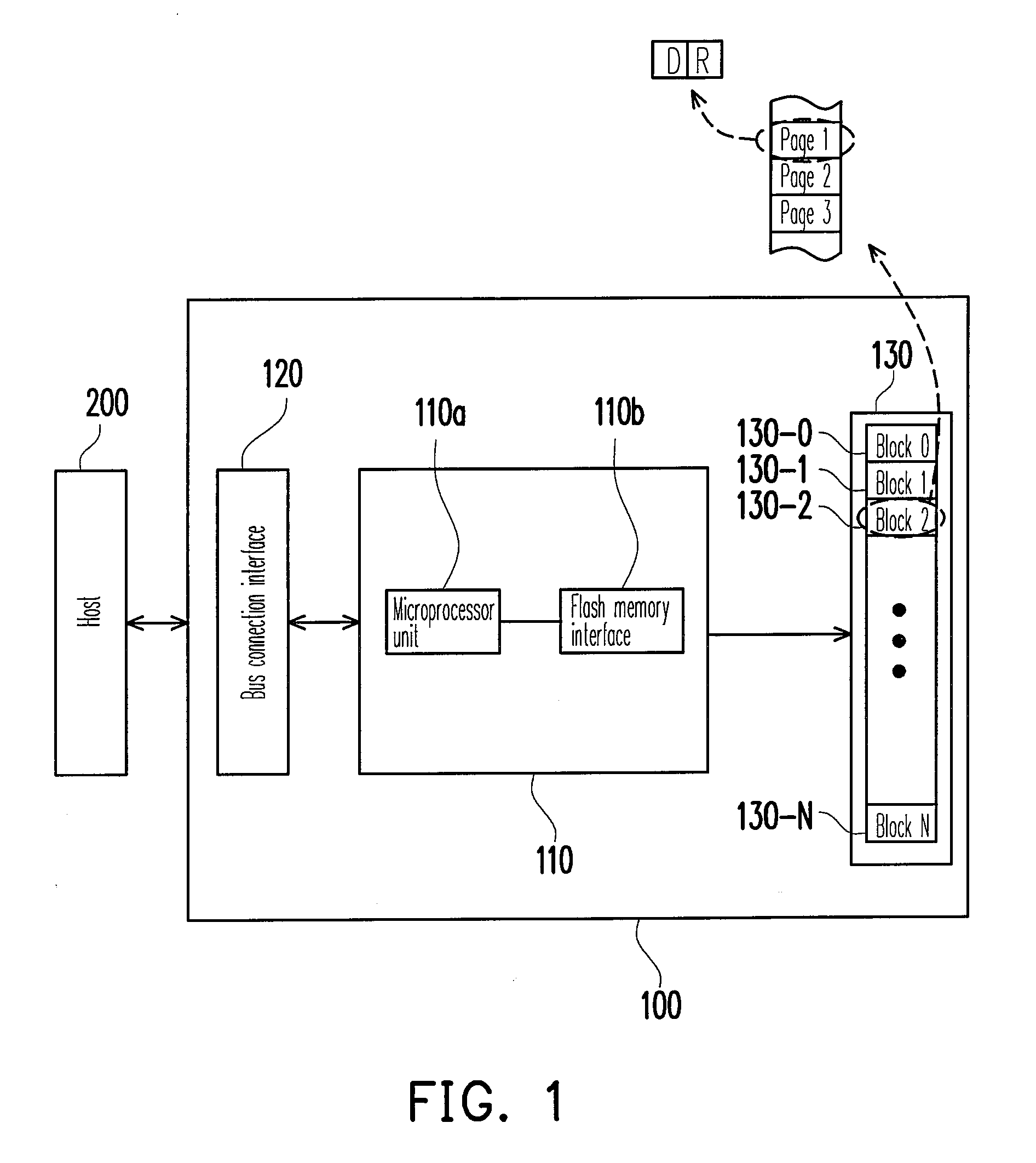
Method for preventing data loss during solder reflow process and memory device using the same
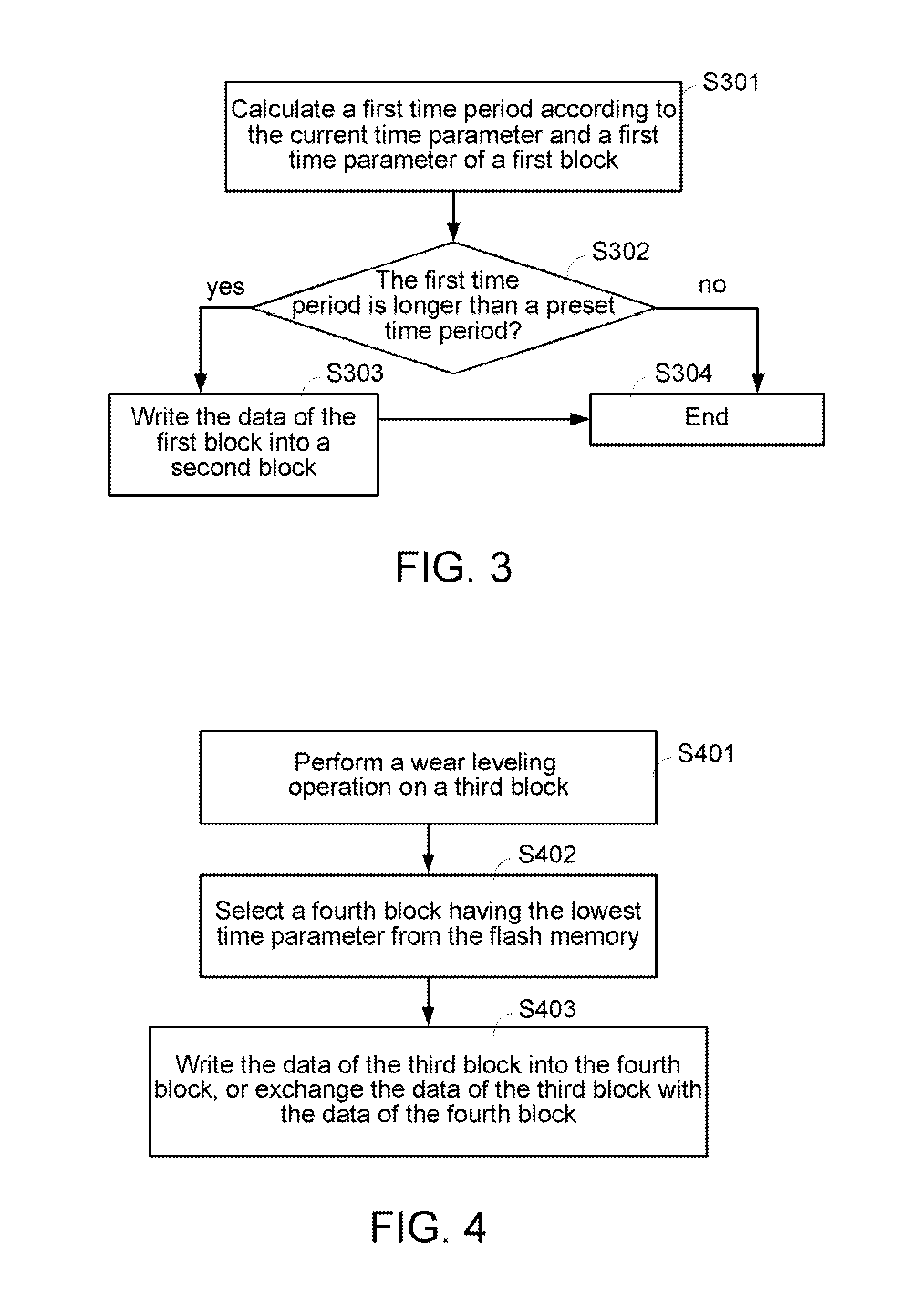
ActiveUS20100169547A1Prevent data lossAvoid data lossMemory architecture accessing/allocationMemory adressing/allocation/relocationMemory blockData loss
The invention provides a method for preventing data loss in a flash memory during a solder reflow process. The flash memory includes a plurality of memory blocks and each memory block includes a plurality of strong pages and weak pages. Preloading data is first received and stored into the strong pages of at least one of first memory block within the flash memory. Then, the flash memory is heated for the solder reflow process. Next, the preloading data is reorganized according to a trigger signal and the strong pages and weak pages of at least one of second memory block within the flash memory are provided for storing the reorganized preloading data.
Owner:SILICON MOTION INC (TW)
Method and apparatus for archiving data during unexpected power loss
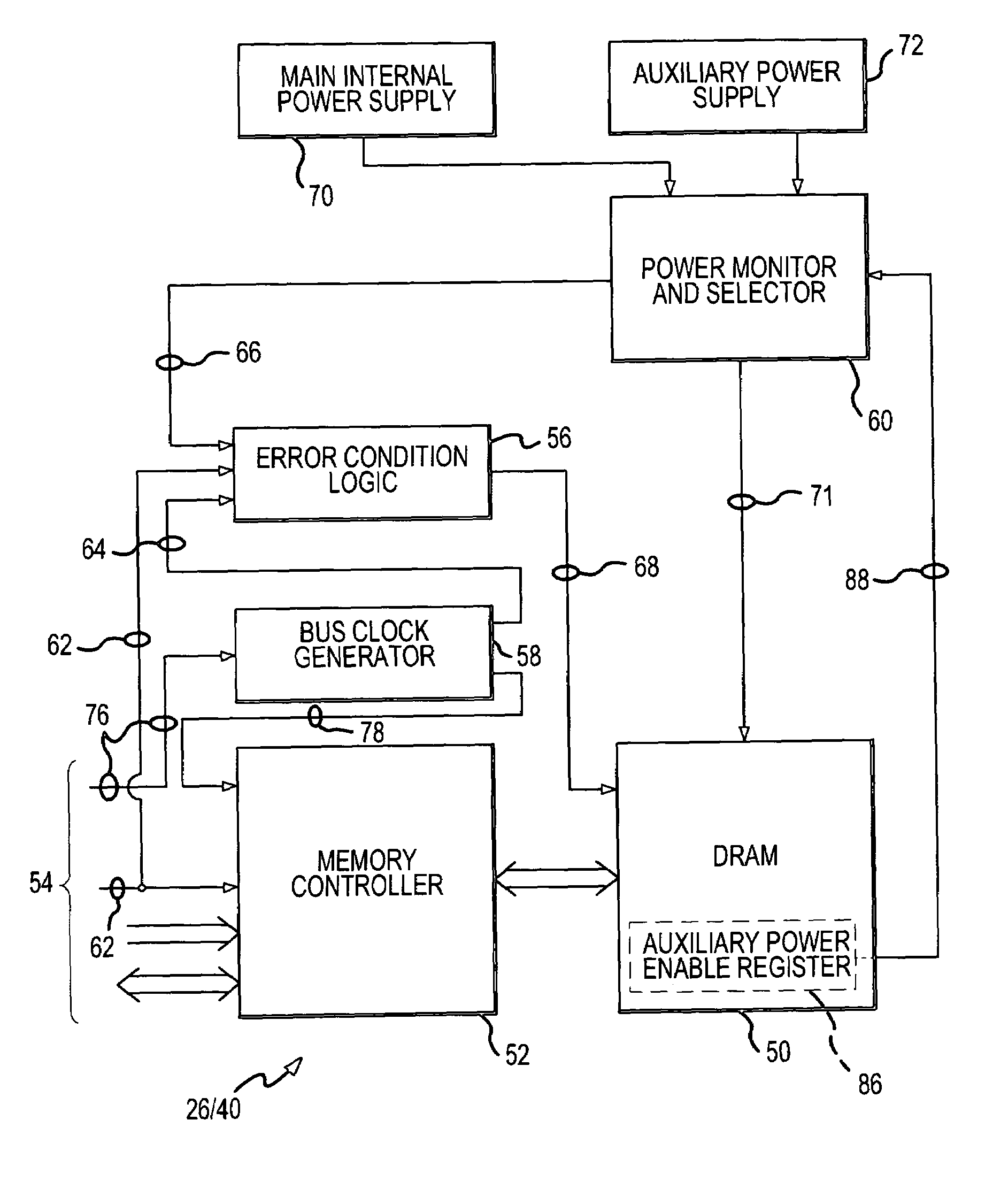
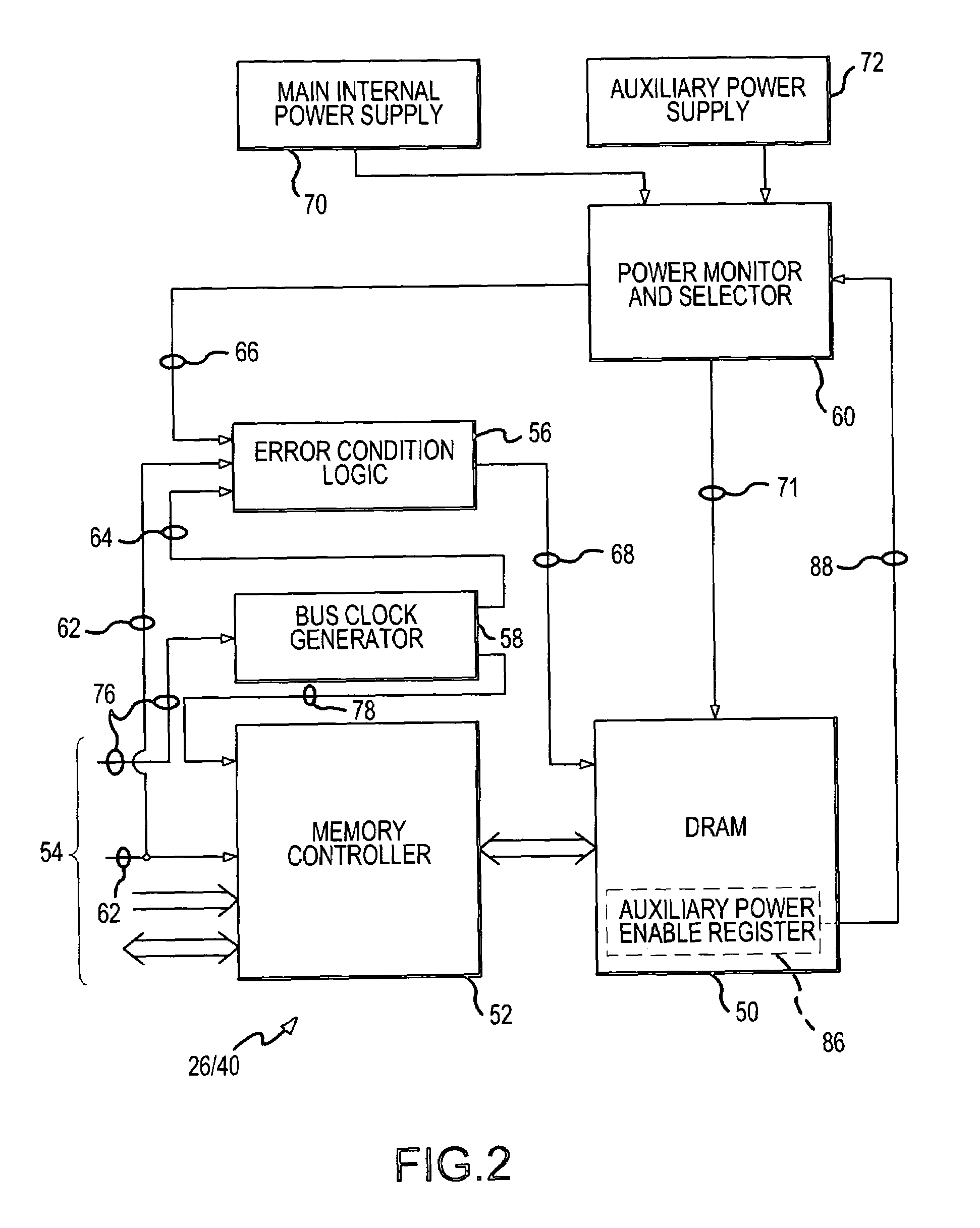
ActiveUS7954006B1Sufficient powerAvoid data lossHardware monitoringPower supply for data processingParallel computingData loss
A method and system for preventing loss of data in a computer interface board during power failure includes providing a secondary data path to a non-volatile storage element from a cache memory of the computer interface board. Components in the secondary data path, such as the cache memory and non-volatile storage element, are powered by a secondary power supply. The cache memory of the computer interface board is a volatile memory. The secondary data path with the non-volatile storage element enables reliable memory operation during both normal and power fail modes. A power failure at the computer interface board is detected. The power failure may result in incomplete transactional data within the cache memory. Upon detection of power failure, the incomplete transactional data at the cache memory is transmitted to the non-volatile storage element through the secondary data path using the power from the secondary power supply. The non-volatile storage element preserves the transactional data of the cache memory during power failure.
Owner:PMC-SIERRA
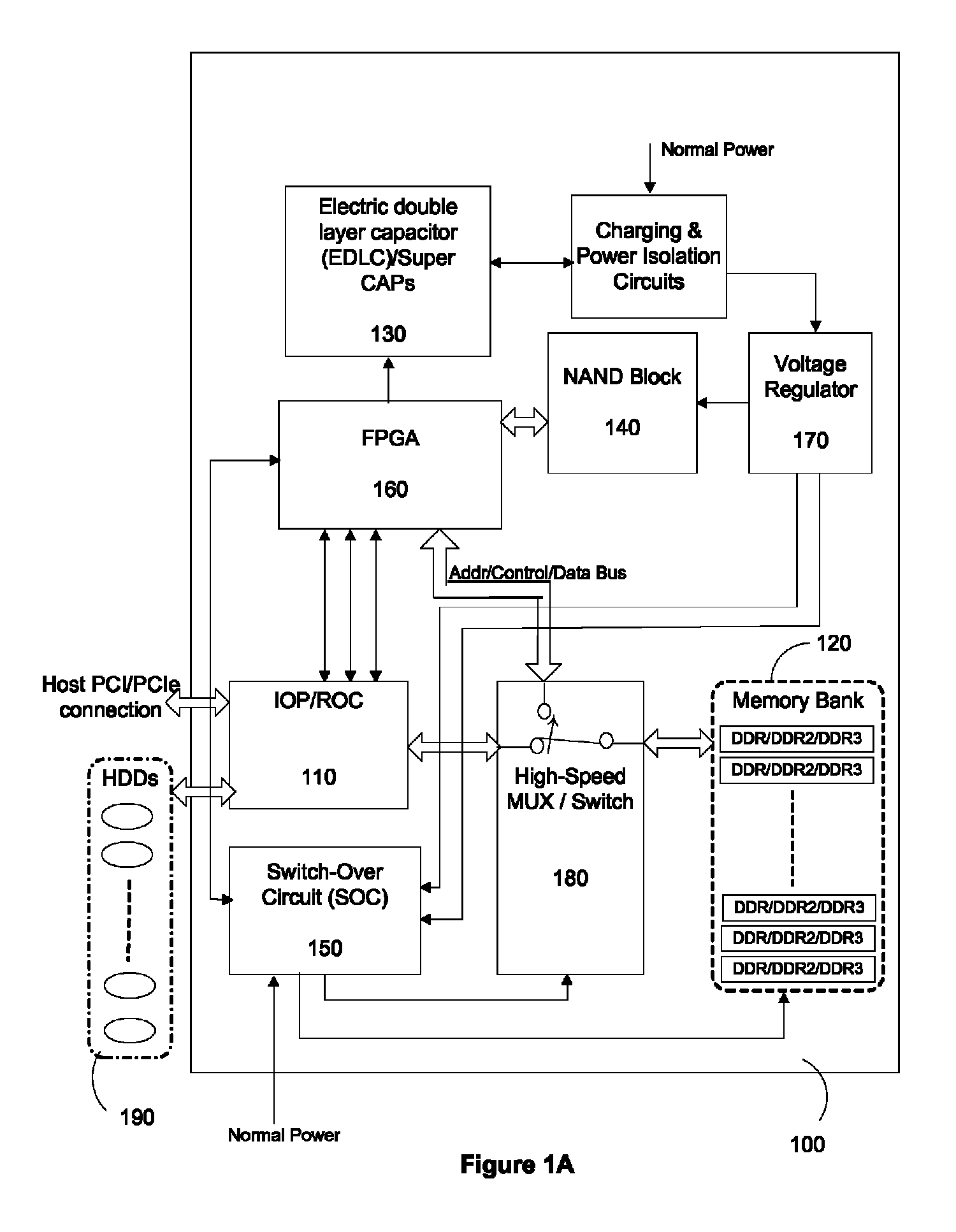
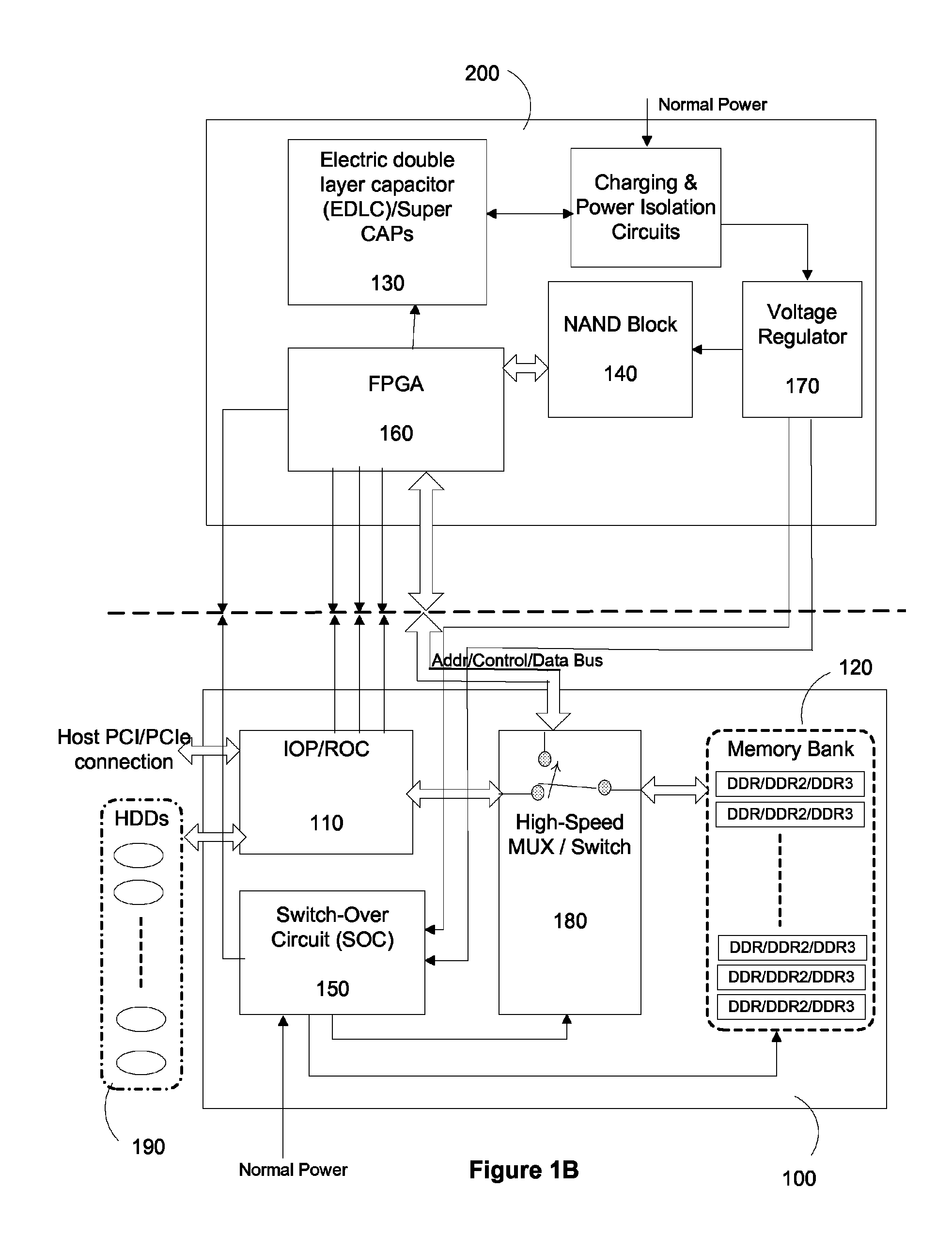
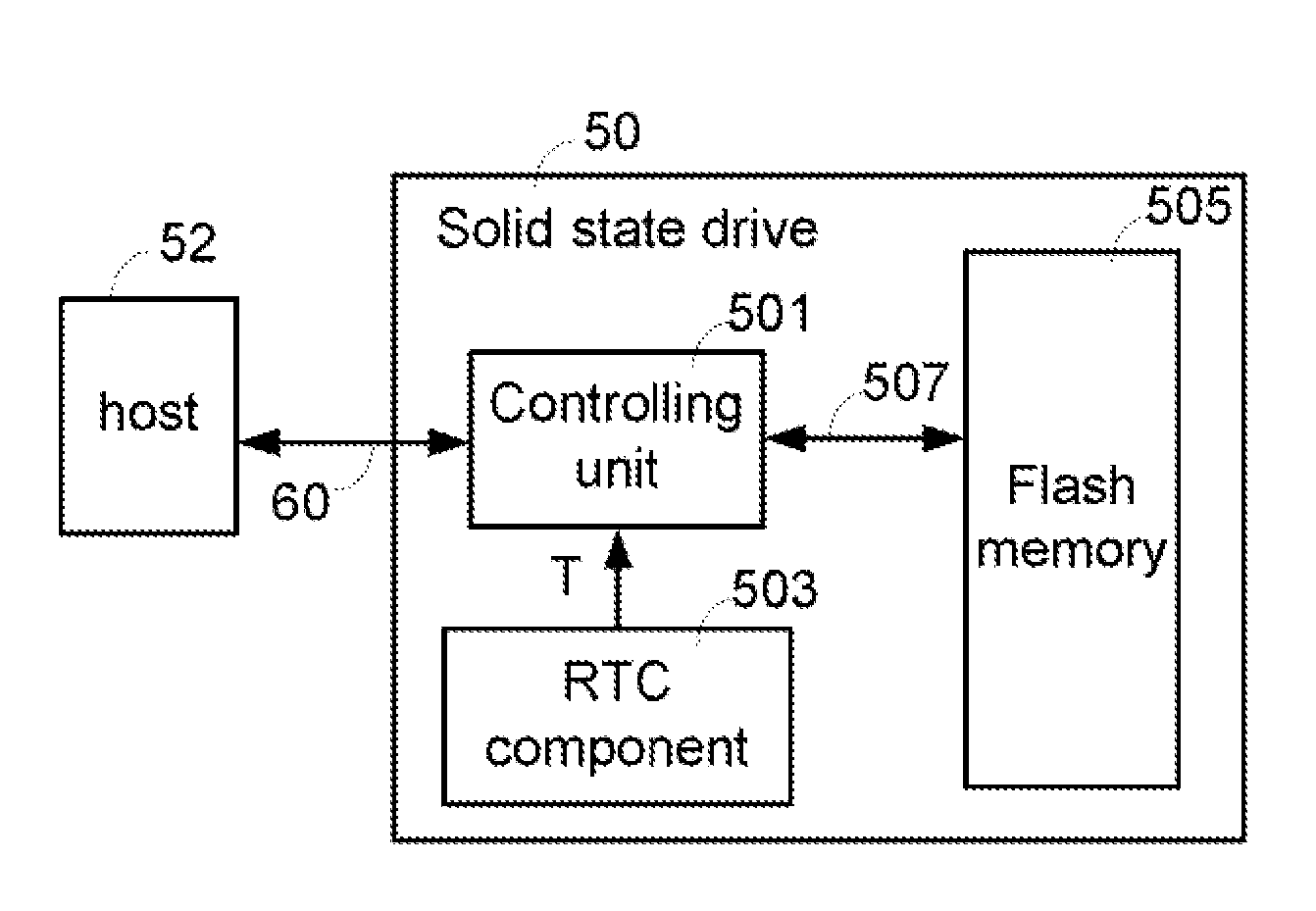
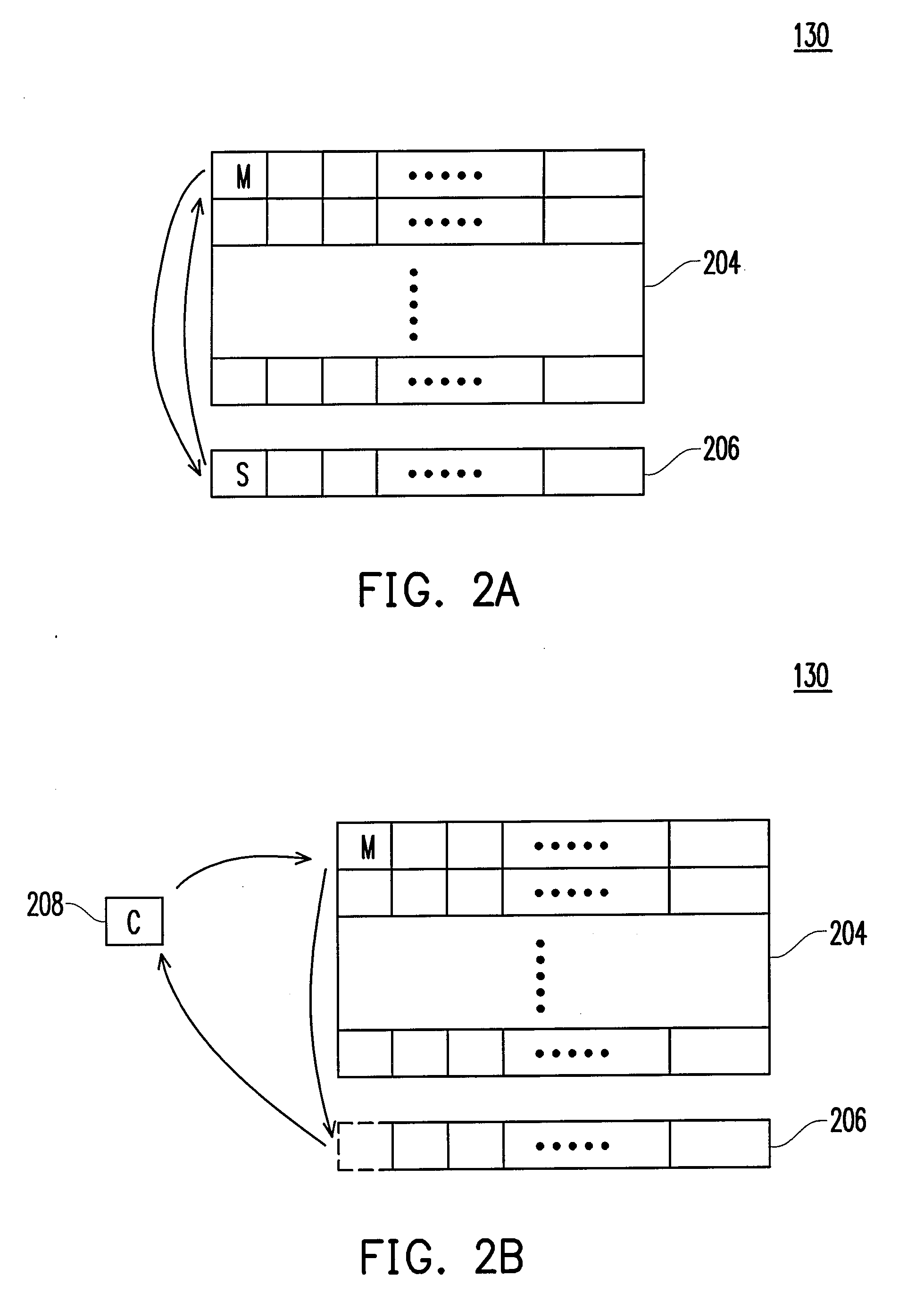
Solid state drive and data control method thereof
InactiveUS20120054414A1Avoid data lossMemory architecture accessing/allocationMemory adressing/allocation/relocationData controlSolid-state drive
A solid state drive includes a flash memory and a controlling unit. The flash memory includes plural blocks. Each block includes plural pages. The controlling unit is in communication with the flash memory. When data of a specified block are erased or data are written into the specified block, the controlling unit provides a time parameter to the specified block. The controlling unit performs a data loss prevention, a wear leveling operation or a garbage collection according to the time parameter.
Owner:LITE ON IT
Collecting data in a batch mode in a wireless communications network with impeded communication
InactiveUS6675203B1Easy to handleAvoid data lossNetwork traffic/resource managementCharacter and pattern recognitionData harvestingWireless network
The method provides for a way to ensure that the application program running on the host computer handles data received from the at least one mobile computer terminals when one of the mobile computer terminals goes out of range of the wireless network. Communication and association may be established between a mobile computer terminal and an access point on a local network. Then, when it has been determined that communications between the mobile computer terminal and the access point have been impeded, the mobile computer terminal may switch to batch mode to continue data collection.
Owner:SYMBOL TECH LLC
Method and apparatus for security management via vicarious network devices
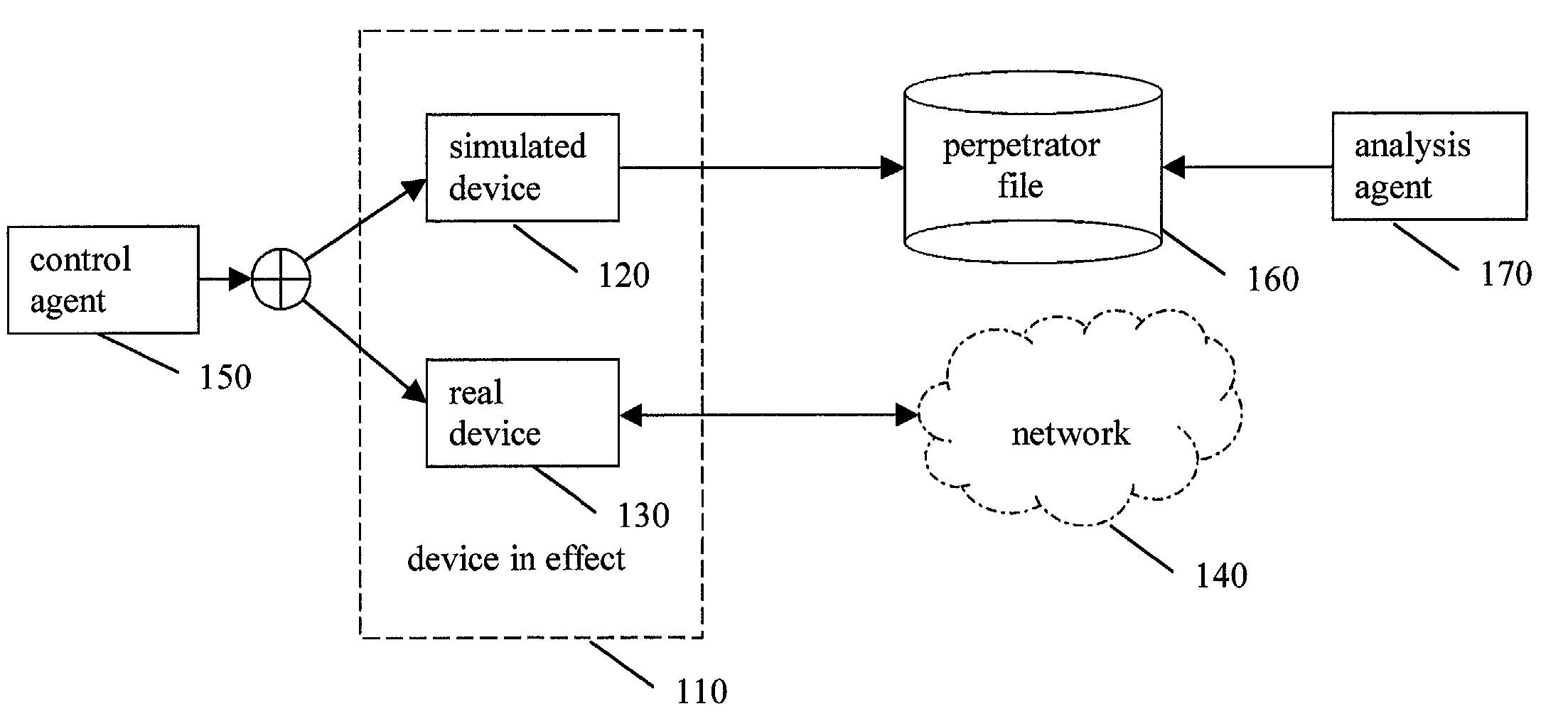
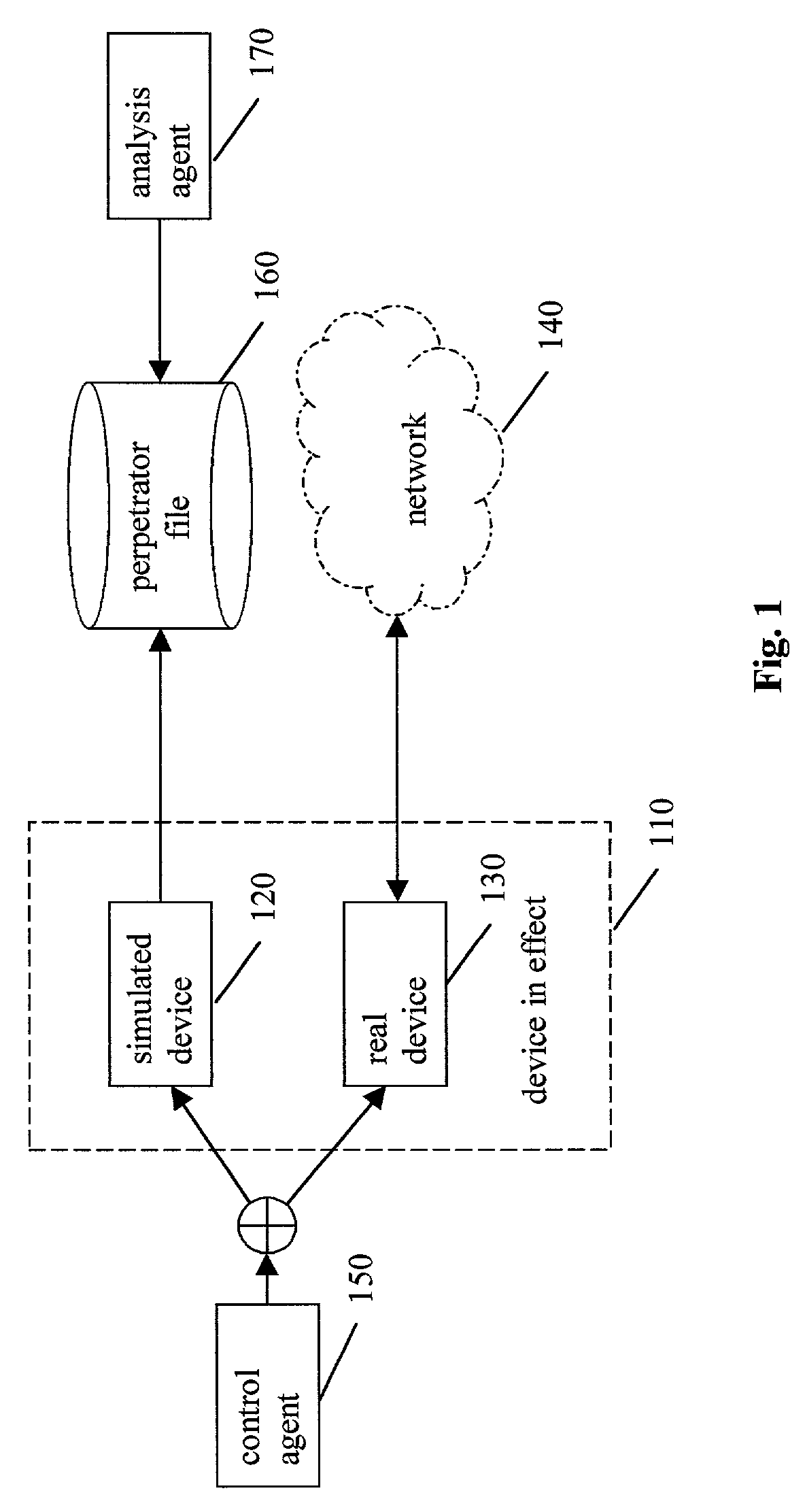
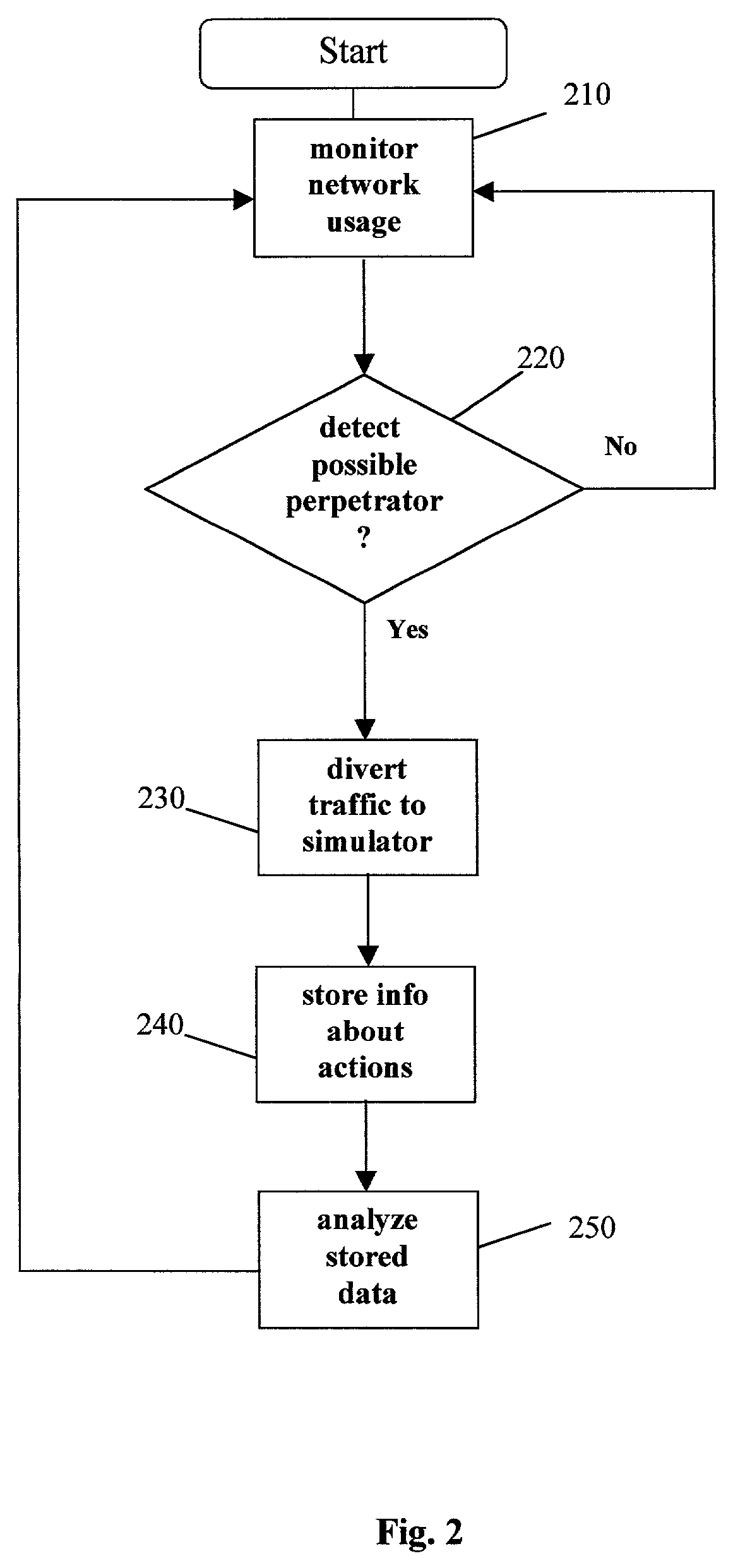
ActiveUS7770223B2Reliable portrayalAvoid data lossMemory loss protectionDigital data processing detailsNetwork isolationSpeech sound
In one embodiment of a method and apparatus for protecting data, voice, and video networks from individuals with malicious intent, a real network or network device has a vicarious simulated counterpart that may take the place of the real device or network upon appropriate triggering. The simulated counterpart behaves like the real device, but records the suspect transactions. The integrity of the real network or device is therefore continuously maintained because the suspect is isolated from the real network and the suspect transactions are not passed on to the actual device or network. The recorded transactions may then be analyzed for purposes of exposing the perpetrator, discovering perpetrator behavior patterns, and identifying device or network security weaknesses.
Owner:COMP ASSOC THINK INC
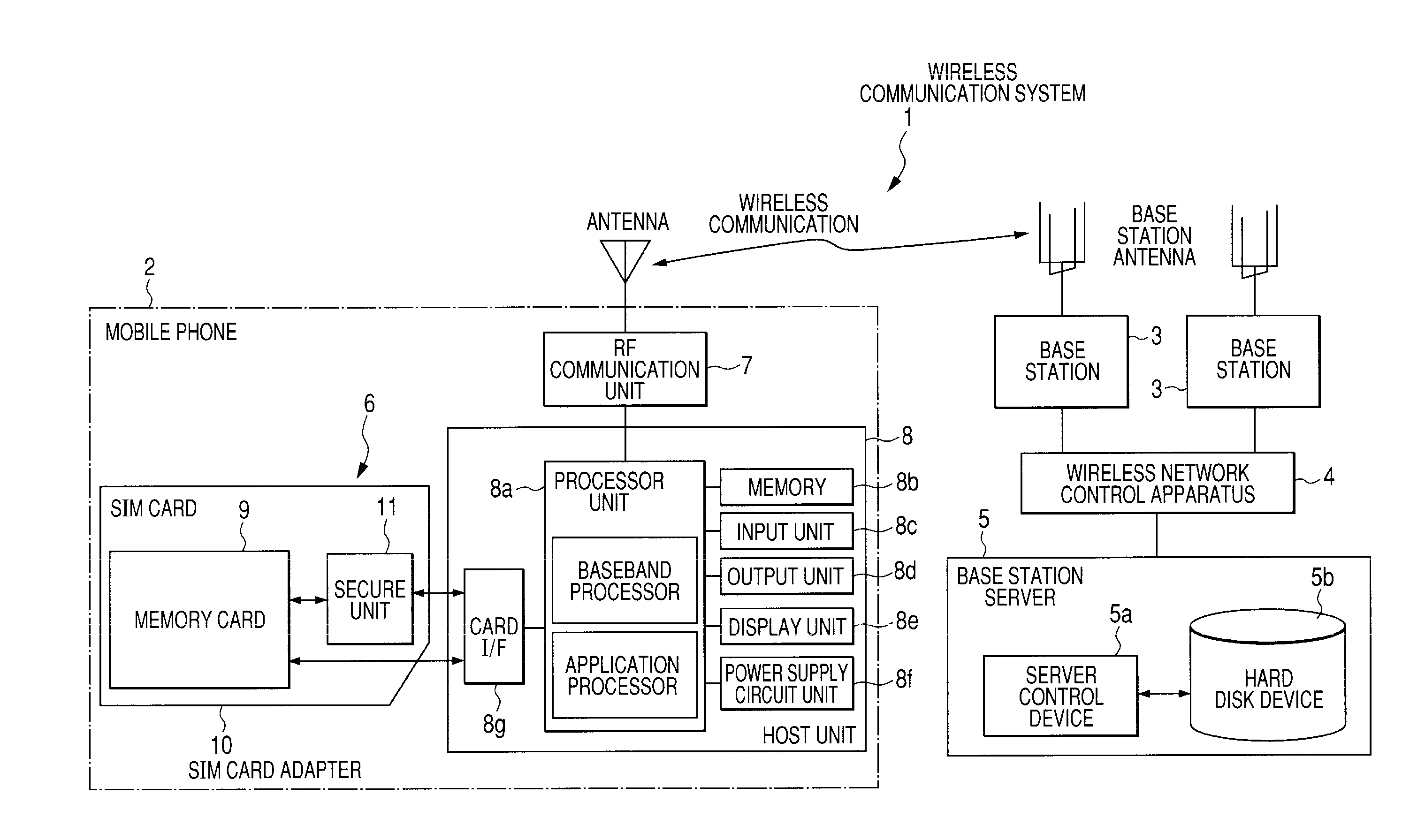
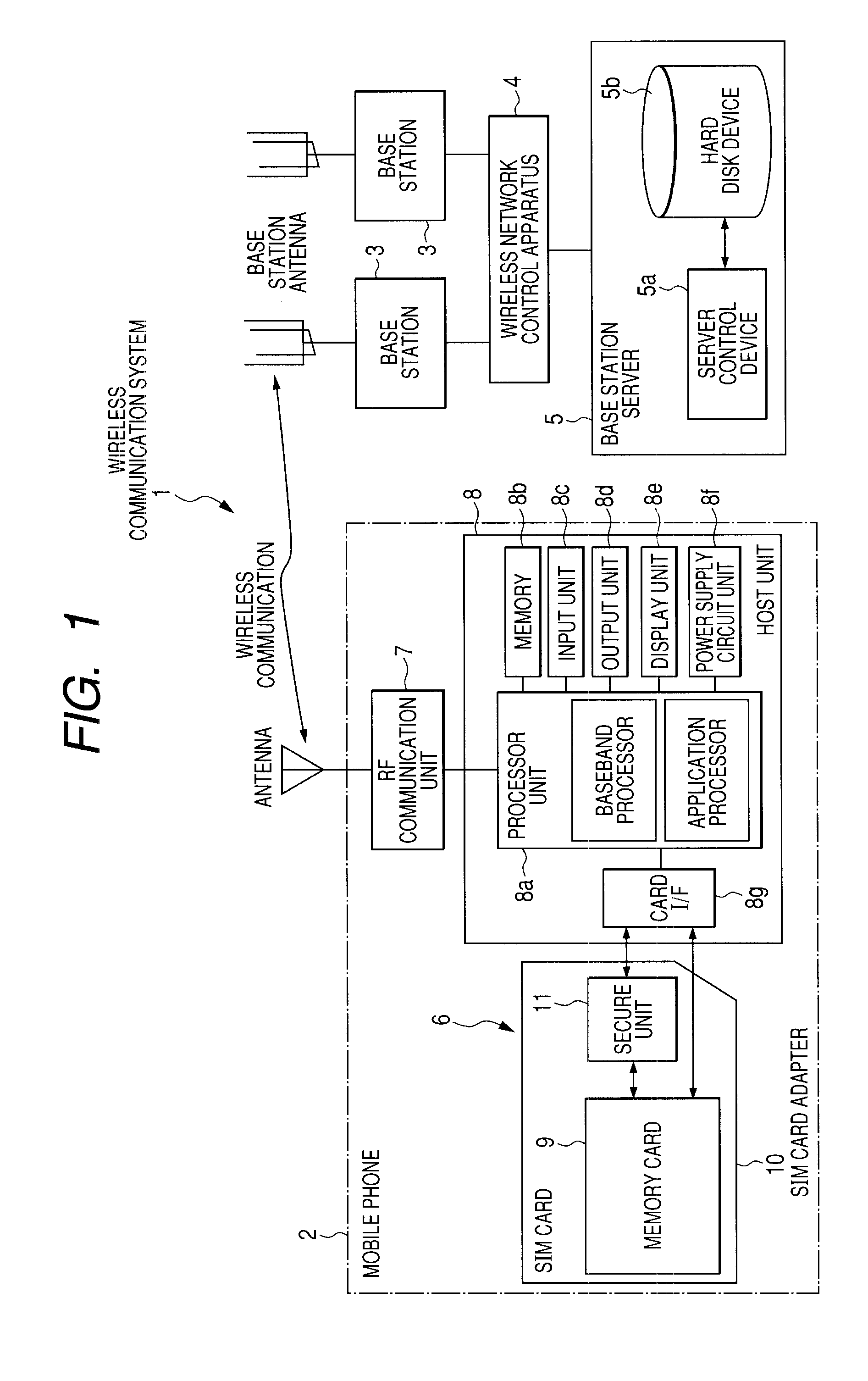
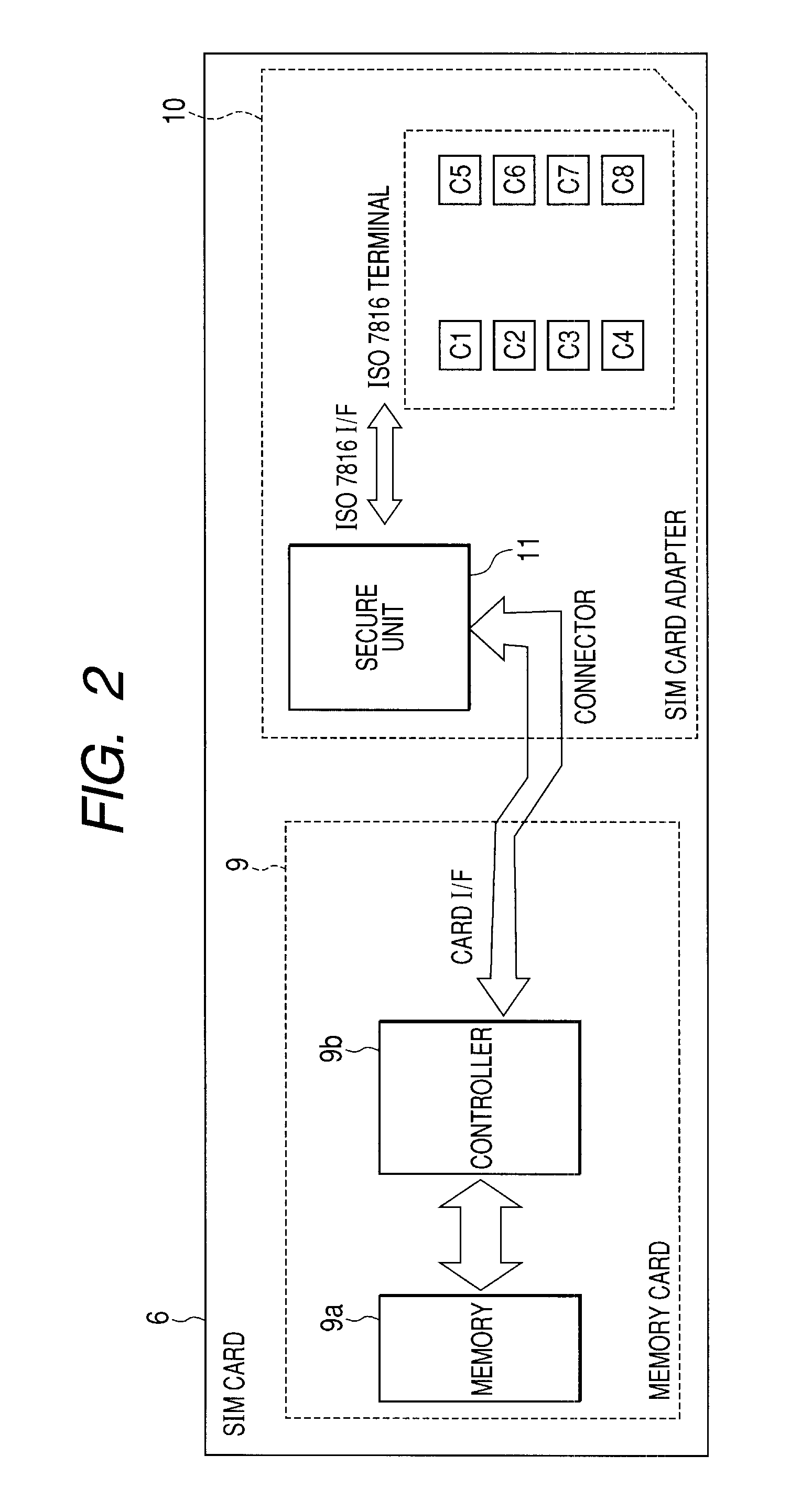
Wireless communication system, sim card, mobile communication terminal, and data guaranteeing method
InactiveUS20080300020A1Avoid data lossAvoid lostSubstation equipmentTransmissionSecure communicationBase station
The loss of data stored in a secure memory card, such as a SIM card, due to the physical destruction thereof is prevented. A host unit performs card authentication of a memory card, and transmits update data for the memory card by security communication to update data when the result of the authentication is OK. Then, the host unit outputs a request for mirror-updating the card data to a base station server. When an access is permitted, the card data is transmitted to the base station server via the host unit to mirror-update the card data. When the mirror-updating of the card data is completed, the base station server returns a completion confirmation to the host unit, so that a data backup process is completed. By thus causing the base station server to mirror-update the data in the memory card, the loss of the stored data is prevented.
Owner:RENESAS TECH CORP
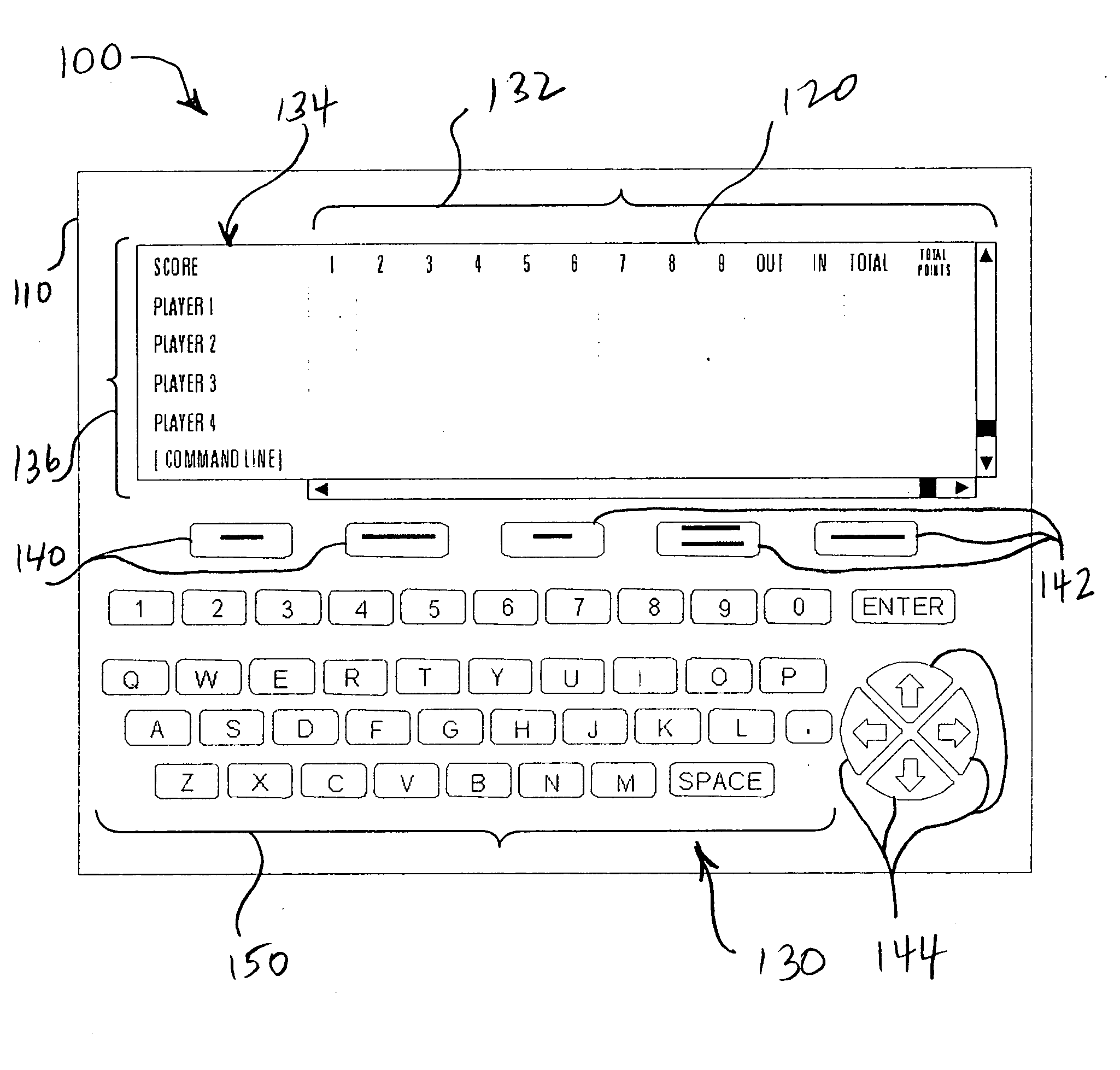
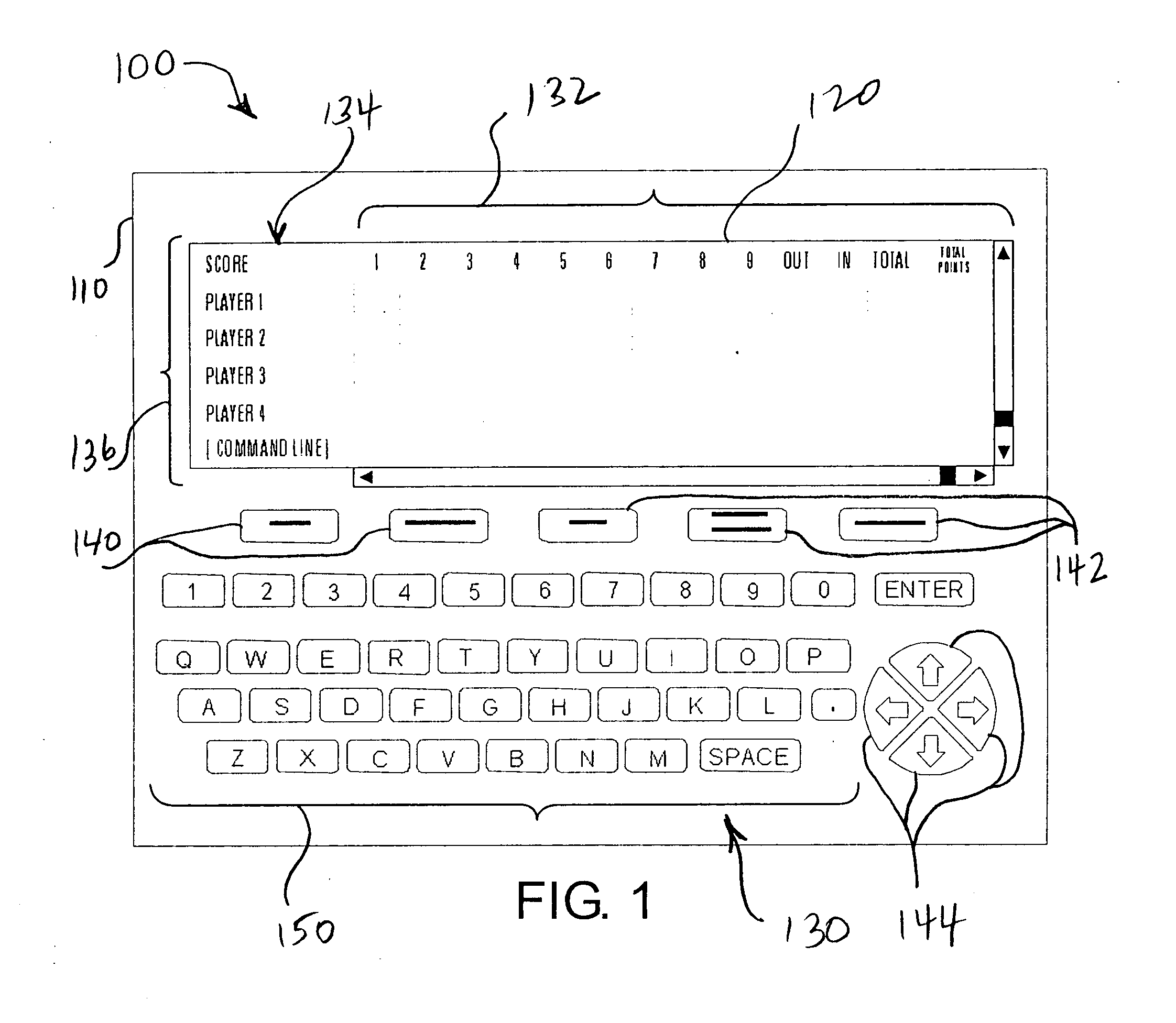
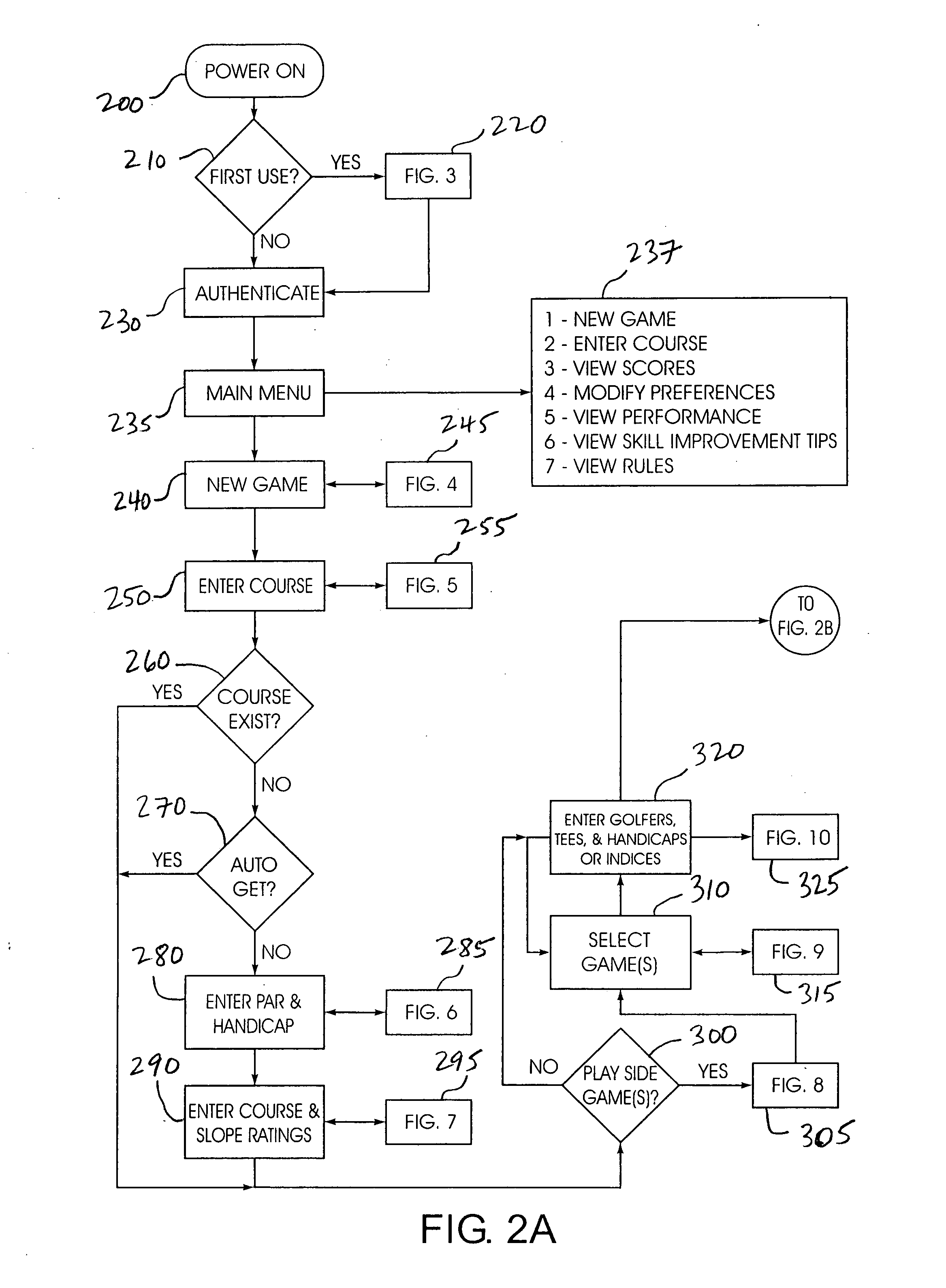
Golf score and information device and system
InactiveUS20050096761A1Avoid data lossImprove skill levelGymnastic exercisingBall sportsGolf course turfDisplay device
A golf score and information device (100, 700, 900) that includes a portable electronic programmable processor and memory unit (110), display (120) and data entry assembly (130), and storage memory (117) operable to automatically or manually receive and send data via a communication circuit. The display (120) and data entry assembly (130) cooperate to visually present continuously scrollable information pertaining to any group of holes of a golf course in a representation of a golf score card. The device (100, 700, 900) is adapted to track current game scores, side games or competitions, hole-by-hole challenges, and to post the results manually and or automatically to a desired score collecting and processing authority.
Owner:FORESCORE GOLF
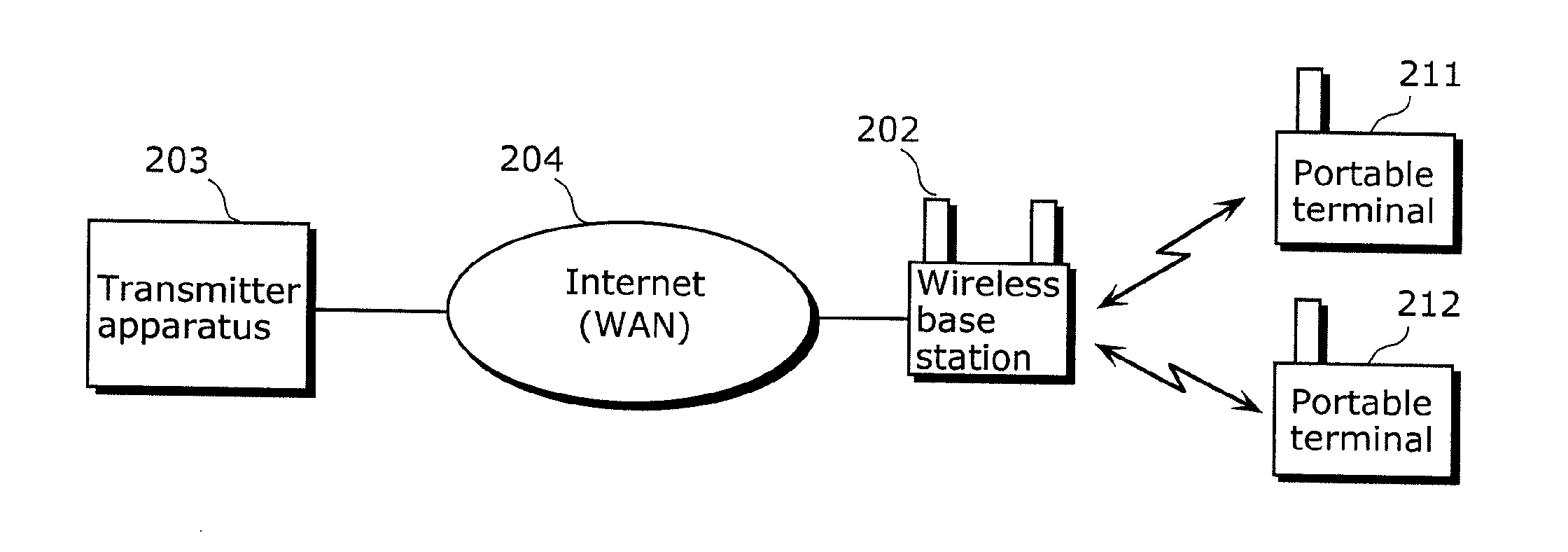
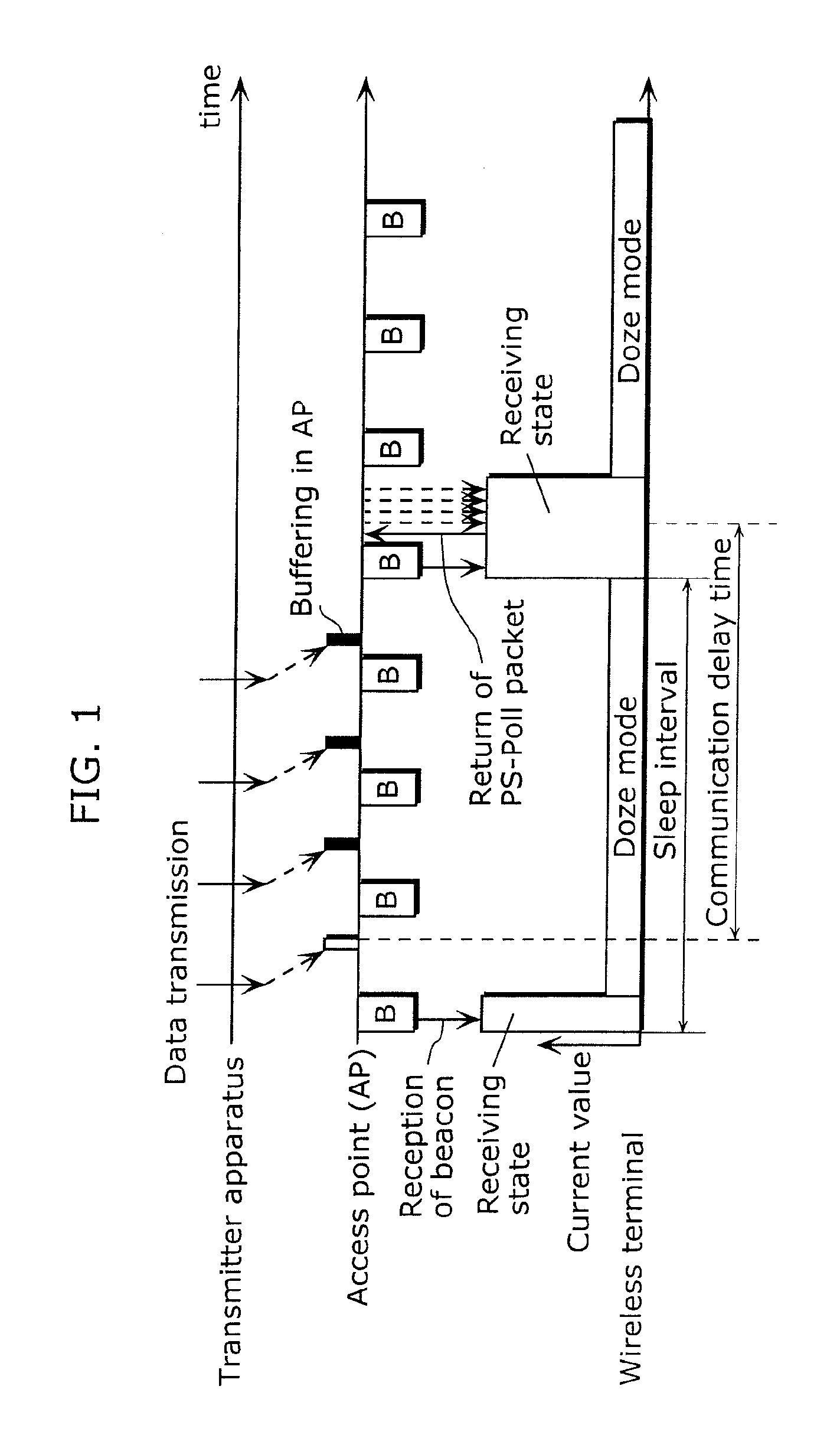
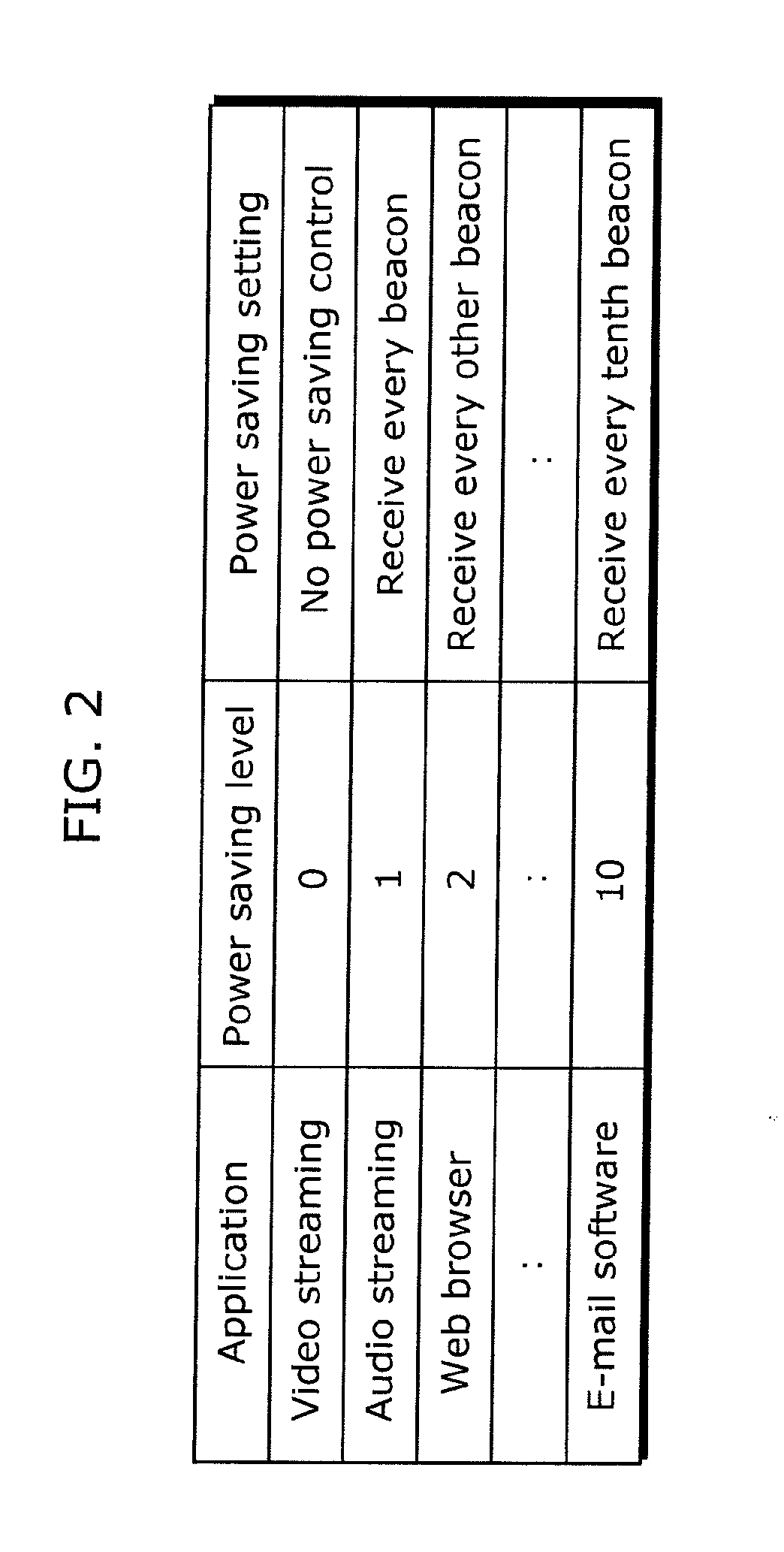
Communication apparatus
InactiveUS20110019555A1Save powerAvoid data lossEnergy efficient ICTPower managementPower savingData transmission
To provide a communication apparatus for achieving further improvements in communication quality and power saving effect, without depending on network environments. A portable terminal (211) as a communication apparatus includes: a communication I / F unit (108) performing data transmission / reception with a transmitter apparatus (203) on a communication protocol having flow control such as TCP; a power control unit (106) switching power on and off to the communication I / F unit (108); and a suppression / resumption control unit (104) determining cycle interval Tc and cycle data size Dc according to communication quality required by a communication application program and, per cycle interval Tc, causing data of cycle data size Dc to be transmitted in a burst state, suppressing data transmission from the transmitter apparatus (203), and causing the power control unit (106) to power off the communication I / F unit (108) while the data transmission is suppressed (T2 to T3), using the flow control mechanism.
Owner:PANASONIC CORP
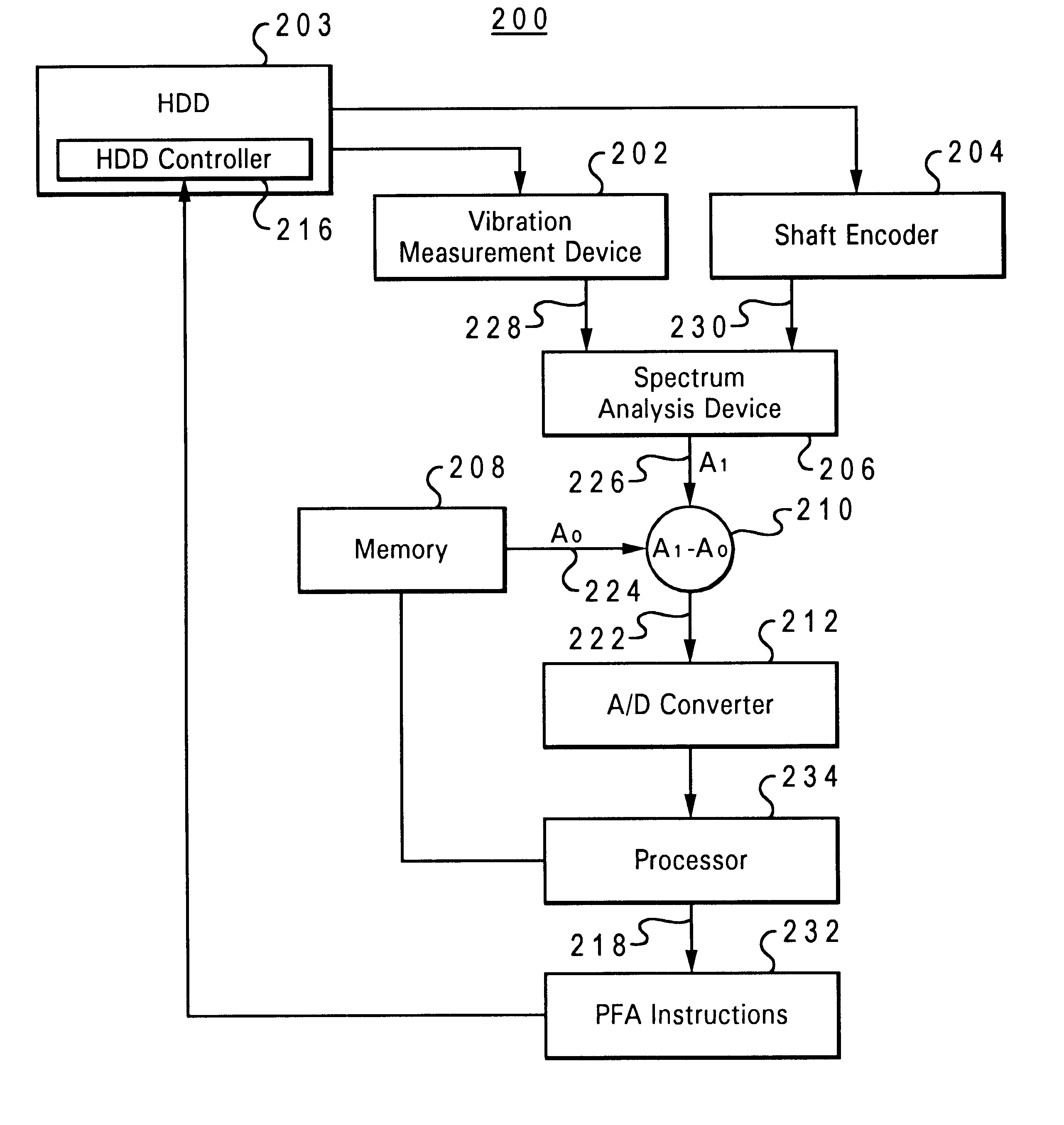
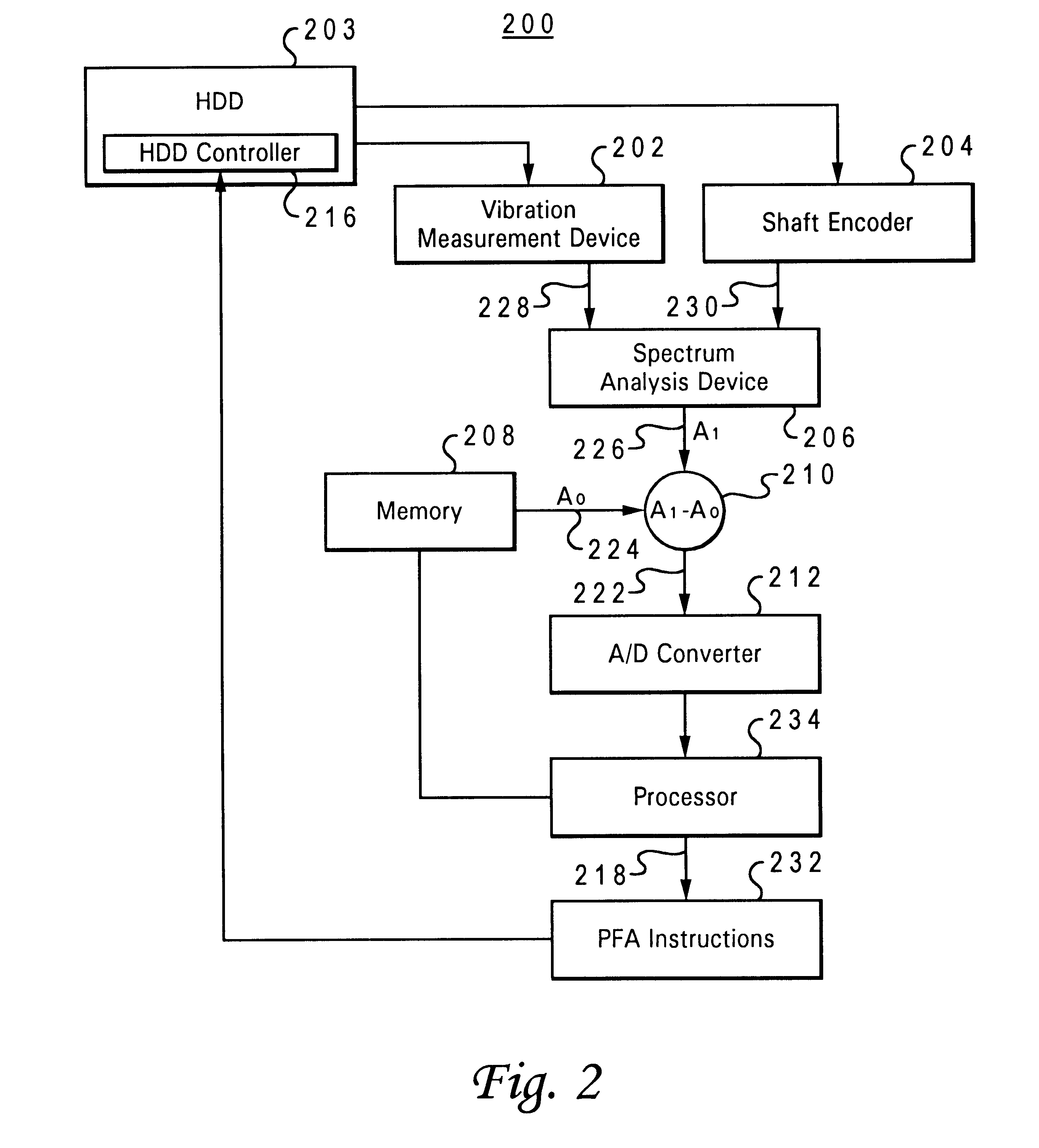
Method and system for predicting disk drive failures
InactiveUS6415189B1Not easy to failAvoid data lossVibration measurement in solidsMaterial analysis using sonic/ultrasonic/infrasonic wavesData processing systemHard disc drive
A method and system within a data processing system for predicting failure of a hard disk drive having a fluid bearing during runtime operation of said hard disk drive, wherein said fluid bearing has an established signature dynamic fluid response. First, a runtime vibration level of the fluid bearing is measured. This runtime vibration level is then translated into a runtime dynamic fluid response which provides an indication of the operating condition of the fluid bearing. The runtime dynamic fluid response is compared with the baseline dynamic fluid response in real-time during operation of the hard disk drive. Finally, in response to a predetermined departure of the runtime dynamic fluid response from the baseline dynamic fluid response, a protective response is initiated, such that data loss within the data storage system due to fluid bearing failure is prevented.
Owner:WESTERN DIGITAL TECH INC
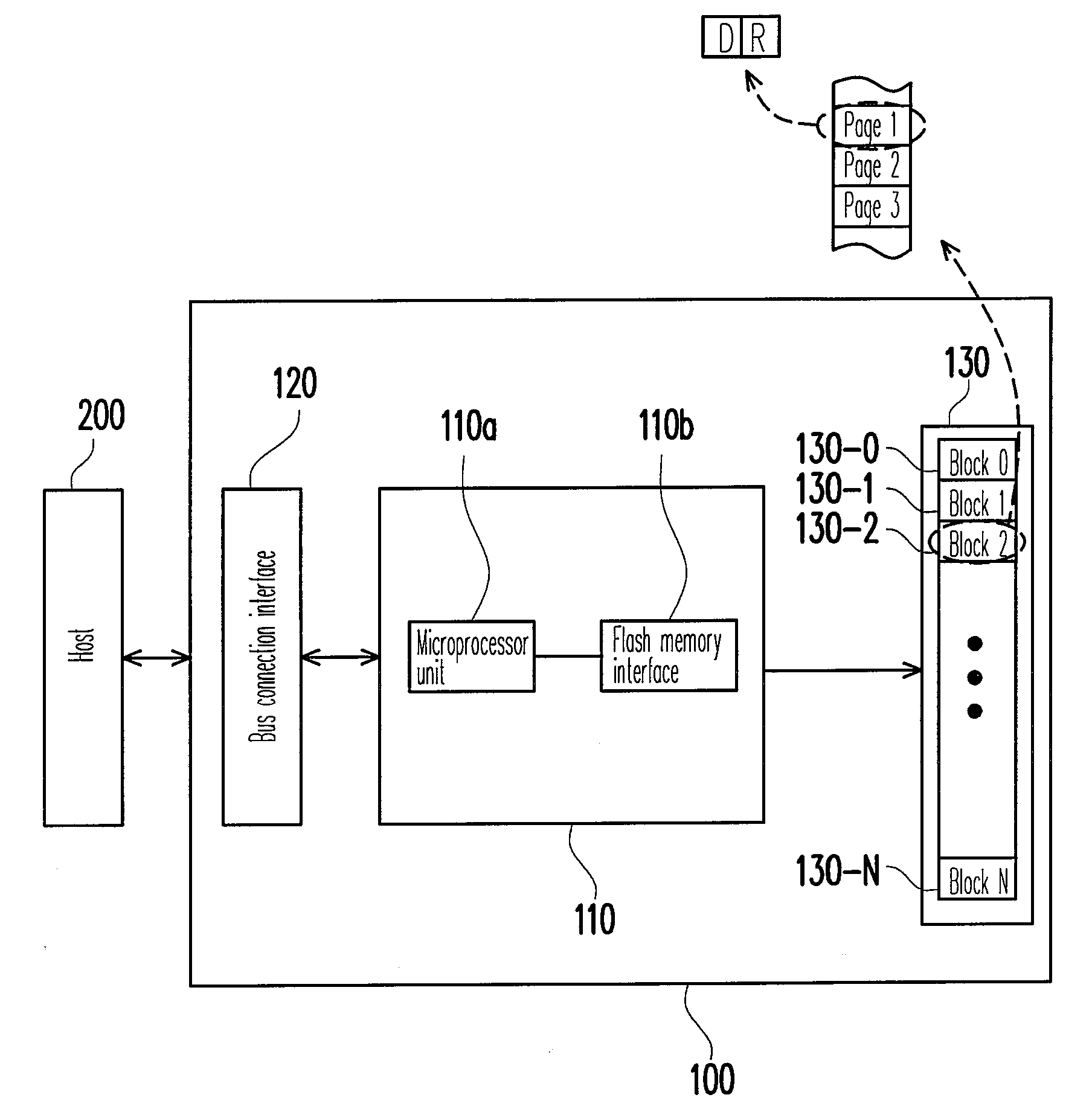
Data reading method for flash memory and controller and storage system using the same
ActiveUS20090216936A1Avoid data lossMemory architecture accessing/allocationMemory adressing/allocation/relocationCopyingData loss
A data reading method suitable for a flash memory storage system having a flash memory is provided, wherein the flash memory is substantially divided into a plurality of blocks and these blocks are grouped into at least a data area and a spare area. The data reading method includes: respectively determining whether the blocks in the data area are frequently read blocks; allocating a buffer storage area corresponding to the frequently read block and copying data stored in the frequently read block to the buffer storage area; and reading the data from the buffer storage area corresponding to the frequently read block when the data stored in the frequently read block is to be read. As described above, data loss caused by read disturb can be effectively prevented.
Owner:SAMSUNG ELECTRONICS CO LTD
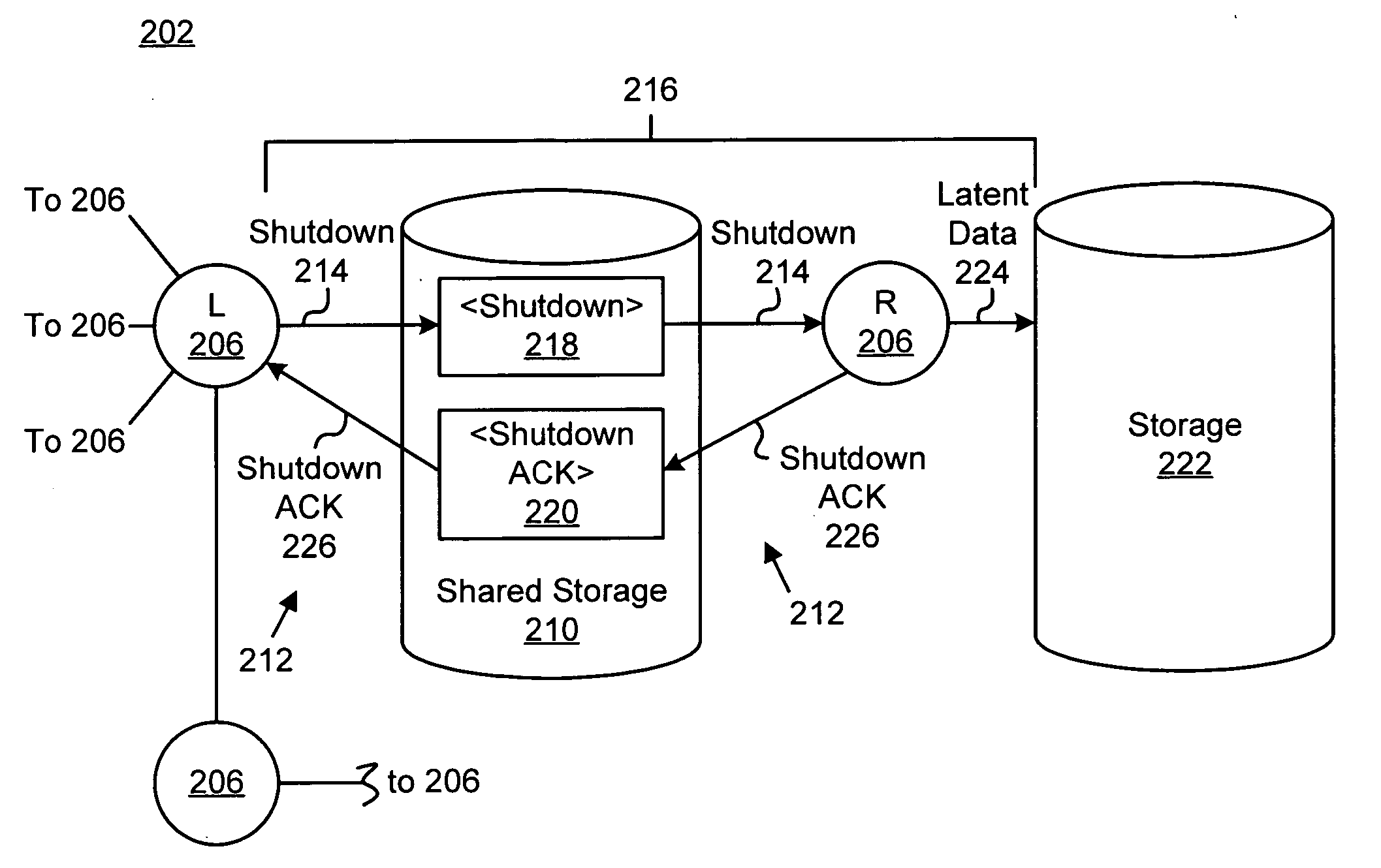
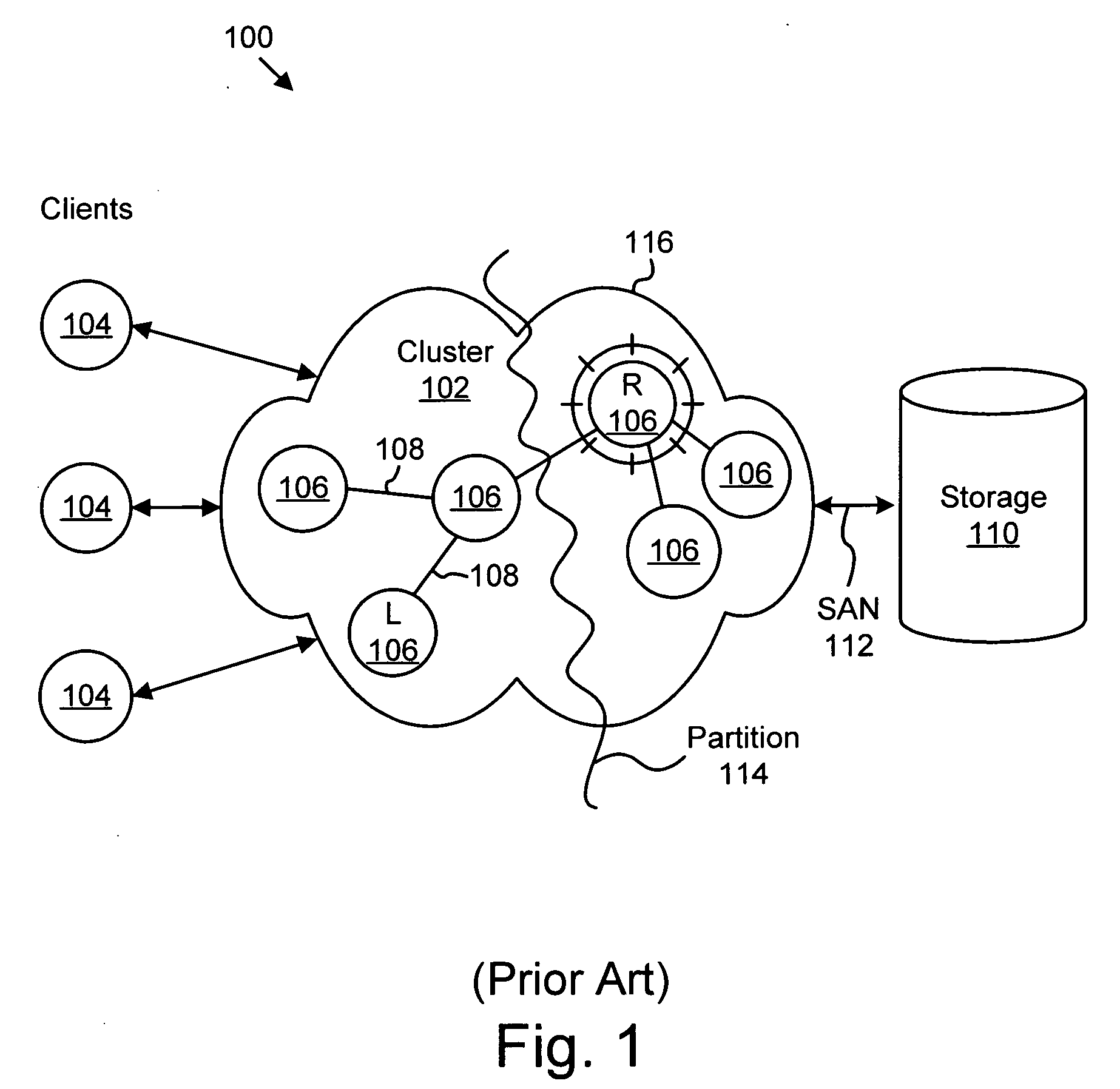
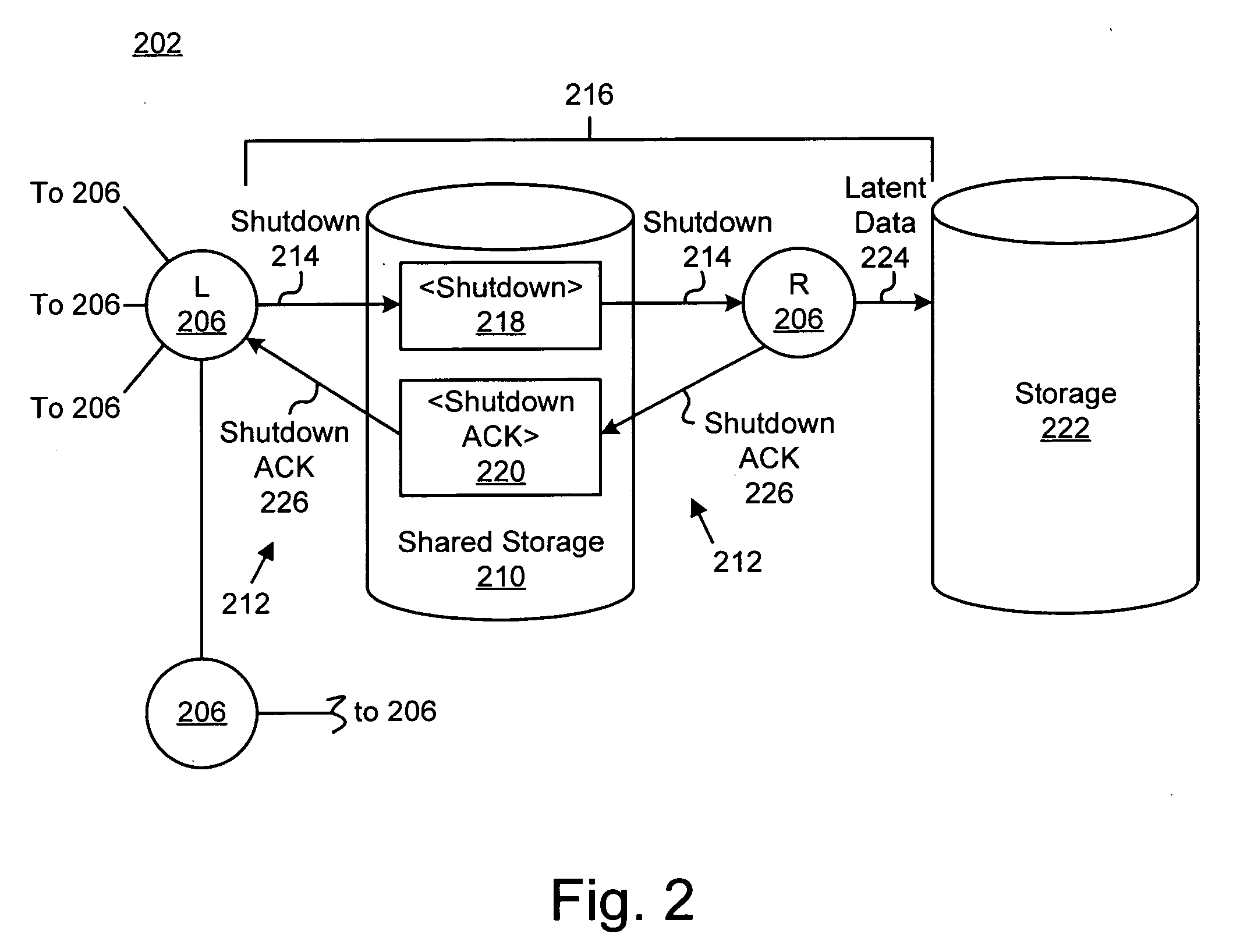
Apparatus, system, and method for verified fencing of a rogue node within a cluster
InactiveUS20050283641A1Maintain data integrityAvoid data lossRedundant hardware error correctionOperating system
An apparatus, system, and method are provided for verified fencing of a rogue node within a cluster. The apparatus may include an identification module, a shutdown module, and a confirmation module. The identification module detects a cluster partition and identifies a rogue node with a cluster. The shutdown module sends a shutdown message to the rogue node using a message repository shared by the rogue node and the cluster. The shutdown message may optionally permit the rogue node to preserve latent I / O data prior to shutting down. The confirmation module receives a shutdown ACK from the rogue node 206. Preferably, the shutdown ACK is sent just prior to the rogue node actually shutting down.
Owner:IBM CORP
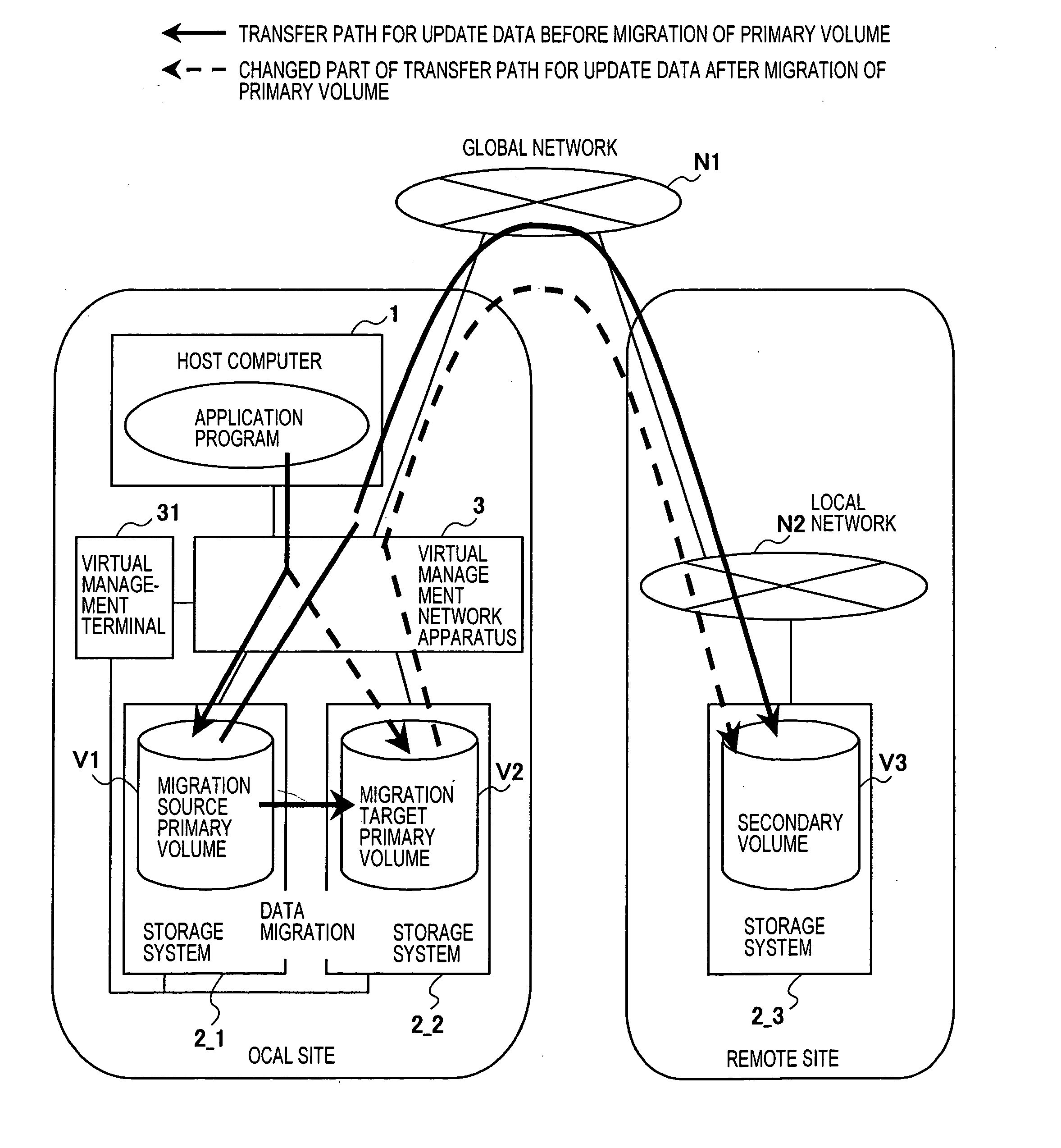
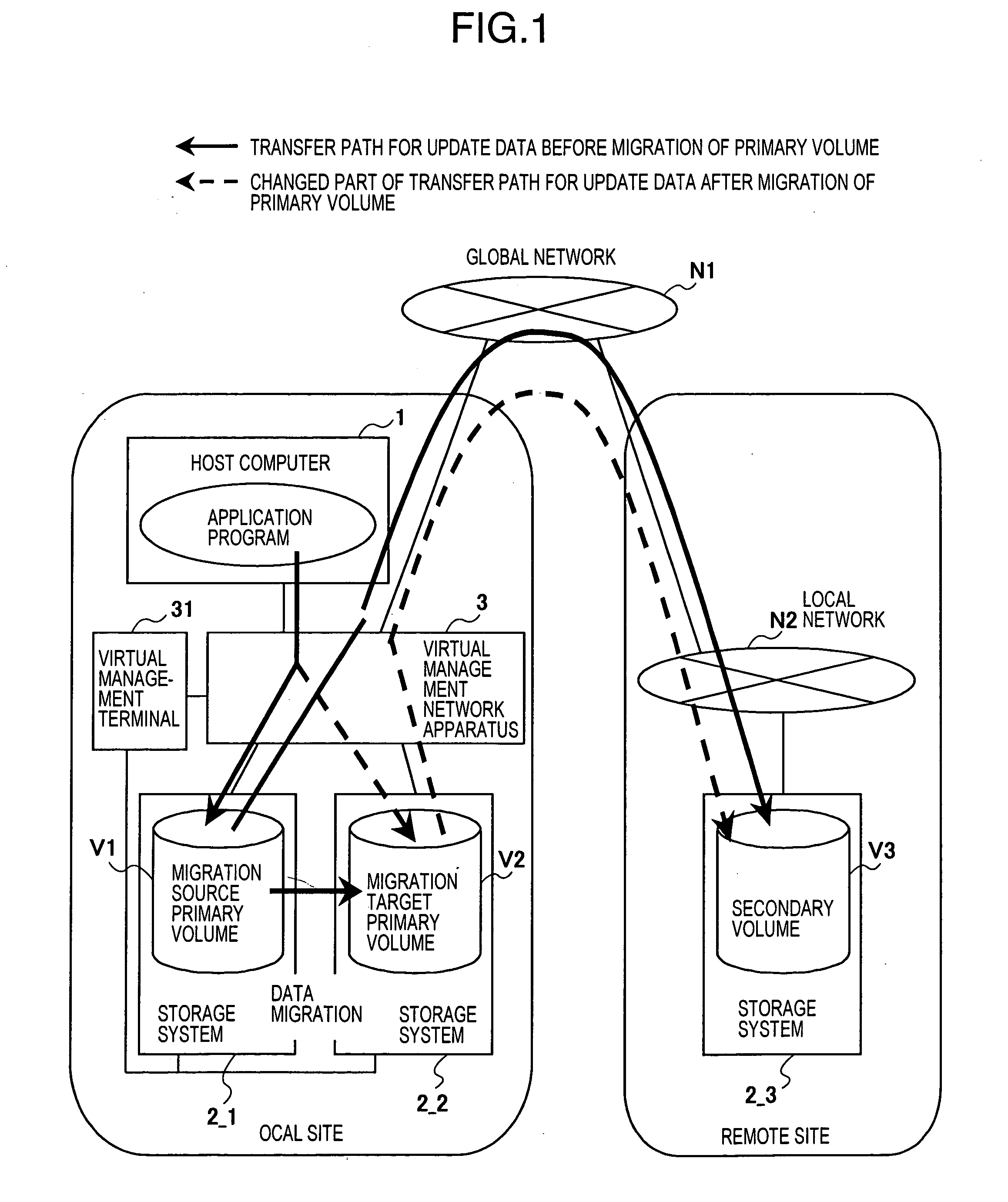
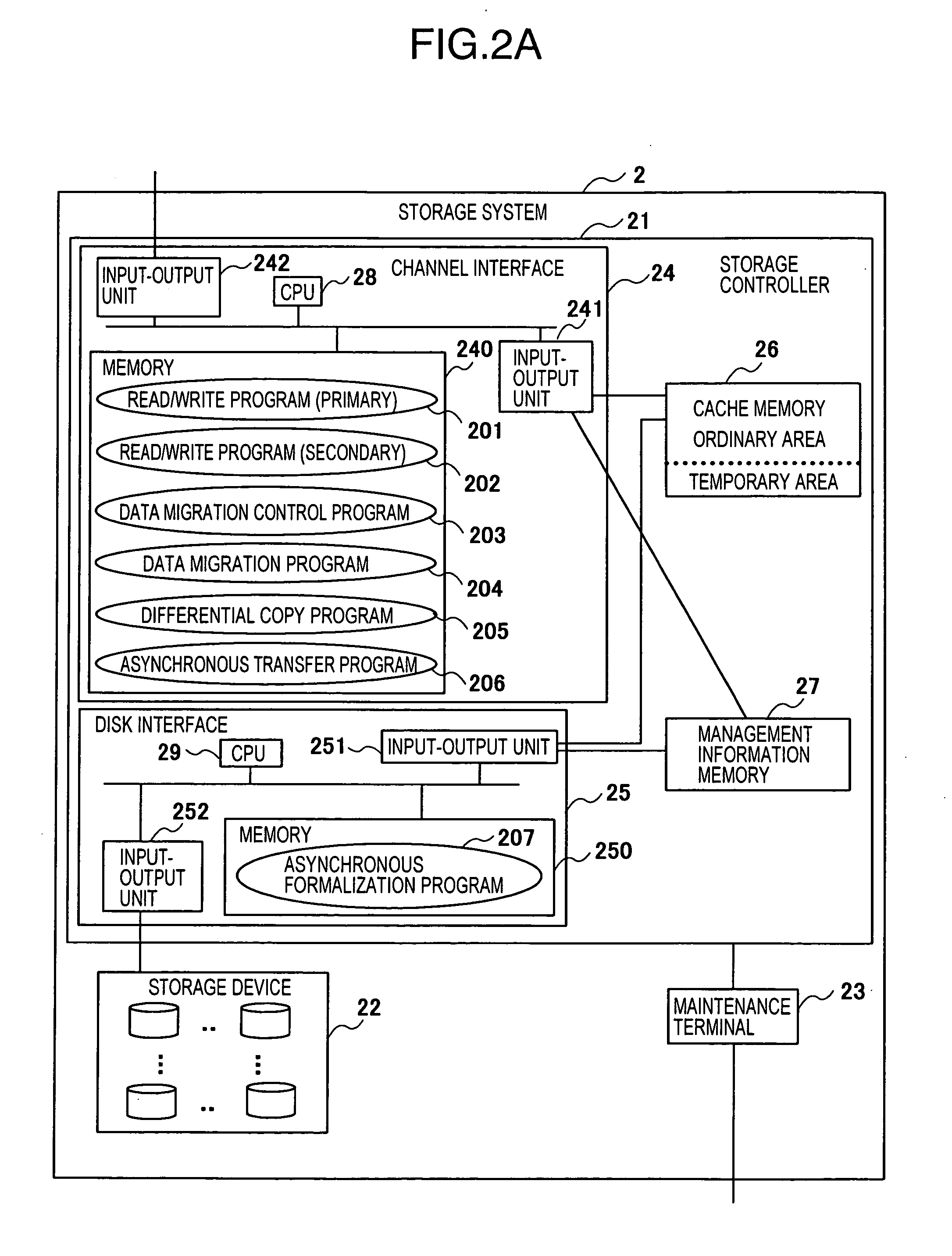
Remote copy system
InactiveUS20050138308A1Avoid data lossInput/output to record carriersMemory loss protectionData storingData store
A remote copy technique according to which data of a primary volume is migrated while continuing remote copy processing and receiving access requests from a host. A remote copy system comprises a first storage system having a first primary volume, a second storage system having a second primary volume and a third storage system having a secondary volume, and remote copying is performed between the first primary volume and the second volume. When data in the first primary volume is migrated to the second primary volume, an access request from the host to the primary volume is transferred to the second primary volume. Further, the second storage system stores write data received from the host and data of the first primary volume received from the storage system, into the second primary volume. Out of data stored in the second primary volume, the second storage system sends data determined by management information received from the first storage system, to the third storage system.
Owner:HITACHI LTD
Method and apparatus to establish safe state in a volatile computer memory under multiple hardware and software malfunction conditions
ActiveUS7139937B1Avoid data lossImprove abilitiesError detection/correctionDigital data processing detailsSignal onSoftware failure
Volatile memory is placed into a data-preserving safe state in a computer system in response to any one of a reduction in power applied to the volatile memory, a bus reset signal on a data communication bus of the computer system, and an absence of a bus clock signal on the bus. The volatile memory is powered from an auxiliary uninterruptible power supply in response to the reduction in power. The volatile memory is also placed into the data-preserving safe state in response to a cessation in executing software instructions by a CPU of the computer system. Placing the volatile memory into the safe state in response to and under these conditions enhances the opportunity to preserve data in response to error and malfunction conditions.
Owner:NETWORK APPLIANCE INC
Protecting information using policies and encryption
ActiveUS8843734B2Ensure confidentialityAvoid data lossUnauthorized memory use protectionHardware monitoringConfidentialityDocumentation
A technique and system protects documents at rest and in motion using declarative policies and encryption. Encryption in the system is provided transparently and can work in conjunction with policy enforcers installed at a system. A system can protect information or documents from: (i) insider theft; (ii) ensure confidentiality; and (iii) prevent data loss, while enabling collaboration both inside and outside of a company.
Owner:NEXTLABS INC
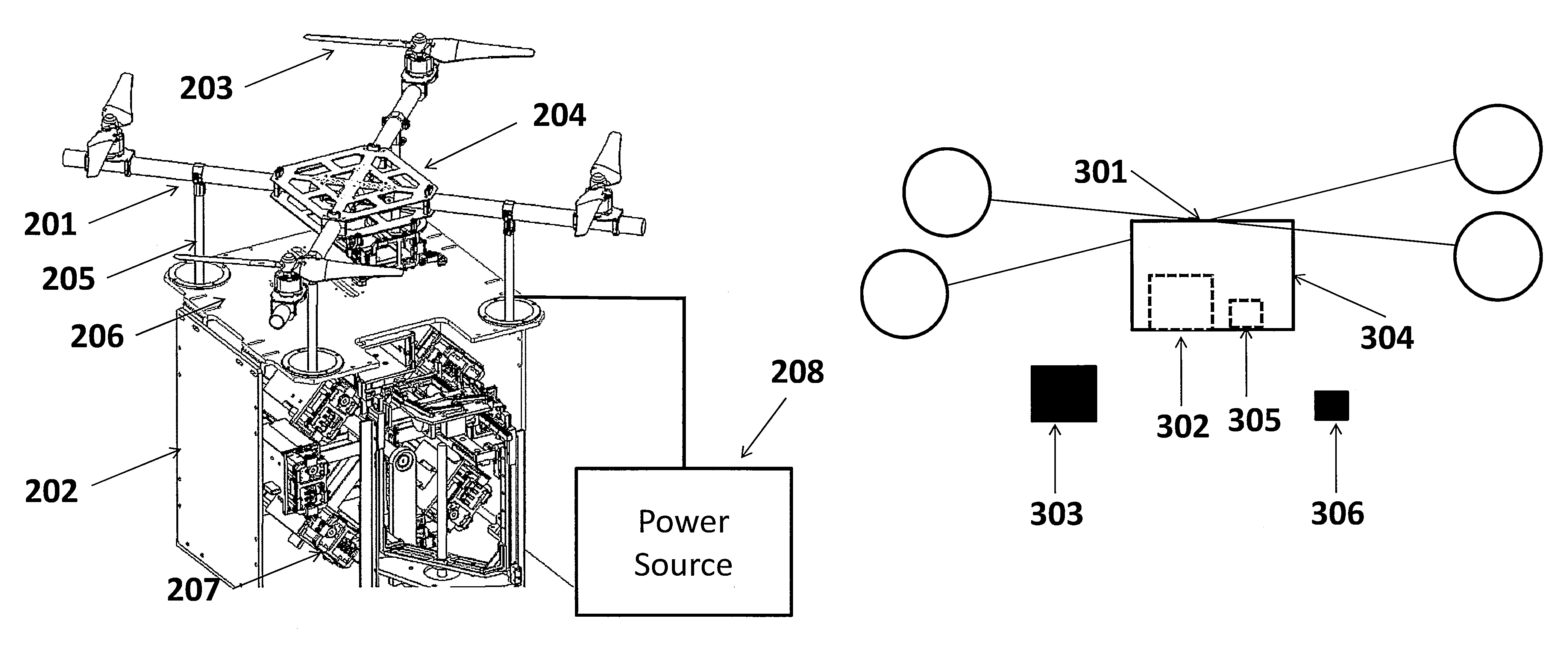
Systems and methods for UAV battery power backup
ActiveUS9434267B2Increase the itineraryAvoid data lossCharging stationsUnmanned aerial vehiclesStandby powerEngineering
Systems and methods are provided for swapping the battery on an unmanned aerial vehicle (UAV) while providing continuous power to at least one system on the UAV. The UAV may be able to identify and land on an energy provision station autonomously. The UAV may take off and / or land on the energy provision station. The UAV may communicate with the energy provision station. The energy provision station may store and charge batteries for use on a UAV. The UAV and / or the energy provision station may have a backup energy source to provide continuous power to the UAV.
Owner:SZ DJI TECH CO LTD
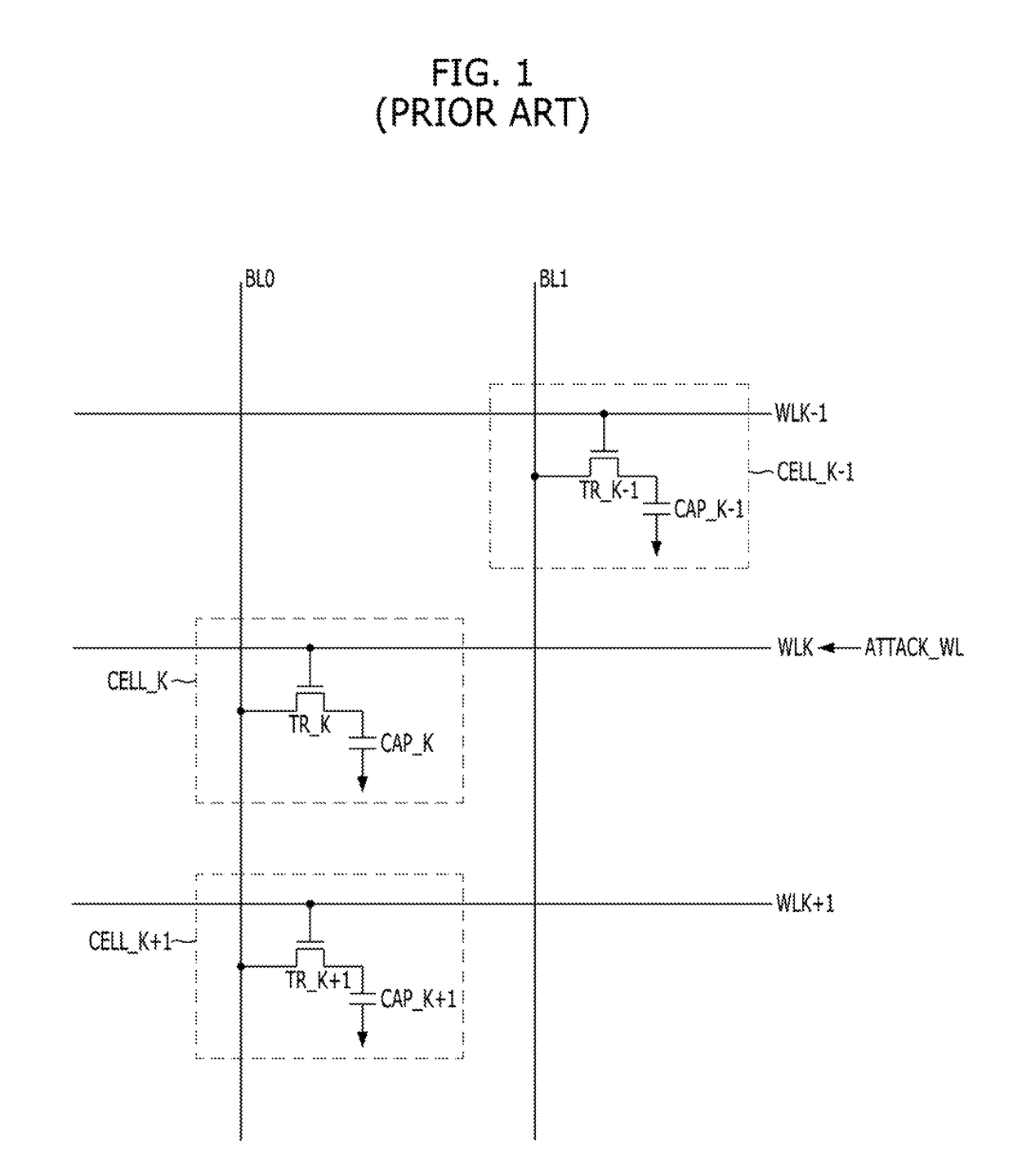
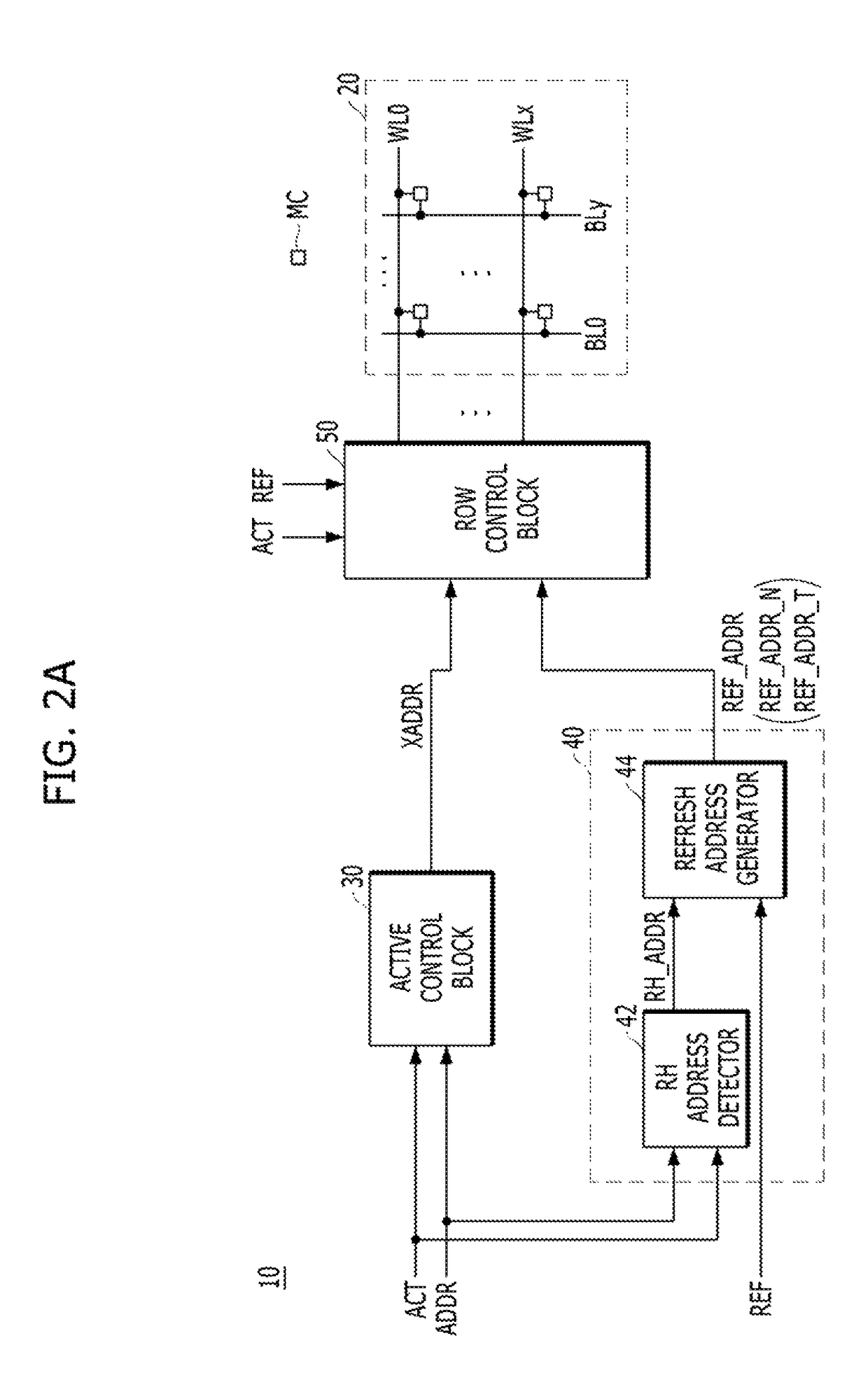
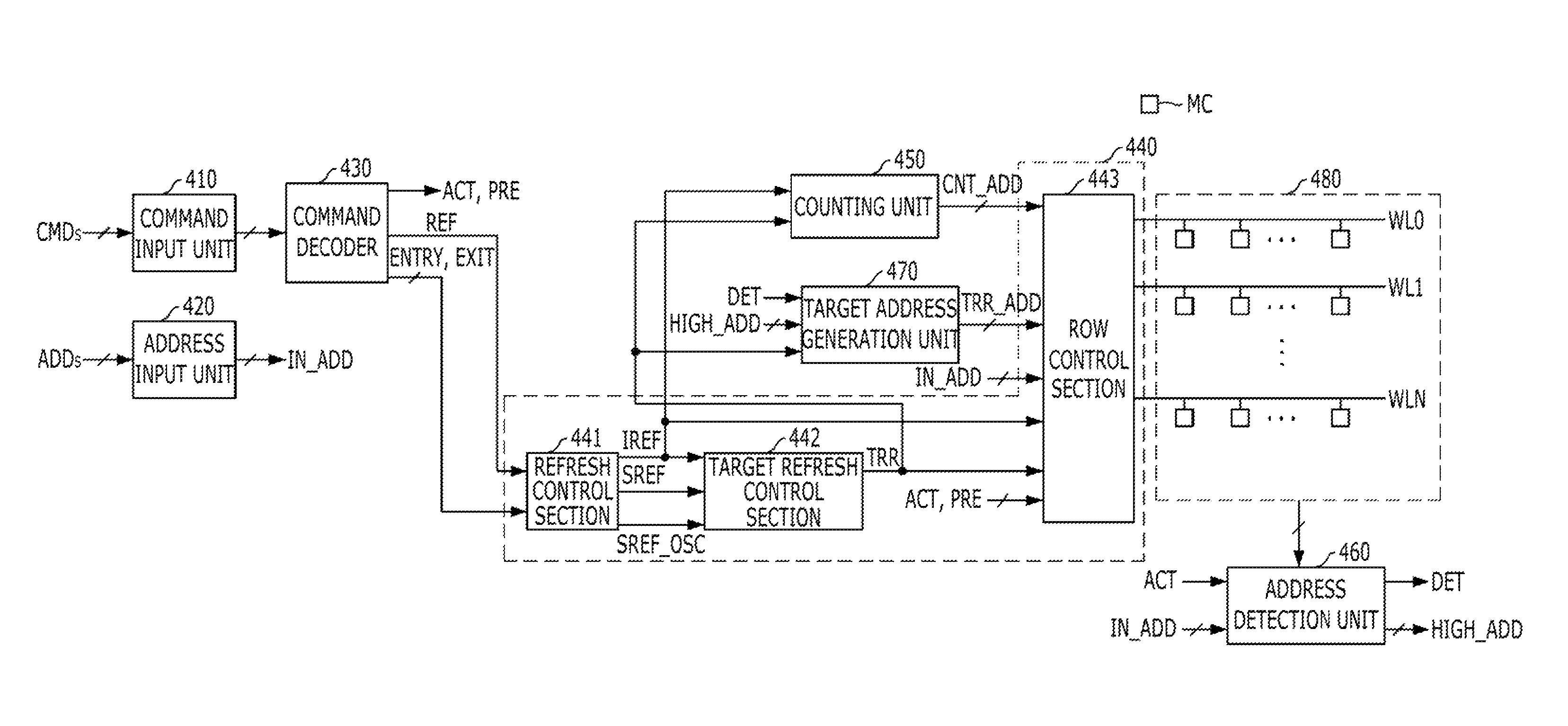
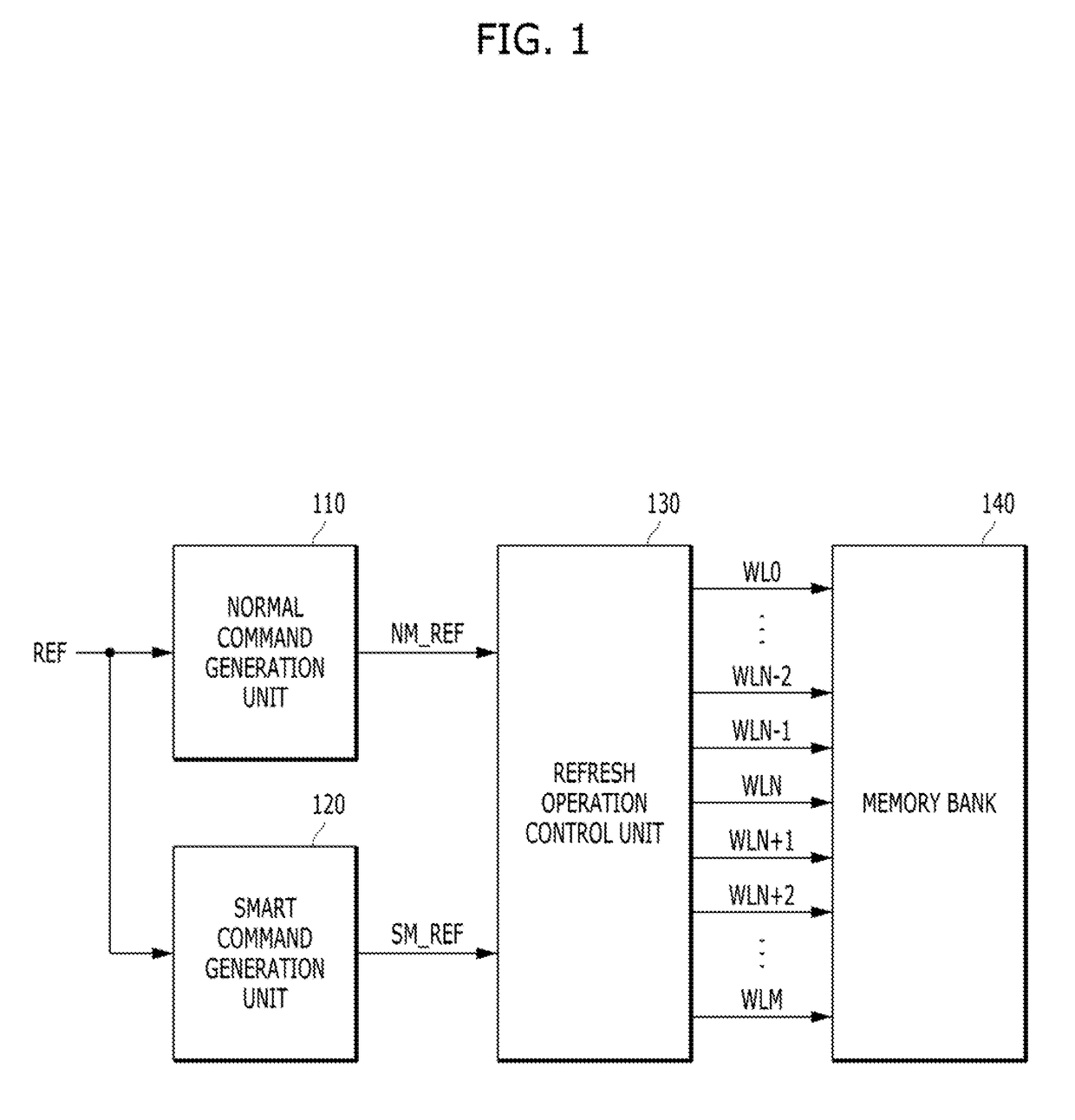
Refresh control circuit for target refresh operation of semiconductor memory device, and operating method thereof
ActiveUS9953696B2Avoid data lossMemory architecture accessing/allocationDigital storageControl circuitBit plane
A semiconductor memory device may include: a memory cell region including a plurality of memory cells coupled between a plurality of word lines and a plurality of bit lines; and a refresh control block suitable for performing a first refresh operation onto the plurality of the word lines in response to a refresh signal, counting the number of active signals that are inputted between at least two neighboring refresh signals and when the counted number of the active signals is equal to or greater than a reference number, performing a second refresh operation onto a word line corresponding to a target address.
Owner:SK HYNIX INC
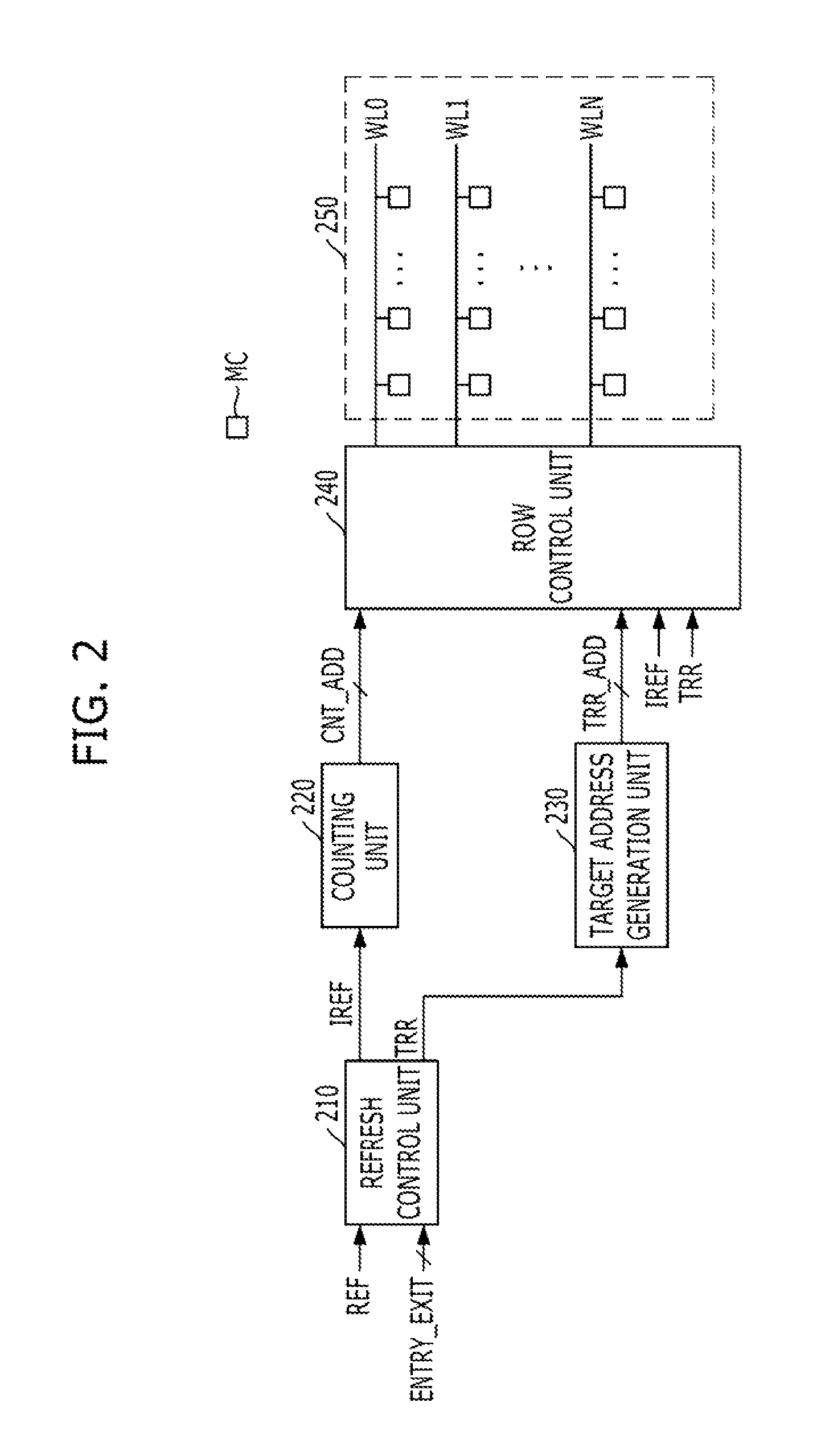
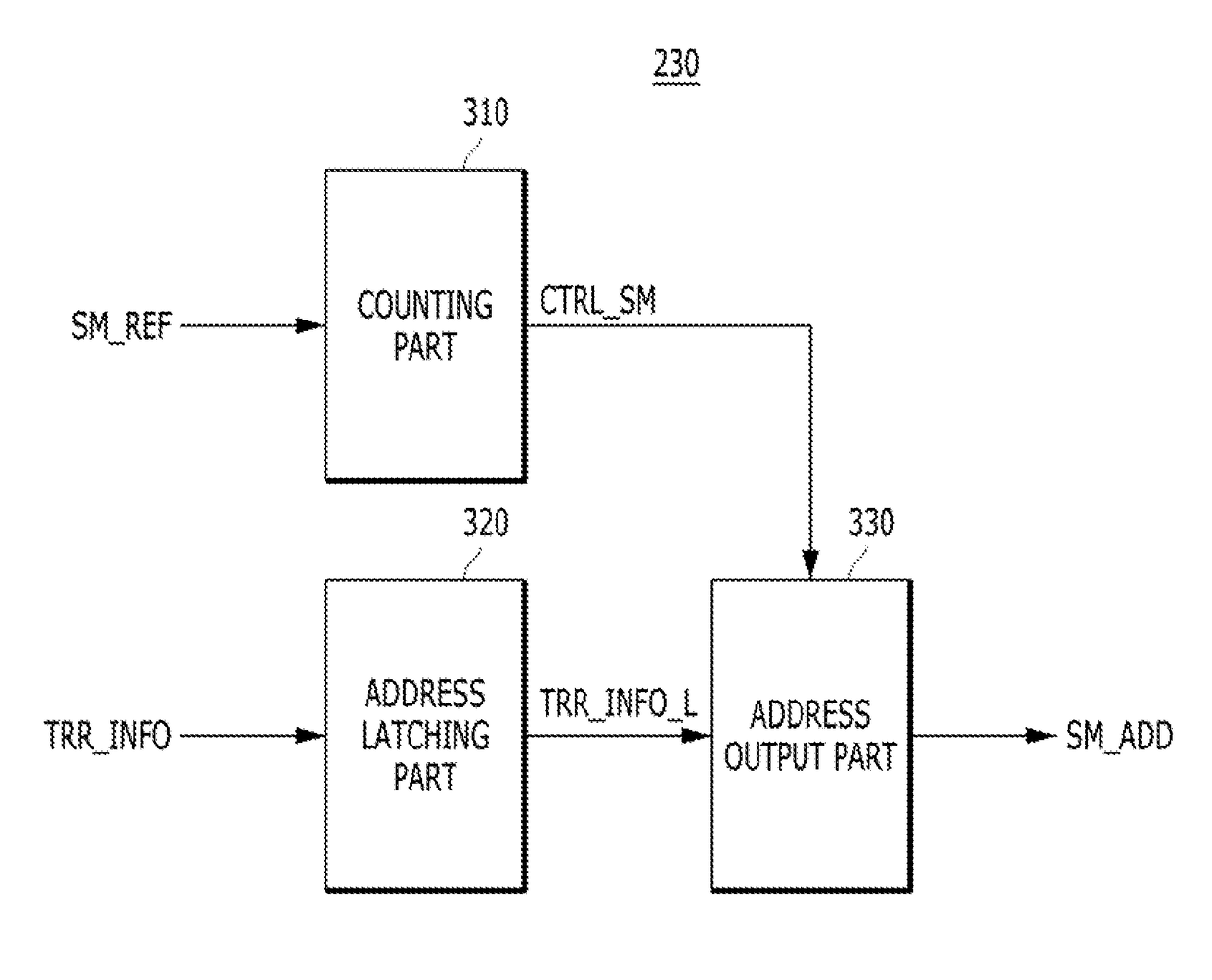
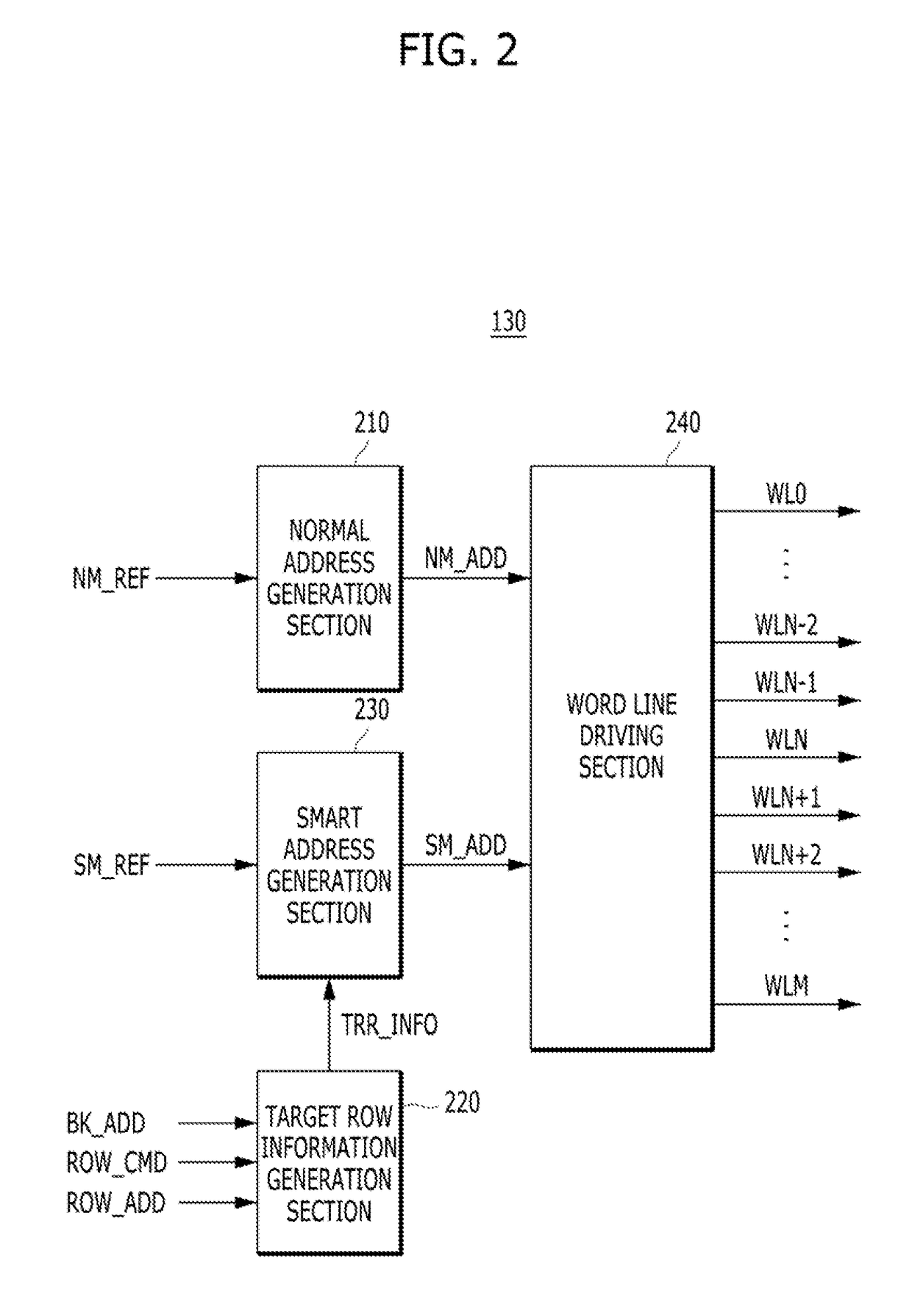
Memory and memory system for periodic targeted refresh
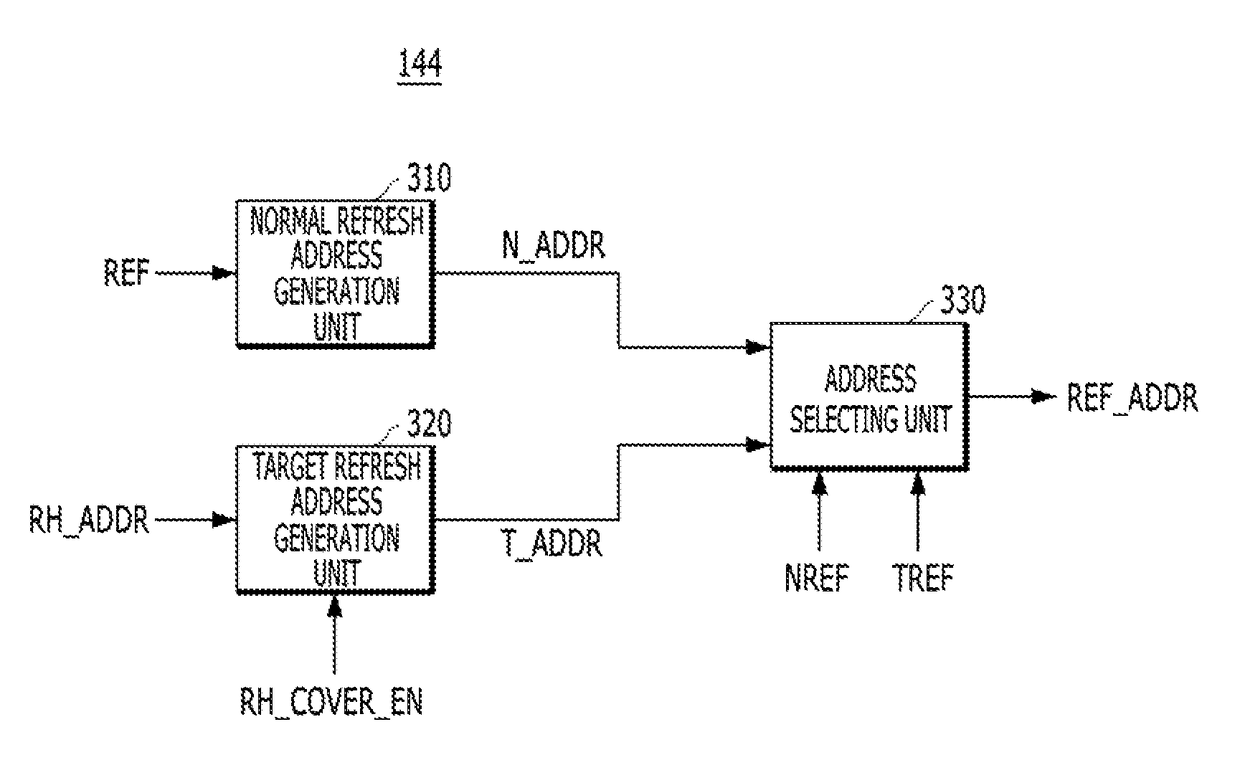
ActiveUS9311985B2Avoid data lossReduce the number of timesDigital storageAddress generation unitMemory systems
A memory includes a plurality of word lines, a target address generation unit generating one or more target addresses by using a stored address, a refresh control section activating a refresh signal in response to a refresh command that is periodically inputted and periodically activating the refresh signal in a self-refresh mode, a target refresh control section activating a target refresh signal when the refresh signal is activated M times, wherein the M is a natural number, and deactivating the target refresh signal in the self-refresh mode, and a row control section sequentially refresh a plurality of first word lines in response to the refresh signal and refreshing a second word line corresponding to the target address in response to the refresh signal when the target refresh signal is activated.
Owner:SK HYNIX INC
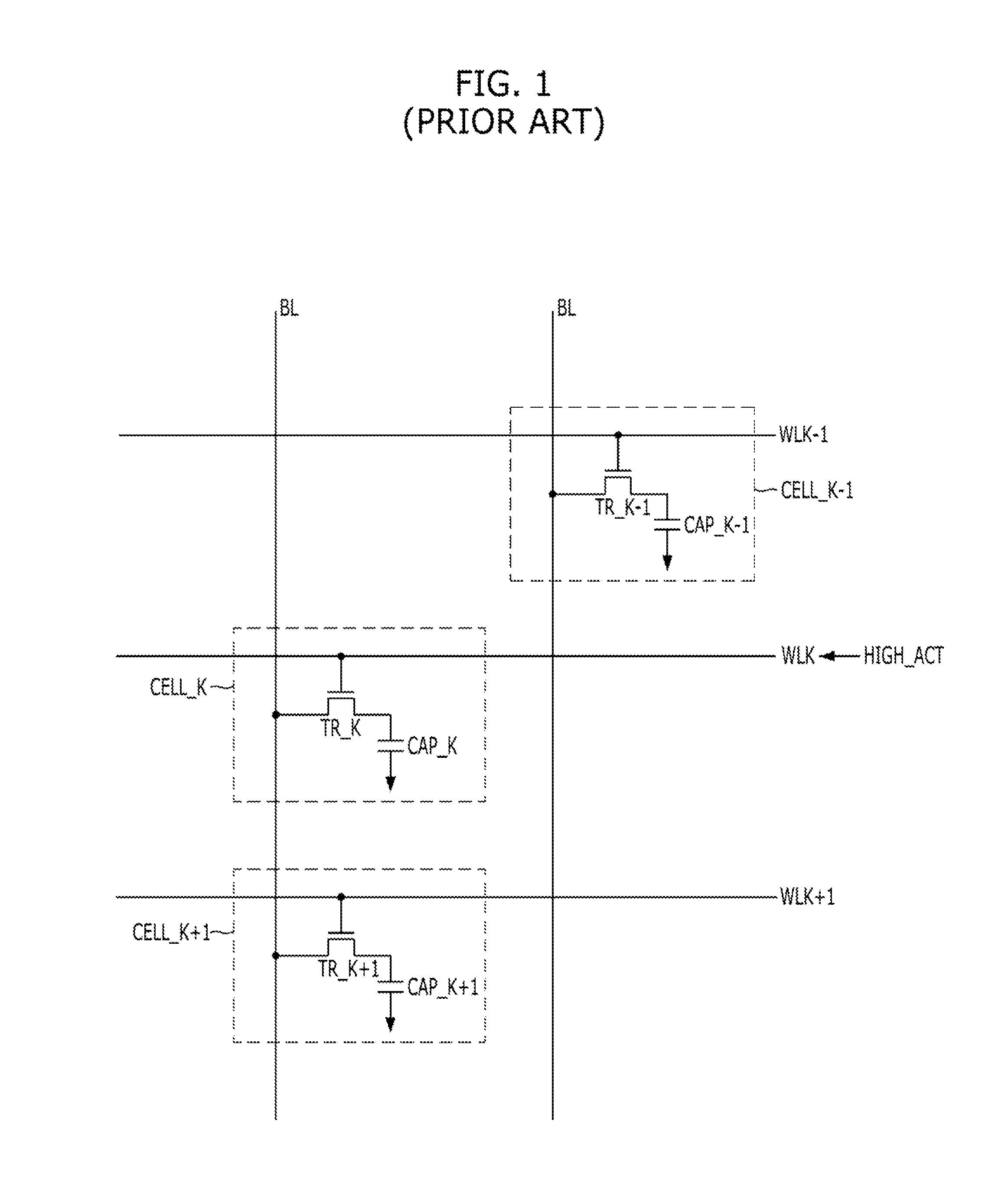
Semiconductor memory device and refresh control method thereof
A semiconductor memory device includes a memory bank including a plurality of word lines, and a refresh operation control unit suitable for performing a first refresh operation for a first adjacent word line group of a target word line of the plurality of word lines, and performing a second refresh operation for a second adjacent word line group of the target word line after the first refresh operation, in response to a smart refresh command.
Owner:SK HYNIX INC
System and method for tracking modified files in a file system
ActiveUS6983296B1Avoid data lossSufficient timeData processing applicationsDigital data processing detailsTransient storageTrace file
A technique keeps track of files that have been modified on a filer server by identifying full pathnames of files that have been modified and maintaining a listing of those pathnames for processing by the file server. The technique is illustratively-implemented by a plurality of processes executing in a file access protocol code layer of a file server embodied as a multi-protocol filer. The processes are configured to identify modified files, load the identified pathnames of the modified files onto a temporary storage element or data structure and maintain those pathnames on the data structure for a predetermined time. Thereafter, the files associated with those pathnames may be processed by a function of the filer.
Owner:NETWORK APPLIANCE INC
Computing system and method for transparent, distributed communication between computing devices
InactiveUS20050235290A1Efficient use of resourcesReduce processing timeInterprogram communicationParallel computingComputing systems
A distributed computing system and method is provided for executing block diagram software applications across multiple computing devices. A first computing device is configured to execute a first block of a block diagram software application to produce an output. The first computing device transparently communicates with a second computing device to provide the output of the first block to a second block of the block diagram software application resident on the second computing device.
Owner:AGILENT TECH INC
Adaptive computing system with modular control, switching, and power supply architecture
InactiveUS20120243160A1Low initial costSimple to deployCasings with display/control unitsPower supply for data processingModularityAdaptive computing
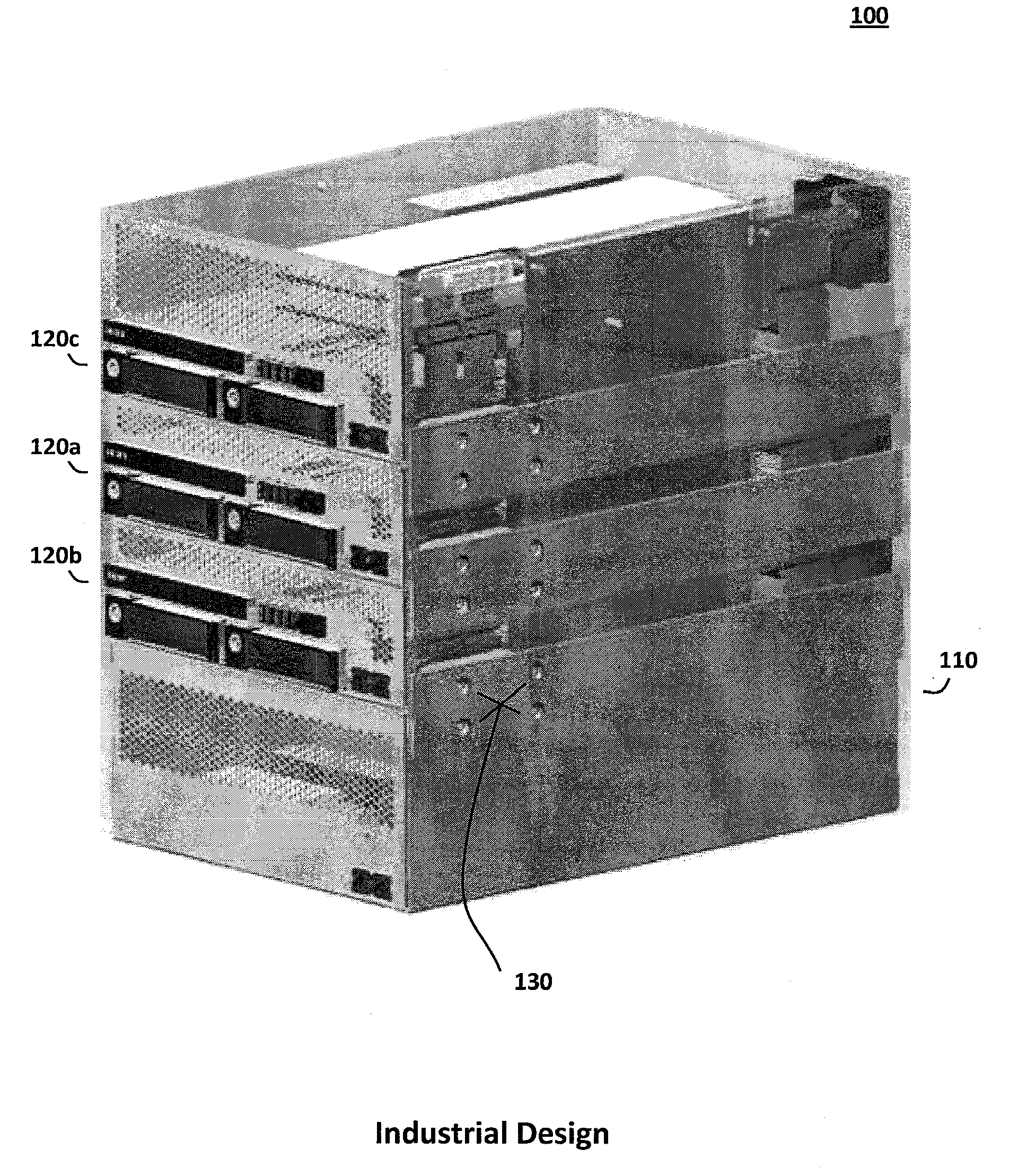
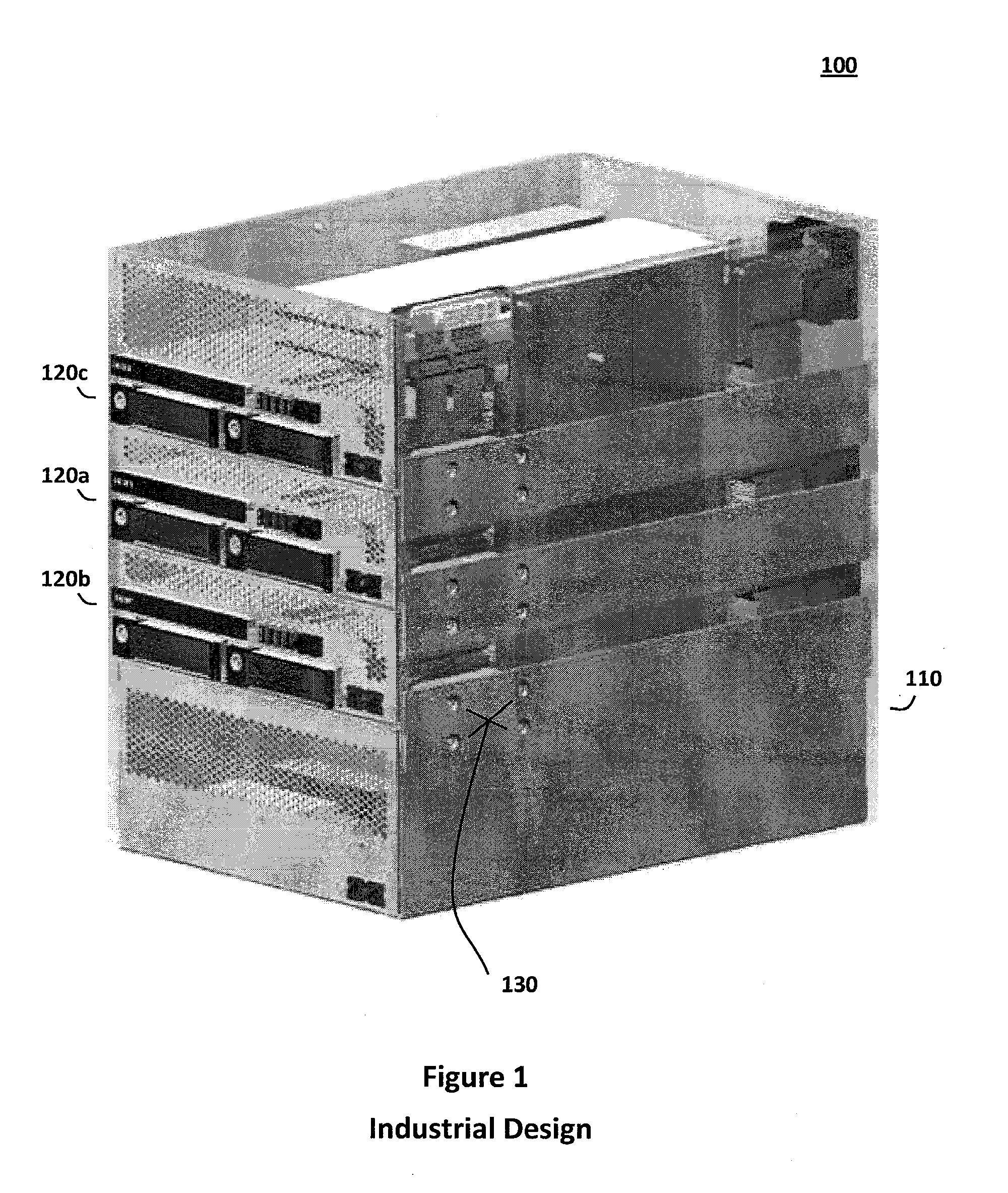
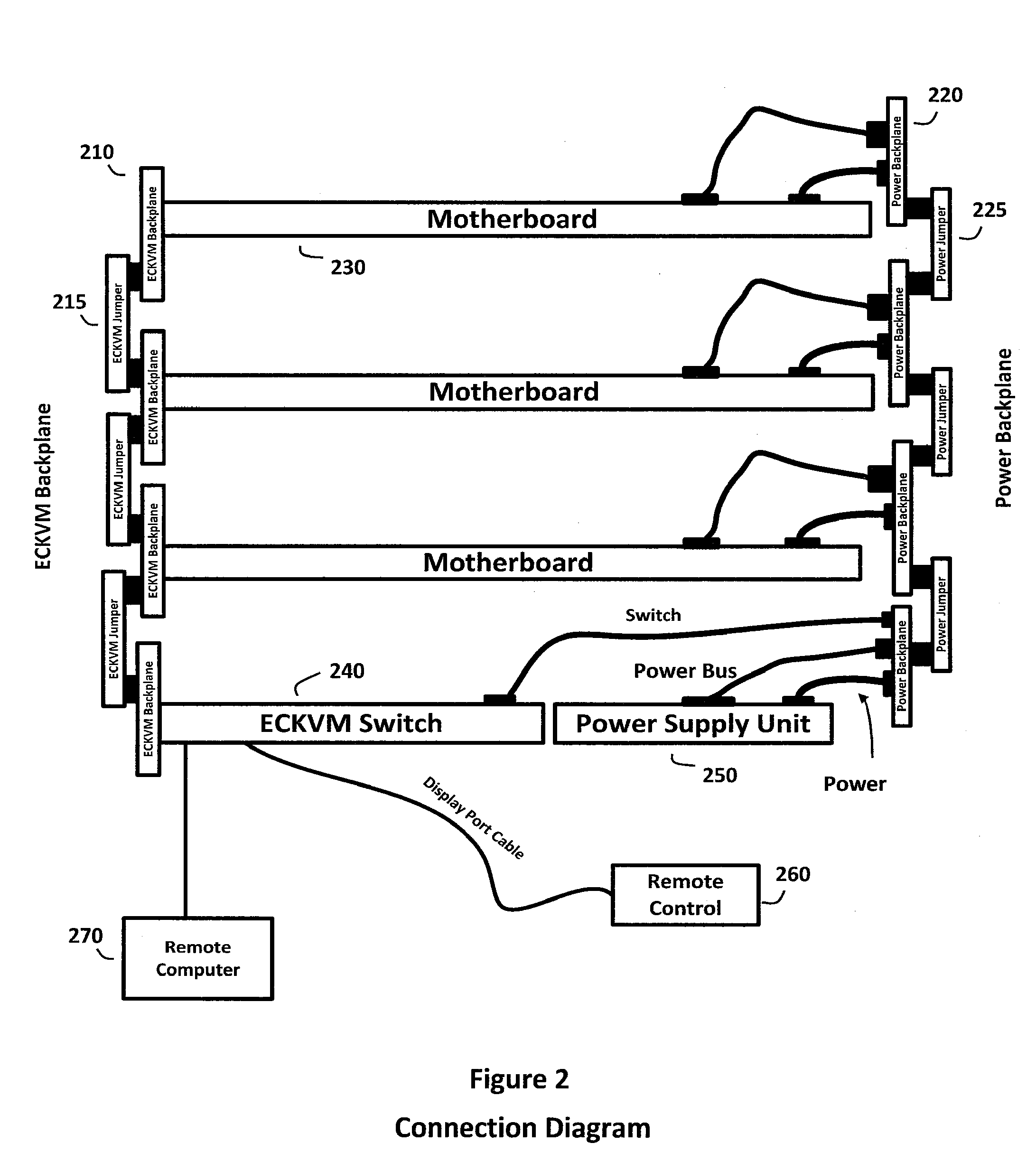
The adaptive computing system described herein may generally include a modular control, switching, and power supply architecture. In particular, the adaptive computing system may provide a platform supporting multiple independent desktop computer modules that occupy less physical space than a standalone commercial computer, provide performance density comparable to current server solutions, and address concerns relating to stability, safety, productivity, performance, assembly, service, and other factors important to diverse desktop computer user communities. Moreover, mechanical, electrical, and functional components associated with the adaptive computing system may have various certifications or otherwise be relied upon to demonstrate compliance with criteria in regulatory, environmental, consumer safety, and other contexts.
Owner:NCS TECH
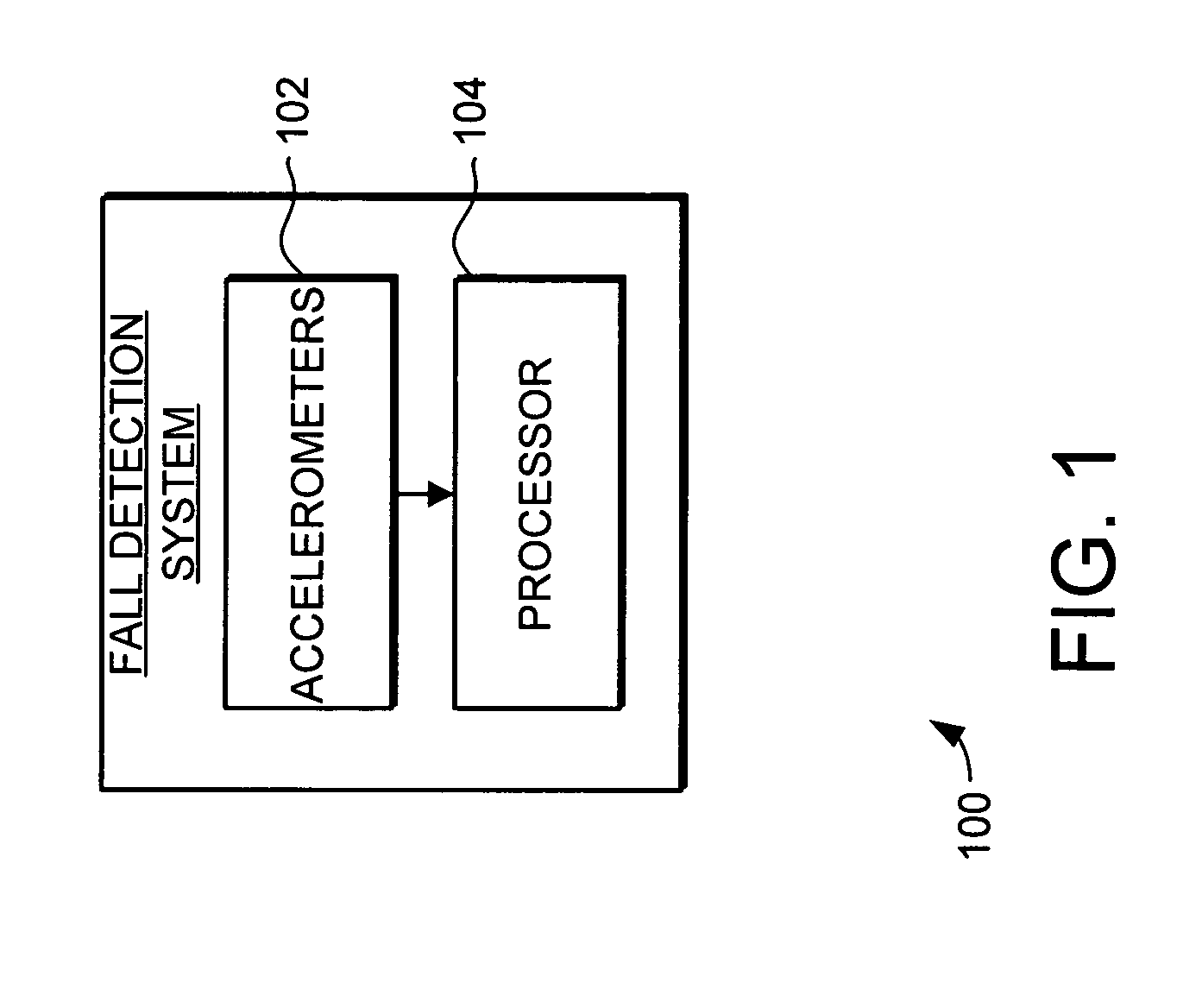
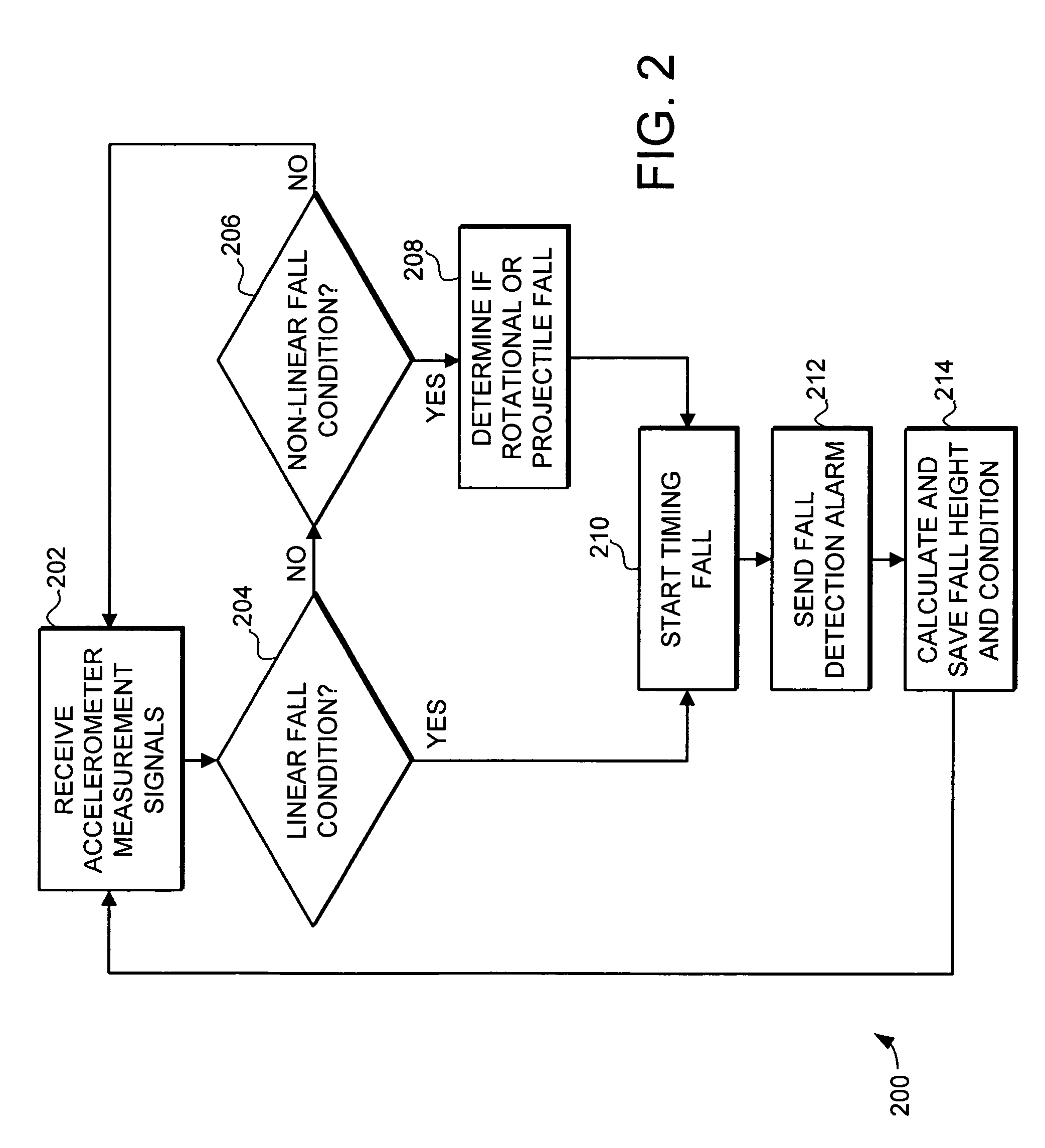
System and method for fall detection
InactiveUS7191089B2Reliably detect fallReduce negative resultDigital computer detailsRecord information storageEngineeringFall detection
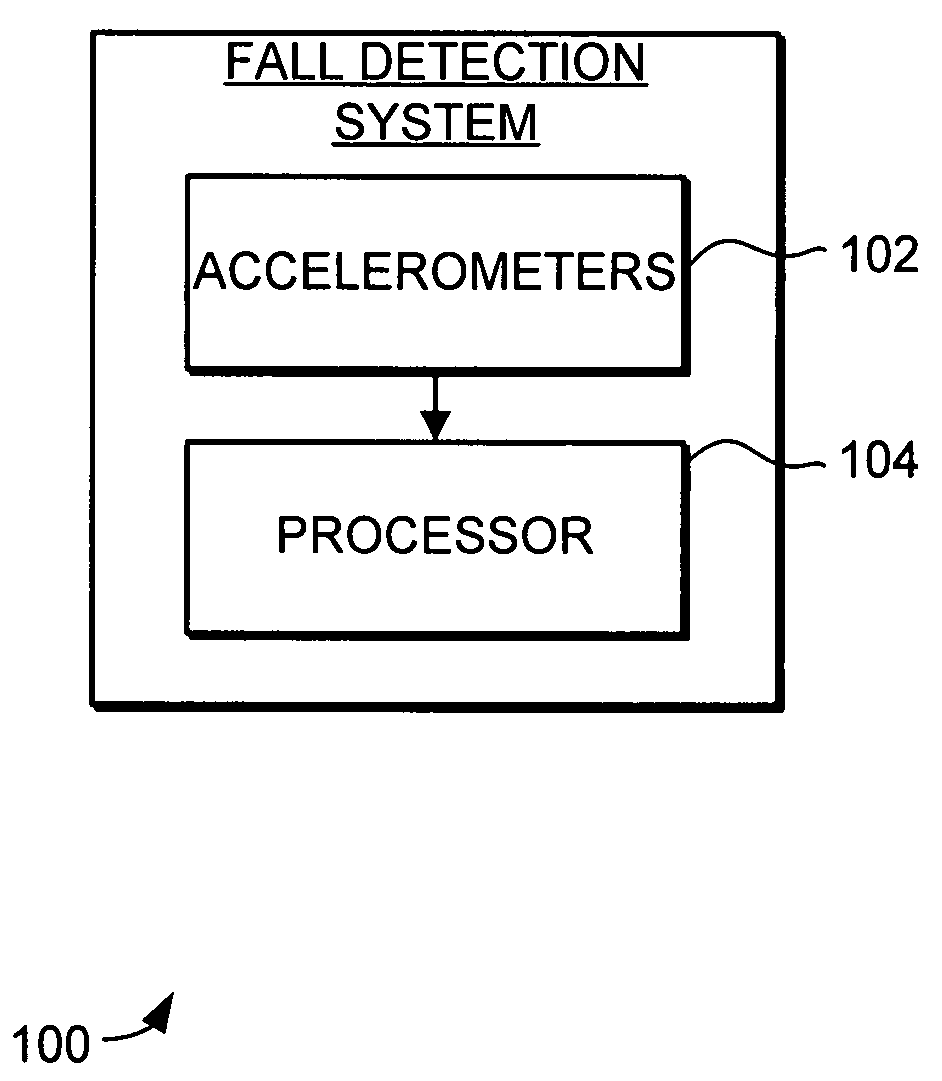
A system and method is provided for electronic device fall detection. The system and method provides the ability to reliably detect falls even in the presence of other motion in the electronic device. The fall detection system includes a plurality of accelerometers and a processor. The plurality of accelerometers provides acceleration measurements to the processor, with these measurements describing the current acceleration of the electronic device in all directions. The processor receives the acceleration measurements and compares the acceleration measurements to a value range to determine if the device is currently falling. Furthermore, the system and method can reliably detect a non-linear fall, such as when the fall is accompanied with device rotation or initiated by additional external force. To detect a non-linear fall, the processor compares combinations of acceleration measurements to a value range and further determines the smoothness of the acceleration measurement combinations.
Owner:NORTH STAR INNOVATIONS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com