Patents
Literature
7899results about "Redundant hardware error correction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
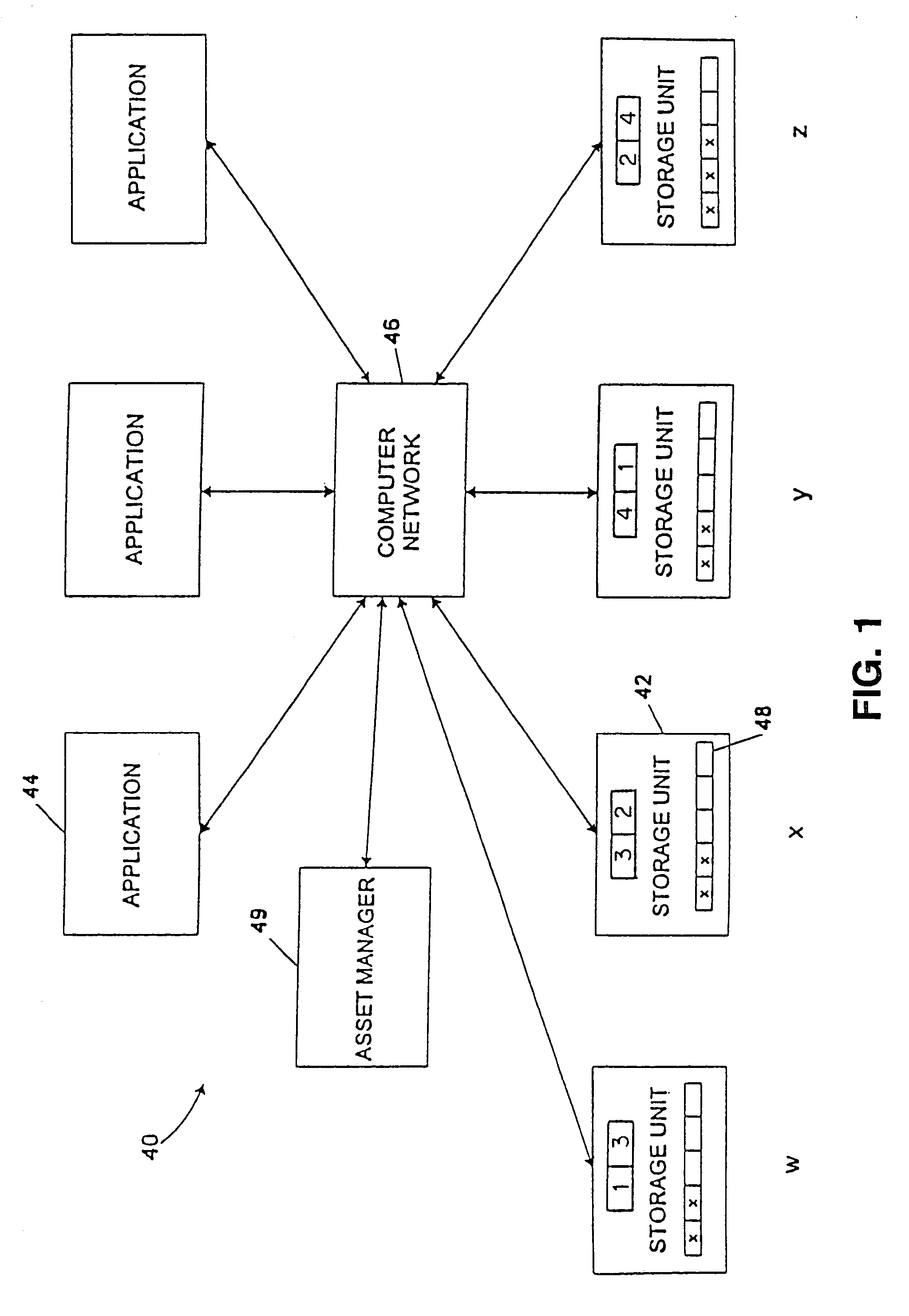
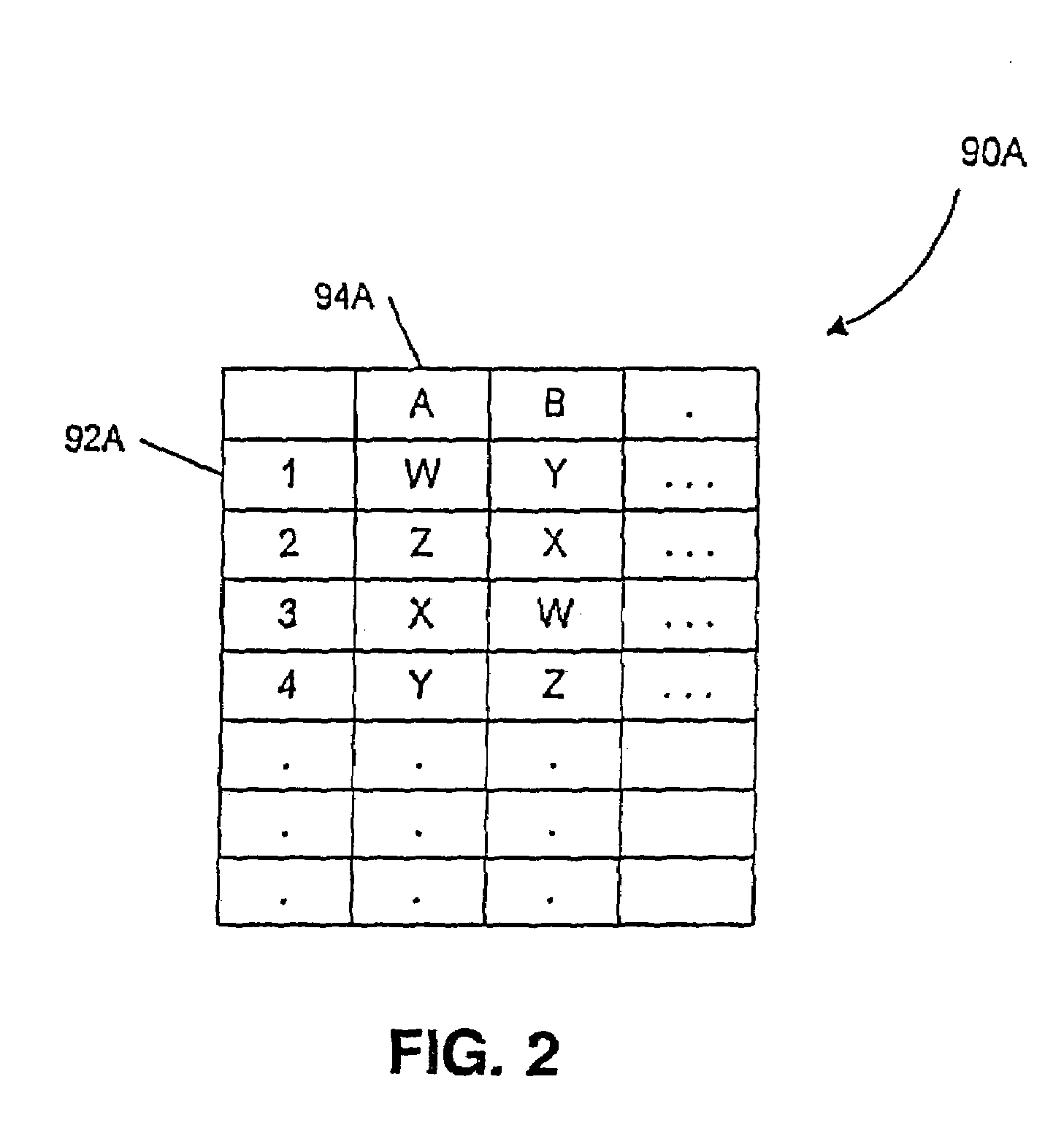
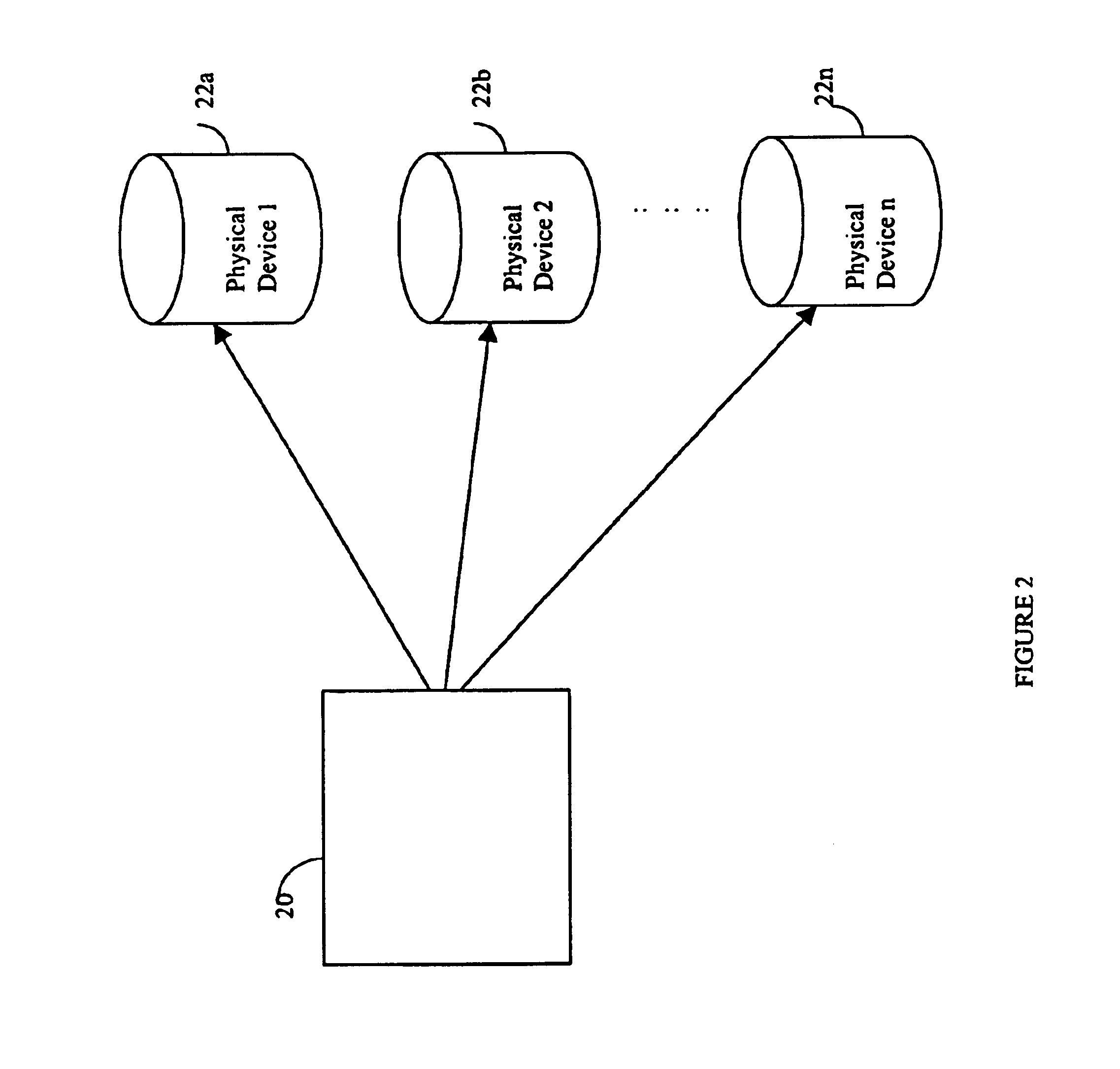
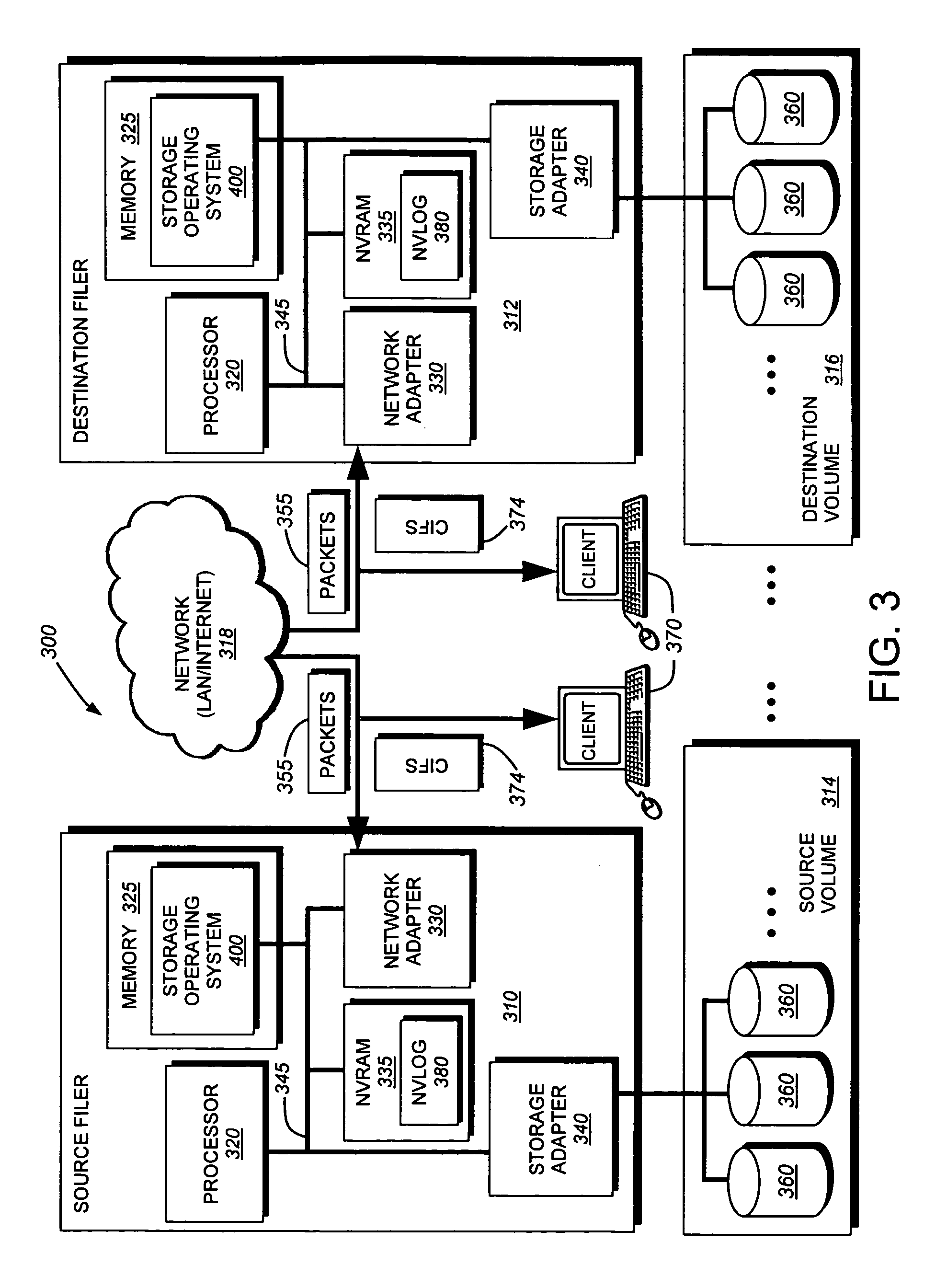
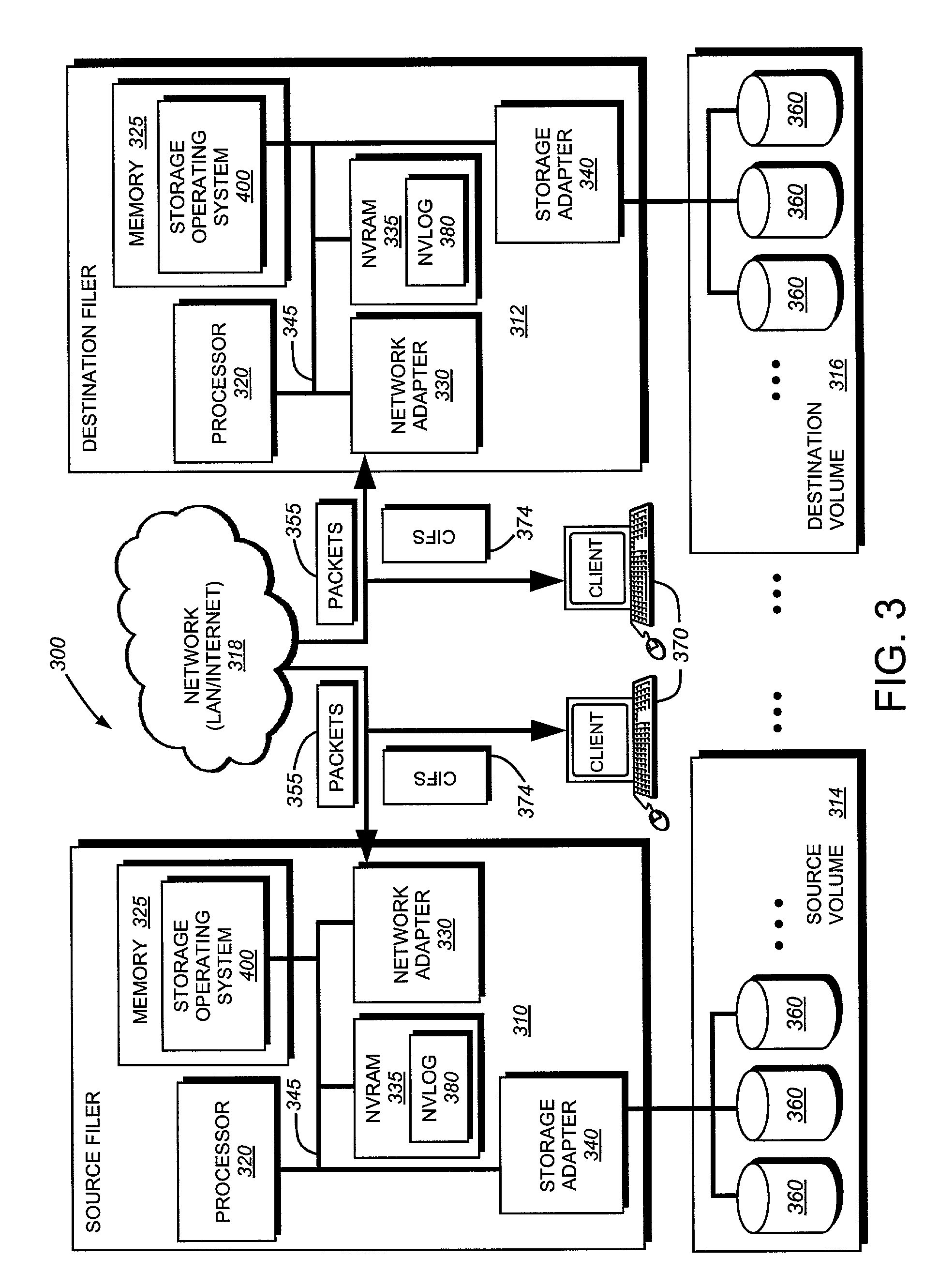
Computer system and process for transferring multiple high bandwidth streams of data between multiple storage units and multiple applications in a scalable and reliable manner
InactiveUS7111115B2Improve reliabilityImprove scalabilityInput/output to record carriersData processing applicationsHigh bandwidthData segment
Multiple applications request data from multiple storage units over a computer network. The data is divided into segments and each segment is distributed randomly on one of several storage units, independent of the storage units on which other segments of the media data are stored. At least one additional copy of each segment also is distributed randomly over the storage units, such that each segment is stored on at least two storage units. This random distribution of multiple copies of segments of data improves both scalability and reliability. When an application requests a selected segment of data, the request is processed by the storage unit with the shortest queue of requests. Random fluctuations in the load applied by multiple applications on multiple storage units are balanced nearly equally over all of the storage units. This combination of techniques results in a system which can transfer multiple, independent high-bandwidth streams of data in a scalable manner in both directions between multiple applications and multiple storage units.
Owner:AVID TECHNOLOGY
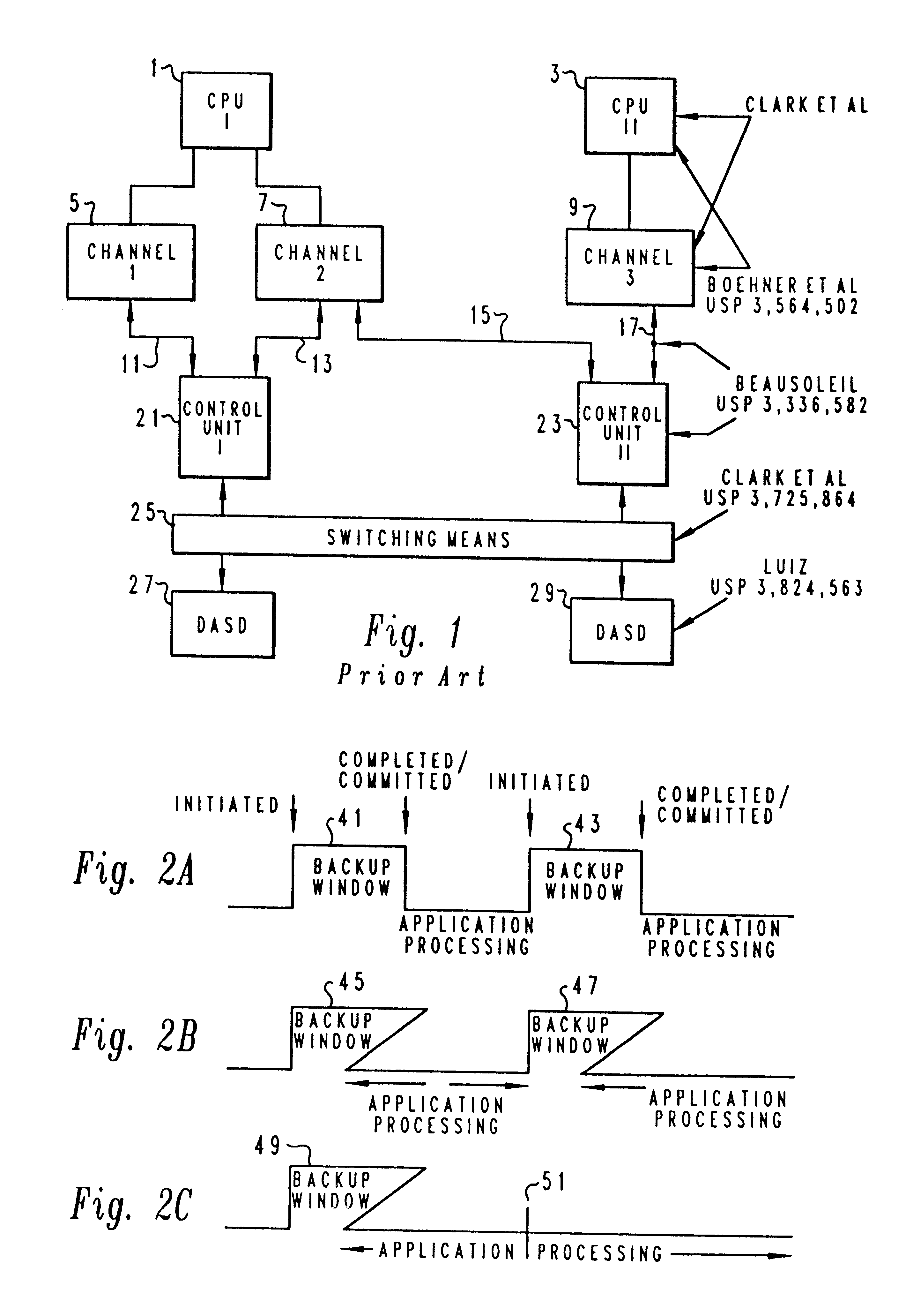
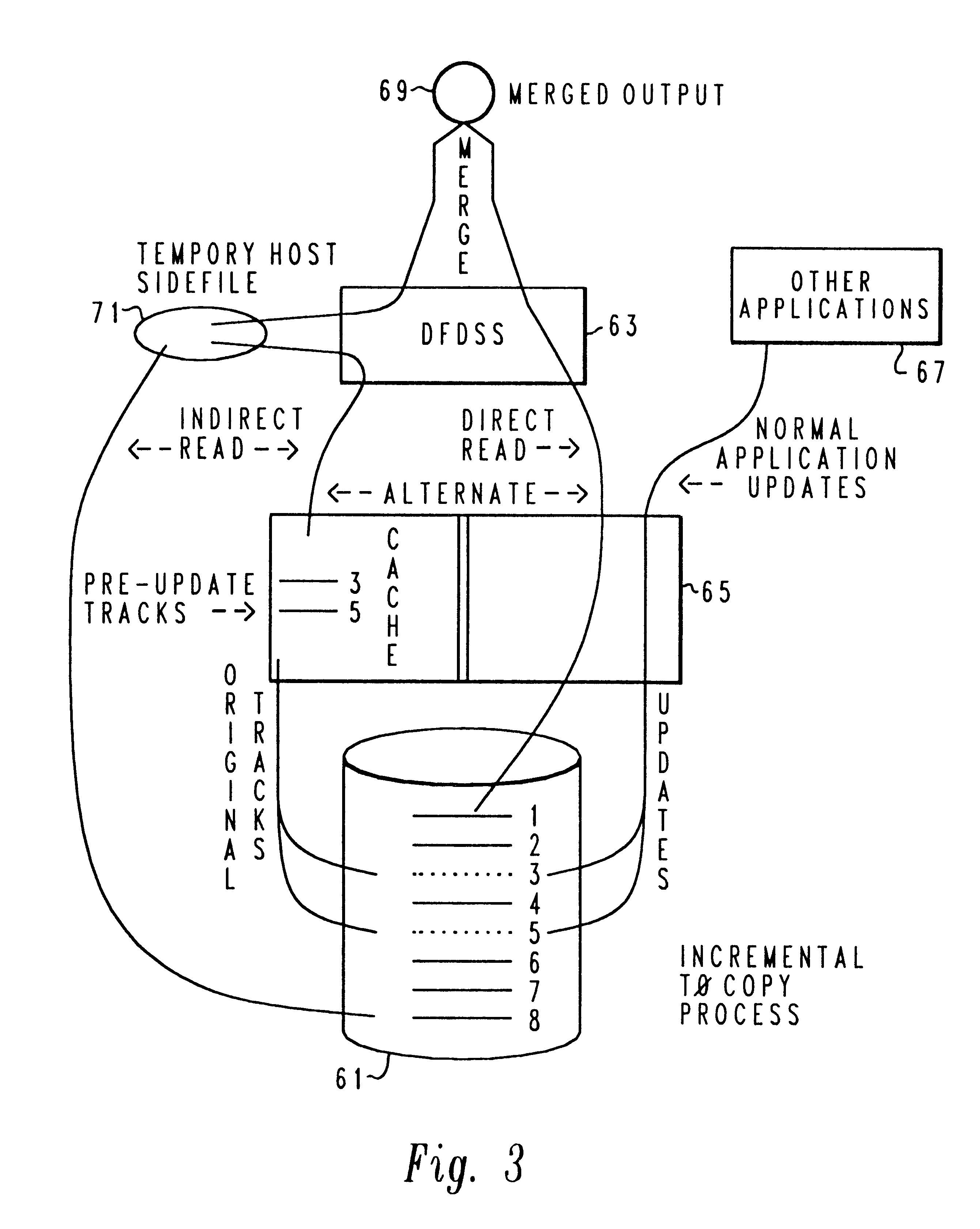
Method and system for incremental time zero backup copying of data
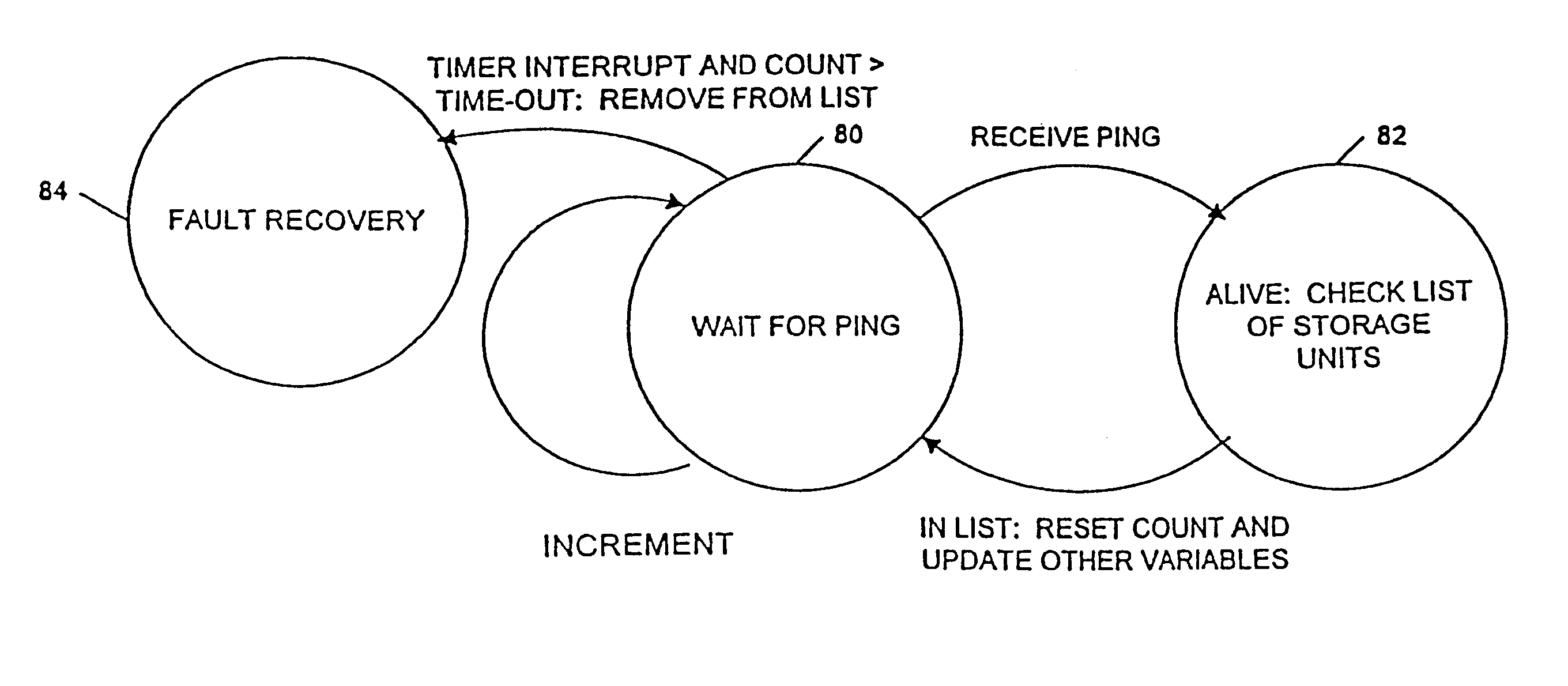
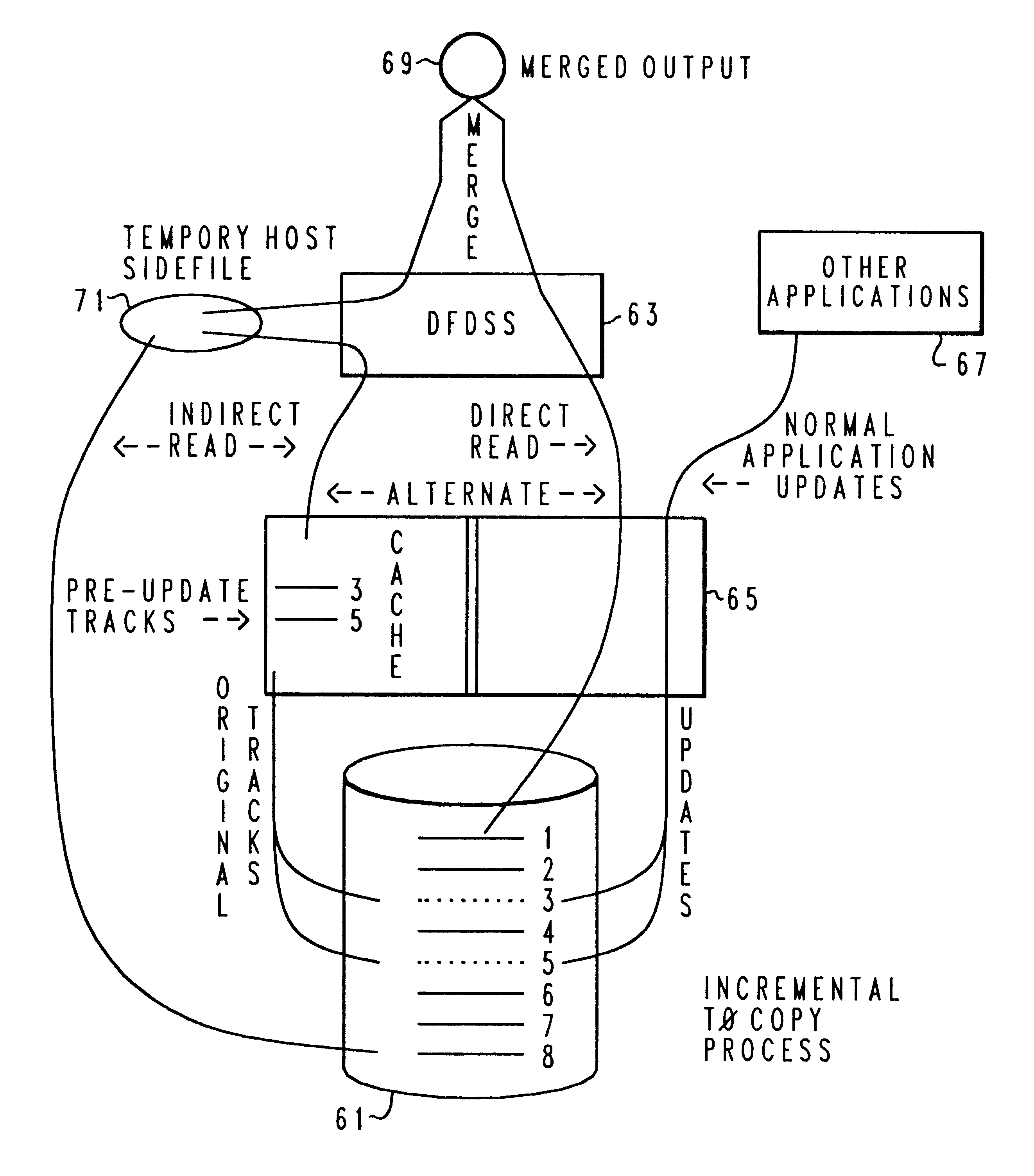
InactiveUSRE37601E1Maintaining continued availability of datasetsReduce suspensionRedundant operation error correctionMemory systemsData processing systemData set
Backup copying of designated datasets representing a first selected point in time consistency may be performed in a data processing system on an attached storage subsystem concurrent with data processing system application execution by first suspending application execution only long enough to form a logical-to-physical address concordance, and thereafter physically backing up the datasets on the storage subsystem on a scheduled or opportunistic basis. An indication of each update to a selected portion of the designated datasets which occurs after the first selected point in time is stored and application initiated updates to uncopied designated datasets are first buffered. Thereafter, sidefiles are made of the affected datasets, or portions thereof, the updates are then written through to the storage subsystem, and the sidefiles written to an alternate storage location in backup copy order, as controlled by the address concordance. At a subsequent point in time only those portions of the designated datasets which have been updated after the first selected period and time are copied, utilizing an identical technique.
Owner:IBM CORP
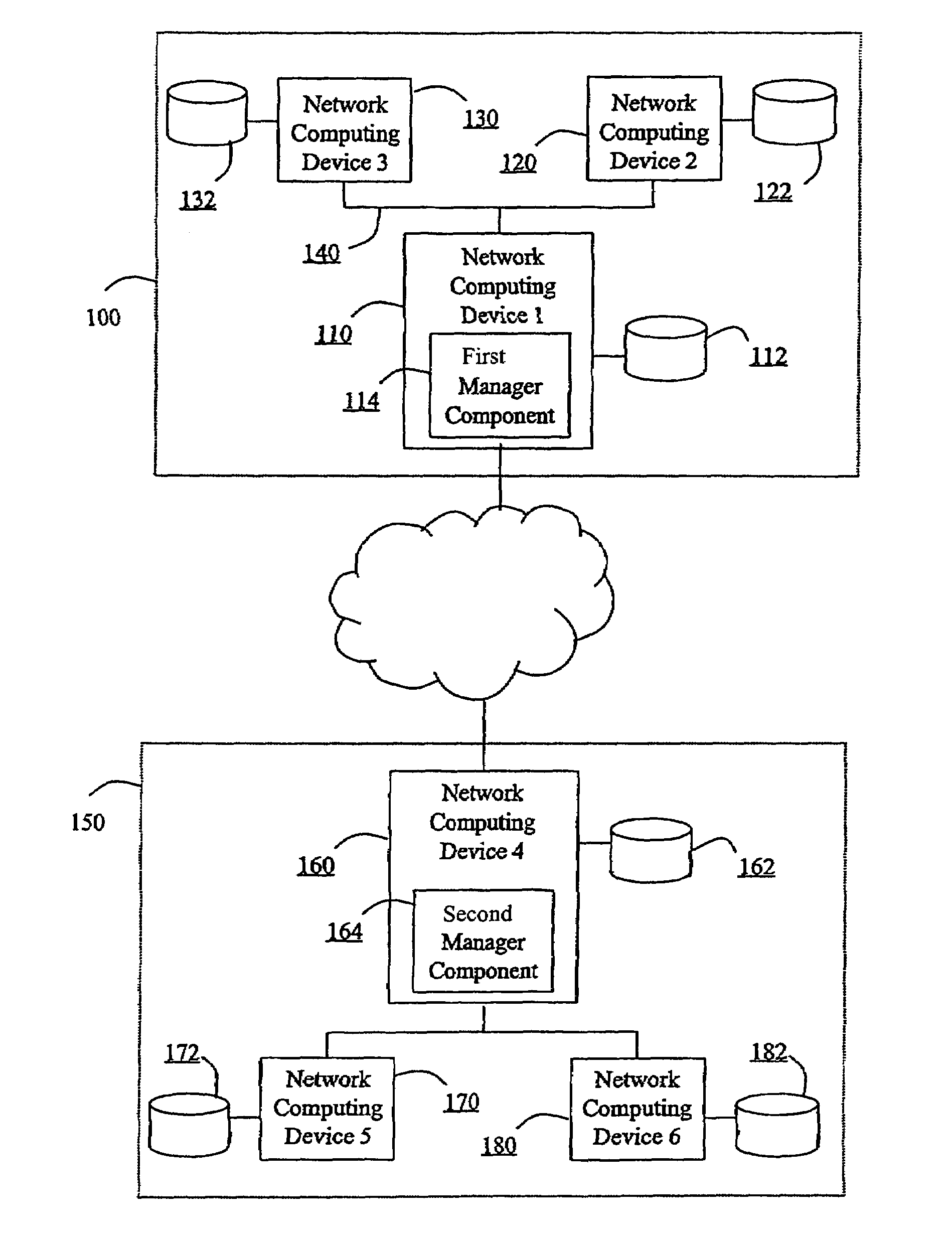
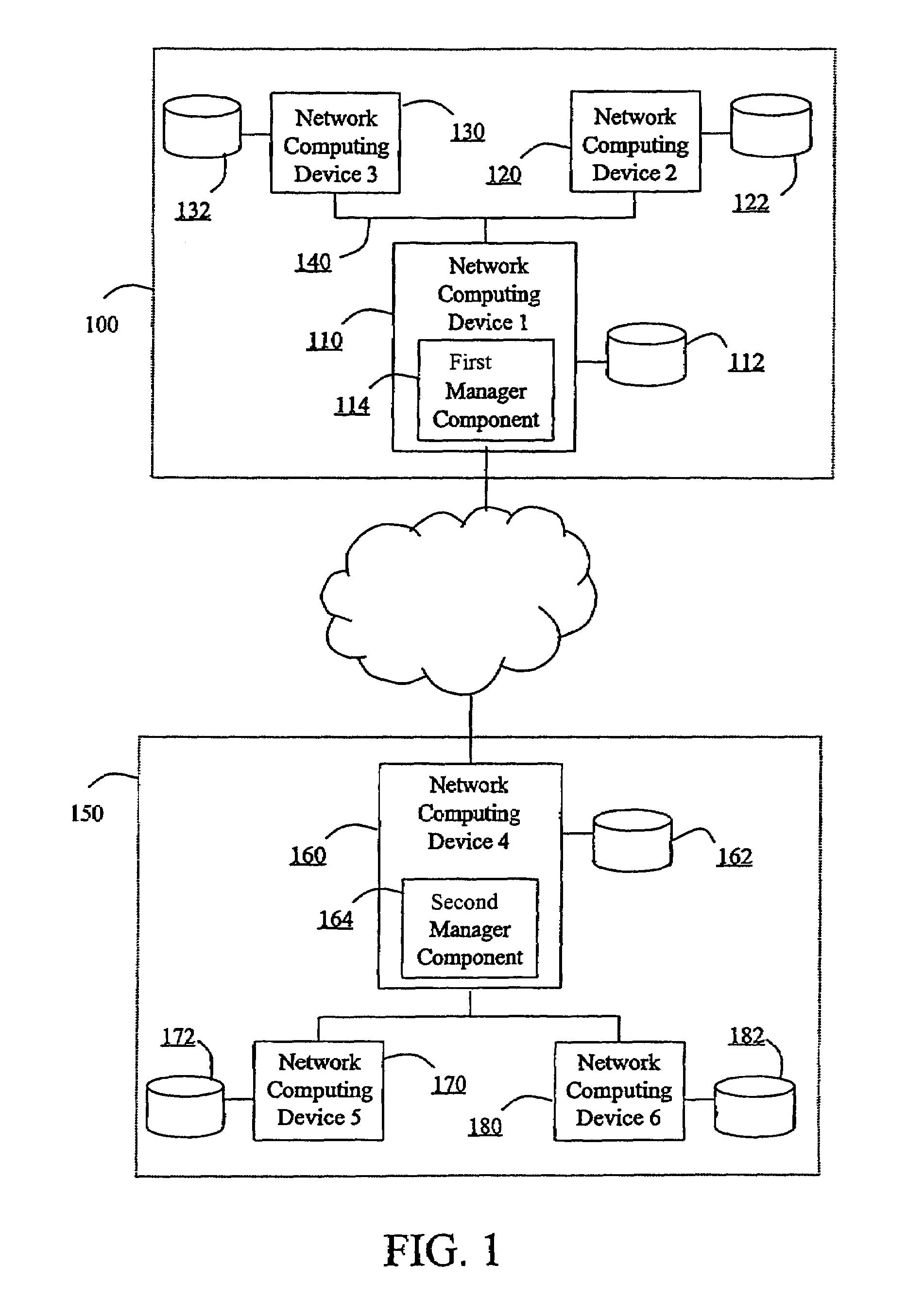
Hierarchical backup and retrieval system
InactiveUS7395282B1Data processing applicationsDigital data processing detailsSoftware agentAdministrative controls
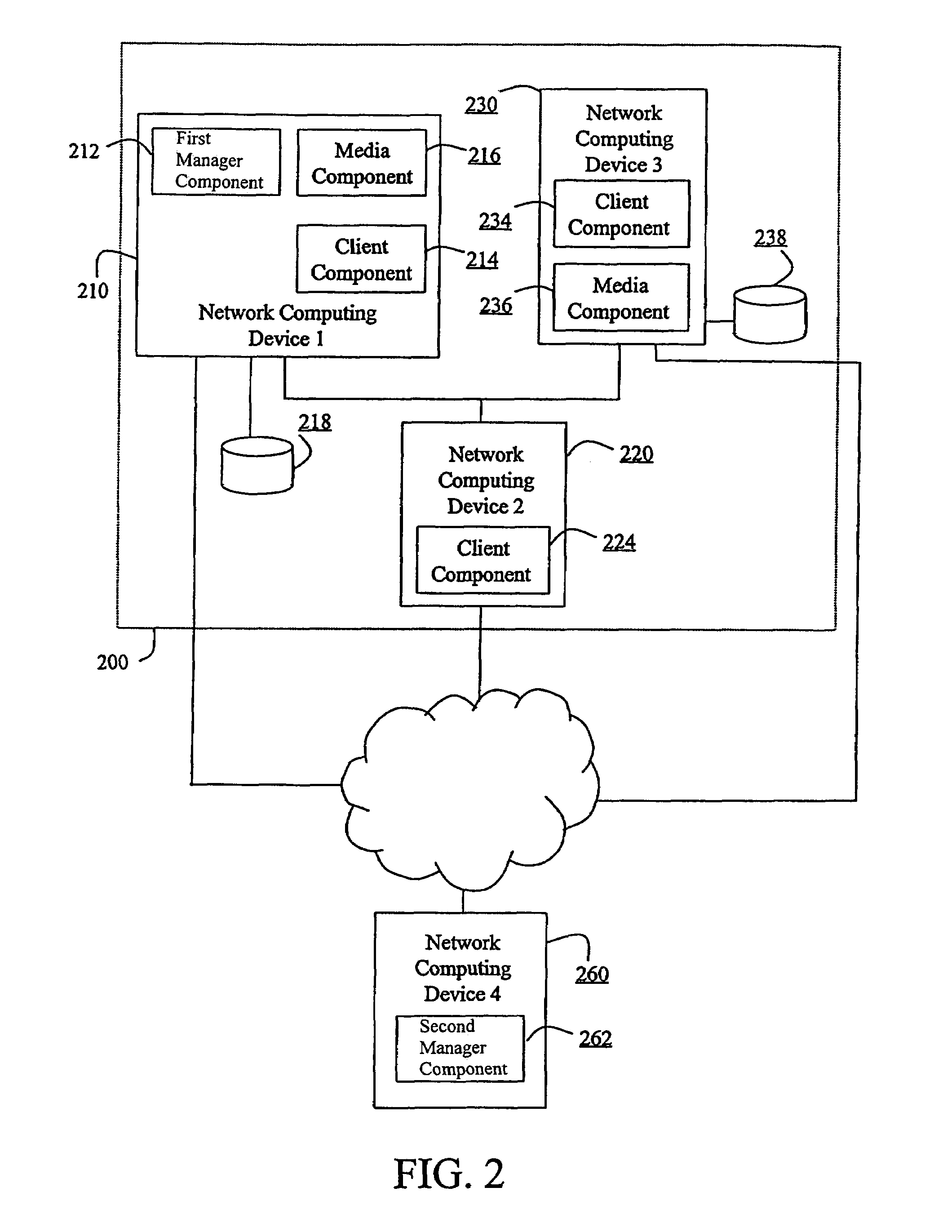
The invention is a hierarchical backup system. The interconnected network computing devices are put into groups of backup cells. A backup cell has a manager software agent responsible maintaining and initiating a backup regime for the network computing devices in the backup cell. The backups are directed to backup devices within the backup cell. Several backup cells can be defined. A manager software agent for a particular cell may be placed into contact with the manager software agent of another cell, by which information about the cells may be passed back and forth. Additionally, one of the software agents may be given administrative control over another software agent with which it is in communication.
Owner:COMMVAULT SYST INC
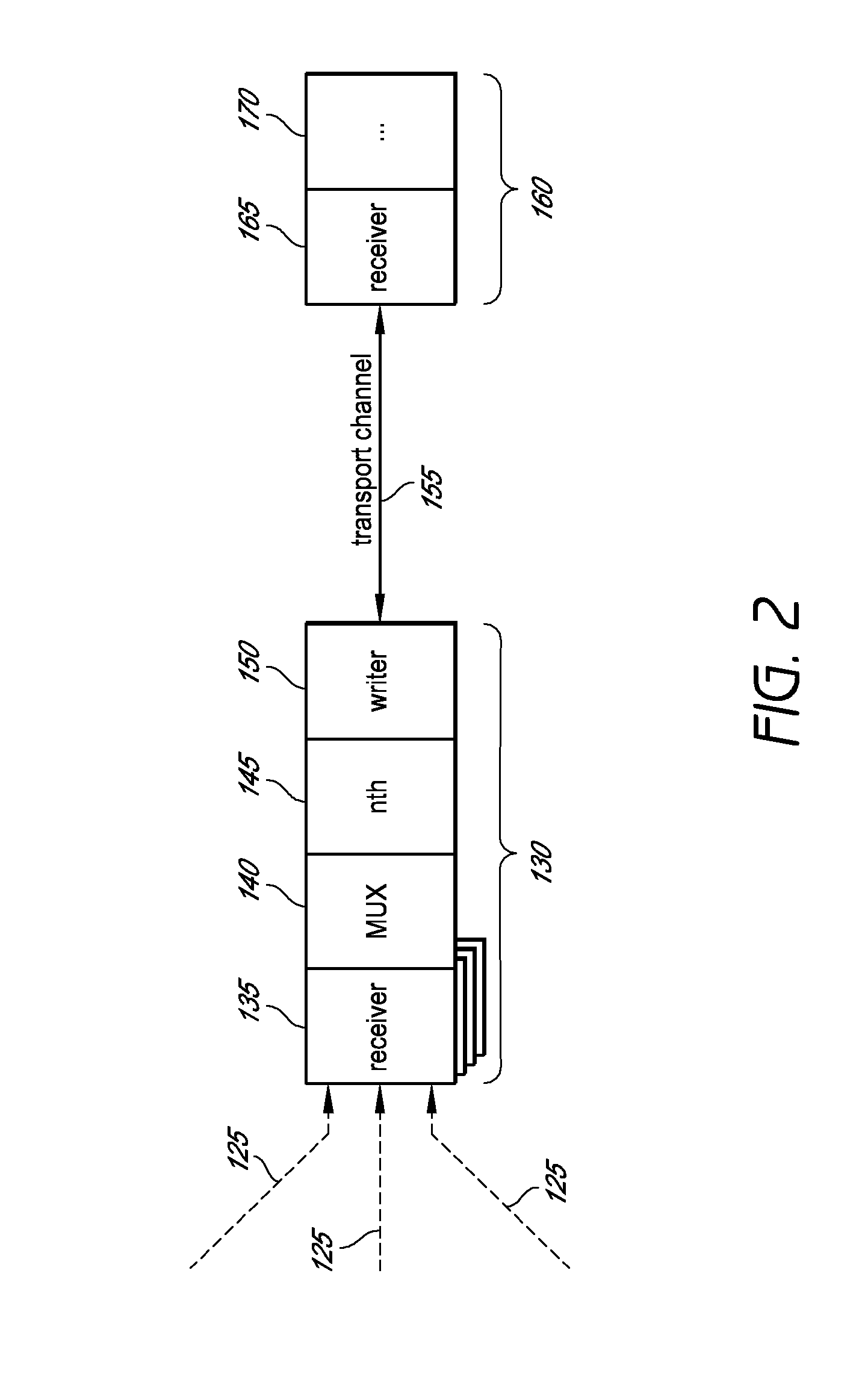
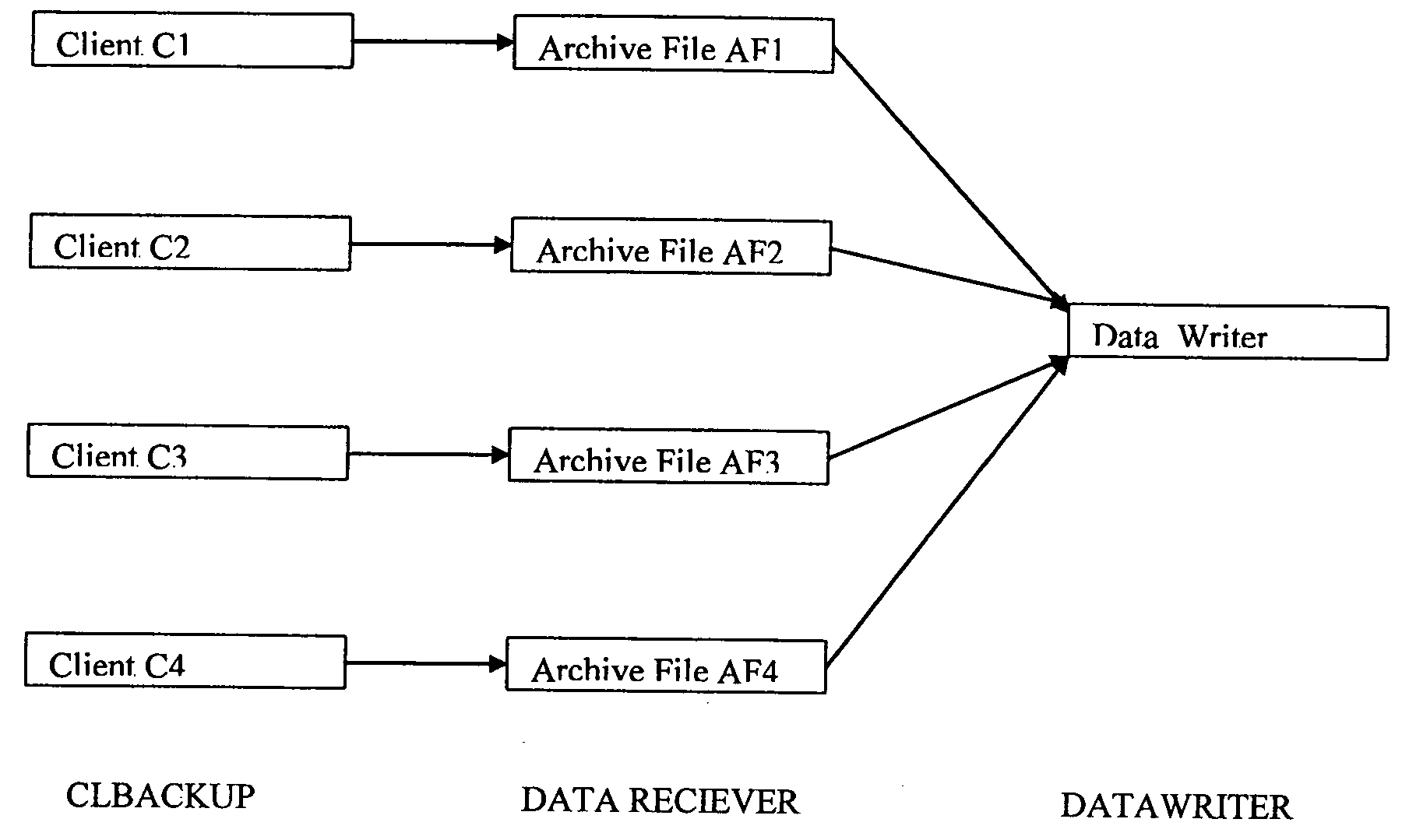
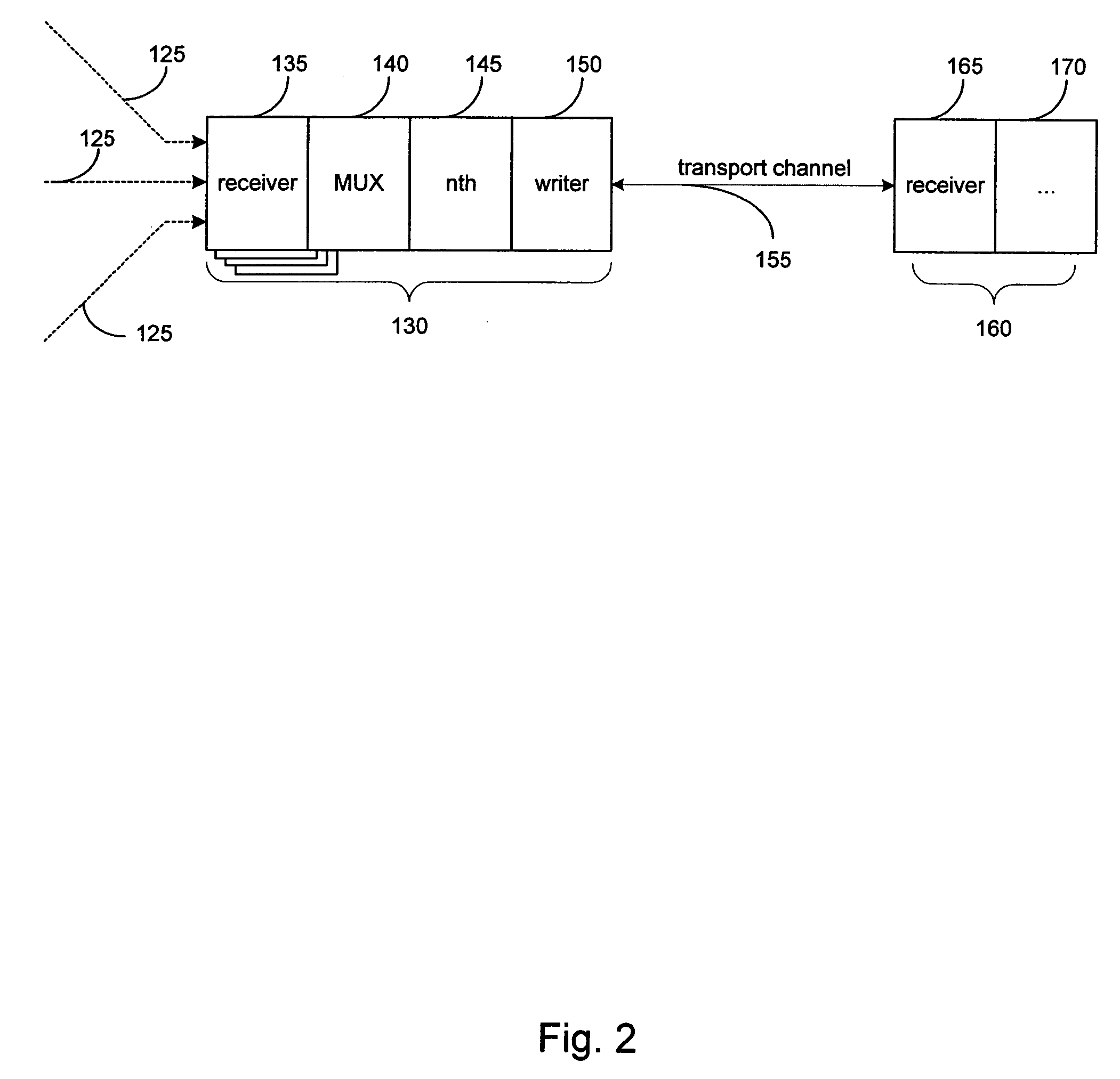
System and method for combining data streams in pipelined storage operations in a storage network
Described herein are systems and methods for multiplexing pipelined data for backup operations. Various data streams are combined such as by multiplexing by a multiplexing module. The multiplexing module combines the data from the various data streams received by receiver module(s) into a single stream of chunks. The multiplexing module may combine data from multiple archive files into a single chunk. Additional modules perform other operations on the chunks of data to be transported such as encryption, compression, etc. The data chunks are transmitted via a transport channel to a receive pipeline that includes a second receiver module and other modules. The data chunks are then stored in a backup medium. The chunks are later retrieved and separated such as by demultiplexing for restoring to a client or for further storage as auxiliary copies of the separated data streams or archive files.
Owner:COMMVAULT SYST INC
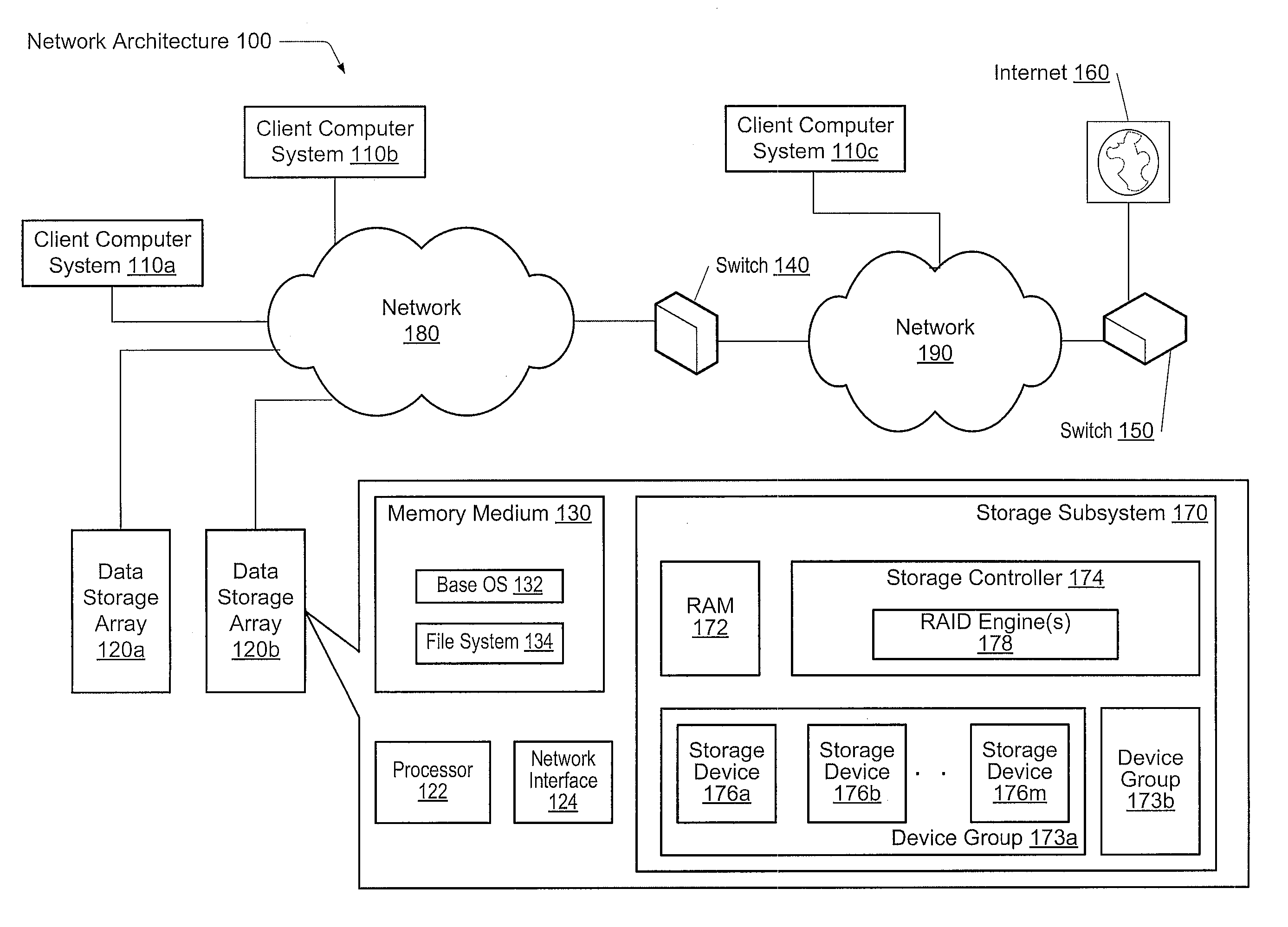
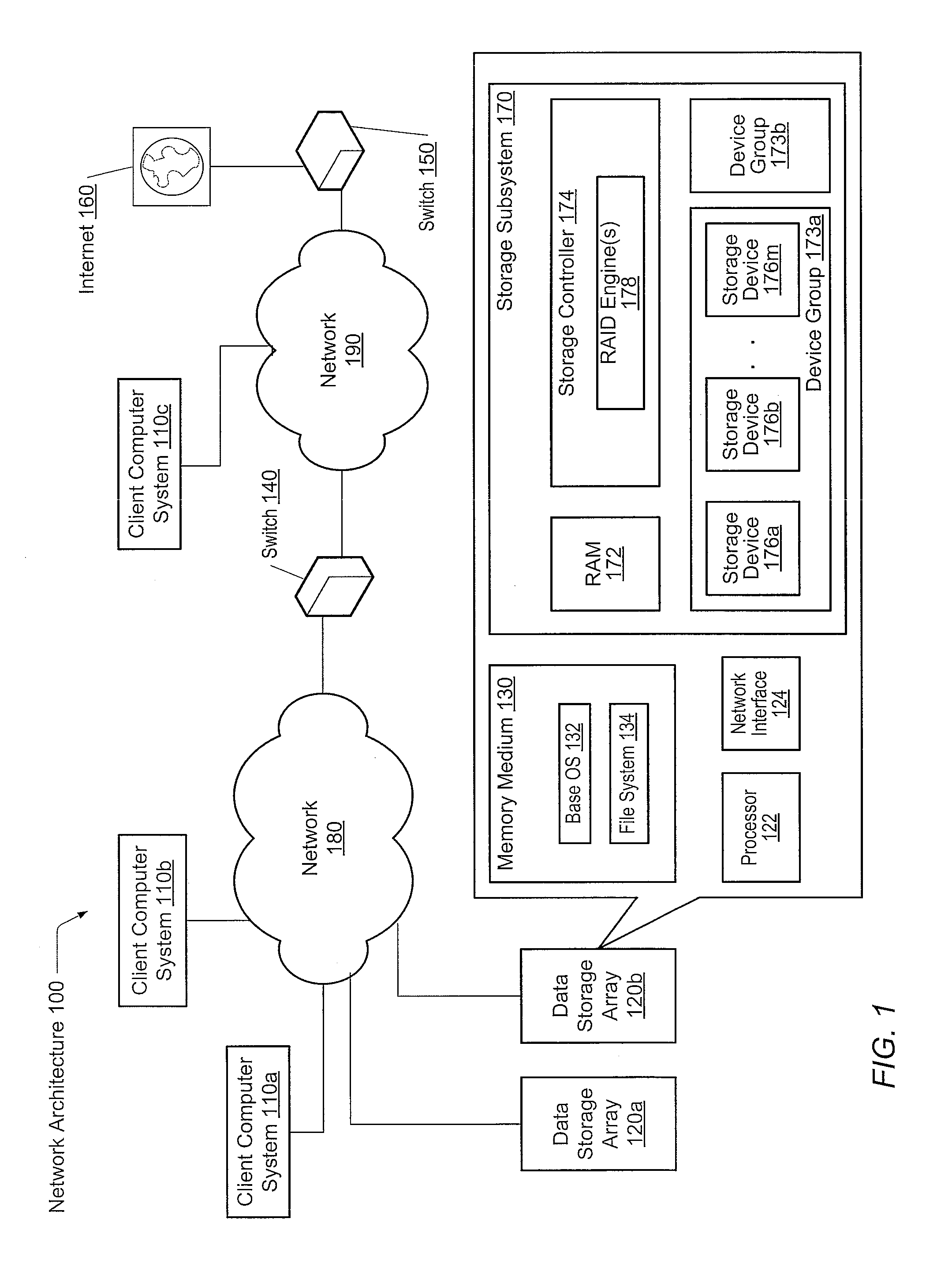
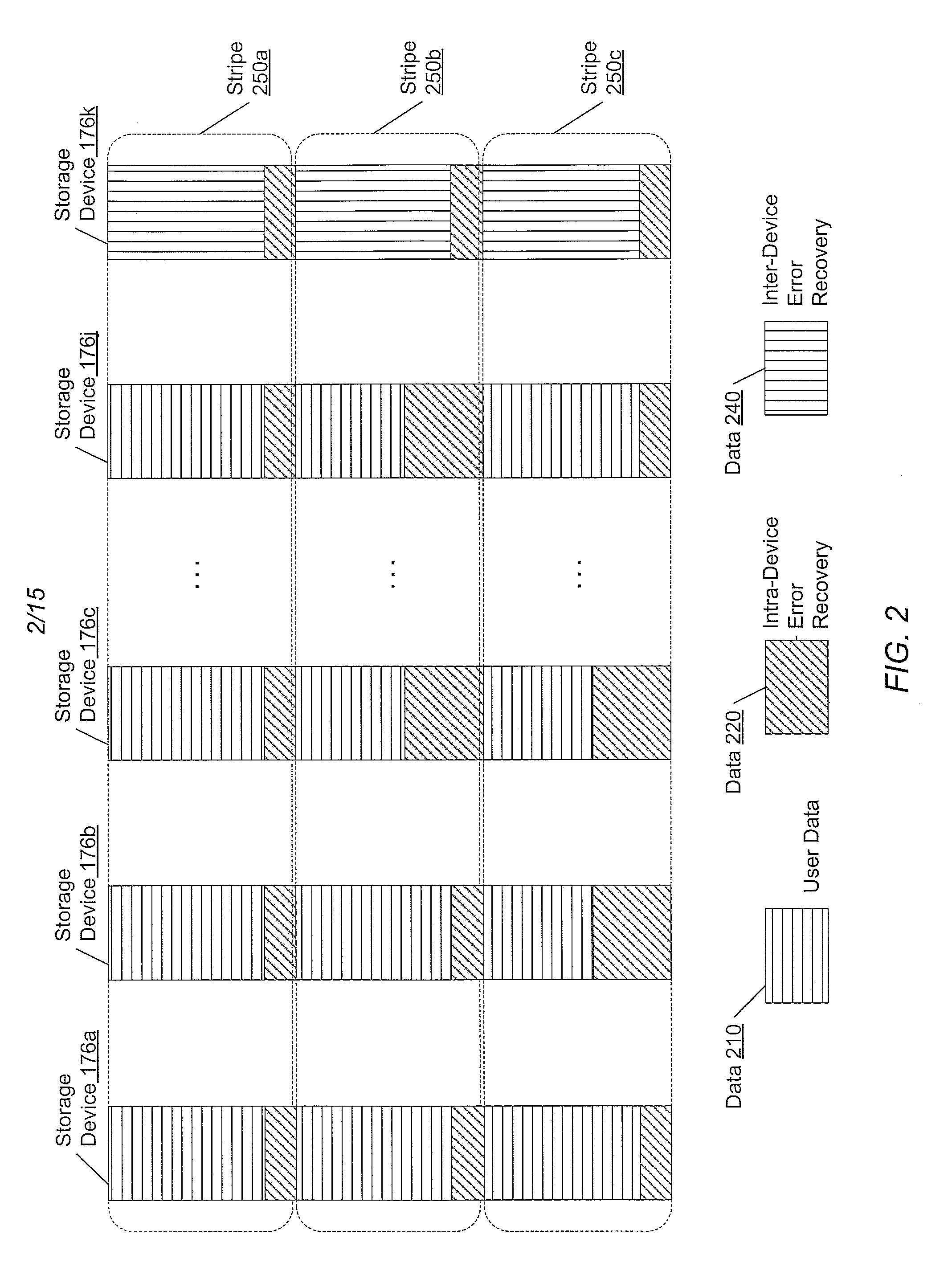
Adaptive raid for an SSD environment
A system and method for adaptive RAID geometries. A computer system comprises client computers and data storage arrays coupled to one another via a network. A data storage array utilizes solid-state drives and Flash memory cells for data storage. A storage controller within a data storage array is configured to determine a first RAID layout for use in storing data, and write a first RAID stripe to the device group according to the first RAID layout. In response to detecting a first condition, the controller is configured to determine a second RAID layout which is different from the first RAID layout, and write a second RAID stripe to the device group according to the second layout, whereby the device group concurrently stores data according to both the first RAID layout and the second RAID layout.
Owner:PURE STORAGE
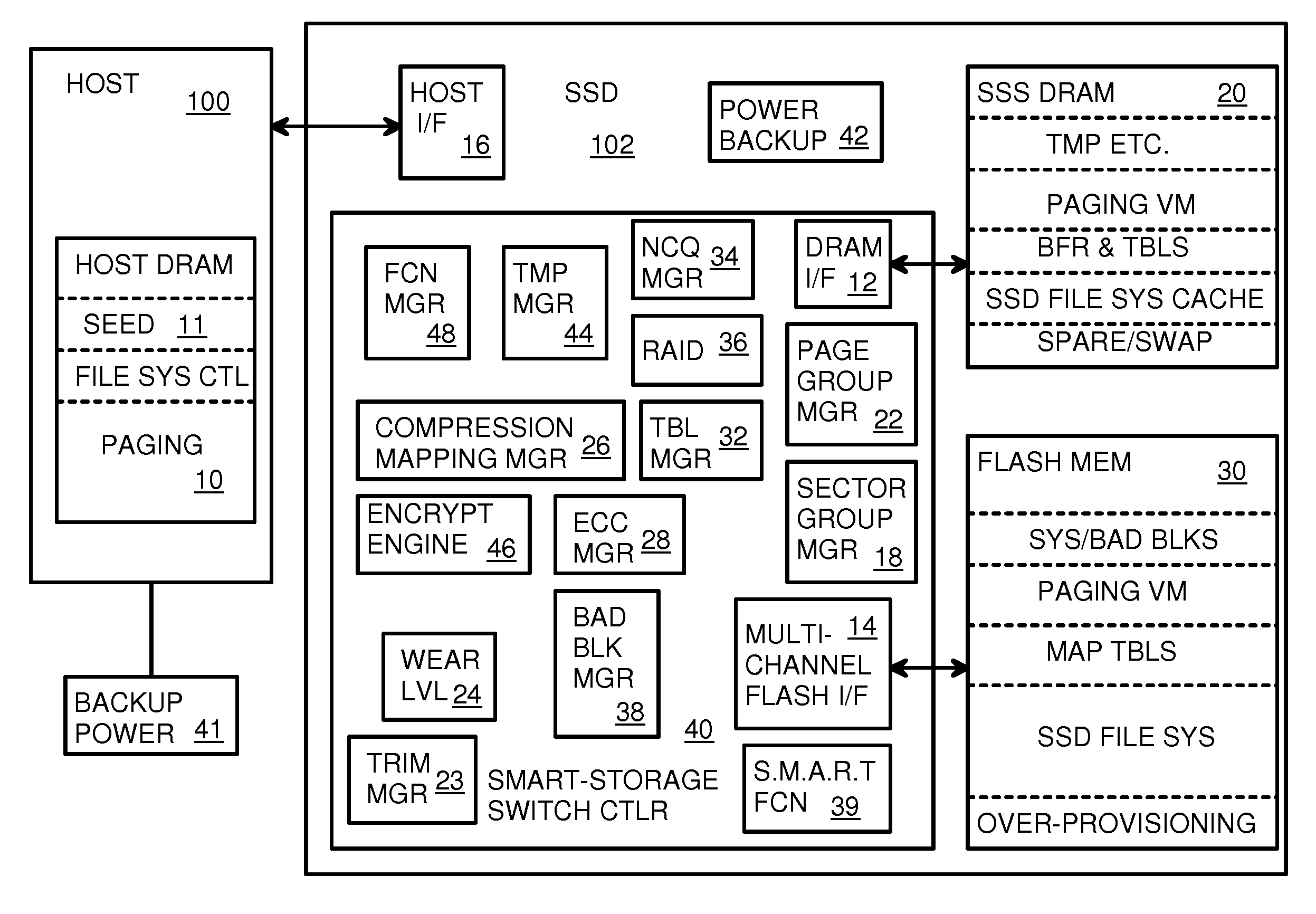
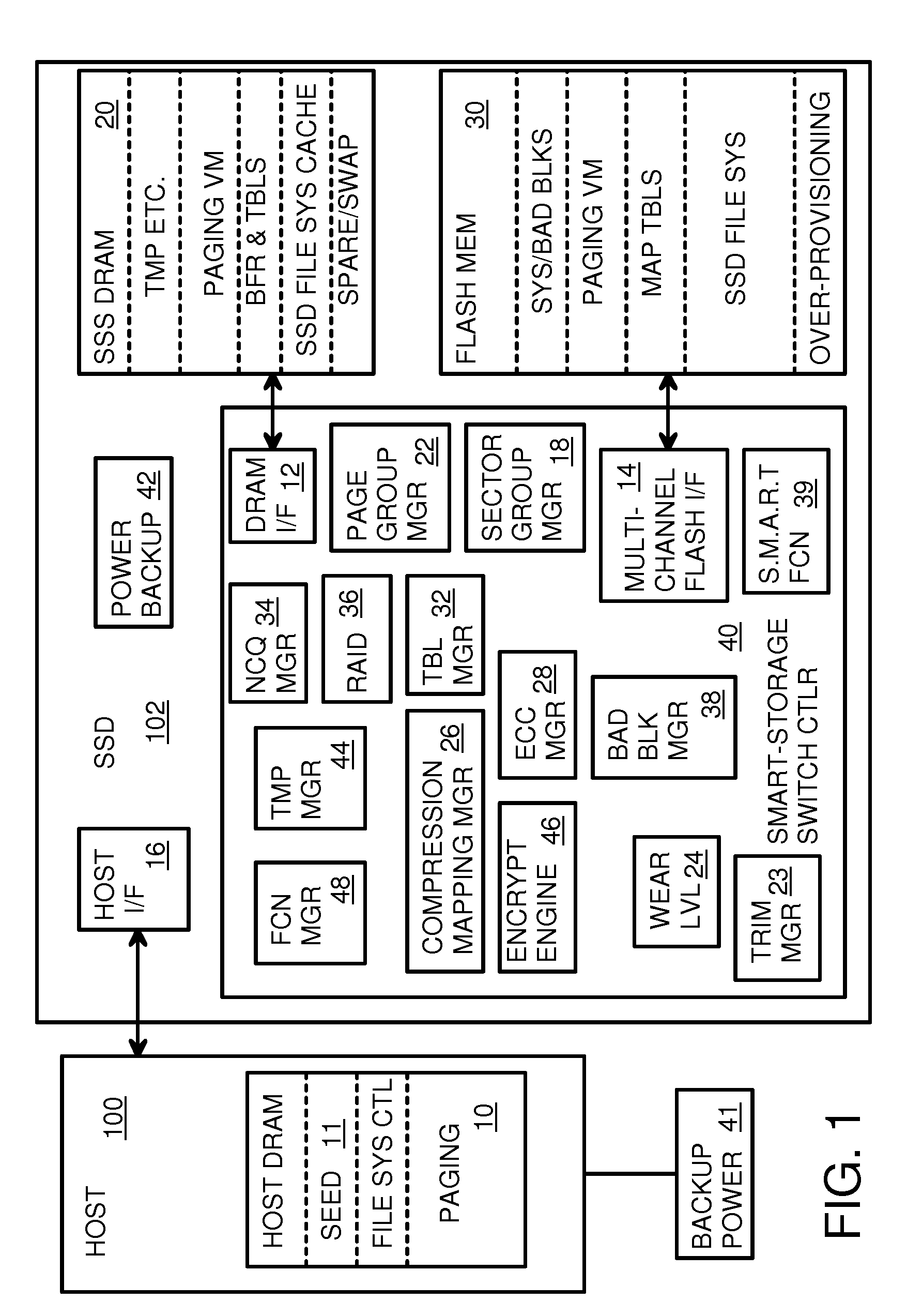
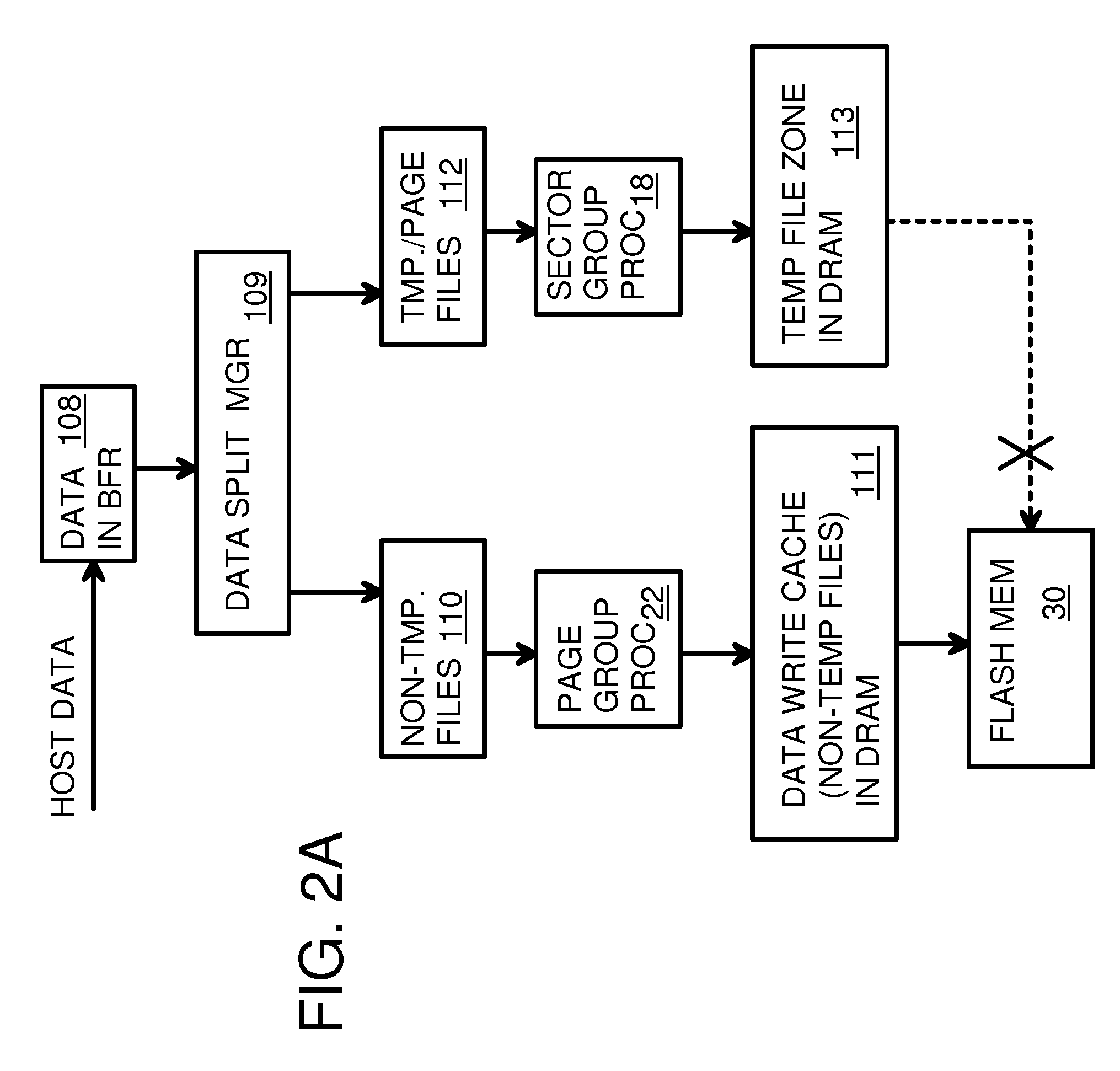
Super-Endurance Solid-State Drive with Endurance Translation Layer (ETL) and Diversion of Temp Files for Reduced Flash Wear
ActiveUS20120284587A1Memory architecture accessing/allocationDigital storageFilename extensionData file
A flash drive has increased endurance and longevity by reducing writes to flash. An Endurance Translation Layer (ETL) is created in a DRAM buffer and provides temporary storage to reduce flash wear. A Smart Storage Switch (SSS) controller assigns data-type bits when categorizing host accesses as paging files used by memory management, temporary files, File Allocation Table (FAT) and File Descriptor Block (FDB) entries, and user data files, using address ranges and file extensions read from FAT. Paging files and temporary files are never written to flash. Partial-page data is packed and sector mapped by sub-sector mapping tables that are pointed to by a unified mapping table that stores the data-type bits and pointers to data or tables in DRAM. Partial sectors are packed together to reduce DRAM usage and flash wear. A spare / swap area in DRAM reduces flash wear. Reference voltages are adjusted when error correction fails.
Owner:SUPER TALENT TECH CORP
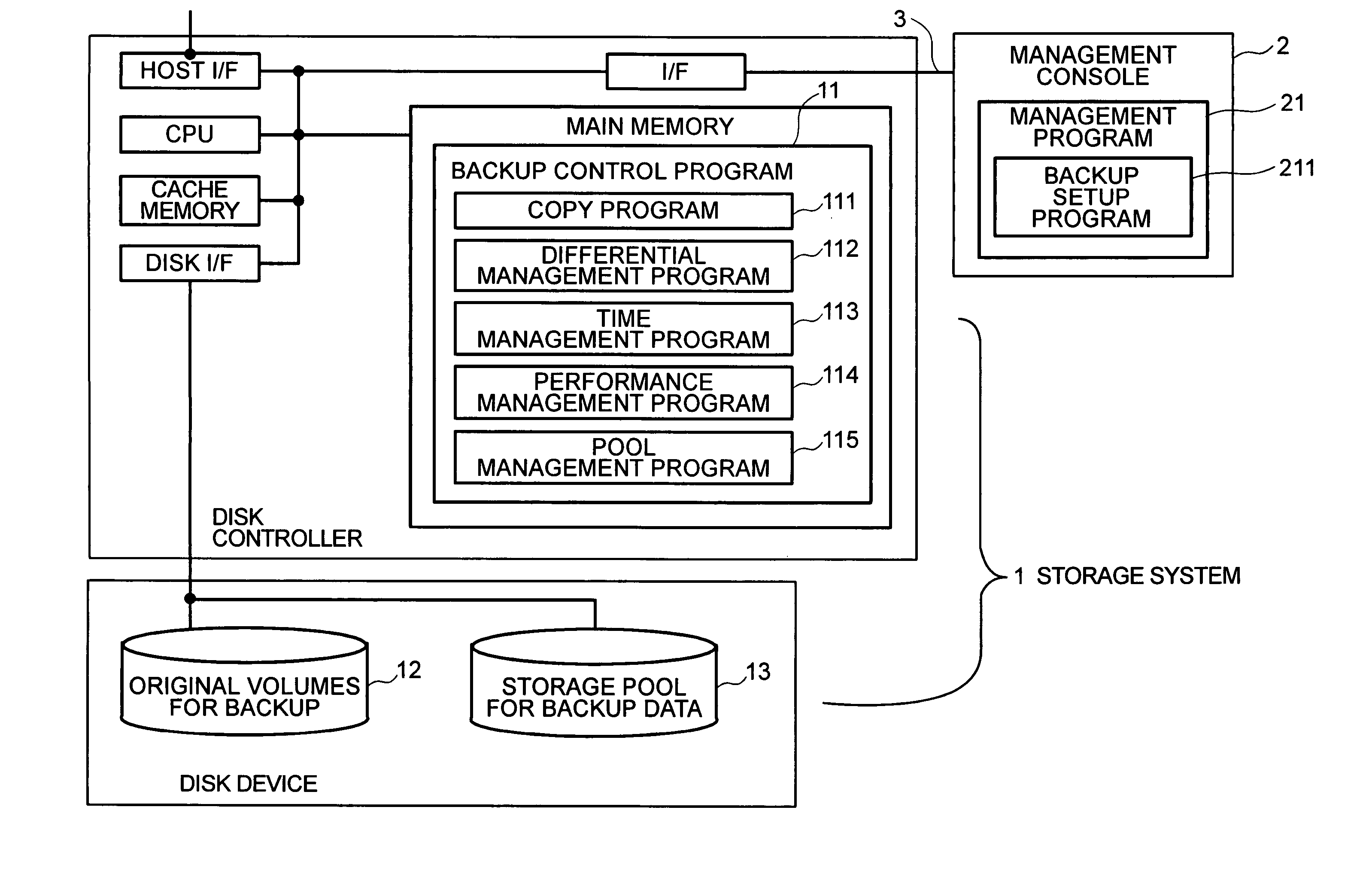
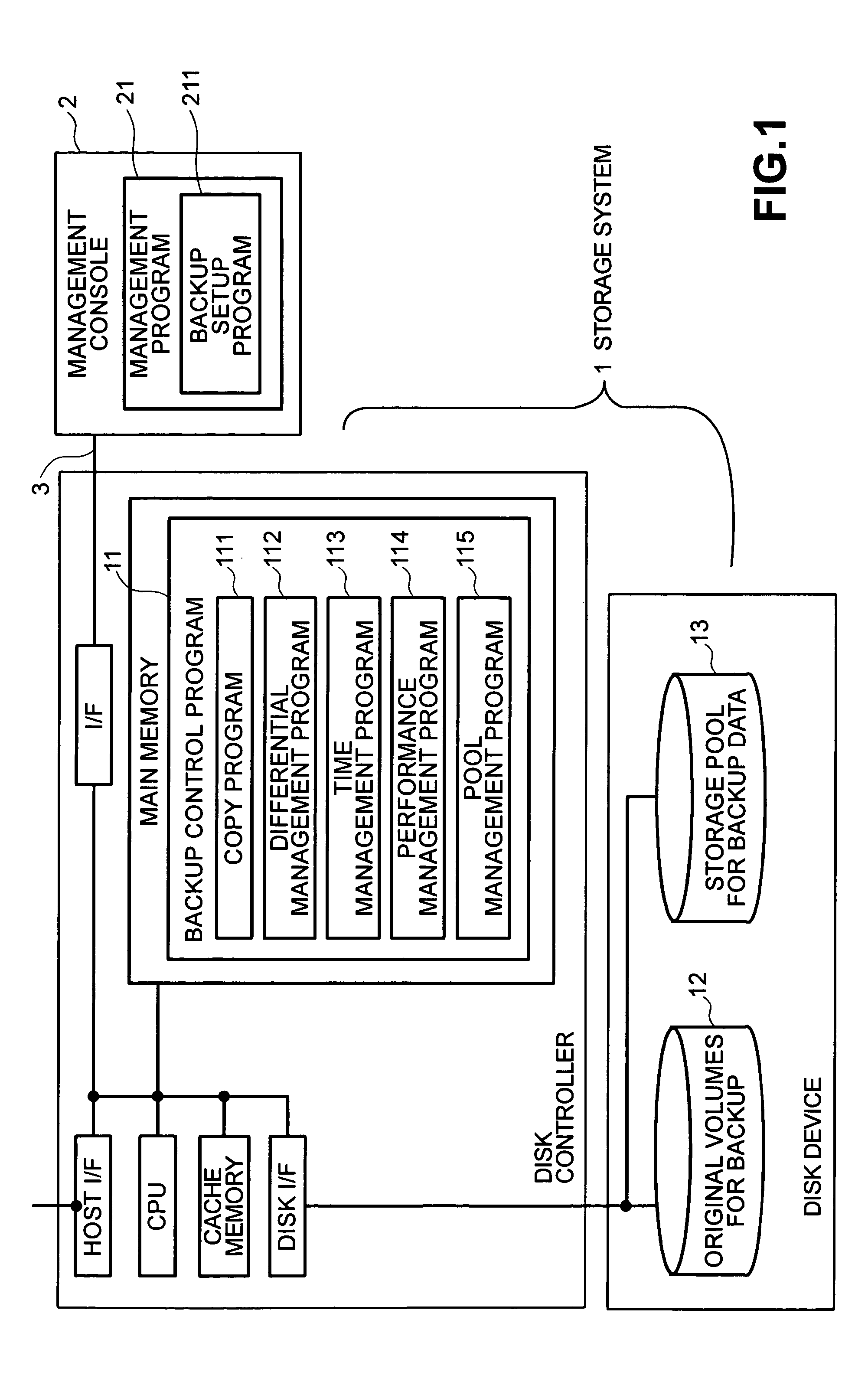
Storage system and method for backup
InactiveUS7085904B2Easy to getReduce the burden onData processing applicationsInput/output to record carriersDisk controllerStorage pool
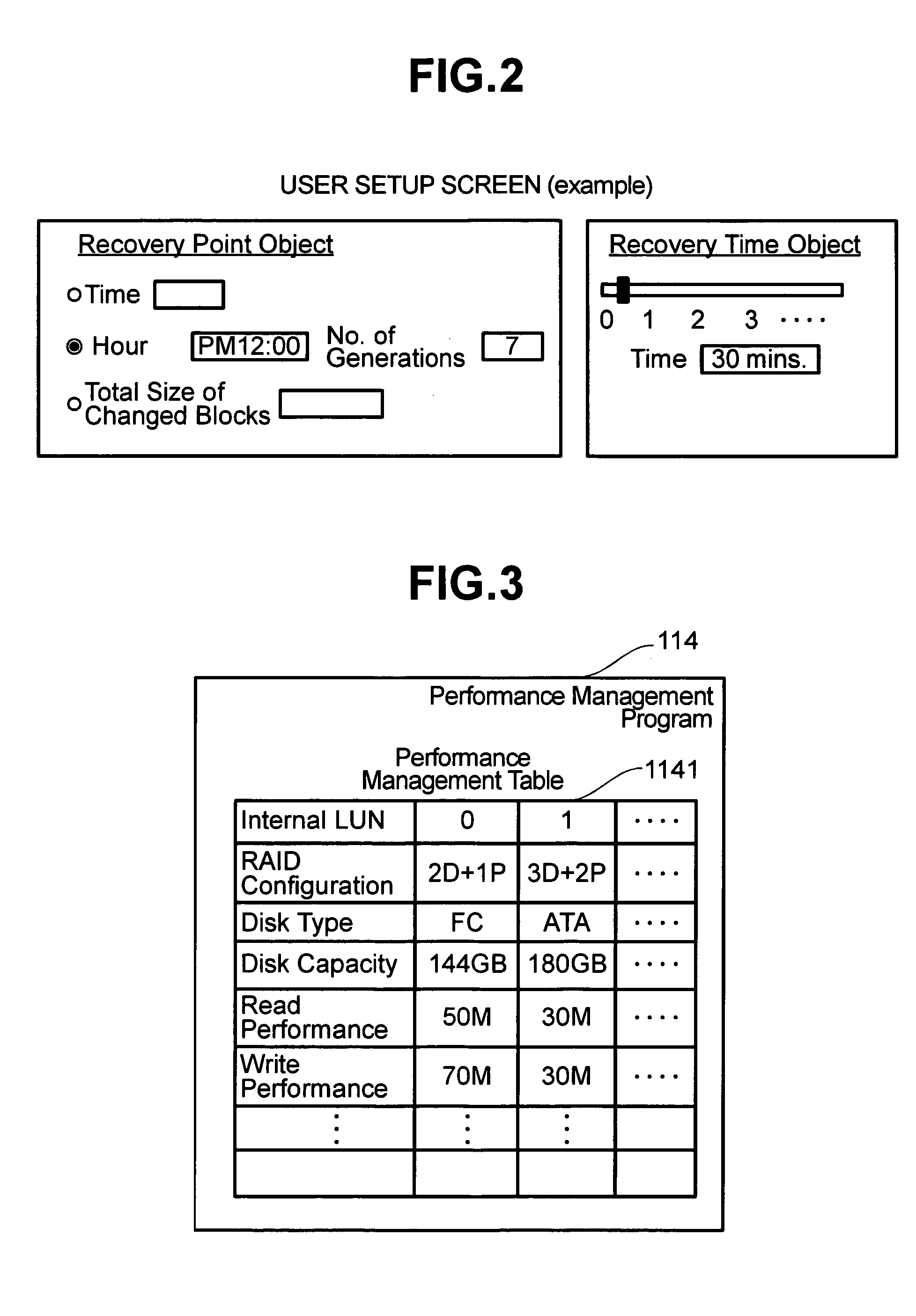
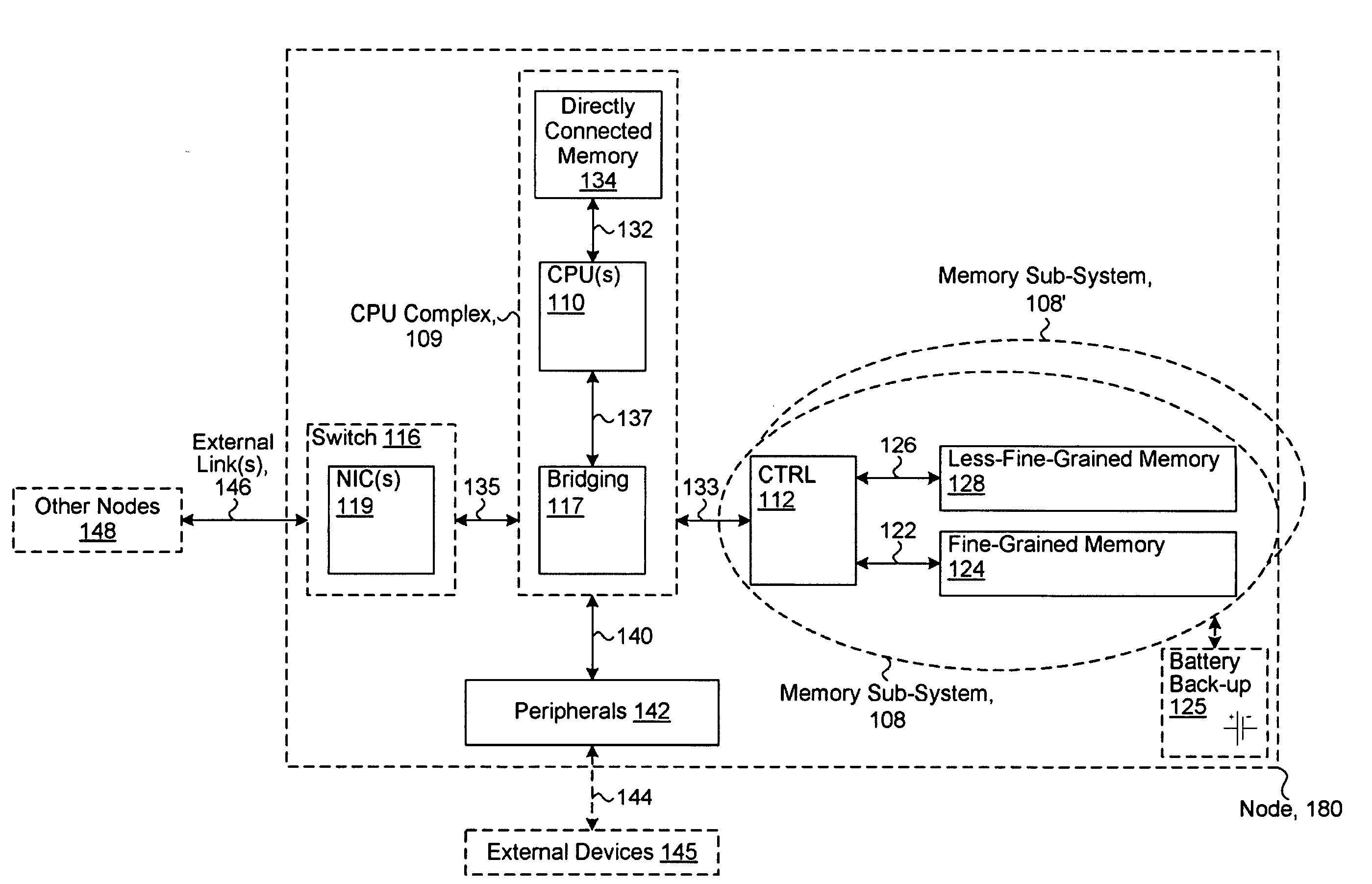
A storage system includes a disk controller and a disk device having original volumes for backup and a storage pool for backup data. It incorporates a differential management program which checks whether the original volumes for backup are updated or not; a pool management program which allocates a disk area to the storage pool for backup data; a performance management program which manages the performance of each volume; and a backup control program which performs total backup control. A backup method by which recovery within a user-specified recovery object time is possible is selected according to the restore performance calculated by the performance management program and the total size of changed blocks after backup acquisition as counted by the differential management program.
Owner:HITACHI LTD
System including a fine-grained memory and a less-fine-grained memory
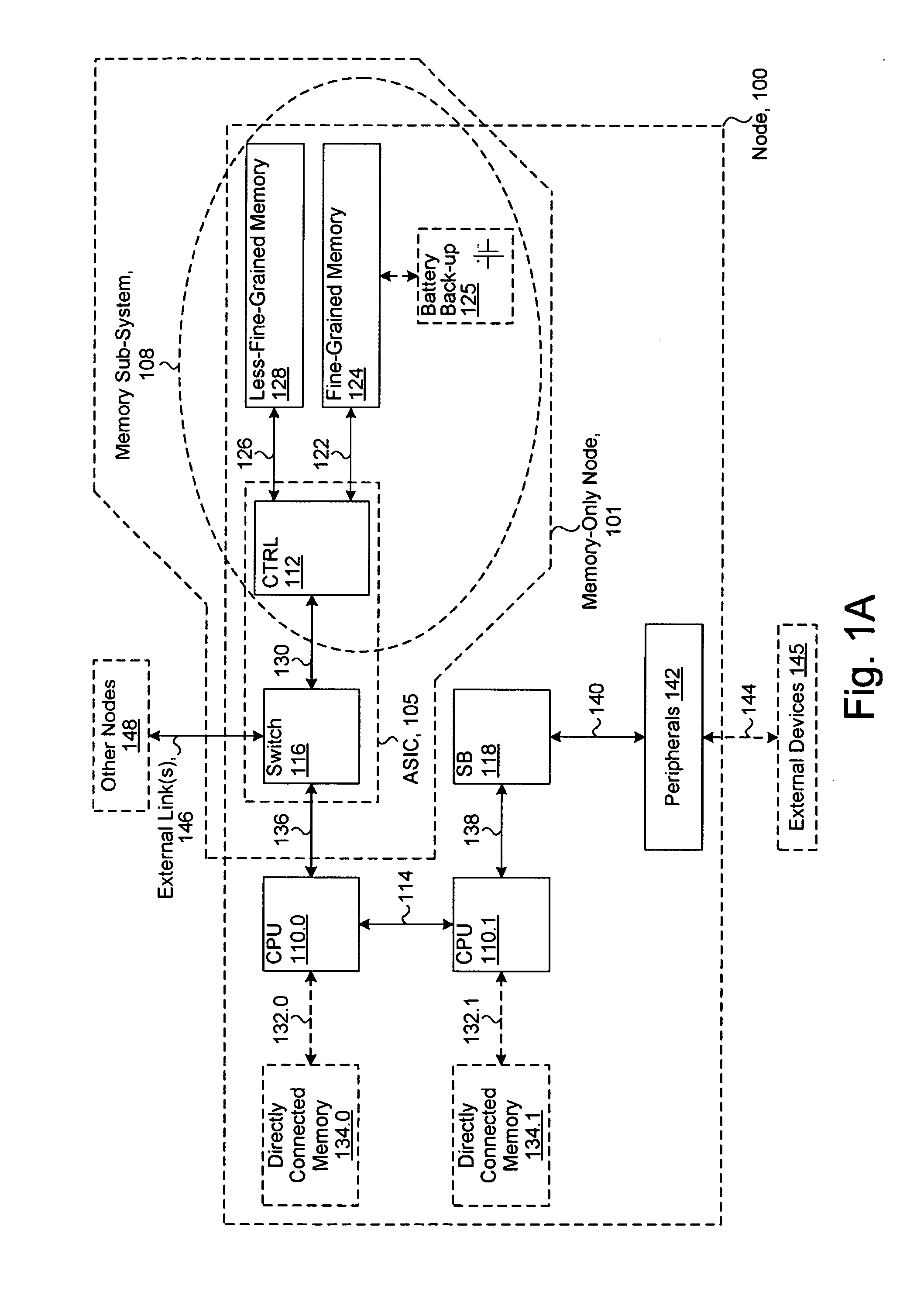
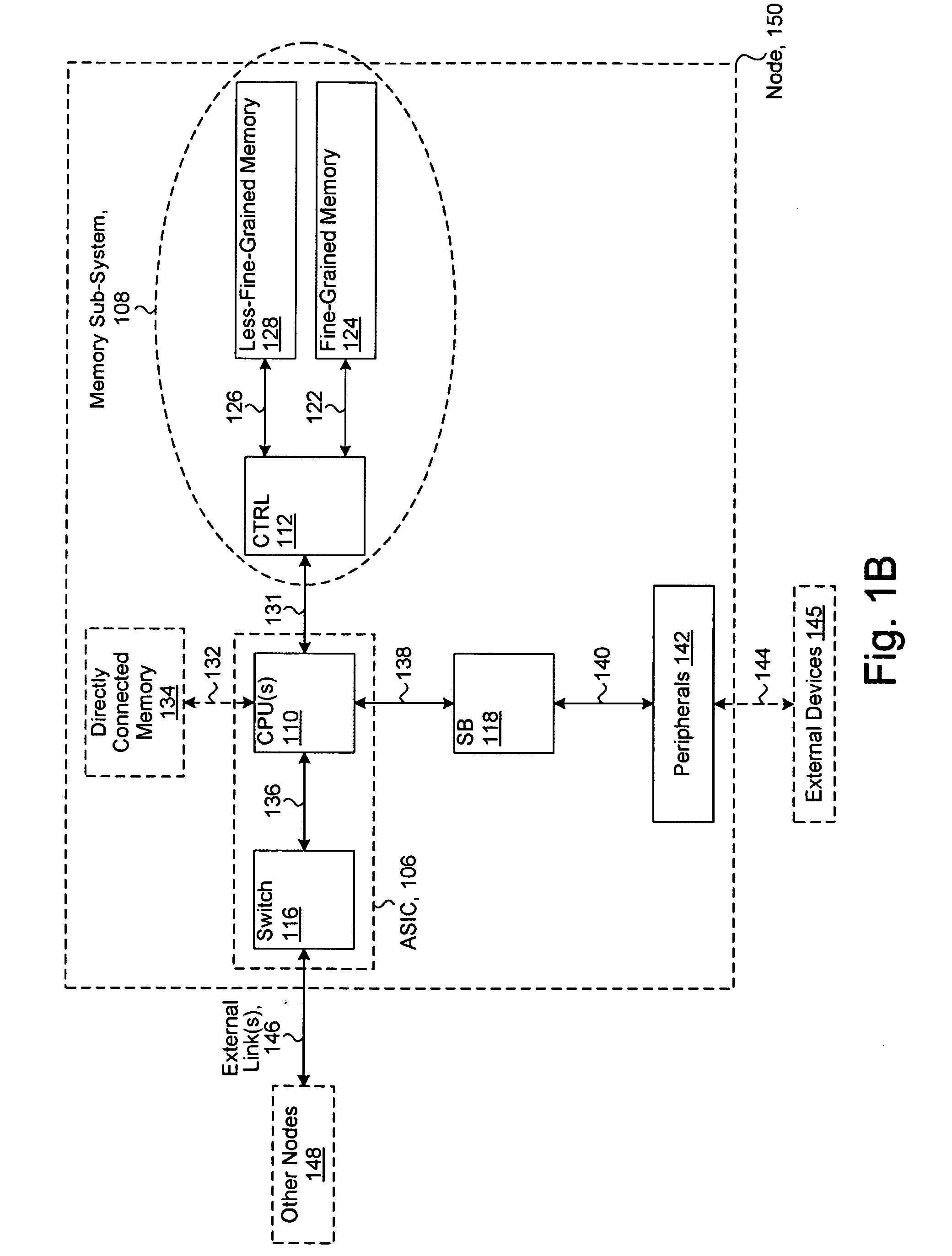
ActiveUS20080301256A1Memory architecture accessing/allocationEnergy efficient ICTData processing systemWrite buffer
A data processing system includes one or more nodes, each node including a memory sub-system. The sub-system includes a fine-grained, memory, and a less-fine-grained (e.g., page-based) memory. The fine-grained memory optionally serves as a cache and / or as a write buffer for the page-based memory. Software executing on the system uses n node address space which enables access to the page-based memories of all nodes. Each node optionally provides ACID memory properties for at least a portion of the space. In at least a portion of the space, memory elements are mapped to locations in the page-based memory. In various embodiments, some of the elements are compressed, the compressed elements are packed into pages, the pages are written into available locations in the page-based memory, and a map maintains an association between the some of the elements and the locations.
Owner:SANDISK TECH LLC
Method and apparatus for storage unit replacement in non-redundant array
InactiveUS6598174B1Lower performance requirementsMaintaining accessMemory loss protectionReliability/availability analysisRAIDData storing
A method and apparatus used in a storage network facilitates the protection of data in, and replacement of, storage devices about to fail before the failure happens. In a network that includes a set of storage devices organized as a non-redundant (for example RAID 0) array, a storage device about to fail in the non-redundant array can be replaced by another storage device, typically from a pool of spares. The method includes detecting a condition of a first particular storage device in the non-redundant array. Conditions which are detected according to various embodiments indicate that the first particular storage device is suffering events indicating that it is likely to fail, or otherwise suffering from reduced performance. The conditions are detected for example, by the receipt of a signal from the storage device itself, or by the monitoring of statistics concerning the performance of the storage device. The method further provides for selecting a particular spare storage device, which can be used in place of the first particular storage device. In response to detecting the condition, data stored in the first particular storage device is migrated to the second particular storage device, and the second particular storage takes the place of the first particular storage device in the non-redundant array. The first particular storage device can then be gracefully removed from the network without loss of service to the clients computers.
Owner:DELL PROD LP
Method and apparatus for independent and simultaneous access to a common data set
InactiveUS6101497AData processing applicationsInput/output to record carriersData processing systemData set
A data network with data storage facilities for providing redundant data storage and for enabling concurrent access to the data for multiple purposes. A first data processing system with a first data facility stores a data base and processes transactions or other priority applications. A second data storage facility, that may be physically separated from the first data storage facility, mirrors the data in the first data storage facility. In a concurrent access operating mode, the second data storage facility makes the data available to an application concurrently with, but independently of, the operation of the other application. On completion of the concurrent operation, the second data storage facility can reconnect with and synchronizes with the first data storage facility thereby to reestablish the mirroring operation.
Owner:EMC CORP
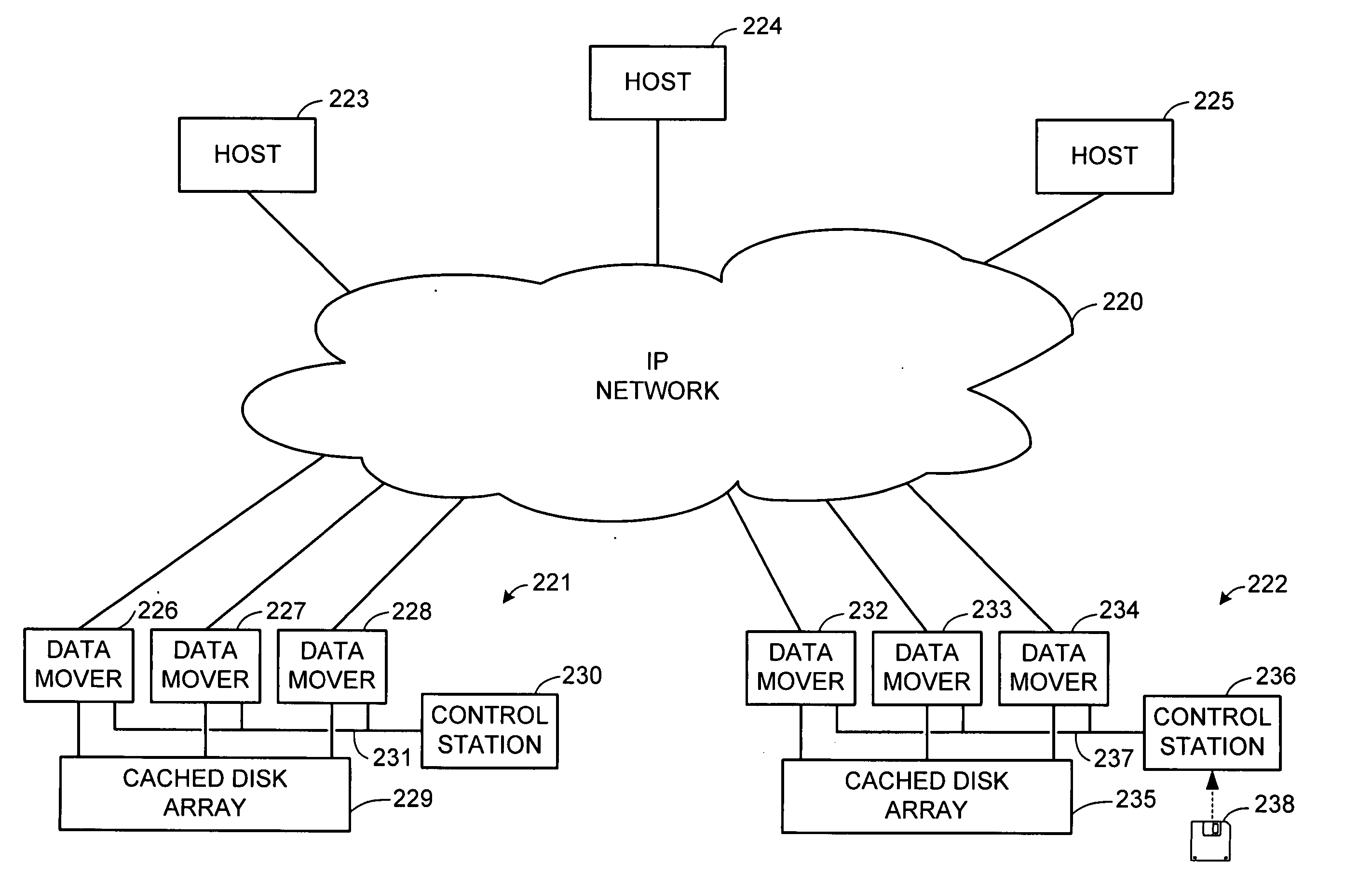
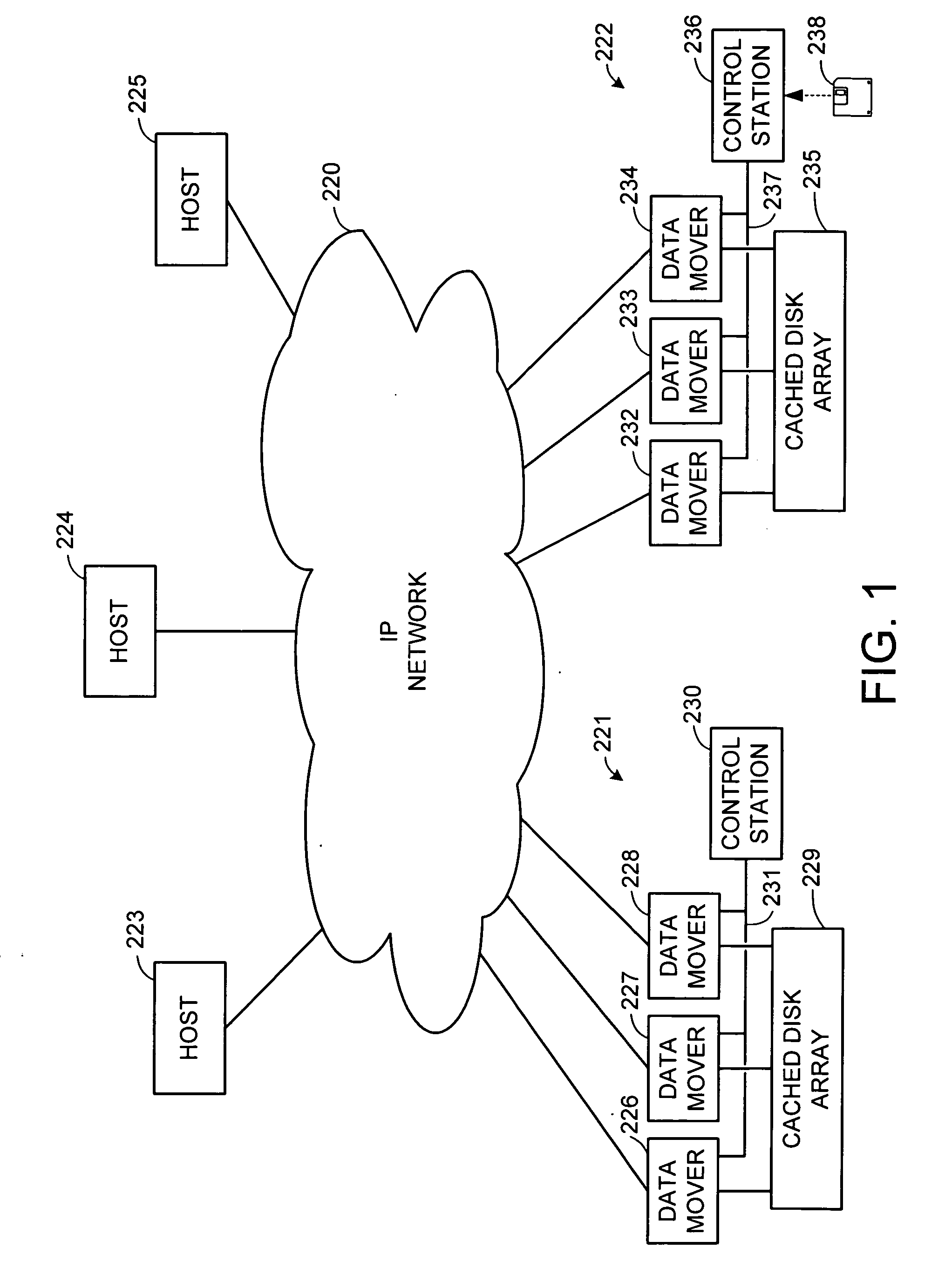
Internet protocol based disaster recovery of a server
For disaster recovery of a file server at an active site, the files that define the user environment of the file server are replicated to a virtual server at a disaster recovery site. To switch over user access from the active site to the disaster recovery site, the disaster recovery system determines whether there are sufficient network interfaces and file system mounts at the disaster recovery site. If so, the required resources are reserved, and user access is switched over. If not, an operator is given a list of missing resources or discrepancies, and a choice of termination or forced failover. Interruptions during the failover can be avoided by maintaining a copy of user mappings and a copy of session information at the disaster recovery site, and keeping alive client-server connections and re-directing client requests from the active site to the disaster recovery site.
Owner:EMC IP HLDG CO LLC
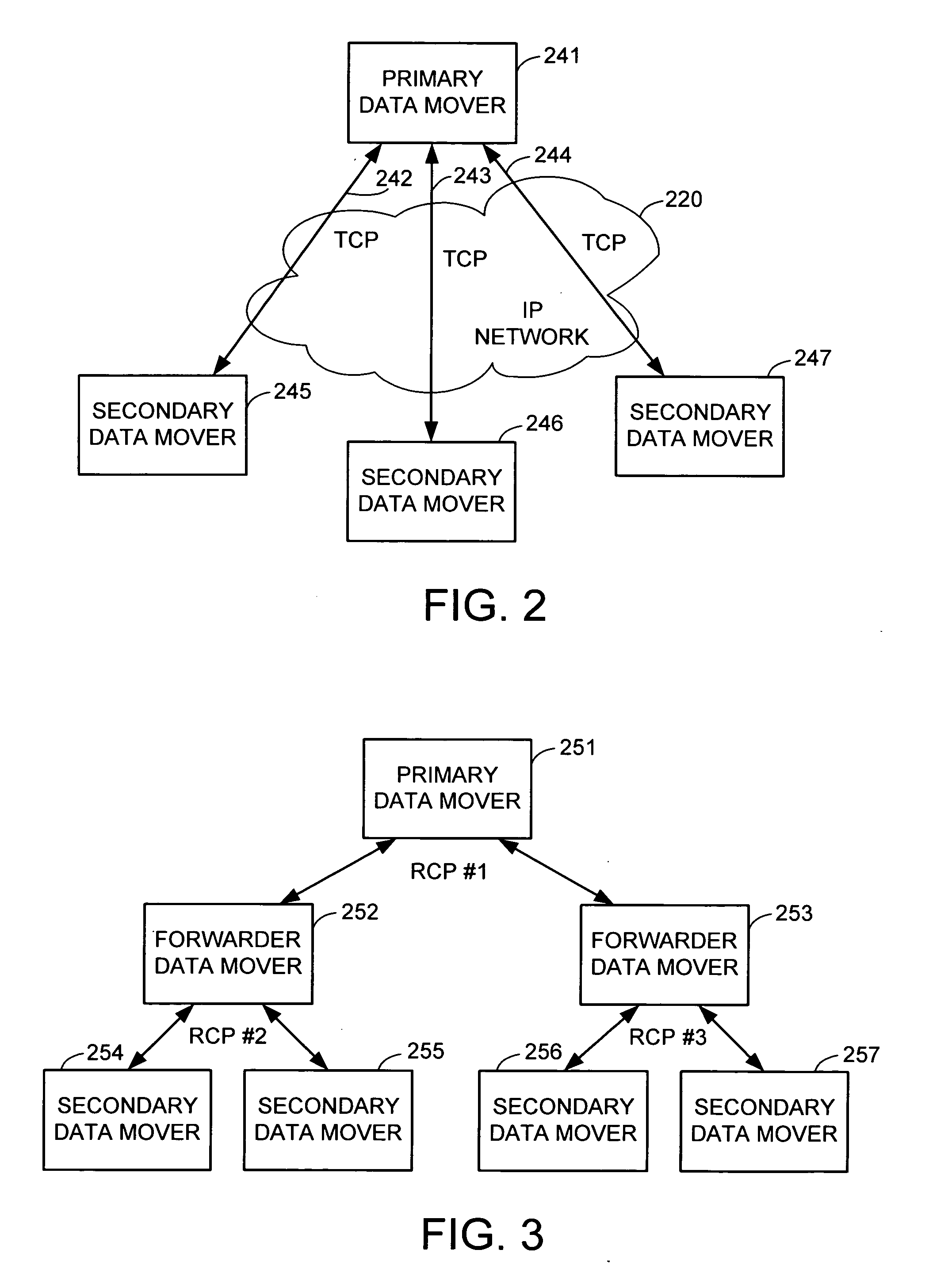
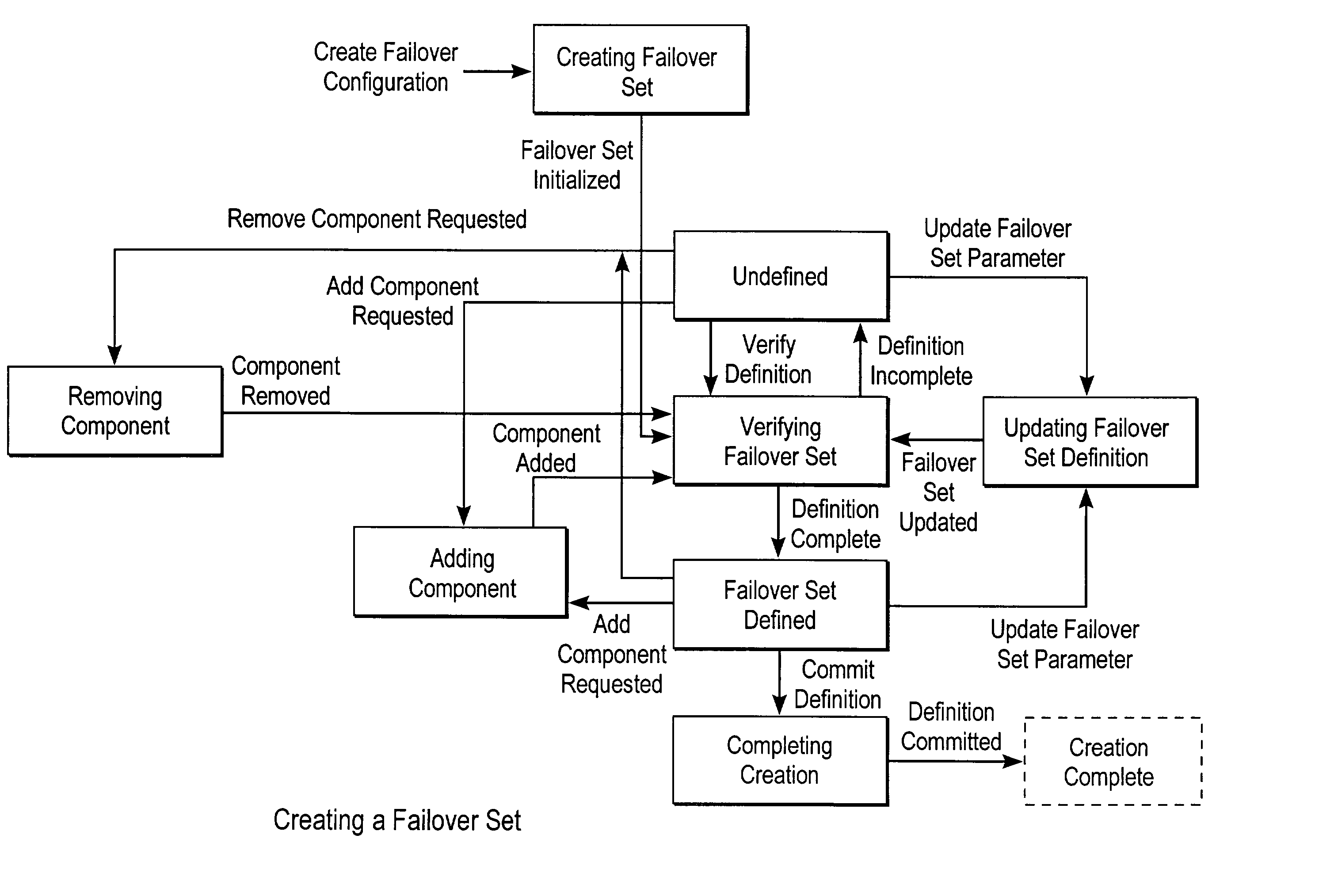
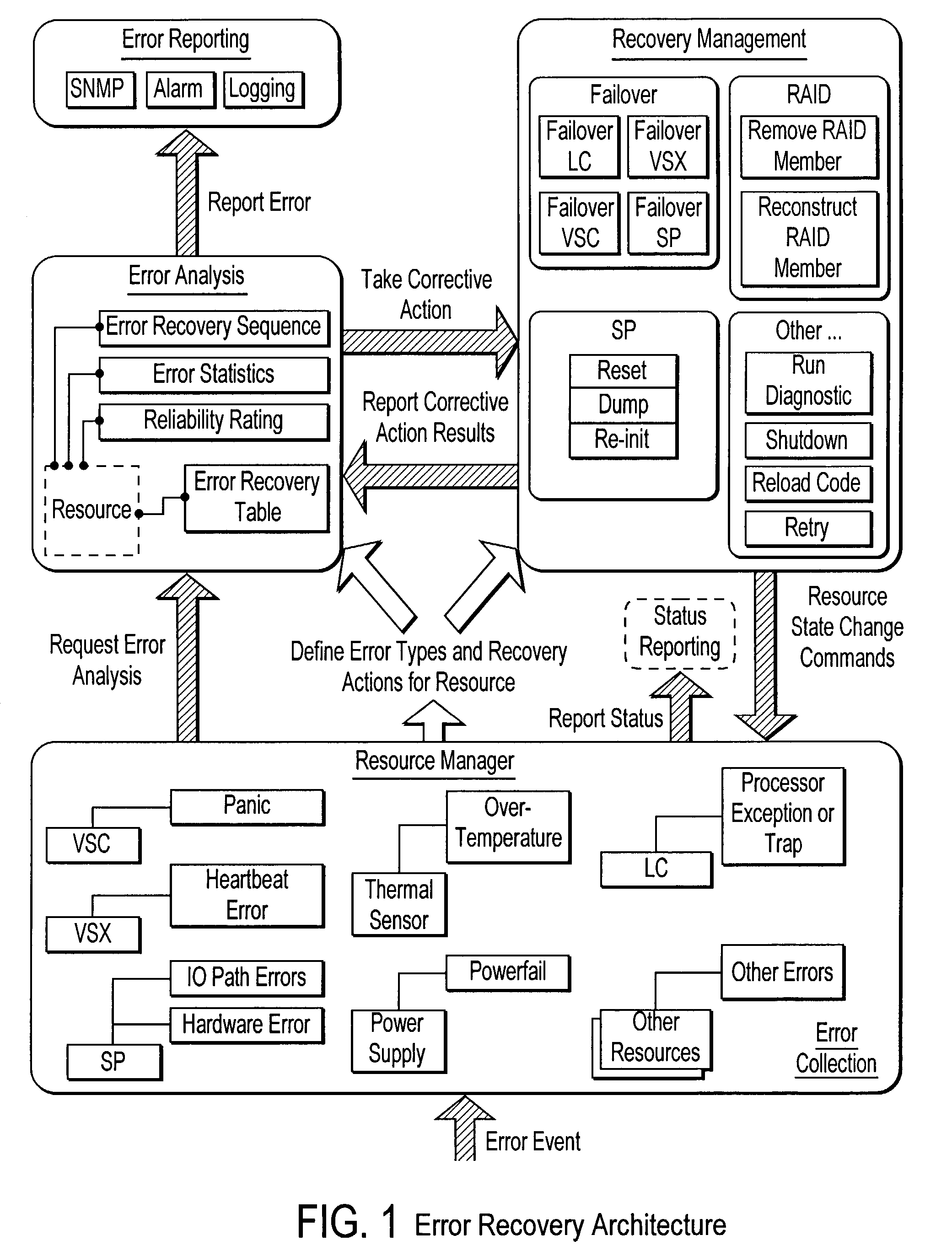
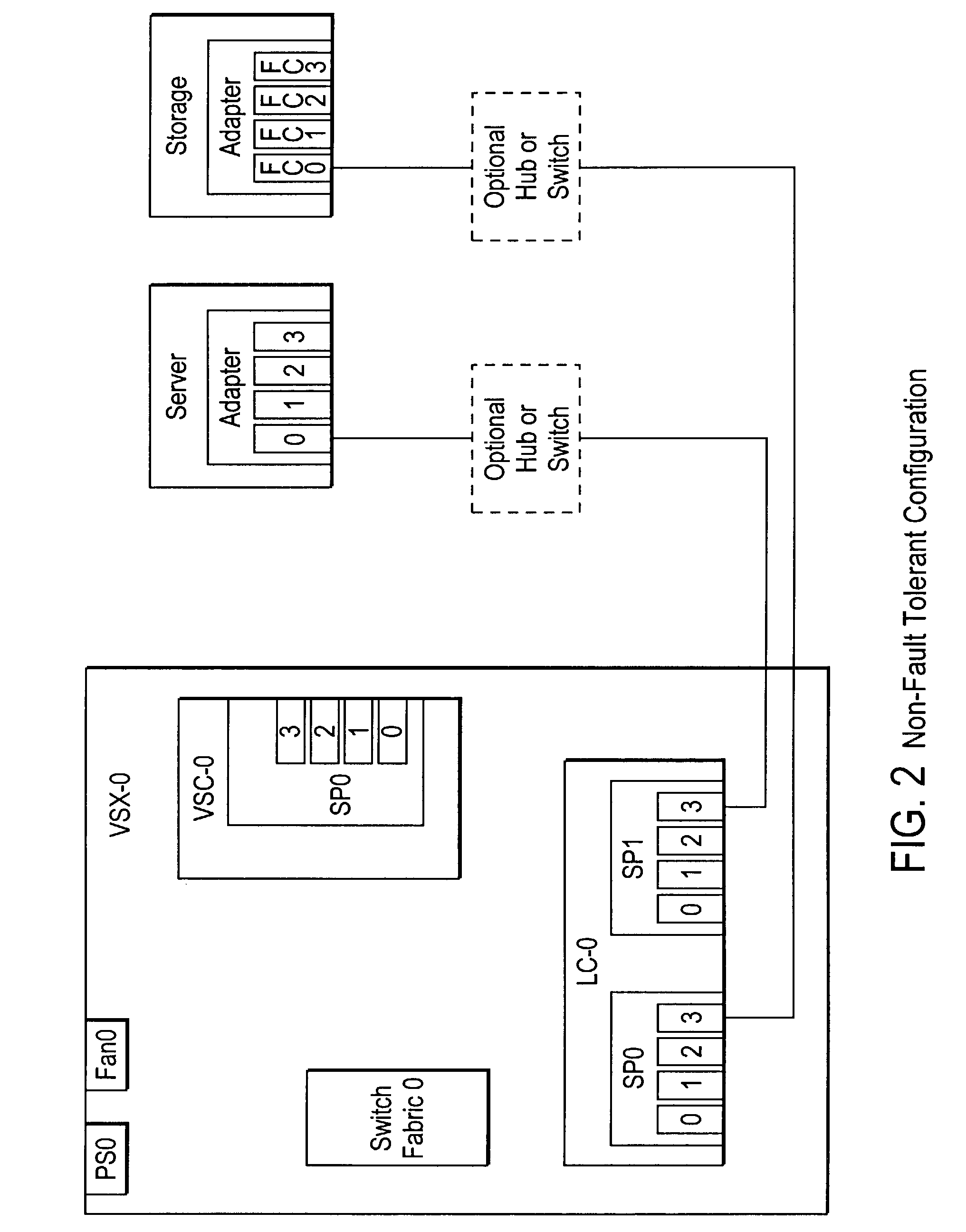
Failover processing in a storage system
InactiveUS7039827B2Improve usabilityInput/output to record carriersDigital data processing detailsFault toleranceFailover
Failover processing in storage server system utilizes policies for managing fault tolerance (FT) and high availability (HA) configurations. The approach encapsulates the knowledge of failover recovery between components within a storage server and between storage server systems. This knowledge includes information about what components are participating in a Failover Set, how they are configured for failover, what is the Fail-Stop policy, and what are the steps to perform when “failing-over” a component.
Owner:NETWORK APPLIANCE INC
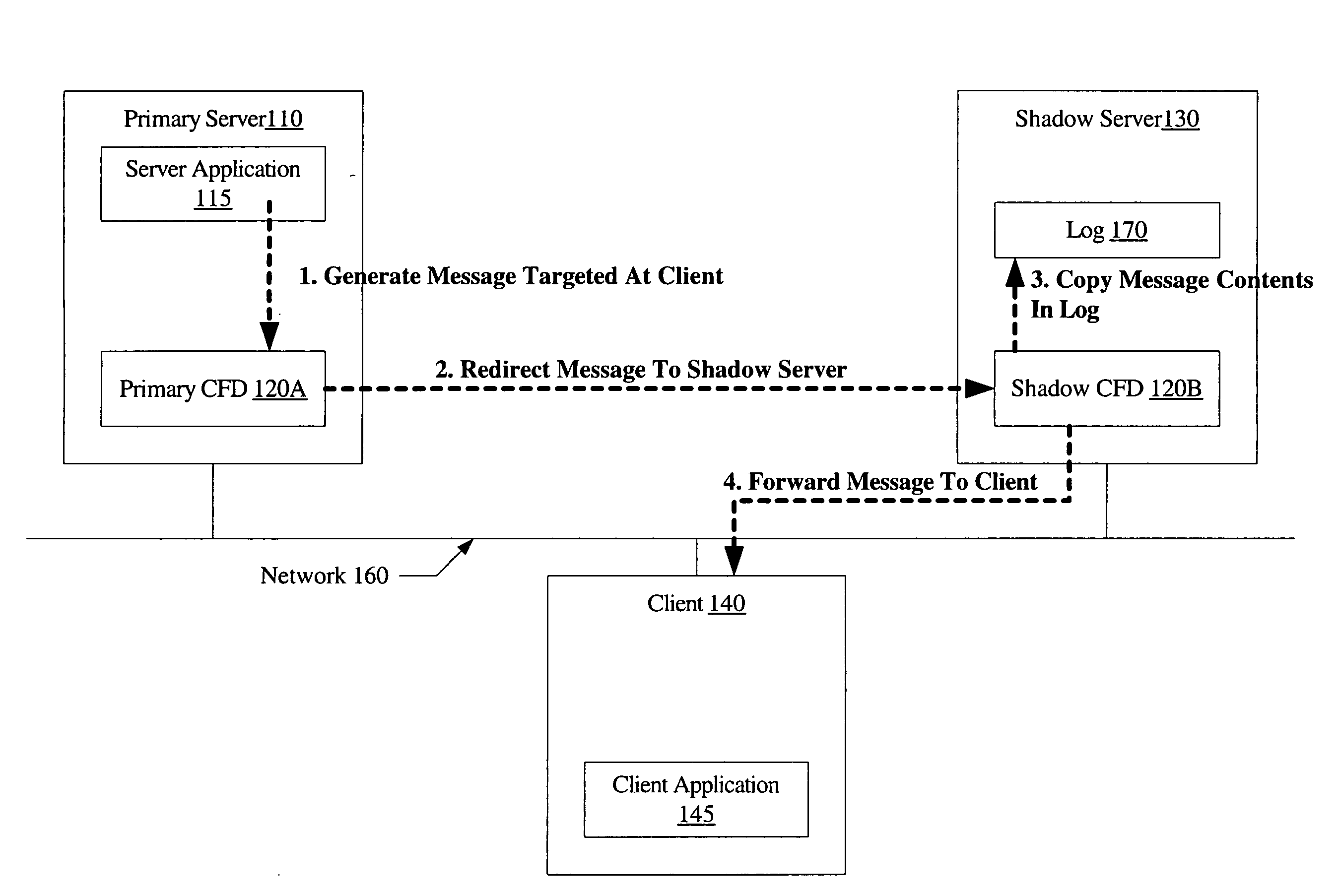
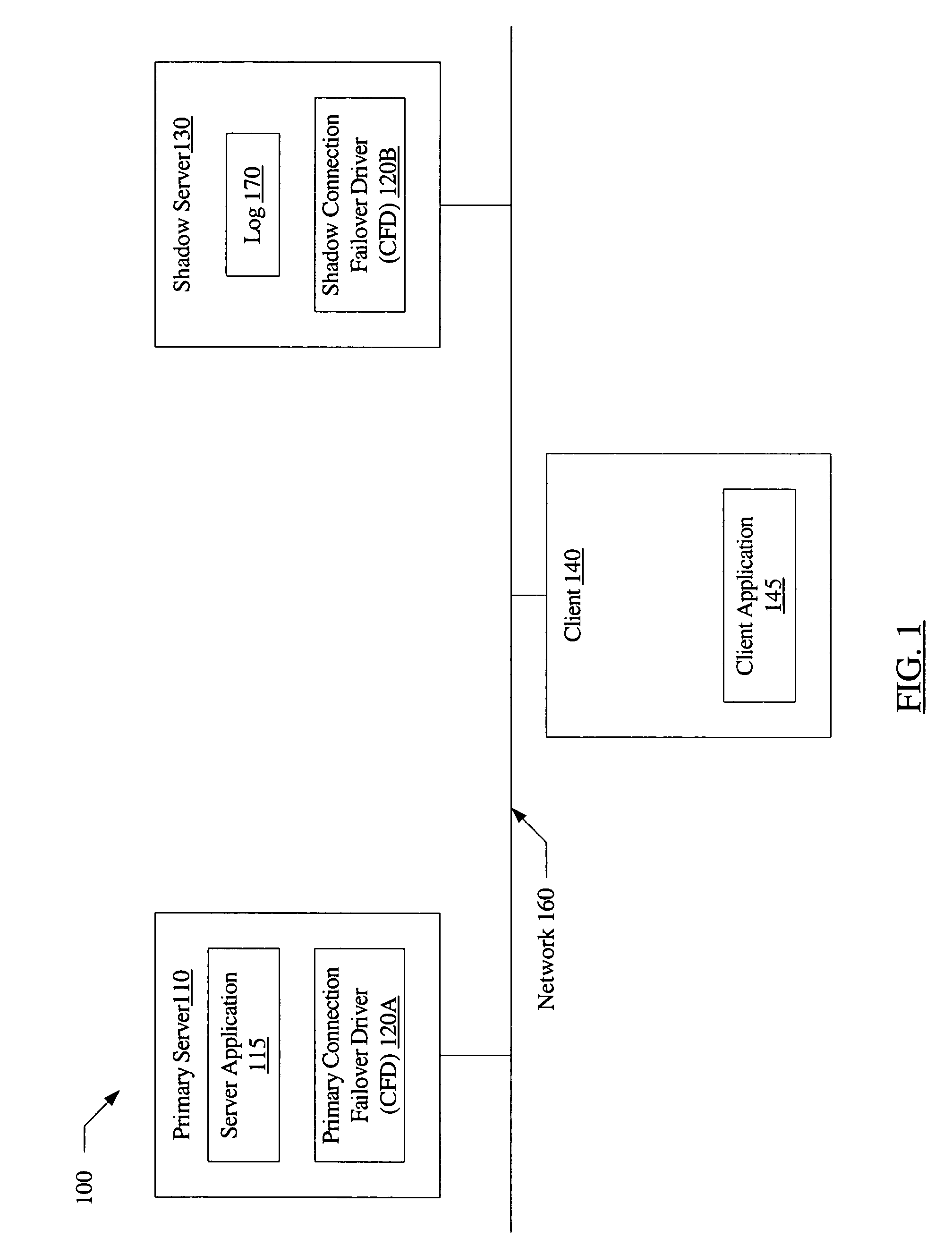
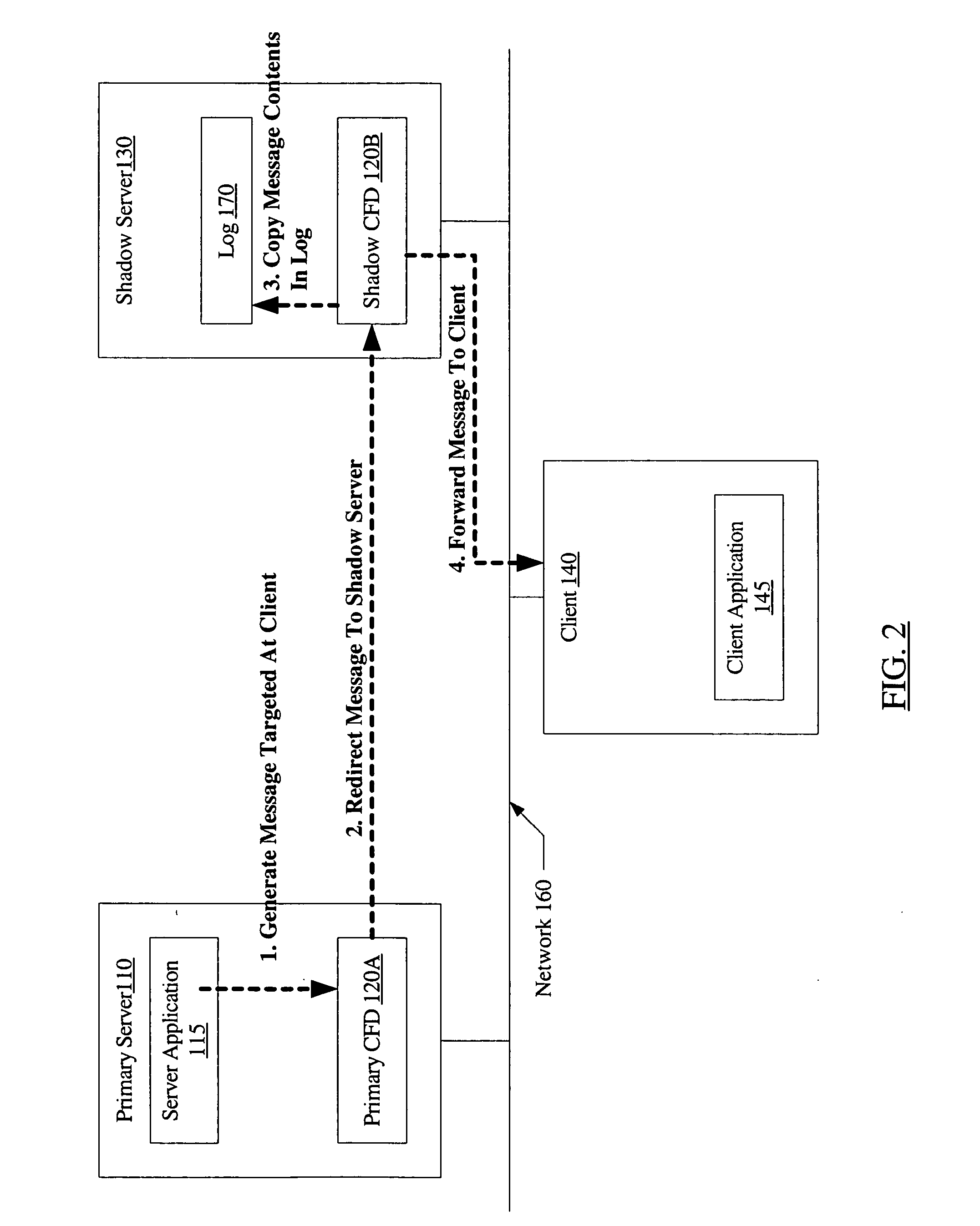
System and method for connection failover using redirection
InactiveUS20060179147A1Multiple digital computer combinationsNetwork connectionsFailoverNetwork connection
A system for connection failover using redirection includes a primary server comprising a primary connection failover driver (CFD), a shadow server comprising a shadow CFD, and a client. The primary and shadow servers and the client are coupled via a network. The primary server and the client are configured to cooperate to establish a network connection. The primary CFD is configured to redirect a first message packet, targeted for transmission to the client over the network connection, to the shadow server. The shadow CFD is configured to copy contents of the first message packet into a log, and forward the first message packet to the client after the contents have been copied.
Owner:SYMANTEC OPERATING CORP
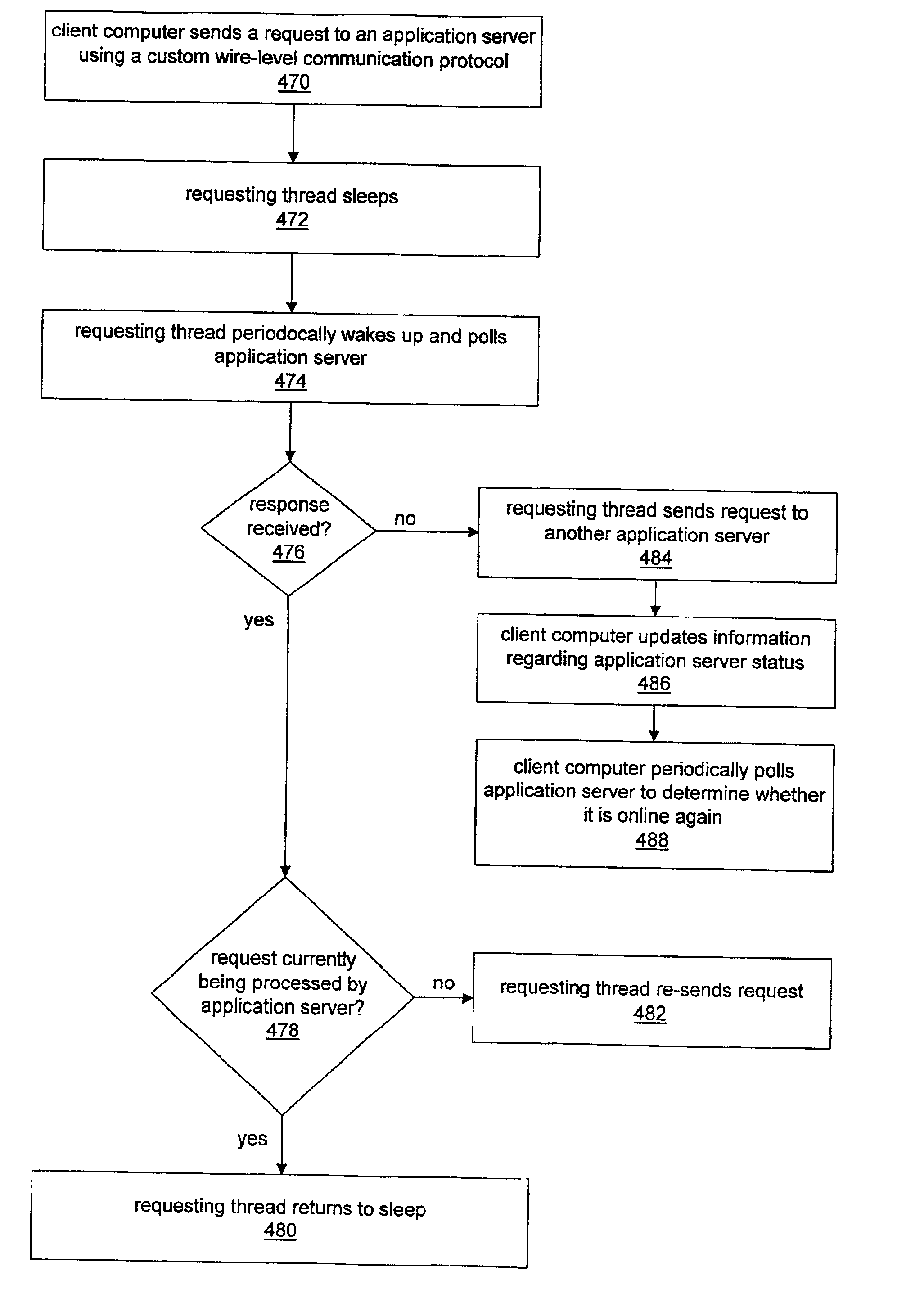
System and method for enabling application server request failover
InactiveUS6859834B1Resource allocationMultiple digital computer combinationsFailoverApplication server
System and method for enabling application server request failover. For each application server request to be performed by a client computer, a requesting thread may be operable to utilize a custom wire-level communication protocol. Request failure detection mechanisms may be built into the custom wire-level communication protocol so that a requesting thread detects a failed request much sooner than if the thread utilized a standard communication protocol and relied on the client computer operating system for notification of failed requests. After sending a request to an application server, a requesting thread may be operable to “sleep” and then periodically wake up to poll the application server computer to determine whether the request has failed. If the requesting thread receives a response from the application server computer indicating that the request is not currently being processed, then the requesting thread may re-send the request. Receiving no response to the poll message may indicate that the application server computer is offline, e.g., due to a failure. The requesting thread may redirect the request to another application server computer if necessary.
Owner:ORACLE INT CORP
High-availability cluster virtual server system
InactiveUS6944785B2Minimize occurrenceImprove system performanceInput/output to record carriersData switching networksFailoverHigh availability
Systems and methods, including computer program products, providing high-availability in server systems. In one implementation, a server system is cluster of two or more autonomous server nodes, each running one or more virtual servers. When a node fails, its virtual servers are migrated to one or more other nodes. Connectivity between nodes and clients is based on virtual IP addresses, where each virtual server has one or more virtual IP addresses. Virtual servers can be assigned failover priorities, and, in failover, higher priority virtual servers can be migrated before lower priority ones. Load balancing can be provided by distributing virtual servers from a failed node to multiple different nodes. When a port within a node fails, the node can reassign virtual IP addresses from the failed port to other ports on the node until no good ports remain and only then migrate virtual servers to another node or nodes.
Owner:NETWORK APPLIANCE INC
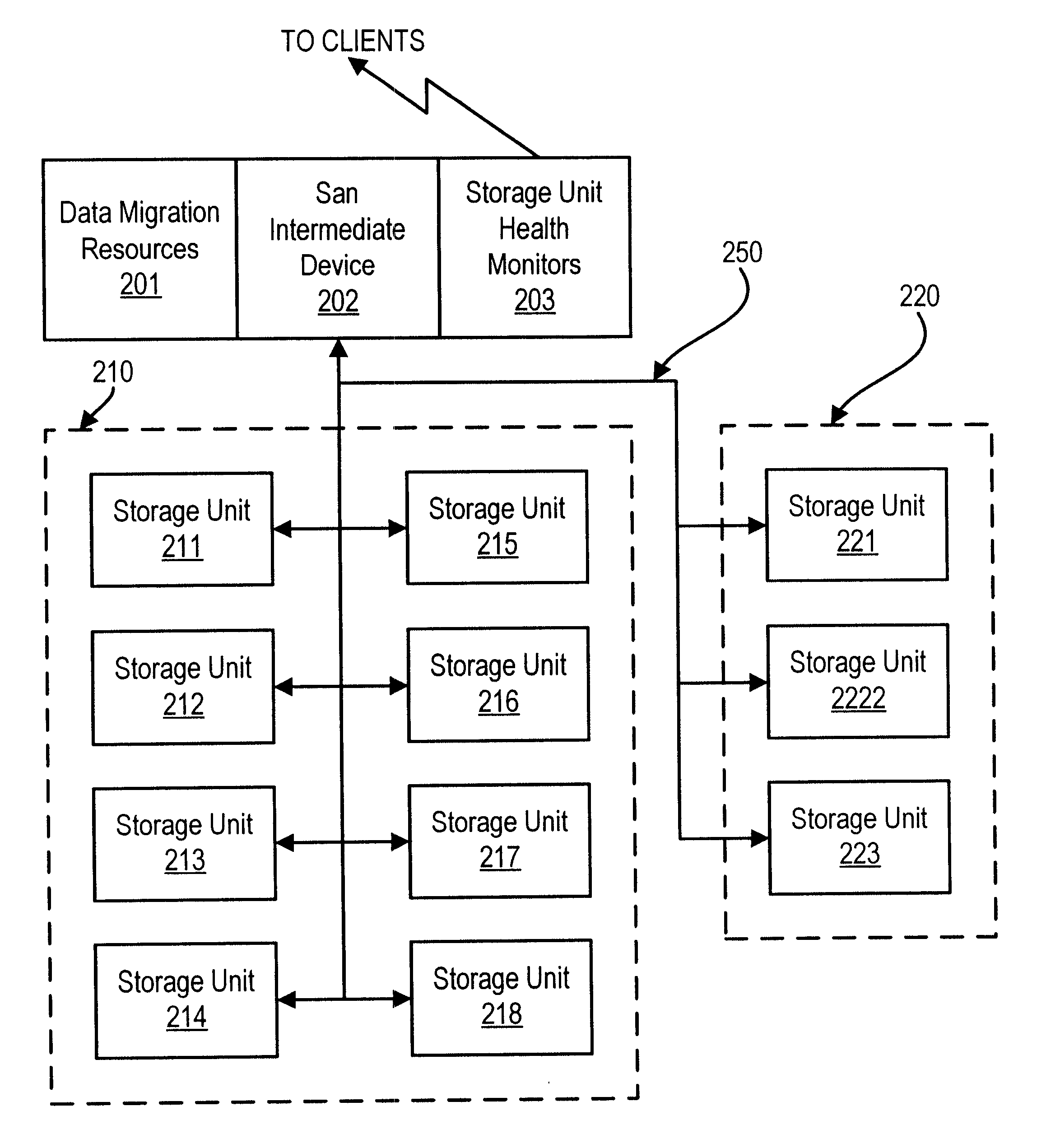
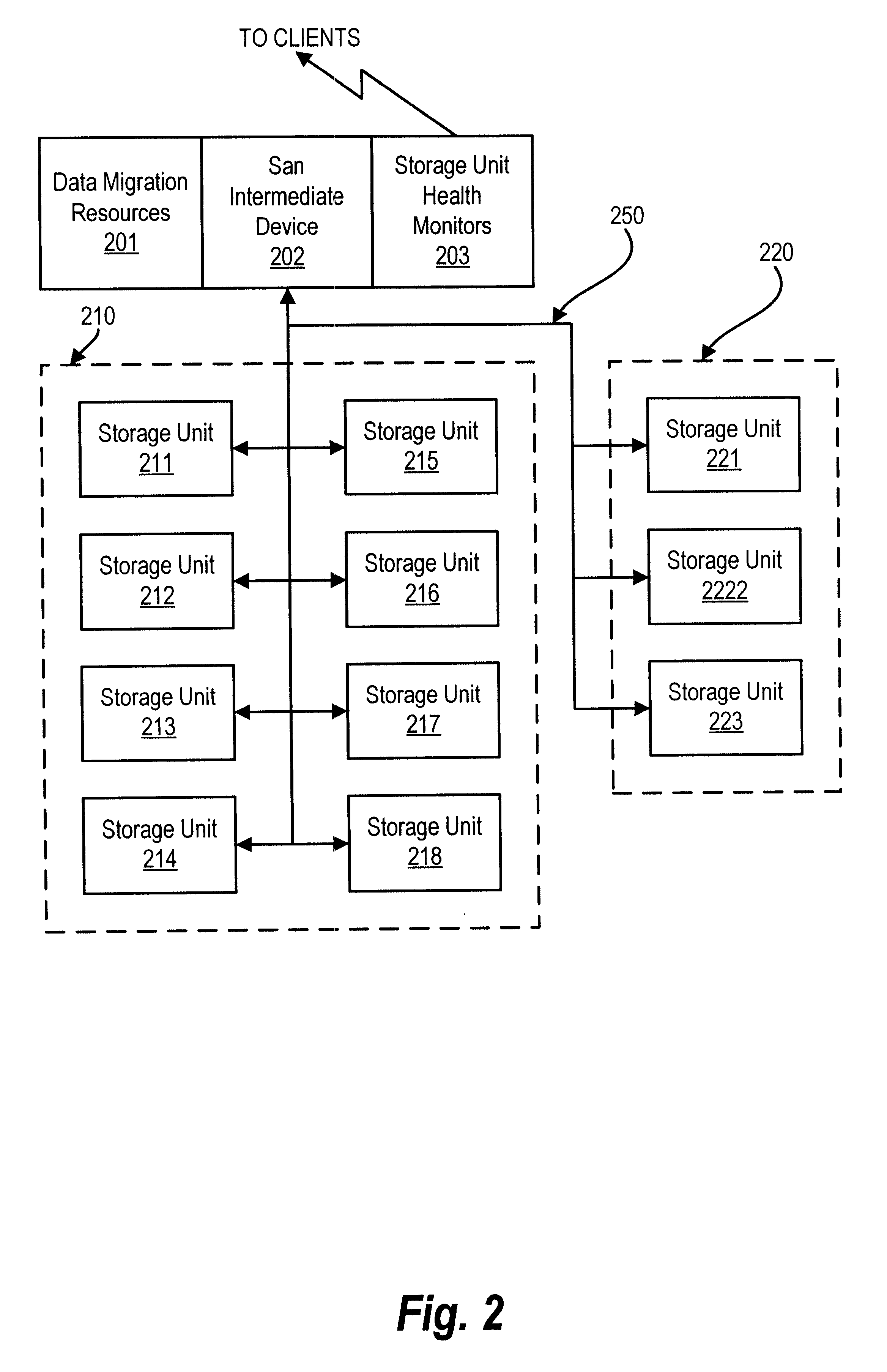
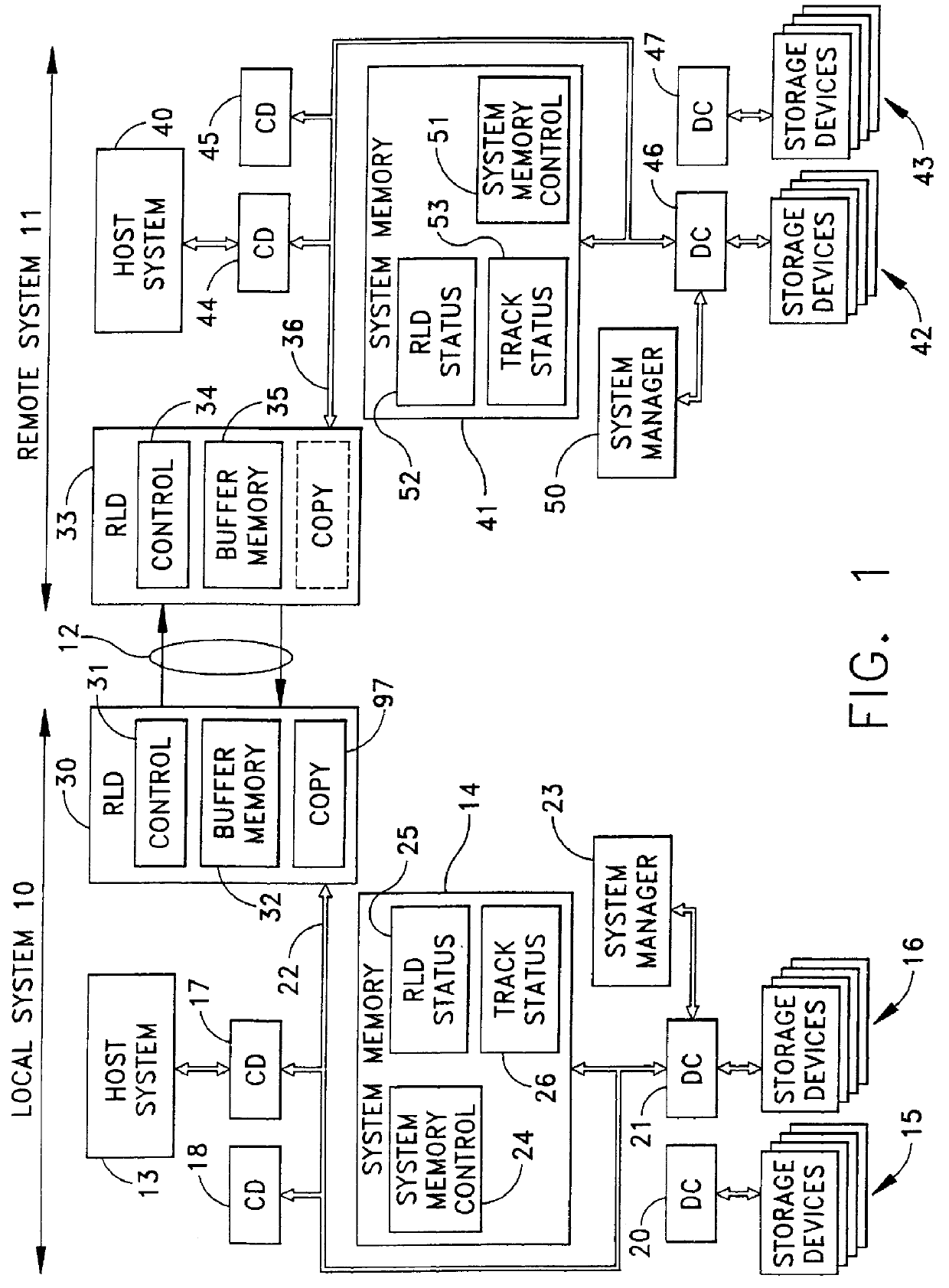
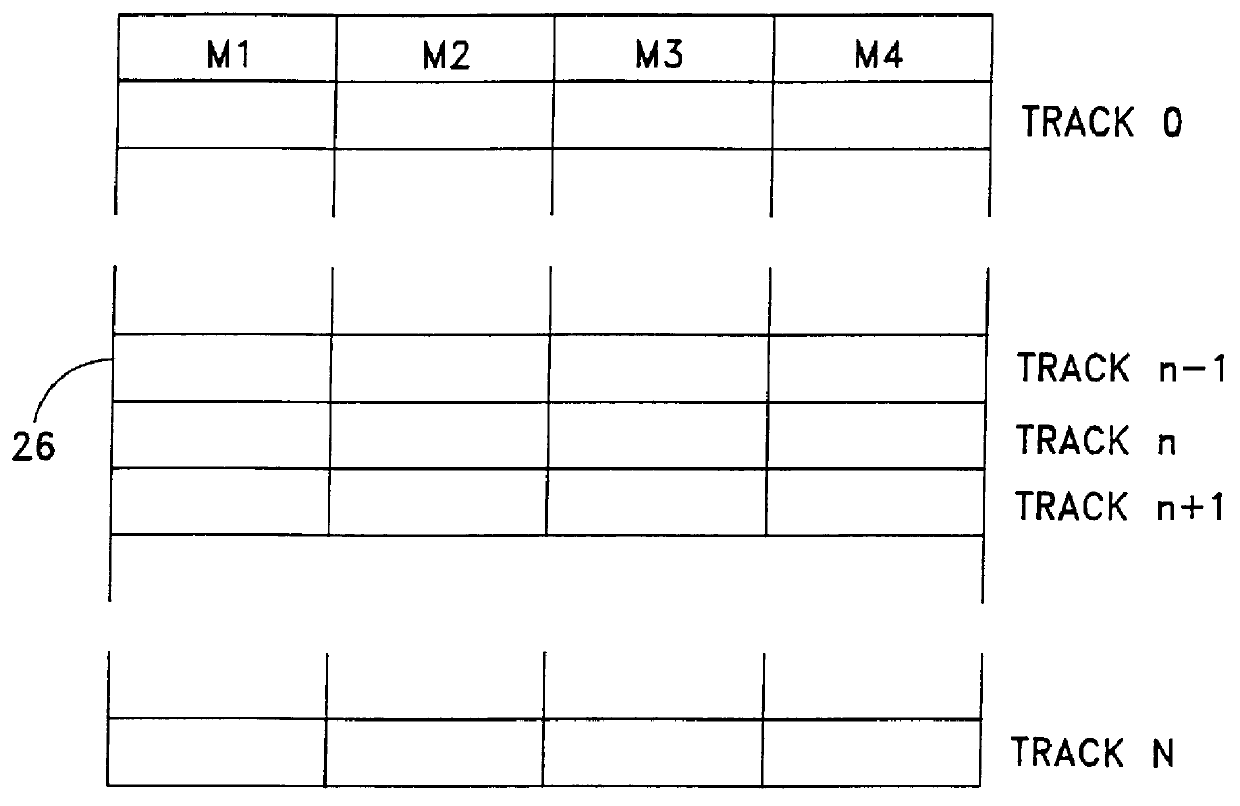
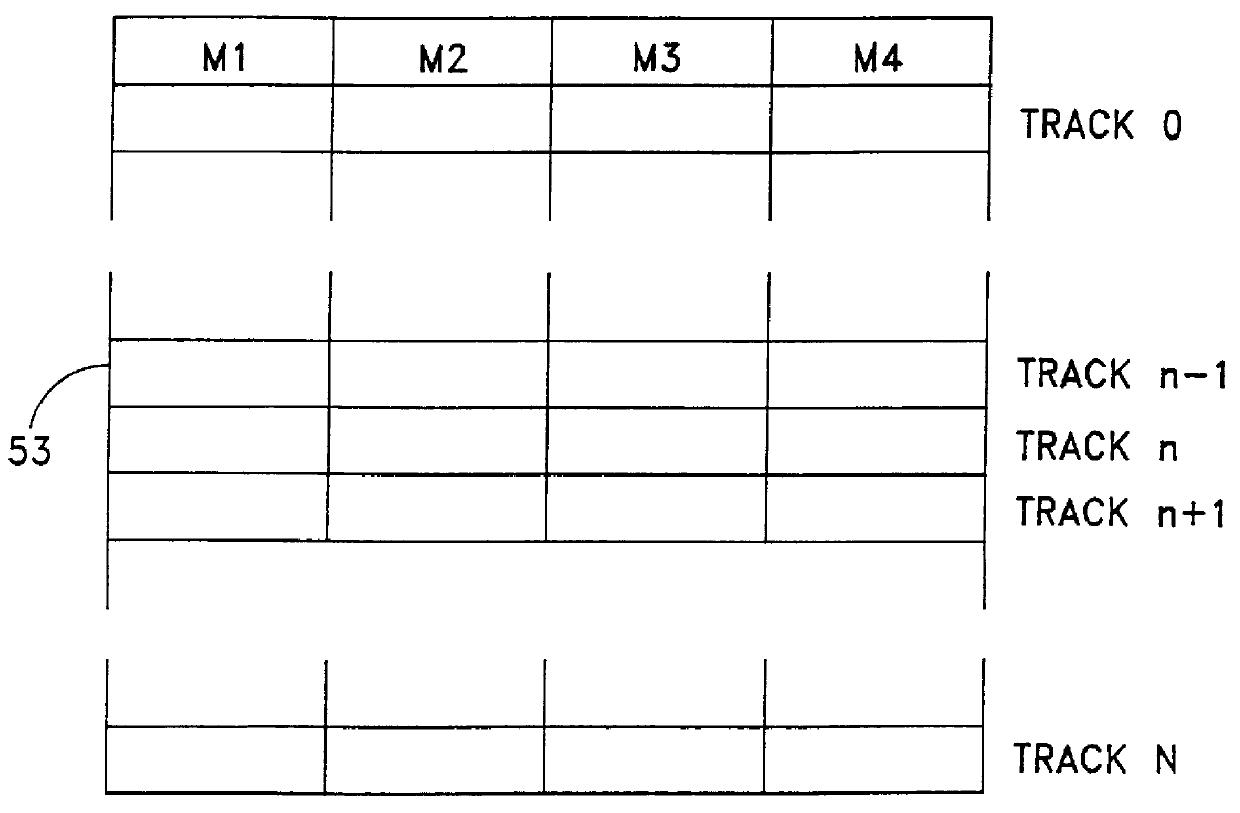
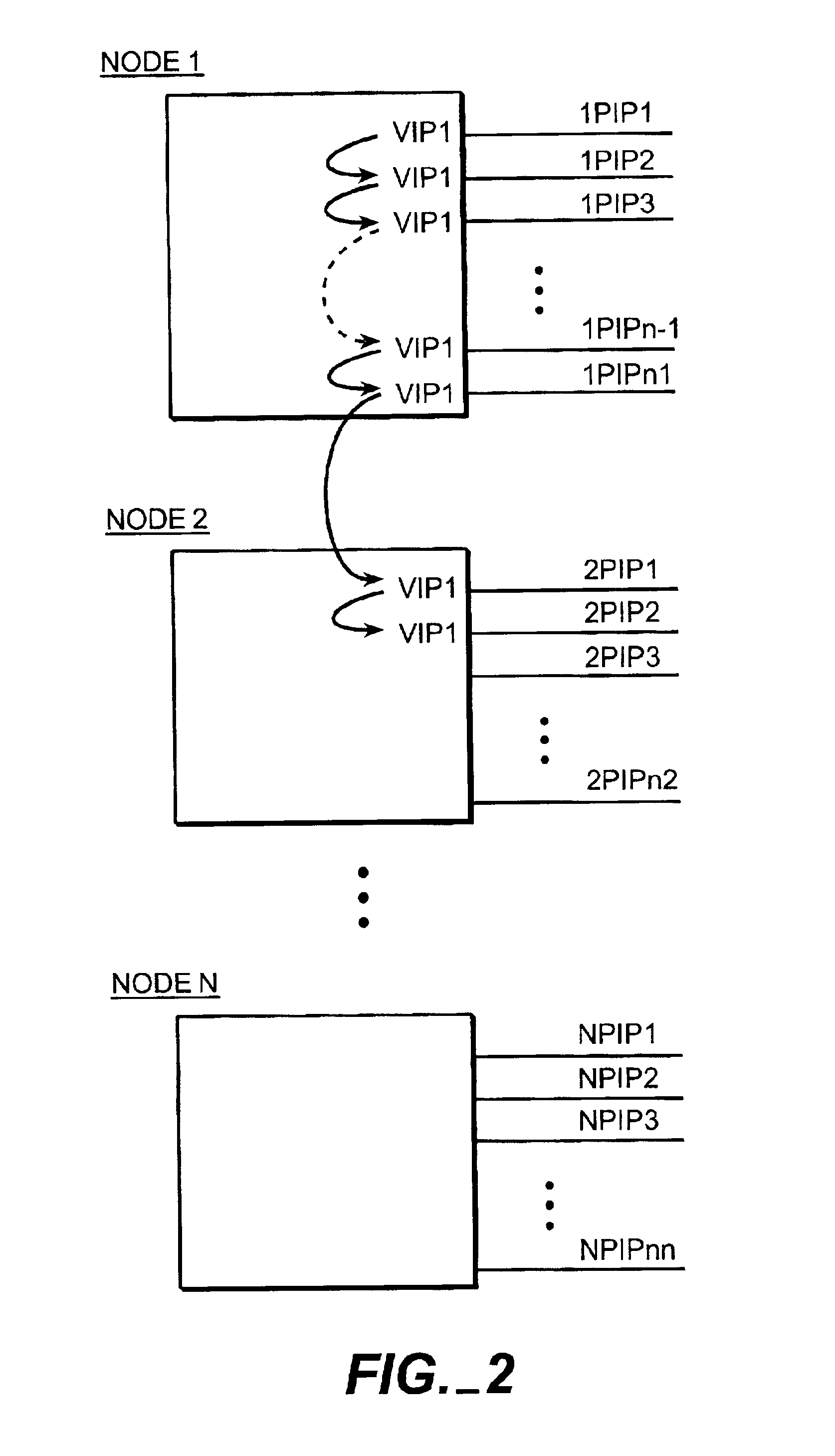
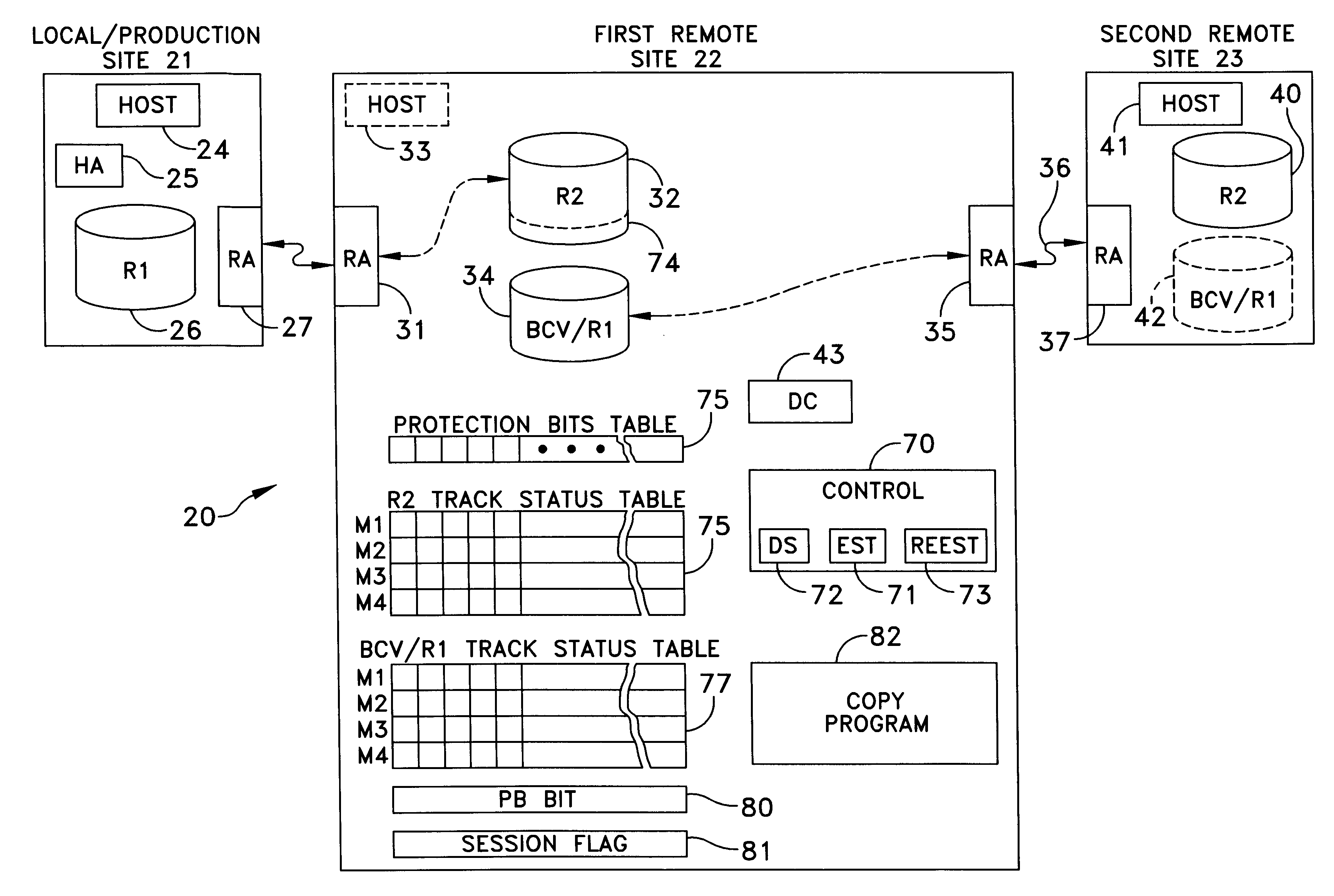
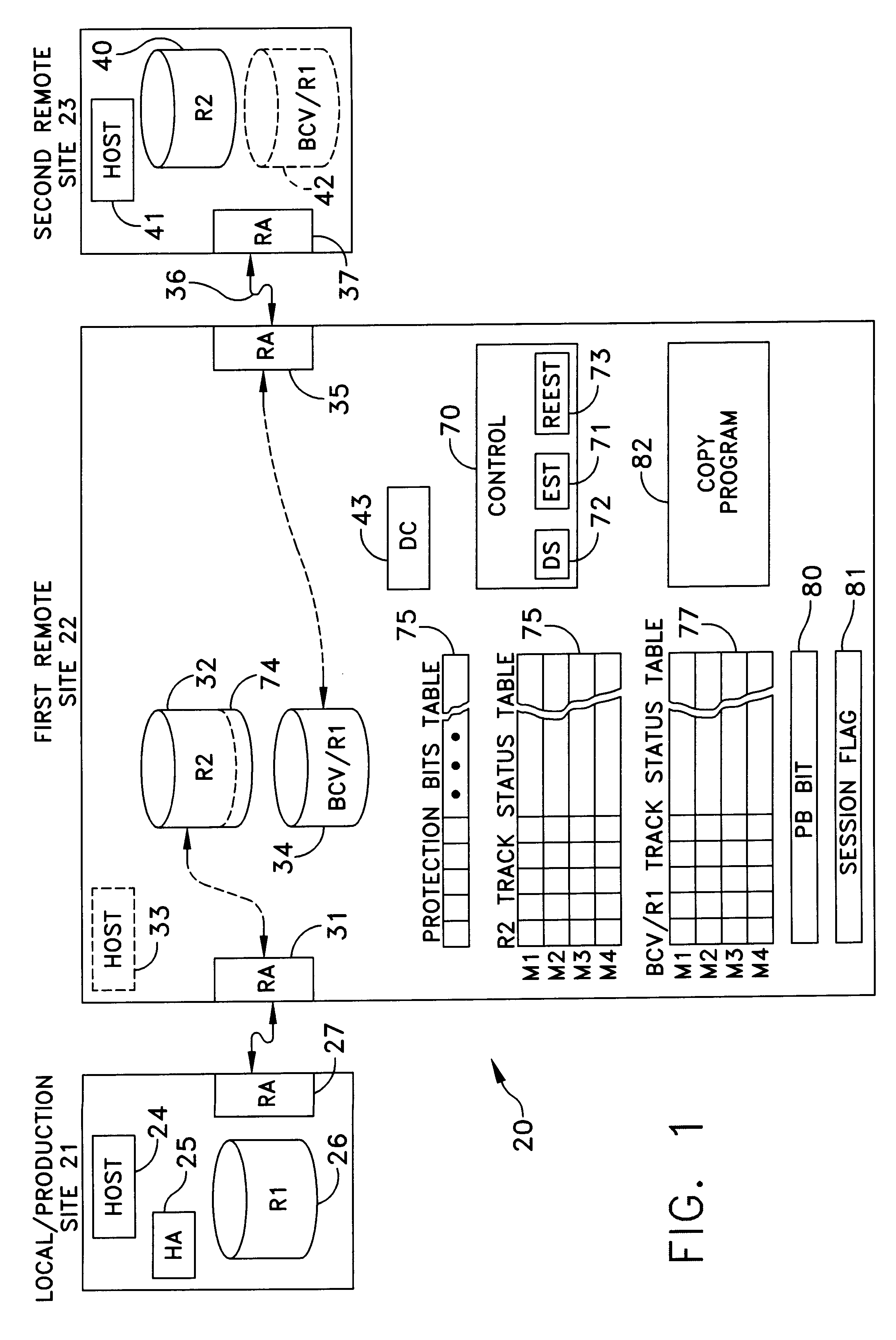
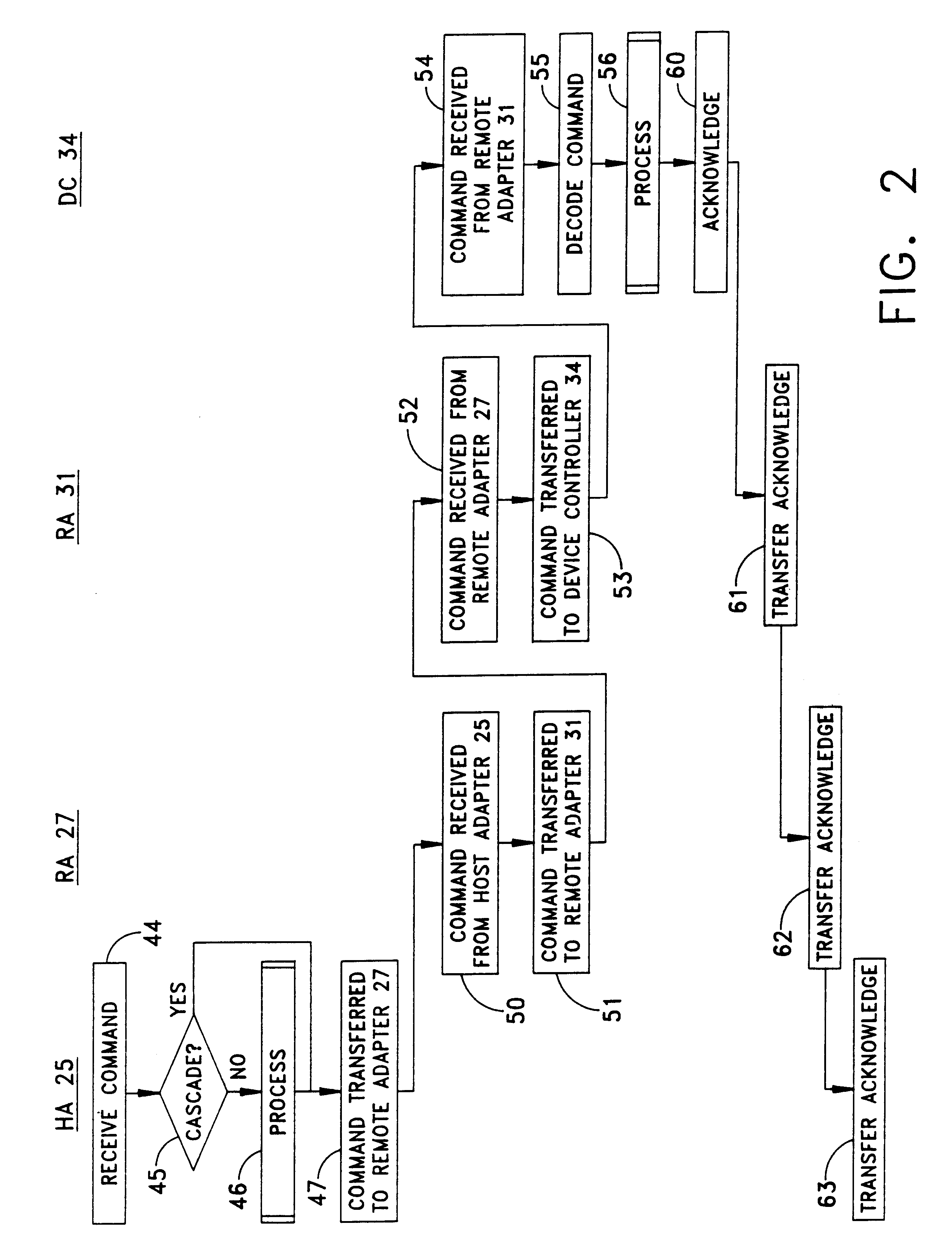
Method and apparatus for cascading data through redundant data storage units
A data storage facility for transferring data from a data altering apparatus, such as a production data processing site to a remote data receiving site. The data storage facility includes a first data store for recording each change in the data generated by the data altering apparatus. A register set records each change on a track-by-track basis. A second data store has first and second operating modes. During a first operating mode the second data store becomes a mirror of the first data store. During a second operating mode the second data store ceases to act as a mirror and becomes a source for a transfer of data to the data receiving site. Only information that has been altered, i.e., specific tracks that have been altered, are transferred during successive operations in the second operating mode. Commands from the local production site initiate the transfers between the first and second operating modes.
Owner:EMC IP HLDG CO LLC
System and method for combining data streams in pipelined storage operations in a storage network
ActiveUS20050246510A1Memory loss protectionRedundant operation error correctionMultiplexingData stream
Described herein are systems and methods for multiplexing pipelined data for backup operations. Various data streams are combined such as by multiplexing by a multiplexing module. The multiplexing module combines the data from the various data streams received by receiver module(s) into a single stream of chunks. The multiplexing module may combine data from multiple archive files into a single chunk. Additional modules perform other operations on the chunks of data to be transported such as encryption, compression, etc. The data chunks are transmitted via a transport channel to a receive pipeline that includes a second receiver module and other modules. The data chunks are then stored in a backup medium. The chunks are later retrieved and separated such as by demultiplexing for restoring to a client or for further storage as auxiliary copies of the separated data streams or archive files.
Owner:COMMVAULT SYST INC
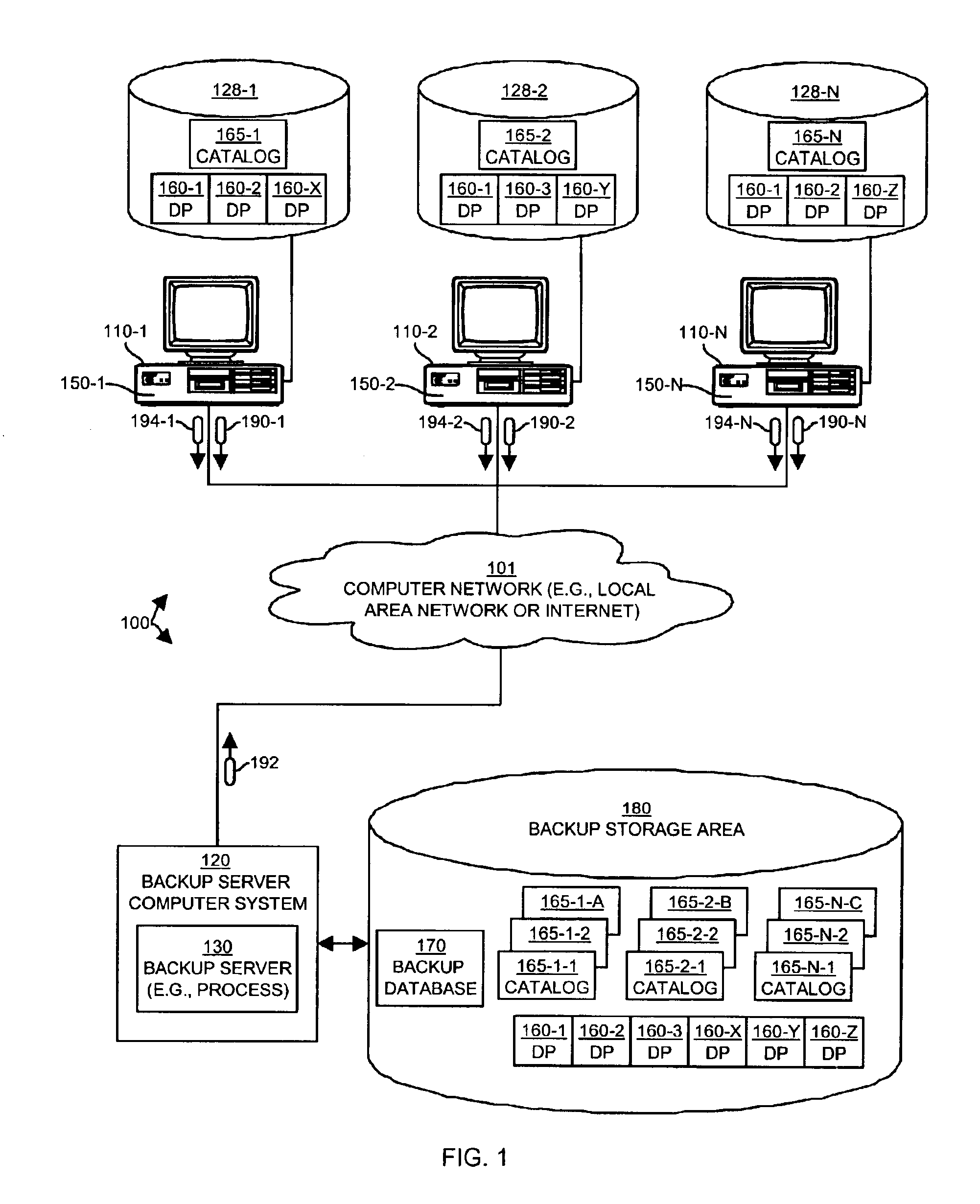
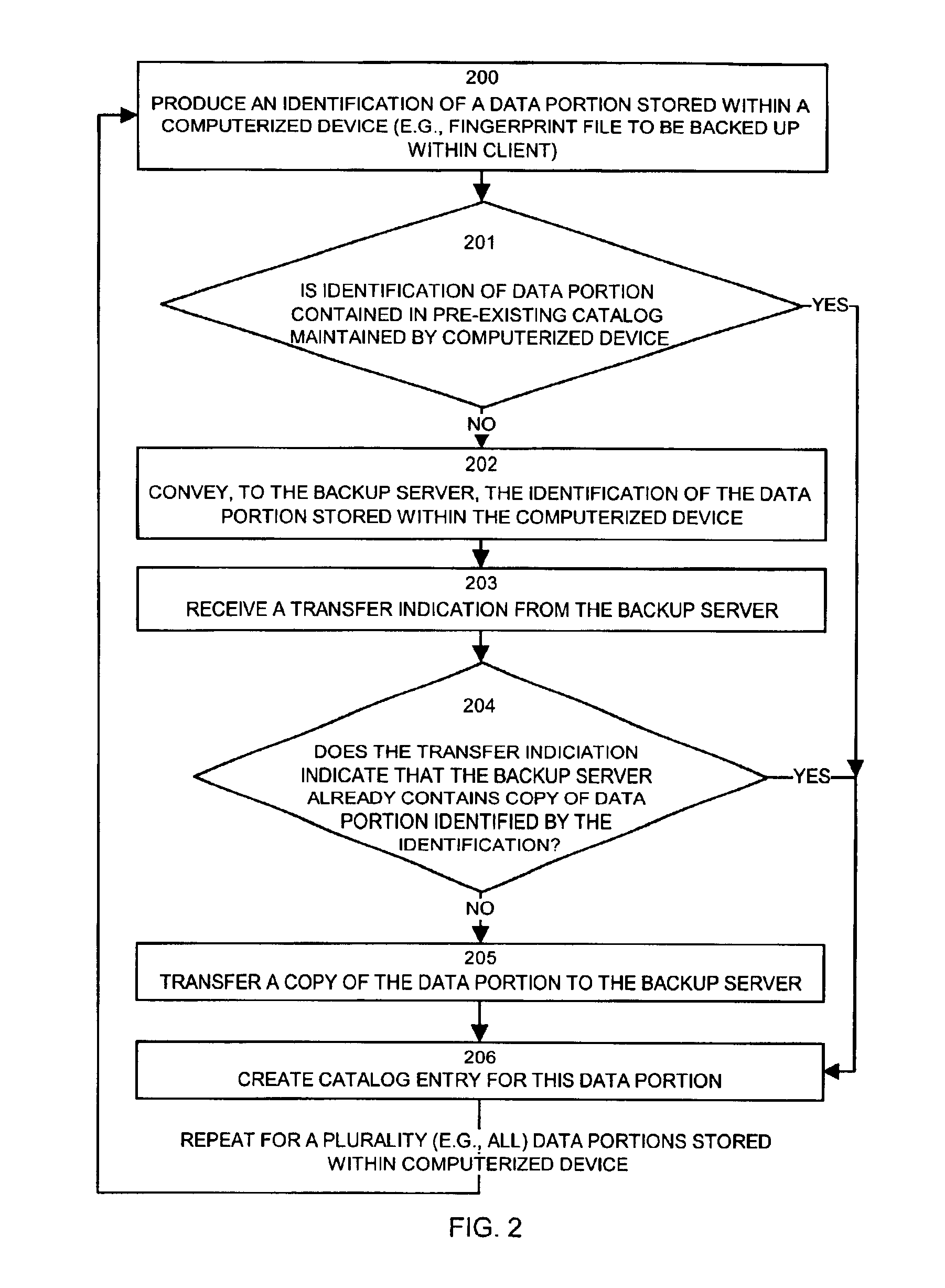
Methods and apparatus for backing up and restoring data portions stored in client computer systems
InactiveUS6865655B1NeedEliminate needData processing applicationsMemory systemsCommunication interfaceClient-side
Mechanisms and techniques operate in a computerized device to perform backup and restore operations on data portions such that if a backup server already has a copy of the content of a data portion, no client computer systems need to transfer a copy of the data portion to the backup server, even if the data portion in those clients has a different name, location, or other attributes. A backup client produces an identification of a data portion stored within a first computerized device to be backed up. The backup client conveys, to a backup server, the identification of the data portion stored within the computerized device and receives, over the communications interface, a transfer indication from the backup server. The backup client determines if the transfer indication indicates that the backup server already contains a copy of the data portion identified by the identification, and if not, the backup client transfers a copy of the data portion from the local storage device to the backup server over the communications interface.
Owner:ORACLE INT CORP
Locking technique for control and synchronization
InactiveUS6973549B1Digital data information retrievalMultiprogramming arrangementsFast pathLocking mechanism
Described are techniques used in a computer system for handling data operations to storage devices. A switching fabric includes one or more fast paths for handling lightweight, common data operations and at least one control path for handling other data operations. A control path manages one or more fast paths. The fast path and the control path are utilized in mapping virtual to physical addresses using mapping tables. The mapping tables include an extent table of one or more entries corresponding to varying address ranges. The size of an extent may be changed dynamically in accordance with a corresponding state change of physical storage. The fast path may cache only portions of the extent table as needed in accordance with a caching technique. The fast path may cache a subset of the extent table stored within the control path. A set of primitives may be used in performing data operations. A locking mechanism is described for controlling access to data shared by the control paths.
Owner:IBM CORP
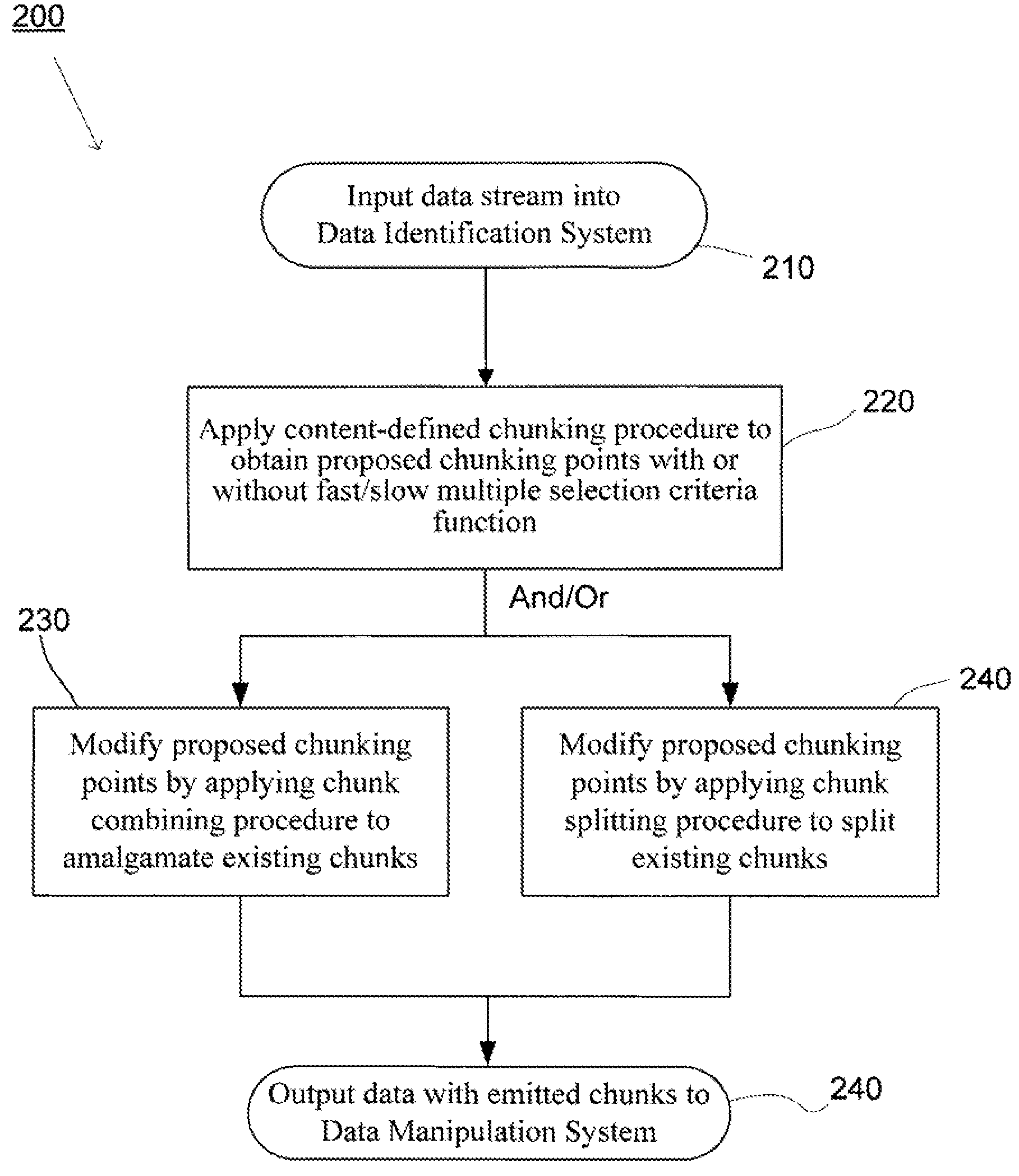
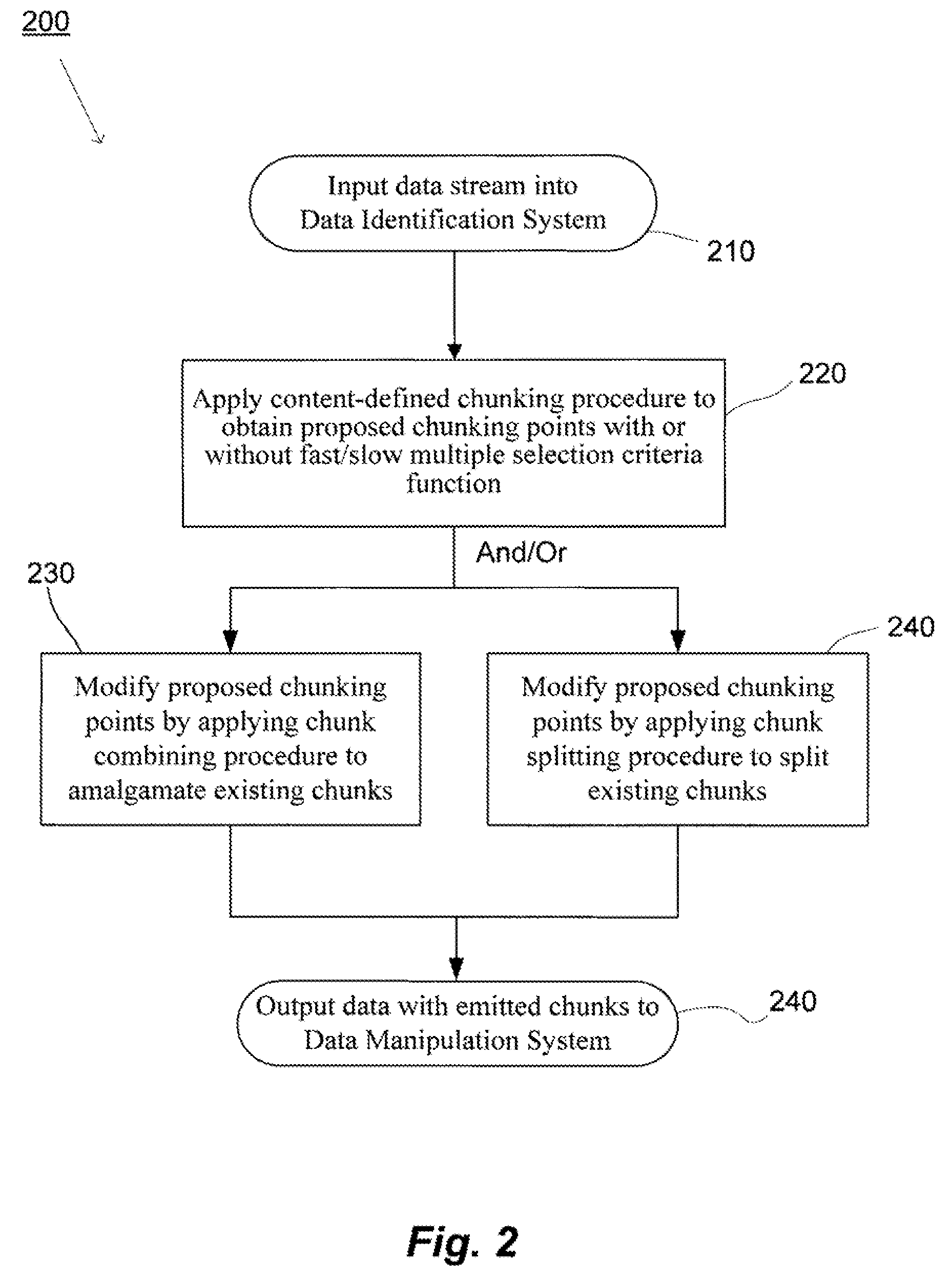
Methods and systems for quick and efficient data management and/or processing
ActiveUS20080133561A1Improve data processing efficiencyReduce quality problemsDigital data information retrievalProgram control using stored programsData managementCombined technique
System(s) and method(s) are provided for data management and data processing. For example, various embodiments may include systems and methods relating to relatively larger groups of data being selected with comparable or better performing selection results (e.g., high data redundancy elimination and / or average chunk size). In various embodiments, the system(s) and method(s) may include, for example a data group, block, or chunk combining technique or / and a data group, block, or chunk splitting technique. Various embodiments may include a first standard or typical data grouping, blocking, or chunking technique and / or data group, block, or chunk combining technique or / and a data group, block, or chunk splitting technique. Exemplary system(s) and method(s) may relate to data hashing and / or data elimination. Embodiments may include a look-ahead buffer and determine whether to emit small chunks or large chunks based on characteristics of underlying data and / or particular application of the invention (e.g., for backup).
Owner:NEC CORP
Controlling data storage in an array of storage devices
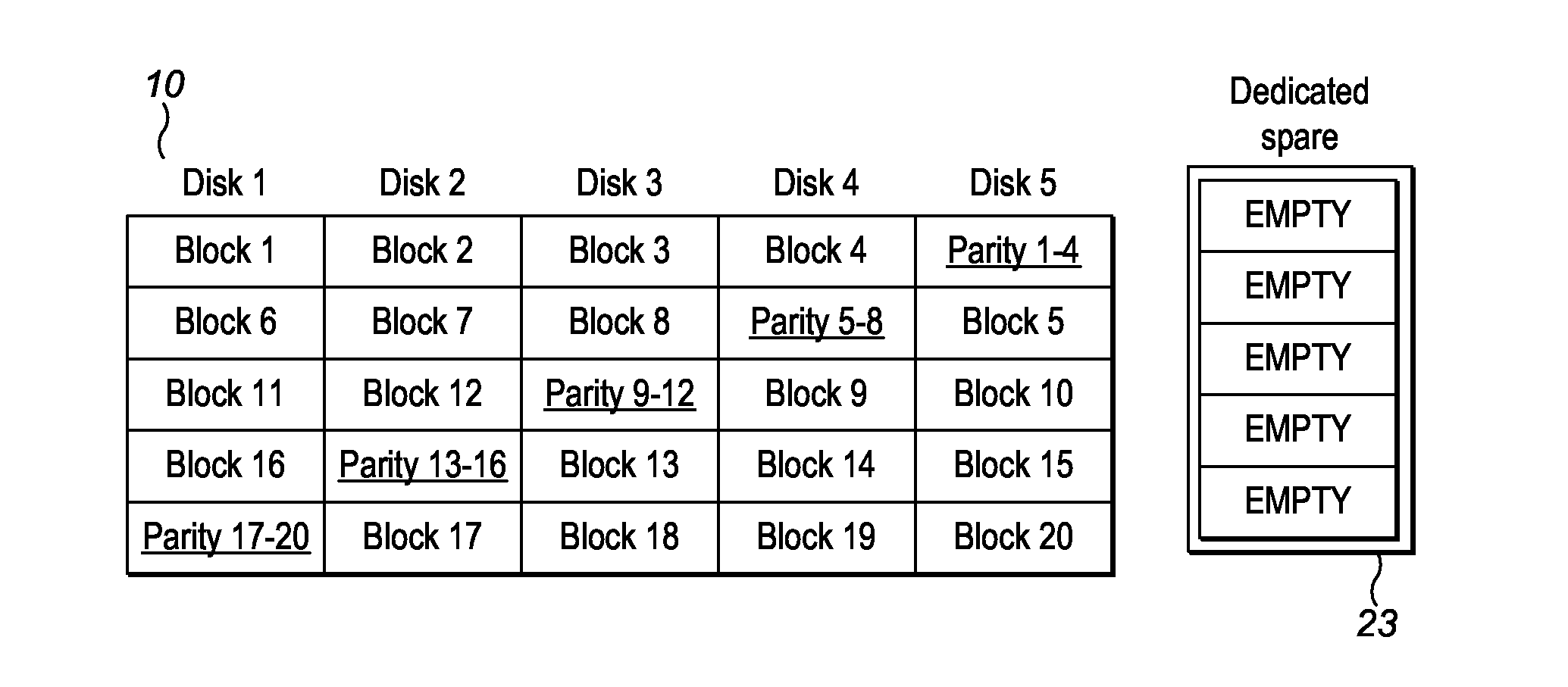
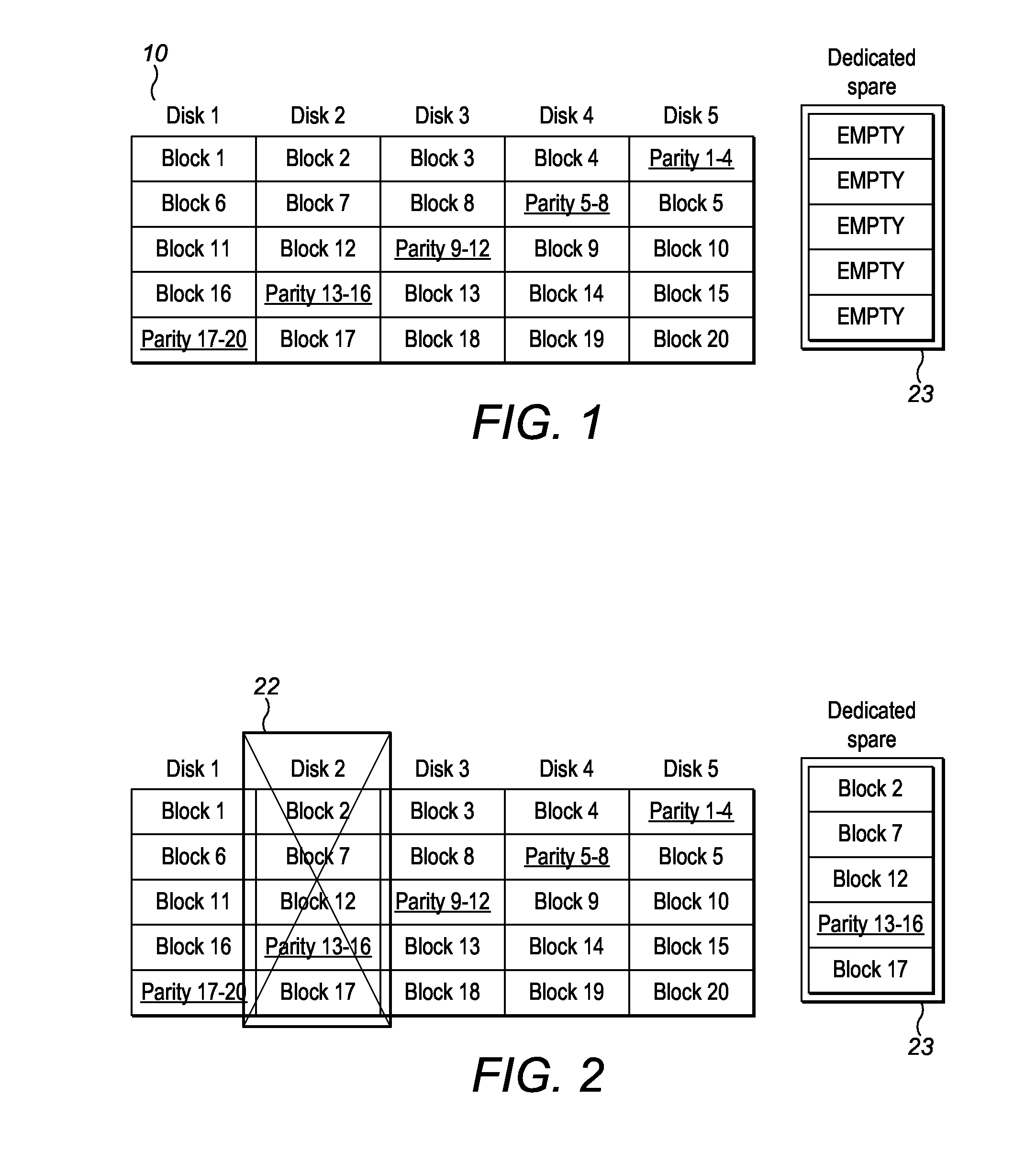
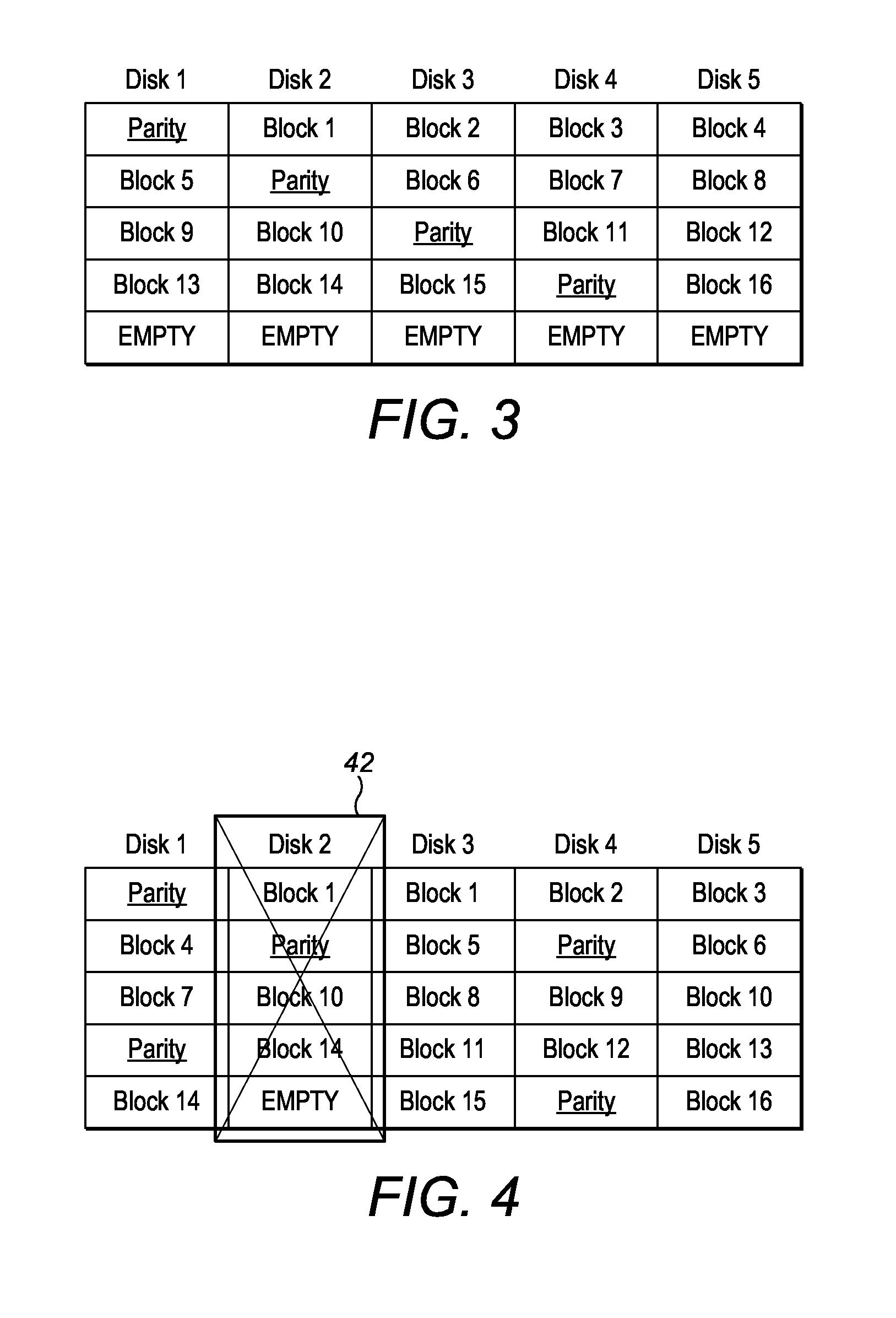
ActiveUS20140325262A1Reduce mismatchLow costRedundant hardware error correctionData storeDevice failure
Methods, apparatus and computer programs have been provided for mitigating a problem of non-optimal recovery from storage device failures. A method involves determining a required write performance for rebuilding data of a failed device, based at least partly on the potential read performance of storage devices in a data rebuild; and allocating a virtual storage area within available storage, which allocation of virtual storage is based at least partly on the required write performance. Data is rebuilt by writing to the allocated virtual storage area, and data recovery is completed by migrating this rebuilt data to at least one data storage device such as a spare physical storage device within the array.
Owner:GLOBALFOUNDRIES US INC
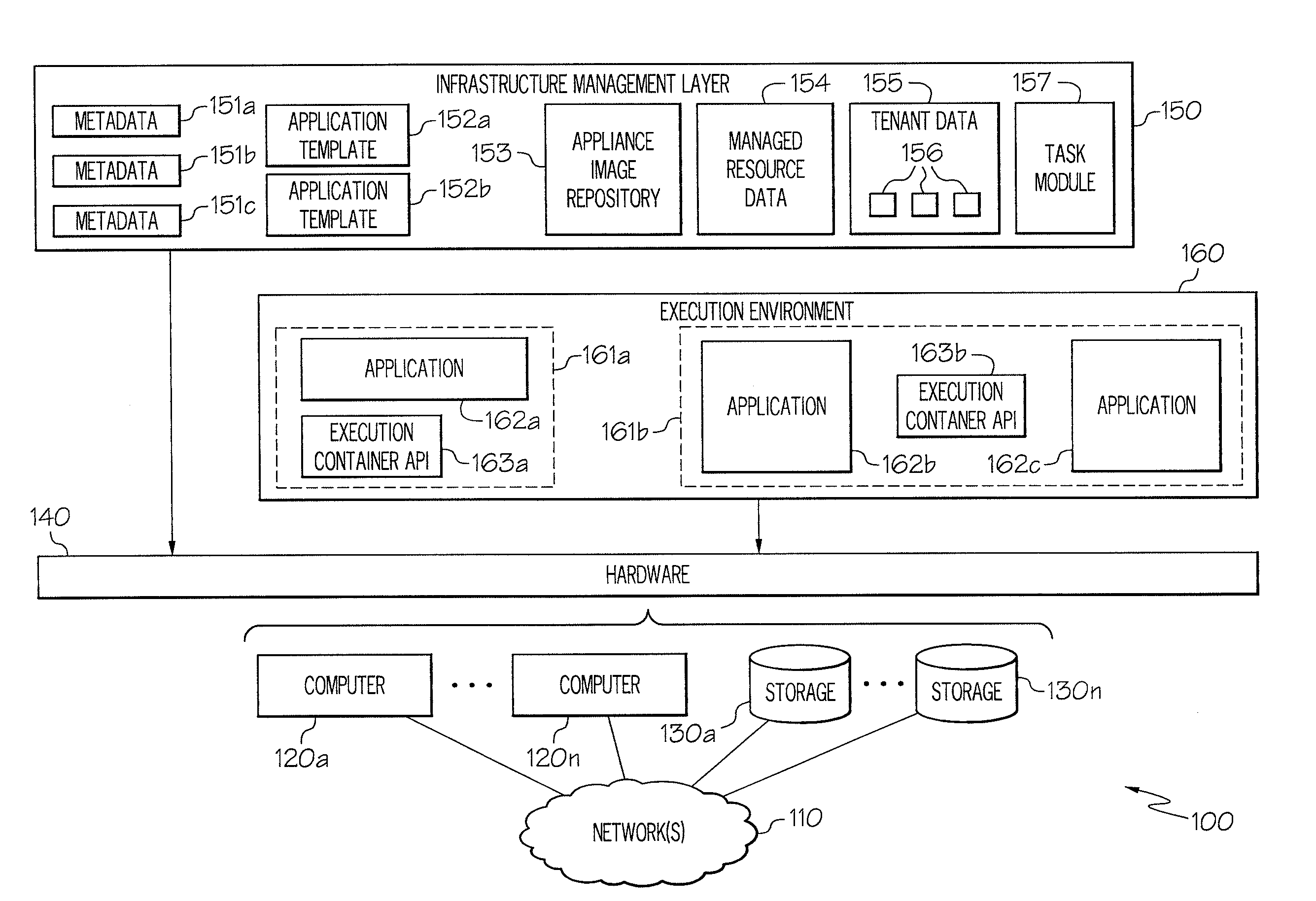
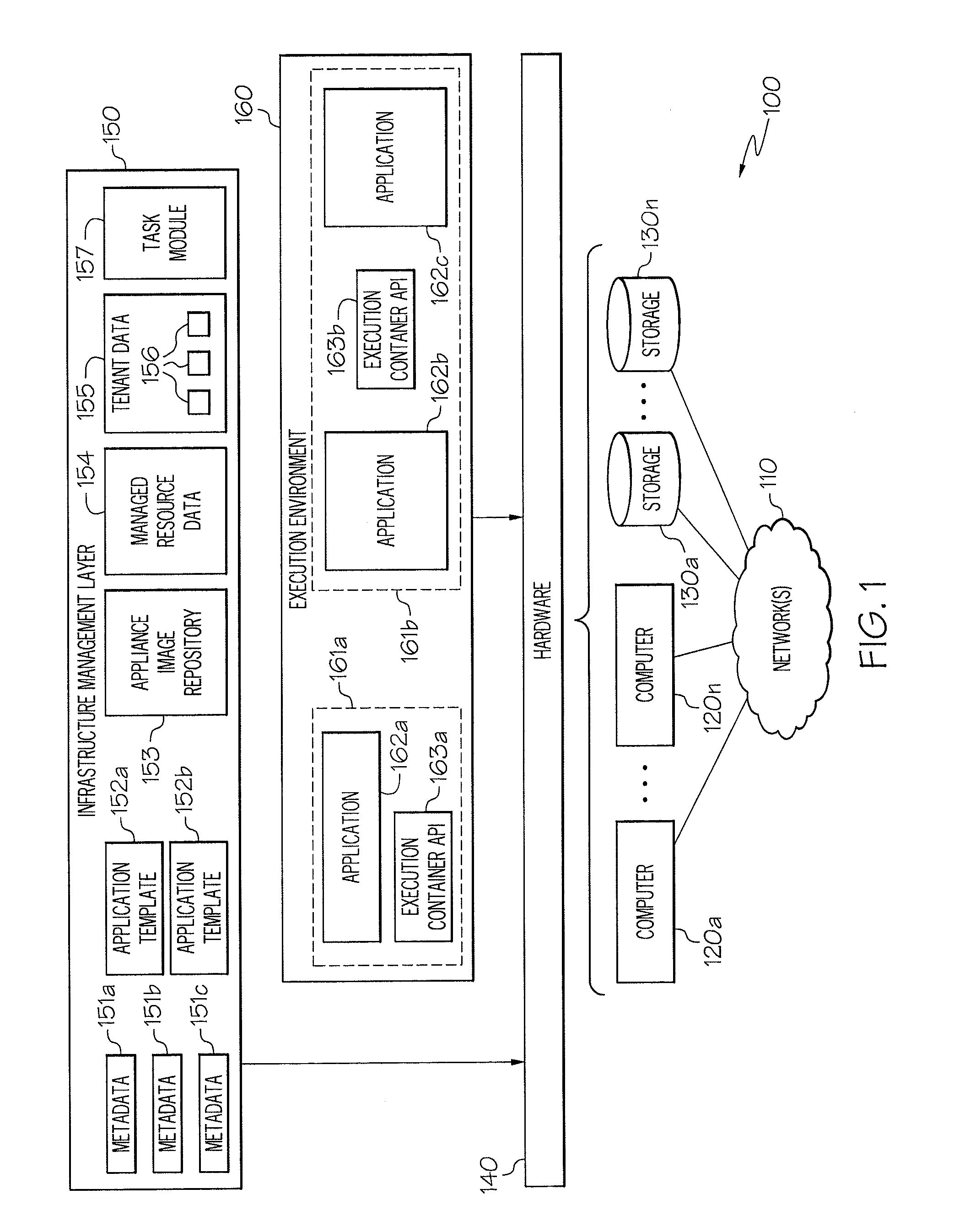
Enhanced Software Application Platform
A system includes information for generating a first appliance based on first appliance information, information for generating a second appliance based on second appliance information, and information for configuring communication between the first appliance and the second appliance. The system further includes at least one processor configured to generate a first volume by copying the first appliance information using a first set of parameters associated with an environment in which the first volume is situated, and generate a second volume by copying the second appliance information using a second set of parameters associated with an environment in which the second volume is situated. The system also includes at least one processor configured to initiate a first appliance instance by executing code from the first volume using information in the third volume, and initiate a second appliance instance by executing code in the second volume using information in a fourth volume.
Owner:CA TECH INC
Computer with switchable components
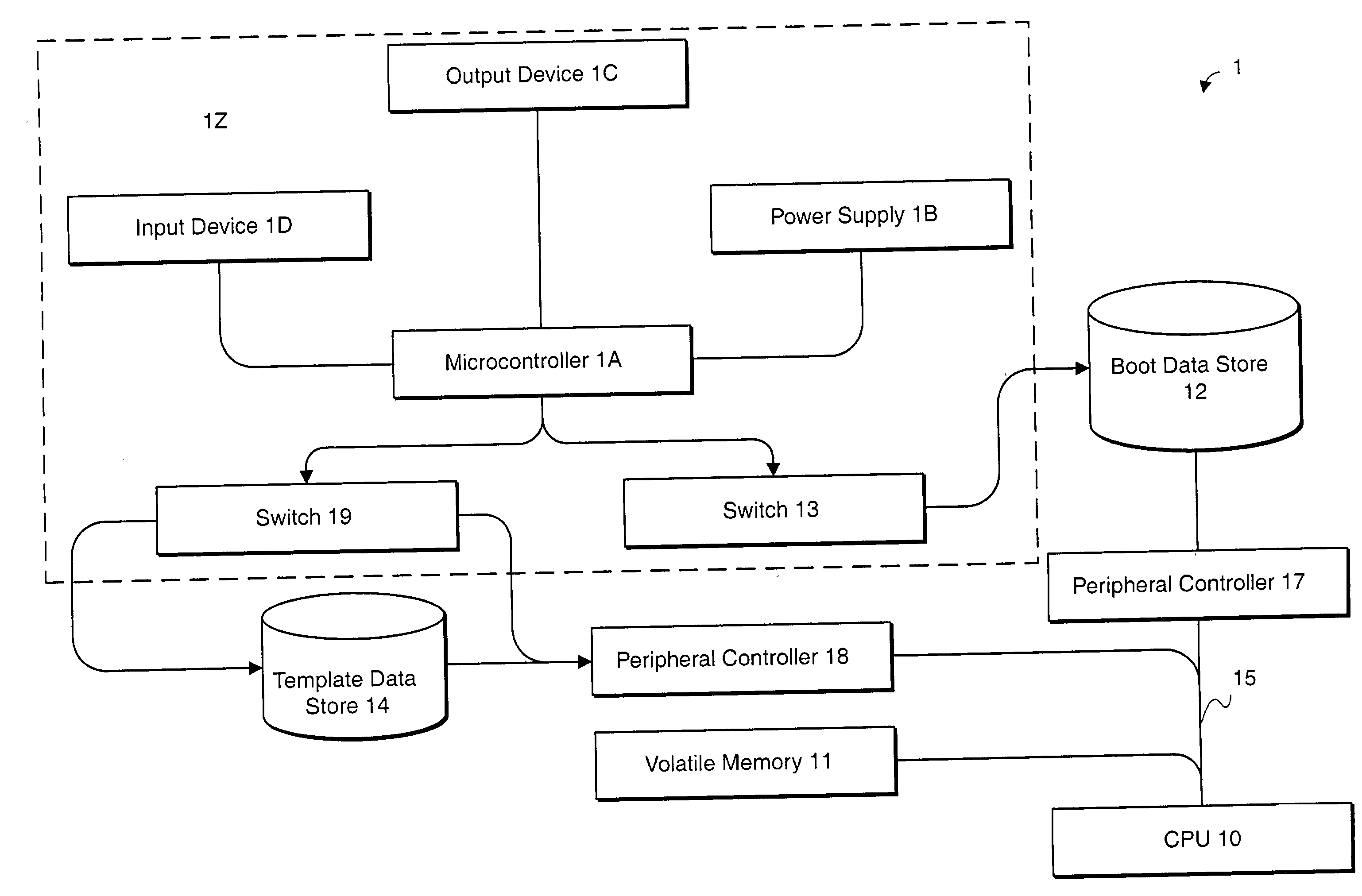
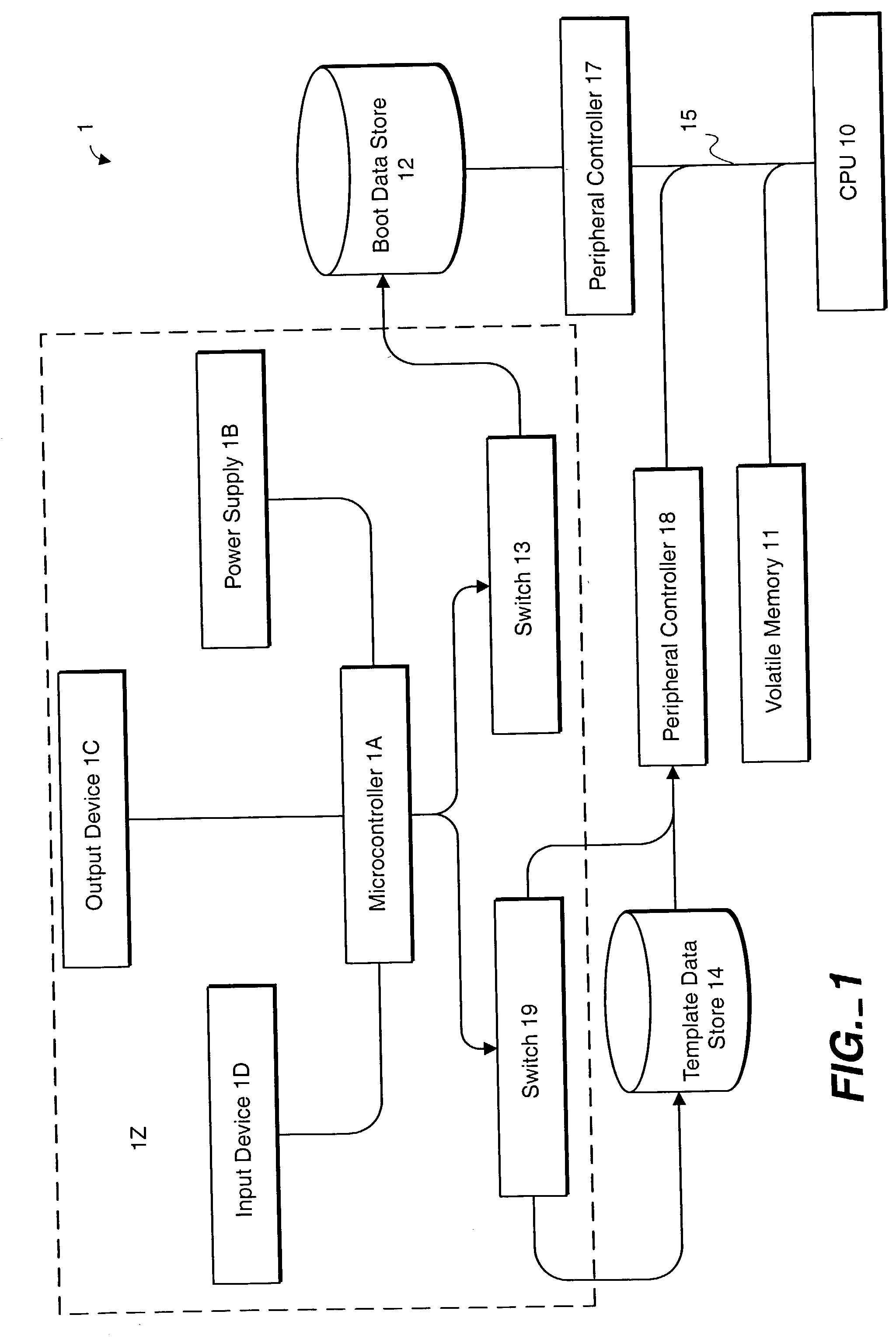
InactiveUS20020188887A1Redundant operation error correctionRedundant hardware error correctionComputerized systemBIOS
A method or system for supporting a computer systems self repair, including the computer executed steps for booting from a first boot device, and booting from a second boot device in response to a signal indicating a need for repair. While booted from the second boot device the computer system is capable of repairing software on the first boot device. The signal may effect a logical or physical switch. Repairing software may be performed in part by copying BIOS, template, backup or archive software from a device other than the first boot device. Repairing software may be performed automatically without direction by a user or according to preset preferences.
Owner:SELF REPAIRING COMP
Inoculation of computing devices against a selected computer virus
ActiveUS7287278B2Avoid infectionMemory loss protectionUnauthorized memory use protectionComputer scienceVirus
In a distributed network having a number of server computers and associated client devices, method of creating an anti-computer virus agent is described. As a method, the inoculation is carried out by parsing a selected computer virus into a detection module that identifies a selected one of the client devices as a target client device, an infection module that causes the virus to infect those target client devices not infected by the selected virus, and a viral code payload module that infects the targeted client device modifying the infection module to infect those computers already infected by the selected virus; and incorporating inoculation viral code in the payload module that acts to prevent further infection by the selected virus.
Owner:TREND MICRO INC
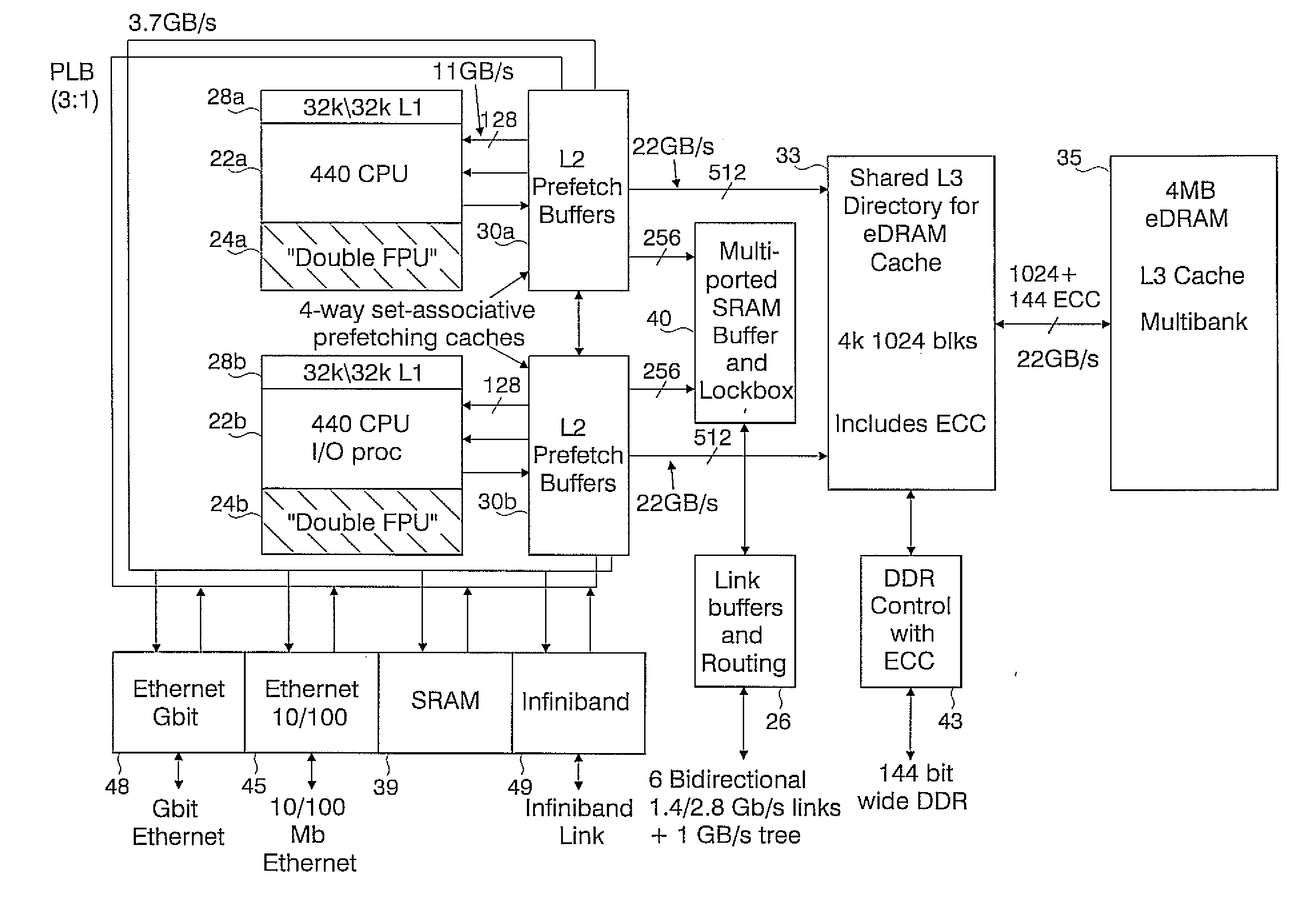
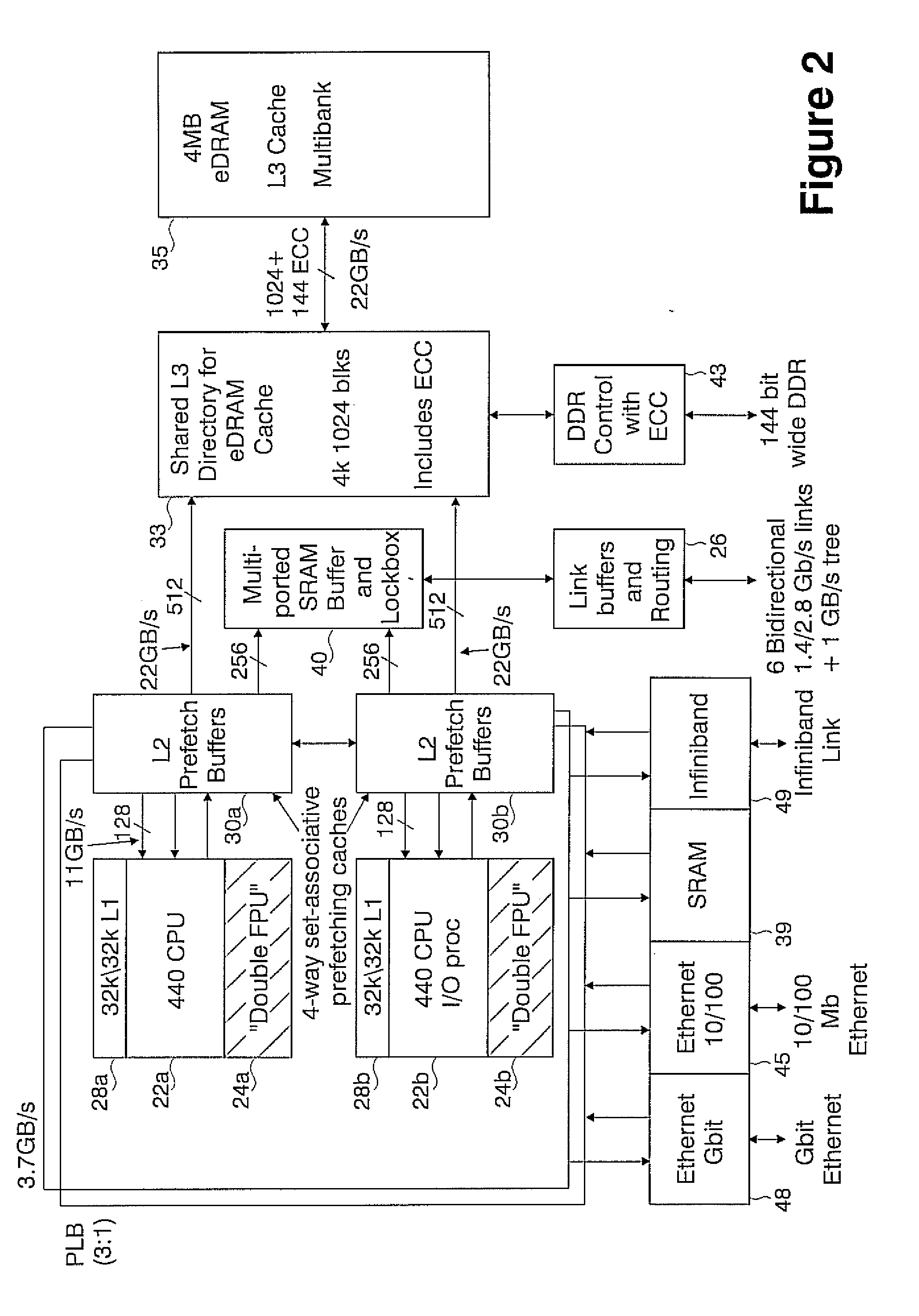
Novel massively parallel supercomputer
InactiveUS20090259713A1Low costReduced footprintError preventionProgram synchronisationSupercomputerPacket communication
Owner:INT BUSINESS MASCH CORP
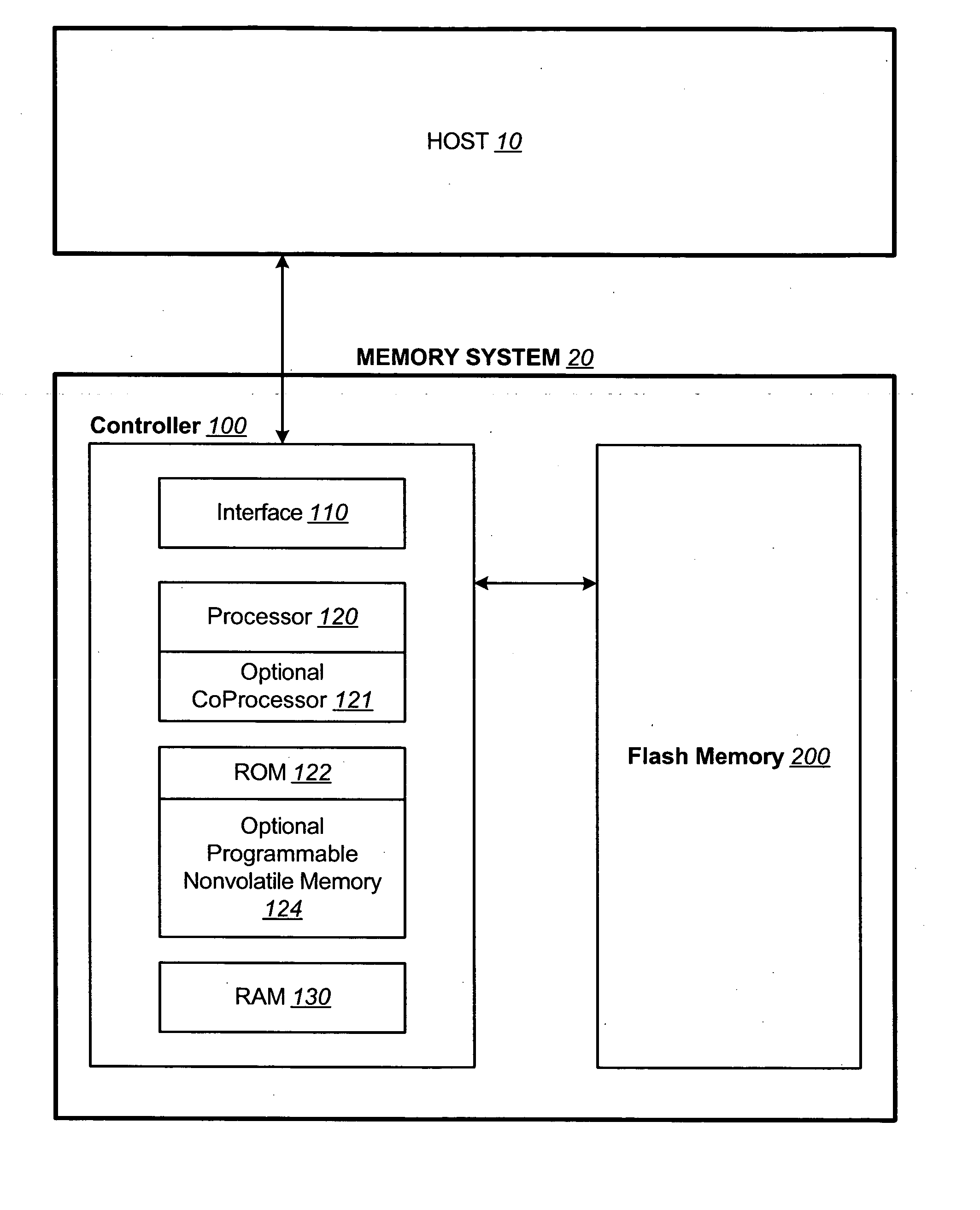
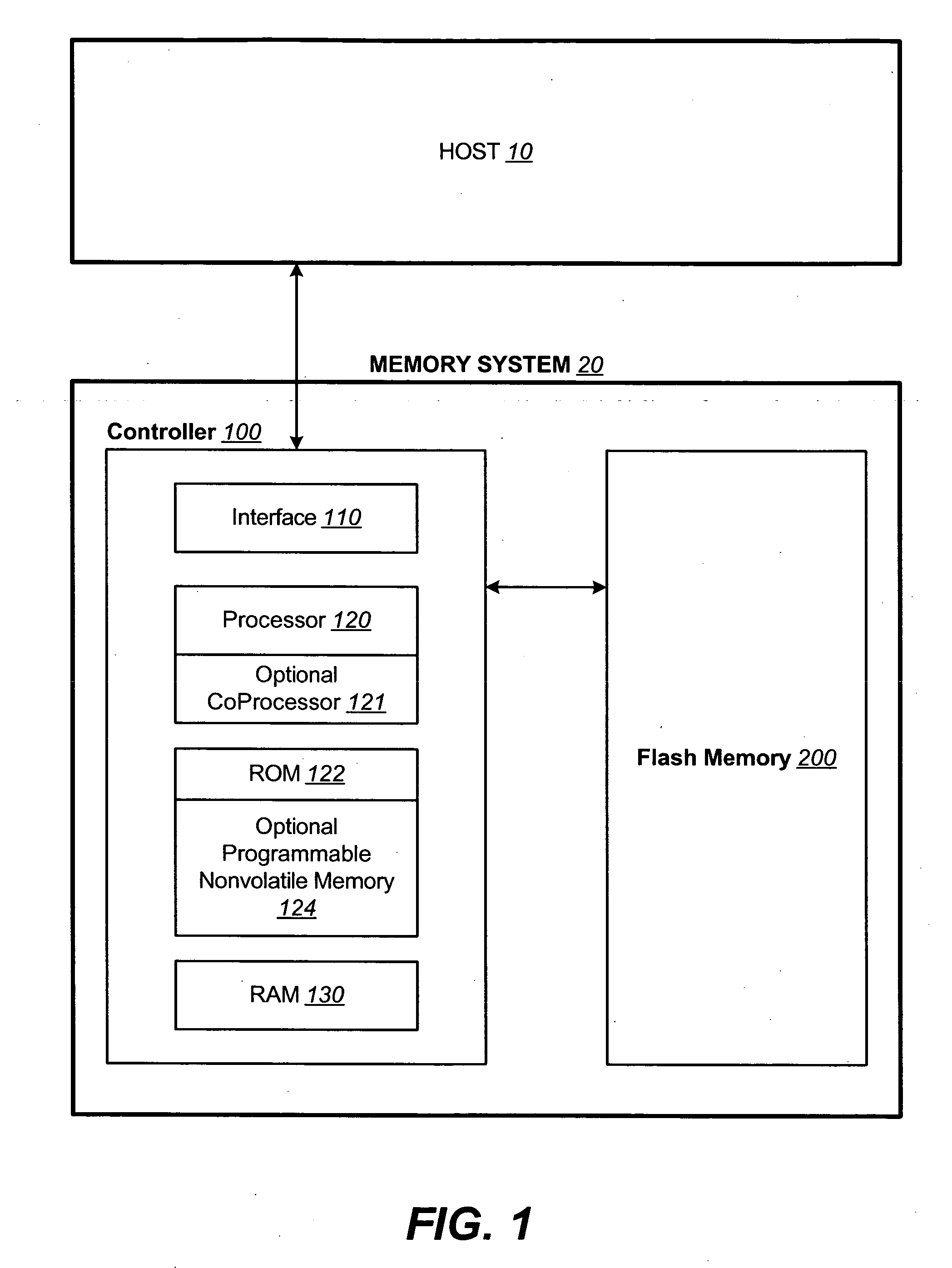
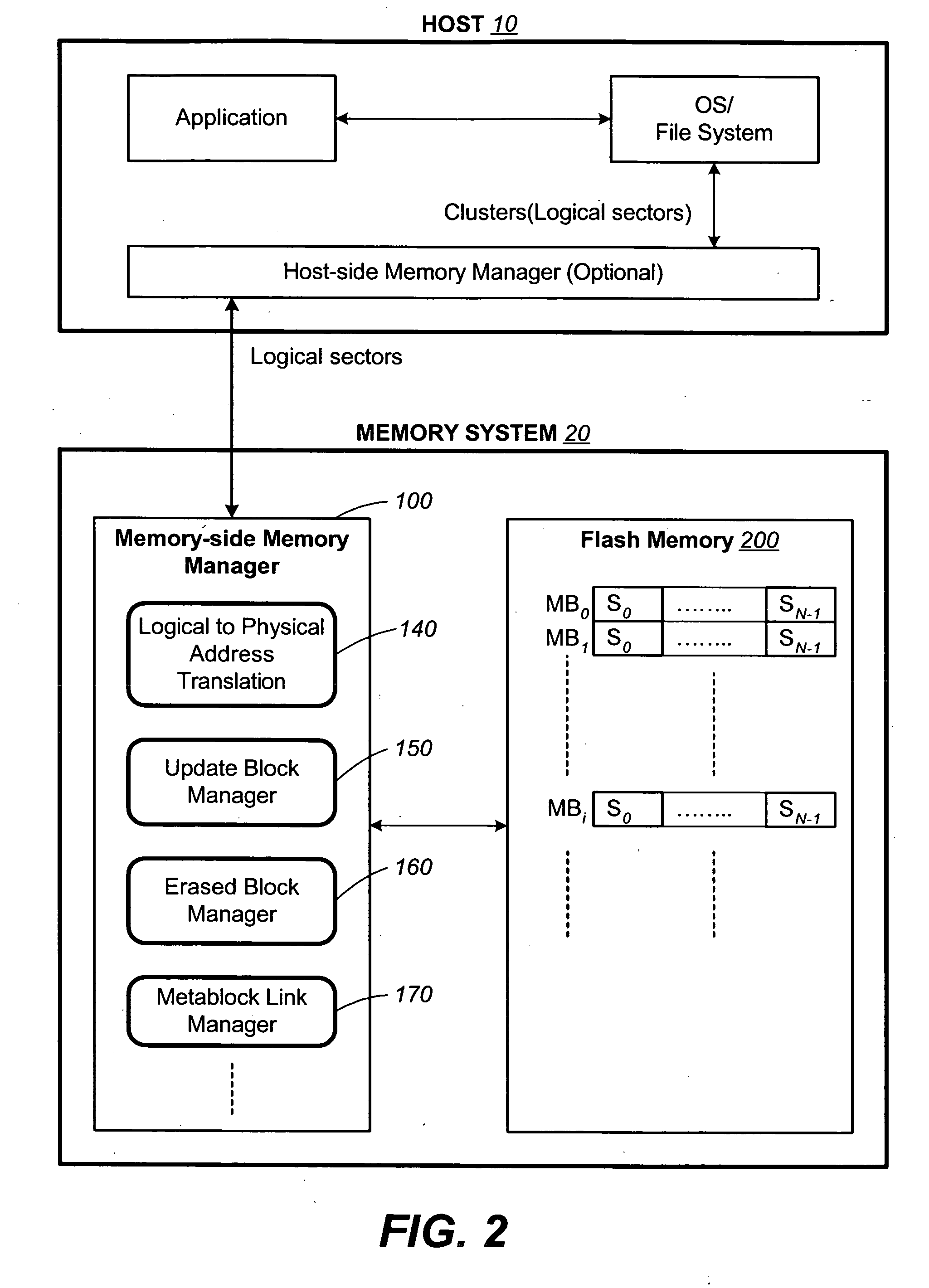
Non-volatile memory and method with non-sequential update block management
InactiveUS20050141312A1Good ECCExtra level of reliabilityMemory architecture accessing/allocationMemory adressing/allocation/relocationLogic cellOperating system
In a nonvolatile memory with block management system that supports update blocks with non-sequential logical units, an index of the logical units in a non-sequential update block is buffered in RAM and stored periodically into the non-volatile memory. In one embodiment, the index is stored in a block dedicated for storing indices. In another embodiment, the index is stored in the update block itself. In yet another embodiment, the index is stored in the header of each logical unit. In another aspect, the logical units written after the last index update but before the next have their indexing information stored in the header of each logical unit. In this way, after a power outage, the location of recently written logical units can be determined without having to perform a scanning during initialization. In yet another aspect, a block is managed as partially sequential and partially non-sequential, directed to more than one logical subgroup.
Owner:SANDISK TECH LLC
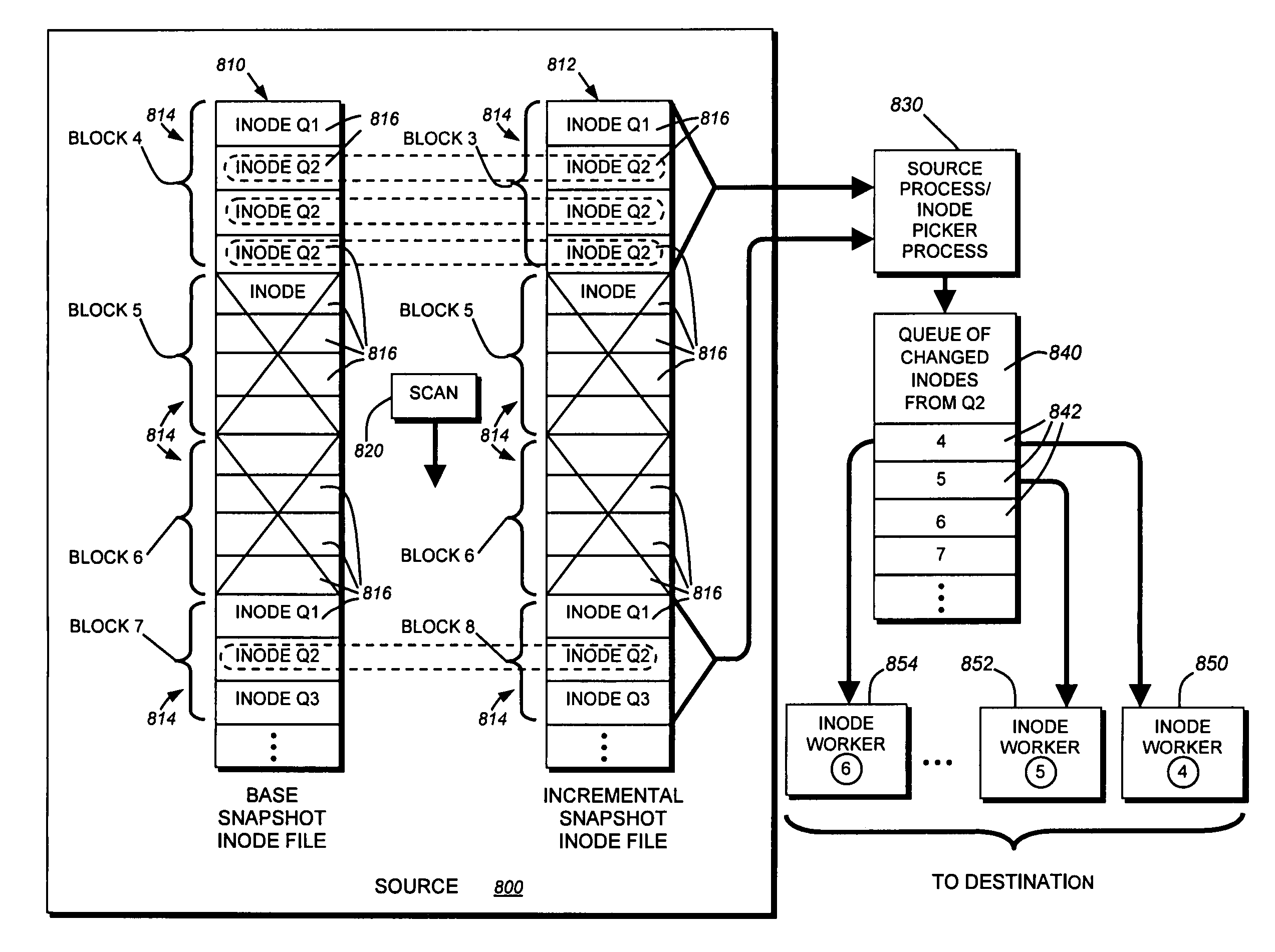
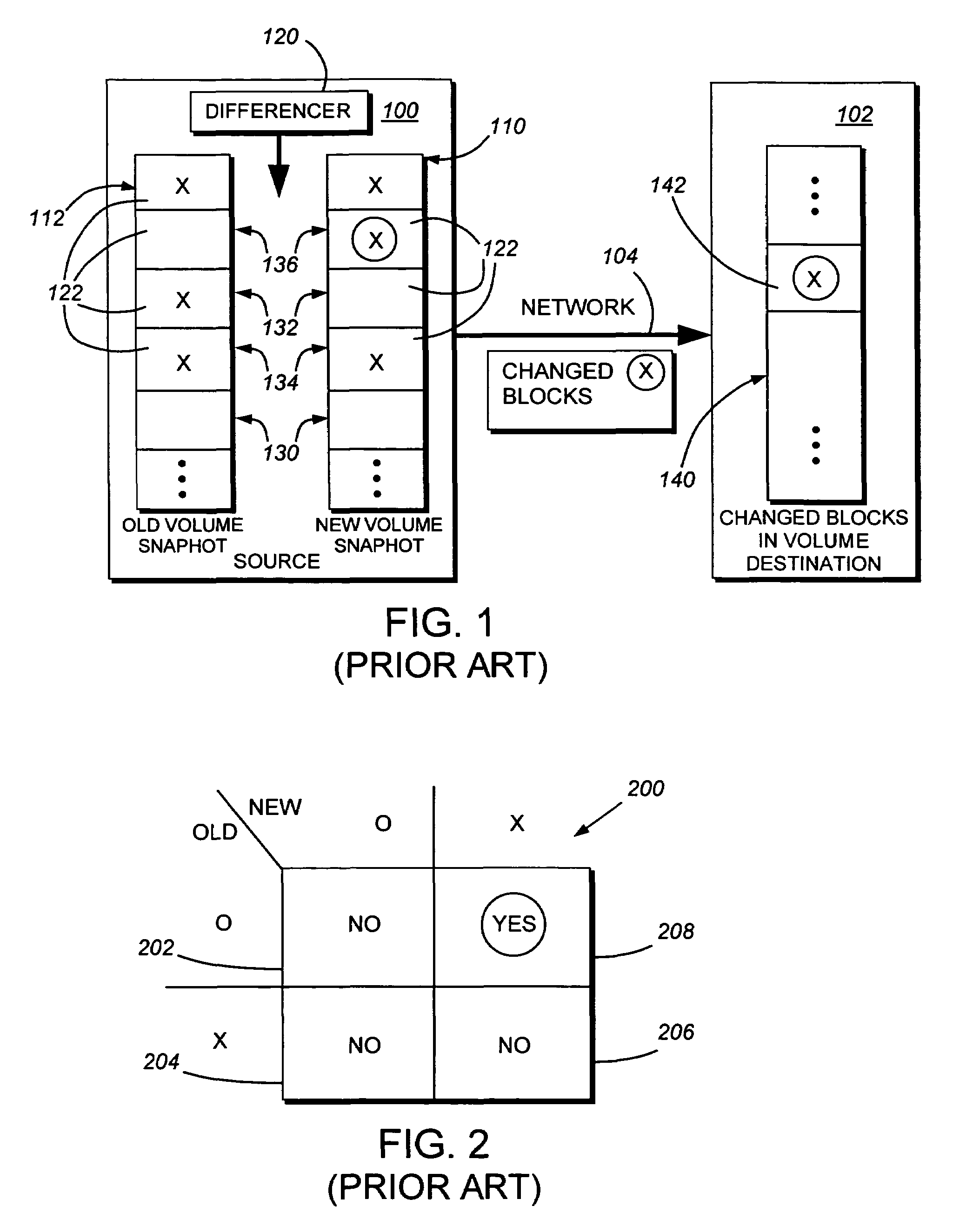
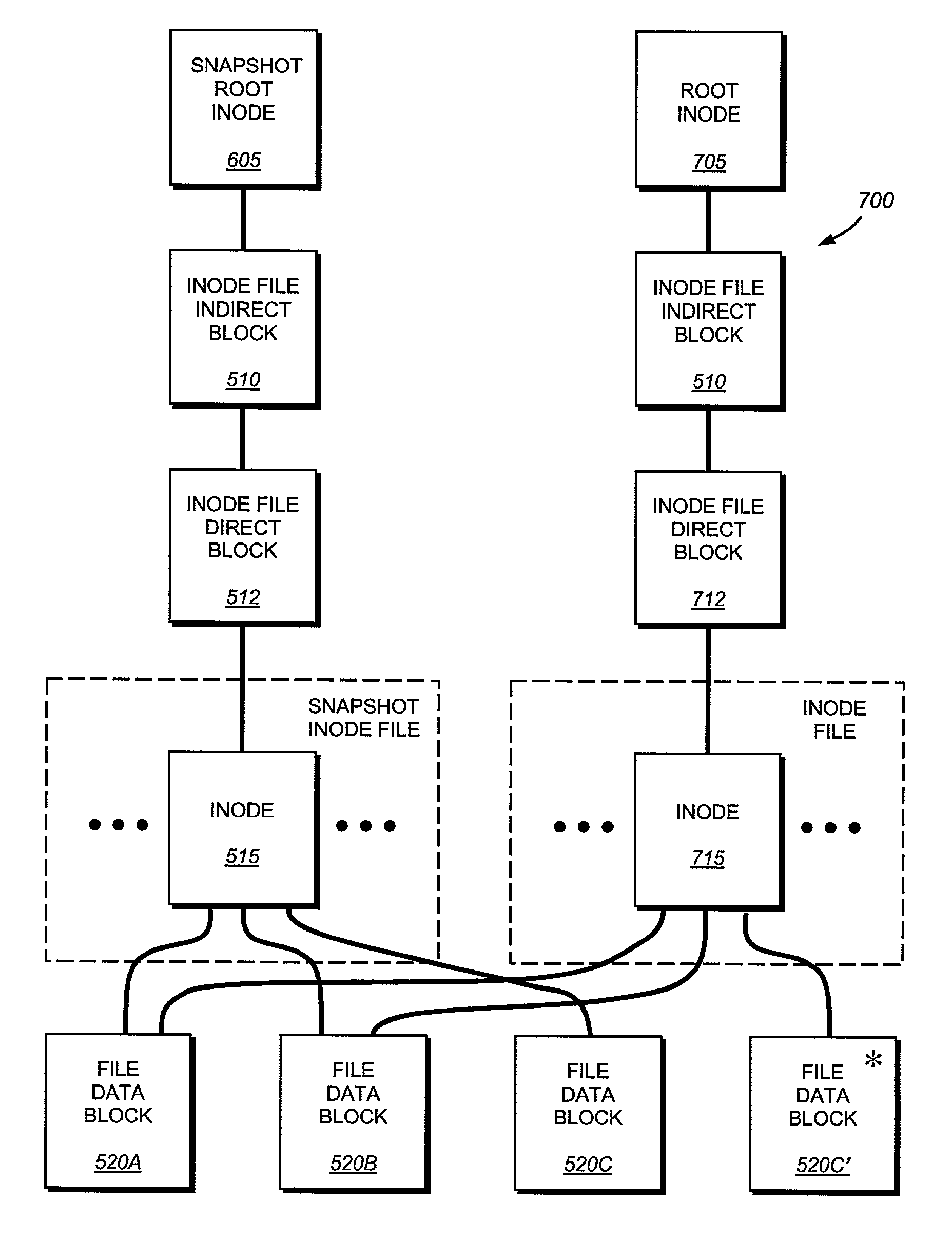
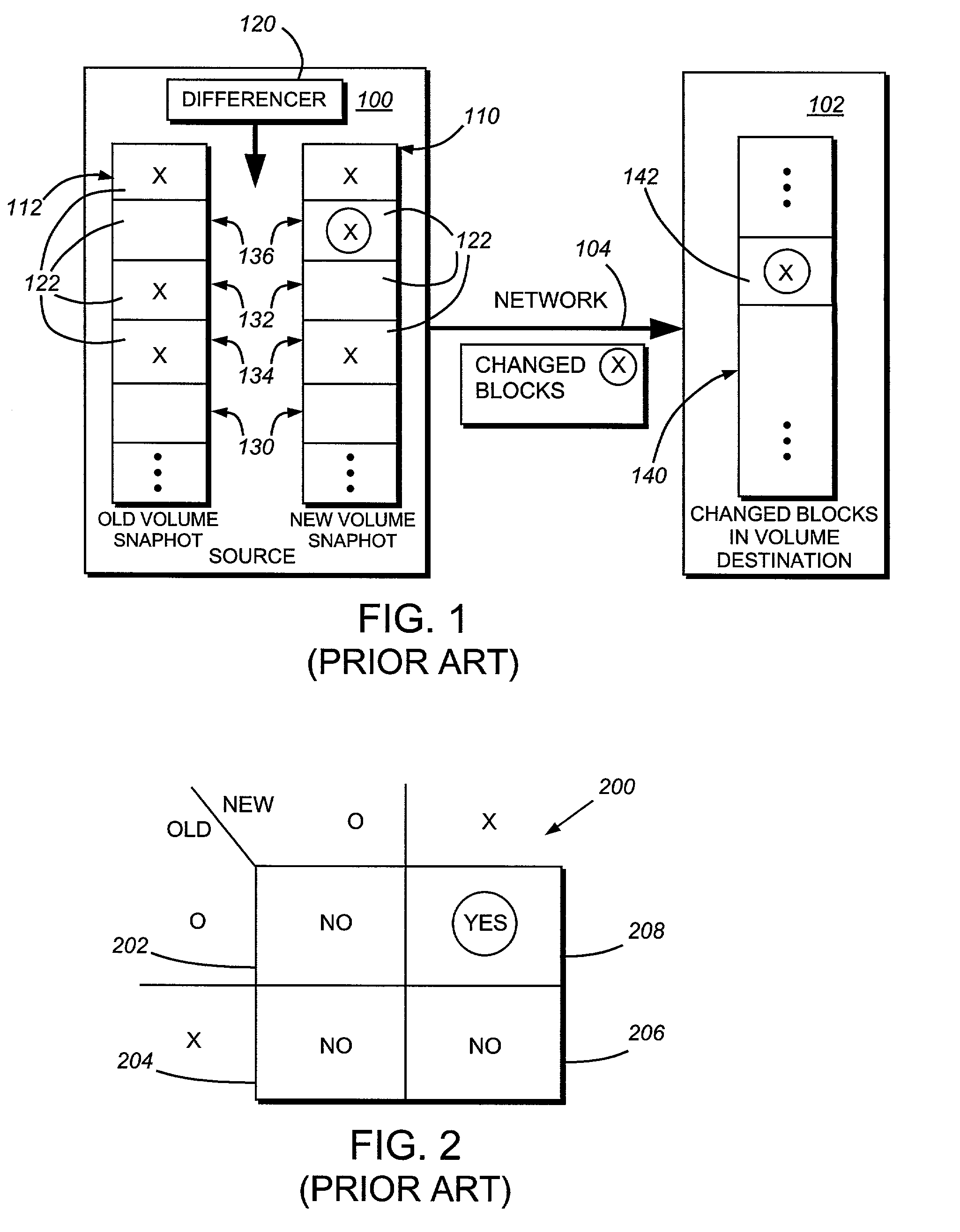
System and method for determining changes in two snapshots and for transmitting changes to destination snapshot
InactiveUS6993539B2Efficient scanningOvercome disadvantagesData processing applicationsSpecial data processing applicationsData streamInode
A system and method for remote asynchronous replication or mirroring of changes in a source file system snapshot in a destination replica file system using a scan (via a scanner) of the blocks that make up two versions of a snapshot of the source file system, which identifies changed blocks in the respective snapshot files based upon differences in volume block numbers identified in a scan of the logical file block index of each snapshot. Trees of blocks associated with the files are traversed, bypassing unchanged pointers between versions and walking down to identify the changes in the hierarchy of the tree. These changes are transmitted to the destination mirror or replicated snapshot. This technique allows regular files, directories, inodes and any other hierarchical structure to be efficiently scanned to determine differences between versions thereof. The changes in the files and directories are transmitted over the network for update of the replicated destination snapshot in an asynchronous (lazy write) manner. The changes are described in an extensible, system-independent data stream format layered under a network transport protocol. At the destination, source changes are used to update the destination snapshot. Any deleted or modified inodes already on the destination are moved to a temporary or “purgatory” directory and, if reused, are relinked to the rebuilt replicated snapshot directory. The source file system snapshots can be representative of a volume sub-organization, such as a qtree.
Owner:NETWORK APPLIANCE INC
System and method for asynchronous mirroring of snapshots at a destination using a purgatory directory and inode mapping
ActiveUS7225204B2Improve versatilityImprove utilizationData processing applicationsDigital data processing detailsInodeComputer science
A system and method for updating a replicated destination file system snapshot with changes in a source file system snapshot, facilitates construction of a new directory tree on the destination from source update information using a temporary or “purgatory” directory that allows any modified and deleted files on the destination active file system to be associated with (e.g. moved to) the purgatory directory if and until they are reused. In addition, an inode map is established on the destination that maps source inode numbers to destination inode numbers so as to facilitate building of the destination tree using inode / generation number tuples. The inode map allows resynchronization of the source file system to the destination. The inode map also allows association of two or more destination snapshots to each other based upon their respective maps with the source.
Owner:NETWORK APPLIANCE INC
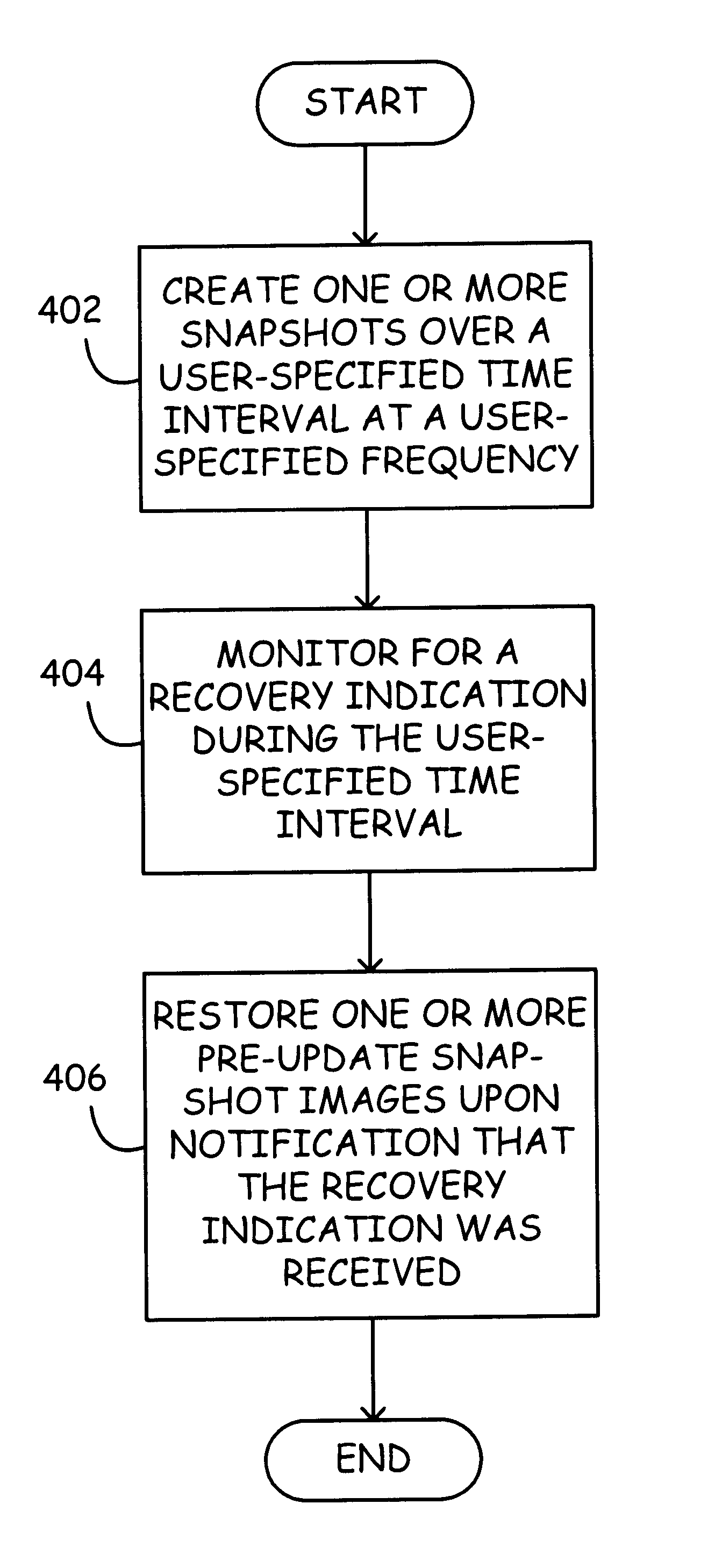
System and method for creating a series of online snapshots for recovery purposes
InactiveUS6799189B2Data processing applicationsMemory adressing/allocation/relocationDatabase fileData mining
A method and system for creating a series of online snapshots for recovery purposes. A series of concurrent, overlapping snapshots (e.g., file snapshots or database file snapshots) may be created over a user-specified time interval at a user-specified frequency. Monitoring for a recovery indication may occur during the user-specified time interval. Once it is established that a "recovery" is necessary, a snapback procedure may be implemented to iteratively restore one or more pre-update snapshot images. Between restore iterations, testing to determine if the problem still exists may occur. When the testing of the data results in a determination that the problem is resolved, no further restores are necessary.
Owner:BMC SOFTWARE
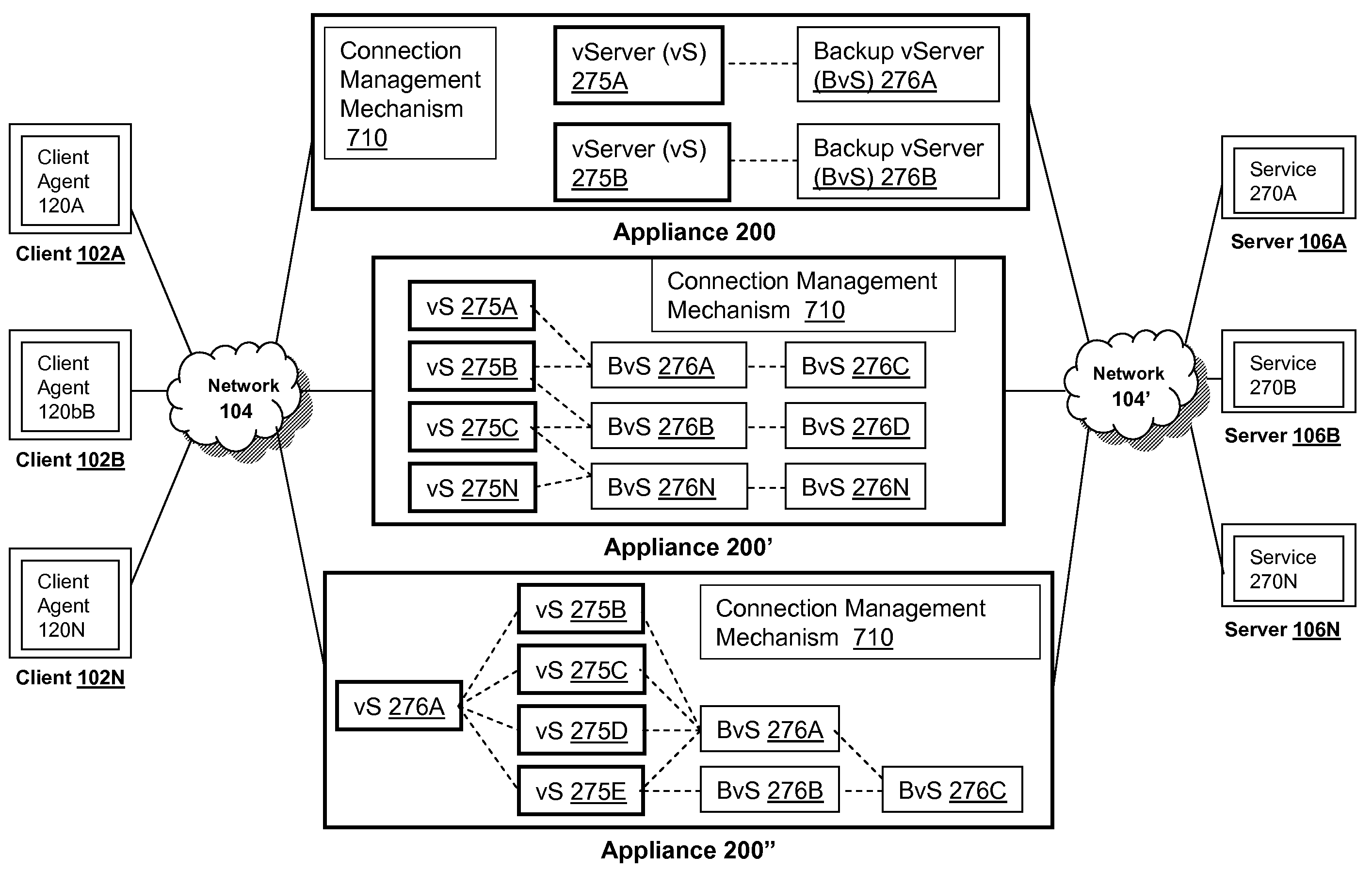
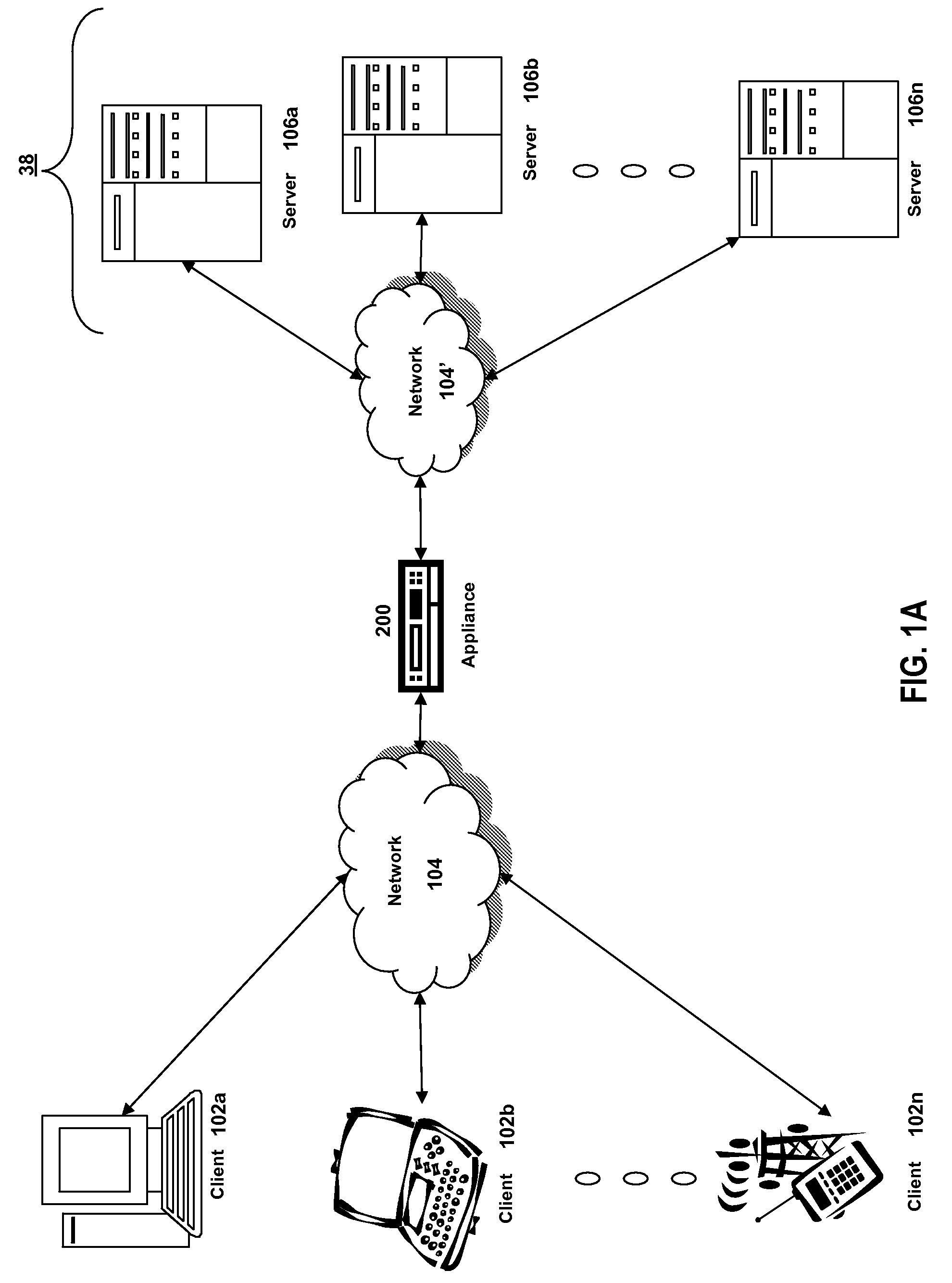
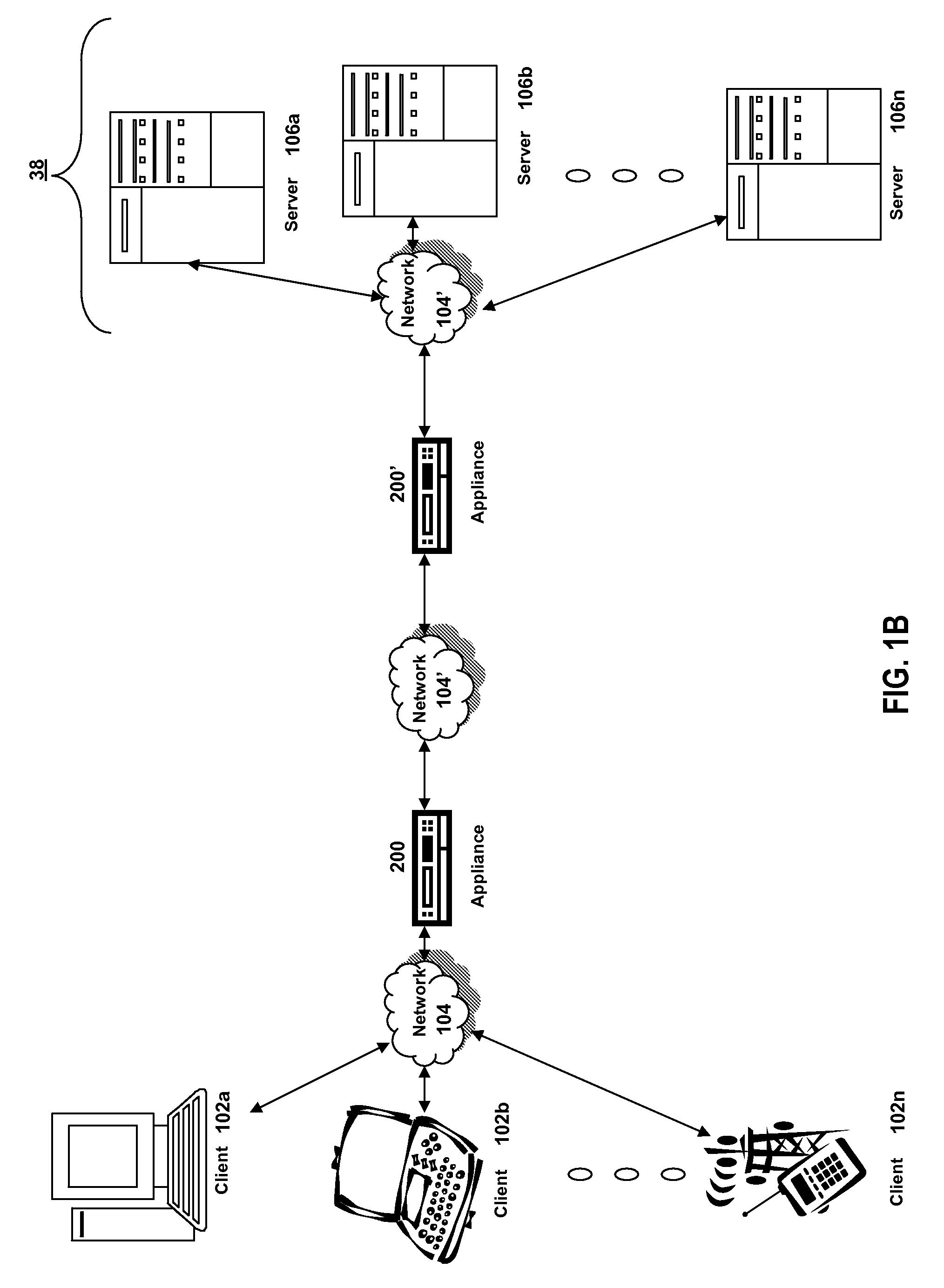
Systems and methods for load balancing via a plurality of virtual servers upon failover using metrics from a backup virtual server
The present invention provides methods and systems for performing load balancing via a plurality of virtual servers upon a failover using metrics from a backup virtual server. The methods and systems described herein provide systems and methods for an appliance detecting that a first virtual server of a plurality of virtual servers having one or more backup virtual servers load balanced by an appliance is not available, identifying at least a first backup virtual server of a one or more backup virtual servers of the first virtual server is available, maintaining a status of the first virtual server as available in response to the identification, obtaining one or more metrics from the first backup virtual server of a one or more backup virtual servers, and determining the load across the plurality of virtual servers using the metrics obtained from the first backup virtual server associated with the first virtual server.
Owner:CITRIX SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com