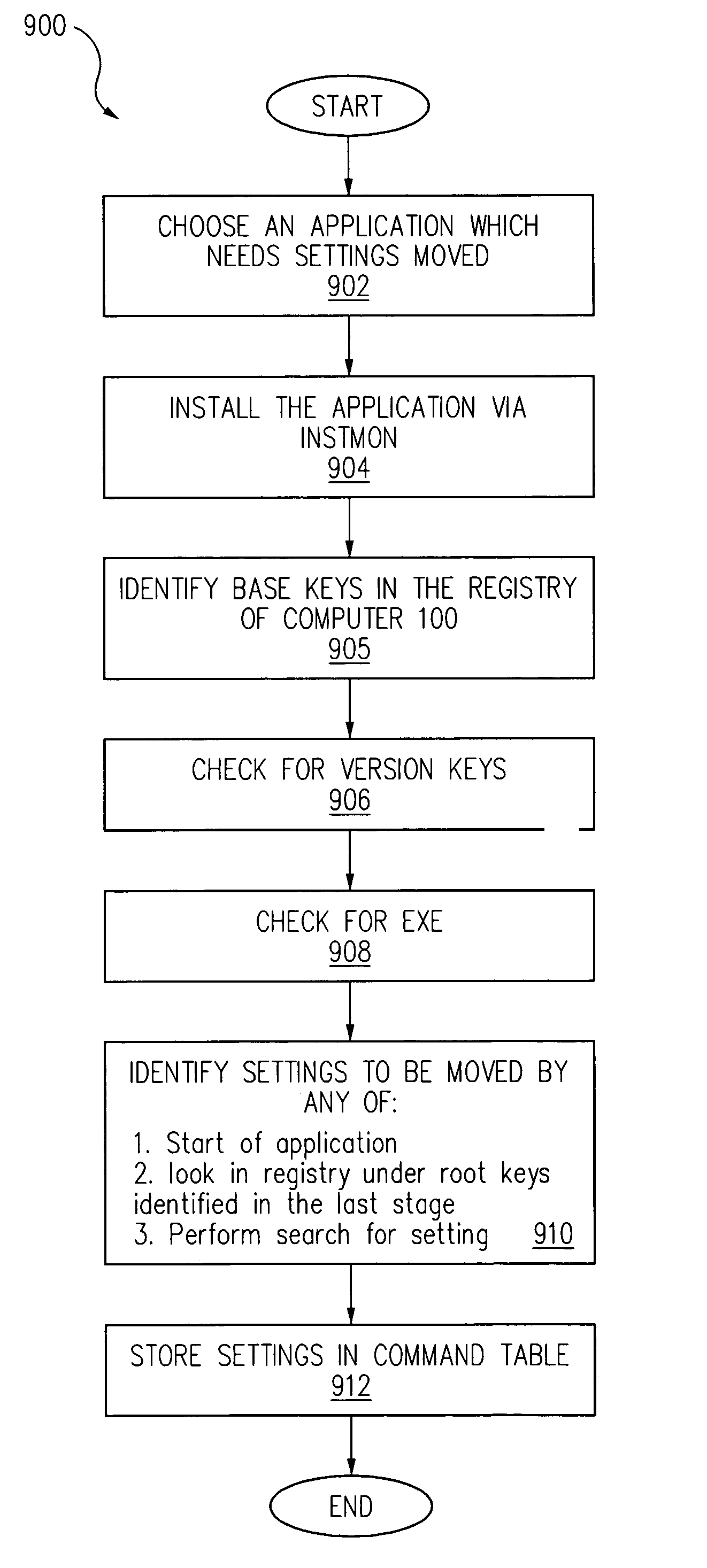
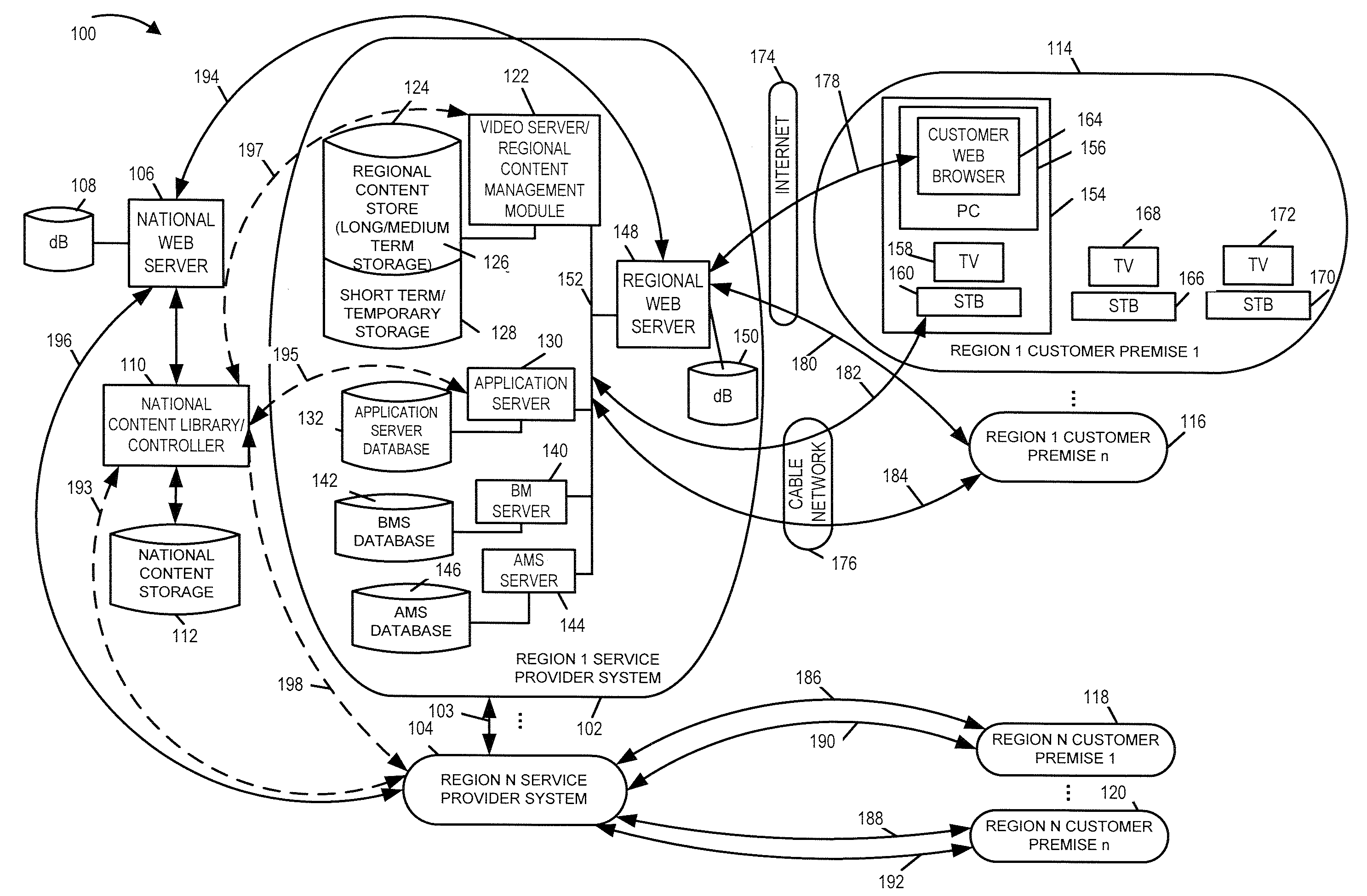
Patents
Literature
1483 results about "Transient storage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Transient Storage. Short lifespan data storage such as a session cookie stored on a browser that is purged from the system when the browser is closed.
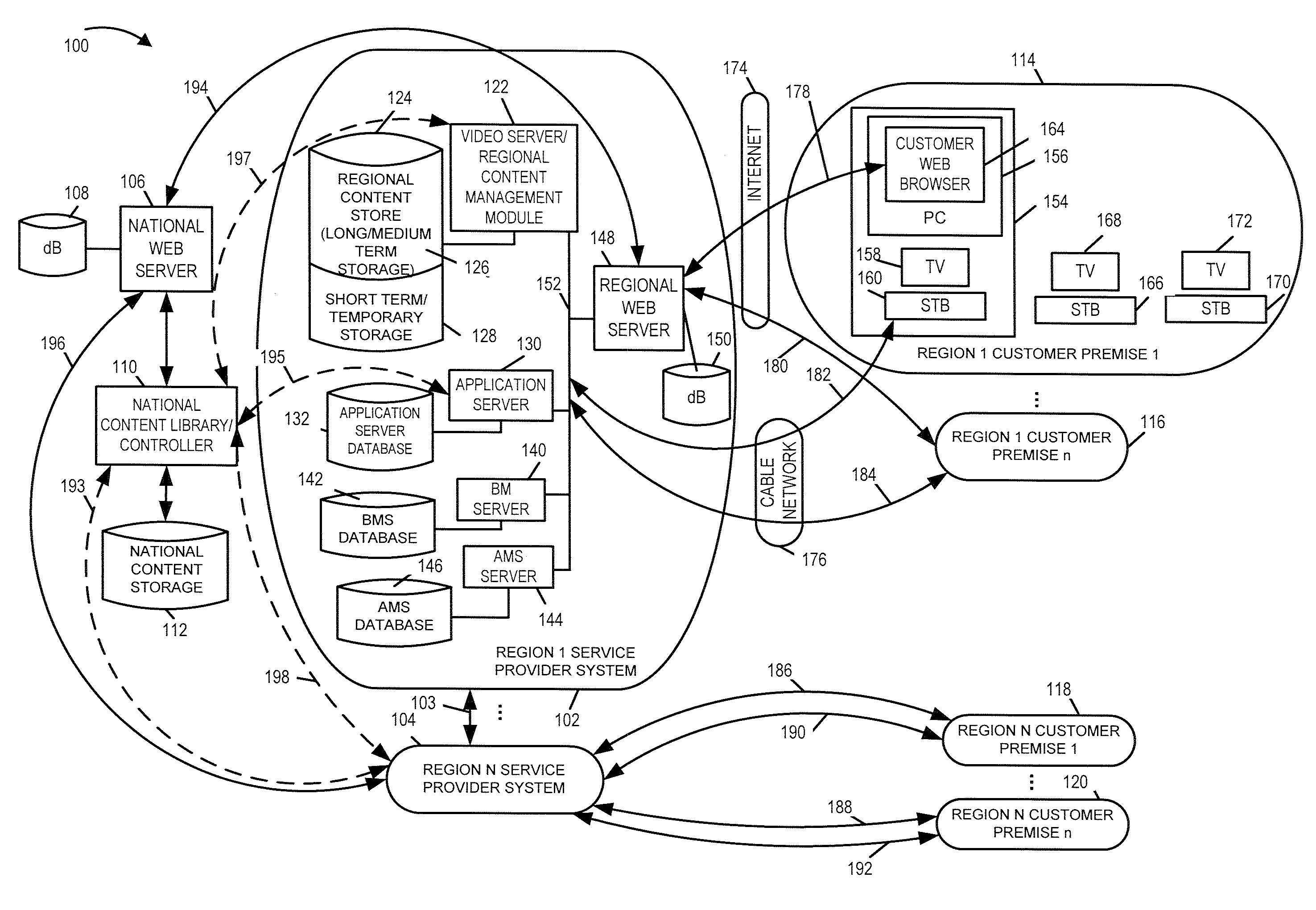
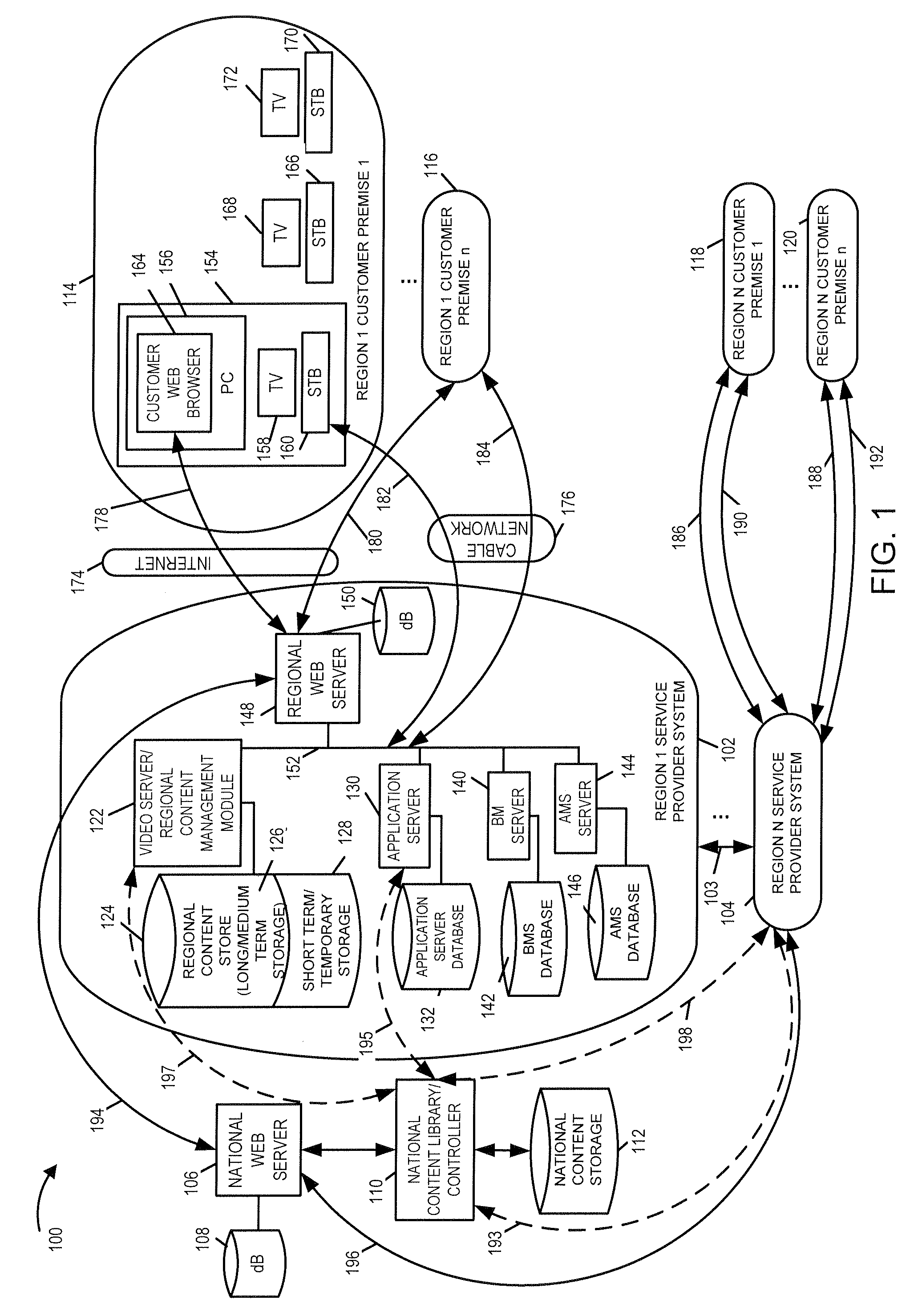
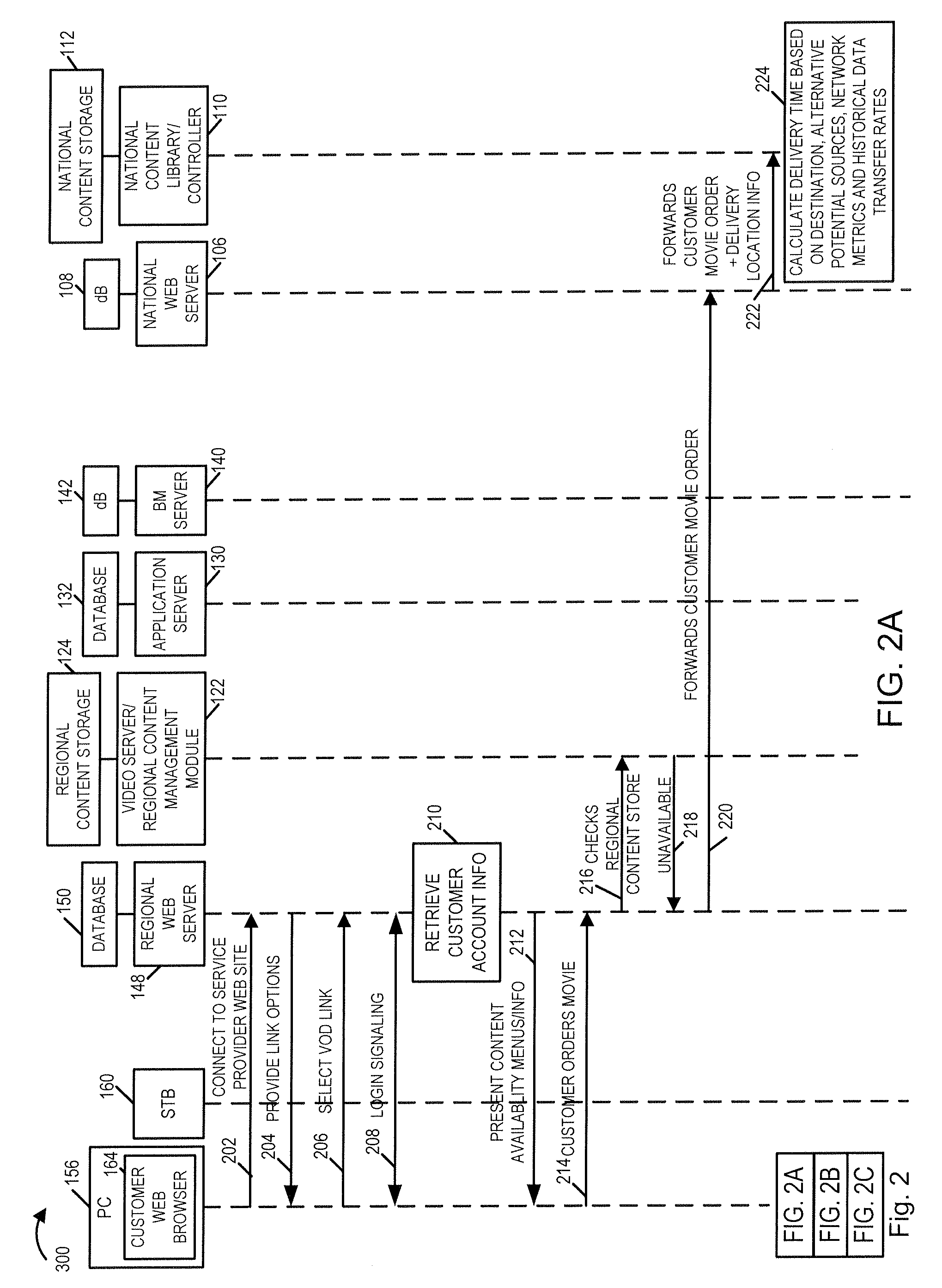
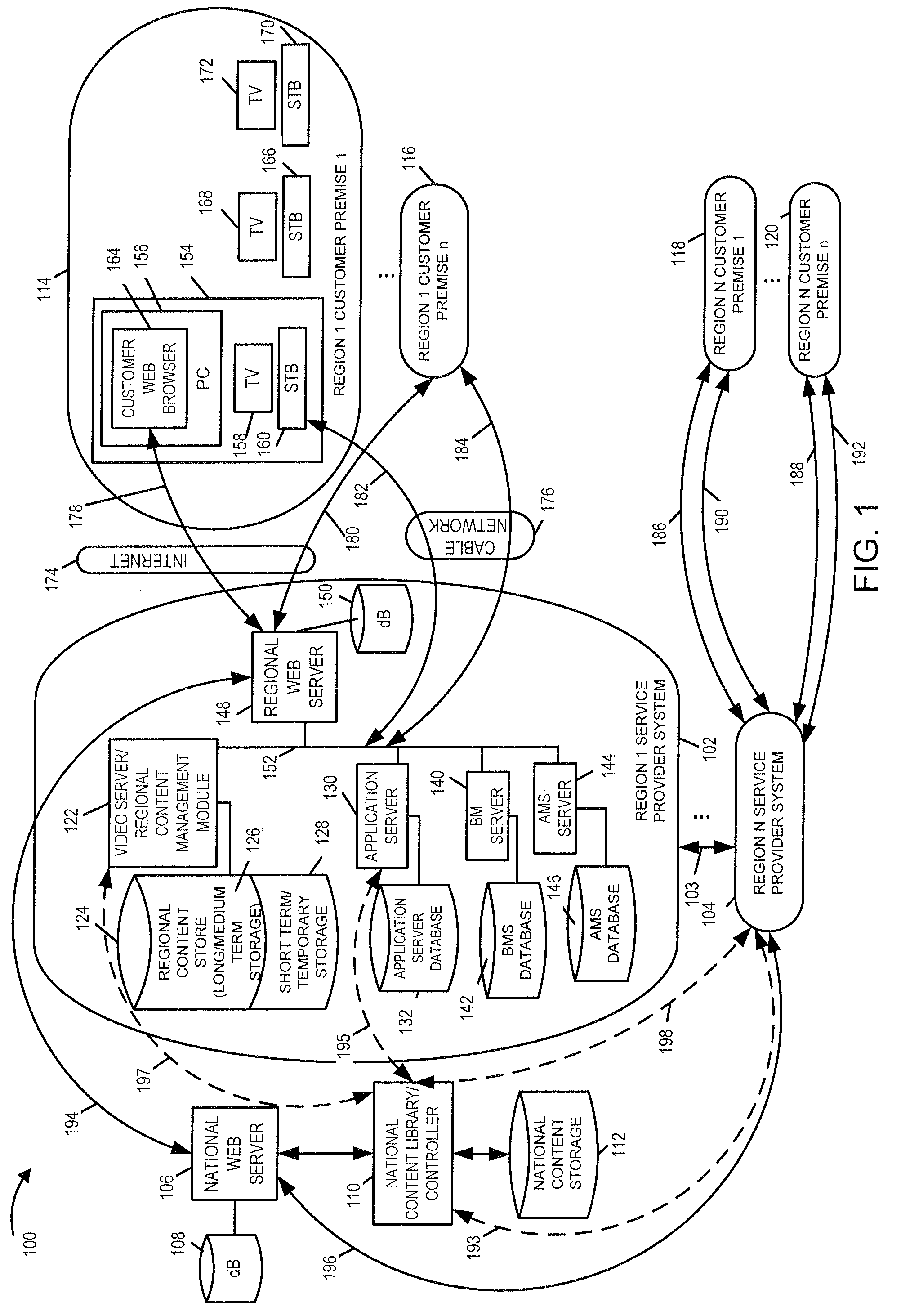
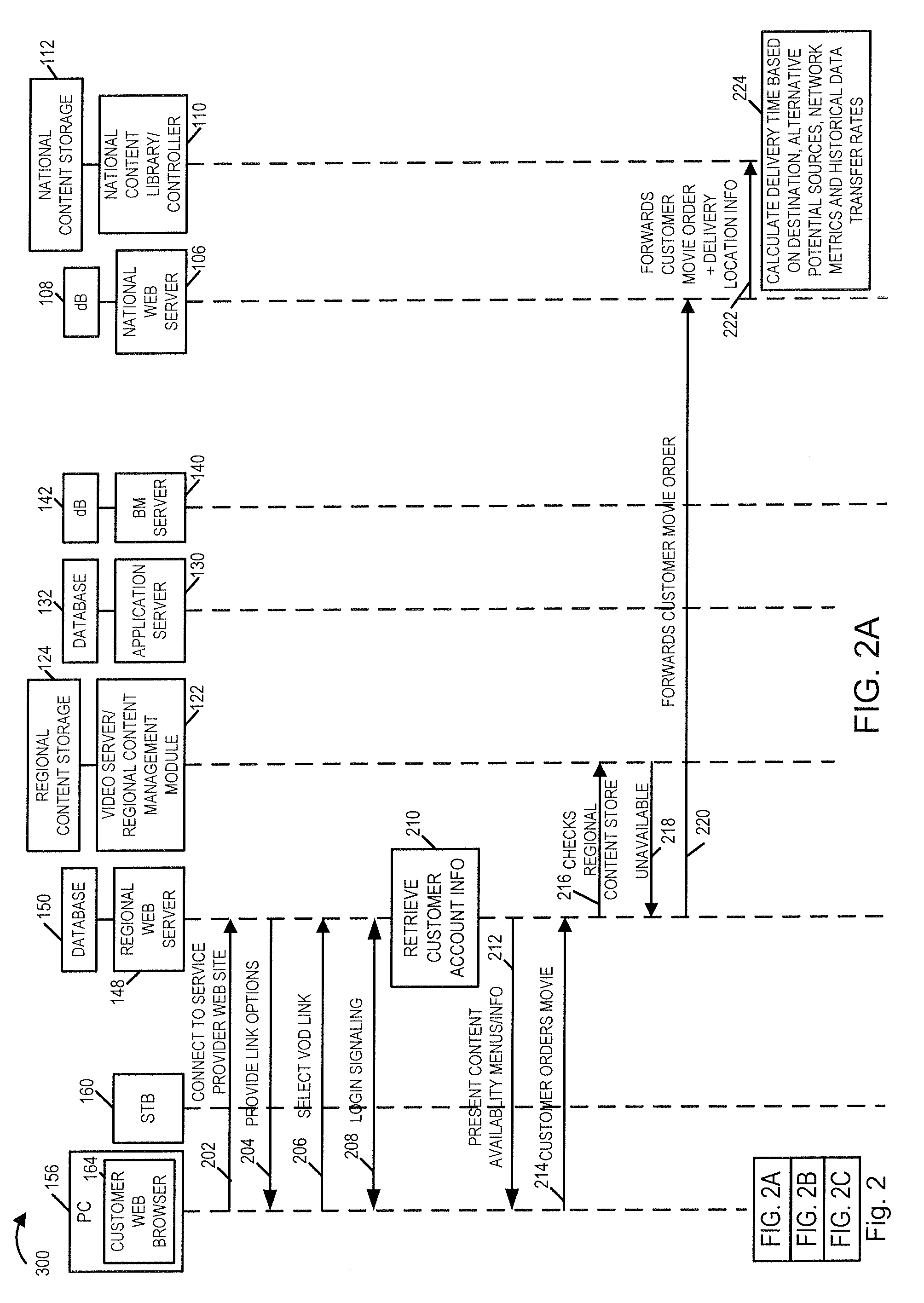
Methods, apparatus and user interface for providing content on demand
ActiveUS20080155613A1Increase storage capacityScalable approachTwo-way working systemsSelective content distributionWorld Wide WebUser interface
Methods and apparatus for supporting content delivery service are described. In accordance with the invention content can be supplied to temporary storage of a regional or local server used to supply the content to a customer's premises when the requested content is not already available in the regional or local server. A content server hierarchy may be implemented with servers higher up in the hierarchy including more content, e.g., titles, than the number of titles stored in the lower level servers. By storing less frequently accessed content in servers higher in the hierarchy and frequently requested titles lower in the hierarchy, a vast number of titles can be supported without overburdening the storage available at local and regional servers. In addition, a national or other server high in the hierarchy can be used to store, move, and distribute local or other content as part of an on demand service.
Owner:TIME WARNER CABLE ENTERPRISES LLC
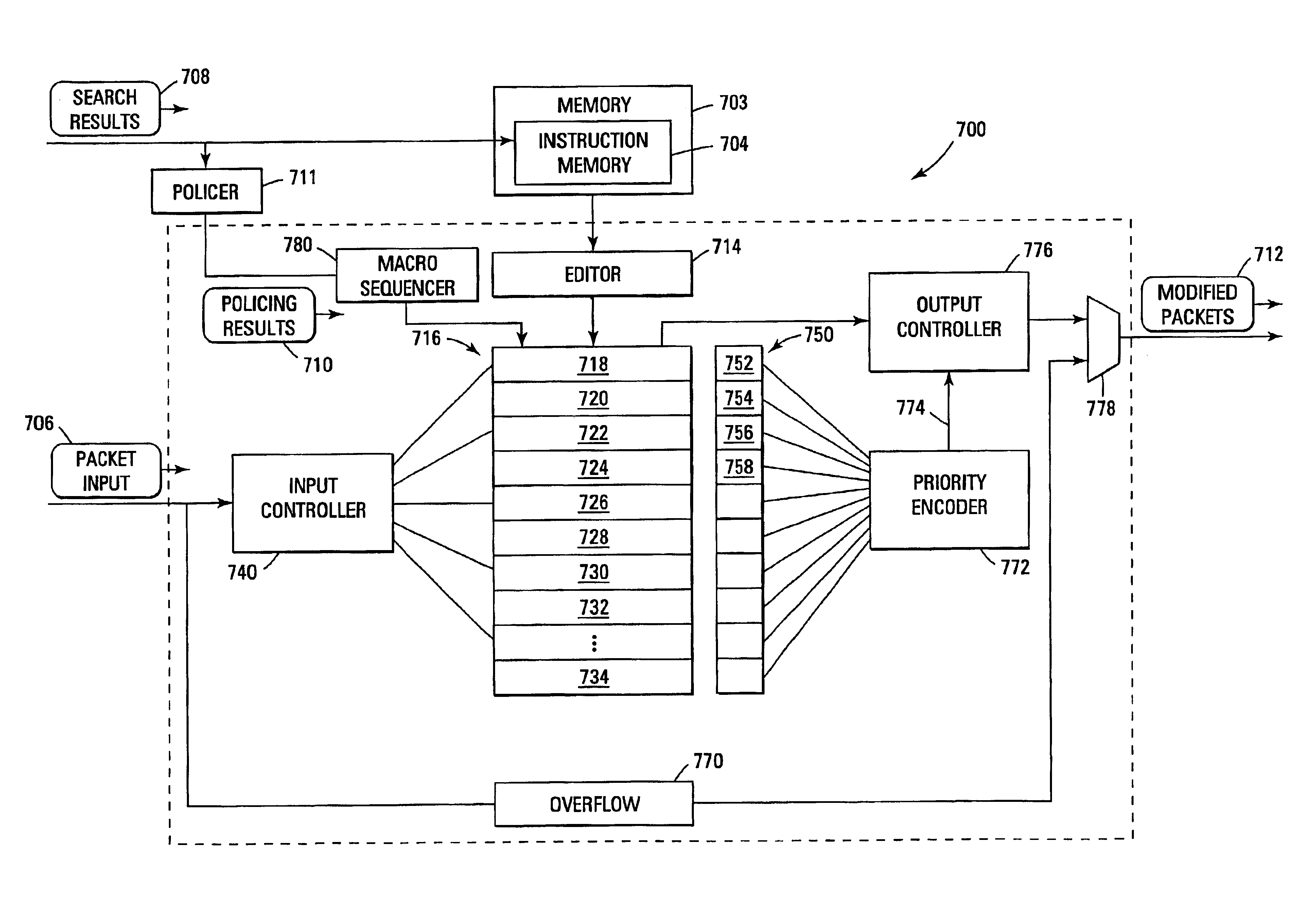
System and method for providing transformation of multi-protocol packets in a data stream
InactiveUS6944168B2Time-division multiplexData switching by path configurationStreaming dataData stream
A system and method for facilitating packet transformation of multi-protocol, multi-flow, streaming data. Packet portions subject to change are temporarily stored, and acted upon through processing of protocol-dependent instructions, resulting in a protocol-dependent modification of the temporarily stored packet information. Validity tags are associated with different segments of the temporarily-stored packet, where the state of each tag determines whether its corresponding packet segment will form part of the resulting modified packet. Only those packet segments identified as being part of the resulting modified packet are reassembled prior to dispatch of the packet.
Owner:RPX CORP
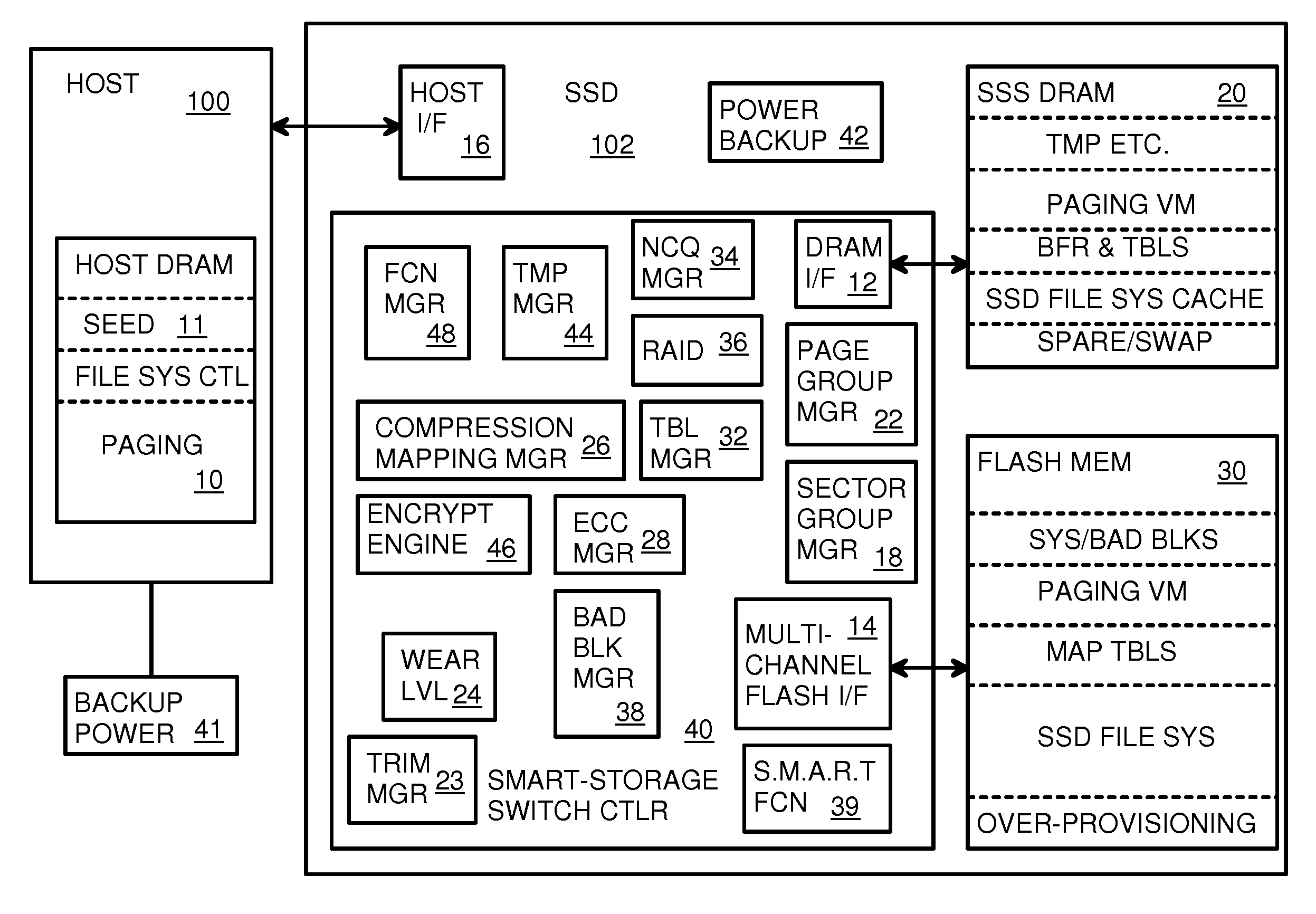
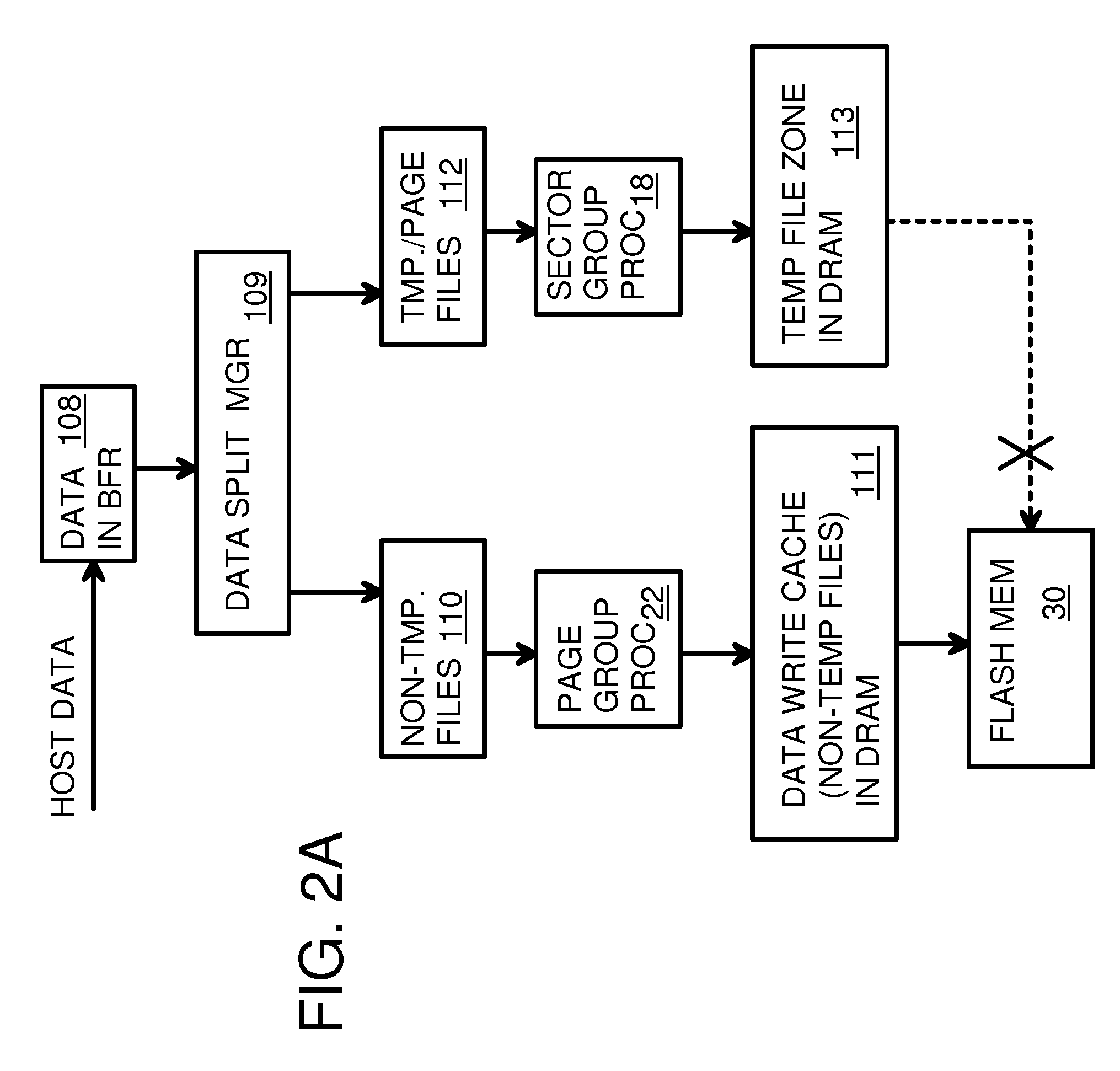
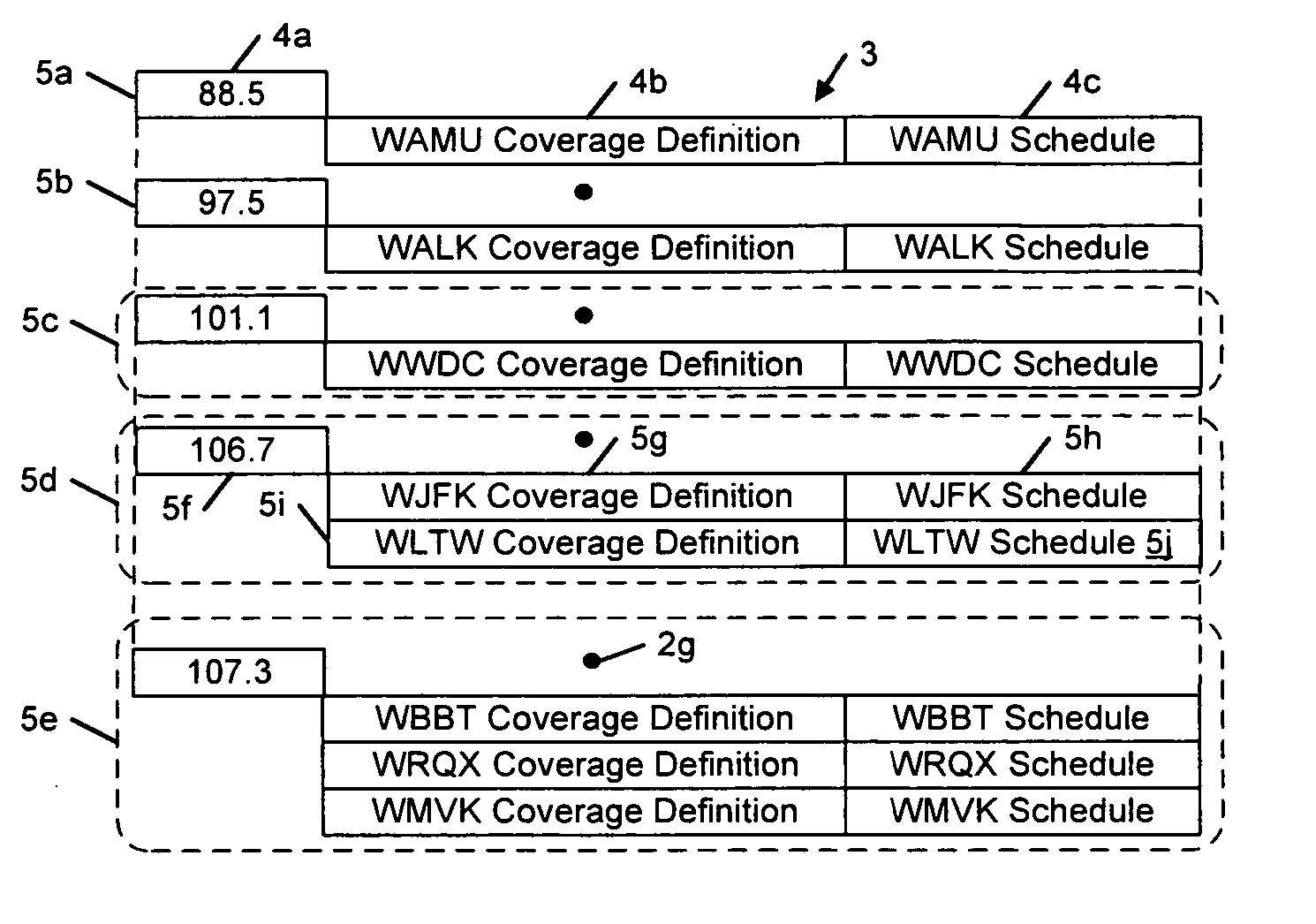
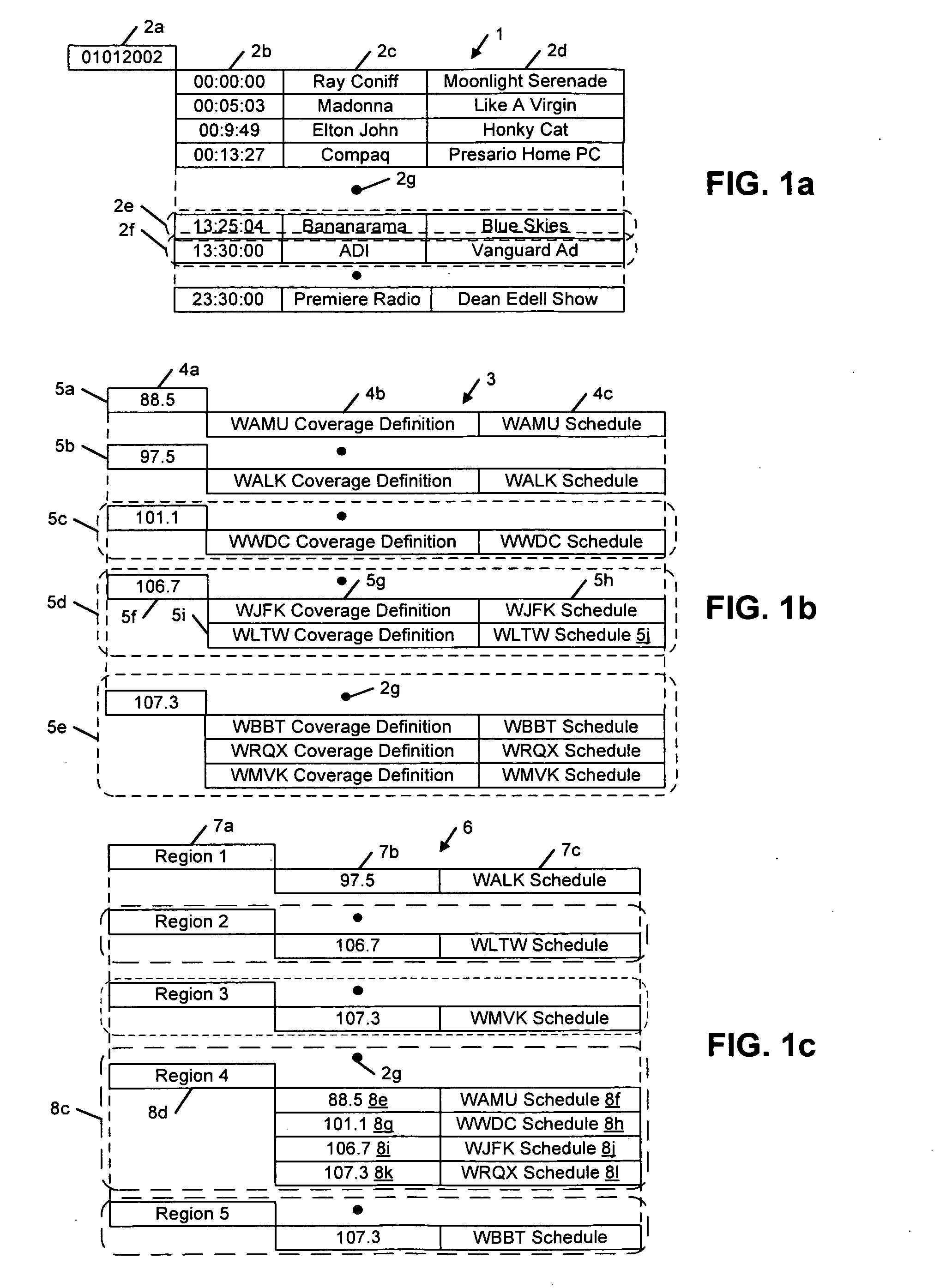
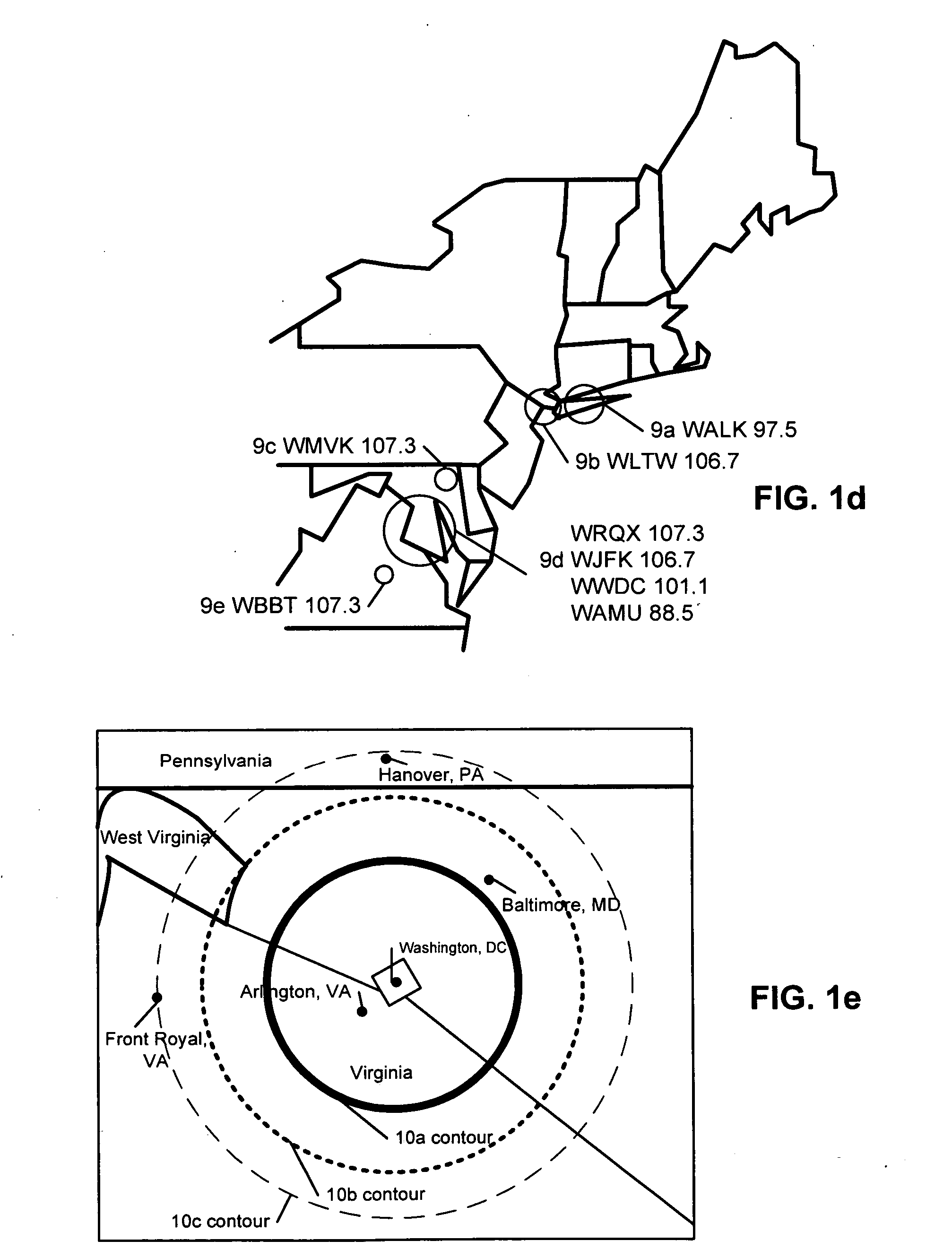
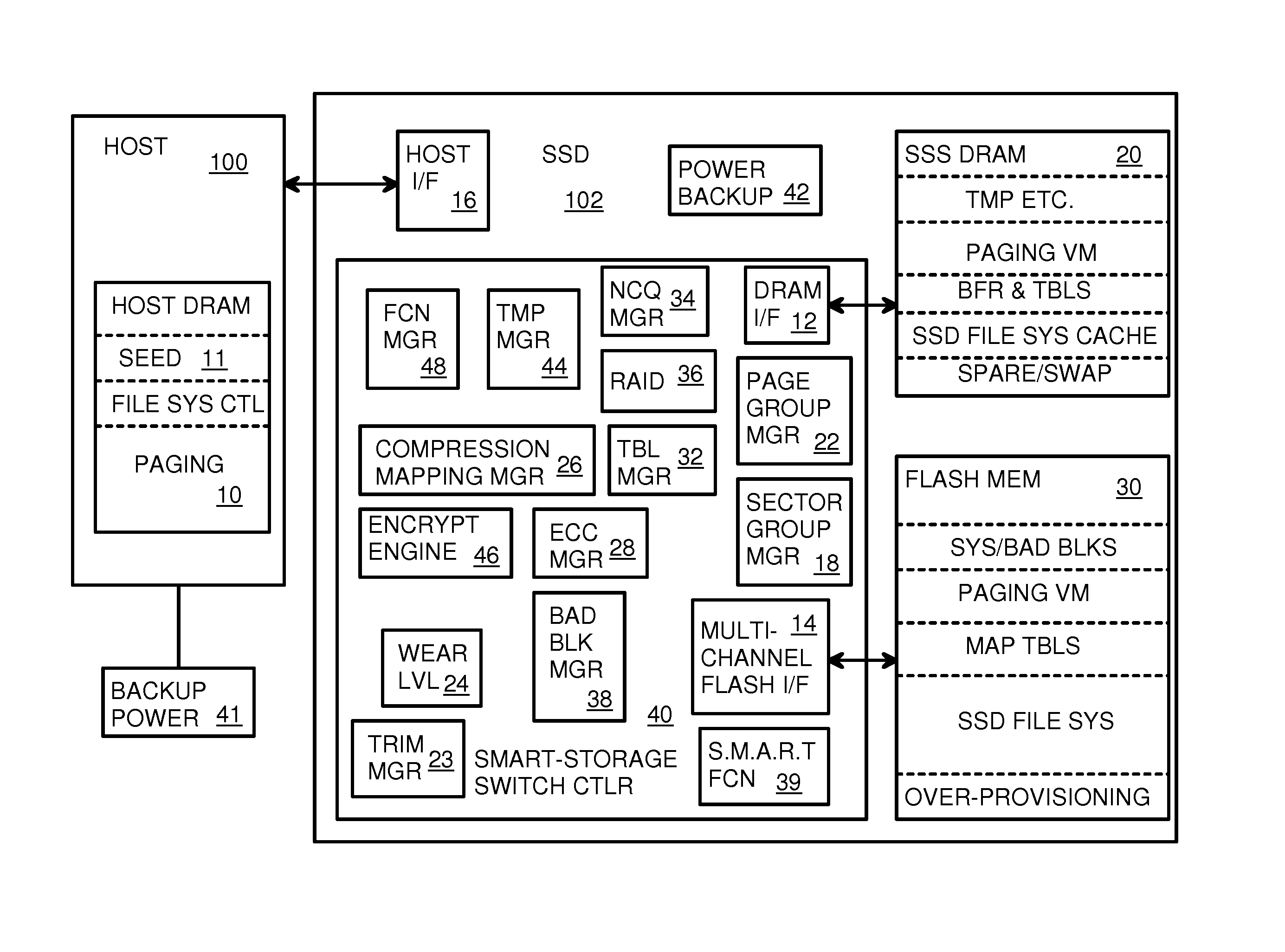
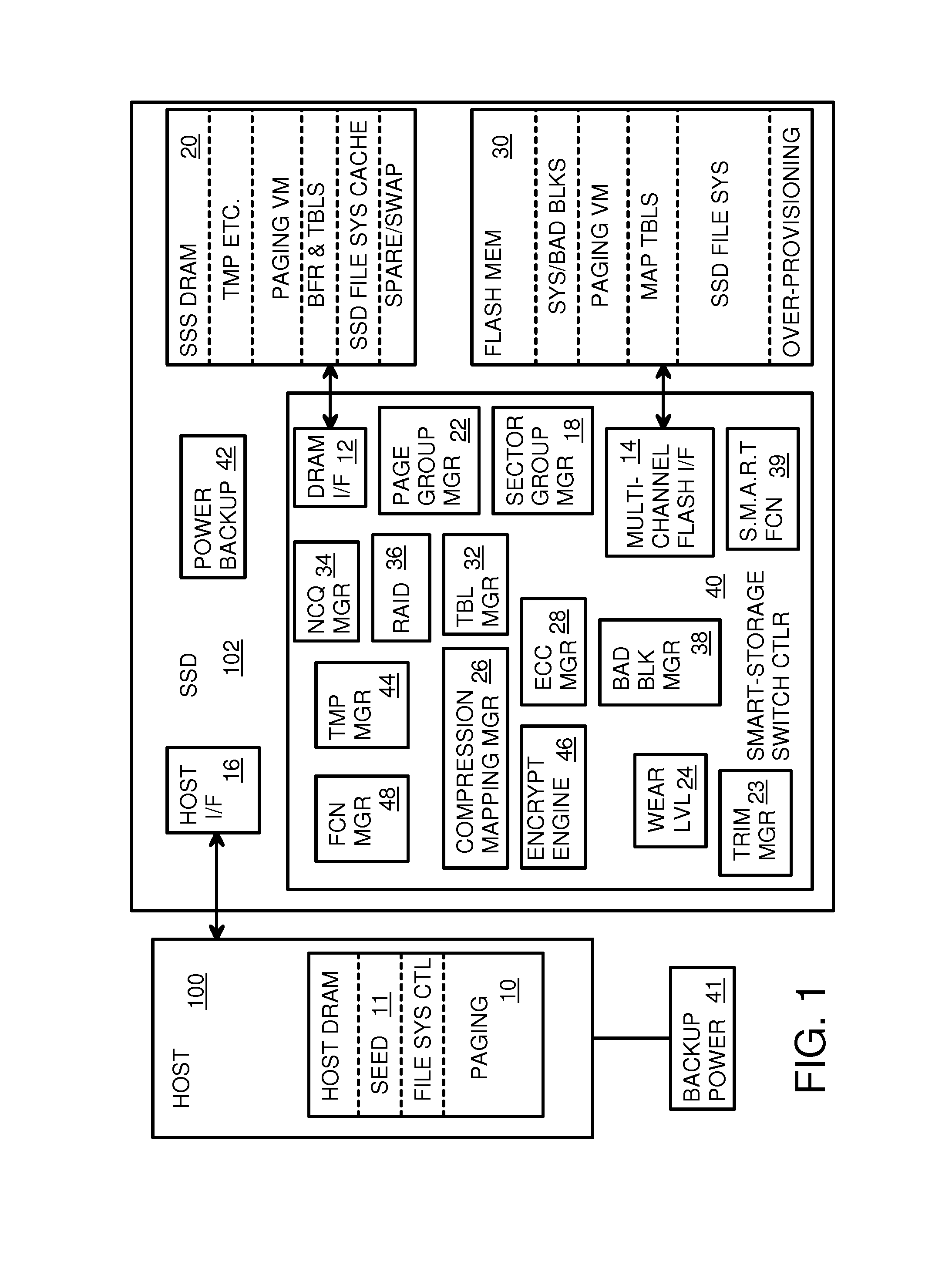
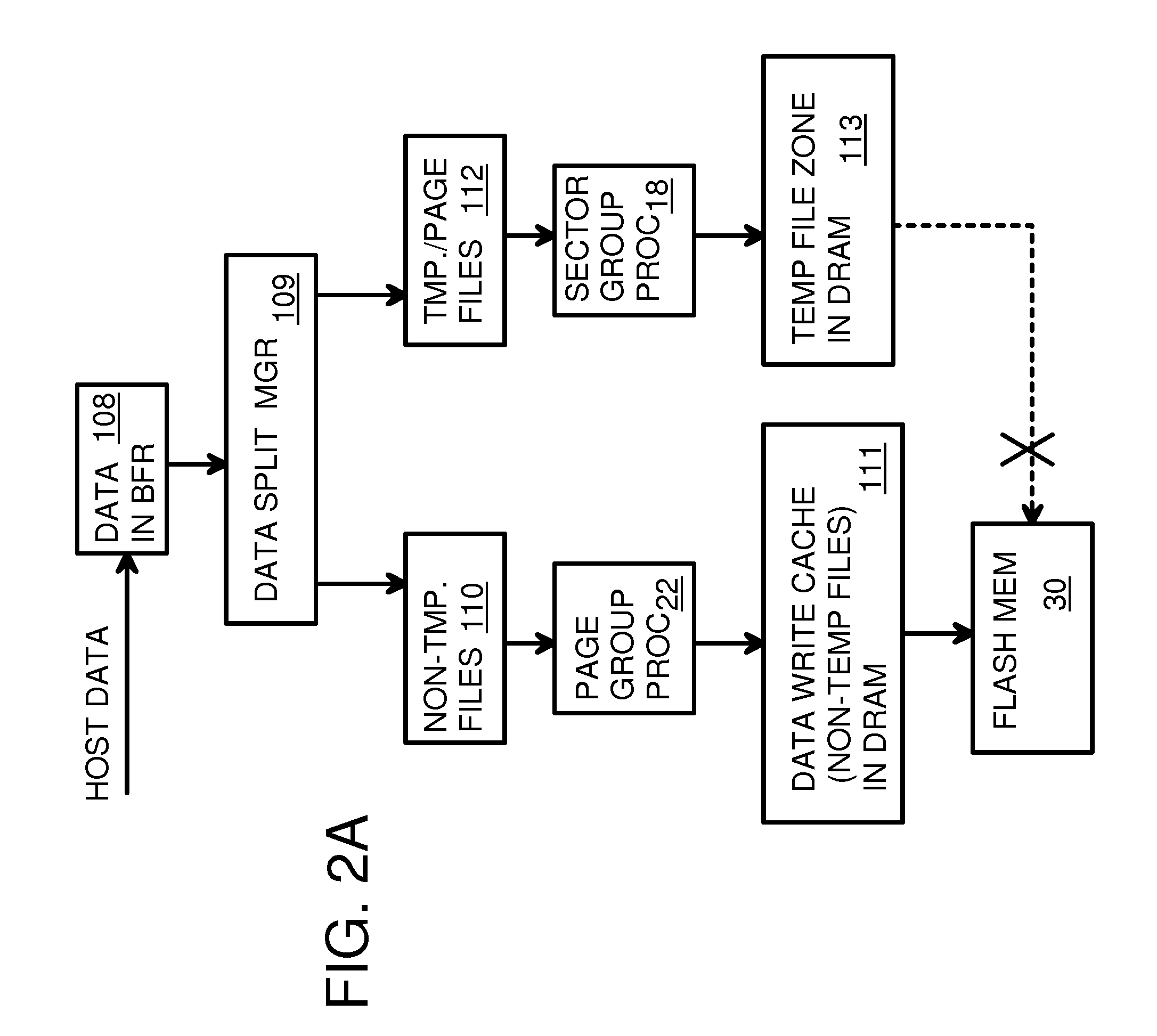
Super-Endurance Solid-State Drive with Endurance Translation Layer (ETL) and Diversion of Temp Files for Reduced Flash Wear
ActiveUS20120284587A1Memory architecture accessing/allocationDigital storageFilename extensionData file
A flash drive has increased endurance and longevity by reducing writes to flash. An Endurance Translation Layer (ETL) is created in a DRAM buffer and provides temporary storage to reduce flash wear. A Smart Storage Switch (SSS) controller assigns data-type bits when categorizing host accesses as paging files used by memory management, temporary files, File Allocation Table (FAT) and File Descriptor Block (FDB) entries, and user data files, using address ranges and file extensions read from FAT. Paging files and temporary files are never written to flash. Partial-page data is packed and sector mapped by sub-sector mapping tables that are pointed to by a unified mapping table that stores the data-type bits and pointers to data or tables in DRAM. Partial sectors are packed together to reduce DRAM usage and flash wear. A spare / swap area in DRAM reduces flash wear. Reference voltages are adjusted when error correction fails.
Owner:SUPER TALENT TECH CORP
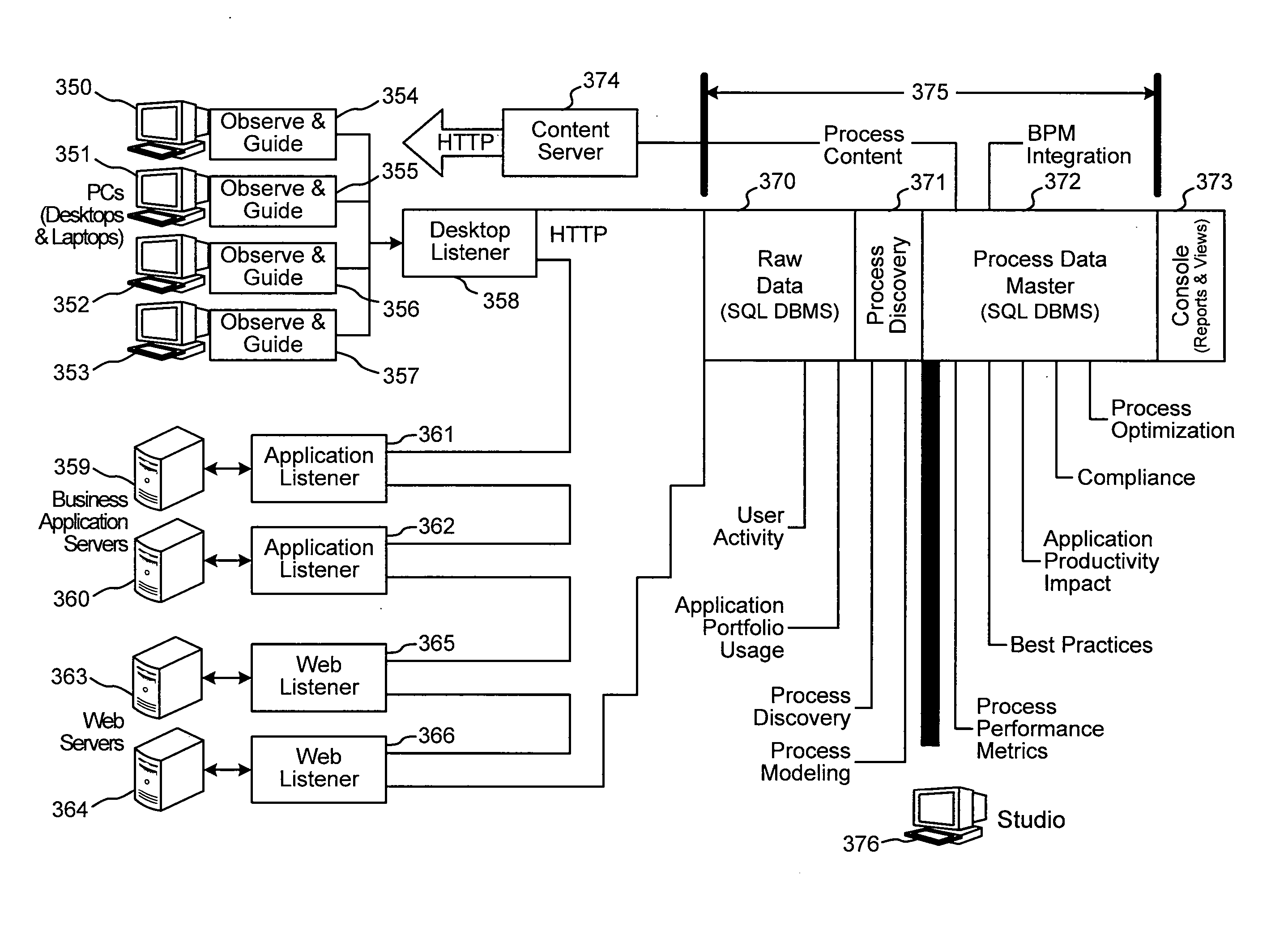
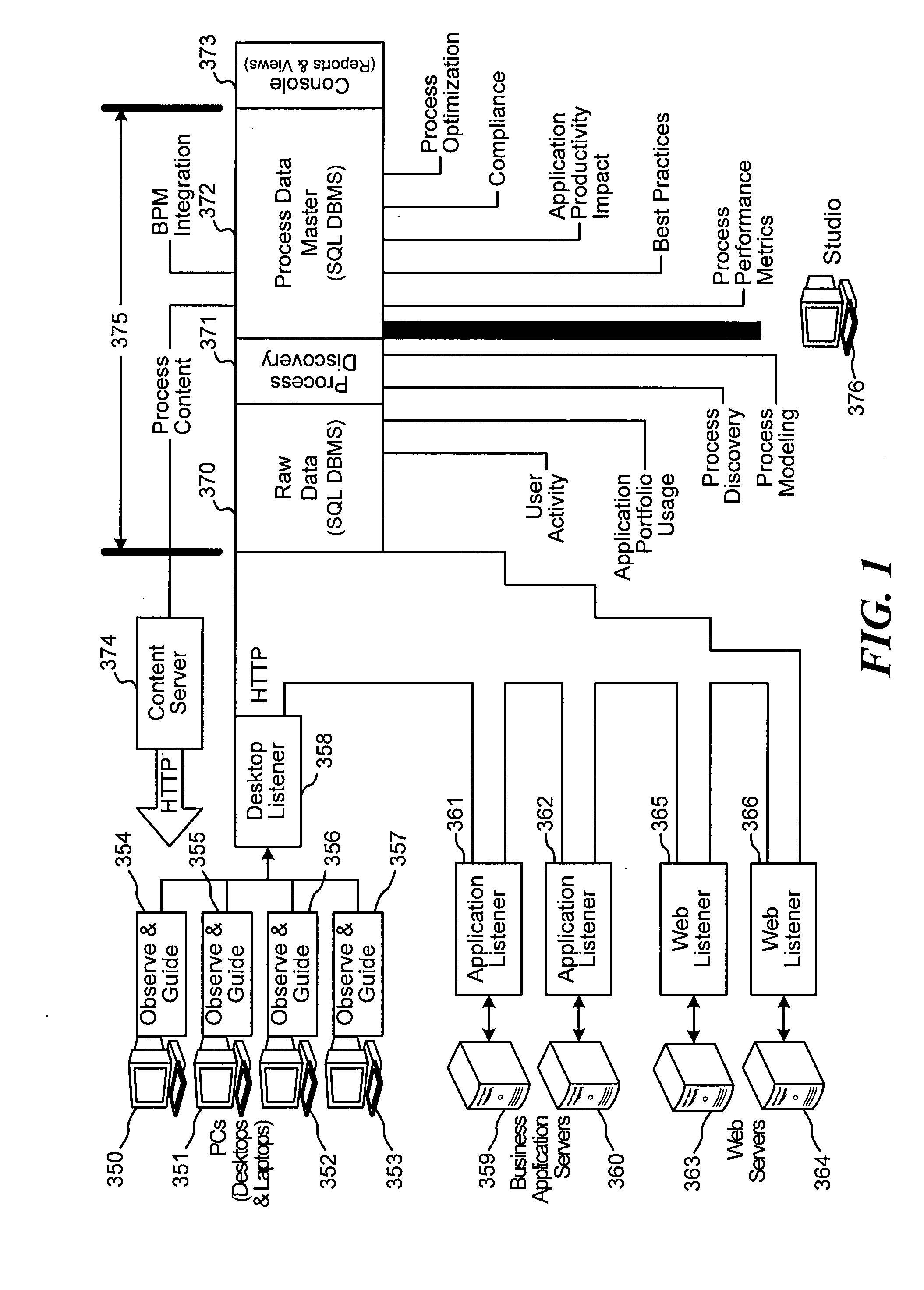
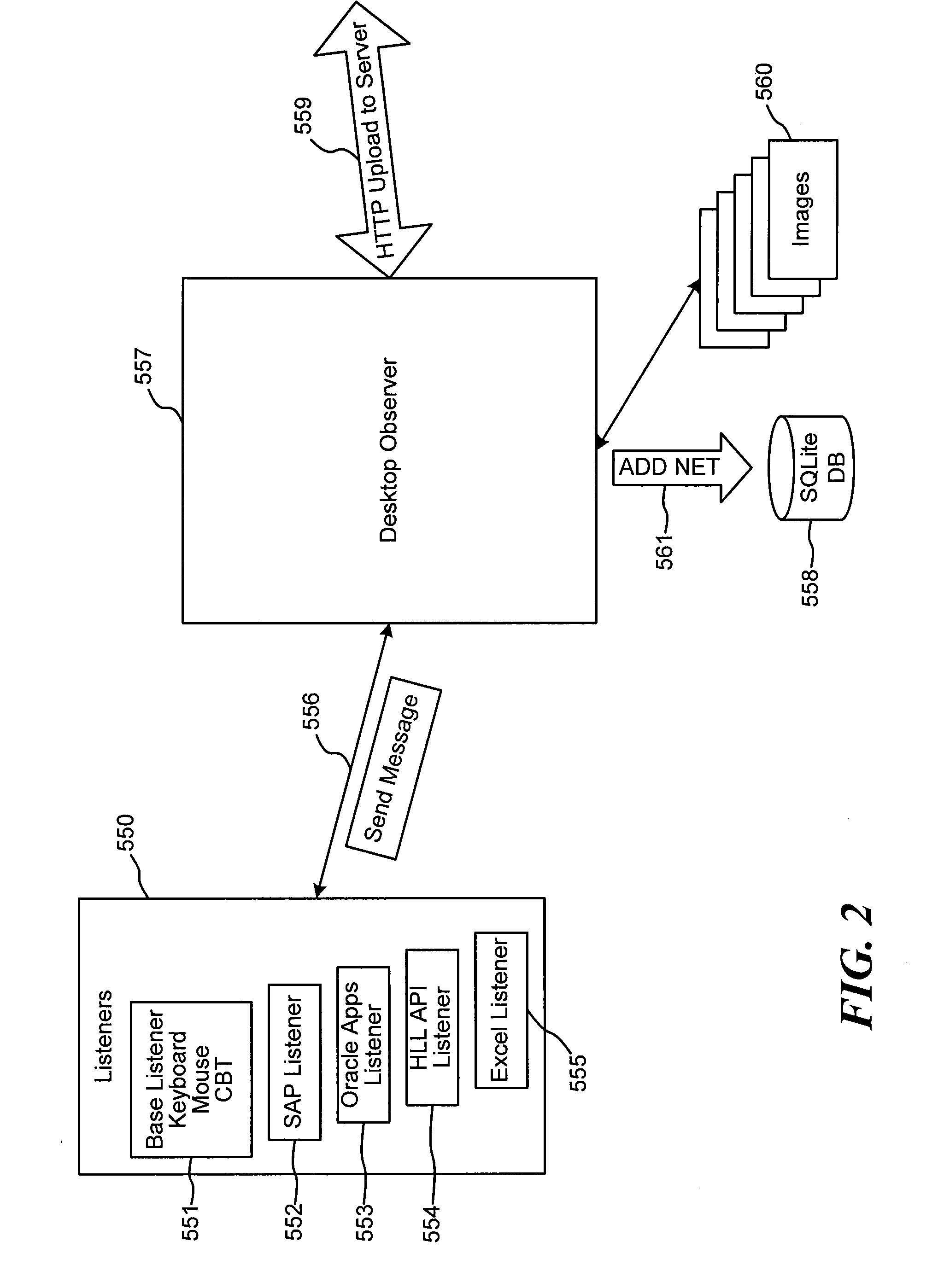
System and method for capture of user actions and use of capture data in business processes
InactiveUS20060184410A1Prevent wrong actionEnsure complianceDigital computer detailsOffice automationGood practiceData storing
Systems and methods are disclosed for capturing data representative of user interactions with a desktop computer, and processing the capture data to identify and analyze business processes performed by the user. The disclosed system comprises listeners that capture key actuations, mouse-clicks, screen information, and other data representative of user interaction with a desktop computer. A desktop observer is provided to accept capture data from listeners, to temporarily store the capture data if necessary, and to pass the capture data to a process intelligence server. The process intelligence server includes a process discovery module the analyzes the capture data and identifies business processes corresponding to the capture data, or models business processes. A process data master storage is provided. A process analysis module is provided to determine performance metrics, best practices, application productivity impacts, compliance, and optimization analysis on the data stored in the process master storage. Methods are disclosed for capture, catalog, combination, correlation, change, compression, and certification.
Owner:QLIP MEDIA
System for transferring customized hardware and software settings from one computer to another computer to provide personalized operating environments
InactiveUS6963908B1Simplify the shipping processOptimization mechanismDigital computer detailsProgram loading/initiatingPersonalizationWeb site
A method and system for transferring information from a first computer-based device to a web site, for temporary storage and later transfer of the stored information from the web site to a second computer-based device. First, a communication link is established between a first computer-based device and the web site. Next, the first computer-based device is scanned, via the web site, to determine the information contained on the first computer-based device. The user then selects which of the scanned information is to be uploaded from the first computer-based device onto the web site for temporary storage. Finally, the selected information is transferred from the first computer-based device onto the web site for temporary storage. Once retrieval of the temporarily stored information is desired, the user establishes a communication link between a second computer-based device and the web site. The second computer-based device is scanned, via the web site, to determine the information contained on the second computer-based device. The temporarily stored information, from the first computer-based device on the web site, is then displayed to the user and the user selects which of this temporary information, from the first computer-based device, is to be downloaded from the web site onto the second computer-based device. The selected information is finally downloaded from the website onto the second computer-based device.
Owner:CLOUDING
Methods and apparatus for supporting content distribution
ActiveUS20080155059A1Reduce deliveryShort amount of timeMultiple digital computer combinationsTwo-way working systemsContent distributionWorld Wide Web
Methods and apparatus for supporting content delivery service are described. In accordance with the invention content can be supplied to temporary storage of a regional or local server used to supply the content to a customer's premises when the requested content is not already available in the regional or local server. A content server hierarchy may be implemented with servers higher up in the hierarchy including more content, e.g., titles, than the number of titles stored in the lower level servers. By storing less frequently accessed content in servers higher in the hierarchy and frequently requested titles lower in the hierarchy, a vast number of titles can be supported without overburdening the storage available at local and regional servers. In addition, a national or other server high in the hierarchy can be used to store, move, and distribute local or other content as part of an on demand service.
Owner:TIME WARNER CABLE ENTERPRISES LLC
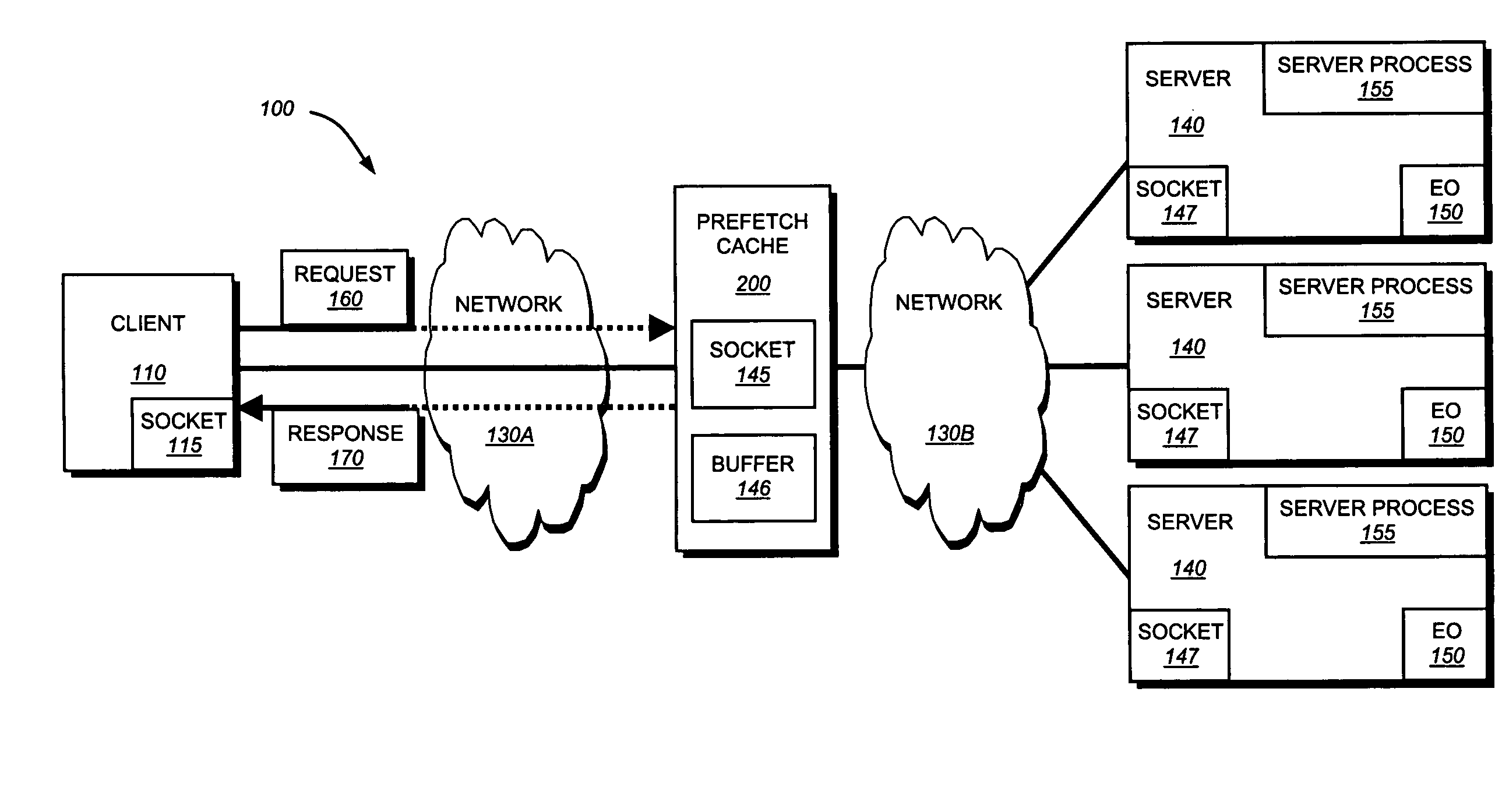
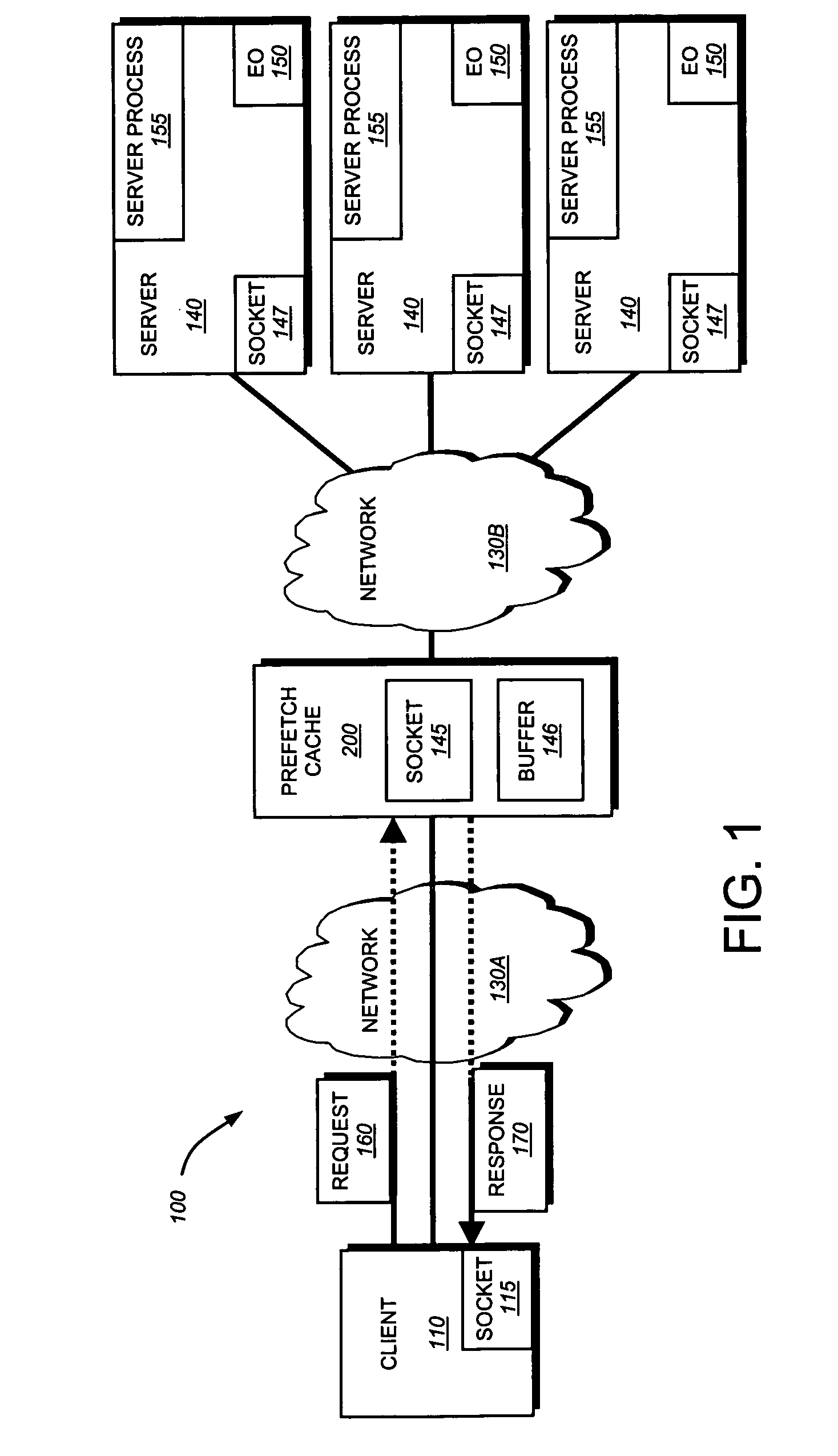
System and method for prefetching uncachable embedded objects
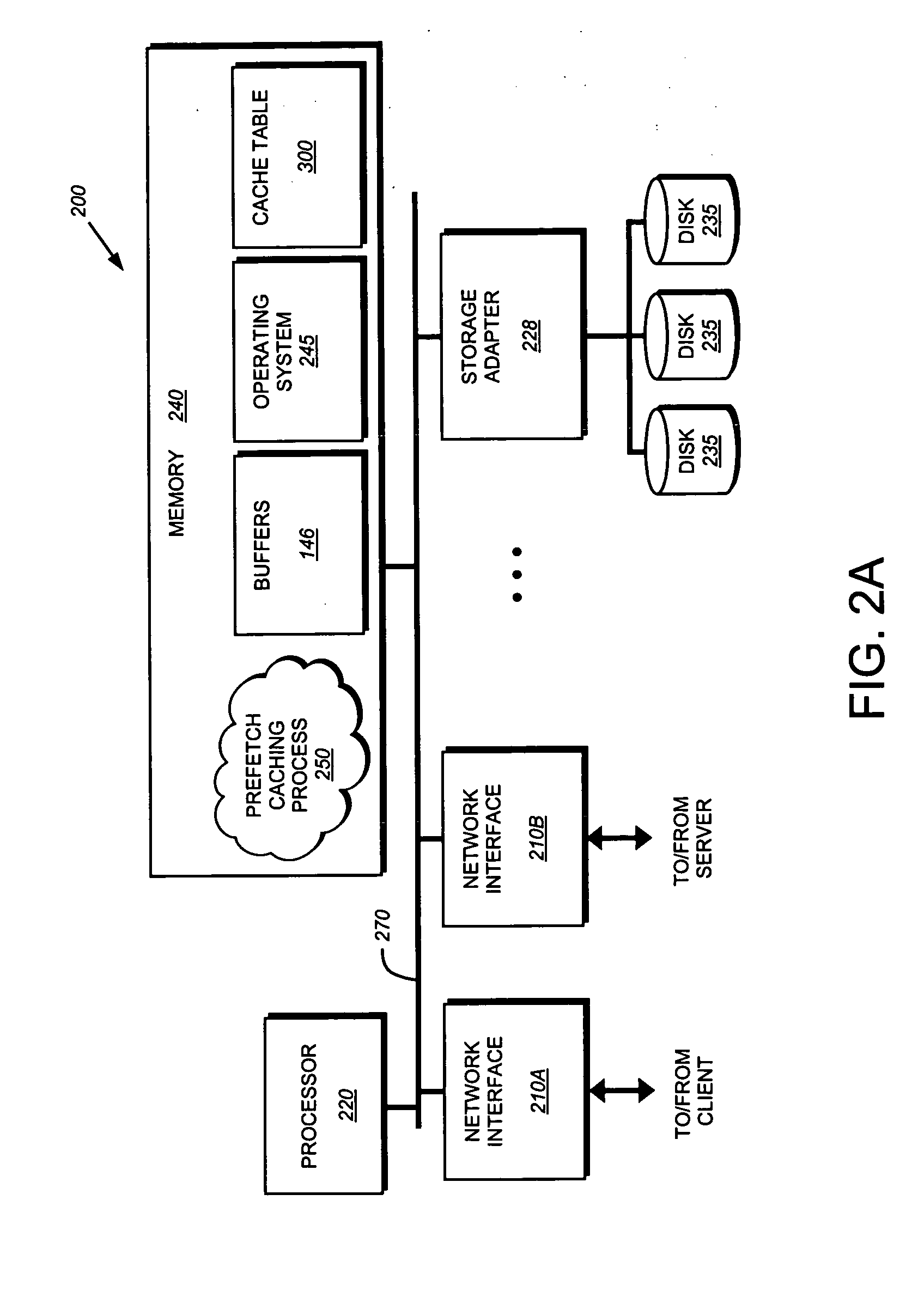
InactiveUS20070250601A1Overcome disadvantagesDigital data information retrievalMultiple digital computer combinationsClient-sideTransient storage
A system and method for prefetching one or more embedded objects marked uncacheable using a staging area on a prefetch cache to temporarily store (load) the uncacheable object. The staging area is a buffer allocated to a socket that is established between a prefetch cache and the server subsequent to the establishment of an initial connection. A prefetch caching process retrieves one or more embedded objects from the server using one or more sockets 145 based on the response sent to the client and a preconfigured set of rules. Additionally, the prefetch caching process determines whether the embedded object is uncacheable. The prefetch caching process then loads the object into the buffer associated with the socket. The prefetch caching process waits a predetermined time period for the cache to receive a client request for the object. If the request is received prior to expiration of the time period, the prefetch caching process sends the object over the socket. Otherwise, the process “flushes” the buffer, thereby discarding the object, and then closes the socket.
Owner:SYMANTEC CORP
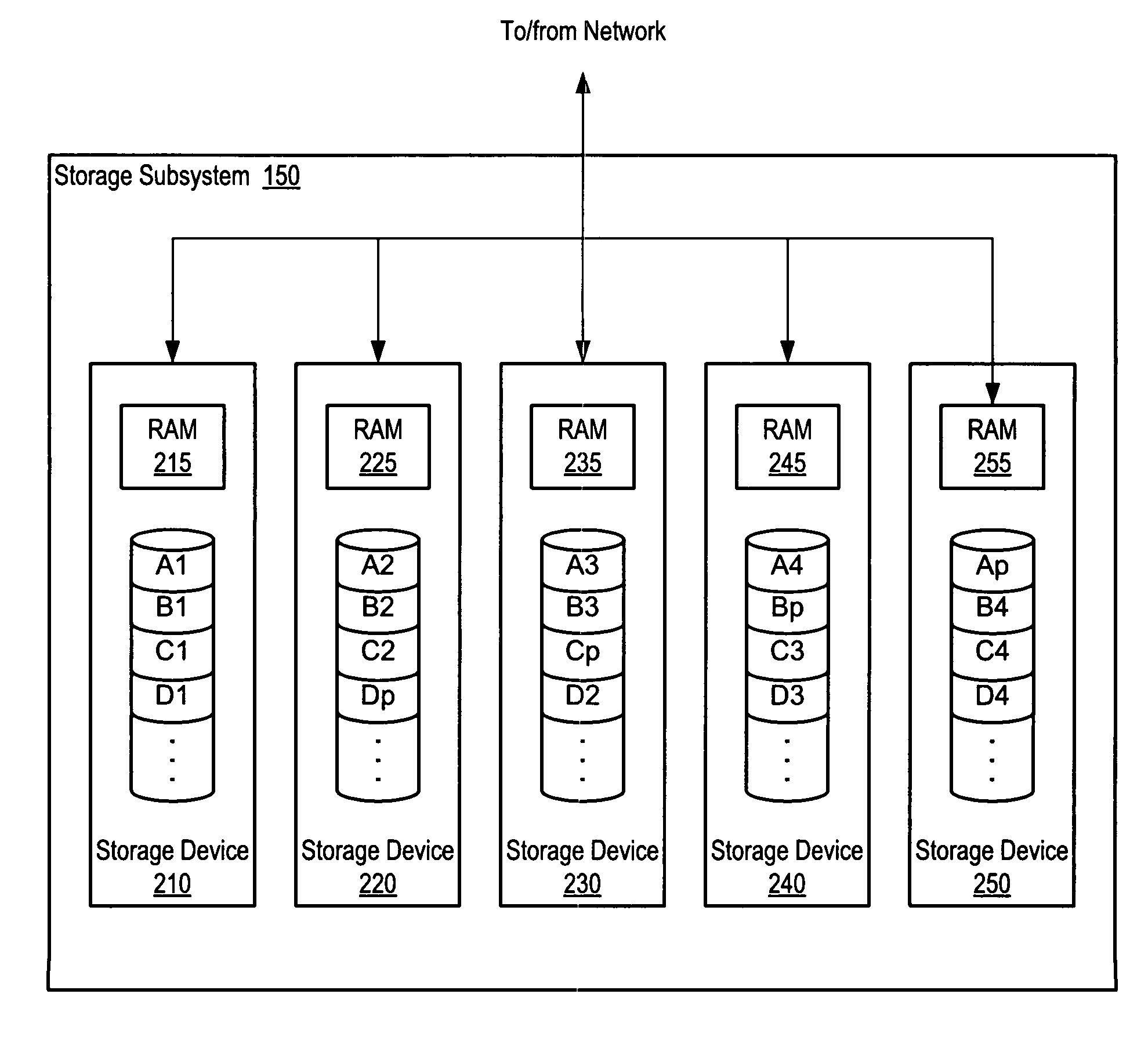
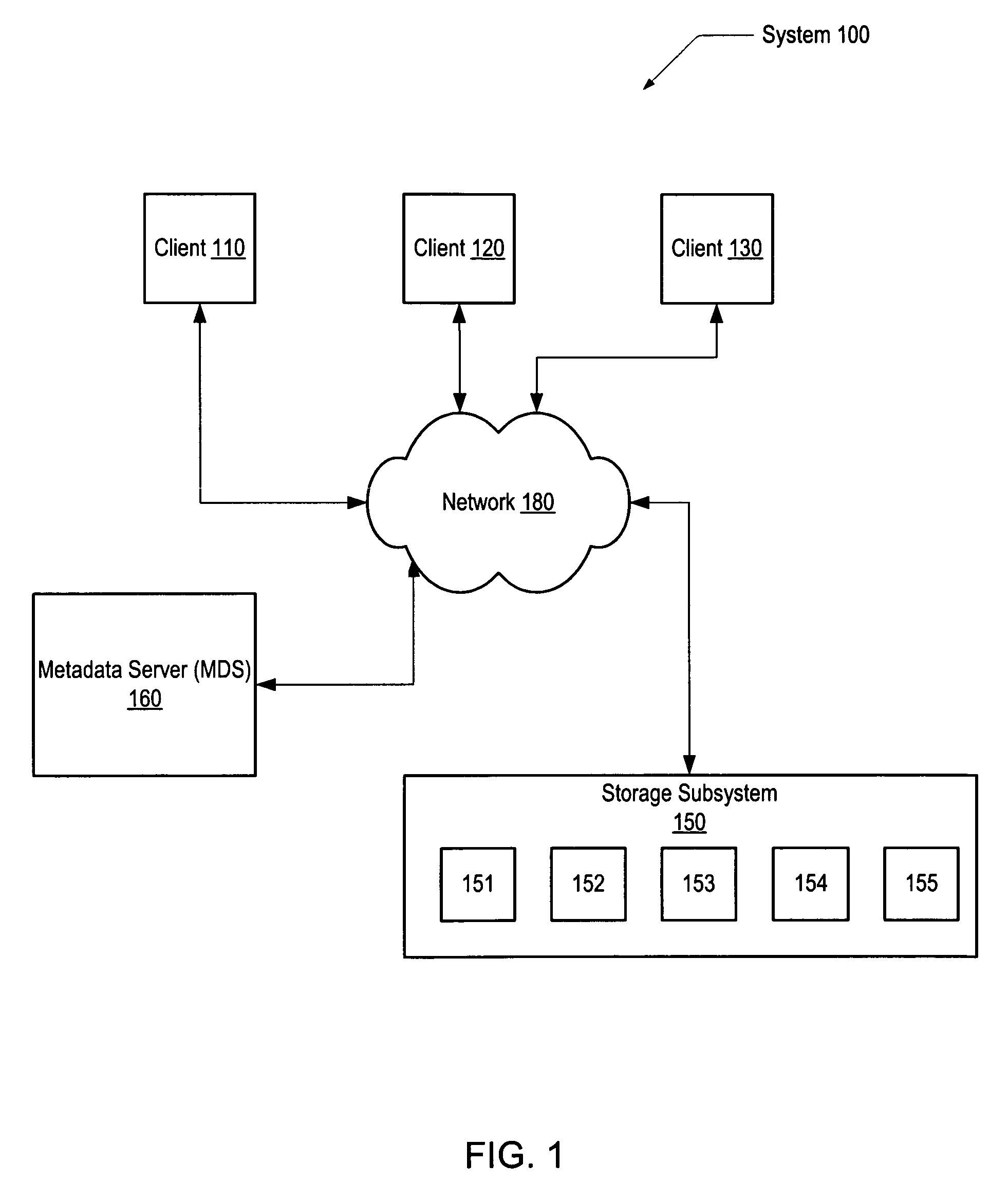
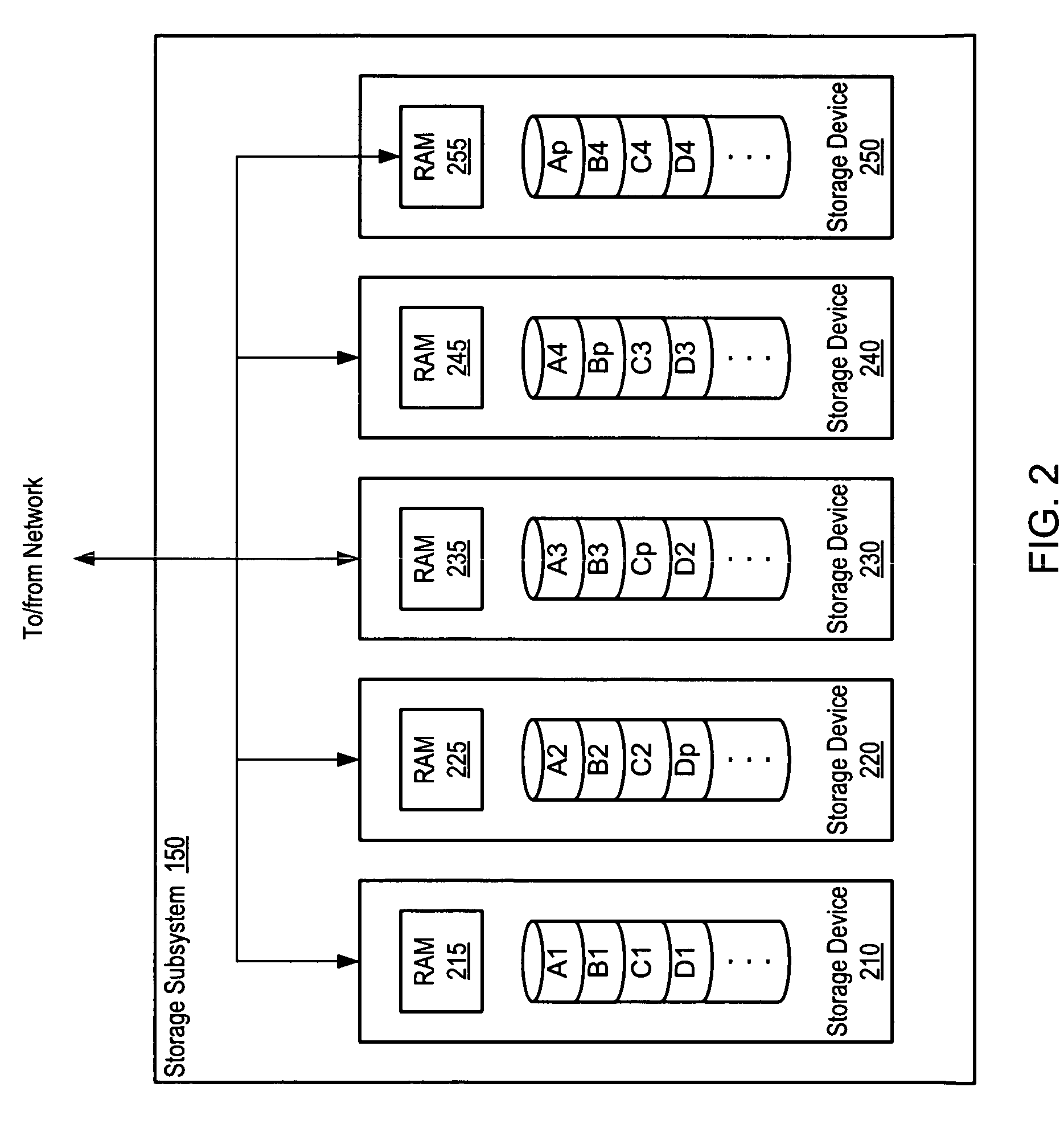
System and method of redundantly storing and retrieving data with cooperating storage devices
A system and method for data storage in an array. A system includes a client coupled to a storage subsystem. The storage subsystem comprises data storage locations addressable as rows and columns in an array. Each column comprises a separate storage device. Each row includes redundant data. For a given row, a coordinating storage device receives data from the client, coordinates computation and storage of redundant data, and forwards data to other storage devices. In response to receiving data targeted for storage in a given storage location, a non-volatile, temporary storage device that is associated with the separate storage device that includes the given storage location buffers the received data. The coordinating storage device conveys a write completion message to the client in response to detecting that the data has been buffered in the non-volatile, temporary storage devices. At least two storage devices are coordinating storage devices in separate rows.
Owner:VERITAS TECH
Method and apparatus for interacting with broadcast programming
ActiveUS20060062363A1Television system detailsReceiver side switchingBroadcast channelsRelevant information
A method of and apparatus for allowing a user using a communications device to interact with first media material that is broadcast on a first broadcast channel y a first broadcast media source and second media material that is broadcast on a second broadcast channel by a second broadcast media source, the first media material and the second media material include a first media item and a second media item, respectively, the first media item and the second media item are associated with a first representation of the first media item and a representation of the second media item, respectively, that are received and presented by a broadcast reception device while the broadcast reception device is tuned to a third broadcast channel. The method includes maintaining in a temporary storage an item identifier, the item identifier identifies one of a first media item-related information and a second media item-related information. Additionally, when the broadcast reception device is tuned to the third broadcast channel and presents the first representation of the first media item, the method includes providing the item identifier as a basis for identifying the first media item-related information, the first media item-related information is a basis for a response to an interactivity activation made in reaction to presentation of the first representation of the first media item by the broadcast reception device. When the broadcast reception device is tuned to the third broadcast channel and presents the first representation of the second media item, the method includes providing the item identifier as a basis for identifying the second media item-related information, the second media item-related information is a basis for a response to an interactivity activation made in reaction to presentation of the representation of the second media item by the broadcast reception device.
Owner:ADAM ALBRETT +1
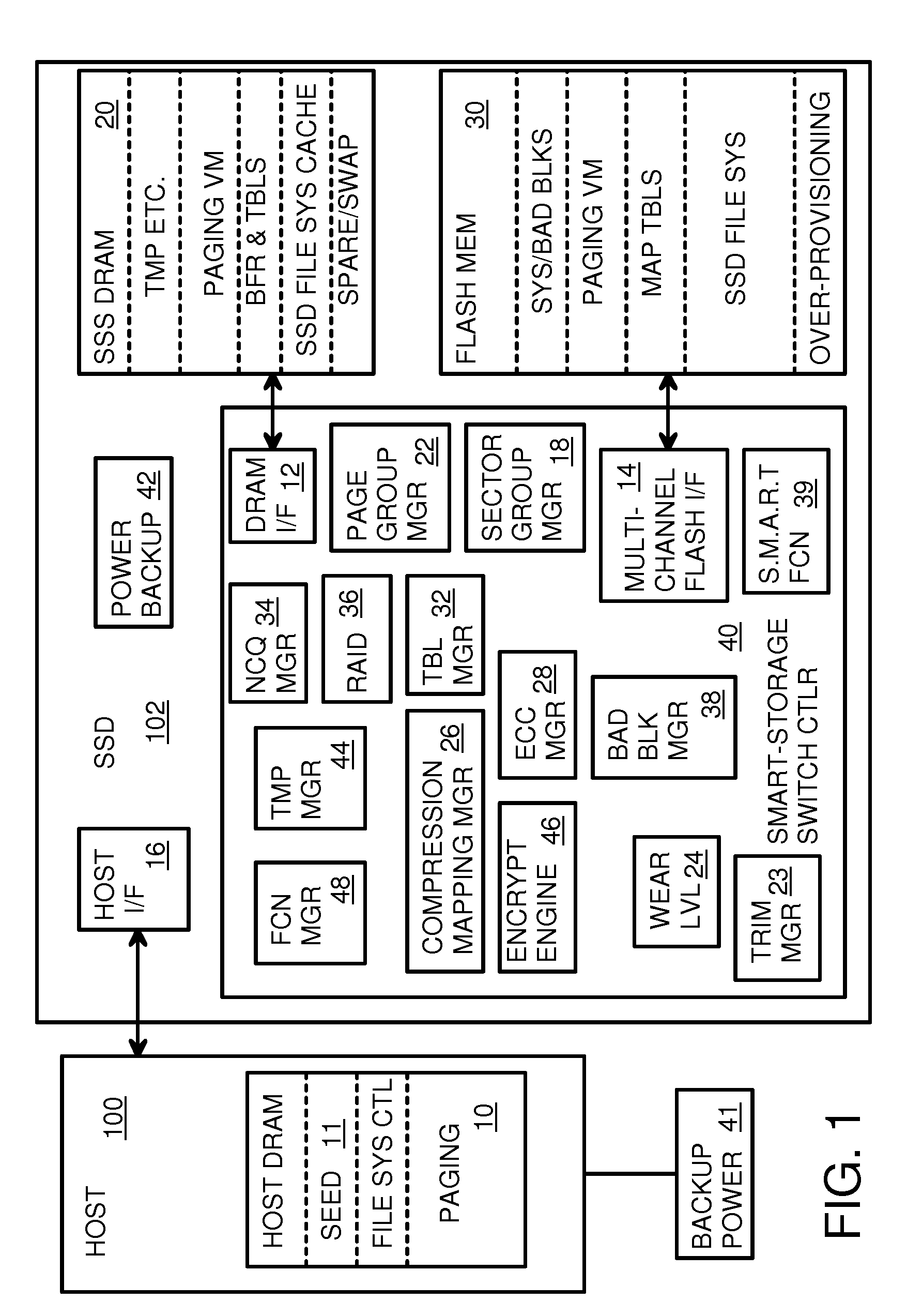
Endurance Translation Layer (ETL) and Diversion of Temp Files for Reduced Flash Wear of a Super-Endurance Solid-State Drive
ActiveUS20150106556A1Memory architecture accessing/allocationMemory adressing/allocation/relocationFilename extensionData file
A flash drive has increased endurance and longevity by reducing writes to flash. An Endurance Translation Layer (ETL) is created in a DRAM buffer and provides temporary storage to reduce flash wear. A Smart Storage Switch (SSS) controller assigns data-type bits when categorizing host accesses as paging files used by memory management, temporary files, File Allocation Table (FAT) and File Descriptor Block (FDB) entries, and user data files, using address ranges and file extensions read from FAT. Paging files and temporary files are never written to flash. Partial-page data is packed and sector mapped by sub-sector mapping tables that are pointed to by a unified mapping table that stores the data-type bits and pointers to data or tables in DRAM. Partial sectors are packed together to reduce DRAM usage and flash wear. A spare / swap area in DRAM reduces flash wear. Reference voltages are adjusted when error correction fails.
Owner:SUPER TALENT TECH CORP
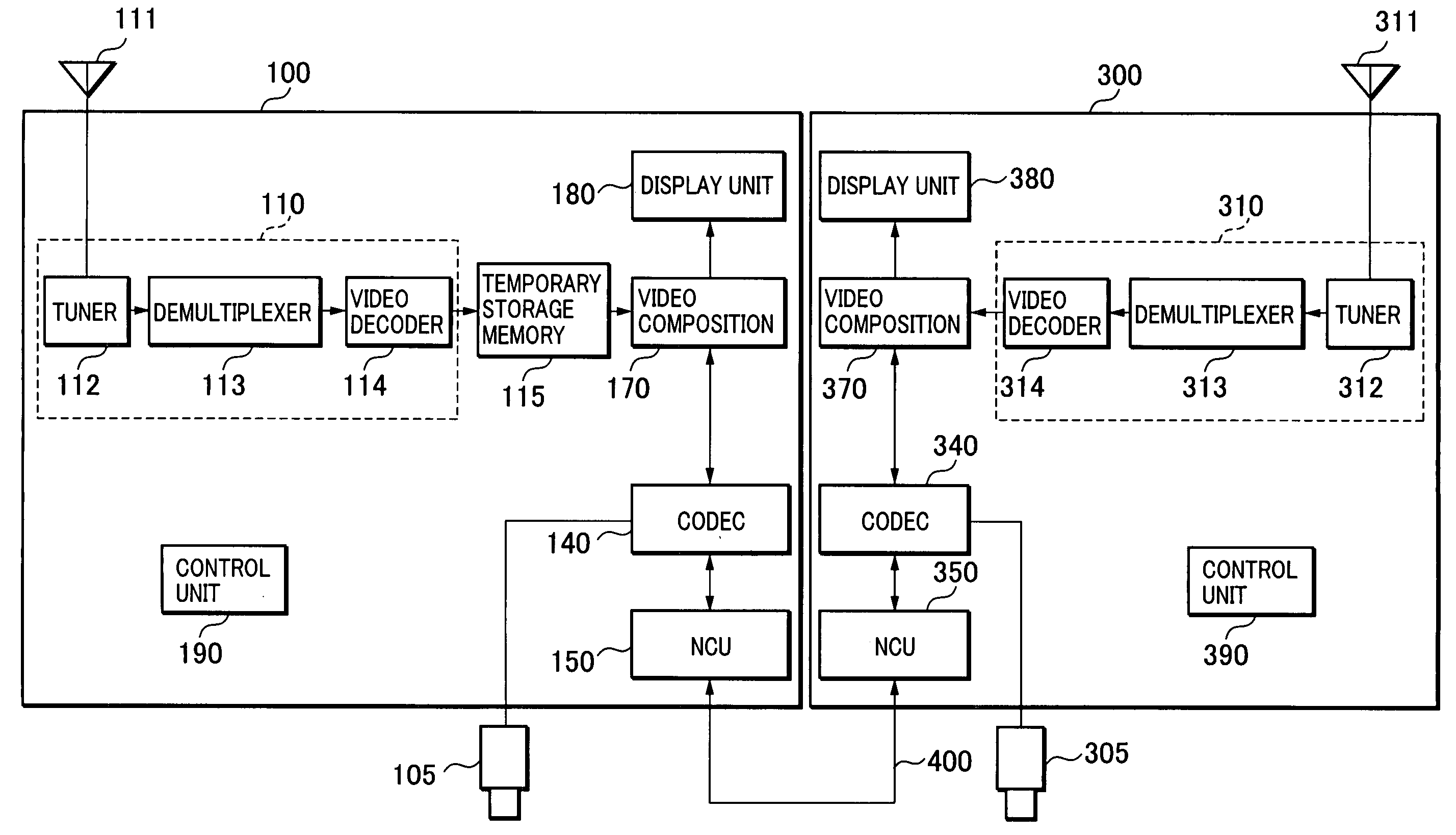
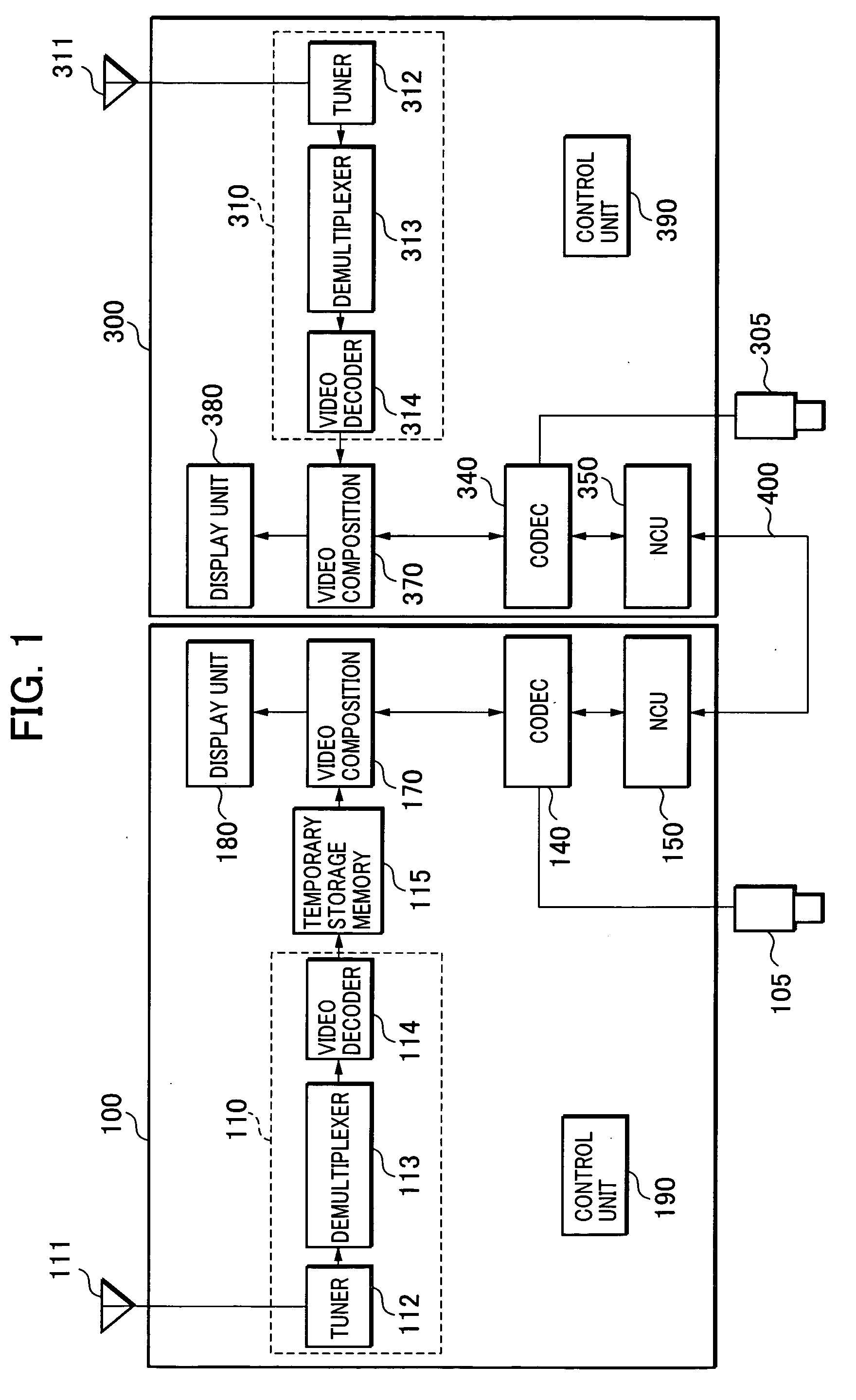
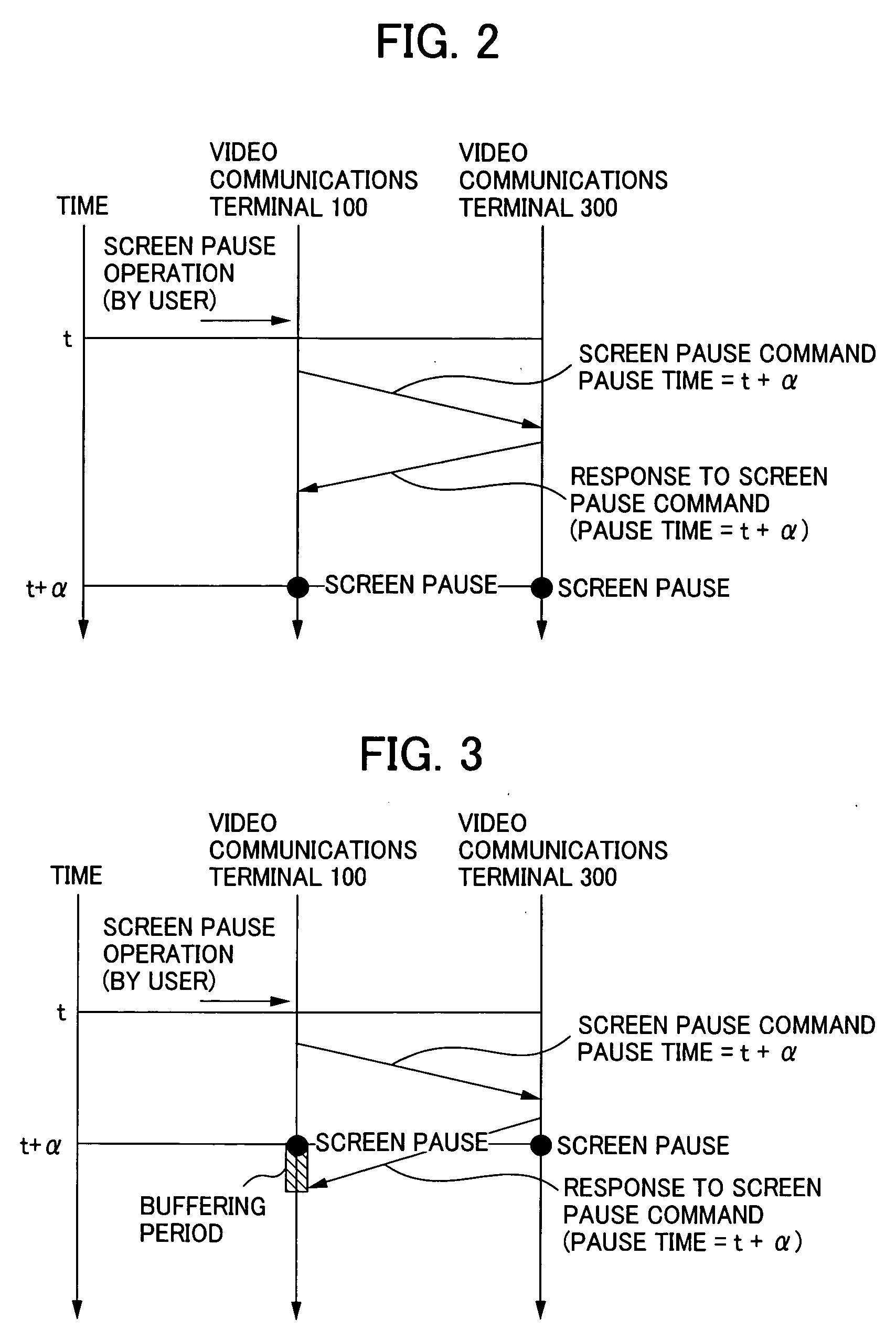
Visual communications system and method of controlling the same
InactiveUS20050166242A1Television system detailsAnalogue secracy/subscription systemsCommunications systemComputer science
A visual communications system and a method of controlling the same for pausing the screens of two terminals at quite the same image. Video communications terminals receive the same channel in their respective broadcast program receiving units. A first video communications terminal temporarily stores the video of the received channel in the temporary storage memory. When a user pauses operation of the first terminal, it temporarily stores a screen pause time obtained by adding a predetermined time to the current time, and transmits a screen pause command and the screen pause time to a second video communications terminal. The second terminal pauses the video at the screen pause time if possible in time. Otherwise, it pauses the video immediately, and transmits a response with its own image pause time to the first terminal. The first terminal displays an image corresponding to the image pause time of the second terminal memory.
Owner:CANON KK
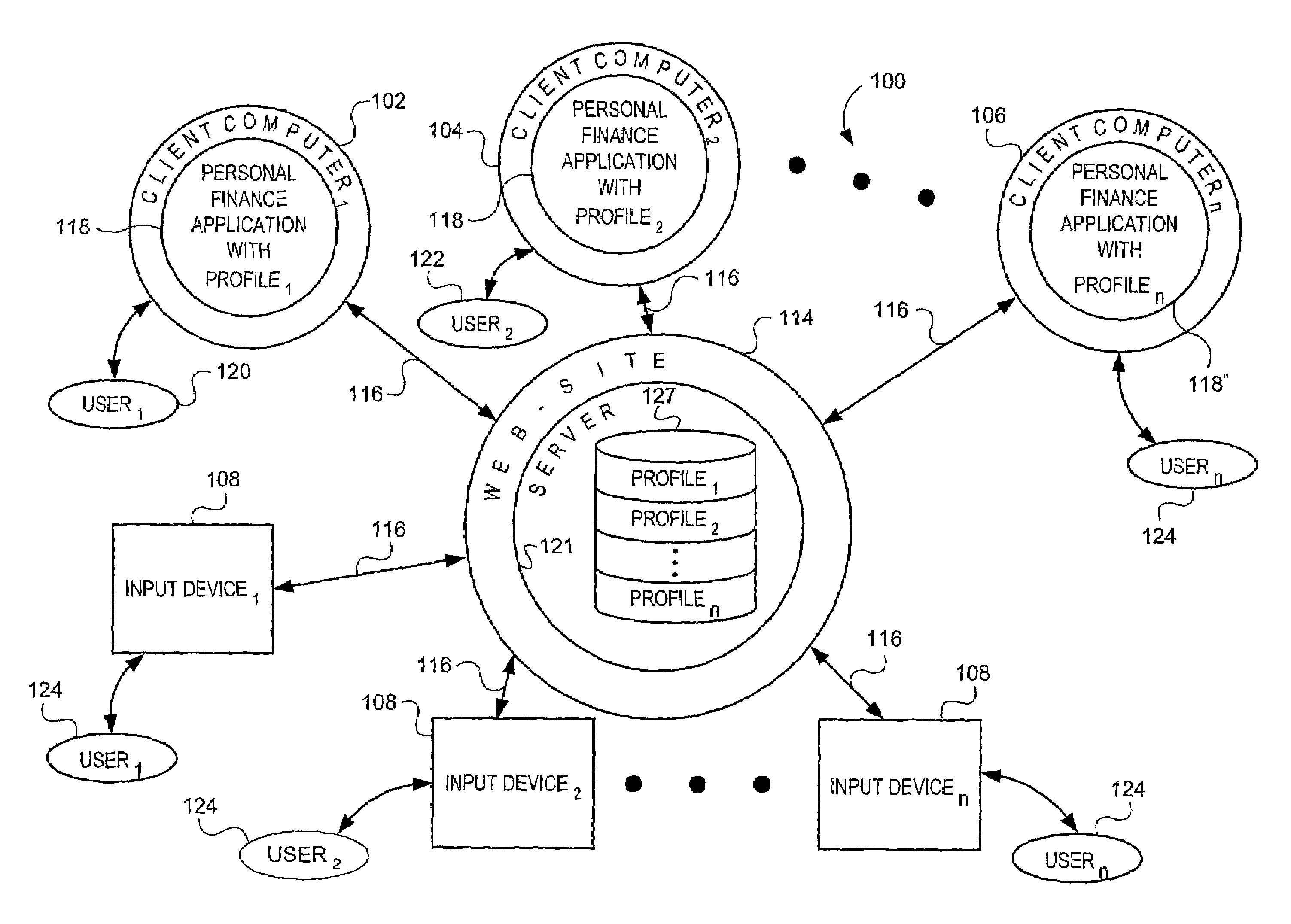
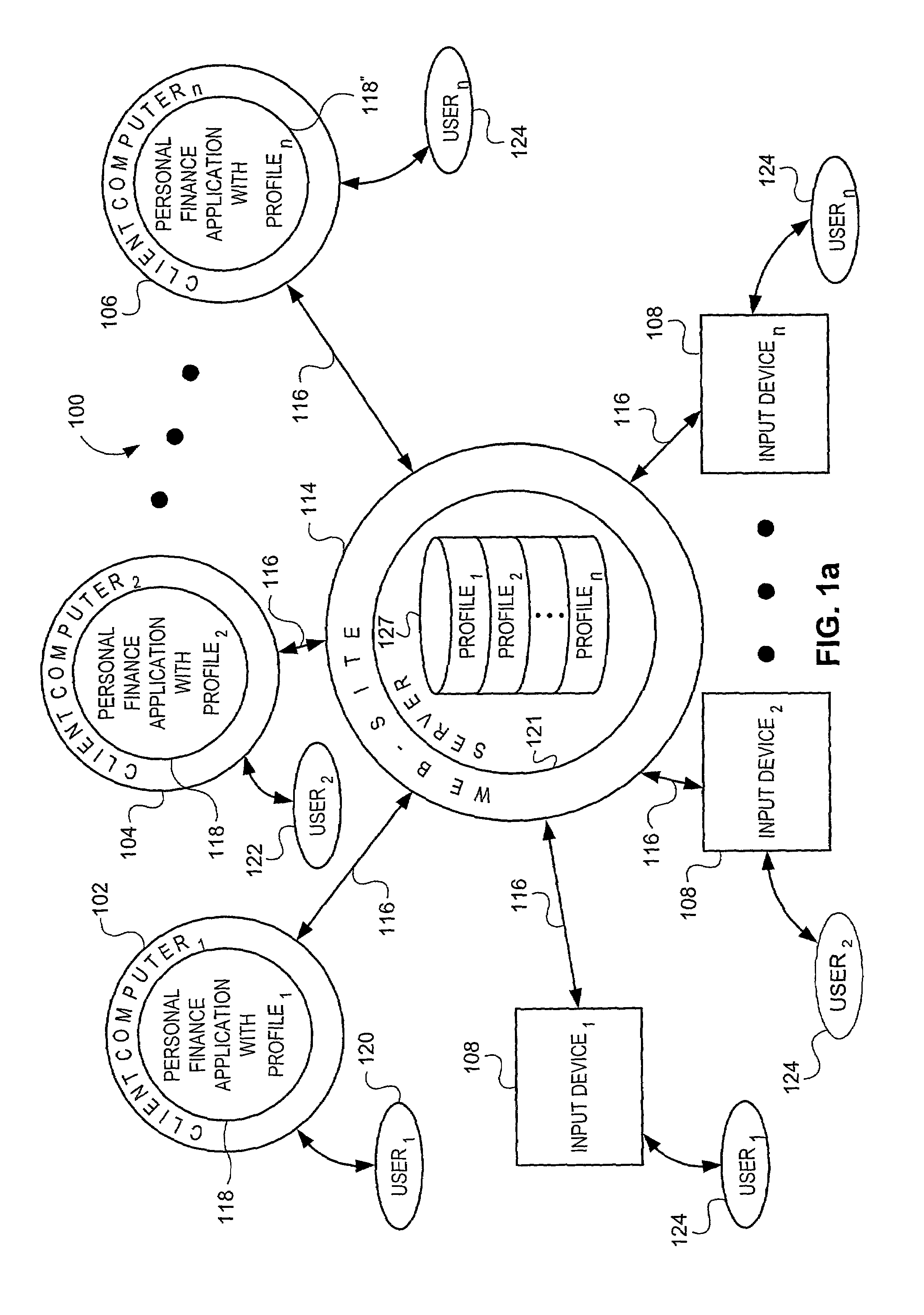
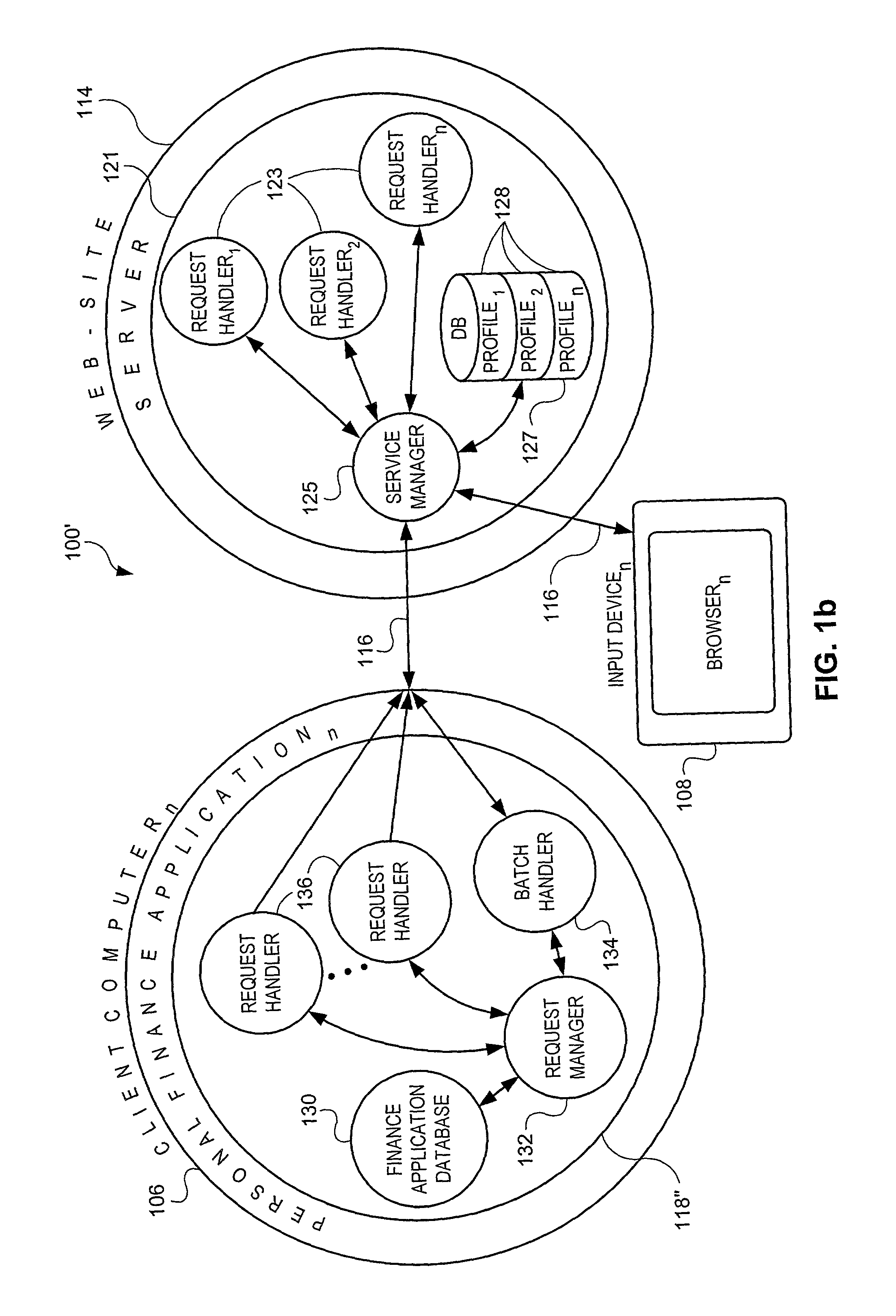
Web-based entry of financial transaction information and subsequent download of such information
InactiveUS7729959B1Reduce probabilityImprove timelinessComplete banking machinesFinanceWeb siteFinancial transaction
The systems, methods and related software products which enable users to temporarily store and subsequently retrieve information are disclosed. The system includes a plurality of input devices, client computers (each having a user-specific personal finance application) and a web-site server with a database. The input devices, client computers and server are communicatively linked via a communication network so that a plurality of users can temporarily store and / or manipulate financial transaction information on the server from any of the input devices. Each user can also transmit financial profile information to the server. This information enables the server to replicate the unique profile characteristics for each of the finance applications. This, in turn, simplifies remote entry of information, subsequent download of that information and integration of such information into each user's personal finance application.
Owner:INTUIT INC
Storage system disposed with plural integrated circuits
InactiveUS8010720B2Increase profitImprove utilization efficiencyTransmissionInput/output processes for data processingSystem configurationEngineering
Owner:HITACHI LTD
Method and system to edit and analyze longitudinal personal health data using a web-based application
In a global computer network, a system for processing personal health records is disclosed. The system includes a web-based application providing an application web server that does not store personal data. A user starts a new session using the application web site and begins entering medical data. During the session, with the user's data in transient storage, the application web site can perform health risk assessments and search other databases to provide information relevant to the user's health. At the end of the session, the user downloads a file that saves all of the data. Next, the application web site erases the user's data from the web site. The user continues data entry in the future by uploading the saved file. Since the user keeps the data, no identification of the user is necessary and privacy is preserved.
Owner:WU HARRY C
Automatic apparatus for storing and dispensing packaged medication and other small elements
The system includes a bin hopper which temporarily stores a plurality of small elements, such as medications. The elements are moved out of the bin and singulated into a one-by-one sequence by a series of singulating conveyors. The resulting sequence of elements is moved onto a main system conveyor where the element is identified and then moved to a loading mechanism which arranges the item so it is ready to be gripped and stored. The system includes a mass storage apparatus comprising a series of four upstanding cylindrical drums, each having a plurality of individually accessible and addressable cell storage locations for the elements. A gripping apparatus removes the elements from the loading mechanism and transfers them to a selected location in a cylindrical drum. When an article is to be dispensed, the drum is rotated so that an ejection arm comes adjacent the desired location in the drum. The ejector arm is actuated, pushing the small element out of its slot, into the center of the drum, where it falls onto a conveyor which moves the dispensed item from the system.
Owner:OMNICELL +1
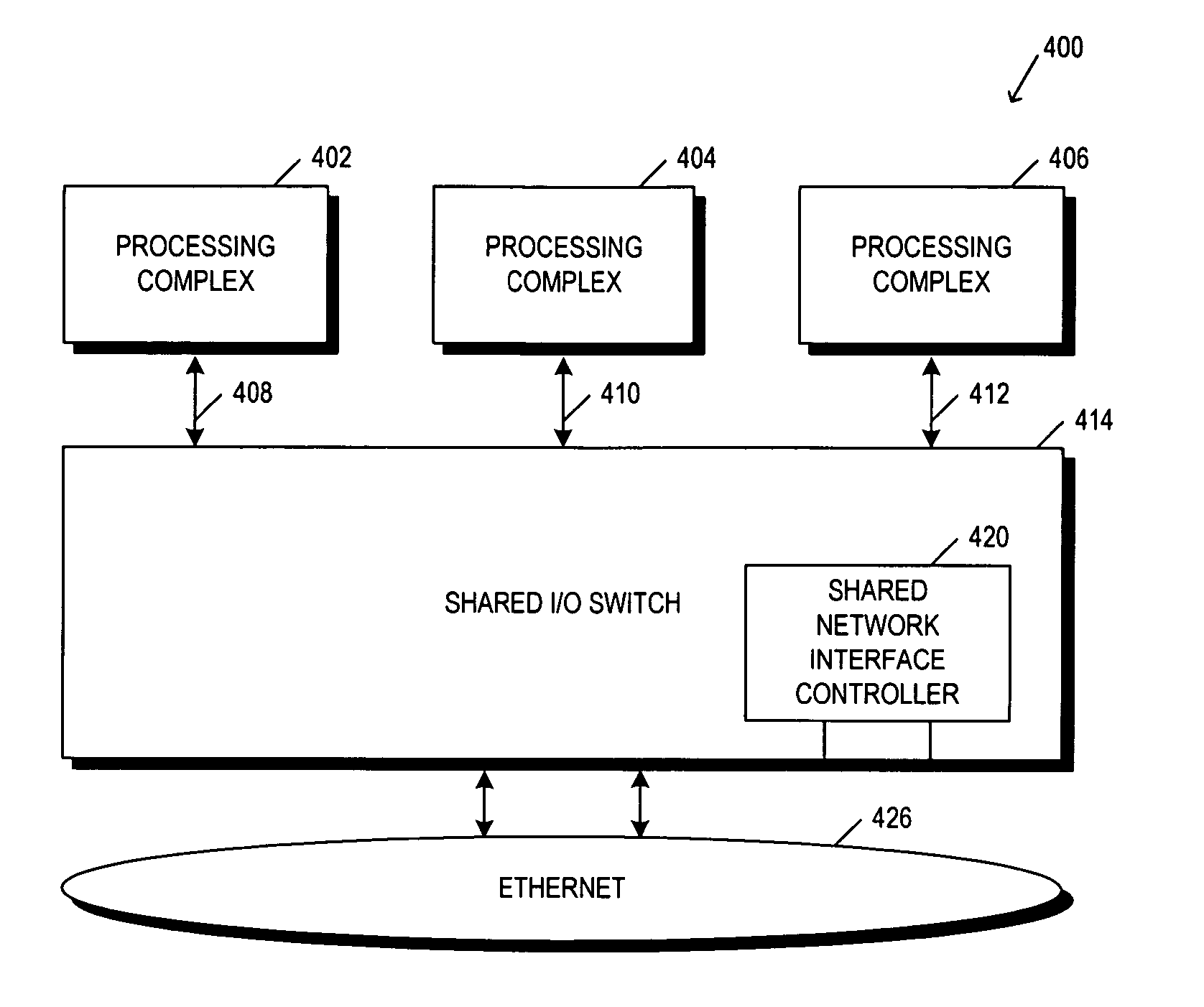
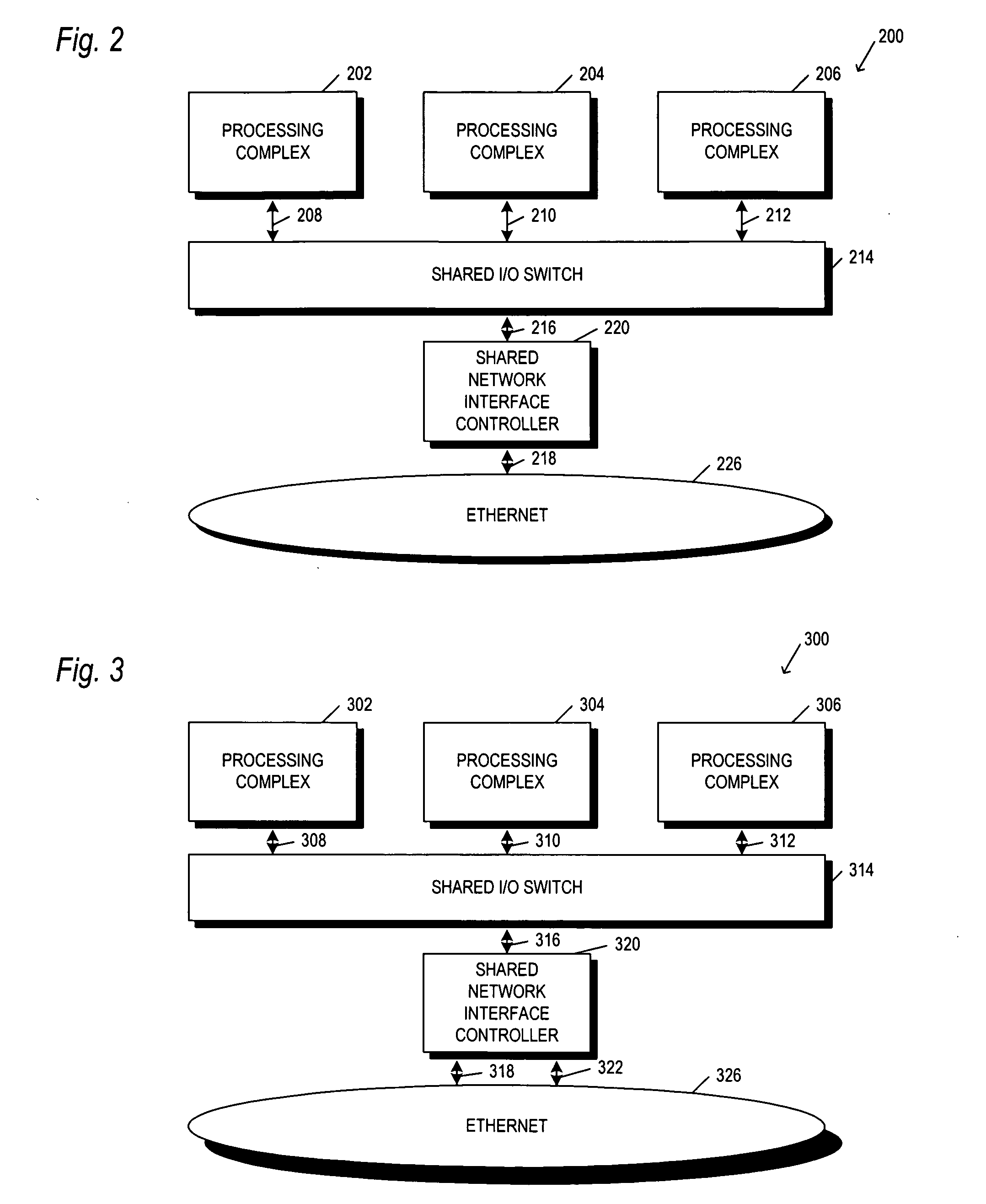
Method and apparatus for a shared I/O network interface controller
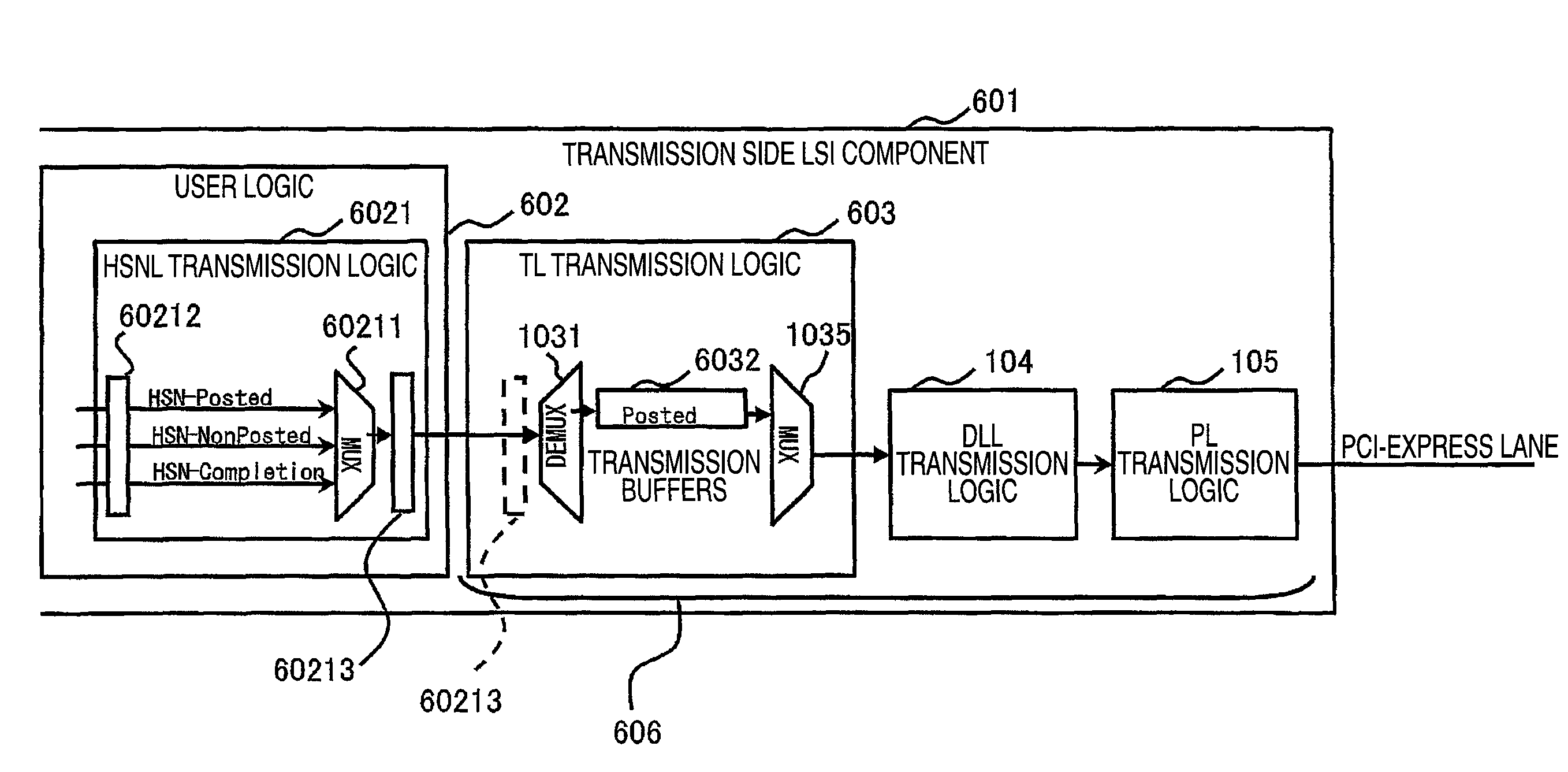
ActiveUS20050053060A1Multiplex system selection arrangementsData switching by path configurationTransient storagePCI Express
An apparatus and method is provided for interfacing a number of computer servers (or operating system domains) to a network such as Ethernet through a shared network interface controller (NIC) which is part of the load-store architecture of the operating system domains. The network interface controller includes a bus interface to couple the controller to a load-store domain bus (such as PCI-Express), the bus including header information to associate data on the bus with an originating operating system domain. The controller also includes transmit / receive logic to connect it to the network. In between the bus interface and the transmit / receive logic is buffering to temporarily store data coming either from the operating system domains or the network. The buffered data is tagged within an identifier to associate it with one or more of the operating system domains. Association logic is further provided to allow the controller to designate, and later lookup which destination MAC address (on the Ethernet side) is associated with which operating system domain. Control Status Registers (CSR's) specific to an operating system domain are duplicated and made available for each domain. Descriptor Register files are also duplicated for each operating system domain. A number of direct memory access (DMA) engines are provided to improve throughput. And, packet replication logic, along with filters (perfect and hash) and VLAN tables are used for looping back packets originating from one of the operating system domains to one or more of the other operating system domains, for server to server communication, multicast and broadcast operations.
Owner:MELLANOX TECHNOLOGIES LTD
System and method for processing transaction data
InactiveUS20040024626A1FinanceMultiple digital computer combinationsMessage queueSoftware architecture
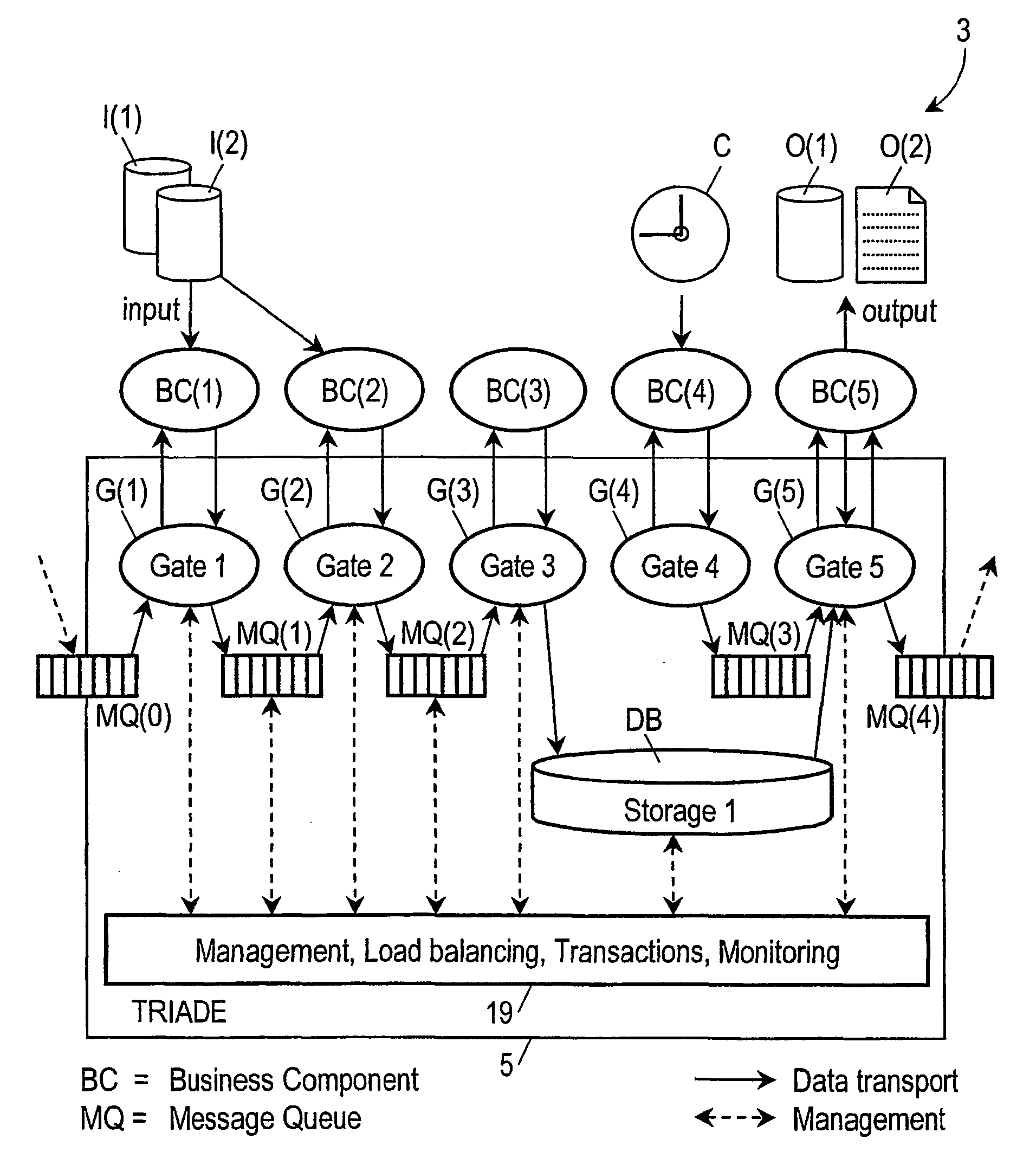
Computer system provided with a software architecture for processing transaction data which comprises a platform (5) with at least one logical processing unit (21) comprising the following components: a plurality of gates (G(k)); one or more message queues (MQ(k)), these being memories for temporary storage of data; one or more databases (DB); a hierarchical structure of managers in the form of software modules for the control of the gates (G(j)), the messages queues (MQ(k)), the one or more databases, the at least one logical processing unit (21) and the platform (5), wherein the gates are defined as software modules with the task of communicating with corresponding business components (BC(j)) located outside the platform (5), which are defined as software modules for carrying out a predetermined transformation on a received set of data.
Owner:NEDERLANDSE ORG VOOR TOEGEPAST-NATUURWETENSCHAPPELIJK ONDERZOEK (TNO)
Method for preventing malicious software installation on an internet-connected computer
ActiveUS20070192854A1Prevents gaining accessAvoid accessMemory loss protectionDigital data processing detailsOperational systemTerm memory
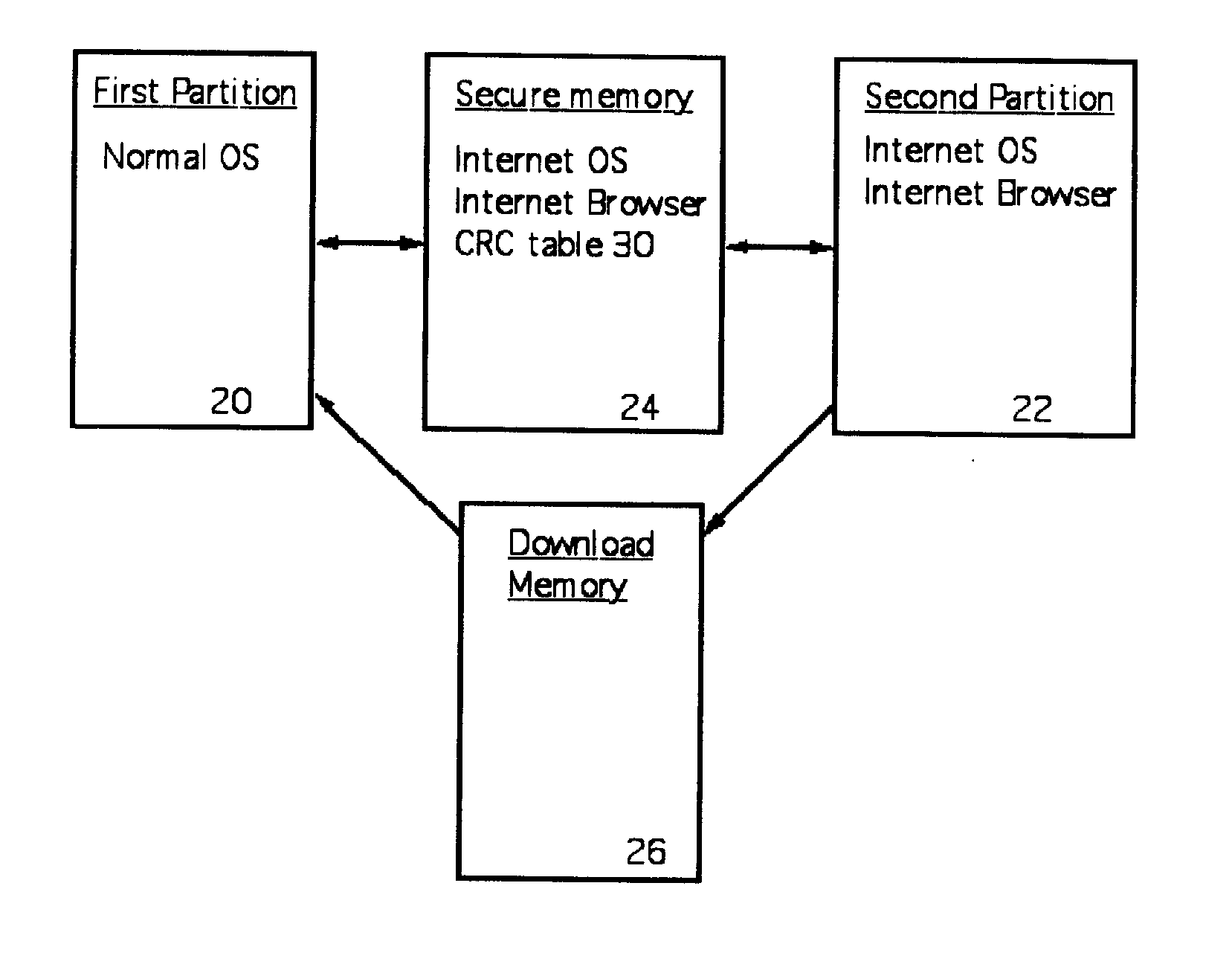
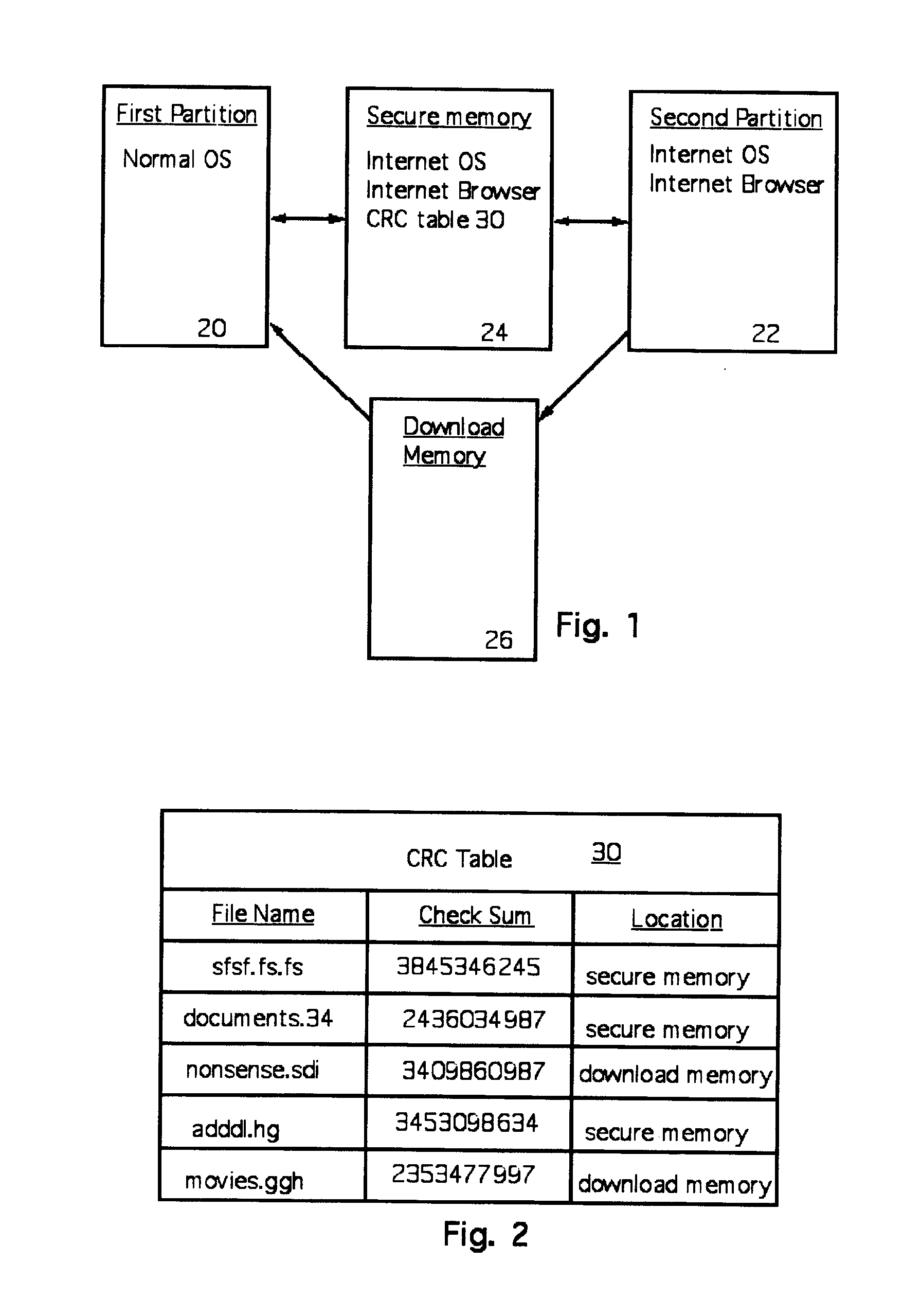
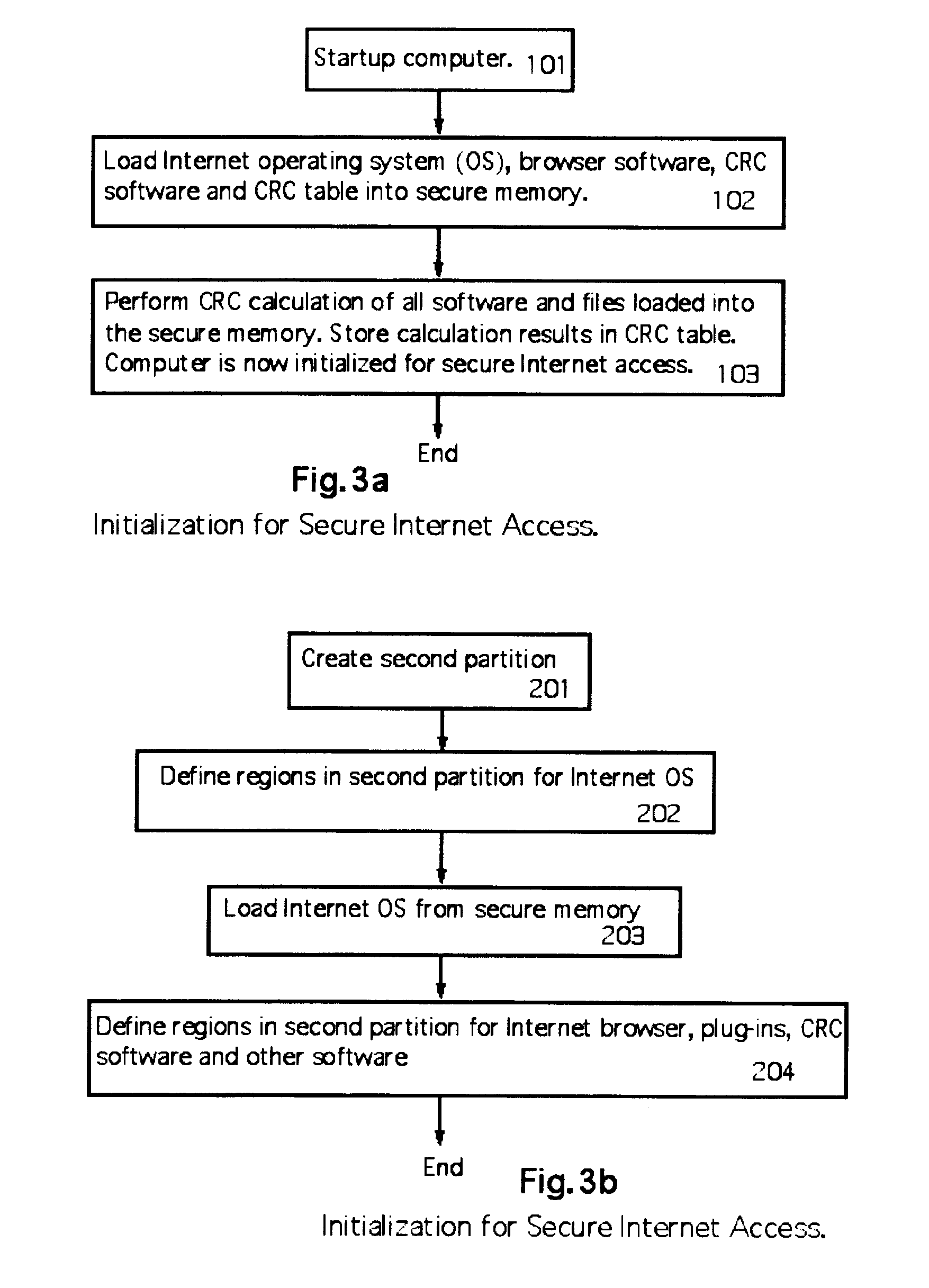
A computer random access memory is divided into first and second partitions. Each partition has its own operating system (OS). The first partition has a conventional OS and is designated for non-Internet use. The second partition is designated for secure Internet access, and has an OS specific for Internet usage. Software in the second partition cannot write or copy files in the second partition. The size of the second partition is fixed and unchangeable while said second partition is open. Each software application in the second partition is allocated a memory region that cannot be changed, thereby preventing memory overflow attacks. A secure memory is designated for temporary storage of software used in the second partition. Cyclic redundancy check (CRC) values are calculated for all files in the secure memory. To detect unauthorized file changes, CRC values are calculated for all files used in the second partition, and checked against values stored in the secure memory. The second partition can write only to a secure memory using a security arrangement such as password protection or a download memory separate from the first partition to allow files stored in the download memory to be examined by scanning and testing from the first partition prior to being stored elsewhere in the computer.
Owner:KYNDRYL INC
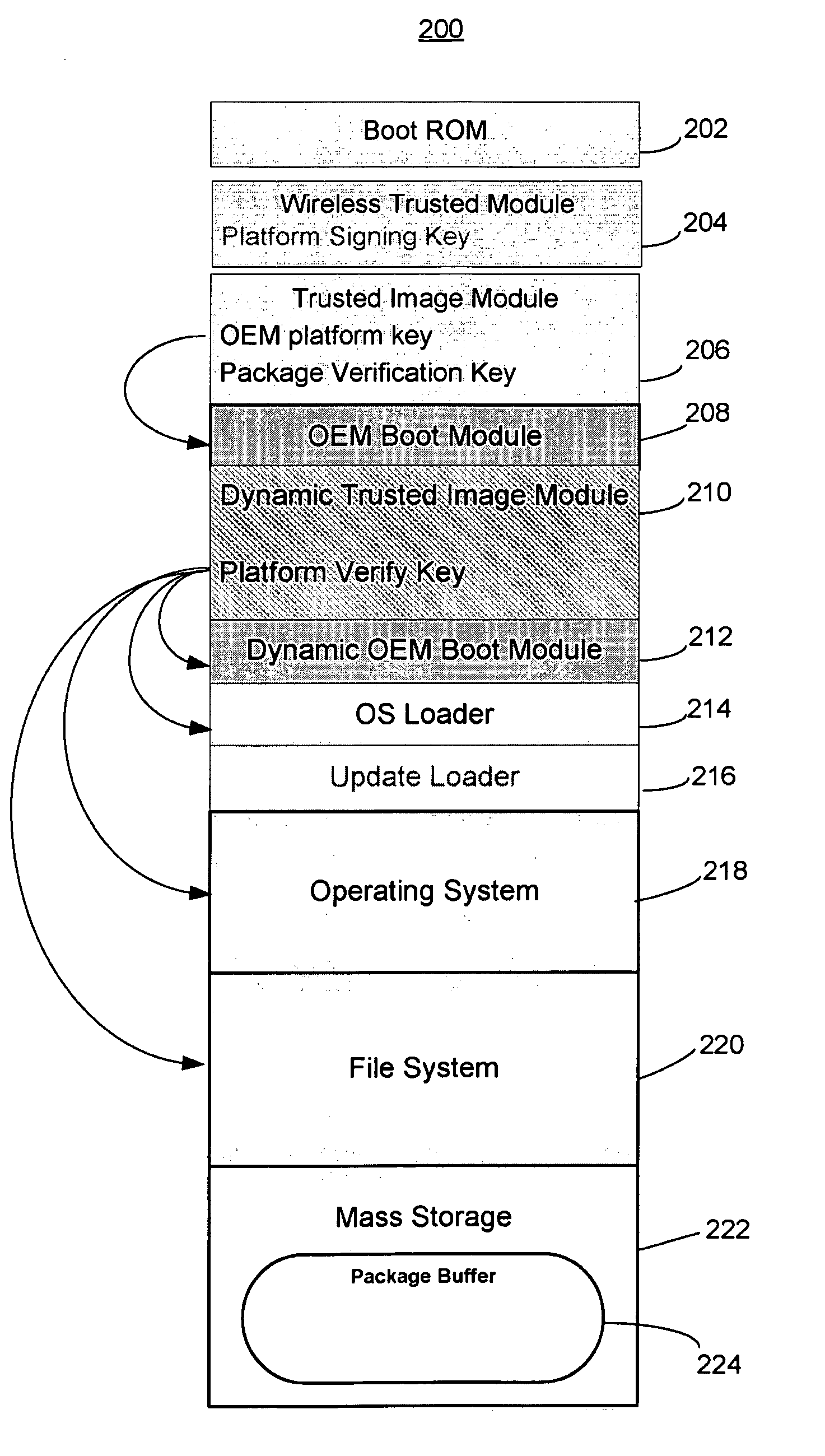
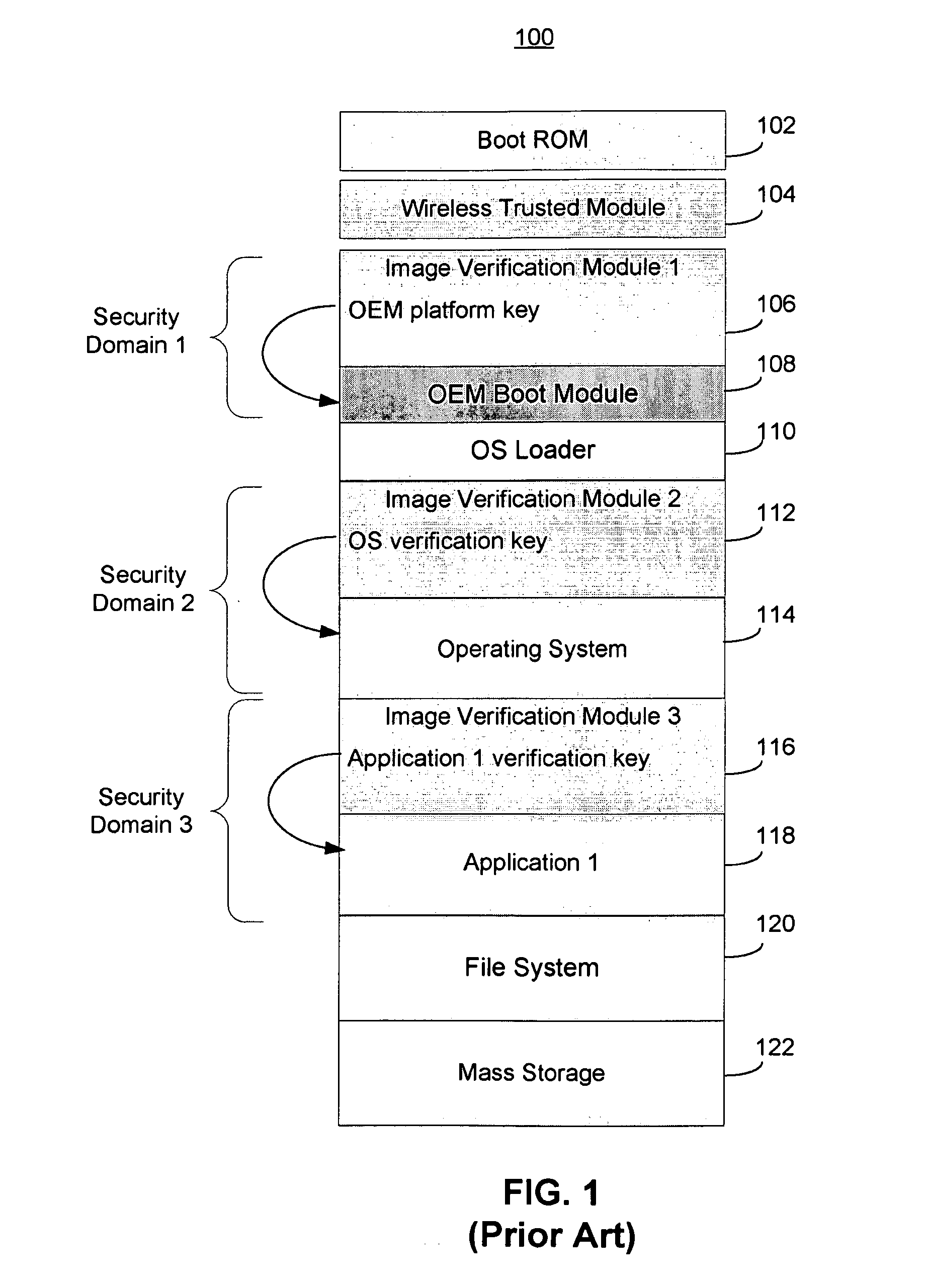
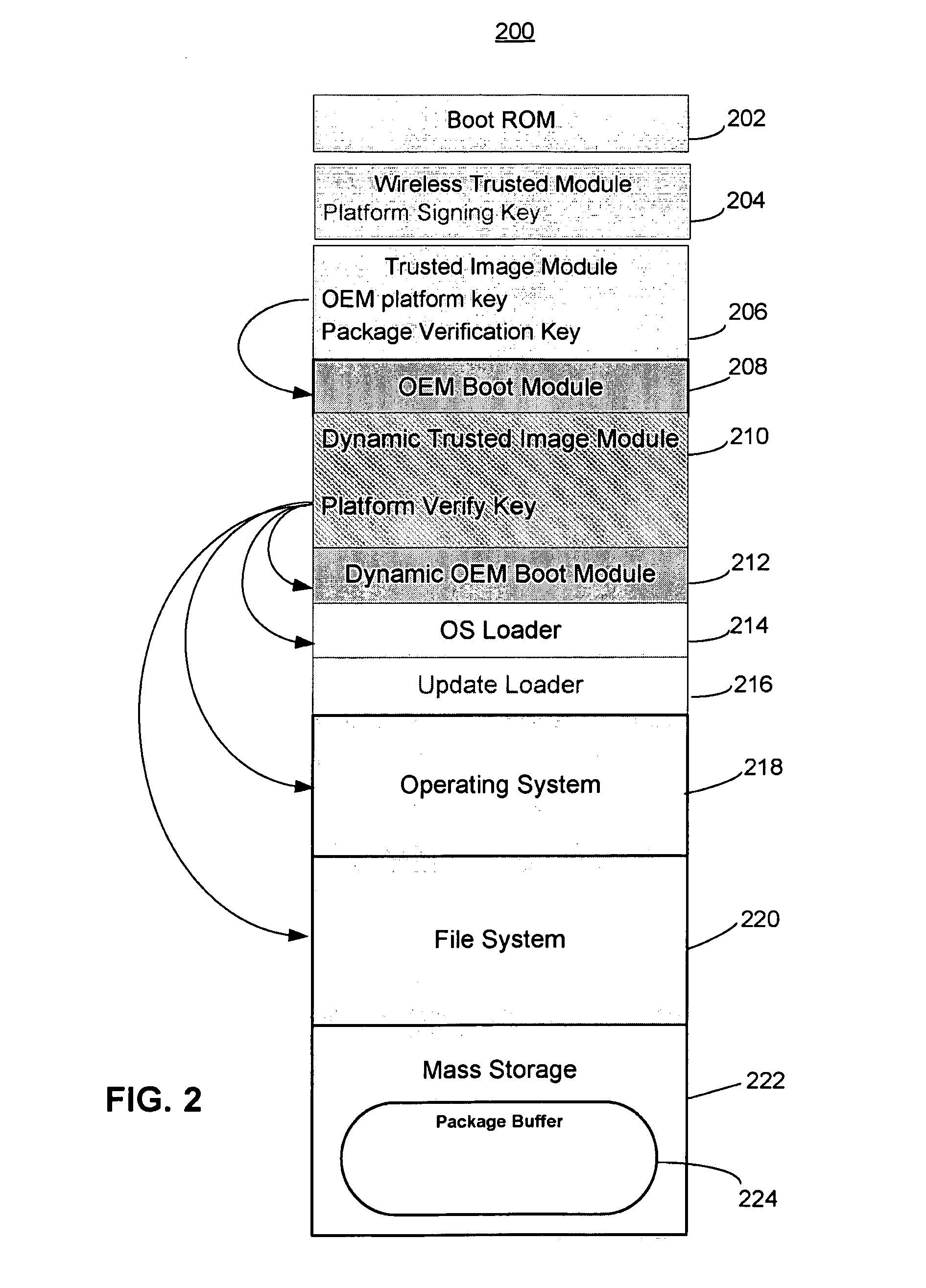
Trusted modular firmware update using digital certificate
An over-the-air firmware update is accomplished in a secure manner using a two-step process. The first step uses an initial boot using a fixed boot program and an authenticated and verified secondary environment to complete starting of only authenticated code. After verifying a pending update, the second step is started with the electronic device being booted into an update mode with an update loader that has exclusive access to a signing key. A dummy update image is loaded into a temporary memory location and a hash is taken. A digital certificate is created corresponding to the update image and signed using the signing key. The update and digital certificate are atomically installed and the signing key is deactivated. Upon reboot, the new image is used for operation and is verified by the hash data and public key in the digital certificate.
Owner:MARVELL ASIA PTE LTD
Data security
InactiveUS20060277413A1Reduce theftPrevent theftUnauthorized memory use protectionHardware monitoringComputer hardwareData field
Data Security methods, computer programs, and systems for encrypting and decrypting data, process sharing, and redundancy. The invention provides techniques for encryption including the encryption of a structured data file where each smallest unit of the data file (e.g., a field in a database record) is encrypted separately. The invention also provides techniques for decrypting such an encrypted data file. Requested fields of data are decrypted, stored in temporary memory, and displayed to the user or used to complete a task. Once the display is over or the task is completed, the decrypted data in temporary memory is deleted. The invention also provides techniques for real time process sharing and redundancy that utilize system characteristics to determine the apportionment of processes.
Owner:DREWS DENNIS T
Handling unavailable memories in distributed storage network
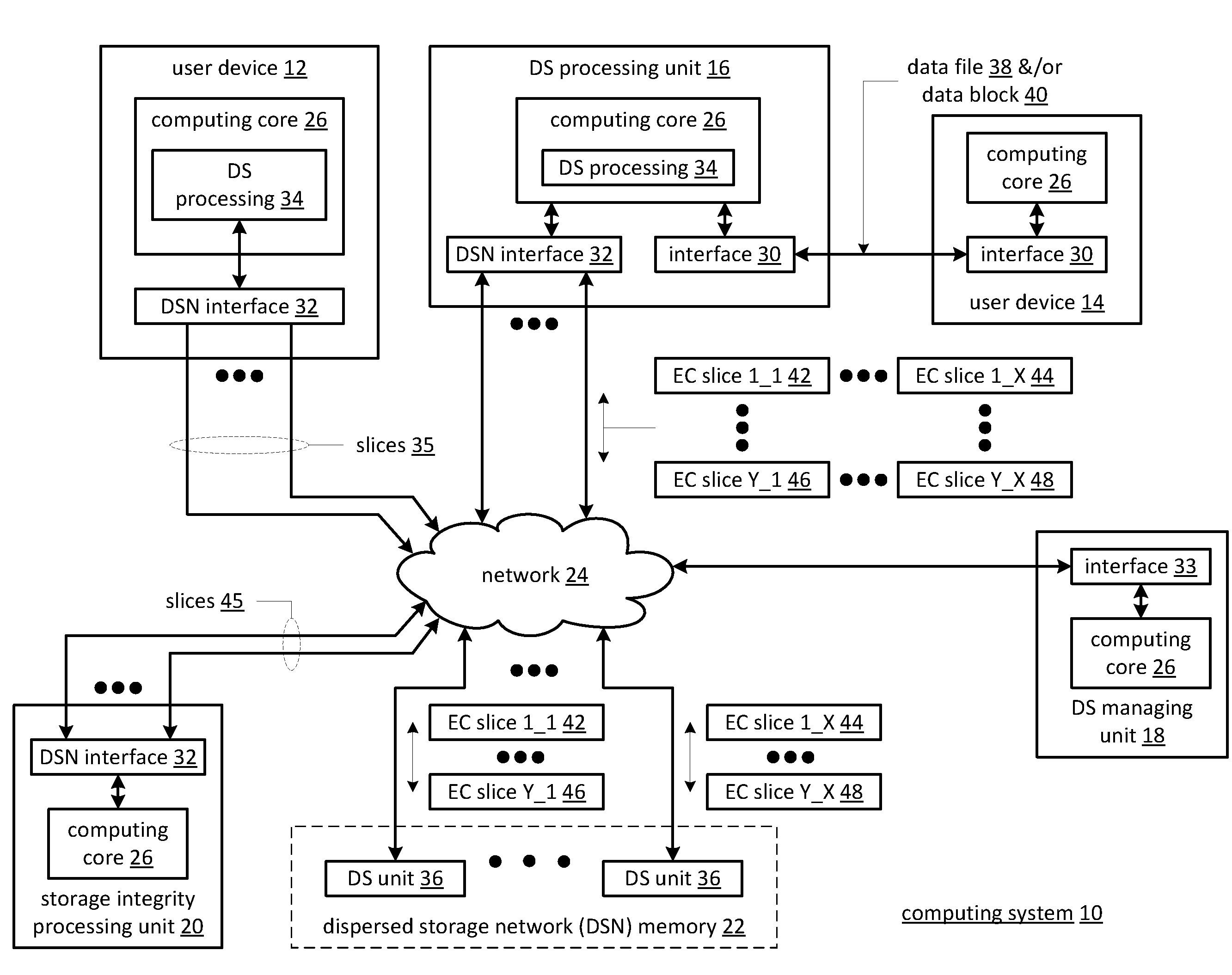
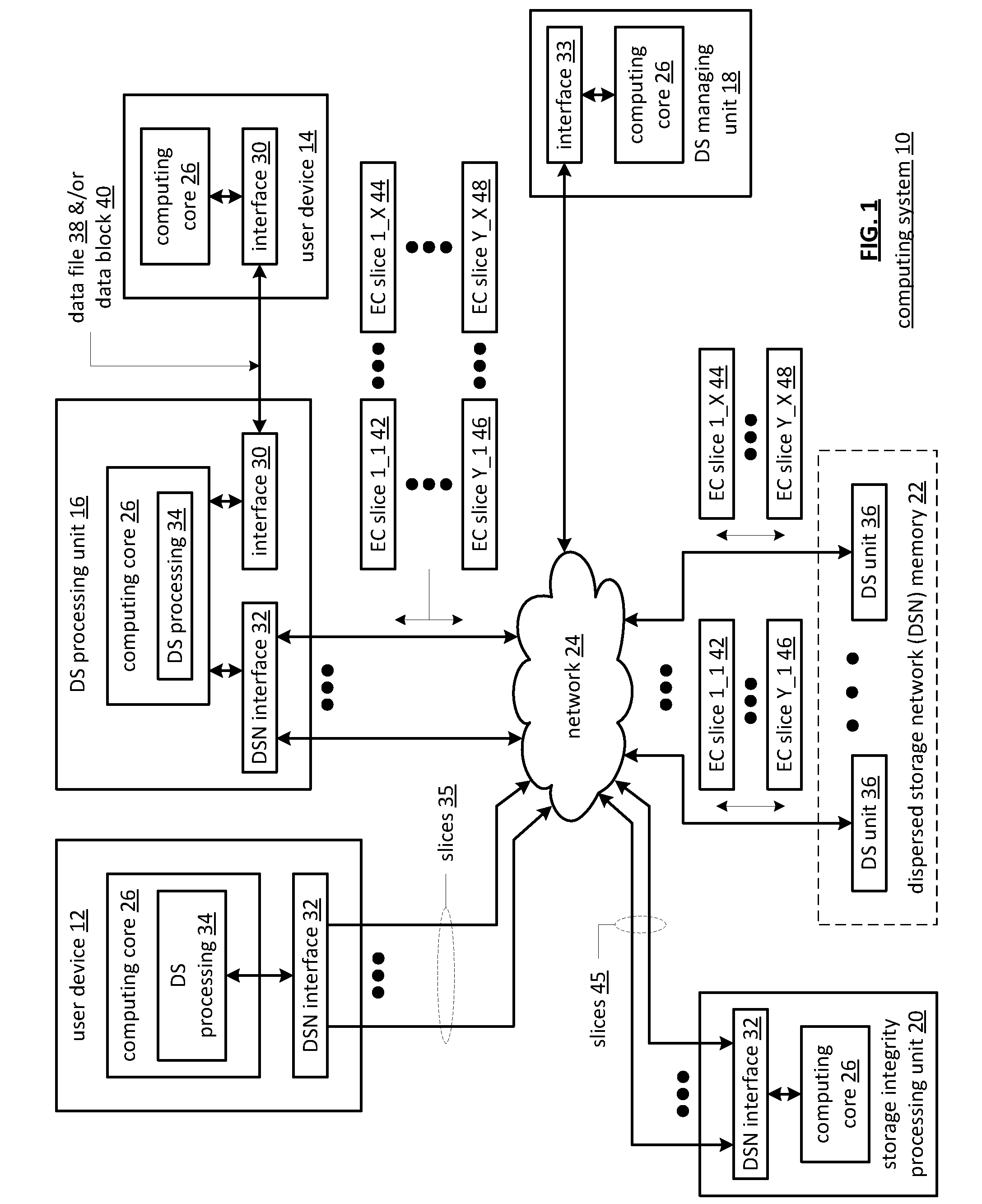
ActiveUS20110078277A1Digital data information retrievalError detection/correctionData segmentStorage area network
A distributed storage network includes a distributed storage processing unit, which generates multiple data slices from a single data segment, and multiple different storage units to store the data slices. Each data slice is assigned to a particular storage unit for storage. The distributed storage processing unit determines which of the storage units are in a ready state, and sends data slices to the ready storage units. Data slices assigned to storage units that are not in a ready state are temporarily stored in a temporary memory, e.g. cache memory, until the storage unit becomes ready. If the intended storage unit remains in a non-ready status for too long, the slices stored in cache memory can be sent to a substitute storage unit, or discarded and reconstructed at a later time.
Owner:PURE STORAGE
Method and apparatus for collecting and reporting consumer trend data in an information distribution system
InactiveUS20020077880A1Better serveTelevision system detailsMarket predictionsData selectionDistribution system
Techniques to collect data indicative of viewer habits and preferences relating to television viewing and / or use of a user interface (e.g., an interactive program guide) provided at the terminal. Various types of information may be collected to identify and track the habits and preferences of the viewers. For example, the viewers' interaction with the terminals, selections made by the viewers, requests for particular programming, demographic information, and others, may be collected for the viewers. These various types of information (i.e., "trend" data) may be continually collected by an application executing at the terminal, temporarily stored in a storage unit, and thereafter reported (e.g., periodically, or upon request) to a head-end of an information distribution system. The head-end may analyze the trend data, and may select and provide programming, advertisements, and other contents targeted to the terminals based on the analyzed data.
Owner:SEDNA PATENT SERVICES
Medical implant having at least two data communication channels
A medical implant has at least one interface for bidirectional wireless data exchange, a data memory, and a controller. The controller and interface perform a wireless data exchange with at least two different external devices, resulting in at least two different data communication channels, one channel being assigned to data communication with the programming device and a second channel being assigned to data communication with a central service center. The medical implant is also designed to receive control commands and / or messages over the second channel while the second channel is active, and to recognize received control commands and / or messages intended for a programming device, store them temporarily in a memory (if necessary), and forward them to a programming device via the first channel when the first channel is active.
Owner:BIOTRONIK SE & CO KG
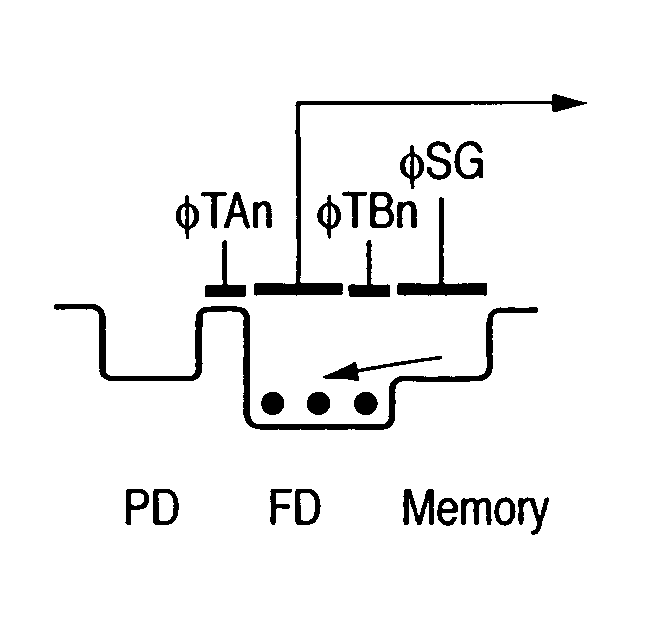
Image capturing apparatus
ActiveUS7733401B2Exclude influenceTelevision system detailsTelevision system scanning detailsElectronic shutterEngineering
An object of the present invention is to eliminate the influences of the leakage etc. of charges from a photodiode to a storage part during the electronic shutter operation. To achieve this object, the present invention includes: a photodiode which generates and accumulates a signal charge according to the amount of light from an object; an amplification part which amplifies a signal charge outputted from the photodiode and outputs the amplified signal to the outside; a storage part which temporarily stores the signal charge; and a transfer device which transfers the signal outputted from the photo-electric conversion device to the storage part via the amplification part.
Owner:CANON KK
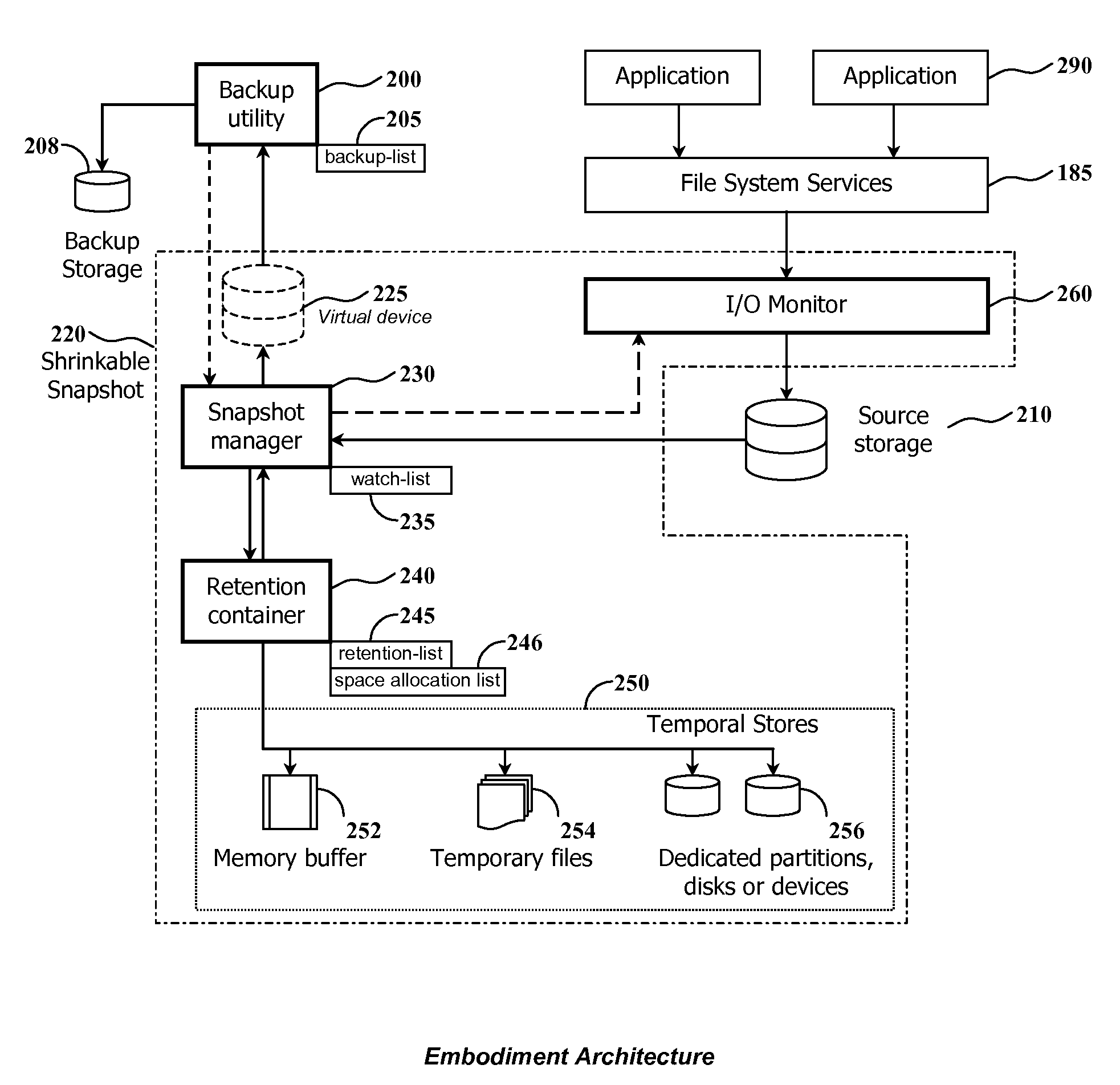
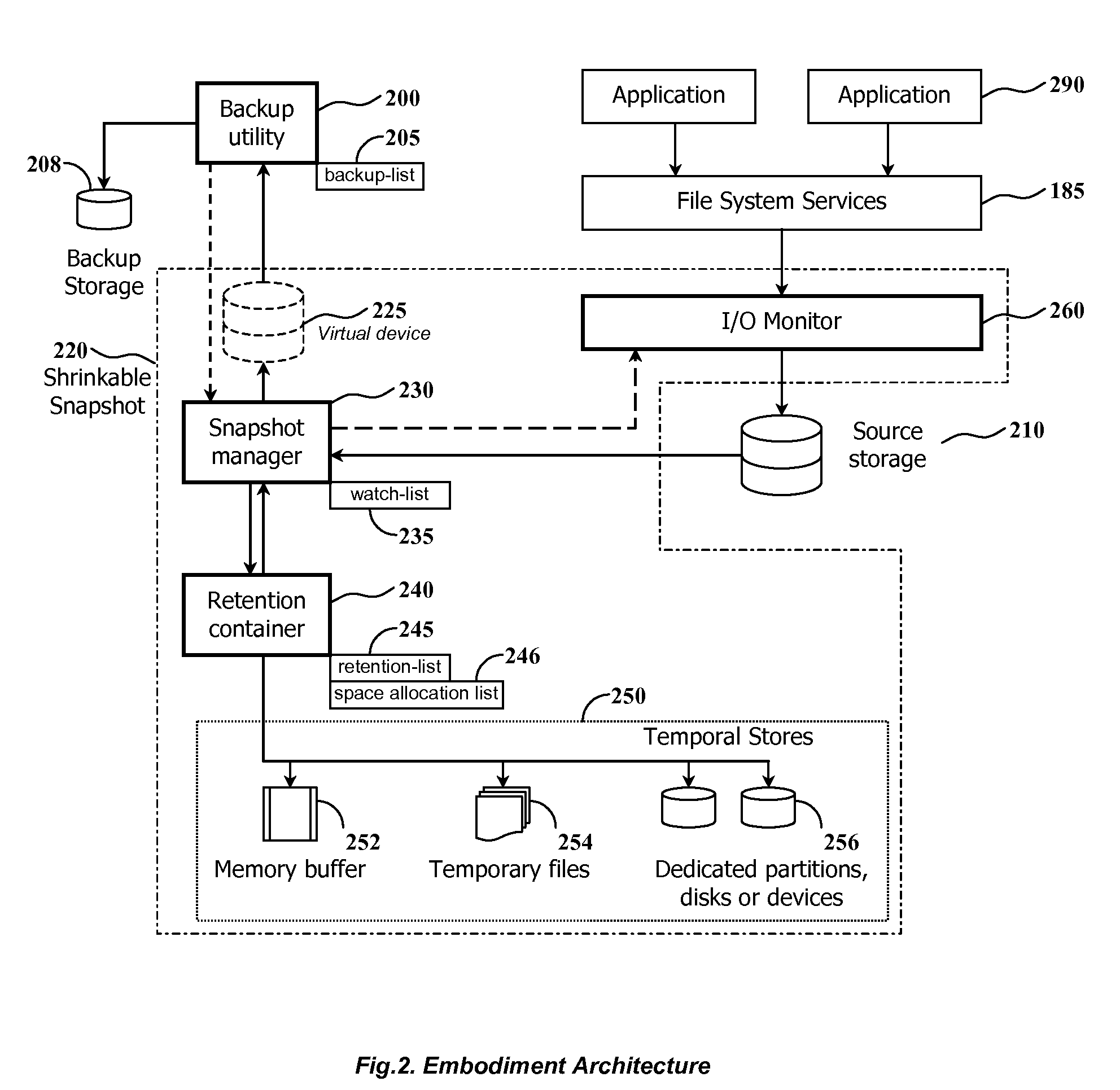
Using shrinkable read-once snapshots for online data backup
InactiveUS20080082593A1Improve performanceEasy to useDigital data information retrievalError detection/correctionRetention timeWatch list
The present invention discloses a method and system for snapshot-based online backup operations permitting reduced requirements to storage capacity and computational overhead for snapshot function.At the beginning of an online backup operation, the backup software system creates a snapshot of source data storage. The snapshot includes a watch-list used for identifying blocks of a source storage which are watched by snapshot management means for update. If a block included into the watch-list was requested for update, the snapshot management means preserve original contents of that block in a retention container for the purpose of temporary store. The retention container includes a set of temporal stores dedicated for transient storing of blocks until they are backed up.The essence of the invention is enabling to exclude blocks from the watch-list and the retention container at any moment within the period of snapshot operation. Therefore it is possible to exclude unnecessary blocks from the scope of blocks managed by the snapshot management means, for the purpose of preserving point-in-time data.Backed up blocks can be operatively excluded from the snapshot so that unchanged blocks are excluded from the watch-list and updated blocks are removed from the retention container. In the latter case temporal stores are shrunk as well. This technique allows to reduce progressively storage expenses and computational overheads required for maintenance of a snapshot being used in the online backup routine.When a volume-level online backup is performed the snapshot is switched to the read-once mode at the beginning of the data copying stage. A backup utility performs sequential read of blocks from the snapshot. The snapshot management means automatically exclude requested blocks from the scope of managed blocks.
Owner:PARAGON SOFTWARE GMBH
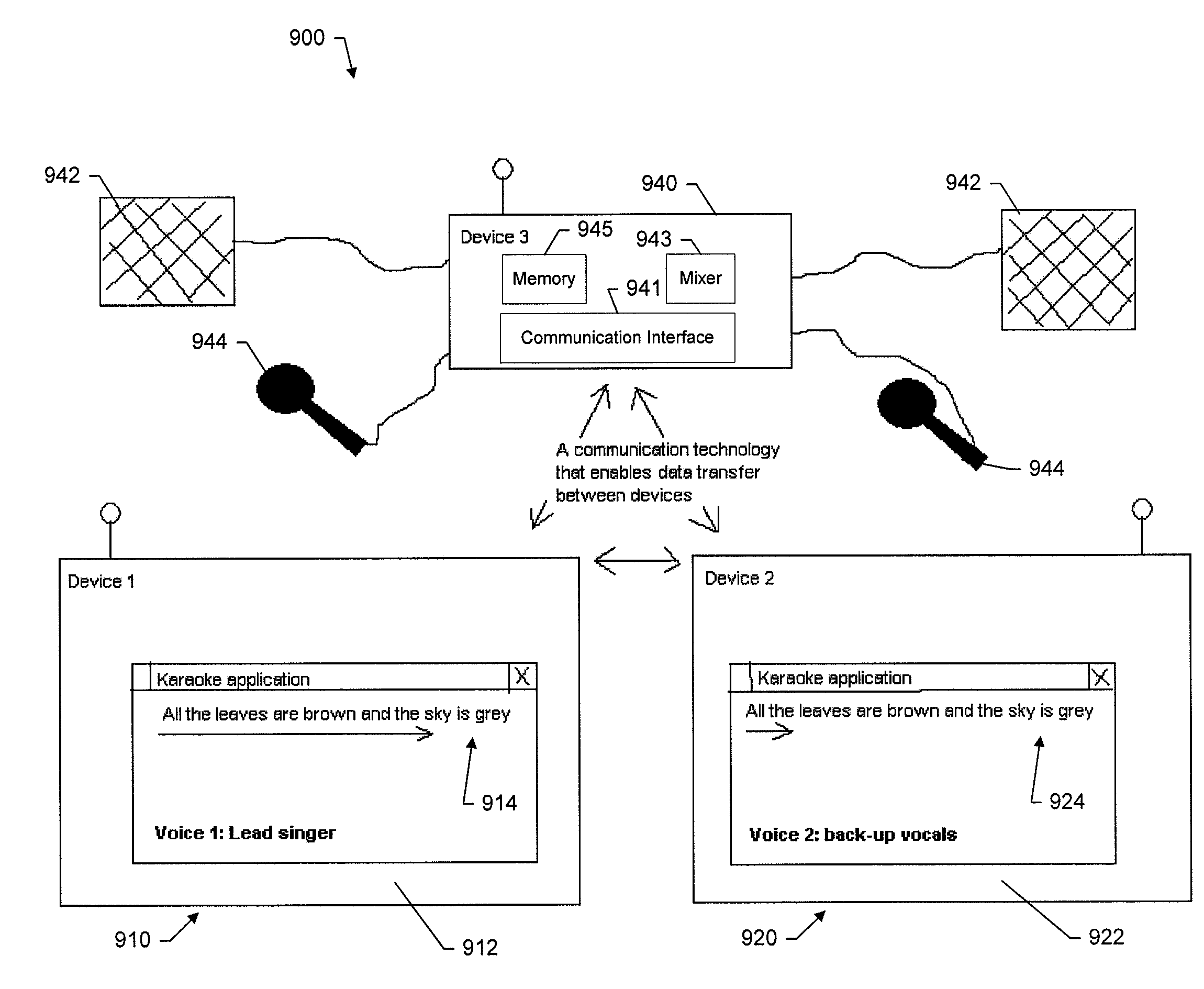
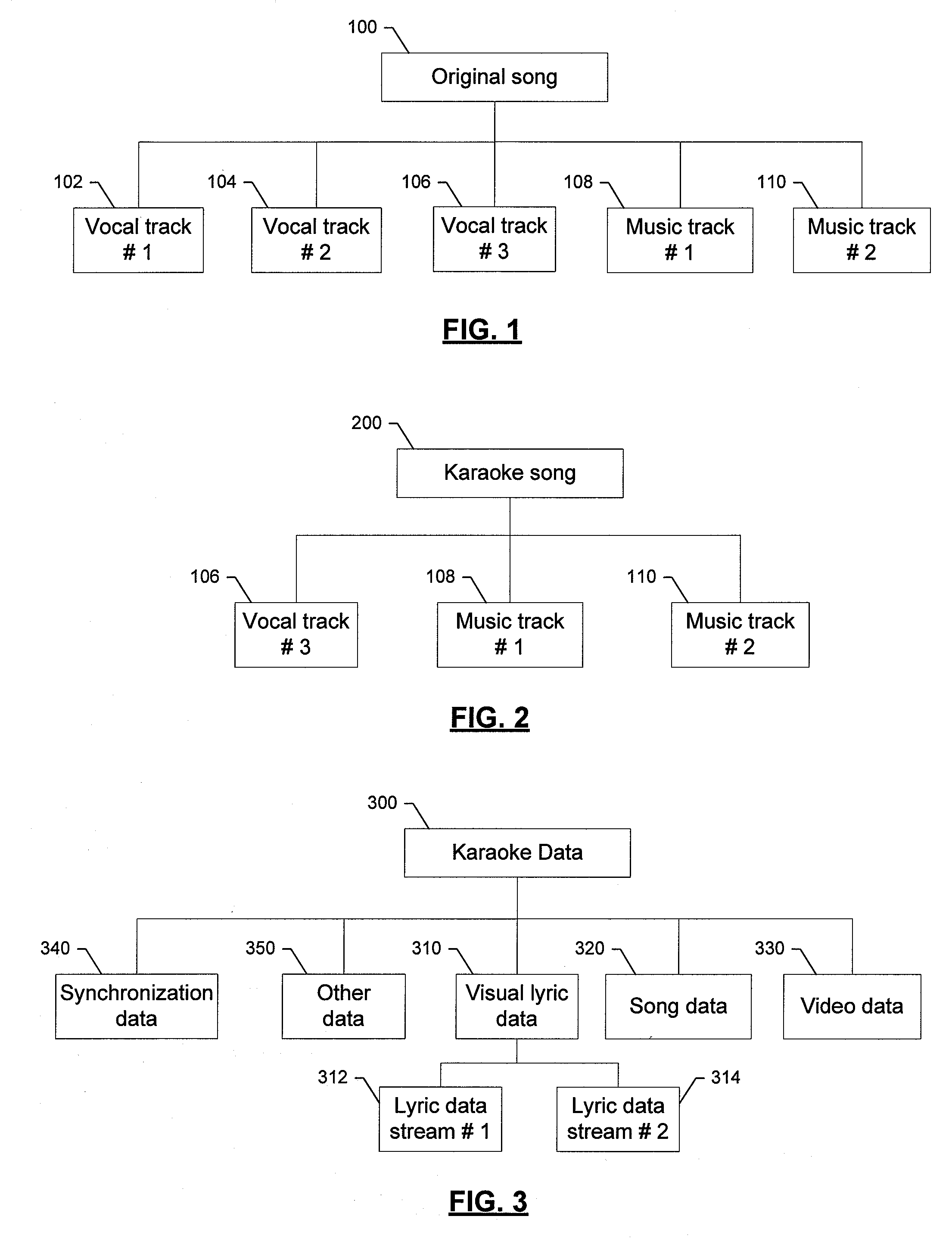
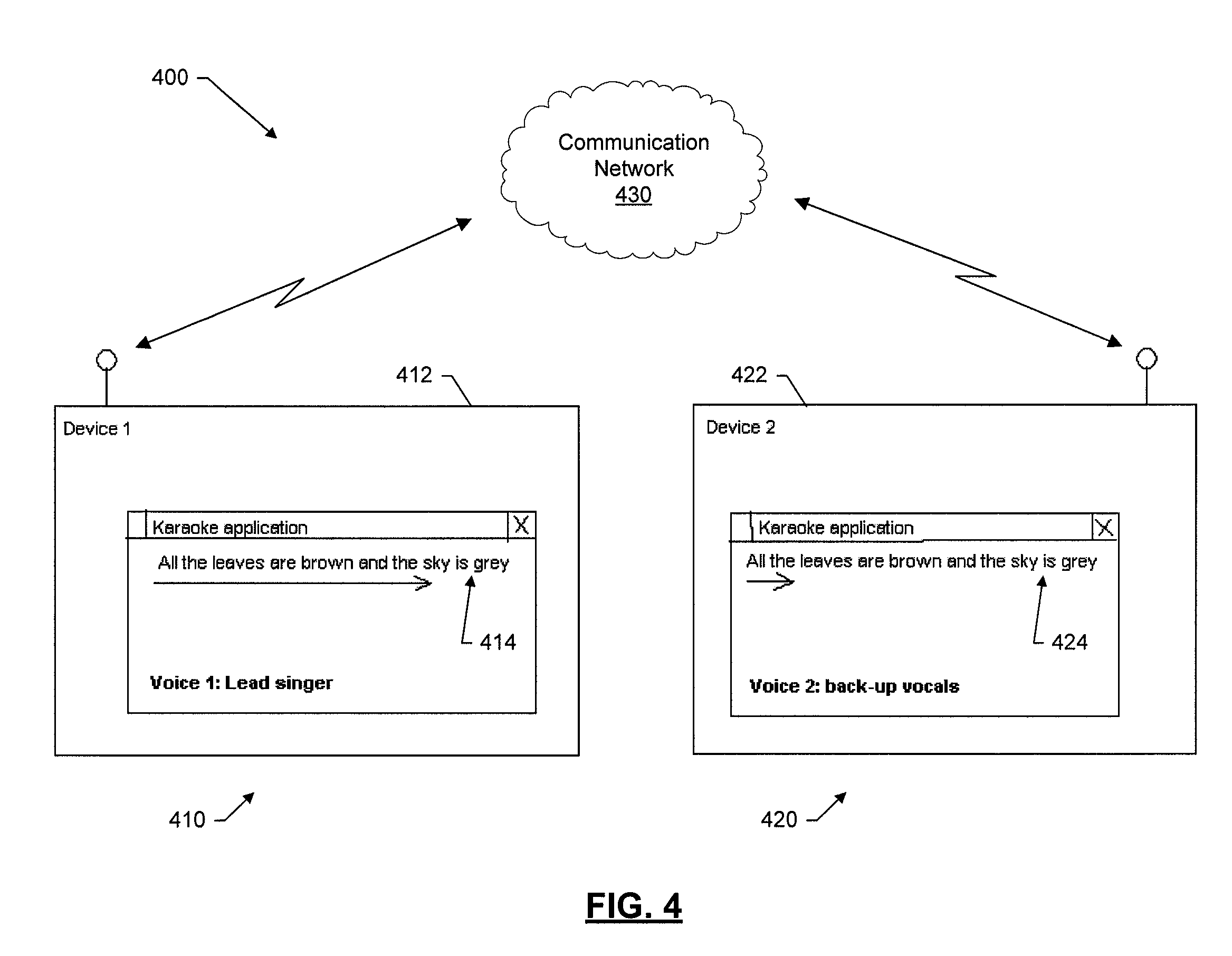
System, method, device, and computer program product providing for a multiple-lyric karaoke system
InactiveUS20080184870A1Improve performanceElectrophonic musical instrumentsData streamDisplay device
Systems, devices, methods, and computer program products are provided for facilitating a group karaoke performance. The system generally comprises at least two devices, each of the at least two devices includes a memory and a display, both operatively coupled to a processor. The memory of each device is configured to at least temporarily store karaoke data including a visual lyric data stream corresponding to one of a plurality of vocal parts in a song. The processor of each device is configured to present the visual lyric information on the display based on the visual lyric data stream stored in the memory. The at least two devices are synchronized so that they can start presenting the visual lyric information essentially at the same time. One of the devices displays visual lyric information for one vocal part of a song and another one of the devices displays visual lyric information for a different vocal part of a song.
Owner:NOKIA CORP
System and method for multi-tiered rule filtering
ActiveUS20050063365A1Digital computer detailsData switching by path configurationElectronic messagingRule sets
A system is described for processing messages and calls comprising: a plurality of filtering modules to apply a corresponding plurality of rule sets in succession to filter incoming and / or outgoing electronic messages and to apply the highest priority rule from among a plurality of rule sets to calls; and a pre-inbox for temporarily storing the calls and / or electronic messages as each of the plurality of rule sets are applied, the calls and / or electronic messages being removed from the pre-inbox and disposed of only after each of the plurality of rule sets have been applied to the calls and / or electronic messages.
Owner:CATALYSTWEB
Systems and methods for selectively performing explicit congestion notification
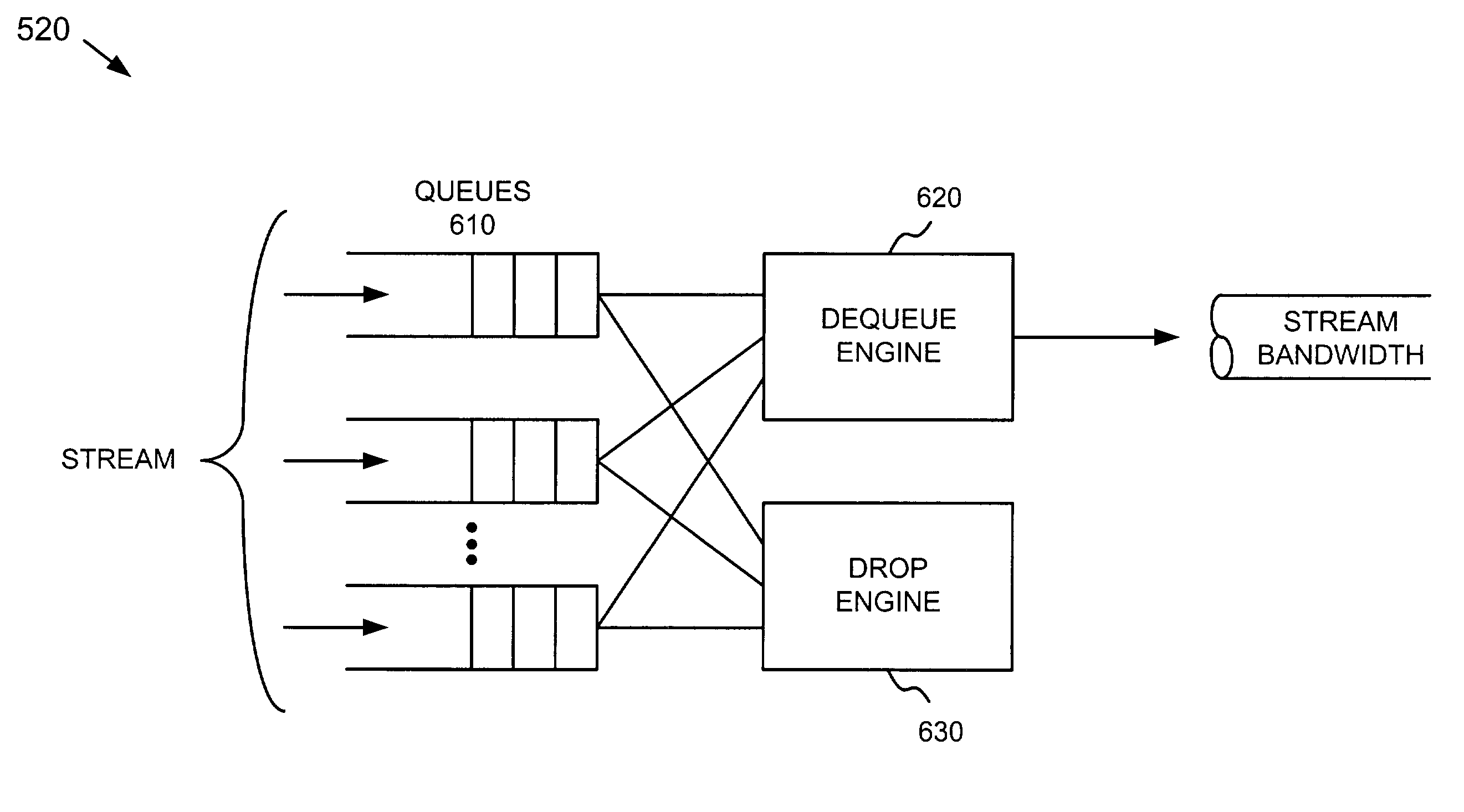
ActiveUS7359321B1Blocking in networkFacilitate communicationError preventionTransmission systemsExplicit Congestion NotificationDistributed computing
A system provides congestion control and includes multiple queues that temporarily store data and a drop engine. The system associates a value with each of the queues, where each of the values relates to an amount of memory associated with the queue. The drop engine compares the value associated with a particular one of the queues to one or more programmable thresholds and selectively performs explicit congestion notification or packet dropping on data in the particular queue based on a result of the comparison.
Owner:JUMIPER NETWORKS INC
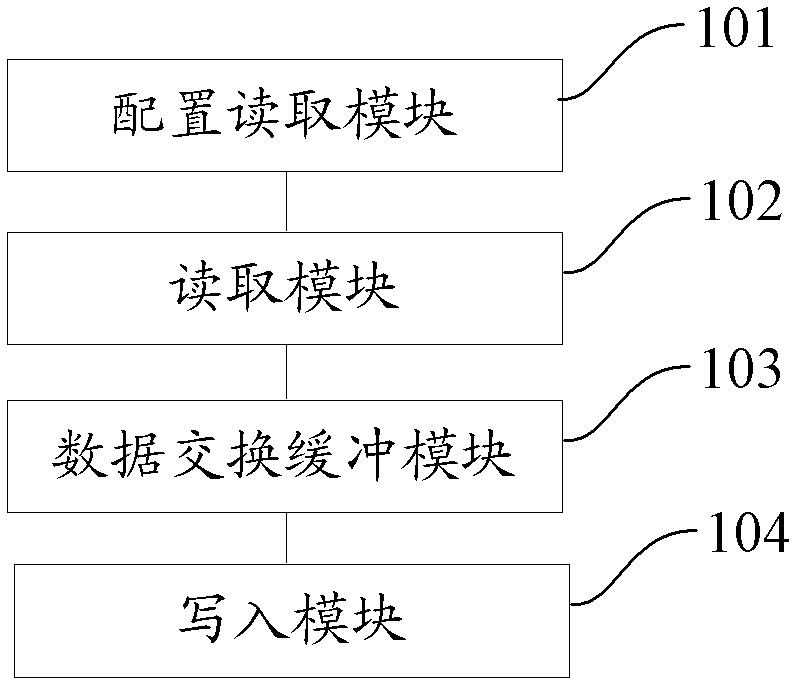
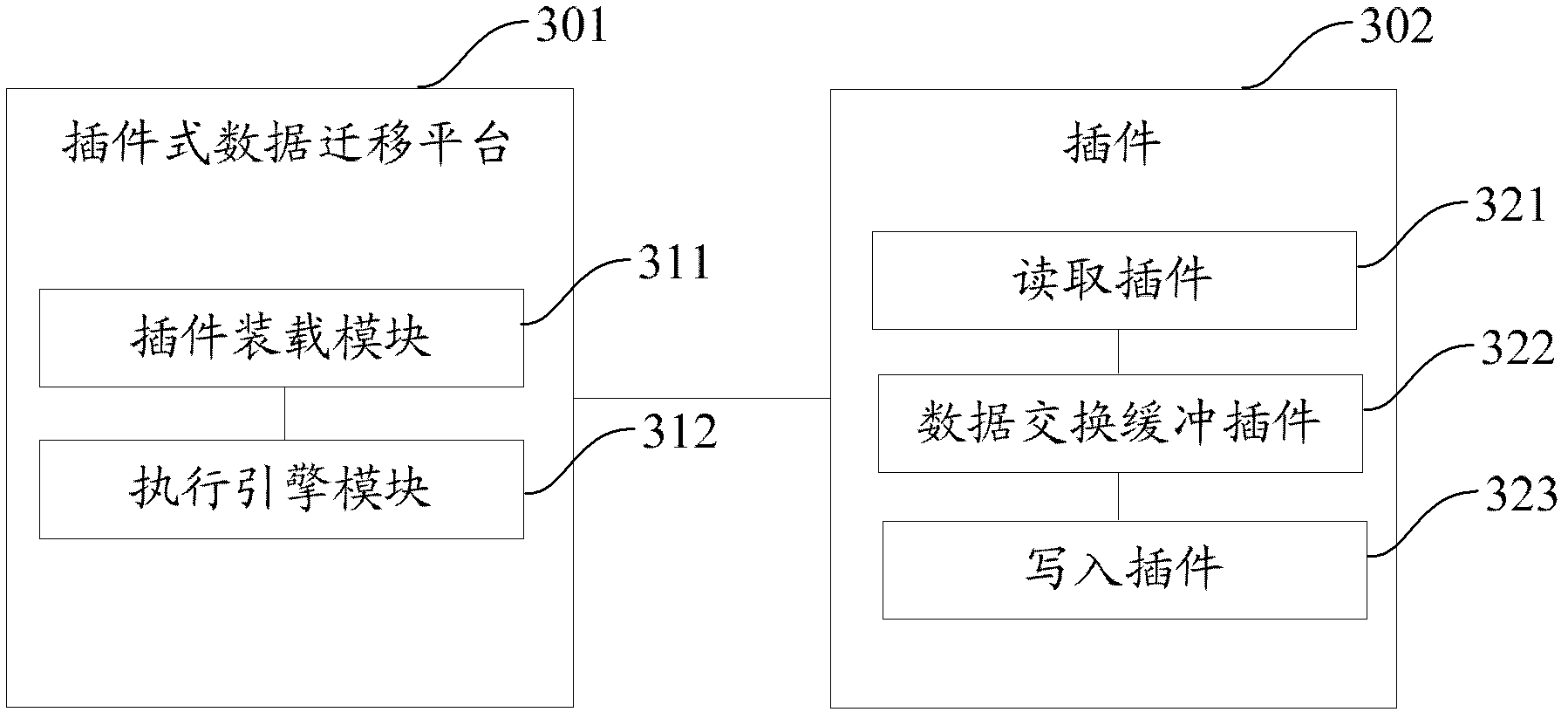
System and method for data migration
ActiveCN102999537AShorten the migration processImprove migration abilitySpecial data processing applicationsData exchangeData conversion
The invention provides a system and a method for data migration. The system specifically comprises a configuration reading module, a reading module, a data exchange buffer module and a writing module, wherein the configuration reading module is used for reading a configuration file of a data migration task, and the configuration file comprises data reading information and data writing information; the reading module is used for reading the data according to the data reading information in the configuration file and converting the read data into an intermediate format to be written into the data exchange buffer module; the data exchange buffer module is used for temporarily storing the written intermediate format data; and the writing module is used for reading the intermediate format data from the data exchange buffer module, writing the information according to the data in the configuration file and converting the intermediate format data into a target format to be written into a target address. By the system, the data migration performance can be improved, and the maintenance cost and the development cost which are spent on data migration are lowered.
Owner:ALIBABA GRP HLDG LTD
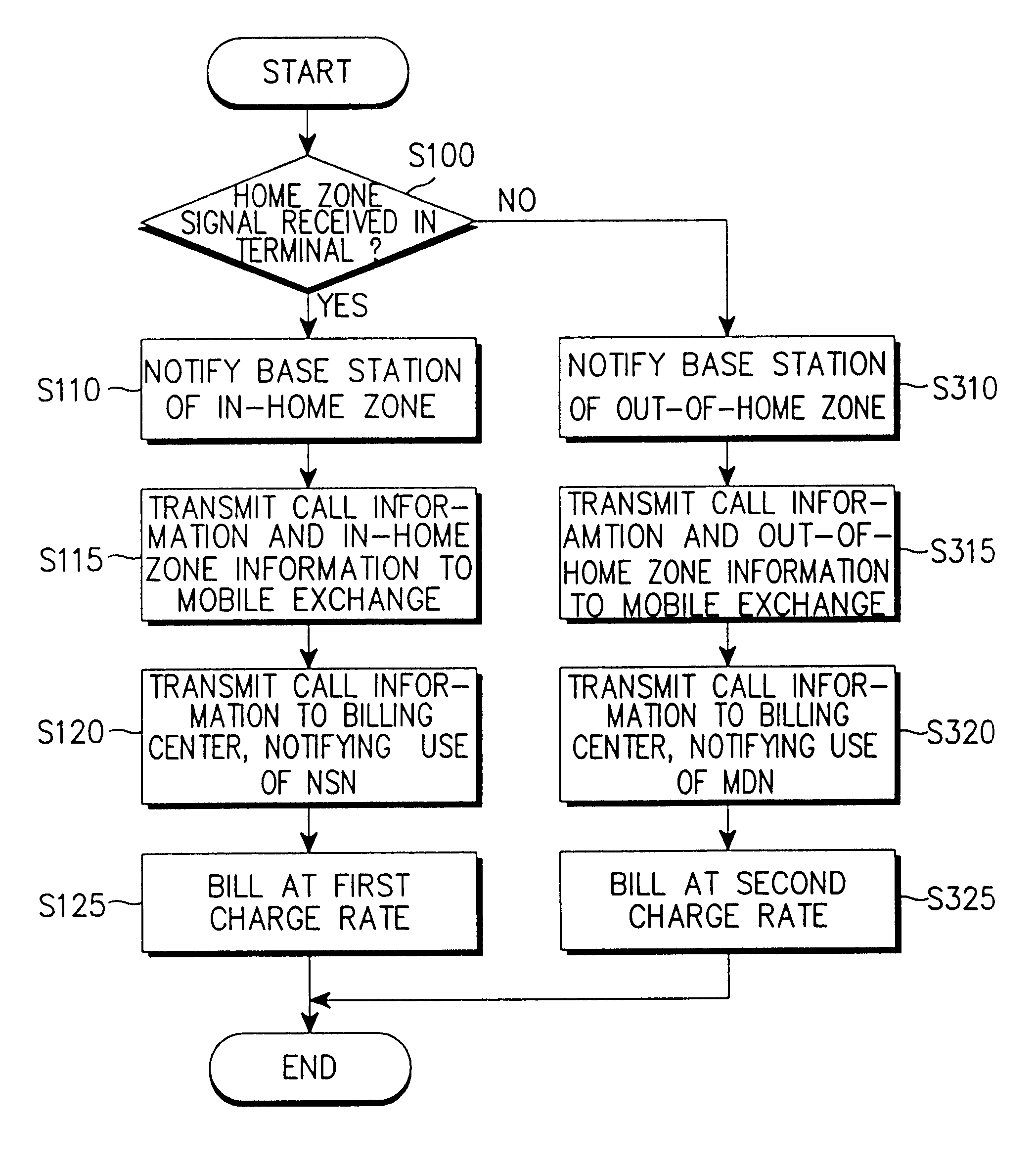
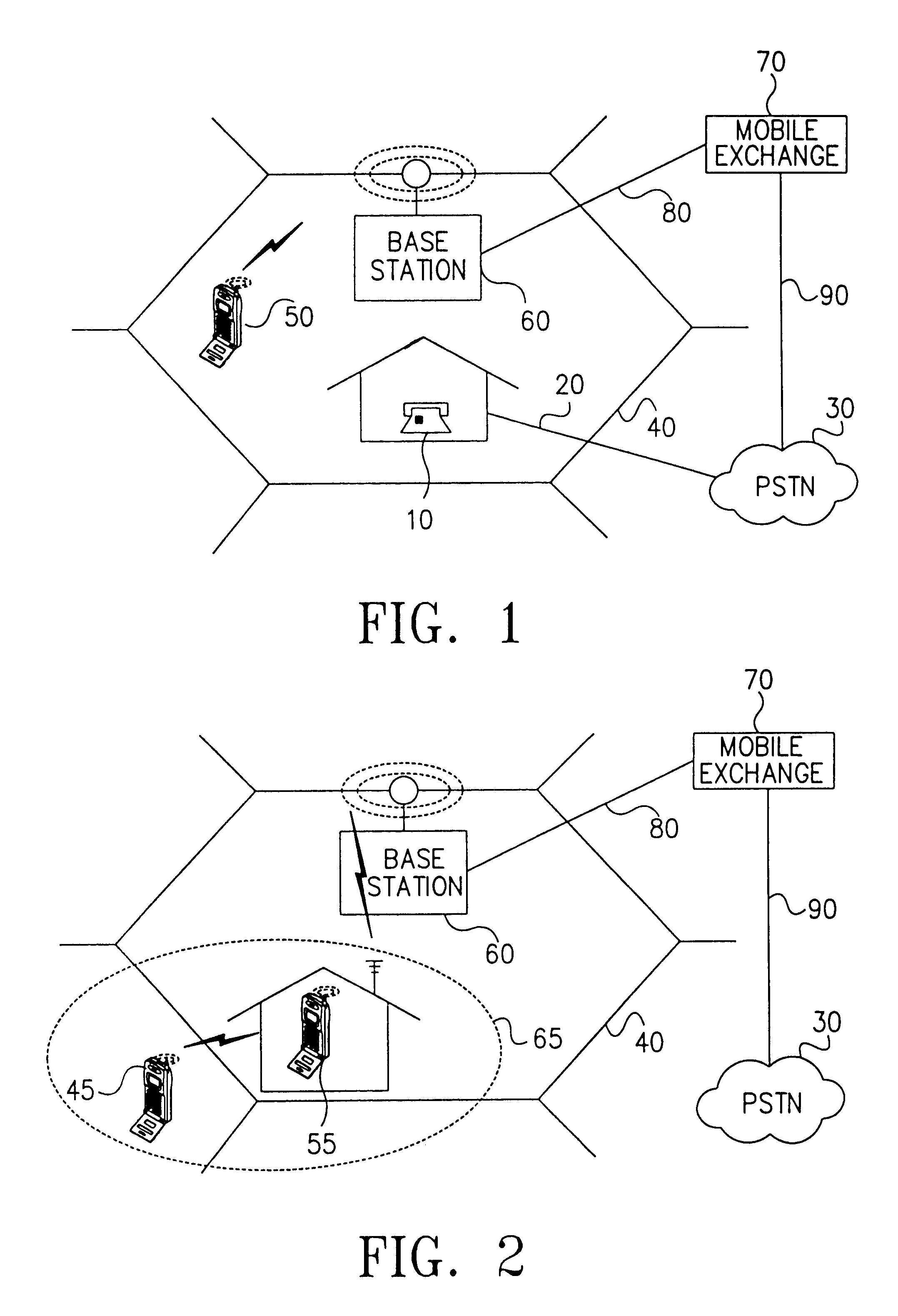
Mobile communication system for home-zone service and method thereof
InactiveUS6671506B1Accounting/billing servicesTelephonic communicationMobile identification numberCharge rate
A mobile communication system for providing a home zone service and a method thereof. In the mobile communication system, a home zone signal generator generates a home zone signal, a mobile radio terminal receives the home zone signal and determines whether the mobile radio terminal is currently within or outside a home zone based on the strength of the home zone signal, and a base station communicates with the mobile radio terminal. A visitor location register temporarily stores a first and a second telephone numbers of a subscriber, wherein each telephone number represents different charge rates. A mobile exchange receives a call information, a mobile identification number, and the home zone in / out information from the base station and selects one of the first and second telephone numbers of a subscriber corresponding to the mobile identification number and the home zone in / out information. A billing center receives the call information and one of the selected first and the second telephone numbers from the mobile exchange and generates a service charge for the call connection.
Owner:SAMSUNG ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com