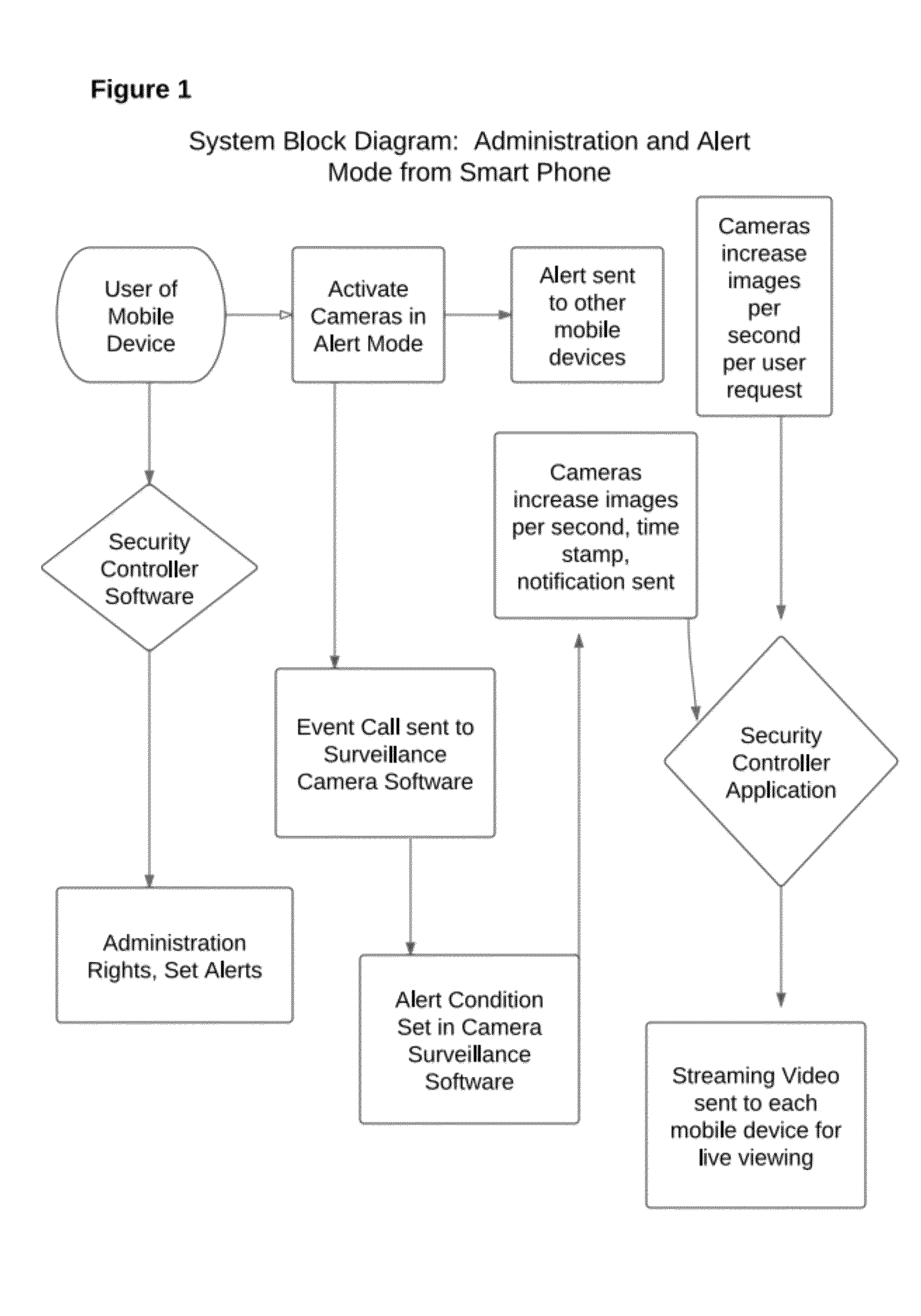
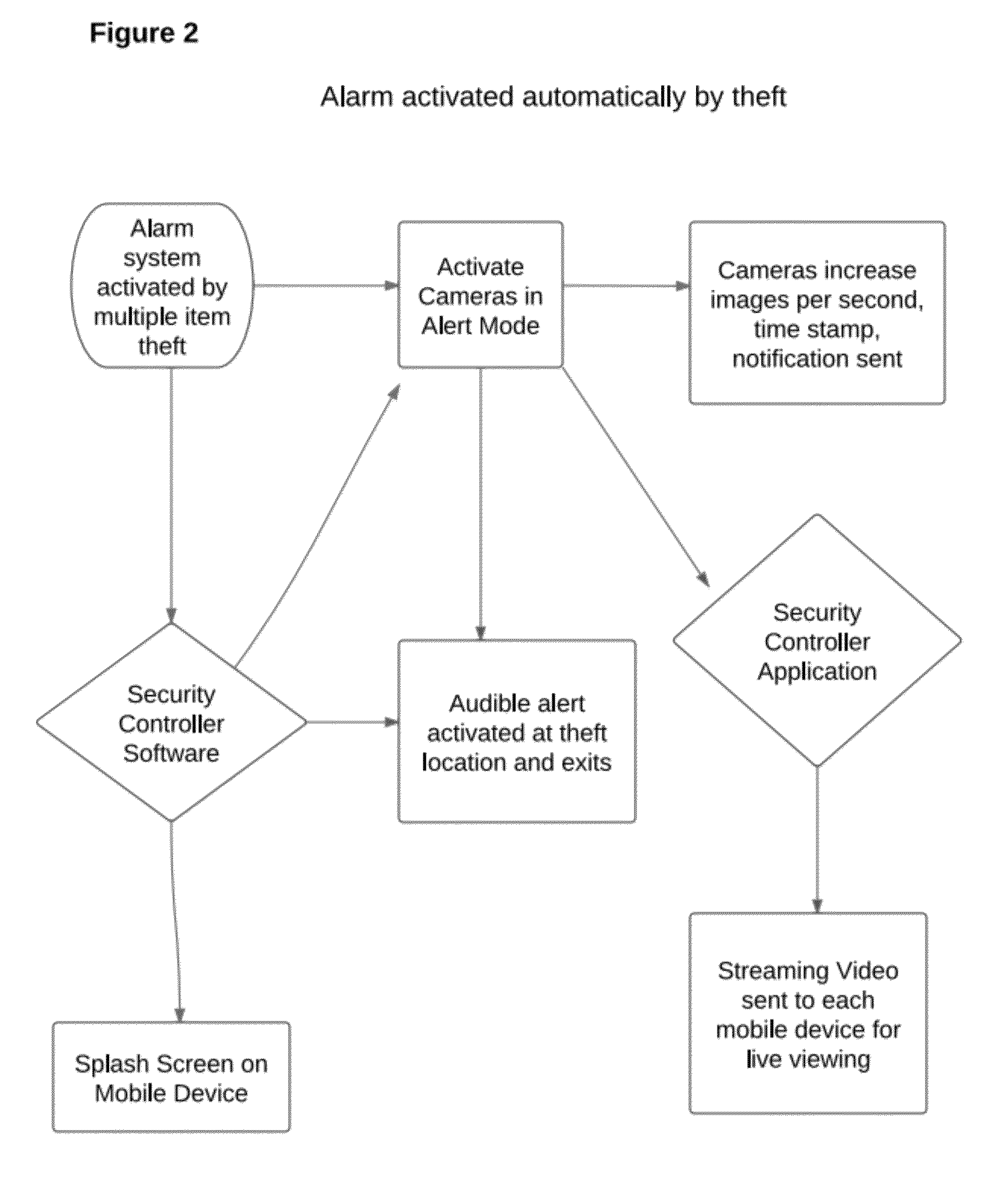
Patents
Literature
330results about How to "Reduce theft" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
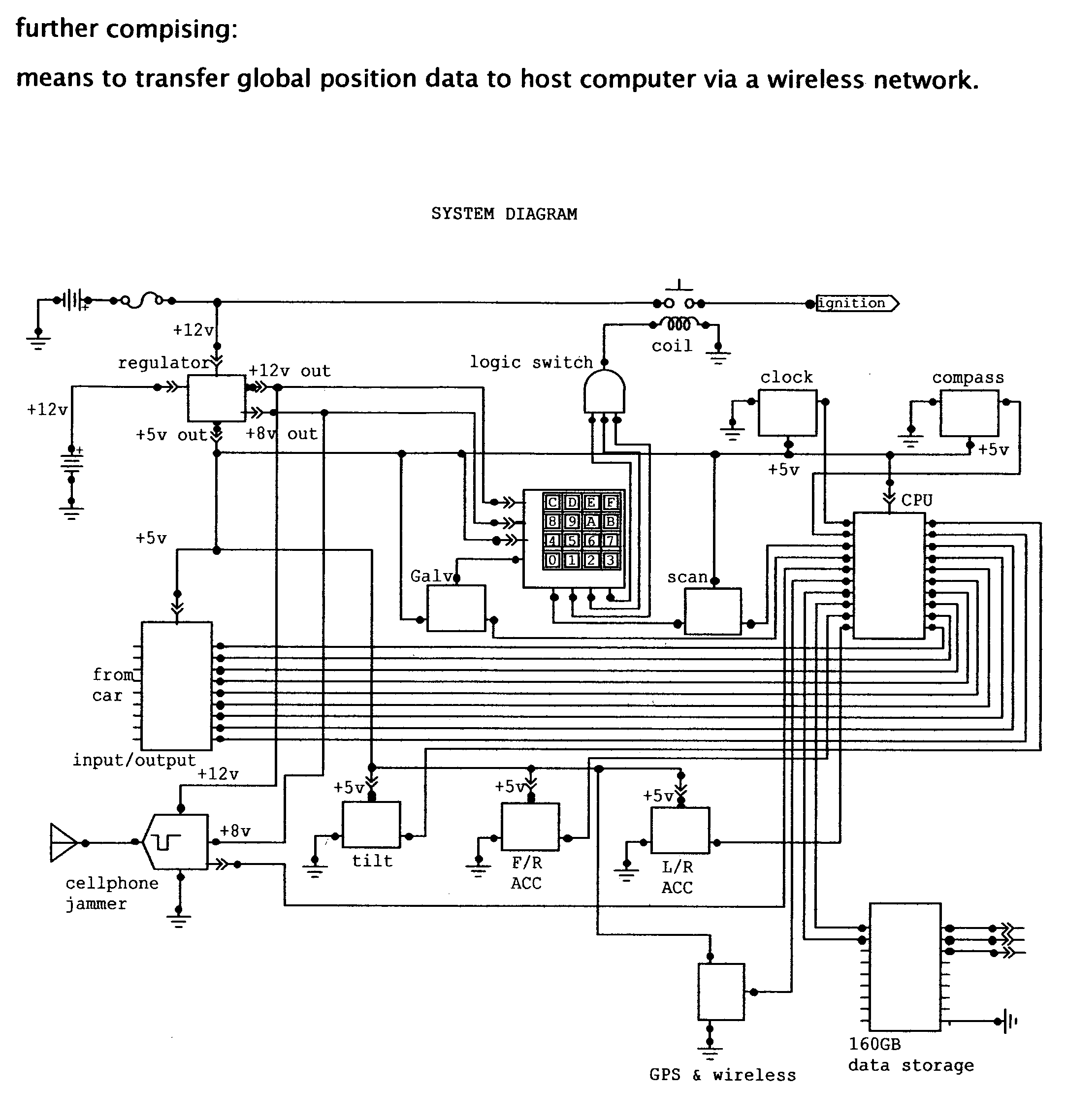
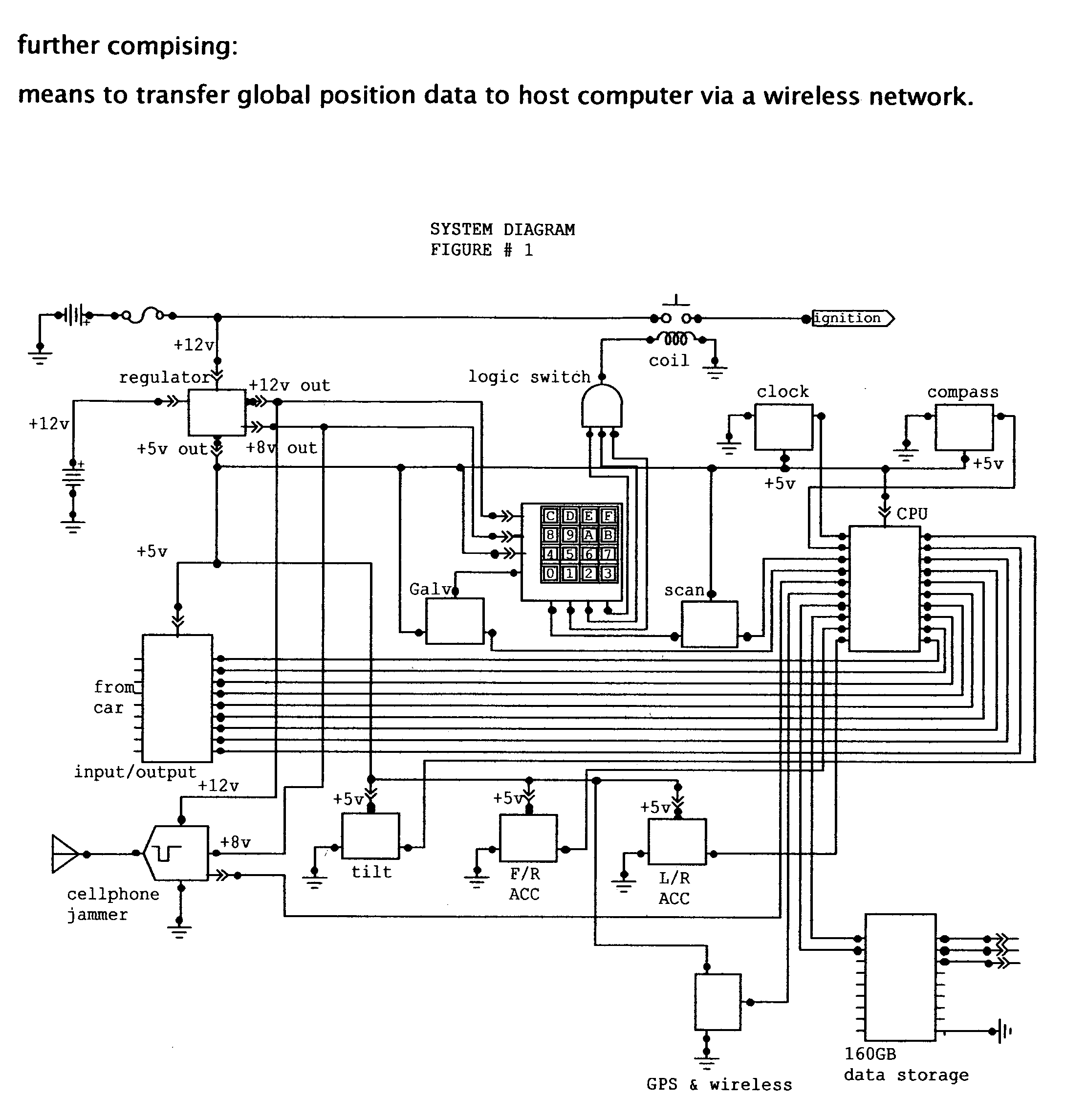
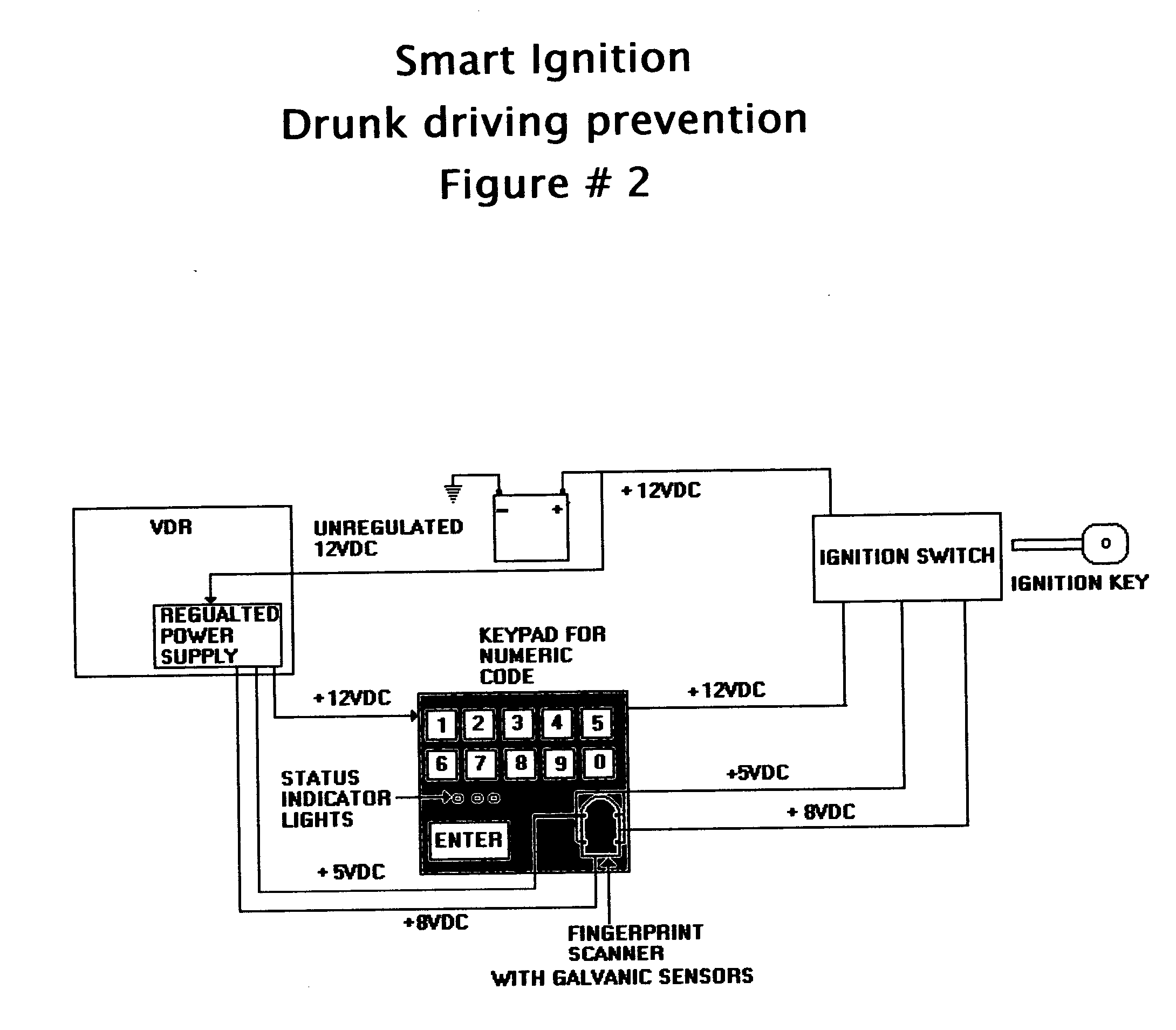
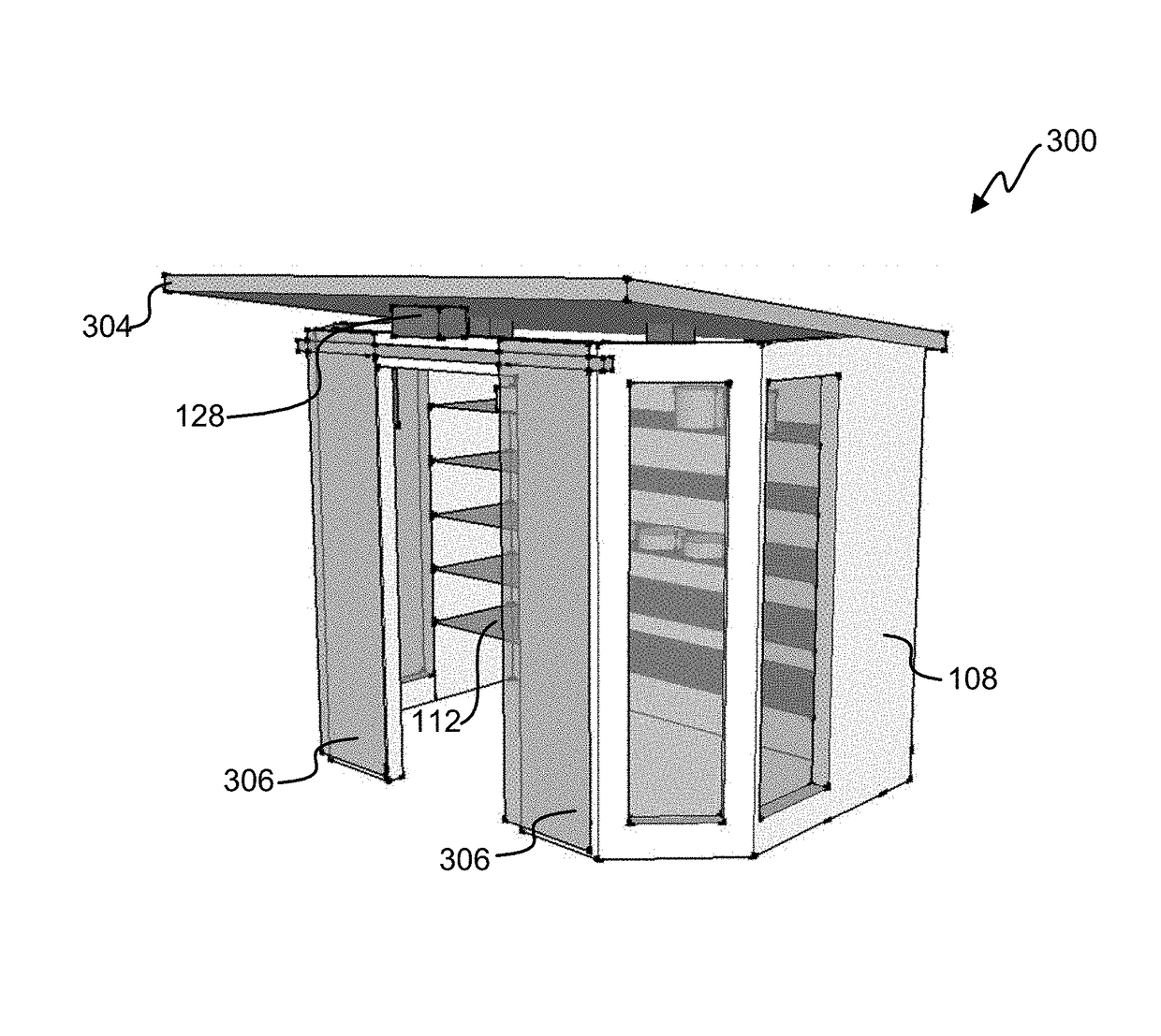
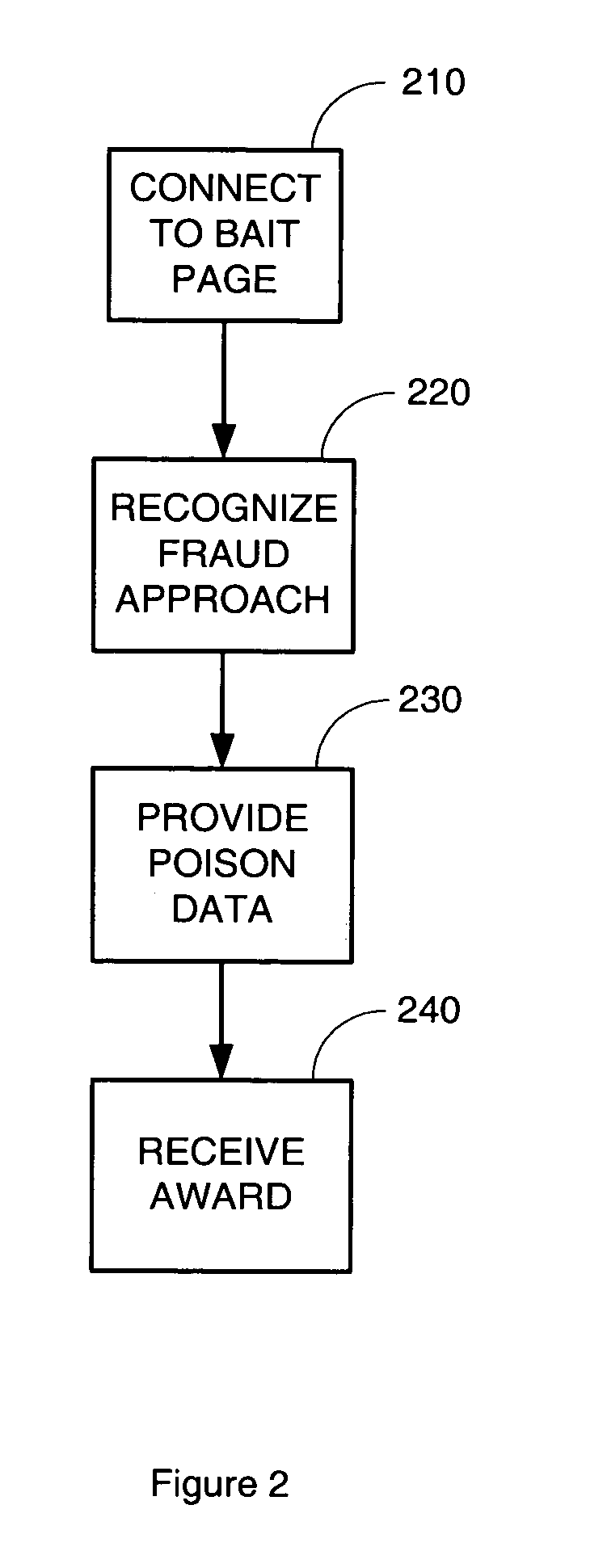
Vehicle data recorder and telematic device
InactiveUS20060212195A1Reduce drunk drivingReduce automobile theftVehicle testingRegistering/indicating working of vehiclesPersonalizationInformation processing
This invention is a vehicle data recorder with the capability to continuously record and store selected data on both driver and vehicle performance that will include but not be limited to, miles driven, speed, acceleration / deceleration, brake activation, seatbelt usage, vehicle direction, steering anomalies, global position, impact forces and direction, transmission status, and alcohol usage. Specifically, this recorder will have extended data storage capacity, a drunk driver prevention smart ignition, real-time GPS data, low-power cell phone jamming, and internal wireless communication capabilities. It uses microprocessor controlled electronics to record, store, and transmit both driver and vehicle performance data in a date and time stamped file which can be utilized to establish personalized insurance rates, assess road tax and use fees, locate “Amber alert” victims or stolen vehicles, and with it's on scene access, provide critical mechanism of injury information to emergency responders.
Owner:VEITH GREGORY W +1
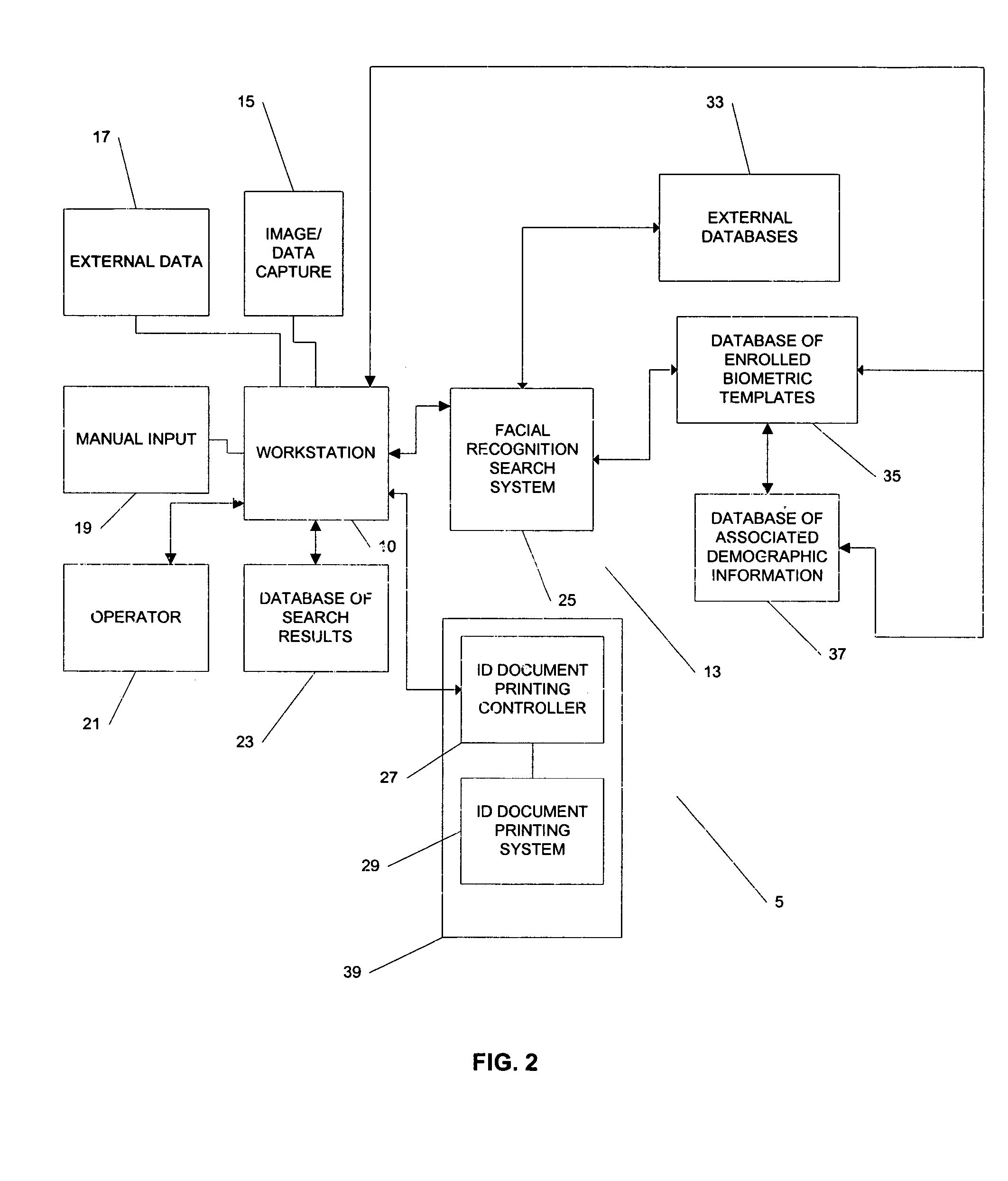
Systems and methods for managing and detecting fraud in image databases used with identification documents
ActiveUS7804982B2Prevent fraudReduce theftCharacter and pattern recognitionIndividual entry/exit registersDocument preparationWorkstation
We provide a system for issuing identification documents to a plurality of individuals, comprising a first database, a first server, and a workstation. The first database stores a plurality of digitized images, each digitized image comprising a biometric image of an individual seeking an identification document. The first server is in operable communication with the first database and is programmed to send, at a predetermined time, one or more digitized images from the first database to a biometric recognition system, the biometric recognition system in operable communication with a second database, the second database containing biometric templates associated with individuals whose images have been previously captured, and to receive from the biometric recognition system, for each digitized image sent, an indicator, based on the biometric searching of the second database, as to whether the second database contains any images of individuals who may at least partially resemble the digitized image that was sent. The a workstation is in operable communication with the first server and is configured to permit a user to review the indicator and to make a determination as to whether the individual is authorized to be issued an identification document or to keep an identification document in the individual's possession.
Owner:L 1 SECURE CREDENTIALING
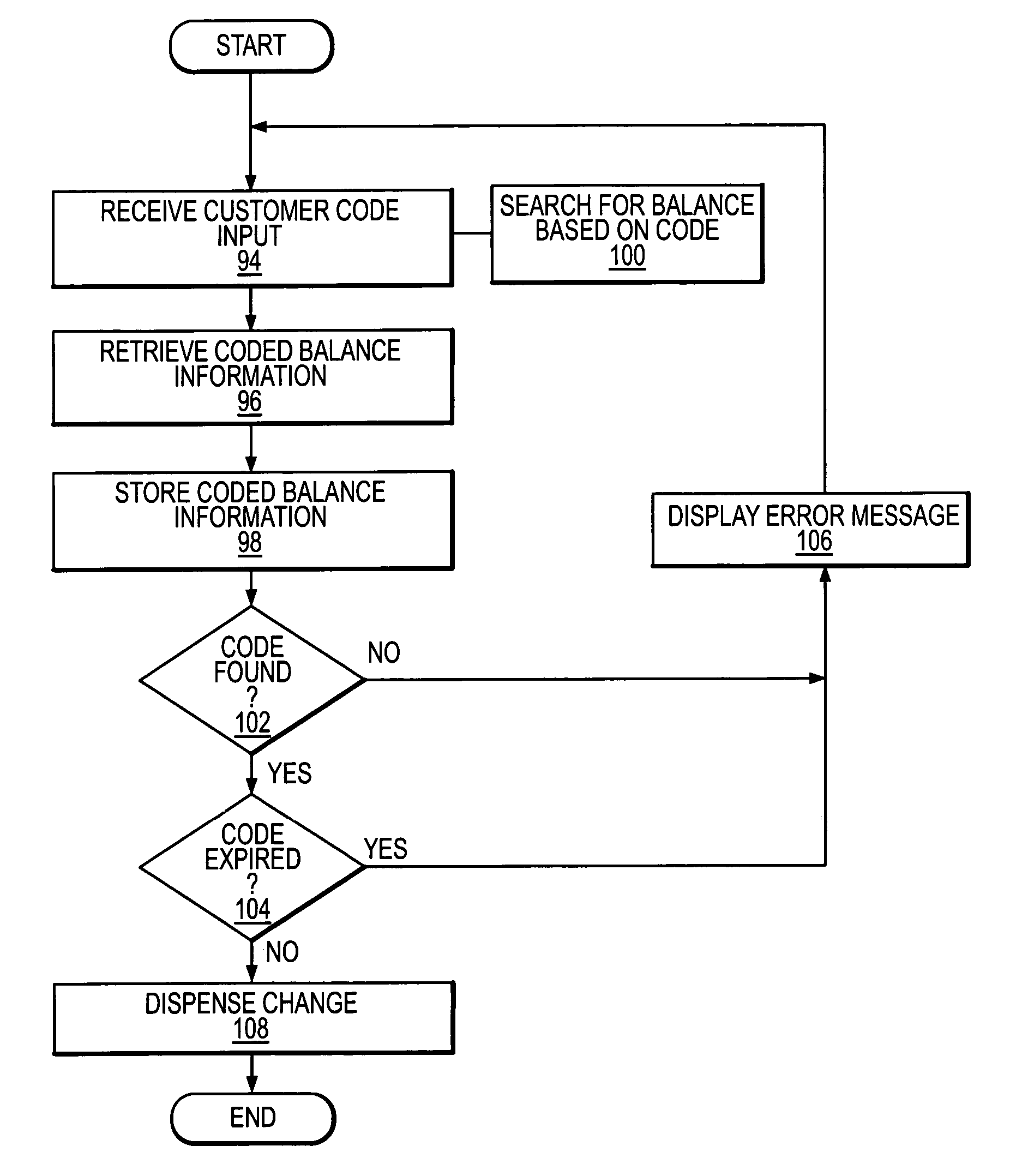
Money dispensing system
InactiveUS20050182681A1Low costReduce errorsApparatus with change-givingPayment architectureCredit cardBarcode
A money managing system for use in a business setting is provided that allows for automated ordering, payment and receipt of change. In a fast food setting, a customer uses a user interface unit to enter an order, indicate the completion of an order and indicate a desired method of payment. The user can then insert coins, paper bills, credit cards, coded tickets, or some combination thereof, in payment. If no change is due, a dispenser is used to generate a receipt. In cases where change is due, the dispenser may further issue a code, for example, in the form of a barcode. The customer's food order can be picked up, for example, at an order window where money handling is not required. The customer may then use the ticket at a money dispensing machine to receive change in the form of coins and / or bills.
Owner:GARY WILLIAMS RETAIL SOLUTIONS
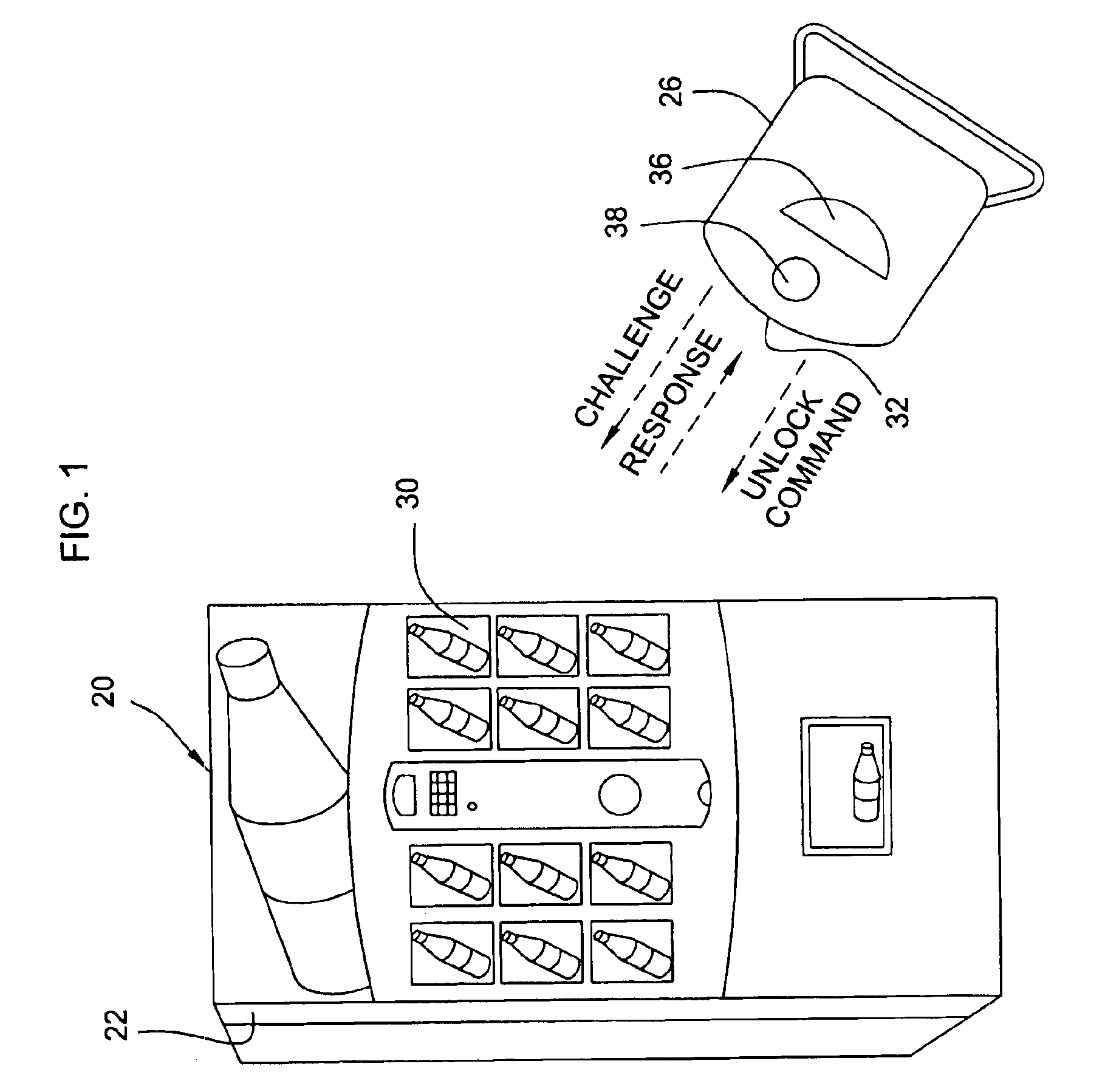
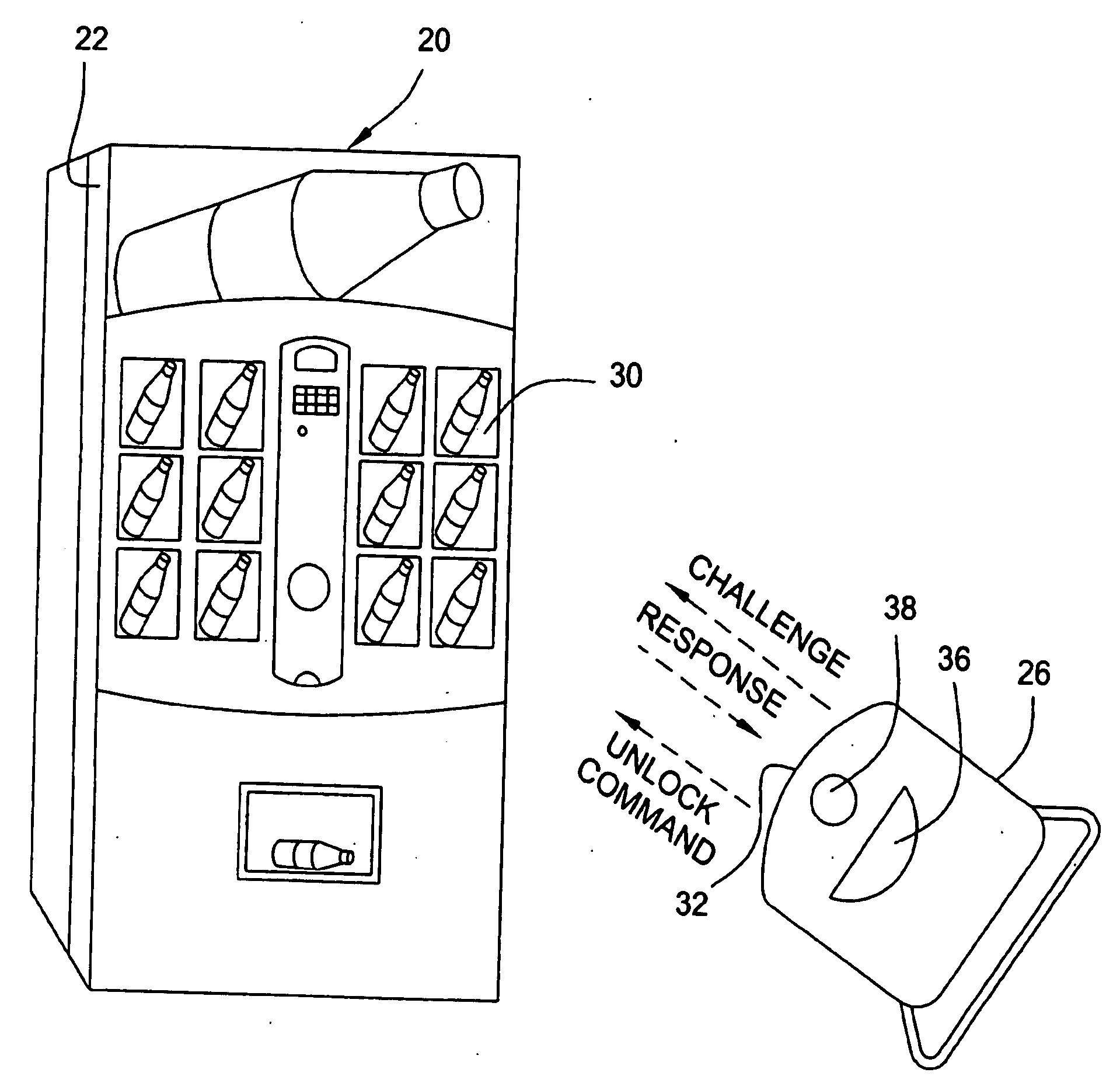
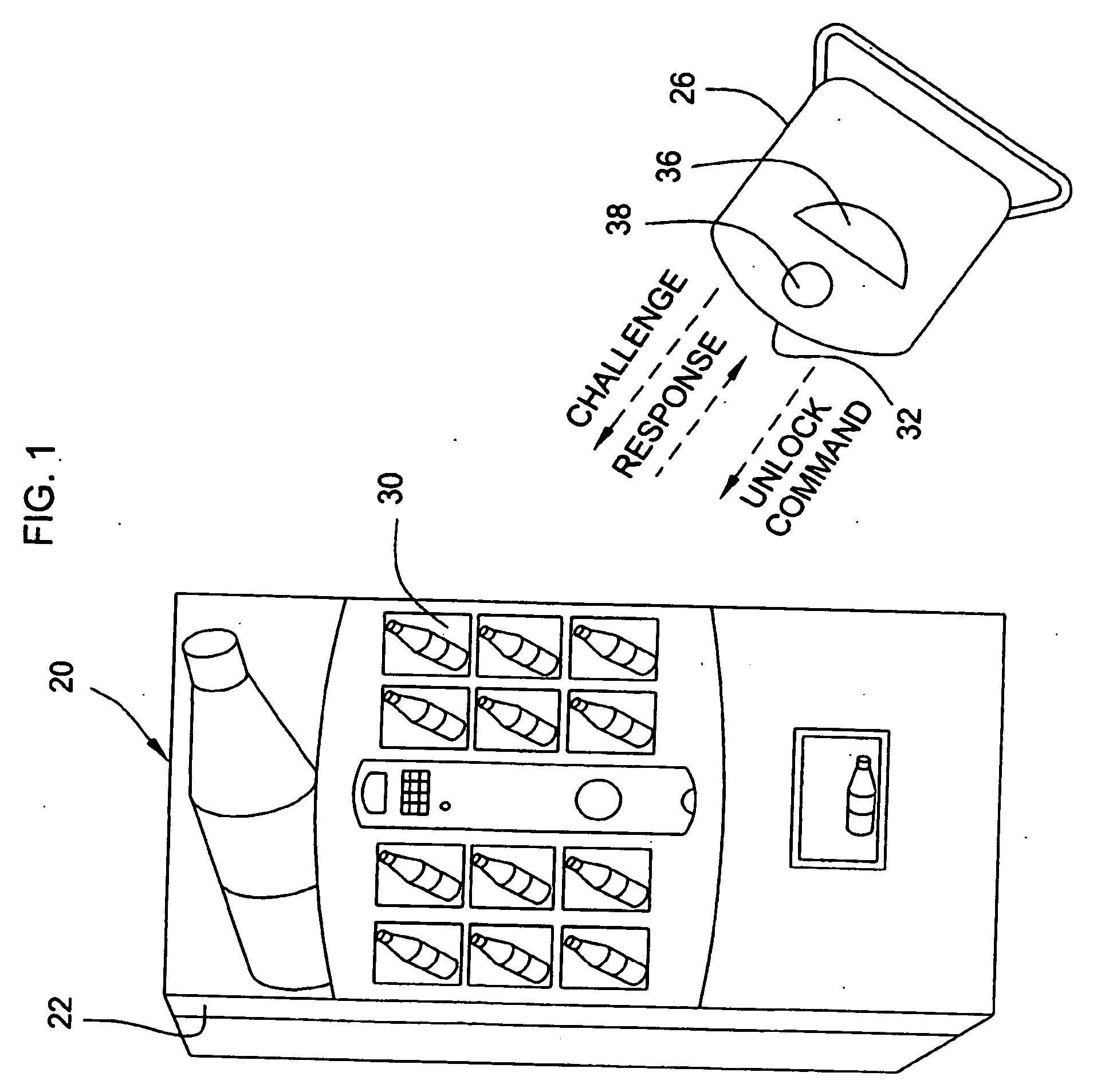
Online challenge-response
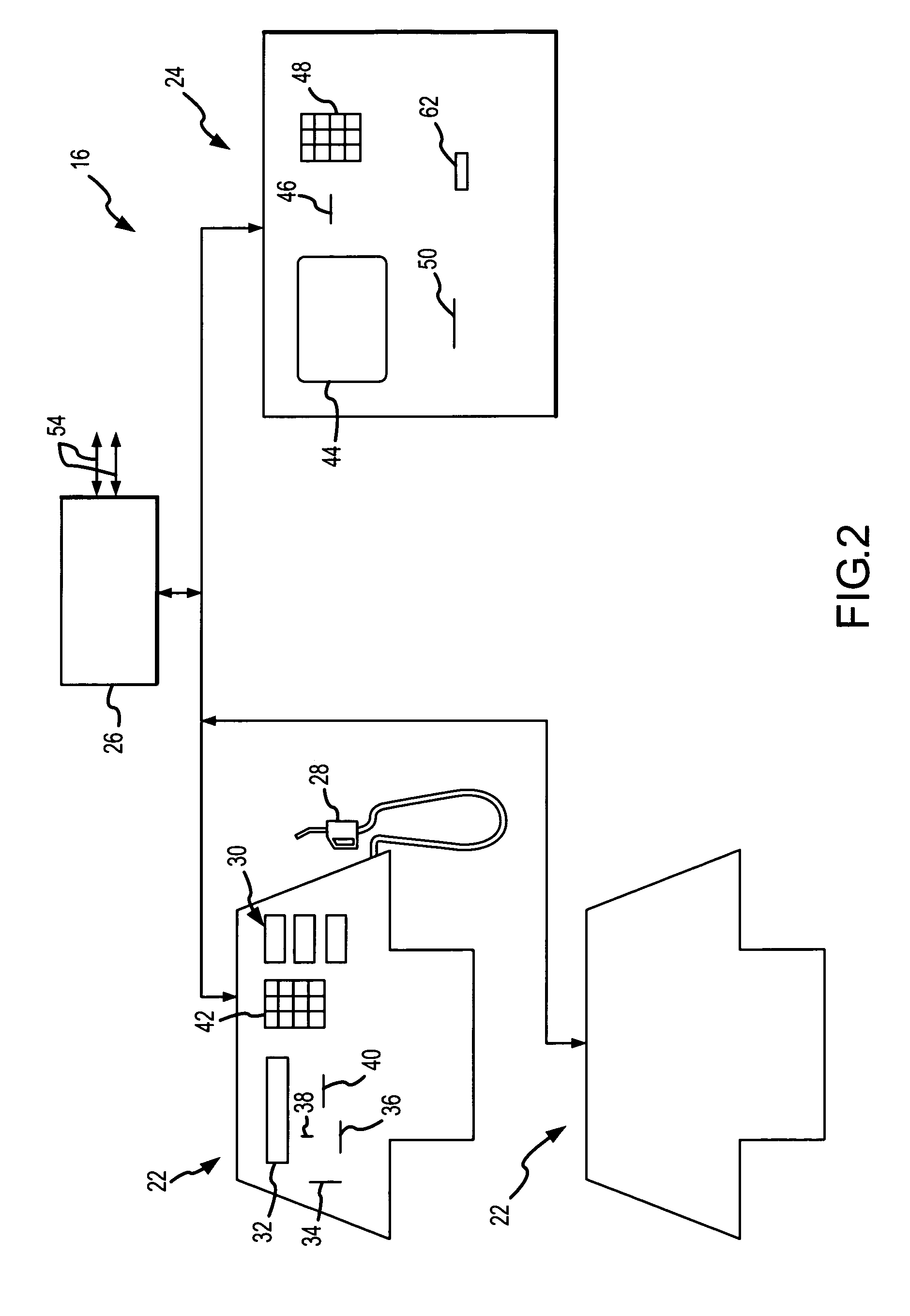
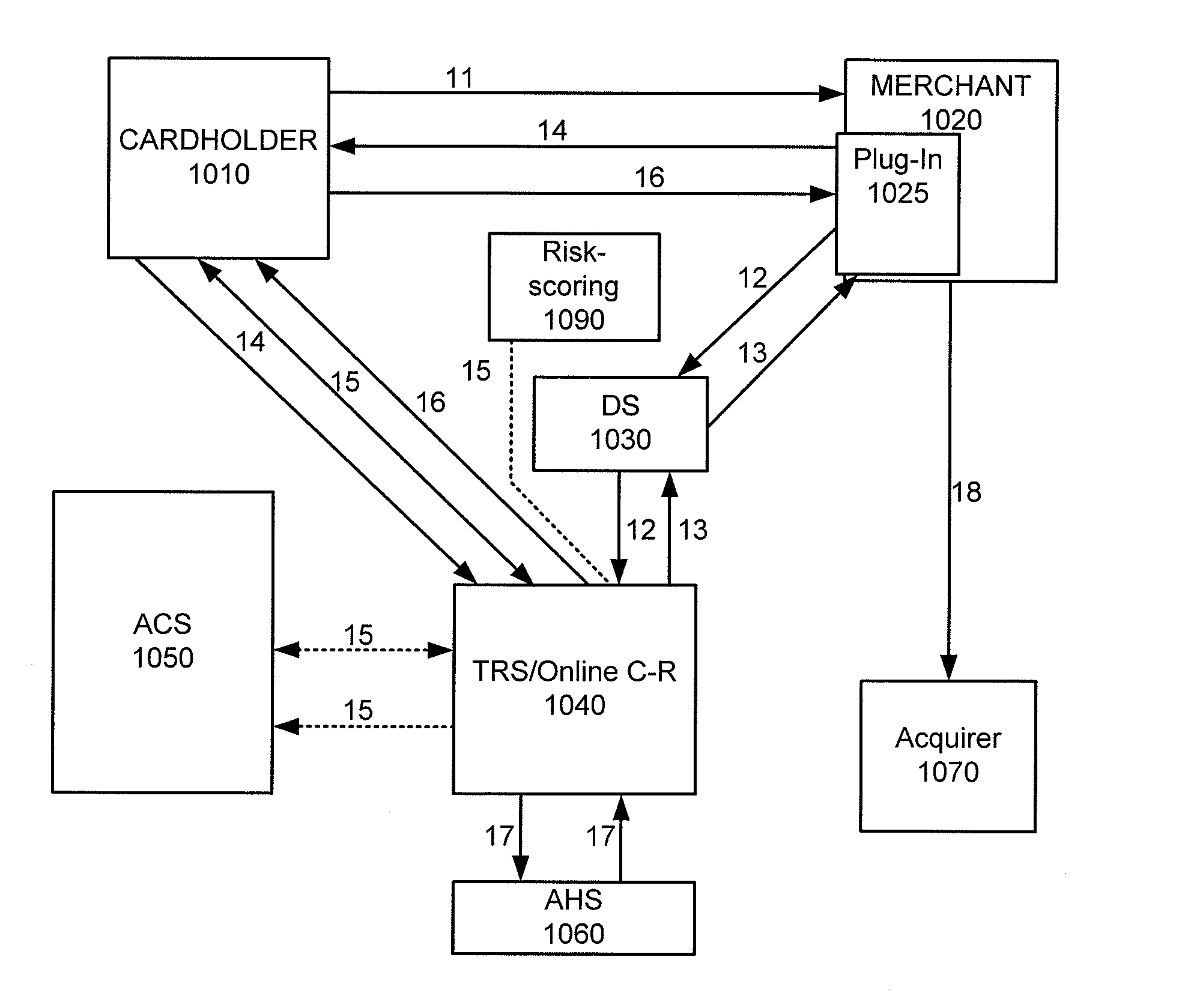
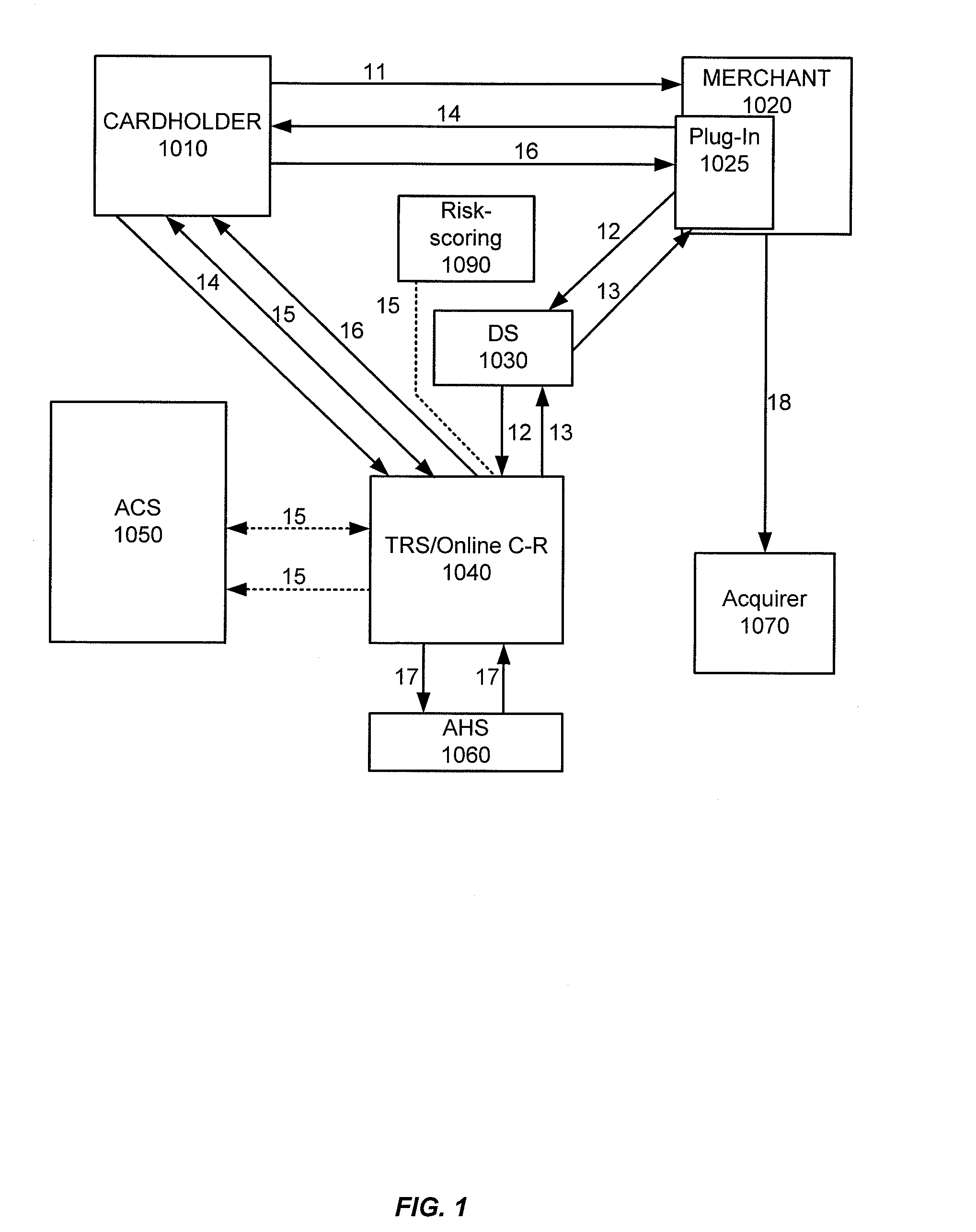
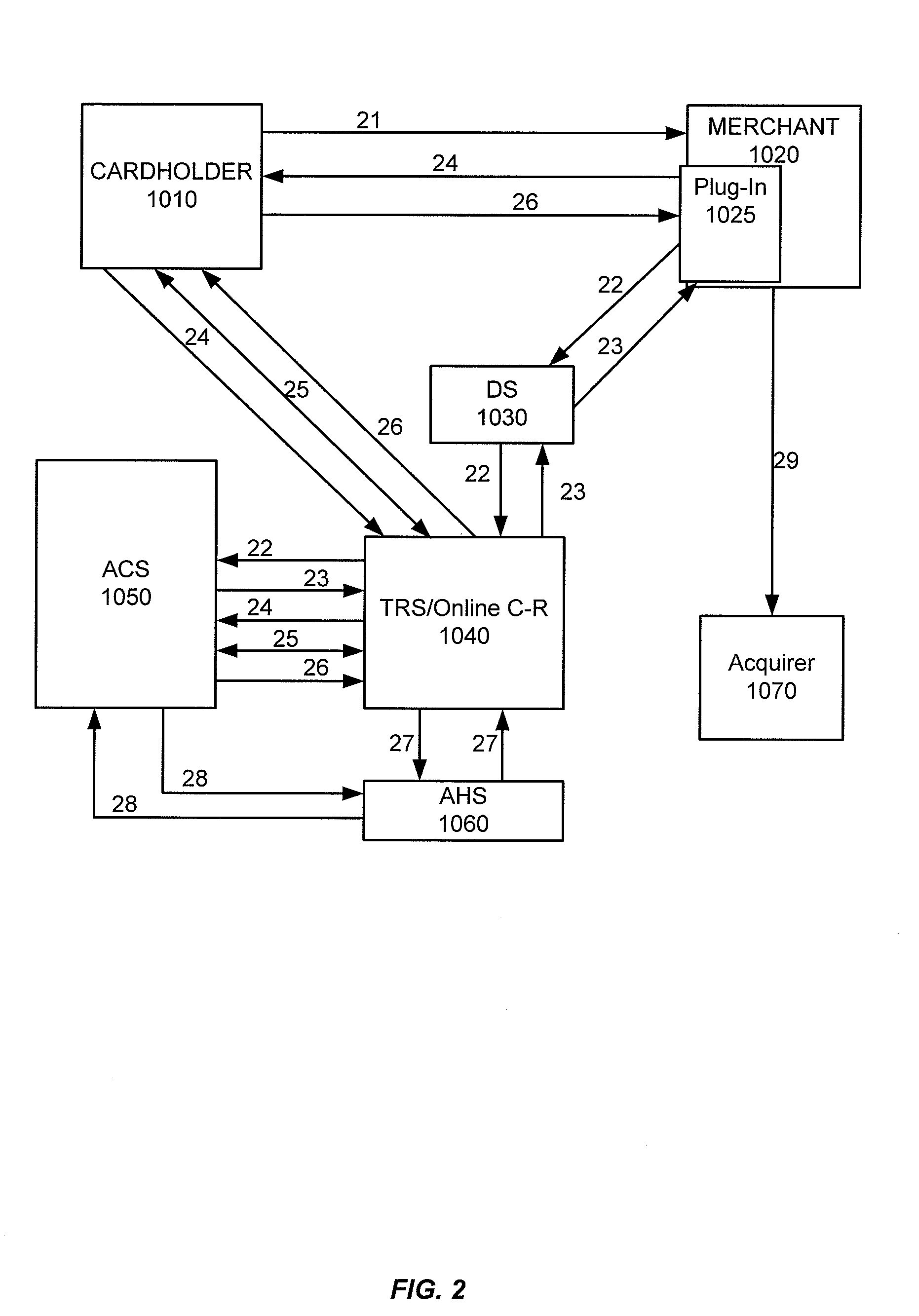
ActiveUS8533118B2Reduce theftSpeed up the processFinanceDigital data processing detailsThird partyChallenge response
Embodiments of the invention enable cardholders conducting an online transaction to be authenticated in real-time using a challenge-response application. The challenge-response application can be administered by an issuer or by a third party on-behalf-of an issuer. A challenge question can be presented to the cardholder, and the cardholder's response can be verified. The challenge question presented can be selected based on an analysis of the risk of the transaction and potentially other factors. A variety of dynamic challenge questions can be used without the need for the cardholder to enroll into the program. Additionally, there are many flexible implementation options of the challenge-response application that can be adjusted based on factors such as the location of the merchant or the location of the consumer.
Owner:VISA INT SERVICE ASSOC
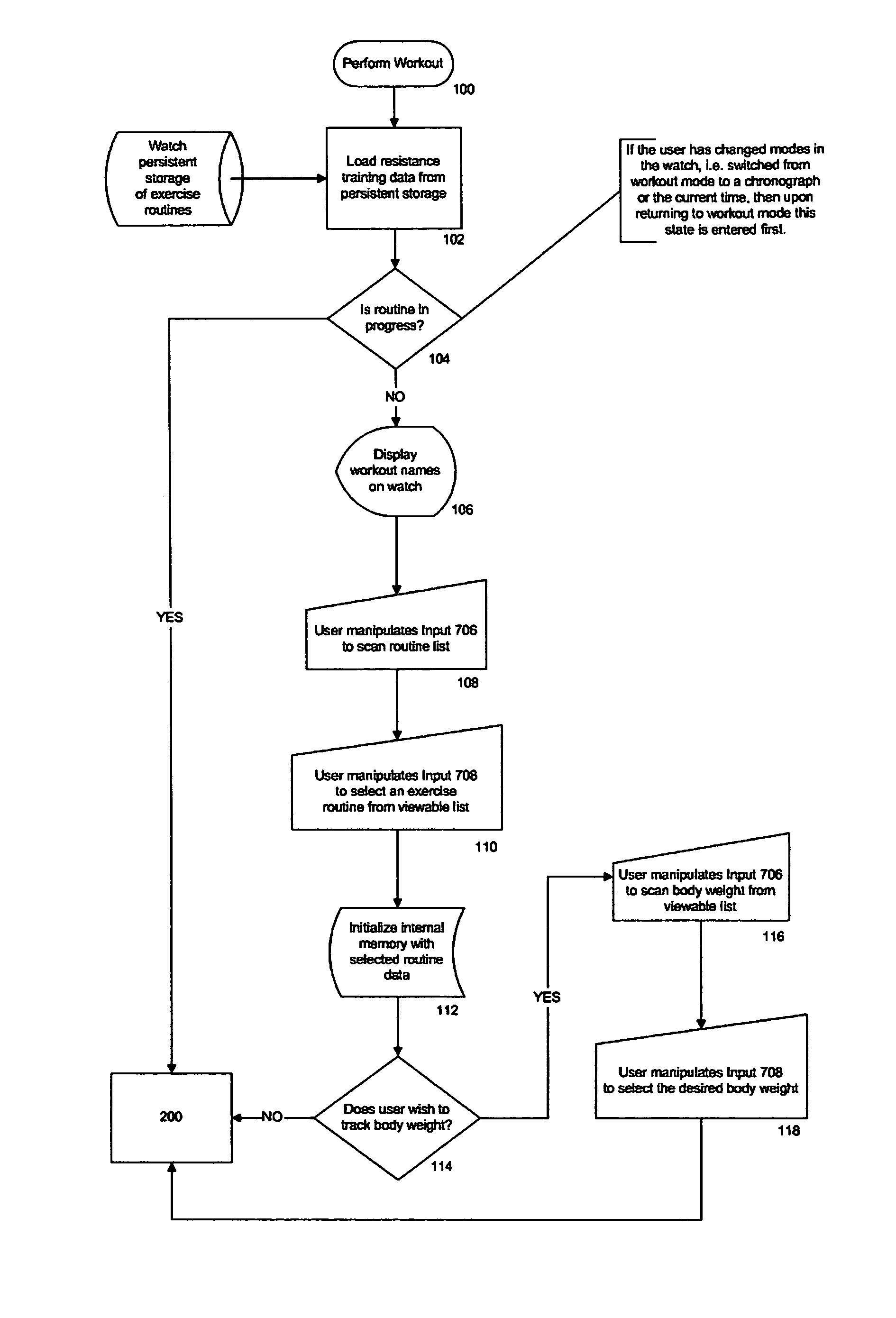
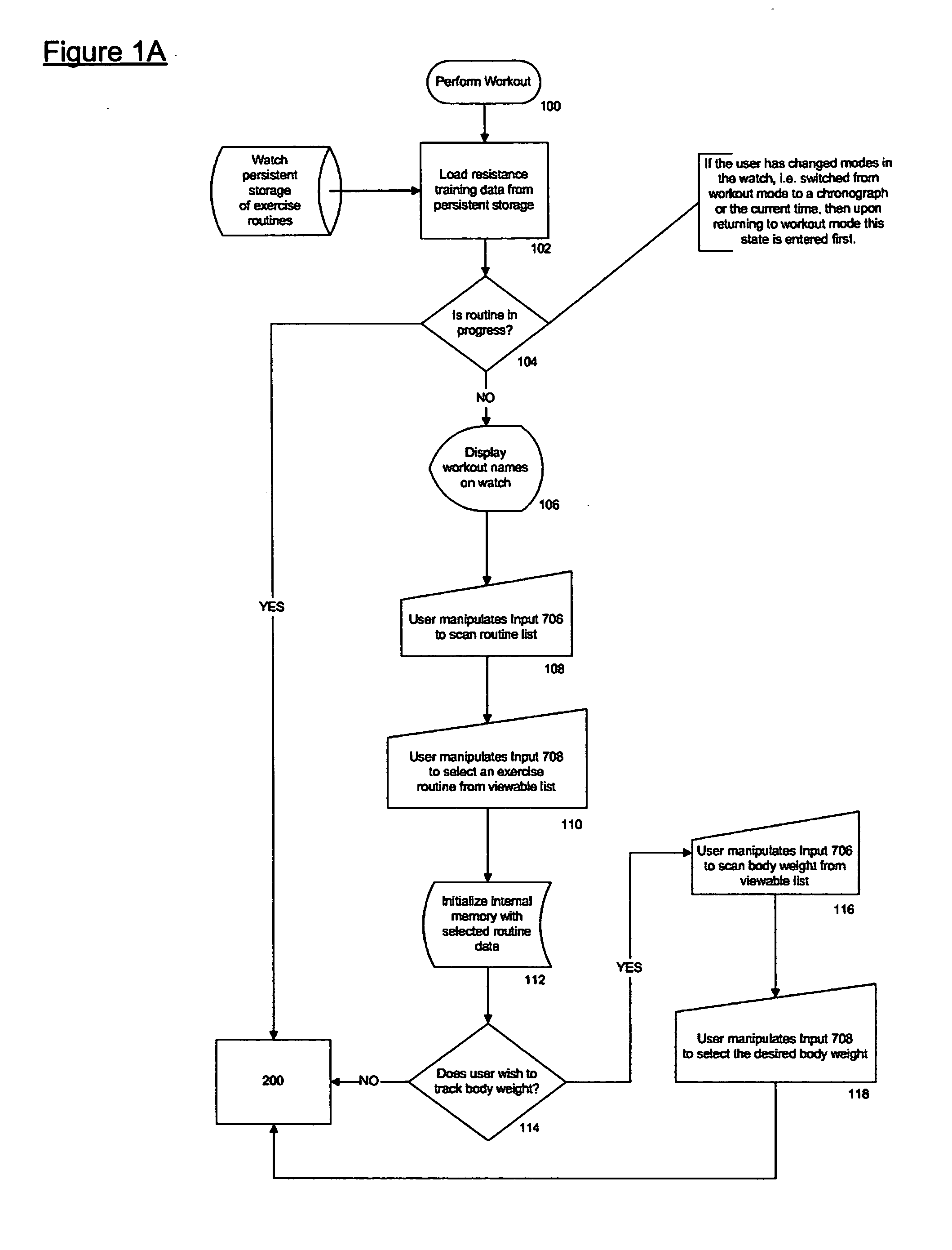
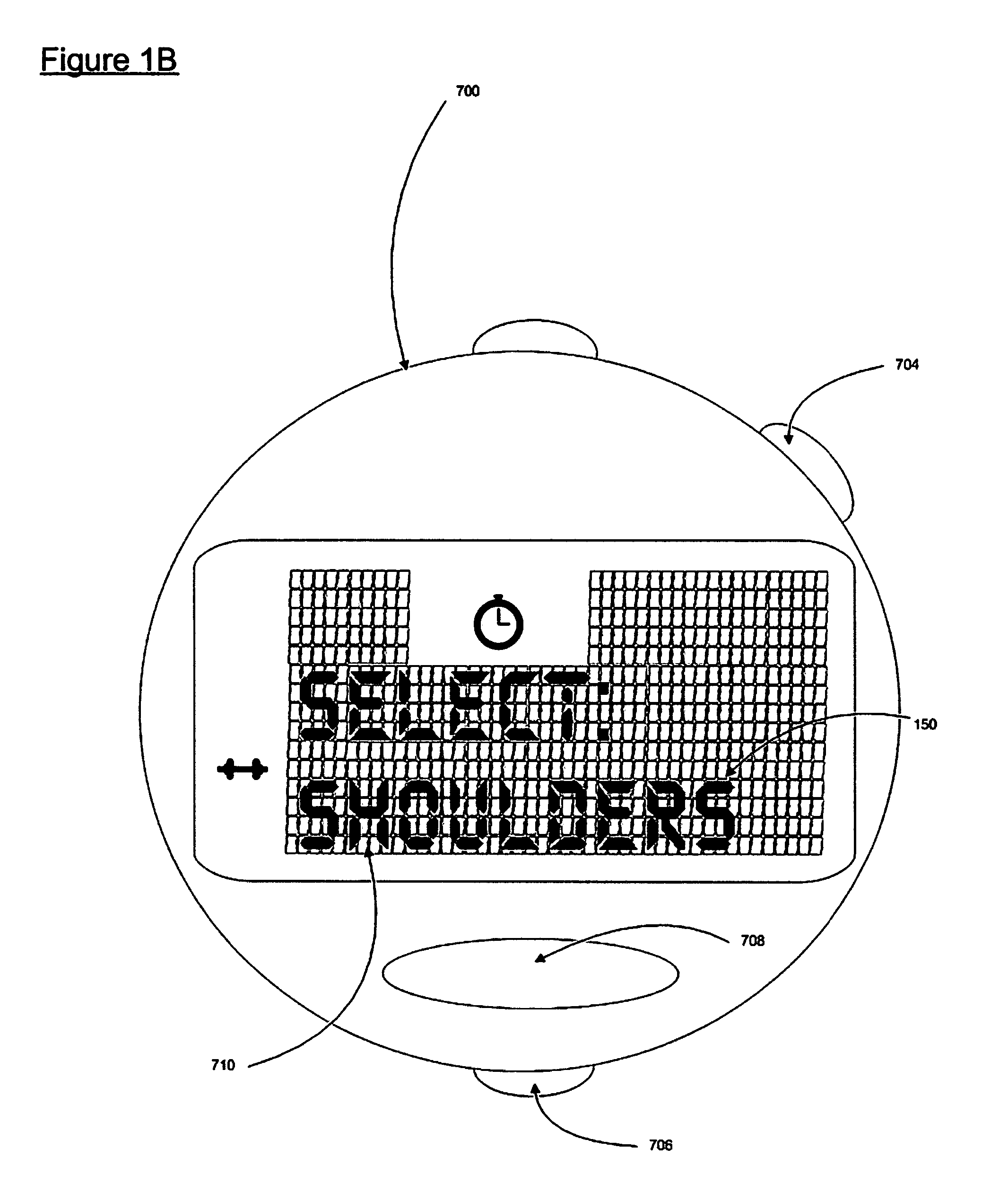
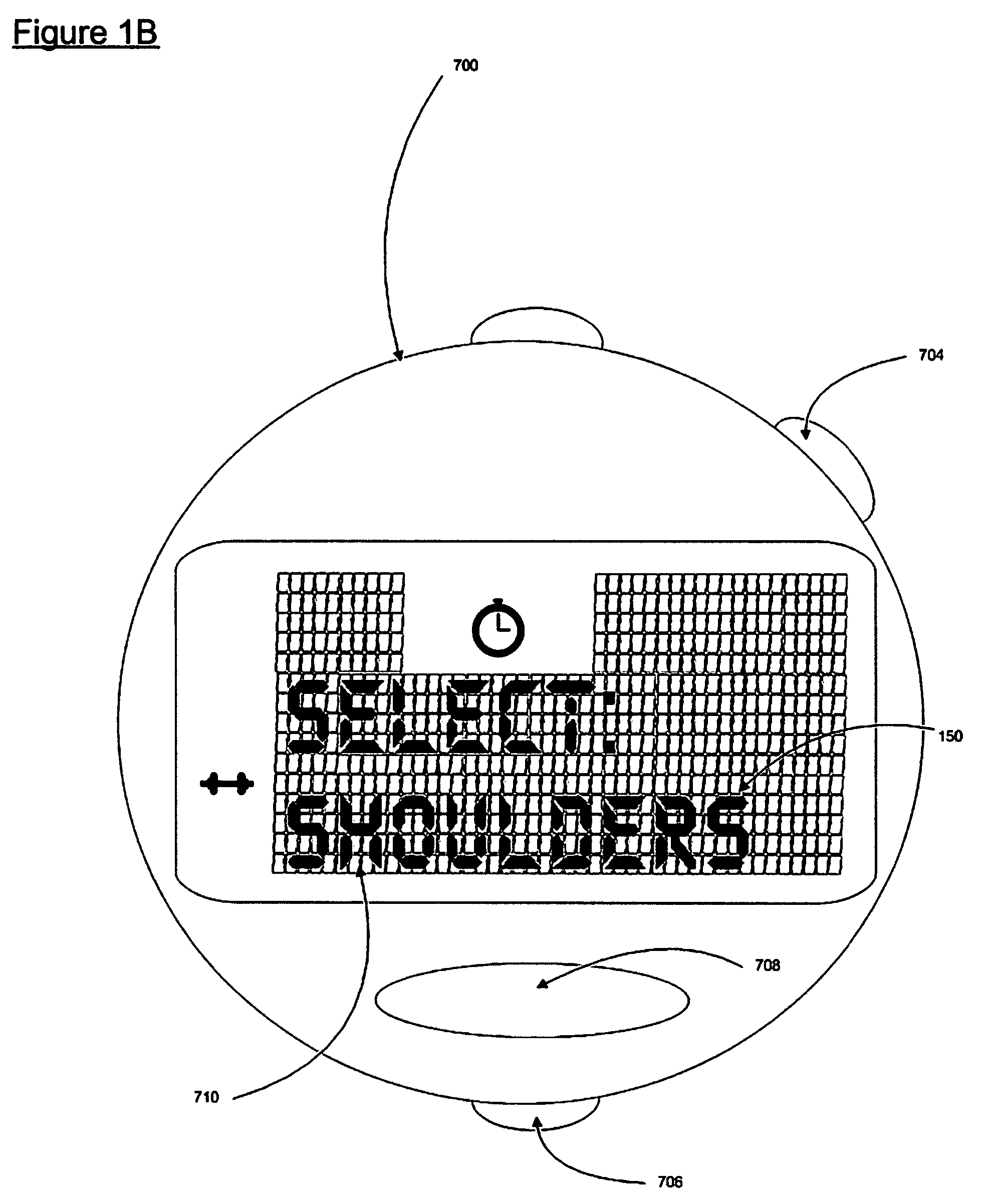
User interface for a resistance training device and method of use
InactiveUS20050209051A1Reduce distractionsImprove usabilityPhysical therapies and activitiesClubsResistance trainingSystems approaches
A system, method, and device for recording and tracking resistance training parameters in connection with a resistance training workout. A specially configured portable recording device has a very compact user interface having an input device with very few inputs. A user may record resistance training parameters directly on the recording device both quickly and easily with few and simple keystrokes, resulting in an improved recording process. A personal trainer or strength coach may track the workouts of multiple exercisers with increased convenience. In a particularly preferred embodiment, the recording device is provided in the body of a sport watch.
Owner:SANTOMASSIMO ROD N +1
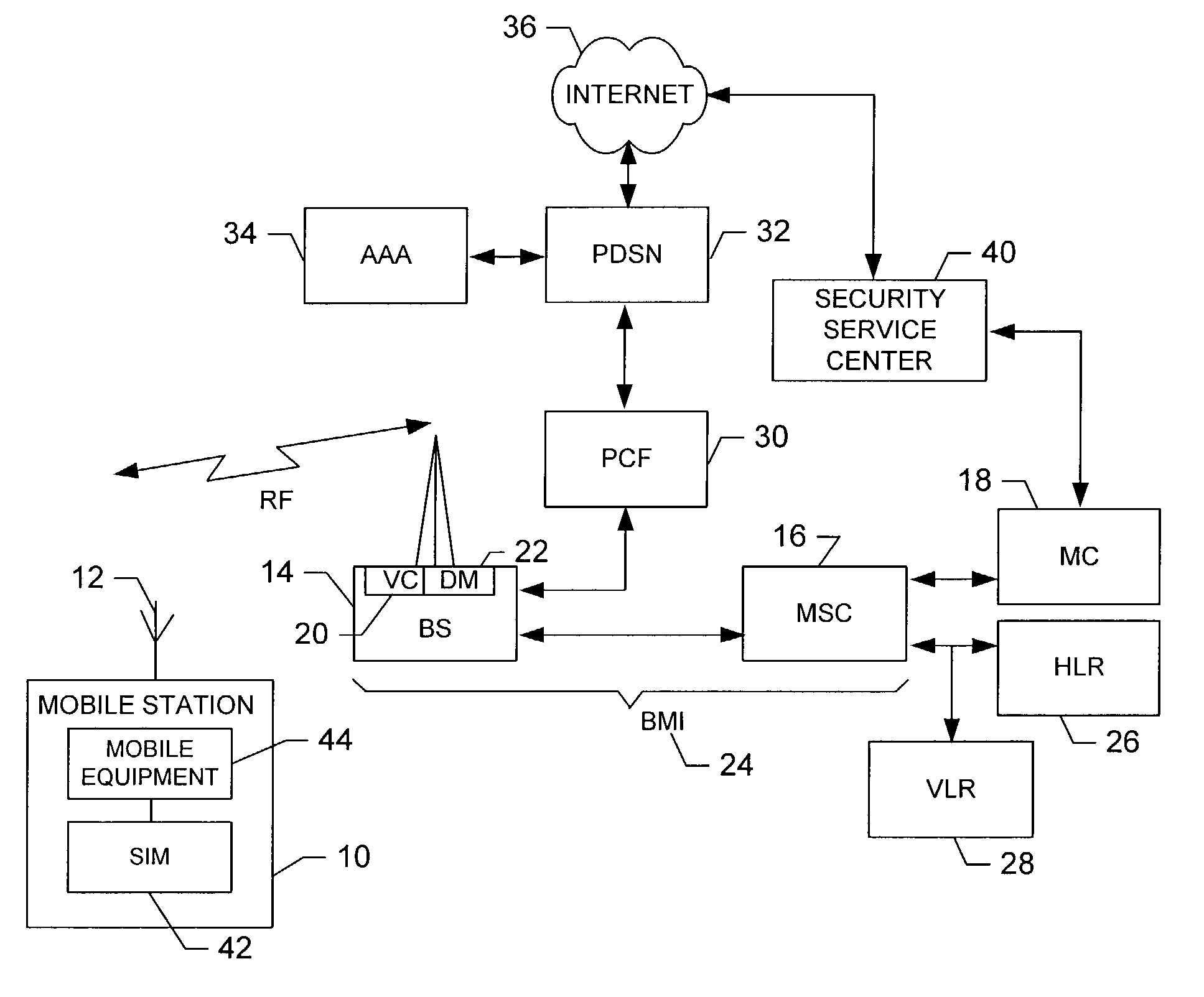
System and method for performing security functions of a mobile station
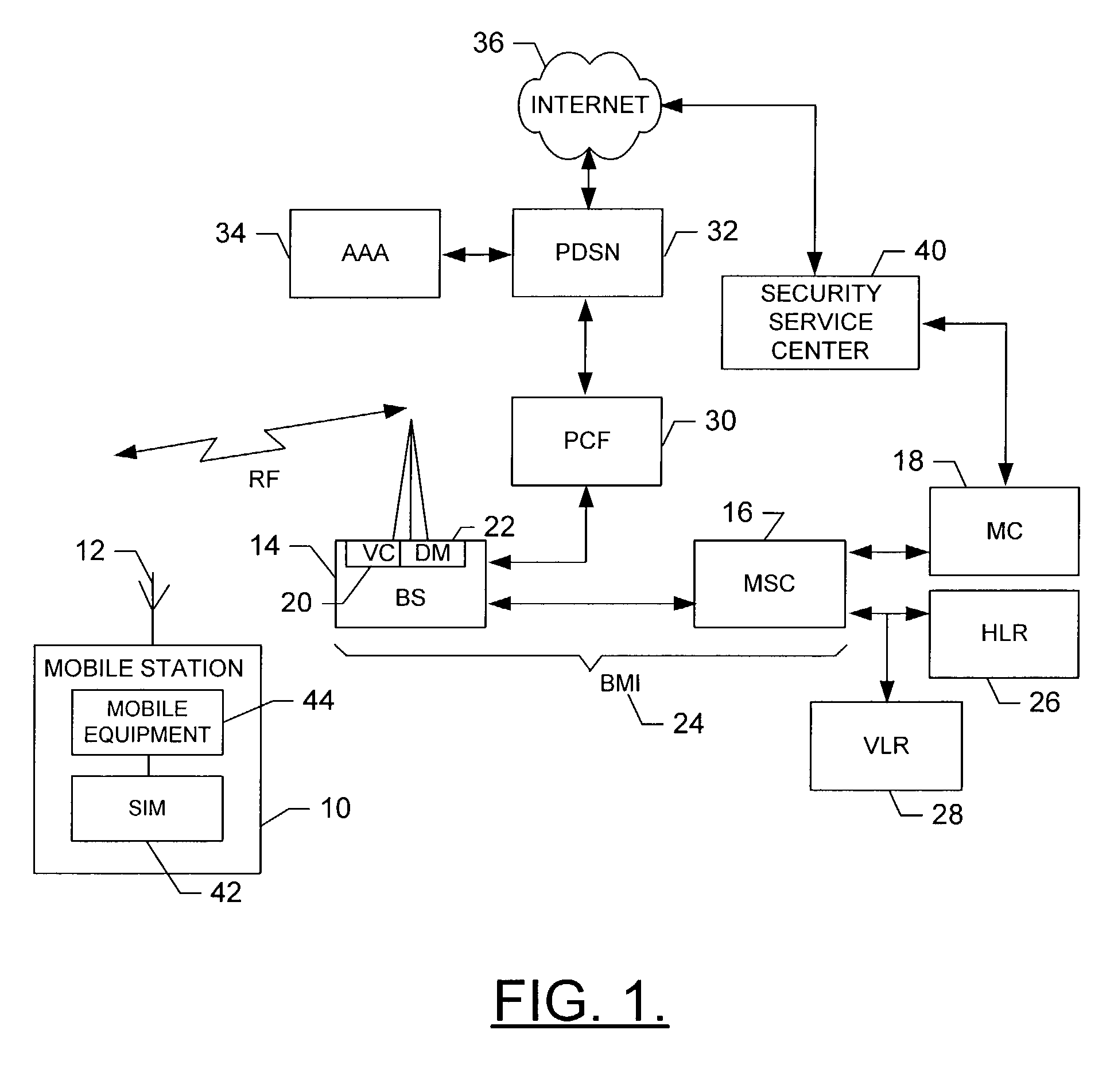
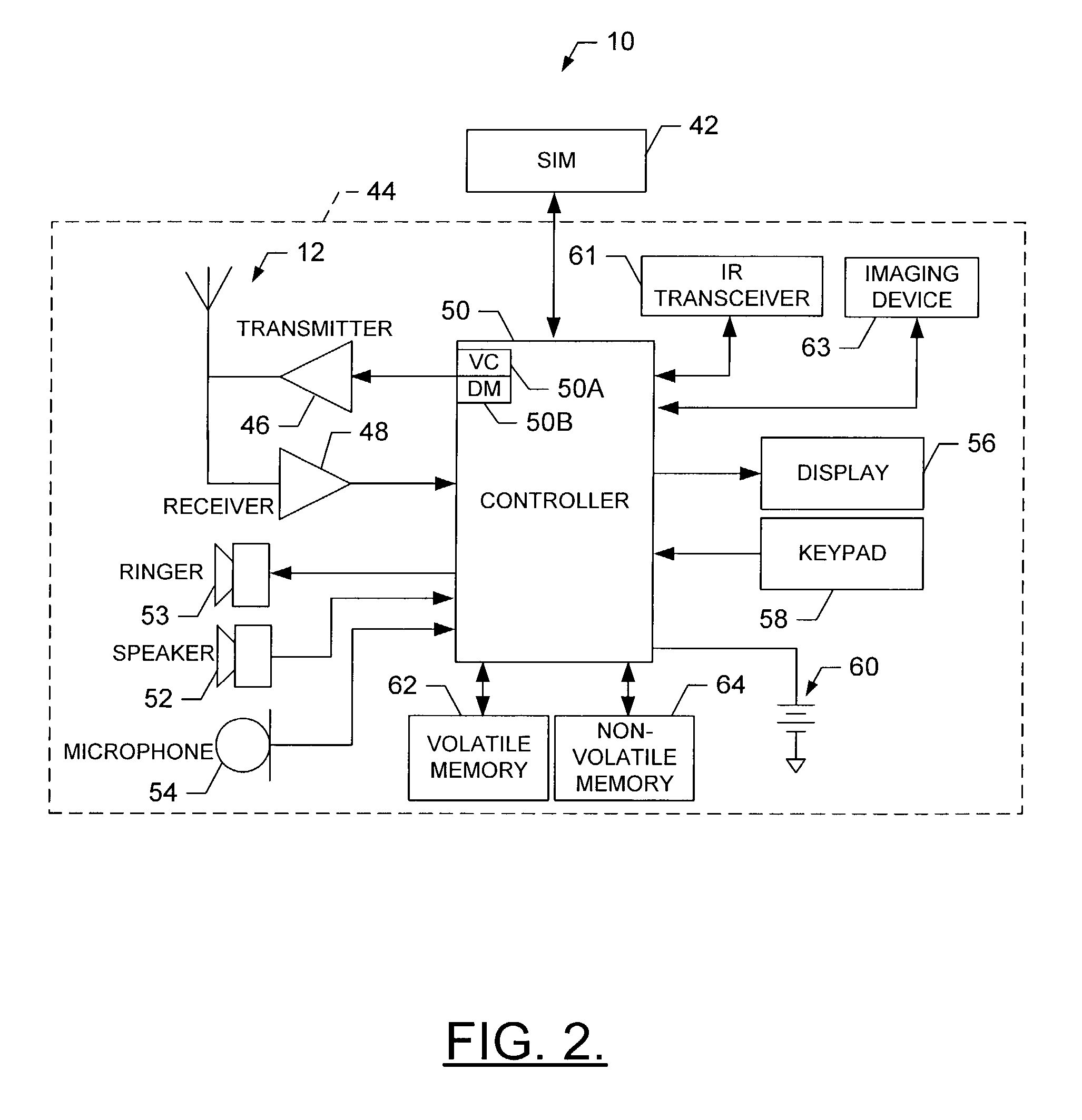
ActiveUS7181252B2Easily maintainableEasily updateableUnauthorised/fraudulent call preventionEavesdropping prevention circuitsIdentification deviceMobile station
A system and method are provided for performing security functions of a mobile station adapted to communicate via a communications network. The mobile station comprises a receiver, a controller, and can also include a ringer and / or a user identifying device. The ringer is capable of generating a ringing tone. The user identifying device can generate data identifying a user of the mobile station. The receiver is capable of receiving at least one security message, where the at least one security message comprises at least one security function. For example, the security function can comprise actuating the ringer to continuously generate the ringing tone, and / or actuating the user identifying device to generate user-identifying data, and thereafter transmitting a status message including the user-identifying data. The controller is therefore capable of interpreting the at least one security message, and thereafter performing the at least one security function.
Owner:PINEAPPLE34 LLC
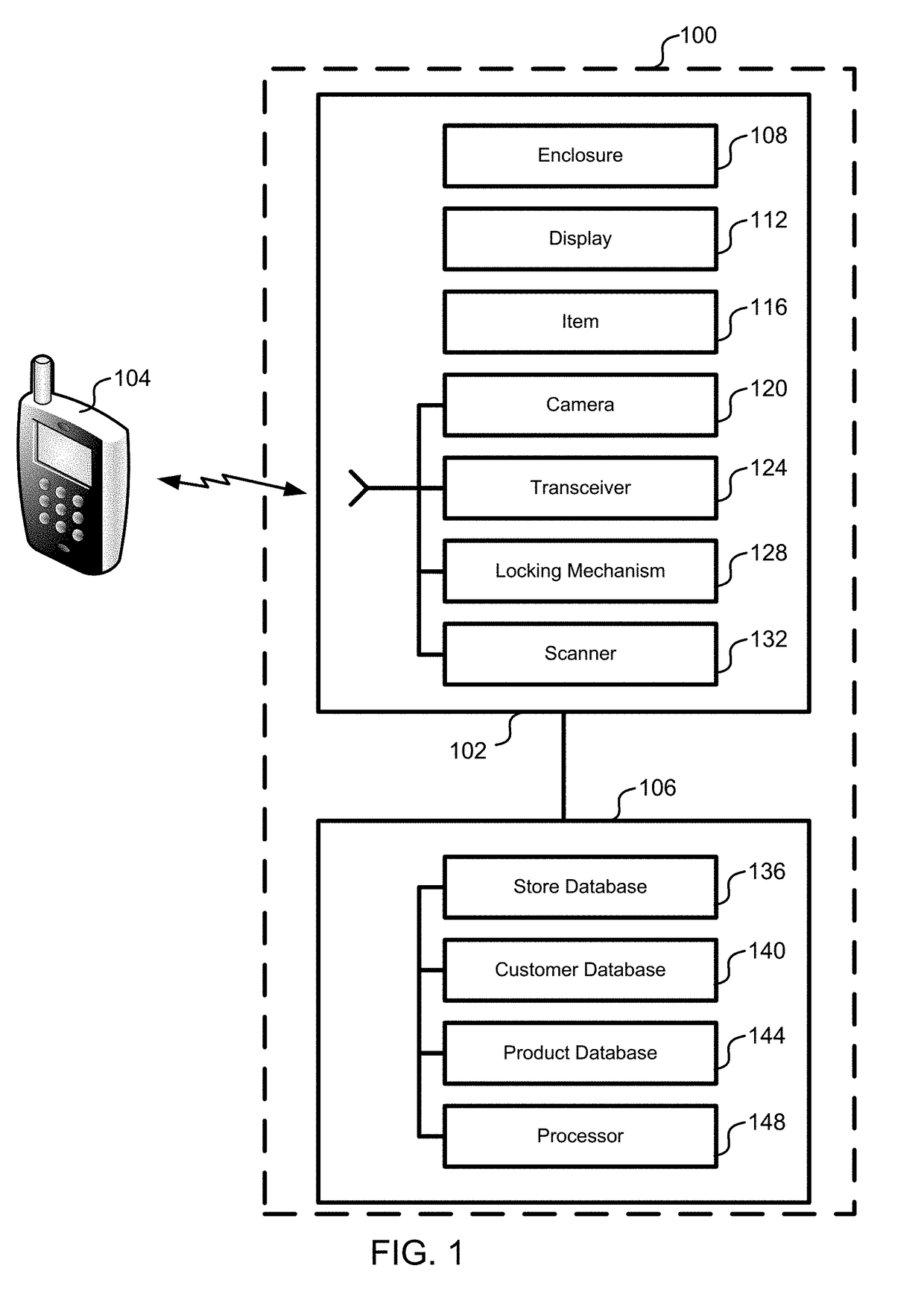
Registry verification for a mechanized store using radio frequency tags
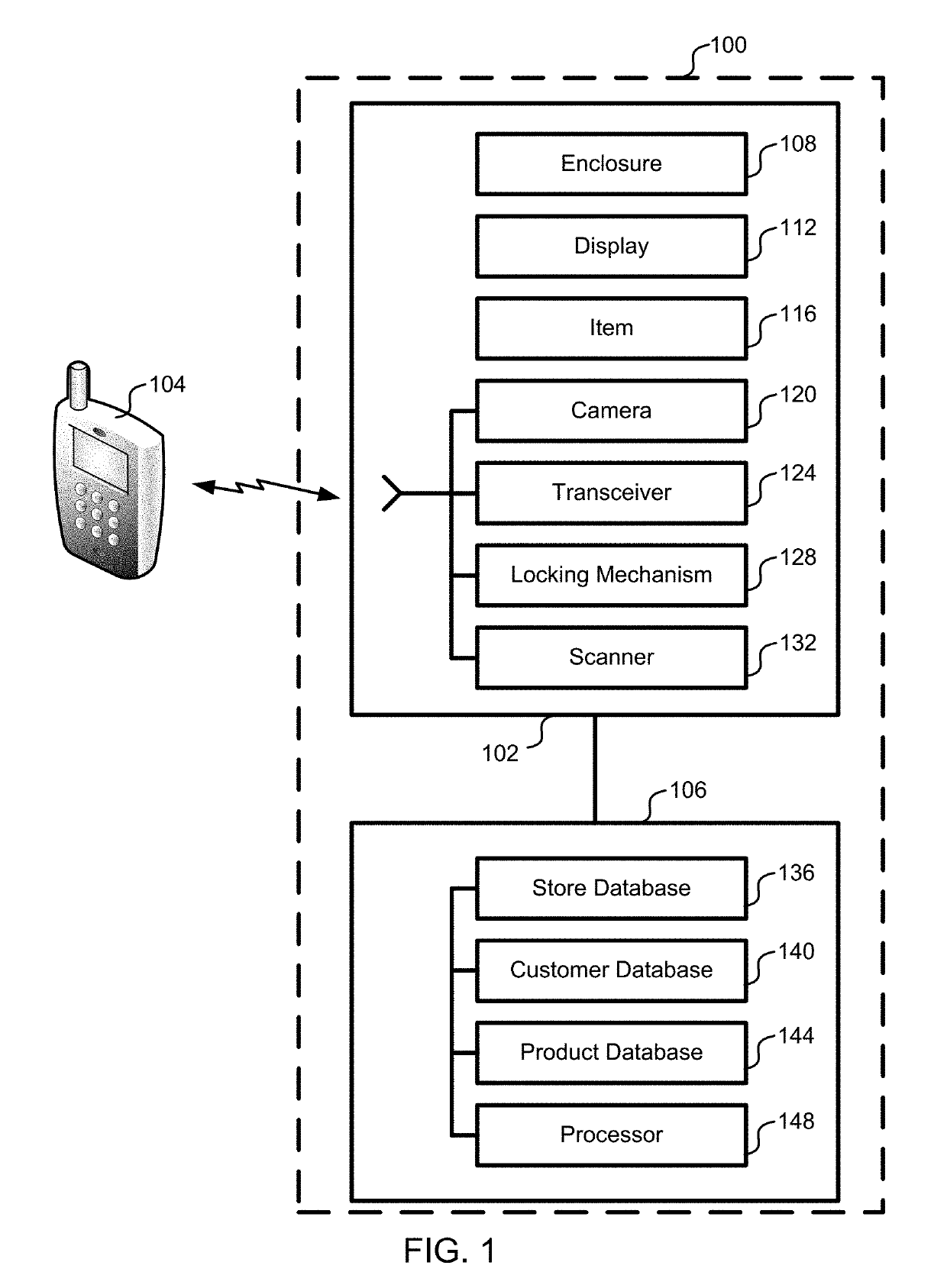
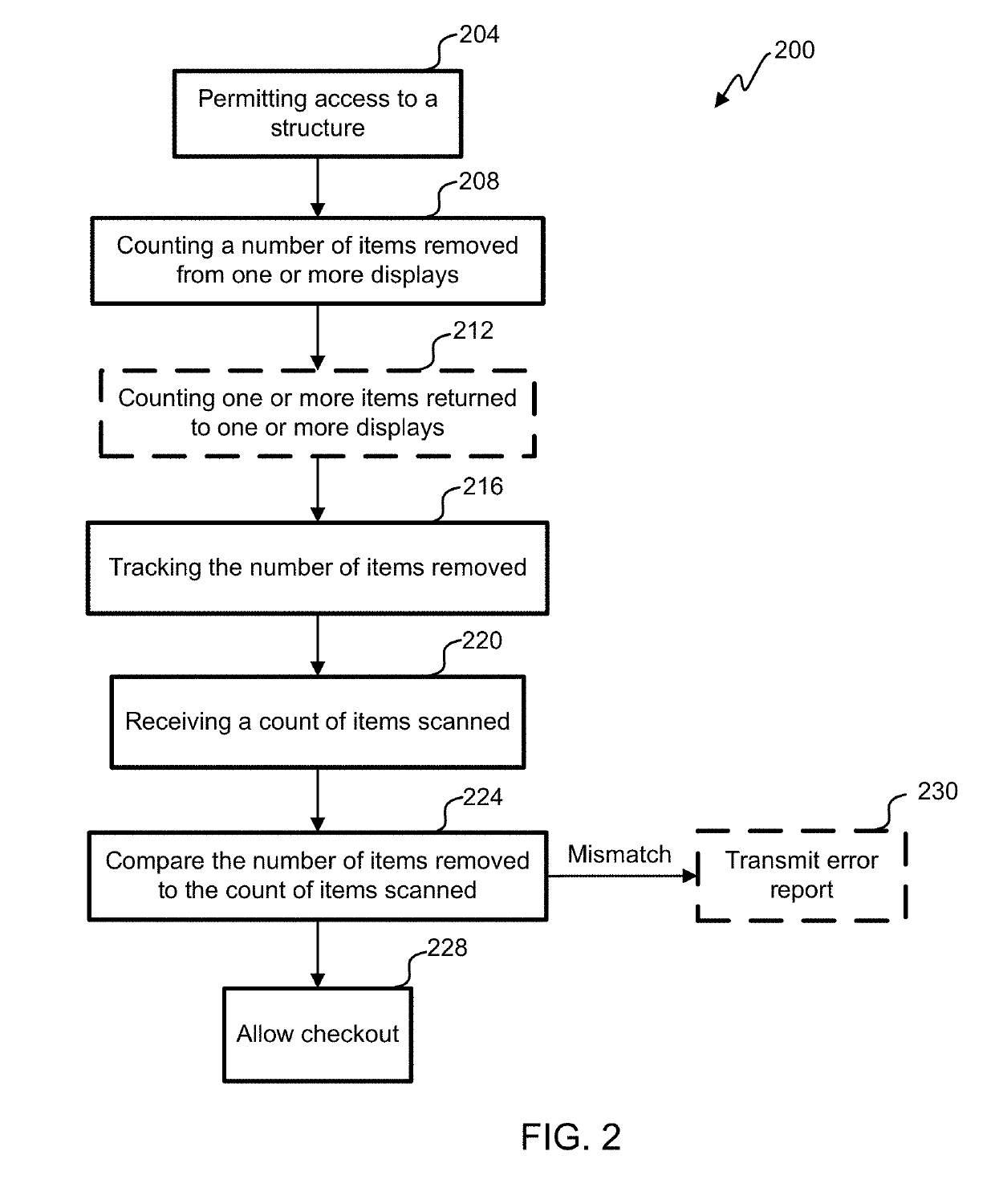
ActiveUS20190147709A1Reduce shop liftingReduce theftCash registersPayment architectureRadio frequencyComputer science
Registry verification is used in a mechanized store. A camera is used to count a first number of items taken by a user. Radio frequency tags are used to determine a second number of items. The first number of items is compared to the second number of items to reduce a likelihood of errors.
Owner:STANDARD COGNITION CORP
Electronically enabling device remotely
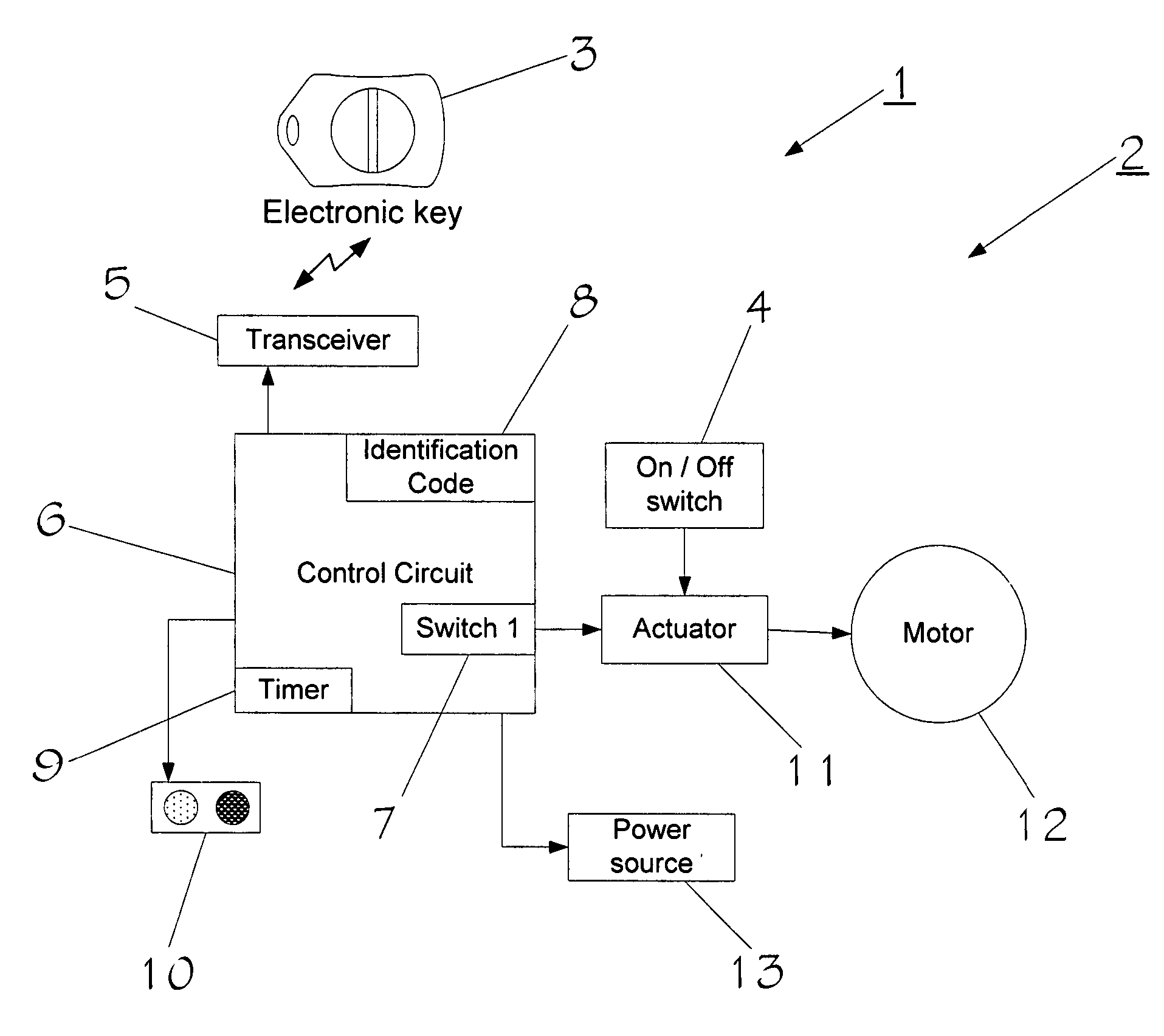
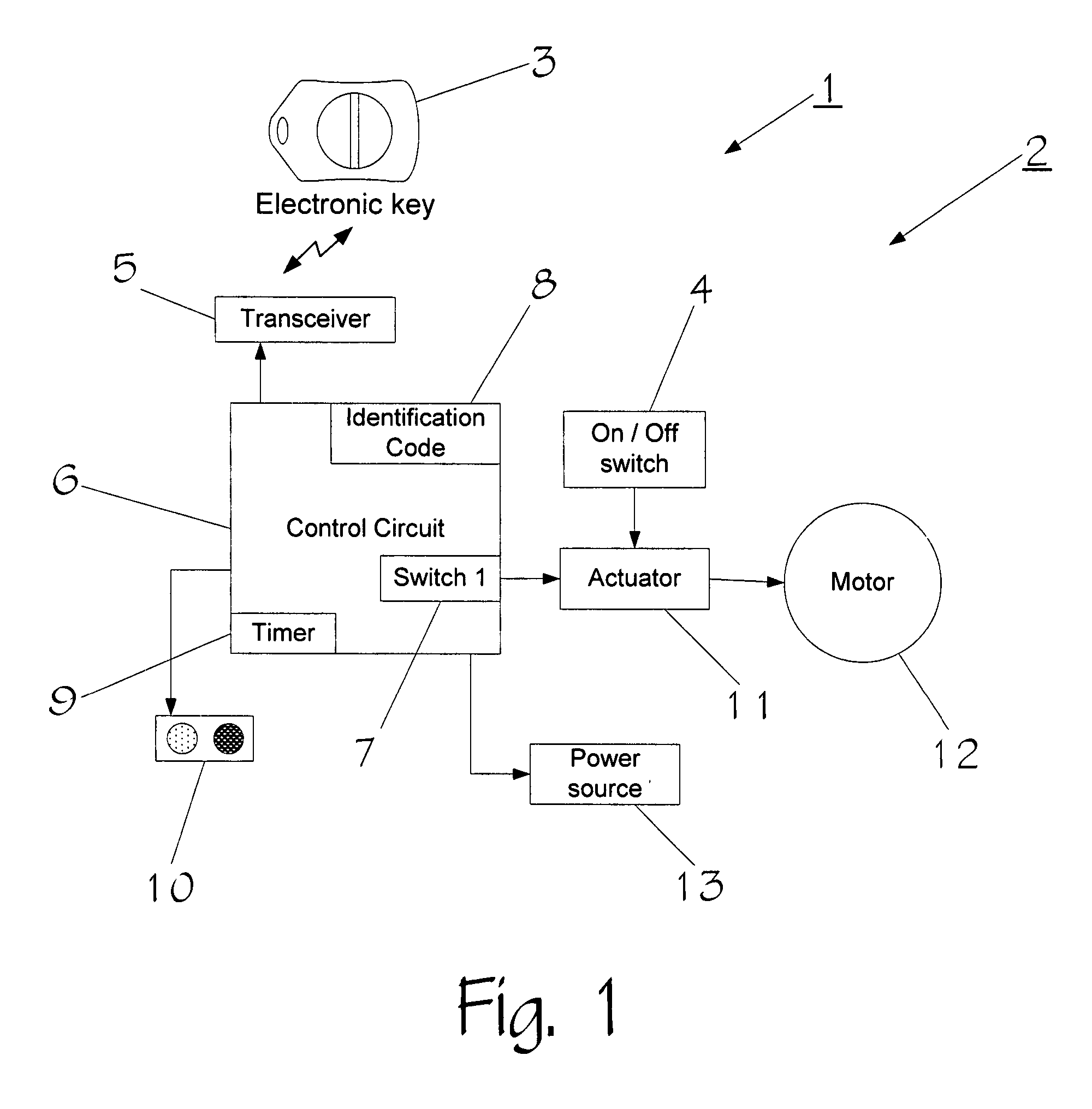
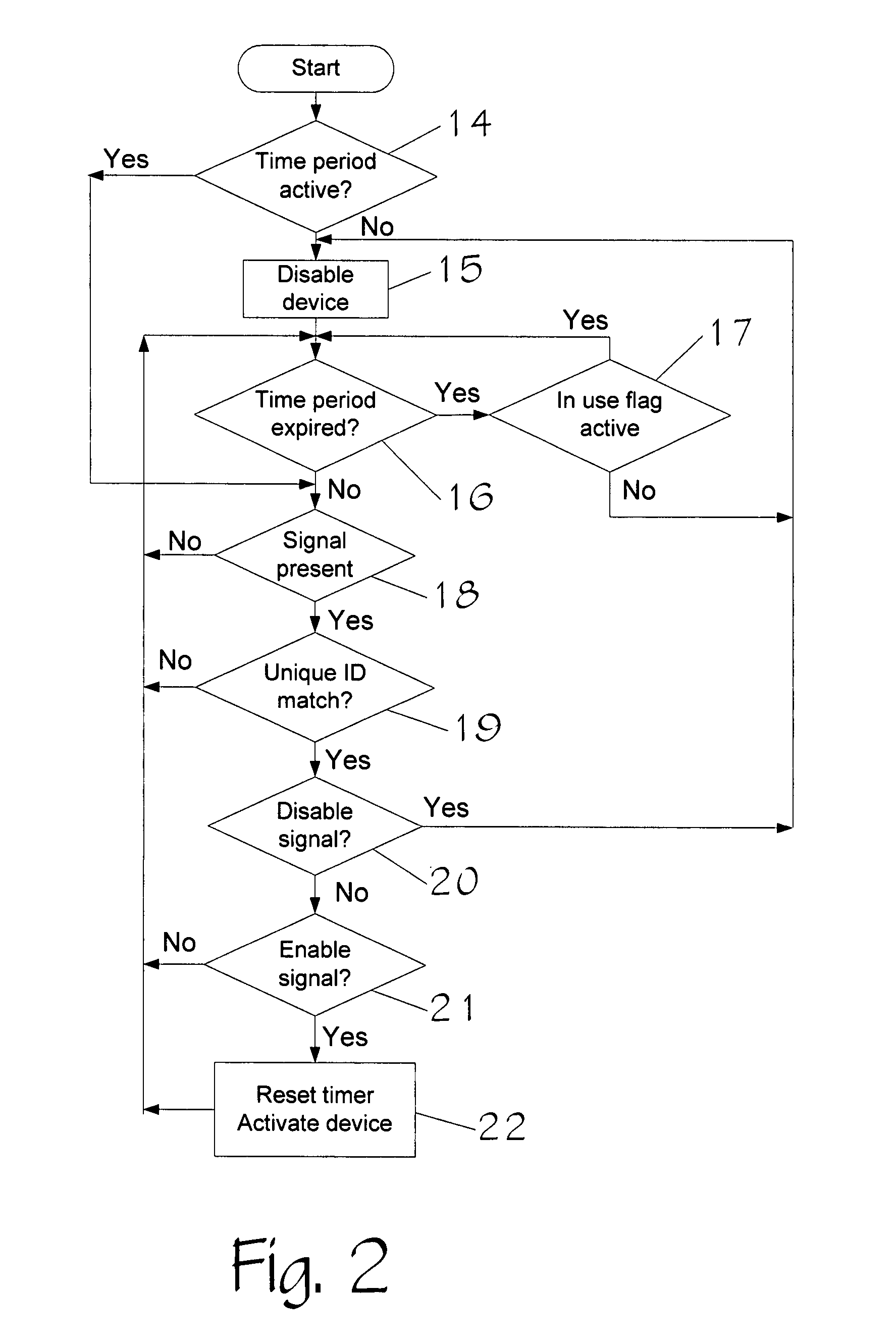
InactiveUS20070252675A1Disabling can be delayedReduce stepsProgramme controlElectric signal transmission systemsElectrical and Electronics engineeringSignal validation
A system has an electronic key that transmits a coded signal and at least one tool or other device that can receive that signal. The coded signal is compared to a coded signal stored in the tool or other device. If the coded signal authenticates the stored signal, the tool is enabled or disabled for a specified amount of time. An on / off switch then enables the user of the tool to turn the tool or other device on and off during the specified amount of time. After the specified amount of time, the tool is disabled so that the tool or other device can no longer be used. Disabling the tool may be delayed if the tool or other device is in use. The tool or other device may also contain a unique identification code that can be read by an interrogating device to identify the tool or other device.
Owner:LAMAR DAVID
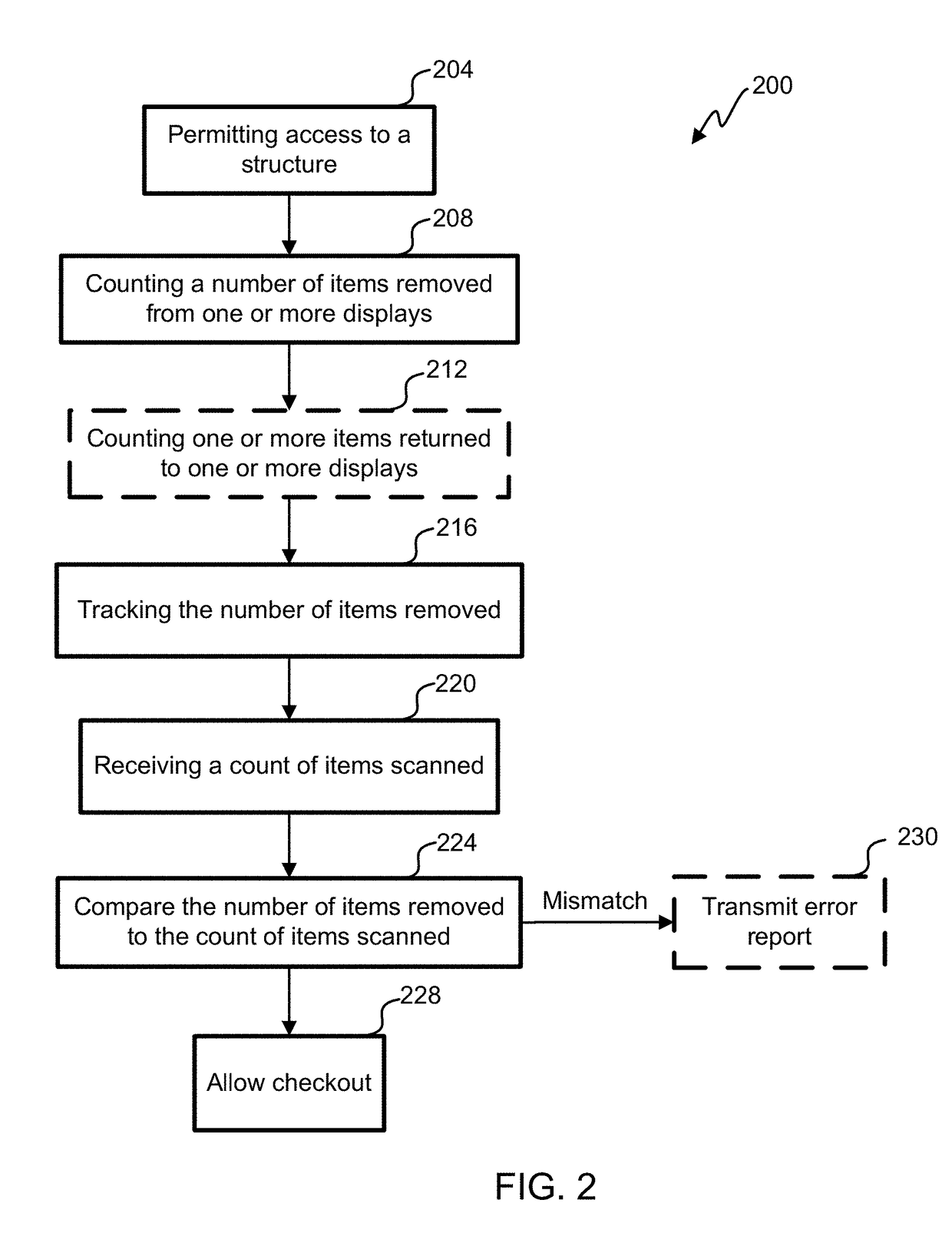
Registry verification for a mechanized store
ActiveUS9886827B2Difficult to manageTime period is limitedCharacter and pattern recognitionCash registersComputer scienceOperating system
Registry verification is used in a mechanized store. A camera is used to count a first number of items taken by a user. The items are scanned to determine a second number of items. The first number of items is compared to the second number of items to reduce a likelihood of errors.
Owner:STANDARD COGNITION CORP
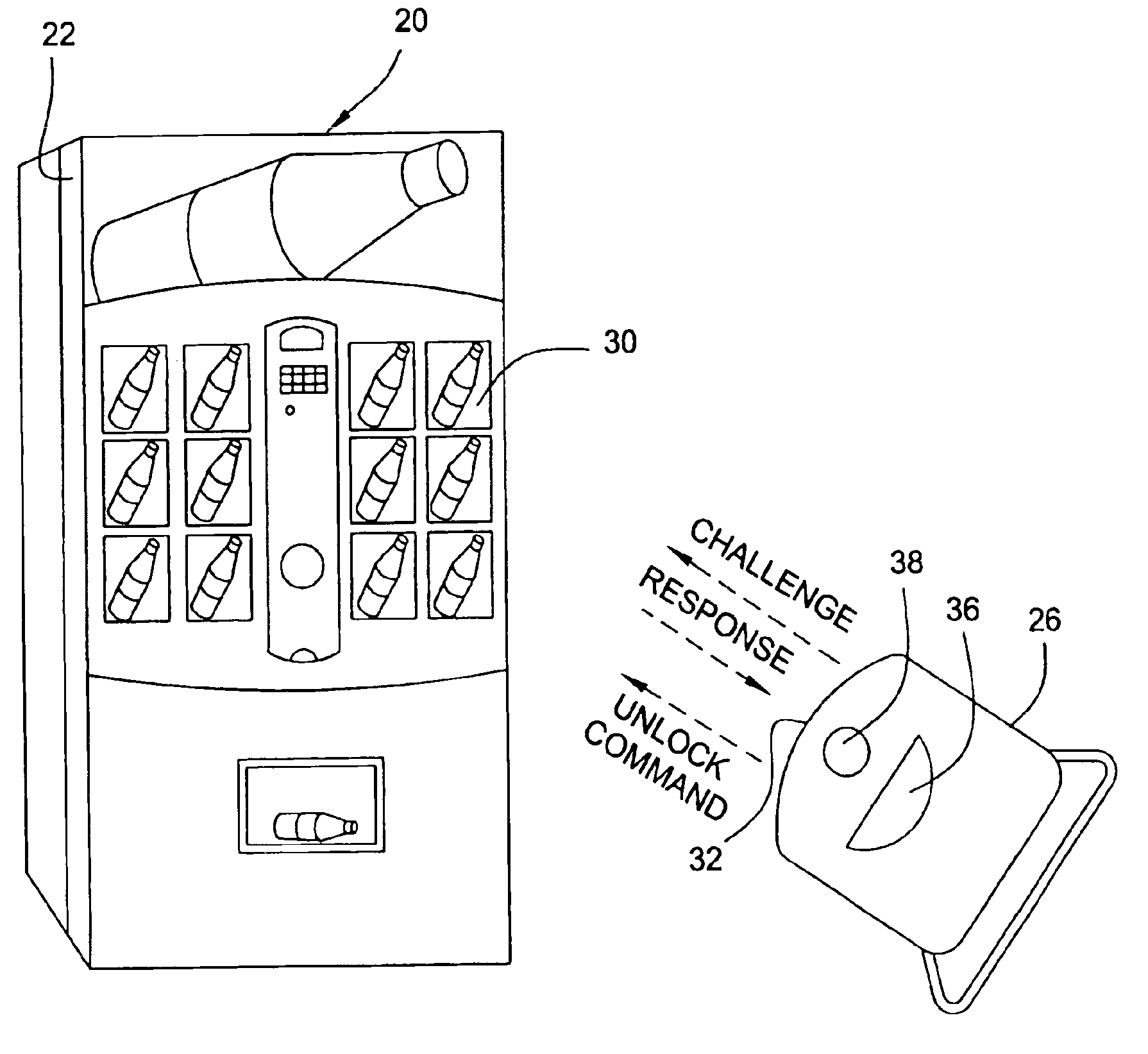
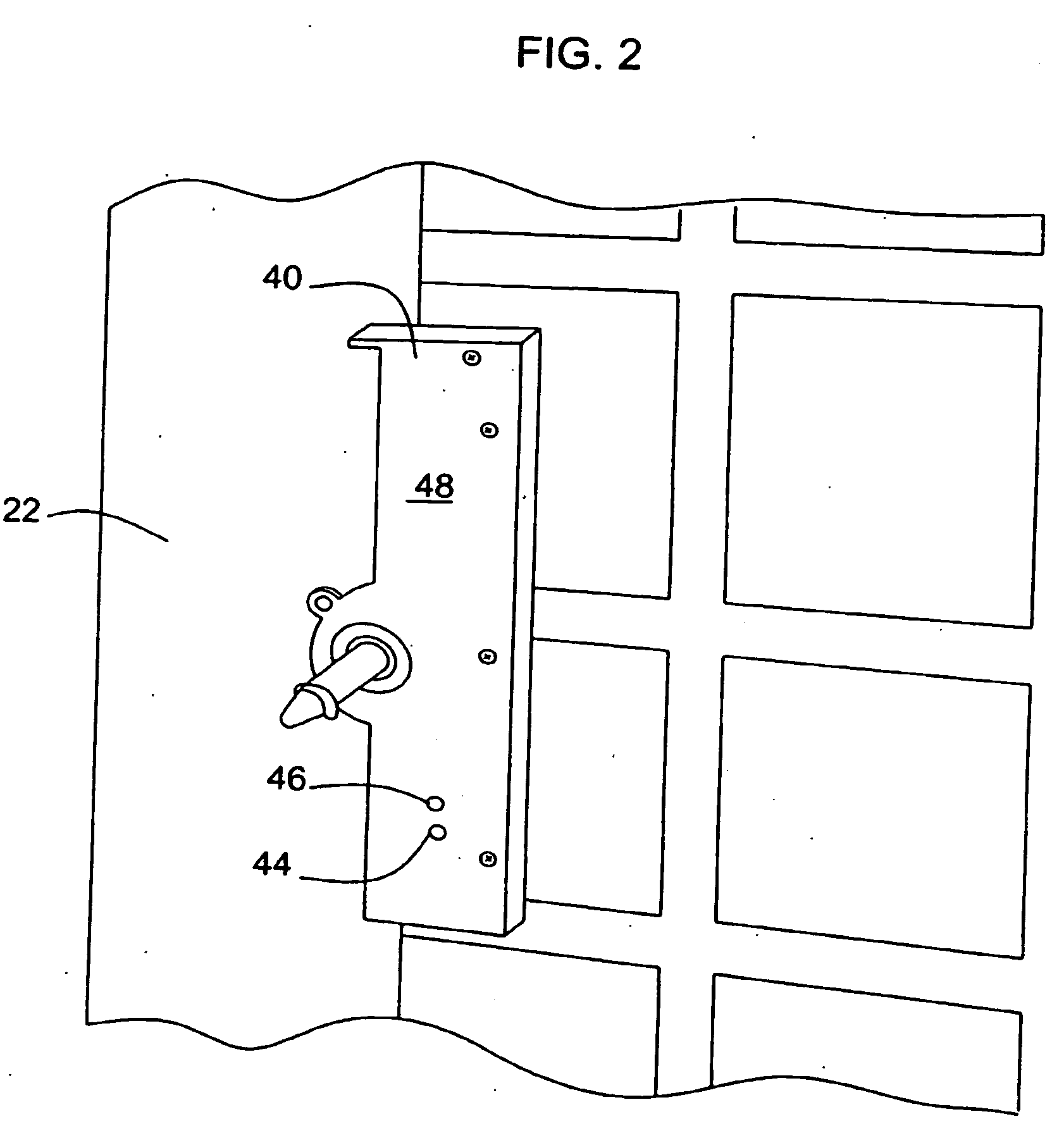
Vending machines with field-programmable locks
InactiveUS6900720B2Easily and inexpensively programmedImprove the level ofFrequency-division multiplex detailsDigital data processing detailsBiological activationHome based
Owner:MICRO ENHANCED TECH
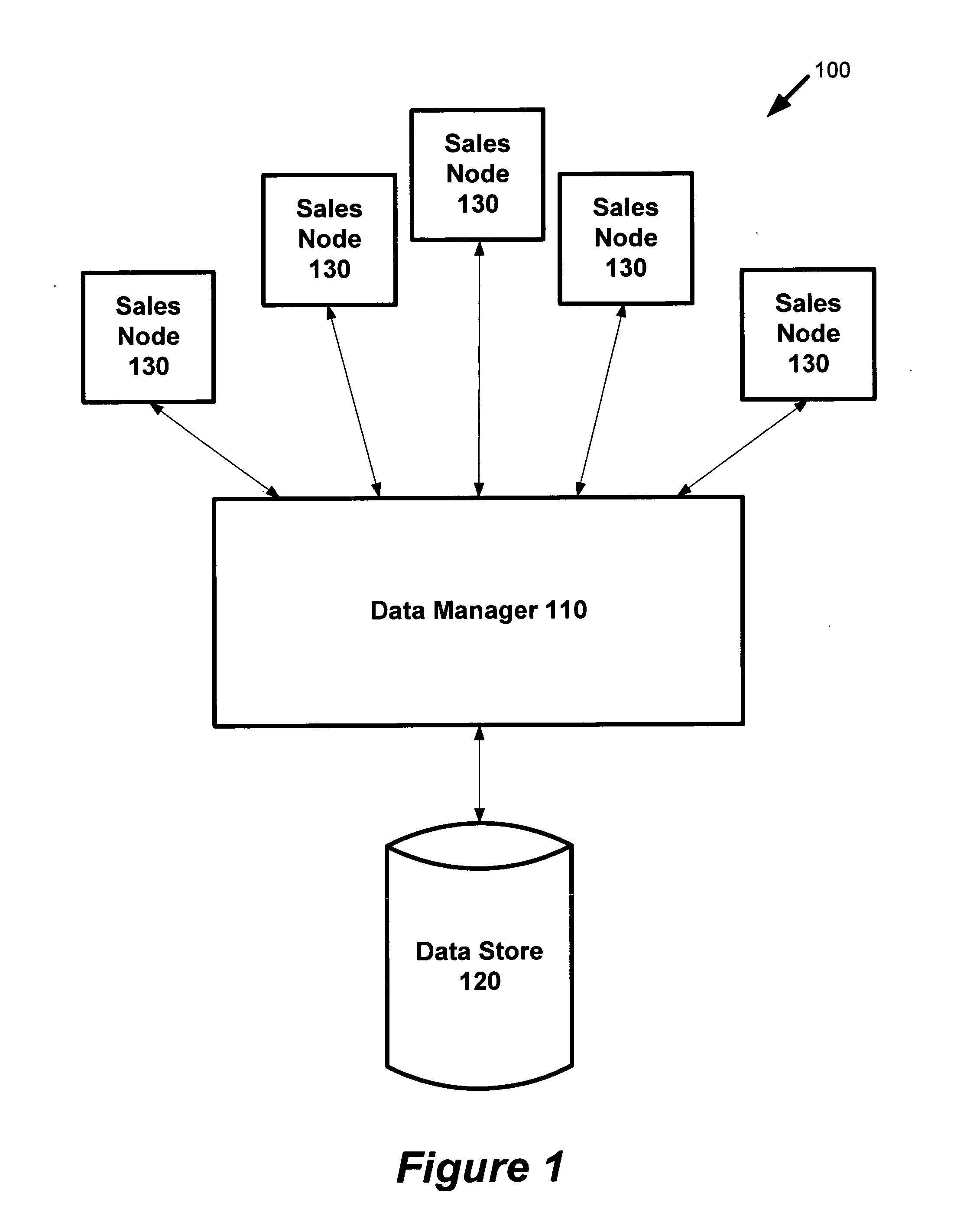
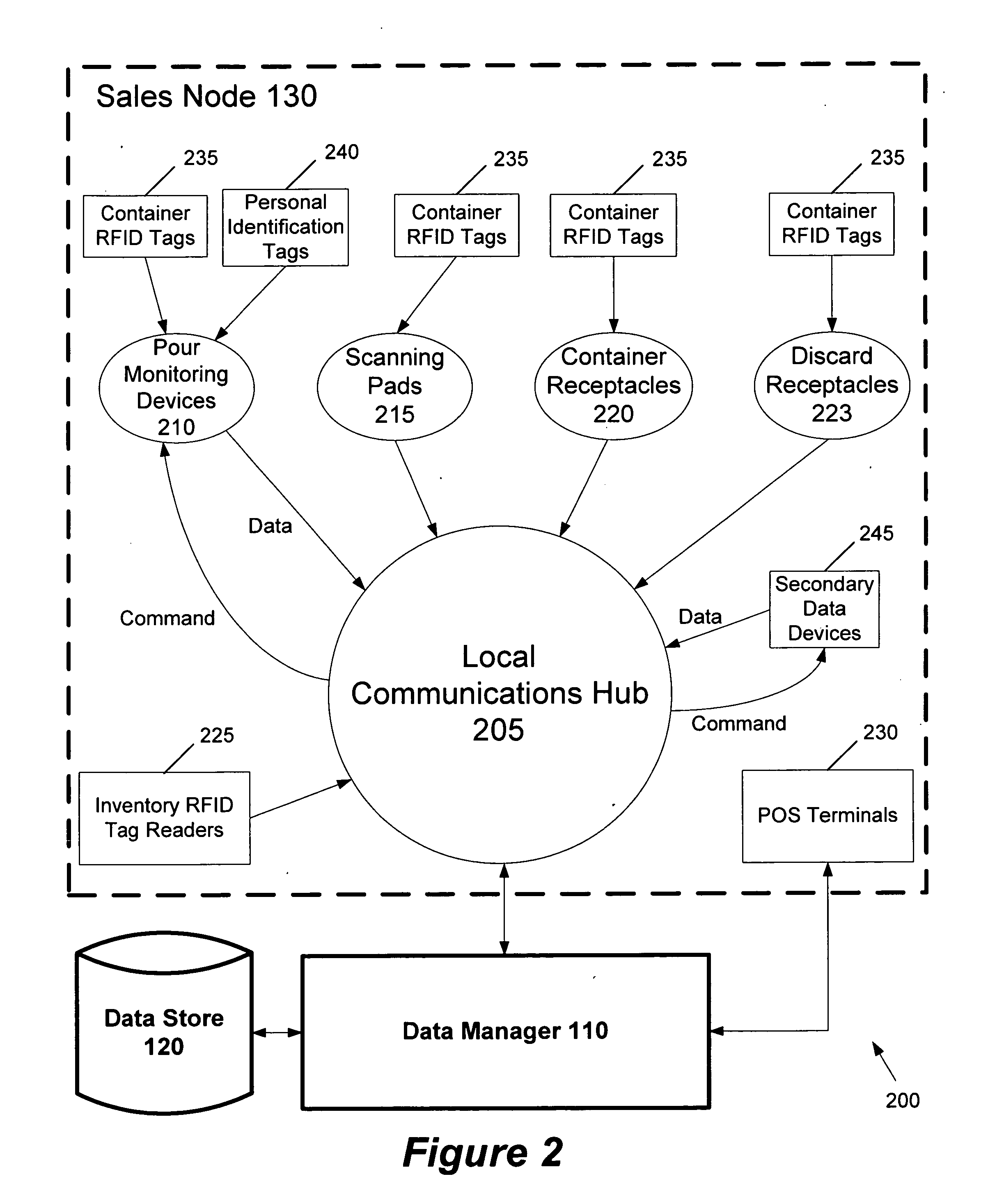
System for beverage dispensing and sales tracking
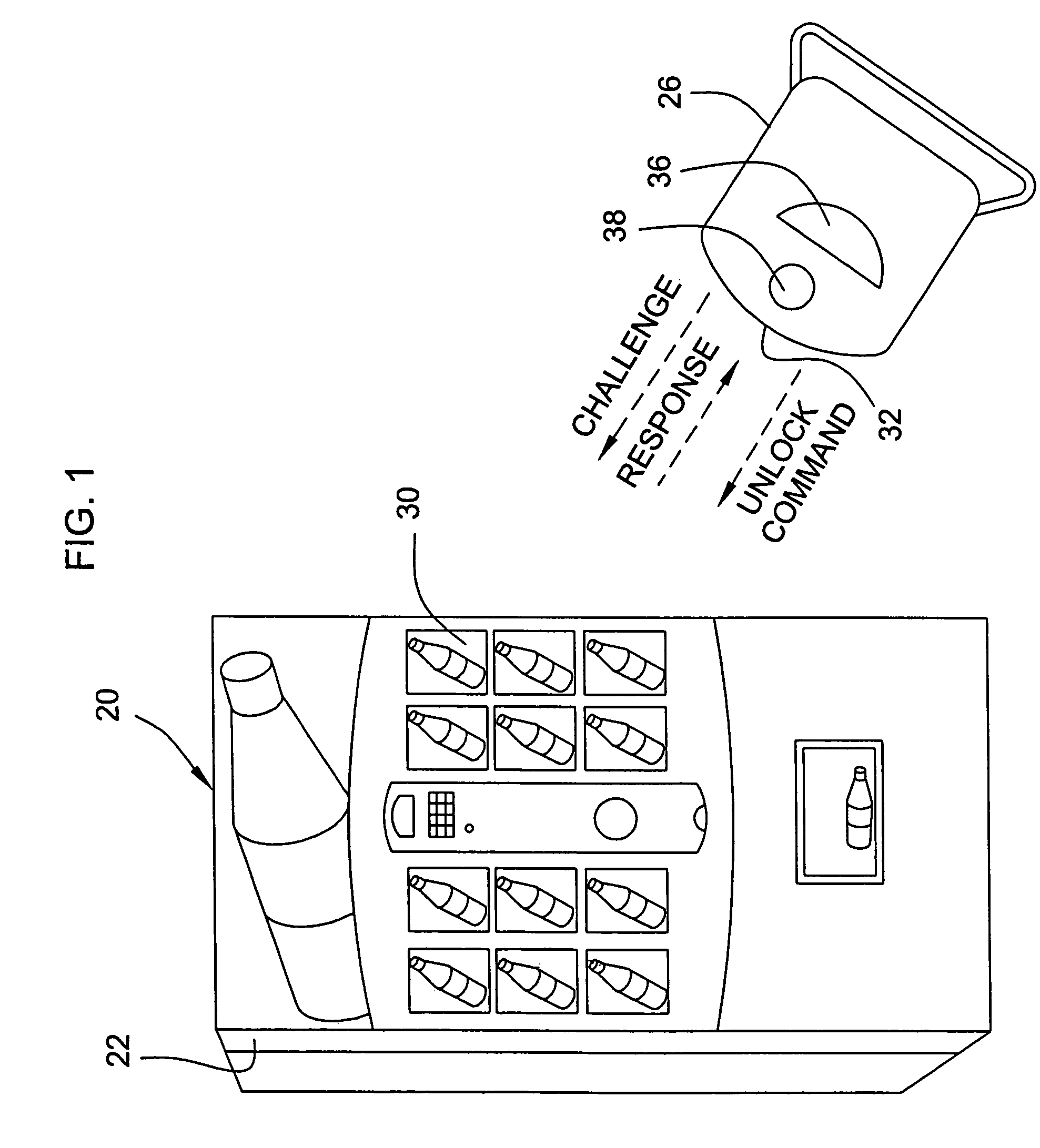
InactiveUS20070214055A1Minimizes inventoryOptimize cash flowHand manipulated computer devicesControlling coin-freed apparatusData managementData steward
Some embodiments provide a system for beverage dispensing and sales tracking. The system includes a data manager, a data store, and one or more sales nodes. In some embodiments, the data manager includes a point-of-sale server function. In some embodiments, the data manager obtains information from the sales nodes related to pouring of beverages, such as liquor. This information may include (1) who poured the drink, (2) where it was poured, (3) when it was poured, and (4) how much was poured. The data manager uses this information to maintain an accurate inventory of beverages and for billing beverage customers. The data manager stores and manipulates this information in the data store.
Owner:TEMKO SETH
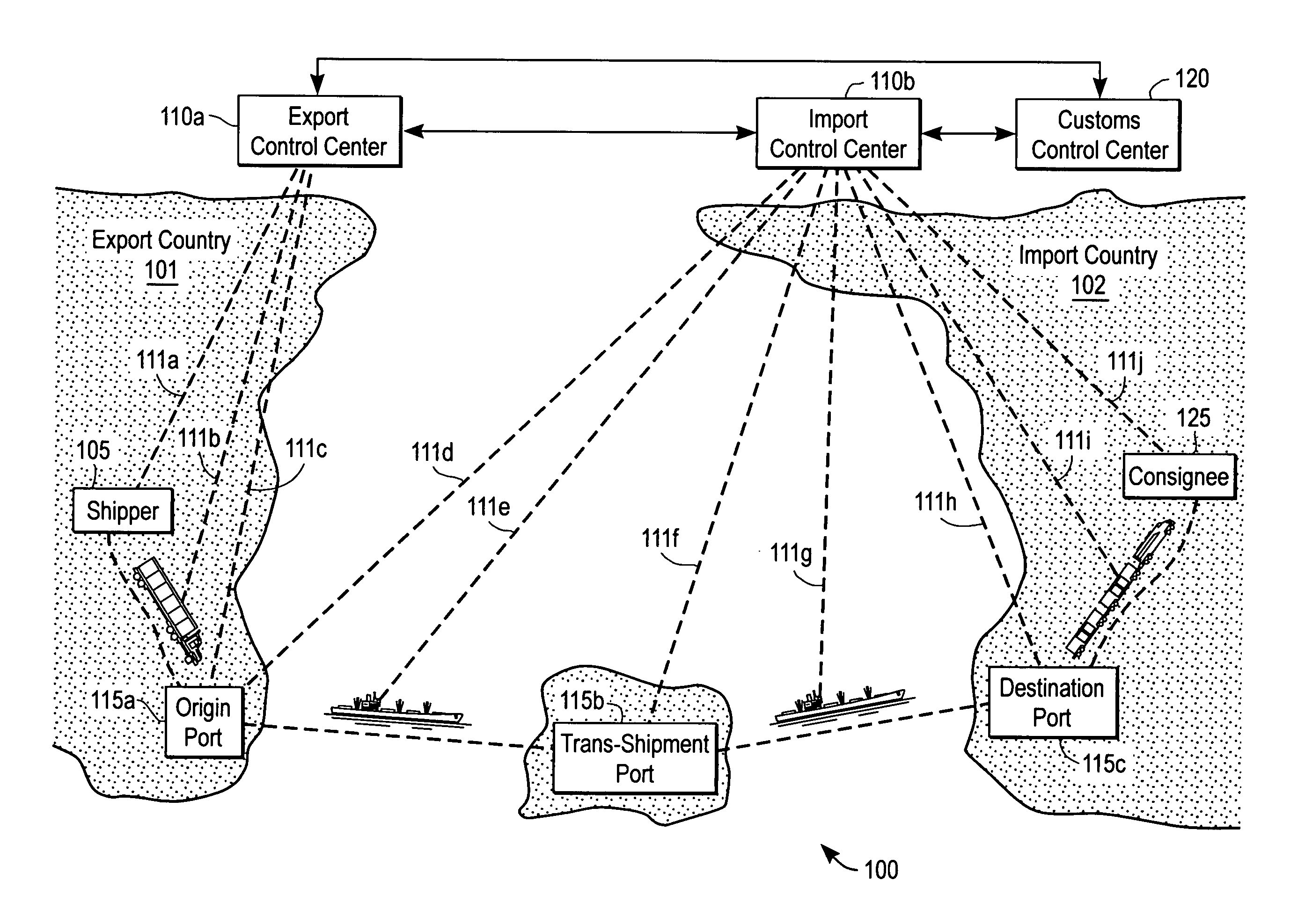
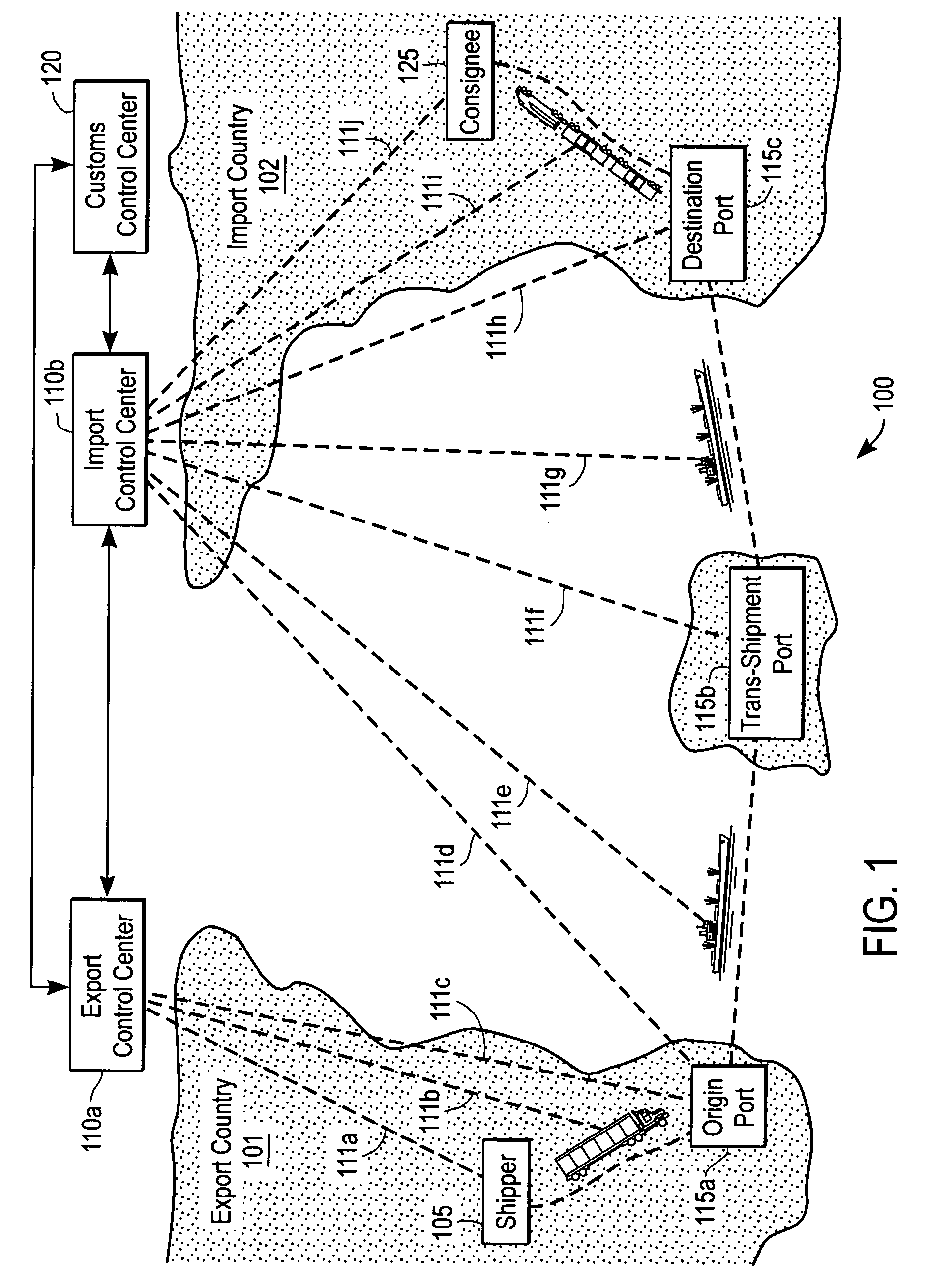
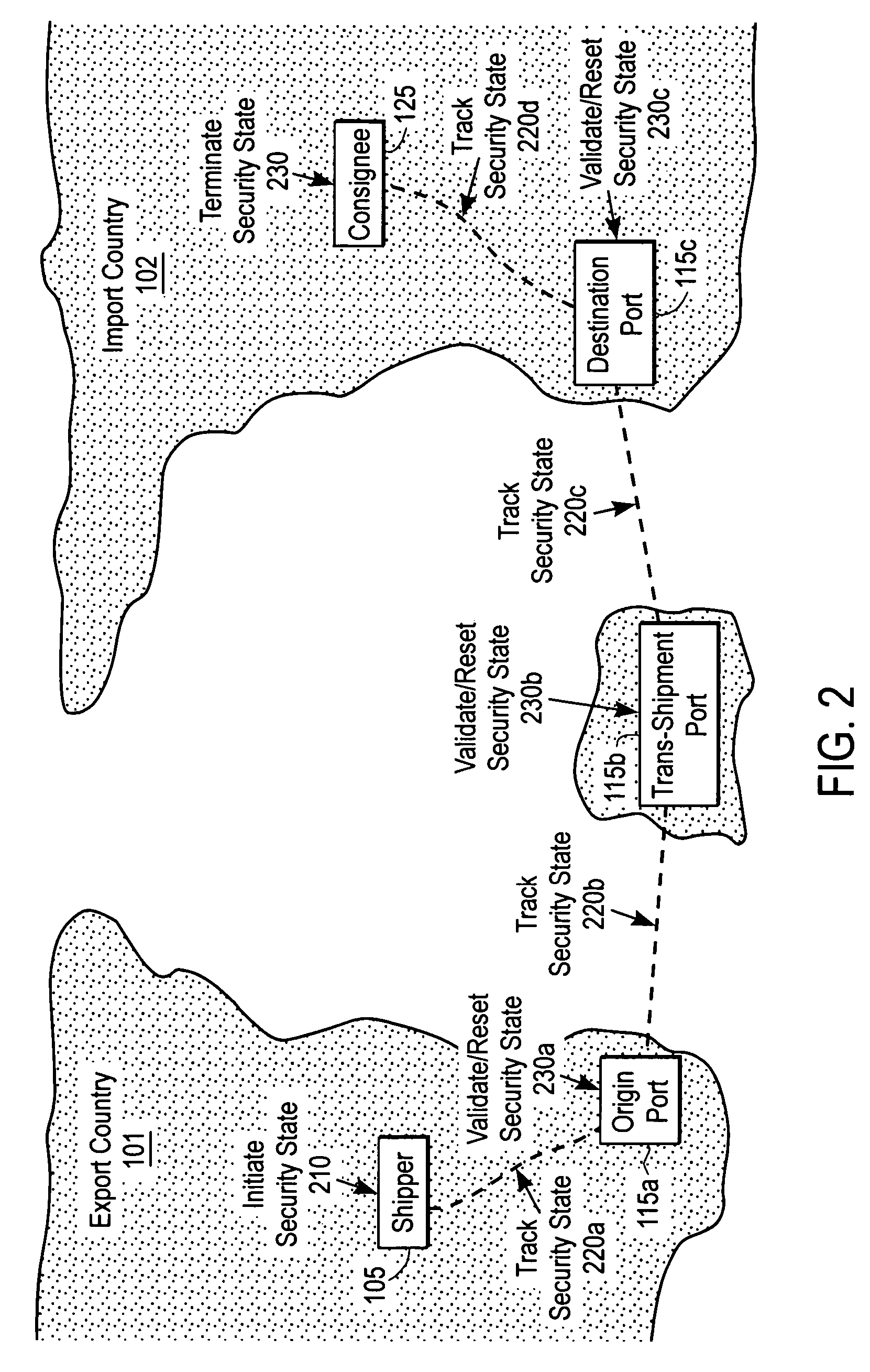
Continuous security state tracking for intermodal containers transported through a global supply chain
ActiveUS7129837B2Inhibitory activityReduce theftTicket-issuing apparatusCommerceSite managerData center
Owner:SAVI TECH INC
Security monitor for PDA attached telephone
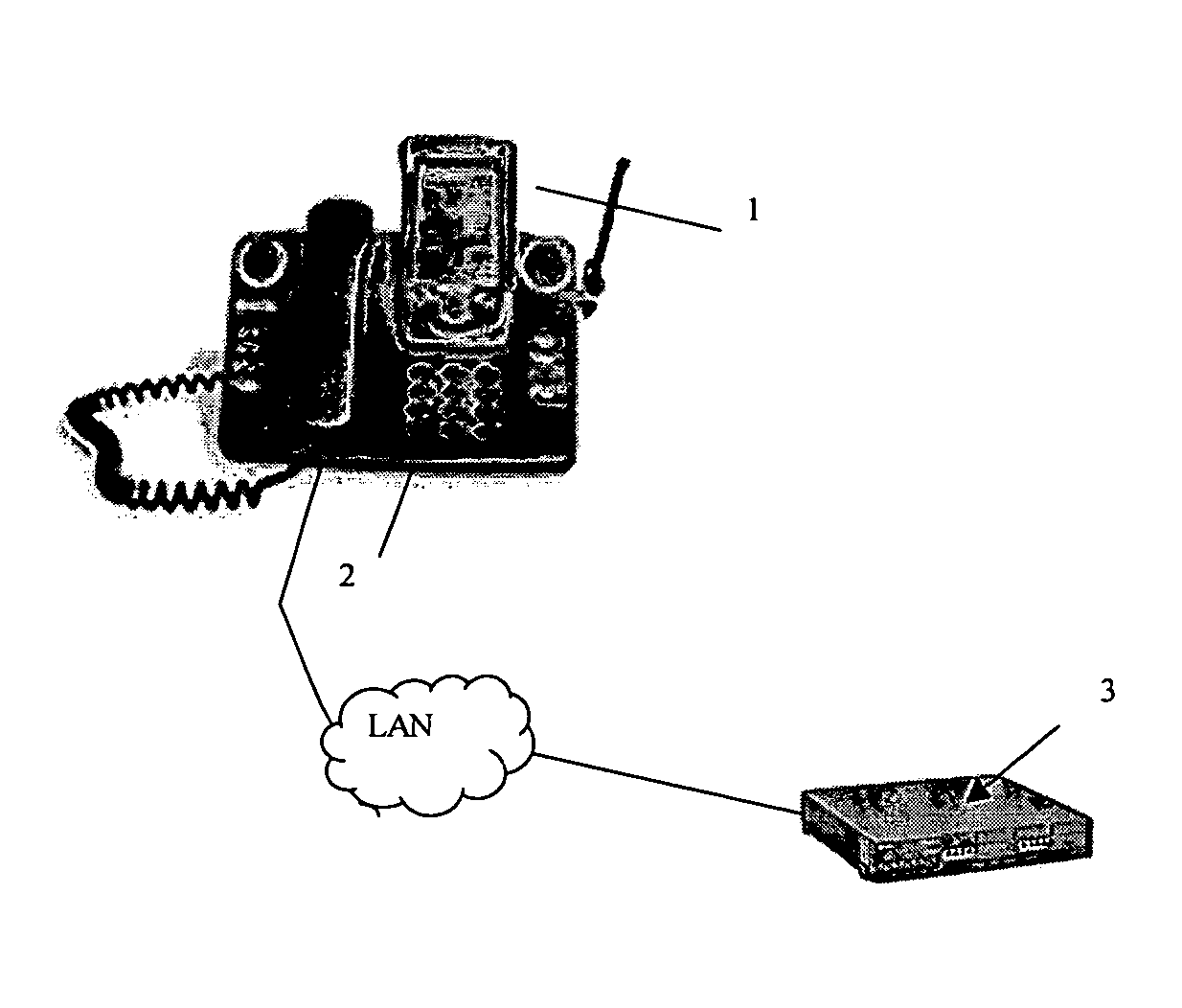
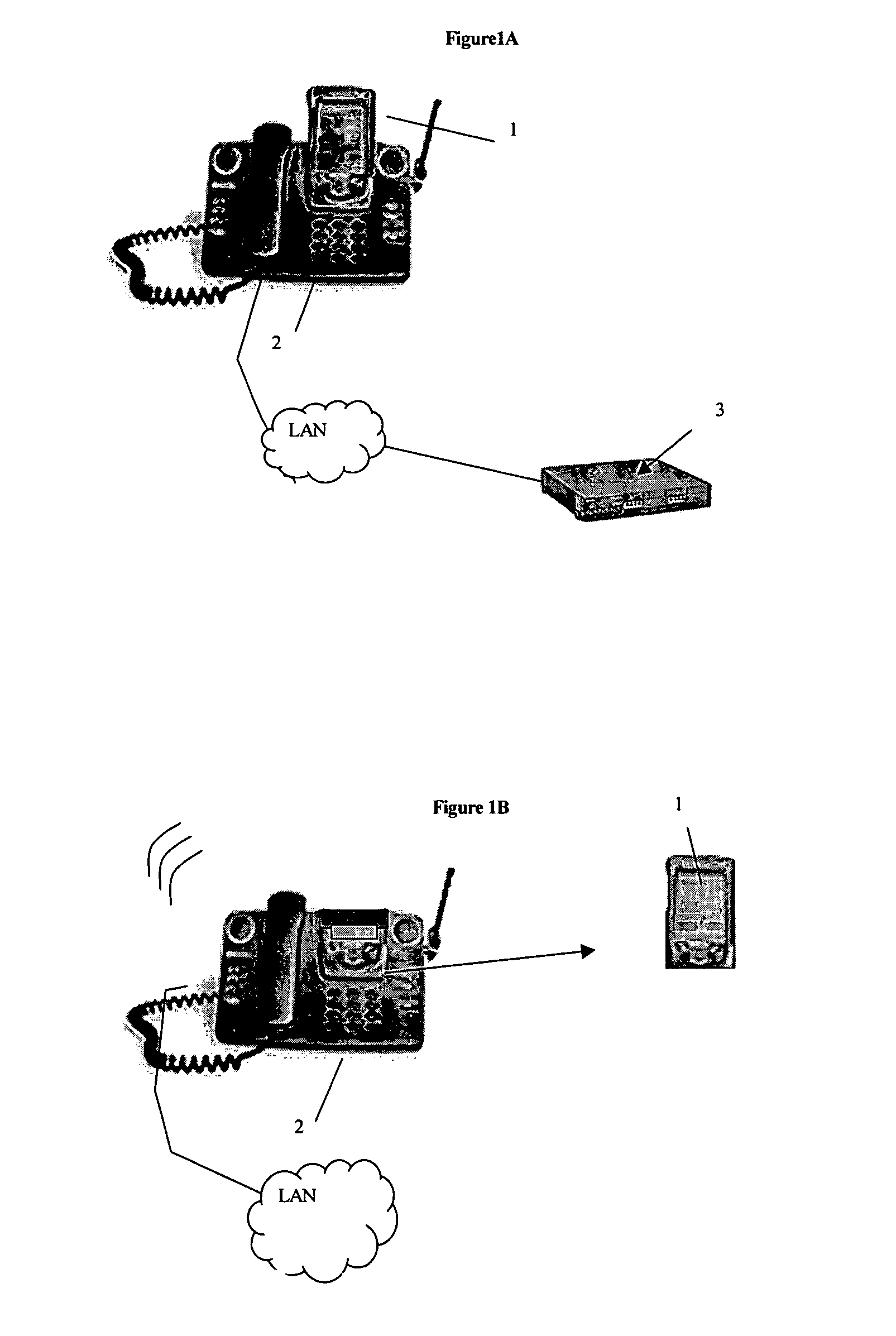
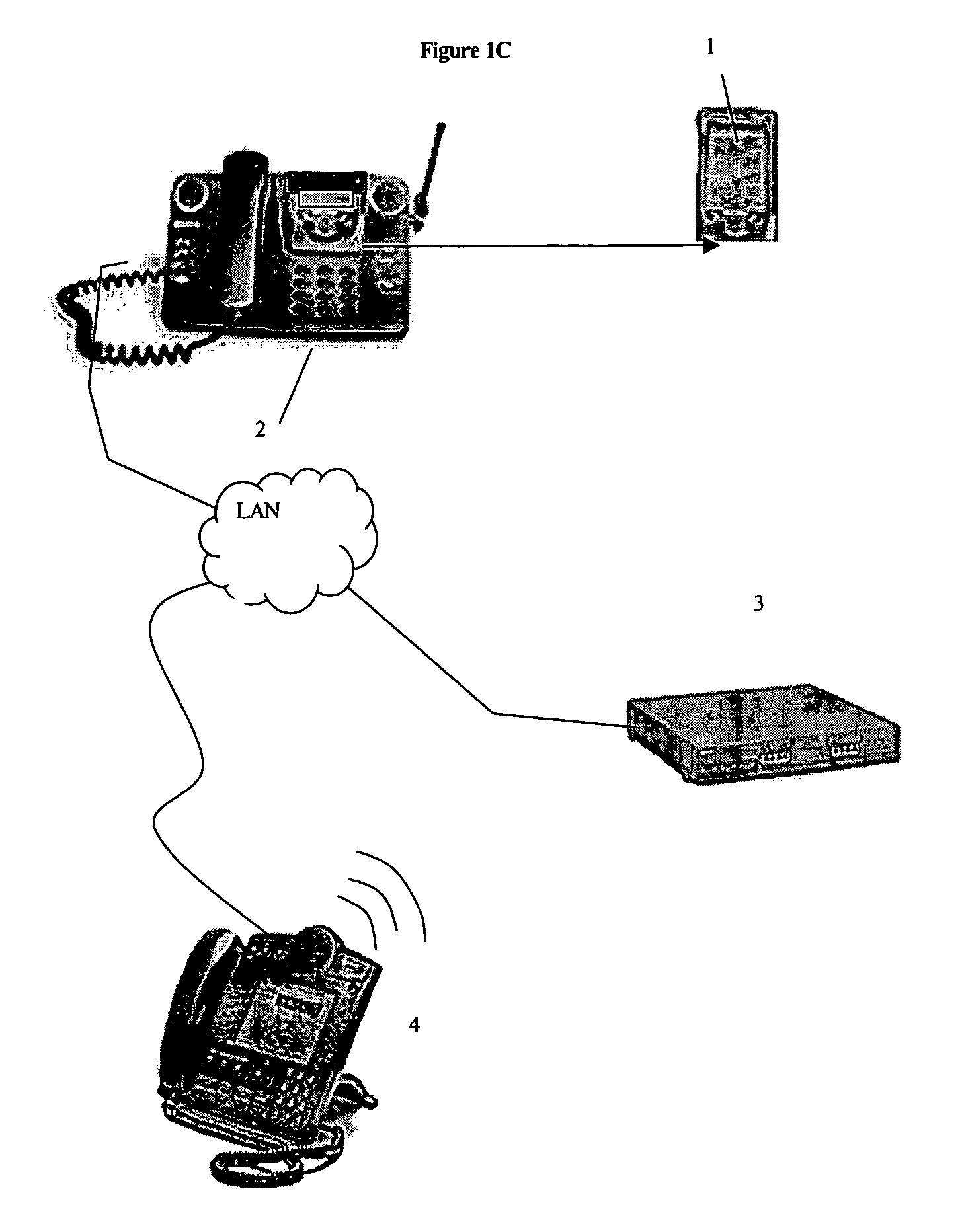
ActiveUS7356835B2Reduce theftSimple and safe processError detection/correctionVolume/mass flow measurementEmail addressPager
A user enabled application for monitoring the presence of a PDA connected to a network via a cradle and, in response, ringing a phone in the vicinity of the PDA. The display on the telephone displays a message that asks the user to enter an access code via the telephone dialpad. If the user enters the correct access code then nothing happens and the phone continues to work as normal. If, however, the correct access code is not entered, the system communicates the unauthorized removal of the PDA to pre-selected phone numbers, pager numbers or email addresses. Appropriate steps can then be taken to try to and recover the missing device.
Owner:MITEL
Mobile device controller application for any security system
InactiveUS8489065B2Easy to useReduce usageColor television detailsClosed circuit television systemsRemote controlTouchscreen
Owner:GREEN ROBERT M +1
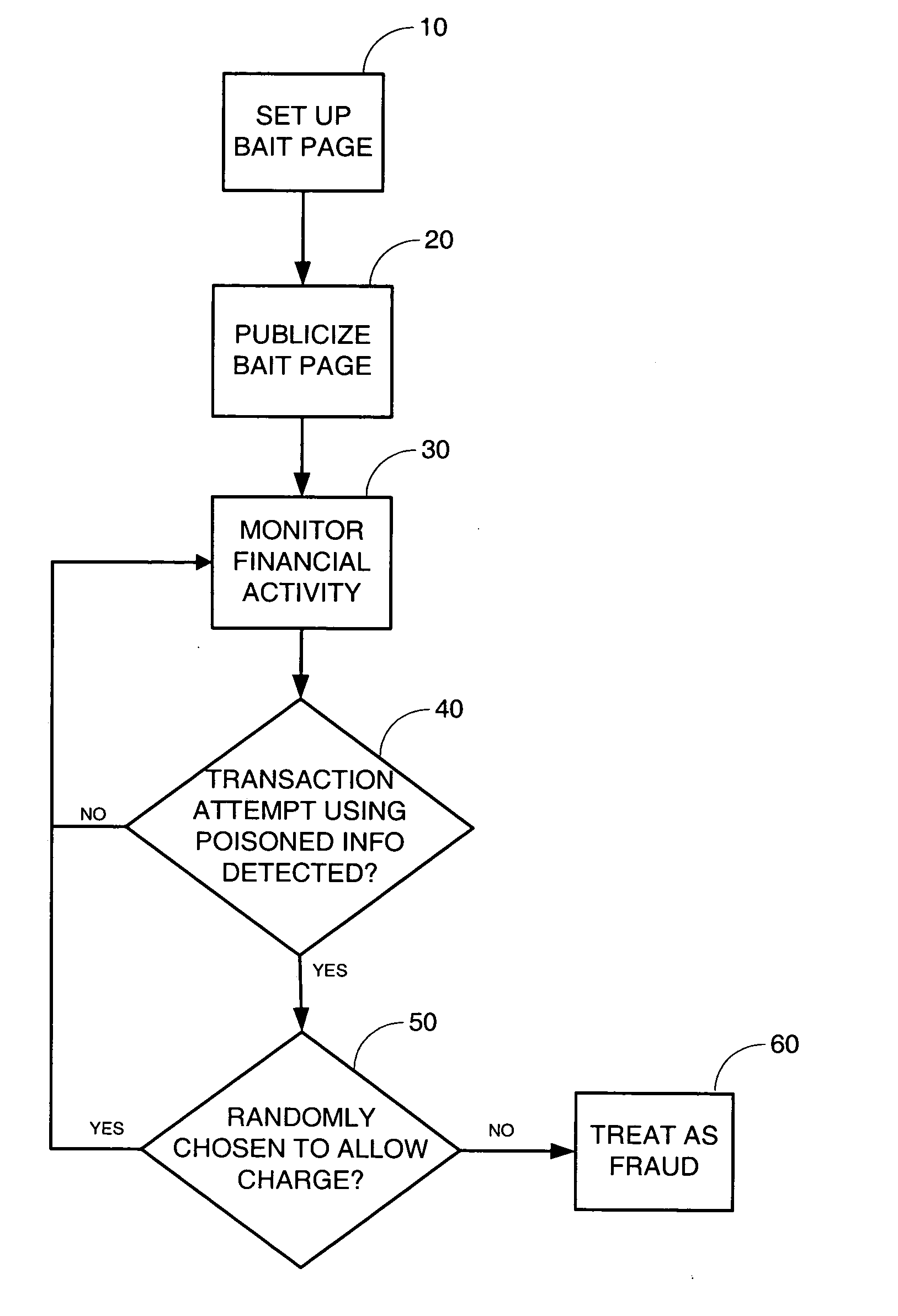
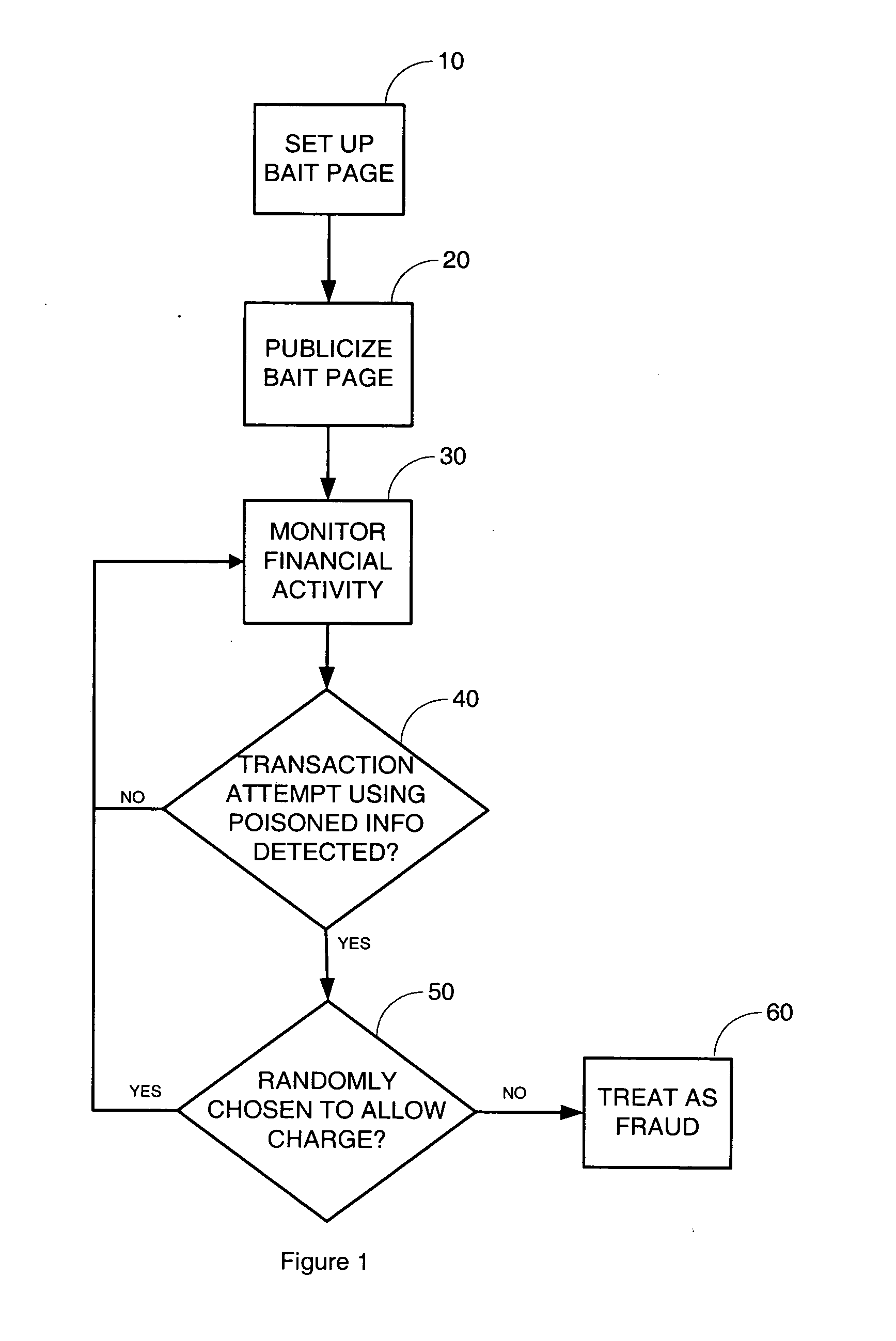
Deterrence of phishing and other identity theft frauds
Techniques are introduced for reducing internet phishing and identity theft and for helping to capture criminals who perpetrate such frauds. Invalid financial data for use in deterring fraud is generated and stored in an electronic database. The invalid financial data is made publicly accessible for use by individuals when approached with a suspicious attempt to obtain financial data. Financial transactions are monitored to detect any attempted use of the invalid financial data stored in the electronic database.
Owner:GALLANT STEPHEN I
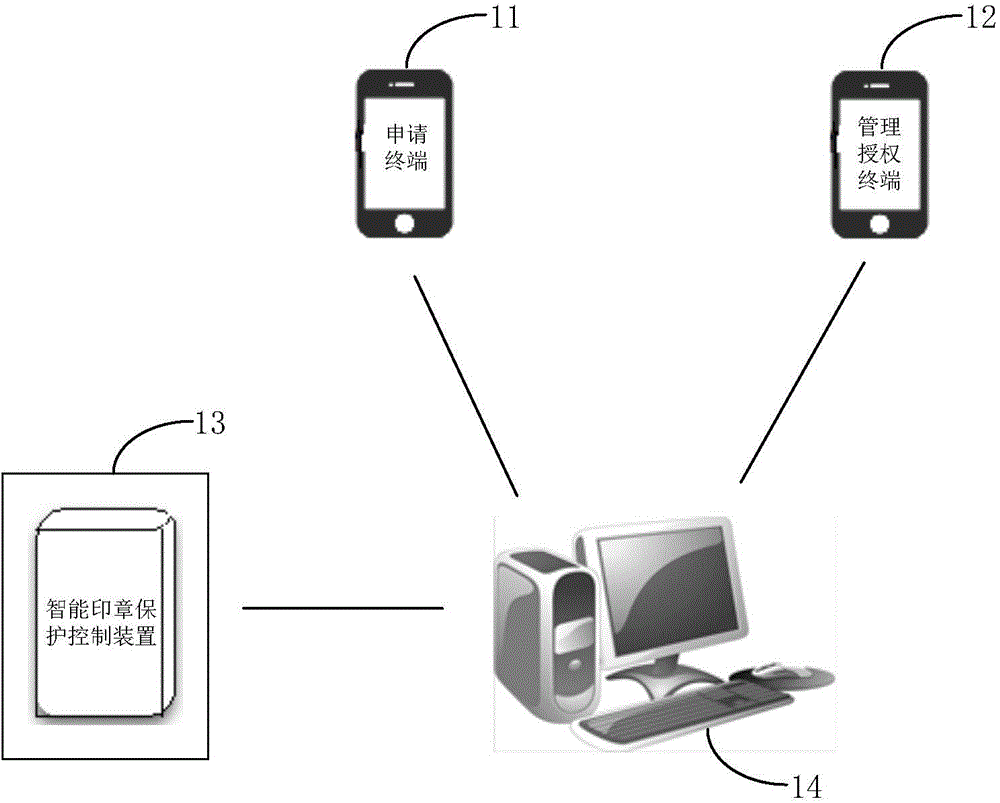
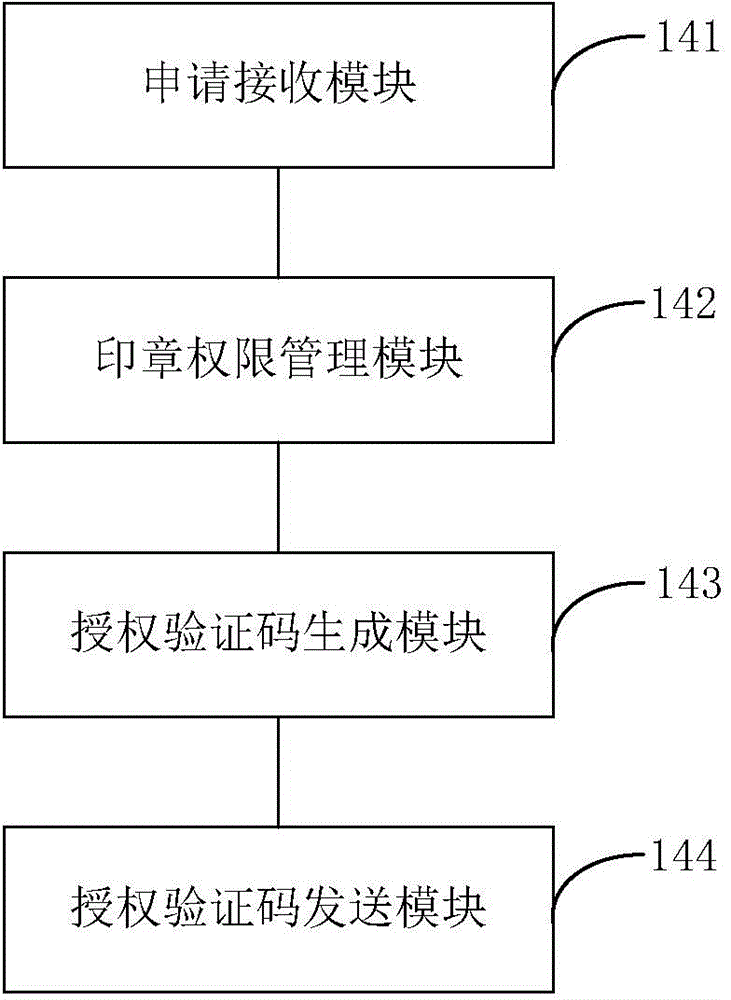
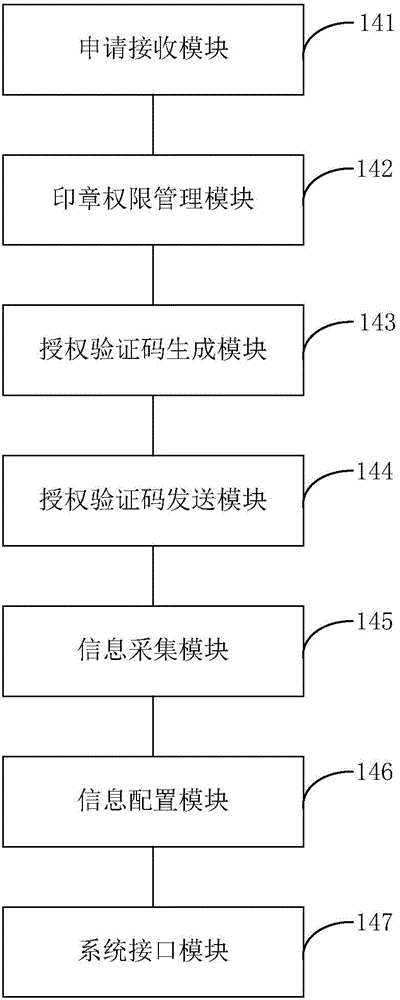
Intelligent stamp protection control device and stamp management system
ActiveCN104156809AReduce theftReduce riskProgramme controlComputer controlAuthorizationManagement system
The invention provides an intelligent stamp protection control device and a stamp management system, wherein the stamp management system includes a request terminal used for sending a stamp use request, a management authorization terminal used for approving stamp use authorization and the intelligent stamp protection control device used for affixing a stamp, wherein the request terminal, the management authorization terminal and the intelligent stamp protection control device are communicated with one another through a wireless network; all authority is set through the stamp management authorization terminal. A stamp management server is also provided for managing and maintaining the intelligent control device use system. The stamp management system provided by the invention provides the possibility of remote operation of stamp management through a network authorization and verification mode, thereby correctly tracking the position of a stamp and supervising, managing, authorizing and safely storing the stamp. The stamp management system also has the advantages of reducing use risks through warning means, simplifying the stamp approval procedure and improving the flexibility of stamp usage, thereby the flat officing needs of the information society and improving work efficiency.
Owner:北京智鉴科技有限责任公司
Vending machines with field-programmable locks
InactiveUS7821395B2Easy and inexpensiveReduce theft and fraudFrequency-division multiplex detailsDigital data processing detailsEngineeringHand held
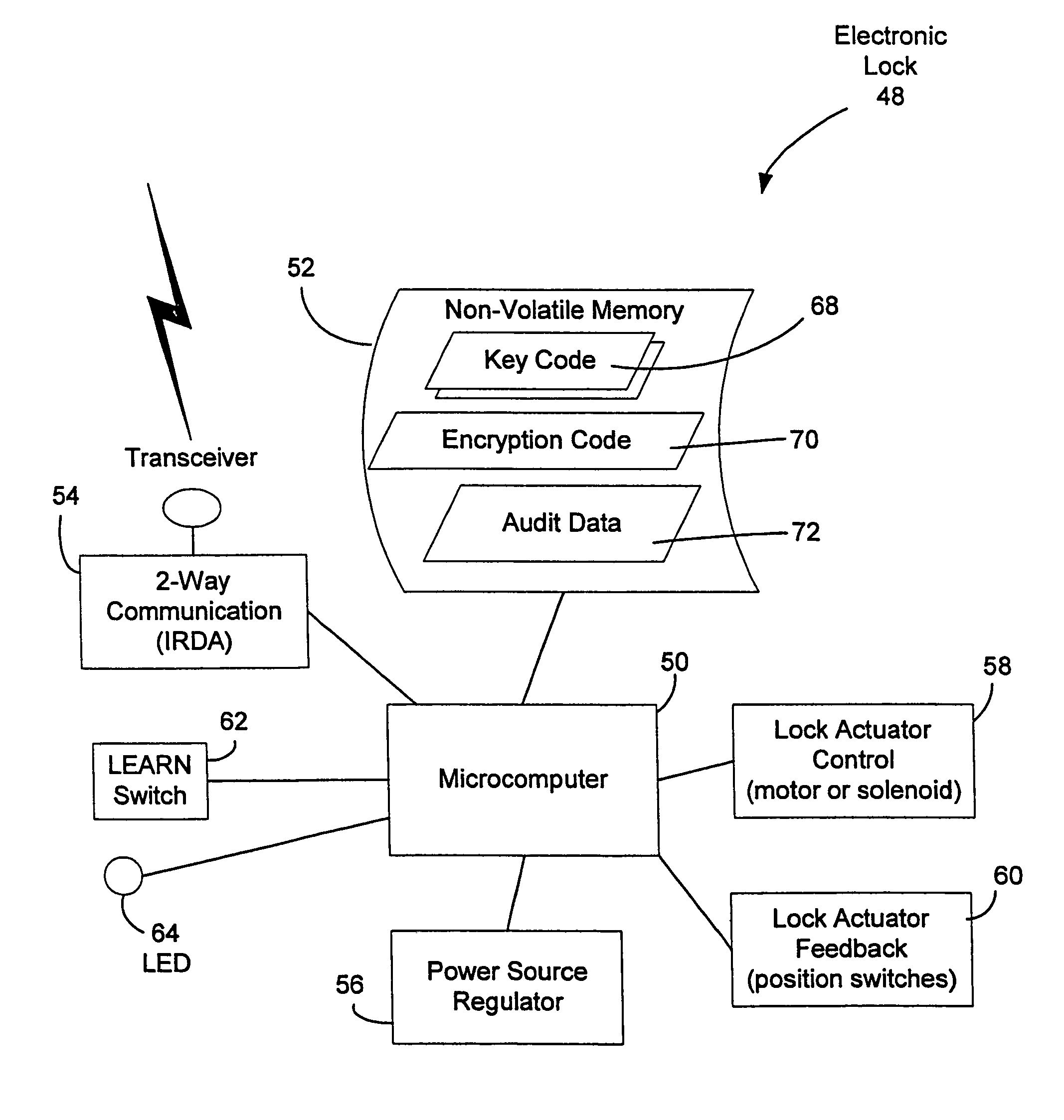
A vending machine uses a field-programmable electronic lock that learns a key code from a corresponding electronic key, a hand-held program unit, or an external computing device via wireless communications. In one mode, the electronic lock has a learning process activation device that is accessible only when the door of the vending machine is in the open position. In another mode, the electronic lock is programmed in the field without first opening the vending machine. A program command and access control data including a new access code are transmitted wirelessly from a hand-held program unit or the like. Alternatively, an external computing device is used to program the electronic lock via long-range wireless communications, and an electronic key is then used to open the electronic lock to physically access the vending machine.
Owner:MICRO ENHANCED TECH
Method and apparatus for tracking the relative value of medical services
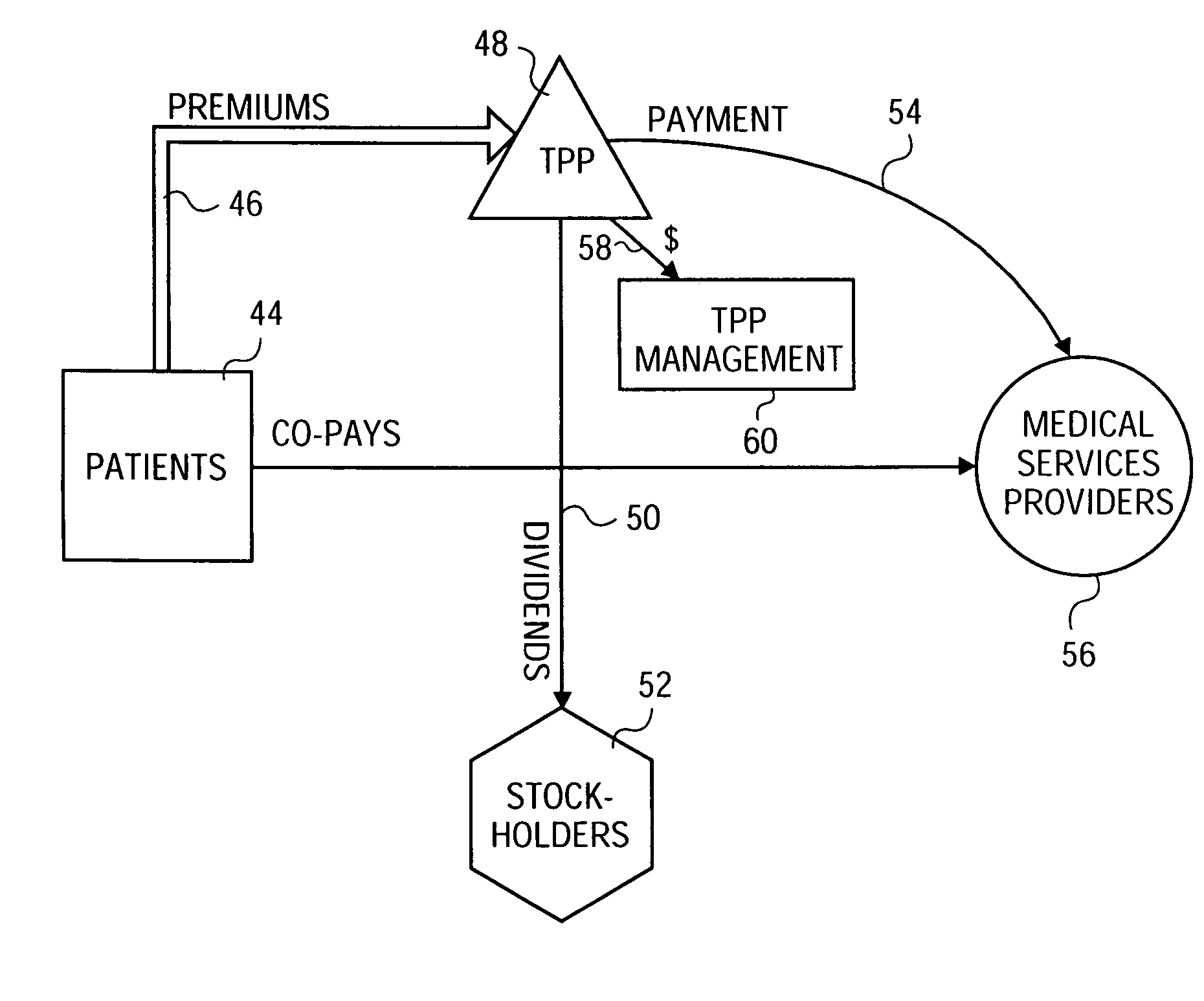
ActiveUS7702522B1Raise the possibilityMaximize profitabilityFinanceBilling/invoicingThird partyRelevant information
Methods and apparatus for tracking and evaluating the relative value, such as the net present value, of medical services provided to patients associated with third party payors (“TPPs”). Under various embodiments of the present invention, the relative value of medical services is considered in evaluating whether to enter into an agreement with a TPP, whether to accept a new patient, when and for how long to schedule a patient appointment, and how long a physician should meet with the patient. Methods and apparatus for improving the efficiency of a medical office are also disclosed whereby a physician may more effectively supply a patient with relevant information and provide prescriptions, record billing information, order supplies, and collect payment for services provided. Methods and apparatus for improving security within a medical office and reducing employee fraud are also disclosed.
Owner:SHOLEM STEVEN L
User interface for a resistance training device and method of use
InactiveUS7510508B2Easy to trackReduce trainingPhysical therapies and activitiesClubsResistance trainingUser interface
A system, method, and device for recording and tracking resistance training parameters in connection with a resistance training workout. A specially configured portable recording device has a very compact user interface having an input device with very few inputs. A user may record resistance training parameters directly on the recording device both quickly and easily with few and simple keystrokes, resulting in an improved recording process. A personal trainer or strength coach may track the workouts of multiple exercisers with increased convenience. In a particularly preferred embodiment, the recording device is provided in the body of a sport watch.
Owner:SANTOMASSIMO ROD N +1
System for using an authorization token to separate authentication and authorization services
ActiveUS20080127317A1Reduce chanceReduce theftDigital data processing detailsUser identity/authority verificationAuthorization certificateAuthentication server
A novel system for utilizing an authorization token to separate authentication and authorization services. The system authenticates a client to an authenticating server; generates an authorization token with the authenticating server and the client; and authorizes services for the client using the generated authorization token.
Owner:FUTUREWEI TECH INC
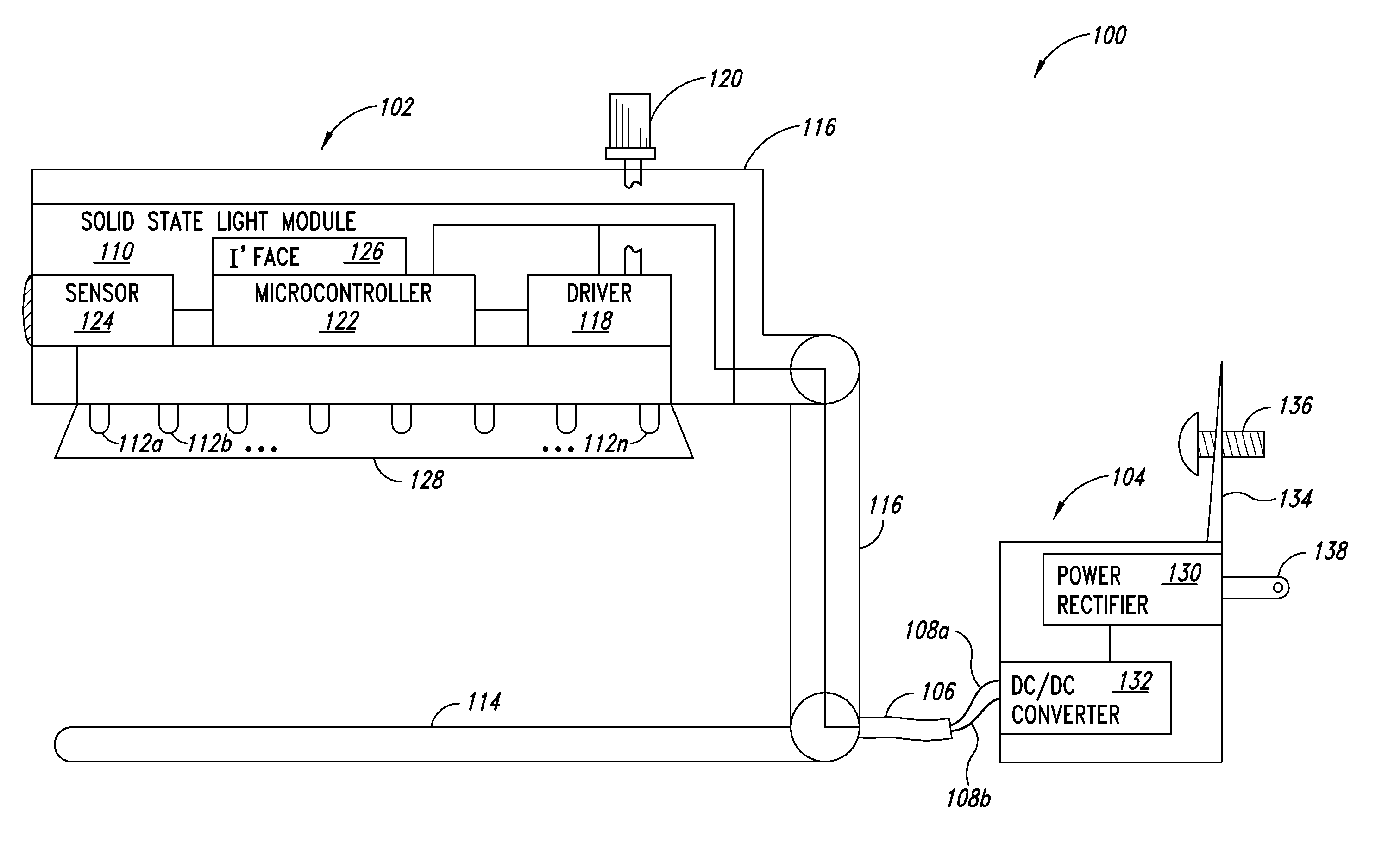
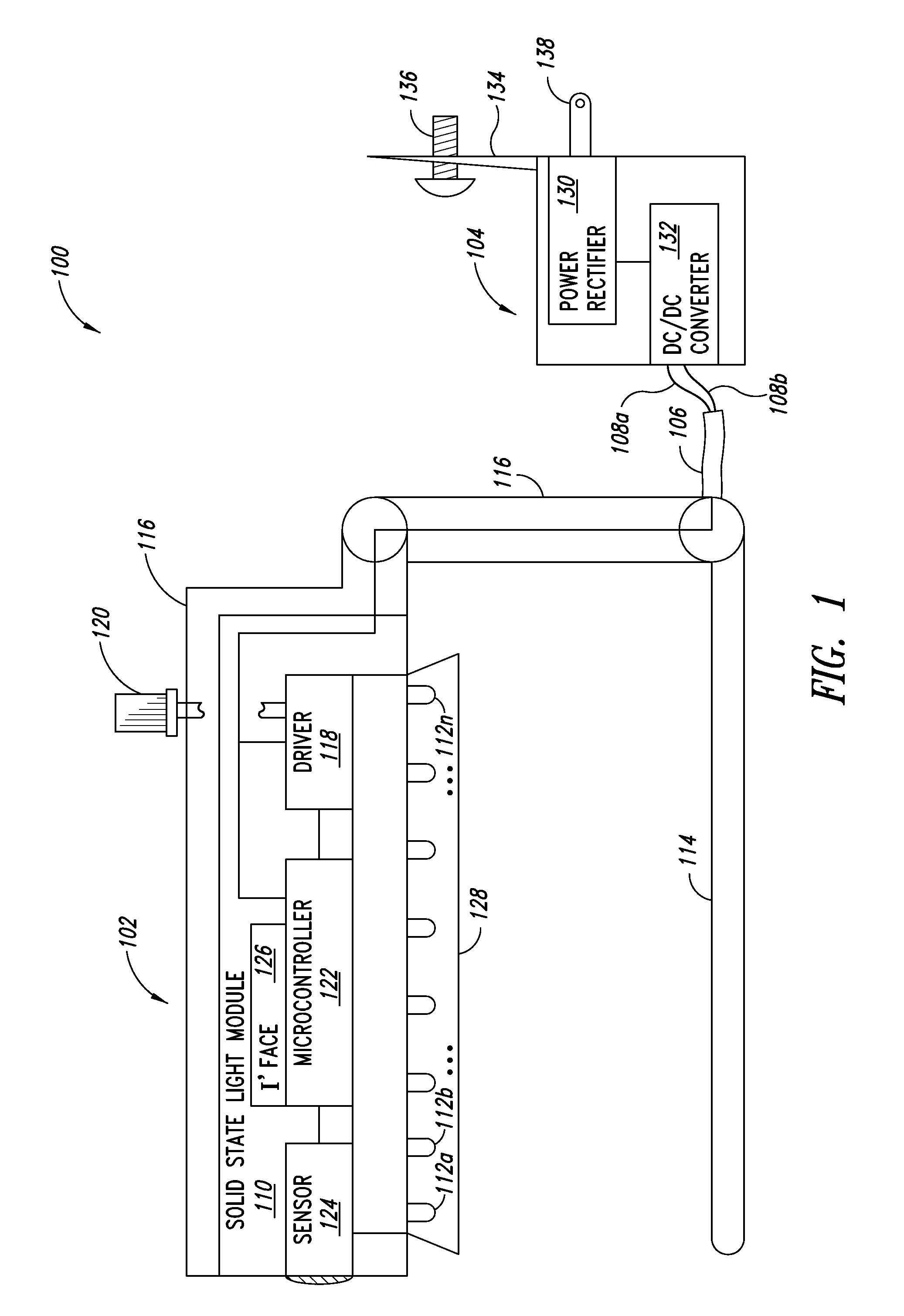
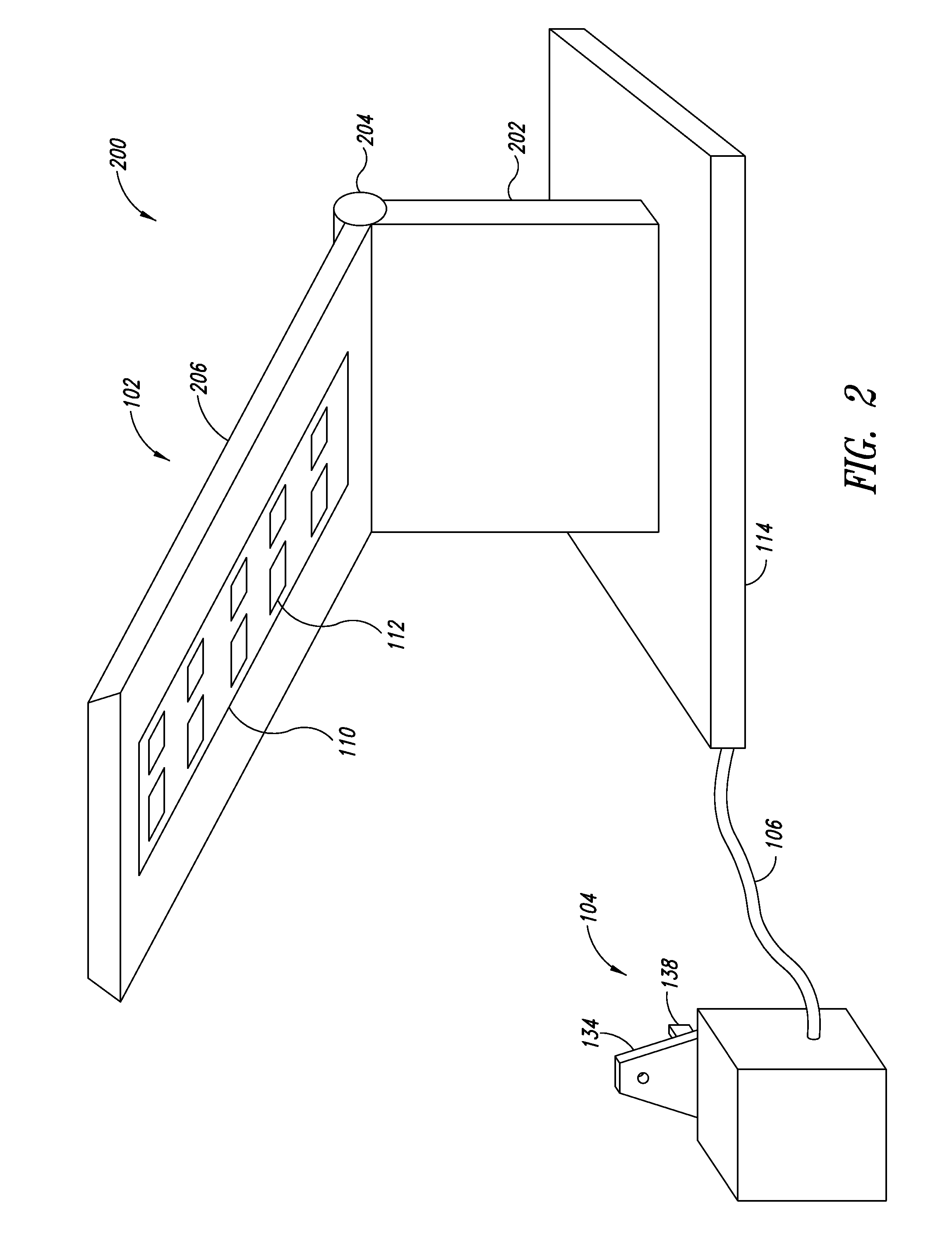
Solid state hospitality lamp
InactiveUS20140055990A1Reduce energy costsLow costNon-electric lightingPoint-like light sourceLight equipmentEngineering
A luminaire includes one or more solid state light modules, each having one or more theft deterrent features. Each of the one or more solid state light modules can include a number of solid state light sources. The one or more solid state light modules can be physically and electrically coupled to the luminaire such that any attempt to remove the solid state light module renders the solid state light module or the solid state light sources permanently inoperable. One or more theft deterrent features may be incorporated into the luminaire to deter theft. In one instance an external power converter supplying the solid state light module can be physically secured to a power source using one or more security mechanisms.
Owner:EXPRESS IMAGING SYST
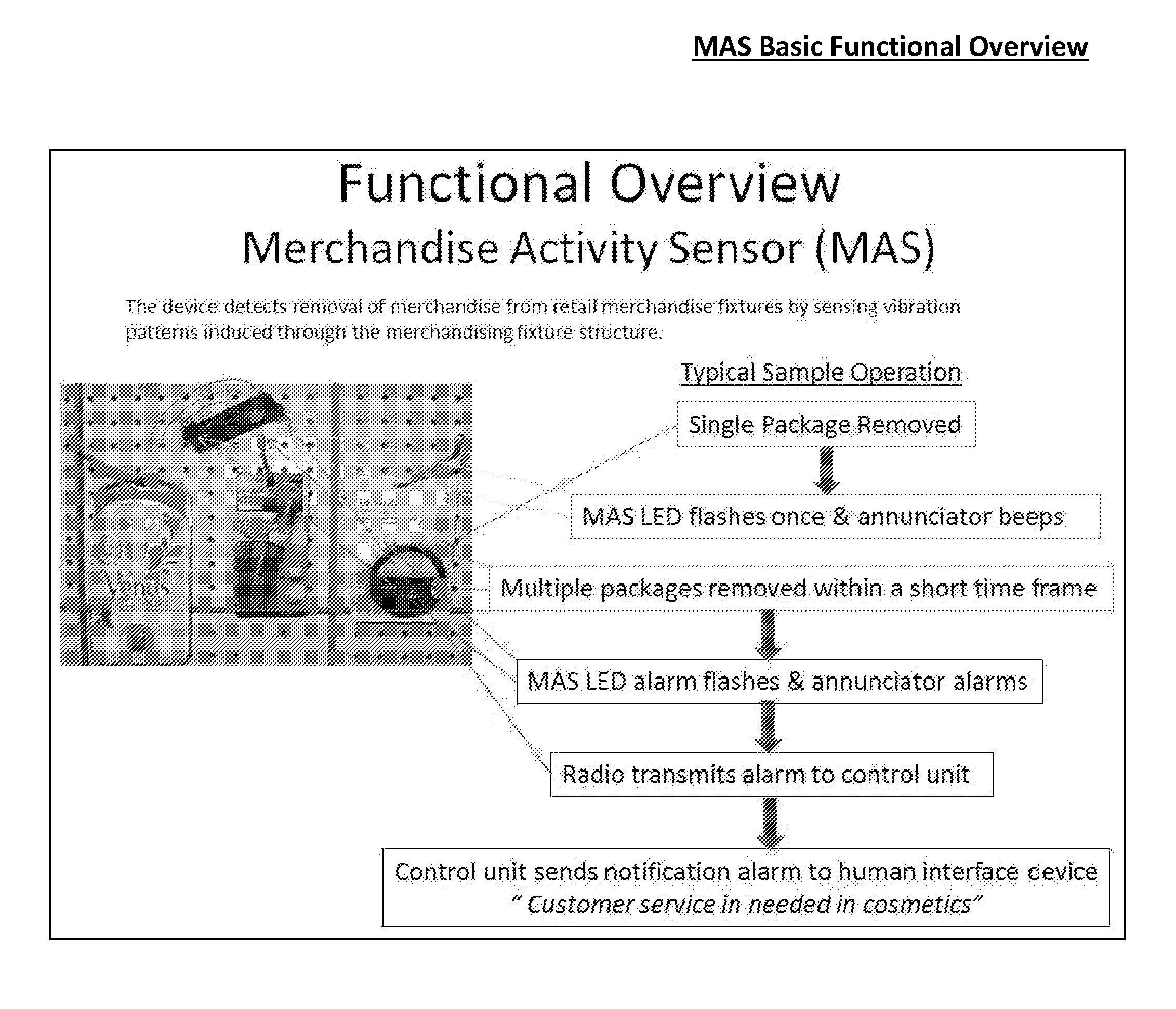
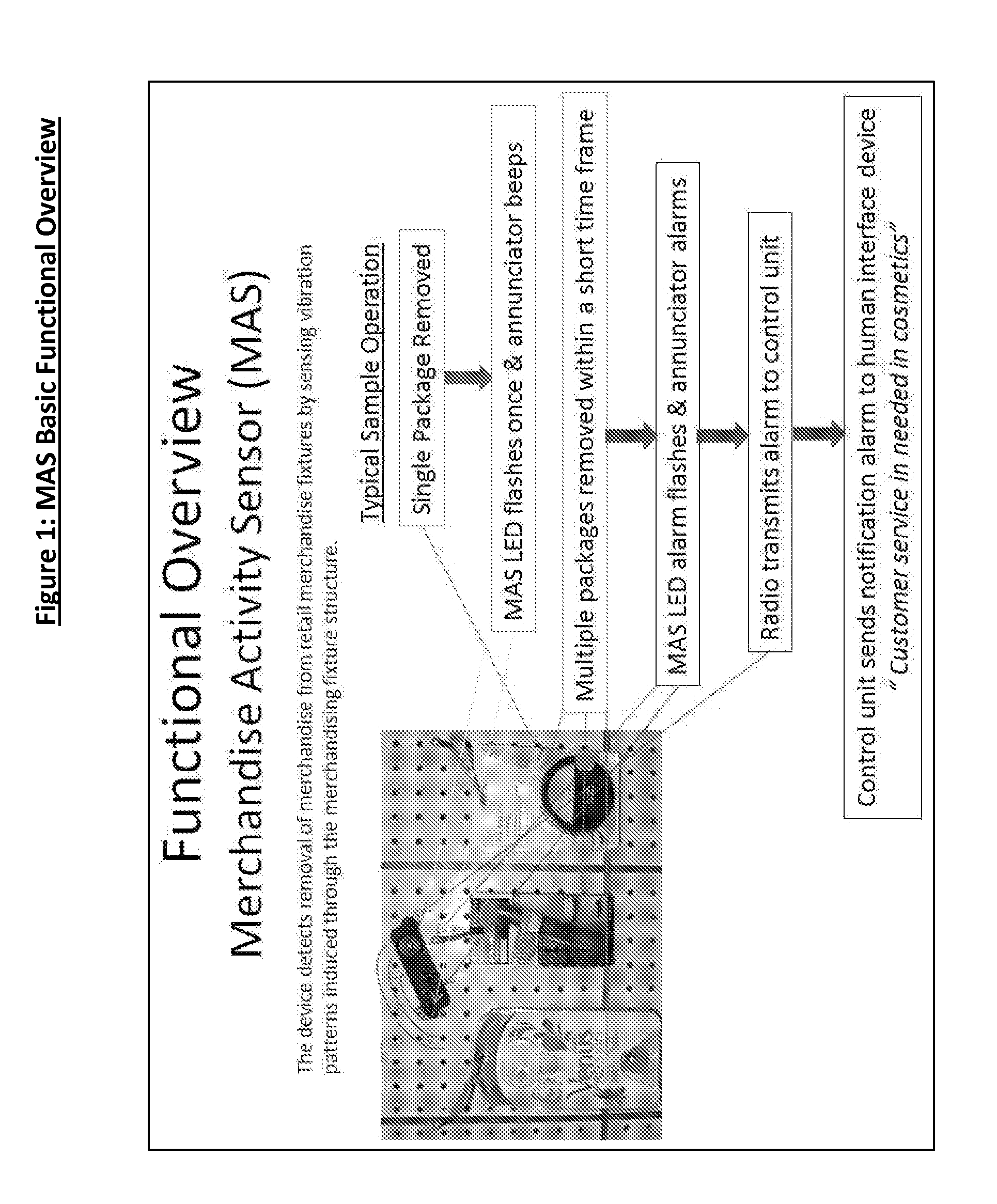
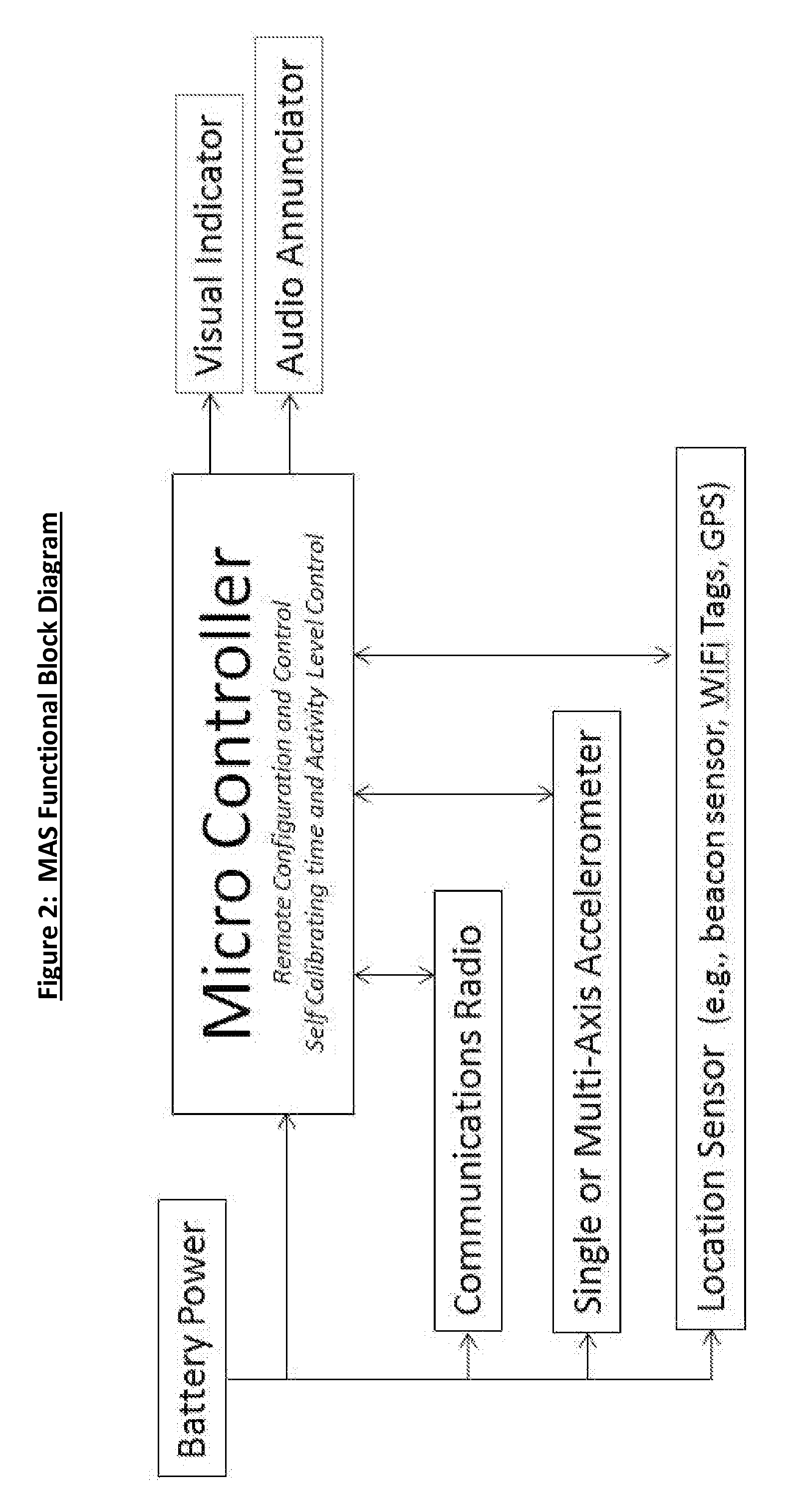
Merchandise Activity Sensor System and Methods of Using Same
ActiveUS20160086460A1Distinctive vibration signatureSimple installationOffice automationBuying/selling/leasing transactionsAnalysis dataEngineering
Apparatus and systems using merchandise activity sensors for increasing the awareness of interactivity with merchandise on retail store displays (shelves, peg hooks, merchandise pushers, and other Point of Purchase displays) in order to facilitate more effective customer service, reduce theft and to provide additional analysis data related to merchandise / shopper interaction.
Owner:INDYME SOLUTIONS LLC
System and method for providing controlled access
InactiveUS20090119698A1User privacy is enhancedAvoid the needProgramme controlElectric signal transmission systemsComputer hardwareWireless transmission
A method for operating a signal receiver which authorizes controlled access, comprising providing an authentication token device having a predetermined usage limit stored therein, providing a reading device for reading the authentication token device, and for implementing the predetermined usage limit while deauthorizing the authentication token device for use with other reading devices, comprising a signal generator for communicating with a signal receiver through a wireless transmission, receiving the wireless transmission at the signal receiver, to permit access based on the received transmission, and upon exceeding the predetermined usage limit, deauthorizing further access.
Owner:EXCEPTIONAL INNOVATION INC
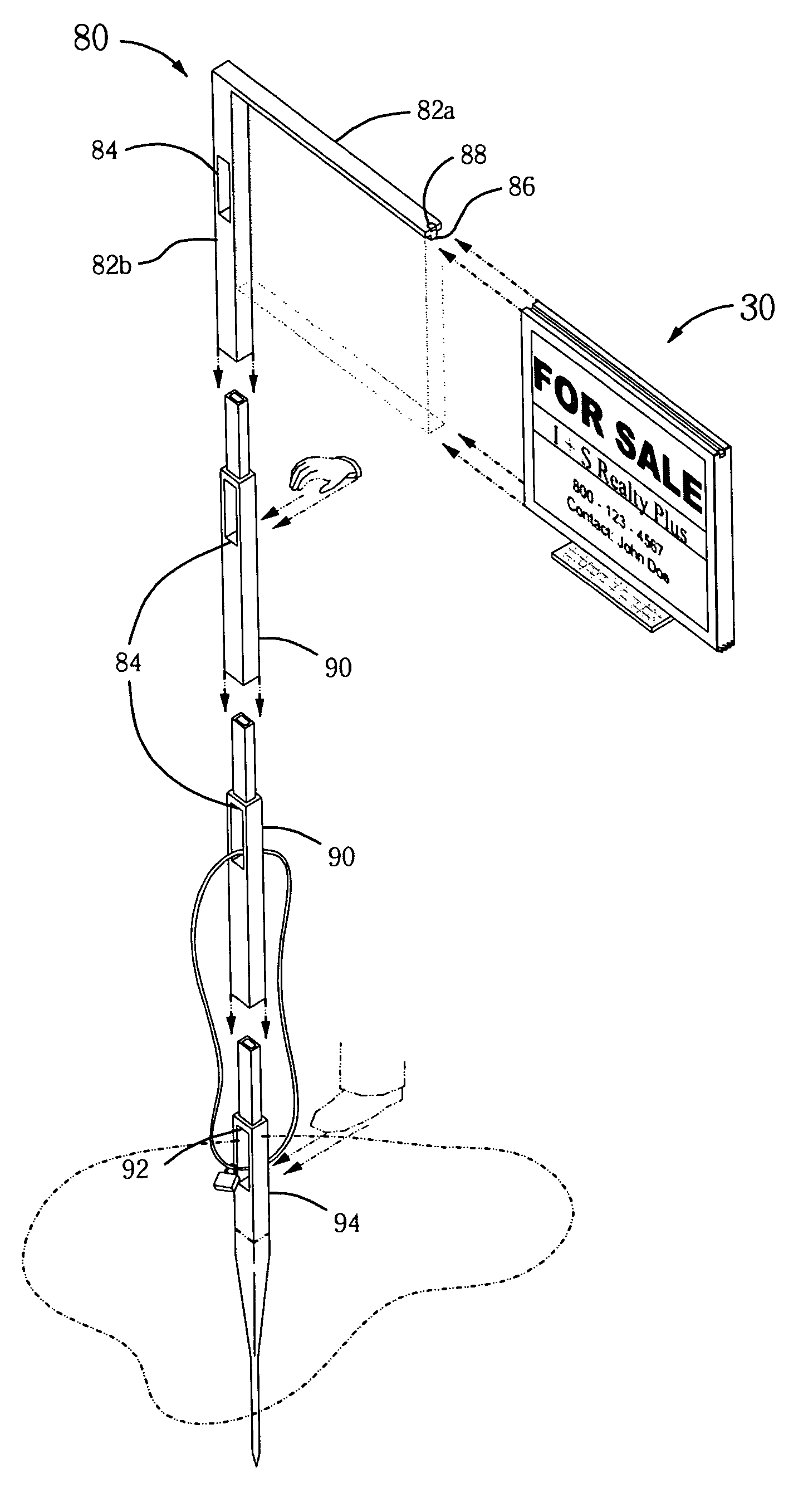
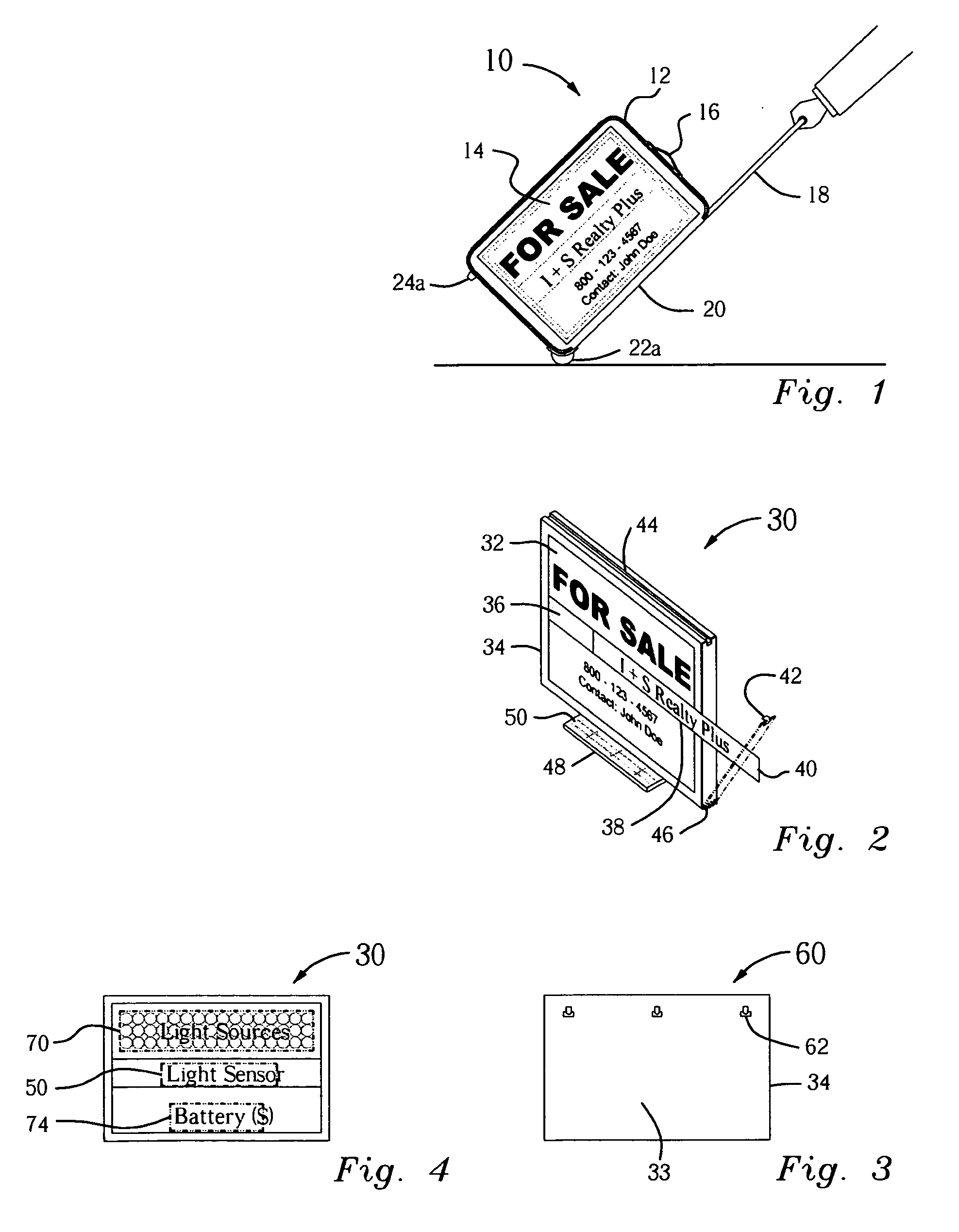
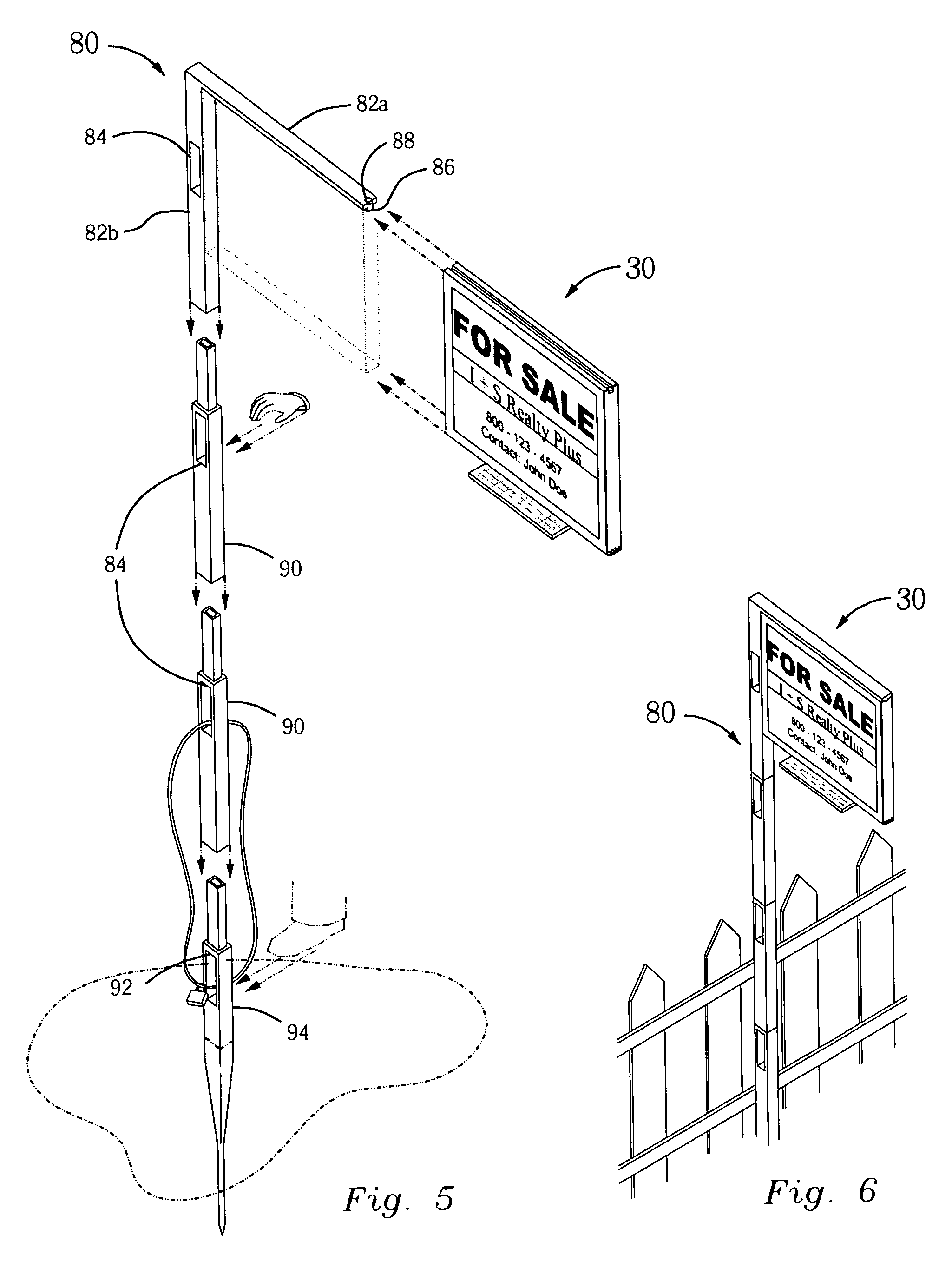
Portable illuminated real estate sign system
InactiveUS20060185203A1Easy to carry and assemble and installReduced vulnerability to and theftAdvertisingIlluminated signsAnti theftLight source
The portable illuminated real estate sign system consists of a carrying case, a sign, and a post. This solar powered illuminated sign is attached to a detachable post that has an anti-theft device. An accompanying bag is used for ease of transport and storage. The sign can be single- or double-sided, having a weatherproof casing, a plastic transparent front and back, and a hinged door to allow signage to be easily changed. Within the sign casing is a solar panel that collects solar energy to charge at least one rechargeable battery, energizing light sources to be turned on by a light sensor from dusk till dawn.
Owner:BITTLE IVY RENE +1
Devices and Methods Useful for Authorizing Purchases Associated with a Vehicle
InactiveUS20090045978A1Easy to installStrong adhesionDetection of traffic movementBuying/selling/leasing transactionsEngineeringEmbedded system
Disclosed are various devices useful as components of a system for authorizing purchases associated with a vehicle that are generally simple to install, operate and maintain and are generally resistant to abuse. Devices disclosed include theft-resistant vehicular identification tags, sealed identification tag reader and variable range tag-readers.
Owner:GASNGO R&D LTD
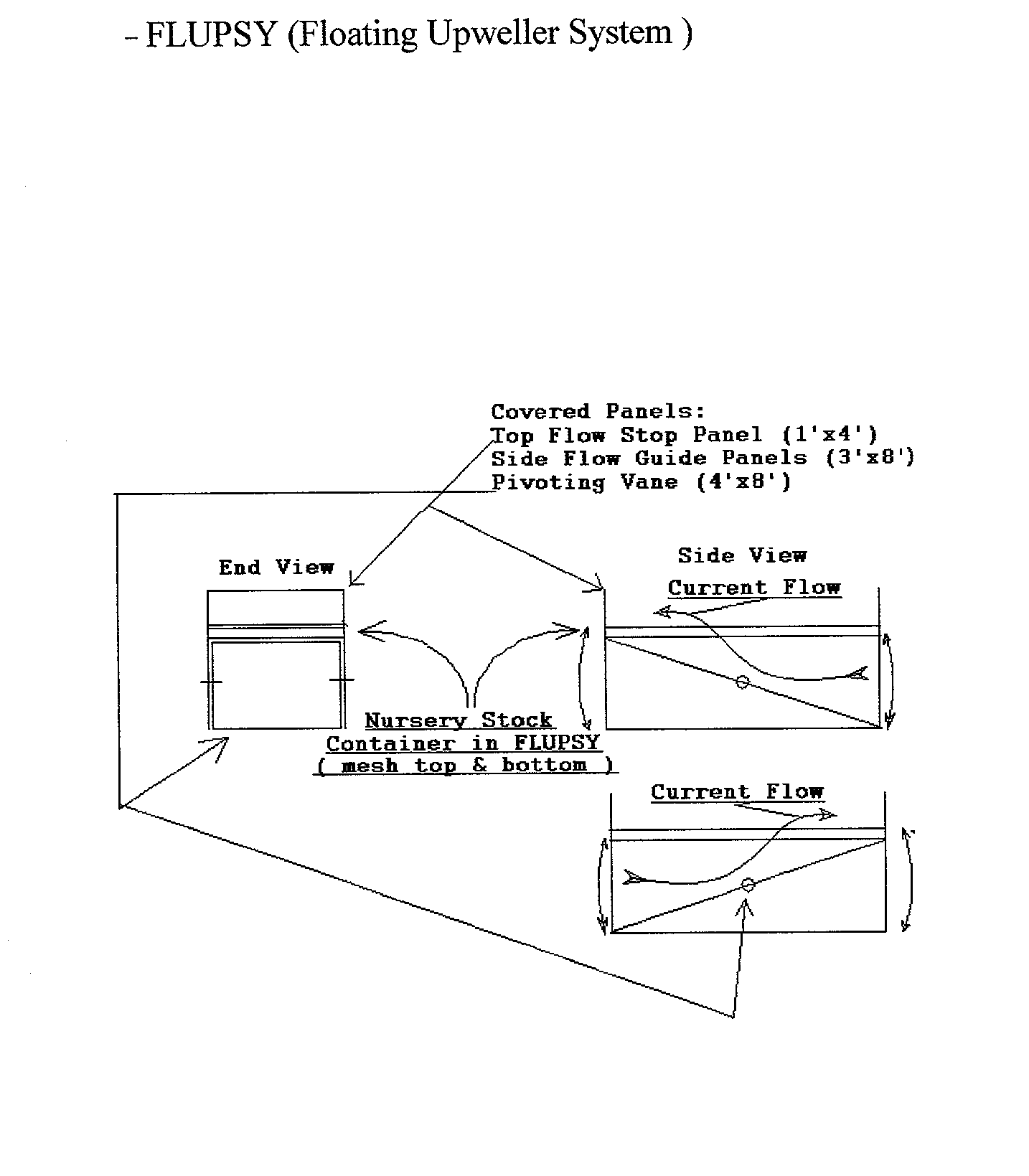
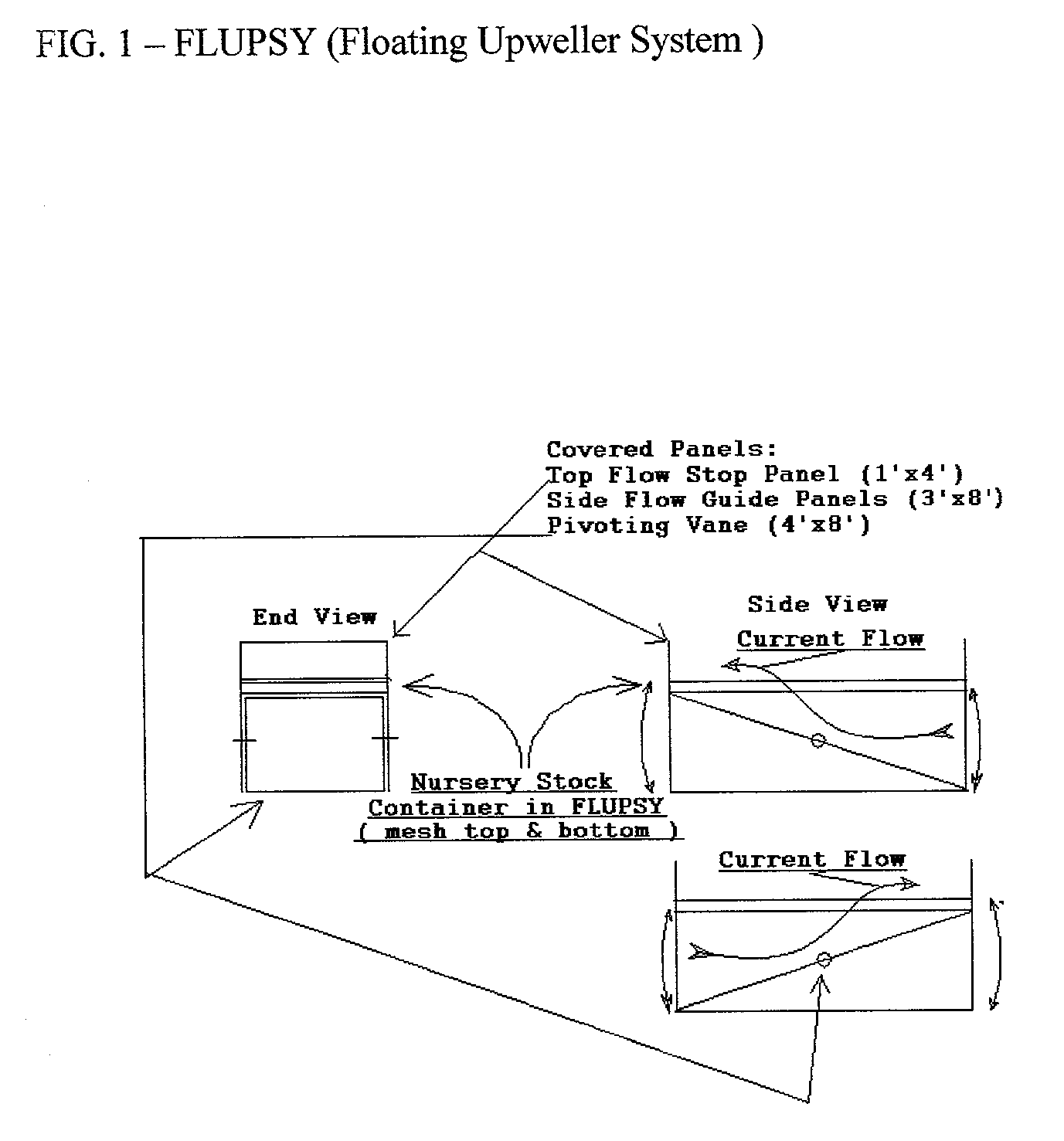
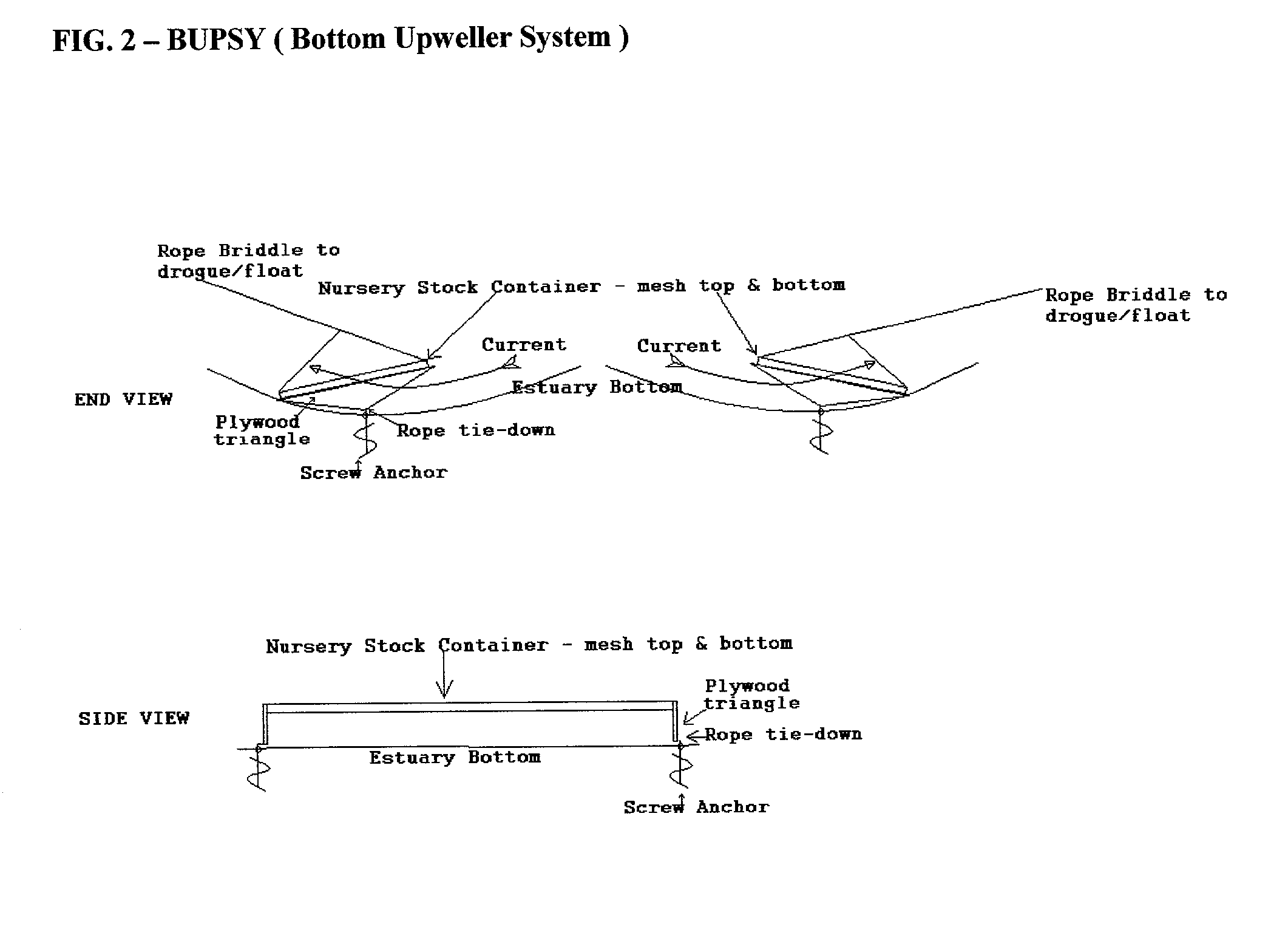
Integrated system for shellfish production: encompassing hatchery, nursery, brood-stock conditioning and market conditioning phases; also water treatment, food supplement, propulsion, anchoring, security, and devices for the integration of neighborhood values and shellfish production.
InactiveUS20030094141A1Reduce theftClimate change adaptationPisciculture and aquariaRiver mouthWater quality
The invention (the process, its supporting devices, and applications) serves the endeavor of shellfish aquaculture. The invention improves and innovates: 1) tidally powered systems for raising shellfish seed, 2) grow-out, 3) brood stock conditioning, 4) market conditioning, & food supplement, 5) hatchery systems, 6) hatchery / nursery integration, resource sharing and optimization, ergonomics and economics, 7) water treatment, 8) Propulsion, 9) Anchorage, 10) Security, and 11) Devices for the Integration of Neighborhood Values and Shellfish Production. Such large increased economies of production suggest new uses for shellfish. Shellfish grow-out can provide cost effective and ecologically advantageous infrastructure benefits to eroding beaches, unstable channels, and water quality and the health of estuaries in general. The system is flexible in operation so that it may maximize the use of estuarine tidal energy and phytoplankton in order to maximize the ecological and economic benefits of the operation. The system is designed with particular attention to Virginia and Federal law so that permitting needs are minimized. Moreover the system is optimized to fit in well with the estuarine community and be a desirable, unobtrusive neighbor.
Owner:DAVIS RUSSELL P
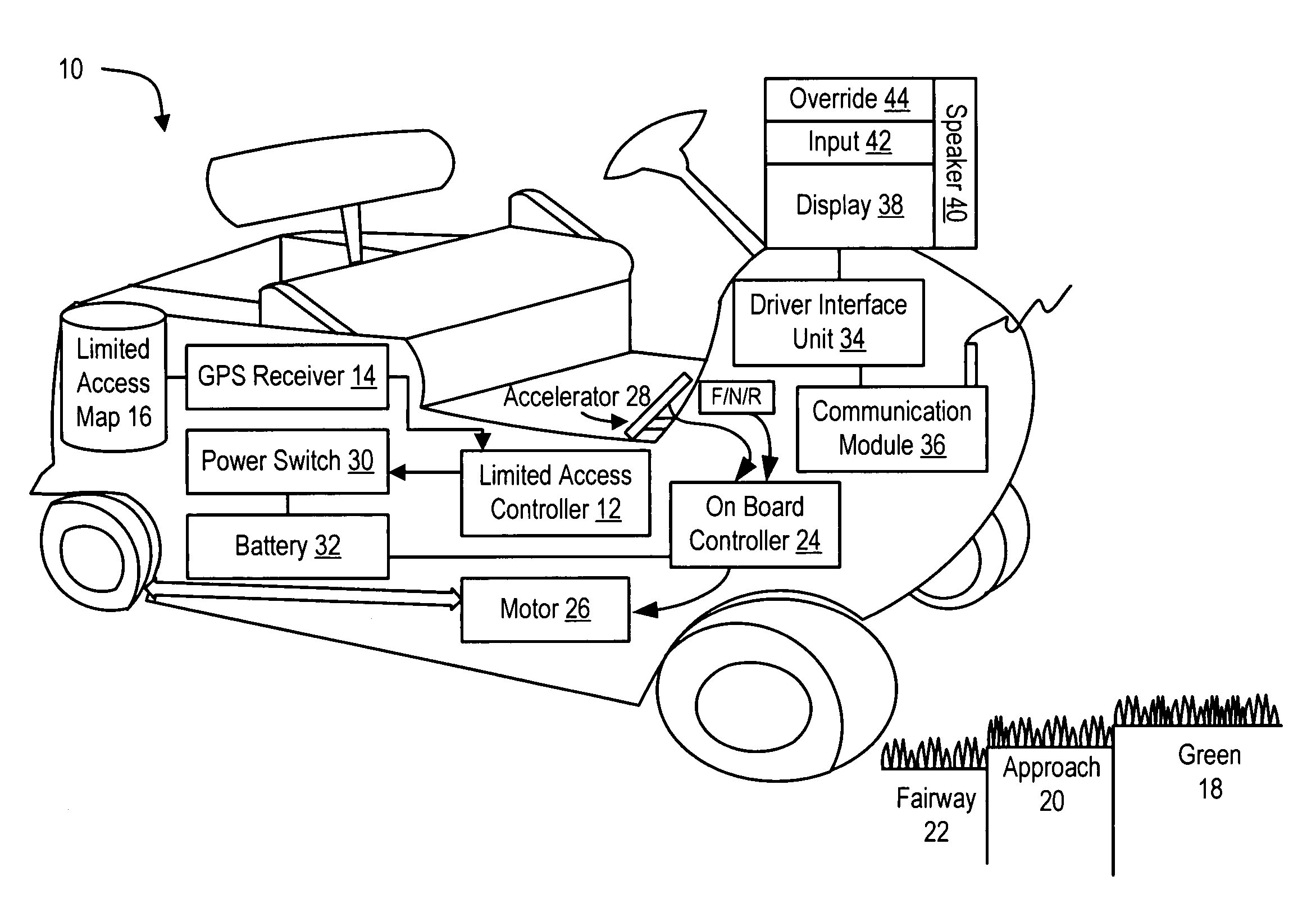
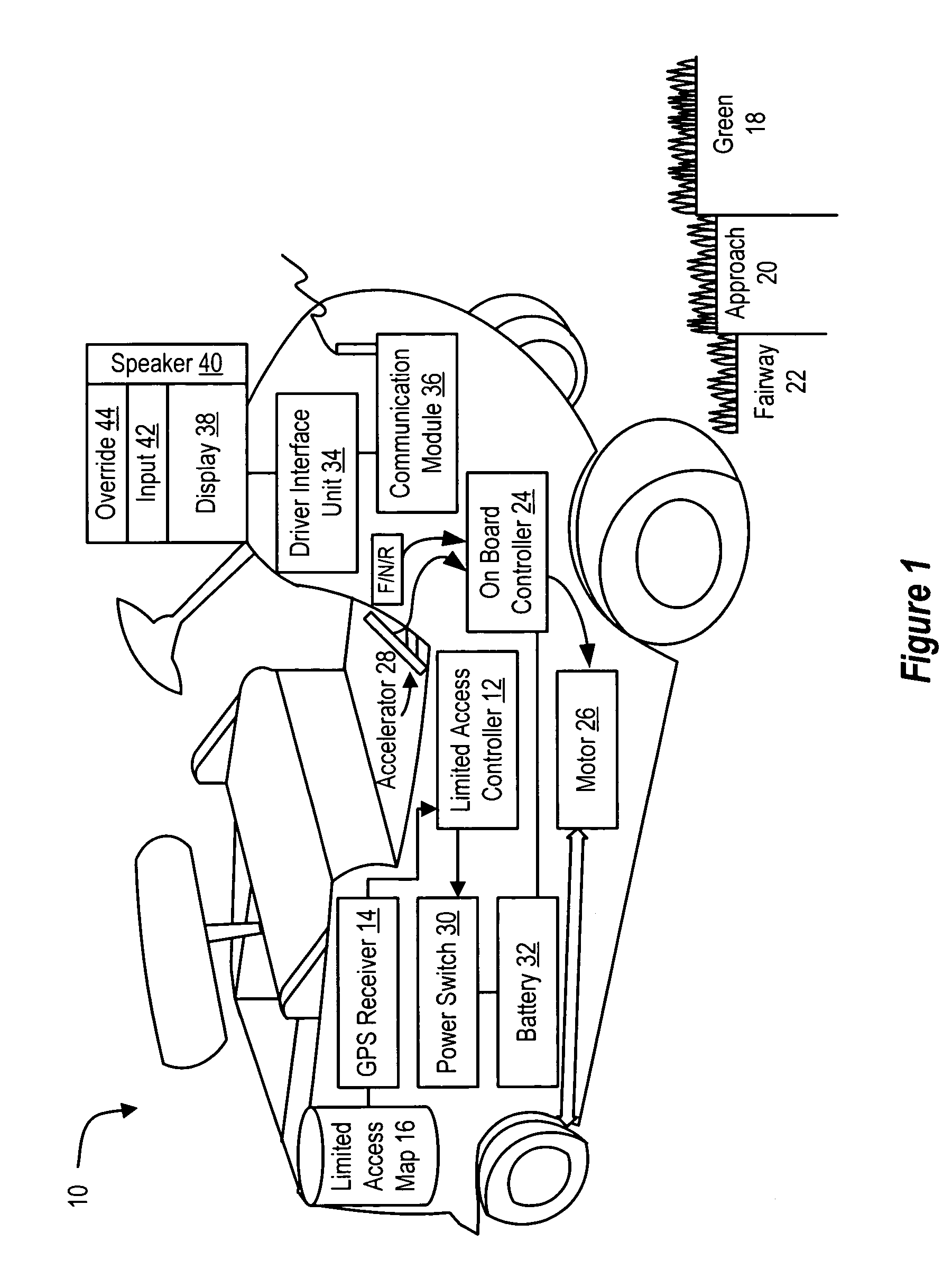
Method and system for golf cart control
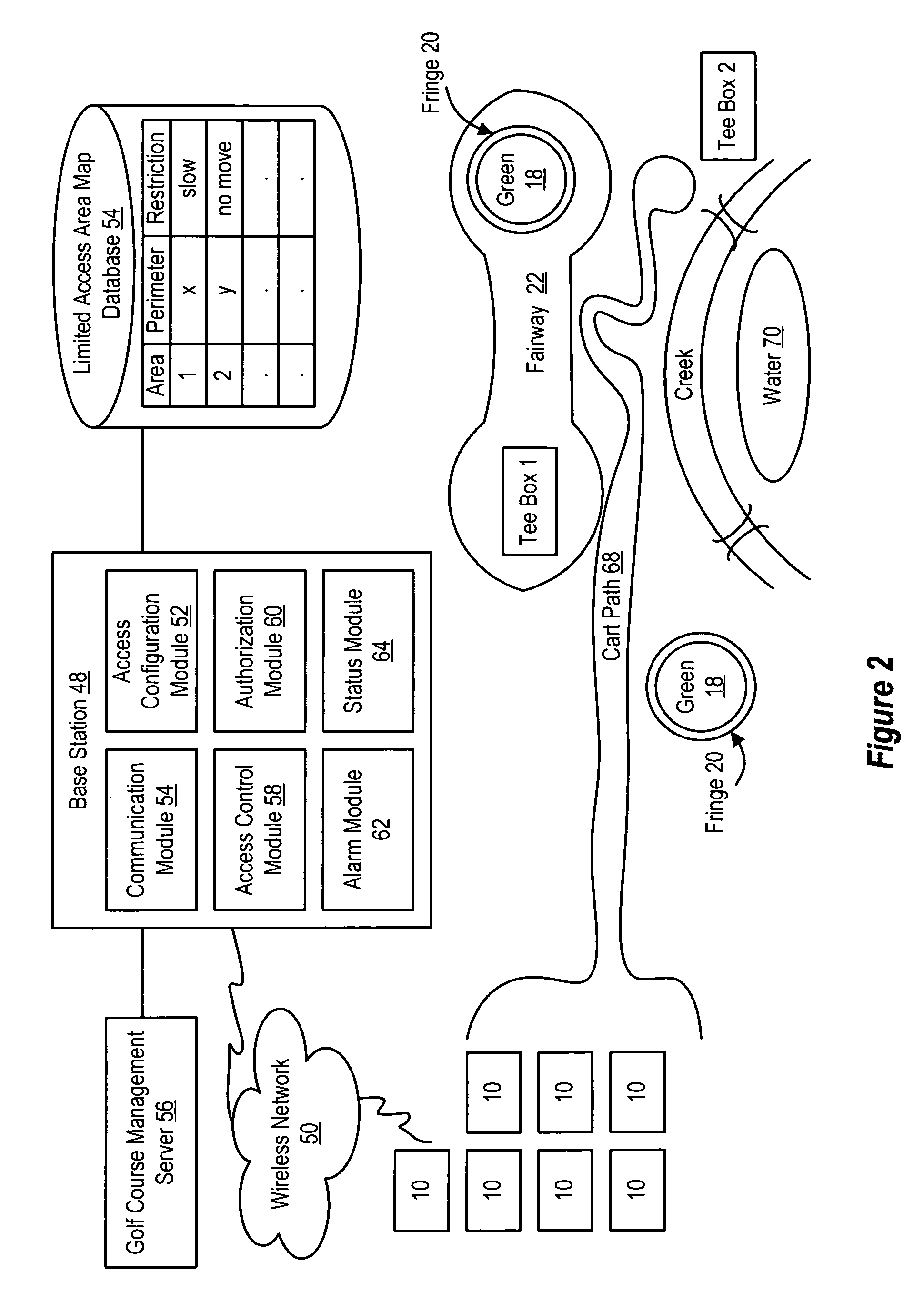
ActiveUS7239965B2Reduce theftDigital data processing detailsPosition fixationMotor speedGolf course turf
Golf cart movements at a golf course are controlled by a limited access controller that compares a golf cart's GPS-determined position against a limited access map to restrict performance of inputs by the golf cart's driver to the golf cart's motor under predetermined conditions, such as if a golf cart enters or has a predetermined likelihood of entering a limited access area. The limited access controller inhibits motor responses, such as by preventing motor operation, limiting available motor speeds, or allowing motor operation only in a vector that removes the golf cart from the limited access area, such as operation in reverse. Golf carts of a golf course communicate with a base station that updates the limited access map by defining limited access area perimeters and allowable actions within a limited access area and that directly commands allowable motor operations. For example, golf carts are prohibited from entering green areas, are restricted to golf cart paths during cart-path-only periods, and are restricted to reduced speeds in driving hazard areas.
Owner:TULIP GRP INVESTMENTS +1
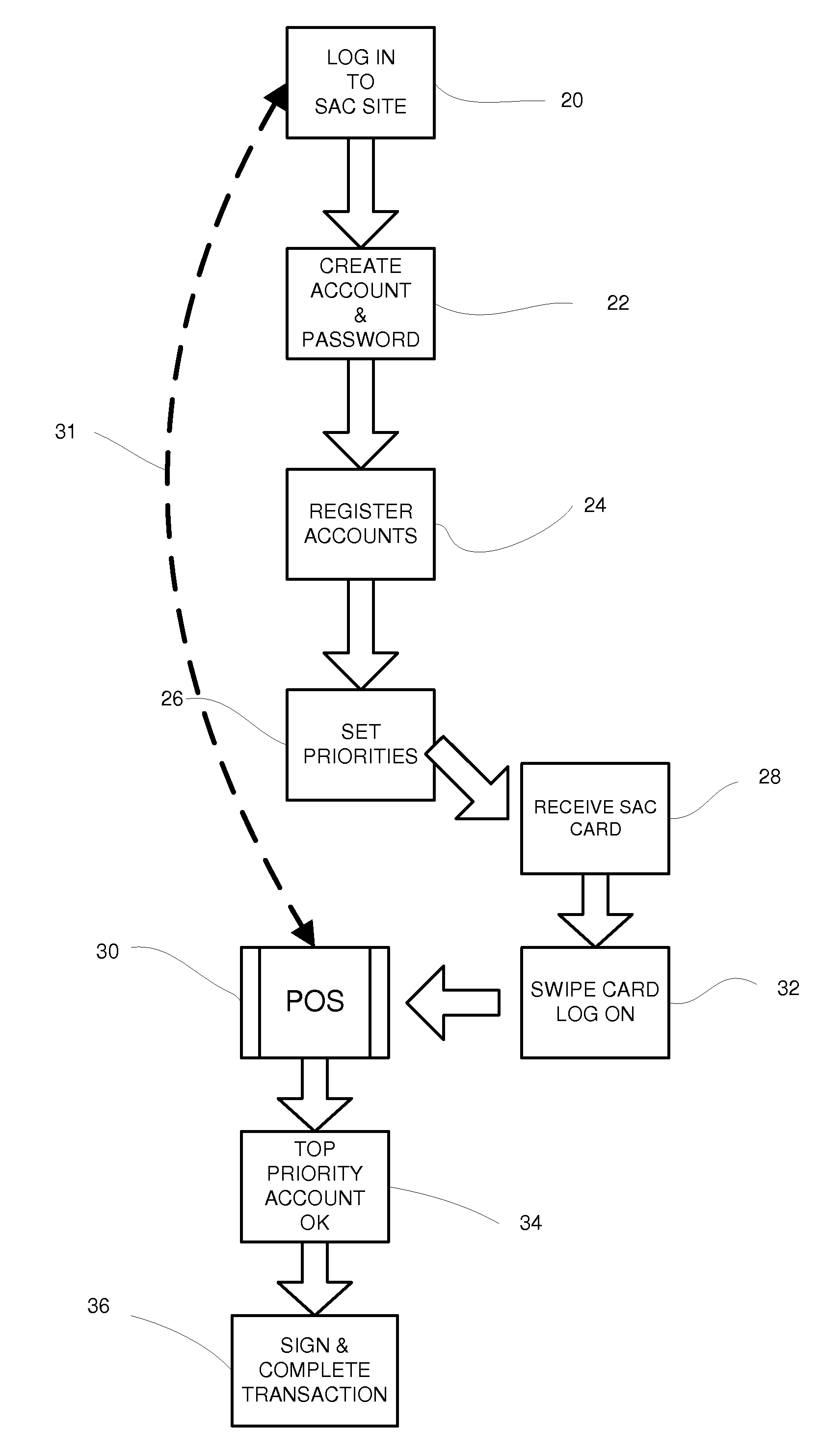
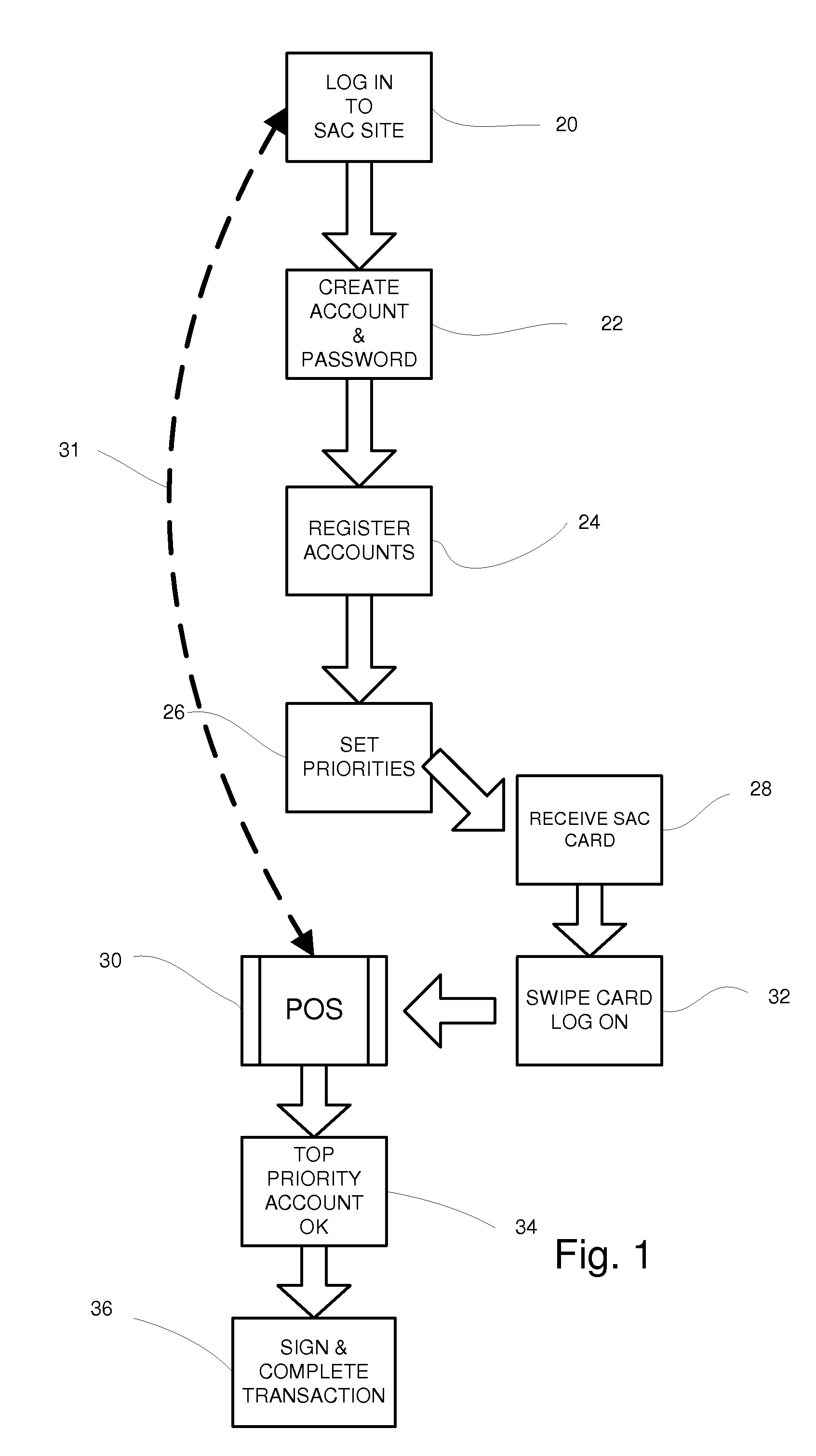
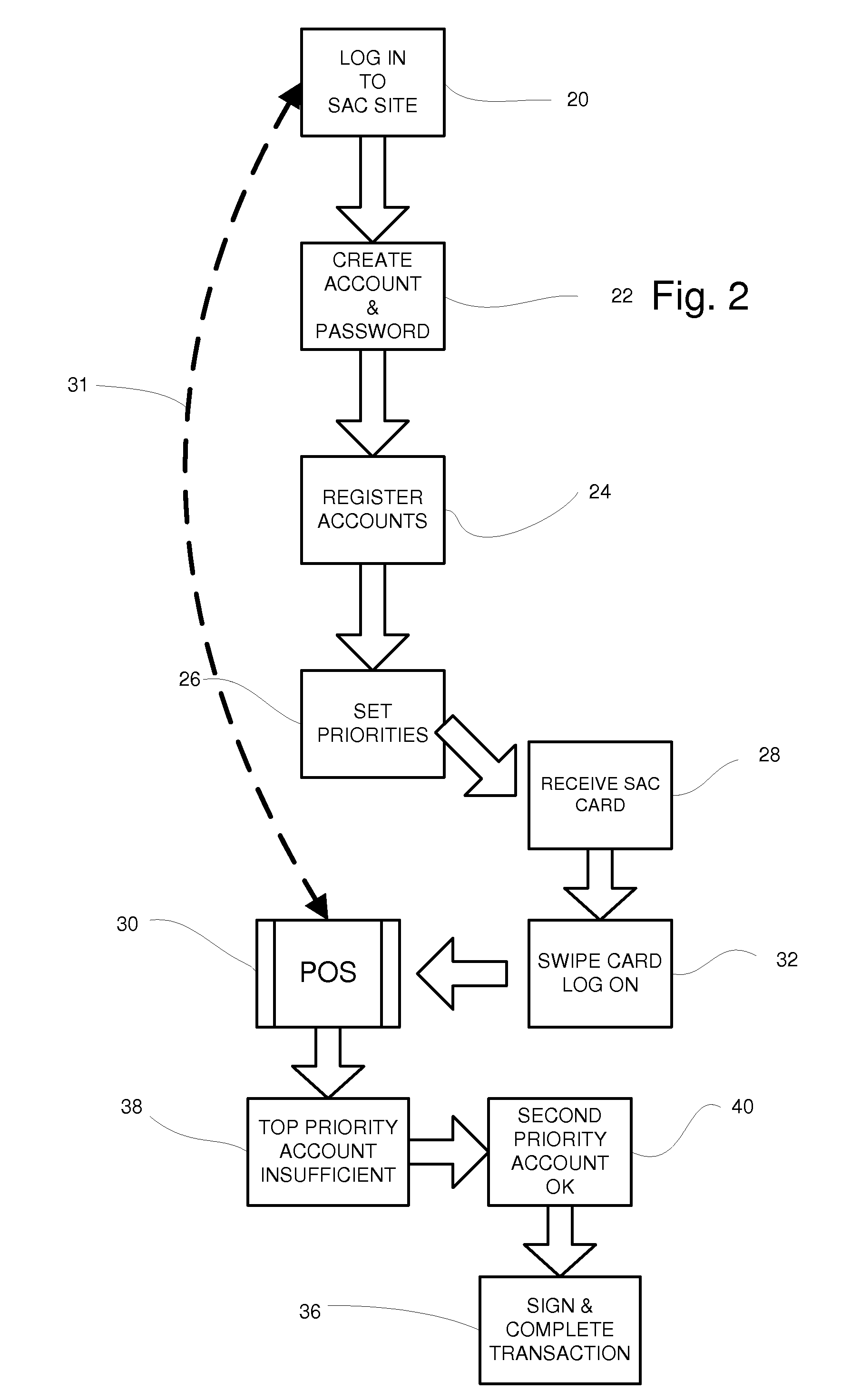
System for managing multiple credit accounts
In an improved method and system for managing consumer credit accounts a consumer registers a plurality of credit accounts through a secure web page establishing a priority of accounts in the process. The web page aggregates data from all of the registered accounts and a single credit card or device is issued to access the aggregated accounts. The single card is used at points of sale like an ordinary credit card except that it requires a password like a debit card. When a purchase is made the request is relayed to the credit account that has the top priority and sufficient available credit. A single card can access a plurality of separate credit accounts so there is no need to carry multiple cards. If the single card is stolen, it can be rapidly inactivated with a single call. It will not be necessary to cancel the underlying accounts.
Owner:SALLY JOSEPH
Vending machines with field-programmable electronic locks
InactiveUS20070096867A1Easily and inexpensively programmedImprove the level ofElectric signal transmission systemsMultiple keys/algorithms usageService personnelBiological activation
A vending machine uses a field-programmable electronic lock that learns a key code from a corresponding electronic key. The electronic lock has a learning process activation device that is accessible when the door of the vending machine is in the open position. Using the learning process activation device, a service person activates the electronic lock to perform a key code learning operation, in which the electronic lock receives a key code transmitted from an electronic key and stores the key code in a non-volatile memory for future access control of the vending machine. Data encryption is employed in the communications between the key and the lock to ensure the security of the communications. A communication device installed in the vending machine for communicating with a home base computer allows the operation of the electronic lock to be remotely controlled for access control and auditing purposes.
Owner:DENISON WILLIAM D +2
Package receiving locker
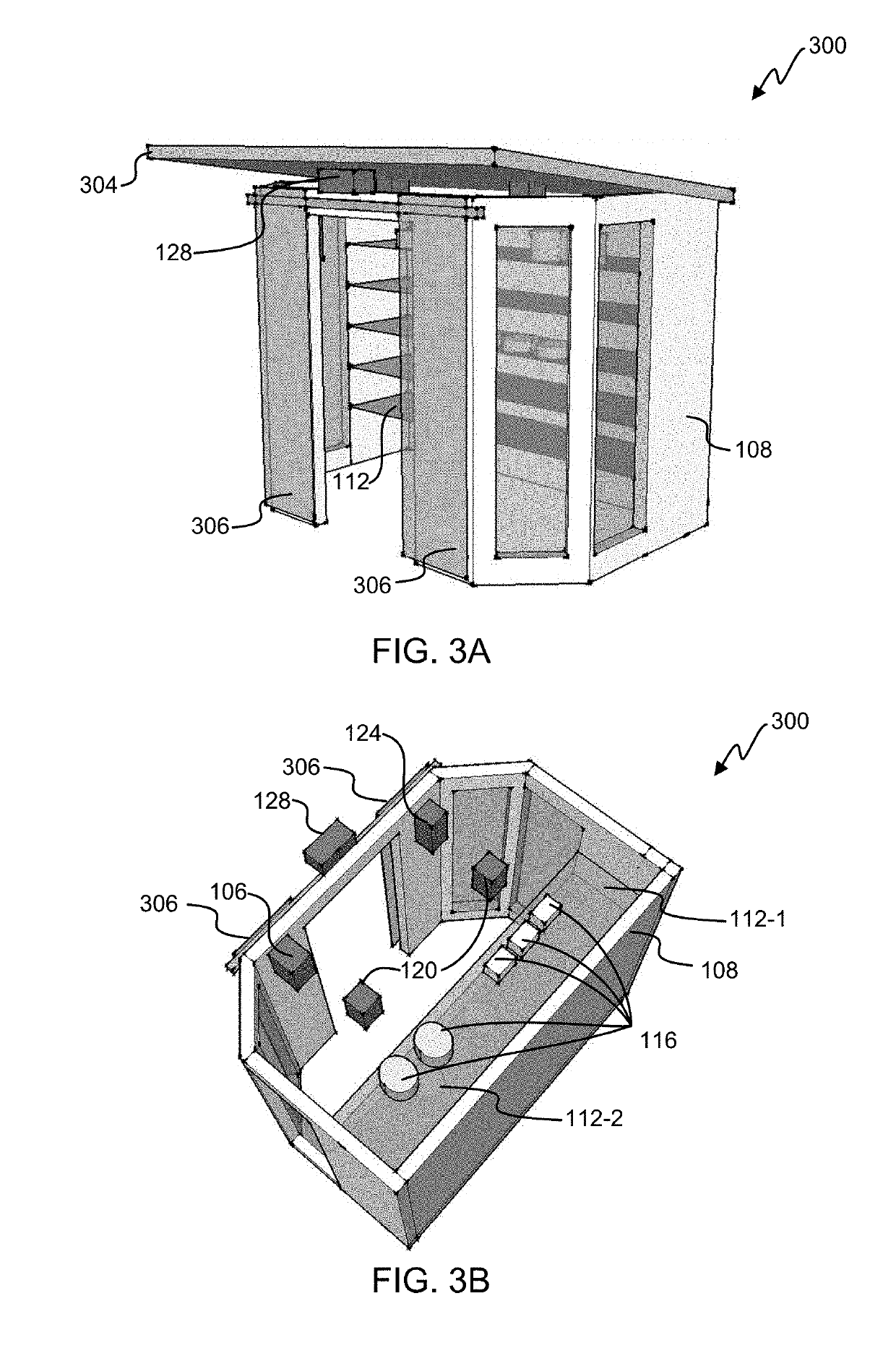
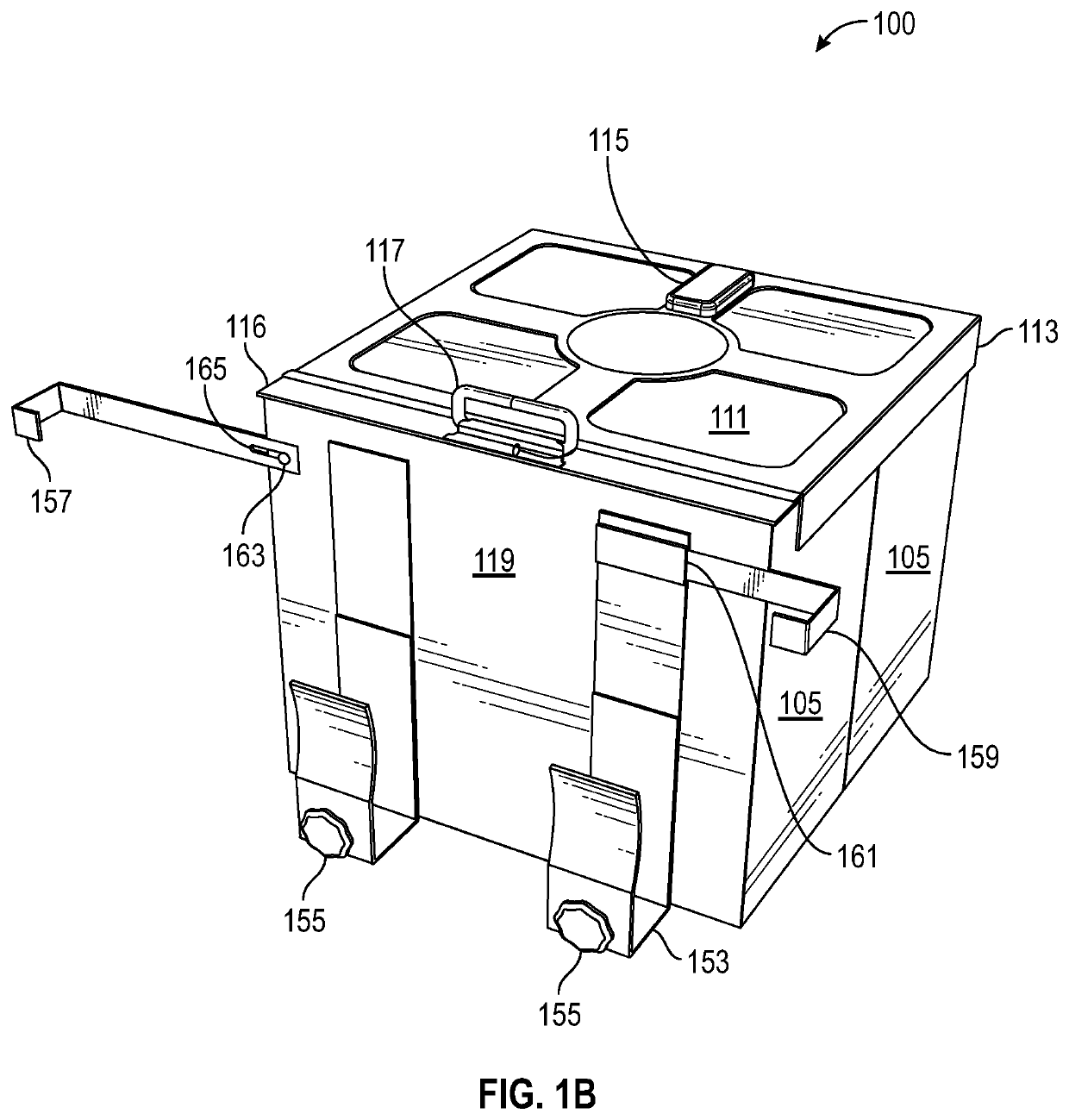
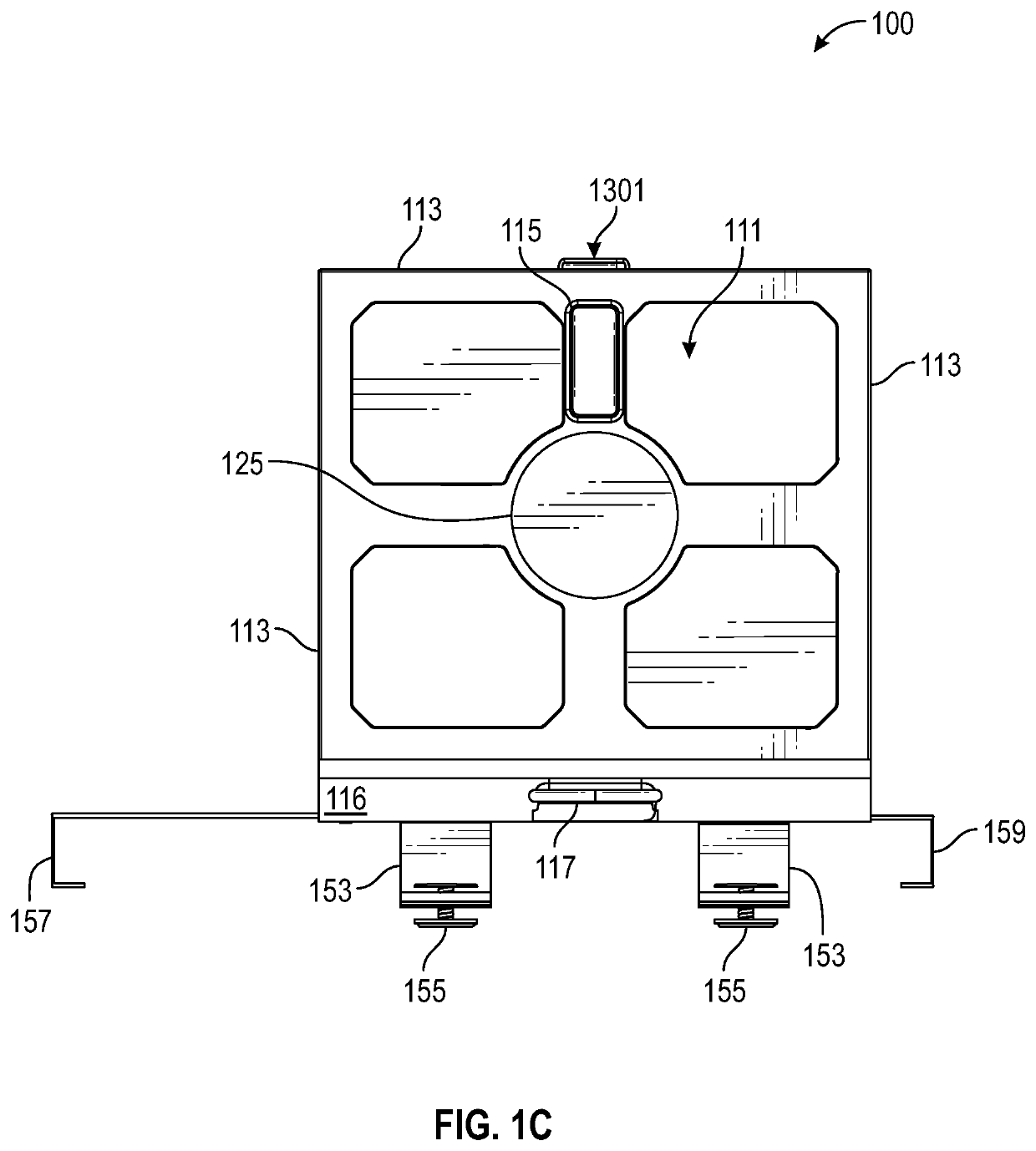
ActiveUS20190350398A1Not to impair operationReduce theftKitchen equipmentDomestic articlesComputer hardwareObject storage
Package-receiving-lockers (PRLs) may have a collapsible-locker portion and door-attachment-structure. PRLs may exist in a substantially collapsed configuration for storing the given PRL or for otherwise minimizing a footprint of the given PRL; and these PRLs may exist in a substantially deployed (expanded) configuration for acting as a secure object storage location. Regardless of configuration (deployed or collapsed), PRLs may be removably attached to side-hinged-doors with the door-attachment-structure, in such a way so as not to impair operation of the given door. The PRLs may have various electronics for facilitating access (e.g., locking and unlocking the collapsible-locker), delivery confirmation, and mitigating theft. These electronics, along with specialized software, may allow an intended recipient (e.g., a buyer), a shipper / delivery person (or shipping / deliver robot), and / or a seller / vendor to access the PRL in a controlled and documented manner. At least some of these electronics may be in wireless communications with other electronic devices.
Owner:SECURUM CAPSA INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com