Patents
Literature
525 results about "Limited access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A limited-access road, known by various terms worldwide, including limited-access highway, dual-carriageway, expressway, and partial controlled access highway, is a highway or arterial road for high-speed traffic which has many or most characteristics of a controlled-access highway (freeway or motorway), including limited or no access to adjacent property, some degree of separation of opposing ...
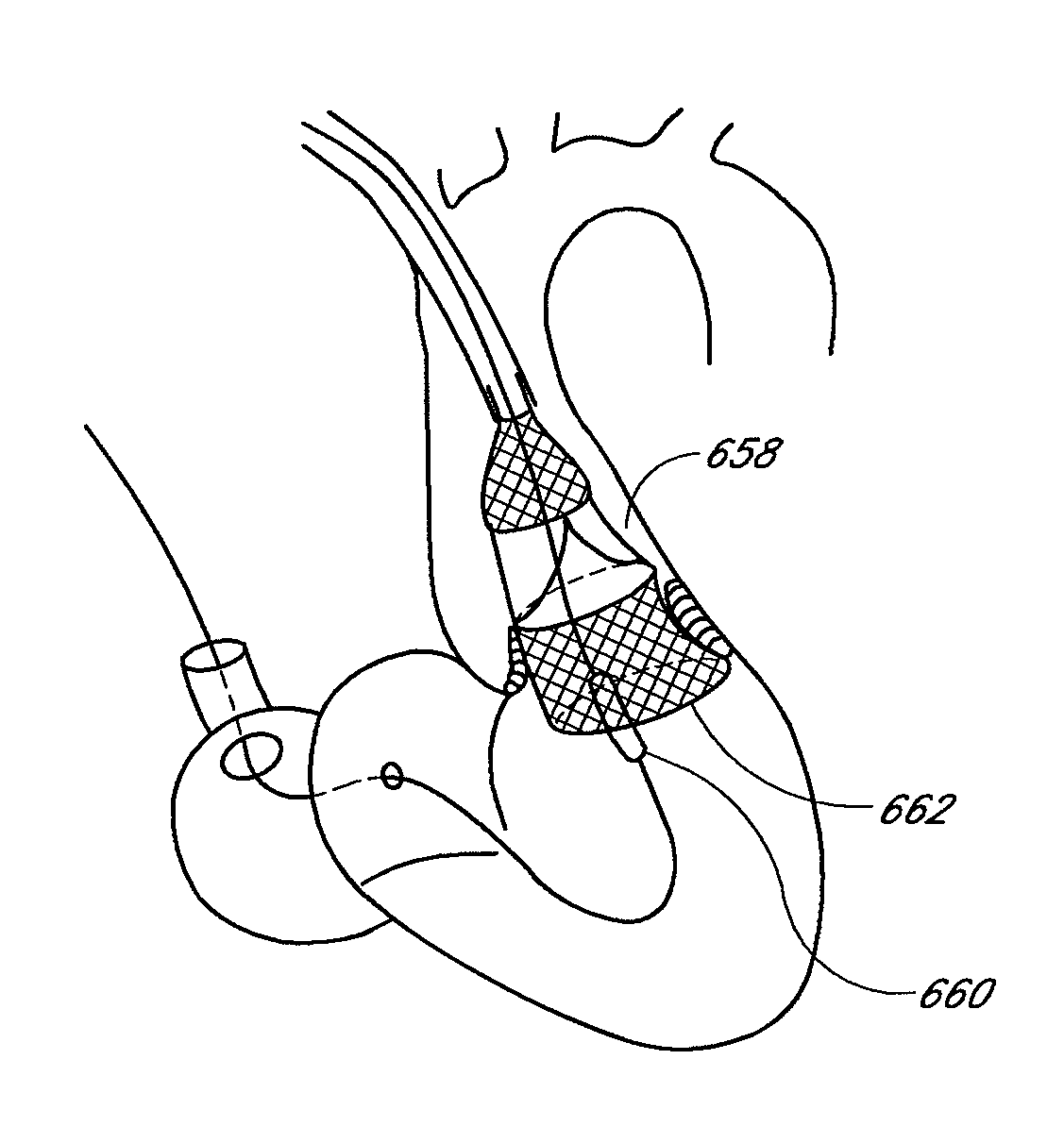
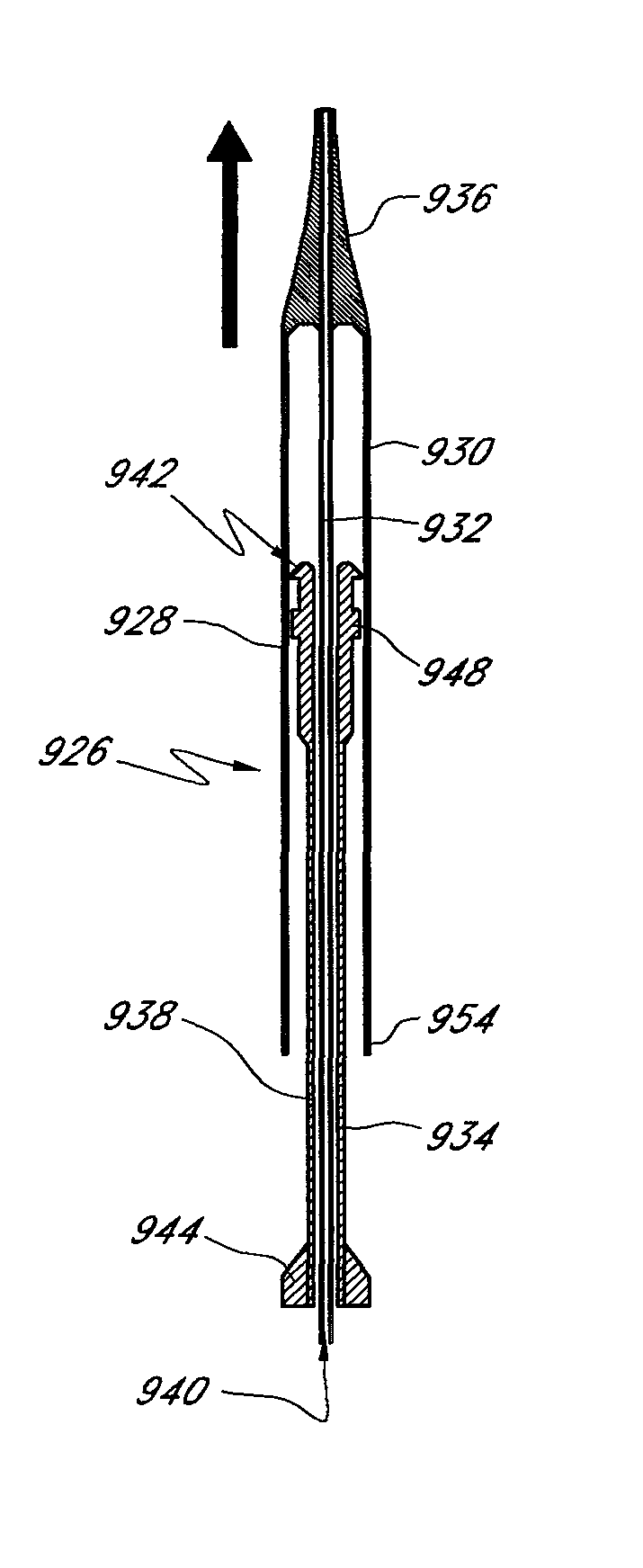
System and method for transapical delivery of an annulus anchored self-expanding valve
ActiveUS20080140189A1Preventing substantial migrationEliminate the problemStentsBalloon catheterLimited accessCardiac muscle
A prosthetic valve assembly for use in replacing a deficient native valve comprises a replacement valve supported on an expandable prosthesis frame. The valve may be delivered transluminally or transmyocardially using a thorascopic or other limited access approach using a delivery catheter. Preferably, the initial partial expansion of the valve is performed against the native valve annulus to provide adequate anchoring and positioning of the valve as the remaining portions of the valve expand. The valve may be delivered using a retrograde or antegrade approach. When delivered using a retrograde approach, a delivery catheter with a pull-back sheath may be used, while antegrade delivery is preferably performed with a delivery catheter with a push-forward sheath that releases the proximal end of the valve first.
Owner:MEDTRONIC ARDIAN LUXEMBOURG SARL
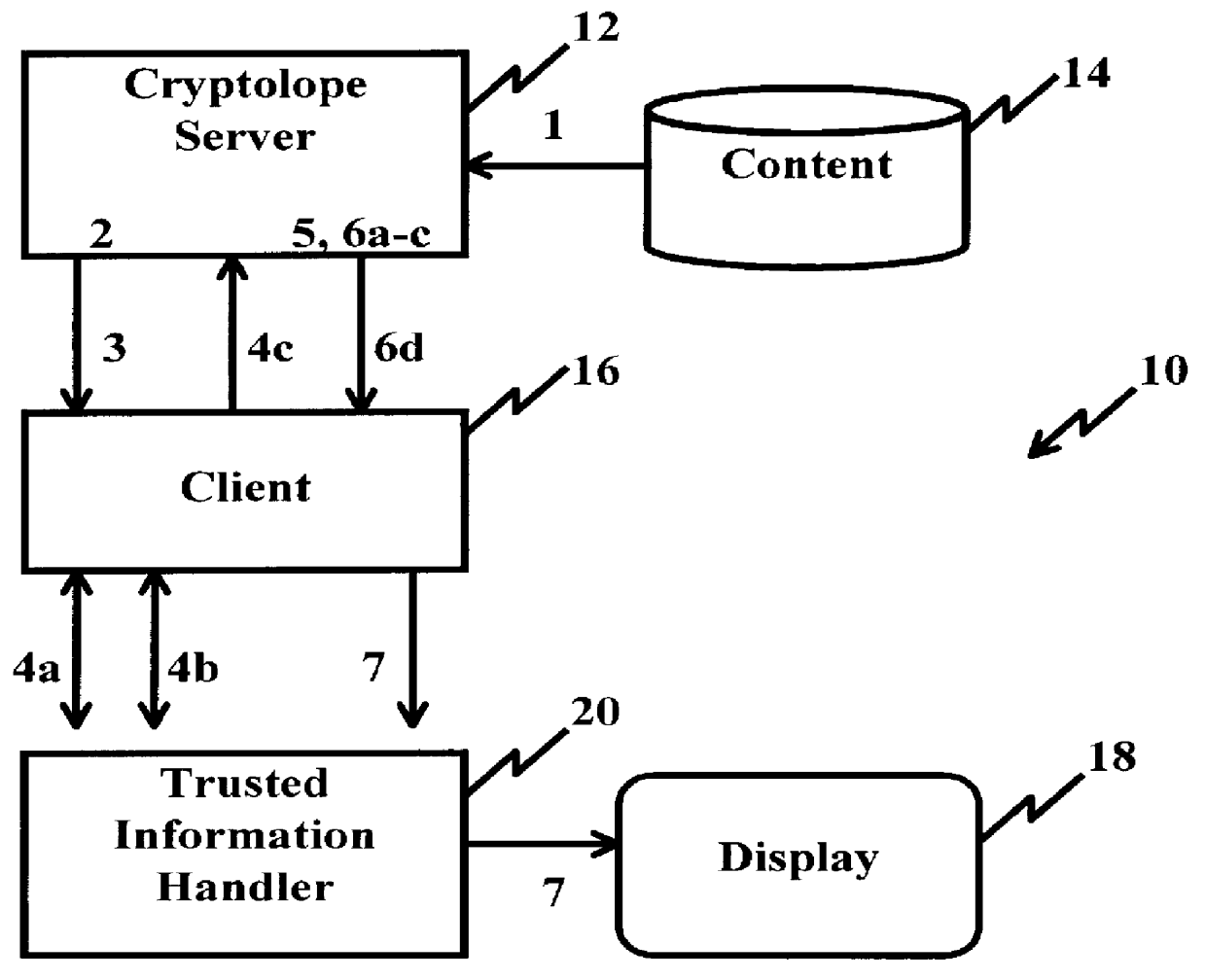
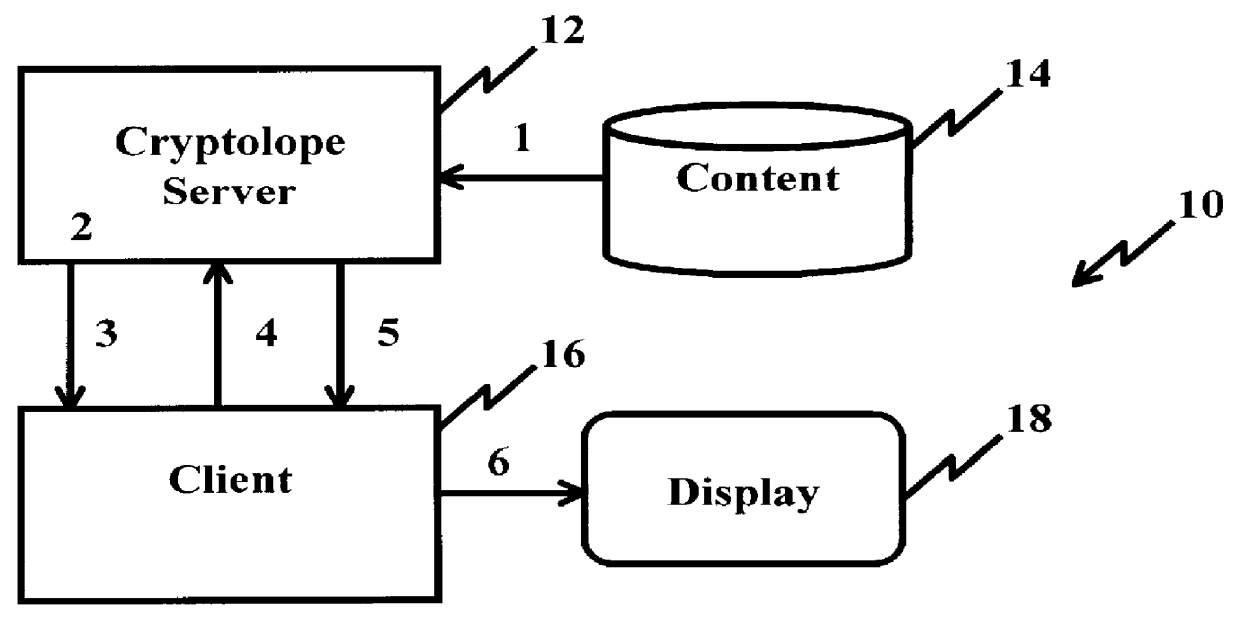
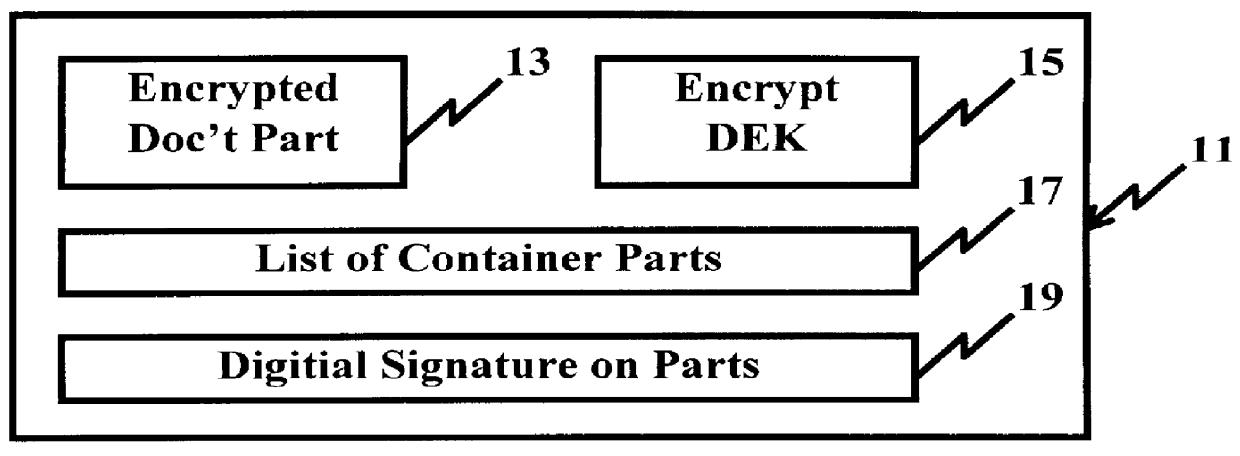
System and method for controlling access rights to and security of digital content in a distributed information system, e.g., Internet
InactiveUS6098056AKey distribution for secure communicationPublic key for secure communicationPersonalizationThe Internet
A system and method for limiting access to and preventing unauthorized use of an owner's digital content stored in an information network and available to clients under authorized conditions. The network includes at least one server coupled to a storage device for storing the limited access digital content encrypted using a random-generated key, known as a Document Encryption Key (DEK). The DEK is further encrypted with the server's public key, using a public / private key pair algorithm and placed in a digital container stored in a storage device and including as a part of the meta-information which is in the container. The client's workstation is coupled to the server for acquiring the limited access digital content under the authorized condition. A Trusted Information Handler (TIH) is validated by the server after the handler provides a data signature and type of signing algorithm to transaction data descriptive of the purchase agreement between the client and the owner. After the handler has authenticated, the server decrypts the encrypted DEK with its private key and re-encrypts the DEK with the handler's public key ensuring that only the information handler can process the information. The encrypted DEK is further encrypted with the client's public key personalizing the digital content to the client. The client's program decrypts the DEK with his private key and passes it along with the encrypted content to the handler which decrypts the DEK with his private key and proceeds to decrypt the content for displaying to the client.
Owner:ACTIVISION PUBLISHING
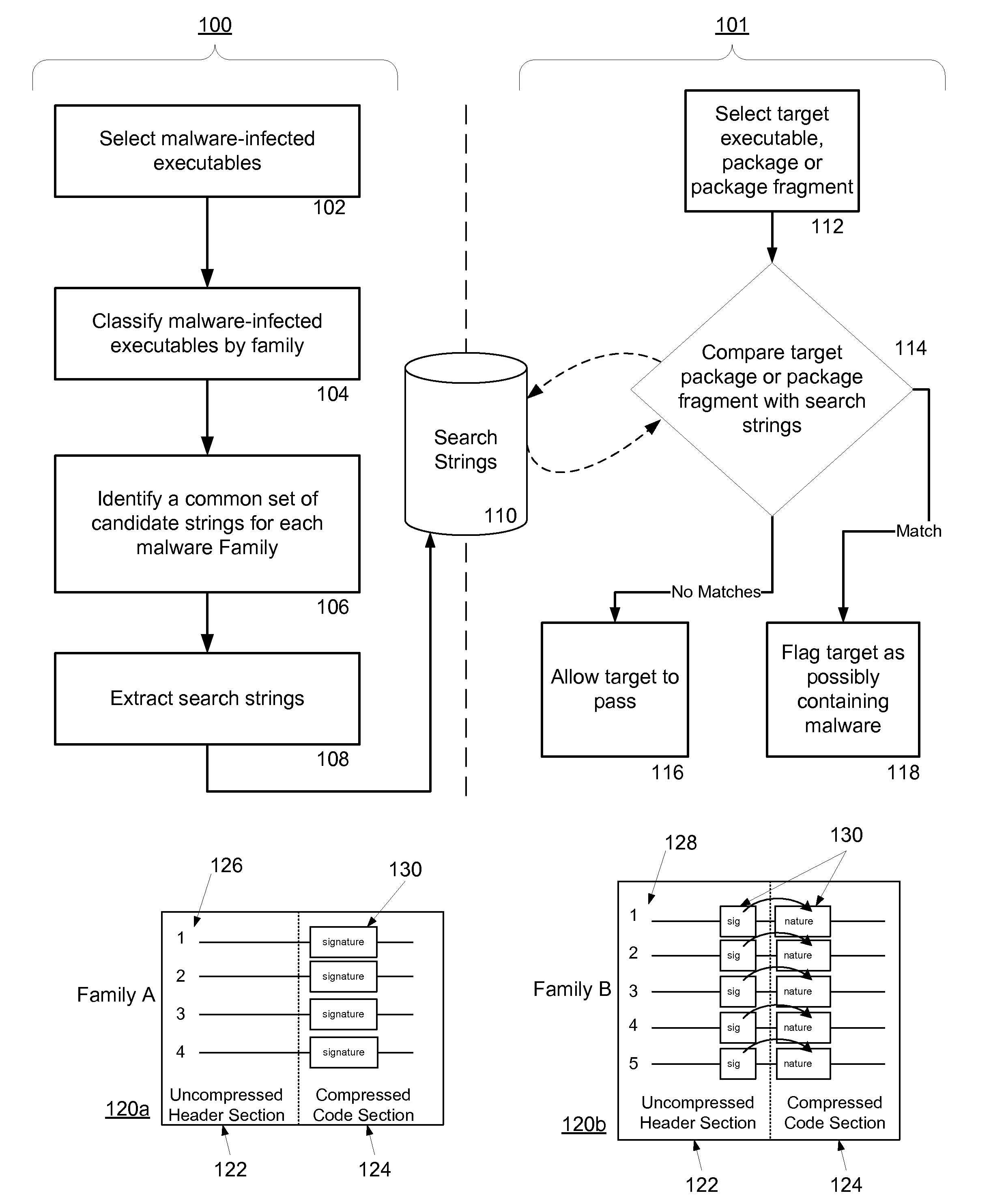
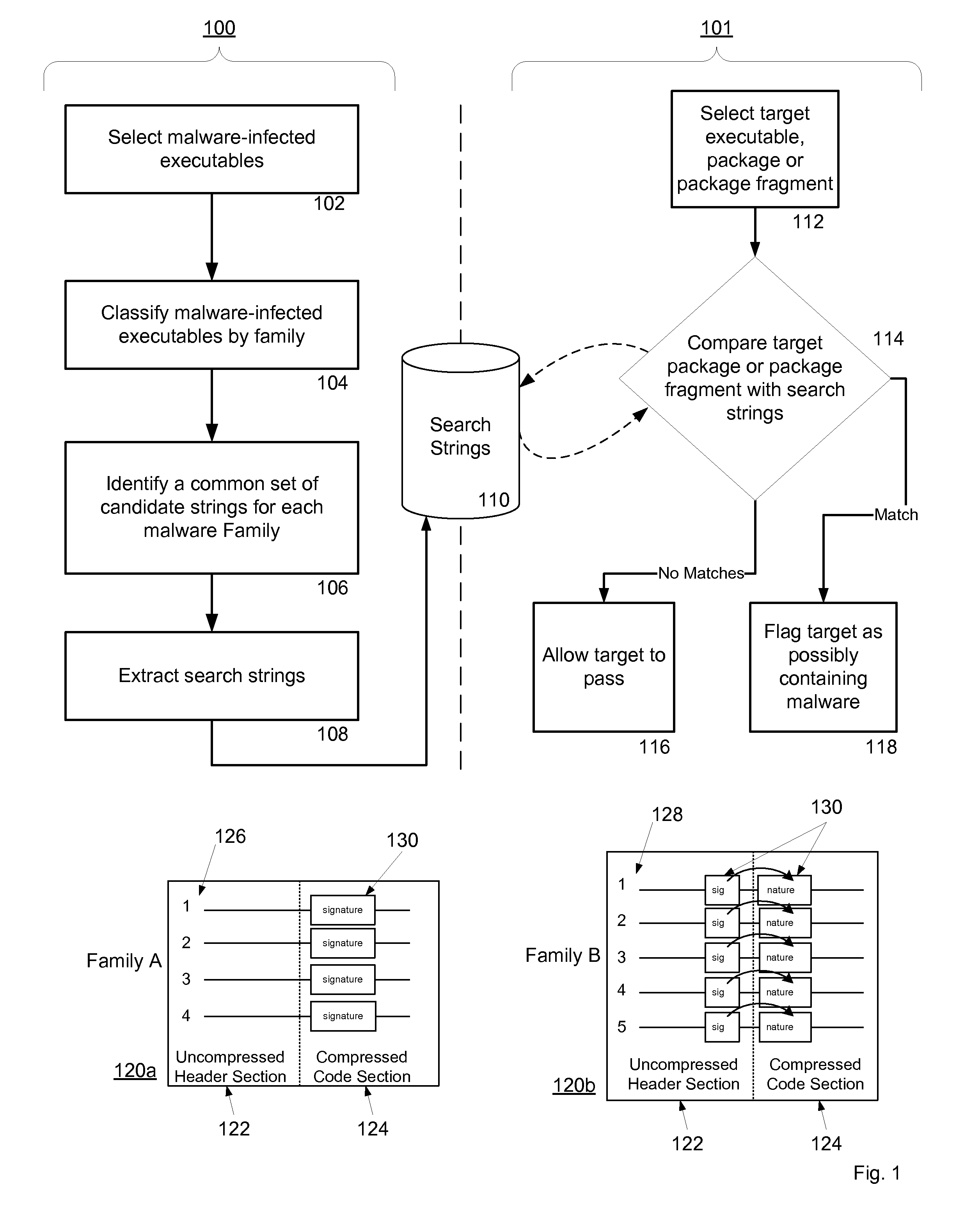
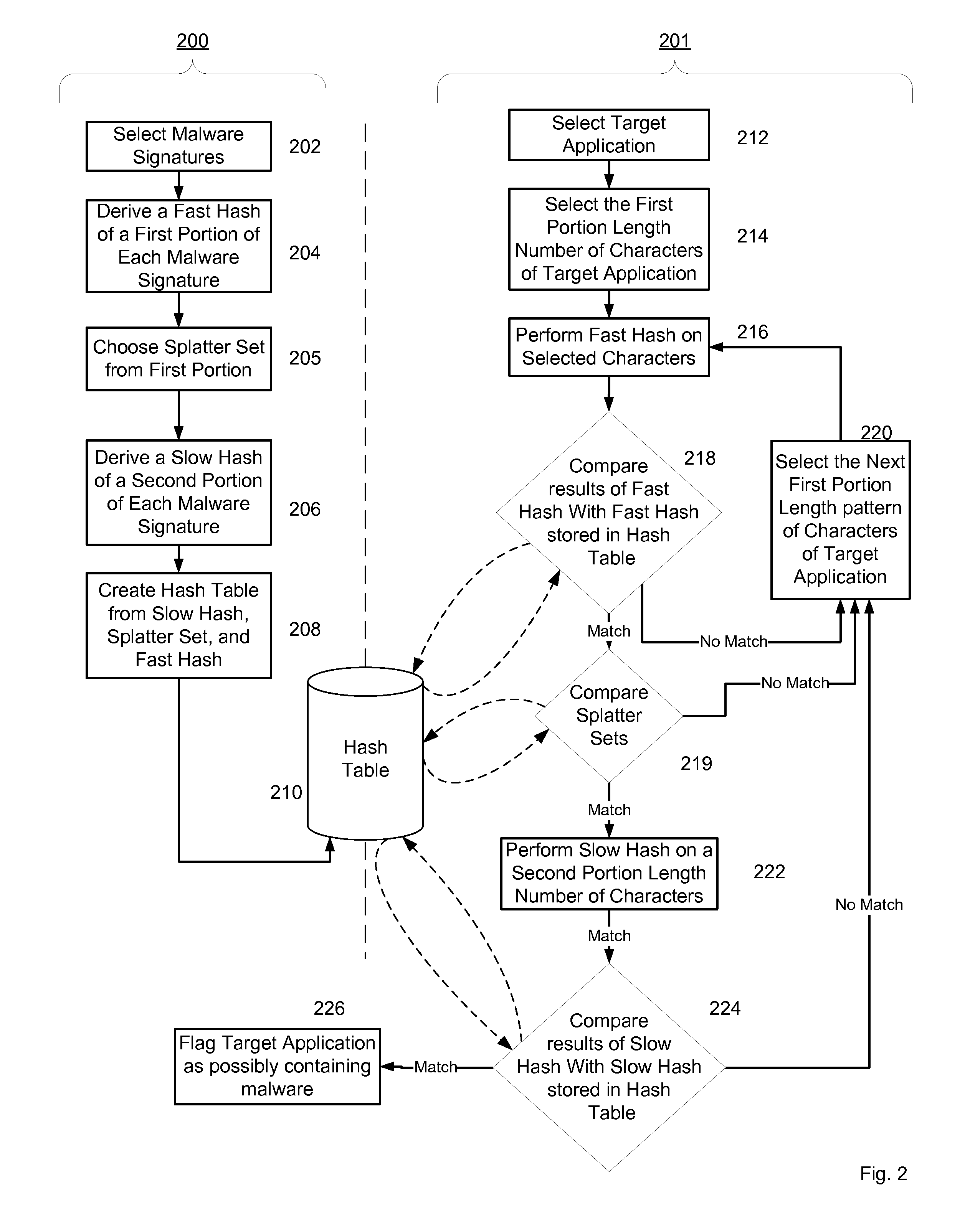
System and method for managing malware protection on mobile devices
ActiveUS20070240220A1Suitable for useReliable detectionMemory loss protectionError detection/correctionLimited accessFeature set
A system and method for detecting malware on a limited access mobile platform in a mobile network. The system and method uses one or more feature sets that describe various non-executable portions of malware-infected and malware-free applications, and compares a application on the limited access mobile platform to the features sets. A match of the features in a suspect application to one of the feature sets provides an indication as to whether the suspect application is malware-infected or malware-free.
Owner:PULSE SECURE
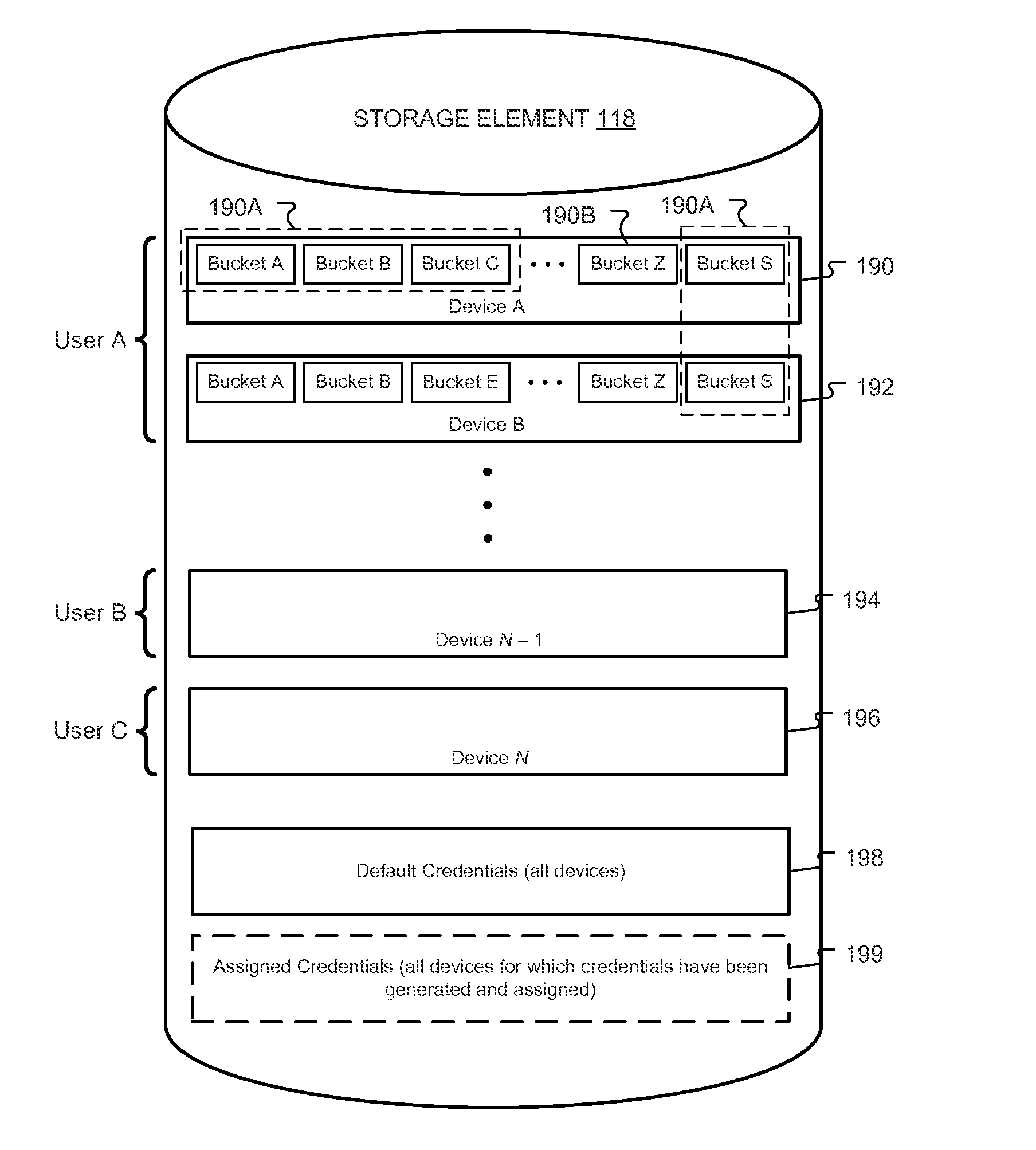
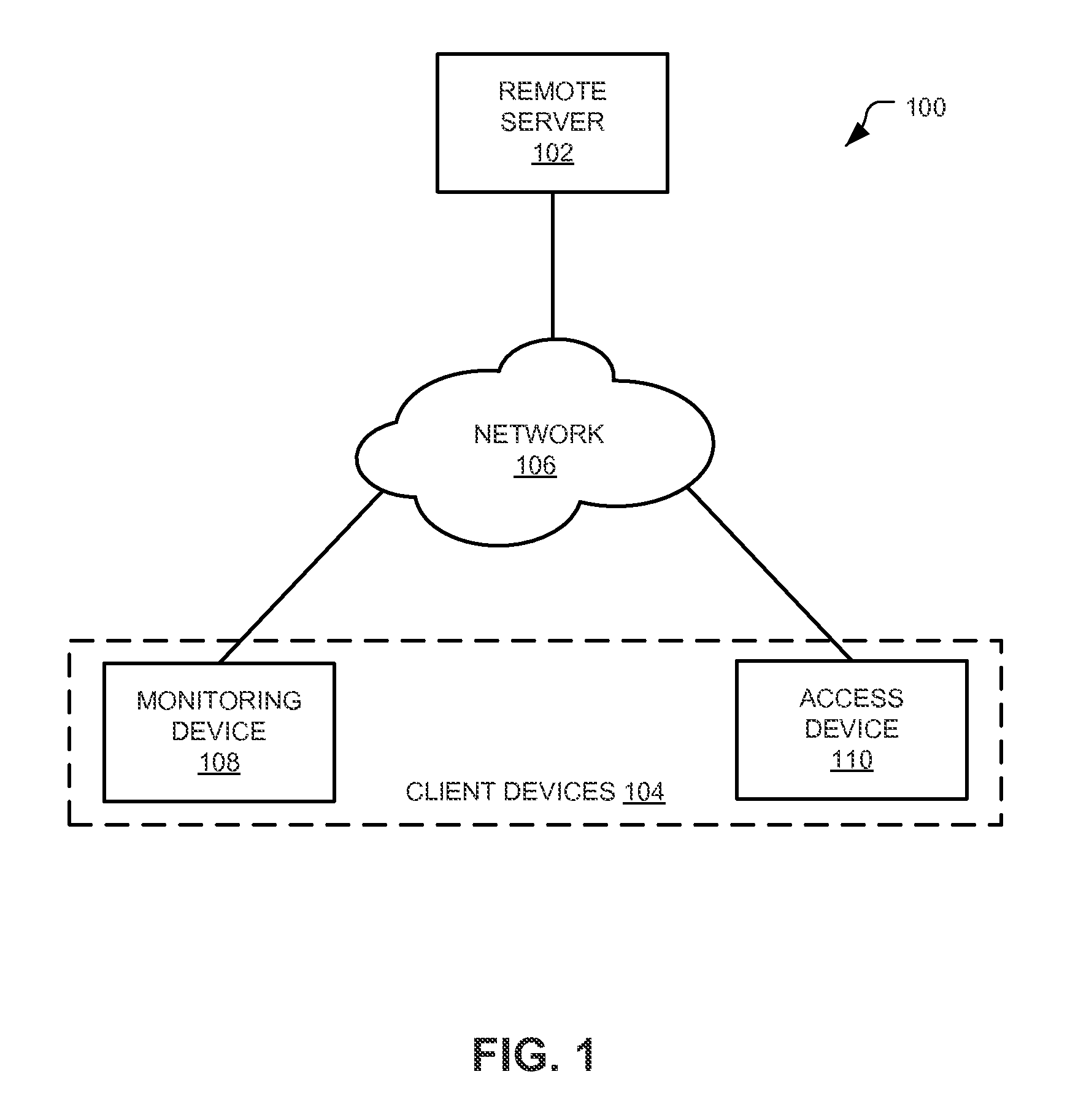
Multi-tiered authentication methods for facilitating communications amongst smart home devices and cloud-based servers
ActiveUS8539567B1Minimize power consumptionReduced power capacityDigital data processing detailsMultiple digital computer combinationsLimited accessCloud base
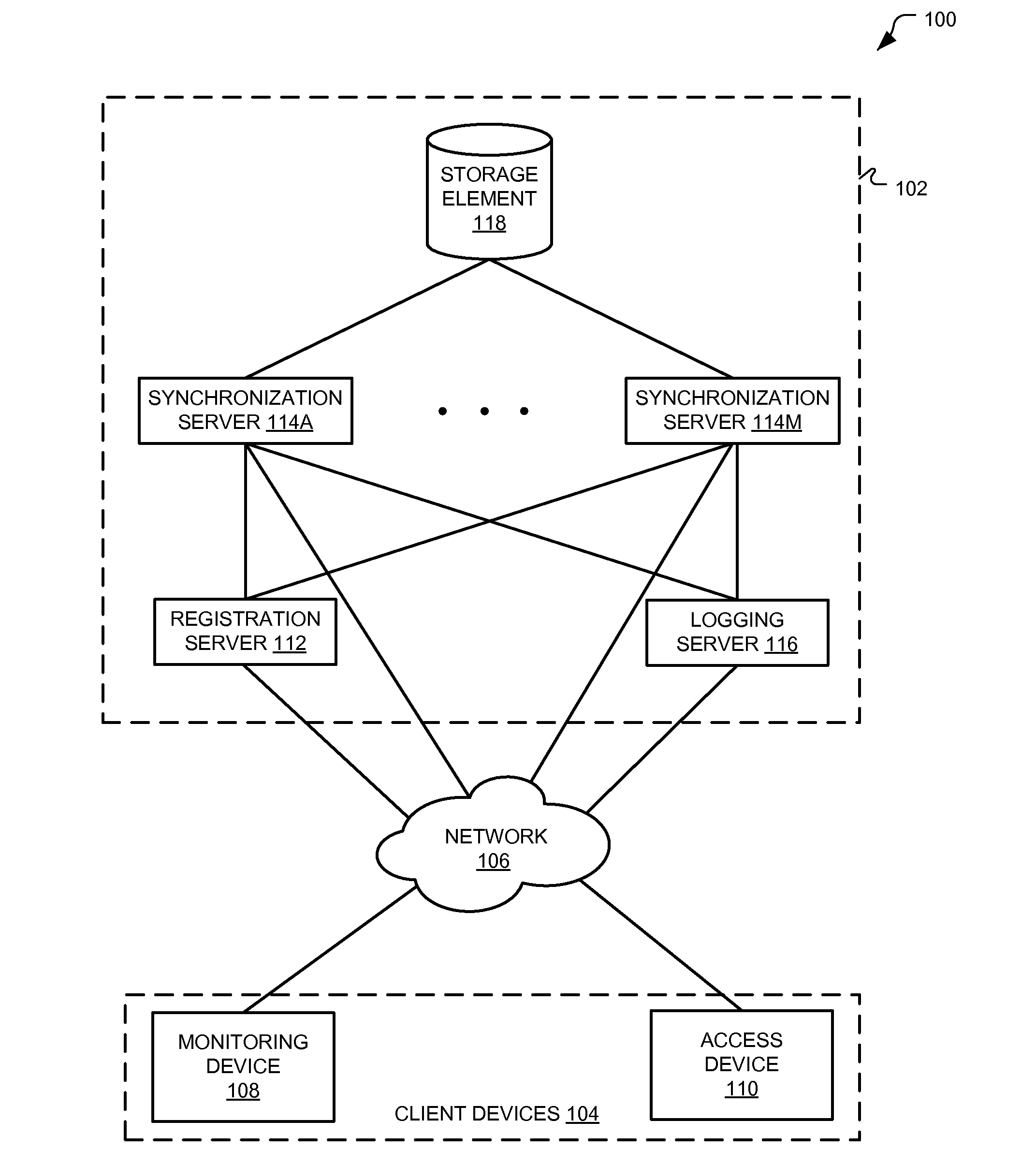
Apparatus, systems, methods, and related computer program products for synchronizing distributed states amongst a plurality of entities and authenticating devices to access information and / or services provided by a remote server. Synchronization techniques include client devices and remote servers storing buckets of information. The client device sends a subscription request to the remote serve identifying a bucket of information and, when that bucket changes, the remote server sends the change to the client device. Authentication techniques include client devices including unique default credentials that, when presented to a remote server, provide limited access to the server. The client device may obtain assigned credentials that, when presented to the remote server, provide less limited access to the server.
Owner:GOOGLE LLC
System and method for transapical delivery of an annulus anchored self-expanding valve
ActiveUS8747459B2Preventing substantial migrationEliminate the problemStentsBalloon catheterLimited accessCardiac muscle
A prosthetic valve assembly for use in replacing a deficient native valve comprises a replacement valve supported on an expandable prosthesis frame. The valve may be delivered transluminally or transmyocardially using a thorascopic or other limited access approach using a delivery catheter. Preferably, the initial partial expansion of the valve is performed against the native valve annulus to provide adequate anchoring and positioning of the valve as the remaining portions of the valve expand. The valve may be delivered using a retrograde or antegrade approach. When delivered using a retrograde approach, a delivery catheter with a pull-back sheath may be used, while antegrade delivery is preferably performed with a delivery catheter with a push-forward sheath that releases the proximal end of the valve first.
Owner:MEDTRONIC ARDIAN LUXEMBOURG SARL
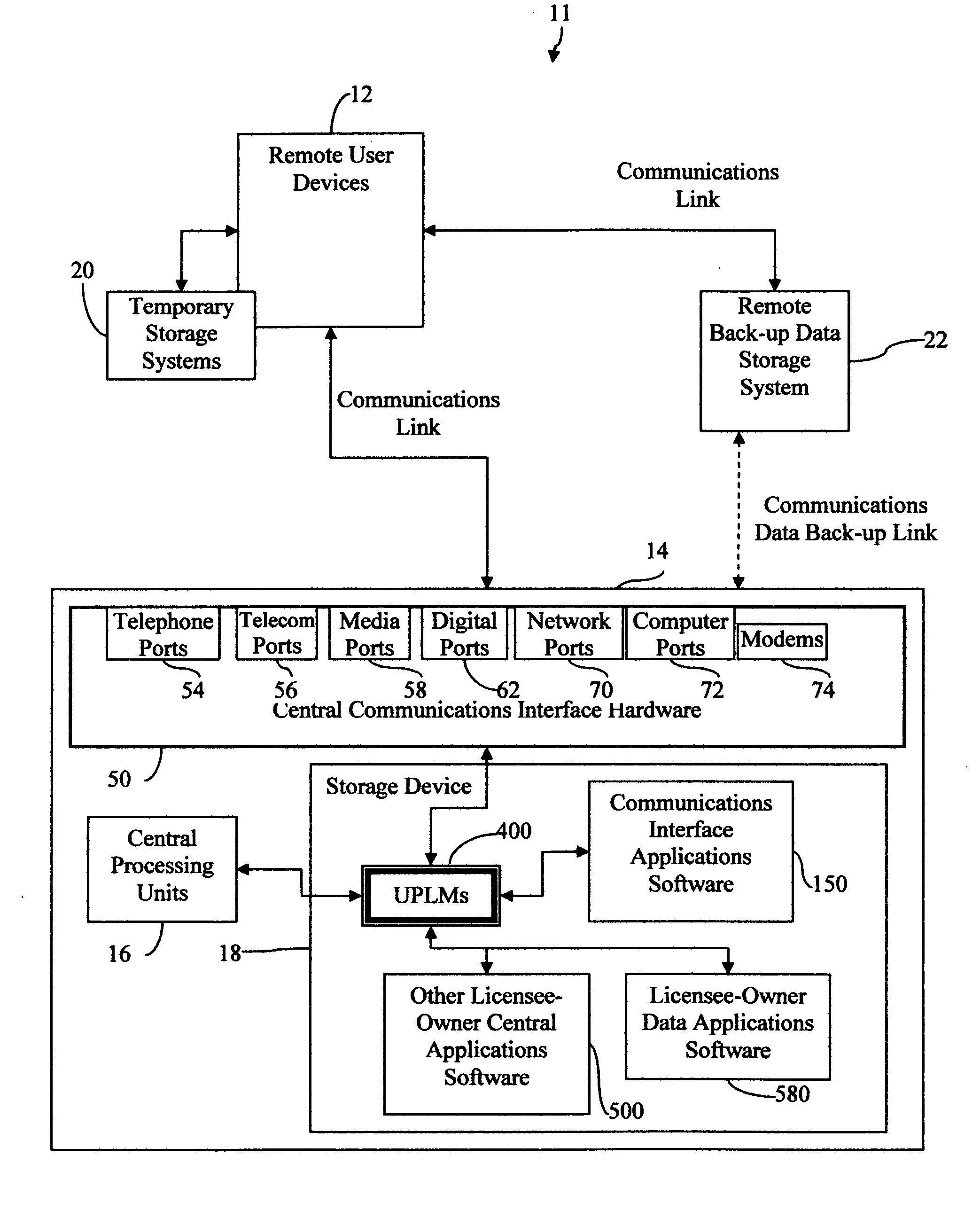
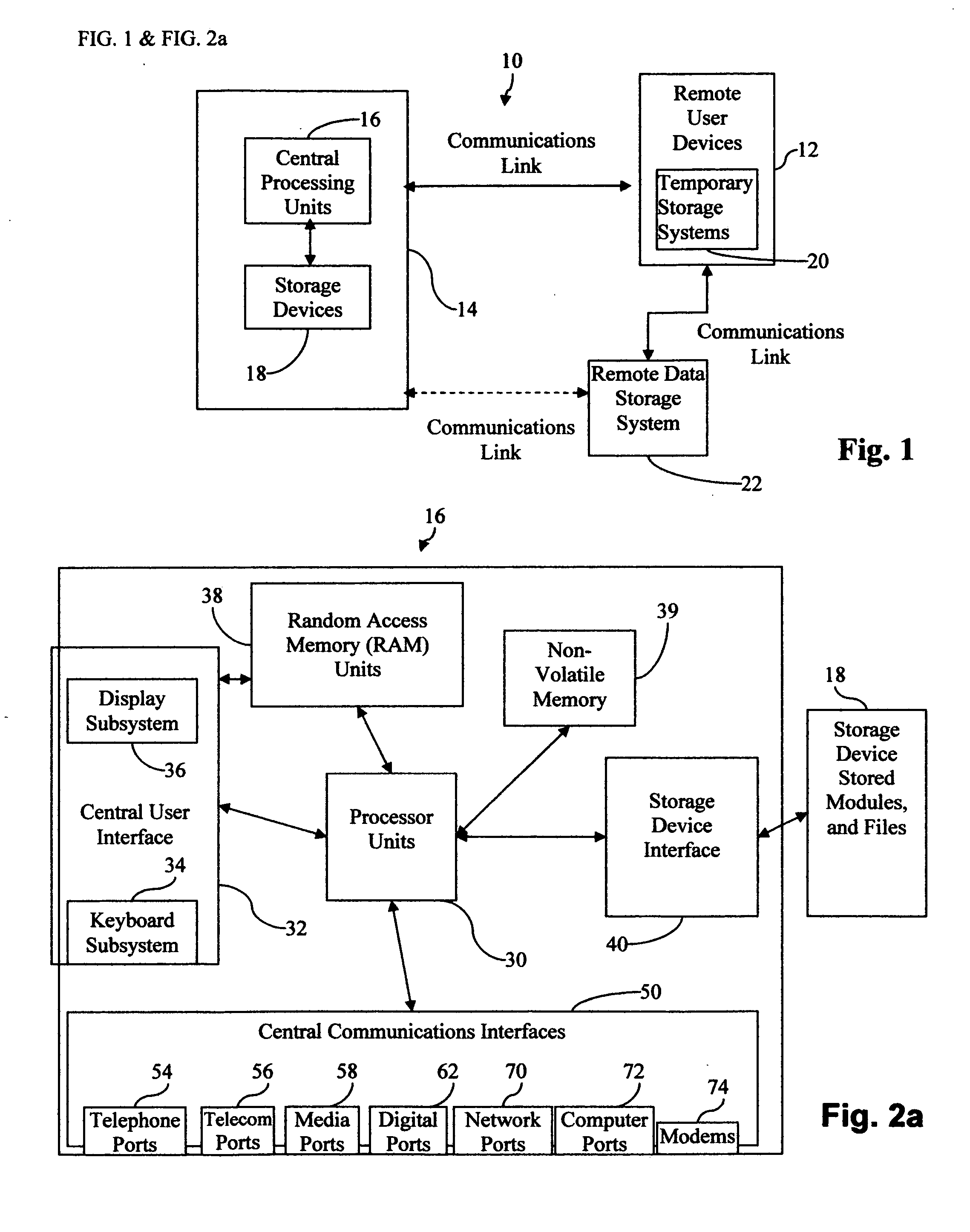
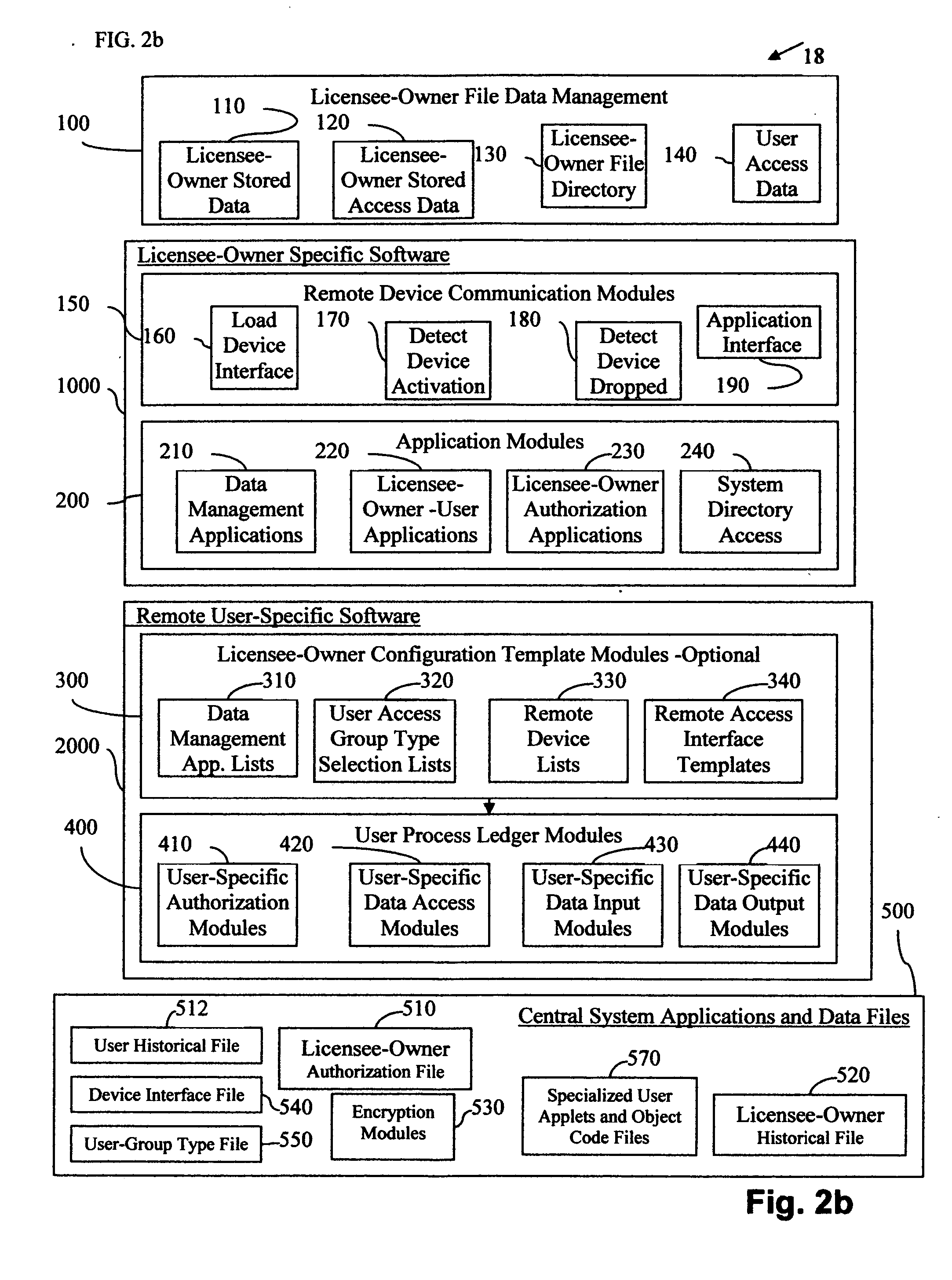
Central work-product management system for coordinated collaboration with remote users
InactiveUS20070143398A1Easy accessFinanceMultiple digital computer combinationsUser deviceWork product
A multi-component system for linking remote uses to a central work-product management system includes central processing device, central storage device, and a selection of different remote access devices and associated central system interface means for remote user to collaborate with central system licensee-owner work-product computer applications. The central storage device stores licensee-owner specific central application software associated with, licensee-owner specific data, and file and data management programs and the associated interface means allowing access to licensee-owner account by custom remote user specific applications The multi-component system for linking a remote user to a licensee-owner central work-product management system and devices are connected by the implementation of custom remote user specific interface applications which communicates with remote user devices, referred to herein as user process ledger modules, or UPLMs. After user recognition and access security is implemented, the UPLMs guide the remote user to limited segments of licensee-owner specific central system data locations implementing specific application procedures in the access to and development of the licensee-owner's and user's work-product. The central processing device implements the communications interface applications which upon remote user connection, recognition, and by access permission, executes associated specific UPLMs to exchange information with the remote user device, and implement any associated applications required for the processing of the remote user specific information, requested data input, data manipulation, or data output. Overall, the system provides an efficient, simple, highly direct, secure limited access mechanism for transferring specific user information from remote locations into an active central licensee-owner specific processing system accurately with minimal knowledge in the area of expertise of licensee-owner file and data management systems and associated application programs required for the development of a licensee-owner work-product.
Owner:GRAHAM JEAN A
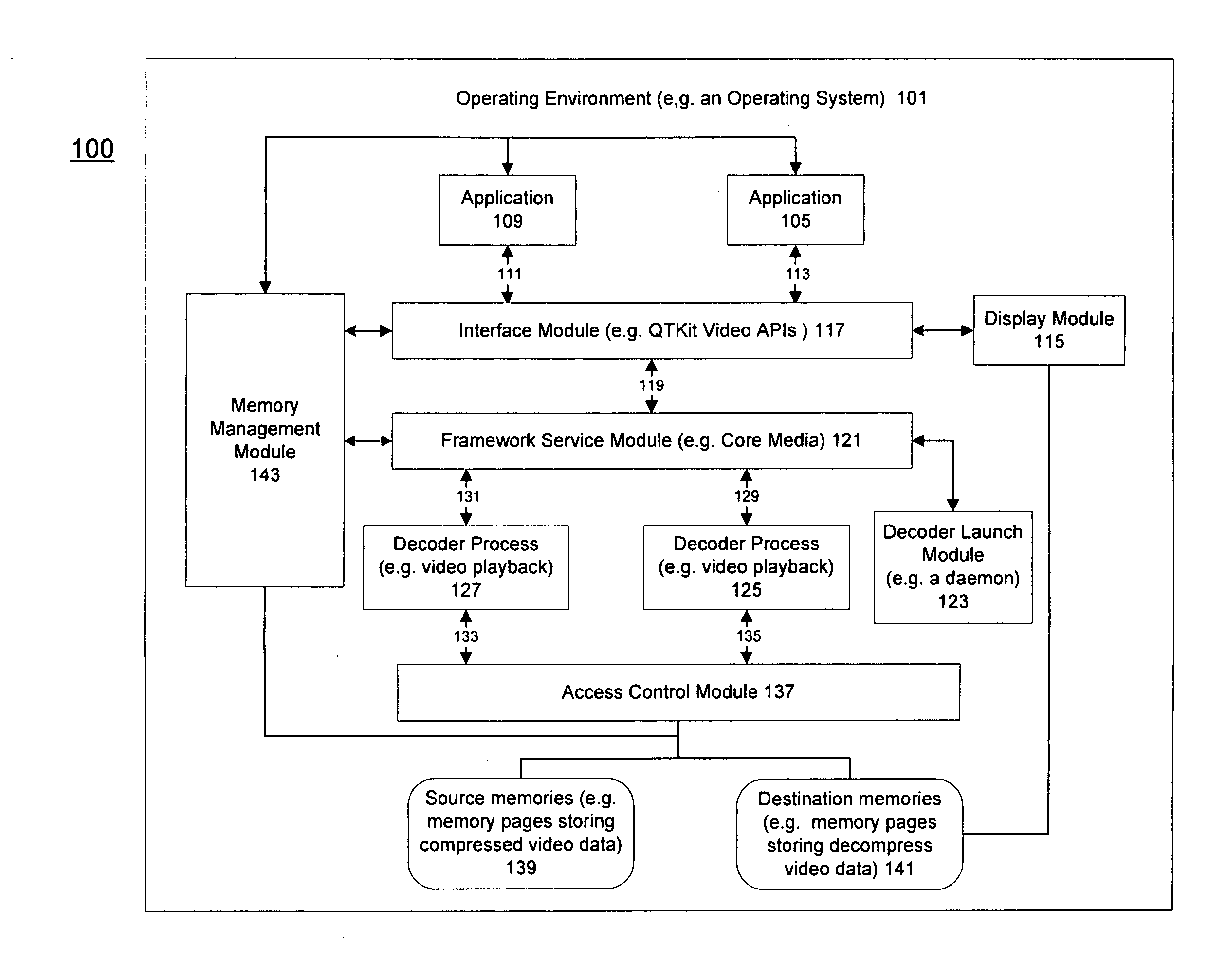
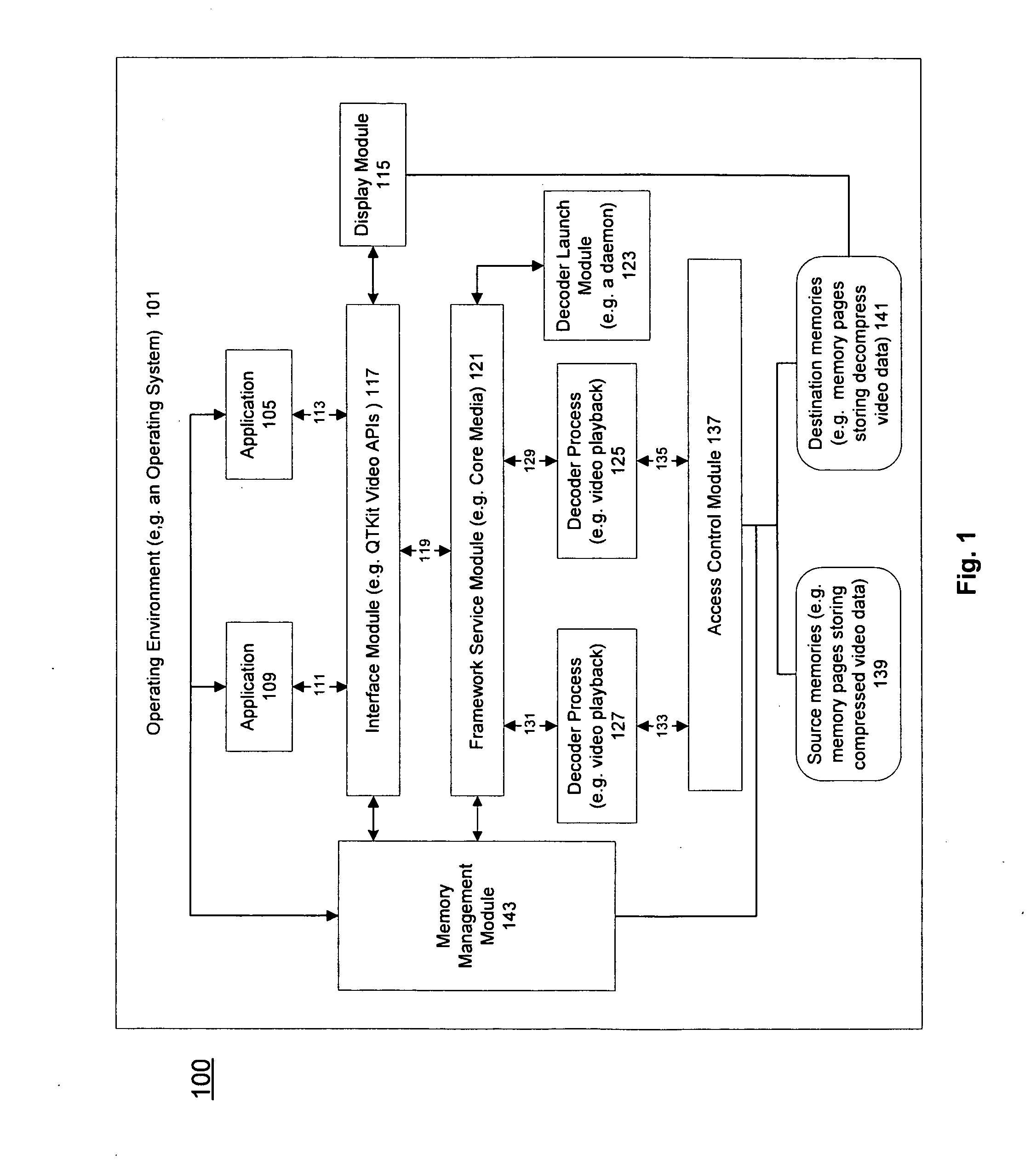
Method and apparatus for protected content data processing
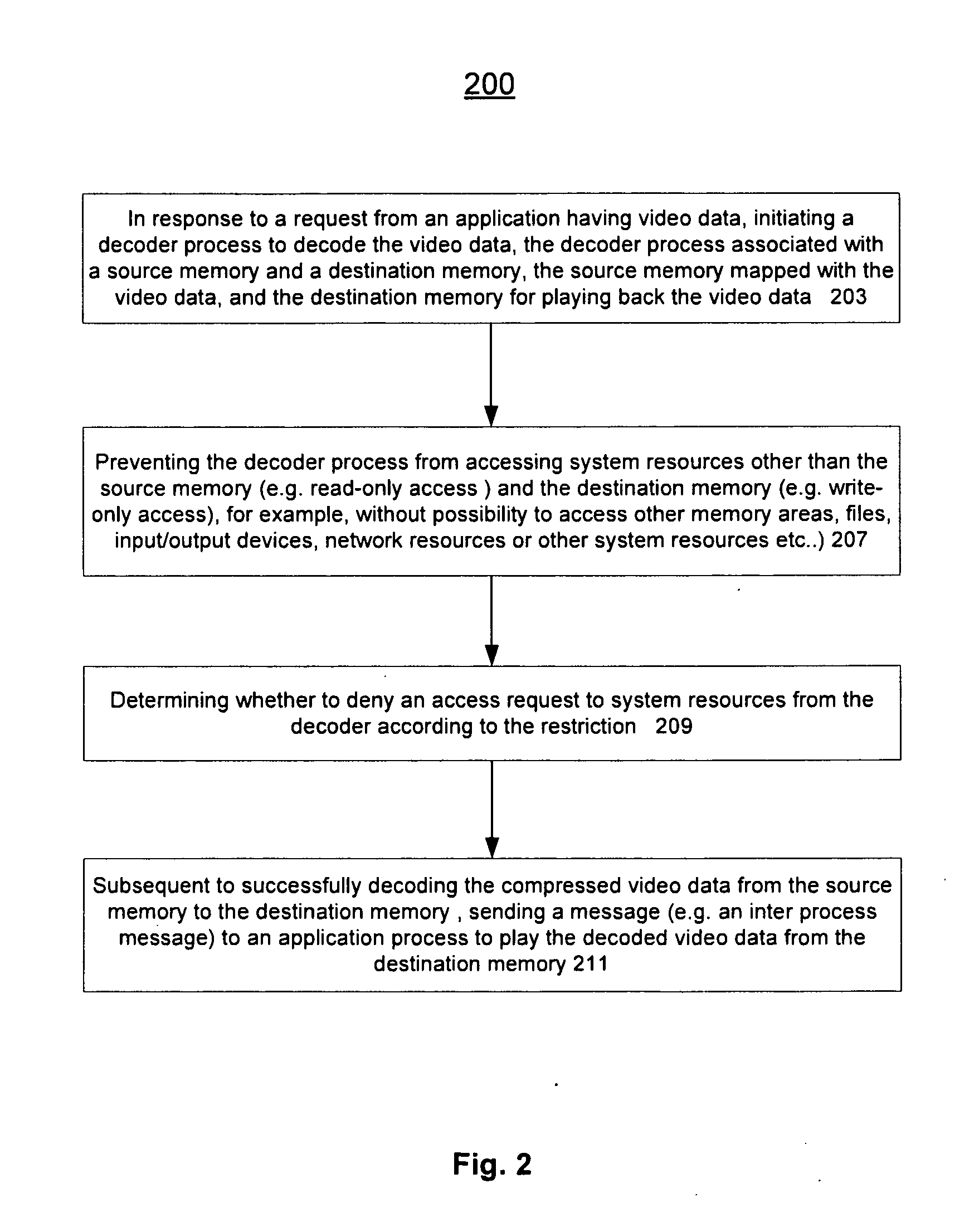
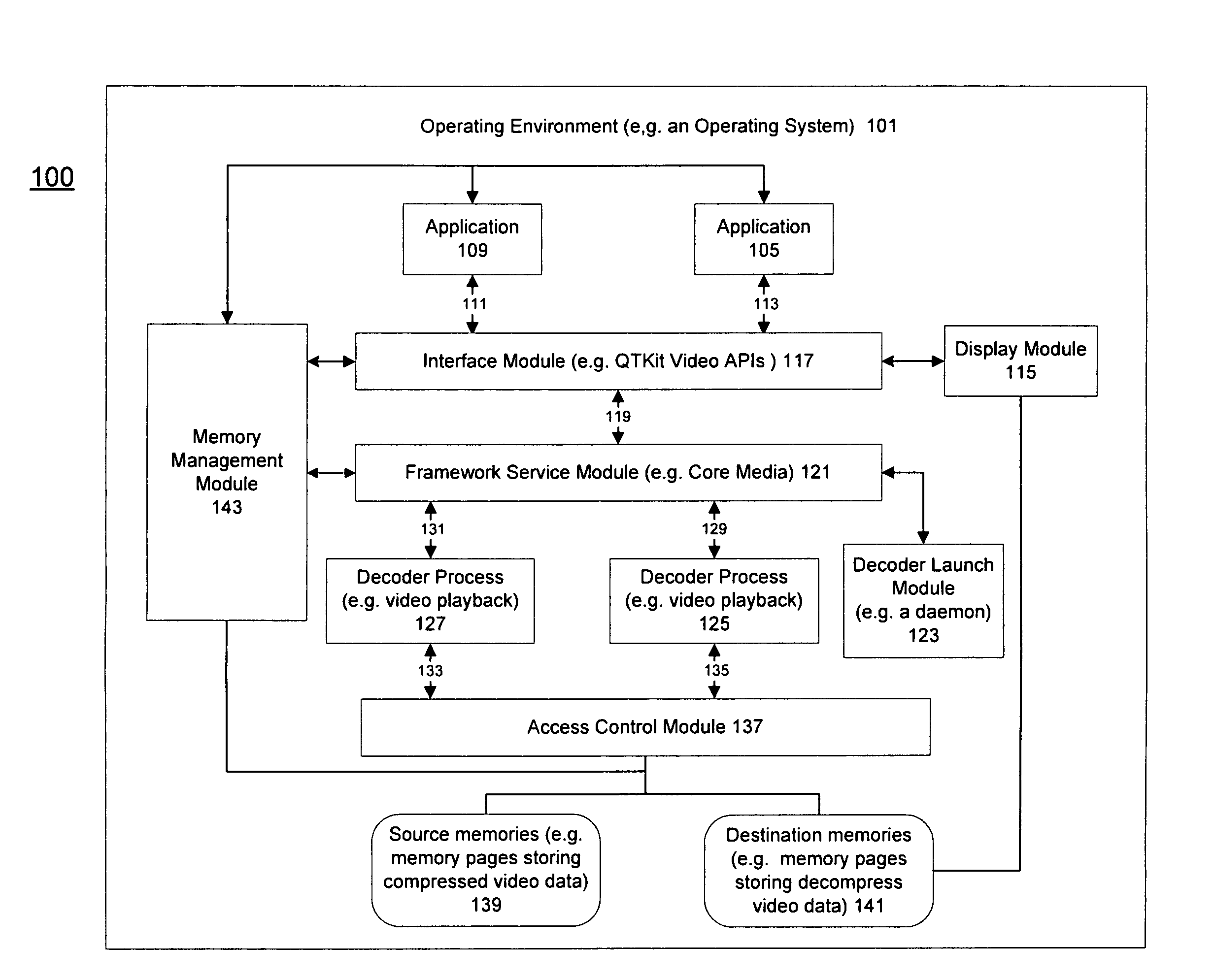
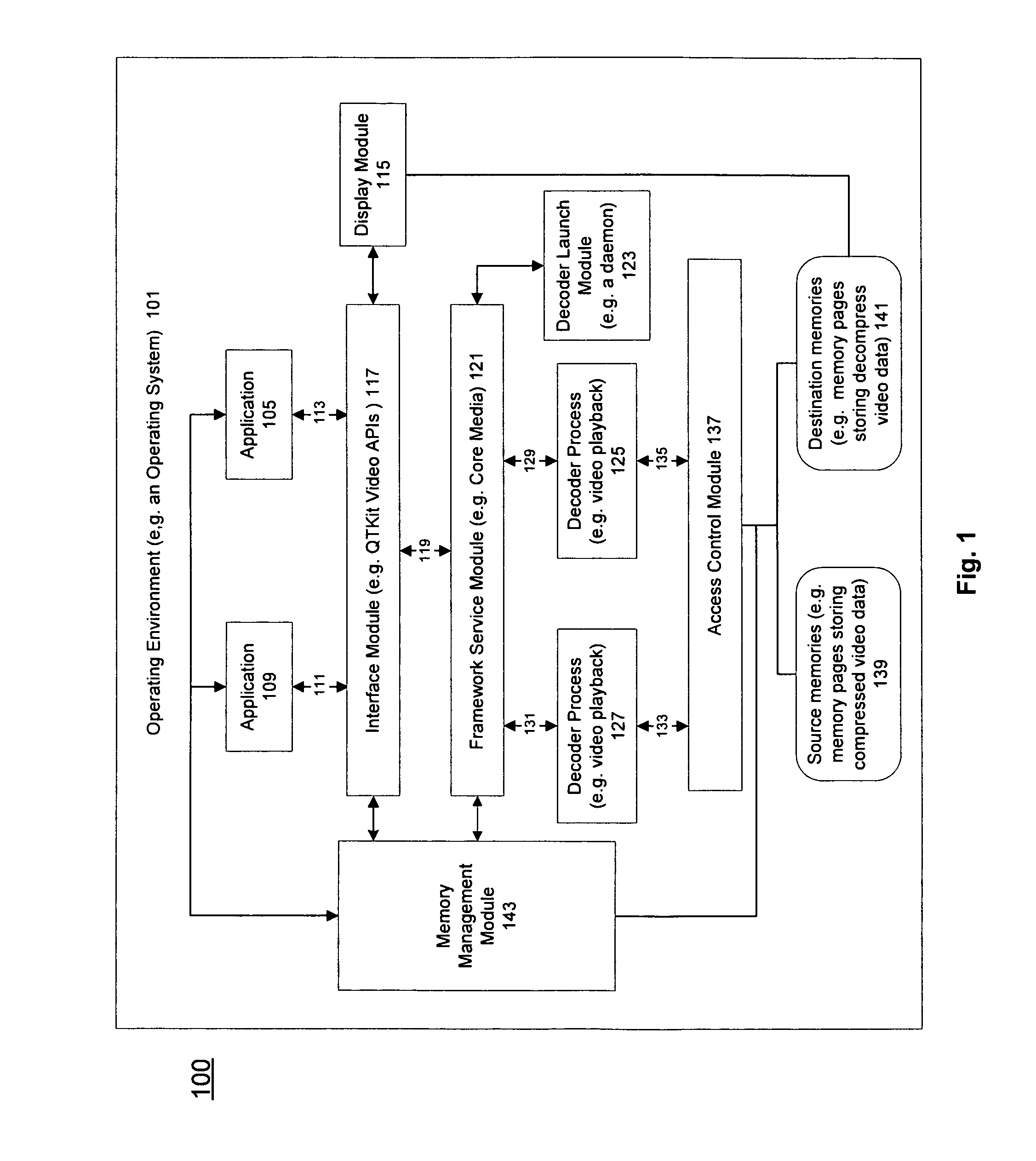
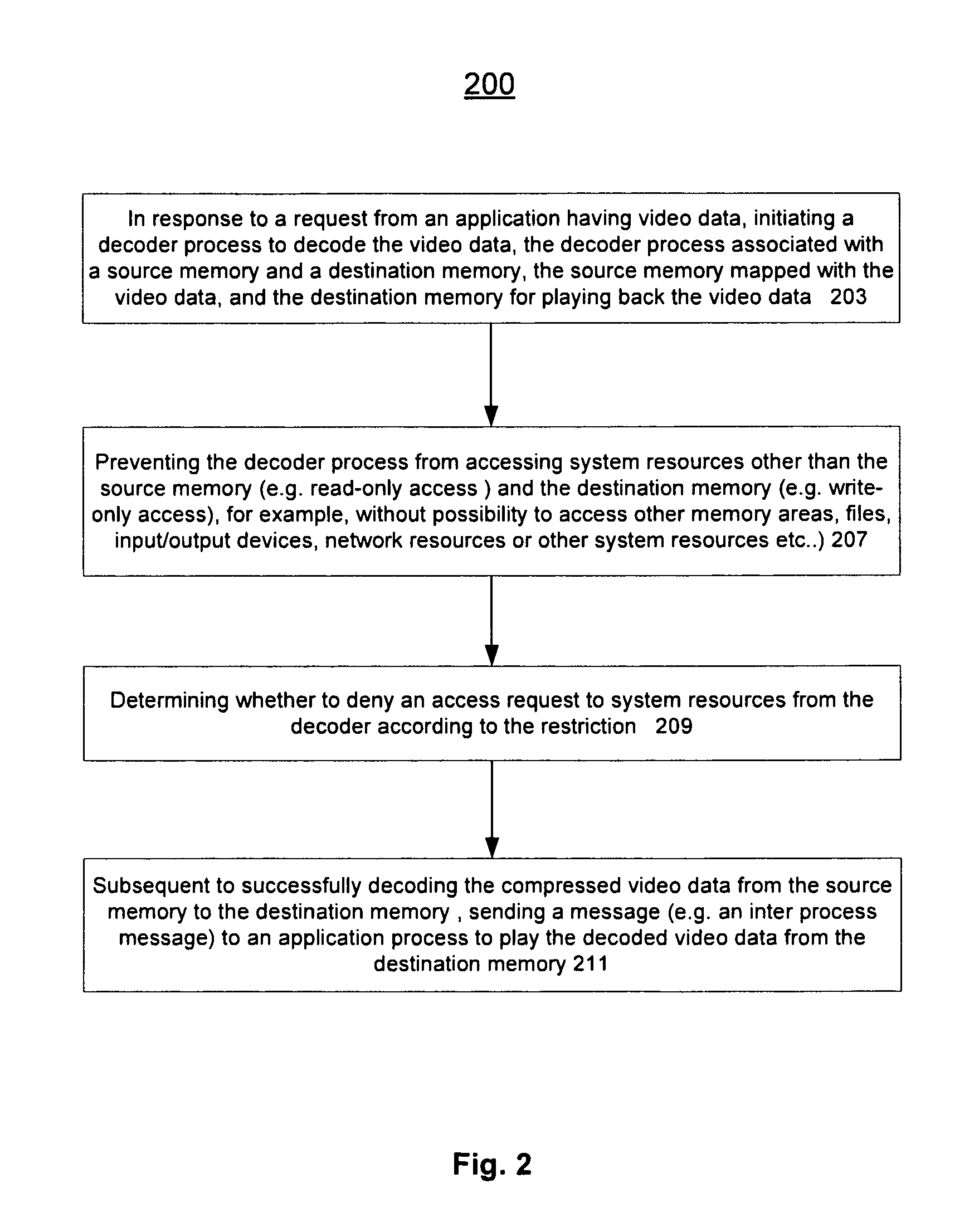
ActiveUS20110004737A1Limited accessAvoid resourcesDigital data processing detailsUnauthorized memory use protectionComputer networkLimited access
Methods and an apparatuses that perform protected content data processing with limited access to system resources are described. One or more regions in a memory (including a source memory and a destination memory) can be allocated and unprocessed content data can be mapped to the source memory. A process can be initialized with the source and destination memories to process the content data. The process can be prevented from accessing resource other than the allocated regions in the memory. The processed content data can be stored in the destination memory. In one embodiment, the content data can include media content. A playing device can be instructed to play the media content based on the processed content data via the destination memory.
Owner:APPLE INC
On-line interactive system and method for transacting business
The present invention includes a method for transacting business over a network between multiple buyers and sellers. In an exemplary embodiment, the invention operates within an improved extranet system which is a secure, limited access network which operates within the larger public packet switched network (Internet) and allows only registered buyers and sellers to access the website while the system communicates with, and takes advantage of, existing credit, billing, collection, clearinghouse, insurance, transportation, tracking and banking systems. The interactive database includes real-time information in connection with a transaction, where the buyer submits a request for product and the request for the product locks out the requested product from selection by any other buyers.
Owner:DUNCAN VENTURES INC
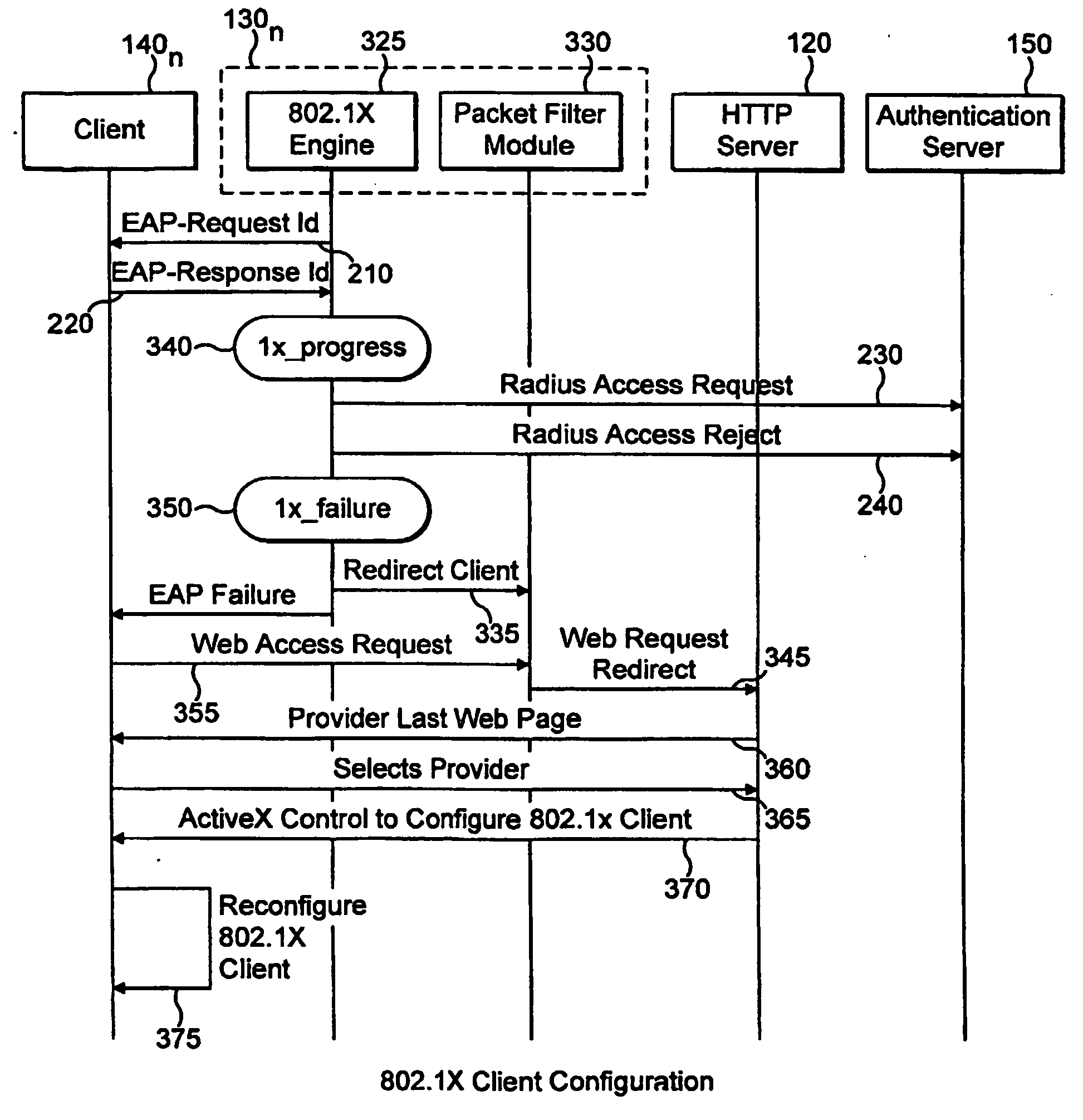
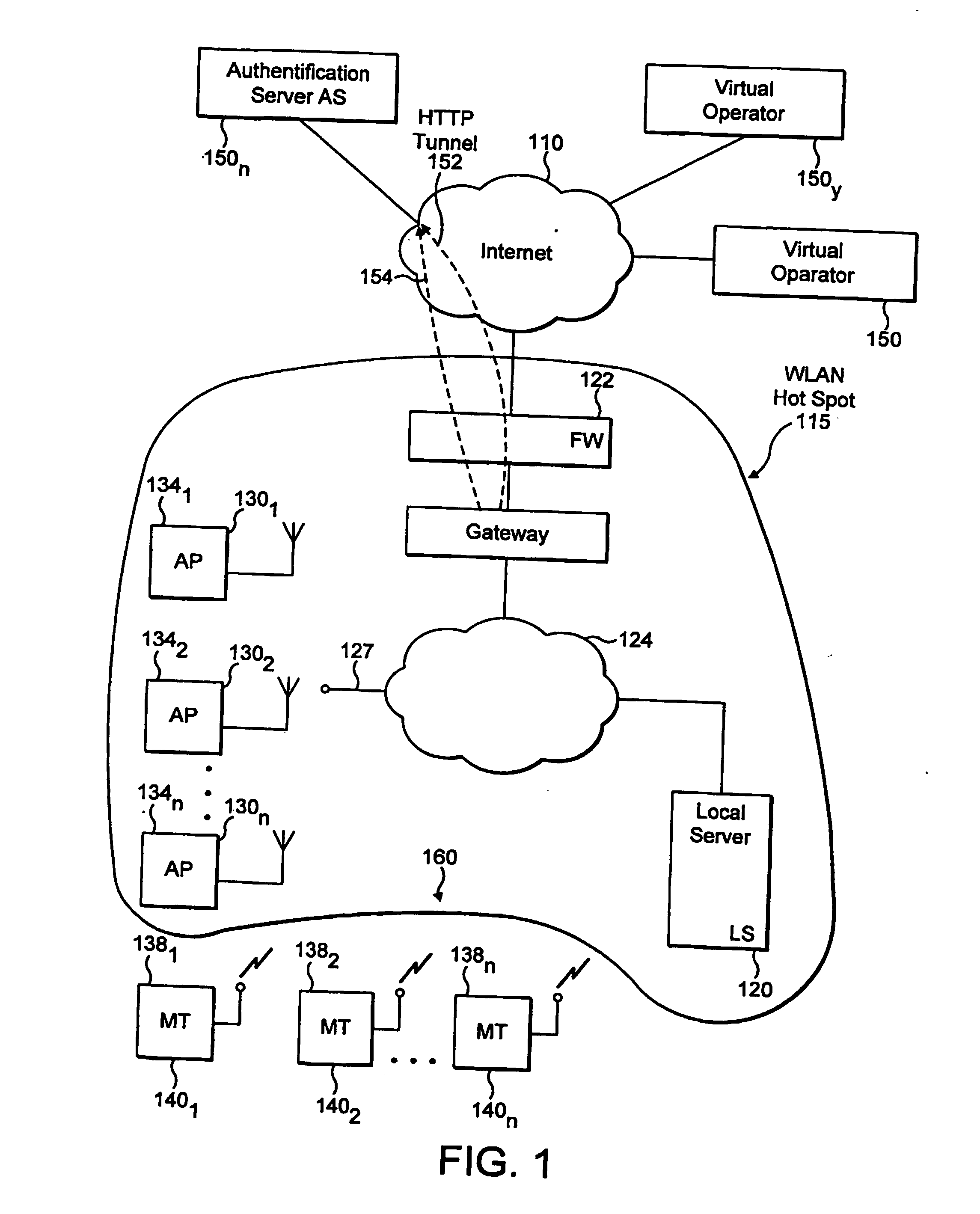
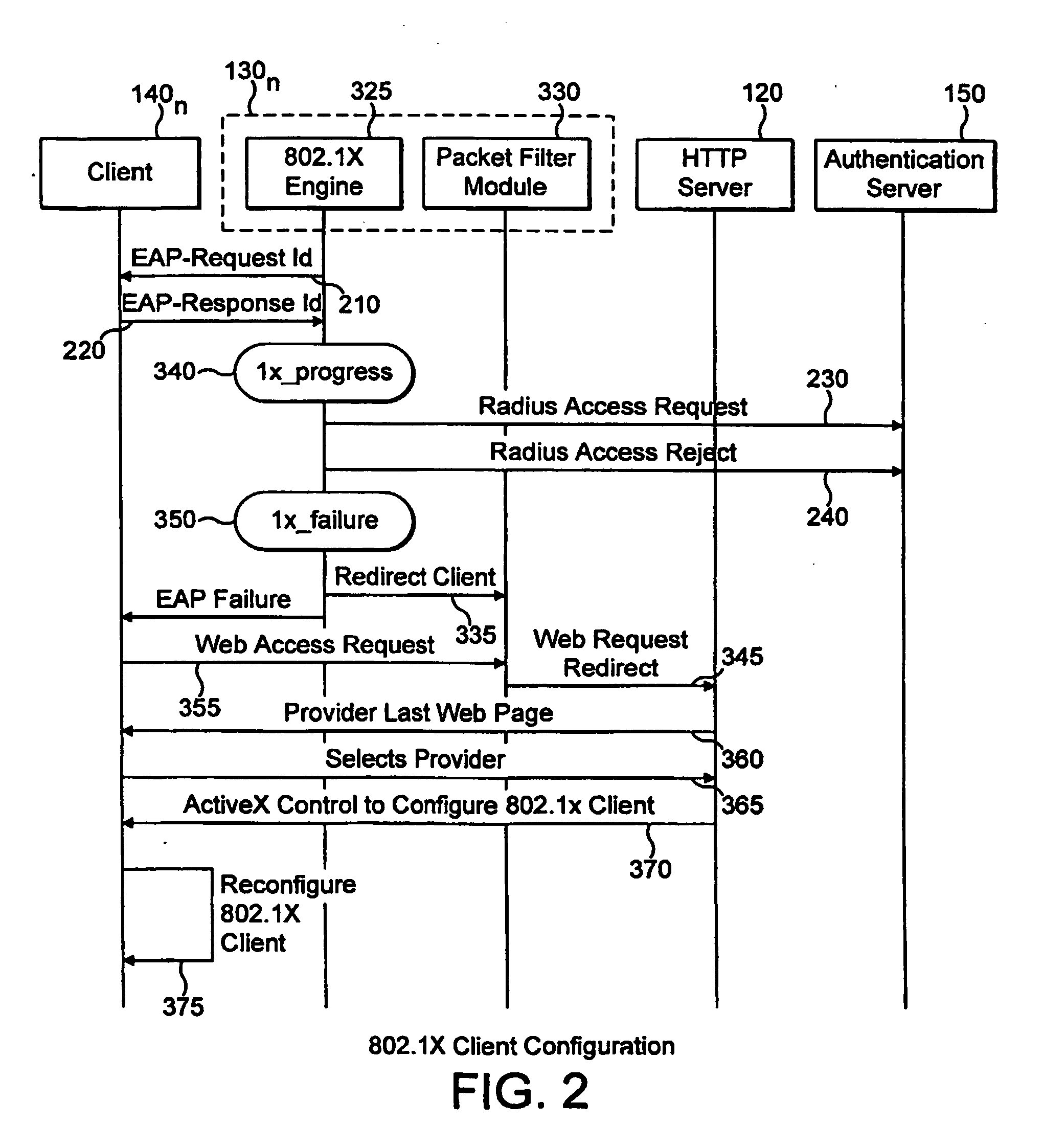
Automatic configuration of client terminal in public hot spot
ActiveUS20060173844A1Easy accessDigital data processing detailsUser identity/authority verificationLimited accessAuto-configuration
The invention herein provides an apparatus and a method for automatically configuring an IEEE 802.1x client terminal to provide limited access in a WLAN environment, specifically utilizing the access point to filter traffic associated with the limited access so as to redirect the client terminal's HTTP request to a designated local web server. The web server responds to the client terminal by requesting information required to establish an authorized communication. Thereafter the client terminal provides information required to establish an authorized communication. In the course of the communication the web server sends information such as transmission rates, new user account creation information, authentication method selection, and access user terms and conditions of acceptance, all typically required to establish an authorized access. The client responds with information, required to establish an authorized communication.
Owner:BOSTON MEDICAL CENTER INC +1
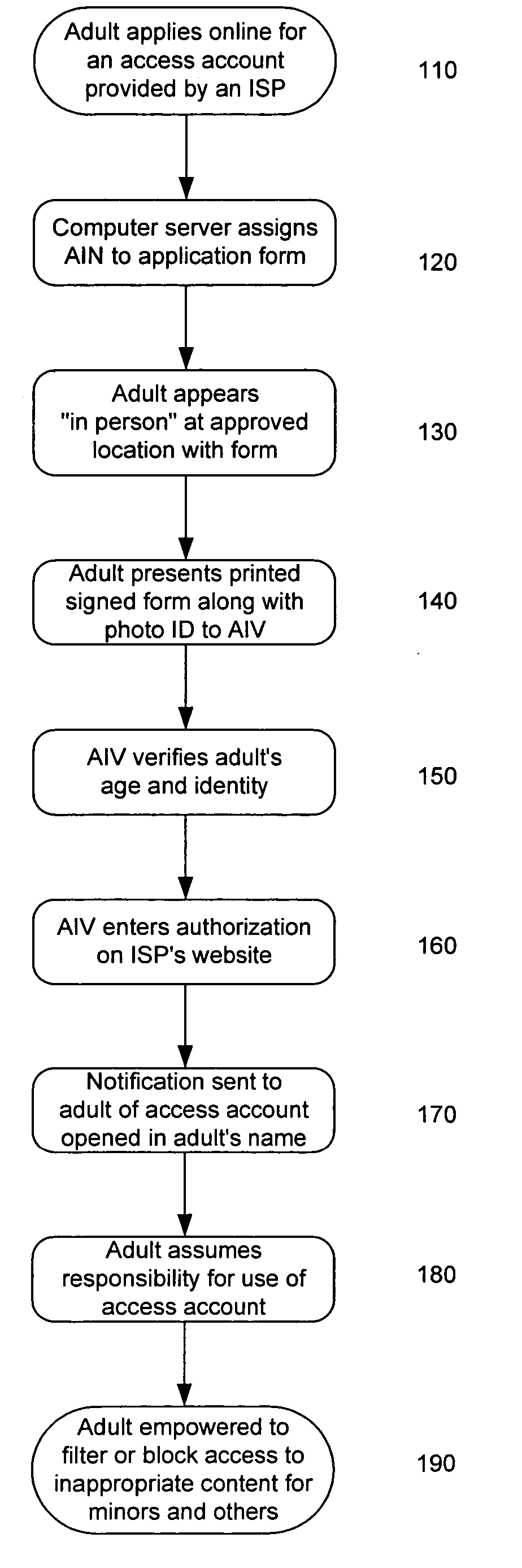
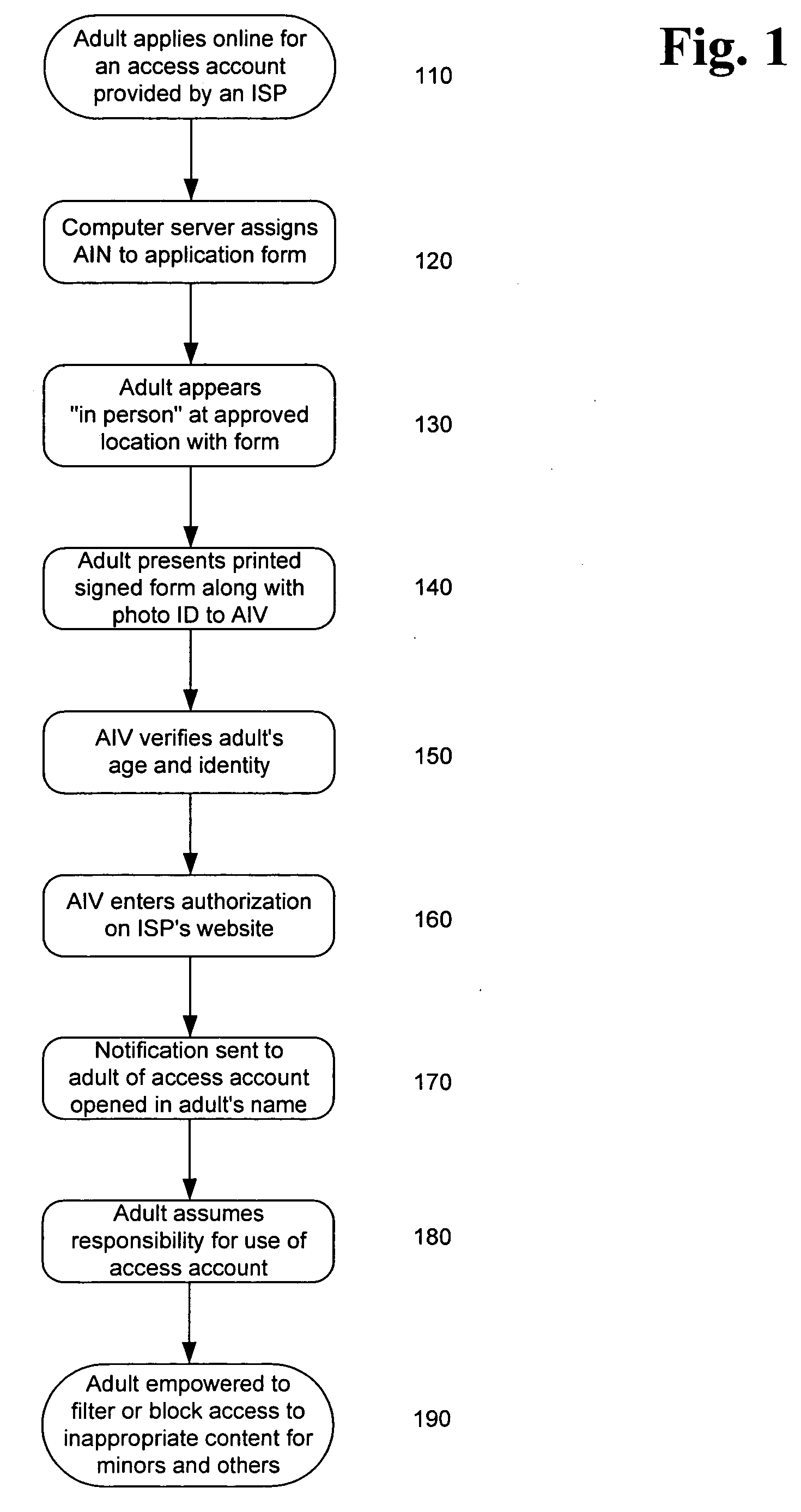
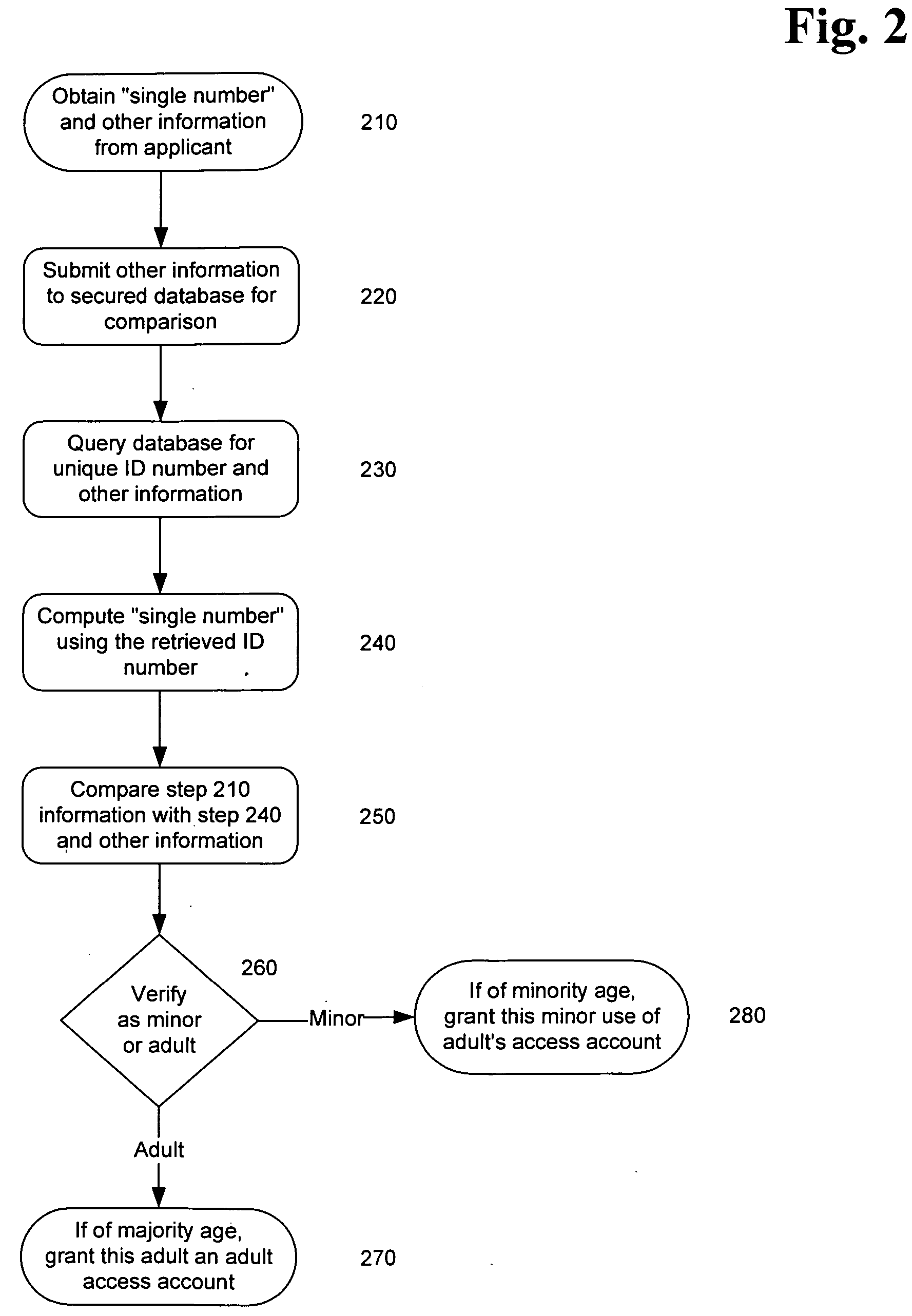
System and method for verifying the age and identity of individuals and limiting their access to appropriate material
InactiveUS20060173792A1Exposure was also limitedPayment architectureSecret communicationLimited accessInternet privacy
Limiting access to the Internet, eCommerce websites, accounts and / or other venues, for example, by providing an Internet access account, and / or other access account, to an “in person” and / or “single number” age verified and identified “adult” who assumes responsibility for use of such account and viewing of appropriate material via such account by “in person” age verified and identified individuals, while being empowered by control of a “single access account” that filters inappropriate material based on (1) user profiles created by age verified and identified adults and stored on provider's “access server” and / or (2) “mandatory” provider imposed filtering.
Owner:GLASS PAUL H
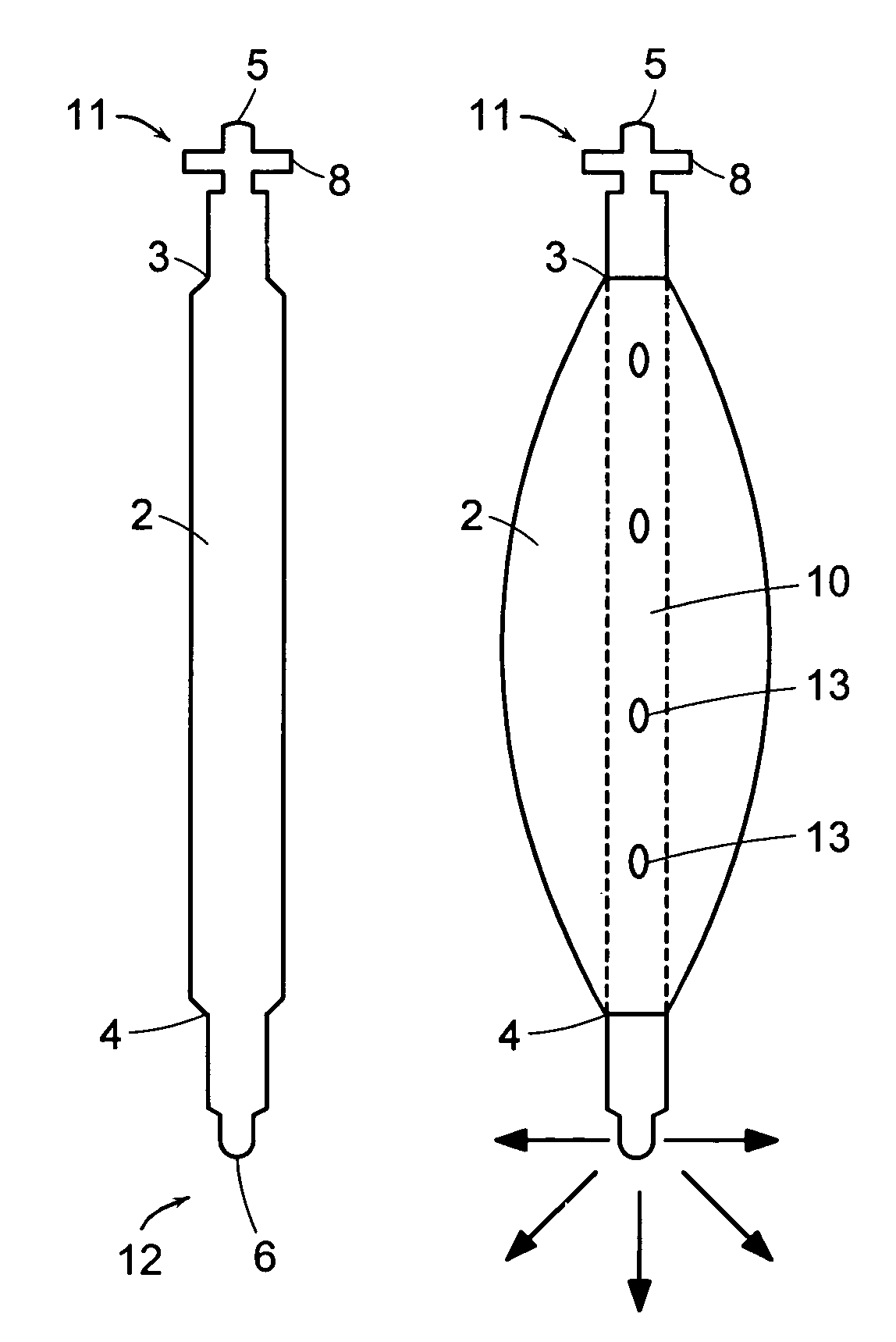
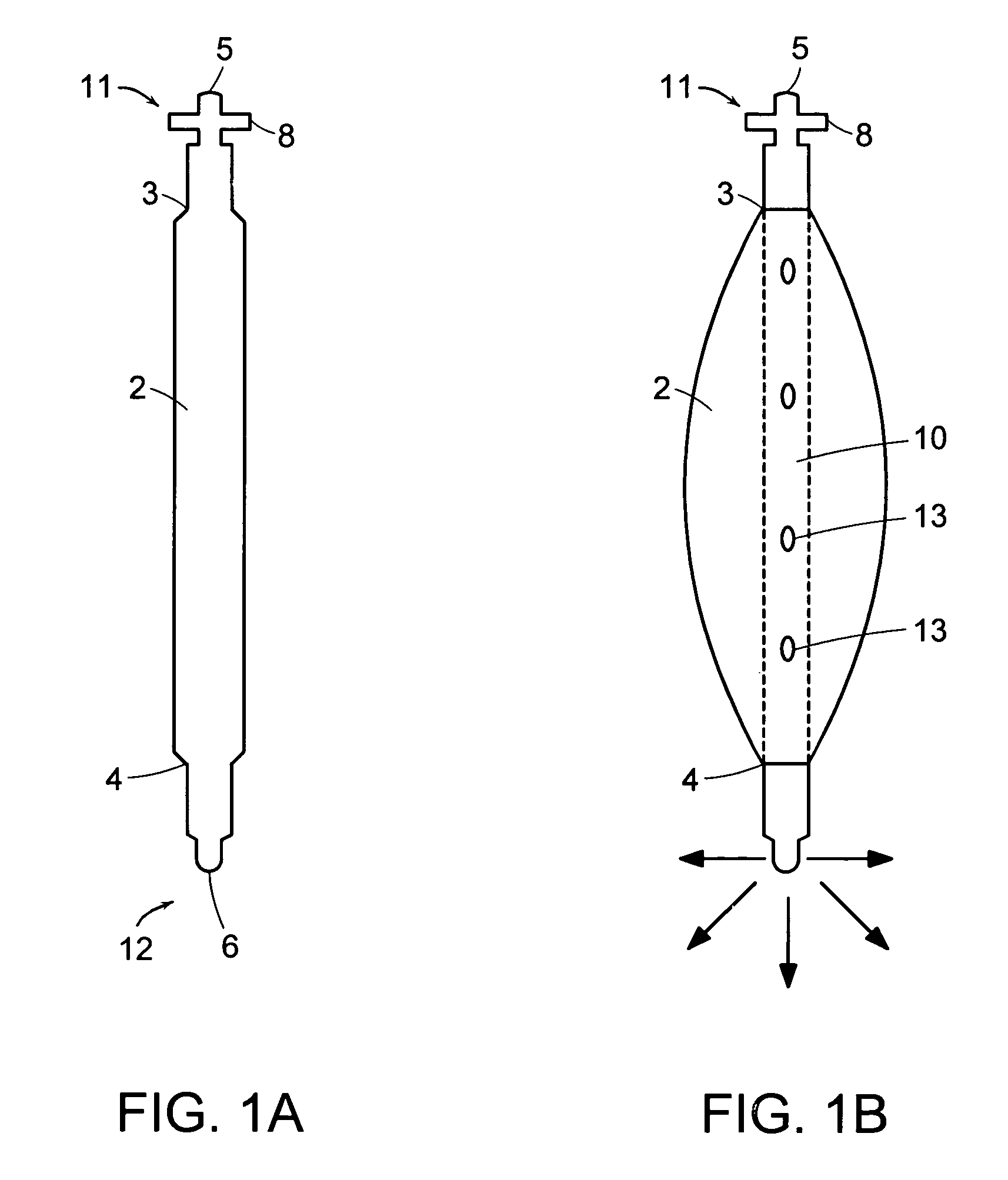
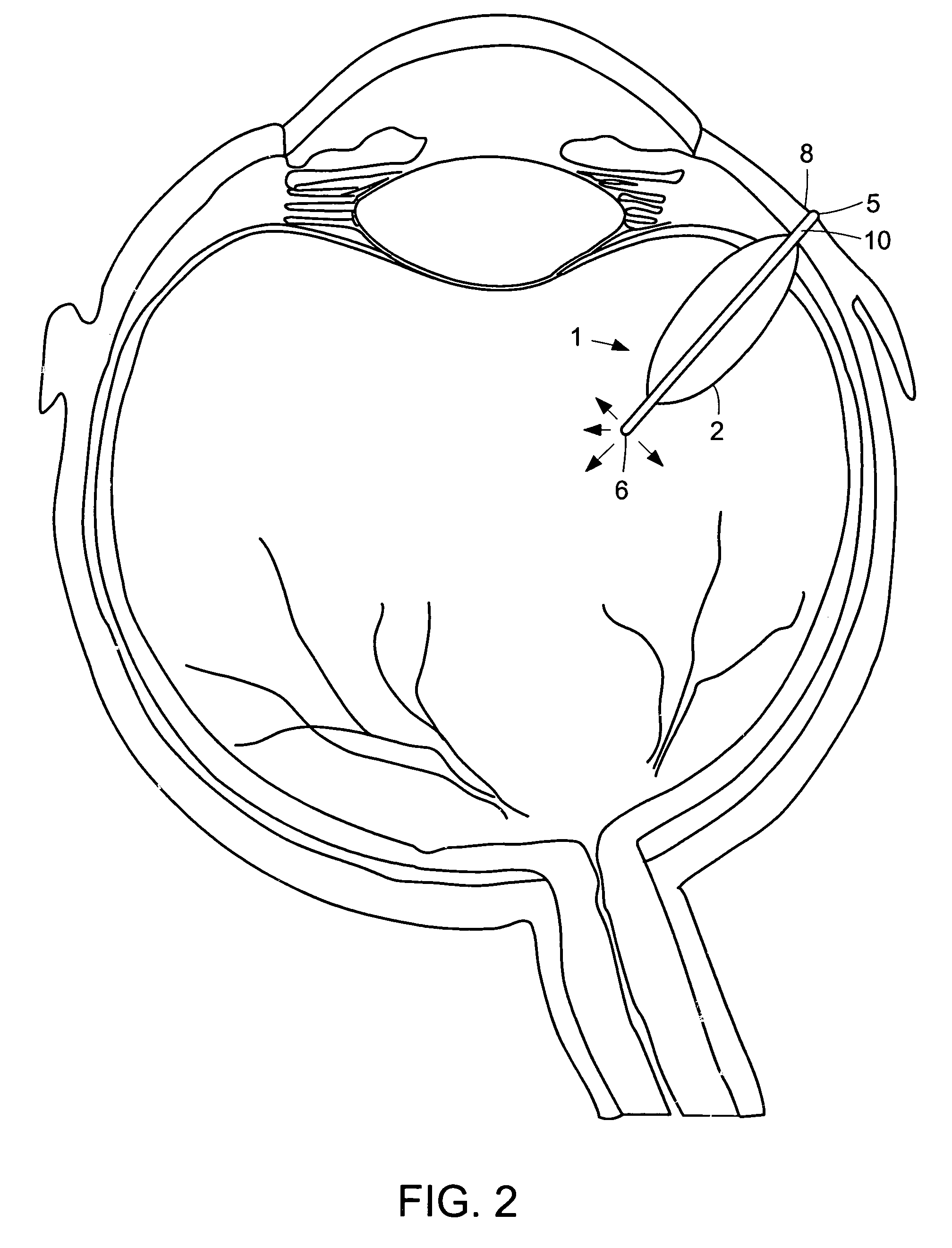
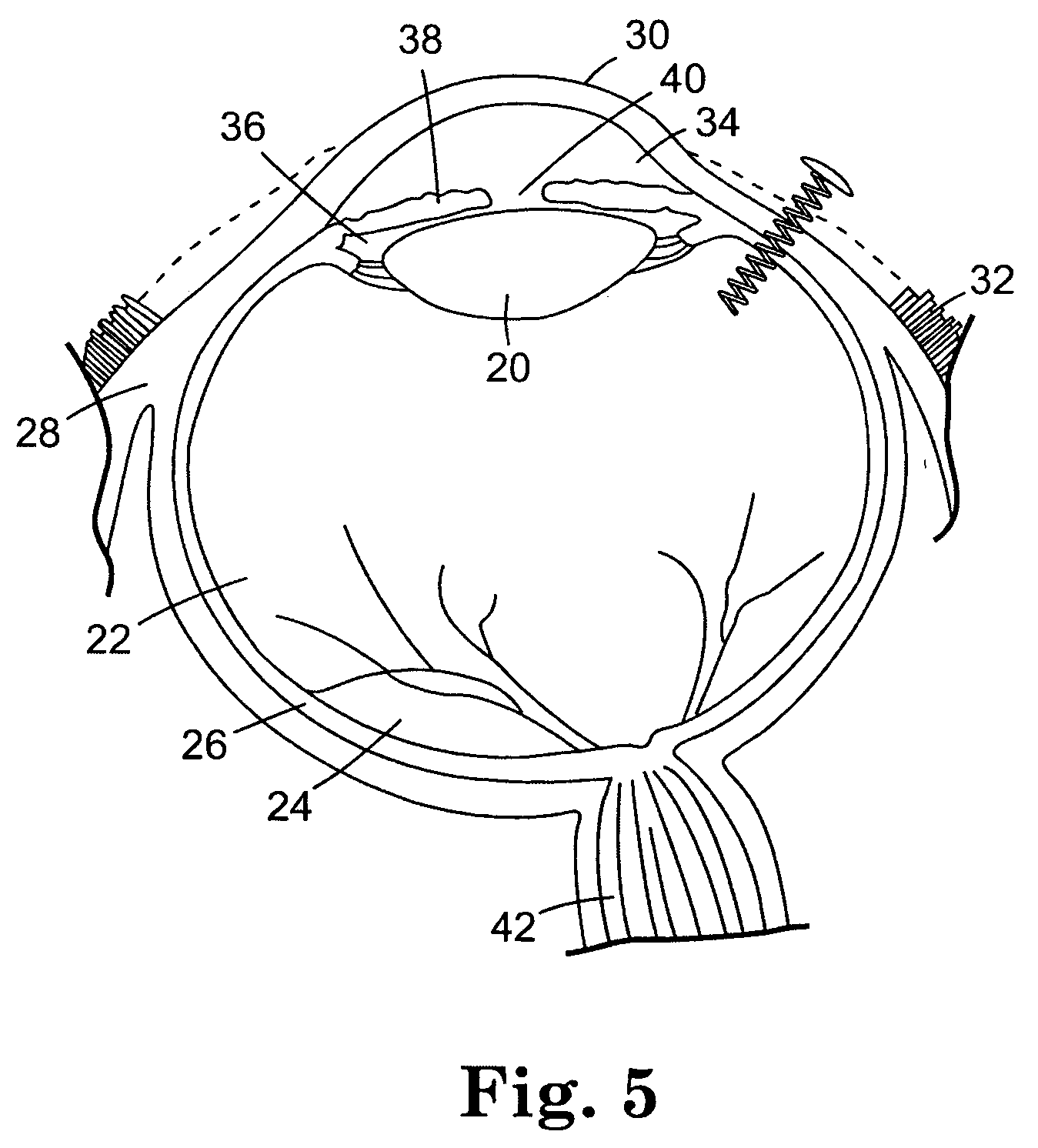
Reservoir device for intraocular drug delivery
ActiveUS7883717B2Eliminate riskMinimally invasiveEye surgeryPharmaceutical delivery mechanismLimited accessSurgery
A delivery device that allows for the sustained release of an agent, particularly useful for the sustained release of a therapeutic agent to limited access regions, such as the posterior chamber of the eye and inner ear. The delivery device is minimally invasive, refillable and may be easily fixed to the treatment area. The delivery device includes a hollow body with an inlet port at its proximal end for insertion of the agent, a reservoir for holding the agent and a delivery mechanism for the sustained delivery of the agent from the reservoir to the patient.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
Lock-free implementation of concurrent shared object with dynamic node allocation and distinguishing pointer value
A novel linked-list-based concurrent shared object implementation has been developed that provides non-blocking and linearizable access to the concurrent shared object. In an application of the underlying techniques to a deque, non-blocking completion of access operations is achieved without restricting concurrency in accessing the deque's two ends. In various realizations in accordance with the present invention, the set of values that may be pushed onto a shared object is not constrained by use of distinguishing values. In addition, an explicit reclamation embodiment facilitates use in environments or applications where automatic reclamation of storage is unavailable or impractical.
Owner:ORACLE INT CORP
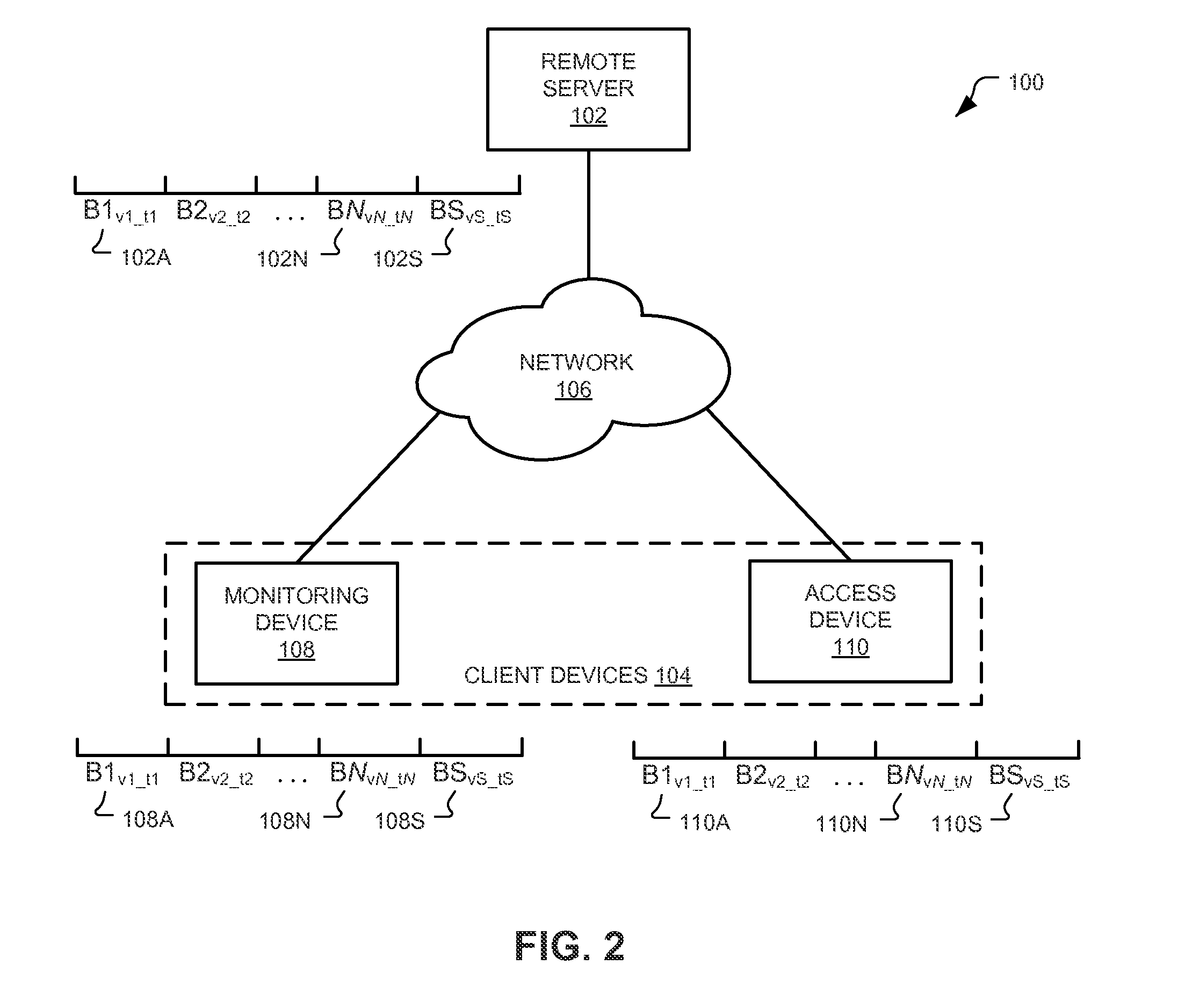
Subscription-Notification mechanisms for synchronization of distributed states
ActiveUS8635373B1Minimize power consumptionReduced power capacityEnergy efficient ICTMultiple digital computer combinationsLimited accessClient-side
Apparatus, systems, methods, and related computer program products for synchronizing distributed states amongst a plurality of entities and authenticating devices to access information and / or services provided by a remote server. Synchronization techniques include client devices and remote servers storing buckets of information. The client device sends a subscription request to the remote serve identifying a bucket of information and, when that bucket changes, the remote server sends the change to the client device. Authentication techniques include client devices including unique default credentials that, when presented to a remote server, provide limited access to the server. The client device may obtain assigned credentials that, when presented to the remote server, provide less limited access to the server.
Owner:GOOGLE LLC
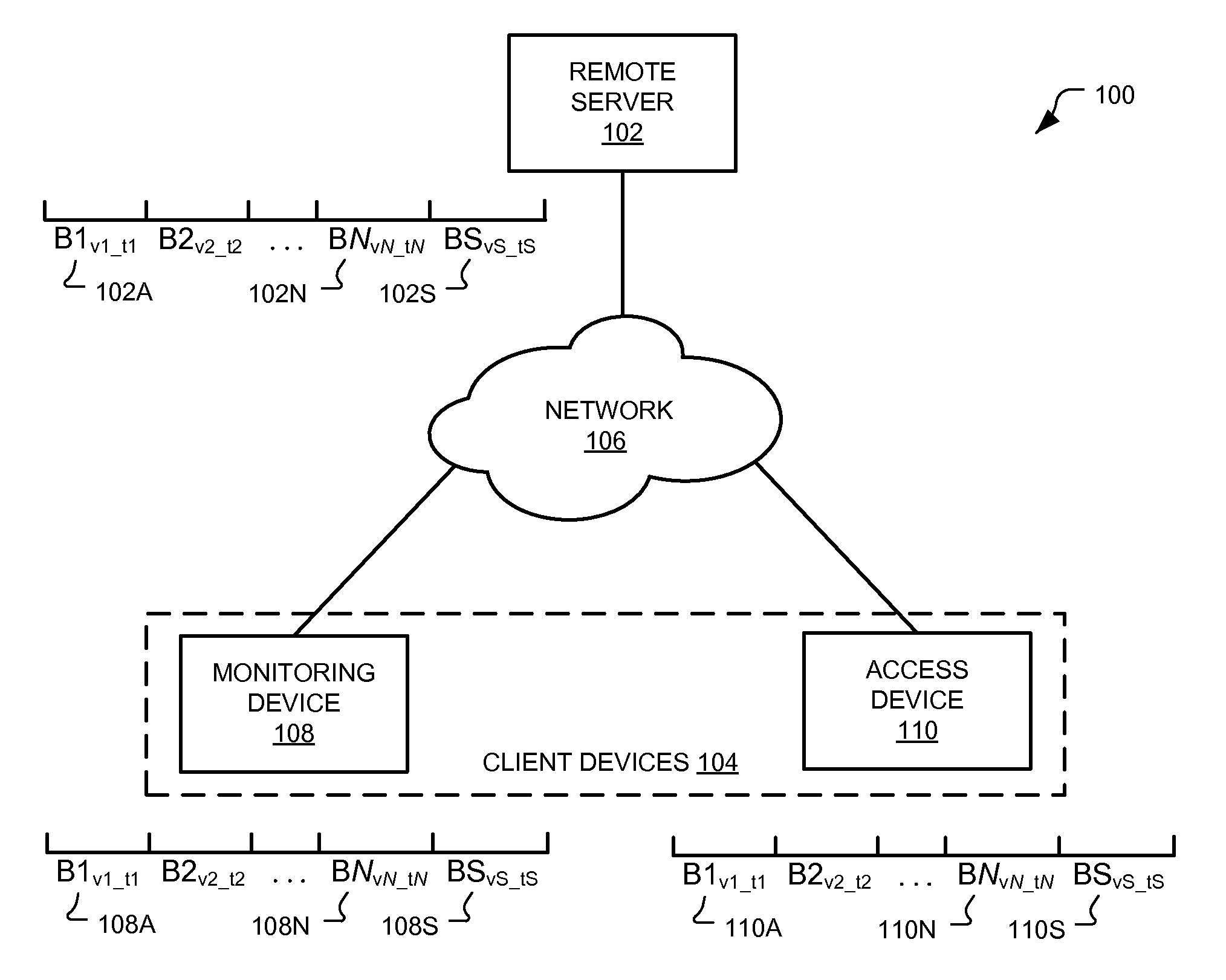
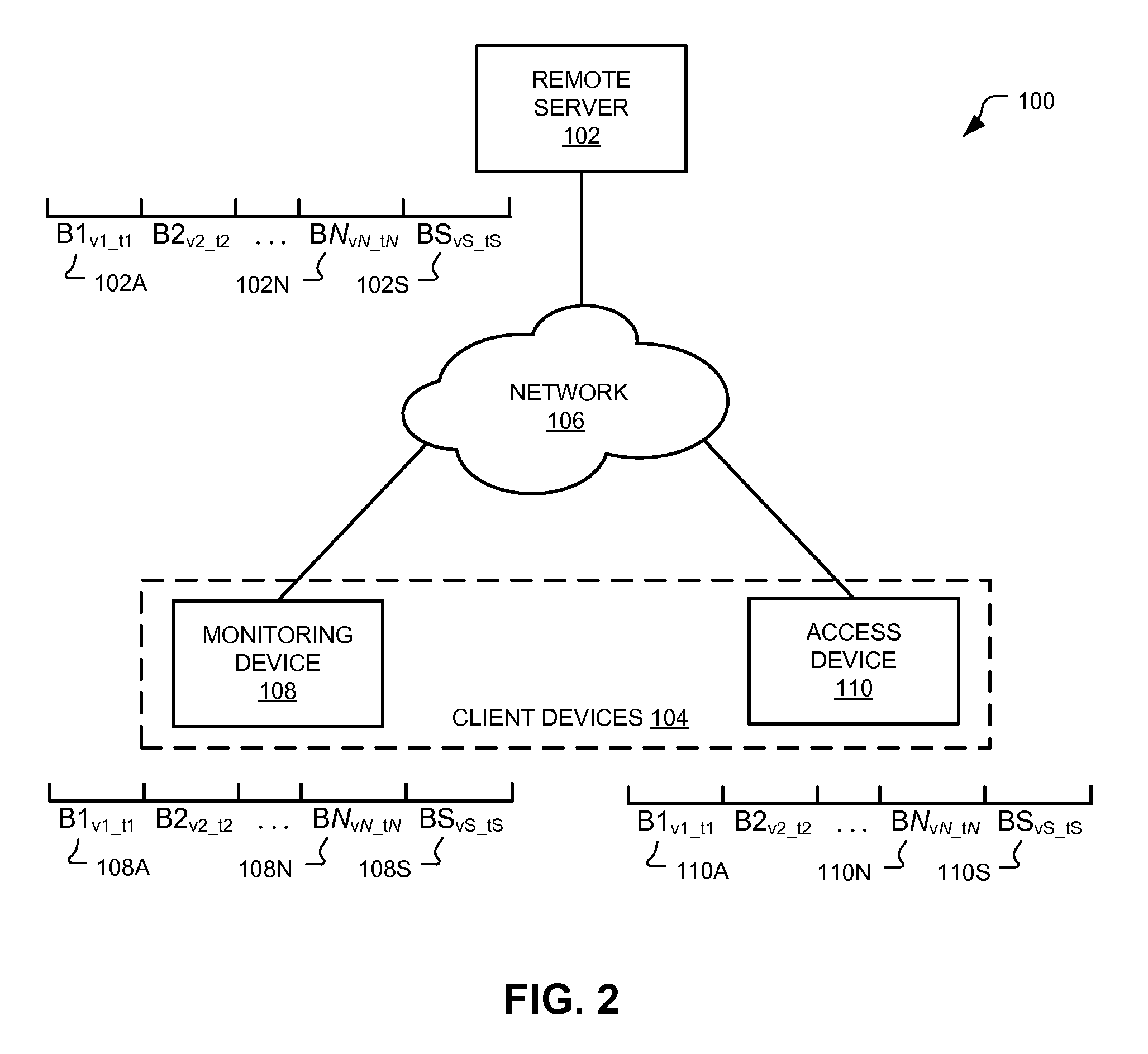
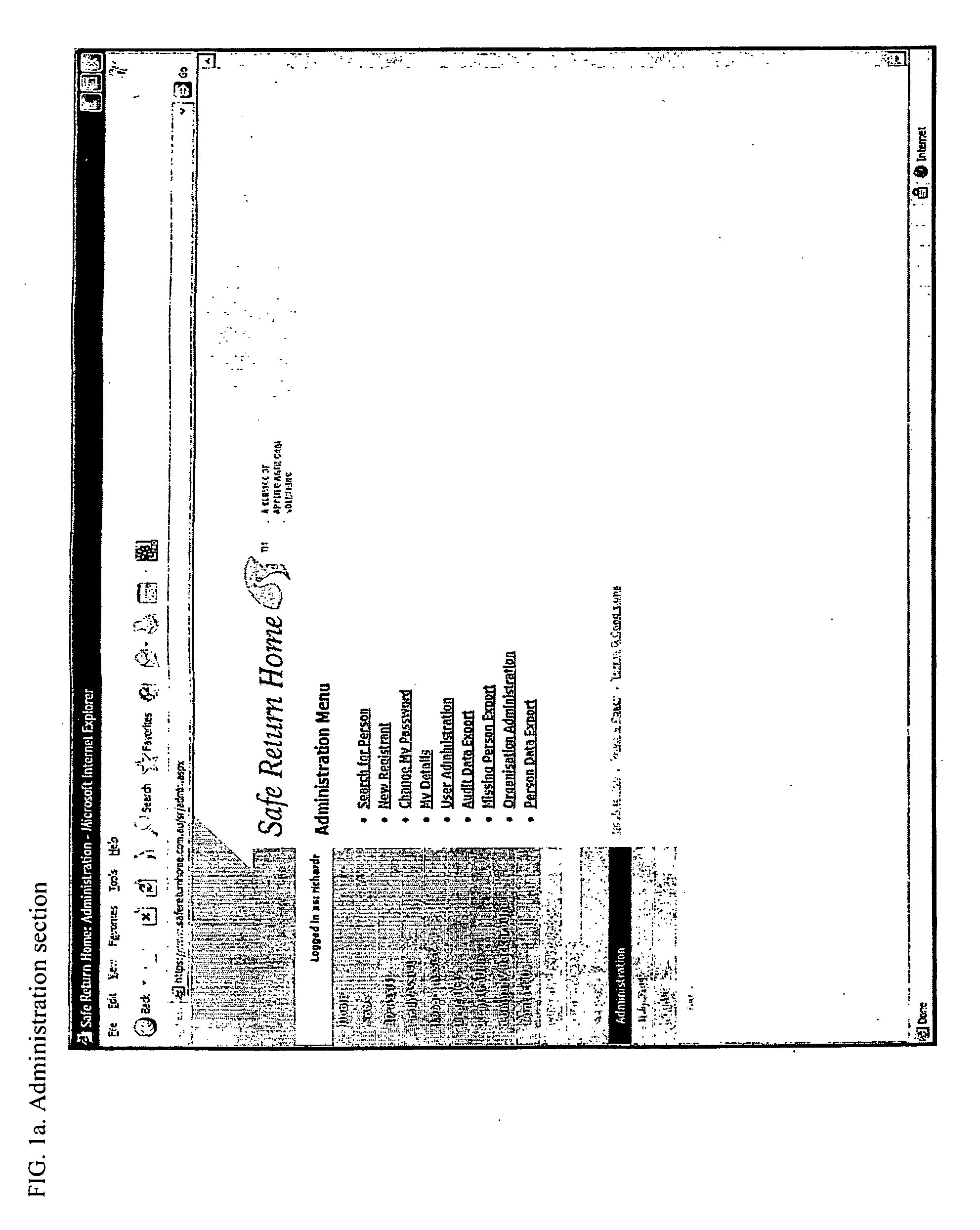
Essential data communication system
InactiveUS20070156692A1Reduce usageData processing applicationsWeb data retrievalCommunications systemLimited access
The present invention provides a communication system forming a safety mechanism for people likely to be disoriented or lost. Using the system, a user provides personal details and defines access restrictions for that data. The access restrictions can include predefined events such s the user being reported lost. The data is disseminated to specified recipients, such as emergency services and police, when conditions of the access restrictions are met. The system has particular application to the location of missing persons.
Owner:ROSEWARNE RICHARD
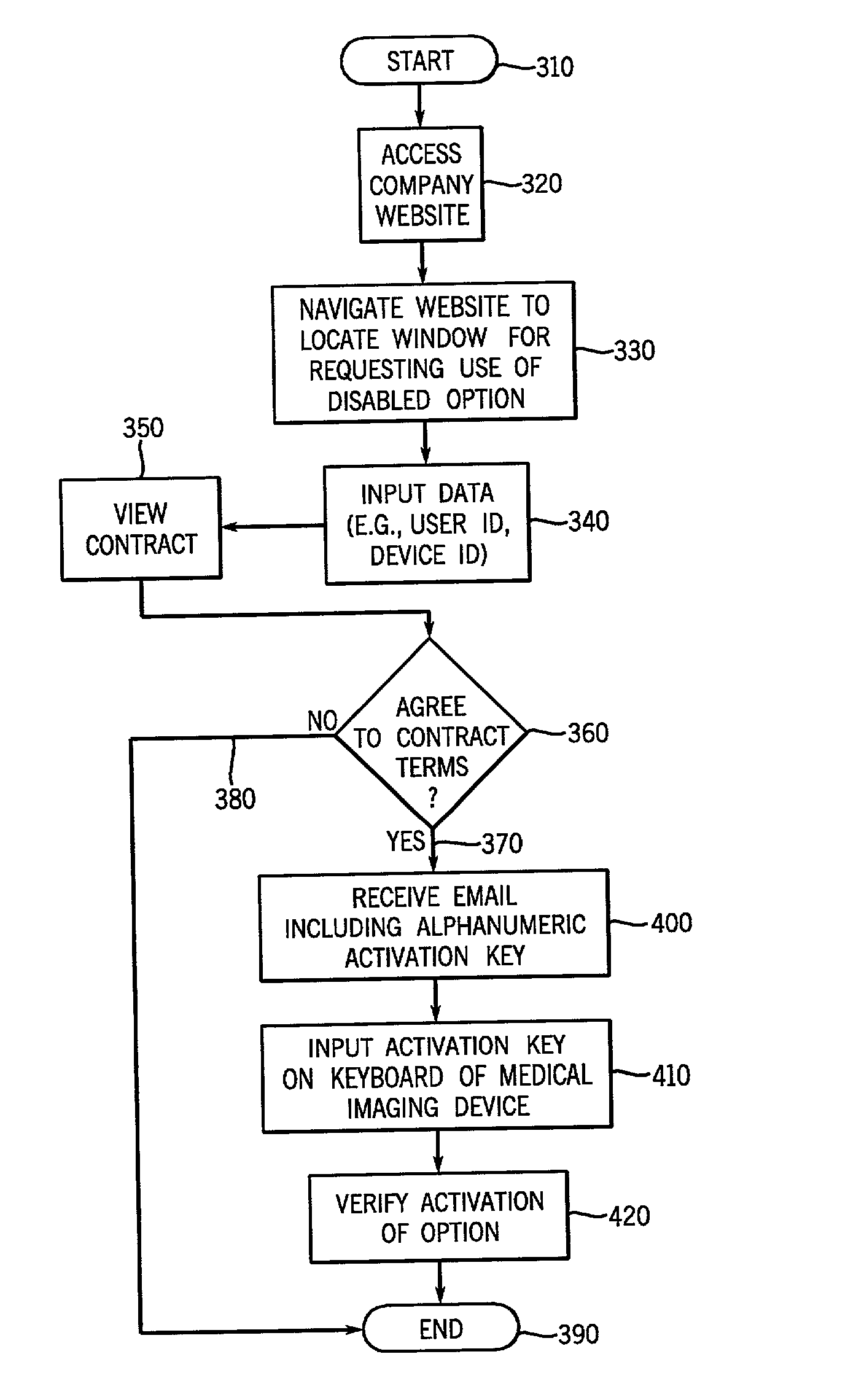
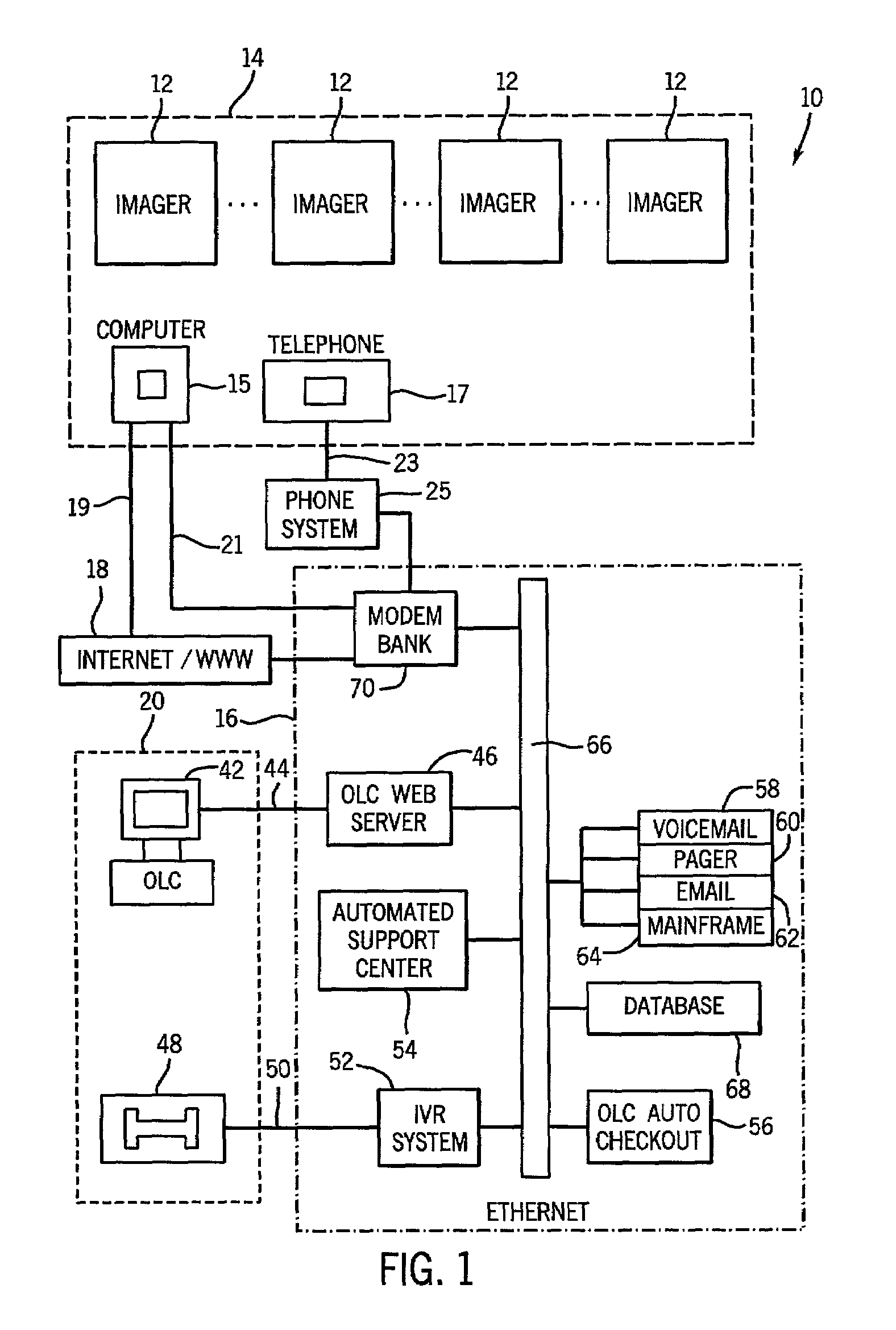
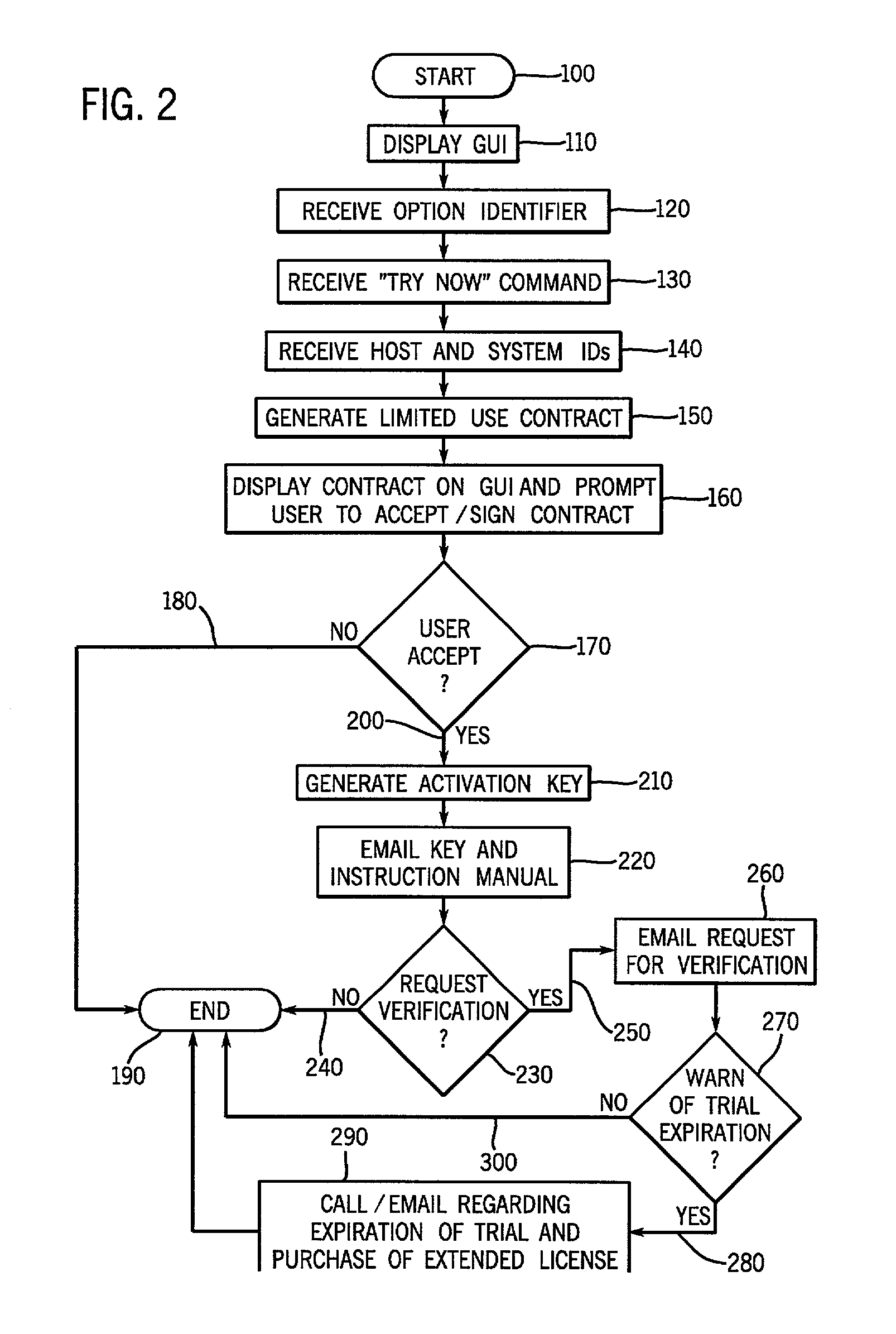
Method and system to grant access to software options resident on a medical imaging device
A system and method are provided that remotely grants limited access and permits use of resident software options in accordance with terms consistent with an access grant. The invention includes receiving an access request from a user to access a software option resident in memory of a device, determining whether to grant access in response to the request, and generating an electronic enabler in response to the access request that is transmitted from a centralized facility to a user of the remote device. The electronic enabler is configured to be input into the device whereupon activation of the option is achieved in accordance with terms of the access grant.
Owner:GE MEDICAL TECH SERVICES
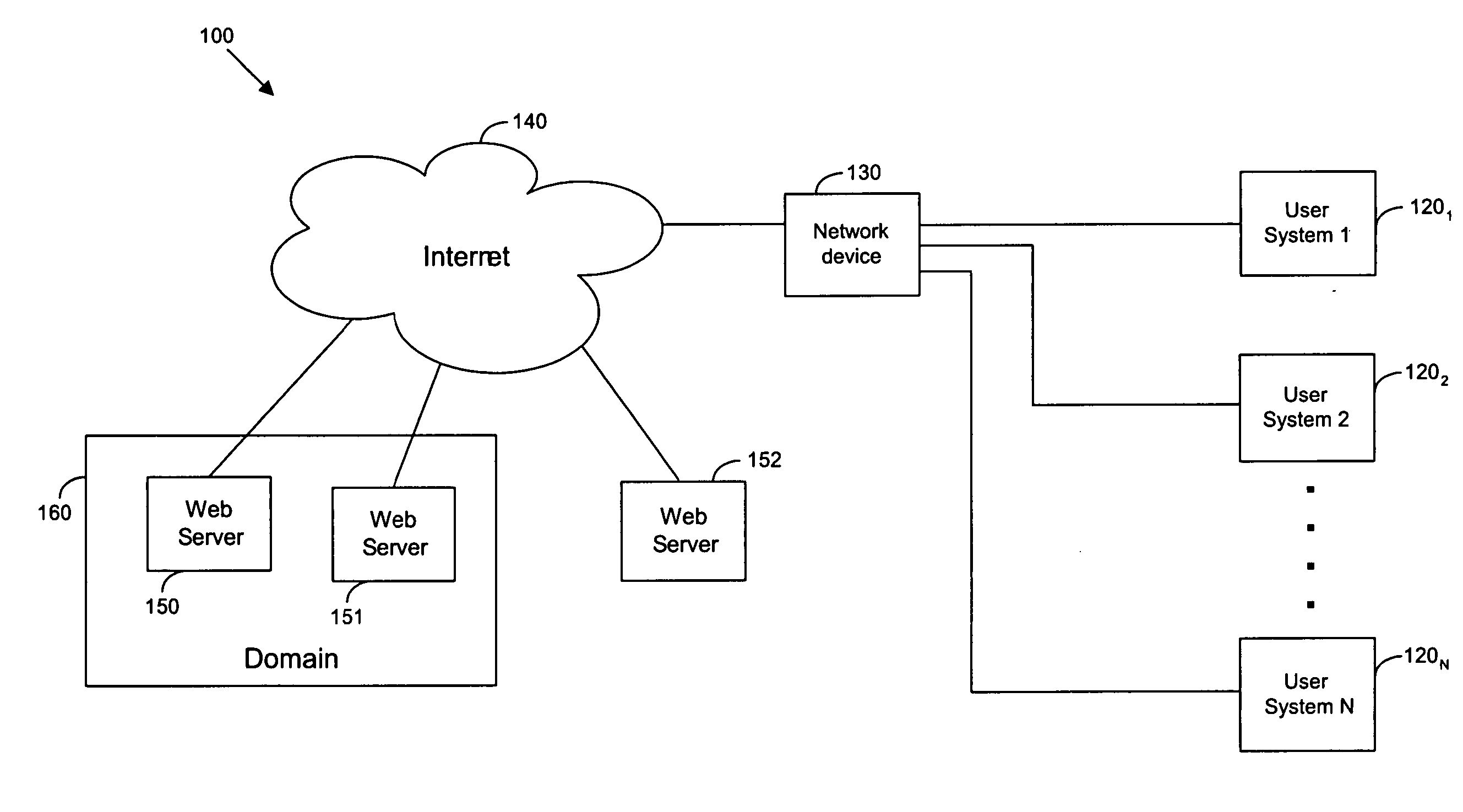
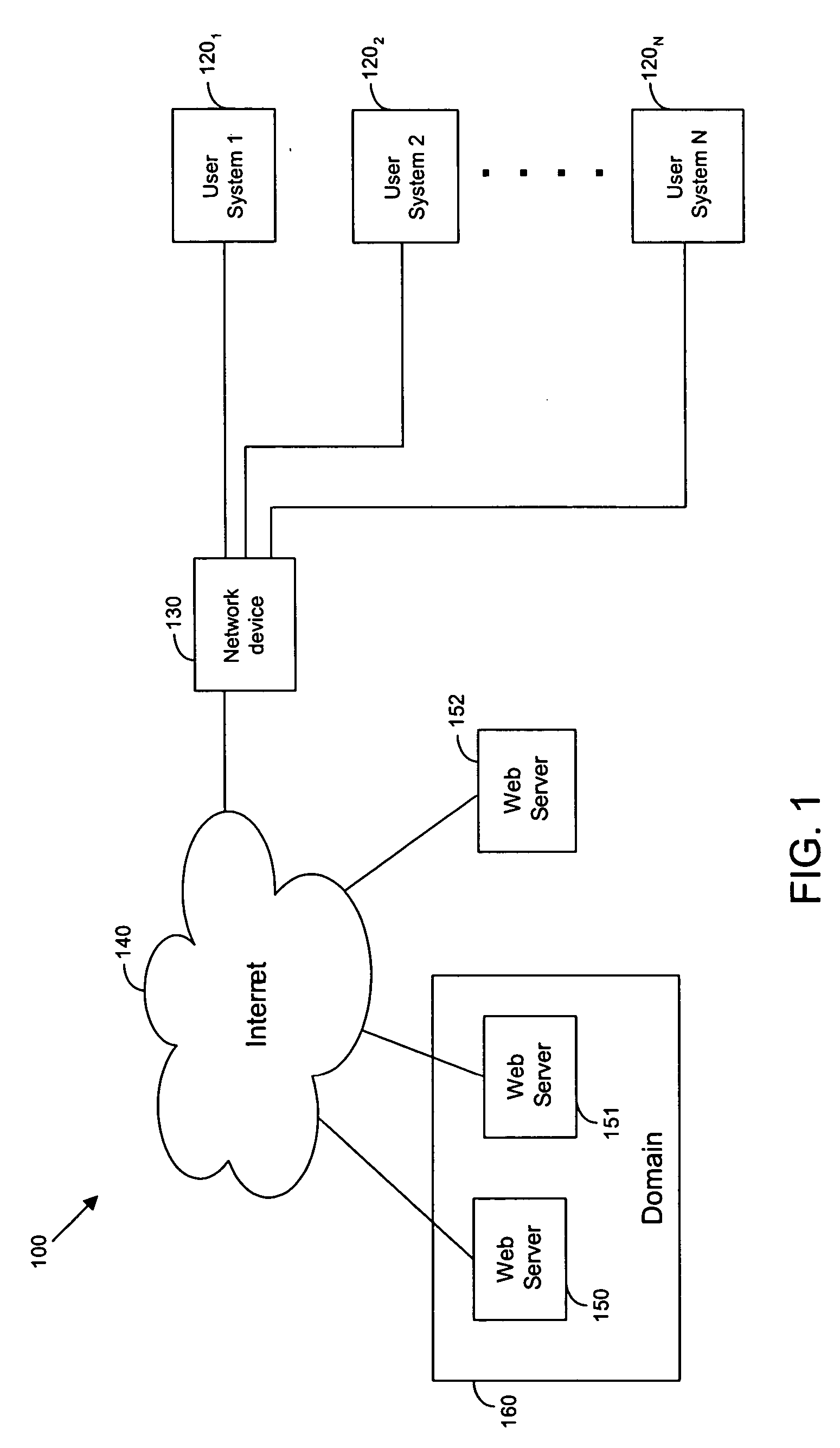
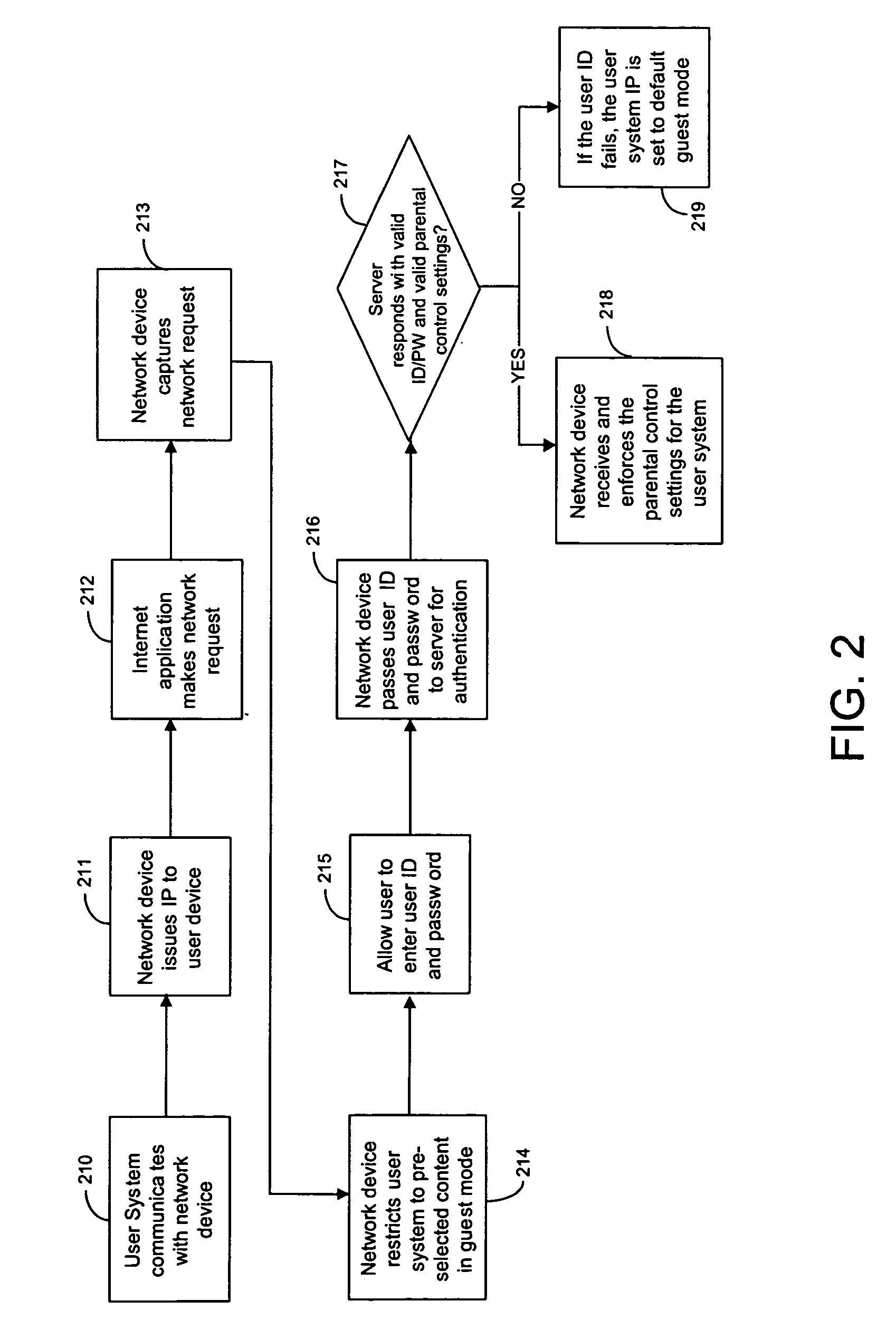
Techniques for parental control of internet access including a guest mode
InactiveUS20050198319A1Limited accessRecord information storageMultiple digital computer combinationsInternet networkLimited access
Techniques are provided for limiting access to Internet content using a parental control filtering system. One or more user systems are connected to the Internet through a network device such as a gateway router. The network device restricts Internet access to pre-selected Internet content in a guest mode without requiring a user to login to a user account. A guest user who does not have a user account is allowed limited access to the Internet through a user system in the guest mode. A user who has a user account can bypass the guest mode and obtain less restrictive access to the Internet by logging into the user account. Parental control settings of any level can be applied to a user account. The parent control setting assigned to a user account are applied to the user system when the user successfully logins to his user account.
Owner:OATH INC
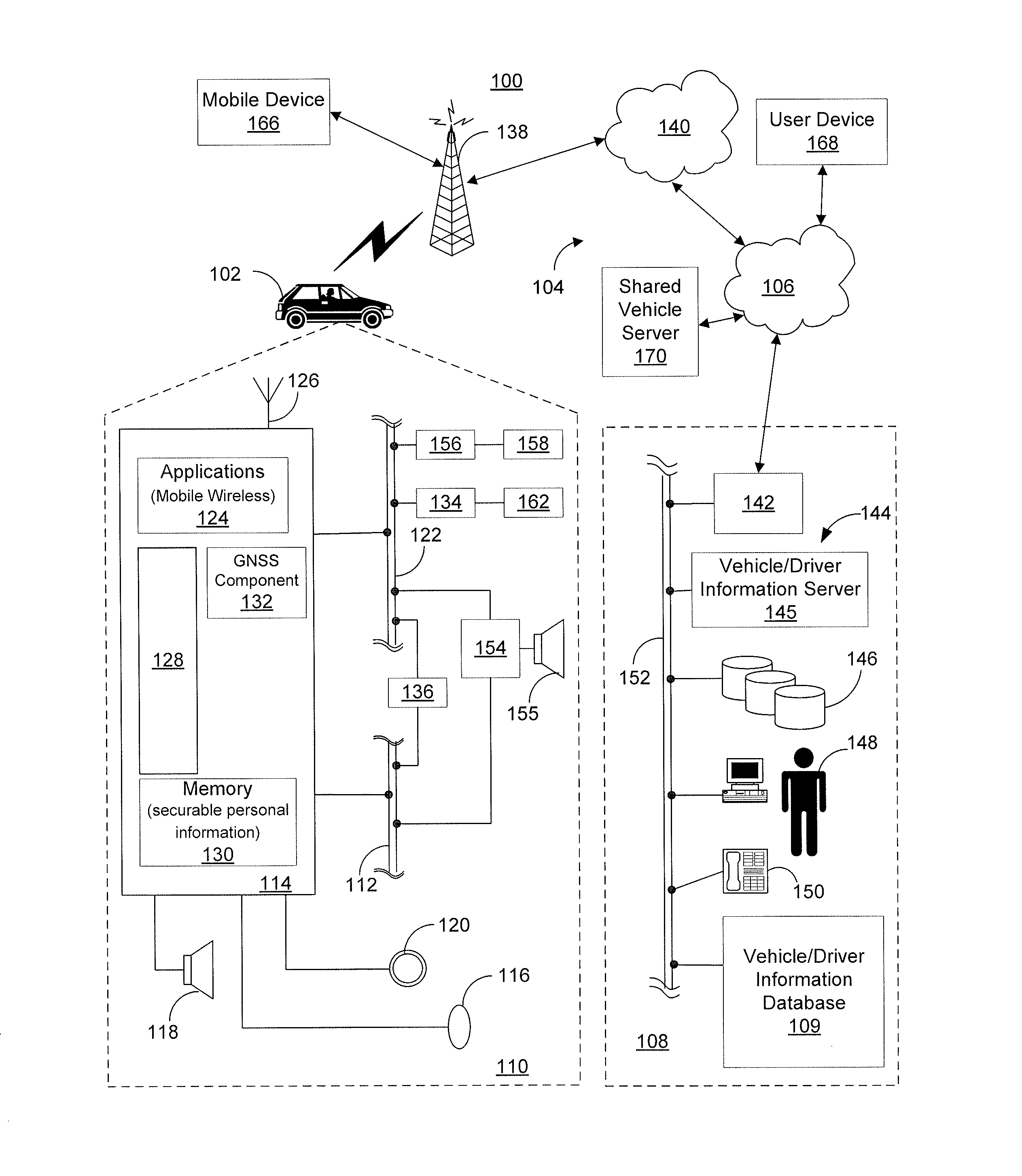
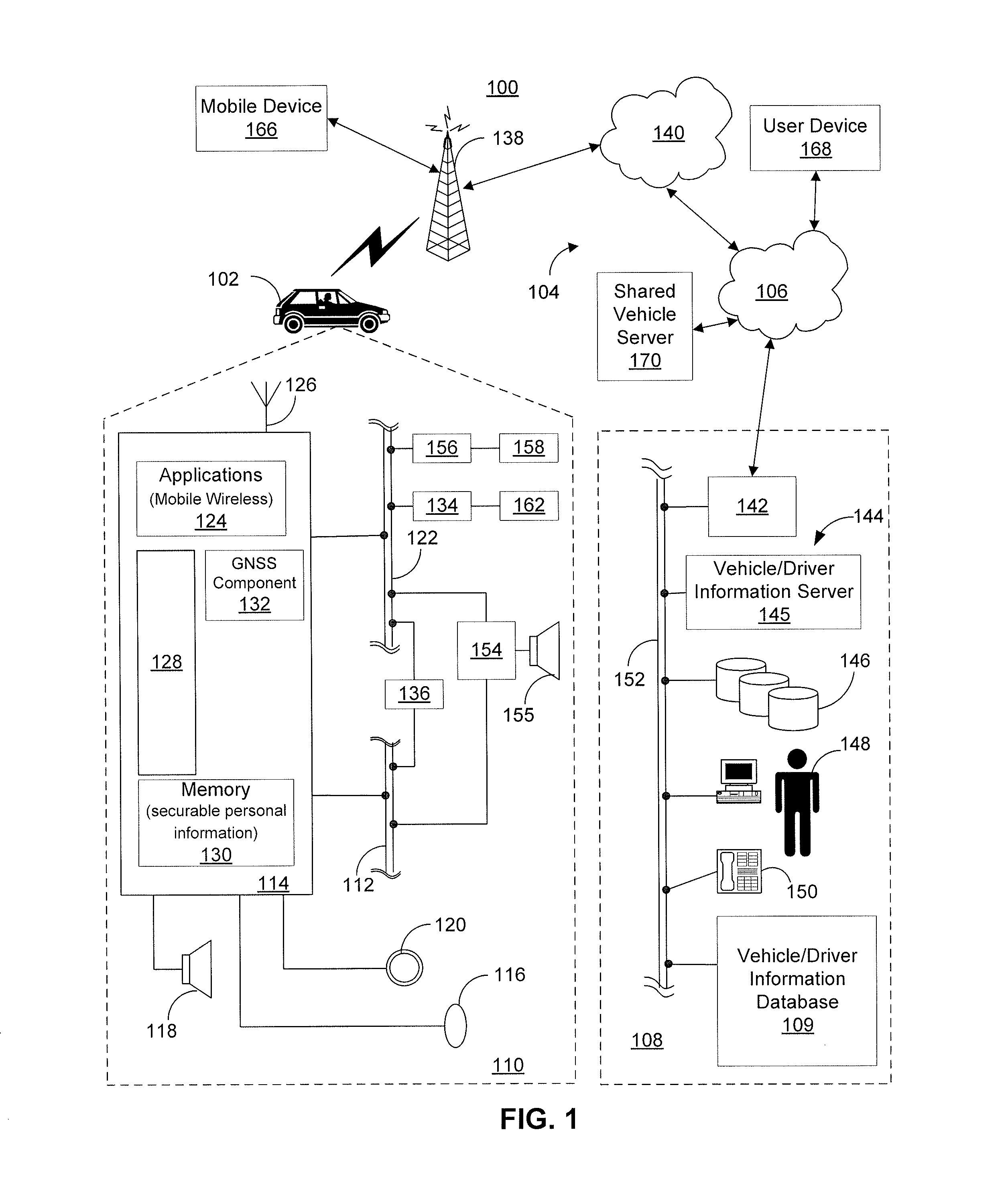
Access control for personalized user information maintained by a telematics unit
ActiveUS9081944B2Digital data authenticationSpecial data processing applicationsPersonalizationLimited access
Owner:GENERA MOTORS LLC
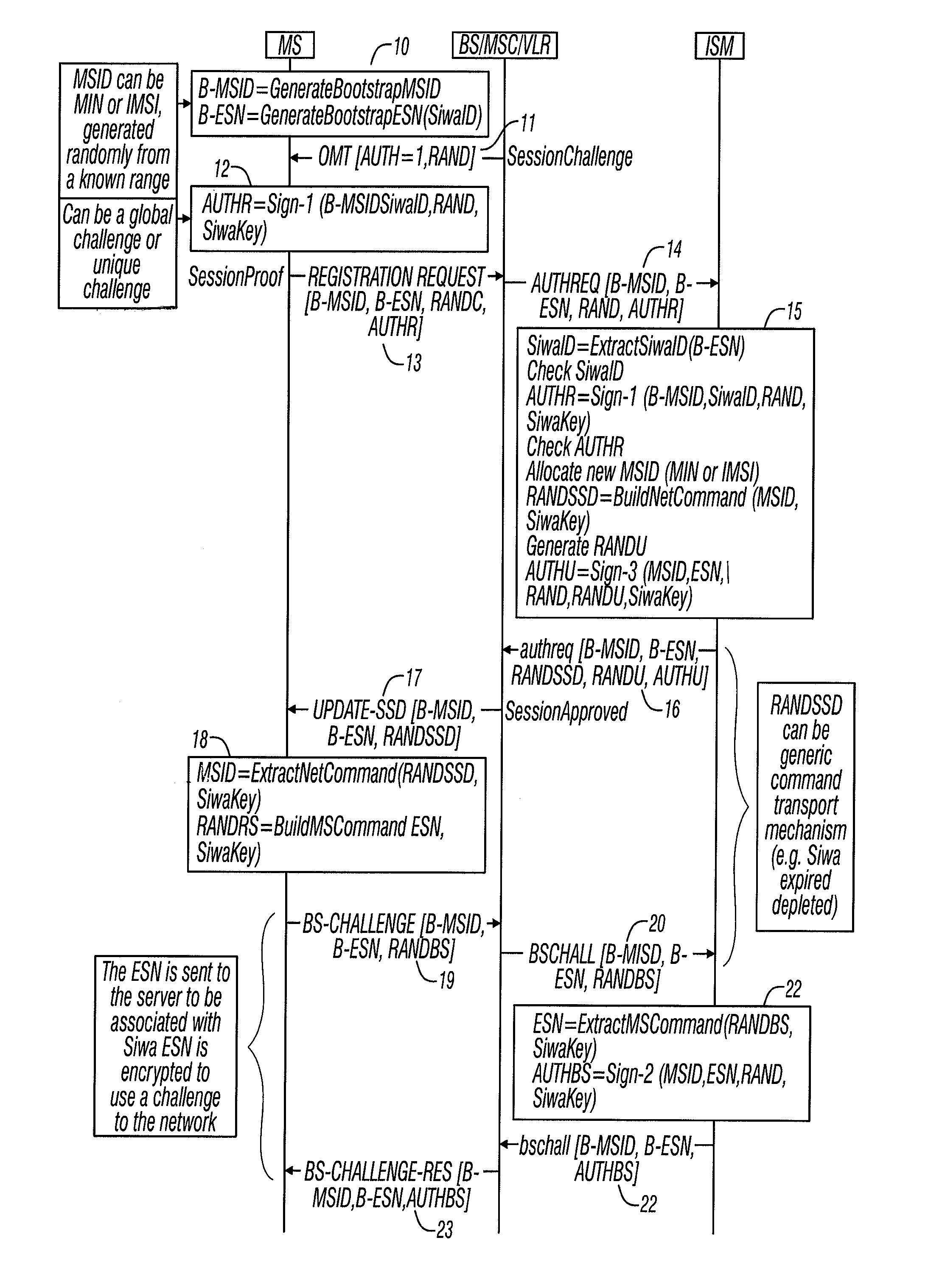
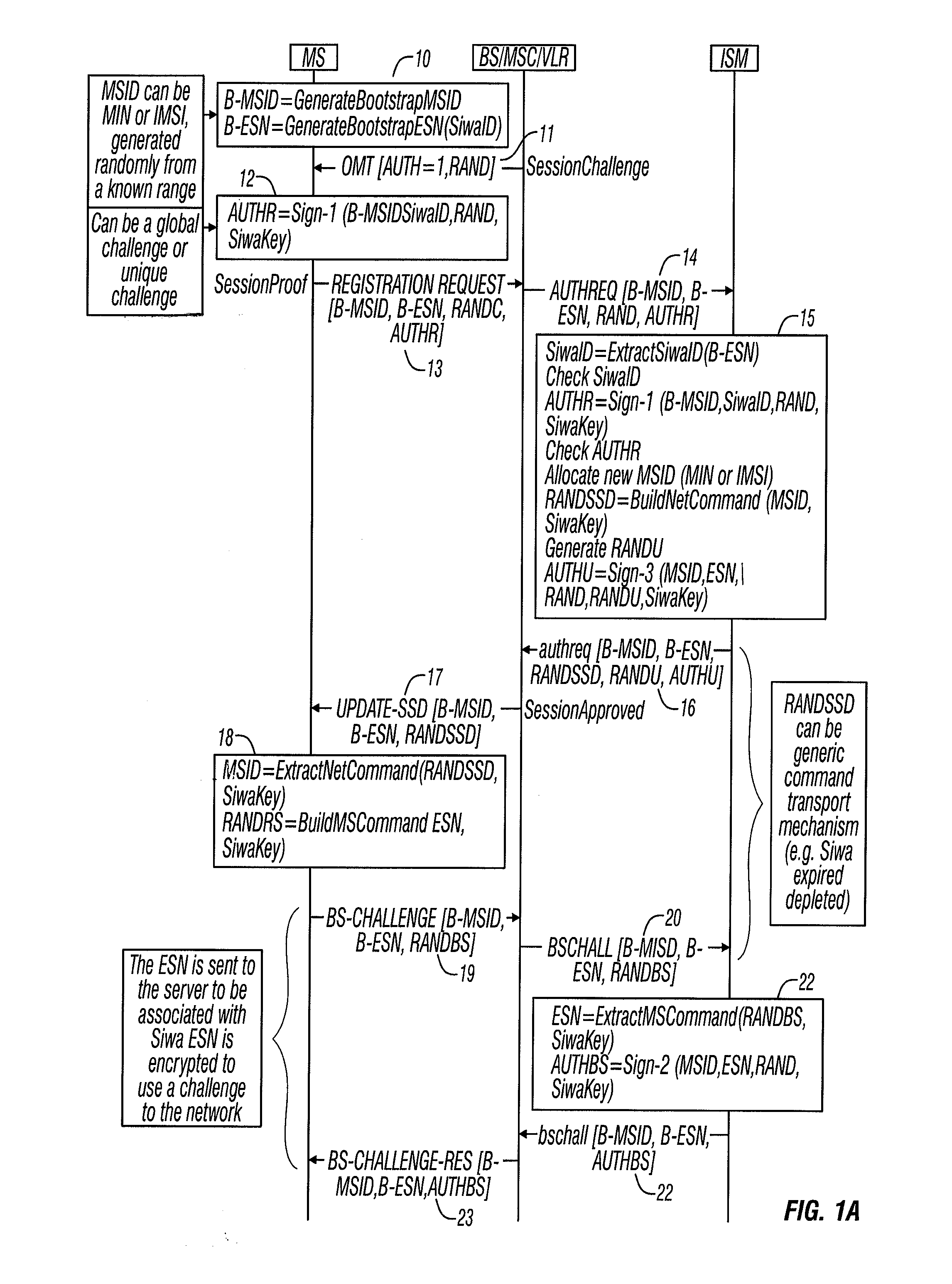
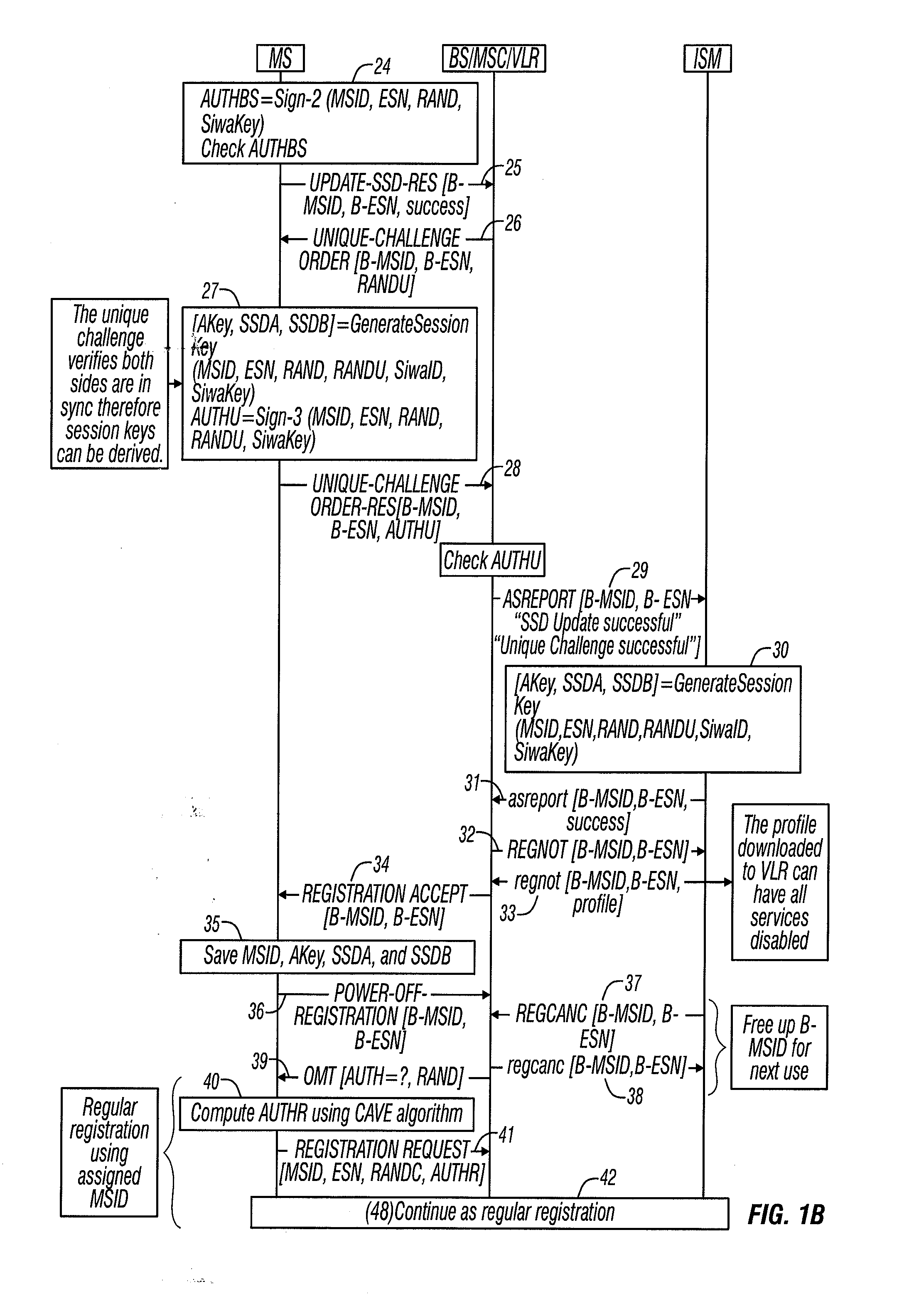
Method and apparatus for secure immediate wireless access in a telecommunications network
InactiveUS20080026740A1Service provisioningUnauthorised/fraudulent call preventionTelecommunications linkLimited access
A wireless telephone and messaging system provides Secure Immediate Wireless Access (SIWA) to wireless telephones onto existing wireless networks. The SIWA protocol uses existing wireless network messaging to exchange information between wireless devices and a network server, referred to herein as an Intelligent Service Manager (ISM). The ISM acts as a gateway between wireless devices and wireless service provider, and provides the wireless devices with an immediate limited or unlimited access to the wireless network. The ISM can also deny access to the wireless network from unauthorized wireless devices.
Owner:EVOLVING SYST LABS INC
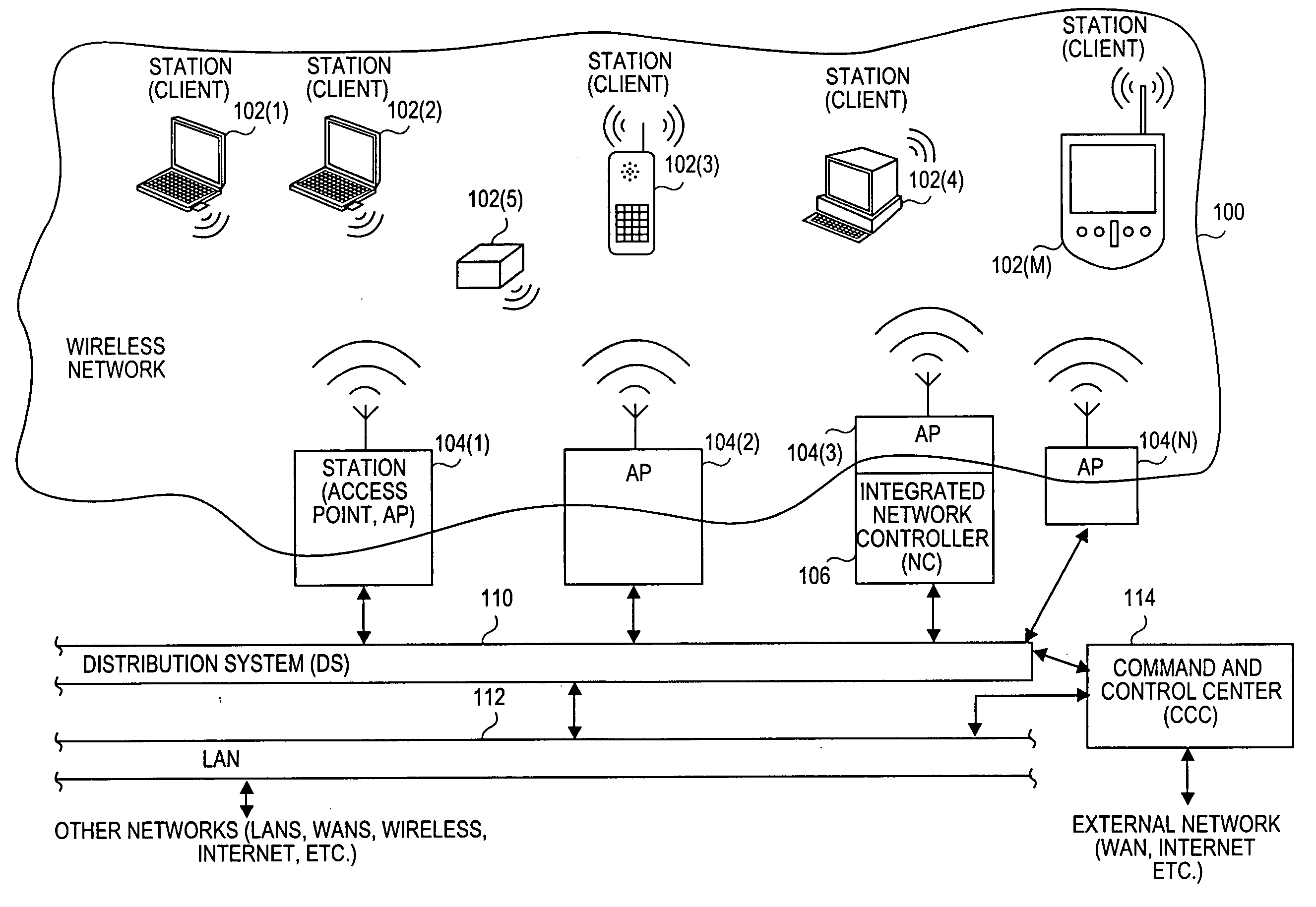
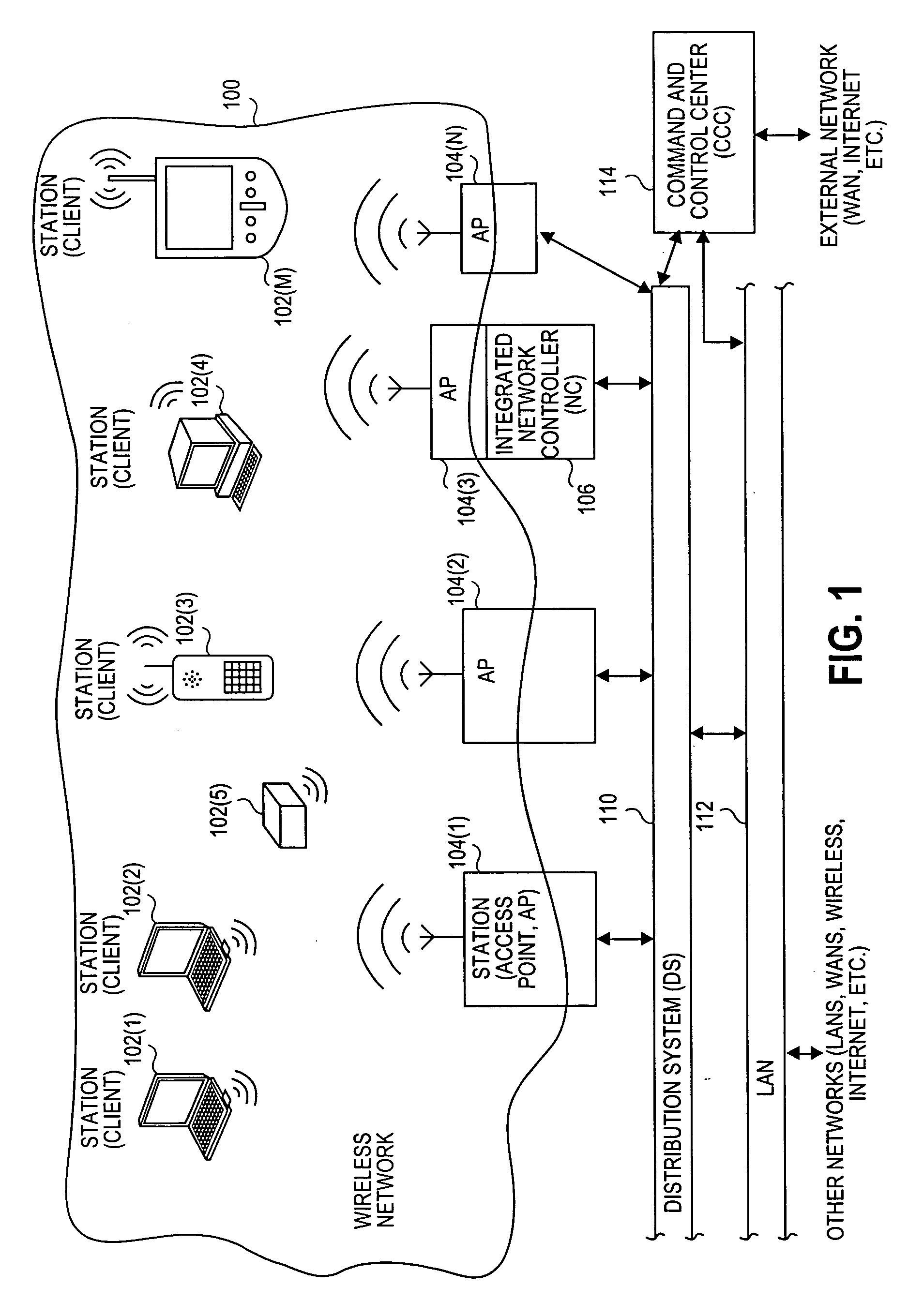
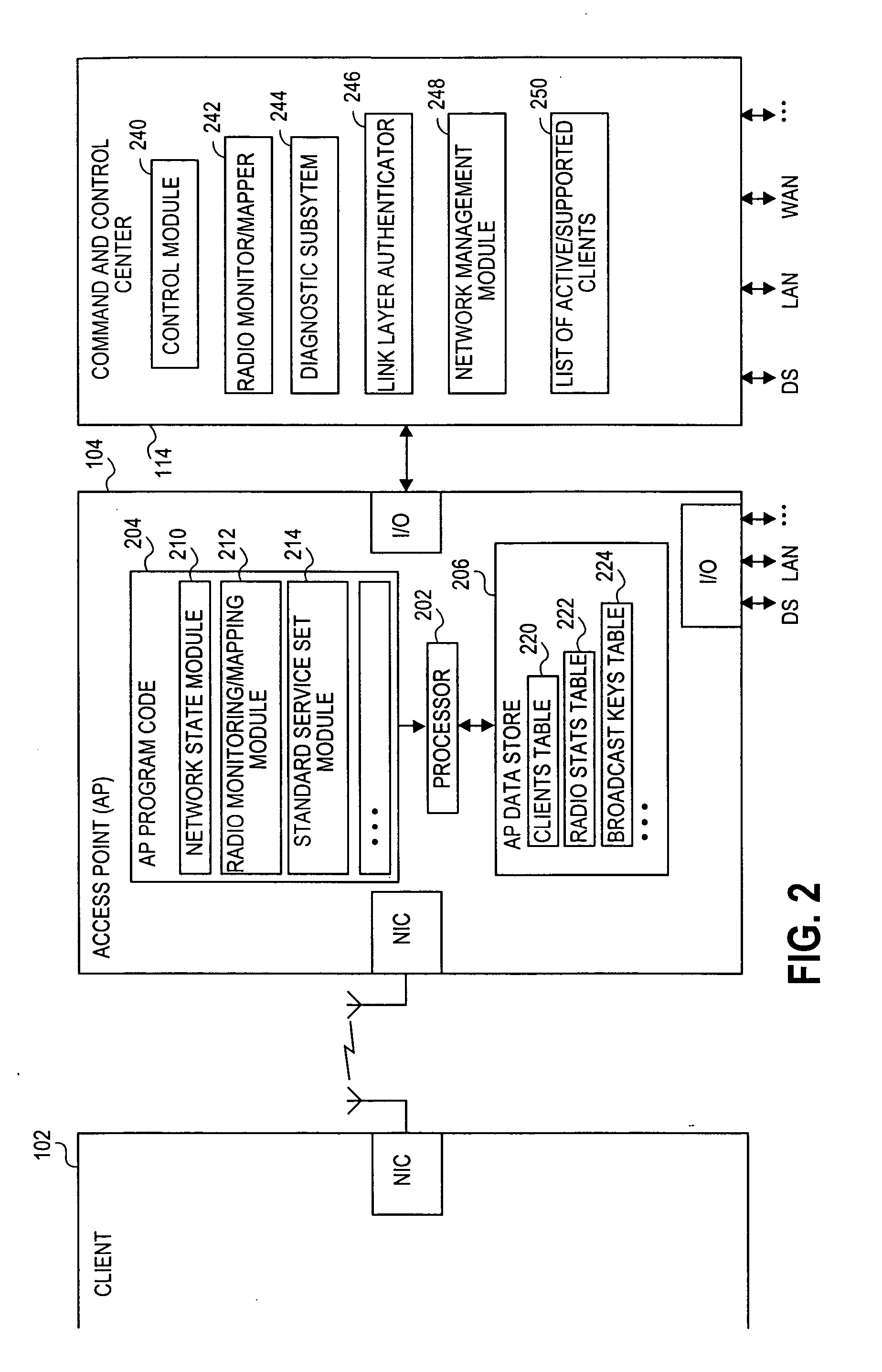
Visitor gateway in a wireless network
ActiveUS20050073979A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsInternet communicationLimited access
A system and method for restricting access to a wireless network is disclosed herein. One or more access points are generally associated with the wireless network (e.g., an IEEE 802.11 wireless network), and a visitor gateway for automatically preventing visiting user from directly entering the wireless network. A command and control center communicates with the access points and the visitor gateway and controls data transfer and routing thereof. The visitor gateway can communicate with a remote computer network (e.g., the Internet) and restricts access to the wireless network by a visiting user through or from the remote computer network. The command and control center also can automatically route the visiting user to the visitor gateway when the visiting user attempts to access an access point associated with the wireless network.
Owner:AVAGO TECH INT SALES PTE LTD
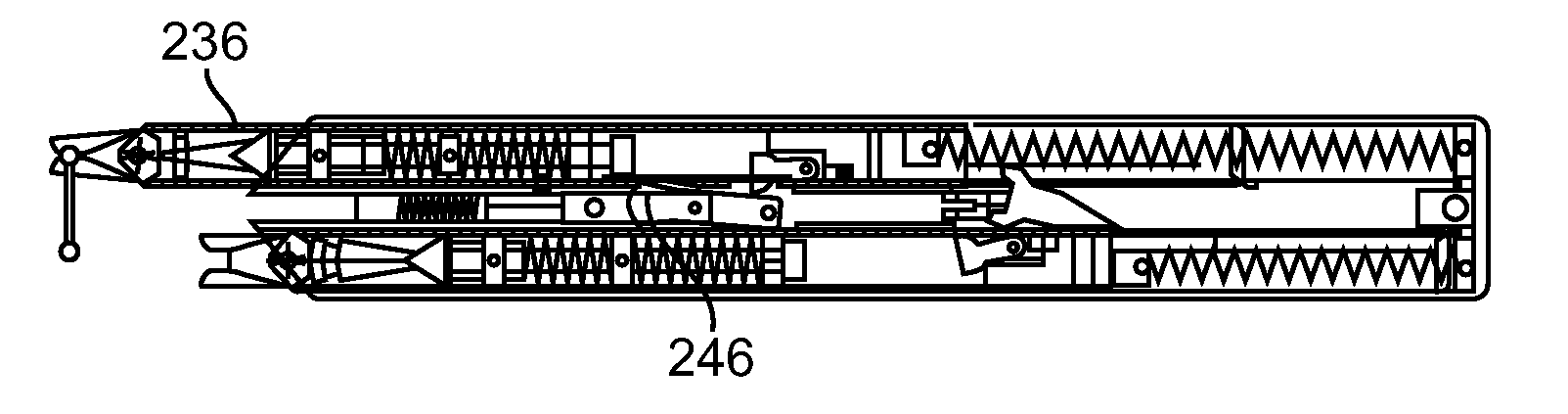
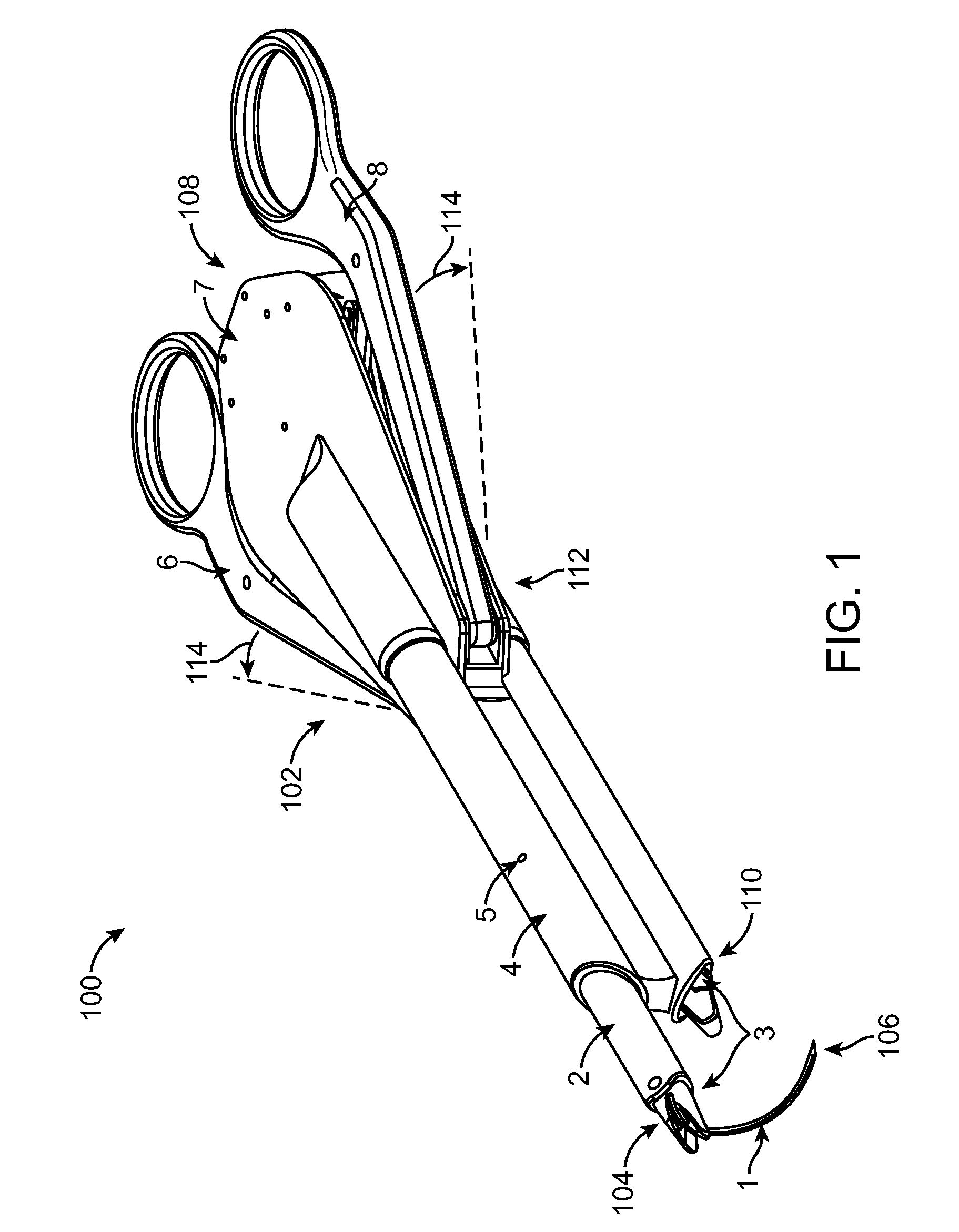
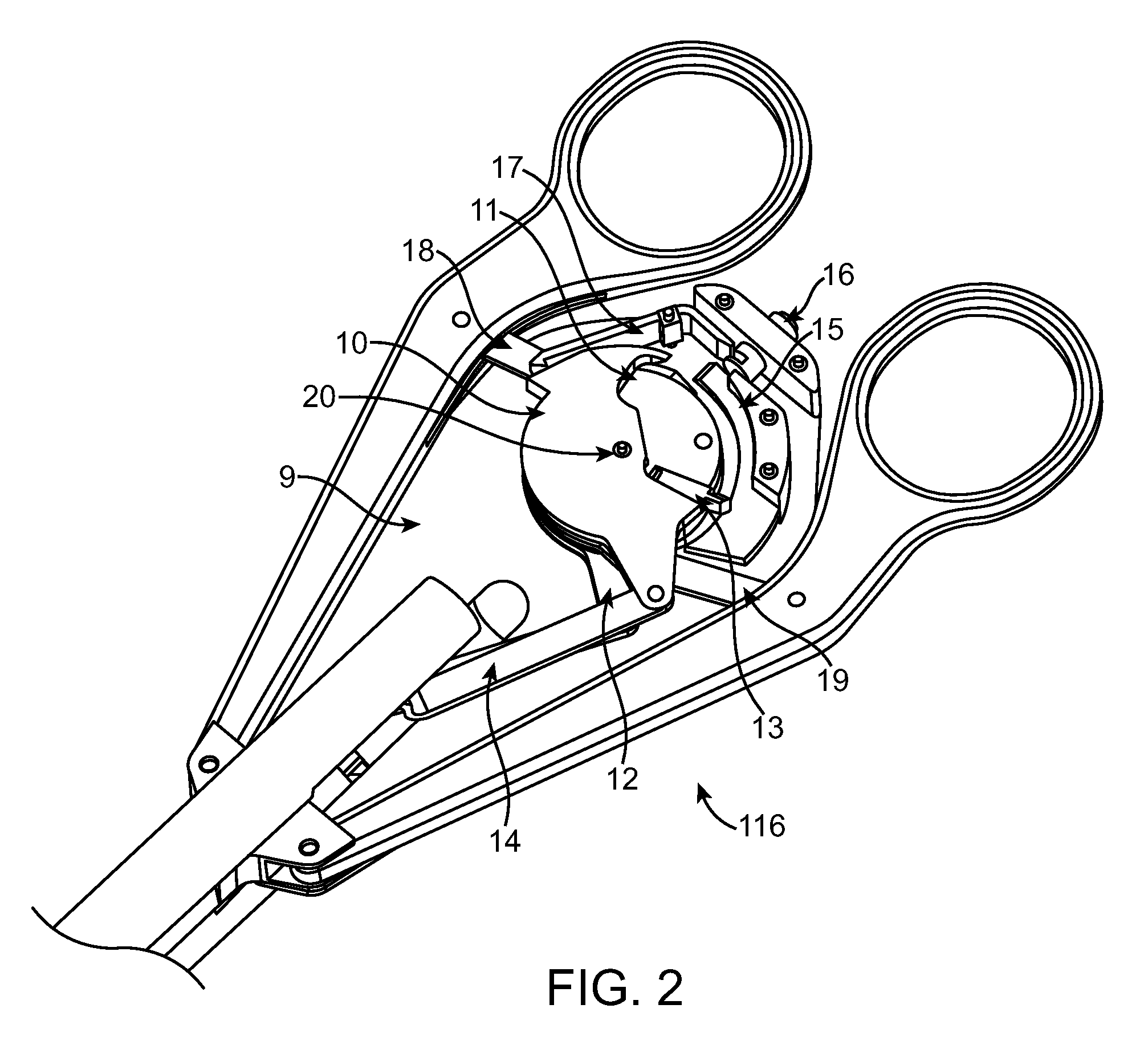
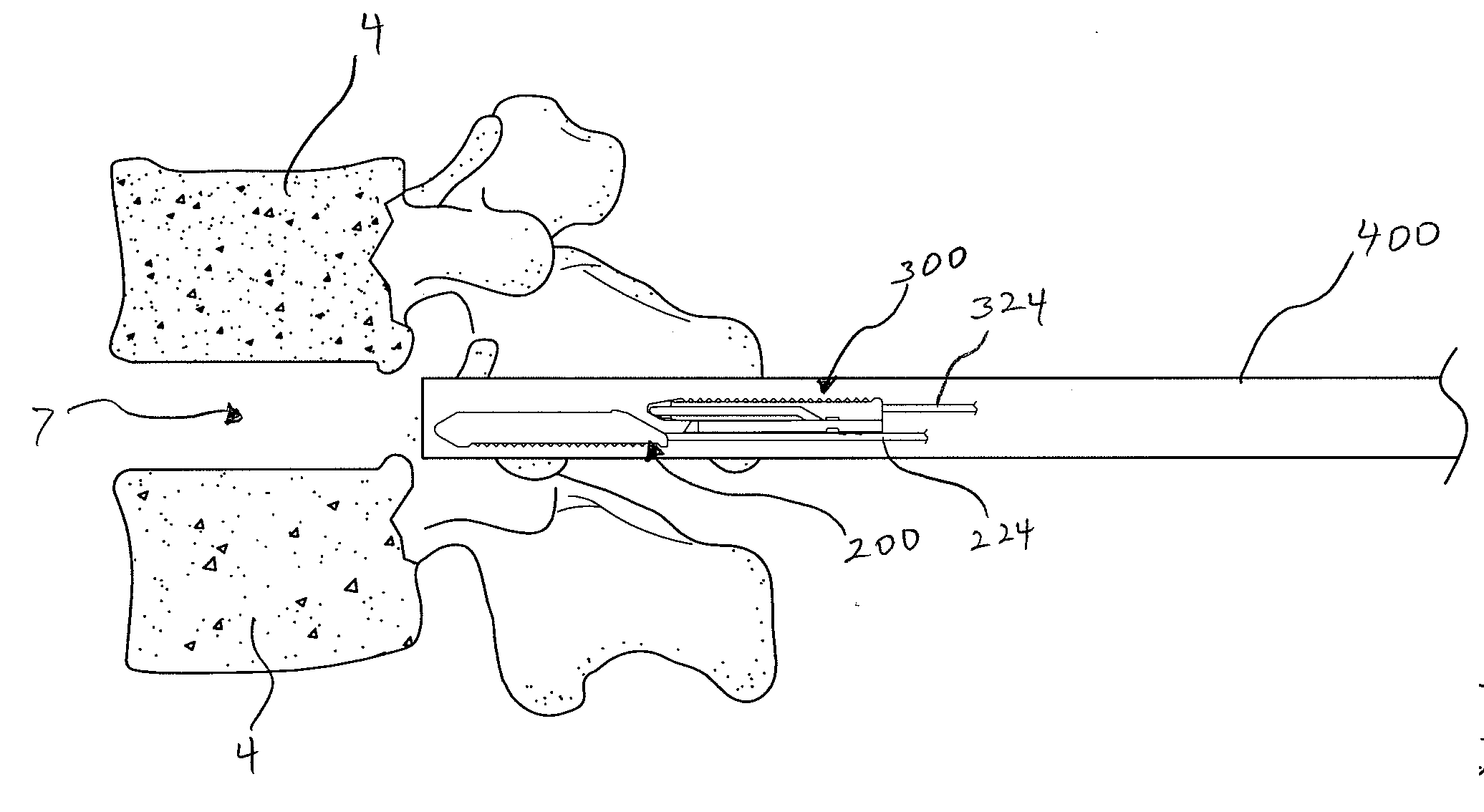
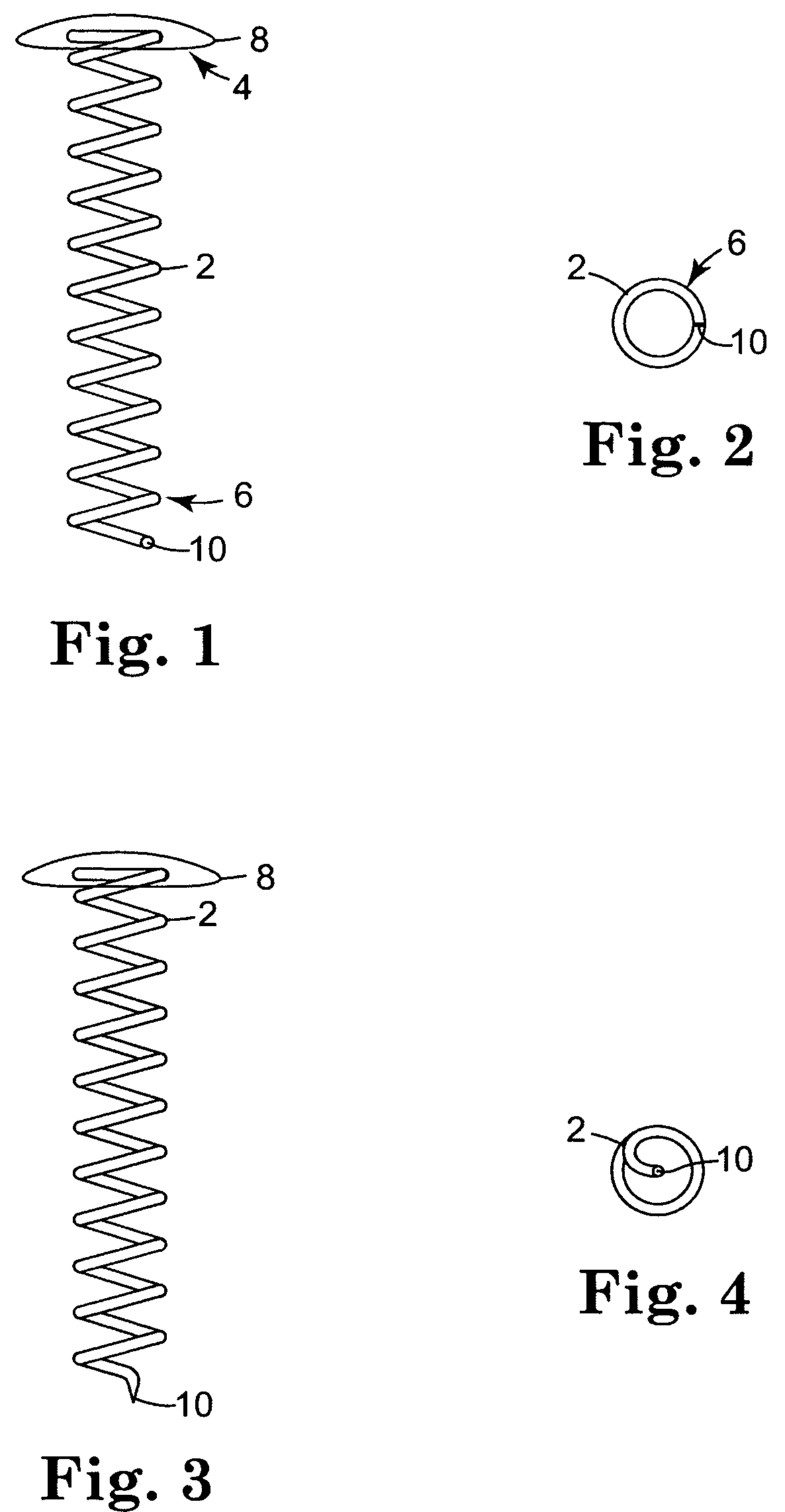
Limited Access Suturing Devices, System, and Methods
ActiveUS20080228204A1Increase speedIncrease usageSuture equipmentsDiagnosticsThroatSurgical operation
Medical suturing devices, systems, and methods will be useful for endoscopic (with or without access ports) or other surgeries in which access is limited, including ear, nose, and throat procedures. Articulation motions may be transferred from a handle to needle grasping jaws using an axial movement of a shaft that has axial stiffness (such as being stiff in compression) and lateral flexibility or an axial movement of a cable. An extension body (within which the shaft or cable moves) between the handle and jaws can be pre-bent or custom bent by the user. Portions of the devices may be disposable, replaceable, and / or reusable. A spring adjacent the clamp may open the clamp or impose a gripping force.
Owner:BOSS INSTR
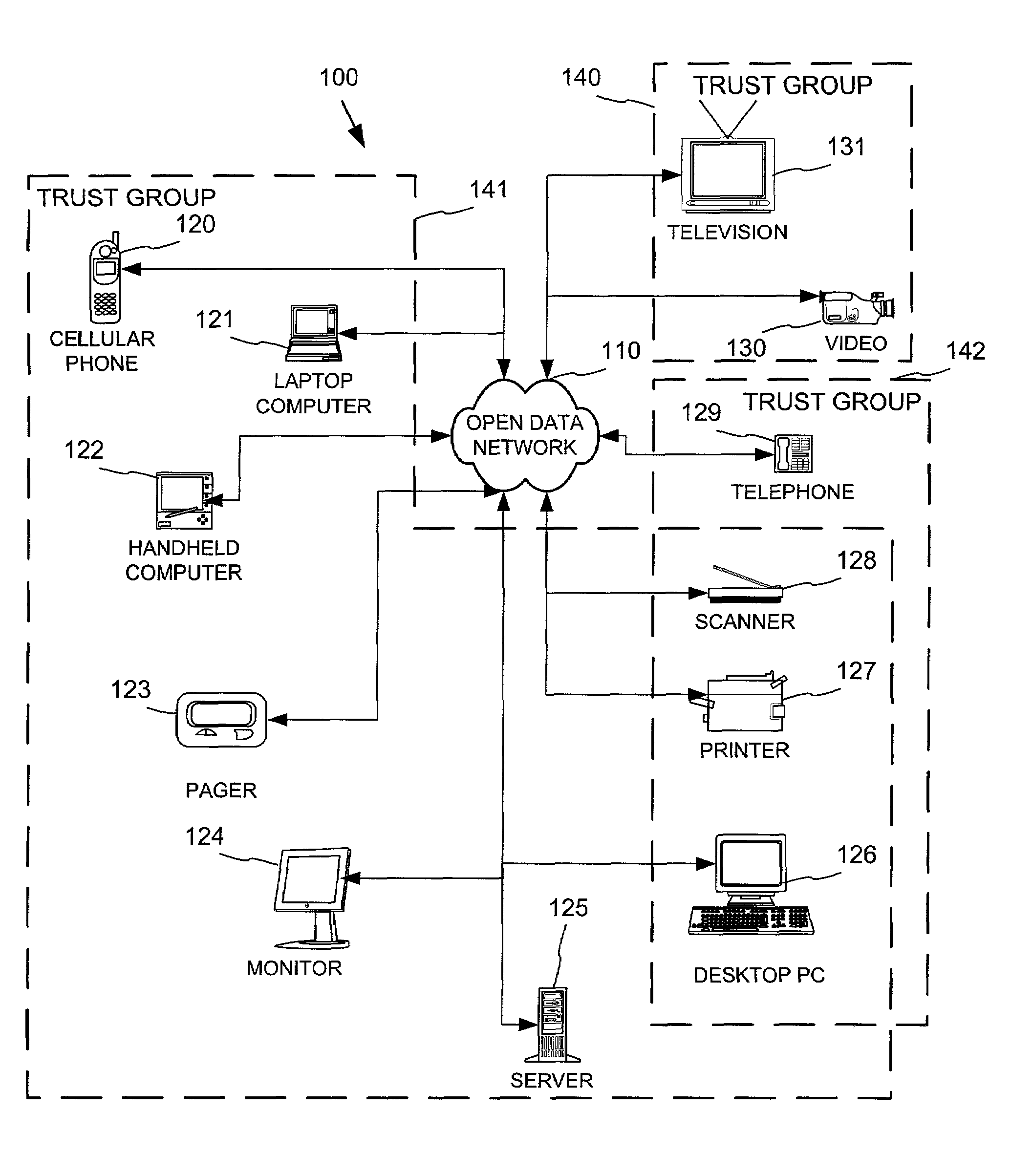
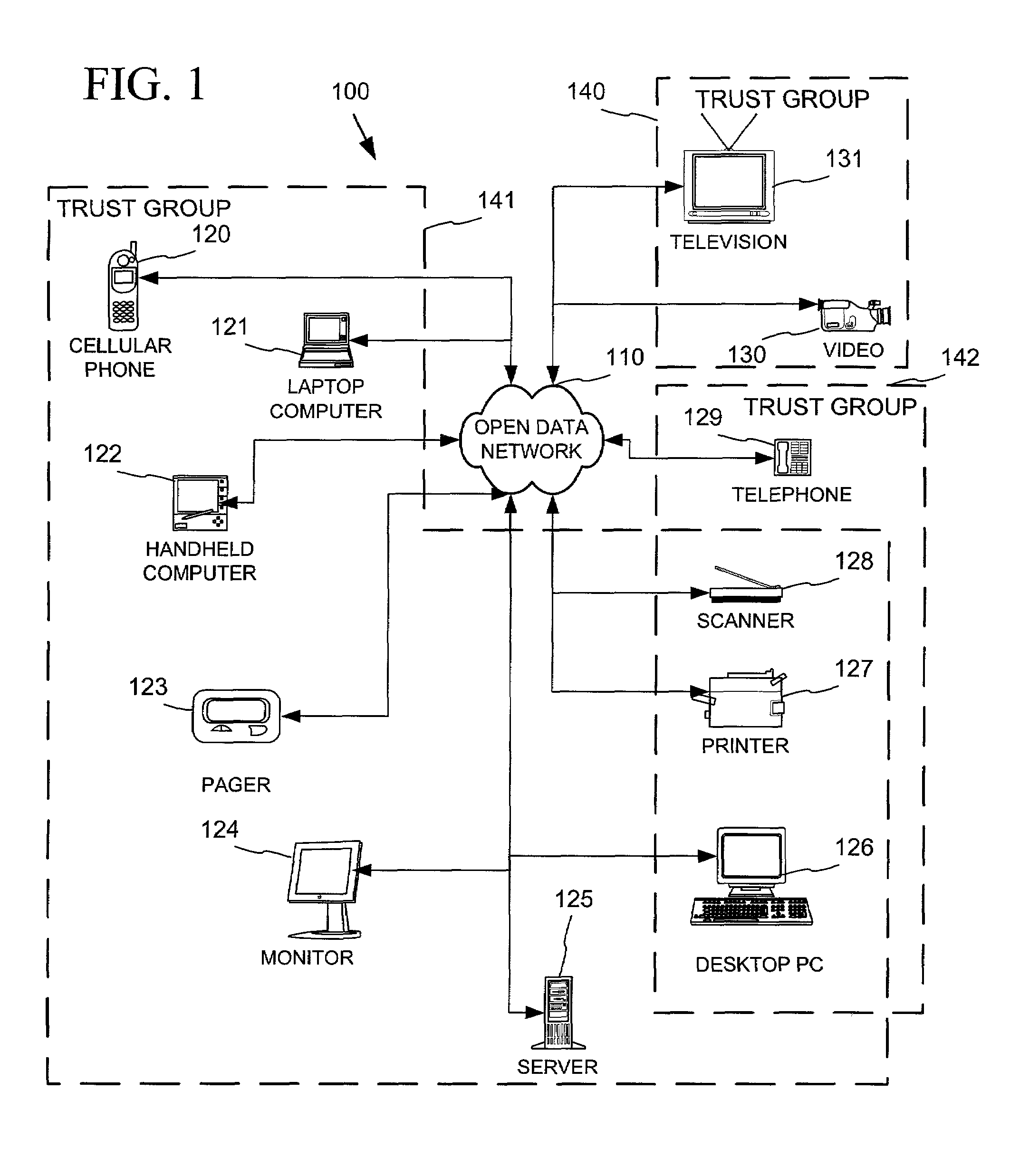
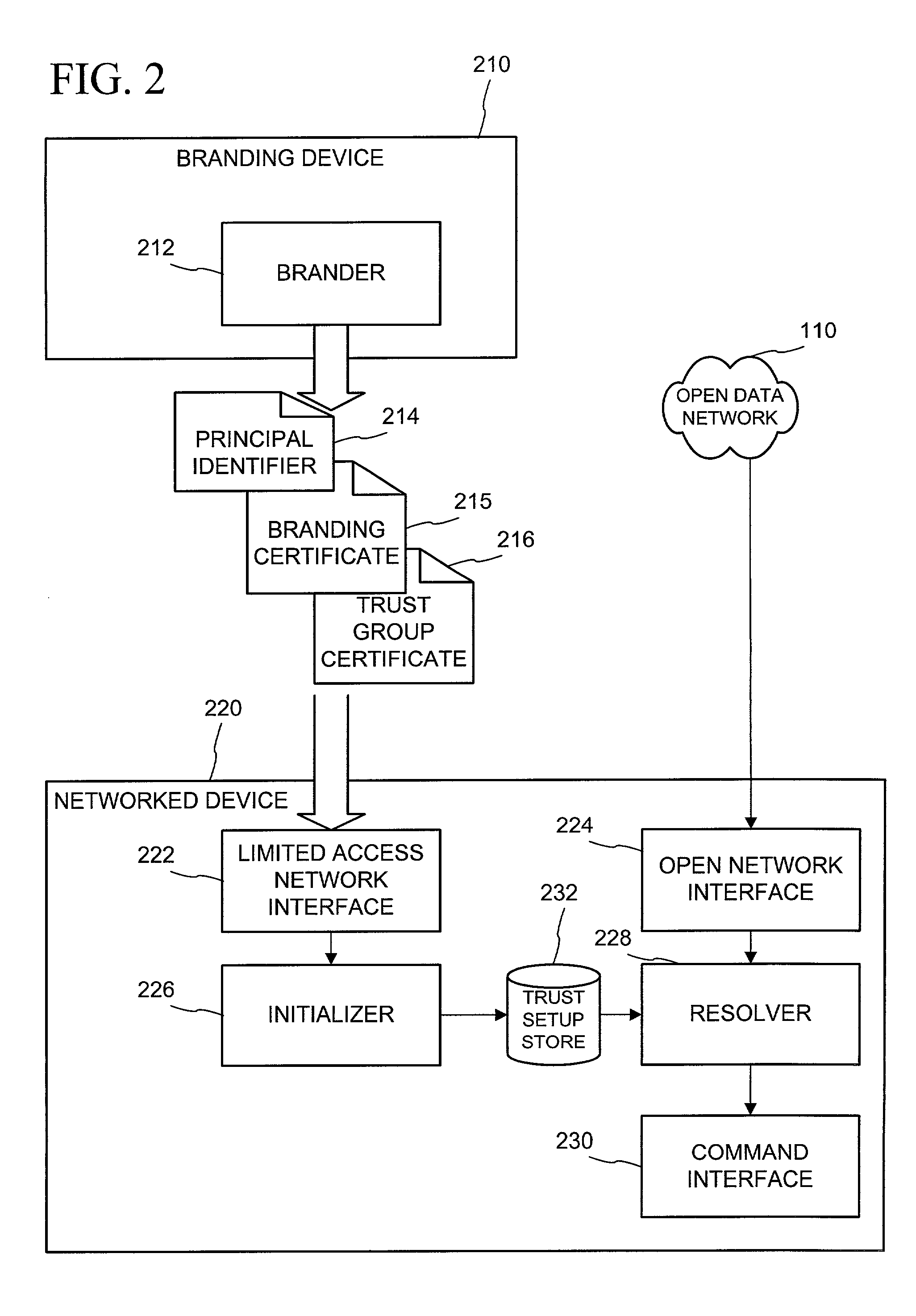
Networked device branding for secure interaction in trust webs on open networks
InactiveUS7500104B2CostSynchronising transmission/receiving encryption devicesDigital data processing detailsLimited accessNetwork media
A branding process provides a networked computing device with initial set up information, including a name, a public / private key pair, and a set of certificates the device will need to inter-operate with other devices in the trust group. A branding device conveys the initial set-up information to the networked computing device via a limited access network interface, or alternatively via a broadcast network media with the device enclosed in a wave guide and / or Faraday cage. The networked computing device can then use the set up information to verify that other devices on the network that seek to interact with the device are also members of the trust group, with which networked computing device can interact.
Owner:MICROSOFT TECH LICENSING LLC
System and method for sending electronic data to inmates
InactiveUS20100299761A1Digital data processing detailsAnalogue secracy/subscription systemsLimited accessRelational database management system
The invention includes delivering and monitoring electronic letters to correction facility inmates while giving supervisory authorities the ability to screen the incoming mail. This may be achieved by providing a database having an entry for each inmate and having a plurality of fields, and by scanning an original letter as an electronic letter and storing each electronic letter sent to a specific inmate in a relational database management system (RDMS) table. Another aspect of the invention involves providing a computer-operated kiosk that may be used by individuals (e.g., inmates) in a restrained environment / restricted-access location (e.g., a prison) to browse through a catalog of available digital media or content, such as music, that may be purchase with credits earned based on work performed by the inmate or bought through some other means, for example by family members of the inmate.
Owner:SECURUS TECH
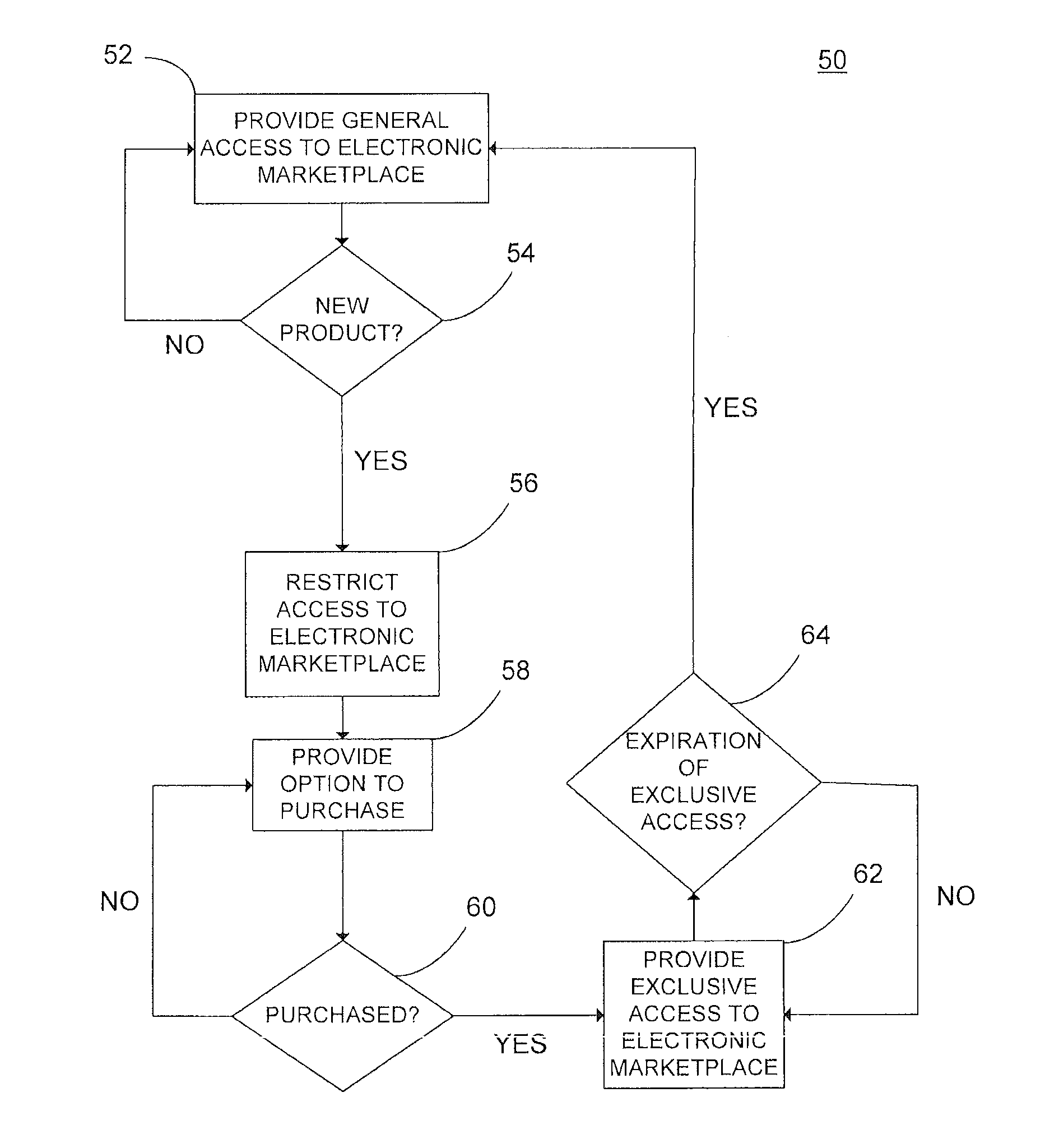
Interactive electronic marketplace
A promotional marketing method for an electronic marketplace, wherein a user gains exclusive, limited access to the marketplace upon purchase of a membership item. Systems and methods for assigning a virtual prize to a buyer within an electronic marketplace. Systems and methods for creating a product line of collectibles and shipping materials based on a theme established from an image of a graphic.
Owner:JENSEN TIFFANY
Multi-Tiered Authentication Methods For Facilitating Communications Amongst Smart Home Devices and Cloud-Based Servers
ActiveUS20140089671A1Digital data processing detailsMultiple digital computer combinationsLimited accessValidation methods
Apparatus, systems, methods, and related computer program products for synchronizing distributed states amongst a plurality of entities and authenticating devices to access information and / or services provided by a remote server. Synchronization techniques include client devices and remote servers storing buckets of information. The client device sends a subscription request to the remote serve identifying a bucket of information and, when that bucket changes, the remote server sends the change to the client device. Authentication techniques include client devices including unique default credentials that, when presented to a remote server, provide limited access to the server. The client device may obtain assigned credentials that, when presented to the remote server, provide less limited access to the server.
Owner:GOOGLE LLC
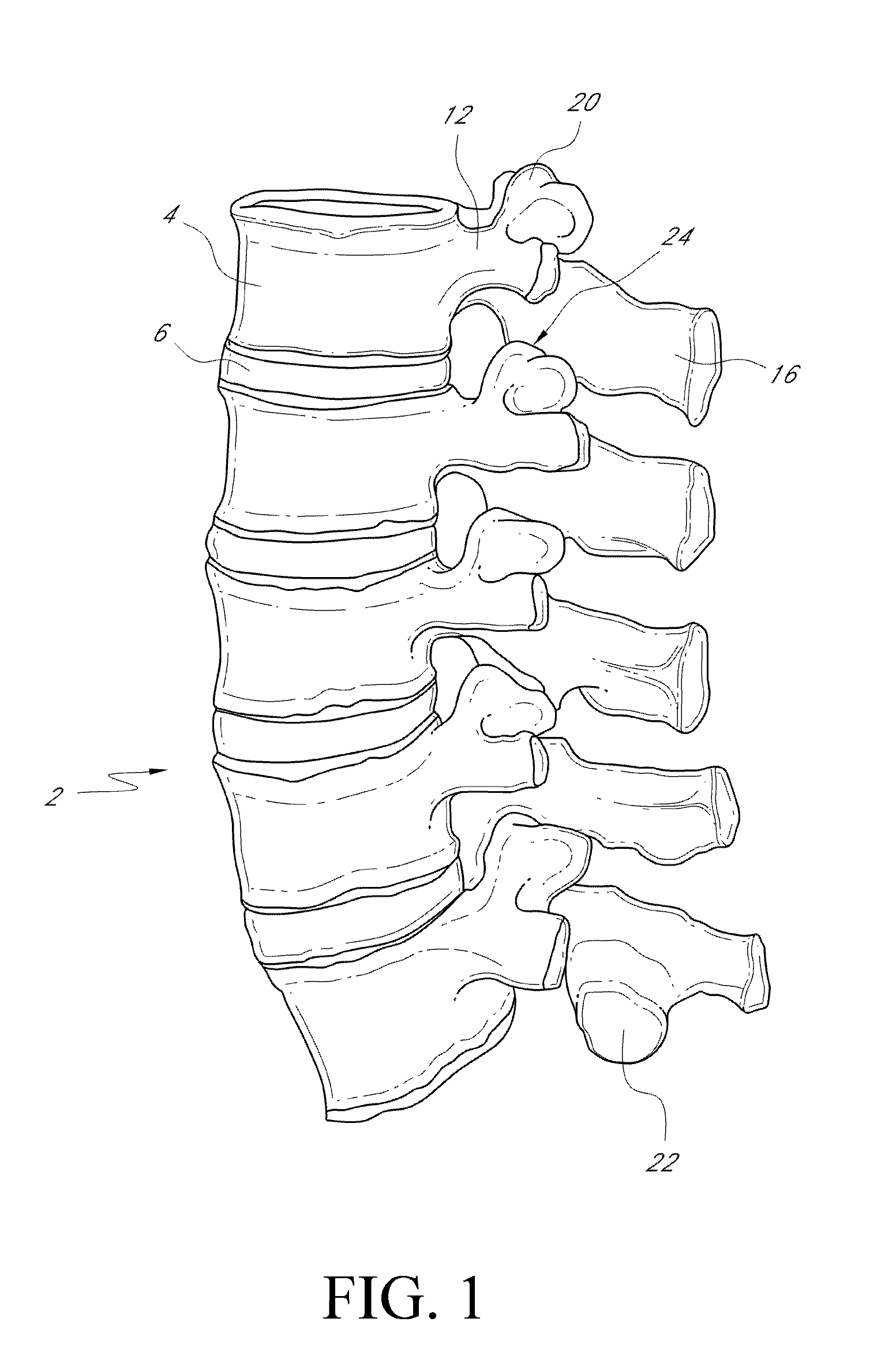
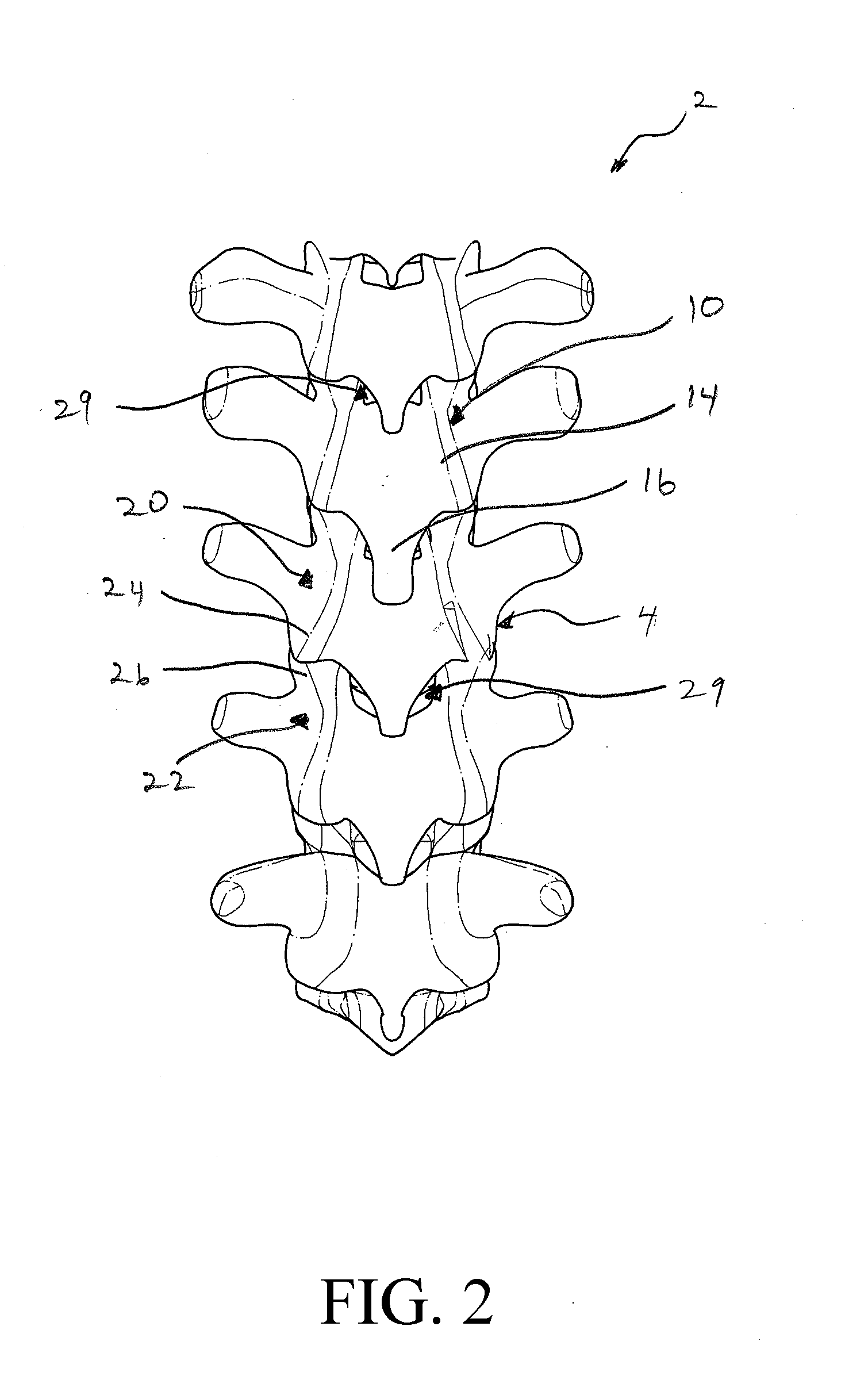
Intervertebral implant
An intervertebral implant and related methods of use are provided for treatment of spaces between two vertebrae. The implant can comprise a first member and a second member that are configured for engagement in a stacked configuration. The first member and second member can be inserted separately so that the intervertebral space can be reached through limited access pathways. The first member and second member can be coupled in situ in the intervertebral space to form an implant of desired height. In this manner, an intervertebral implant having final dimensions that would not fit through a limited access pathway can be implanted through the access pathway by inserting the implant in separate member pieces.
Owner:INTERVENTIONAL SPINE
Biodegradable ocular devices, methods and systems
InactiveUS20060024350A1Volume maximizationControl releaseSurgeryPharmaceutical delivery mechanismLimited accessActive agent
The invention provides implantable medical devices that are fabricated of biodegradable materials for delivery of bioactive agent to limited access regions of a patient's body, such as the eye. The invention further provides methods of treatment utilizing the devices.
Owner:SURMODICS INC
Method and apparatus for protected content data processing
ActiveUS8225061B2Digital data processing detailsUnauthorized memory use protectionLimited accessComputer network
Owner:APPLE INC
Biodegradable controlled release bioactive agent delivery device
InactiveUS20060034891A1Minimize damageInterference minimizationPharmaceutical delivery mechanismEye treatmentControlled releaseLimited access
The invention provides implantable medical devices that are fabricated, at least in part, from biodegradable polymeric material. The implantable medical devices are used to provide bioactive agent to a treatment site, and are particularly useful for treatment of limited access regions of the body.
Owner:SURMODICS INC
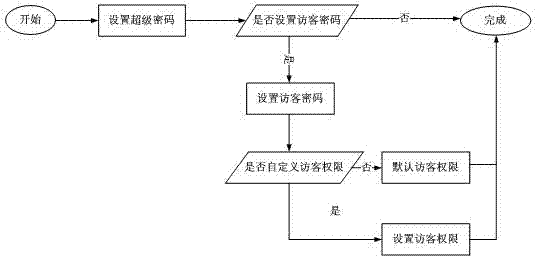
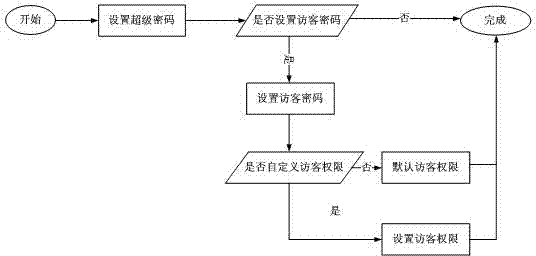
Method for setting permission password for mobile phone
InactiveCN102457619AProtect privacy and securityPrivacy protectionSubstation equipmentLimited accessDocumentation procedure
The invention discloses method for setting a permission password for a mobile phone. The method comprises the steps as follows: 1, entering a permission password setting program; 2, setting the highest permission password; 3, judging whether a visitor password is set or not, if yes, Step 4 is executed, otherwise, setting of the permission password is finished; 4, executing the program of setting a visitor password; 5, judging whether visitor permission is user-defined or not, if yes, Step 6.1 is executed, otherwise, Step 6.2 is executed; 6.1, setting visitor permission; 6.2, defaulting the visitor permission set by the system; and 7, accomplishing setting of the permission password. When the permission password is used for unlocking, whether a password inputted by a user is the highest permission password or the visitor permission password can be judged, if the password is the highest permission password, all the functions, applications and documentations of the mobile phone are opened, and if the password is the visitor permission password, the functions, applications and documentations of the mobile phone are used in a limited way. The method can protect data privacy of a user through passwords with different permissions and restrict access, and has the advantages of simplicity and convenience in operation, and easiness in implementation.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Breast biopsy and therapy system for magnetic resonance imagers
The present invention describes a device for performing breast biopsies and / or therapy within magnetic resonance imaging (MRI) systems. The apparatus includes a RF receiver antenna for magnetic resonance imaging of the breast. The RF coil includes openings in the front and side to provide access to the breast during the procedure. Compression plates are integrated into the breast coil which compress the breast either laterally or in the head / feet direction as required for optimal access to the breast. The apparatus includes a mechanical device for positioning interventional instruments in the breast such as biopsy or therapy instruments. The mechanical positioning devices position the instrument along the desired trajectory to the target site and insert the instrument into the breast while the patient remains inside the MRI scanner. Real time MR images may be acquired during instrument alignment and insertion to verify the trajectory. The mechanical positioning devices allow manipulation of instruments in any type of MRI scanner, including high field MRI systems with cylindrical magnets. The positioning devices provide a means to overcome limited access to the patient in MRI scanners. The positioning devices may be manually operated by means of gears, drive shafts, cables or other mechanical means. Or they may be electronically controlled by means of MR compatible motorized drive systems. The devices may be remotely controlled from outside the magnet for MRI systems that have limited access to the patient in the magnet. An interface between the electronically controlled drivers and the MRI scanner computer can provide robotic control of the instrument.
Owner:LAMPMAN DAVID A +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com