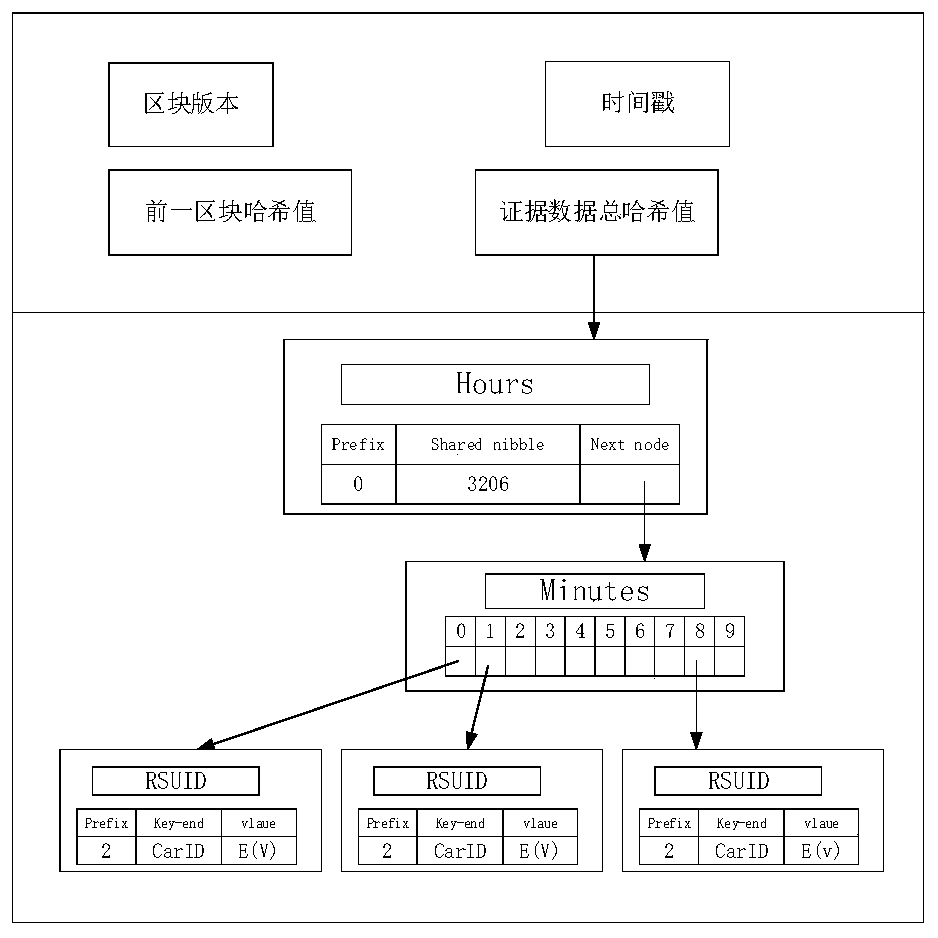
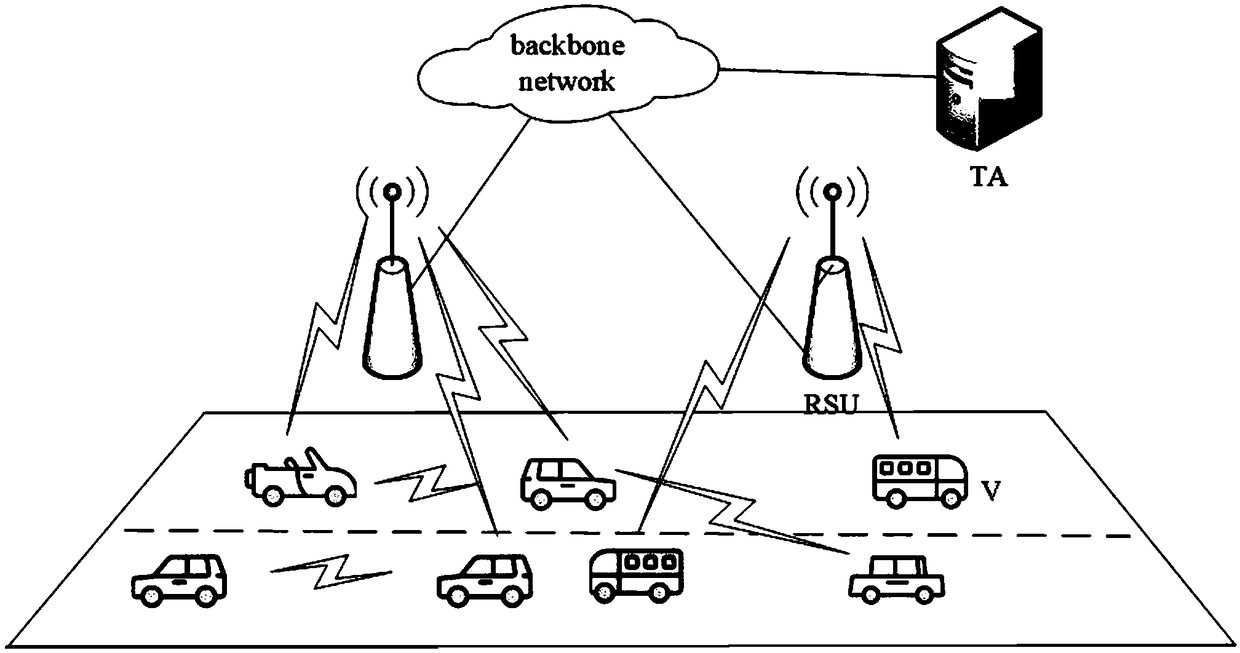
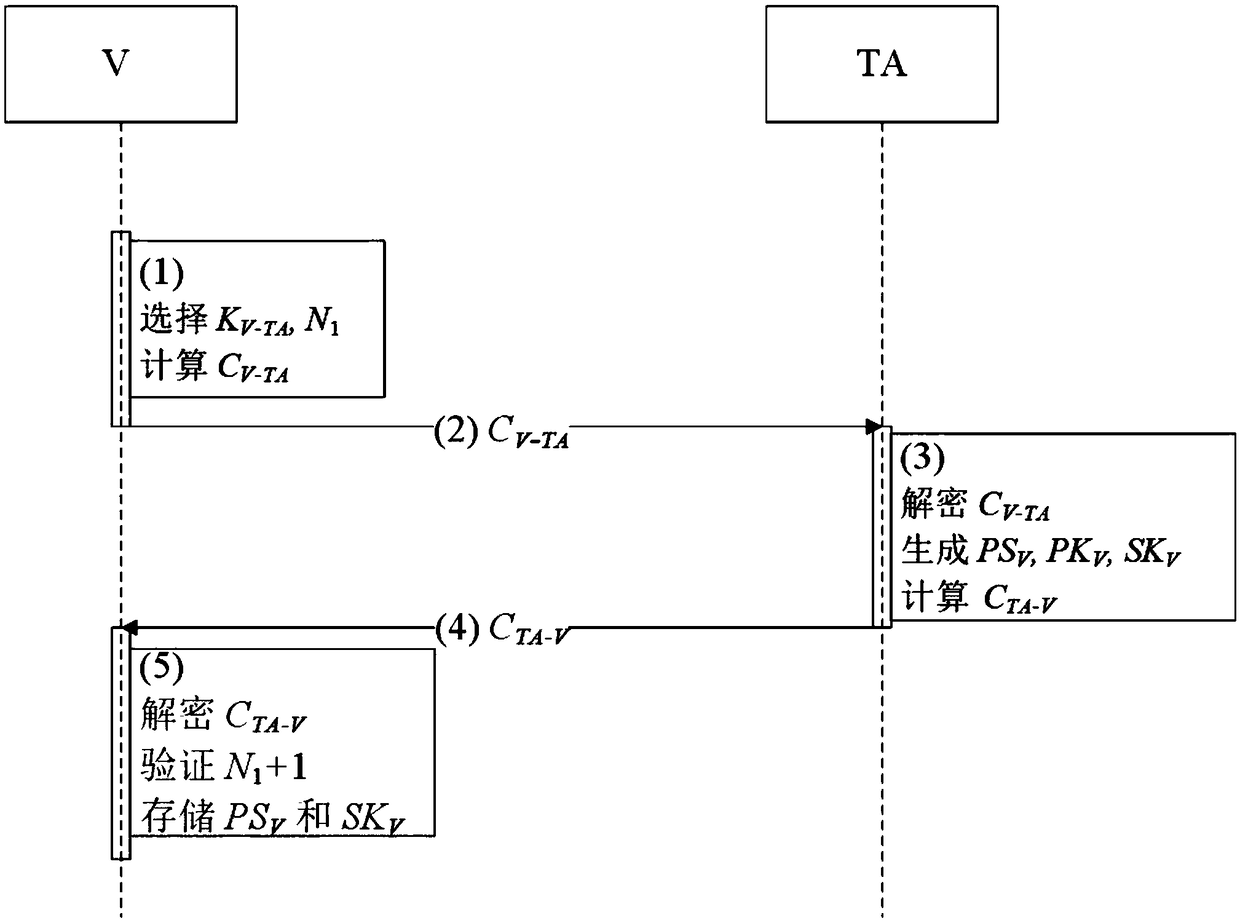
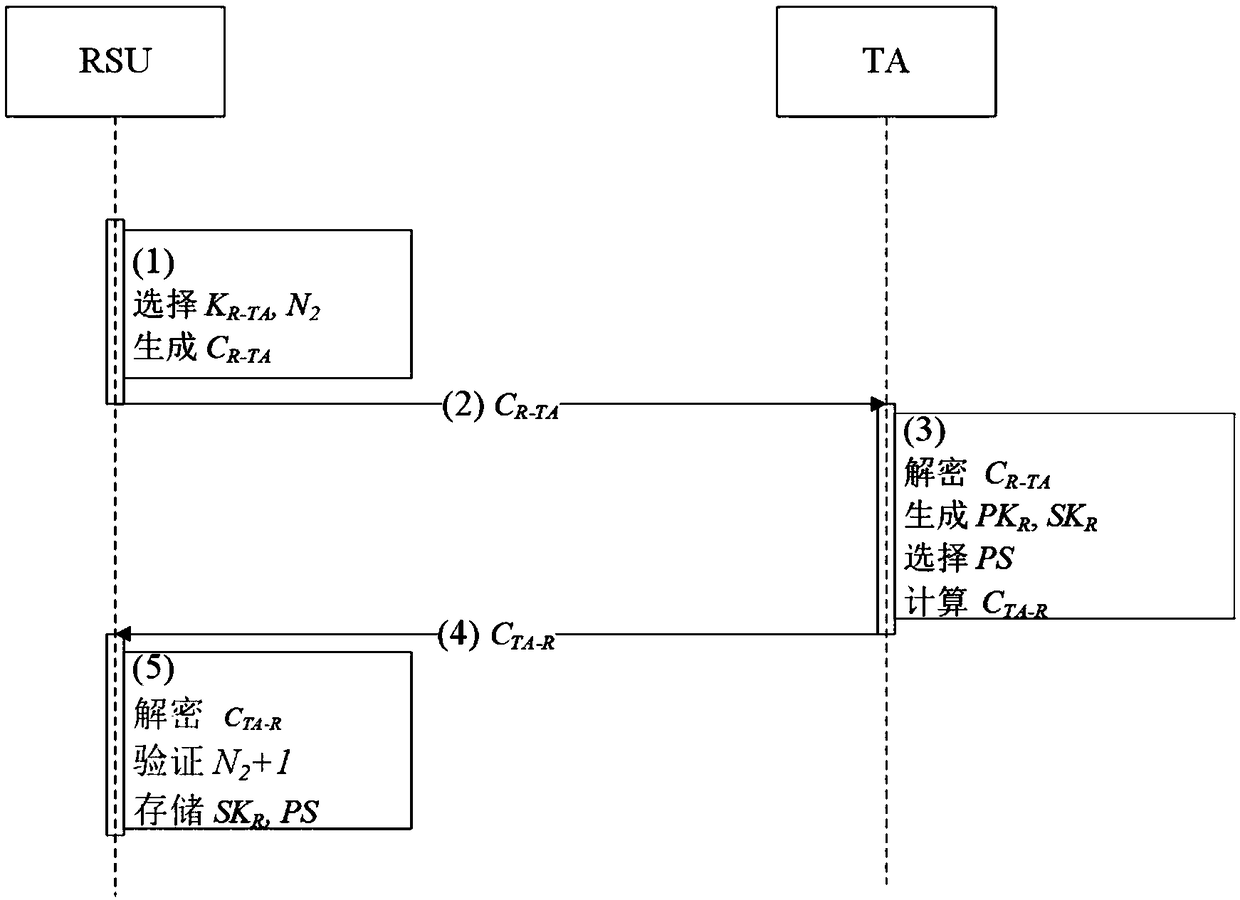
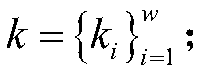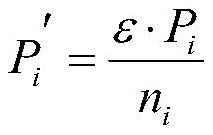Patents
Literature
343results about How to "Protect privacy and security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
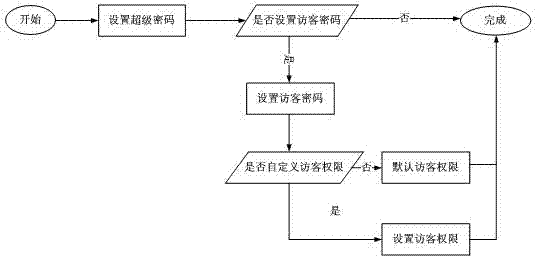
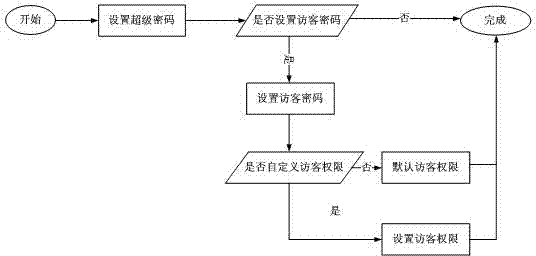
Method for setting permission password for mobile phone
InactiveCN102457619AProtect privacy and securityPrivacy protectionSubstation equipmentLimited accessDocumentation procedure
The invention discloses method for setting a permission password for a mobile phone. The method comprises the steps as follows: 1, entering a permission password setting program; 2, setting the highest permission password; 3, judging whether a visitor password is set or not, if yes, Step 4 is executed, otherwise, setting of the permission password is finished; 4, executing the program of setting a visitor password; 5, judging whether visitor permission is user-defined or not, if yes, Step 6.1 is executed, otherwise, Step 6.2 is executed; 6.1, setting visitor permission; 6.2, defaulting the visitor permission set by the system; and 7, accomplishing setting of the permission password. When the permission password is used for unlocking, whether a password inputted by a user is the highest permission password or the visitor permission password can be judged, if the password is the highest permission password, all the functions, applications and documentations of the mobile phone are opened, and if the password is the visitor permission password, the functions, applications and documentations of the mobile phone are used in a limited way. The method can protect data privacy of a user through passwords with different permissions and restrict access, and has the advantages of simplicity and convenience in operation, and easiness in implementation.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
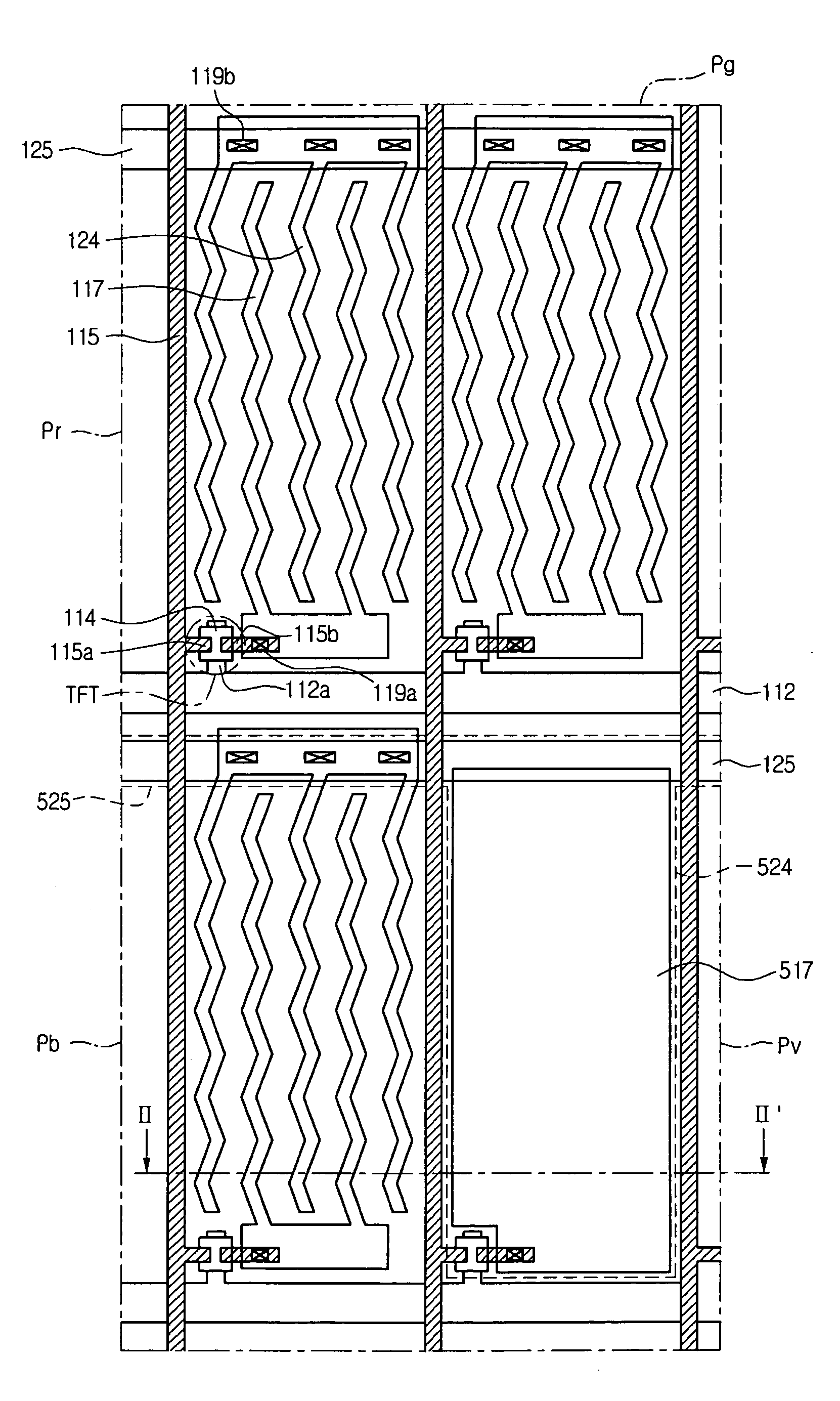
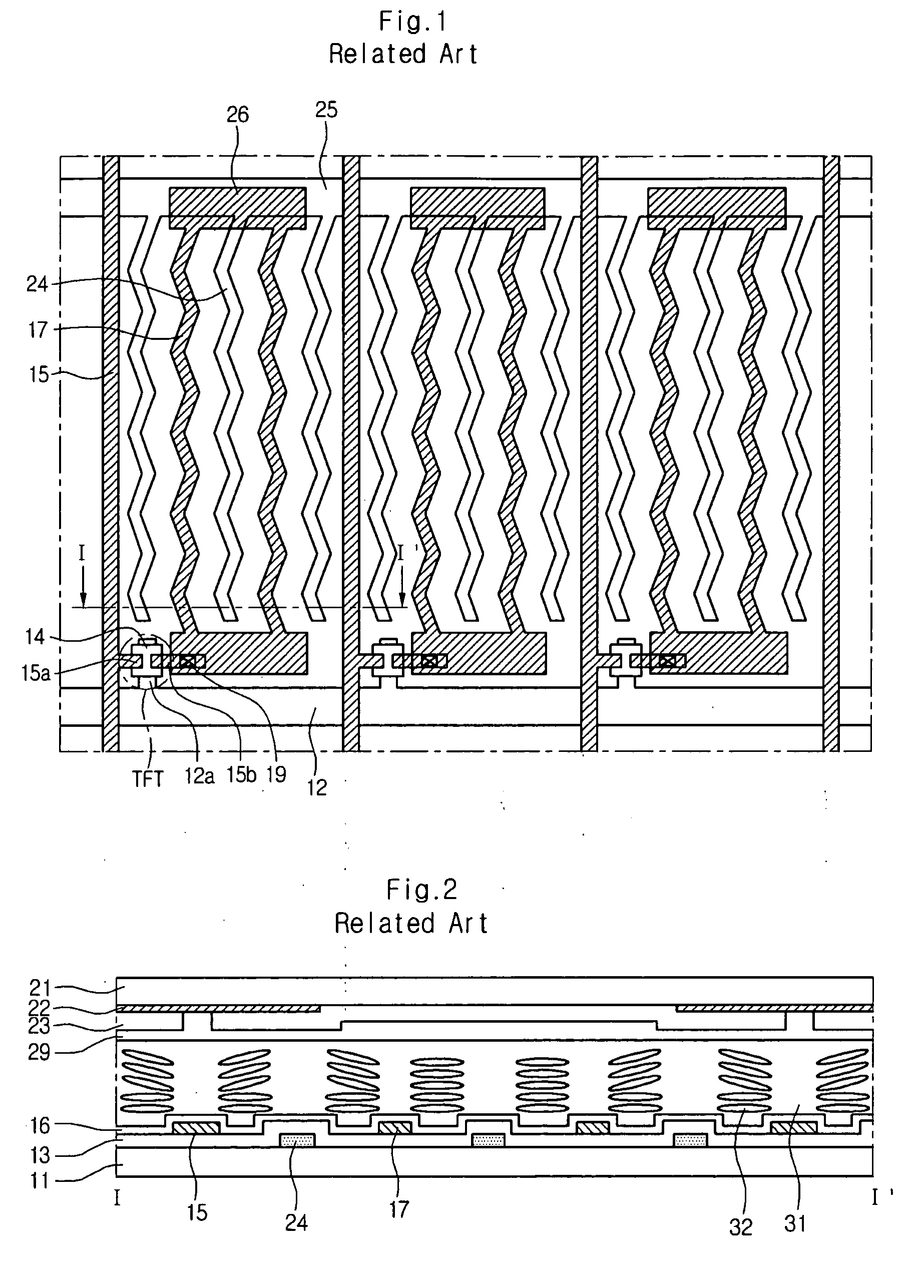
In-plane switching mode liquid crystal display device with adjustable viewing angle and method of fabricating the same
ActiveUS20070121047A1Protect privacy and securityPrivacy protectionNon-linear opticsLiquid-crystal displayLiquid crystal
An in-plane switching mode liquid crystal display device includes a first substrate and a second substrate, gate lines and data lines intersecting each other on the first substrate and defining red, green, blue sub-pixels, and viewing angle controlling sub-pixels, thin film transistors at the intersections of the gate lines and the data lines, first pixel electrodes and first common electrodes spaced apart from each other and alternately disposed at the red, green, and blue sub-pixels, second pixel electrodes at the viewing angle controlling sub-pixels, second common electrodes on the second substrate and at positions corresponding to the second pixel electrodes, and a liquid crystal layer between the first substrate and the second substrate.
Owner:LG DISPLAY CO LTD
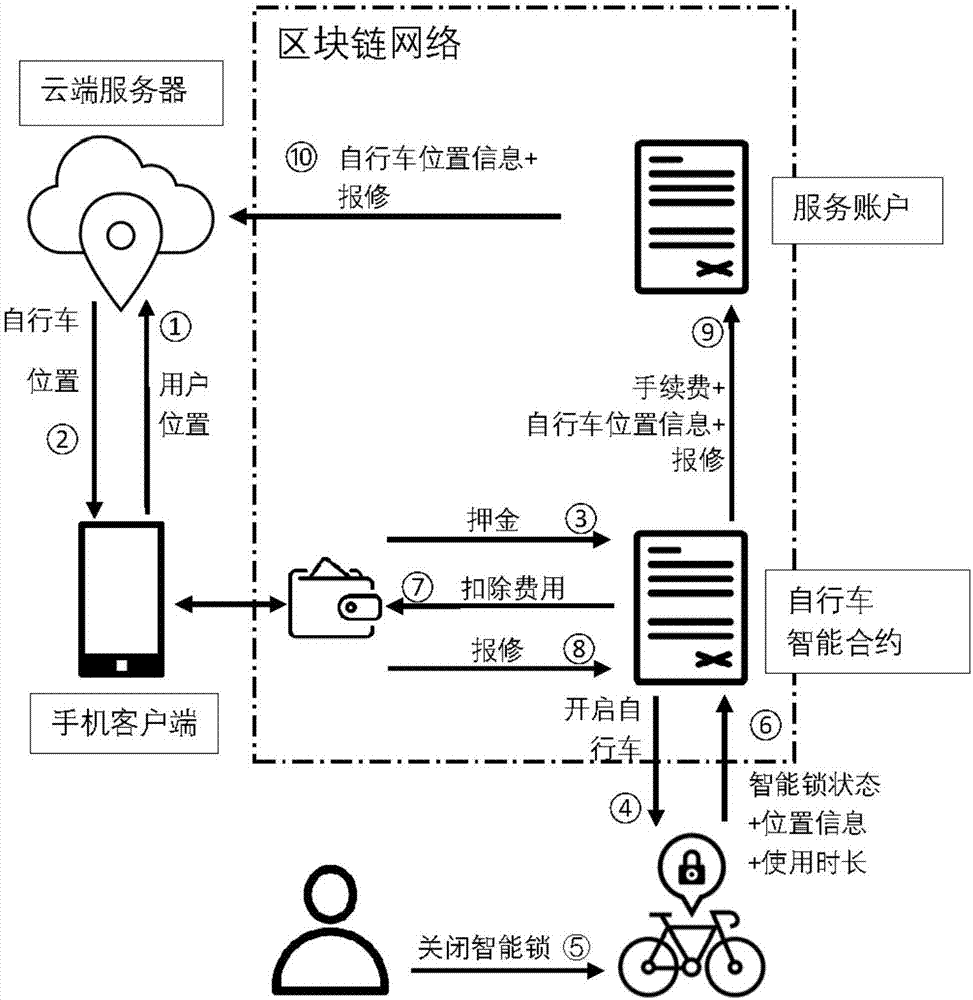
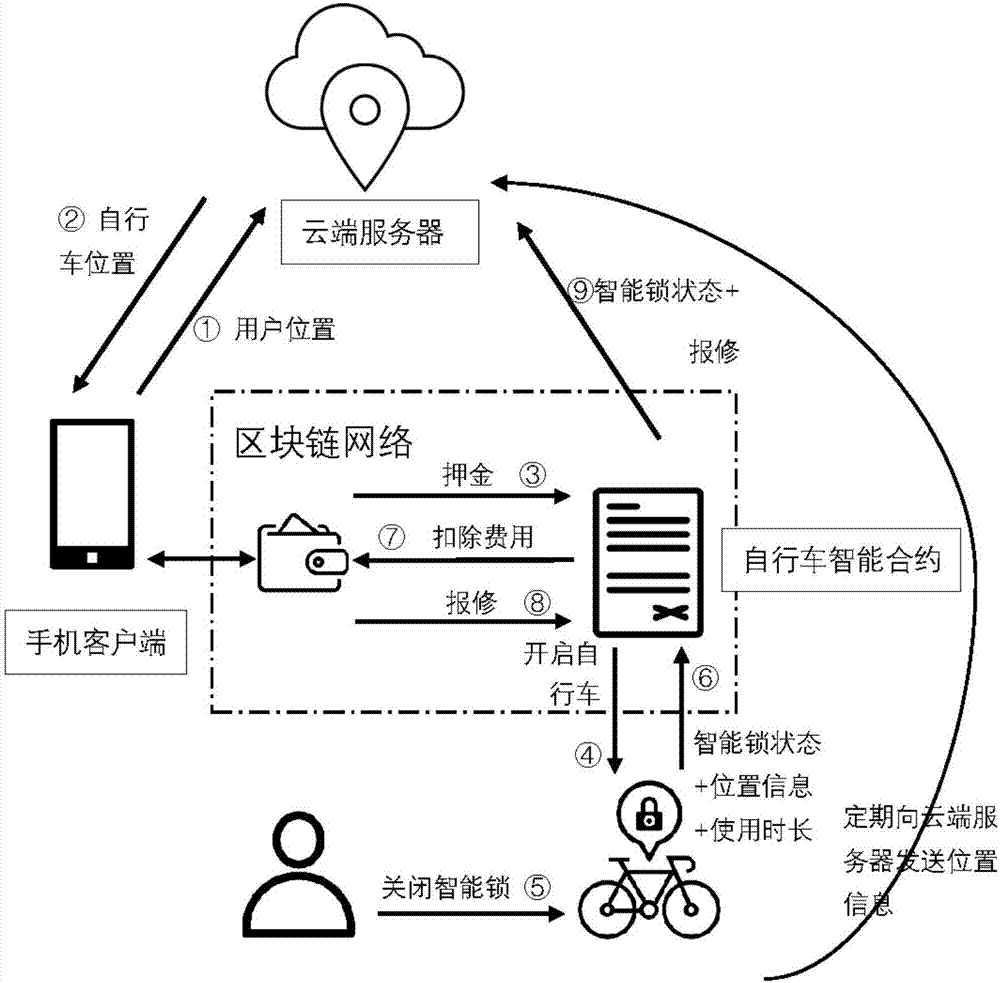
End-to-end bike sharing system and method based on blockchain
ActiveCN107993359AEnsure safetyLow costApparatus for meter-controlled dispensingTransmissionThird partyBike sharing
The invention discloses an end-to-end bike sharing system and method based on blockchain. The system comprises a system administrator, a cloud server, bike owners, bike users and a blockchain network;the blockchain network contains accounts, bike smart contracts and nodes; there is no need for the bike users to download multiple different applications any more, after registration, deposits are paid to the bike smart contracts, the blockchain network does not contain third parties, and the users only need to apply to the bike smart contracts when the deposits need to be returned, so that the phenomenon of difficult deposit returning is effectively avoided; the payment process does not rely on third-party payment software, so that needed commission charge is effectively reduced. Transactioninformation is stored by the nodes in the blockchain network together, each node stores all transaction data in the network totally redundantly, and once the data in one node is tampered with, othernodes raise objections, so that a whole database is high in safety, and private security of the bike users and the bike owners can be protected.
Owner:ZHEJIANG UNIV
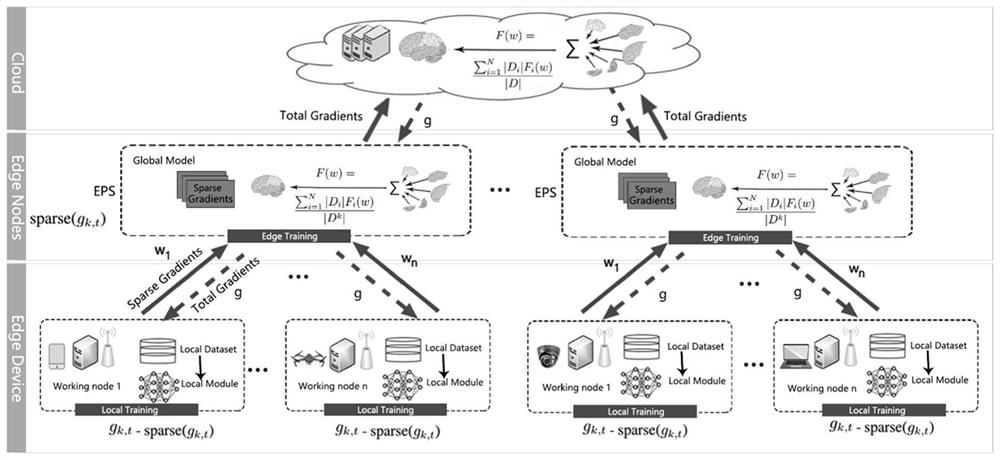
Federal learning computing unloading computing system and method based on cloud side end
InactiveCN112817653AMake up for deficienciesAccurate decisionProgram initiation/switchingResource allocationComputation complexityEdge node
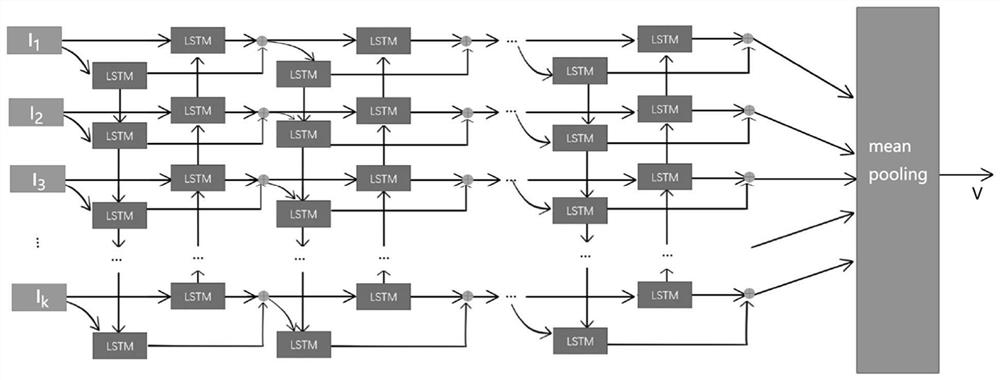
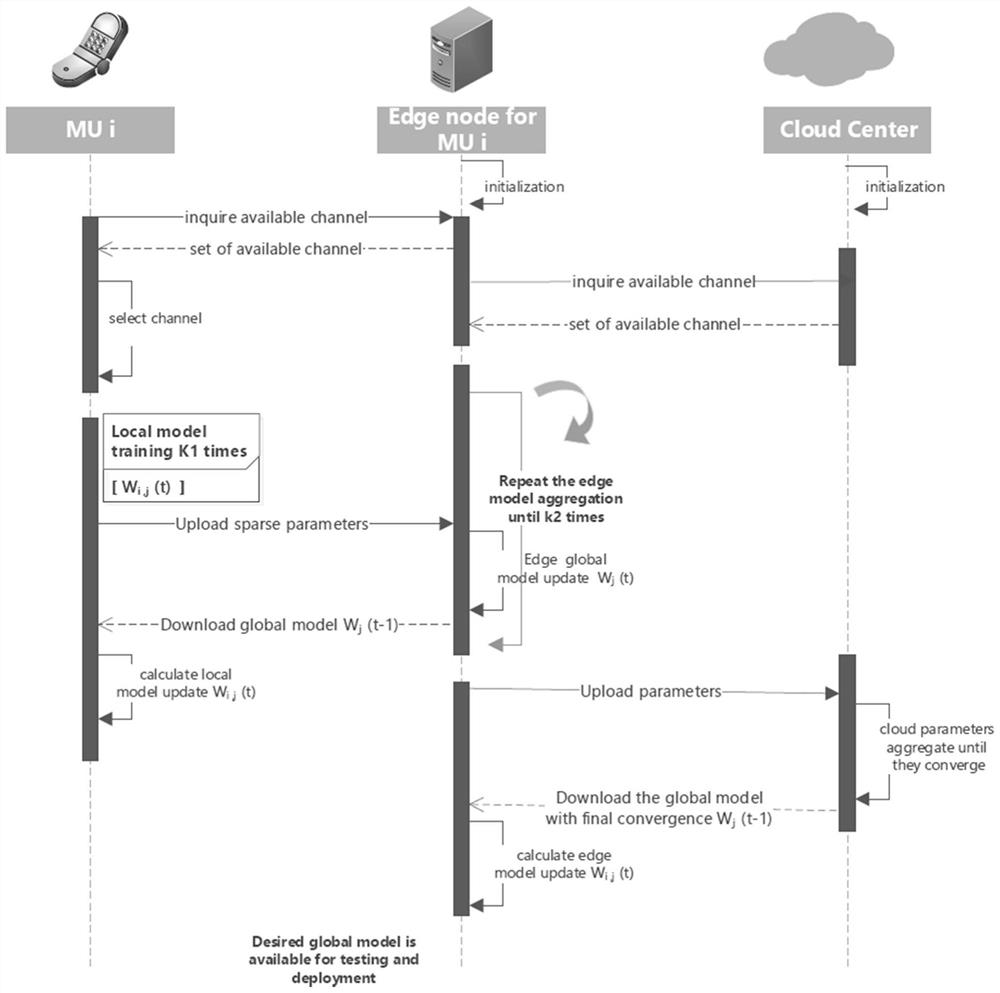
The invention discloses a federated learning computing unloading resource allocation system and a method based on a cloud side end, and aims to make an accurate decision for computing task unloading and resource allocation, eliminate the need for solving a combinatorial optimization problem and greatly reduce the computing complexity. Based on cloud side three-layer federated learning, the adjacent advantage of edge nodes to a terminal is comprehensively utilized, core powerful computing resources in cloud computing are also utilized, the problem that the computing resources of the edge nodes are insufficient is solved, a local model is trained at each of multiple clients to predict an unloading task. A global model is formed by periodically executing one-time parameter aggregation at an edge end, the cloud end executes one-time aggregation after the edge executes the periodic aggregation until a global BiLSTM model is formed through convergence, and the global model can intelligently predict the information amount of each unloading task. Therefore, guidance is better provided for calculation unloading and resource allocation.
Owner:XI AN JIAOTONG UNIV
Transparent encryption and decryption method for intelligent terminal file
ActiveCN104331644AProtect privacy and securityPrevent theftDigital data protectionProgram/content distribution protectionEncryption
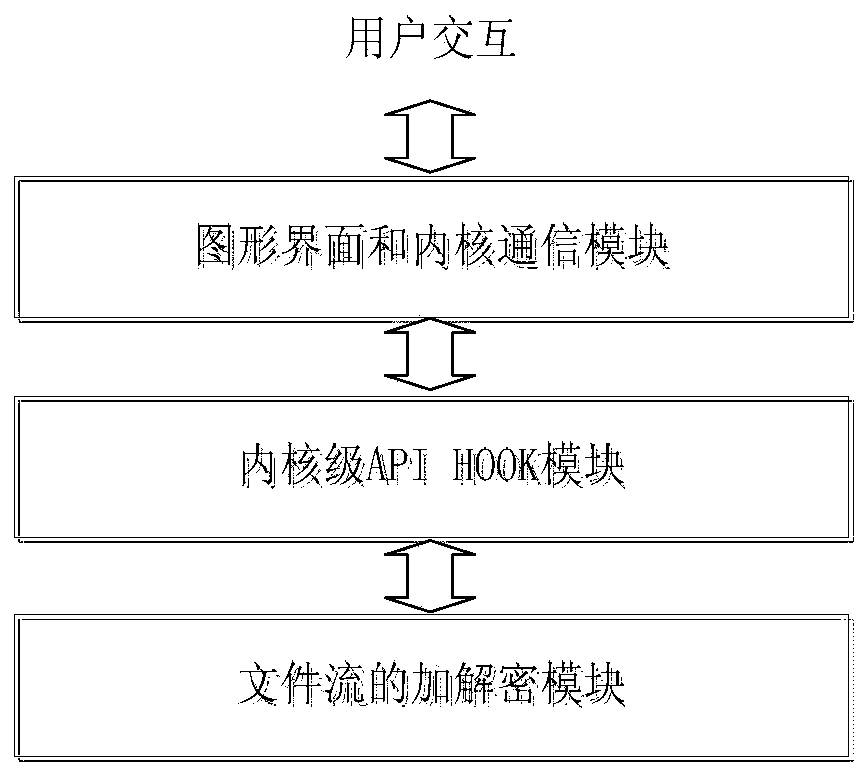
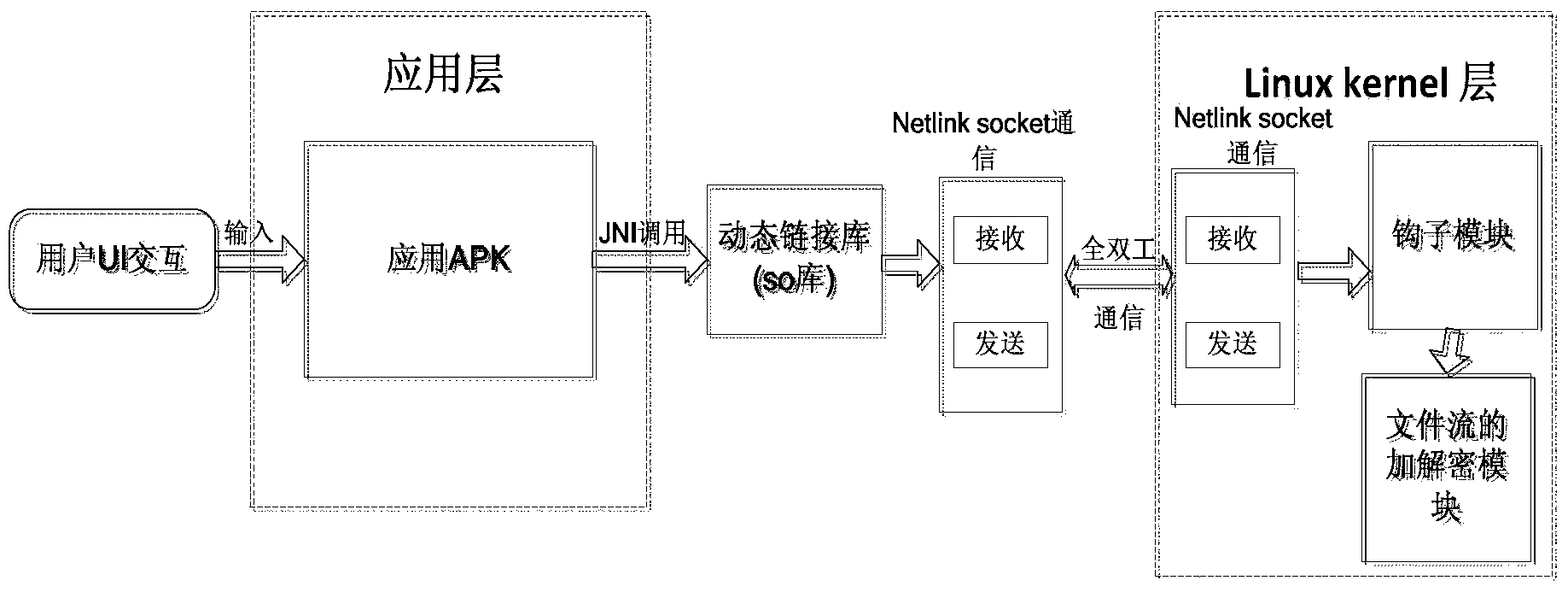
The invention provides a transparent encryption and decryption method for an intelligent terminal file. The method comprises the following steps: setting an authorized progress list and a to-be-protected file list on an application layer and sending the authorized progress list and the to-be-protected file list to a dynamic link library. so; acquiring an operation command for an operation file from an access progress, calling for the dynamic link library. so through JNI, and transmitting the name of the access progress, the address of the operation file and the operation command to a hook module of a nucleus layer of an operating system of the intelligent terminal when the dynamic link library. so determines that the access progress is the authorized progress and the operation file is the to-be-protected file; seeking for a system call table by the hook module; acquiring the address of a system call function corresponding to the operation command from the system call table; replacing the address of the system call function in the system call table with the address of the function with a decryption function preset in the nucleus layer.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Fingerprint recognition apparatus, fingerprint recognition method and terminal device for same
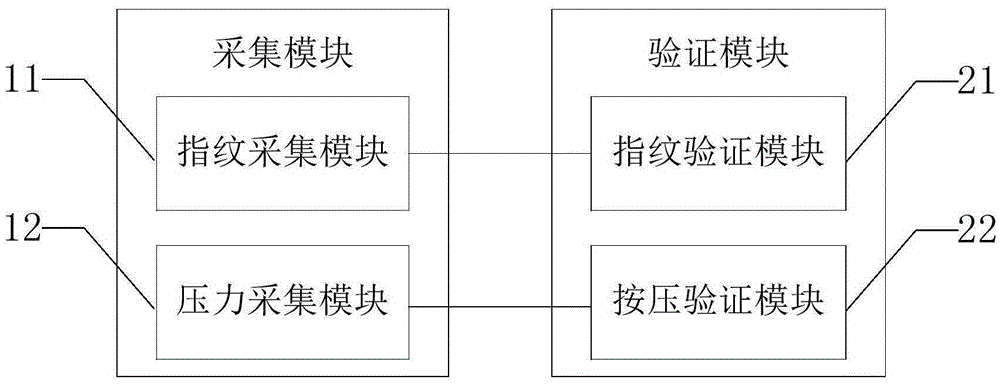
InactiveCN105404875AHigh precisionProtect privacy and securityCharacter and pattern recognitionPattern recognitionTerminal equipment
The present disclosure provides a fingerprint recognition apparatus, a fingerprint recognition method and a terminal device for the same. The fingerprint recognition apparatus comprises: a fingerprint acquisition module, used for acquiring fingerprint data of a detected finger after the detected finger is placed on a fingerprint detection region, wherein the fingerprint detection region is located above a plurality of pressure detection regions; a pressure acquisition module, used for acquiring a pressure value of each pressure detection region that is pressed by the detected finger; a fingerprint authentication module which is coupled to the fingerprint acquisition module and is used for verifying whether the acquired fingerprint data is matched with pre-stored fingerprint data; and a press authentication module which is coupled to the pressure acquisition module and is used for verifying whether the pressure value of each pressure detection region is matched with a preset pressure value interval. According to the fingerprint recognition apparatus, the fingerprint recognition method and the terminal device for the same, which are provided by the present disclosure, precision of fingerprint recognition can be improved, and privacy and property security of a user of an electrical device can be protected.
Owner:NANCHANG OUFEI BIOLOGICAL IDENTIFICATION TECH
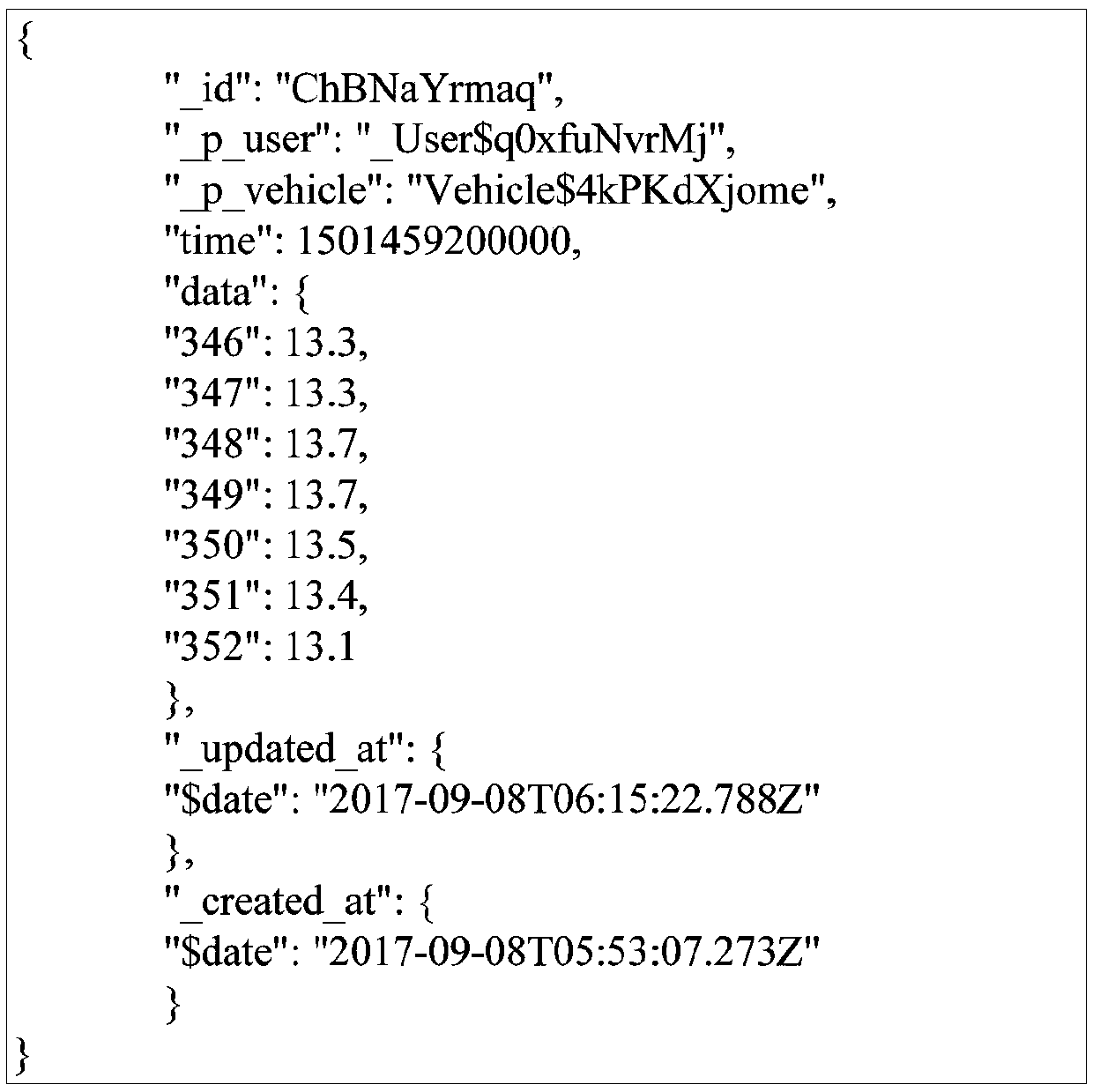
Data processing method and device, medium and terminal
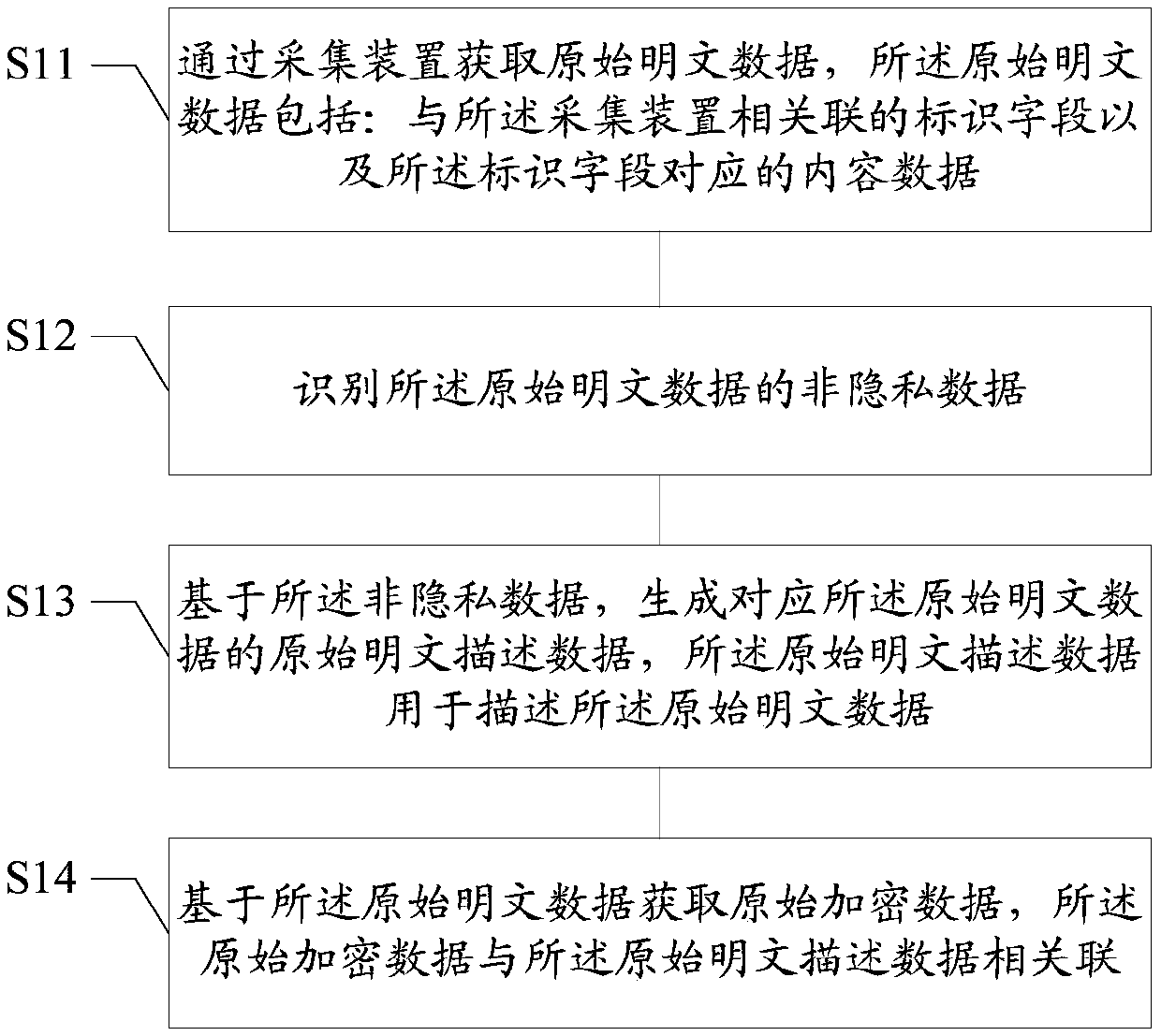
Embodiments of the invention disclose a data processing method and device, a medium and a terminal. The data processing method comprises the following steps of acquiring original plaintext data through an acquisition device, wherein the original plaintext data comprises an identification field associated with the acquisition device and content data corresponding to the identification field; identifying non-privacy data of the original plaintext data on the basis of the identification field; generating original plaintext description data corresponding to the original plaintext data on the basisof the non-privacy data, wherein the original plaintext description data is used for describing the original plaintext data; and obtaining original encrypted data based on the original plaintext data, wherein the original encrypted data is associated with the original plaintext description data. According to the technical scheme, the security of data in a data trading process can be improved.
Owner:石更箭数据科技(上海)有限公司
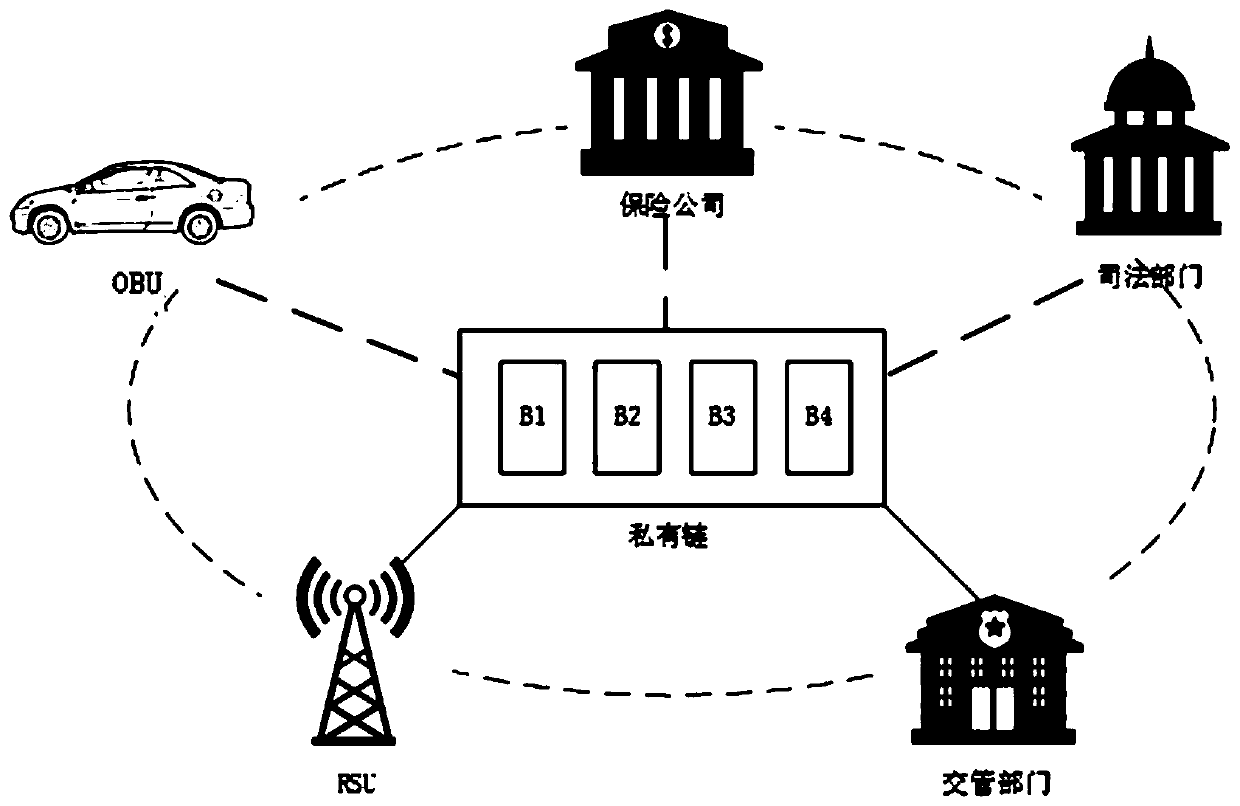
Electronic evidence obtaining device and method based on block chain in Internet-of-Vehicles environment
ActiveCN111464980AProtection against the risk of tamperingImprove access efficiencyData processing applicationsParticular environment based servicesComputer networkTraffic crash
The invention provides an electronic evidence obtaining device and method based on a block chain in an Internet-of-Vehicles environment. The method comprises the following steps of S10, offline registration, S20, vehicle online identity registration, S30, real-time evidence storage and S40, query and evidence obtaining. According to the electronic evidence obtaining device and method based on theblock chain in the Internet-of-Vehicles environment, the block chain technology is used for traffic accident electronic evidence obtaining, the integrity, non-repudiation and permanence of evidence are guaranteed through the characteristics of block chain distributed data storage and the like, many problems of traditional traffic accident evidence obtaining are solved, and the evidence obtaining efficiency is high.
Owner:NANTONG UNIVERSITY
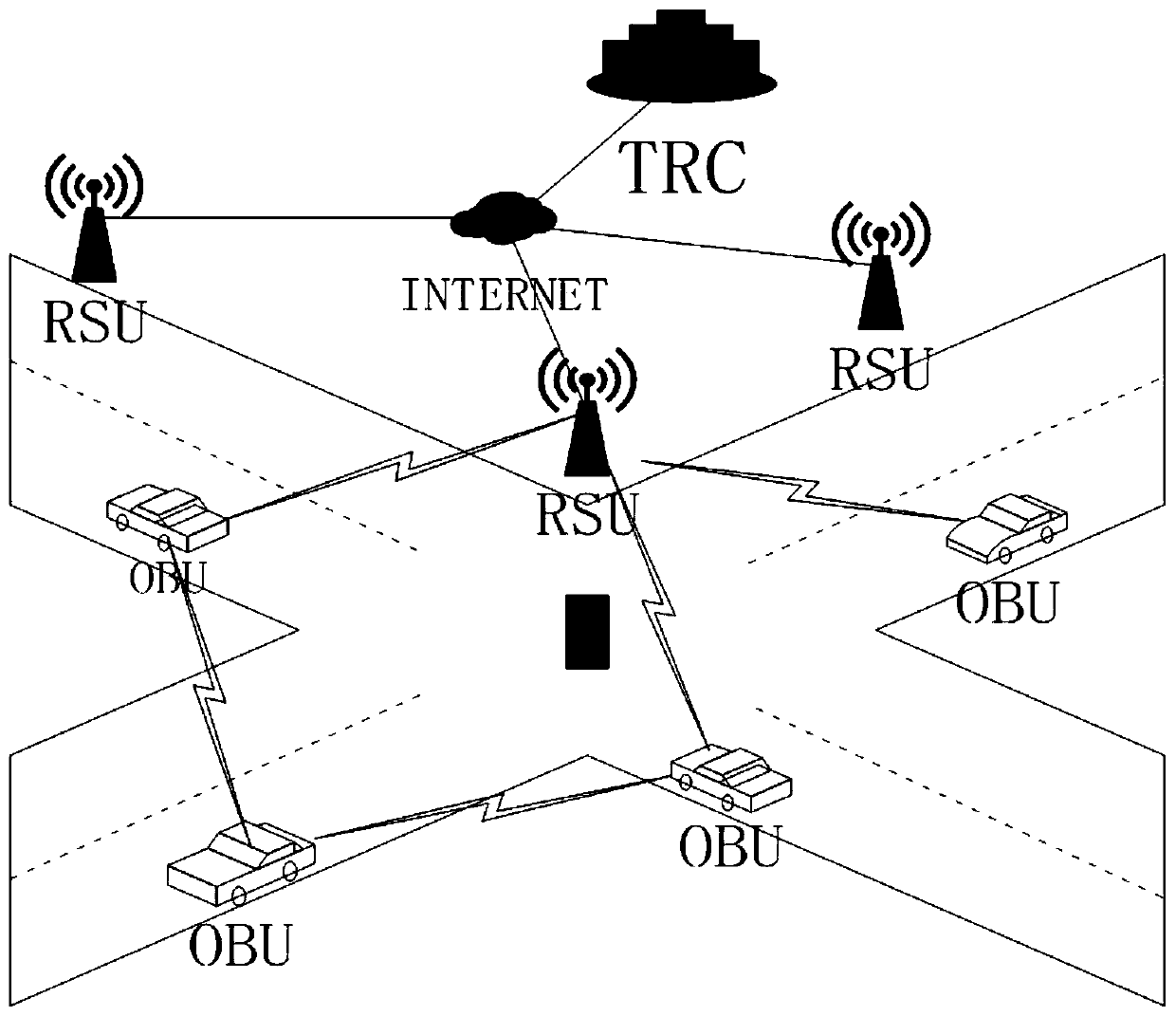
Vehicle-mounted-network anonymous-communication system based on ring signature and method
ActiveCN109412816AProtect privacy and securityGuarantee authentication efficiencyUser identity/authority verificationSecurity arrangementThird partyCommunications system
The invention relates to the technical field of network security, and provides a vehicle-mounted-network anonymous-communication system based on ring signature. The system includes a third-party trustinstitution, road side units and vehicles. The invention also provides a method of using the above system for vehicle-mounted-network anonymous-communication. The third-party trust institution firstly publishes public parameters, then the vehicles and the road side units apply for registration to the third-party trust institution, the third-party trust institution issues pseudonyms and public andprivate keys for the vehicles, and issues public and private keys and initial pseudonym ring members for the road side units, and then states of the vehicles in a vehicle-mounted network are monitored; and initial accessing authentication is carried out with a road side unit RSU if a vehicle accesses the vehicle-mounted network for the first time, and switching accessing authentication is carriedout with a road side unit RSU' if the vehicle does out access the vehicle-mounted network for the first time, and two-way authentication is carried out under assistance of a road side unit if a vehicle Vi is ready to communicate with a vehicle Vj. The system and the method integrate pseudonym certificate and group signature technology, and can fully protect privacy safety of communicators on thepremise of ensuring authentication efficiency.
Owner:NORTHEASTERN UNIV
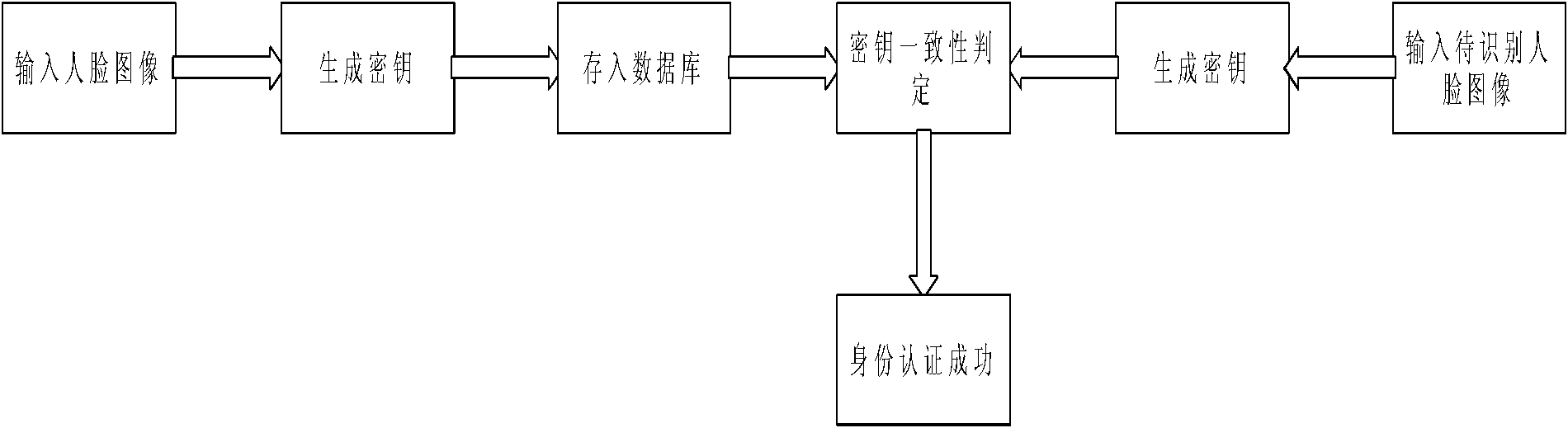
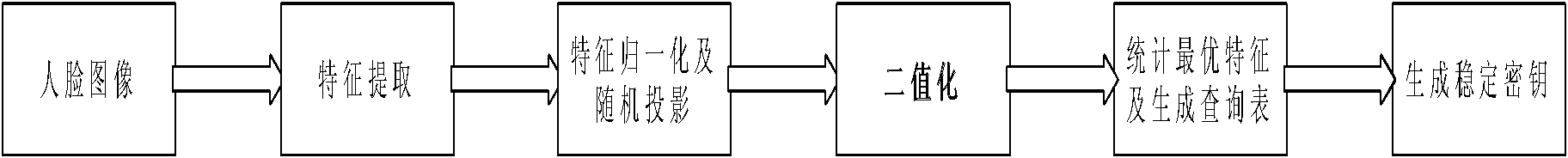
Facial feature cryptographic key generation-based internet identity authentication method
InactiveCN102111418AAvoid enteringProtect privacy and securityUser identity/authority verificationCharacter and pattern recognitionFeature matchingAuthentication system
The invention discloses a facial featured cryptographic key generation-based internet identity authentication method, which relates to the technical fields of biological feature recognition and authentication and password application. The method comprises an identity registration stage and an identity authentication stage. In the identity registration stage, a stable cryptographic key is generated by utilizing a facial feature method based on random projection and statistical optimum, stored into a database and used for performing identity authentication on a user. In the identity authentication stage, the steps of feature extraction, feature random projection, cryptographic key generation and feature error correction are performed on a face image by adopting a method consistent with the method for generating the cryptographic key in the identity registration stage, and then a feature matching operation is performed to realize the identity authentication of the user. By the method, a face template is effectively protected from attacks in a face recognition process, good references and choices are provided for the generation, management and the like of the cryptographic key required by an identity authentication system in real life, and the problem of internal diversity in biological feature recognition is effectively solved; and the method is simple and easy.
Owner:BEIJING UNIV OF TECH
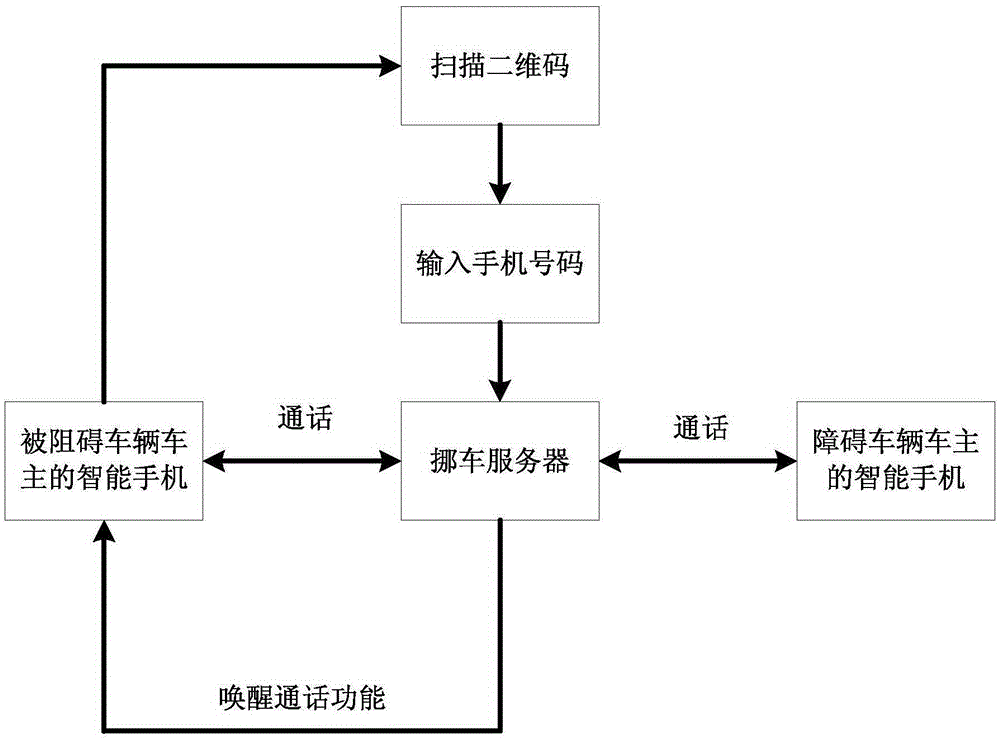
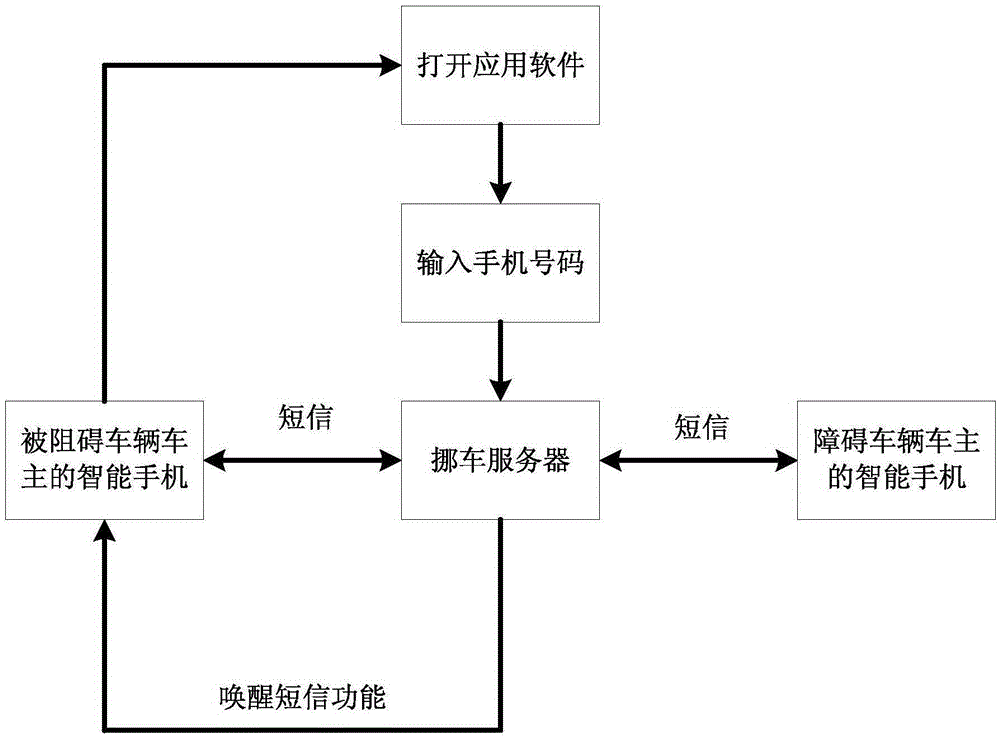
Communication method and system applied to vehicle moving
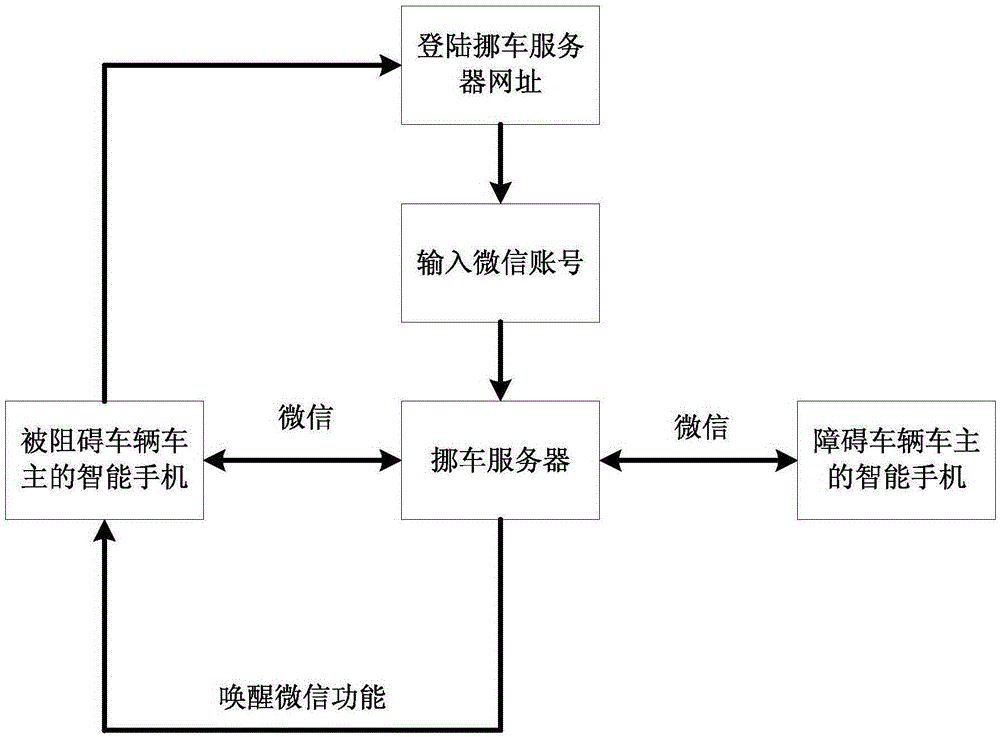
InactiveCN105430039AProtect privacy and securityProtect information securityTransmissionInformation securityReal-time computing
The invention discloses a communication method and a system applied to vehicle moving. When driving difficulty occurs, an owner of a blocked vehicle regards a vehicle-moving server platform as an intermediate medium so that the communication with an owner of a blocking vehicle is realized, and the problem of driving difficulty is solved in time. Besides, in a communication process of both vehicle owners, both of them cannot obtain information of the other so that individual privacy and information security of the owners are protected.
Owner:SHENZHEN VCYBER TECH
Hide display starting device and hide display starting method for application programs
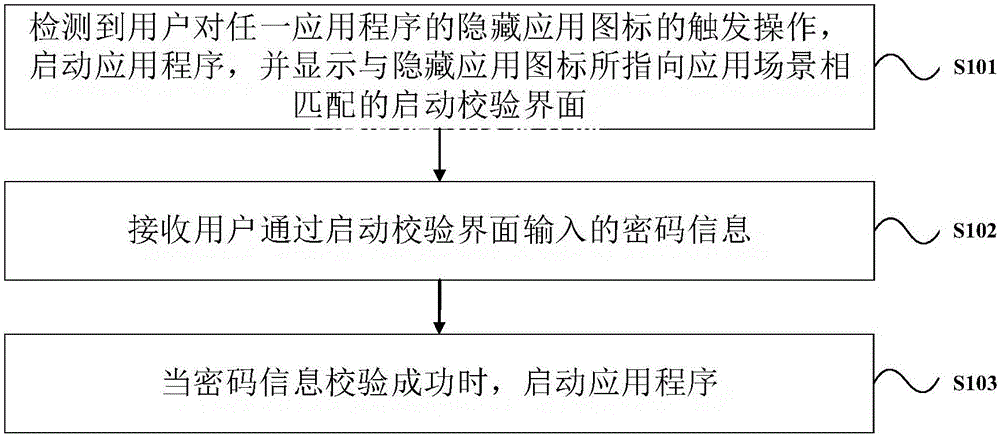
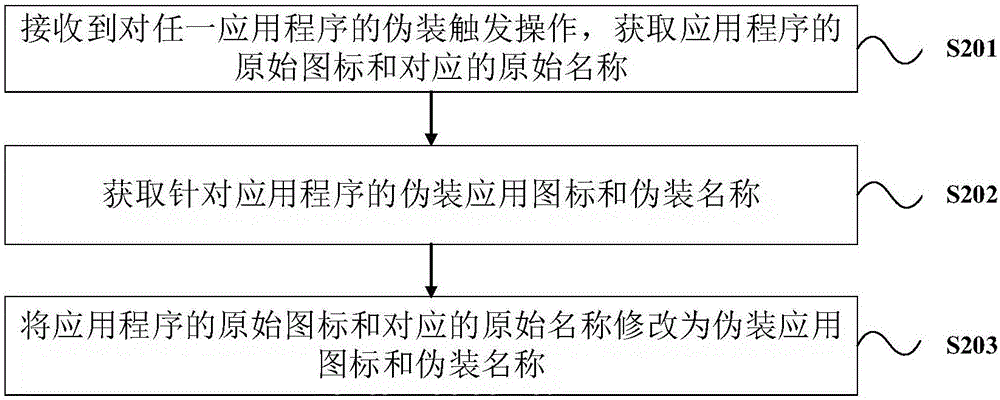
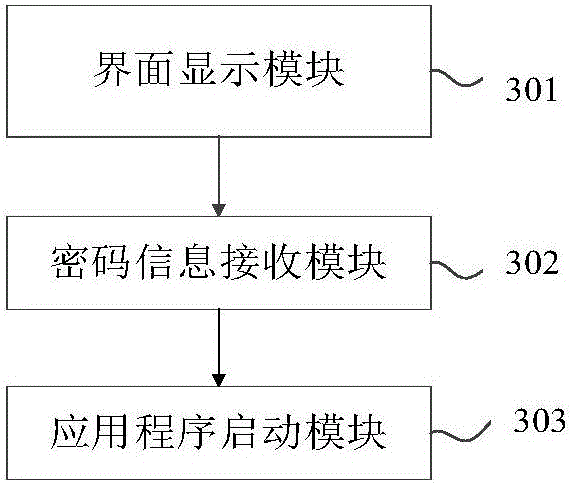
ActiveCN106446632AImprove experienceFull camouflageDigital data authenticationExecution for user interfacesTerminal equipmentComputer terminal
The invention provides a hide display starting device and a hide display starting method for application programs. The method includes: when trigger operations applied by a user to a hide application icon of any application program are detected, starting the application program, and displaying a starting verification interface matched with an application scene pointed by the hide application icon; receiving code information inputted by the user through the starting verification interface; starting the application program if code information verification is successful. By adoption of the technical scheme, high privacy of the user can be guaranteed in the application program even under the condition of unlocking of a screen of terminal equipment, the application program is prevented from being used by any person except for the user of the terminal equipment, and accordingly privacy safety of user data in the application program can be effectively protected, and user experience is improved.
Owner:BEIJING QIHOO TECH CO LTD +1
Method and device for protecting privacy
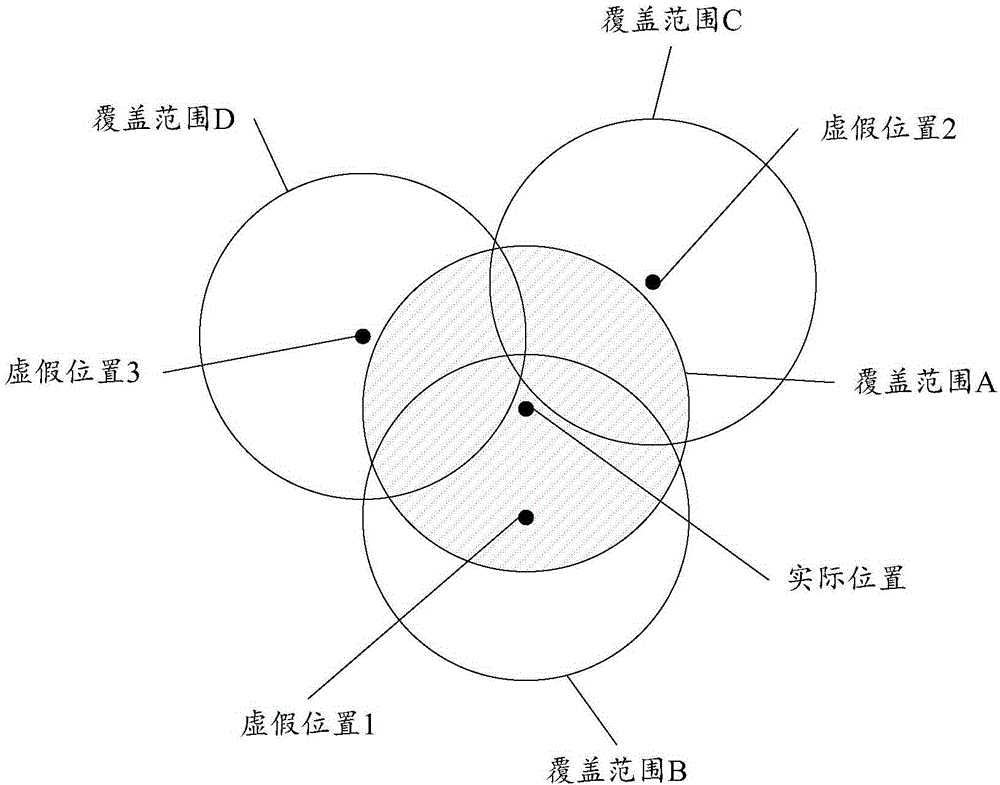
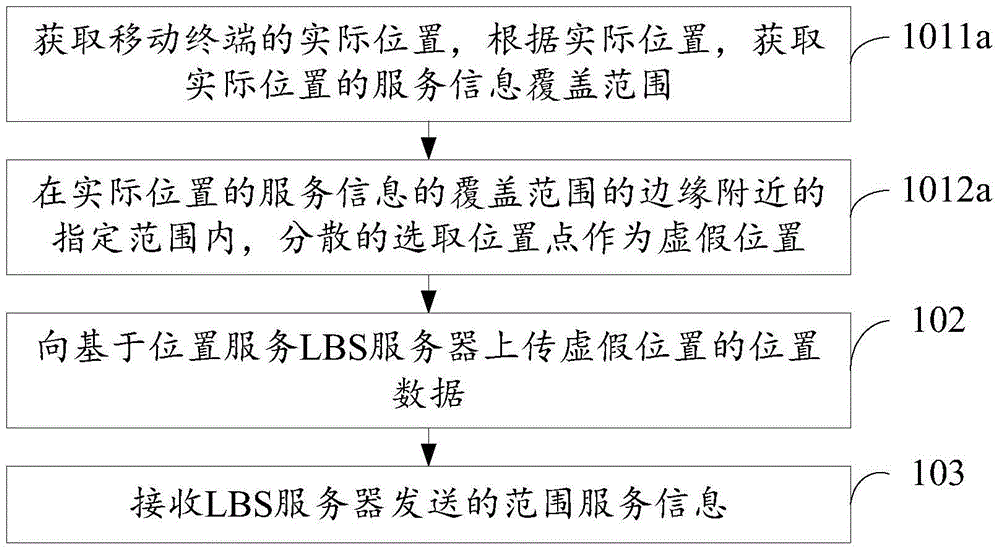
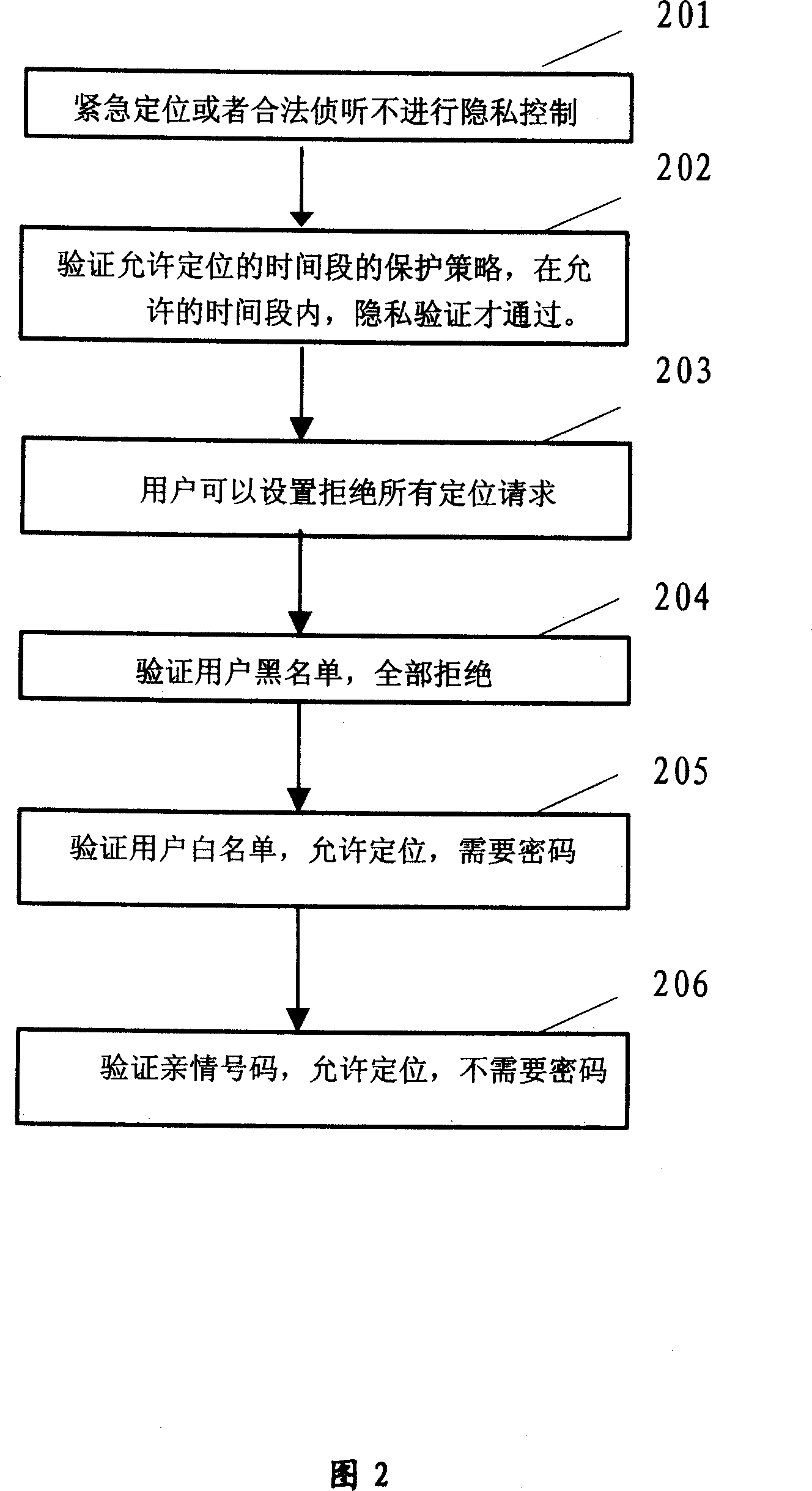
InactiveCN104010272AProtect privacy and securityReduce the risk of privacy breachesLocation information based serviceSecurity arrangementInformation technologyElectronic information
The embodiment of the invention discloses a method and device for protecting privacy and relates to the technical field of electronic information. According to the method and device, position information and privacy leakage of a user can be reduced. The method includes the steps that the actual position of a mobile terminal is obtained, a false position is selected according to the actual position, and the coverage range of service information of the actual position is within the coverage range of service information of the false position; data of the false position are uploaded to an LBS server; the range service information sent by the LBS server is received and at least includes the service information of the false position, and the service information of the false position is obtained through the LBS server according to the data of the false position. The method and device are suitable for scenes where the privacy of the user is protected in LBS.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
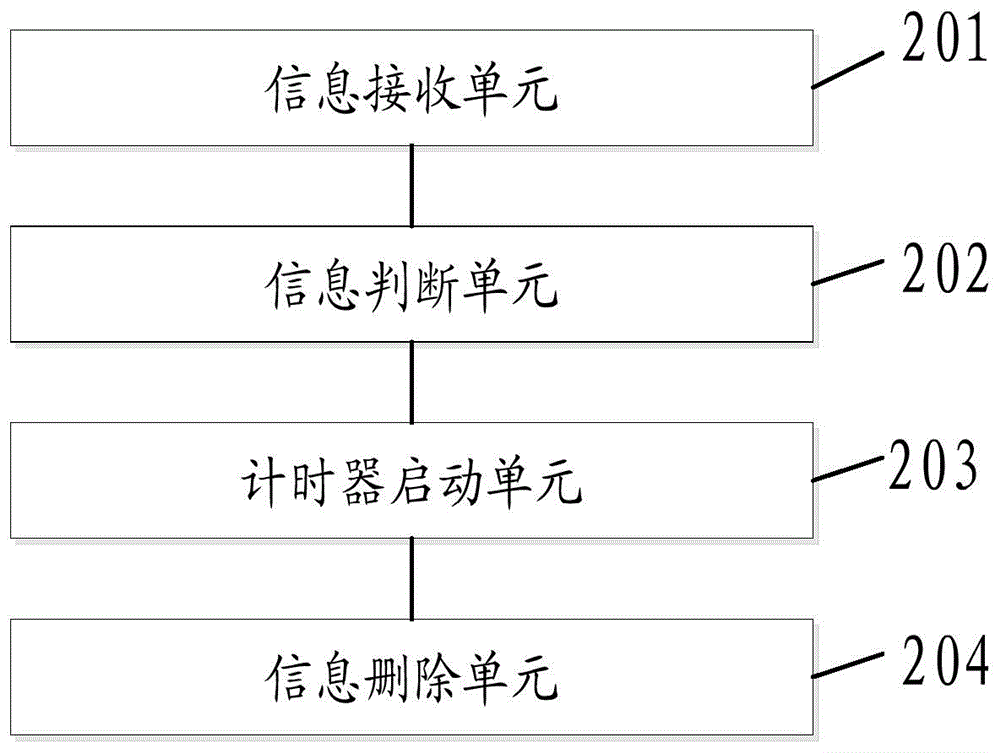
Method and device for automatically deleting information
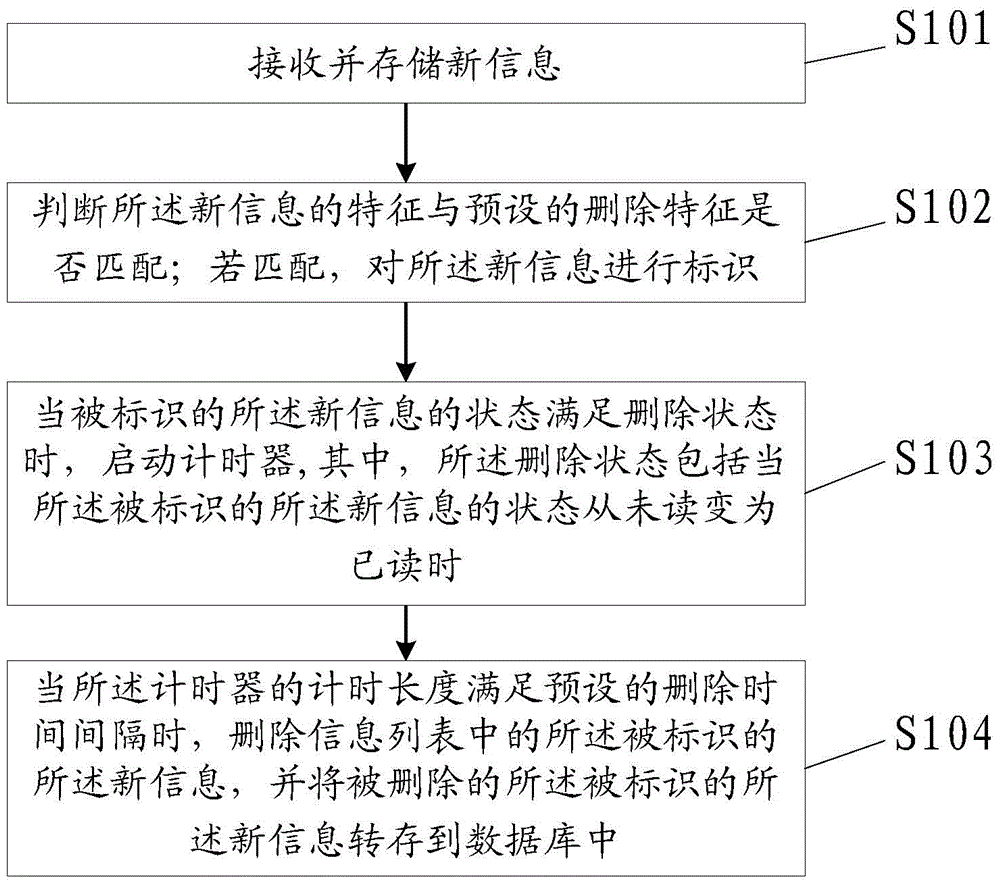
The invention discloses a method and a device for automatically deleting information. The method for automatically deleting information comprises the following steps: receiving and storing new information; judging whether the characteristic of the new information is matched with a preset deleting characteristic or not; if so, identifying the new information; when the state of the identified new information satisfies a deleting state, starting a timer; and when the timing length of the timer satisfies a preset deleting time interval, deleting the identified new information in an information list, and unloading the deleted identified new information in a database, wherein the deleting state comprises a state in which the state of the identified new information turns from an unread state to a read state. By adopting the method provided by the invention, information needing to be deleted can be deleted automatically after being read, so that convenience is brought to a user during use, and the privacy security of the user is protected.
Owner:北京数字天域科技有限责任公司
Mobile APP registration method and device and mobile APP registration login method and device
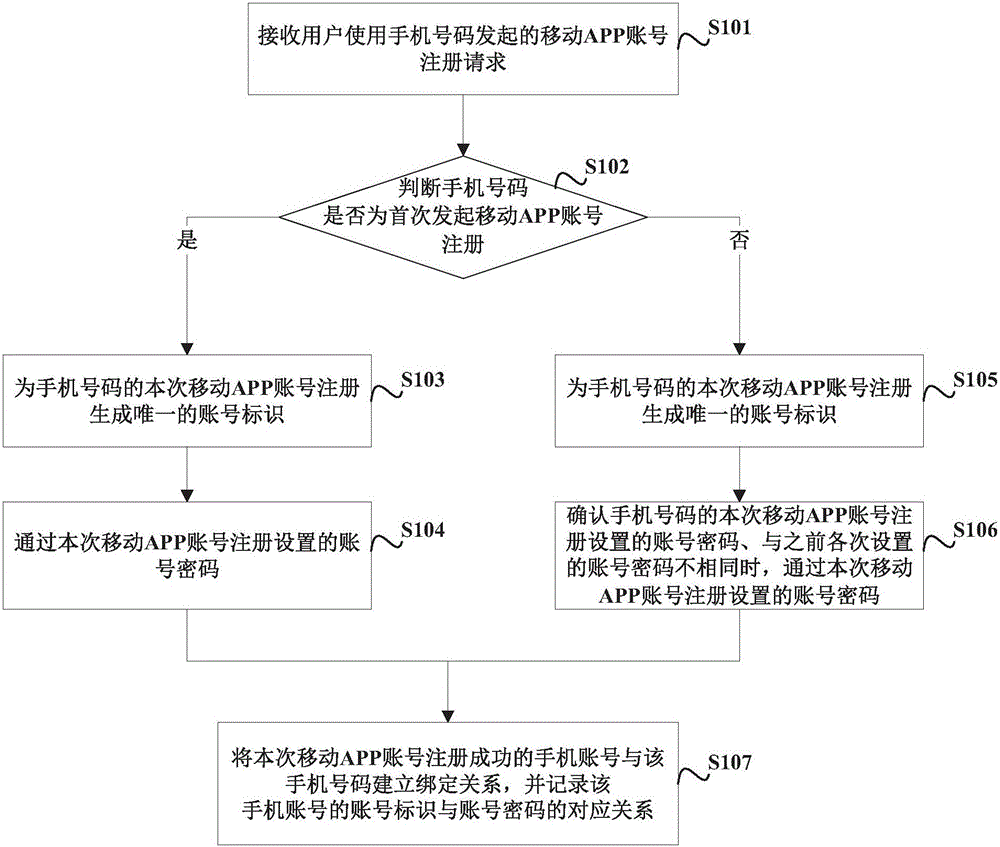
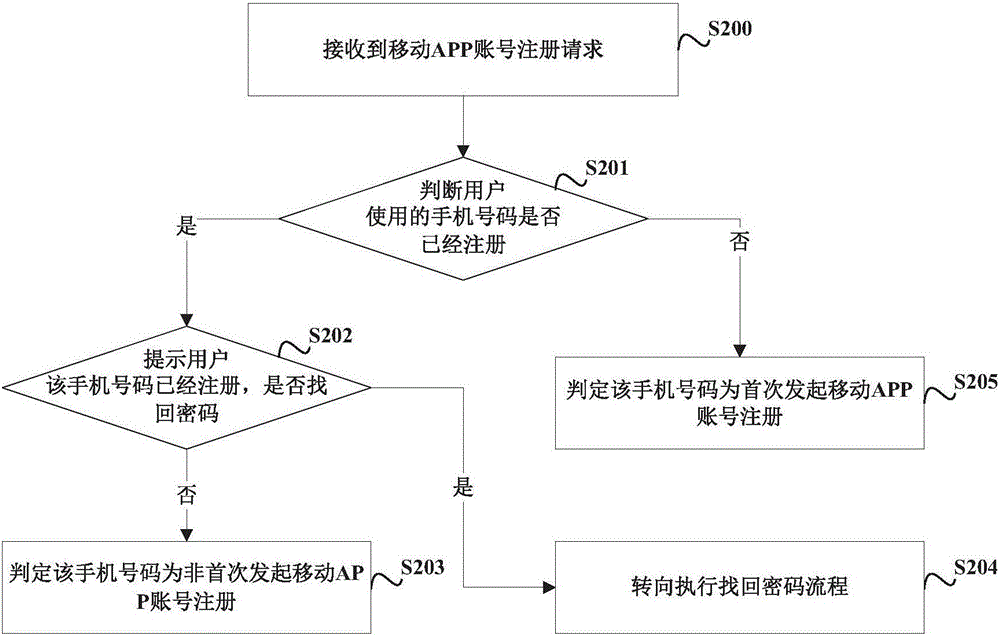
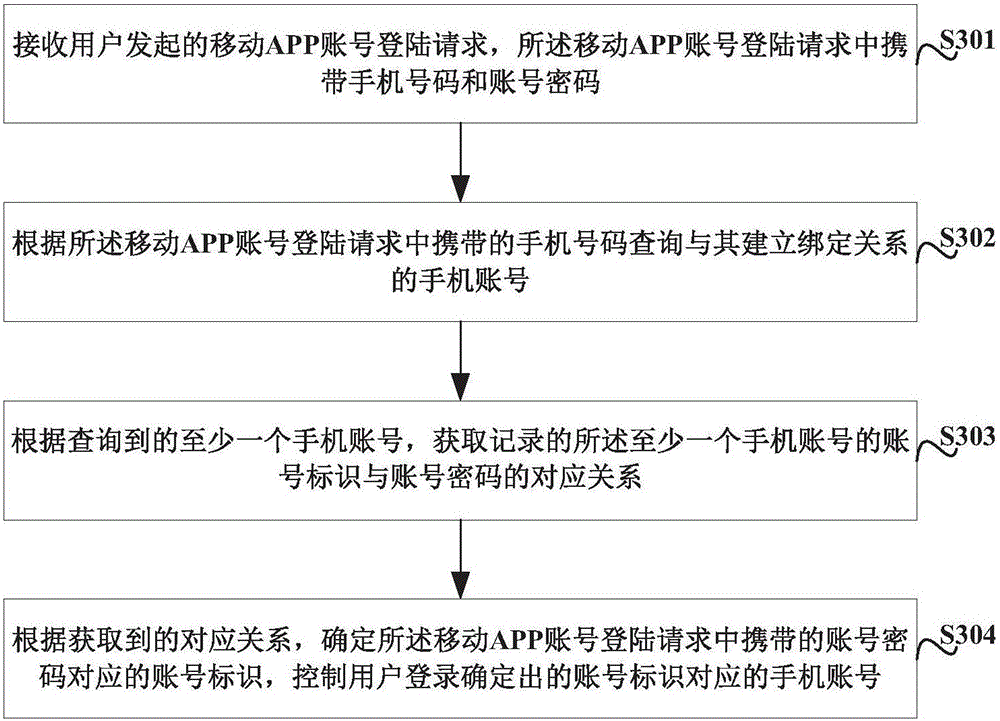
InactiveCN105956435AImprove experienceProtect privacy and securityDigital data authenticationMobile appsMobile Telephone Number
The embodiment of the invention provides a mobile APP registration method and device and a mobile APP registration login method and device, and is used for solving the problem that a mobile phone number repeatedly registers mobile APPs by aiming at a phenomenon that a mobile network operator issues numbers for the second time or multiple times. The mobile APP registration method comprises the following steps: receiving a mobile APP account registration request initiated by a user through a mobile phone number; generating a unique account identifier for the current-time mobile APP account registration of the mobile phone number when a judgment result shows that the mobile phone number does not initiate the mobile APP account registration for the first time; when a confirmation result shows that an account password set through the current-time mobile APP account registration of the mobile phone number is different from the account password previously set each time, causing the account password set by the current-time mobile APP account registration to pass; and establishing a binding relationship for the mobile phone account which succeeds in the current-time mobile APP account registration with the mobile phone number, and recording a corresponding relationship between the account identifier and the account password of the mobile phone account.
Owner:MICRO DREAM TECHTRONIC NETWORK TECH CHINACO
Privacy control method for position service
InactiveCN101026869AProtect privacy and securityRadio/inductive link selection arrangementsLocation information based serviceCommunications systemInternet privacy
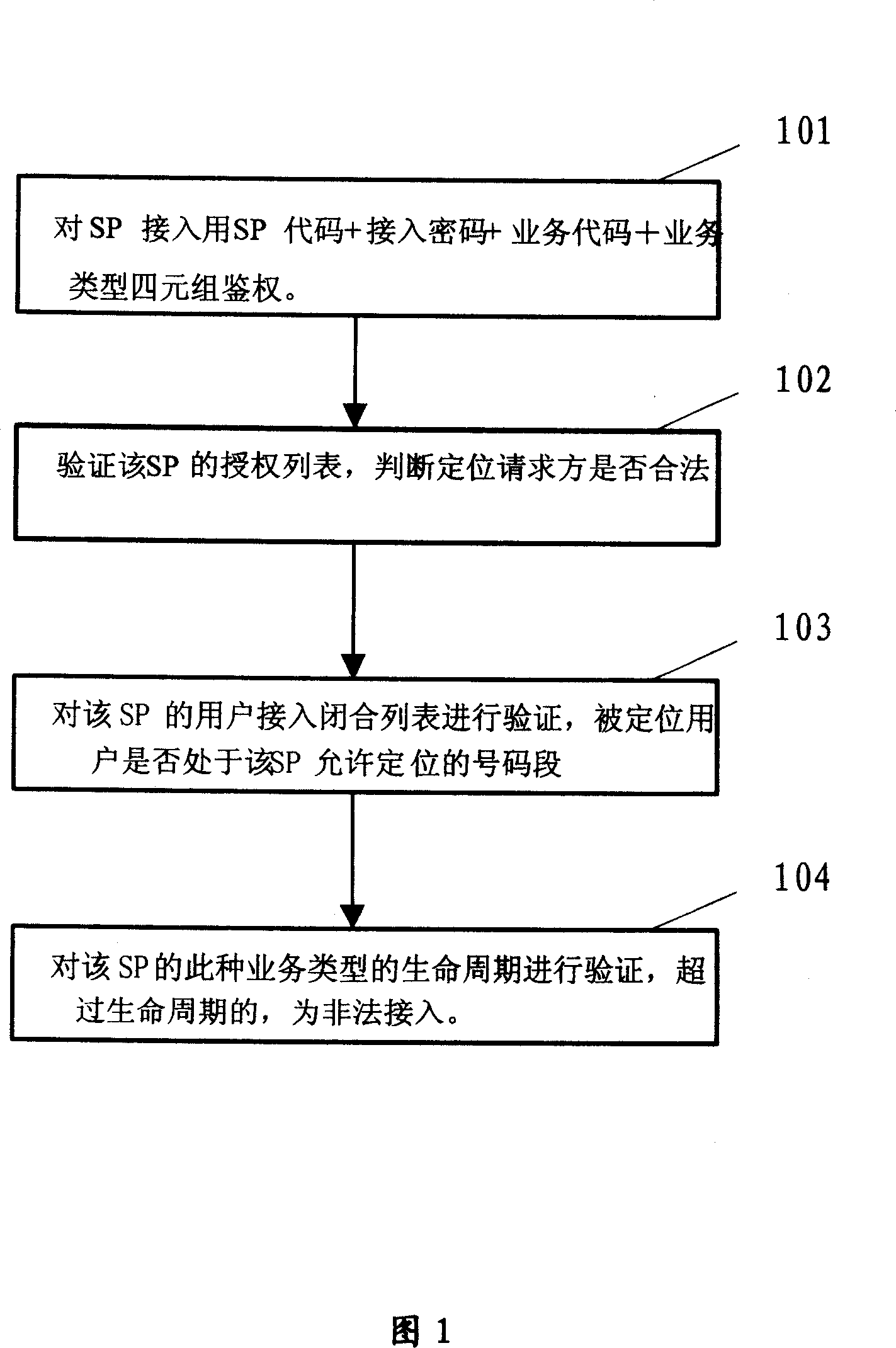
Being in use for position service subsystem (PSS) in radio comm system, the method includes following steps: recording info of authorized list of service provider (ALSP), info of user access close list (UACL), and information of authorized list provided contract signed user in position service sub system; after receiving positioning request, based on info of service provider, and info of positioning request party included in the request, PSS validates ALSP and UACL to determine positioning validation; based on information of the party to be positioned included in the received positioning request, PSS validates the authorized list provided by the party to be positioned, and determines number of the positioning request party in the authorized list; PSS executes positioning request, and returns positioning result back to positioning request party. The method implements protection for right of privacy of user position.
Owner:ZTE CORP
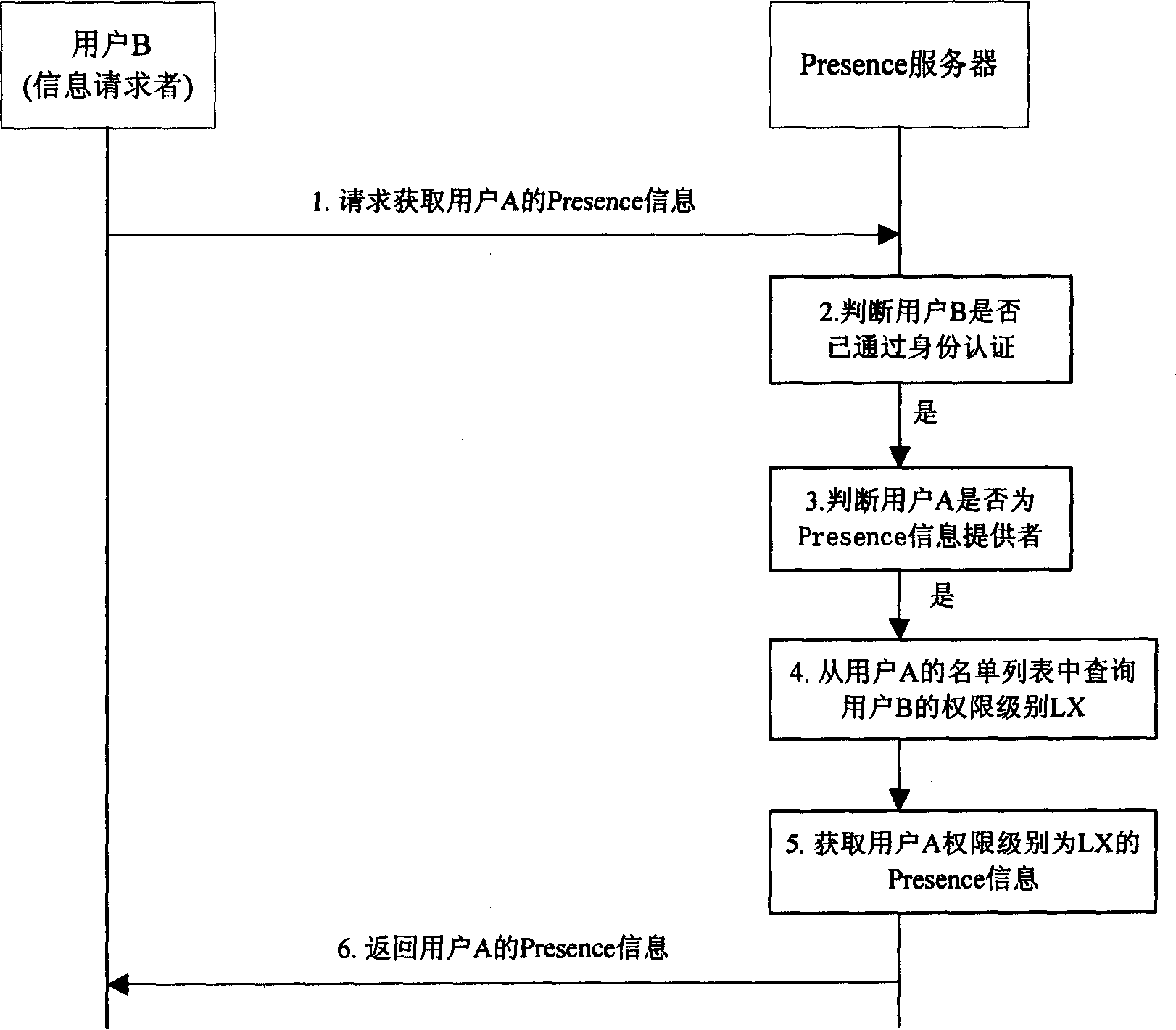
Method for realizing information grading authorized access in presenting service system
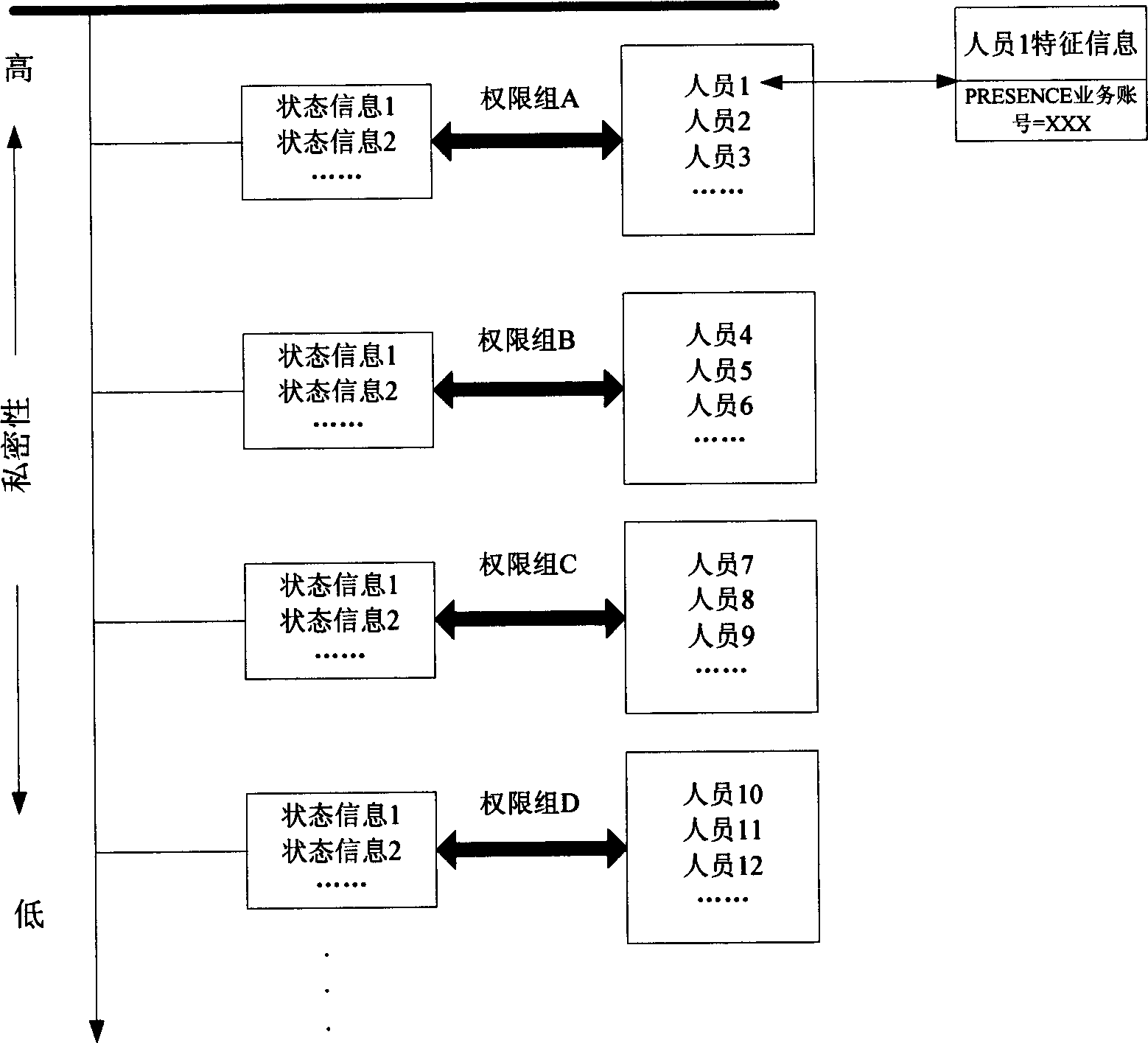
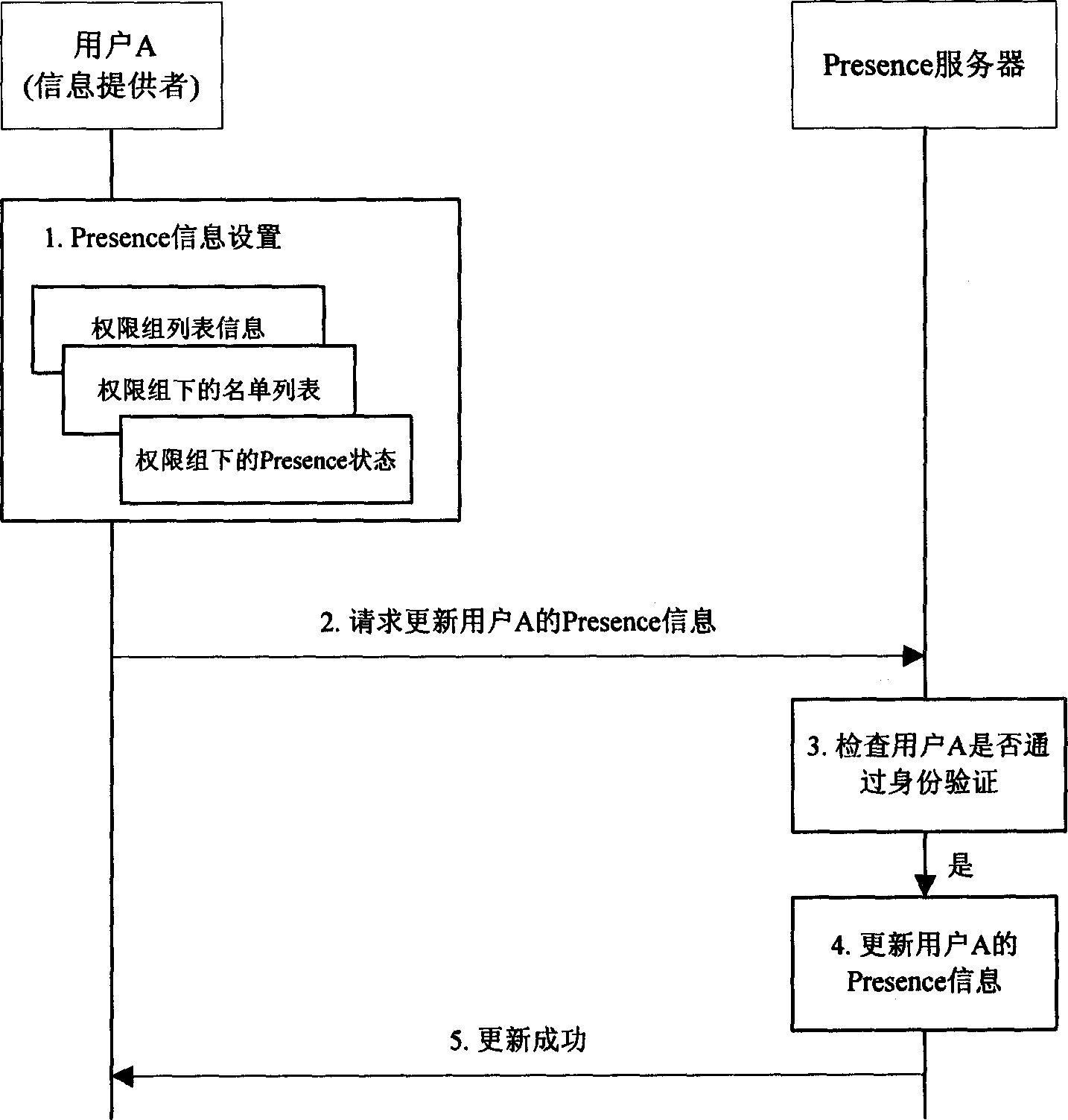
InactiveCN1787528AGuarantee normal implementationProtect privacy and securityData switching networksService systemAuthorization
This invention discloses a method for realizing information hierarchical authorization access in a presence service system including two steps: a user refreshes its own presence service information hierarchical access strategy to a presence service server, which sends information to the user requiring for obtaining the information based on the strategy set by the user, which can realize the complete Presence information hierarchical authorization access system.
Owner:ZTE CORP
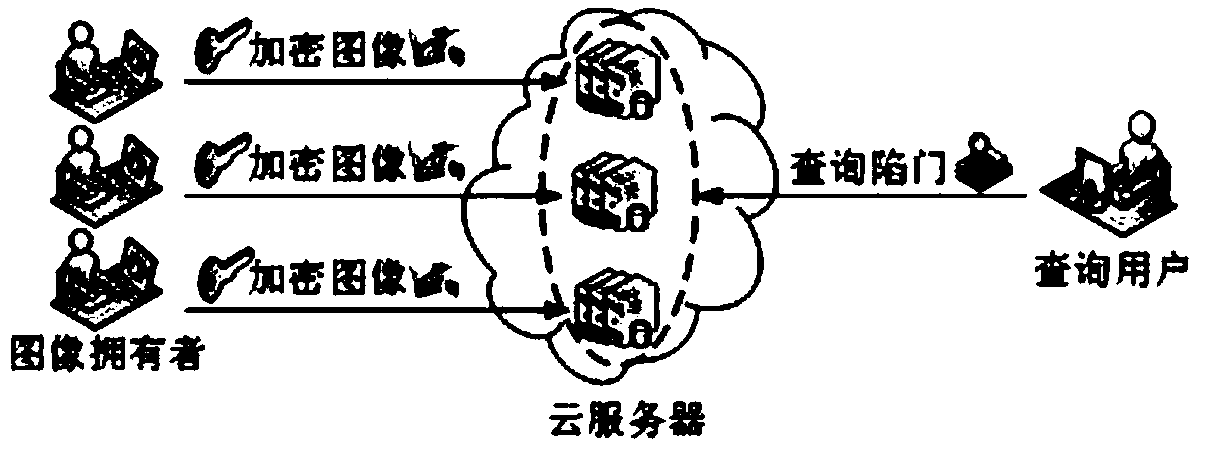
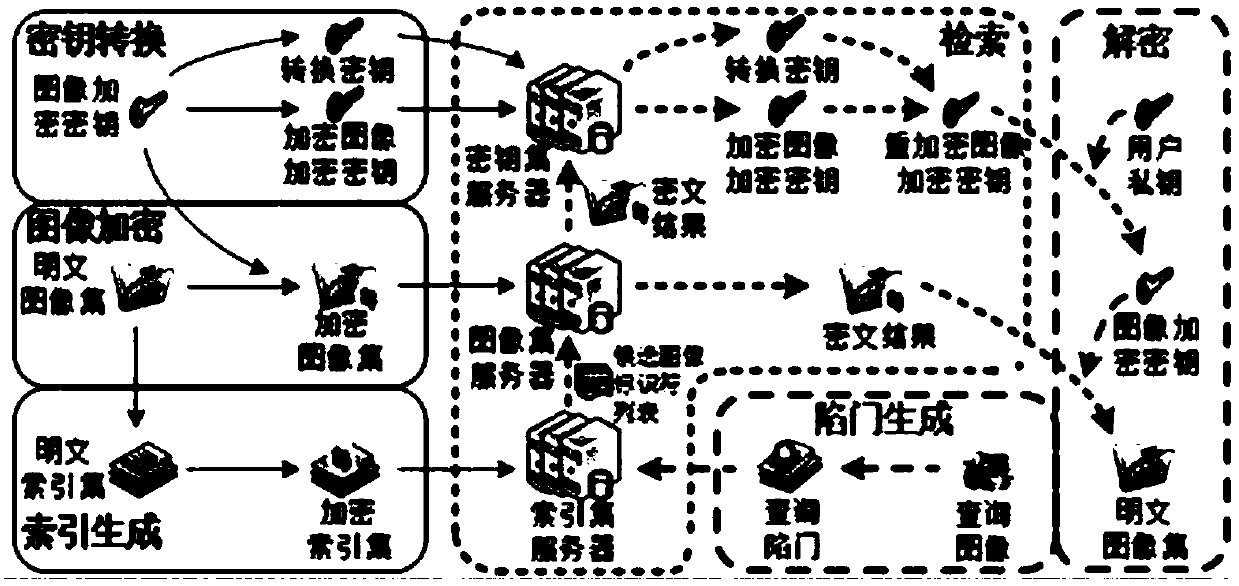
An encrypted image retrieval method supporting multiple keys
ActiveCN109543061AProtect privacy and securityImprove retrieval speedKey distribution for secure communicationMetadata still image retrievalFeature vectorPlaintext
The invention discloses an encrypted image retrieval method supporting multiple keys. The invention utilizes proxy re-encryption technology to convert different image encryption keys into the form that the inquiry user can decrypt with his private key, applies local sensitive hash algorithm to pre-classify the image set, improves the retrieval speed, and then encrypts the image feature vector withthe safe nearest neighbor algorithm to improve the retrieval precision. The invention supports a query user to query image sets from different encryption keys by using a query trap under a multi-keyscenario, and the user can only decrypt the query result by using a legal private key. The invention can protect data privacy and safety, and the cloud server cannot obtain any plaintext information from the ciphertext set, the index set and the ciphertext key set, nor can it obtain any plaintext information from the query trap. The invention is efficient and feasible in practical application.
Owner:XIDIAN UNIV
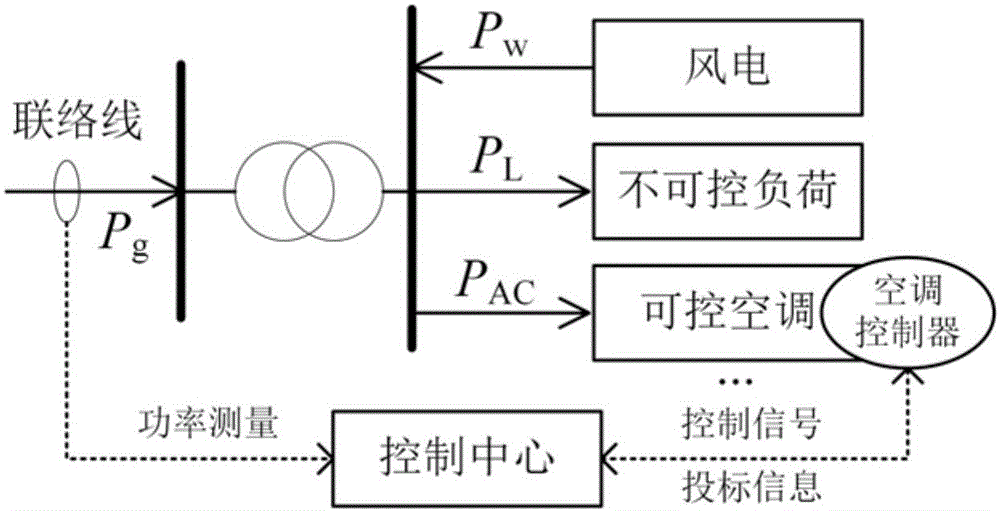
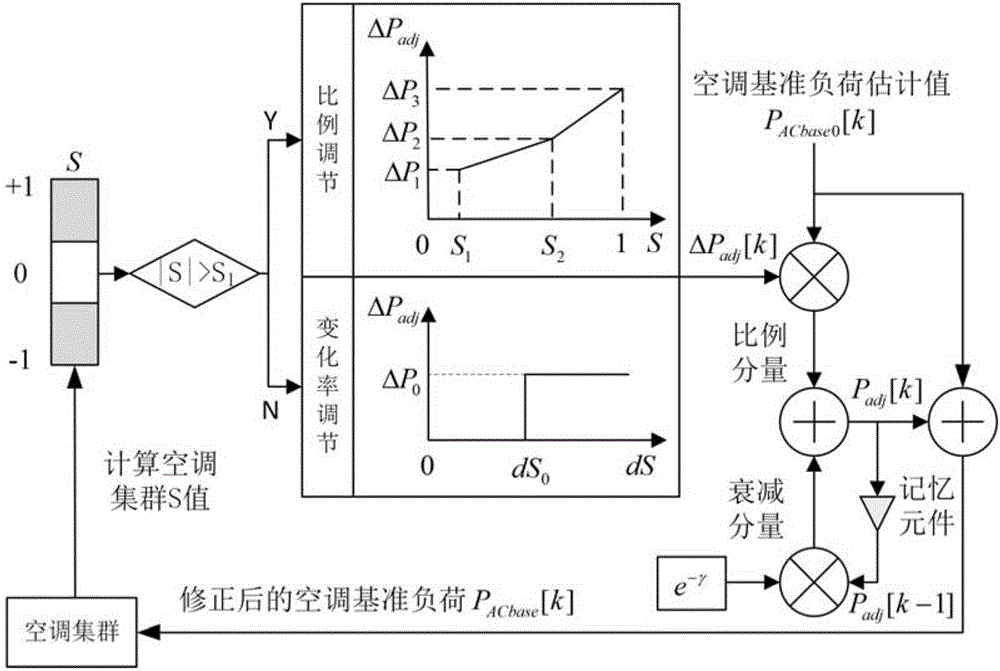
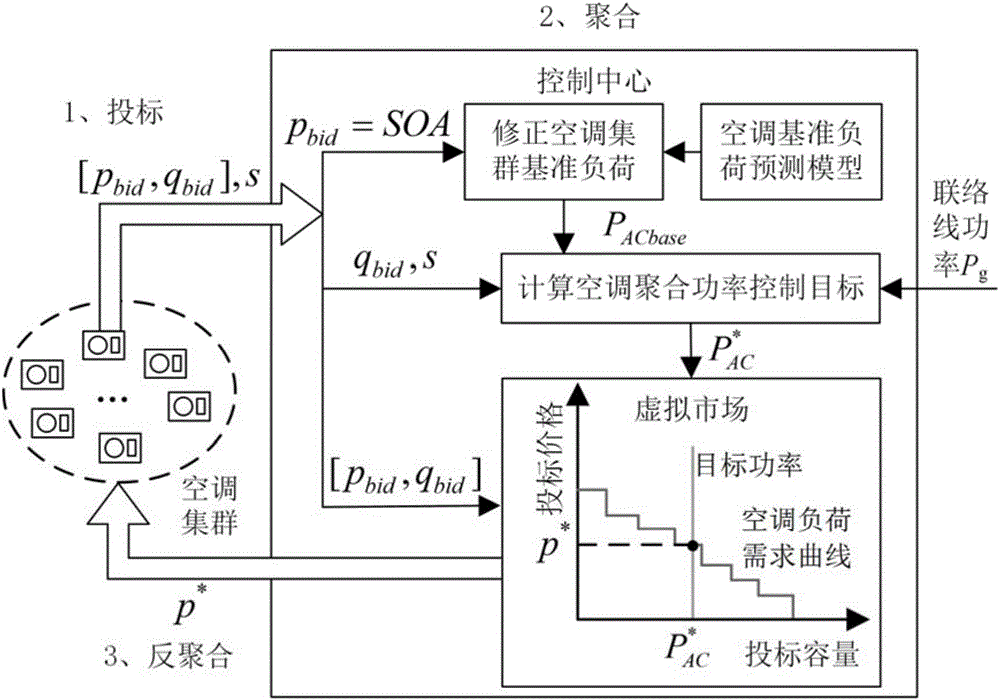
Air conditioning load coordination control method of stabilizing power fluctuation of micro-grid linking-up road
ActiveCN106655221AMeet differentiated comfort requirementsProtect privacy and securityLoad forecast in ac networkPower oscillations reduction/preventionUser privacyPower control
The invention relates to an air conditioning load coordination control method of stabilizing power fluctuations of a micro-grid linking-up road. The method includes the following steps: 1) calculating an air conditioning an aggregation power control target for air conditioning clusters on the basis of low pass filter principles; and 2) for an air-conditioning individual, coordinately distributing the air conditioning an aggregation power control target to all air conditioning loads on the basis of market control. Compared with the prior art, the method has the advantages that different comfort requirements of users can be met, user privacy and power utilization safety can be fully protected, and thus the user experience of implementation of the method can be improved. The method greatly simplifies downlink control for a control center, only needs to measure power of a linking-up road, and effectively reduces the implementing cost.
Owner:SHANGHAI JIAO TONG UNIV
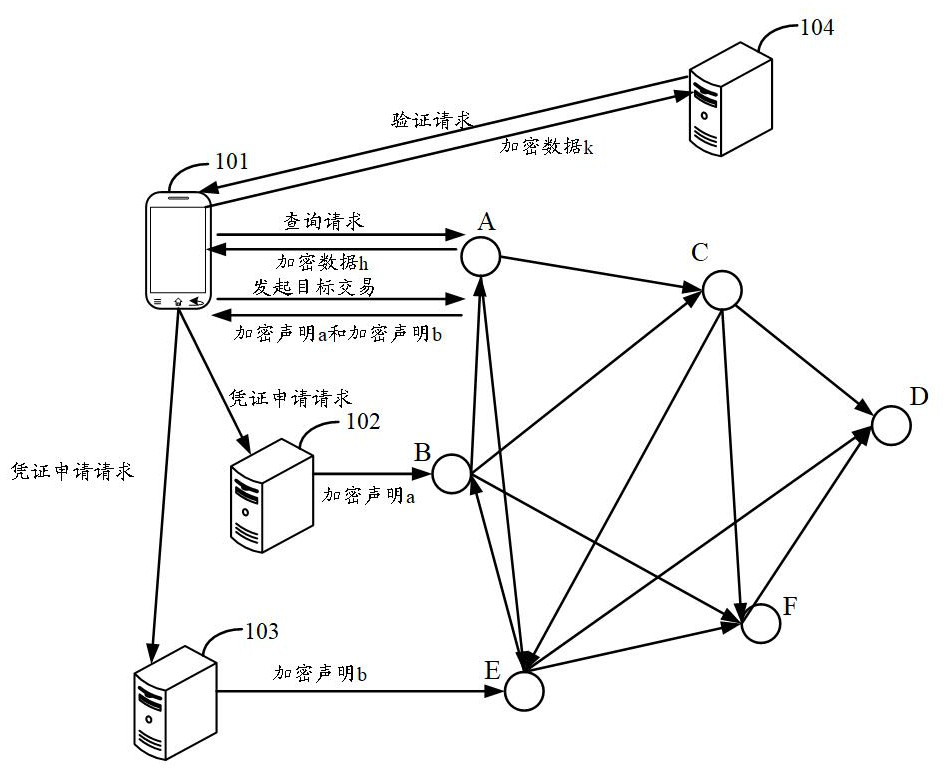
Privacy protection method and device based on block chain and electronic equipment
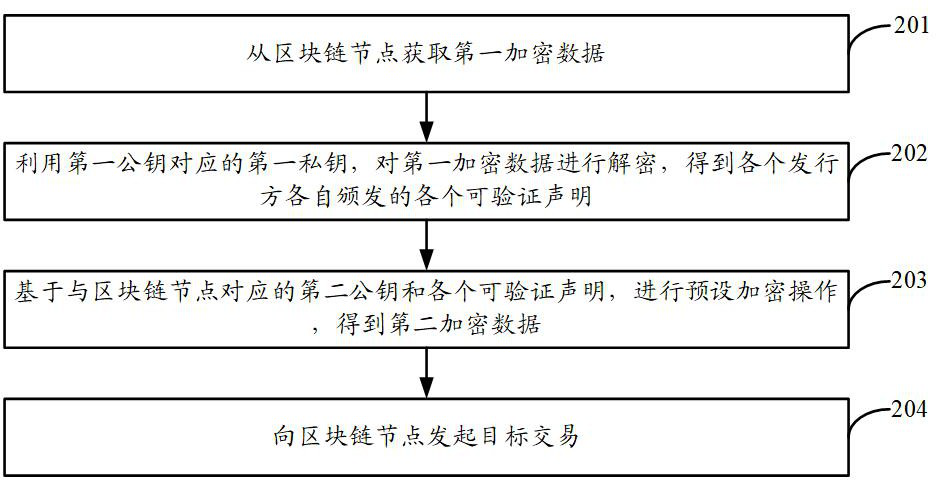
ActiveCN112199714AProtect privacy and securityCo-operative working arrangementsDigital data protectionDigital identityPrivacy protection
The embodiment of the invention provides a privacy protection method and device based on a block chain and electronic equipment. The method is applied to a distributed digital identity system client,a target account is logged in the client, and the method comprises the steps of acquiring first encrypted data from a block chain node; decrypting the first encrypted data by using a first private keycorresponding to the first public key to obtain each verifiable declaration issued by each issuer; performing a preset encryption operation based on a second public key corresponding to the block chain node and each verifiable declaration to obtain second encrypted data; and sending the second encrypted data to the block chain node, and initiating a target transaction to the block chain node, sothat the block chain node performs a preset decryption operation on the second encrypted data and then performs joint calculation to obtain a target identity certificate of the target user. Therefore,when joint calculation is carried out on the verifiable declarations issued by multiple issuers, the privacy of the user is not leaked, and the privacy security of the user is protected.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
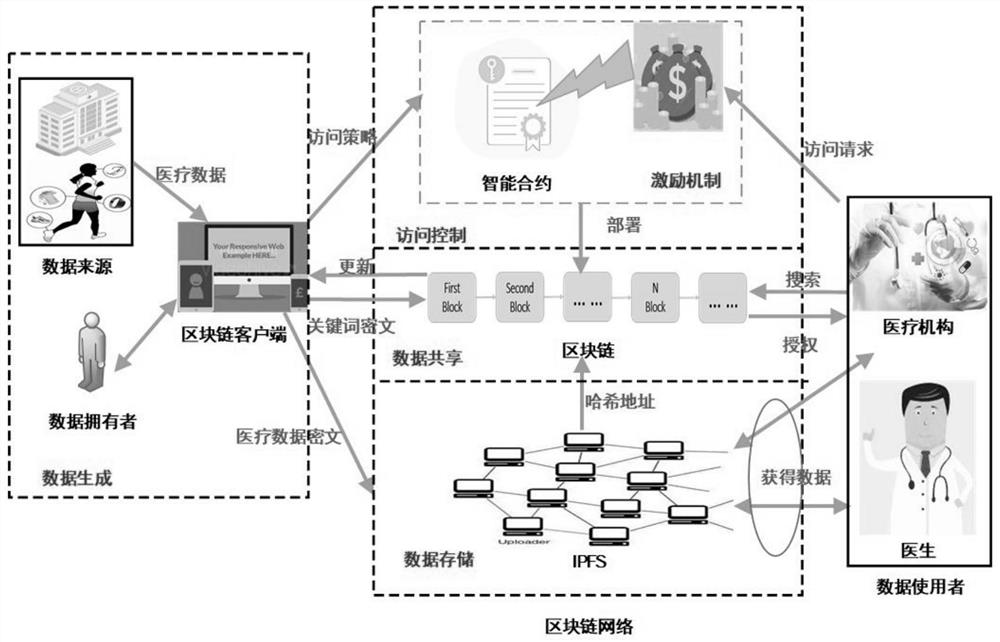
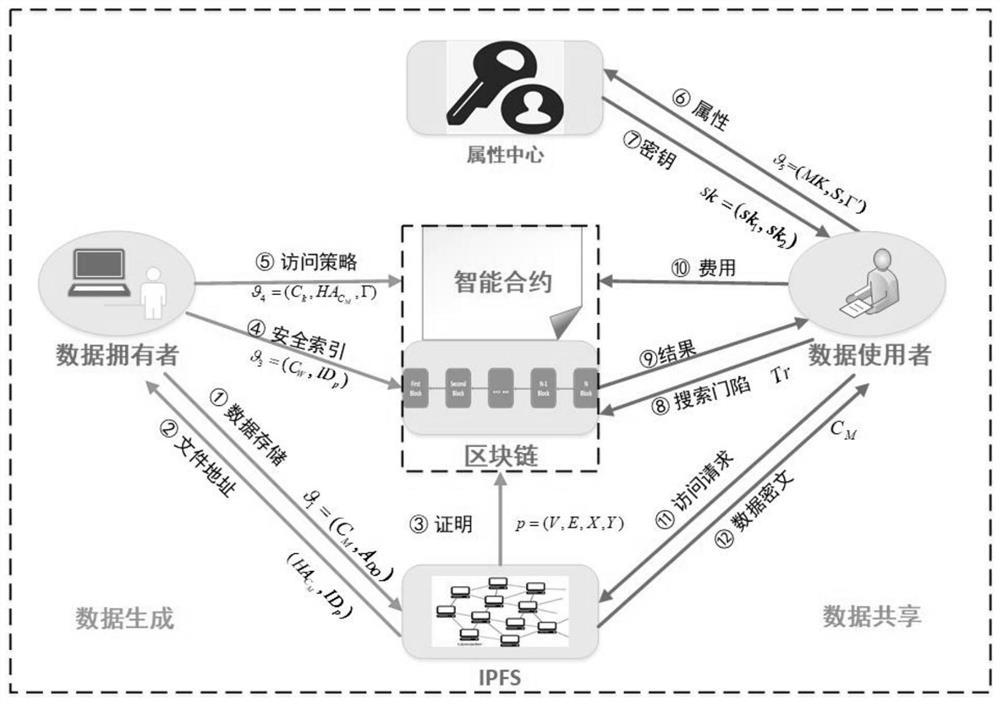
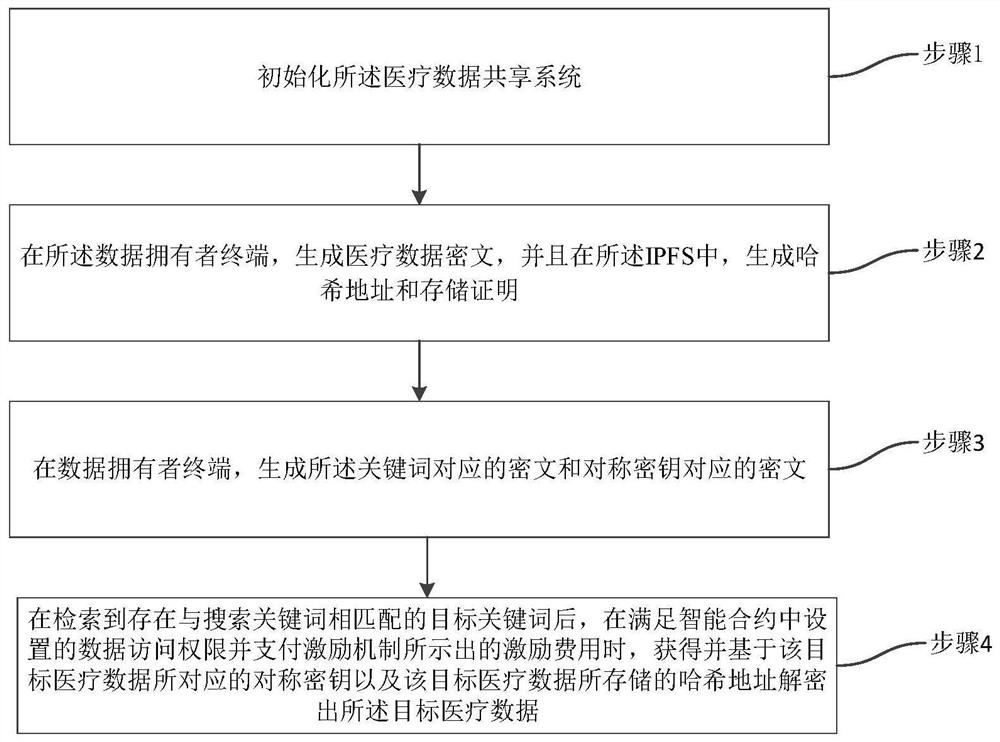
Medical data security sharing system and method based on IPFS and alliance chain
PendingCN111916173AEnable secure storageImplement fine-grained access controlDigital data protectionFile metadata searchingSafe storageData security
Owner:ANHUI NORMAL UNIV
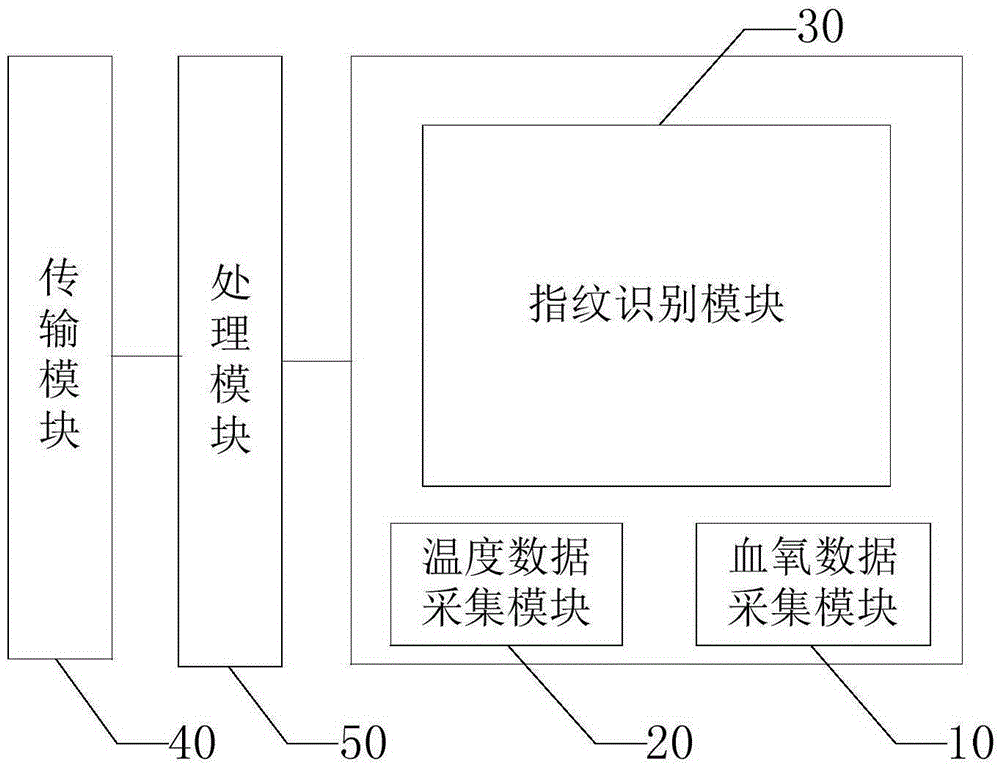
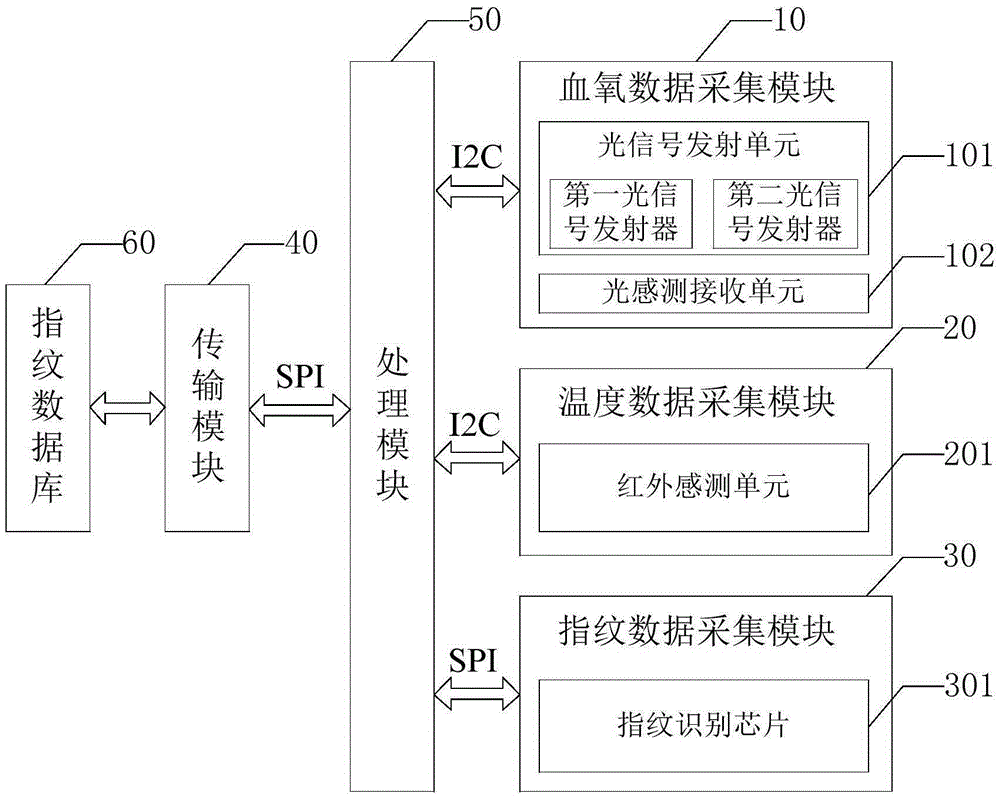
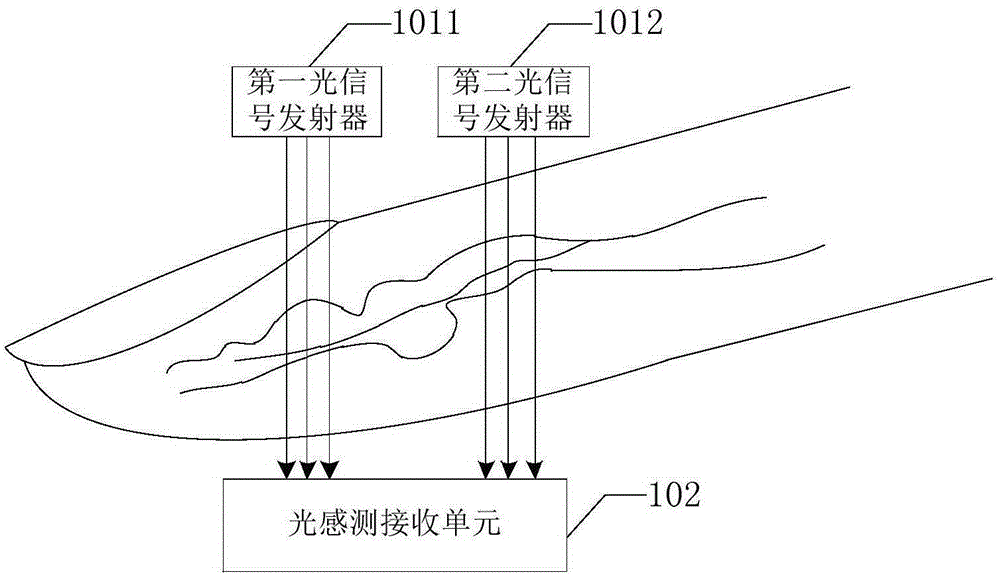
Fingerprint identification device, fingerprint identification method and terminal device
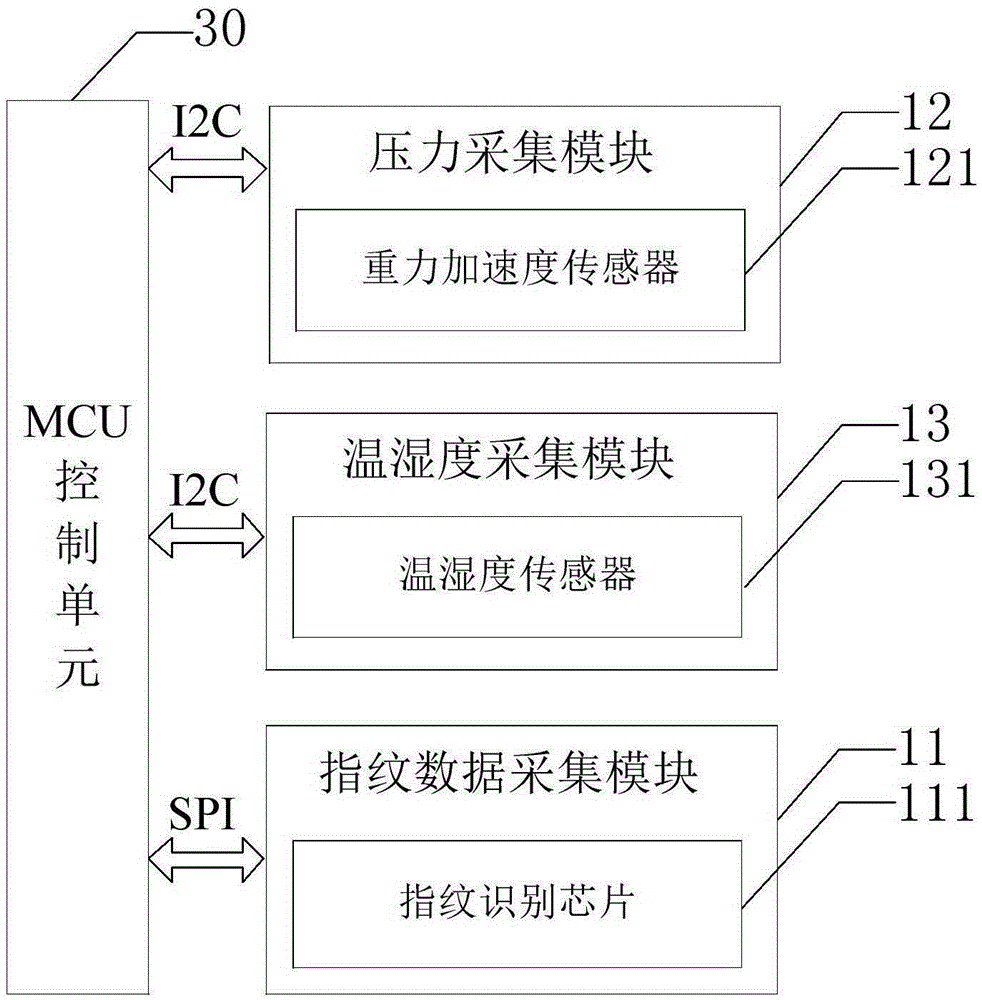
InactiveCN105279504AHigh precisionProtect privacy and securityMatching and classificationDetecting live finger characterData acquisitionTerminal equipment
The invention provides a fingerprint identification device, a fingerprint identification method and a terminal device. The fingerprint identification device comprises: an oxyhemoglobin data acquisition module, for acquiring oxyhemoglobin saturation data of detected tissues; a temperature data acquisition module, for acquiring temperature data of the detected tissues; a fingerprint identification module, for acquiring fingerprint data of the detected tissues; a transmission module, which is coupled with the fingerprint identification module; and a processing module, which is coupled with the oxyhemoglobin data acquisition module, the temperature data acquisition module and the transmission module and is used to analyze the oxyhemoglobin saturation data and the temperature data, judge whether the oxyhemoglobin saturation data and the temperature data are within the preset range, and control the transmission module to transmit the fingerprint data of the detected tissues to a fingerprint database for fingerprint identification when both the oxyhemoglobin saturation data and the temperature data are within the preset range. The invention can prevent the potential safety hazards of the prior art of identify recognition with a fake body.
Owner:NANCHANG OUFEI BIOLOGICAL IDENTIFICATION TECH
Interface sharing method and electronic equipment
ActiveCN111107222AProtect privacy and securityAccurate and convenient interactionSubstation equipmentExecution for user interfacesOperating systemElectronic equipment
The invention discloses an interface sharing method and electronic equipment. The method comprises the steps that under the condition that a first interface is displayed, first input is received; in response to the first input, interface sharing information is sent to second electronic equipment, so that the second electronic equipment displays a second interface; wherein the display content of the second interface corresponds to the authority of the first interface and the authority of the second electronic equipment. Embodiments of the present invention, a user can set the sharing permissionof the display content on the first electronic equipment on the second electronic equipment according to the privacy requirement. Therefore, when the first electronic equipment shares the shared first interface to the second electronic equipment, the second electronic equipment can determine the display content of the second interface according to the sharing permission of the first interface andthe second electronic equipment, so that the privacy safety of a user is effectively protected, and the information interaction is more accurate and convenient.
Owner:VIVO MOBILE COMM CO LTD
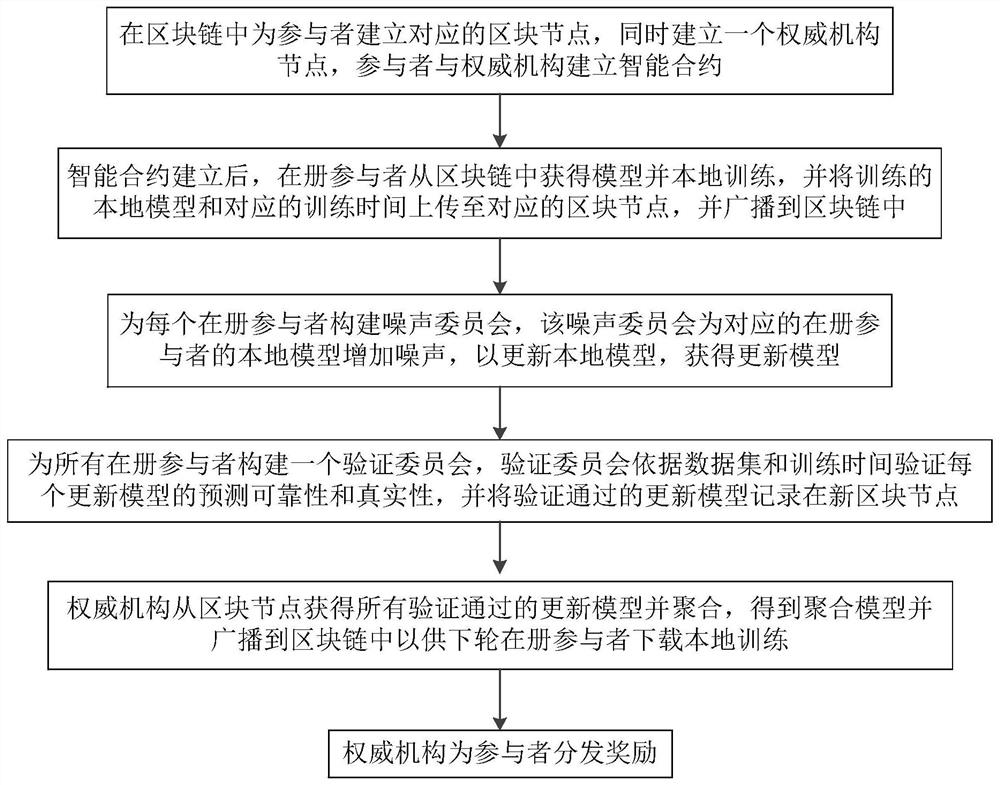
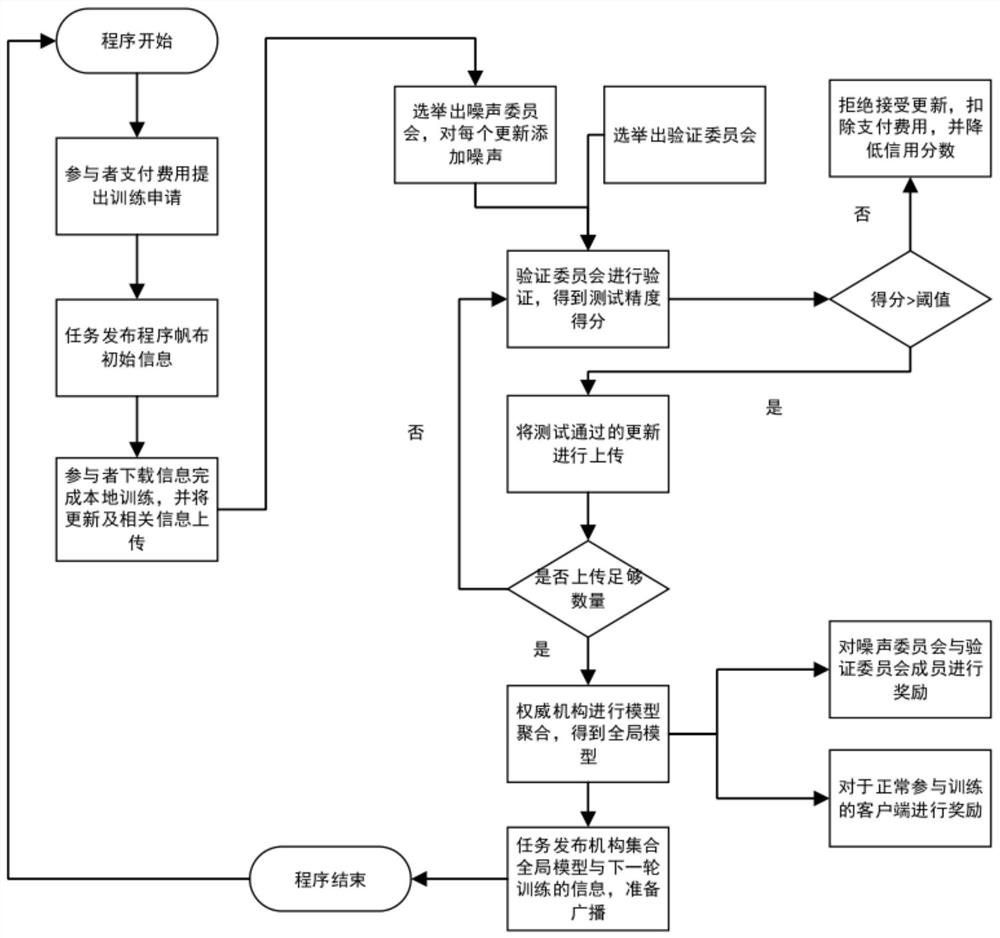
Federated learning defense method based on block chain
PendingCN112434280AProtect privacy and securityAchieve defenseFinanceDigital data protectionData setEngineering
The invention discloses a federated learning defense method based on a block chain. The method comprises the following steps: a participant establishing an intelligent contract with an authority; obtaining the model from the block chain by the participant in the book, carrying out local training, uploading the trained local model and the corresponding training time to the corresponding block node,and broadcasting the local model and the corresponding training time to the block chain; constructing a noise committee of a noise committee for each on-book participant, and adding noise to the local model of the corresponding on-book participant by using the noise committee to update the local model to obtain an updated model; constructing a verification committee for all in-book participants,verifying the prediction reliability and authenticity of each update model by using the verification committee according to the data set and the training time, and recording the update model passing the verification in a new block node; and the authority obtaining all the updated models passing the verification from the block nodes and aggregating the updated models to obtain an aggregated model,and broadcasting the aggregated model to the block chain for the next round of in-book participants to download local training.
Owner:ZHEJIANG UNIV OF TECH
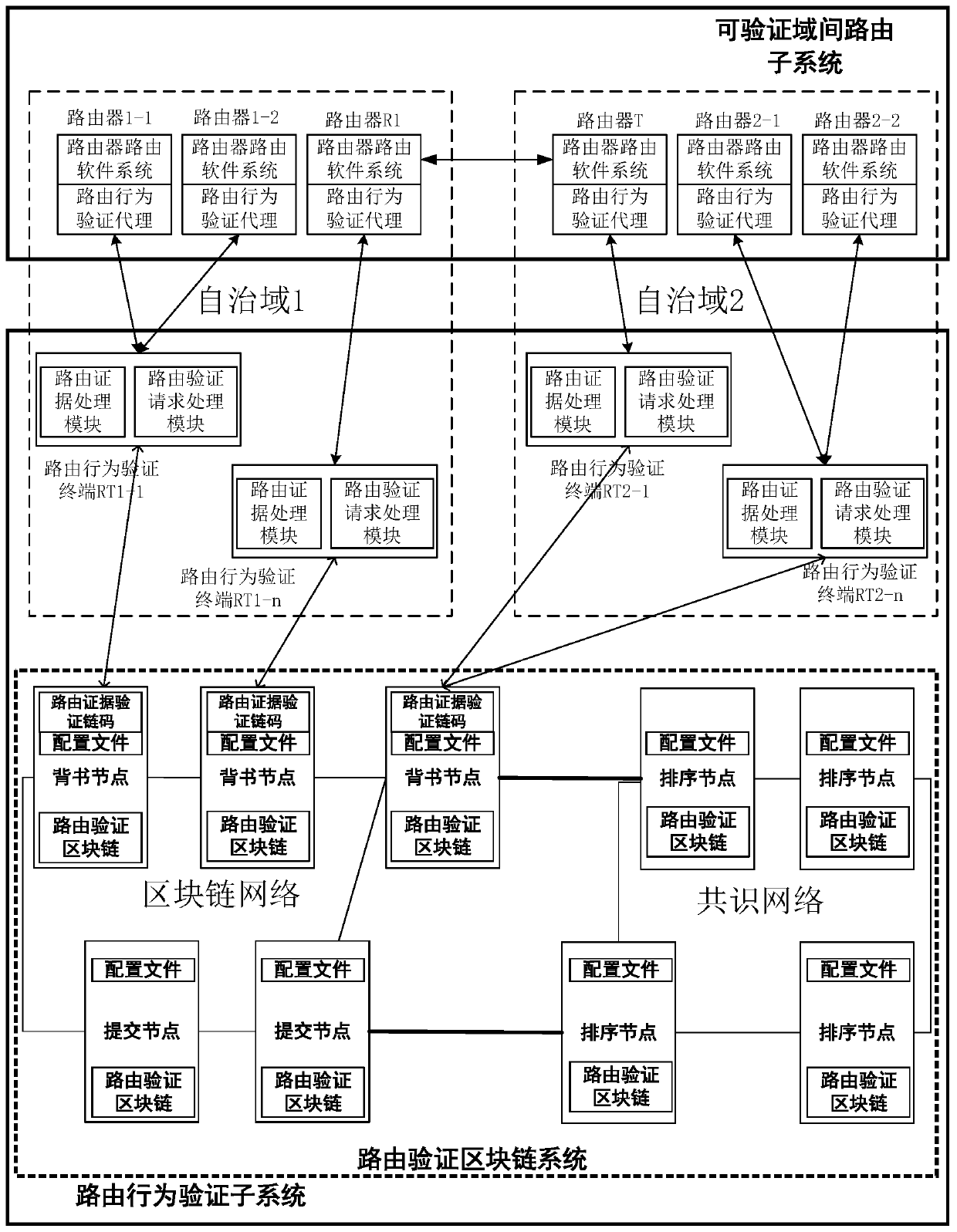
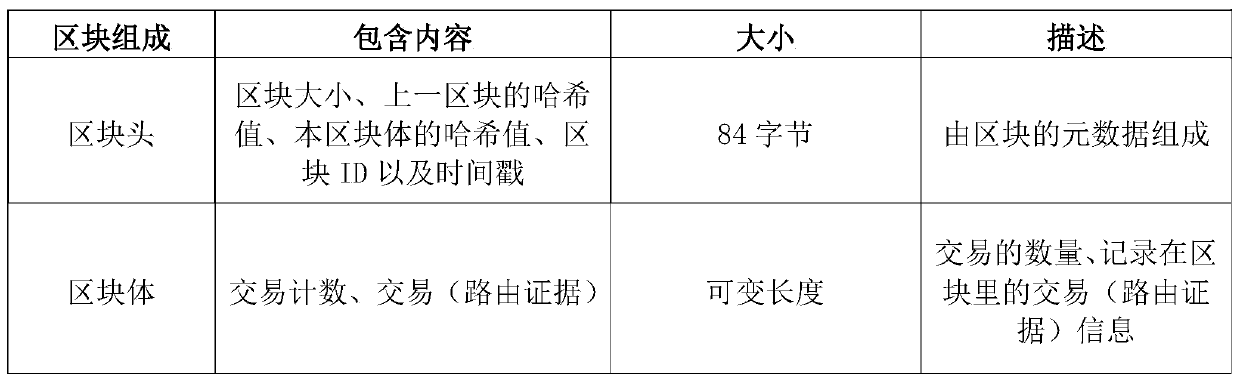
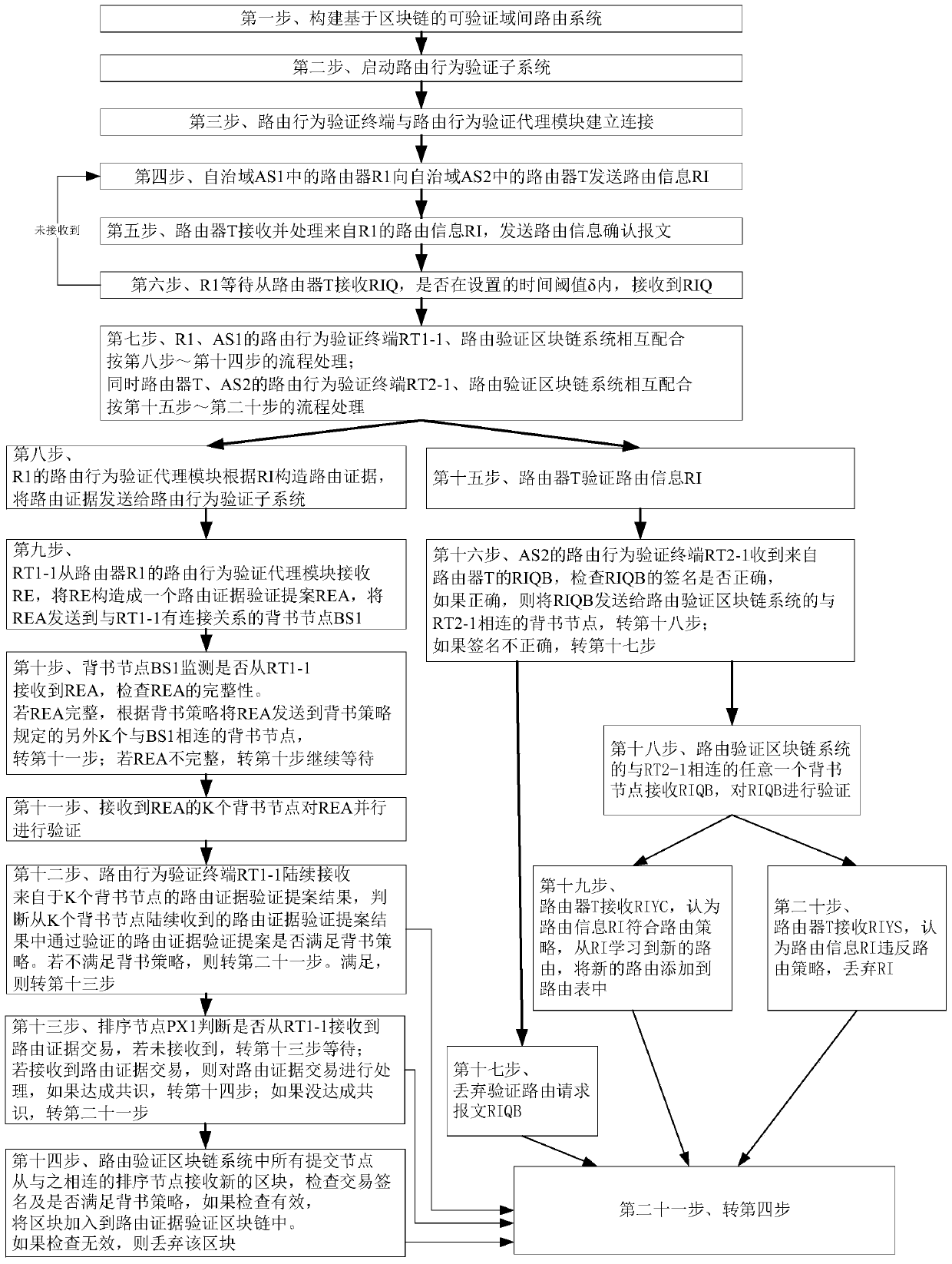
Verifiable inter-domain routing verification method based on block chain
ActiveCN110855565AProtect privacy and securityIncrease the difficultyUser identity/authority verificationPublic key infrastructure trust modelsEngineeringFinancial transaction
The invention discloses a verifiable inter-domain routing verification method based on a block chain. According to the technical scheme, the method comprises the following steps: constructing a verifiable inter-domain routing system based on a block chain, wherein the verifiable inter-domain routing system is composed of verifiable inter-domain routing and a routing behavior verification subsystem; the routing behavior verification subsystem is composed of a routing behavior verification terminal and a routing verification block chain system. A sender router R1, a routing behavior verificationterminal of an autonomous domain to which the R1 belongs and a routing verification block chain system construct routing evidences, verify proposal of the routing evidences, verify and endorse the proposal, judge whether an endorsement strategy is met or not, generate routing evidence transactions, perform consensus sorting on the transactions and update a routing verification block chain; and the receiver router T, the routing behavior verification terminal of the autonomous domain to which the router T belongs and the routing verification blockchain system construct a verification routing request message, and retrieve whether routing evidence corresponding to the routing request exists or not. According to the method, the problem that routing strategies are violated due to routing single-point attacks and routing multi-point collusion attacks can be verified.
Owner:GUANGZHOU UNIVERSITY
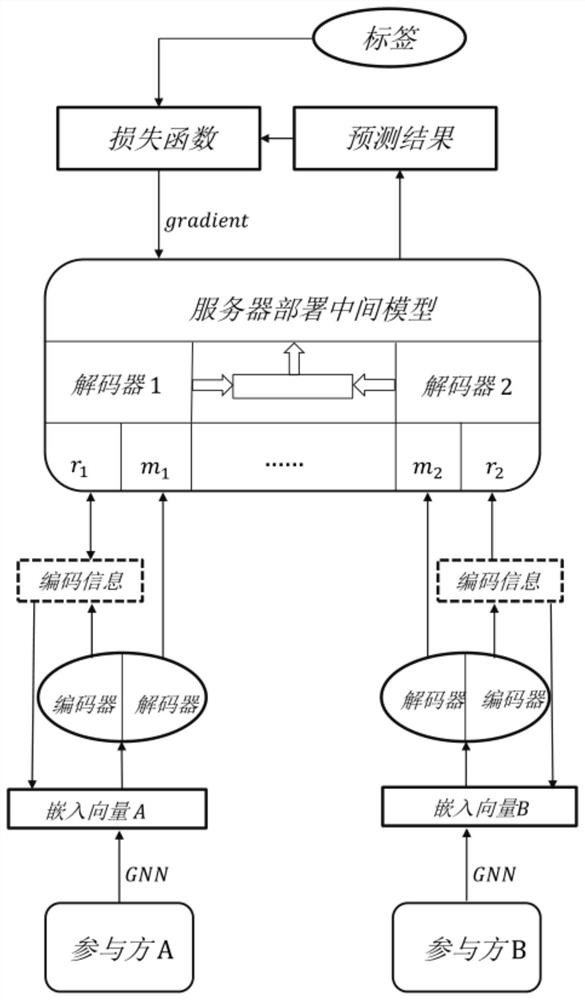
Vertical federated learning defense method based on auto-encoder
PendingCN112464290AProtect private informationProtect privacy and securityImage codingDigital data protectionAlgorithmEdge model
The invention discloses a vertical federated learning defense method based on an auto-encoder. The method comprises the steps that (1) a terminal trains an edge model through local data, and aggregates the embedding features of adjacent nodes of each layer in the edge model in a training process; (2) the terminal constructs and trains an auto-encoder comprising an encoder and a decoder to obtain encoder parameters and decoder parameters, and encodes the embedded features by using the encoder to obtain encoding information; (3) the terminal uploads the decoder parameters to the server, and after the server constructs a decoding model according to the decoder parameters and carries out message verification with the terminal, the terminal uploads coded information to the server; and (4) the server decodes the received coded information by using the decoding model to obtain decoded information, aggregates all decoded information to obtain embedded information, trains the global model by using the embedded information, and feeds back gradient information to each terminal after training. The malicious participant can be effectively prevented from stealing the private data.
Owner:ZHEJIANG UNIV OF TECH
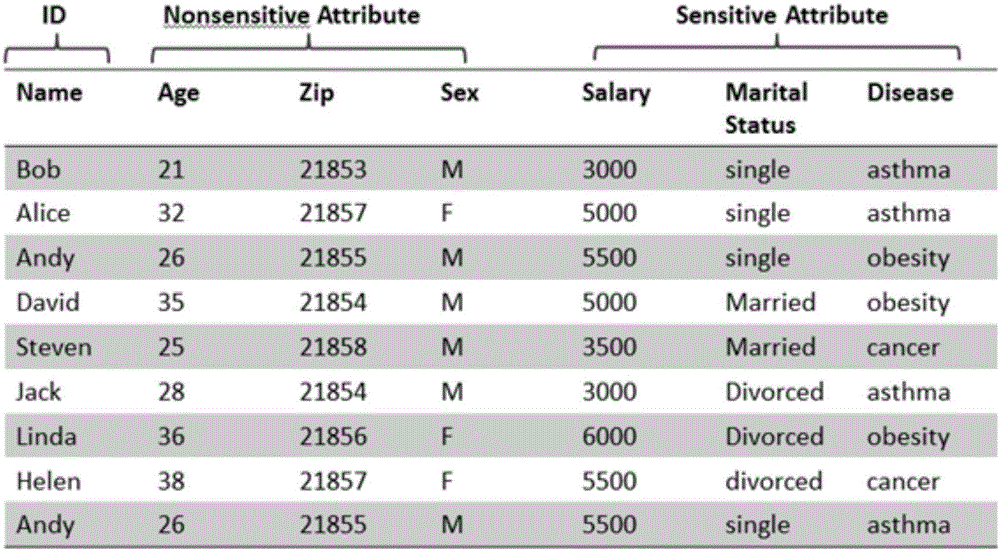
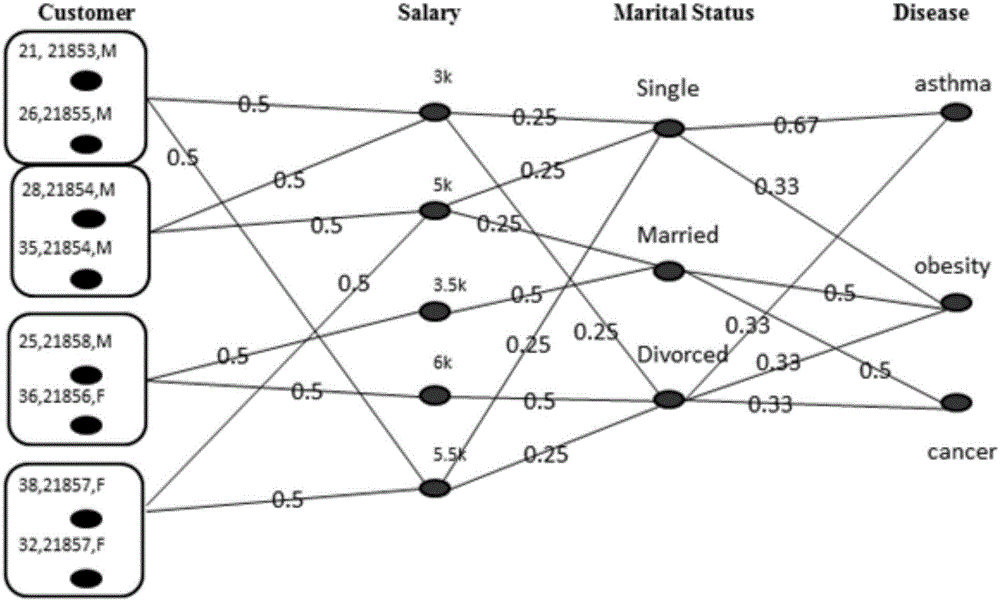
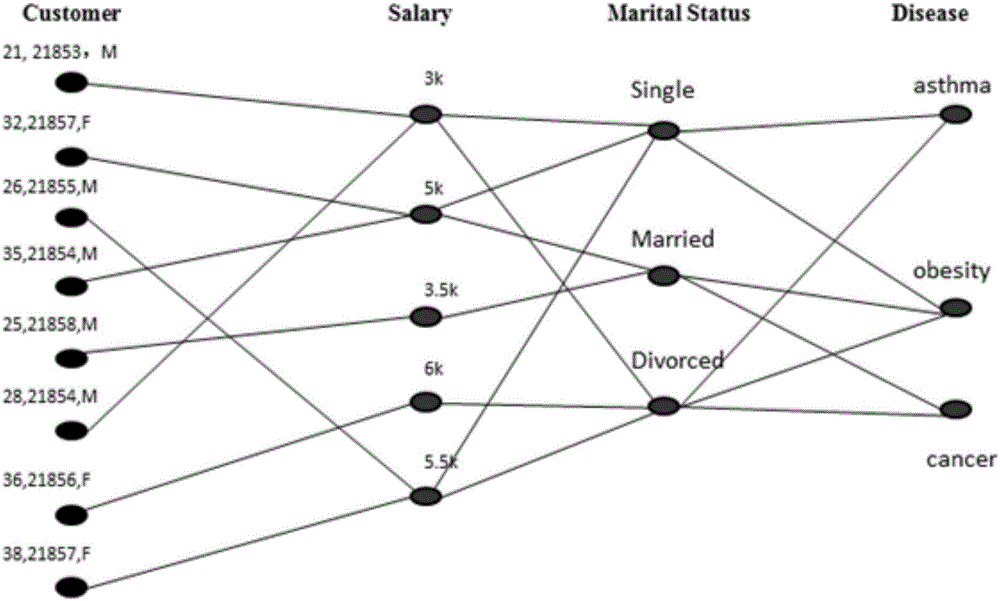
Multi-partite graph privacy protection method published based on multi-dimension sensitive data
ActiveCN106650487AProtect multiple sensitive attributesProtect privacy and securityDigital data protectionPrivacy protectionMultiple dimension
The invention discloses a multi-partite graph privacy protection method published based on multi-dimension sensitive data. The multi-partite graph privacy protection method mainly comprises the steps of constructing original table data into two large parts of a multi-partite graph form and a privacy protection strategy based on the multi-partite graph. An ID is adopted as one type of nodes, a quasi-identity sign corresponding to the ID is expressed through a form of label, each sensitive property is shown through the adoption of one type of the nodes, and if one user has a certain sensitive property, one side must exit between two nodes so as to show the relevance. A clustering method is adopted to conduct grouping, users in the same group are regarded as one super node, the relevance degree between the sensitive properties and the users is shown through a side with weight, the weight of the side is the probability that the group of the users have the sensitive properties, the relevance degree among the properties is also shown through the side with weight, so that the purposes that the relevance among the properties is preserved, and multiple sensitive properties and correlated privacy security thereof are effectively protected are achieved.
Owner:GUANGXI NORMAL UNIV
Storage card locking method and system
InactiveCN102646075AFreedom of operationEasy to operateUnauthorized memory use protectionComputer hardwareOperational system
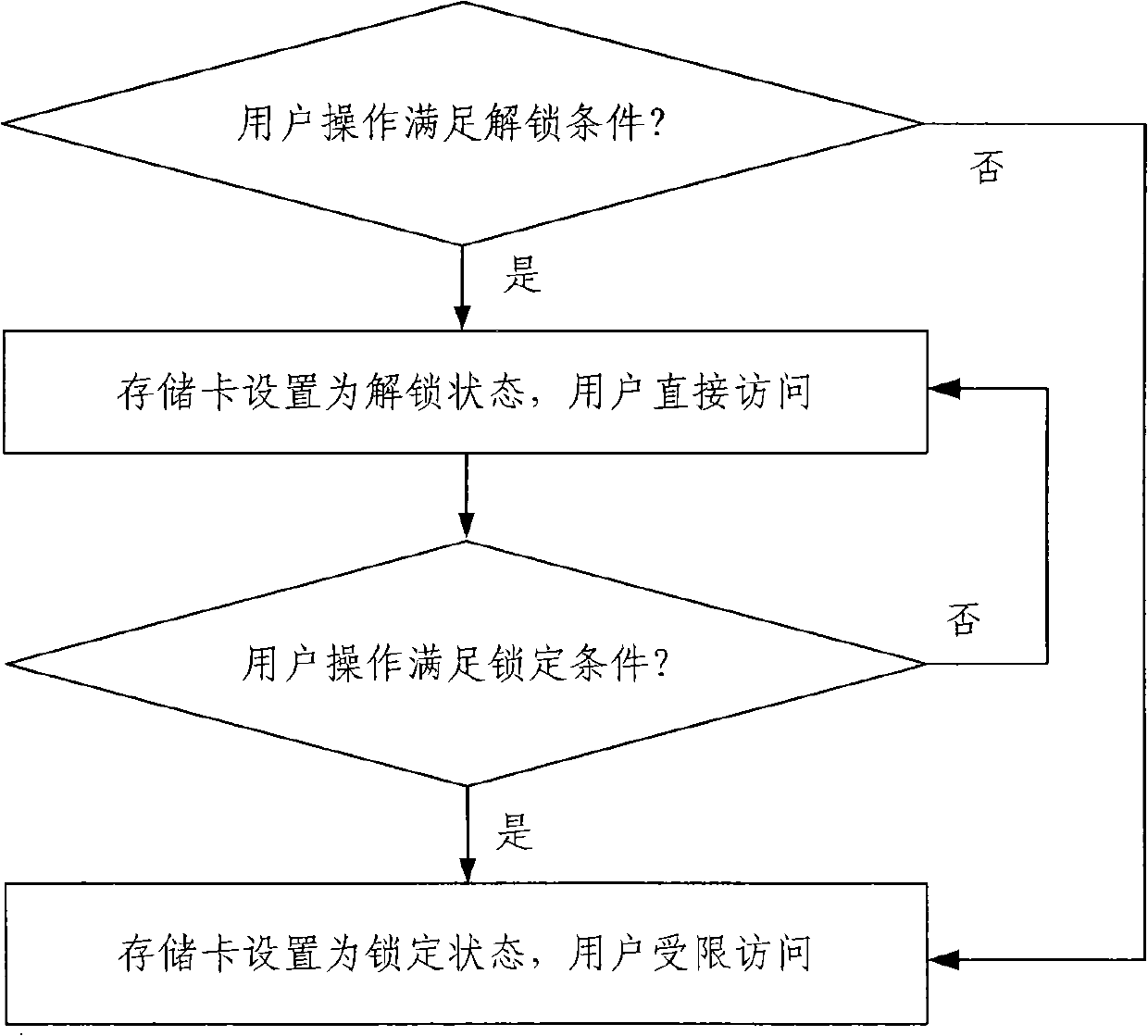
The invention relates to the technical field of content protection of storage cards and discloses a storage card locking method and system. The method comprises the following steps: S1, a user accesses data on a storage card, an operating system uses a universal command to perform operation, a storage card controller intercepts the operation and performs verification, if unlocking conditions are met, the step S2 is implemented, otherwise, the state of the storage card is kept in a locking state; S2, the storage card controller is used for converting the state of the storage card to an unlocking state; S3, the storage card controller is used for judging whether the logic of the operating system against the current operation of the storage card meets the locking conditions, if so, the step S4 is implemented, otherwise, the state of the storage card is kept in the unlocking state; and S4, the storage card controller is used for setting the storage card in the locking state. According to the method disclosed by the invention, the leakage of important data of the storage card can be prevented, the safety is enhanced, and the privacy of the user is protected; and in addition, the universal command is used for verification, thus the operation of the system is facilitated and the compatibility is ensured.
Owner:兰宦泽 +2
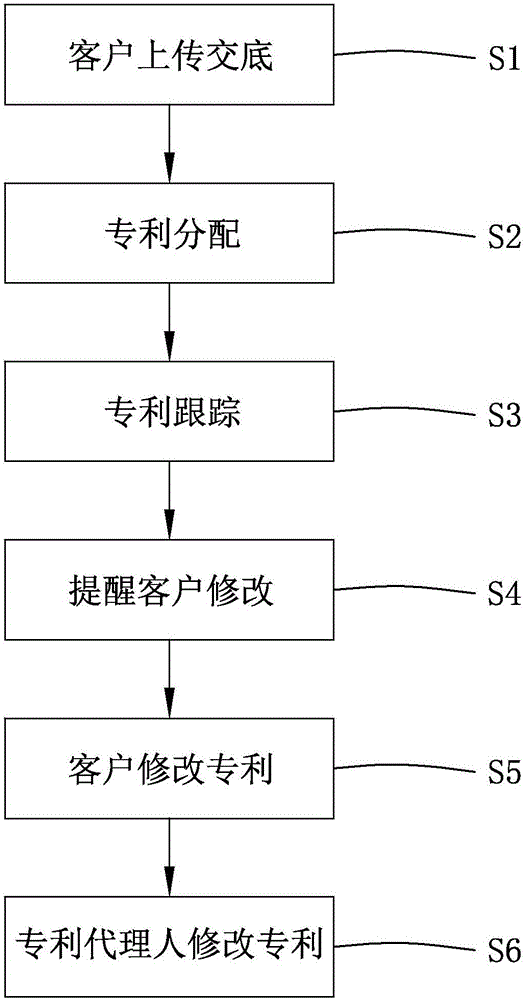
Case tracking interaction system and method
InactiveCN105956955ARealize real-time trackingProtect privacy and securityData processing applicationsSpecial data processing applicationsInteraction systemsLibrary science
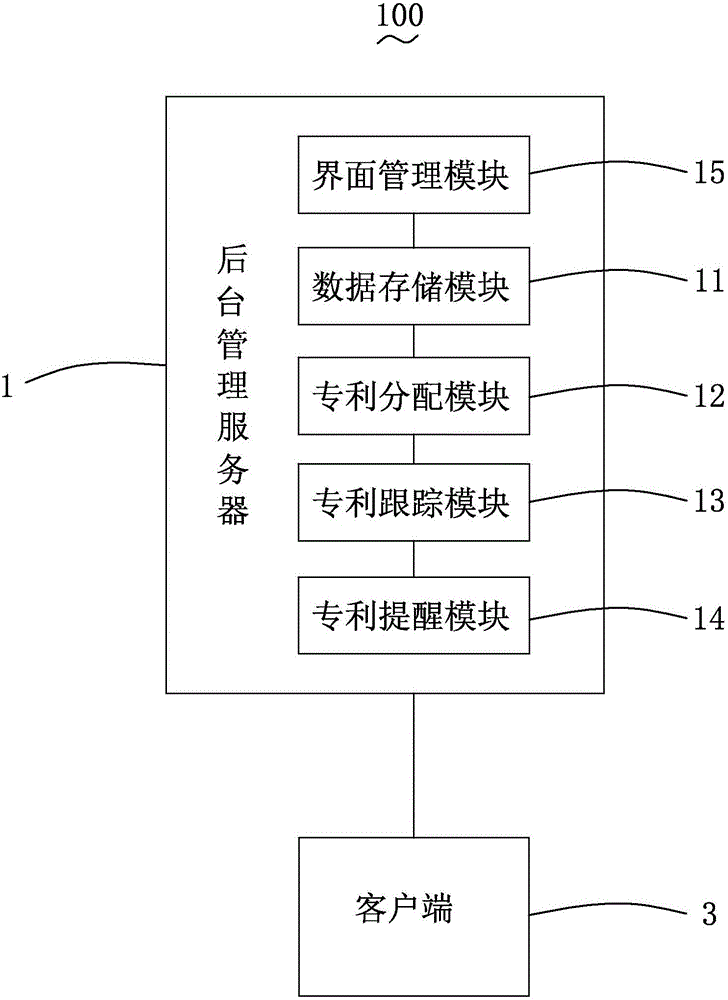
The invention discloses a case tracking interaction system comprising a background management server and a client connected with the background management server. The background management server comprises a data storage module, a patent distribution module, a patent tracking module, a patent reminding module, and an interface management module. The invention further discloses a case tracking interaction method. Compared with the related technology, the invention provides a case tracking interaction system which enables customers to check the progress of a patent and make modification in a timely manner.
Owner:CHANGSHA LUZHI INFORMATION TECH
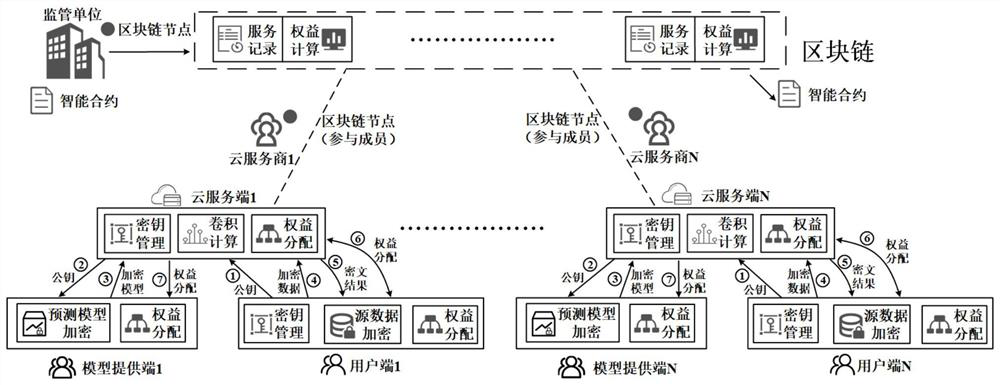
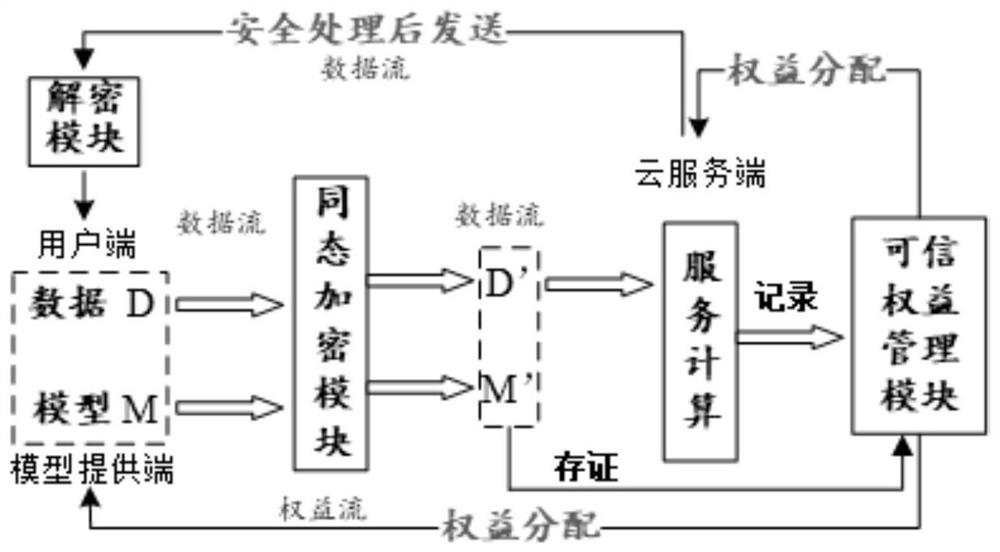
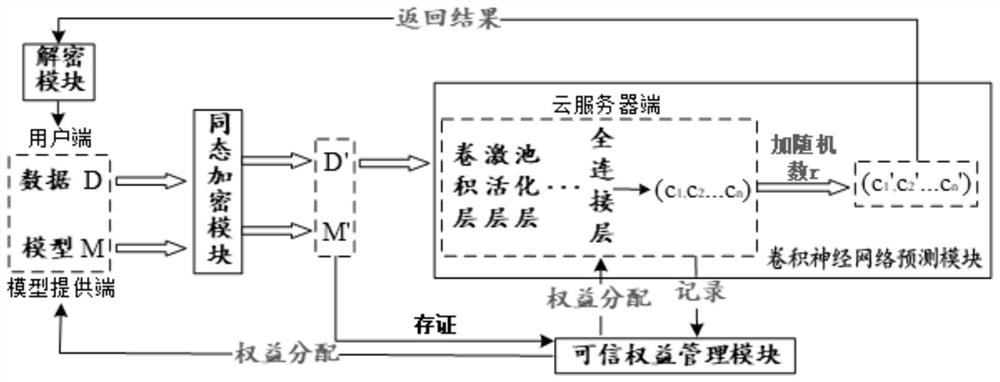
Credible privacy intelligent service computing system and method based on block chain
ActiveCN112347495AImprove securityImprove protectionFinanceDatabase distribution/replicationComputational modelKey generator
The invention provides a credible privacy intelligent service computing system based on a block chain, which performs computing service, encryption service and credible right and interest service, andcomprises a user end, a model providing end and a cloud server end , the user side is a user of service computing and is provided with a data and public and private key generator, and the user end puts forward demand and request service and starts the whole service process after authority is obtained; the model providing end obtains the encrypted public key from the cloud server end, encrypts thetrained prediction model by using the public key, provides the encrypted prediction model to the cloud server end, provides a classification label at the same time, and obtains a rights and interestsdistribution result and corresponding cost after the calculation service is completed; and the cloud server end is used for providing computing resources and model services and completing the requestof the user end. The invention further provides a calculation method and a calculation model, a homomorphic encryption method is adopted, and the calculation model comprises a credible privacy service calculation sub-model, a prediction service privacy calculation sub-model and a prediction service rights and interests evaluation sub-model.
Owner:BEIJING WUZI UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com