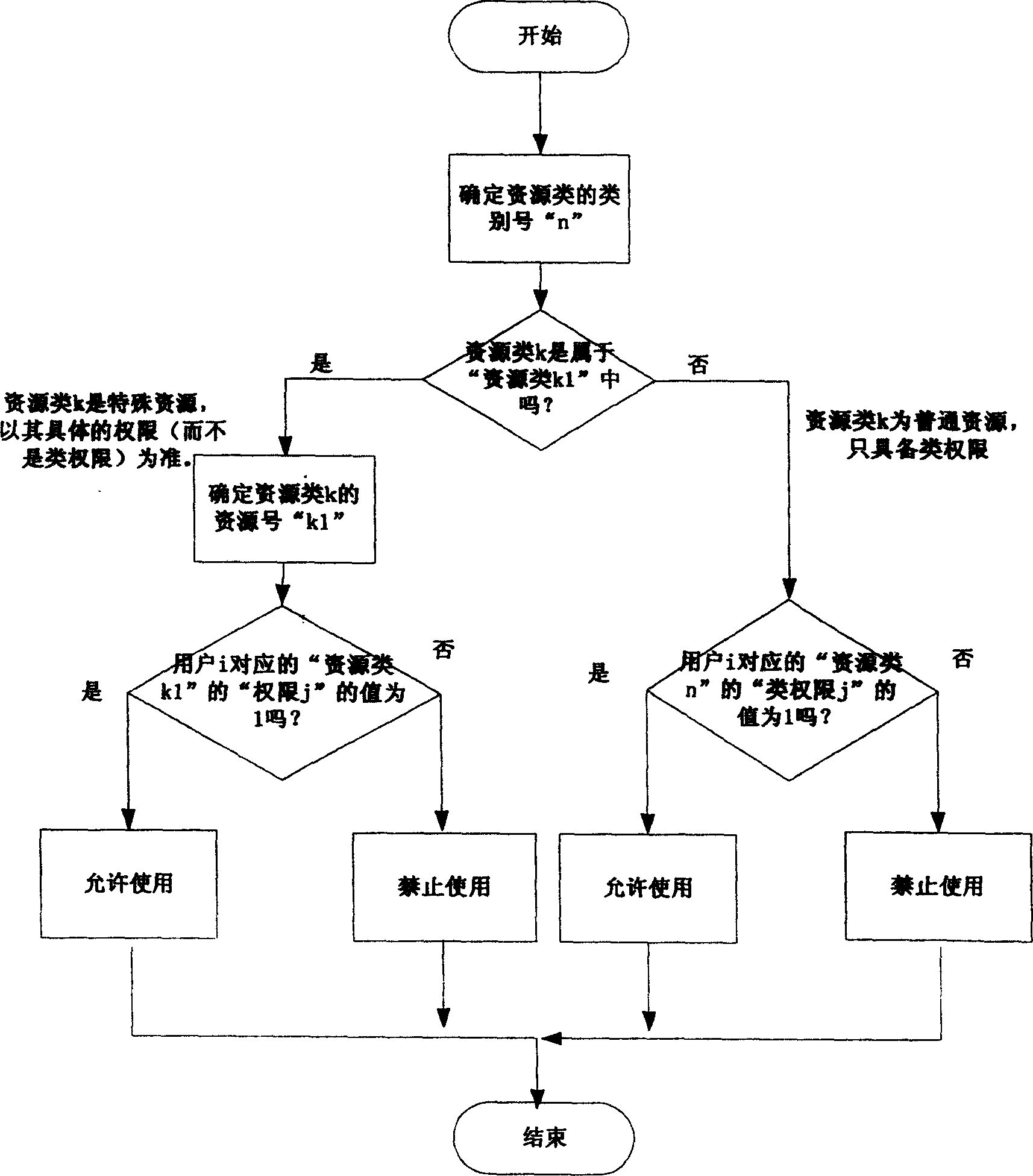
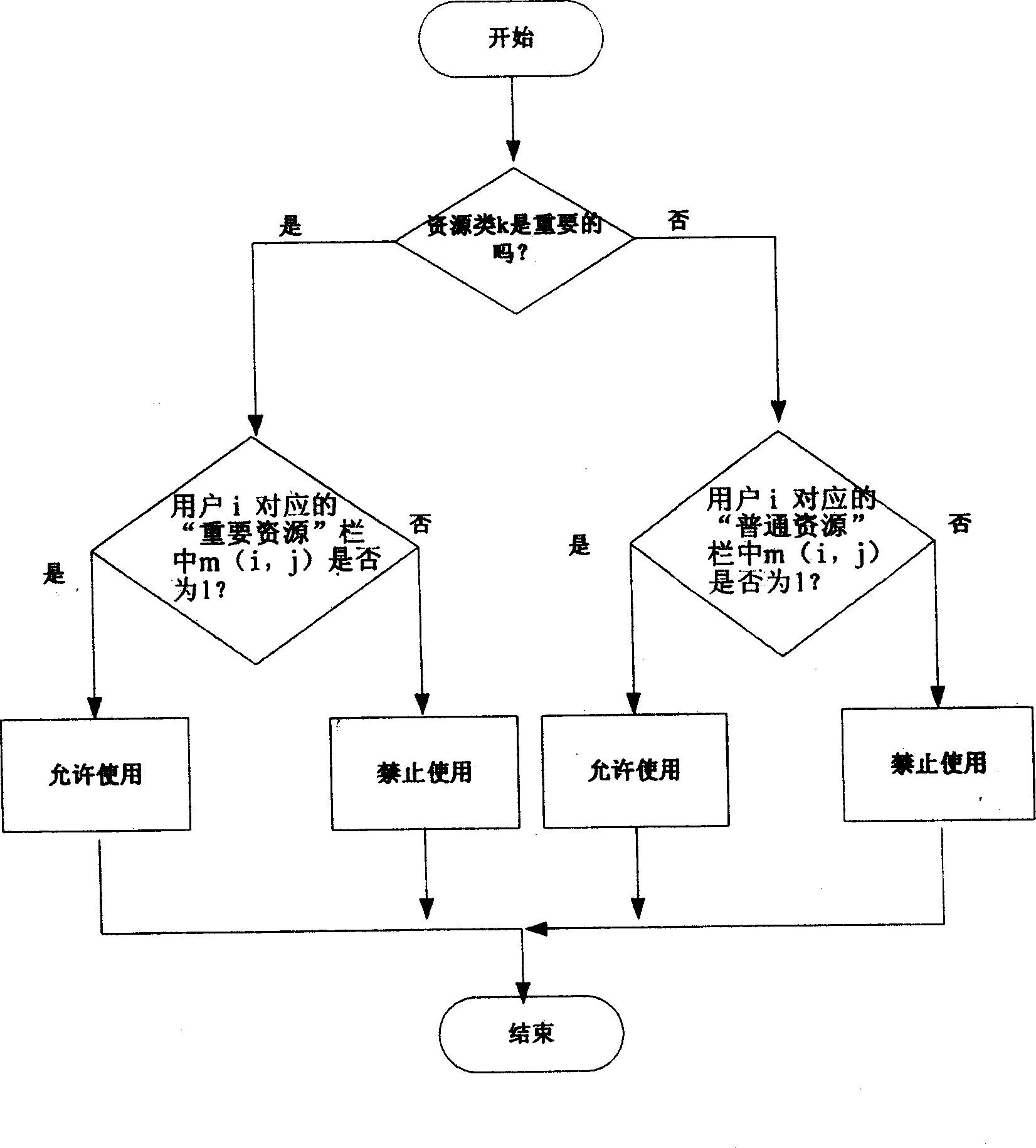
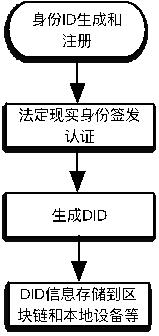
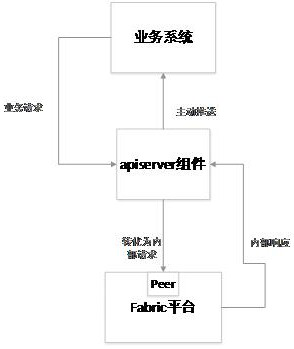
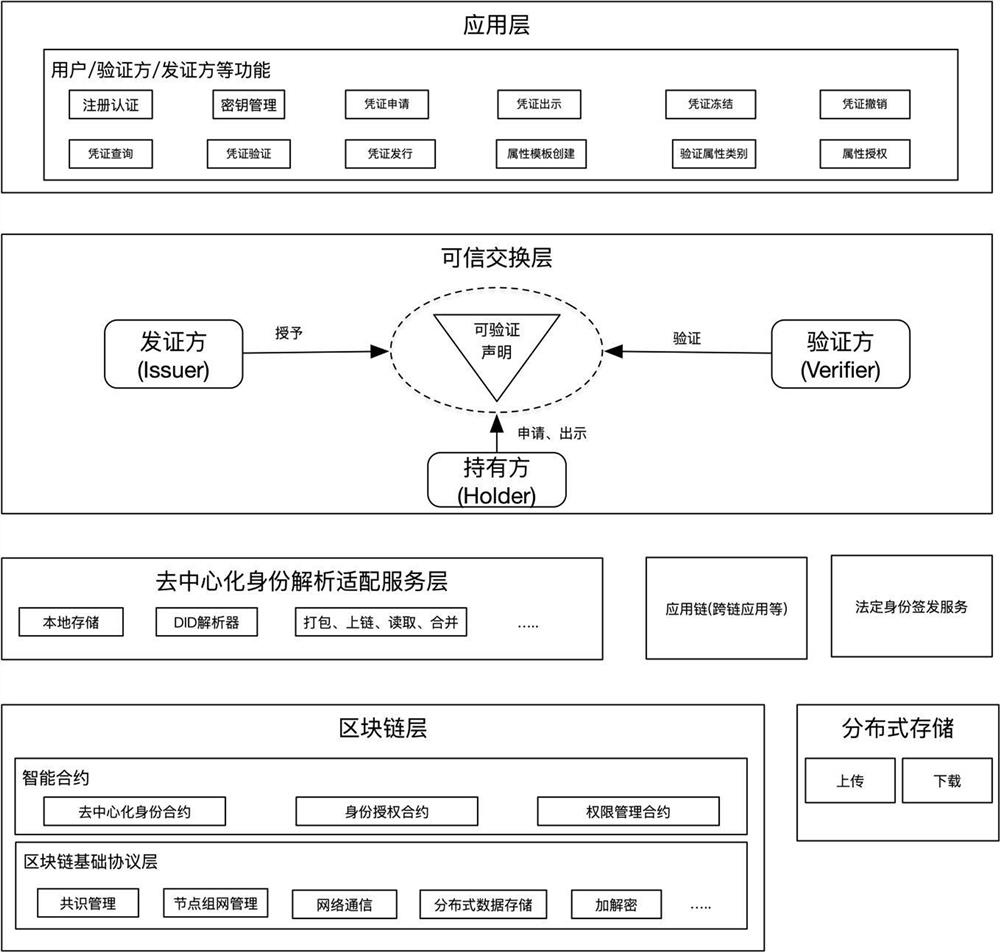
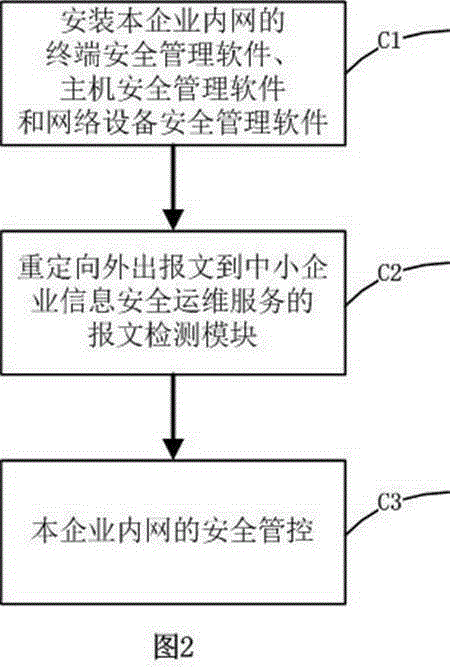
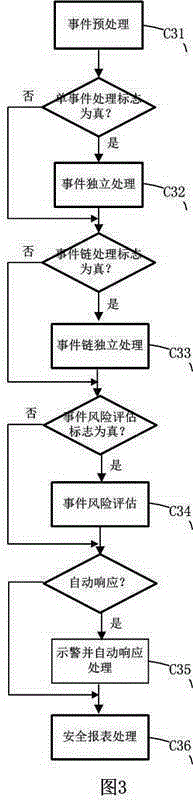
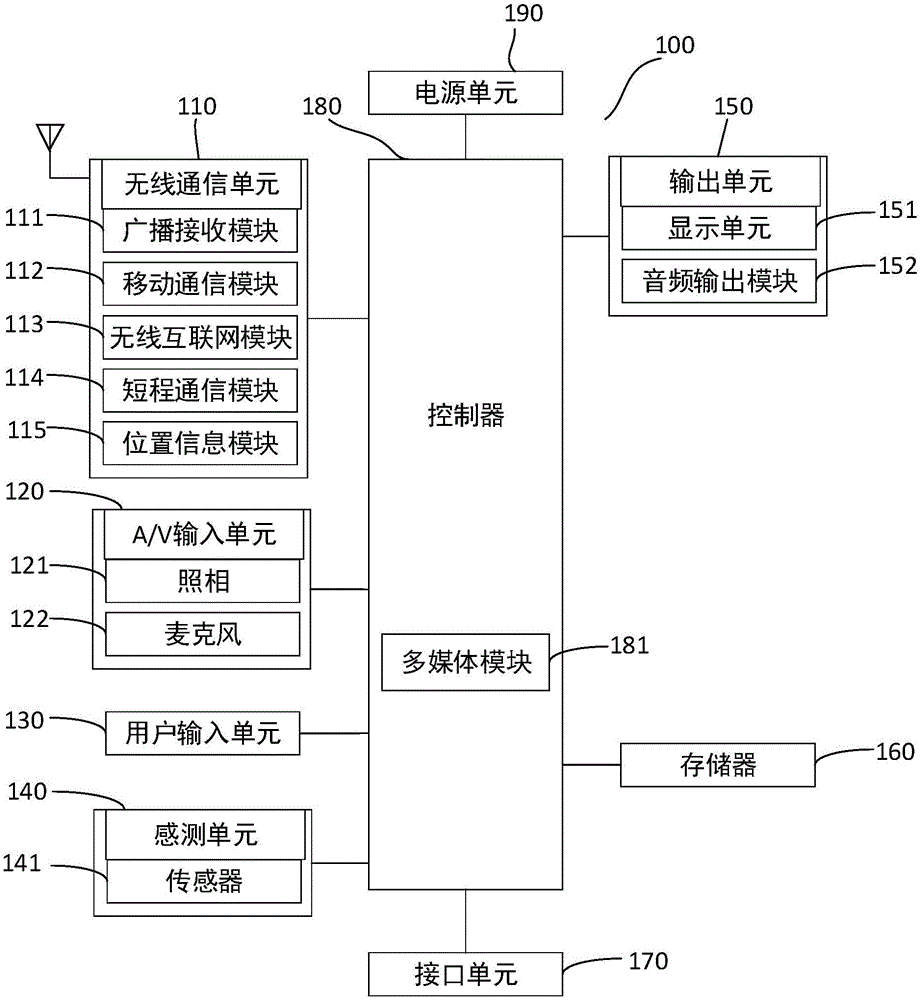
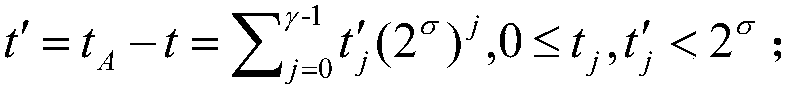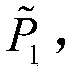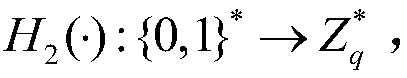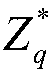Patents
Literature
297results about How to "Protect private information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
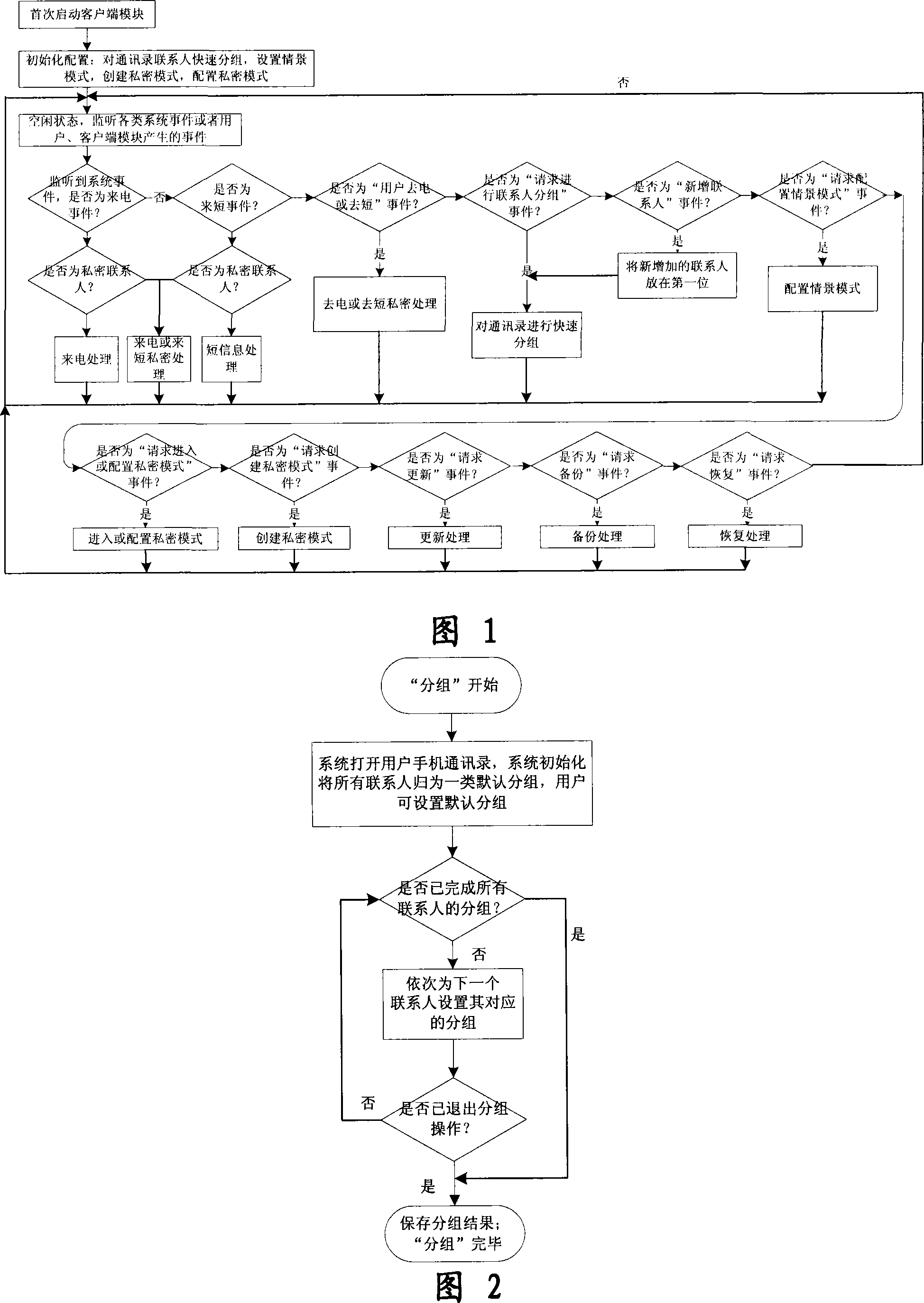
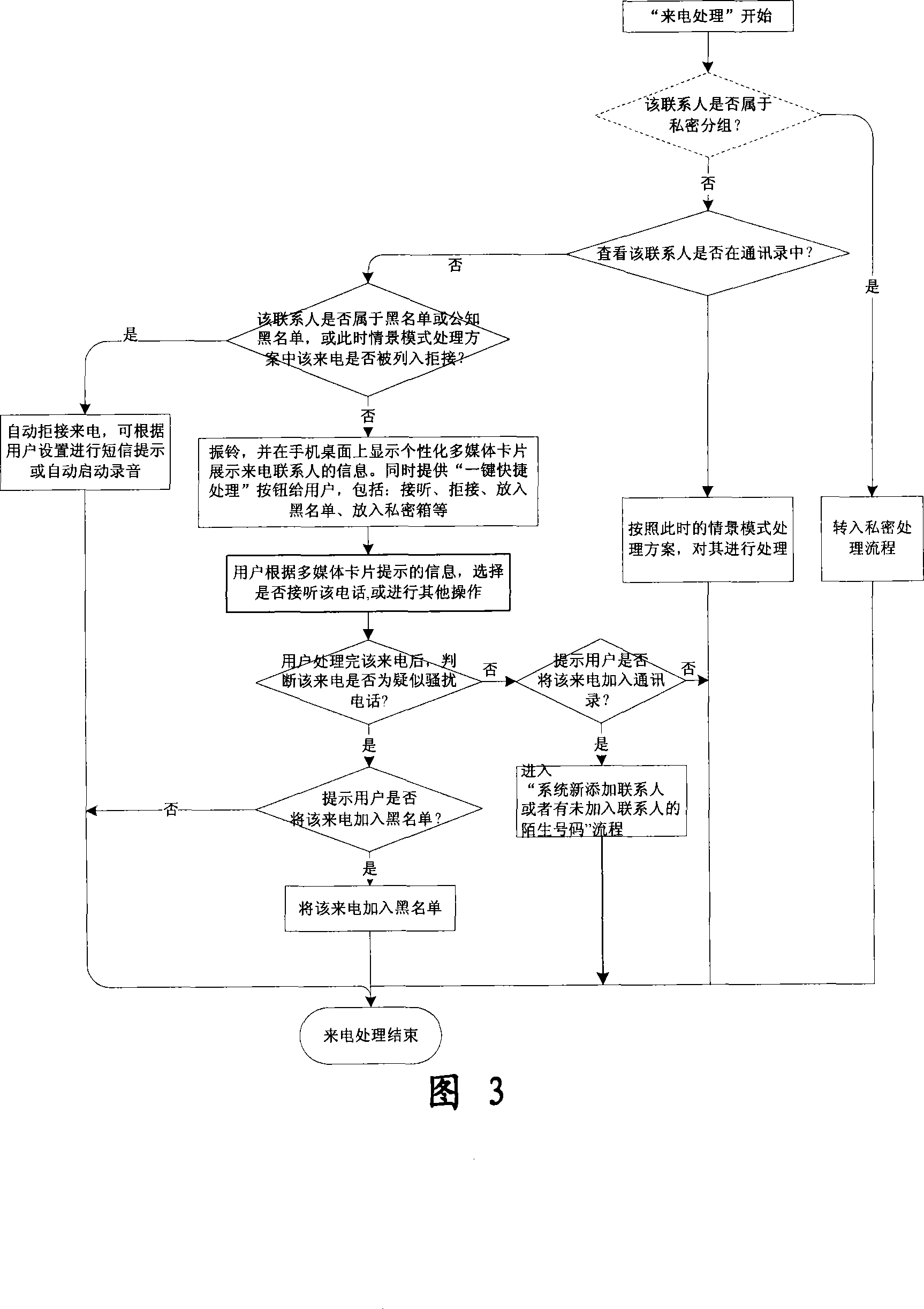
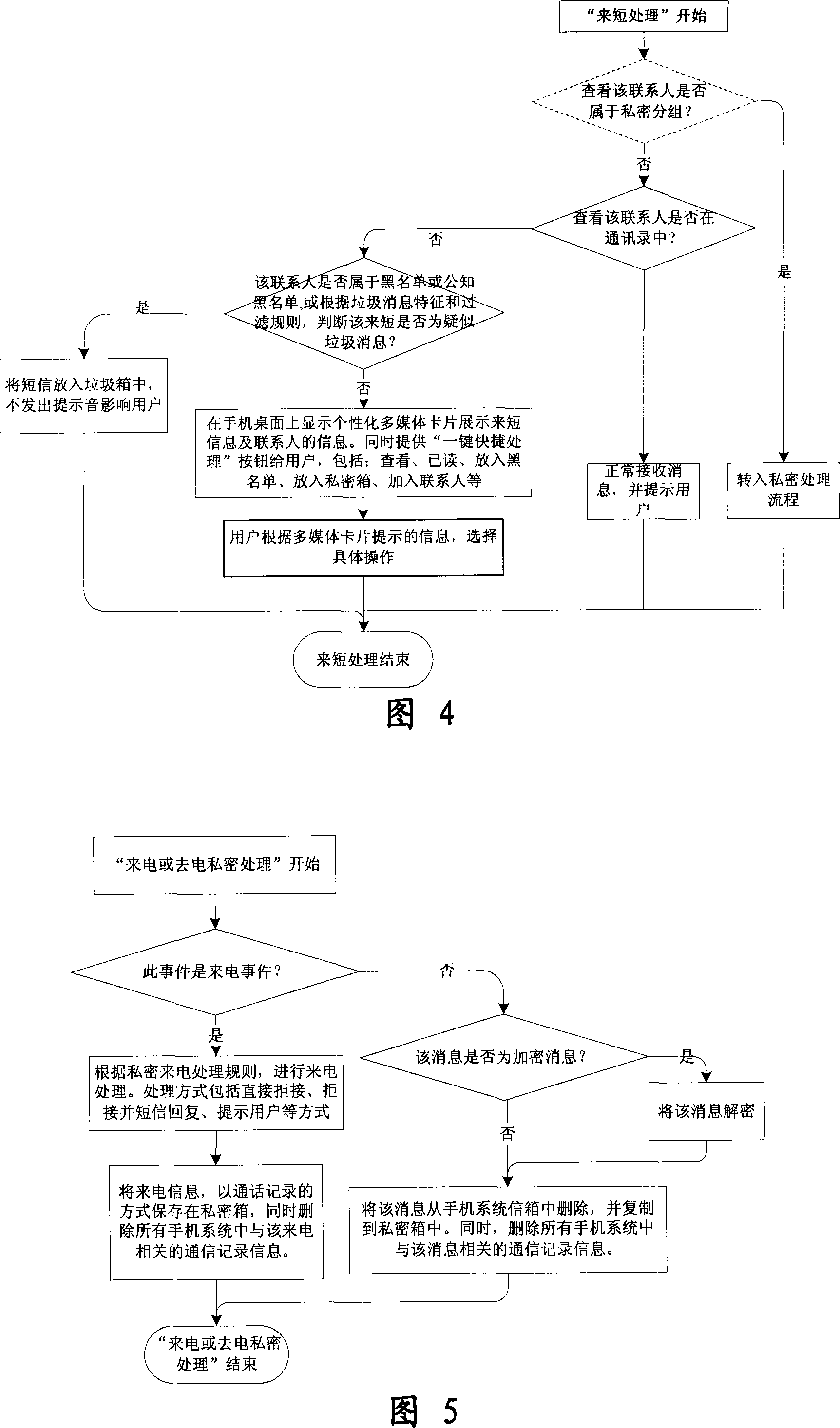
Mobile phone telephone and message anti-disturbance and private communication method and system
InactiveCN101184264AImprove filtering effectOptimize the effect of anti-harassmentRadio/inductive link selection arrangementsSubstation equipmentPrivate communicationSocial statistics
The invention relates to a processing method and the system of anti-harassment of mobile phone calls and messages and private communication, which is as follow: when grouping the contacts in the mobile phone address list according to different classes, a private group of private communicating contacts is added, and different scene modes of the user are set; when receiving a mobile phone call or a message (text message, multimedia message), depending on the grouping sort of the contact of the incoming call or the message or the multimedia message, and the current scene of the user, together with the behavior characteristics of the harassing call and the spam message with the database information of the public harassing message issued by the authoritative institution or obtained from social statistics, the corresponding process to the call, the message and the multimedia message of the mobile phone is executed to reduce harassment; meanwhile the communication records of incoming, dialed calls and message, multimedia message with the contacts in the private grouping are encrypted and preserved to protect the personal privacy of the user. The invention has the advantages of adopting the operating steps of uniform process, and resolving synthetically the harassment of calls, messages and multimedia messages for the mobile phone and the private protection.
Owner:BEIJING NETQIN TECH
Method for Replacing Traditional Payment and Identity Management Systems and Components to Provide Additional Security and a System Implementing Said Method
InactiveUS20140108241A1Improve securityReduce in quantityFinanceComputer security arrangementsComputer hardwarePayment
An electronic wallet system that protects payment accounts, identification and other personal information found within a typical wallet with a secure electronic vault (first) device that can be part of a physical wallet, insert to a wallet, or in other embodiments, wearable / portable devices. A unique biometrically enabled multi-factor authentication process ensures only owners of the information can copy the information to the device or retrieve it thereafter. Authenticated users may then select payment, identification, medical or virtually any private information via touch display or voice command on the vault or on another (second) device that operates in conjunction with the vault. The second device comprises, for example, a programmable card with dynamic magnetic stripe, cell phone, or other wearable technology, that initiates and processes a payment and / or transfer of private information.
Owner:GARMIN INT
Method for protecting privacy of smart contract of block chain, and medium
ActiveCN108418783AIncrease flexibilityImprove privacyFinanceUser identity/authority verificationZero-knowledge proofUser privacy
The invention discloses a method for protecting the privacy of a smart contract of a block chain, which can verify correction of a transaction while covering transaction details, and can verify validity and effectiveness of an operation while protecting the user privacy. The technical scheme of the method is as follows: addition is used for homomorphically encrypting privacy data in the block chain, and non-interactive zero knowledge is generated in the transaction process for proving the effectiveness of the transaction.
Owner:JUZIX TECH SHENZHEN CO LTD +1
Method for realizing classification management of use right of mobile terminal user
InactiveCN1845032ALow costImprove versatilityDigital data processing detailsRadio/inductive link selection arrangementsComputer terminalDocumentation
The invention relates to a method for realizing access grade management of movable terminal user. It is characterized in that: the movable terminal grades itself resources as document, function, etc, and grade manage its user; then building access database of access of each resource to be stored in memorizer; when user uses one resource, the system will find the access of user at said resource via said access database, to decide to execute relative document or transfer program module or not, to realize the access grade management on the user. The invention can effectively protect the privacy and commercial secret, without disturbing others.
Owner:杭州波导软件有限公司
Multi-dimensional digital identity authentication system based on block chain
InactiveCN112580102ASupport large-scale accessSupport for customizable identity certificatesDigital data protectionDigital data authenticationEngineeringData store
The invention discloses a multi-dimensional digital identity authentication system based on a block chain, and relates to the technical field of block chains. The system comprises: a block chain layerused for storing and anchoring a DID document and other data needing distributed storage content; a decentralized identity analysis adaptation service layer which is used for providing a unified DIDdocument analysis service for the block chain layer, and the service can be connected with other application chains at the same time to carry out cross-chain application; a trusted exchange layer which is used for obtaining a DID document through an identity on a user agent registration chain, applying for various verifiable certificates to a certificate issuer by depending on the DID document, and finally providing the DID and the verifiable certificates to a verifier to complete a verification process; and an application layer which is used for constructing a web, wherein an application of the mobile client is provided for a terminal user to use. The system supports cross-chain and cross-platform interoperation, and can be expanded in various different modes.
Owner:ZHENGZHOU UNIV
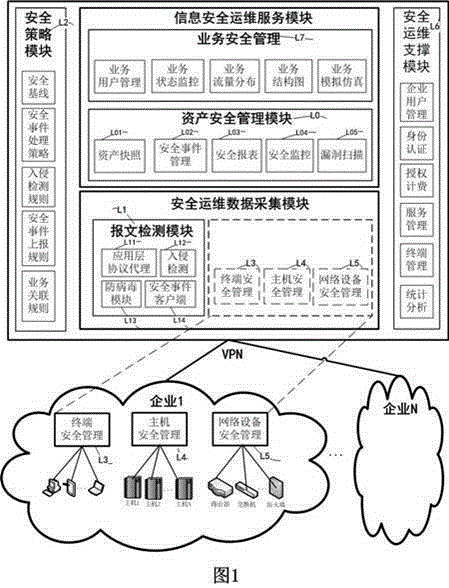
System and method for supplying information security operation service to medium-sized and small enterprises
InactiveCN105391687AImprove securityReduce security operation and maintenance costsNetworks interconnectionBaseline dataInformation security
The invention discloses a system for supplying information security operation service to medium-sized and small enterprises. The system comprises the components of a security operation data acquiring module, a security operation service module, a security operation supporting module and a security policy module. The security operation data acquiring module comprises a message detecting module, a terminal security management module, a host security management module and a network equipment security management module. The security operation service module comprises an asset management module and a service management module. The security operation supporting module performs the functions of enterprise user management, identity authentication, authorization charging, service management, terminal management and statistical analysis. The security policy module is used for setting security baseline data, a security event processing strategy, an invasion detecting rule, a security event reporting rule and a service association rule.
Owner:NANJING LIANCHENG TECH DEV
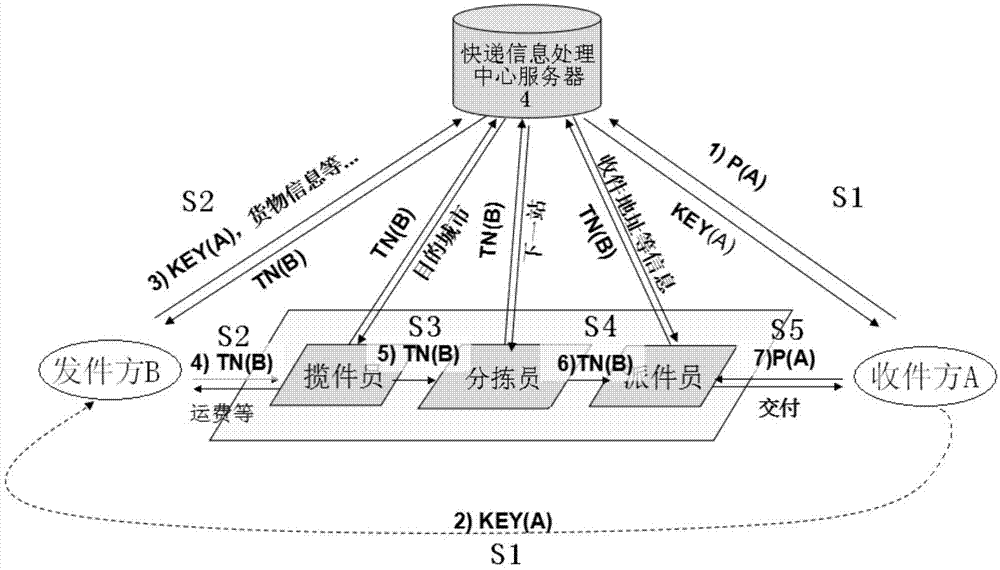
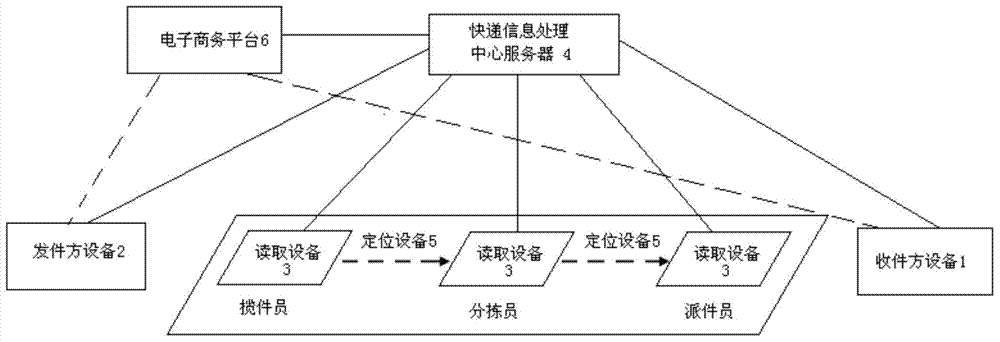
Confidential express method and system thereof
InactiveCN104123624AProtect private informationImprove confidentialityLogisticsInformation processingPassword
The invention discloses a confidential express method. The method comprises the following steps: establishing an express information processing center; encrypting and saving the address information and receiving password of a recipient and generating a key code through a server; sending the key code to an initiator through the recipient; sending the key code, the goods information and the initiator identification to the server through the initiator for encrypting, saving and generating a bill number; sending the goods together with the bill number; reading the bill number and checking the goods information by an undertaking worker; transporting the goods to a sorting place to enter the transfer stage after checking; reading out the bill number by a sorting worker; sorting the goods according to a targeted city; transferring to the next station until arriving at the delivery station of the targeted city; reading the bill number by an express delivery worker to obtain the receiving address and contact mode; delivering the goods to the recipient; sending the receiving password to the server to verify to obtain the goods by the recipient. With the adoption of the confidential express method, the information of the recipient and the initiator can be effectively prevented from leaking; in addition, a complete system of signing after receiving is provided. The invention also discloses a confidential express system.
Owner:EAST CHINA NORMAL UNIV
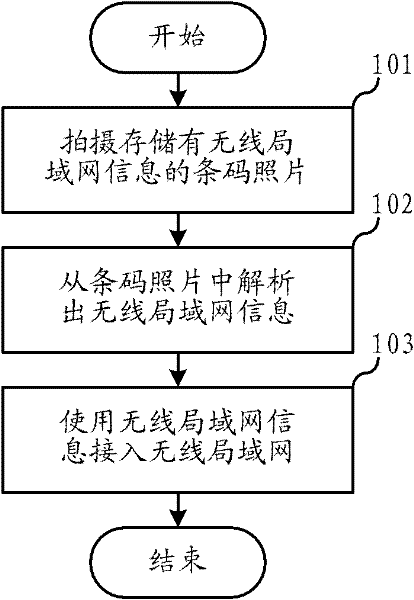
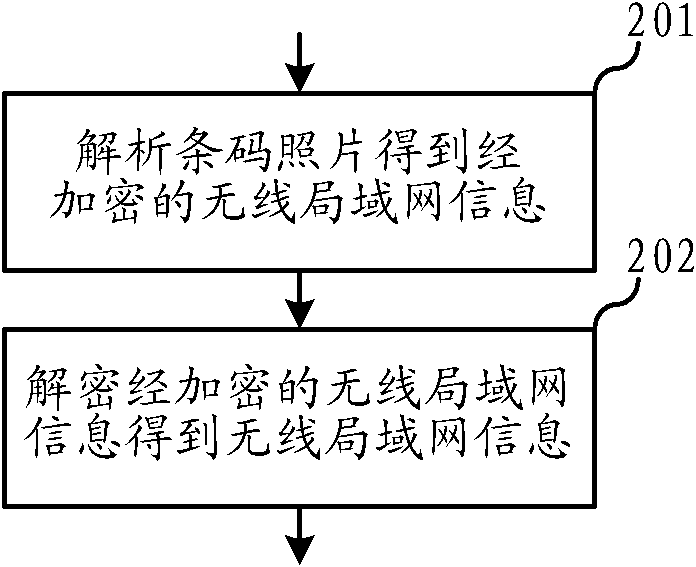
Method for rapidly accessing to wireless local area network and mobile terminal thereof
InactiveCN102395216AImprove securityEasy access rights managementConnection managementSecurity arrangementPasswordBarcode
The invention relates to the wireless network field and discloses a method for rapidly accessing to a wireless local area network and a mobile terminal thereof. By using the method for rapidly accessing to the wireless local area network, the mobile terminal can conveniently access to the wireless local area network. Simultaneously, network privacy information can be protected and network safety stabilization can be strengthened. The method for rapidly accessing to the wireless local area network of the invention comprises the following steps: shooting a barcode photo which stores wireless local area network information, wherein the wireless local area network information comprises a service set identifier (SSID) and a password; analyzing the wireless local area network information from the barcode photo; using the wireless local area network information to access to the wireless local area network.
Owner:上海云联计算机系统有限公司
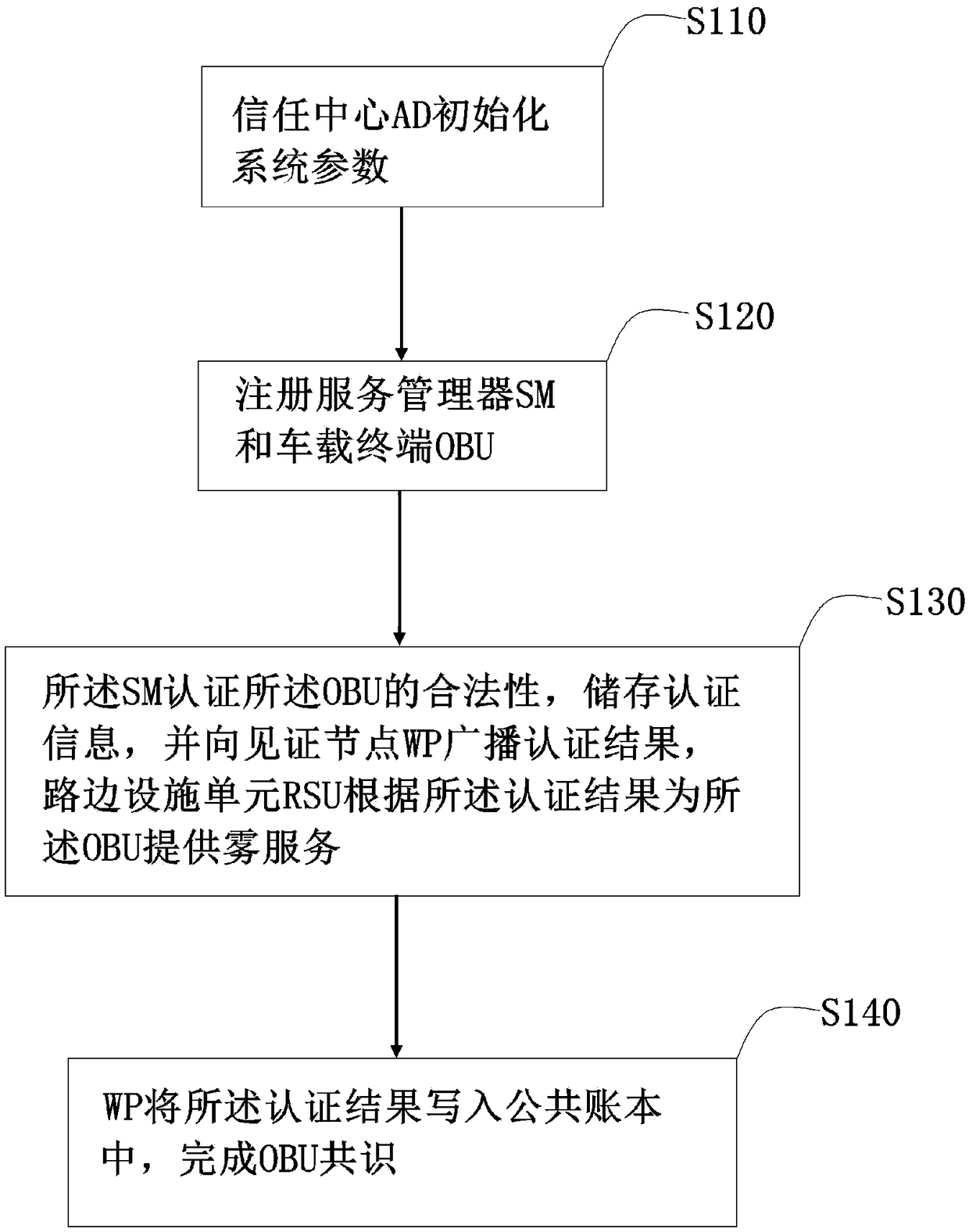
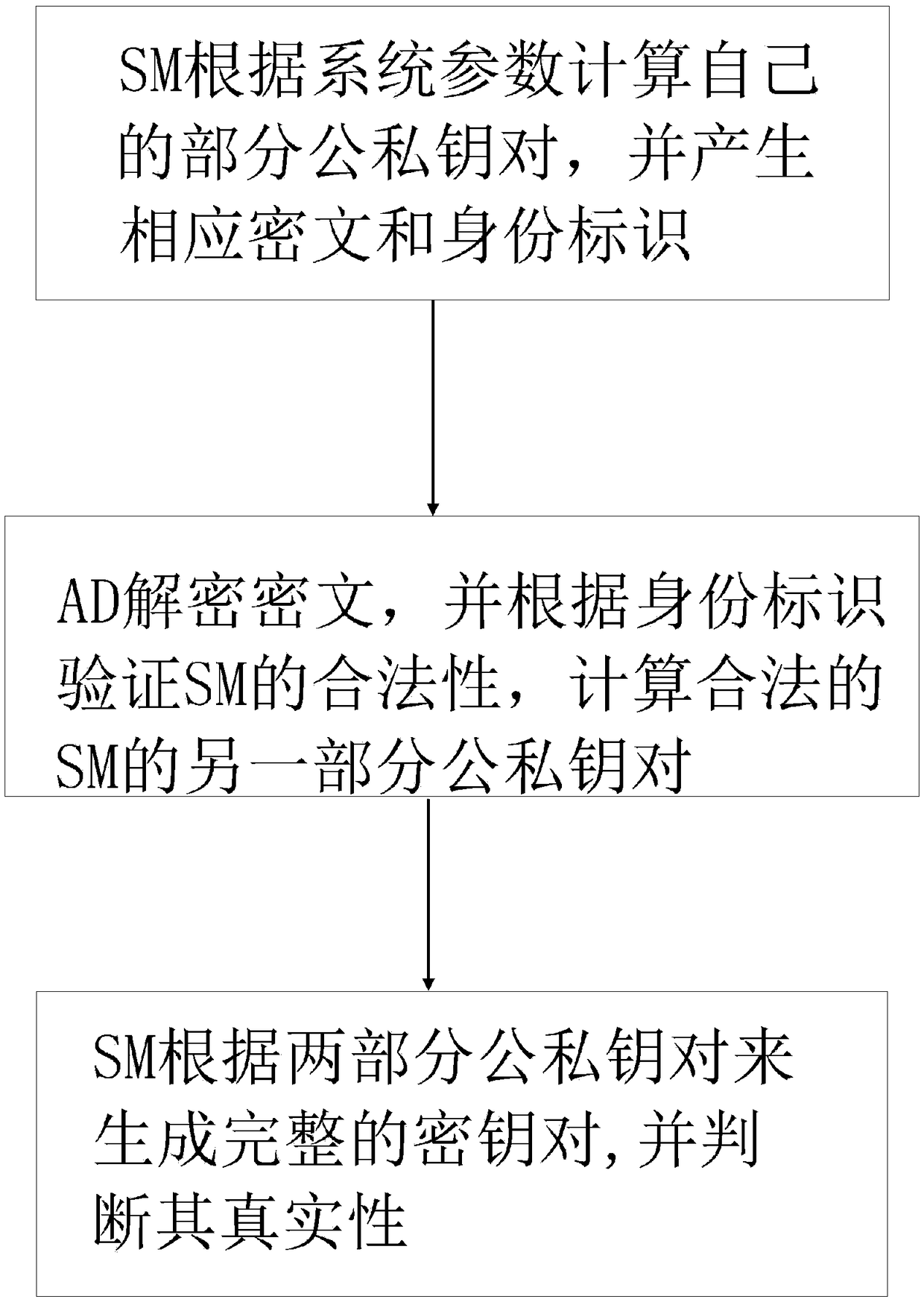
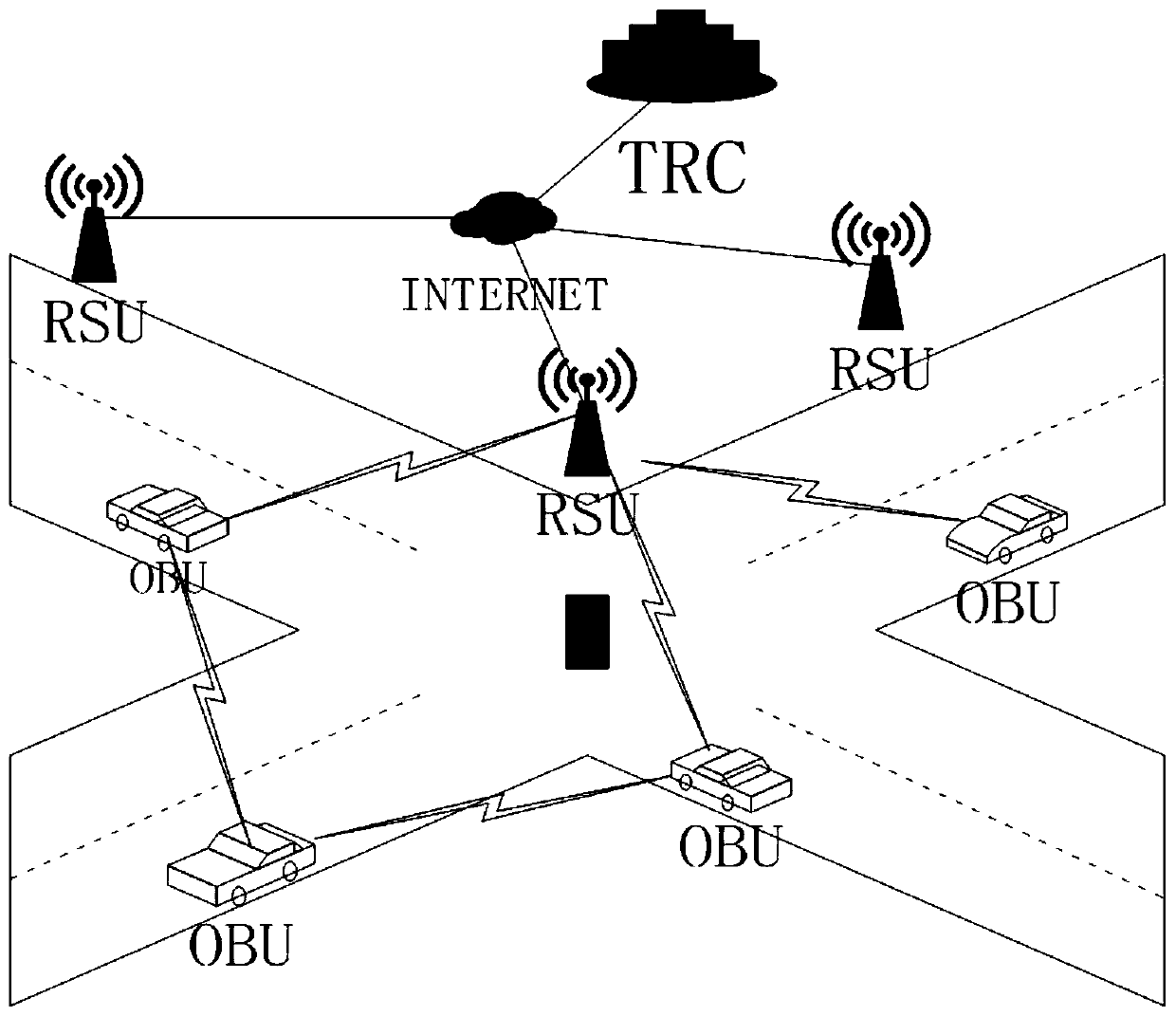
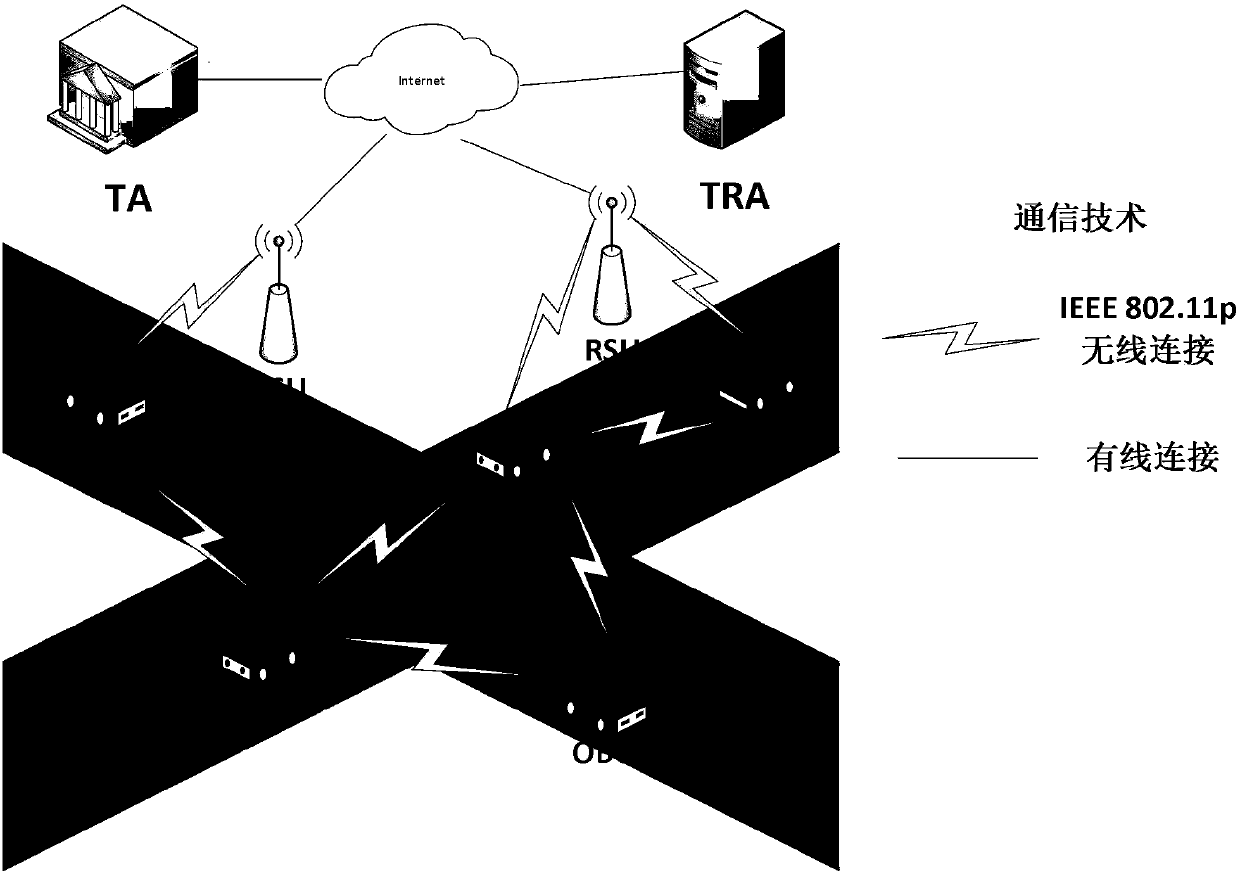
Vehicle fog data light-weight anonymous access authentication method based on blockchain assistance
InactiveCN109194610AProtect private informationEnhanced anonymityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPublic accountOn board
The present invention provides a vehicle fog data light-weight anonymous access authentication method based on blockchain assistance, and relates to the technical field of network communication safetyof urban traffic operation management. The method comprises the steps of: arranging one witness node (WP) in a management range of each service manager (SM), initializing system parameters through antrusted center AD, and registering the SM and a OBU (On Board Unit); allowing the SM to authenticate the validity of the OBU, storing the authentication information, broadcasting an authentication result to the WP, and providing fog service to the OBU according to the authentication result by a roadside facility unit RSU; and writing the authentication result into a public account by the WP to complete OBU consensus. The vehicle fog data light-weight anonymous access authentication method based on blockchain assistance can protect the user privacy information while ensuring the identity authenticity of a vehicle user accessing the fog service so as to achieve the vehicle anonymous authentication and allow users to select the time and the frequency of replacement of the pseudonym by themselves; the non-interactive autonomous cross-domain authentication is achieved, and the communication delay is effectively reduced; and moreover, the authentication information management is simplified,and the risk that a single database is tampered is effectively avoided.
Owner:BEIJING JIAOTONG UNIV
IOV (Internet of Vehicles) anonymous authentication system with controllable link, and IOV anonymous authentication method
ActiveCN109391631AProtect private informationRealize controllable linkKey distribution for secure communicationEncryption apparatus with shift registers/memoriesService providerTrusted authority
The invention discloses an IOV (Internet of Vehicles) anonymous authentication system with a controllable link, and an IOV anonymous authentication method, and relates to the IO field. The system includes a system initialization module which is used for completing the initialization work of an IOV system and a TA (trusted authority); a registration module which is used for completing the registration of an OBU (onboard unit) and an RSU (roadside unit) to the TA; an OBU joining module which is used for obtaining a group certificate from the RSU when the OBU enters the communication range of a new RSU; a signature module which is used for completing the signature of a vehicle about a message; an authentication module which is used for completing the signature information authentication afterthe OBU receives the signature information; a link module which is used by an SP (service provider) to determine whether the two signature messages are linkable or not; an identity tracking module which is used for completing the process that the TA exposes the real identity of a signer of a valid signature message. The construction of the system uses a more lightweight elliptic curve operation to make the authentication process more efficient.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
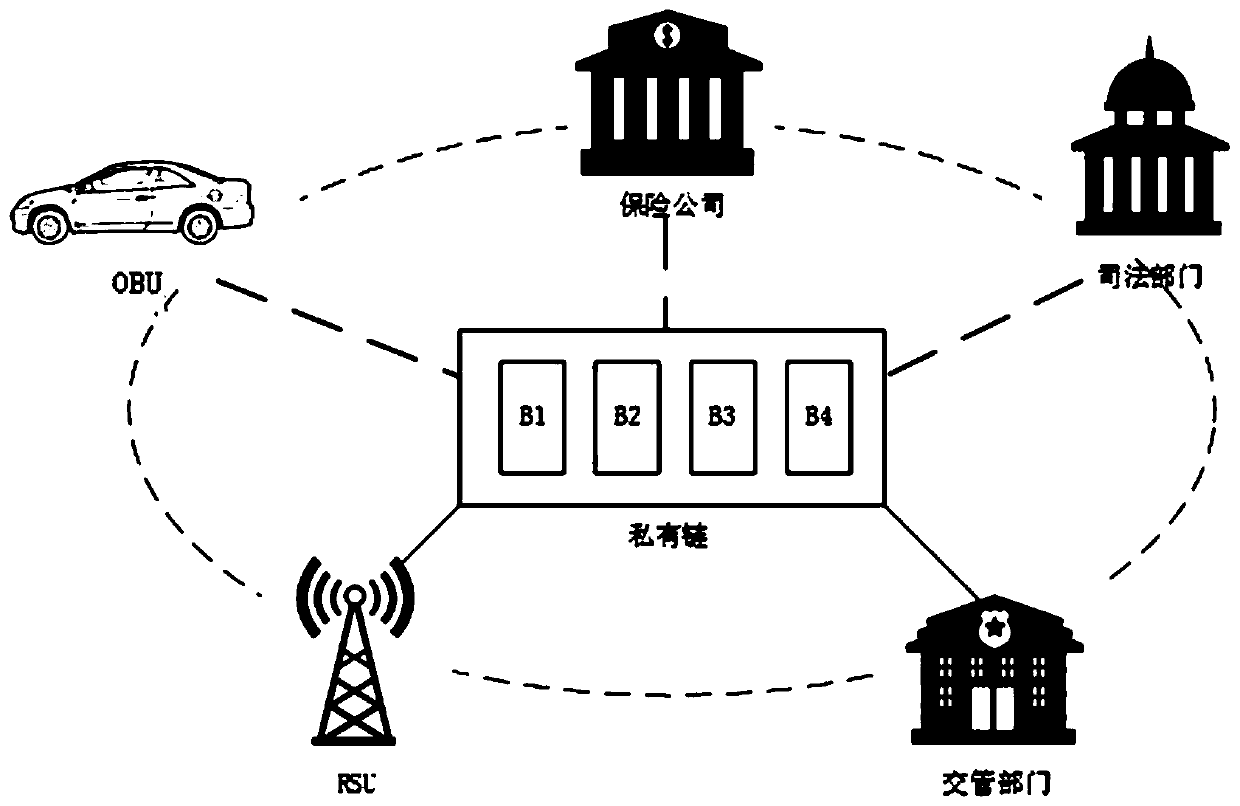
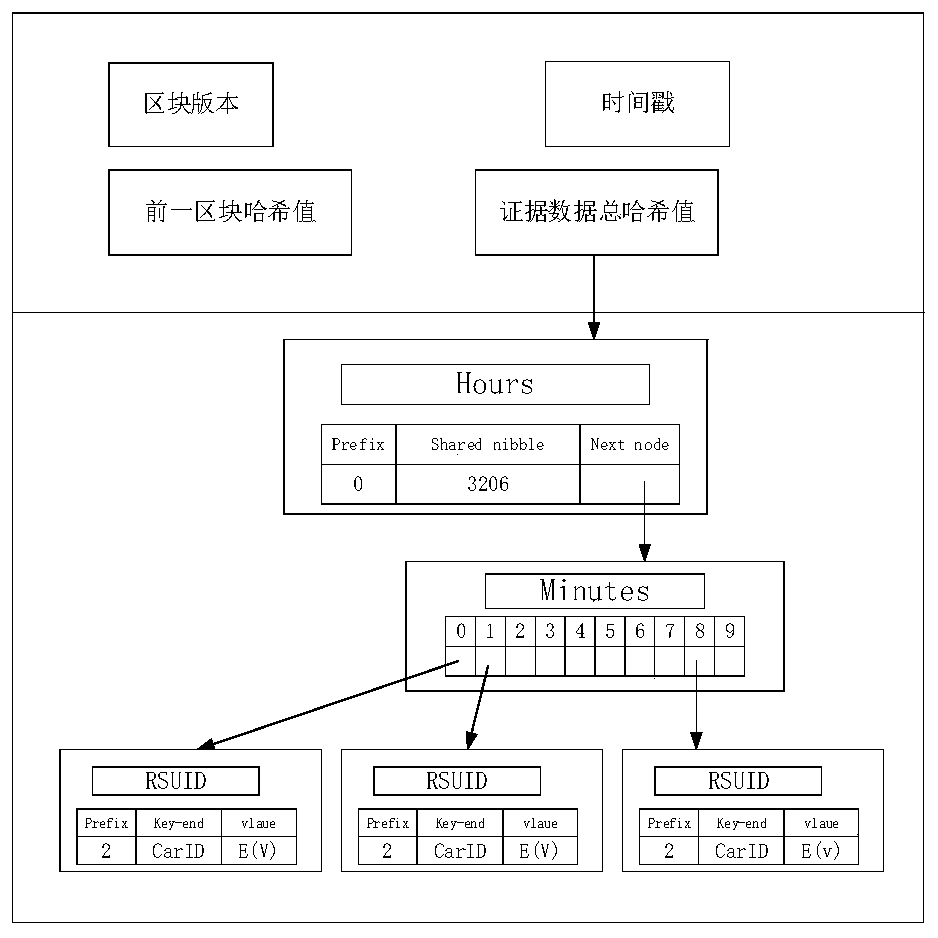
Electronic evidence obtaining device and method based on block chain in Internet-of-Vehicles environment
ActiveCN111464980AProtection against the risk of tamperingImprove access efficiencyData processing applicationsParticular environment based servicesComputer networkTraffic crash
The invention provides an electronic evidence obtaining device and method based on a block chain in an Internet-of-Vehicles environment. The method comprises the following steps of S10, offline registration, S20, vehicle online identity registration, S30, real-time evidence storage and S40, query and evidence obtaining. According to the electronic evidence obtaining device and method based on theblock chain in the Internet-of-Vehicles environment, the block chain technology is used for traffic accident electronic evidence obtaining, the integrity, non-repudiation and permanence of evidence are guaranteed through the characteristics of block chain distributed data storage and the like, many problems of traditional traffic accident evidence obtaining are solved, and the evidence obtaining efficiency is high.
Owner:NANTONG UNIVERSITY
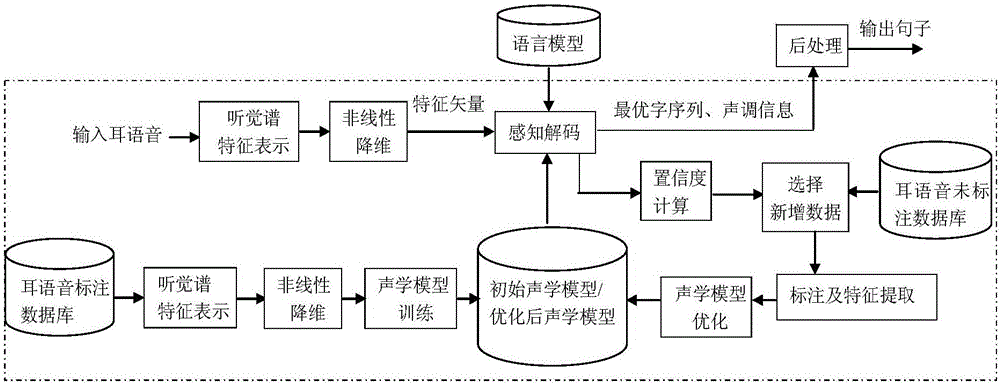
Whisper speech feature extraction method and system
ActiveCN106571135AImprove distinguishabilityImprove robustnessSpeech recognitionFeature vectorFeature Dimension
The invention discloses a whisper feature extraction method which is characterized by comprising the following steps of (1) whisper speech auditory spectrum feature representation; (2) feature dimension reduction and robust performance analysis; the feature dimension reduction and robust performance analysis include three contents: (a) the low-dimensional topological structure features are extracted from the high-dimensional auditory spectrum; (b) topological structure feature time sequence analysis is performed; and (c) topological structure feature stability analysis is performed; and (3) acoustic model optimization is performed; the training mechanism of performing passive learning and then active learning is adopted in acoustic model optimization so as to enhance the adaptive performance of the model. According to the whisper speech feature extraction method, dimension reduction is performed on the auditory perception spectrum features to obtain the topological structure features, and the distinguishability of the whisper speech features is strengthened by strengthening the time sequence weight of the features. The distance between the feature vectors of different meanings is maximized through two target functions, and the distance between the feature vectors of the same meaning is also minimized so as to enhance the robustness of the features.
Owner:SUZHOU UNIV
Method and device for tracking positioning of mobile terminal device and mobile terminal device thereof
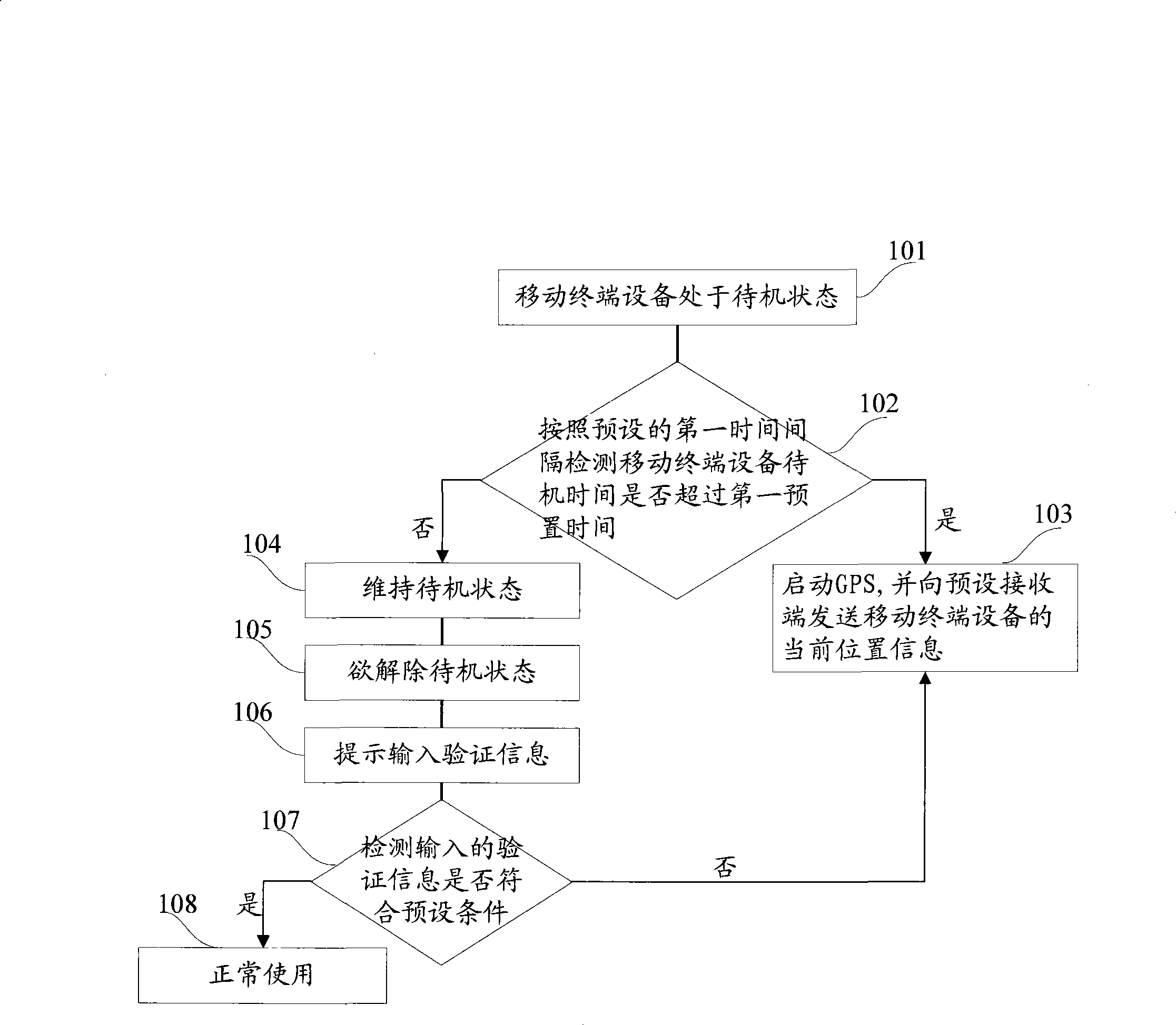
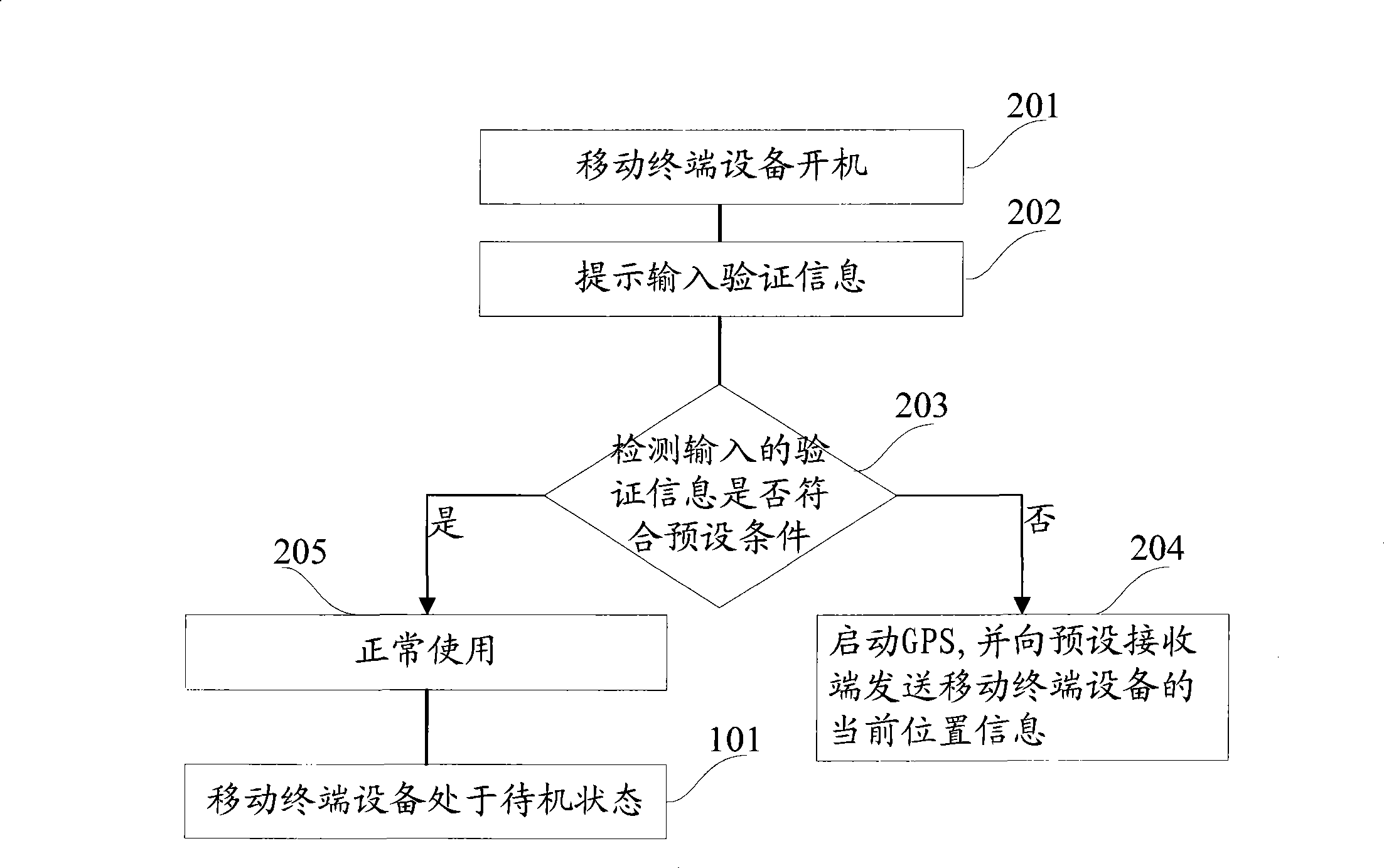
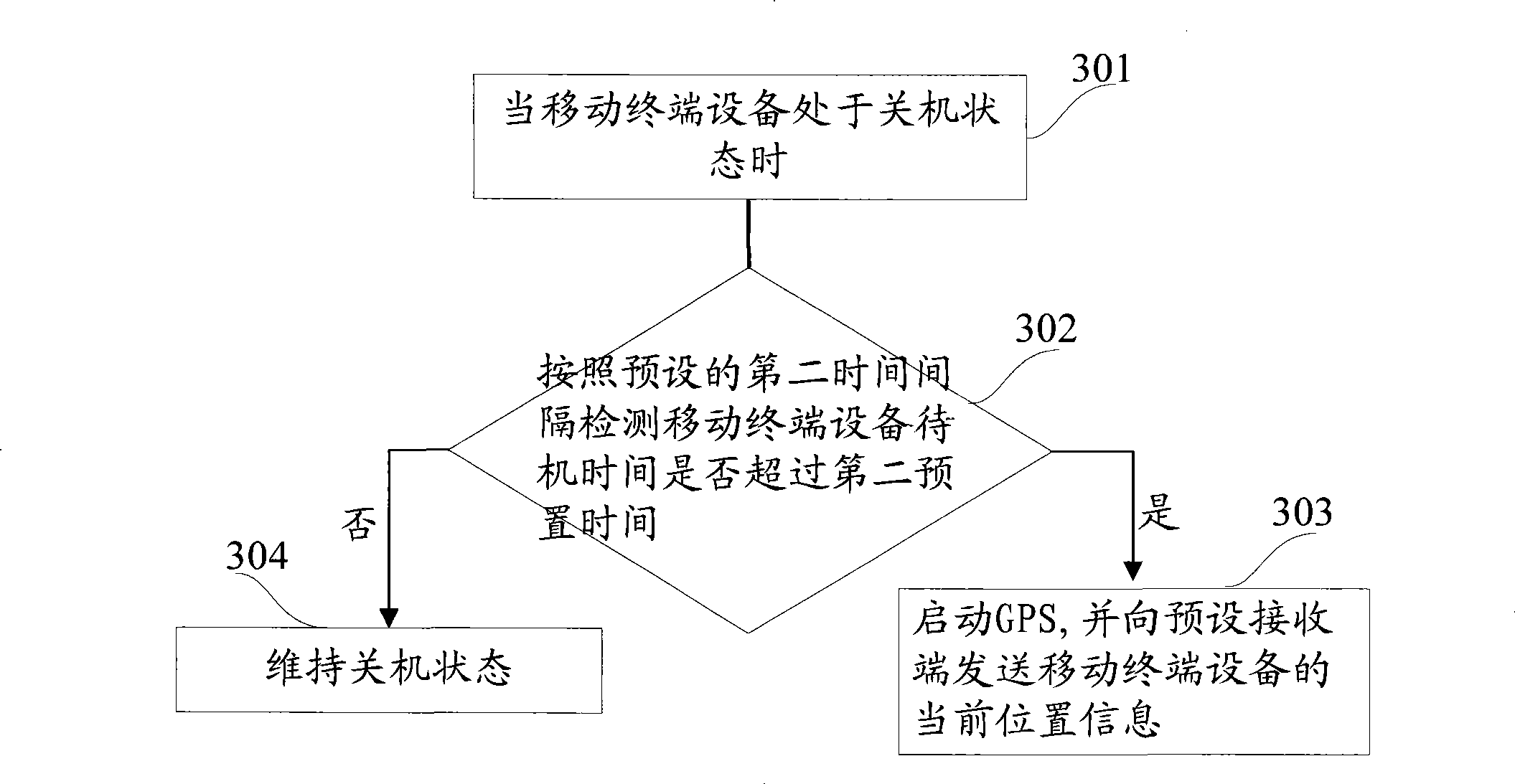
InactiveCN101399881ASave powerProtect the owner's private informationSubstation equipmentWireless communicationEngineeringTerminal equipment
The invention provides a method and a device for tracing and locating a movable terminal. The method includes: when the movable device is arranged in a standby state, whether the standby time of the movable terminal device exceeds a first preset time or not is detected according to a preset first time interval; if not, then GPS is started and the current position information of the movable terminal device is transmitted to a preset receiving terminal; if not, then maintaining the standby state; when the standby state is released, then the movable terminal device indicates to input verification information; if the input verification information meets a preset condition, then the movable terminal device is normally used; if not, then the GPS is started and the current position information of the movable terminal device is transmitted to the preset receiving terminal.
Owner:VIMICRO CORP
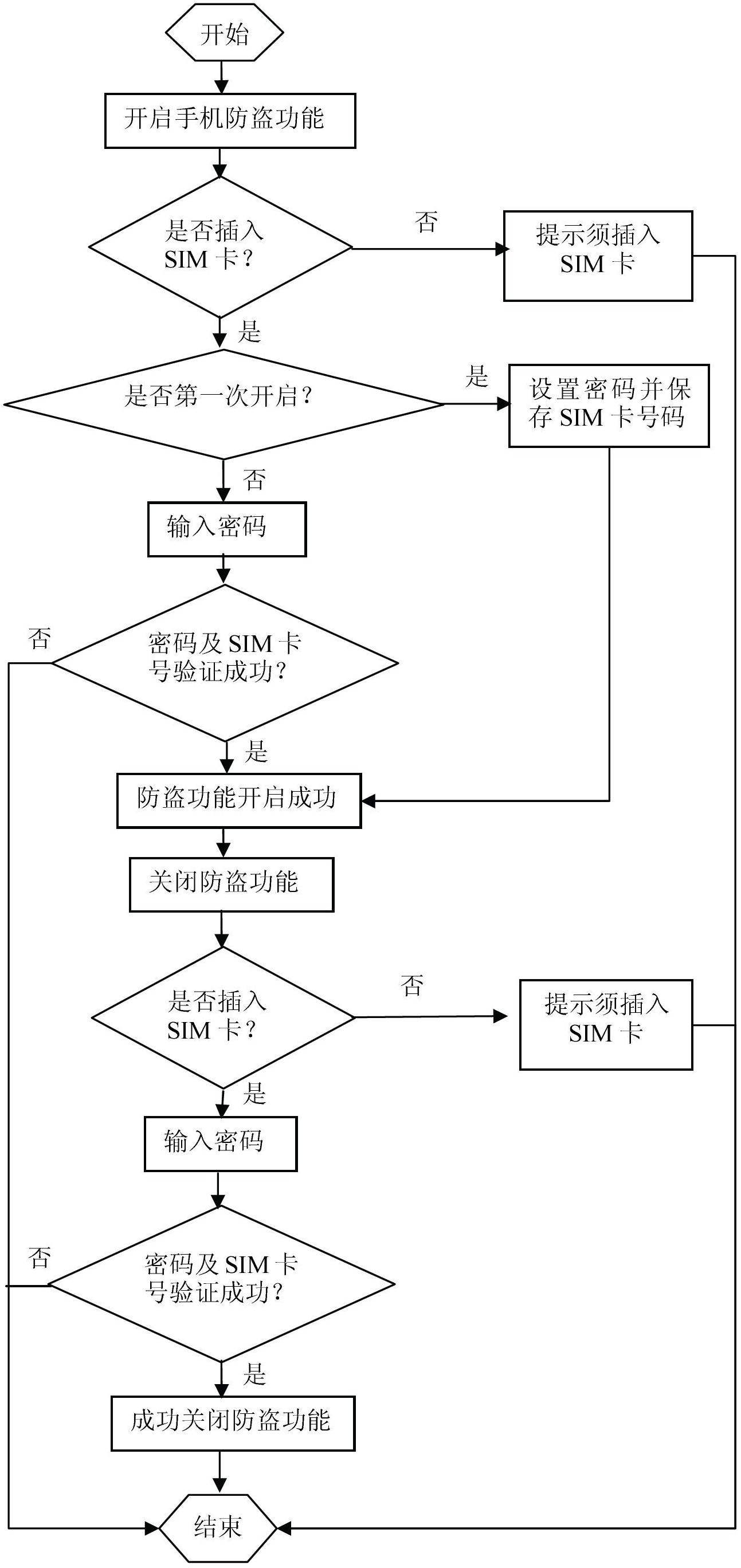
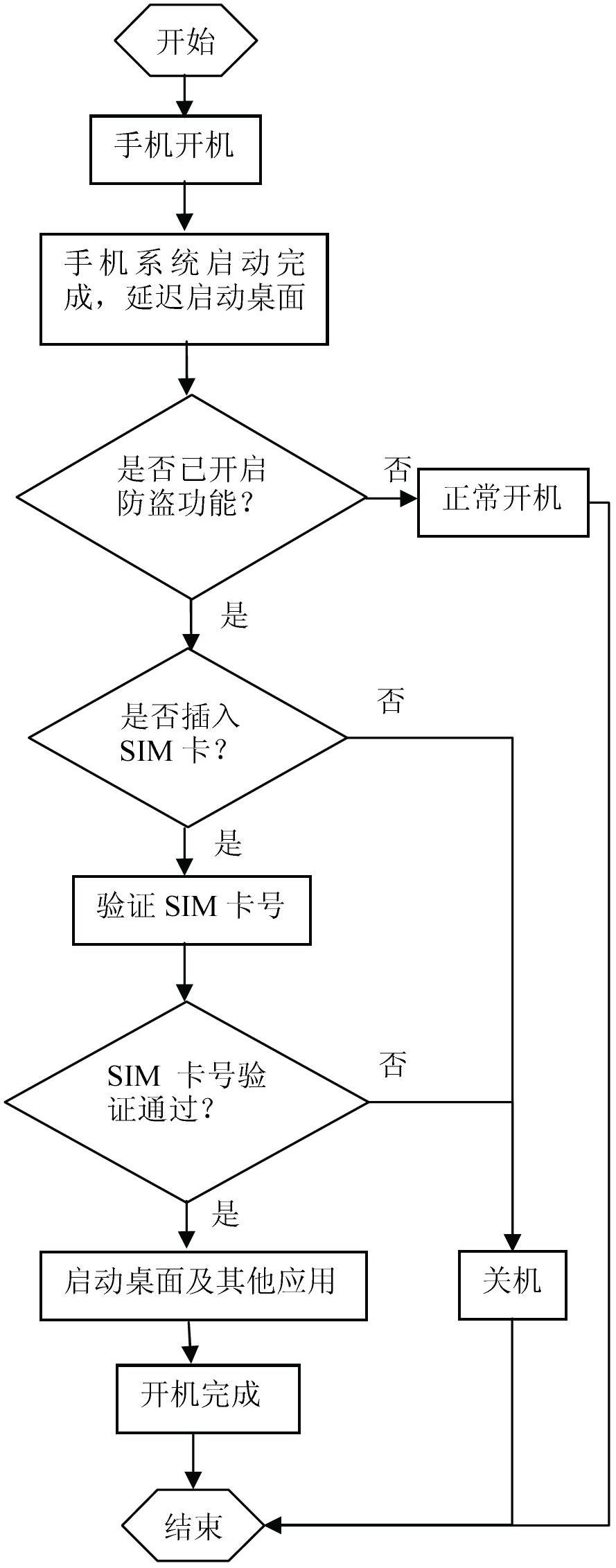
Mobile phone antitheft method
ActiveCN102694920AUnable to obtain authorizationProtect private informationSubstation equipmentPasswordUser input
The invention relates to a mobile phone antitheft method. The mobile phone antitheft method includes: 1101) starting mobile phone antitheft; 1102) judging whether an SIM (subscriber identity module) card is inserted into a mobile phone or not, entering next step if yes, and otherwise, exiting; 1103) judging whether the mobile phone antitheft is started for the first time or not, setting an antitheft password, storing an SIM card number and entering a step 1105) if yes, and otherwise, entering next step; 1104) entering next step if a user input password and an SIM card are consistent with the stored antitheft password and the SIM card number respectively, and otherwise, exiting; and 1105) recording a starting sign. The mobile phone antitheft method further includes: 1201) detecting and judging whether an antitheft function is started or not, entering next step if yes, and otherwise, exiting after the mobile phone is normally turned on; 1202) judging whether the SIM card is inserted into the mobile phone or not, entering next step if yes, and otherwise, turning off the mobile phone or exiting after use is prohibited; and 1203) judging whether the SIM card is consistent with the stored SIM card number, turning on the mobile phone normally if yes, and otherwise, turning off the mobile phone or prohibiting use.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
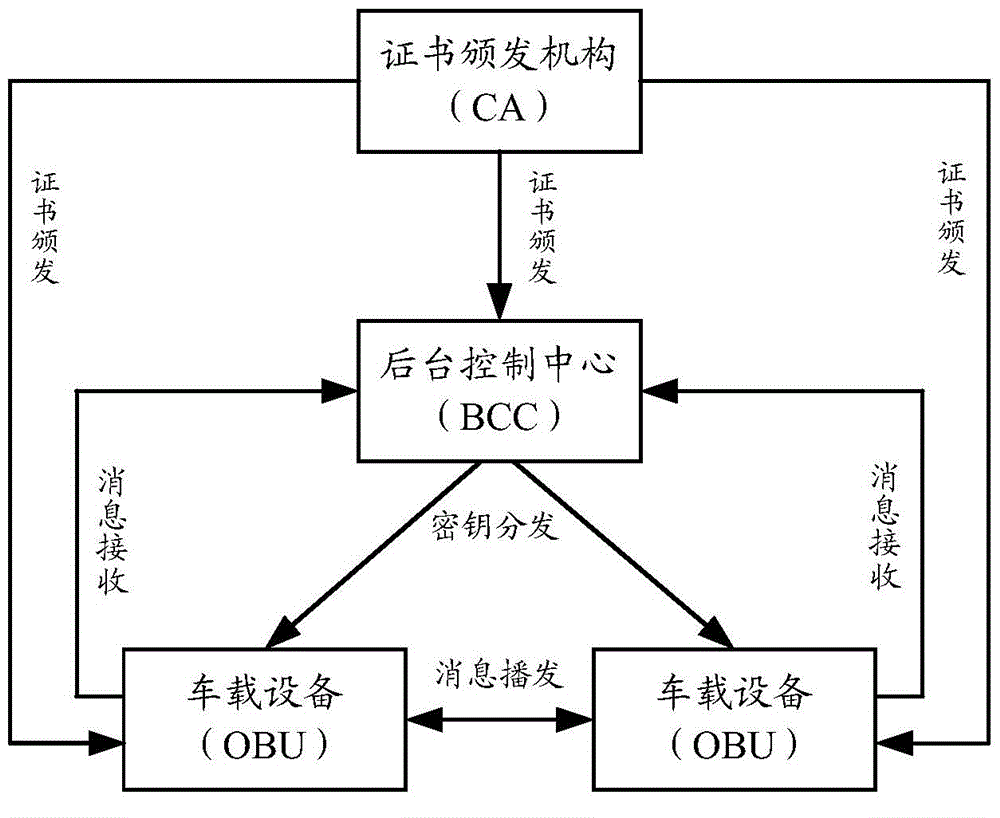
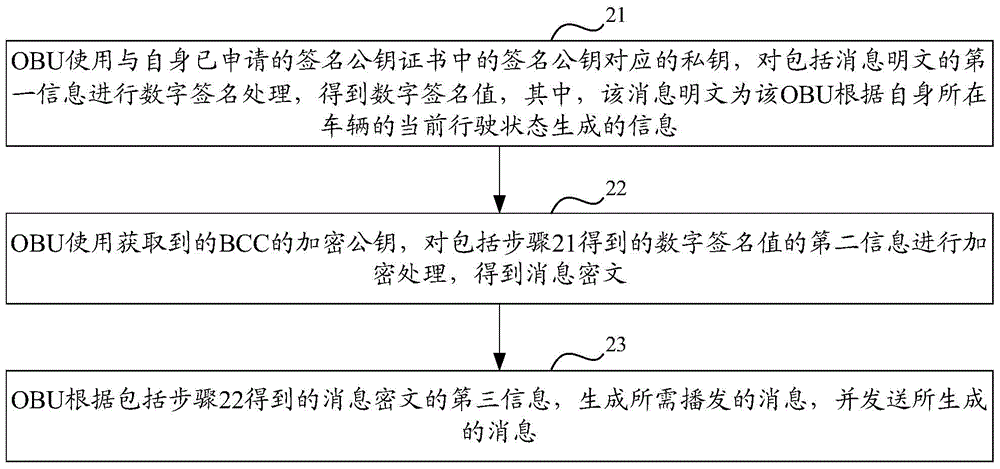
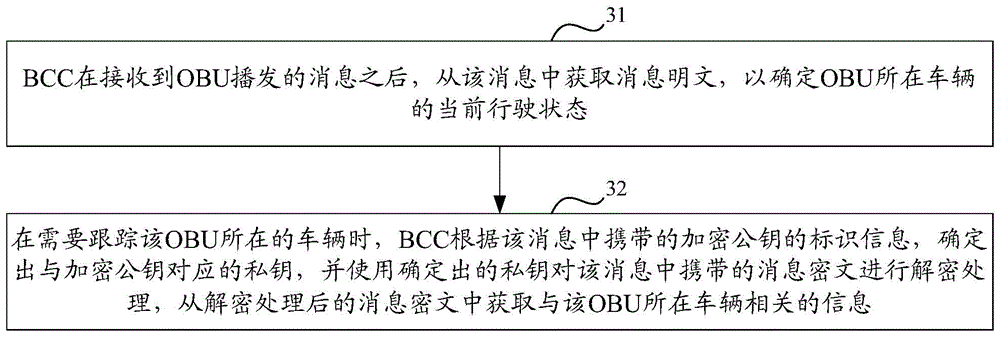
Message generation and authentication methods and equipment in Internet-of-vehicles system
The invention discloses message generation and authentication methods and equipment in an Internet-of-vehicles system. The message generation method comprises the steps as follows: an OBU (On-Board Unit) uses a private key corresponding to a signed public key in a signed public key certificate applied by the OBU to digitally sign first information including message plaintext to obtain a digital signature value; the OBU uses an acquired encrypted public key of a BCC (Background Control Center) to encrypt second information of the digital signature value to obtain a message ciphertext; and the OBU generates a message needing broadcasting according to third information including the message ciphertext, and sends the generated message. As the OBU uses the acquired encrypted public key of the BCC to encrypt the second information of the digital signature value to obtain the message ciphertext, a private key corresponding to the encrypted public key is needed to decrypt the message ciphertext. Therefore, other OBUs cannot decrypt the message ciphertext when receiving the message, and the private information of a vehicle where the message sending OBU is located is protected.
Owner:DATANG GOHIGH INTELLIGENT & CONNECTED TECH (CHONGQING) CO LTD
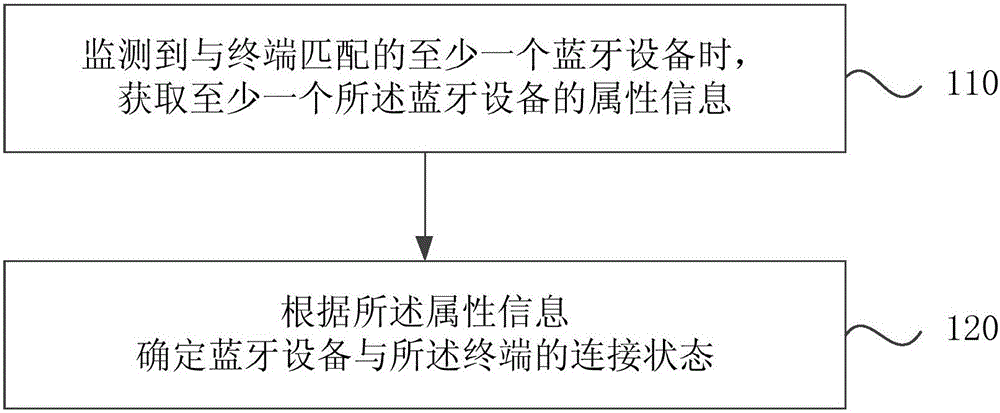
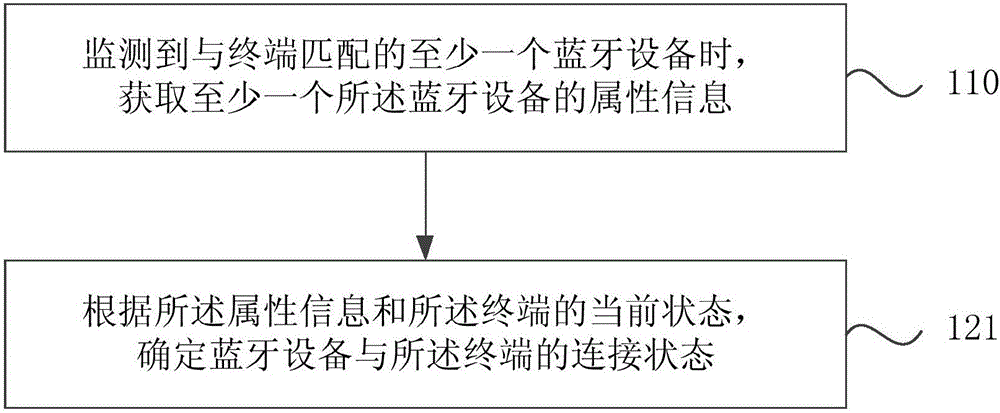
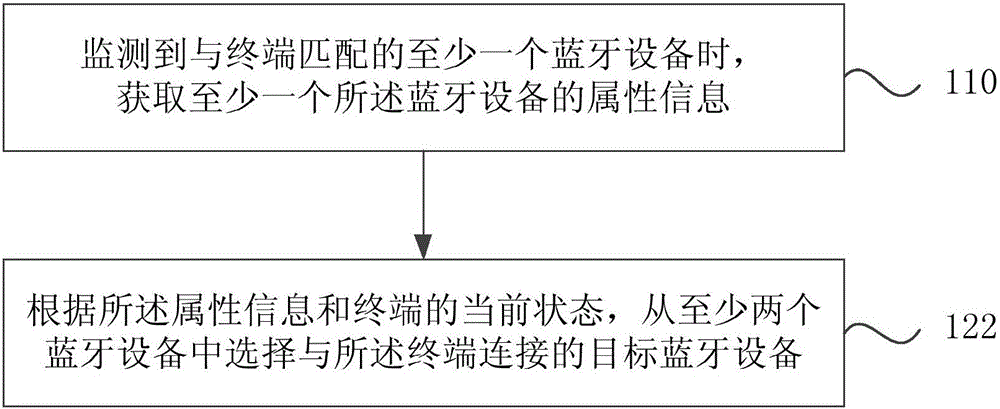
Bluetooth equipment connection method and device
InactiveCN106131971AEnsure safetyProtect private informationConnection managementPersonalizationBluetooth
The invention discloses a Bluetooth equipment connection method and device, relating to the technical field of electronic information application, wherein the Bluetooth equipment connection method comprises the following steps of: obtaining attribute information of at least one Bluetooth equipment while monitoring at least one Bluetooth equipment matched with a terminal; and determining the connection state between the Bluetooth equipment and the terminal according to the attribute information. According to the technical scheme provided in the invention, the connection state between the Bluetooth equipment and the terminal is determined through the obtained attribute information of the Bluetooth equipment in the at least one Bluetooth equipment matched with the terminal; the terminal is not directly connected with the Bluetooth equipment; therefore, the safety of the Bluetooth equipment connected with the terminal can be ensured better; simultaneously, individual requirements of users are satisfied; the existing connection scheme between the terminal and the Bluetooth equipment is optimized; and thus, the user experience is improved.
Owner:LETV HLDG BEIJING CO LTD +1
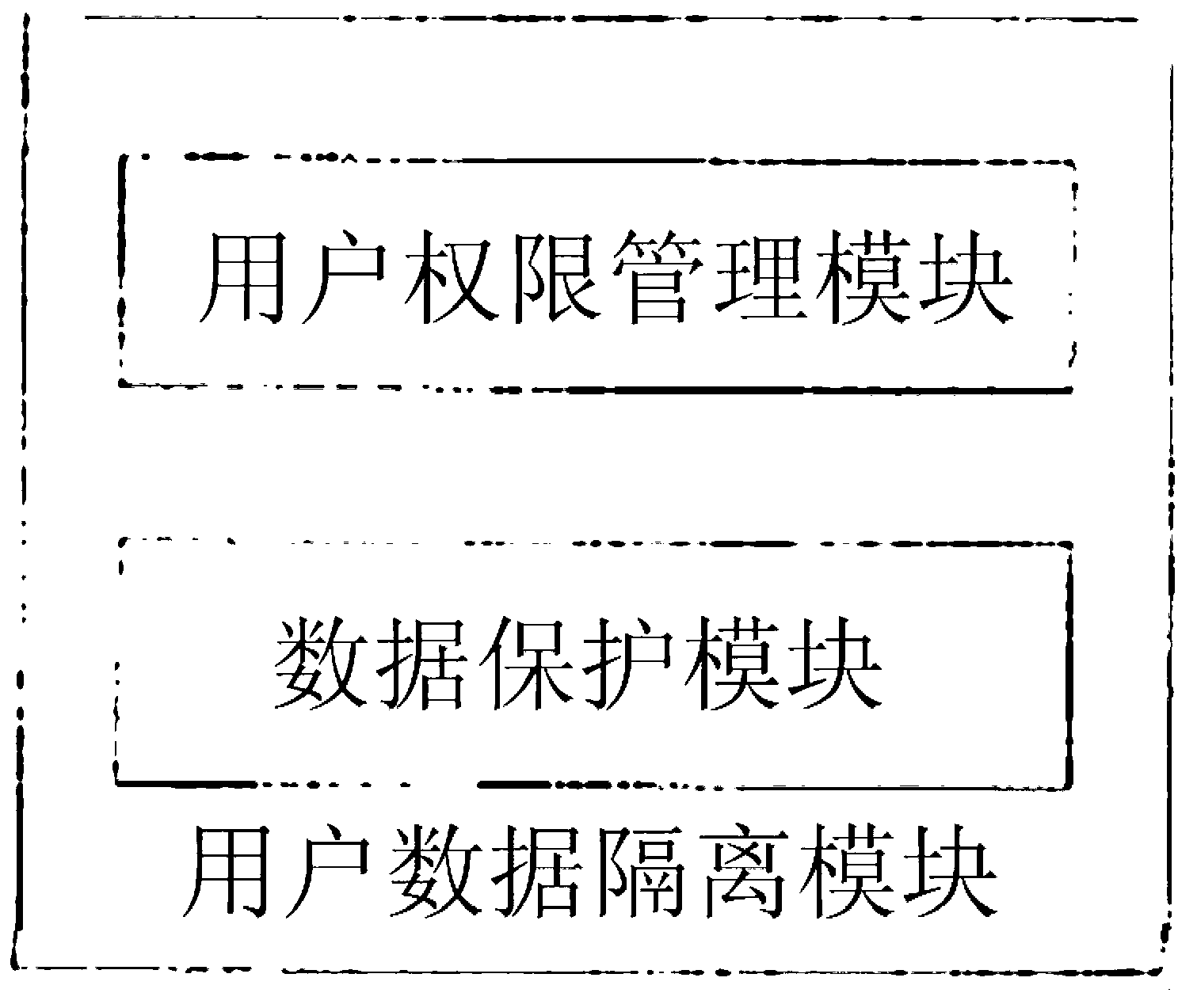
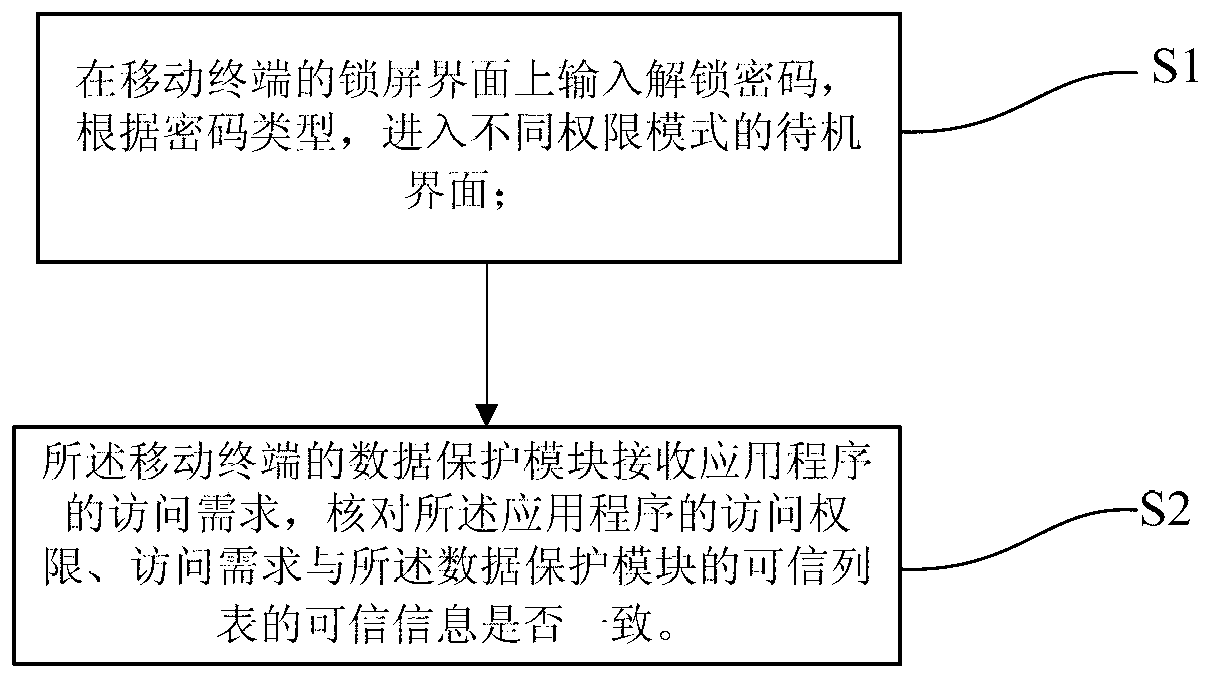
Safety system and safety protection method for mobile terminal
InactiveCN103313238APrevent disclosure or theft of personal informationProtect private informationSecurity arrangementApplication softwareTerminal system
The invention discloses a safety system for a mobile terminal. The safety system comprises a user data isolation module; the user data isolation module comprises a user authority management module and a data protection module and is used for protecting privacy data of a user; the user can enter standby interfaces corresponding to different authority passwords by the aid of the user authority management module; the data protection module is arranged between application and a database interface and is used for managing user data access authority of application programs. The invention further discloses a safety protection method for the mobile terminal. The safety system and the safety protection method have the advantages that the real data can be protected by the system for the mobile terminal, personal information of the mobile terminal is prevented from being revealed or stolen, and the privacy information of the user can be effectively protected.
Owner:TIANYI TELECOM TERMINALS
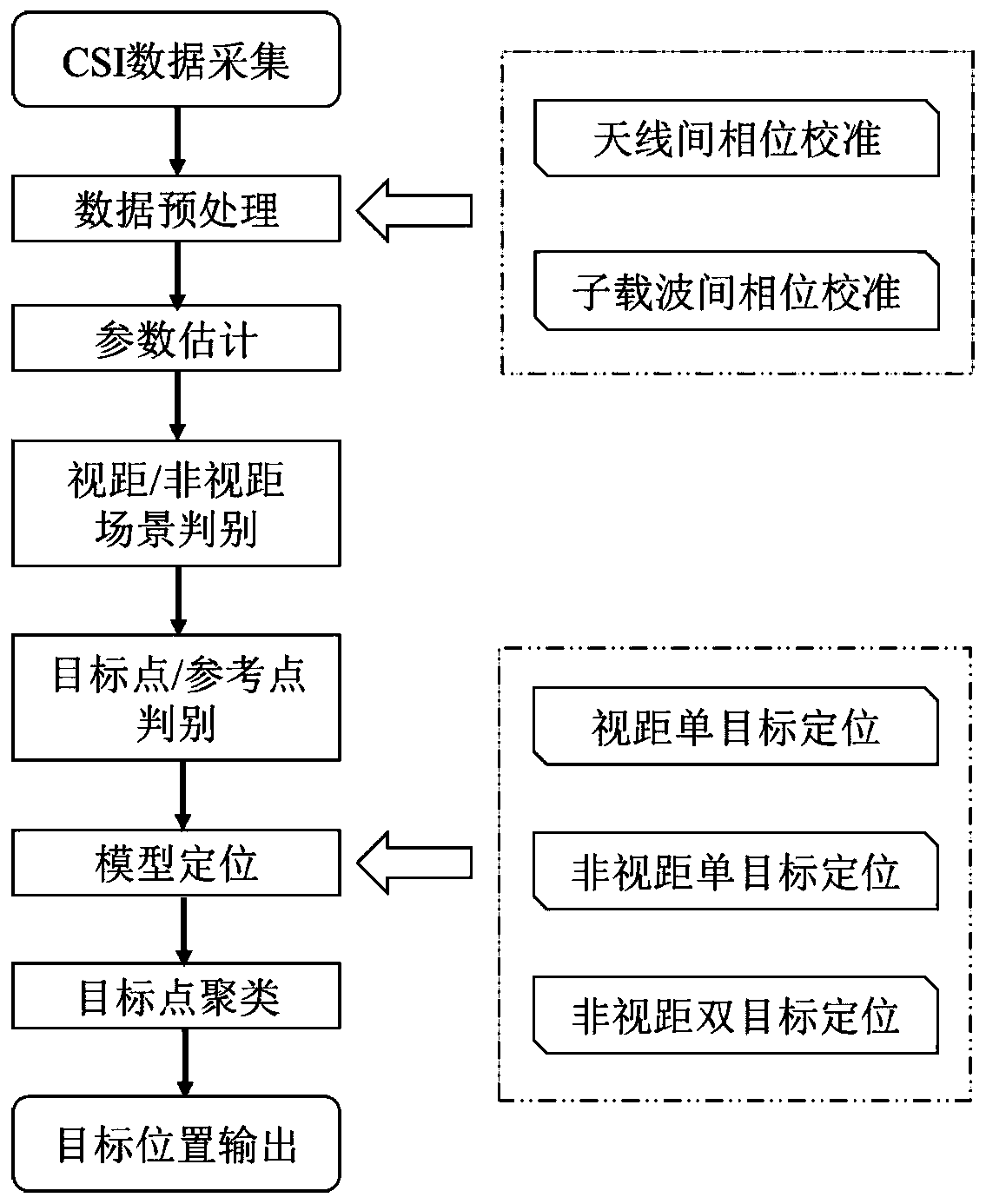
Passive indoor positioning method based on Wi-Fi
ActiveCN111521969AHigh precisionHigh positioning accuracyParticular environment based servicesPosition fixationChannel state informationCluster algorithm
The invention provides a passive indoor positioning method based on Wi-Fi. Indoor target position optimization positioning is carried out by using multipath information. The method comprises the stepsof firstly, acquiring channel state information data, and preprocessing the channel state information data; secondly, performing parameter estimation by utilizing an improved multi-signal classification algorithm to obtain parameter information such as arrival angles, signal flight time and departure angles of multiple paths; then, performing target positioning by utilizing a complementary relationship among the parameters; and finally, performing positioning correction by using a clustering algorithm to obtain a final target position. Due to the fact that the multipath information is fully utilized, the method has a better positioning effect on daily typical scenes, especially non-line-of-sight scenes.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
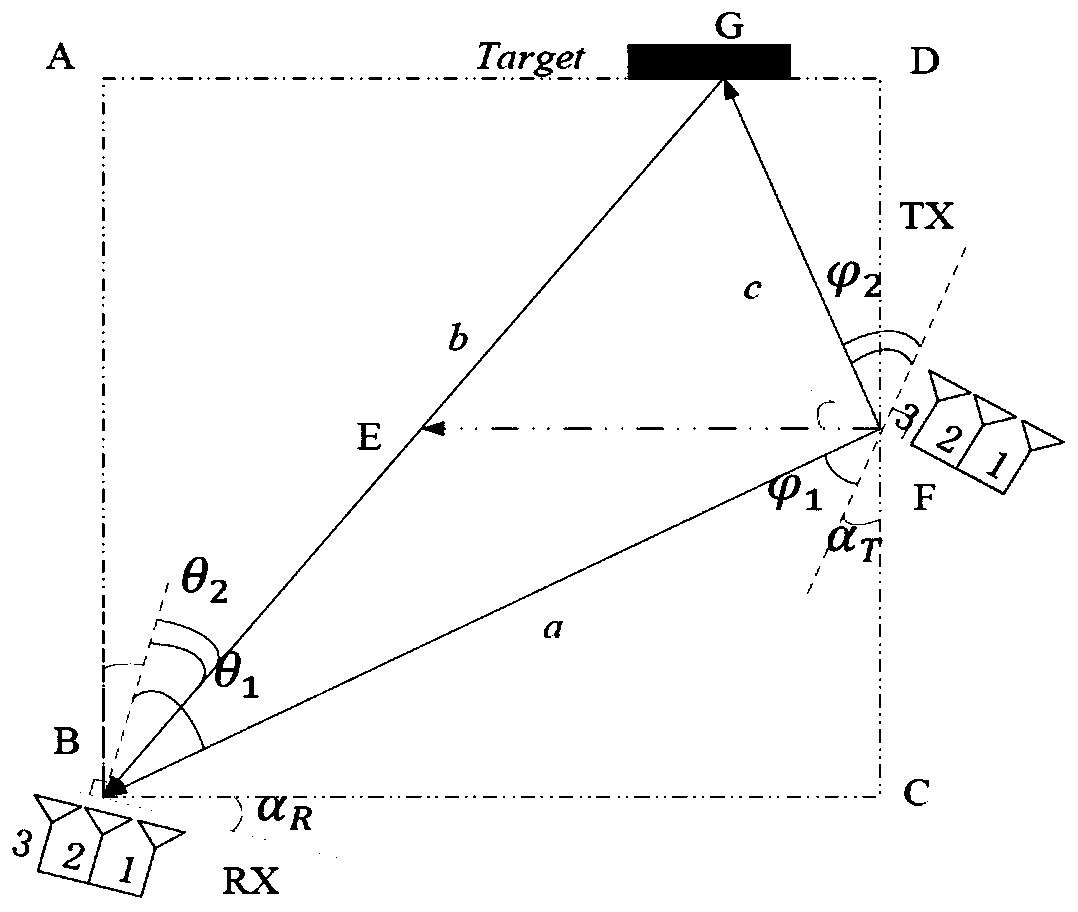
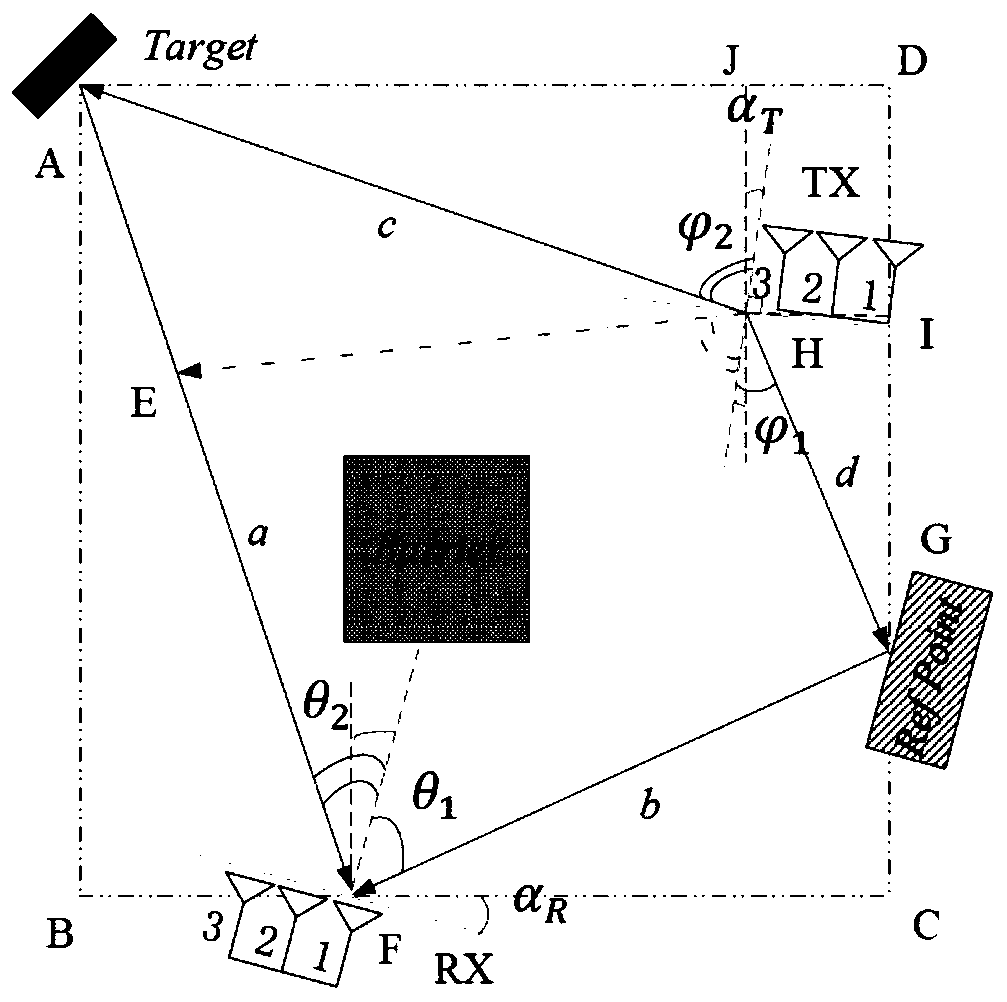
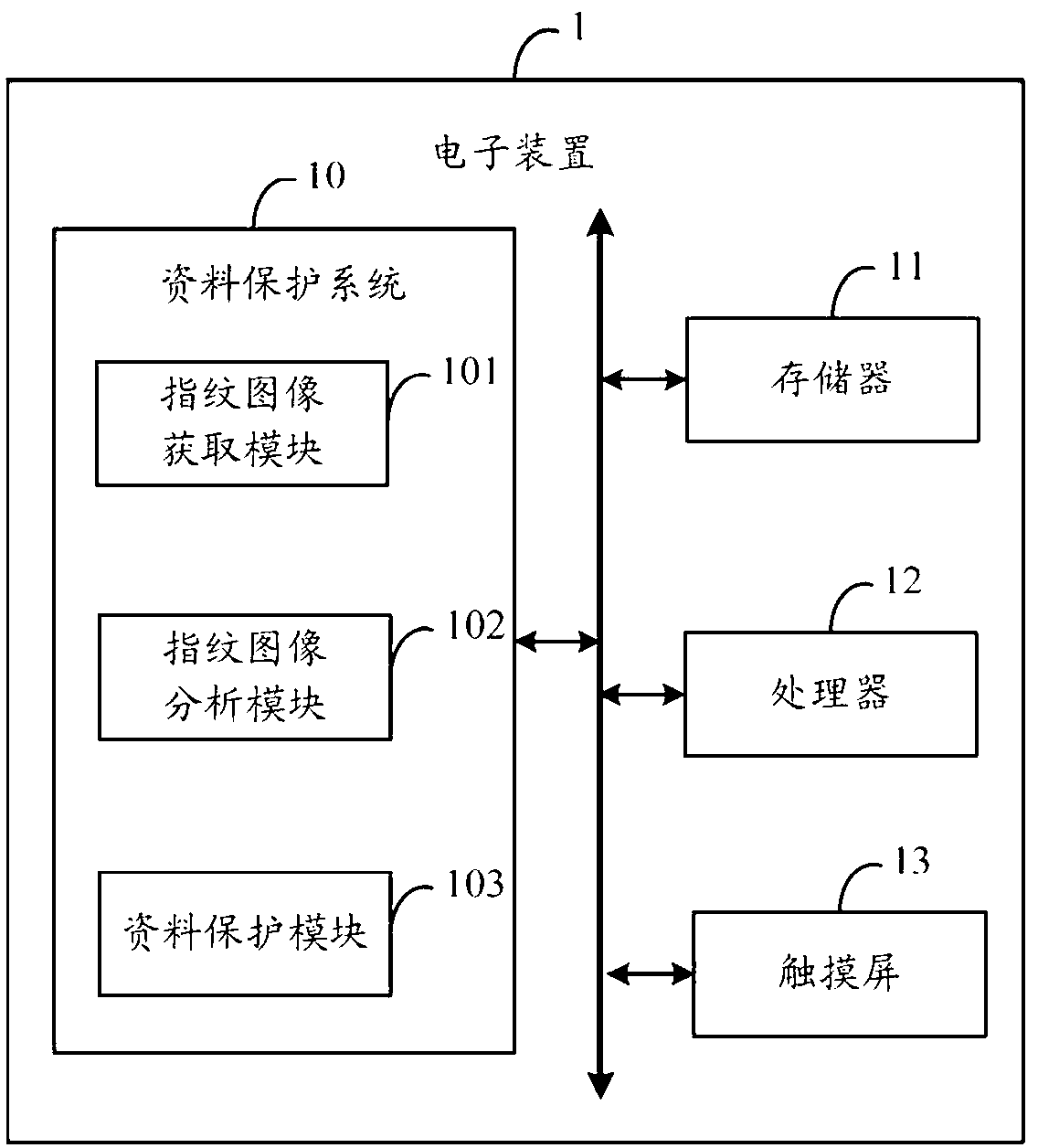
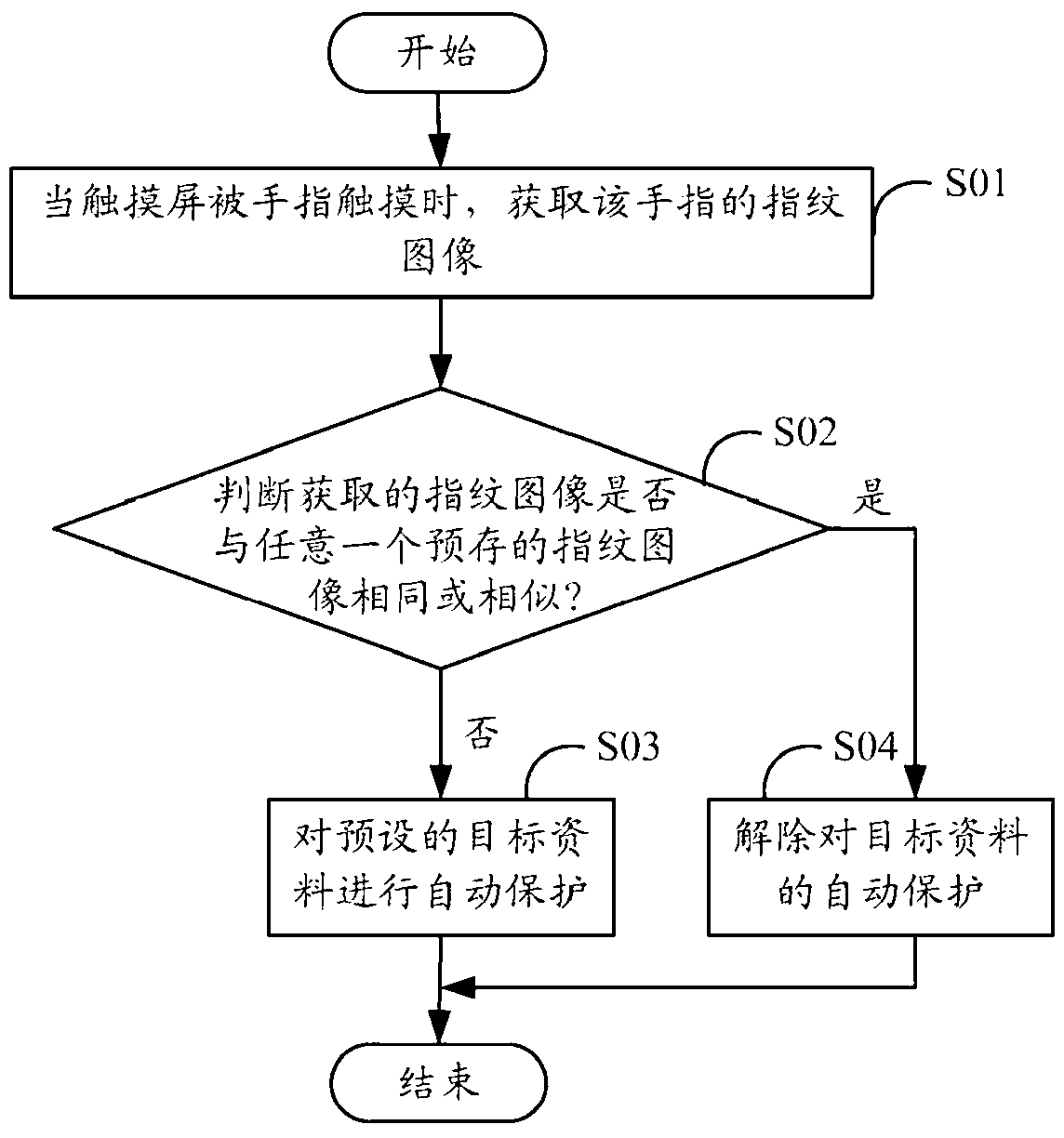
Electronic device as well as fingerprint identification-based data protection system and method thereof
InactiveCN103294963AProtect private informationDigital data protectionDigital data authenticationComputer hardwareCapacitance
Owner:FU TAI HUA IND SHENZHEN +1
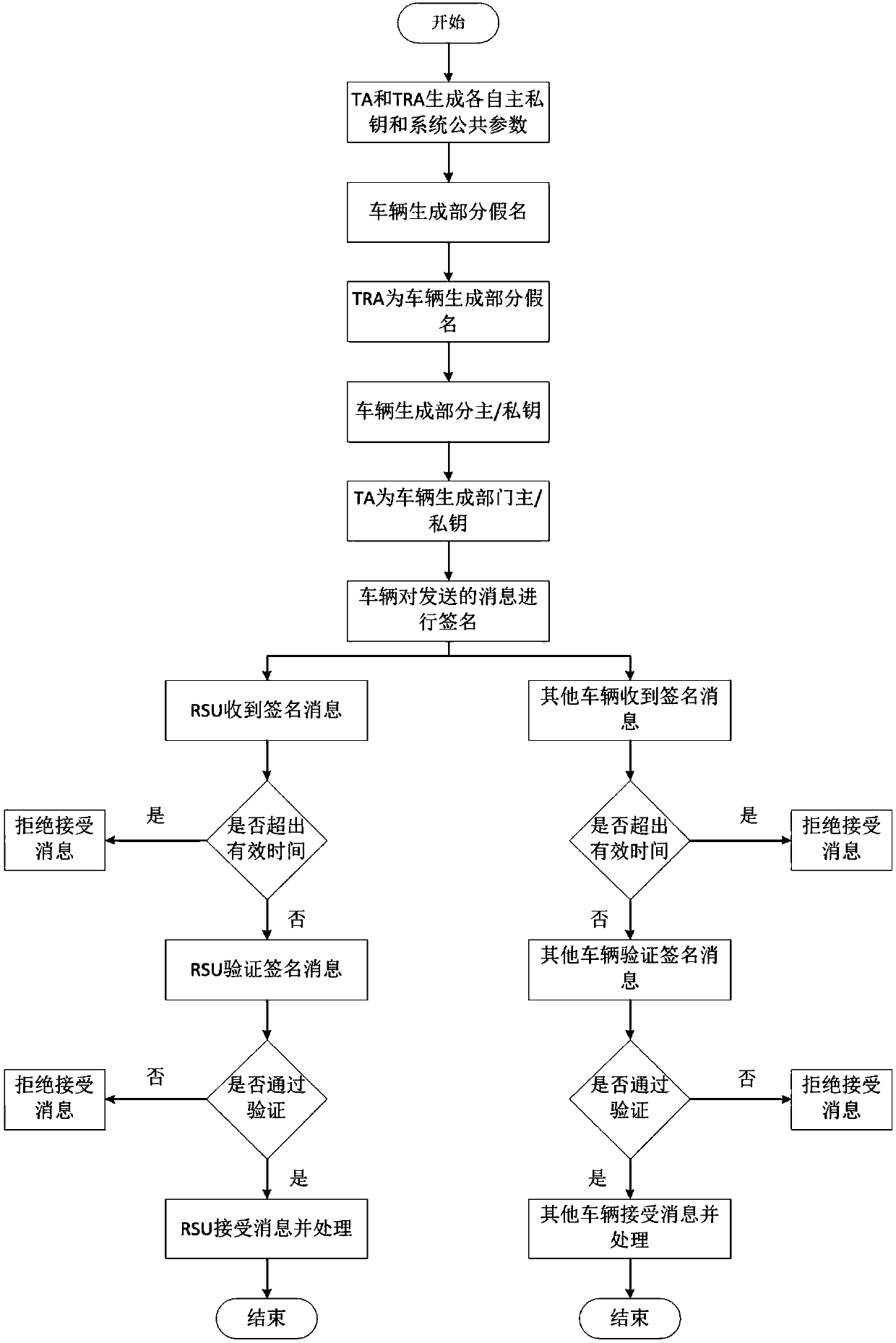
Non-bilinear mapping certificateless signature-based vehicle self-assembly network authentication method
ActiveCN107947932APrivacy protectionProtect private informationKey distribution for secure communicationPublic key for secure communicationUser privacyMessage passing
The invention relates to a non-bilinear mapping certificateless signature-based vehicle self-assembly network authentication method, belonging to the field of data security. The method is based on a scheme of protecting privacy of a user and improving the efficiency of message signature authentication, and can protect privacy information of the user in a message passing authentication process; ifthe transmitted message is illegal, a TRA(tracing authority) uses a tracking secret key to track the real identity of a vehicle; in a process of message verification, bilinear mapping is not used, andmessage batch transmission and batch authentication are also supported, so that the method is suitable for rapid transmission and authentication operations of the message in a vehicle networking environment with higher mobility. The method provided by the invention can protect the privacy information of the user in the message passing authentication process; furthermore, if the transmitted message is illegal, the tracking authoritative center TRA can track the real identity of the vehicle by means of the private key; in the process of message verification, the mechanism does not use the bilinear mapping and also supports the message batch transmission and batch authentication, so that the method is suitable for rapid transmission and authentication of the message in the vehicle networkingenvironment with higher mobility.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Method and terminal device for protecting privacy information
ActiveCN106687969AImprove protectionAvoid presentingDigital data authenticationSubstation equipmentInternet privacyTerminal equipment
Owner:HUAWEI TECH CO LTD
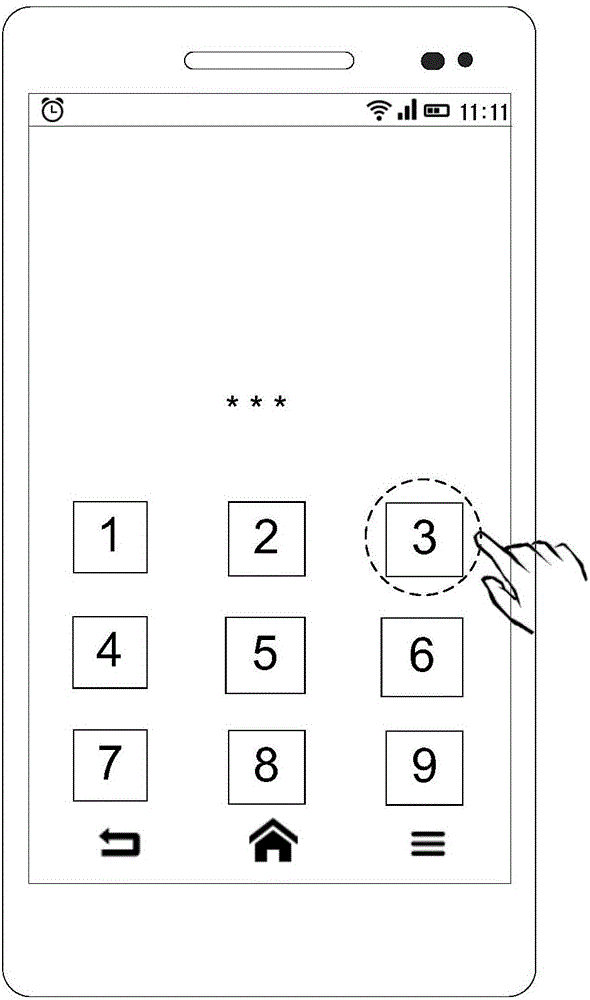
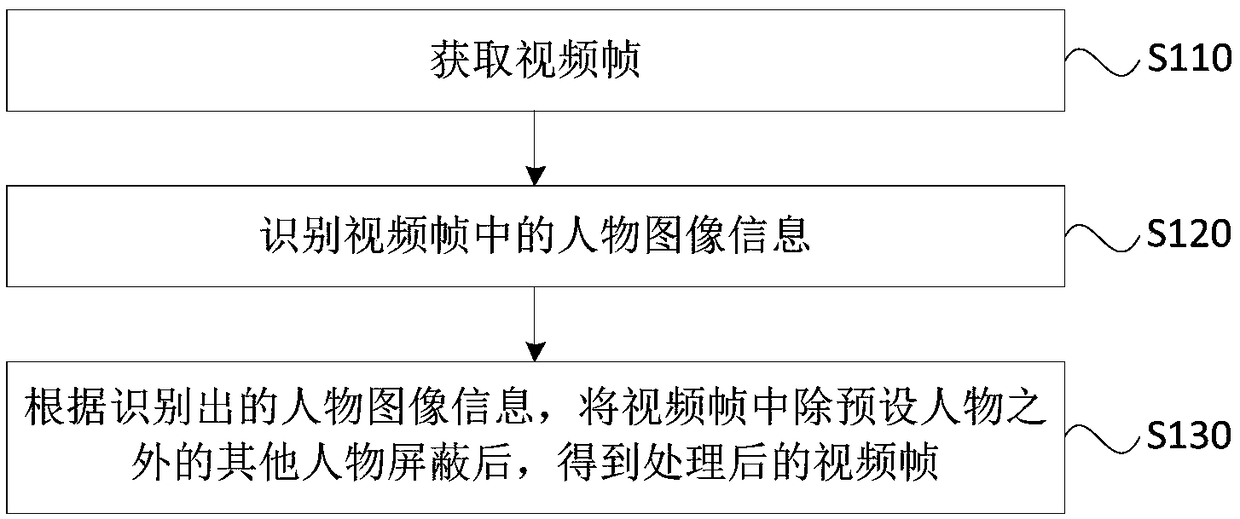
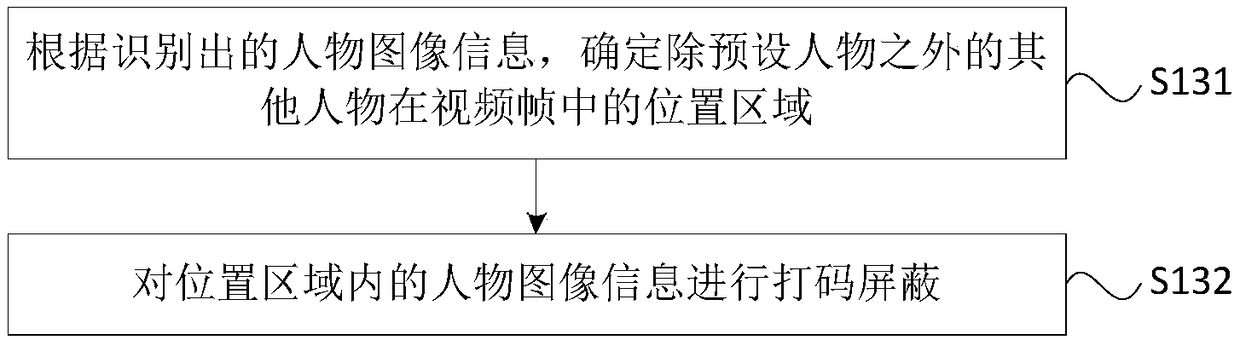
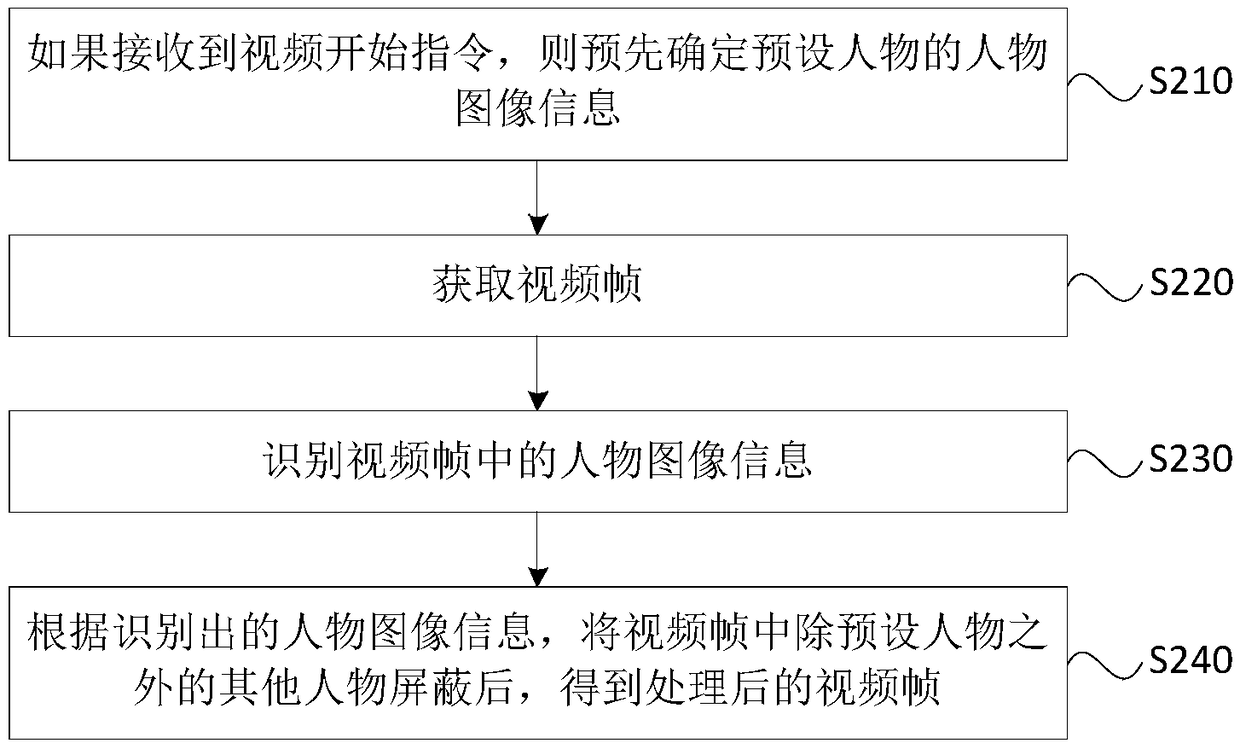
Video processing method and apparatus, terminal and storage medium
InactiveCN108848334AProtect private informationReduce the risk of privacy breachesTwo-way working systemsSelective content distributionComputer graphics (images)Video processing
The embodiment of the invention discloses a video processing method and apparatus, a terminal and a storage medium. The method comprises the following steps: obtaining a video frame; identifying character image information in the video frame; and shielding other characters excluding a preset character in the video frame according to the identified character image information to obtain a processedvideo frame. By adoption of the technical scheme provided by the embodiment of the invention, by shielding the other characters excluding the preset character in the video frames in a video process, the information of the other characters who do not participate in a video in the surrounding environment of the video is shielded, thereby protecting the privacy information of the other characters, reducing the risks of accidental privacy leakage and improving the privacy security.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
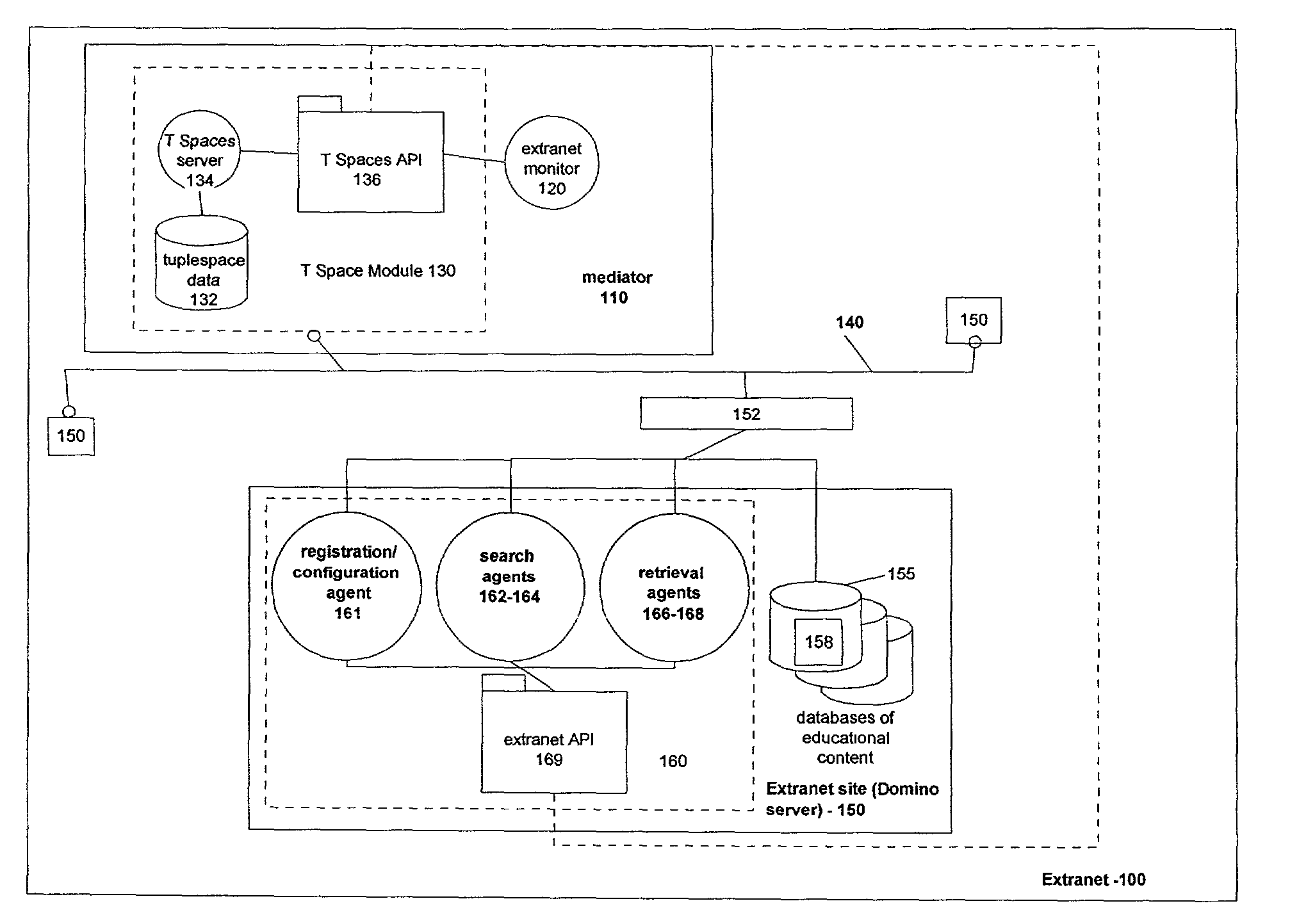
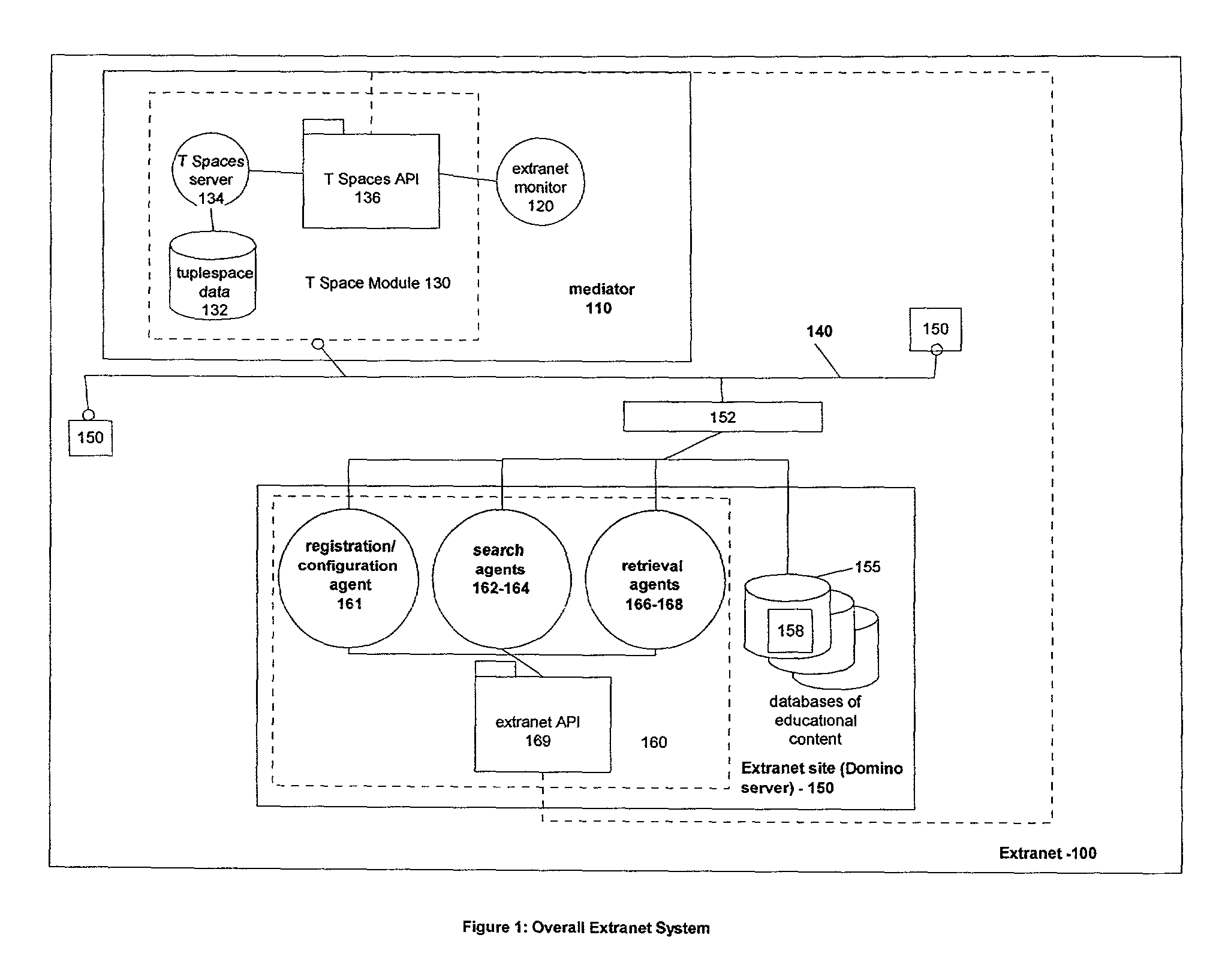
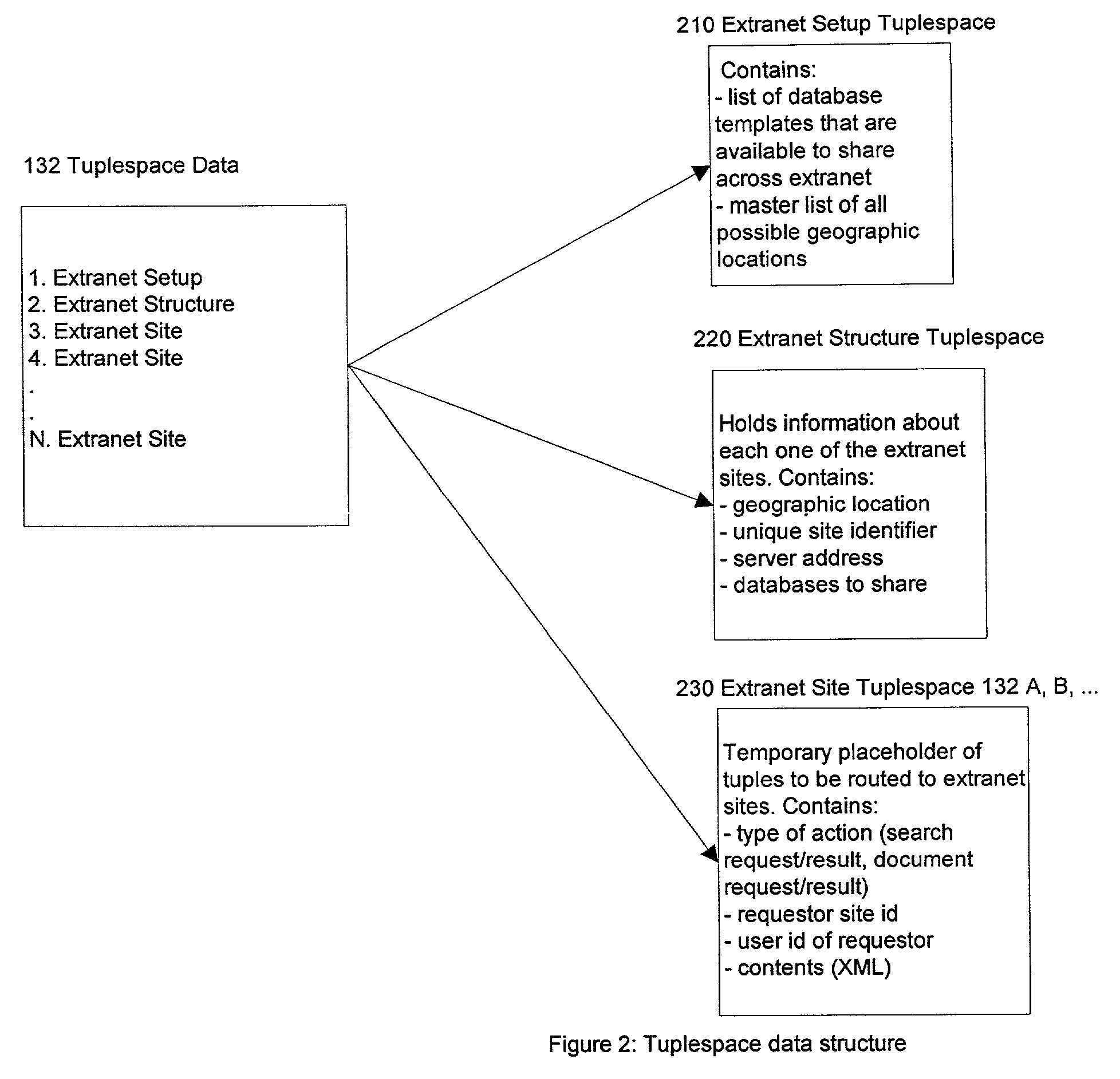
System and method for sharing, searching, and retrieving web-based educational resources
InactiveUS7188150B2Protect private informationData processing applicationsWeb data retrievalShared resourceExtranet
A system and method that enables sharing of resources and materials on a worldwide basis is disclosed. This system and method creates a secure extranet, with member sites communicating through a shared mediator service. The extranet protects private information at each site, yet allows searching and sharing of resources by authorized users of any extranet site. A preferred embodiment is an extranet of Lotus Notes / Domino servers, where information can be shared via the extranet without requiring cross-certification or replication among the servers.
Owner:IBM CORP
Multi-user management method of electronic equipment
InactiveCN102833383AProtect private informationProtect Confidential InformationSubstation equipmentEngineeringMobile phone
The invention discloses a multi-user management method of electronic equipment. The multi-user management method comprises the following steps of: Step 1, creating management, and Step 2, executing an operation, wherein the Step 1 comprises the following steps of: Step 111, creating permission groups of application programs or files; Step 112, setting functional items comprised by the permission groups; and Step 113, setting authentication information corresponding to the permission groups, wherein the authentication information is a code generated by computation according to characters input by a user or a code generated by conversion according to the operation of a user. The multi-user management method of the electronic equipment disclosed by the invention can carry out authentication and permission management in a way of inputting the characters by the user or in a way of operating by the user, so that other users rather than an owner of a mobile phone can use the mobile phone normally but cannot perceive private information that is protected, in this way, the private information of the owner is protected without being perceived.
Owner:HUAQIN TECH CO LTD
Multi-source encrypted image retrieval method supporting privacy protection
ActiveCN108256031AReduce overheadSolve the problem of image privacy protectionTransmissionSpecial data processing applicationsPrivacy protectionImaging Feature
The invention provides a multi-source encrypted image retrieval method supporting privacy protection, and belongs to the technical field of encrypted image retrieval. The method comprises the steps that thought encryption image features of secure multiparty computation is used, an image owner makes images, encrypted with a private key, of the owner and the image features outsourced to a cloud server, and the cloud server performs retrieval in an encrypted image library submitted by a user and returns the encrypted retrieval result to a query user. Accordingly, the image privacy protection problem occurring when multiple image owners outsource the images to a cloud for retrieval can be solved, the image owner and the user do not need a communication secret key, the communication cost is reduced, and the actual application prospect is better met; meanwhile, a new image similarity measurement method is provided, by means of the measurement method, the phenomenon that in the retrieval process, similarity information between the images stored in the cloud server is revealed to the cloud server can be prevented, and the private information of the images on the cloud server is further protected.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Method and platform for demonstrating multi-dimensional multi-industry information of two-dimensional codes
ActiveCN108229195AExpand the scope of application scenariosImplement security managementDigital data protectionSensing by electromagnetic radiationMulti dimensionalWorld Wide Web
Owner:高江涛
Method for Replacing Traditional Payment and Identity Management Systems and Components to Provide Additional Security and a System Implementing Said Method
ActiveUS20170132613A1Reduce in quantityProtect private informationDigital data protectionPayment architectureComputer hardwarePayment
An electronic wallet system that protects payment accounts, identification and other personal information found within a typical wallet with a secure electronic vault (first) device that can be part of a physical wallet, insert to a wallet, or in other embodiments, wearable / portable devices. A unique biometrically enabled multi-factor authentication process ensures only owners of the information can copy the information to the device or retrieve it thereafter. Authenticated users may then select payment, identification, medical or virtually any private information via touch display or voice command on the vault or on another (second) device that operates in conjunction with the vault. The second device comprises, for example, a programmable card with dynamic magnetic stripe, cell phone, or other wearable technology, that initiates and processes a payment and / or transfer of private information.
Owner:GARMIN INT
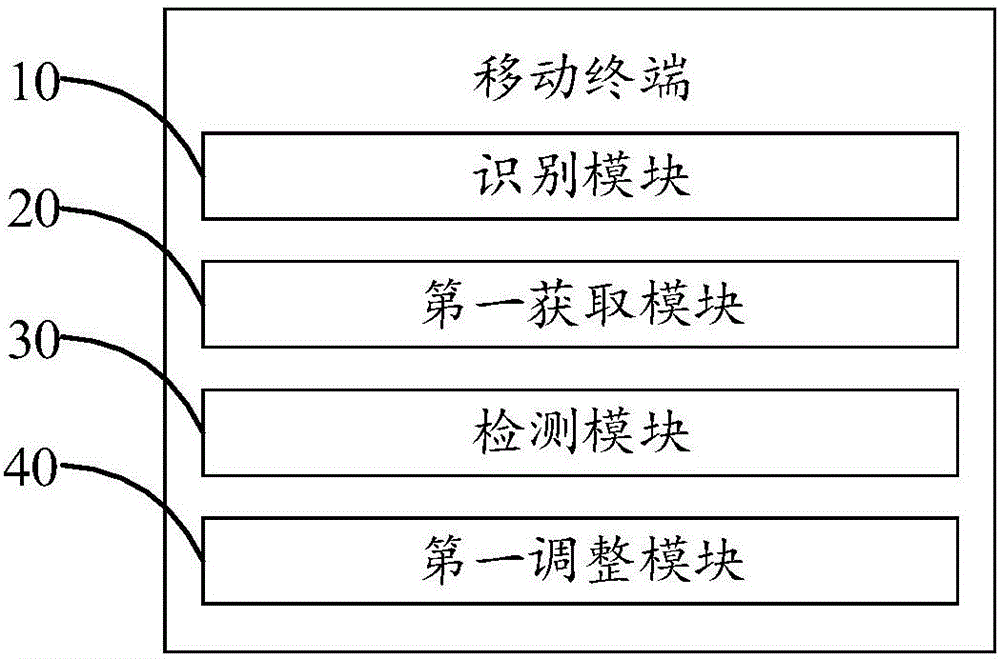
Privacy information protection method and mobile terminal
InactiveCN106550134AProtect private informationImprove experienceSubstation equipmentBrightness perceptionComputer engineering
The invention discloses a mobile terminal which comprises an identification module for identifying currently displayed content information of the mobile terminal to determine whether the content information meets a first preset condition, a first acquisition module for acquiring position information of the mobile terminal when the content information meets the first preset condition, a detection module for detecting the degree of noise in an environment to which the mobile terminal belongs when the position information meets a second preset condition, and a first adjustment module for adjusting the brightness of a display screen of the mobile terminal to preset brightness and / or adjusting the visual angle of the display screen to a preset visual angle when the degree of noise is greater than a preset threshold value. The invention further discloses a privacy information protection method. The mobile terminal and the privacy information protection method realize adjustment of the brightness and / or the visual angle of the display screen according to the content information displayed on the display screen of the mobile terminal, namely the environment to which the mobile terminal belongs, so that privacy information of the user is protected.
Owner:NUBIA TECHNOLOGY CO LTD
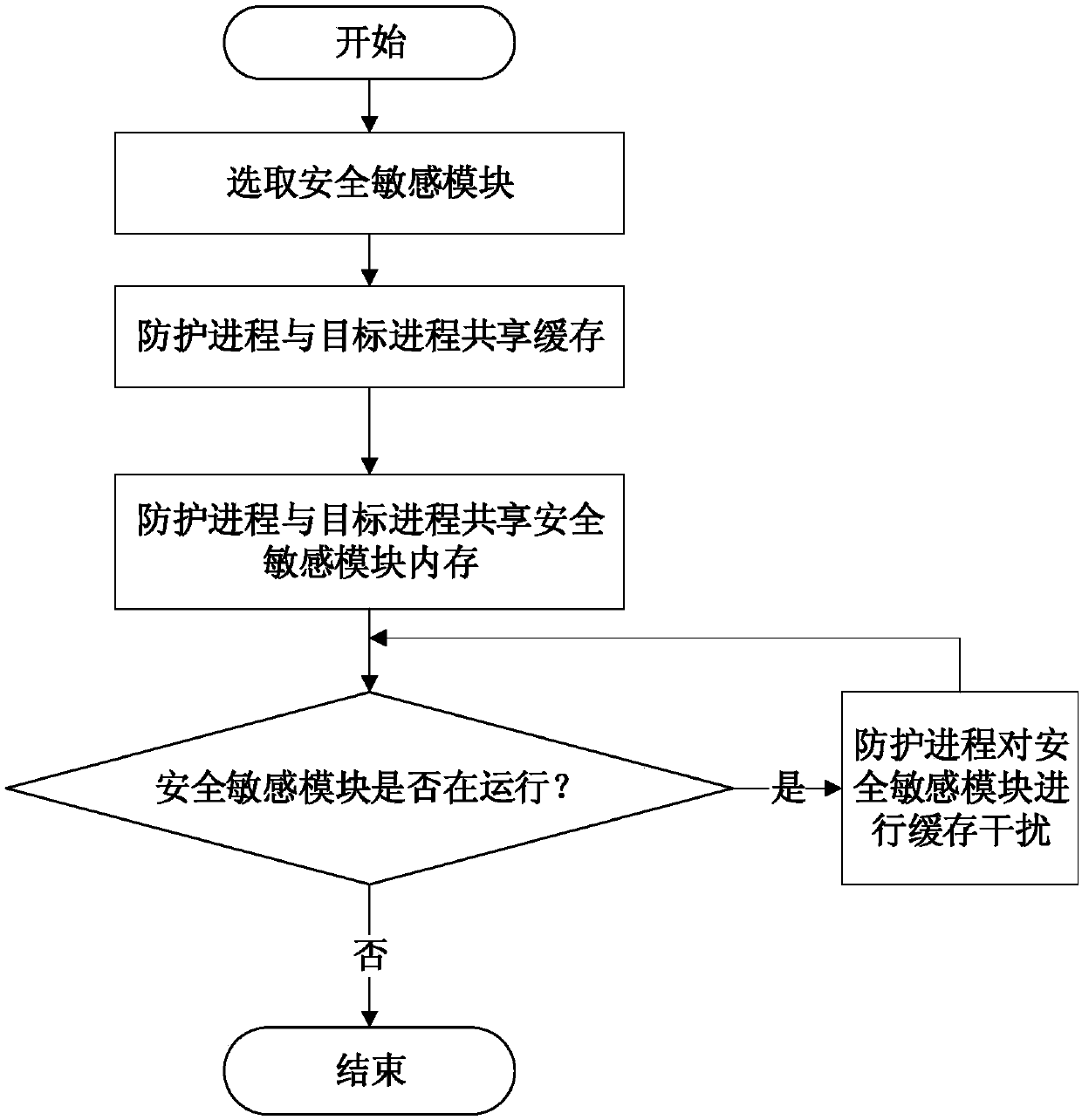
Flush-Reload cache side channel attack defense method and device in cloud environment
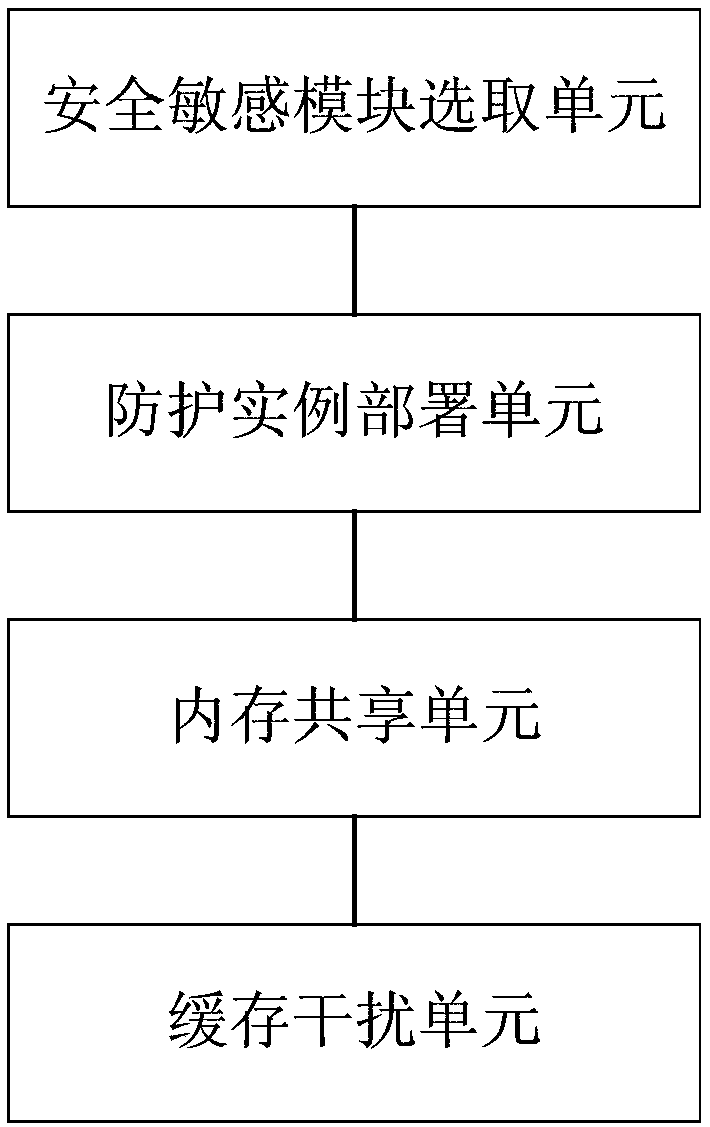
ActiveCN107622199AProtect private informationReduce aggressionInterprogram communicationPlatform integrity maintainanceUser privacyComputer module
The invention relates to a Flush-Reload cache side channel attack defense method and device in a cloud environment. The method comprises the following steps: 1) selecting a safety-sensitive module tobe protected; 2) sharing CPU (Central Processing Unit) caches between a protection process and a target process; 3) sharing the memory of the safety-sensitive module between the protection process andthe target process; and 4) when the target process runs the safety-sensitive module, obfuscating the shared memory of the safety-sensitive module according to a certain strategy by the protection process to interfere a caching state in order to defend Flush-Reload cache side channel attacks. Through adoption of the Flush-Reload cache side channel attack defense method and device, noise is continuously introduced into a high-speed cache channel utilized by Flush-Reload attacks in order to interfere an attack instance, so that user privacy information can be protected effectively.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Vertical federated learning defense method based on auto-encoder
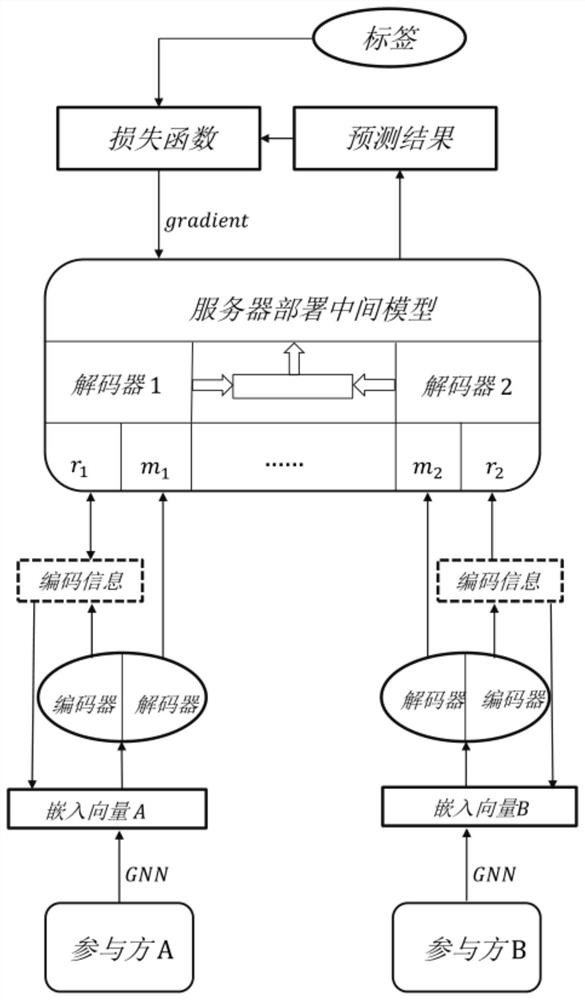
PendingCN112464290AProtect private informationProtect privacy and securityImage codingDigital data protectionAlgorithmEdge model
The invention discloses a vertical federated learning defense method based on an auto-encoder. The method comprises the steps that (1) a terminal trains an edge model through local data, and aggregates the embedding features of adjacent nodes of each layer in the edge model in a training process; (2) the terminal constructs and trains an auto-encoder comprising an encoder and a decoder to obtain encoder parameters and decoder parameters, and encodes the embedded features by using the encoder to obtain encoding information; (3) the terminal uploads the decoder parameters to the server, and after the server constructs a decoding model according to the decoder parameters and carries out message verification with the terminal, the terminal uploads coded information to the server; and (4) the server decodes the received coded information by using the decoding model to obtain decoded information, aggregates all decoded information to obtain embedded information, trains the global model by using the embedded information, and feeds back gradient information to each terminal after training. The malicious participant can be effectively prevented from stealing the private data.
Owner:ZHEJIANG UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com