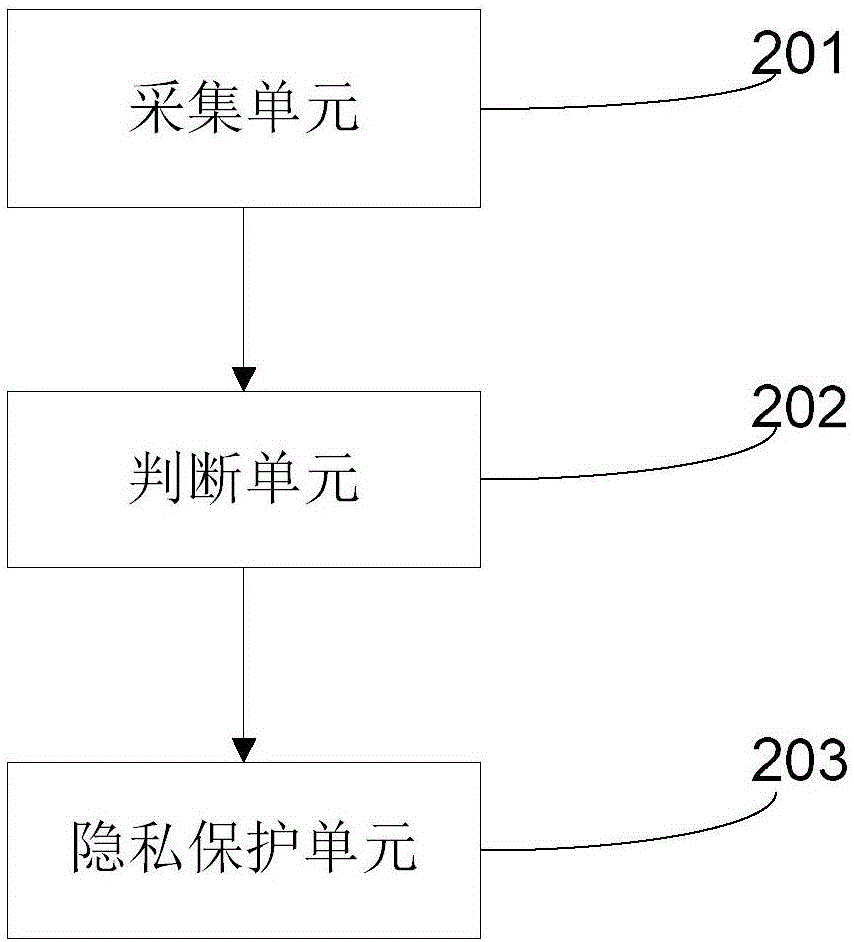
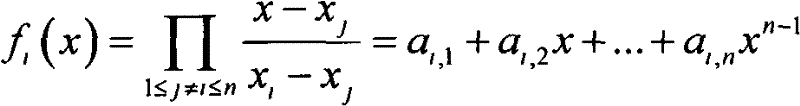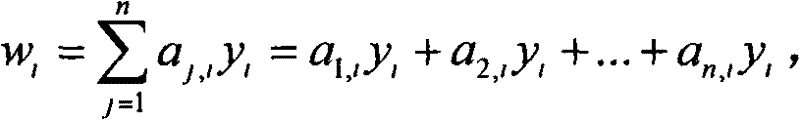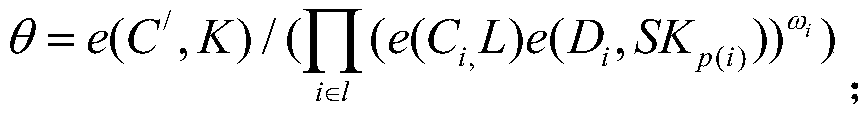Patents
Literature
63results about How to "Solve the problem of privacy protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
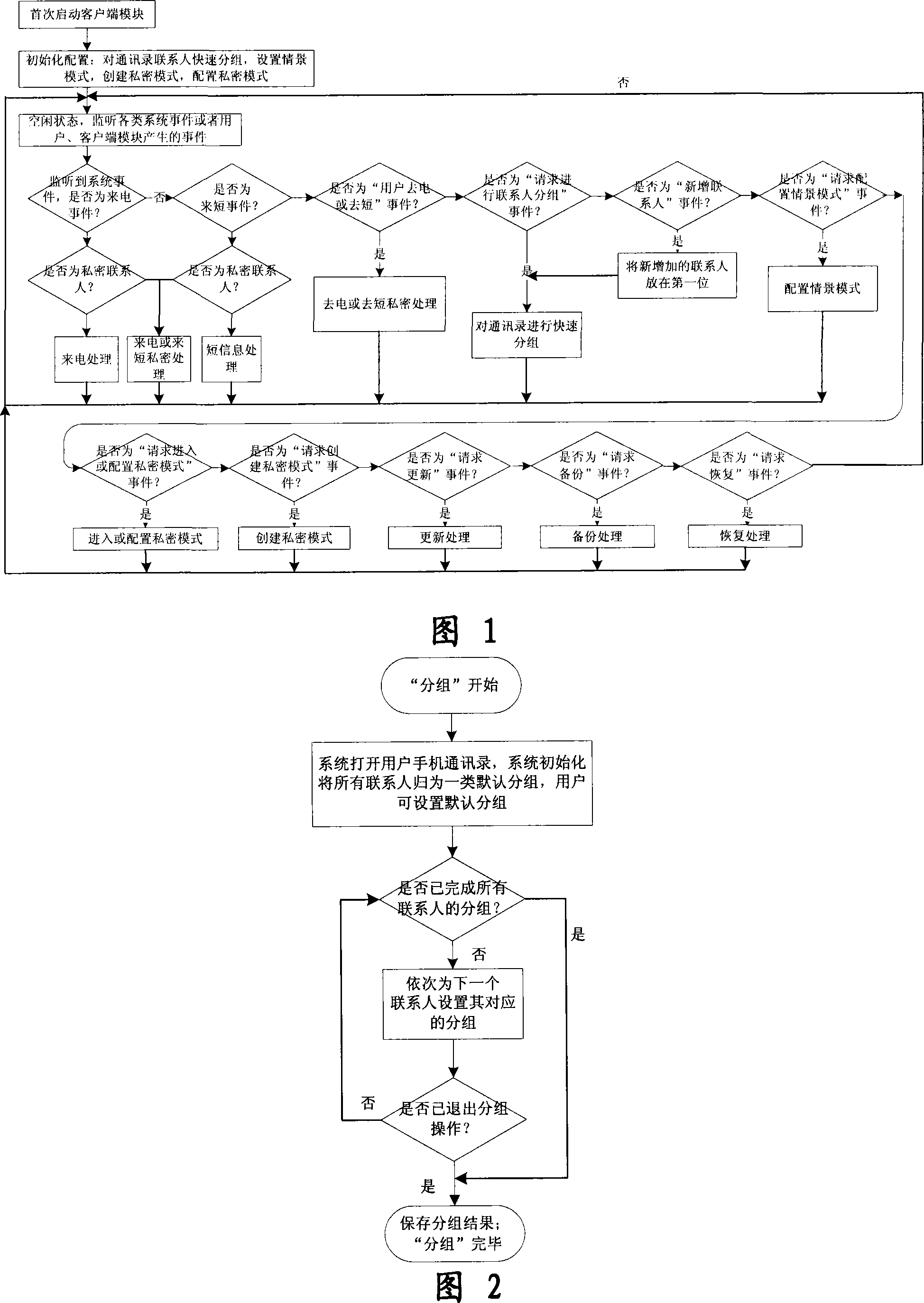
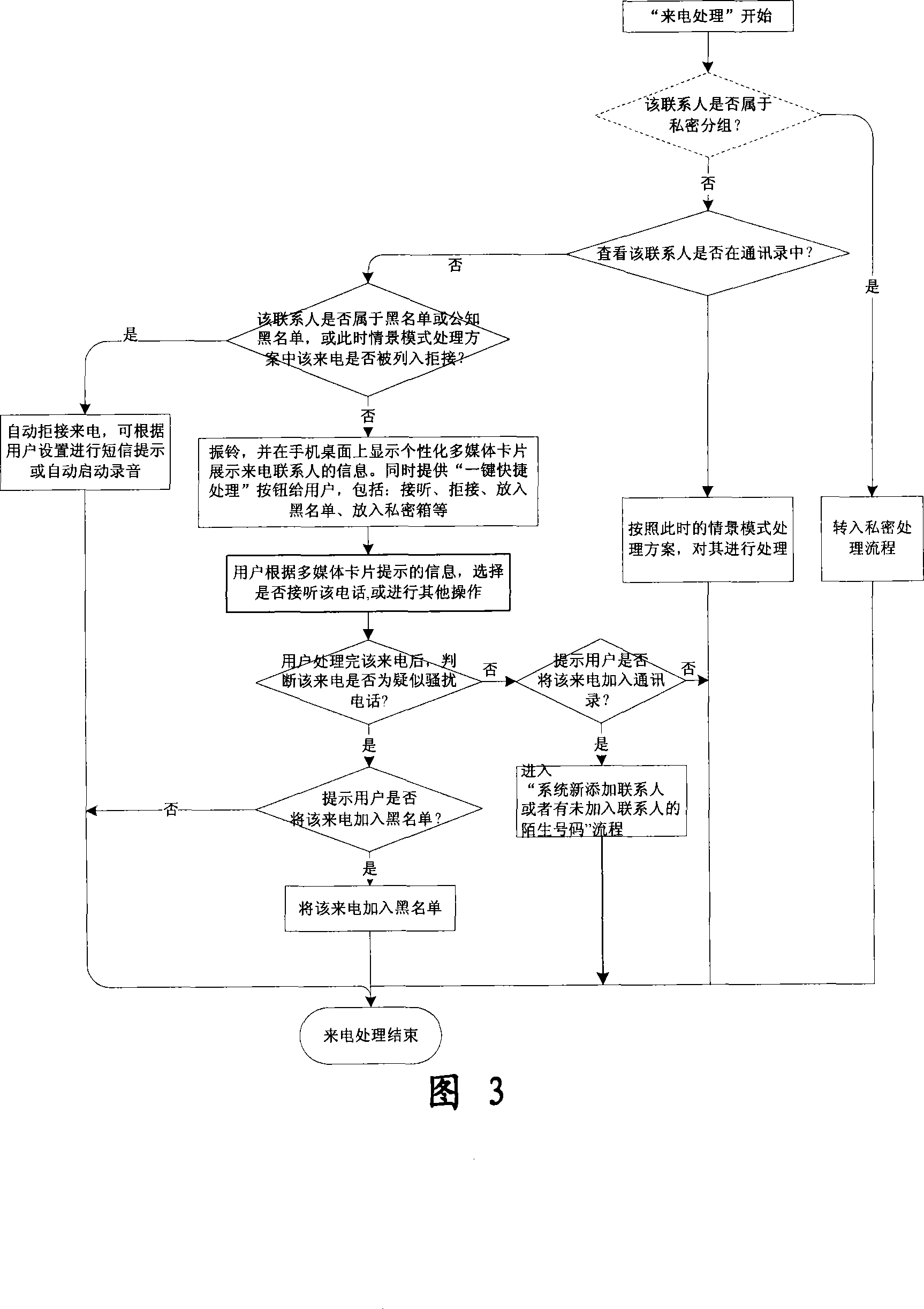
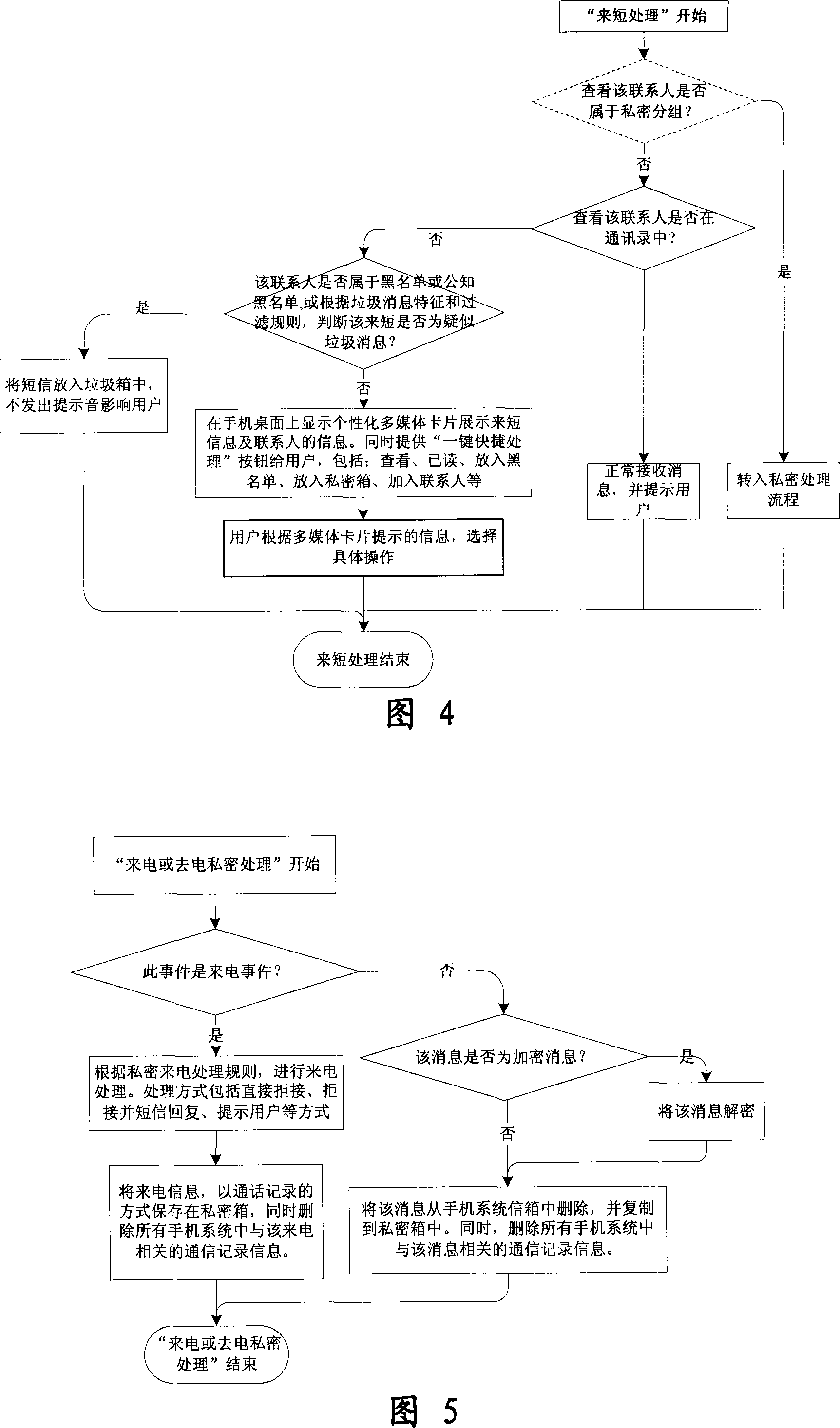
Mobile phone telephone and message anti-disturbance and private communication method and system
InactiveCN101184264AImprove filtering effectOptimize the effect of anti-harassmentRadio/inductive link selection arrangementsSubstation equipmentPrivate communicationSocial statistics
The invention relates to a processing method and the system of anti-harassment of mobile phone calls and messages and private communication, which is as follow: when grouping the contacts in the mobile phone address list according to different classes, a private group of private communicating contacts is added, and different scene modes of the user are set; when receiving a mobile phone call or a message (text message, multimedia message), depending on the grouping sort of the contact of the incoming call or the message or the multimedia message, and the current scene of the user, together with the behavior characteristics of the harassing call and the spam message with the database information of the public harassing message issued by the authoritative institution or obtained from social statistics, the corresponding process to the call, the message and the multimedia message of the mobile phone is executed to reduce harassment; meanwhile the communication records of incoming, dialed calls and message, multimedia message with the contacts in the private grouping are encrypted and preserved to protect the personal privacy of the user. The invention has the advantages of adopting the operating steps of uniform process, and resolving synthetically the harassment of calls, messages and multimedia messages for the mobile phone and the private protection.
Owner:BEIJING NETQIN TECH
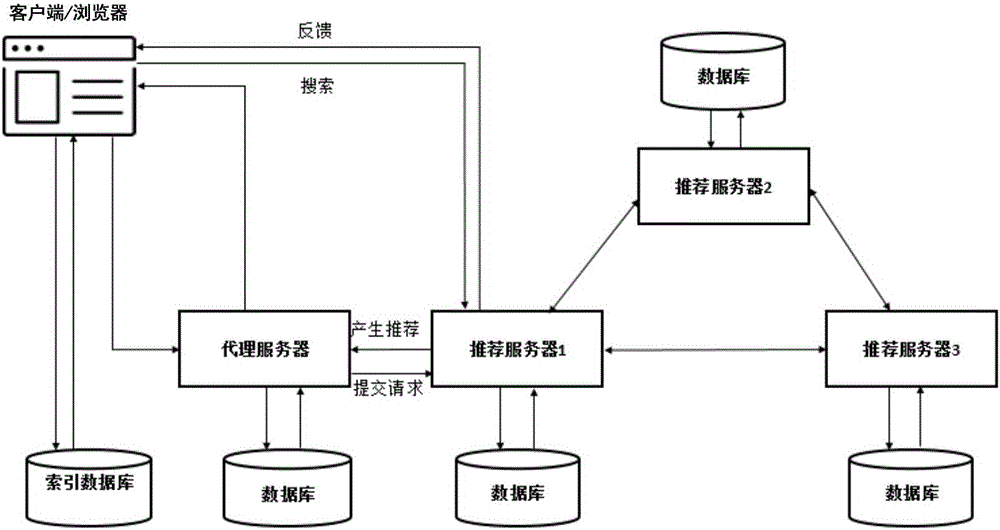
Recommendation system with hierarchical privacy protection function and operation method on basis of recommendation system
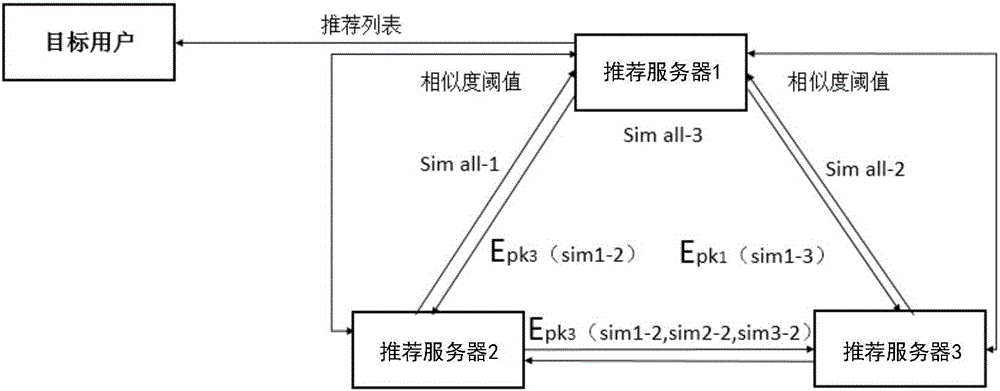
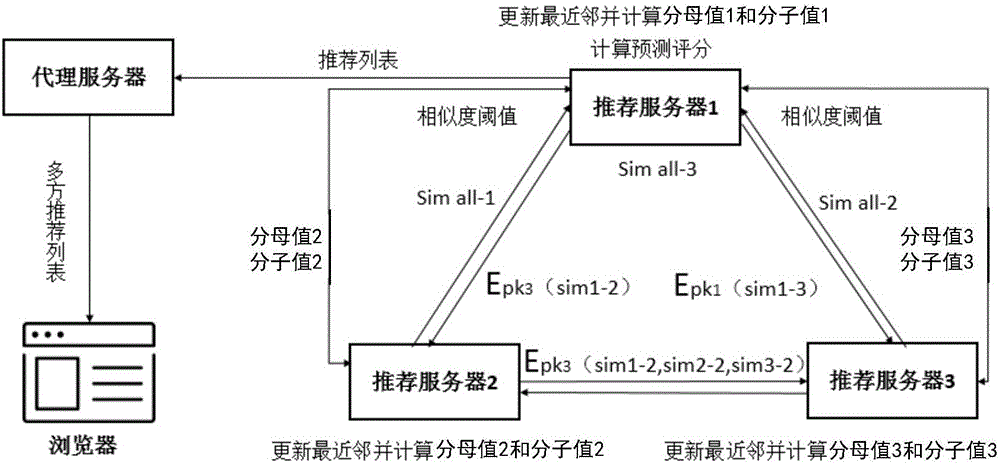
ActiveCN106202331ASolve the problem of privacy protectionImprove toleranceDigital data protectionSpecial data processing applicationsUser inputPrivacy protection
The invention discloses a recommendation system with a hierarchical privacy protection function and an operation method on the basis of the recommendation system. The recommendation system comprises a client / browser, a database of the client / browser, a proxy server, a database of the proxy server, a plurality of recommendation servers and databases of the recommendation servers. Interfaces for exchanging data with the servers can be provided by the client / browser and the database of the client / browser, personal information and service requests which are inputted by users can be received, the personal information can be stored in the database of the client / browser, the service requests can be transmitted to the proxy server, and recommendation results fed by the recommendation servers can be displayed for the users; the service requests of the users can be received by the proxy server and the database of the proxy server, the proxy server and the database of the proxy server can respond to the service requests, the recommendation results of the recommendation servers can be received, and recommendation can be carried out for the users according to the recommendation results; project resources in the recommendation system can be stored and managed by the recommendation servers and the databases of the recommendation servers, and recommendation which meets the service requests of the users can be collaboratively generated according to score information of the users. The recommendation system and the operation method have the advantage that privacy of the users can be protected when the recommendation system is used in application scenes such as recommendation, query and small data cold start.
Owner:COMMUNICATION UNIVERSITY OF CHINA
Differential privacy protection method for online social network based on stratified random graph
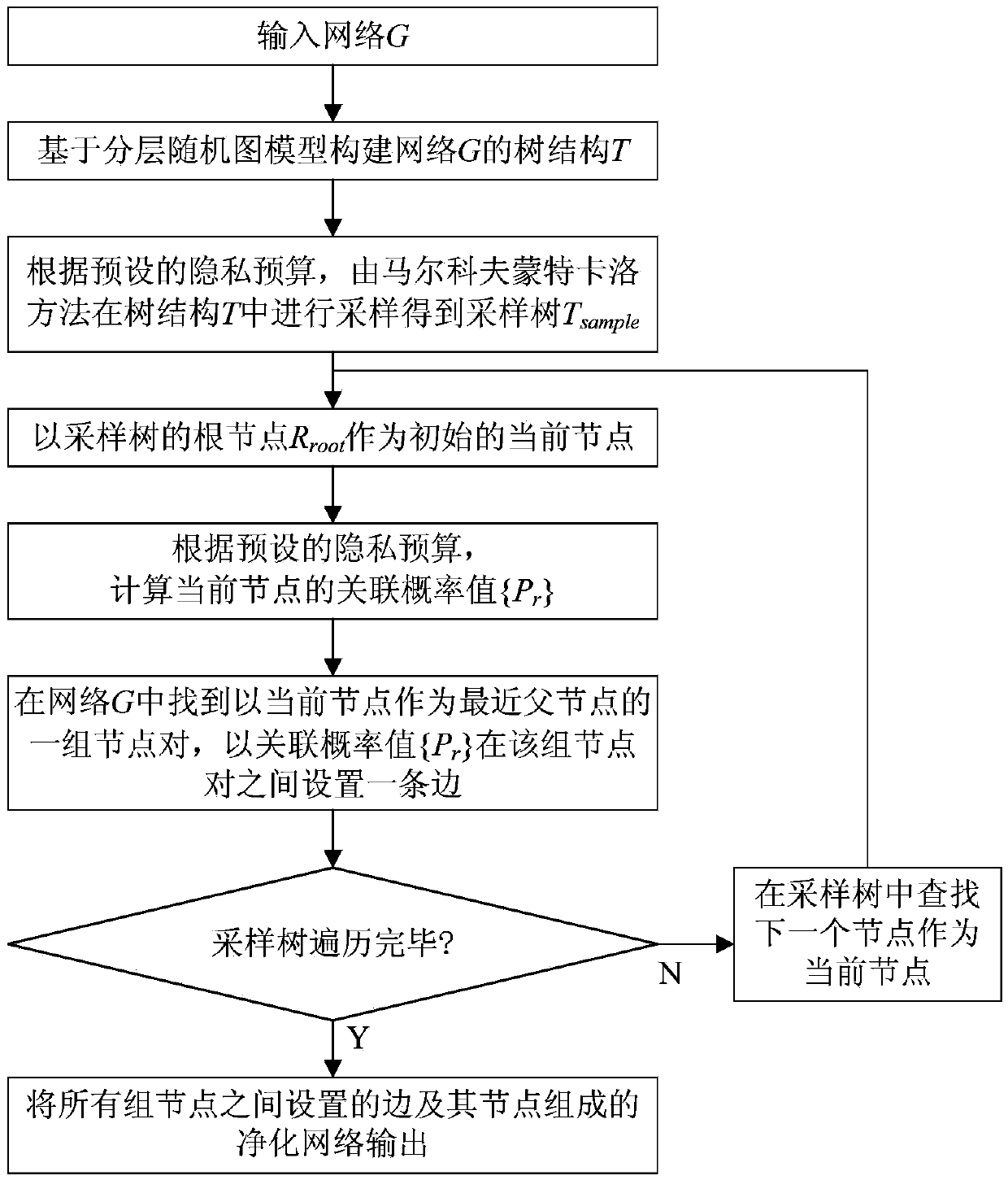
InactiveCN105376243ASolve the problem of privacy protectionGuaranteed availabilityTransmissionNODALRelationship - Father
The invention discloses a differential privacy protection method for an online social network based on a stratified random graph. The differential privacy protection method comprises the following steps: inputting a network; constructing a tree structure of the network based on a stratified random graph model; sampling in the network through a Markov chain Monte Carlo method according to a preset privacy budget so as to obtain a sampled tree; taking the root node of the sampled tree as an initial current node; calculating an associated probability value of the current node according to the preset privacy budget; finding out a set of node pairs by taking the current node as the nearest father node in the network, and setting an edge among the set of node pairs according to the associated probability value; judging whether traversal of the sampled tree is completed or not, and if not, continuously traversing the next node in the sampled tree; and otherwise, outputting a purified network composed of edges arranged among all the sets of nodes and nodes thereof. According to the invention, the privacy protection problem of sensitive structural data information in the social network can be solved; differential privacy protection requirements can be satisfied; and simultaneously, the good data availability is kept.
Owner:NAT UNIV OF DEFENSE TECH
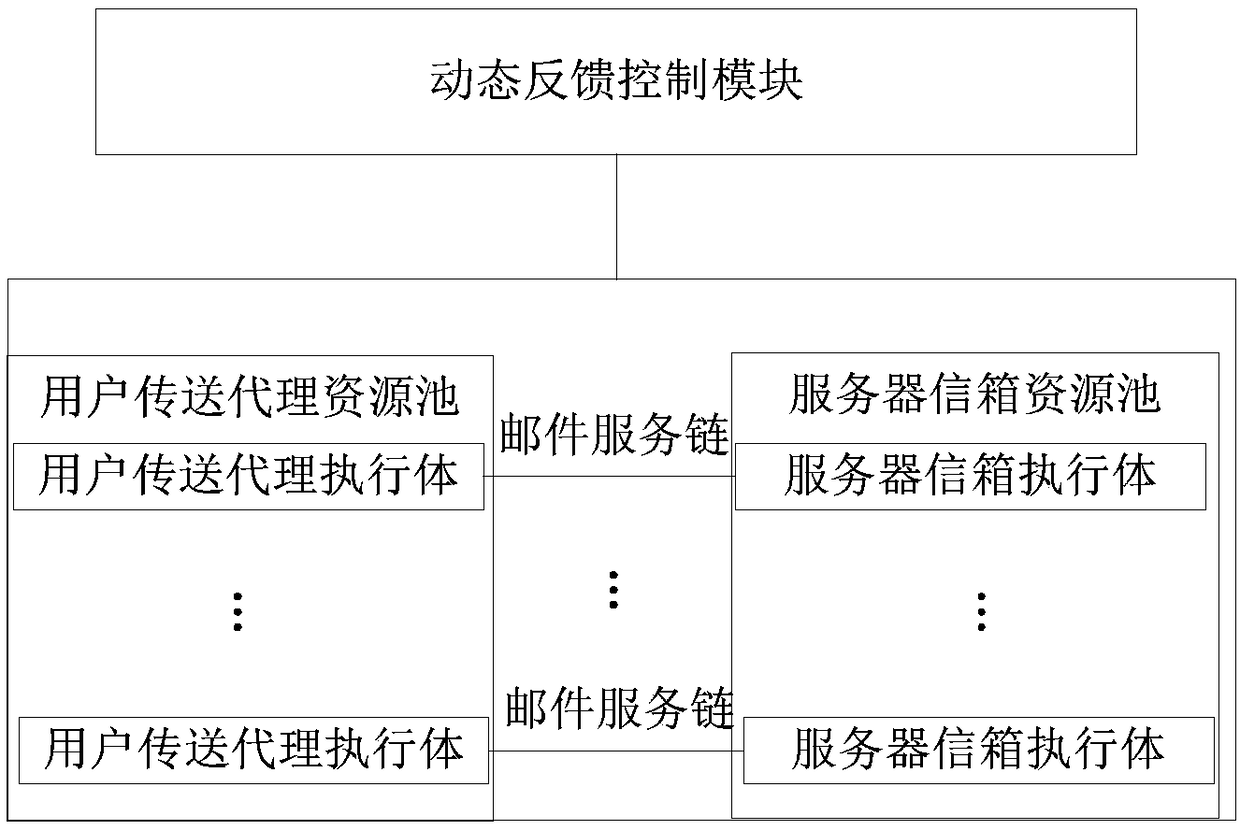
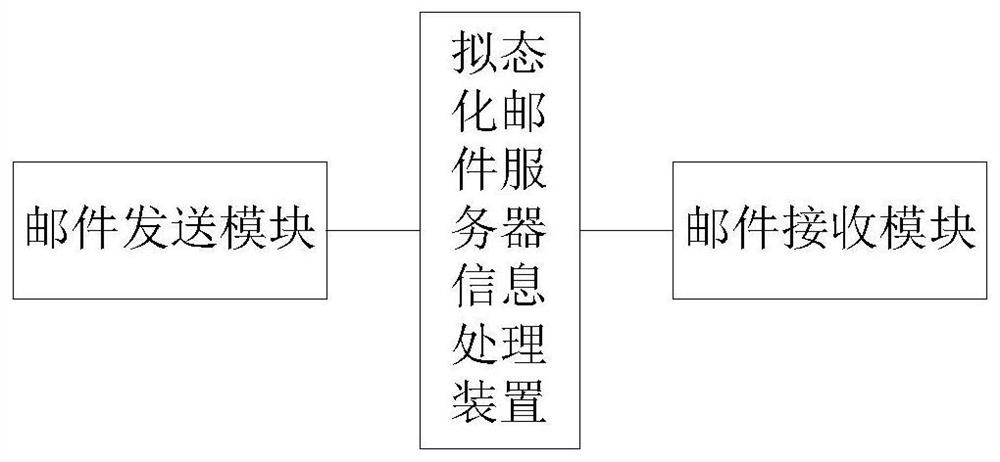
Mimetic mail server information processing device and mail service processing method, device and mail system
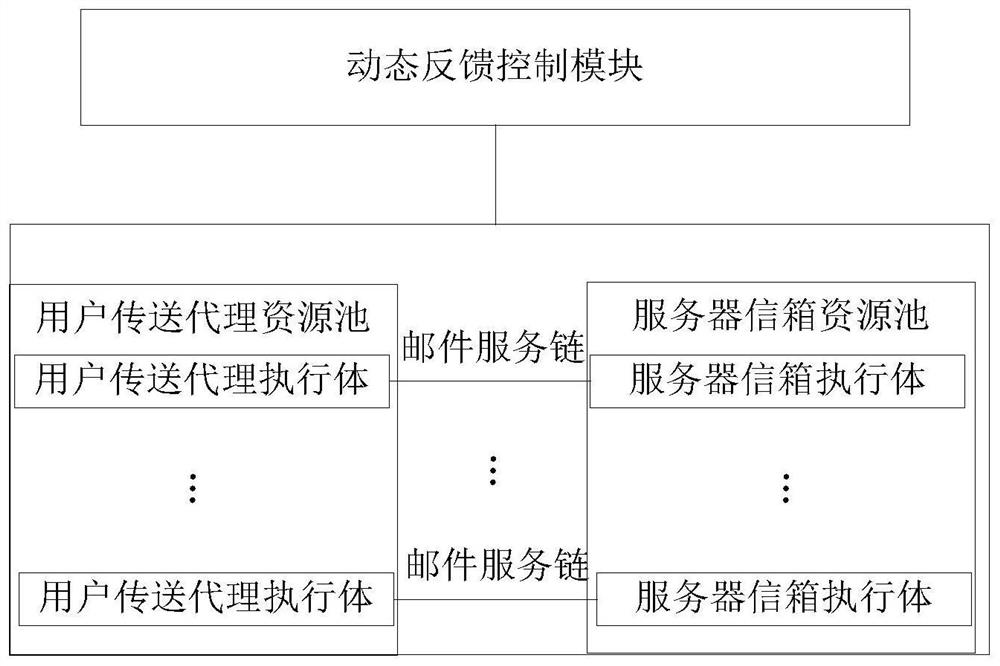
ActiveCN108833417AMeet security needsSolve the problem of building homogeneityData switching networksResource poolInformation processing
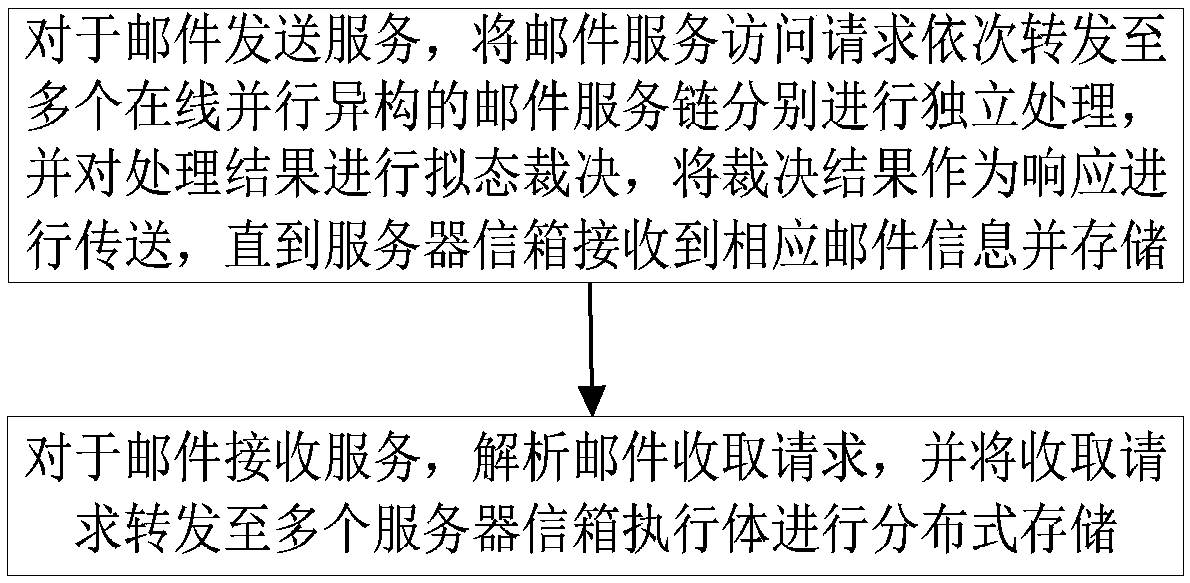
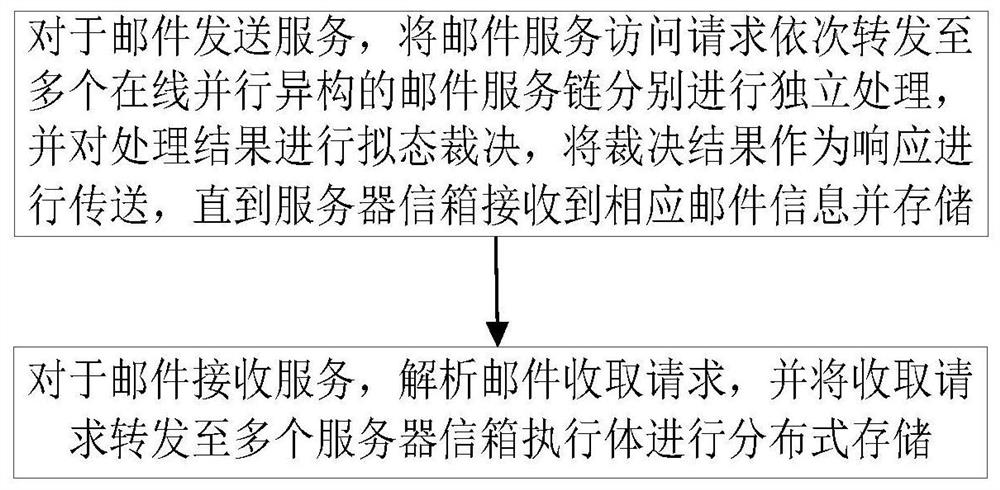
The invention relates to a mimetic mail server information processing device and a mail service processing method, device and a mail system. The information processing device comprises a resource poolcomposed of a user transfer proxy component and a server mailbox component, multiple parallel heterogeneous mail service chains composed of various components randomly selected from the resource pool, and a dynamic feedback control module, wherein the user transfer proxy component includes a number of heterogeneous user transfer proxy executors, and the server mailbox component includes a numberof server mailbox executors; and the dynamic feedback control module is used to monitor the operation of each executor and perform dynamic scheduling on various components. According to the scheme ofthe invention, the diversified executors are created, multiple processing results are subjected to mimetic decision output, the security performance of the mail system services can be improved, the initiative, variability and randomness of the mail system defense capability can be improved, the problem of privacy protection can be effectively solved, a more secure mail server solution can be provided, and the important guiding significance can be provided for the mail system security technologies.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Mixed randomization privacy protection method of social network data dissemination
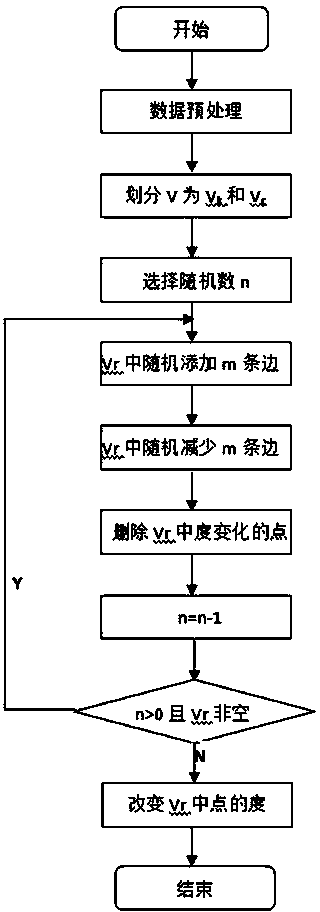
ActiveCN103902924ADoes not affect the natureDoes not affect qualityData processing applicationsDigital data protectionThird partyK-anonymity
The invention discloses a mixed randomization privacy protection method of social network data dissemination. The mixed randomization privacy protection method includes the steps that top points V of an undirected graph G(V,E) for expressing social network data are divided into a set Vk and a set Vr according to degree numbers with k-anonymity as a condition, wherein the set Vk comprises the points with the degree numbers meeting the k-anonymity condition, and the set Vr comprises the points with the degree numbers not meeting the k-anonymity condition; the points in the set Vk are not processed; randomization protection processing is carried out on the points in the set Vr. According to the mixed randomization privacy protection method, an existing k-anonymity method and an existing randomization method are combined, the number of users of the social network is not changed, influences on the nature and the quality of data provided for third parties are small, the processing process is simple, and the processing speed is high; after processing is carried out, the social network data of each person can be in one of the two following protection states: the degree natures are not changed, and the social network data of the person are located in other at least k persons same as the person in degree nature, or the degree natures are changed; relocation attacks with structure background knowledge can be prevented through the protection, and the demands of the users of the social network for the privacy safety are met.
Owner:北京睿航至臻科技有限公司
Method and system for implementing internet advertisement telephone
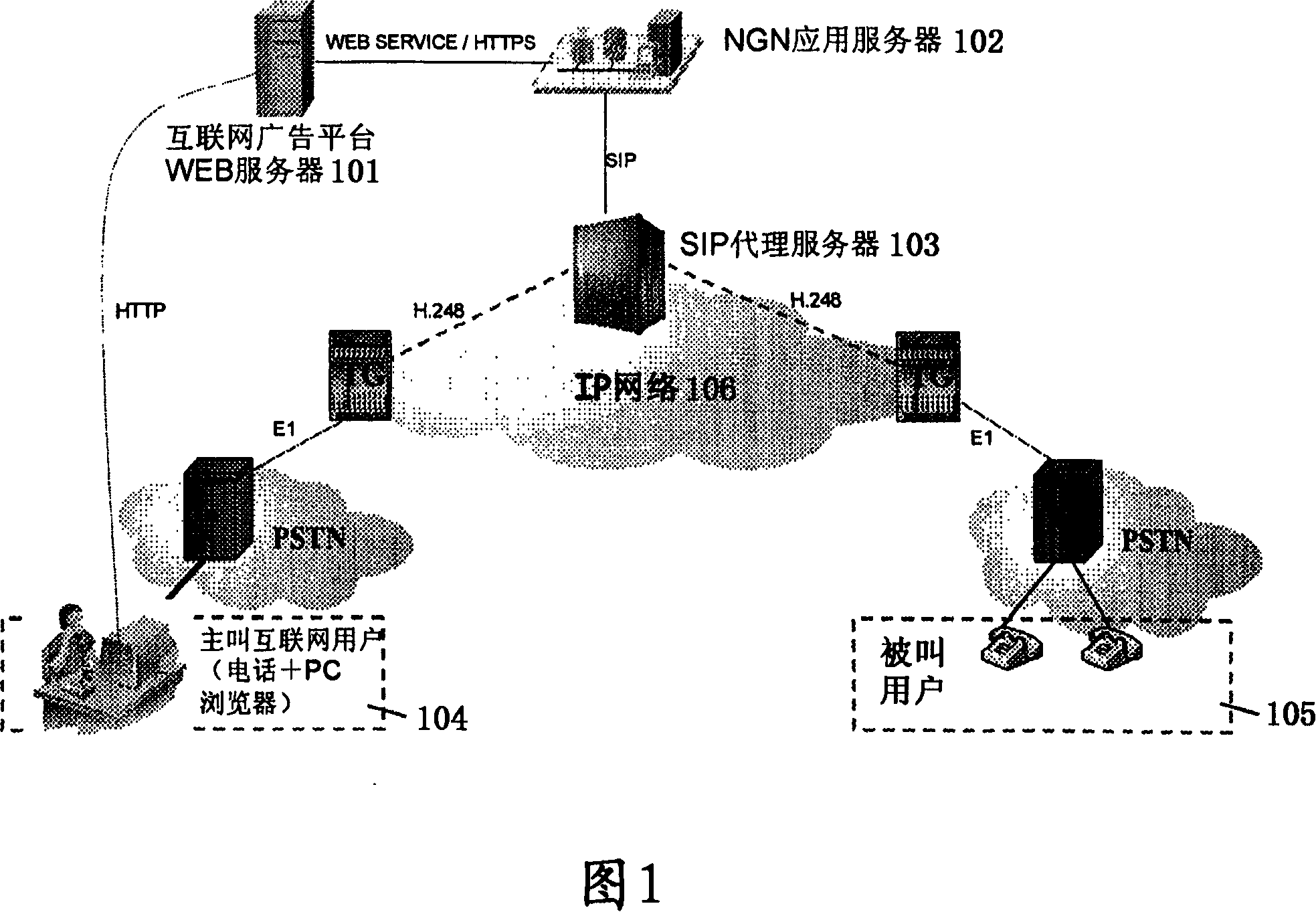
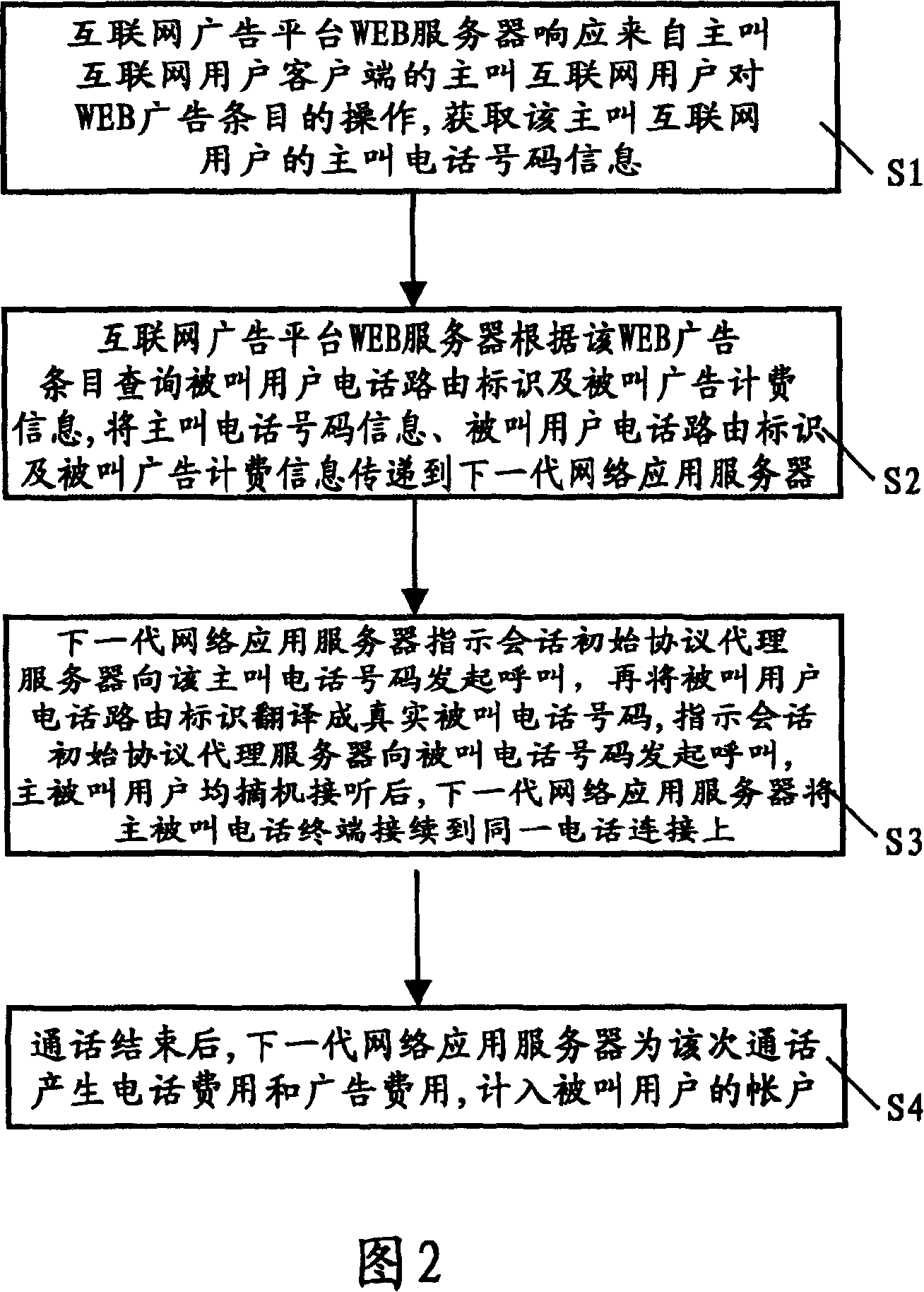
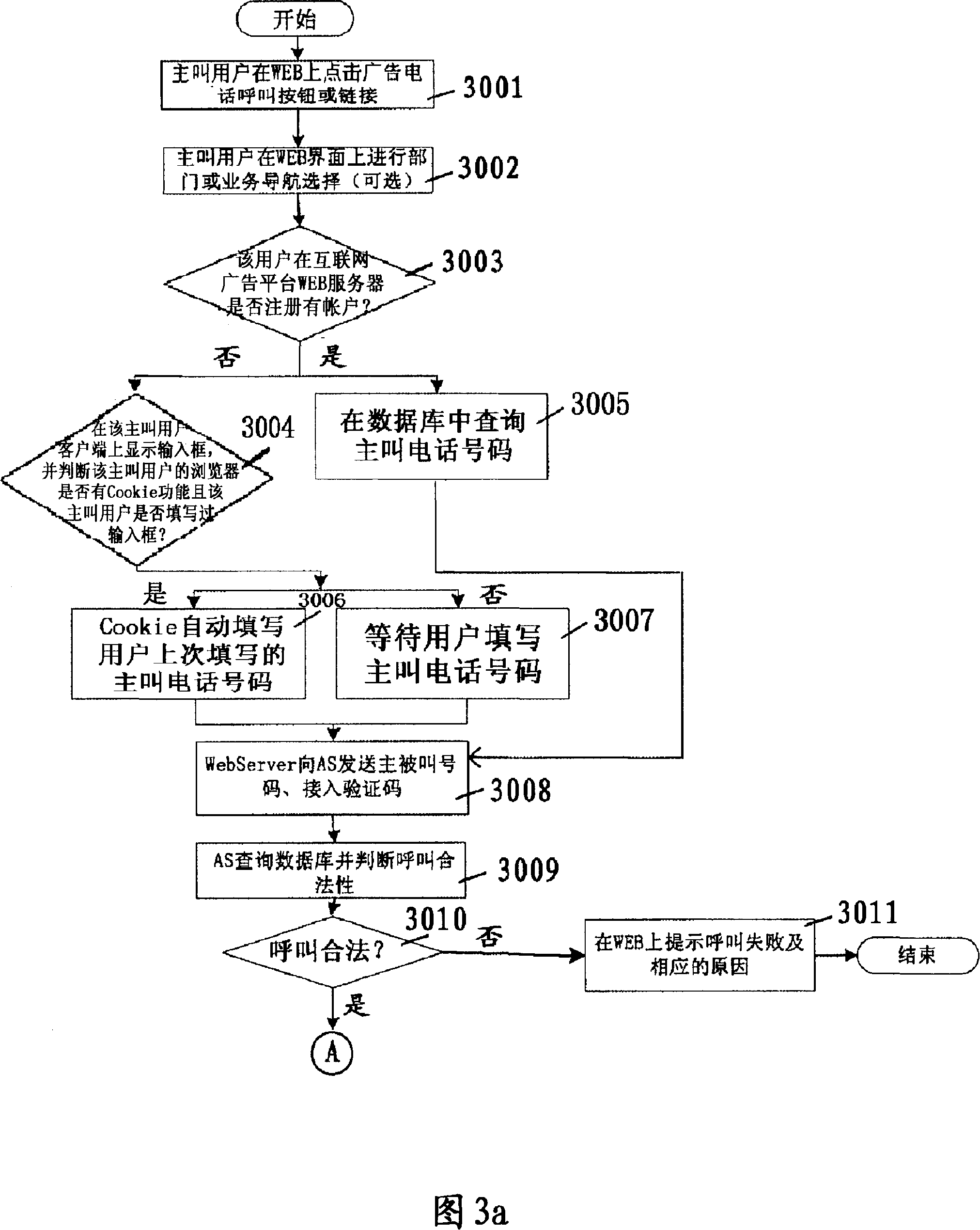
ActiveCN101141517AImprove experienceImprove advertising effectivenessInterconnection arrangementsSpecial service for subscribersApplication serverProtocol Agent
The present invention relates to an implement method of an Internet advertisement telephone, which comprises the following procedures: an Internet advertisement platform WEB server responds the operation to a WEB advertisement item by a calling user, and inquires the calling telephone number information of the calling Internet user, the called telephone route identification, and the called advertisement charging information, and transmits the information to the next generation network application server; a next generation network application server indicates the session inception protocol proxy service to initiate the call to the calling party and the called party telephone number, and connects the calling user with the called user; when the call is finished, the next generation network application server records the relative charge of the call which comprises the telephone charge and the advertisement charge into the account of the called user, and returns certain telephone utilization amount to the calling user. The present invention can form an actuation system to the clicked Internet user, and advance the deep communication contact between the user and the advertisement delivery enterprise.
Owner:CHINA TELECOM CORP LTD
A differential privacy processing and publishing method for social network data
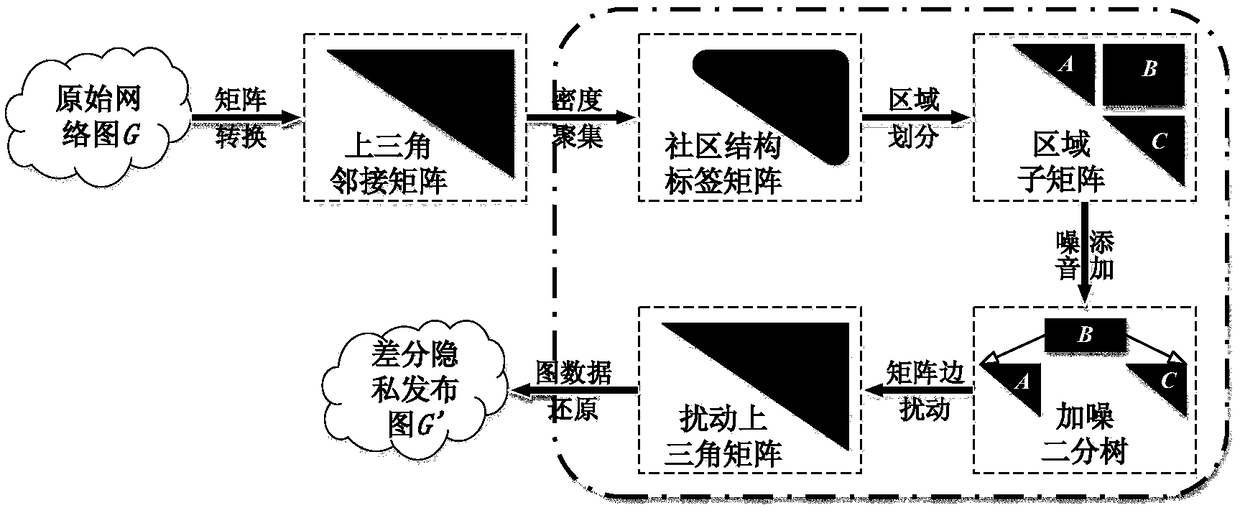
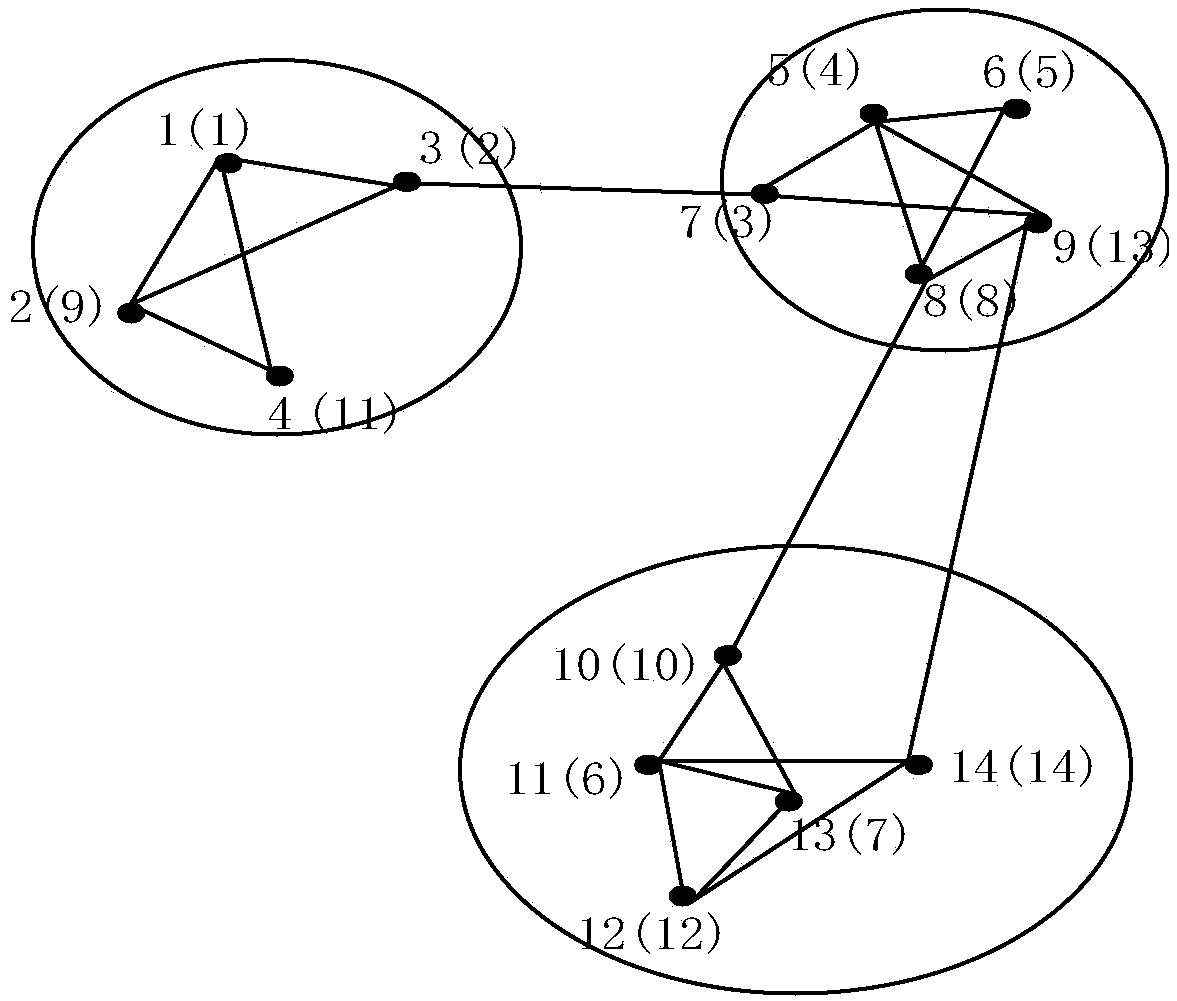
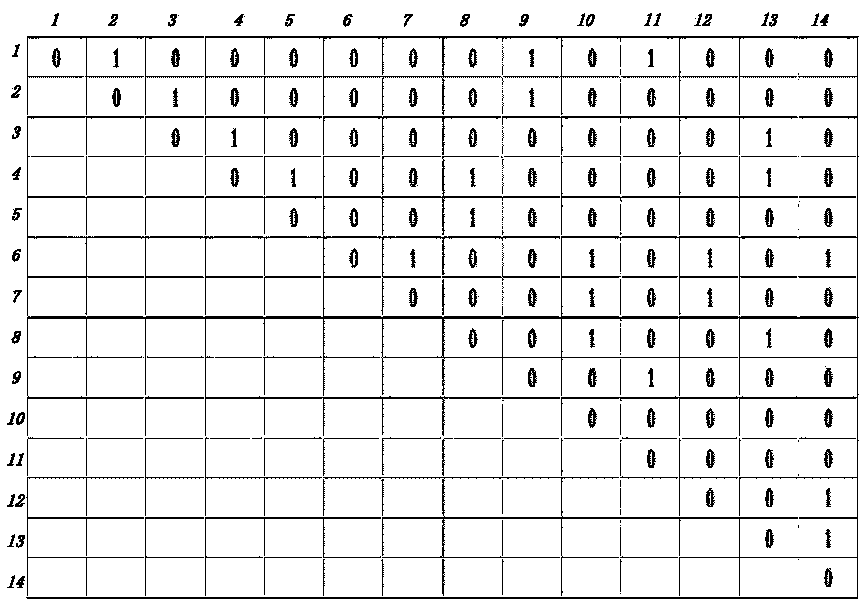
ActiveCN109299615ASolve the problem of privacy protectionImprove protectionData processing applicationsDigital data protectionSocial graphDistribution method
The invention discloses a differential privacy processing and publishing method for social network data. The method utilizes the fast community detection and differential noising to identify the structural labels of the social network and generate the node labels which make the community nodes gather. The method is based on the adjacency matrix processing of the social network graph. At the same time, the data-independent adaptive method and binary tree structure are used to determine the dense region of the generated upper triangular adjacency matrix. Finally, the noisy adjacency matrix is reconstructed by matrix processing and the network graph is published. The invention introduces the concept of community grouping, which not only protects the data privacy of the social network but alsoensures the better data functionality, and the method of using the upper triangular matrix to reconstruct the density of the sub-region can effectively improve the data processing efficiency, and theoptimal noise-adding edge distribution method designed according to different densities also ensures the privacy protection degree of the scheme.
Owner:NANJING UNIV OF POSTS & TELECOMM
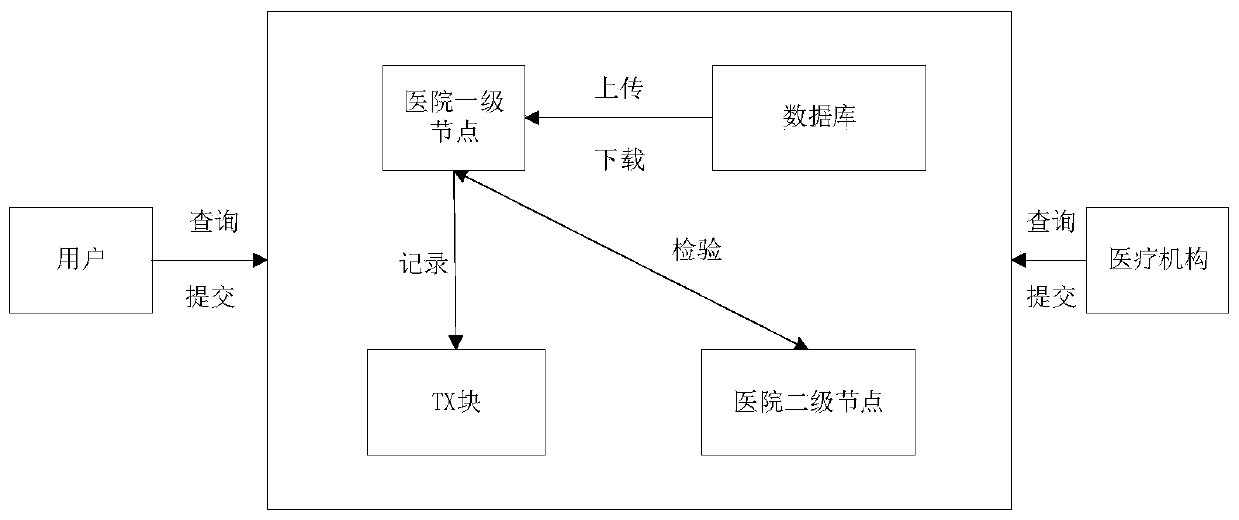
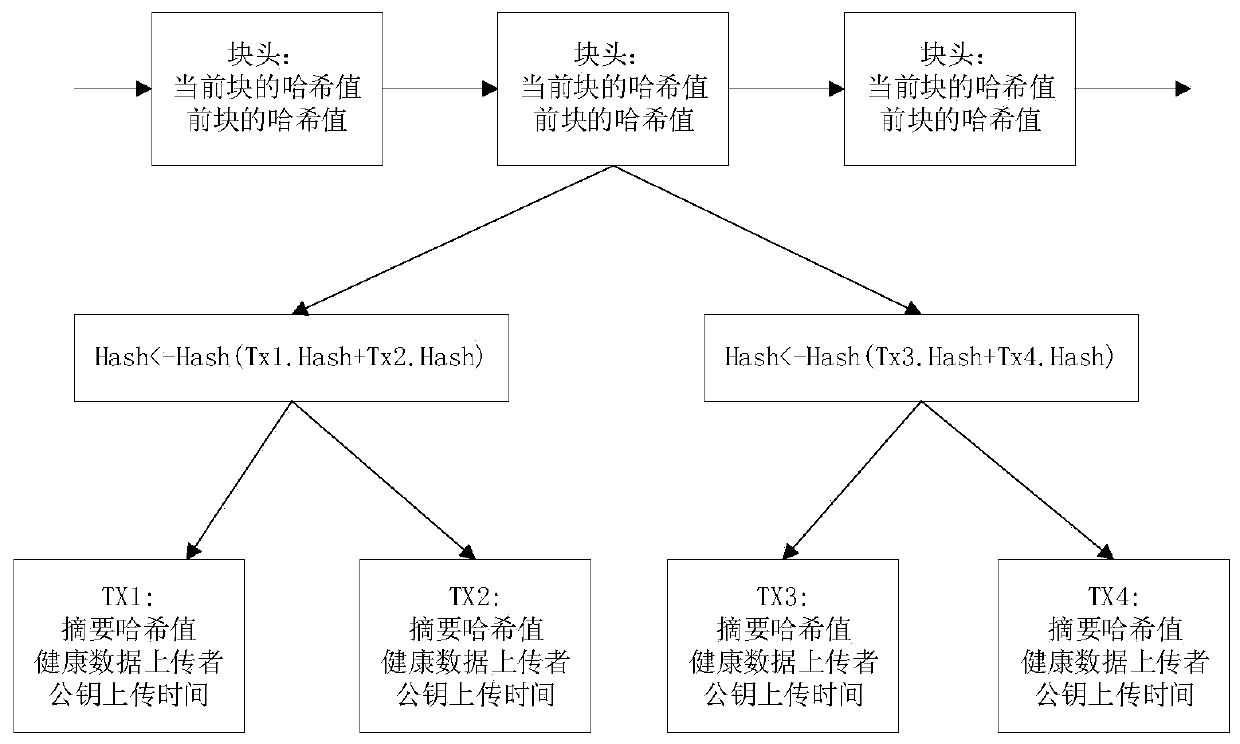
Medical data sharing method based on block chain
InactiveCN111444258ASolve the problem of privacy protectionReduce turnaround timeKey distribution for secure communicationDatabase distribution/replicationPasswordThe Internet
The invention provides a medical data sharing method based on a block chain, which comprises the following steps: S1, a node registers a public key on the Internet, the node is a node in an alliance group, and the public key is a 32-bit identifier; s2, the mechanism encrypts the data through a public key and then uploads the data to a database; s3, the client sends a request to the main node, broadcasts the request after receiving the request and reaches a consensus; s4, the data is uploaded to a blockchain database; s5, a block chain is formed by the block, the node is interacted by using aninterface provided by a web, and a private key of the user is encrypted by using a password; s6, when the user inquires the data, an identity authentication mode is adopted, and the user can upload the data and can also inquire the data. According to the decentralized, traceable and tamper-proof data sharing method based on the block chain, the data can be shared, and meanwhile the safety of the data can be guaranteed.
Owner:JIANGSU RONGZE INFORMATION TECH CO LTD
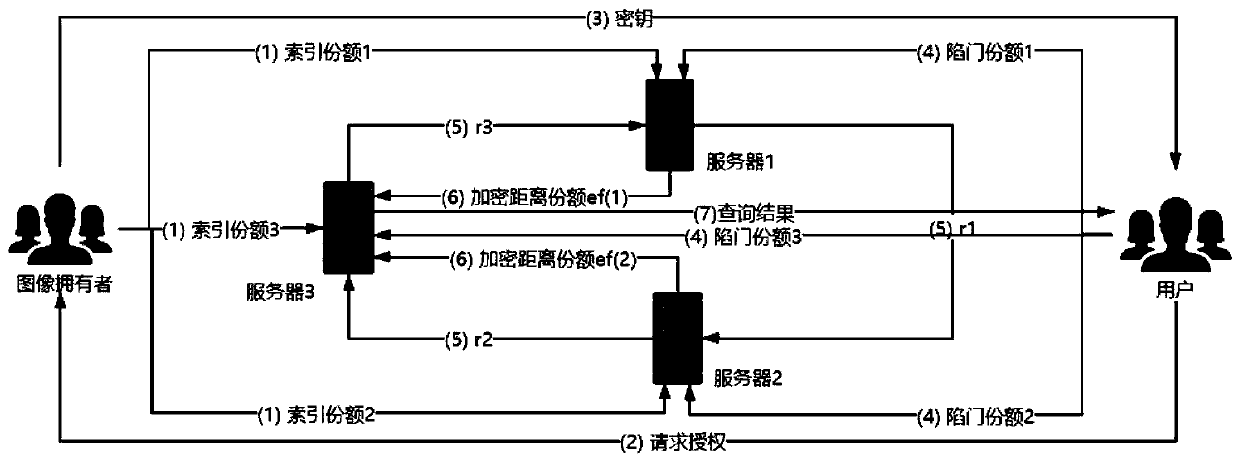
Image security retrieval method based on secret sharing in cloud environment
ActiveCN111541679AProtection securityIncrease the difficultyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextEngineering
The invention aims to provide an image security retrieval scheme based on secret sharing in a cloud environment, which realizes security retrieval of a cloud image by constructing an index share and atrap door share. A data owner generates a ciphertext image and an index share and uploads the ciphertext image and the index share to a cloud, during query, a user generates a trap door share and sends the trap door share to the cloud, and the cloud can calculate a distance share and return the ciphertext image closest to the query image, so that the security problem caused by using a unified keyfor encryption in an existing scheme can be solved. In order to prevent an attacker from analyzing image similarity information according to an original Euclidean distance to speculate an image, a random number and a secure multi-party calculation method are used to encrypt a distance share. The security of the scheme depends on a secret sharing technology, the common precision loss problem in image security retrieval is solved, and the retrieval precision is almost consistent with that of plaintext domain image retrieval.
Owner:WUHAN UNIV
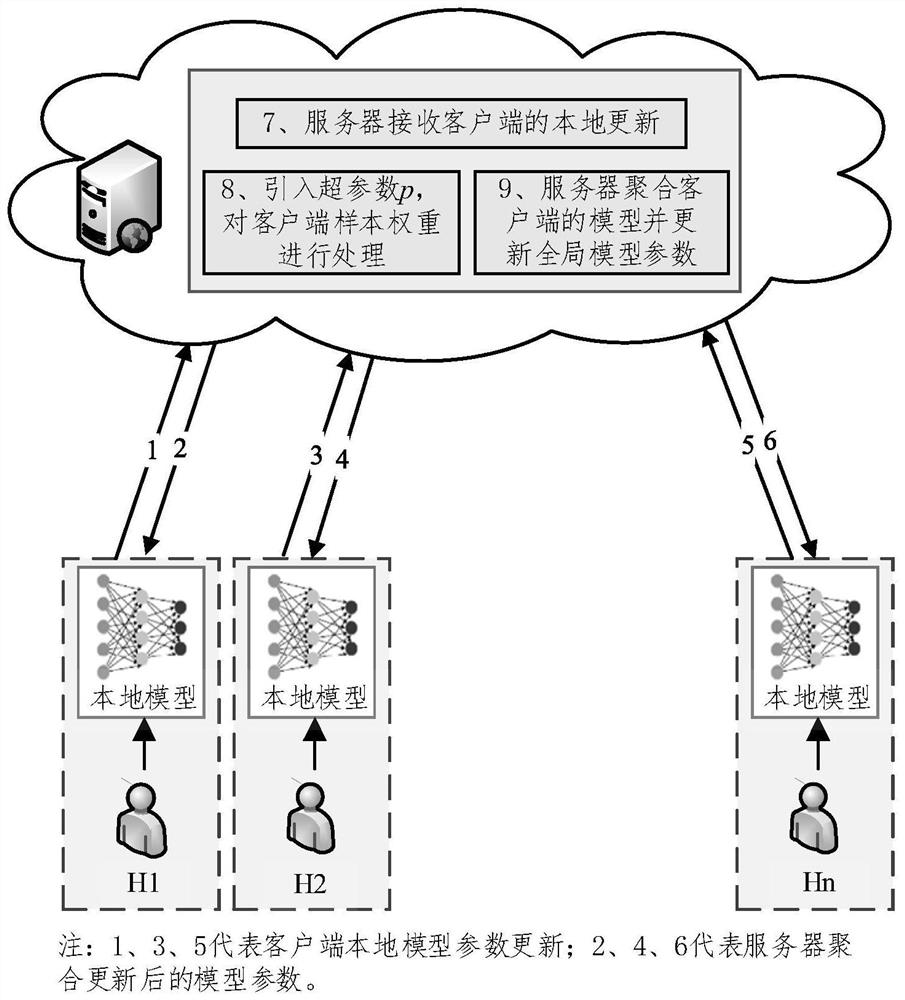
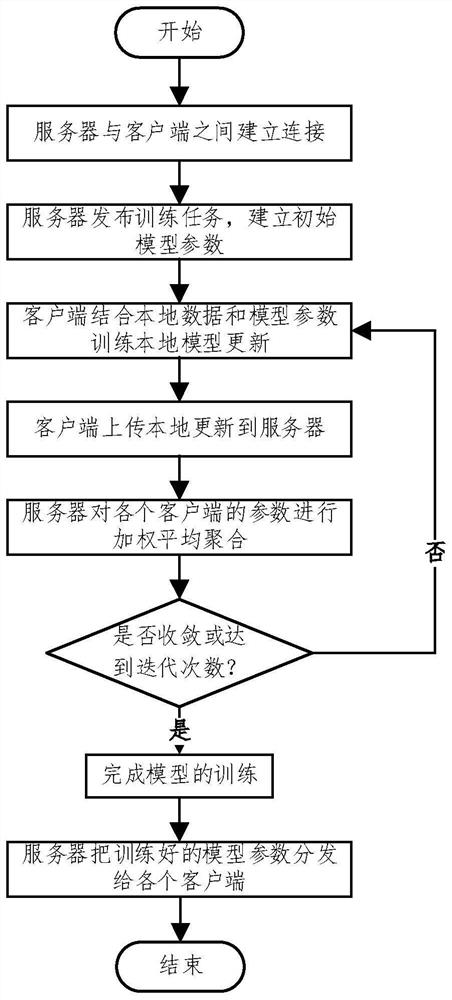
Federal learning-based human activity identification method and system
PendingCN114386621ASolve the problem of privacy protectionAchieve protectionEnsemble learningDigital data protectionEngineeringArtificial intelligence
The invention provides a human activity identification method and system based on federal learning. The method comprises the steps that 1, a server determines training tasks and corresponding activity data features, generates initial model parameters and issues the initial model parameters to all clients; 2, each client performs local training according to the received initial model parameters or new global model parameters in combination with local activity data of the client, generates local update parameters and uploads the local update parameters to a server; step 3, the server performs weighted average aggregation on the received local update parameters of each client to generate new global model parameters, and issues the new global model parameters to each client; and step 4, repeatedly executing the step 2 to the step 3 until a training stop condition is met to obtain a final global model parameter, and issuing the final global model parameter to each client by the server. According to the method, the accuracy of HAR recognition is improved while the privacy of the user is protected.
Owner:HENAN UNIVERSITY
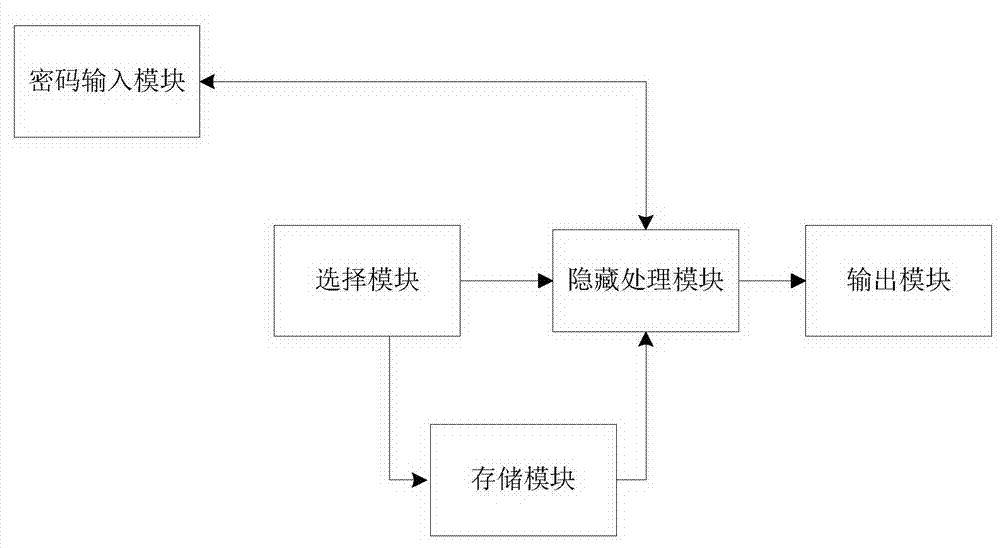
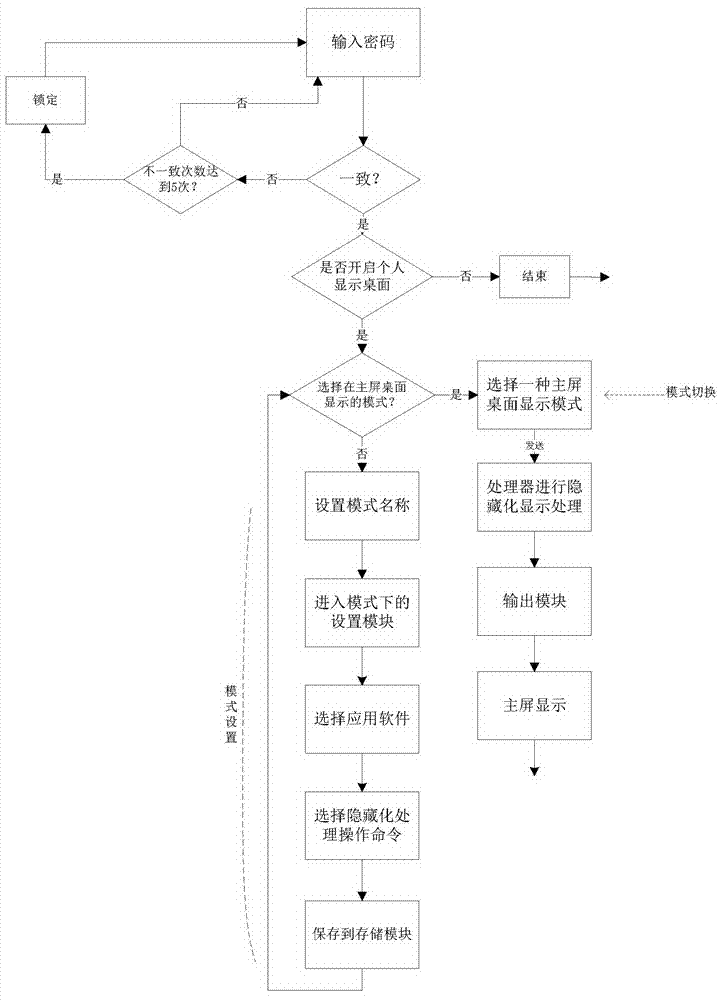
Desktop software filtering system
ActiveCN104715173ASolve complexitySolve the problem of privacy protectionDigital data authenticationUser inputPassword
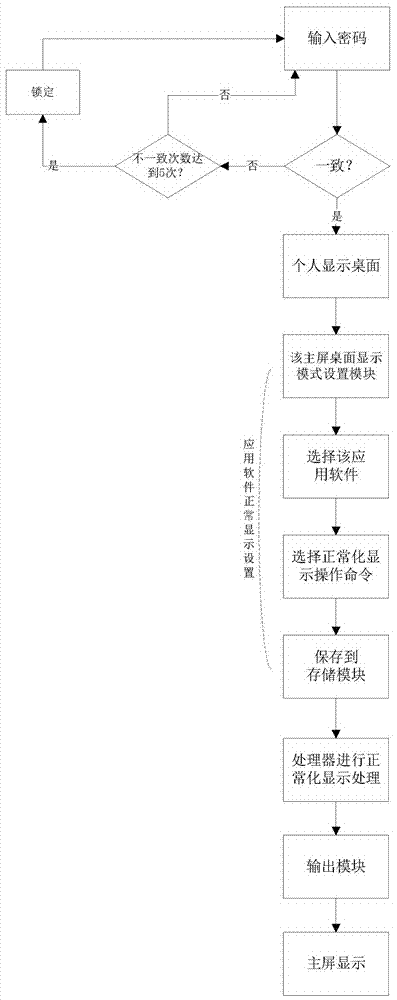
The invention discloses a desktop software filtering system. The desktop software filtering system comprises a password input module, a selecting module, a storage module, a hidden processing module and an output module, wherein the password input module is connected with a personal display desktop; the selecting module is connected with the personal display desktop and the storage module; the hidden processing module is connected with the storage module, the selecting module, the output module and the password input module; the storage module is used for storing password parameters, pattern names and operation commands; the password input module is used for password unlocking and enters the personal display desktop mode when the password input by a user is correct; the selecting module is used for collecting the pattern names set by the user, application software selected by the user and the operation commands selected by the user and carried out on the application software, and transmitting the operation commands to the hidden processing module; the hidden processing module is used for processing the application software, and the application software is output to a main screen desktop through the output module.
Owner:SOI MICRO CO LTD
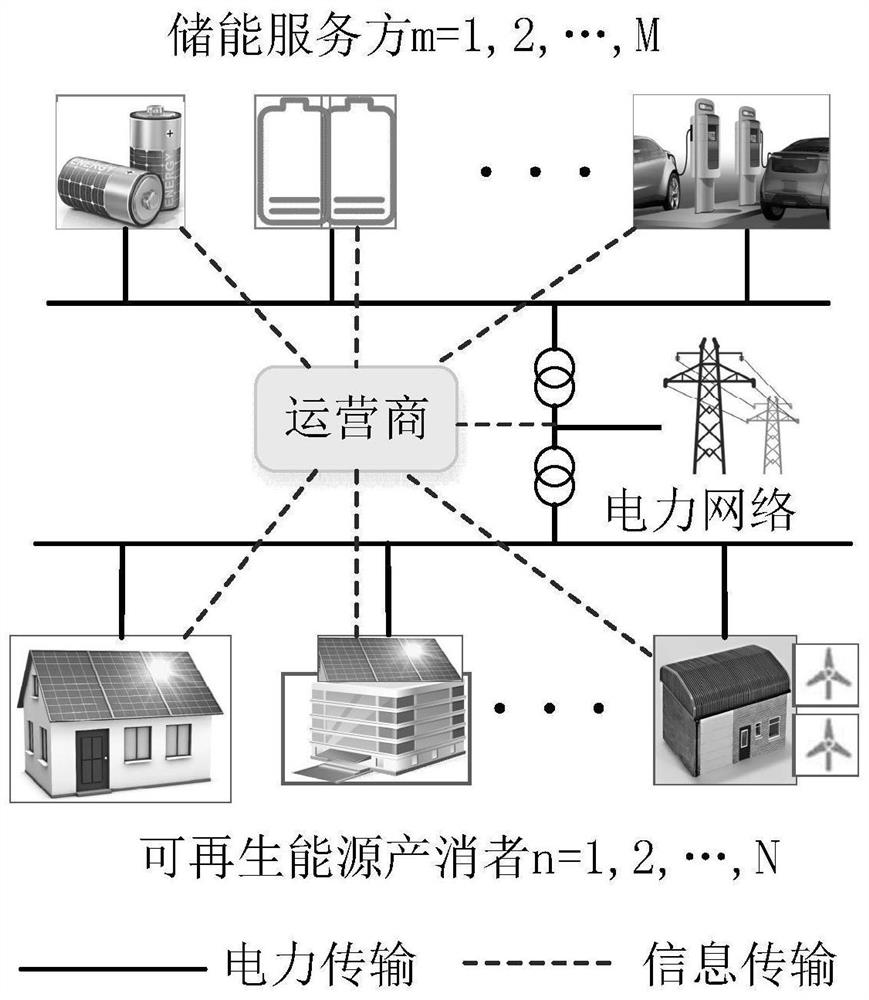
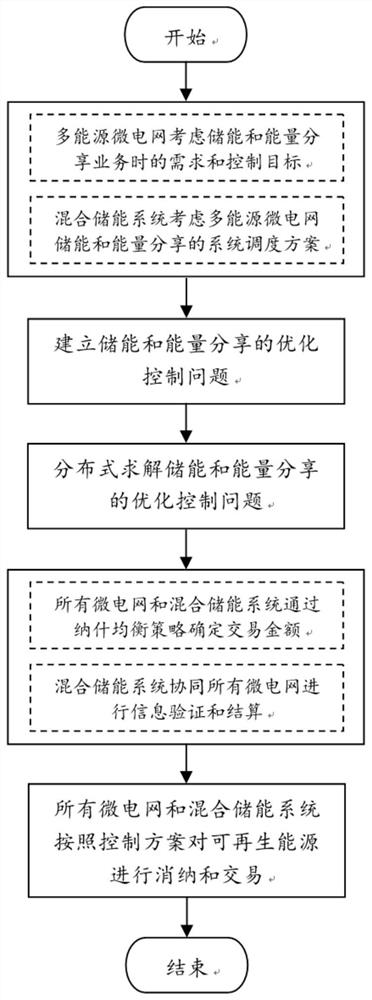
Shared energy storage control method and system for distributed renewable energy producers and disasters
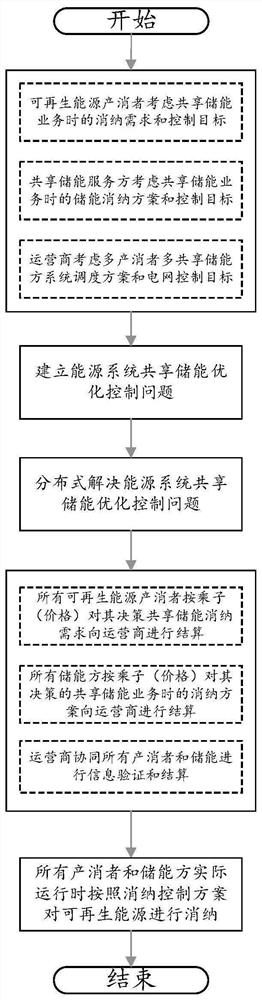
PendingCN111899054AImplement deprecationReduce deprecationMarket predictionsForecastingPower usageLoad following power plant
The invention discloses a shared energy storage control method and system for distributed renewable energy producers and disasters, and belongs to the field of energy consumption. The method comprisesthe following steps: minimization of the total energy cost of all prosumers, energy storage parties and operators participating in shared energy storage is taken as an objective function, wherein theenergy transaction cost in the power market takes downlink and uplink energy of an interface between an operator and a power system as decision-making quantity; the dispatchable load of the prosumergenerates benefits through power utilization, and actually control flexible load energy consumption in each prosumer control time period and energy consumption indirectly put forward to the energy storage party through an operator can serve as decision-making quantities; the energy storage loss cost of the energy storage parties takes the charging and discharging speed of each energy storage partyin the control time period and energy consumption proposed by a prosumer and indirectly received by an operator as decision variables, and constraint conditions are constructed for each decision variable to construct an energy system shared energy storage optimization control model; and the shared energy storage optimization control model of the energy system is solved by adopting distributed optimization to obtain a control scheme for multi-energy storage sharing by the prosumer.
Owner:HUAZHONG UNIV OF SCI & TECH +1
Data security sharing method, system and device
ActiveCN111901309AImprove protectionSolve the problem of privacy protectionFinanceTransmissionData securityFederated learning
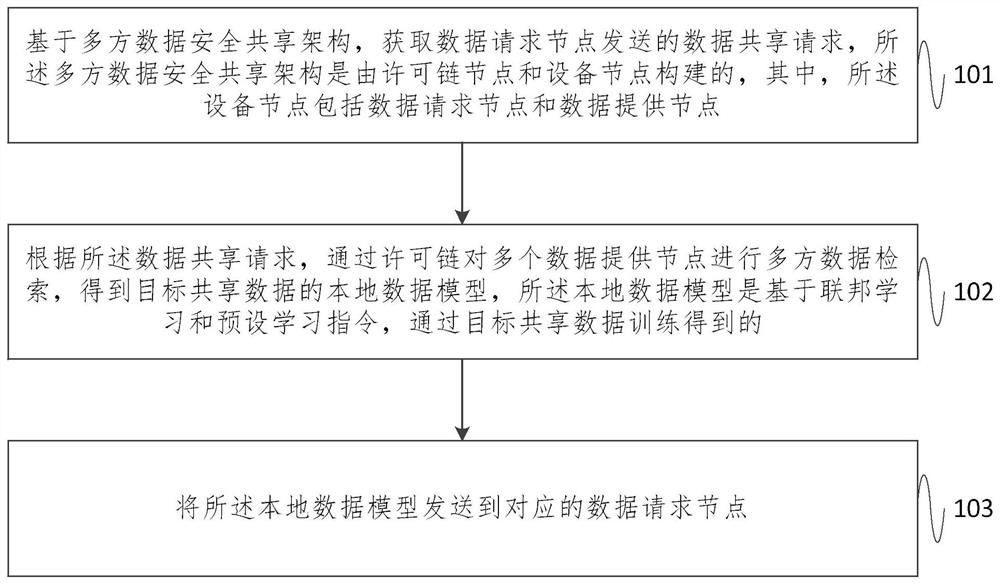
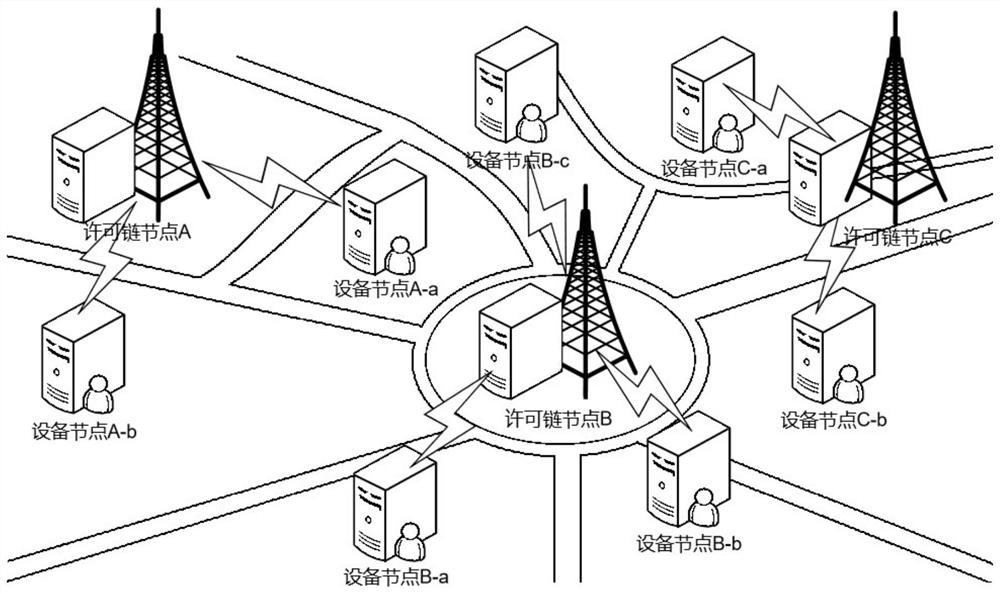
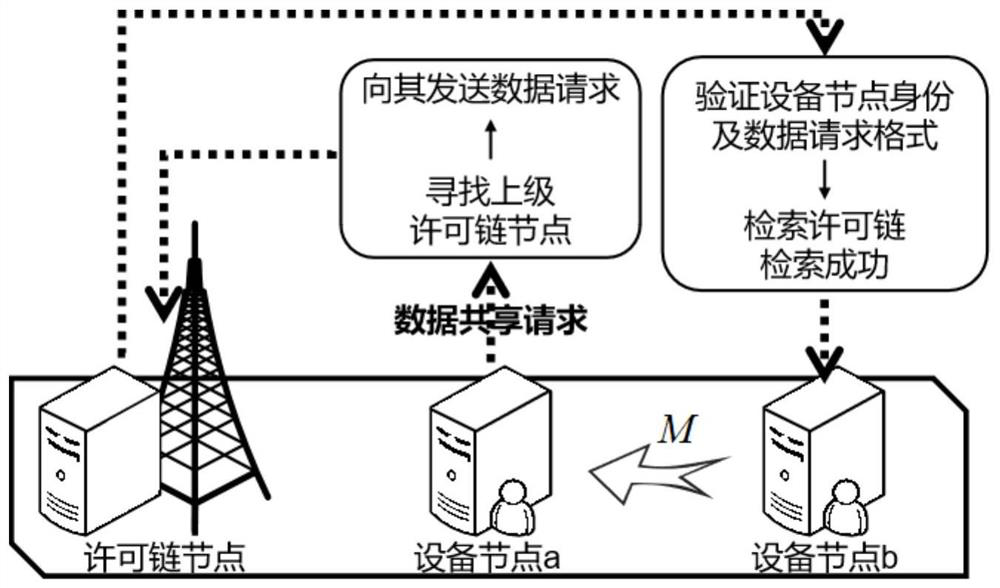
The embodiment of the invention provides a data security sharing method, system and device, and the method comprises the steps: obtaining a data sharing request transmitted by a data request node based on a multi-party data security sharing architecture which is constructed by a license chain node and an equipment node; according to the data sharing request, carrying out multi-party data retrievalon a plurality of data providing nodes through a permission chain to obtain a local data model of target shared data, and obtaining the local data model through target shared data training based on federated learning and a preset learning instruction; and sending the local data model to a corresponding data request node. According to the embodiment of the invention, a decentralized trusted transaction environment is established, so that the transaction process is transparent to two transaction parties; and through a federated learning technology, the original data does not need to be transmitted in a data sharing process, so that the protection degree of user data privacy is increased from the source.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
A spatial network query method capable of protecting privacy
ActiveCN109728904AEnsure safetyEfficient use ofKey distribution for secure communicationGeographical information databasesPrivacy protectionUser privacy
The invention relates to the technical field of data processing, in particular to a privacy protection method for spatial network query. The method is based on the following steps: constructing encrypted spatial network data; Generating a security query request; Basic security space network query processing; Heuristic security space network query processing; By applying the method provided by theinvention, the security spatial network query can be realized in an outsourcing scene, and the security of sensitive information such as spatial network data and query requests and user privacy information in the query process is ensured; The spatial network data in the outsourcing scene is effectively utilized; On the premise that data privacy security is guaranteed, the requirement of a user forspatial network query in practical application is met, and a safe and efficient spatial network query system under a data encryption framework is formed.
Owner:SHENYANG AEROSPACE UNIVERSITY
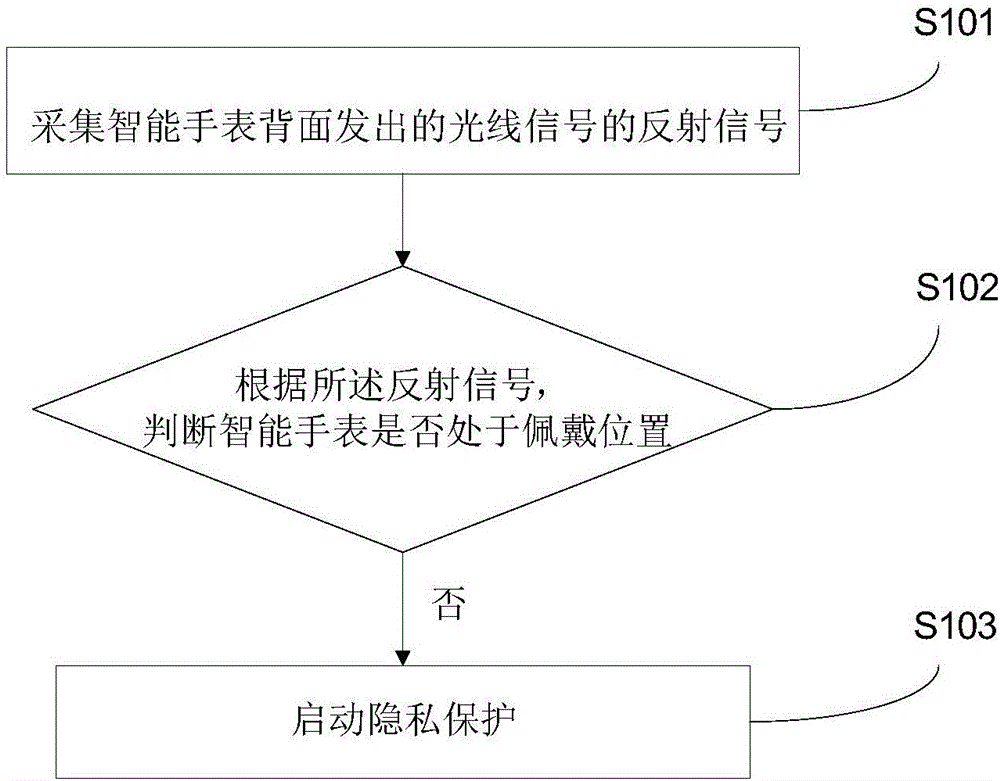
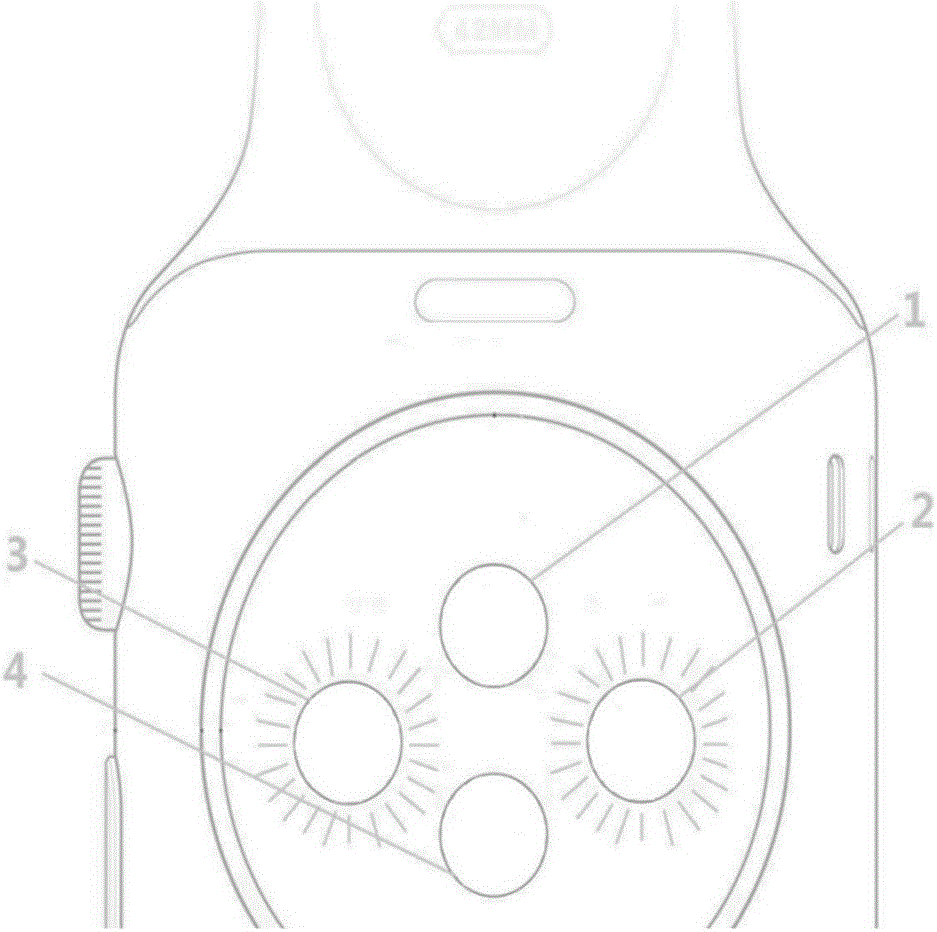
Privacy protection method and privacy protection device for smart watch
InactiveCN106570361AIncrease overheadSolve the problem of privacy protectionDigital data authenticationPrivacy protectionEngineering
The invention provides a privacy protection method for a smart watch. The privacy protection method for a smart watch includes the steps: acquiring a reflection signal of a light signal emitted from the surface of a smart watch; according to the reflection signal, determining whether the smart watch is in the wearing position; if not, entering the next step; and starting privacy protection. The privacy protection method for a smart watch has the advantages that as long as the smart watch is not in the wearing state, privacy protection can be automatically started, so that the privacy protection problem in a daily social contact scene is effectively solved. Besides, the privacy protection method for a smart watch utilizes sensor equipment which is commonly used by a current smart watch, thus having no demand for increasing hardware cost additionally. The invention also provides a privacy protection device for a smart watch.
Owner:HANGZHOU LIANLUO INTERACTIVE INFORMATION TECH CO LTD
Construction method for authorizing listener anonymity set in broadcasting program
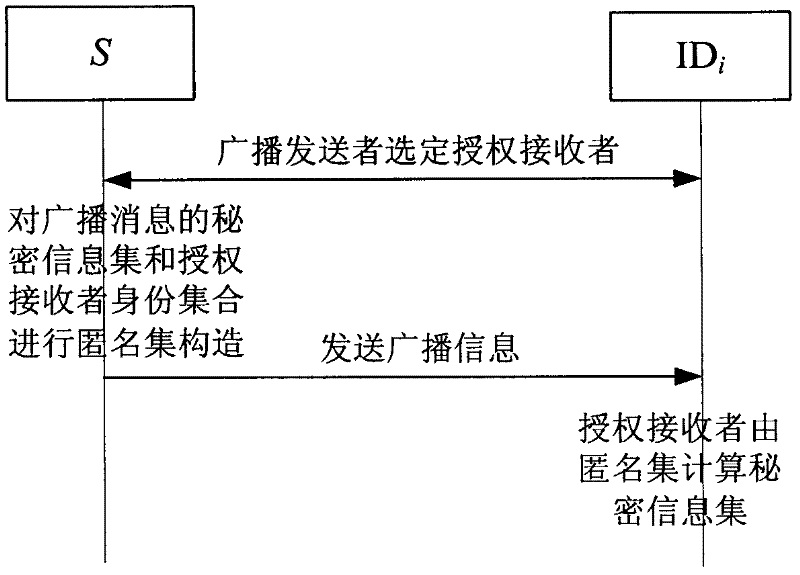
InactiveCN102510379ASolve the problem of privacy protectionTransmissionBroadcast systems controlPrivacy protectionAnonymity
The invention discloses a construction method for authorizing listener anonymity set in a broadcasting program, which solves the technical problem of the prior art that: when the broadcasting is encrypted, the authorized listener identity information is exposed. A Lagrange interpolation function is used to realize the construction of the anonymity set of the authorized listener in the broadcasting program based on identity and the broadcasting information does not contain the authorized listener identity list information. The identity of the authorized listener is not directly visually shown, thus the information of the authorized listener can not be obtained by an attacker and all the authorized listeners which receive a same message can not obtain any information from other authorized listeners except itself, therefore the privacy protection problem of the authorized listeners can not be solved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV +1
Steel quality guarantee book privacy protection and sharing method and system based on block chain
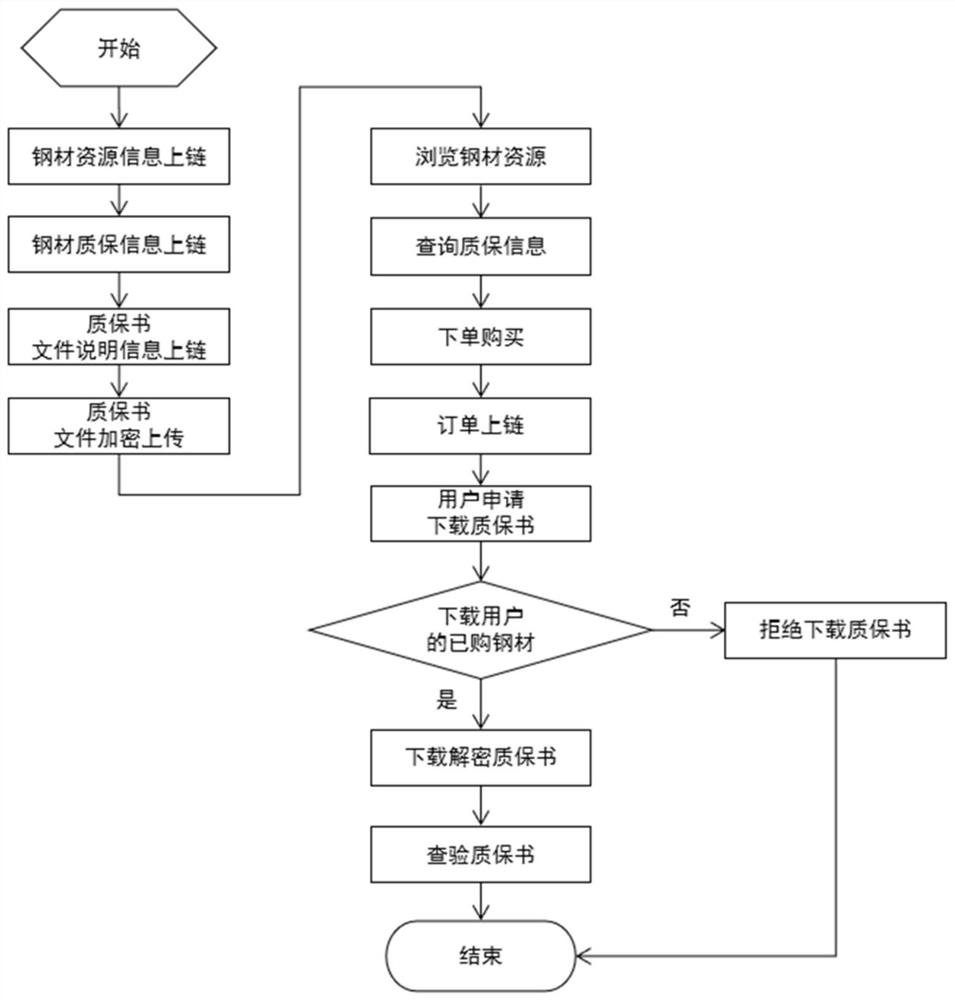
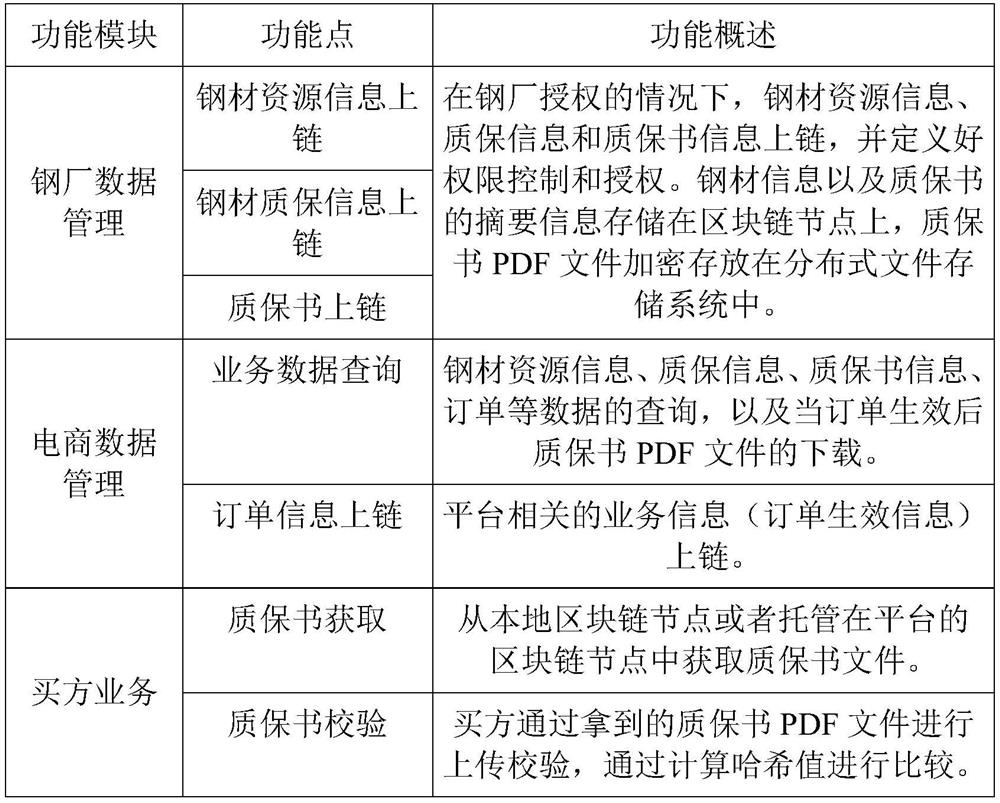
ActiveCN111783127AGuaranteed to be true and effectiveSolve inspection problemsDigital data protectionFile access structuresResource informationPrivacy protection
The invention relates to a steel quality guarantee book privacy protection and sharing method and system based on a block chain. The method comprises the steps that a block chain platform is constructed, and a steel production institution and a steel sales institution are accessed to the block chain platform based on unique identity authentication information; the block chain platform receives thesteel resource information, the quality guarantee information and the quality guarantee document description information which are signed and uploaded by the steel production institution, and storesthe encrypted quality guarantee document into a distributed document storage module; the block chain platform feeds back corresponding quality guarantee information when receiving a query request of the steel sales institution; and after receiving purchase confirmation information of the steel sales institution, the blockchain platform calls a corresponding encrypted quality guarantee document from the distributed file storage module in response to a download request and feeds back the encrypted quality guarantee document, and the encrypted quality guarantee document is downloaded by a purchased user after being decrypted. Compared with the prior art, the method has the advantages of high information security and the like.
Owner:欧冶云商股份有限公司
Certificate-based equality test encryption method
InactiveCN109889332AAvoid Hosting IssuesSolve the problem of privacy protectionKey distribution for secure communicationCiphertextInformation security
The invention discloses a certificate-based equality test encryption method, and belongs to the technical field of cloud computing and information security. The method is characterized in that a certificate-based encryption technology is used in a constructional column to construct the method, and the certificate with a short lifetime is used in the technology, so that the tedious certificate management problem caused by a public key infrastructure encryption technology is avoided to a certain extent, and meanwhile, the key hosting problem of an identity-based encryption technology does not exist. The method is safer. Meanwhile, an equality test technology is used, and compared with a previous searchable encryption technology. The method can only be applied to the ciphertext encrypted by the same public key. In order to be more suitable for cloud servers storing different user encrypted data, the equality test encryption method can support retrieval of ciphertext encrypted by the samepublic key and can also retrieve ciphertext encrypted by different public keys.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
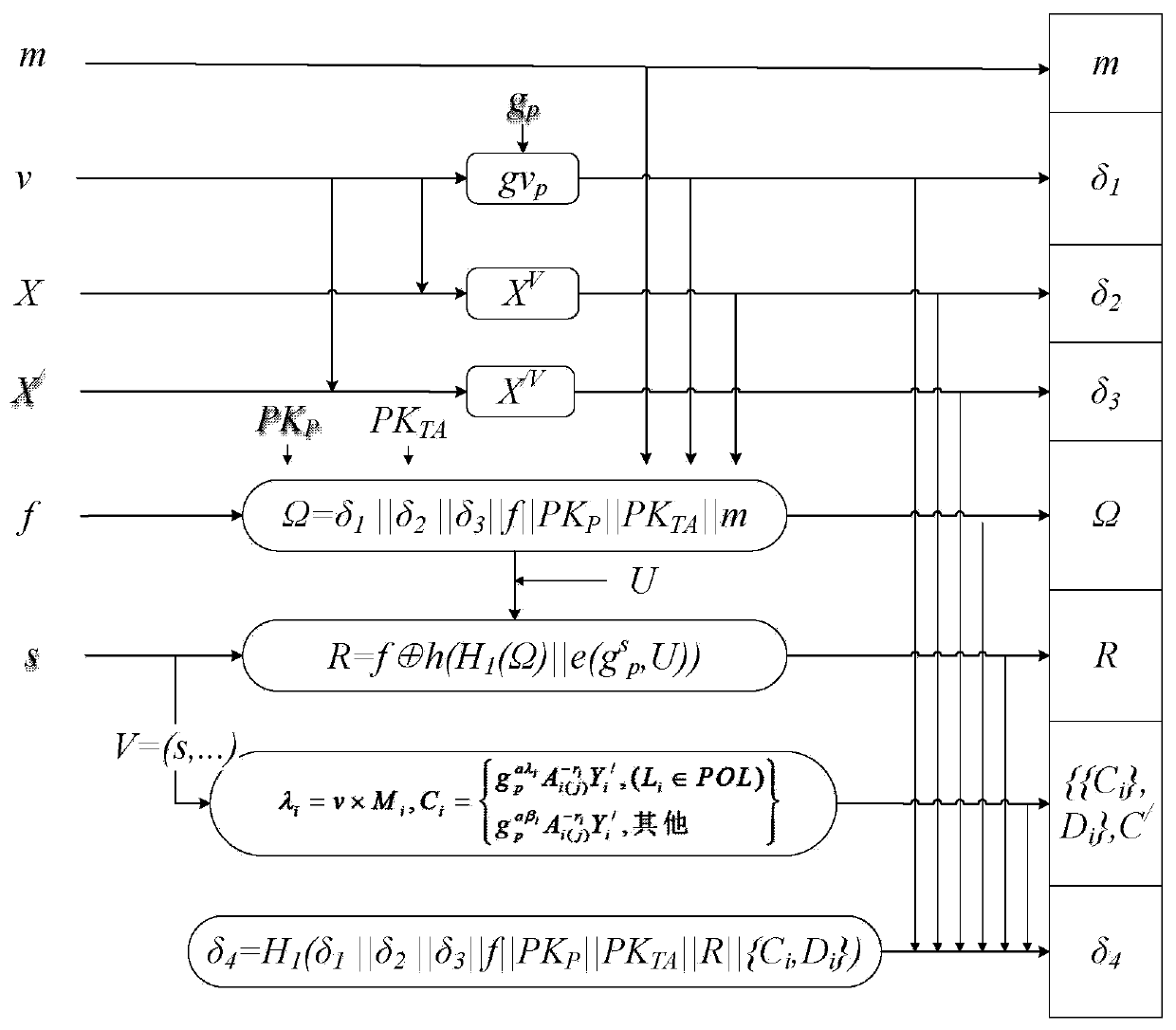
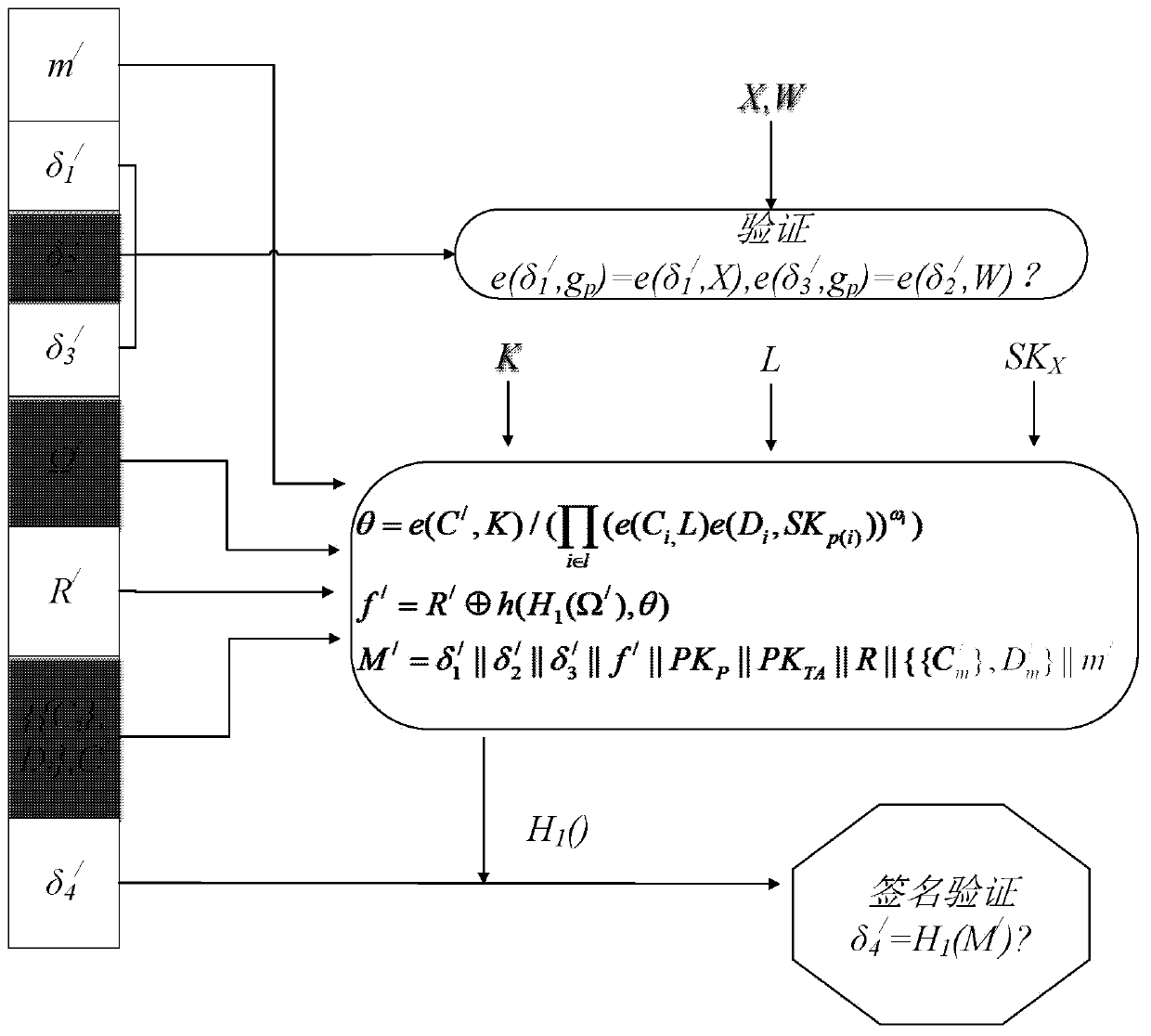
Strategy control signature method supporting privacy protection
ActiveCN111431715ASolve the problem of privacy protectionKey distribution for secure communicationPublic key for secure communicationAccess structurePrivacy protection
The invention discloses a strategy control signature method supporting privacy protection. The idea of strategy control signature is introduced, the access strategy is embedded into the signature, a sender is allowed to specify a receiver with the attribute to verify the authenticity of the message, when sensitive data is processed, the privacy of the sender to the message and more application scenes are improved, and fine-grained permission control over the verifier is achieved. Meanwhile, global attributes are set, noise attributes are increased, a linear secret sharing matrix (LSSS) is adopted as an access structure, the expression capacity is high, a three-prime-number-sum-order bilinear group is used for hiding an actual access strategy, the processed global attributes are disclosed,and the verification efficiency and the feasibility of actual application are improved.
Owner:武汉力龙信息科技股份有限公司
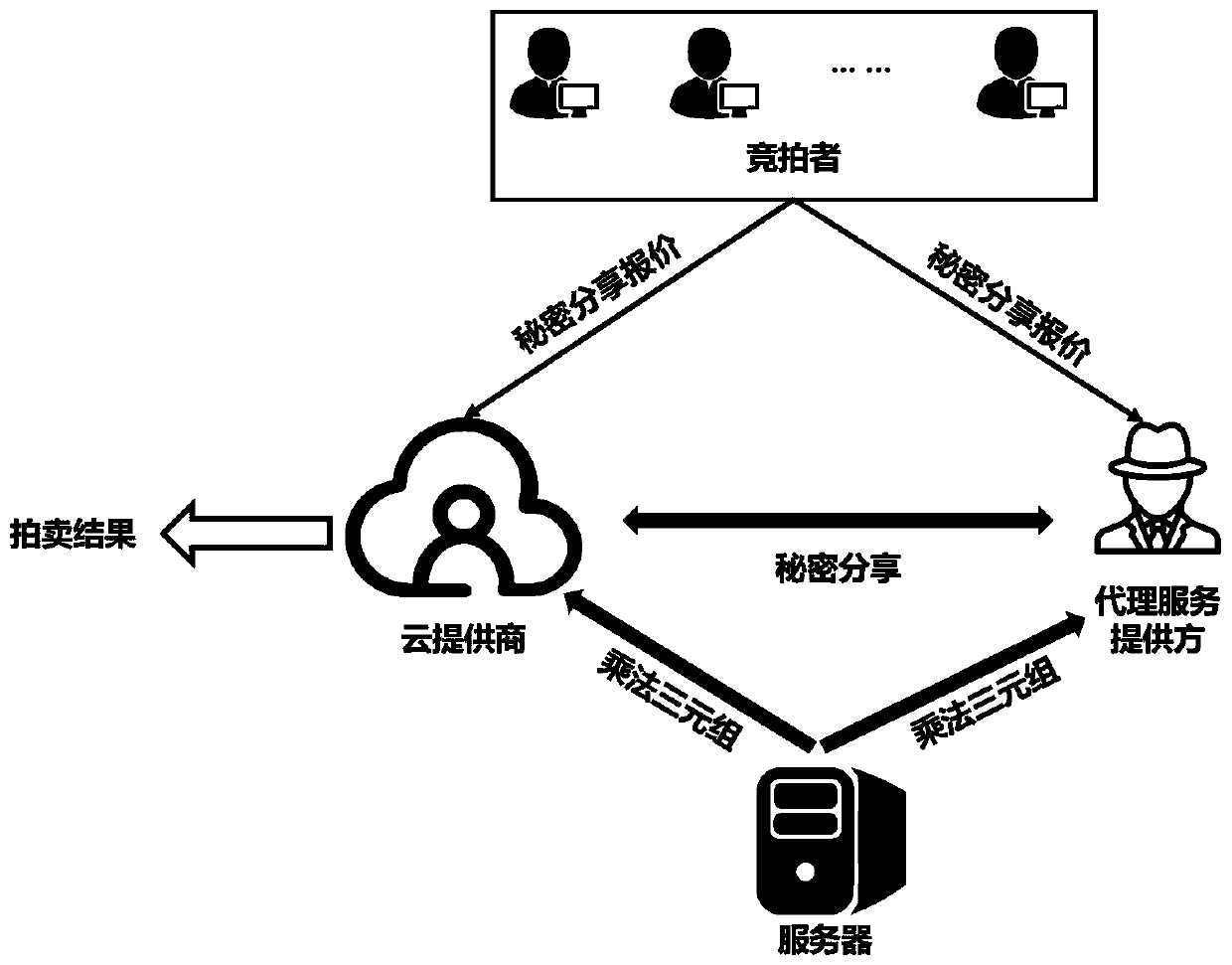
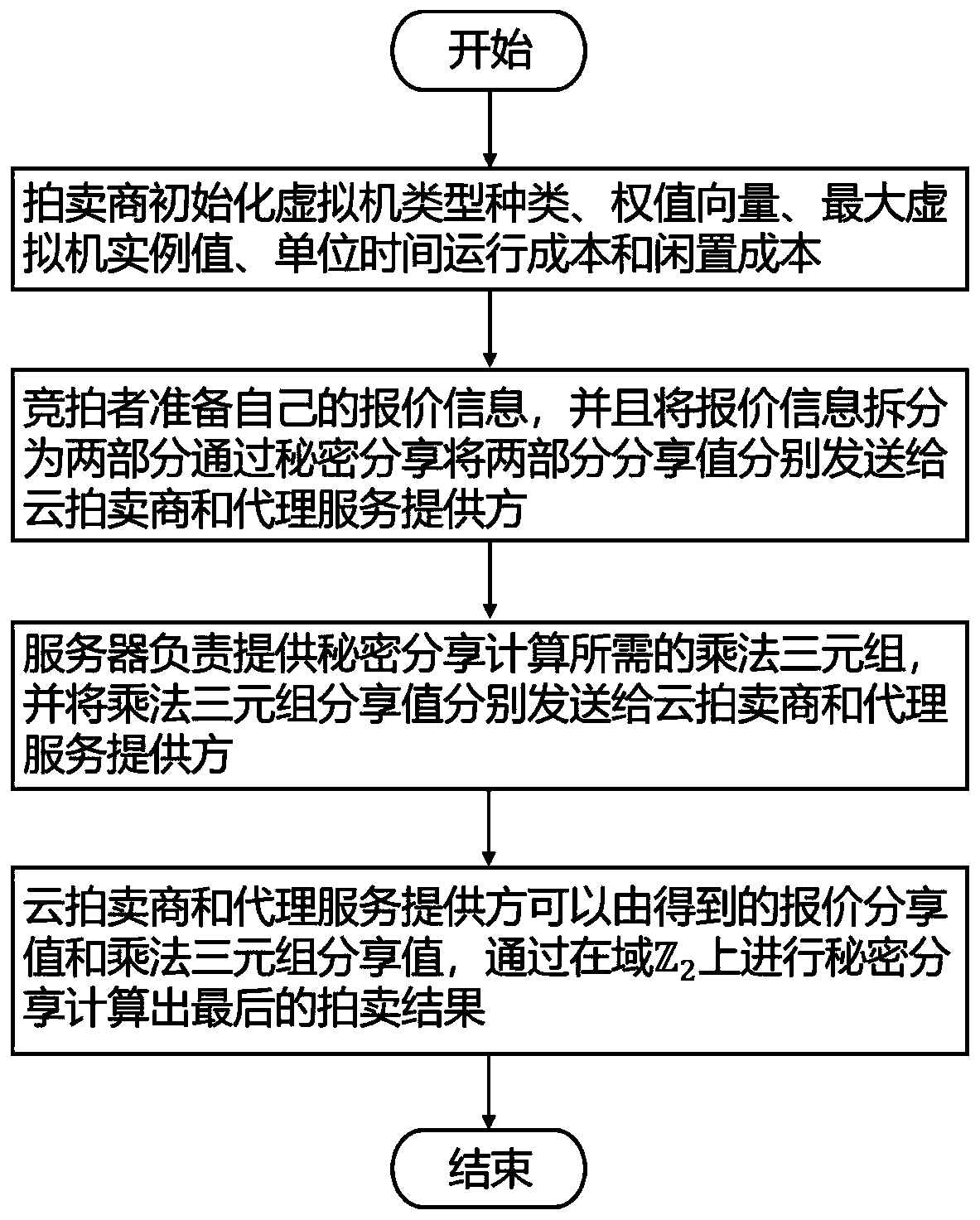
Dynamic virtual machine distribution method based on combined cloud auction mechanism and privacy protection
ActiveCN110460440AProtect Quote InformationSolve the problem of privacy protectionKey distribution for secure communicationResource allocationDistribution methodDynamic resource
The invention discloses a dynamic virtual machine distribution method based on a combined cloud auction mechanism and privacy protection. The method is applied to a dynamic resource allocation cloud auction scene composed of n bidders, a cloud auction provider for providing m virtual machine instances, an agent service provider and a trusted server, and comprises the following steps: S1, an initialization stage; S2, a quotation submitting stage; and S3, a secret sharing calculation stage. According to the method, the problem that privacy protection is not considered in current dynamic virtualmachine instance allocation in the cloud can be solved, so that related information of a final auction result is not leaked, quotation related information of bidders is protected, and the security ofdynamic virtual machine instance allocation in the cloud is improved.
Owner:ANHUI UNIVERSITY
Video shielding method and device, computer equipment and readable storage medium
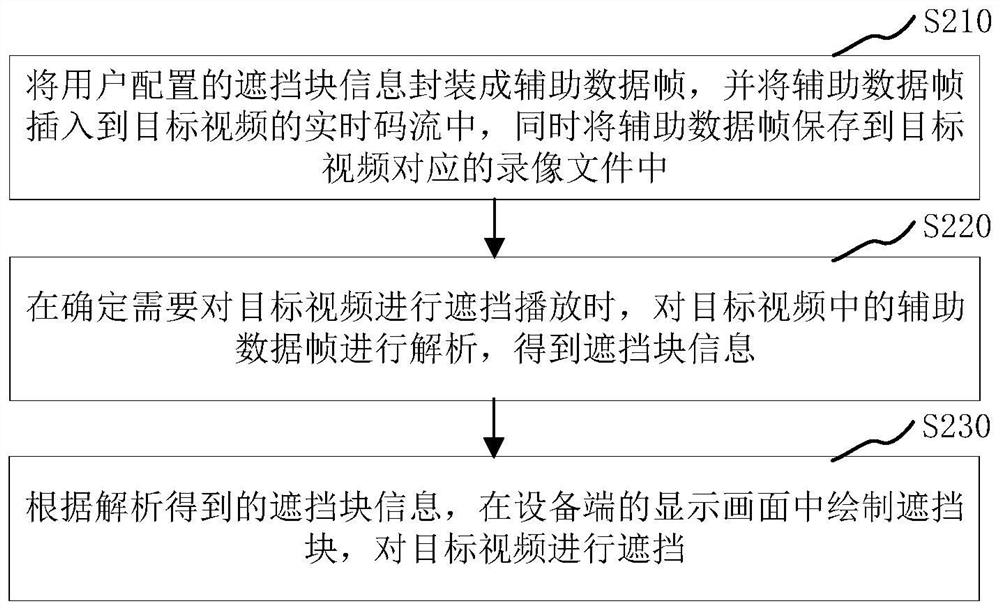
PendingCN114143503AAddress privacy protectionSolve the problem of privacy protectionClosed circuit television systemsSelective content distributionComputer equipmentPrivacy protection
The invention relates to a video shielding method and device, computer equipment and a computer readable storage medium, and the method comprises the steps: storing shielding block information configured by a user in a real-time code stream of a target video and a video file corresponding to the target video in a mode of packaging an auxiliary data frame; an auxiliary data frame in a target video is analyzed according to requirements to obtain shielding block information, a shielding block is drawn on a display picture according to the shielding block information so as to achieve video shielding, and when the access mode of a rear-end device to a front-end device is third-party protocol access and video shielding configuration cannot be issued to the front-end device, the shielding block information is drawn on the display picture according to the shielding block information so as to achieve video shielding. The video shielding function can be directly realized in the display picture of the back-end equipment, and the problem that privacy protection cannot be performed in the display picture of the back-end equipment is effectively solved.
Owner:ZHEJIANG DAHUA TECH CO LTD
Privacy protection method and privacy protection device
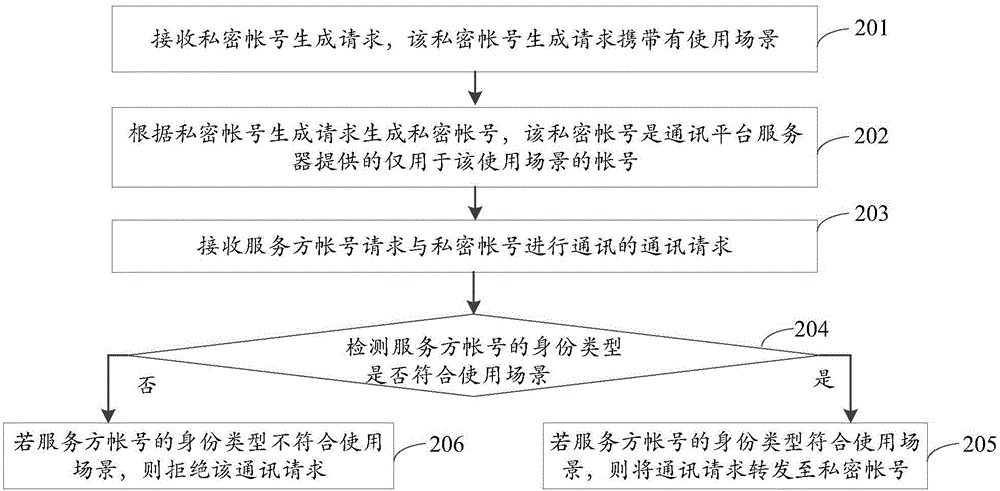
ActiveCN104967605ASolve the problem of privacy protectionAvoid harassmentTransmissionPrivacy protectionInformation security
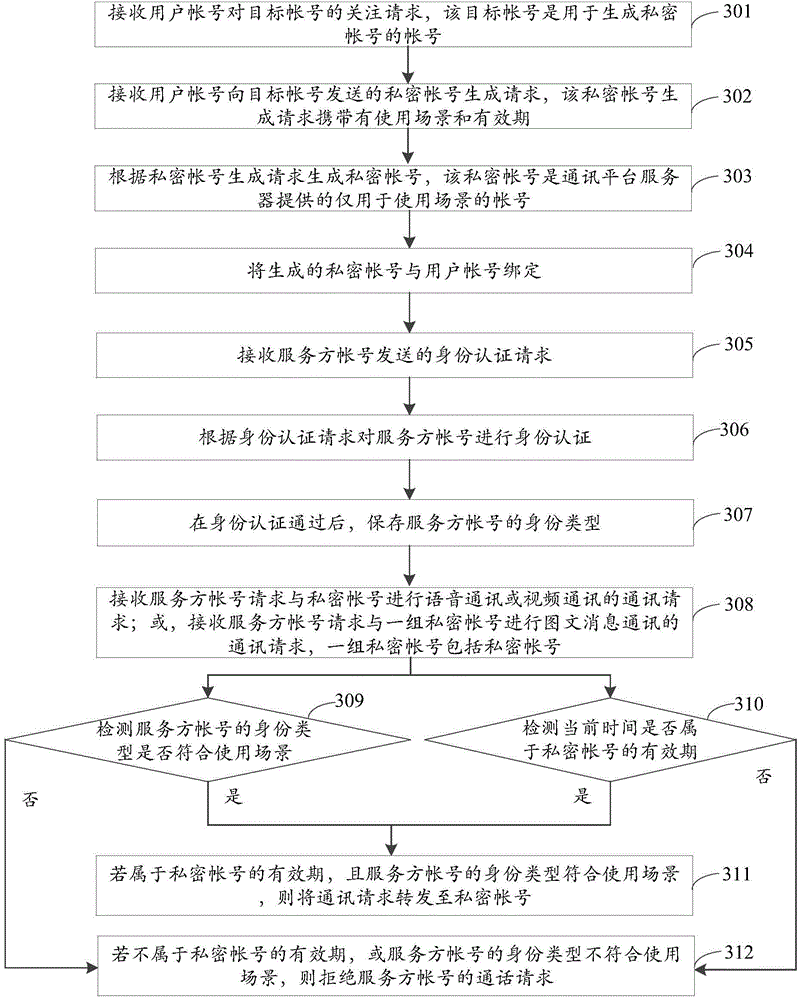
The present invention discloses a privacy protection method and a privacy protection device, and belongs to the information safety field. The method comprises the steps of receiving a private account generation request; generating a private account according to the private account generation request; receiving a communication request of a service party account of requiring to communicate with the private account; detecting whether the identity type of the service party account accords with a use scene; if the identity type of the service party account accords with the use scene, forwarding the communication request to the private account. According to the present invention, by generating the private account of a user, when the communication request of the service party account is received, and if the identity of the service party account accords with the use scene preset by the user, the communication request is forwarded to the private account, and the communication requests which are sent by the service party account and do not accord with the use scene preset by the user are filtered, thereby solving the problem that users are harassed by the malicious calls and that can not be completely solved by the prior art, and realizing the effect of preventing the users from being harassed by the malicious calls that do not accord with the use scene.
Owner:TENCENT TECH (SHENZHEN) CO LTD
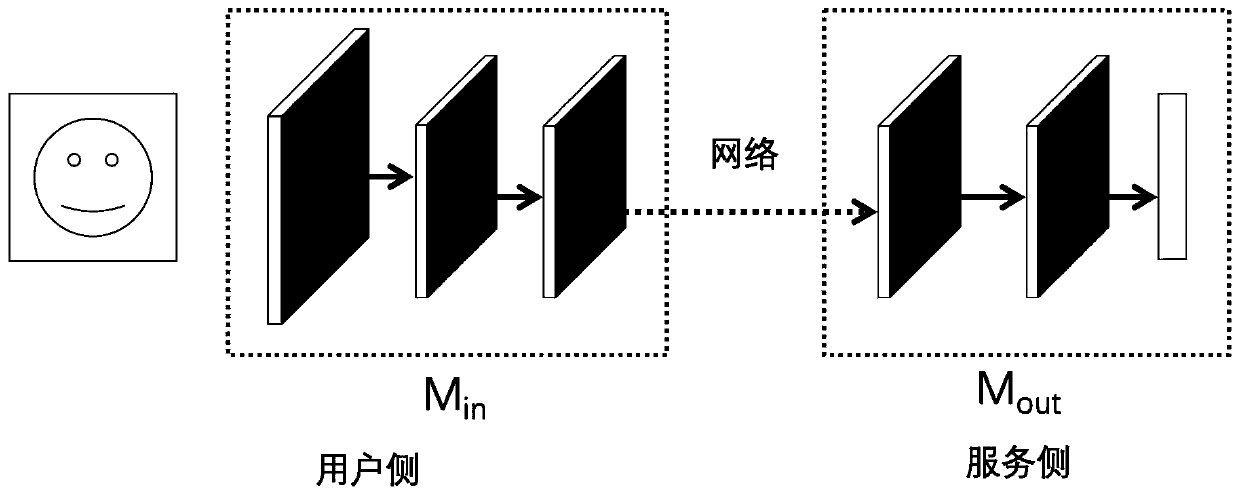
Data and model safety protection method of face recognition system
ActiveCN110598464AProtection securitySolve the problem of privacy protectionDigital data protectionNeural architecturesIntelligent algorithmsNetwork model
The invention provides a data and model safety protection method of a face recognition system, belongs to the technical field of safety protection of an artificial intelligence algorithm in application, and the purposes of protecting the safety of private data of a user and protecting a model of the system from being infringed and used are achieved by separating an input end and an output end of the model. According to the method, the calculation orderliness of the neural network model is reasonably utilized, and the problem of privacy protection of face recognition model providers and customers is solved.
Owner:INSPUR GROUP CO LTD
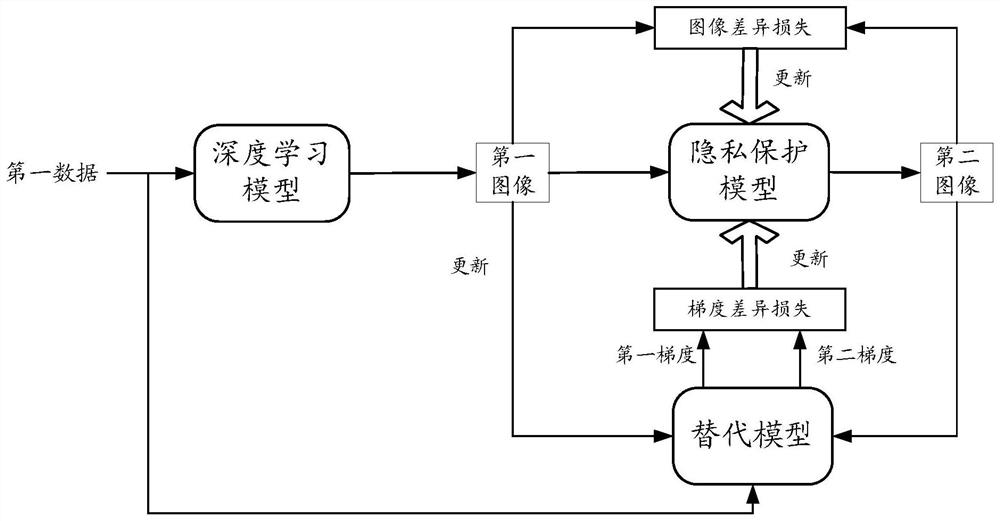
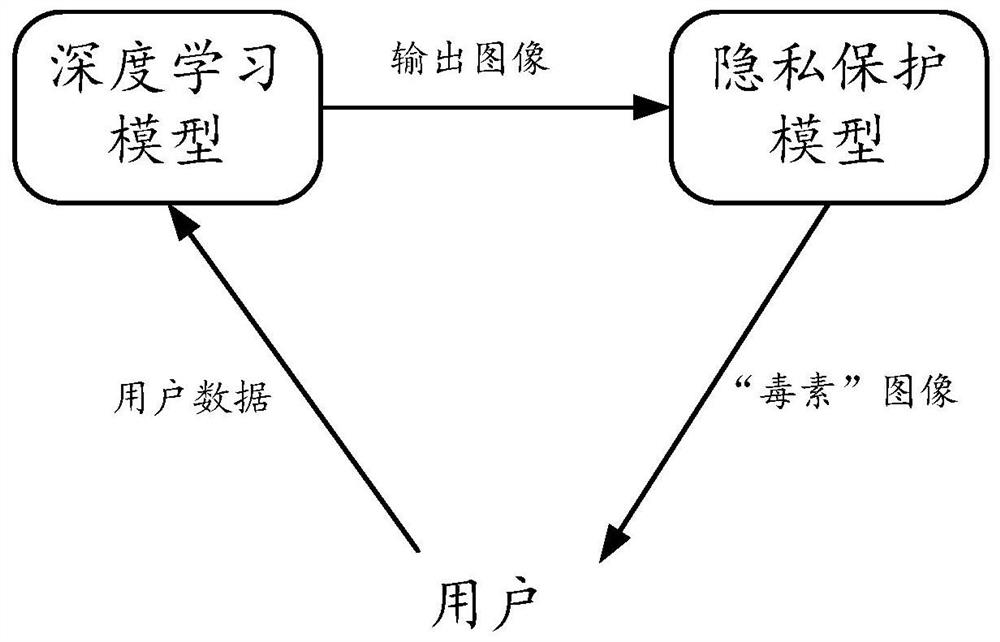
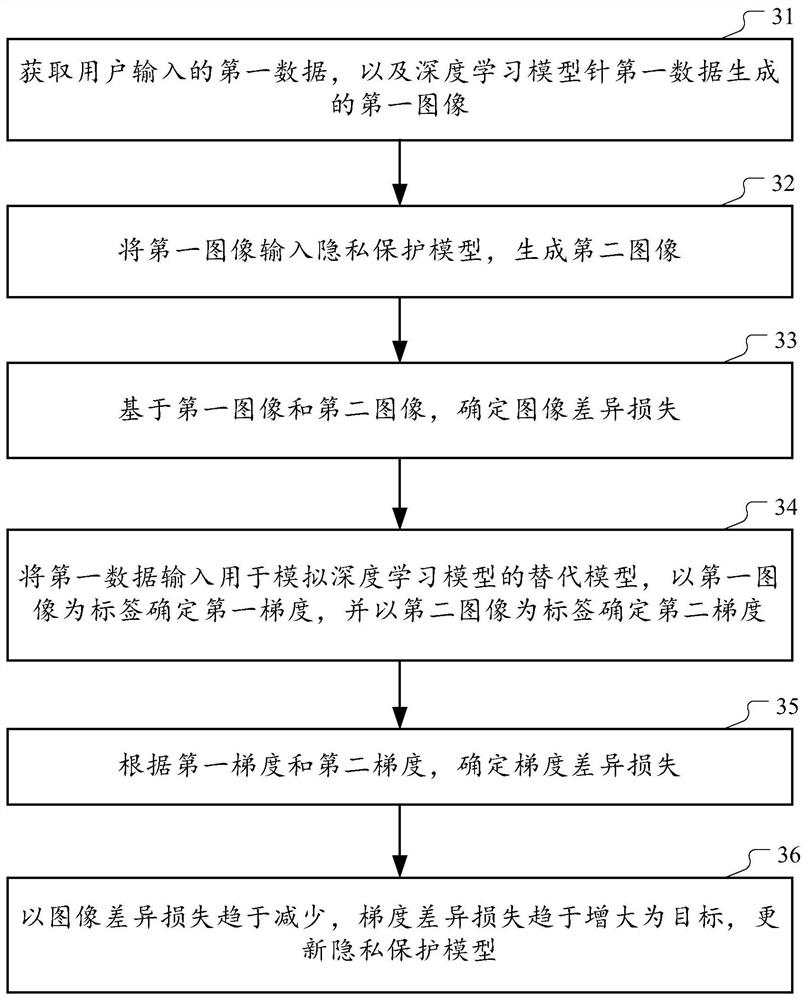
Method for training privacy protection model and privacy protection method and device
PendingCN112487479ASolve the problem of privacy protectionCharacter and pattern recognitionDigital data protectionAlgorithmPrivacy protection
Embodiments of the invention provide a privacy protection model training method, a privacy protection method and a privacy protection device. The privacy protection model is used for providing model privacy protection for a pre-trained deep learning model, an output result of the deep learning model is an image, and the training method comprises the steps of obtaining first data, and a first imagegenerated by the deep learning model for the first data; inputting the first image into the privacy protection model to generate a second image; determining an image difference loss based on the first image and the second image; inputting the first data into a substitution model for simulating a deep learning model, determining a first gradient by taking the first image as a label, and determining a second gradient by taking the second image as a label; determining gradient difference loss according to the first gradient and the second gradient; and updating the privacy protection model by taking image difference loss tending to be reduced and gradient difference loss tending to be increased as targets.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Mail System Based on Mimic Defense
ActiveCN108833417BMeet security needsSolve the problem of building homogeneityData switching networksResource poolInformation processing
The present invention relates to a mimetic mail server information processing device, mail service processing method, device and mail system, wherein the information processing device includes: a resource pool composed of a user transmission agent component and a server mailbox component; the user transmission agent component includes A number of heterogeneous user transfer agent execution bodies, the server mailbox component contains several server mailbox execution bodies; multiple parallel heterogeneous mail service chains composed of various components selected from the resource pool randomly; used to monitor the operation of each execution body and A dynamic feedback control module for dynamic scheduling of various components. The present invention creates a variety of executors, performs mimetic judgment output on multiple processing results, improves the security performance of the mail system service, improves the initiative, variability and randomness of the defense ability of the mail system, effectively solves the privacy protection problem, and can effectively solve the problem of privacy protection. Providing a more secure mail server solution has important guiding significance for mail system security technology.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Privacy protection encrypted data query method based on fog assistance
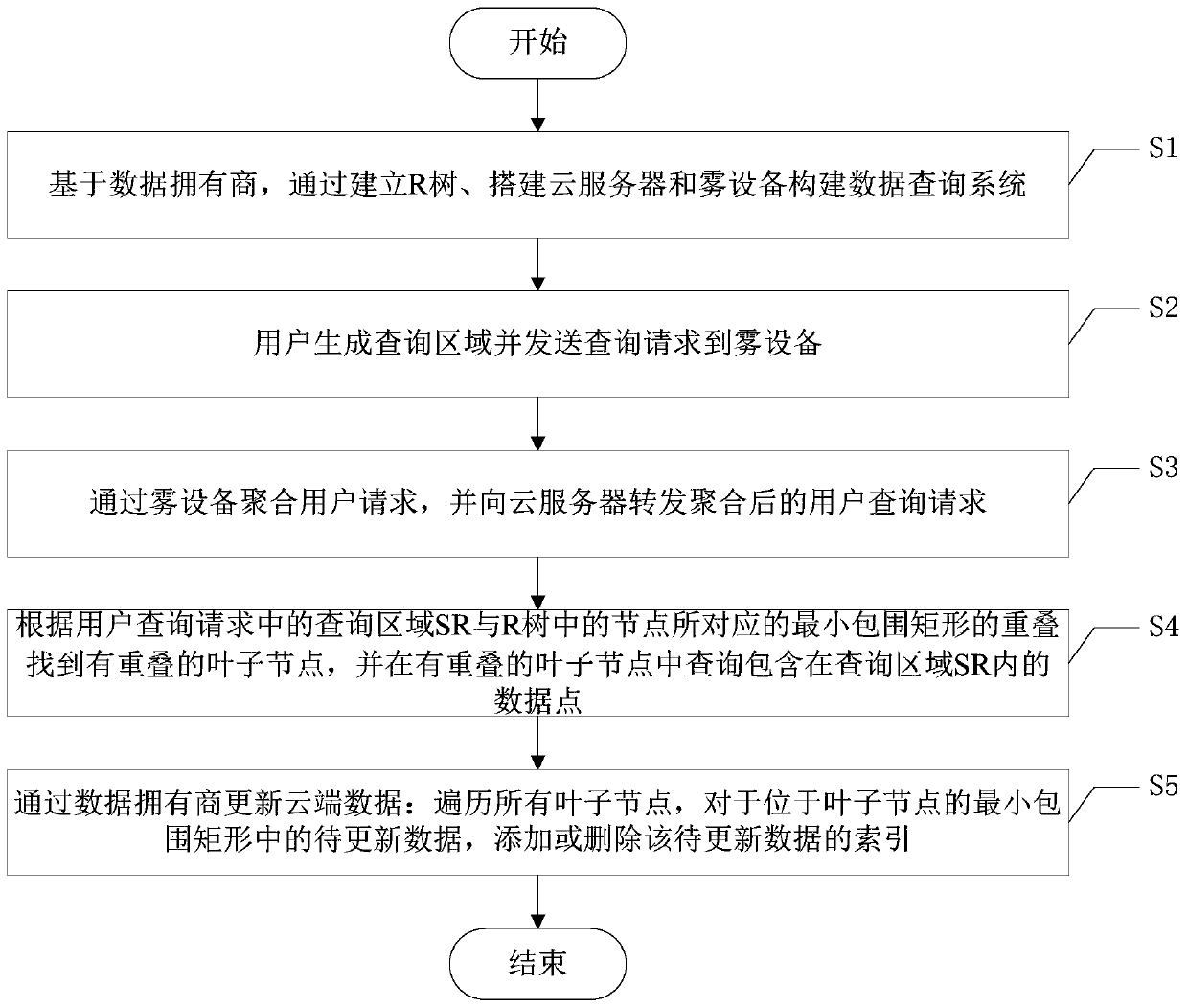
ActiveCN110601812ASolve the problem of privacy protectionImprove query efficiencyKey distribution for secure communicationDigital data protectionMinimum bounding rectangleInternet privacy
The invention discloses a privacy protection encrypted data query method based on fog assistance, and the method comprises the following steps: S1, building an R tree, a cloud server and fog equipmentbased on a data owner, and building a data query system; s2, enabling the user to generate a query area and send a query request to the fog device; s3, aggregating the user requests through fog equipment, and forwarding the aggregated user query requests to a cloud server; and S4, finding leaf nodes with overlap according to the overlap of the query area SR in the user query request and the minimum bounding rectangle corresponding to the nodes in the R tree, and querying data points contained in the query area SR in the leaf nodes with overlap. According to the invention, a light data outsourcing privacy protection structure is constructed, and the data privacy of a data owner and the query privacy of a user are protected under the structure.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA +1
Business video telephone set with hidden camera
ActiveCN102186048ADoes not damage aestheticsExtend your lifeTelevision system detailsColor television detailsKey pressingPrivacy protection
Owner:NANJING NANFANG TELECOMM
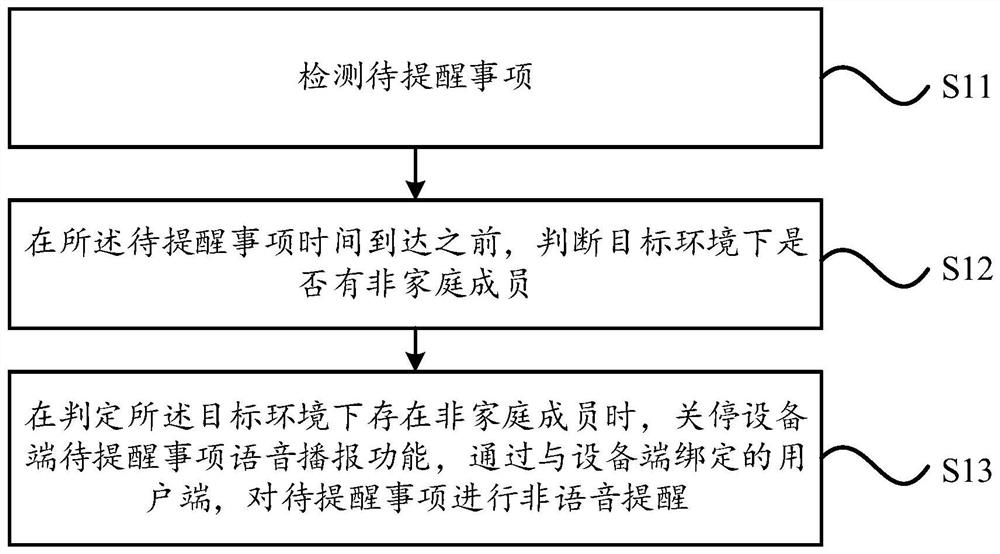
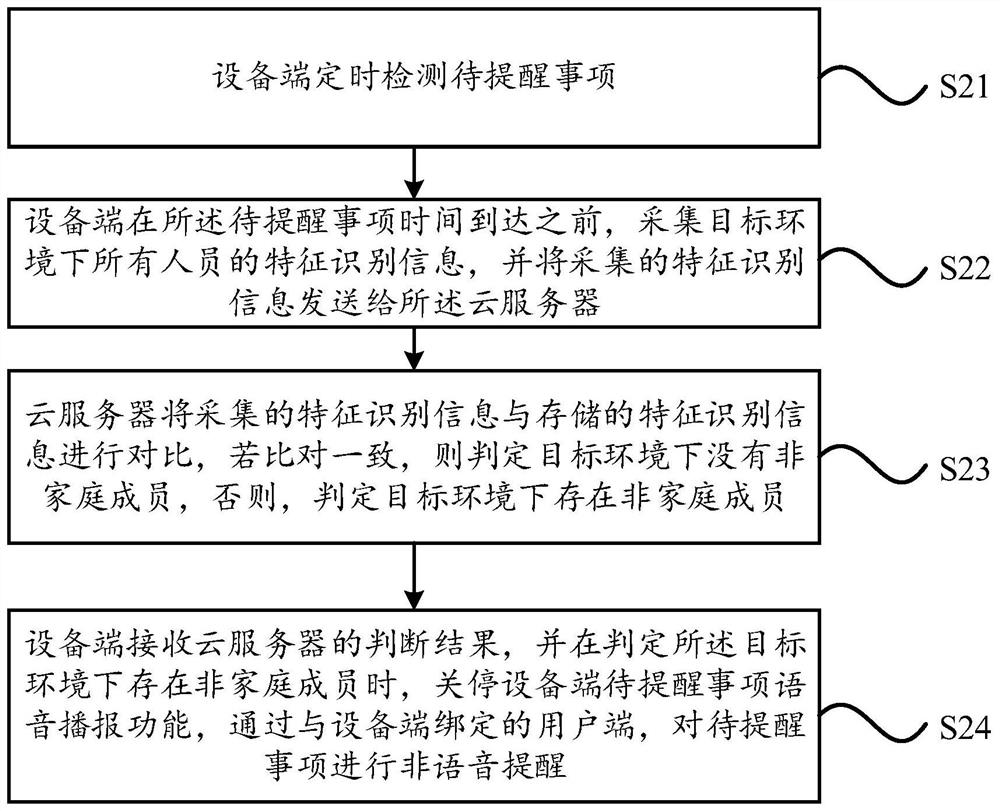
Device end voice reminding method and system and household appliance
InactiveCN113765757ASolve the problem of privacy protectionImprove experienceSubstation equipmentHome automation networksPrivacy protectionEngineering
The invention relates to a device end voice reminding method and system and a household appliance. The method comprises the following steps: detecting a to-be-reminded item; before the time of the to-be-reminded item arrives, judging whether a non-family member exists in a target environment or not; and when it is judged that the non-family members exist in the target environment, turning off a voice broadcast function of a to-be-reminded item of an equipment end, and performing non-voice reminding on the to-be-reminded item through a user end bound with the equipment end. According to the technical scheme, the to-be-reminded item is detected, whether the non-family members exist in the target environment or not is judged before the time of the to-be-reminded item is up, and when it is judged that the non-family members exist in the target environment, the to-be-reminded item voice broadcast function of the equipment end is shut down, non-voice reminding is performed on the to-be-reminded item through the user side bound with the equipment side, so that voice reminding or non-voice reminding is performed on the to-be-reminded item according to the user scene, the privacy protection problem when non-family members exist is solved, and the user experience is improved.
Owner:GREE ELECTRIC APPLIANCES INC
Block chain-based energy data trusted sharing system and method
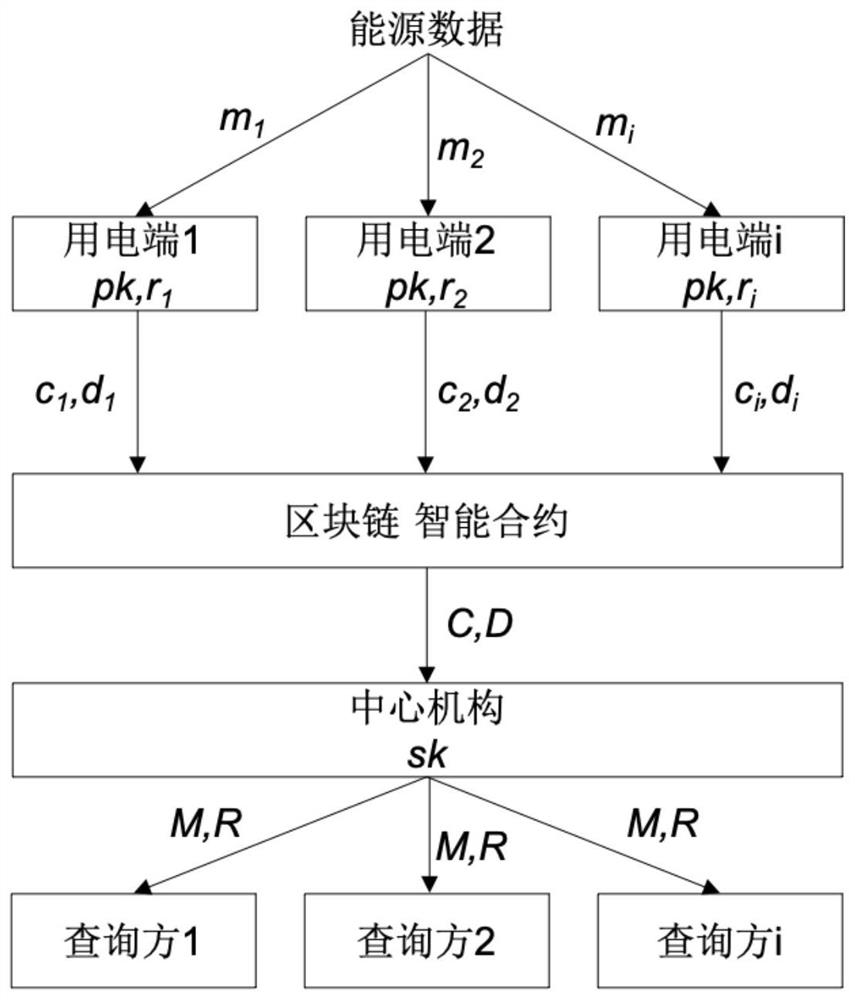
PendingCN113660226AAchieve sharingSolve the problem of privacy protectionCommunication with homomorphic encryptionComputer networkPrivacy protection
The invention relates to an energy data credible sharing system and method based on a block chain. The system comprises a plurality of electricity utilization ends, the block chain, an intelligent contract on the block chain, a central mechanism and a plurality of statistical result query parties. The plurality of power utilization terminals are respectively connected with the block chain and the smart contract on the block chain, the output ends of the block chain and the smart contract on the block chain are connected with the central mechanism, the output end of the central mechanism is respectively connected with the statistical result query party, the statistical result query party makes a query result request to the central mechanism, and the central mechanism decrypts and shows the query result. According to the invention, the privacy protection problem in energy data sharing management can be solved.
Owner:STATE GRID TIANJIN ELECTRIC POWER +1
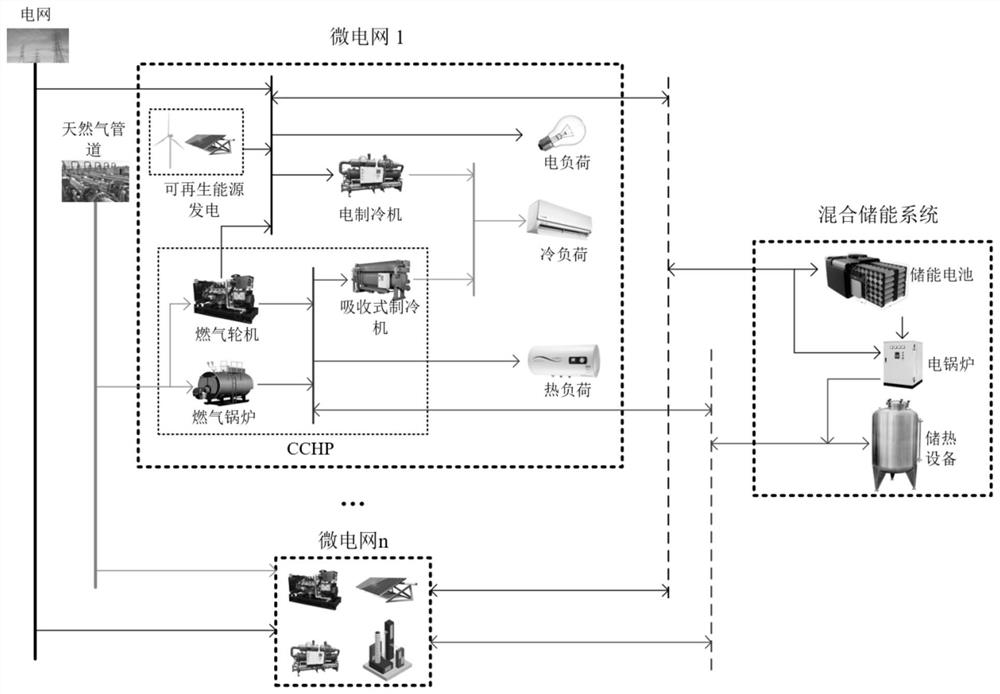
Renewable energy source-oriented multi-energy microgrid shared energy storage control method and system
PendingCN114123260AImplement deprecationReduce deprecationForecastingSingle network parallel feeding arrangementsNew energyMicro grid
The invention discloses a renewable energy source-oriented multi-energy microgrid shared energy storage control method and system, and belongs to the field of new energy consumption. Comprising the following steps: minimizing the total energy cost of all multi-energy microgrids and hybrid energy storage systems participating in shared energy storage as a target function; the energy flow between the micro-grid and the hybrid energy storage system is used as a decision variable; the method comprises the following steps: by taking electric quantity and natural gas quantity purchased from the outside of a micro-grid and energy flow in a single micro-grid as decision variables, and taking energy storage loss cost of a hybrid energy storage system, charging and discharging speed of the hybrid energy storage system and thermoelectric conversion of the hybrid energy storage system as decision variables, constructing constraint conditions for each decision variable; a hybrid energy storage system shared energy storage optimization control model is constructed; and solving the shared energy storage optimization control model of the hybrid energy storage system by adopting distributed optimization to obtain a control scheme that a plurality of micro-grids share a single hybrid energy storage system.
Owner:HUAZHONG UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com