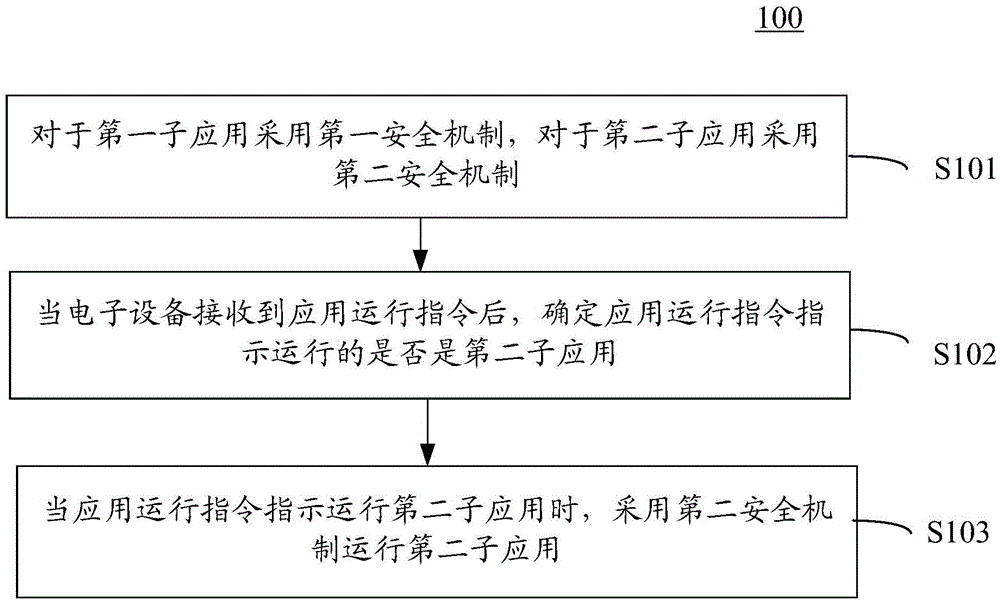
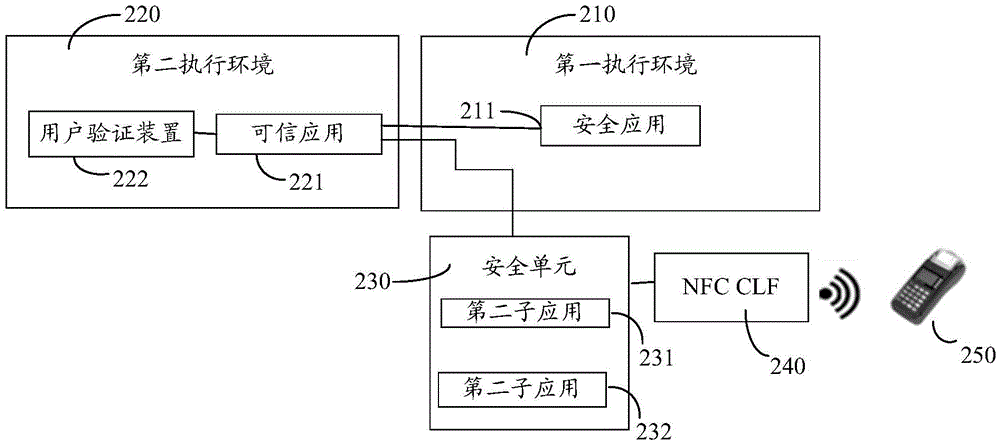
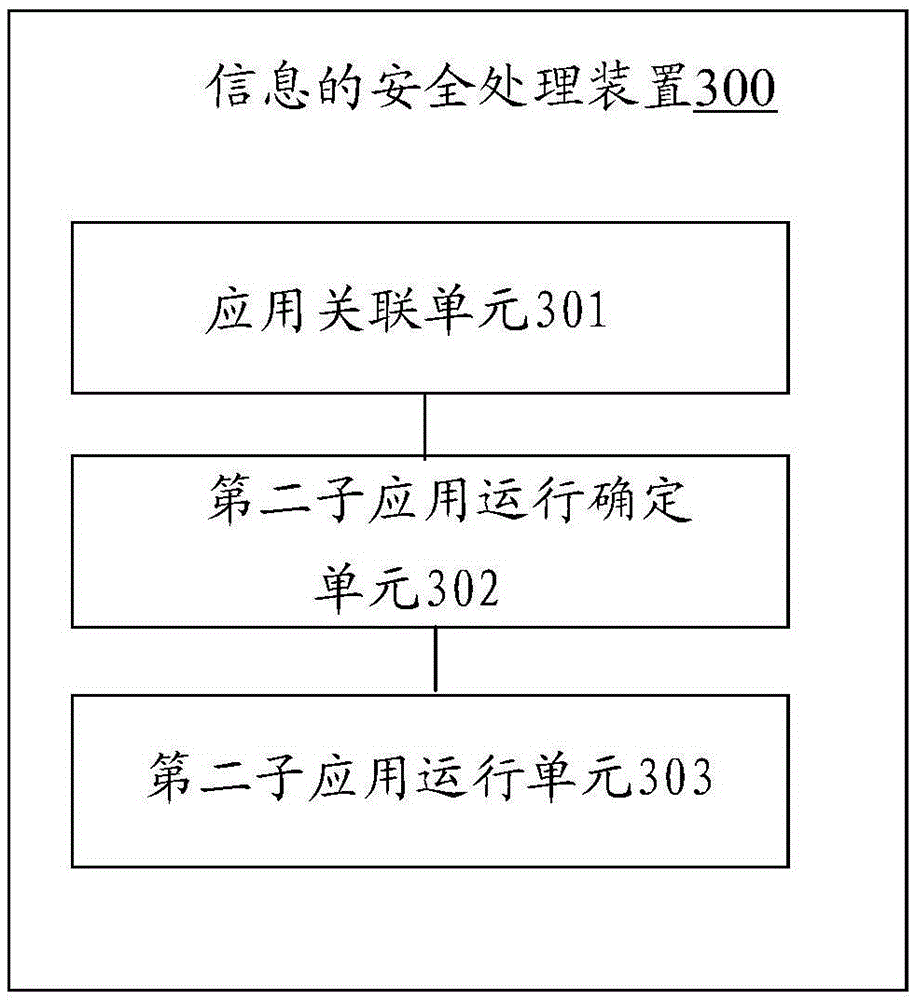
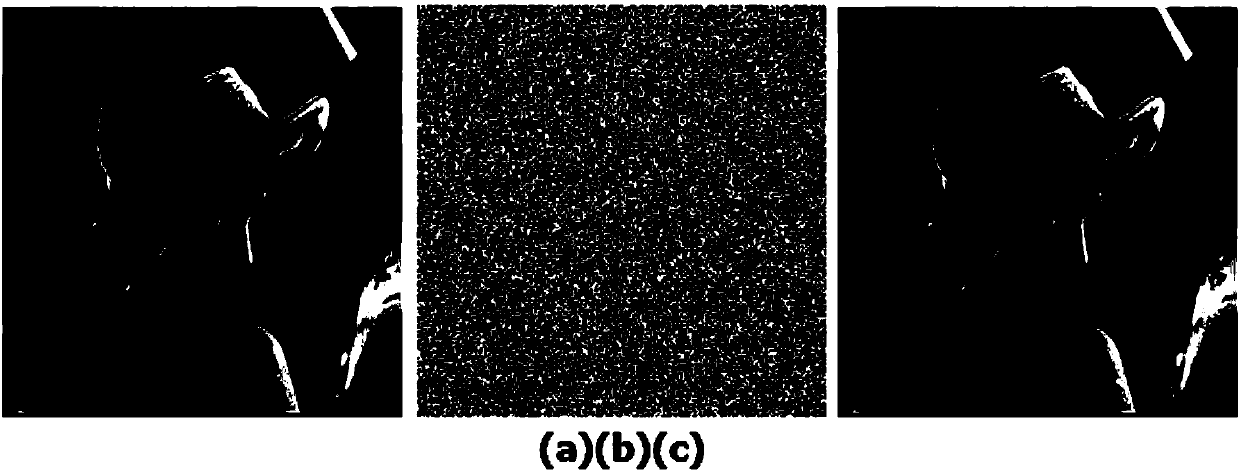
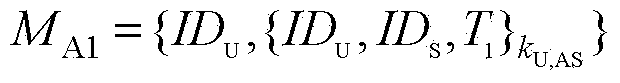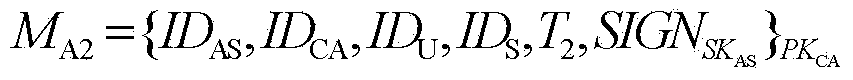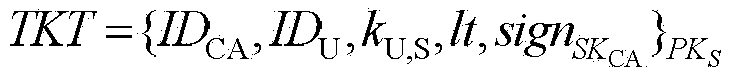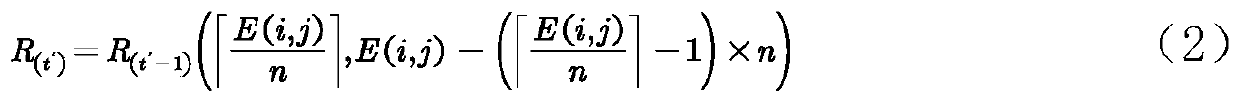Patents
Literature
200results about How to "High security requirements" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
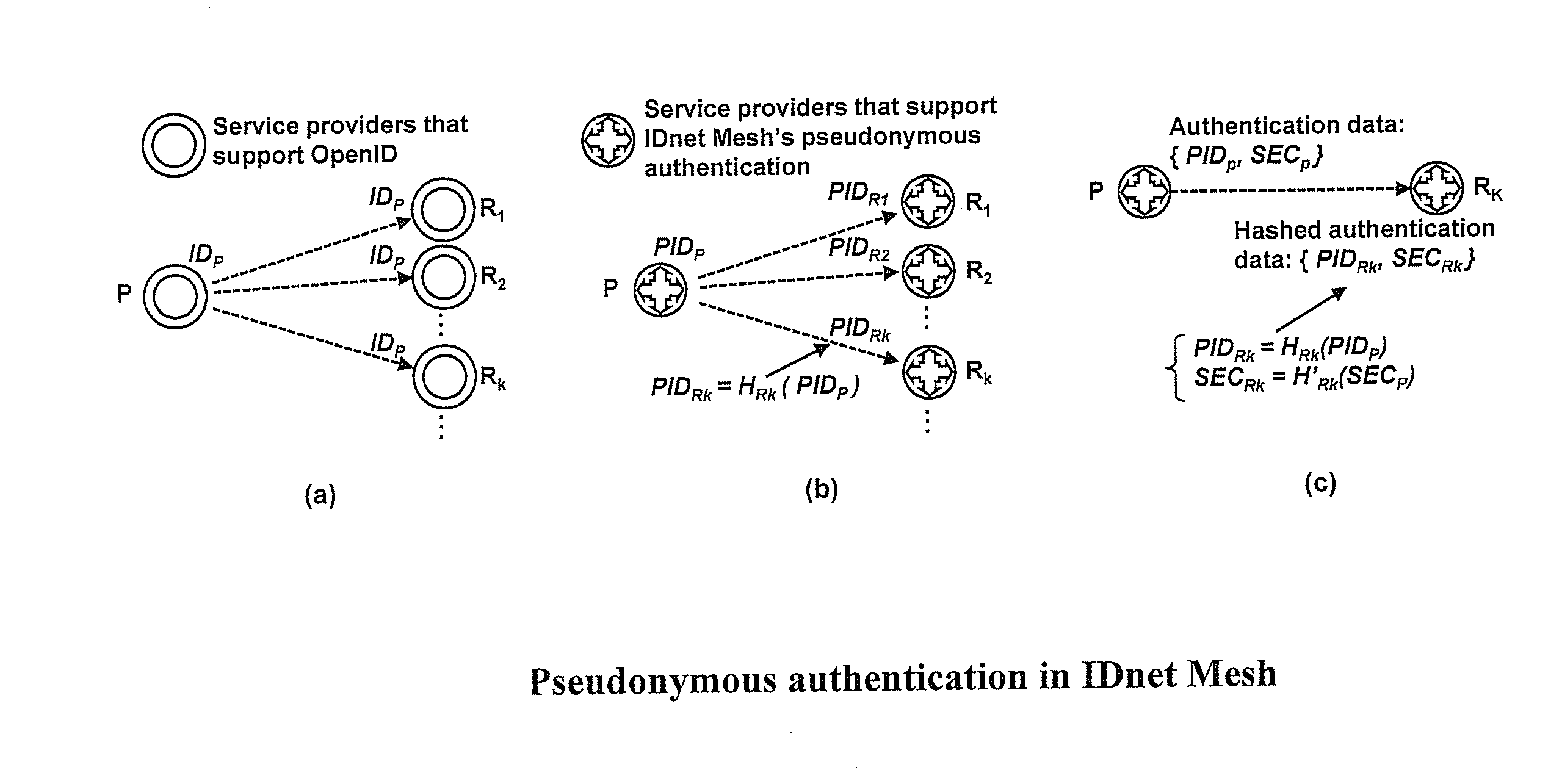
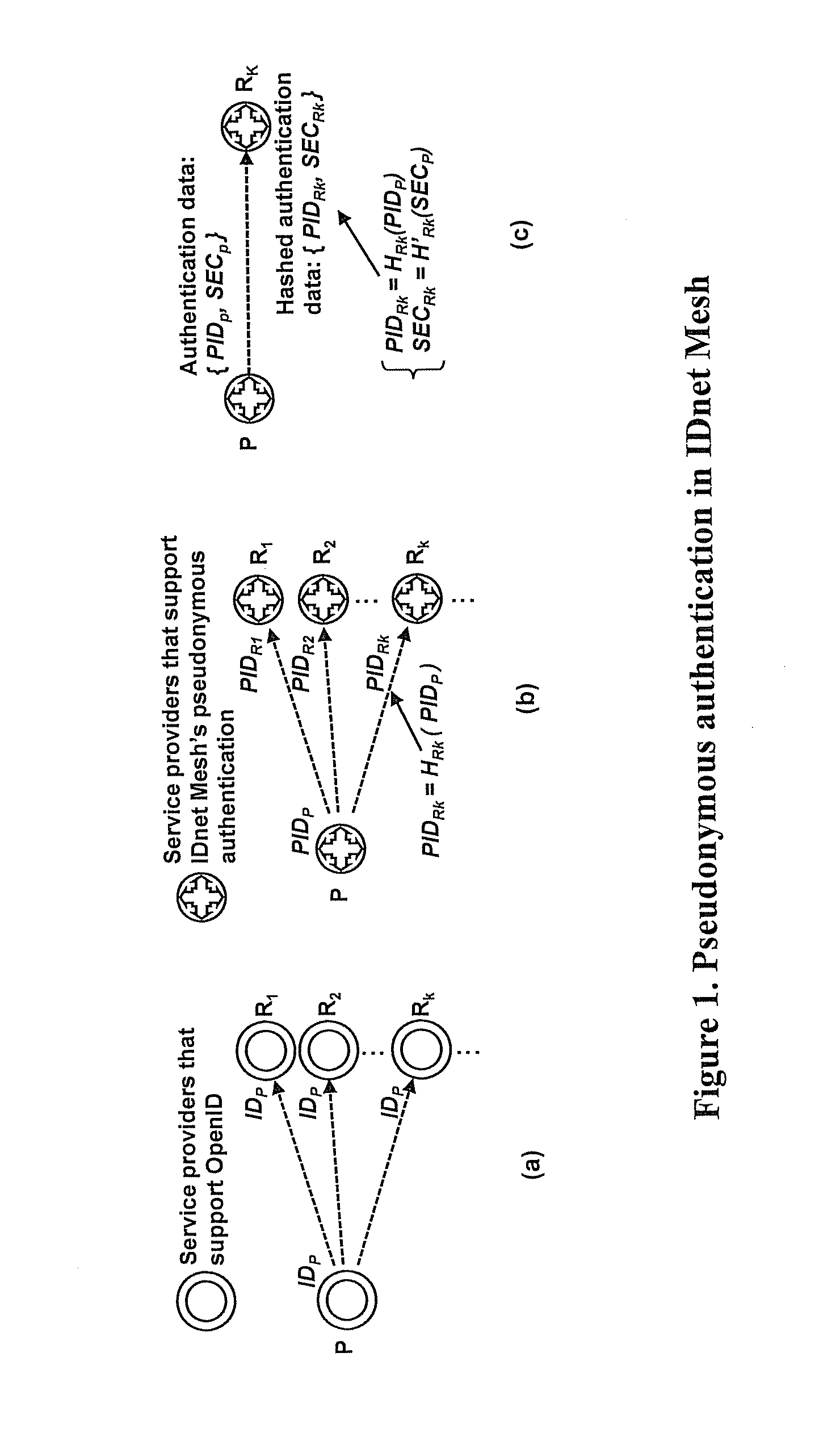
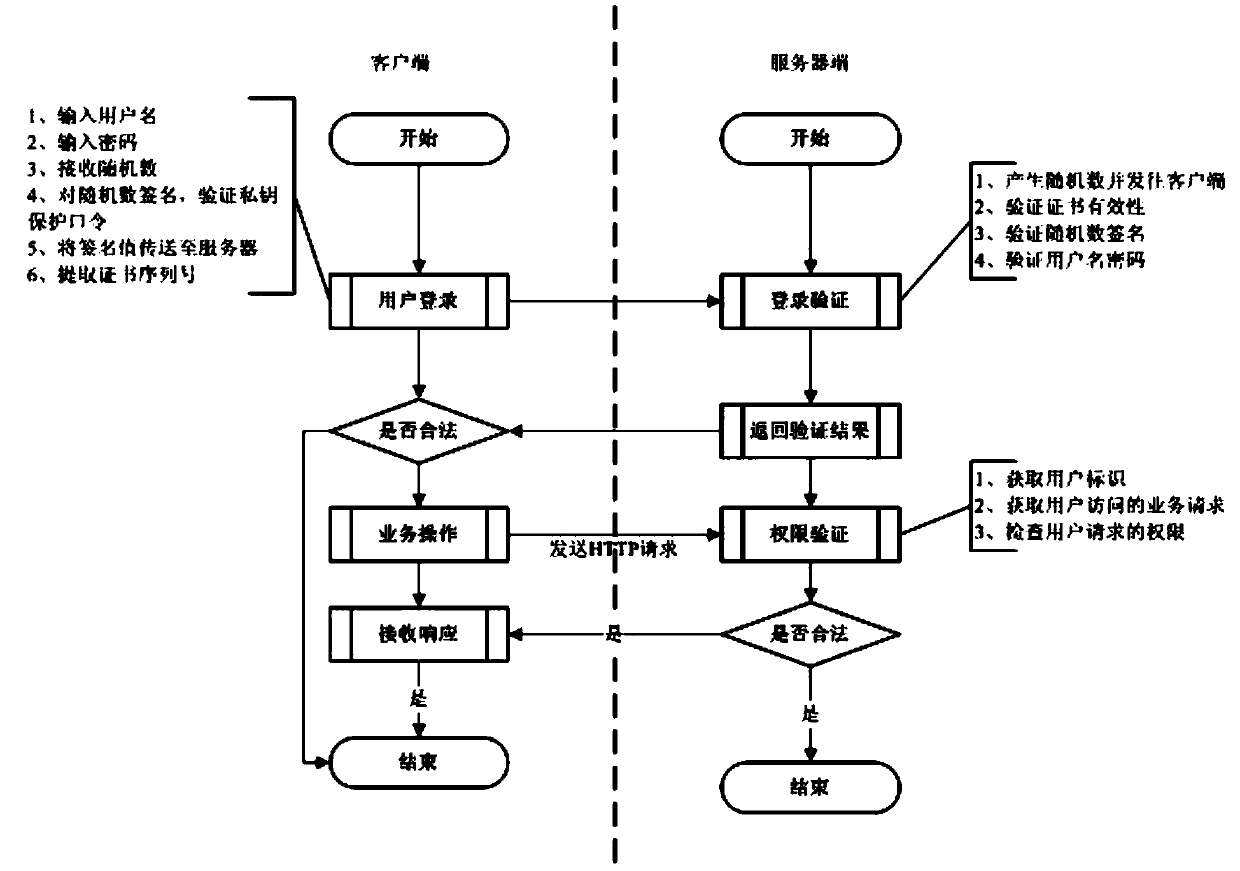
Pseudonymous public keys based authentication
InactiveUS20110302412A1High security requirementsImprove securityUser identity/authority verificationAuthentication systemNon-repudiation
Systems and methods for pseudonymous public keys based authentication are described that enable an authentication to achieve pseudonymity and non-repudiation, for example, at the same time. Pseudonymity may provide, for example, that a user can show to different parties different digital identifiers for authentication instead of, for example, always using a single digital identifier everywhere, which may lead to a breach of privacy. Non-repudiation may provide, for example, that the authentication data at the server side can be used, for example, to verify a user's authentication request, but not to generate an authentication request, which might lead to user impersonation. A user may use a physical token to generate the authentication request corresponding to the user's identity to pass the authentication.
Owner:NORTHWESTERN UNIV
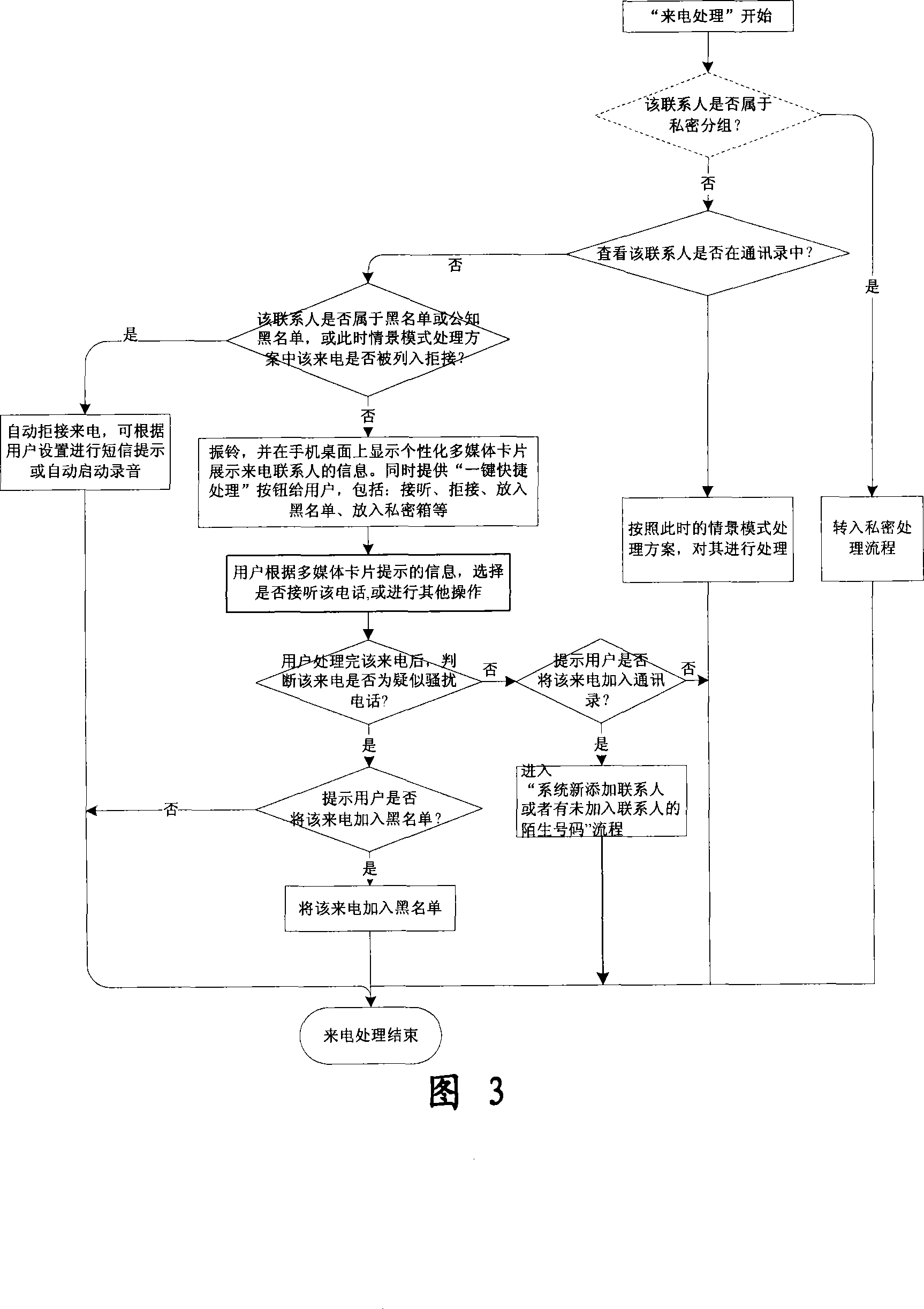
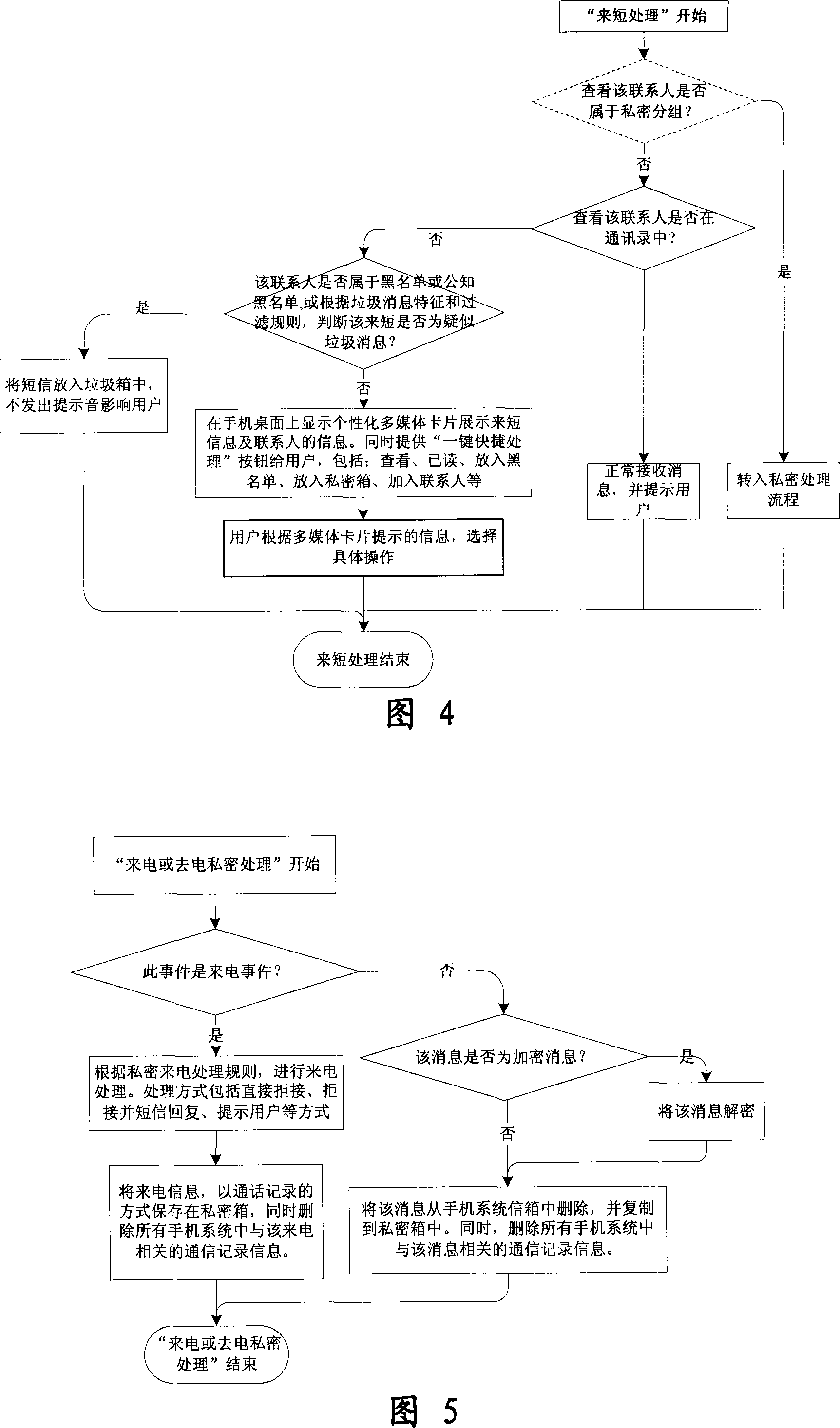
Mobile phone telephone and message anti-disturbance and private communication method and system
InactiveCN101184264AImprove filtering effectOptimize the effect of anti-harassmentRadio/inductive link selection arrangementsSubstation equipmentPrivate communicationSocial statistics
The invention relates to a processing method and the system of anti-harassment of mobile phone calls and messages and private communication, which is as follow: when grouping the contacts in the mobile phone address list according to different classes, a private group of private communicating contacts is added, and different scene modes of the user are set; when receiving a mobile phone call or a message (text message, multimedia message), depending on the grouping sort of the contact of the incoming call or the message or the multimedia message, and the current scene of the user, together with the behavior characteristics of the harassing call and the spam message with the database information of the public harassing message issued by the authoritative institution or obtained from social statistics, the corresponding process to the call, the message and the multimedia message of the mobile phone is executed to reduce harassment; meanwhile the communication records of incoming, dialed calls and message, multimedia message with the contacts in the private grouping are encrypted and preserved to protect the personal privacy of the user. The invention has the advantages of adopting the operating steps of uniform process, and resolving synthetically the harassment of calls, messages and multimedia messages for the mobile phone and the private protection.
Owner:BEIJING NETQIN TECH
Method for cross-isomerism domain identity authentication and session key negotiation based on access authorization ticket
ActiveCN103780618AHigh security requirementsStrong computing powerUser identity/authority verificationPublic key authenticationKey-agreement protocol
The invention provides a method for cross-isomerism domain identity authentication and session key negotiation based on an access authorization ticket. The method mainly comprises the steps that firstly, a first-level trust relationship is established between a CA of a PKI domain and an AS of a Kerberos domain through a distributed trust model based on a public key authentication mechanism; on the basis, the authorization ticket allowing an outer-domain user to have access to resources of the domain is generated and distributed by the CA or the AS united with a TGS, and through design of a two-way cross-domain authentication and key negotiation protocol based on a symmetric key cryptosystem, a second-level trust relationship allowing the outer-domain user to have access to the resources of the domain is established. On the premise that the requirements for safety of the levels are satisfied, the calculated amount and the communication traffic of a terminal are effectively reduced, public key encryption and decryption operations of a Kerberos domain terminal can be completely avoided, and the implementation is good in the cross-isomerism domain identity authentication process of a dynamic distributed type system, session key negotiation is completed when identity authentication is conducted, and the protocol efficiency is high.
Owner:四川华创智能科技有限公司
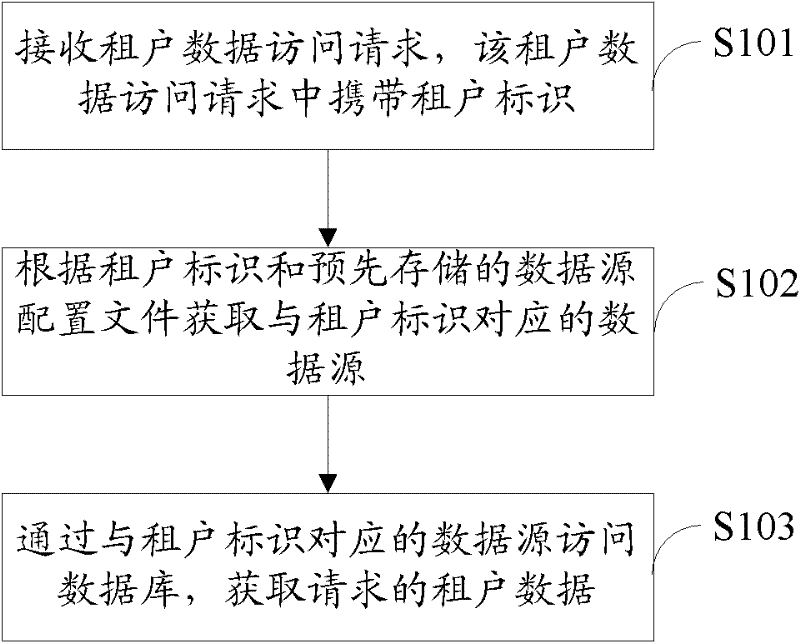
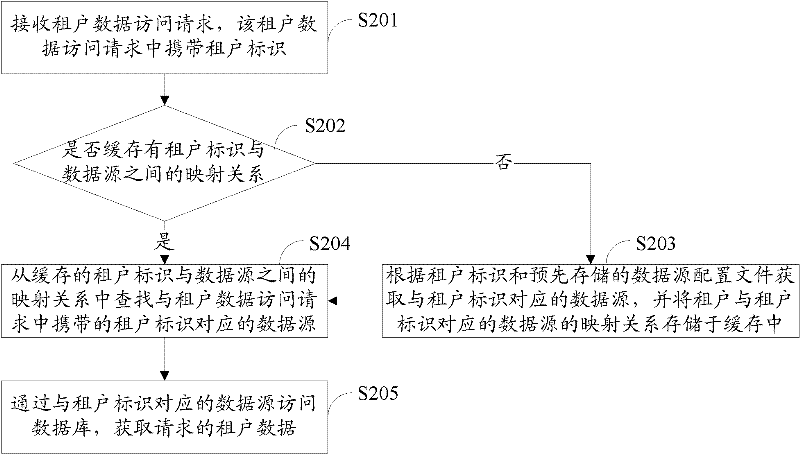
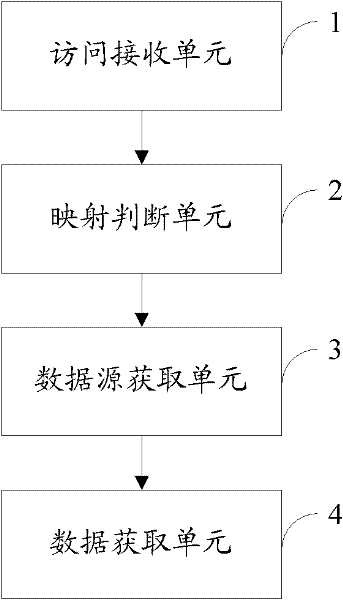
Multi-tenant-oriented data acquisition method, device and system
InactiveCN102456028AImprove the isolation effectHigh security requirementsSpecial data processing applicationsData sourceData acquisition
The invention is applicable to the field of computer software and provides a multi-tenant-oriented data acquisition method, device and system. The method comprises the following steps: receiving a tenant data access request which carries tenant identifiers; obtaining data sources corresponding to the tenant identifiers according to the tenant identifiers and data source configuration files stored in advance; and obtaining the requested tenant data via data source access databases corresponding to the tenant identifiers. The method, the device and the system provided by the invention have the advantages that: one or more data source configuration files can be actually configured according to different application scenarios; therefore the method can be used in different application scenarios and is more widely applied; and a data source configuration file is configured independently for the tenants requiring high isolation performance and security and is used for managing the data sources related to the tenants, thus the requirement of some tenants for high isolation performance and security is met further.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
Electronic contract off-line signing method based on trusted third party
ActiveCN103873255APrevent tamperingHigh security requirementsUser identity/authority verificationCommerceThird partyElectronic contracts
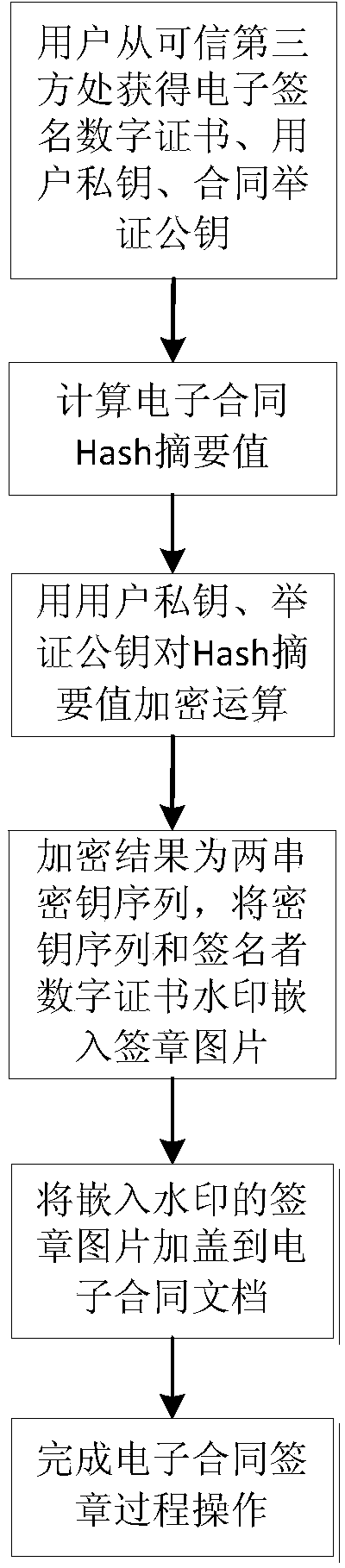
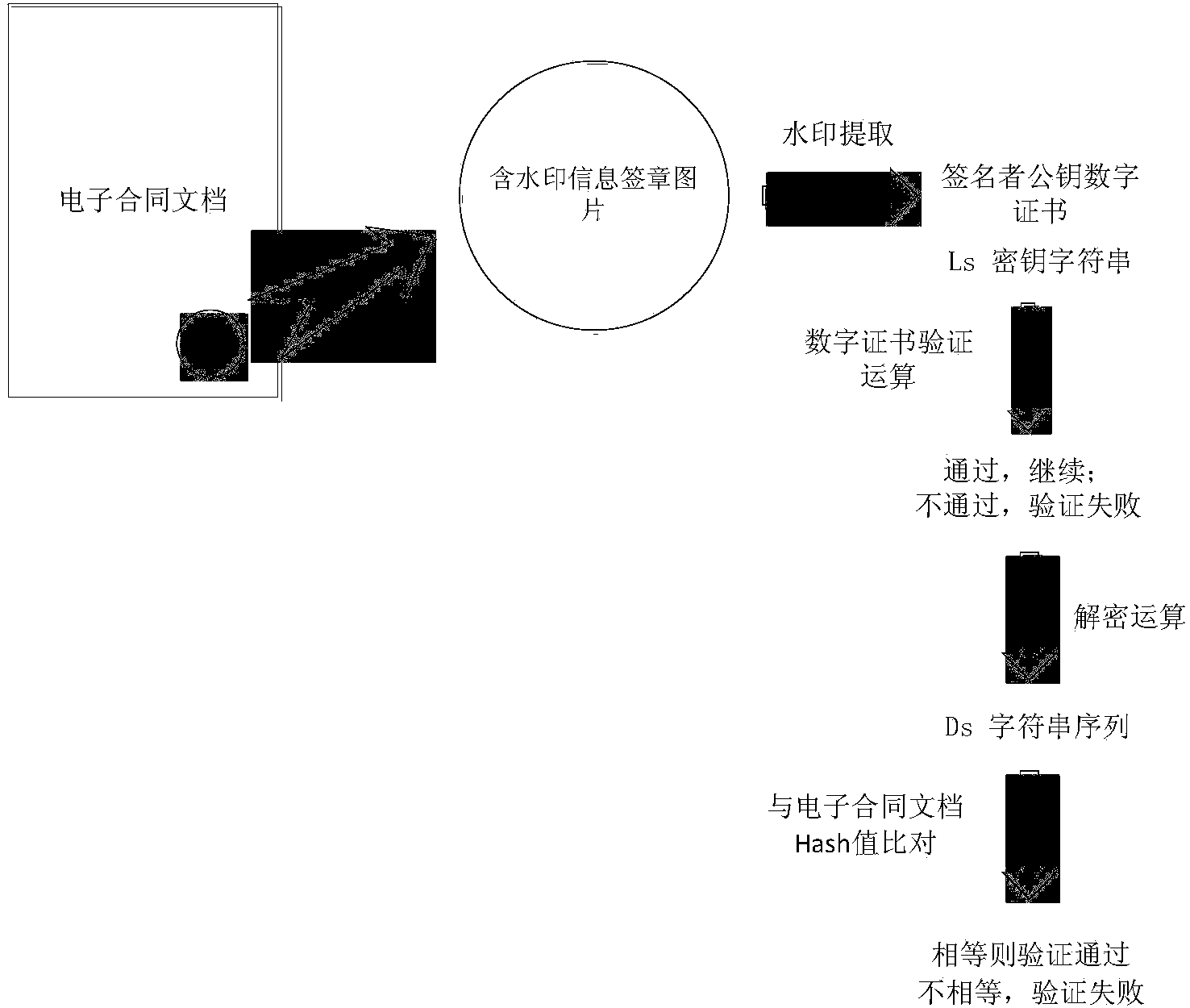
The invention relates to an electronic contract off-line signing method based on a trusted third party. According to the electronic contract off-line signing method based on the trusted third party, an electronic signature digital certificate, a user private key and a contract proof public key are obtained from the trusted third party by a user; then, the Hash digest value of the electronic contract is calculated; the Hash digest value is subjected to encryption operation by the user private key and the proof public key; an encryption result is two strings of key sequences; finally, the key sequences and the digital certificate watermark of a signer are embedded into a signature picture; then signature picture embedded with the watermark is stamped to an electronic contract document. According to the electronic contract off-line signing method based on the trusted third party, which is disclosed by the invention, the requirement on the contract signing platform safety in the contract signing process can be favorably lowered, and the contract signing platform can finish the electronic contract signing process only by taking the responsibilities of approving and putting to the proof to the electronic signature without damaging the safety.
Owner:HANGZHOU DIANZI UNIV
Material of polyethylene in super high molecular weight for obstruction guard of highway, and fabricating method
InactiveCN1958274AReduce harmGood value for moneyDomestic articlesUltrahigh molecular weightCarbon steel
An anticollision protecting fence material for highway is prepared from ultrahigh molecular weight polyethene (UHMWPE) through pre-swelling, dissolving and pugging in dual-screw extruder, extruding out for shaping, and stretching for strengthening. It has high longitudinal tension strength (100-180 MPa) and large longitudinal elongation rate at break (50-350%).
Owner:肖久梅 +1
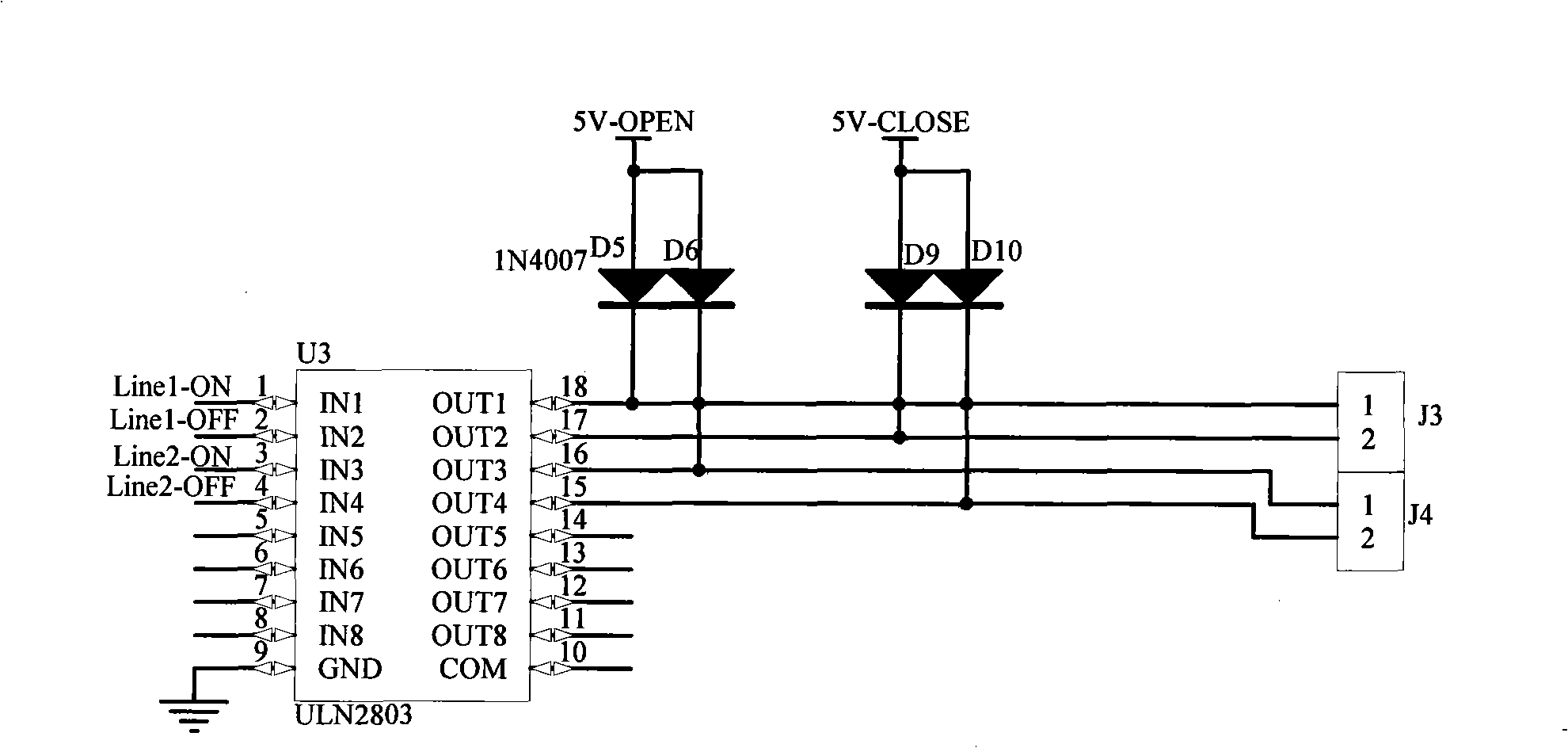
Valve controller based on ZigBee communication technology and control method thereof
ActiveCN101349914AFlexible networkingHigh security requirementsWatering devicesCultivating equipmentsAutomatic controlControl system
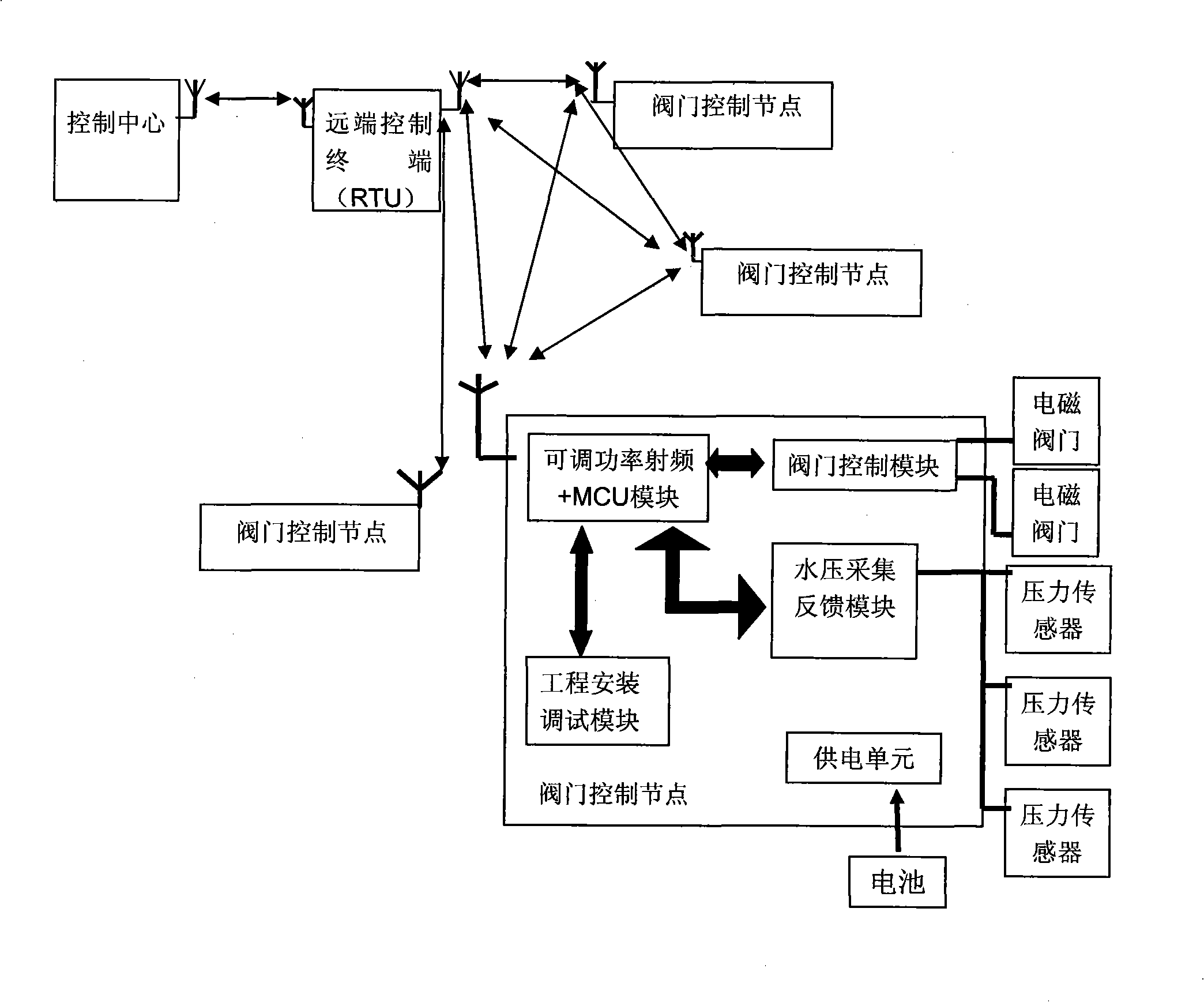
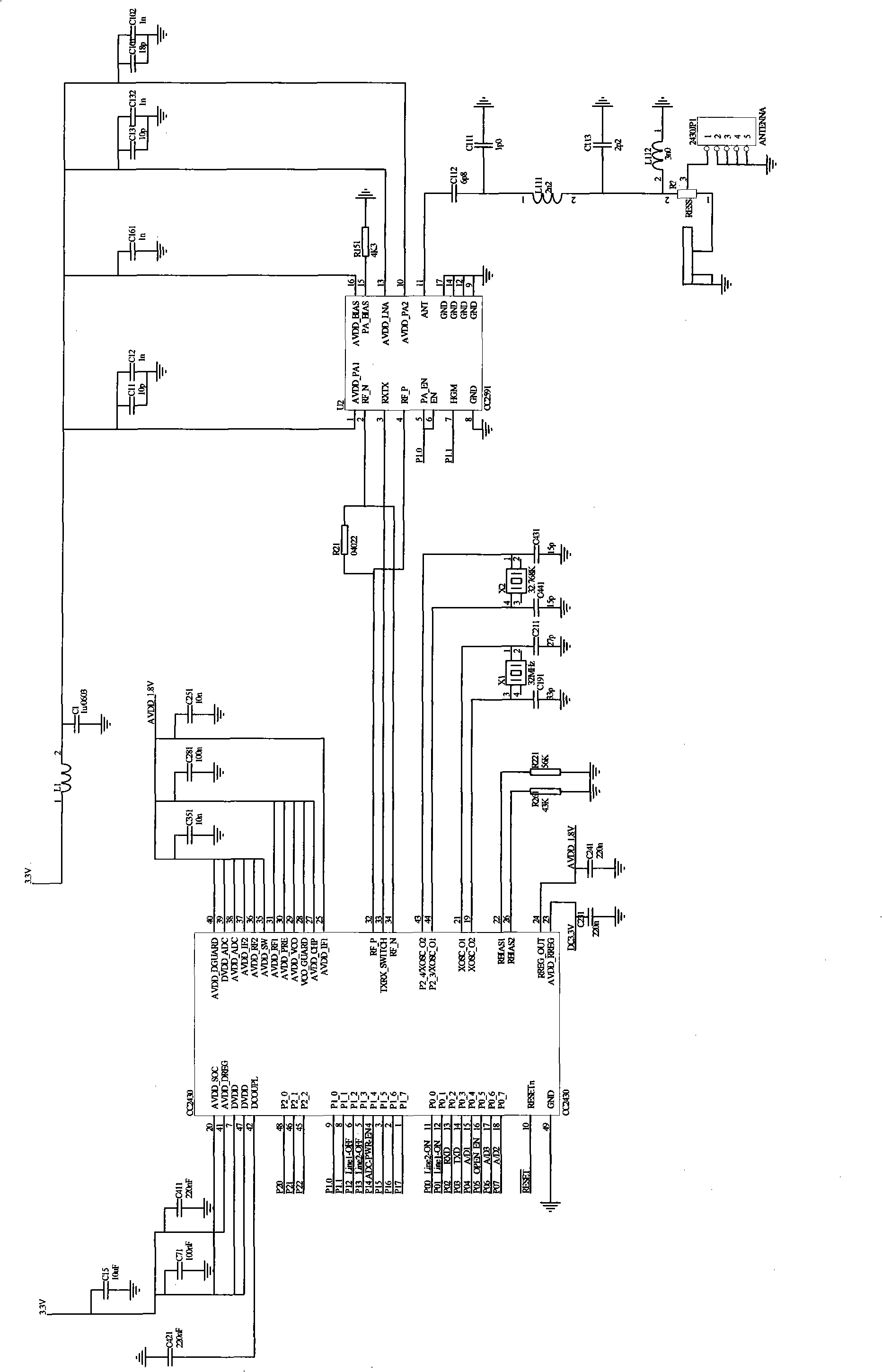
The invention relates to a valve controller based on ZigBee communication technique and a control method, belonging to the water saving irrigation automatic control system, wherein the valve controller is composed of a adjustable power radio frequency and central control module, a valve control module, a water pressure acquisition feedback module, a project installment debugging module and a power supply unit, the power supply unit has three power supply paths while a 3.3V power supply is normally opened, a 5.5V power supply and a 500mA large current power supply controlling the switch of an electromagnetic valve can be turned off, the control center and the valve control nodes form a ZigBee net communication, the radio frequency is adjustable according to distance. The invention uses a working mode of integral awake and integral dormancy for the valve controller to switch the electromagnetic valve and feedback information. The invention has ultra low power consumption, can realize ZigBee communication after using a battery, and has high reliability, high safety, simple installment, simple debugging and intelligent water quantity measurement. The invention can give full play to the advantages of mulch drip irrigation technique and is beneficial for engineering realization.
Owner:CHENGDU WANJIANGGANGLI TECH
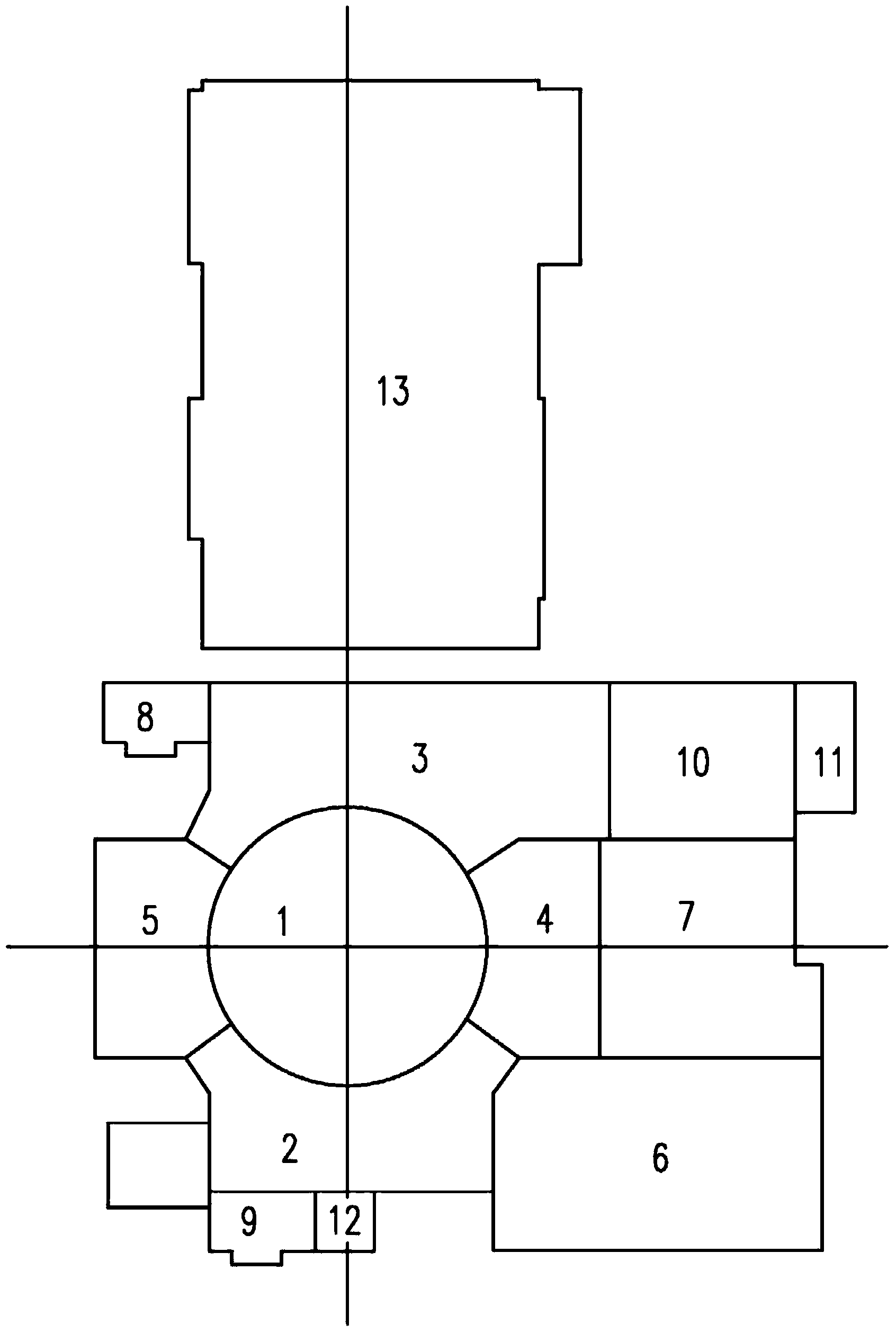
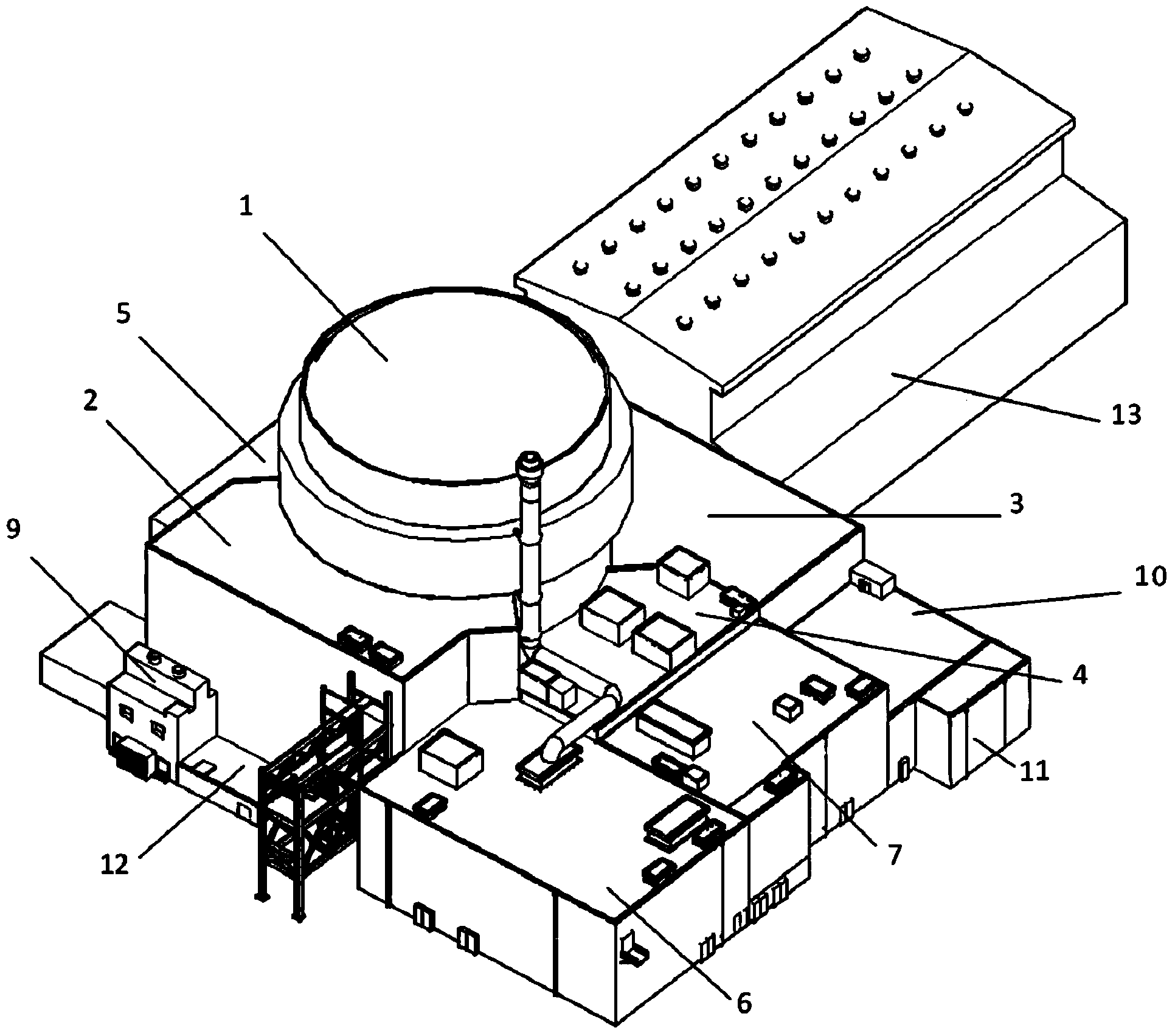
Main machine hall group arrangement method of nuclear power plant
ActiveCN103850483AImprove waterproof performanceImprove seismic performanceIndustrial buildingsNuclear plantNuclear engineering
The invention discloses a main machine hall group arrangement method of a nuclear power plant and relates to the technical field of nuclear power, and the main machine hall group arrangement method is used for solving the problem that an compact and efficient arrangement method capable of meeting enabling and non-enabling safety facility arrangement requirements, which is used for solving the reasonable equipment arrangement of a nuclear island plant does not exist in the prior art. The scheme provided by the invention is as follows: according to the main machine hall group arrangement method of the nuclear power plant, a main machine hall group comprises a nuclear island and a conventional island, and a nuclear island machine hall group comprises a reactor machine hall with a double-layer safety shell, an electric machine hall, a safety machine plant, a fuel machine hall, a nuclear auxiliary machine hall, a nuclear waste machine hall, an operation service machine hall, an emergency diesel generator machine hall and a nuclear-island fire-fighting water machine hall. According to the nuclear-island machine hall group arrangement method, a novel nuclear power plant single-pile arrangement structure is adopted and comprises an enabling and non-enabling combined safety system, has stronger capability of resisting severe external events, meets the requirement of a third-generation nuclear power technology, is beneficial to improvement on the safety of the whole nuclear power plant, and can be used for enhancing the nuclear safety acceptability of the public.
Owner:CHINA NUCLEAR POWER ENG CO LTD
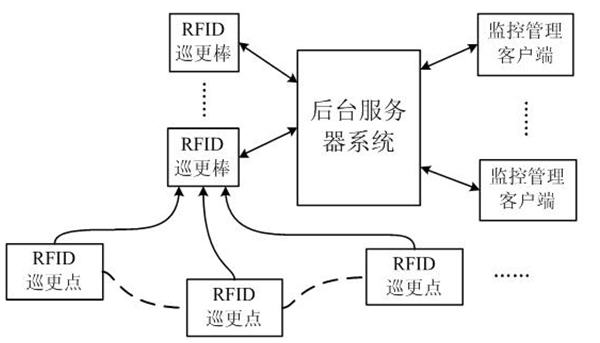
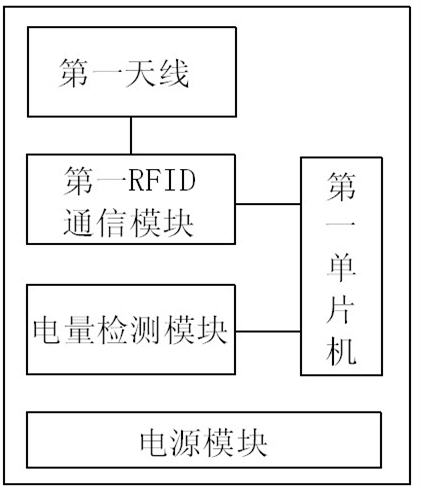
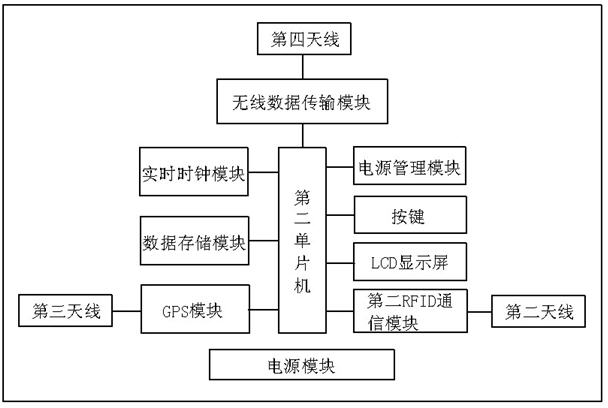
Real-time night patrol system based on radio frequency identification technology
InactiveCN102385764AImprove real-time performanceHigh precisionChecking time patrolsCo-operative working arrangementsGeolocationComputer science
The invention discloses a real-time night patrol system based on radio frequency identification technology, which includes an RFID (radio frequency identification technology) night patrol point, an RFID night patrol club, a background server system and a monitoring and managing client, wherein an active RFID label is adopted to replace the night patrol point; and RFID label read-write equipment, a wireless data transmission module and a GPS positioning module are integrated in the RFID night patrol club. When the night patrol point is within the recognizable range of the RFID night patrol club, the RFID night patrol club can automatically collect the night patrol information, and transmits real time, geographic position and night patrol club information to the background server system through wireless data transmission technology; and the management staff knows the night patrol staff information in real-time through a monitoring and managing software by operating the monitoring and managing client, and issues a command through the background server system; as a result, the real-time property of the night patrol data and the accuracy in dispatching the night patrol staff are improved, and the problem that the data is delayed in the conventional night patrolling process is solved.
Owner:NINGBO TONGYI WULIAN TECH
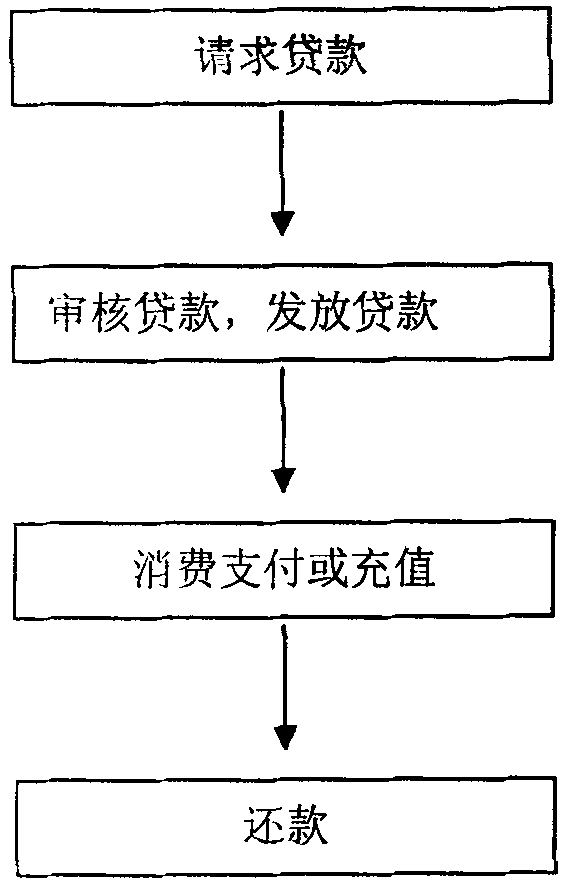
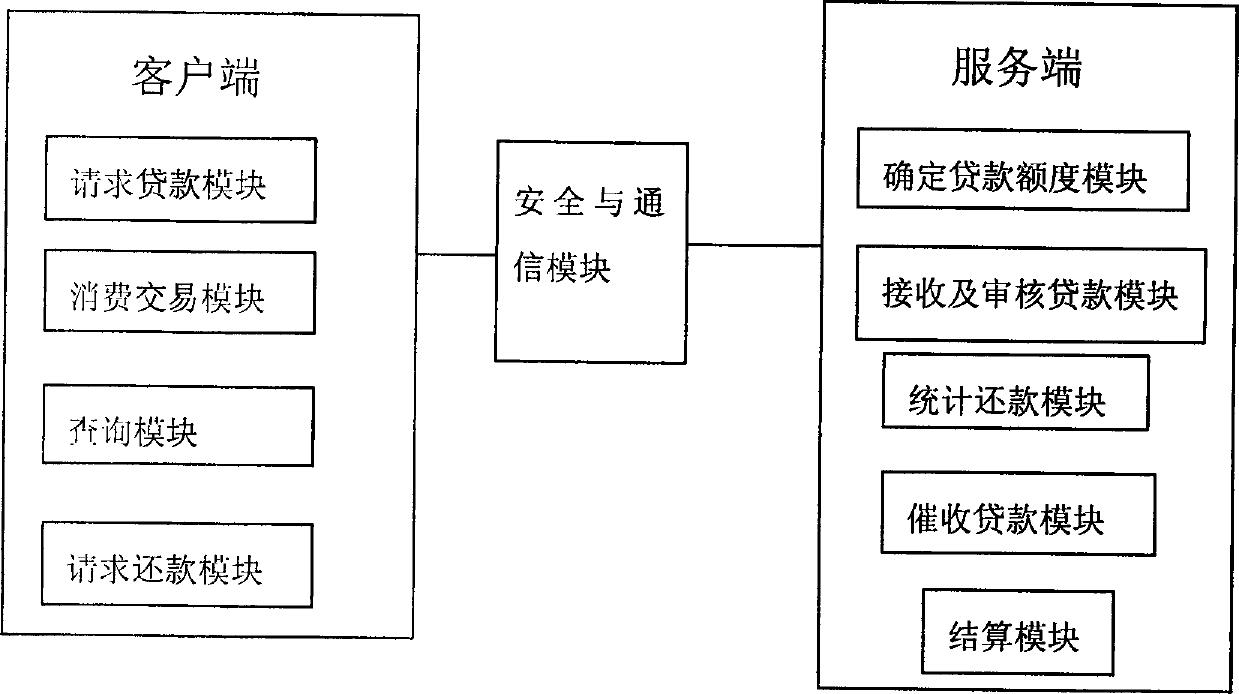
Online virtual currency third-party credit method and data processing system thereof
The invention provides an online virtual currency third-party credit method and a data processing system thereof. The online virtual currency third-party credit method includes steps of determining user credit line, user loan application, third-party credit supplier assessment and lending, user recharging or trading by loan, user repayment and payment requesting, settlement of a third-party credit supplier and a platform supplier and the like. The data processing system comprises a client and a server, the client realizes users' various service requests and the server processes the users' service requests. By the aid of the online virtual currency third-party credit method and the data processing system, value of personal online digital assets is explored, trade is promoted by means of load leverage and simple consumption payment ways, trade scale is enlarged, and the platform supplier is assisted in exploring and keeping high-quality users, and user experience is improved.
Owner:孔庆发 +1
System and method for realizing security storage and access control of data
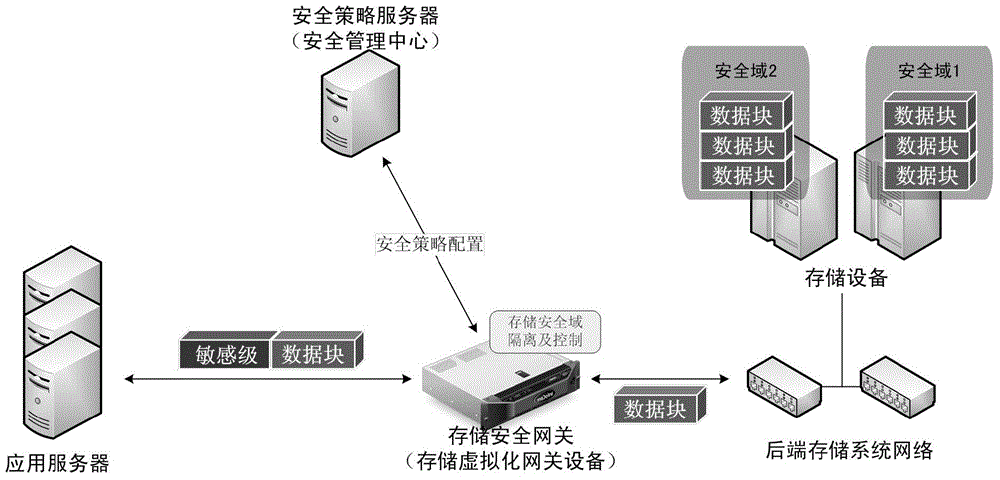
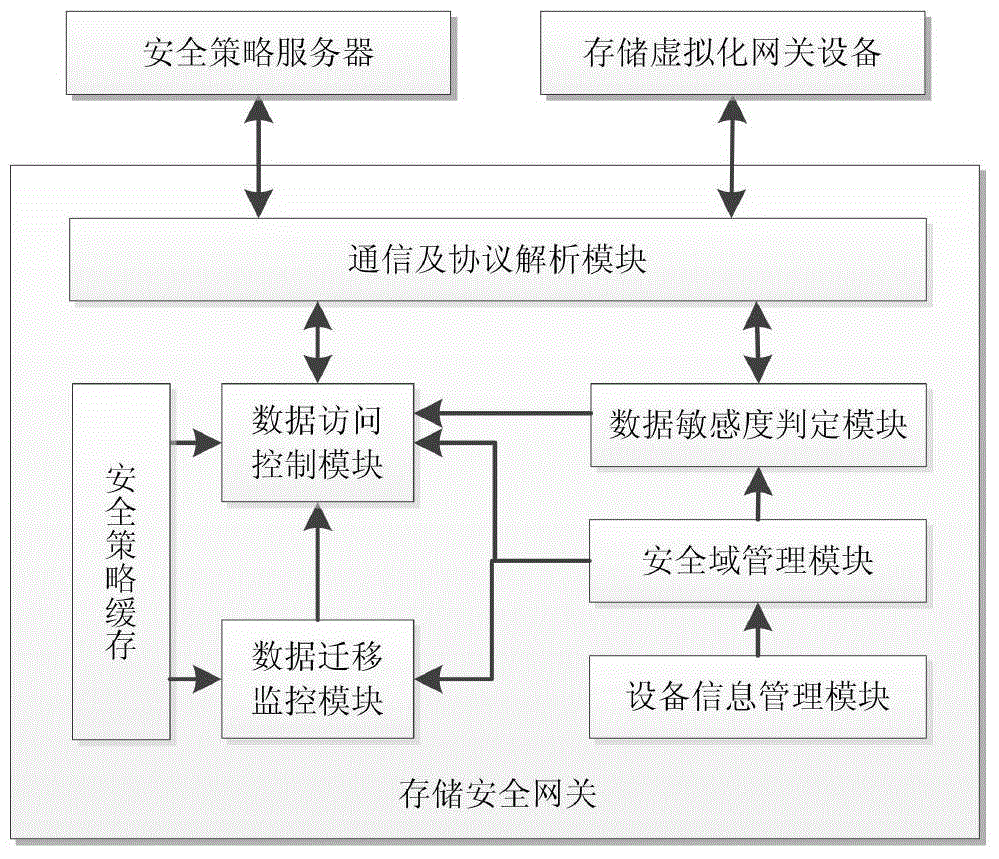
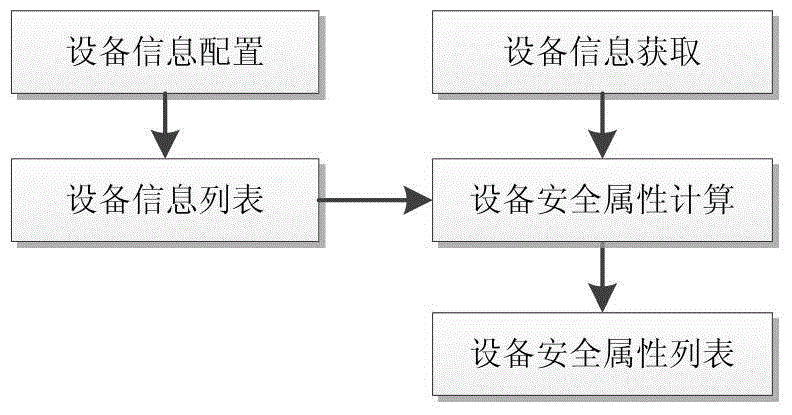
ActiveCN104660578AMeet the need for protectionHigh security requirementsTransmissionStorage securitySecurity domain
The invention discloses a system and method for realizing the security storage and the access control of data. The system comprises an application server, a storage security gateway, a security strategy server and a backend storage system, wherein the storage security gateway is additionally arranged between the application server and the backend storage system so as to realize the partition, the isolation and the access control of data security domains. The storage security gateway and a storage virtualization gateway can synergistically work, and data can be stored in the manner of the security domains on an actual physical medium by utilizing a virtualization technique. When a data access request arrives at the storage virtualization gateway, the storage virtualization gateway can invoke the functions of the storage security gateway so as to realize the isolation and the access control of the data security domains. Because all data requests for access to the backend storage system can be processed by the storage security gateway, security control is guaranteed to be performed on the single path of data without being bypassed. In addition, security control is realized at the bottom layer of data access, so that attack means to data by upper application layers can be effectively avoided.
Owner:董唯元
Information transmission method, system and device
InactiveCN101316424AHigh security requirementsImprove securityInternal/peripheral component protectionDigital data authenticationInformation transmissionSecurity information
Owner:ALIBABA GRP HLDG LTD
Arc extinction brush and method for eliminating electric arc of power generator with this arc-extinction brush
InactiveCN101237108ADoes not affect productionNo need to shed loadRotary current collectorCurrent collector maintenanceIndiumSilver iodide
The present invention relates to an arc extinction brush, comprising a solid mixture brush body, wherein, the solid mixture brush body consists of a solid lubricant, wax, and a fast film formation substance; the solid lubricant is any of tin, lead, indium, cadmium, silver and oxides thereof; the fast film formation substance is any of molybdenum disulfide, tungsten disulfide, silver iodide, lithium carbonate, barium carbonate or sodium silicate. The present invention also comprises a method of using the arc extinction brush to eliminate electric arc of brushes for generators. The arc extinction brush is used to replace a brush to participate in motor operation and is matched with the operation of eliminating a bad oxide film, and after the arc extinction brush is repeatedly put into operation, the arc extinction brush can help form a good oxide film, so as to eliminate electric arc of brushes for generators and to reduce the sliding friction and self-vibration of brushes.
Owner:黄继林
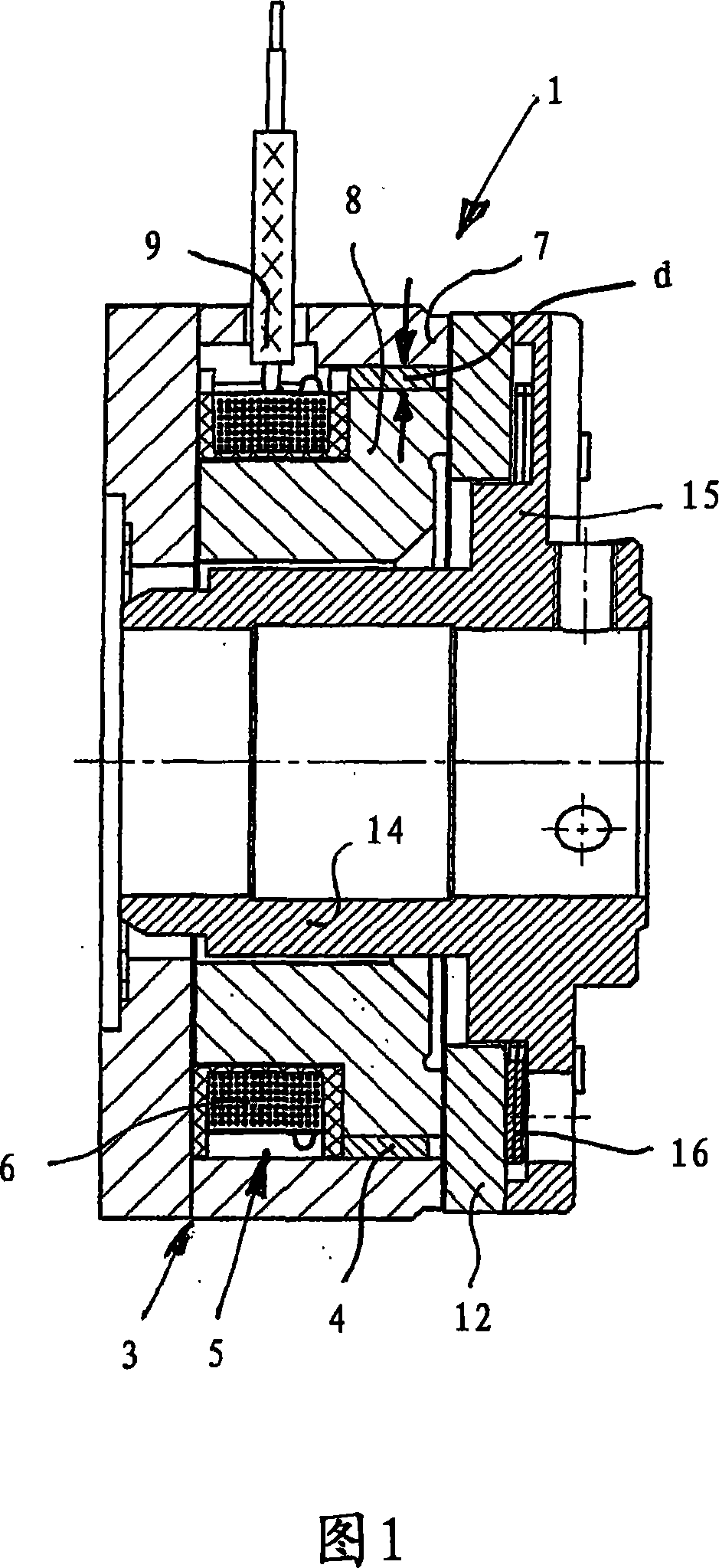
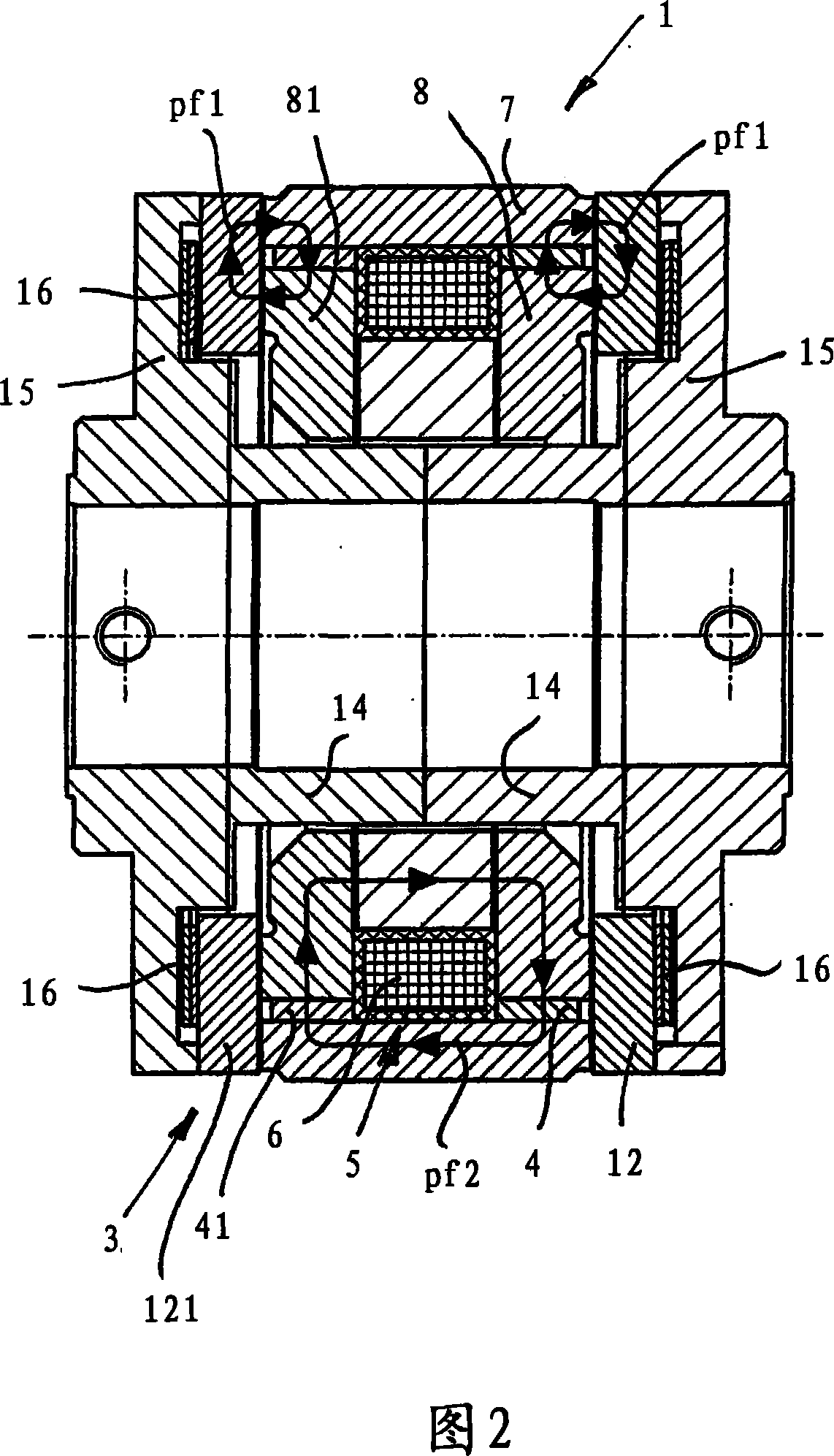
Electromagnetic permanent magnet brake
ActiveCN101115937AConstant torqueRaise or enlarge the magnet surfaceAxially engaging brakesBrake actuating mechanismsMagnetic tension forceSpring force
An electromagnetic brake (20), in particular for an electric drive is provided, having a brake body (3), which is provided with a sleeve-shaped permanent magnet (4), an electromagnet (5) with an exciting coil (6), an external ring in the form of an external pole and an internal ring (8) in the form of an internal pole, wherein an armature disc (12) rotatably connected to a shaft is attractable against the brake body (3) or the external or internal ring surfaces by the permanent magnet (4) force acting against a return spring force. When the exciting coil is powered, the permanent magnet (4) magnetic field is compensated in such a way that the armature disc (12) is lifted up from the brake body (3) by the spring force, thereby allowing the brake to be released. A radial cross-sectional dimension or cross-sectional thickness d of the permanent magnet (4) is smaller than the axial dimension thereof and a spatial arrangement, viewed in the axial direction, is provided between the armature disc (12) and the exciting coil (6) in the area radially external with respect to the exciting coil (6) or the housing thereof.
Owner:KENDRION VILLINGEN GMBH
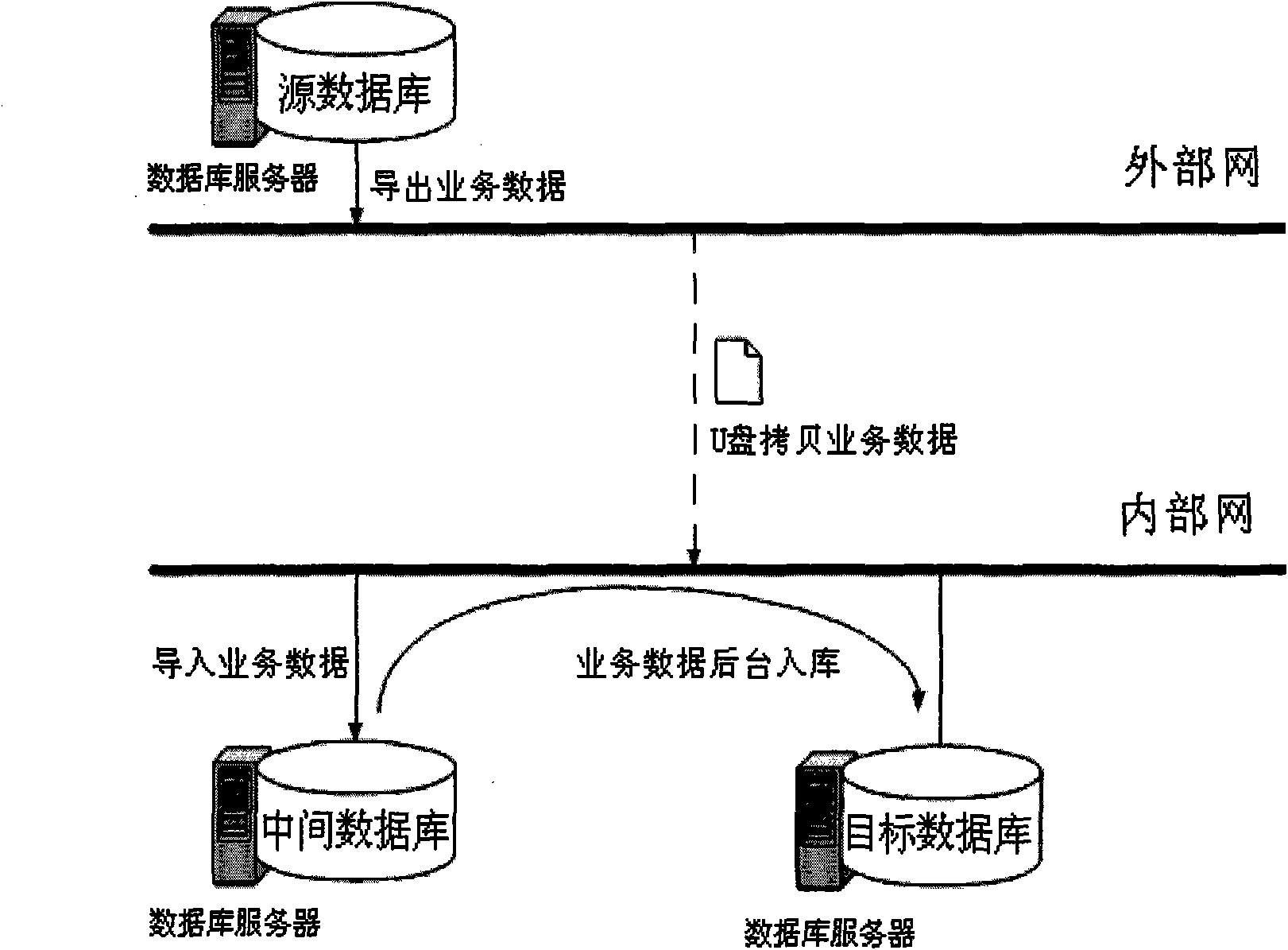
Method for synchronizing data between different databases under physical isolating condition
InactiveCN101620624AStable jobIncrease flexibilitySpecial data processing applicationsData synchronizationTarget database
The invention provides a method for synchronizing data between different databases under a physical isolating condition in order to ensure the stability of inputting data to a target database. Through building a temporary middle database inside an intranet, a synchronous buffering is realized between different network environmental databases, at the same time, the requirements of synchronization and the completeness of the data can be satisfied, and the flexibility of the operation is improved through designing a metadata table. The method has a high demand on safety and needs the intranet and an outer net to be isolated physically; the data with large data quantity can work stably in the different databases during synchronizing through the method.
Owner:THE FIRST RES INST OF MIN OF PUBLIC SECURITY +1
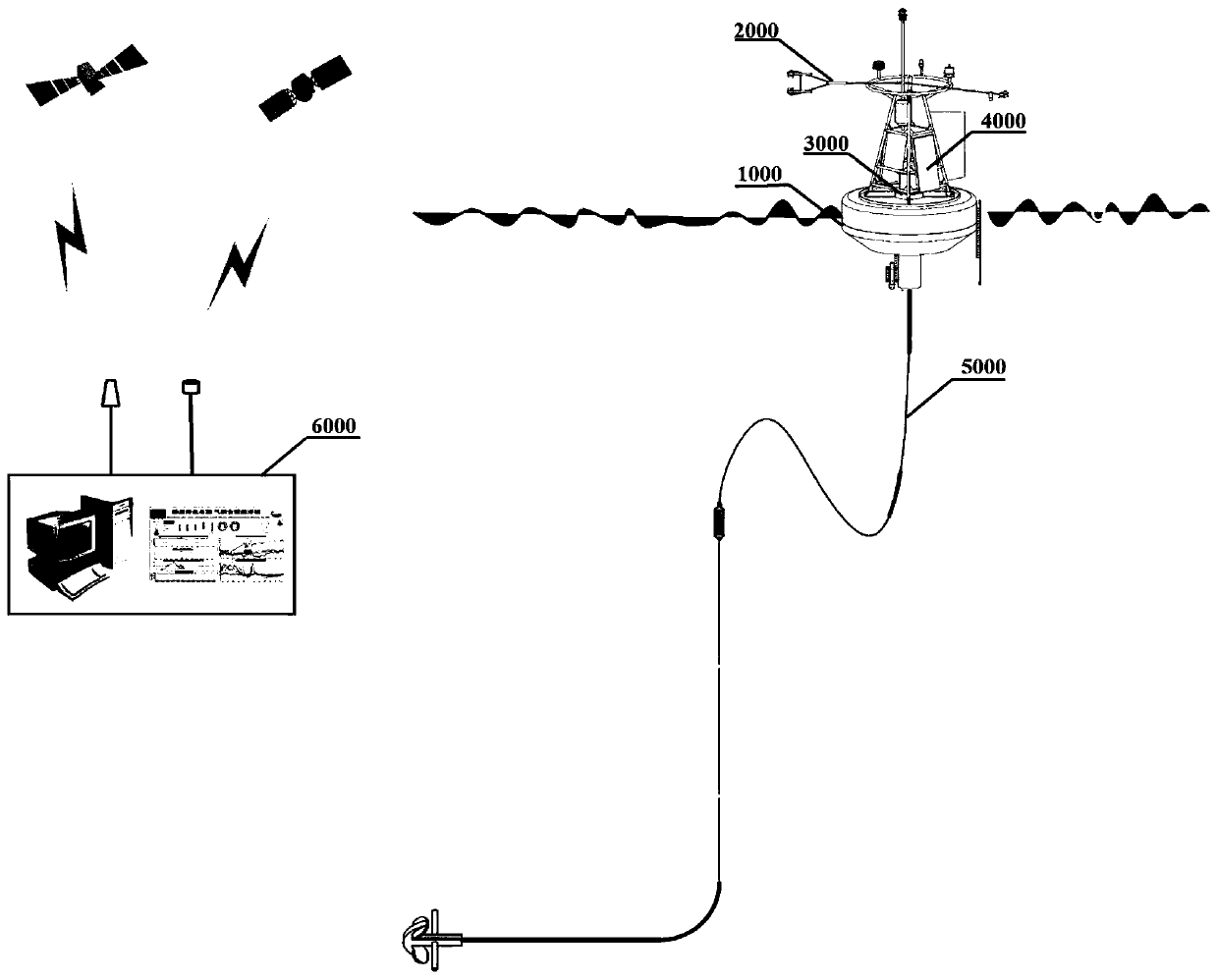
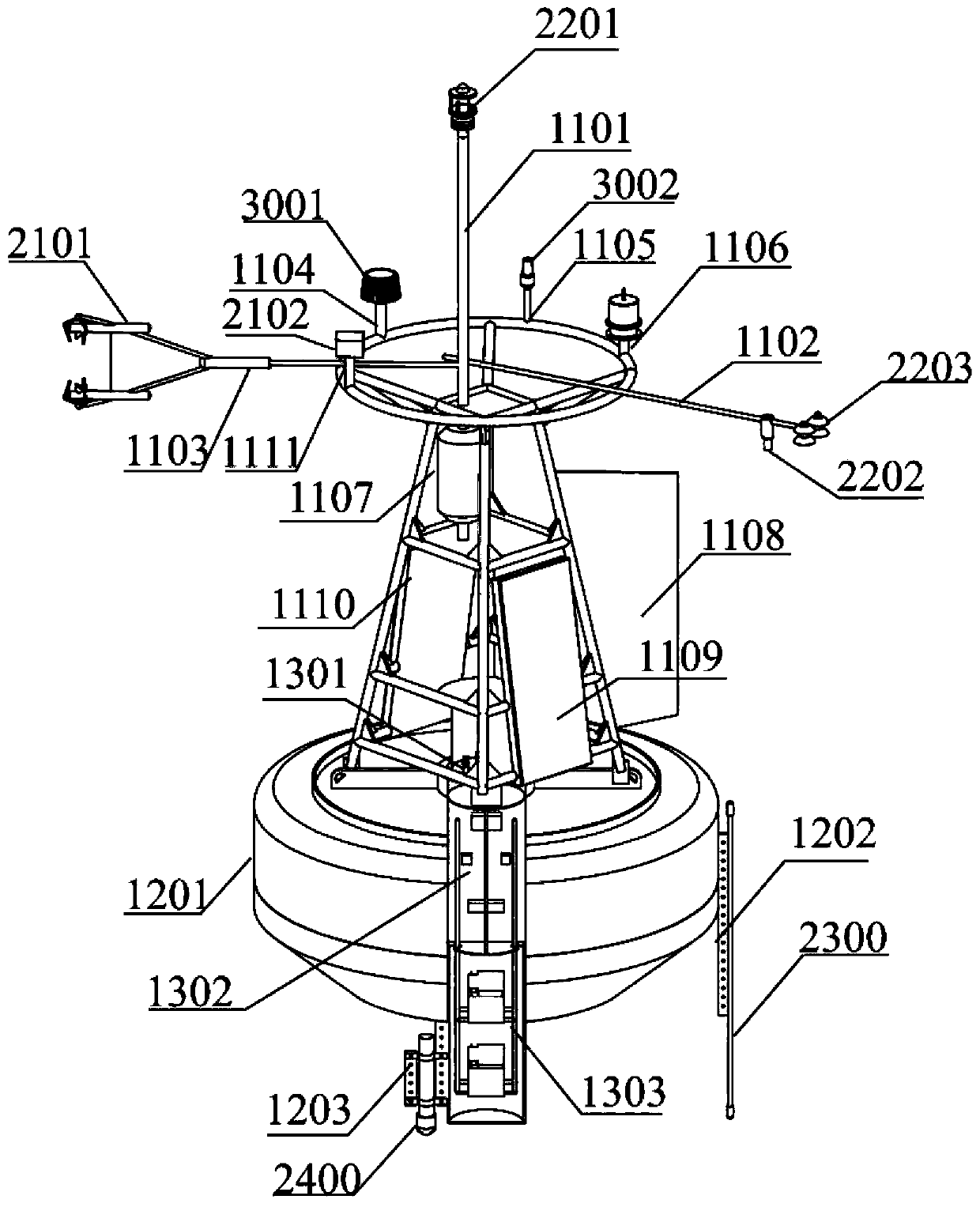
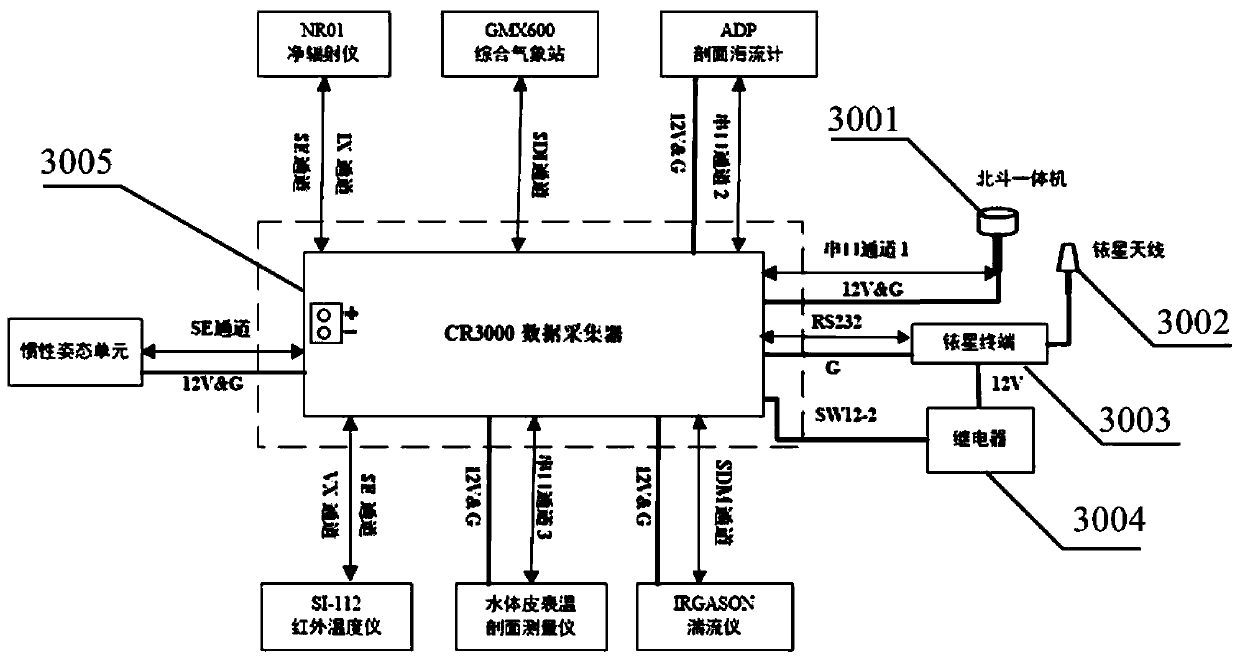
Sea-gas coupled real-time observation buoy system based on Beidou satellite and Iridium satellite double-satellite communication
ActiveCN110203333AHigh security requirementsReduced security requirementsBatteries circuit arrangementsWaterborne vesselsIridiumOpen sea
The invention discloses a sea-gas coupled real-time observation buoy system based on Beidou satellite and Iridium satellite double-satellite communication. The sea-gas coupled real-time observation buoy system comprises a sea-gas coupled observation sensor unit, a data collecting communication control unit, an anchoring unit, a buoy body platform, a power supplying unit and a data processing center. The buoy data collecting communication control unit adopts a Beidou satellite system to transmit conventional block method sea-gas flux, upper-layer sea current profile and buoy operation state parameters which have high requirements on data safety and low requirements on the communication quantity, and adopts an Iridium satellite system to transmit high frequency eddy related and high-resolution seawater skin surface temperature profile data which have high requirements on the communication quantity. A buoy can synchronously observe turbulence flux parameters of an eddy-related method of amovable platform, flux parameter of a block method, the seawater 0-1.0 m high-resolution skin surface temperature profile and the 0-70 m upper-layer sea current profile in real time in real time. Thesea-gas coupled real-time observation buoy system is suitable for being released in deep and open sea, and has the characteristics of diverse sea-gas interface observation parameter, safe data transmission and the like.
Owner:SOUTH CHINA SEA INST OF OCEANOLOGY - CHINESE ACAD OF SCI
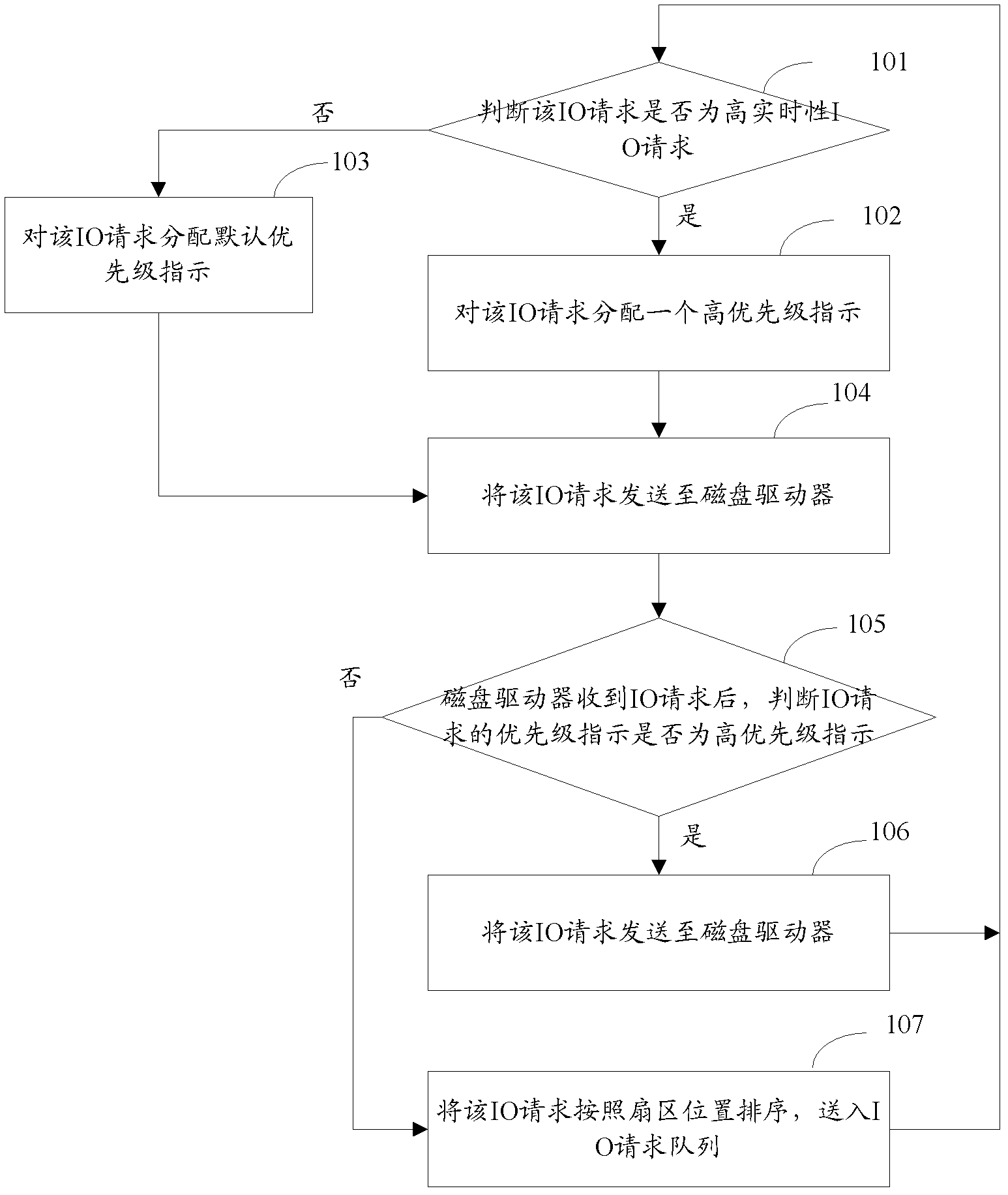
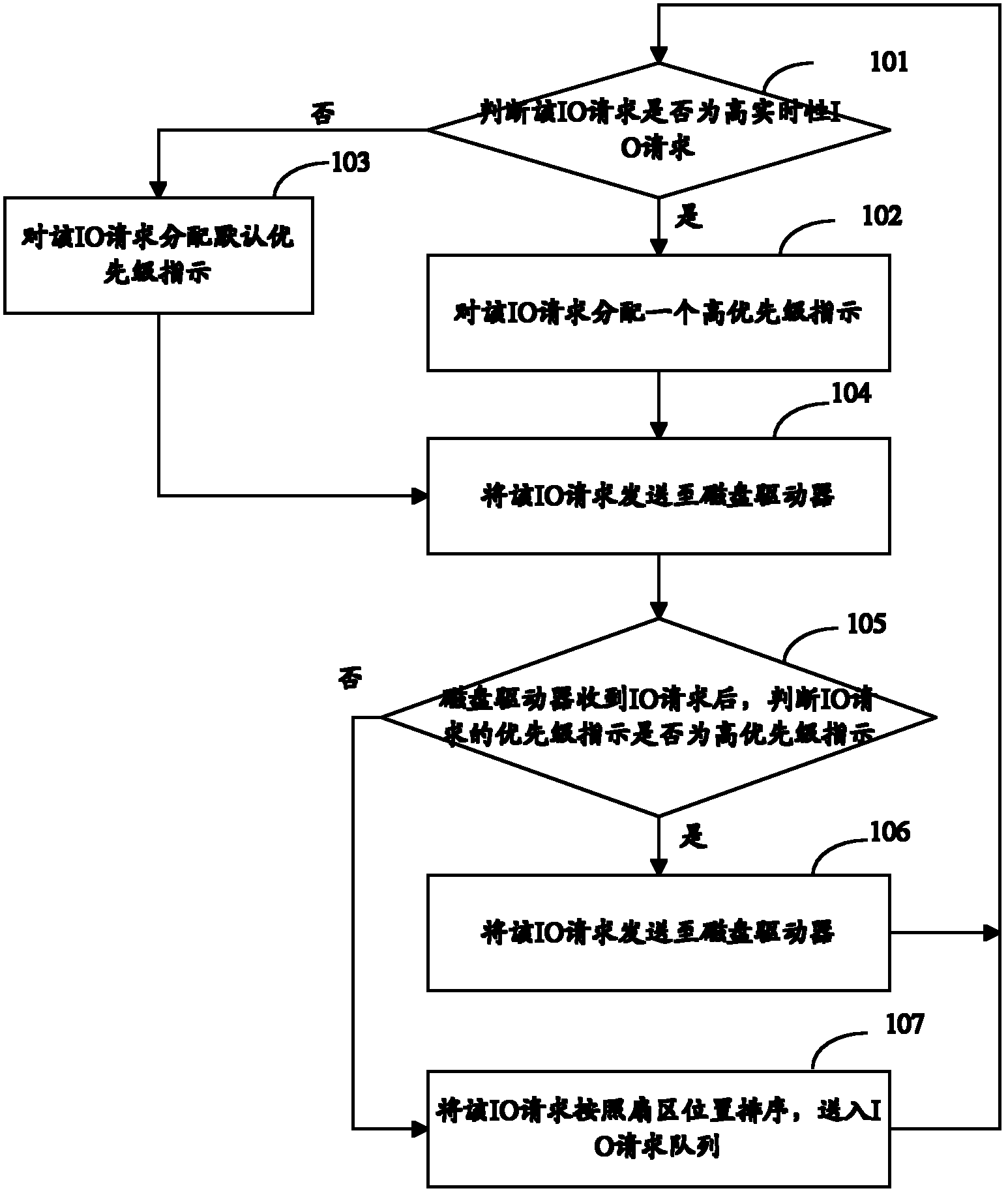
Method for scheduling input output (IO) request queue of disk
InactiveCN102402401AHigh real-time requirementsHigh security requirementsInput/output to record carriersFile systemRequest queue
The invention provides a method for scheduling an input output (IO) request queue of a disk. The method comprises the following steps of: A, when a file system generates IO requests, judging whether the IO requests are high-real-time-performance IO requests, if so, executing the step B, otherwise, executing the step C; B, allocating high-priority instructions to the IO requests, and then executing the step C; C, sending the IO requests to a disk driver; D, after the disk driver receives the IO requests, judging whether the IO requests include the high-priority instructions, if so, executing the step E, otherwise, executing the step F; E, sending the IO requests to the forefront position of the IO request queue, and returning to the step A; and F, sorting the IO requests according to the position of a sector, sending the IO requests into the IO request queue, and returning to the step A.
Owner:云海创想信息技术(无锡)有限公司 +1
Information security processing method and security processing apparatus
InactiveCN105574723AHigh security requirementsImprove ease of useProtocol authorisationPaymentLow demand
The invention provides an information security processing method and security processing apparatus applied to electronic equipment; a security application can be implemented on the electronic equipment; the information safe processing method comprises the steps of enabling the security application to be associated with a first sub application and a second sub application; adopting a first security mechanism for the first sub application while adopting a second security mechanism for the second sub application; after the electronic equipment receives an application running instruction, determining whether the second sub application is indicated by the application running instruction to be implemented or not; if the second sub application is indicated by the application running instruction to be implemented, adopting the second security mechanism to enable the second sub application to be implemented, wherein the first sub application is different from the second sub application; and the security level of the second security mechanism is higher than that of the first security mechanism. By adoption of the mobile terminal security payment scheme provided by the invention, the security of applications having high demand on security is ensured, and the convenience in use of applications having low demand on security is improved as well.
Owner:LENOVO (BEIJING) LTD
Pixel and DNA cross dynamic chaotic cipher-based image encryption method and device
The present invention relates to a pixel and DNA cross dynamic chaotic cipher-based image encryption method and device. The method comprises the following processing of ranking the pixels of a plaintext image to obtain a first index matrix, and carrying out the first chaotic coding on the plaintext image according to the first index matrix to obtain a first intermediate image; ranking the rows andthe columns of the first intermediate image separately to obtain a row index matrix and a column index matrix, and scrambling the first intermediate image according to the row and column index matrixes to obtain a second intermediate image; converting each pixel in the second intermediate image into a 4-base DNA sequence, selecting eight kinds of coding rules satisfying a Watson-Crick complementrule according to the second chaotic coding, adopting the above eight kinds of coding rules to carry out the complementary DNA coding on each DNA sequence in the second intermediate image to obtain athird intermediate image, and then carrying out the DNA subtraction, add operation and xor operation on the third intermediate image to obtain a fourth intermediate image; carrying out the adjacent DNA coding on the fourth intermediate image to obtain a final ciphertext image.
Owner:SHANDONG ZHENGZHONG COMP NETWORK TECH CONSULTING
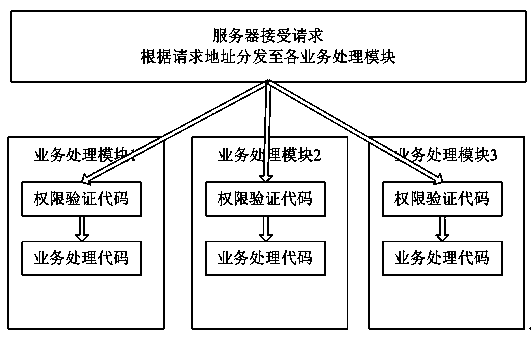
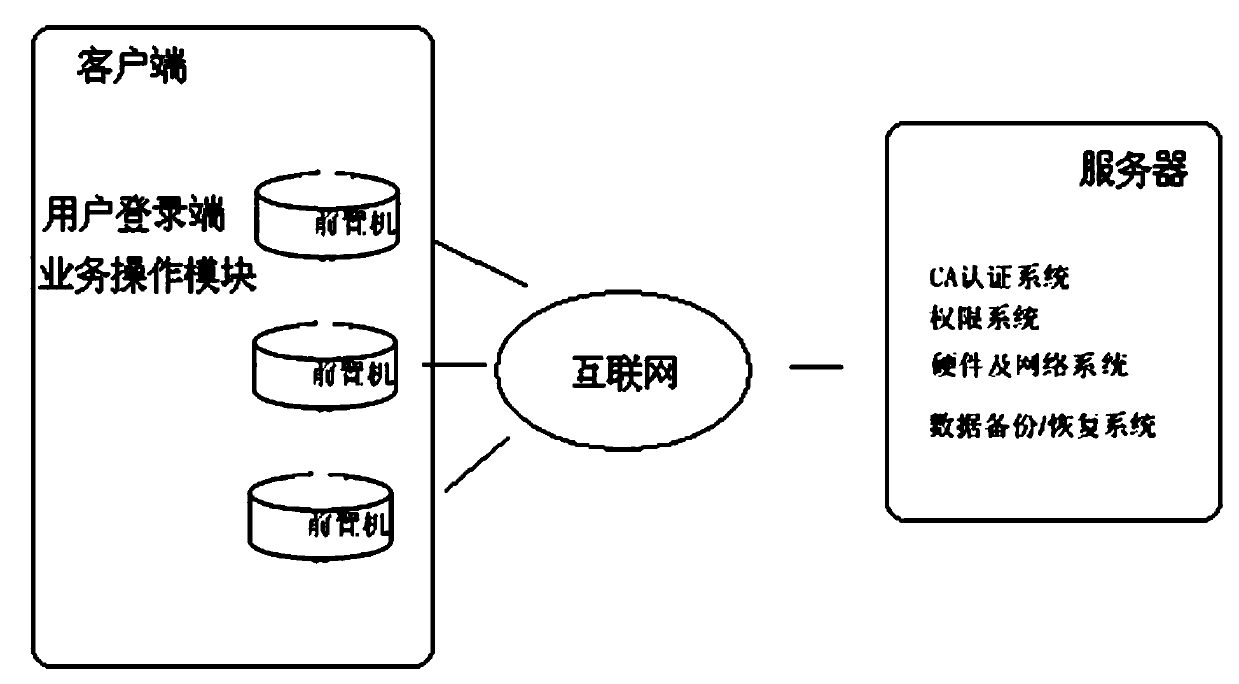
Permission validation system and permission validation method for safety production comprehensive supervision
ActiveCN103473489AImprove scalabilityHigh security requirementsDigital data authenticationTransmissionInternet communicationValidation methods
The invention relates to the technical field of supervision systems and discloses a permission validation system and a permission validation method for safety production comprehensive supervision. The permission validation system comprises a client and a server side, wherein the client is communicated with the server side by a plurality of front-end processors through the Internet; each front-end processor of the client is provided with a user login end module and a service operation end module; the server side is provided with a login permission validation module and a service operation validation module which are correspondingly communicated with the user login end module and the service operation end module of each front-end processor through the Internet; an Internet communication protocol of the client and the server side is the HTTP (Hyper Text Transport Protocol). According to the permission validation system and the permission validation method, permission validation can be carried out on the access request each time; when a user accesses a server through the Internet, an address of a user request is obtained and is compared with a user permission information database; when the permission passes, the request is permitted; when the permission does not pass, the request is returned back; the permission validation system is flexible and strong in expandability.
Owner:LUOYANG HONGZHUO ELECTRONICS INFORMATION TECH
Method and device for security check of liquid article
InactiveCN104089944AAccurate analysisImprove accuracyRaman scatteringMaterial analysis by transmitting radiationSecurity checkPack material
The invention discloses a method and a device for security check of a liquid article. The method is characterized by comprising the following steps: firstly determining whether the package of the liquid article is transparent, semi-transparent or opaque; carrying out the Raman spectrum analysis on the detected liquid article by utilizing a Raman spectrum module under the situation that the package of the liquid article is transparent or semi-transparent, and judging whether the detected liquid article is a hazardous article or a suspicious article; and checking the detected liquid article by utilizing a ray two-energy scanning technology under the situation that the package of the detected liquid article is opaque, and judging whether the detected liquid article is the hazardous article or the suspicious article. The method has the advantages of high check speed, capability of recognizing the substance, applicability to the packaging materials in different shapes and different types, high accuracy of the check result and the like. The method and the device are suitable for the security check in public fields with high security check requirement, complicated detected liquid articles, a great number of people and high personnel flow rate and the like.
Owner:NUCTECH CO LTD
An image interpolation space completely reversible separable ciphertext domain information hiding algorithm
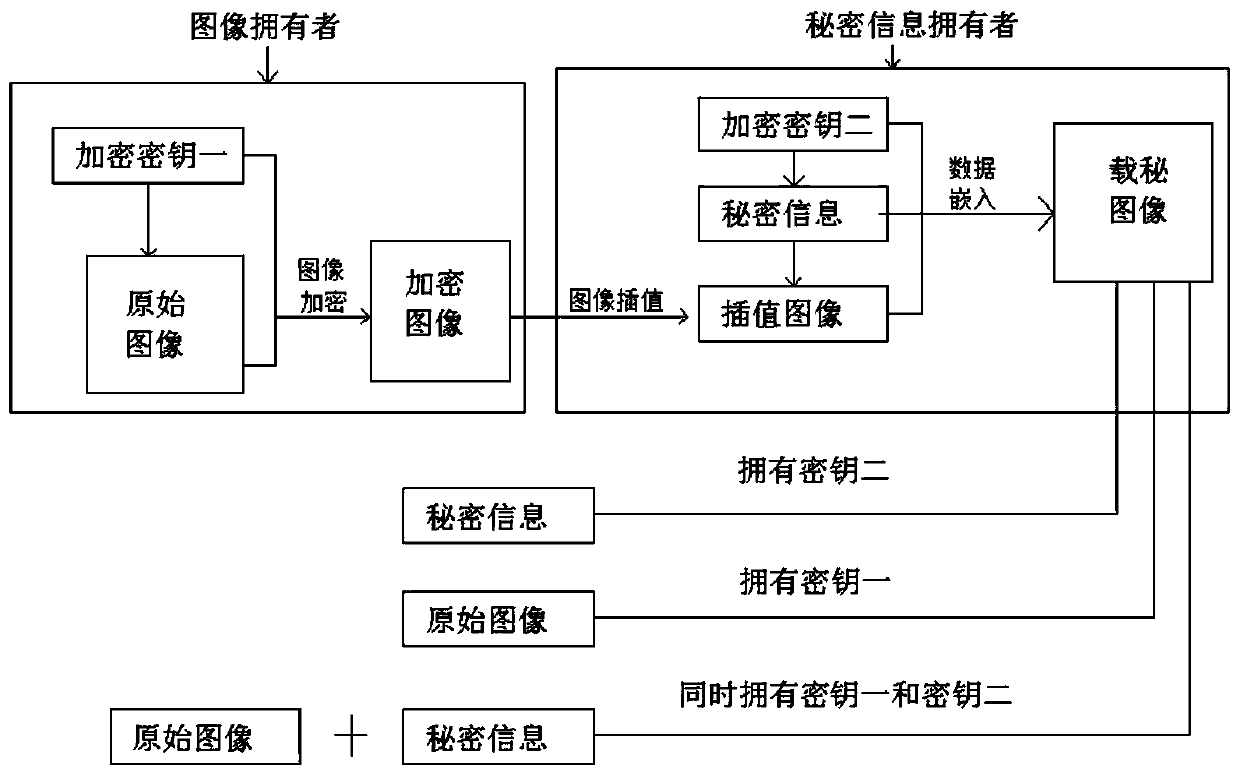
ActiveCN109800585AMeet safety requirementsImprove securityDigital data protectionImage data processing detailsPlaintextCiphertext
The invention provides an image interpolation space completely reversible separable ciphertext domain information hiding algorithm. The method comprises the following steps of: giving out a conditionrequired by a traversal matrix suitable for image encryption, constructing the traversal matrix by utilizing a chaotic pseudo-random number generator, carrying out a decryption algorithm of the traversal matrix and diffusion and restoration of pixels, generating an encrypted image and realizing secret information hiding in an encrypted image interpolation space; according to the invention, the matrix is traversed;, pixel diffusion and interpolation hiding can realize confidentiality of a carrier image and a secret image. The distribution of a ciphertext image histogram and a secret carrying image histogram is uniform. The image is flat, and a decoder cannot obtain the original image and the secret key information from the histogram; Attacks such as statistical characteristics of the plaintext image are well defended. The security requirement of the carrier image is met, meanwhile. The original image can be restored in a lossless mode, secret information can be extracted, watermark extraction and image decryption are independent, completely separated and exchangeable, and the method has the advantage of being high in security.
Owner:王继军 +1
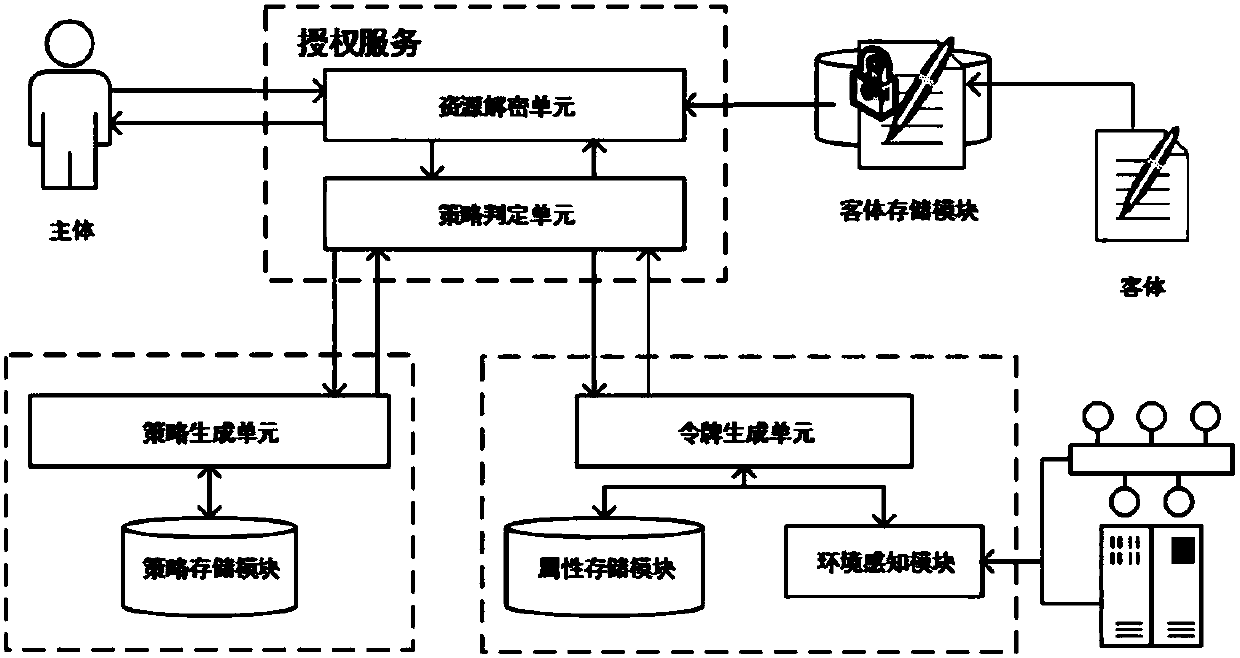
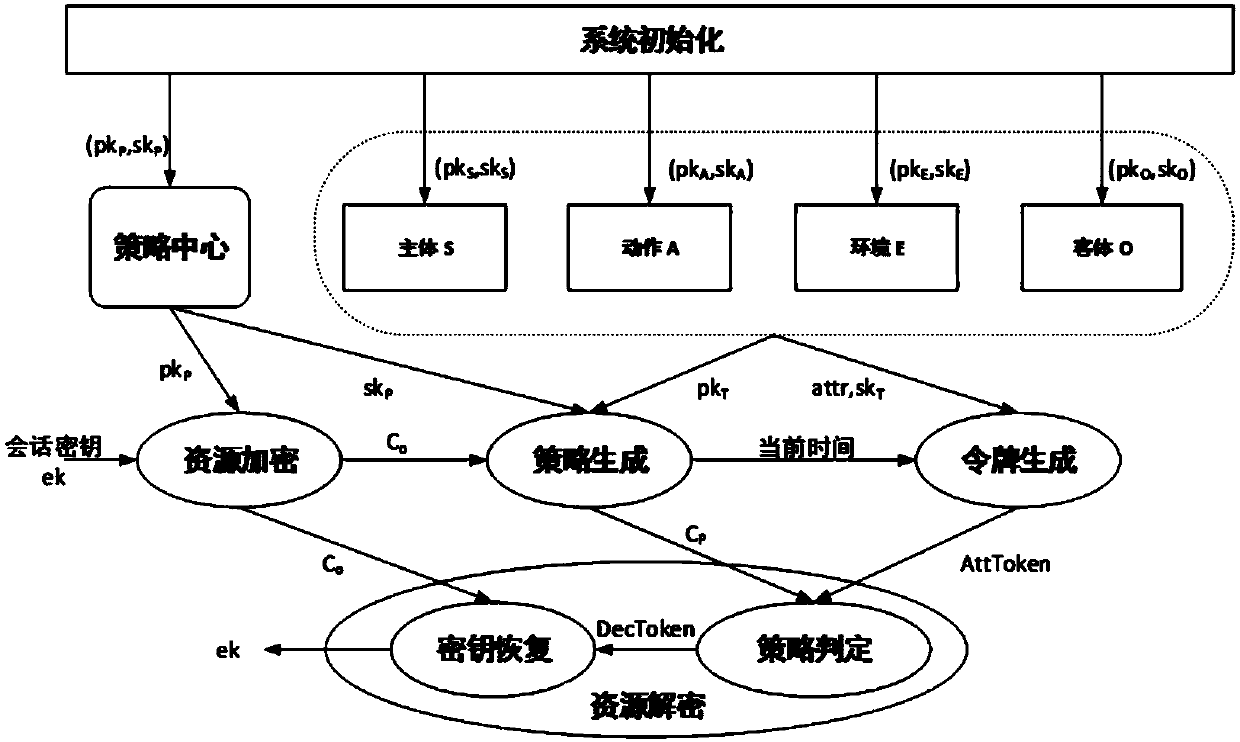
Cryptography attribute-based access control method and system based on dynamic rule
ActiveCN107864139AHigh security requirementsGuaranteed unforgeabilitySecuring communicationExtensibilityUnsafe environment
The invention relates to a cryptography attribute-based access control method and system based on a dynamic rule, mainly belonging to the technical field of information. In the cryptography attribute-based access control system based on the dynamic rule, protected objects are stored in a encrypted form, and only the requests satisfying the requirements of access policies in the attribute-based access control can be authorized to decrypt the objects, therefore, it can be ensured that data in an unsafe environment can be accessed with authorization according to a security policy, and meanwhile,the extensibility of the policies and the dynamic acquisition of the attributes are also supported. The cryptography attribute-based access control method and system based on the dynamic rule are divorced from the traditional encryption system framework, and are a new attribute-based access control model, method and system supporting the cryptography decision. The cryptography attribute-based access control method and system based on the dynamic rule can achieve more secure, diversified, dynamic and flexible access authorization, which are suitable for large-scale organizations or informationsystems, and can be applied to the environments such as cloud computing, grid computing, distributed computing, and so on.
Owner:UNIV OF SCI & TECH BEIJING
Composite non-electrolyte additive for improving high-temperature safety performance of battery
InactiveCN102544601AImprove securityEnsure safetySecondary cells servicing/maintenanceElectricityAlkylphosphate
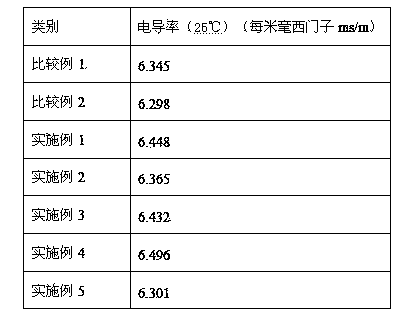
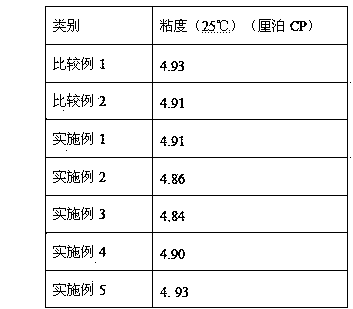
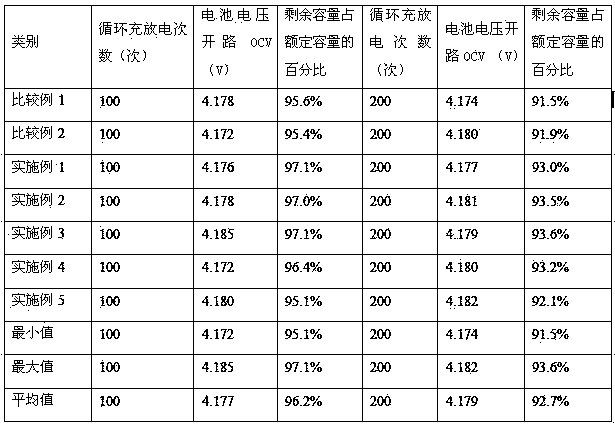
The invention discloses a composite nonaqueous electrolyte additive for improving the high-temperature safety performance of a battery. The safety and flame retardancy of the battery in a high-temperature state can be effectively improved, and the electrolyte is prevented from combusting and exploding due to battery overheating. The non-electrolyte additive for improving the high-temperature safety performance of the battery consists of fluorinated carbonic ester and alkyl phosphate. The non-electrolyte additive is an additive capable of effectively improving the safety of the battery in the high-temperature state; and the safety of the battery in the high-temperature state is effectively guaranteed, the electrical property of the battery is not influenced, and a requirement of customers on the high safety of the battery can be well met. The non-electrolyte additive can be applied to the conventional lithium ion batteries and lithium battery systems.
Owner:SHANGHAI INST OF SPACE POWER SOURCES
Visible-code-based payment method and system with multiple security combination mechanisms
InactiveCN103886449AImprove securitySave on roaming chargesPayments involving neutral partyProtocol authorisationSelf-serviceSmart client
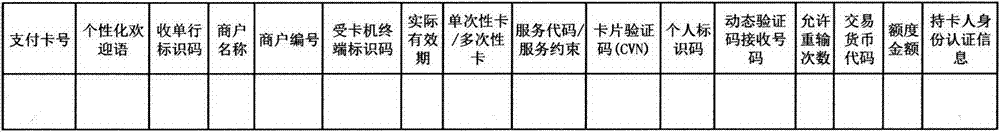
The invention relates to a visible-code-based payment method and system with multiple security combination mechanisms, wherein the visible code is a two-dimension code or a bar code or a character code or combination of the two-dimension code, the bar code and the character code. The visible-code-based payment method and system with the multiple security combination mechanisms is characterized in that on the basis of an existing transaction payment system (such as an Internet channel, a mobile intelligent client terminal, an ATM, a POS and a counter), payment card information used for authentication during transaction payment is generated in a self-service mode in a card issuing bank / card issuing mechanism system by a cardholder, the payment card information at least comprises a payment card number, personalized welcomes, an acquiring bank identification code, a commercial tenant name, a commercial tenant code, a card acceptor terminal identification code, an actual validity period, a one-time / multi-time card, a service code / service constraint, a CVN, a personal identification code, a dynamic verification code receiving number, the allowed retyping frequency, a transaction money code, limit amount, cardholder identity authentication information (such as the cardholder identification numbers, fingerprints, a digital certificate and a seal impression) and the like, the payment card information is used as the basis of the multiple security combination authorization mechanisms, and the payment card numbers can be applied to the transaction payment method and system through the visible code (such as the two-dimension code, the bar code, the character code and the combination of the two-dimension code, the bar code and the character code).
Owner:闻进
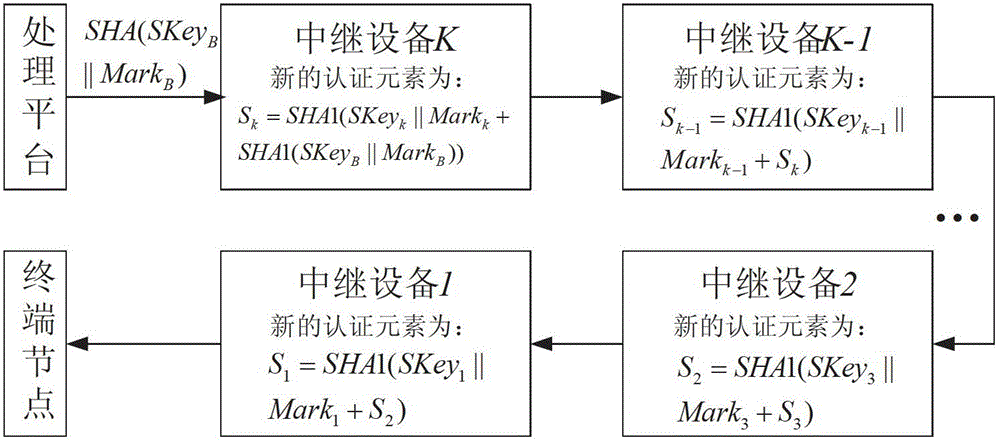
Two-way link security authentication method for wireless relay network
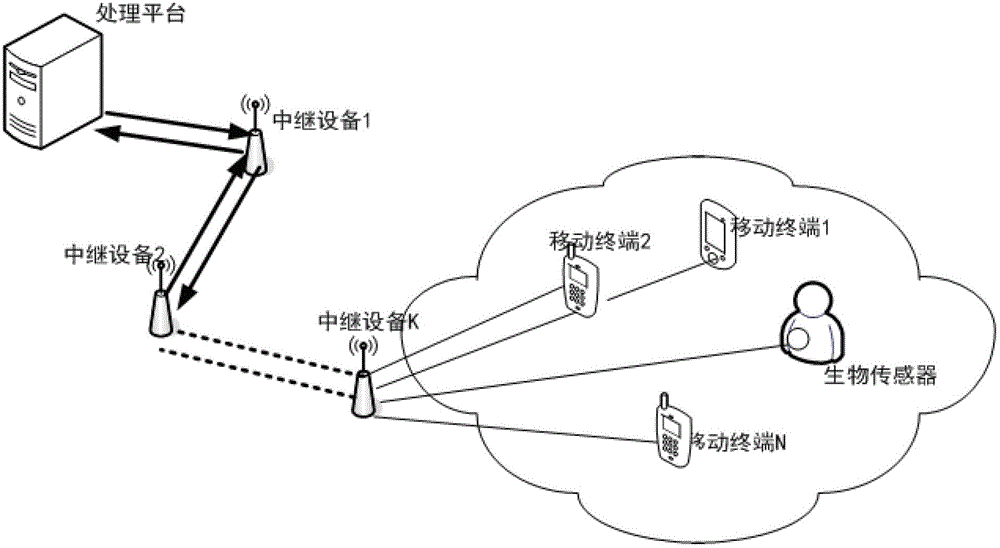
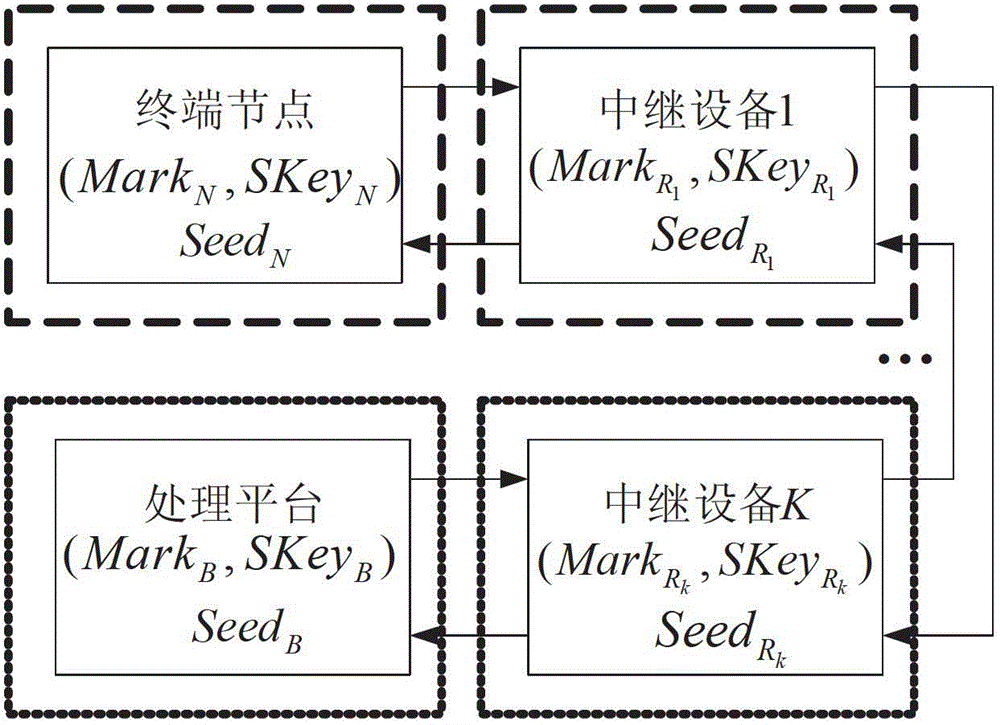
InactiveCN102724197AIncreased forward brute force complexityHigh security requirementsTransmissionSecurity arrangementMobile wireless sensor networkWireless mesh network
The invention discloses a two-way link security authentication method for a wireless relay network. The wireless relay network comprises a terminal node, M relay equipment and a processing platform. The method is a solution to the problems of low operational capability and low security of the terminal node in a link with the relay equipment in a wireless sensor network. By the participation of the relay equipment, a part of computational load of two authentication parties is transferred to the relay equipment, so that the complexity of an authentication process is improved, and difficulty in the cracking of an attacker is greatly improved along with the addition of the relay equipment. Moreover, the relay equipment participates in the update of an authentication information flow by using own private information, so that the processing platform and the terminal node also can indirectly authenticate the legality of the identity of the relay equipment.
Owner:SHANGHAI JIAO TONG UNIV
Horizontal rotation structure of ultra-large-tonnage asymmetric hybrid girder cable-stayed bridge and construction method thereof
PendingCN107964877AConstruction safetyShort construction periodBridge erection/assemblyCable stayedProcess complexity
The invention relates to the bridge construction technique, specifically to a horizontal rotation structure of an ultra-large-tonnage asymmetric hybrid girder cable-stayed bridge and a construction method thereof. The horizontal rotation structure of the ultra-large-tonnage asymmetric hybrid girder cable-stayed bridge comprises a concrete foundation pile, a bearing platform, rotating disks and a rotation sliding rail, wherein the bearing platform is divided into an upper bearing platform and a lower bearing platform; the rotation sliding rail is divided into support legs and a slideway; the upper bearing platform is provided with an upper rotating disk and the support legs; the lower bearing platform is provided with a lower rotating disk, a position-fixing pin and the slideway; the upperrotating disk and the lower rotating disk are connected by the position-fixing pin; the upper rotating disk fits the lower rotating disk; and the support legs fit the slideway. The horizontal rotationstructure of the ultra-large-tonnage asymmetric hybrid girder cable-stayed bridge and the construction method have obvious effects on solving the problems of complex construction process and high construction costs of a horizontal rotation structure of a large-tonnage asymmetric hybrid girder cable-stayed bridge in the prior art, and have the advantages of simple construction procedures, high construction speed, safety, reliability and low construction costs.
Owner:CHINA RAILWAY NO 9 GRP 2ND ENG +2
Electrolyte capable of improving security property of lithium ion battery
InactiveCN103779608AEnsure safetyMeet the needs of high securitySecondary cellsOrganic electrolytesSolventVinylene carbonate
The invention discloses an electrolyte capable of improving the security property of a lithium ion battery. The electrolyte is prepared by mixing of electrolyte salt, organic solvents and additives, wherein the electrolyte salt is solid solvent LiBOB; the organic solvents are ethylene carbonate EC, propylene carbonate PC and ethyl methyl carbonate EMC; the additives are vinylene carbonate VC, vinyl ethylene carbonate VEC, trimethylene sulfite PS and tributyl phosphate TBP. By using the novel electrolyte salt and the functional additives, the thermal stability of the lithium ion battery is improved, on premise of ensuring the battery circulation property, the security property of the battery is effectively improved, and the problems that the battery is combusted and exploded under an overheating condition are avoided. By applying the electrolyte, the reliability and the security of the lithium ion battery are improved, the quality of the lithium ion battery is greatly improved, and the market application prospect of products of battery production factories is improved, so that the successful development of the novel electrolyte has great production practice significance.
Owner:TECHN CENT FOR SAFETY OF INDAL PRODS TIANJIN ENTRY EXIT INSPECTION QUARANTINE BUREAU
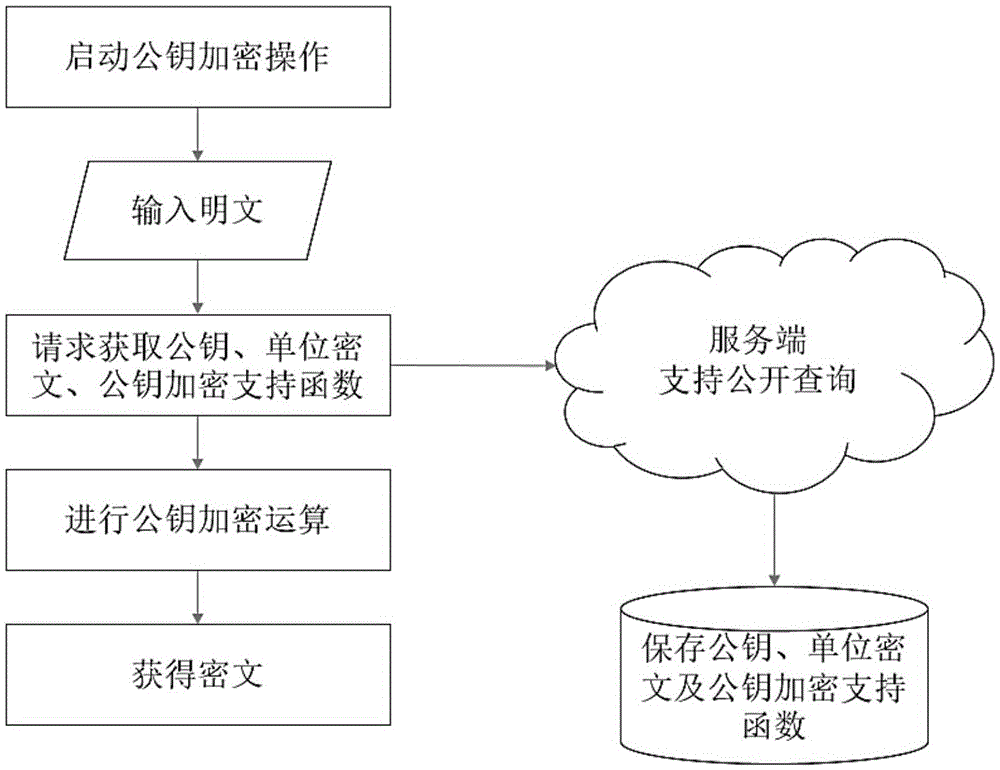
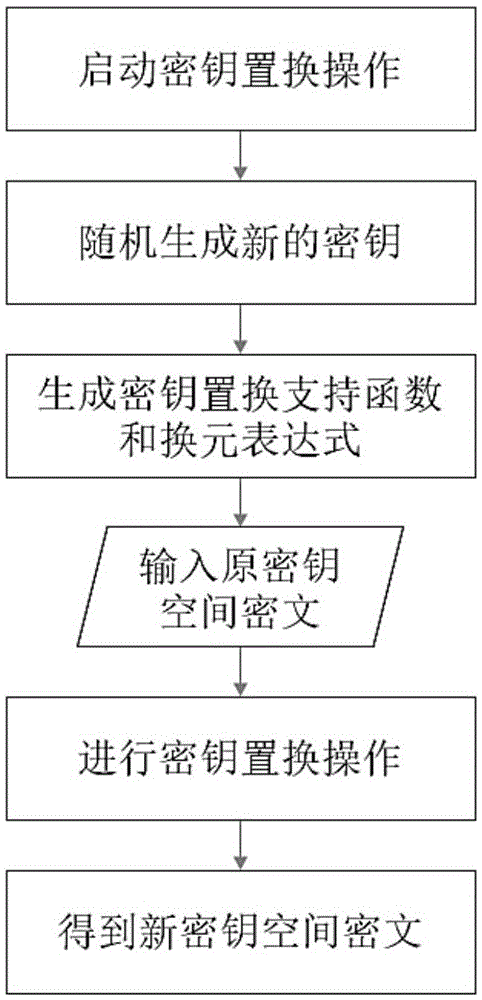
Asymmetric FHE (Fully Homomorphic Encryption) method and secret key substitution and cipher text delivery methods thereof
ActiveCN107181584AOverall small sizeLow speedKey distribution for secure communicationCommunication with homomorphic encryptionPlaintextNon symmetric
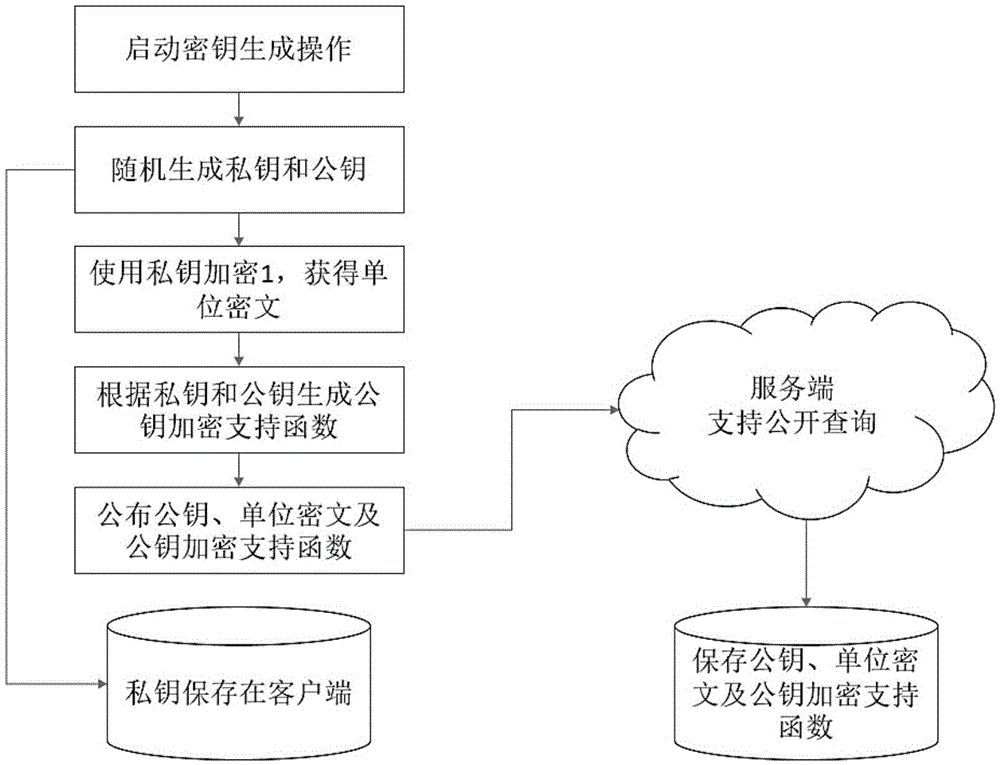
The invention relates to an asymmetric FHE method and secret key substitution and cipher text delivery methods thereof. A private key and a public key are generated randomly, and the secret key is used to generate an operation support function, a unit cipher text of secret key encryption and a public key encryption operation support function; a plaintext is encrypted to generate a cipher text, namely, the secret key is used for encryption directly to obtain a direct cipher text, or the public key corresponding to the secret key is used to carry out encryption operation to obtain a compatible cipher text in the same secret key space; and when the cipher text needs to be delivered to the receiving end safely, the sending, receiving and server ends or the sending and receiving ends complete delivery of the cipher text. Operation of the cipher text is carried out directly without leakage of the plaintext, a safe data storage and operation environment is provided, the computing speed is improved substantially compared with the prior art, the required cipher text volume and expansion speed are lower, the methods can be realized in different manners, and a data owner can use different cloud computing services needless of worrying about leakage of sensitive and secrete data.
Owner:上海麟羿信息科技有限公司
Safe authentication and encrypted communication method
InactiveCN101447873AEasy to useExpand the scope ofPublic key for secure communicationUser identity/authority verificationSecure communicationConfidentiality
The invention discloses a safe communication authentication and encrypted communication method comprising three parts: the method for realizing the establishment of a digital signature by a signature institution or a digital publisher, the method for authenticating the signature in application and the method for establishing the encrypted communication in the application. The safe communication authentication and encrypted communication method can conveniently utilize Internet, a public telephone network, and the like for realizing the point-to-point bidirectional digital signature authentication, the encrypted communication function and other functions, thereby ensuring the credibility and the authenticity of both communication parties and realizing the safety and the confidentiality.
Owner:HANGZHOU EASTCOM FINANCIAL TECH +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com