Visible-code-based payment method and system with multiple security combination mechanisms
A safe and mechanism-based technology, applied in the payment and system fields based on multiple security combination mechanisms of visible codes, can solve problems such as the impossibility of holding a large amount of payment certificates, the inability to use high-security mechanisms, and the short effective period of use, etc., to achieve Reduce roaming charges, reduce operation and maintenance costs, and improve security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
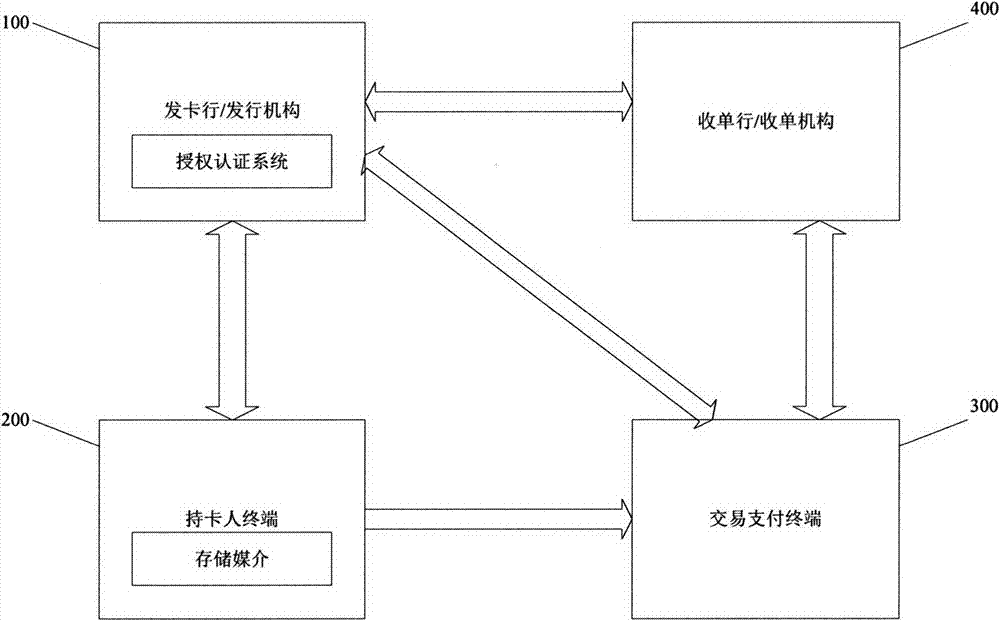
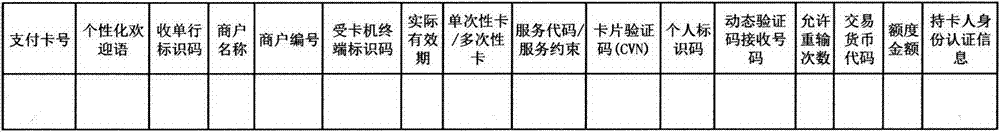
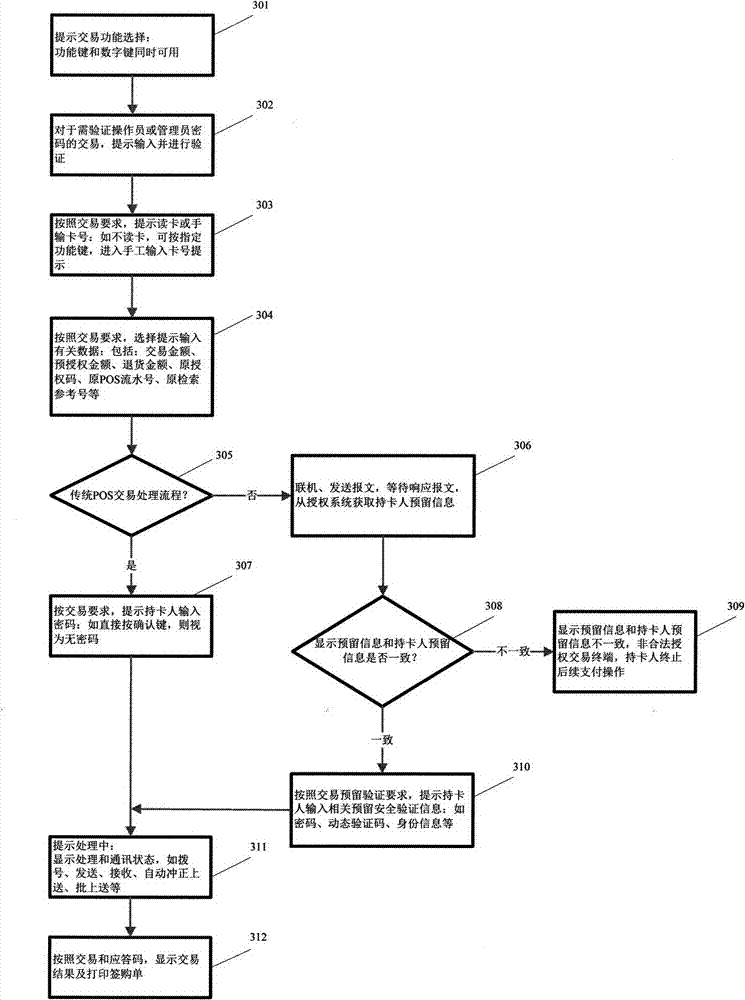
[0027] The cardholder uses the master account to log in to the card issuing bank / issuer system (100) of the master account online through a terminal (200) device (net banking, mobile banking, mobile smart client, etc.), and self-generates payment card information for transaction payment ( Including but not limited to the following: payment card number, personalized welcome message, acquiring bank identification code, merchant name, merchant number, terminal identification code of card accepting machine, actual validity period, single-use card / multi-use card, service code / service Constraints, card verification code (CVN), personal identification code, dynamic verification code receiving number, allowable re-entry times, transaction currency code, credit amount, cardholder identity authentication information (cardholder ID number, fingerprint, digital cert...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com