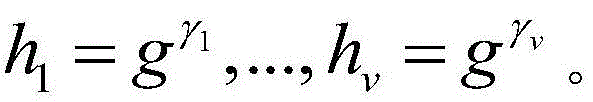Patents
Literature
12928results about How to "Protection security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information security management and control method under cloud manufacturing environment
InactiveCN102710605ASolve the problem of update and maintenanceAvoid complex proceduresPublic key for secure communicationUser identity/authority verificationConfidentialityPrivate network
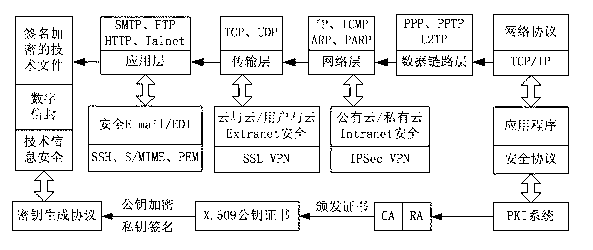
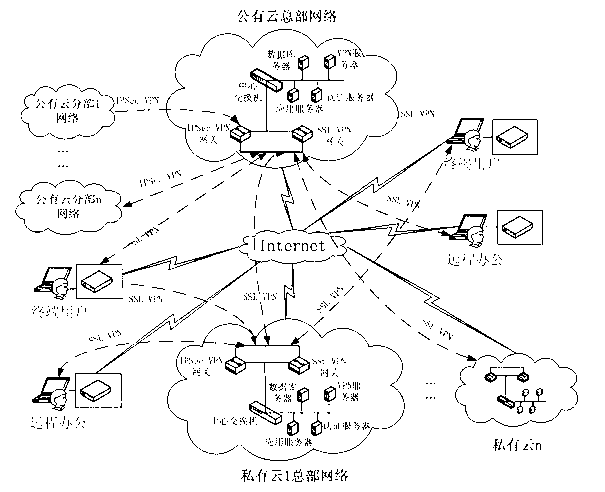
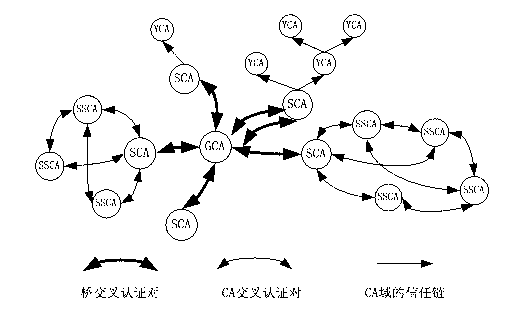
The invention discloses an information security management and control method under a cloud manufacturing environment. On the basis of a network security protocol, a password technology and a public key infrastructure (PKI), comprehensive security guarantee is supplied to information interaction among cloud internal networks, between one cloud and another cloud, and between a user and each cloud by using implementation technologies and methods, such as a virtual private network (VPN) based on multiple layers of protocols, a digital envelope and a password algorithm; Intranet, Extranet and Internet of a cloud manufacturing system are covered; comprehensive management and control technical information files are stored and transmitted to each used loop; a session key (SK) which is randomly produced by using a key production protocol is used for symmetrically encrypting the technical information files; and a receiver public key obtained according to a PKI digital certificate asymmetrically encrypts the SK to form the digital envelope for protecting the technical information files and the SK. The information security management and control method has the characteristics of being high in confidentiality, high inefficiency, flexible in arrangement and the like and can be widely applied to the cloud manufacturing system and other network manufacturing systems.
Owner:CHONGQING UNIV
Multifunctional intelligent rehabilitation robot for assisting stand and walk
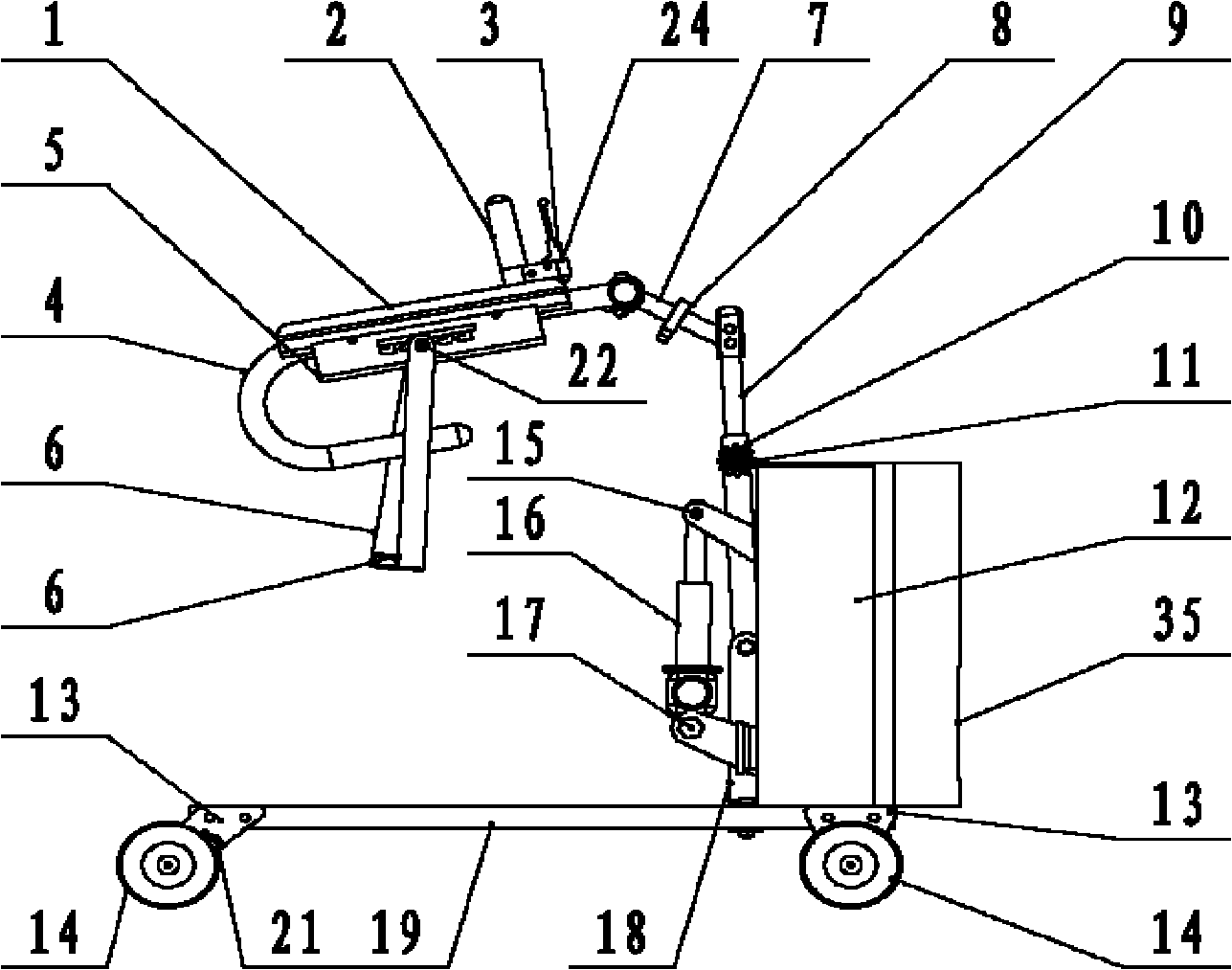
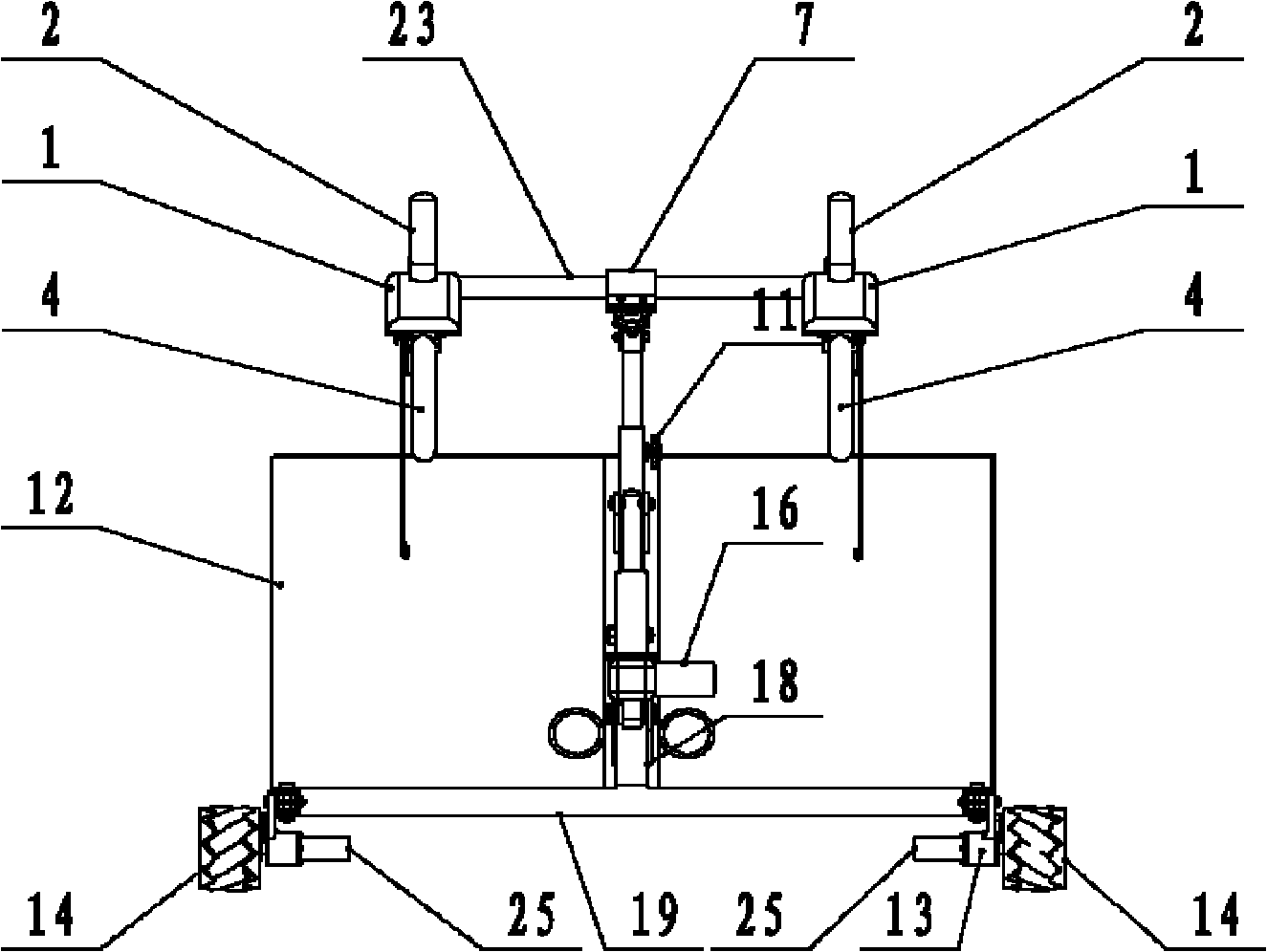
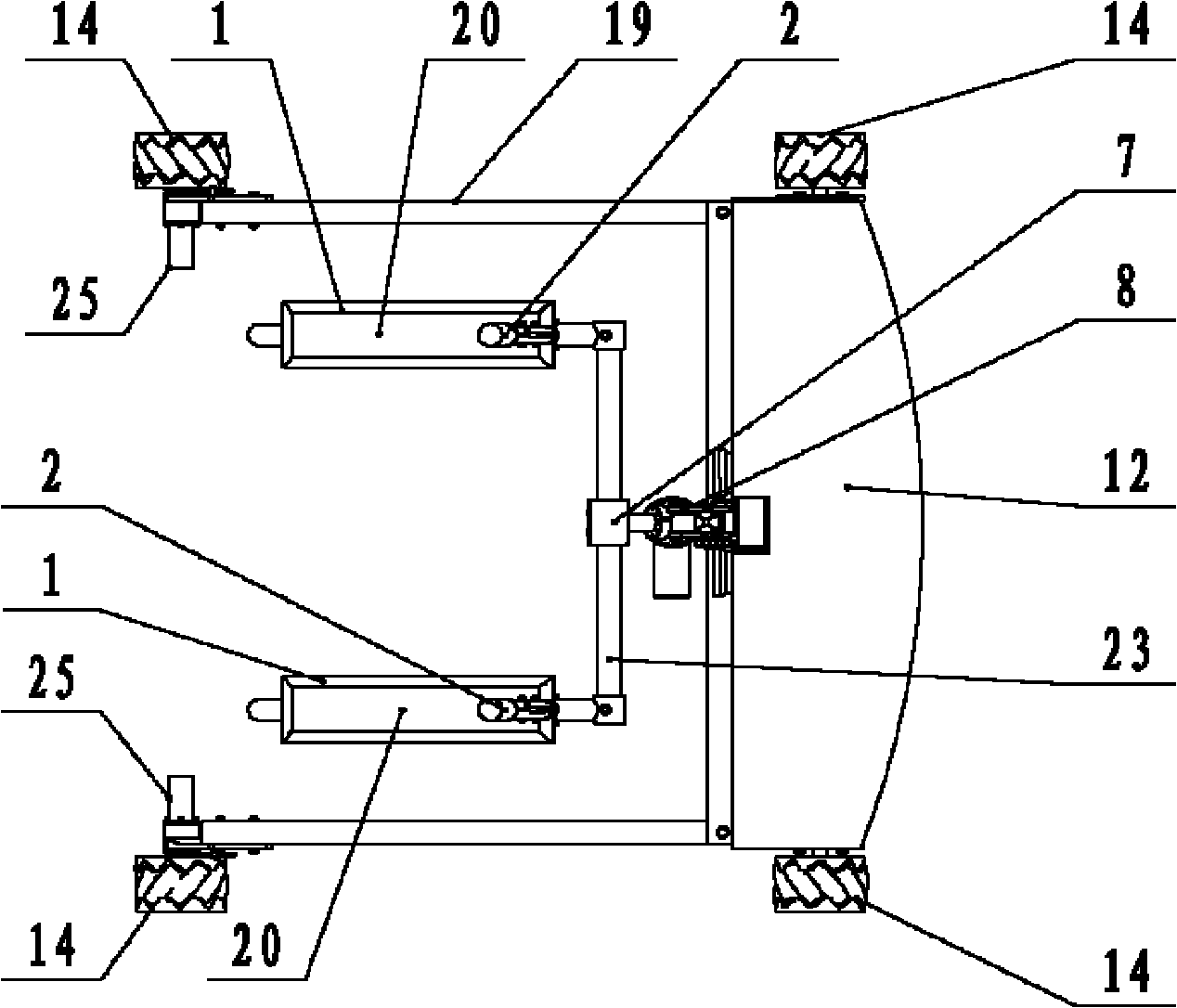
The invention discloses a multifunctional intelligent rehabilitation robot for assisting stand and walk. The whole robot comprises three parts basically: a mechanical stand assisting device, a chassis moving device and a monitoring control device, wherein the mechanical stand assisting device comprises a support base, a swing arm, an electric push rod and a handrail device; the chassis moving device comprises a base, a motor fixing frame, four Mecanum wheels, a braking ratchet wheel, a braking sheet, and the like; the monitoring control device comprises a force sensor array, a vision sensor, a distance-measuring sensor, and the like; and in addition, the robot also comprises a power source storage battery, and the like. The robot can realize the auxiliary stand and walk assistance to a user, can lift the user up safely and comfortably under the condition of sitting posture, judge the motion intention of the user in the walking process and carry out all-sided collaborative motion; meanwhile, the robot can also detect the moving tread of the user so as to judge the stability of the user and do corresponding assistance to the user at the real time; and the robot can safely and effectively assist patients with lower limbs being injured to carry out rehabilitation training and assist the daily activities of weak old people.
Owner:HUAZHONG UNIV OF SCI & TECH
Integrated digital transfusion apparatus and transfusion monitoring and management method thereof
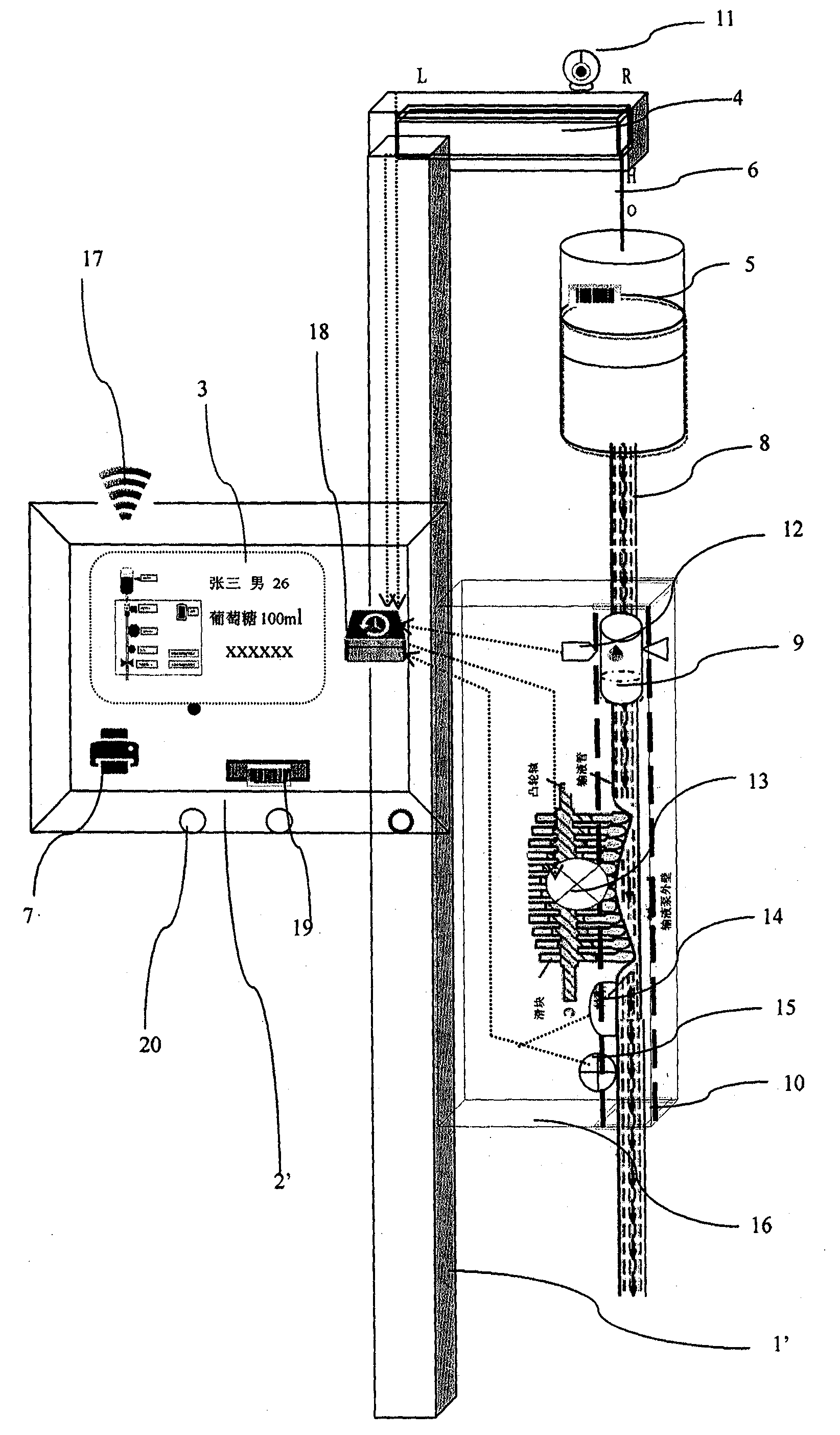
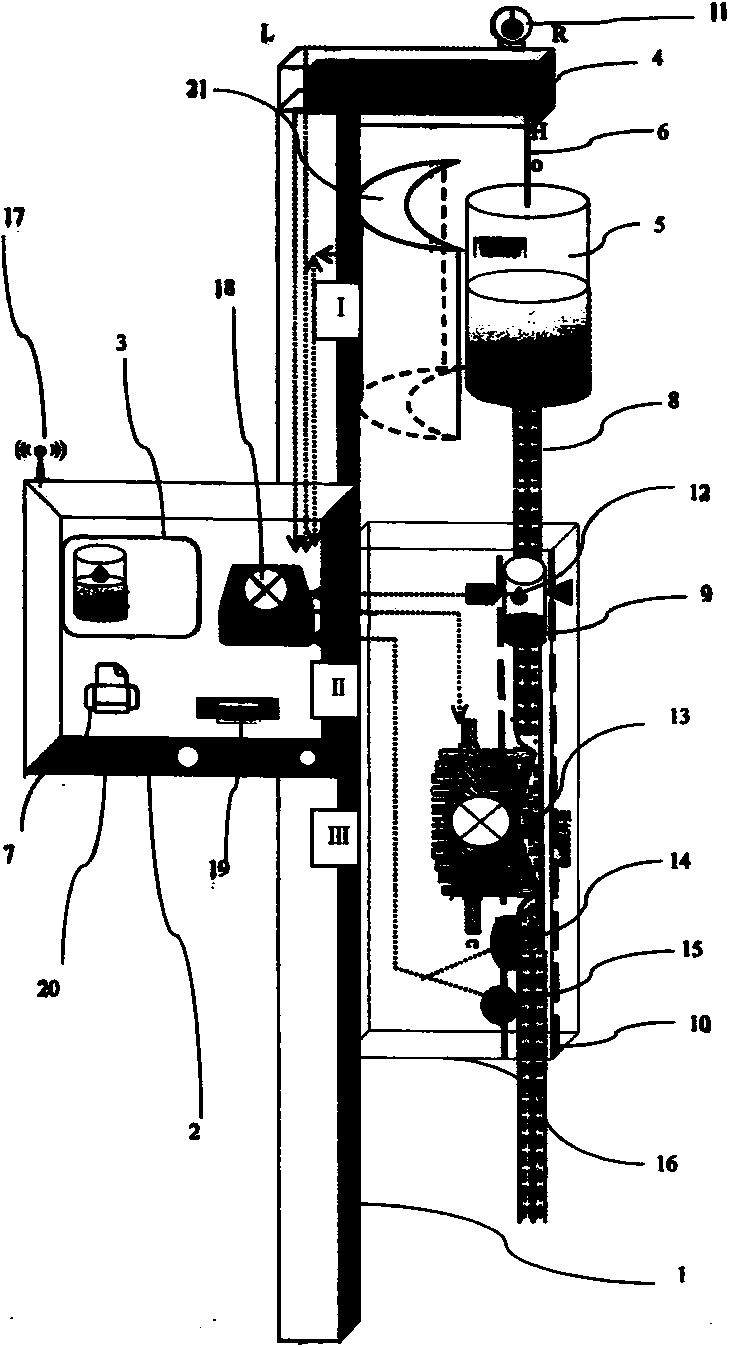
InactiveCN103816582AAspect mobileEnsure the safety of infusionFlow monitorsSpecial data processing applicationsPeristaltic pumpControl system
The invention discloses an integrated digital transfusion apparatus and a transfusion monitoring and management method thereof. The integrated digital transfusion apparatus is mainly structurally characterized in that a shell of devices including a control system, a display and the like and a transfusion tube clip and device shell are respectively fixed onto an integrated transfusion support and device shell. A touch display, a microprocessor, a microphone / speaker, a scanner, a wireless network connection device, a miniprinter, a transfusion tube, a Murphy dripper clamping groove, a finger peristaltic pump, a photoelectric droplet detection device, a pressure detector and an ultrasonic bubble detector are mounted on the integrated digital transfusion apparatus. Data acquired by different parts in the transfusion apparatus are used for mutual comparison of transfusion parameters. Software computation and simulation techniques are used during transfusion, and nurses can well know detailed transfusion conditions of each patient in transfusion by directly observing simulated transfusion bottles / bags and tubes and simulated transfusion apparatuses on software of the transfusion apparatuses and software on external computers, setting operation of various transfusion parameters, setting alarm thresholds of the various transfusion parameters and the like.
Owner:葛锋
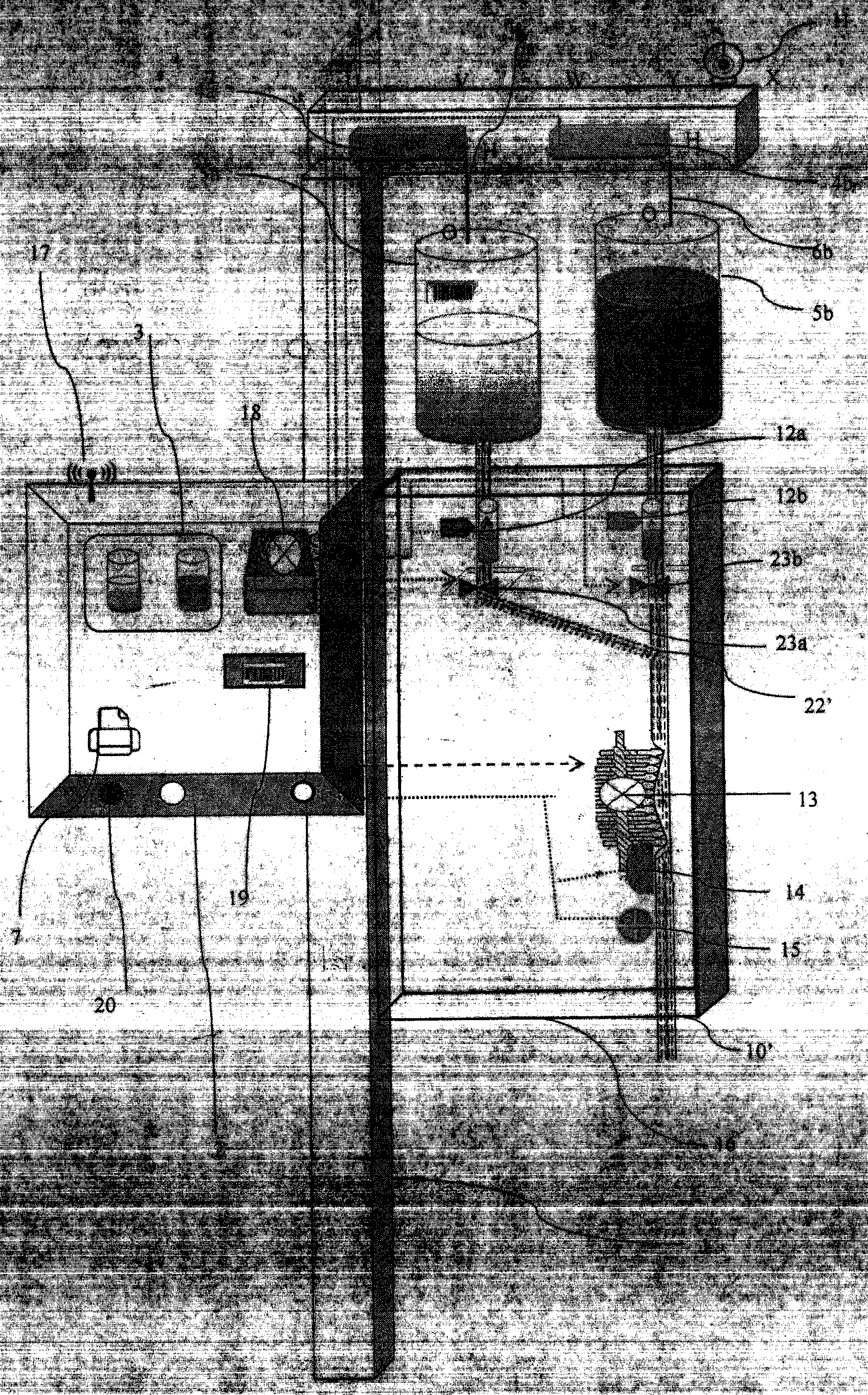
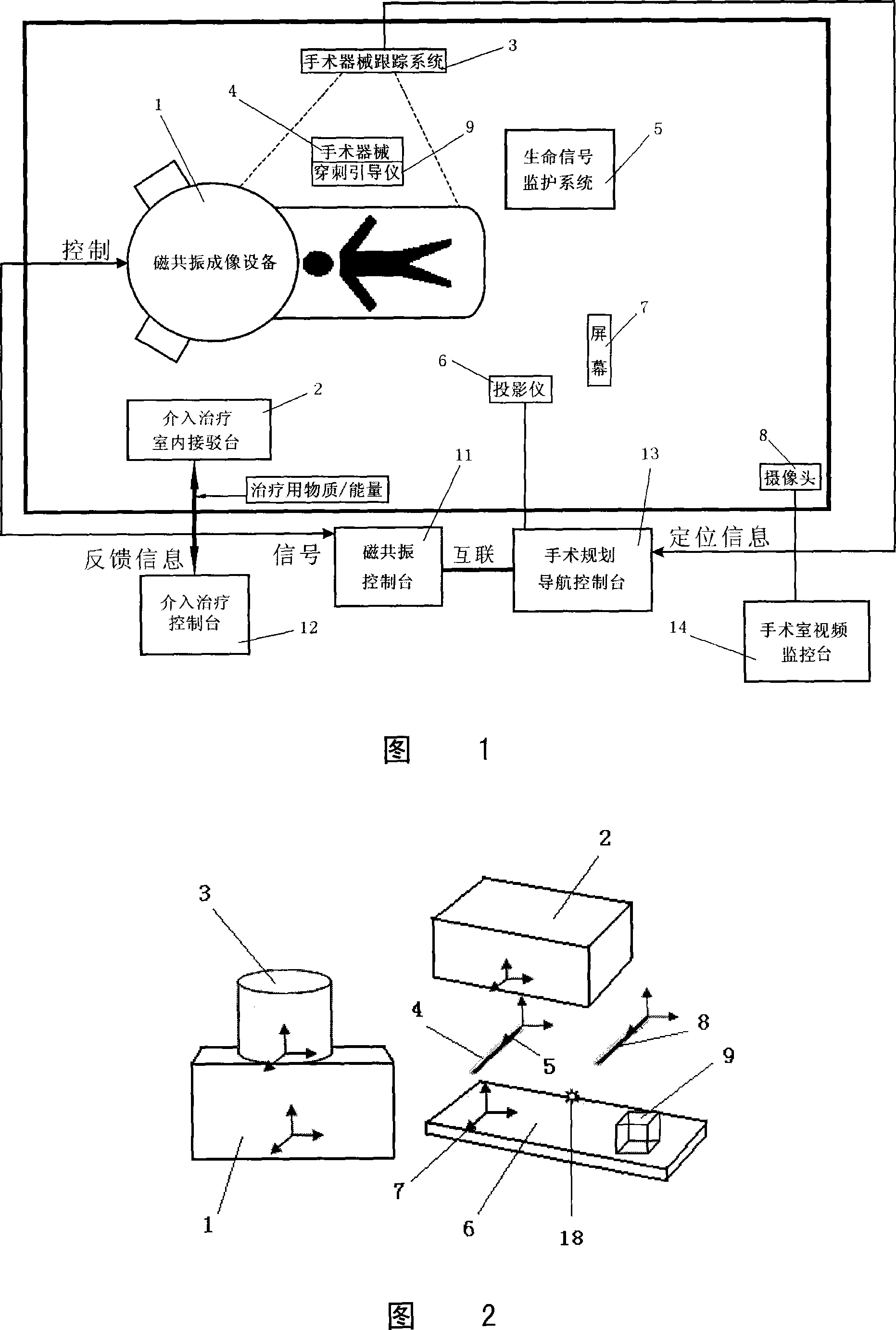
Surgical operation system under the guide of magnetic resonant image and the operation navigating method
ActiveCN101019765APrecise Navigation EffectGuaranteed navigation accuracySurgeryDiagnostic recording/measuringSurgical operationDisplay device
The present invention is surgical operation system under the guide of magnetic resonant image and the operation navigating method. The surgical operation system includes magnetic resonant imaging equipment, a tracking system, a surgical instrument, a sick bed, a control and display device, a computer with relevant software. It features the calibrating pin and calibrating mode, and the tracer with different coordinate systems for measuring pose and calibrating. The present invention can realize the precise location of the operational equipment relative to the magnetic resonant image and operation navigation.
Owner:SYMBOW MEDICAL TECH
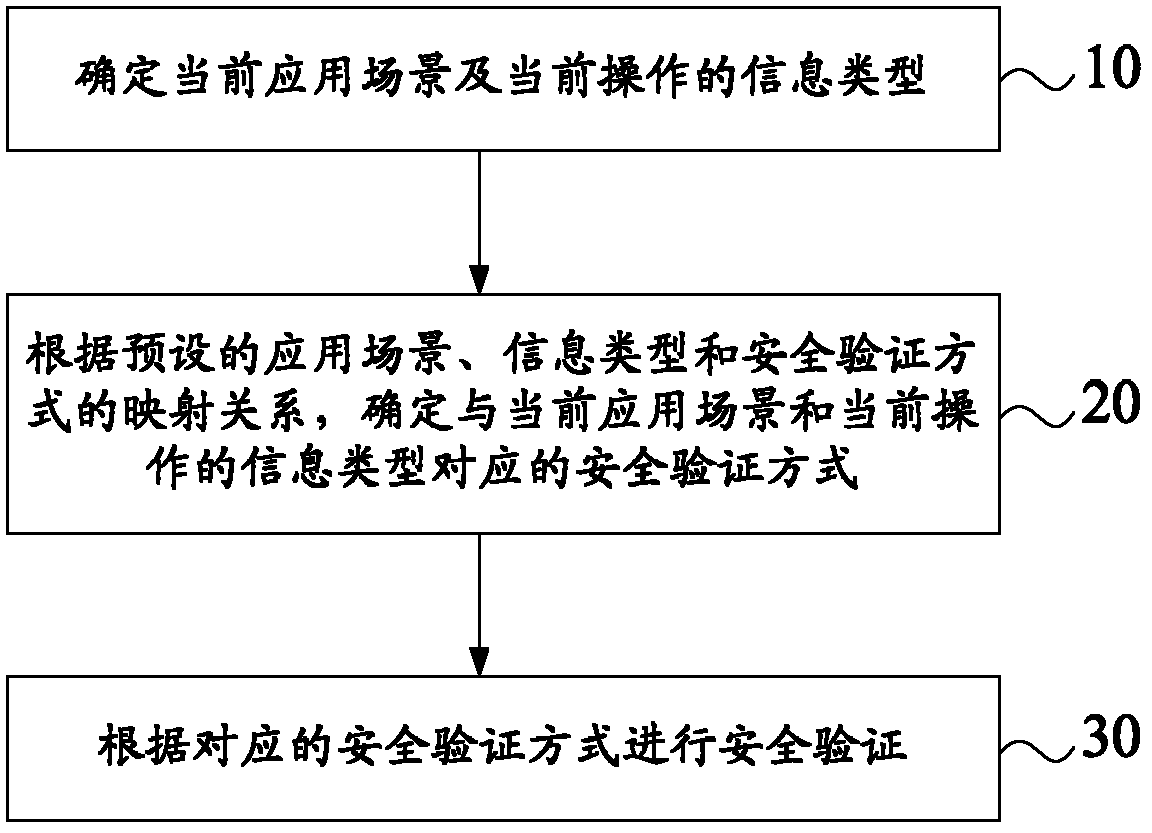
Safety verification method and equipment
InactiveCN102685106AImprove operational convenienceProtection securityUser identity/authority verificationSpeech analysisInformation typeUnsafe environment
The invention provides a safety verification method and equipment. The safety verification method comprises the following steps of: determining a current application scene and an information type of current operation; determining a safety verification mode corresponding to the current application scene and the information type of the current operation according to a mapping relation among the pre-supposed application scene, the information type and the safety verification mode; and performing safety verification according to the corresponding safety verification mode. By adopting the technical scheme, the pre-supposed safety verification mode matched with the current application scene is selected according to the application scene in which a user is located. According to the dynamic safety verification mode, the operation convenience of the user in a safe environment can be enhanced, and the safety of private information and data of the user in an unsafe environment can also be protected as far as possible.
Owner:BEIJING BENY WAVE SCI & TECH
Multiple-degree-of-freedom anti-explosion mechanical arm
InactiveCN101797748AAvoid damageSo as not to damageProgramme-controlled manipulatorJointsJoint componentDistributed control system
A multiple-degree-of-freedom anti-explosion mechanical arm relates to an anti-explosion mechanical arm. The anti-explosion mechanical arm comprises a six-degree-of-freedom joint component, a double-camera system, a distributed control system and an expansion system, wherein a front paw can be operated flexibly and diversely through the cooperative control of six joints; the double-camera system is used to provide front vision for rear operating staff so that the mechanical arm can be conveniently controlled to complete special tasks, the double-camera system comprises a main camera fixed on a front arm and a front-end camera fixed on a paw joint; the main camera has broad vision, the focus of the front-end camera is fine; the distributed control system is used to control the synergy movement of the six-degree-of-freedom component and various movements of the six-degree-of-freedom component, the distributed control system comprises a distributed control module, a magnetic absolute position sensing system and the like; and the expansion system is used to add different functions to meet different demands and increase the application range of the mechanical arm.
Owner:武汉若比特机器人有限公司
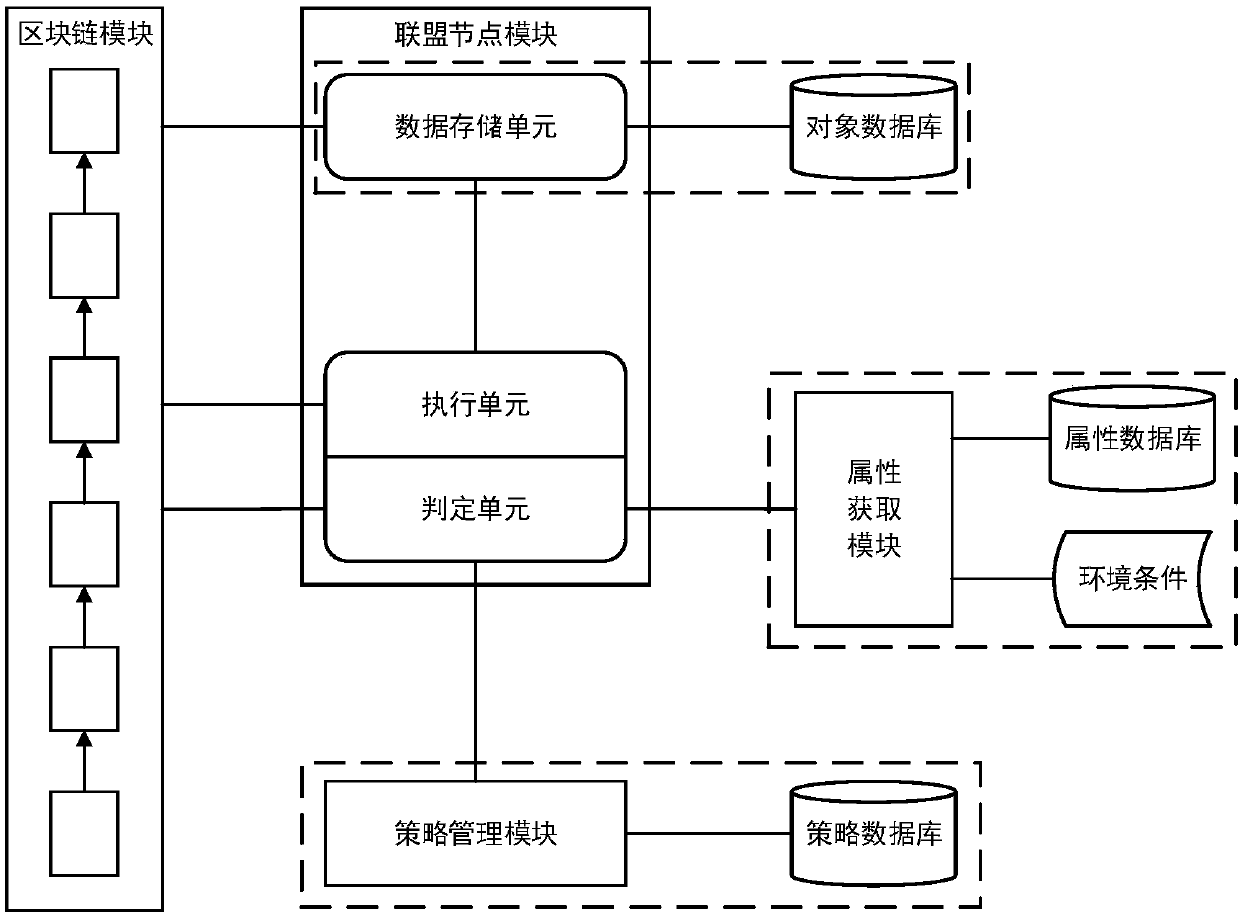
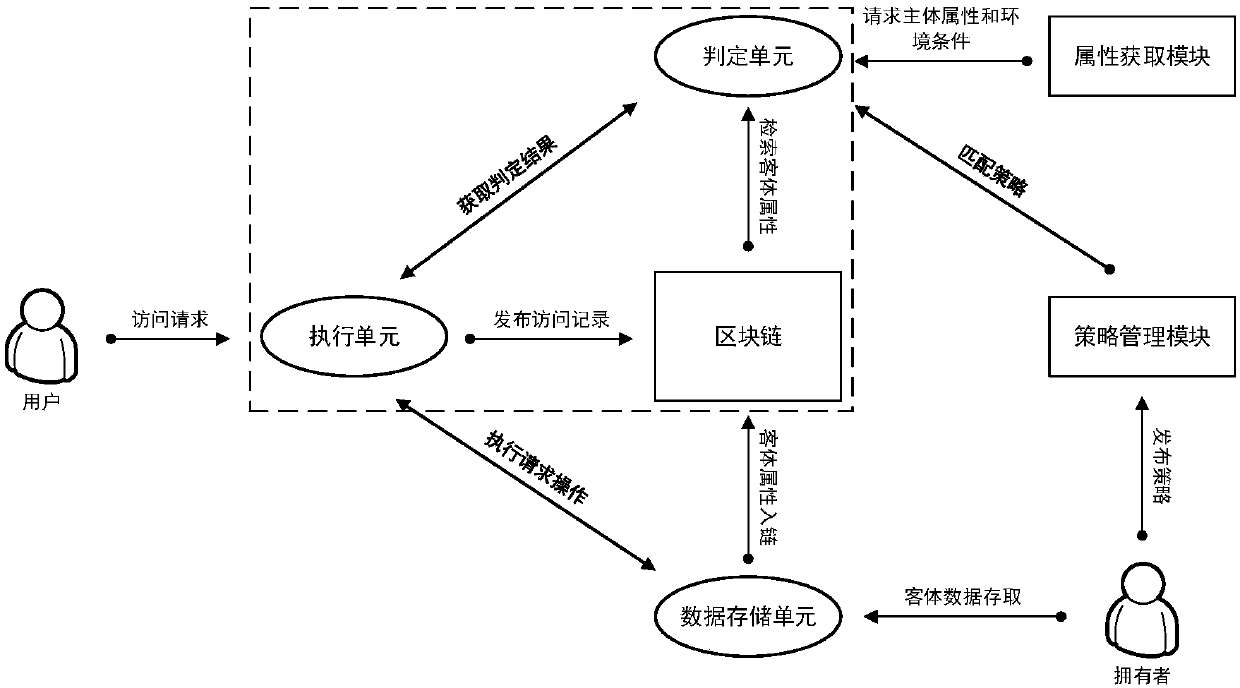
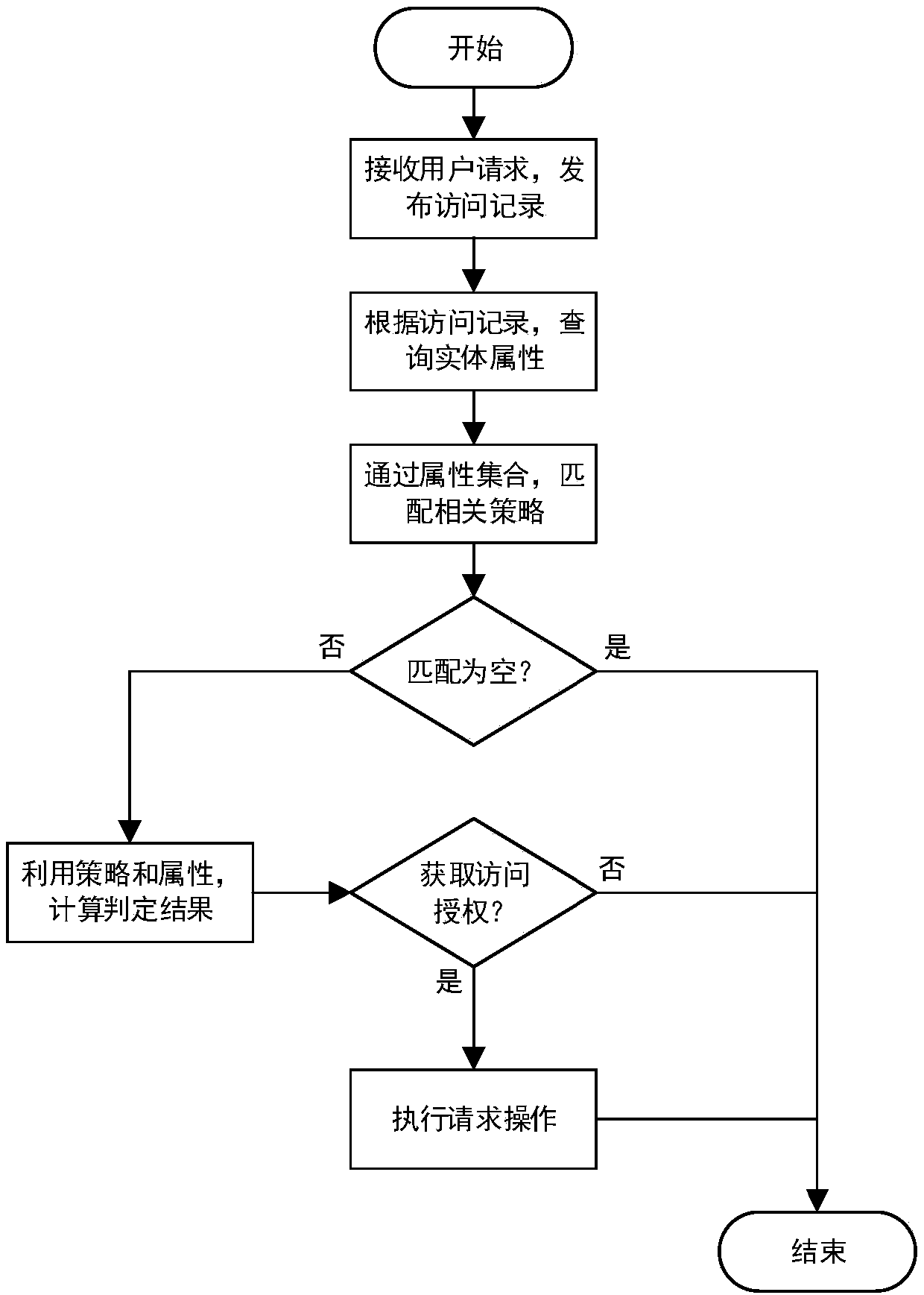
Access control method and system based on block chain technology
ActiveCN108123936AResistance to failureResist being attackedFinancePayment protocolsAuthorization ModeData privacy protection
The invention provides an access control method and system based on block chain technology. The block chain technology is combined with attribute-based access control in the method, and the method comprises the following steps: adding an object in a chain, binding a judgment process of attribute and strategy on all block chain nodes with reference to the strategy. The access authorization is converted from a centralized manner into a distributed manner, the consistency check of the judgment results in the whole network is achieved by using a consensus mechanism of the block chain, and the authorized operations for accessing the recorded transactions are permanently recorded on the block chain. The method has the advantages of anti-single point failure, flexible authorization mode, accurateaccess boundary, and record auditability. The access control method and system provided by the invention are applicable to operating environments such as enterprises and governments that have the need of data privacy protection and realize multi-branch cooperation work based on a block chain platform, the access permissions of users in the system can be dynamically and scalably managed, fine-grained permission management is achieved for the strategy and the attribute, and the access control method and system are of important practical significance for protecting the security of information systems in a distributed network environment.
Owner:UNIV OF SCI & TECH BEIJING
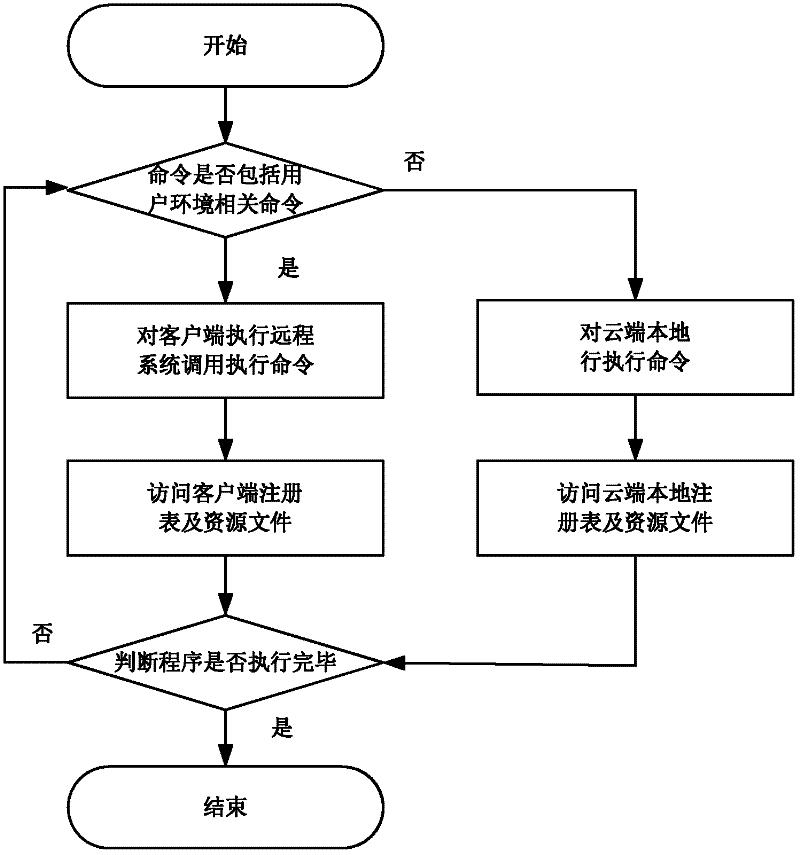
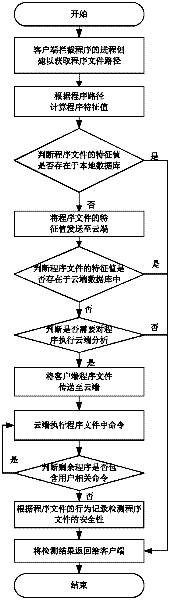
Active defense method based on cloud platform
The invention discloses an active defense method based on a cloud platform. The active defense method comprises the following steps of: intercepting progress establishment by a client to acquire a program file route of a progress; calculating a characteristic value of a program file according to the program file route; judging whether the characteristic value of the program file exists in a local database; if the characteristic value of the program file does not exist in the local database, sending the characteristic value of the program file to a cloud end; judging whether the characteristic value of the program file exists in a database of the cloud end; if the characteristic value of the program file does not exist in the database of the cloud end, judging whether cloud end analysis is required to be performed on the program file; if the cloud end analysis is required to be performed on the program file, sending the program file to the cloud end; executing a command in the program file by the cloud end; judging whether the residual commands in the program file do not comprise commands related to a user environment; if the residual commands in the program file do not comprise commands related to the user environment, executing the residual commands; and detecting the security of the program file according to a behavior record of the program file, and returning a detection result back to the client.
Owner:HUAZHONG UNIV OF SCI & TECH
Method and system for optimal scheduling on joint flood control for cascade reservoir groups
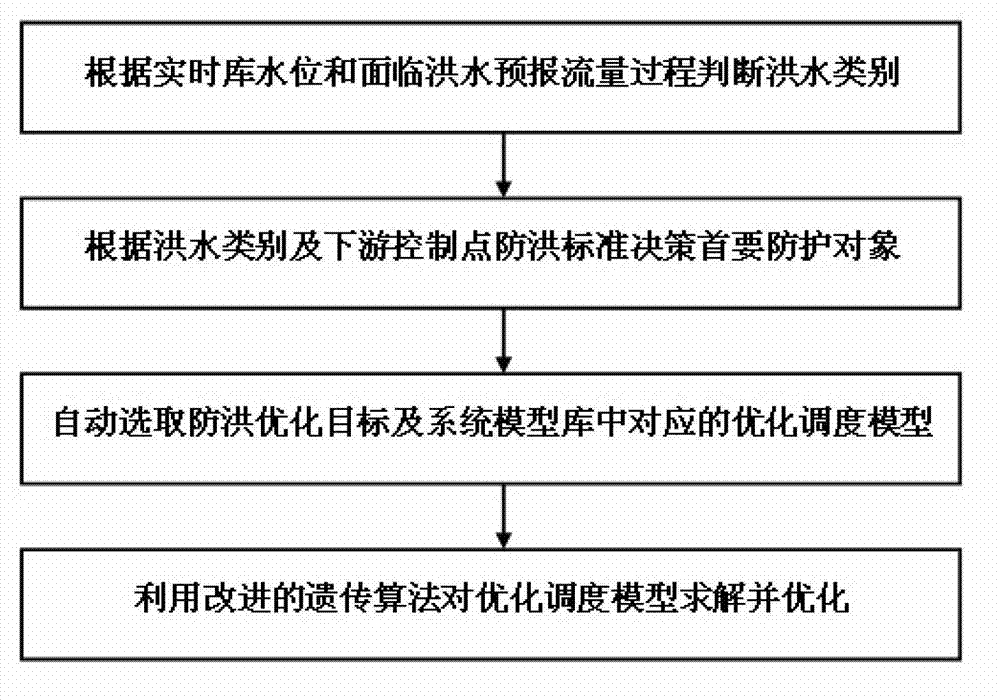
InactiveCN102817335AProtection securityImprove decision-making efficiencyClimate change adaptationForecastingTraffic volumeFlood control
The invention discloses a method and a system for optimal scheduling on joint flood control for cascade reservoir groups. The method includes the steps of firstly, determining flood type according to real-time reservoir level and the process of forecasting runoff in case of flood; secondly, deciding a primary protection object according to the flood type and downstream control-point flood control standards; thirdly, automatically selecting flood control optimization objectives and corresponding optimization scheduling models in a system model base; and fourthly, solving and optimizing the optimization scheduling model by modified genetic algorithm. The method and the system dynamically judge the level of flood and finish hierarchical scheduling based on the level of flood. In addition, projection of downstream protection objects, dam safety and flood recycling are achieved by selecting proper optimization scheduling objectives according to comprehensive information of the reservoirs, such as regulation performance, scheduling period and reliability in forecast flood during hierarchical scheduling, efficiency in decisions for the reservoir groups is improved, and mass data statistics show that the decision efficiency is improved by about 30% by the method and the system.
Owner:GUIZHOU WUJIANG HYDROPOWER DEV
Safe vehicle passing system and method
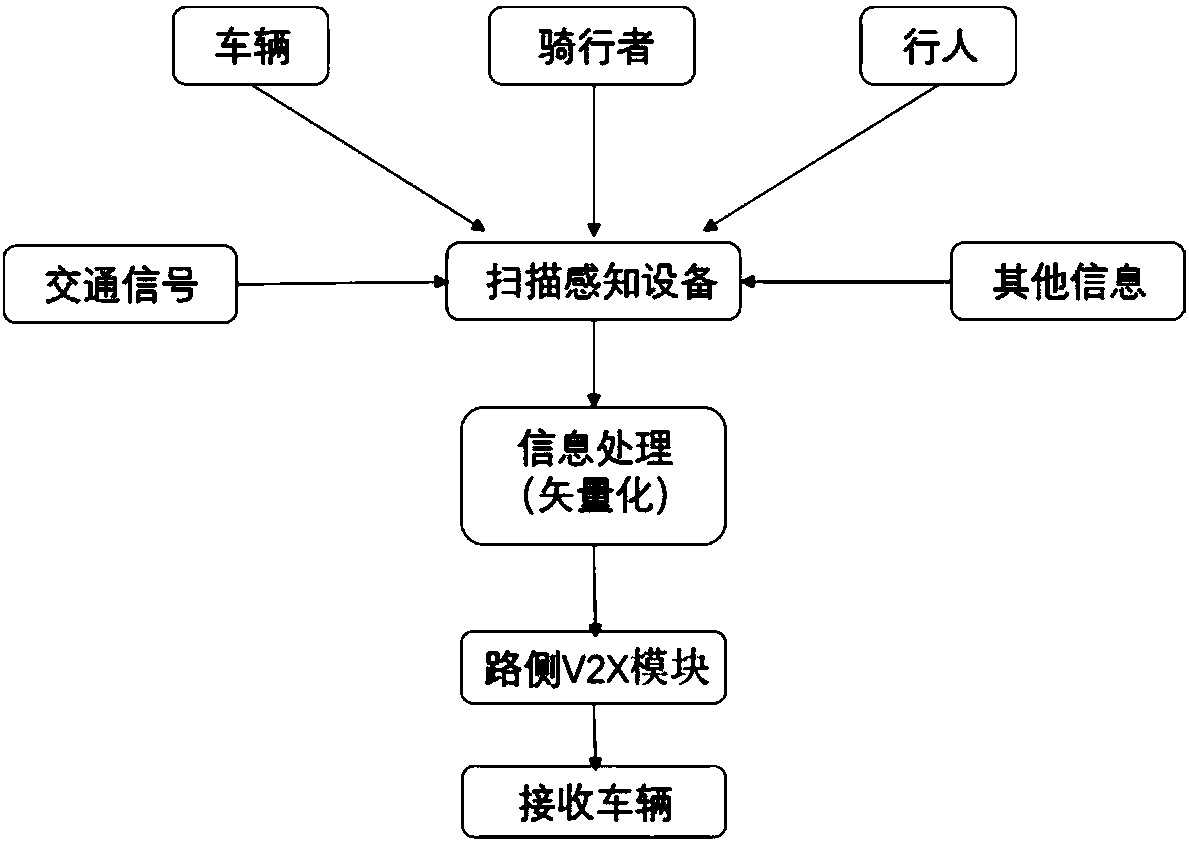
ActiveCN108417087AIncrease coverageImprove usabilityParticular environment based servicesDetection of traffic movementRoad userNear road
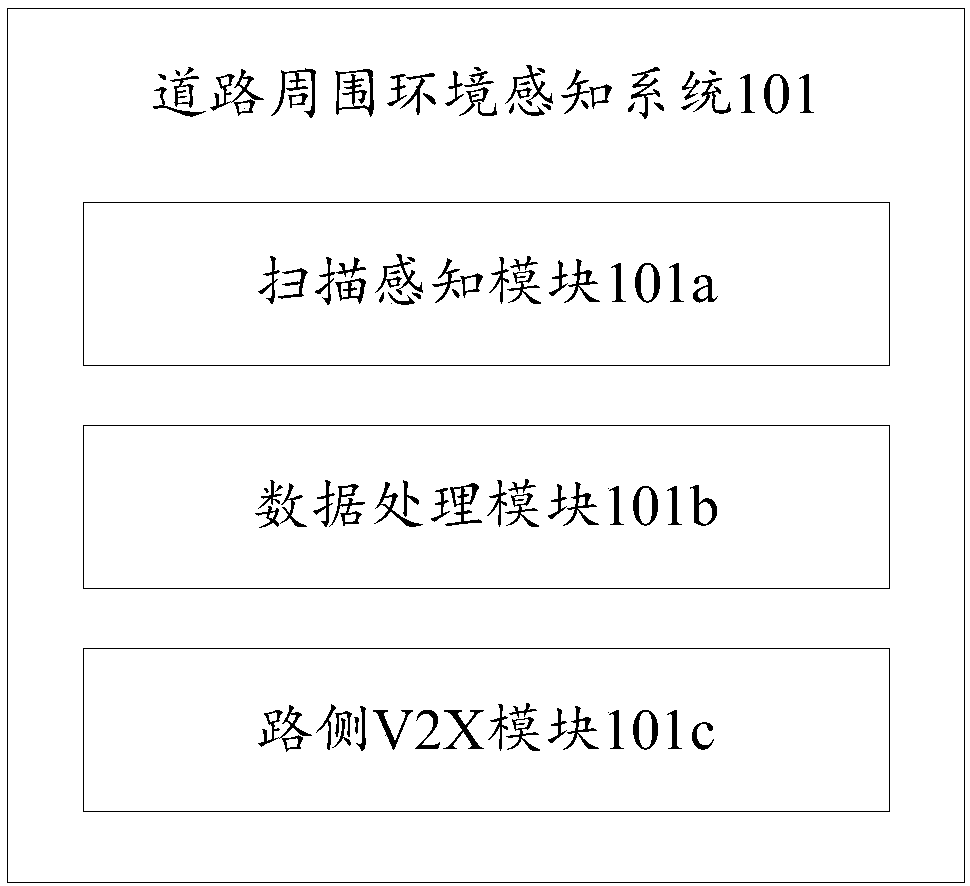
The invention discloses a safe vehicle passing system comprising an ambient road environment sensing system and a vehicle-mounted terminal. The ambient road environment sensing system is used for acquiring sensing information of an ambient environment of a road in real time, processing the sensing information to obtain driving assistance information of the vehicle, and sending the driving assistance information of the vehicle to the vehicle-mounted terminal. The vehicle-mounted terminal is used for receiving the driving assistance information of the vehicle and planning a driving track based on the driving assistance information of the vehicle and information collected by the vehicle. In addition, the invention also discloses a safe vehicle passing method based on the safe vehicle passingsystem. According to the invention, information various participants on road is obtained by scanning; near road environment information is provided for vehicles having V2X receiving devices fully; andthus the road right and safety of the vulnerable road user can be protected fully.
Owner:ZHEJIANG GEELY AUTOMOBILE RES INST CO LTD +1
Electric pressure cooker
The invention relates to the field of kitchen appliances, in particular to an electric pressure cooker. The electric pressure cooker comprises a pot body, a pot cover hinged to the pot body and an inner pot placed in the pot body; a first clamping member used for connecting the inner pot, a second clamping member used for connecting the pot body, a handle acting on the first clamping member and acover opening button acting on the second clamping member are arranged on the pot cover; a baffle plate is linked on the handle; when the pot cover and the inner pot are in a clamping state, the action of the second clamping member of the cover opening button is limited by the baffle plate, and therefore the clamping connection state between the pot cover and the pot body cannot be removed by thecover opening button. The cover of the electric pressure cooker can only be opened when pressure does not exist in the pot and when the electric pressure cooker is in an unlocking state after cookingis completed, and the safety of a user is ensured.
Owner:HANGZHOU YONGYAO TECH
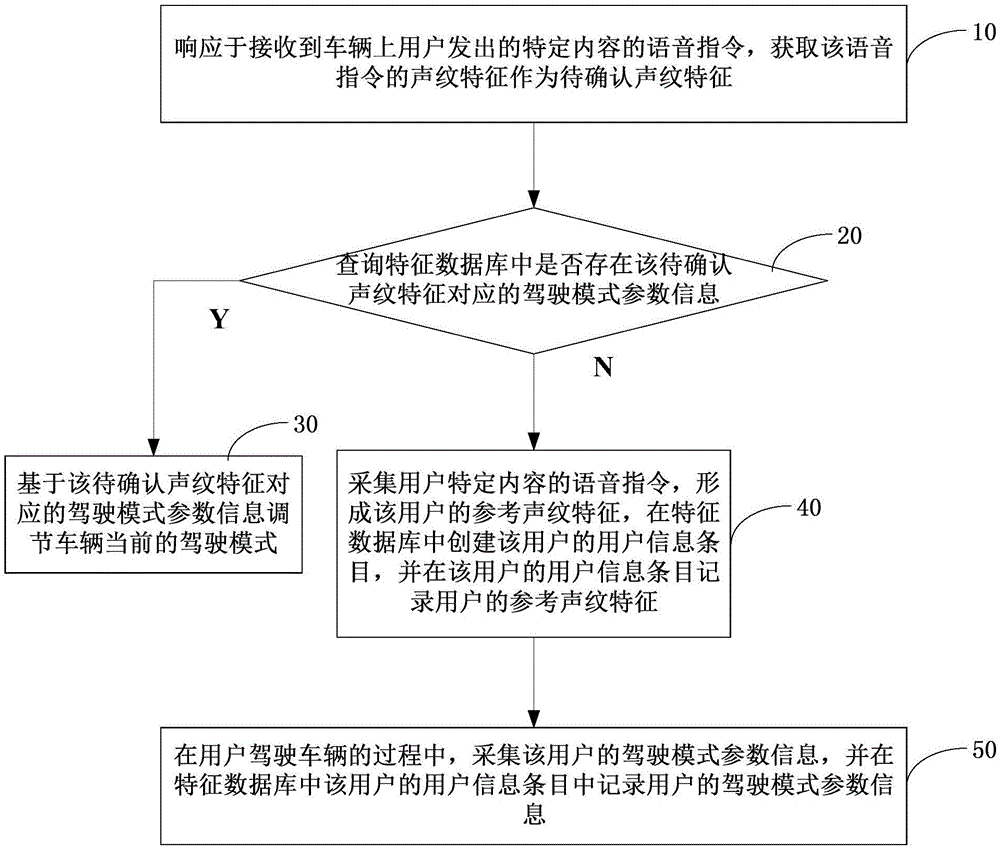
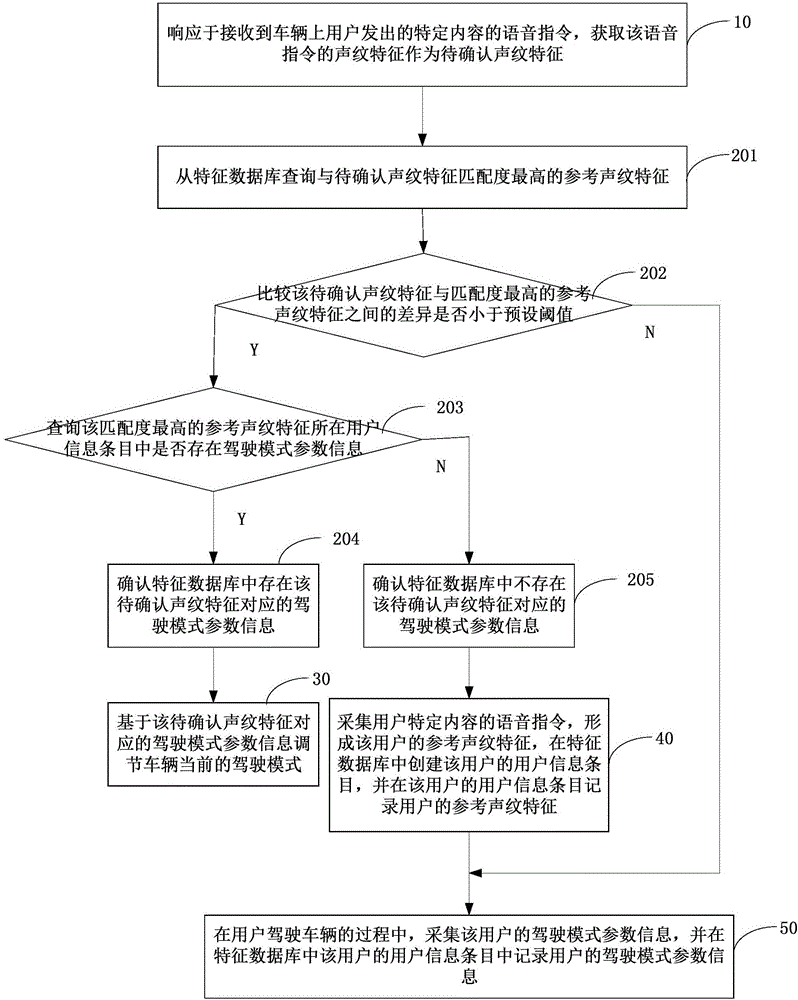
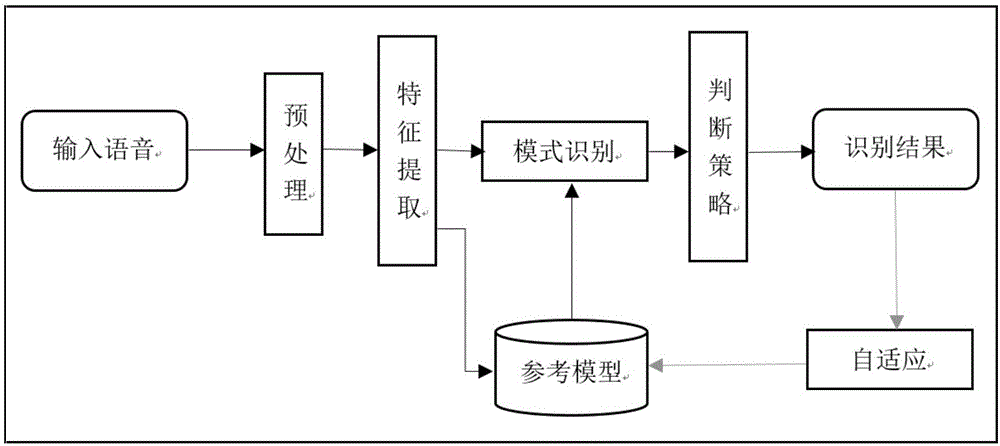
Method, device and system for adjusting driving modes and vehicle
ActiveCN106683673ARealize automatic adjustmentProtection securitySpeech recognitionPersonalizationVehicle driving
The invention discloses a method, a device and a system for adjusting driving modes and a vehicle. The method includes receiving a voice instruction; querying feature databases; determining parameter information of the driving modes on the basis of to-be-confirmed voiceprint features; acquiring the voice instruction and acquiring the parameter information of the driving modes in driving procedures. The method, the device, the system and the vehicle have the advantages that the vehicle can be adjusted to be in the most familiar and habitual driving modes by the aid of the single voice instruction, and accordingly users can be positioned in habitual driving environments without manually adjusting the parameter information of the driving modes; the parameter information of the driving modes of the users can be automatically acquired in the vehicle driving procedures of the users without being manually set by the users, the tedious properties of user operation can be prevented, specific physical buttons can be omitted, and influence on the aesthetics of internal environments of the vehicle can be prevented; the quantity of the parameter information of the driving modes of the users is unlimited for the same vehicle, and the personalized driving modes of the various users can be implemented.
Owner:ZHICHEAUTO TECH BEIJING
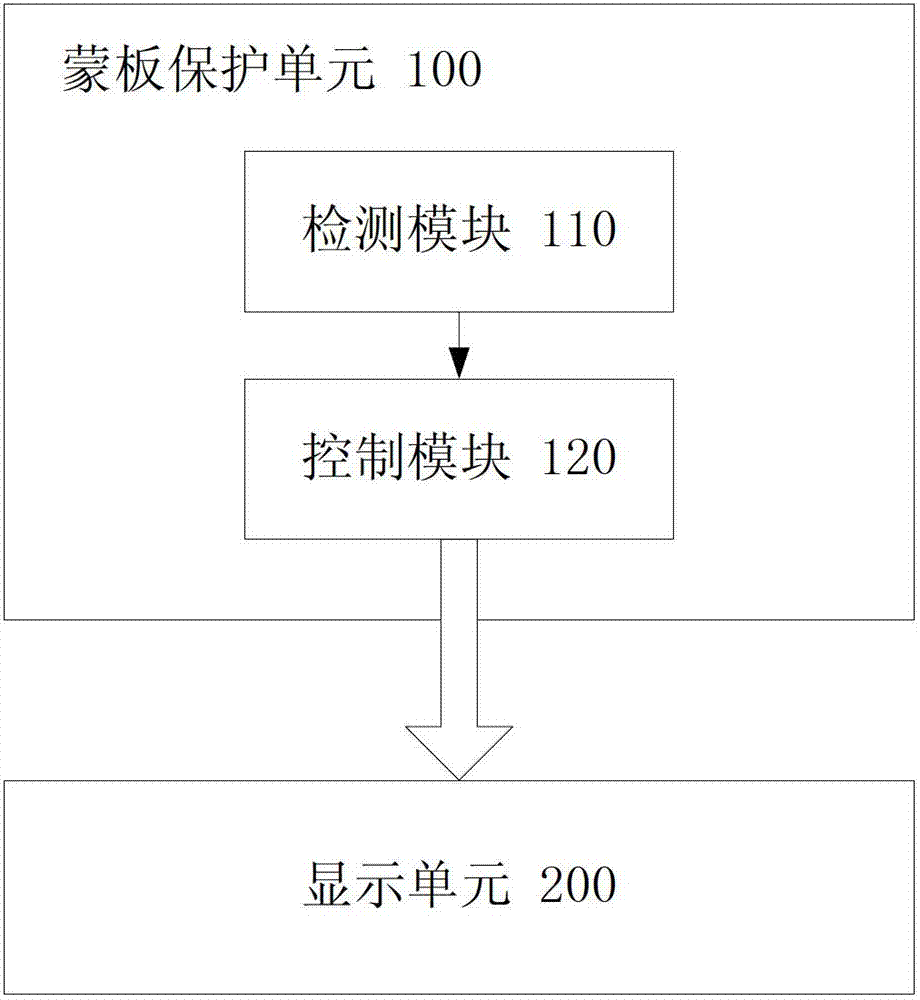
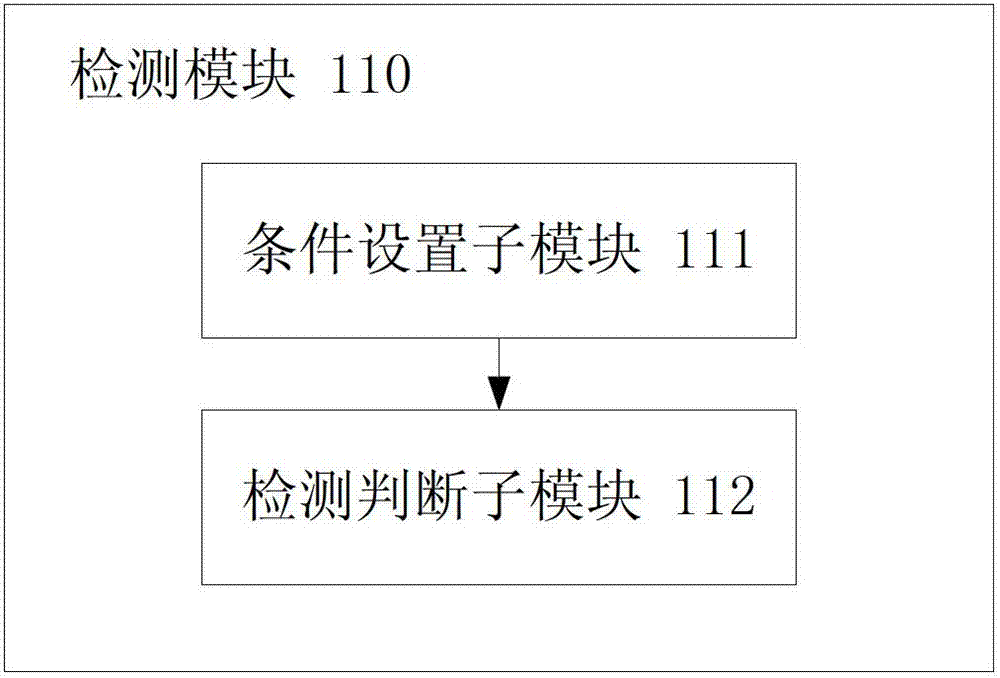
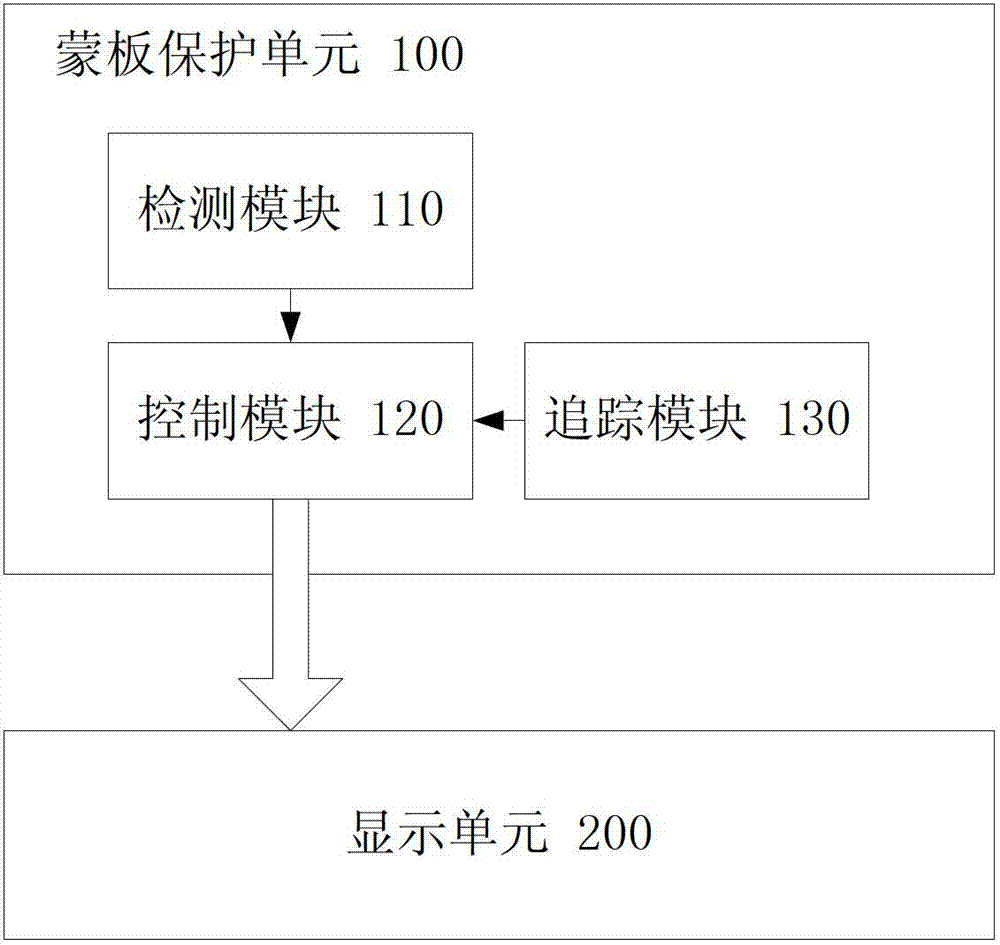
Mobile terminal and anti-spy method thereof
ActiveCN103077361ADoes not restrict field of viewImprove experienceDigital data protectionInternal/peripheral component protectionComputer scienceField of view
The invention relates to a mobile terminal and an anti-spy method thereof. The method comprises the following steps of: detecting current content displayed by a screen of the mobile terminal; and when the content or an application with privacy properties is detected, displaying a mask in a preset zone of the current screen of the mobile terminal so as to protect the current content displayed by the screen of the mobile terminal. Through the application of the technical scheme of the invention, the screen content of the mobile terminal can be protected, the cost is low, few system resources are occupied, the vision of a user cannot be limited, and great experience is brought to the user.
Owner:DONGGUAN YULONG COMM TECH +1
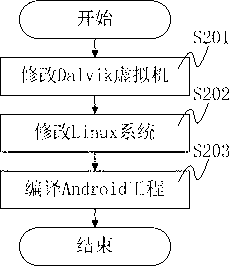
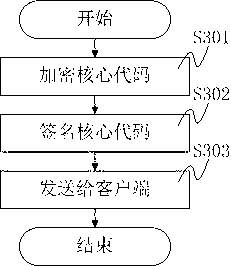
Android platform software protecting system, method and equipment
The invention mainly discloses a system and method for protecting application software in an Android system from reverse analysis and decryption. The method mainly comprises the following steps: increasing interfaces for a LiDalvik virtual machine and a Linux system library in the Android system, so that the Android has a capability of directly loading a DEX format file and an SO format file from a memory; storing a core code of the application software in an online server, encrypting and signing the core code, sending the core code to the application software installed at a client end; after receiving the core code, verifying the signature and decrypting the core code by the application software; storing a plaintext into the memory, and directly loading the plaintext into the system; invoking the code; and releasing the memory. The method greatly improves the difficulty in performing reverse analysis and decryption by an attacker, so that the safety of the Android application software can be effectively protected.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
Device with culture relics exhibiting and protecting function
InactiveCN101390700APrevent oxidationInhibition of photodegradationShow cabinetsShow shelvesMicroorganismGlass cover
The invention provides a device which can exhibit and protect cultural relics. The device is characterized in that the device comprises a base; a base plate is arranged at the top of the base; the bottom of a glass cover is fixed on the base plate through a safety lock reed, and a safety alarm is arranged on the safety lock reed; a gland bush is arranged at the butt joint of the glass cover and the base plate; a rotating bushing is arranged at the middle part of the base plate and a gland bush is arranged on the rotating bushing; rotating shafts are arranged inside the rotating bushing and the base; showcase stands are arranged at the top parts of the rotating shafts, and step motors are arranged at the tail ends of the rotating shafts; a temperature sensor, a pressure sensor, a humidity sensor and a gas composition sensor are arranged at two sides of the base plate; and a cavity refrigerating / heating device is arranged at the bottom of the base plate. The device has the advantages that the device can well exhibit the cultural relics and can create a manual protecting environment without damages. The device prevents oxidation, photodegradation, overheating volatilization, mould development and microorganisms and has the function of protecting the cultural relics and the precious article inside the cavity.
Owner:DONGHUA UNIV
Equipment and method for automatically disassembling and recycling power battery
ActiveCN105070971AActive collectionHigh degree of automationWaste accumulators reclaimingBattery recyclingManipulatorPower battery
The invention discloses equipment and a method for automatically disassembling and recycling a power battery. The equipment comprises a rack, a loading bin, a loading manipulator, a horizontal mobile platform, a clamping and positioning mechanism, a cutting mechanism, a core taking mechanism, a residual energy detection system, an auxiliary loading device and a visual system; a series of automated technological process such as loading, clamping, battery head cutting, separation of a cell and a battery case, unloading and the like of the power battery can be realized, and meanwhile, visualized remote monitoring on the whole technological process is realized through matching with the visual system. Besides, the cutting mechanism and the core taking mechanism are covered with inner protection covers, the whole equipment adopts an all-closed type outer protection cover, so that noise and dust in the equipment can be effectively isolated, and safety of operators and the equipment is protected.
Owner:SHENYANG INST OF AUTOMATION GUANGZHOU CHINESE ACAD OF SCI +1
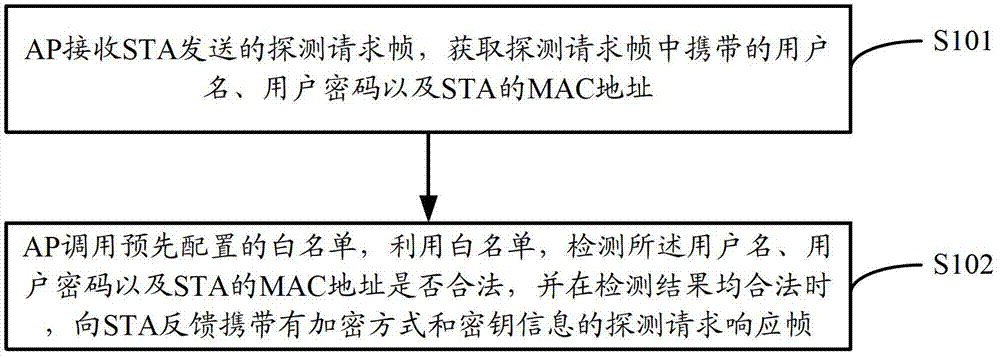
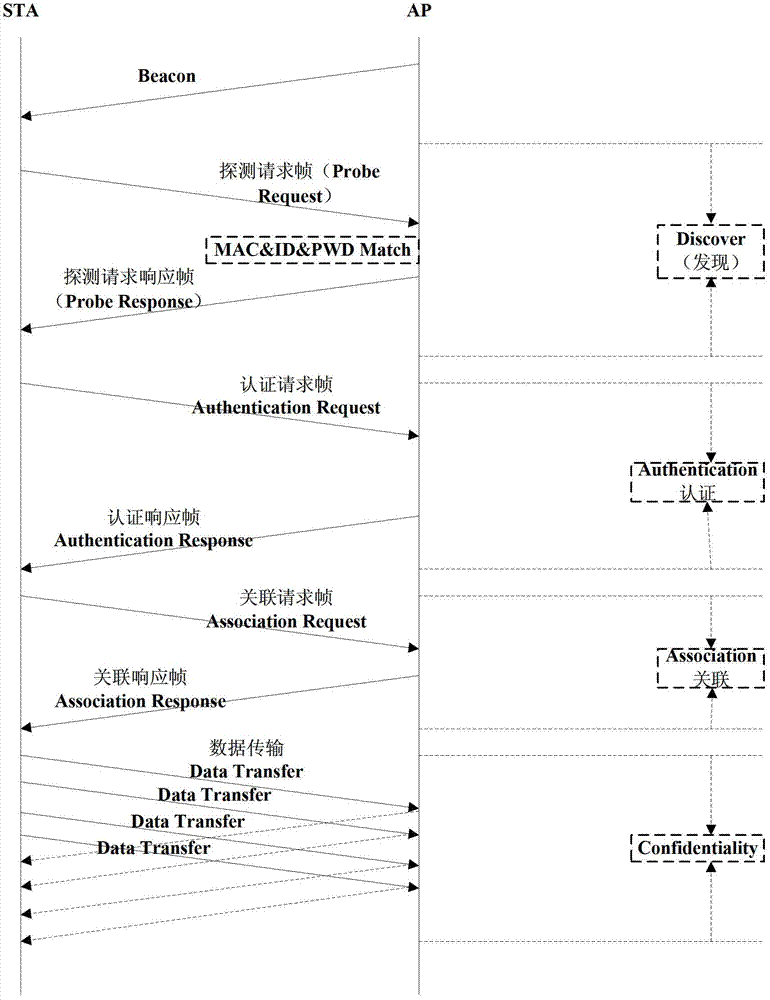
Wireless network safe access method, apparatus and system
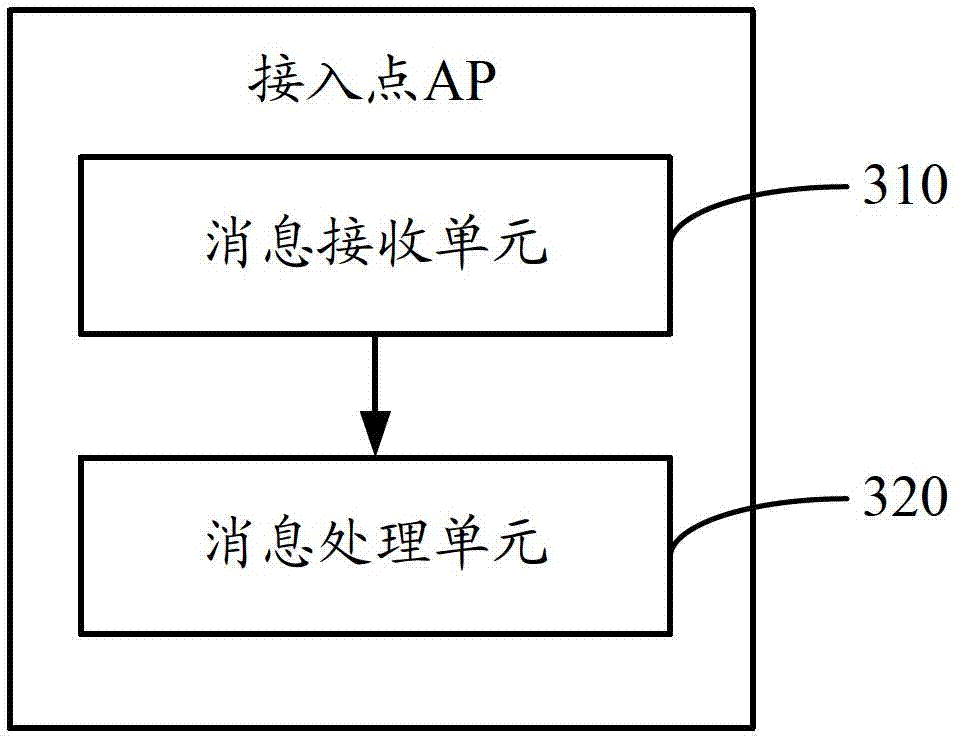
The invention discloses a wireless network safe access method, apparatus and system. The method comprises the following steps: an access point (AP) receiving a detection request frame sent by a station (STA), and obtaining a user name, a user password, and the MAC address of the STA which are carried by the detection request frame; and the AP scheduling a white list configured in advance, utilizing the white list to detect whether the user name, the user password and the MAC address of the STA are valid, and feeding a detection request response frame carrying an encryption mode and secret key information back to the STA when detection results are valid. Through the access method provided by the invention, it is not necessary for a user to carry out complex configuration, be aware of which encryption algorithm is adopted by the AP and input a complex WLAN password so that the use of the user is facilitated; and besides, the white list is arranged for detecting the validity of the access user in a binding mode, so that safety of a wireless network can be effectively protected.
Owner:ZTE CORP
Application installation control method, related system and related device
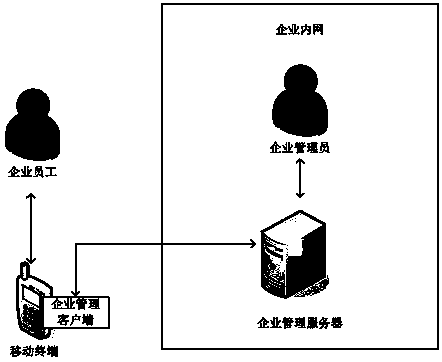
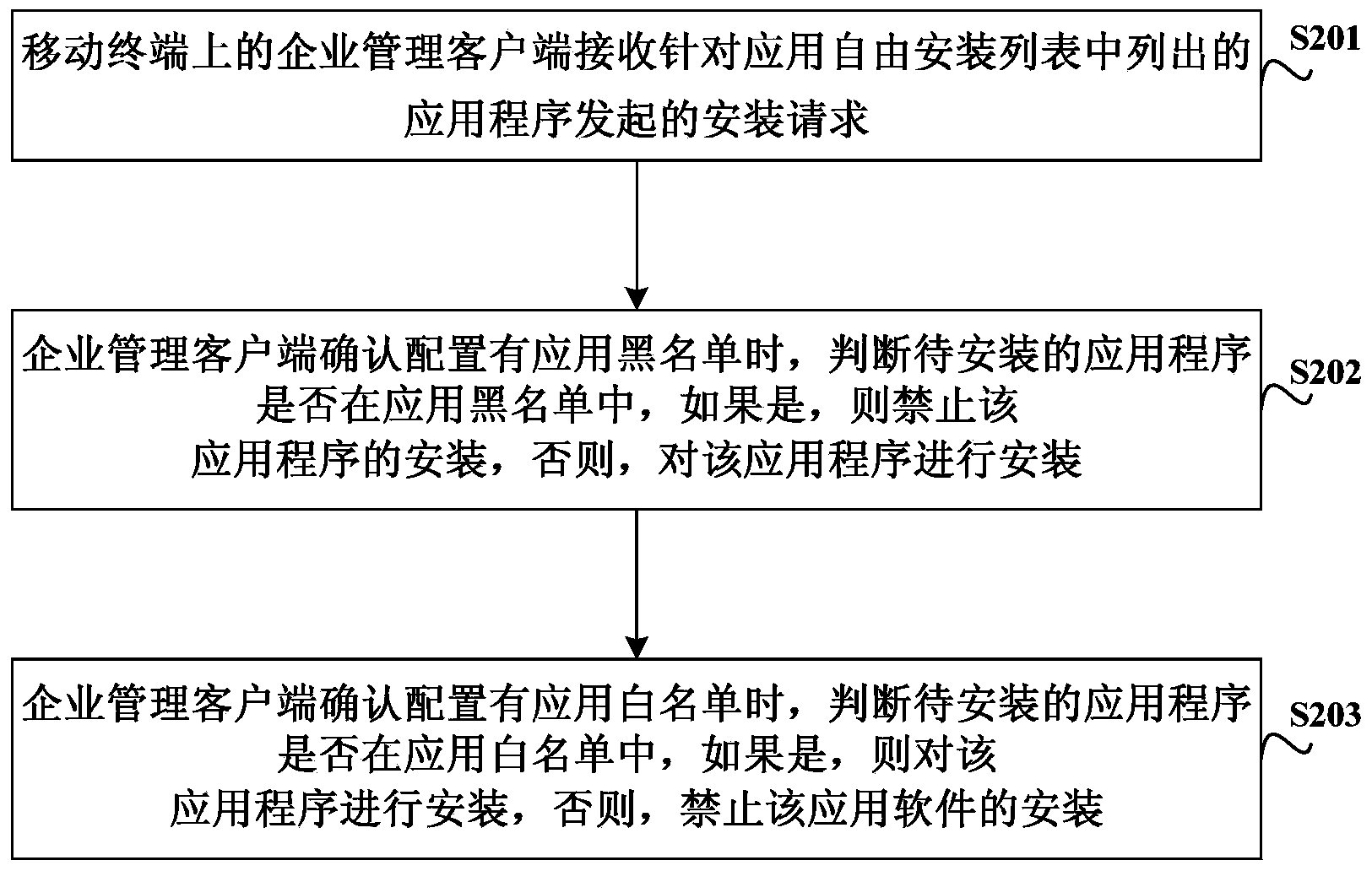
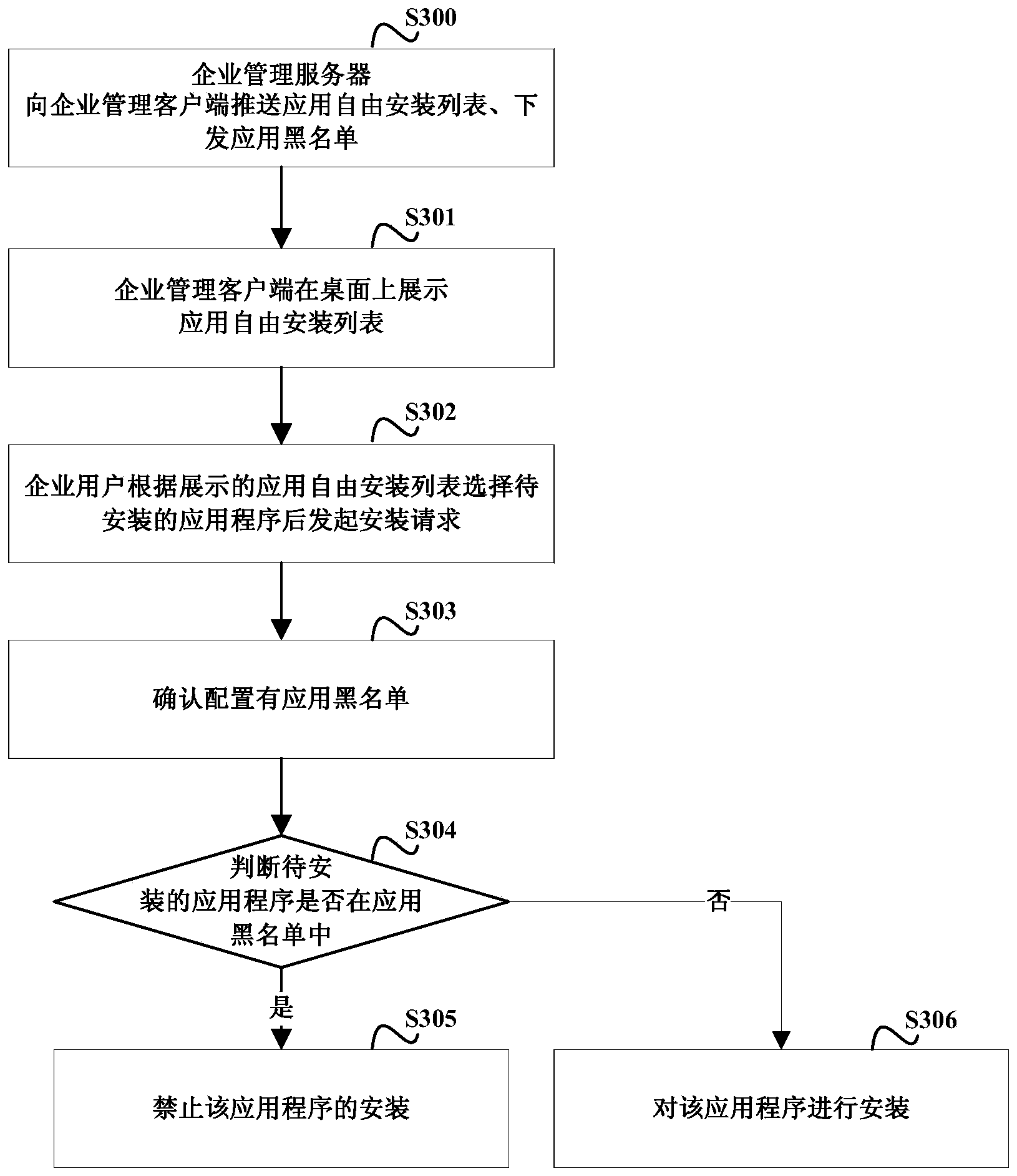
InactiveCN103646215AGuaranteed safety and reliabilityProtection securityPlatform integrity maintainanceWhitelistClient-side
The invention discloses an application installation control method, a related system and a related device, which are used to achieve safety management of applications on a mobile terminal. The application installation control method includes the following steps: an enterprise management client on the mobile terminal receives an installation request for an application listed in a list of applications for free installation; in case the enterprise management client is for sure configured with an application blacklist, whether the application to be installed is in the application blacklist is judged, the installation of the application is prohibited if the application to be installed is in the application blacklist, and the installation of the application proceeds if the application to be installed is not in the application blacklist; in case the enterprise management client is for sure configured with an application whitelist, whether the application to be installed is in the application whitelist is judged, the installation of the application proceeds if the application to be installed is in the application whitelist, and the installation of the application is prohibited if the application to be installed is not in the application whitelist. The invention adopting the technical scheme can effectively protect the information security of enterprises.
Owner:BEIJING QIHOO TECH CO LTD +1
Double authentication-based word document electronic seal system and method
InactiveCN101894238AImplement an authentication policyProtection securityDigital data protectionImage data processing detailsElectronic documentDigital signature
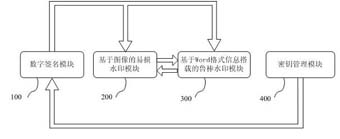
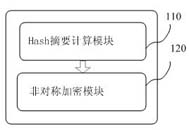
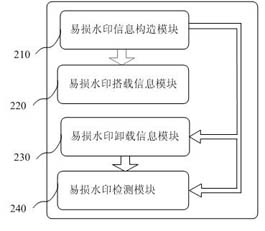
The invention discloses a double authentication-based word document electronic seal system and method. The system of the invention comprises a digital signature module, a BMP image-based fragile watermarking module, a word format information carrying-based robust watermarking module and a key management module. A double-authentication mechanism is adopted to realize the authentication of electronic seal; when the fragile watermarking is invalid, the robust watermarking can not only complete the inspection of the document, but also generate a document source analysis report and a tamper detection report to clear the issuer information of the file and the specific tampered position and ensure the integrity, truth, reliability and nonrepudiation of the electronic document. The invention has a perfect electronic seal management system and an identity authentication strategy based on hardware, and can provide further detection function for the tampered document and store the summary information of the document by means of the fragile image watermarking and the robust watermarking. The invention also discloses a double authentication-based word document electronic seal method.
Owner:NAVAL UNIV OF ENG PLA
High-voltage direct-current breaker
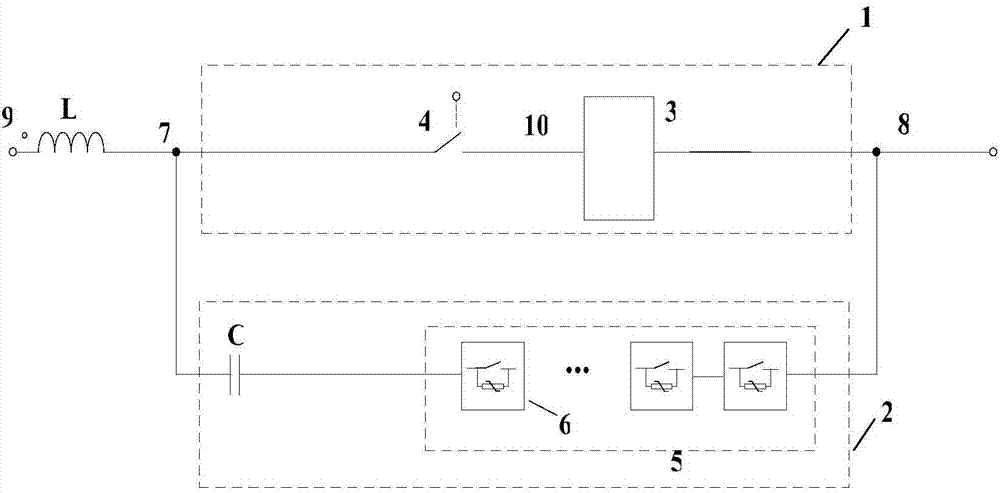
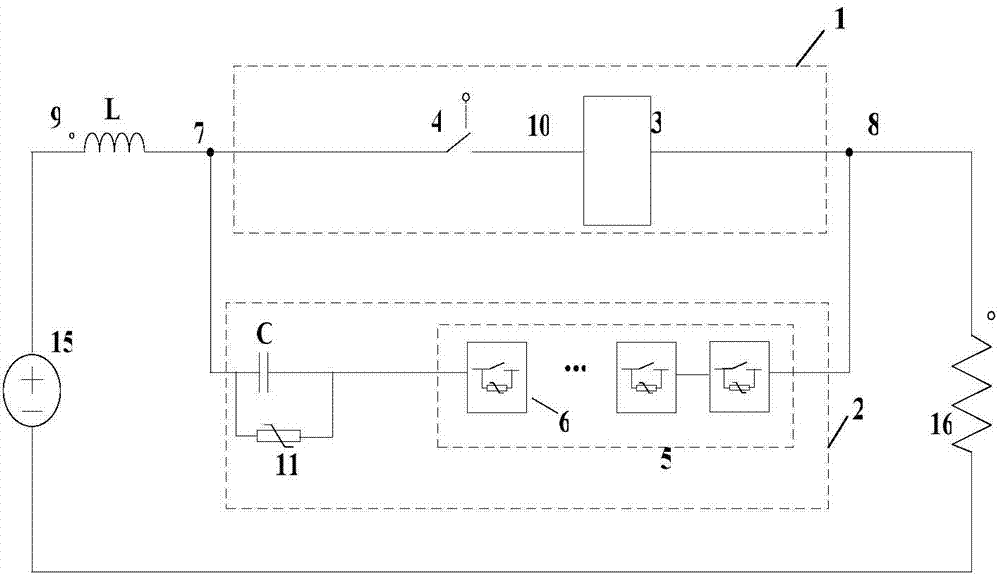
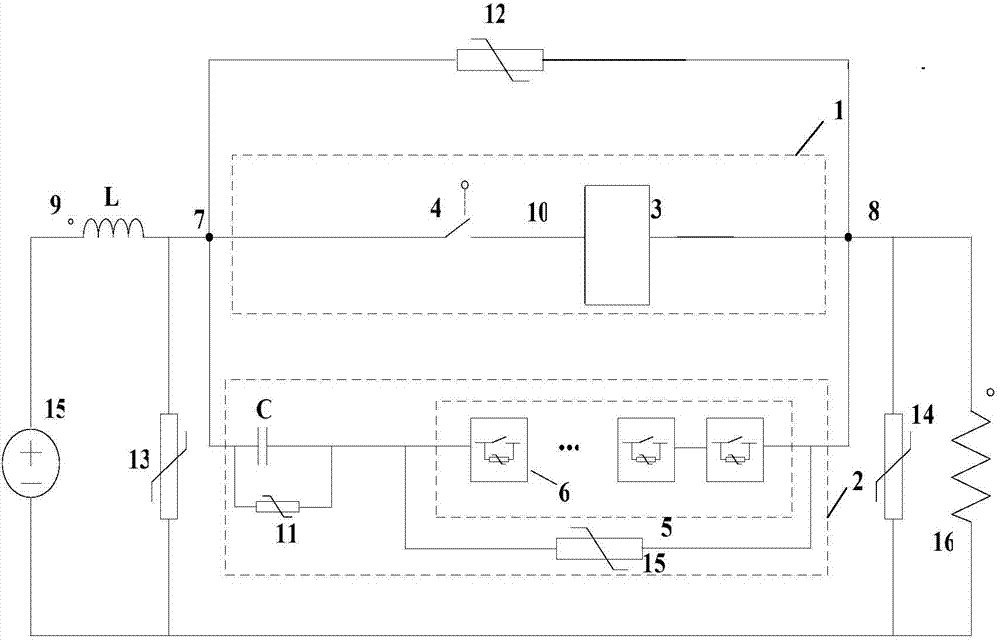
ActiveCN103618298AFast topology breakingAchieve zero arc breakingEmergency protective arrangements for limiting excess voltage/currentPower flowHigh-voltage direct current
A high-voltage direct-current breaker is composed of an initial current path (1) and a fail current interdicting path (2). The initial current path (1) comprises at least one electric electronic switch module (3) and a mechanical switch (4), and the fail current interdicting path (2) comprises an initial capacitor (C) and a modular switching subunit series connection component (5). The modular switching subunit series connection component (5) is formed by connecting a plurality of sub units (6) in series. When a high-voltage direct-current electric transmission line fails, the opening and closing of a fail electric transmission line can be rapidly achieved.
Owner:INST OF ELECTRICAL ENG CHINESE ACAD OF SCI
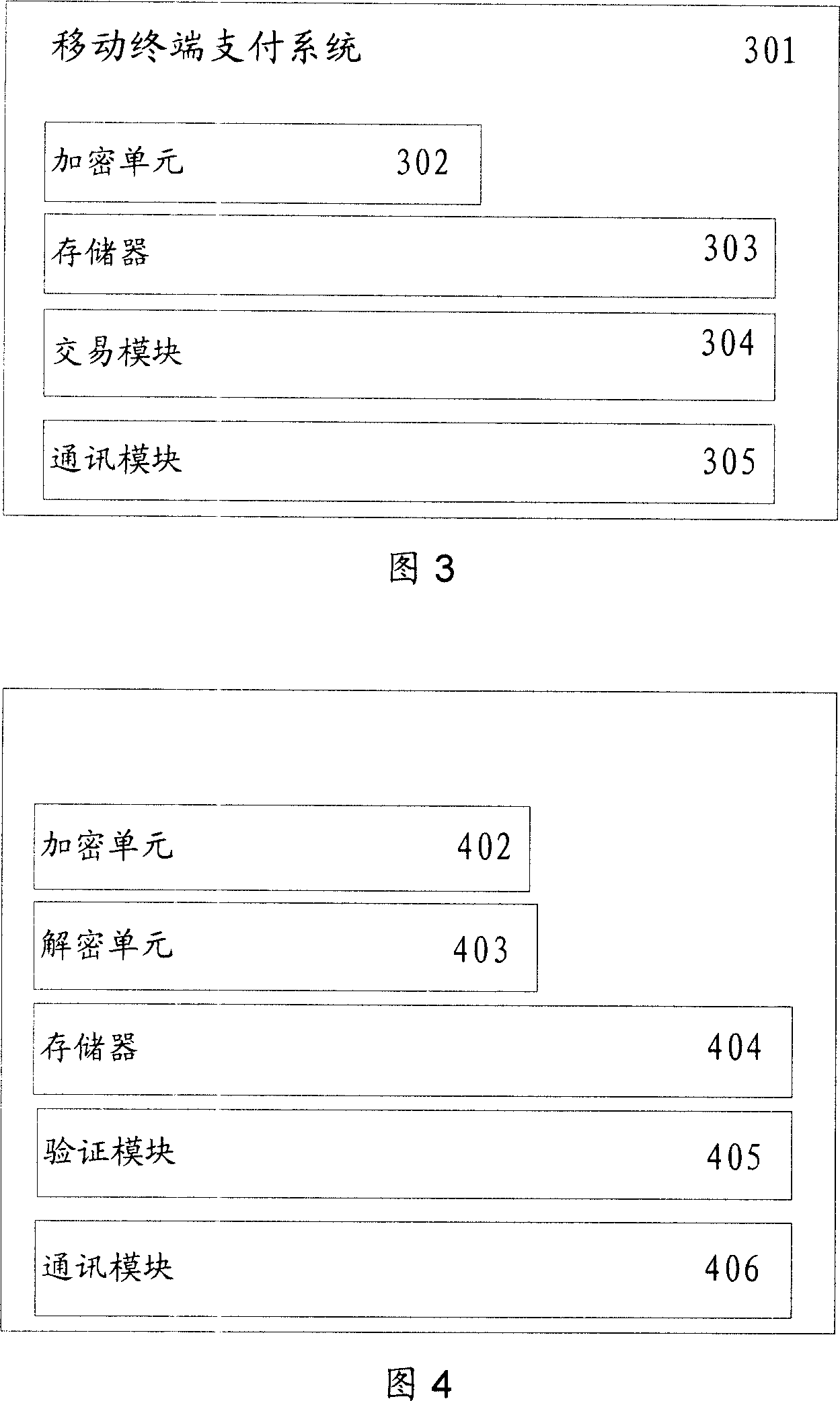
Safety data transmission method and paying method, paying terminal and paying server
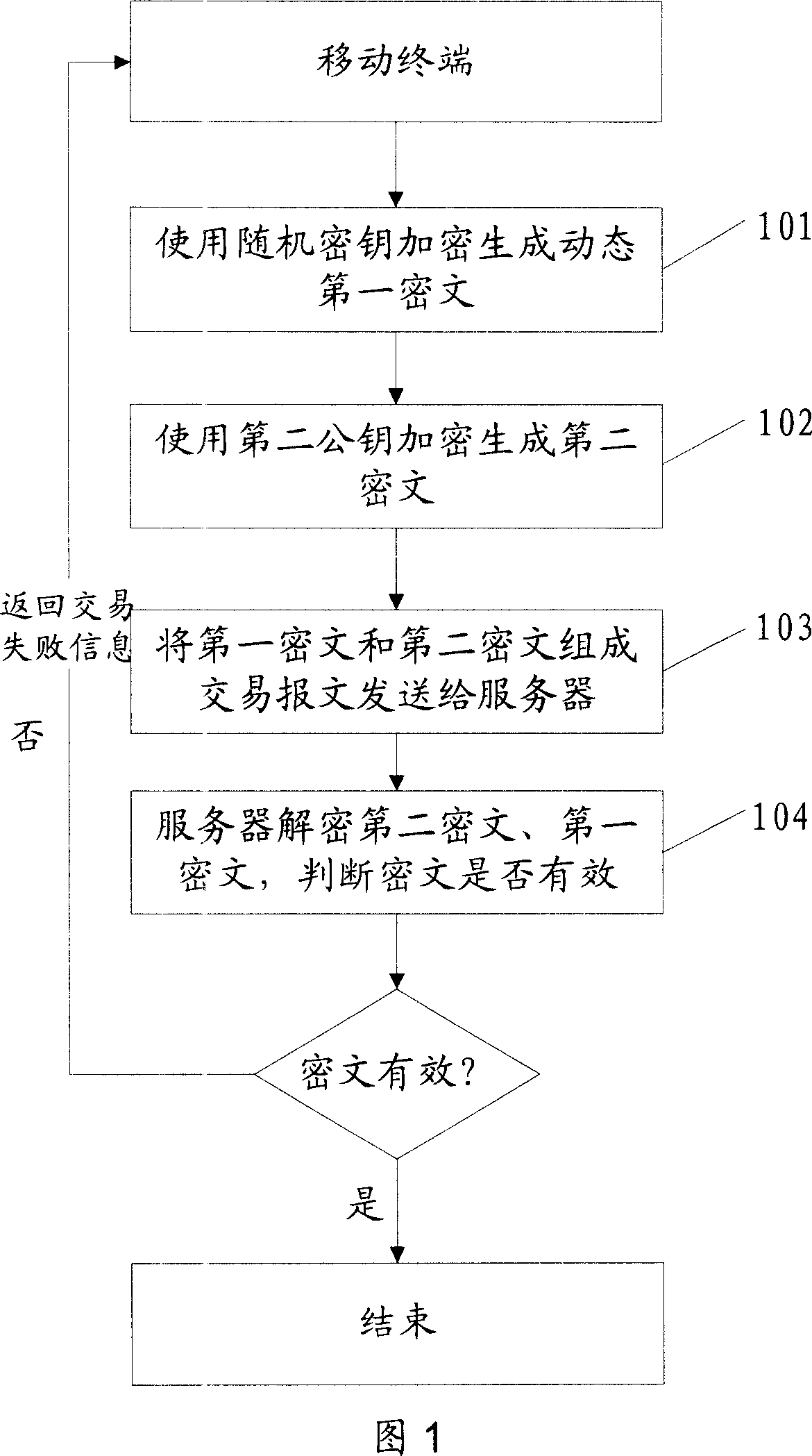
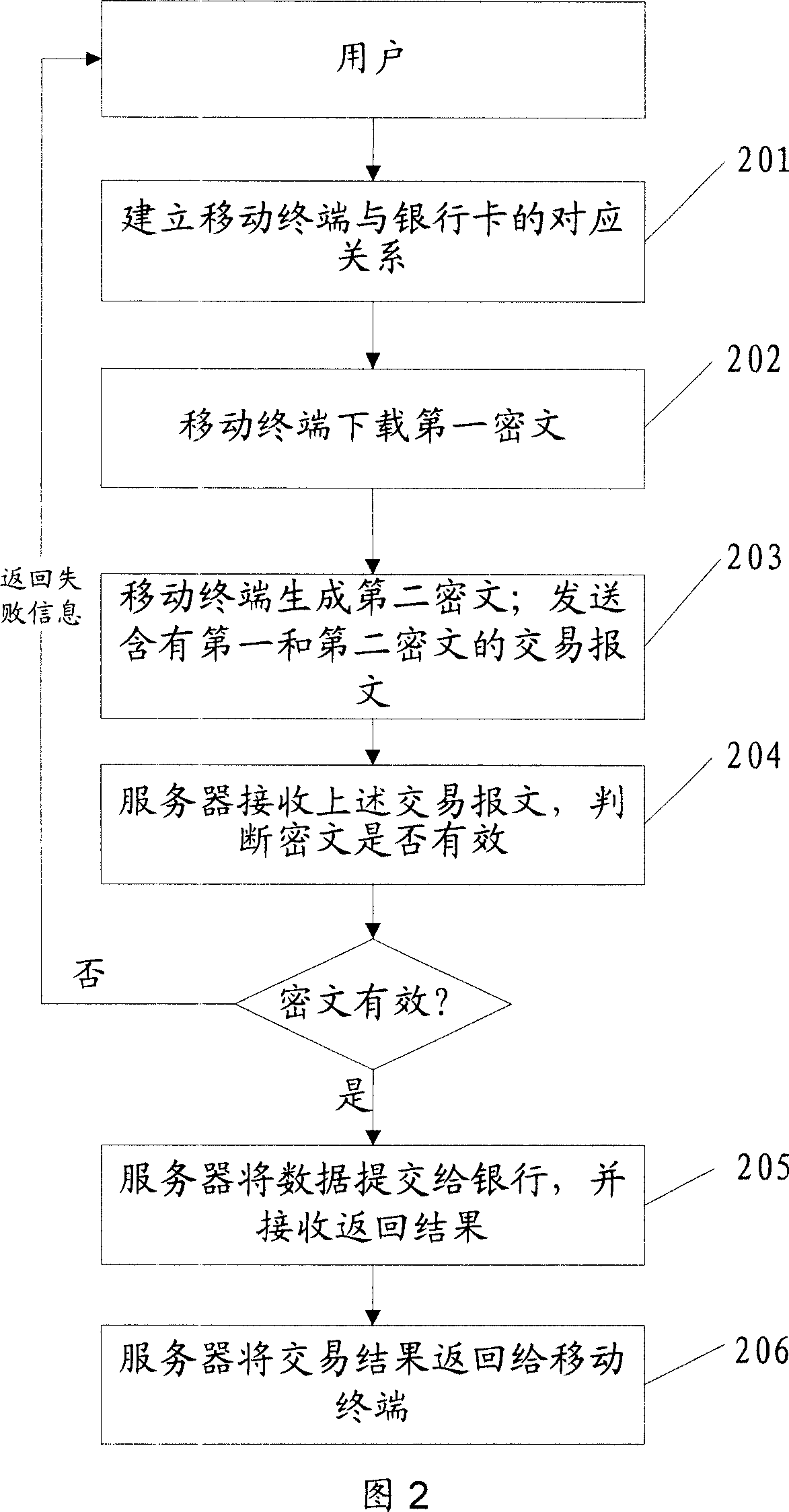
ActiveCN101098225AProtection securityEnsure safetyUser identity/authority verificationPayment architectureTime markPassword
The invention discloses a safe data transmission method, comprising that a mobile terminal uses a second public key to encrypt the personal password of bank card to generate a second cryptogram, the mobile terminal combines the first and second cryptograms into a trade report to be sent to a server, while the first cryptogram contains card track information stored in the mobile terminal, the server decrypts the first and second cryptograms, for best, the mobile terminal can use random password to encrypt the first cryptogram to generate a dynamic first cryptogram, while the random password is generated by relative algorism according to dynamic factor. The invention uses asymmetry encrypt technique to encrypt the data sent by mobile terminal, and uses random password to generate dynamic cryptogram, and generates the cryptogram with living period according to time mark, therefore, the transmission safety of finance data as cark track information or the like is effectively protected via the combined encrypt methods, to realize mobile payment.
Owner:CHINA UNIONPAY
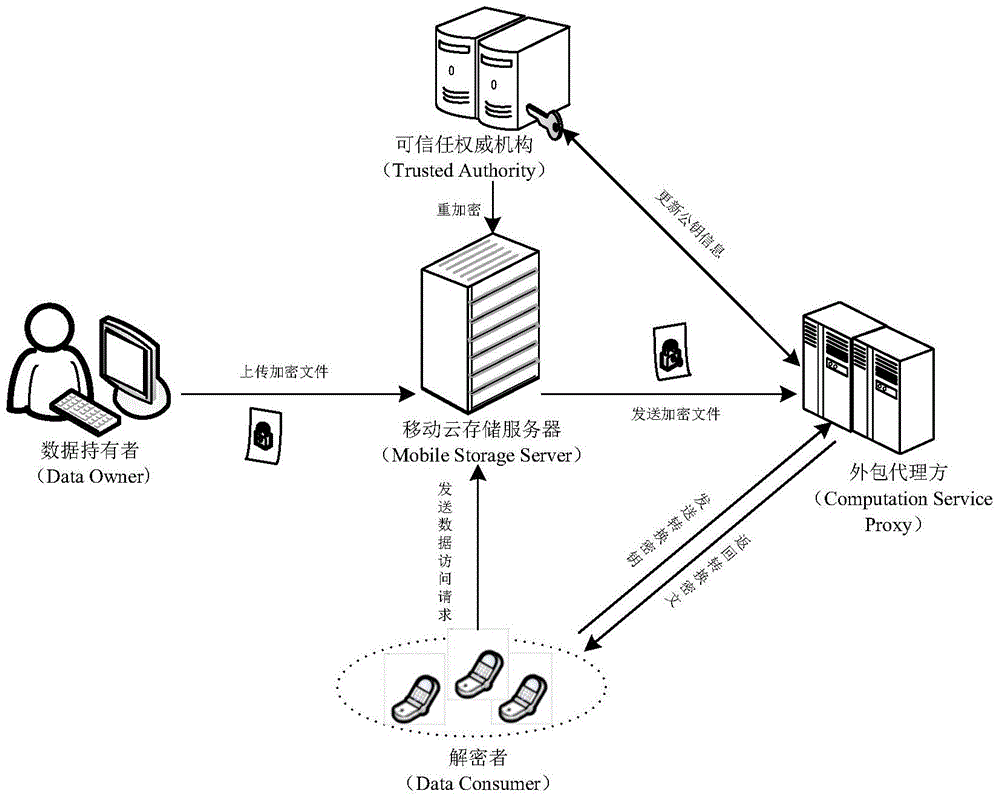
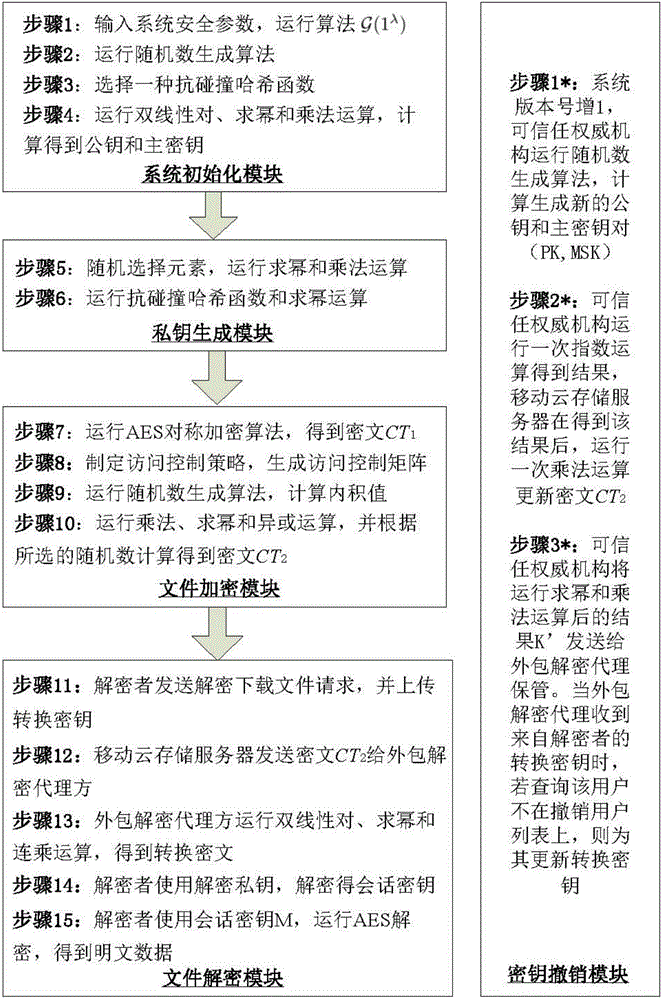
Revocable key external package decryption method based on content attributes
ActiveCN104486315APrevent unauthorized accessProtection securityUser identity/authority verificationComputer hardwareTrusted authority
The invention relates to a revocable key external package decryption method based on content attributes. For a trusted authority, 1, initialization is carried out, and system parameters are output; 2, a random number generation algorithm operates; 3, a collision-resistant Hash function is selected, and the Hash value is calculated; 4, a public key and a main key are calculated; 5, the random number is selected, and exponentiation calculation and multiplication are carried out; 6, the collision-resistant Hash function operates, the exponentiation operation is carried out, and a decryption key is obtained. For a data holder, 7, AES data encryption is carried out; 8, an access control matrix is generated; 9, a random number is selected, and an inner product is calculated; 10, multiplication, exponentiation and exclusive-or operation is operated, and ciphertexts are obtained. For a decryption operator, 11, a decryption request and a transformation key are sent. For a mobile storage serve provider, 12, CT2 is sent to an external package decryption agency. For the external package decryption agency, 13, the transformation key is utilized, and the transformation ciphertext is calculated. For the decryption operator, 14, a conversation key is obtained through calculation; 15, AES data decryption is carried out.
Owner:HANGZHOU INNOVATION RES INST OF BEIJING UNIV OF AERONAUTICS & ASTRONAUTICS
Anti-monitoring method and system for mobile terminal
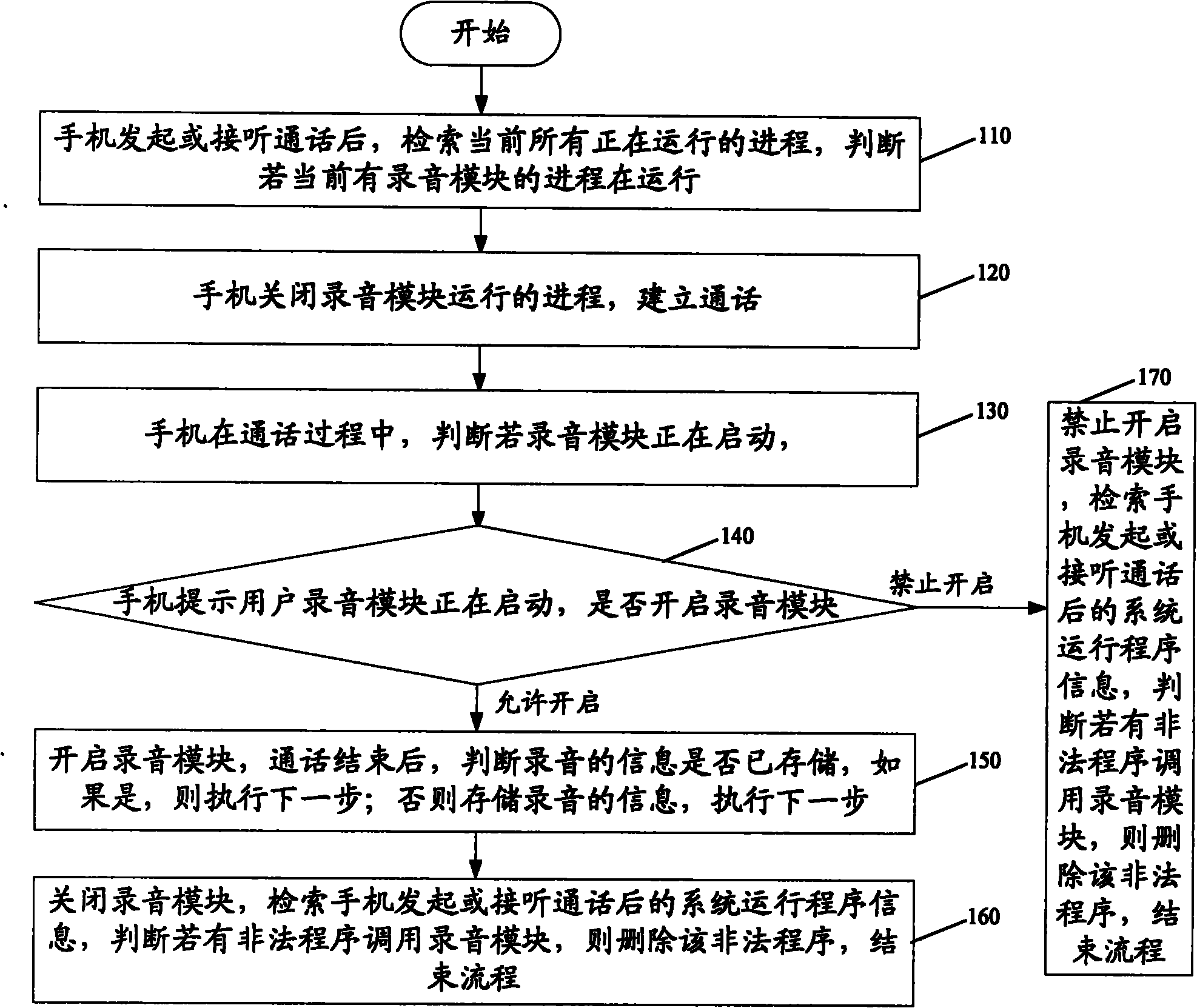
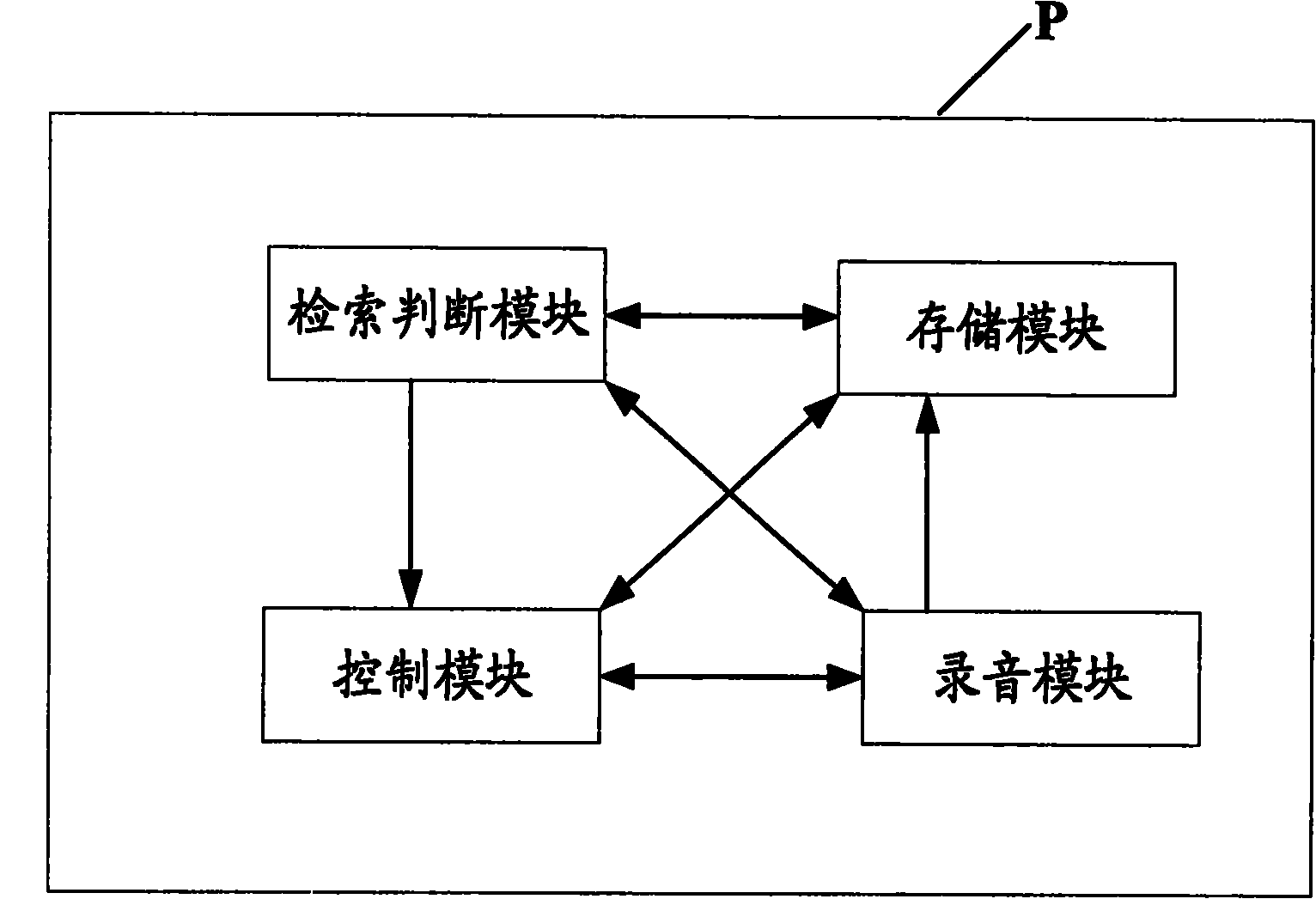
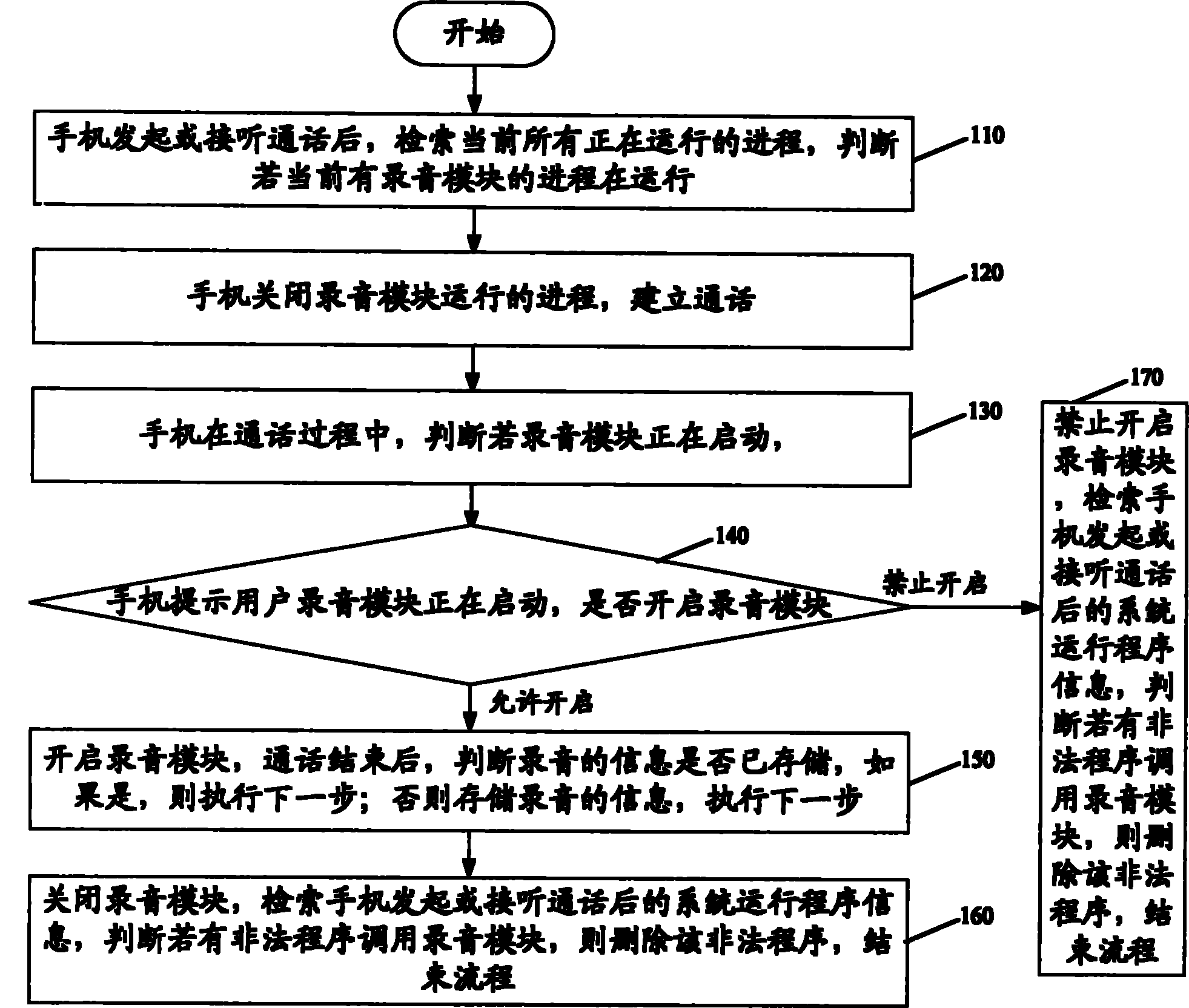
The invention provides an anti-monitoring method and system for a mobile terminal. The anti-monitoring method comprising the following steps: when the mobile terminal initiates or answers a call, indexing the process of an existing running program; and if judging that the process of a sound recording module runs currently, closing the process of the sound recoding module, and establishing conversation. The anti-monitoring method and system are used to ensure that conversation content of a user can not be recorded and spread illegally during the conversation, thus effectively protecting individual privacy and safety of the user, and improving degree of satisfaction of the user.
Owner:BEIJING QIHOO TECH CO LTD
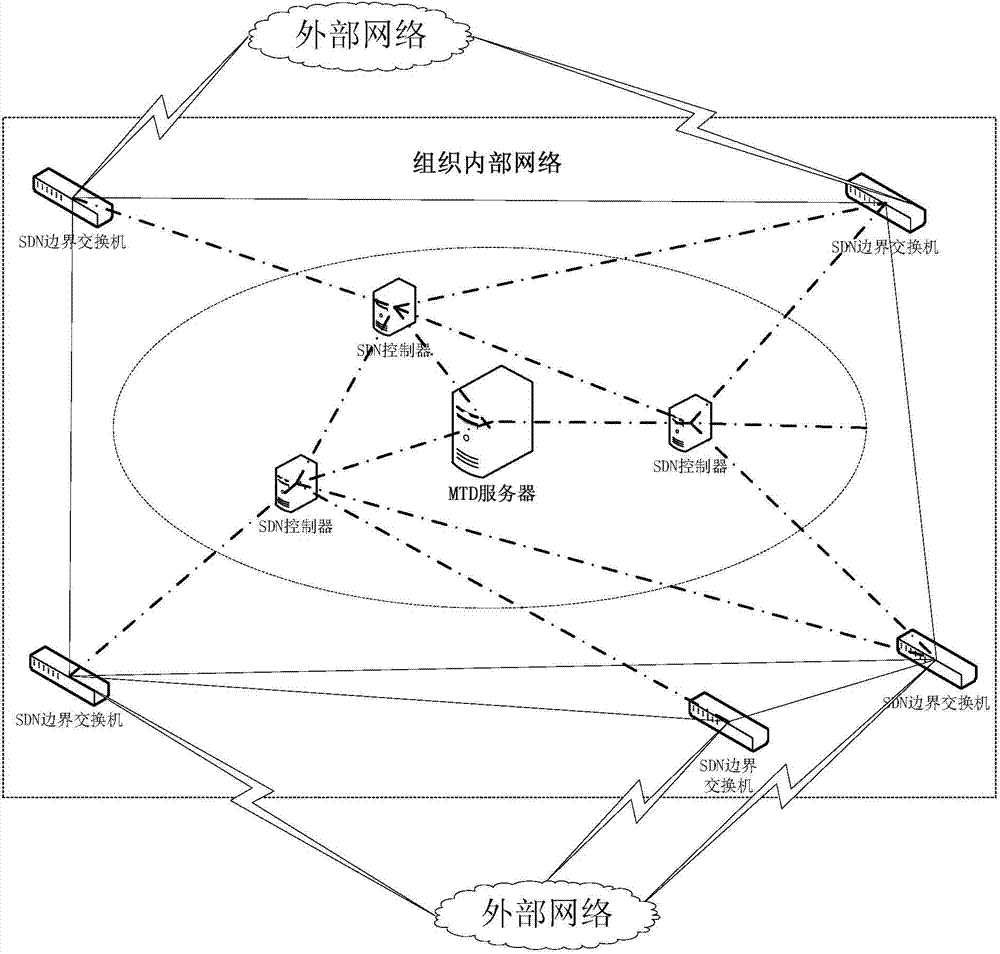
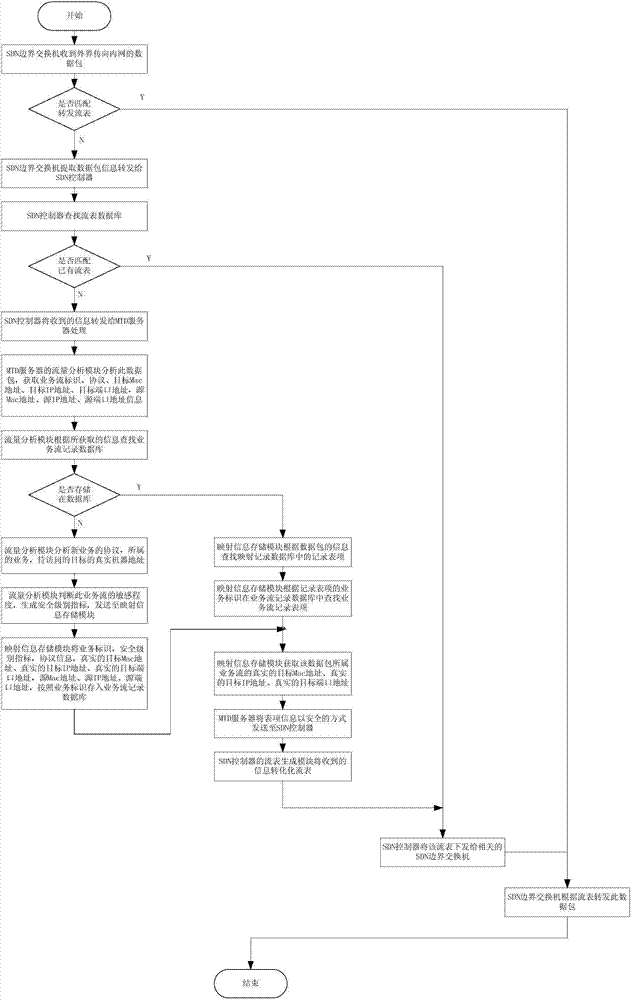
Moving target defense system and moving target defense method for SDN (self-defending network)
InactiveCN104506511AProtection securityIncrease the difficultyTransmissionTraffic flow analysisSafety Communications
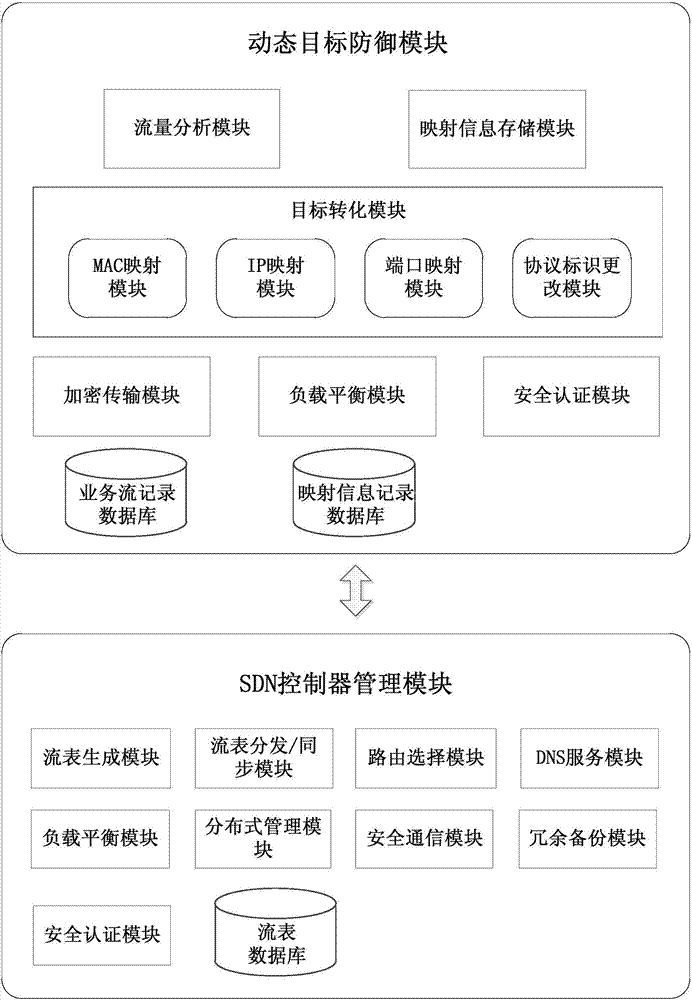
The invention discloses a moving target defense system for an SDN (self-defending network). The system consists of a moving target defense module and an SDN controller management module; the moving target defense module comprises a flow analysis module, a mapping information storage module, a target conversion module, an encryption transmission module, a load balance module, a safety authentication module, a business flow recording database and a mapping information recording database; the SDN controller management module comprises a flow table generation module, a flow table distribution / synchronization module, a route selection module, a DNS service module, a load balance module, a distributed management module, a safety communication module, a redundant backup module, a safety authentication module and a flow table database; furthermore, the invention also discloses a moving target defense method for the SDN. Through the moving target defense system and the moving target defense method disclosed by the invention, the difficulty of an attacker to detect a target is increased further, and therefore the safety of an intranet is comprehensively protected.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
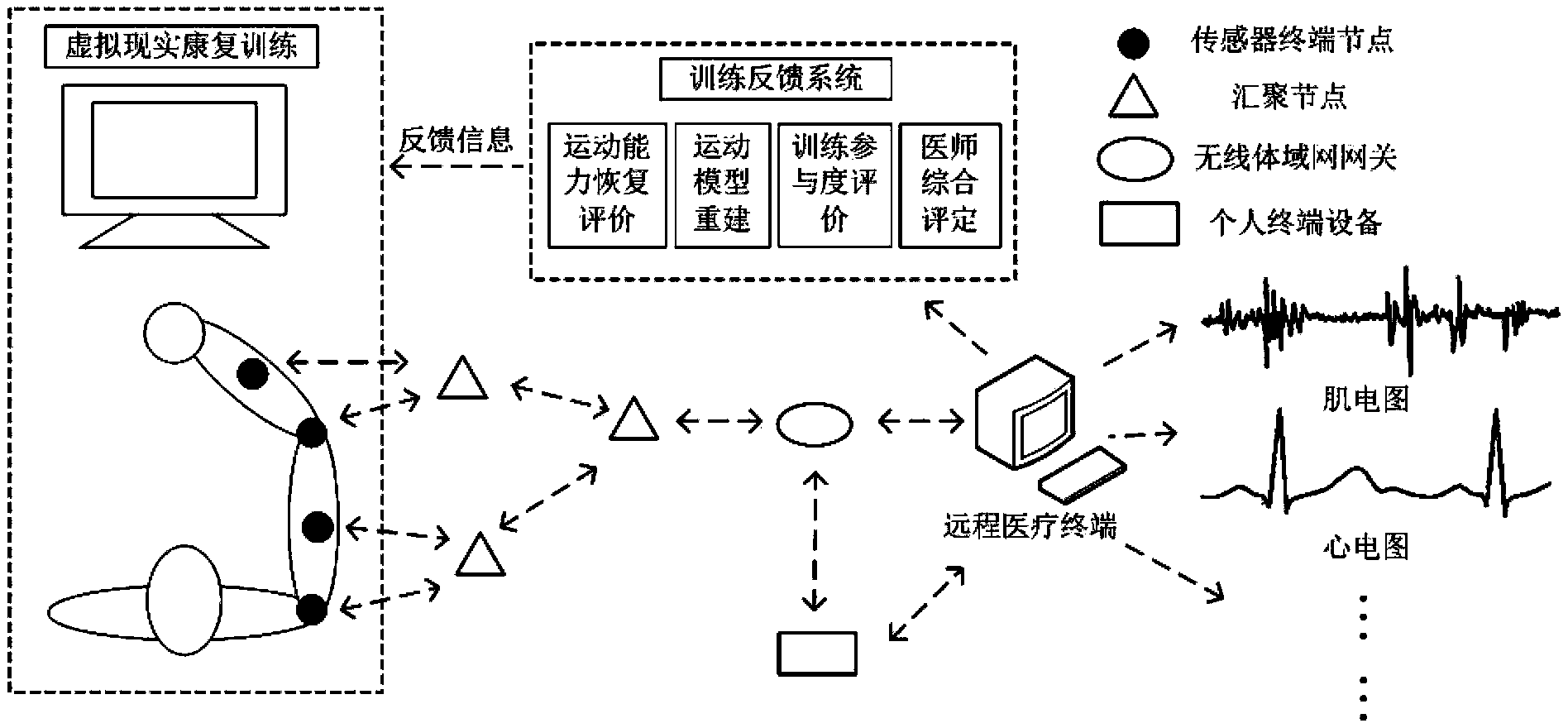
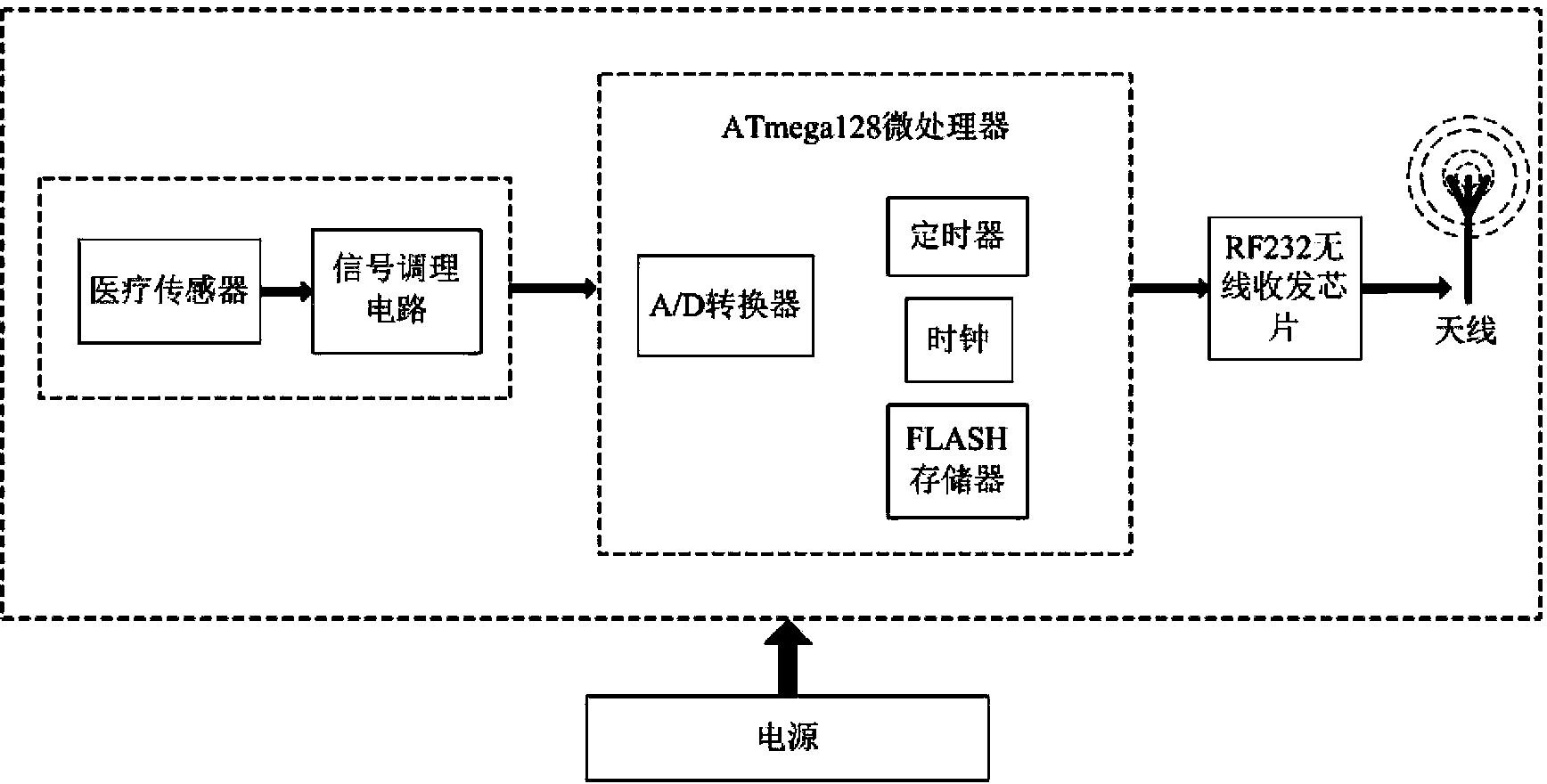
Motor function rehabilitation monitoring system based on wireless body area network
InactiveCN103479362AExpand the scope of activitiesReduce labor intensityDiagnostic recording/measuringSensorsWireless transceiverInformation feedback
The invention discloses a motor function rehabilitation monitoring system based on a wireless body area network. The system comprises a sensor terminal node, a wireless gathering node, a wireless body area network gateway, a personal terminal, a remote medical terminal and an information feedback system, wherein the sensor terminal node comprises a medical sensor, a signal conditioning circuit, a microprocessor unit and a wireless transceiver unit which are sequentially connected, the medical sensor sends collected data into the signal conditioning circuit for preprocessing, and the wireless transceiver unit is controlled to perform wireless transmission after the data is processed by the microprocessor unit; the data collected by the sensor terminal node sequentially passes through the wireless gathering node and the wireless body area network gateway and is respectively transmitted into the personal terminal and the remote medical terminal, and the data is transmitted into the information feedback system after being processed by the remote medical terminal, and is displayed by a 3D model built through the information feedback system. The monitoring system can be used for monitoring the exercise rehabilitation situation of a patient in real time, providing reasonable guidance and advices for subsequent rehabilitation training and improving the rehabilitation training effect.
Owner:NANJING UNIV OF POSTS & TELECOMM
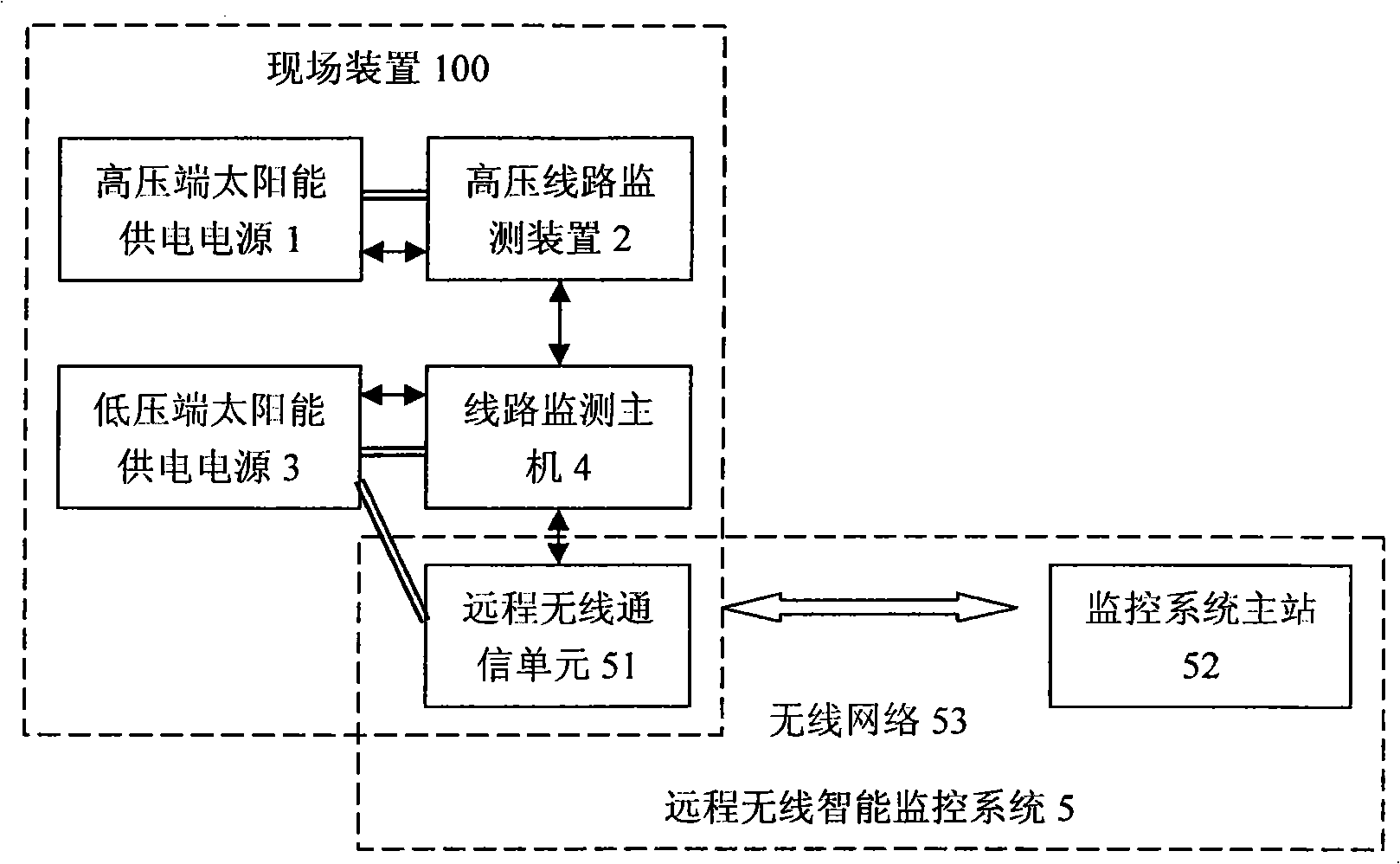
Ultra-high pressure circuit monitoring system for solar power generation
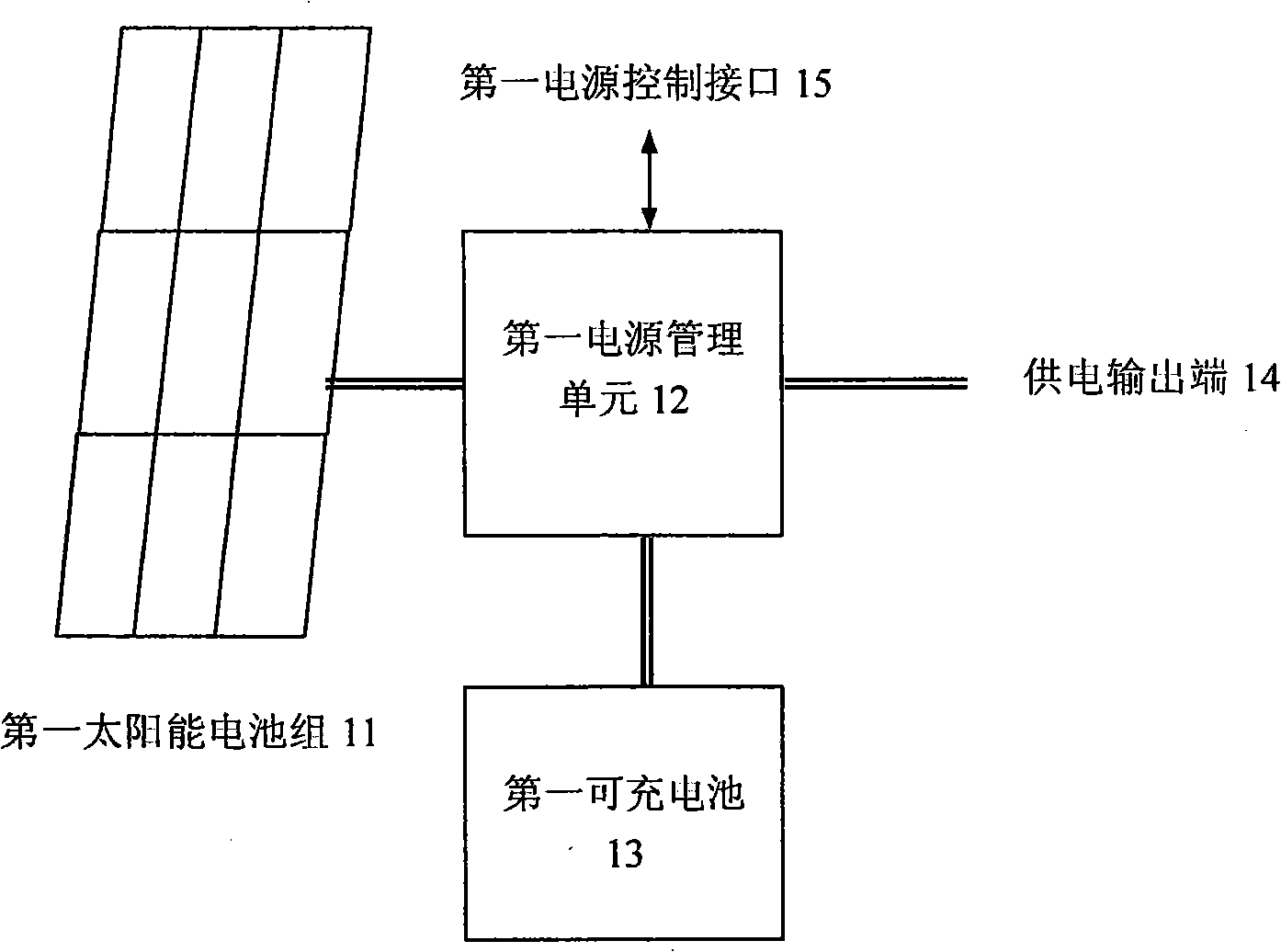
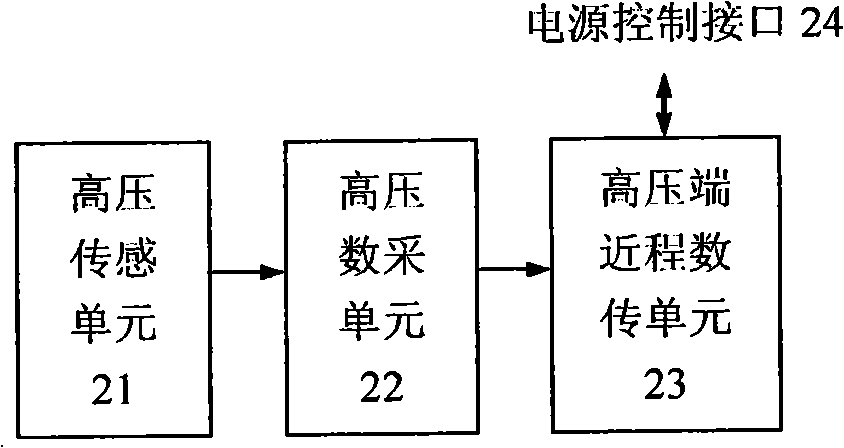
InactiveCN101359022ARealize long-term online operationSolve power problemsData switching by path configurationFault locationTime informationUltra high pressure
The invention relates to a solar-powered ultra-high voltage line monitoring system, comprising a high-voltage side solar power supply, a high voltage line monitoring device, a low-voltage side solar power supply, a line monitoring host computer and a remote wireless intelligent monitoring system. The high-voltage side solar power supply and the low-voltage side solar power supply comprise solar batteries, rechargeable batteries and power management units; the high voltage line monitoring device and the line monitoring host computer comprise sensing units as well as data acquisition and recording units for detecting and processing field parameters of various lines; and the remote wireless intelligent monitoring system comprises a wireless communication unit and a monitoring system master station. The high-voltage side solar power supply, the high voltage line monitoring device, the low-voltage side solar power supply, the line monitoring host computer and the remote wireless intelligent monitoring system compose a field device which collects and records the running status and fault information of high-voltage lines through solar power and transmits the running status and fault information to the monitoring system master station through the remote wireless communication unit so as to provide real-time information for power line monitoring.
Owner:SOUTHEAST UNIV +2
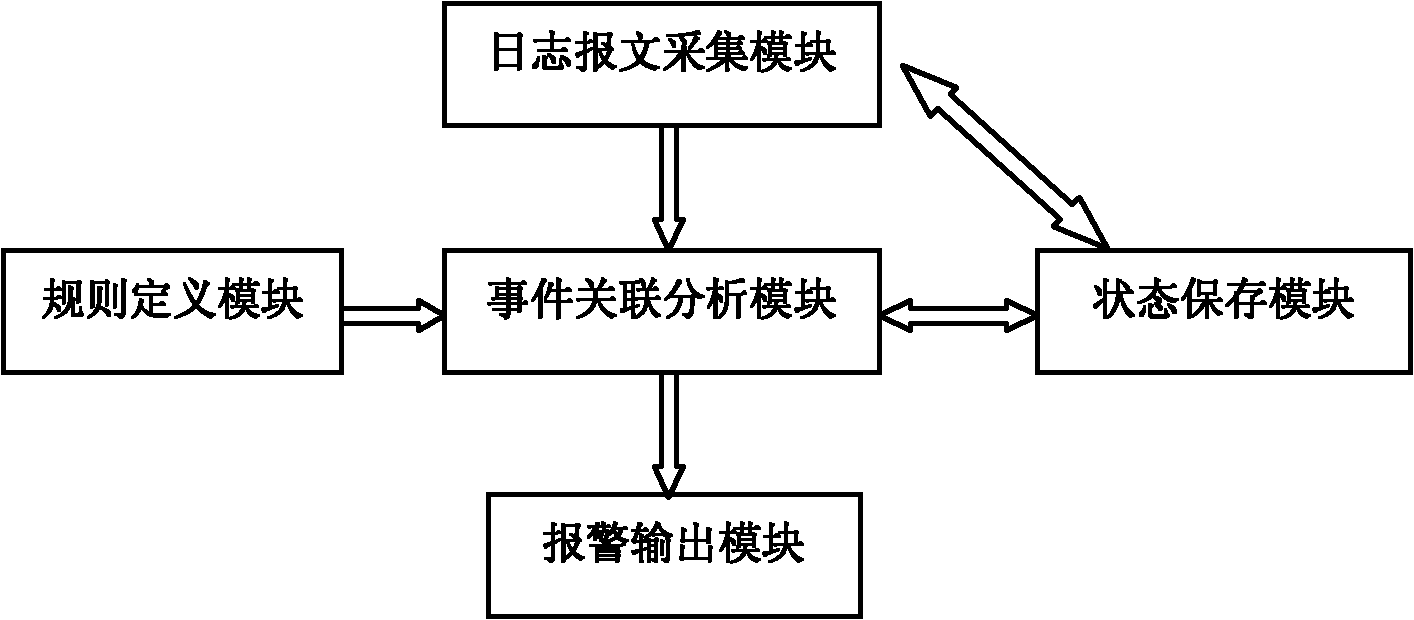
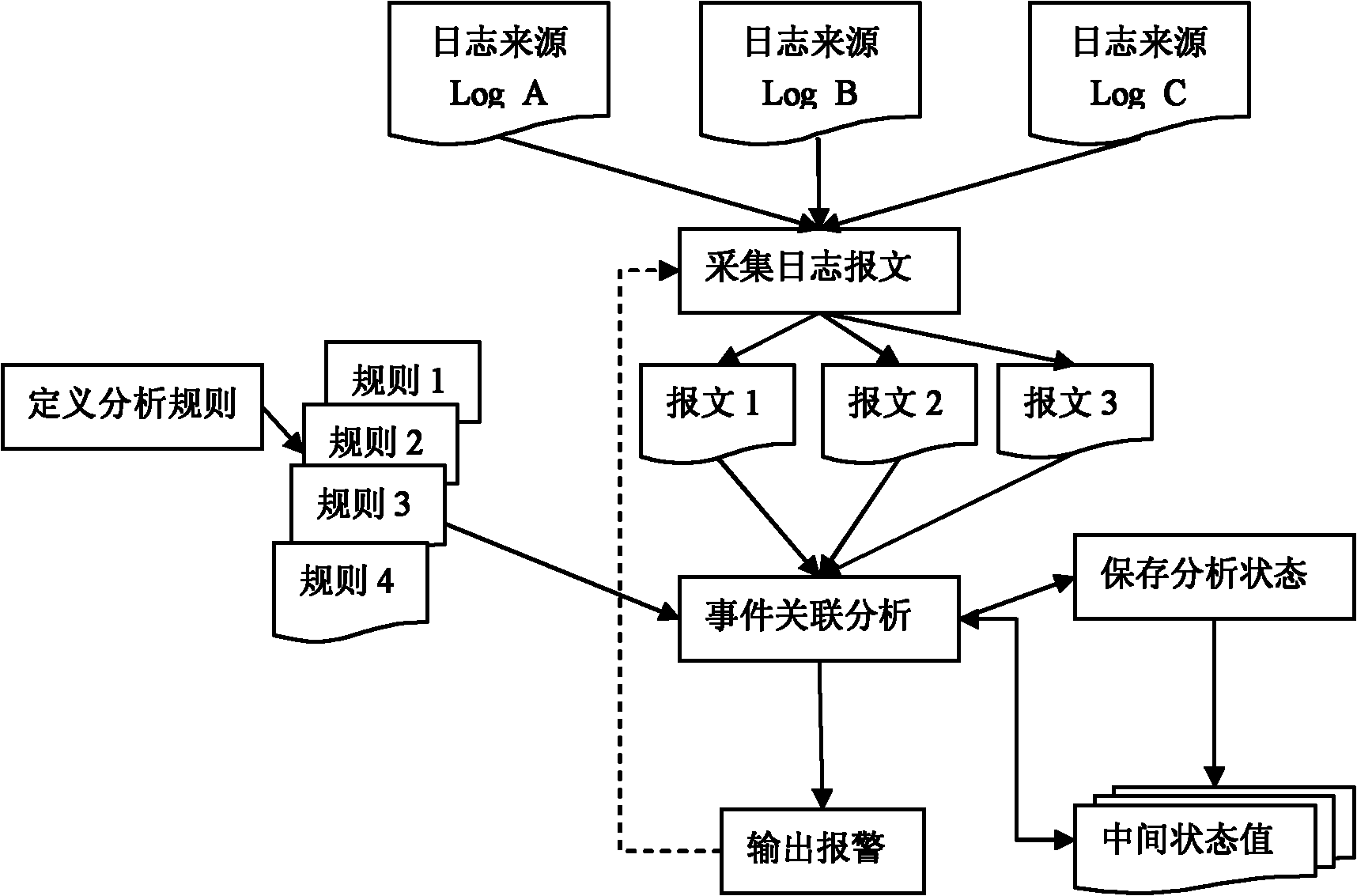
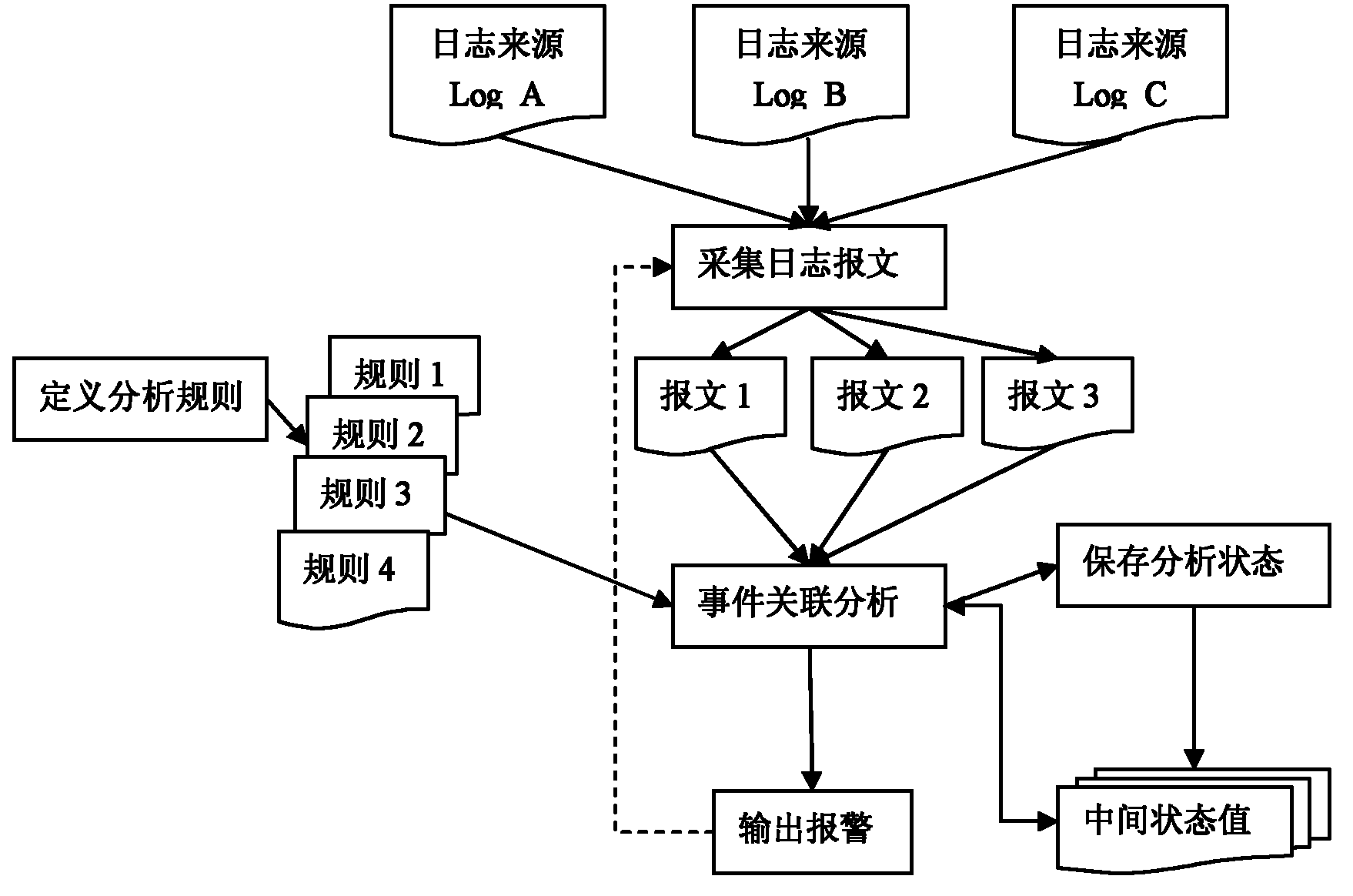
Log event correlation analysis method and device capable of concurrent and interrupted analysis
InactiveCN102158355AProtection securityImprove accuracyData switching networksIntermediate stateNetwork management
The invention discloses a log event correlation analysis method and a device capable of concurrent and interrupted analysis. The method comprises the following steps: firstly defining an analysis rule and uploading the rule to an event correlation analysis module; acquiring a log message of each log source in sequence, and uploading the log messages to the event correlation analysis module; analyzing logs by the event correlation analysis module; storing intermediate state variables of the existing event correlation analysis to a state storage module in the analysis process; and if certain correlated event is triggered in the analysis process, sending an alarming signal of the correlated event outwards. The device comprises a rule definition module, a log message acquisition module, an alarm output module and an event correlation analysis module. According to the invention, the concurrent and interrupted analysis can be carried out on the multiple logs, thus strengthening the log audit function of network monitoring and a network management system, improving the accuracy of network early warming, and ensuring the safety of the network monitoring and the network management system.
Owner:GUANGZHOU LANKE TECH
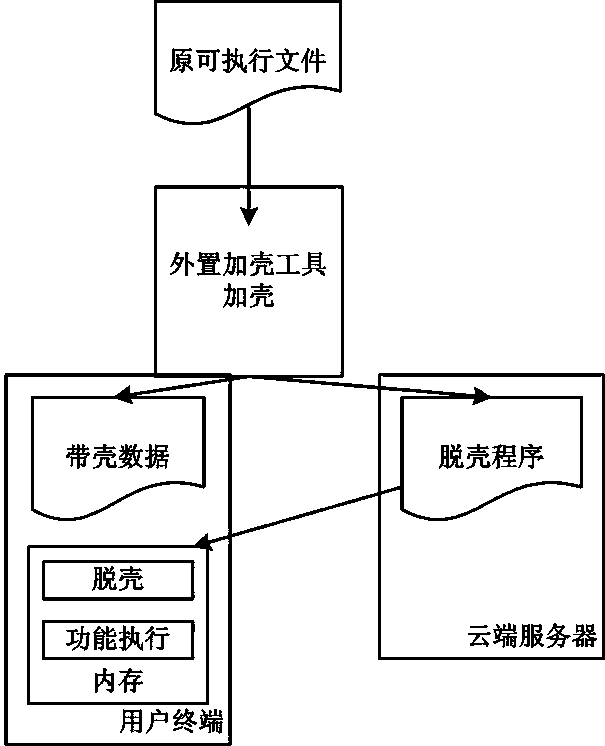
Shell adding and removing method for Android platform application program protection
InactiveCN103530535AProtect confidentialityProtection securityProgram/content distribution protectionApplication softwareCommercial software
The invention discloses a shell adding and removing method for Android platform application program protection. The method includes the shell adding step and the shell removing step for an original executive file of an Android platform application program. The shell adding step refers to the step that the file format structure of the original executive file is analyzed through an externally-arranged shell adding tool, and a source program is encrypted to form data with a shell. The shell removing step refers to the step that before the application program operates, a shell removing program is preferentially loaded and operates in a memory of a mobile terminal, source program decrypting is carried out on the data with the shell, and then the original executive file is loaded to the memory and normally operates. Due to the adoption of the technical scheme of shell adding and removing, innovative thinking and feasible technical solving ways are provided for application shell adding and removing under an Android platform, and the shell adding and removing method can be used for protecting the executive file of the mobile platform, prevent the program from being attacked by hacker means like decompilation, guarantee confidentiality of commercial software and protect user application safety.
Owner:JIANGSU PAYEGIS INFORMATION SECURITY TECH CO LTD
Network safety isolating and information exchanging system and method based on proxy mapping
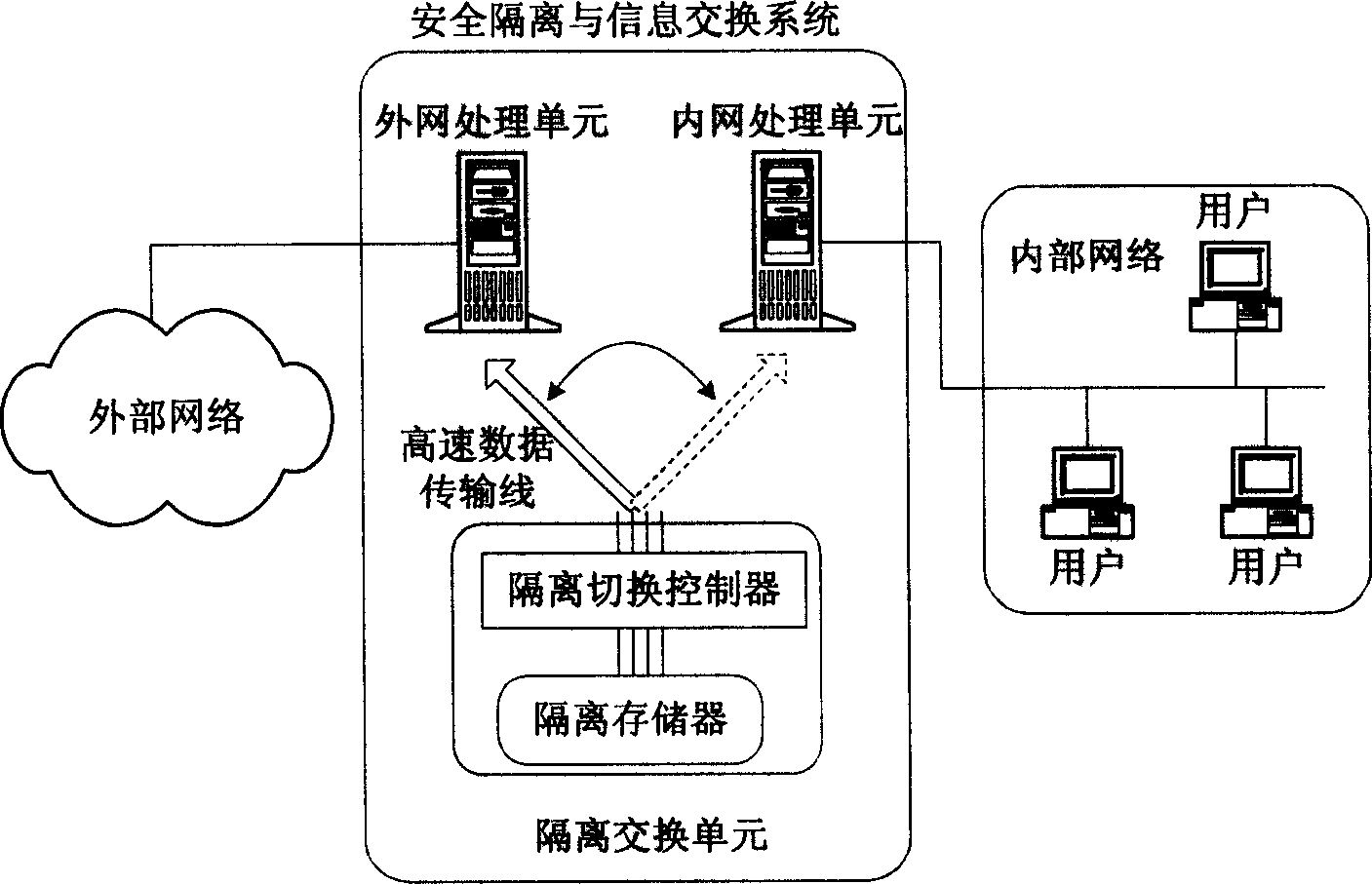
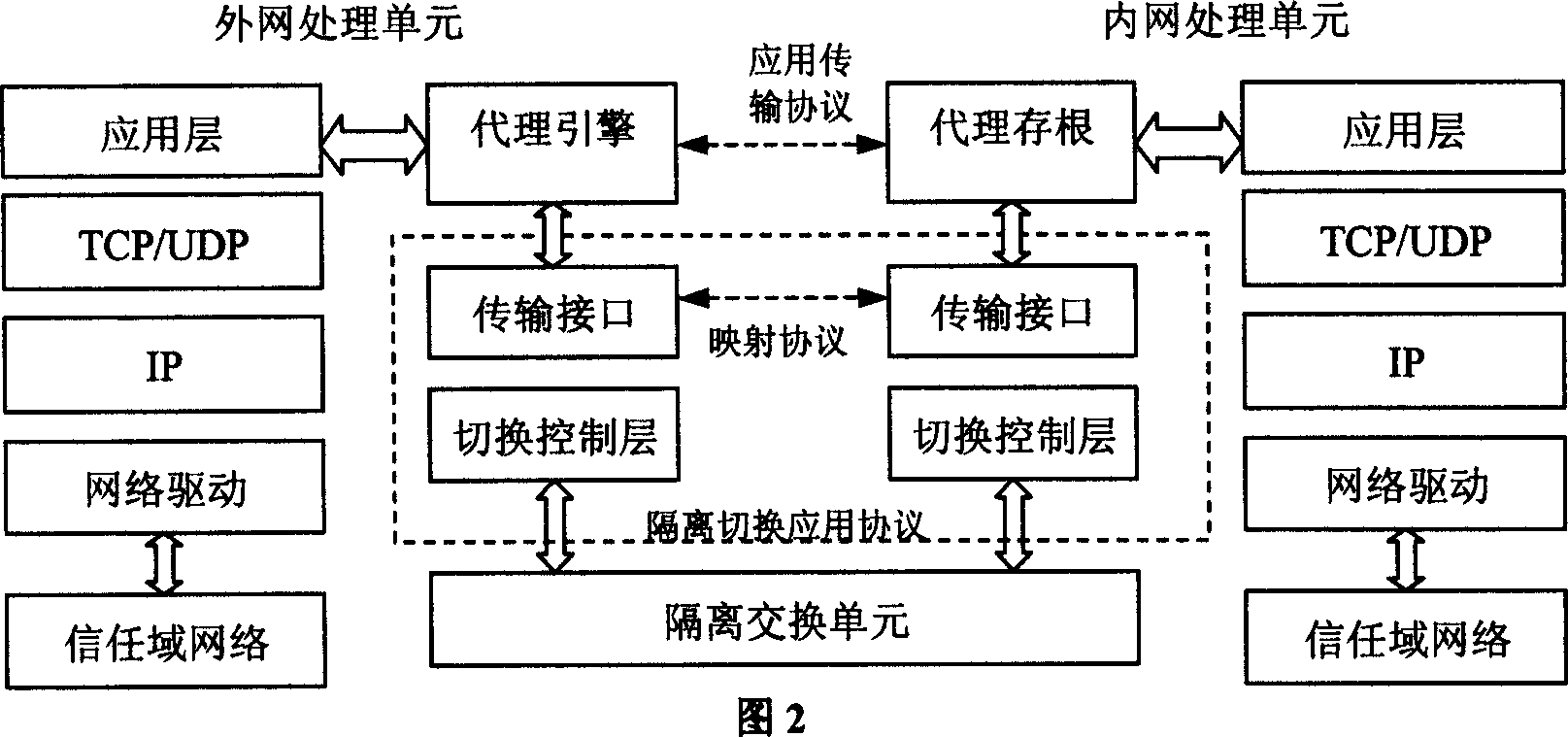
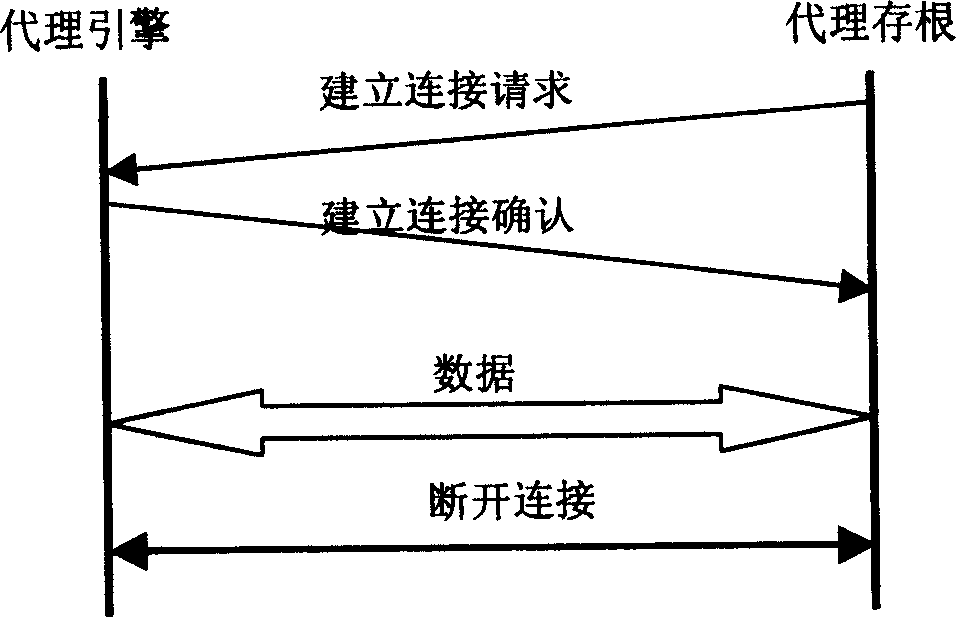
InactiveCN1571398AResist attackProtection securitySubstation remote connection/disconnectionStore-and-forward switching systemsClient-sideNetwork data
The invention relates to network security isolation based on agent mapping and information exchanging system and its method. It uses in information exchanging field and network data exchanging field. The in-out net processing units are each connected to the inner net and the outer net in the system. Isolation exchanging unit includes isolation switching controller and isolation storage. The in-out net processing units are connected to the isolation switching controller through high speed data transmission line. The isolation switching controller is connected to the isolation storage. Only one of the in-out net processing units can assess the isolation storage. The in-out net processing units exchange the information through the isolation exchanging unit. The inner net processing unit includes an agent stub and the outer net processing unit includes an agent engine. The method of the invention is that the inner defined transmission interface is called by the agent stub and the agent engine, and the date is exchanged between the in-out net processing units by isolation exchanging unit. So this can construct an information exchanging channel between the inner net client end and the outer net server in the form of agent mapping.
Owner:SHANGHAI JIAO TONG UNIV
All-directional intelligent monitoring method for bank ATMs
ActiveCN102622818AAvoid long guardReduce labor costsComplete banking machinesClosed circuit television systemsMicrowave detectorsCard reader
The invention relates to an all-directional intelligent monitoring method, in particular to an all-directional intelligent monitoring method for bank ATMs (Automated Teller Machines). The all-directional intelligent monitoring method is characterized in that at least four paths of videos can be monitored in real time, an emergency alarm and a non-emergency alarm can be given for the monitoring behavior of each path of video, and various unconventional behaviors can be identified by the aid of external shock sensors, microwave detectors, acoustic sensors and other various sensors. The video comprises at least one ATM panel video, at least one ATM scene video, at least one wide-angle scene video of a self-service bank where the ATMs are mounted, and at least one ATM cash replenishing room video. By adopting the technology provided by the invention, such abnormal behaviors as mounting fake keyboards, mounting fake card readers, mounting or dismounting a keyboard shield, maliciously sticking strips, operating the ATMs for a long time and the like can be intelligently identified during monitoring of ATM panel video. Therefore, the method is suitable for large-scale installation in banks.
Owner:BEIJING HISIGN TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com