Information security management and control method under cloud manufacturing environment
A technology of information security and cloud manufacturing, which is applied in the direction of public key for secure communication, user identity/authority verification, electrical components, etc., and can solve problems such as not supporting certificate operation and certificate login
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
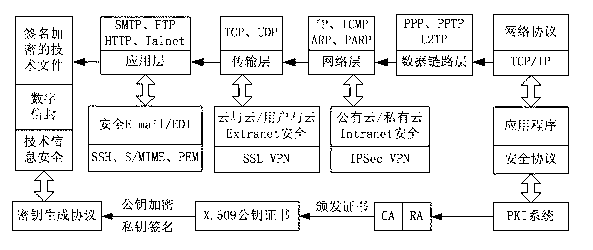
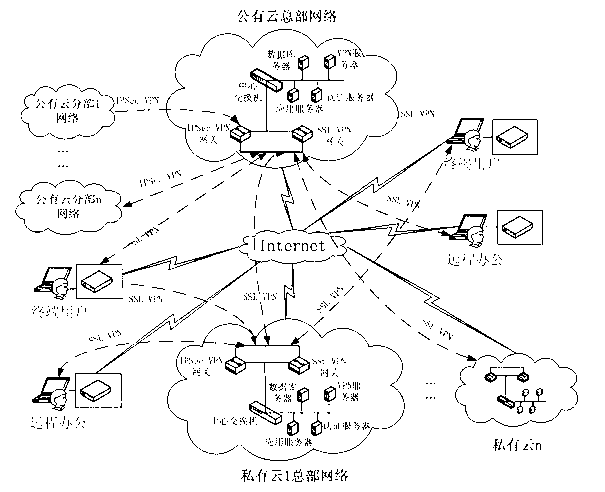
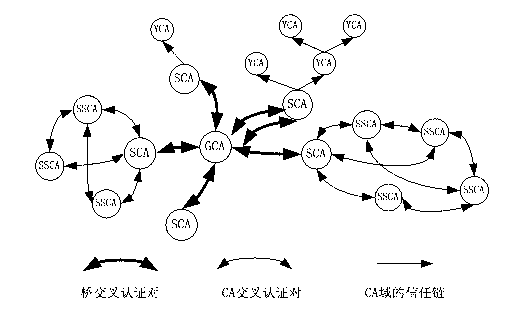
[0064] The present invention establishes a secure tunnel VPN based on multi-layer protocols such as secure Internet protocol (IPSec), secure socket layer protocol (SSL), S / MIME, PEM, SSH, etc., and realizes the network security access of cloud manufacturing system Intranet, Extranet and Internet ; Through the issuance of X.509 digital certificates based on the public key infrastructure PKI system, and the use of digital envelope technology to protect the session key SK, two-way identity authentication, digital signatures, and technical information encryption between users and cloud servers can be realized. Guarantee the confidentiality, integrity, non-repudiation, availability and controllability of the whole process of information transmission, sharing and use, su...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com