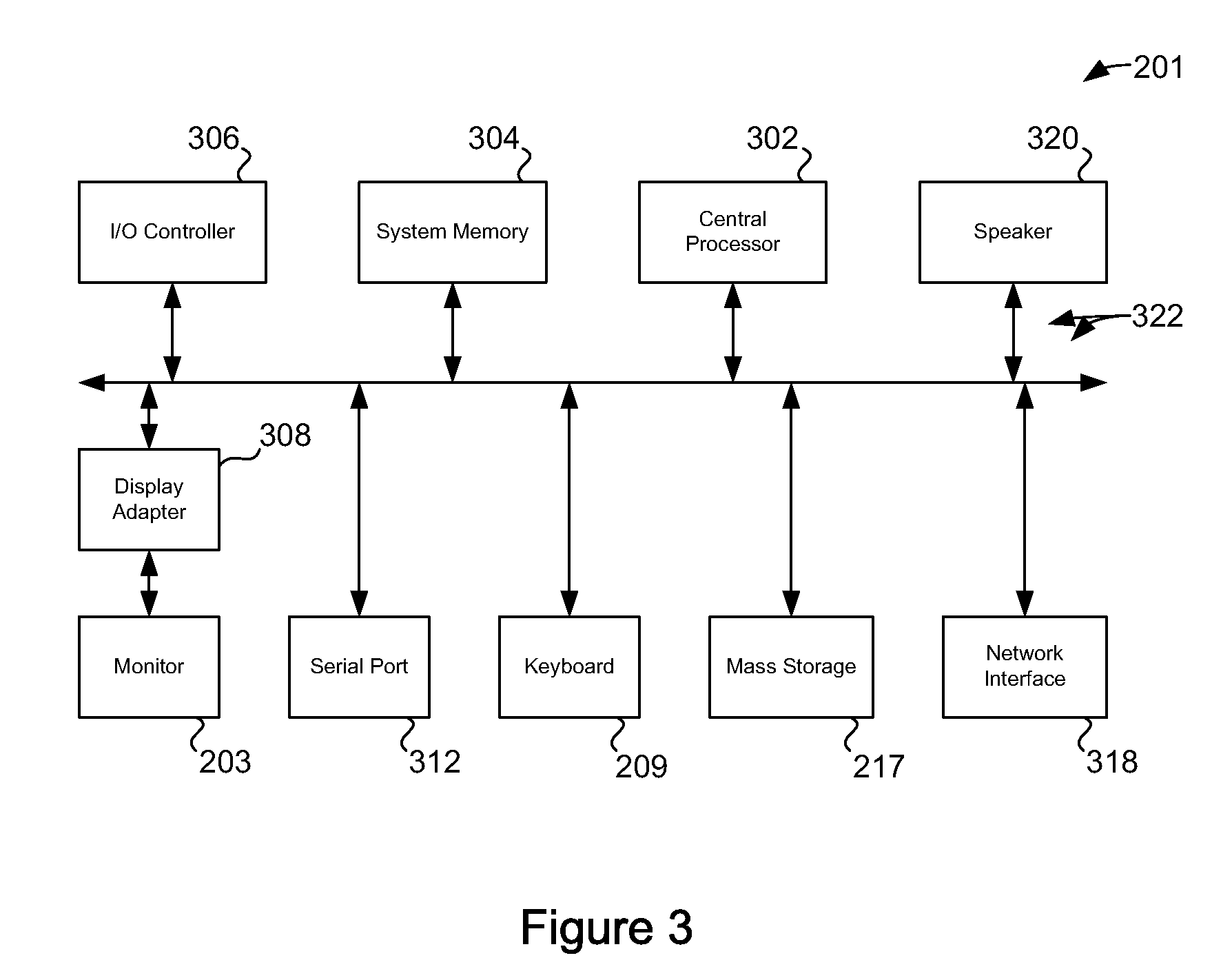
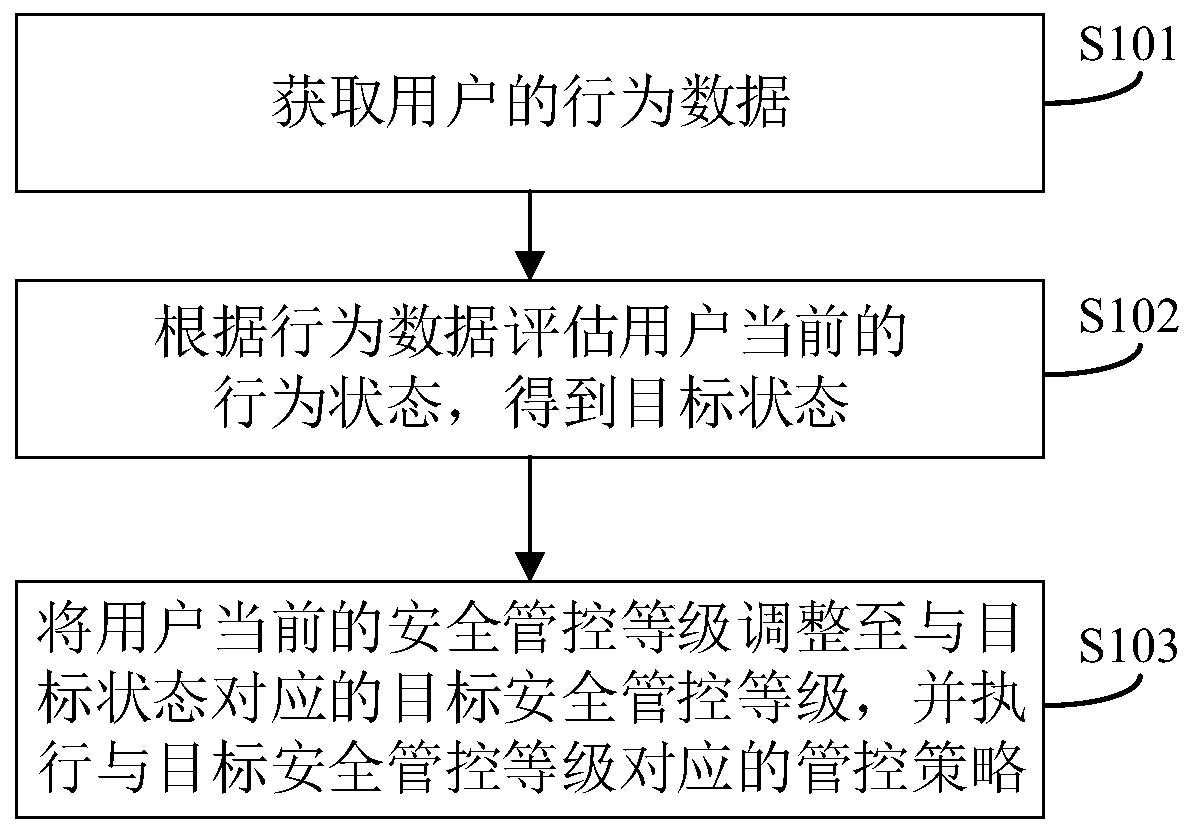
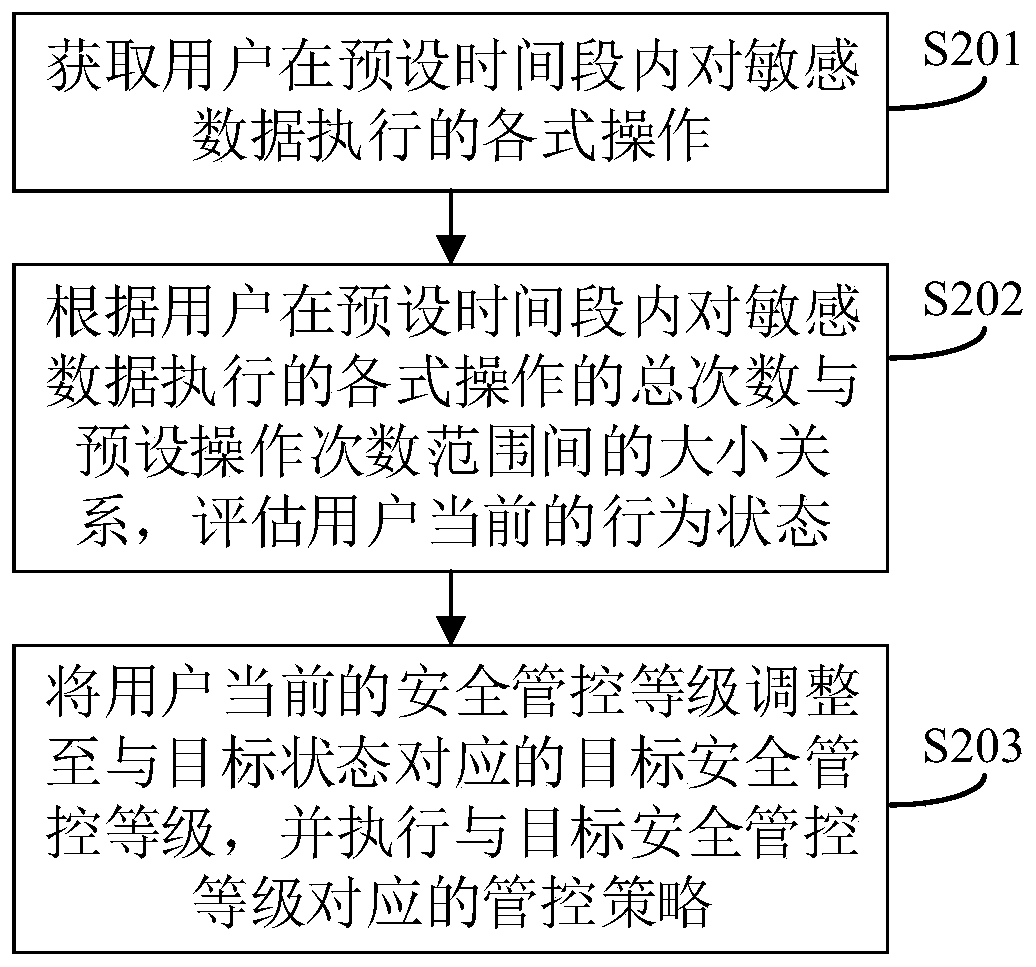
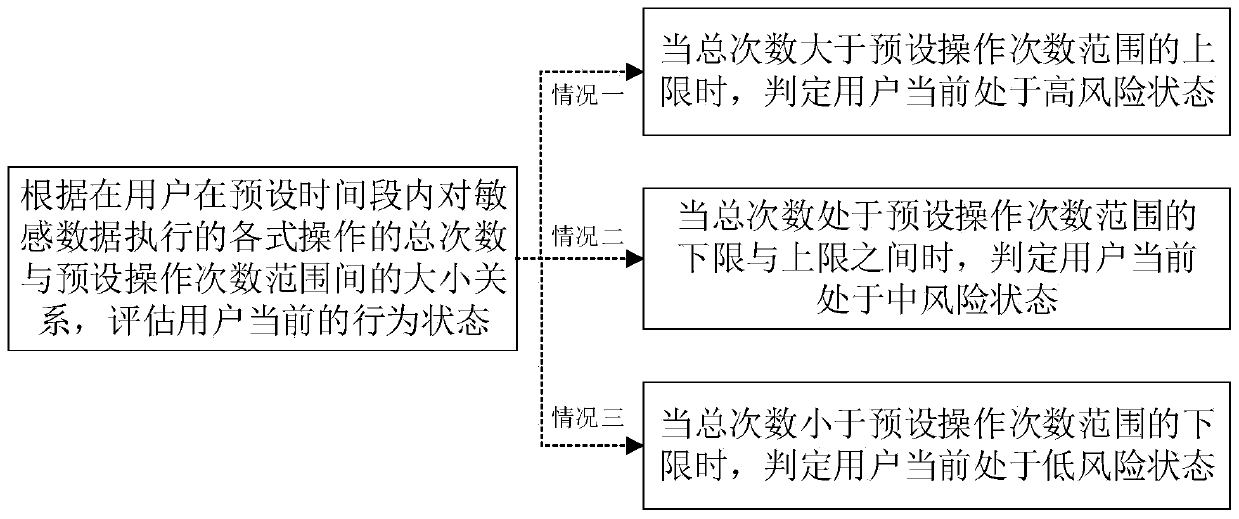
Patents
Literature
211 results about "Information security management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information security management (ISM) describes controls that an organization needs to implement to ensure that it is sensibly protecting the confidentiality, availability, and integrity of assets from threats and vulnerabilities. By extension, ISM includes information risk management, a process which involves the assessment of the risks an organization must deal with in the management and protection of assets, as well as the dissemination of the risks to all appropriate stakeholders. This of course requires proper asset identification and valuation steps, including evaluating the value of confidentiality, integrity, availability, and replacement of assets. As part of information security management, an organization may implement an information security management system and other best practices found in the ISO/IEC 27001, ISO/IEC 27002, and ISO/IEC 27035 standards on information security.
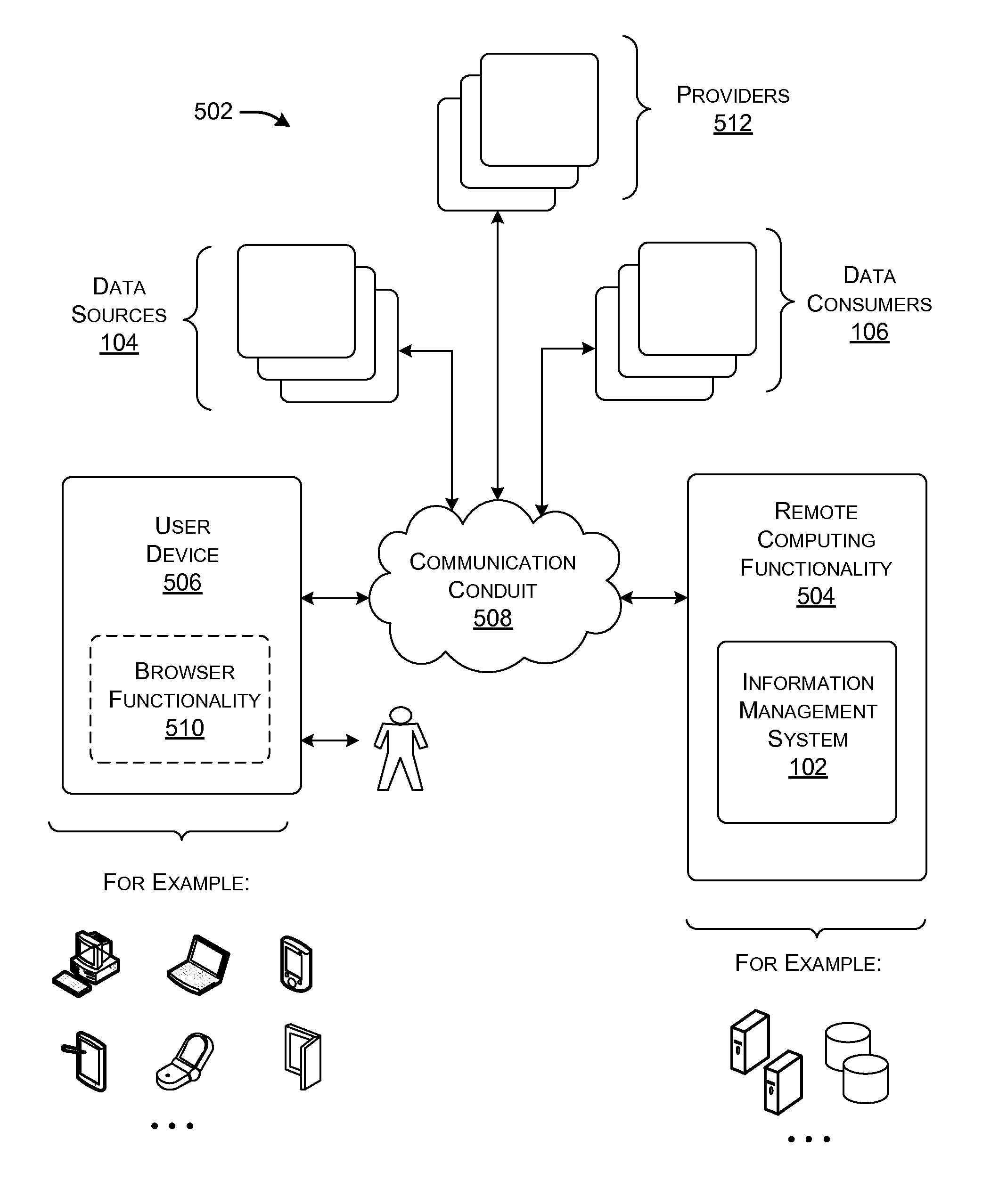
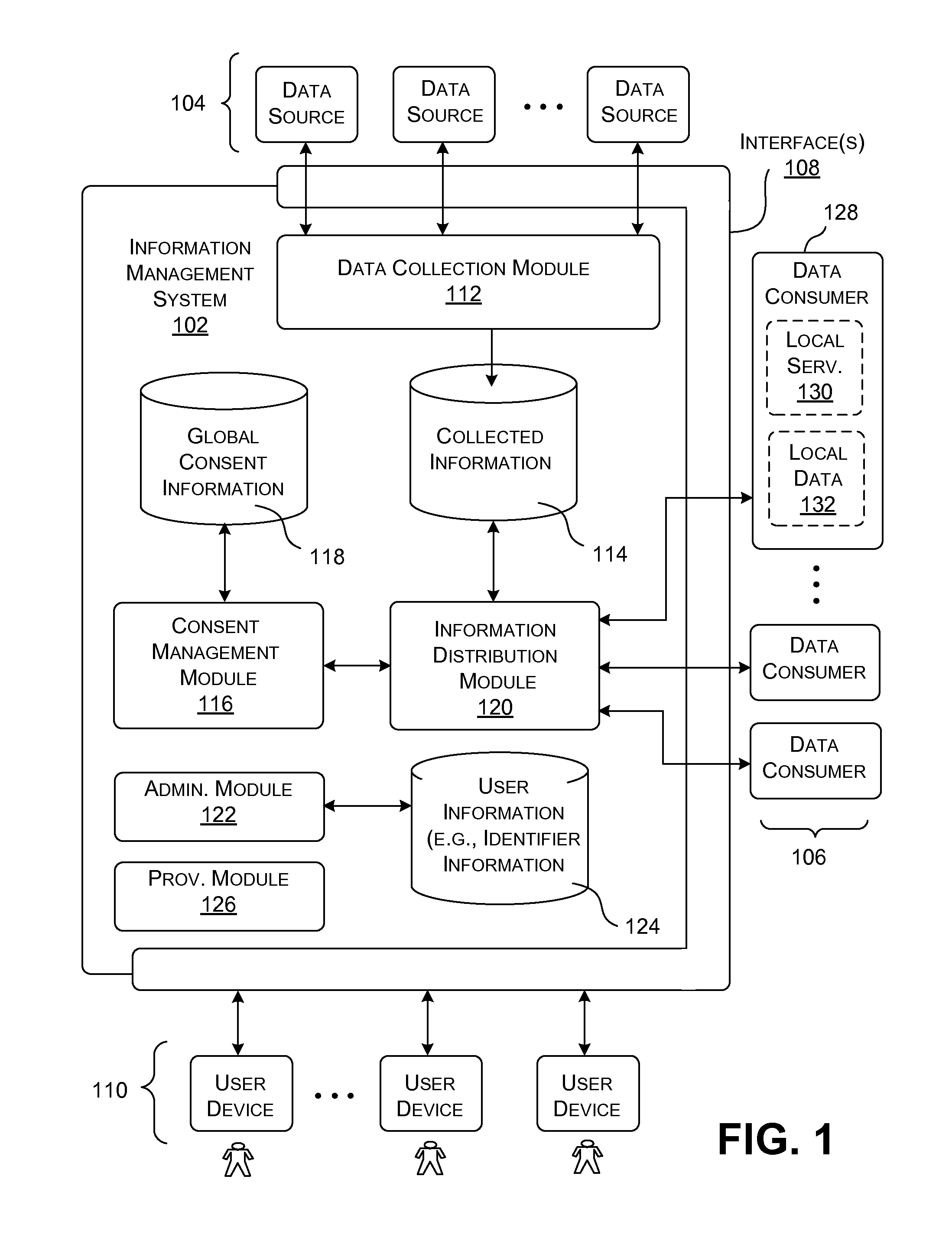
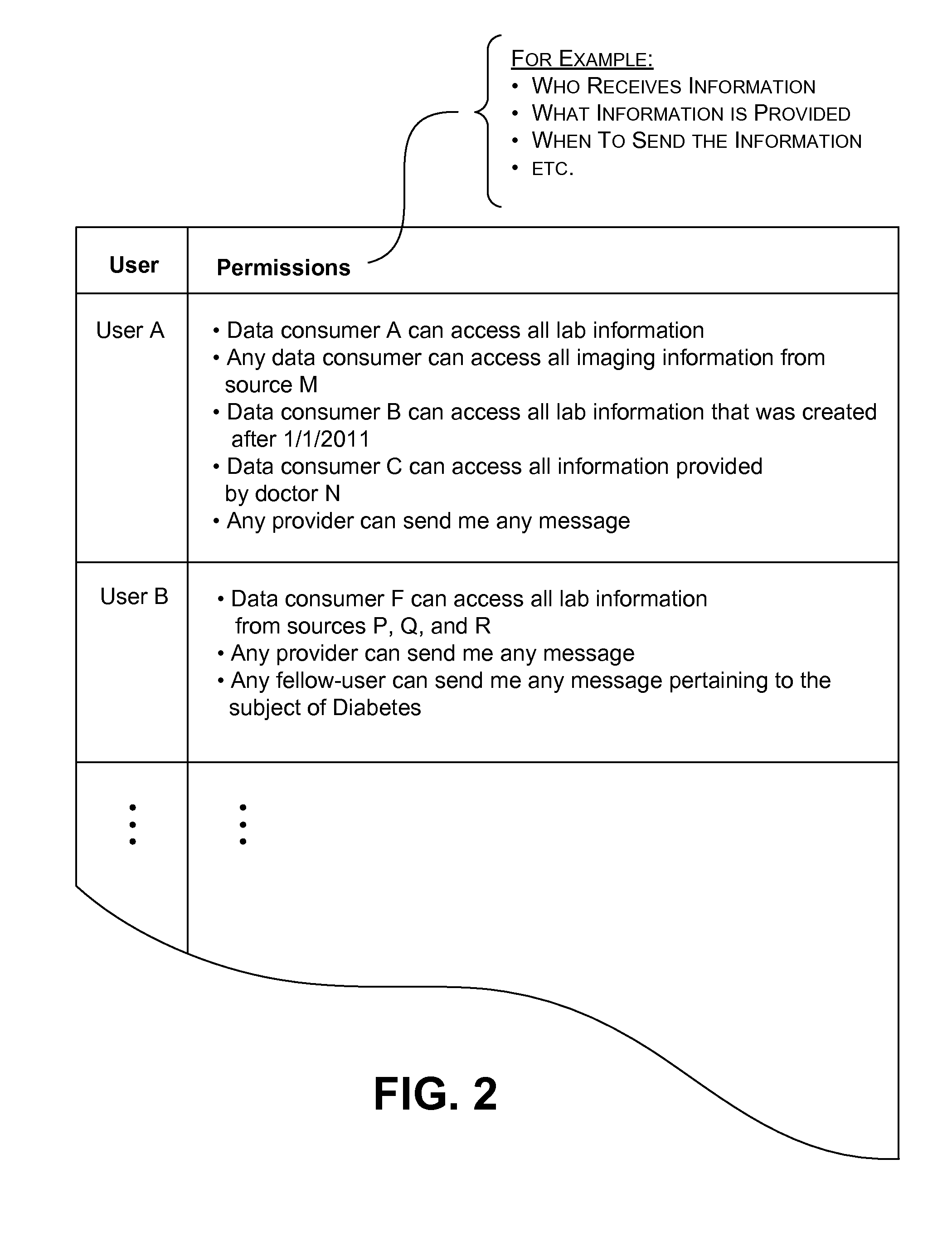
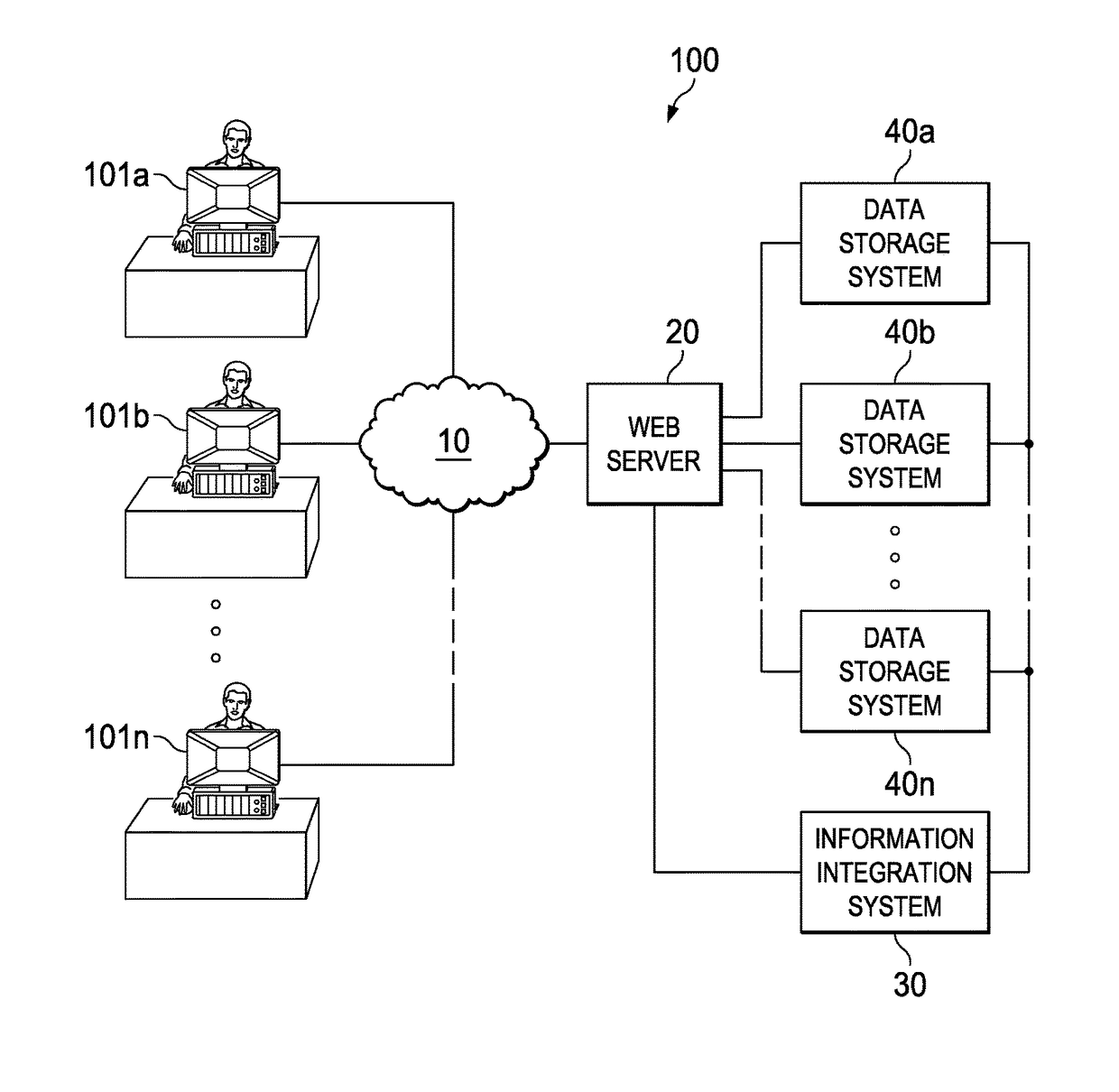
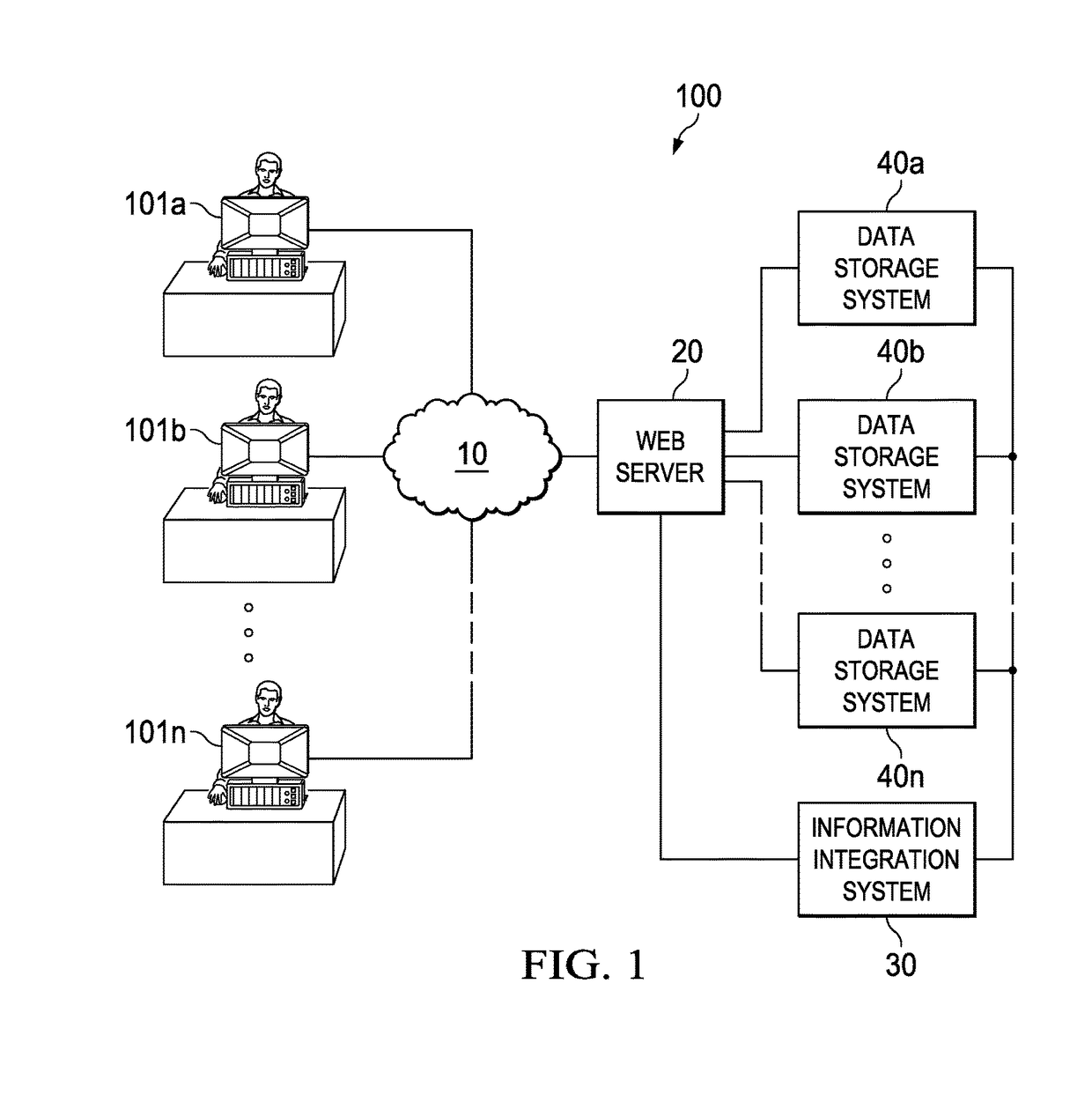
Distributing collected information to data consumers based on global user consent information
InactiveUS20120254320A1Well formedTelemedicineMultiple digital computer combinationsInformation functionDatasource
An information management system is described herein which maintains collected information that pertains to users, received from one or more data sources. The information management system also maintains a store of consent information. The consent information describes, for each user, at least one permission rule (established by the user) which enables at least one data consumer to receive at least part of the collected information for that user. Upon the occurrence of a triggering event, an information distribution module operates by distributing identified part(s) of the collected information to appropriate data consumer(s), as governed by the consent information. In this manner of operation, the consent information functions as global metadata which, from a centralized platform, governs the dissemination of the collected information to any data consumer in an application-agnostic manner.
Owner:MICROSOFT TECH LICENSING LLC
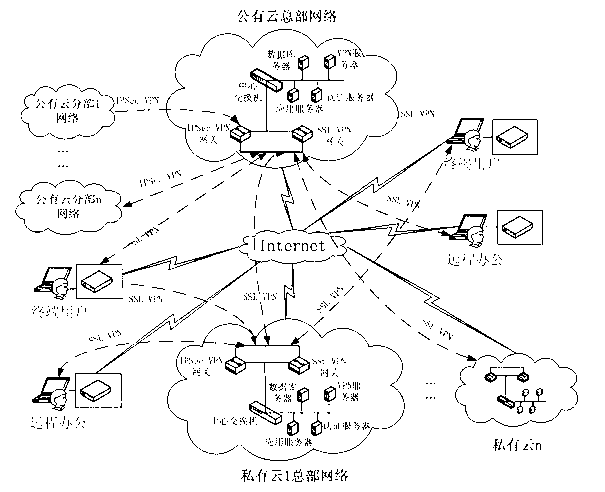
Information security management and control method under cloud manufacturing environment
InactiveCN102710605ASolve the problem of update and maintenanceAvoid complex proceduresPublic key for secure communicationUser identity/authority verificationConfidentialityPrivate network
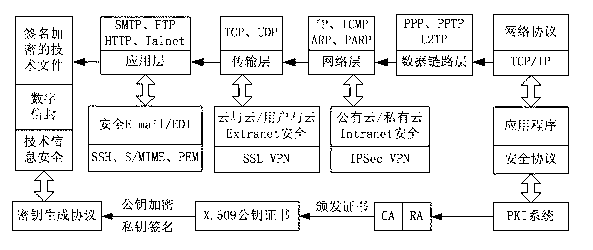
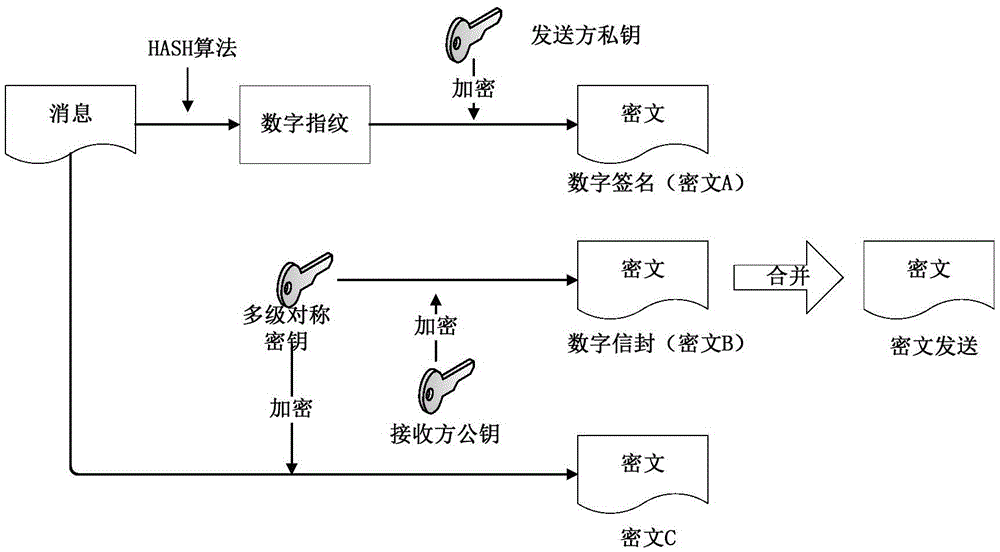
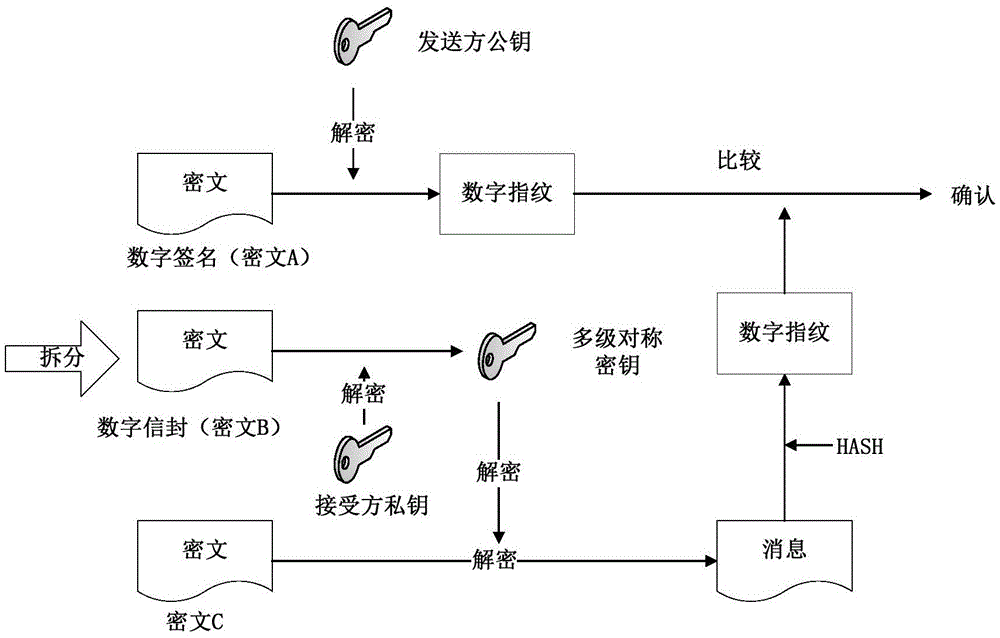
The invention discloses an information security management and control method under a cloud manufacturing environment. On the basis of a network security protocol, a password technology and a public key infrastructure (PKI), comprehensive security guarantee is supplied to information interaction among cloud internal networks, between one cloud and another cloud, and between a user and each cloud by using implementation technologies and methods, such as a virtual private network (VPN) based on multiple layers of protocols, a digital envelope and a password algorithm; Intranet, Extranet and Internet of a cloud manufacturing system are covered; comprehensive management and control technical information files are stored and transmitted to each used loop; a session key (SK) which is randomly produced by using a key production protocol is used for symmetrically encrypting the technical information files; and a receiver public key obtained according to a PKI digital certificate asymmetrically encrypts the SK to form the digital envelope for protecting the technical information files and the SK. The information security management and control method has the characteristics of being high in confidentiality, high inefficiency, flexible in arrangement and the like and can be widely applied to the cloud manufacturing system and other network manufacturing systems.
Owner:CHONGQING UNIV
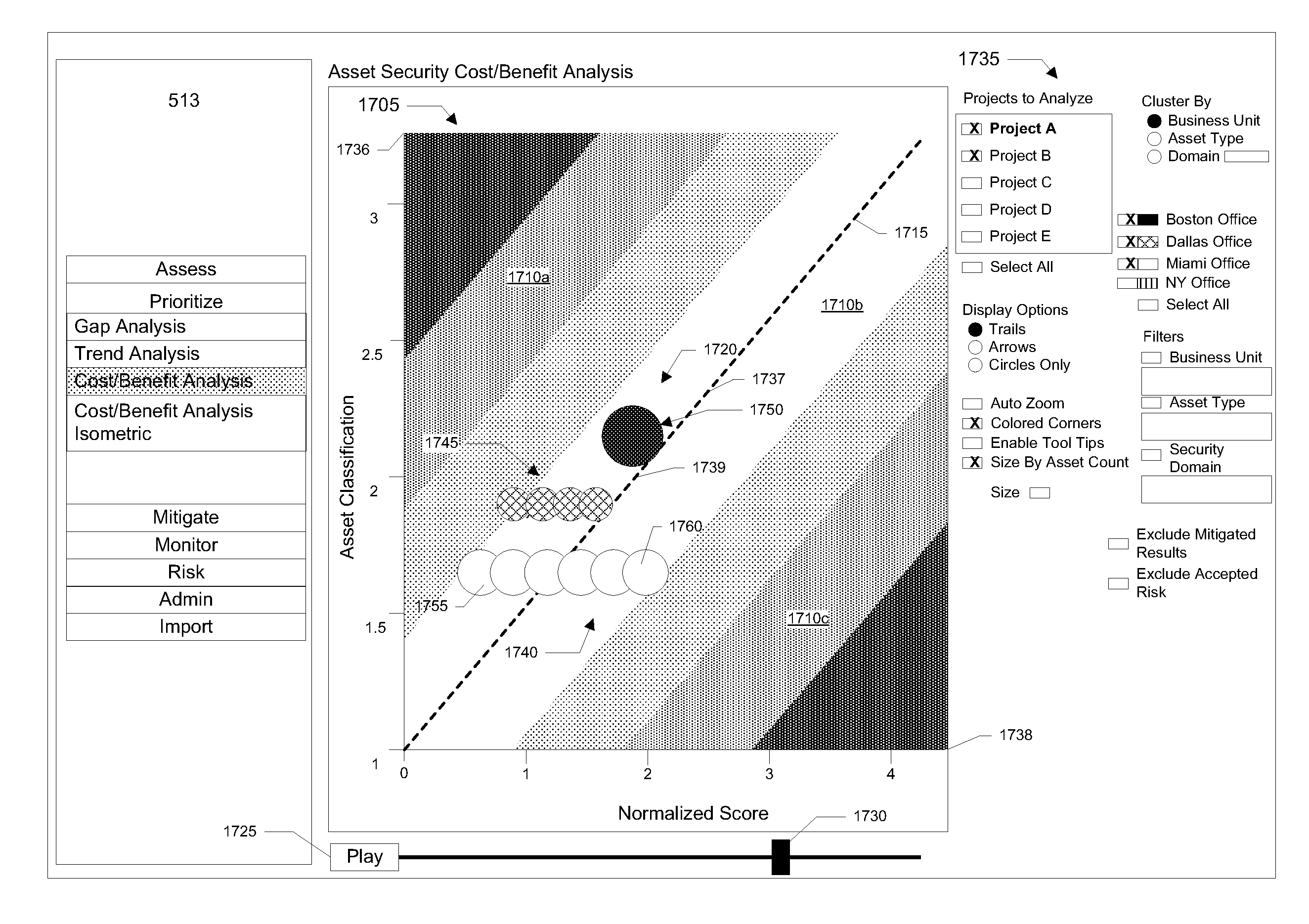
Enterprise Information Security Management Software Used to Prove Return on Investment of Security Projects and Activities Using Interactive Graphs
InactiveUS20100095235A1Shorten the timeReduce laborData processing applicationsInput/output processes for data processingGraphicsAnimation
Asset security is tracked and managed by the system. In a specific implementation, assets are entered into the system. The system automates gathering security information about the asset by, for example, sending out surveys and aggregating the responses. The system performs a security gap analysis by comparing the responses against a security maturity model. Tasks can be assigned to various users and then tracked so that vulnerabilities can be addressed. The system generates interactive summary reports (e.g., charts, graphs, animation) to help users make security decisions. Graphs may be temporally animated so that users can see and analyze changes over time.
Owner:ALLGRESS
Information security management improvement system
ActiveUS10860721B1Improving information security management systemWeb data indexingPlatform integrity maintainanceInformation security managementSecurity framework
Systems, methods, and non-transitory mediums for assessing and improving the information security management health of an organization may be used to generate a baseline assessment measuring a level of compliance with proper security framework elements as well as a level of cross-management, interaction, or engagement across four essential information security domains including a benchmark domain, a measurement domain, a decision domain, and an execution domain using a domain-element table with a plurality of measurement types associated with criteria for progressing through an increasing level of difficulty tiered scoring system established by selected frameworks, policies, standards, and guidelines while also providing a path to improve upon a baseline assessment.
Owner:GENTILE MIKE
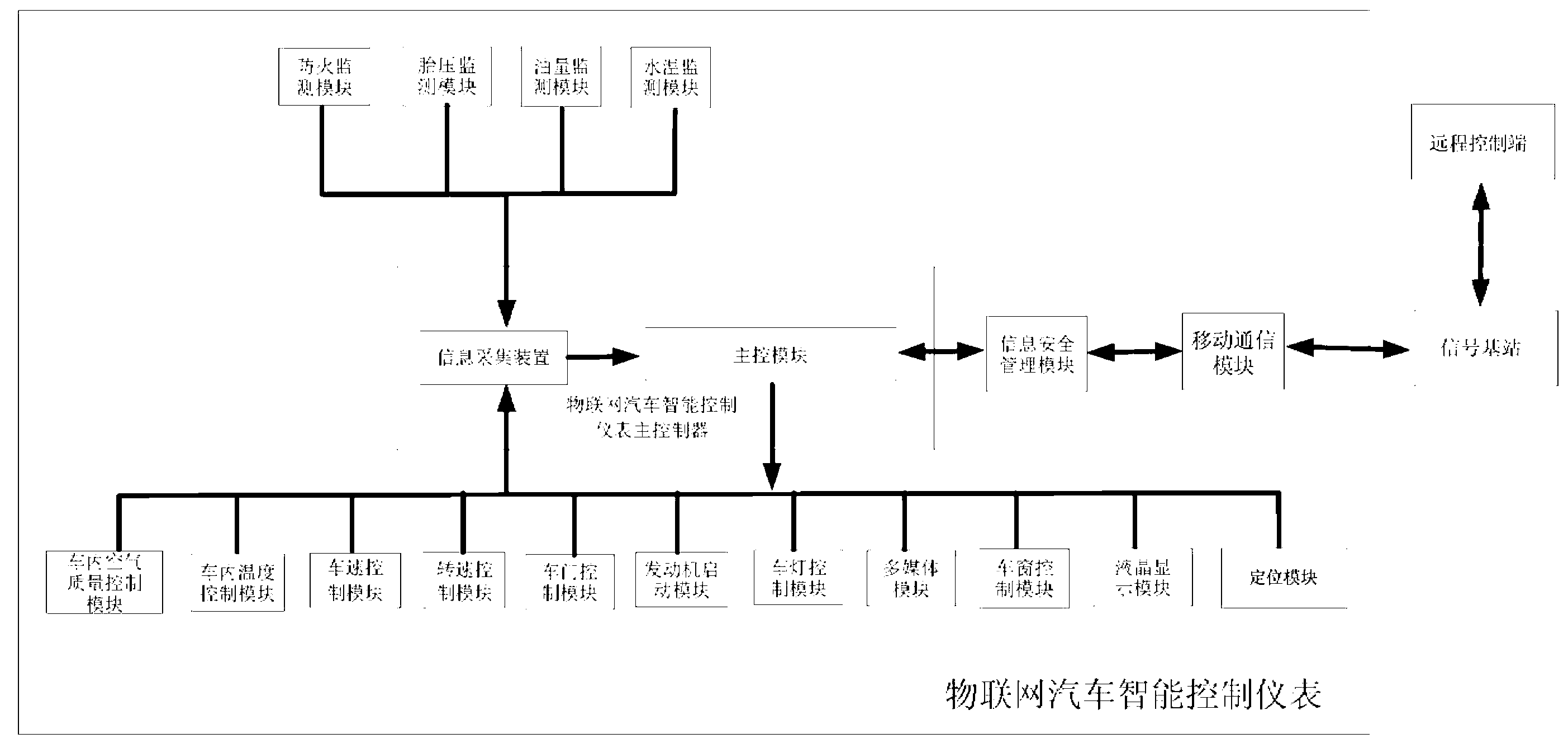
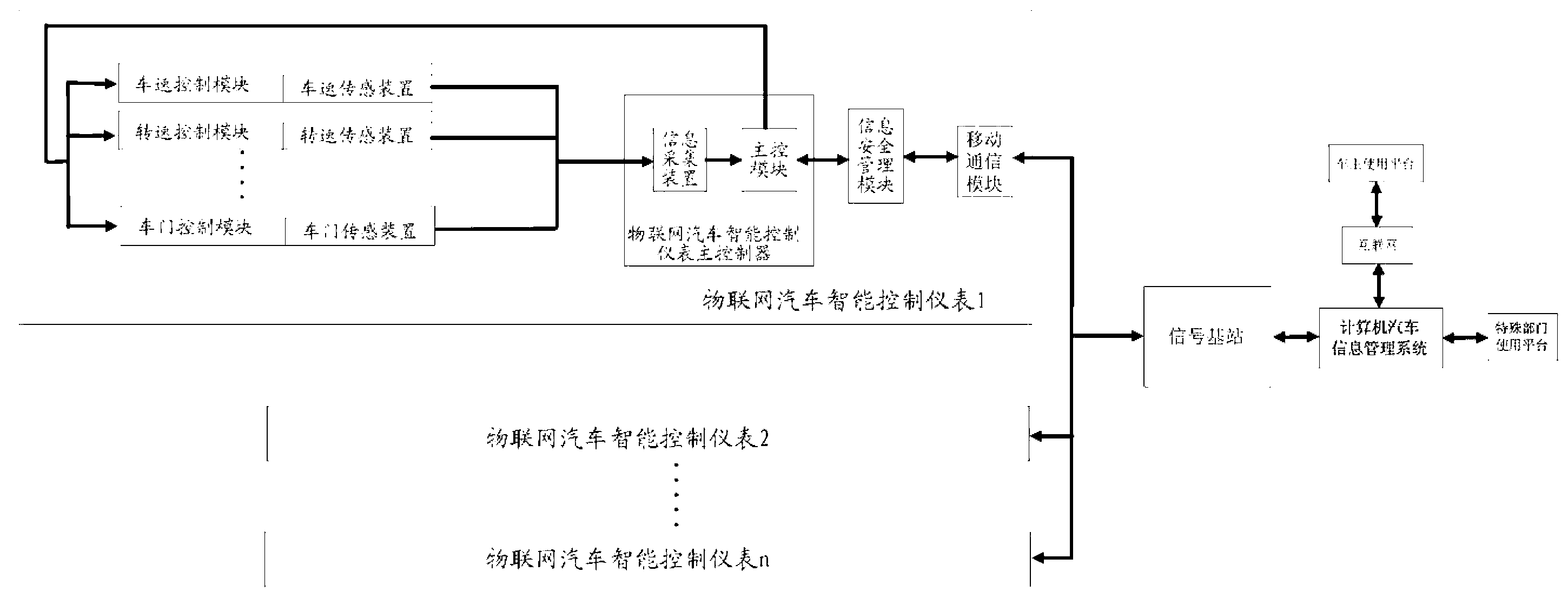
Internet of things automotive intelligent control instrument and internet of things automotive intelligent management system
ActiveCN103309315ASimple structureConvenient Management FunctionParticular environment based servicesIn-vehicle communicationDashboardThe Internet
The invention discloses an internet of things automotive intelligent control instrument and an internet of things automotive intelligent management system. The internet of things automotive intelligent control instrument belongs to an automotive instrument and comprises a main controller of the internet of things automotive intelligent control instrument, wherein the main controller of the internet of things automotive intelligent control instrument terminal is respectively connected with multiple functional modules in an automobile and is also connected with an information security management module, the information security management module is connected with a signal base station through a mobile communication module and is connected with a remote control end through the signal base station, and various data and control instructions are transmitted between the main controller of the internet of things automotive intelligent control instrument terminal and the remote control end through the information security management module and the mobile communication module; the main controller of the internet of things automotive intelligent control instrument is connected with the remote control end through the signal base station by using the mobile communication module, and the main controller is remotely controlled and monitored by the remote control end, so that convenient management functions are provided for car owners, the national security department, the traffic management department, the police security department and the like.
Owner:眉山秦川智能传感器有限公司
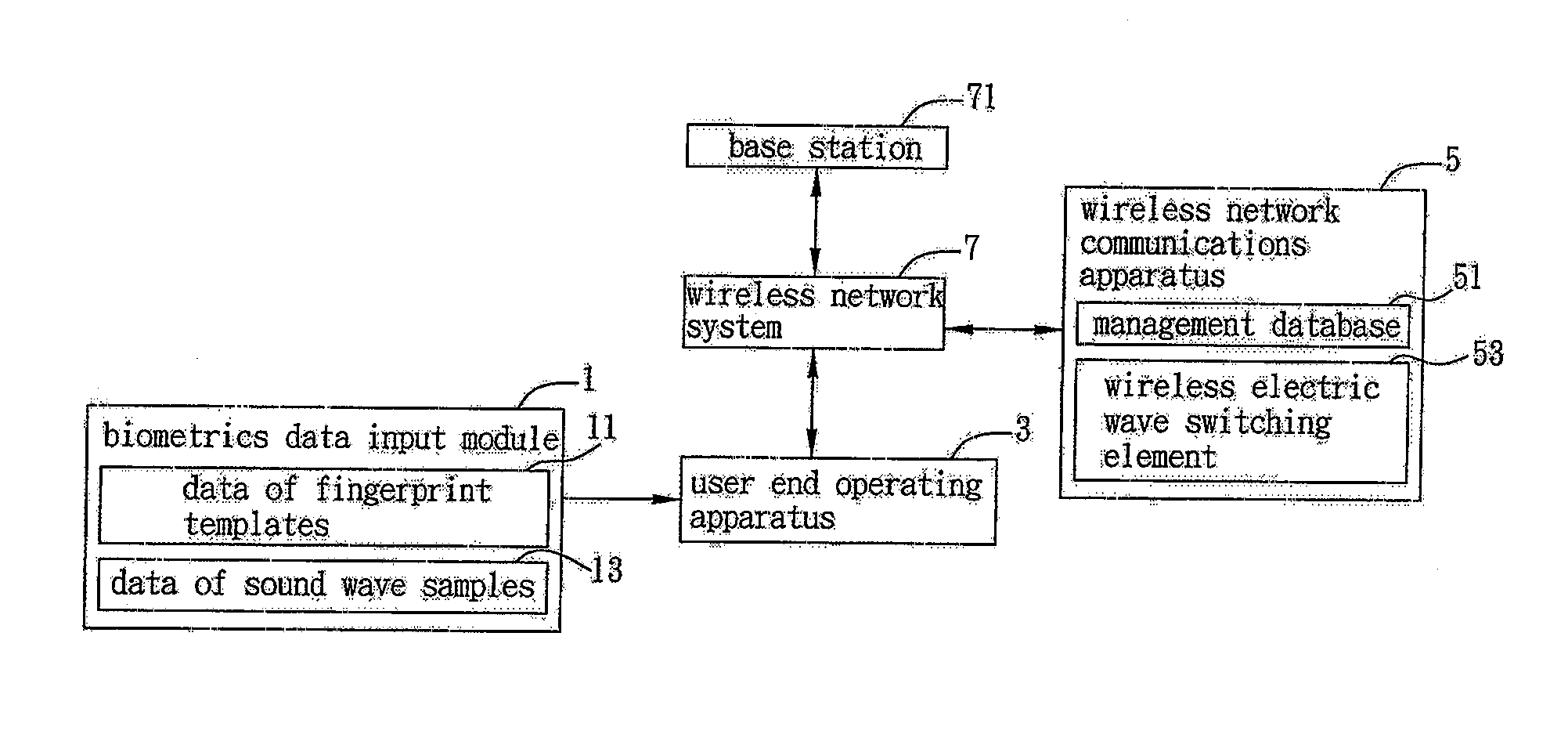
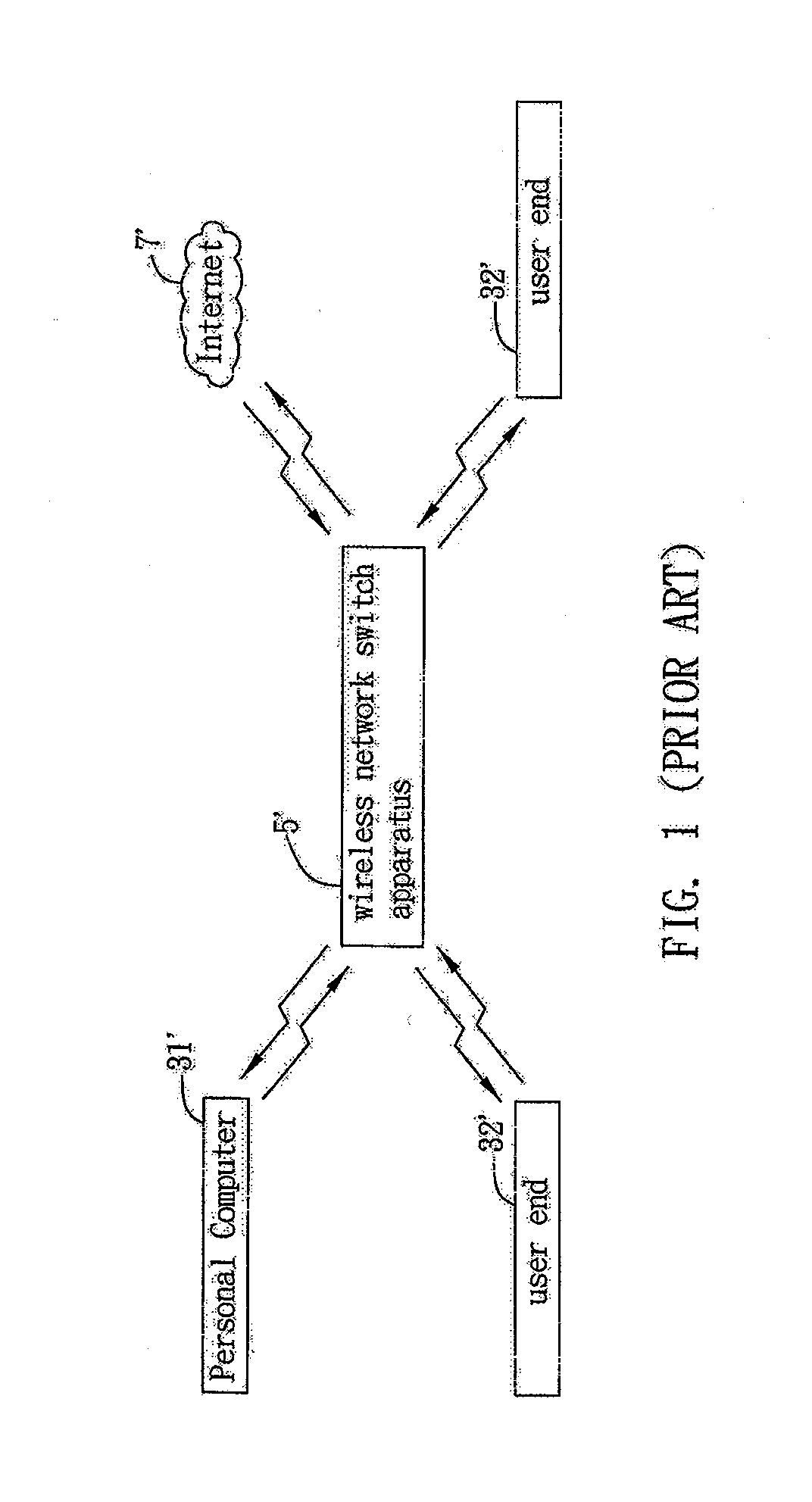
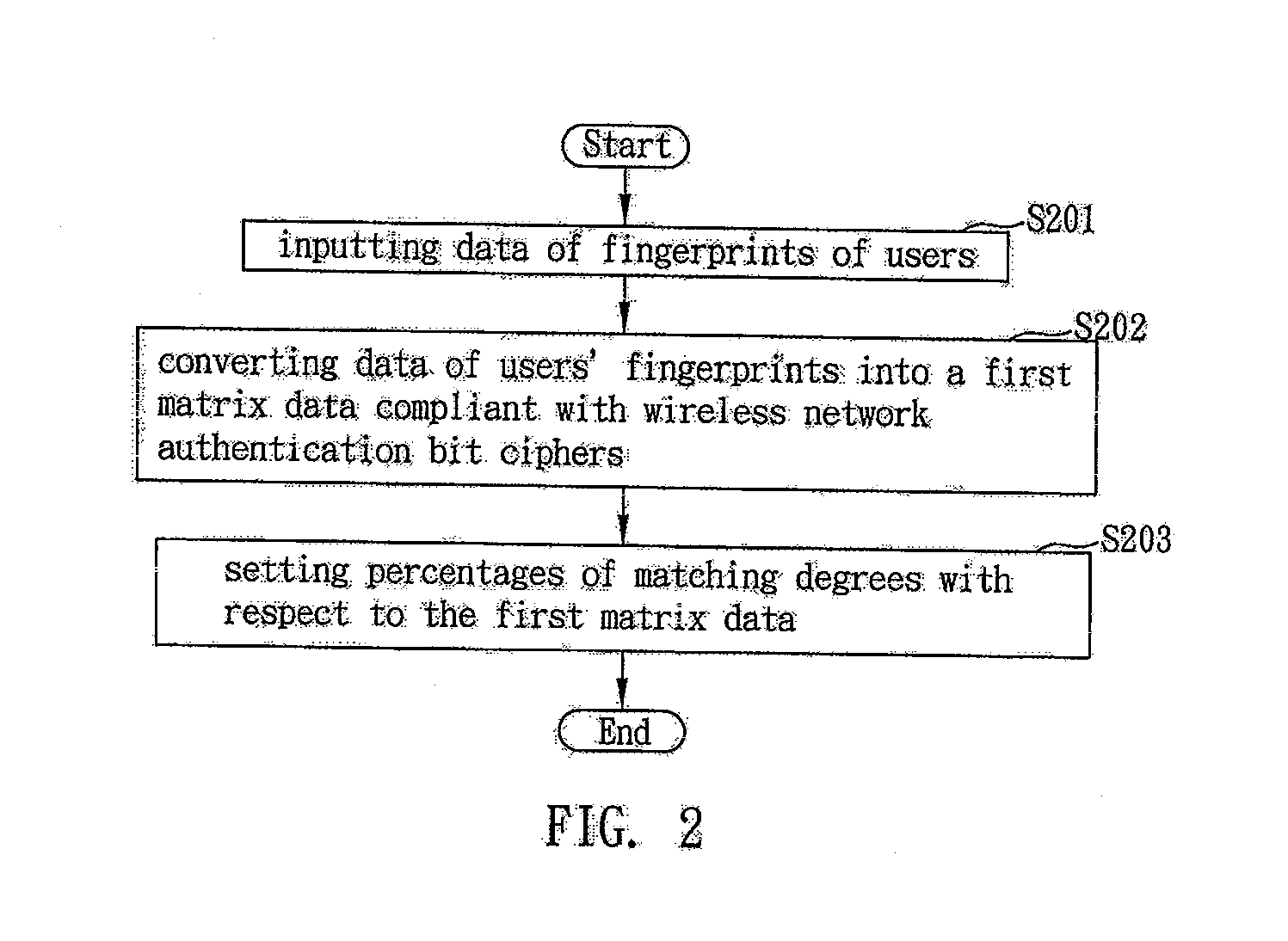
Fingerprint authentication method for accessing wireless network systems
ActiveUS20070239991A1Quality improvementImprove securityDigital data processing detailsInformation formatNetwork connectionInformation security management
This invention provides a fingerprint authentication mechanism for accessing the wireless network system that is applicable to a wireless network communications apparatus, the mechanism including the steps of inputting data of users' fingerprints and converting the same into matrix data compliant with wireless network authentication bit ciphers; setting thresholds for pattern identification with respect to the matrix data as an authentication basis for determining if the user has access rights to the network system upon receipt of a request signal for network connection sent from a user end; and analyzing if the captured fingerprint of the user matches with the preset authentication data to determine if the wireless network communications apparatus is to be started for network connection, thereby increasing the quality, usability and safety of the wireless network connection to achieve an easier scheme of information security management.
Owner:MITAC INT CORP
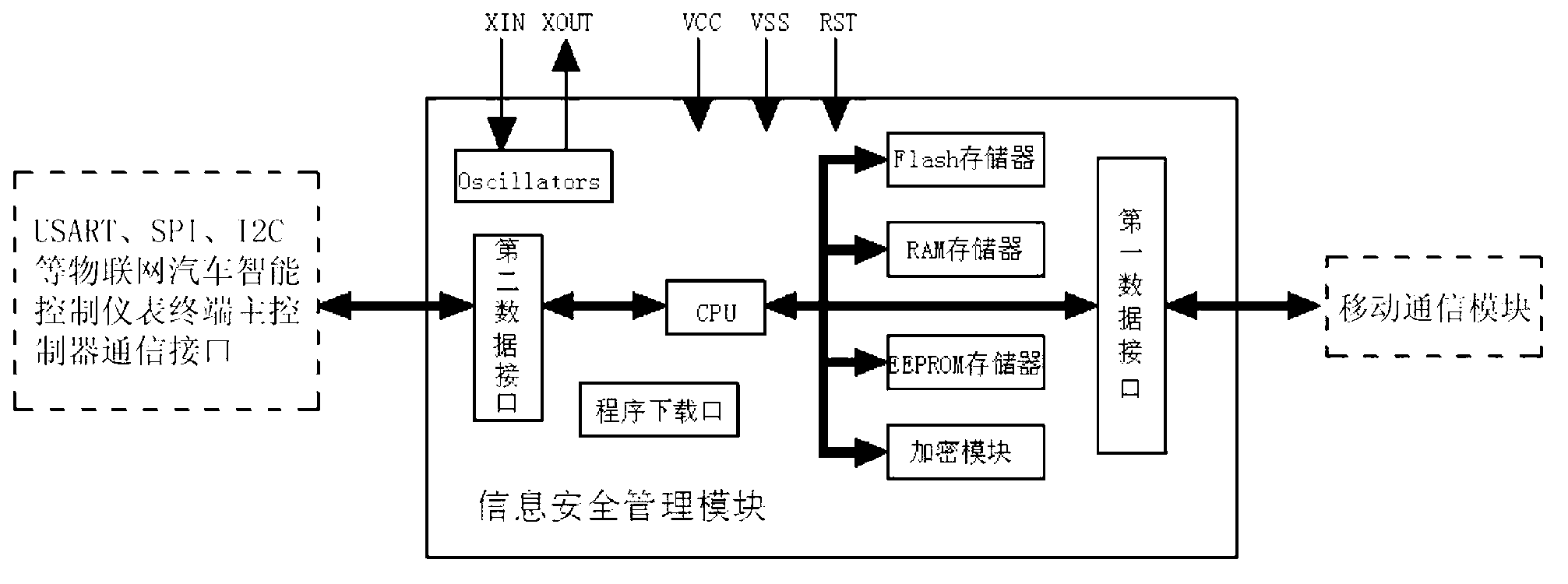
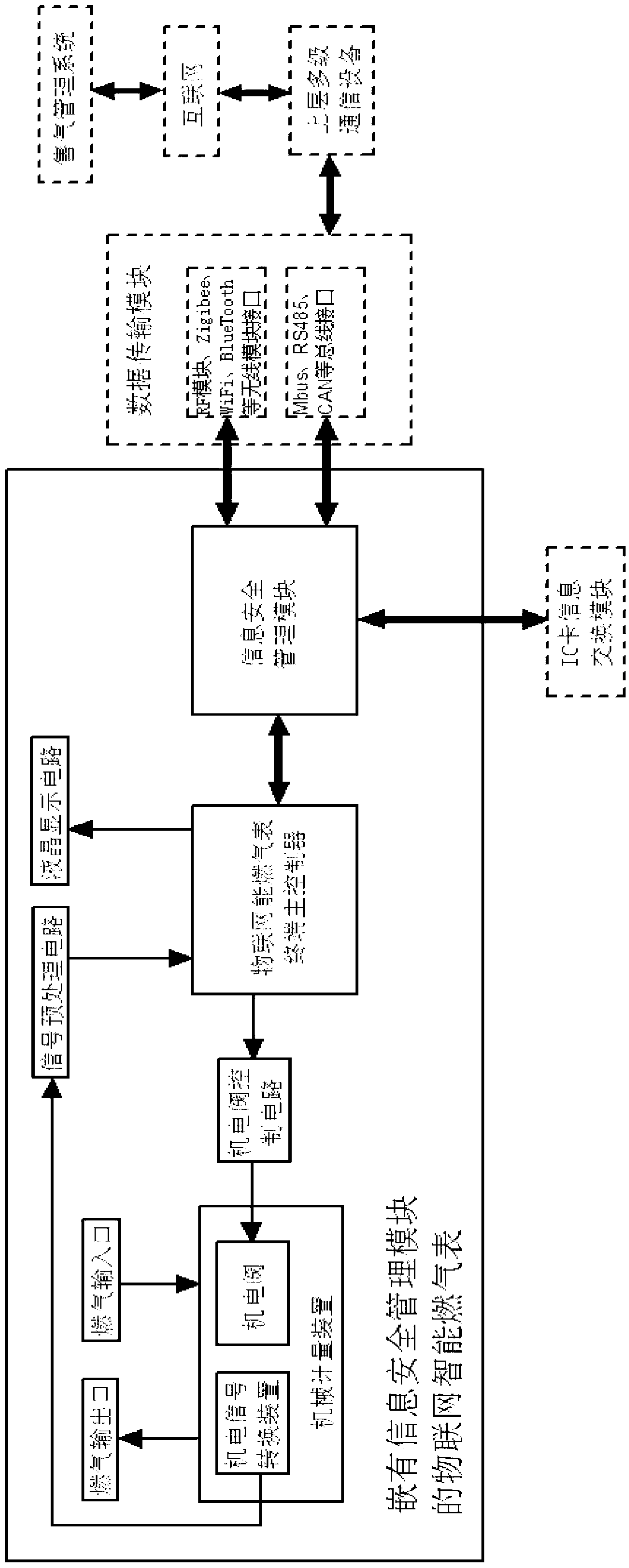
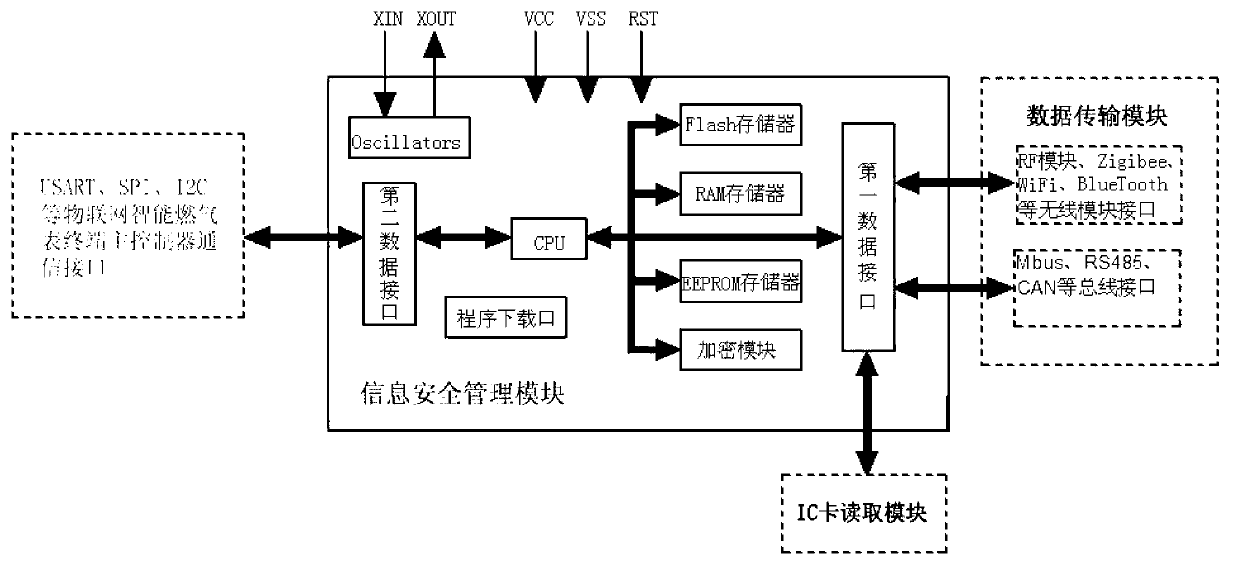
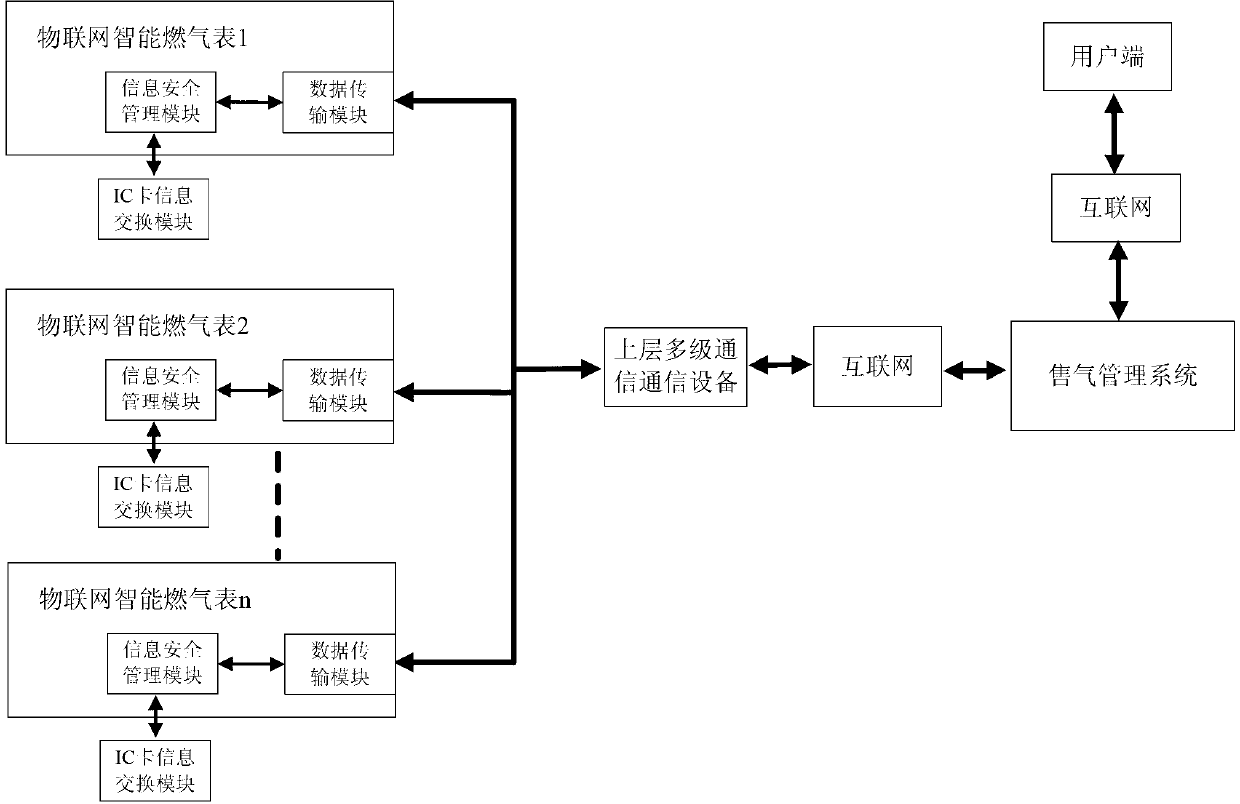
Internet of things intelligent gas meter embedded with information security management module
ActiveCN103106744ASimple structureGuaranteed independenceApparatus for hiring articlesRemote controlThe Internet
The invention discloses an internet of things intelligent gas meter embedded with an information security management module. The information security management module comprises a processor, a first data interface, a second data interface and a flash storer, wherein the processor is respectively connected into the first data interface, the second data interface and the flash storer. When the information security management module exchanges data with an internet of things remote control terminal, identity authentication is conducted, and the communicating validity of the information security management module and the internet of things remote control terminal is ensured. A terminal master controller of the internet of things intelligent gas meter can be communicated with the outside only through the information security management module. The internet of things intelligent gas meter embedded with the information security management module is simple in structure of module, can be connected into a gas management system in a seamless mode through the internal information security management module, achieves dispersion manufacture and unified management of the internet of things intelligent gas meter, and is wide in range of application.
Owner:CHENGDU QINCHUAN IOT TECH CO LTD
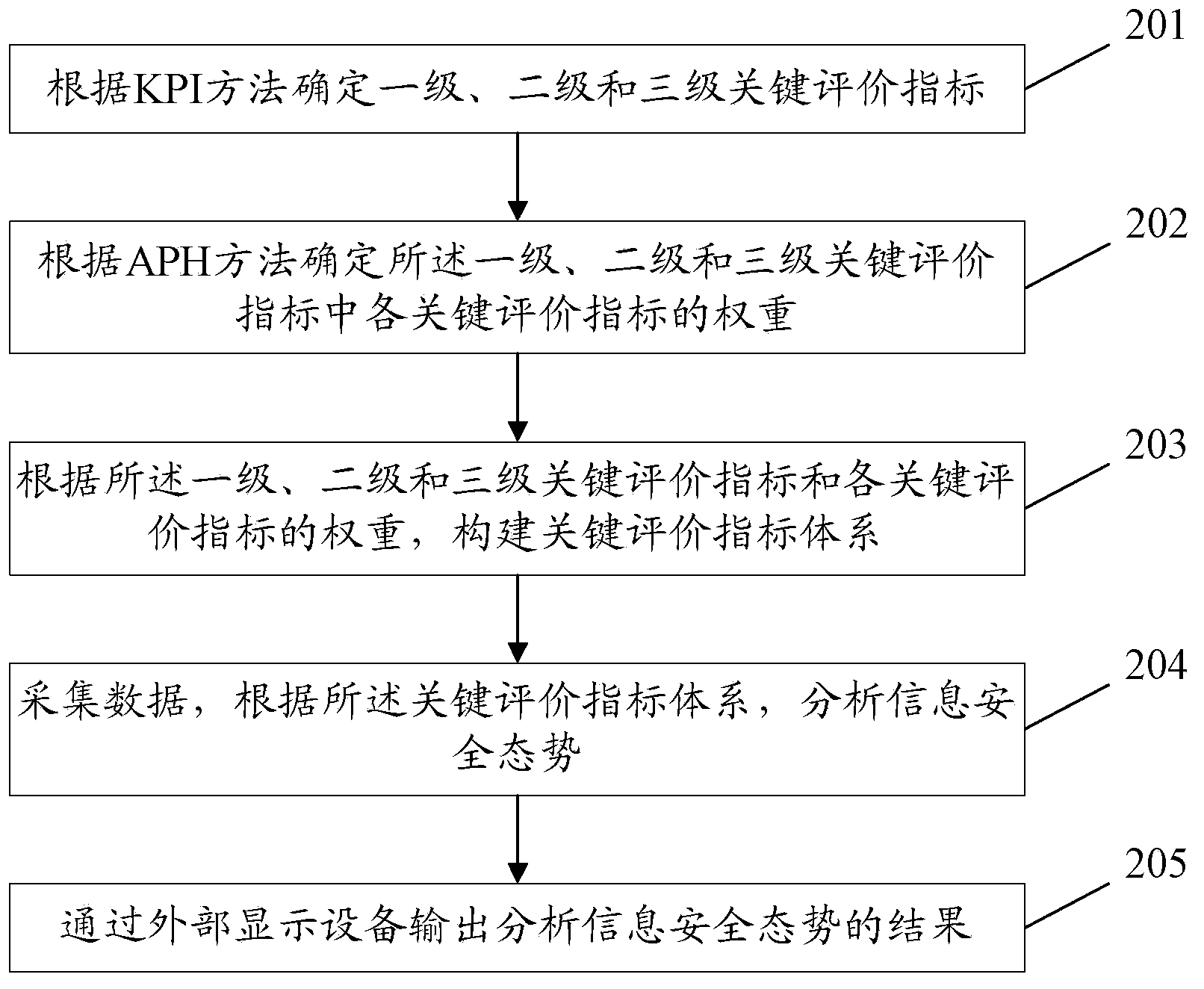
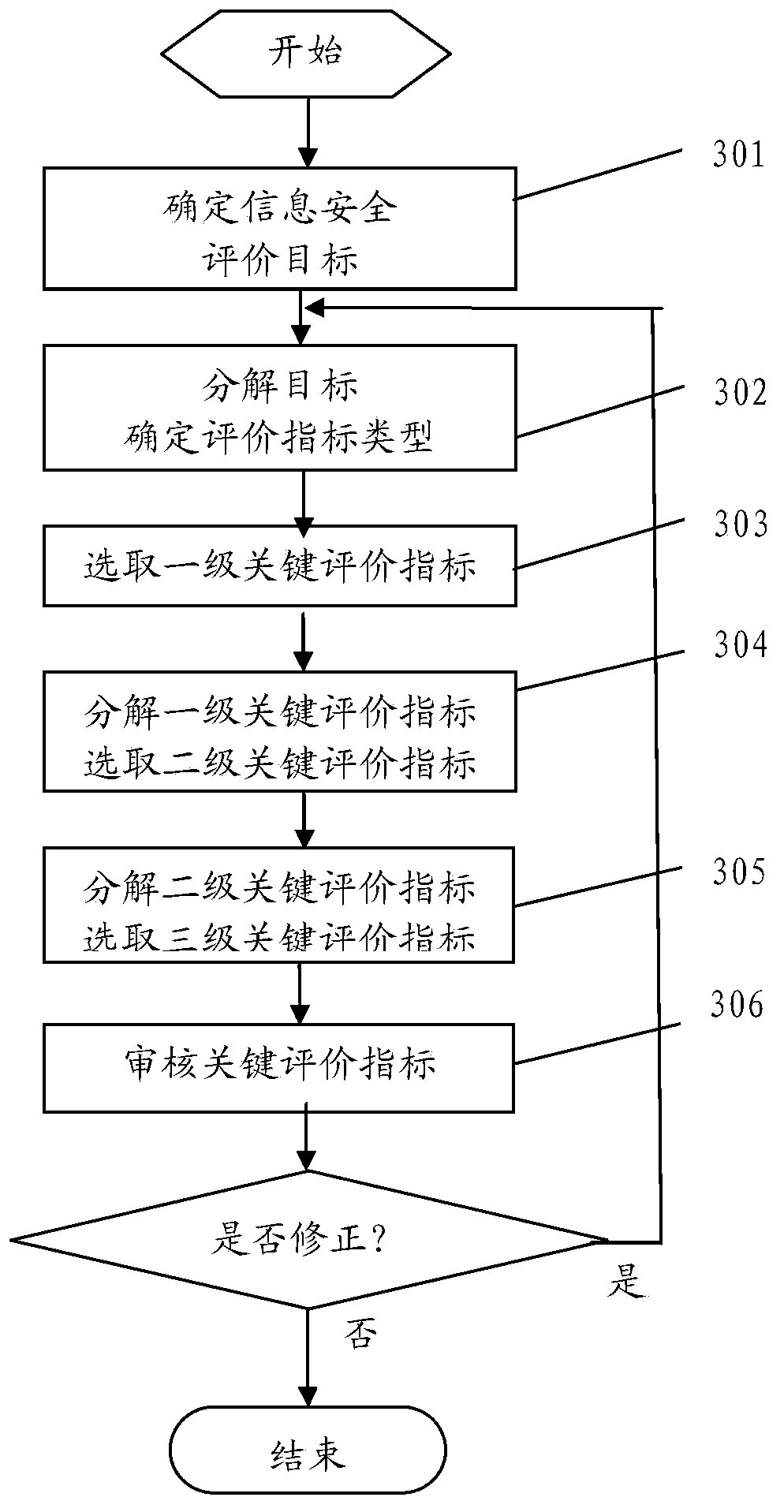
Information security situation analysis method and system
ActiveCN103581155AAddress Security ManagementData switching networksInformation security managementIndex system
The invention provides an information security situation analysis method and system, and relates to the technical field of network and information security. The information security situation analysis method and system achieve the aim of effective information security management. The information security situation analysis method comprises the steps that first-level, second-level and third-level key evaluation indexes are determined according to the KPI method; the weight of each key evaluation index in the first-level, second-level and third-level key evaluation indexes is determined according to the AHP method; a key evaluation index system is constructed according to the first-level, second-level and third-level key evaluation indexes and the weight of each key evaluation index; data is collected, and information security situation is analyzed according to the key evaluation index system. According to the technical scheme, the information security situation analysis method and system are applied to network information security, and achieve analysis and management of information security.
Owner:GUIZHOU POWER GRID INFORMATION & TELECOMM
An information security management platform
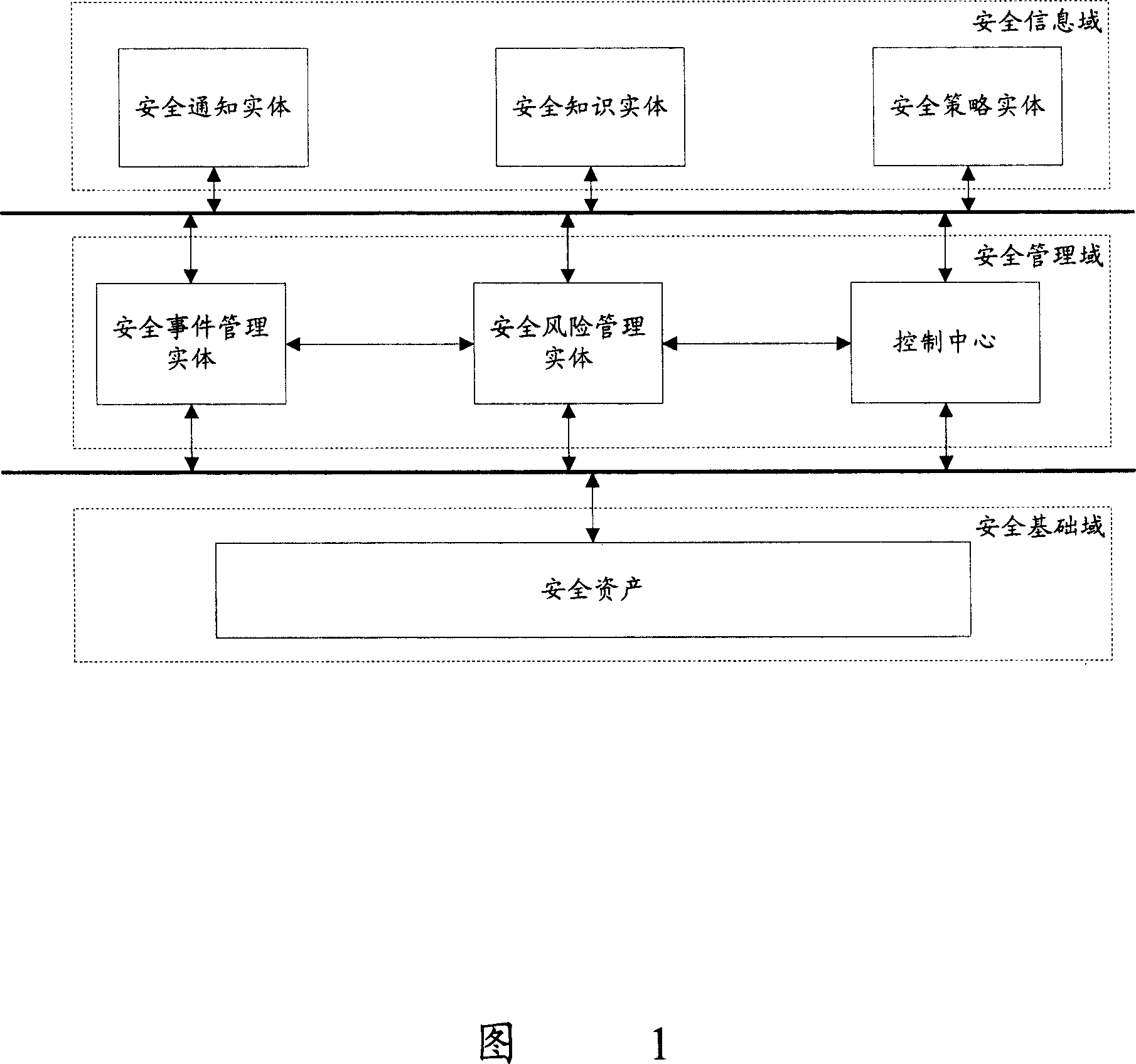
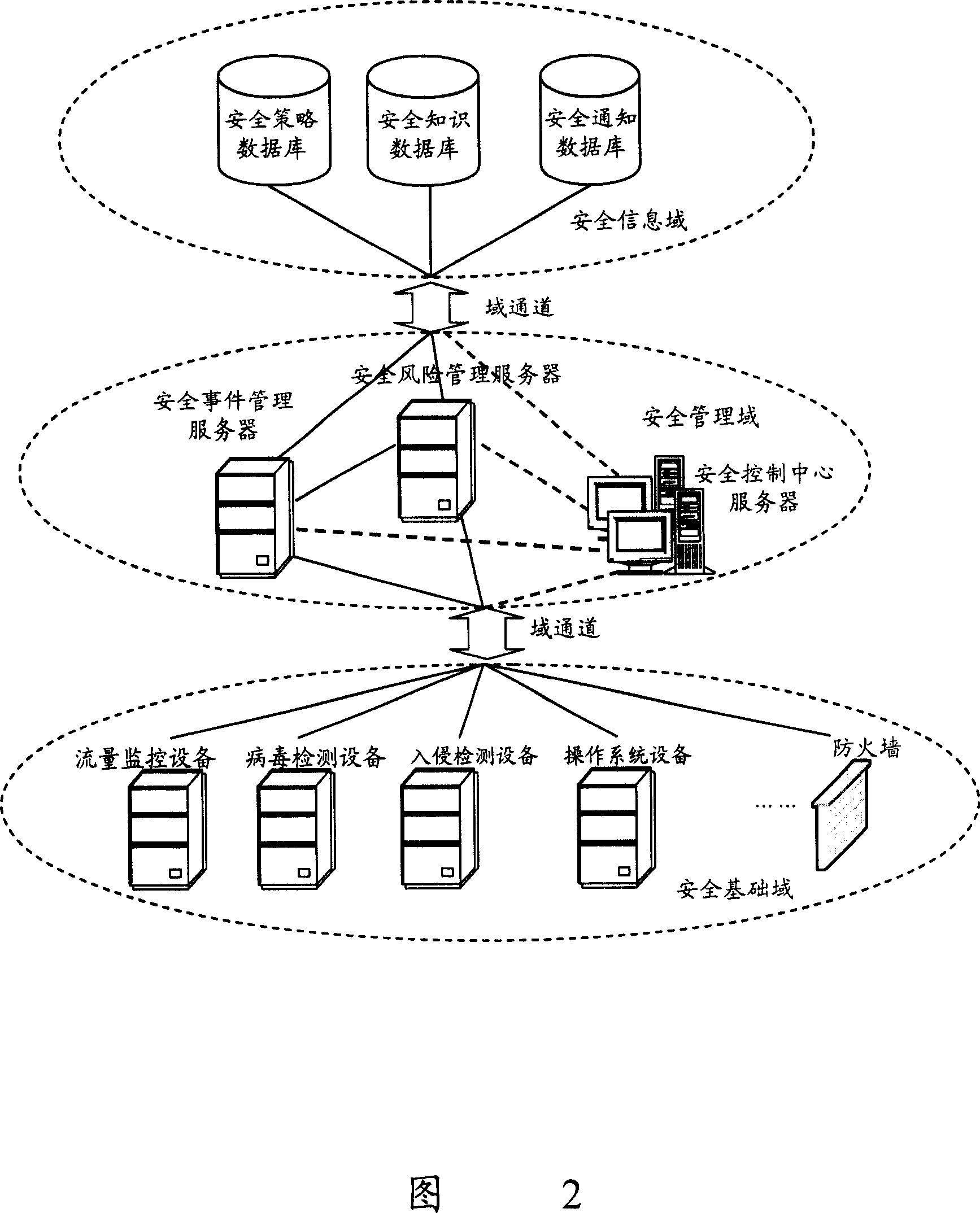
InactiveCN101056198ADynamic and flexible security managementImplement security task managementData switching networksSecure stateInformation security management
The invention discloses an information safety management platform, which includes: safety base domain, for monitoring the network safety status, generating and sending the safety report to the safety management domain; safety management domain, for receiving the safety report from the safety base domain, and extract the safety information from the safety information domain, according to the analysis for the safety report received from the relevant safety information, acquire the network safety alarm and network safety configuration suggestions; the safety information domain, used for saving the safety information and output to the safety management domain. The invention may realize the automatic management of dynamic network information safety.
Owner:HUAWEI TECH CO LTD
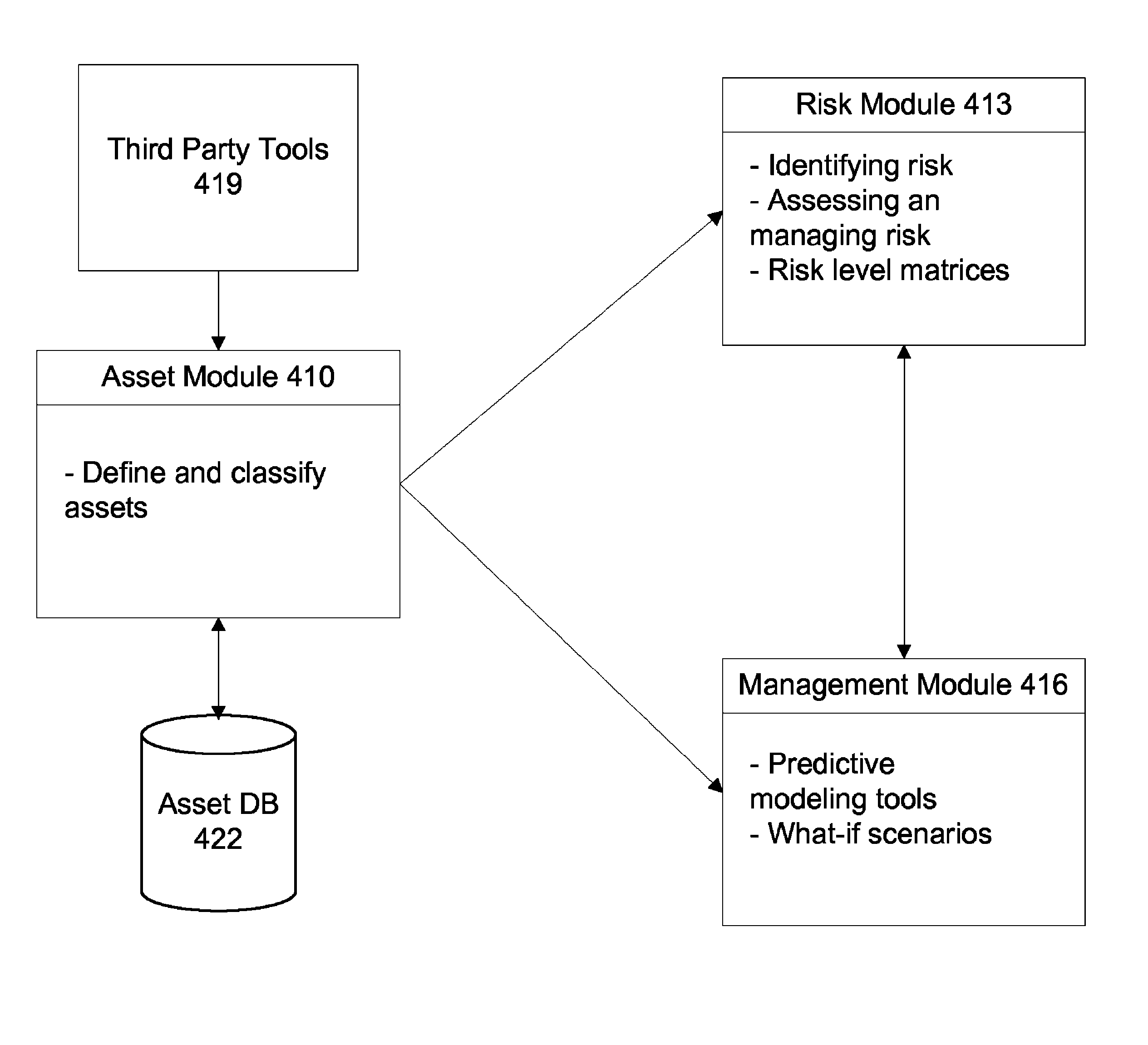
Enterprise information security management software for prediction modeling with interactive graphs
InactiveUS8516594B2Analysis can be performedLoses credibilityDrawing from basic elementsMemory loss protectionGraphicsSecurity measurement
Various baseline security measurements of assets are collected and calculated by the system. A user creates a what-if scenario by changing one or more baseline security measurements. The system generates interactive, animated graphs that compare the baseline security measurements against the what-if scenario.
Owner:ALLGRESS
ERP information management system for building material enterprise
InactiveCN106096906AVarious and accurate screening conditionsEasy to manageOffice automationManagement unitInformation security management
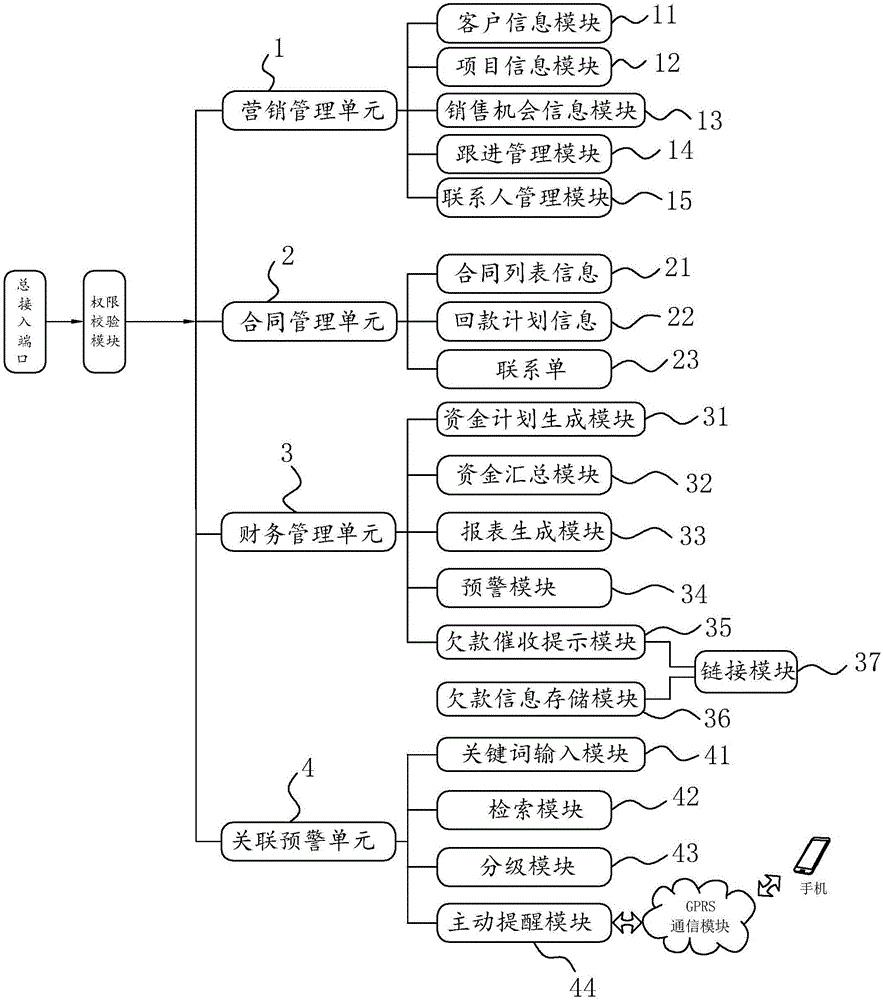
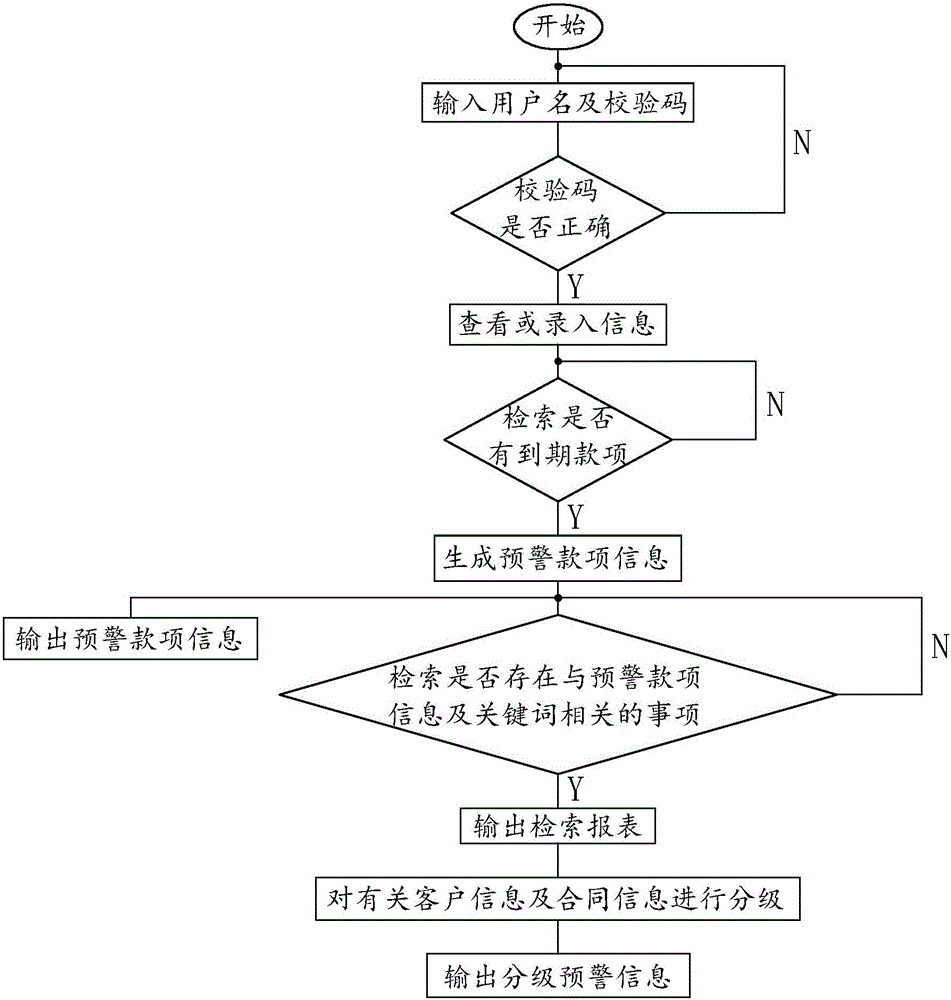
The invention discloses an ERP (Enterprise Resource Planning) information management system for a building material enterprise. The system comprises a marketing management unit, a contract management unit, a finance management unit and an associated early warning unit, wherein the associated early warning unit comprises a keyword input module that comprises a keyword input interface, a retrieval module that retrieves the marketing management unit, the contract management unit and the finance management unit according to a keyword or early warning money information, screens out information associated with the early warning money information and outputs a retrieval report, and a grading module that outputs graded early warning information according to a degree of correlation between the retrieval report and the early warning money information. According to the system, the associated early warning unit is arranged, and the system automatically retrieves all information related to a client and other clients associated with the client when one client in the system breaks a contract, so that an enterprise manager can know and understand the default risk possibly existent in other links or the clients more clearly and the bad debt risk of enterprise fund is lowered.
Owner:杭州与溪科技发展有限公司
Classified management method applied to security baseline software
InactiveCN106055984AImprove securityImprove efficiencyPlatform integrity maintainanceNODALInformation security management
The invention provides a classified management method applied to security baseline software, pertaining to the technical field of host security. The method comprises following respects including nodal point management, strategy management, knowledge base management, resource management, user management, log forms, alarm management and a security center. The classified management method applied to security baseline software has following beneficial effects: the method can be applied to the government, and enterprises and institutions so that comprehensive security kernel configuration services for computer terminals can be provided to help government-related departments set up a system for standardizing terminal security management, thereby obtaining the best management effect. The security and operation and management efficiency of computer terminals can be significantly improved so that security of government information is ensured.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Intelligent network automobile information security risk assessment method and system
PendingCN112329022AFacilitate the automation processQuality assurancePlatform integrity maintainanceTransmissionIntelligent NetworkInformation security management
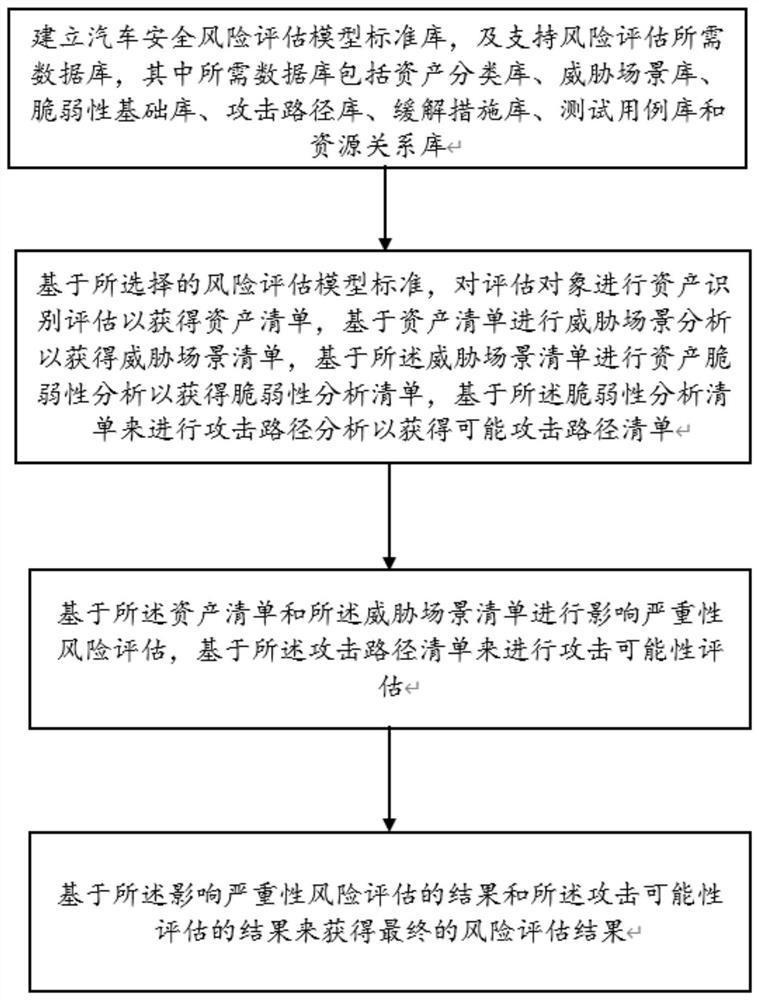
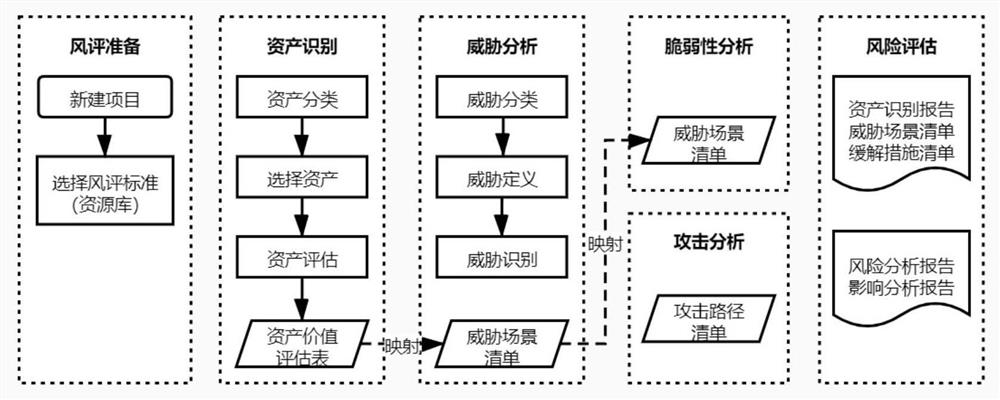
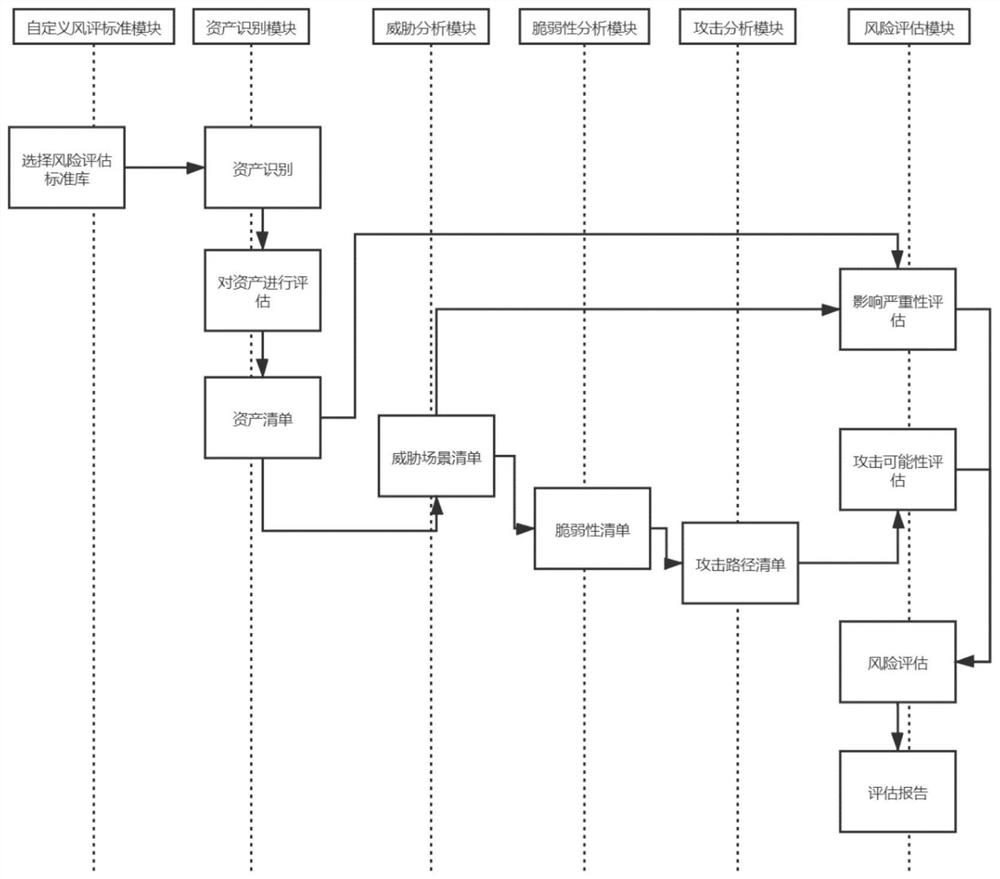
The invention discloses an intelligent network automobile information security risk automatic evaluation method and system. The method comprises steps of sequentially carrying out the risk evaluationaccording to steps, asset recognition, threat analysis, vulnerability analysis and attack path analysis after an evaluation object is selected; after preliminary risk assessment, a threat severity andinfluence severity analysis report being generated, the threat severity of an assessment object being subjected to grade assessment, and the influence caused by the threat severity being assessed; then, risk disposal and mitigation measures being implemented, and threats and influences brought by the threats of the evaluation object being reduced; and finally, generating a risk assessment report.The method is advantaged in that the range of the method covers automobile information safety management, including automobile information safety comprehensive management, product development periodinformation safety management and information safety management after product mass production, and information safety risk assessment automation of software and hardware related to network communication (including an automobile internal network) of an intelligent networked automobile in the automobile design, research, development and manufacturing process is achieved; and efficiency is improved.
Owner:浙江长三角车联网安全技术有限公司
Host security detection method and system based on central management
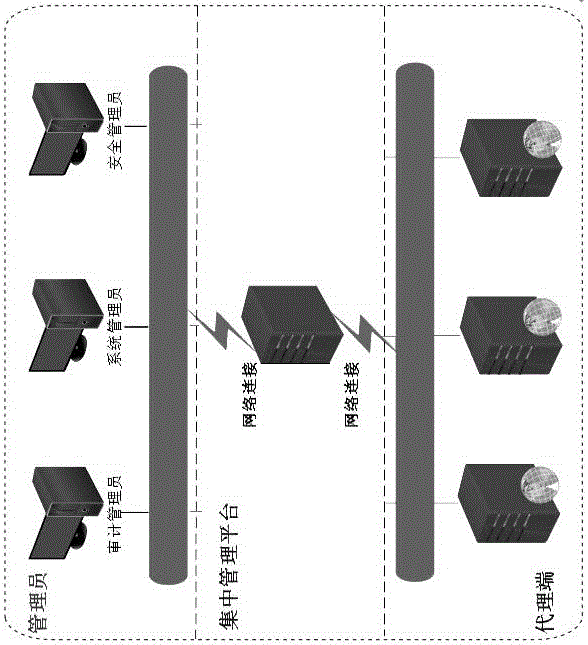
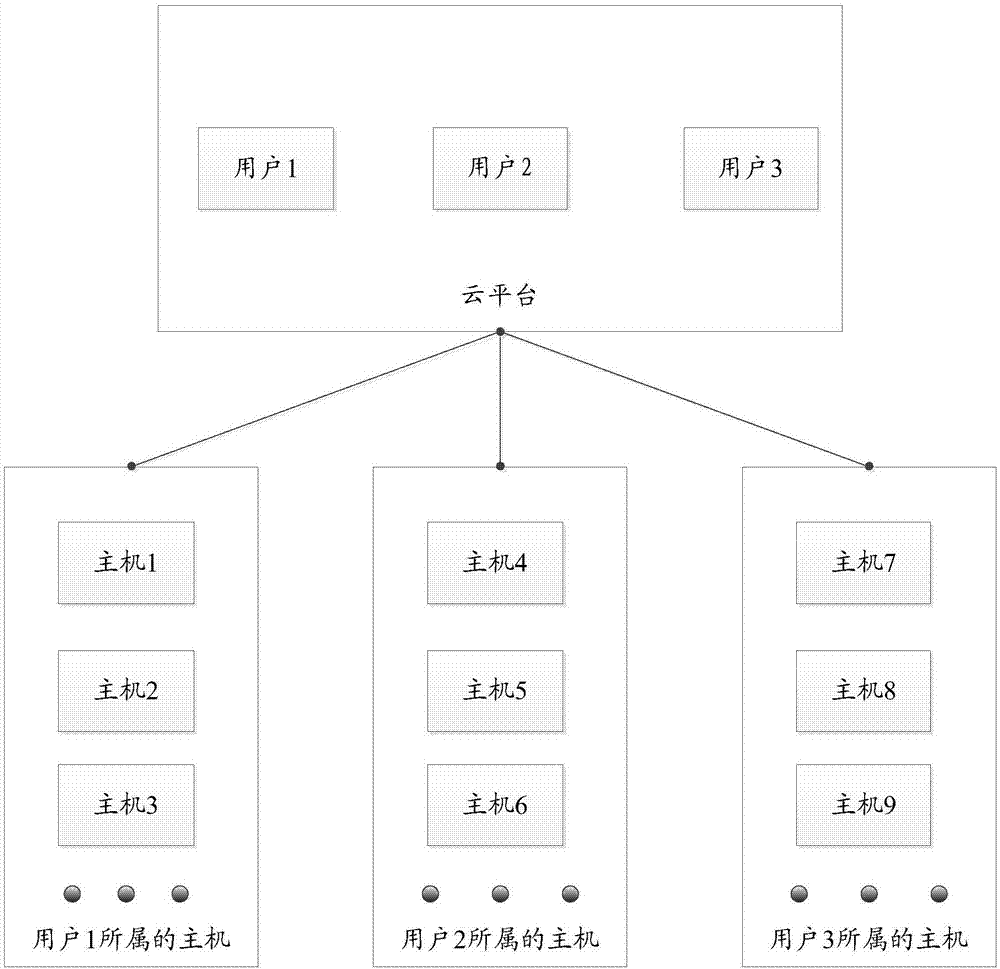
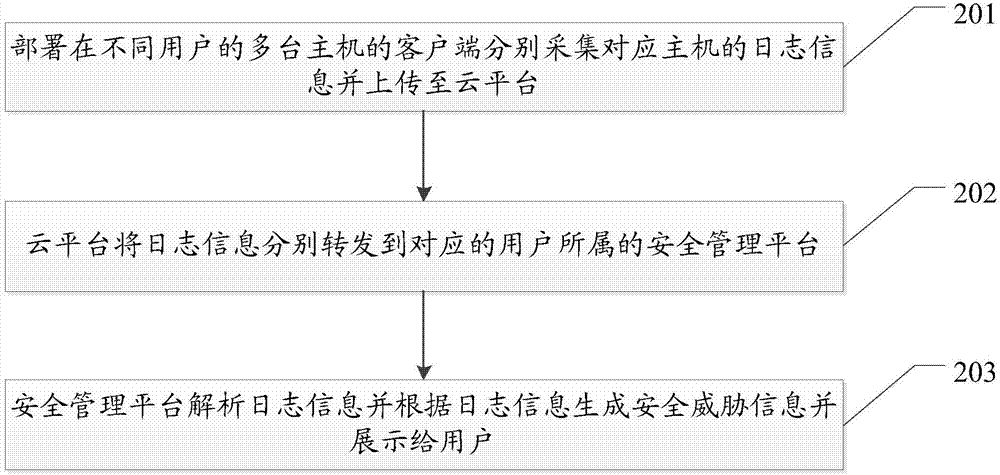
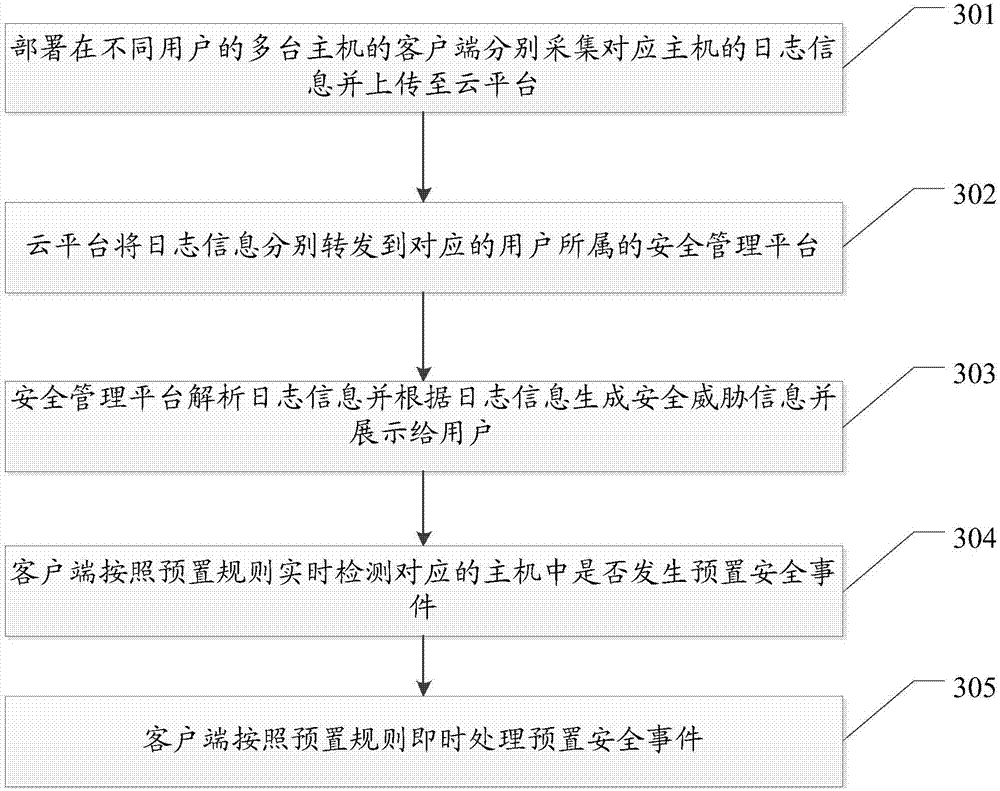
ActiveCN107295021AReduce resource overheadImprove Security Monitoring EfficiencyTransmissionInformation security managementCentralized management
The embodiment of the invention provides a host security detection method and system based on central management, and the method and system are used for improving the efficiency of host security detection based on central management. The method comprises the steps: clients in multiple hosts of different users separately acquire log information of corresponding hosts and upload to a cloud platform, the cloud platform is arranged in public network, and one client is arranged on each to-be-security detected host; the cloud platform separately forwards the log information security management platforms which users corresponding to the log information belong, and the cloud platform comprises at least one security management platform; and the security management platforms separately analyze the log information and generate security threat information according to the log information and display to the users.
Owner:SANGFOR TECH INC
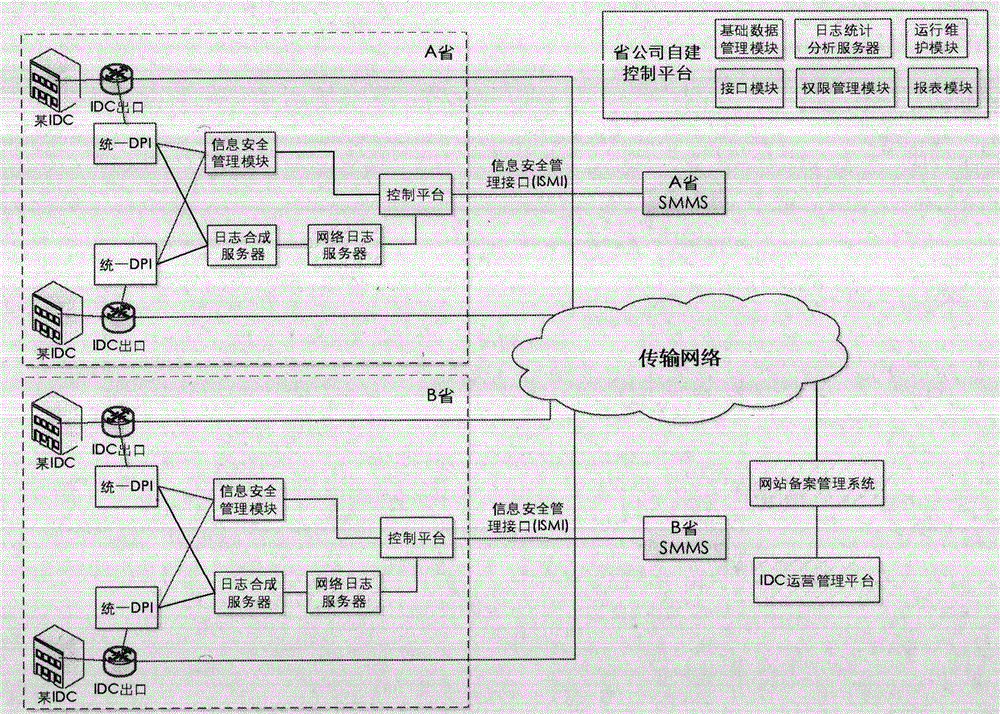
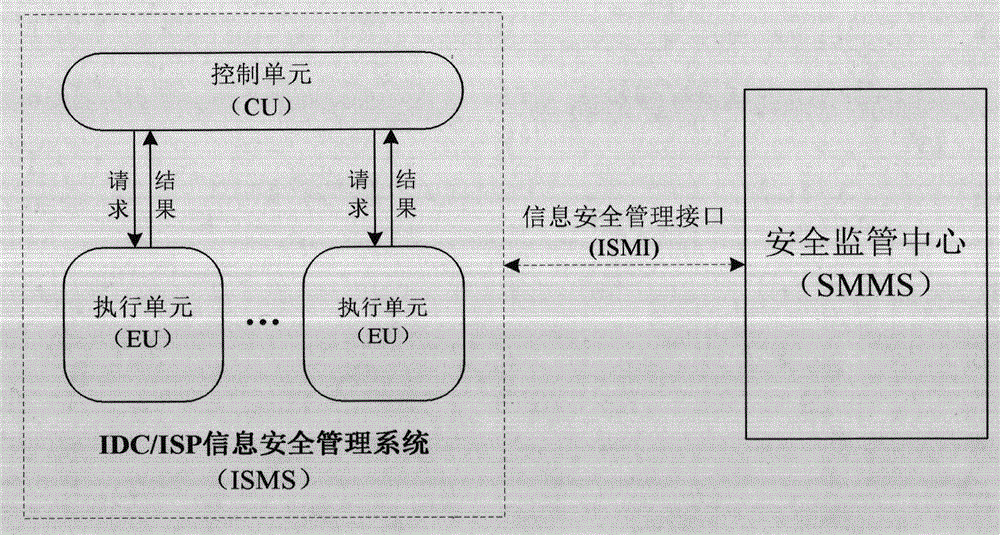
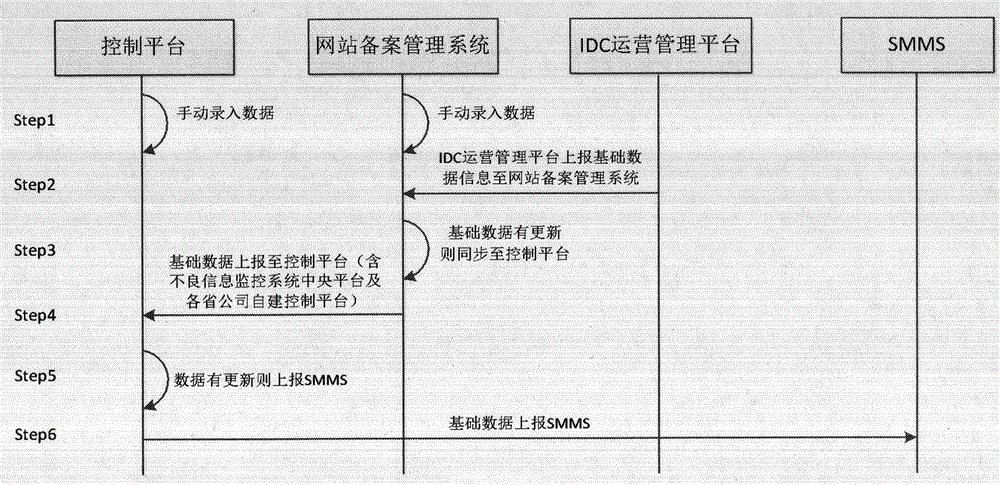
Internet data center/Internet service provider (IDC/ISP) information security management system and information management method thereof
InactiveCN105490831AA comprehensive understanding of social conditions and public opinionData switching networksSpecial data processing applicationsWeb siteSafety management systems
The invention relates to information security management, in particular to an Internet data center / Internet service provider (IDC / ISP) information security management system and an information management method thereof for performing basic data management, access log management and information security management on an IDC / ISP. The IDC / ISP information security management system consists of a control platform, a website record management system, an IDC operation management platform, a provincial end execution system and a uniform DPI equipment system which are in butt joint.
Owner:北京东方通网信科技有限公司
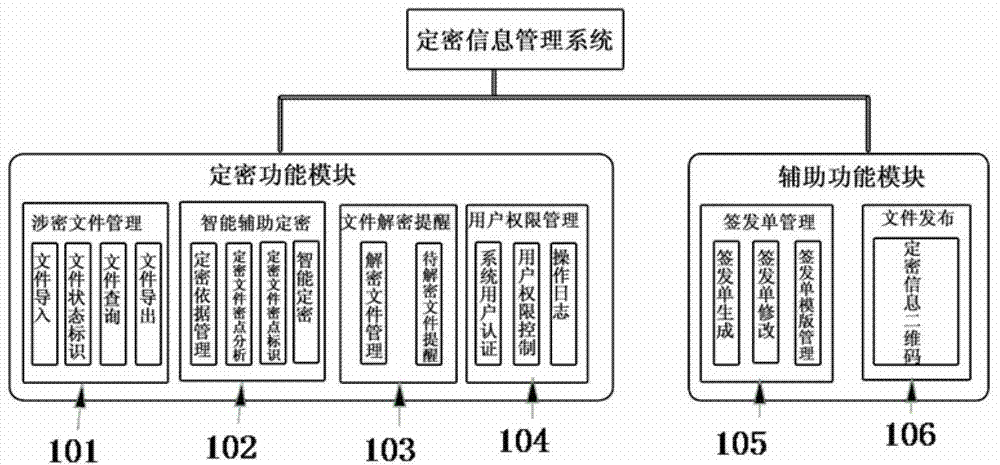
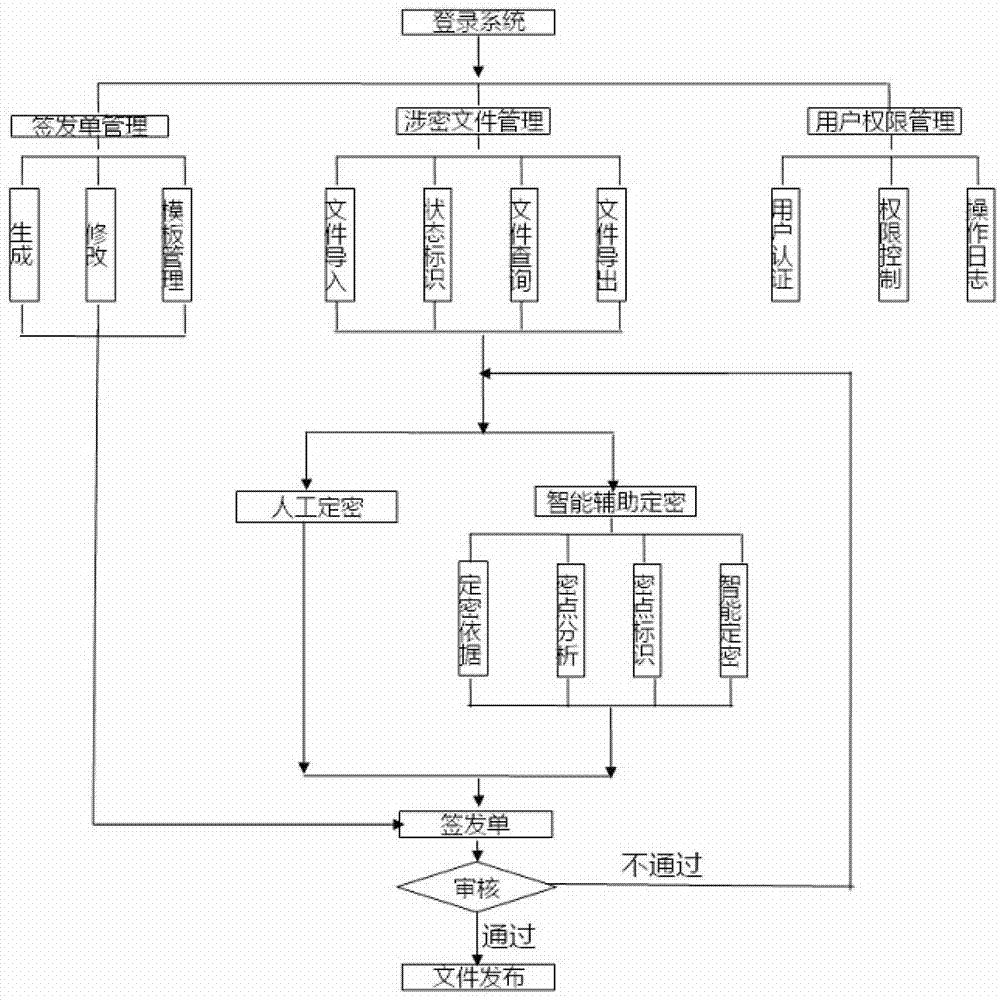
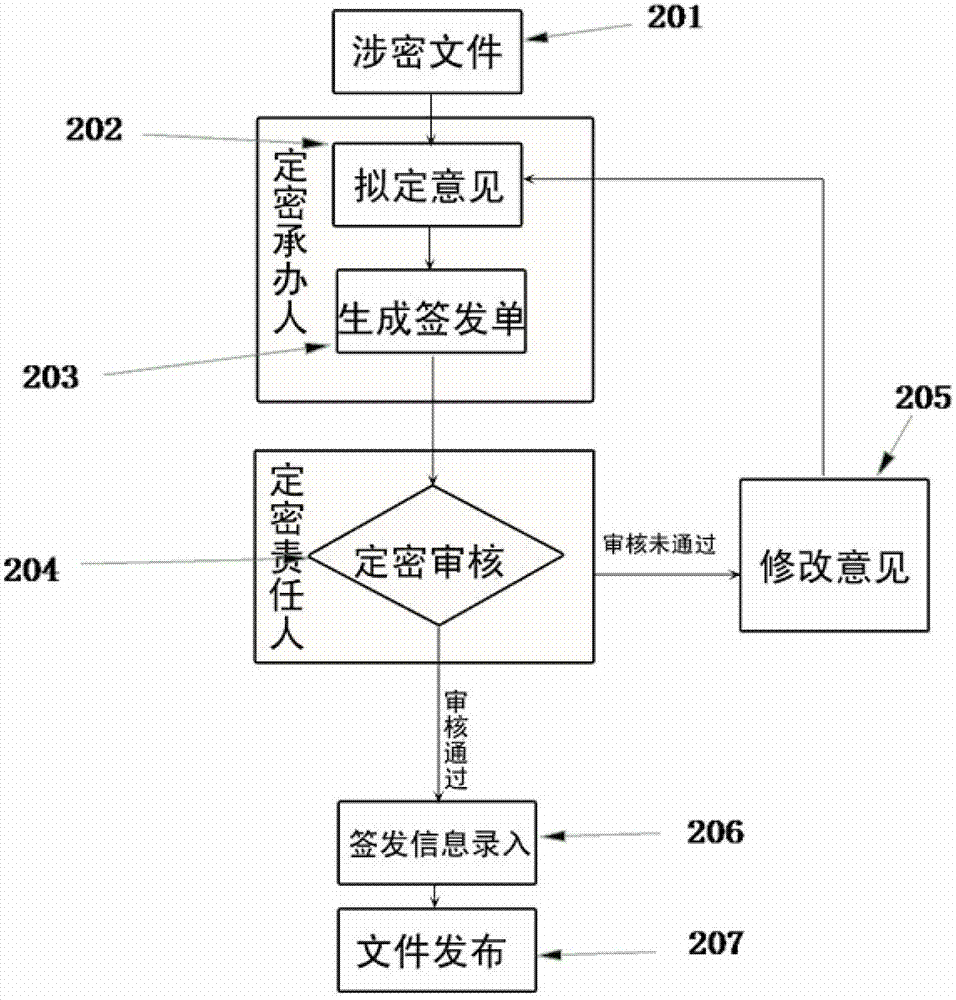
Secret-level setting information management system and secret-level setting information management method
ActiveCN103093154AImprove the standardization of confidentialityImprove confidentiality management levelDigital data protectionDigital data authenticationLog managementComputer module
The invention discloses a secret-level setting information management system and a secret-level setting information management method. The secret-level setting information management system comprises a classified document management module (101), an intelligent auxiliary secret-level setting module (102), a document decryption reminding module (103), a user authorization management module (104), a signing and issuing bill management module (105) and a document issuing module (106), wherein the classified document management module (101) is used for uniformly storing and managing electronic edition classified documents of the secret-level setting information management system, the intelligent auxiliary secret-level setting module (102) is used for conducting auxiliary and secret-level setting management for documents to be classified, the document decryption reminding module (103) is used for conducting automatic reminding decryption, decryption deadline changing and management of decryption documents for the decryption documents according to the decryption deadline, the user authorization management module (104) is used for conducting authority management and operation log management for a system user, the signing and issuing bill management module (105) is used for uniformly storing and managing a document signing and issuing bill template in a 'what you see is what you get' mode and generating a document signing and issuing bill and the document issuing module (106) is used for providing an external extending program interface for the secret-level setting information management system. The secret-level setting information management system and the secret-level setting information management method standardize secret-level setting procedures and improve secret-level setting standardability of a secret-level setting undertaker.
Owner:SHANDONG ZHONGFU INFORMATION IND
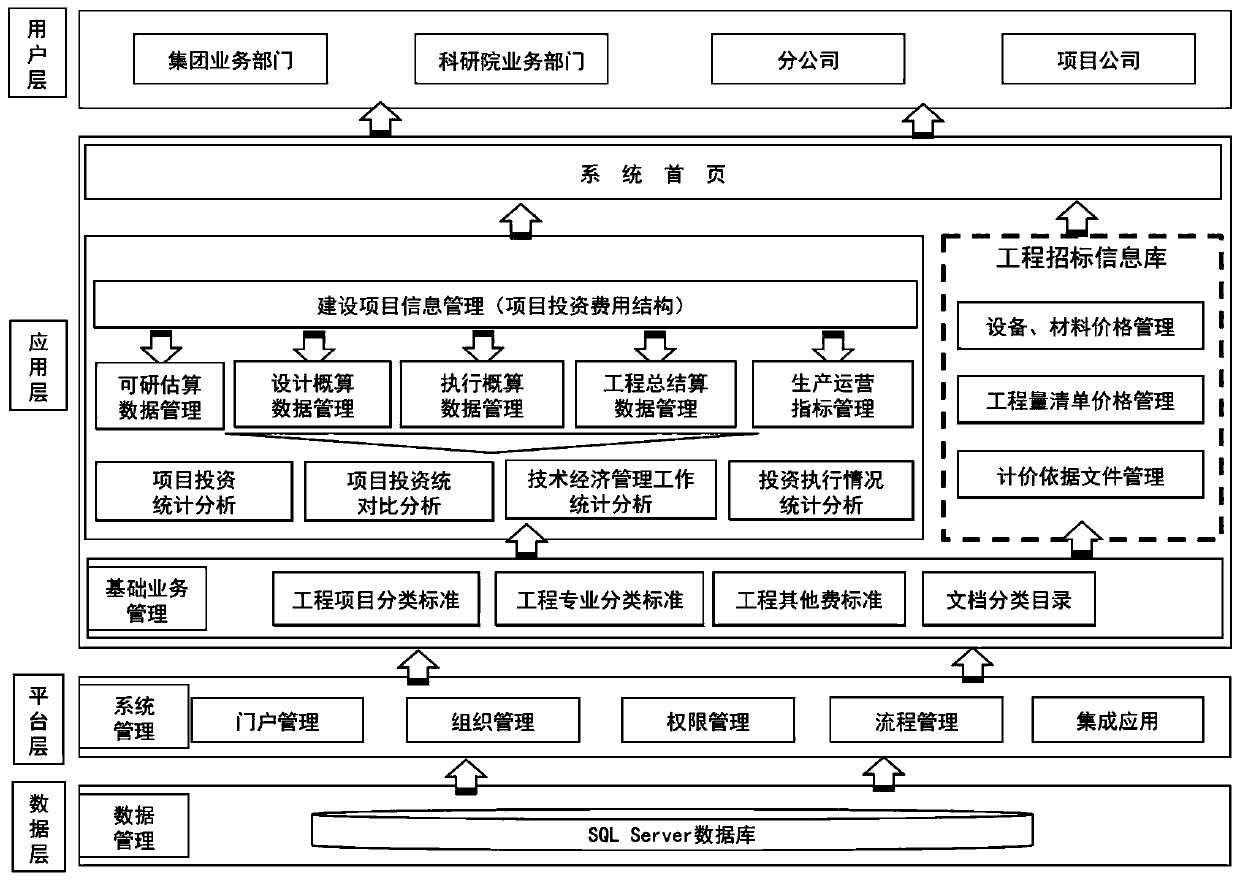
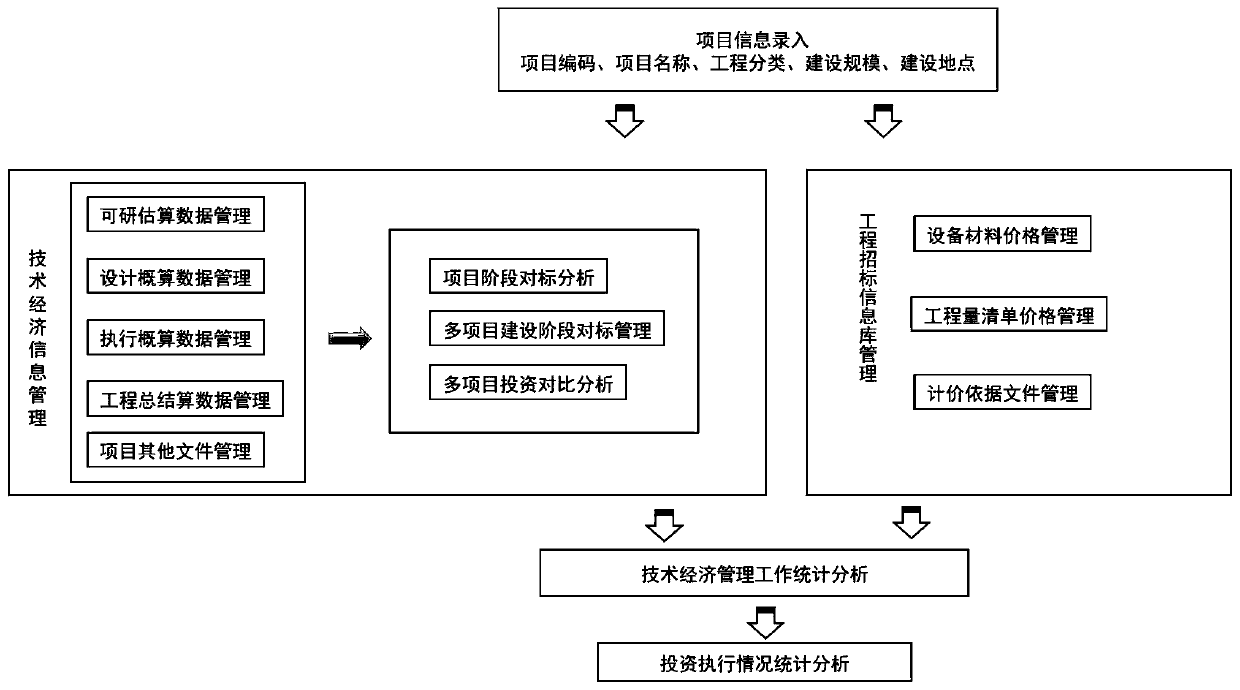
An electric power engineering project technical and economic information system
The invention relates to a power generation project technical and economic information system, and belongs to the technical field of informatization. The system comprises construction project basic information, technical and economic information management, a project bidding information base and system management. The system is composed of a user layer, an application layer, a platform layer and adata layer, the user layer can meet applications of a management unit, a service unit and a use unit, the application layer achieves basic service management, and the platform layer meets basic function setting of system application. The data layer provides management for data storage and setting of the system; System mainly comprises data entry, Data processing, Data analysis, Data cloud storage, data display and information security management are carried out, investment data storage and application of all stages of the whole life cycle of a project are achieved through program setting, data capture and computational programming, benchmarking analysis of technical and economic information of all stages of a single project and multiple projects is achieved, and references are provided for project investment decision making, optimization design, project implementation and production operation.
Owner:中国大唐集团科学技术研究总院有限公司
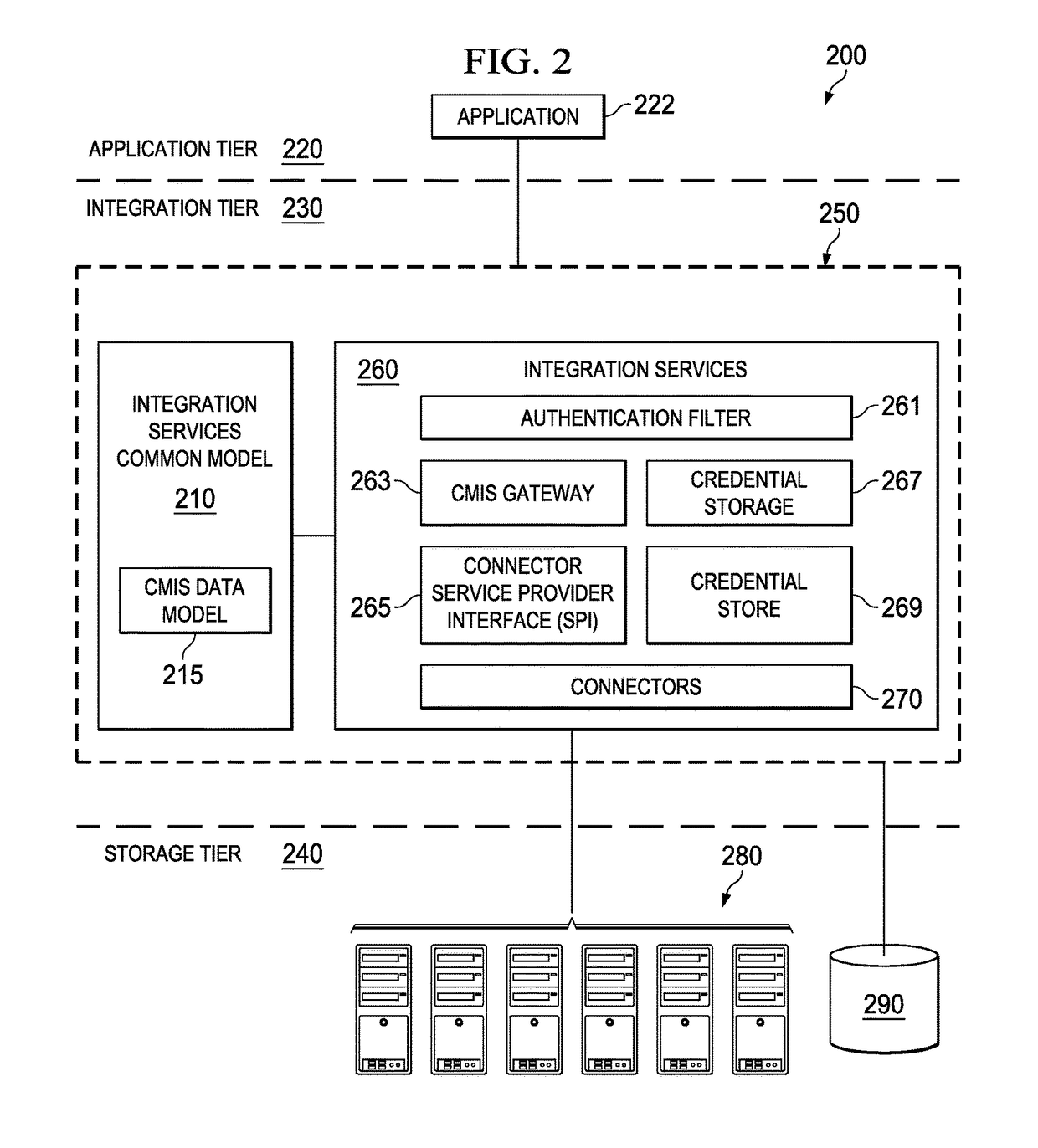
Systems, methods and computer program products for information management across disparate information systems
ActiveUS9898537B2Extend control and influenceEasy to controlDatabase distribution/replicationTransmissionInformation security managementApplication software
An information integration system may include a set of integration services embodied on one or more server machines in a computing environment. The set of integration services may include connectors communicatively connected to disparate information systems. The connectors are configured for integrating data utilizing a common model comprising a content management interoperability services data model, common property definitions, and a common security model particularly defined for use by the set of integration services. Responsive to a user query to search disparate information systems or a subset thereof, an application may communicate metadata of interest contained in the user query to a search engine which locates, via a unified index, requested data from the disparate information systems or a subset thereof. The search engine returns search results referencing the requested data to the application which interprets the search results and displays a visualization thereof on a client device.
Owner:OPEN TEXT SA ULC
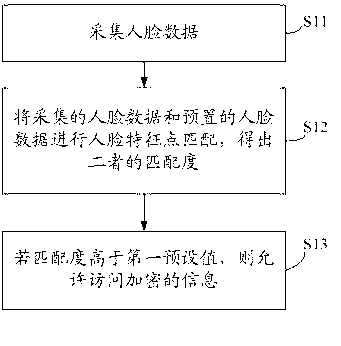
Information security management method and mobile terminal
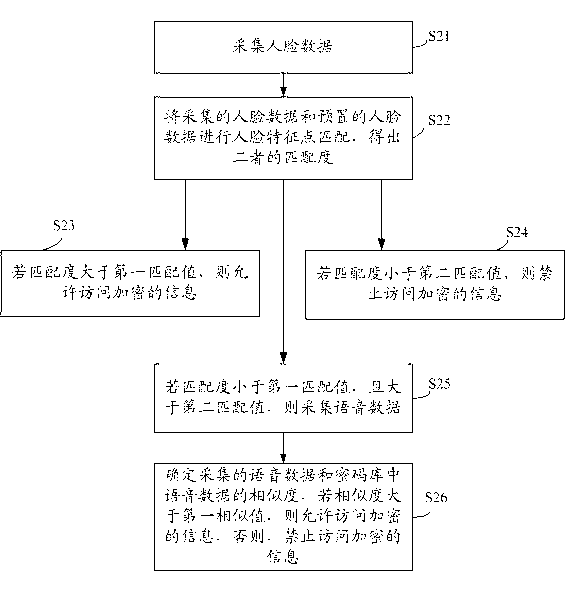
InactiveCN103164645ASafe and effective protectionDon't worry about inconvenienceCharacter and pattern recognitionDigital data authenticationPasswordInformation security management
The invention discloses an information security management method. The information security management method comprises the following steps: human face data are collected; feature point information in the human face data is extracted, the feature point information is matched with feature point information in human face data in a password bank, and matching degree of the collected human face data and the human face data in the password bank is determined; and if the matching degree is larger than a first matching value, encrypted information is allowed to be visited. The invention further discloses a mobile terminal. By adopting the information security management method and the mobile terminal, information security on the mobile terminal can be protected effectively and safely.
Owner:KONKA GROUP
IMA processor system information security management method
ActiveCN105530092AEffectively manage usage rightsControl traffic flowMultiple keys/algorithms usageDigital data protectionInformation transmissionInformation access
The invention discloses an IMA processor system information security management method, comprising following steps: 1), information security management total method: 1.1), dividing IMA processor system information into four security levels of top secret, confidential, secret and ordinary information, managing the information; setting the security level of the top secret information to be highest, setting the security level of the ordinary information to be lowest; 1.2), storing the secret and ordinary information in a processor system, forbidding storing the top secret and confidential information in the processor system, only temporarily loading the top secret and confidential information through a data loader; 1.3), identifying and encrypting the top secret, confidential and secret information according to the levels; 1.4), carrying out information access authority management and control according to corresponding security levels. According to the IMA processor system information security management method provided by the invention, the information using authority is effectively managed; the information transmission flow direction is controlled; and the information security storage access problem of the IMA processor system resulted from high resource sharing and high data fusion is solved.
Owner:XIAN AVIATION COMPUTING TECH RES INST OF AVIATION IND CORP OF CHINA
Information management system and method based on personal credit data
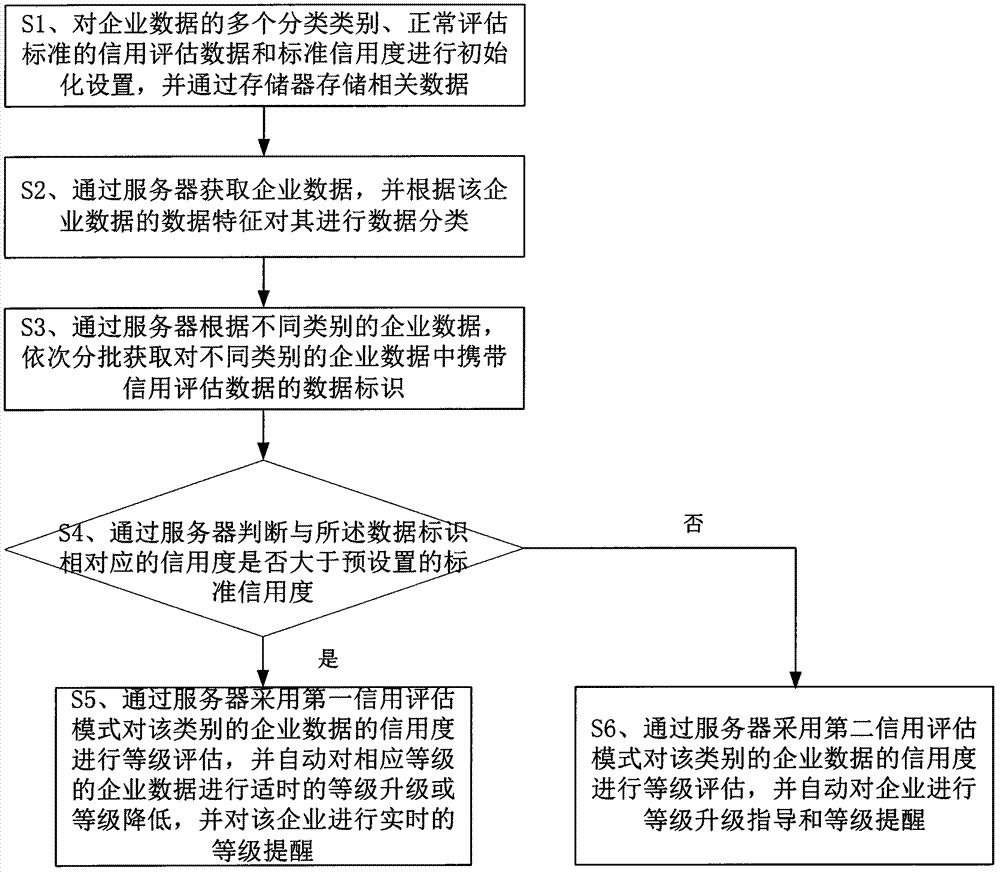
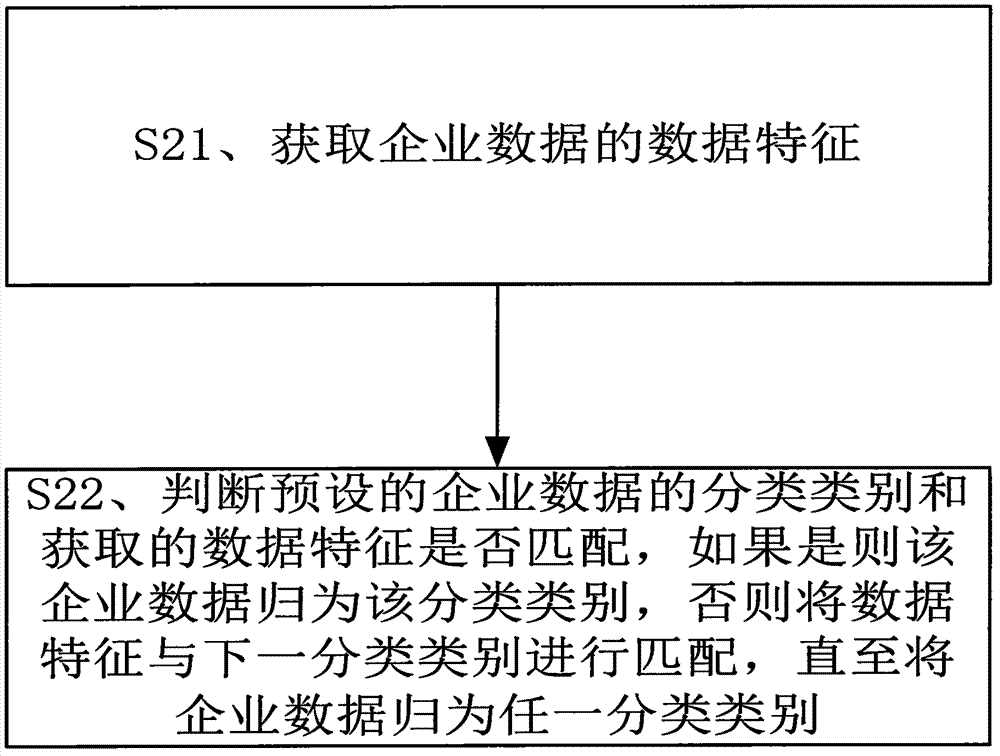
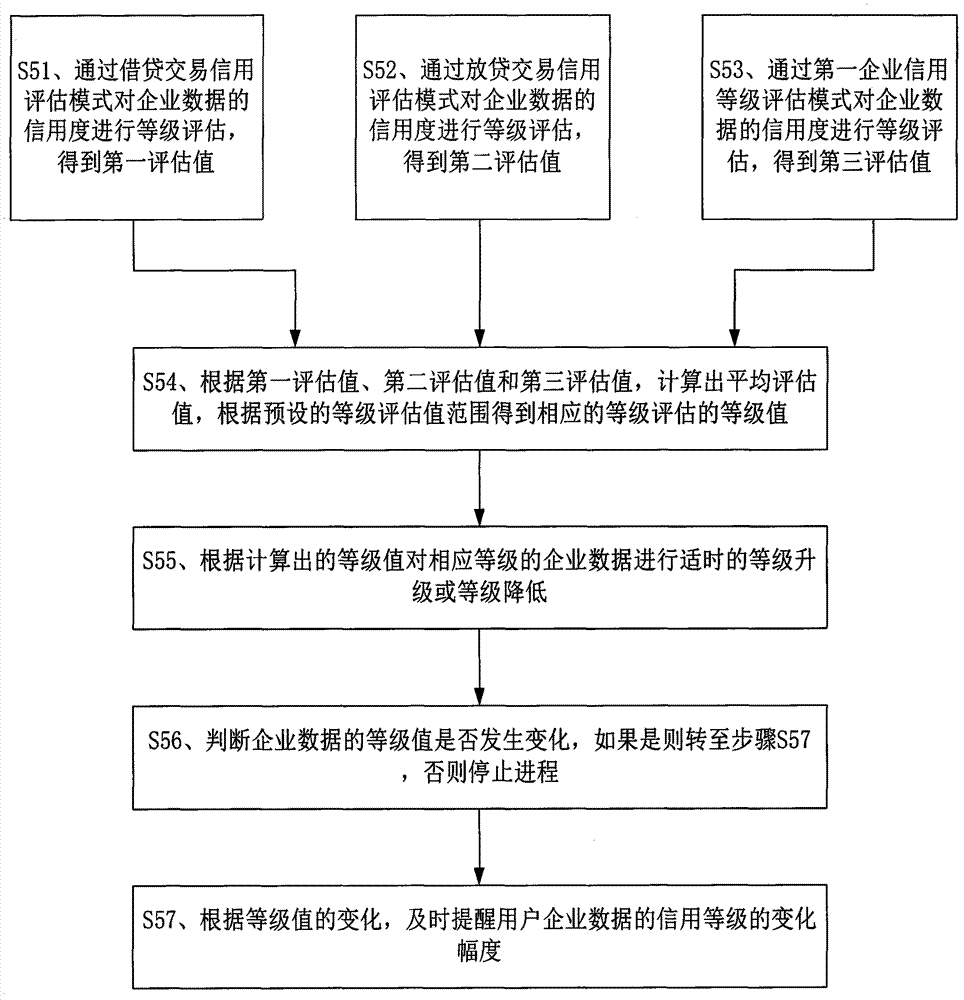
InactiveCN104850939ATimely reminder of changesSolve the problem of large amount of calculation and difficult statisticsResourcesInformation security managementAssessment data
The invention discloses an information management system and an information management method based on personal credit data. The information management system comprises a server and a storage. The information management method comprises the steps of: presetting credit assessment data and standard credit degree of normal assessment standards of multiple classification types about enterprise data, and storing relevant data through the storage; acquiring the enterprise data through the server, and subjecting the enterprise data to data classification according to data features of the enterprise data; sequentially acquiring data identities carrying credit assessment data in enterprise data of different types in batches according to the enterprise data of different types through the server; and judging whether the credit degree corresponding to the data identities is greater than the preset standard credit degree through the server. The personal information data integration system and method have the beneficial effects of solving the problems that the big data is large in calculation complexity and not easy to count, reducing error rate, realizing real-time assessment of credit rating and real-time prompting of credit rating variation based on the enterprise data, and bringing convenience for enterprises to adjust their business model timely.
Owner:XINERLAING DATA TECH SHANGHAI CO LTD
Method and device for information security management and storage medium
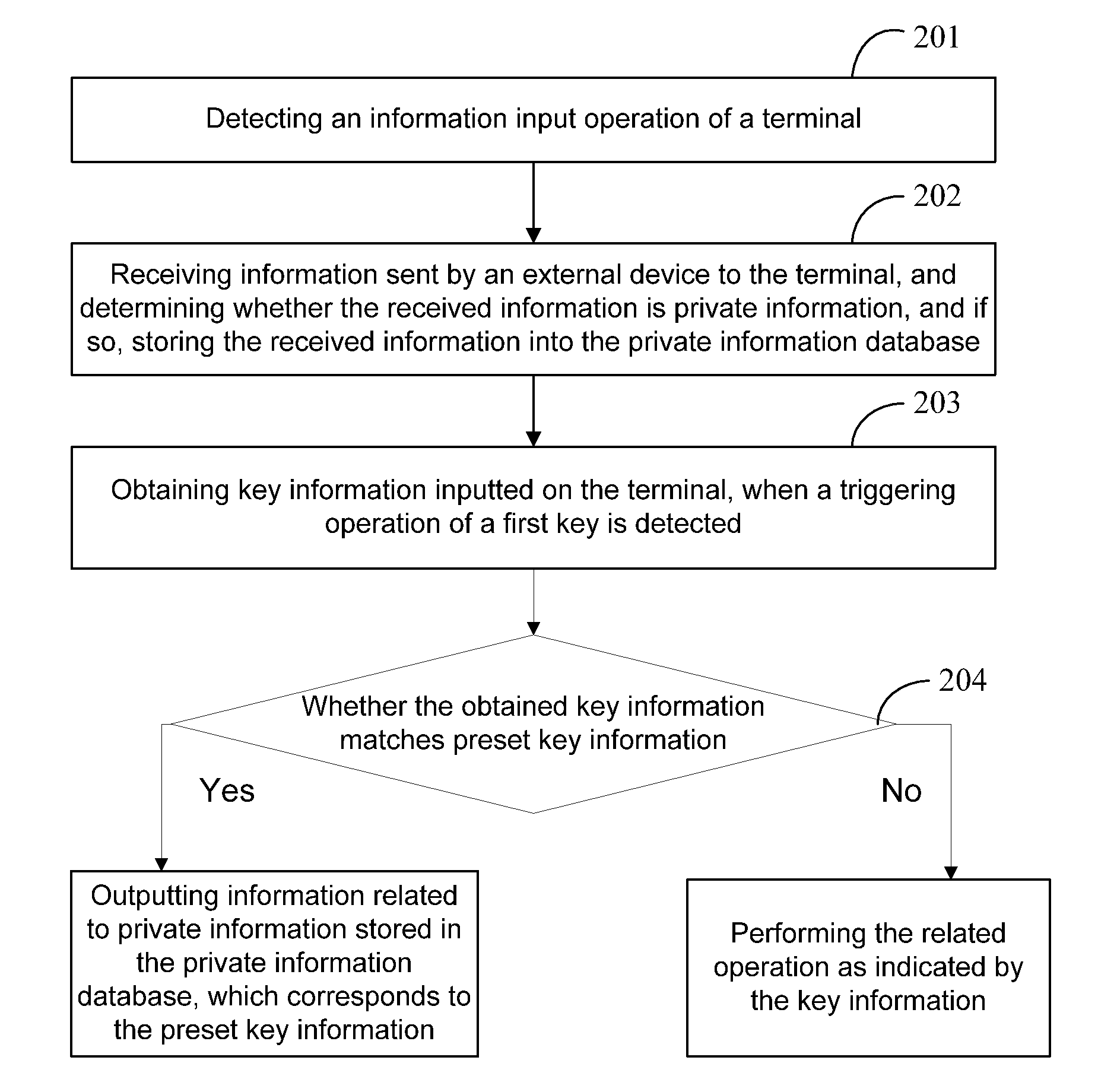
ActiveUS20140324912A1Improve information securityEnhanced informationDigital data processing detailsDigital data protectionUser needsPassword
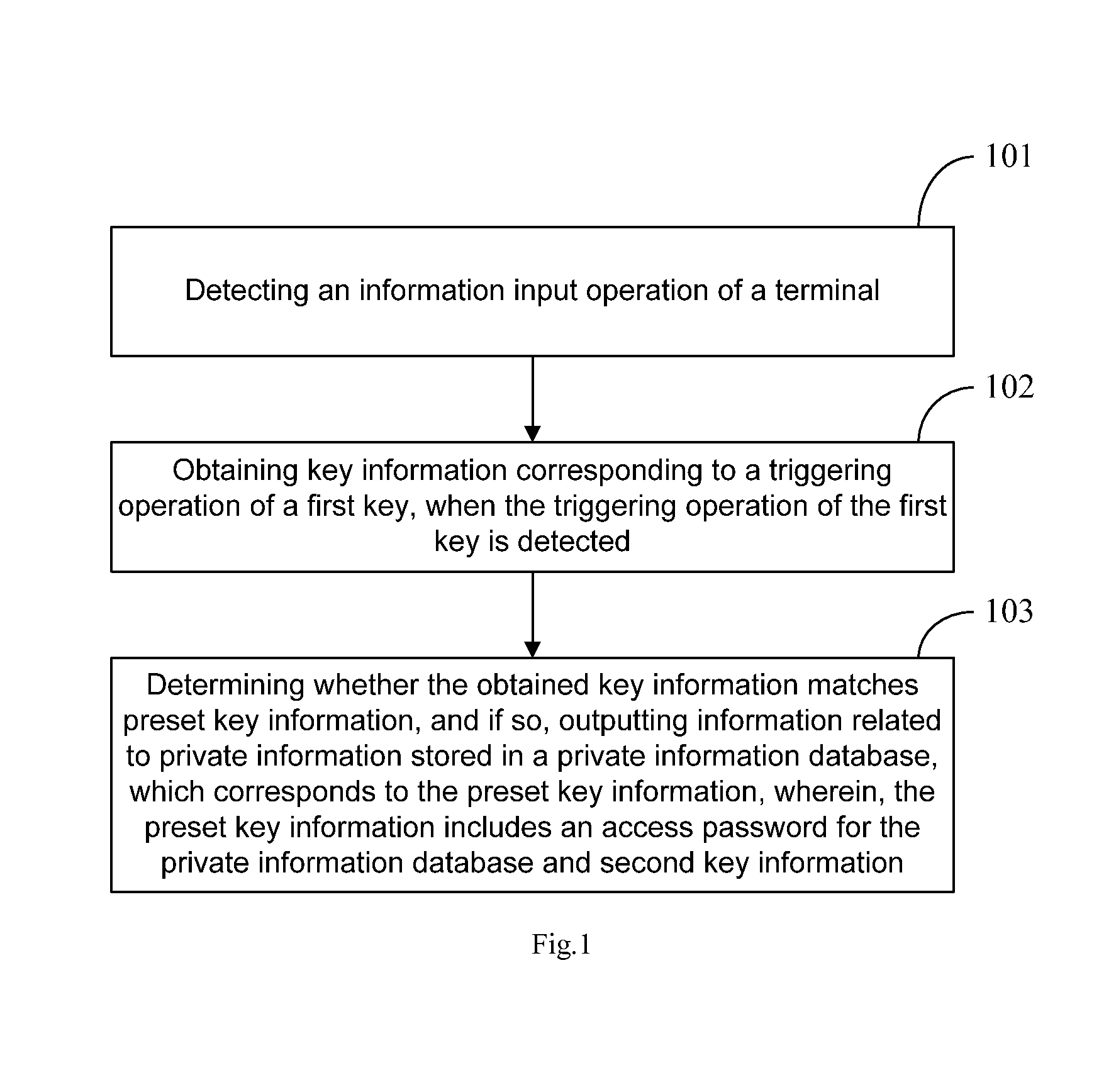
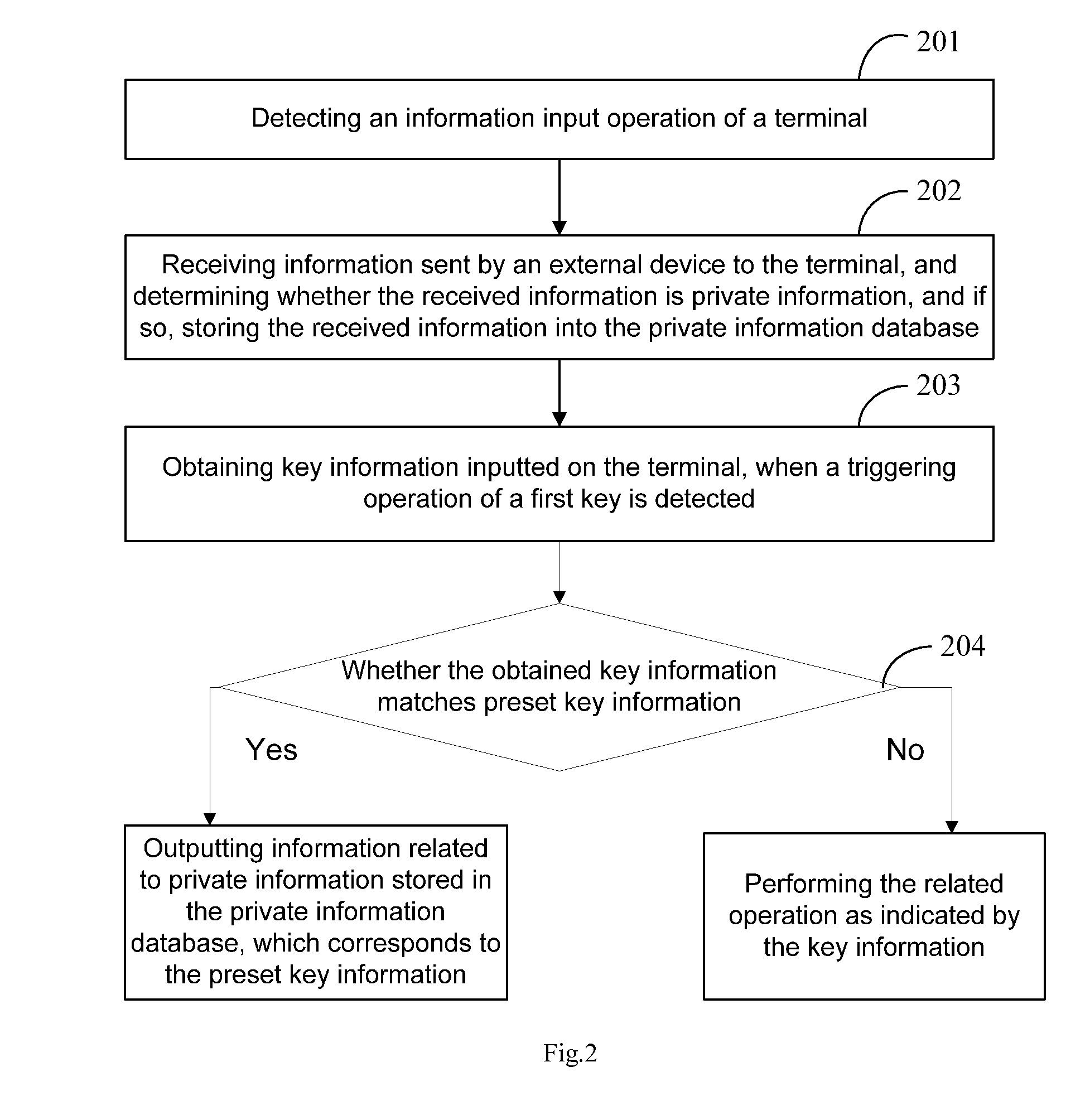
The invention discloses a method and a device for information security management, and a storage medium, in the field of information security technologies. The method comprises: detecting an information input operation of a terminal; obtaining key information corresponding to a triggering operation of a first key, when the triggering operation of the first key is detected; determining whether the obtained key information matches preset key information, and if so, outputting information related to private information stored in a private information database, which corresponds to the preset key information, wherein, the preset key information includes an access password for the private information database and second key information. In the invention, a user needs not access a private space to check private information; instead, the user only needs to input the preset key information to query the information related to the private information. Therefore, the security of the private information is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Security policy flow down system
ActiveUS20130167191A1Easy to analyzeMemory loss protectionError detection/correctionProgram planningSecurity compliance
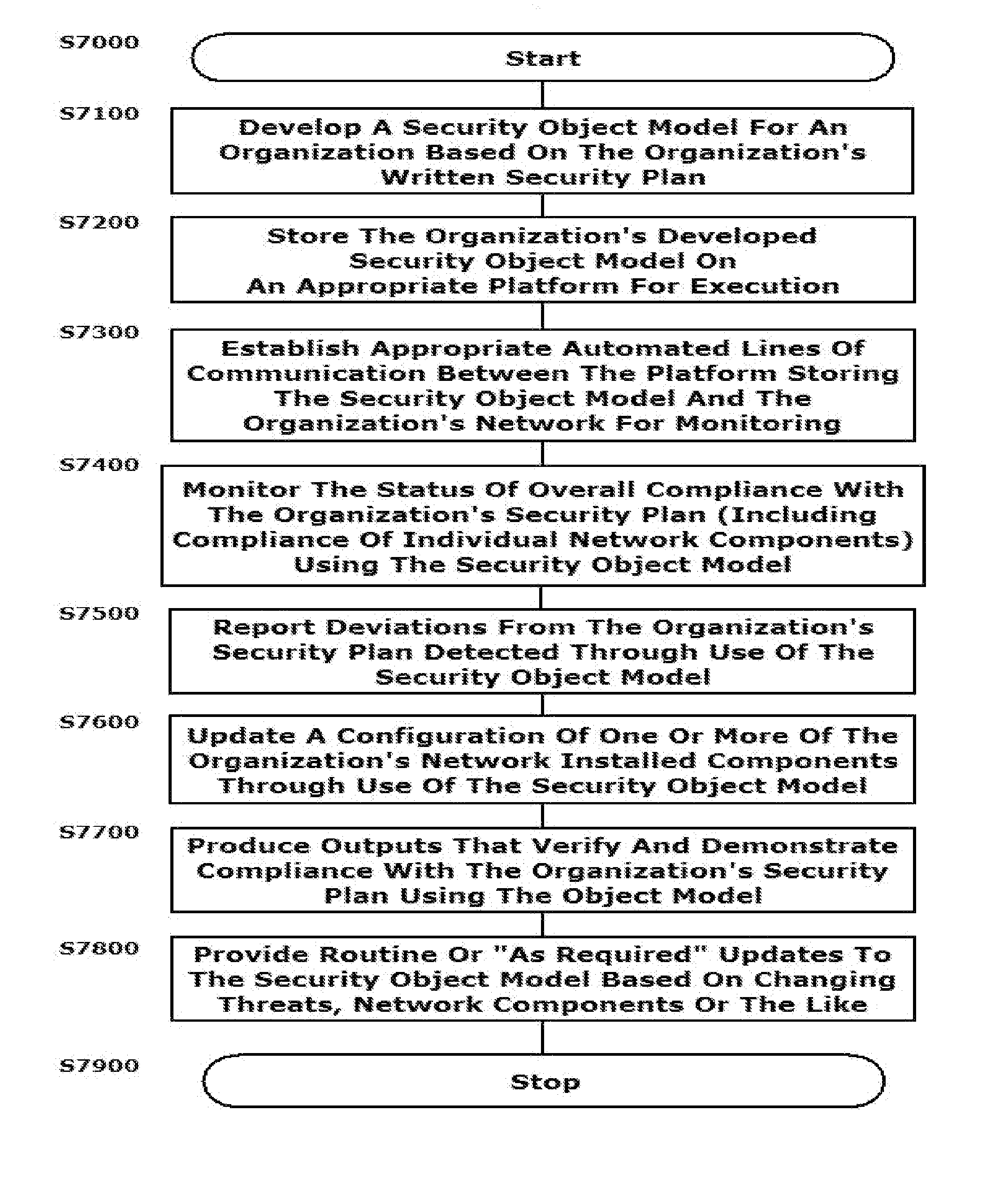
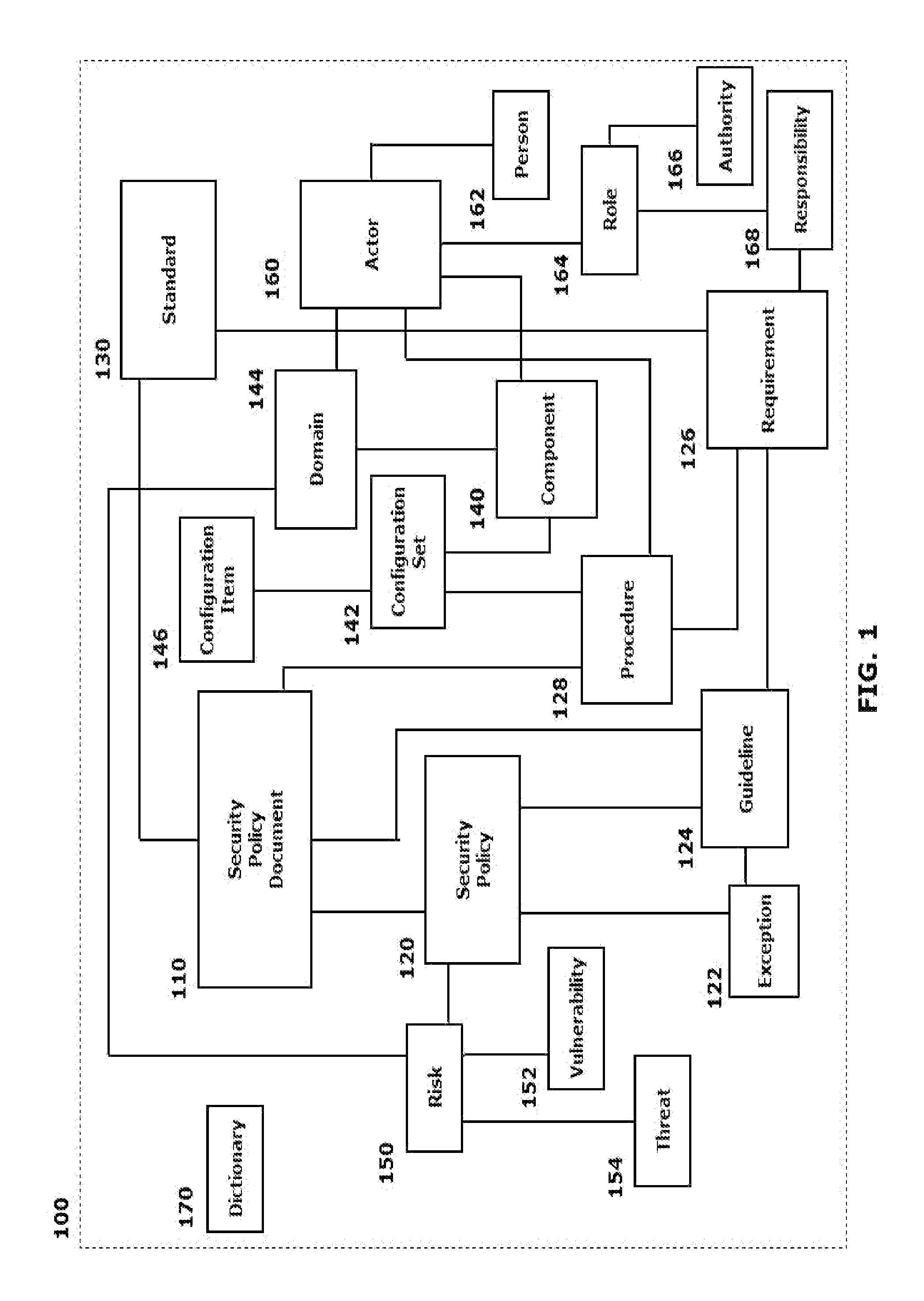
A system and method are provided that distill an organization's information security plan into a detailed and unambiguous security object model. The developed security object model provides a visualization of complex relationships between individual elements and levels that is usable to carry into effect the organization's information security plan. Configuration control and a verifiable level of security compliance are provided through implementation of the organization's information security plan by the developed security object model. The developed security object model is hosted on a computing platform in communication with at least the organization's network to provide information security plan compliance, configuration control and gap analysis in a usable form to the organization.
Owner:LOCKHEED MARTIN CORP
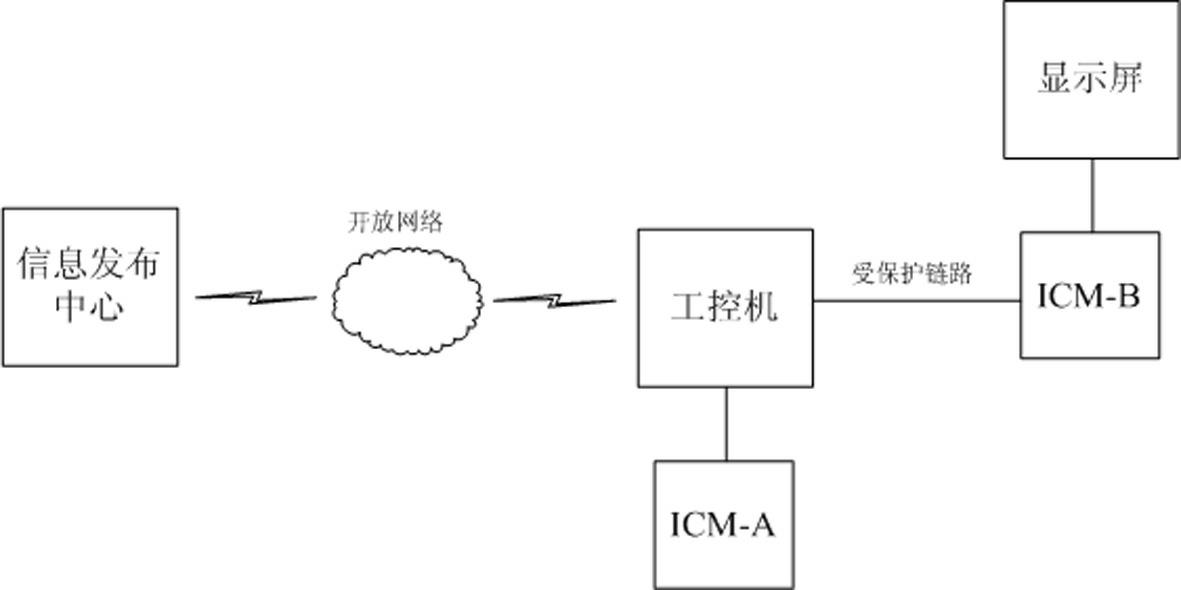
Equipment for traffic guidance information security management
InactiveCN102594564AValidity certificationSolve the contradiction between public opinion security needsPublic key for secure communicationUser identity/authority verificationData displayInformation security management
The invention discloses equipment for traffic guidance information security management. The equipment is characterized by comprising encryption authentication equipment ICM-A and decryption transmission equipment ICM-B; and the design for adopting modular development and universal cryptographic service API (Application Program Interface) is realized. The equipment for traffic guidance information security management, disclosed by the invention, has the advantages that 1) valid authentication is carried out on guidance information received by traffic information nodes; 2) data displayed by the information nodes is protected; and 3) an industrial personal computer is protected. At present, the information security management equipment is directly applied in a display management system of traffic management guidance information of the intelligent traffic field. The equipment solves the contradiction between the actual condition that the information is accessed into a traffic display screen by an open network and the public information opinion security requirement.
Owner:NO 709 RES INST OF CHINA SHIPBUILDING IND CORP
Mobile phone information security management method based on multiple authority modes
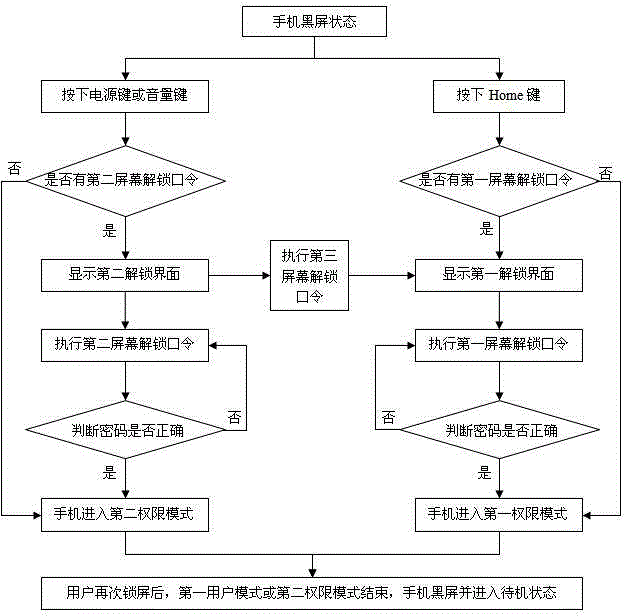
ActiveCN104902074AImprove information securityProtect personal privacySubstation equipmentUser inputPassword
The invention discloses a mobile phone information security management method based on multiple authority modes. In a blank-screen state of a mobile phone, a power or volume key is pressed to activate a mobile phone screen; if a user does not set a second screen unlocking password, the mobile phone directly enters the second authority mode; and if the user sets the second screen unlocking password, the mobile phone displays a second unlocking interface, the user inputs the second screen unlocking password, and then the mobile phone directly enters the second authority mode. In the blank-screen state of the mobile phone, a Home key is pressed to activate the mobile phone screen; if the user does not set a first screen unlocking password, the mobile phone directly enters a first user mode; and if the user sets the first unlocking password, a corresponding first unlocking interface is displayed, the user executes the preset first unlocking password, and the mobile phone enters the first user mode after the password is successfully matched. After the user locks the screen again, the first user mode or the second authority mode ends, the screen of the mobile phone is blank, and the mobile phone enters a standby state.
Owner:SHANGHAI GUAN AN INFORMATION TECH
Information security management method, terminal device, and computer readable storage medium
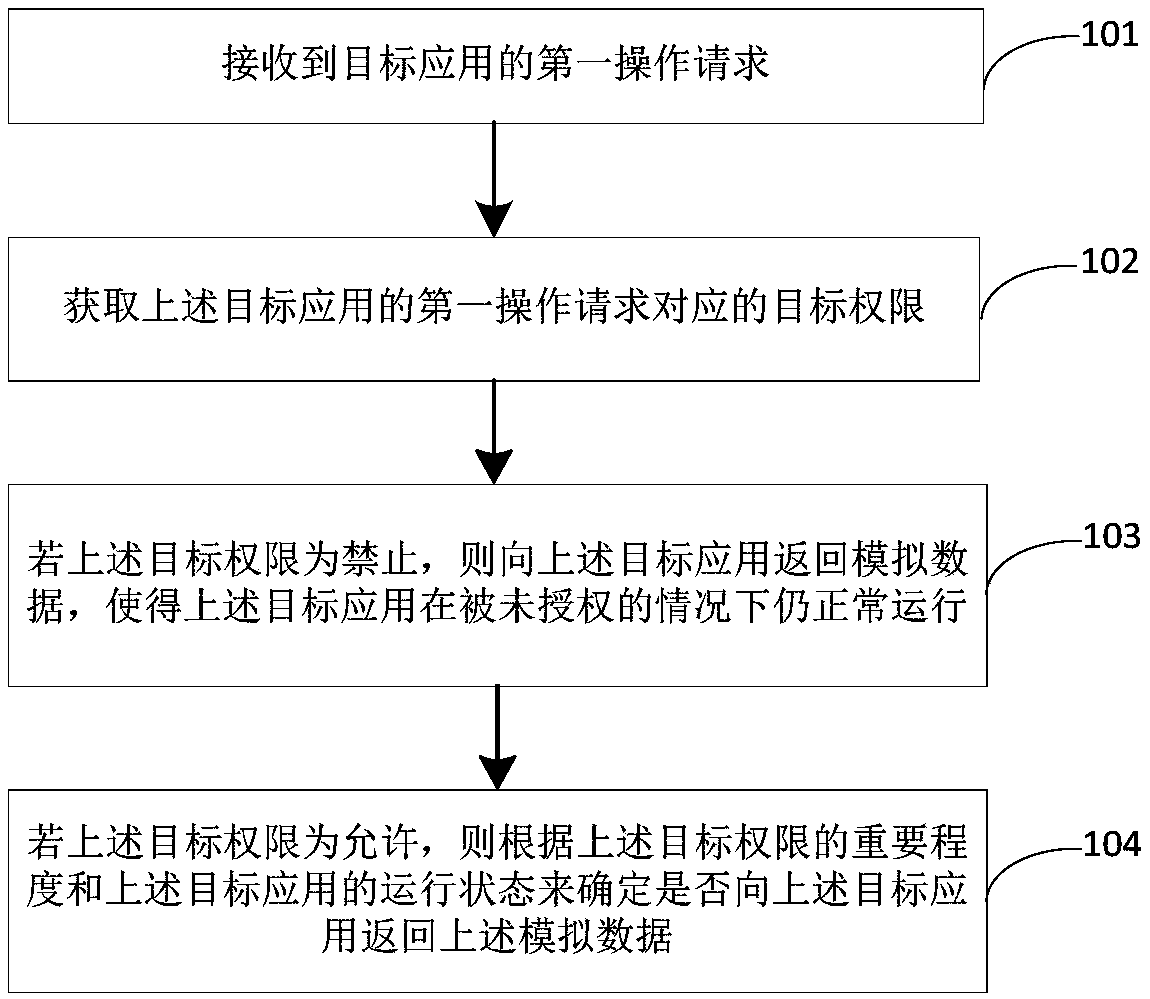
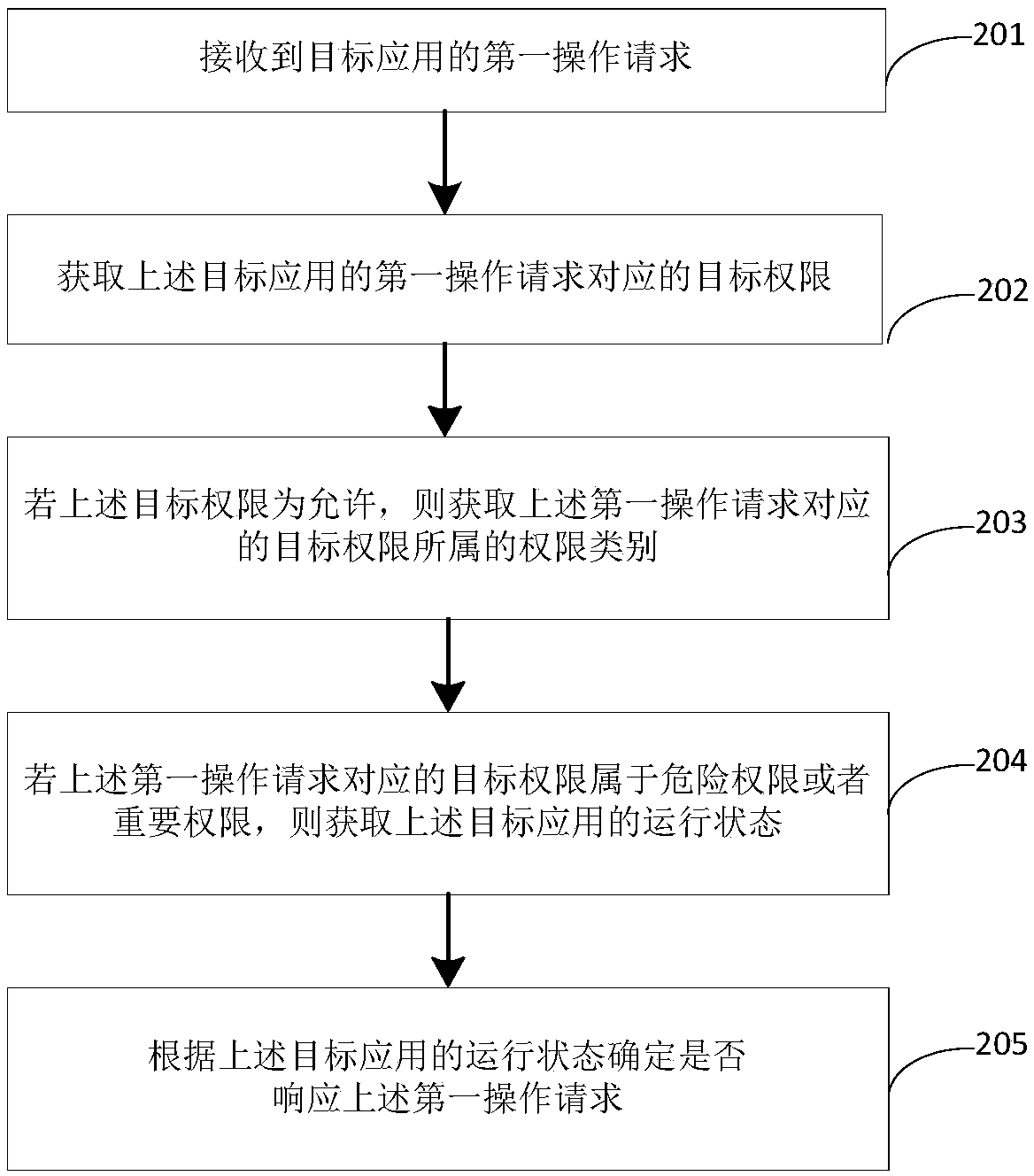
InactiveCN108932435AGuaranteed privacy and securityGuarantee property securityDigital data protectionInformation security managementTerminal equipment
Embodiments of the invention disclose an information security management method, a terminal device, and a computer readable storage medium. The method comprises: receiving a first operation request ofa target application; obtaining a target authority corresponding to the first operation request of the target application; if the target authority is forbidden, returning simulated data to the targetapplication, to make the target application still operate normally under an unauthorized condition; if the target authority is allowed, determining whether to return the simulated data to the targetapplication according to degree of importance of the target authority and operating states of the target application. Through sending the simulated data to the application, the target application canbe ensured to operate normally under an unauthorized condition.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method and system for internal security management and control of enterprise data
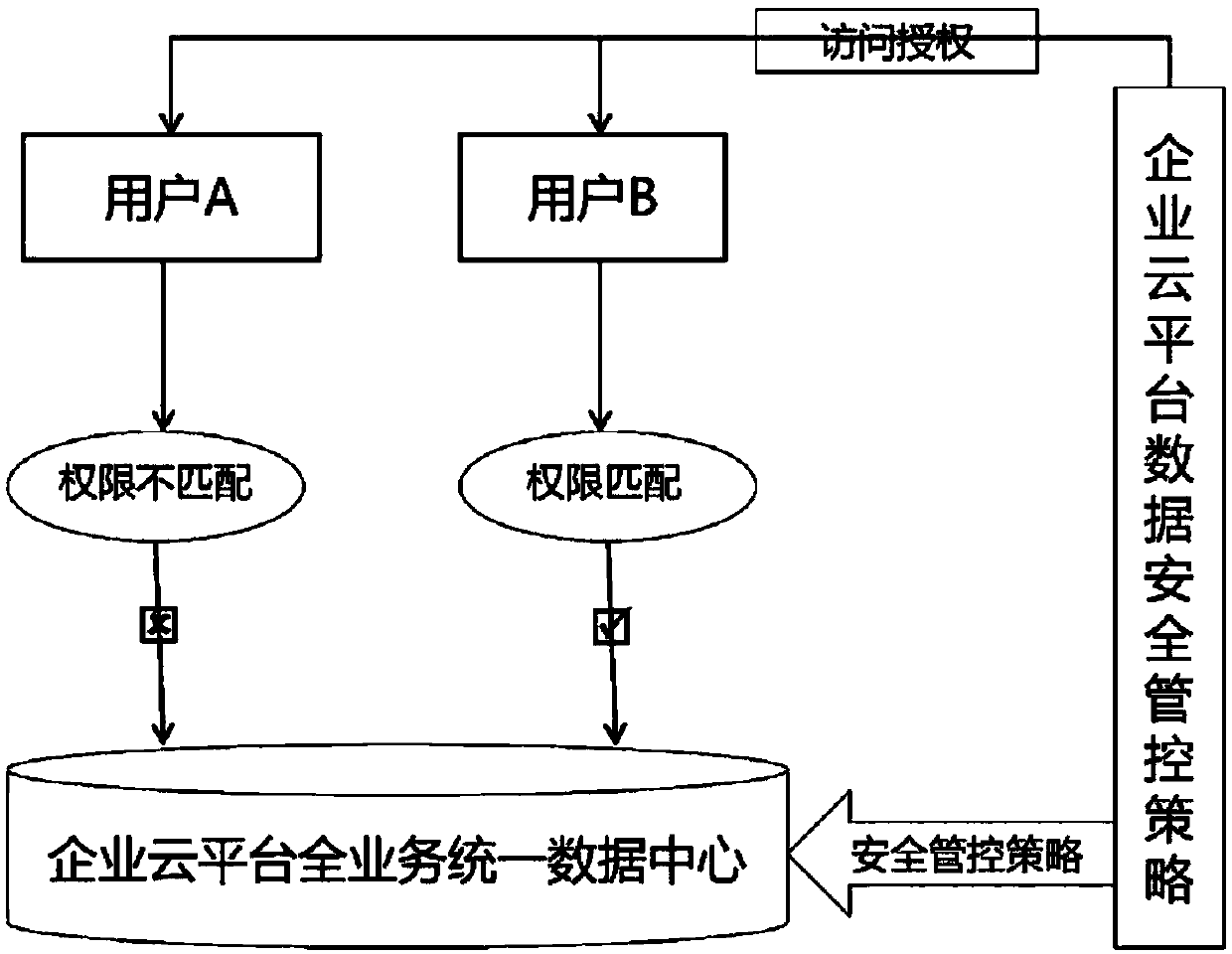
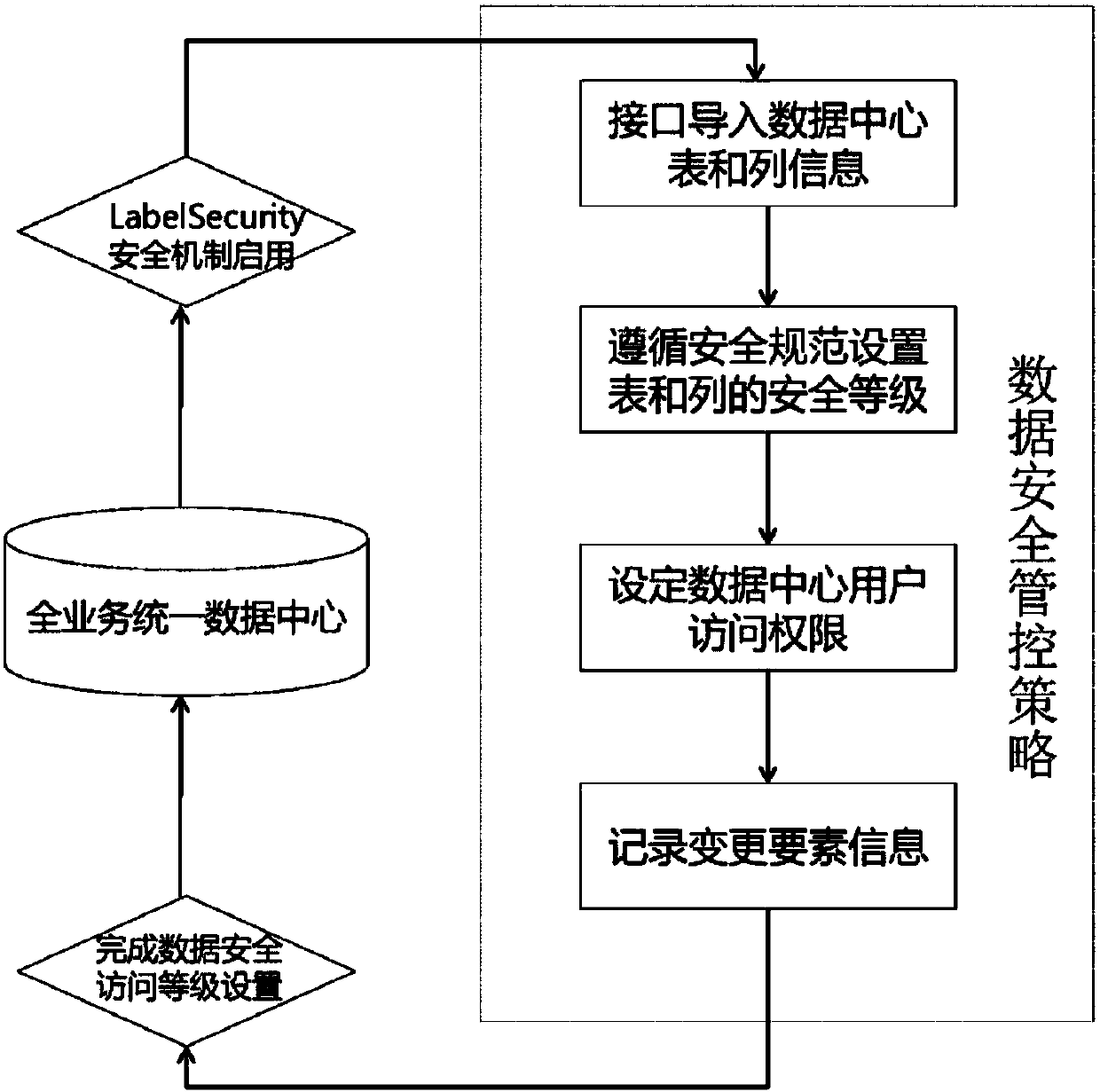
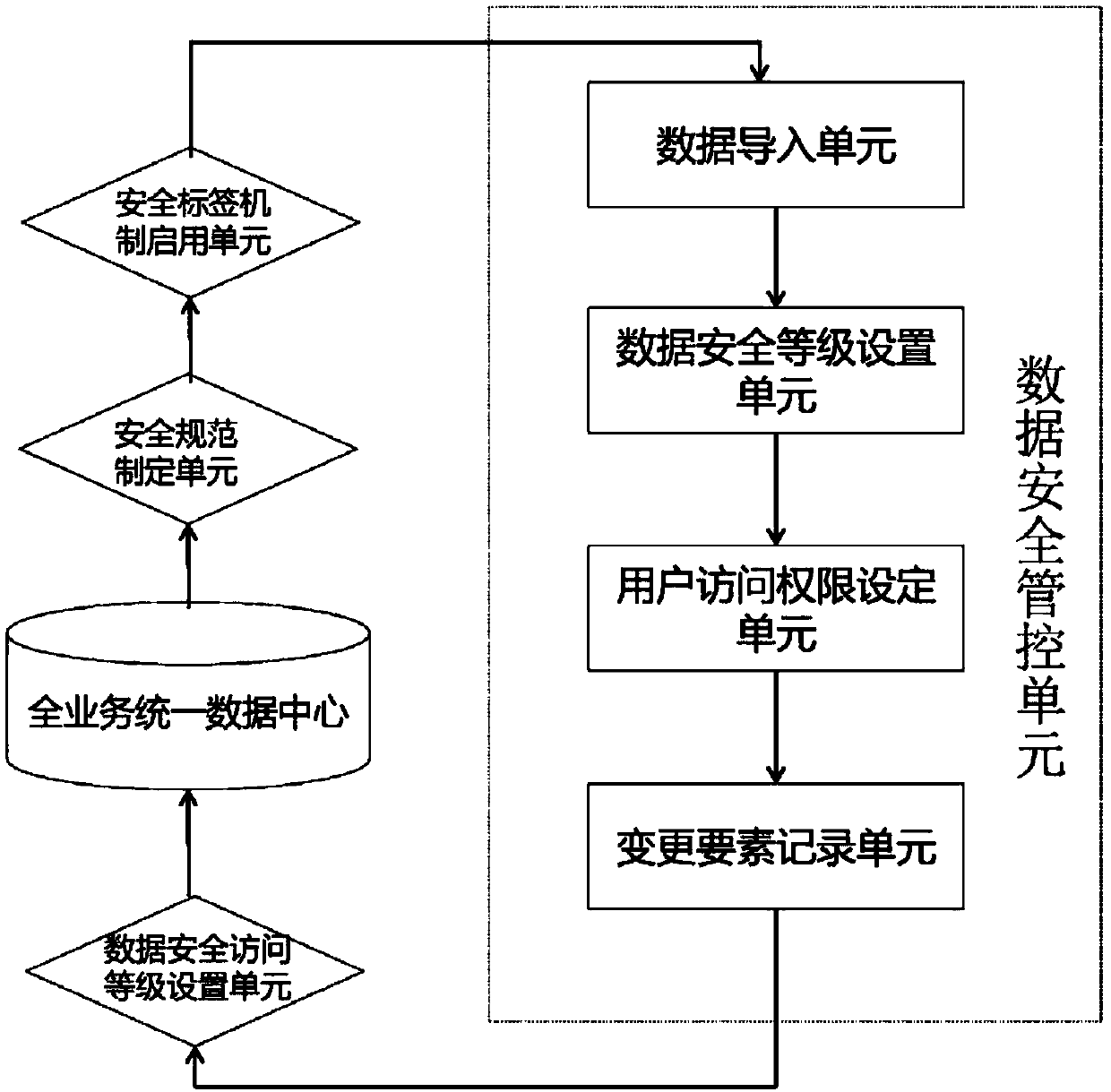
ActiveCN107944284AAbnormal behavior can be traced backEnsure safetyDigital data protectionOpen dataConfidentiality
The present invention discloses a method and a system for internal security management and control of enterprise data. The method disclosed by the present invention is based on a full-service unifieddata center built by an enterprise cloud platform, the full-service unified data center comprises structured data in a unified view area and in a digital warehouse area, and after carrying out actualoperating environment risk analysis on the structured data, from the perspective of the security lifecycle, the entire data protection security specification is formulated; based on the security specification, the LabelSecurity security tag mechanism is enabled on the enterprise cloud platform, and the data access levels of the enterprise cloud platform are divided into four levels of confidentiality of open data, internal data, secret data and confidential data by the security tags; and through the LabelSecurity access mechanism, different effective security control strategies are implementedfor different columns of the data in the same table. According to the method and system disclosed by the present invention, secure tracking and management and control of the service data within the life cycle is ensured; and at the same time, a friendly visual operation is ensured during the entire data management and control process.
Owner:ELECTRIC POWER RES INST OF STATE GRID ZHEJIANG ELECTRIC POWER COMAPNY +1
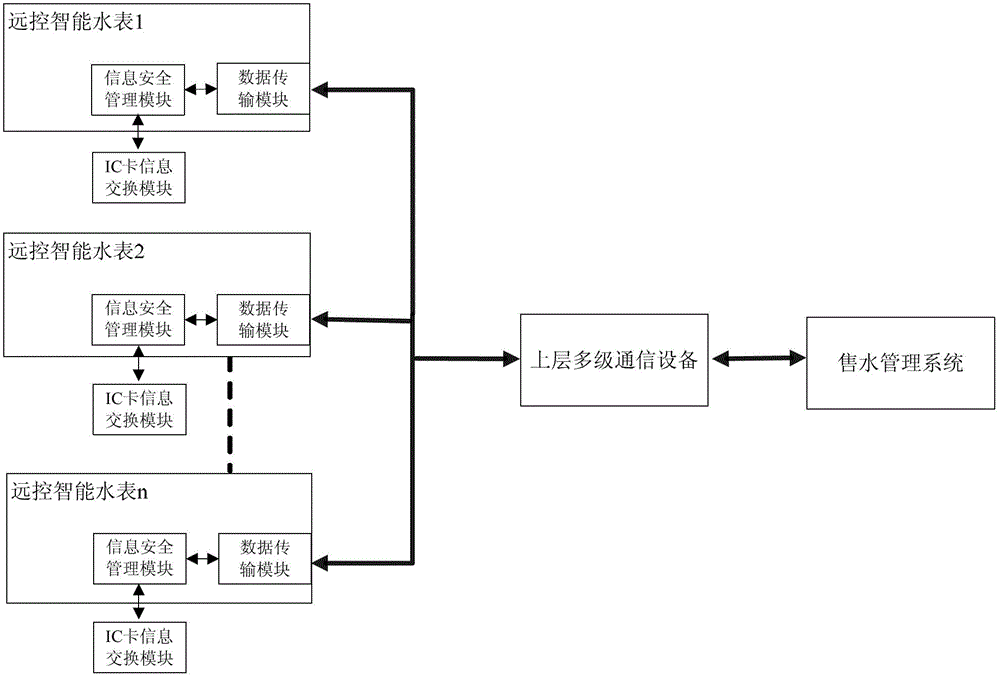
Information security management module of remote-control intelligent water meters
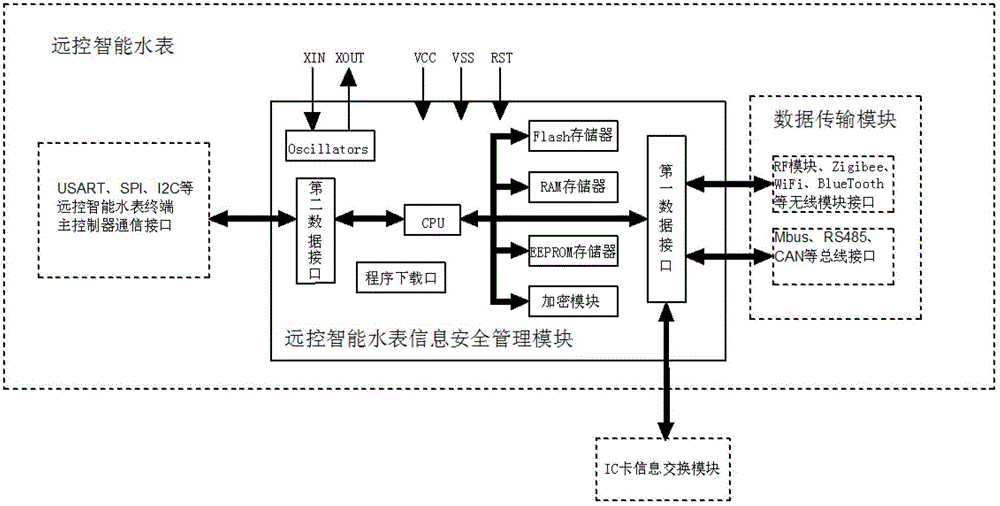
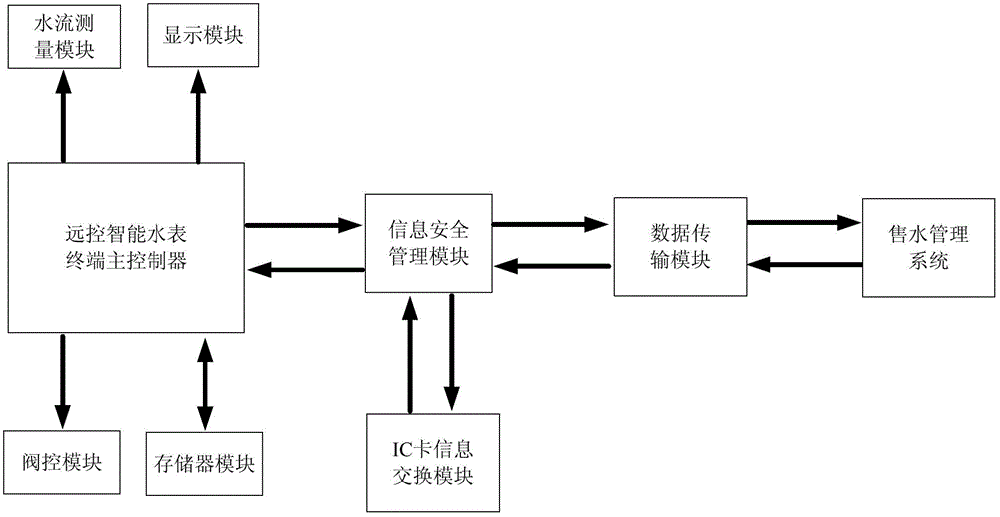
ActiveCN103152166AGuaranteed legalityGuaranteed independenceEncryption apparatus with shift registers/memoriesTransmission technologyStructure of Management Information
The invention discloses an information security management module of remote-control intelligent water meters, belonging to an auxiliary management device of the remote-control intelligent water meters. The information security management module comprises a processor, a first data interface, a second data interface and a FLASH storage unit, wherein the processor is respectively connected into the first data interface, the second data interface and the FLASH storage unit; identity authentication is carried out on the information security management module when the information security management module carries out data exchange with a water selling management system by a data transmission module, so that the legality of communication between the information security management module and the water selling management system is ensured, and a master controller of remote-control intelligent water meter terminals can communicate with outside only by the information security management module; and simultaneously, the information security management module is simple in structure, can be embedded into various remote-control intelligent water meters, is compatible to the master controller at the meter end by multiple communication transmission technologies and a bus interface, is accessed into a water supplying management system in a seamless manner, realizes dispersed manufacture and unified management of the remote-control intelligent water meters, and is wide in application range.
Owner:CHENGDU QINCHUAN IOT TECH CO LTD
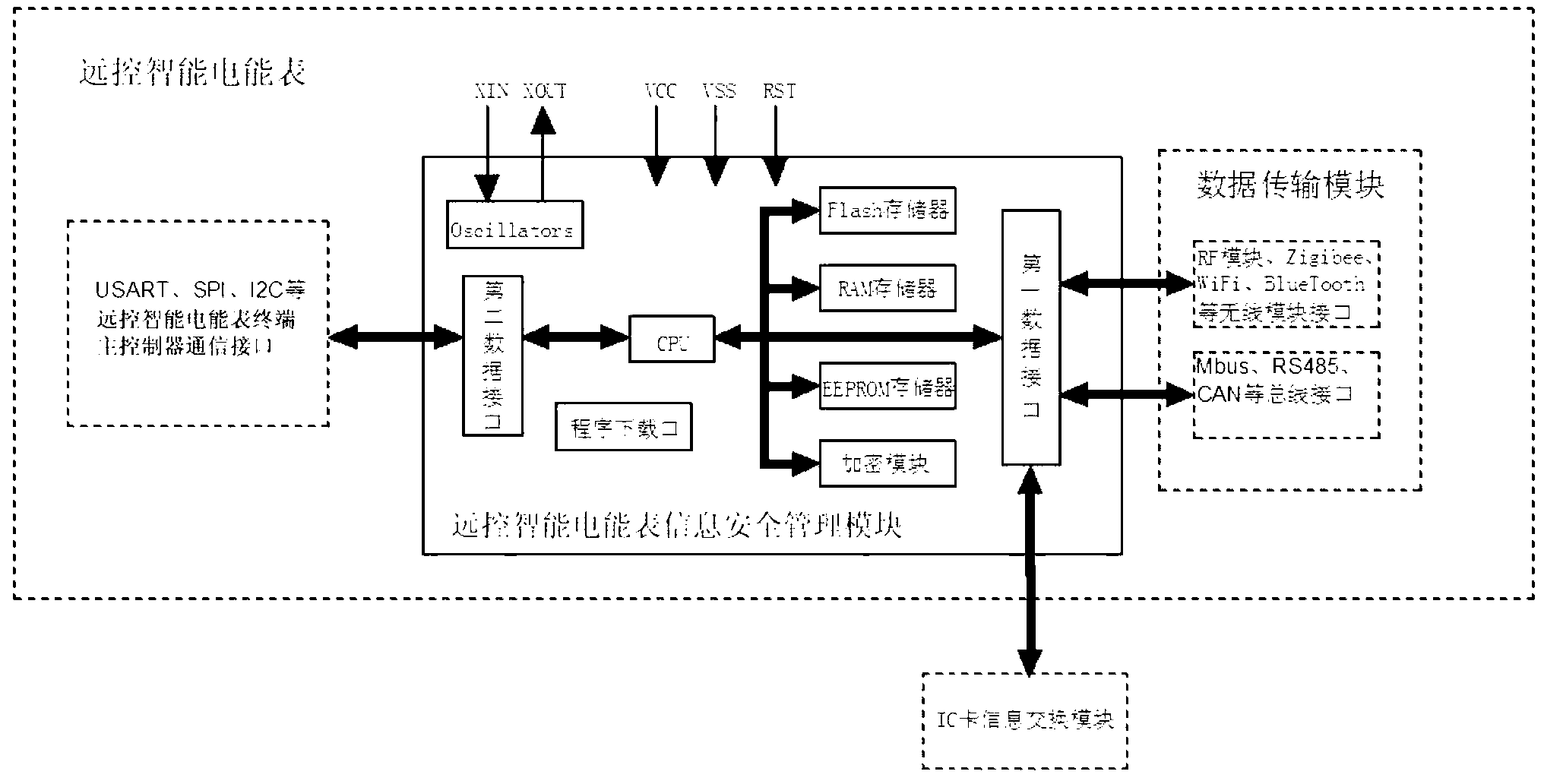
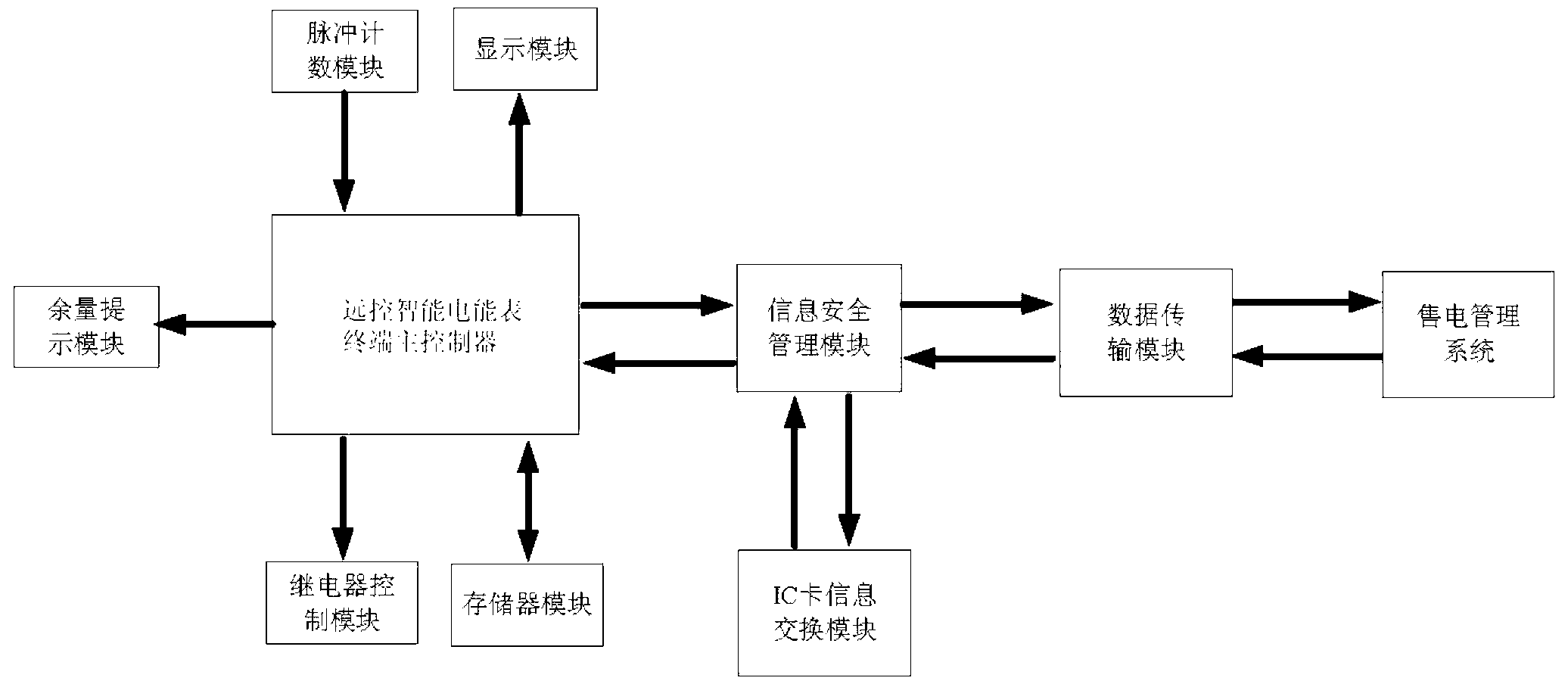
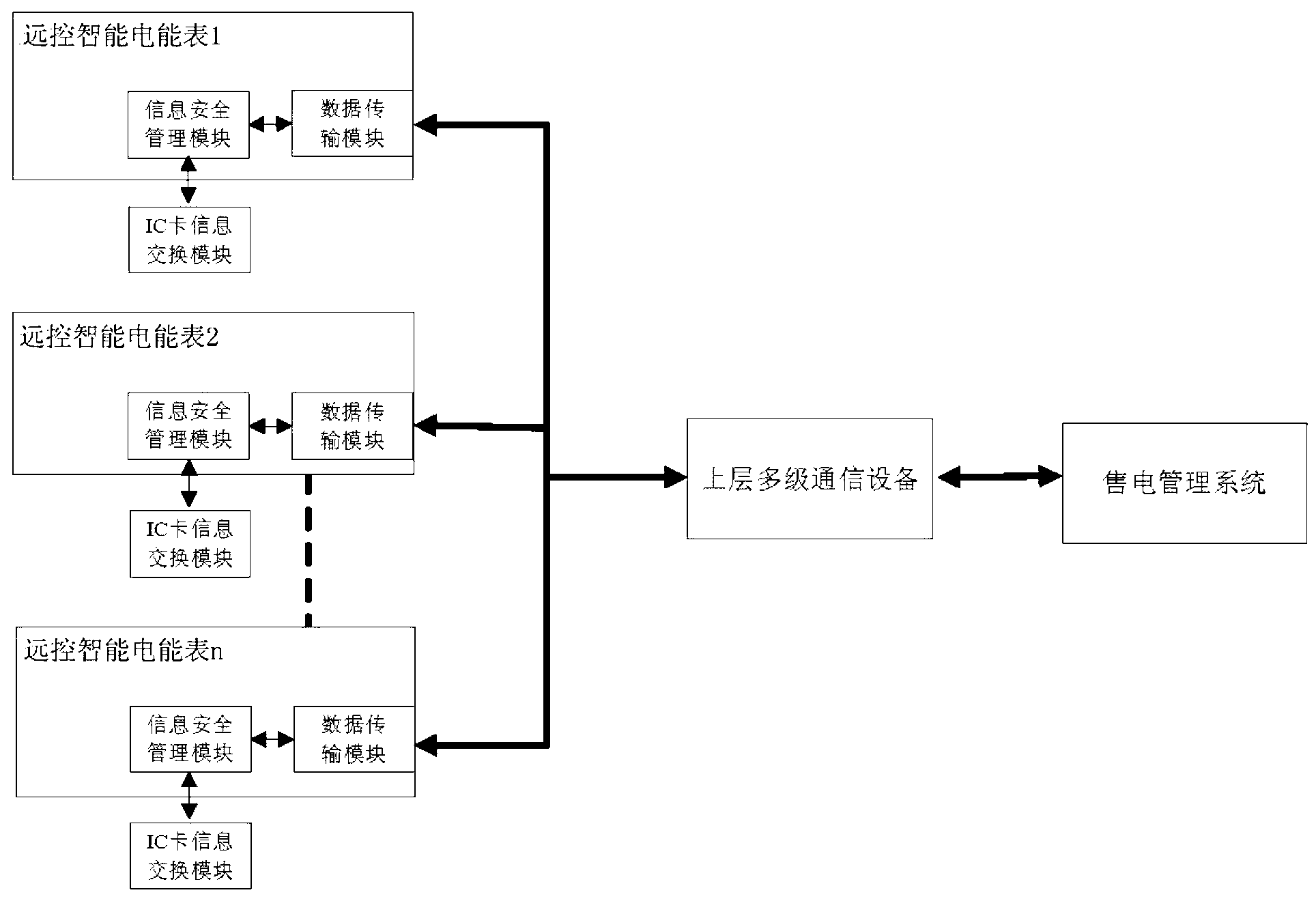
Information security management module of remote control intelligent electric energy meter
ActiveCN103218876AGuaranteed independenceSimple structureApparatus for hiring articlesTransmission technologyInformation security management
The invention discloses an information security management module of a remote control intelligent electric energy meter, which belongs to a management assistance device of the remote control intelligent electric energy meter. The information security management module comprises a processor, a first data interface, a second data interface and a FLASH memorizer, wherein the processor is respectively accessed to the first data interface, the second data interface and the FLASH memorizer. The information security management module disclosed by the invention is subjected to identity authentication while being subjected to data exchange with an electricity selling management system through a data transmission module, the legality of communication between the information security management module and the electricity selling management system can be ensured, and a terminal main controller of the remote control intelligent electric energy meter can be in communication with the outside just by means of the information security management module; and meanwhile, the information security management module disclosed by the invention has a simple structure, can be embedded in remote control intelligent electric energy meters of various types, can be compatible with the terminal main controller of the remote control intelligent electric energy meter through various communication transmission technologies and bus interfaces and can be seamlessly accessed to a power supply management system, distributed manufacturing and unified management of the remote control intelligent electric energy meter can be realized, and the application range is wide.
Owner:眉山秦川智能传感器有限公司
Information security management and control method, system and device and readable storage medium
PendingCN109800589ADetect a mismatchFlexible adjustmentDigital data protectionDigital data authenticationEvaluation resultControl system
The invention discloses an information security management and control method. The method is different from the prior art in which a fixed authority is set for each employee. According to the invention, evaluation is carried out in real time based on the behavior data capable of reflecting the user behavior state; According to the invention, the security management and control level of the corresponding user is dynamically adjusted according to the evaluation result, so that each user has a non-invariable authority, the phenomenon that the current behavior of the user is not matched with the current security management and control level can be more timely perceived, then flexible adjustment is performed, the internal invasion difficulty is higher, and the information is safer. The invention further discloses an information security management and control system and device and a computer readable storage medium which have the above beneficial effects.
Owner:SANGFOR TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com