Method and system for internal security management and control of enterprise data
A security control and enterprise data technology, applied in the field of information system data security, can solve problems such as data security difficulty and data leakage, and achieve the effect of friendly visual operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
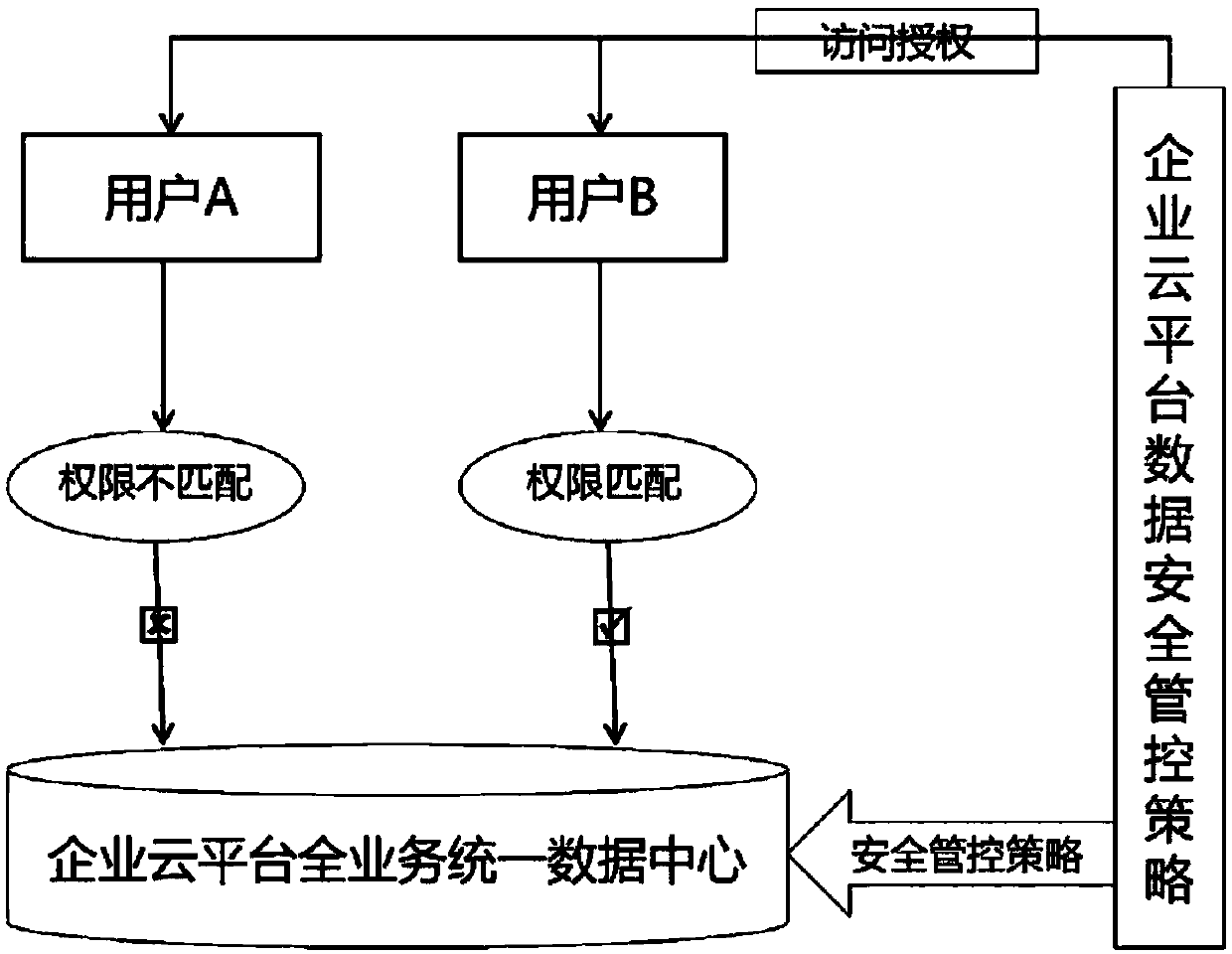
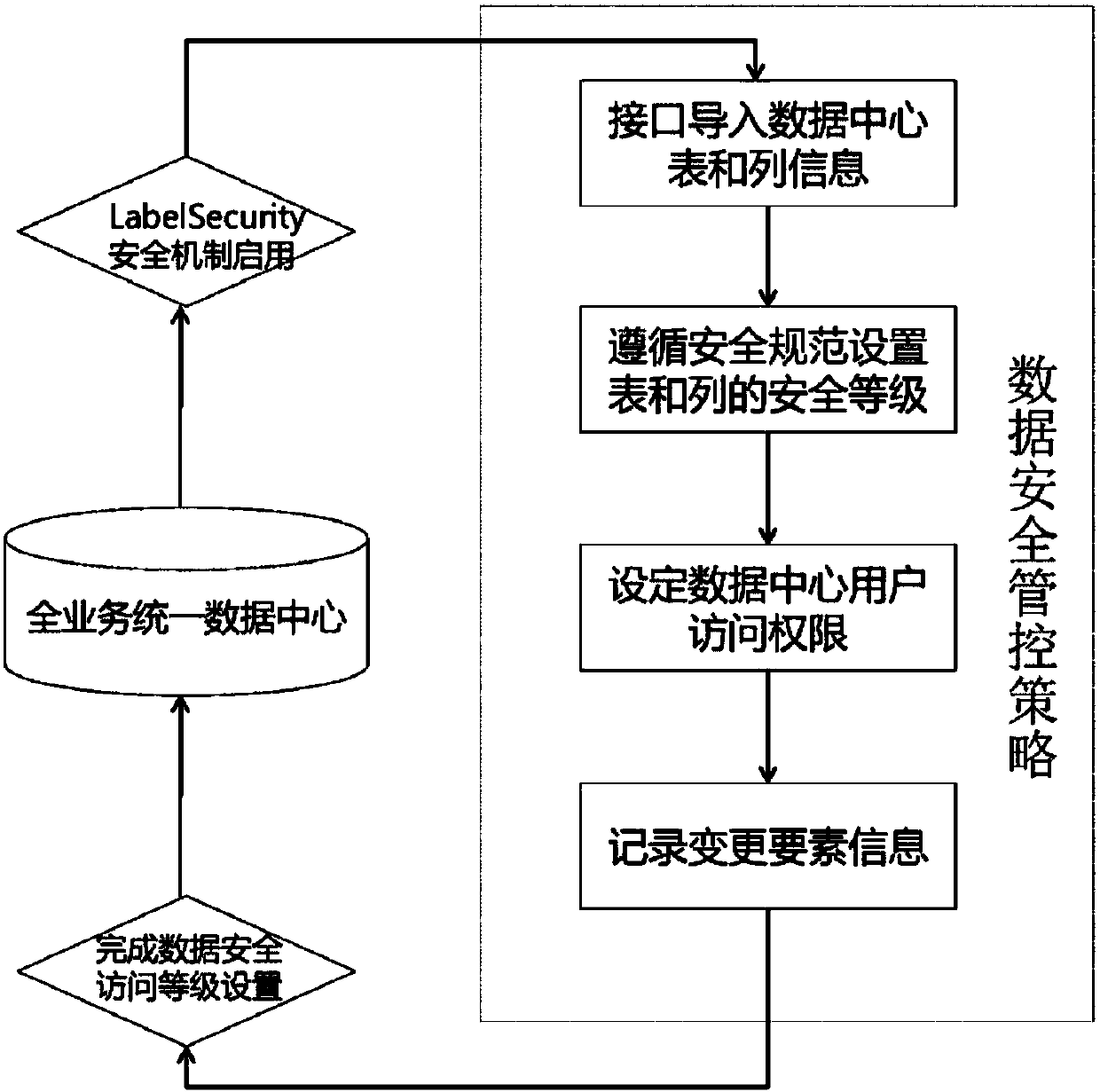
[0029] This embodiment provides a method for internal security management and control of enterprise data, such as Figure 1-2 As shown, it is based on the full-service unified data center built on the enterprise cloud platform. The full-service unified data center includes structured data in the unified view area and data warehouse area. Formulate security specifications for the entire data protection from the perspective of the security life cycle;
[0030] Based on the above security specifications, the LabelSecurity security label mechanism is enabled on the enterprise cloud platform, and the security label distinguishes the data access level of the enterprise cloud platform into four levels of confidentiality: public data, internal data, confidential data, and confidential data; and through The LabelSecurity access mechanism implements different effective security control strategies for different columns of the same table data.
[0031] After the security label mechanism ...
Embodiment 2
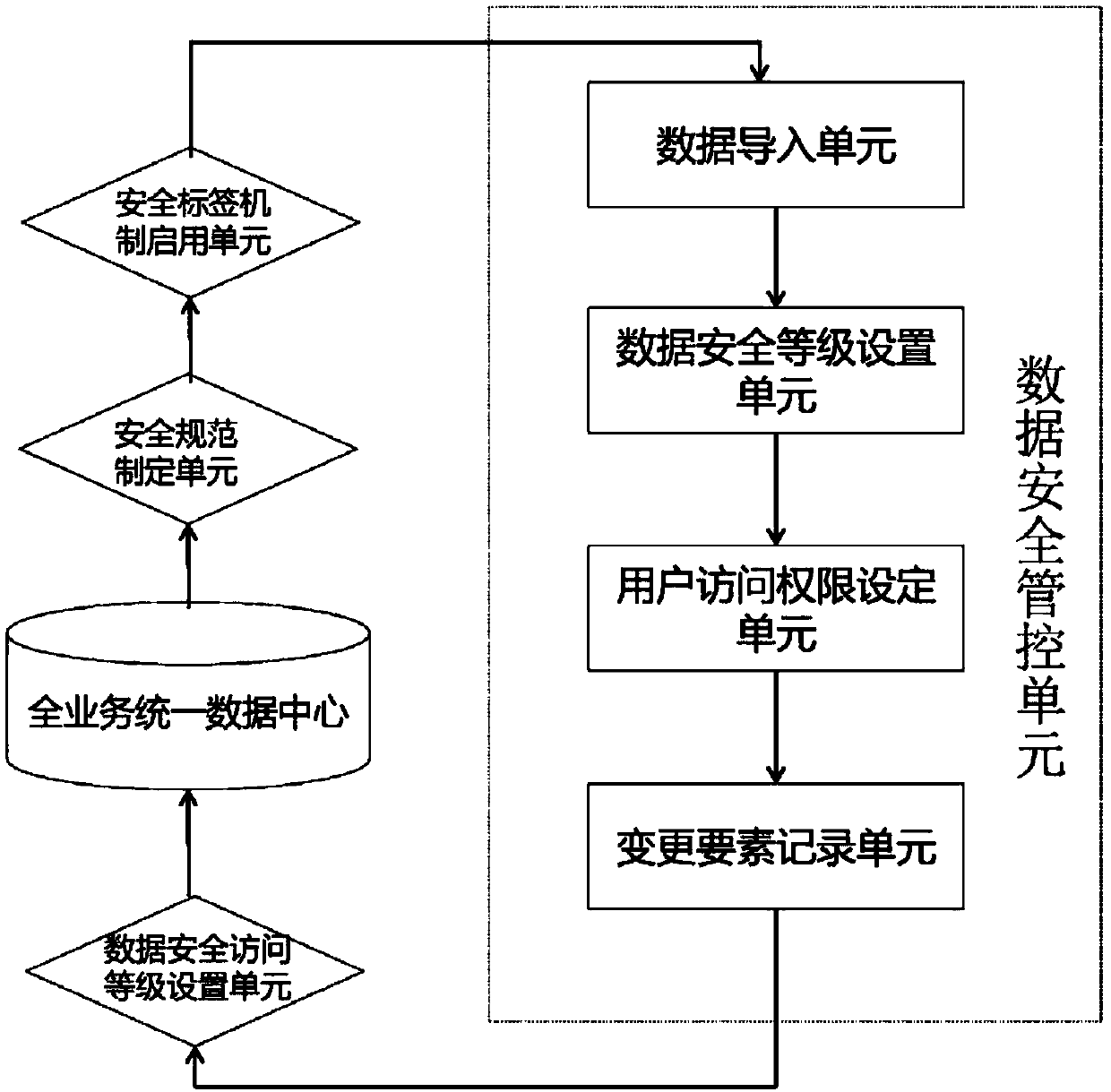
[0037] This embodiment provides a system for internal security management and control of enterprise data, such as image 3 shown, which includes:
[0038] Full-service unified data center: A full-service unified data center based on the enterprise cloud platform, including structured data in the unified view area and data warehouse area;
[0039] Security label mechanism enabling unit: used to enable the LabelSecurity security label mechanism;
[0040] Security specification formulation unit: After analyzing the actual operating environment risk of the structured data in the unified view area and the data warehouse area, formulate the security specification for the entire data protection from the perspective of the data security life cycle;
[0041] Data security management and control unit: Based on the above security specifications, the LabelSecurity security label mechanism is enabled on the enterprise cloud platform, and the security label distinguishes the data access le...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com