Patents
Literature
574results about How to "Ensure integrity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
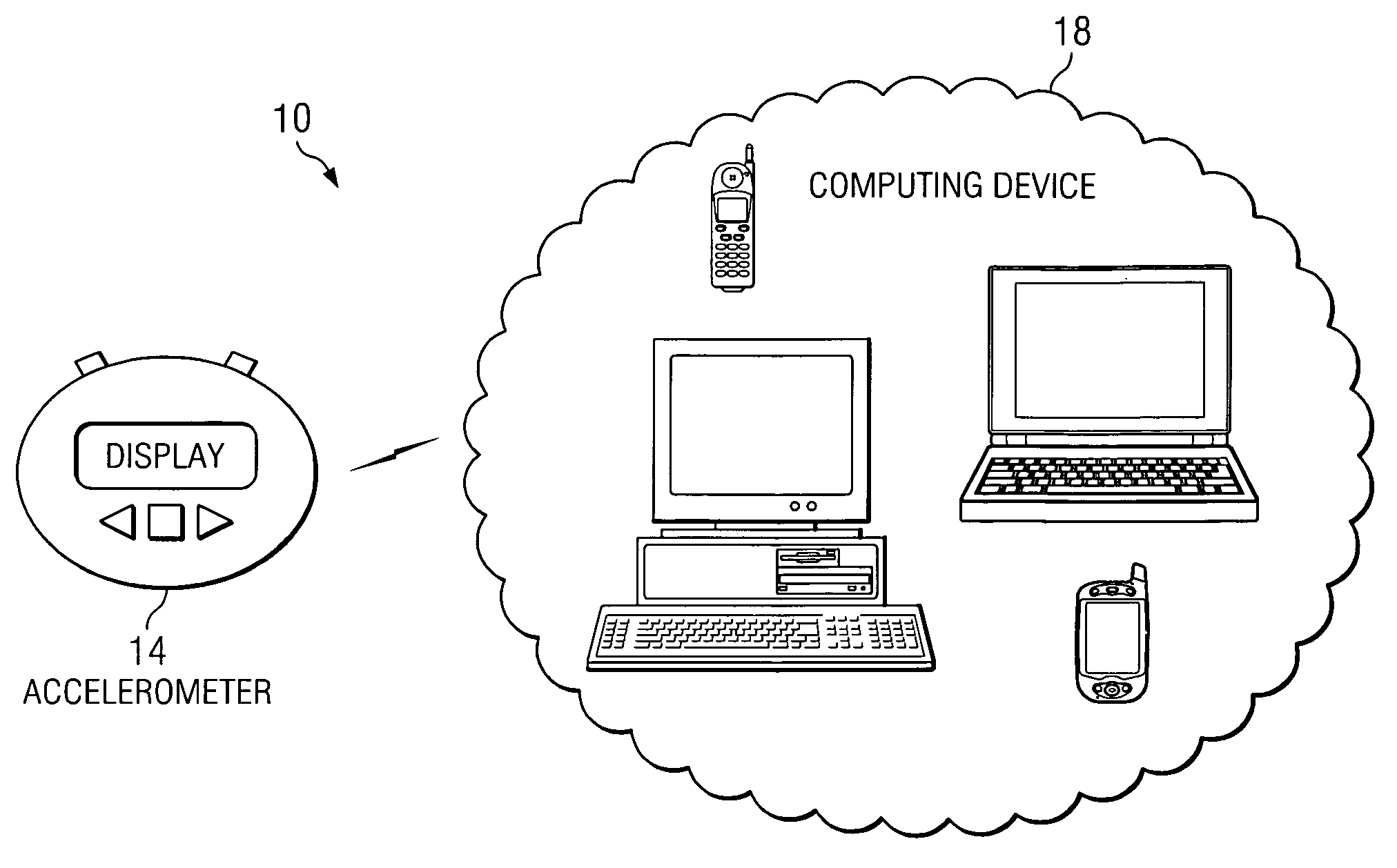
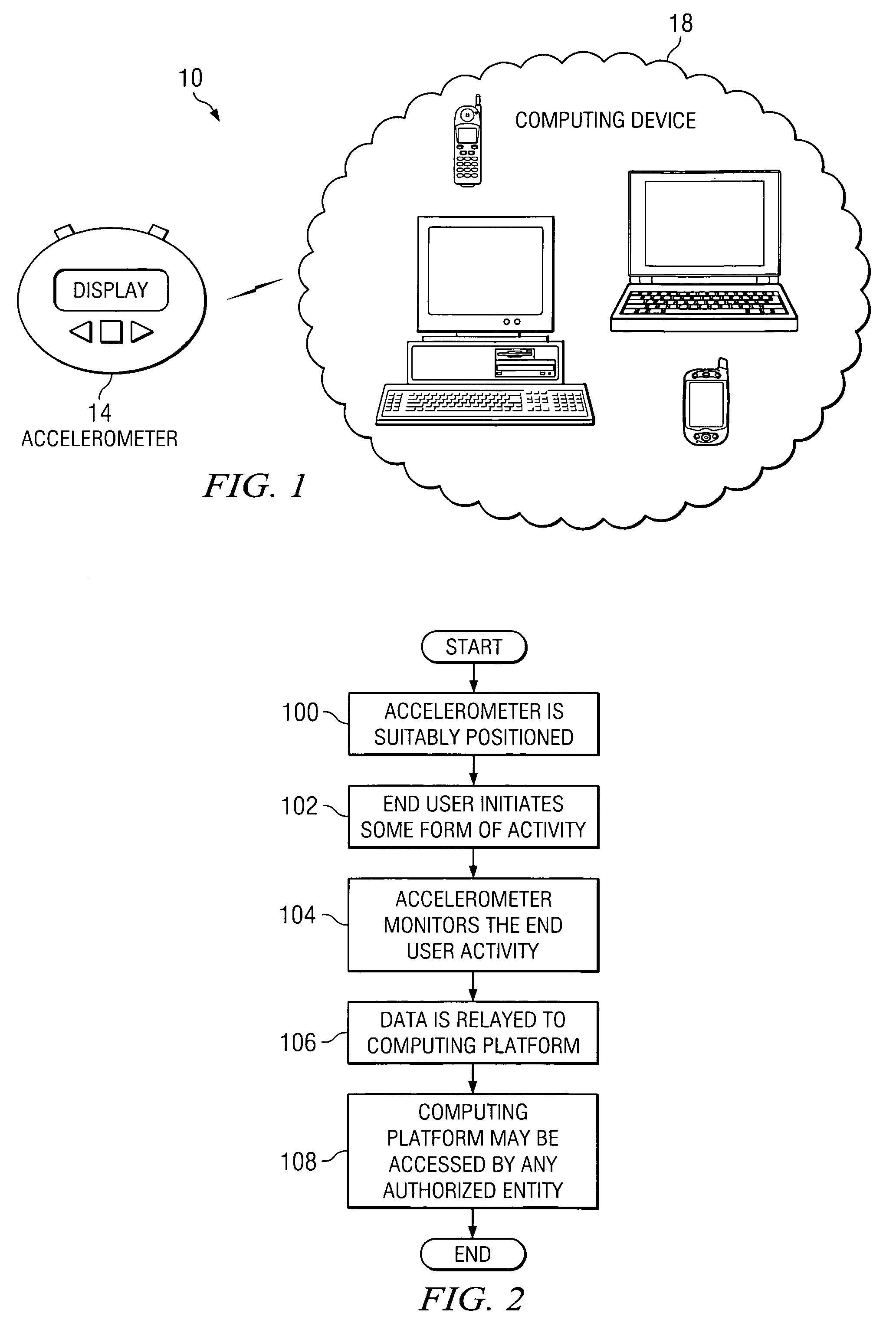
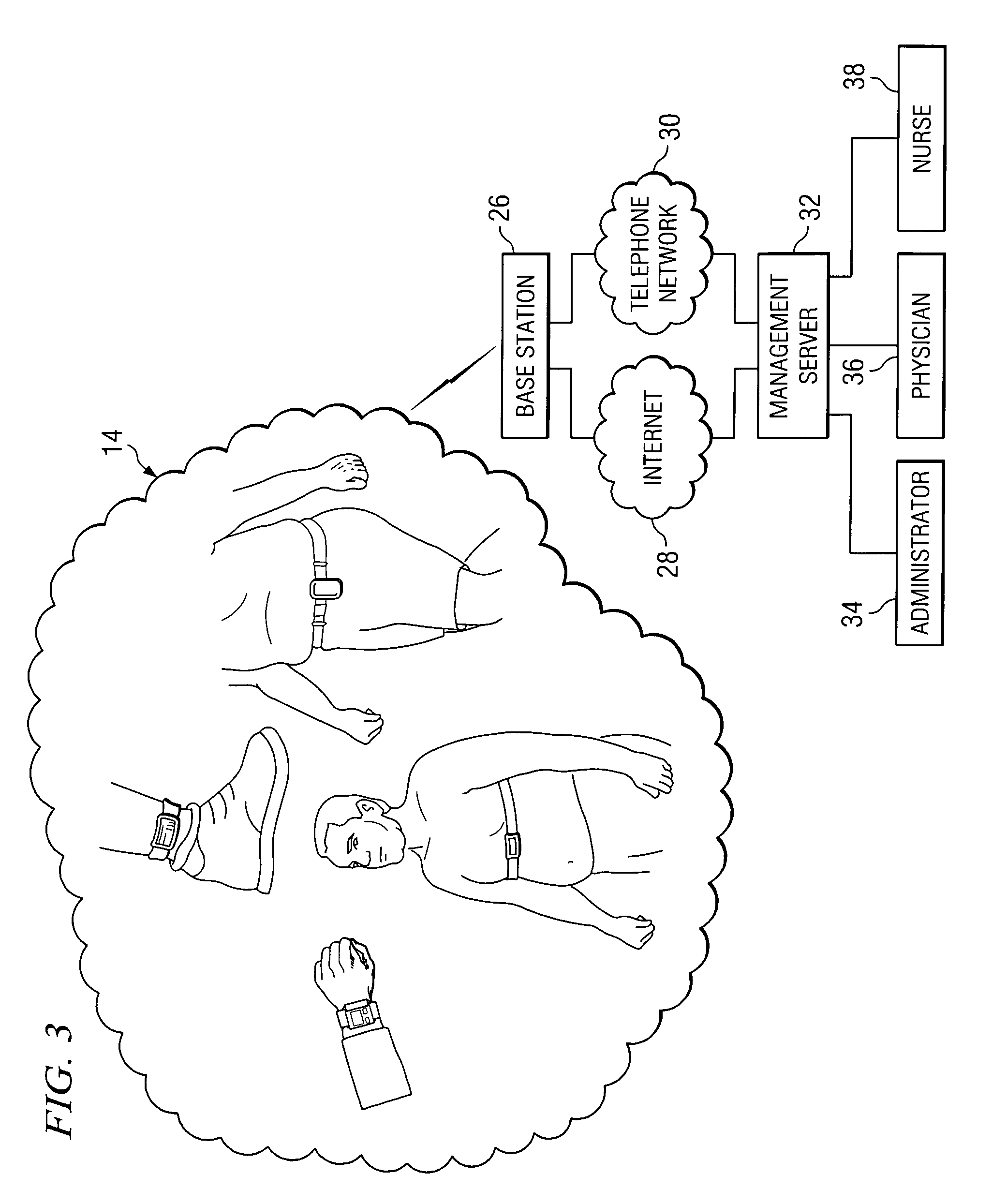
Accelerometer for data collection and communication
ActiveUS7373820B1Easy data collectionSimple processGymnastic exercisingInertial sensorsAccelerometerData shipping
A method for communicating data is provided that includes collecting data associated with an individual using an accelerometer. The accelerometer is operable to monitor activity associated with the individual. The method also includes communicating the data to a computing device, which can receive the data and perform any number of operations.
Owner:KERSH RISK MANAGEMENT
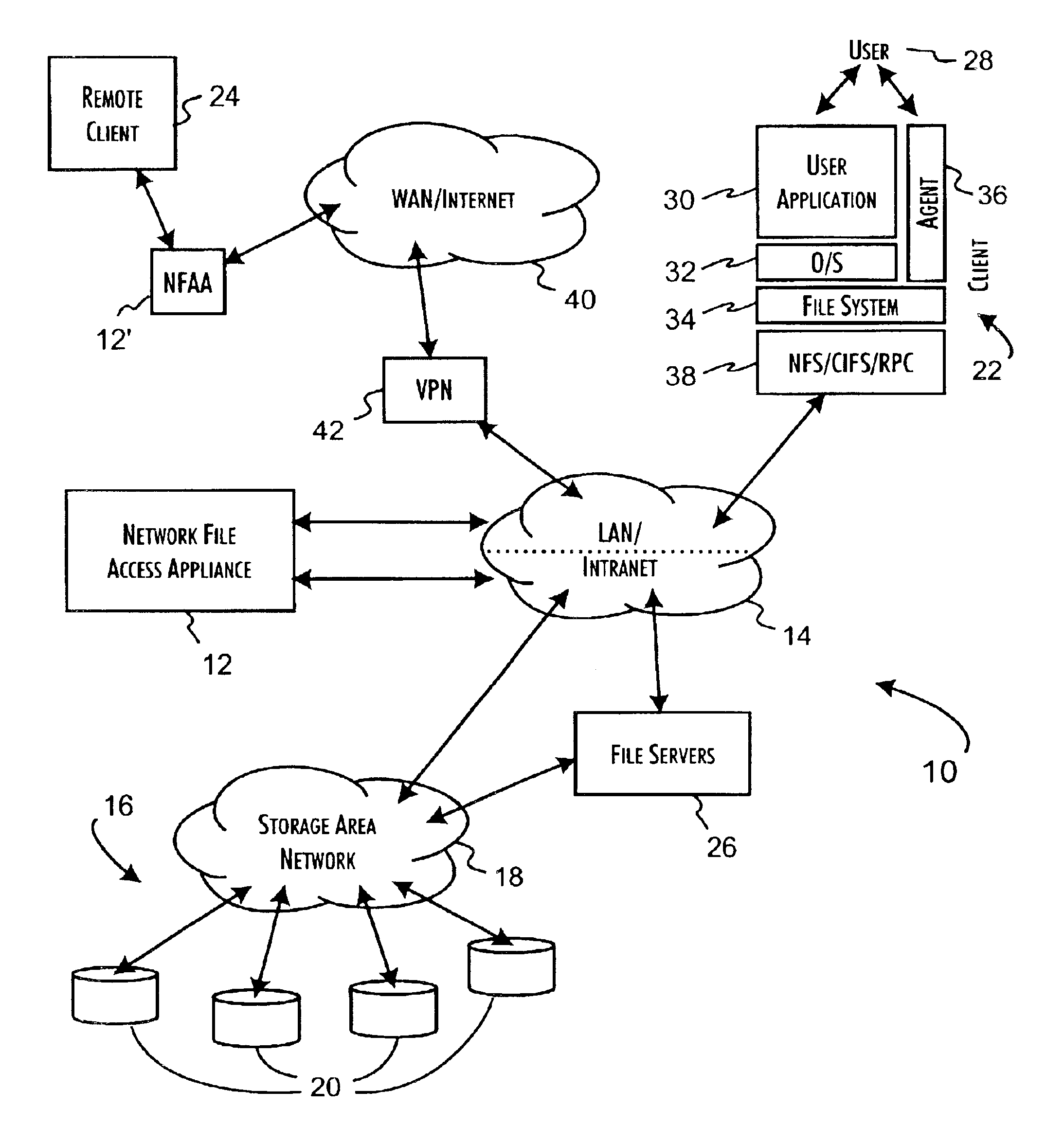
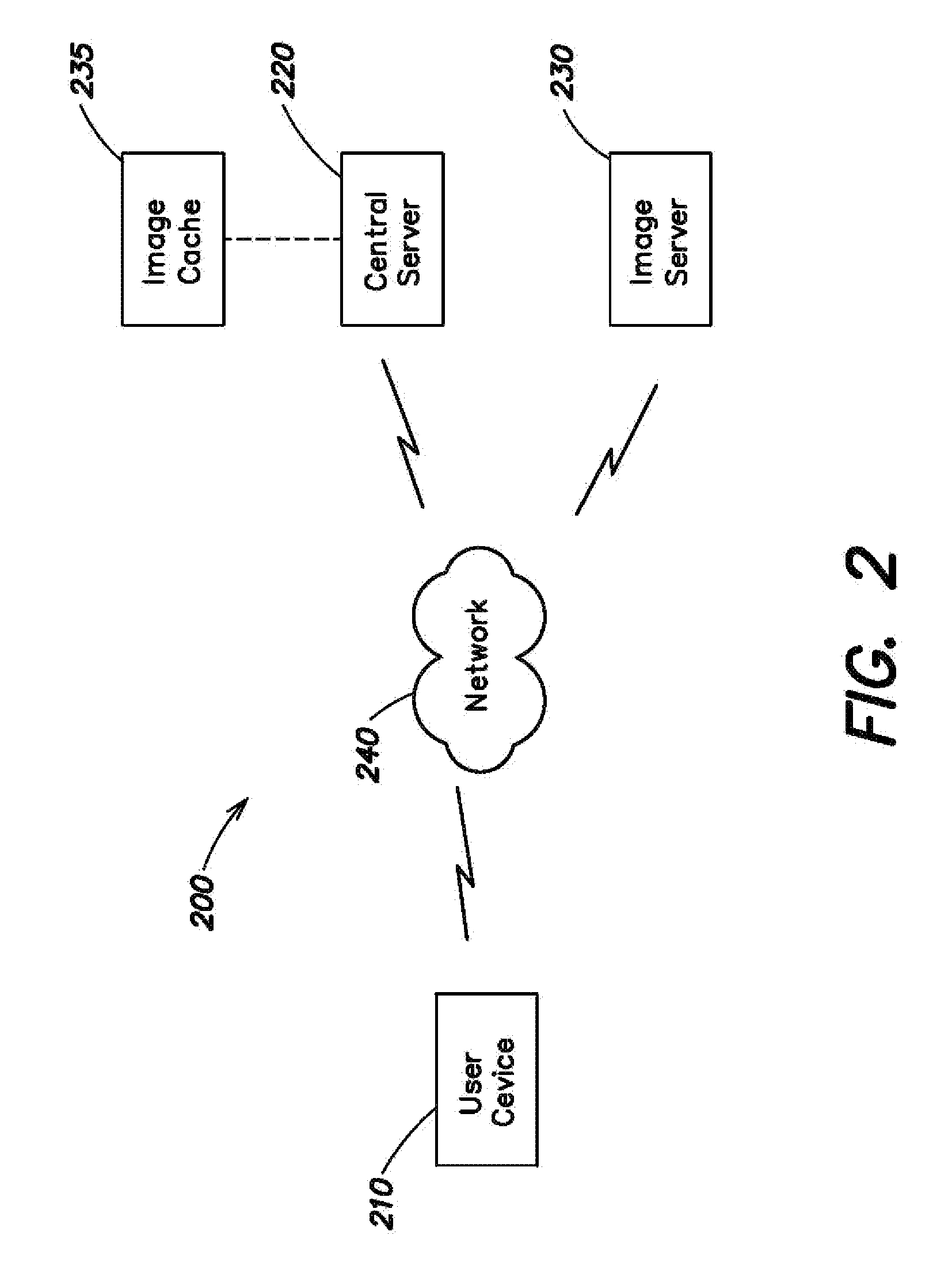
Secure network file access controller implementing access control and auditing
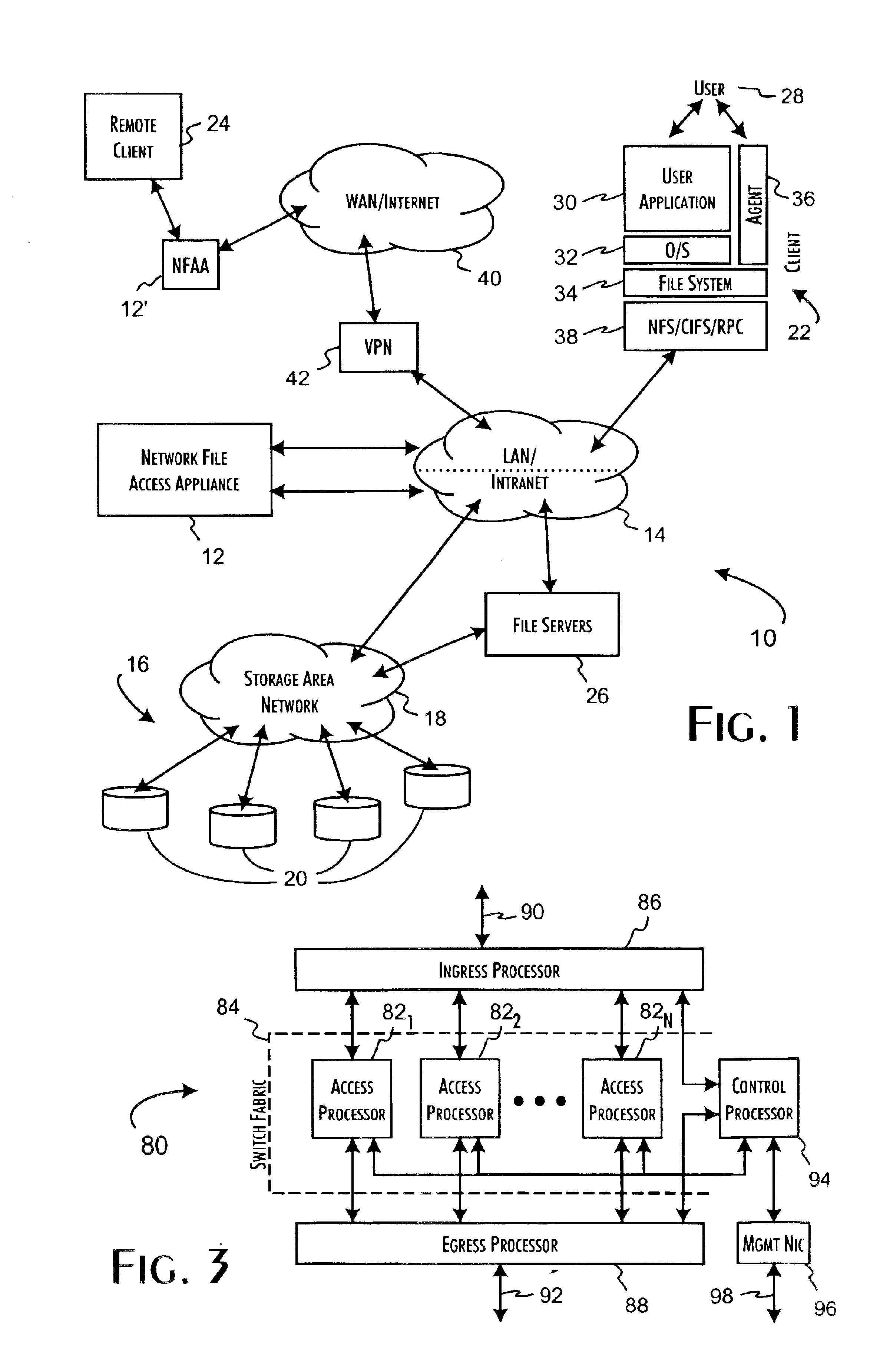
InactiveUS6931530B2Ensure integritySafe storageDigital data processing detailsUser identity/authority verificationReference mapSecure transmission
A network file access appliance operates as a secure portal for network file access operations between client computer systems and network storage resources. The file access appliance terminates network file access transactions, identified by packet information including client system, mount point, and file request identifiers, between client systems and mount points supported by the access controller. A policy parser determines, based on the packet information, to selectively initiate network file access transactions between the access controller and network storage resources to enable completion of selected network file access transactions directed from the clients to the network file access appliance. The network file access transactions directed to the network storage resources are modified counterparts of policy selected client network file access transactions modified to reference mapped network storage resource mount points and support the secure transfer and storage of network file data.
Owner:THALES DIS CPL USA INC
System and Method to Facilitate Creation of Educational Information
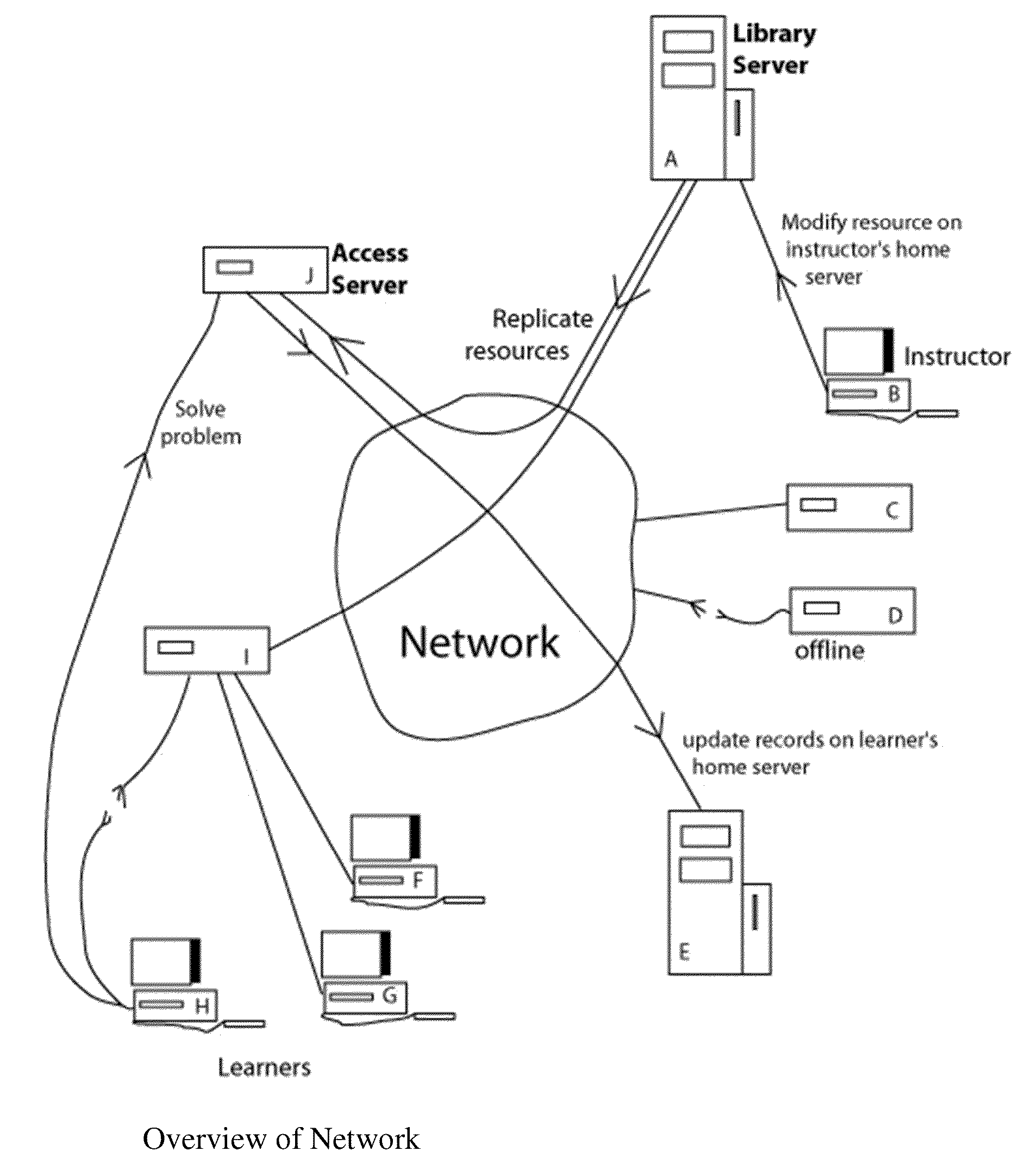
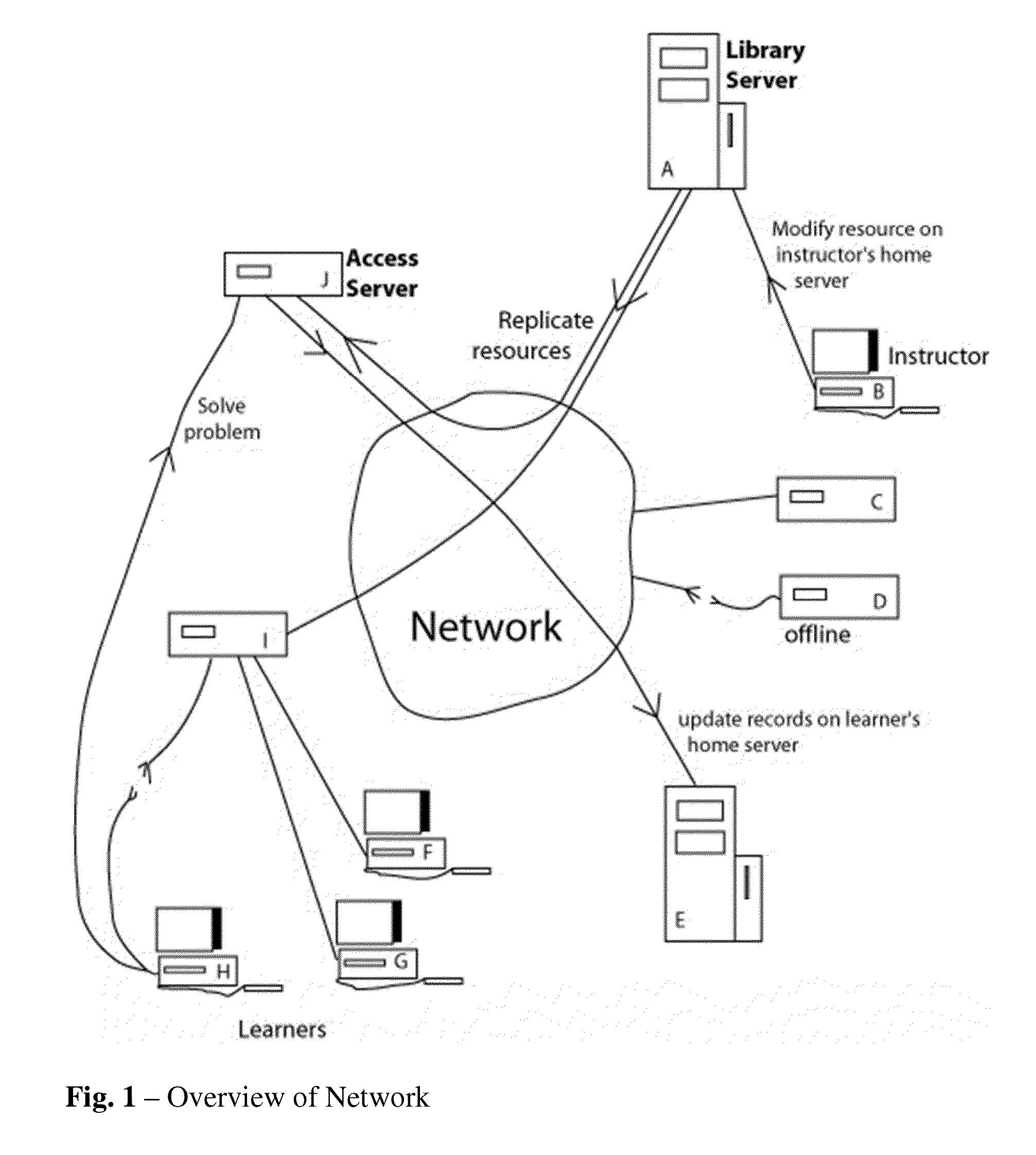
InactiveUS20130130221A1Avoid overload situationsAvoid single points of failure in the networkPayment architectureElectrical appliancesComputerized systemDissemination
The computer-implemented system to facilitate creation of educational information employs a networked computer system that stores at least one resource in association with a first electronic file, storing metadata information about usage of the resource. A resource assembly tool implemented by a computer is programmed to access the networked computer system to display information to an instructor about at least one resource, including the metadata information. This aids the instructor in selecting resources for inclusion in educational information being created. The resource assembly tool is configured to assemble the educational information to include resources selected for inclusion being created for dissemination to learners via said networked computer system. The networked computer system is further configured to capture information about usage of the resource and to update the stored metadata information to reflect said captured information.
Owner:BOARD OF TRUSTEES OPERATING MICHIGAN STATE UNIV
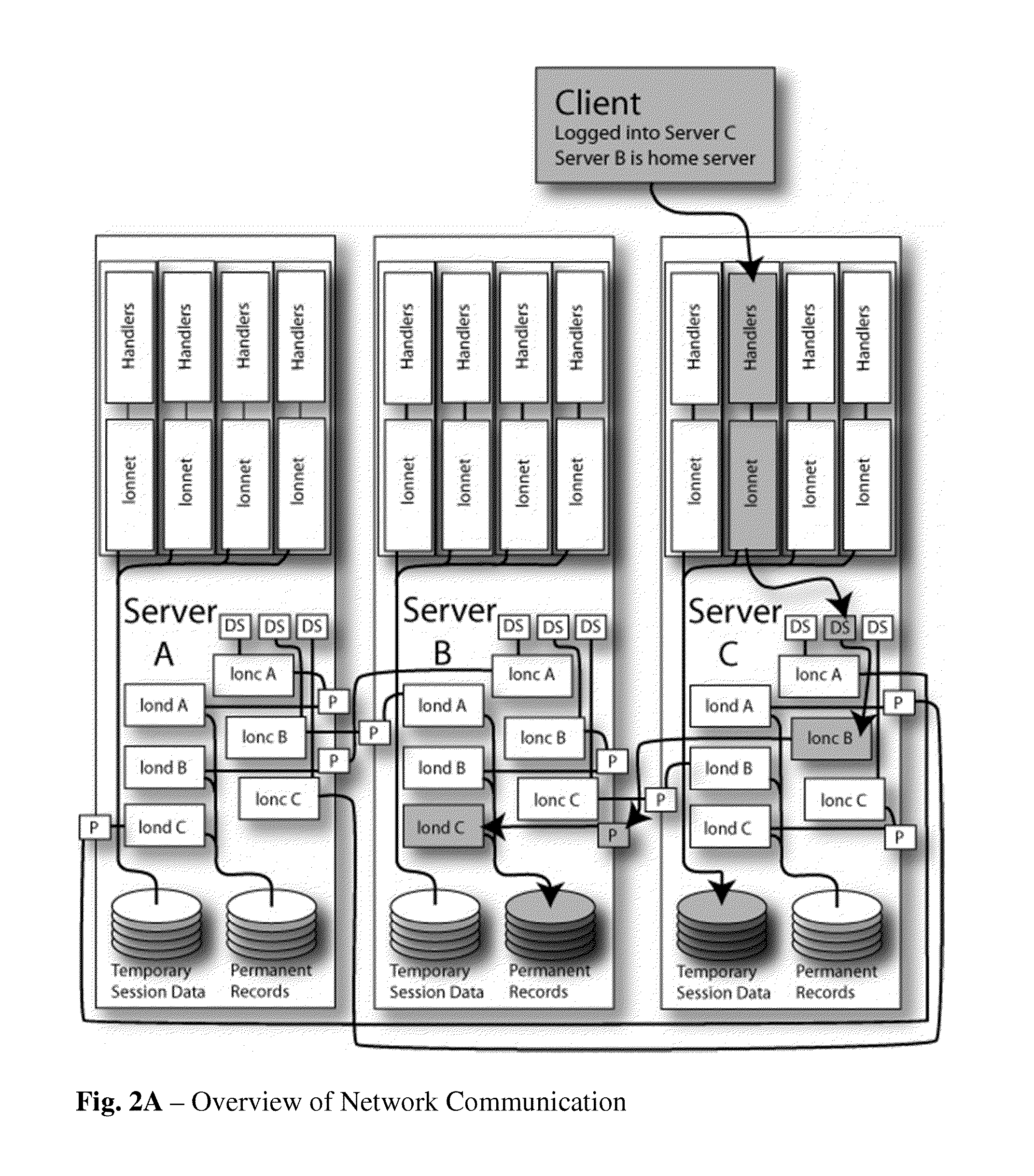
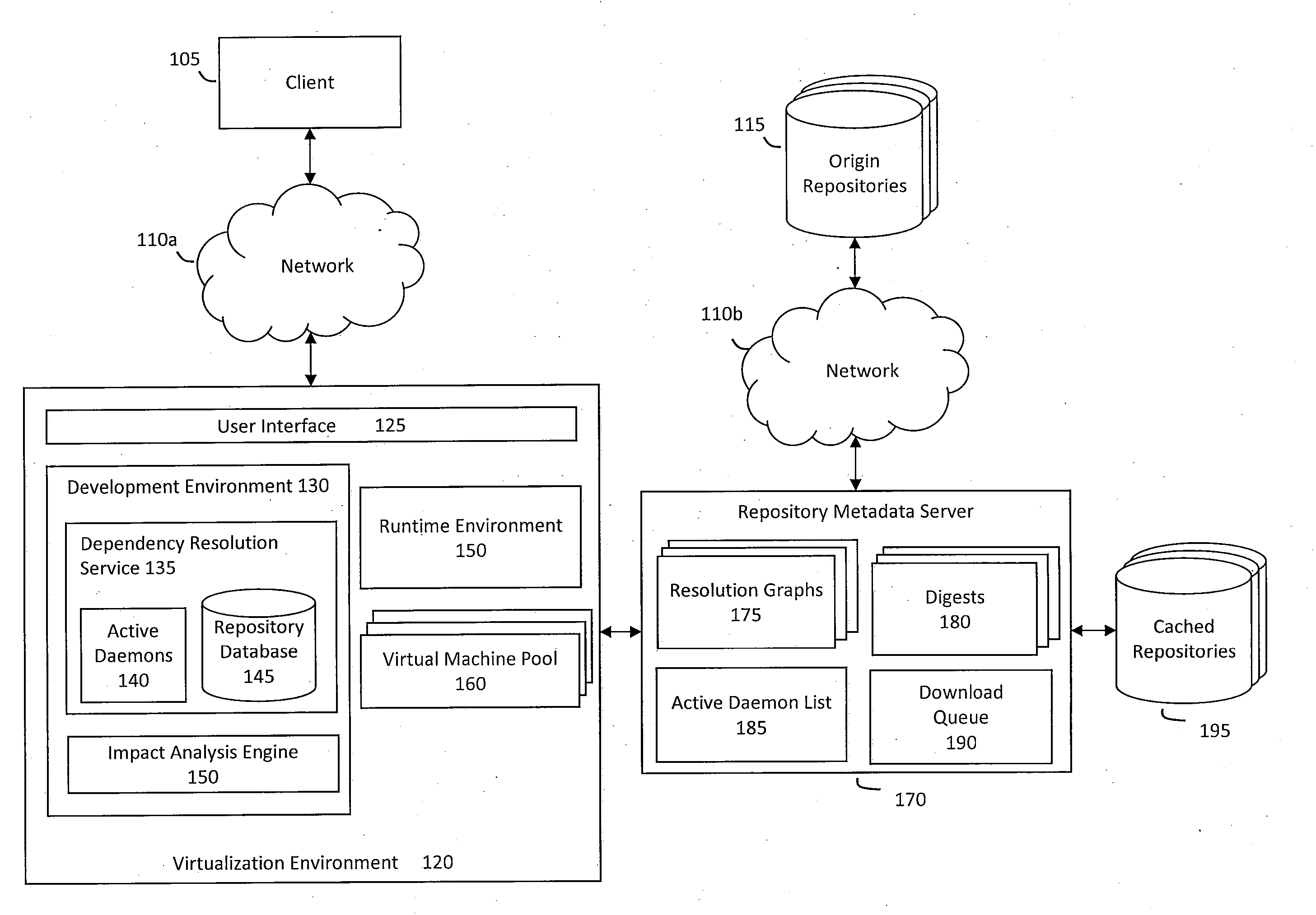
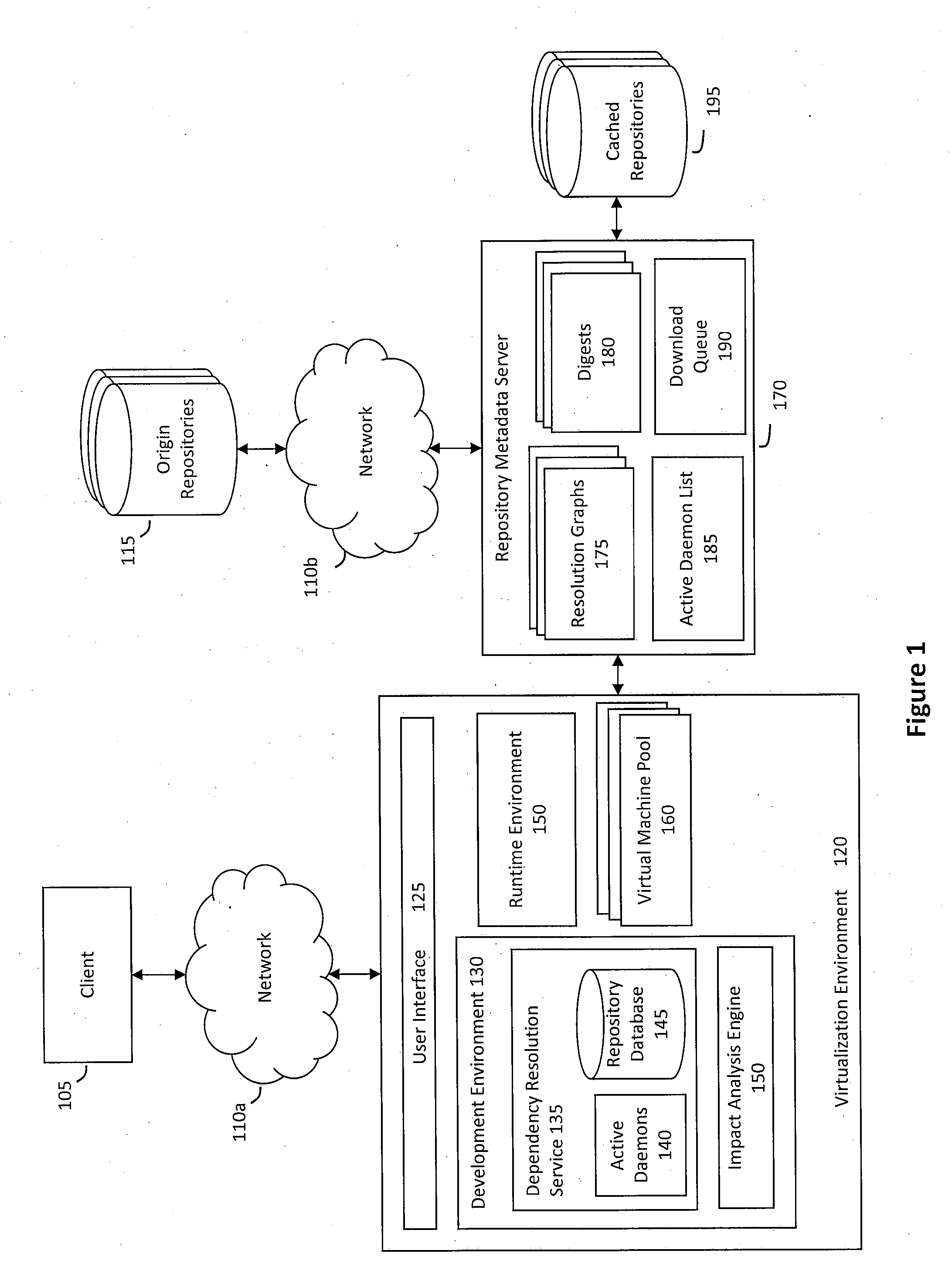
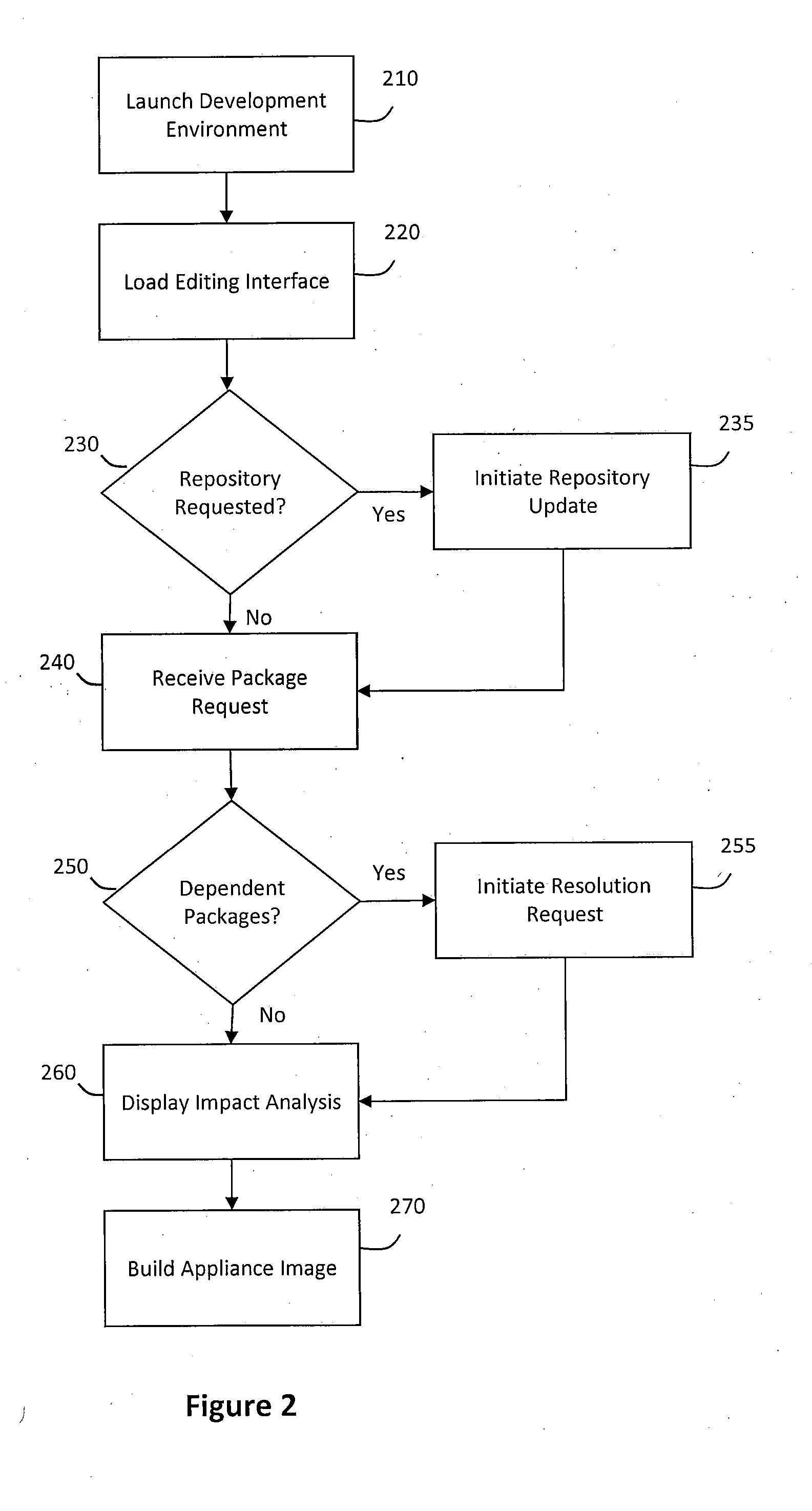
System and method for building virtual appliances using a repository metadata server and a dependency resolution service
ActiveUS20090300604A1Easy to buildEasy to configureError detection/correctionProgram loading/initiatingWeb serviceImage resolution
A system and method for building virtual appliances using a repository metadata server and a dependency resolution service is provided. In particular, a hosted web service may provide a collaborative environment for managing origin repositories and software dependencies, whereby remote clients may follow a simple and repeatable process for creating virtual appliances. For example, the repository metadata server may cache and parse metadata associated with an origin repository, download software from the origin repository, and generate resolution data that can be used by the dependency resolution service. The dependency resolution service may then use the resolution data to resolve dependencies for a package selected for an appliance, wherein the dependencies may include packages that are required, recommended, suggested, banned, or otherwise a dependency for the selected package.
Owner:ORACLE INT CORP
Distributed virtual environment
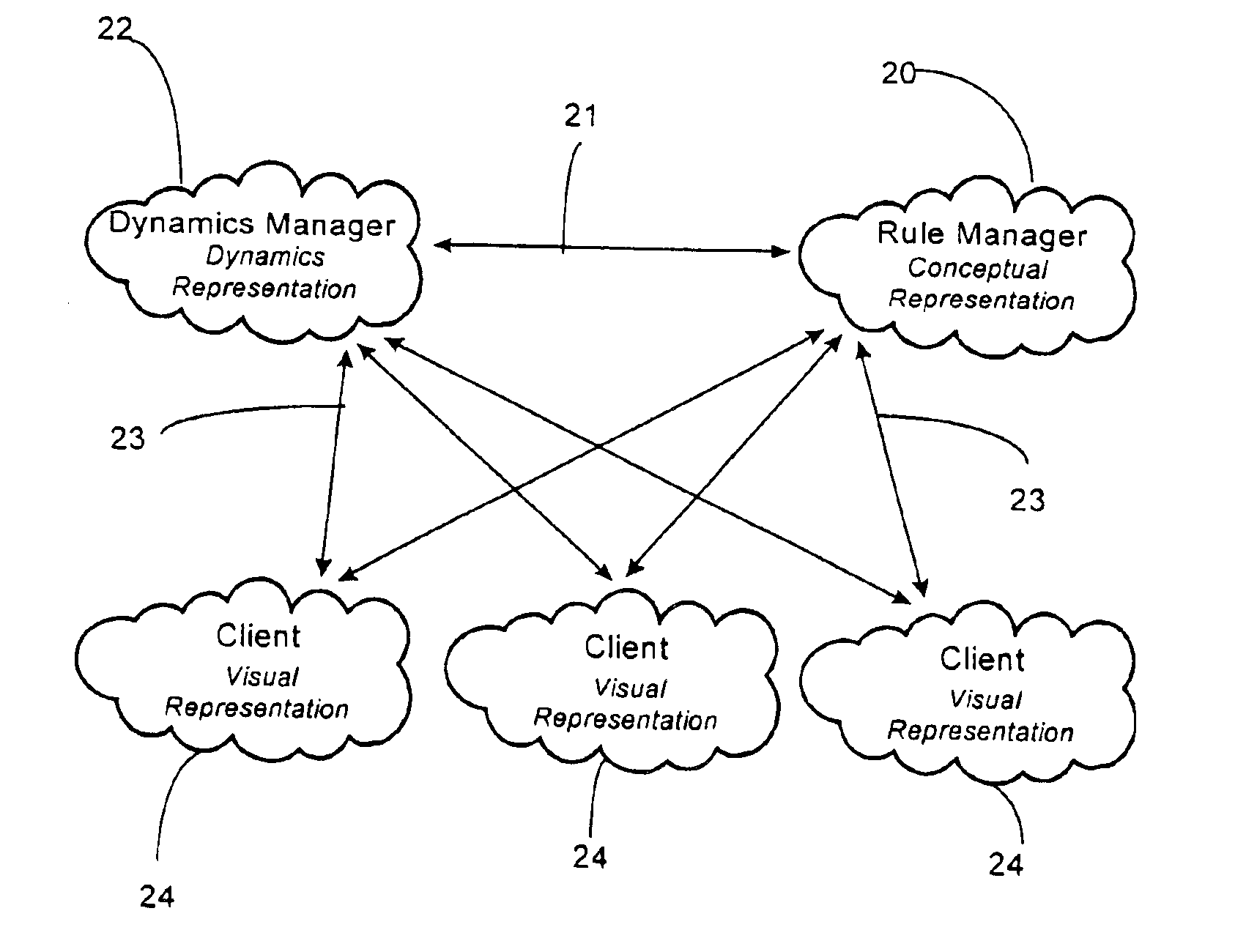
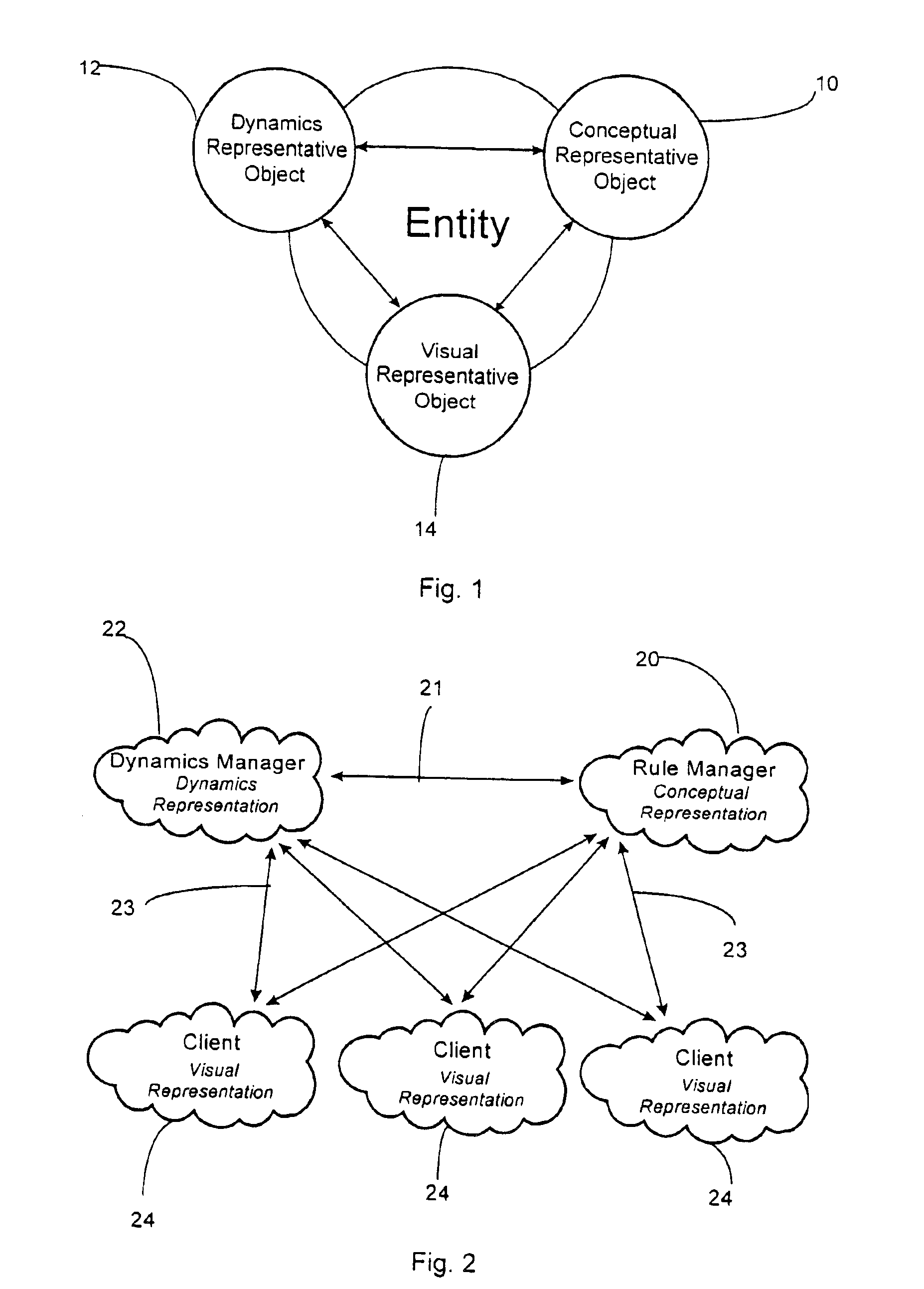
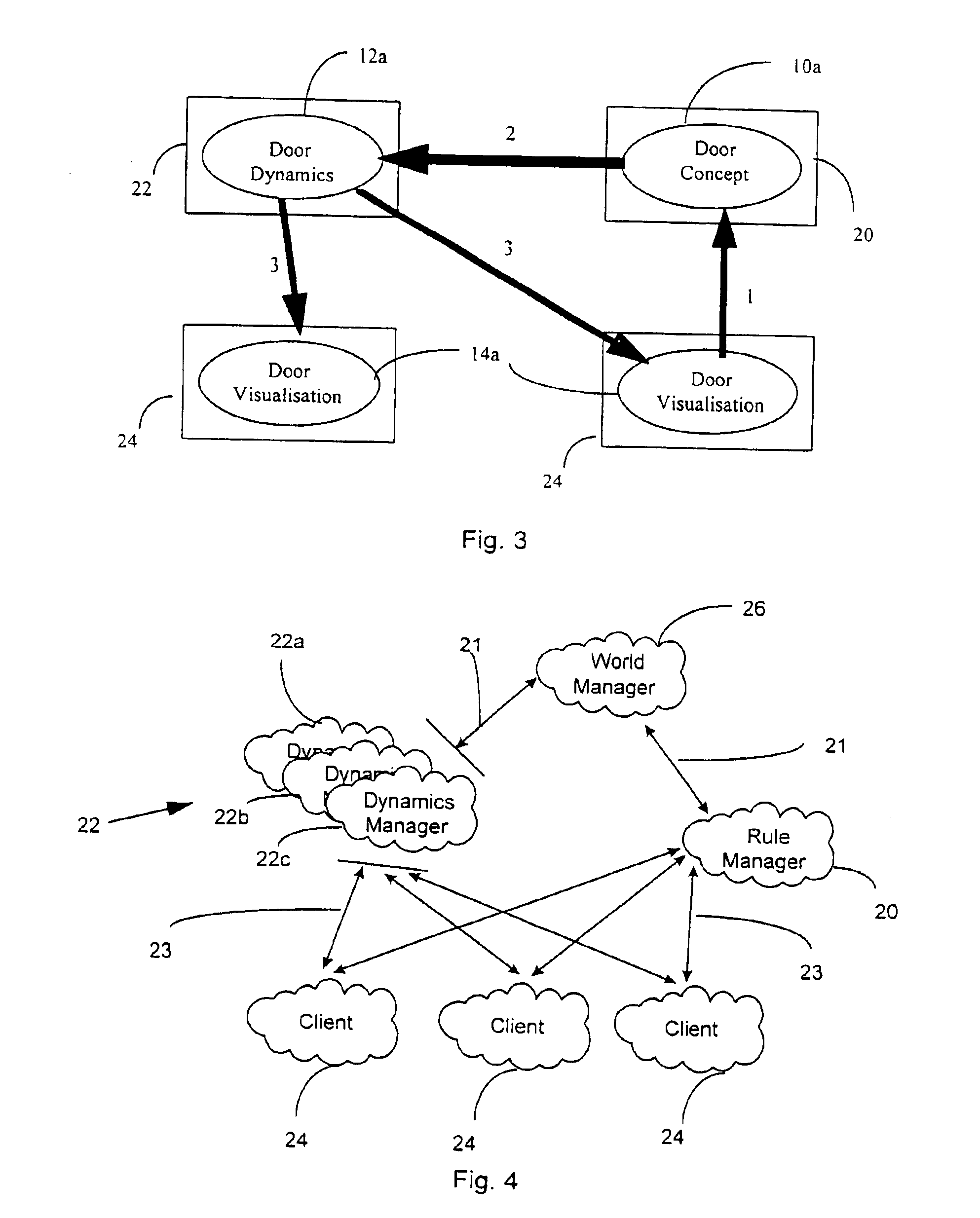
InactiveUS6912565B1Reduce upstream traffic requirementEnsure consistencyMultiple digital computer combinationsVideo gamesDynamic modelsClient-side
A distributed virtual environment includes one or more entities represented in the virtual environment by at least a conceptual entity-model, a dynamic entity-model and a visual entity-model each of the entity models being mutually independent. A server provides a conceptual-model manager, arranged to provide conceptual entity-models, one or more dynamic-model managers arranged to provide dynamic entity-models, and one or more client apparatuses arranged to provide a visual-model manager arranged to provide visual entity-models. Communications is arranged to allow transmission of messages between the conceptual-model manager, one or more dynamic-model managers and one or more visual-model managers.
Owner:BRITISH TELECOMM PLC
Inventory control and prescription dispensing system
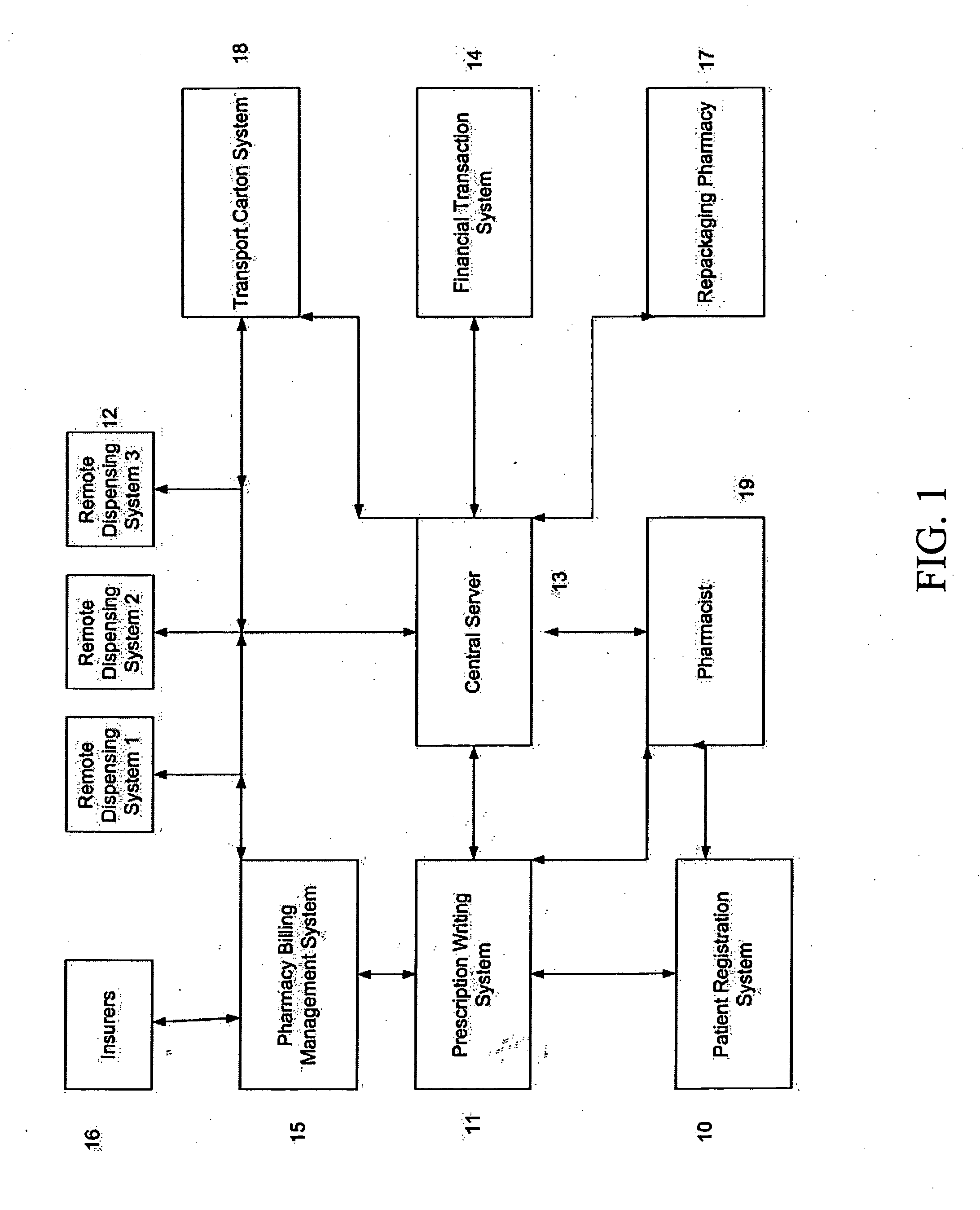
ActiveUS20070043469A1Ensure integrityEnsure safetyDrug and medicationsCoin-freed apparatus detailsEngineeringPatient registration
An inventory control and prescription management and dispensing system including a dispensing vault for storing and dispensing prescriptions, the dispensing vault in communication with a central computer system that, in turn, communicates with prescription providers, insurance companies, and other third parties; the dispensing vault including robotic means for randomly accessing pre-filled prescriptions within the vault, with the vault further including RFID, bar code, and other means for verifying the content and internal location of pre-filled prescriptions; a customer interface that uses customer biometrics to ID a customer to ensure that prescriptions are only dispensed to the correct person; a patient registration system in communication with the central computer system for collecting insurance, doctor, biometric, and other information to facilitate transactions; a labeling system for labeling pre-filled prescriptions with customer specific information upon dispensing; transport container that integrate into the dispensing vault and provide secure transportation from a pharmaceutical manufacturer or repackager to the dispensing vault, security provided through RFID tags which communicate with the central computer to verify that the transport container contains the correct formulary and that the integrity of the container (temperature range, time in transit, tampering) has not been compromised; a payment system integral to the dispensing vault that is in communication with third party banks and pharmacy billing management systems, credit agencies and the central computer; a verification system for ensuring that pre-filled bottles received from the manufacturer (before they are placed into the storage locations inside the vault) have not had their integrity compromised, with this system evaluating each container's weight, size, moisture content, shape, velocity change, color, pattern, and physical integrity (all comparisons made against standards stored in the central computer).
Owner:DRAPER LONNIE
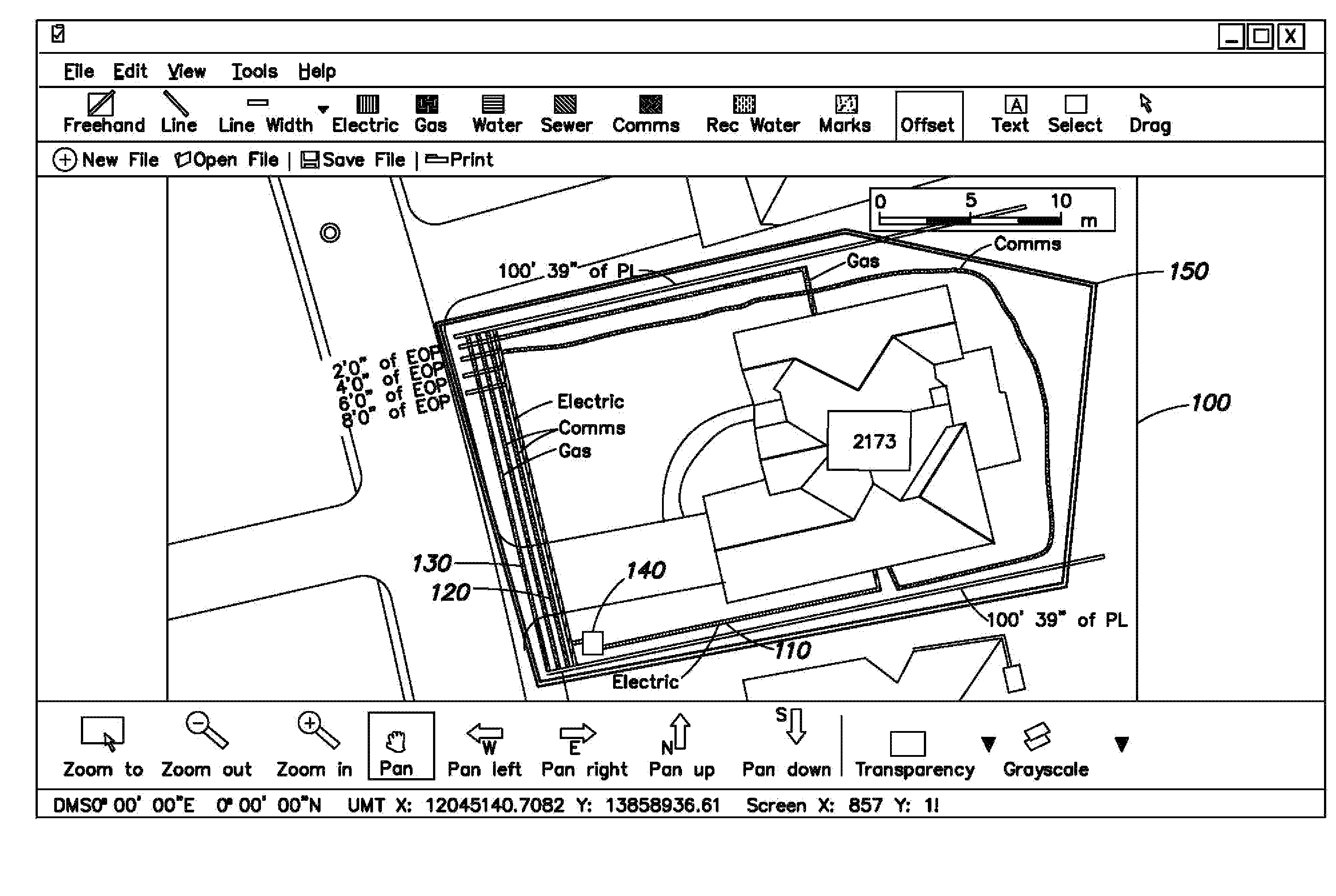
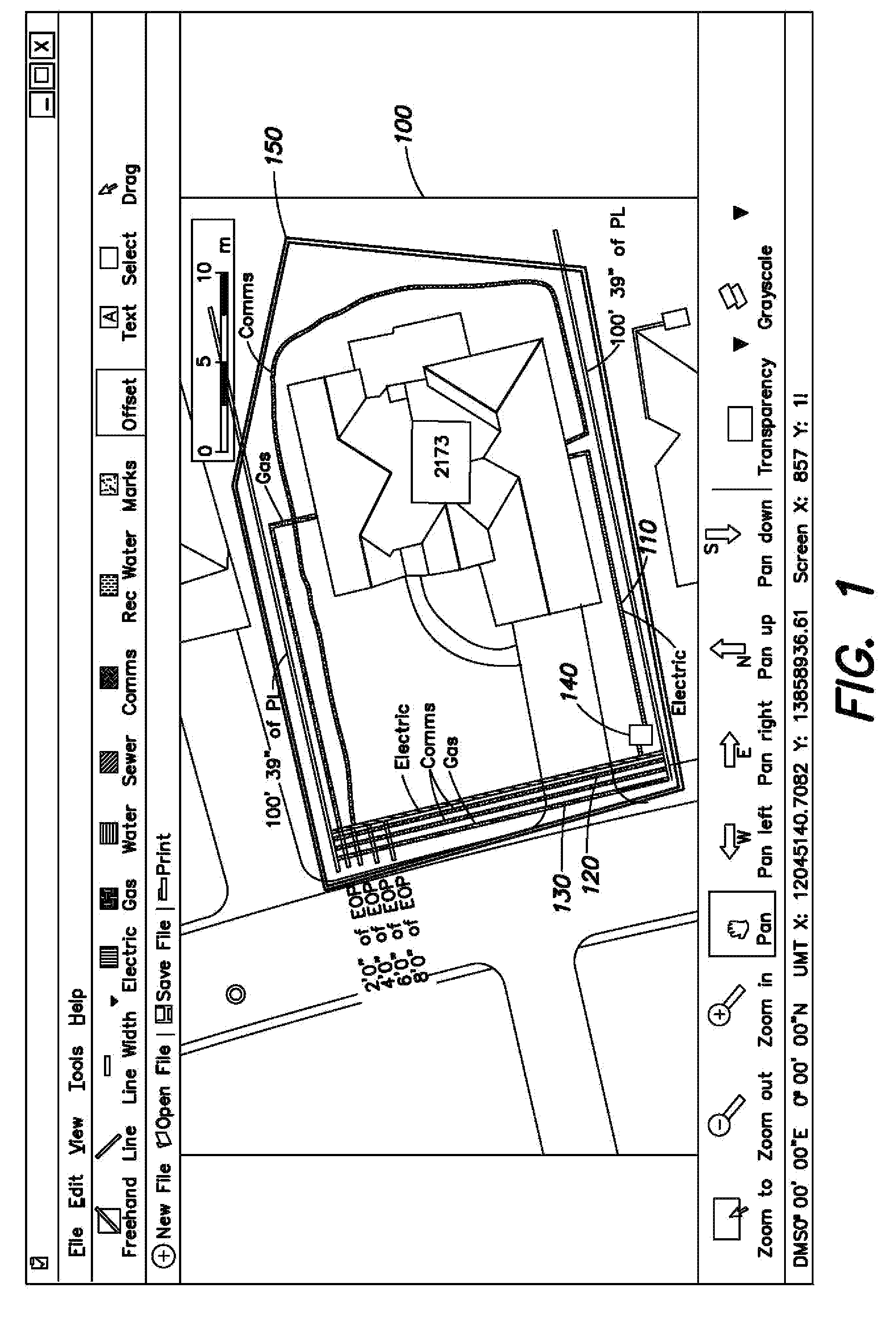
Methods, apparatus and systems for generating digital-media-enhanced searchable electronic records of underground facility located and/or marking operations
ActiveUS20110285749A1Facilitate viewingEnsure integrityData processing applicationsCathode-ray tube indicatorsElectronic recordsEngineering
Generating a digital-media-enhanced electronic record of a locate and / or marking operation performed by a locate technician. The locate and / or marking operation comprises locating and / or identifying, using at least one physical locate mark, a presence or an absence of at least one underground facility within a dig area, wherein at least a portion of the dig area may be excavated or disturbed during excavation activities. A location of the at least one underground facility and / or the at least one physical locate mark is electronically rendered on a display device so as to generate an electronic visual representation of the locate and / or marking operation. At least one digital media file representation of a corresponding digital media file relating to at least one aspect of the locate and / or marking operation or an environment of the dig area is also electronically rendered on the display device, so as to generate a digital-media-annotated representation of the locate and / or marking operation. Information relating to the digital-media-annotated representation of the locate and / or marking operation is electronically transmitted and / or stored so as to generate the digital-media-enhanced electronic record of the locate and / or marking operation.
Owner:CERTUSVIEW TECH
System and method for used vehicle valuation based on actual transaction data provided by industry participants
A vehicle valuation system supplies accurate wholesale, retail, purchase, and reconditioning values of used automobiles based upon actual transaction data for selected geographical areas. The system validates transaction data to ensure data integrity. A transaction database is populated with validated transaction data received, either automatically from an application such as a dealer management system or upon dealer submission, via online communication. Valuation requests may be submitted from client computers, which may include remote computing devices such as personal computers, laptop computers and handheld computers based upon manual and / or scanned entries. In response to valuation requests, the system searches the transaction database for a matching record and returns the resulting wholesale, retail, purchase, and reconditioning values to a user either via a web application or mobile PDA application.
Owner:HEDY SHAD
Multi-level security network system
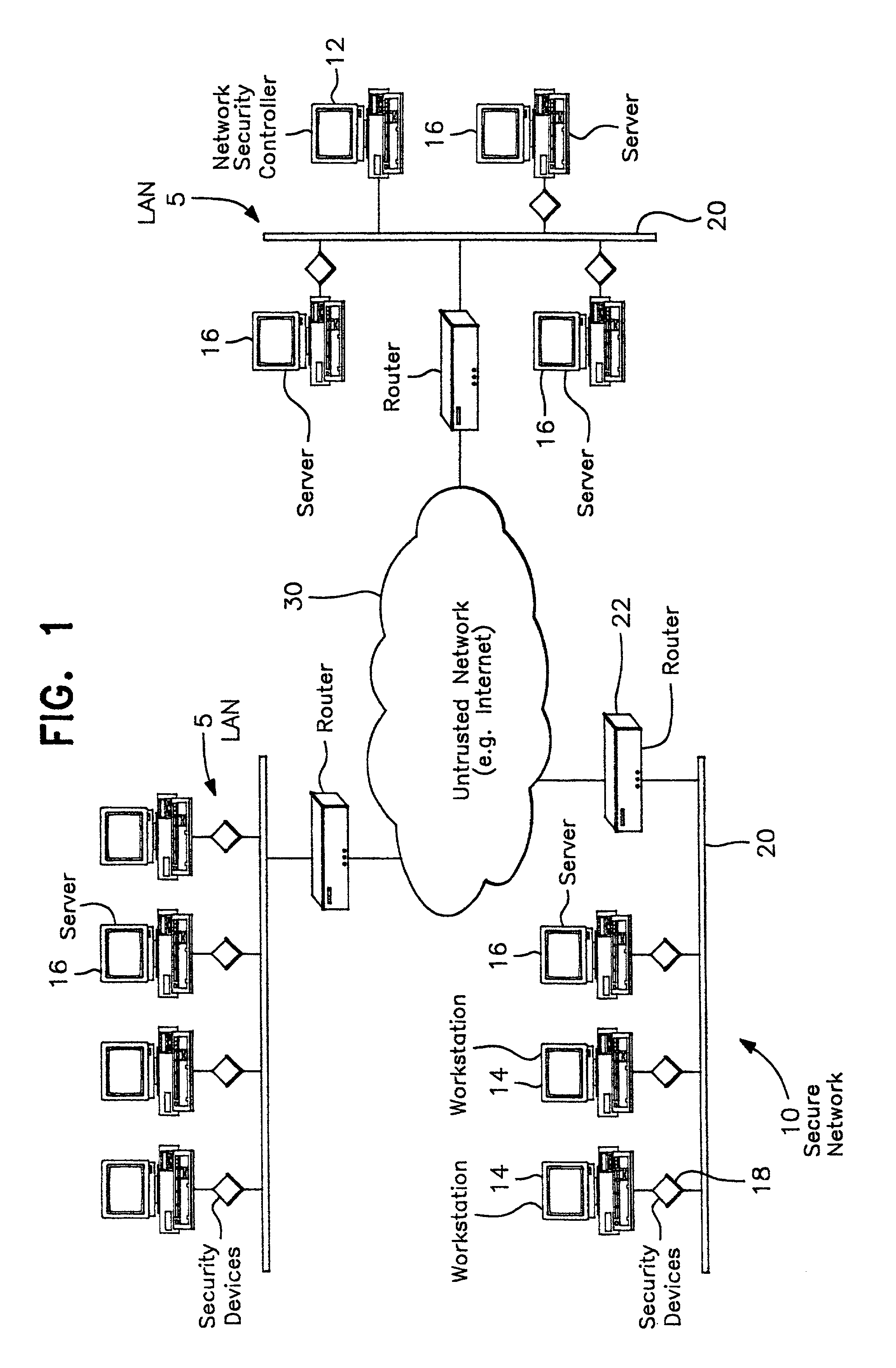
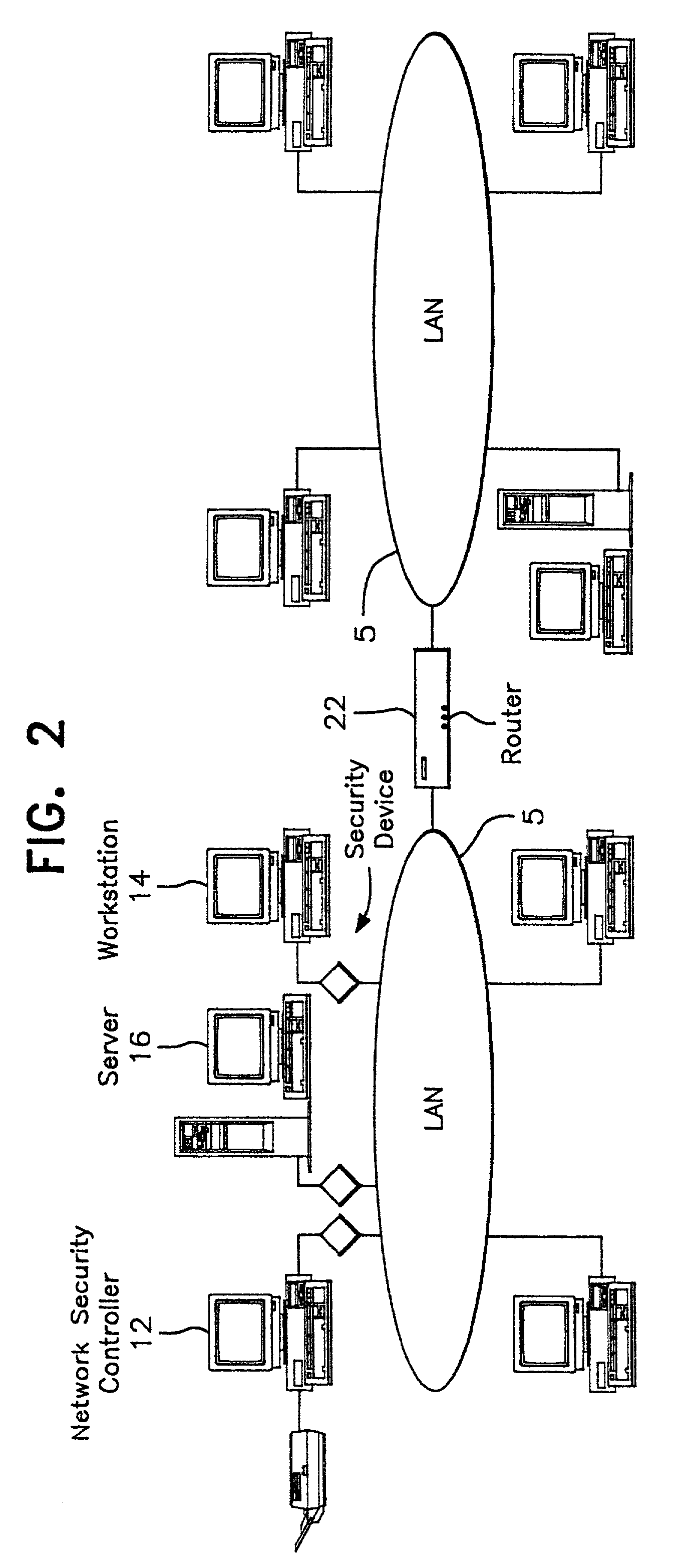
InactiveUS7069437B2Ensure integrityDigital data processing detailsComputer security arrangementsPrivate networkThe Internet
A network prevents unauthorized users from gaining access to confidential information. The network has various workstations and servers connected by a common medium and through a router to the Internet. The network has two major components, a Network Security Center (NSC) and security network interface cards or devices. The NSC is an administrative workstation through which the network security officer manages the network as a whole as well as the individual security devices. The security devices are interposed between each of workstation, including the NSC, and the common medium and operate at a network layer (layer 3) of the protocol hierarchy. The network allows trusted users to access outside information, including the Internet, while stopping outside attackers at their point of entry. At the same time, the network limits an unauthorized insider to information defined in their particular security profile. The user may select which virtual network to access at any given time. The result is trusted access to multiple secure Virtual Private Networks (VPN), all from a single desktop machine.
Owner:CRYPTEK INC
Streaming Method and System for Processing Network Metadata
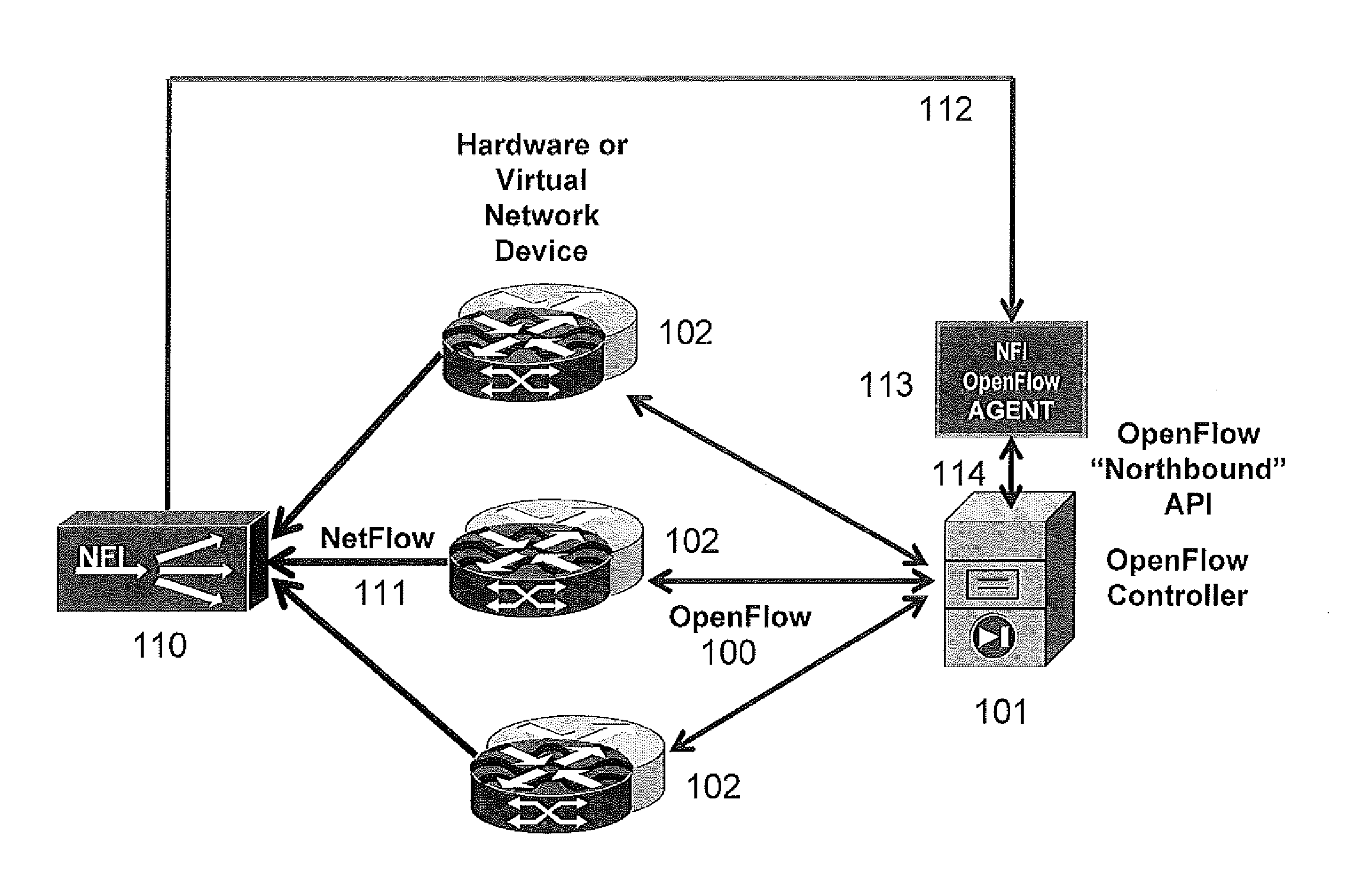
InactiveUS20140075557A1Easy to deployImprove system throughputMemory loss protectionError detection/correctionInternet trafficTemplate based
An improved method and system for processing network metadata is described. Network metadata may be processed by dynamically instantiated executable software modules which make policy-based decisions about the character of the network metadata and about presentation of the network metadata to consumers of the information carried by the network metadata. The network metadata may be type classified and each subclass within a type may be mapped to a definition by a unique fingerprint value. The fingerprint value may be used for matching the network metadata subclasses against relevant policies and transformation rules. For template-based network metadata such as NetFlow v9, an embodiment of the invention can constantly monitor network traffic for unknown templates, capture template definitions, and informs administrators about templates for which custom policies and conversion rules do not exist. Conversion modules can efficiently convert selected types and / or subclasses of network metadata into alternative metadata formats.
Owner:NETFLOW LOGIC
Variable encryption scheme for data transfer between medical devices and related data management systems
InactiveUS7027872B2Ensure authenticityEnsure integrityElectrotherapyData processing applicationsData centerData management
Owner:MEDTRONIC INC
Data processing method
ActiveUS20070014394A1Increased complexityDifficult to applyMathematical modelsUnauthorized memory use protectionComputer hardwareMagnetic tape
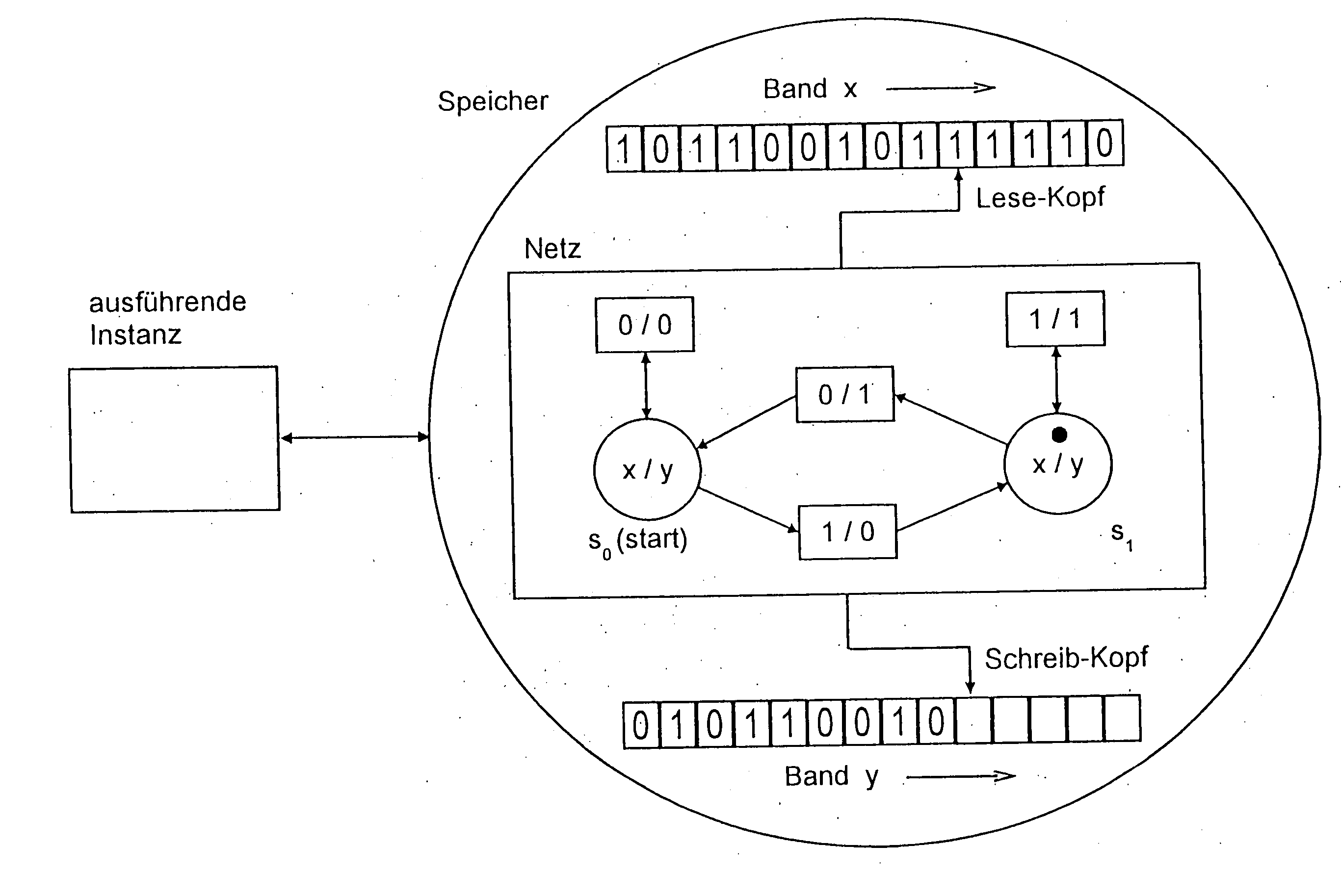
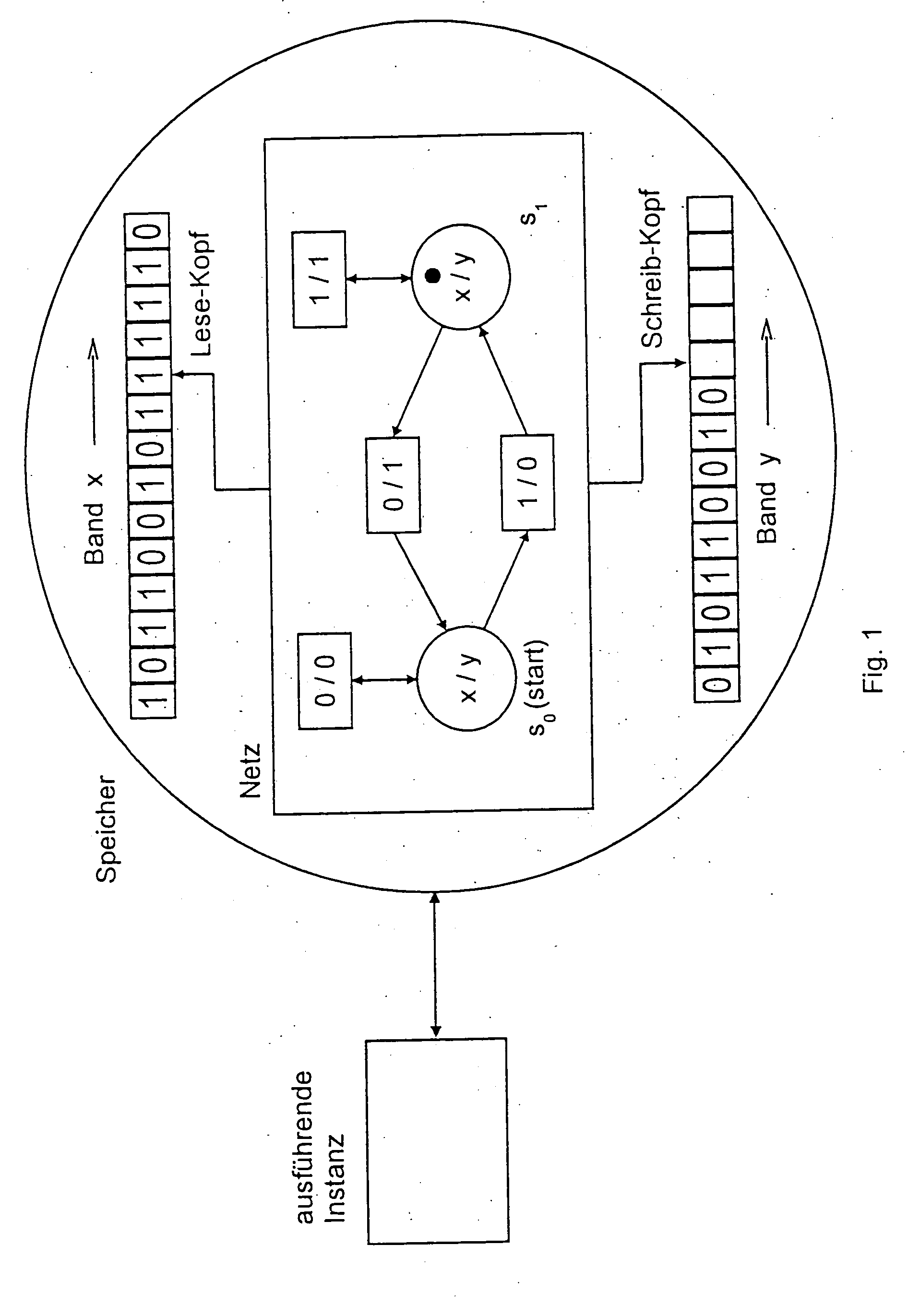
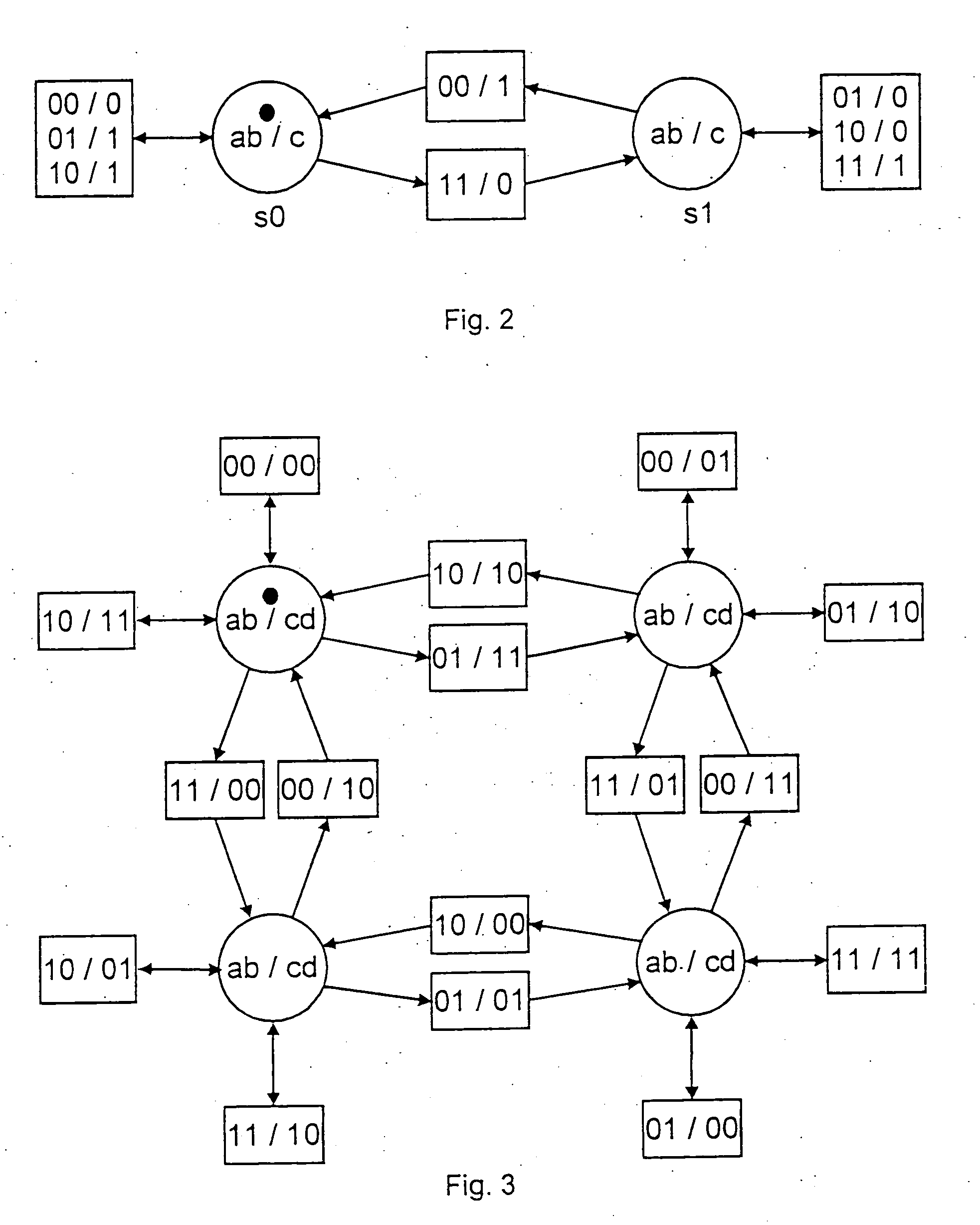
Method for processing data, in which a Petri net is encoded, written into a memory and read and excuted by at least one instance, wherein transitions of the Petri net read from at least one tape and / or write on at least one tape symbols or symbol strings, with the aid of at least one head. [FIG. 1]. In an alternative, data-processing, co-operating nets are composed, the composition result is encoded, written into a memory and read and executed from the memory by at least one instance. In doing this, components can have cryptological functions. The data-processing nets can receive and process second data from a cryptological function which is executed in a protected manner. The invention enables processing of data which prevents semantic analysis of laid-open, possibly few processing steps and which can produce a linkage of the processing steps with a hardware which is difficult to isolate.
Owner:WHITECRYPTION
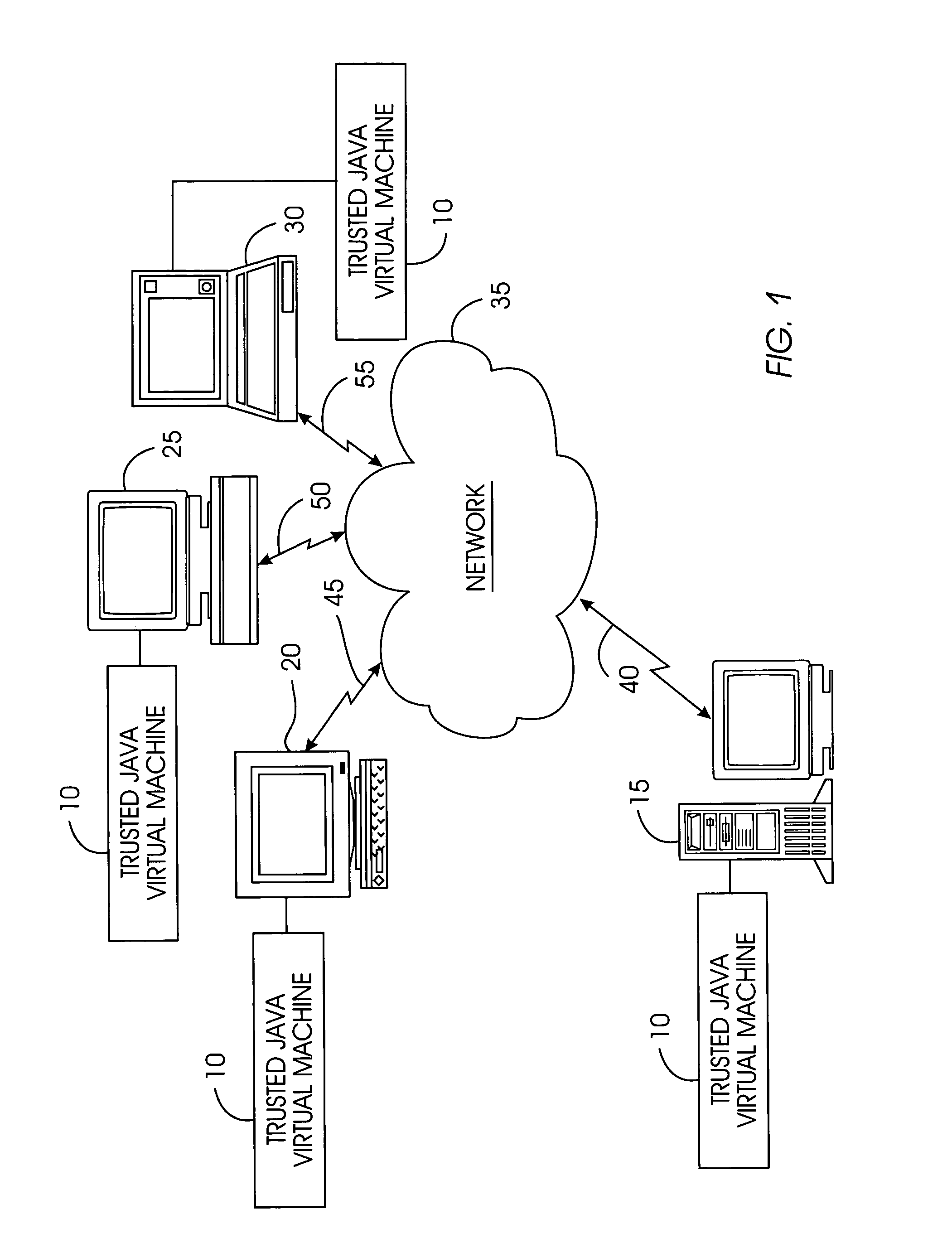
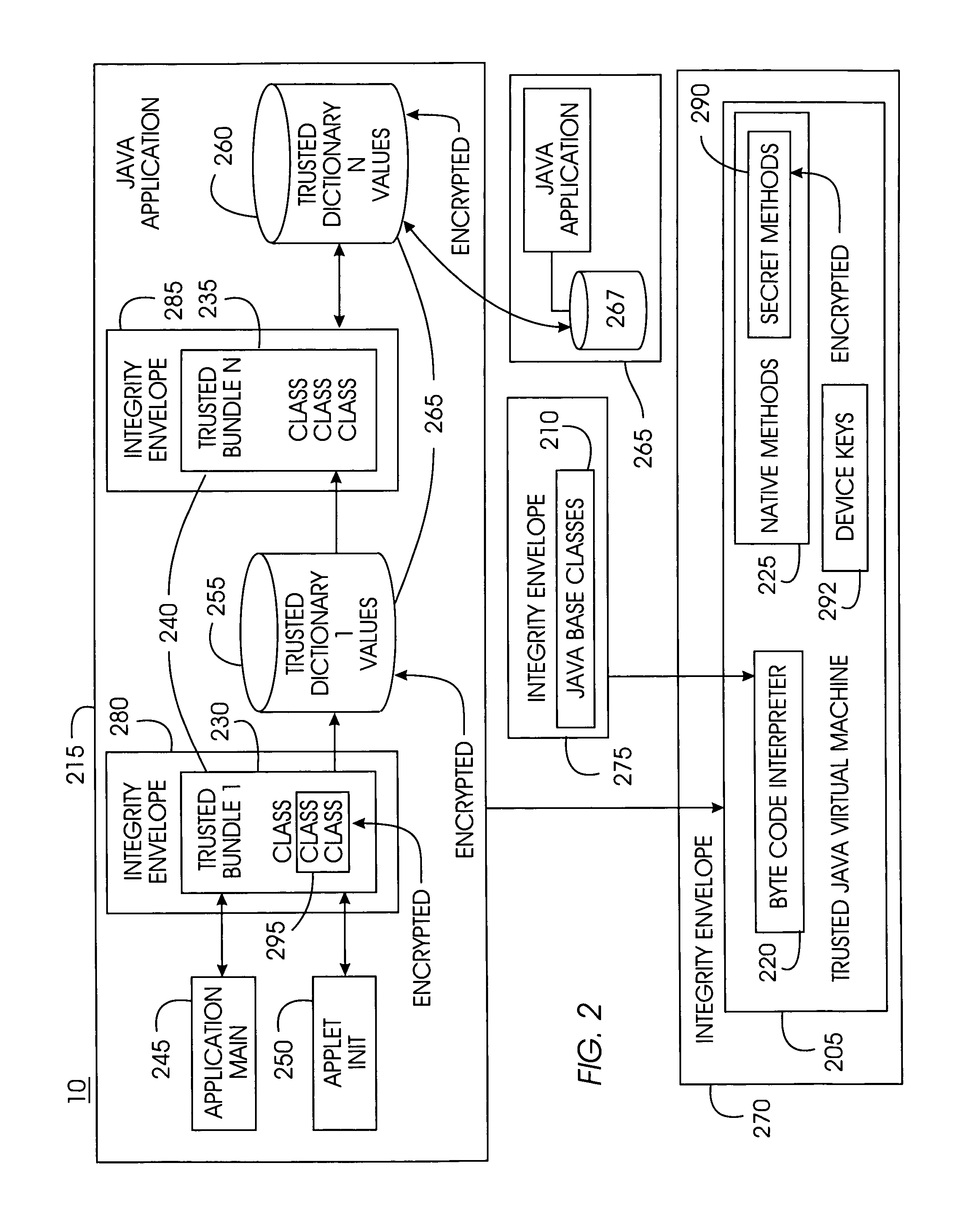
Tamper-resistant trusted java virtual machine and method of using the same
InactiveUS7516331B2Slow processEnsure integrityProgram control using stored programsUser identity/authority verificationOpen sourceProgram security
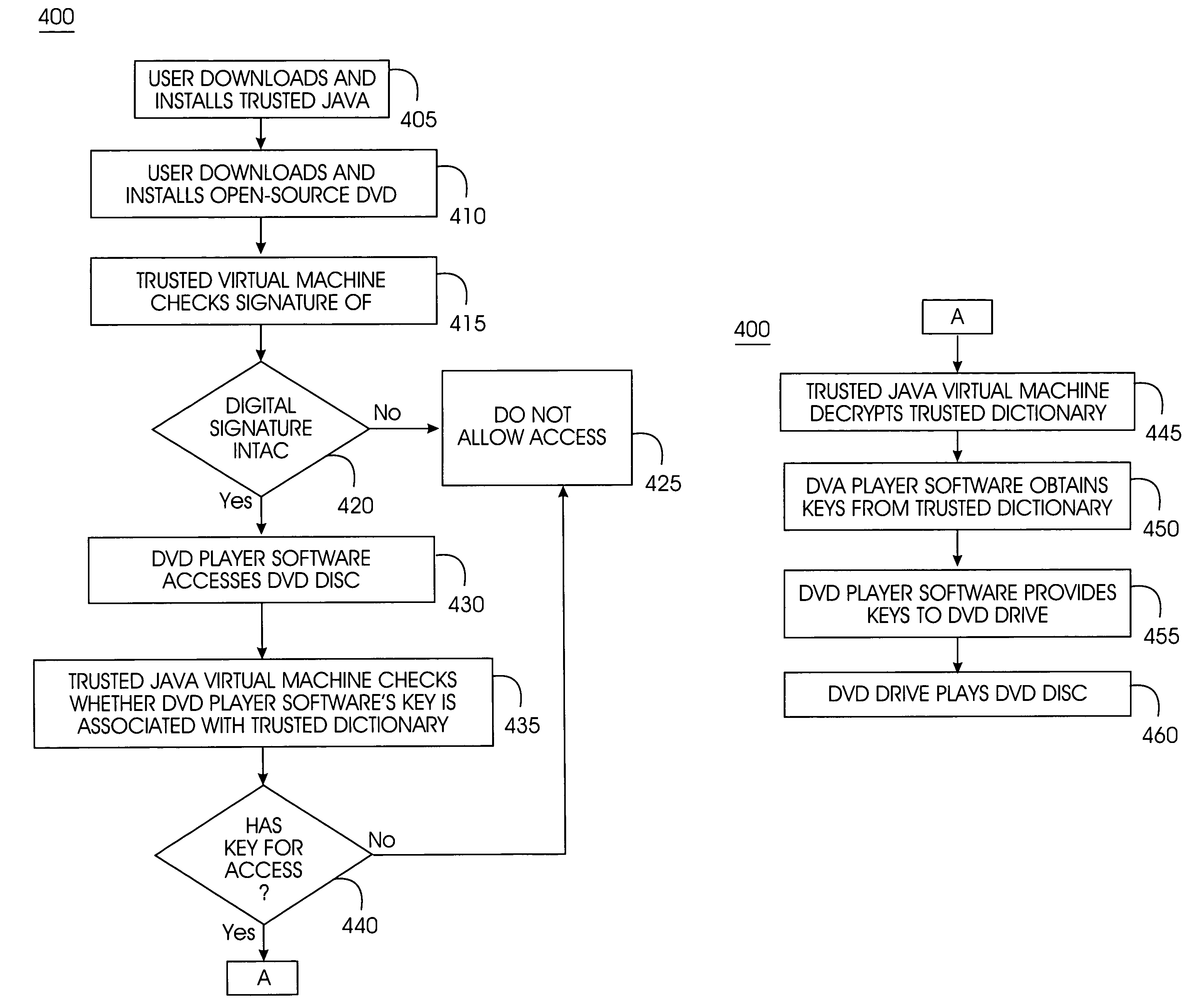
A trusted Java virtual machine provides a method for supporting tamper-resistant applications, ensuring the integrity of an application and its secrets such as keys. The trusted Java virtual machine verifies the integrity of the Java application, prevents debugging of the Java application, and allows the Java application to securely store and retrieve secrets. The trusted Java virtual machine environment comprises a TrustedDictionary, a TrustedBundle, an optional encryption method for encrypting and decrypting byte codes, and an underlying trusted Java virtual machine. The encrypted TrustedDictionary protects data while the TrustedBundle protects programming code, allowing applications to store secret data and secure counters. The application designer can restrict TrustedBundle access to only those interfaces that the application designer explicitly exports. The open source code may optionally be encrypted. Secrets required by the open source programming code of the application are encrypted in TrustedDictionary.
Owner:INT BUSINESS MASCH CORP
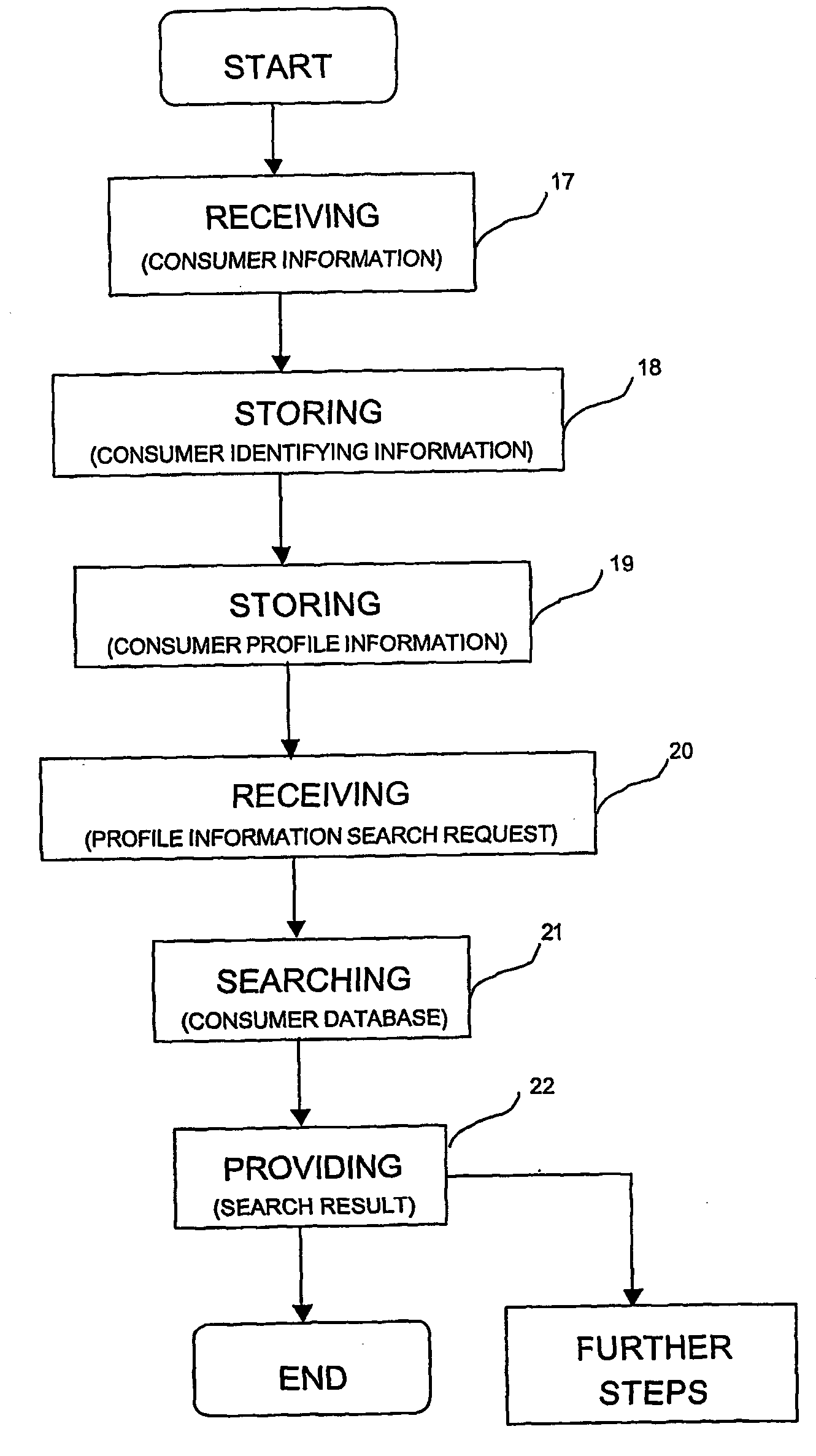
System for permission-based communication and exchange of information
InactiveUS20050131757A1Accurate dataEffectively and efficiently capturingDigital data information retrievalSpecial data processing applicationsInformation searchingInformation exchange
A method and system for permission-based communication and exchange of information by means of a neutral and unified database in which consumers remain anonymous. The method involves receiving and storing consumer information corresponding to a number of individual consumers via a consumer information receiver, the consumer information including both consumer-identifying information and consumer profile information for each consumer. The method also involves receiving a profile information search request which specifies at least one consumer profile criterion. The method also involves searching the consumer database to identify selected records which match the consumer profile criterion in order to obtain a search result. The method also involves providing the search result to the requestor via a search result provider, and wherein the search result does not include any consumer-identifying information.
Owner:PUREPROFILE MEDIA PLC
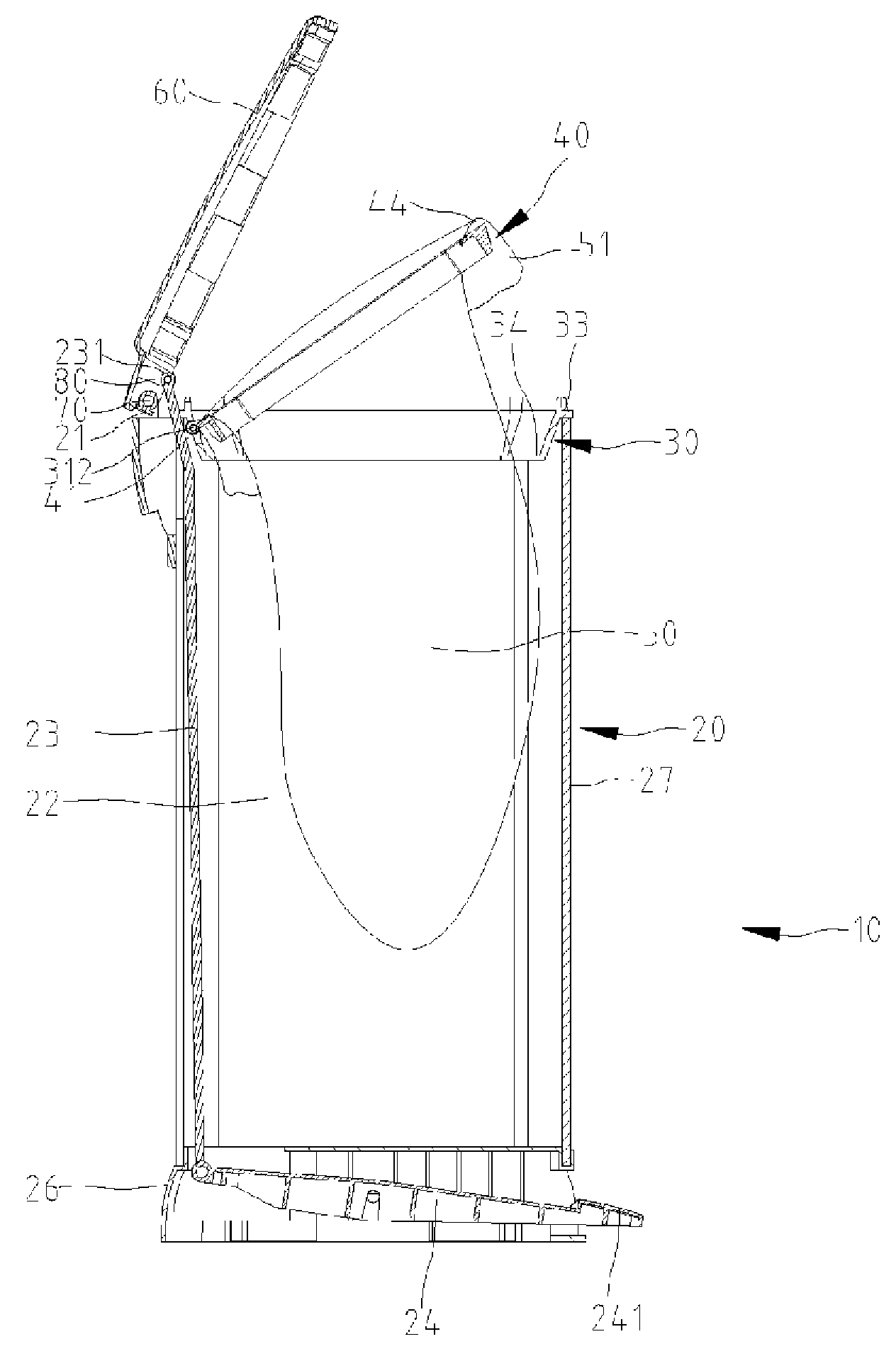
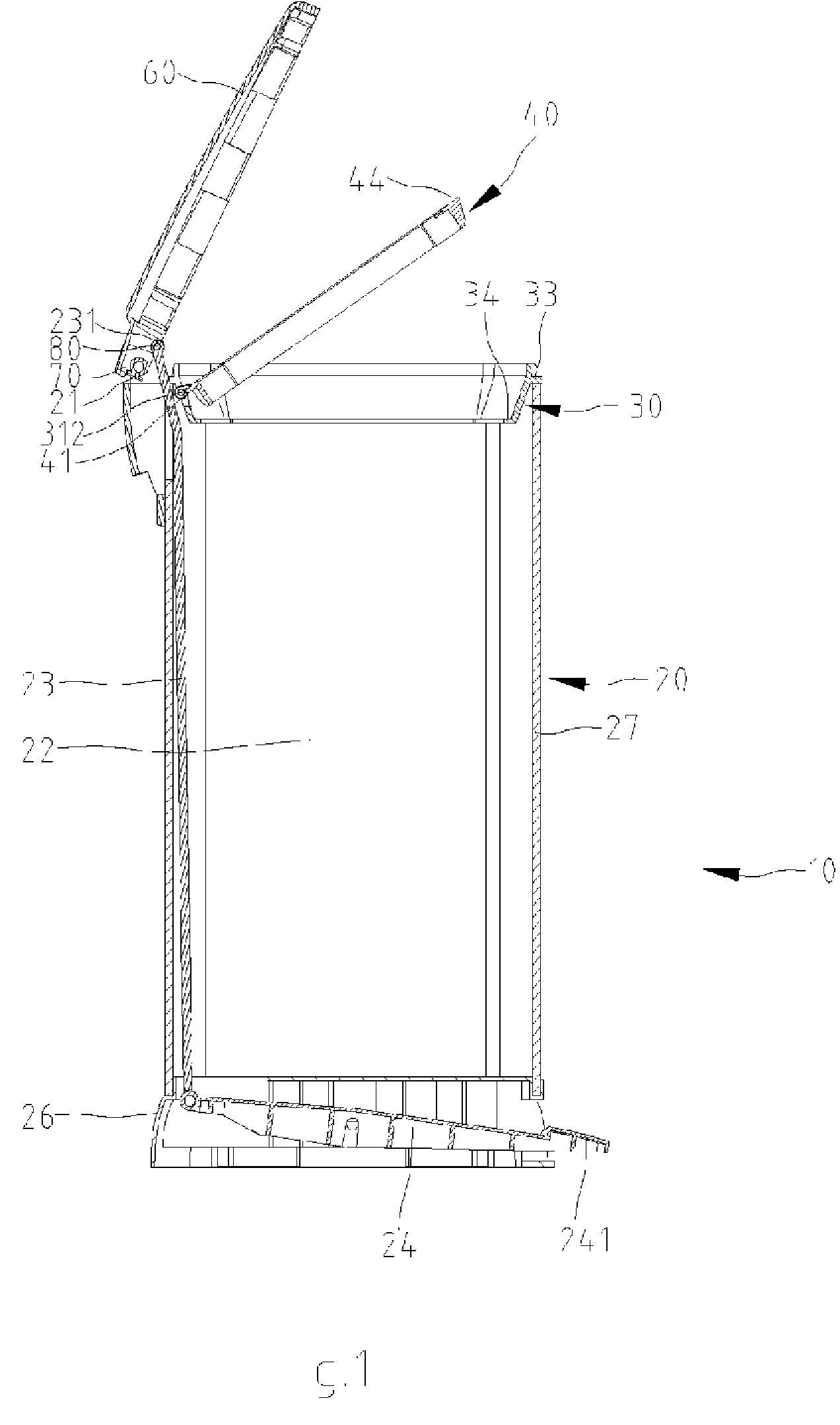
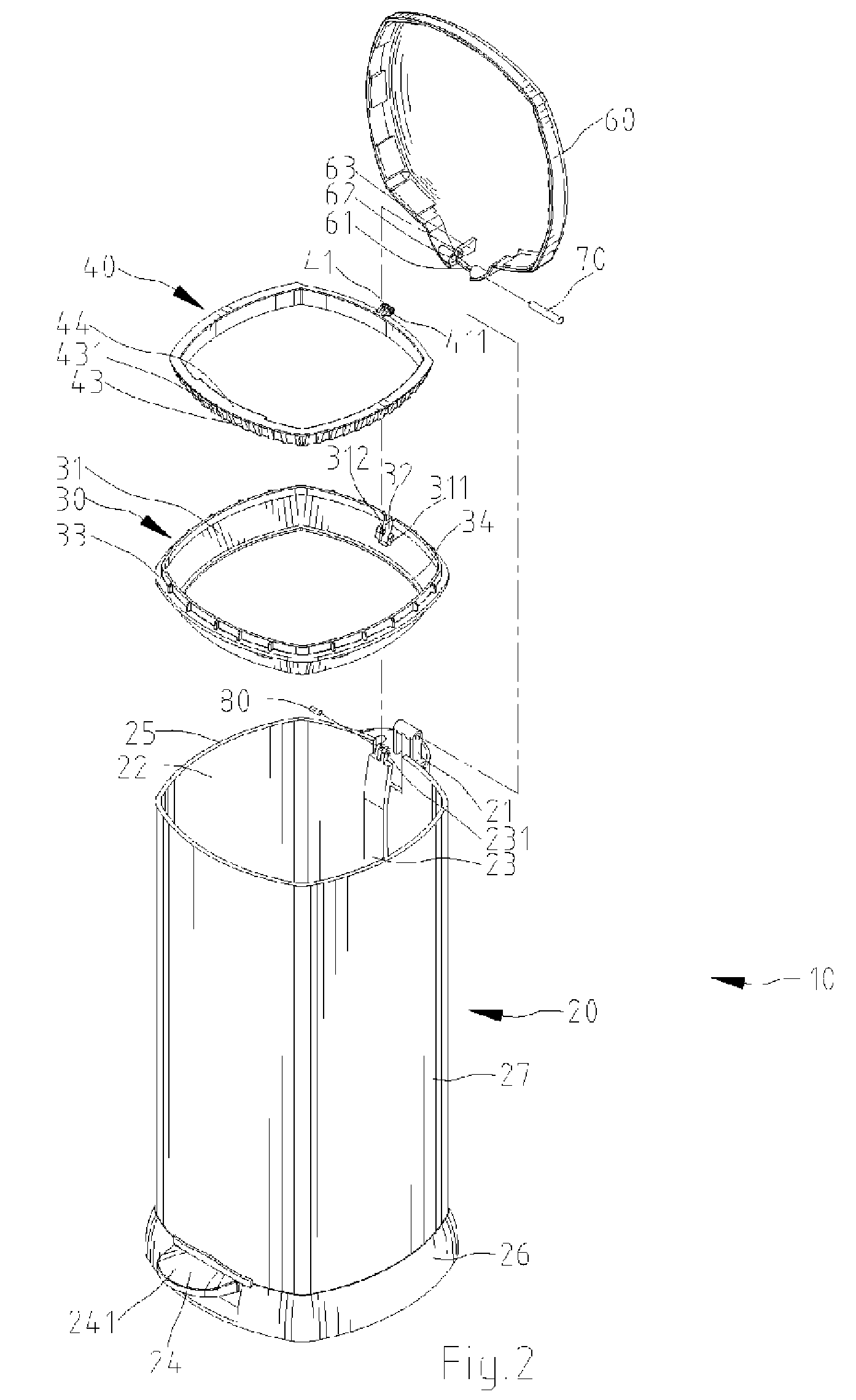
Garbage bin
Owner:LIN TSONG YOW
Method and apparatus for encryption, method and apparatus for decryption, and computer-readable medium storing program
InactiveUS7184549B2Ensure integrityEncryption apparatus with shift registers/memoriesSecret communicationComputer hardwarePlaintext
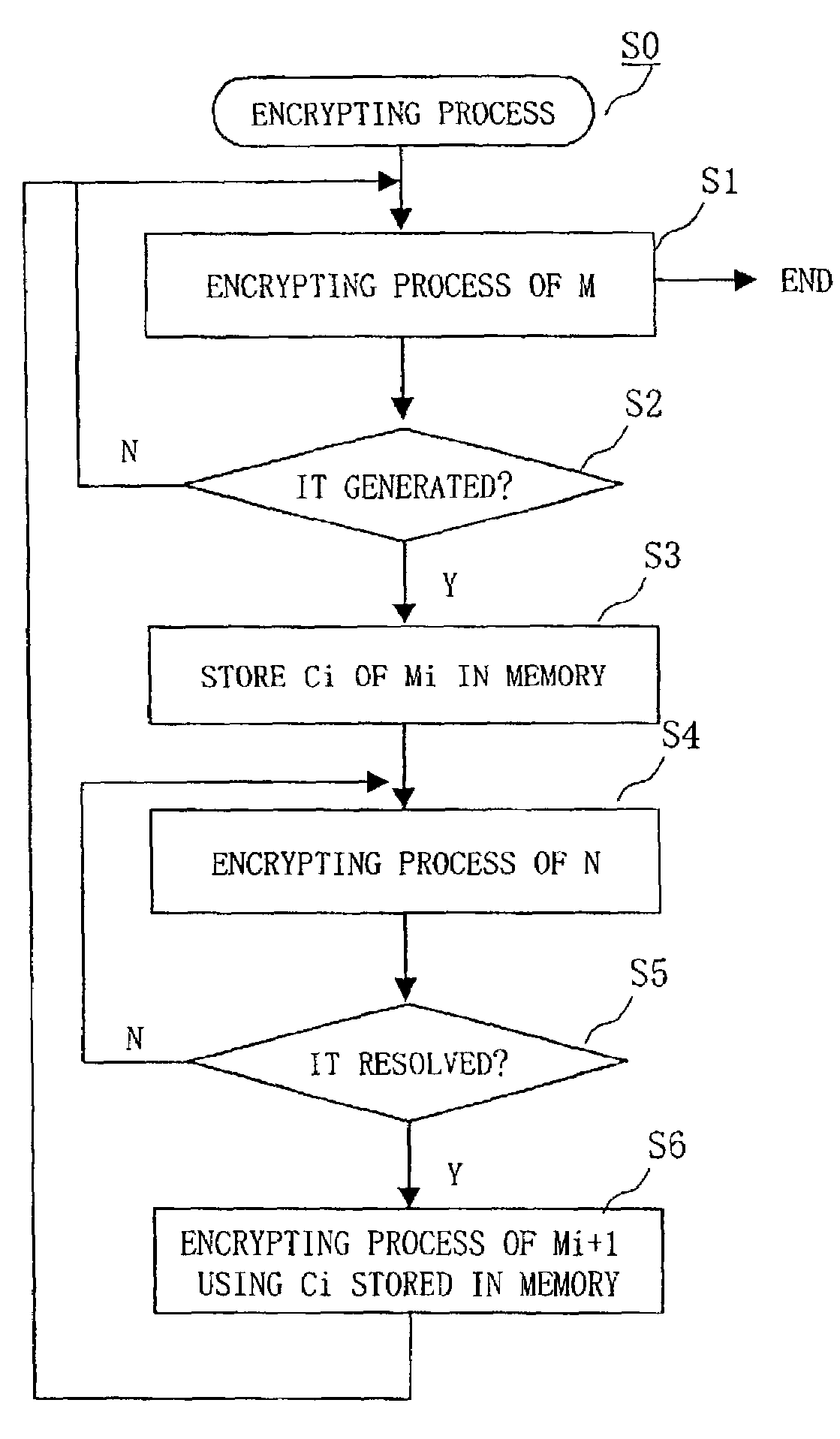
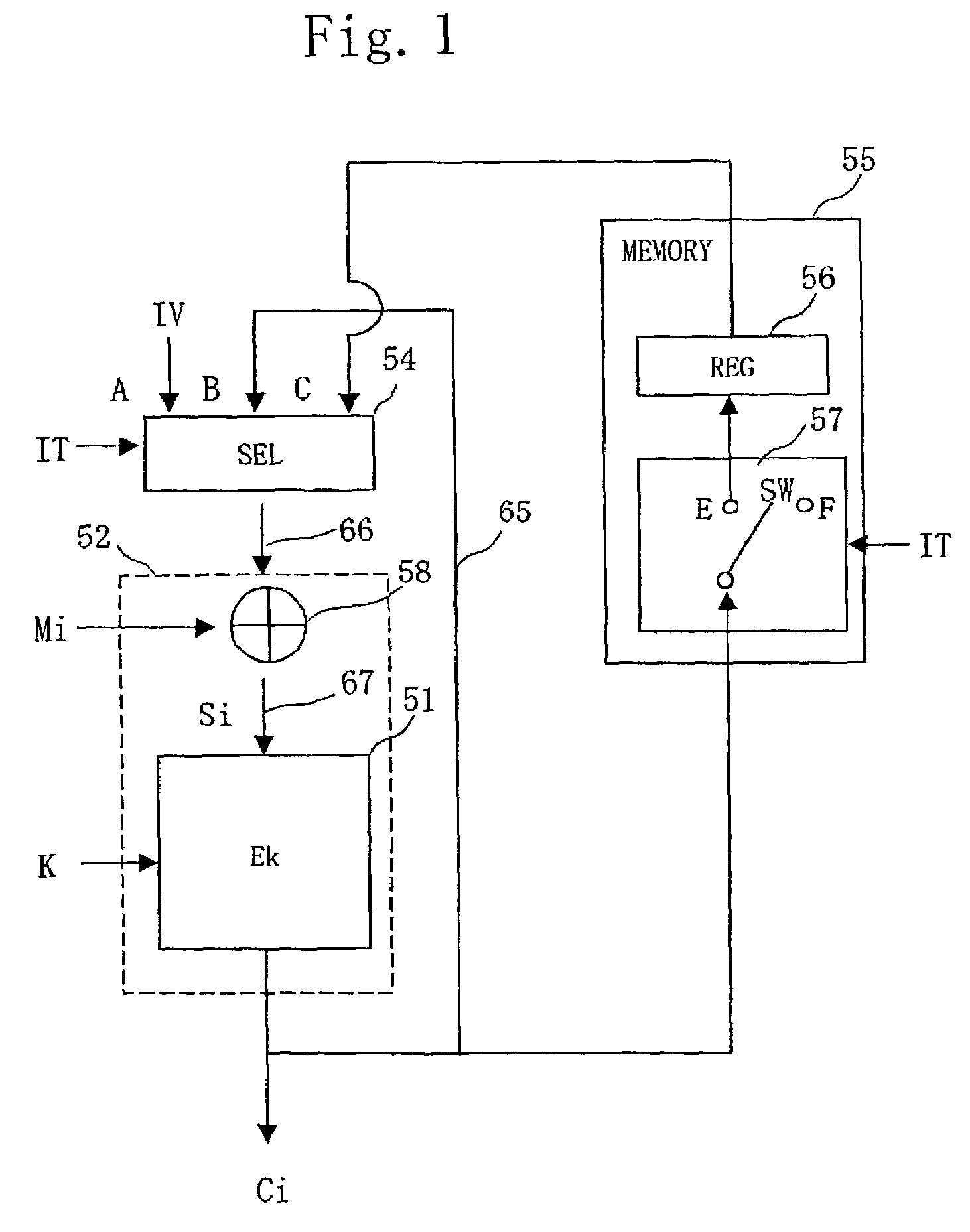
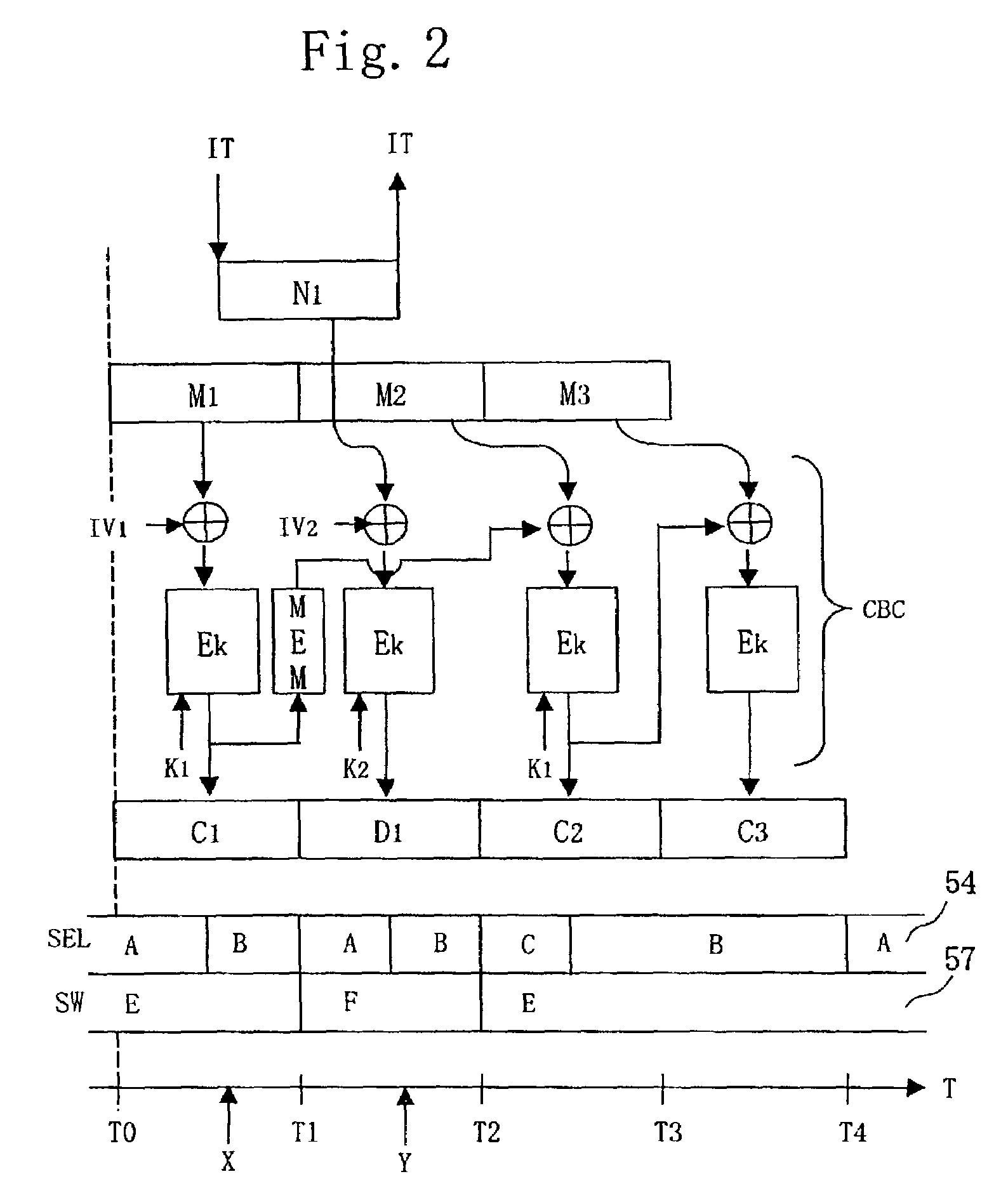
To encrypt another piece of data during encrypting process of a certain piece of data, a memory 55 is provided in parallel with a feedback line 65 which feeds back data from an encrypting module 51using an encryption key K to a selector 54. When an interrupt IT for processing plaintext block data N1 is generated while plaintext block data M1 is processed, ciphertext block data C1 at timing of generation of the interrupt IT is made to be stored in a register 56. The ciphertext block data C1 stored in the memory 55 is made to be selected by the selector 54 at timing of completion of processing the plaintext block data N1, and processing the plaintext block data M1+1 is started.
Owner:MITSUBISHI ELECTRIC CORP
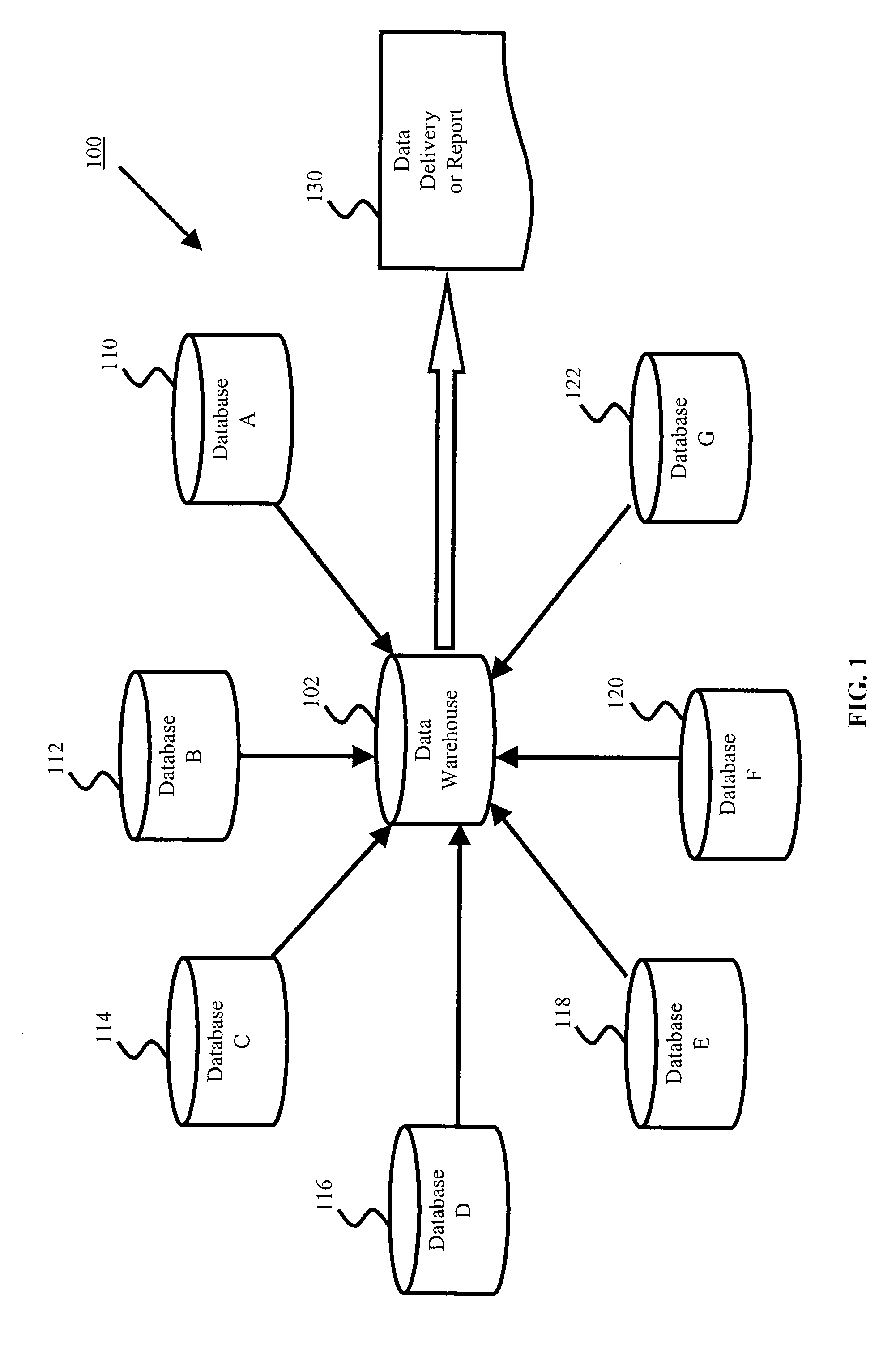
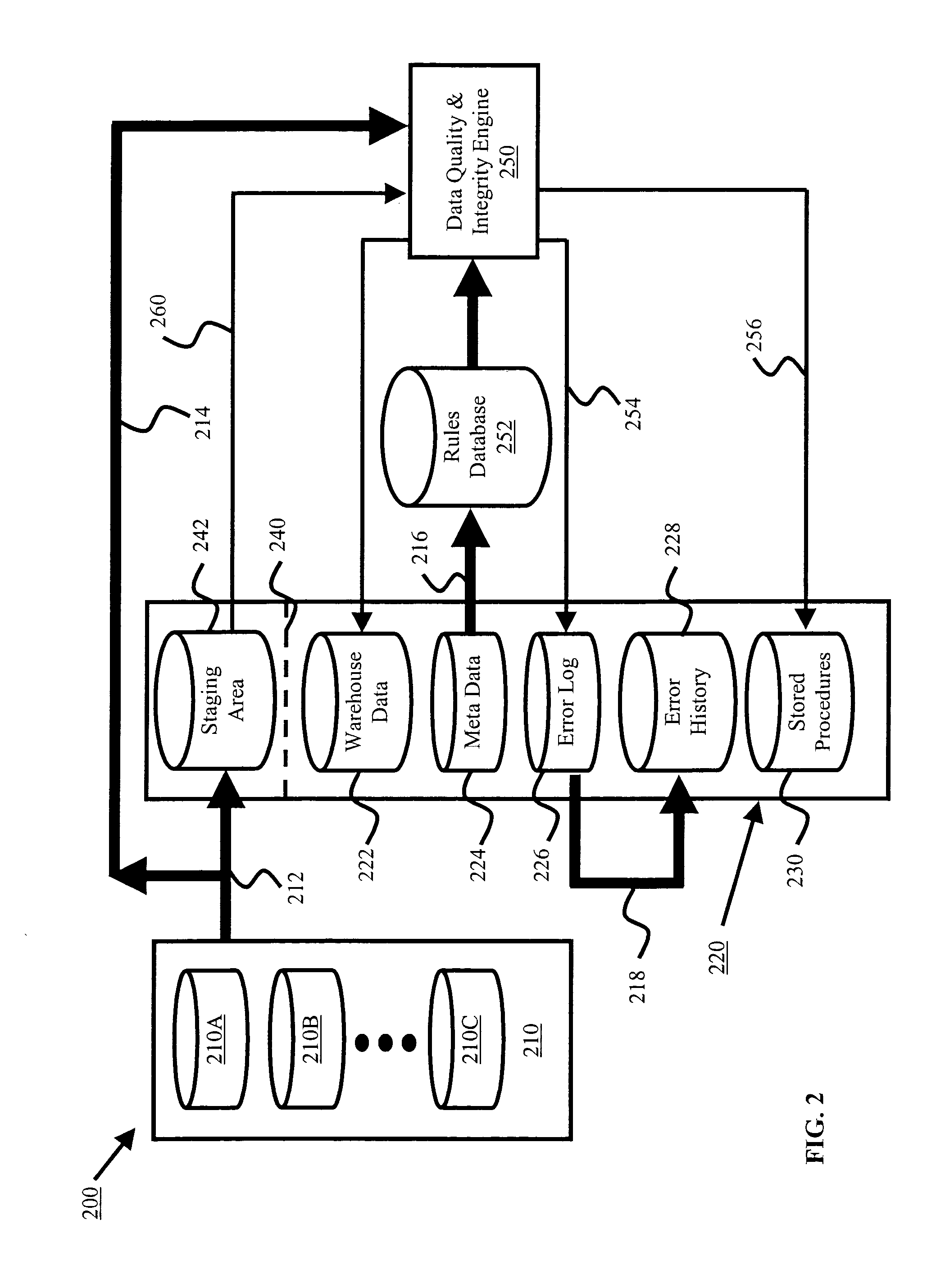
Data quality & integrity engine
InactiveUS20050066240A1Ensure integrityEnsure qualityError detection/correctionOffice automationSearch data structureData set
Methods, systems, and computer program products for ensuring data quality and integrity of a data set derived from a data source are described. The data source may be one or more data repositories or data warehouses, or one or more transaction systems. Data from the data source may be stored in a staging area. A data repository is built using the data. The data repository comprises a data structure that forms a model of the data from the data source. The building step involves applying business rules from a rules database to the data. The business rules are dependent upon meta data. The building step further involves detecting any errors in the data and storing data satisfying the business rules in the data repository. A log of any detected errors may be maintained in the data repository.
Owner:TENIX INVESTMENTS
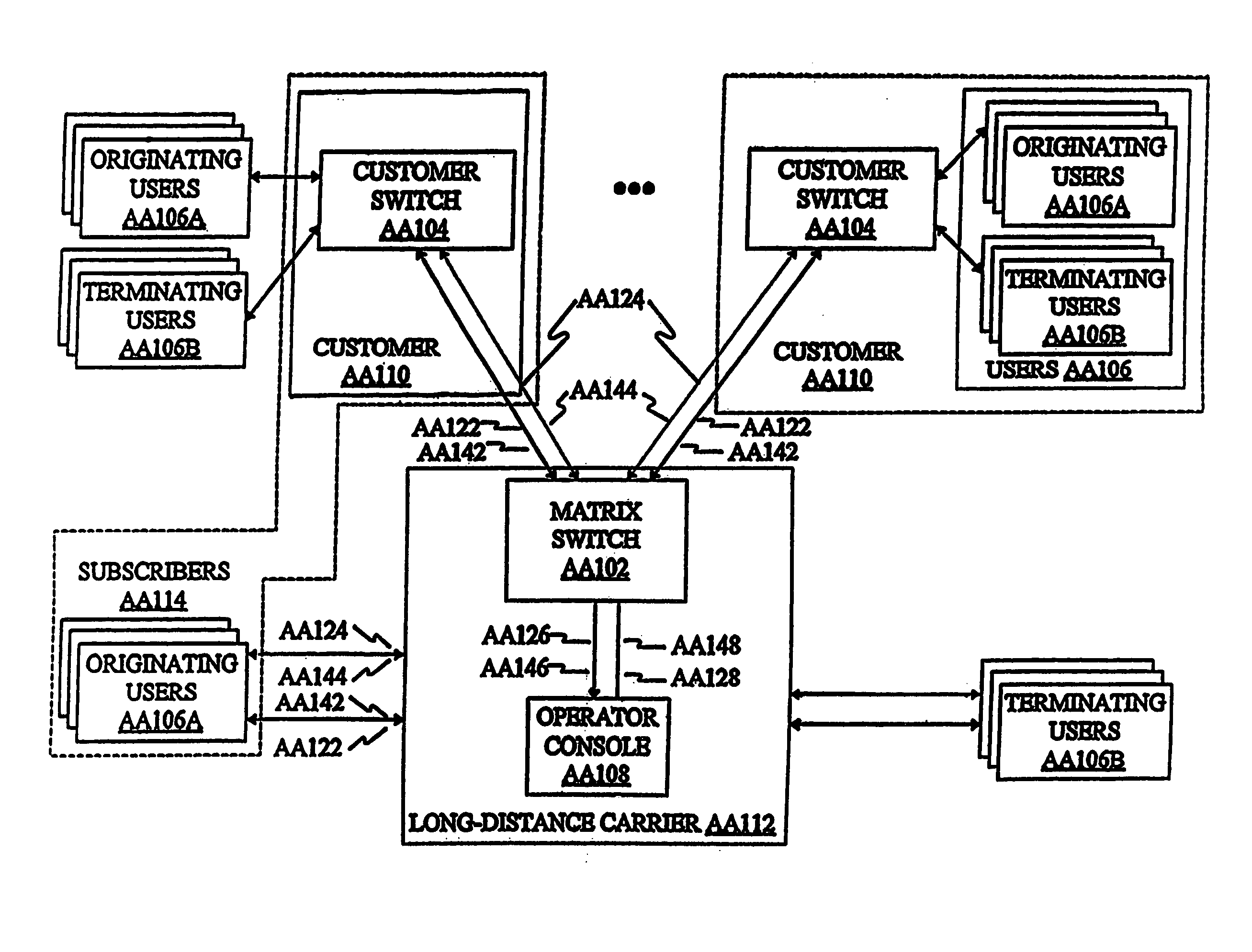
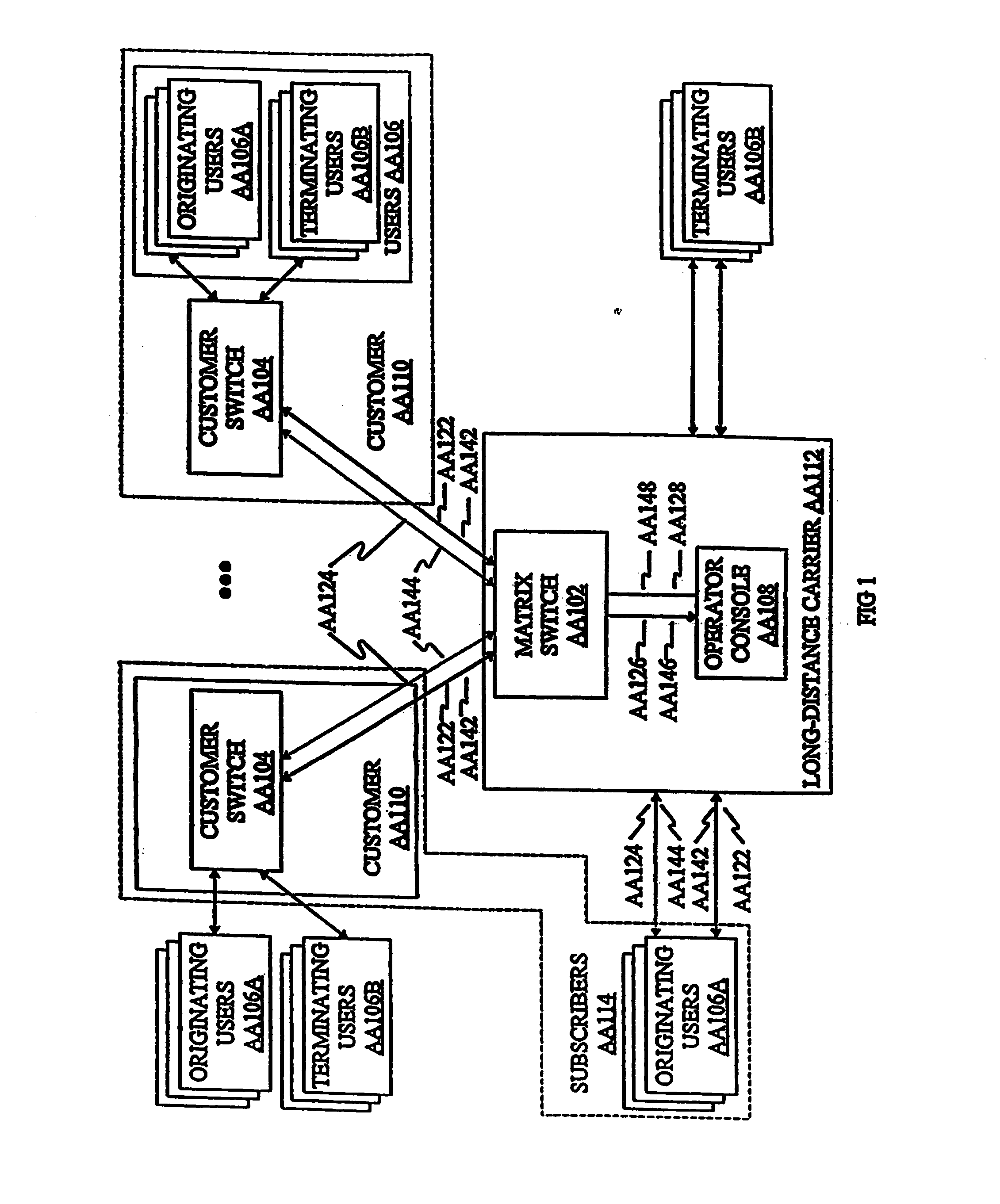
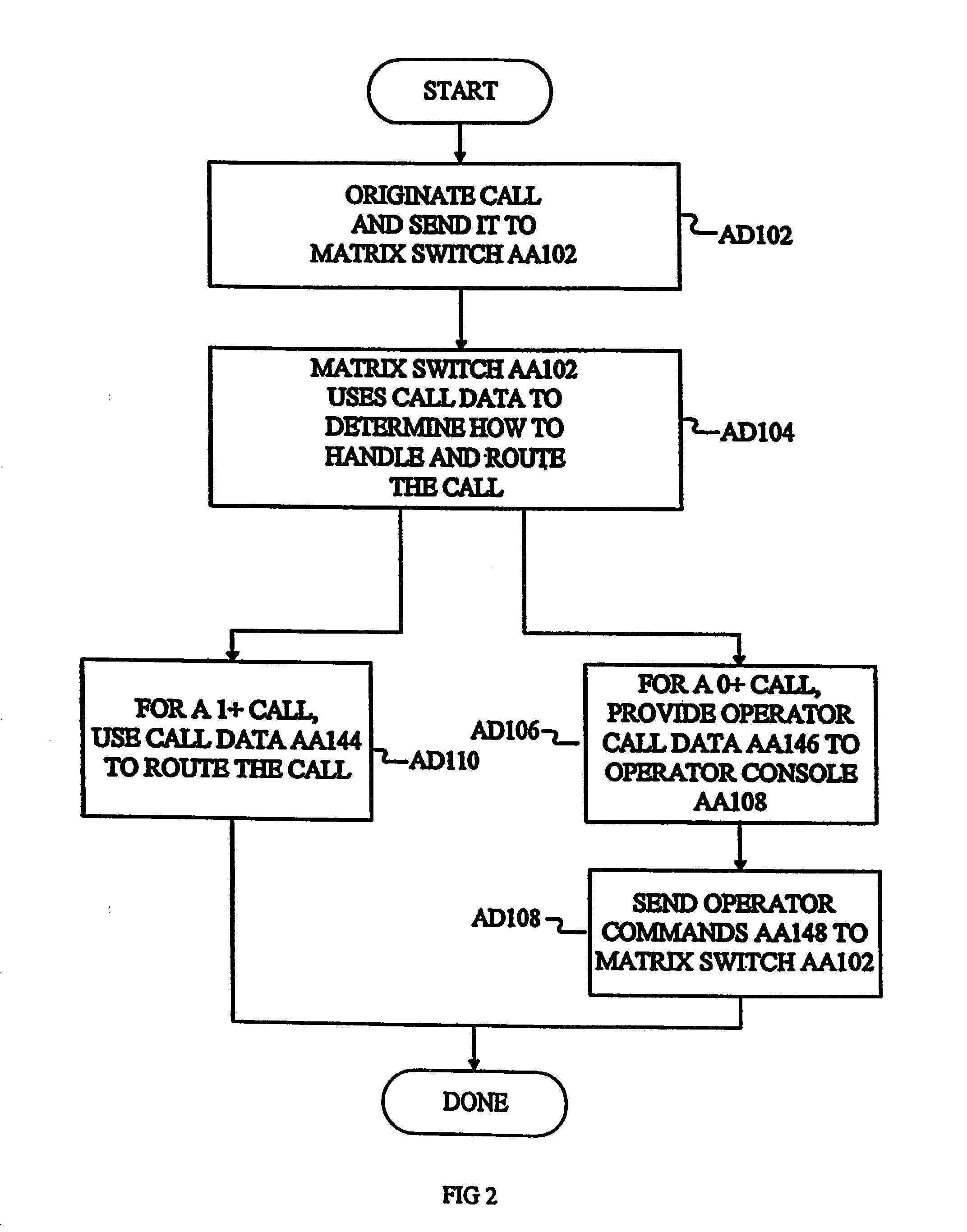
Call-processing system and method
InactiveUS20060251226A1Easy to operateEnsure integrityMultiplex system selection arrangementsInterconnection arrangementsHandling systemDistributor
A system and method for processing telephone calls and providing enhanced services is presented. The call processing system includes a network control processor for controlling the processing and routing of the calls and for providing enhanced features, and a matrix switch for routing calls from an originating location to a terminating location. Operator consoles can be included to provide operator assistance to the caller. The network control processor comprises a central message processor that receives call data, determines the type of call, determines the processing required, and determines whether operator assistance is required. A call route distributor allocates an operator console to the call if required. A billing server is used to track billing information for the call while it is in progress. A database server is provided for database look-ups and storage. The call processing system also includes a validation system, a billing system, a distribution system, and a fraud detection and prevention system. The validation system is used to validate call information to determine whether the call can be placed. The billing system determines rates for calls and calculates the cost of completed calls. The distribution system distributes changes that are made to a master database to the appropriate slave database. The fraud detection and prevention system monitors originating and in-process calls to detect and possibly prevent possible fraudulent uses of phone services and systems. A client interface is provided to facilitate communications among applications and DEF records are used to define specific call processing actions.
Owner:GLOBAL CROSSING TELECOMM
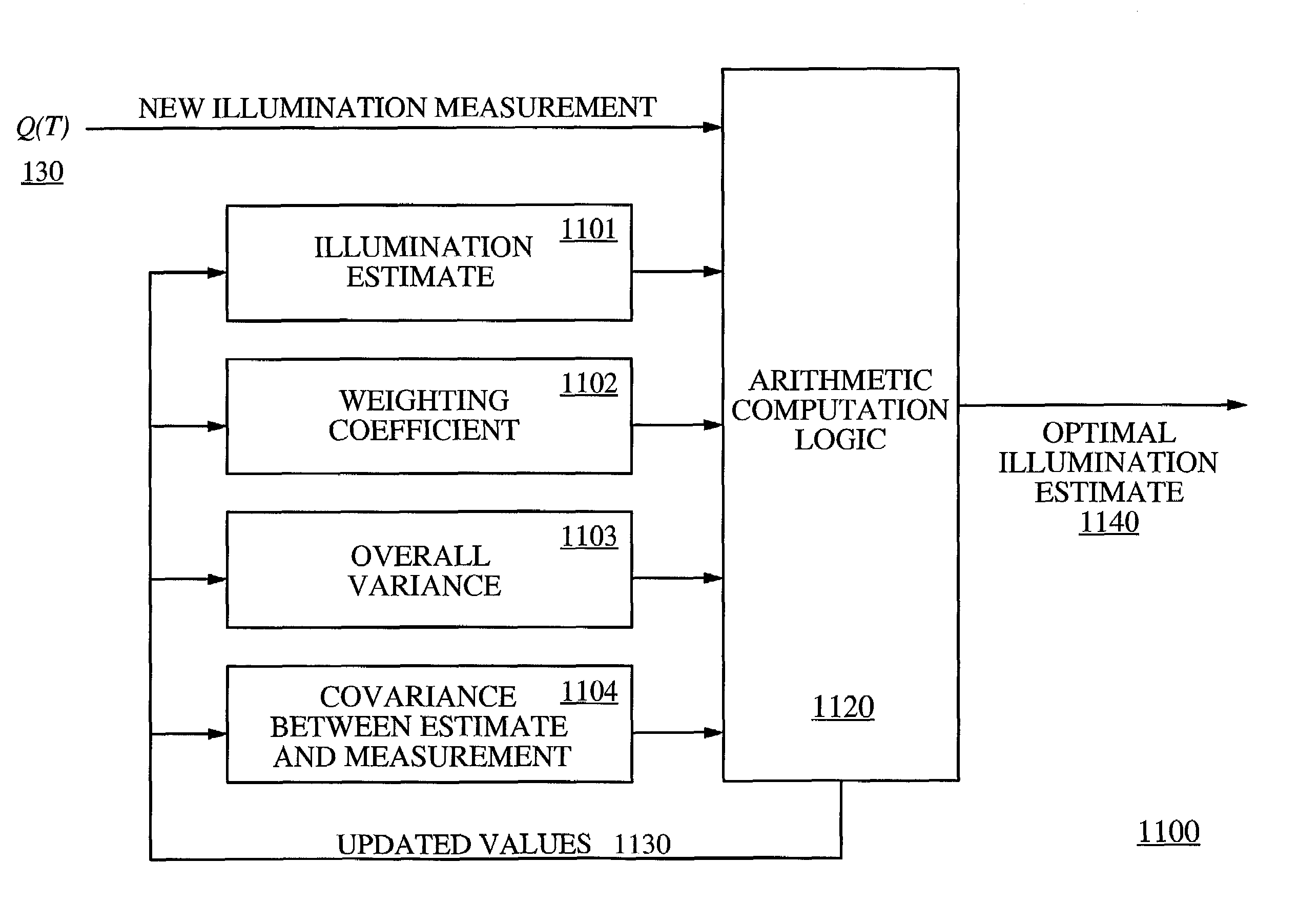
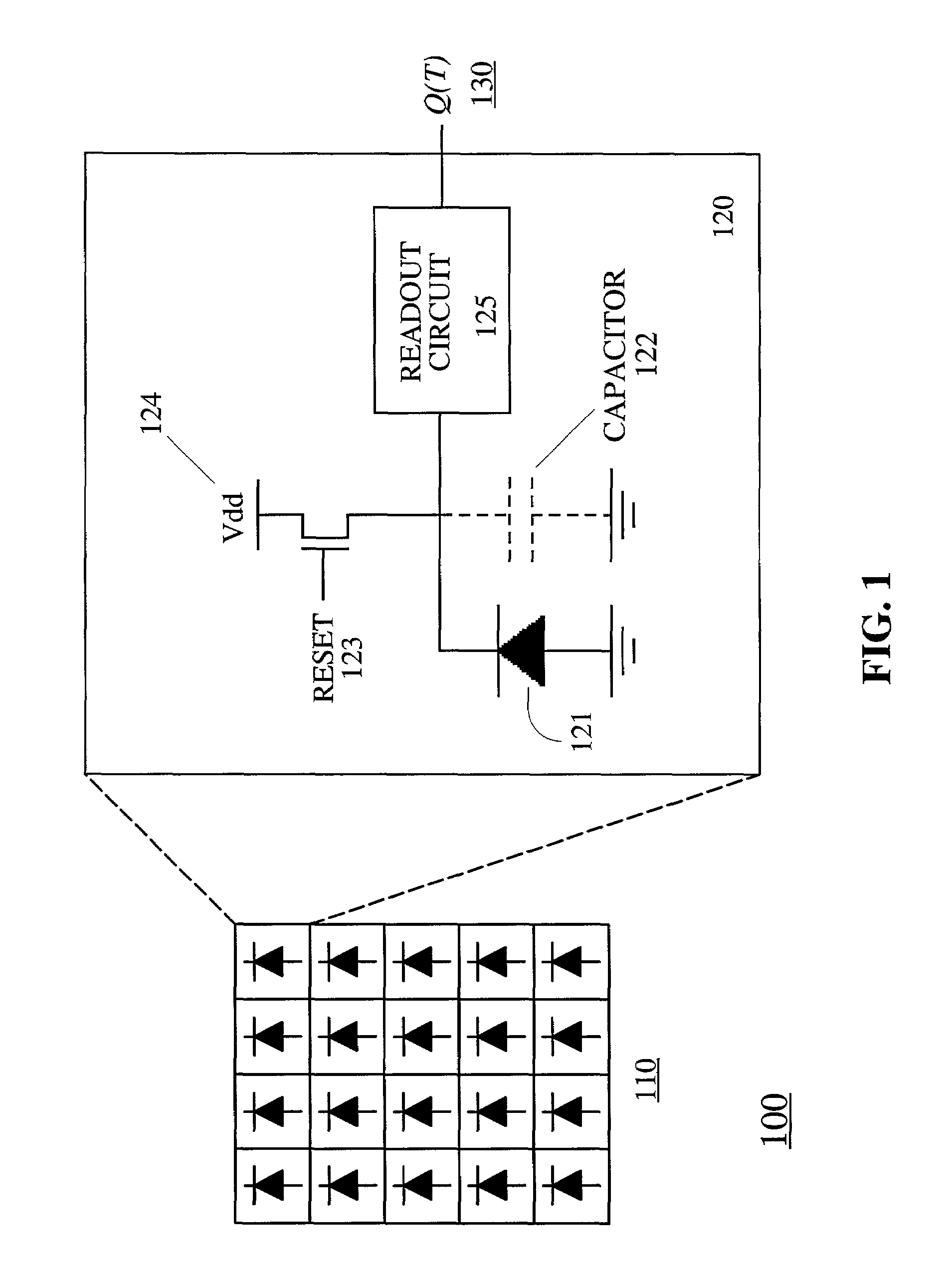
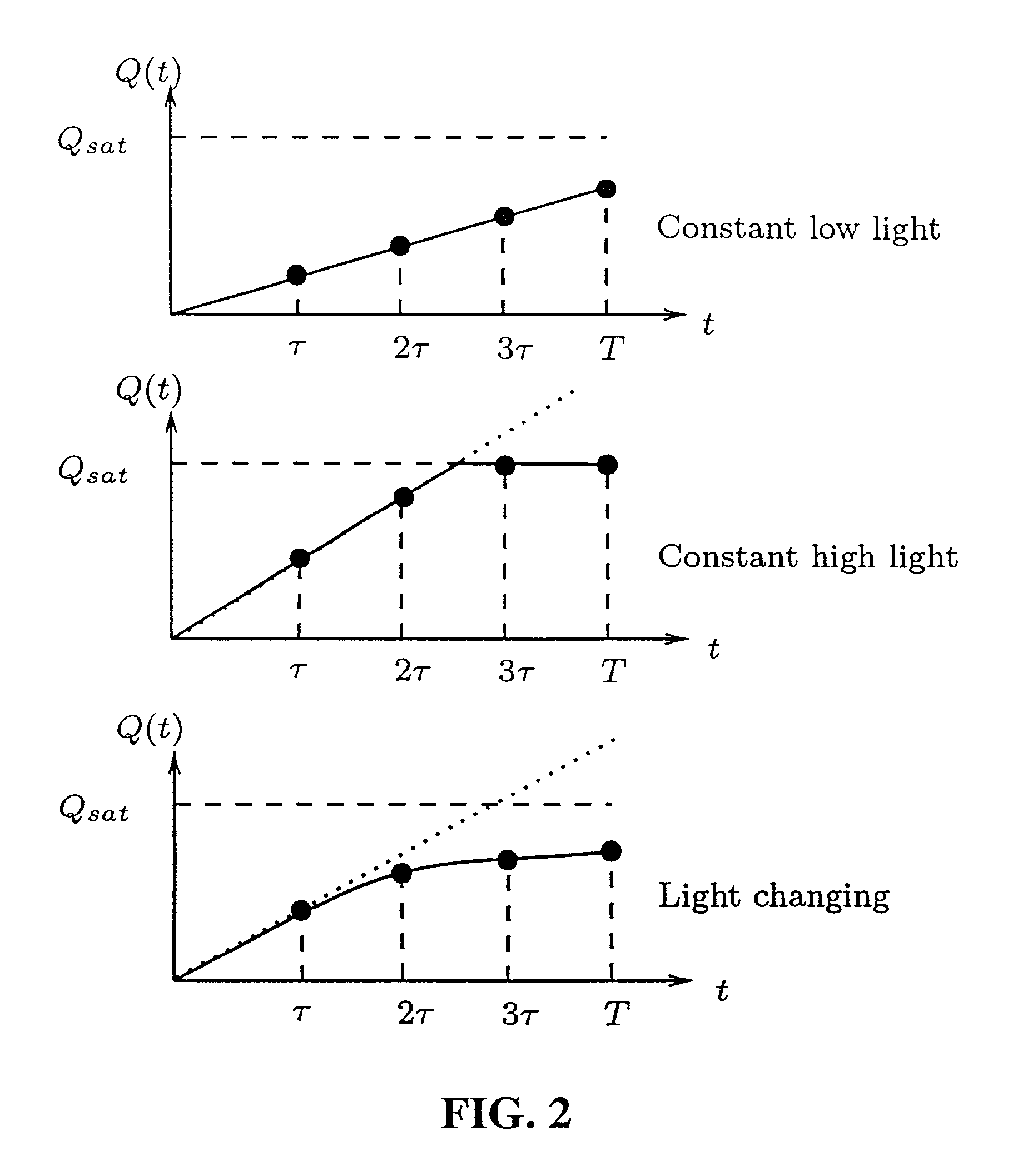
Motion/saturation detection system and method for synthesizing high dynamic range motion blur free images from multiple captures
ActiveUS7061524B2Improve dynamic rangeEasy to optimizeTelevision system detailsTelevision system scanning detailsHigh-dynamic-range imagingSingle chip
Motion / Saturation detection system and method for synthesizing high dynamic range motion blur free images from multiple captures, the system and method utilizing photocurrent estimation to reduce read noise and enhance dynamic range at the low illumination end, saturation detection to enhance dynamic range at the high illumination end, and motion blur detection to ensure the photocurrent estimation is not corrupted by motion. Motion blur detection also makes it possible to extend exposure time and to capture more images, which can be used to further enhance dynamic range at the low illumination end. The present invention operates completely locally, making it well suited for single chip digital camera implementations.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
Method, device, and system of securely storing data
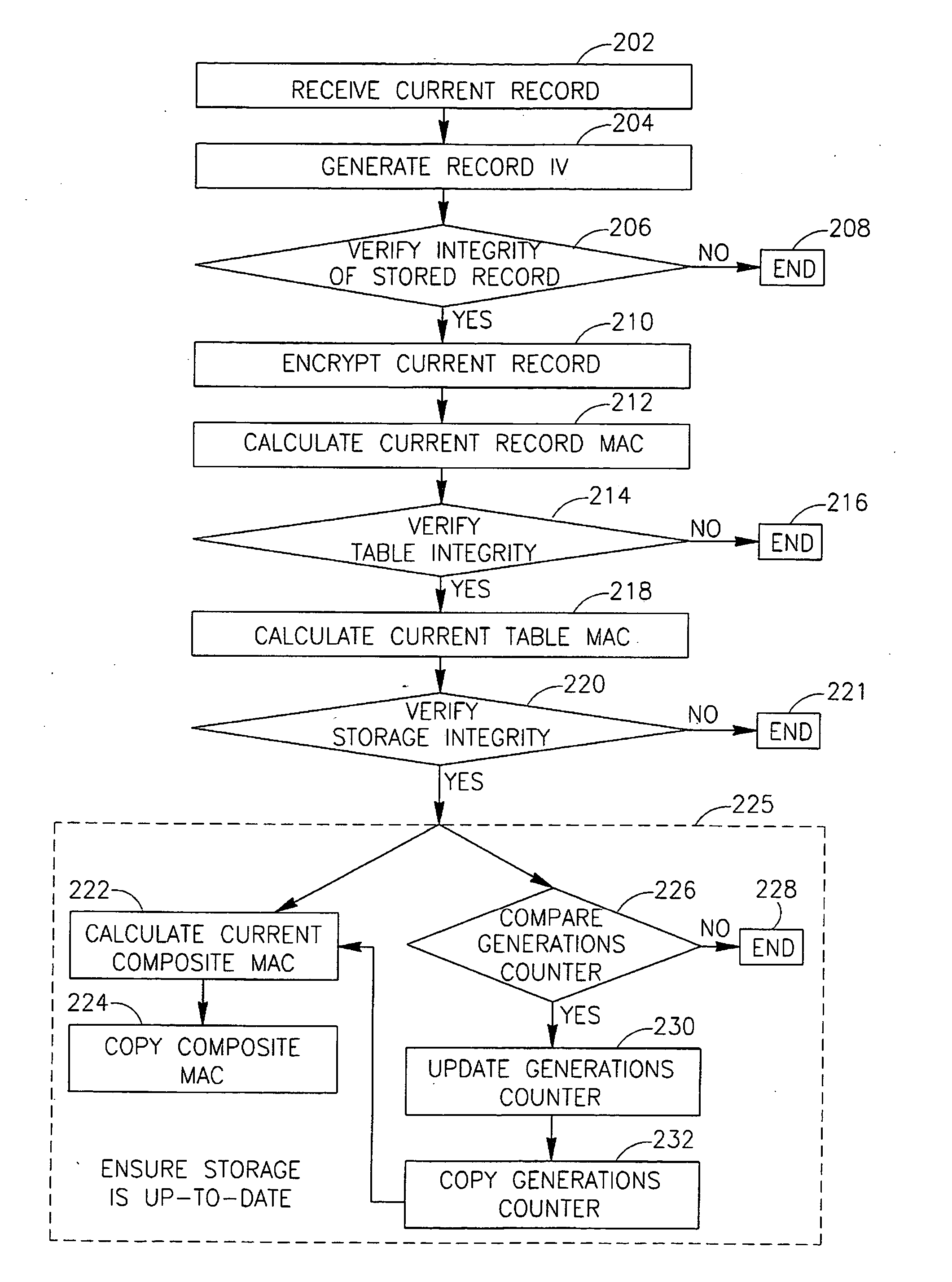
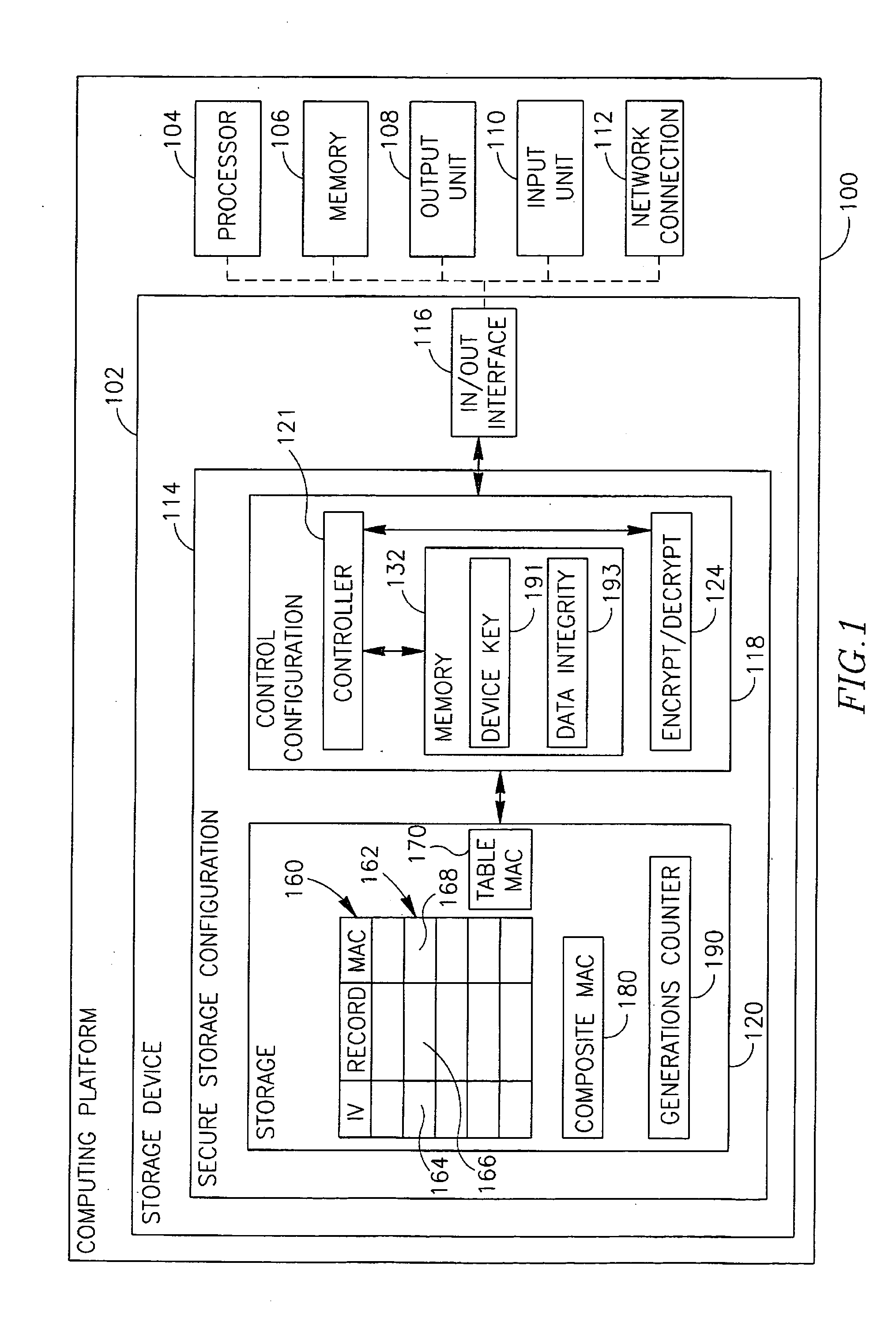
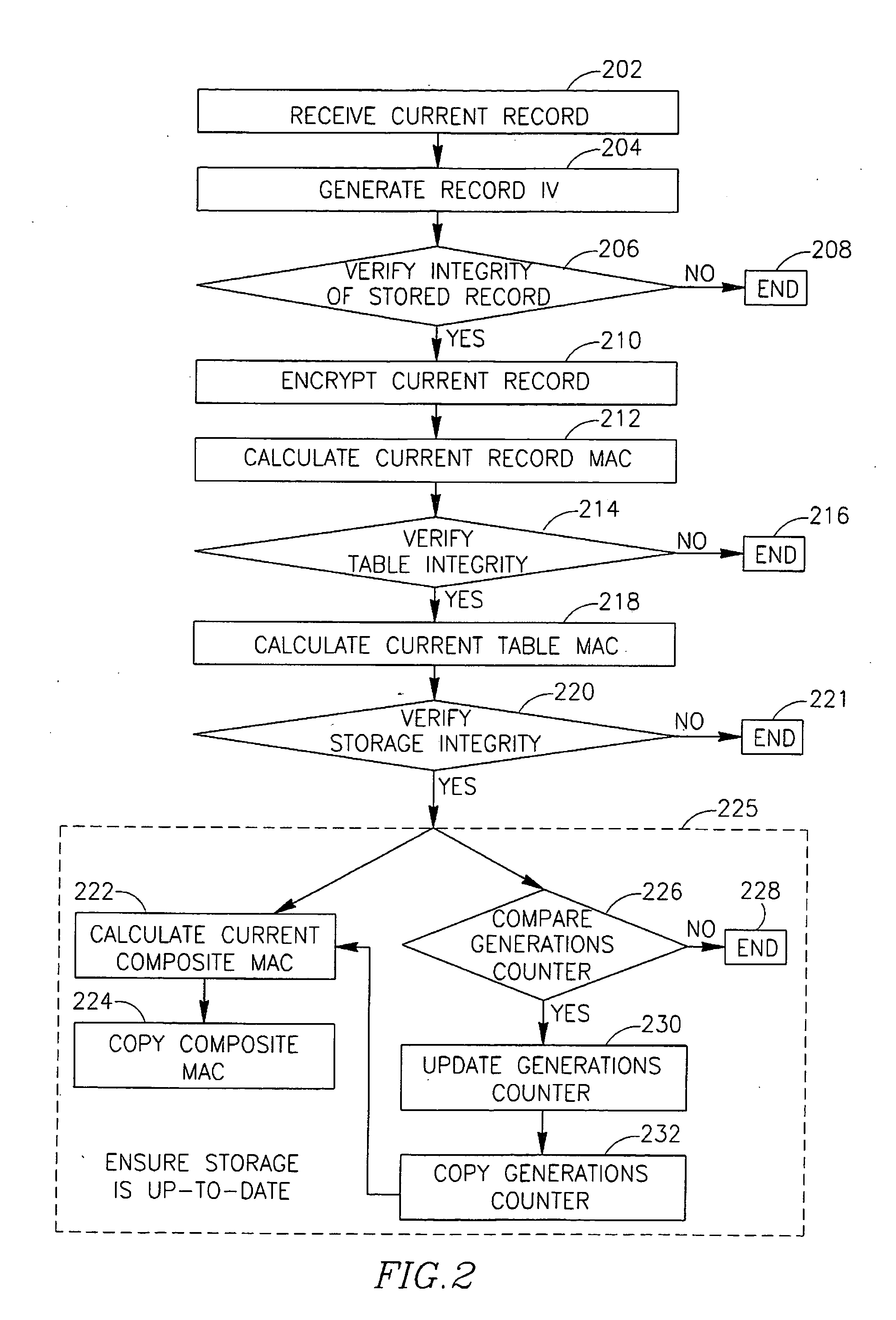
InactiveUS20060107047A1Preventing unauthorized disclosureEnsure integrityUser identity/authority verificationRecord information storageEncryptionData records
Some demonstrative embodiments of the invention include a method, device an / or system of securely storing data, for example, by preventing unauthorized disclosure of the stored data, and / or ensuring the integrity of the stored data. An apparatus able to securely store data may include, according to some demonstrative embodiments of the invention, a secure control configuration, which may include a secure memory to securely store a key; an encryption module to generate an encrypted record by encrypting a data record to be stored using the key; and a controller to generate authentication information for authenticating the integrity of the encrypted record based on the key. The apparatus may also include a storage for storing the encrypted record and the authentication information. Other embodiments are described and claimed.
Owner:ARM LTD +1
Respiratory masks with gusseted cushions
ActiveUS8297283B2Level of comfortEnsure integrityRespiratory masksBreathing masksEngineeringRespiratory mask
Cushions for respiratory face masks have a frame-connecting portion, a face-contacting portion, and a gusset portion disposed between and joining the frame-connecting and face-contacting portions. The gusset portion preferably includes at least one perimetrical region which having a laterally projecting exterior gusset section and a laterally projecting interior gusset section. According to one aspect, the laterally projecting exterior and interior gusset sections are disposed about the entire perimeter to the gusset portion so as to establish a substantially constant widthwise dimension thereof about the gusset's entire perimeter.
Owner:RESMED LTD
Secured microcontroller architecture
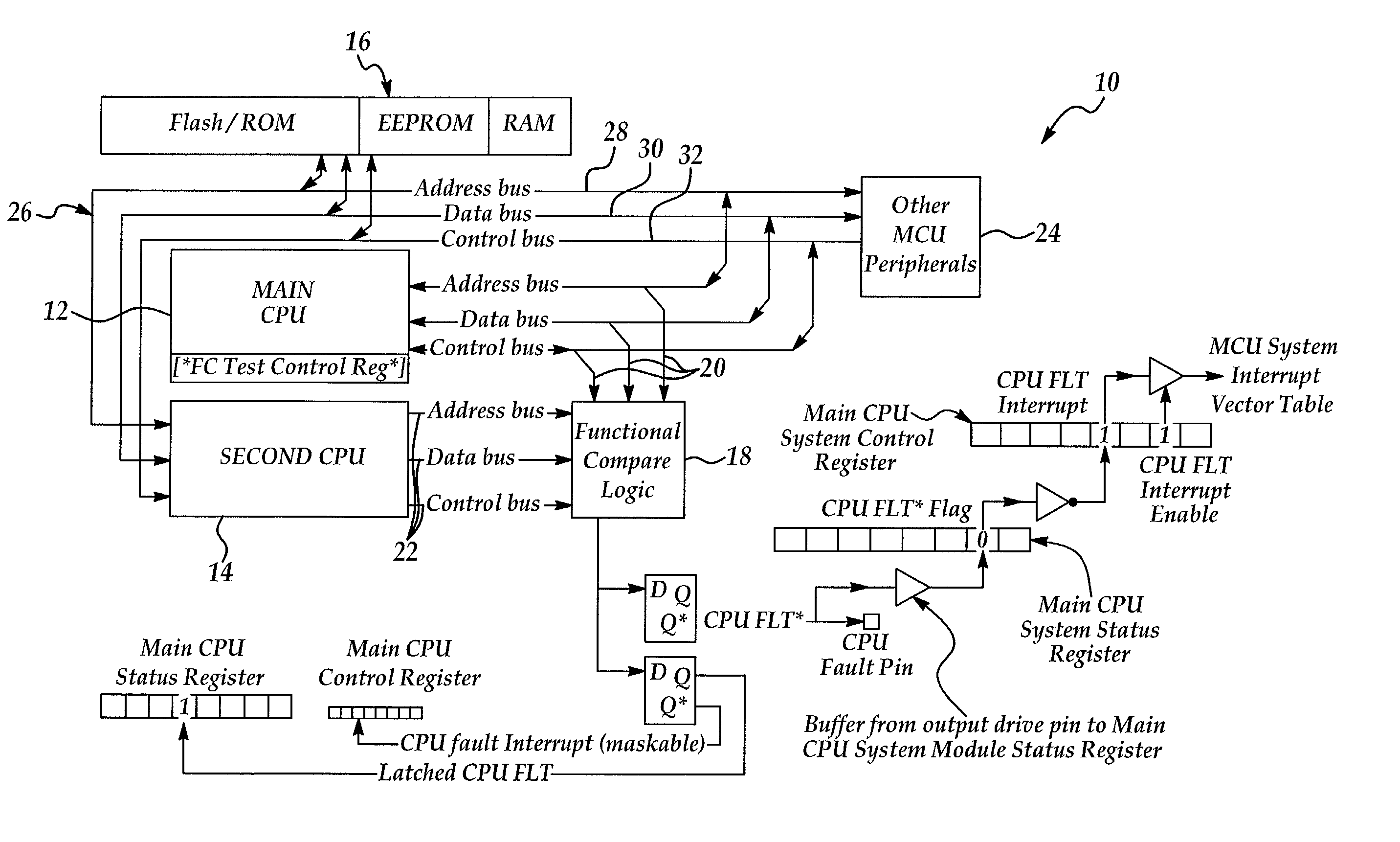
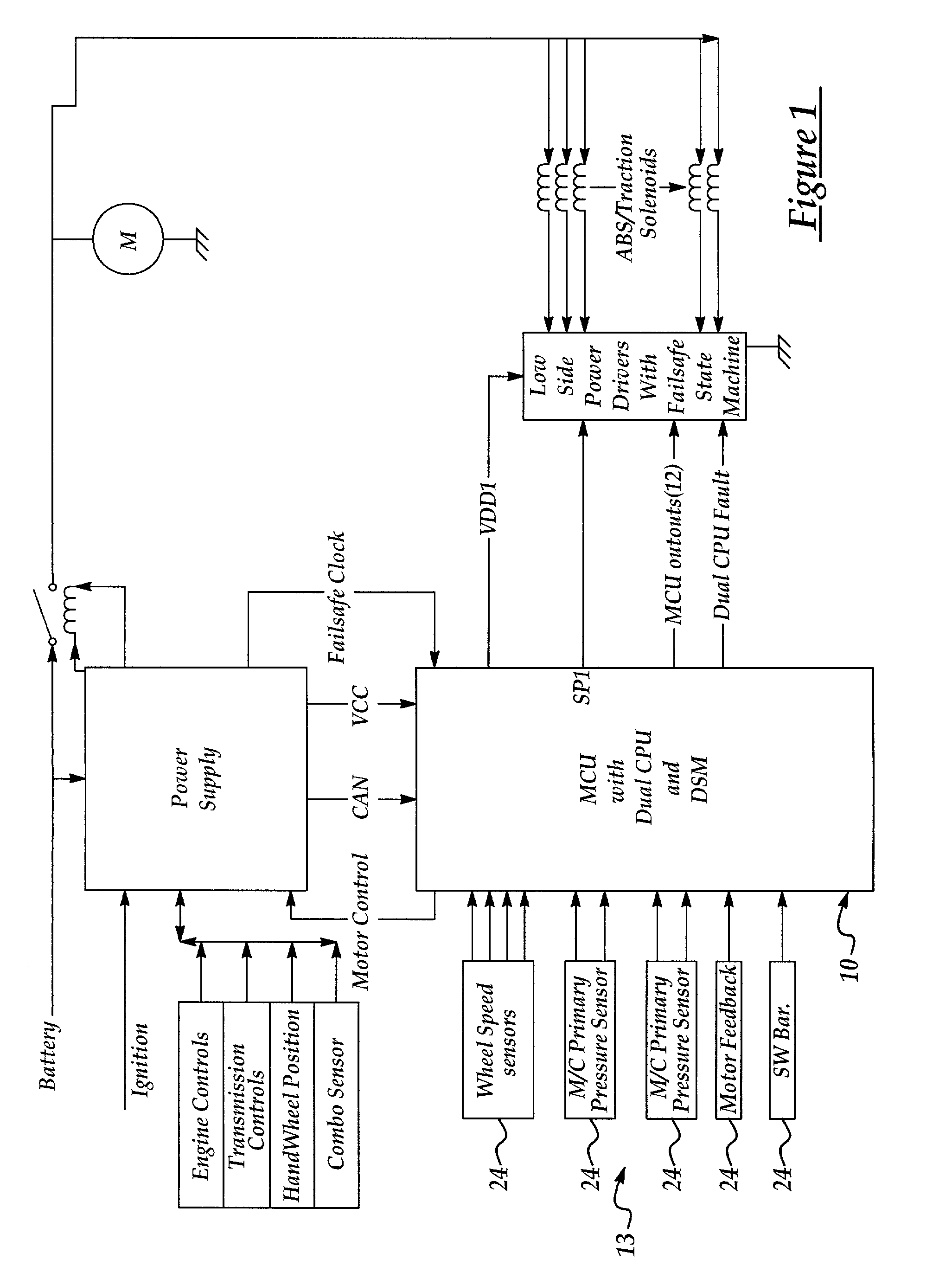
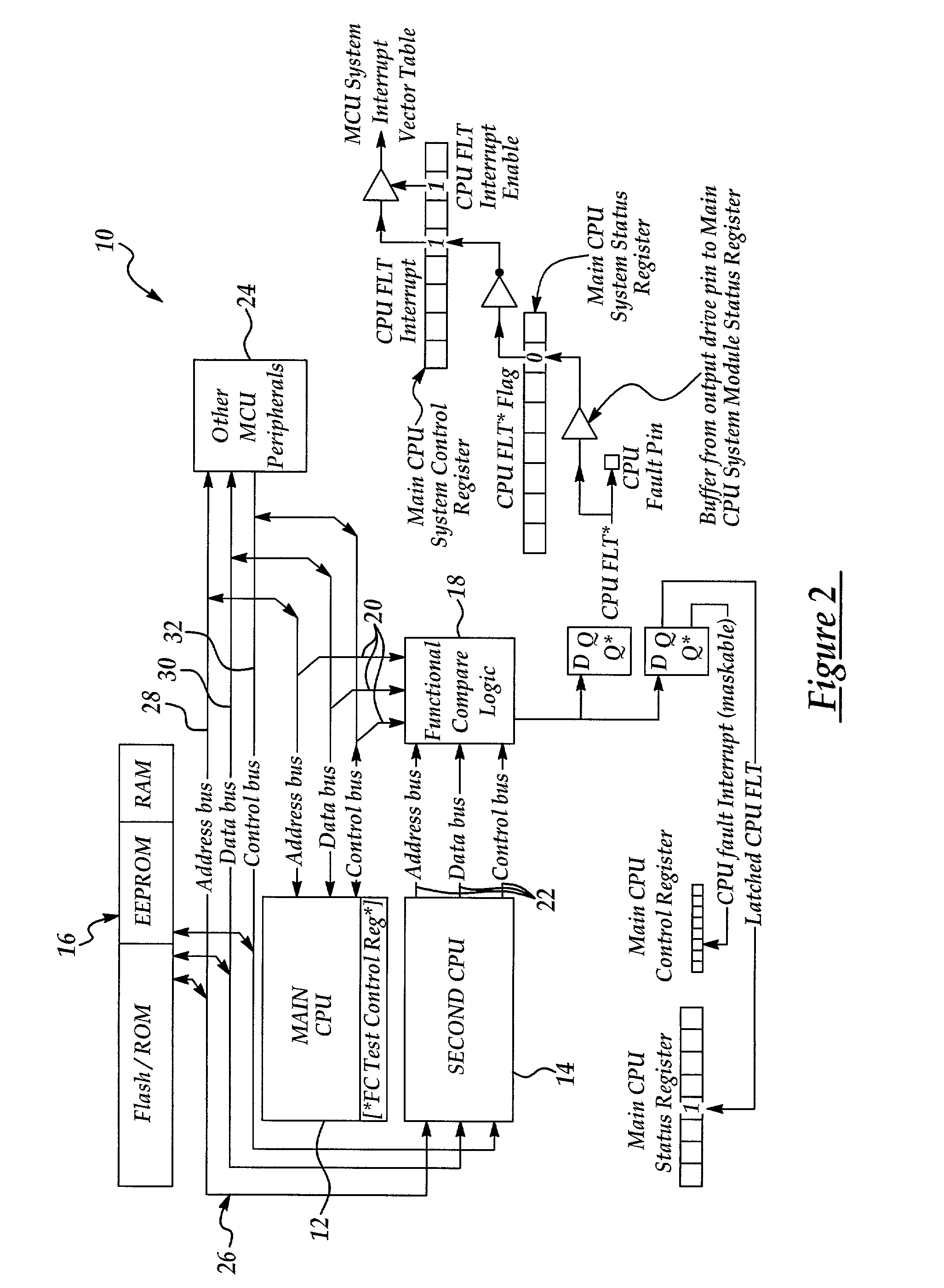
InactiveUS6981176B2Reduce sensitivityImprove system reliabilityVehicle testingRegistering/indicating working of vehiclesMicrocontrollerParallel computing
A microcontroller unit (MCU) having a primary, or main, processing unit, a secondary processing unit coupled to the primary processing unit, and a common memory coupled to the primary and secondary processing units is disclosed. A functional compare module is coupled to the primary processing unit and the secondary processing unit for comparing a primary output of the primary processing unit and a secondary output of the secondary processing units to detect a fault if the primary output and the secondary output are not the same. The invention provides a method for detecting a fault in the MCU including the steps of reading a control algorithm stored in the common memory by the primary processing unit, reading the control algorithm stored in the common memory by the secondary processing unit, comparing the primary output and the secondary output and responsively detecting a fault, if the primary output does not match the second output.
Owner:SAMSUNG ELECTRONICS CO LTD
User authentication based on asymmetric cryptography utilizing RSA with personalized secret
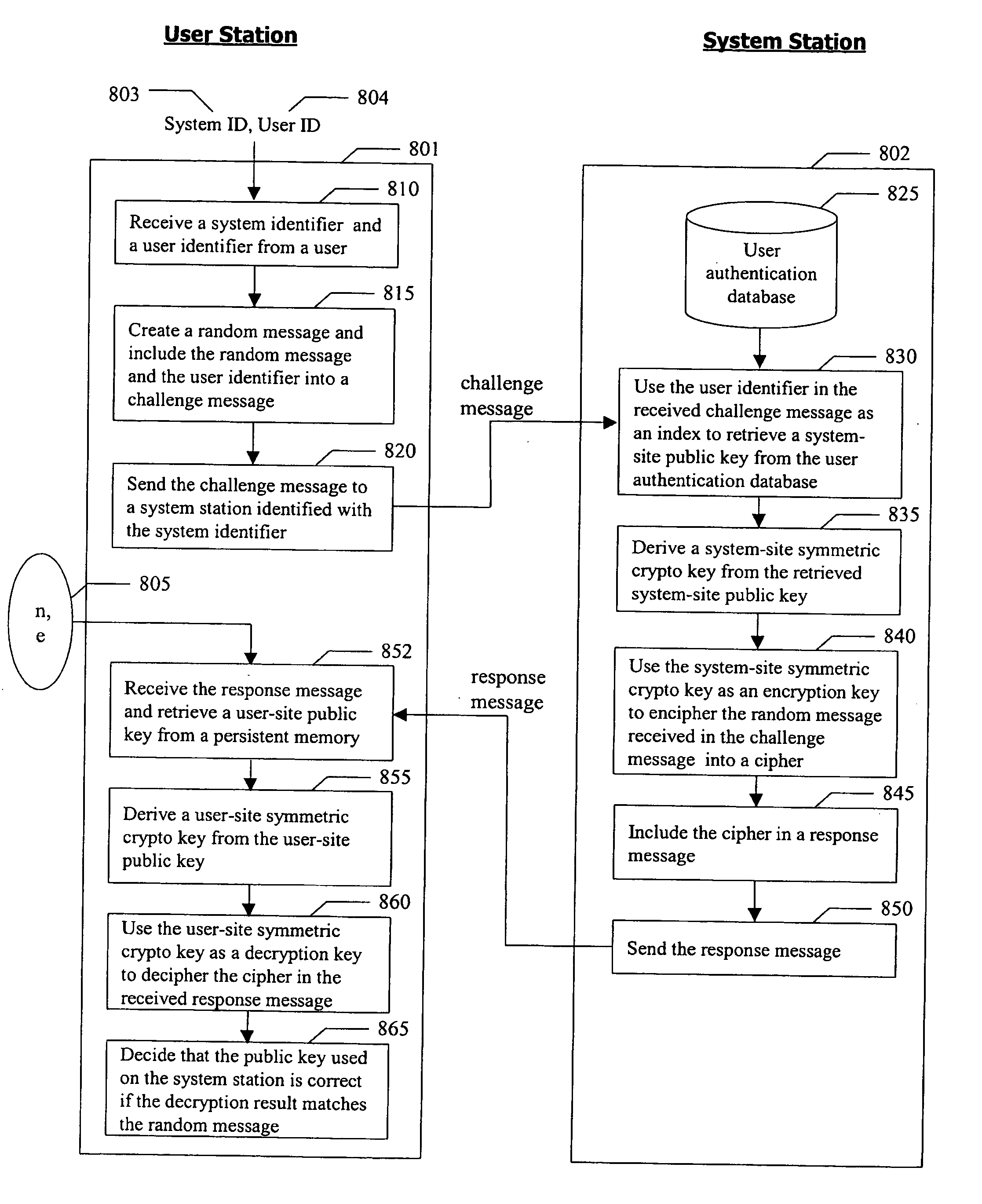
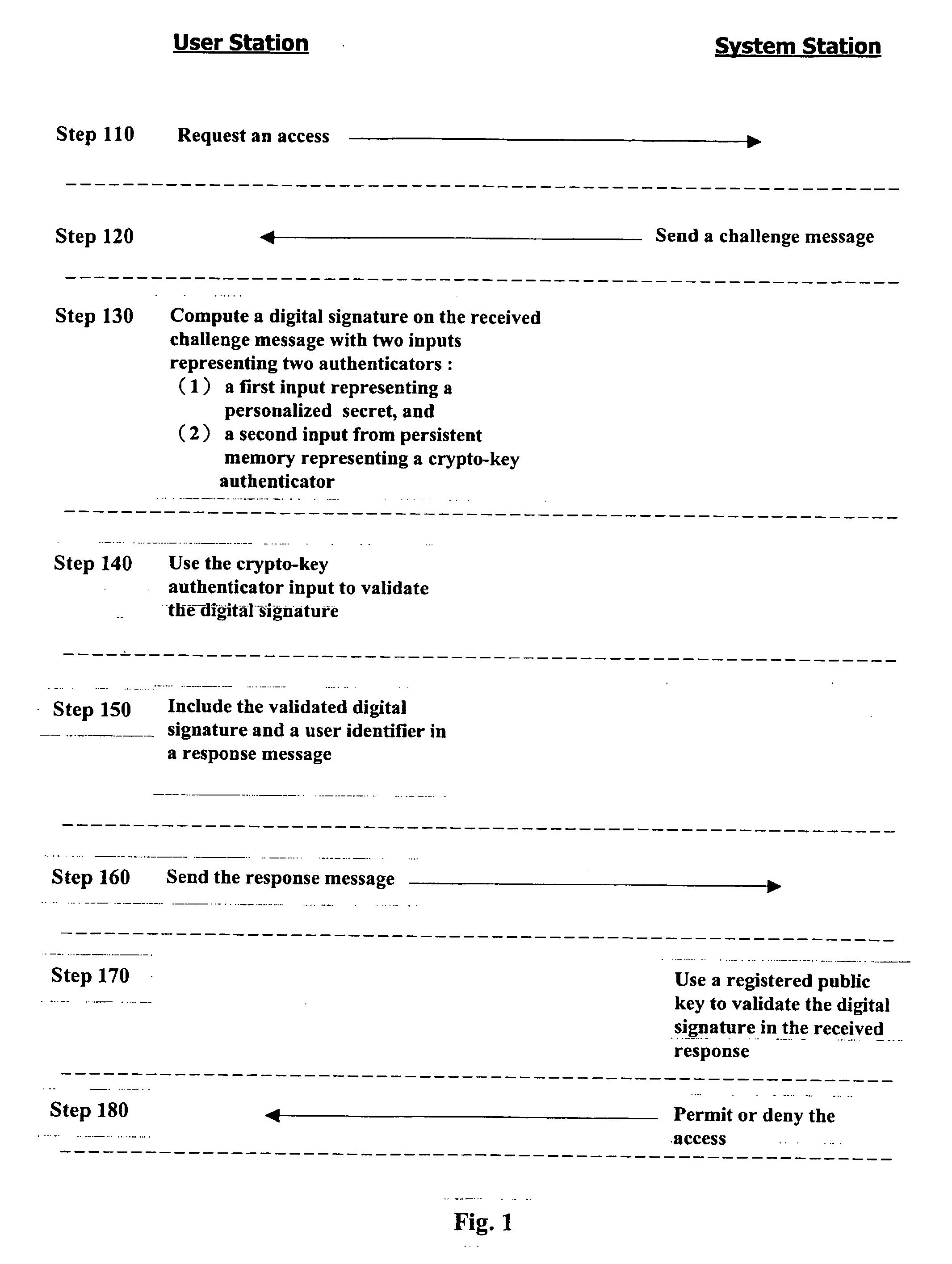
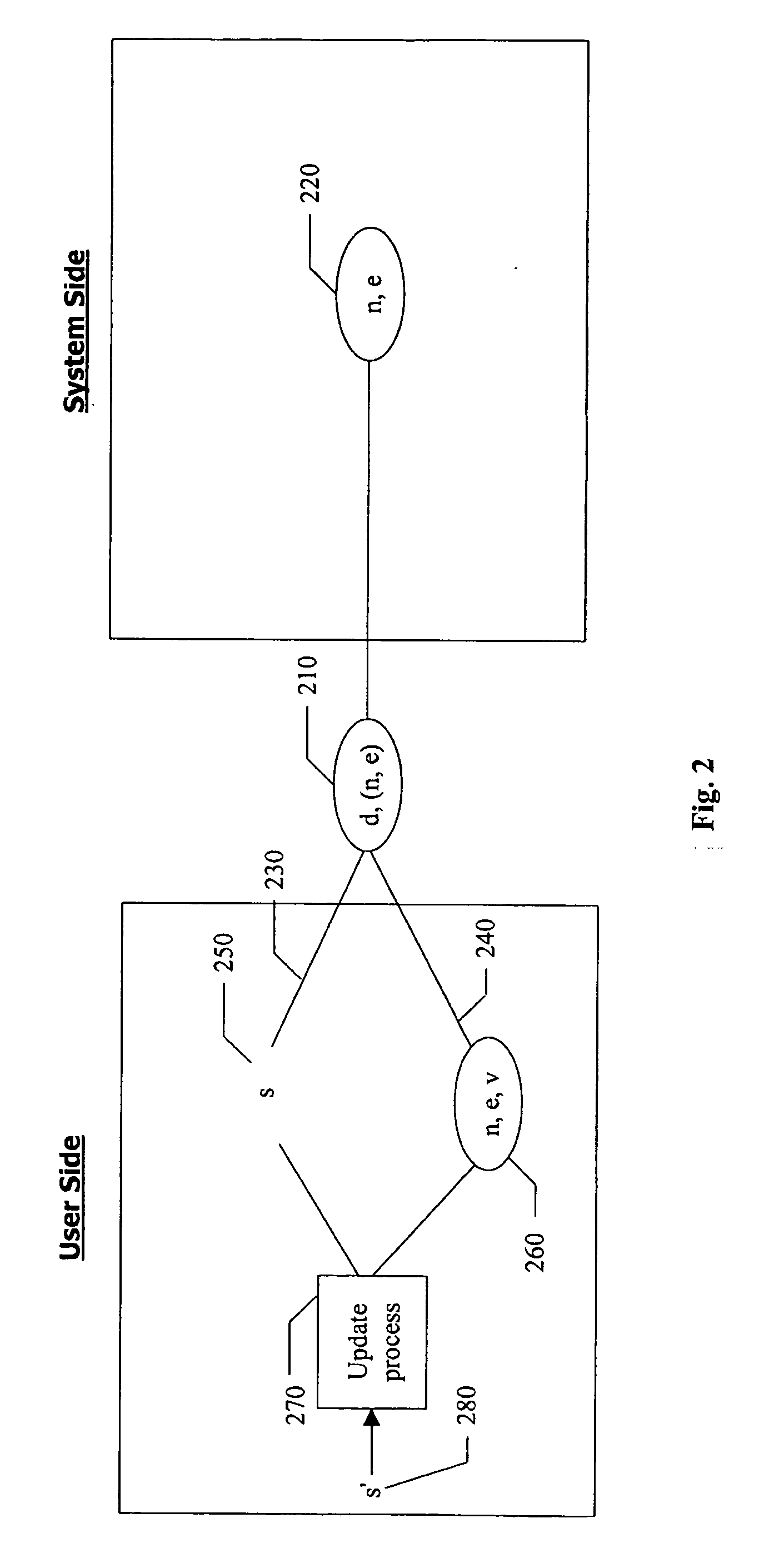
InactiveUS20070081667A1Ensure integrityDigital data processing detailsPublic key for secure communicationPersonalizationCryptographic key generation
A method for authenticating a user to a computer system is disclosed, comprising using a first input and a second input in producing a digital signature in response to a challenge. The digital signature is valid when the first input matches a personalized secret and the second input matches a trio comprising a public modulus, a public exponent, and a private-key-dependent exponent. Selection of the personalized secret is discretionary and changeable. A crypto-key generation process uses the personalized secret and two primes as input to produce the trio. The public modulus and public exponent of the trio form a public key used in digital signature validation. Also disclosed is a business method that replaces the conventional public-key certificate with an agreement on the user's public key.
Owner:CHANG GUNG UNIVERSITY
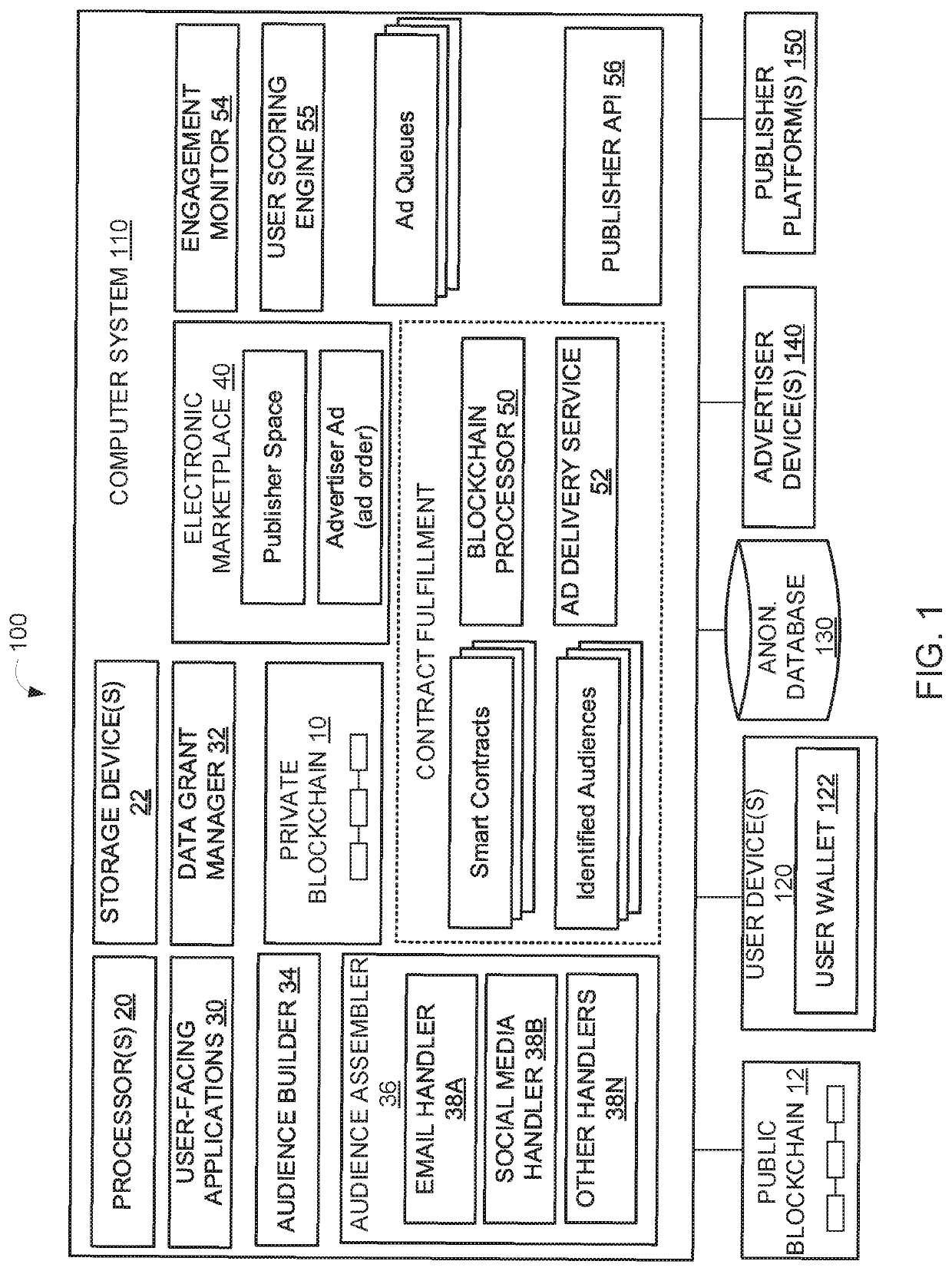
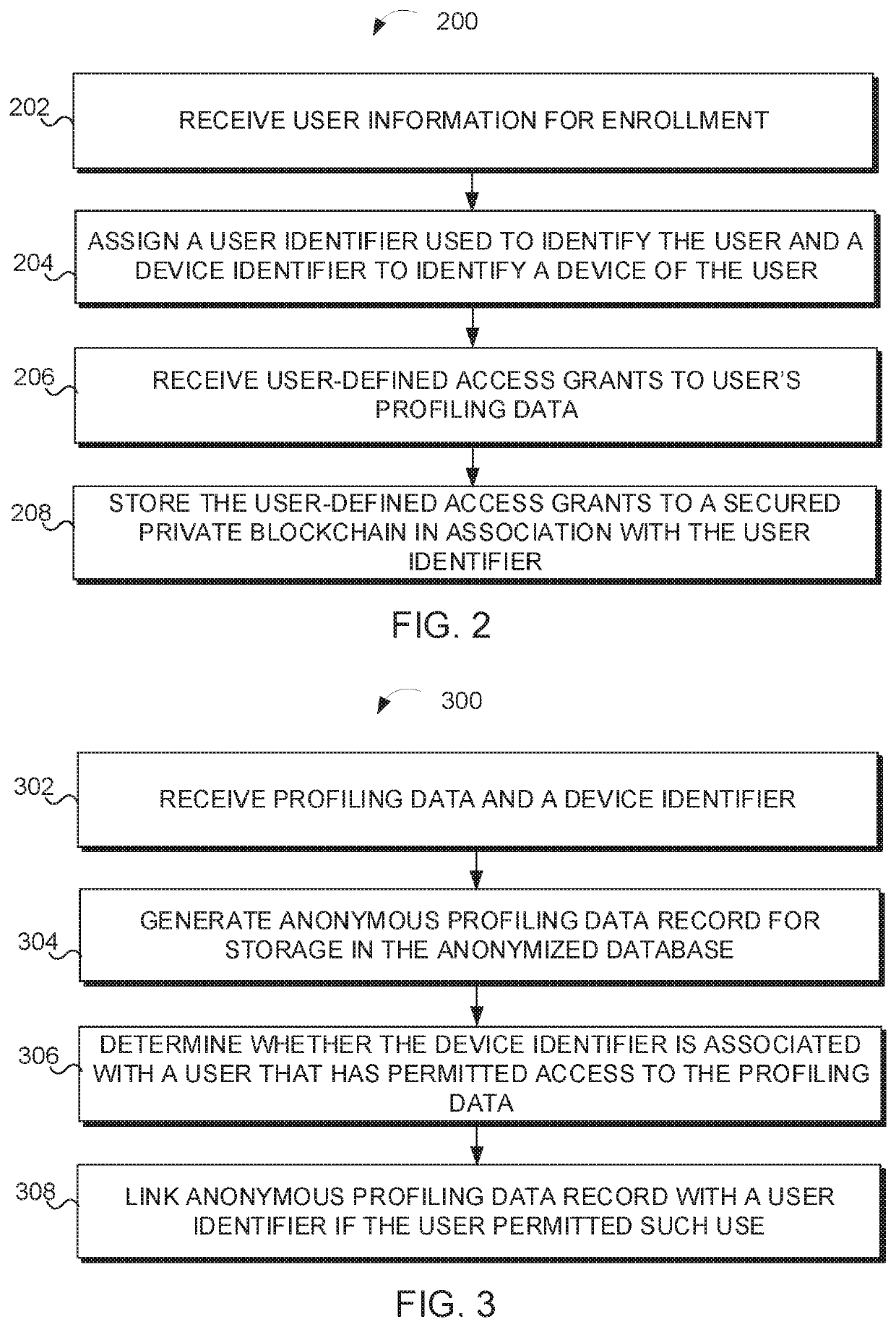
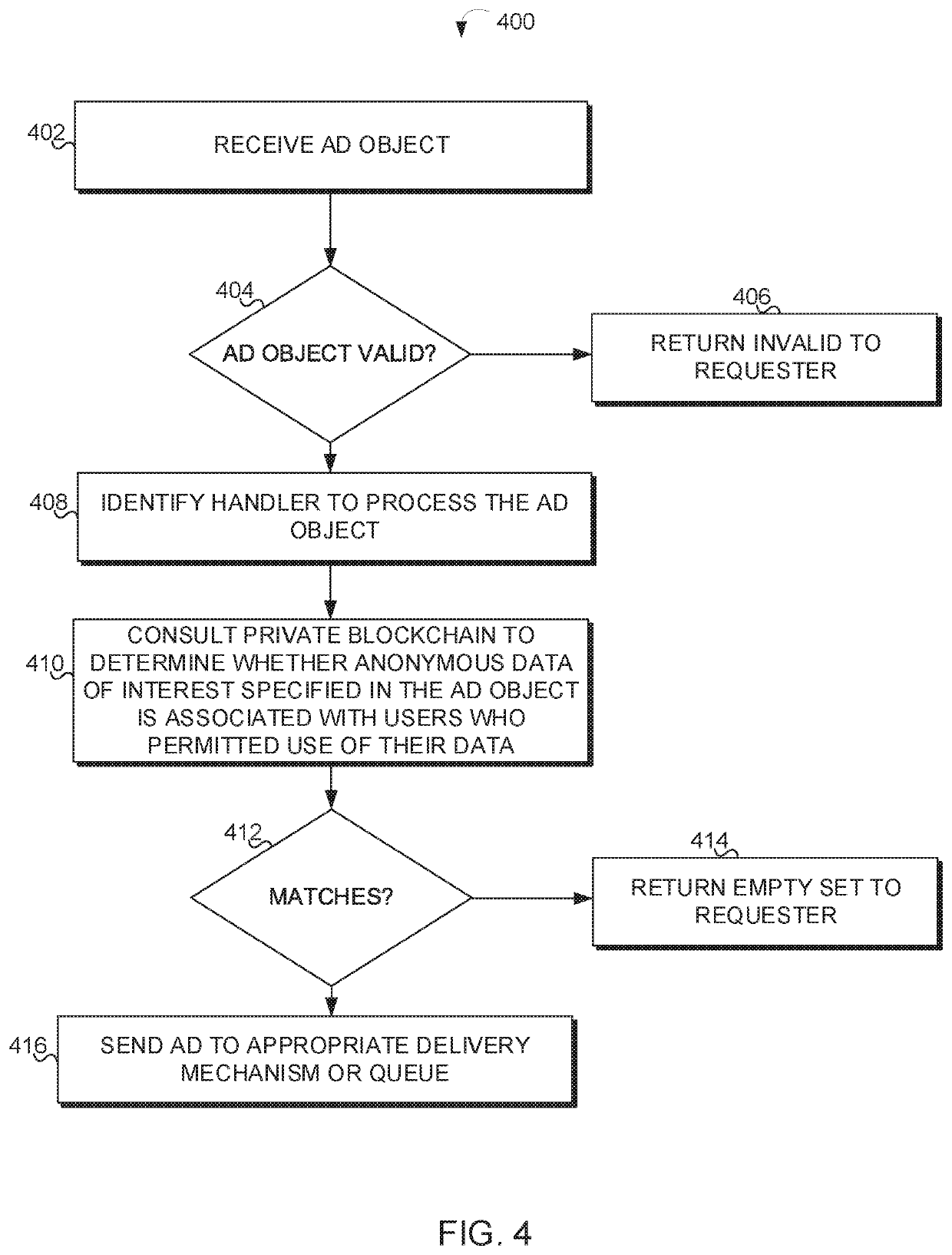
User control of anonymized profiling data using public and private blockchains in an electronic ad marketplace
ActiveUS20190370866A1Ensure integrityAdvertisementsEncryption apparatus with shift registers/memoriesAnalysis dataInternet privacy
The disclosure relates to securing and enabling user control of profiling data, blockchain-driven matching of users and advertiser-identified anonymous profiling data records of interest, and smart contracts encoded by blockchain for executing transactions. The system may include an anonymized database of profiling data, which is unlinked to any user. The system may implement a private blockchain to store user-defined settings that provide user control over whether and how the profiling data may be used. If a grant to use the data is received, a link is stored that allows the system to identify a user associated with the anonymous profiling data records. If the grant is revoked, the link may be removed. The system may also implement public blockchain technology to record a public information relating to grants, online marketing transactions, making them verifiable, immutable, and transparent for various stakeholders including advertisers, publishers, and users.
Owner:CONCORD TECH
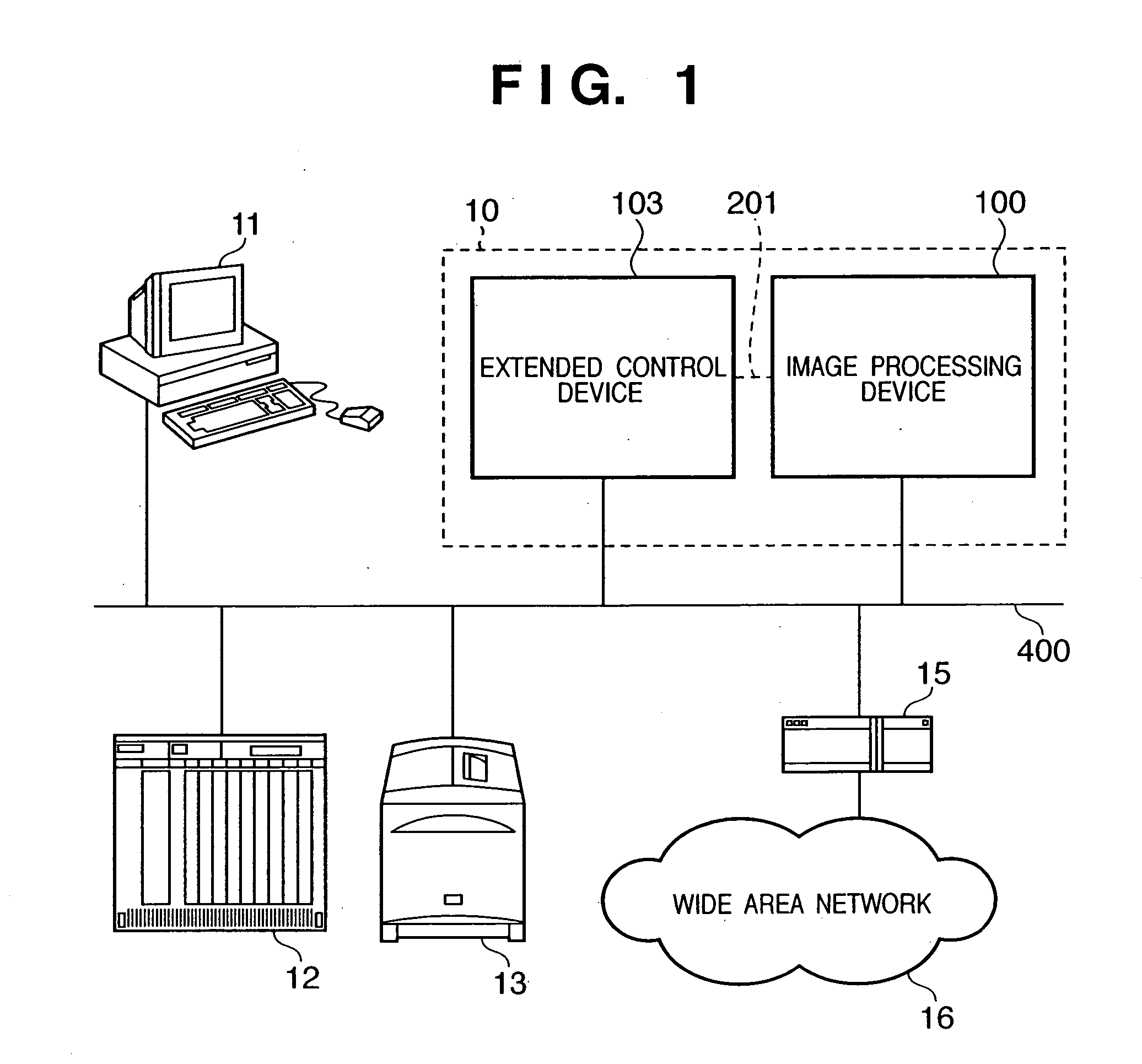
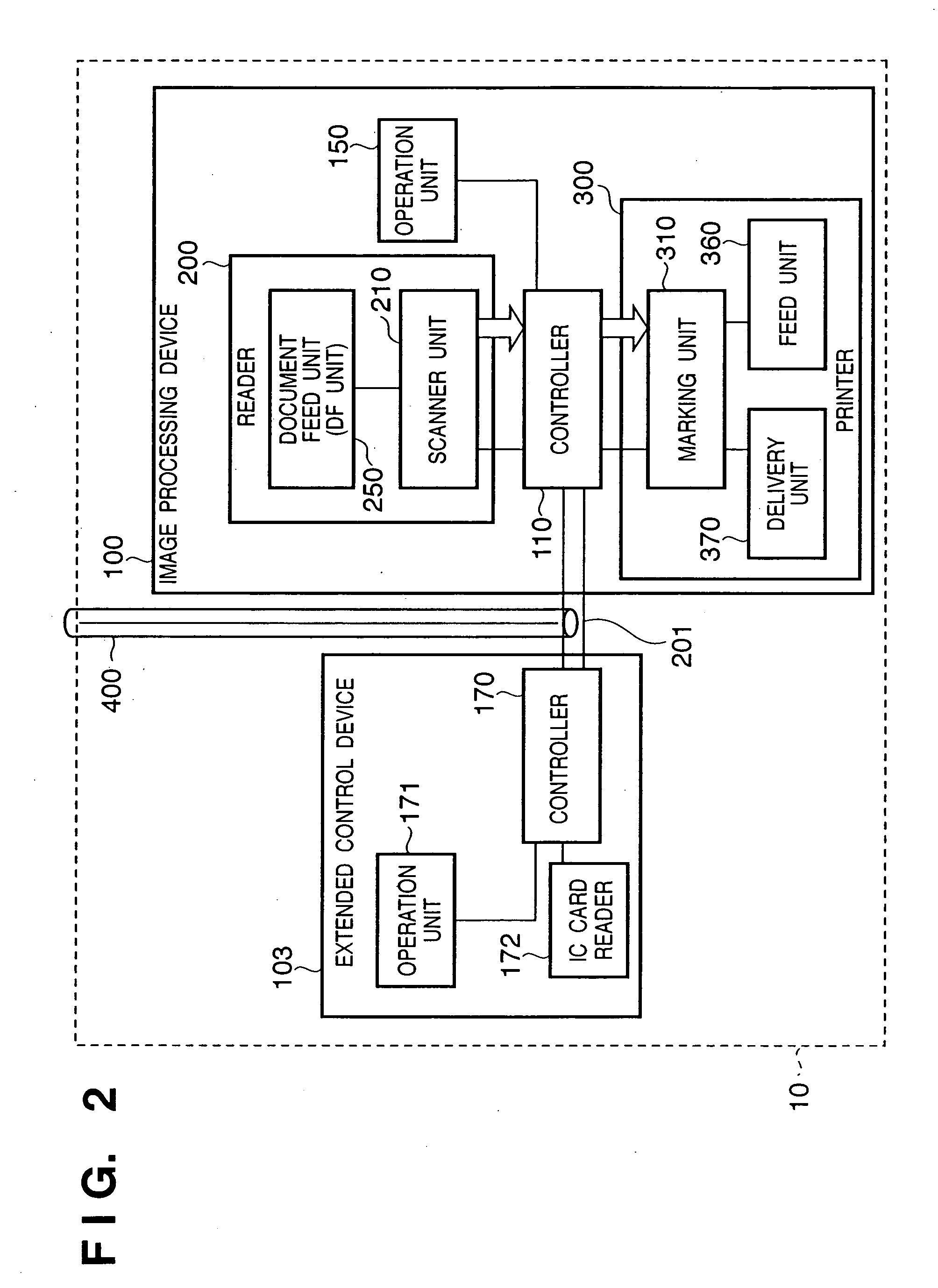
Image processing system
InactiveUS20050243364A1Ensure integrityKey distribution for secure communicationElectric signal transmission systemsData shippingControl equipment
An image processing system including an image processing device and a control device which controls data transfer to said image processing device is provided. When the control device is connected to the image processing device via the network, the control device encrypts the decrypted data and transfers the encrypted data to the image processing device via the network, and when the control device is connected to the image processing device via a leased cable, the control device transfers the decrypted data to the image processing device via the cable.
Owner:CANON KK
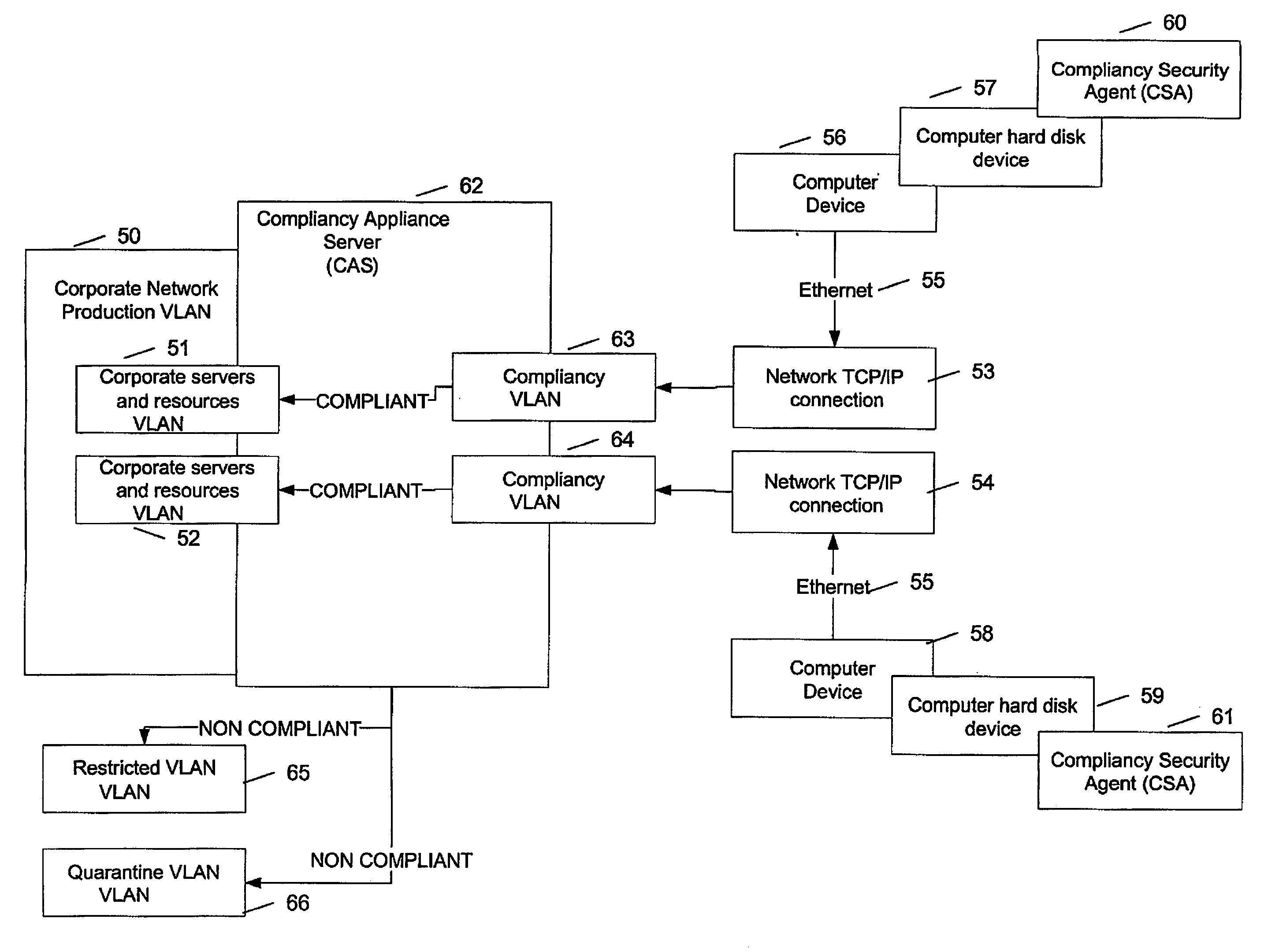
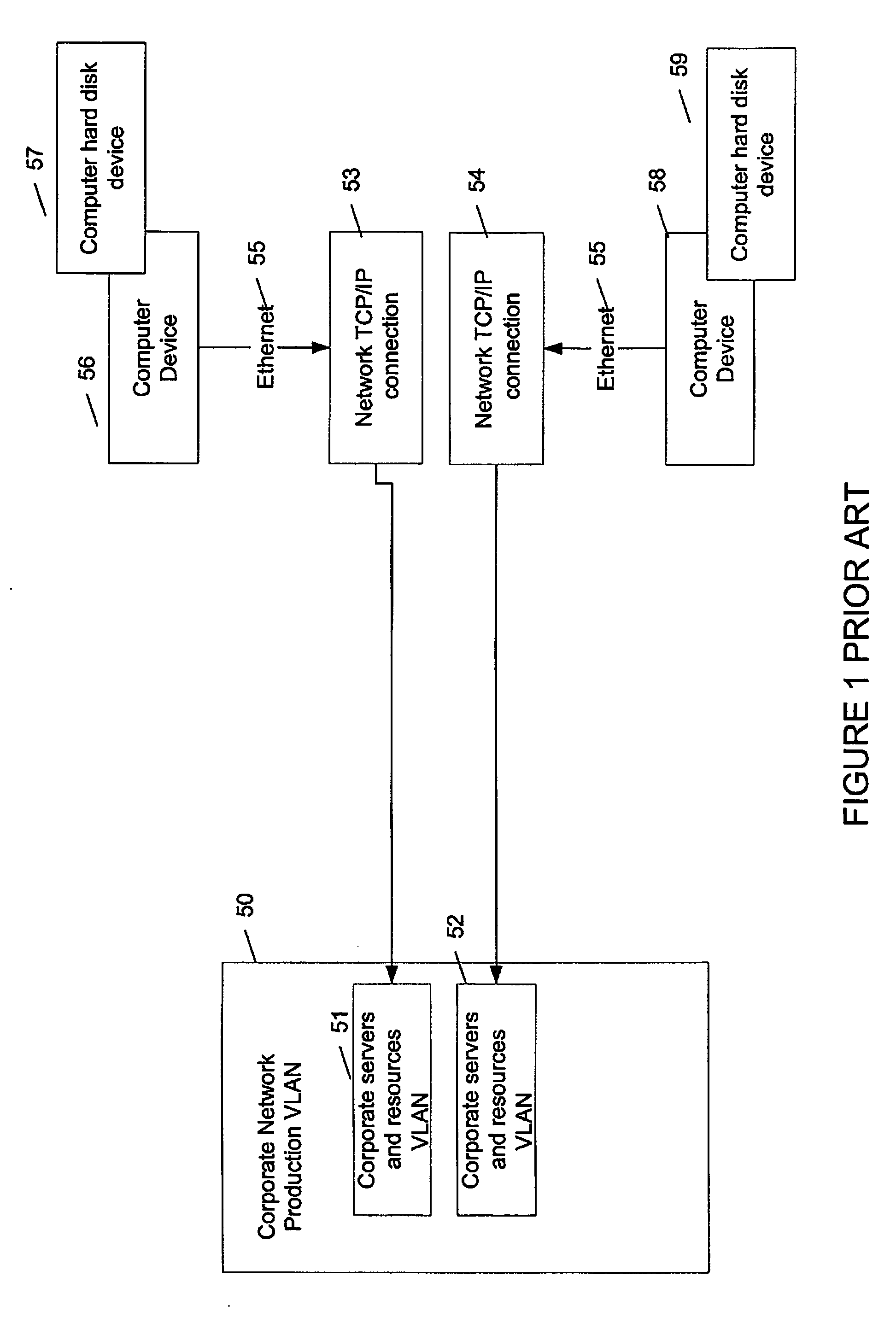
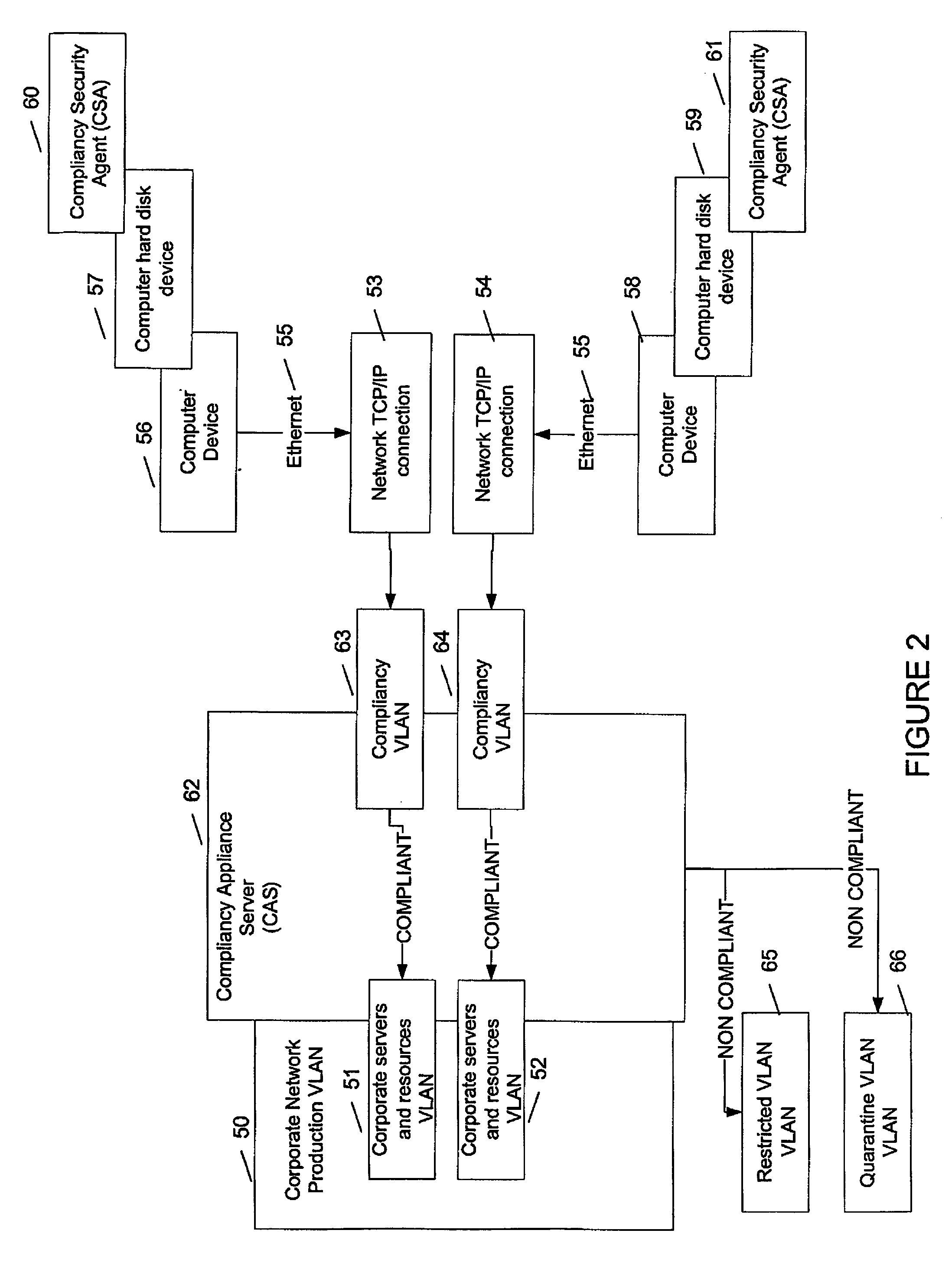
Compliance verification and OSI layer 2 connection of device using said compliance verification
InactiveUS20060203815A1Avoid loopholesPreserving network integrityData switching by path configurationNetwork connectionsCorporate networkIp address
The method comprises installing an agent software on the device; detecting a boot-up of the device; providing the device with a temporary IP address upon boot-up, the temporary IP address being within a compliancy network, logically separate from the corporate network; providing a list of compliance rules to be verified for the device; sending the agent the list of compliance rules; verifying a state of the device for each rule; transmitting a result of the state obtained for each compliance rule; deciding on compliance of the device using the result; instructing a switch port at OSI layer 2 to connect the device to the corporate network if the decision determines compliance; instructing a switch port at OSI layer 2 to connect the device to a network logically separate from the corporate network in case of non-compliance.
Owner:TELUS COMM
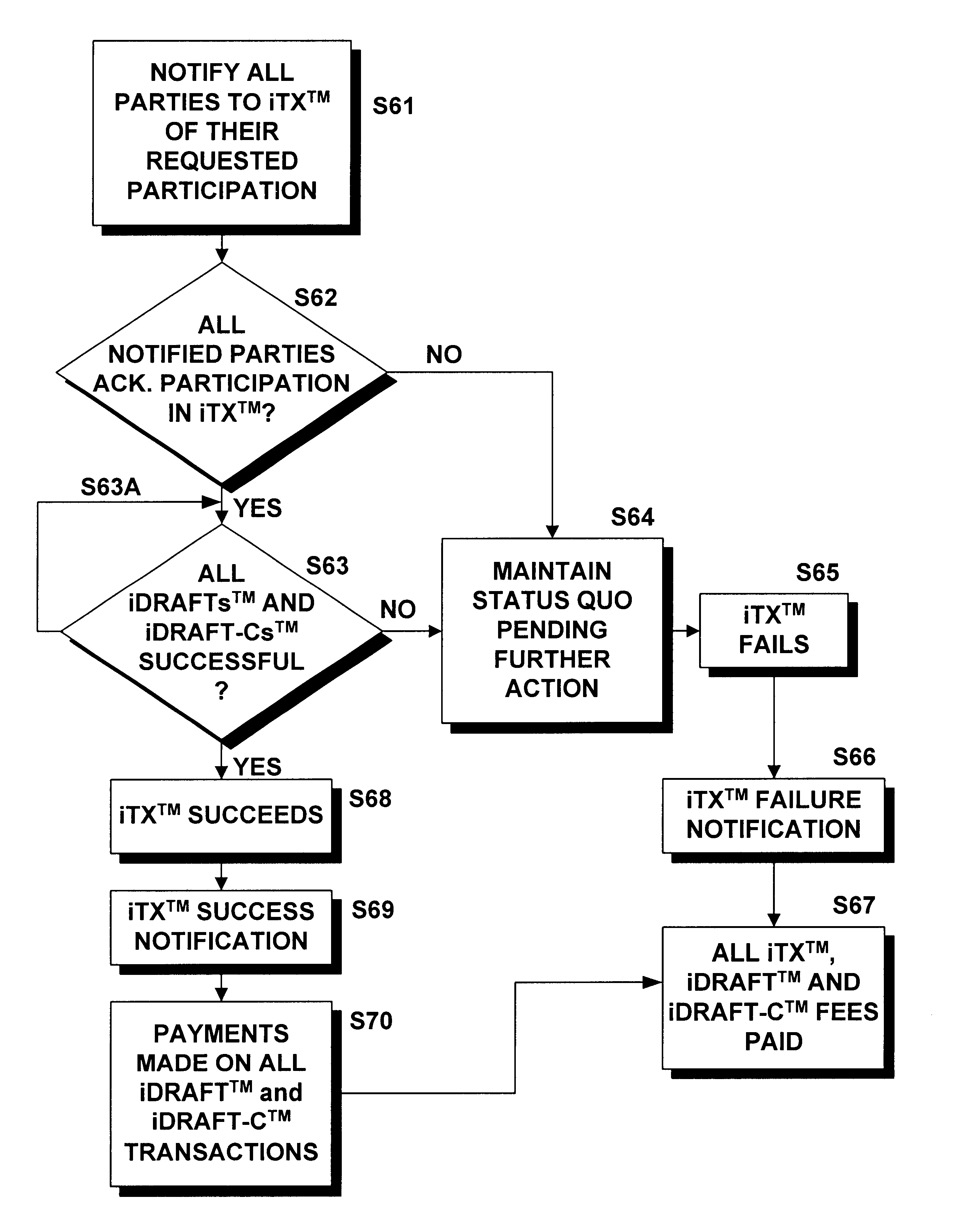
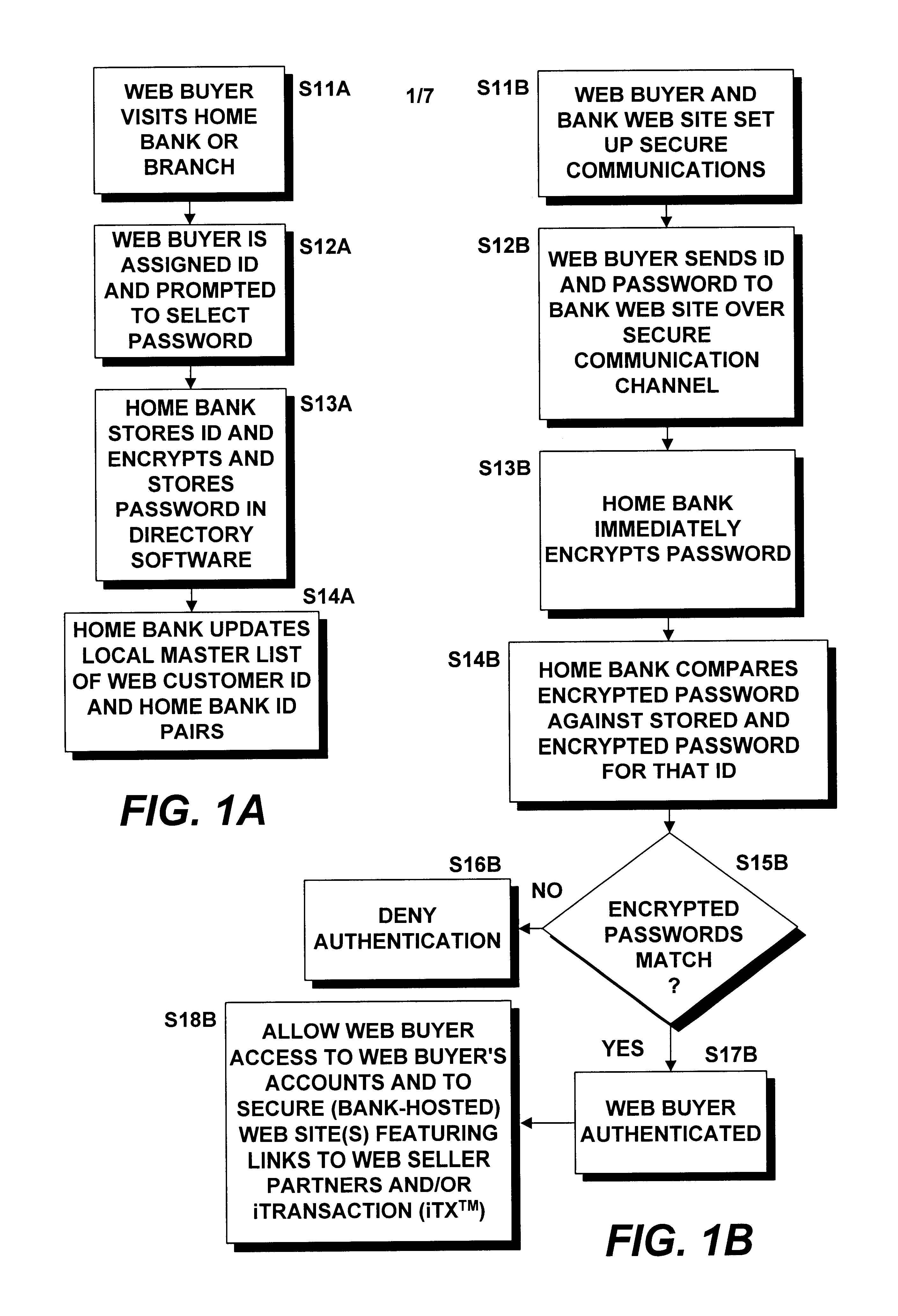
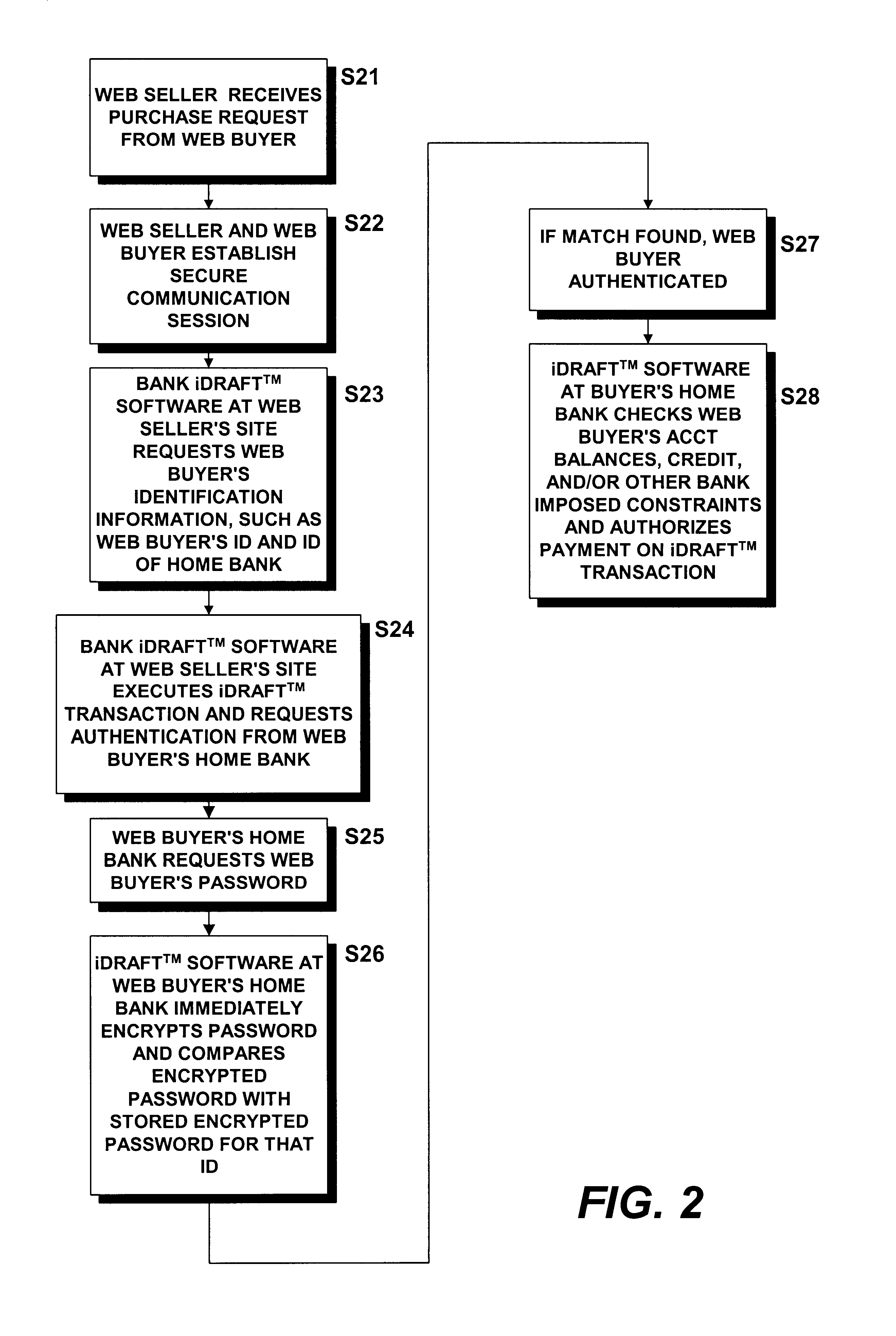
Methods and systems for carrying out directory-authenticated electronic transactions including contingency-dependent payments via secure electronic bank drafts
InactiveUS6941282B1Ensure integrityEnsure safetyFinancePayment circuitsCredit cardDocumentation procedure
Disclosed herein are computer-implemented methods and systems for securely carrying out electronic transactions including electronic drafts, wherein payment on at least one of the drafts is contingent upon the removal of an associated contingency. The method may include steps of establishing a secure computer site accessible only by authenticated parties to the transaction and by any authenticated contingency approver. The site includes a representation of the transaction that includes a representation of each of the plurality of drafts and an option to remove any contingencies associated therewith. Parties and contingency approvers requesting access to the computer site are authenticated by encrypting identification information provided by the requesting party or contingency approver over a secure channel and successfully matching the encrypted identification information with an encrypted identifier that is stored by a bank, the encrypted identifier being unique to the requesting party or contingency approver. Payment on the constituent drafts of the transaction are released by the bank only when the option to remove each contingency associated with the draft is timely exercised by an authenticated party or authenticated contingency remover that is authorized to remove the contingency. Complex transactions may thereby be carried out securely, remotely and without compromising personal and / or financial information. The invention obviates the need to disseminate identification surrogates such as credit card numbers over public networks as well as the need to rely upon in-person holographic signatures on paper documents for authentication purposes.
Owner:ORACLE INT CORP
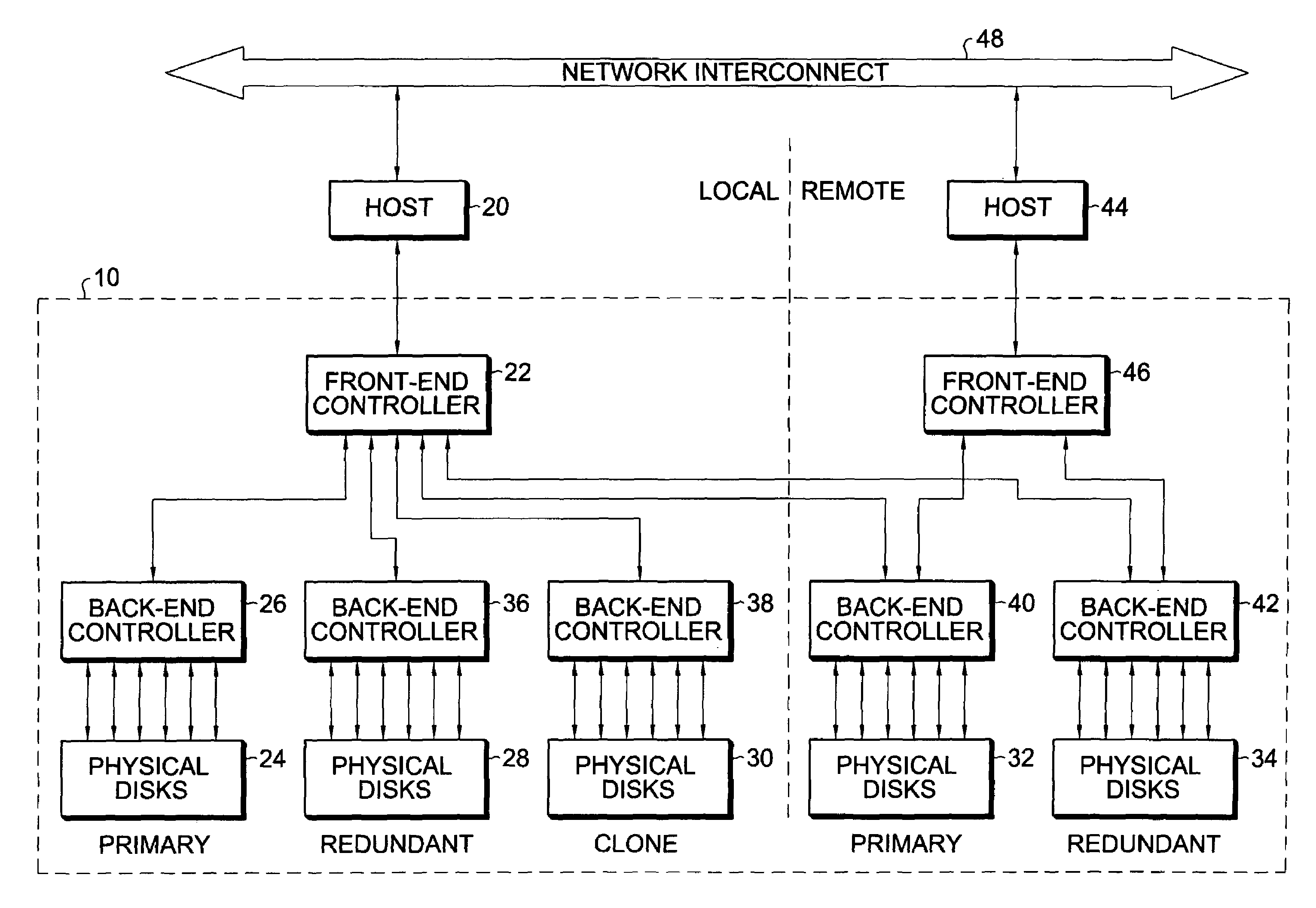
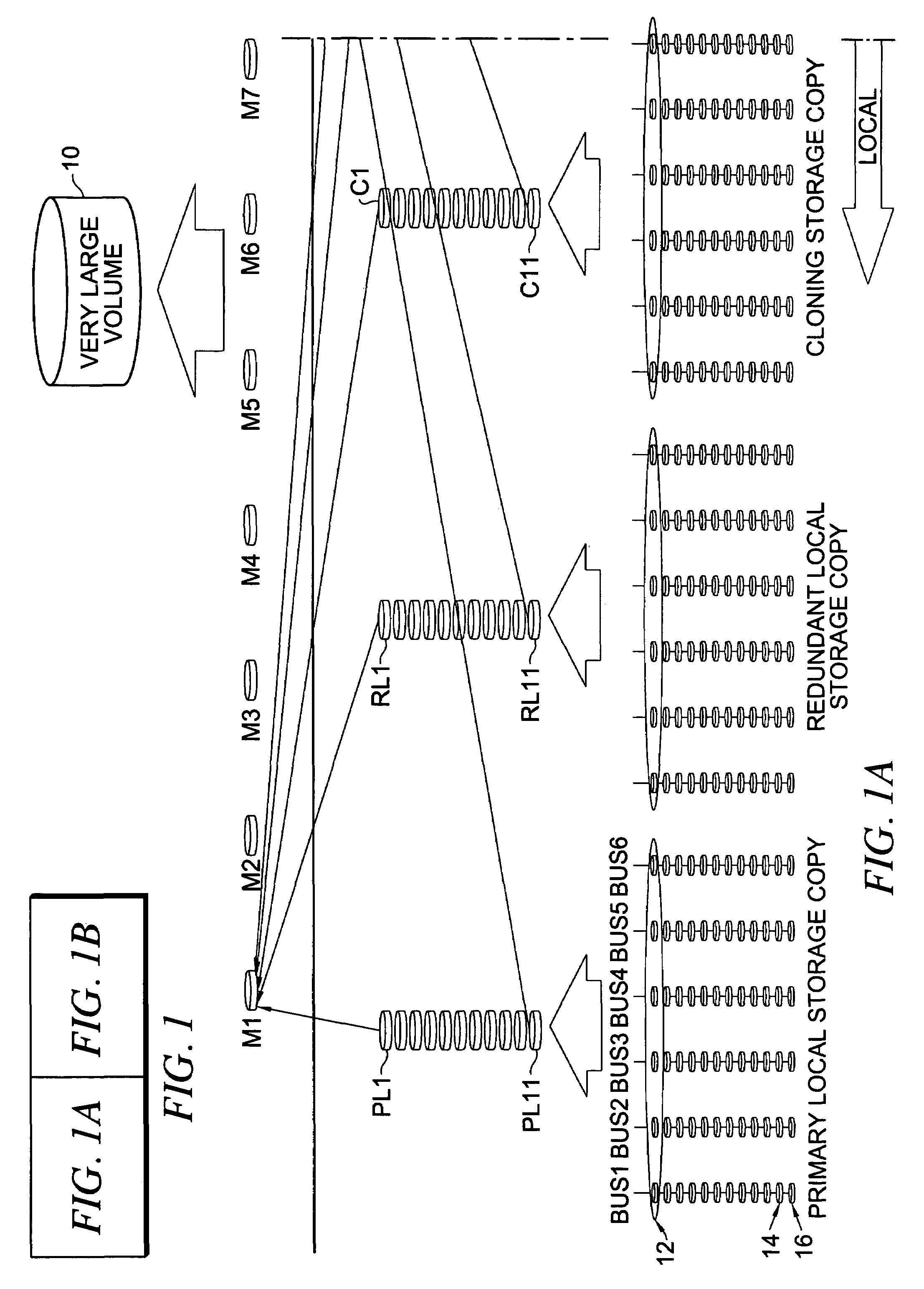
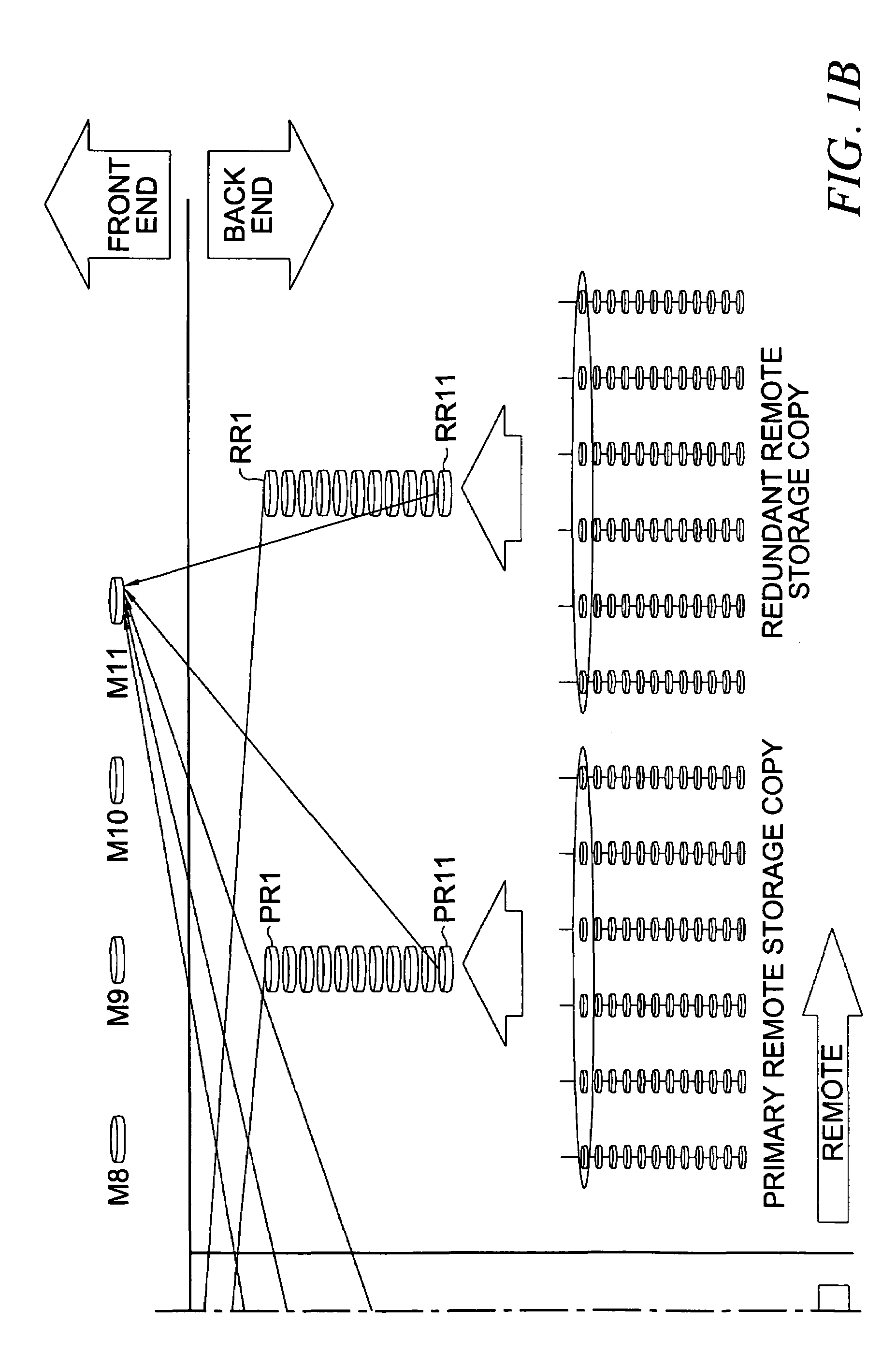
Apparatus and method for providing very large virtual storage volumes using redundant arrays of disks
InactiveUS7000069B2Ensure integrityInput/output to record carriersRedundant data error correctionRAIDComputer architecture
A very large virtual storage volume formed by distributing disks in multiple, multi-disk RAID (redundant array of independent disks) sets across busses of a back-end controller. The multiple RAID sets are striped by a front-end controller connected to the back-end controller and presented to a host computer as a very large virtual storage volume.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
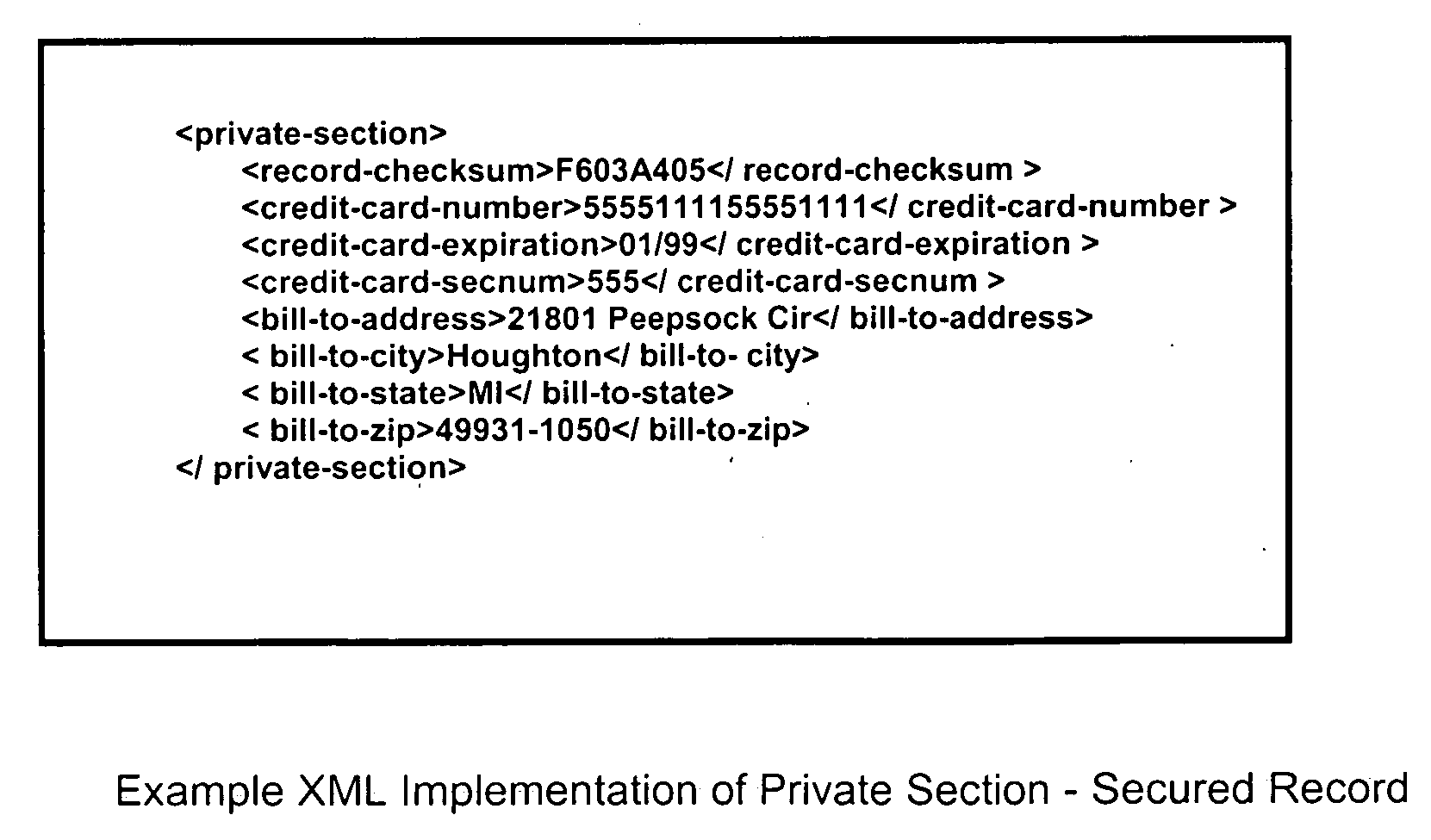
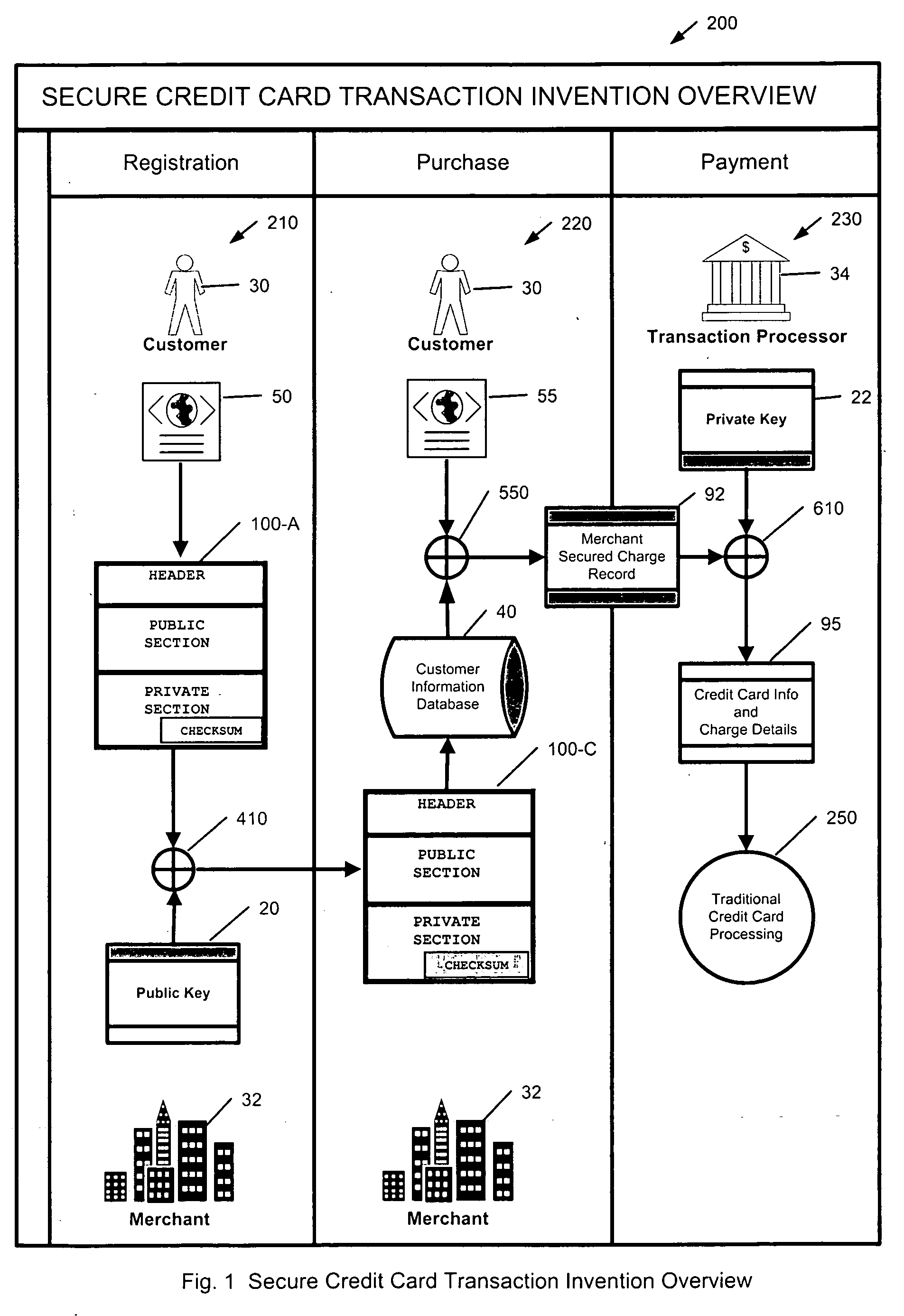
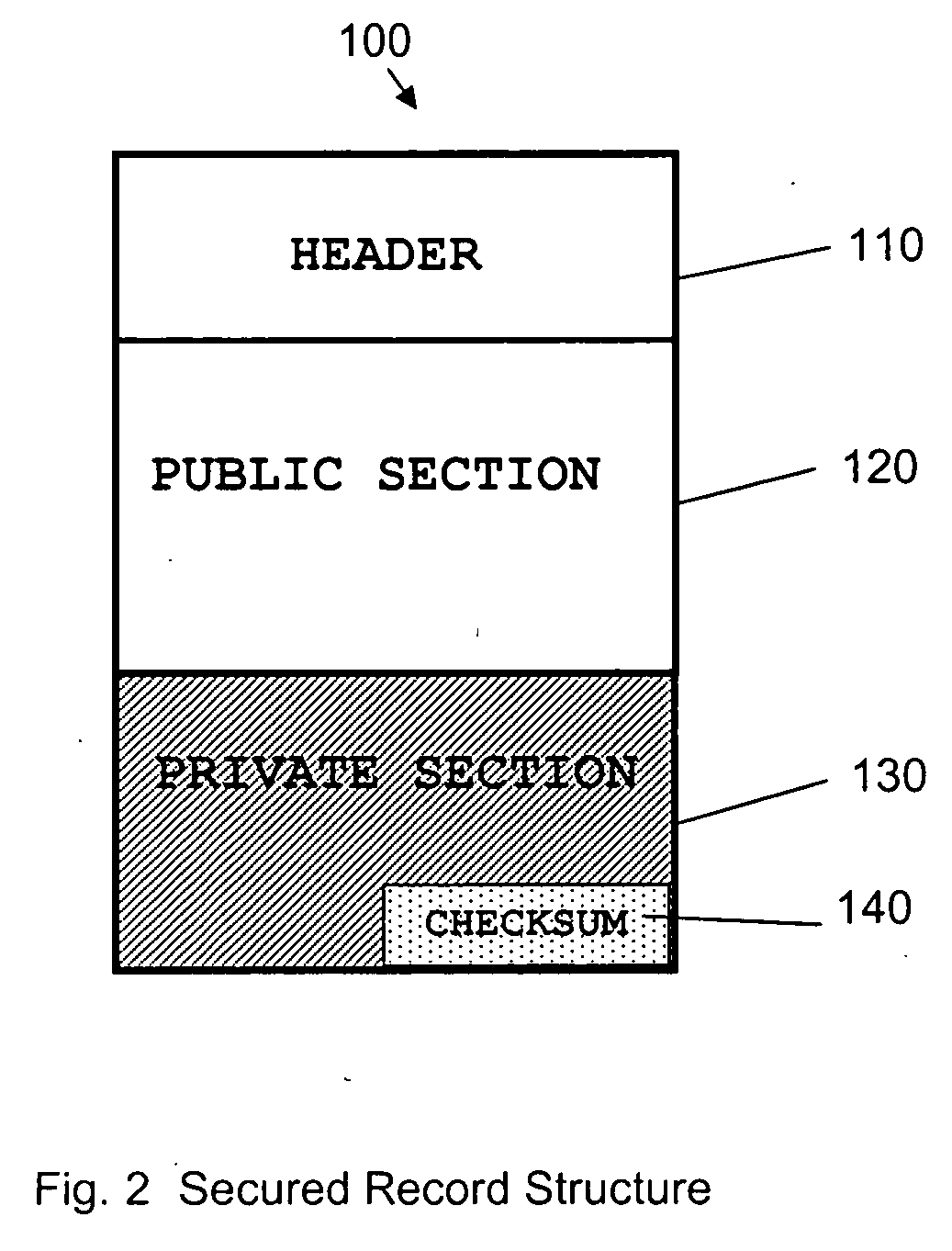
Method to secure credit card information stored electronically
InactiveUS20060282372A1Ensure integrityMinimize expirationAcutation objectsFinanceCredit cardChecksum
A method by which merchants who store sensitive credit card information can secure the information from theft, while minimizing the impact on the customer, as well as minimizing the cost of implementation. The merchant uses a special secured record for the storage of the credit card information for a specific customer. The record consists of two parts. The first part of the record contains public information which is visible to anyone with access to the record. The public information includes the merchant identity, along with information that constrains the use of the record, such as limits on the type of purchase, amount of purchase, or frequency of purchase, as well as the expiration date of the record, approved shipping addresses, and other constraints that make the record effectively useless to anyone except the merchant who created and stored the record, as well as limiting possible abuse by said merchant. The second part of the record contains private information which is encrypted so as to be visible only to parties authorized to view the information. The private part of the record will contain the sensitive credit card information, along with a checksum of the contents of the record. When the record is submitted to the clearing entity, the private part of the record is decrypted using the appropriate key. The checksum is used to verify that the record has not been modified, and that the public and private sections correspond to each other. Once the record is validated, constraints are applied, and if met, the credit card information is used to process the transaction.
Owner:ENDRES TIMOTHY GERARD +1
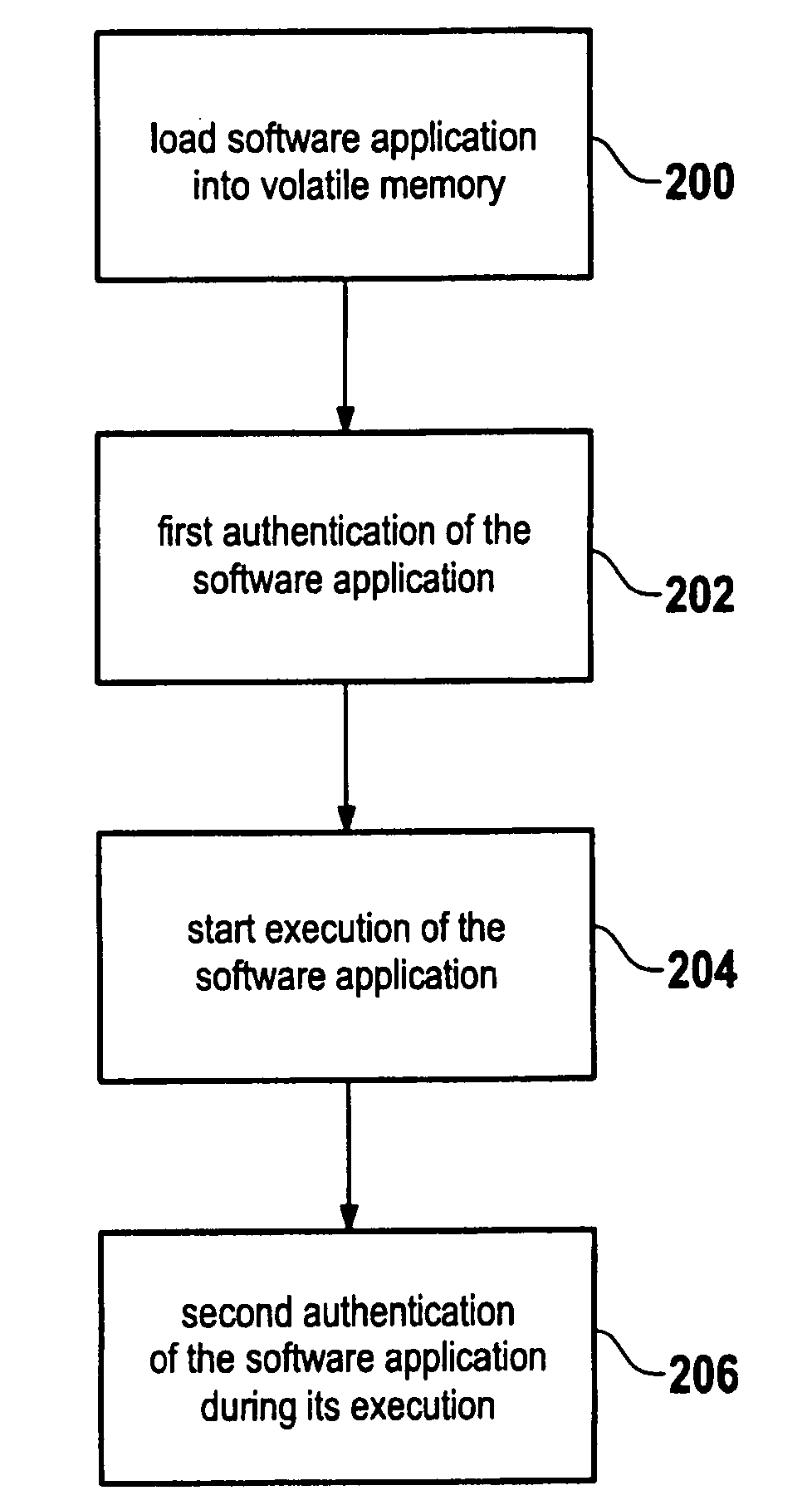
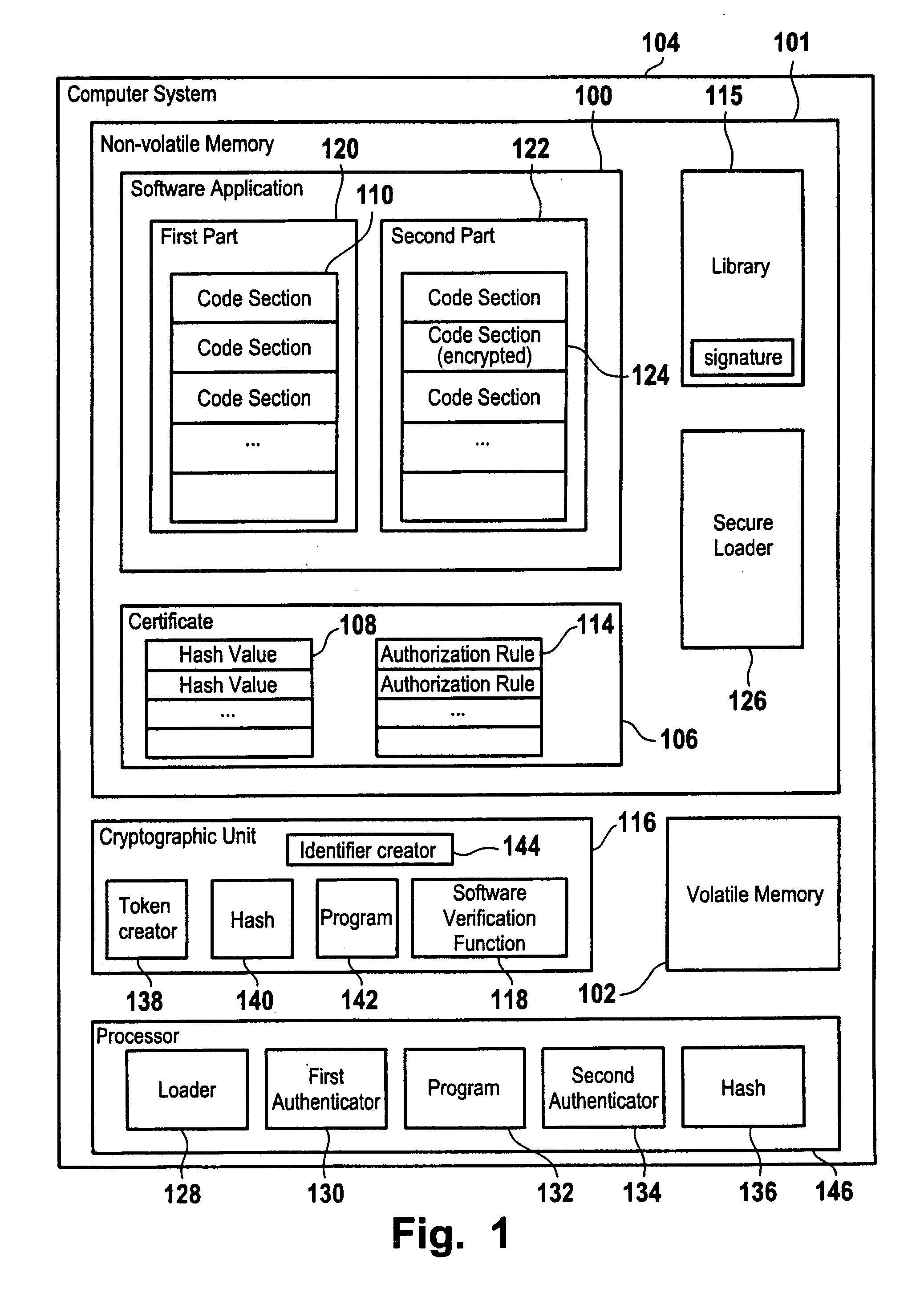
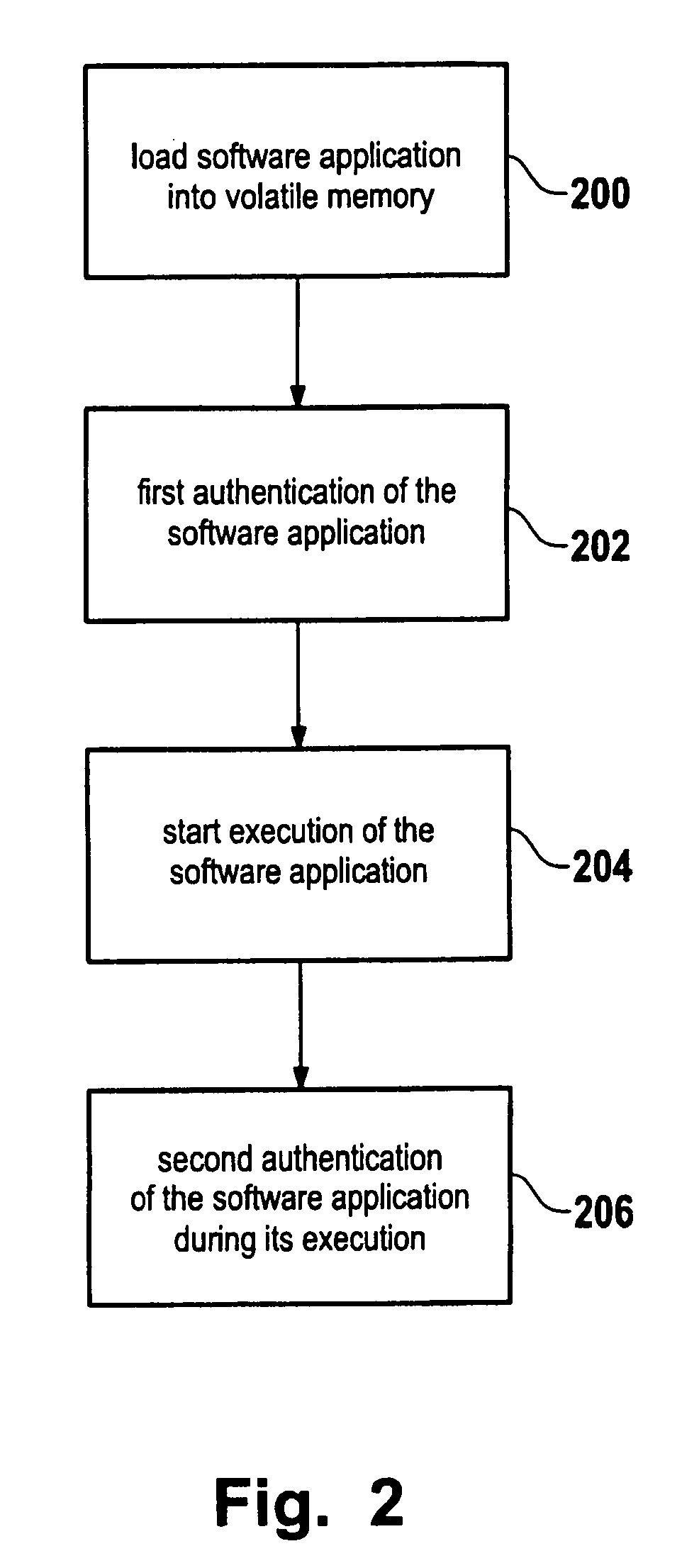
Computer security method and computer system
ActiveUS20070220500A1Ensure integrityExecution of applicationUnauthorized memory use protectionHardware monitoringDigital rights managementAuthorization
A method for secure loading, integrity checking of the runtime image and control over the runtime execution of applications which ensures that a software application loads only code it was authorized to load, and that the software application is monitored for unauthorized modifications of the runtime image. The method proposed can be used as a basis for further enforcing of authorization rules during the execution of an application, e.g. for Digital Rights Management.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com