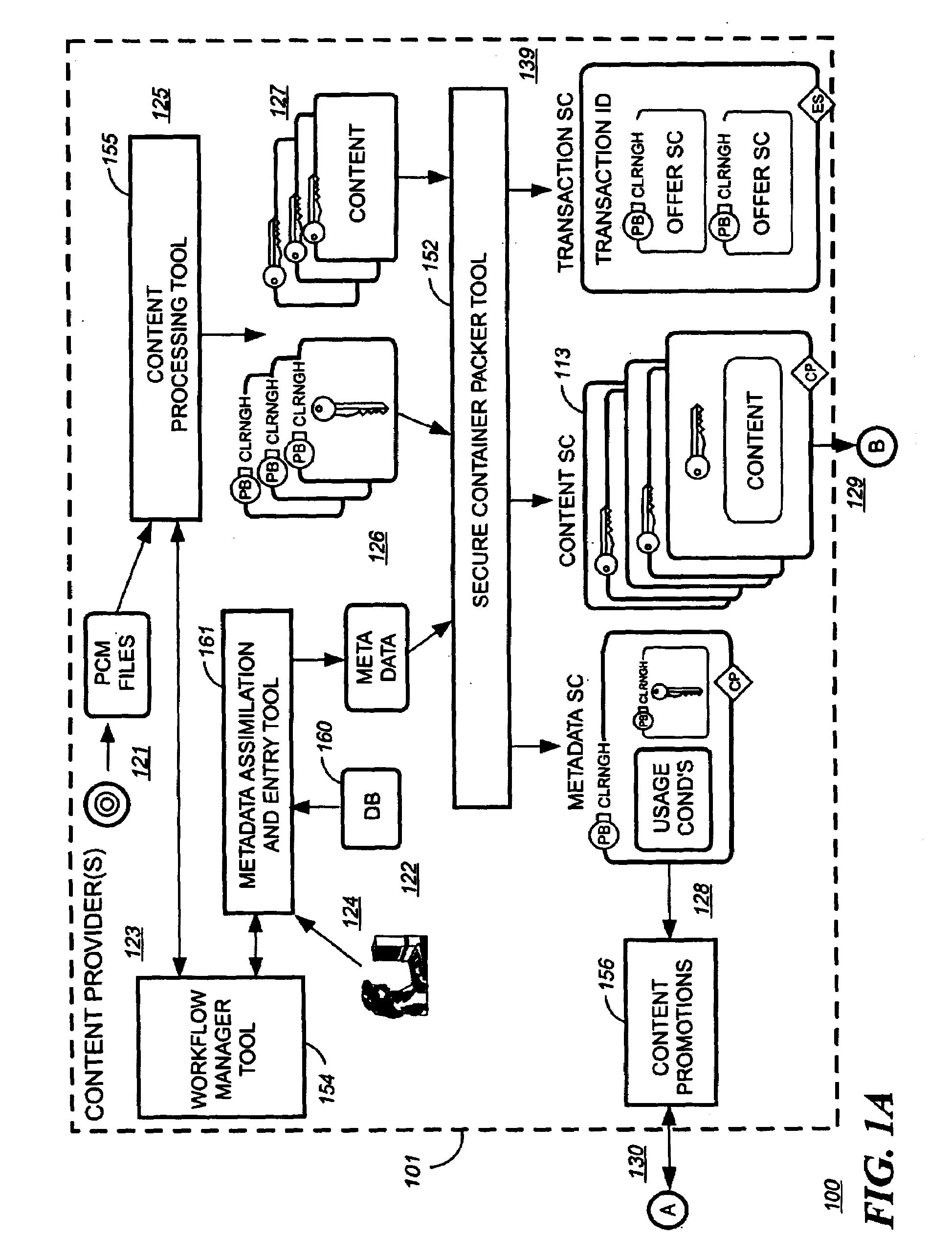
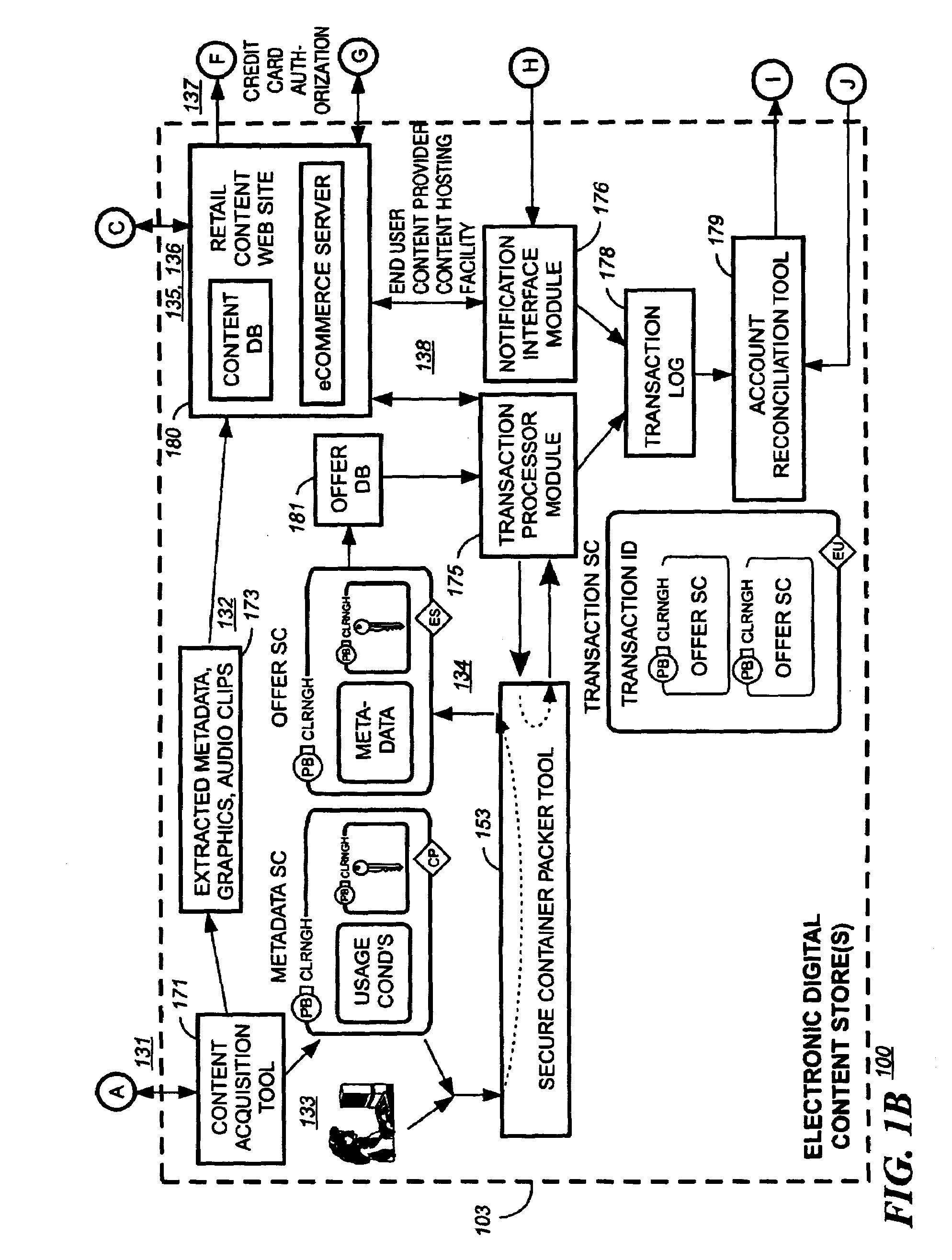
Patents
Literature
1282 results about "Digital rights management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Digital rights management (DRM) tools or technological protection measures (TPM) are a set of access control technologies for restricting the use of proprietary hardware and copyrighted works. DRM technologies try to control the use, modification, and distribution of copyrighted works (such as software and multimedia content), as well as systems within devices that enforce these policies.
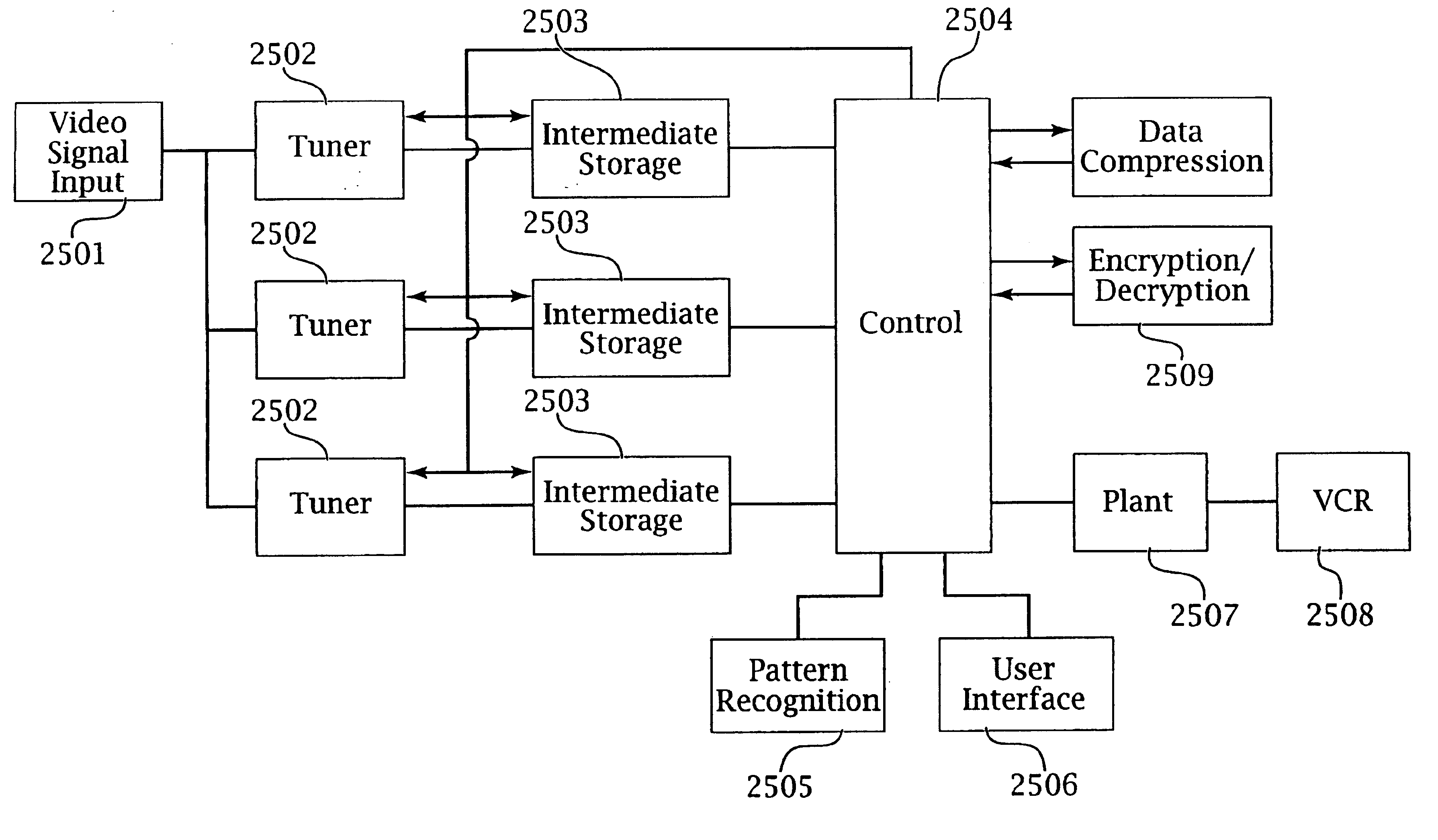
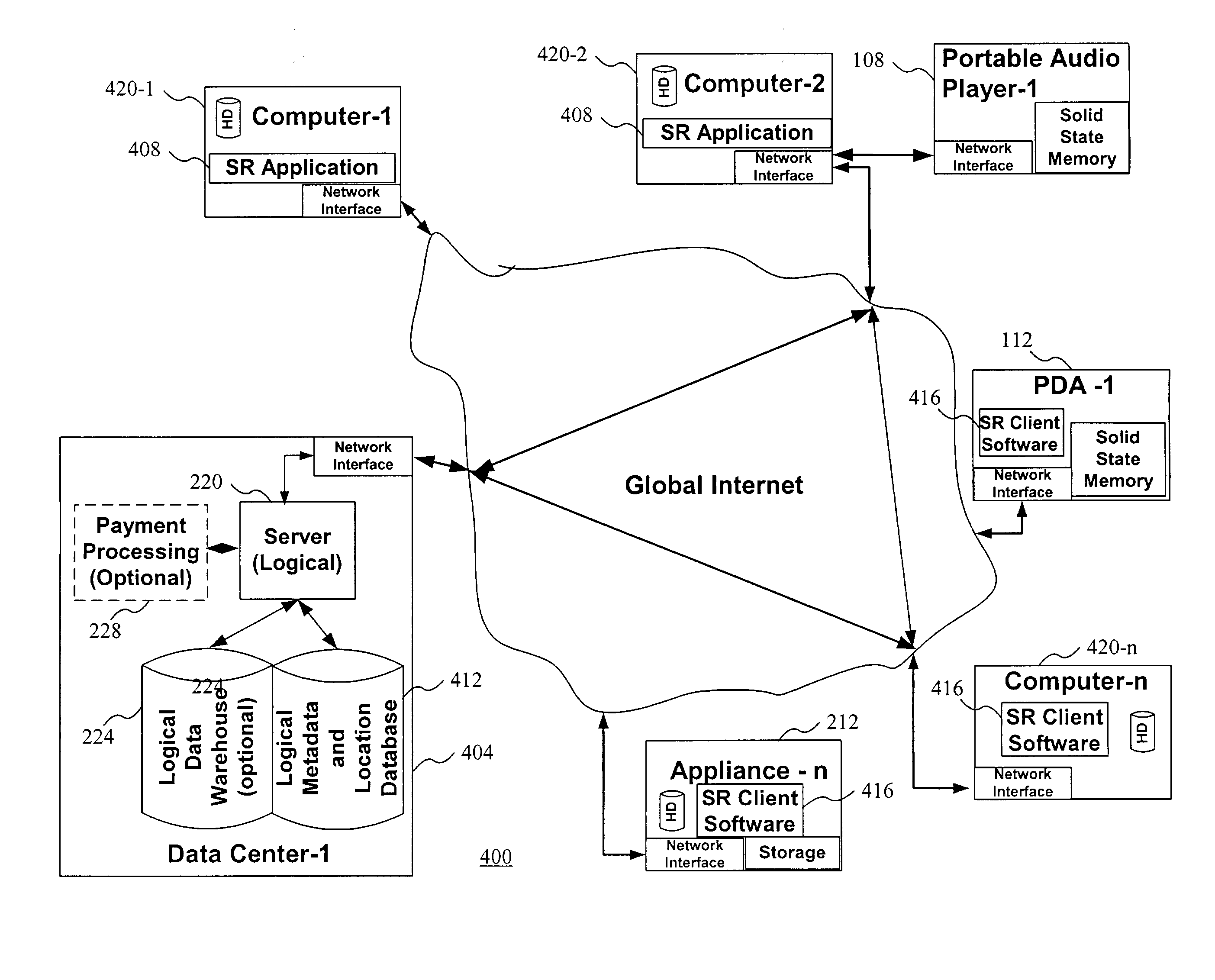
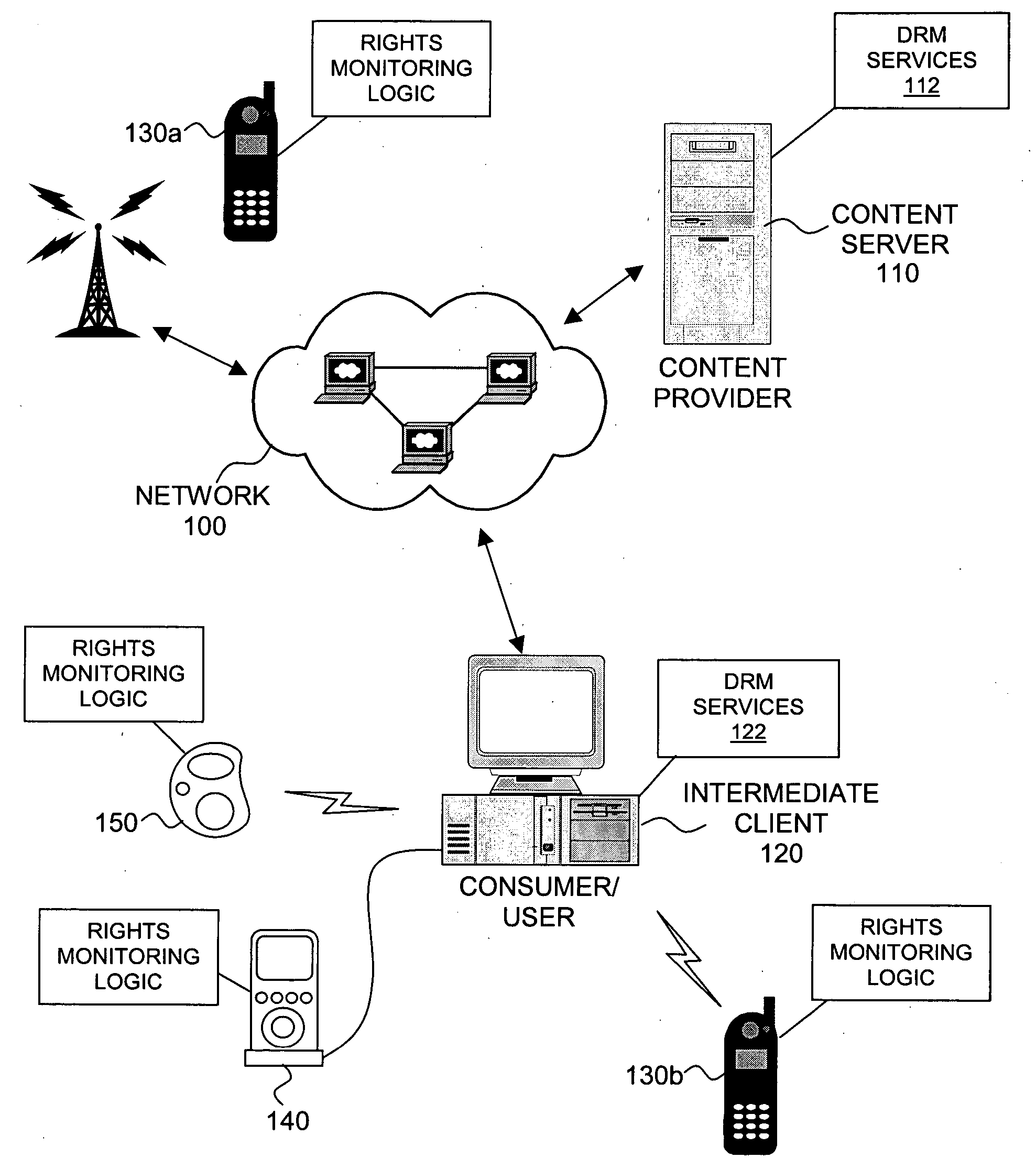
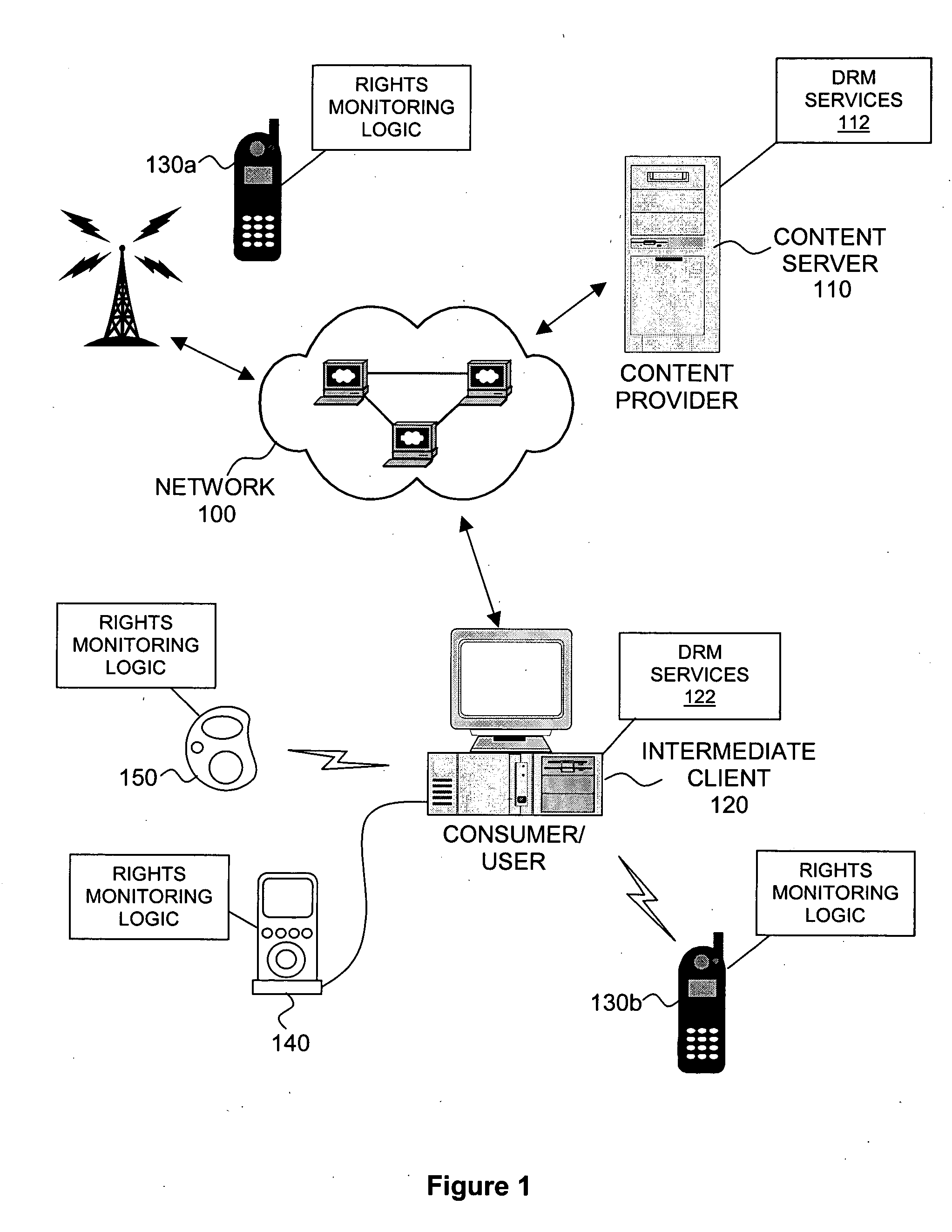
Intelligent electronic appliance system and method
InactiveUS6850252B1Minimize timeEasy to implementAnalogue secracy/subscription systemsCharacter and pattern recognitionAdaptive user interfaceDigital rights management
An intelligent electronic appliance preferably includes a user interface, data input and / or output port, and an intelligent processor. A preferred embodiment comprises a set top box for interacting with broadband media streams, with an adaptive user interface, content-based media processing and / or media metadata processing, and telecommunications integration. An adaptive user interface models the user, by observation, feedback, and / or explicit input, and presents a user interface and / or executes functions based on the user model. A content-based media processing system analyzes media content, for example audio and video, to understand the content, for example to generate content-descriptive metadata. A media metadata processing system operates on locally or remotely generated metadata to process the media in accordance with the metadata, which may be, for example, an electronic program guide, MPEG 7 data, and / or automatically generated format. A set top box preferably includes digital trick play effects, and incorporated digital rights management features.
Owner:BLANDING HOVENWEEP
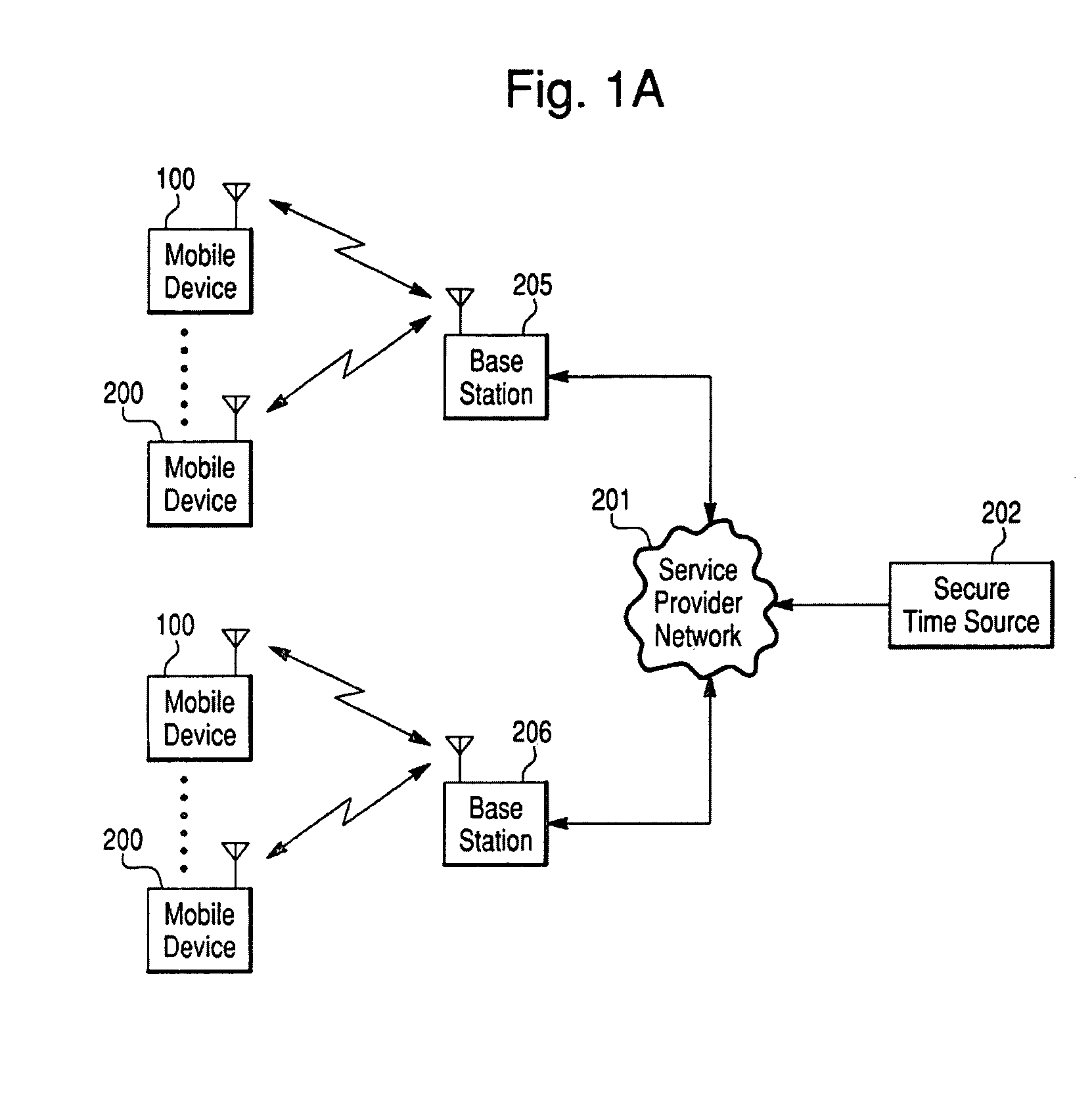
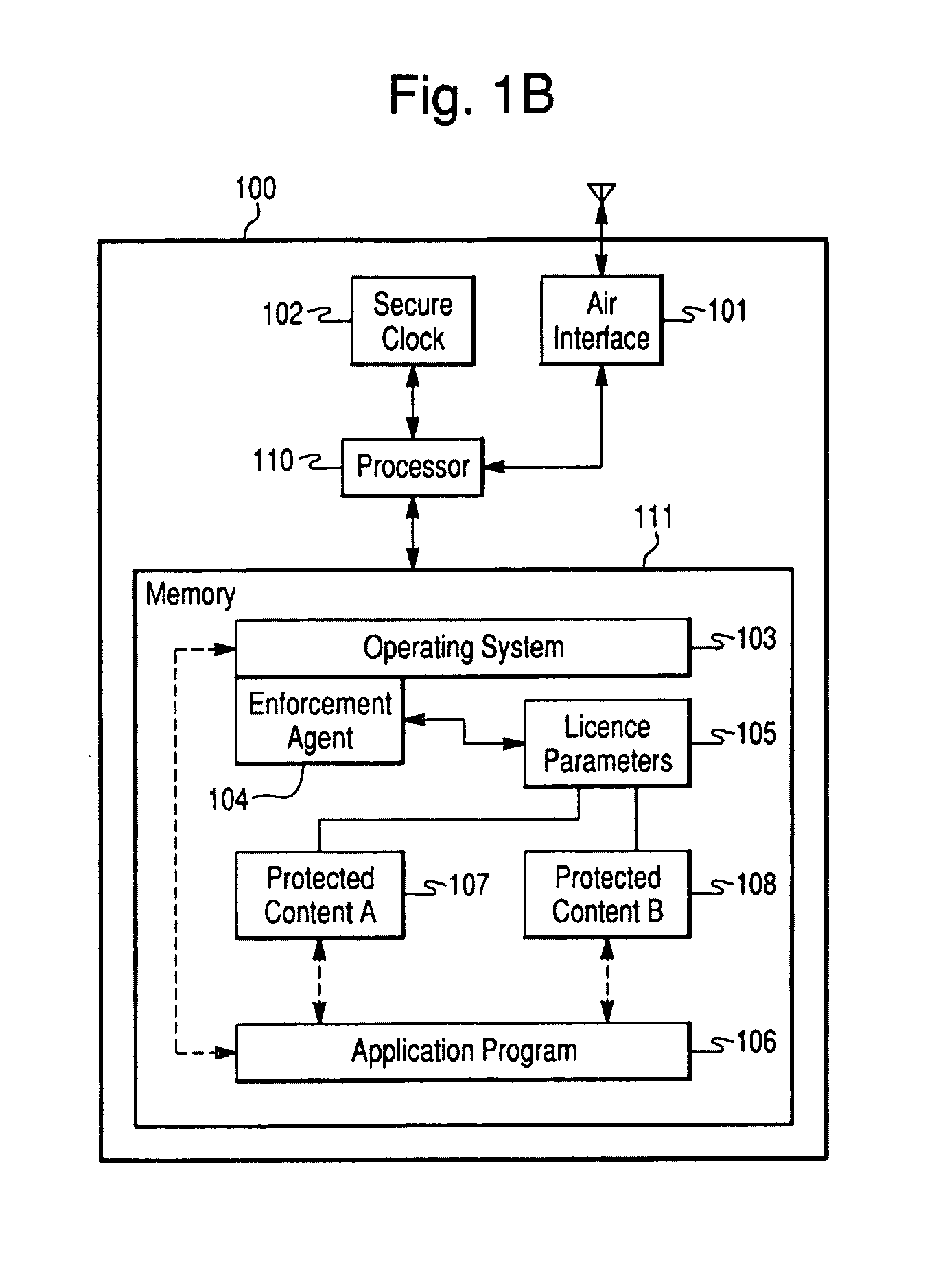
Digital rights management in a mobile environment
ActiveUS20110225417A1Facilitating access to contentOptimization of content deliveryOffice automationResourcesComputer hardwareDigital rights management
Embodiments provide a method that causes a plurality of virtual machine instructions to be interpreted for indications of a mobile device's hardware identification information, thus forming a plurality of hardware instruction interpretations. The embodiment also combines each of the plurality of hardware instruction interpretations and hashes the combination to form a quasi-hardware device identifier. An encryption process is based on the quasi-hardware encryption device identifier and the media is then encrypted using the encryption process. The encrypted media is transferred to the mobile device wherein the mobile device decrypts the media based at least in part on the mobile device's internal knowledge of the quasi-hardware device identification.
Owner:DIRECTV LLC
Digital rights management in a mobile communications environment
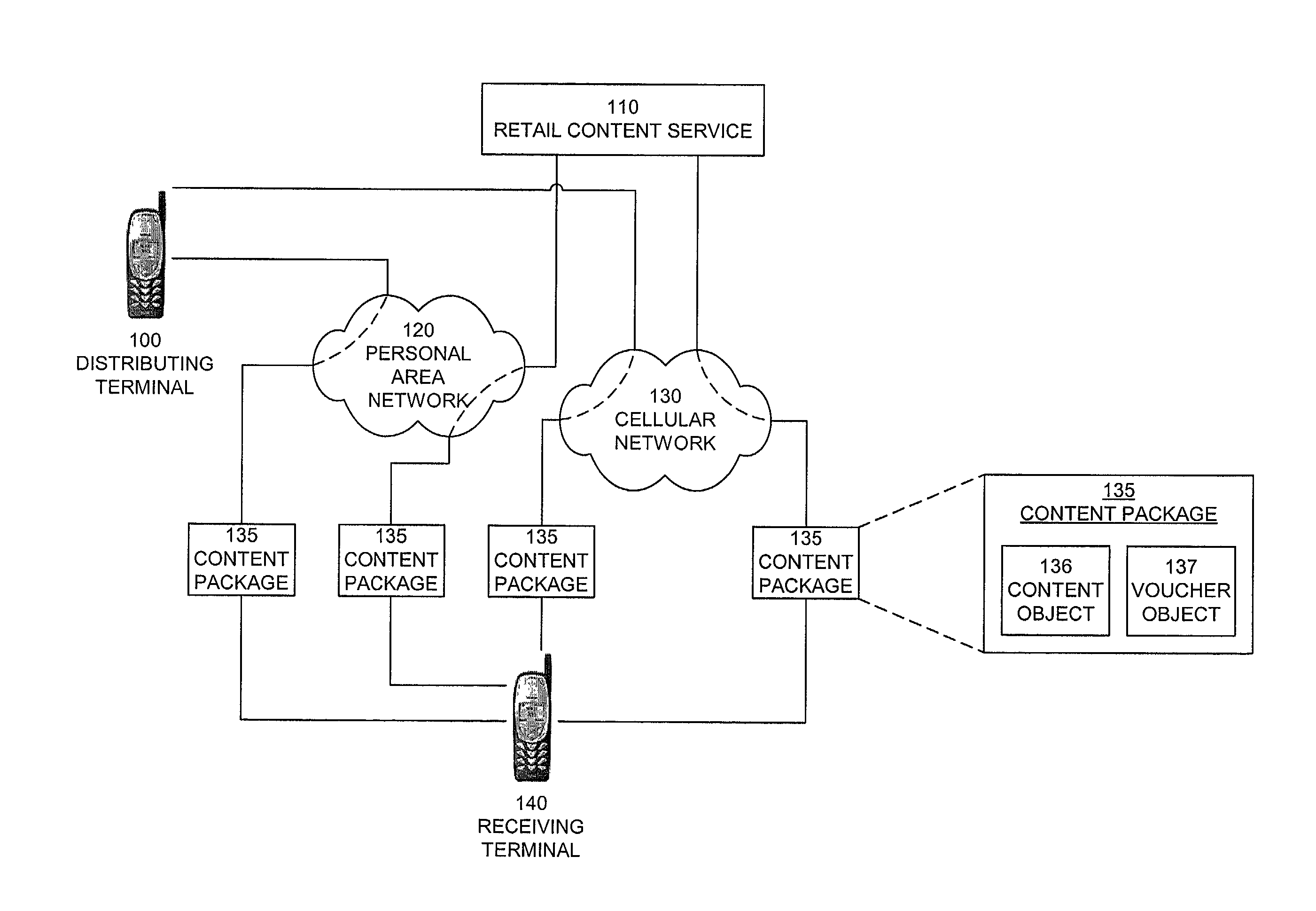
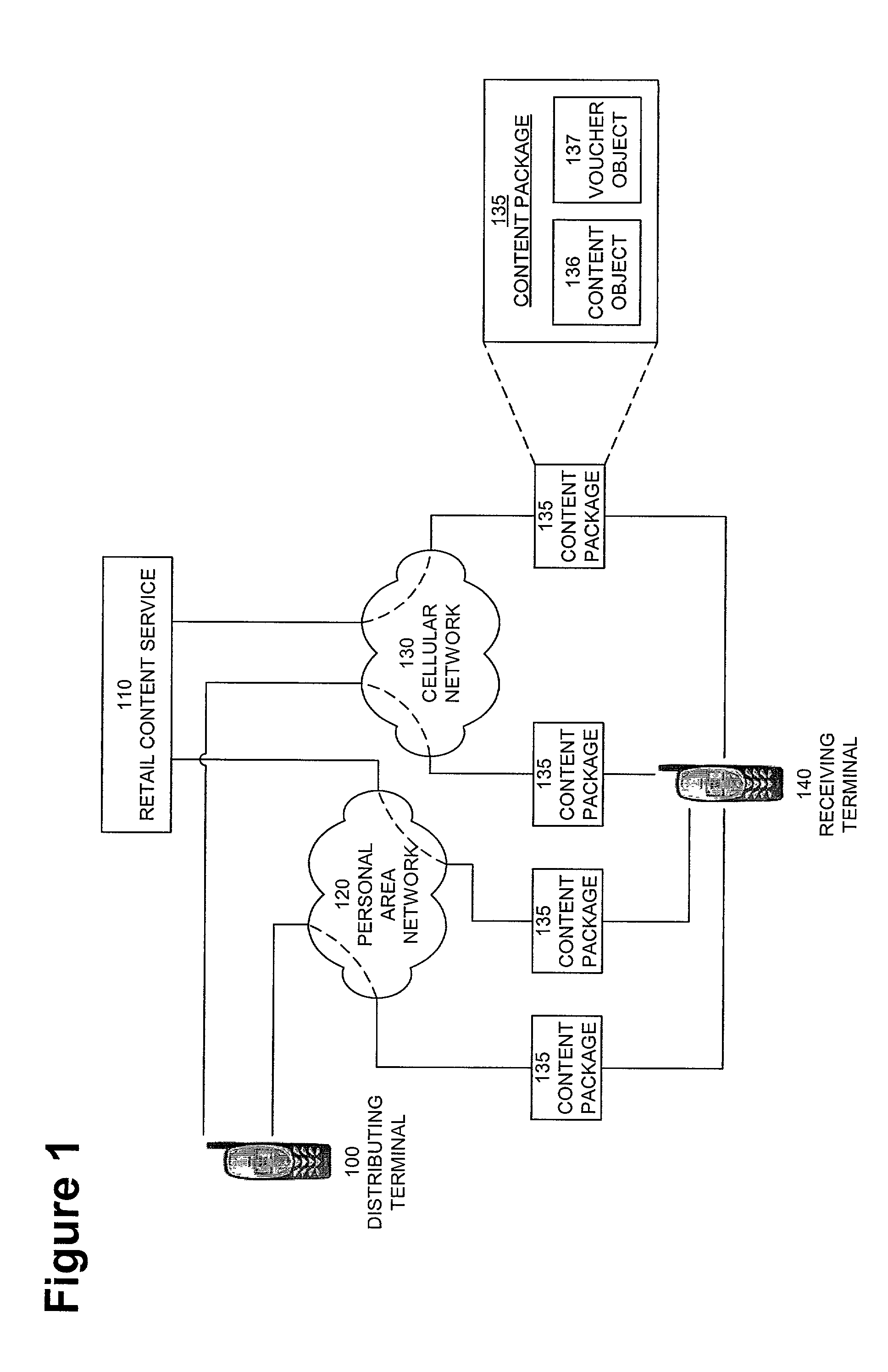
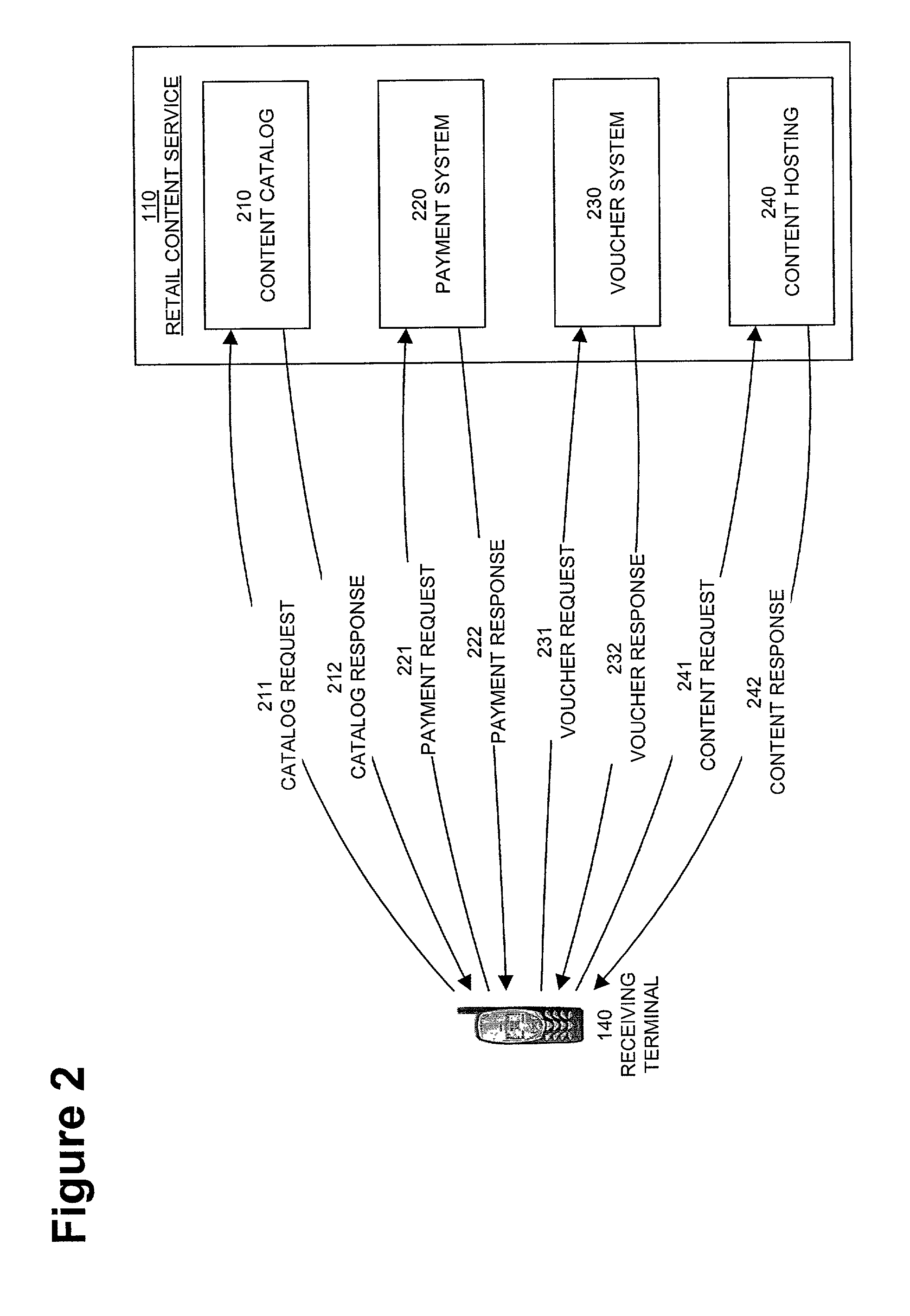
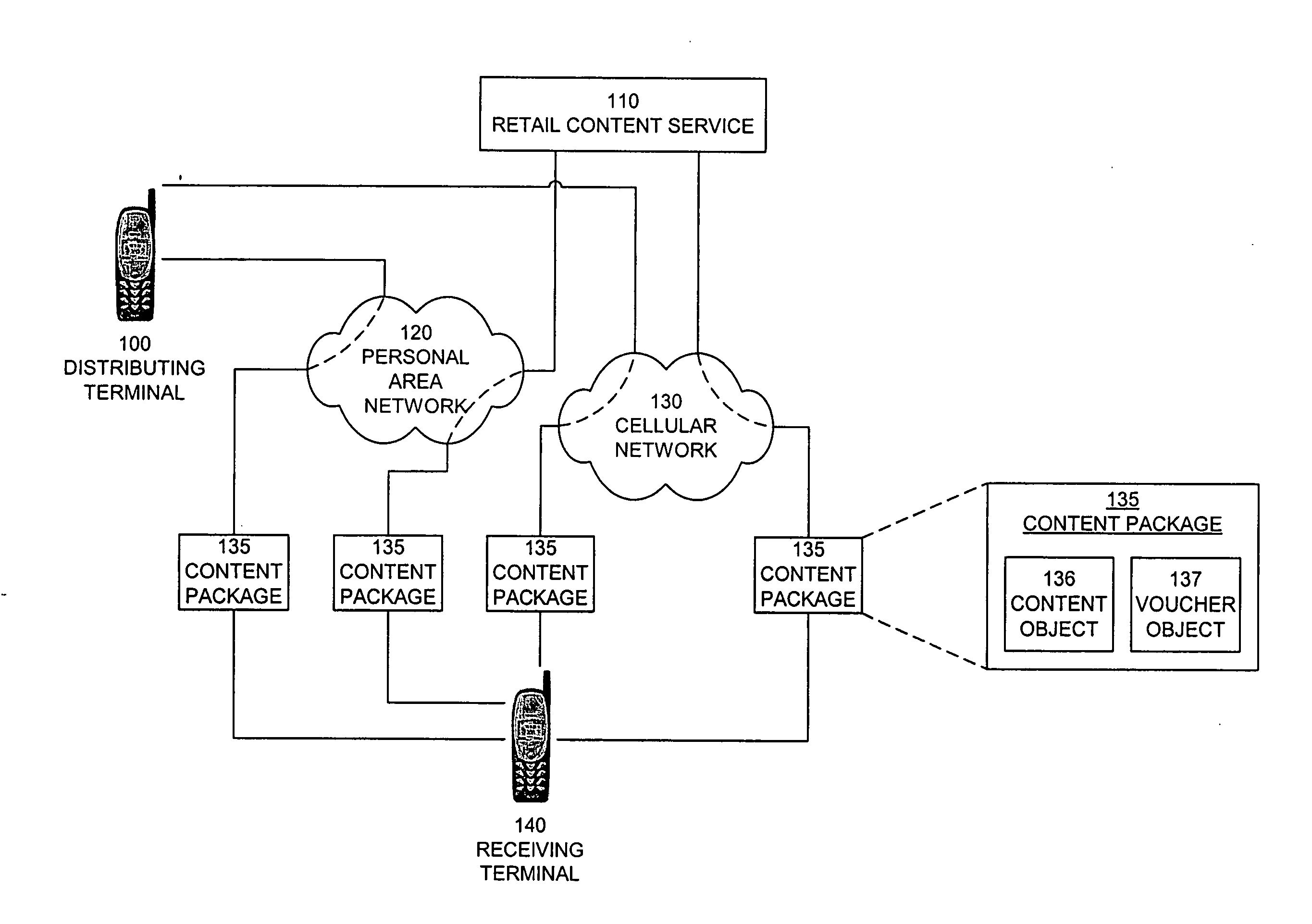
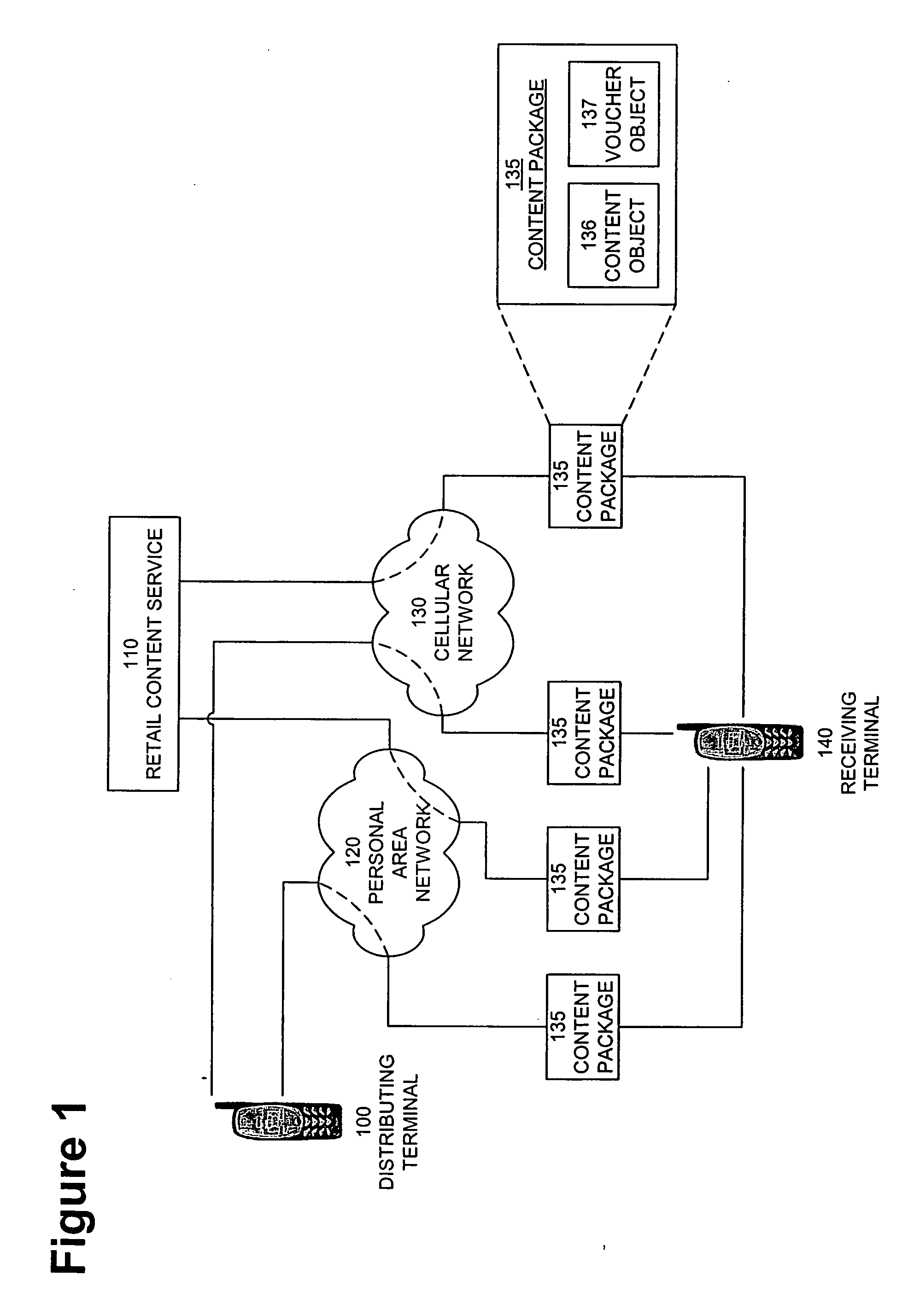
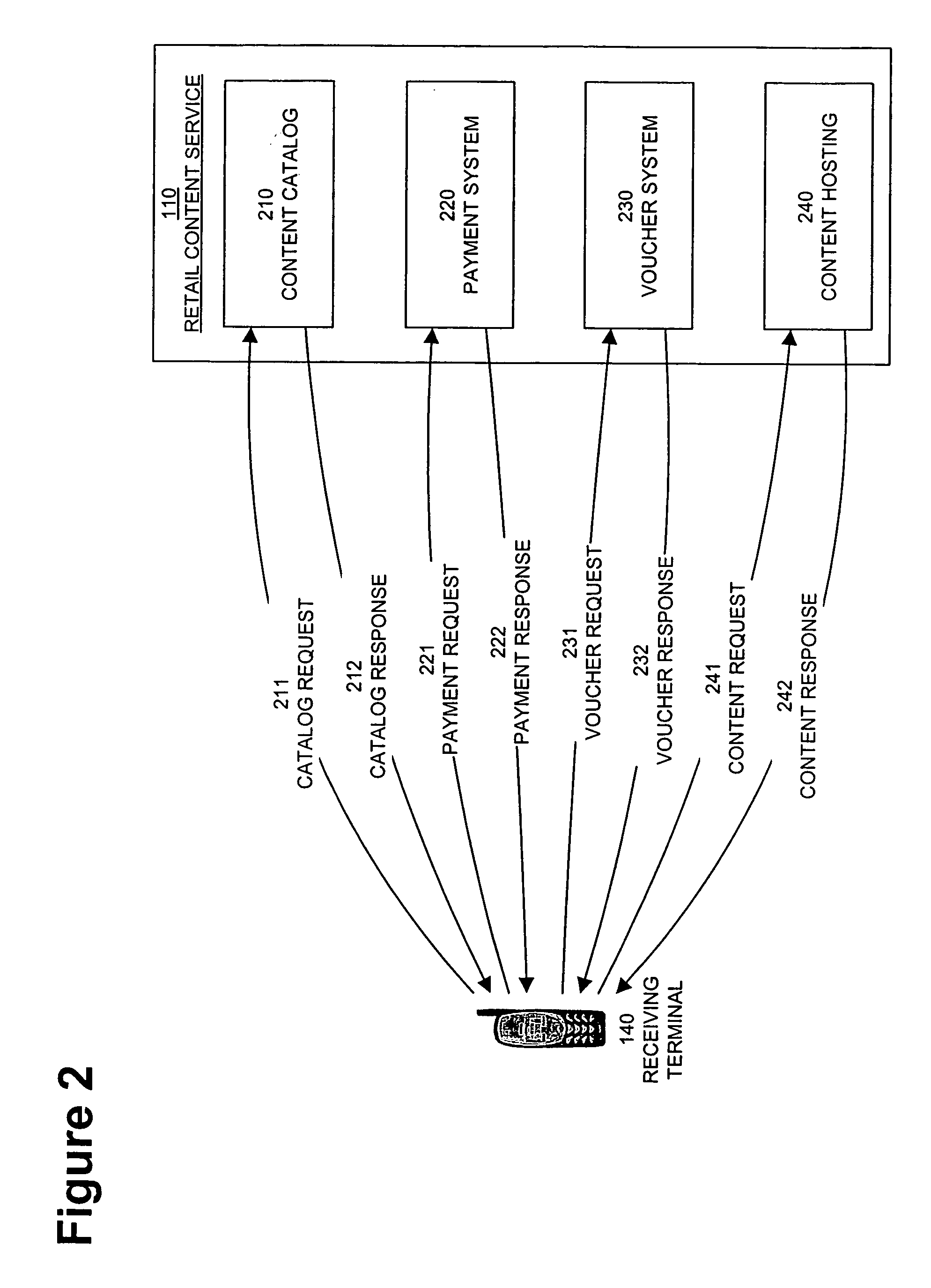
InactiveUS20050004875A1Payment architectureProgram/content distribution protectionVoucherDigital rights management
A method, system, and computer program product for enabling a wireless device in a mobile communication environment to obtain rights to protected content of a digital asset. The digital asset is downloaded to the wireless device from any one of a plurality of content servers or other wireless devices. The digital asset comprising a content ID, content encrypted with a content key, and information on obtaining rights to the content being expressed in a voucher generated by a voucher server in the network. The method, system, and computer program product also creates the digital asset for downloading to a wireless device from one of a plurality of content servers in a network and generates a voucher at the voucher server.
Owner:NOKIA TECHNOLOGLES OY
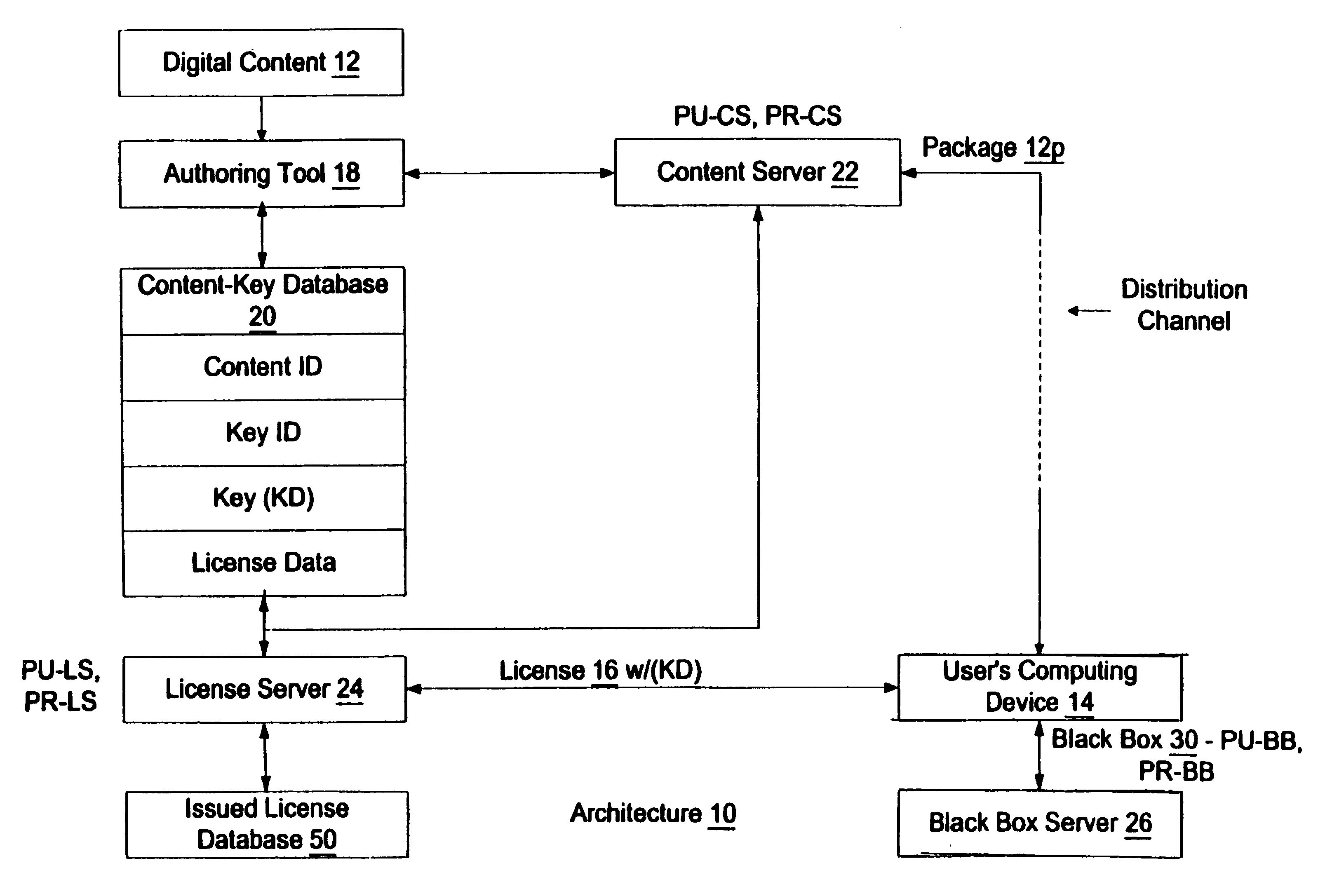
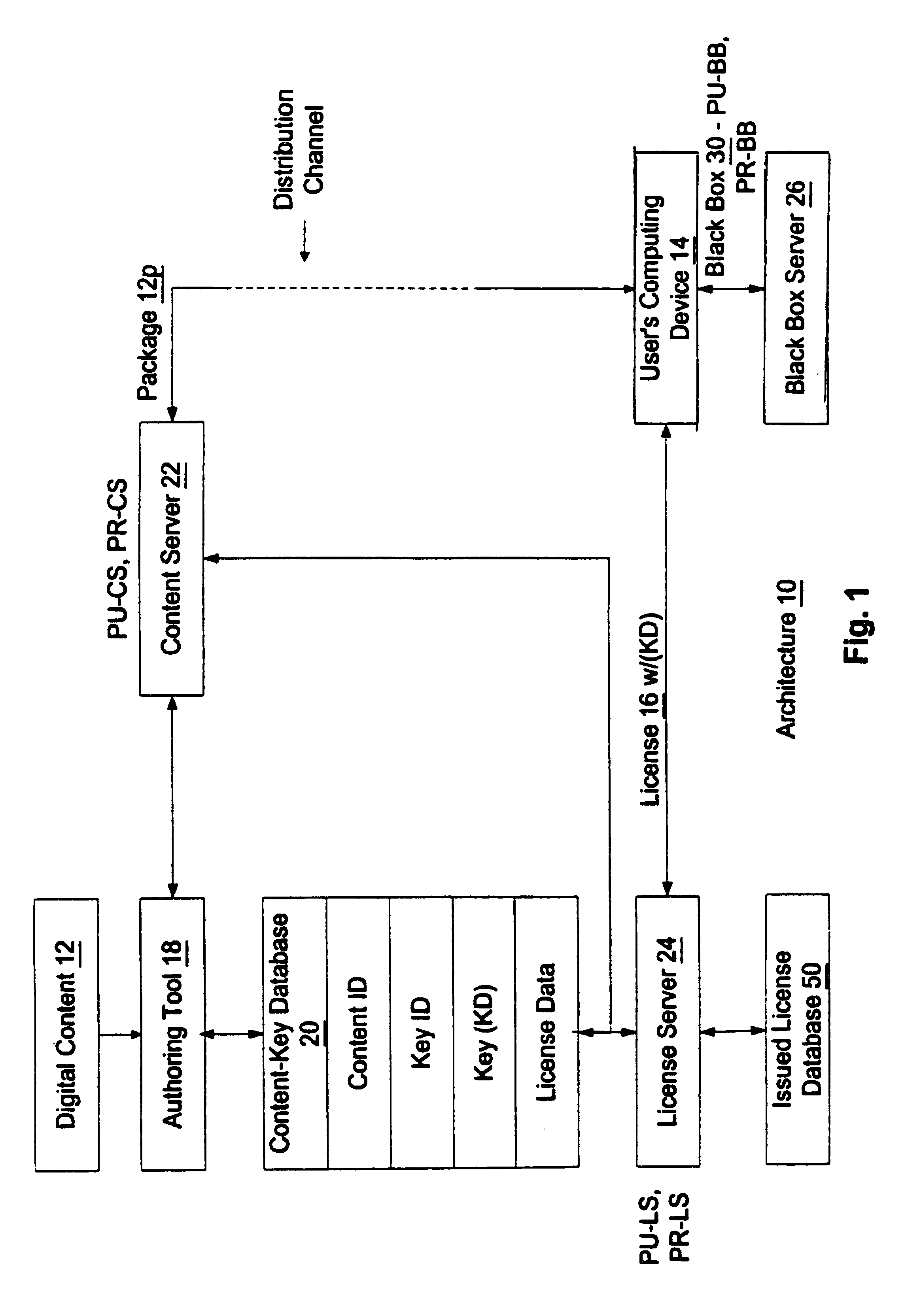
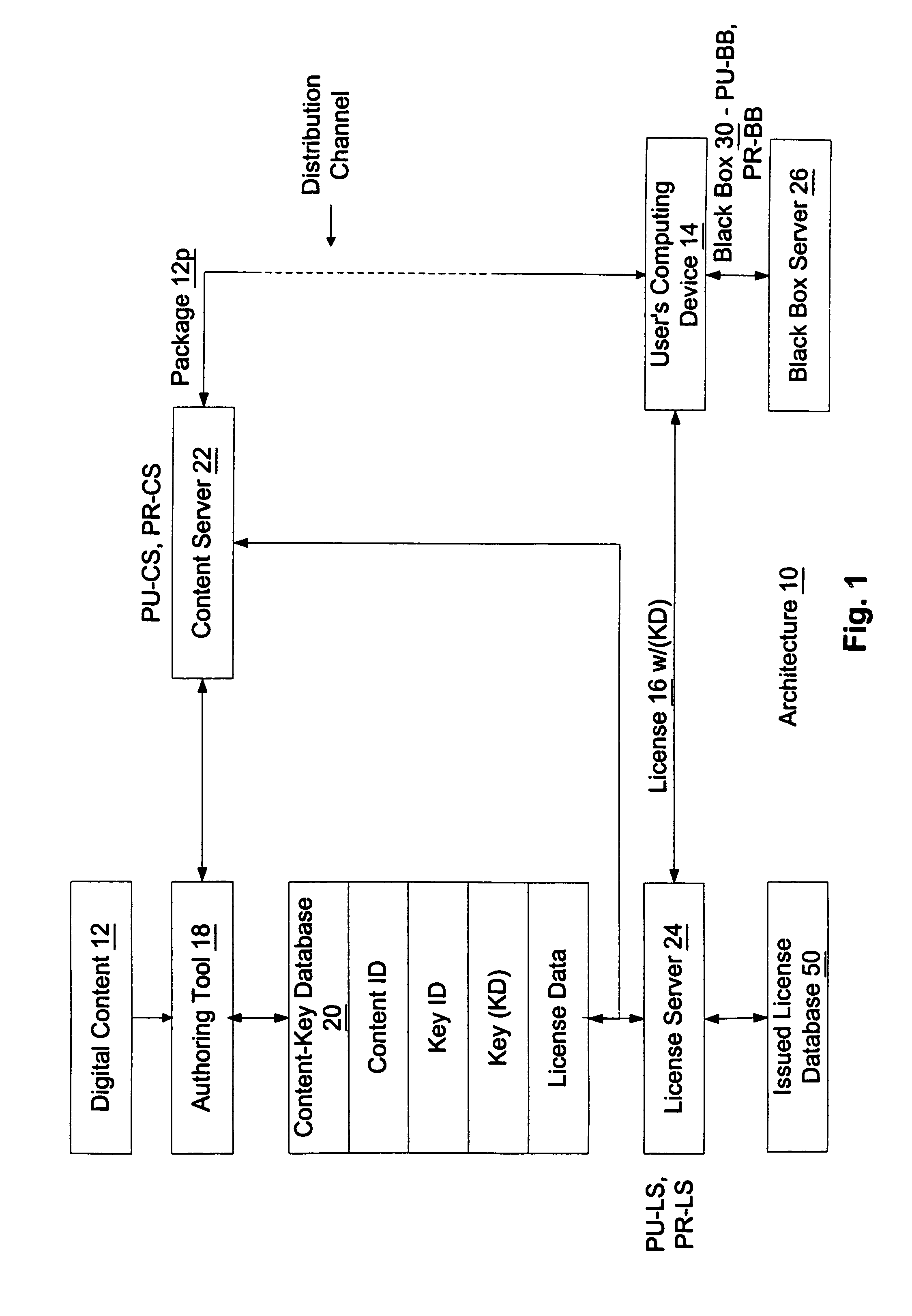
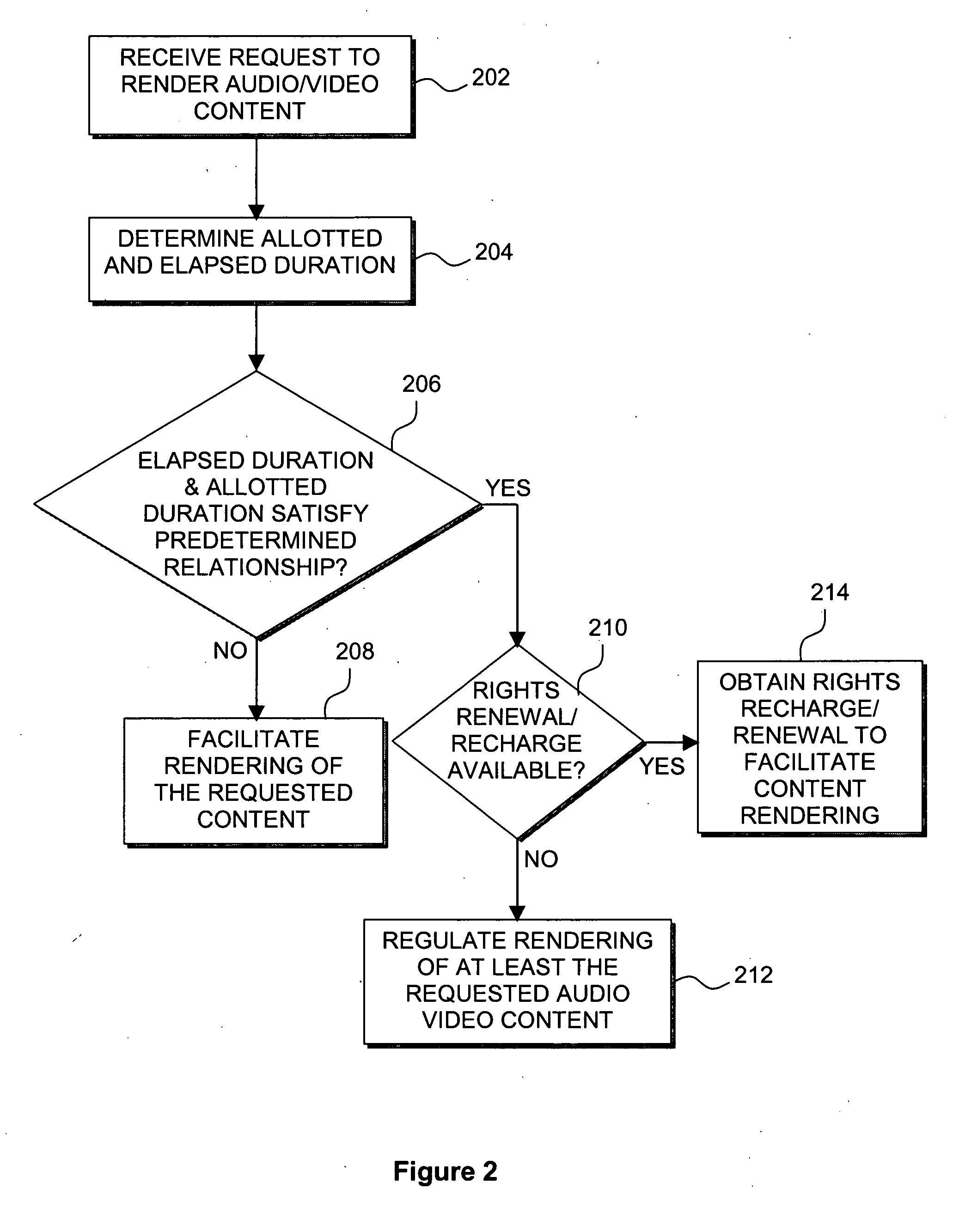
Enforcement architecture and method for digital rights management
InactiveUS7103574B1Satisfies needKey distribution for secure communicationDigital data processing detailsDigital contentNumber content
An enforcement architecture and method for implementing digital rights management are disclosed. Digital content is distributed from a content server to a computing device of a user and received, and an attempt is made to render the digital content by way of a rendering application. The rendering application invokes a Digital Rights Management (DRM) system, and such DRM system determines whether a right to render the digital content in the manner sought exists based on any digital license stored in the computing device and corresponding to the digital content. If the right does not exist, a digital license that provides such right and that corresponds to the digital content is requested from a license server, and the license server issues the digital license to the DRM system. The computing device receives the issued digital license and stores the received digital license thereon.
Owner:MICROSOFT TECH LICENSING LLC
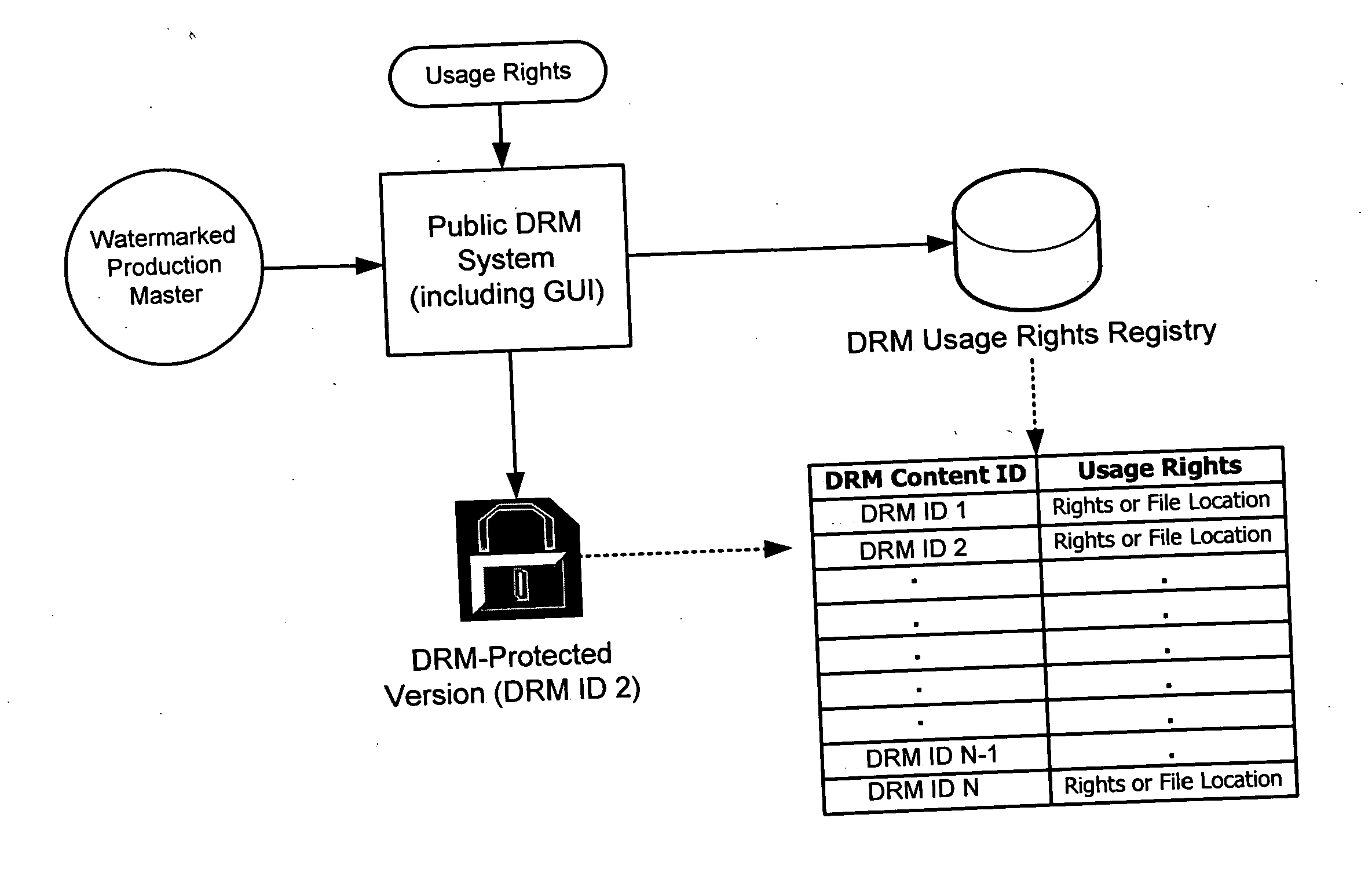
Rights management systems and methods using digital watermarking
ActiveUS20060062426A1Difficult to controlDifficult to trackUser identity/authority verificationAnalogue secracy/subscription systemsContent IdentifierRights management
A digital watermark (DWM) content identifier is steganographically embedded in content. The DWM content identifier provides a link to a rights registry storing usage rights associated with the content. In some implementations the rights registry provides an association between the DWM content identifier and a digital rights management (DRM) content identifier. The DRM content identifier is used to find associated usage rights. The DWM content identifier can also be used to transfer content from a first DRM system to a second DRM system.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
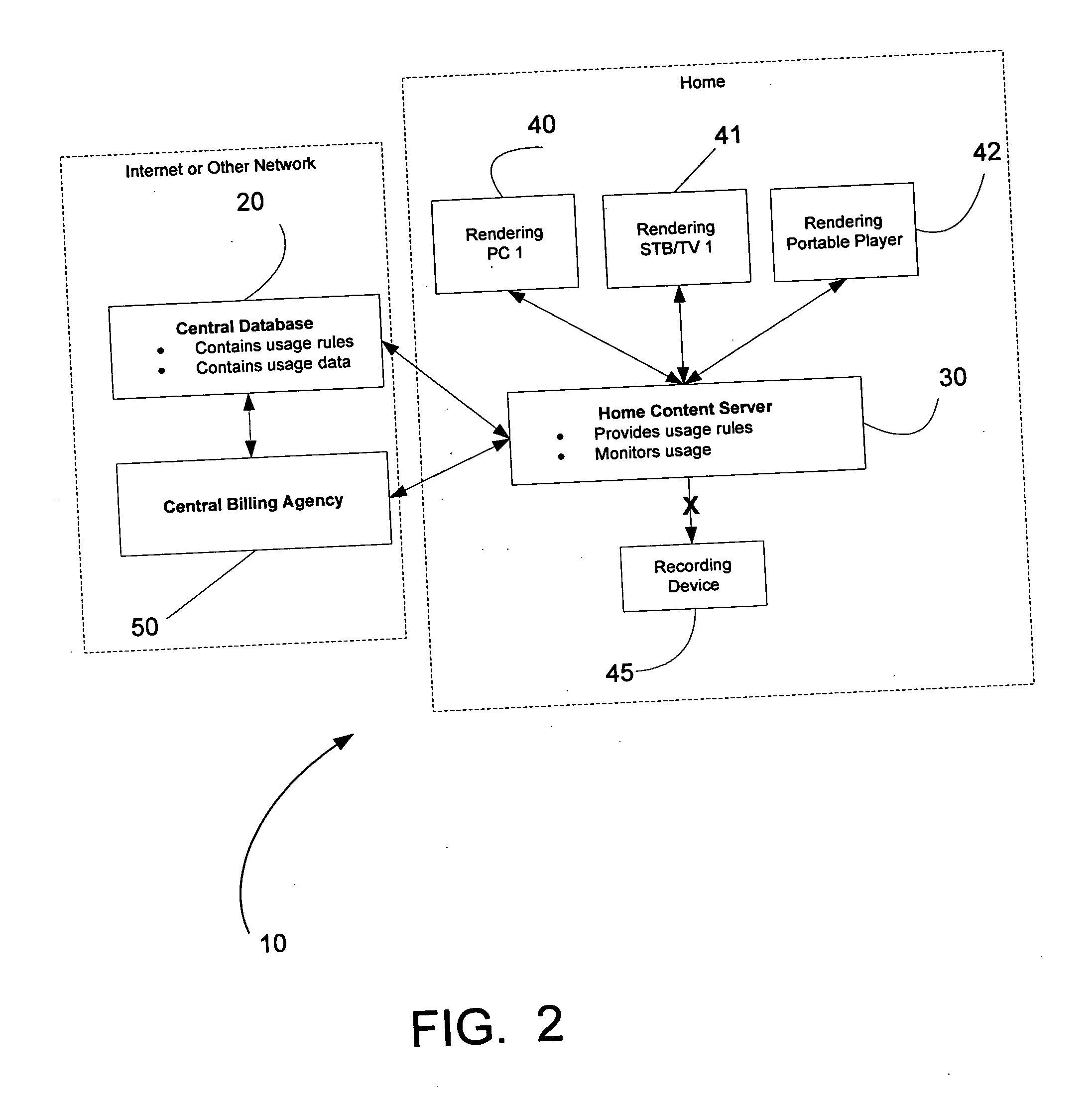
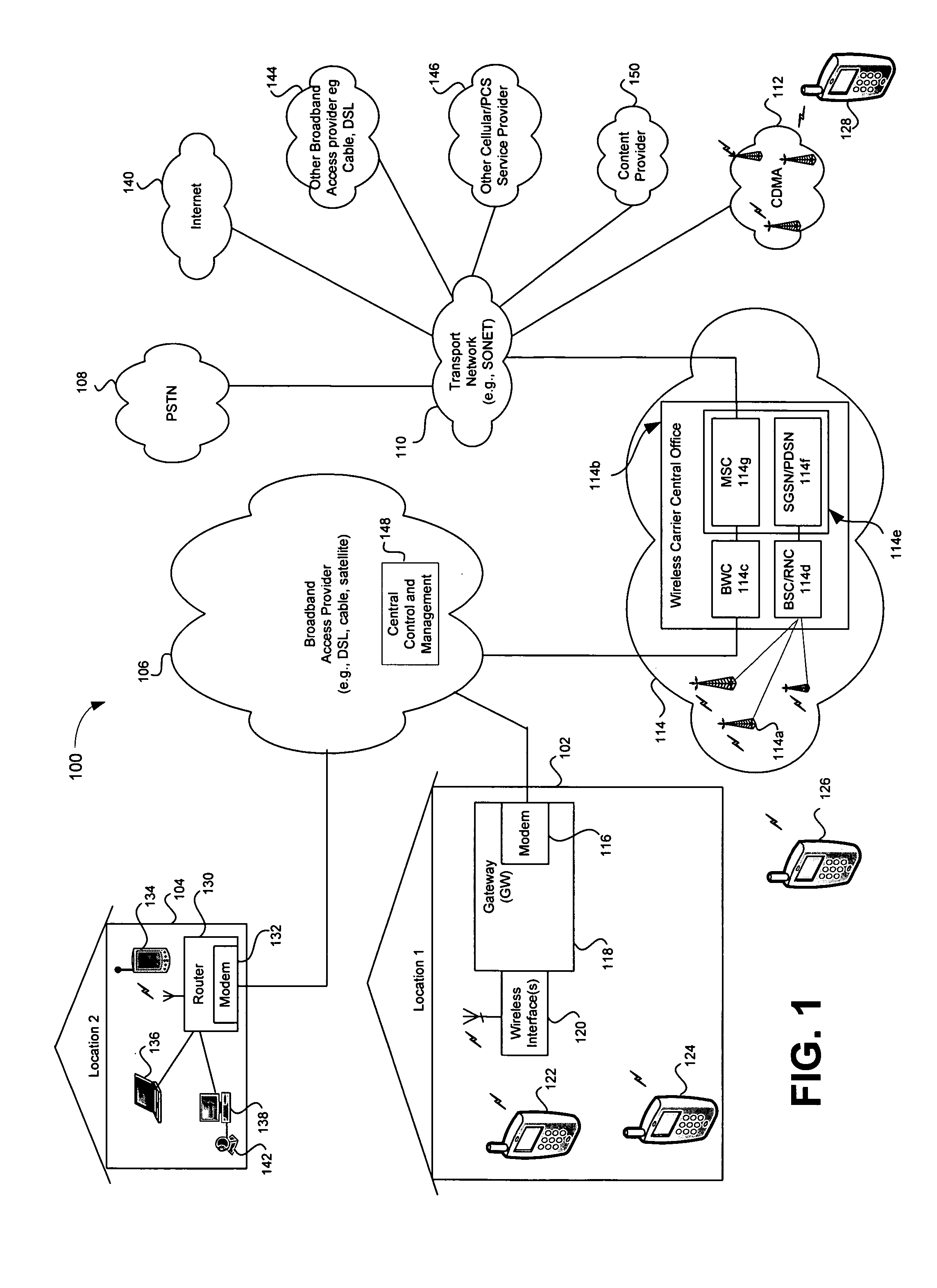
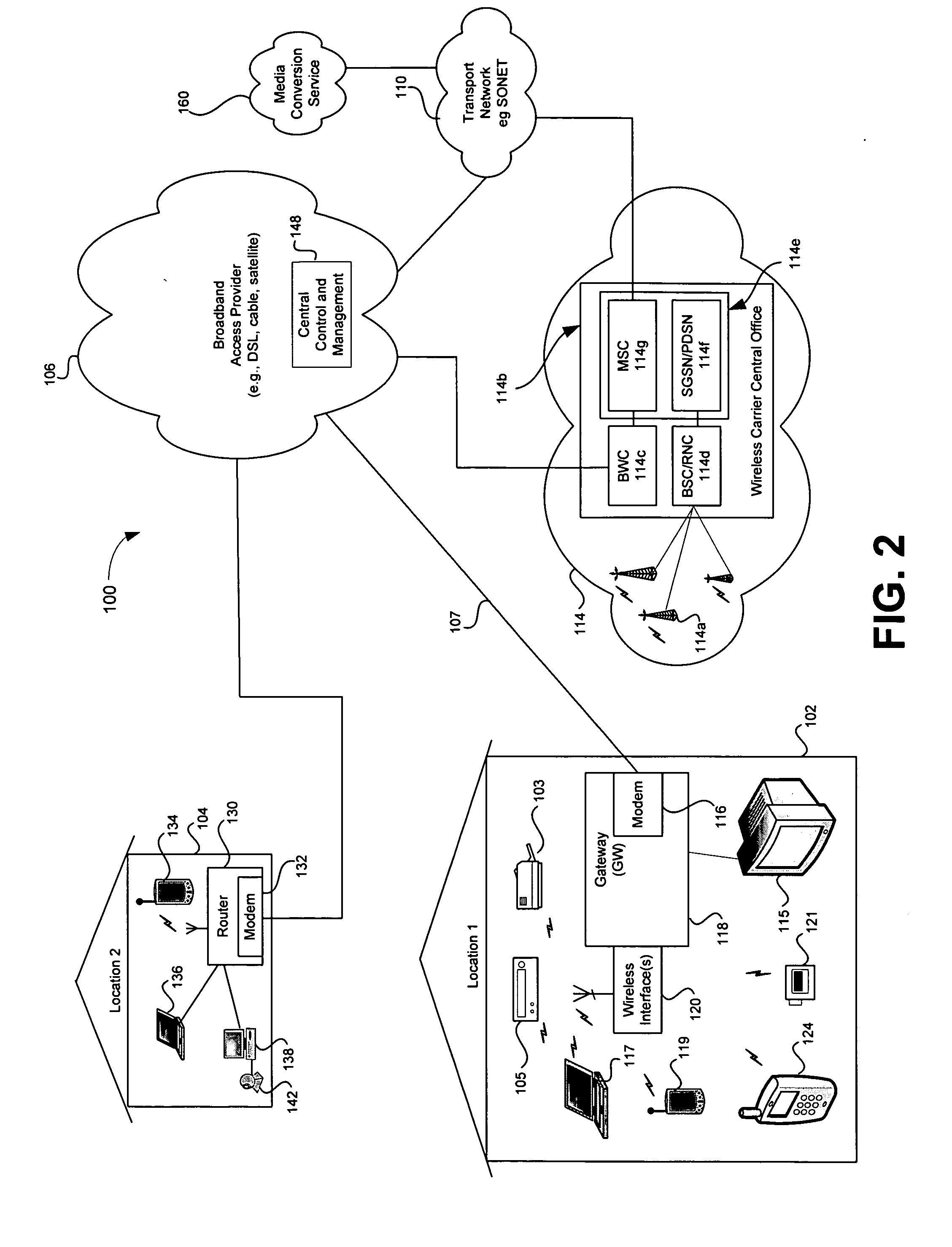
Providing automatic format conversion via an access gateway in a home
InactiveUS20050232284A1Information formatTime-division multiplexQuality of serviceComputer compatibility
A system and method supporting the automatic conversion of multimedia information from a first format to a second format in a broadband access gateway and / or network-based server are disclosed. The broadband access gateway and / or network-based server may convert multimedia information that is in a format that an access device is not capable of processing. The gateway and / or server may automatically detect the format incompatibility, and may automatically convert or arrange for conversion of the multimedia information to a format that is compatible with the access device, based upon compatibility information associated with the access device. The conversion may be based upon a set of user-defined quality of service criteria, and may be subject to the control of digital rights management parameters associated with the requested multimedia information. The user of the access device may be prompted when the conversion is expected to impact the quality of the multimedia information being played, and the user may be offered options that permit the user to minimize the impact upon the user.
Owner:AVAGO TECH INT SALES PTE LTD
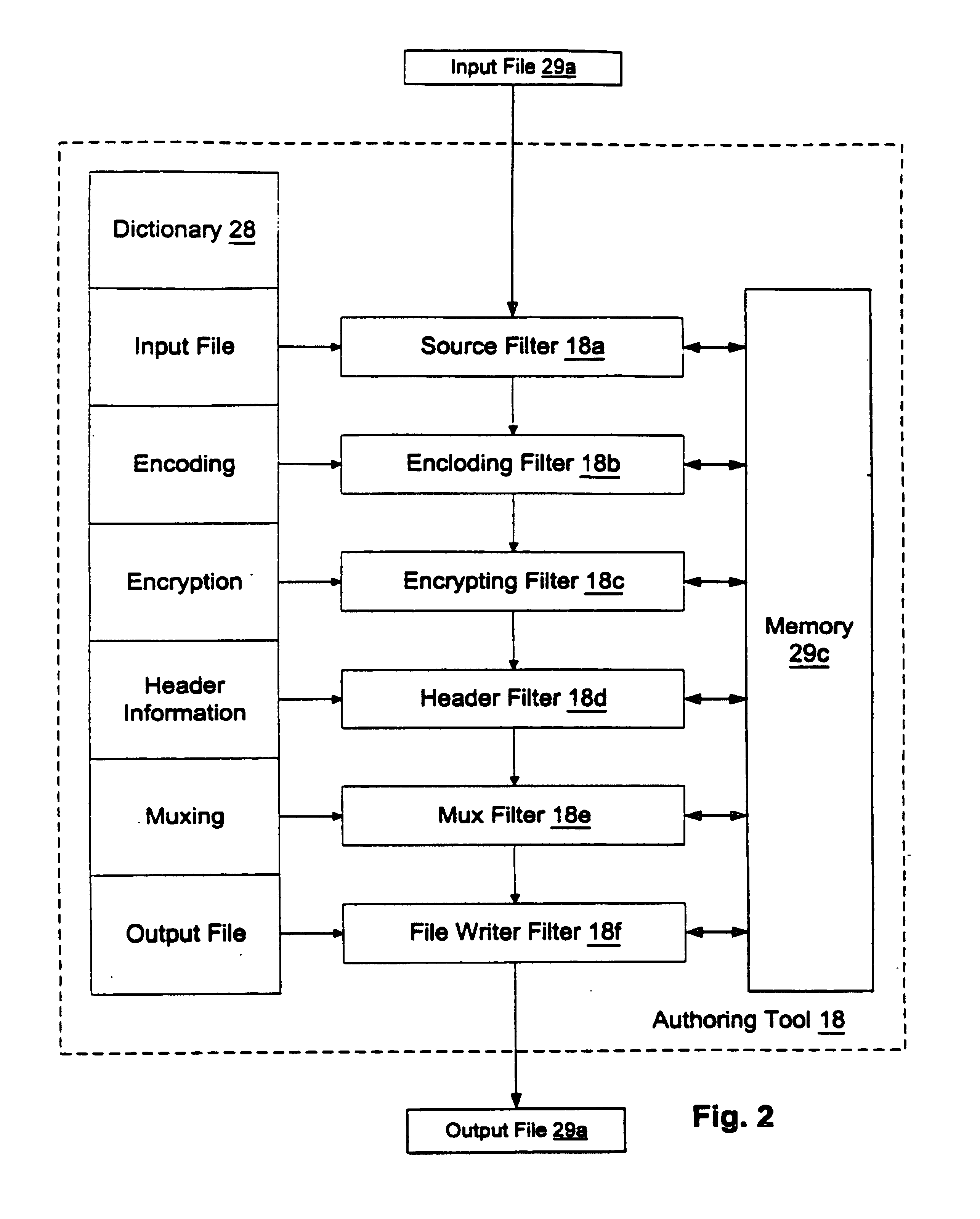
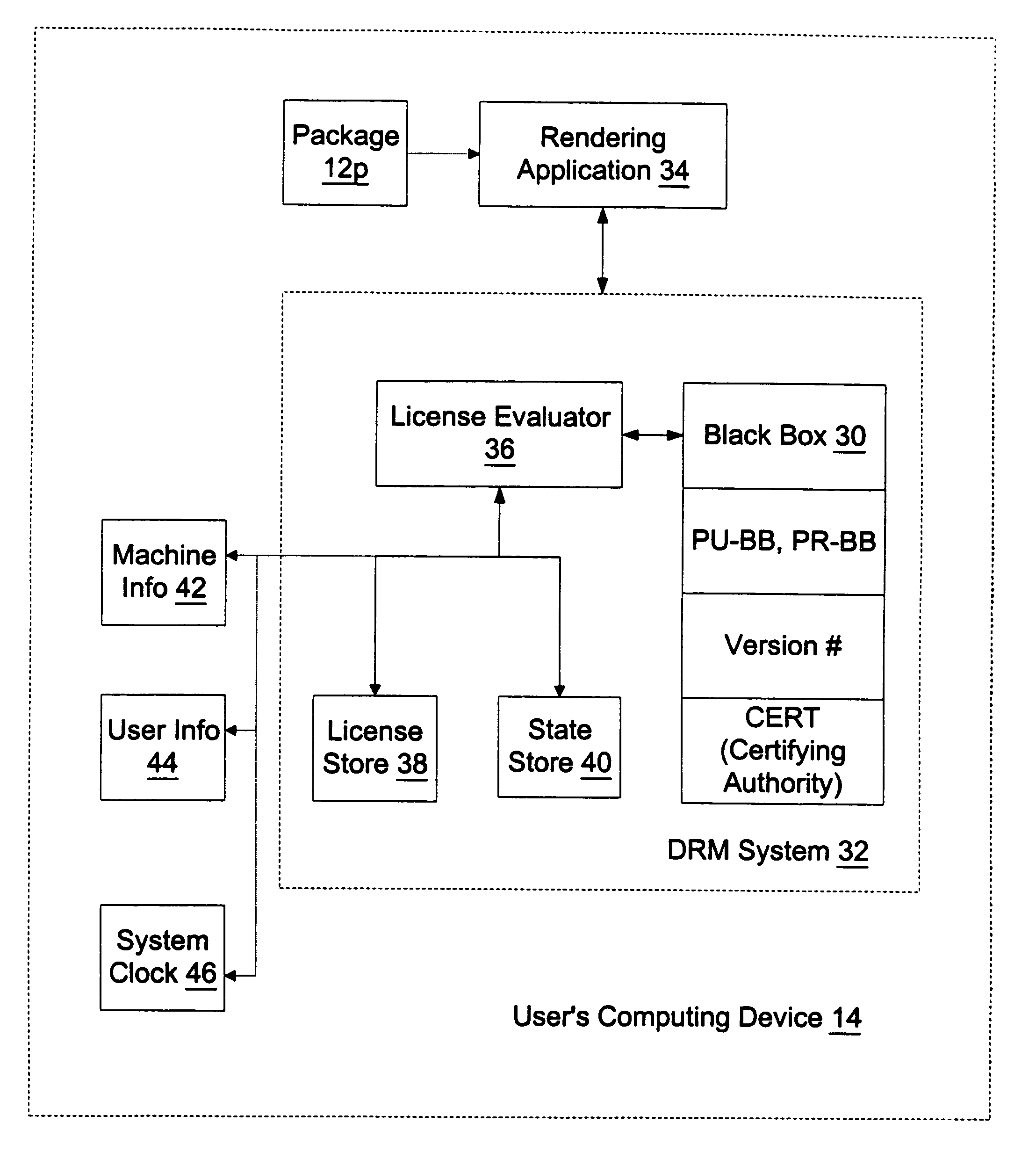
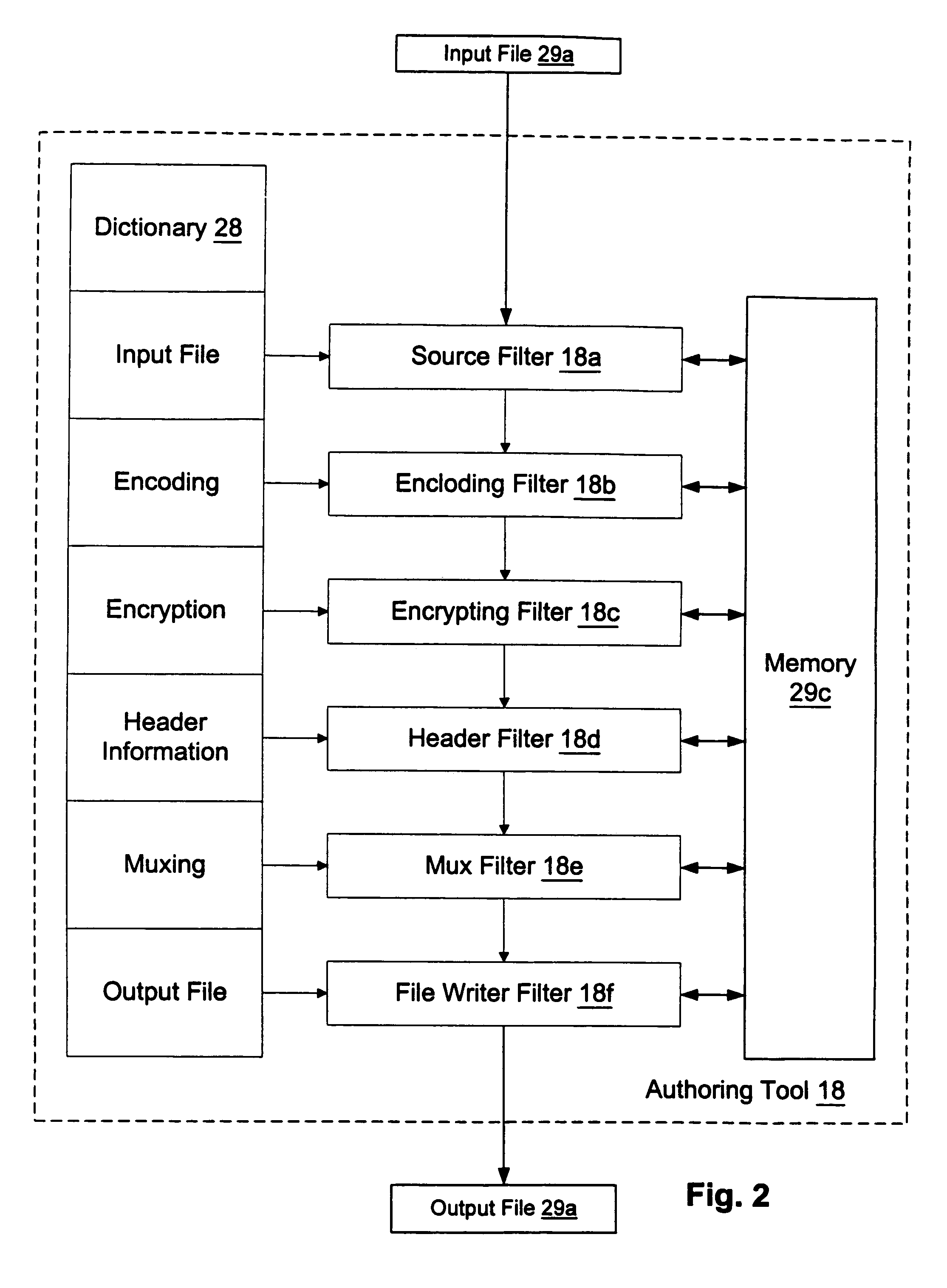
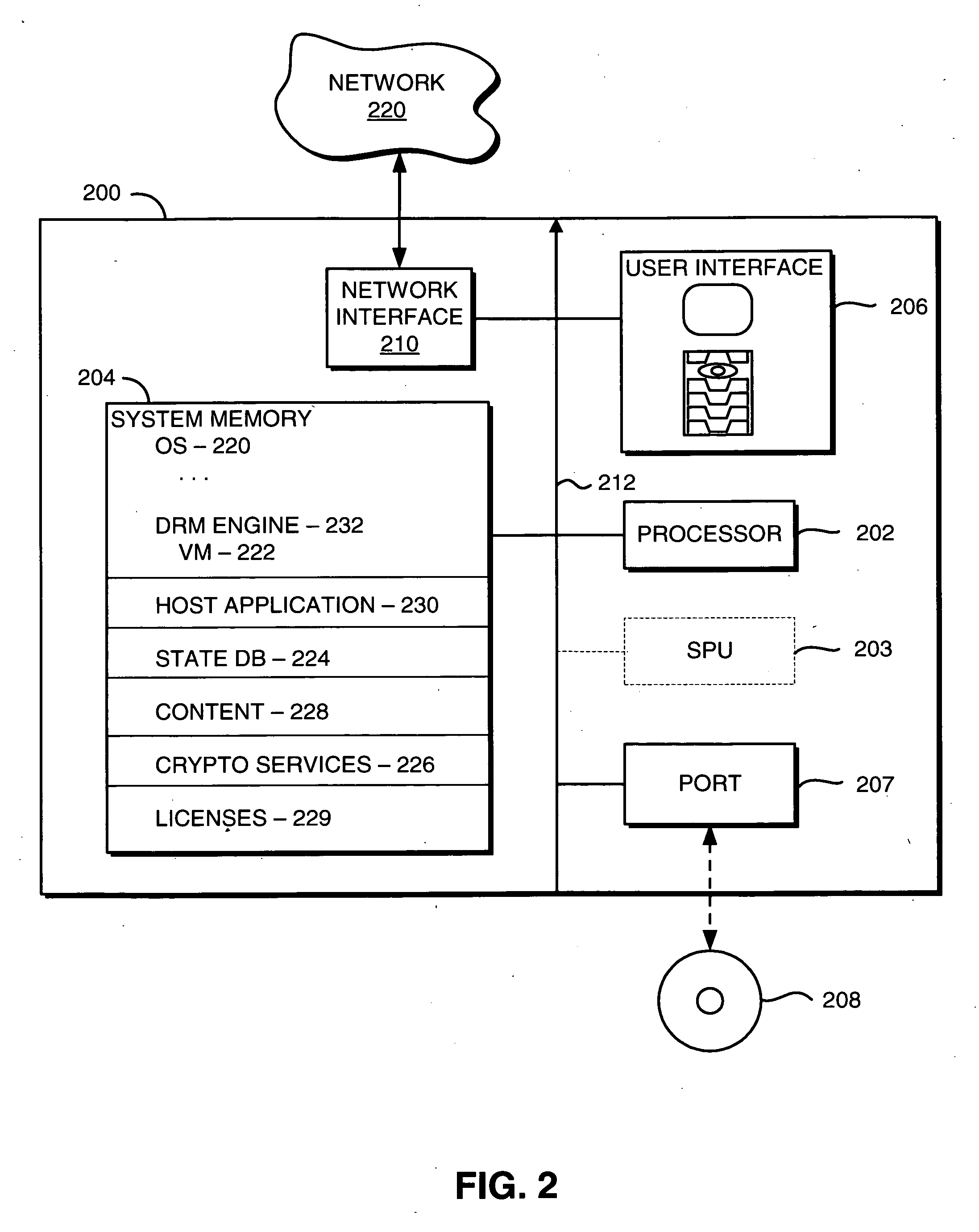
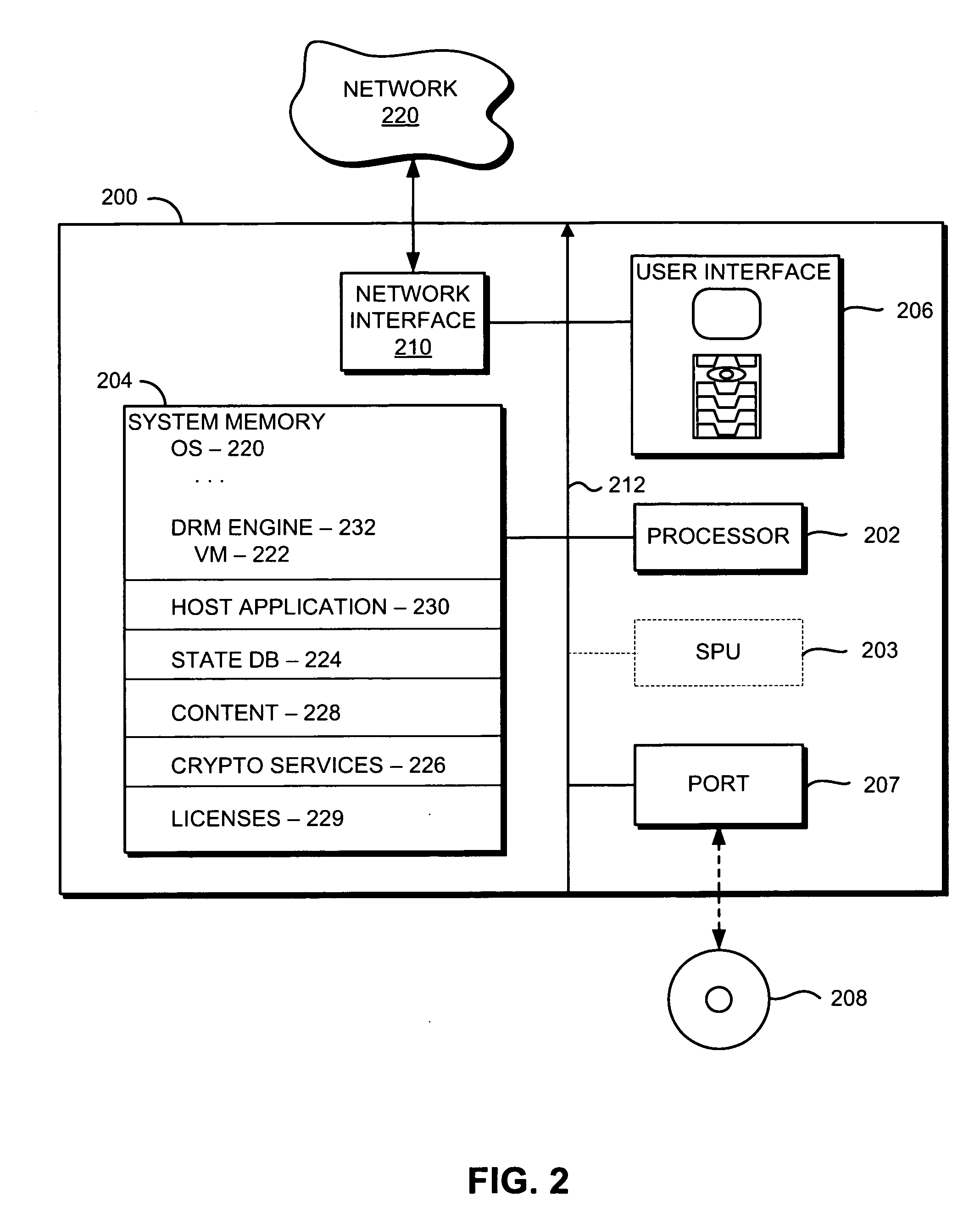
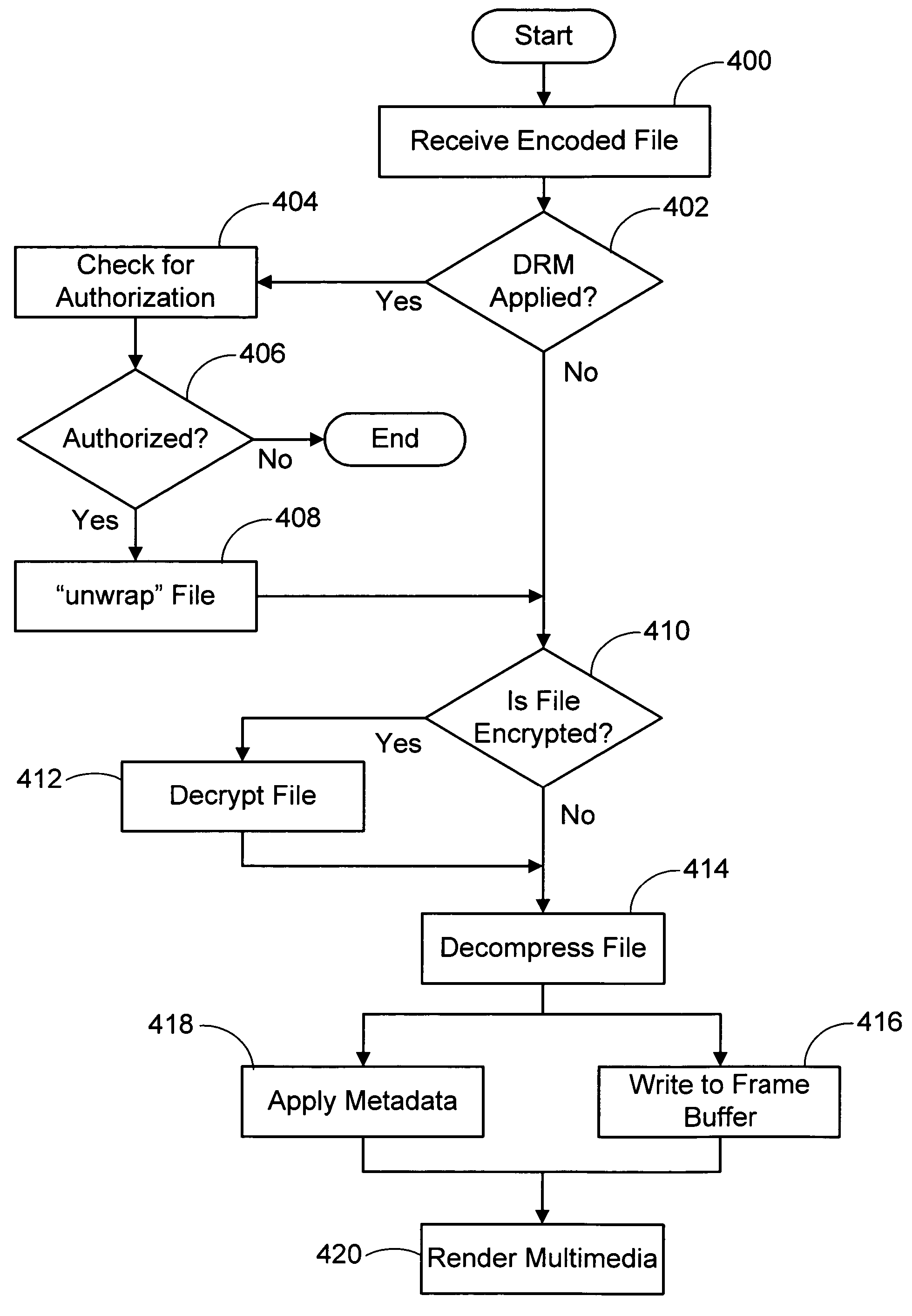
Structural of digital rights management (DRM) system
InactiveUS7024393B1Satisfies needData processing applicationsDigital data processing detailsDigital contentDigital rights management
A digital rights management (DRM) system operates on a computing device when a user requests that a protected piece of digital content be rendered by the computer device in a particular manner. The DRM system has a license store, a license evaluator, and a state store. The license store stores digital licenses on the computing device. The license evaluator determines whether any licenses stored in the license store correspond to the requested digital content and whether any such corresponding licenses are valid, reviews license rules in each such valid license, and determining based on such reviewed license rules whether such license enables the requesting user to render the requested digital content in the manner sought. The state store maintains state information corresponding to each license in the license store, where the state information is created and updated by the license evaluator as necessary.
Owner:MICROSOFT TECH LICENSING LLC
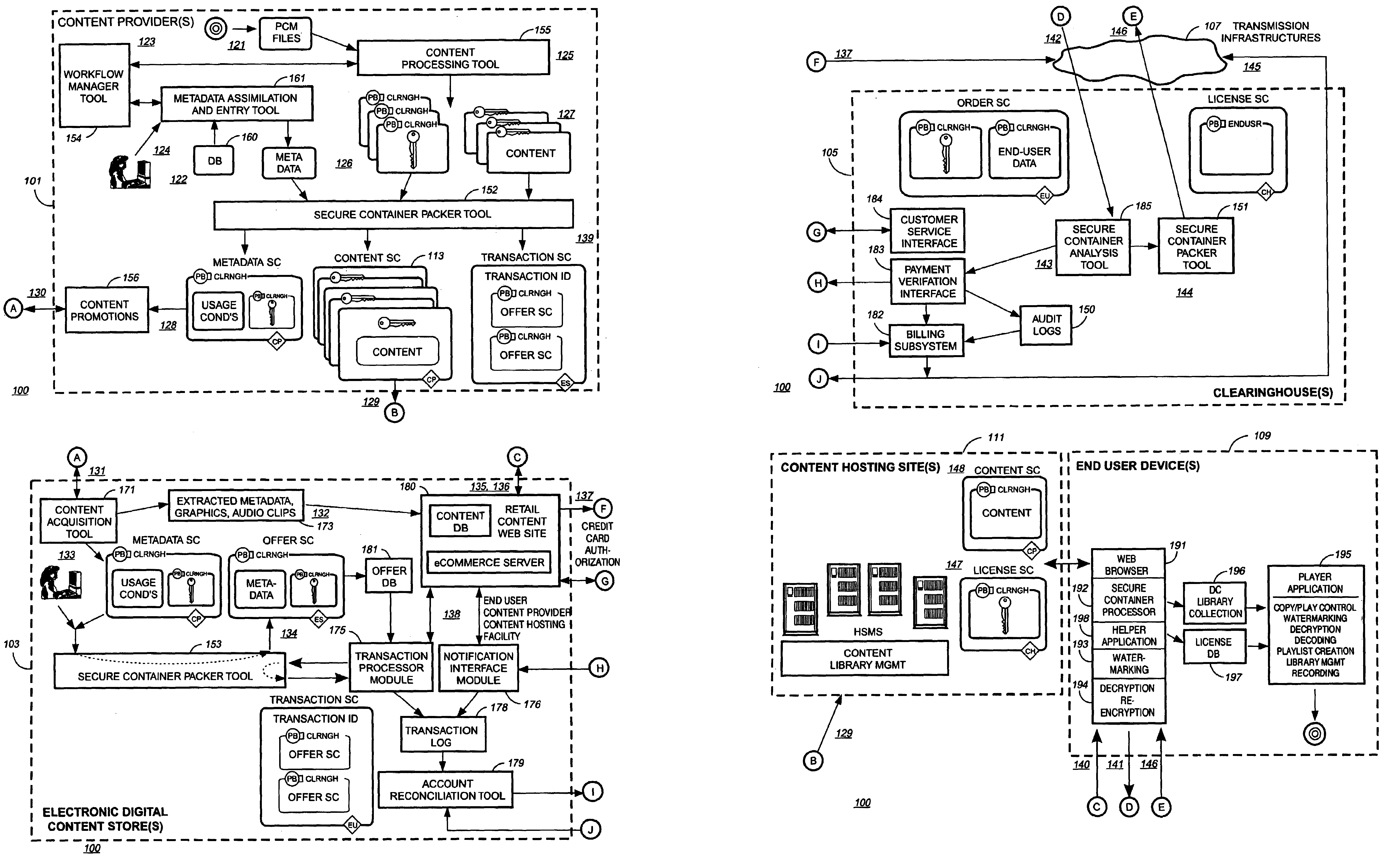
Methods for rights enabled peer-to-peer networking
InactiveUS20030120928A1User identity/authority verificationUnauthorized memory use protectionDigital rights managementRights management
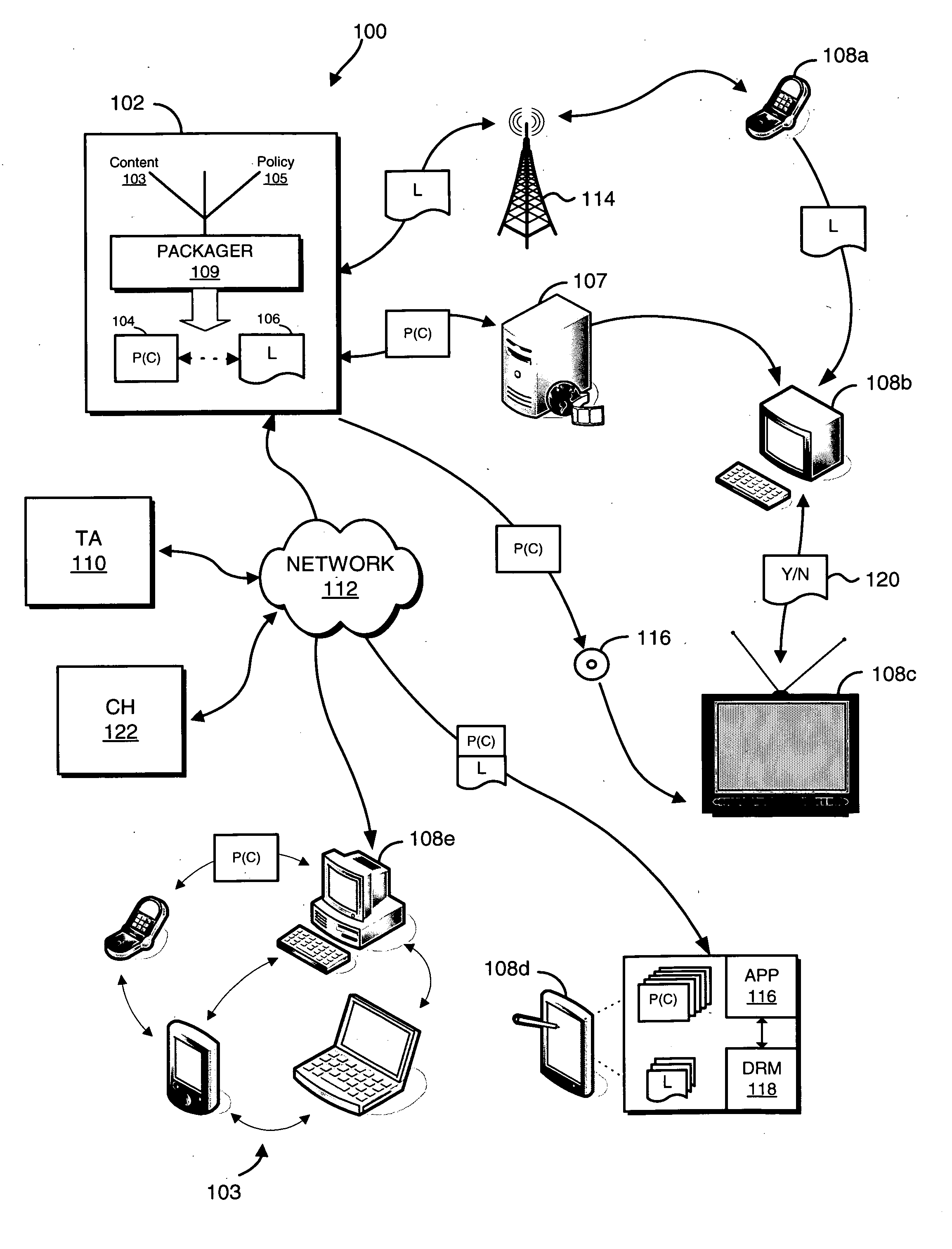
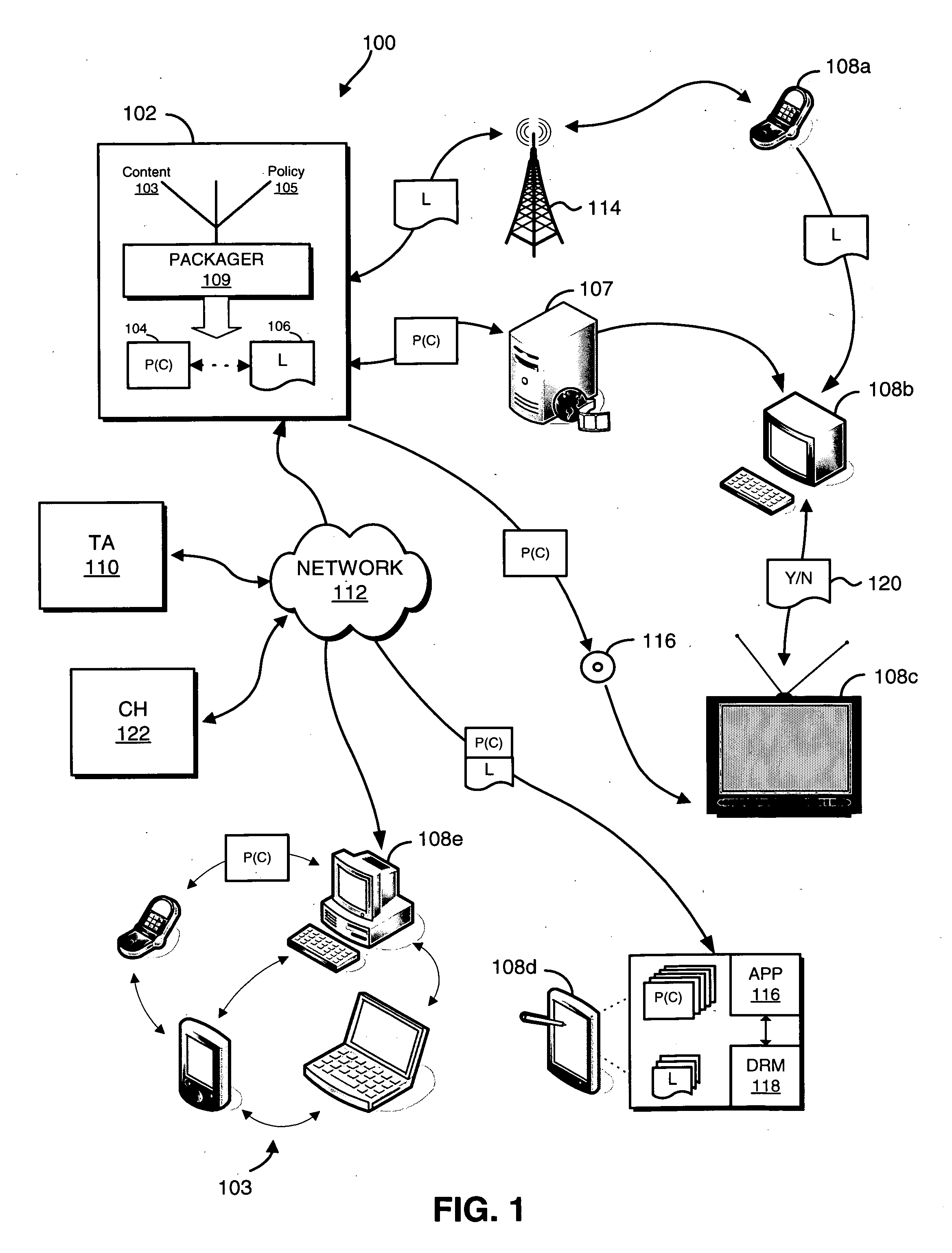
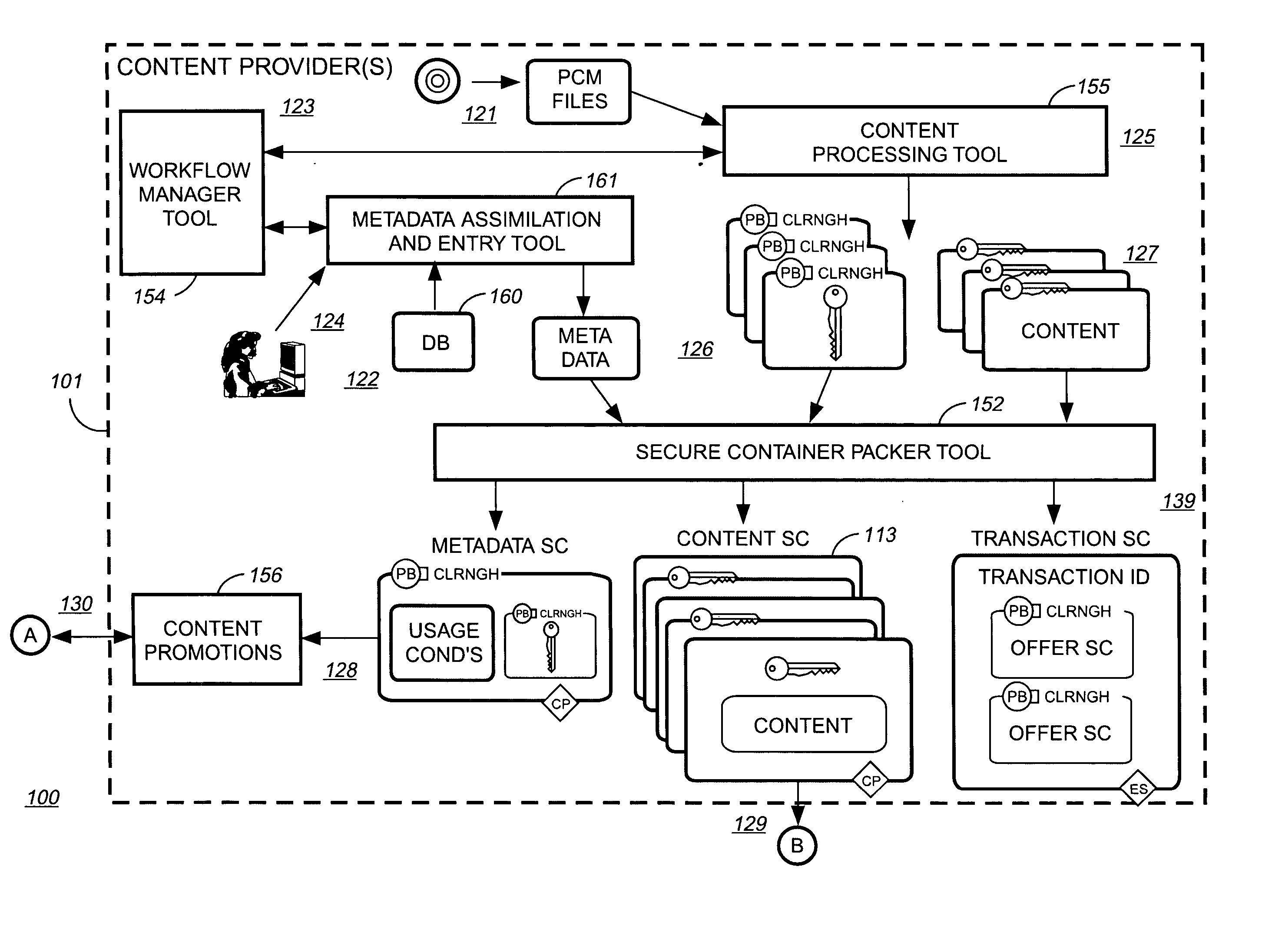
The present invention relates to digital rights management. In one embodiment, persons, processes, and / or computers and appliances locate, share, publish, retrieve, and use all kinds of digital information that has been protected using digital rights management technologies. Rights management includes securely associating rules for authorized use with the digital information. Rules and / or digital information may be encapsulated in a cryptographically secure data structure or "container" ("CSC") to protect against unauthorized use, to ensure secrecy, to maintain integrity, and to force the use of a rights management system to access the protected information. Attributes or metadata information describing at least some of the rules ("rules-metadata information") and optionally any associated rule parameter data with respect to the protected information are created. This rules-metadata information may be organized, structure, encoded, and / or presented using a self-defining data structure such as those created using Extensible Markup Language (XML). In one embodiment, the XML-encoded rules-metadata information is also made available unencrypted, in plain text, to facilitate P2P search and file transfer. Having at least some of the rules-metadata information outside or external to a CSC allows greater flexibility in searching based at least in part upon the rules-metadata information. Some embodiments may hold the rules-metadata information in a separate CSC. Putting the rules-metadata information in a separate CSC more easily allows authentication and maintains the integrity of the rules-metadata information. In another embodiment, the rules metadata may be in an unencrypted portion of a CSC itself or concatenated with a CSC in a single file.
Owner:CATO MILES +2
Binding a digital license to a portable device or the like in a digital rights management (DRM) system and checking out/checking in the digital license to/from the portable device or the like
InactiveUS7073063B2Key distribution for secure communicationDigital data processing detailsDigital contentDigital rights management
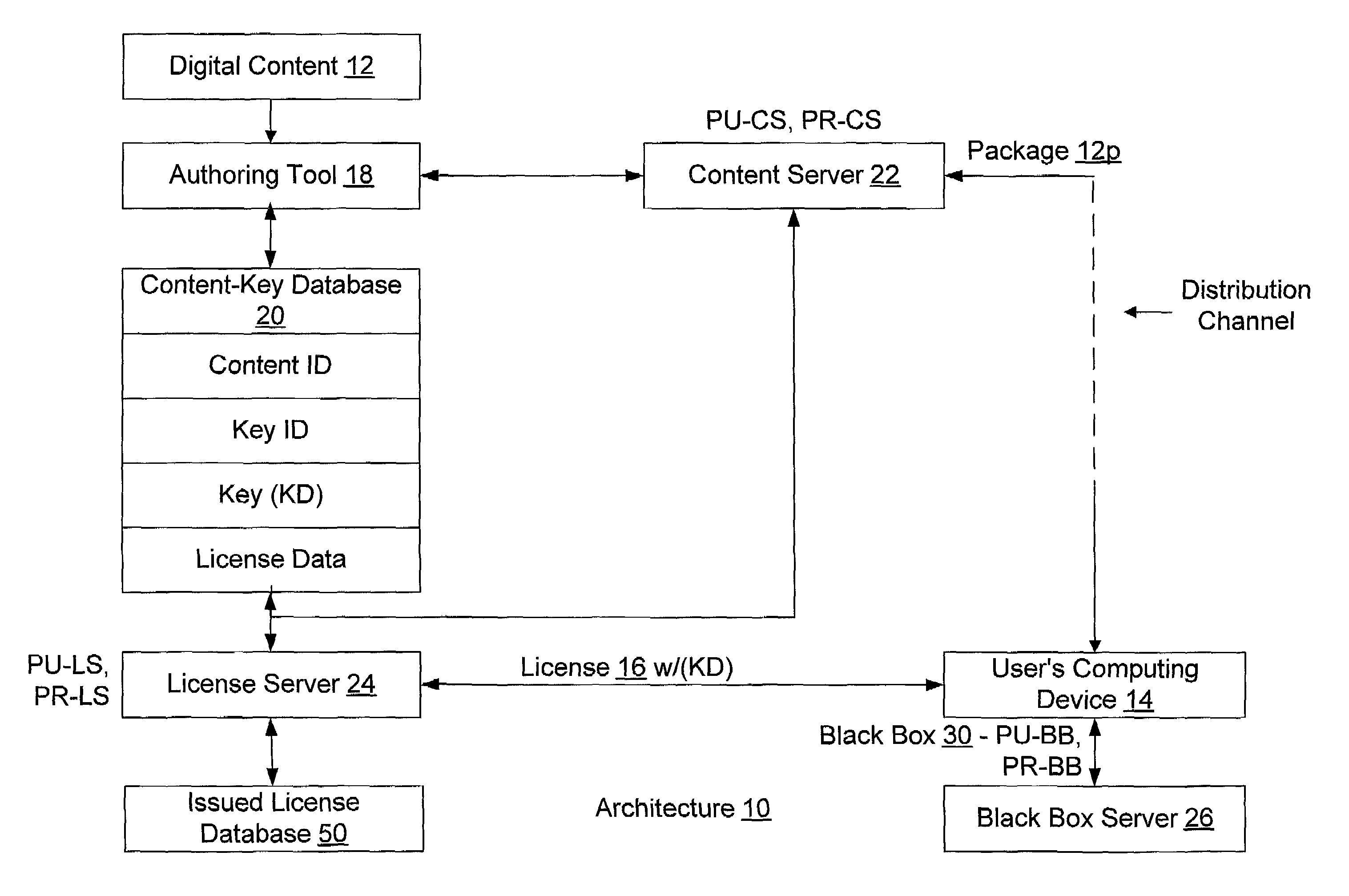
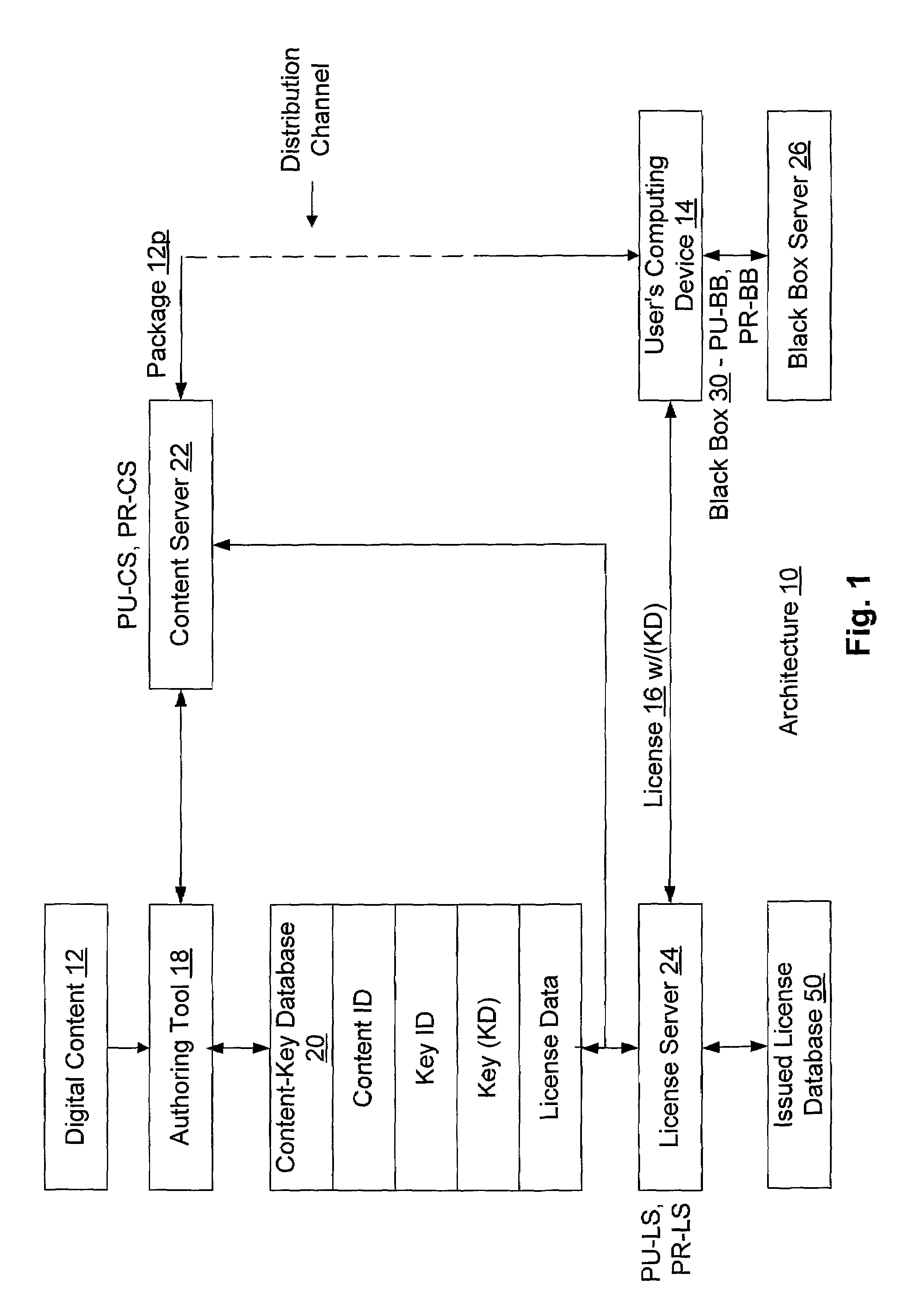
To render digital content encrypted according to a content key (KD) on a first device having a public key (PU1) and a corresponding private key (PR1), a digital license corresponding to the content is obtained, where the digital license includes the content key (KD) therein in an encrypted form. The encrypted content key (KD) from the digital license is decrypted to produce the content key (KD), and the public key (PU1) of the first device is obtained therefrom. The content key (KD) is then encrypted according to the public key (PU1) of the first device (PU1 (KD)), and a sub-license corresponding to and based on the obtained license is composed, where the sub-license includes (PU1 (KD)). The composed sub-license is then transferred to the first device.
Owner:MICROSOFT TECH LICENSING LLC
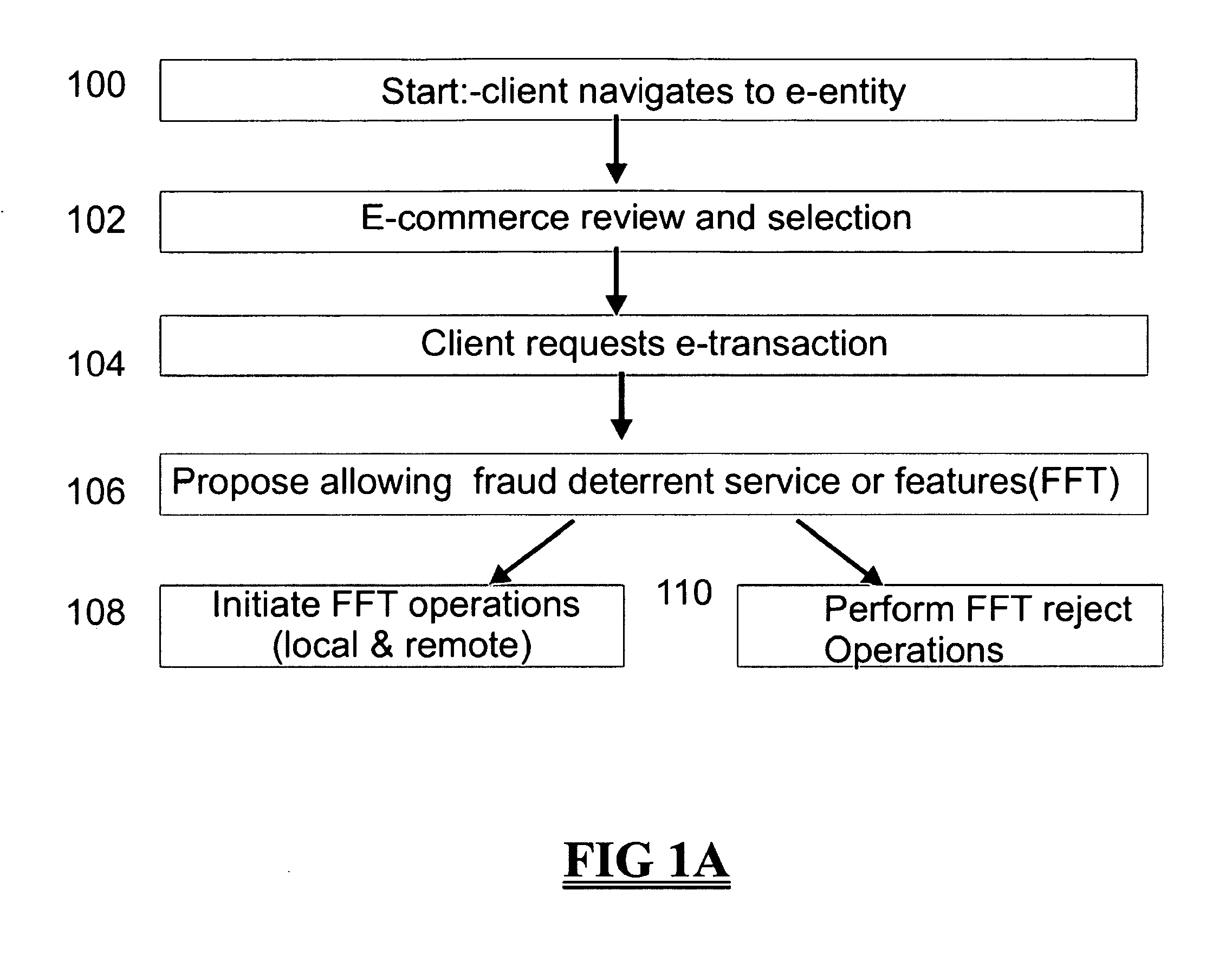
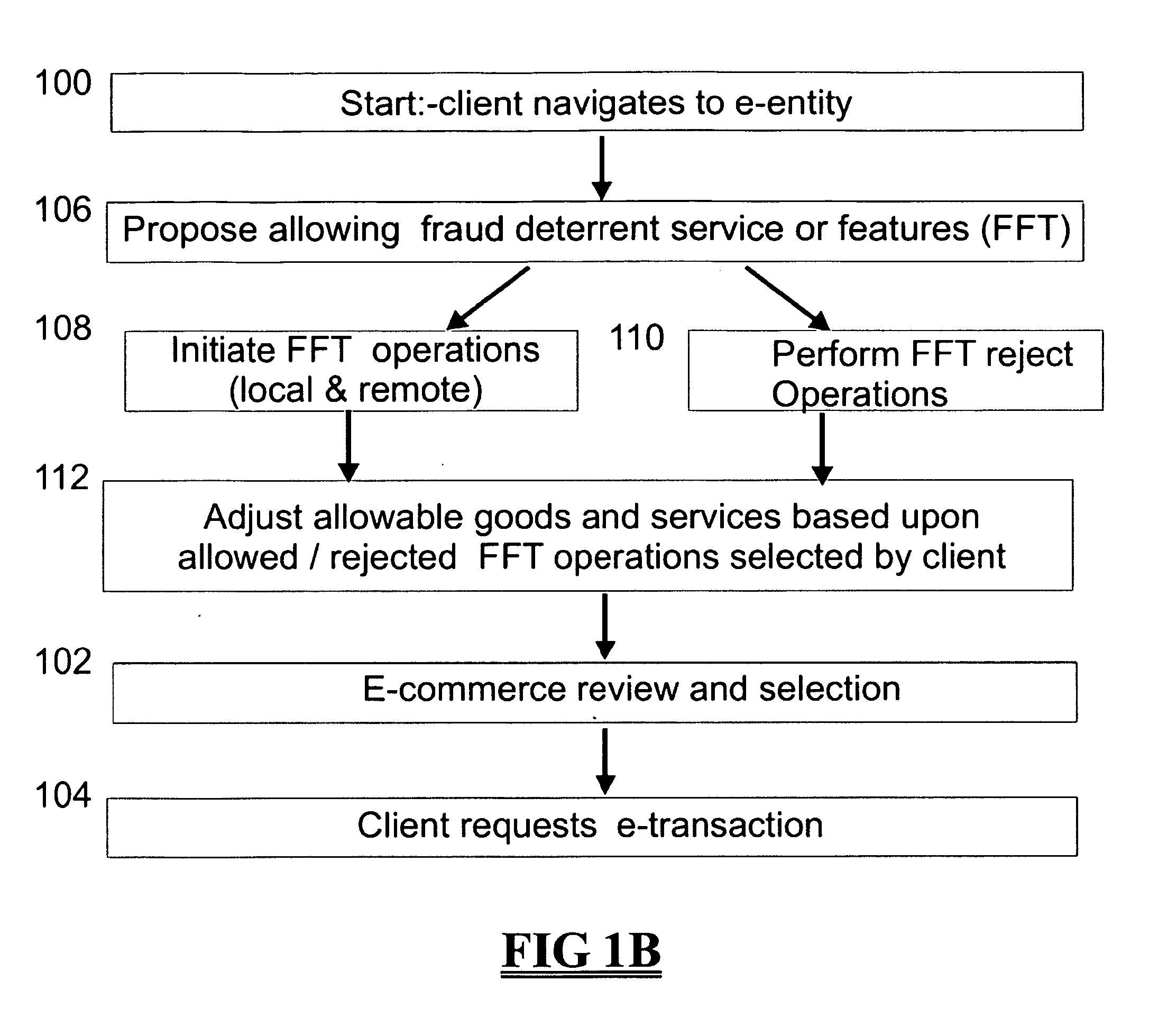
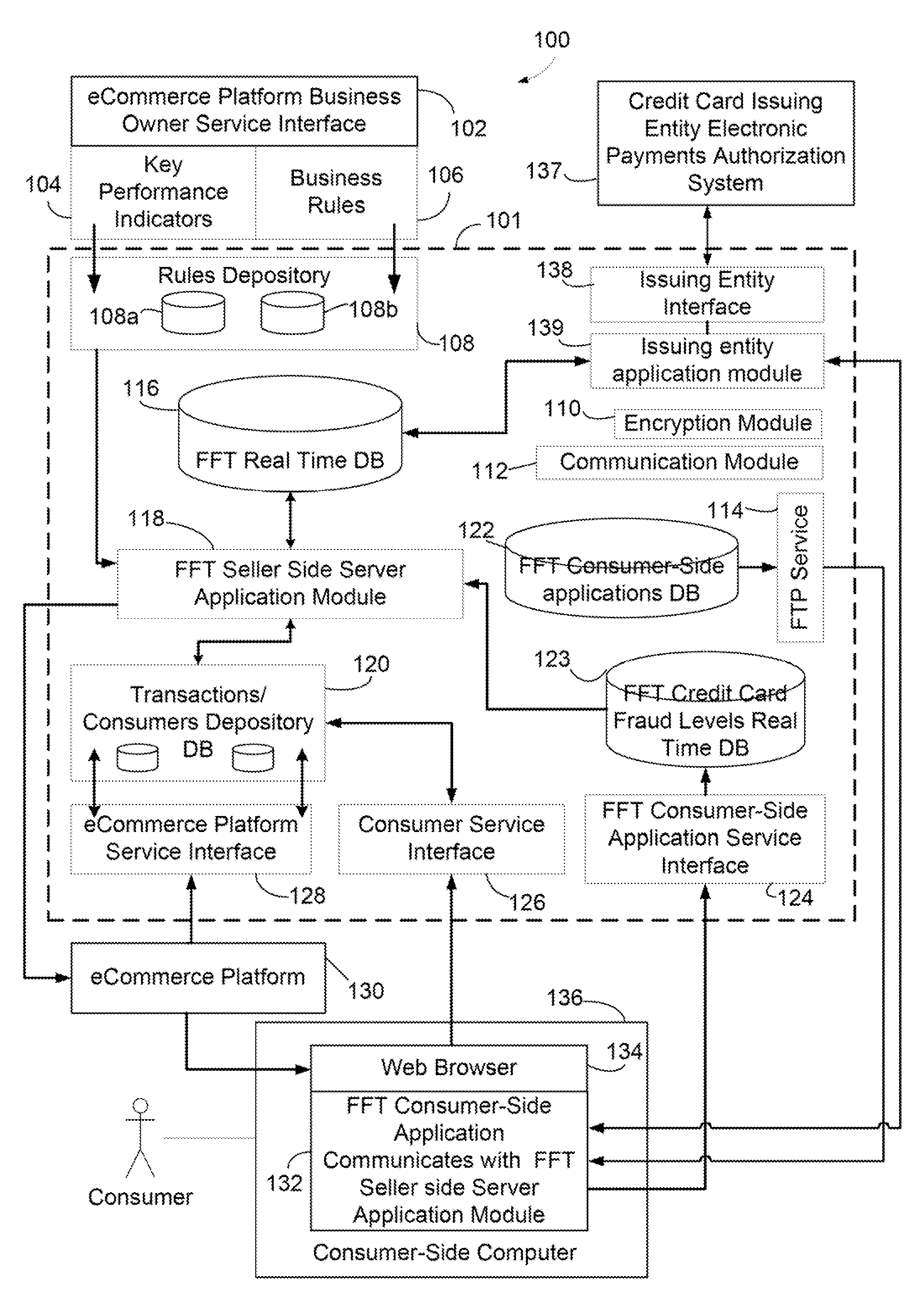
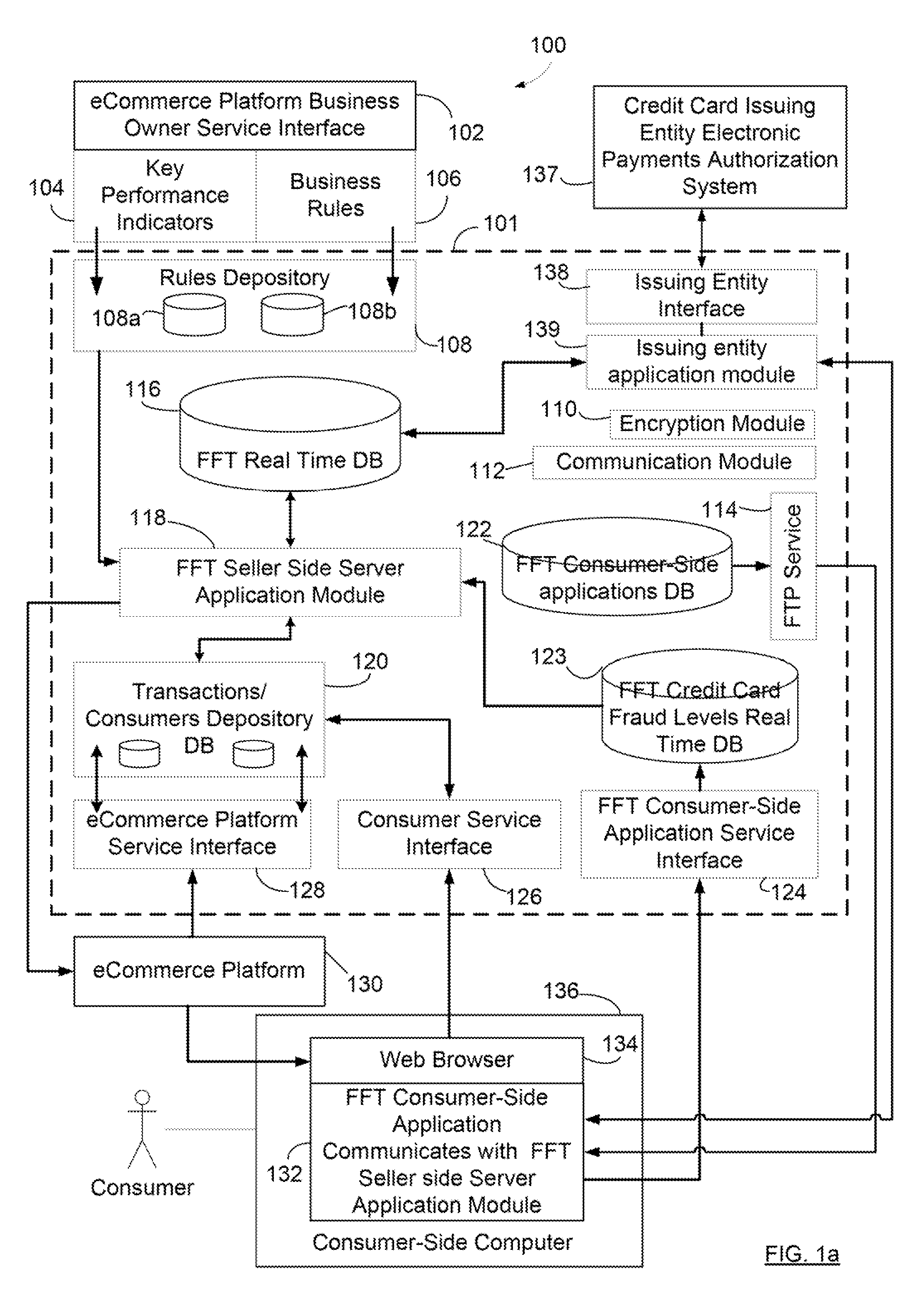
Systems and methods for facilitating electronic transactions and deterring fraud
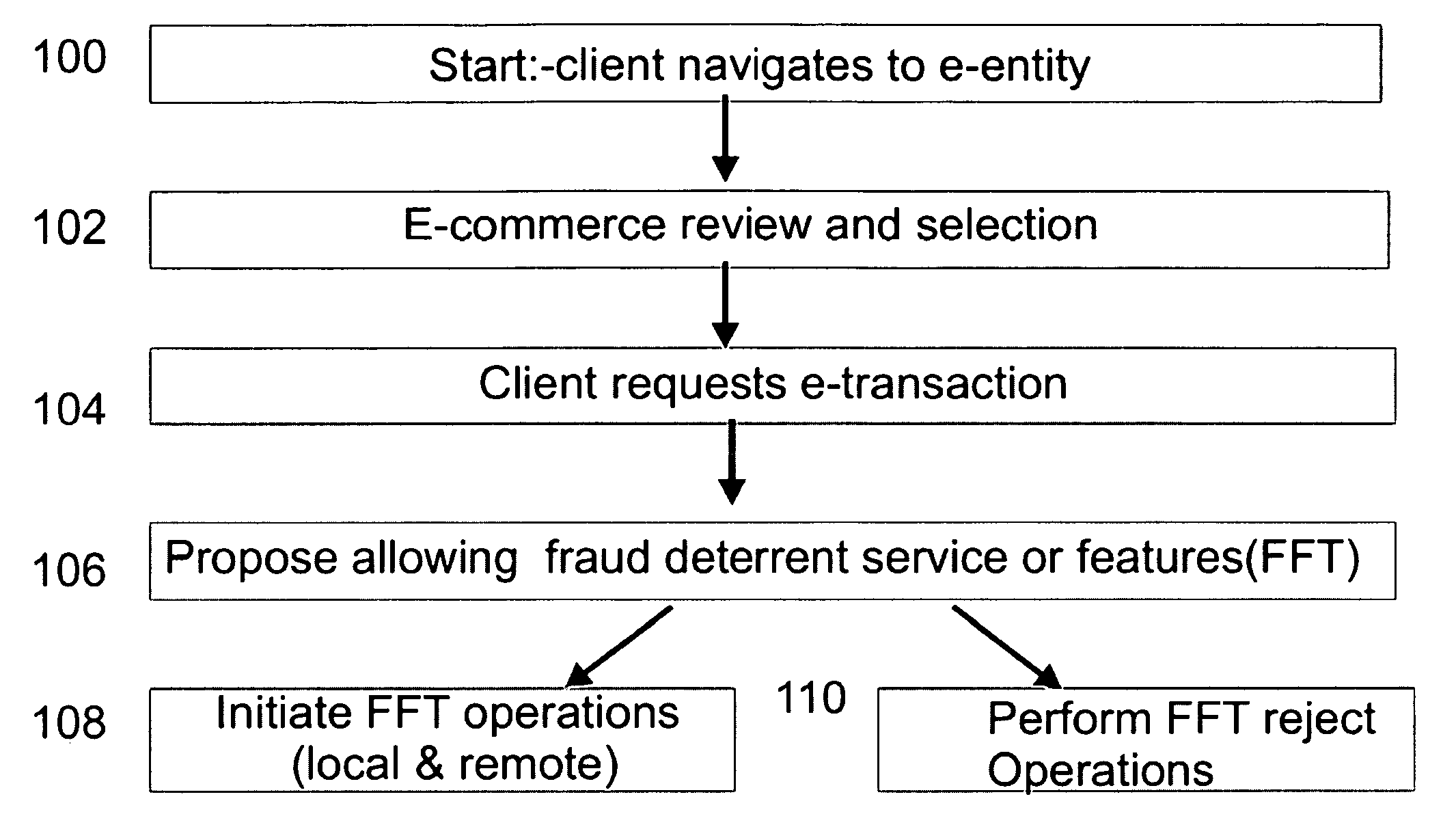
Systems and methods are described for providing fraud deterrents during e-commerce, e-transactions, and digital rights management and access. One or more fraud deterrents may be automatically selected by a client, seller, bank, or other 3rd party and may be implemented or presented to the client as a potential fraud deterrent option that may be chosen. Fraud deterrent options may be provided which are associated with particular aspects of the transaction including a client's profile, the value of an item, or the preferences of the seller. The fraud deterrent features can be provided as part of a digital shopping cart and may be highly customized by the client including allowing the client to customize conceptual passwords which are presented during subsequent transactions.
Owner:JOHN MICHAEL SASHA
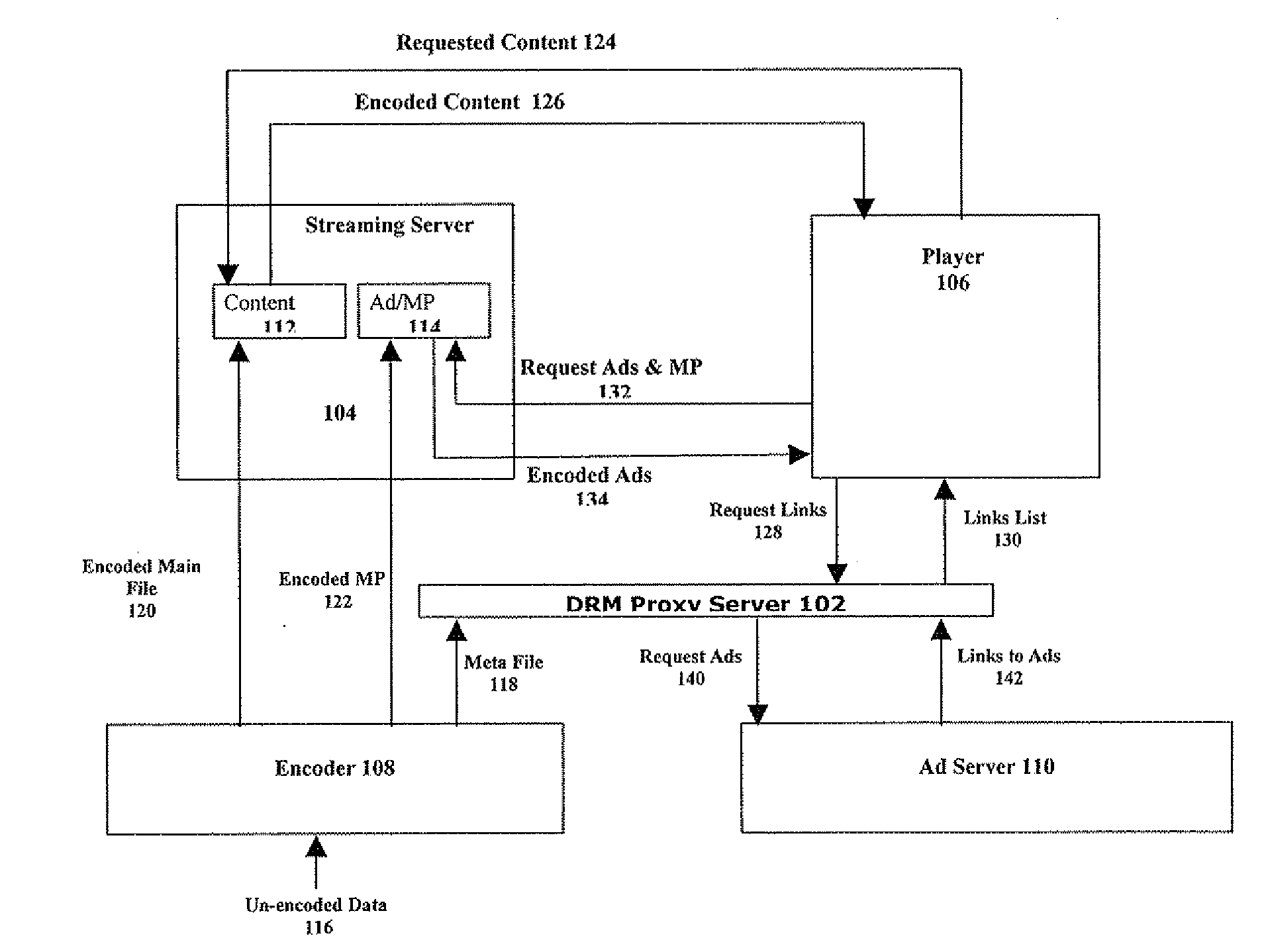
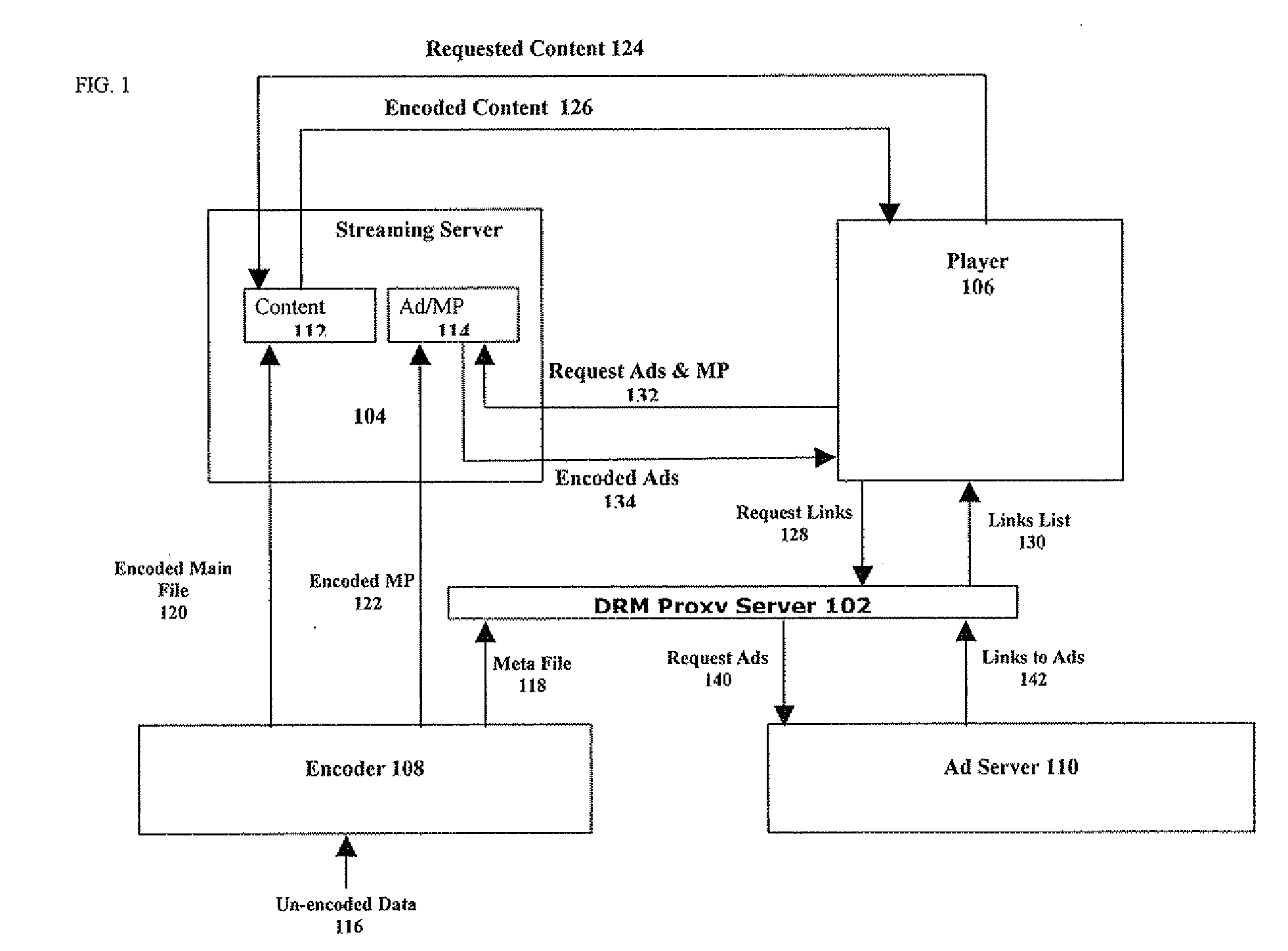
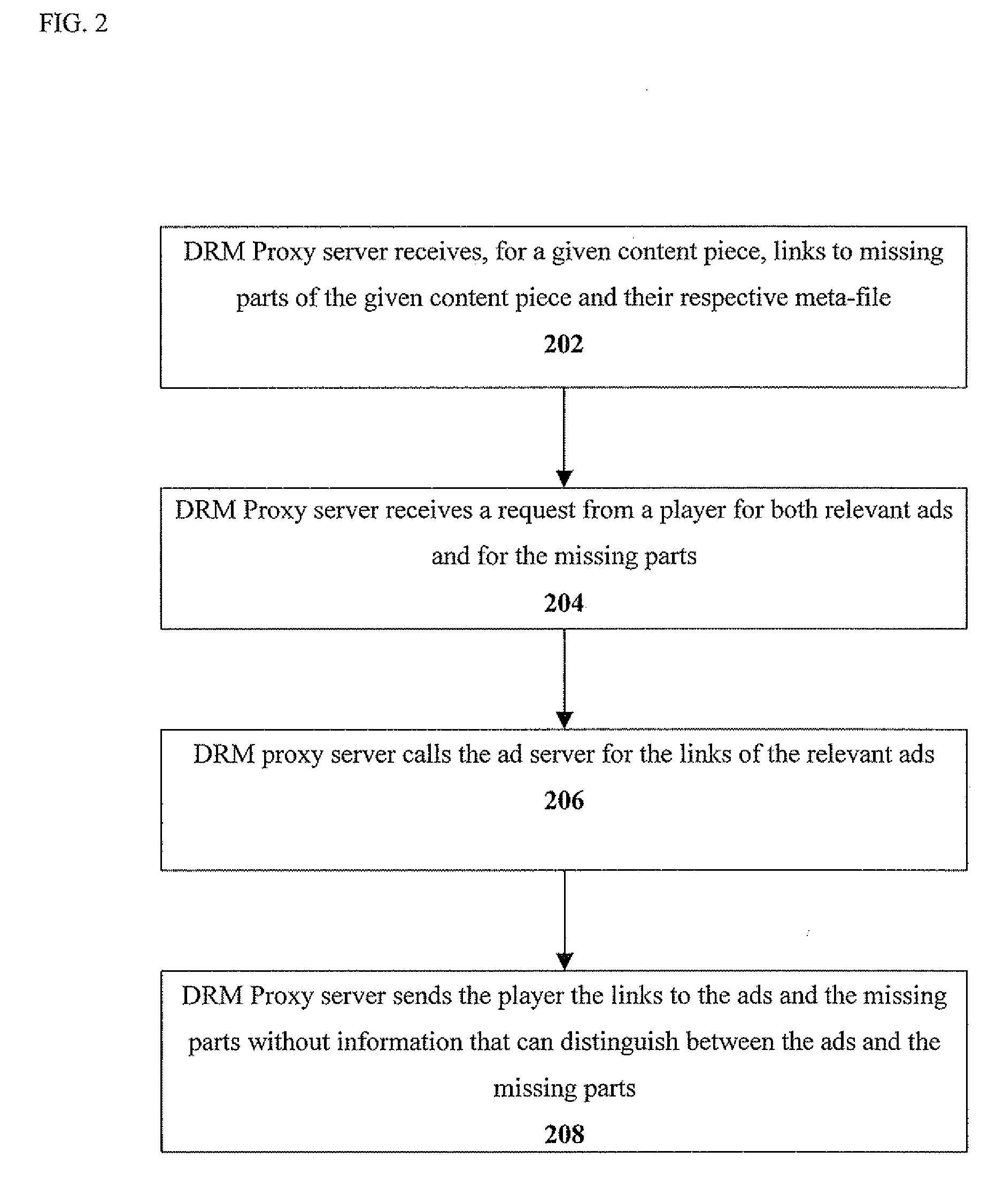
Method and system for preventing ad stripping from ad-supported digital content
InactiveUS20080319862A1Prevent hackingHarming viewing experienceAdvertisementsMultiple digital computer combinationsDigital contentDigital rights management
Methods for preventing ad stripping from ad-supported digital content include removing part of the content, and using a digital rights management (DRM) proxy server to provide links to any removed content part and to ads to be inserted in the content to a player who plays the content with the ads. The DRM proxy server ensures that the player cannot distinguish between removed content parts and the ads. A system enabling the method includes in addition to the DRM server and player an encoder used to remove at least one part from the content, encode the remaining content and the removed part and supplying links to each removed part to the DRM proxy server. The system further includes an ad server used to provide links to ads to the DRM proxy server.
Owner:HIROMEDIA
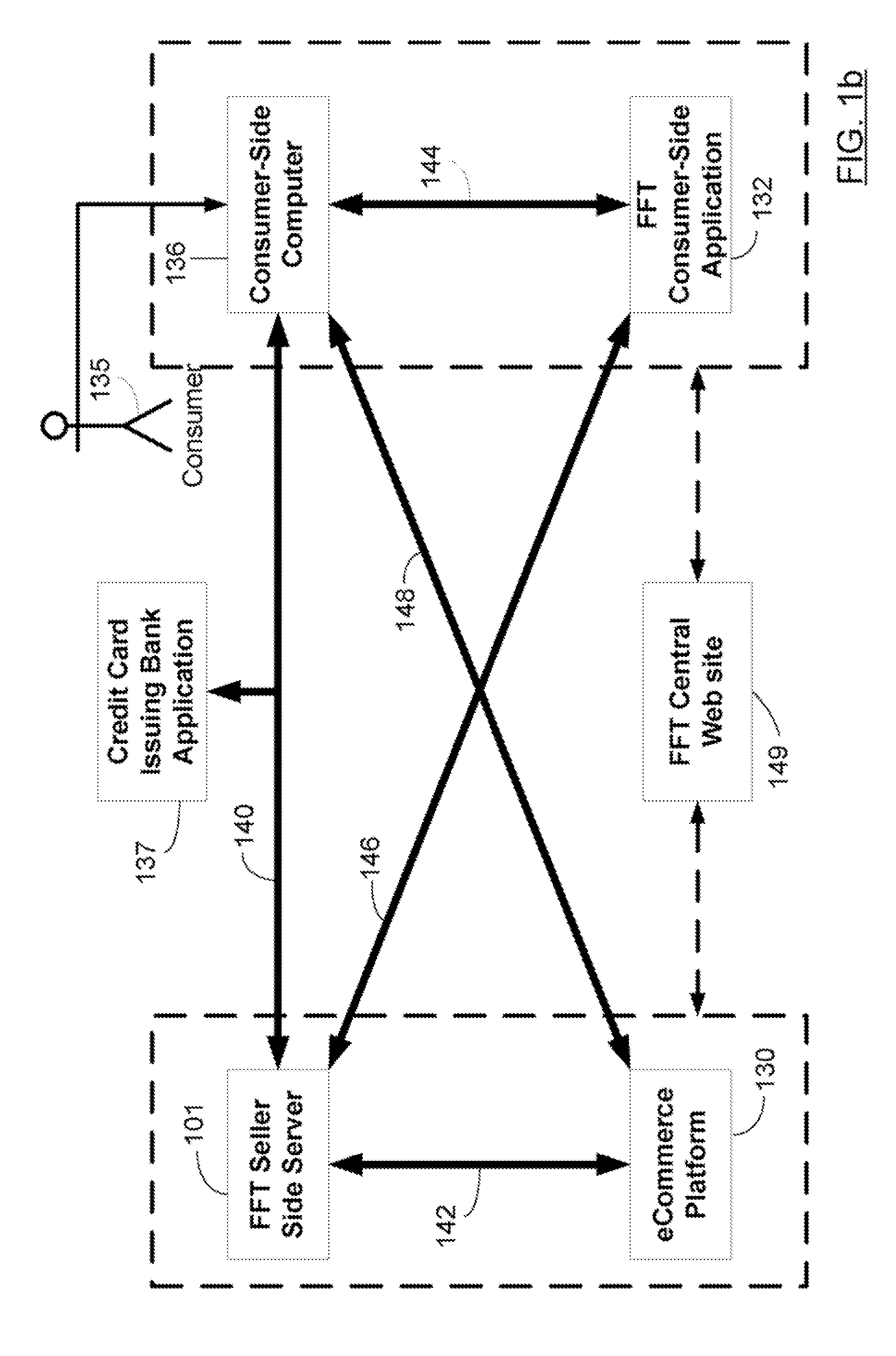
Systems and Methods for Automatic and Transparent Client Authentication and Online Transaction Verification
Systems and methods are described for providing fraud deterrents, detection and prevention during e-commerce, e-transactions, digital rights management and access control. Fraud deterrent levels may be automatically selected by a requesting transaction approval entity server (and can be related to level of risk, or security, related to fraud) or may be selected by a consumer. These deterrent levels can determine the manner in which the transaction occurs as well as the types of information that must be provided and validated for successful approval of the transaction. The client can associate their credit card with a specific device, an e-identity, such as an instant messaging identity, and the e-identity is contacted as a part of finalizing a payment transaction so that a client response of ‘approve’ or ‘reject’ can be obtained. The anti-fraud technology also provides for management and storage of historical transaction information. Entity-to-client communication occurs according to merchant permission parameters which are defined by the client and which enable messages sent by the entity to be automatically allowed, rejected, and managed in other ways as well.
Owner:JOHN MICHAEL SASHA
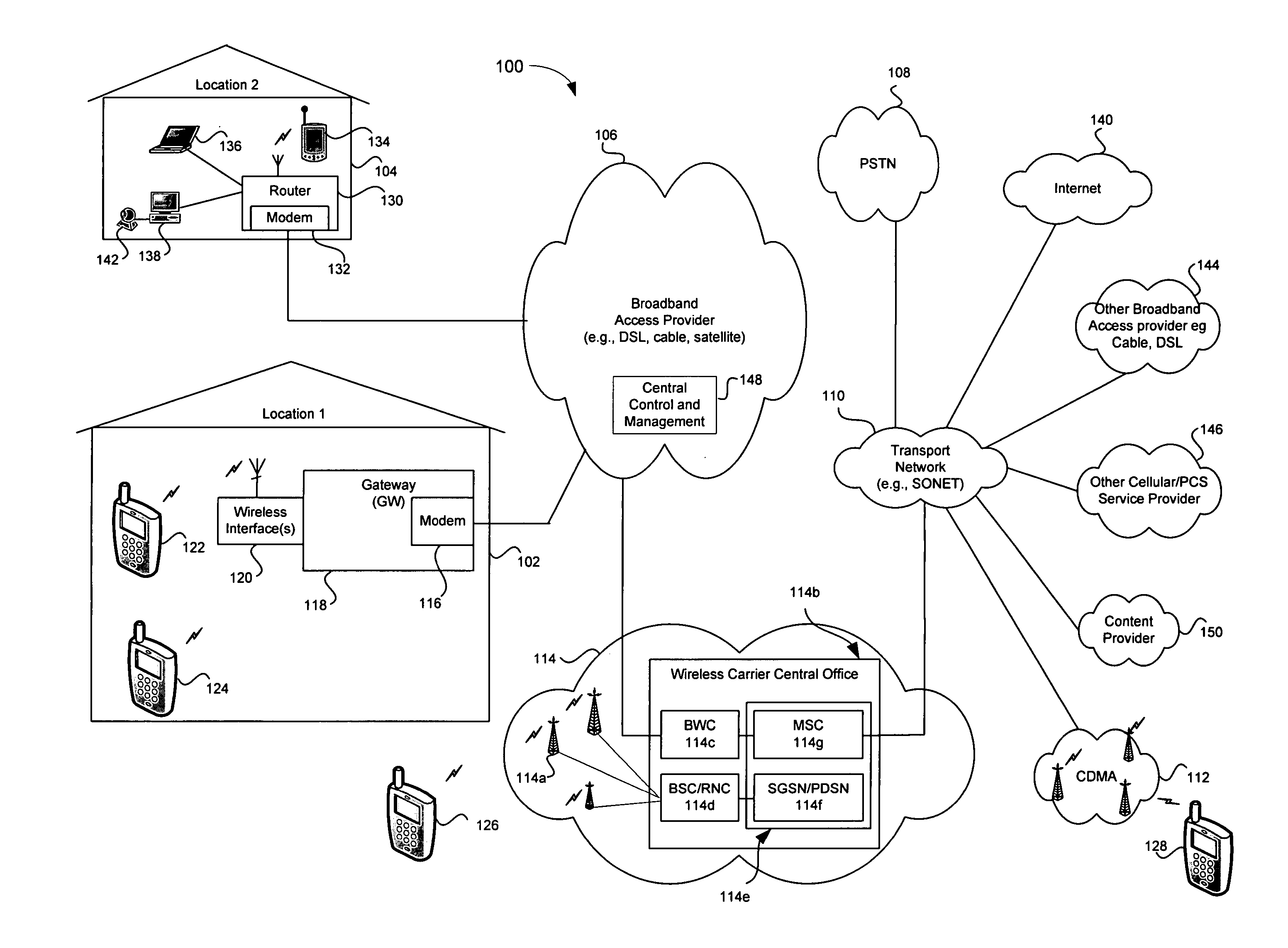
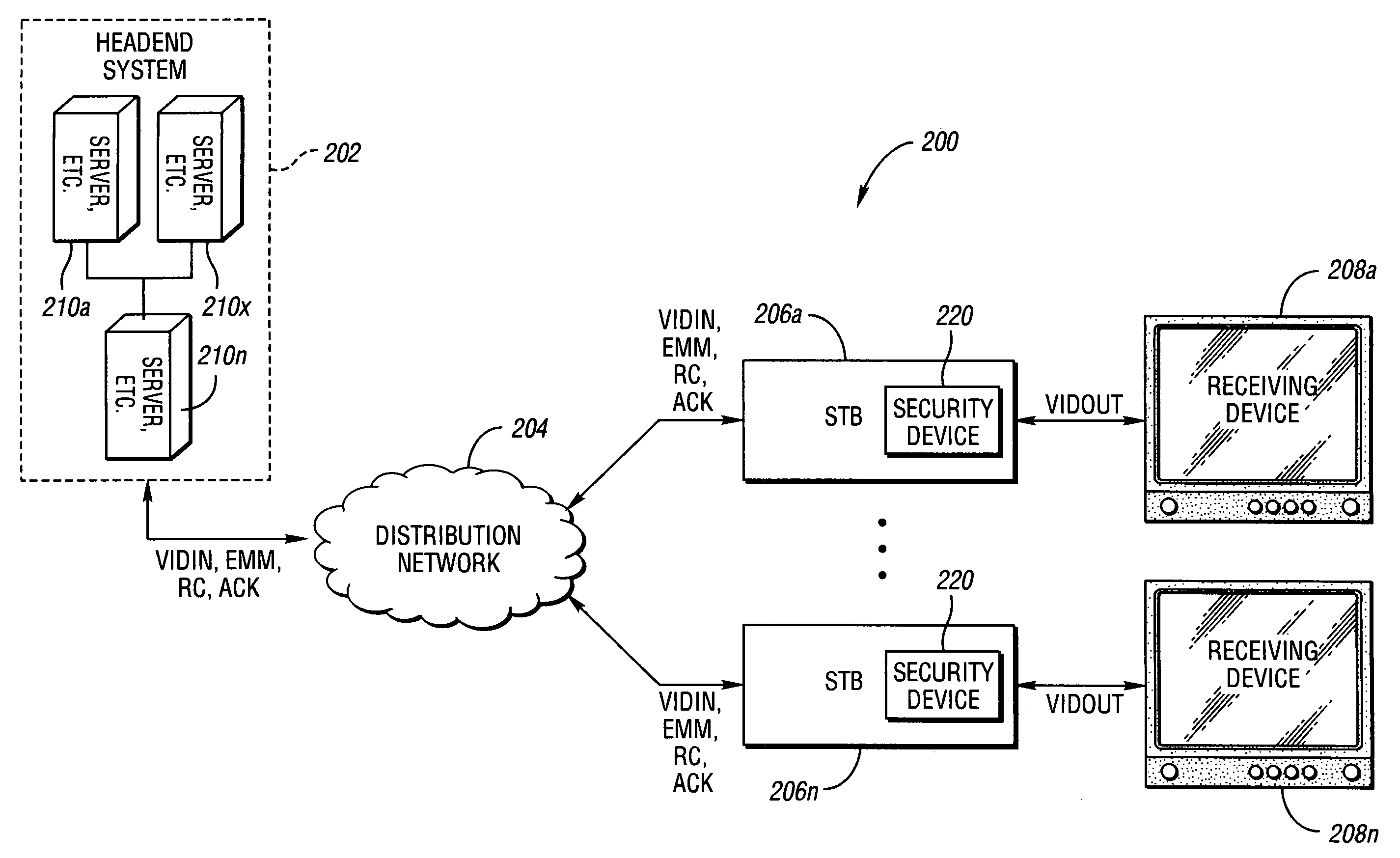
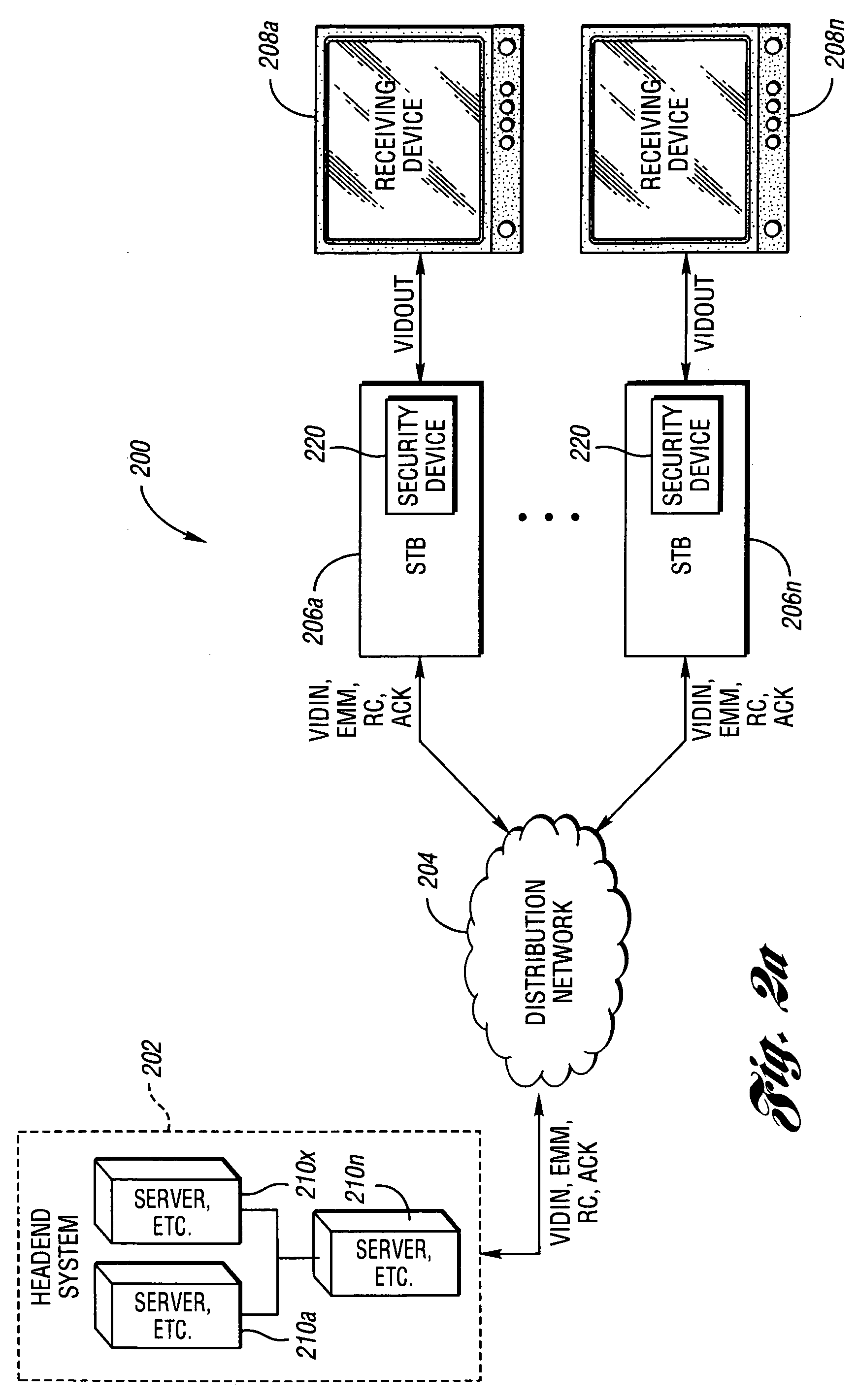
System and method for secure conditional access download and reconfiguration
ActiveUS20060137015A1Overcome deficienciesDigital data processing detailsUser identity/authority verificationSecurity softwareConditional access
A method of securely downloading at least one of conditional access software (CAS), Digital Rights Management software (DRMS), Trusted Domain Software (TDS), and Gaming Security Software (GSS) includes presenting a specialized entitlement management message (EMM) to initiate the download to a receiver security device using a supervisory logon key (SLK) split to logon with a second split contained inside the receiver security device, presenting a receiver digitally signed random challenge from the receiver security device to a sender security server to establish authentication of the receiver security device to the sender security server, and signing and returning the receiver random challenge from the sender security server to the receiver security device with a sender random challenge to establish authentication of the sender security server to the receiver security device.
Owner:COMCAST CABLE COMM LLC
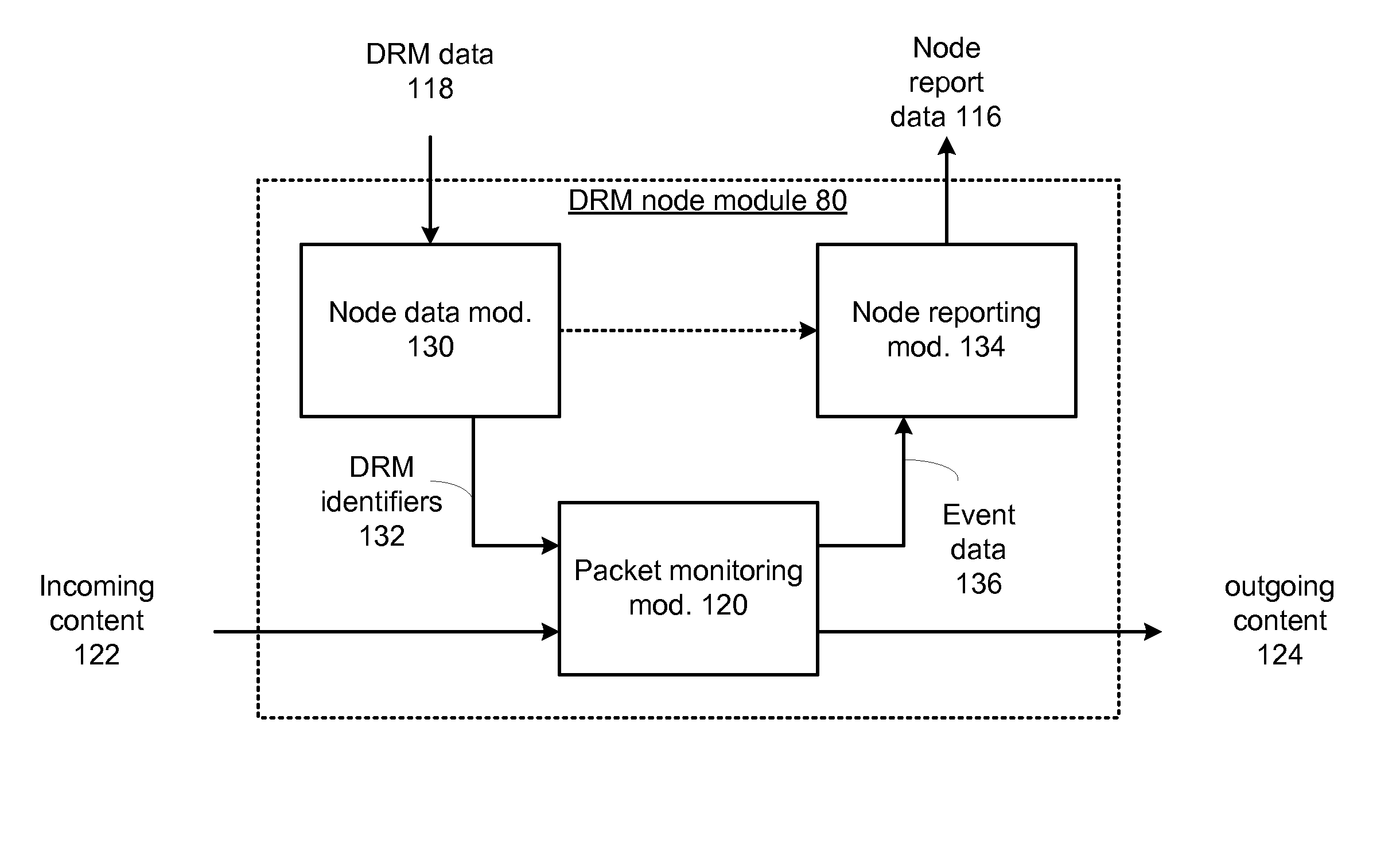
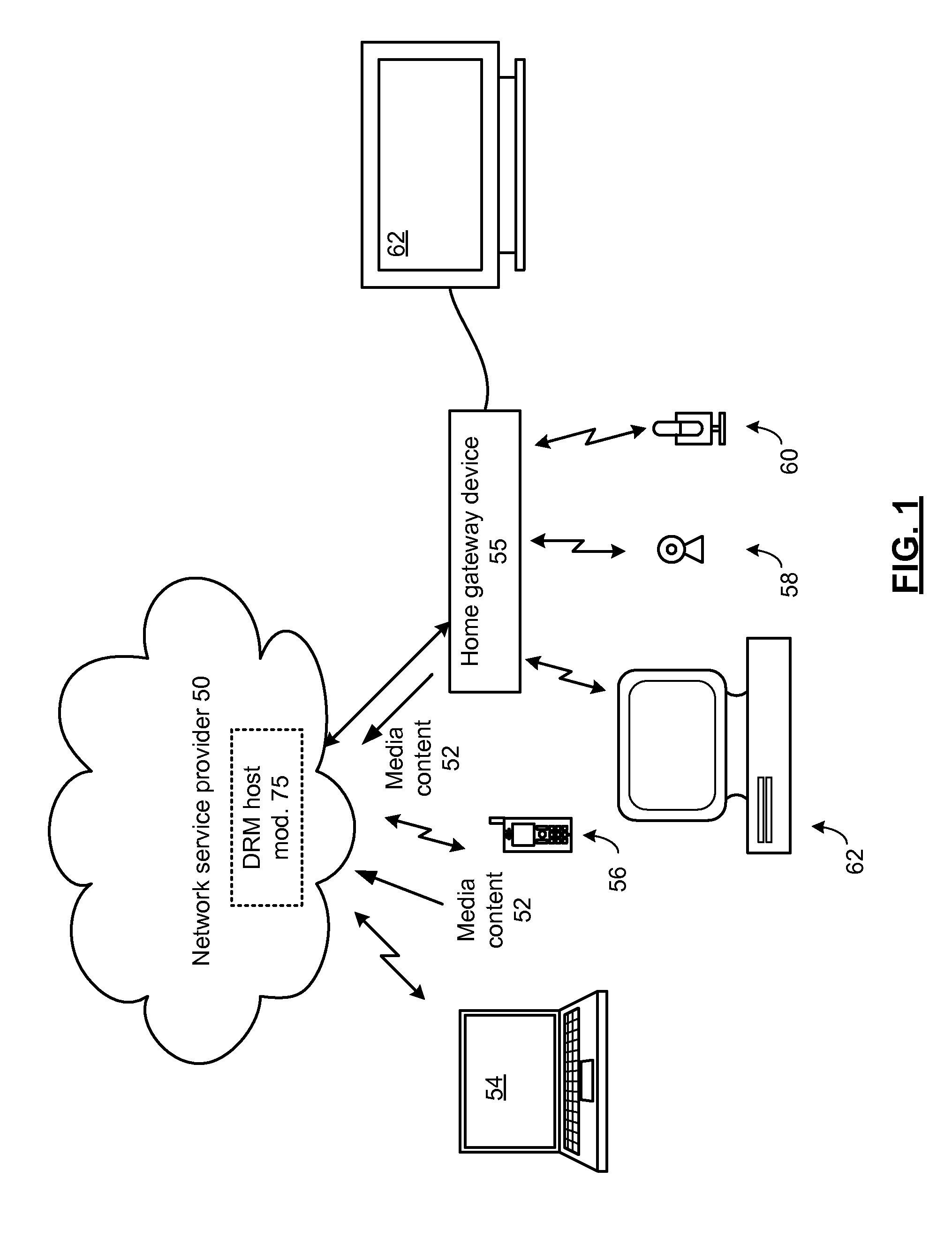
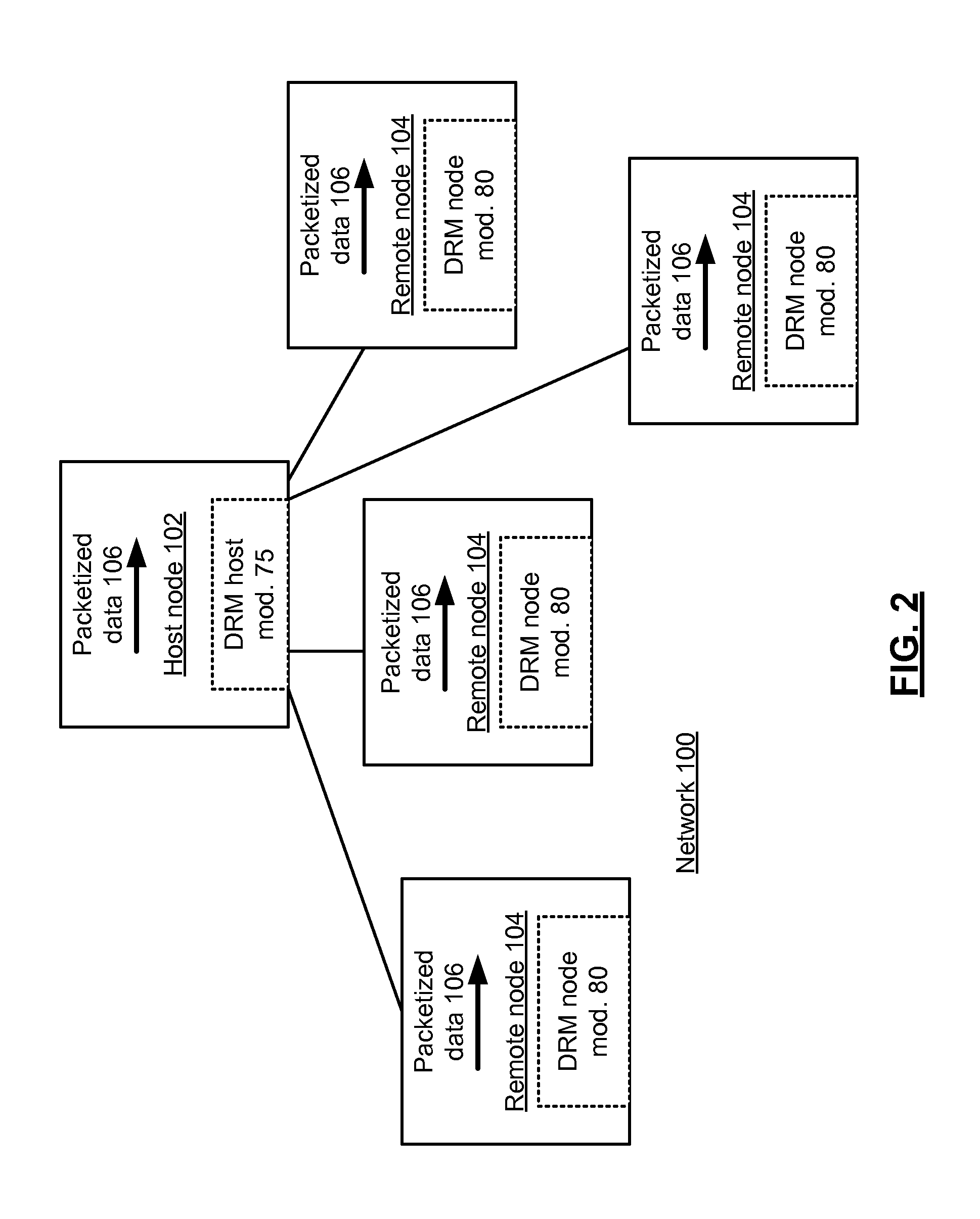
Distributed digital rights management node module and methods for use therewith
A digital rights management (DRM) node module for use in a node of a public data includes a node data module that stores DRM data associated with a plurality of digital files, the DRM data including a plurality of DRM identifiers. A packet monitoring module receives the plurality of DRM identifiers from the node data module, that receives packets containing incoming content and compares the incoming content to the DRM identifier, and generates event data when the incoming content matches at least one of the DRM identifiers. A node reporting module receives the event data, and generates node report data based on the event data.
Owner:AT&T INTPROP I LP
Digital rights management engine systems and methods
ActiveUS20070100701A1Limited accessHand manipulated computer devicesDigital data protectionRights managementDigital rights management
Systems and methods are described for performing digital rights management. In one embodiment, a digital rights management engine is provided that evaluates license associated with protected content to determine if a requested access or other use of the content is authorized. In some embodiments, the licenses contain control programs that are executable by the digital rights management engine.
Owner:INTERTRUST TECH CORP
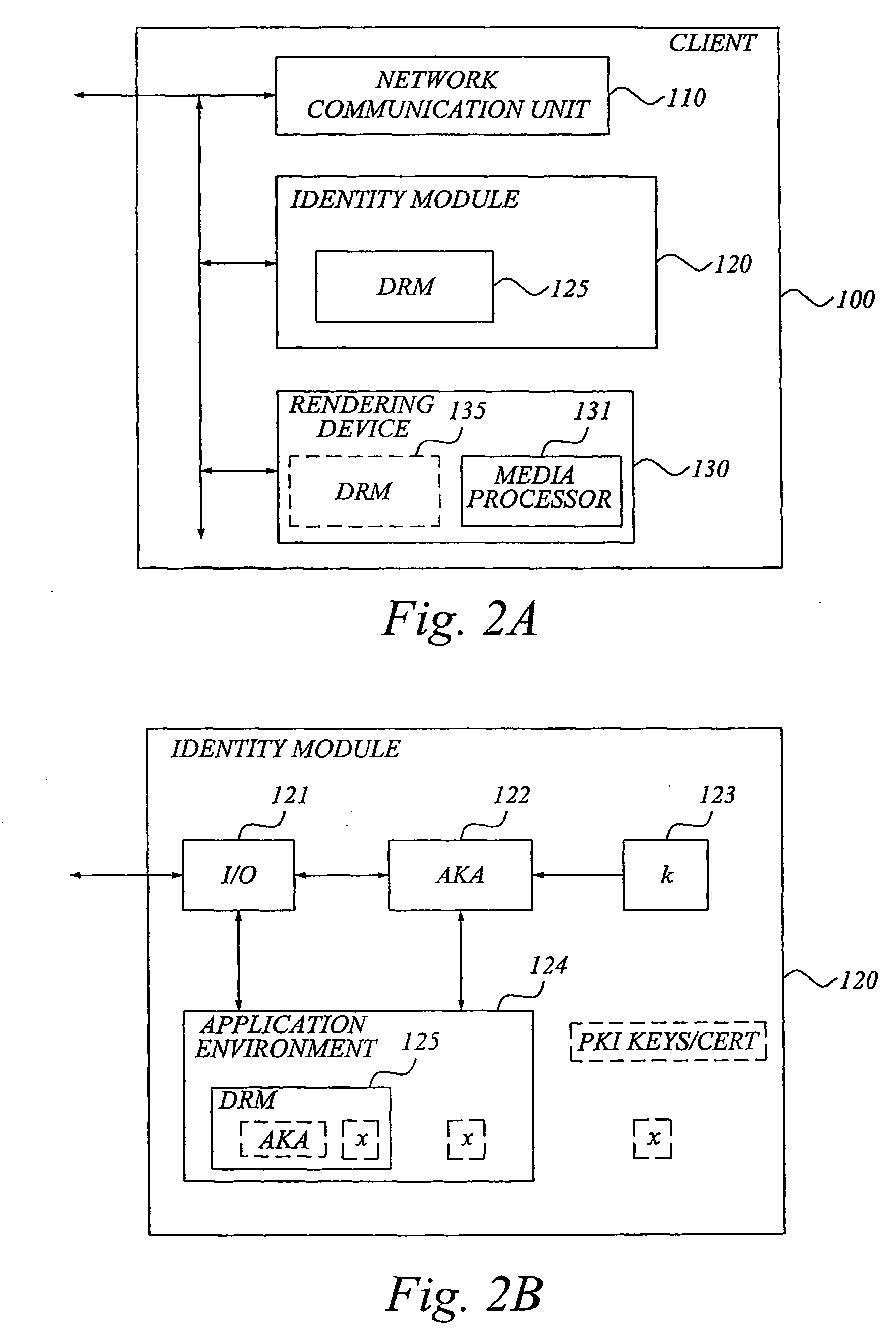
Robust and flexible digital rights management involving a tamper-resistant identity module
ActiveUS20050278787A1Easy to replaceEasy to upgradeDigital data processing detailsAnalogue secracy/subscription systemsDigital contentDigital rights management
The invention relates to digital rights management, and proposes the implementation of a DRM agent (125) into a tamper-resistant identity module (120) adapted for engagement with a client system (100), such as a mobile phone or a computer system. The DRM agent (125) is generally implemented with functionality for enabling usage, such as rendering or execution of protected digital content provided to the client system from a content provider In general, the DRM agent (125) includes functionality for cryptographic processing of DRM metadata associated with the digital content to be rendered. In a particularly advantageous realization, the DRM agent is implemented as an application in the application environment of the identity module. The DRM application can be preprogrammed into the application environment, or securely downloaded from a trusted party associated with the identity module. The invention also relates to a distributed DRM module, with communication between distributed DRM agents (125, 135) based on usage-device specific key information.
Owner:TELEFON AB LM ERICSSON (PUBL)
Digital rights management negotiation for streaming media over a network
ActiveUS7382879B1Avoid necessityData processing applicationsDigital data processing detailsNetwork addressingNetwork address
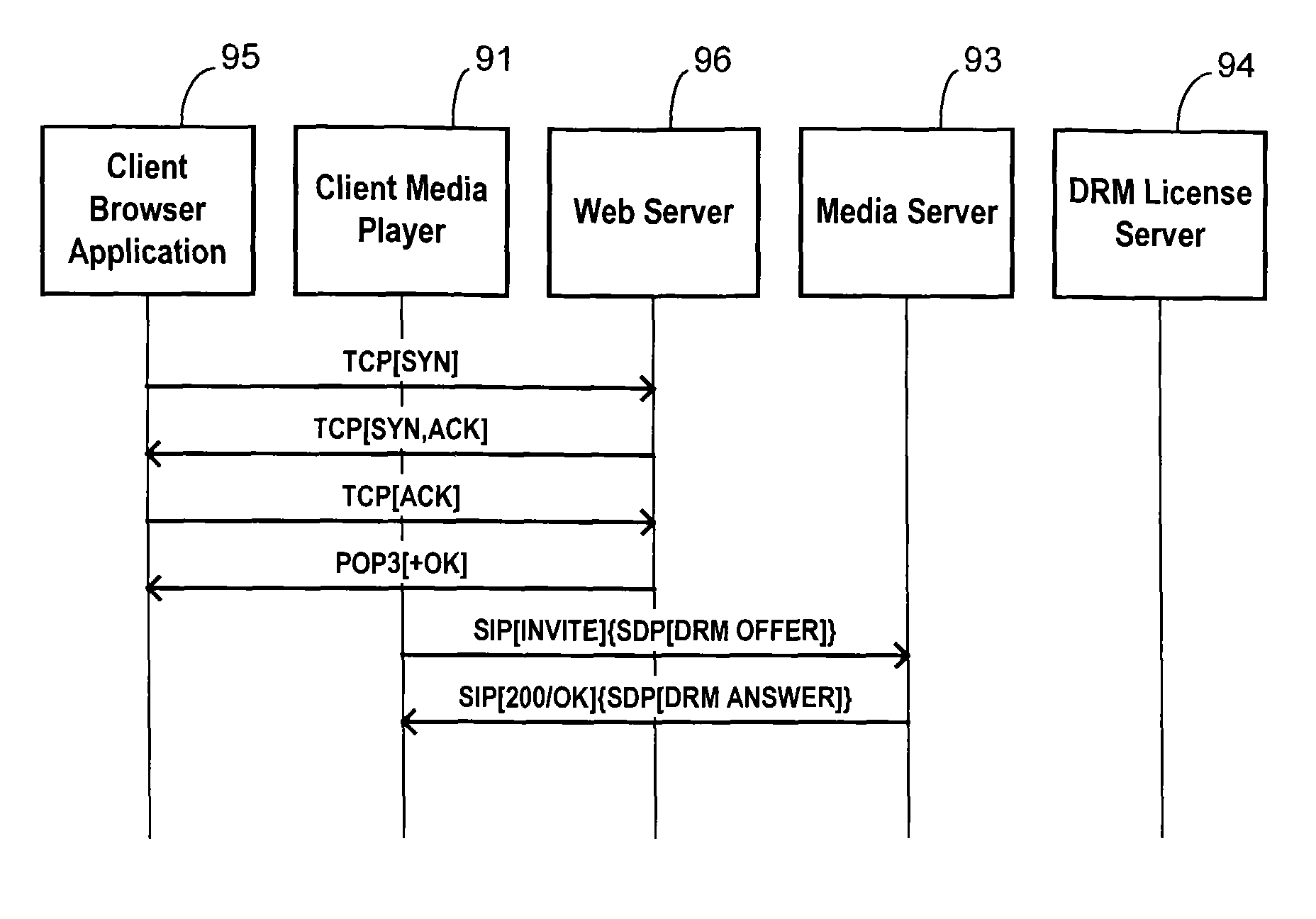
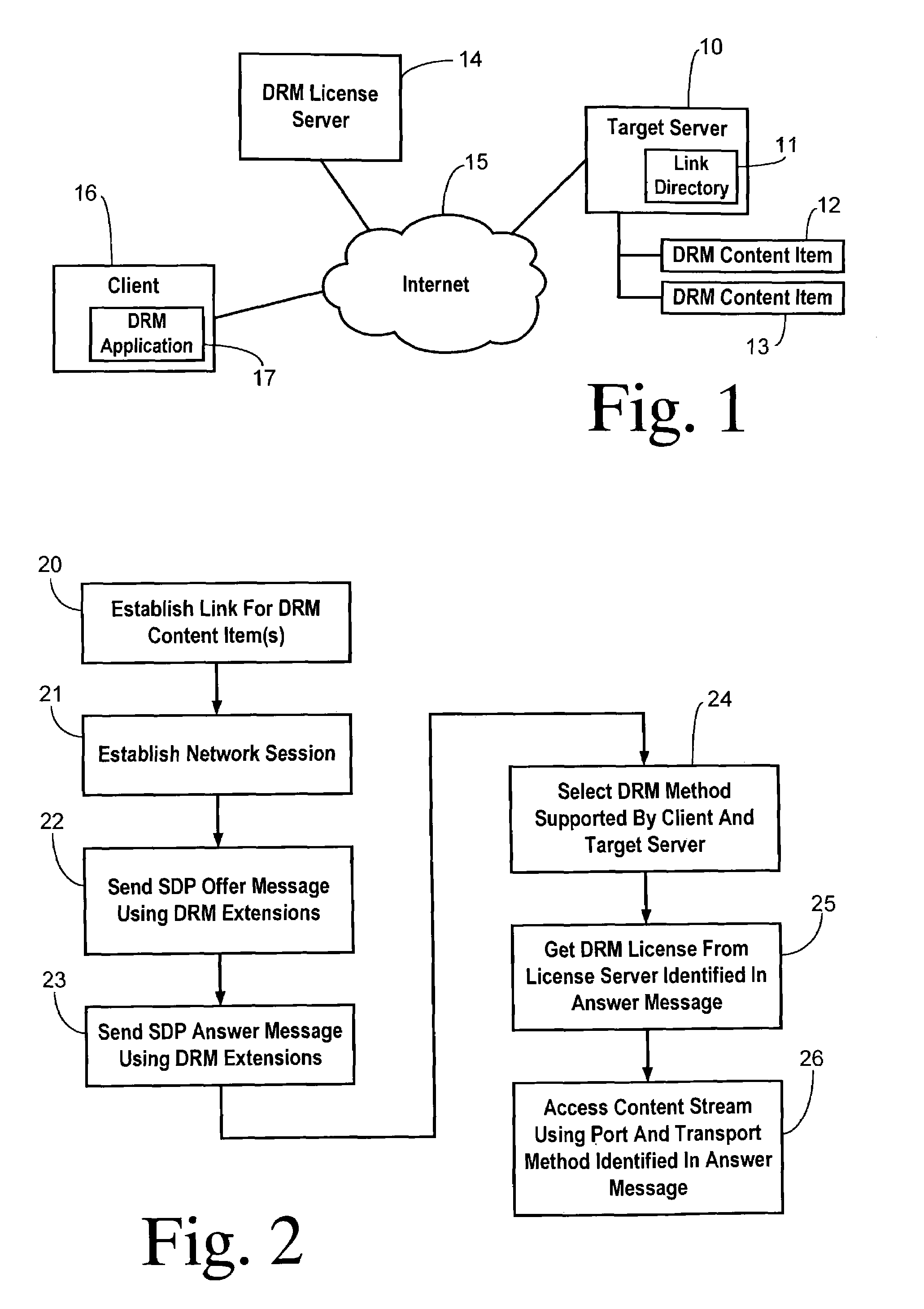
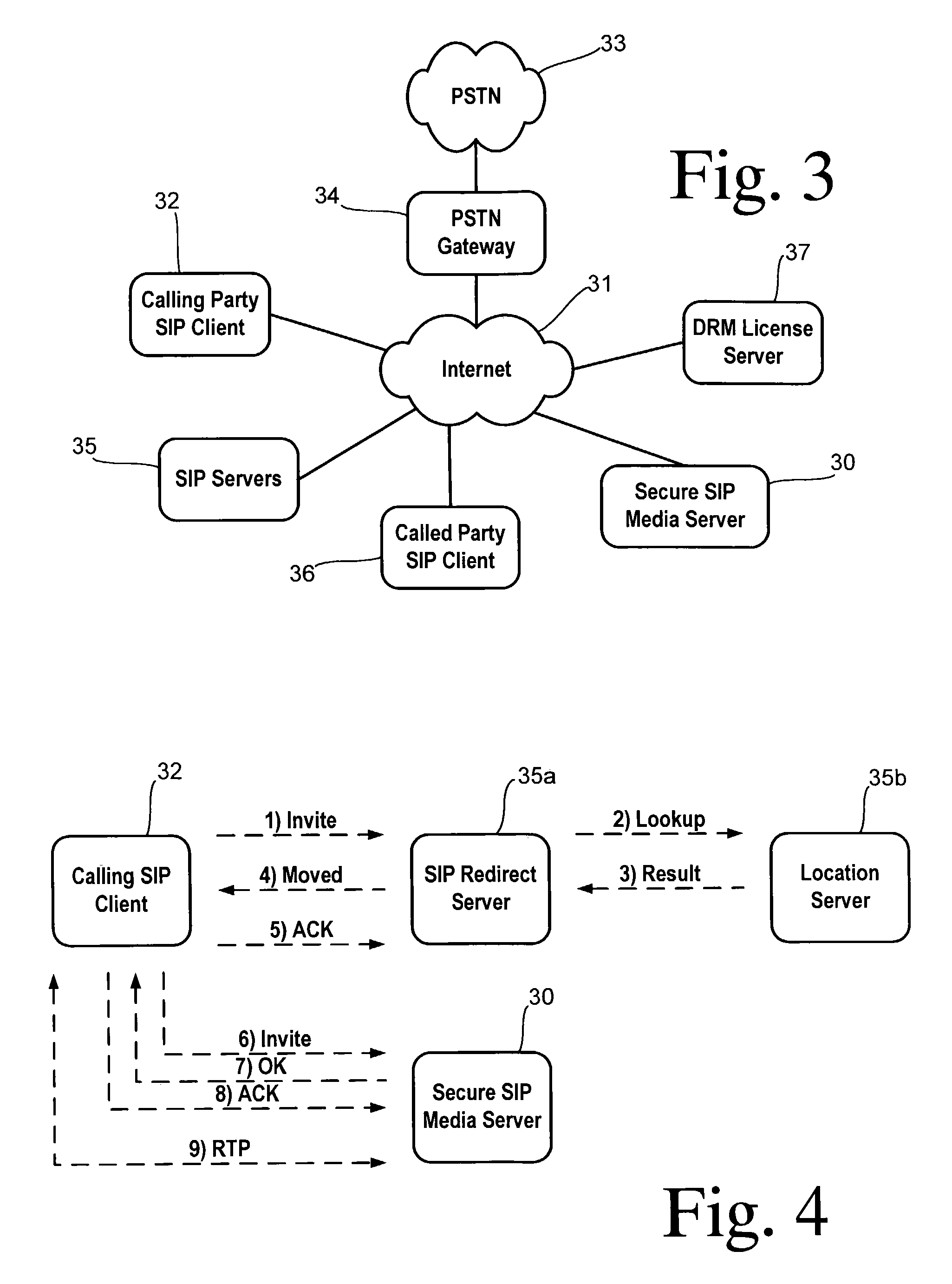
A digital rights management (DRM) method is negotiated prior to initiating delivery of a DRM encoded content item over a digital network between a client and a target server. The client identifies a link to the target server for accessing the DRM encoded content item. The client initiates a network session with the target server. The client sends an offer message to the target server containing a list of at least one supported DRM method. The target server sends an answer message to the client containing a corresponding list 1) indicating whether each DRM method listed in the offer message is supported by the target server, and 2) providing a network address of a DRM license server for each supported DRM method. The client selects a supported DRM method. The client obtains a DRM license using the network address listed for the selected DRM method. The target server delivers the DRM encoded content item to the client using the selected DRM method.
Owner:T MOBILE INNOVATIONS LLC
Updating usage conditions in lieu of download digital rights management protected content
InactiveUS20060089912A1Digital data processing detailsRecord information storageDigital rights managementEnd user
A method on an end user system for creating additional copies onto at least one computer readable medium such as CDs, DVDs, ZipDisks™, tape, Flash memory, and RAM. The method comprising the steps of: receiving encrypted content with associated usage conditions and a first hash value; receiving a selection from an end user to create at least one copy of the-encrypted content onto at least one computer readable medium; sending a request to an online electronic store of the encrypted content selected to be copied; receiving from the electronic store a description of the content selected to be copied along with a second hash value; and determining if the first hash value received is identical to the second hash value and if the first hash and the second hash value is identical authorizing the creating additional copies onto at least one computer readable medium.
Owner:IBM CORP
Digital rights management engine systems and methods
InactiveUS20070204078A1Limited accessValidity is limitedDigital data protectionProgram/content distribution protectionDigital rights managementLicense
In one embodiment, a digital rights management engine is provided that evaluates license associated with protected content to determine if a requested access or other use of the content is authorized. In some embodiments, the licenses contain control programs that are executable by the digital rights management engine.
Owner:INTERTRUST TECH CORP
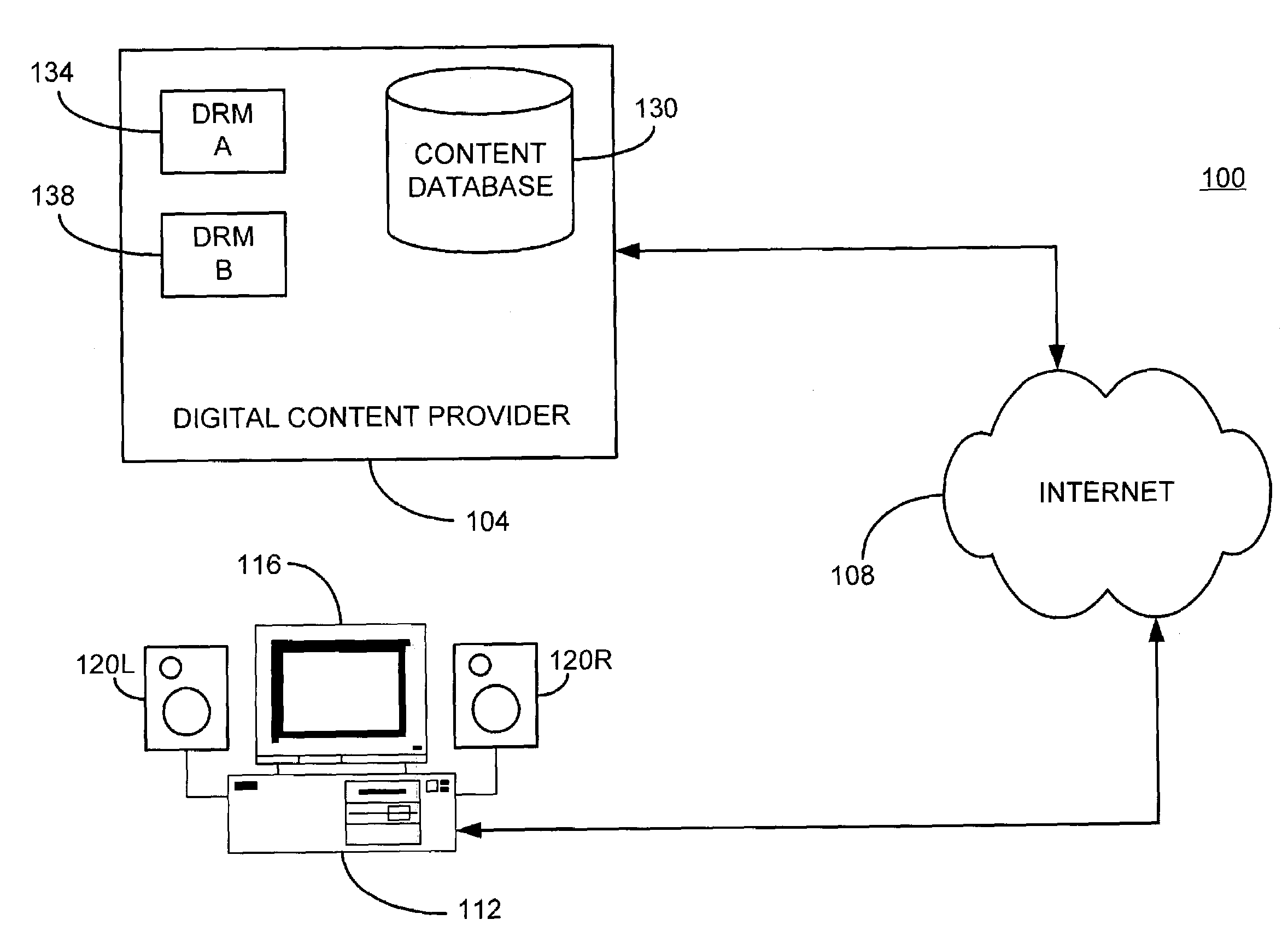
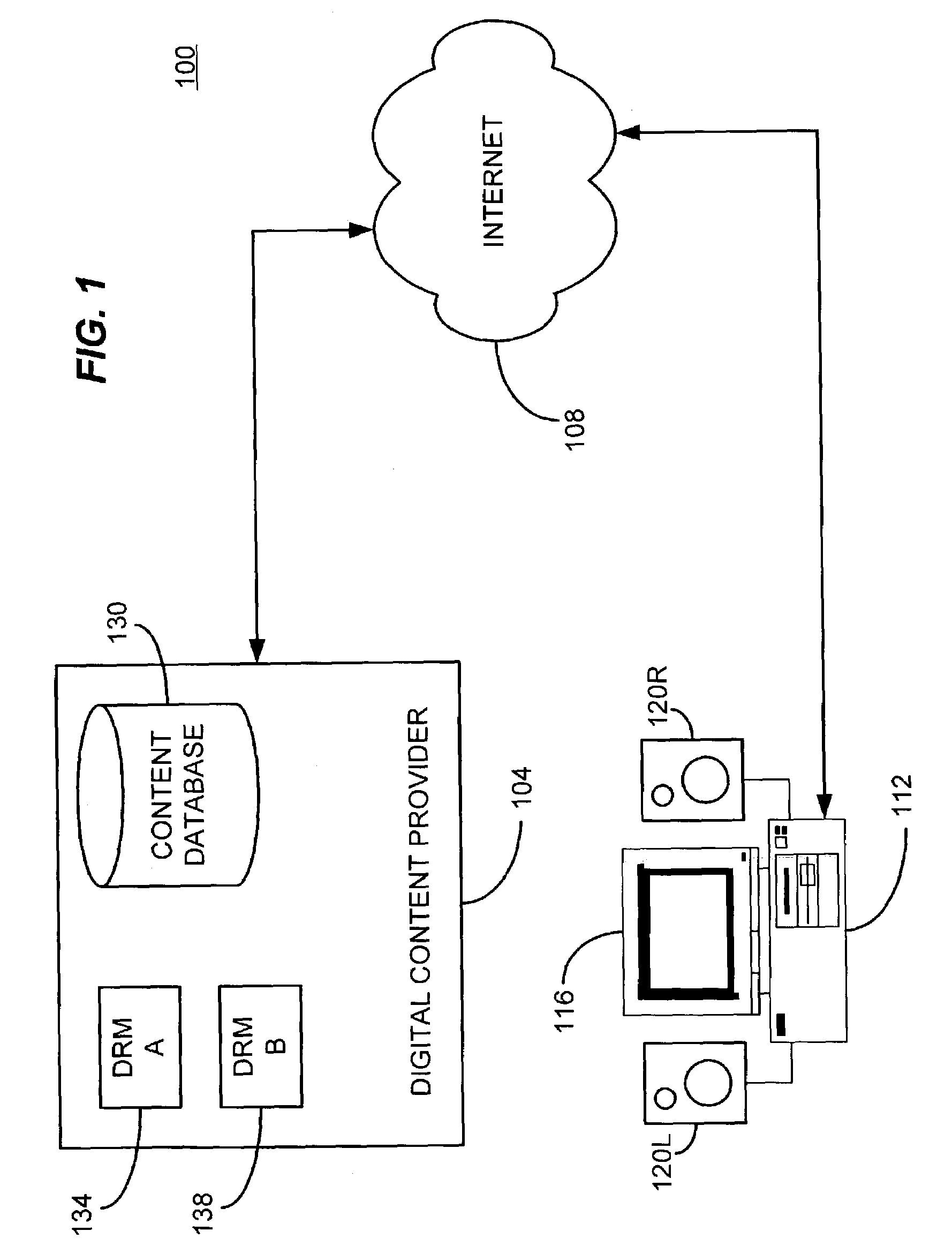
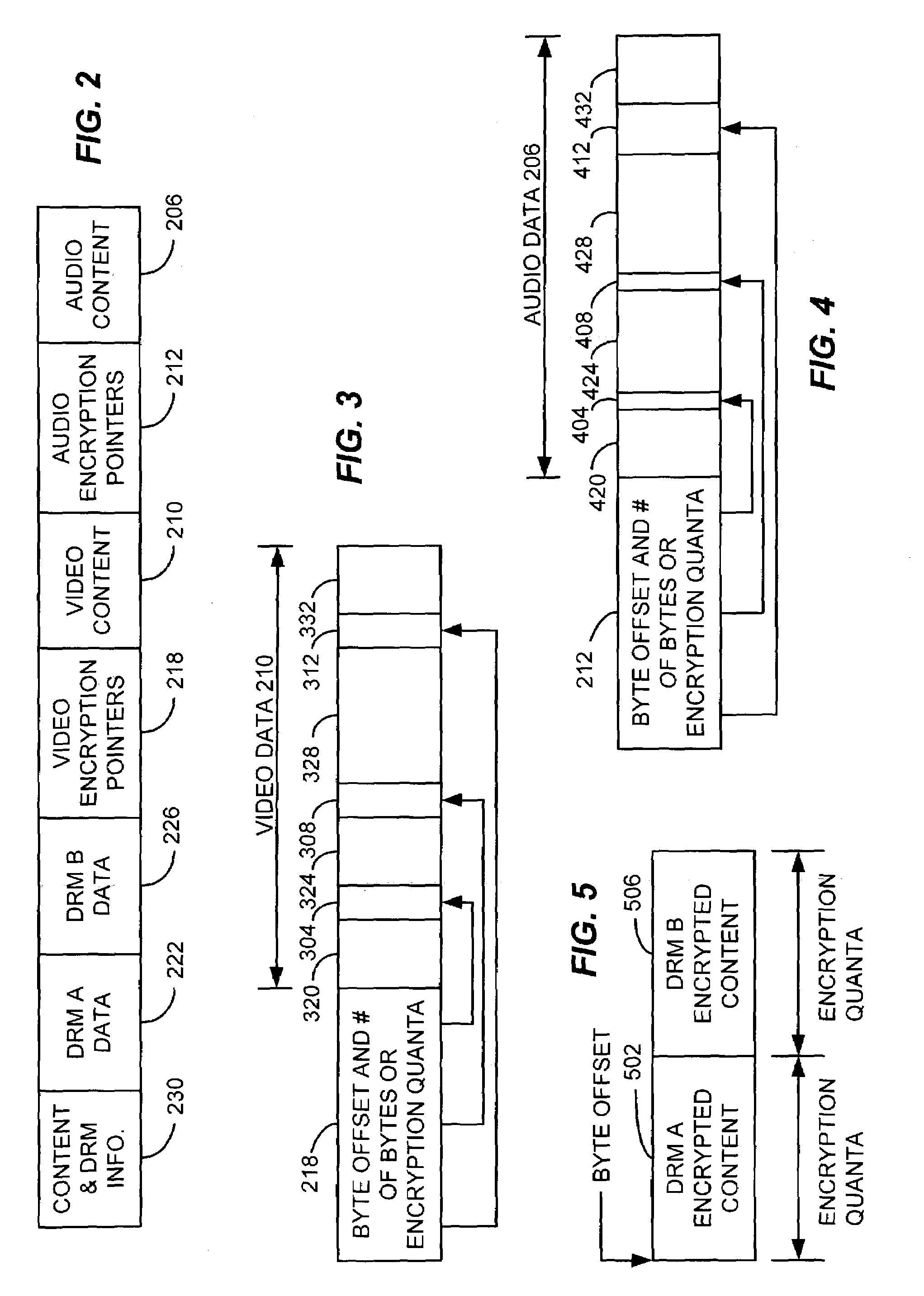
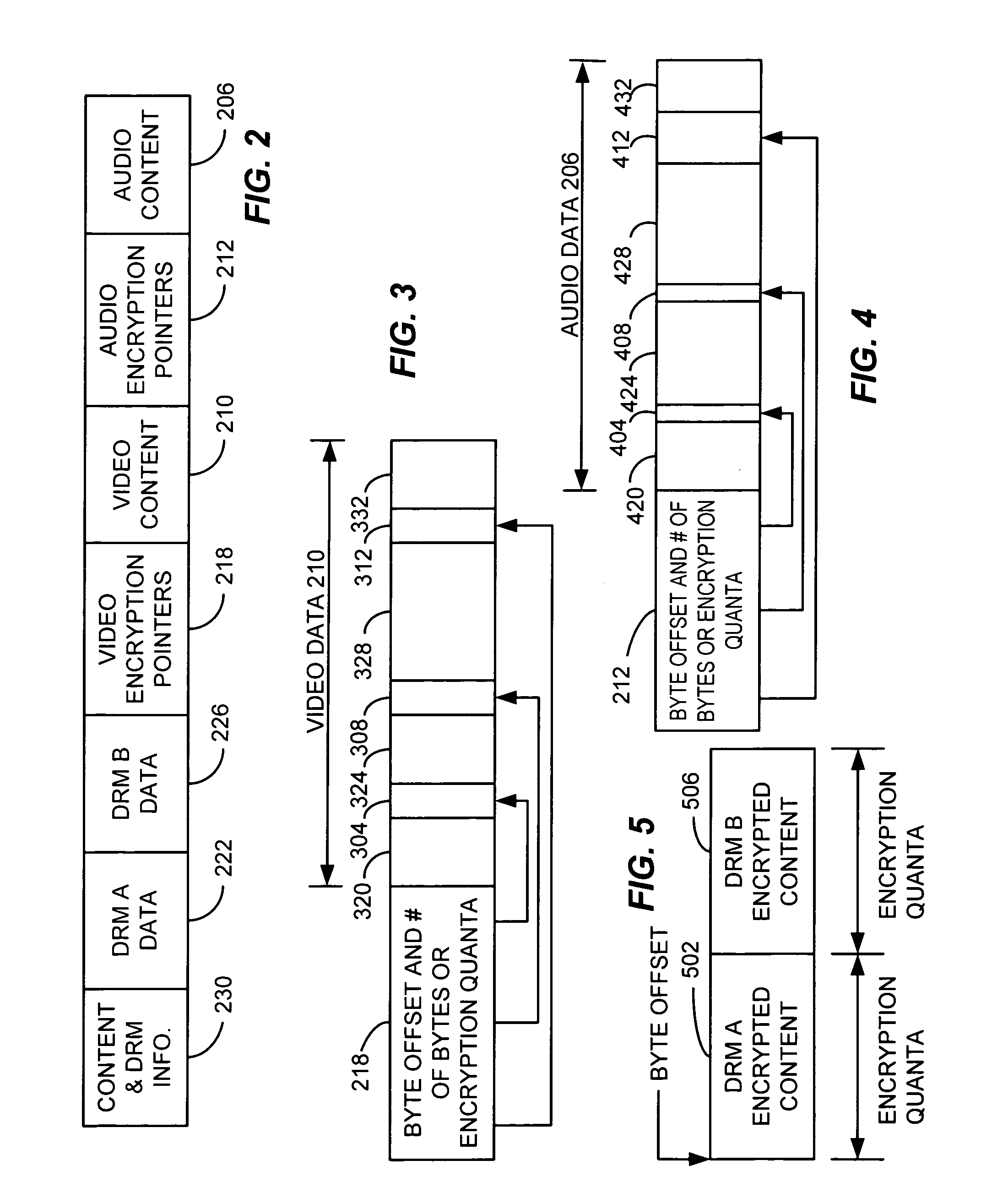
Content distribution for multiple digital rights management
InactiveUS7120250B2Television system detailsKey distribution for secure communicationContent distributionDigital content
A method and apparatus for enabling use of multiple digital rights management scenarios (DRM). Unencrypted data representing digital content is examined to identify at least segments of content for encryption. The identified segments of content are duplicated and then encrypted using a first encryption method associated with a first DRM to produce first encrypted segments. Duplicates are encrypted using a second encryption method associated with a second DRM to produce second encrypted segments. A set of pointers are generated that point to the first and second encrypted segments content. A file is then created containing first and second encrypted segments of content, pointers and unencrypted content along with DRM rights data to produce a selectively encrypted multiple DRM enabled file.
Owner:SONY CORP +1
Digital rights management and data license management
InactiveUS20080228578A1Surpasses efficiencySurpasses convenience factorAdvertisementsDigital computer detailsDigital contentWeb service
A system and method for the exchanging, distributing and managing digital content, along with providing users with the ability to sell and transfer digital rights of products or services purchased from other users, wherein the system and method are used to manage synchronization and the use of applications, web services and media in combination with different digital rights management (DRM) solutions to authenticate and authorize such transactions.
Owner:ALEX MASHINSKY FAMILY TRUST +1
Method and apparatus for managing policies for time-based licenses on mobile devices
ActiveUS8544105B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsInternet privacyUsability
Owner:QUALCOMM INC
Method and apparatus to decode a streaming file directly to display drivers
InactiveUS20050195205A1Eliminating intermediate processingEliminating storage stepCathode-ray tube indicatorsDigital video signal modificationLiquid-crystal displayComputer graphics (images)
Owner:MICROSOFT TECH LICENSING LLC
System and method for allowing creators, artsists, and owners to protect and profit from content
InactiveUS20070156594A1Great dealGood wayDigital data processing detailsAnalogue secracy/subscription systemsDigital contentThumbnail
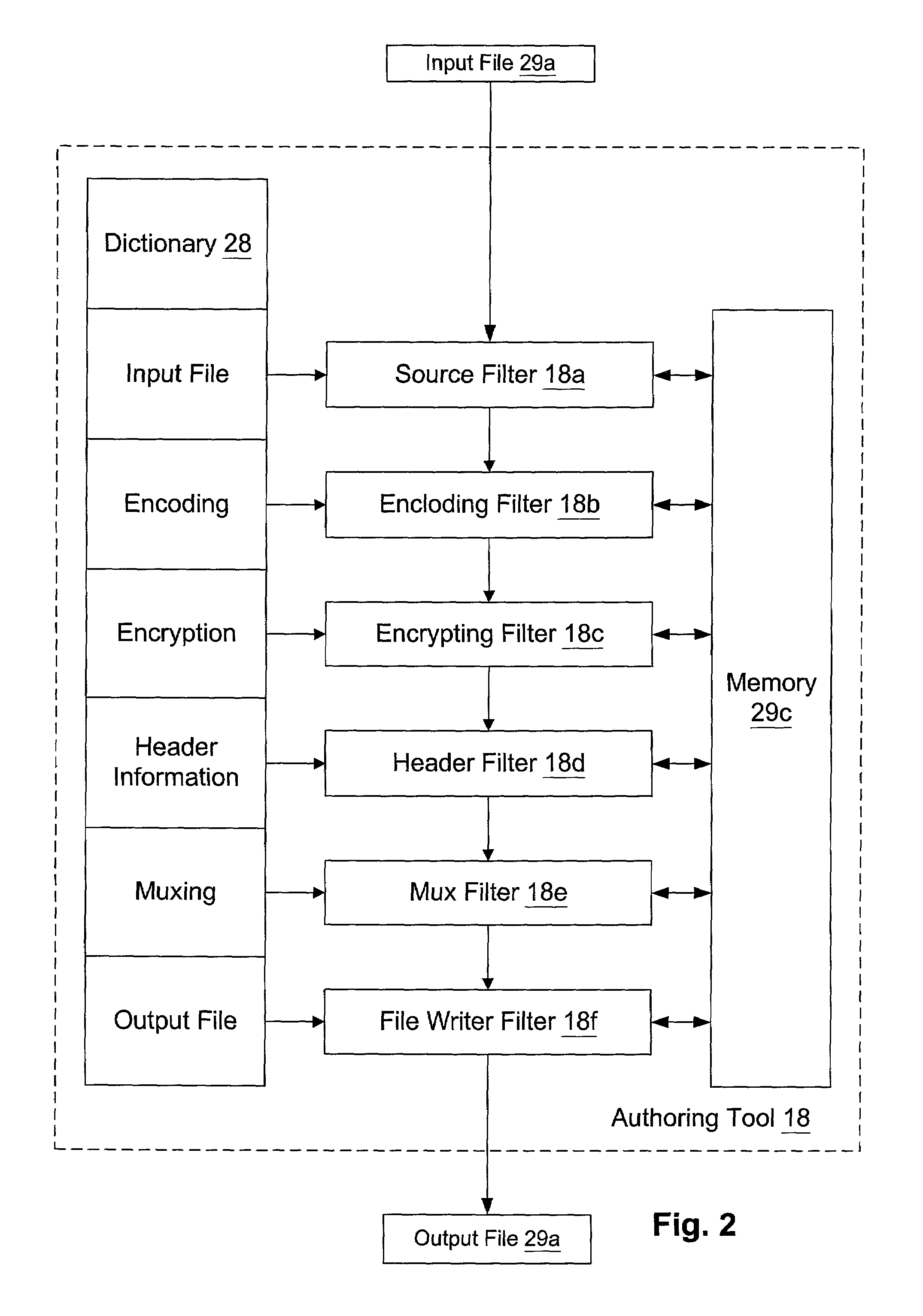
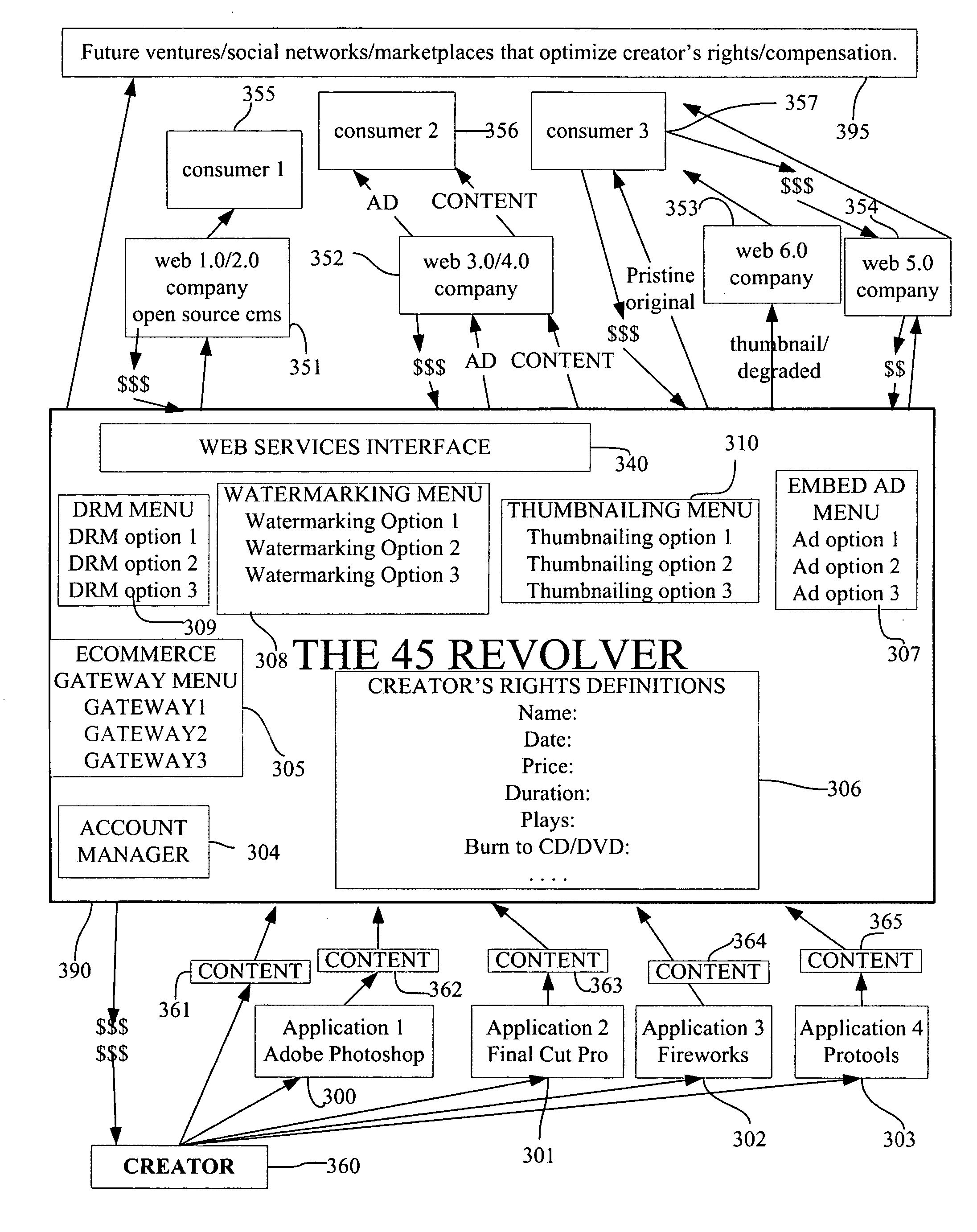
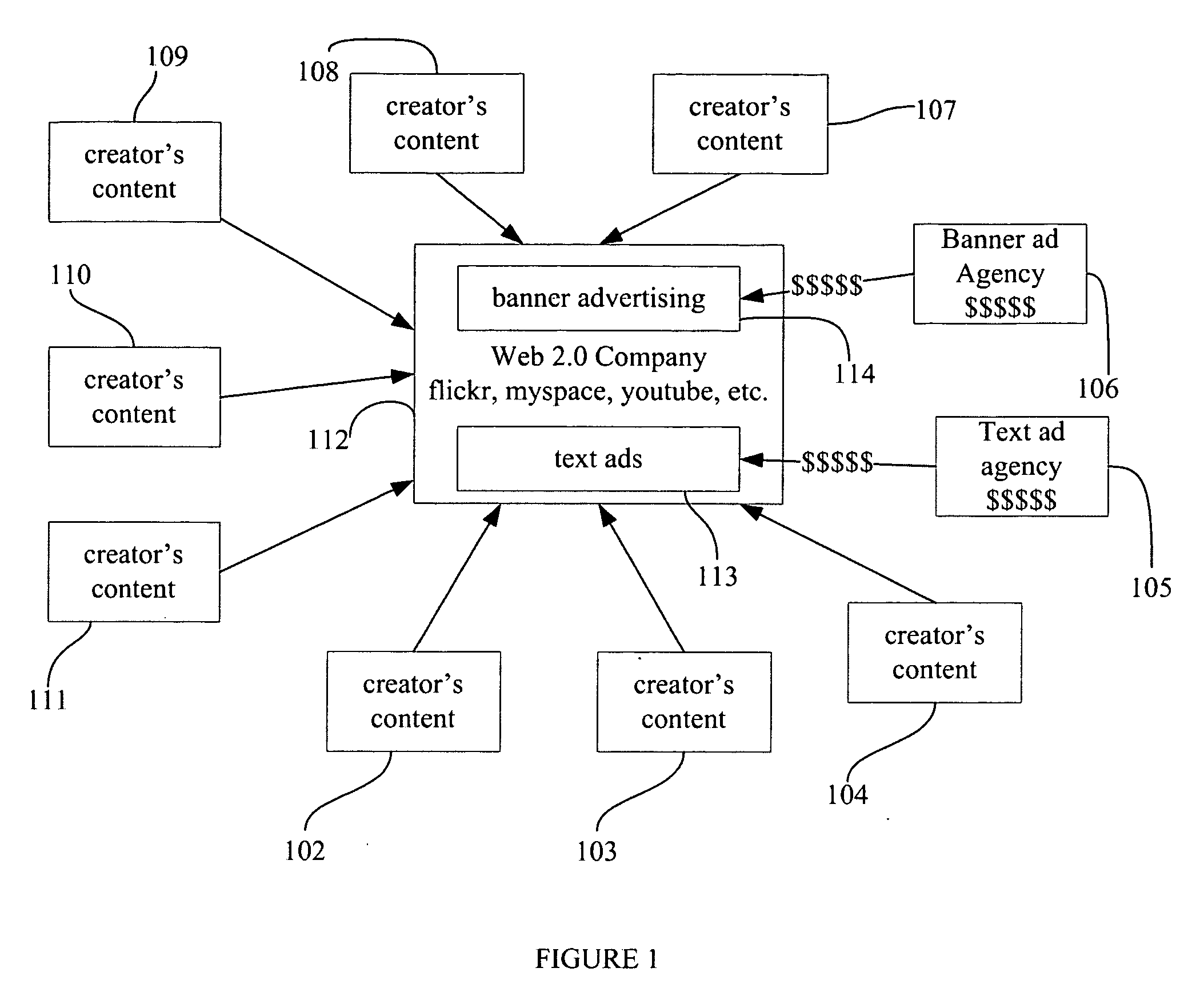
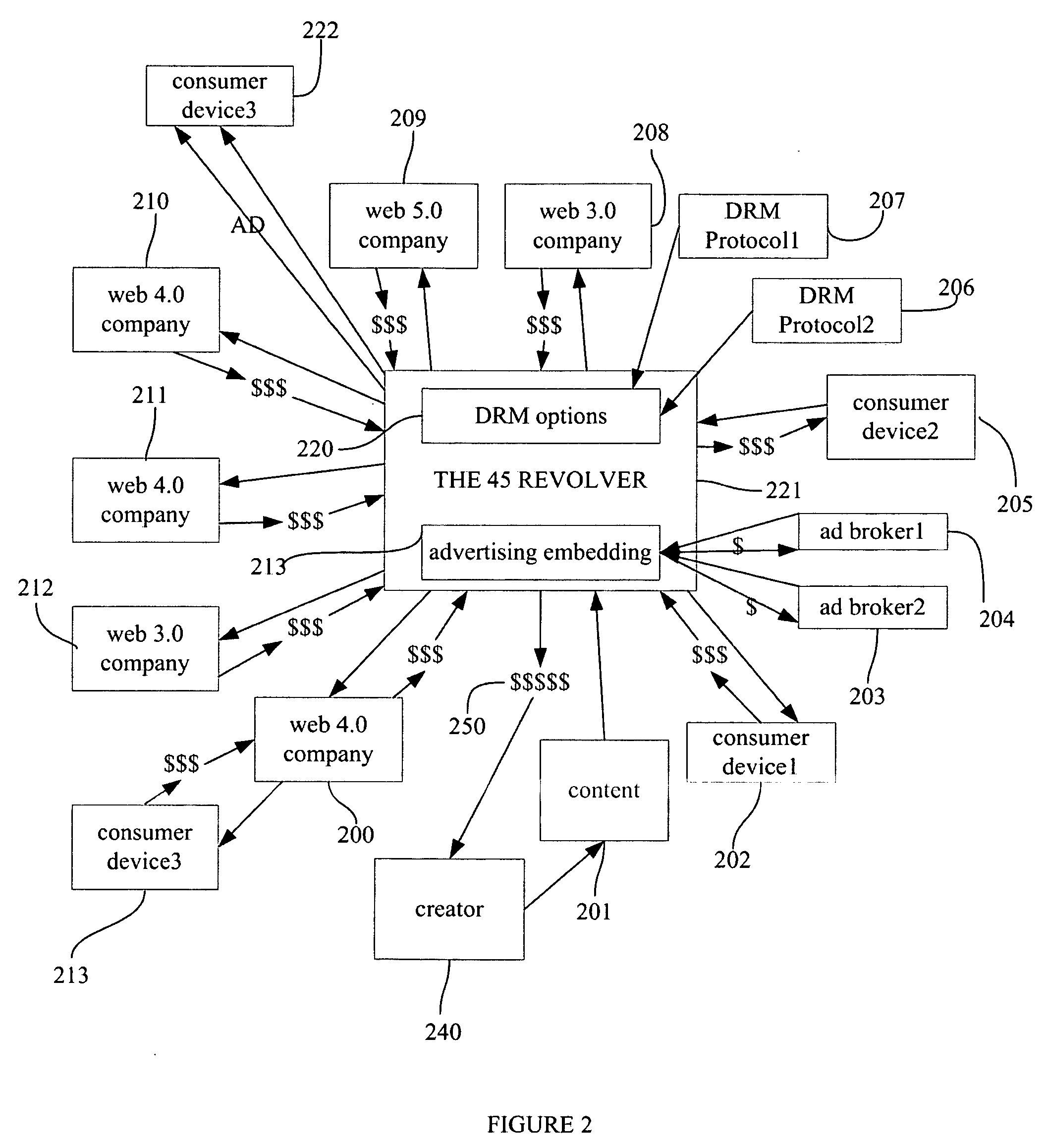
The present invention offers novel and superior means for protecting and profiting from digital content. The rights-centric, creator-centric digital rights management application will lead to greater revenue and rights for artists, and a new era of creator's entrepreneurship, as opposed to the dominant aggregator's entrepreneurship. The present invention offers a simple interface for creators, artists, users, and owners to define rights, select from a plurality of DRM options, advertising options, watermarking options, thumbnailing options, syndication options, and publish, share, sell, and distribute their content in a plurality of manners. This invention has far-ranging ramifications, as it causes DRM providers, device manufacturers, web companies, social networks, and content marketplaces to more directly compete with one-another to provide the creator and content owner the best compensation for their work. Creators can bypass the traditional and new middlemen, define their rights, sell their content, and enhance profits.
Owner:MCGUCKEN ELLIOT
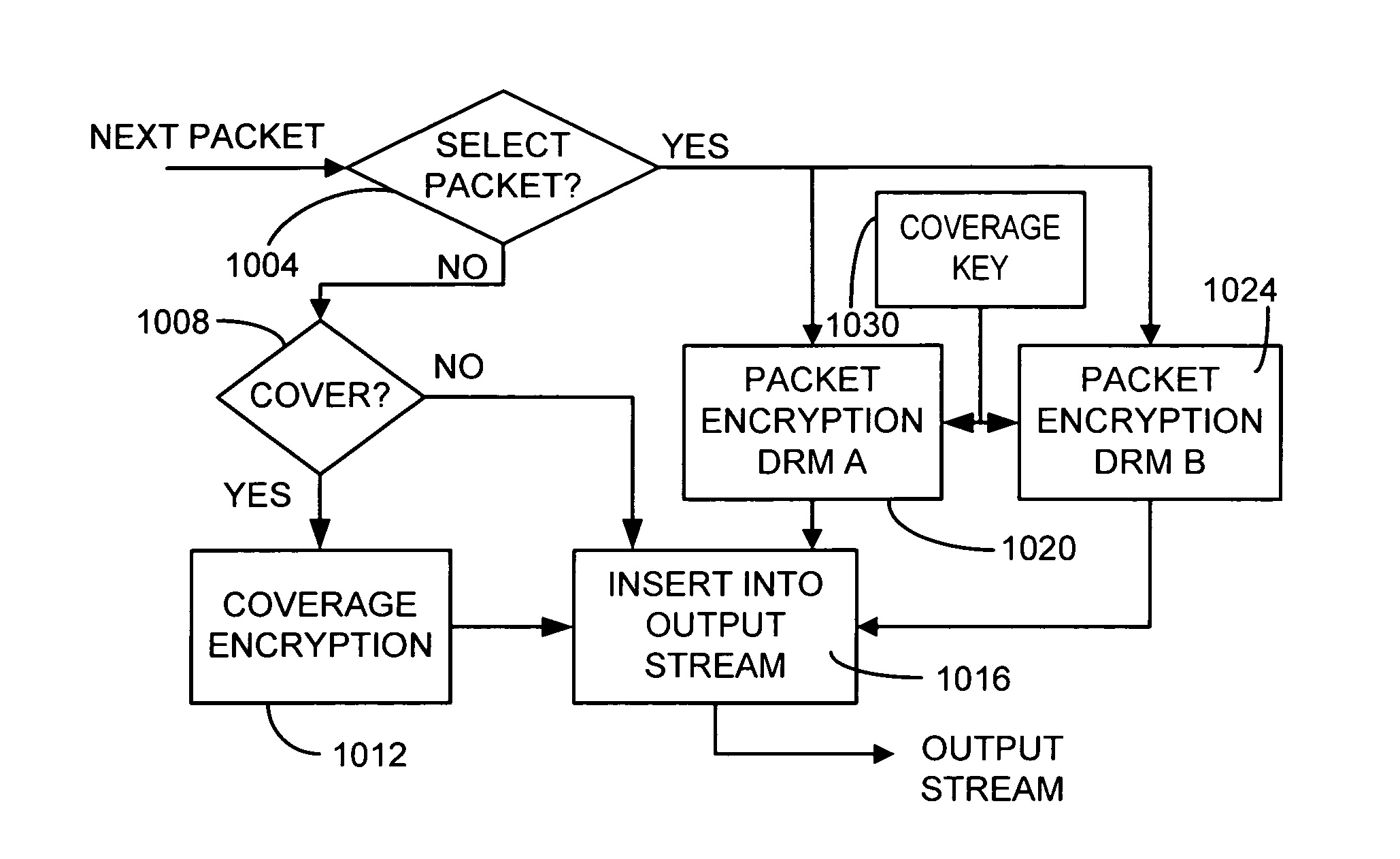
Selective encryption with coverage encryption
ActiveUS20050192904A1Multiple keys/algorithms usagePayment architectureDigital contentDigital rights management
A method and apparatus for enabling use of multiple digital rights management scenarios (DRM). Unencrypted data representing digital content is examined to identify at least segments of content for DRM encryption. The identified segments of content are duplicated and then encrypted using a first encryption method associated with a first DRM to produce first encrypted segments. Duplicates are encrypted using a second encryption method associated with a second DRM to produce second encrypted segments. At least a portion of segments not selected for DRM encryption are encrypted using a coverage encryption method. The coverage encryption key is encrypted by each of a third and fourth encryption methods associated with the first and second DRMs respectively. This abstract is not to be considered limiting, since other embodiments may deviate from the features described in this abstract.
Owner:SONY CORP +1
Digital rights management in a mobile environment
ActiveUS9124650B2Facilitate personalization of user experienceEasy to integratePayment architectureOffice automationComputer hardwareDigital rights management
Owner:DIRECTV LLC
Digital rights management in a mobile communications environment
InactiveUS20070112676A1Payment architectureProgram/content distribution protectionDigital rights managementVoucher
The invention provides a method, system, and computer program product to control the access, copying, and / or transfer of a digital asset by mobile, wireless devices using a digital voucher. The digital voucher references a primary content that contains all of the expression for that particular asset and a secondary content that contains information that can be distilled out as a preview. The information in the primary content can be limited to a specified duration or a specific number of viewings. The author, owner, or possessor of the digital asset specifies the terms and conditions for distribution of the digital asset. The digital voucher authorizes the mobile, wireless device to access a specified primary or secondary content that may be located elsewhere in the network. The mobile, wireless device can download a copy of portions or all of the content depending on the terms specified in the voucher.
Owner:NOKIA CORP
Digital rights management of a digital device
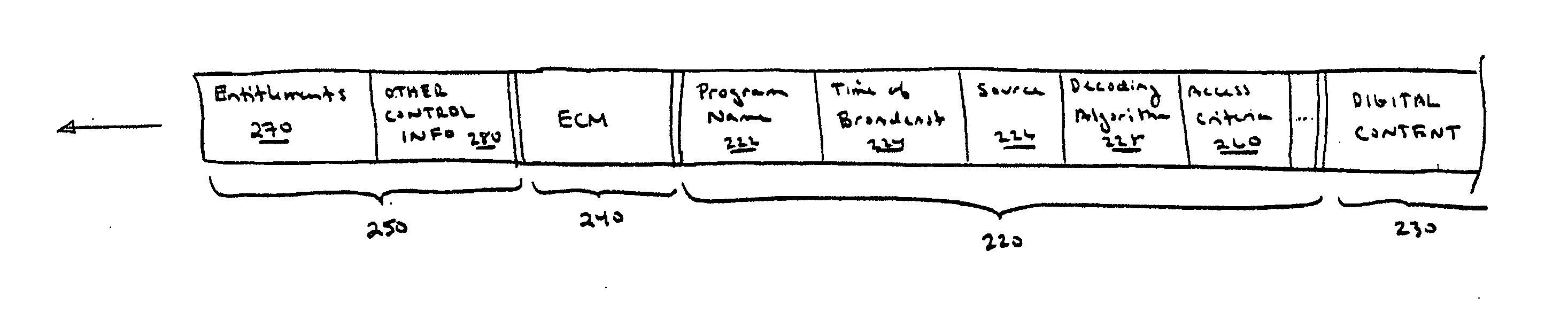
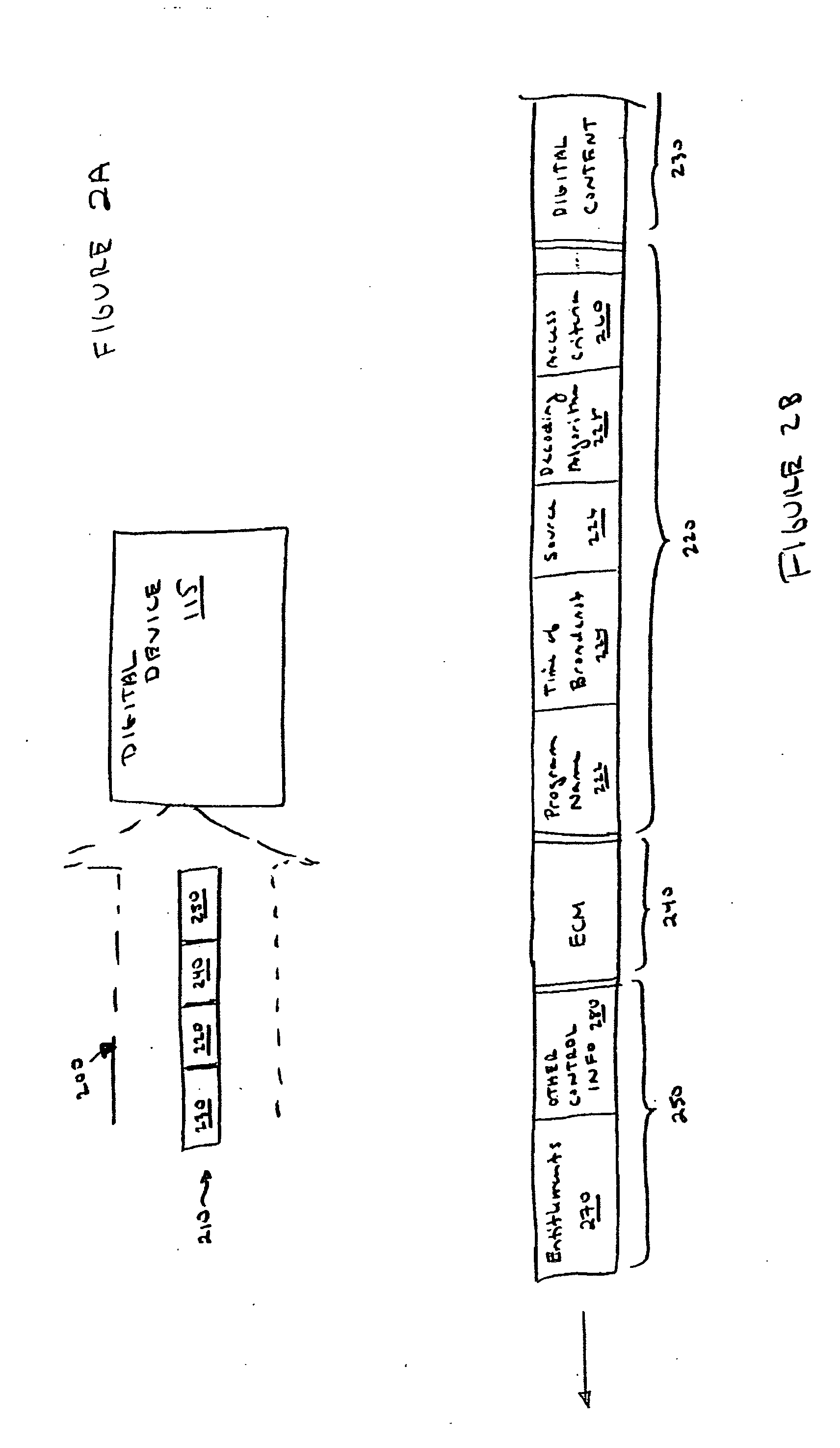
ActiveUS20050063541A1Television system detailsUnauthorized memory use protectionDigital contentRights management
According to one embodiment, an apparatus involves the descrambling of scrambled digital content using a one-time programmable key and digital rights management. The apparatus comprises a processor and a descrambler. The processor is adapted to execute a Digital Rights Management (DRM) function in order to determine whether each entitlement needed to access the digital content is pre-stored. The descrambler is adapted to decrypt encrypted information using a Unique Key stored within the one-time programmable memory. After determining that each entitlement needed to access the digital content is pre-stored, the decrypted information is used to generate a key, which is used to decrypt at least one service key for descrambling the scrambled digital content.
Owner:SONY CORP +1
Digital rights management for content rendering on playback devices
ActiveUS20050114896A1Static indicating devicesComputer security arrangementsComputer hardwareDigital rights management
Owner:INTEL CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com