Patents
Literature
896 results about "Number content" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
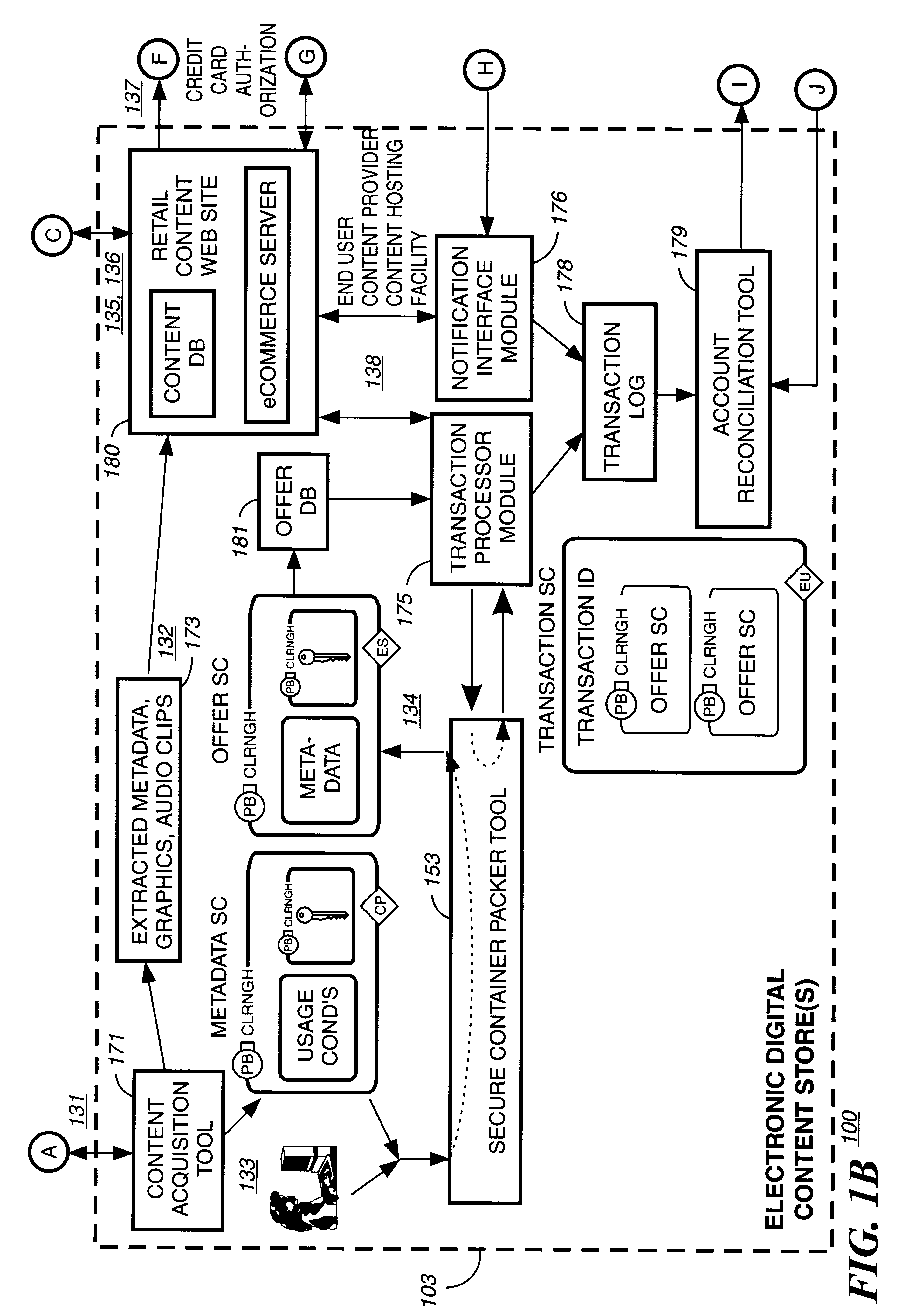
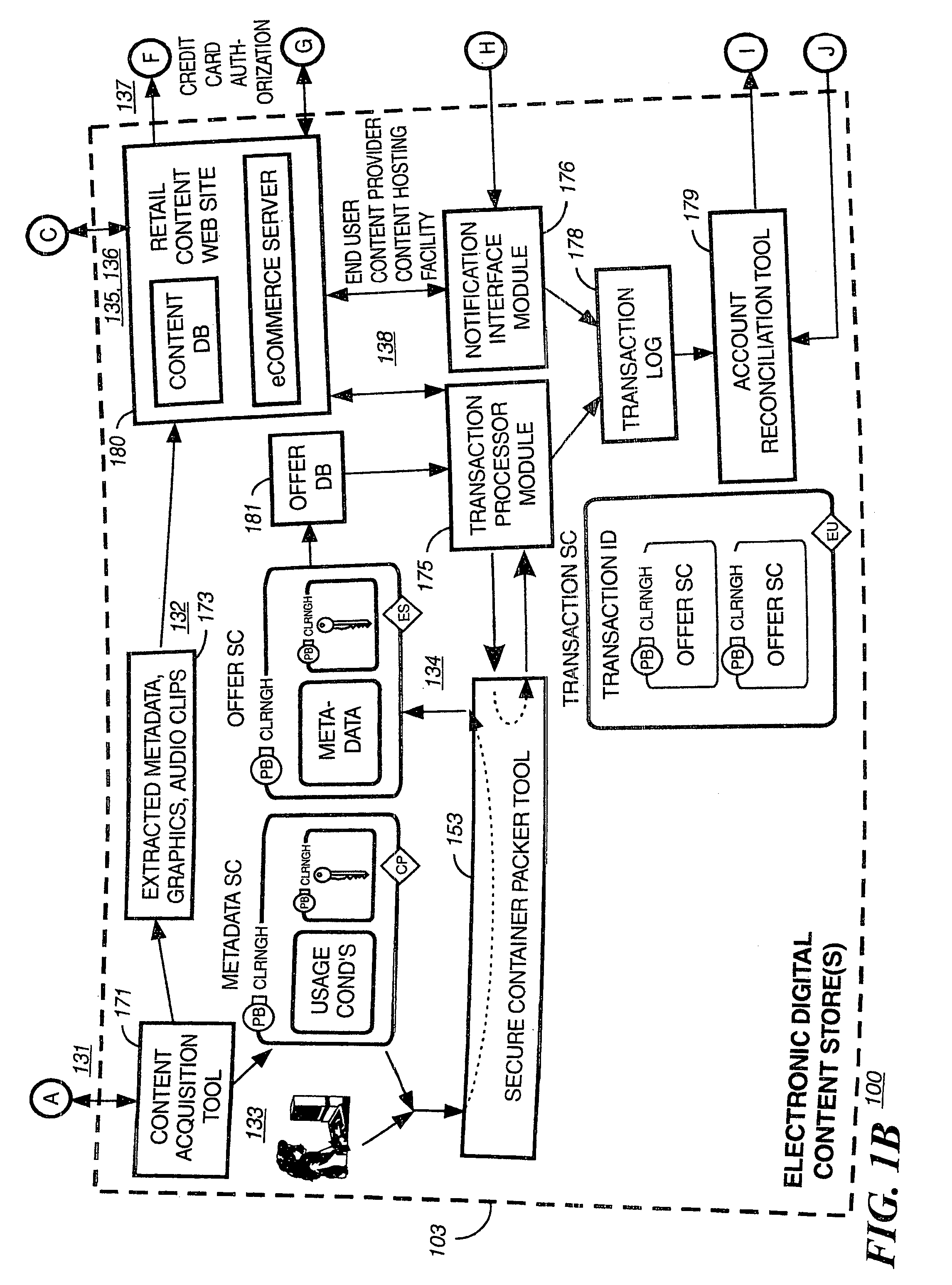
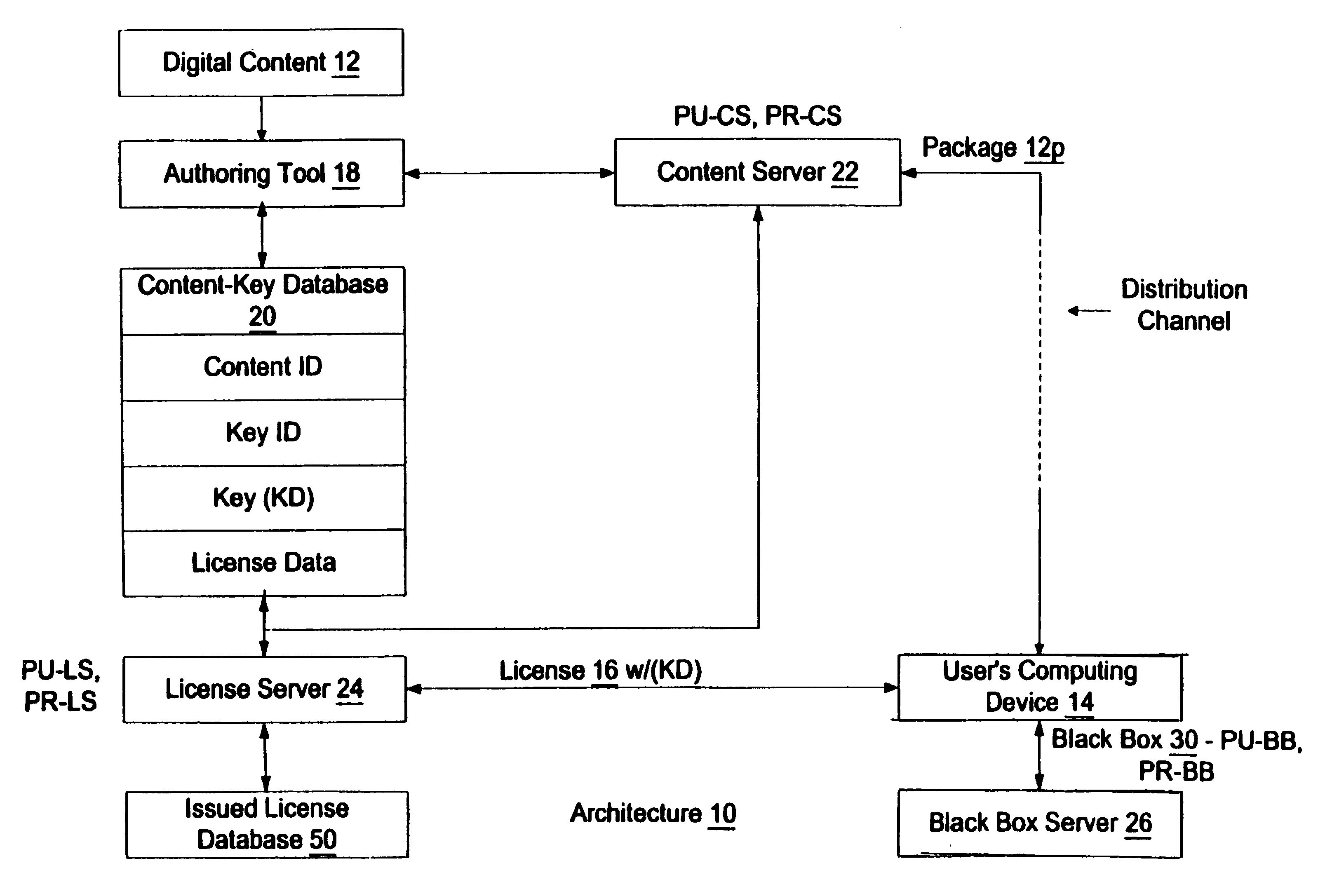
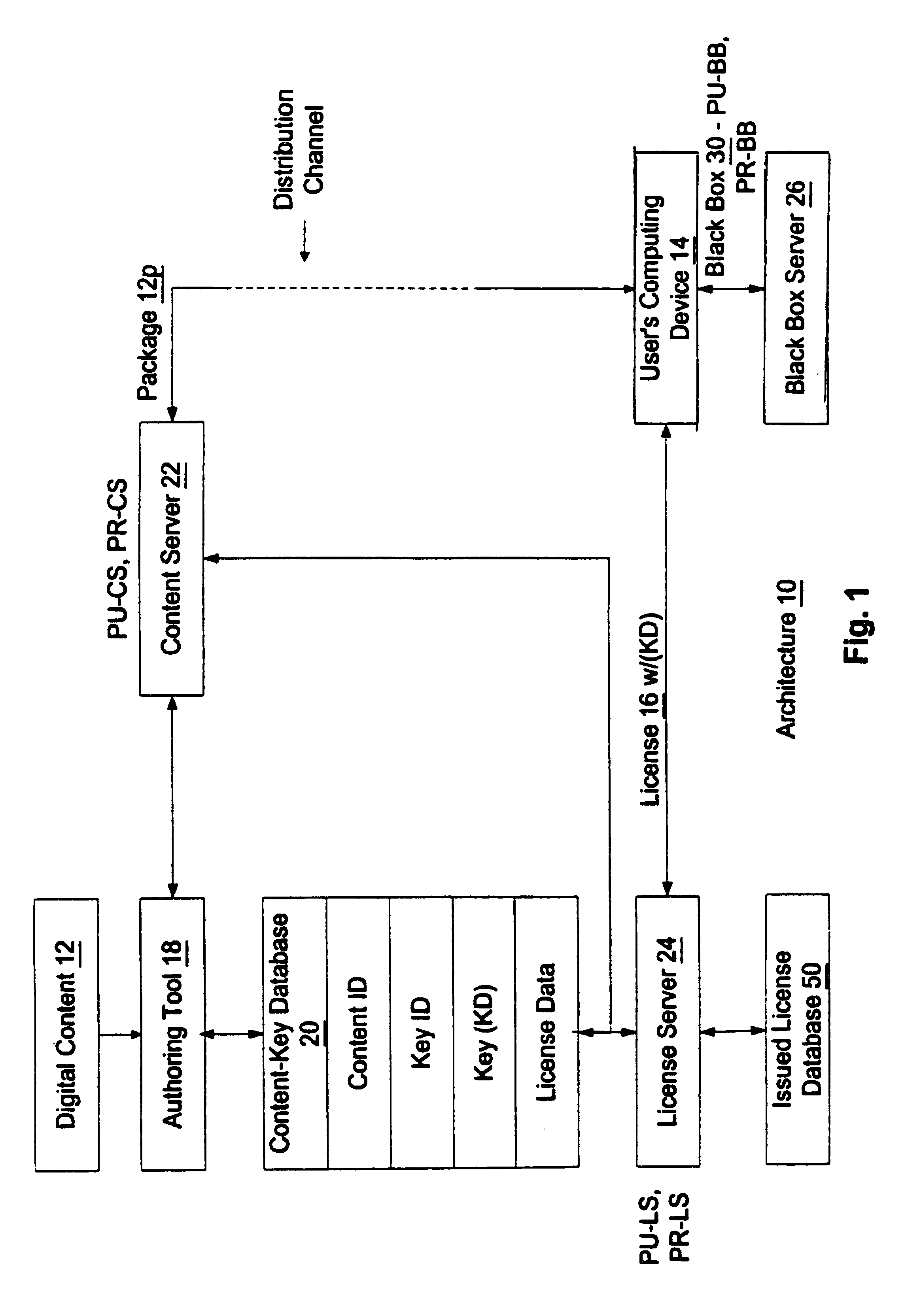
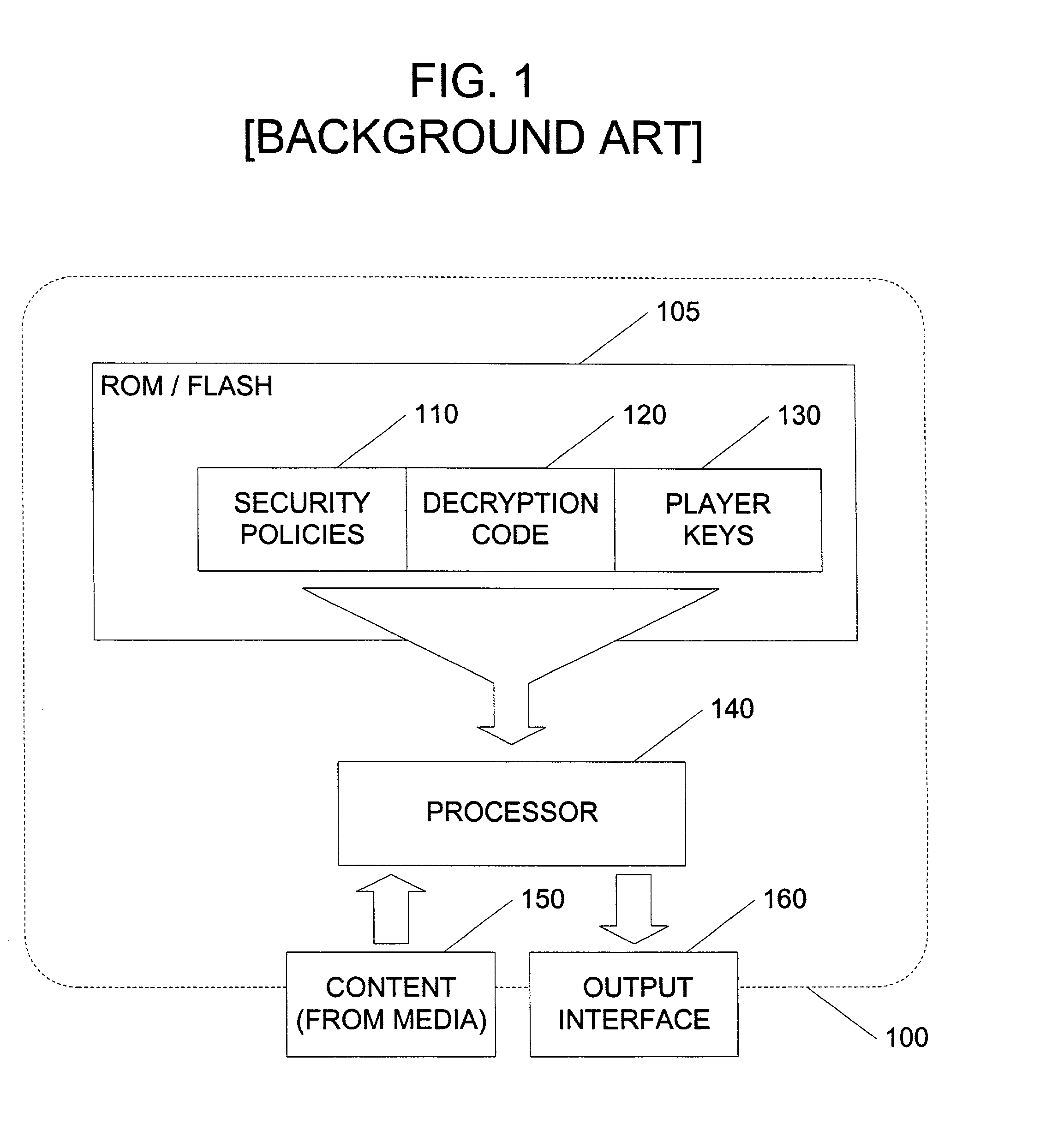
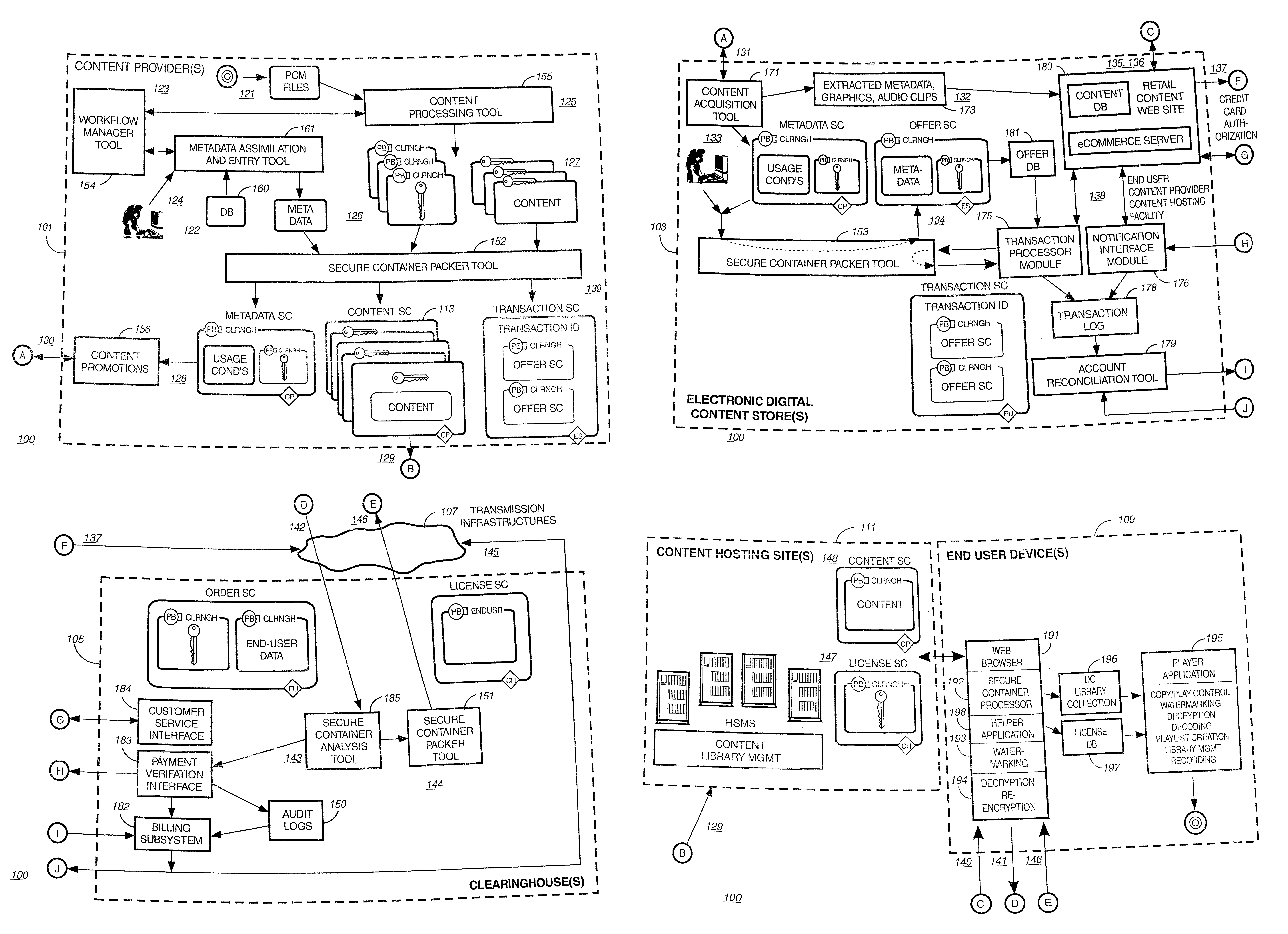
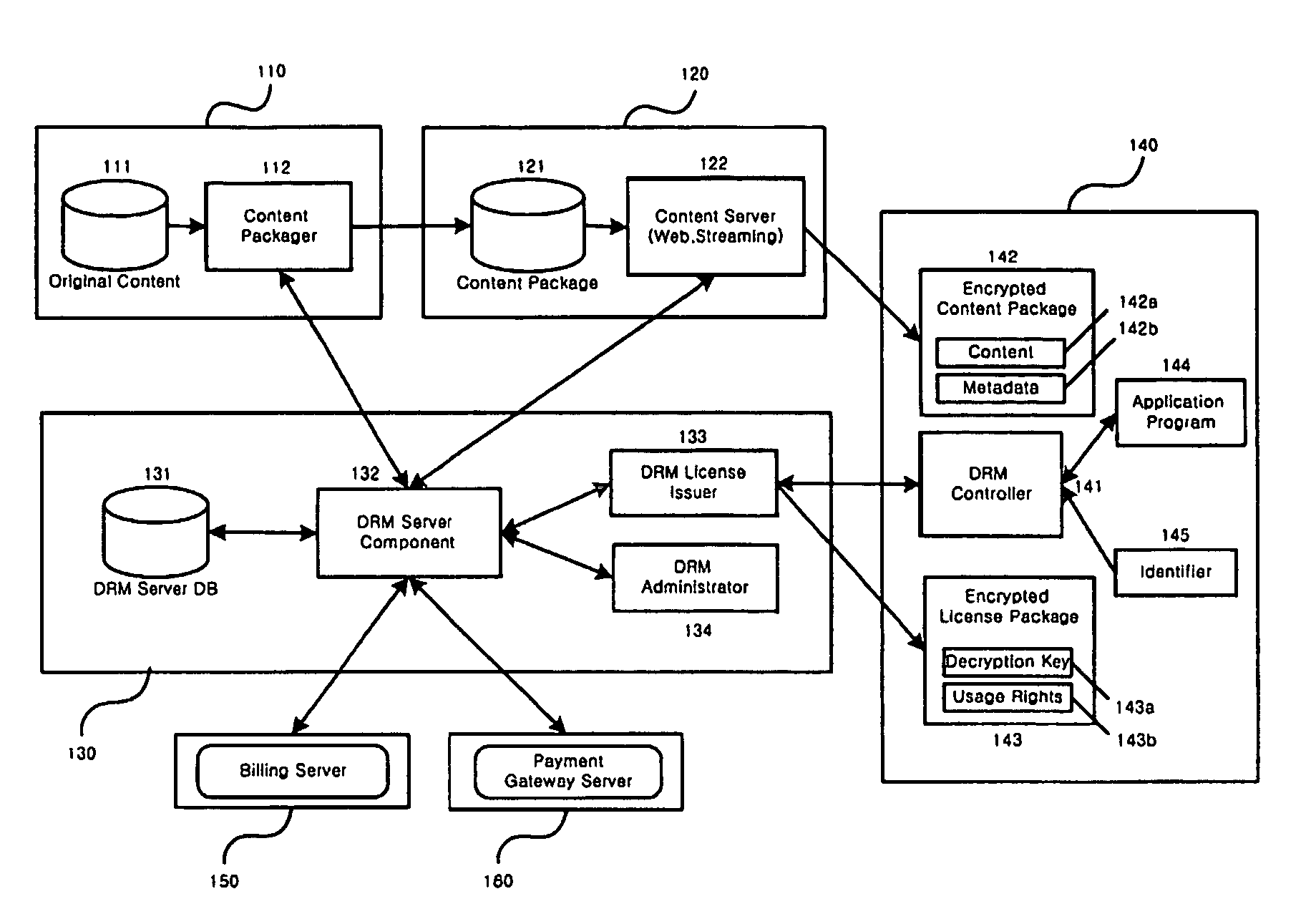
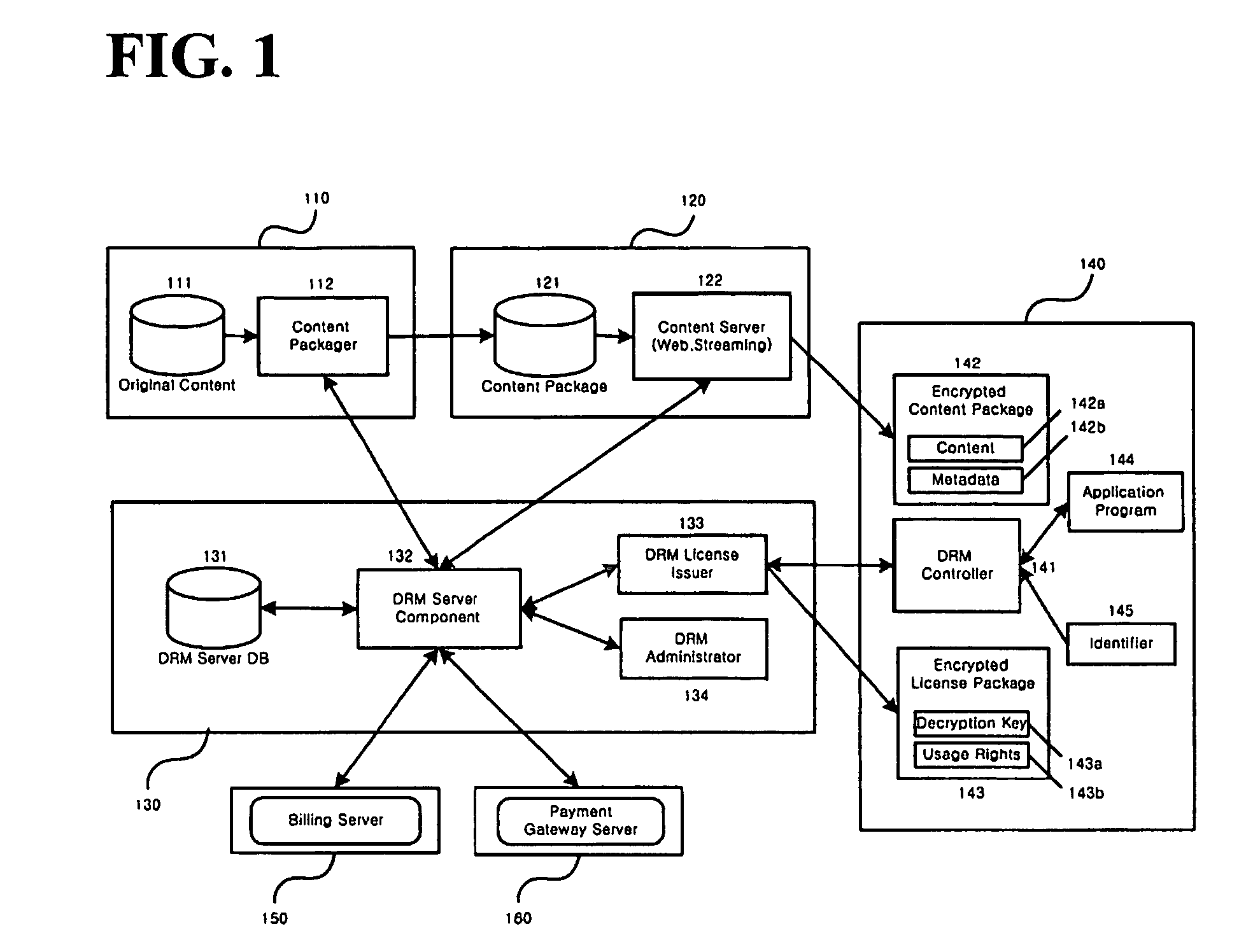
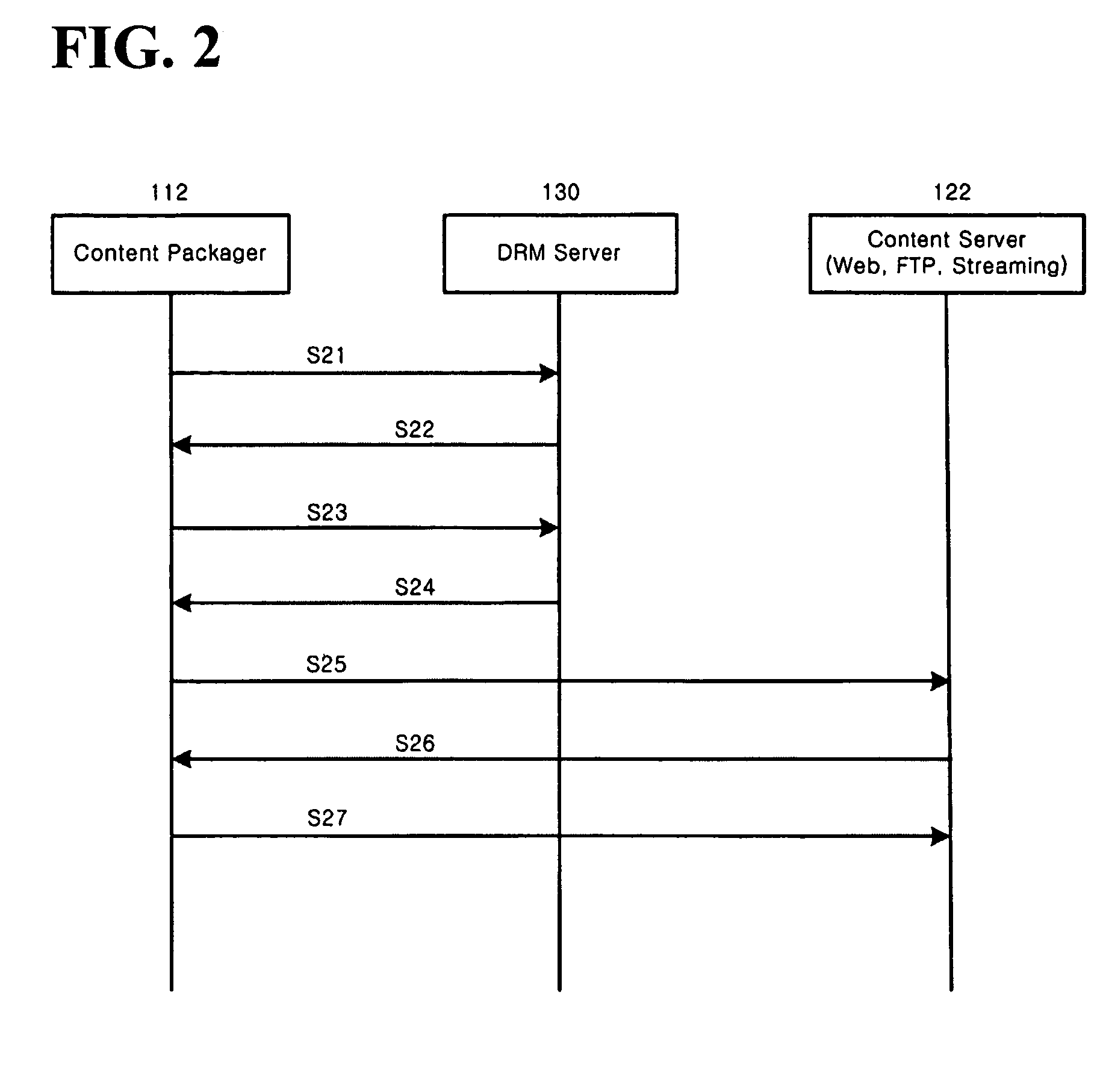
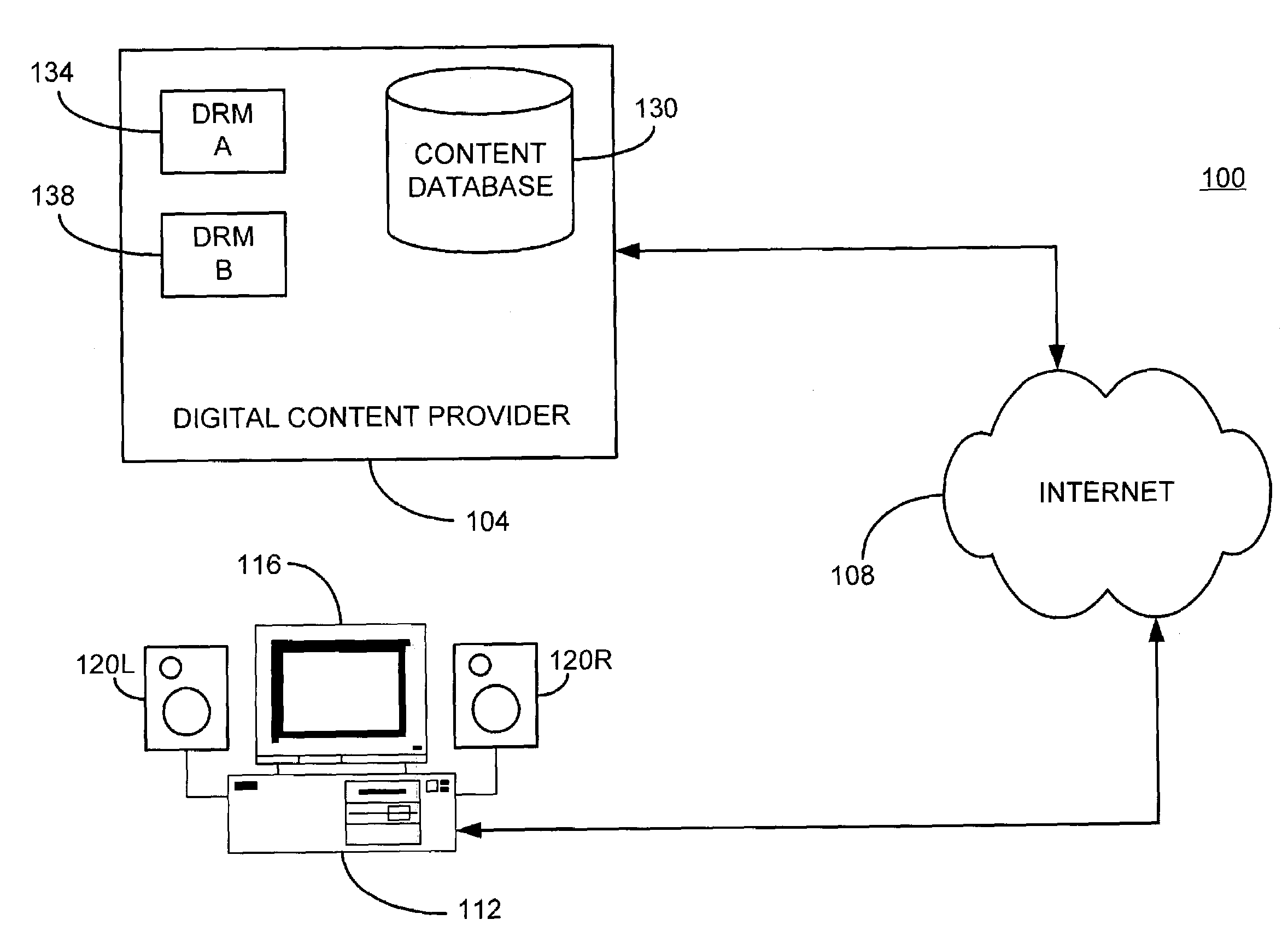
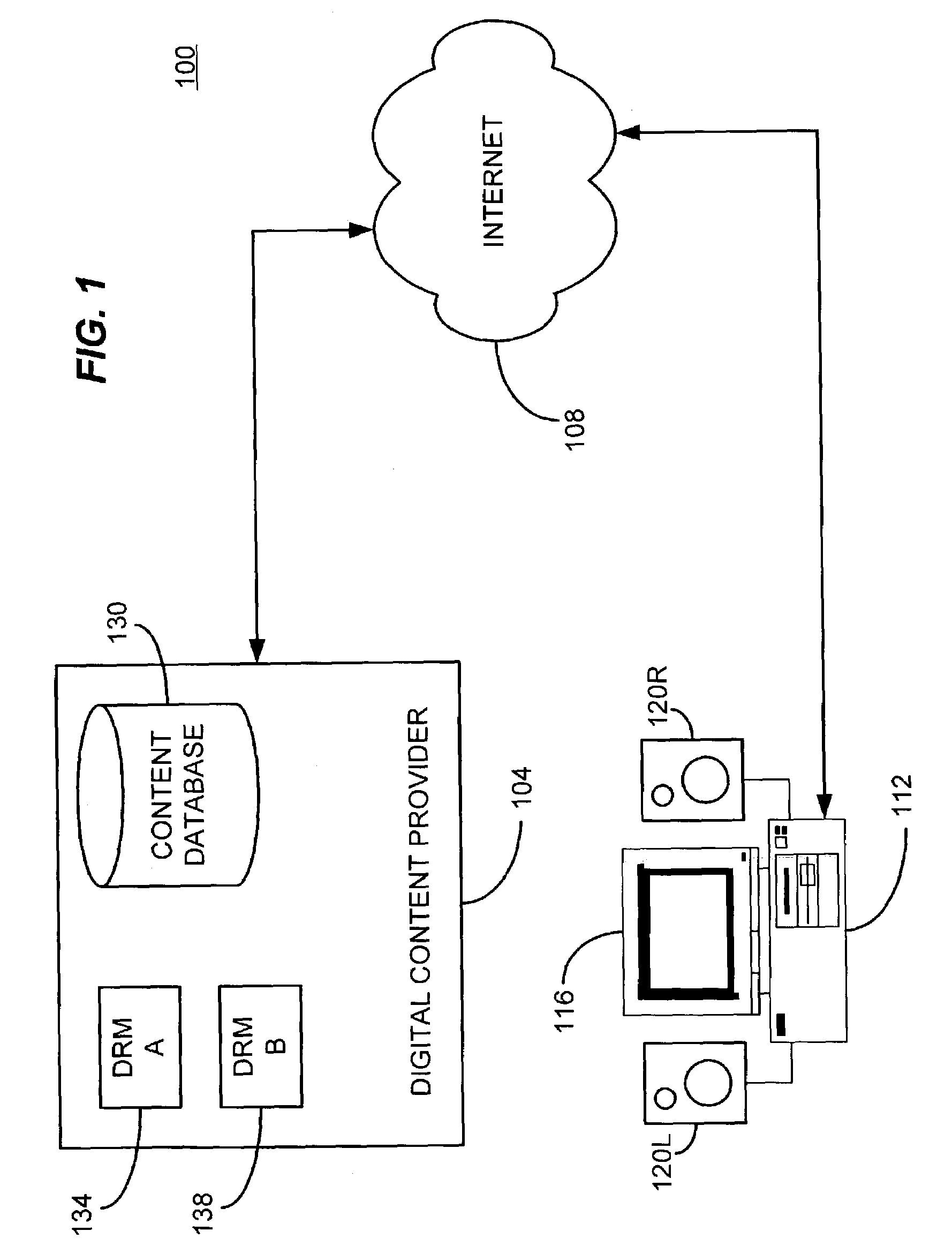
Automated method and apparatus to package digital content for electronic distribution using the identity of the source content
InactiveUS6345256B1Key distribution for secure communicationDigital data processing detailsDigital contentNumber content
A method to automatically retrieve data associated with content. An identifier is read that is stored on electronic readable medium storing content. The identifier is used to search a database for data associated with the content. Data that is associated with the content is retrieved as guided by the database. And the data retrieved is used to create a version of the content for electronic distribution. In accordance with another aspect of the invention, a computer readable medium is described to carry out the above method.
Owner:INT BUSINESS MASCH CORP
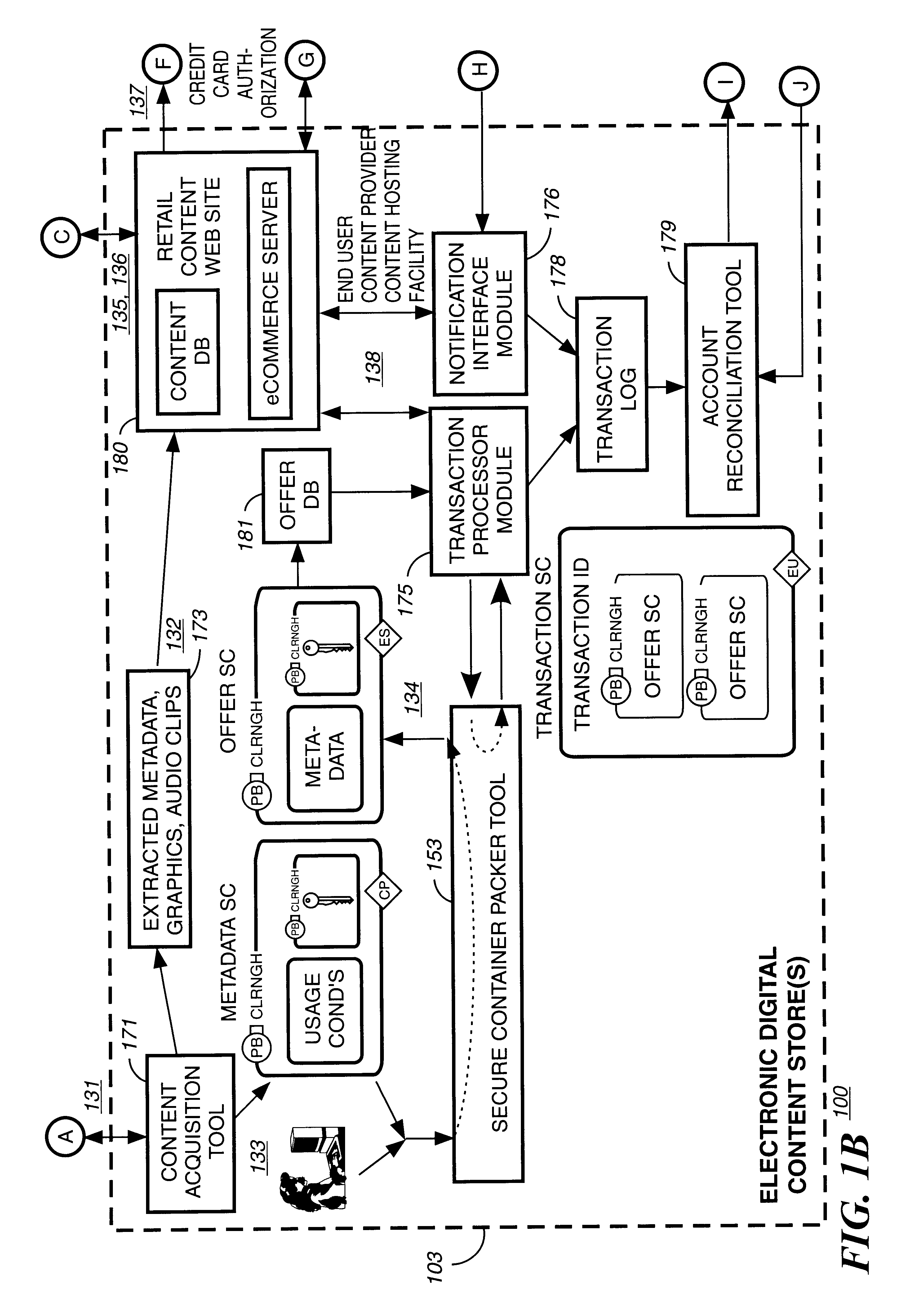
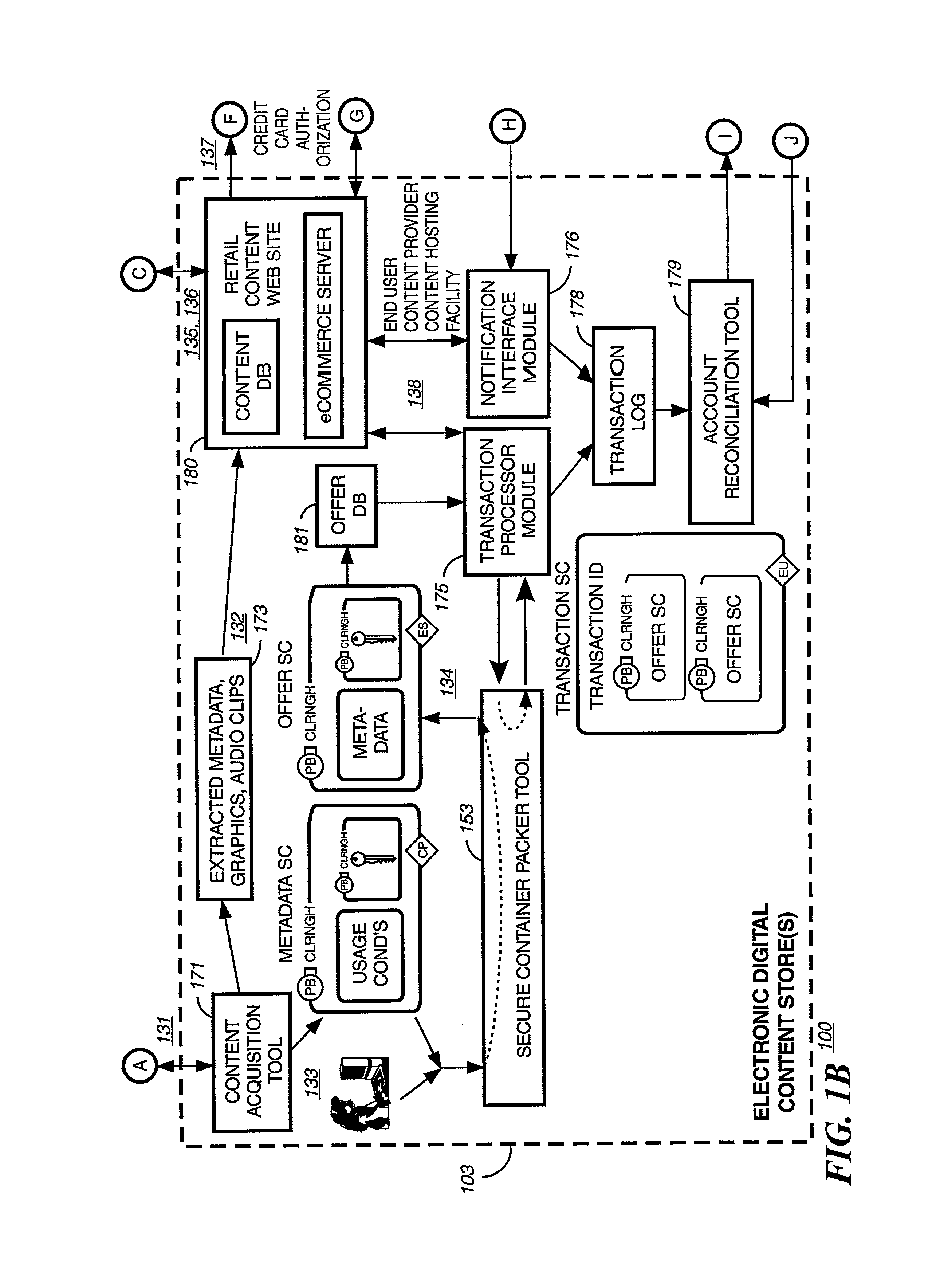
Secure electronic content distribution on CDS and DVDs
InactiveUS6611812B2Key distribution for secure communicationDigital data processing detailsDigital contentComputer terminal
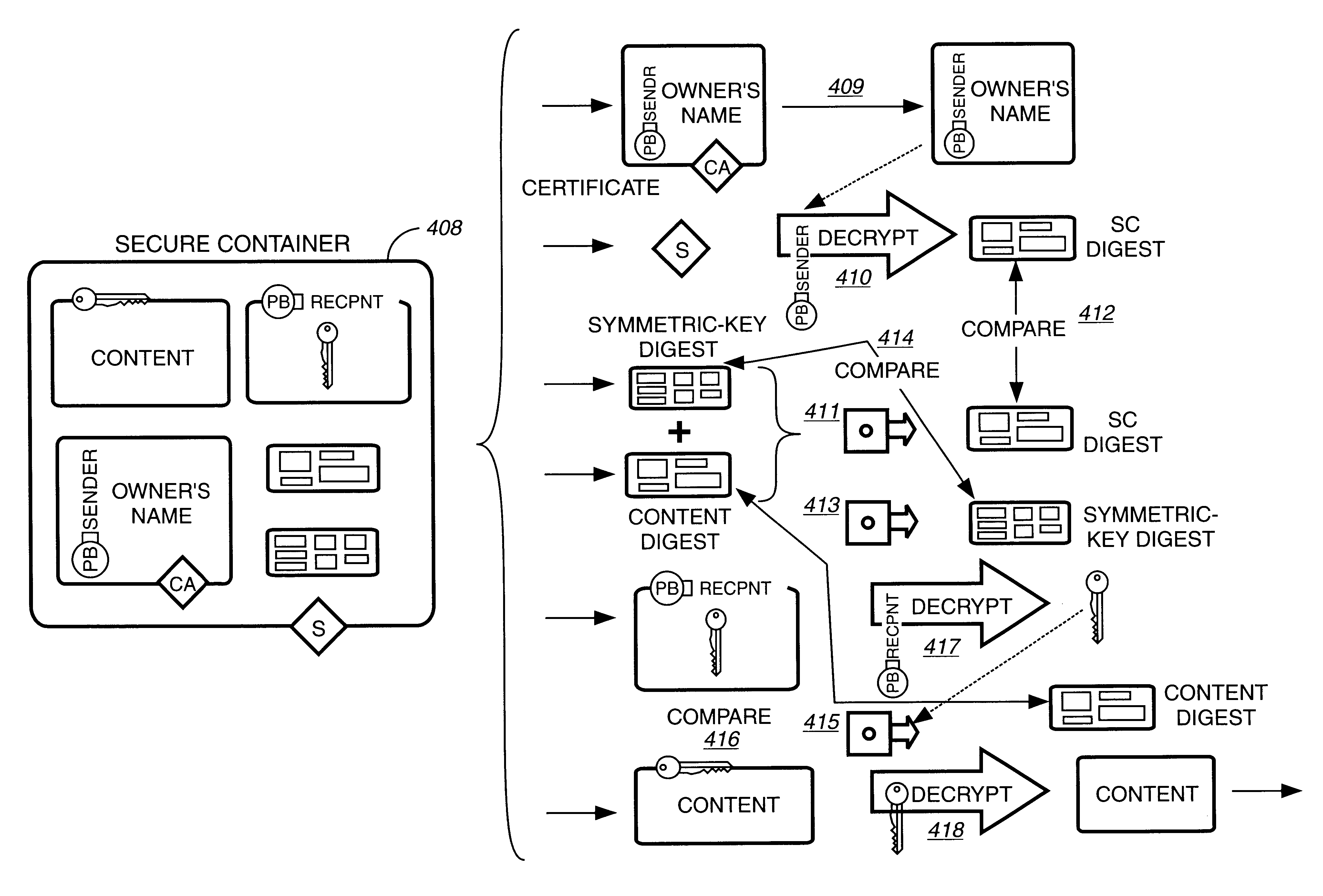
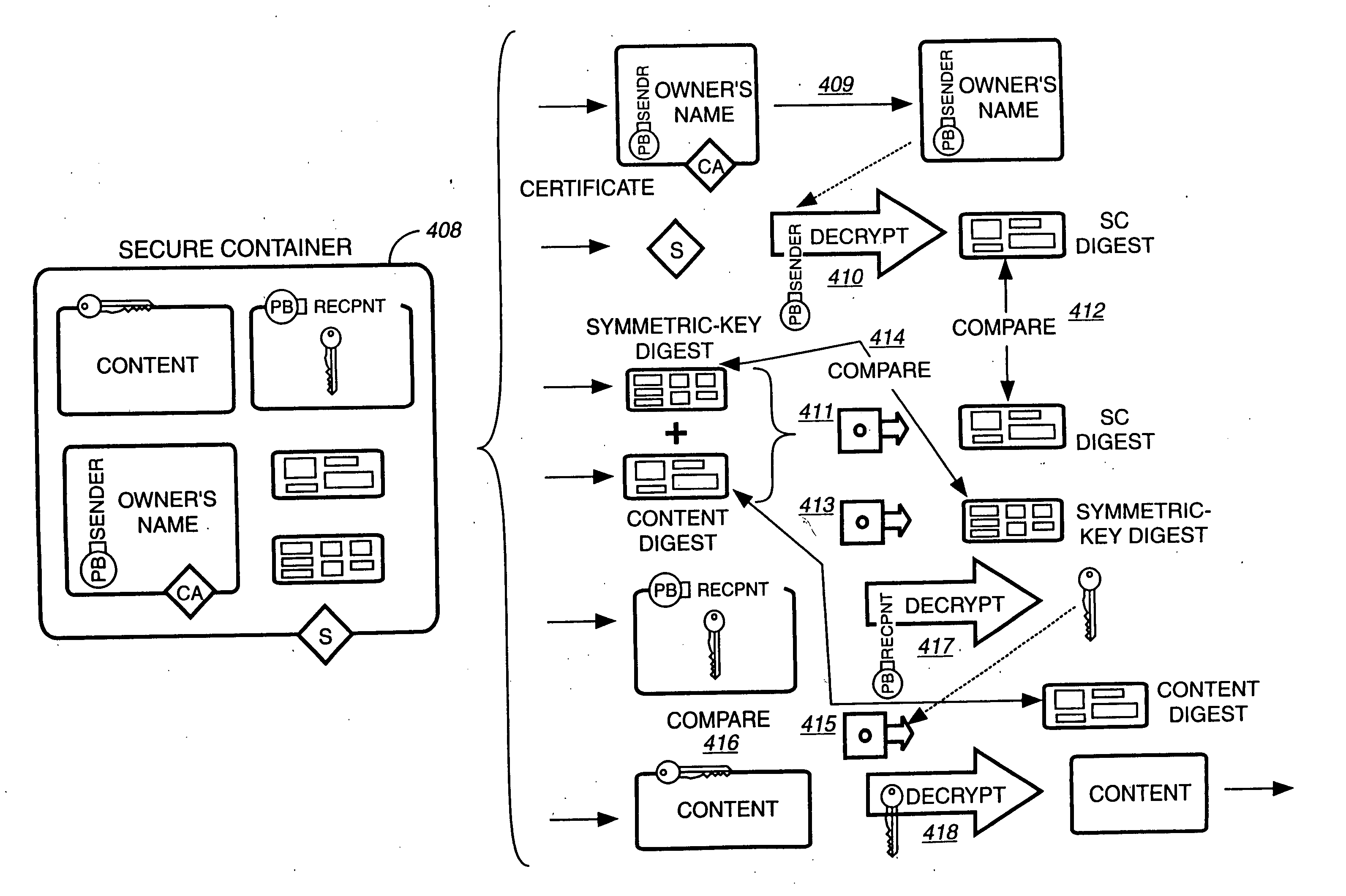
A method to delivery encrypted digital content to a end user system for playing the content comprising the steps of: reading from a computer readable medium metadata which has previously associated with the content. A user selects from the metadata associated content to decrypt and the end user system establishes a secure connection with an authorization authority for decrypting the content. The end user system receives a secure container containing the decrypting key for decrypting at least part of the previously encrypted content as permitted. The system creates a secure container using the encrypting key from a clearing house, wherein the secure container has an encrypting key therein from the end user system; transferring the secure container to the clearing house for authentication of permission to decrypt the content. The system receives from the clearing house, a secure container encrypted using the encrypting key of the end user system containing the decrypting key for decrypting at least part of the previously encrypted content stored on the computer readable medium as permitted; and playing at least part of the previously encrypted content by decrypting the secure container using the encrypting key of the end user system to access the decrypting key for decrypting at least part of the encrypted content.
Owner:WISTRON CORP
Method and apparatus to create encoded digital content
InactiveUS6263313B1Electrophonic musical instrumentsKey distribution for secure communicationDigital contentNumber content
Owner:LEVEL 3 COMM LLC
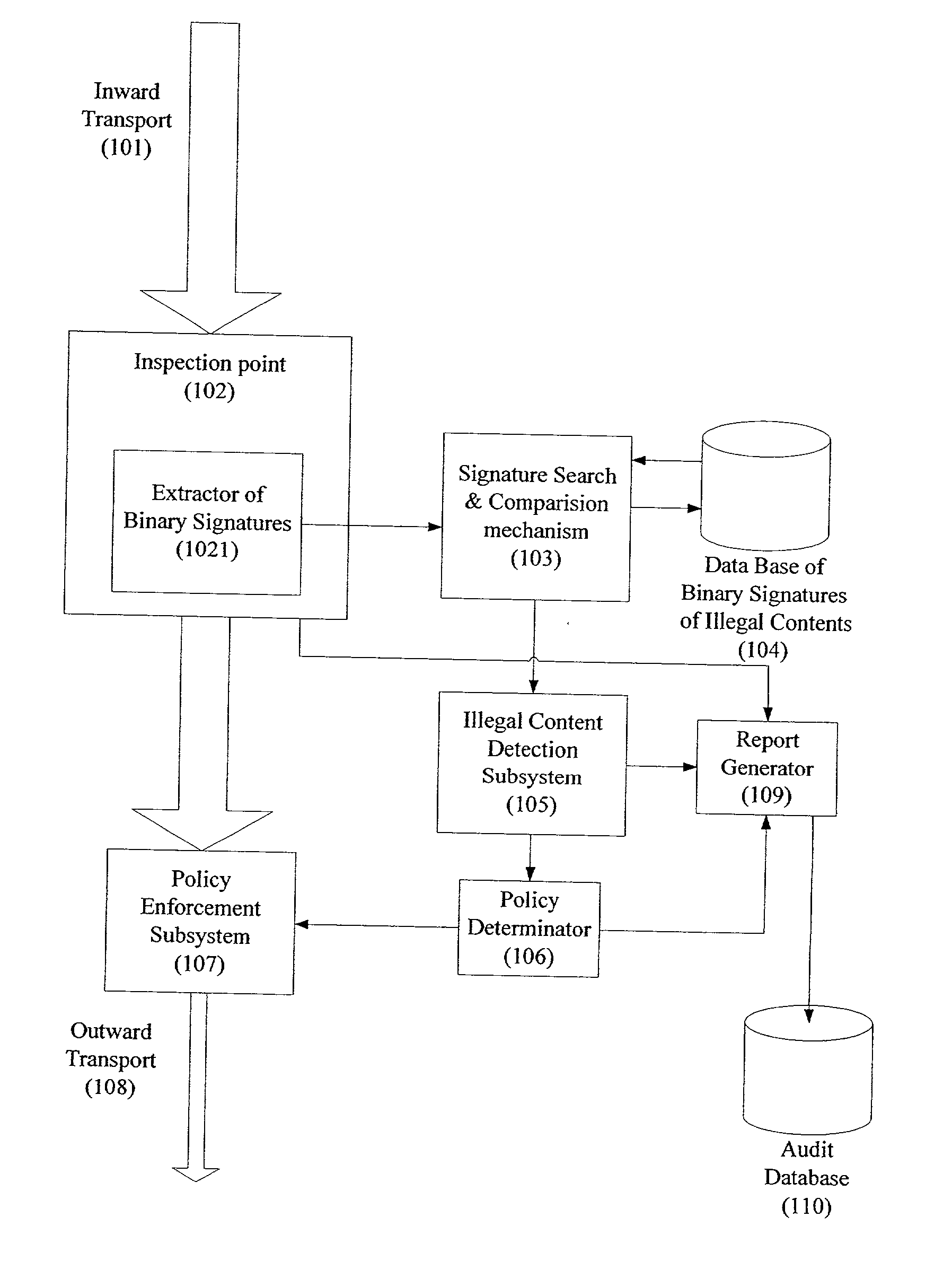
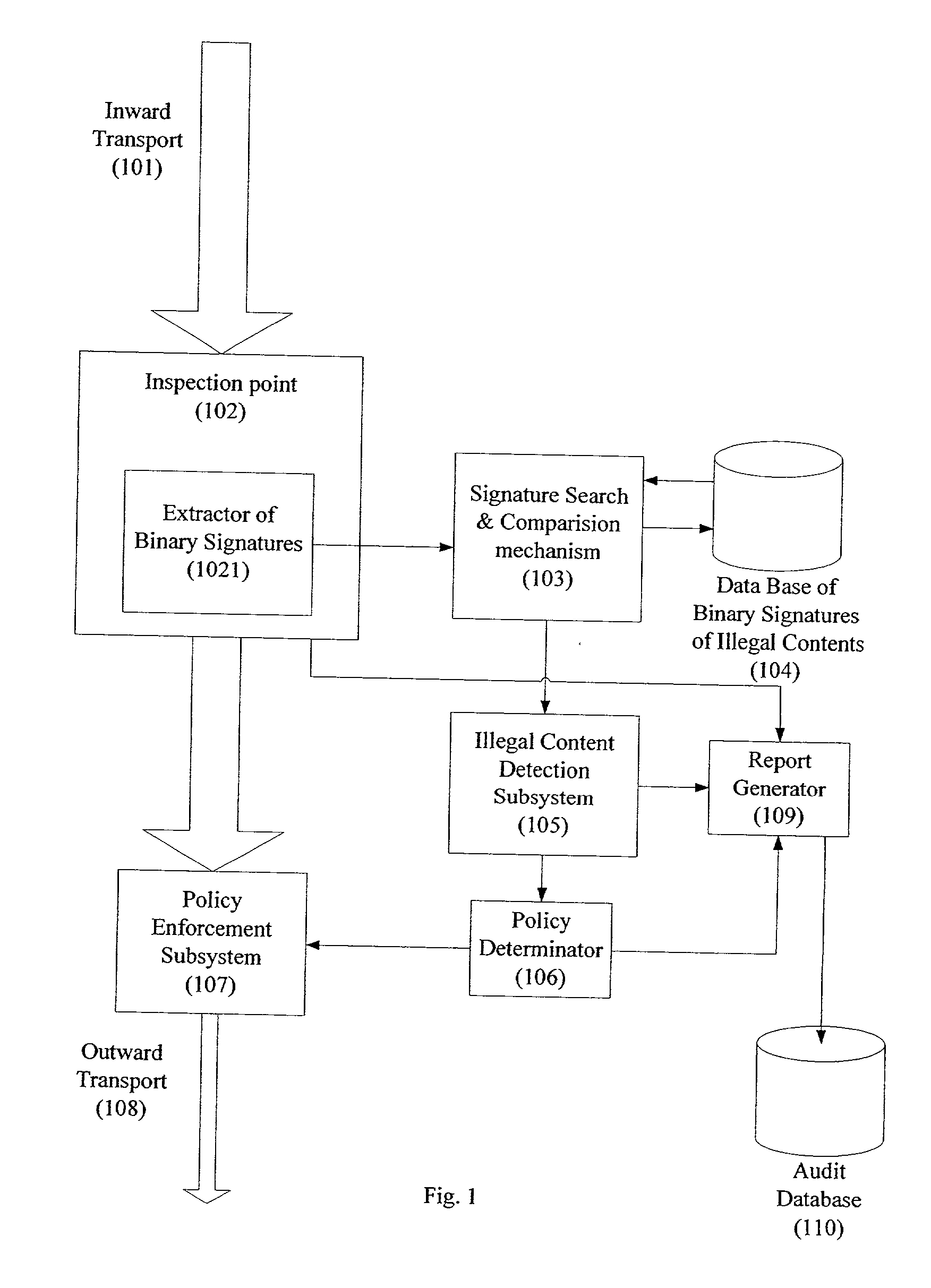
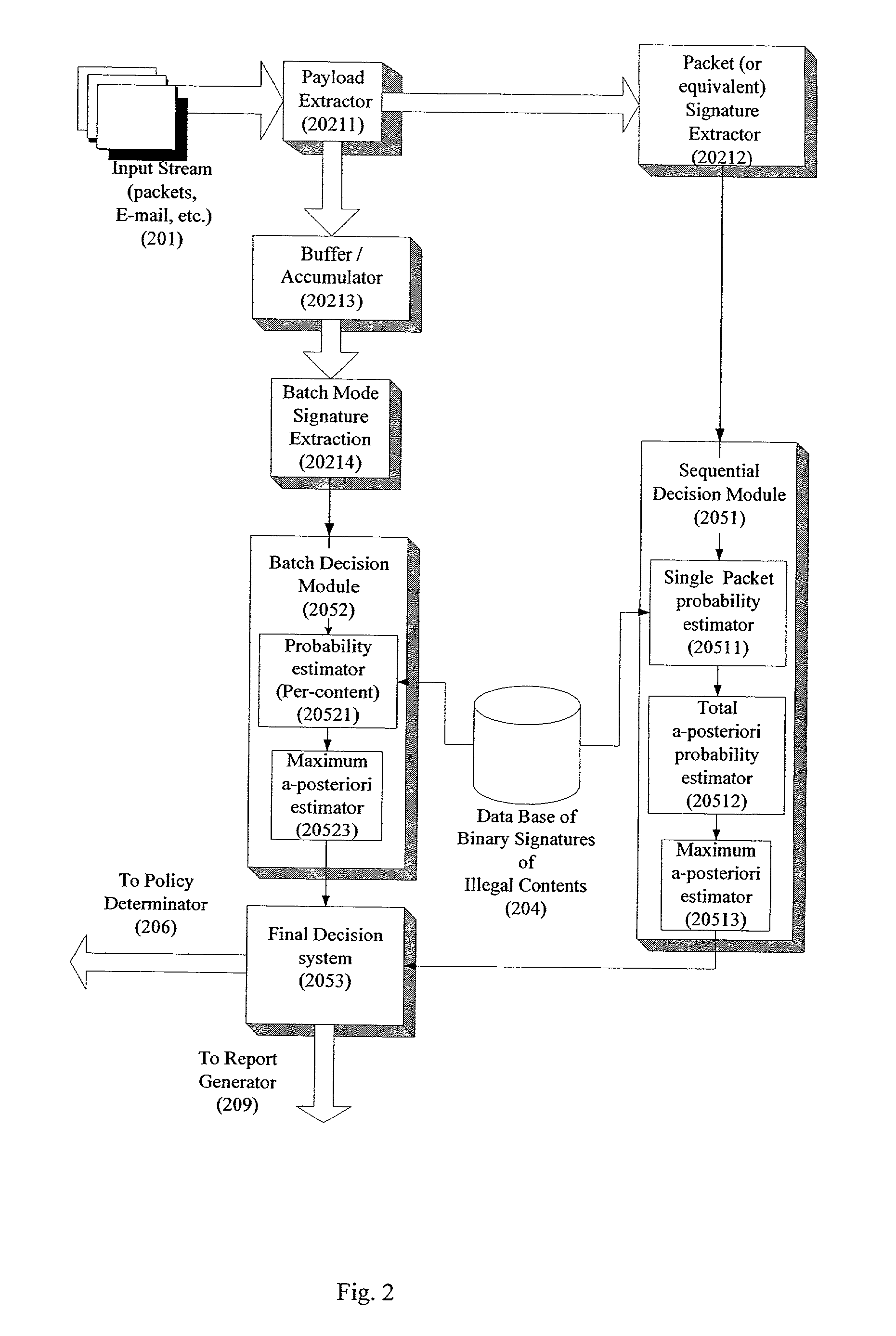
System and method for monitoring unauthorized transport of digital content
ActiveUS20020129140A1Reduce decreaseAttenuation bandwidthMemory loss protectionError detection/correctionDigital contentNumber content
A system for network content monitoring and control, comprising: a transport data monitor, connectable to a point in a network, for monitoring data being transported past said point, a signature extractor, associated with said transport data monitor, for extracting a derivation of said data, said derivation being indicative of content of said payload, a database of preobtained signatures of content whose movements it is desired to monitor, and a comparator for comparing said derivation with said preobtained signatures, thereby to determine whether said payload comprises any of said content whose movements it is desired to monitor. The monitoring result may be used in bandwidth control on the network to restrict transport of the content it is desired to control.
Owner:FORCEPOINT LLC
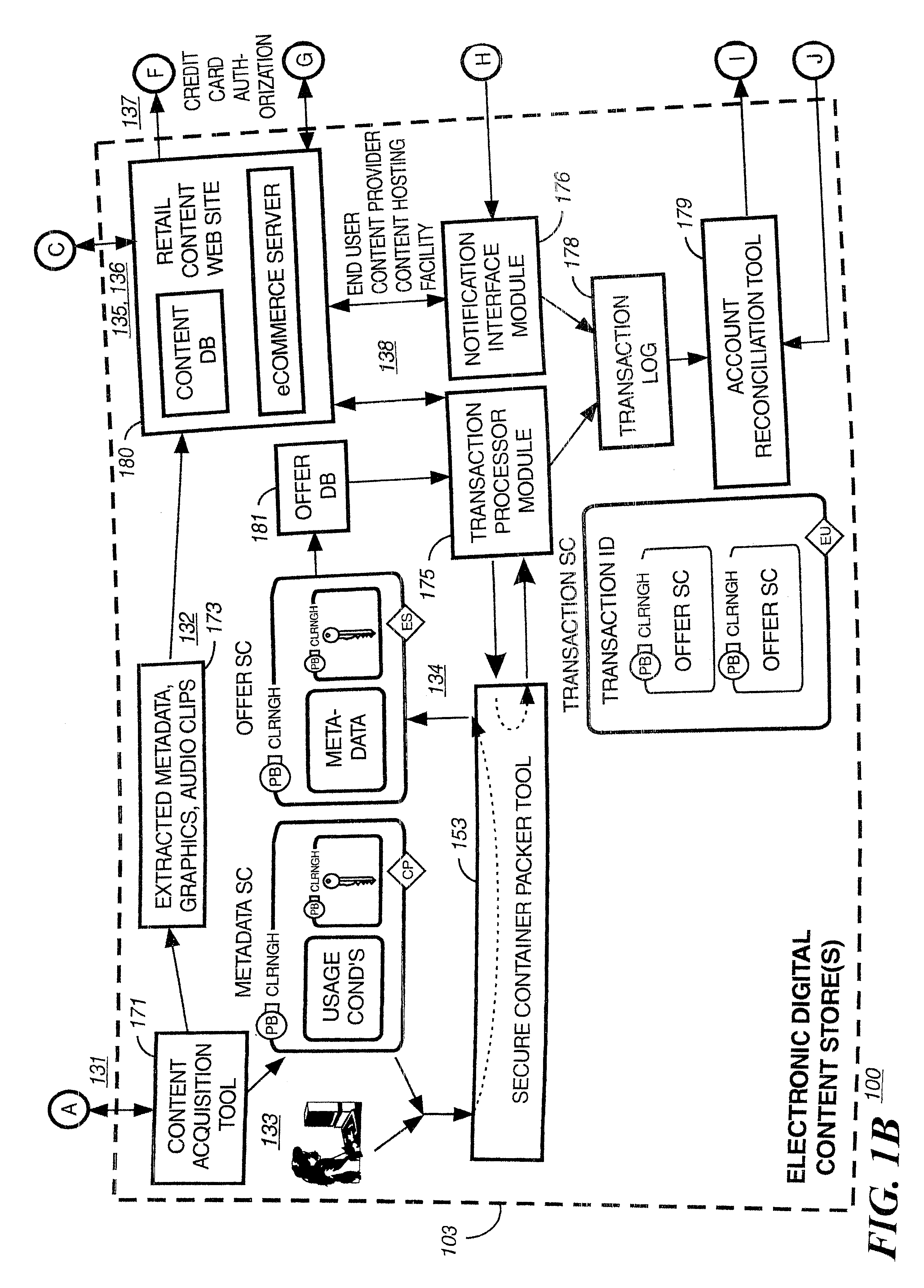
Method and apparatus for uniquely identifying a customer purchase in an electronic distribution system
InactiveUS6389403B1Key distribution for secure communicationDigital data processing detailsContent IdentifierUser device
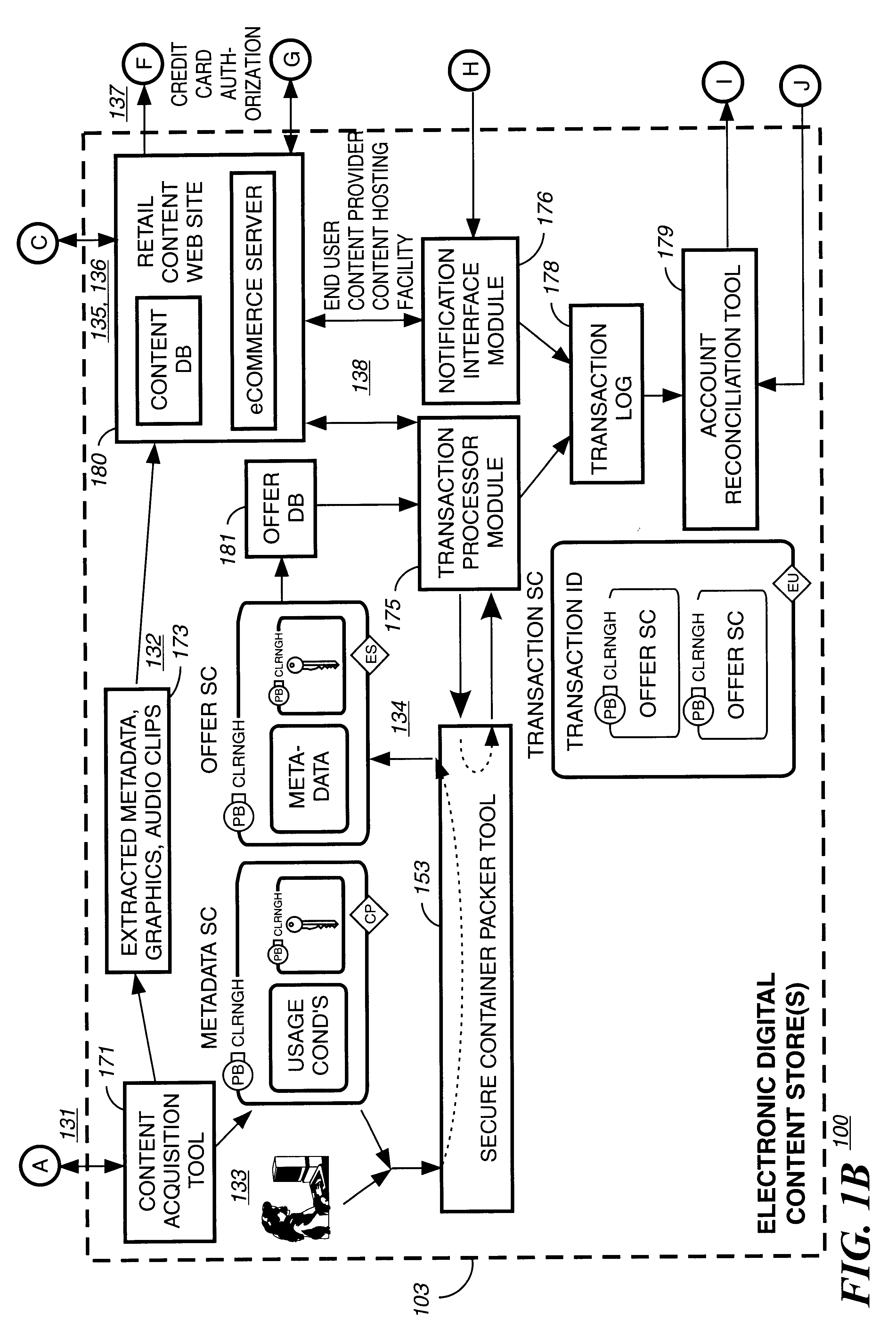
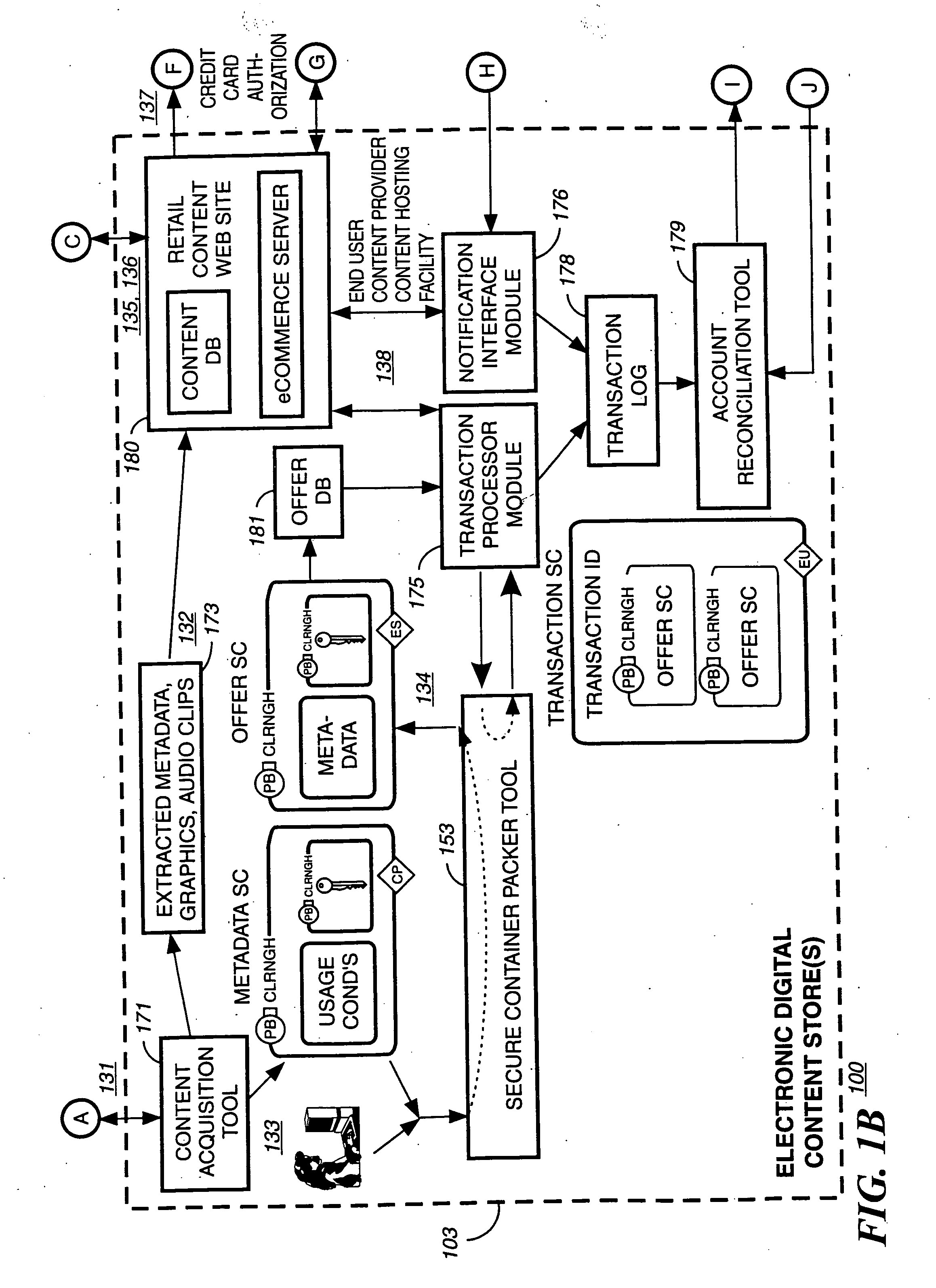
A system for tracking usage of digital content on user devices. Content sites for distributing digital content over a computer readable medium to users. The content sites associate unique content identifier with the content associated. Electronic stores coupled to a network sell licenses to play digital content data to users. The licenses contain a unique transaction identifier for uniquely identifying the transaction, and the licenses contain a unique item identifier for uniquely identifying at least one item in the transaction. Content players, which receive from the network the licensed content data, are used to play the licensed content data. The content players produce a purchase identifier based upon the mathematical combination of the content identifier, the transaction identifier and the item identifier.
Owner:WISTRON CORP
Method and apparatus for scheduling presentation of digital content on a personal communication device
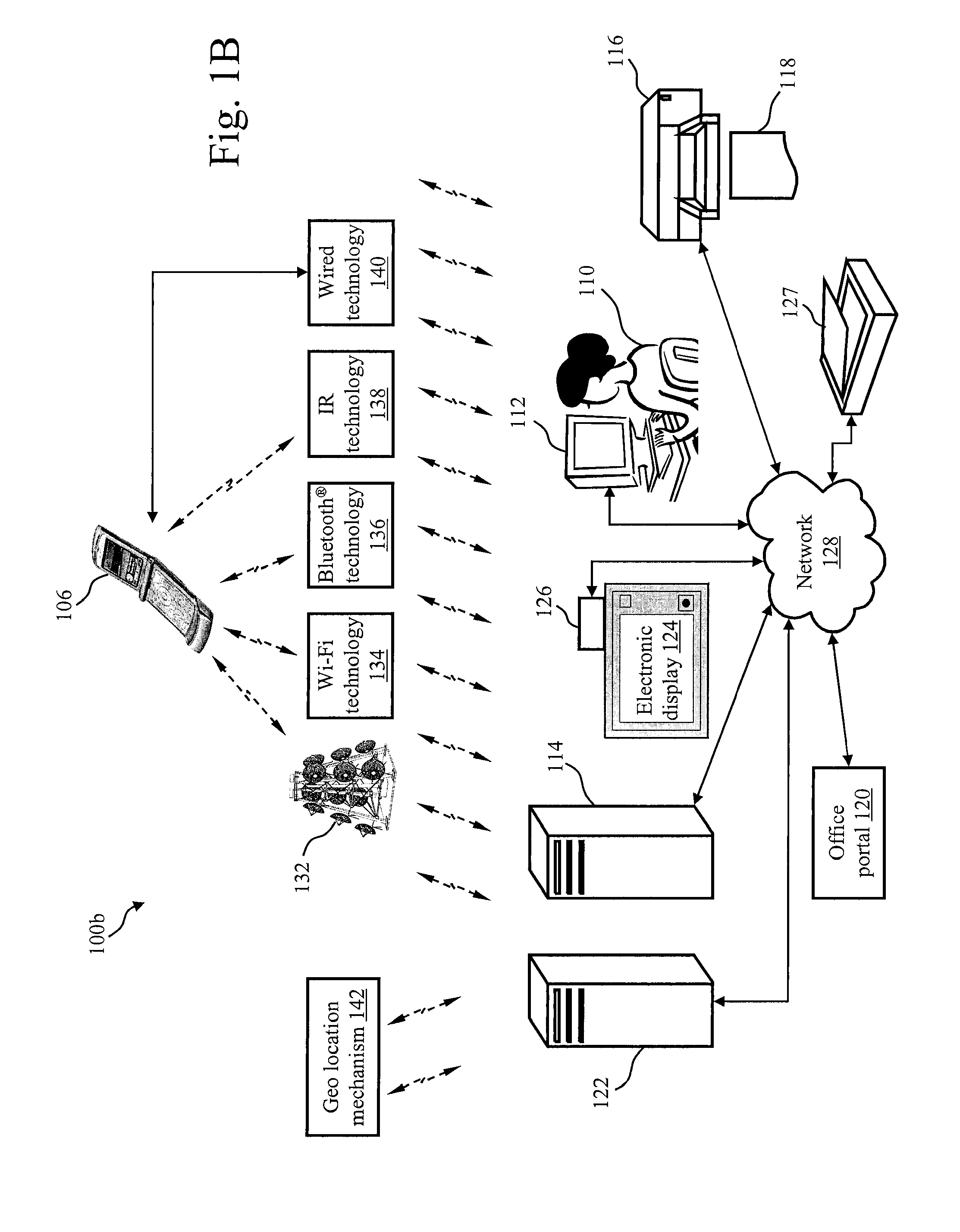
InactiveUS20050043060A1Increase probabilityLevel of controlDigital data information retrievalNetwork traffic/resource managementTelevision setLocation aware
A method and apparatus wherein a software scheduling agent resides on a communication network and / or client device, such as location-aware wireless communication appliances, television set top boxes, or other end user client devices is disclosed. The software scheduling agent is part of a probabilistic modeling system in which the scheduler operates to perform constrained random variation with selection. Digital content is generated, organized, and stored on the communication network and / or the client devices. An electronic digital content wrapper, which holds information in the form of data and metadata related to the digital content is associated with each item of digital content. Contextual profiles for each user and each item of digital content are established by the users and the network and maintained by a service provider on the communication network. The software scheduling agent compares the contextual digital content profile for each item of digital content to the contextual user profile for each user to determine which digital content should be offered for presentation to each user. The comparison and determination of which items of digital content should be offered for presentation to which users is performed by a process of constrained random variation. After the software scheduling agent determines which items of digital content would most likely be relevant or interesting to the user, the digital content is transmitted, either in whole or in part, at predetermined times over the communication network to the appropriate client devices. The digital content is then stored, either in whole or in part, in cache memory on the client device until an appropriate time when the digital content is digitally packaged and presented to particular users over those user's client devices.
Owner:WIRELESS AGENTS
Super-distribution of protected digital content
Briefly according to the present invention, a system, computer readable medium and method to deliver encrypted digital content to from a first system for playing the content to a second system for playing the content. The method on the first user system comprising the steps of: reading from a computer readable medium metadata which has previously been associated with the content; selecting from the metadata associated content to decrypt; establishing a secure connection with an authorization authority, such as a clearinghouse, for decrypting the key used to encrypt the content; receiving a secure container containing the decrypting key for decrypting at least part of the previously encrypted content as permitted; decrypting the content and then encrypting the content with a new encryption key that is generated locally on the end user system.
Owner:WISTRON CORP
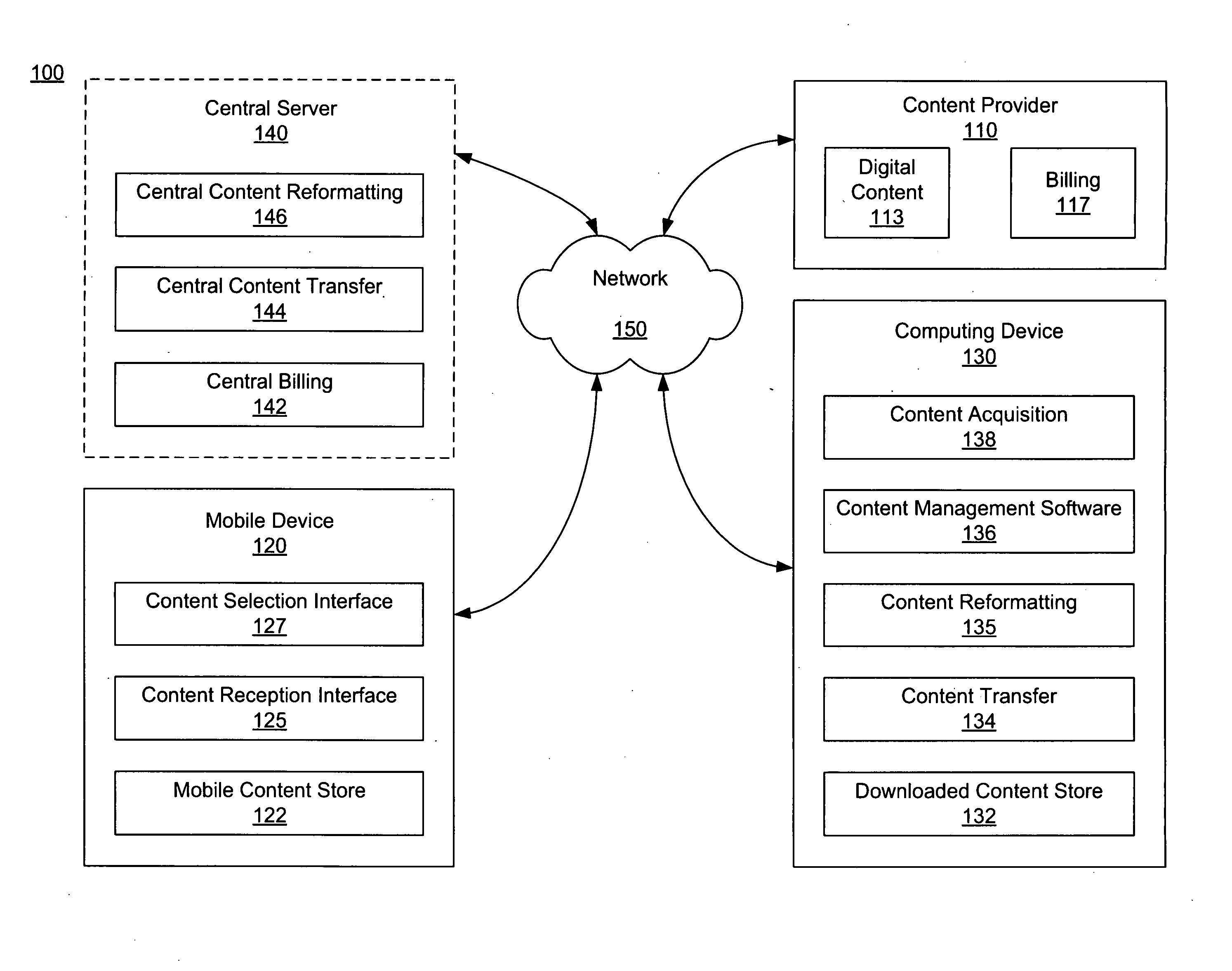
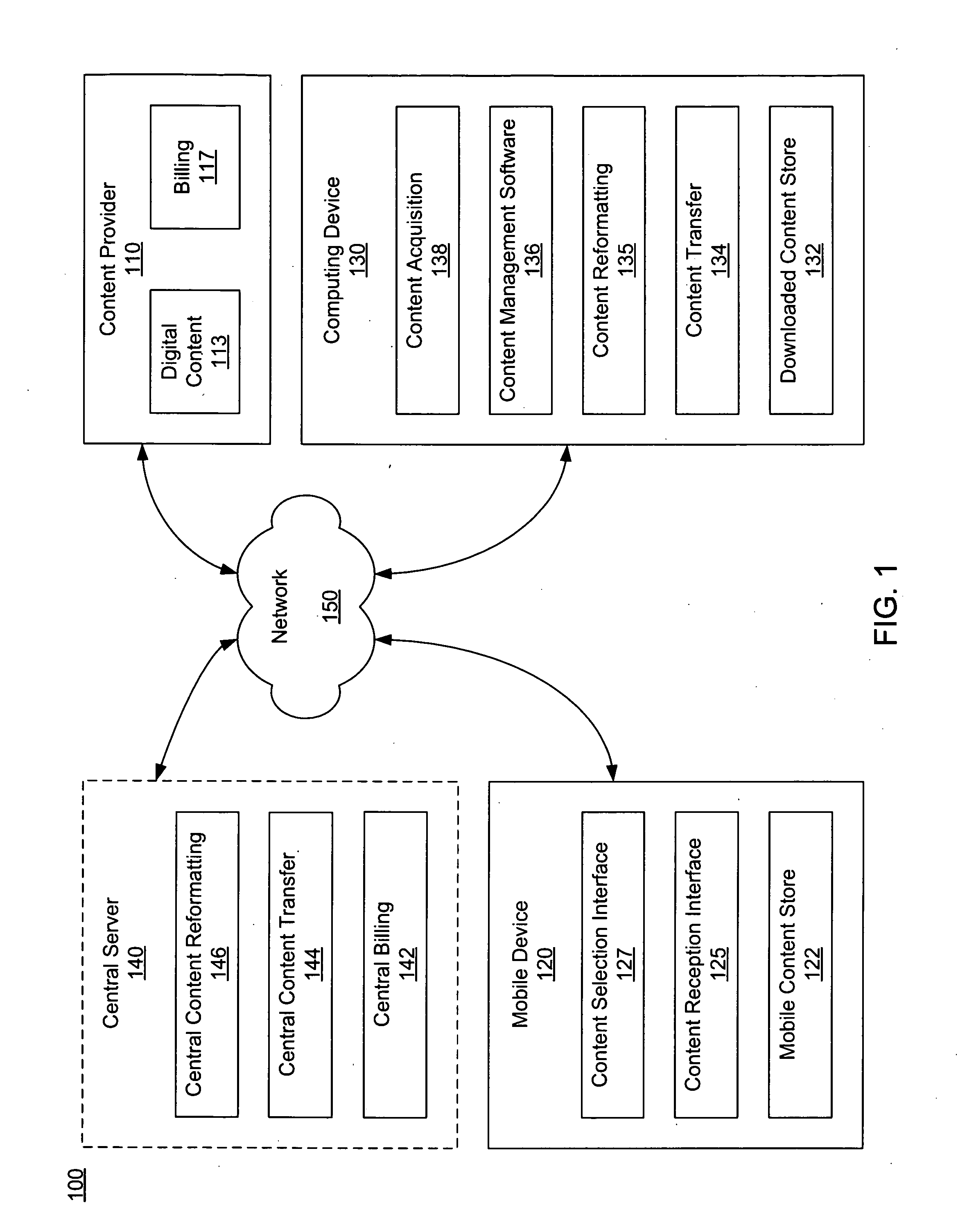
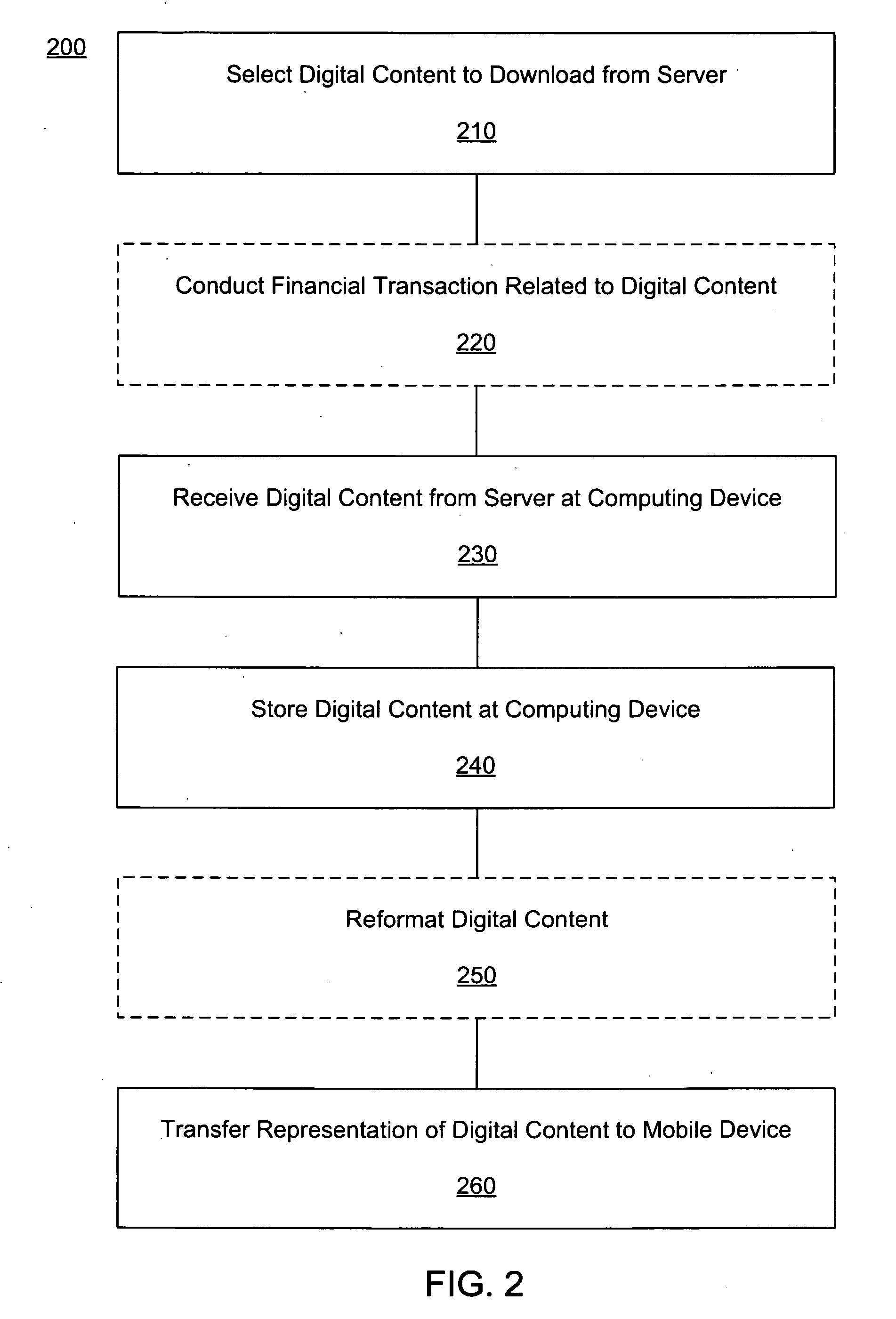
Content delivery to a mobile device from a content service
InactiveUS20090157792A1Reduce rateReduce resolutionComplete banking machinesTelephonic communicationService provisionDigital content
Systems and methods for delivering digital content to a mobile device from a digital content provider are disclosed. Digital content is selected using a selection interface on the mobile device. The selected content is then transferred to a computing device by the digital content provider and subsequently transferred to the mobile device by the computing device. In some embodiments, the digital content is reformatted before being transferred to the mobile device. The digital content may be streamed from the computer system to the mobile device. A service provider of a network through which the mobile device connects to the digital content provider may bill a user of the mobile device on behalf of the digital content provider. The digital content provider may bill the user of the mobile device using a Premium SMS service.
Owner:SEVEN NETWORKS INC
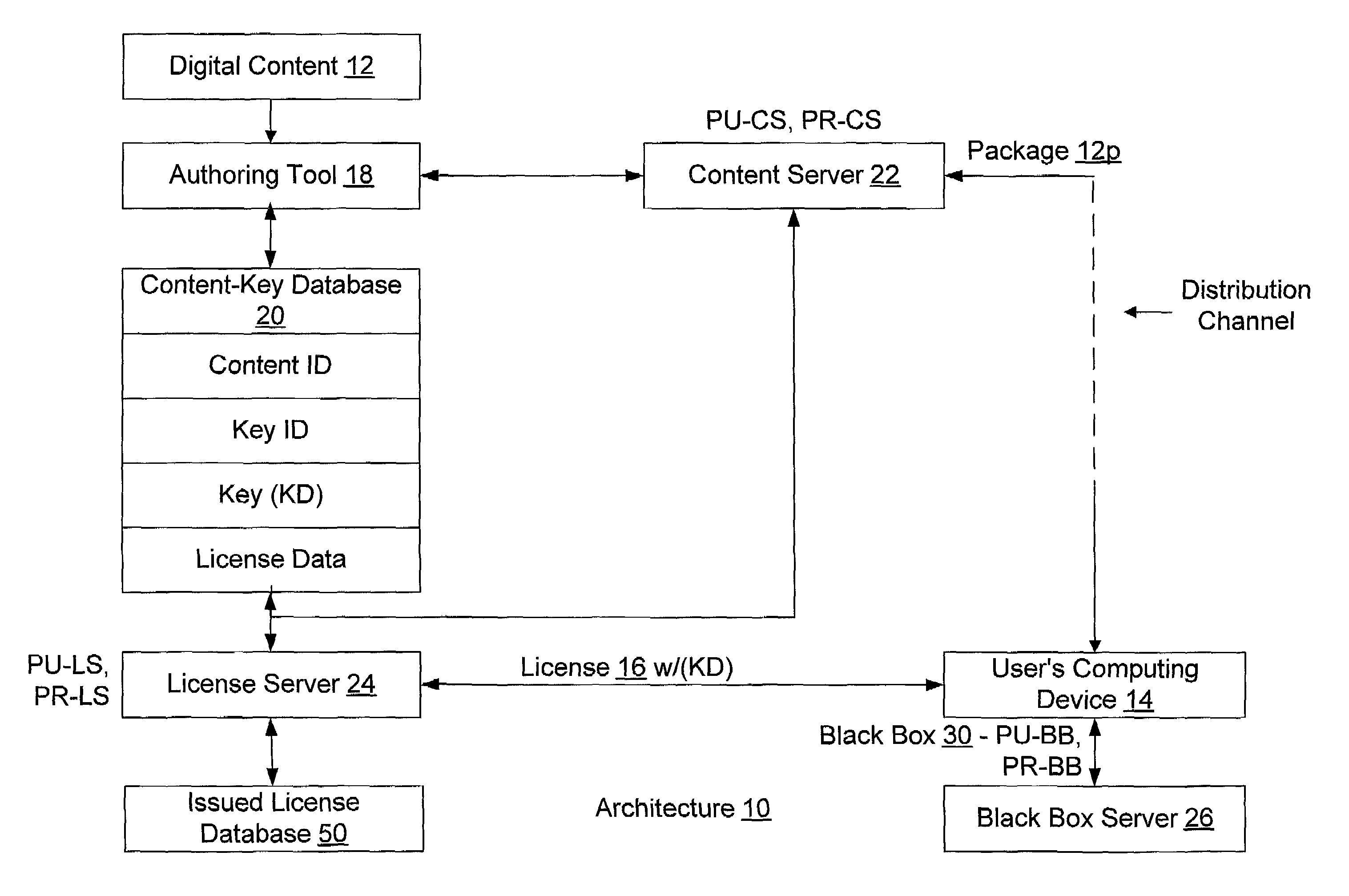
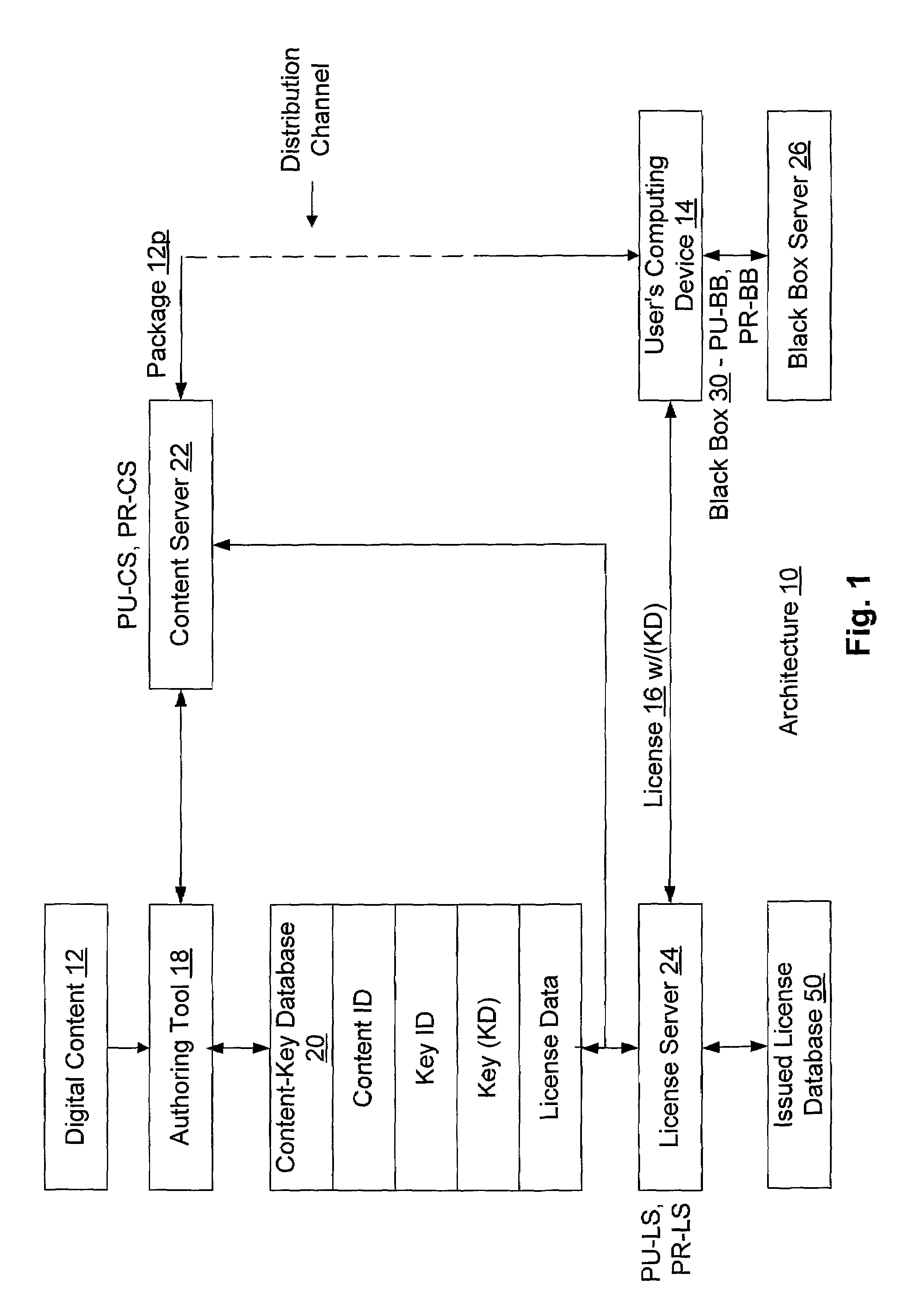
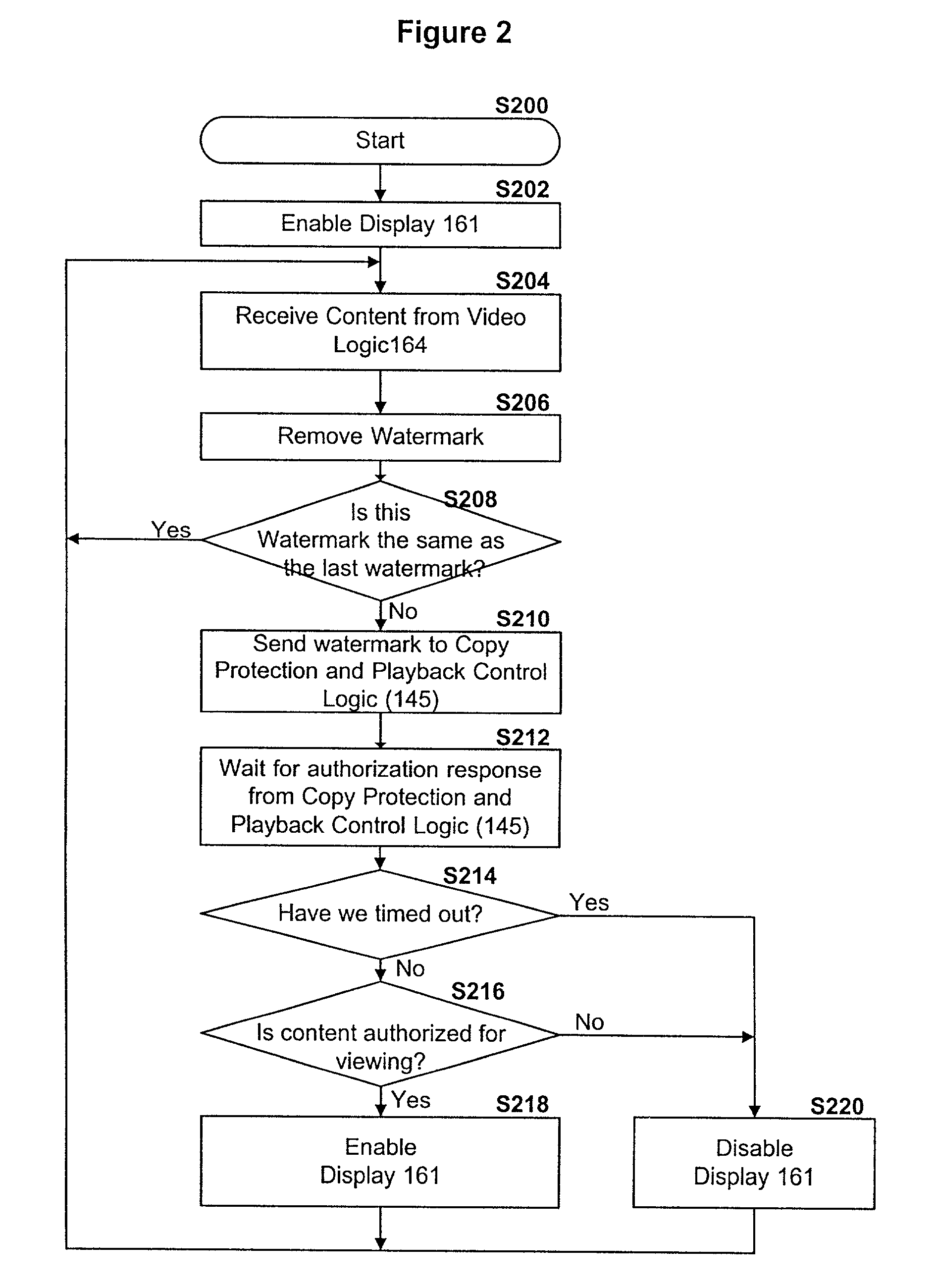
Enforcement architecture and method for digital rights management
InactiveUS7103574B1Satisfies needKey distribution for secure communicationDigital data processing detailsDigital contentNumber content
An enforcement architecture and method for implementing digital rights management are disclosed. Digital content is distributed from a content server to a computing device of a user and received, and an attempt is made to render the digital content by way of a rendering application. The rendering application invokes a Digital Rights Management (DRM) system, and such DRM system determines whether a right to render the digital content in the manner sought exists based on any digital license stored in the computing device and corresponding to the digital content. If the right does not exist, a digital license that provides such right and that corresponds to the digital content is requested from a license server, and the license server issues the digital license to the DRM system. The computing device receives the issued digital license and stores the received digital license thereon.
Owner:MICROSOFT TECH LICENSING LLC
Client content management and distribution system
InactiveUS20010010046A1Wide bandwidthBroadcast transmission systemsPayment architectureGraphicsGraphical user interface
A method for distribution to and management of an inventory of digital content in a digital content vending machine, DCVM. The DCVM includes an infrastructure and an inventory in a client on a personal computer, PC. The infrastructure presents a graphical user interface on the client containing a plurality of stores operated by vendors. Customers shop in the stores by viewing information about and selecting assets inventory. One or more master servers are provided to update the infrastructure and inventory.
Owner:DIGITAL DELIVERY NETWORKS
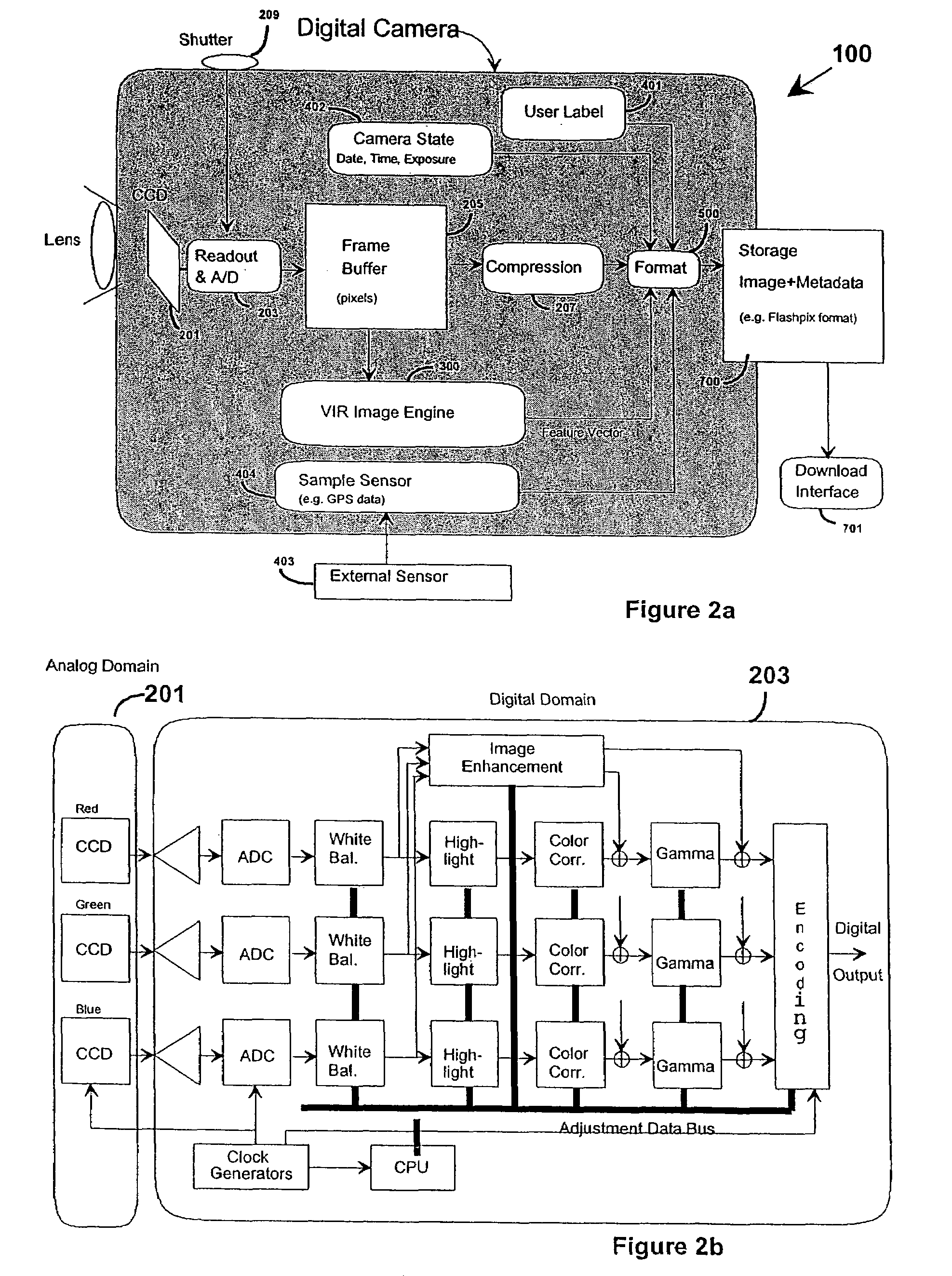
Embedded metadata engines in digital capture devices
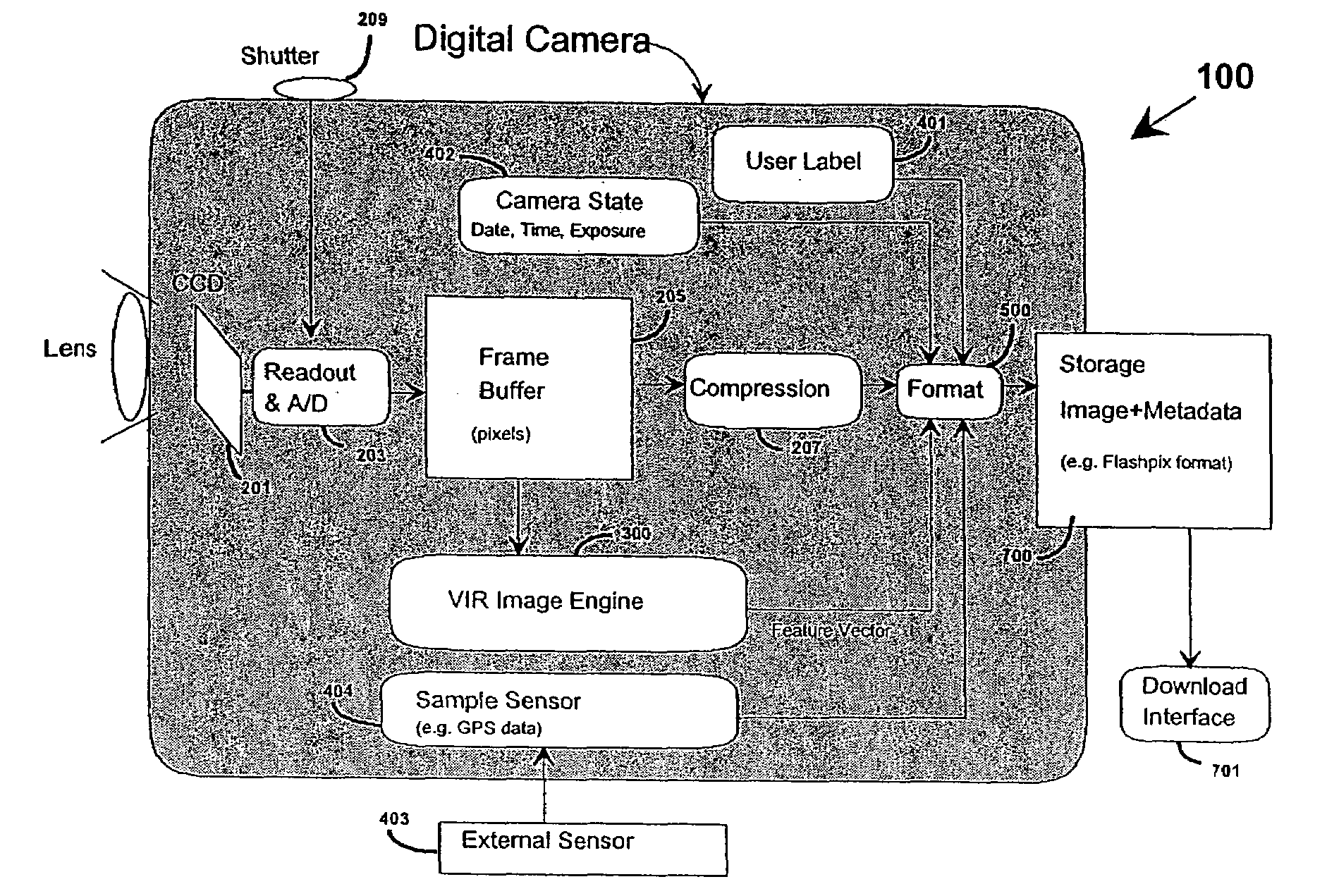
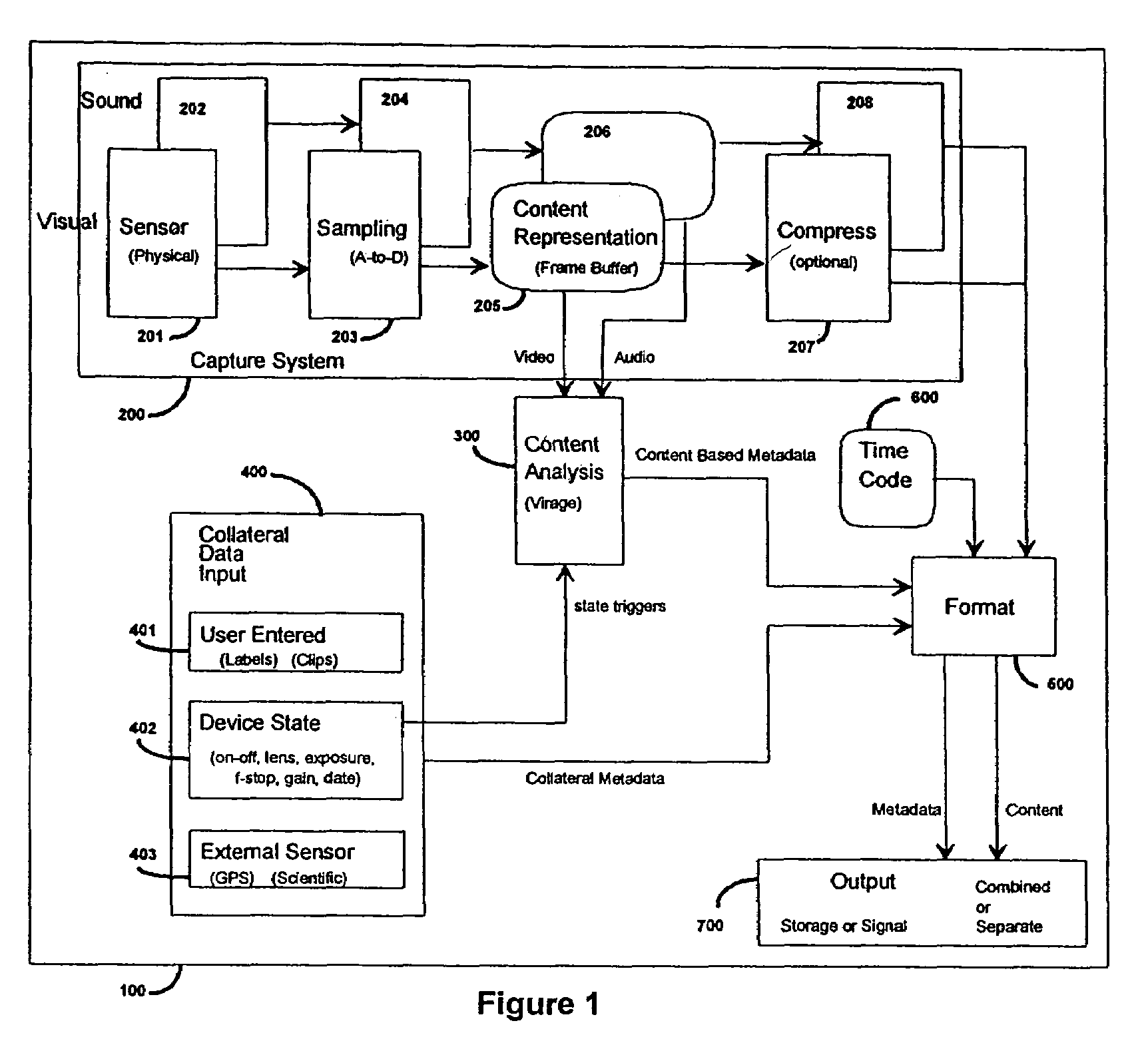
InactiveUS7403224B2Improving access and utilizationLow costTelevision system detailsColor television signals processingDigital videoDigital content
A digital capture system, such as a digital still camera or digital video recorder, has an embedded real-time content-based analysis function in the capture device to extract metadata from the digital signals. In one embodiment, metadata (descriptive information about the digital content) is formatted and stored separately from the content. In another embodiment, the metadata may be formatted and combined with the digital content in a container format such as MPEG-7, QuickTime, or FlashPix.
Owner:MICRO FOCUS LLC
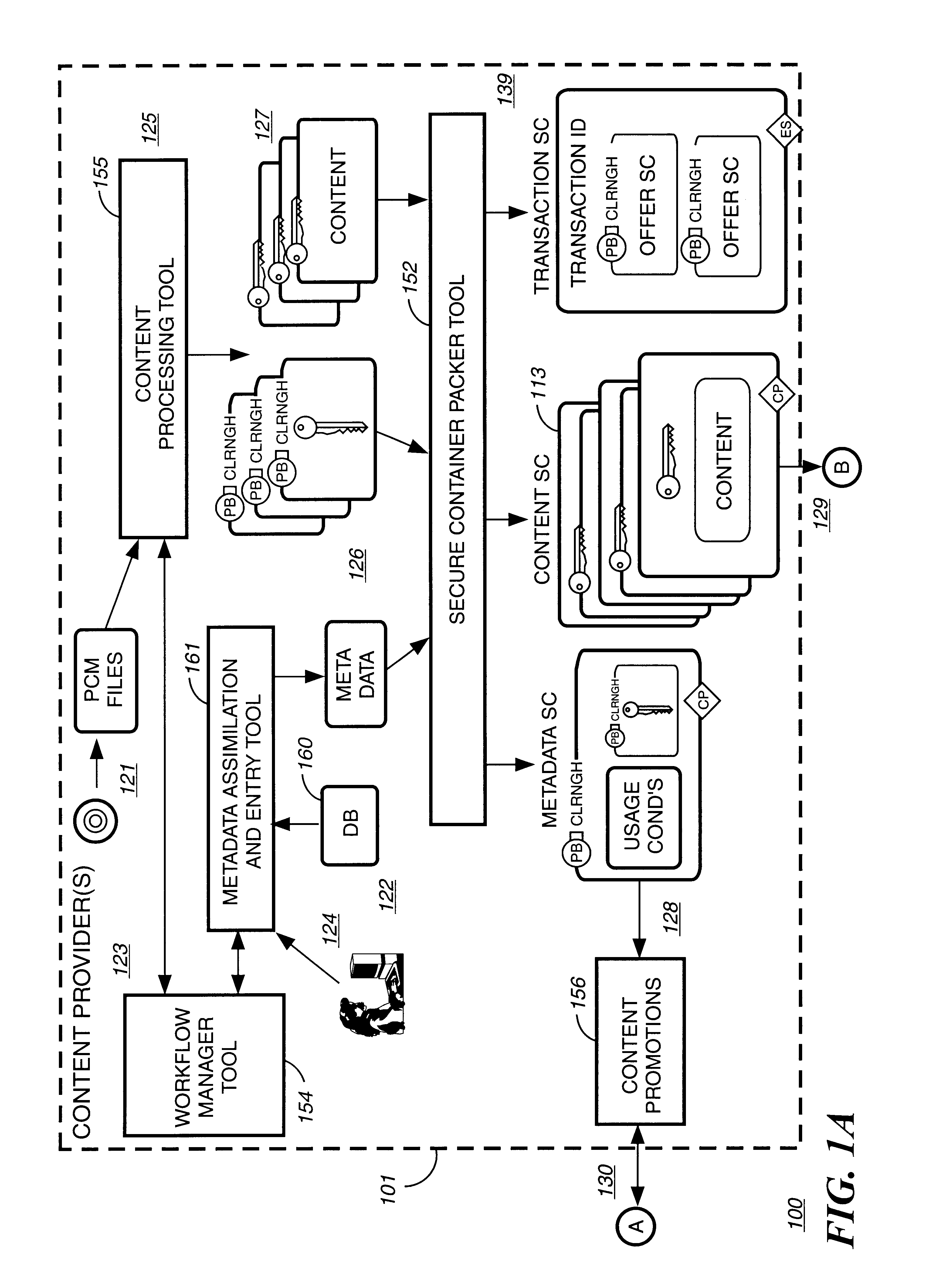
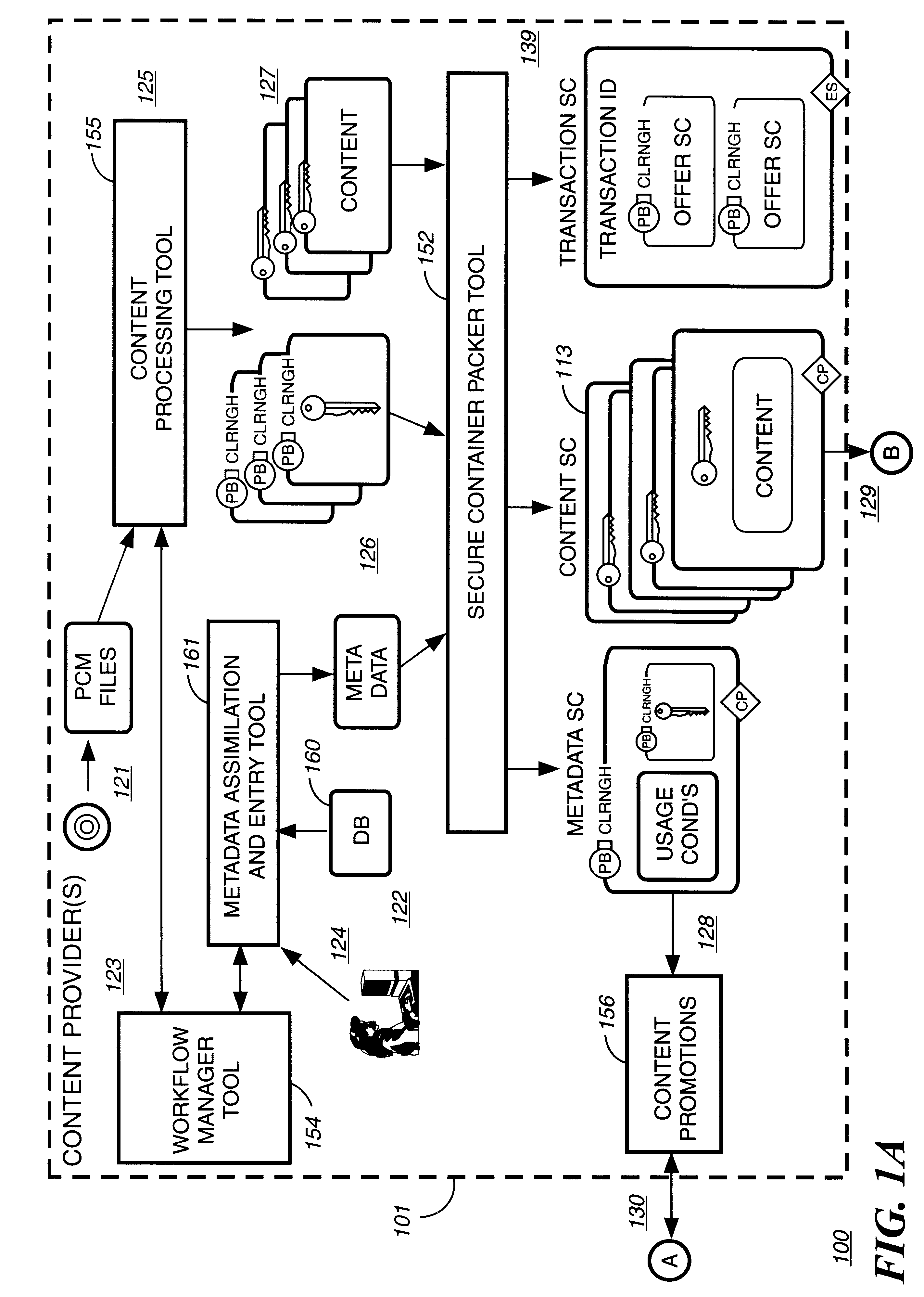
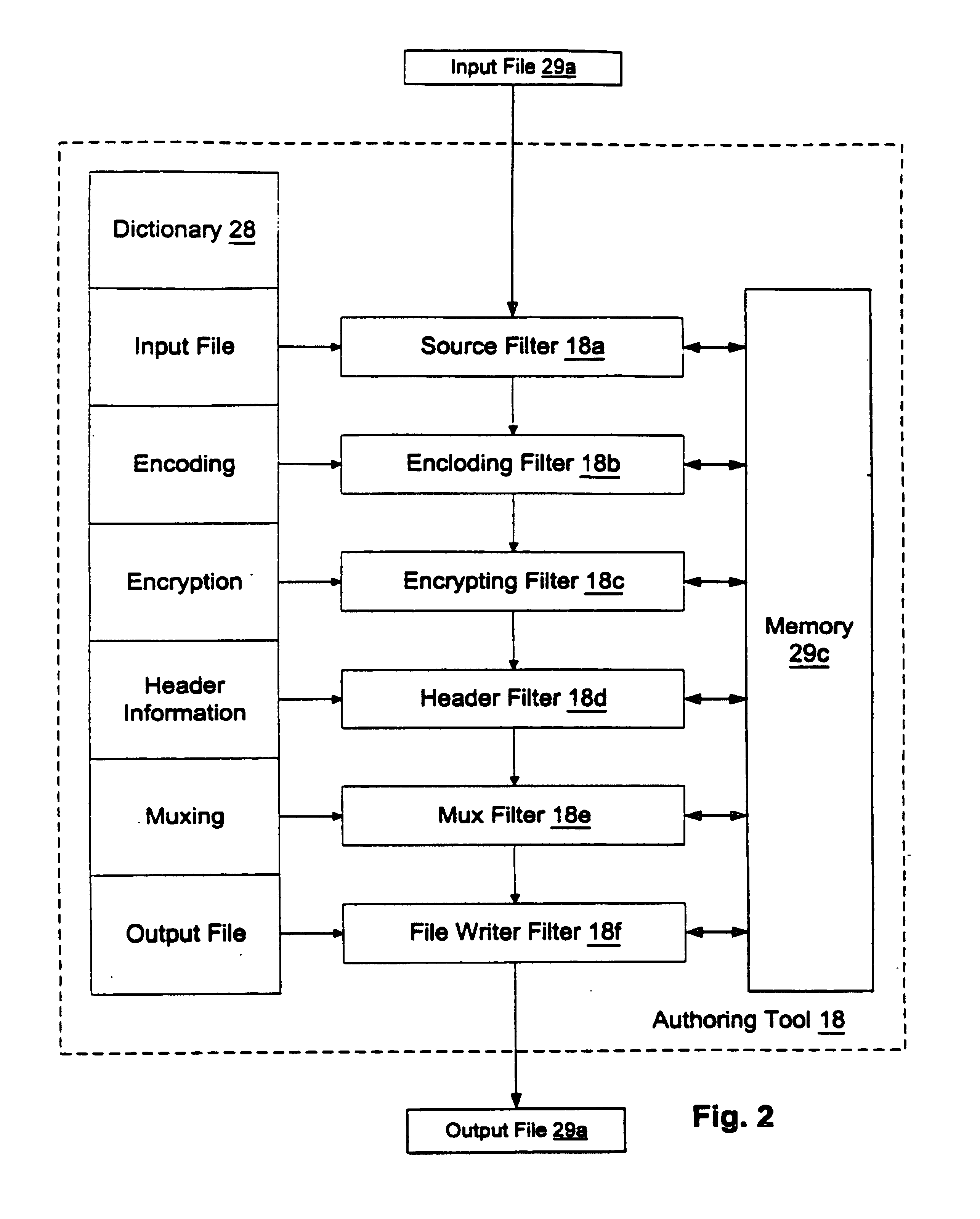
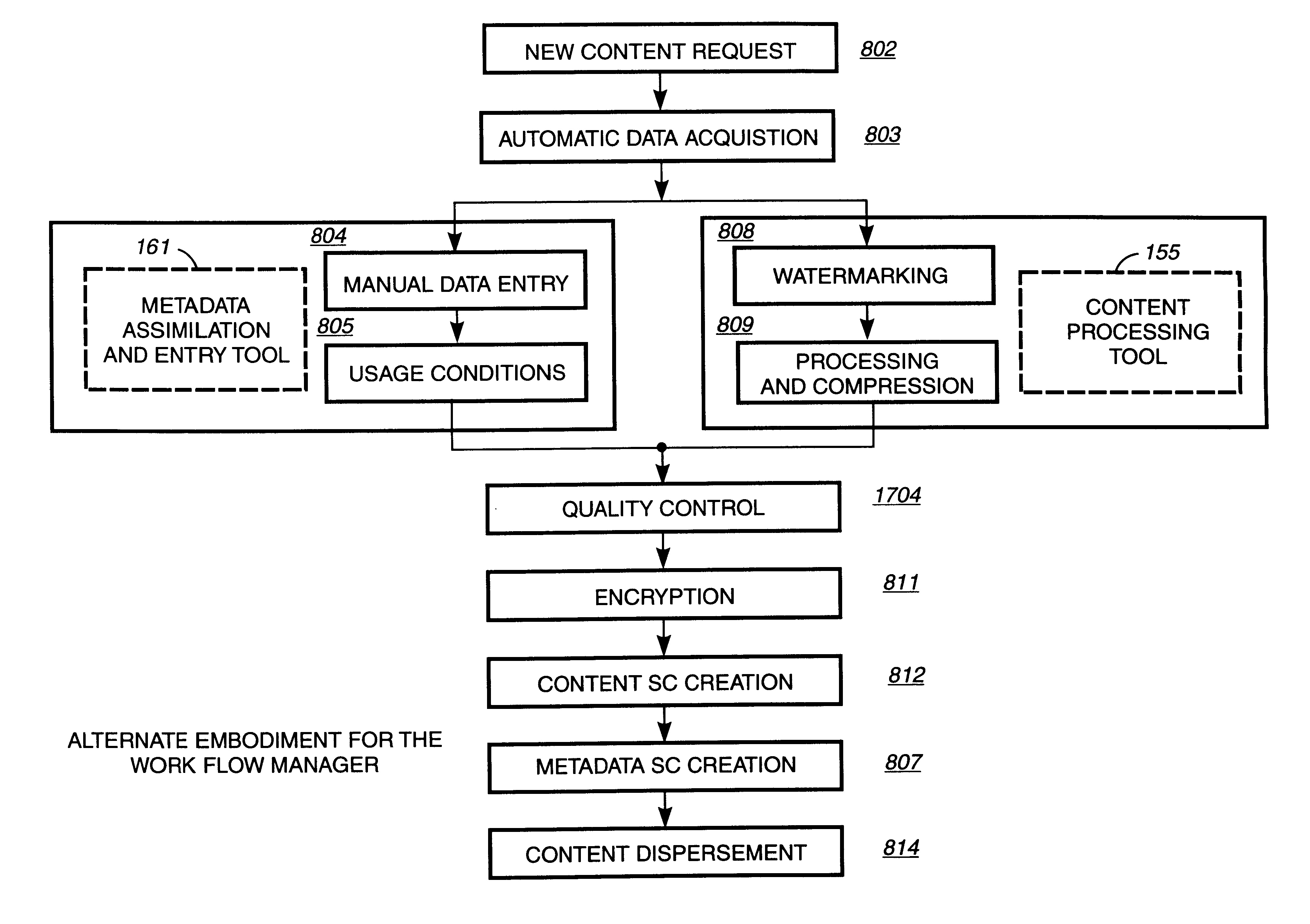
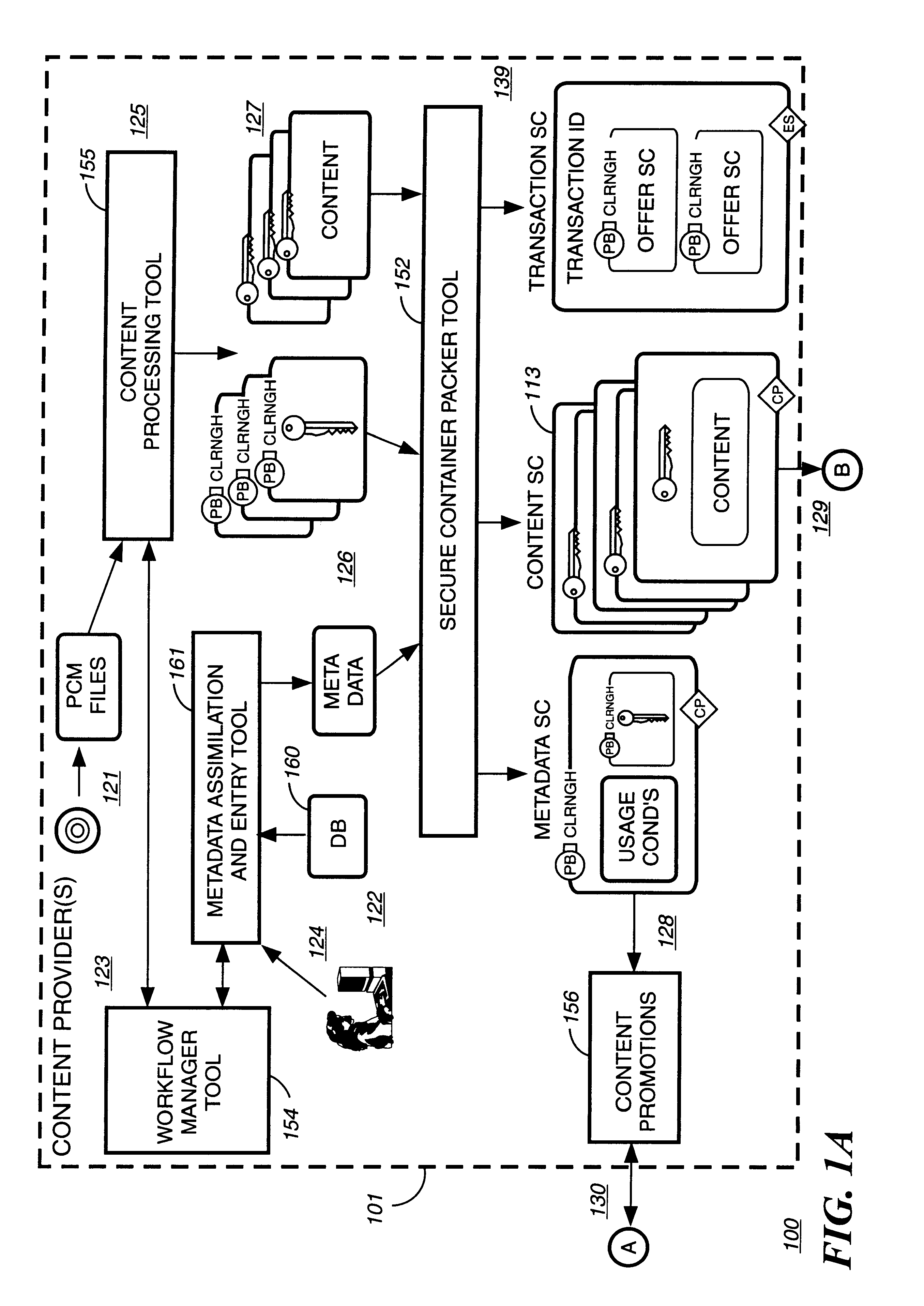
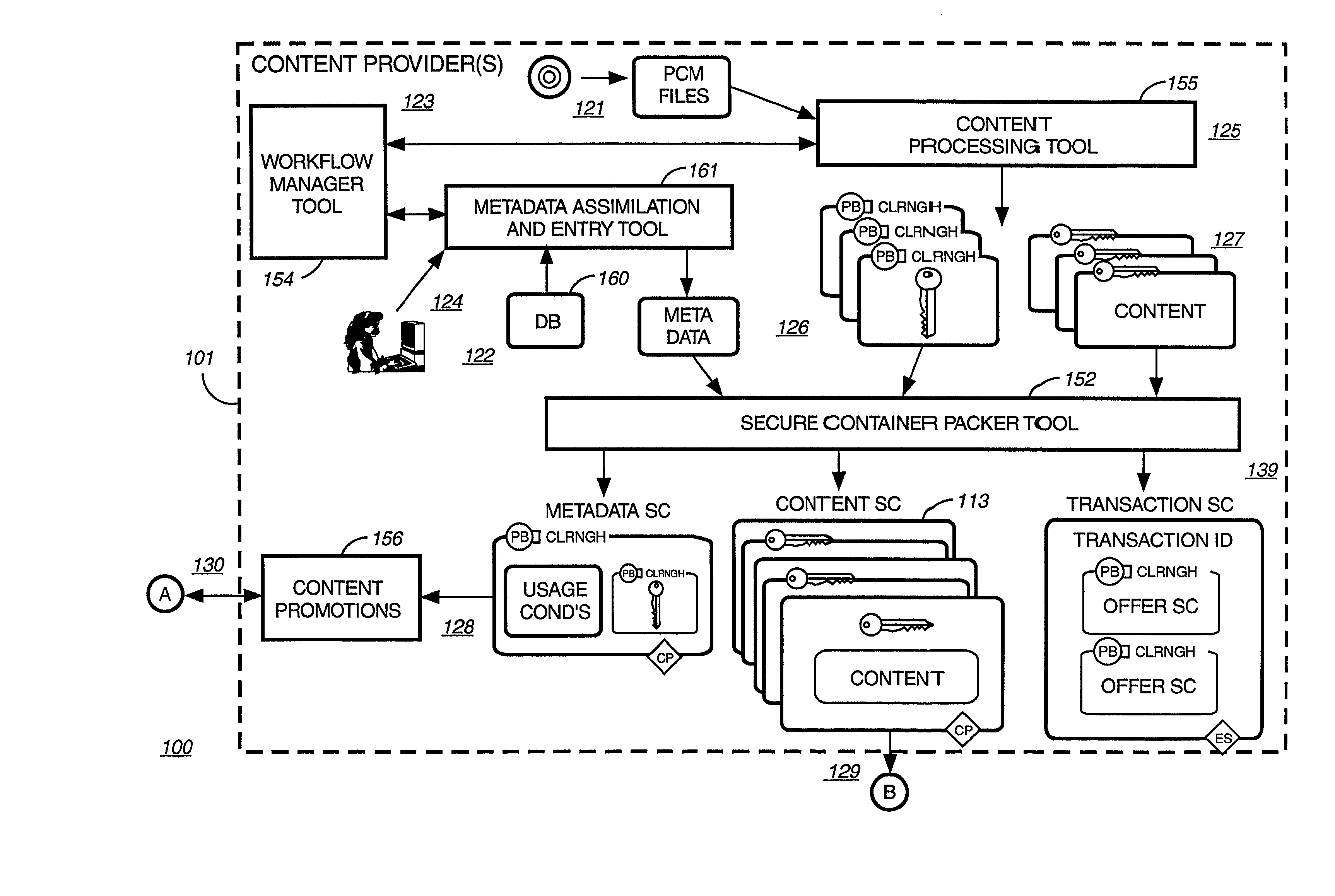
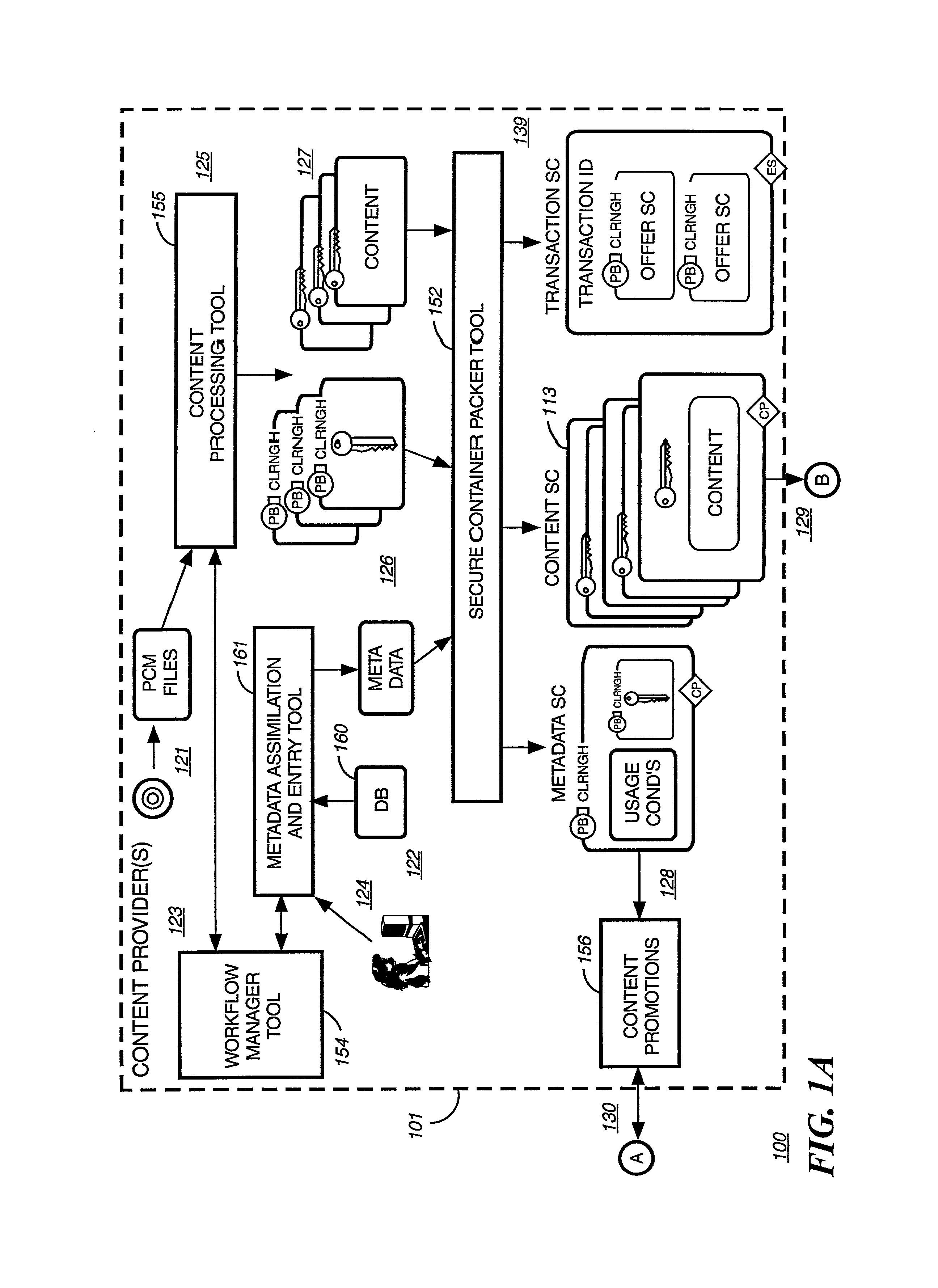
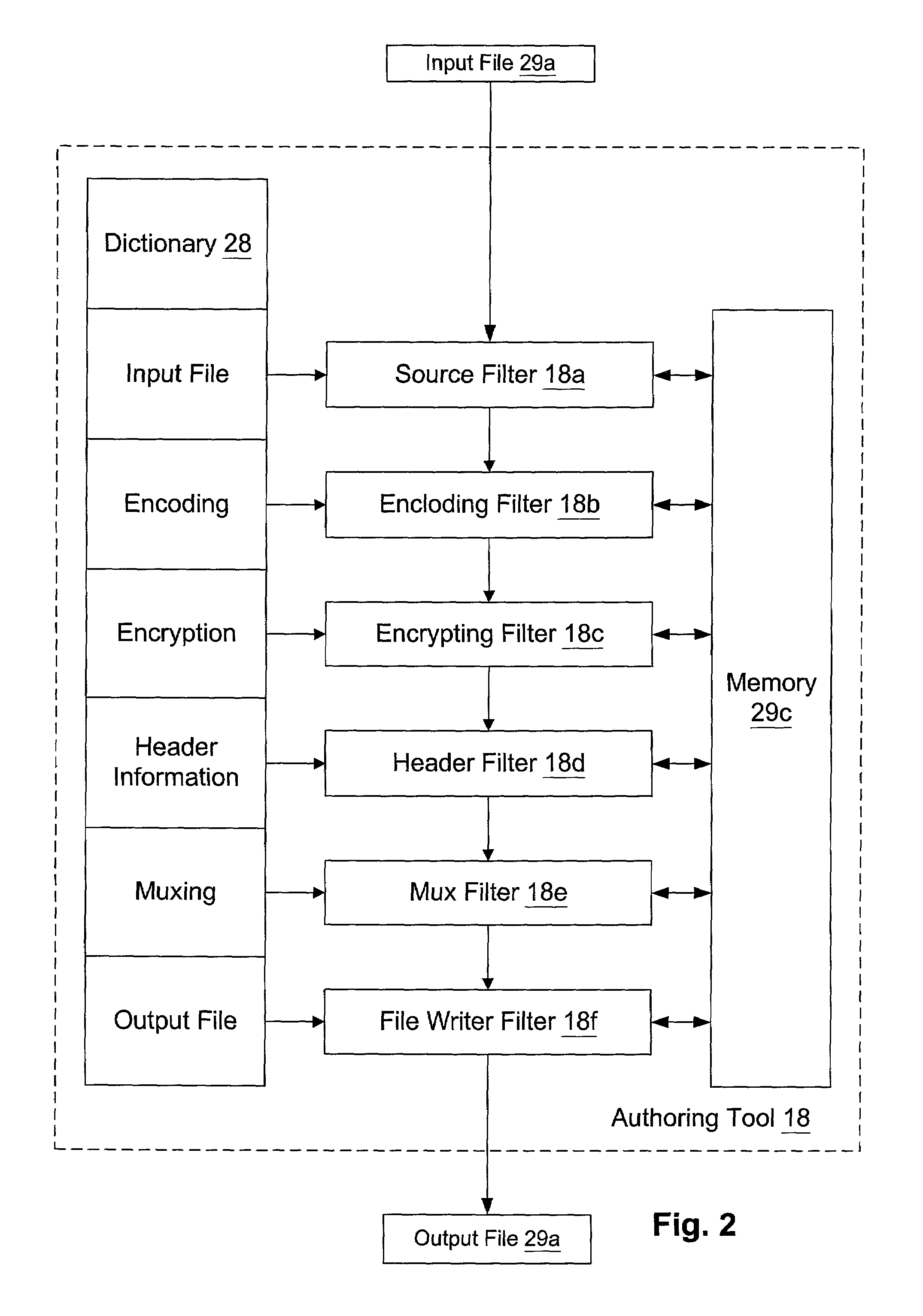
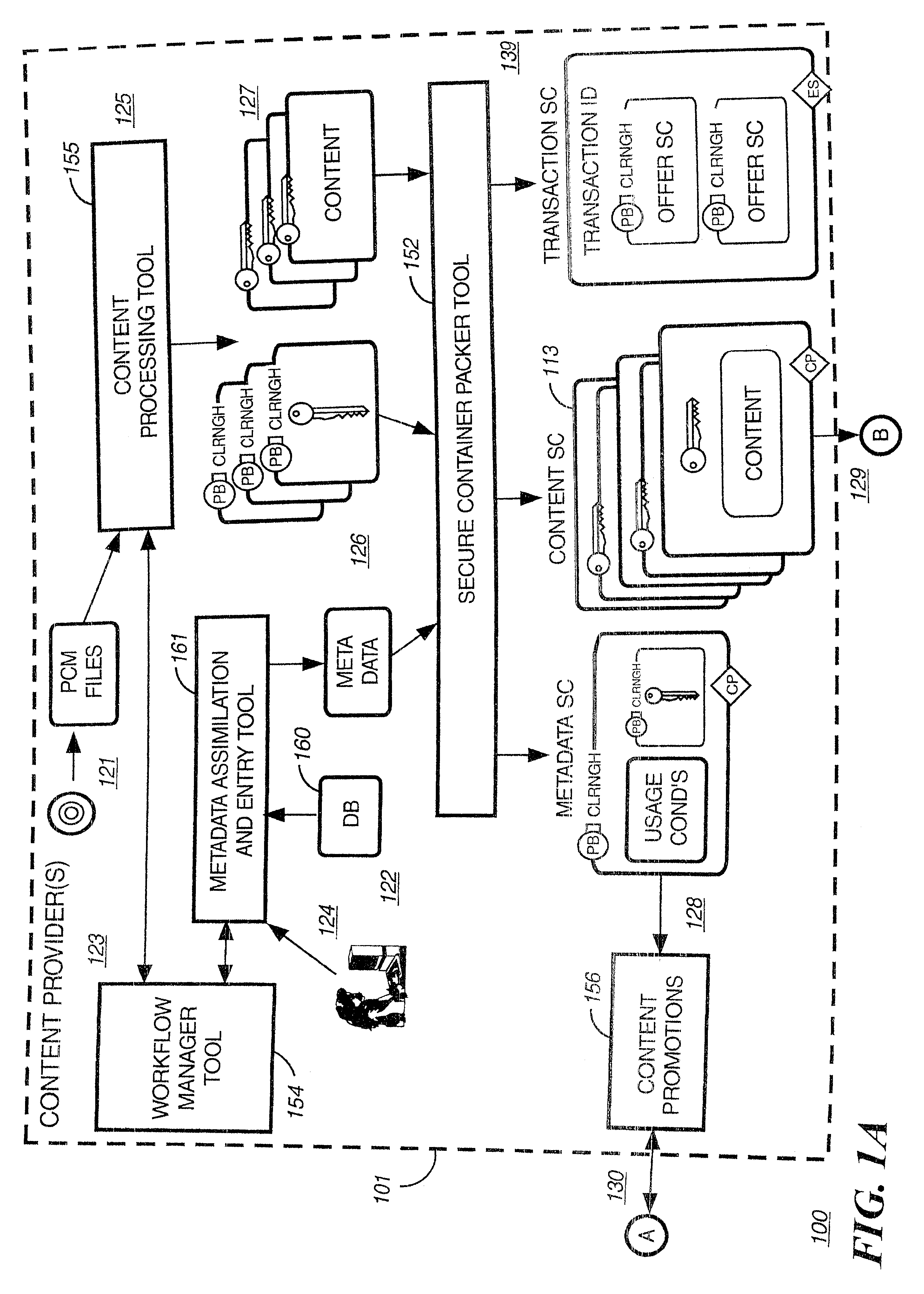
Digital content preparation system
InactiveUS6959288B1Key distribution for secure communicationPublic key for secure communicationDigital contentNumber content
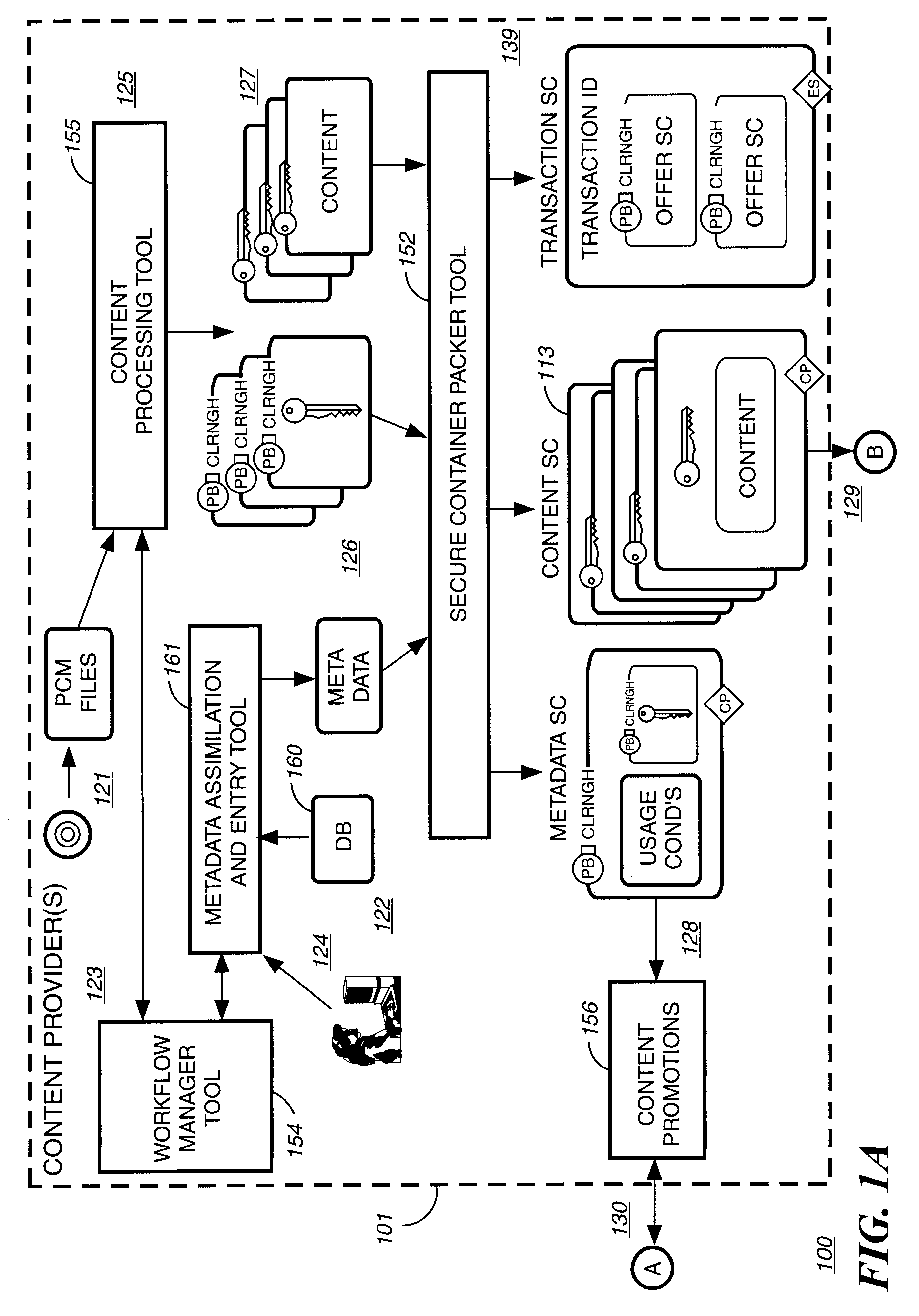
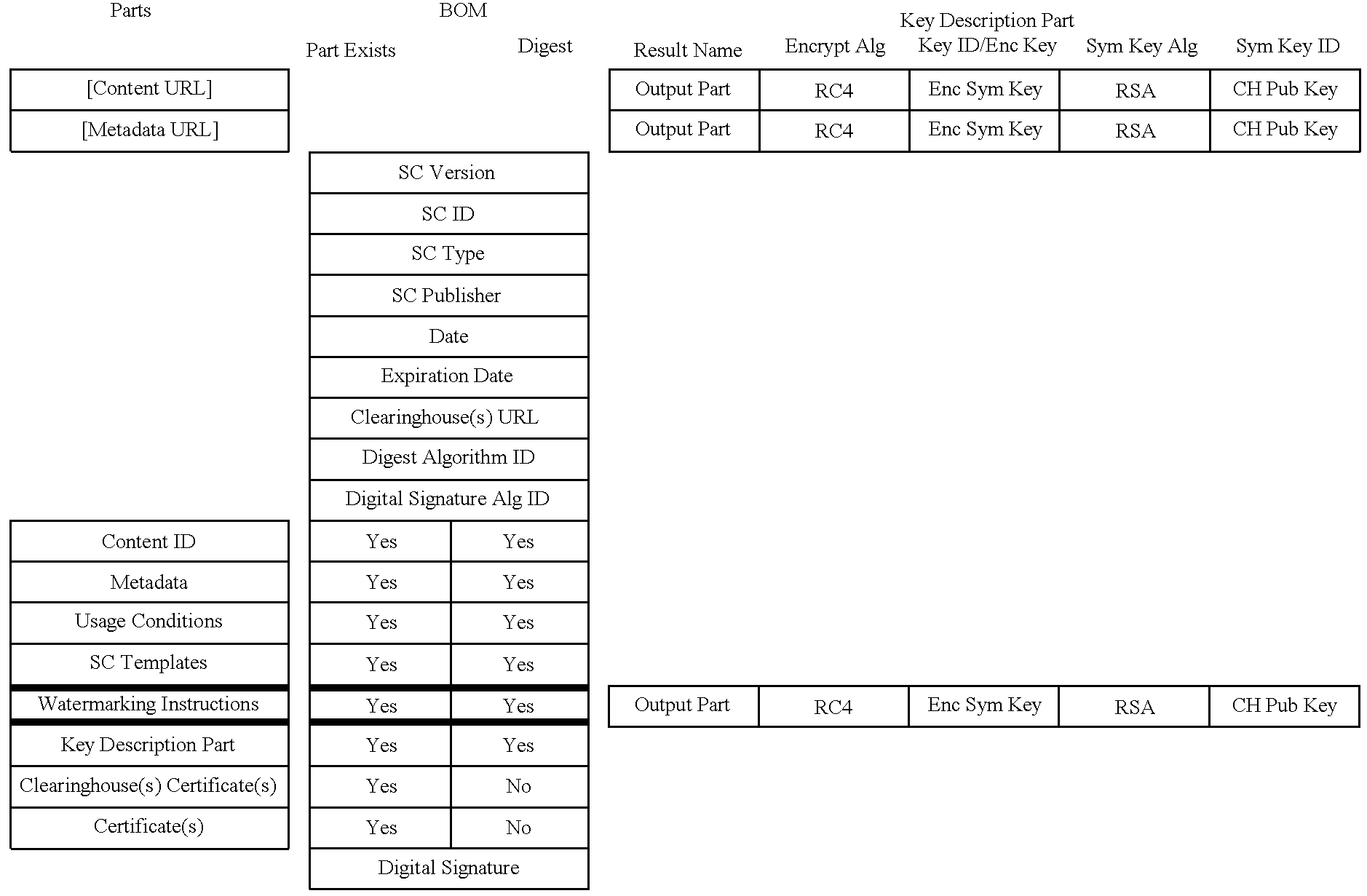
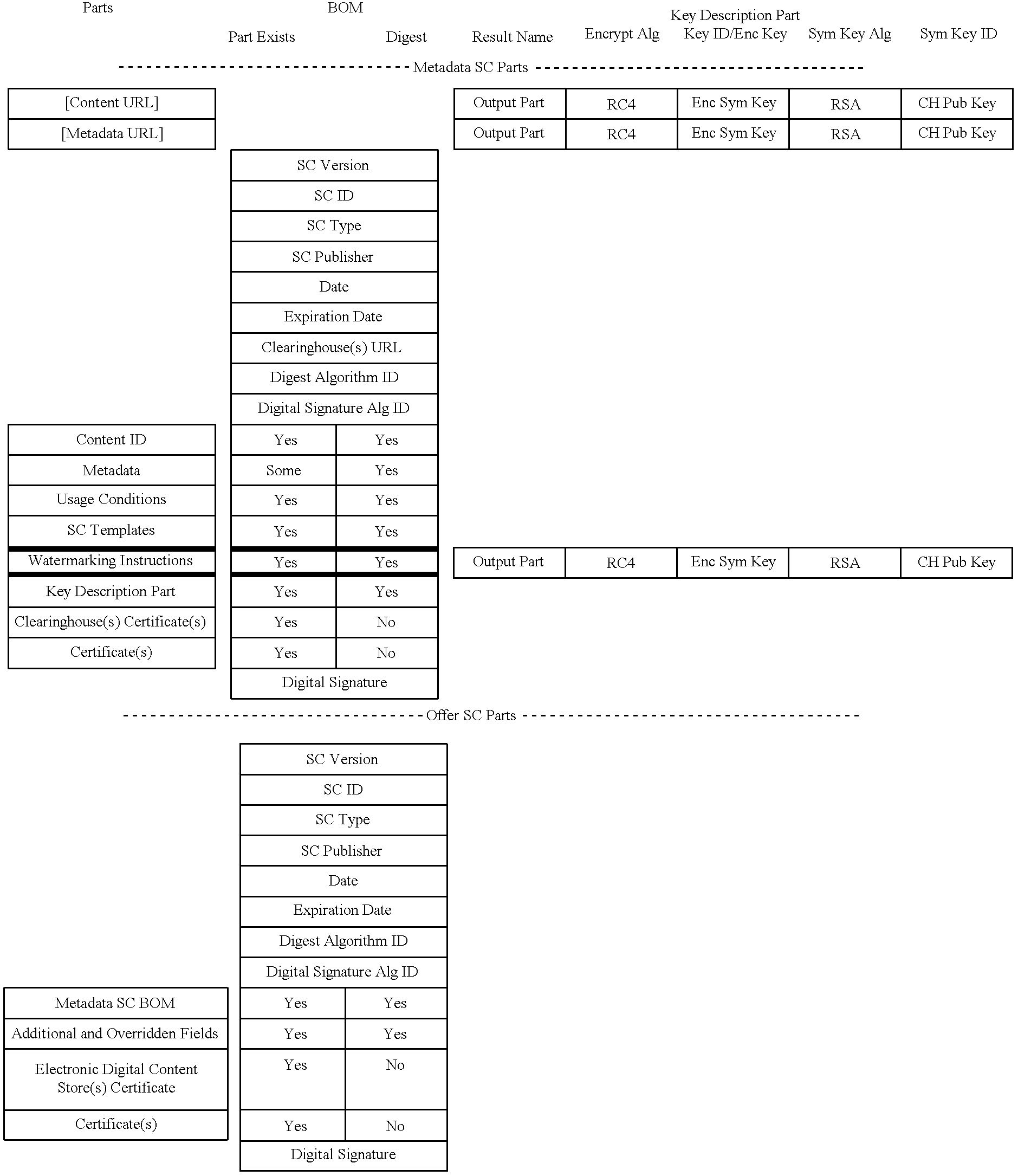
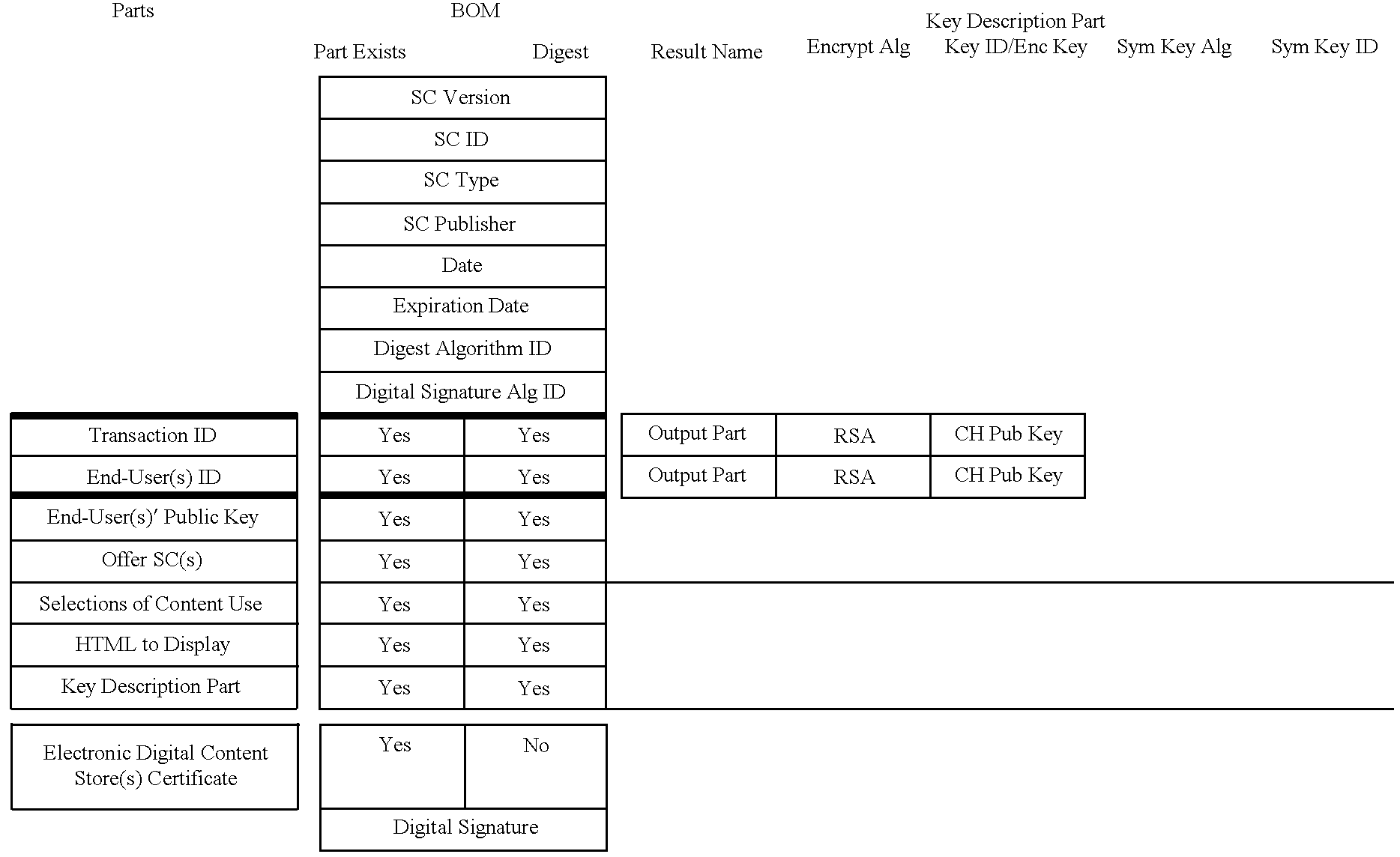
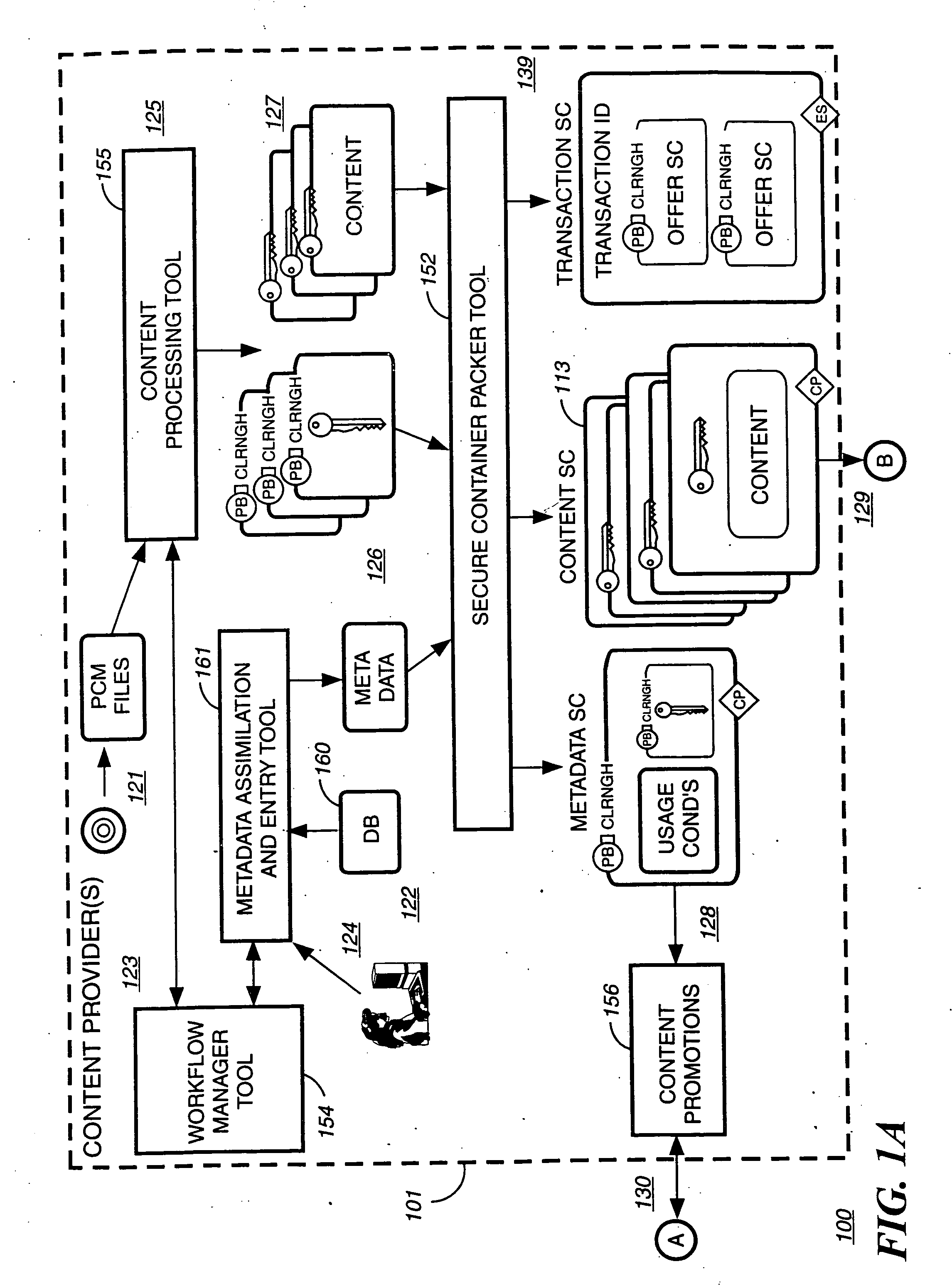
A digital content preparation system that includes a metadata acquisition tool for acquiring metadata associated with the digital content, and a digital content processor for processing the digital content by performing at least one of watermarking, encoding, and encrypting. A work flow manager manages processings by the metadata acquisition tool and the digital content processor. In one preferred embodiment, the metadata acquisition tool includes an automatic metadata acquisition tool and a manual metadata acquisition tool, and the digital content processor includes an encoder and an encrypter. The present invention also provides a method for preparing digital content. According to the method, metadata associated with the digital content is acquired, and the digital content is processed by at least one of watermarking, encoding, and encrypting. Processings in the acquiring step and the processing step are managed. In a preferred method, the acquiring step includes automatically retrieving at least a portion of the metadata and allowing manual entry of at least a portion of the metadata, and the processing step includes encoding the digital content and encrypting the encoded digital content.
Owner:IBM CORP
Copy protection system for portable storage media
InactiveUS6950941B1Limited abilityKey distribution for secure communicationData processing applicationsDevice formDigital content
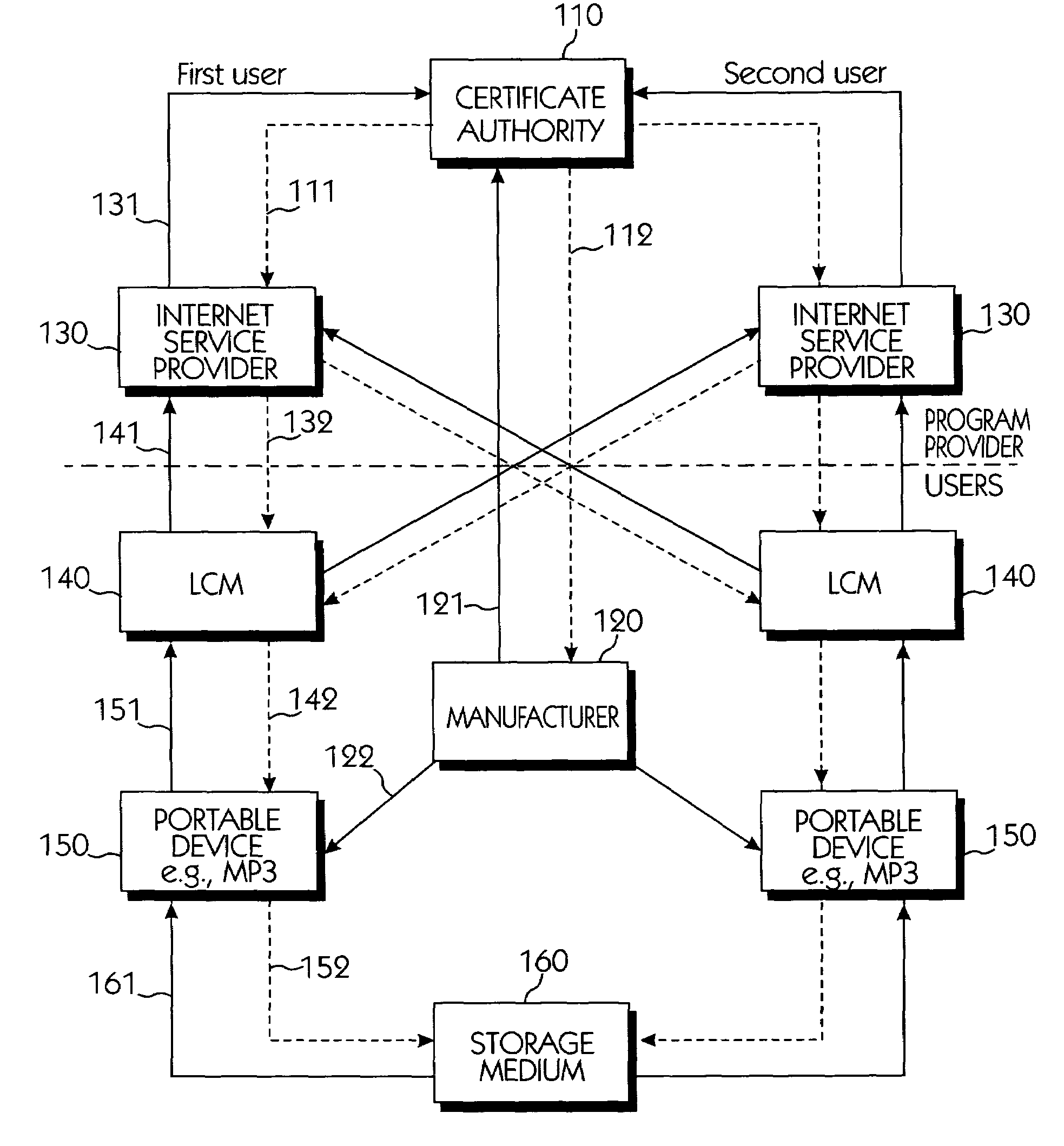
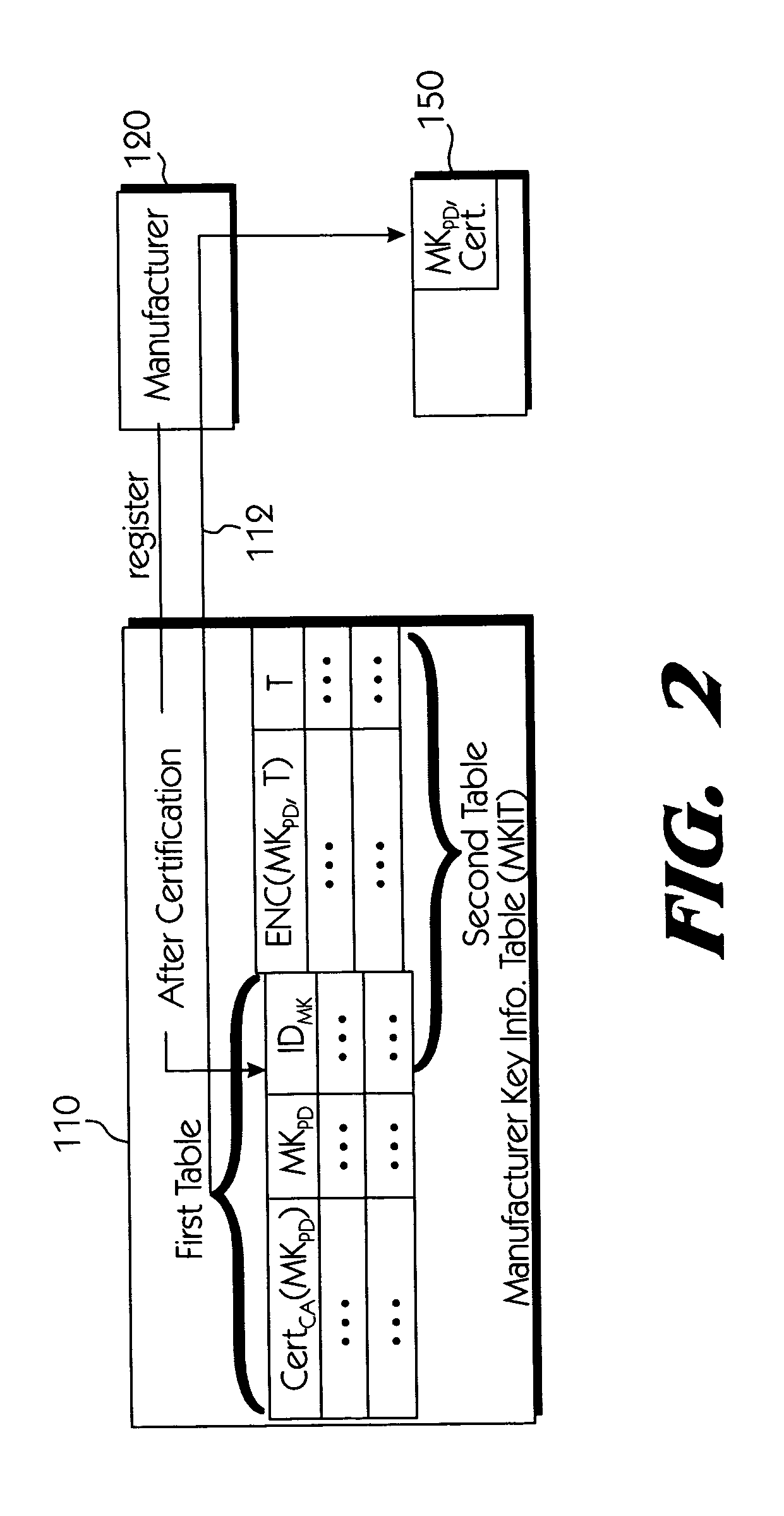
Systems connected to users generate a plurality of keys which are mutually shared, and download and upload digital contents by using secret channels formed between the systems. An information provider receives an authorization from a certificate authority. A licensed SDMI compliant module (LCM) is authenticated through the information provider, and the information provider and the LCM form a channel. A portable device is authenticated from the information provider through the LCM, and the LCM and the portable device form a channel. The digital content between the LCM and the portable device is downloaded and uploaded according to respective control state data of the LCM and the portable device. The system can use a physical address of a bad sector formed in the portable medium during the manufacturing process for preventing an illegal copy of the downloaded digital contents through the portable device after the digital contents have been downloaded.
Owner:SAMSUNG ELECTRONICS CO LTD
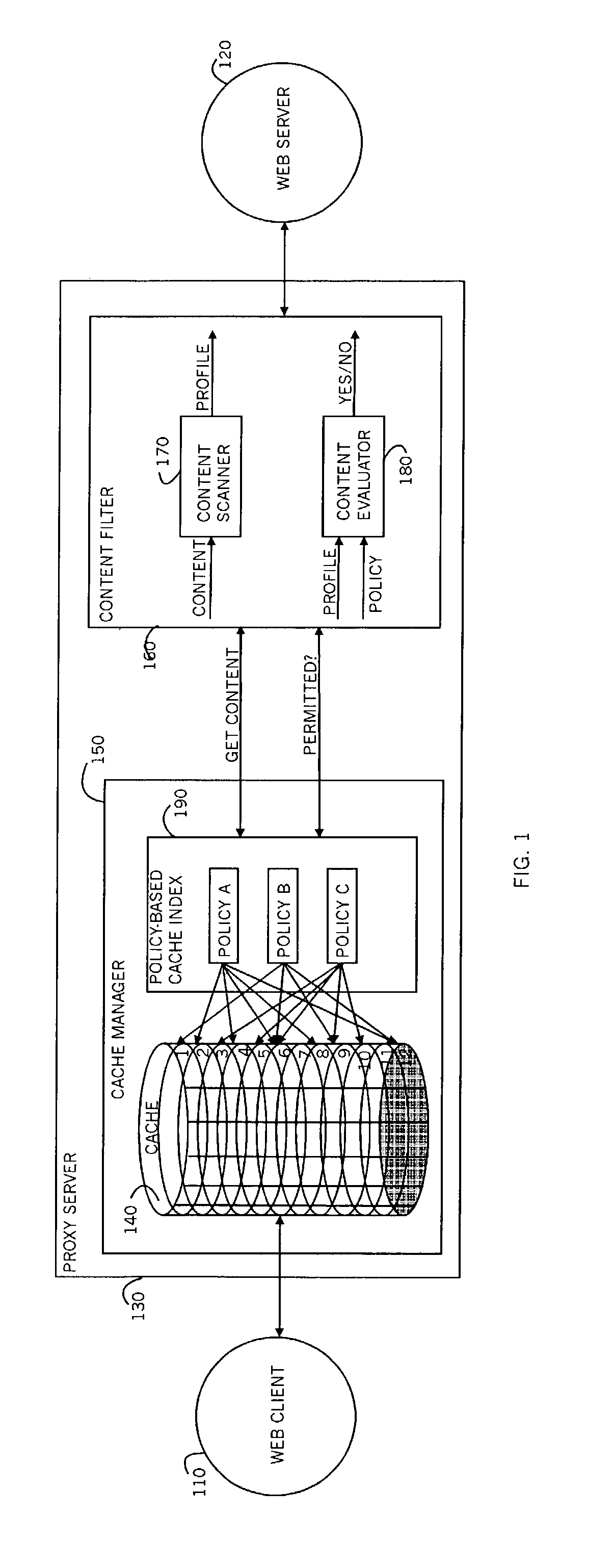
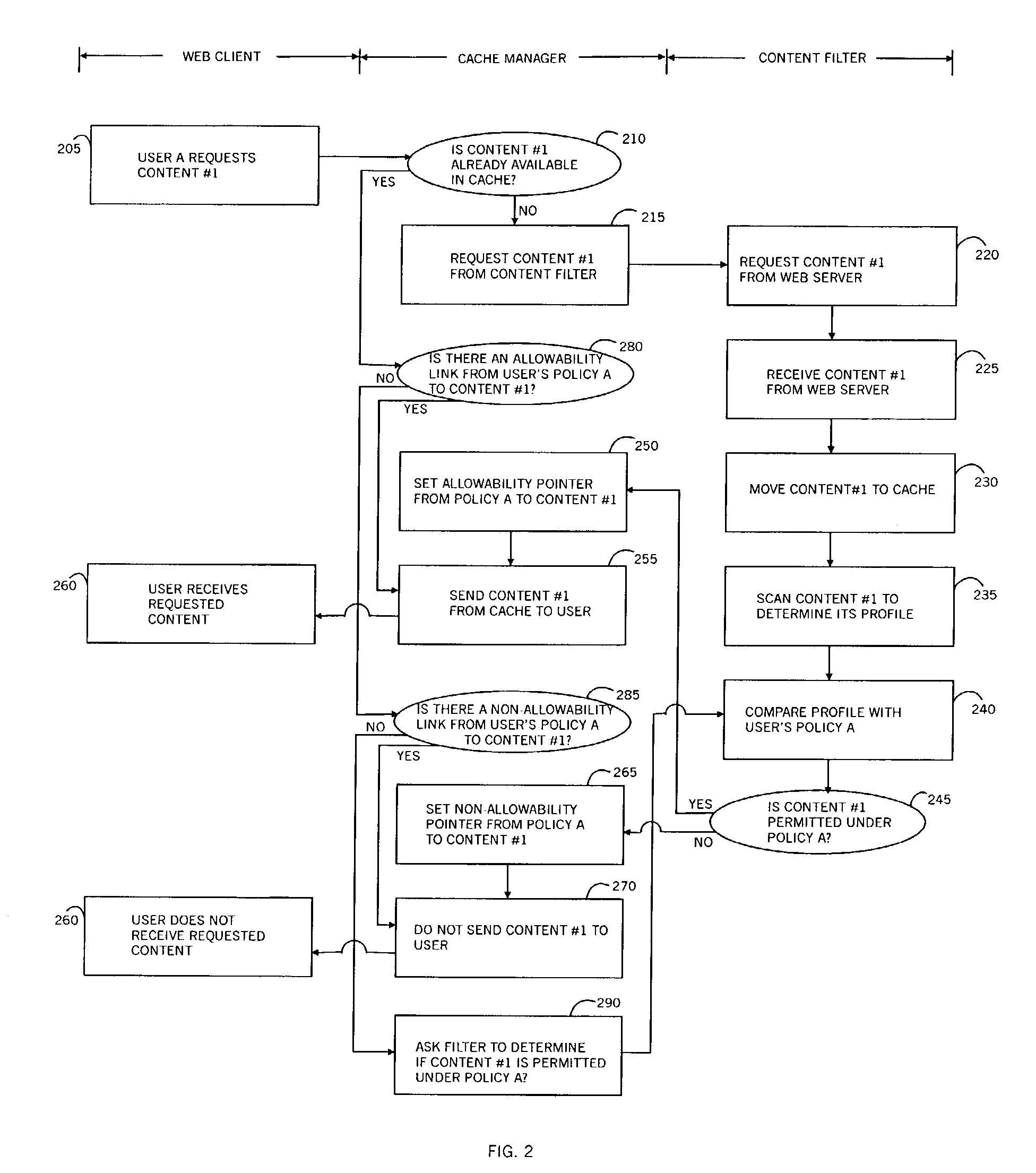
Policy-based caching
InactiveUS6965968B1Enhances conventional cachingBlock deliveryDigital data information retrievalComputer security arrangementsDigital contentNumber content
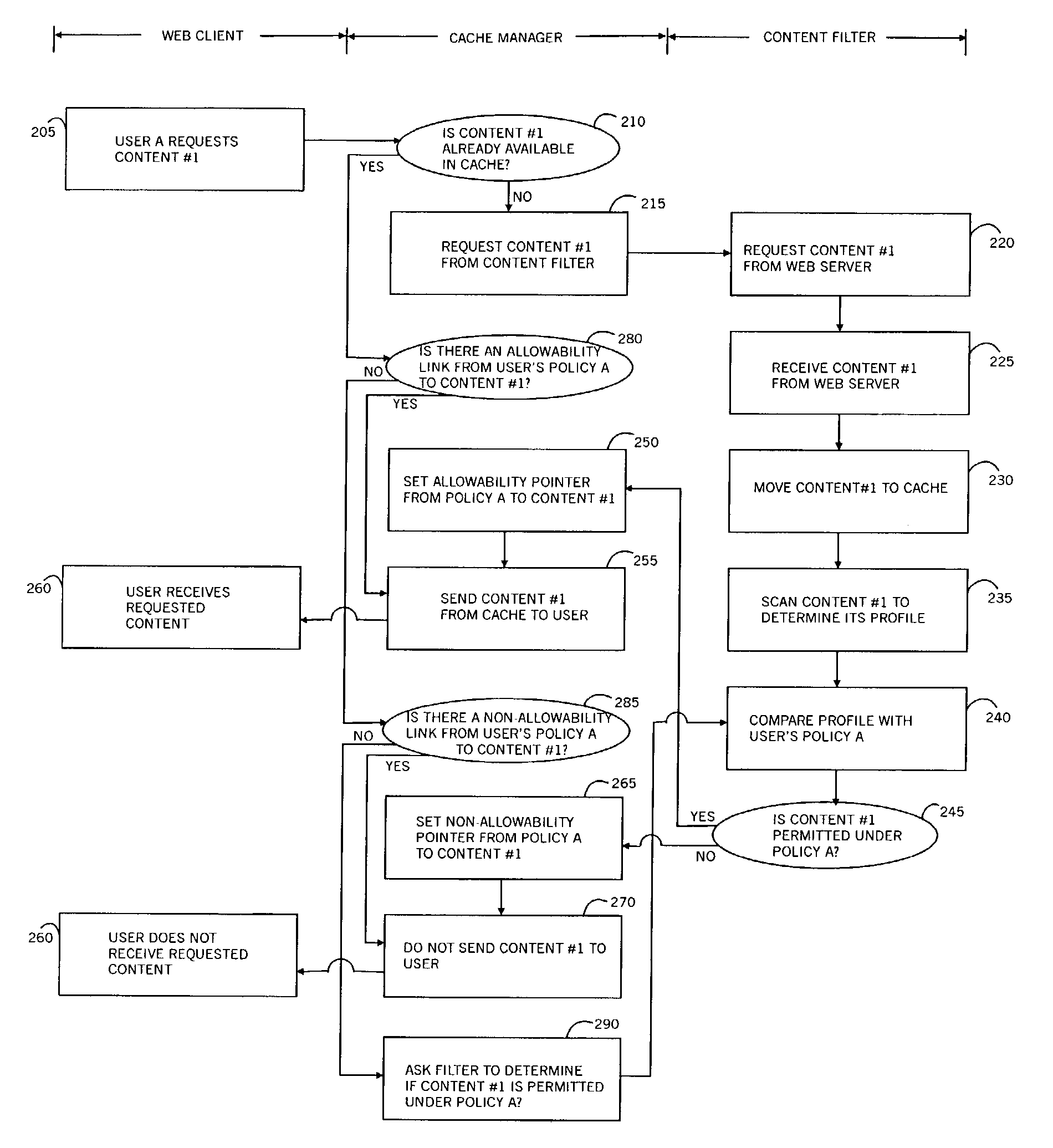
A policy-based cache manager, including a memory storing a cache of digital content, a plurality of policies, and a policy index to the cache contents, the policy index indicating allowable cache content for each of a plurality of policies, a content scanner for scanning a digital content received, to derive a corresponding content profile, and a content evaluator for determining whether a given digital content is allowable relative to a given policy, based on the content profile. A method is also described and claimed.
Owner:FINJAN LLC
Method and system for downloading digital content over a network
InactiveUS20050021398A1Easy to controlEasy to identifyAdvertisementsMultiple digital computer combinationsDigital dataGraphics
A system and method for managing the acquisition of desired digital data files by a user over a network where royalty fees can be collected from advertisers for the payment of royalties to the owners of the desired digital data files. This invention facilitates the transfer and legalization of such data files as audio files, video files, graphics files, text files and multimedia files in an efficient commercial manner which provides and uses marketing information in the selection of appropriate advertisements.
Owner:WEBHOUND CORP
Dual display apparatus and methodology for broadcast, cable television and IPTV
InactiveUS20080098450A1Facilitate conductionConvenient transactionDigital computer detailsAnalogue secracy/subscription systemsOperational systemDigital content
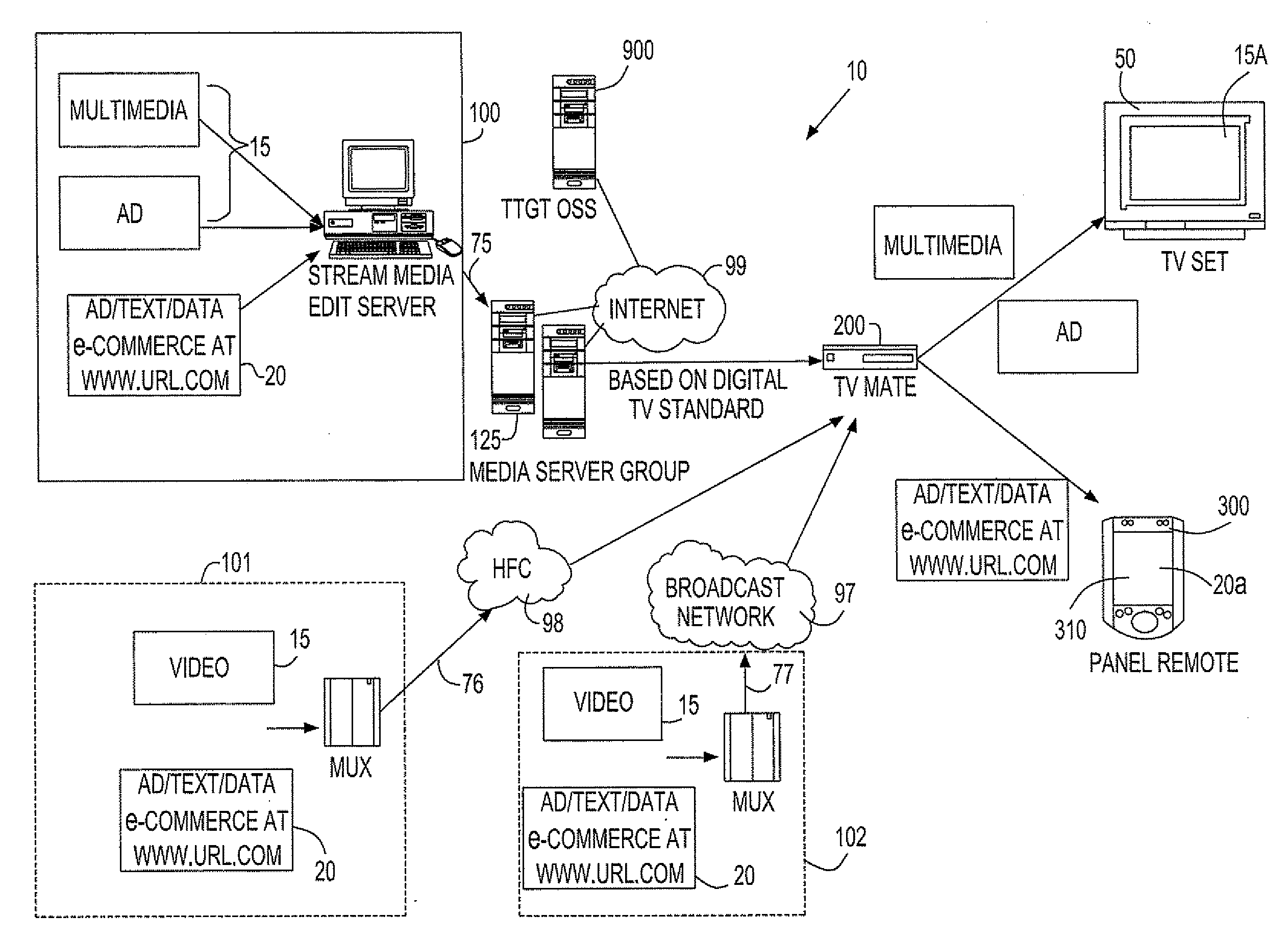
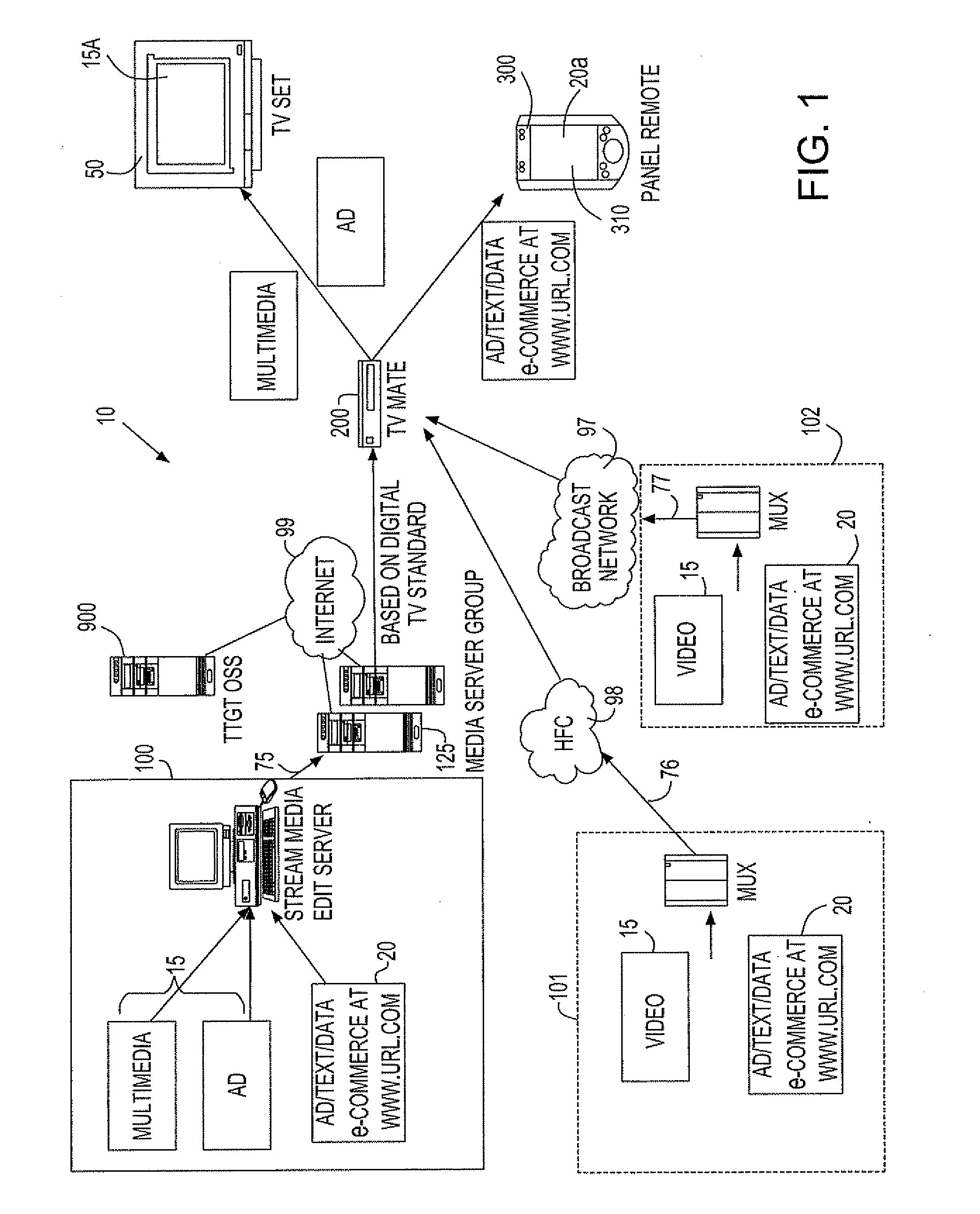
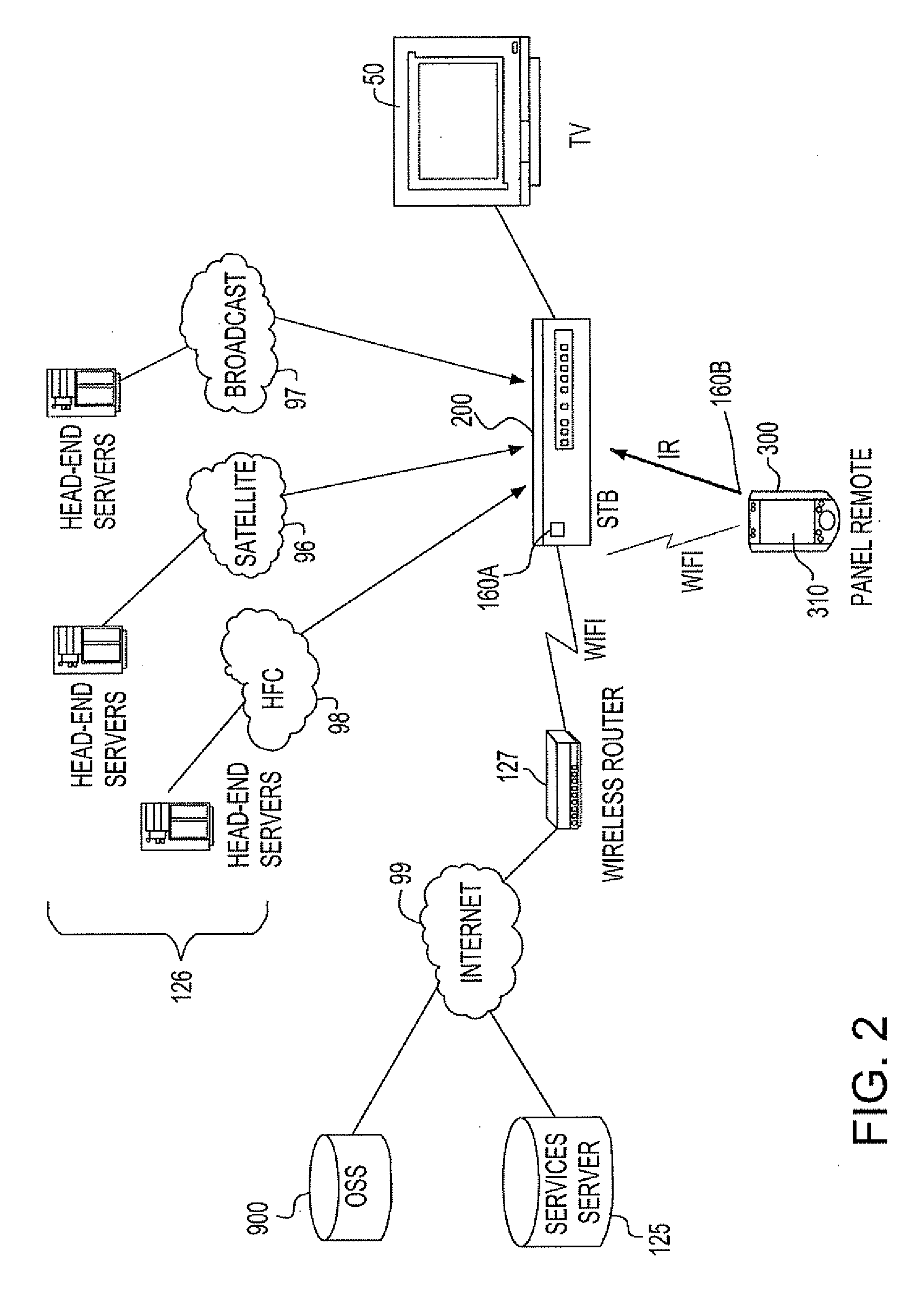
A set top box (“STB”) apparatus configurable for handling broadcast, cable television and Internet protocol television (“IPTV”) formats by multiple operators via a single flexible operating system is provided. The set top box is enabled to receive and run different operating systems from multiple providers or operators. In another aspect, a dual mode display feature enables viewing of digital content via a first display device while enabling browsing and e-commerce functionality via an associated remote device.
Owner:TOPTREND GLOBAL TECH
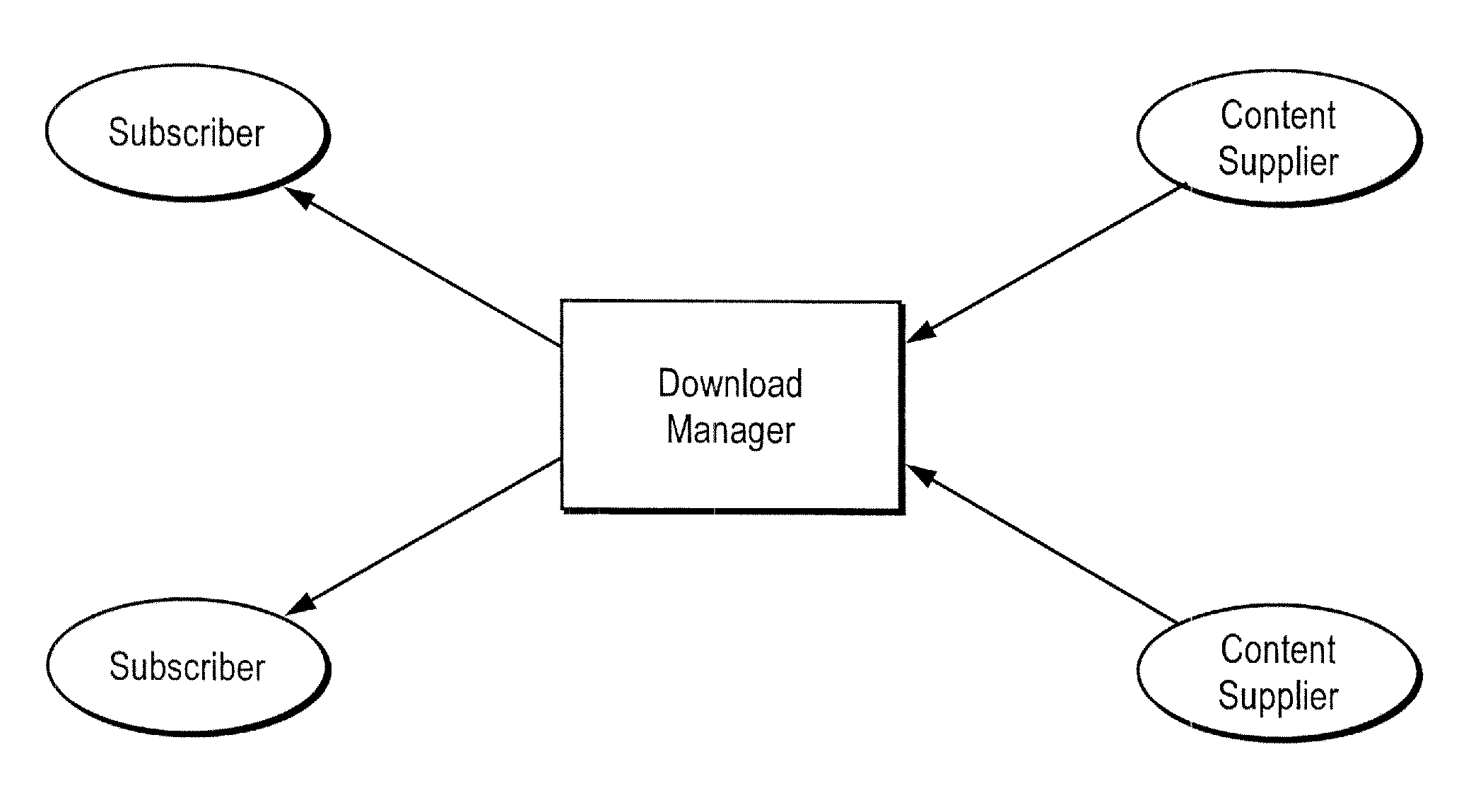
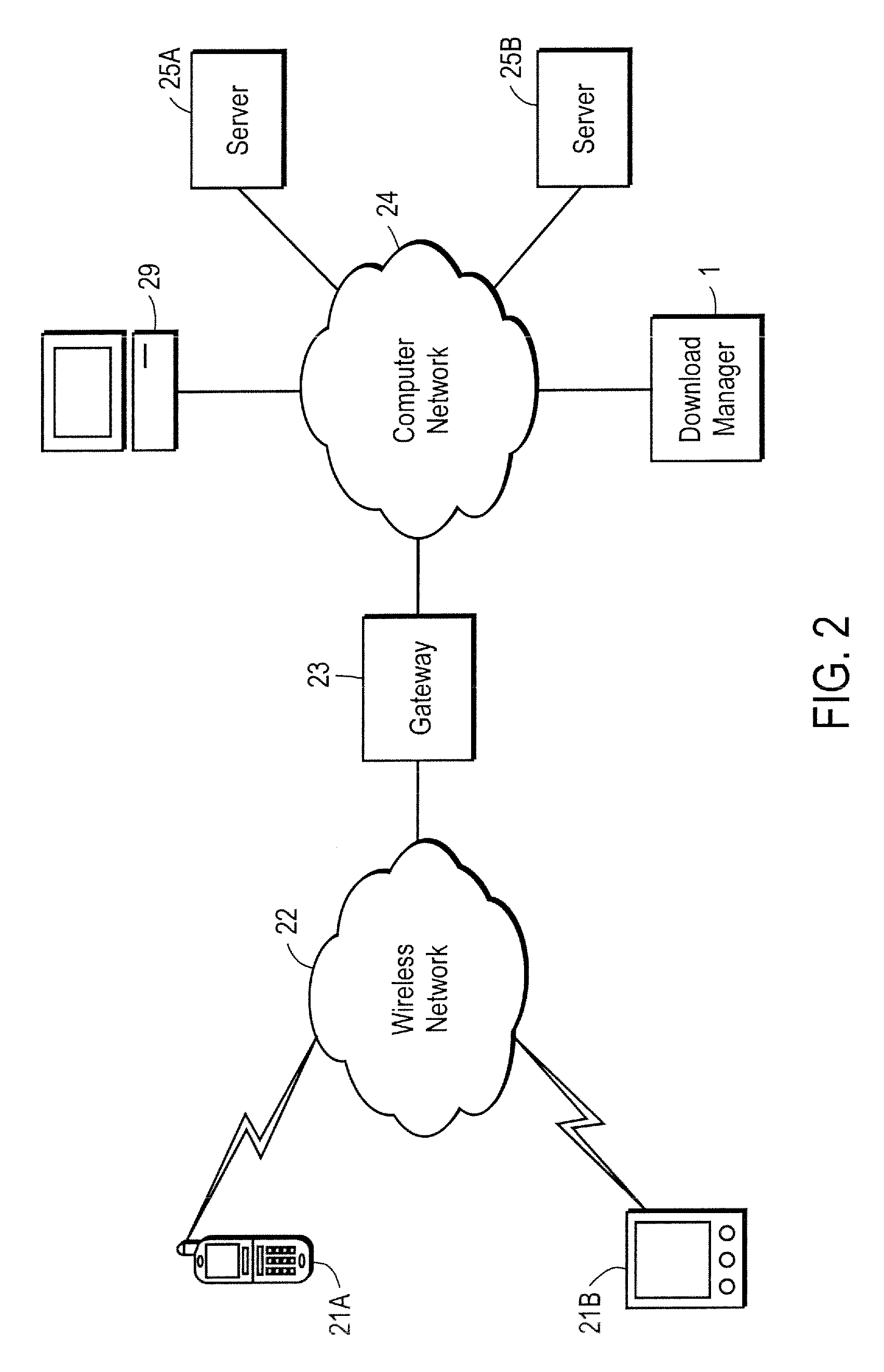
Domain-based management of distribution of digital content from multiple suppliers to multiple wireless services subscribers
ActiveUS7299033B2Digital data information retrievalSpecial service for subscribersDigital contentBusiness enterprise
A network server system includes a download manager that manages the publication, purchase and delivery of digital content from multiple content suppliers to wireless services subscribers in multiple domains. Each domain is defined as a different grouping of subscribers, such as a wireless carrier or subsidiary thereof, a business enterprise, or other defined group of subscribers. The download manager maintains data defining the multiple domains and associations between the domains and wireless services subscribers. Digital content suppliers can publish and manage their products on the server system via a computer network and make their products available to the subscribers for purchase or licensing. The subscribers in each of the domains can access the server remotely to purchase rights to download and use the digital content on associated wireless communication devices.
Owner:UNWIRED PLANET
Content security layer providing long-term renewable security
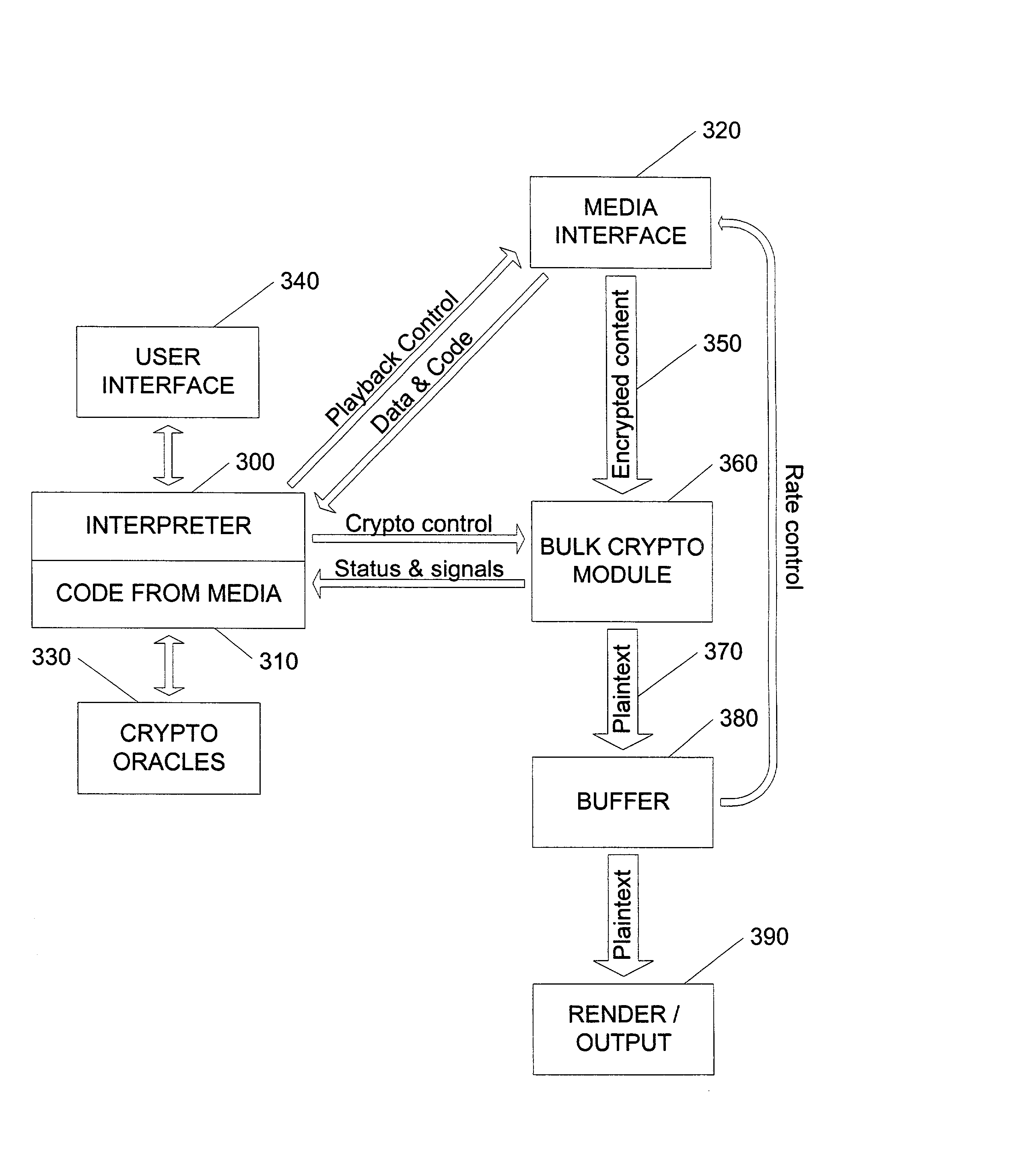
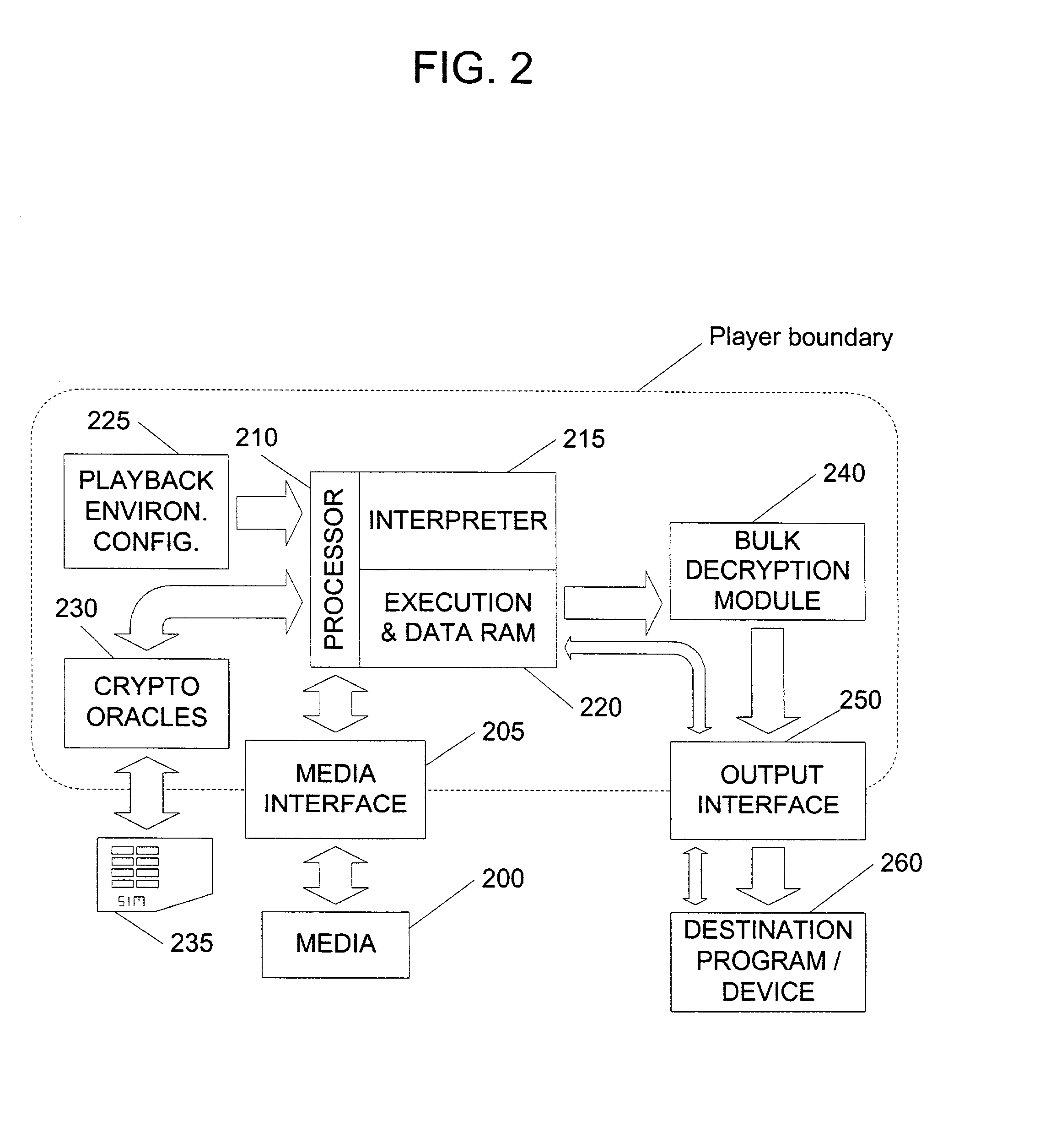
InactiveUS20020141582A1Unparalleled flexibilityIncrease sampling rateTelevision system detailsKey distribution for secure communicationAttackMediaFLO
In an exemplary embodiment, digital content is mastered as a combination of encrypted data and data processing operations that enable use in approved playback environments. Player devices having a processing environment compatible with the content's data processing operations are able to decrypt and play the content. Players can also provide content with basic functions, such as loading data from media, performing network communications, determining playback environment configuration, controlling decryption / playback, and / or performing cryptographic operations using the player's keys. These functions allow the content to implement and enforce its own security policies. If pirates compromise individual players or content titles, new content can be mastered with new security features that block the old attacks. A selective decryption capability can also be provided, enabling on-the-fly watermark insertion so that attacks can be traced back to a particular player. Features to enable migration from legacy formats are also provided.
Owner:ROVI SOLUTIONS CORP
Secure electronic content distribution on cds and dvds
InactiveUS20030105718A1Key distribution for secure communicationDigital data processing detailsDigital contentComputer terminal
A method to delivery encrypted digital content to a end user system for playing the content comprising the steps of: reading from a computer readable medium metadata which has previously associated with the content. A user selects from the metadata associated content to decrypt and the end user system establishes a secure connection with an authorization authority for decrypting the content. The end user system receives a secure container containing the decrypting key for decrypting at least part of the previously encrypted content as permitted. The system creates a secure container using the encrypting key from a clearing house, wherein the secure container has an encrypting key therein from the end user system; transferring the secure container to the clearing house for authentication of permission to decrypt the content. The system receives from the clearing house, a secure container encrypted using the encrypting key of the end user system containing the decrypting key for decrypting at least part of the previously encrypted content stored on the computer readable medium as permitted; and playing at least part of the previously encrypted content by decrypting the secure container using the encrypting key of the end user system to access the decrypting key for decrypting at least part of the encrypted content.
Owner:WISTRON CORP
Binding a digital license to a portable device or the like in a digital rights management (DRM) system and checking out/checking in the digital license to/from the portable device or the like
InactiveUS7073063B2Key distribution for secure communicationDigital data processing detailsDigital contentDigital rights management
To render digital content encrypted according to a content key (KD) on a first device having a public key (PU1) and a corresponding private key (PR1), a digital license corresponding to the content is obtained, where the digital license includes the content key (KD) therein in an encrypted form. The encrypted content key (KD) from the digital license is decrypted to produce the content key (KD), and the public key (PU1) of the first device is obtained therefrom. The content key (KD) is then encrypted according to the public key (PU1) of the first device (PU1 (KD)), and a sub-license corresponding to and based on the obtained license is composed, where the sub-license includes (PU1 (KD)). The composed sub-license is then transferred to the first device.
Owner:MICROSOFT TECH LICENSING LLC
Method for determining internet users geographic region
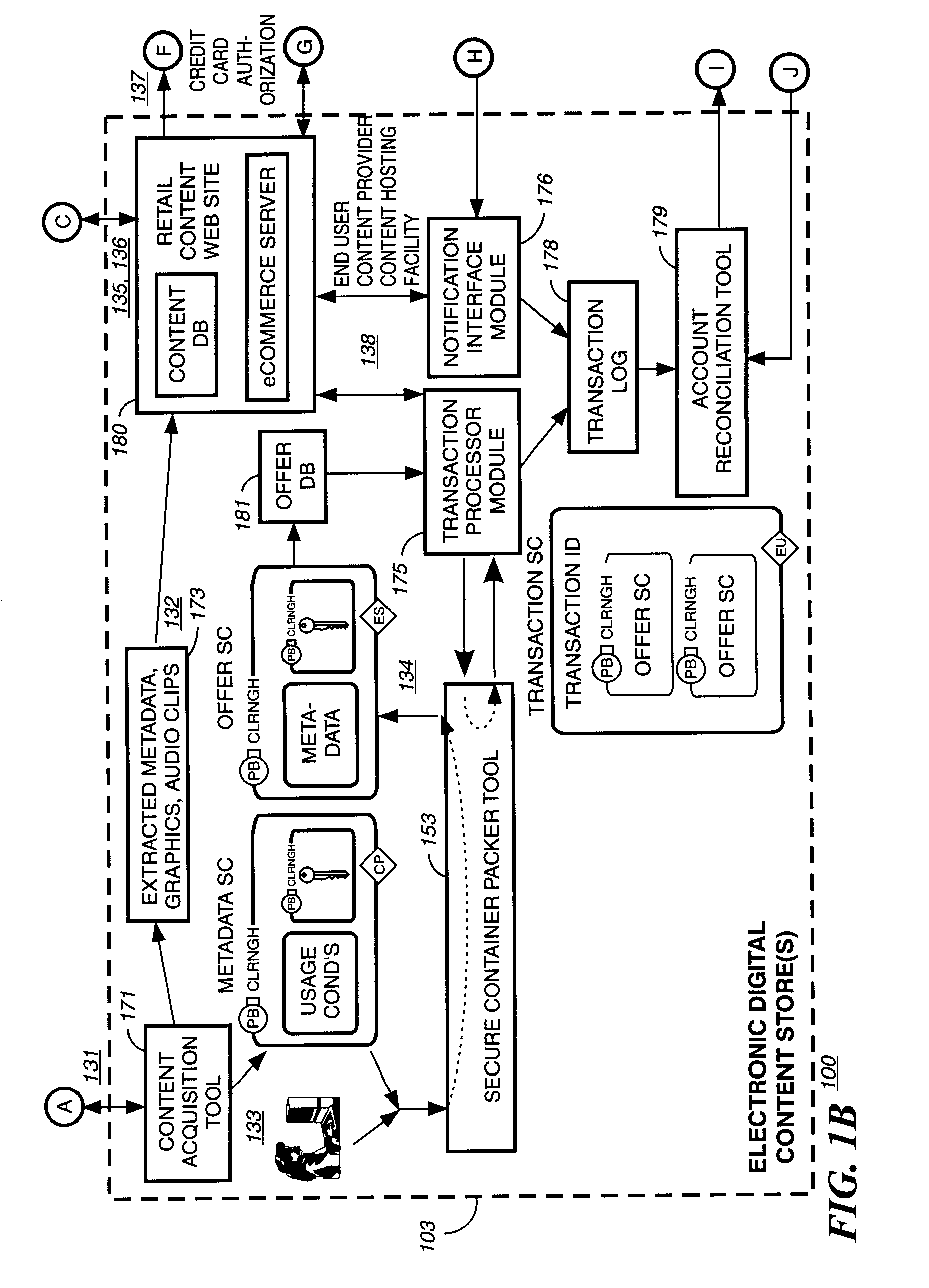
InactiveUS6859791B1Digital data processing detailsRecord information storageCredit cardGeographic regions
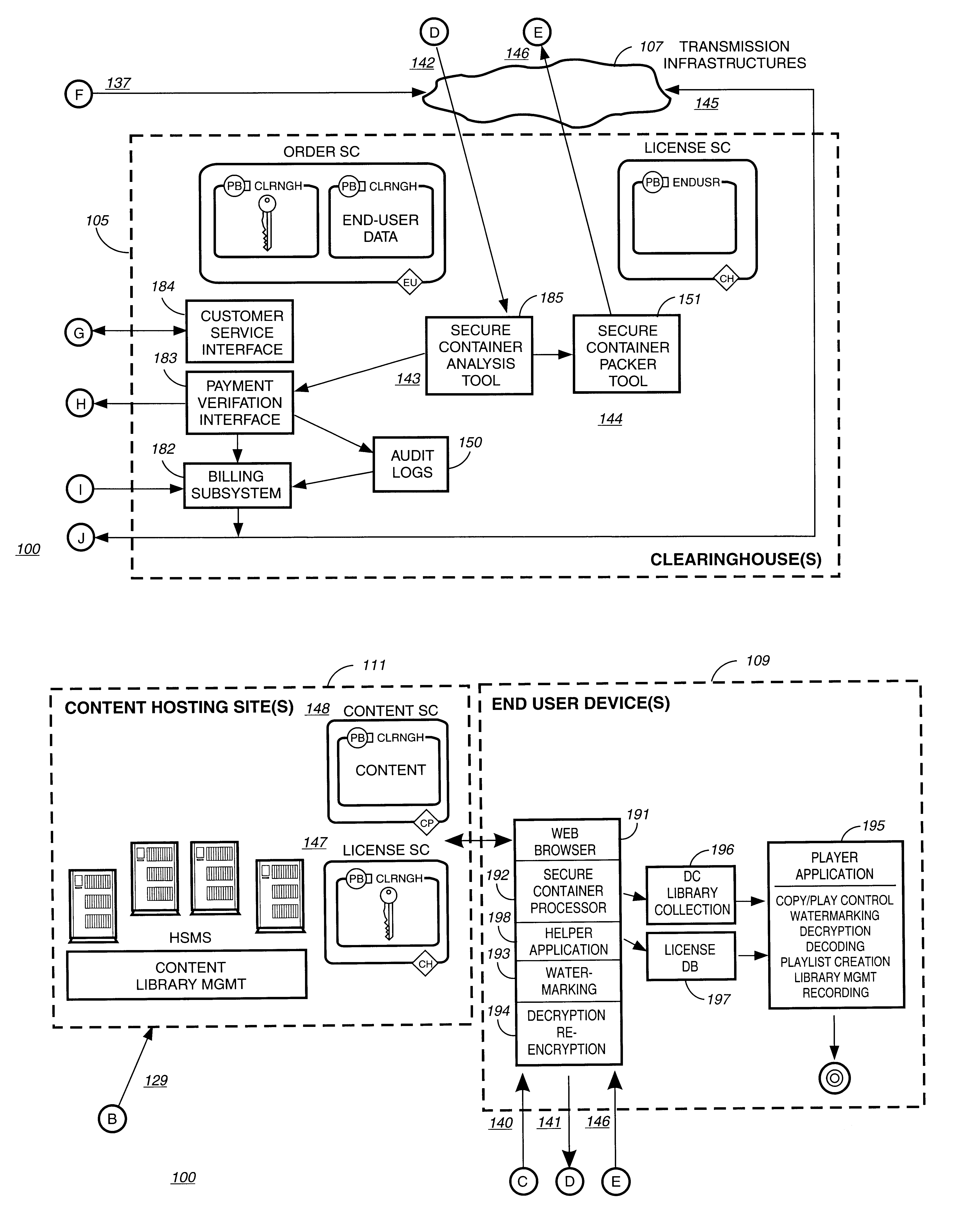
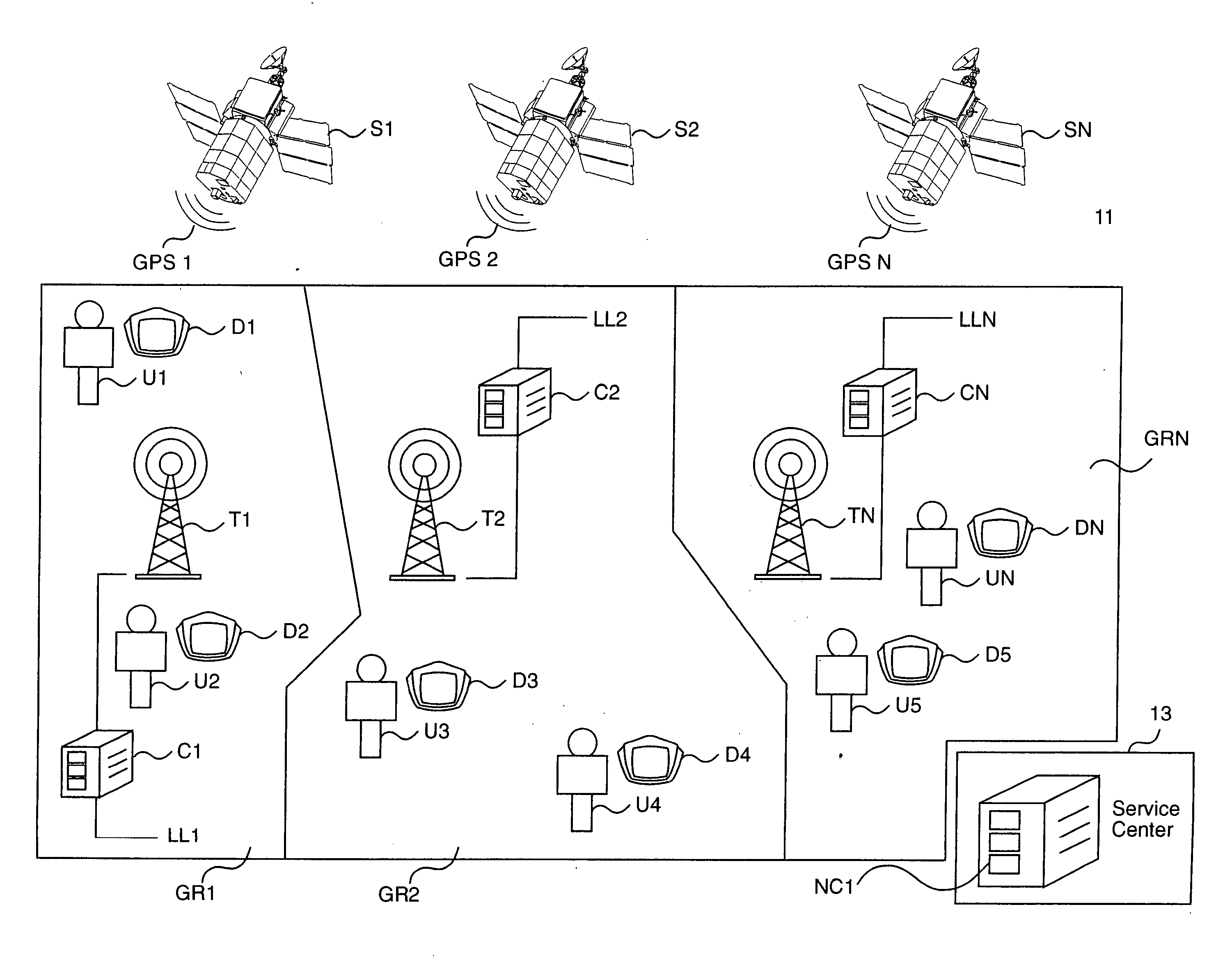
A method at a clearing house to verify the geographic region of an end user device for receiving encrypted digital content. In one embodiment the geographic region is a country. The method comprising three sub-methods. In the first sub-method the address is verified by determining the credit card clearing address of the end user using an address verification system. In the second sub-method the address is verified by determining the IP address of the end user device requesting delivery of the encrypted digital content. And in the third sub-method the address is verified by checking that the IP address of the end user device requesting delivery of the encrypted digital content is the identical IP address of the end user device requesting a license to use the encrypted digital content. Depending on predetermined system settings, one or more of the above combination of the three sub-methods is then checked, before authorizing the decrypting of the encrypted digital content includes decrypting the encrypted digital content if the address verification system returns an address in a predetermined geographic region and the IP address of the end user device is in a predetermined geographic region.
Owner:LEVEL 3 COMM LLC
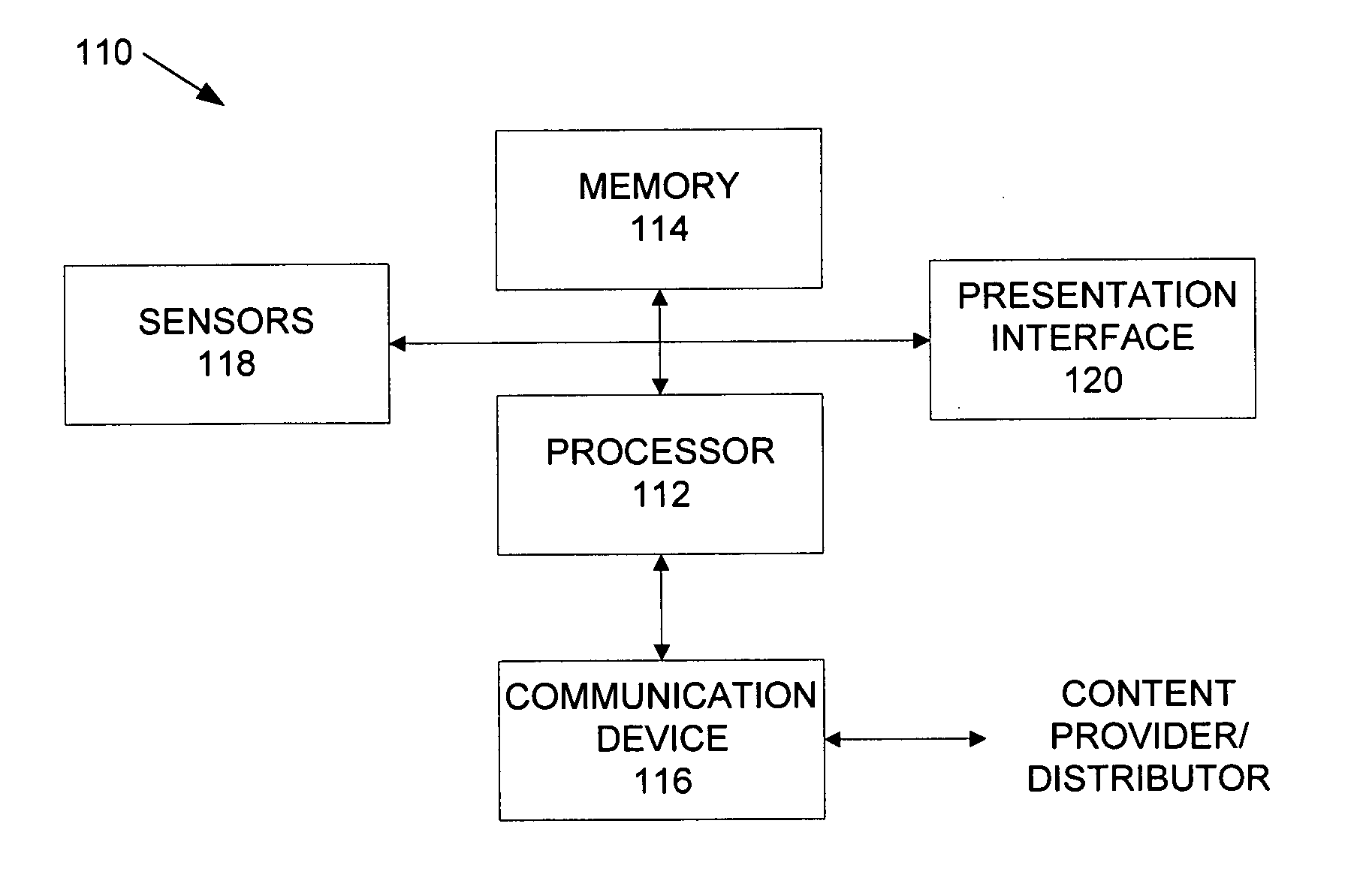
Using sensors to provide feedback on the access of digital content
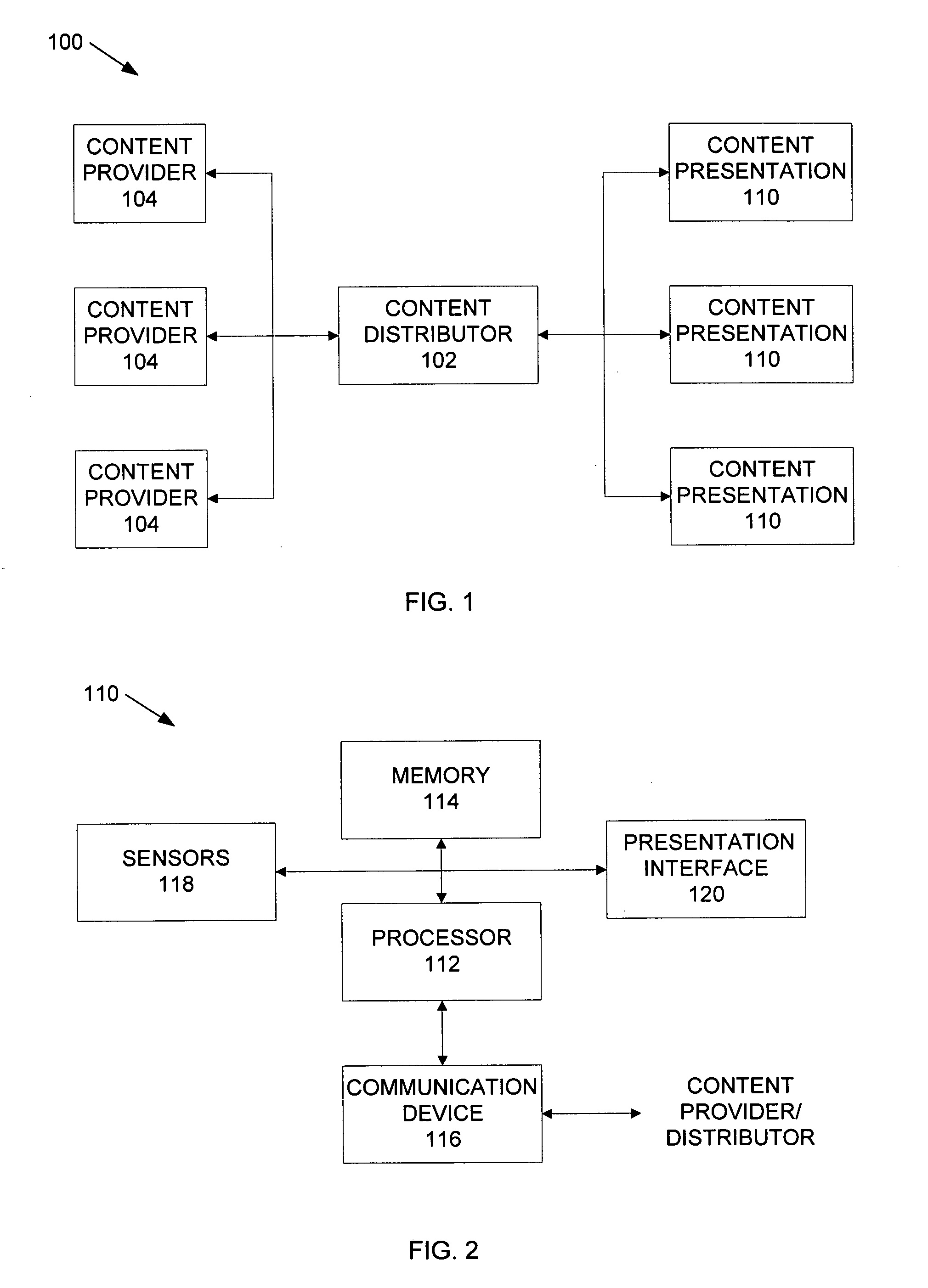
InactiveUS20070150916A1Analogue secracy/subscription systemsBroadcast components for monitoring/identification/recognitionGraphicsDigital content
A system according to the present disclosure presents content to a user and provides feedback to a content provider without requiring the viewer to explicitly take action. A content presentation unit, such as a digital picture frame or public display, may be any device that continuously and / or sequentially displays graphical, audio and other presentations that may be sensed by a user, generally without intervention by the user. The unit may include sensors that detect when a human expresses interest in specific content, and in various embodiments, determines a type of emotional response experienced by the user regarding the content. Particular sensors may include eye-contact, touch, motion and voice, though other sensors may also be used. The response information can be combined to provide feedback to the content provider that the content was experienced, and may determine various data, such as the duration of attention to the content and any detected emotional response to it.
Owner:PALO ALTO RES CENT INC
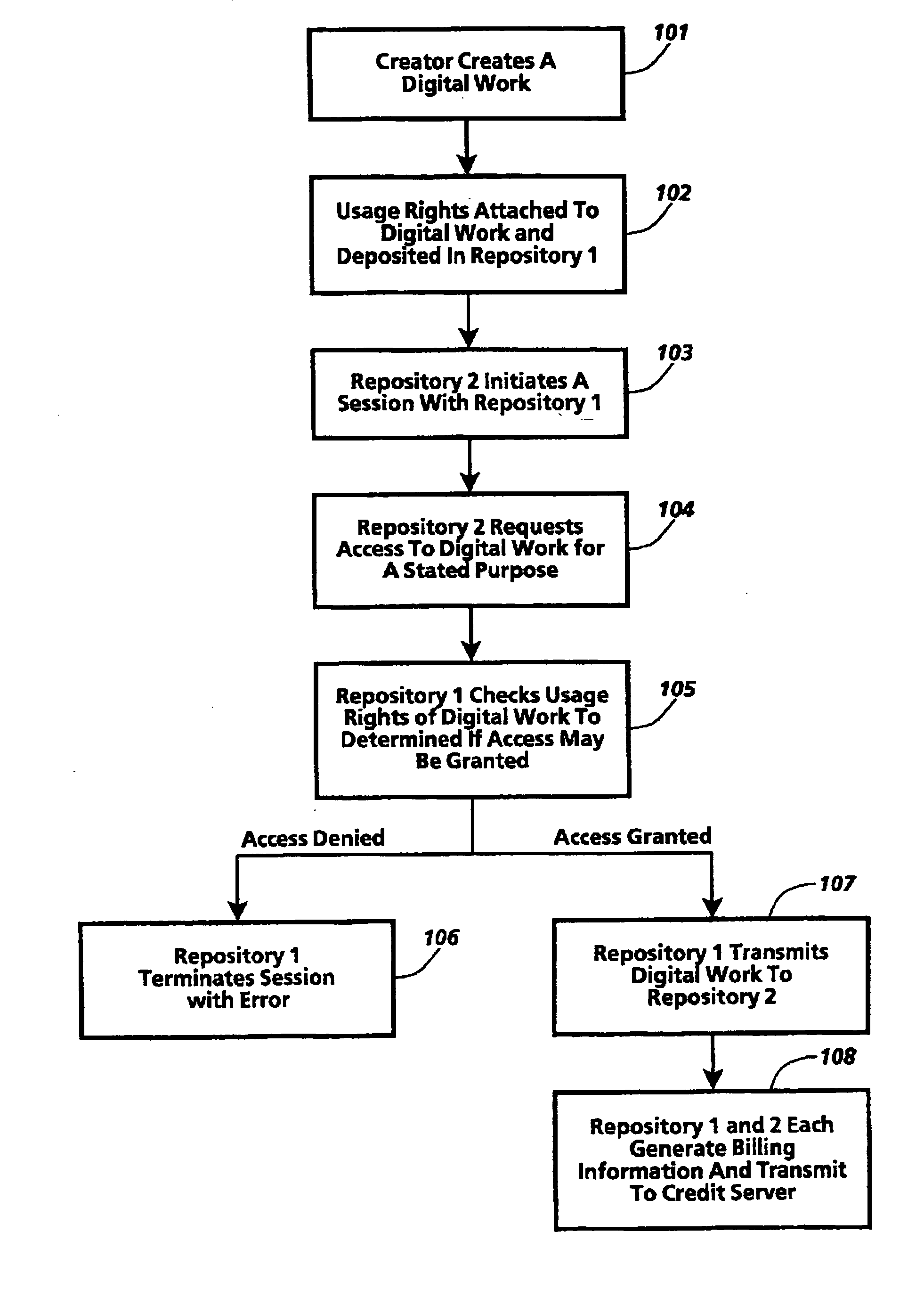
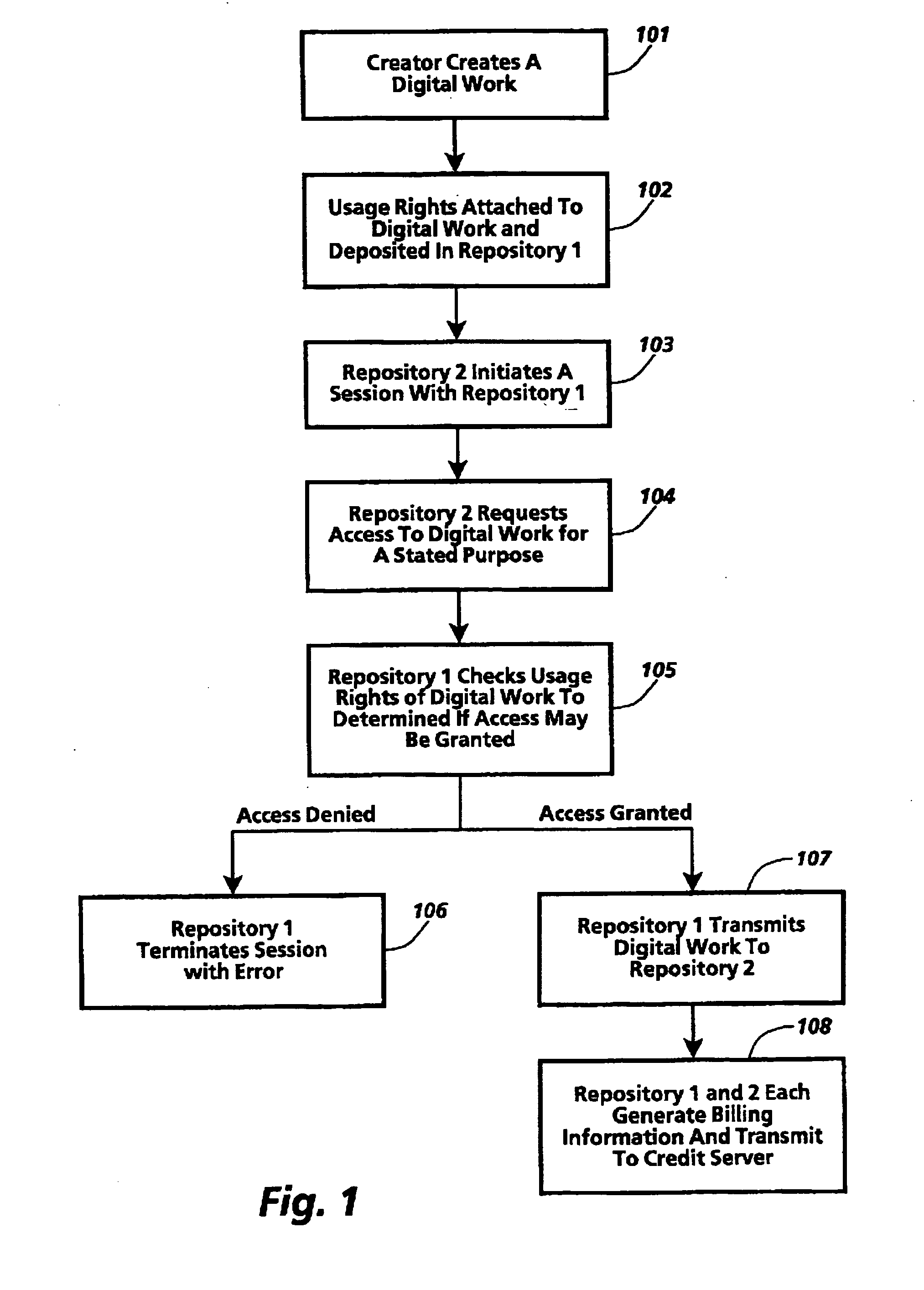
Triggering applications based on a captured text in a mixed media environment
ActiveUS20070050360A1Easy to optimizeFacilitate methodMultimedia data indexingSpecial data processing applicationsInformation retrievalApplication software
A Mixed Media Reality (MMR) system and associated techniques are disclosed. The MMR system provides mechanisms for forming a mixed media document that includes media of at least two types (e.g., printed paper as a first medium and digital content and / or web link as a second medium). In one particular embodiment, the MMR system includes an action processor and method, and MMR documents with an associated action. The MMR document structure is particularly advantageous because the ability to specify different actions for different MMR documents, combined with the ability to create any number of MMR documents for a particular location on any media, allows the MMR architecture to serve as a universal trigger or initiator for additional processing. In other words, addition processing or actions can be triggered or initiated based on MMR recognition. The action processor receives the output of the MMR recognition process which yields an MMR document including at least one action. The action processor executes that action which includes various commands to the MMR system or other systems coupled to the MMR system. The MMR system architecture is advantageous because an action can be executed by pointing the capture device at a block of text, and the action is performed. Example actions include retrieving the text in electronic form to the capture device, retrieving the specification for the action, inserting data to a MMR document, transferring data between documents, purchasing items, authoring actions or reviewing historical information about actions. The MMR system includes a variety of user applications (one or more actions) initiated by the MMR recognition of a text patch such as information retrieval for a travel guide book, stock listings or advertisements; information capture such as recording content from a conference, recording and storing multimedia associated with the document, capturing information for a calendar and on the fly authoring; purchasing media files for storage on any part of an MMR document.
Owner:RICOH KK
Method and system for the information protection of digital content
ActiveUS7484103B2Digital data processing detailsAnalogue secracy/subscription systemsDigital contentNetwork packet
The present invention relates to the information protection of digital content transferred by streaming and download service through wire or wireless Internet network. The information protection system in this invention suggests a drastic prevention method of copyrights infringement such as illegal copy and unauthorized distribution of digital content, by using of the encryption, decryption, distribution, and authentication technologies. This invention suggests the control technology of general viewer program, not the specific viewer program for information protection, using a network filter driver for streaming and file system filter driver for download service. The main function of network and file system filter driver is the filtering operation such as a hooking, changing, decrypting, and restoring of message and data packet, and transferring to the viewer program. The main idea and technology of this invention suggest higher secure and efficient digital information protection system for live / VOD / HTTP streaming and download service.
Owner:WOO JE HAK +6
Method, system and device for providing educational content
InactiveUS20050086172A1Metering/charging/biilling arrangementsDigital data processing detailsDigital contentNumber content
A system, method and device for controlling the use of digital content in accordance with usage rights information associated with the digital content and specifying a manner of use for the digital content, including generating a request, from a client device, for digital content; receiving the request at a content distributor repository; downloading the content and usage rights information associated with the content from the content distributor repository to the client device; enforcing the usage rights information with a repository coupled to the client device to render the content by a rendering engine of the client device only in accordance with the manner of use.
Owner:CONTENTGUARD HLDG
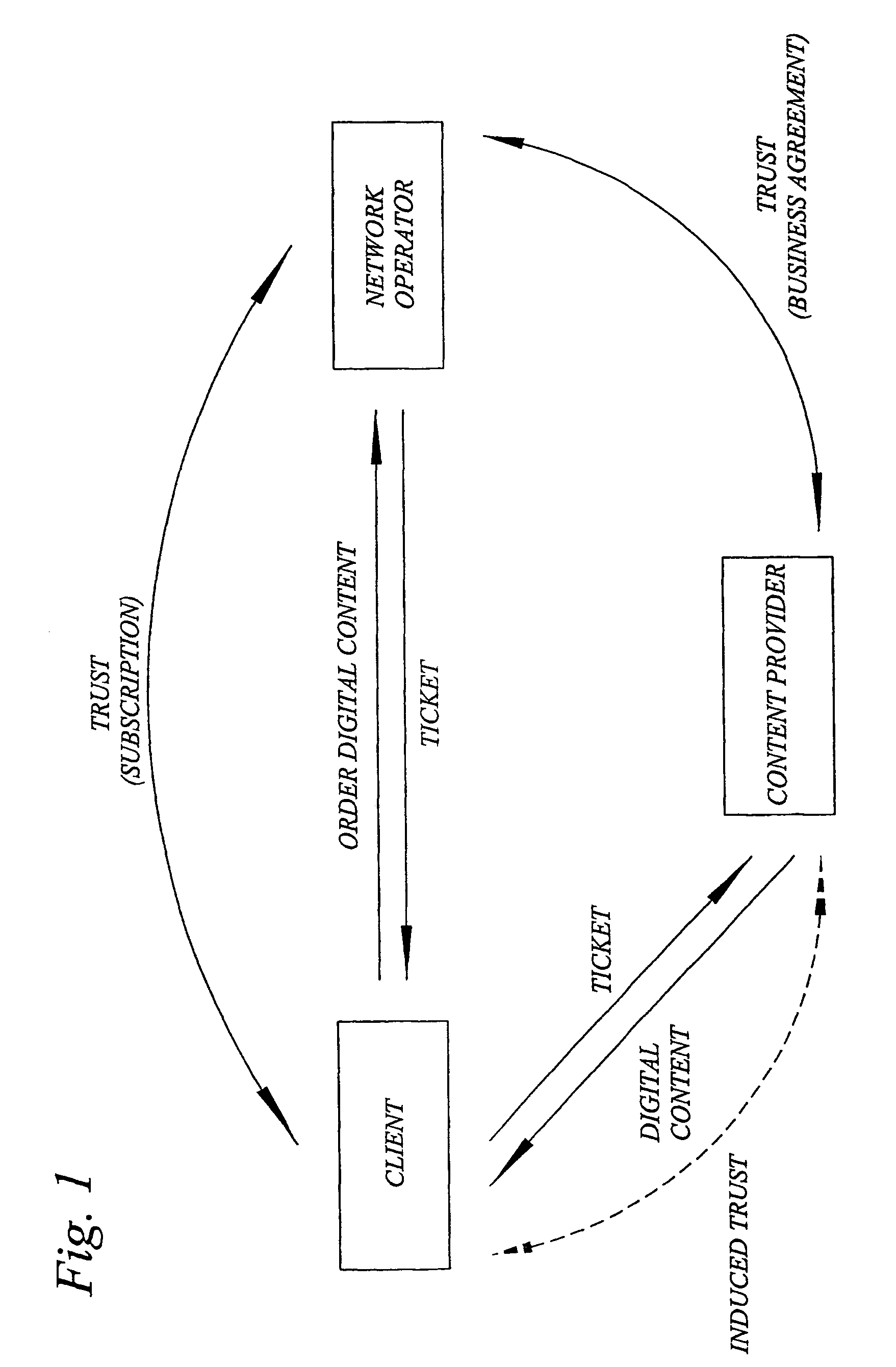
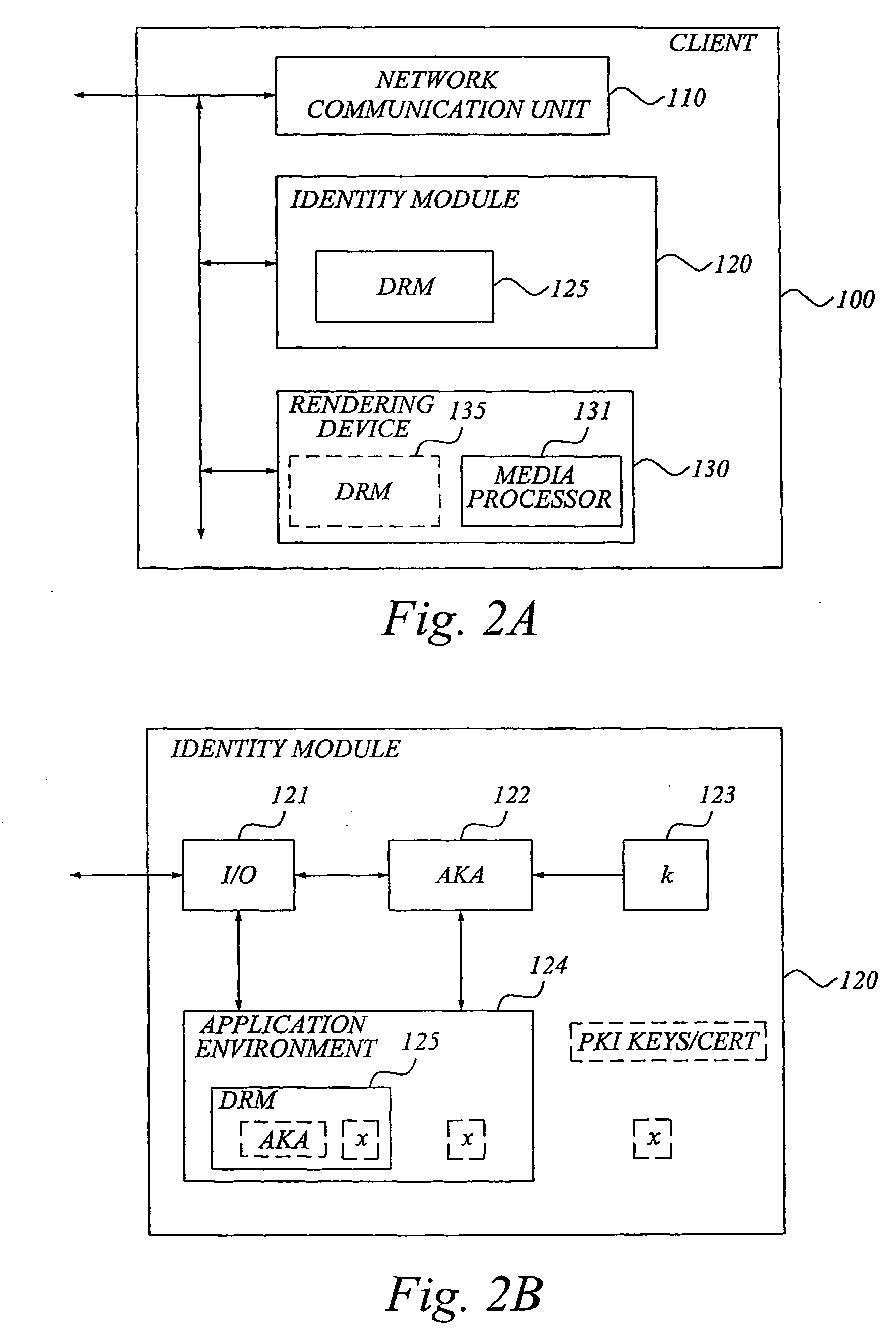
Robust and flexible digital rights management involving a tamper-resistant identity module
ActiveUS20050278787A1Easy to replaceEasy to upgradeDigital data processing detailsAnalogue secracy/subscription systemsDigital contentDigital rights management
The invention relates to digital rights management, and proposes the implementation of a DRM agent (125) into a tamper-resistant identity module (120) adapted for engagement with a client system (100), such as a mobile phone or a computer system. The DRM agent (125) is generally implemented with functionality for enabling usage, such as rendering or execution of protected digital content provided to the client system from a content provider In general, the DRM agent (125) includes functionality for cryptographic processing of DRM metadata associated with the digital content to be rendered. In a particularly advantageous realization, the DRM agent is implemented as an application in the application environment of the identity module. The DRM application can be preprogrammed into the application environment, or securely downloaded from a trusted party associated with the identity module. The invention also relates to a distributed DRM module, with communication between distributed DRM agents (125, 135) based on usage-device specific key information.
Owner:TELEFON AB LM ERICSSON (PUBL)
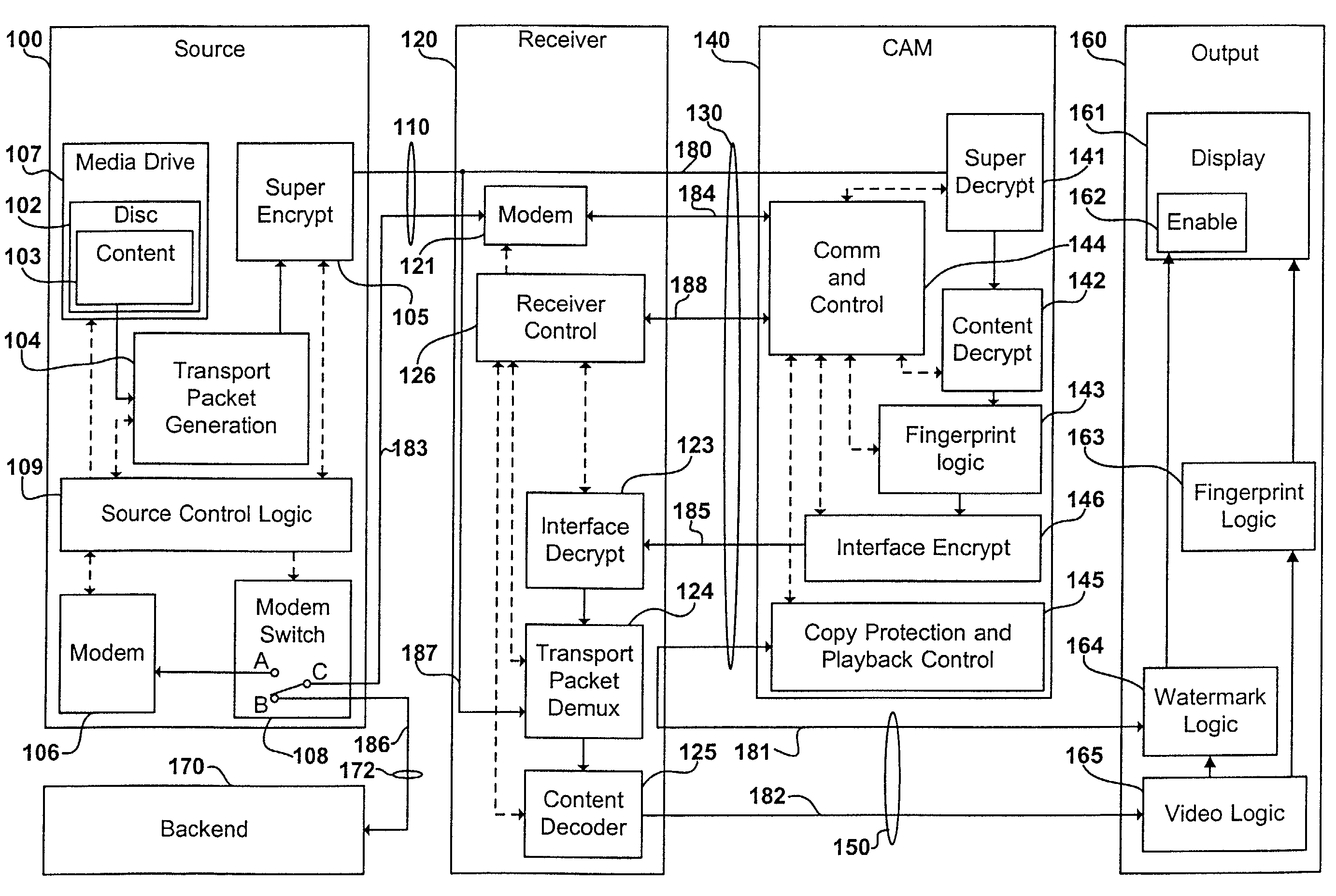
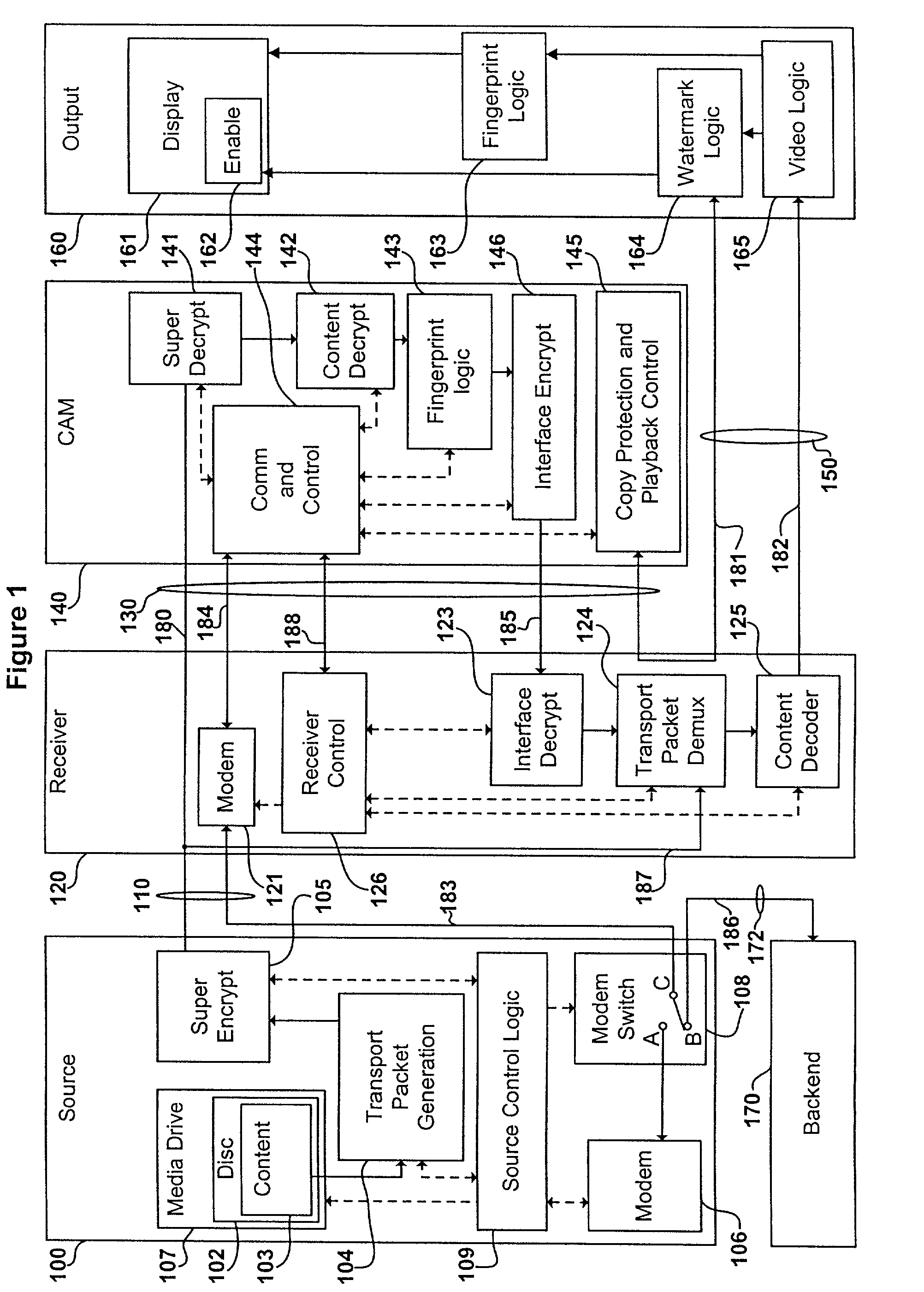
Digital content distribution system and method
InactiveUS7162642B2Prevent unauthorized accessObtaining unauthorized accessDigital data processing detailsUser identity/authority verificationContent distributionDigital content
A content distribution system and method which prevents unauthorized access to secured content such as movies and music. The apparatus includes a source, a receiver, an authorized security device such as a conditional access module (CAM) for decrypting authorized content, an output device for outputting content and a backend for managing accounts and system operations. One aspect of this invention provides a mechanism for providing secured content on a medium such as a DVD optical disc. These devices may verify that there is authorization to play the secured content, add watermarks to the secured content, convert the secured content to a displayable form and provide a means for preventing output of the secured content.
Owner:GOOGLE LLC
Content distribution for multiple digital rights management
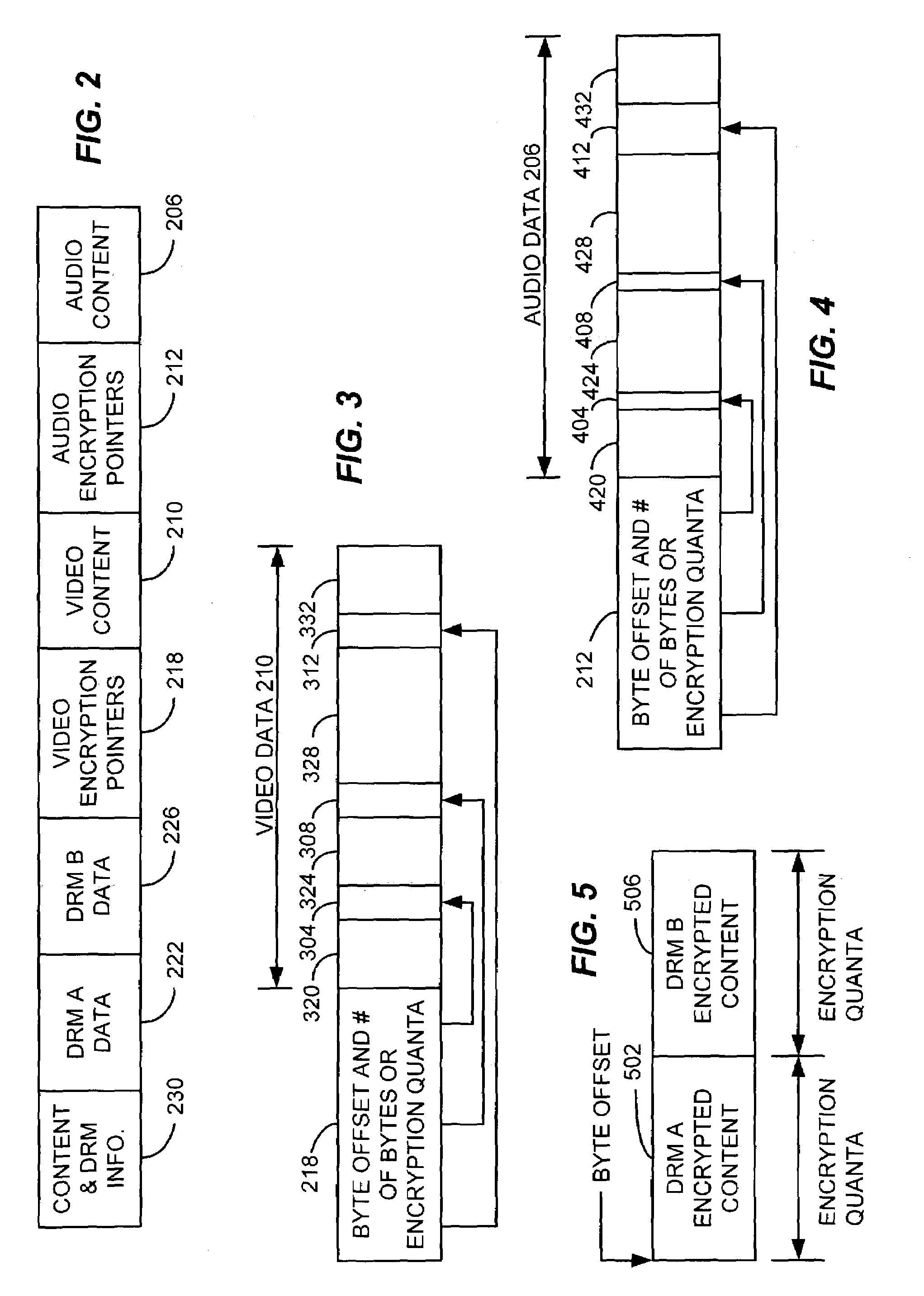
InactiveUS7120250B2Television system detailsKey distribution for secure communicationContent distributionDigital content
A method and apparatus for enabling use of multiple digital rights management scenarios (DRM). Unencrypted data representing digital content is examined to identify at least segments of content for encryption. The identified segments of content are duplicated and then encrypted using a first encryption method associated with a first DRM to produce first encrypted segments. Duplicates are encrypted using a second encryption method associated with a second DRM to produce second encrypted segments. A set of pointers are generated that point to the first and second encrypted segments content. A file is then created containing first and second encrypted segments of content, pointers and unencrypted content along with DRM rights data to produce a selectively encrypted multiple DRM enabled file.
Owner:SONY CORP +1
Digital content distribution using web broadcasting services
InactiveUS20060053077A1Website content managementElectronic credentialsBroadcast channelsDigital content
Owner:INT BUSINESS MASCH CORP
Digital Content Protection Method and Apparatus
InactiveUS20020099948A1Improve securityMinimizes probabilityKey distribution for secure communicationDigital data processing detailsDigital signatureDigital content
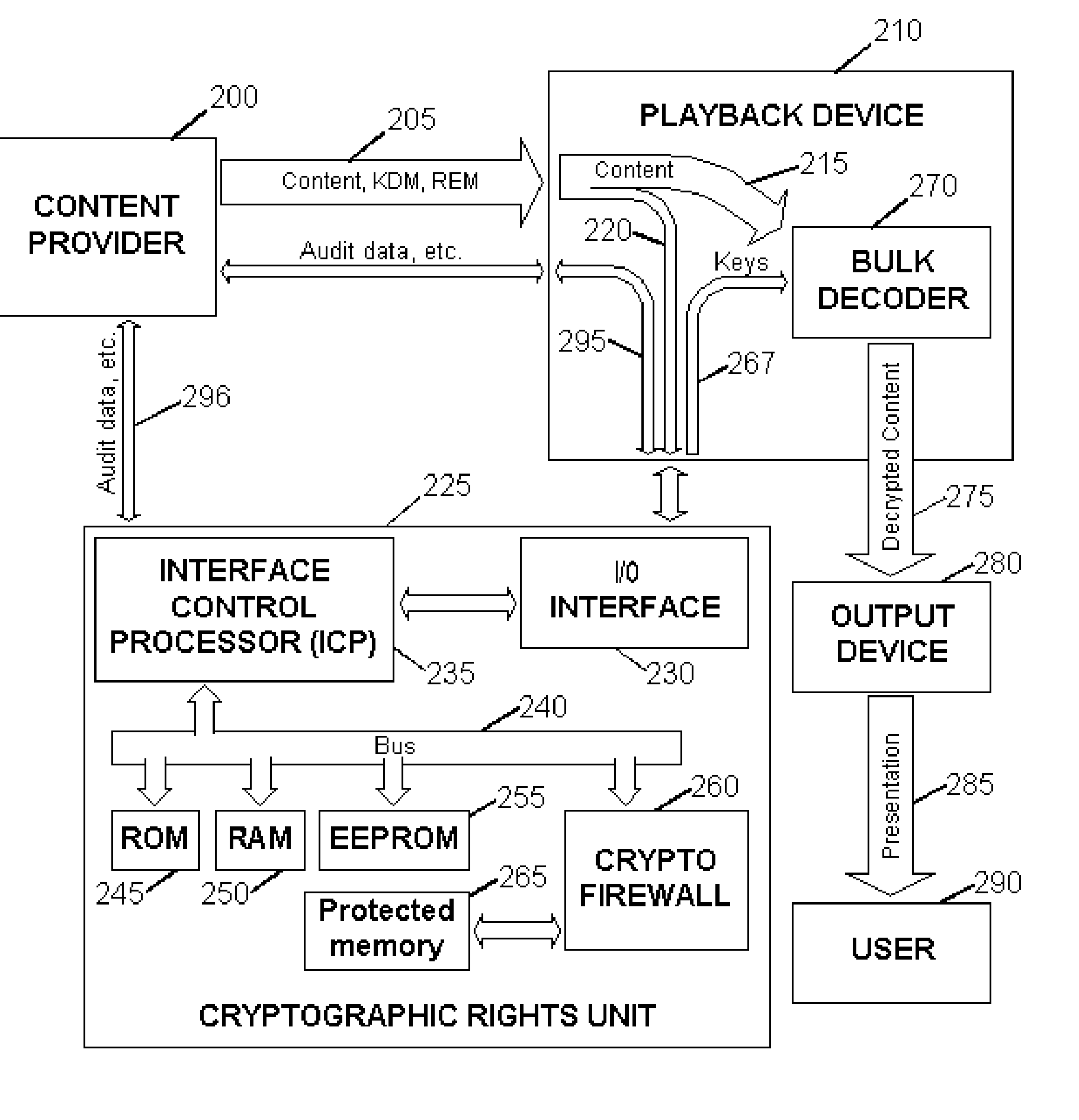
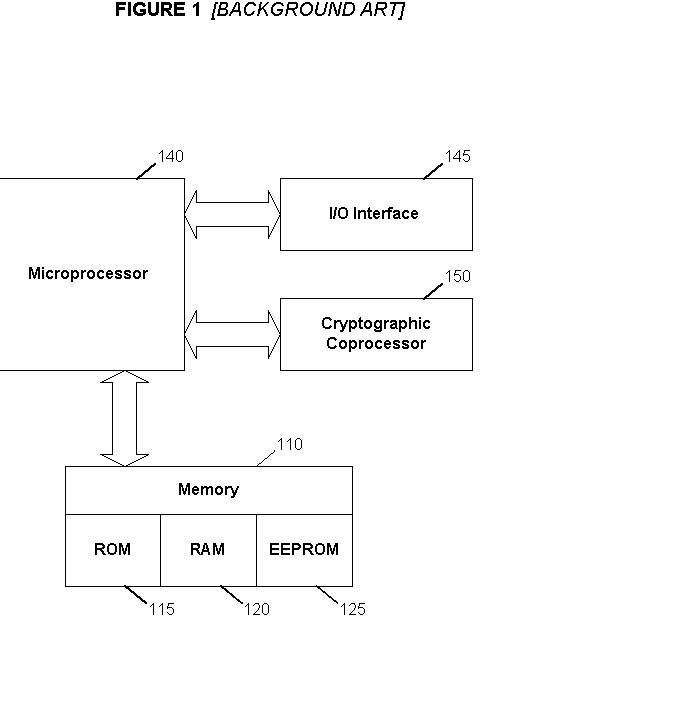
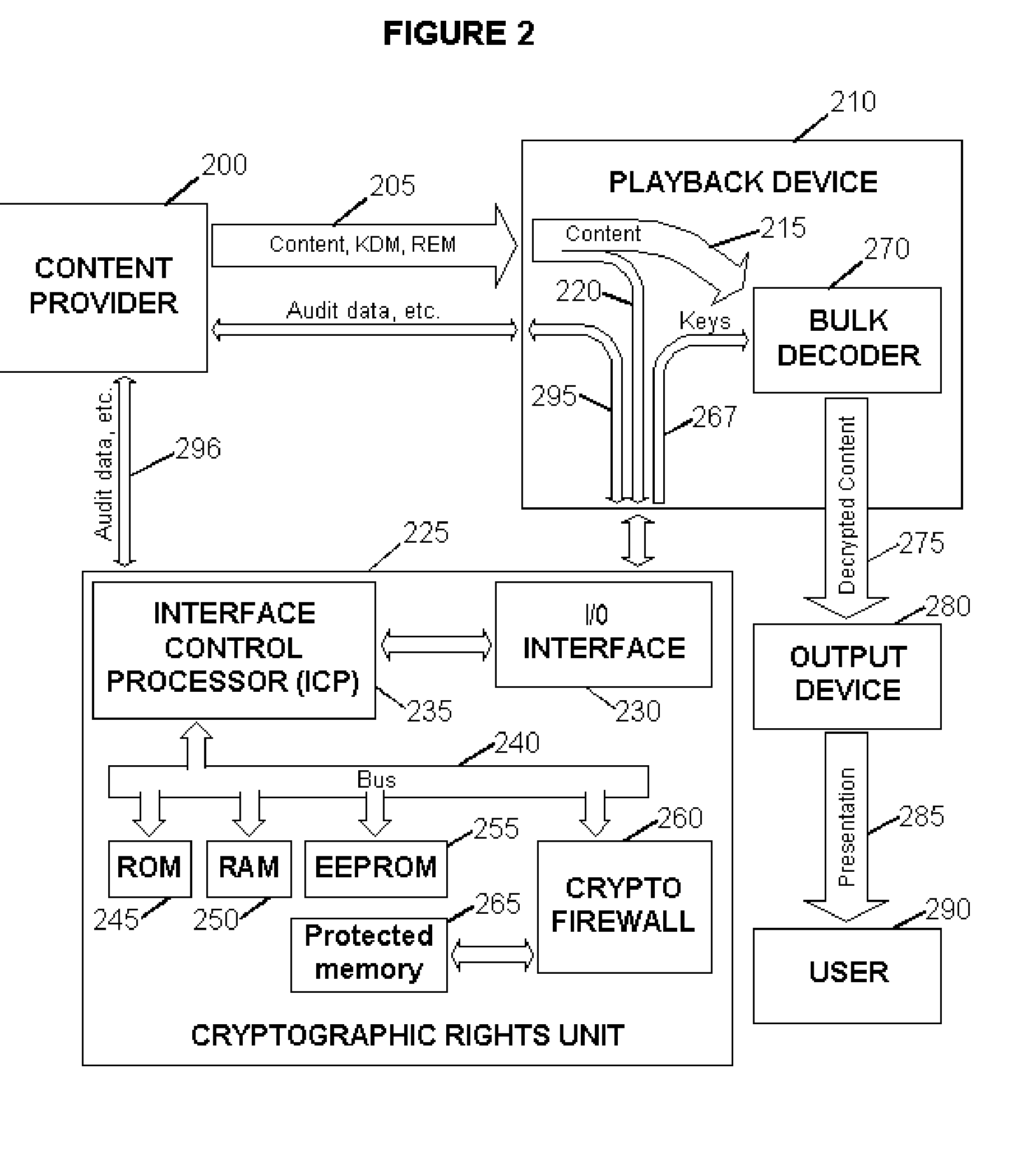
<heading lvl="0">Abstract of Disclosure< / heading> Before use, a population of tamper-resistant cryptographic enforcement devices is partitioned into groups and issued one or more group keys. Each tamper-resistant device contains multiple computational units to control access to digital content. One of the computational units within each tamper-resistant device communicates with another of the computational units acting as an interface control processor, and serves to protect the contents of a nonvolatile memory from unauthorized access or modification by other portions of the tamper-resistant device, while performing cryptographic computations using the memory contents. Content providers enforce viewing privileges by transmitting encrypted rights keys to a large number of recipient devices. These recipient devices process received messages using the protected processing environment and memory space of the secure unit. The processing result depends on whether the recipient device was specified by the content provider as authorized to view some encrypted digital content. Authorized recipient devices can use the processing result in decrypting the content, while unauthorized devices cannot decrypt the content. A related aspect of the invention provides for securing computational units and controlling attacks. For example, updates to the nonvolatile memory, including program updates, are supported and protected via a cryptographic unlocking and validation process in the secure unit, which can include digital signature verification.
Owner:CRYPTOGRAPHY RESEARCH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com