Patents
Literature
41837 results about "Data bank" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
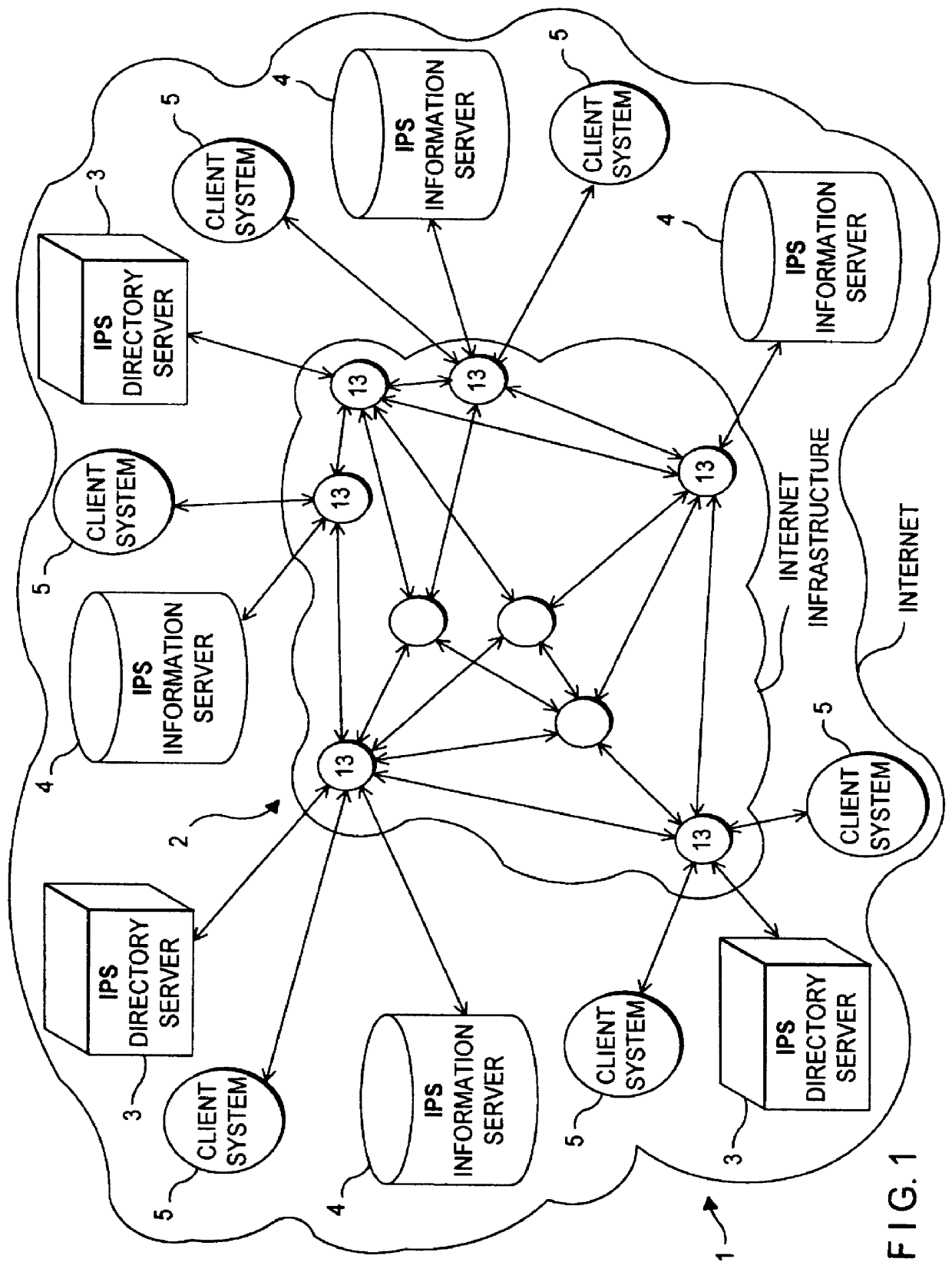
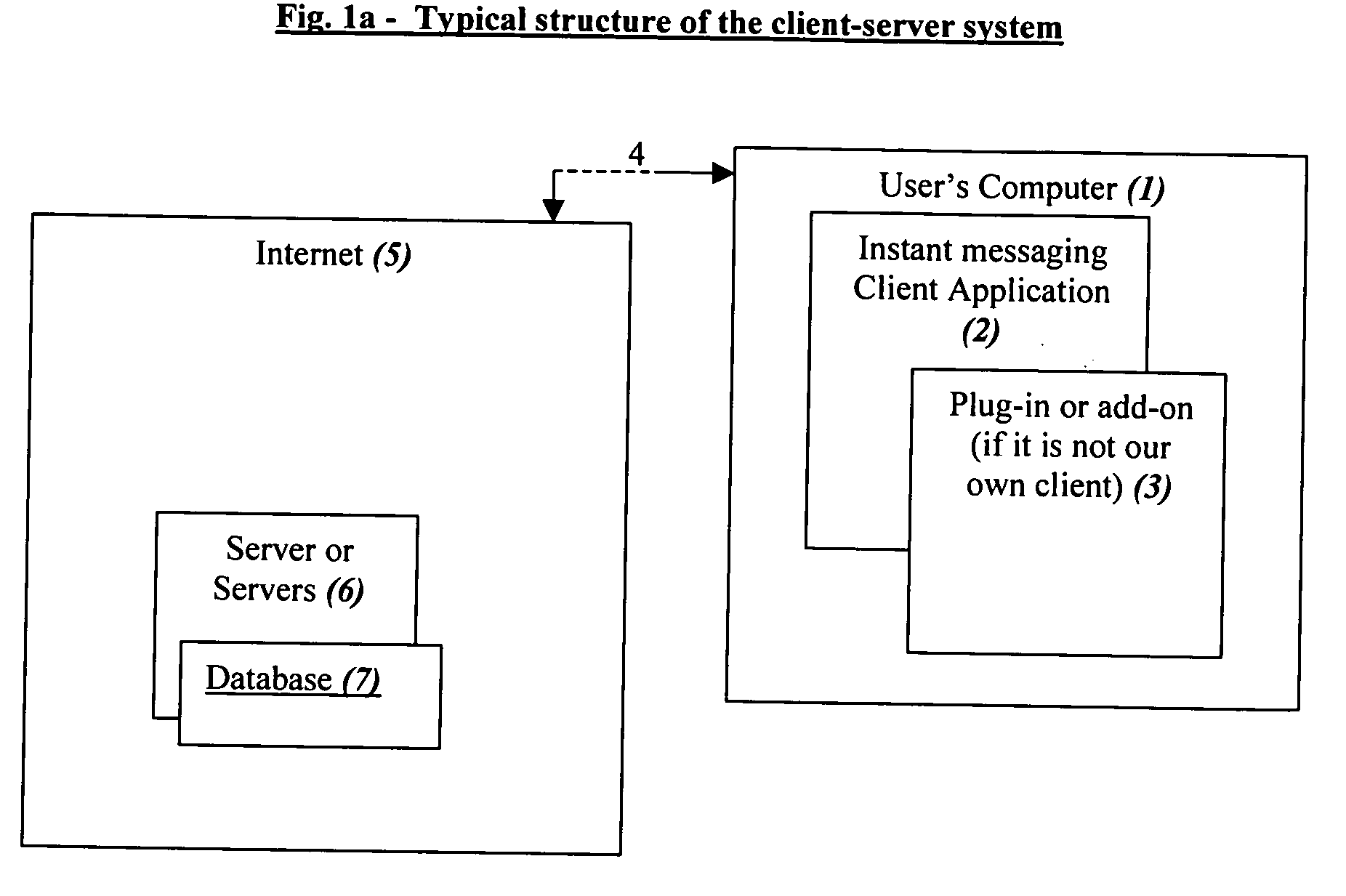
In telecommunications, computing, and information architecture, a data bank or databank is a repository of information on one or more subjects – a database – that is organized in a way that facilitates local or remote information retrieval and is able to process a large number of continual queries over a long period of time. A data bank may be either centralized or decentralized, though most usage of this term refers to centralized storage and retrieval of information, by way of analogy to a monetary bank. The data in a data bank can be anything from scientific information like global temperature readings, and governmental information like census statistics, to financial-system records like credit card transactions, or the inventory available from various suppliers.
Audio visual player apparatus and system and method of content distribution using the same
InactiveUS20060008256A1None of methods is secureTelevision system detailsColor television signals processingContent distributionVideo player
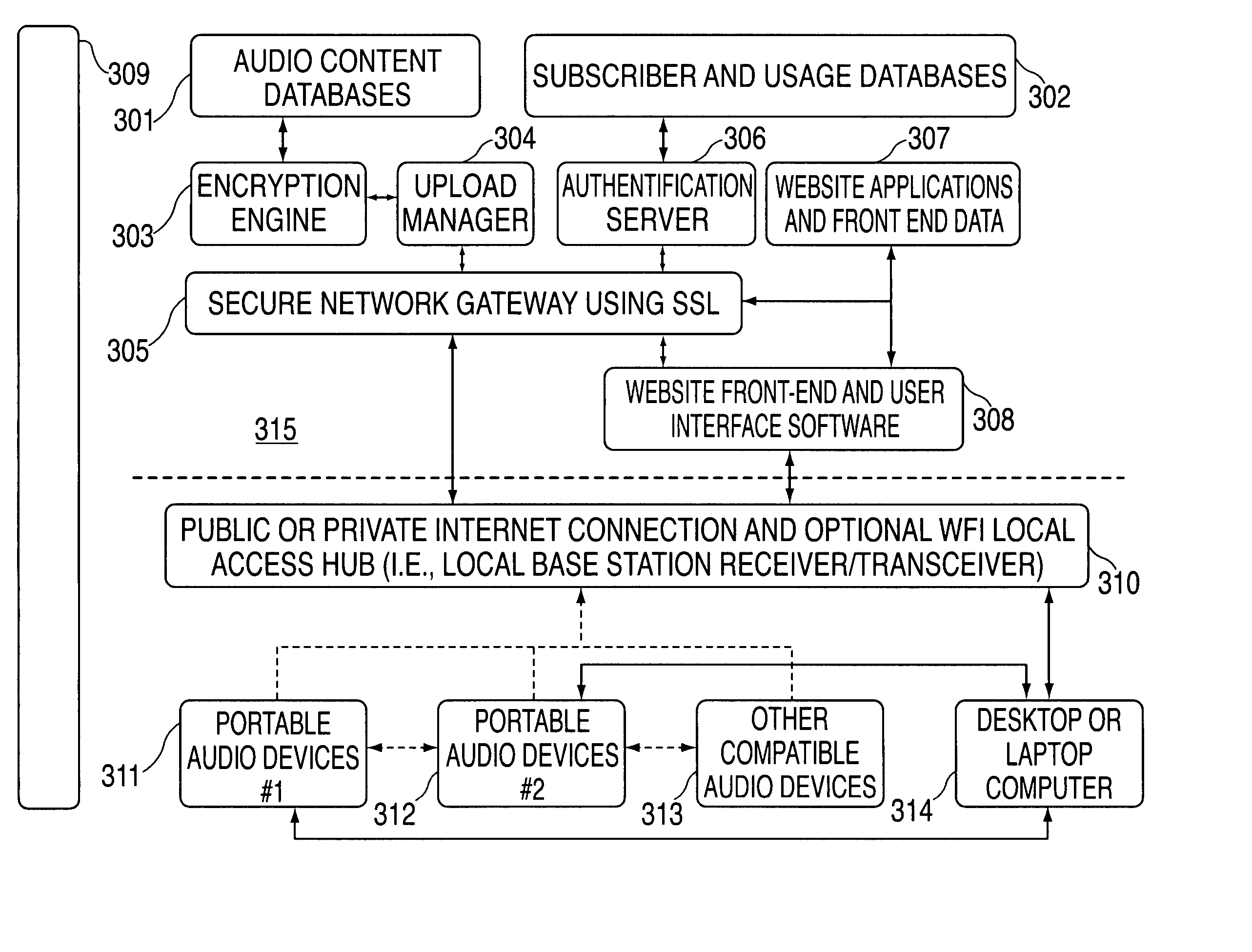
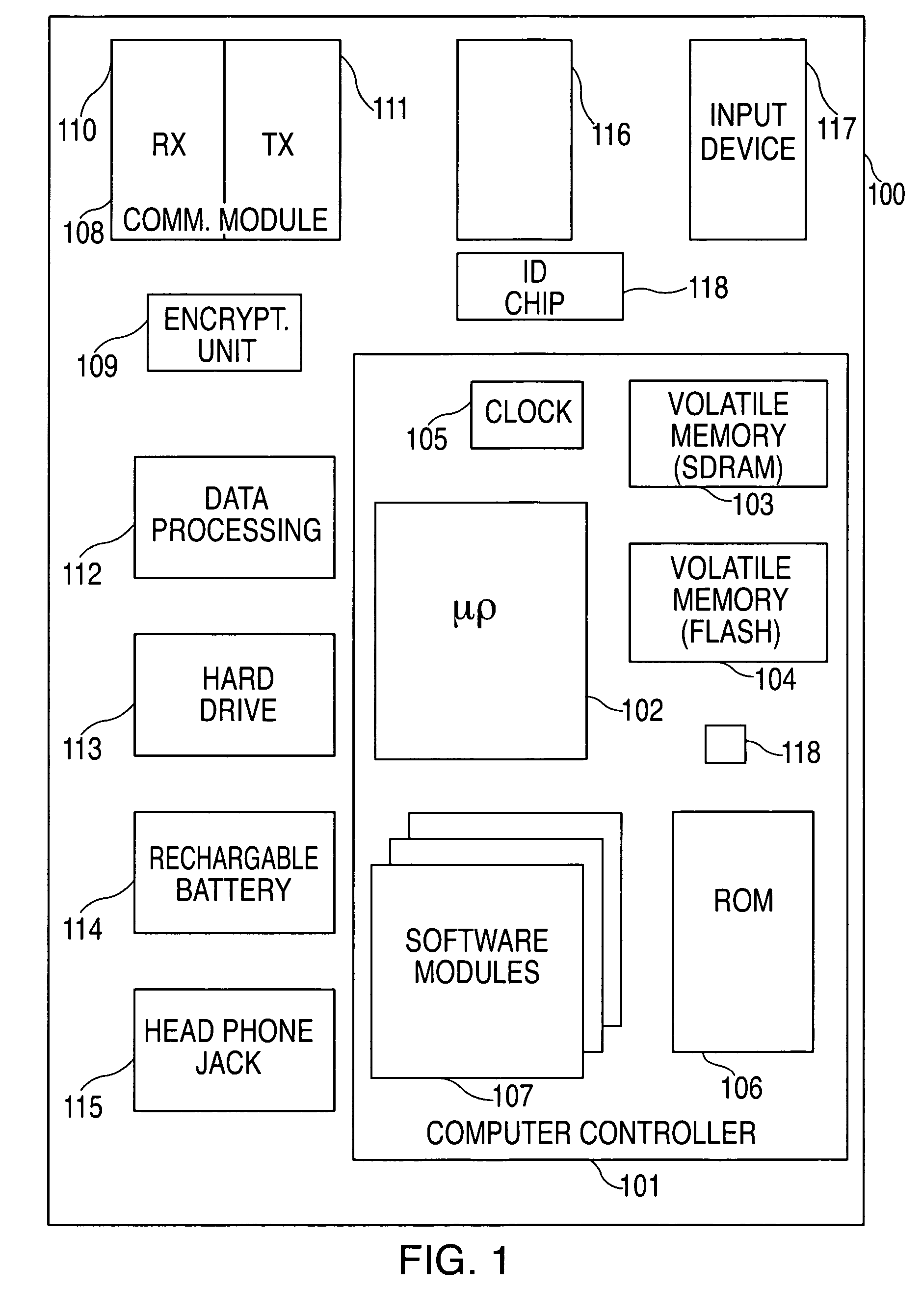
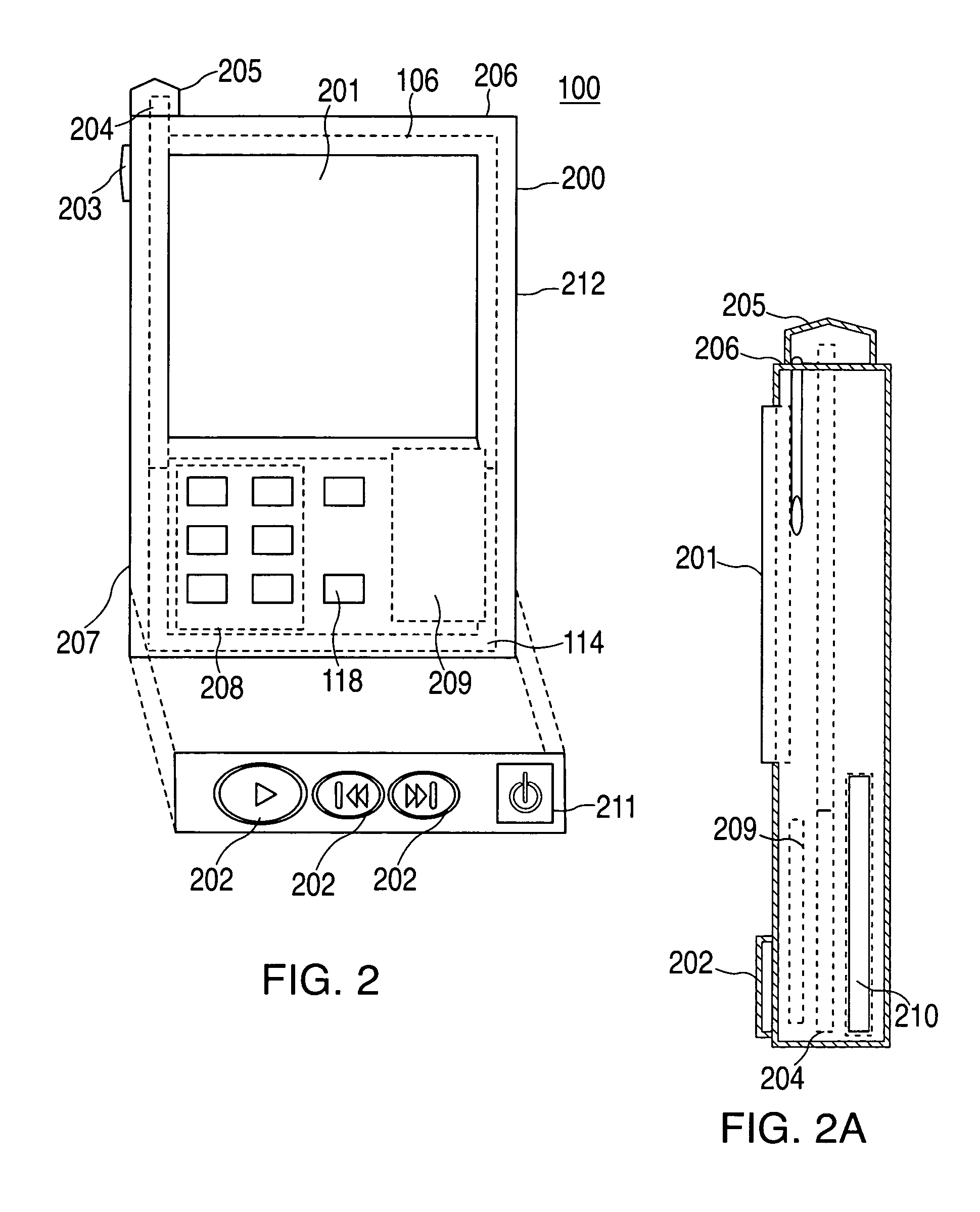
A portable wireless communications subscriber audio and / or video player apparatus and system and method for selecting, requesting, downloading, and playing audio and / or video data content files from an Internet-based database server. The wireless link is preferably implemented in accordance with the WiFi protocol, which allows connectivity to the Internet by being in proximity with a local base station or WiFi hotspot (i.e., publicly available local wireless access hub connected to the Internet). The portable wireless communications subscriber audio and / or video player apparatus and system preferably include a security means for monitoring and blocking unauthorized use of the player apparatus and system. The player apparatus further preferably has the capability to communicate with other neighboring player apparatus for the purpose of exchanging content data files, playlists and personal messages.
Owner:SANDISK TECH LLC
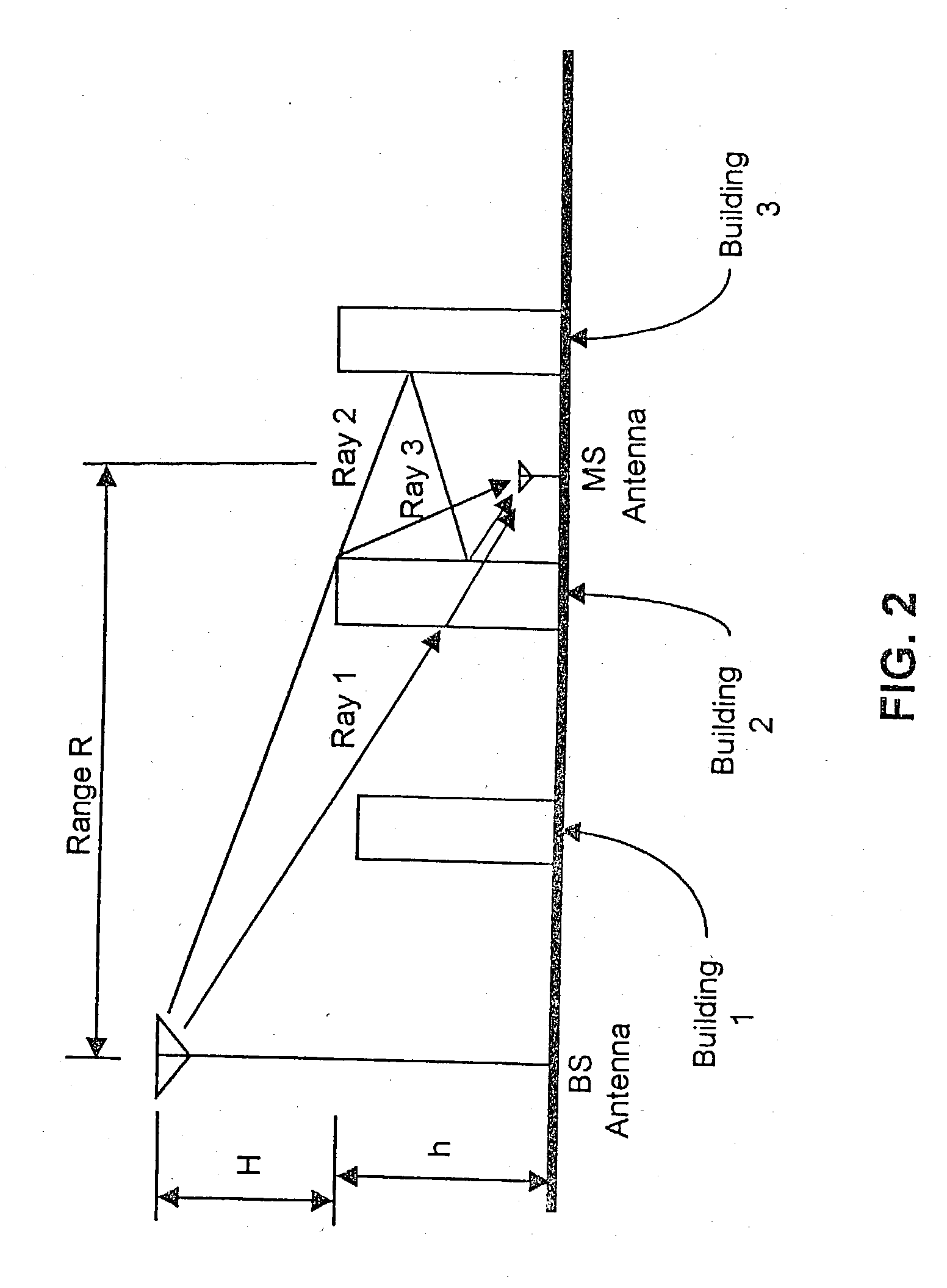
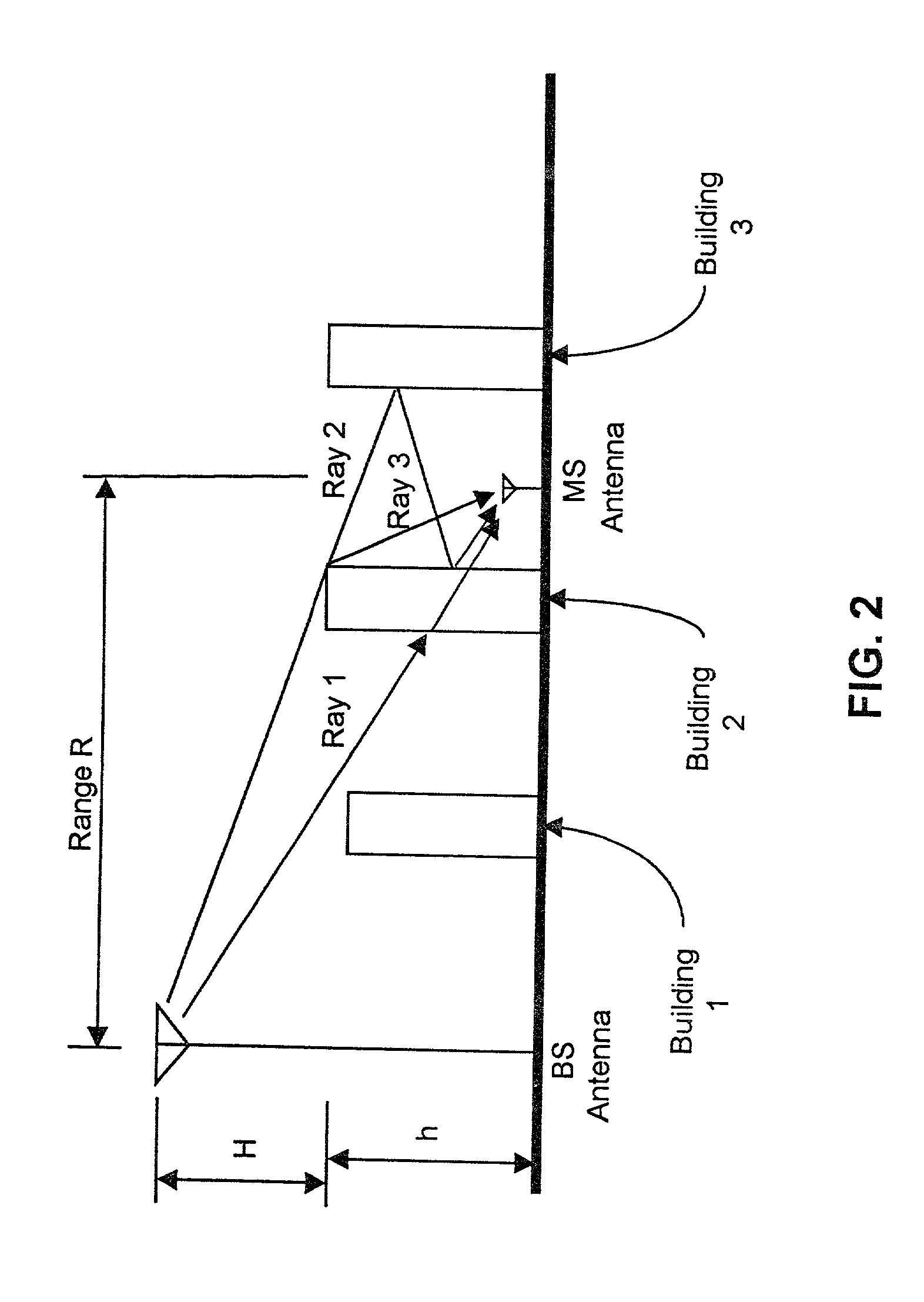
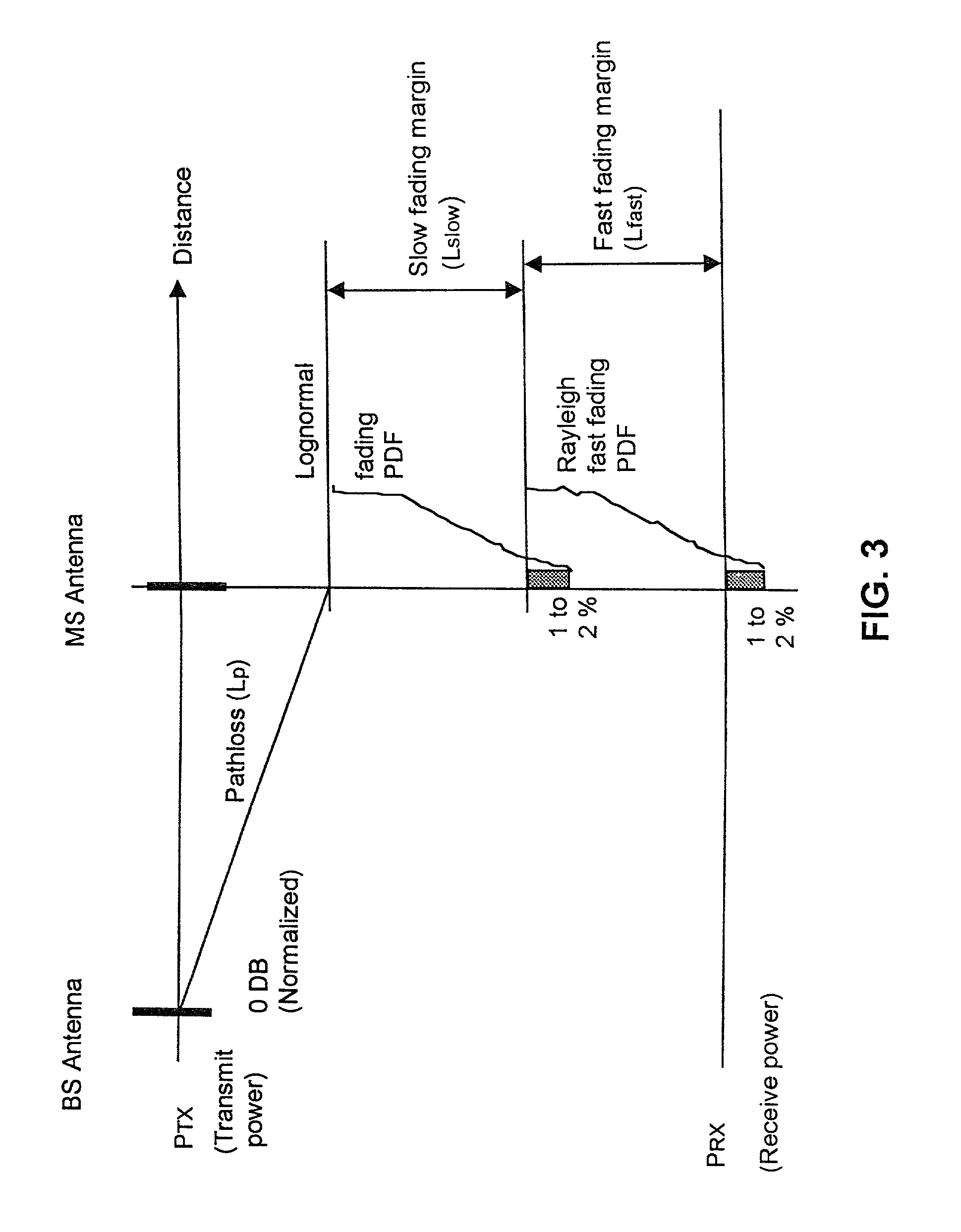
Wireless location using multiple location estimators
InactiveUS6249252B1Effectively and straightforwardly resolvedAmbiguity and conflictDirection finders using radio wavesBeacon systems using radio wavesTerrainHeuristic
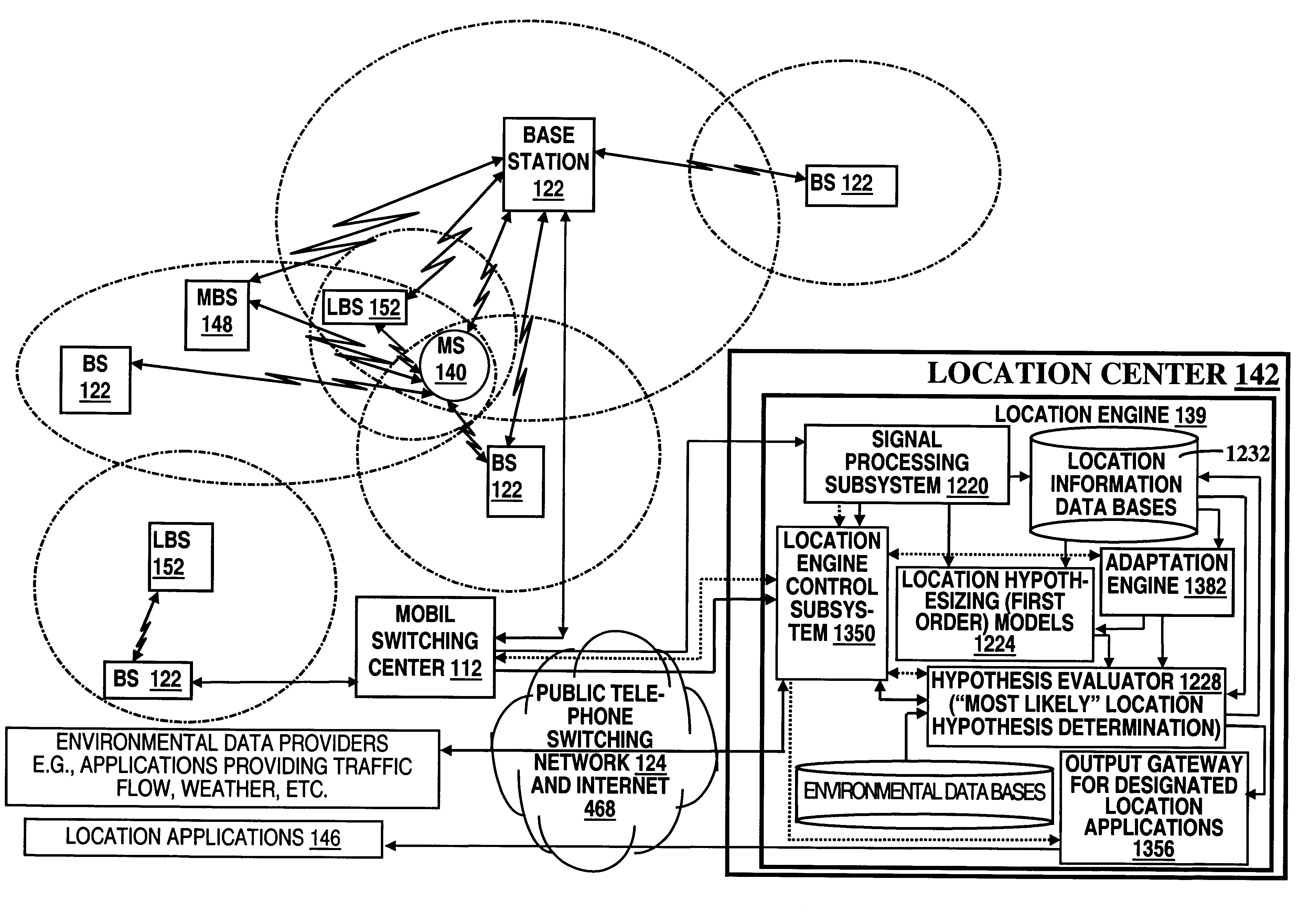
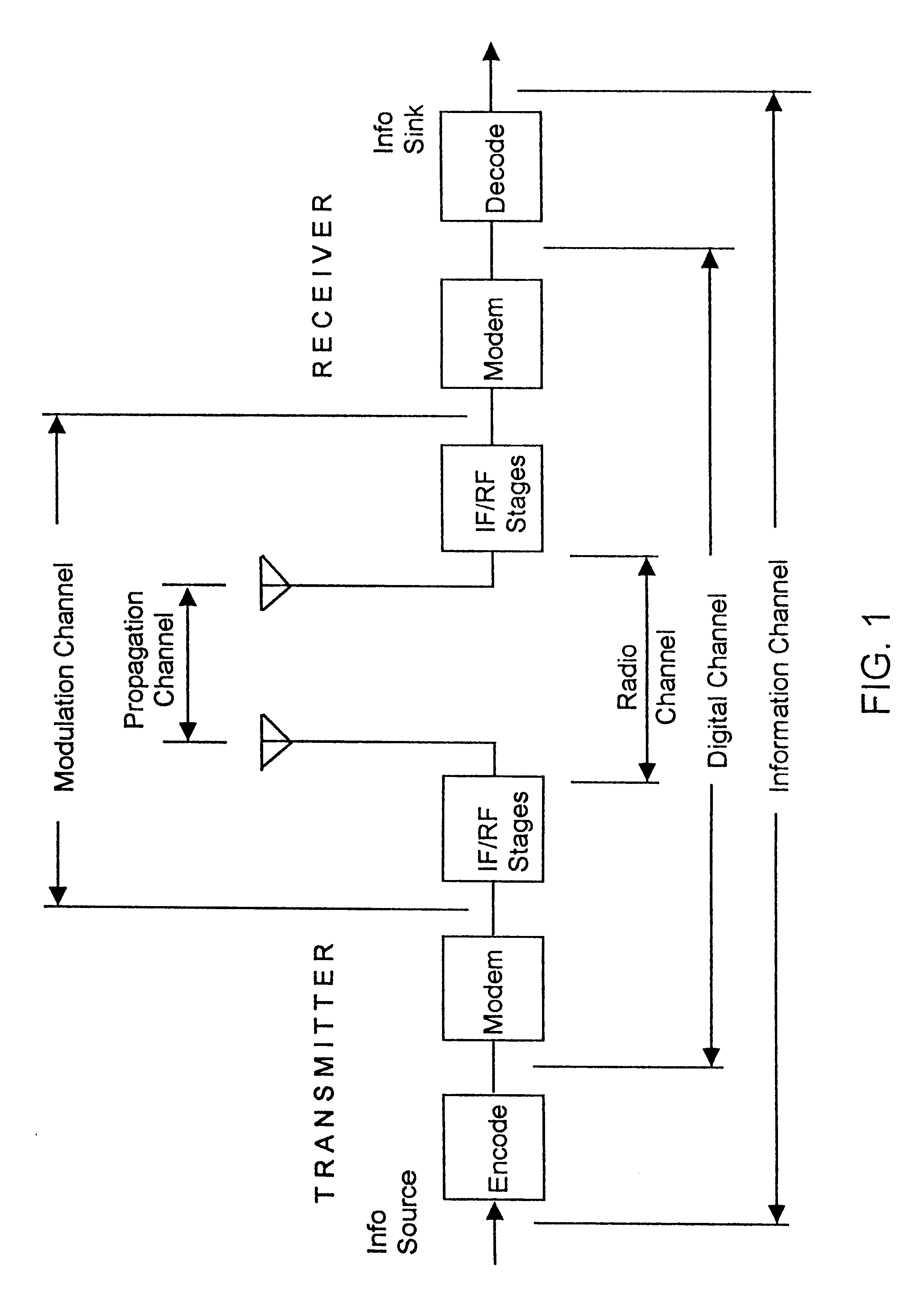
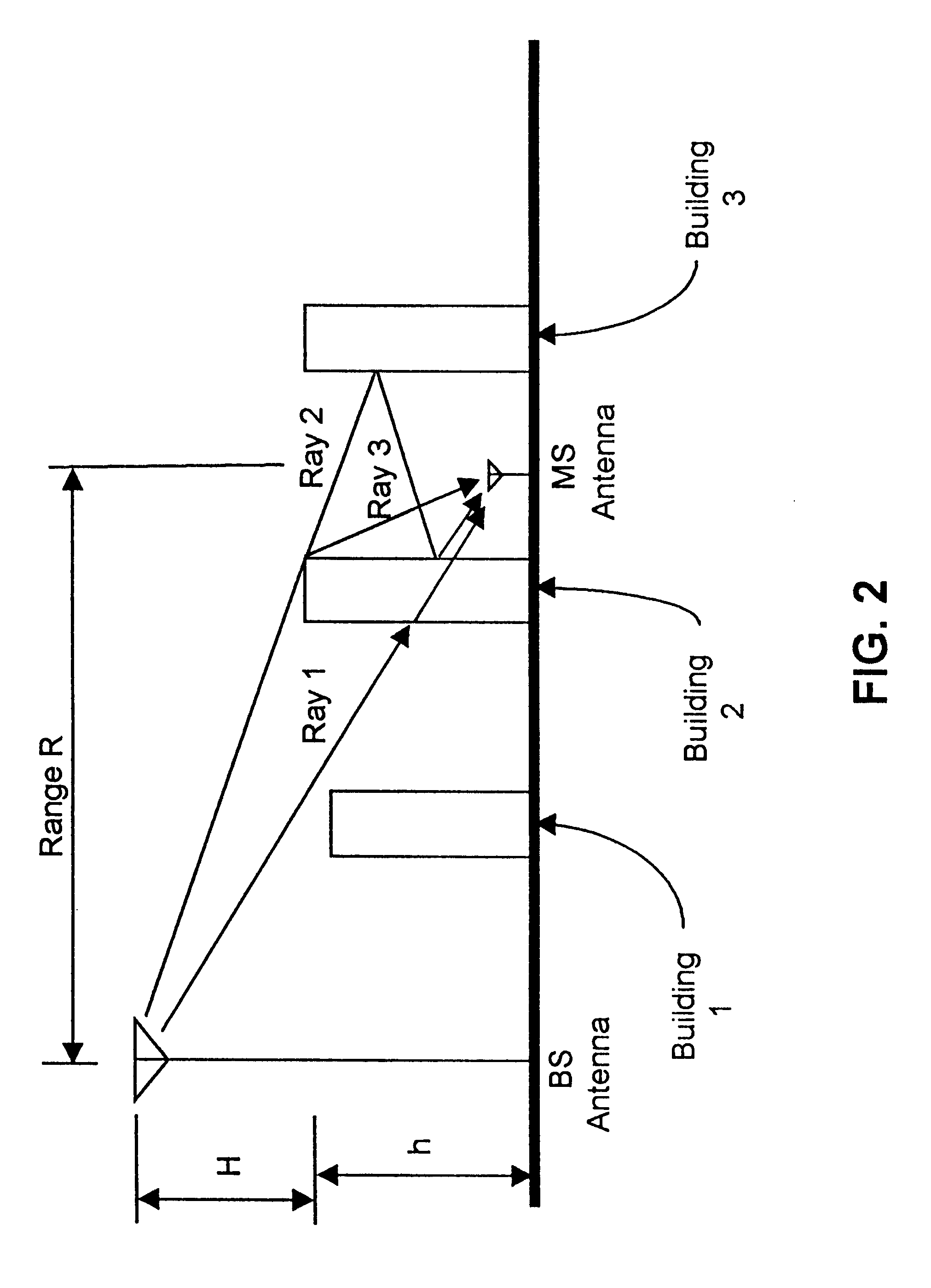
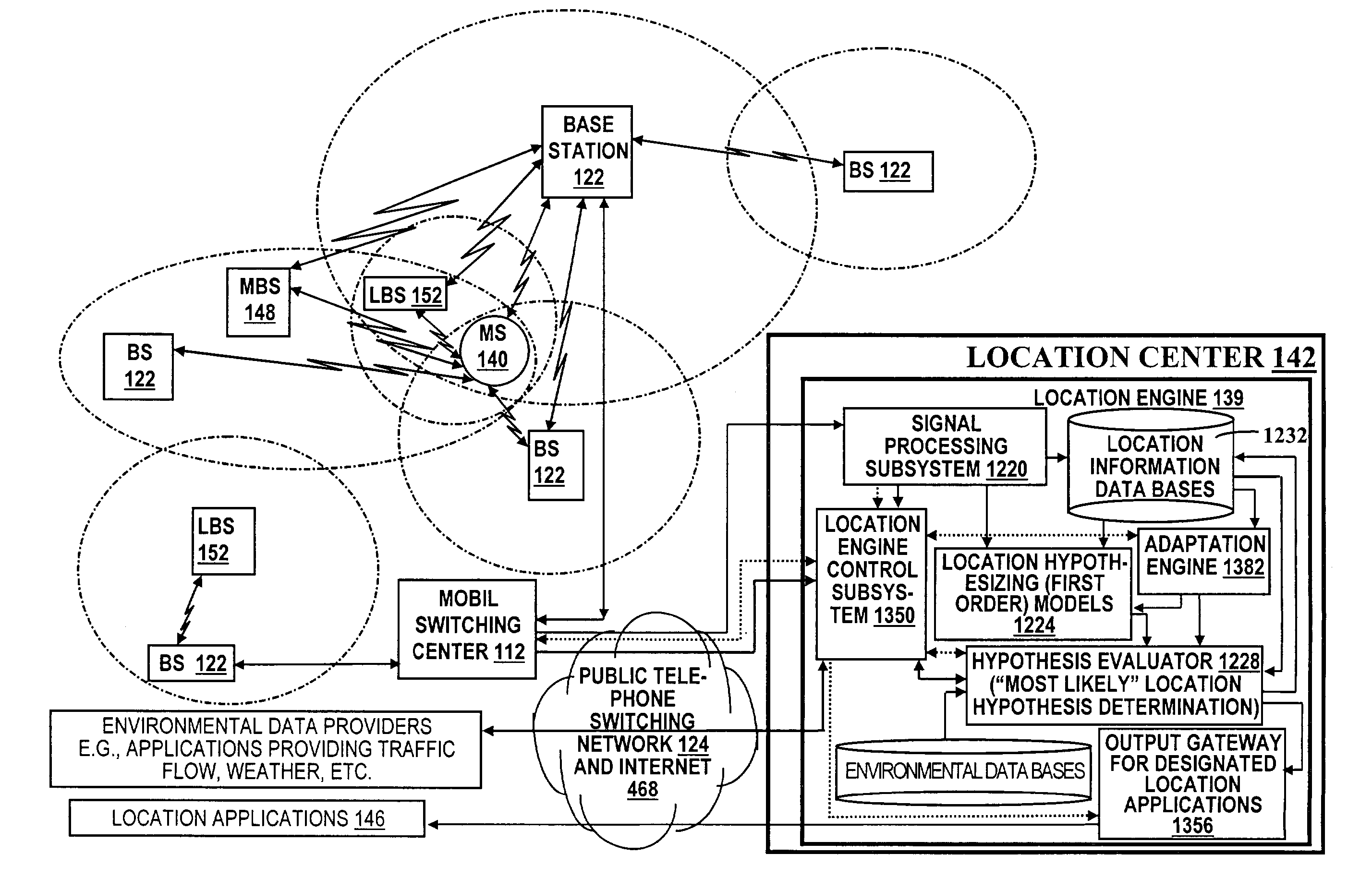
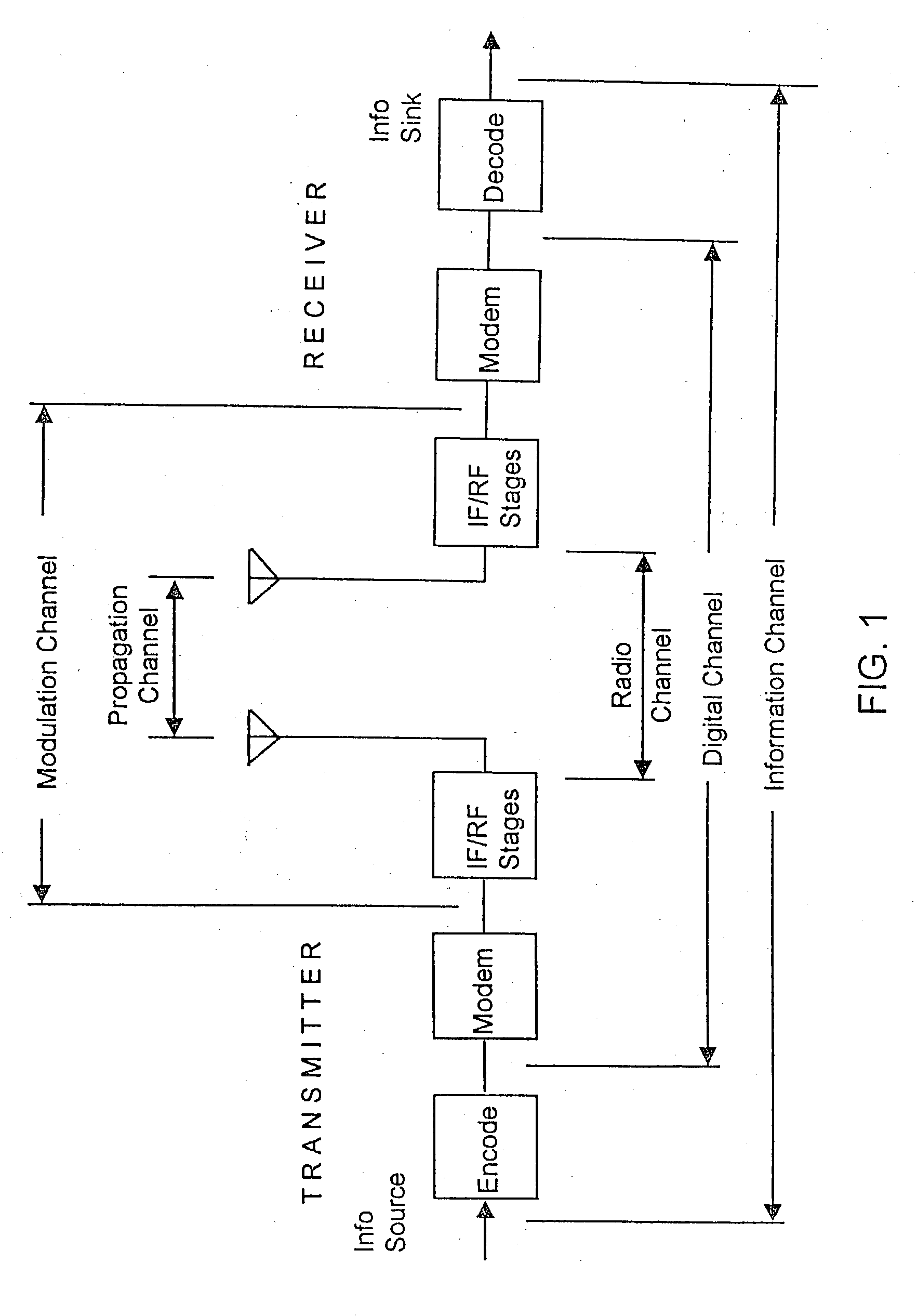
A location system is disclosed for commercial wireless telecommunication infrastructures. The system is an end-to-end solution having one or more location centers for outputting requested locations of commercially available handsets or mobile stations (MS) based on, e.g., CDMA, AMPS, NAMPS or TDMA communication standards, for processing both local MS location requests and more global MS location requests via, e.g., Internet communication between a distributed network of location centers. The system uses a plurality of MS locating technologies including those based on: (1) two-way TOA and TDOA; (2) pattern recognition; (3) distributed antenna provisioning; (5) GPS signals, (6) angle of arrival, (7) super resolution enhancements, and (8) supplemental information from various types of very low cost non-infrastructure base stations for communicating via a typical commercial wireless base station infrastructure or a public telephone switching network. Accordingly, the traditional MS location difficulties, such as multipath, poor location accuracy and poor coverage are alleviated via such technologies in combination with strategies for: (a) automatically adapting and calibrating system performance according to environmental and geographical changes; (b) automatically capturing location signal data for continual enhancement of a self-maintaining historical data base retaining predictive location signal data; (c) evaluating MS locations according to both heuristics and constraints related to, e.g., terrain, MS velocity and MS path extrapolation from tracking and (d) adjusting likely MS locations adaptively and statistically so that the system becomes progressively more comprehensive and accurate. Further, the system can be modularly configured for use in location signing environments ranging from urban, dense urban, suburban, rural, mountain to low traffic or isolated roadways. Accordingly, the system is useful for 911 emergency calls, tracking, routing, people and animal location including applications for confinement to and exclusion from certain areas.
Owner:TRACBEAM
Applications for a wireless location gateway
InactiveUS20040198386A1Easy to implementEffectively and straightforwardly resolvedPosition fixationRadio/inductive link selection arrangementsTerrainInternet communication
A location system is disclosed for commercial wireless telecommunication infrastructures. The system is an end-to-end solution having one or more location centers for outputting requested locations of commercially available handsets or mobile stations (MS) based on, e.g., CDMA, AMPS, NAMPS or TDMA communication standards, for processing both local MS location requests and more global MS location requests via, e.g., Internet communication between a distributed network of location centers. The system uses a plurality of MS locating technologies including those based on: (1) two-way TOA and TDOA; (2) pattern recognition; (3) distributed antenna provisioning; (5) GPS signals, (6) angle of arrival, (7) super resolution enhancements, and (8) supplemental information from various types of very low cost non-infrastructure base stations for communicating via a typical commercial wireless base station infrastructure or a public telephone switching network. Accordingly, the traditional MS location difficulties, such as multipath, poor location accuracy and poor coverage are alleviated via such technologies in combination with strategies for: (a) automatically adapting and calibrating system performance according to environmental and geographical changes; (b) automatically capturing location signal data for continual enhancement of a self-maintaining historical data base retaining predictive location signal data; (c) evaluating MS locations according to both heuristics and constraints related to, e.g., terrain, MS velocity and MS path extrapolation from tracking and (d) adjusting likely MS locations adaptively and statistically so that the system becomes progressively more comprehensive and accurate. Further, the system can be modularly configured for use in location signaling environments ranging from urban, dense urban, suburban, rural, mountain to low traffic or isolated roadways. Accordingly, the system is useful for 911 emergency calls, tracking, routing, people and animal location including applications for confinement to and exclusion from certain areas.
Owner:DUPRAY DENNIS J
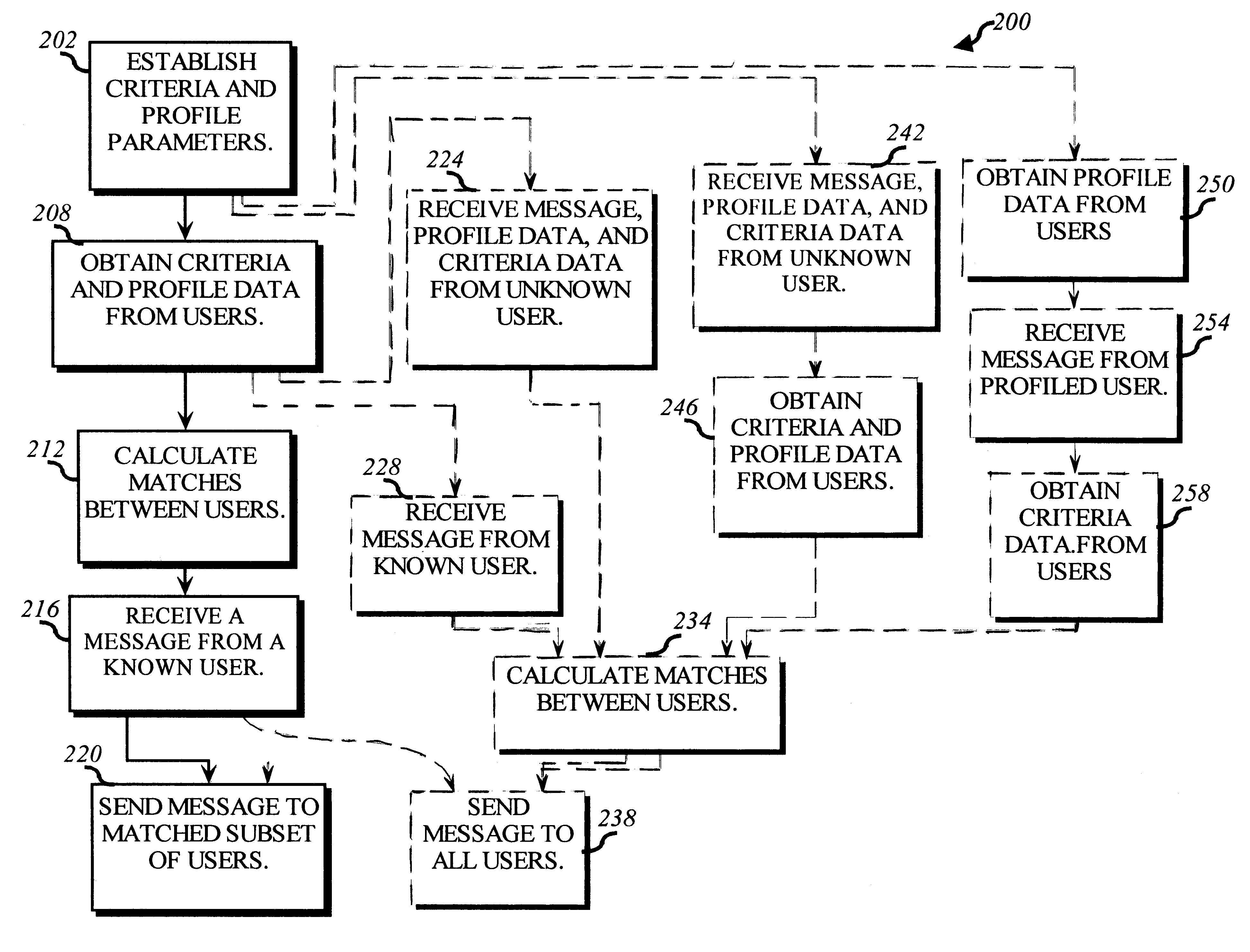
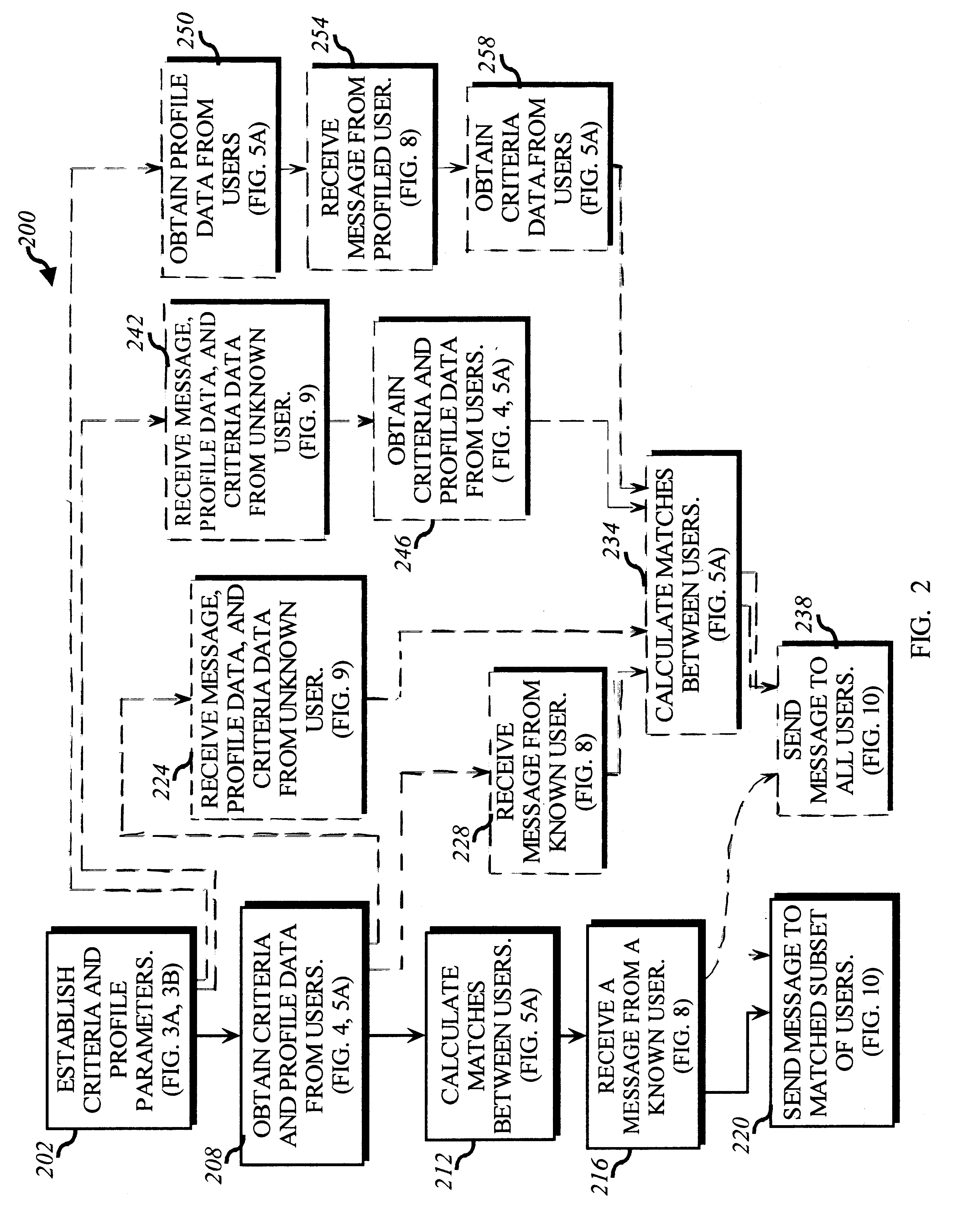
Dynamically matching users for group communications based on a threshold degree of matching of sender and recipient predetermined acceptance criteria
InactiveUS6480885B1Quality of communicationReduce in quantitySpecial service provision for substationMultiprogramming arrangementsPersonalizationWeb service
A method for enabling users to exchange group electronic mail by establishing individual profiles and criteria, for determining personalized subsets within a group. Users establish subscriptions to an electronic mailing list by specifying user profile data and acceptance criteria data to screen other users. When a user subscribes, a web server establishes and stores an individualized recipient list including each matching subscriber and their degree of one-way or mutual match with the user. When the user then sends a message to the mailing list, an email server retrieves 100% her matches and then optionally filters her recipient list down to a message distribution list using each recipient's message criteria. The message is then distributed to matching users. Additionally, email archives and information contributions from users are stored in a database. A web server creates an individualized set of web pages for a user from the database, containing contributions only from users in his recipient list. In other embodiments, users apply one-way or mutual criteria matching and message profile criteria to other group forums, such as web-based discussion boards, chat, online clubs, USENET newsgroups, voicemail, instant messaging, web browsing side channel communities, and online gaming rendezvous.
Owner:TUMBLEWEED HLDG LLC
Systems and Methods to Target Predictive Location Based Content and Track Conversions
ActiveUS20080248815A1Particular environment based servicesDevices with GPS signal receiverCommunications systemMobile device
Methods and systems that record the location of a user and transmit targeted content to a user based upon their current and past location information. A network is configured to include a server programmed with a database of targeted content, a database of location information, a database of user information, a database searching algorithm, and a wireless communication system capable of communicating with the user's mobile device. The location of the mobile device is ascertained and recorded. The location information is analyzed to determine the routes taken by the user, businesses visited by the user, and other behaviors of the user. Targeted content is sent to the mobile device of the user and whether the user visits the physical locations associated with the targeted content is monitored. Payment systems, phone exchange systems, and other features may also be integrated to provide detailed conversion tracking to producers of targeted content and business owners.
Owner:META PLATFORMS INC
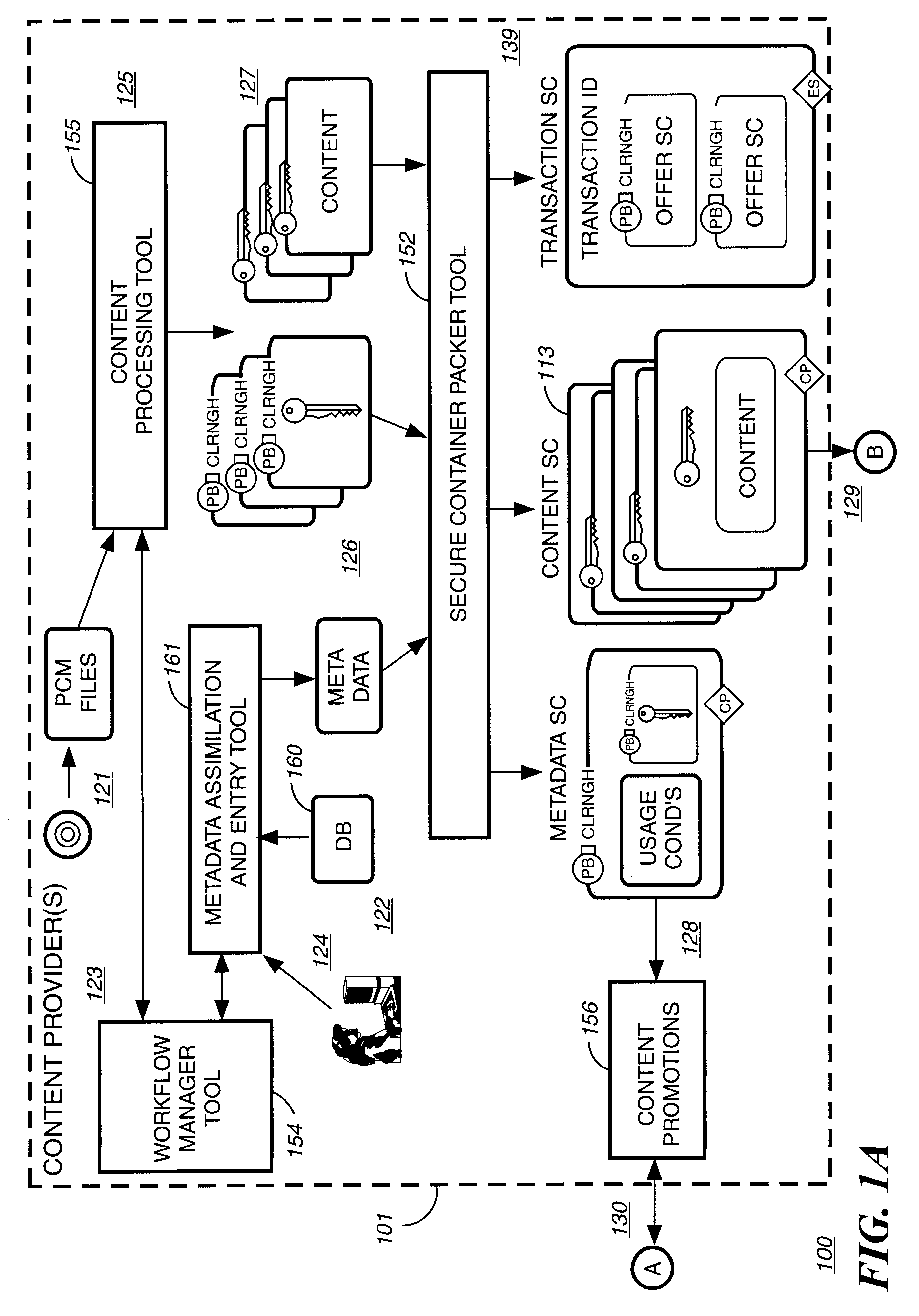
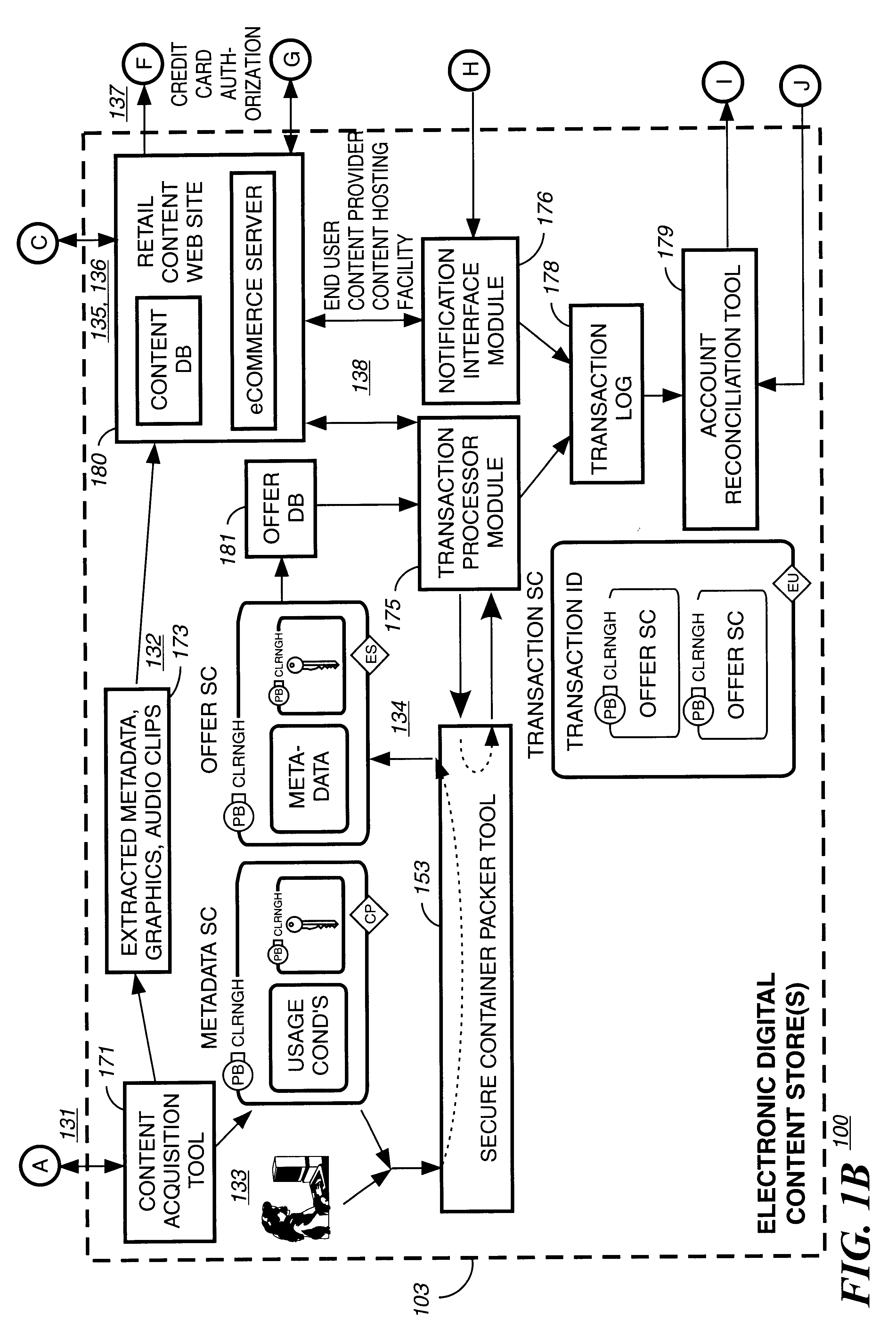
Automated method and apparatus to package digital content for electronic distribution using the identity of the source content
InactiveUS6345256B1Key distribution for secure communicationDigital data processing detailsDigital contentNumber content
A method to automatically retrieve data associated with content. An identifier is read that is stored on electronic readable medium storing content. The identifier is used to search a database for data associated with the content. Data that is associated with the content is retrieved as guided by the database. And the data retrieved is used to create a version of the content for electronic distribution. In accordance with another aspect of the invention, a computer readable medium is described to carry out the above method.
Owner:INT BUSINESS MASCH CORP
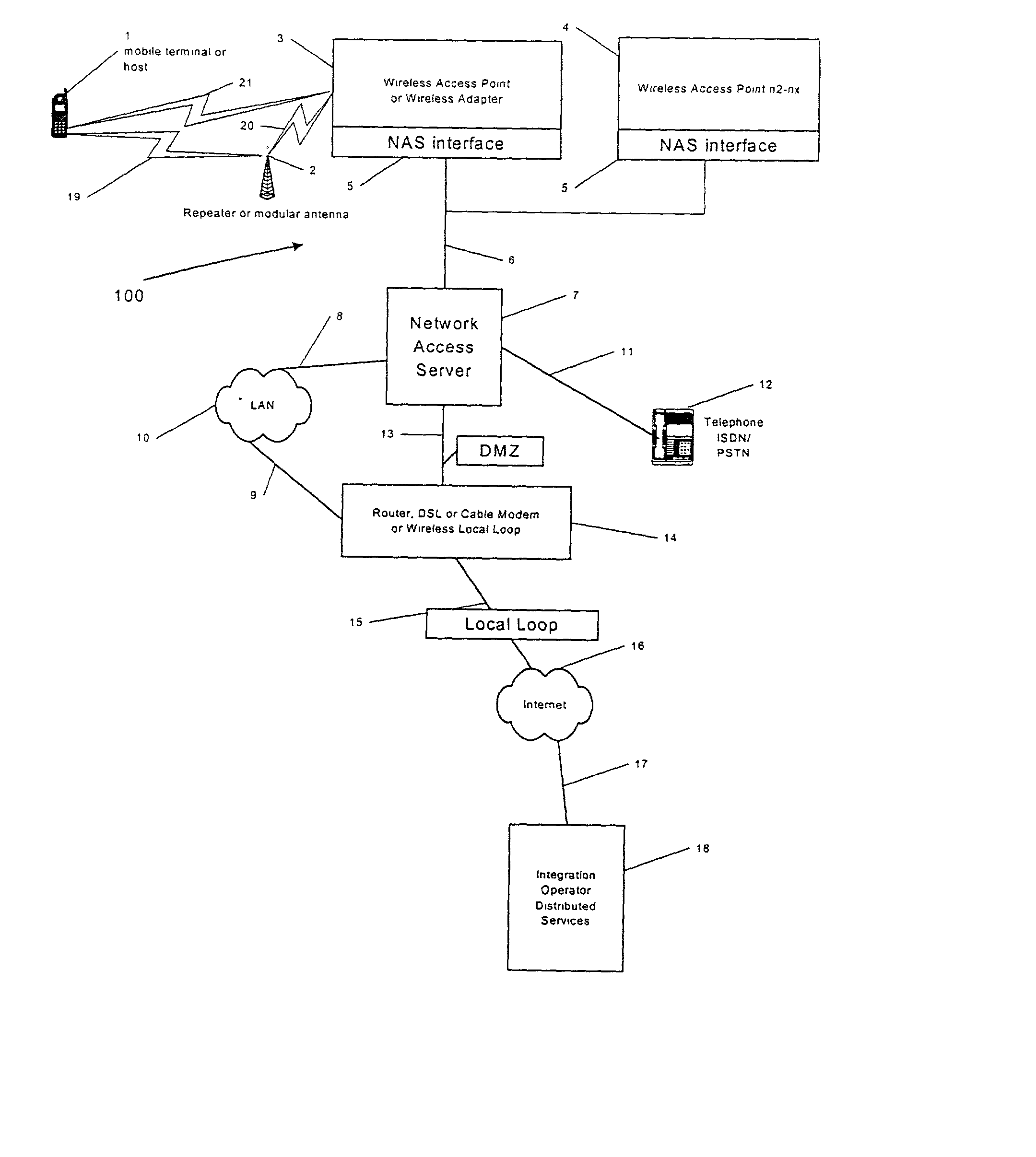
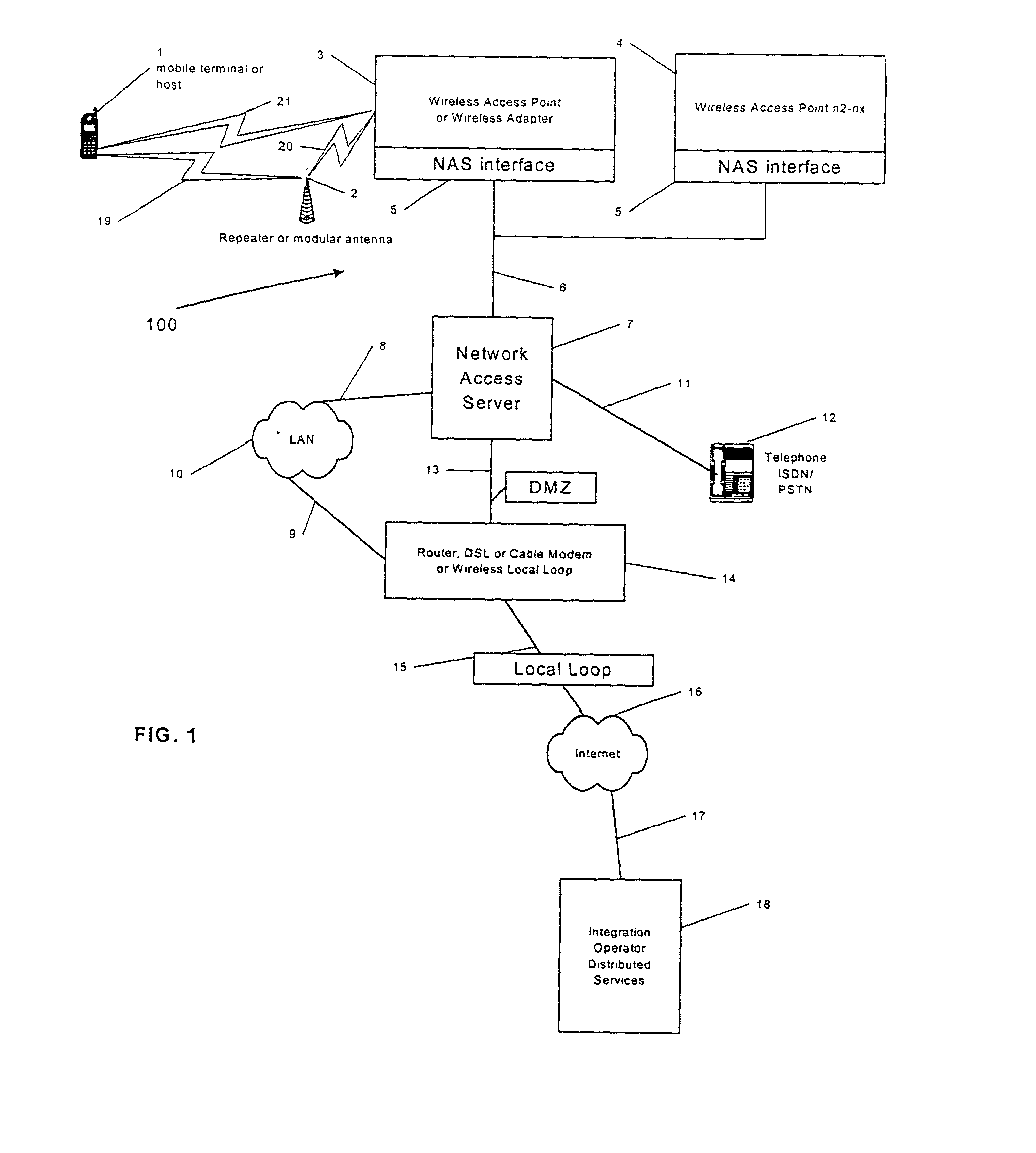
Integrating public and private network resources for optimized broadband wireless access and method
InactiveUS20020075844A1Network traffic/resource managementNetwork topologiesNetwork access serverPrivate network
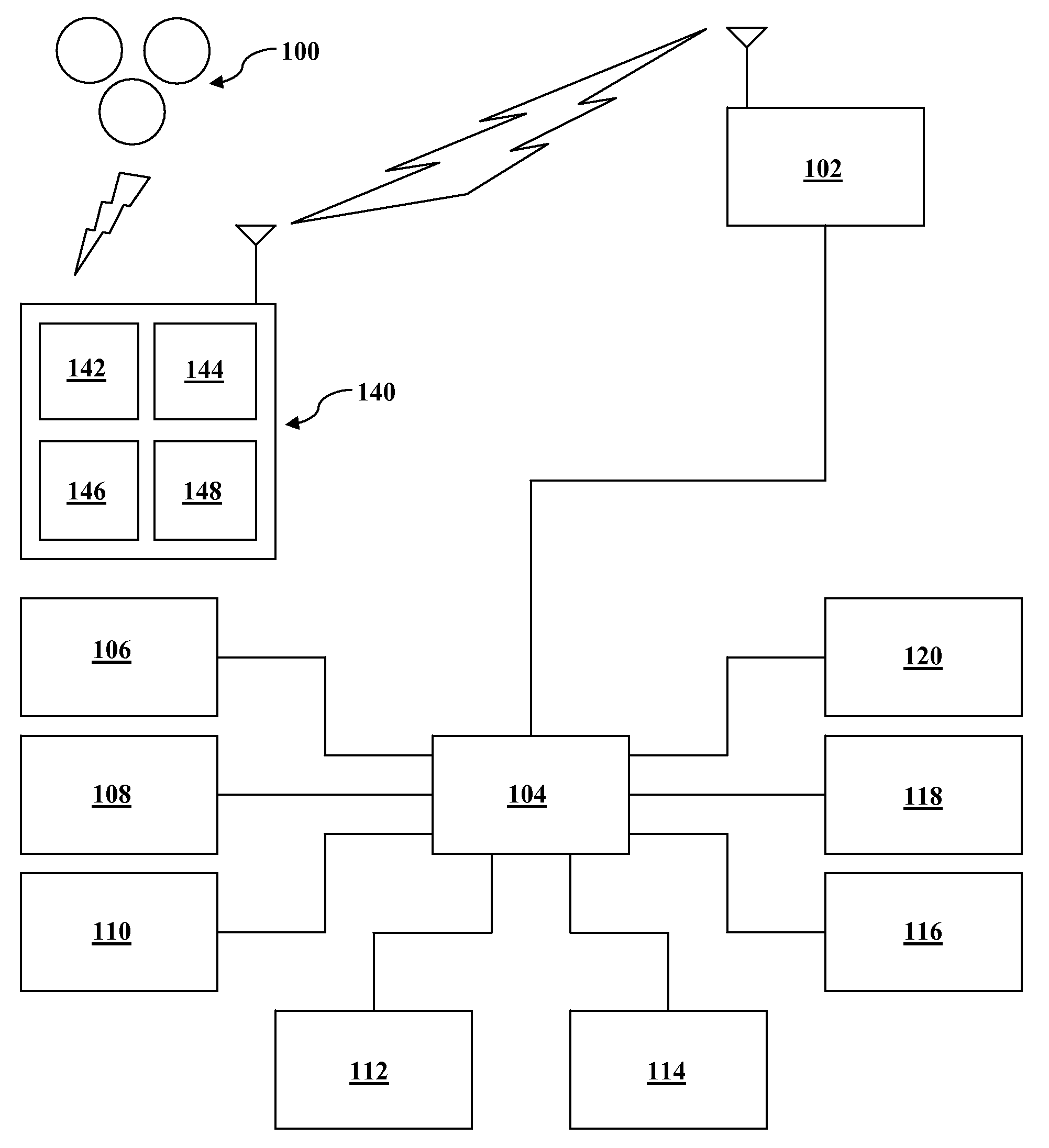
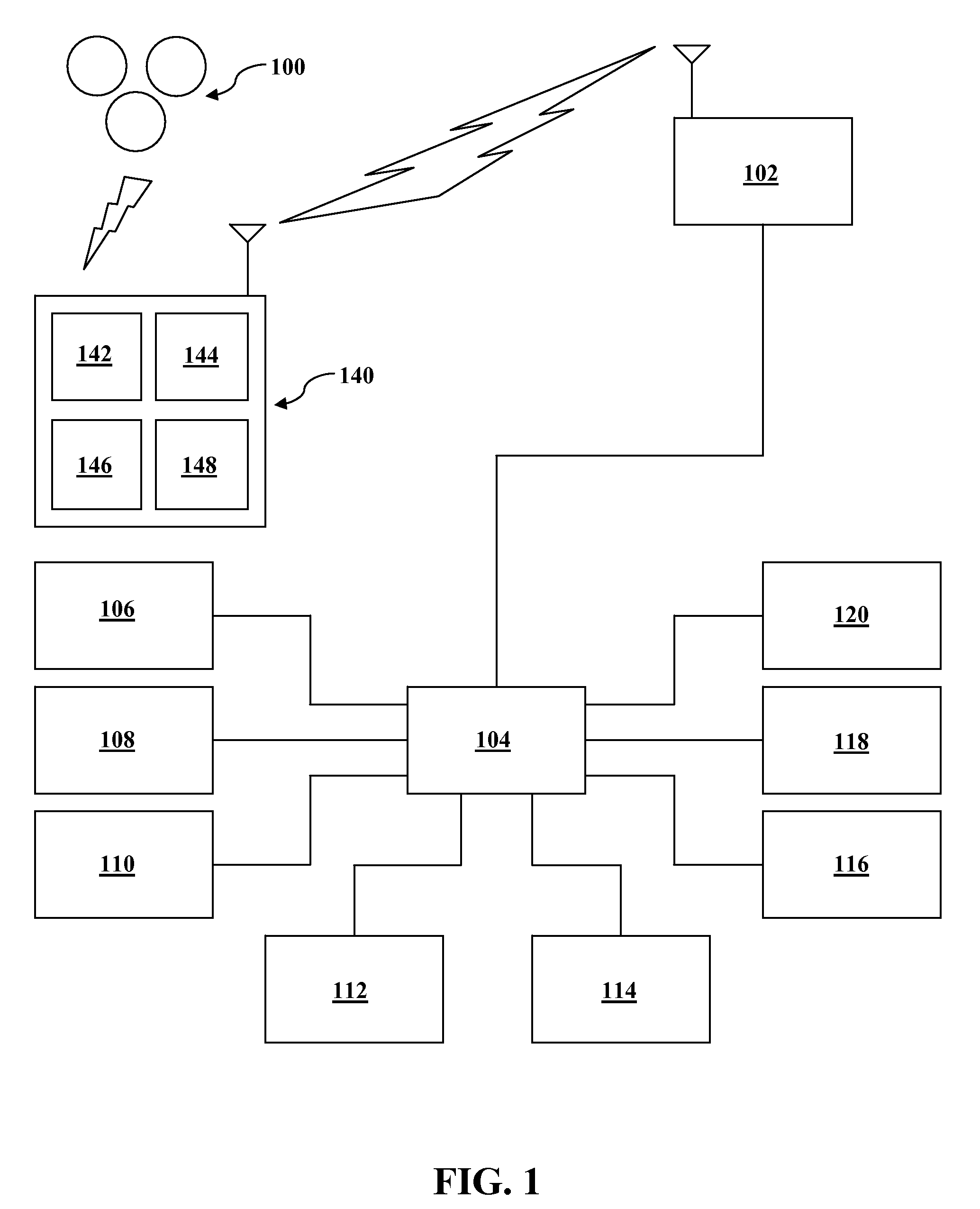
A system and method are disclosed for providing ubiquitous public network access to wireless, mobile terminals using private networks having private network access points and connections with the public network. The wireless, mobile terminals are permitted to use wireless, radio frequency communication devices comprising private network access points. A network access server (NAS) is associated with each wireless, radio frequency communication device and provides an interface between the wireless, mobile terminals and the private network. The NAS controls registration of wireless, mobile terminals as subscribers, and provides public network access to the mobile terminals through the private network's access point and public network connection. The NAS also restricts access by the mobile terminals to the private network, meters network useage by the mobile terminals, and controls use of bandwidth by the mobile terminals. The NAS also interfaces with integration operator distributed services over the public network. The integration operator services include databases and servers for storing and providing subscriber and network provider information for subscriber registration, network access and useage control, and accounting purposes. The NAS may be provided as a standalone element embodied in a computer, or may be integrated with the wireless radio frequency device and / or a network adaptor device for the private network.
Owner:NTT DOCOMO DCMR COMM LAB USA
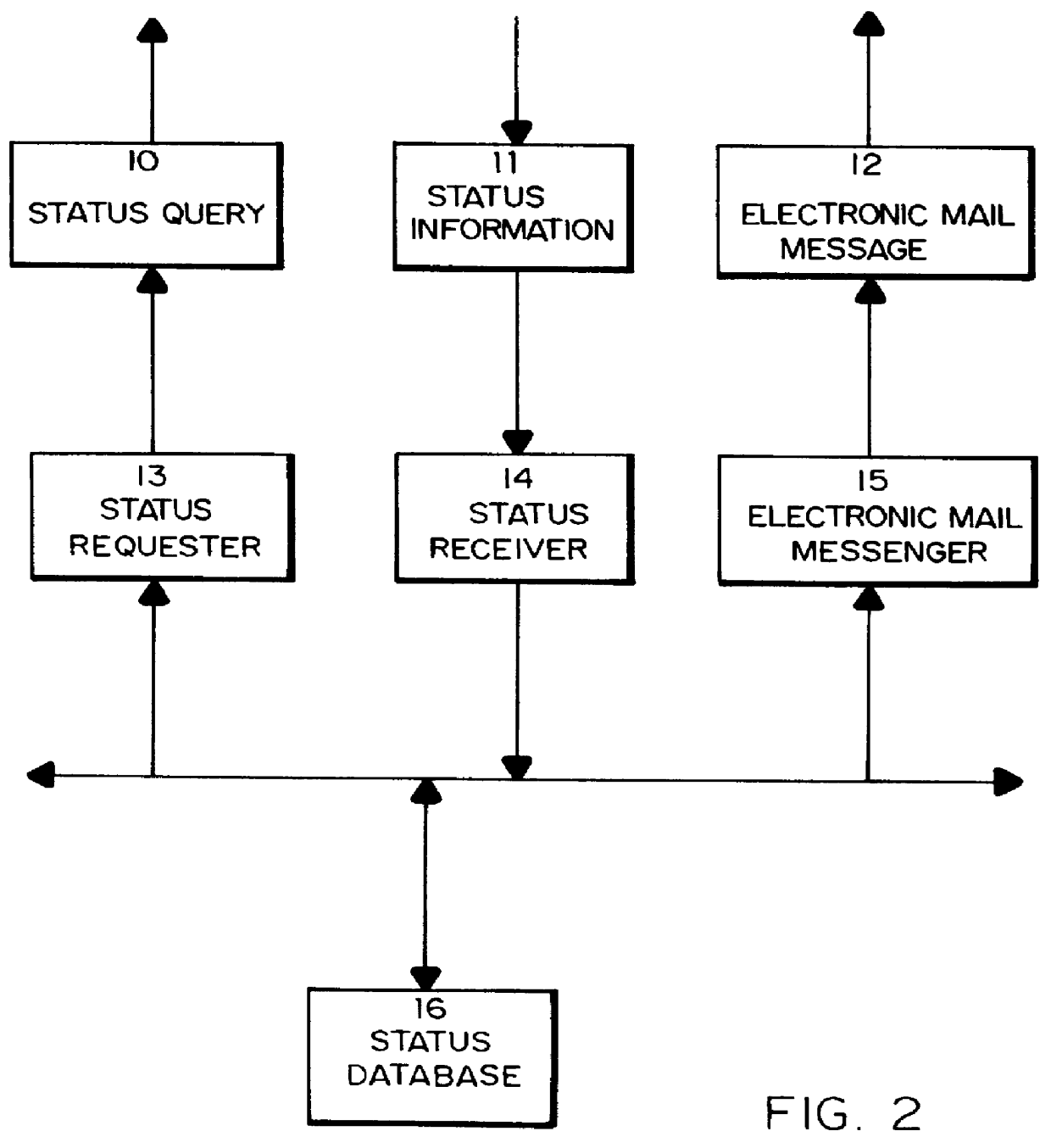
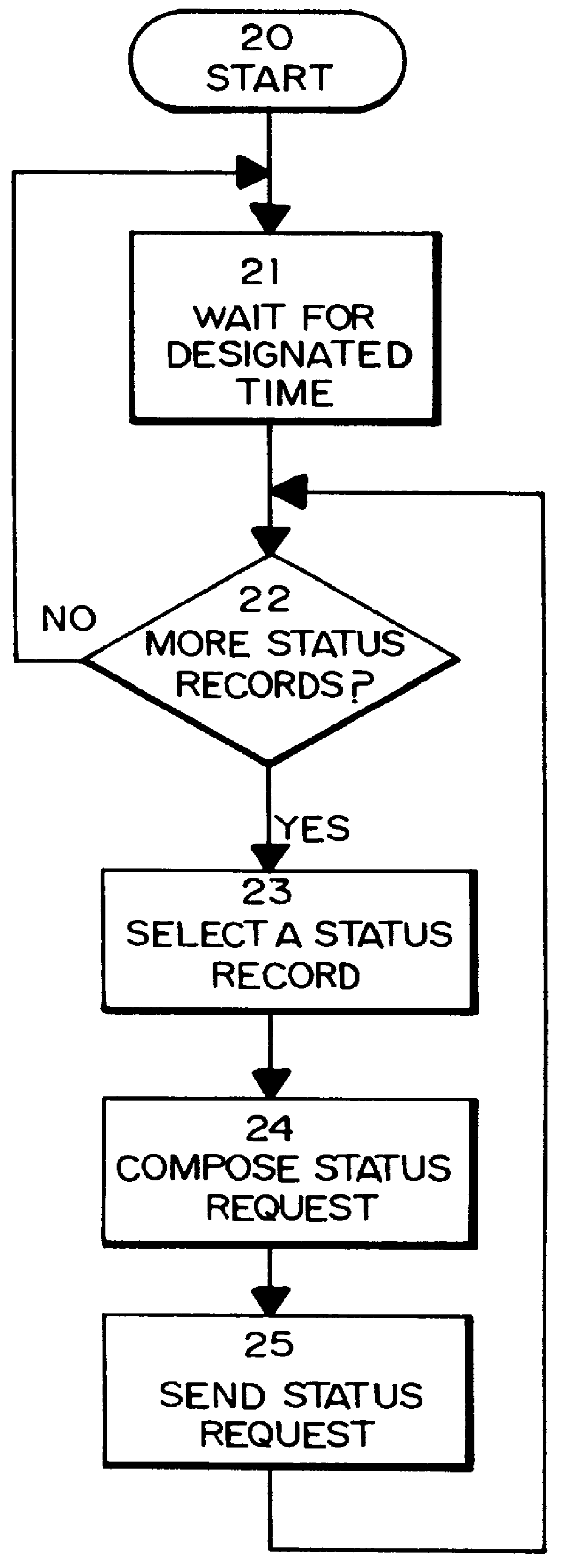
Method for supplying automatic status updates using electronic mail
A method is disclosed for automatically updating the status of customers' orders and shipments via electronic mail without using a human attendant to create and send the electronic mail messages. Preferably implemented in software, the updating method allows a large set of customers to be periodically updated over a computer or communications network via electronic mail. The method utilizes a database for maintaining order and shipping status and other relevant information.
Owner:EBAY INC
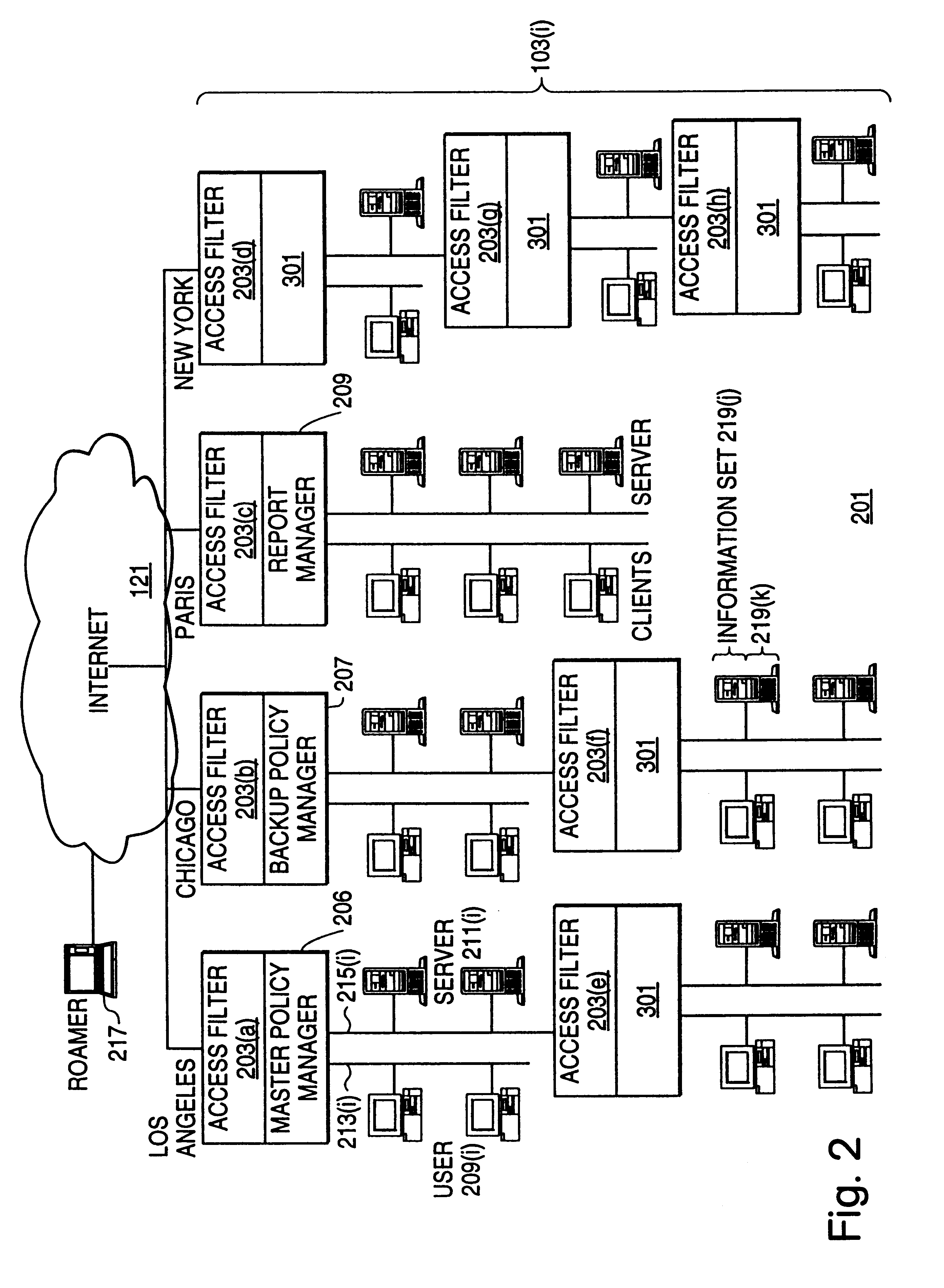
Distributed administration of access to information
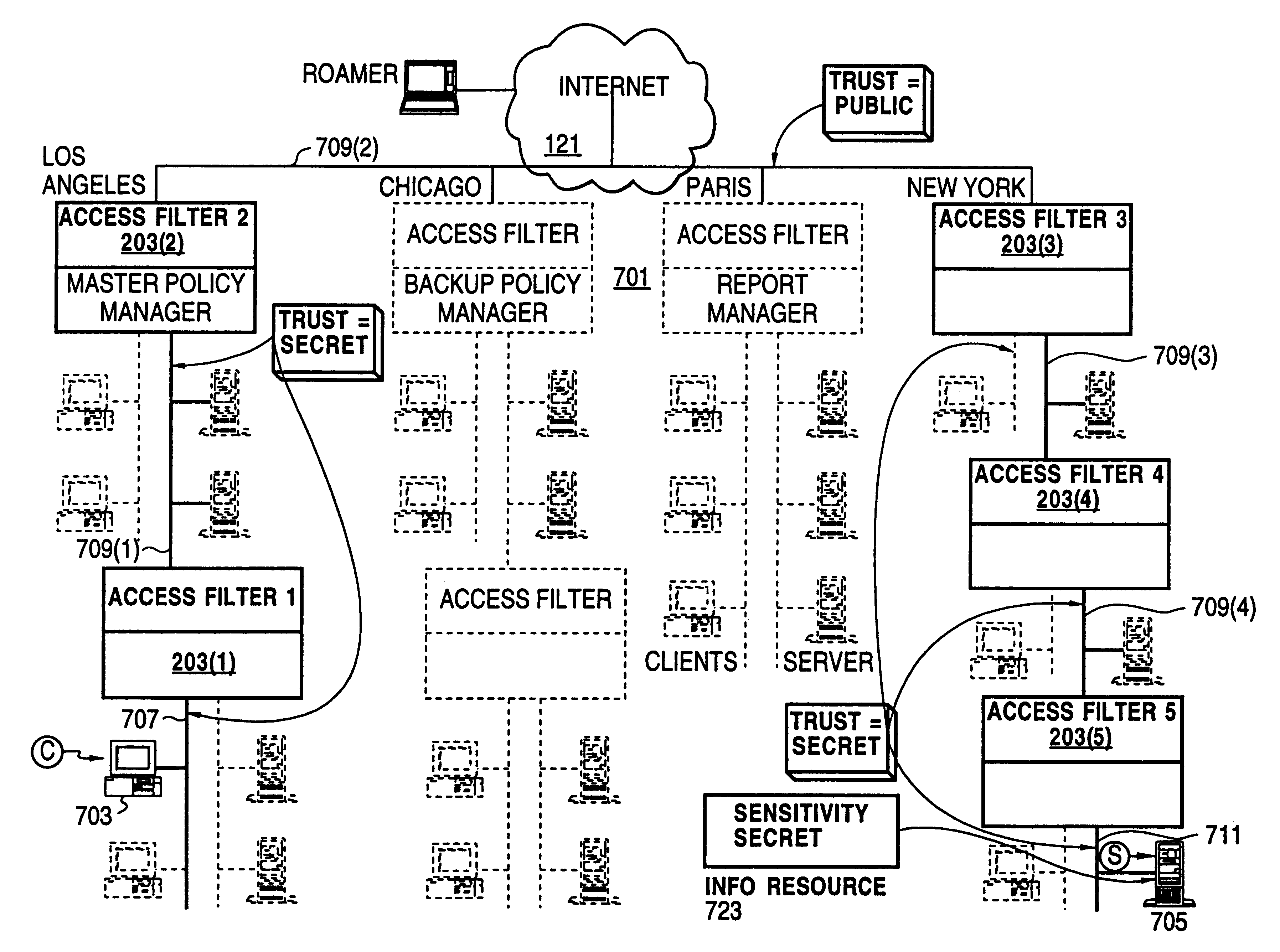
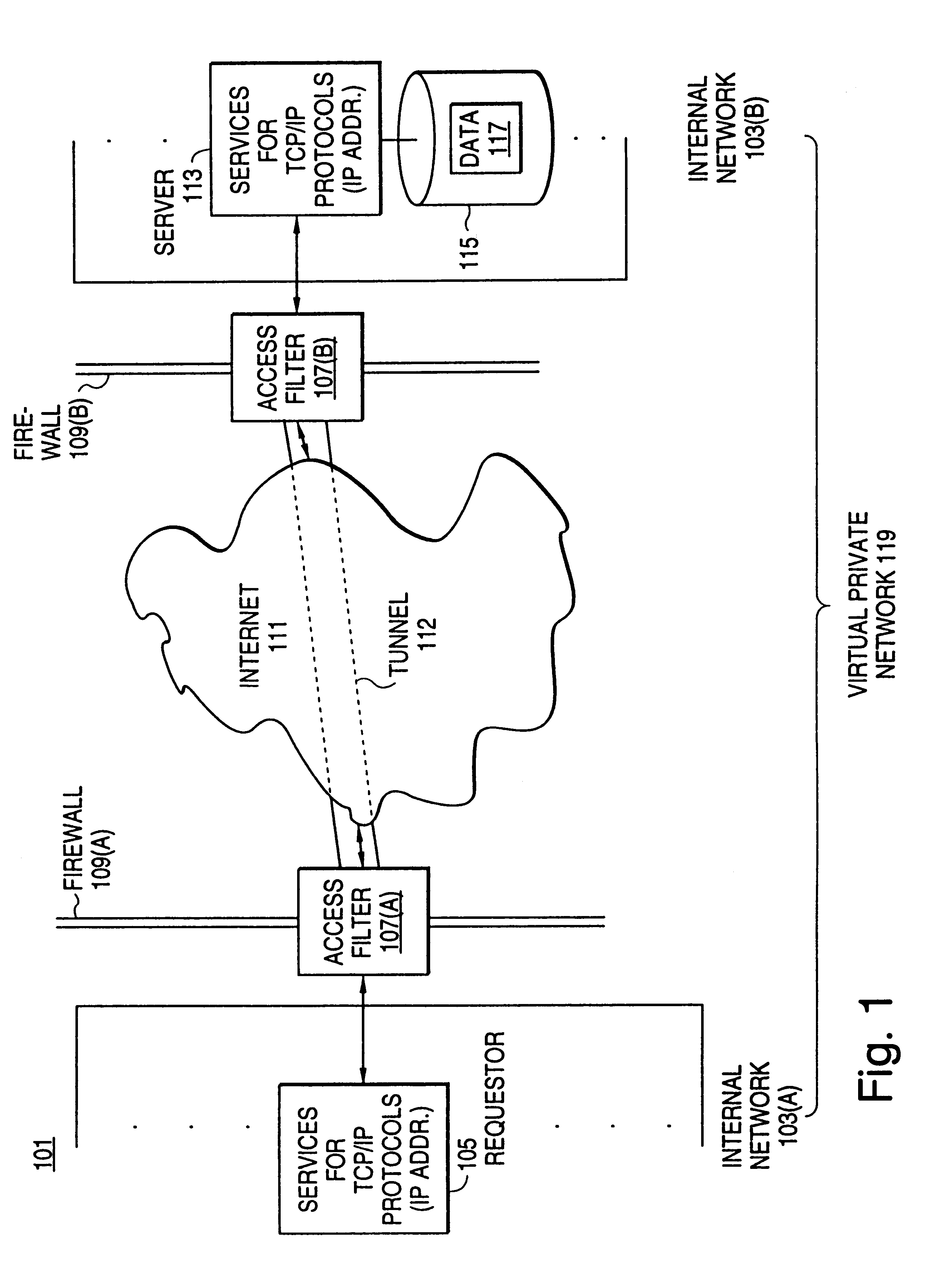
InactiveUS6408336B1Digital data processing detailsMultiple digital computer combinationsPrivate networkInformation resource
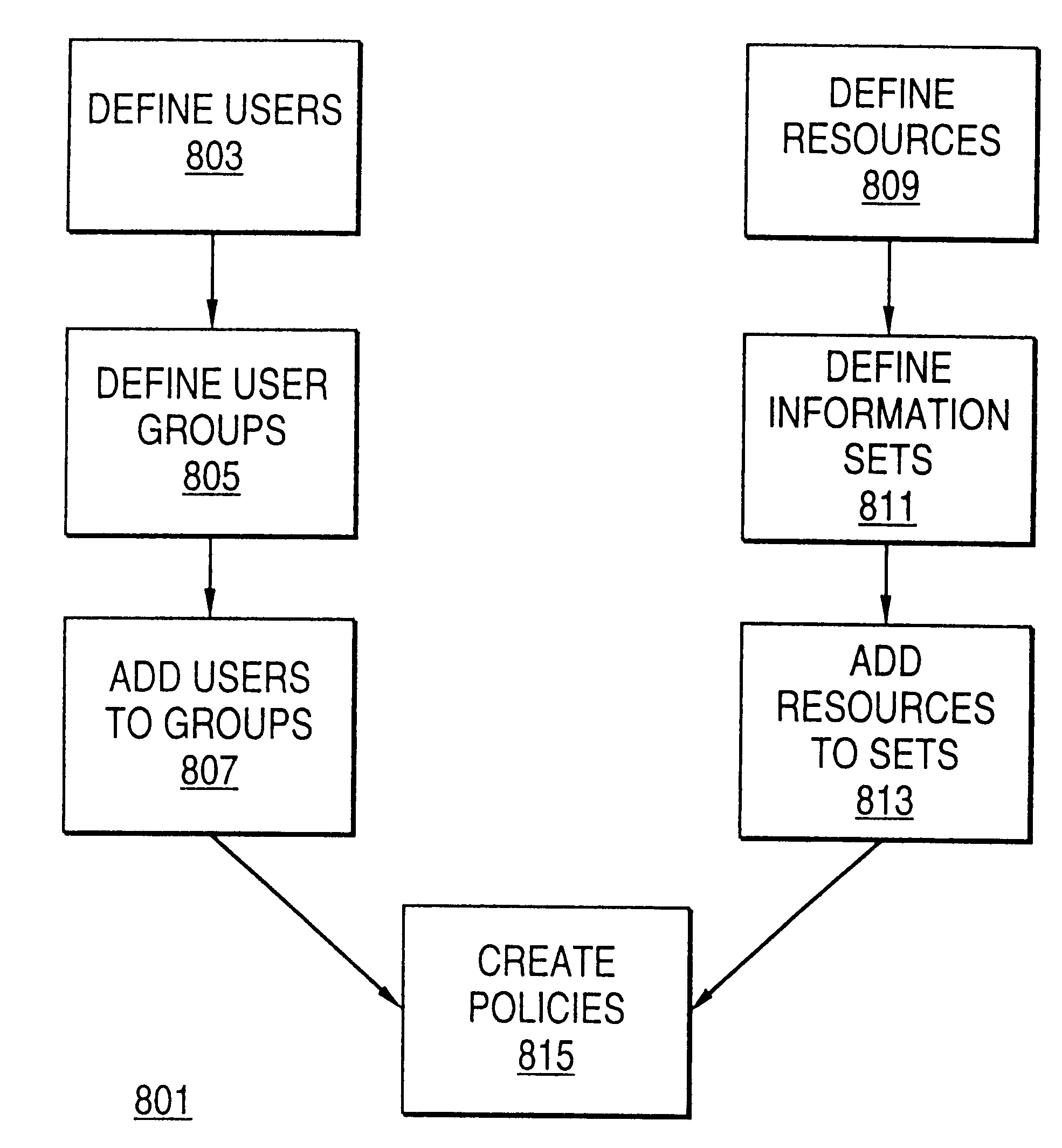
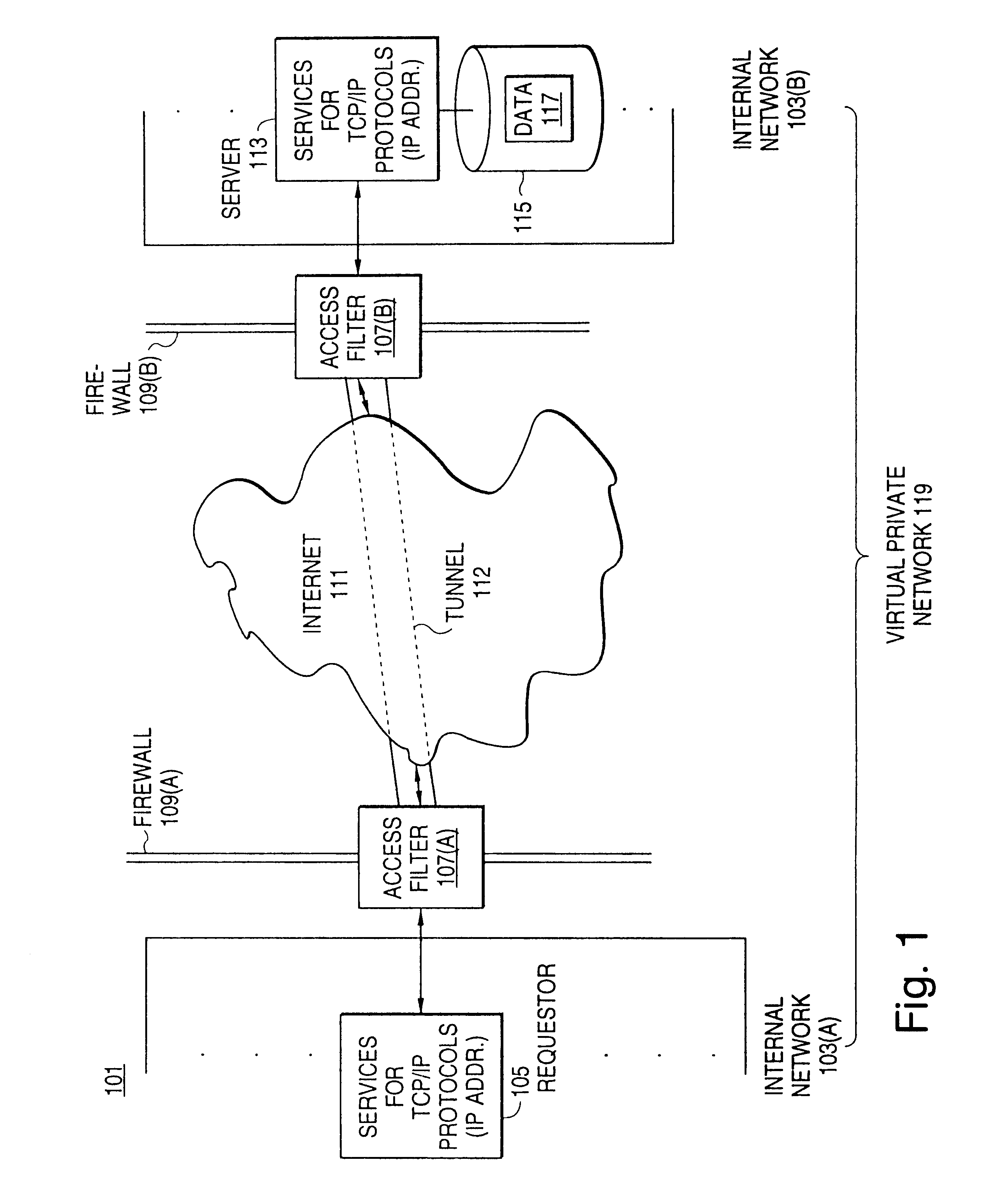
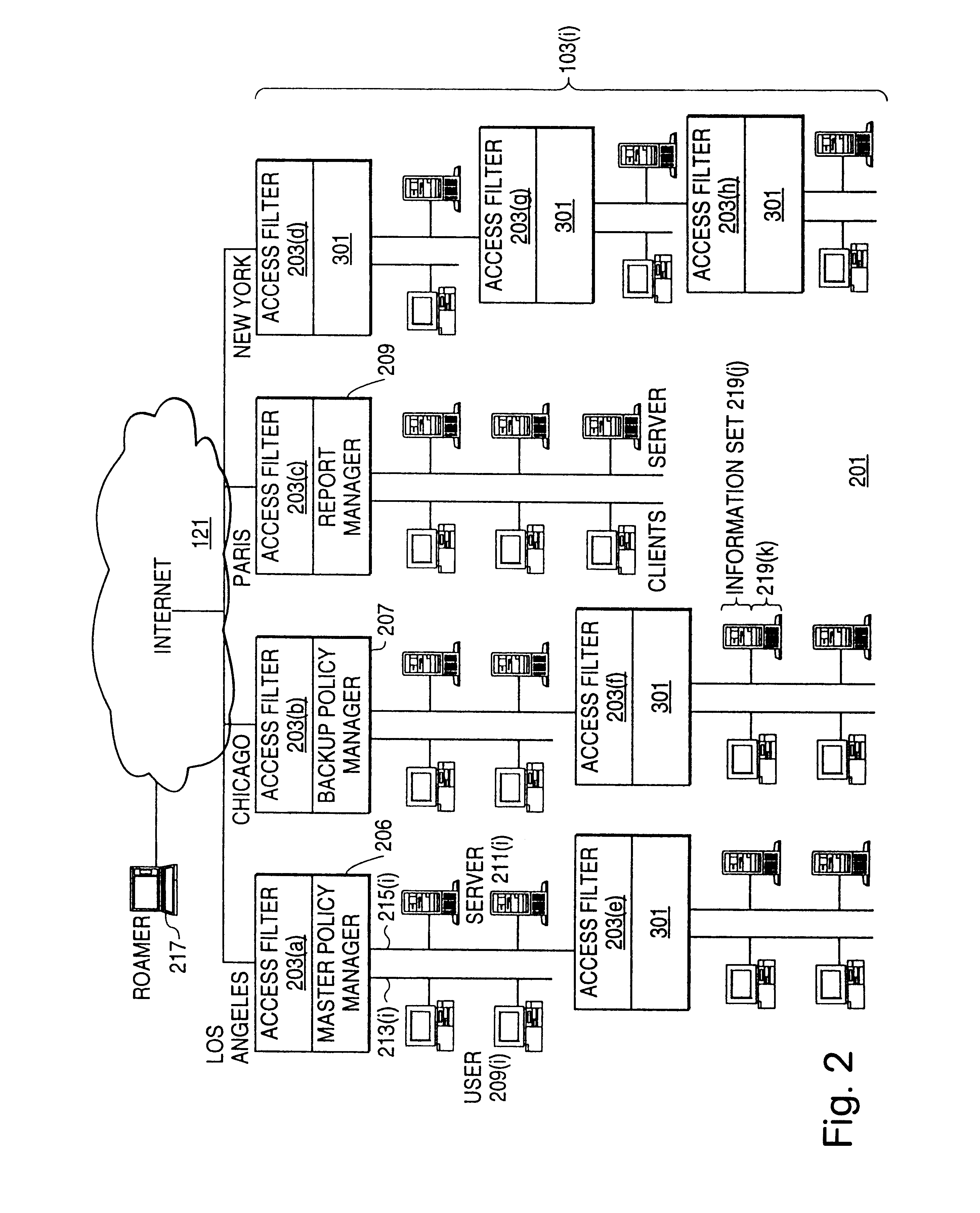
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
Wireless location using signal fingerprinting
InactiveUS20010022558A1Low costSpectrum efficiencyDirection finders using radio wavesBeacon systems using radio wavesInternet communicationCall tracing
A location system is disclosed for commercial wireless telecommunication infrastructures. The system is an end-to-end solution having one or more location centers for outputting requested locations of commercially available handsets or mobile stations (MS) based on, e.g., CDMA, AMPS, NAMPS or TDMA communication standards, for processing both local MS location requests and more global MS location requests via, e.g., Internet communication between a distributed network of location centers. The system uses a plurality of MS locating technologies including those based on: (1) two-way TOA and TDOA; (2) pattern recognition; (3) distributed antenna provisioning; and (4) supplemental information from various types of very low cost non-infrastructure base stations for communicating via a typical commercial wireless base station infrastructure or a public telephone switching network. Accordingly, the traditional MS location difficulties, such as multipath, poor location accuracy and poor coverage are alleviated via such technologies in combination with strategies for: (a) automatically adapting and calibrating system performance according to environmental and geographical changes; (b) automatically capturing location signal data for continual enhancement of a self-maintaining historical data base retaining predictive location signal data; (c) evaluating MS locations according to both heuristics and constraints related to, e.g., terrain, MS velocity and MS path extrapolation from tracking and (d) adjusting likely MS locations adaptively and statistically so that the system becomes progressively more comprehensive and accurate. Further, the system can be modularly configured for use in location signaling environments ranging from urban, dense urban, suburban, rural, mountain to low traffic or isolated roadways. Accordingly, the system is useful for 911 emergency calls, tracking, routing, people and animal location including applications for confinement to and exclusion from certain areas.
Owner:TRACBEAM
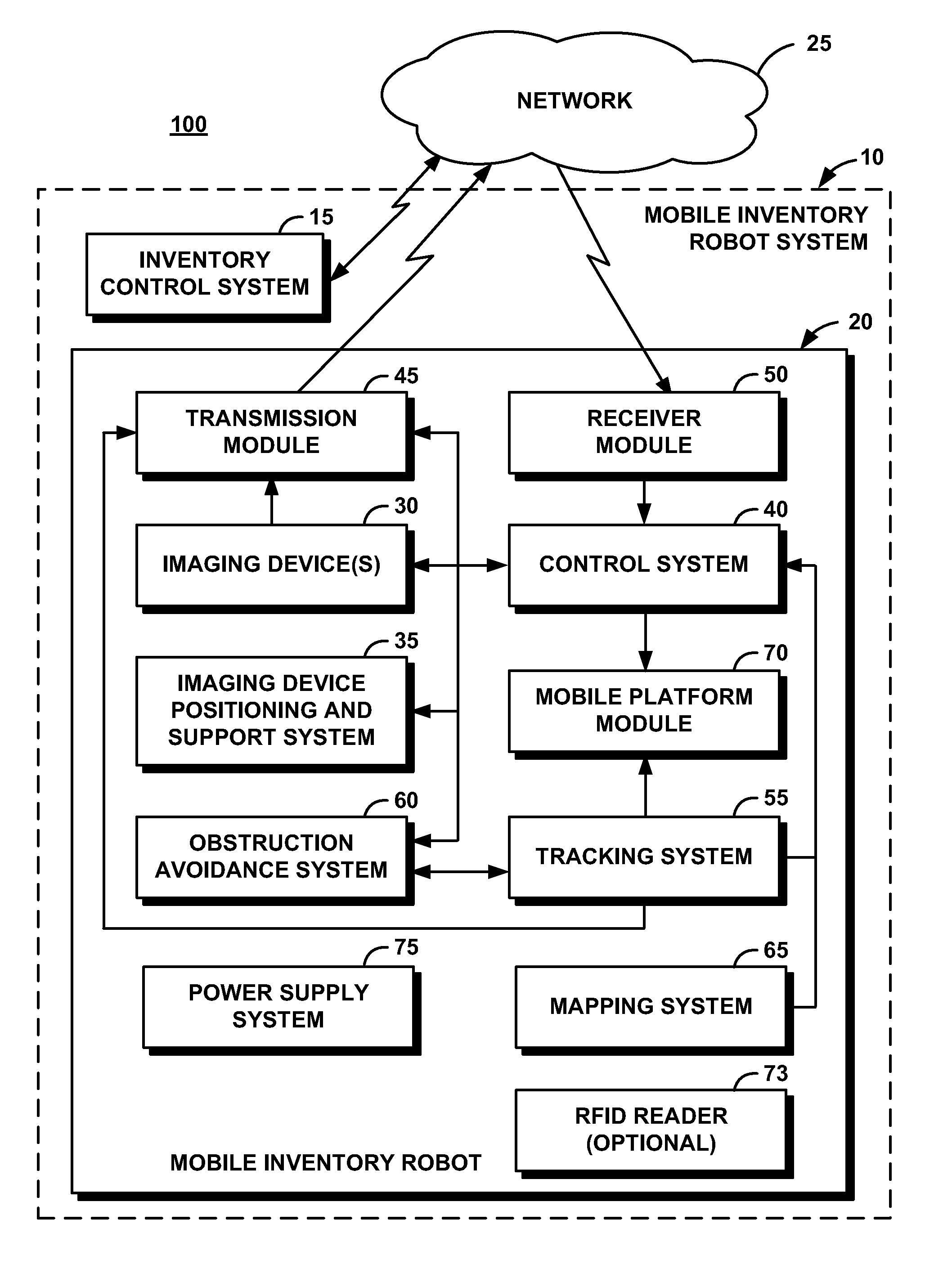
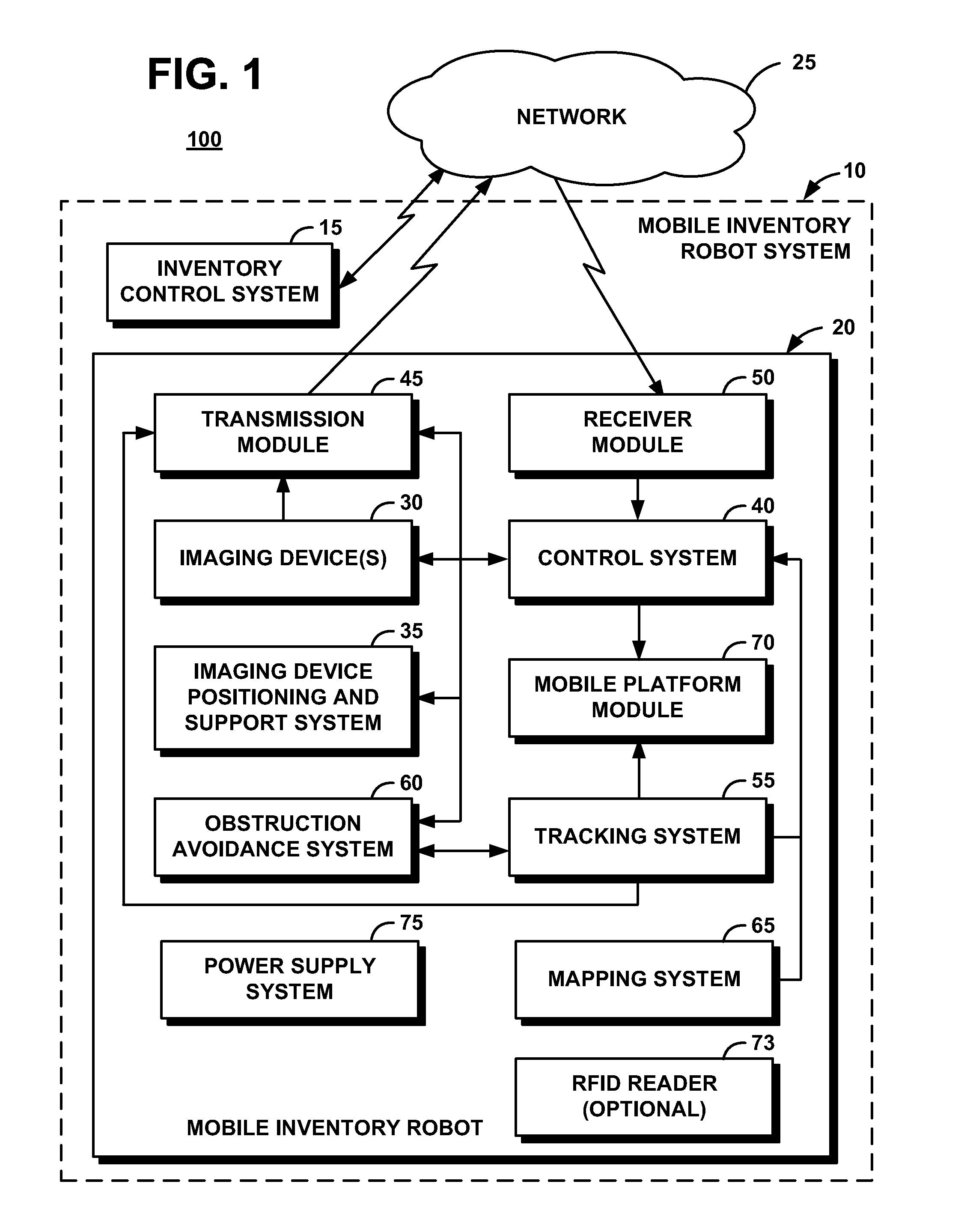
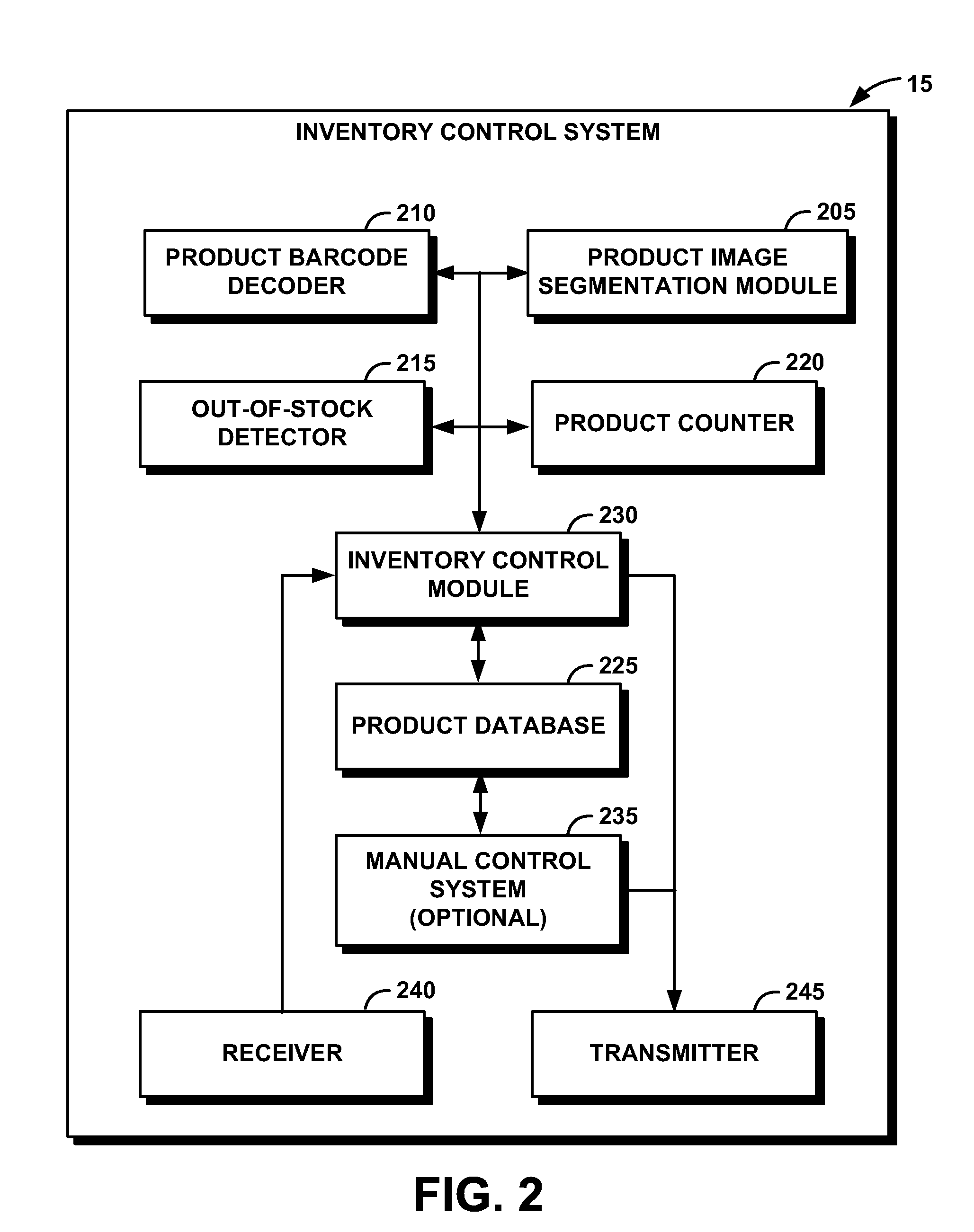
System and Method for Performing Inventory Using a Mobile Inventory Robot
InactiveUS20080077511A1Still image data retrievalVehicle position/course/altitude controlRobotic systemsBarcode
A mobile inventory robot system generates an inventory map of a store and a product database when a mobile inventory robot is manually navigated through the store to identify items on shelves, a location for each of the items on the shelves, and a barcode for each of the items. The system performs inventory of the items by navigating through the store via the inventory map, capturing a shelf image, decoding a product barcode from the captured shelf image, retrieving a product image for the decoded product barcode from the product database, segmenting the captured shelf image to detect an image of an item on the shelves, determining whether the detected image matches the retrieved image and, if not, setting an out-of-stock flag for an the item.
Owner:IBM CORP
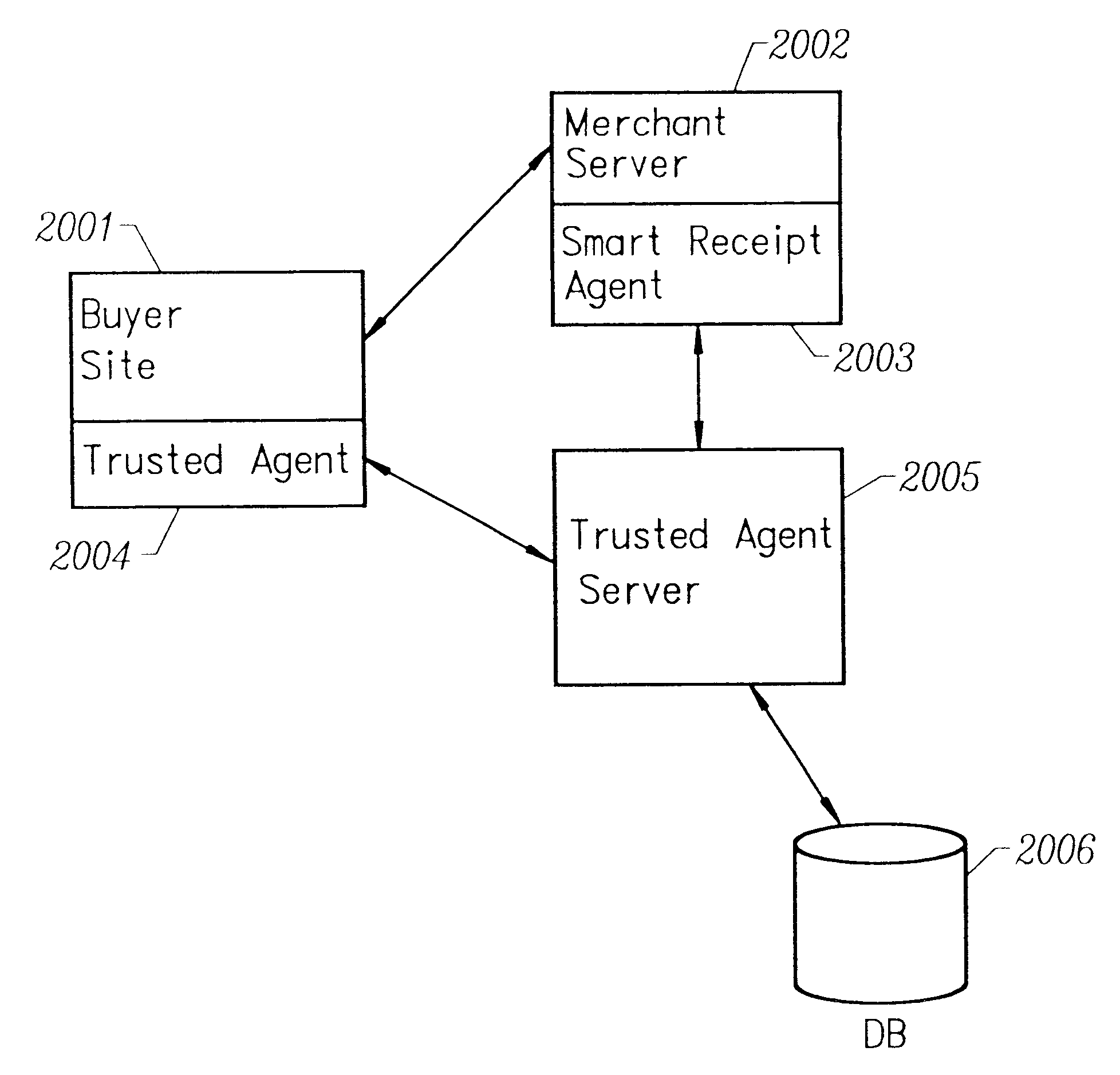
Smart electronic receipt system
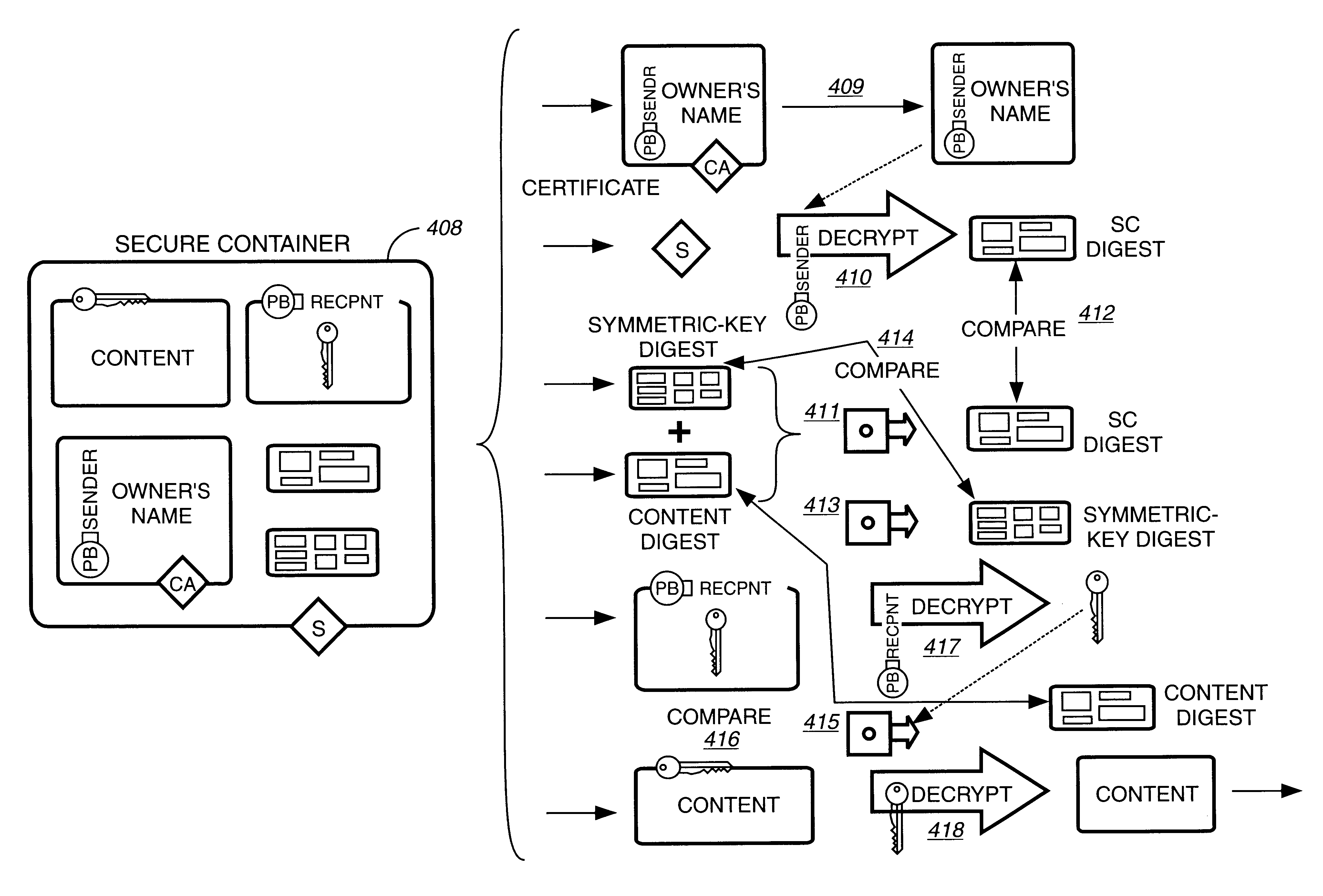
A smart electronic receipt system that provides intelligent receipts, called Smart Receipts, that electronically document a transaction between two parties and maintains a persistent connection between the two parties following a successful online transaction. A Trusted Agent on the Buyer's client system creates an order record which is stored in a database on a Trusted Agent Server and starts the transaction process with the merchant. A Smart Receipt is delivered by a Smart Receipt Agent over a secure connection from the merchant to the Trusted Agent Server upon successful completion of a purchase and reflects the details of the transaction. It is stored in a secure database on the Trusted Agent Server and is made available to the Buyer (user) through a Trusted Agent located on his machine. The Trusted Agent Server compares the order record Limited Edition Digital Objects (LEDOs) stored in database with the Smart Receipt's LEDO to find the corresponding order record. The Smart Receipt provides the customer with detailed information about an online purchase in a standardized format. Hyperlinks embedded in the Smart Receipt enable the customer to access customer service and order status. The merchant may also embed addition-al services within the Smart Receipt, including special offers for future purchases. Offers provided in a Smart Receipt can be personalized to a user's preferences which are stored on the Trusted Agent Server. Each Smart Receipt is comprised of a chain of LEDOs with each LEDO object having a unique owner. A Smart Receipt is a dynamic entity and is continuously updated until the Buyer deletes it from the Trusted Agent Server.
Owner:THE BRODIA GROUP
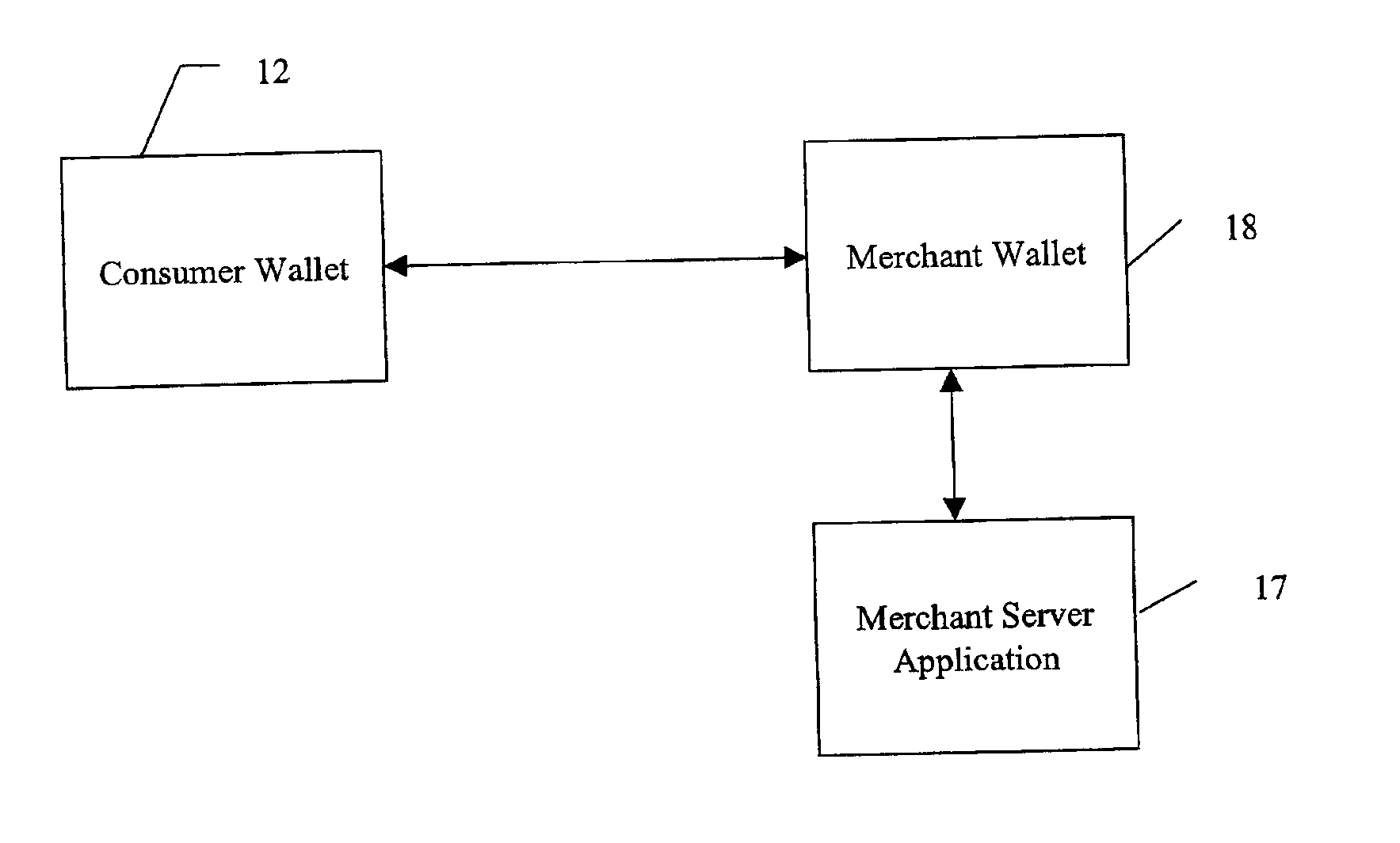
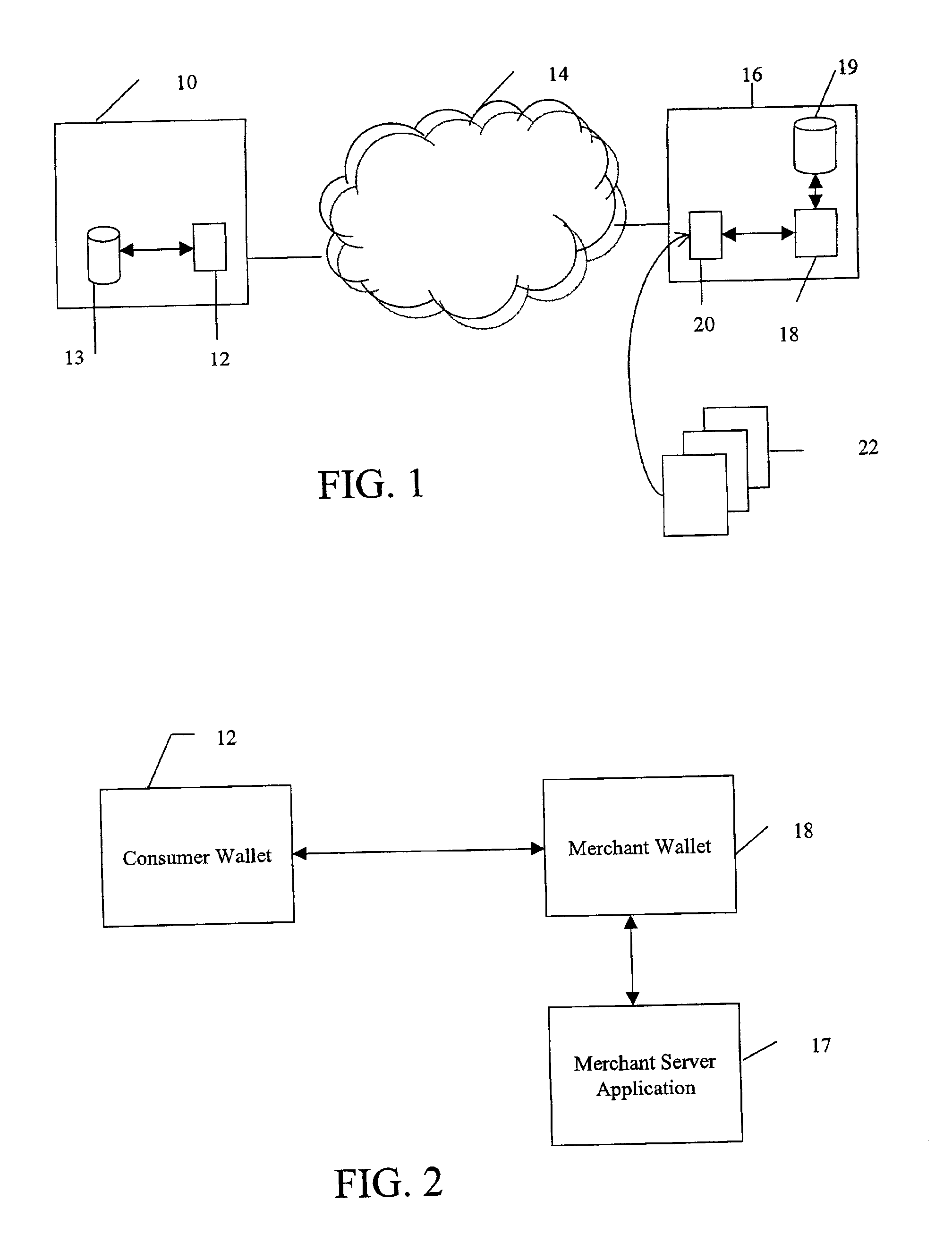
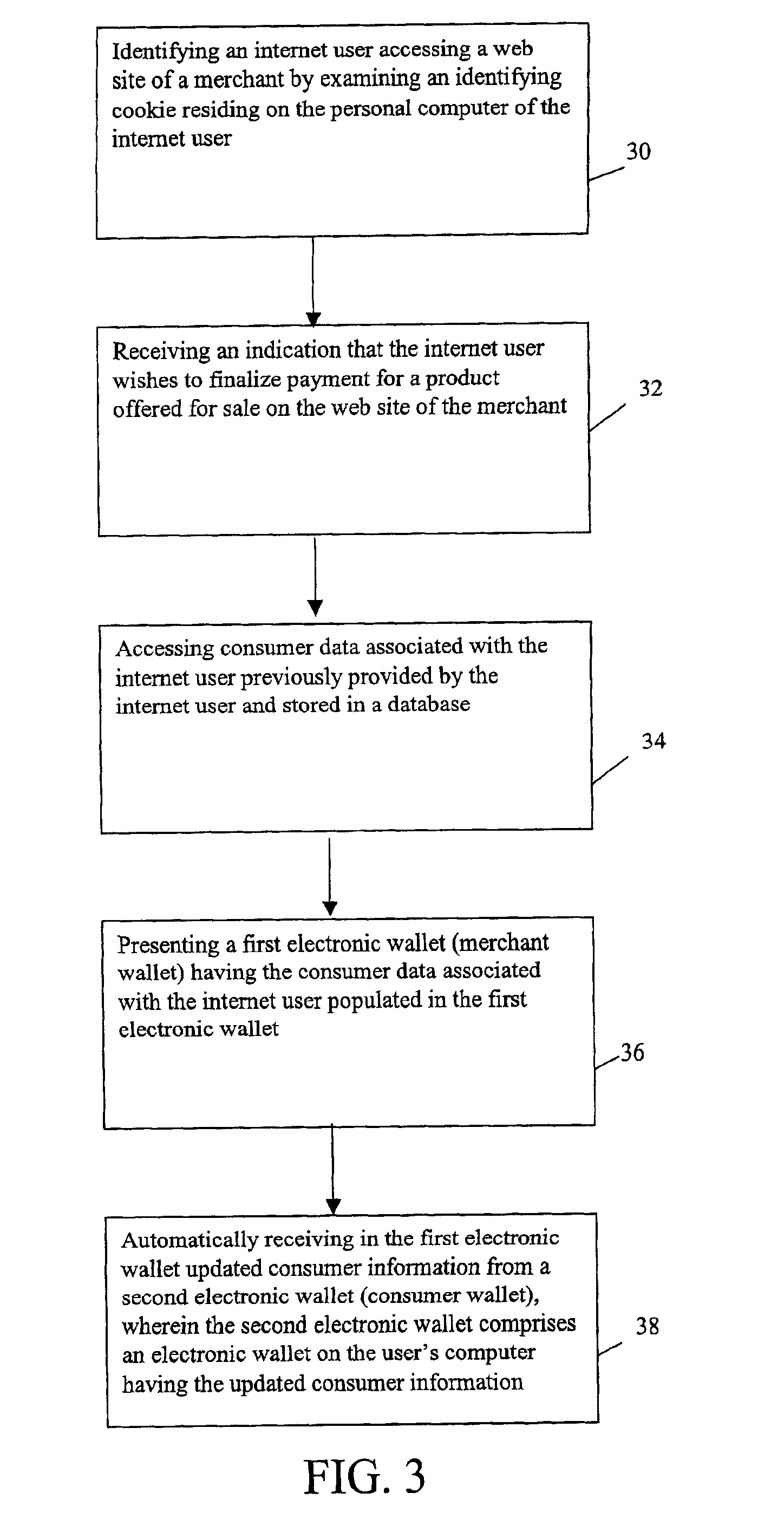
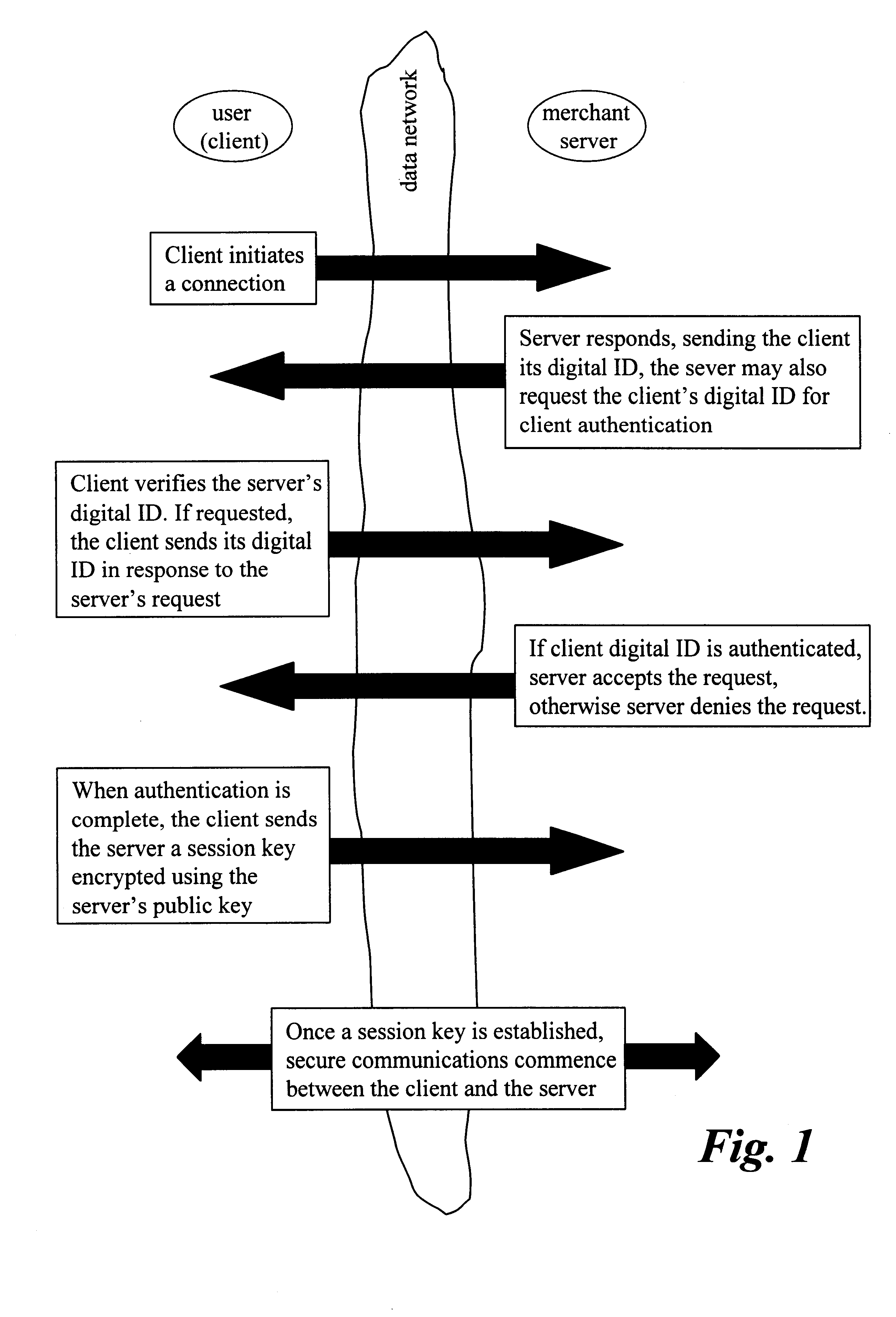
System and method for use of distributed electronic wallets
InactiveUS6873974B1Avoid burdenImprove efficiencyComplete banking machinesFinanceMerchant servicesCredit card
Methods and systems whereby two electronic wallets communicate and exchange information. In one such system, a consumer's personal electronic wallet communicates with the exclusive or preferred wallet of a web merchant. In one such system, an internet consumer registers with a web merchant's exclusive or preferred electronic wallet (“merchant wallet”) and provides consumer information (e.g., credit card number, mailing address, and other information) to the merchant wallet, which is stored by the merchant wallet in a database on the merchant server. Such information may be automatically populated by the consumer's personal electronic wallet. The consumer maintains current consumer information in a consumer electronic wallet on the consumer's personal computer. When the consumer visits the merchant site again, and orders goods or services, the merchant's preferred wallet can be automatically updated by the consumer's electronic wallet if any of the data in the merchant's wallet has changed. For example, the consumer wallet examines the information in the merchant wallet to determine if the information in the merchant wallet conforms to the current information in the consumer wallet. If the information does not conform, the consumer wallet communicates the current consumer information to the merchant wallet.
Owner:CITIBANK
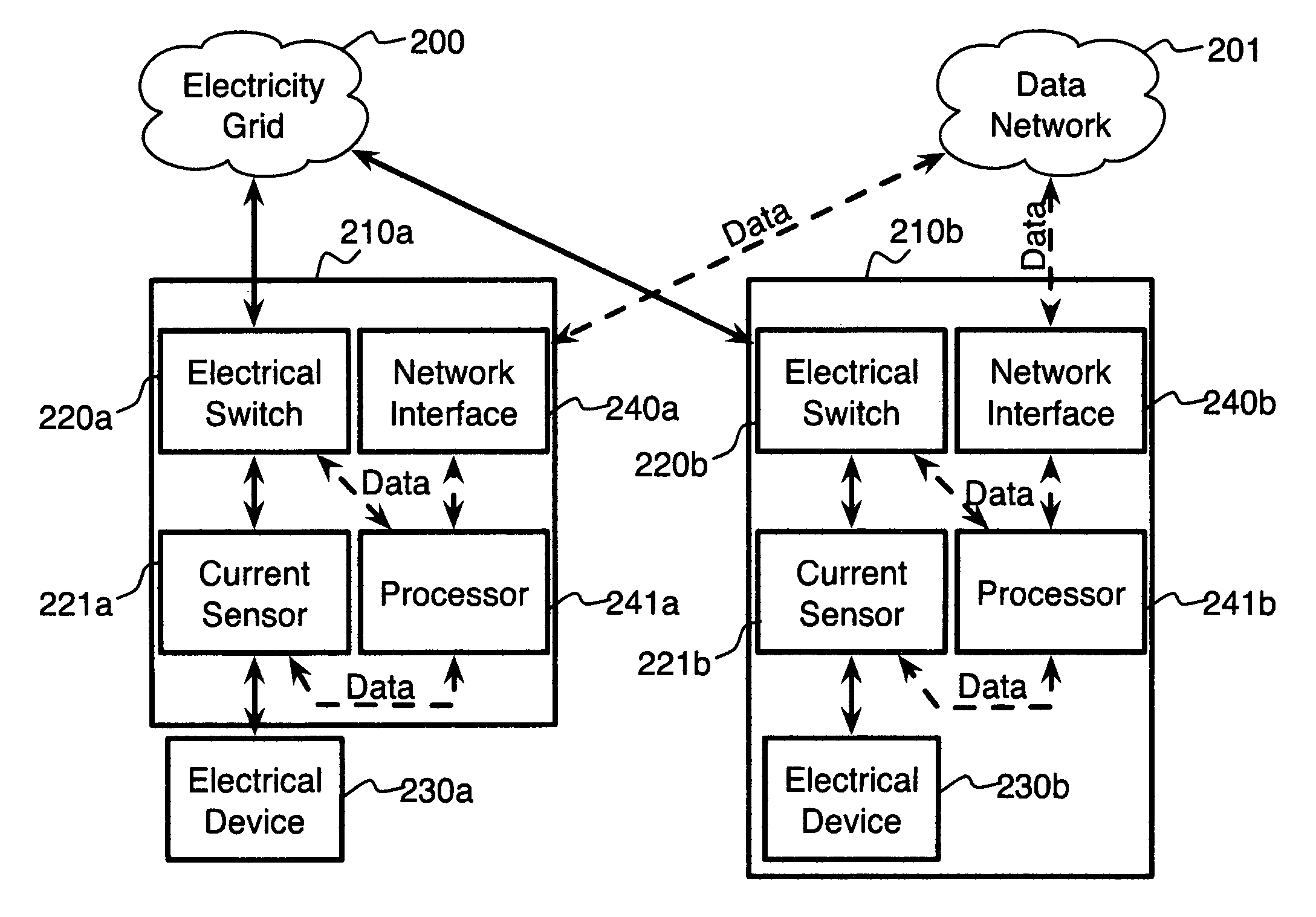
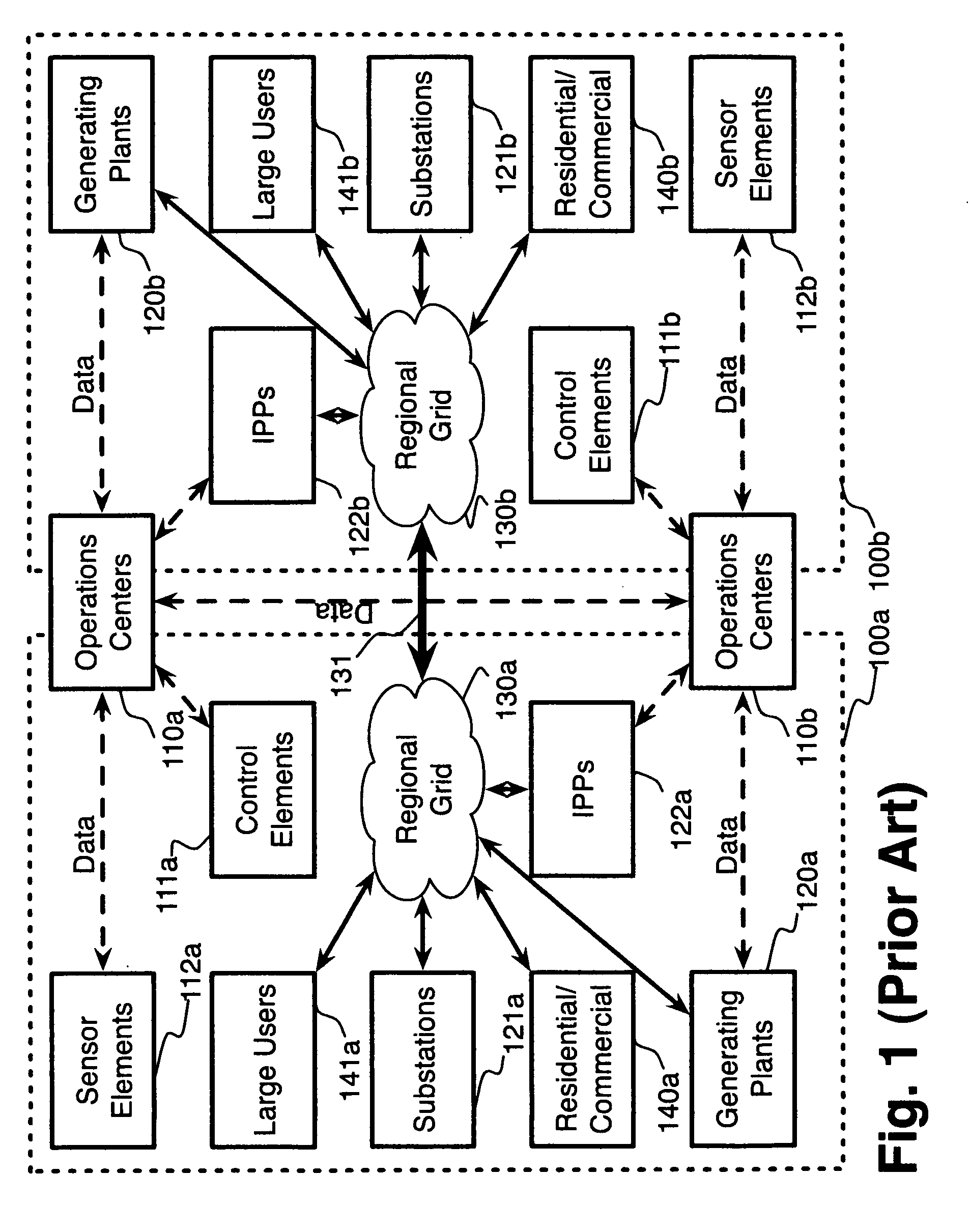
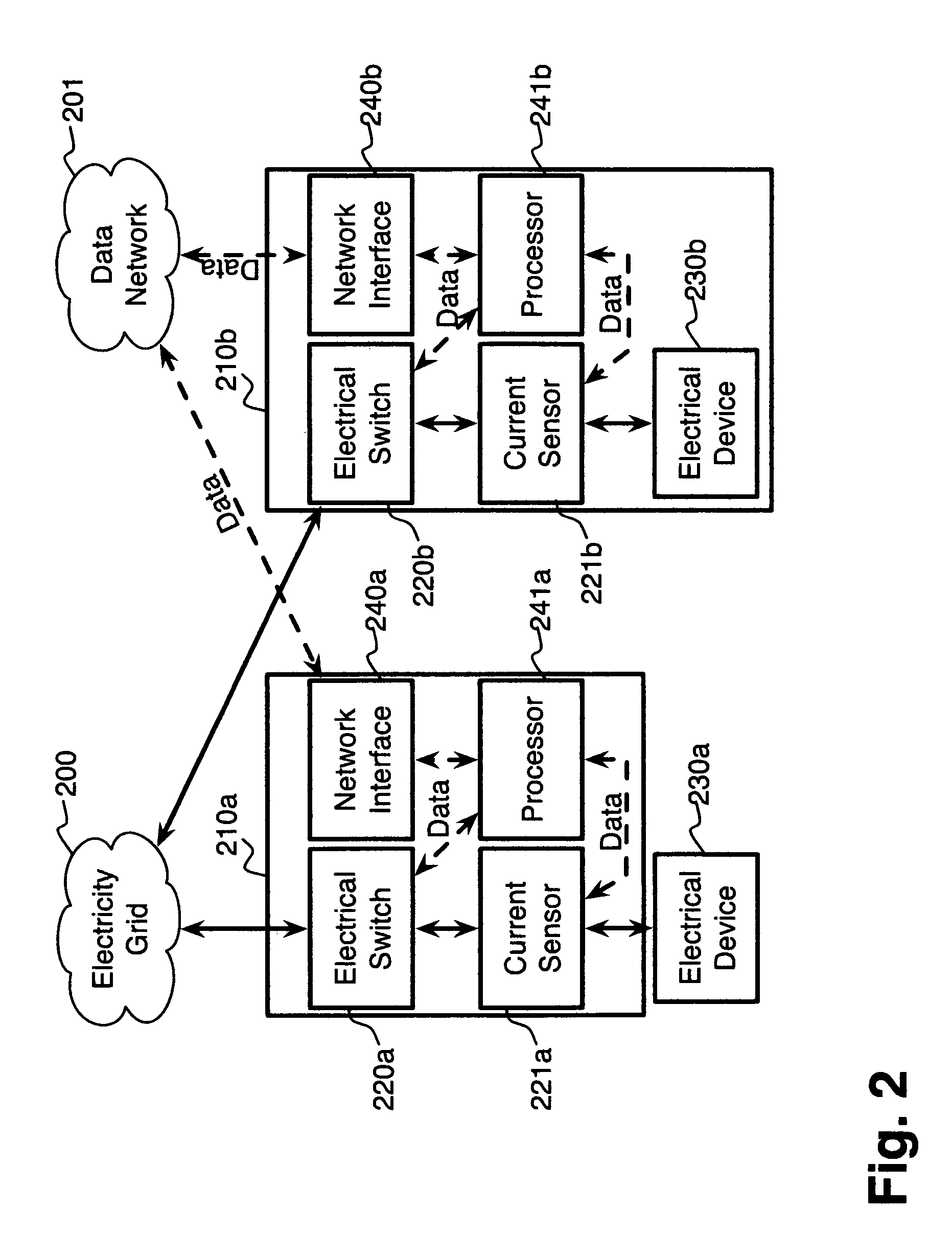
System and method for electric grid utilization and optimization
InactiveUS20100217550A1Selective ac load connection arrangementsElectric devicesSimulationTransmission loss
A system for electric grid utilization and optimization, comprising a communications interface executing on a network-connected server and adapted to receive information from a plurality of iNodes, the plurality of iNodes comprising a source iNode, a sink iNode, and a plurality of transmission or distribution iNodes, an event database coupled to the communications interface and adapted to receive events from a plurality of iNodes via the communications interface, a modeling server coupled to the communications interface, and a statistics server coupled to the event database and the modeling server, wherein the modeling server, on receiving a request to establish an allocation of at least one of transmission losses, distribution losses, and ancillary services to a specific sink iNode, computes at least one virtual path for flow of electricity between a source iNode and the specific sink iNode and wherein the modeling server further computes, for each transmission or distribution iNode included in the computed virtual path, at least one energy loss and allocates a portion thereof to the specific sink iNode, is disclosed.
Owner:CRABTREE JASON +4
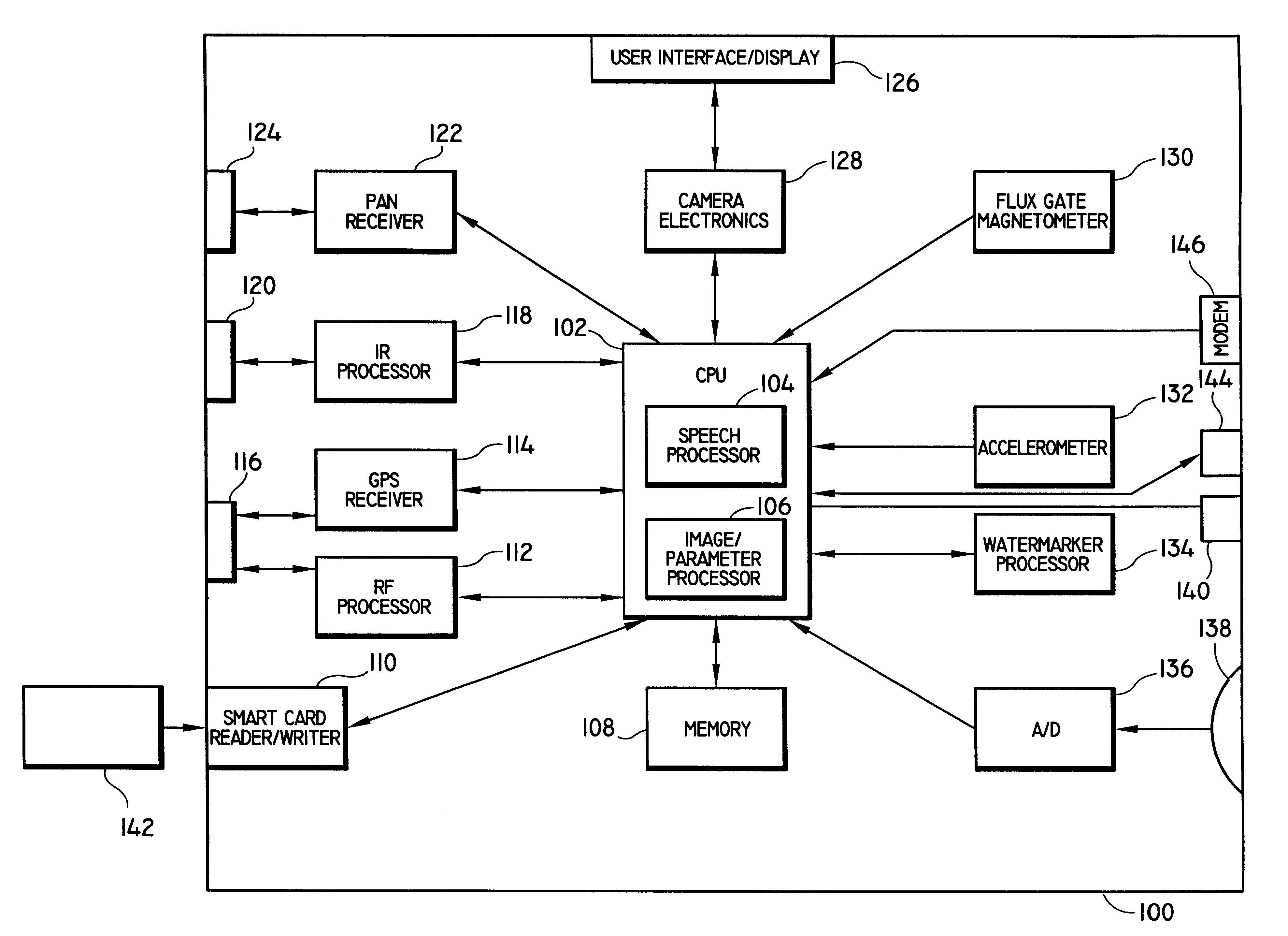
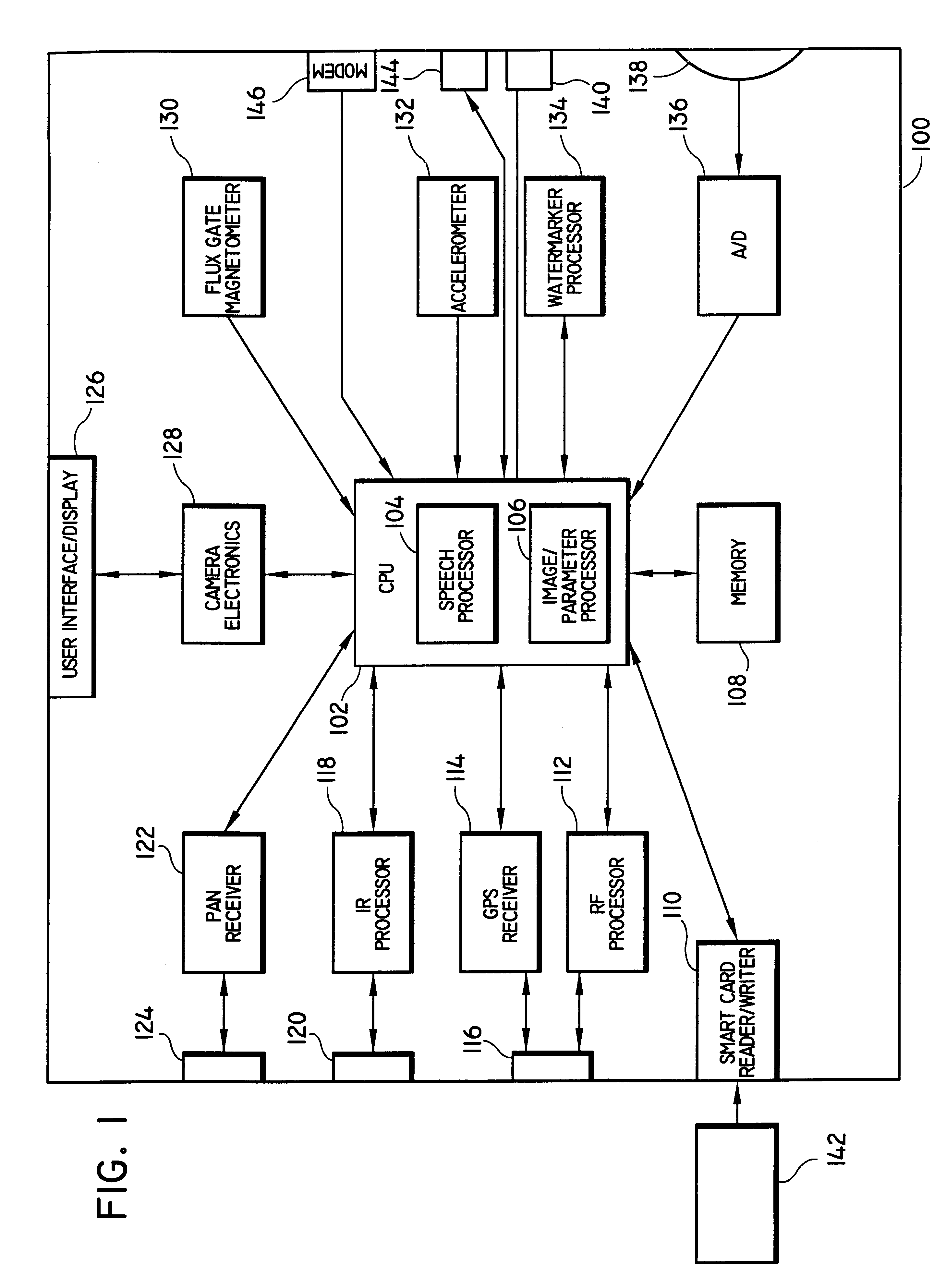
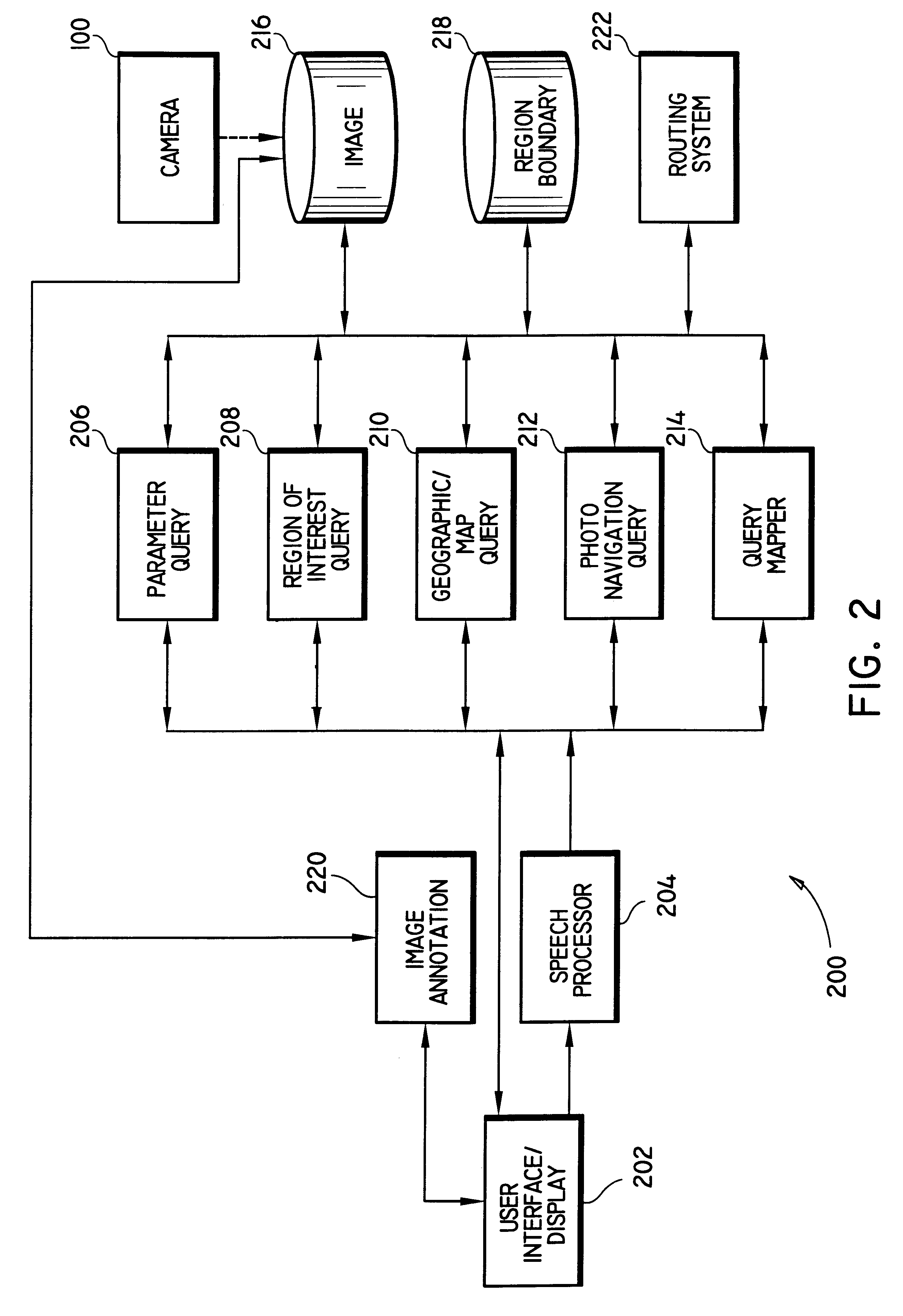
System and methods for querying digital image archives using recorded parameters
System and methods for querying digital image archives containing digital photographs and / or videos (collectively, "digital images"). The digital images are indexed in accordance with a plurality of recorded parameters including time, date and geographic location data (altitude and longitude), as well as image data such as lens focal length, auto focus distance, shutter speed, exposure duration, aperture setting, frame number, image quality, flash status and light meter readings, which are used for searching a database consisting of the digital images. These images are preferably generated by an image capturing system which is capable of measuring and recording a plurality of parameters with each captured digital image. The image retrieval system allows a querying user to search the image archive by formulating one or more of a plurality of query types which are based on the recorded parameters, and then retrieve and display those images having the specified parameters.
Owner:IBM CORP
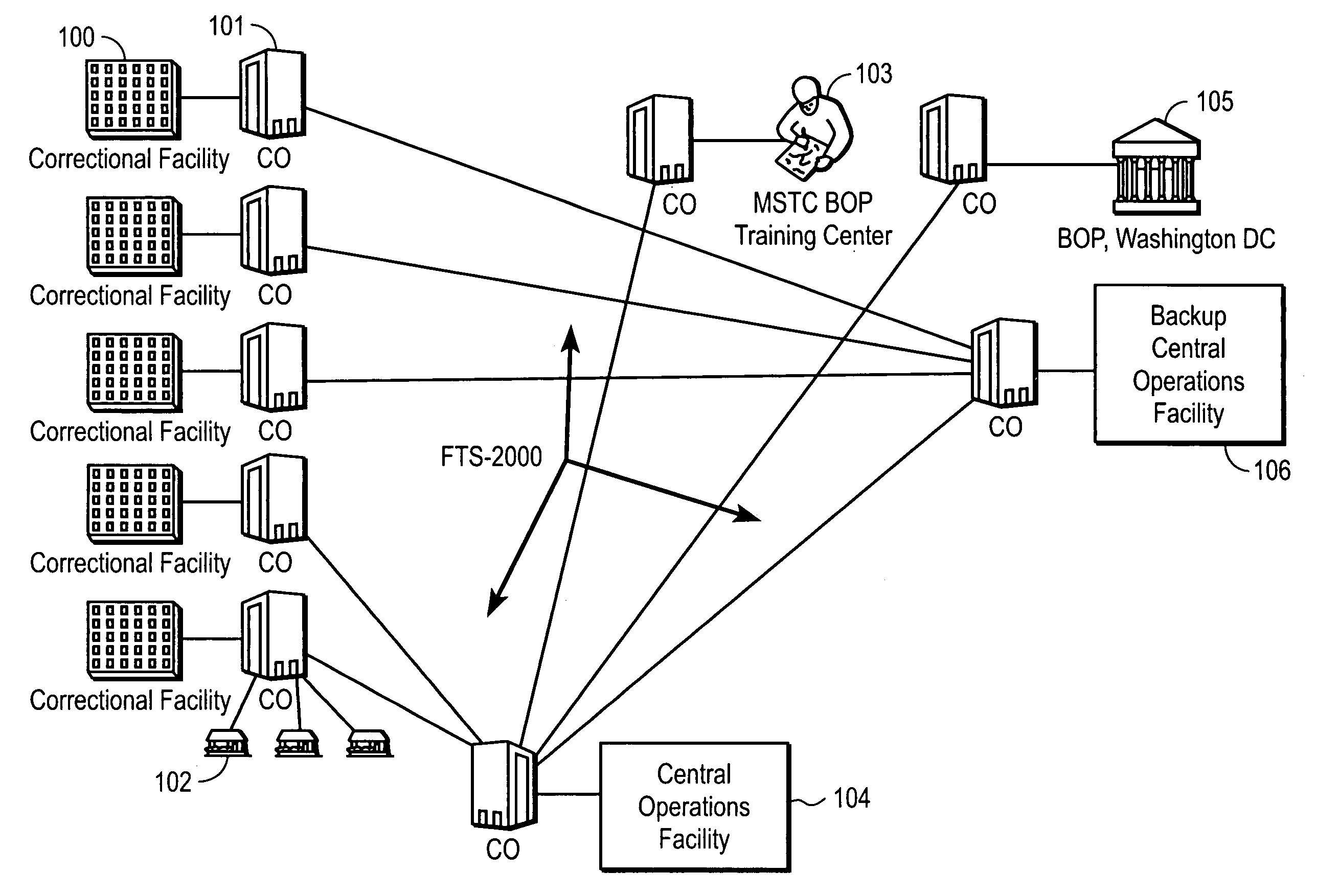
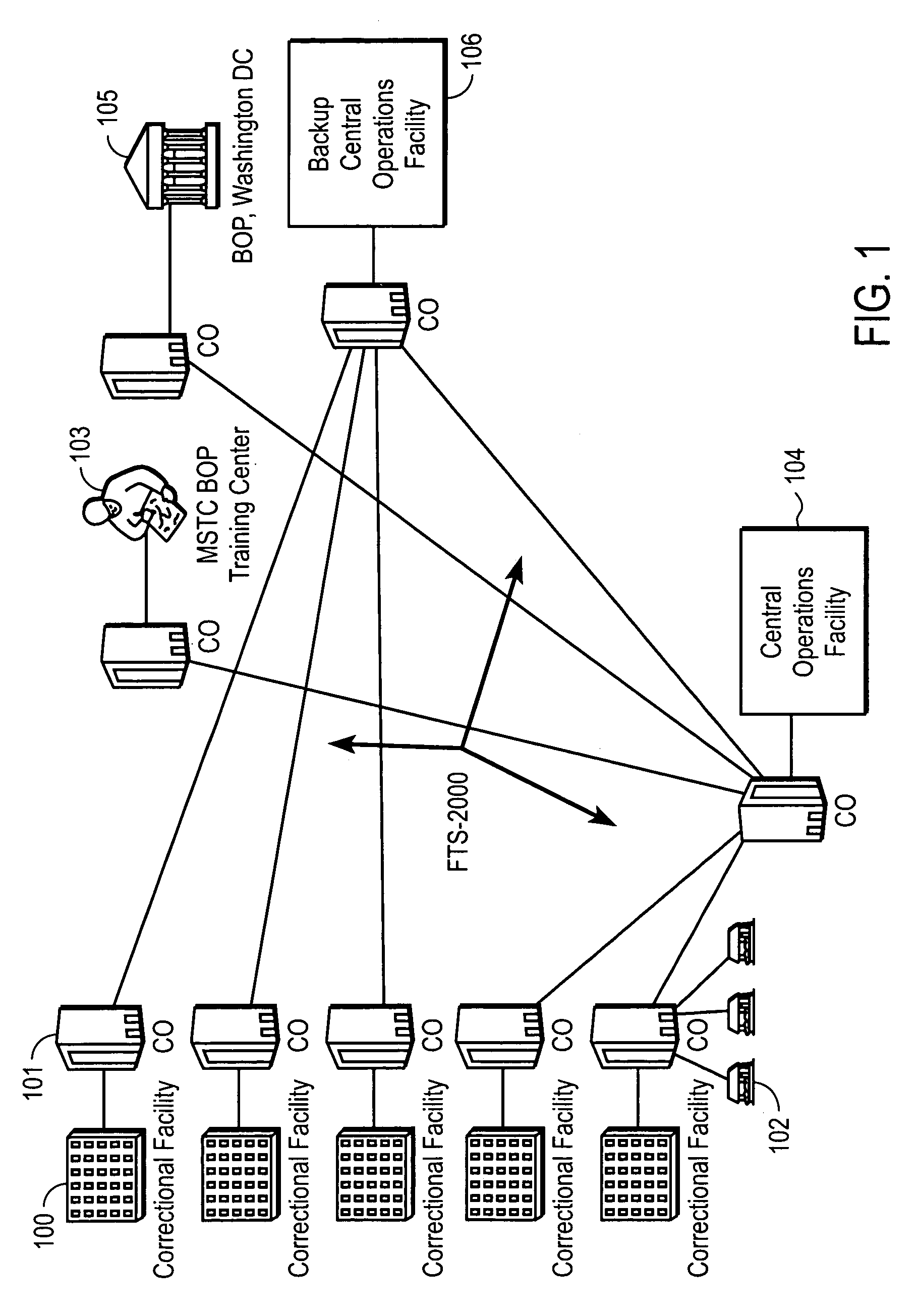
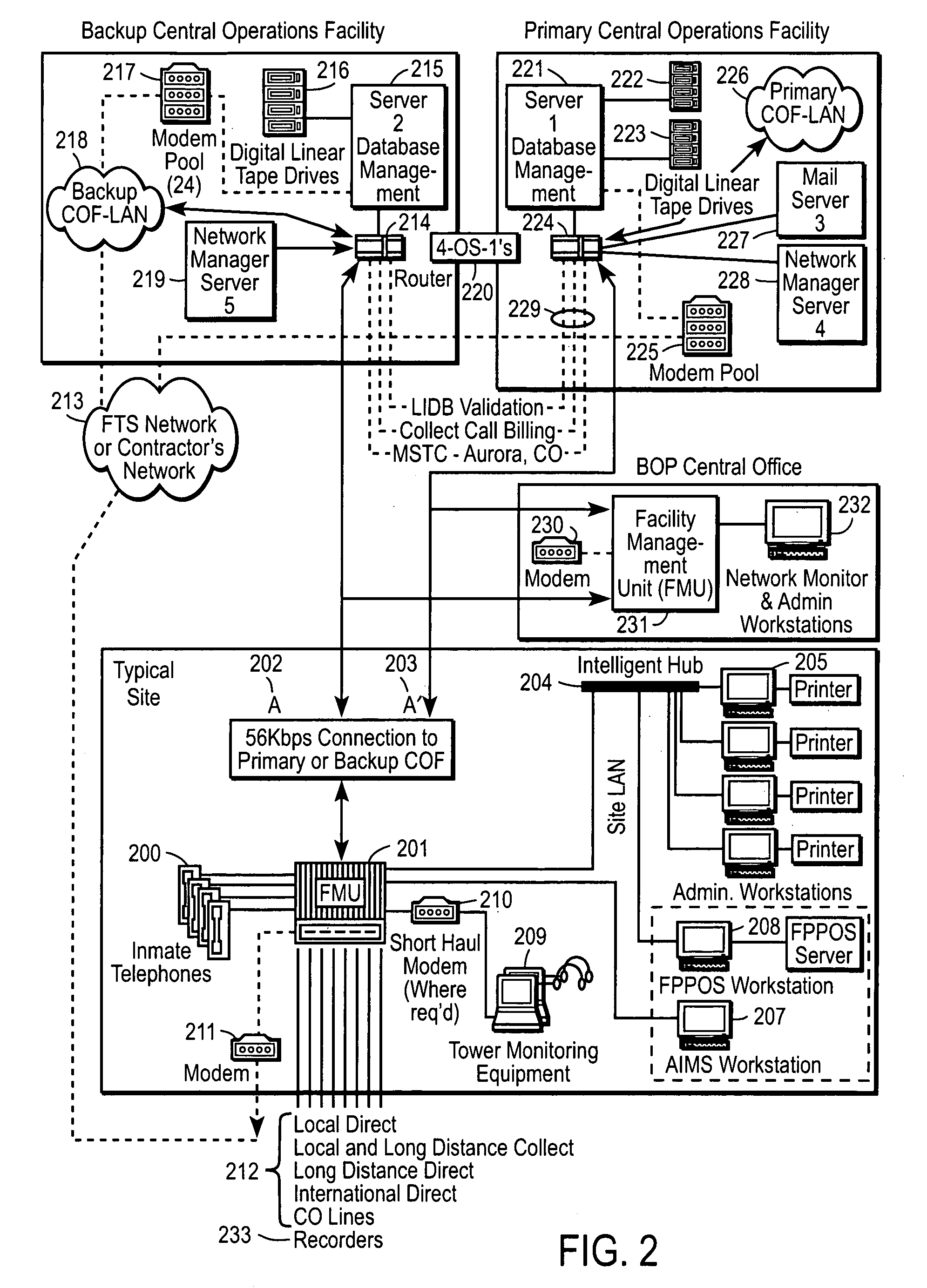
Computer-based method and apparatus for controlling, monitoring, recording and reporting telephone access
InactiveUS7106843B1Improve securityLow costUnauthorised/fraudulent call preventionEavesdropping prevention circuitsManagement unitCentralized management
A method and apparatus for managing institutional telephone activity utilizing a computer-based telephony management unit to connect institutional telephones with outside telephone lines. The unit provides institutional users with fully automated, direct dial and collect calling privileges for local, long distance, and international calls. The unit contains a database for storing the calling privileges and restrictions of institutional users, for recording calling transactions made by the users, and for managing user monetary accounts. The unit can record up to 400 hours of conversation in a digital format. The unit provides various administrative capabilities, including user account management, audit trails, transaction reports, centralized management and report capabilities, and detection of fraudulent calling.
Owner:AMERICAN CAPITAL FINANCIAL SERVICES +1
Method of and system for finding and serving consumer product related information over the internet using manufacturer identification numbers
InactiveUS6064979AHigh acceptanceMultiple digital computer combinationsApparatus for meter-controlled dispensingRelevant informationHome page
A method of and system for finding and serving consumer product-related information on the Internet comprising a database serving subsystem which stores: a plurality of manufacturer identification numbers (MINs) assigned to a plurality of manufacturers of consumer products; a plurality of home-page specifying URLs symbolically linked to the plurality of MINs; a plurality of universal product numbers (UPN) assigned to a plurality of consumer products made by the plurality of manufacturers; and a plurality of product-information specifying URLs symbolically linked to the plurality of UPNs. During operation, a client subsystem transmits to the database serving subsystem, a request for information which includes the UPN assigned to the consumer product on which product-related information is being sought. The database serving subsystem automatically compares the UPN against the stored plurality of MINs, and automatically returns to the client subsystem, one or more of URLs symbolically linked to the UPN, if URLs have been symbolically linked to the UPN within the database serving subsystem. However, if no URLs have been symbolically linked to the UPN, then the database serving subsystem automatically returns the home-page specifying URL symbolically linked to the MIN contained within the UPN in the request. By virtue of this novel MIN-based search mechanism embodied within the database serving subsystem, client subsystems are automatically provided with the home-page of the manufacturer's World Wide Web (WWW) site in situations where product-information specifying URLs have not yet been symbolically linked with the UPN on any one of the manufacturer's products.
Owner:PERKOWSKI THOMAS J
System and method for monitoring unauthorized transport of digital content
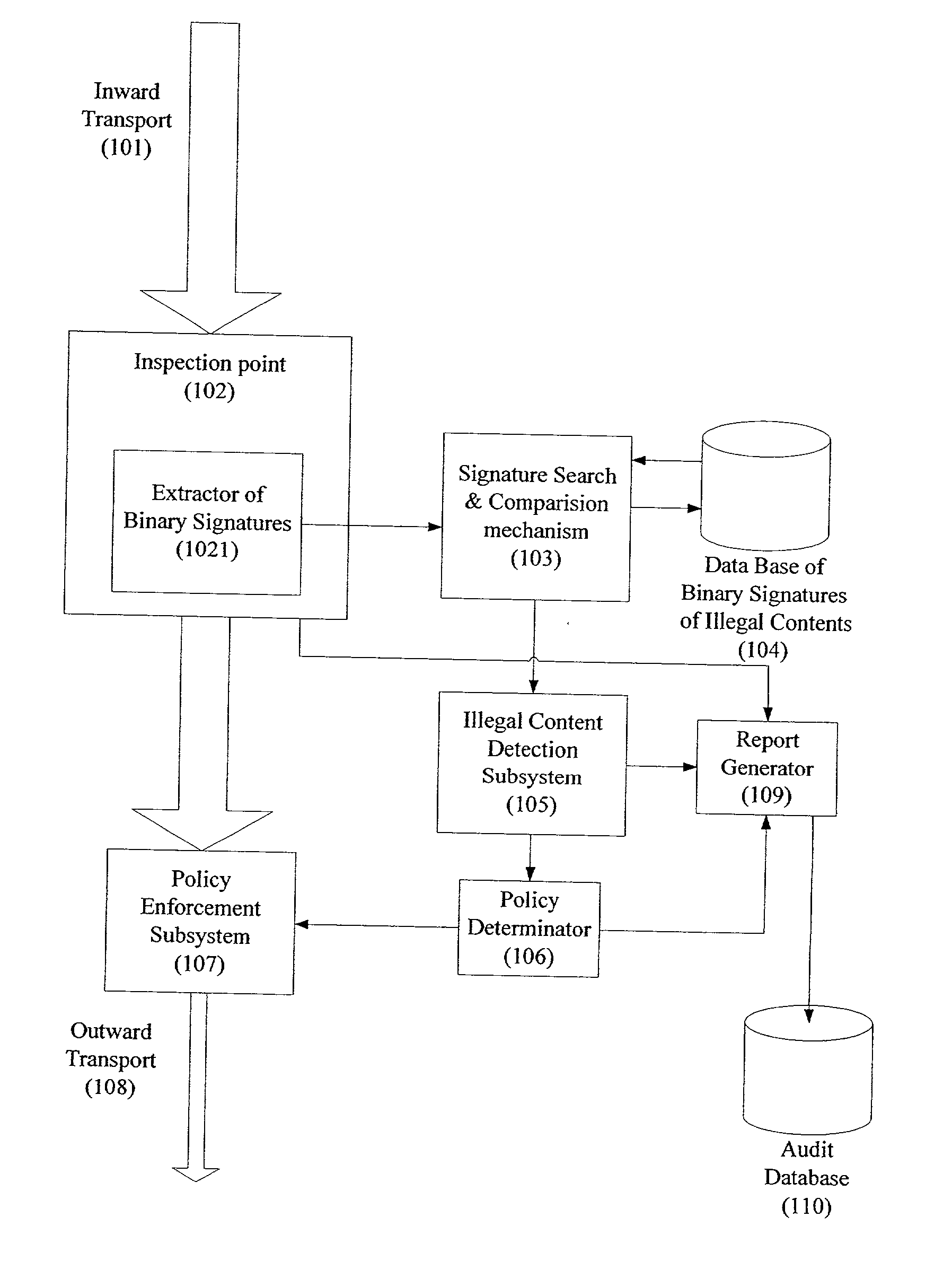
ActiveUS20020129140A1Reduce decreaseAttenuation bandwidthMemory loss protectionError detection/correctionDigital contentNumber content
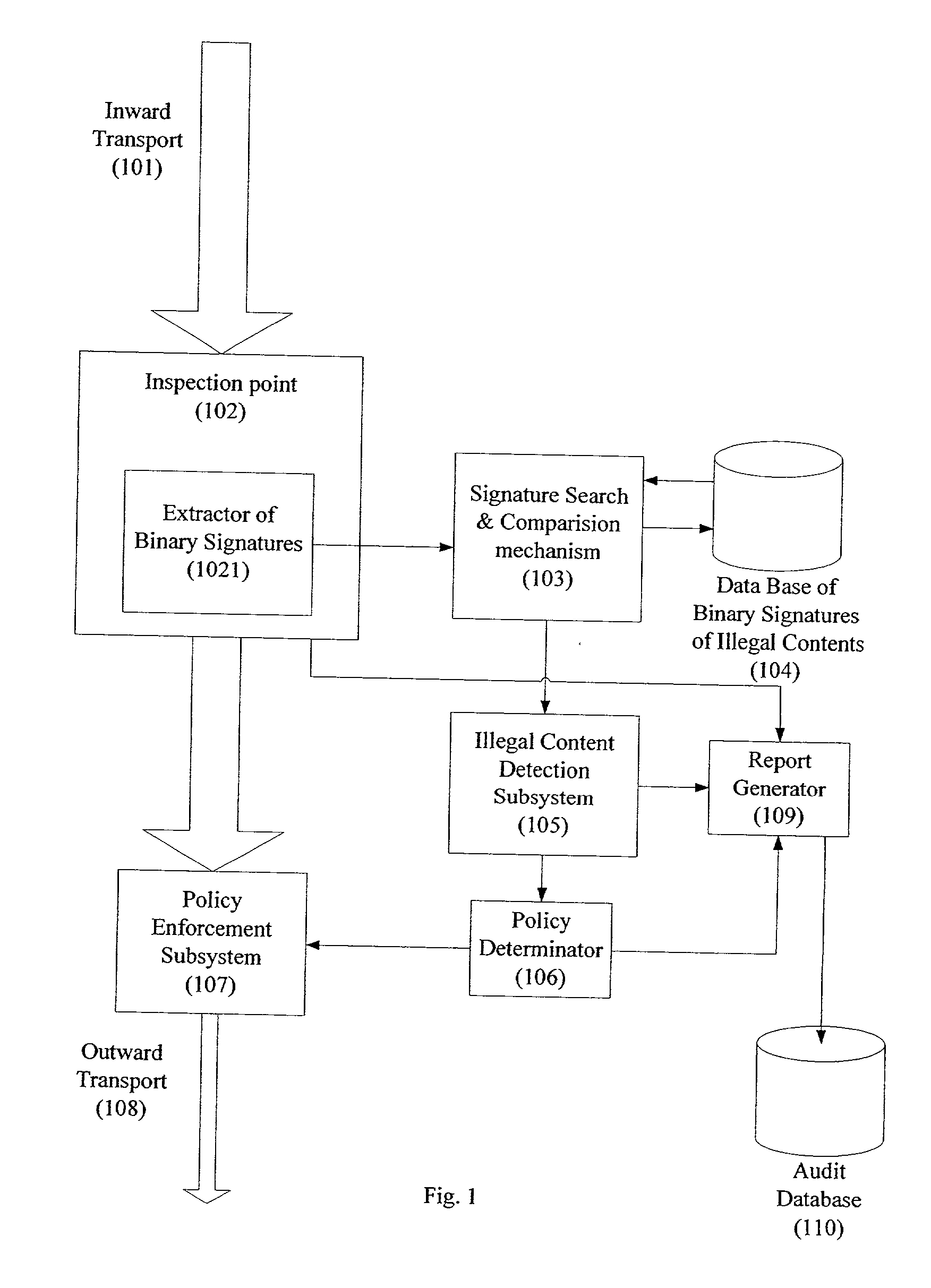
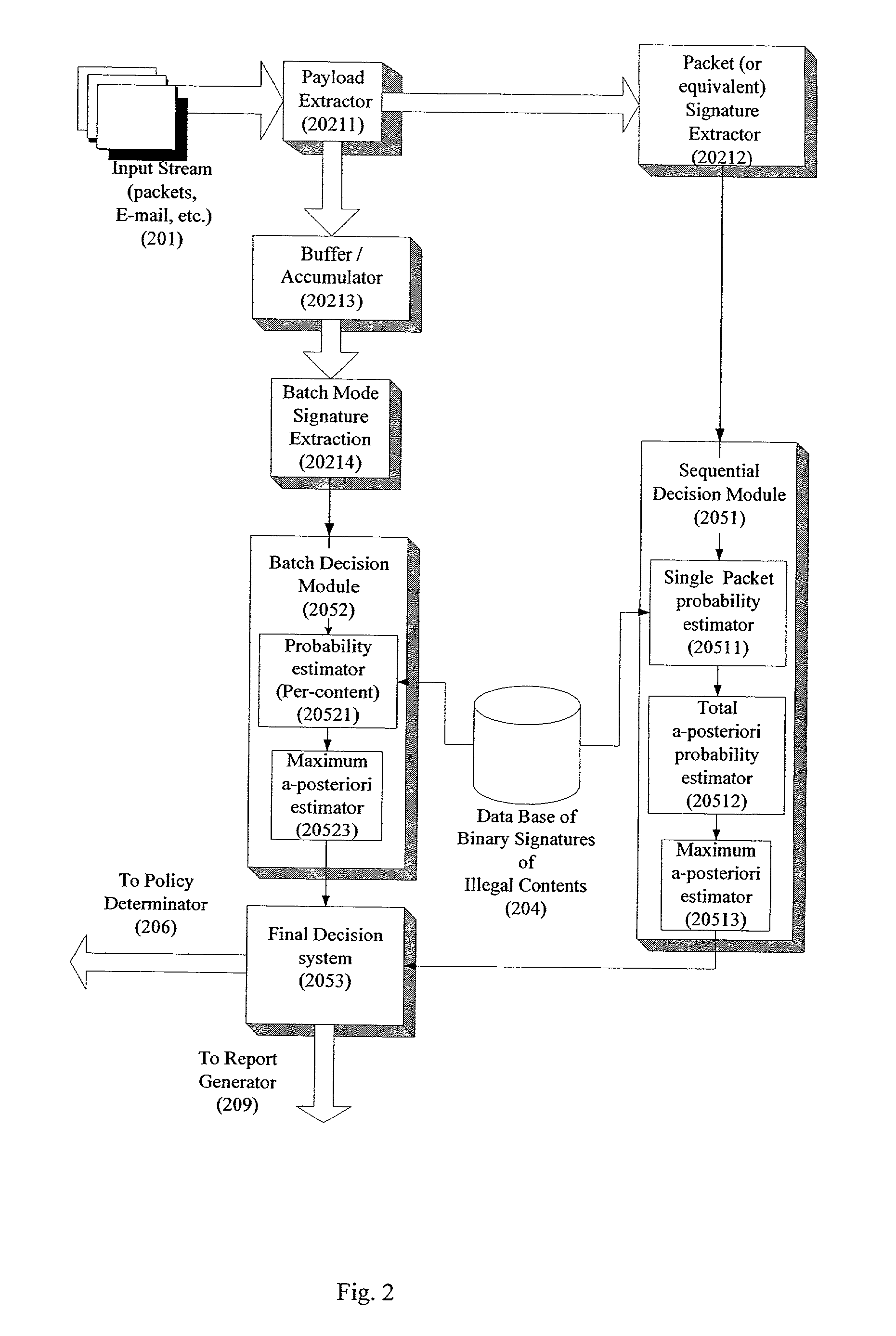
A system for network content monitoring and control, comprising: a transport data monitor, connectable to a point in a network, for monitoring data being transported past said point, a signature extractor, associated with said transport data monitor, for extracting a derivation of said data, said derivation being indicative of content of said payload, a database of preobtained signatures of content whose movements it is desired to monitor, and a comparator for comparing said derivation with said preobtained signatures, thereby to determine whether said payload comprises any of said content whose movements it is desired to monitor. The monitoring result may be used in bandwidth control on the network to restrict transport of the content it is desired to control.
Owner:FORCEPOINT LLC
Secure delivery of information in a network
InactiveUS6178505B1User identity/authority verificationData switching networksPrivate networkInformation resource
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
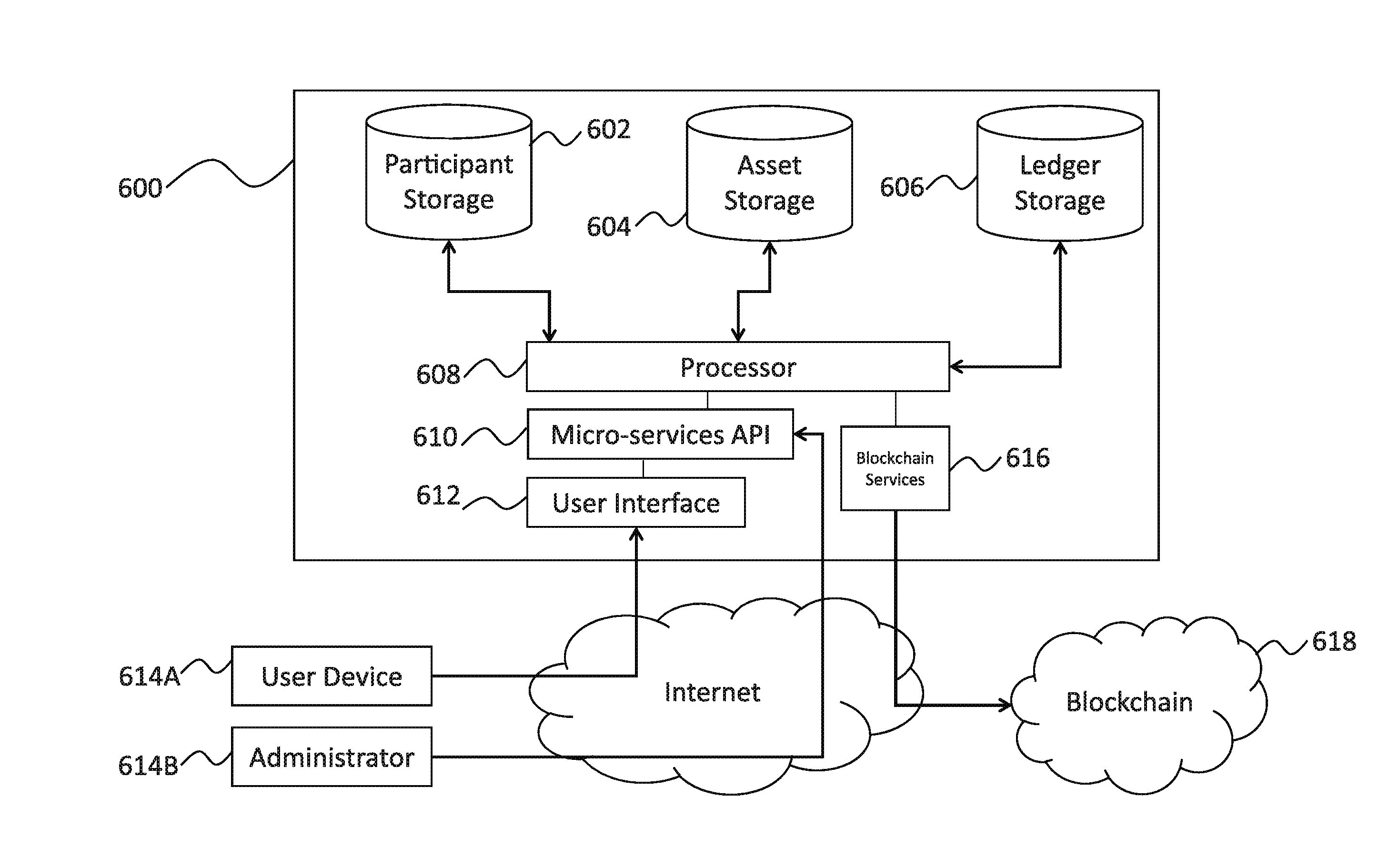
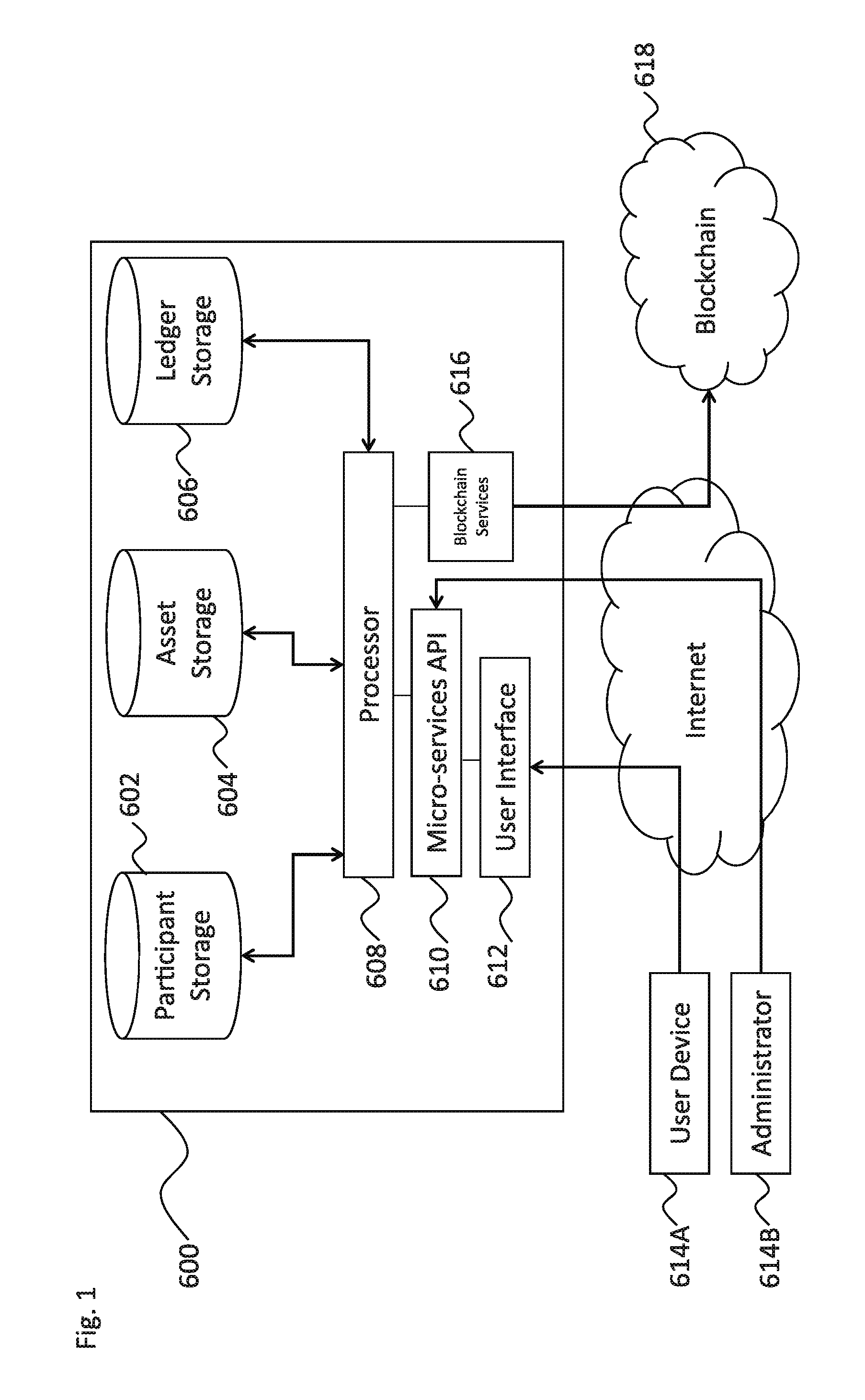
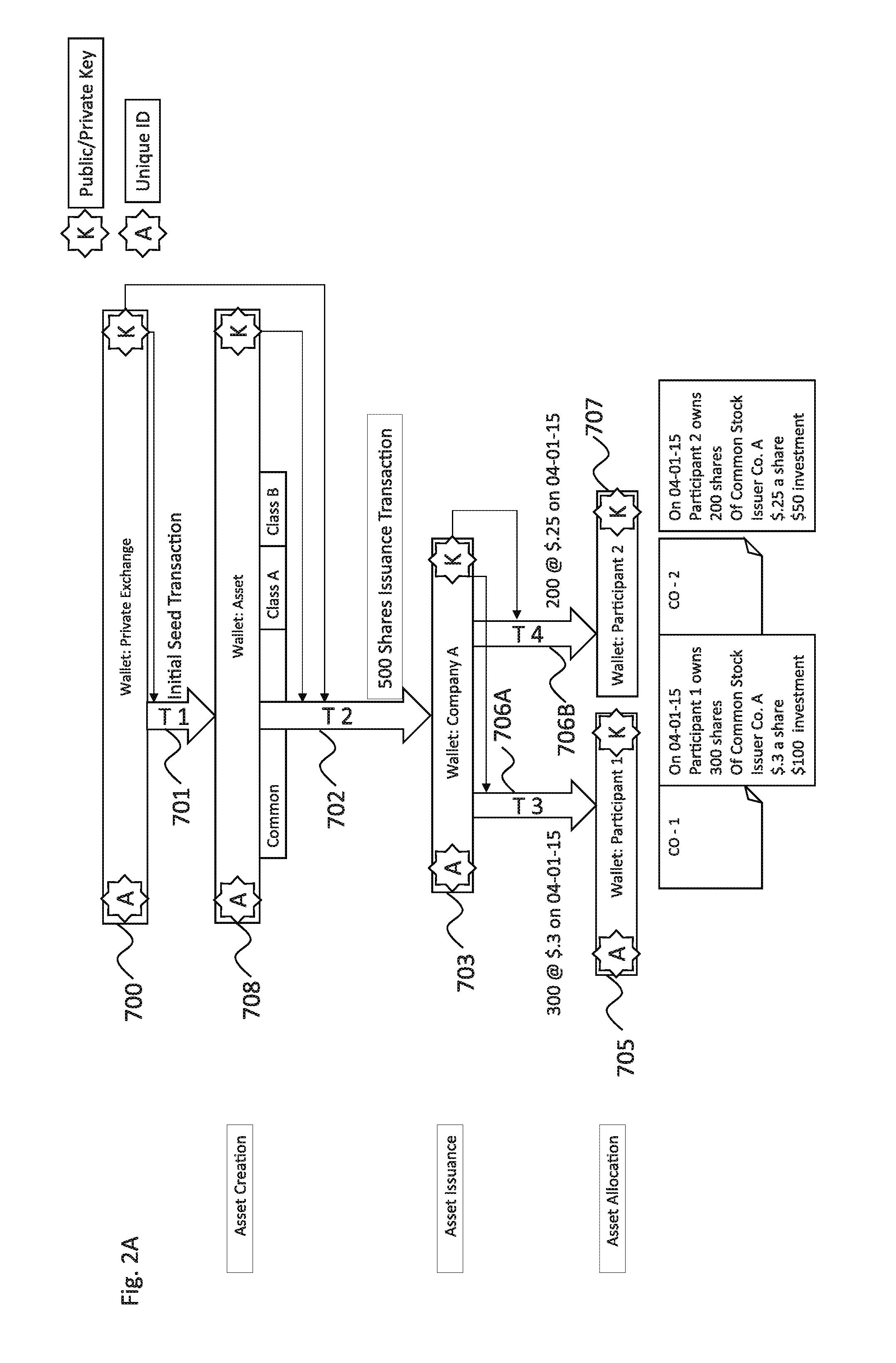
Systems and methods of secure provenance for distributed transaction databases
ActiveUS20170005804A1Direct accessImprove usabilityUser identity/authority verificationDigital data protectionFinancial transactionHandling system
An electronic resource tracking and storage computer system is provided that communicates with a distributed blockchain computing system that includes multiple computing nodes. The system includes a storage system, a transceiver, and a processing system. The storage system includes an resource repository and transaction repository that stores submitted blockchain transactions. A new resource issuance request is received, and a new resource is added to the resource repository in response. A new blockchain transaction is generated and published to the blockchain. In correspondence with publishing to the blockchain, the transaction storage is updated with information that makes up the blockchain transaction and some information that was not included as part of the blockchain transaction. The transaction storage is updated when the blockchain is determined to have validated the previously submitted blockchain transaction.
Owner:NASDAQ INC
Parimutuel wagering system with opaque transactions
InactiveUS20050096124A1Apparatus for meter-controlled dispensingBuying/selling/leasing transactionsDeposit accountCredit union
A seamless ledger-based wagering system is provided wherein a secure, flexible and automated database method and apparatus is used for retrieving information and accounting for wagers in an electronic wagering format. The accounting system can be a ledger wherein funds are accounted for by a financial structure (e.g., financial institution such as a bank, credit union, savings and loan, deposit account, and the like) so that funds may be transferred through an intermediate transaction (e.g., the electronic wager entered onto the account) on the ledger and committed to payment at the ultimate target of the transfer (e.g., the pari-mutuel site, and ancillary recipients of wagering monies, such as horseman's associations, totalisator companies, automated machine lessors, track association, governmental agencies and the like). As the financial records from the financial structure never ‘sees’ the wagering facility in the transaction, transferring funds or guaranteeing funds to the intermediate transaction on a ledger, the entire transaction is in compliance with state and national regulations prohibiting or limiting or rendering illegal the availability of funds in the wagering transaction or transferring funds into a wagering account.
Owner:ASIP HLDG INC
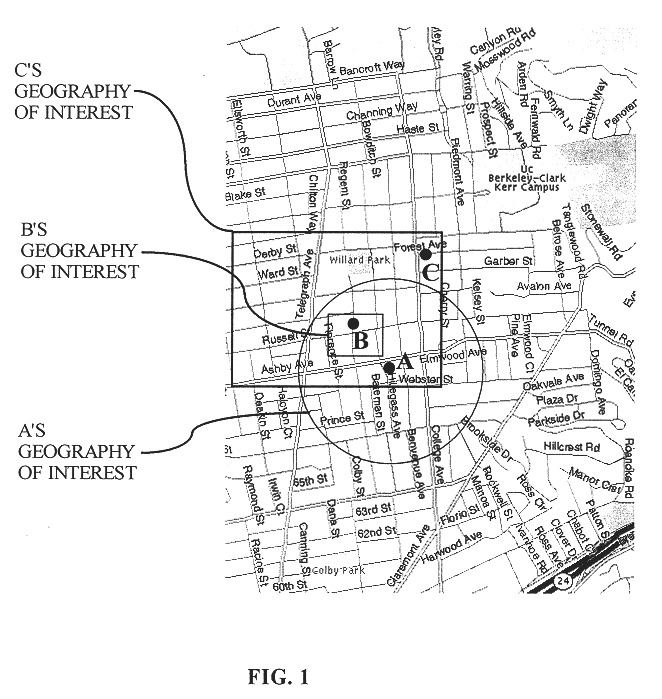
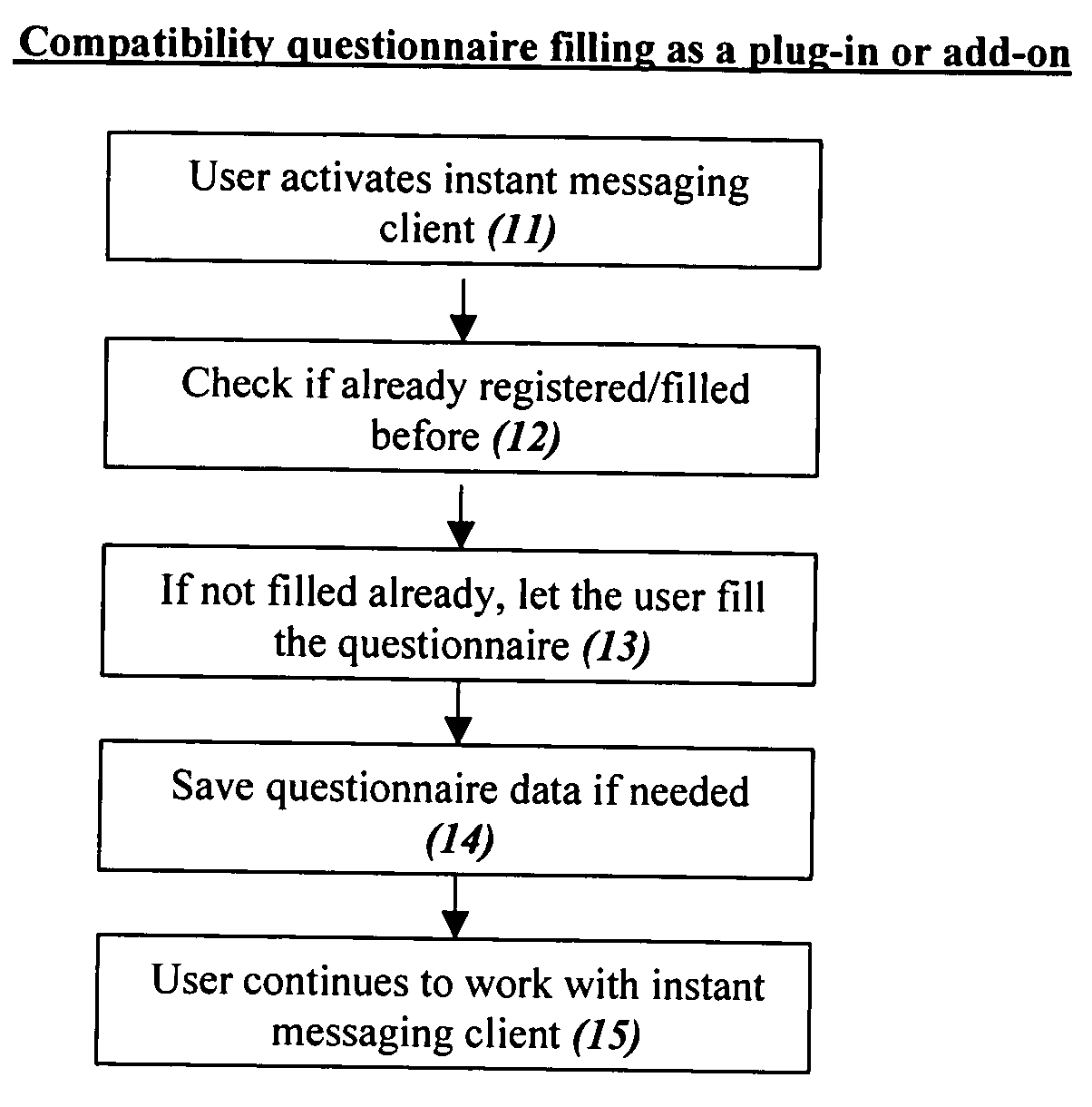
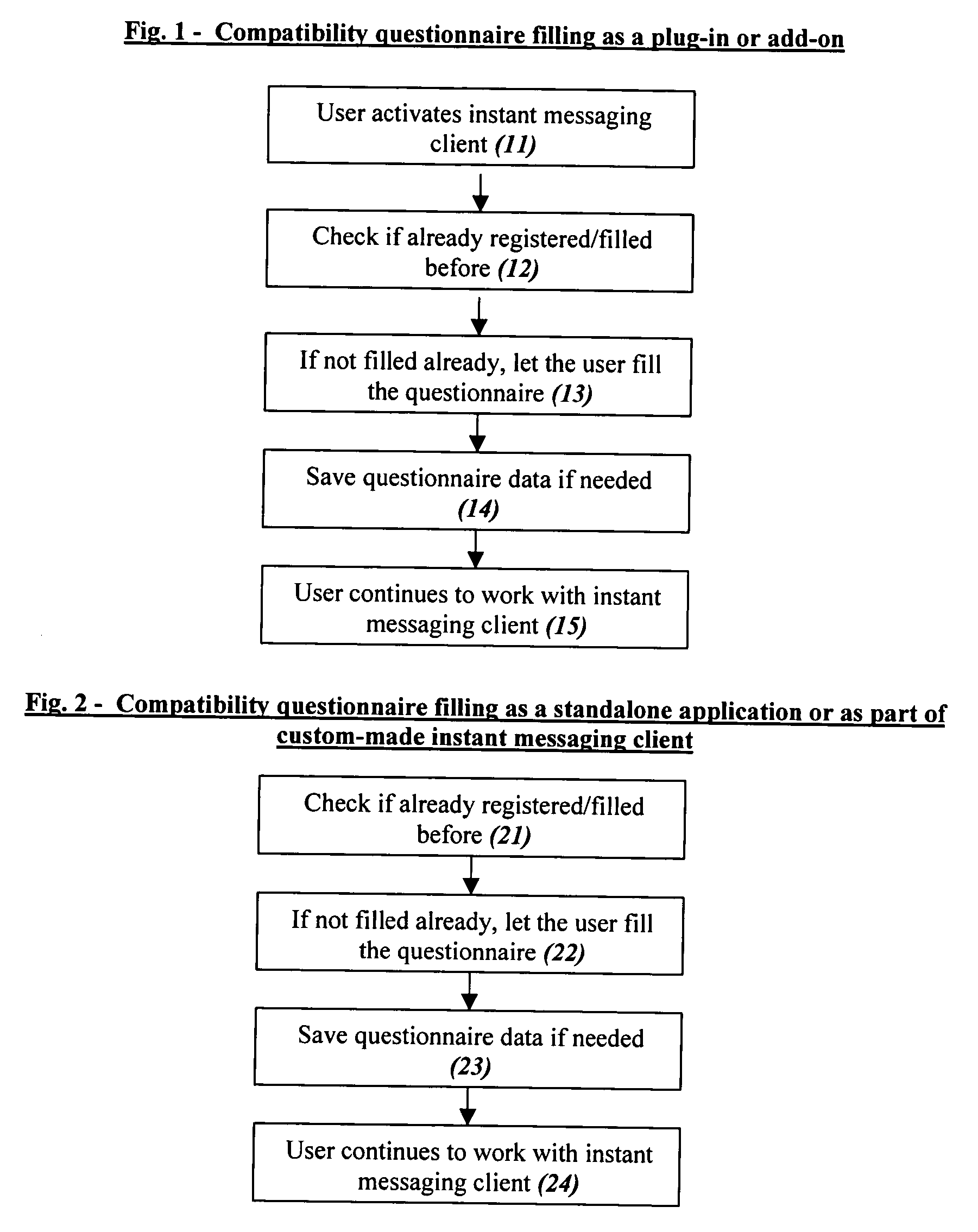
System and method for searching, finding and contacting dates on the Internet in instant messaging networks and/or in other methods that enable immediate finding and creating immediate contact
InactiveUS20050086211A1Highly integratedIncrease motivationWeb data indexingDigital data processing detailsWeb siteNetwork on
Computer dating is applied to instant messaging, in a novel, systematic and flexible way. This system and method enable the user to search and find instantly compatible dates in instant messaging networks on the basis of attribute search or 1-way compatibility search or 2-way compatibility search, and to search either for potential dates that are currently Online or also for dates that are currently Offline. Many additional features are described, and especially for example features that are based on improved integration between computer dating and instant messaging. Important features include for example: a. Integration of the dating environment with the contactee list (buddy list). b. Generating a list of compatible dates with different markings for people that are online or offline or a list divided into sub-lists or separate lists according to this. c. Applying a reverse variation by adding Instant messaging features to an Online dating site. d. Automatic instant notification when a new highly compatible date is available, instead of only periodical reports. e. Using a database of systematic pictures to which the users relate in defining their own appearance and the appearance of the desired date. f. Automatic finding of duplicate records. g. Addition of “OR” and / or “IF” relationships between questions instead of only the usual “AND”.
Owner:MAYER YARON
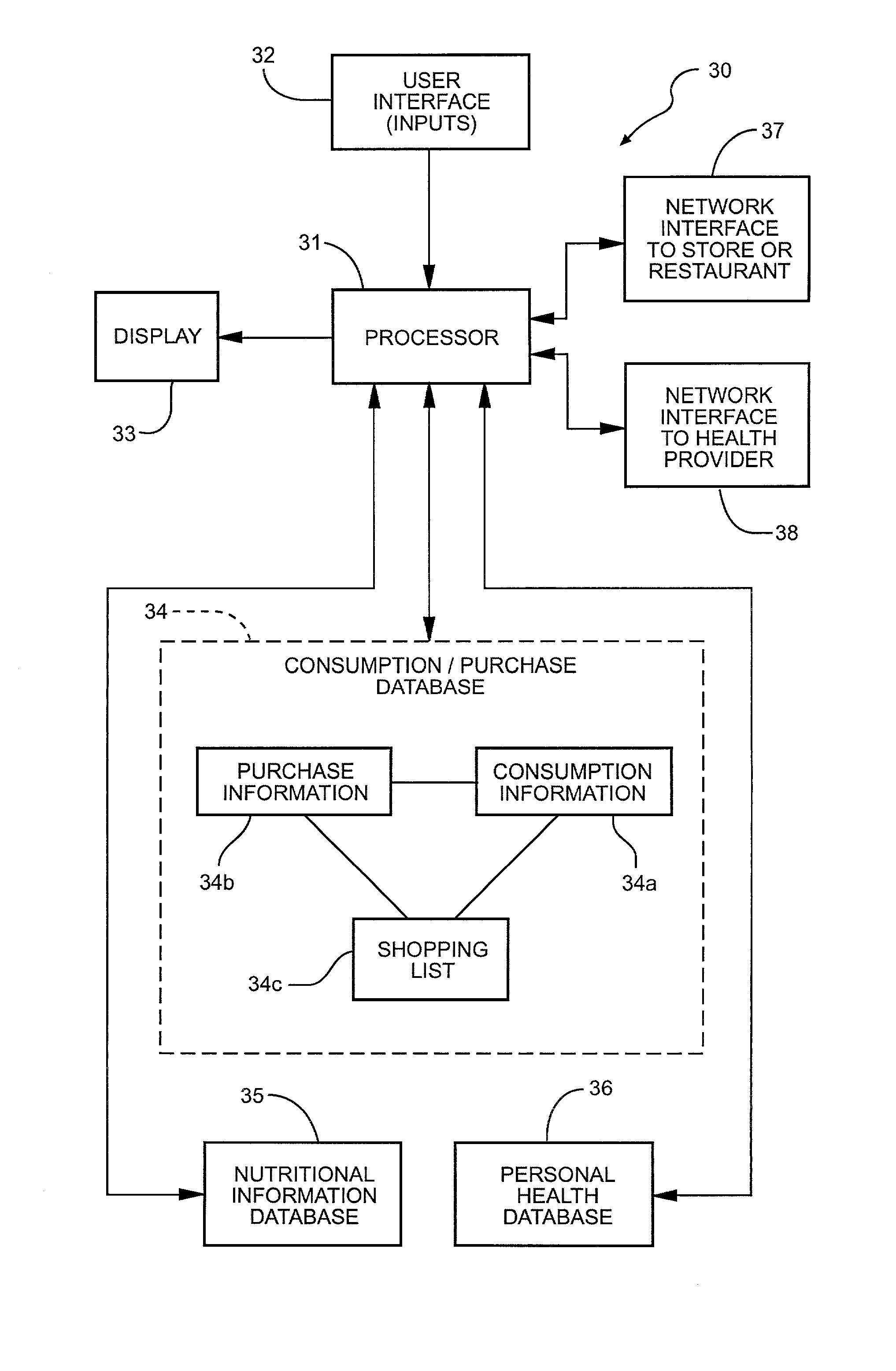
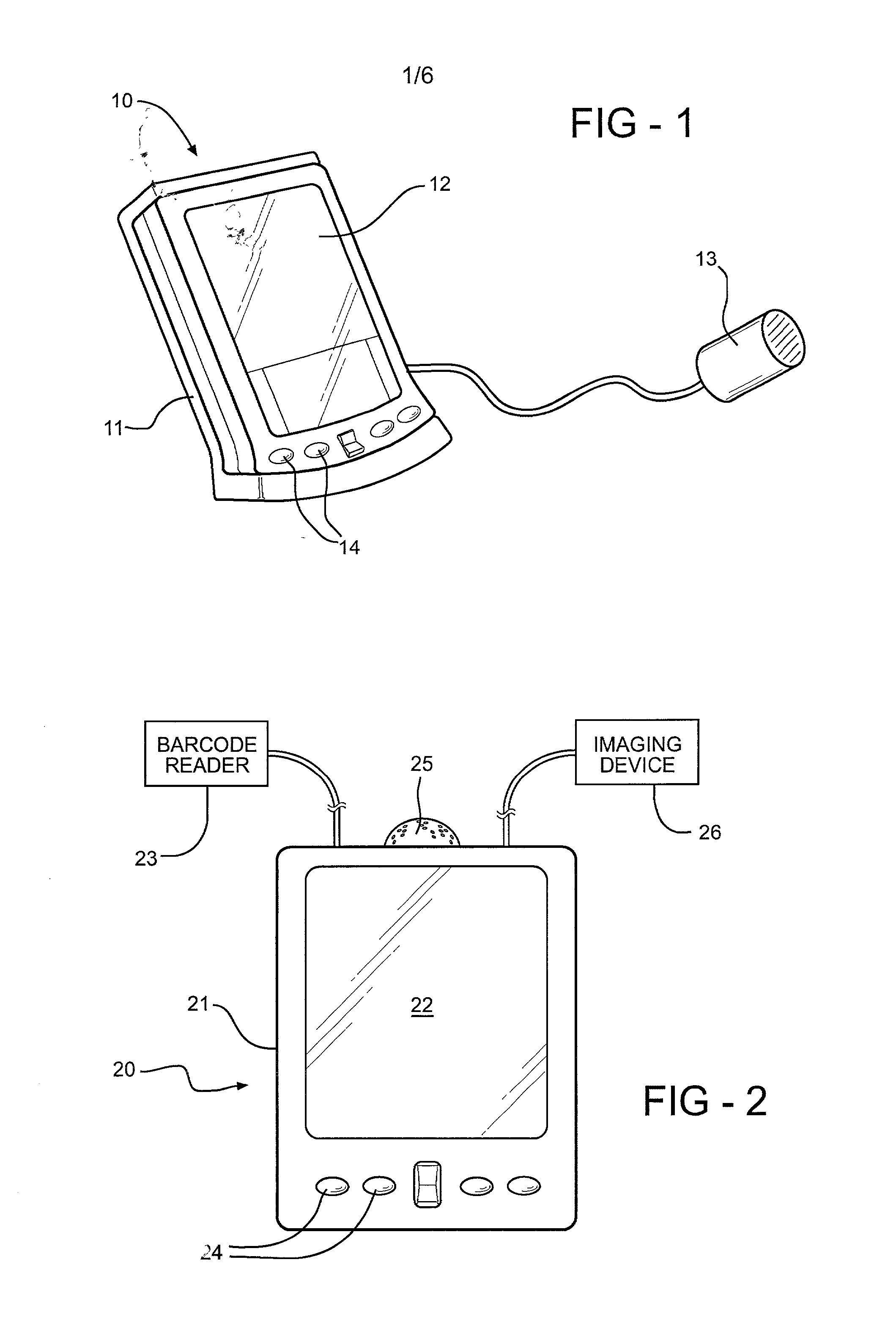
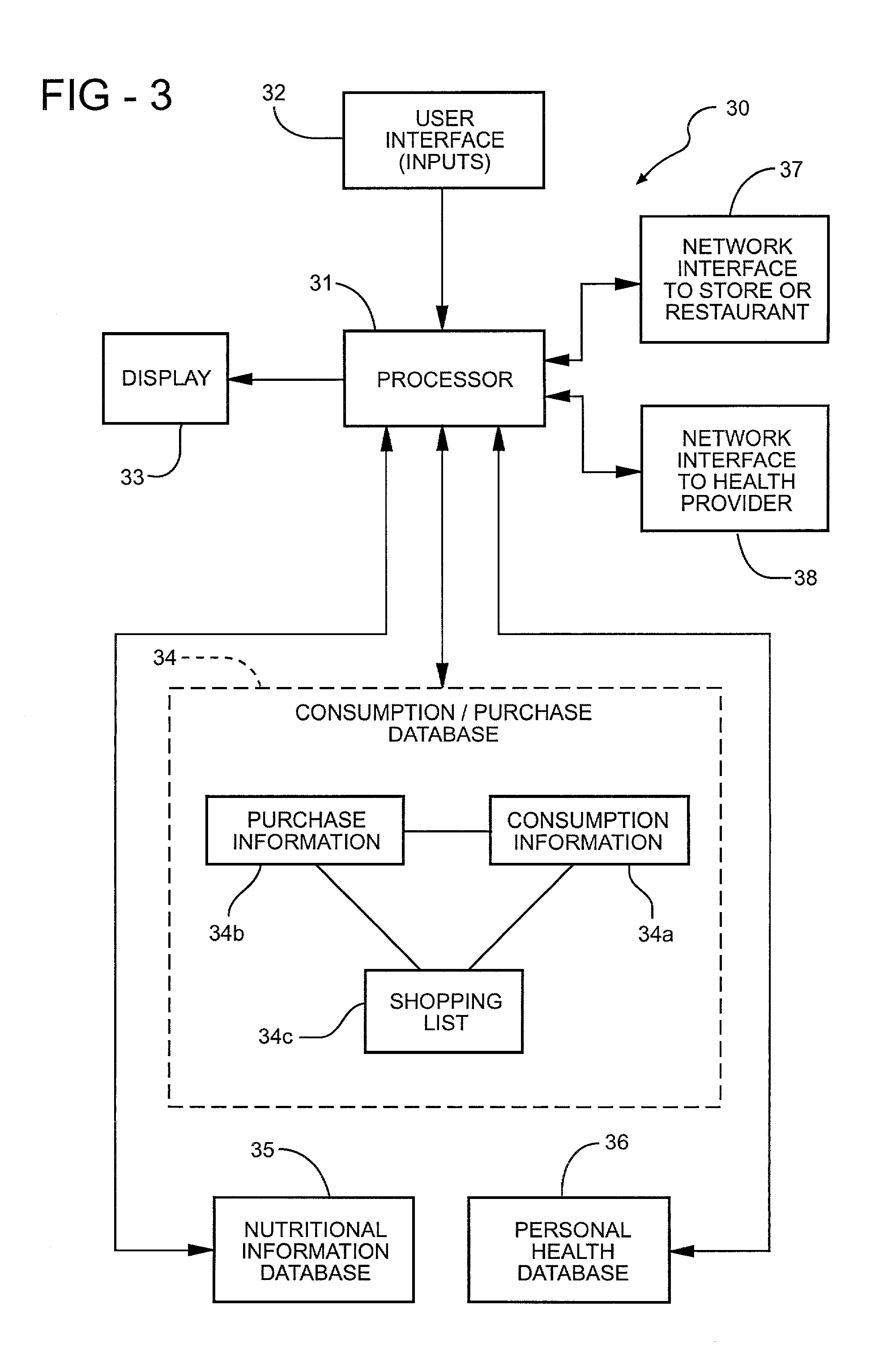
Portable computing apparatus particularly useful in a weight management program
InactiveUS20020027164A1Accurate recordPhysical therapies and activitiesNutrition controlProper timeMedical prescription
Portable computing apparatus for aiding a user in the monitoring of the consumption of consumable items, such as food items or prescribed medicaments, and reordering such items includes a common database for use in monitoring the items as consumed, and for preparing the reorder list at the proper time. The apparatus preferably includes an imaging device for recording the image of the item to be consumed, and recognition circuitry for utilizing the recorded image to identify the item and also to provide information concerning its nutritional content in a weight management program. The consumable item may also be identified in other manners, such as by a barcode reader, or a voice-recognition circuit.
Owner:HEALTHETECH
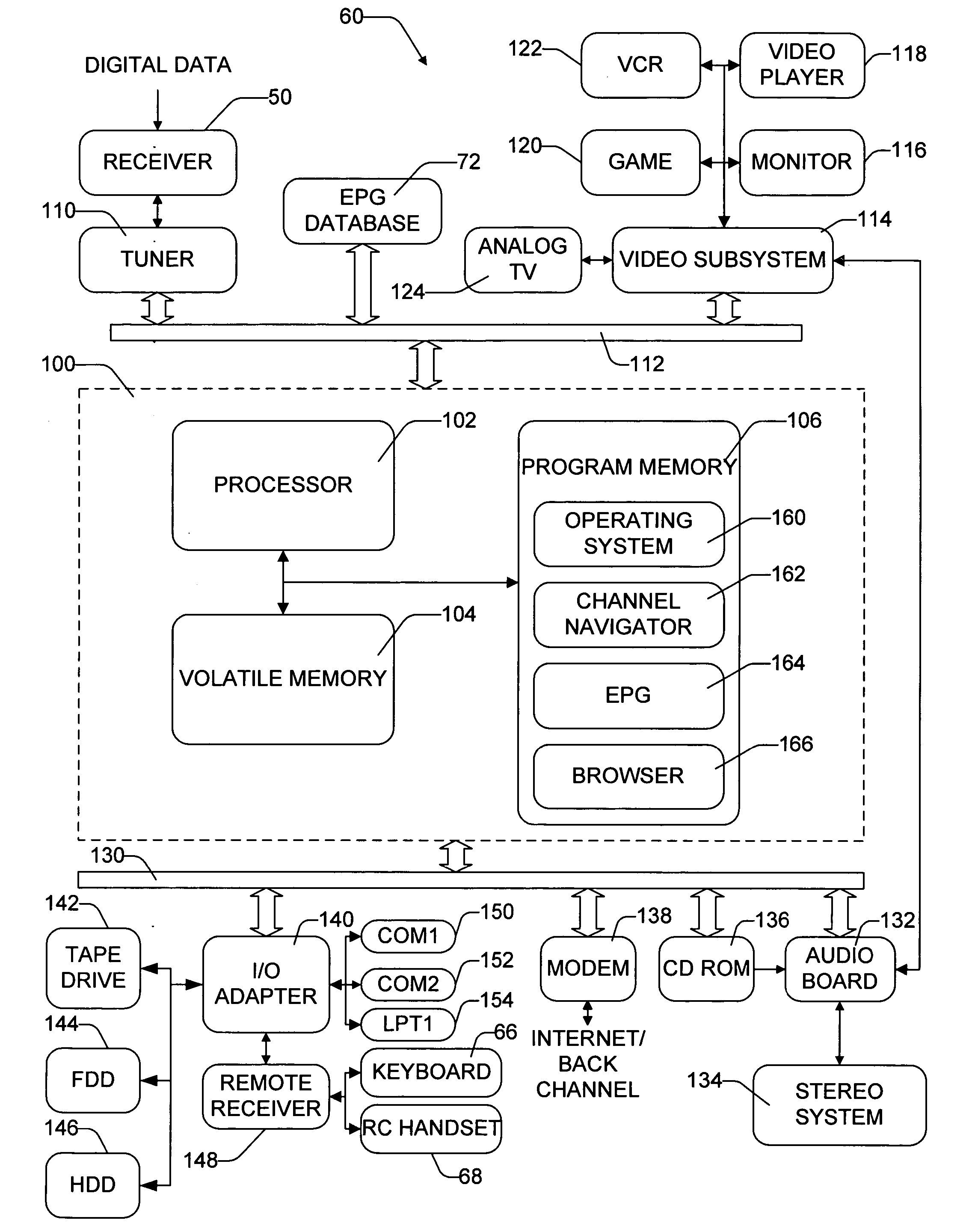
Query-based electronic program guide
InactiveUS20050278741A1Facilitate simpleFacilitate complex searchTelevision system detailsGHz frequency transmissionOperating systemElectronic program guide
An electronic program guide (EPG) organizes and presents programming information to the viewer and allows for creation of queries to facilitate both simple and complex searches of the programming information. According to one aspect, the EPG is configured to automatically identify programs that a viewer is likely to prefer. The EPG collects viewing preferences of a viewer and, based upon the these viewing preferences, automatically develops queries for identifying programs that the viewer is likely to want to watch. The EPG further enables multiple viewers to merge their individual queries into one composite query or to run queries in background to periodically check for programs and notify the viewer when a program is identified. Queries are saved in an EPG database in a hierarchic structure with directories and sub-directories to make it easy for a viewer to organize and retrieve queries. Another aspect concerns creating queries for a channel, network name or program name using a 10-key keypad. The viewer enters digits in the number or name, one digit at a time. With each entry, the viewer might intend to enter a number or letter. The EPG is configured to interpret the data as representing all possible choices, including the number and letters associated with the key. For instance, when a viewer depresses the key with number “5,” the EPG interprets that data to mean “5” or “j” or “k” or “1.” The EPG identifies all programs, channels, and networks which begin with the number or letters. As the viewer continues to enter data, the list of programs, channel, and networks dynamically narrows so that after a few button presses, the viewer is presented with a short list of possible choices.
Owner:ROVI TECH CORP
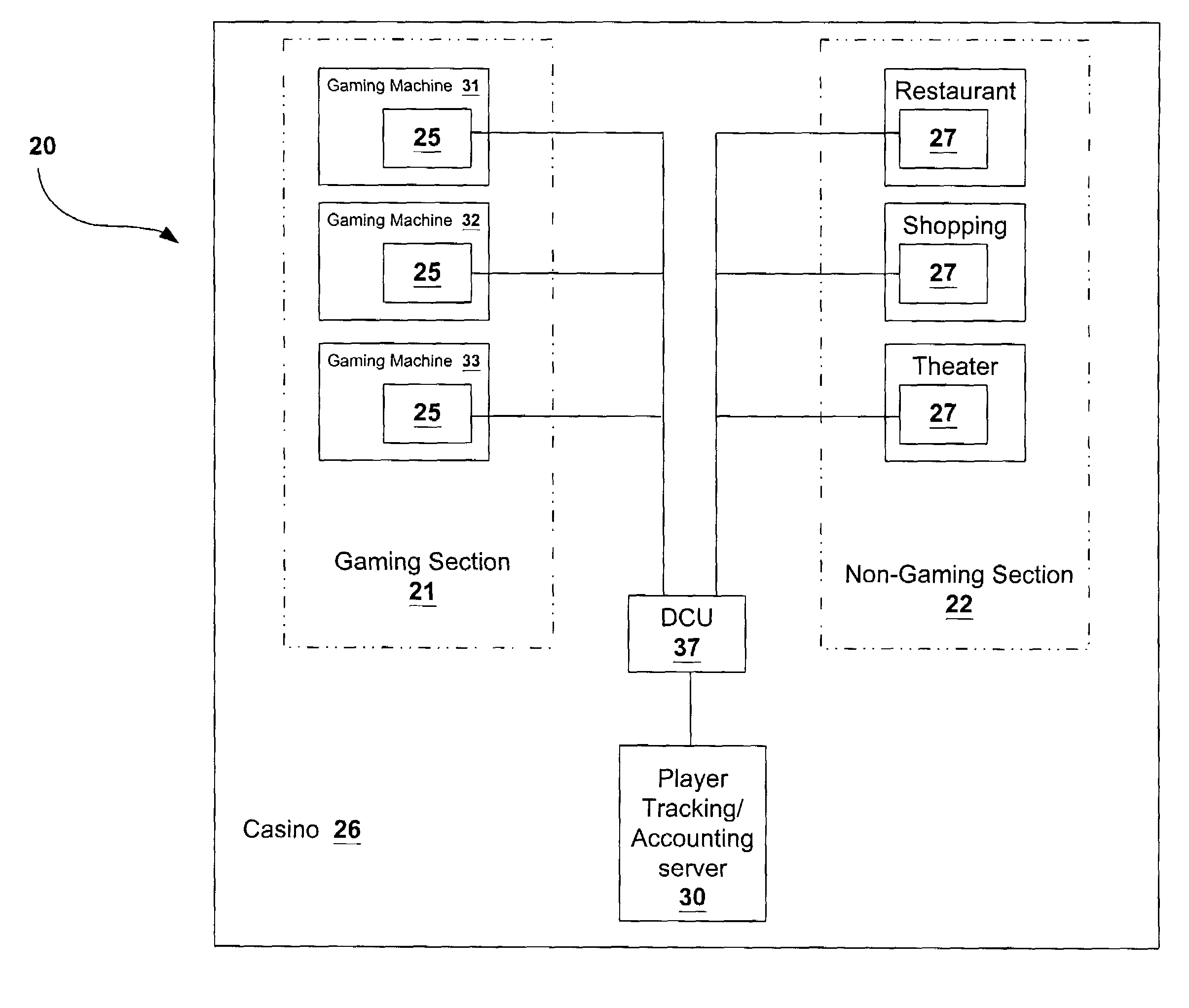
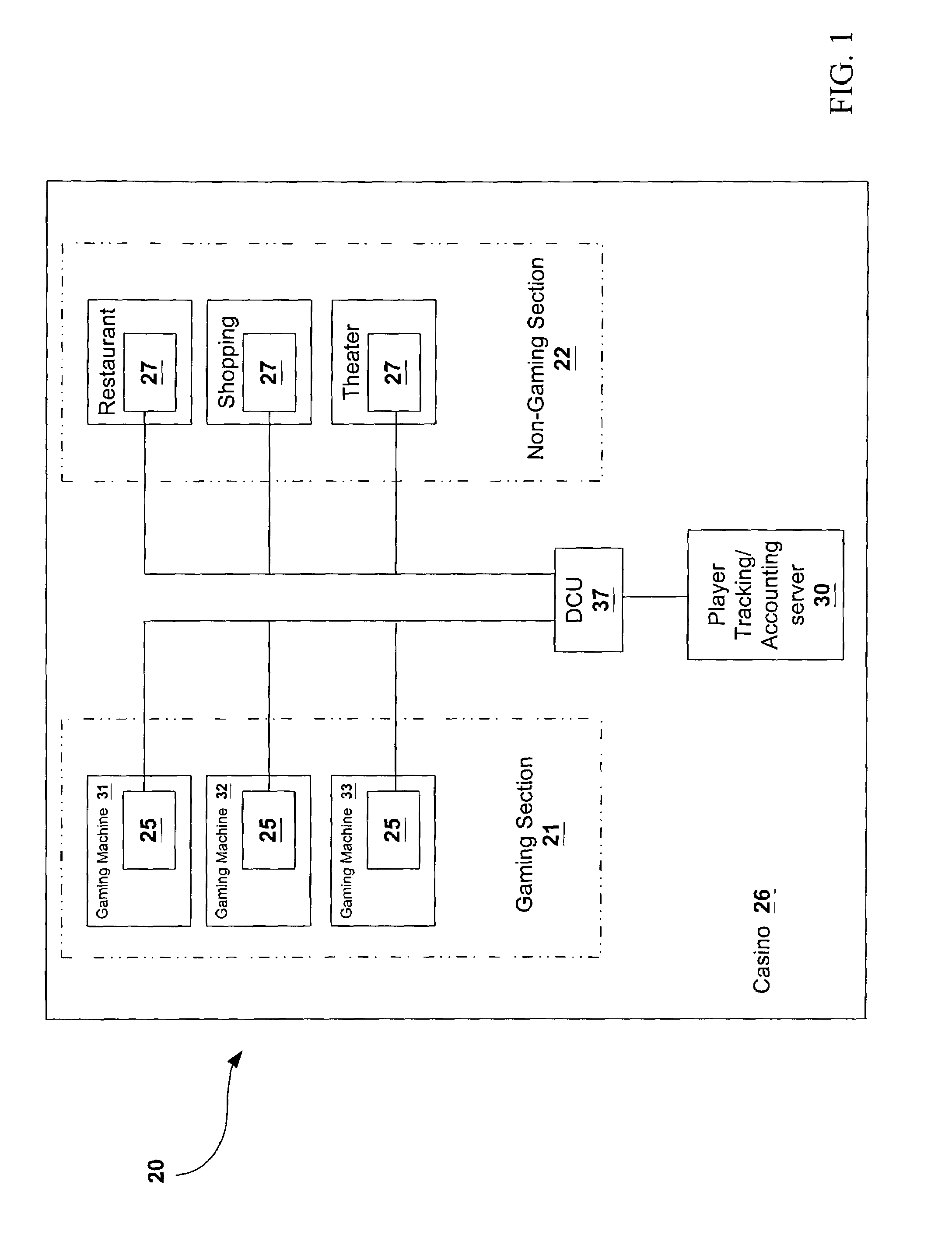
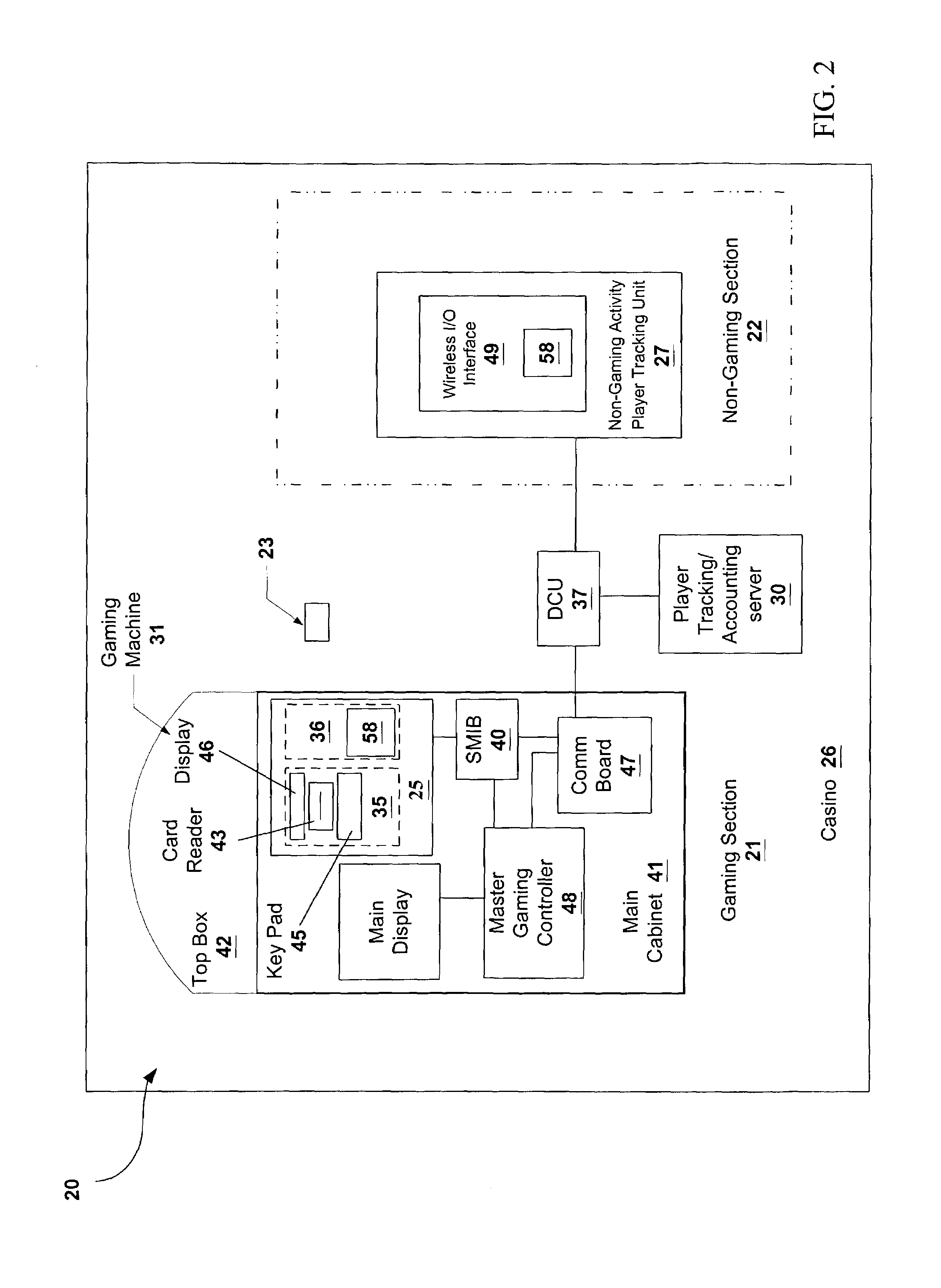
Player tracking assembly for complete patron tracking for both gaming and non-gaming casino activity
InactiveUS7311605B2Apparatus for meter-controlled dispensingVideo gamesComputerized systemEngineering
A player tracking system for tracking customer activity for a casino establishment having gaming sections and non-gaming sections. The player tracking system includes a plurality of player tracking cards for distribution to respective participating customers that incorporate respective customer accounts associated with respective customer IDs. The system further includes a plurality of gaming activity player tracking units positioned in the gaming section of the casino establishment proximate the gaming activity which cooperates with the player tracking cards to monitor the gaming activity data of the respective customer, and a plurality of non-gaming activity player tracking units positioned in the non-gaming section of the casino establishment proximate the non-gaming activity which cooperates with the player tracking cards to monitor the non-gaming activity data of the respective customer. A computer system includes a database of the respective customer accounts associated with respective customer Ids, and each gaming activity player tracking unit and each non-gaming activity player tracking unit coupled to the computer system to process the respective gaming activity data and non-gaming activity data for each respective customer.
Owner:IGT
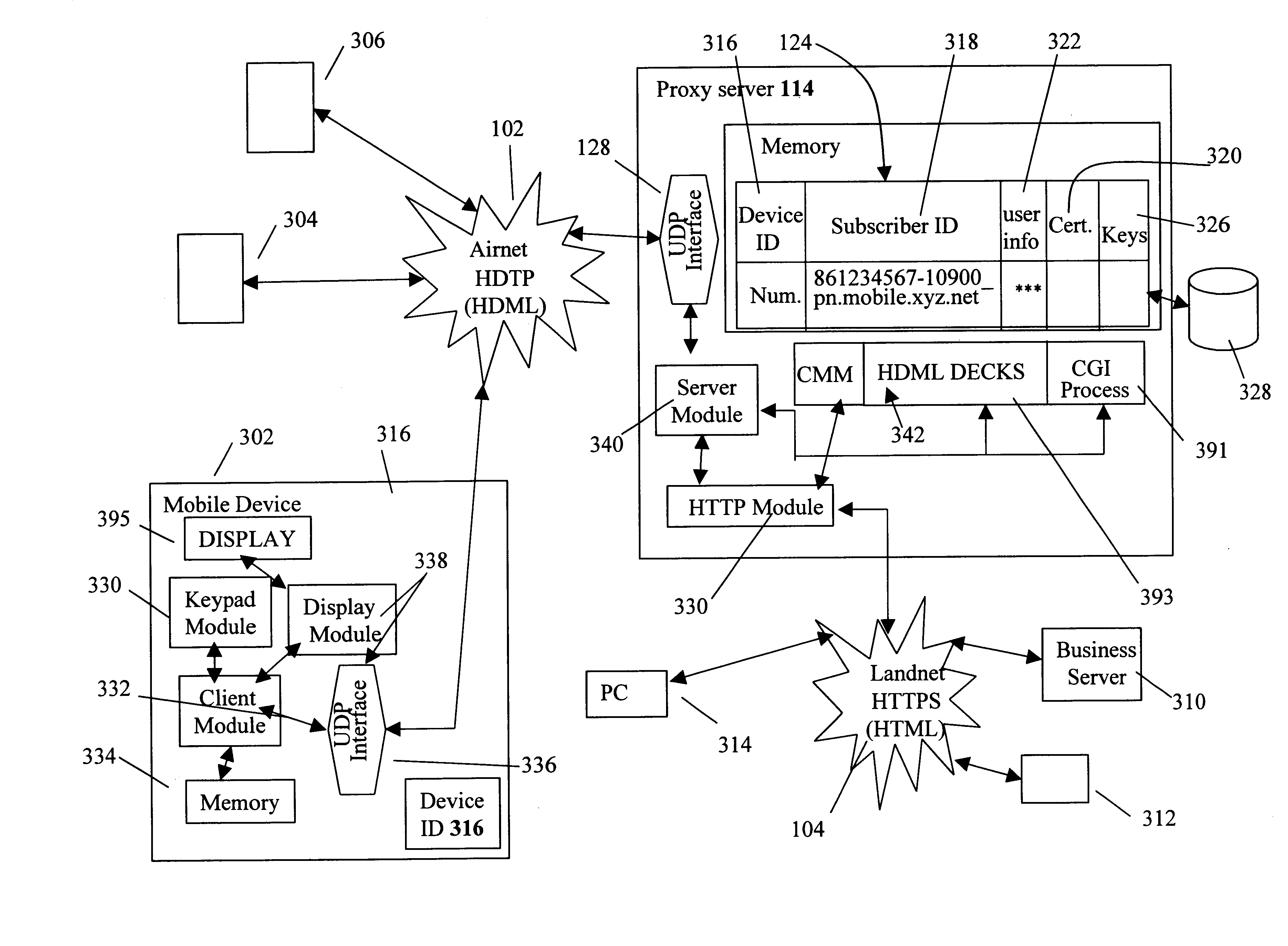
Centralized certificate management system for two-way interactive communication devices in data networks
InactiveUS6233577B1Key distribution for secure communicationData processing applicationsServer applianceCommunication device
The present invention discloses a central certificate management system for thin client devices in data networks and has particular applications to systems having a large number of the thin clients serviced by a proxy server through which the thin clients communicate with a plurality of secure server computers over a data network. According to one aspect, the present invention provides a certificate management module that causes the server device to manage digital certificates for each of the thin client devices. To minimize the latency of obtaining certificates for each of the thin client devices, the certificate management module reserves a fixed number of free certificates signed by a certificate authority and their respective private keys in a certificate database and frequently updates the free certificate according to a certificate updating message. Whenever a user account is created for a thin client device, the certificate management module fetches one or more free certificates from the certificate database and associate the fetched certificates to the created account and meanwhile the certificate management module creates new free certificates with the certificate authority to fill in the certificate database. Apart from the tradition of obtaining certificates locally in client devices that normally have sufficient computing power, the present invention uses the computing resources in a server device to carry out the task of obtaining and maintaining certificates asynchronously in the proxy server and further. These and other features in the present invention dramatically minimize the demands for computing power and memory in thin client devices like mobile devices, cellular phones, landline telephones or Internet appliance controllers.
Owner:UNWIRED PLANET
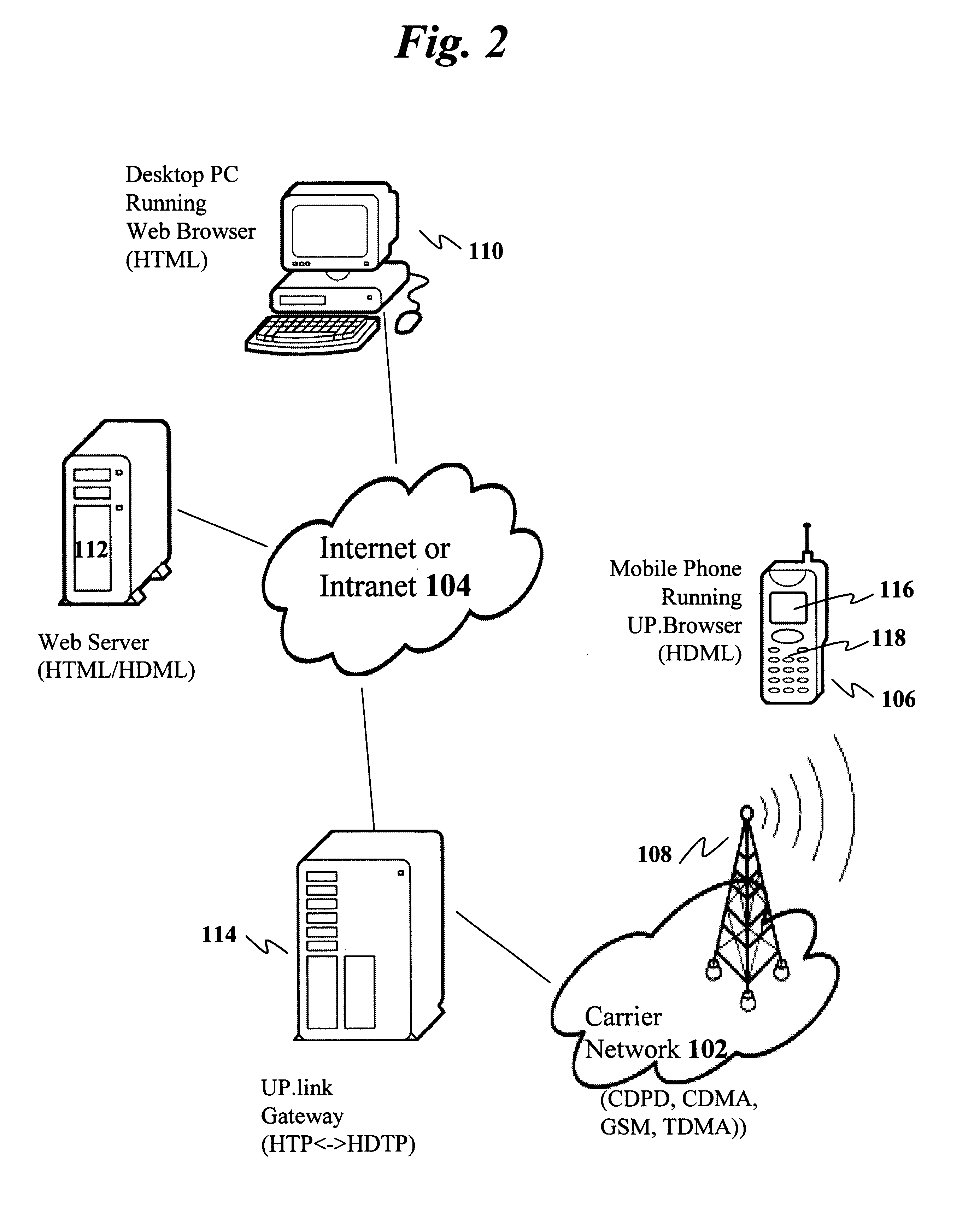
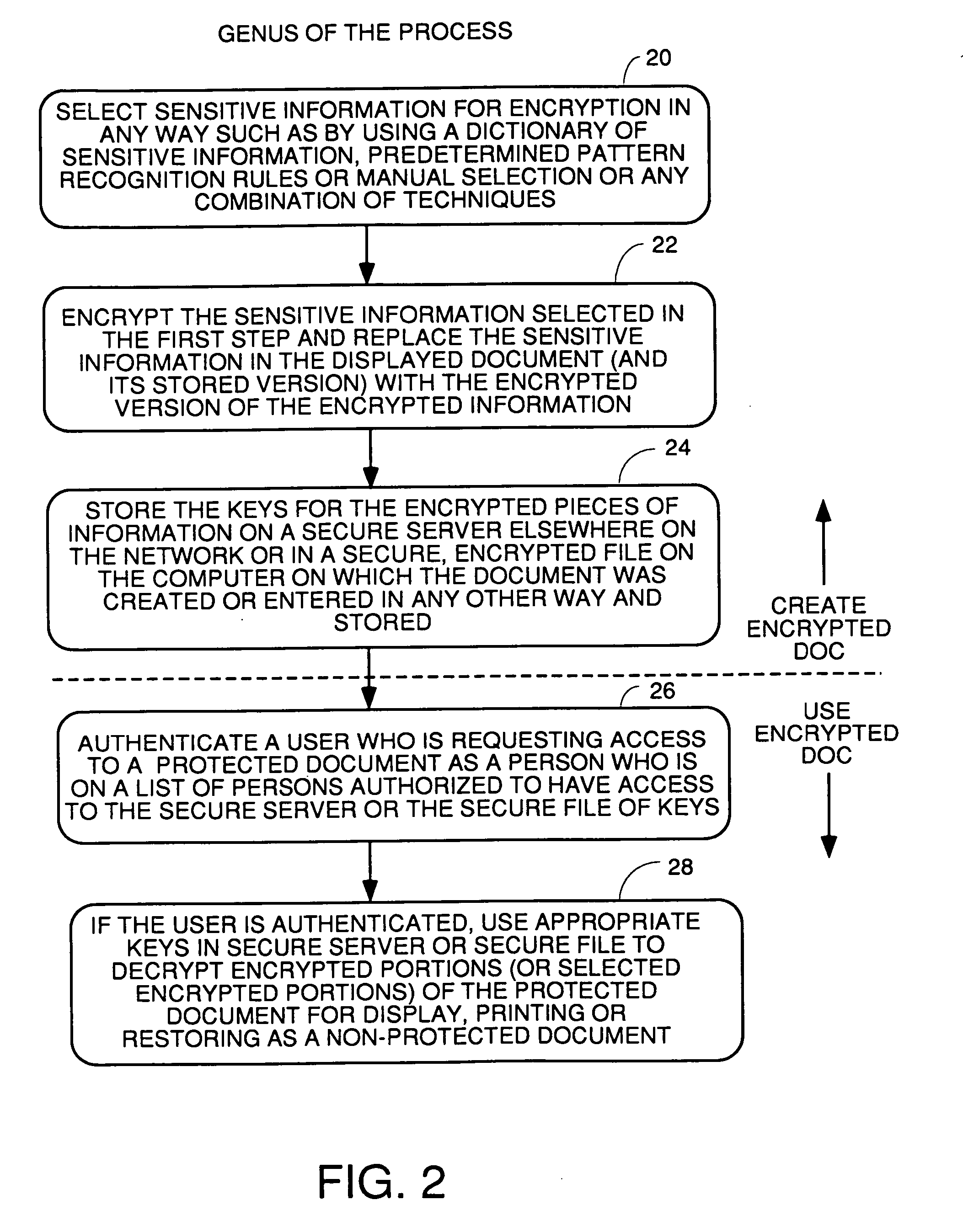
Method and apparatus for recognition and real time protection from view of sensitive terms in documents
InactiveUS20060075228A1Computer security arrangementsSecuring communicationInternet privacyClient-side
A process for automatically selecting sensitive information in any form of document being displayed and / or generated on a computer to select sensitive information for protection by encryption, redaction or removal of only the sensitive text. Selection is done by using pattern recognition rules, dictionaries of sensitive terms and / or manual selection of text. The sensitive text is automatically protected on the fly in the same manner as a spell checker works so that the sensitive information immediately is removed and replaced with the encrypted or redacted version or a space and a pointer to where the decryption key or the original of the redacted or removed text is stored. Other embodiments require manual approval of automatically selected text prior to protection. For encryption embodiments, the keys used to encrypt the sensitive information in each document are stored in a table or database, preferably on a secure key server so that they do not reside on the computer on which the partially redacted document is stored. Embodiments to protect the body of emails and attachments in either the email client or web mail environment are also disclosed.
Owner:INFOSAFE
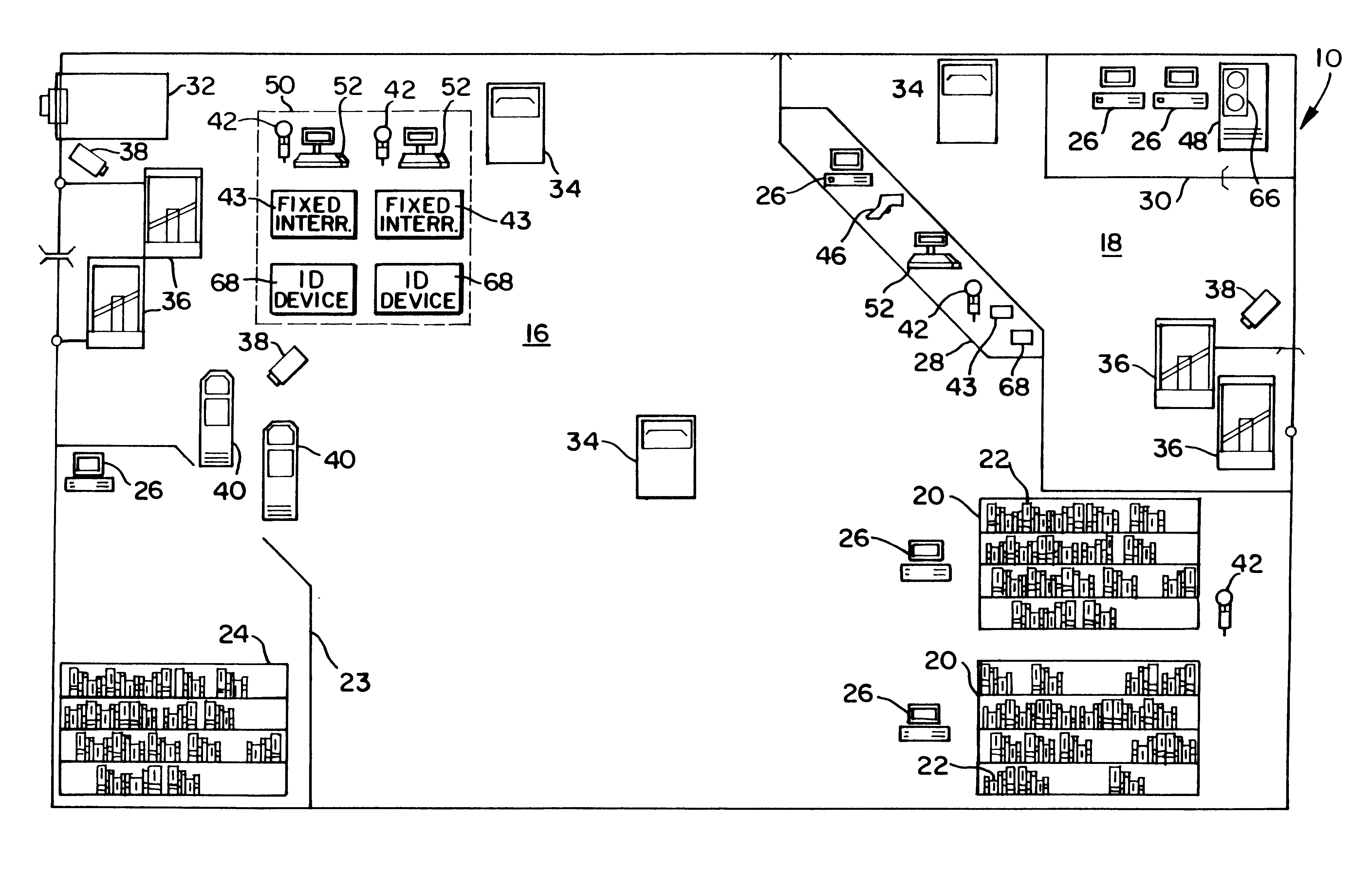
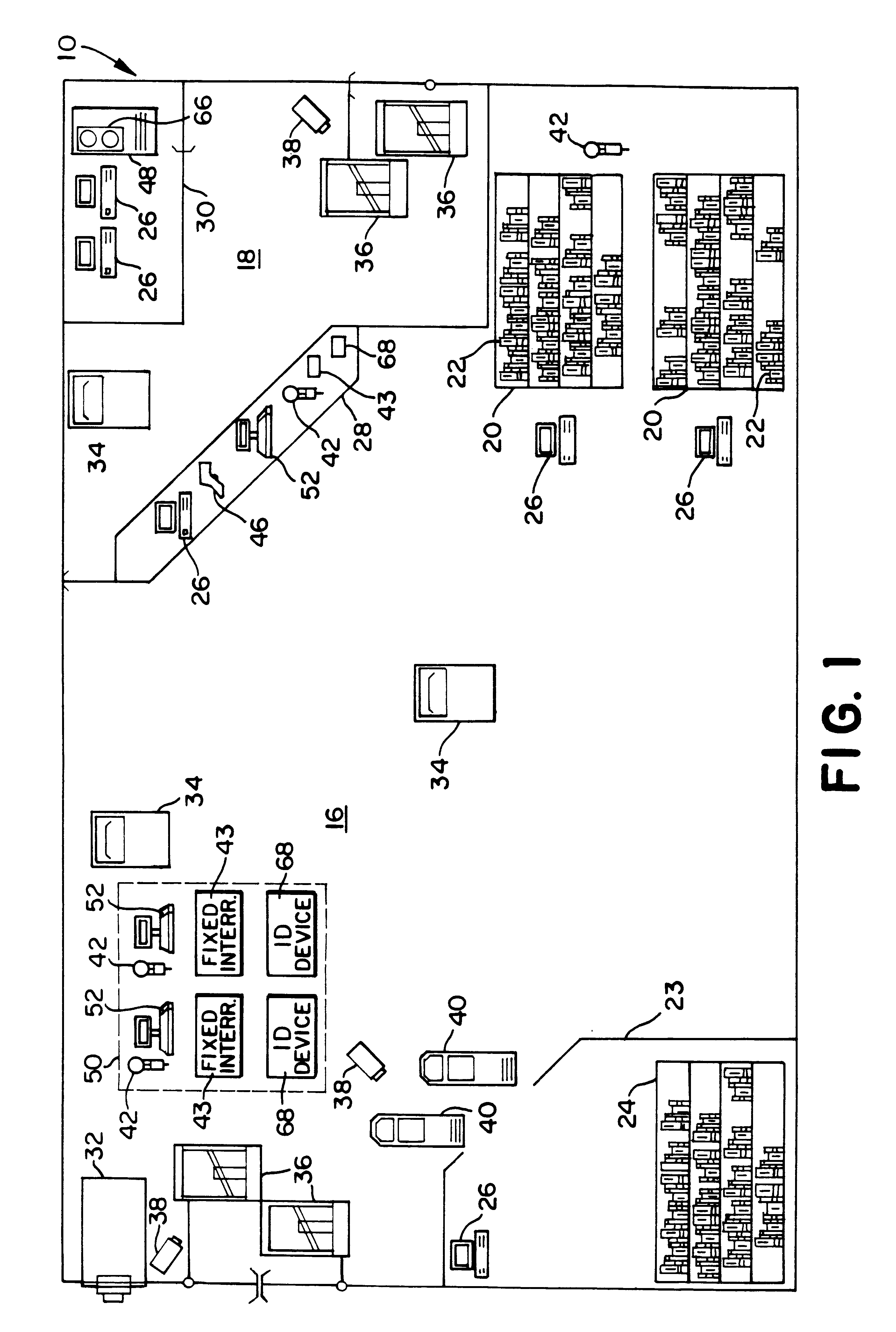
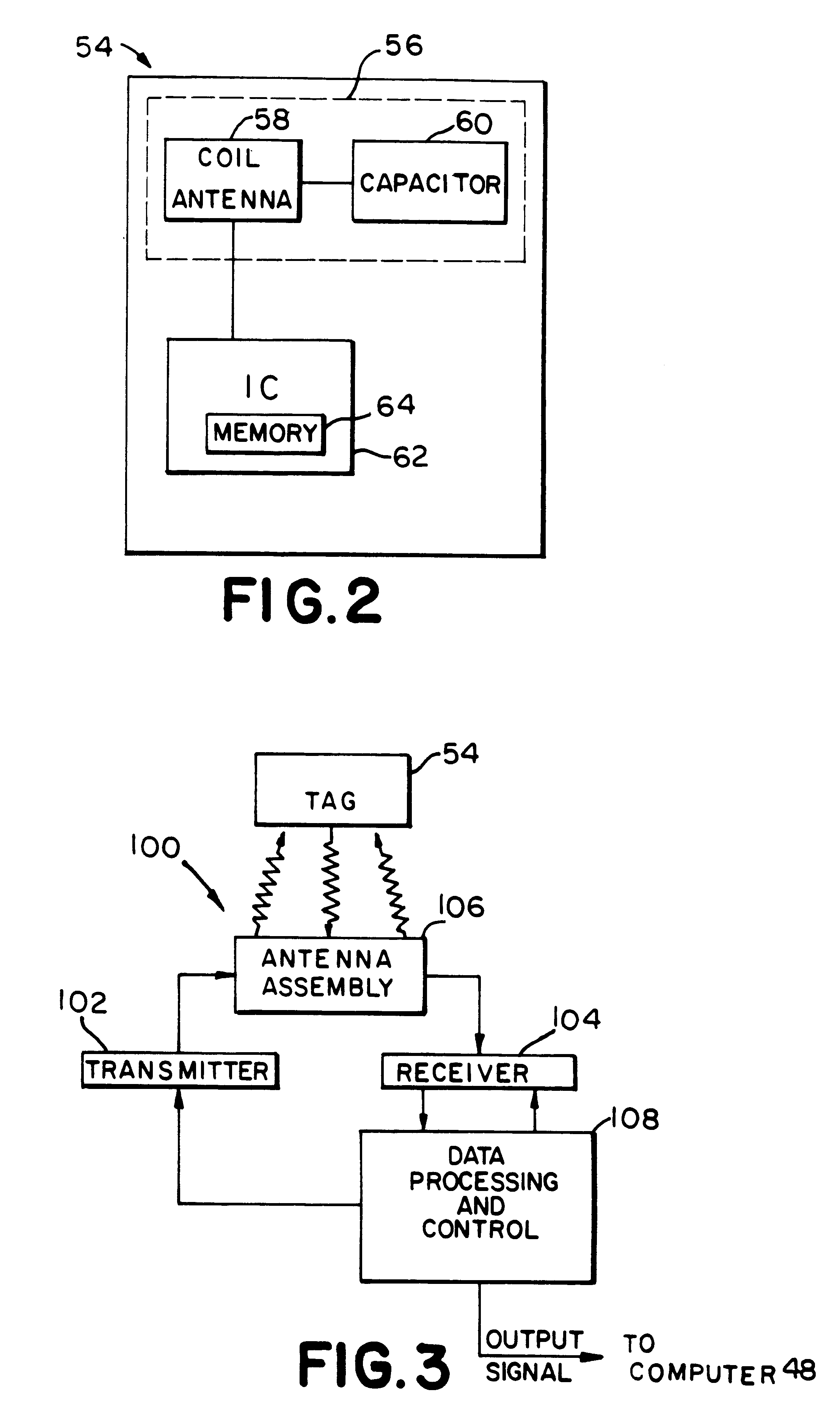
Inventory system using articles with RFID tags
InactiveUS6195006B1Electric signal transmission systemsDigital data processing detailsControl systemMobile RFID
An article inventory control system for articles, such as books, uses RFID tags attached to each article. Each tag has a unique identification or serial number for identifying the individual article. An inventory database tracks all of the tagged articles and maintains circulation status information for each article. Articles are checked out of the library using a patron self-checkout system. Checked out articles are returned to the library via patron self-check in devices. The shelves are periodically scanned with a mobile RFID scanner for updating inventory status.
Owner:CHECKPOINT SYST INC
User interaction with voice information services
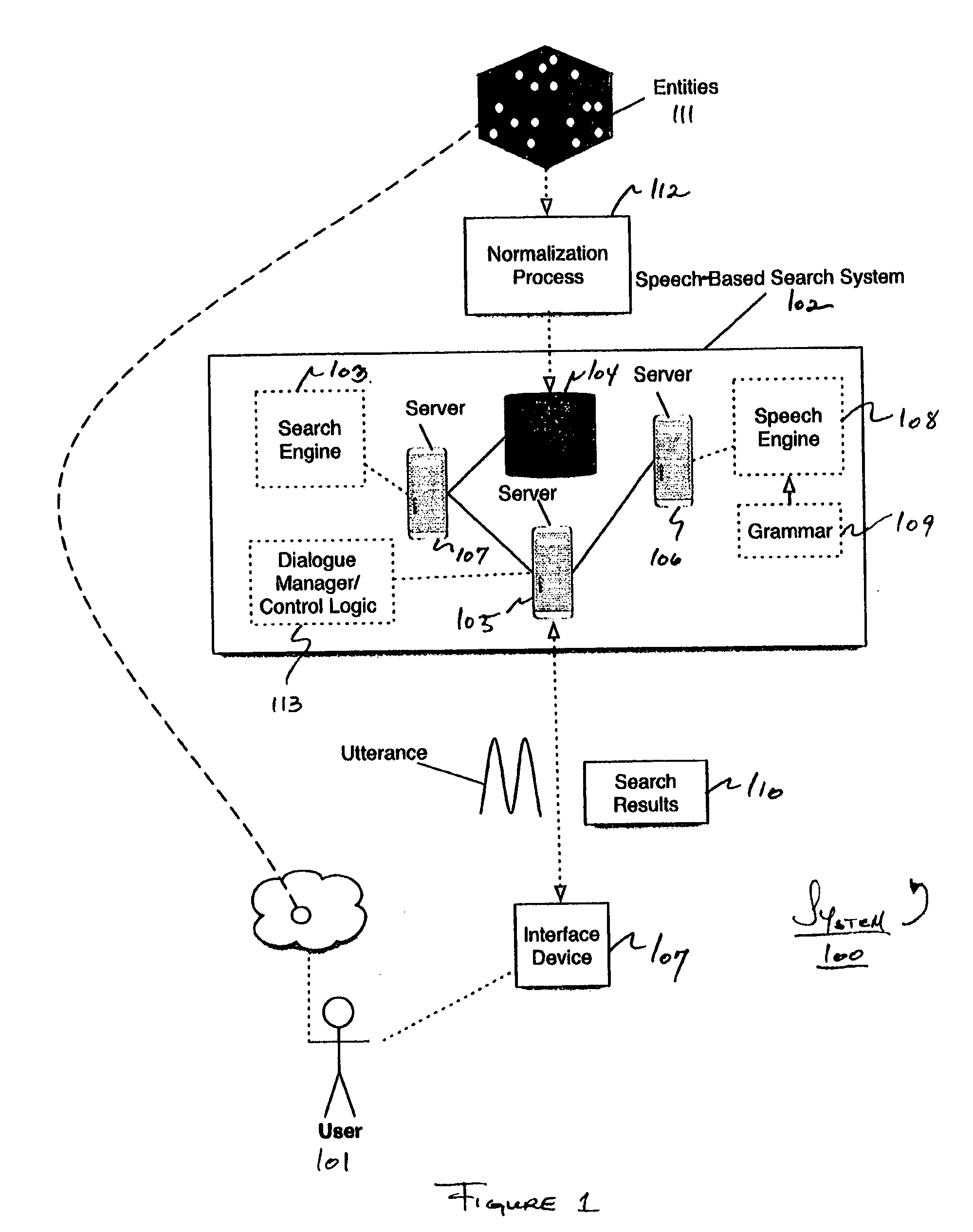
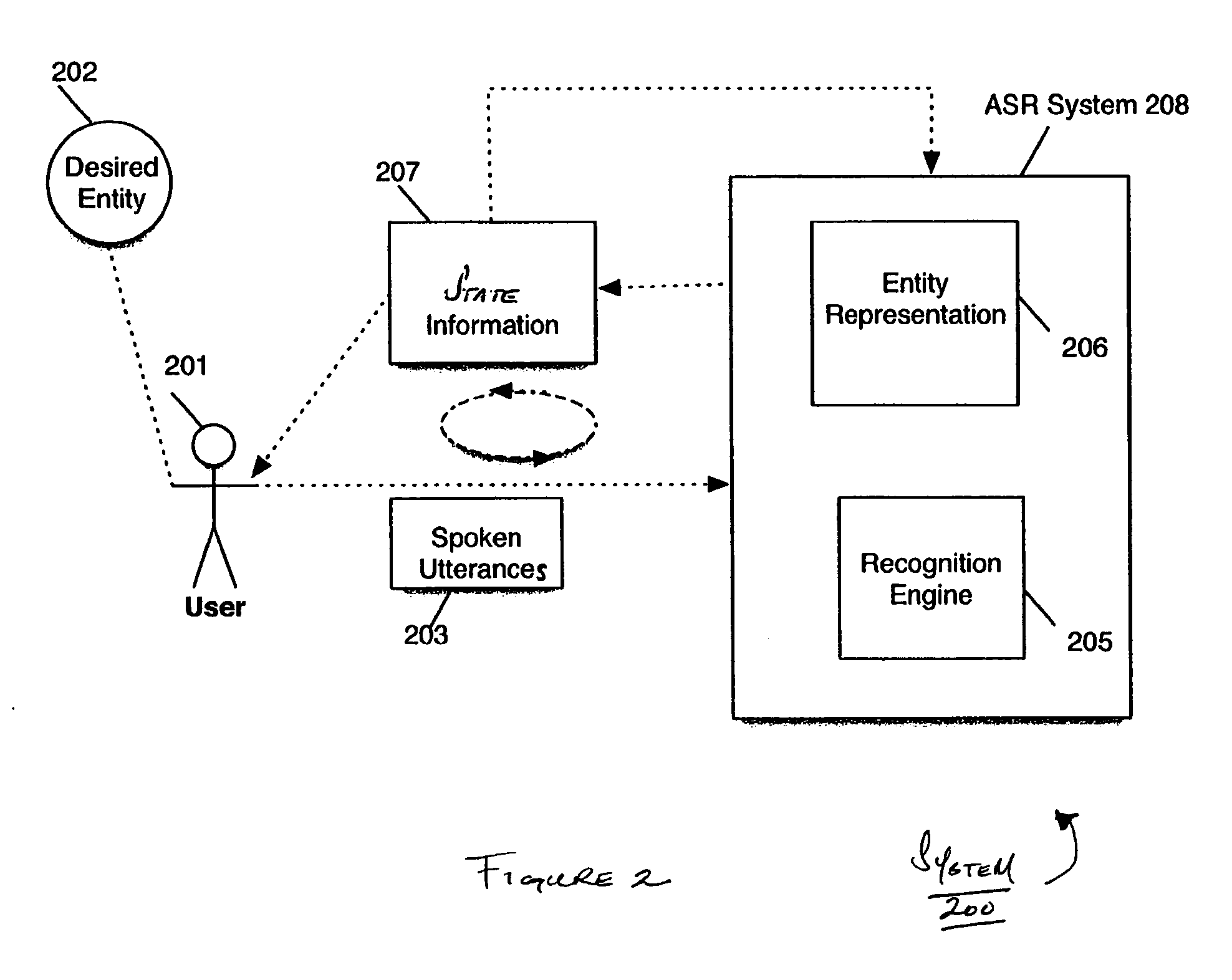
InactiveUS20060143007A1Reduce inputThe result is accurateSpeech recognitionAutomatic speechAncillary service
An iterative process is provided for interacting with a voice information service. Such a service may permit, for example, a user to search one or more databases and may provide one or more search results to the user. Such a service may be suitable, for example, for searching for a desired entity or object within the database(s) using speech as an input and navigational tool. Applications of such a service may include, for instance, speech-enabled searching services such as a directory assistance service or any other service or application involving a search of information. In one example implementation, an automatic speech recognition (ASR) system is provided that performs a speech recognition and database search in an iterative fashion. With each iteration, feedback may be provided to the user presenting potentially relevant results. In one specific ASR system, a user desiring to locate information relating to a particular entity or object provides an utterance to the ASR. Upon receiving the utterance, the ASR determines a recognition set of potentially relevant search results related to the utterance and presents to the user recognition set information in an interface of the ASR. The recognition set information includes, for instance, reference information stored internally at the ASR for a plurality of potentially relevant recognition results. The recognition set information may be used as input to the ASR providing a feedback mechanism. In one example implementation, the recognition set information may be used to determine a restricted grammar for performing a further recognition.
Owner:MICROSOFT TECH LICENSING LLC
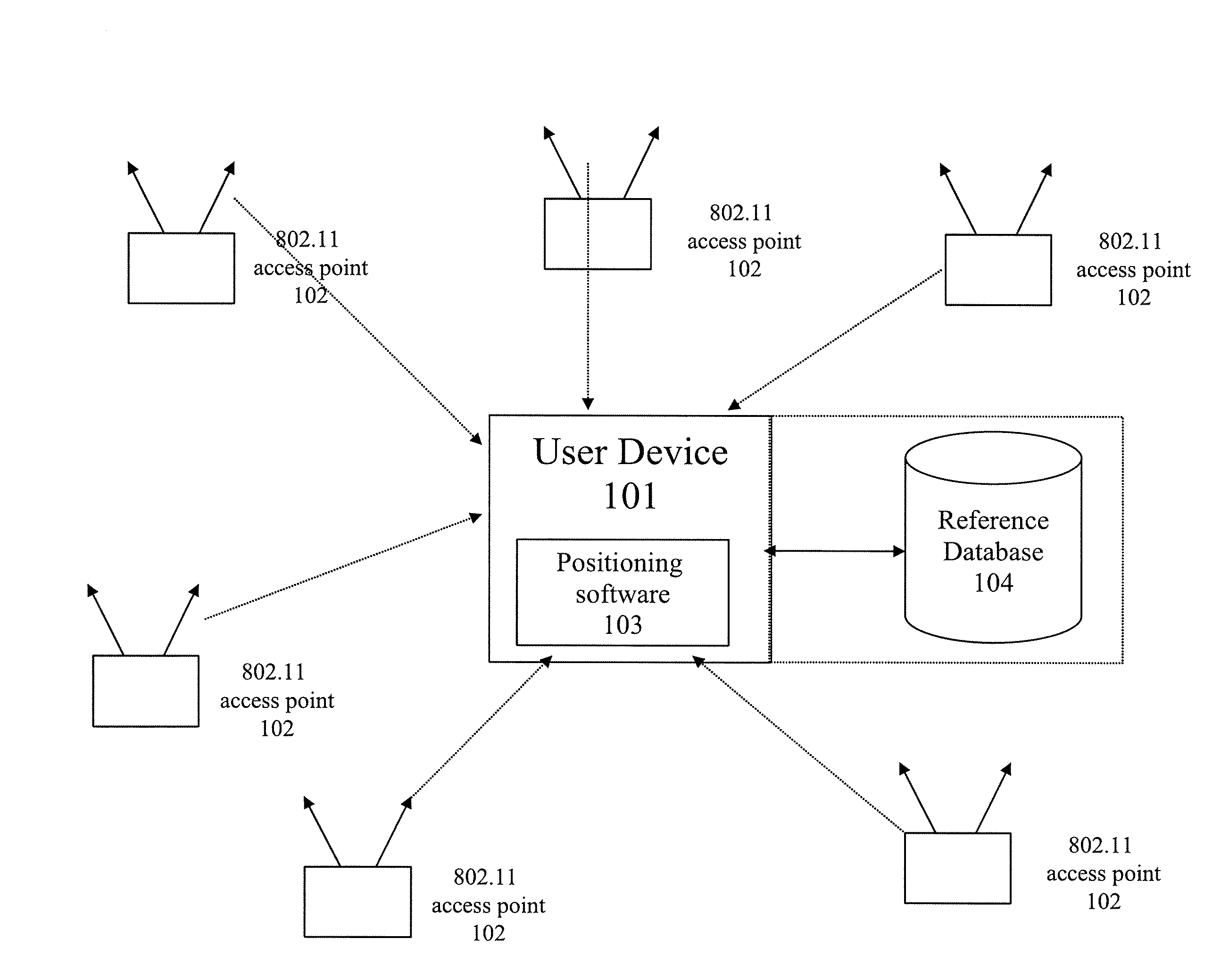
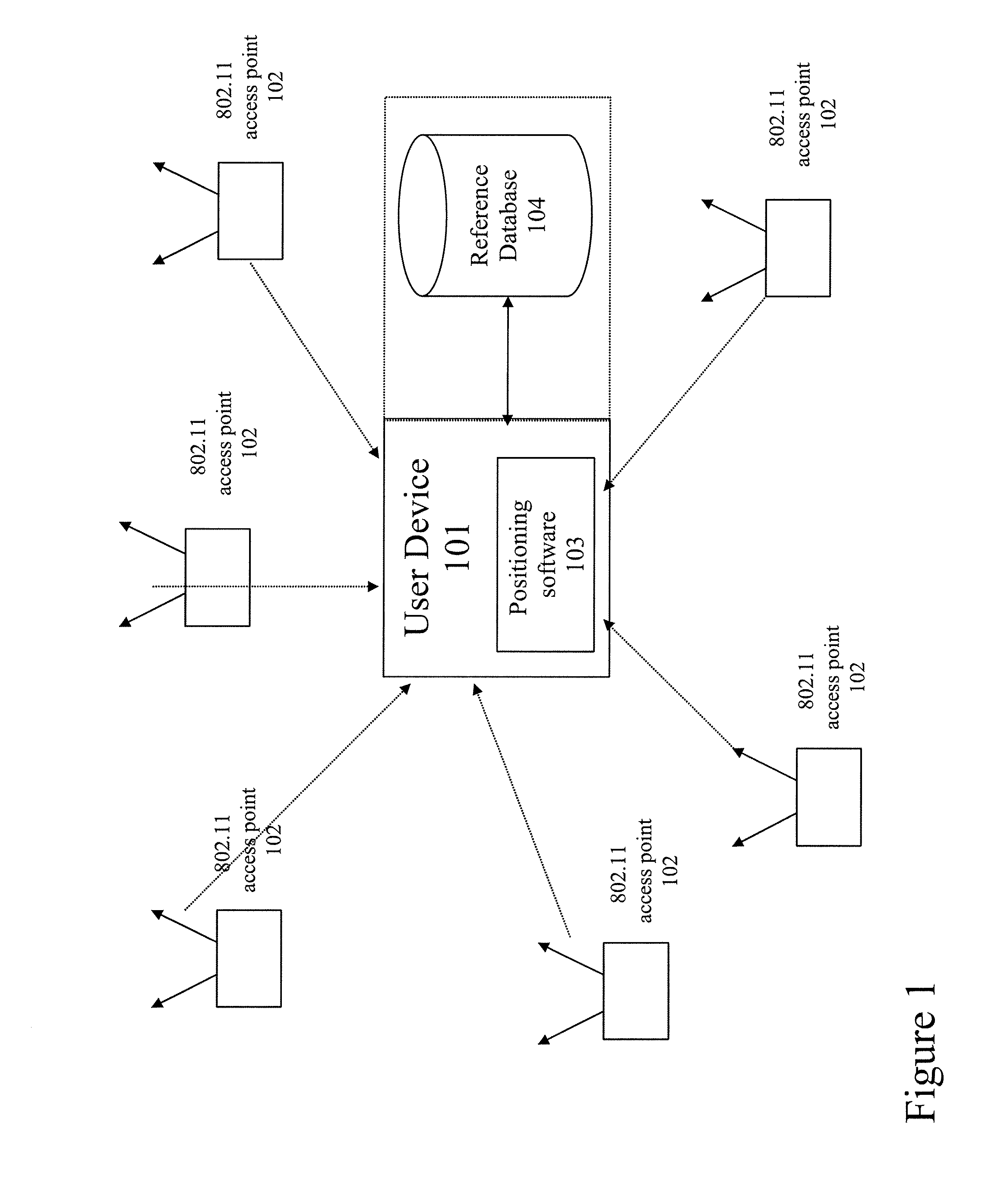
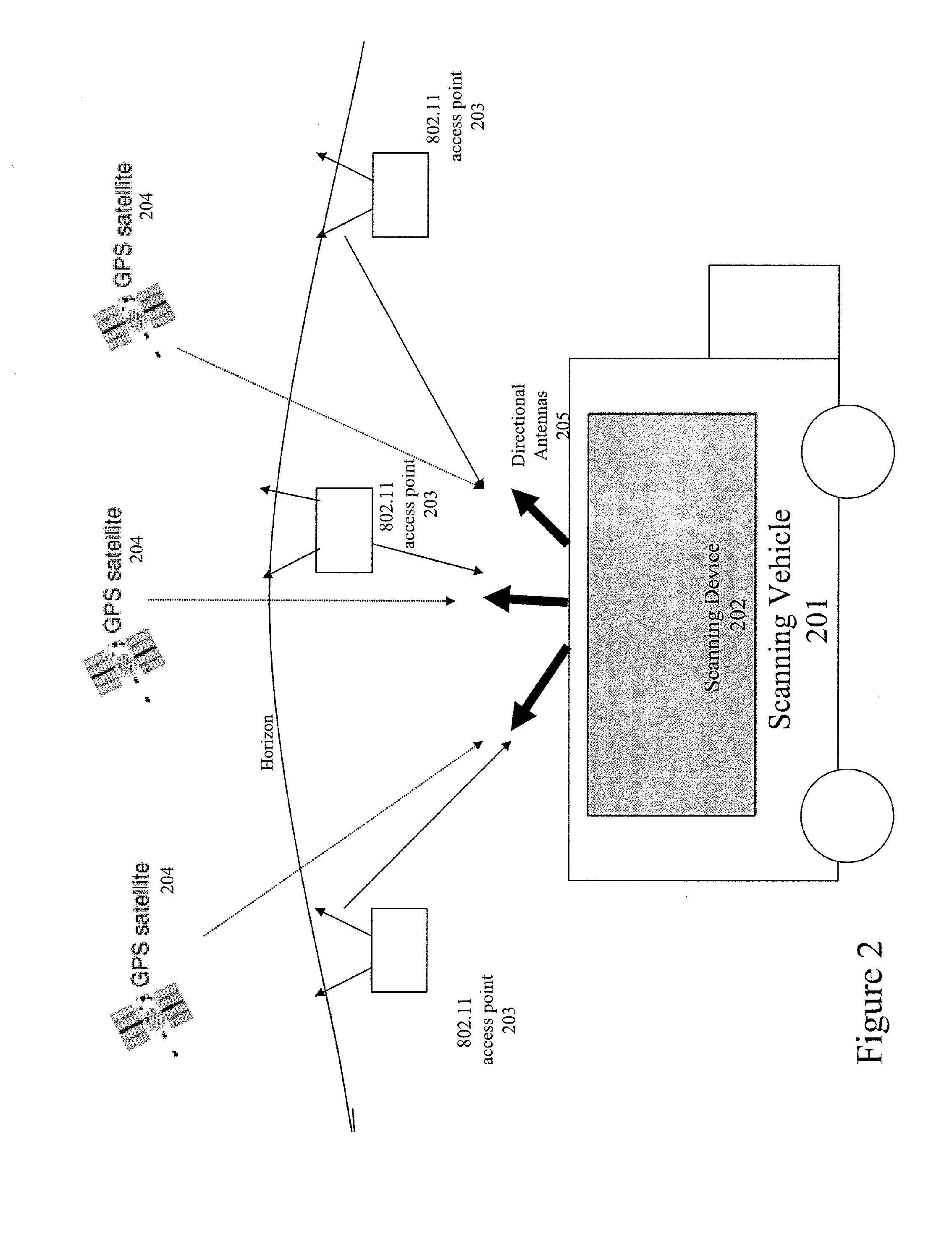
Method and system for selecting and providing a relevant subset of wi-fi location information to a mobile client device so the client device may estimate its position with efficient utilization of resources
Methods and systems for selecting and providing a relevant subset of Wi-Fi location information to a mobile client device so the client device may estimate its position with efficient utilization of resources.A method of providing a relevant subset of information to a client device is based in part on scanning for Wi-Fi access points within range of the client device, using a Wi-Fi database that covers a large target region to retrieve information about these access points, using this information to estimate the position of the mobile client device, selecting a limited region in the vicinity of the estimated location of the client device, and providing information about Wi-Fi access points within this limited region to the client. For efficient transfer and maintenance of data, the target region may be divided into a hierarchy of fixed geographical tiles.
Owner:SKYHOOK WIRELESS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com