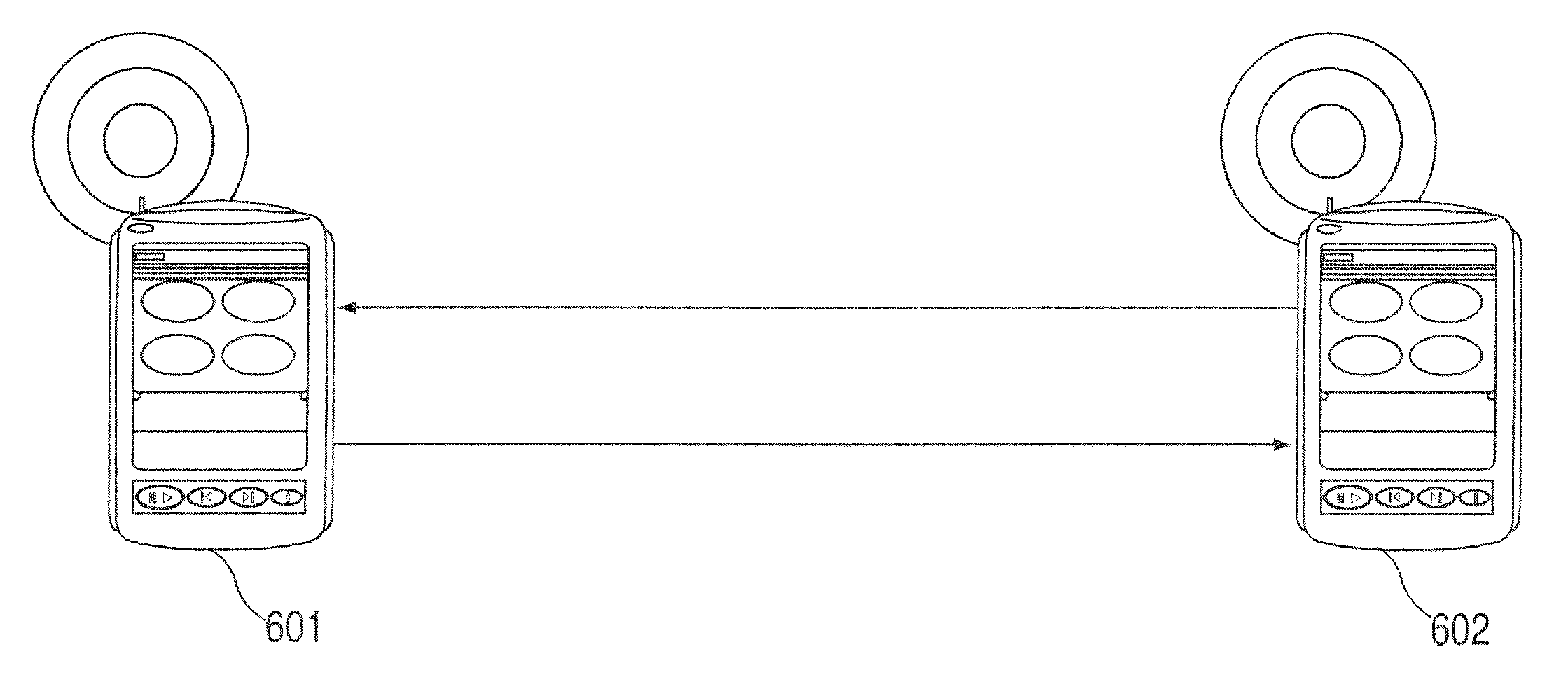Patents
Literature
81results about How to "None of methods is secure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
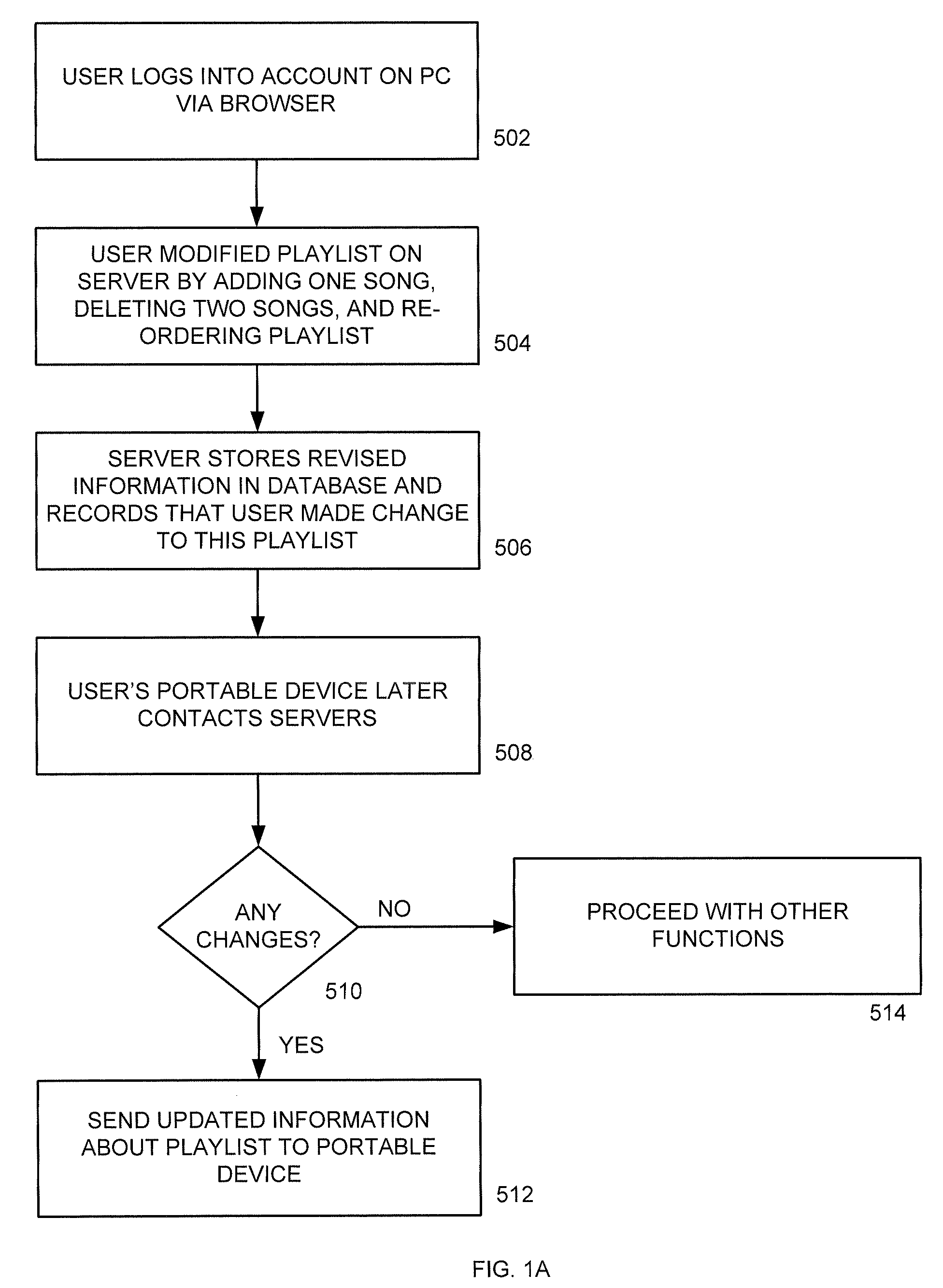
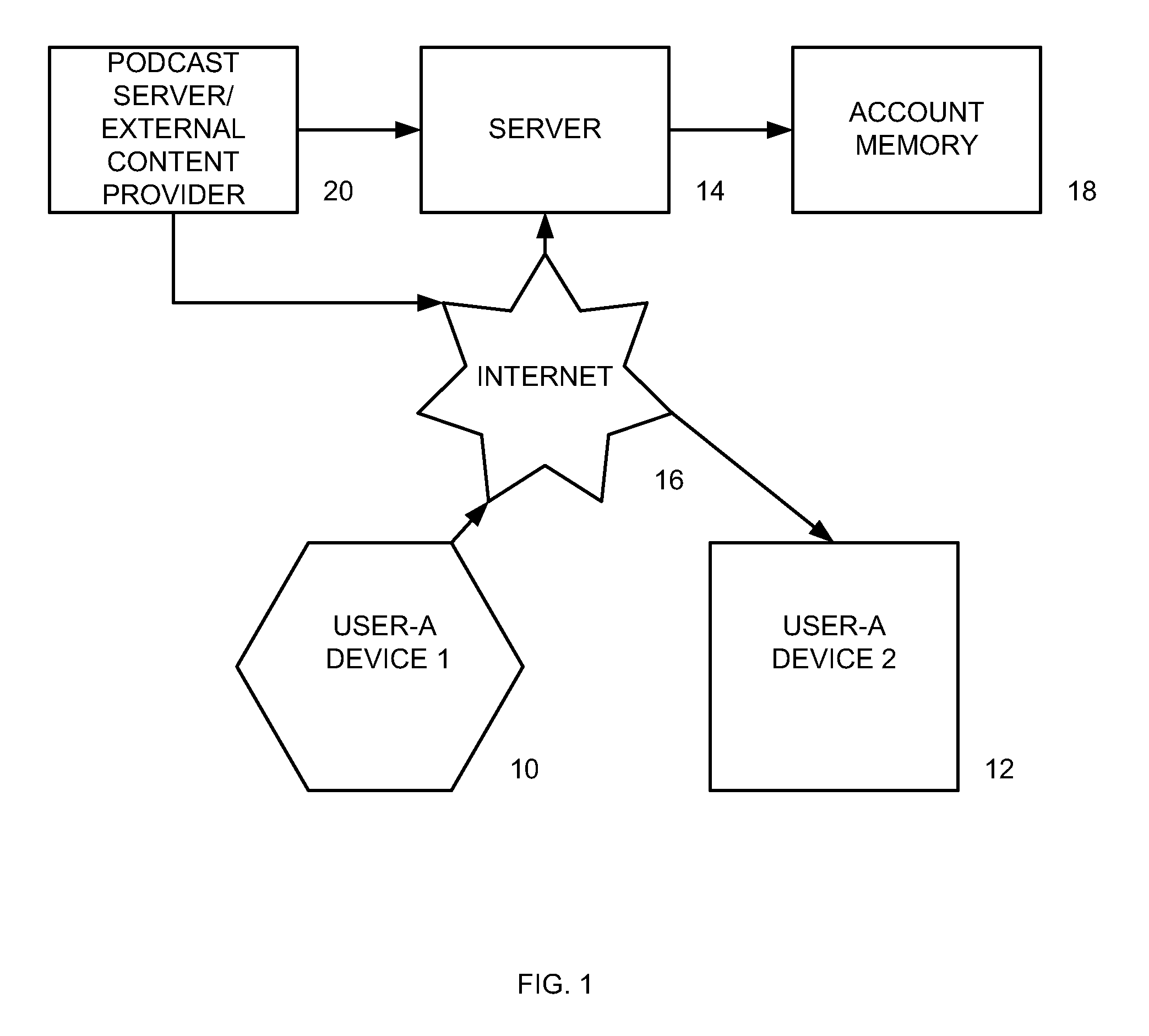
Audio visual player apparatus and system and method of content distribution using the same
InactiveUS20060008256A1None of methods is secureTelevision system detailsColor television signals processingContent distributionVideo player
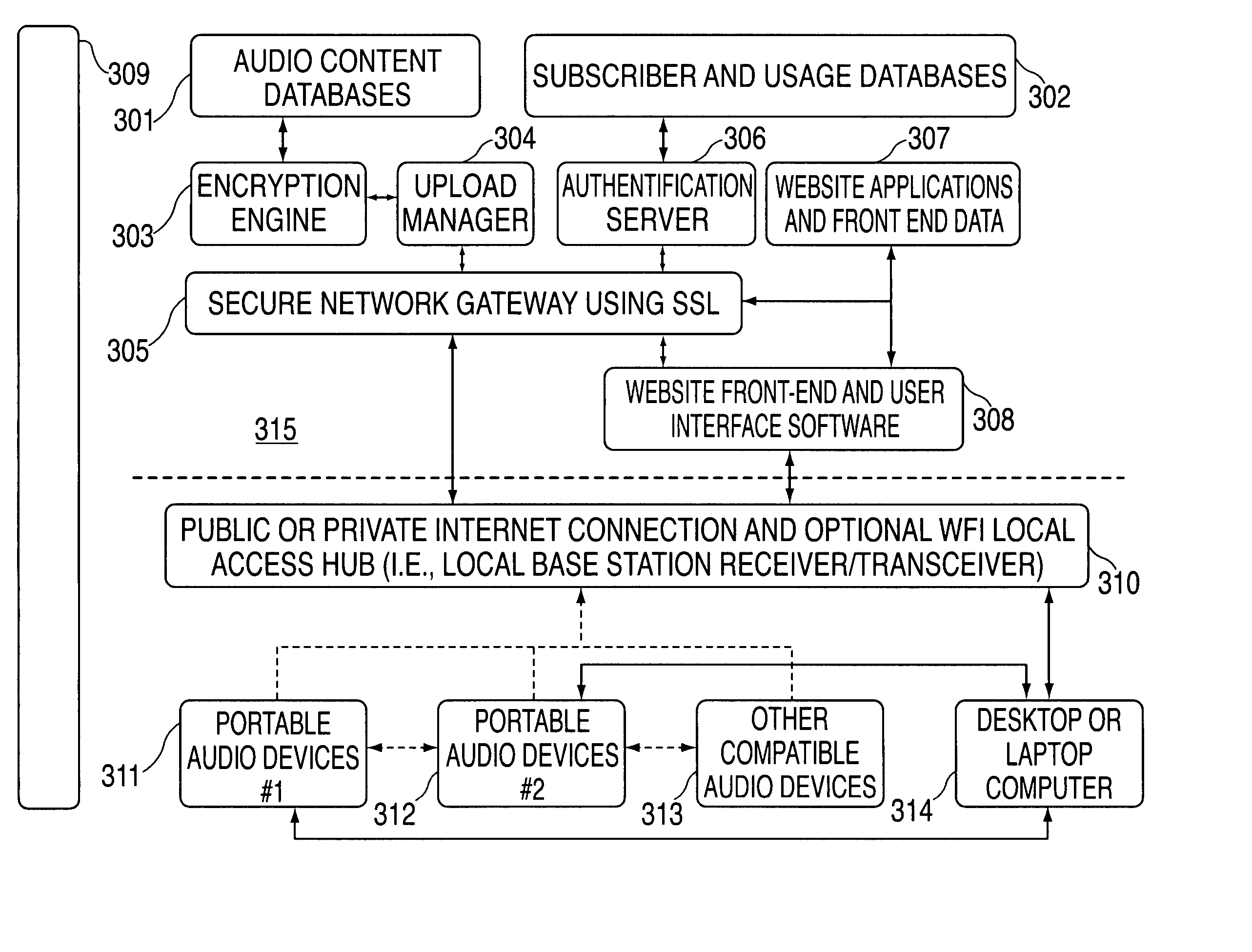
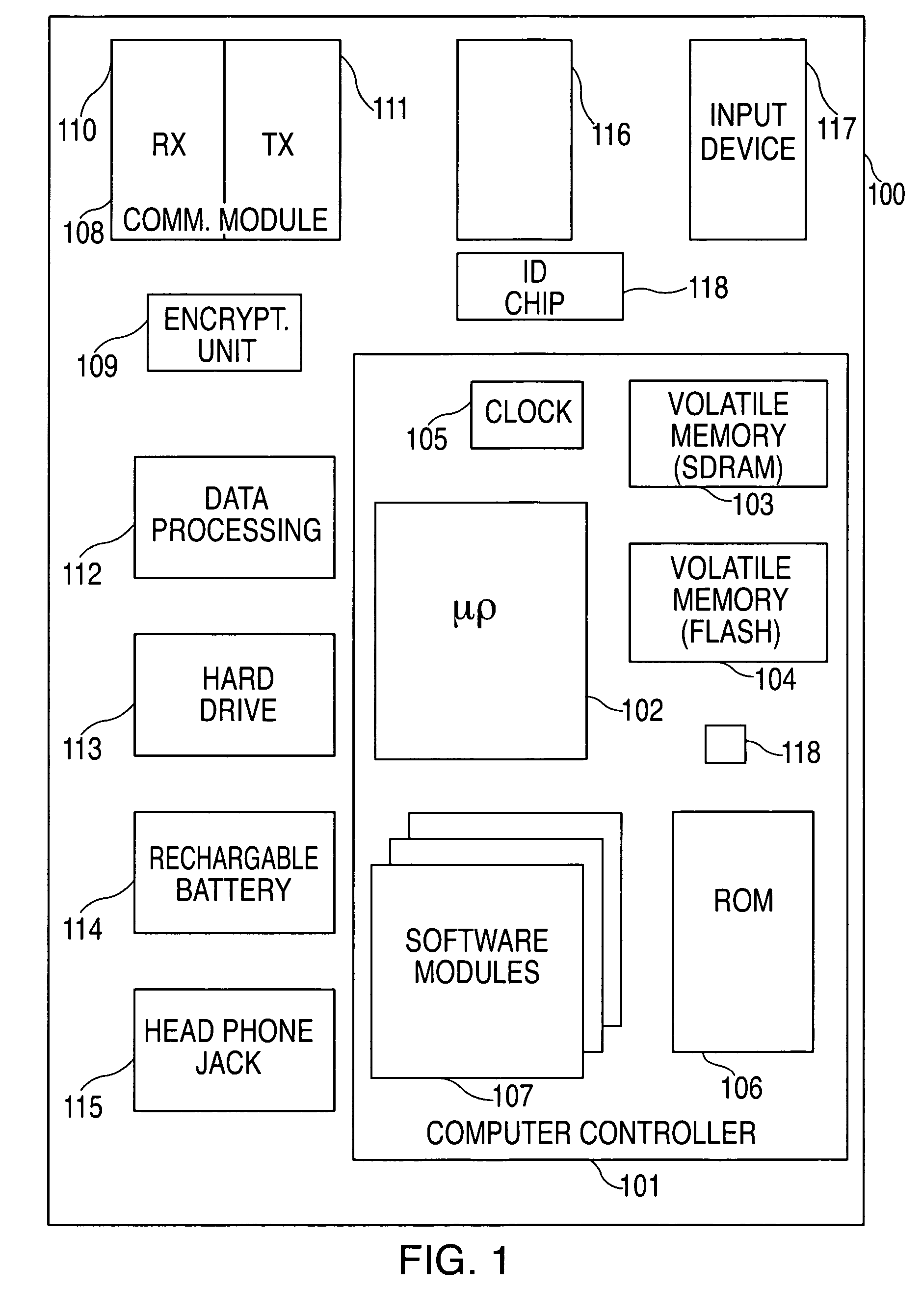
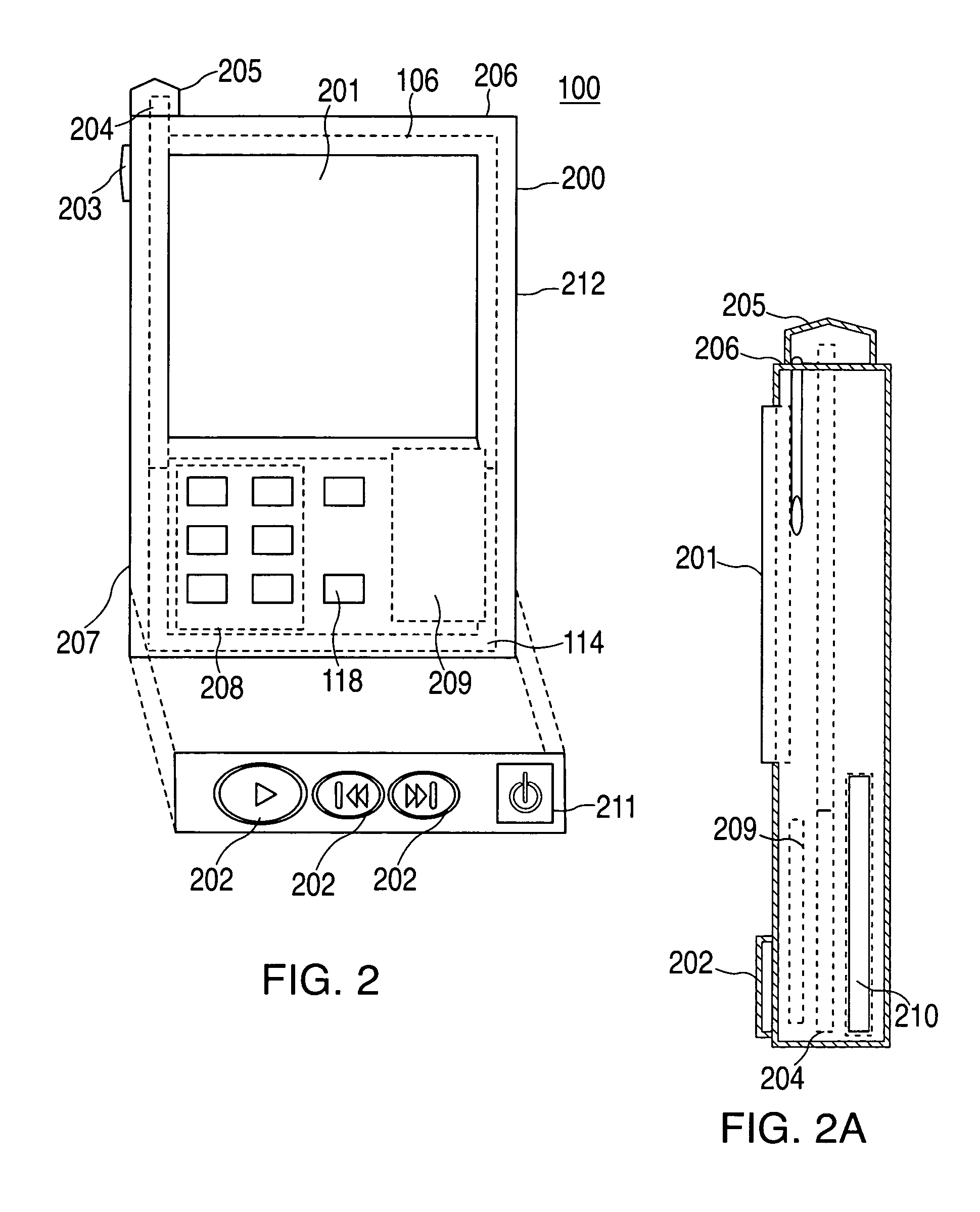
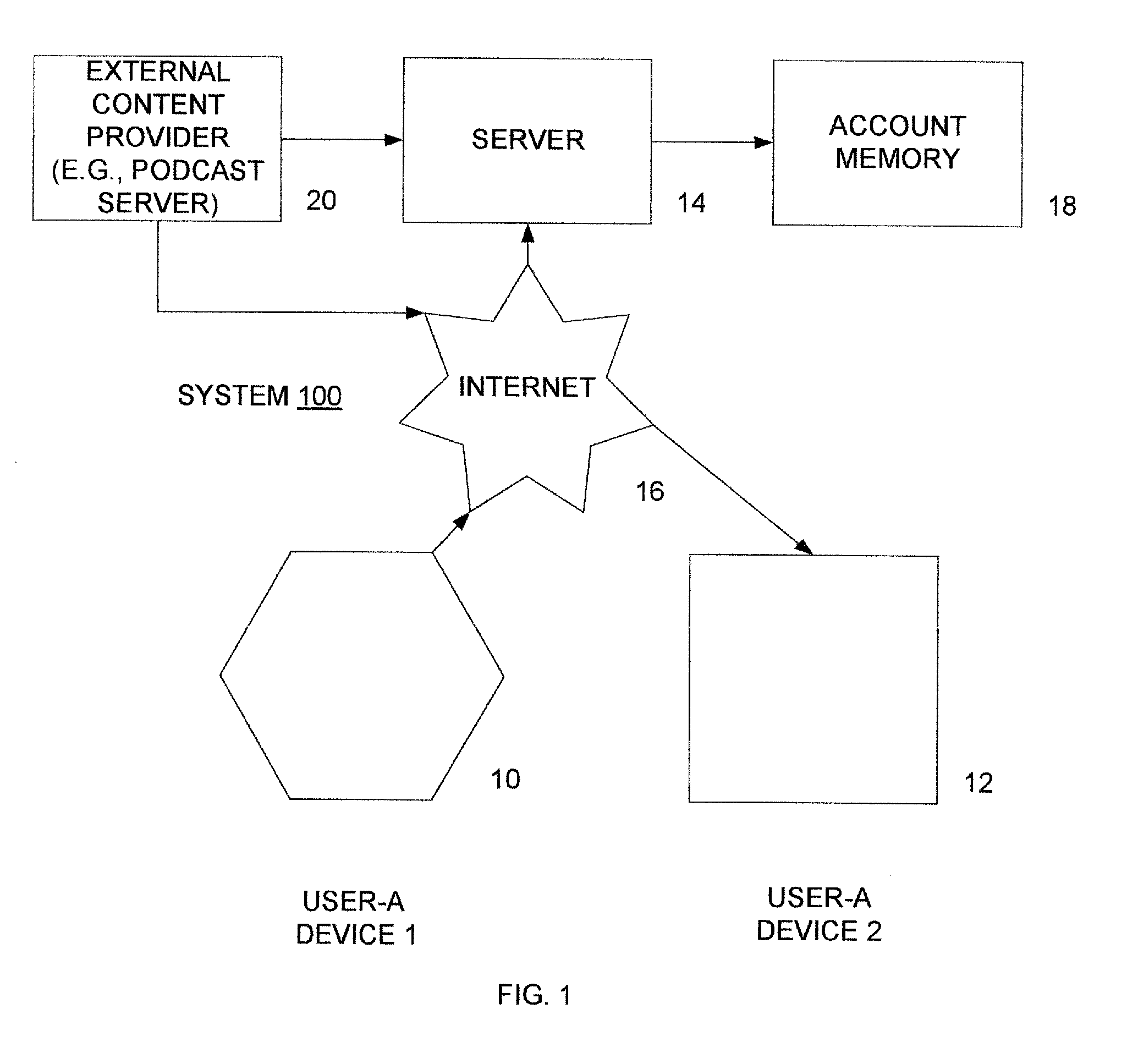
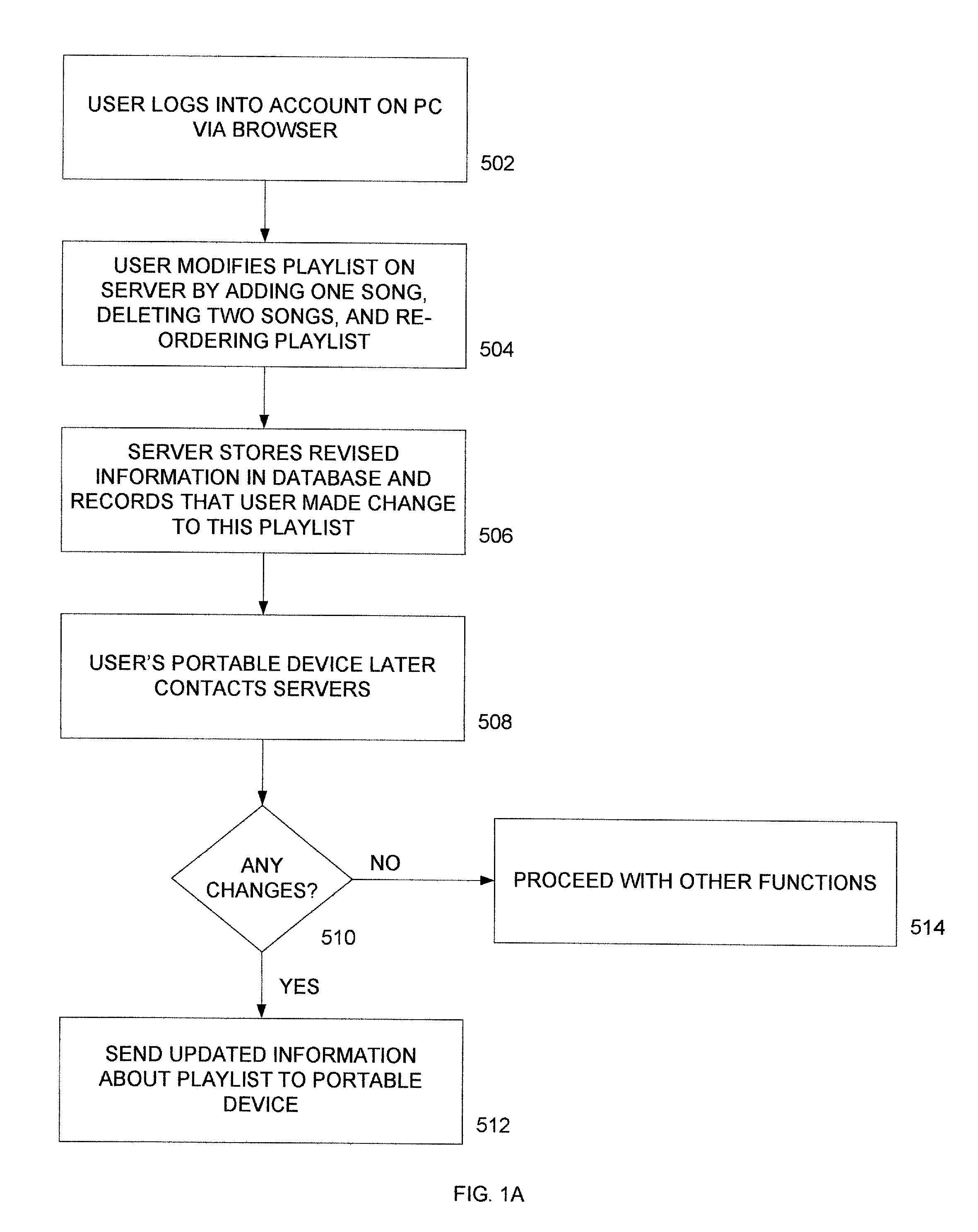
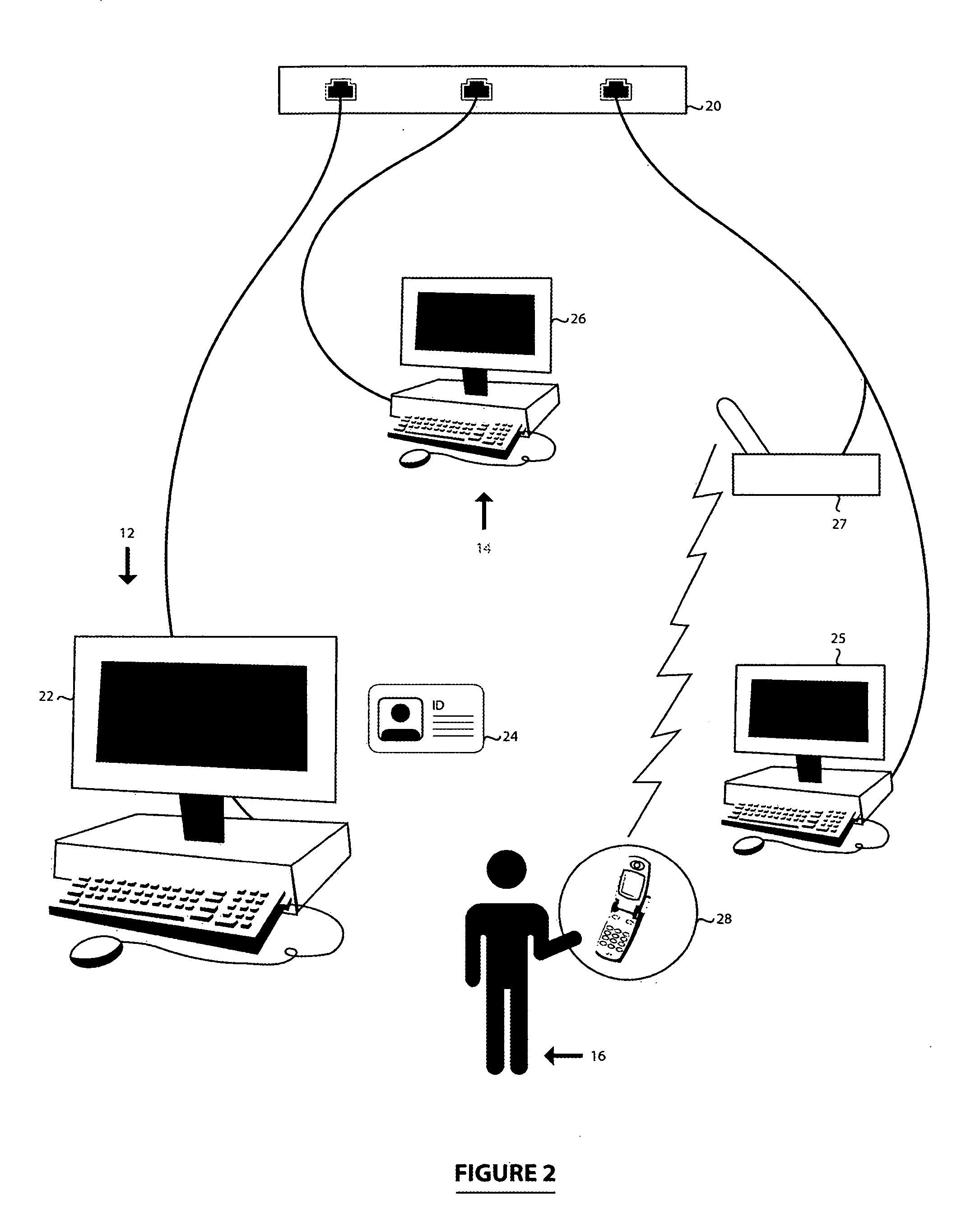
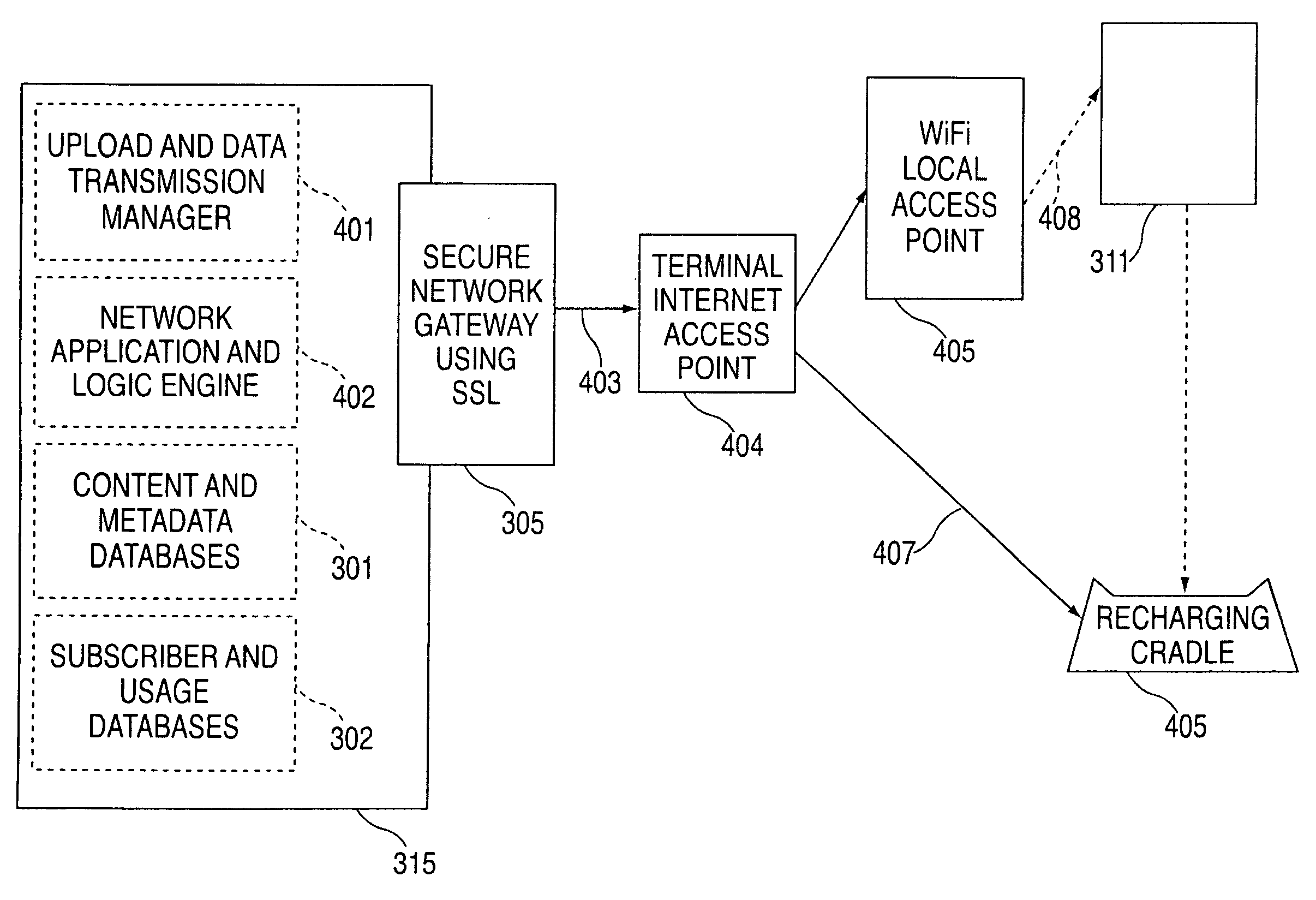
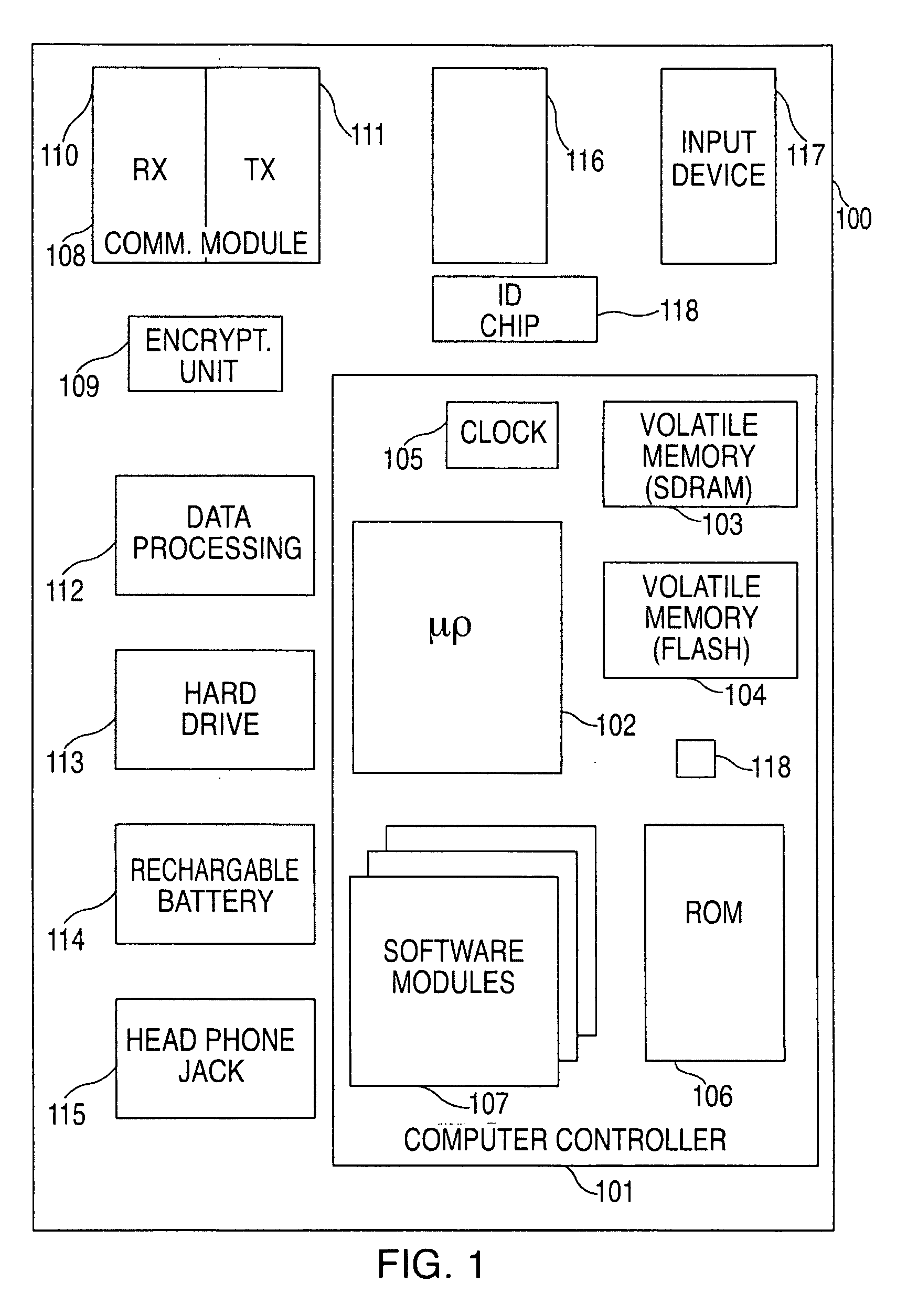
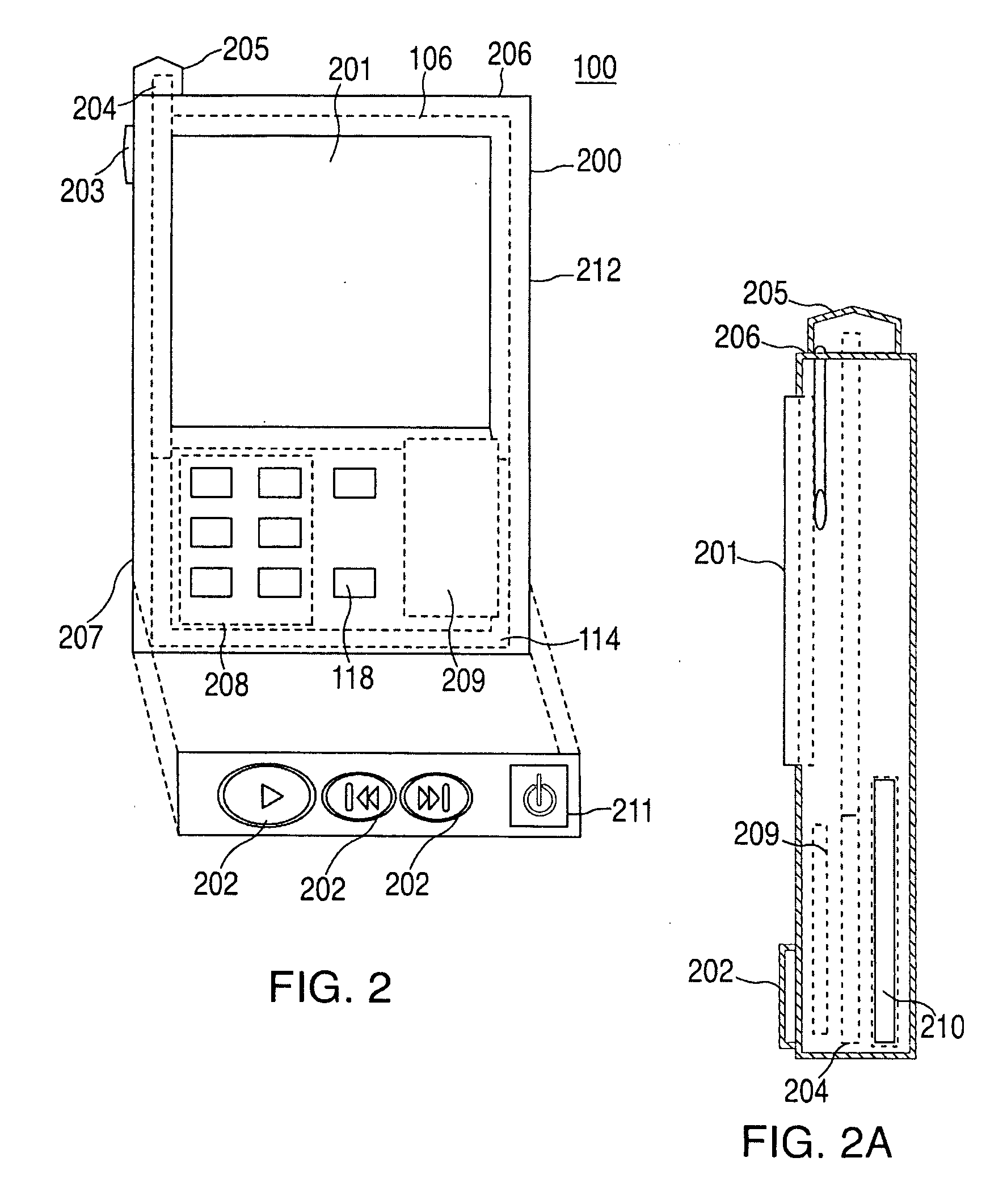
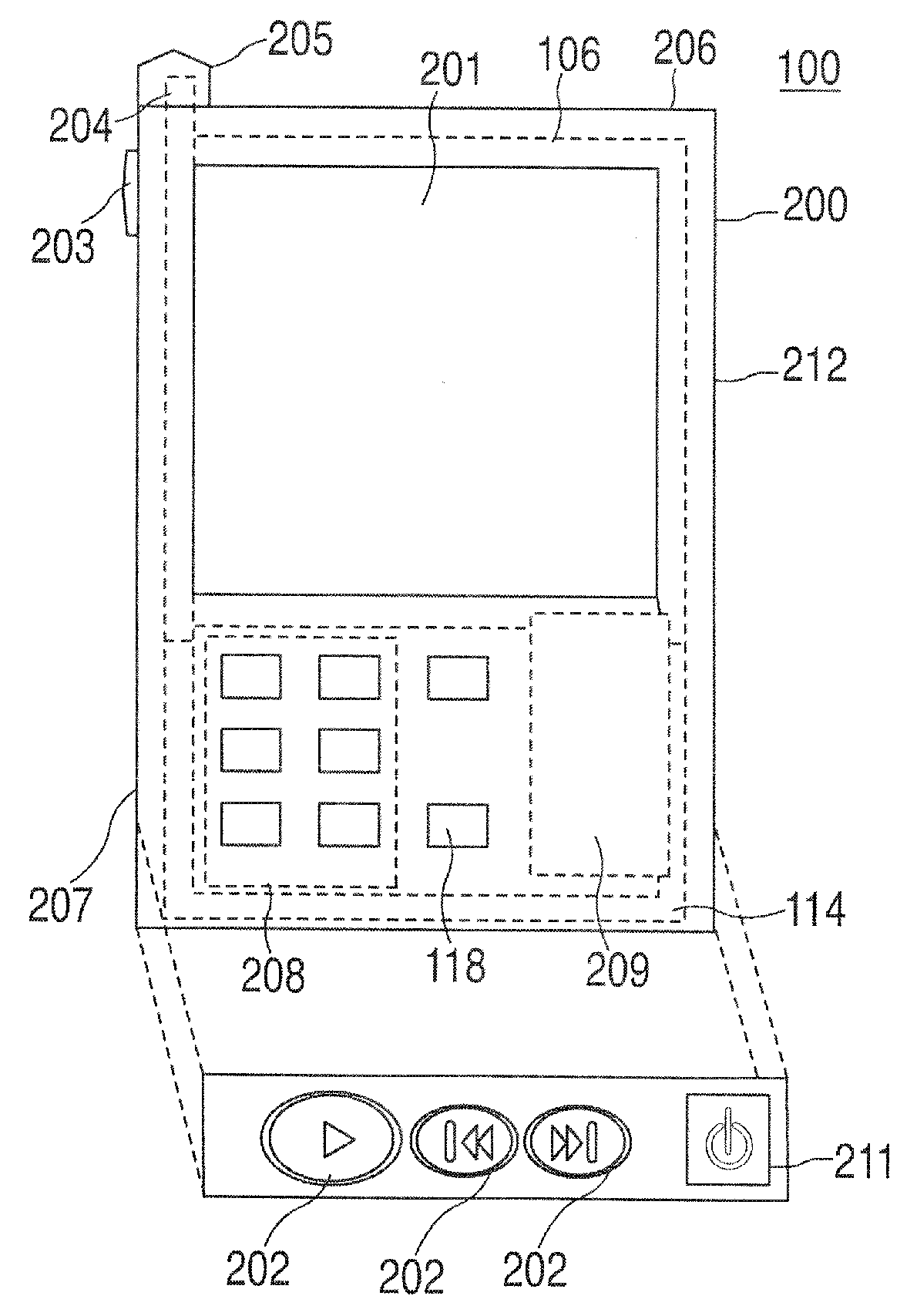
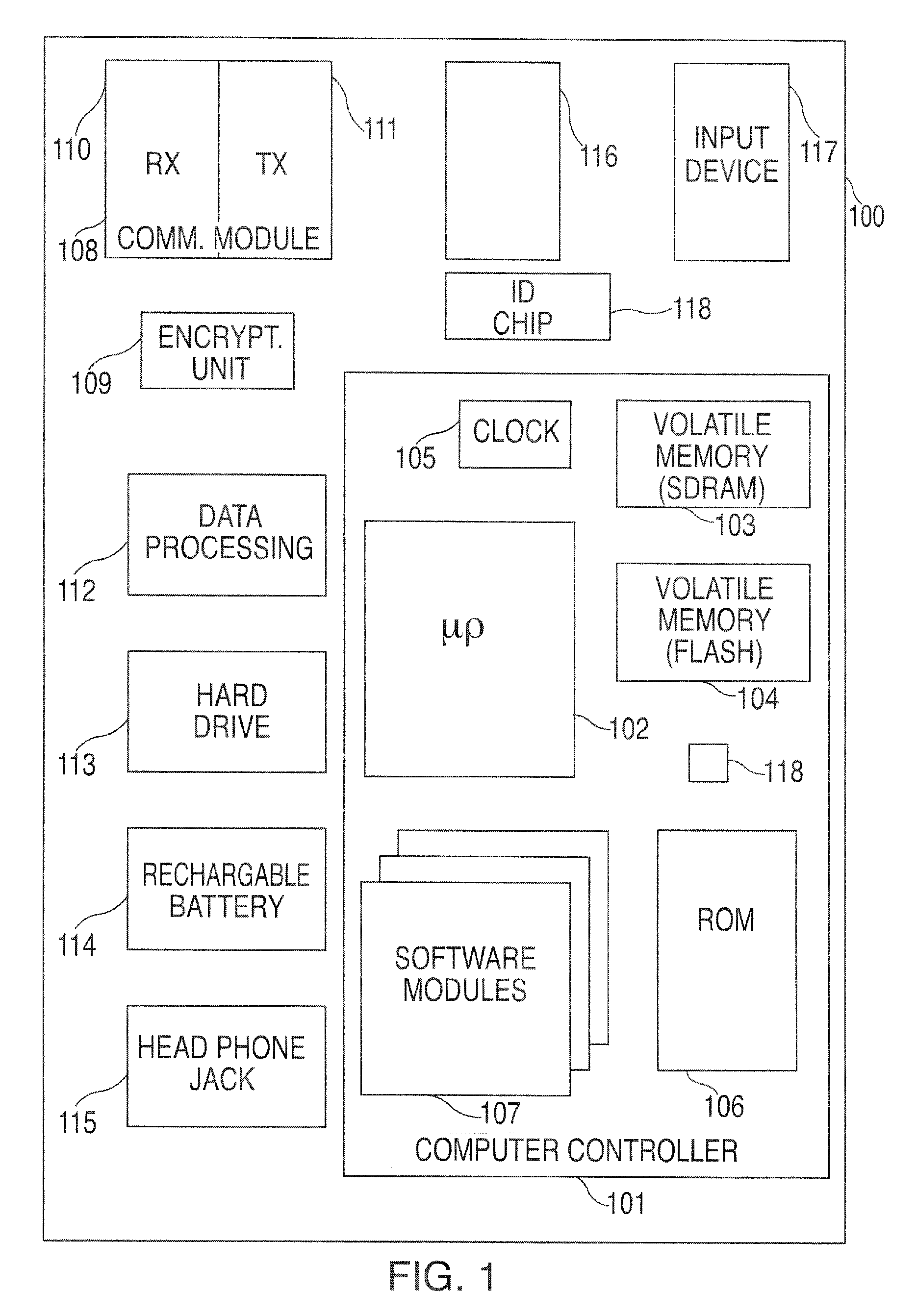
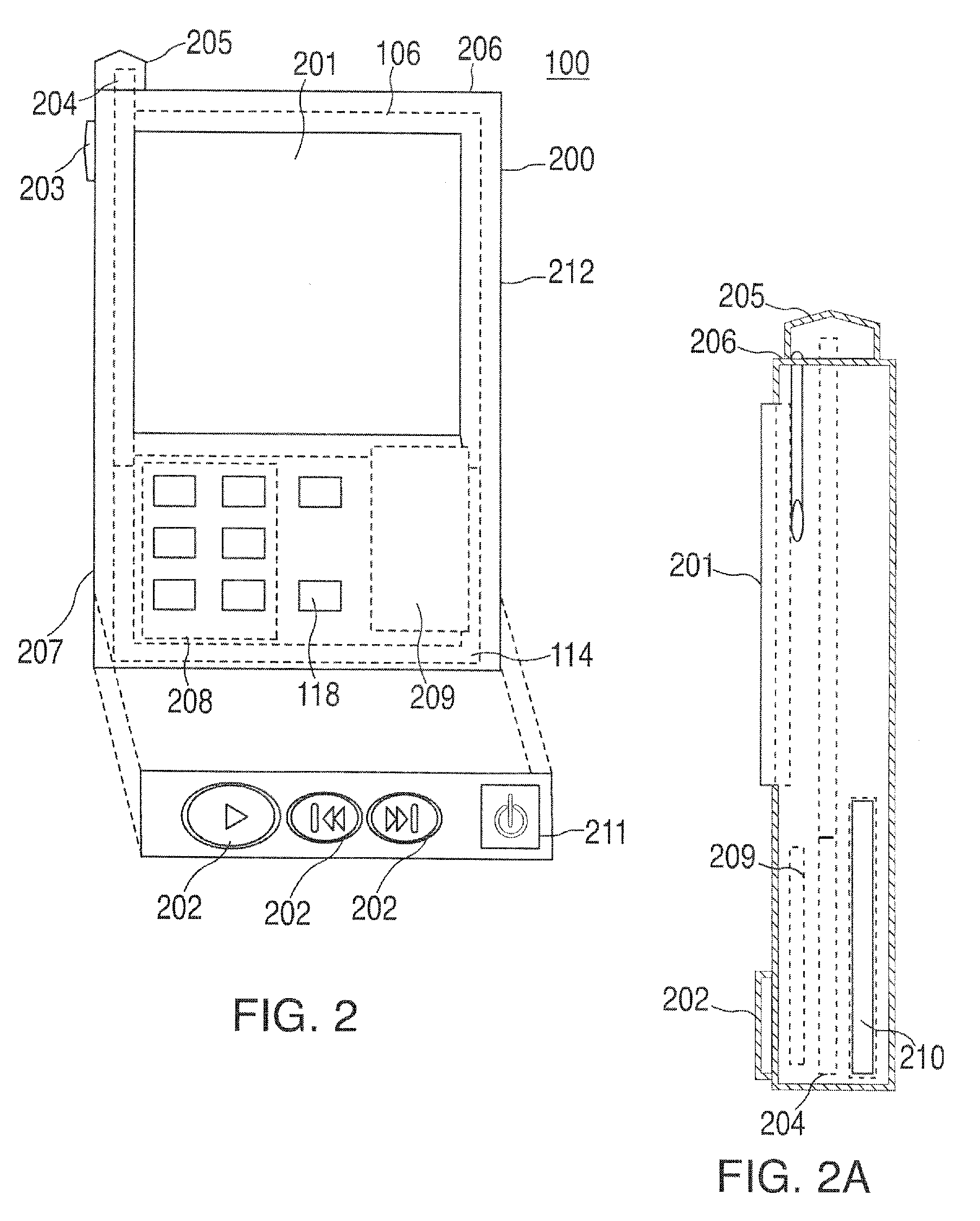
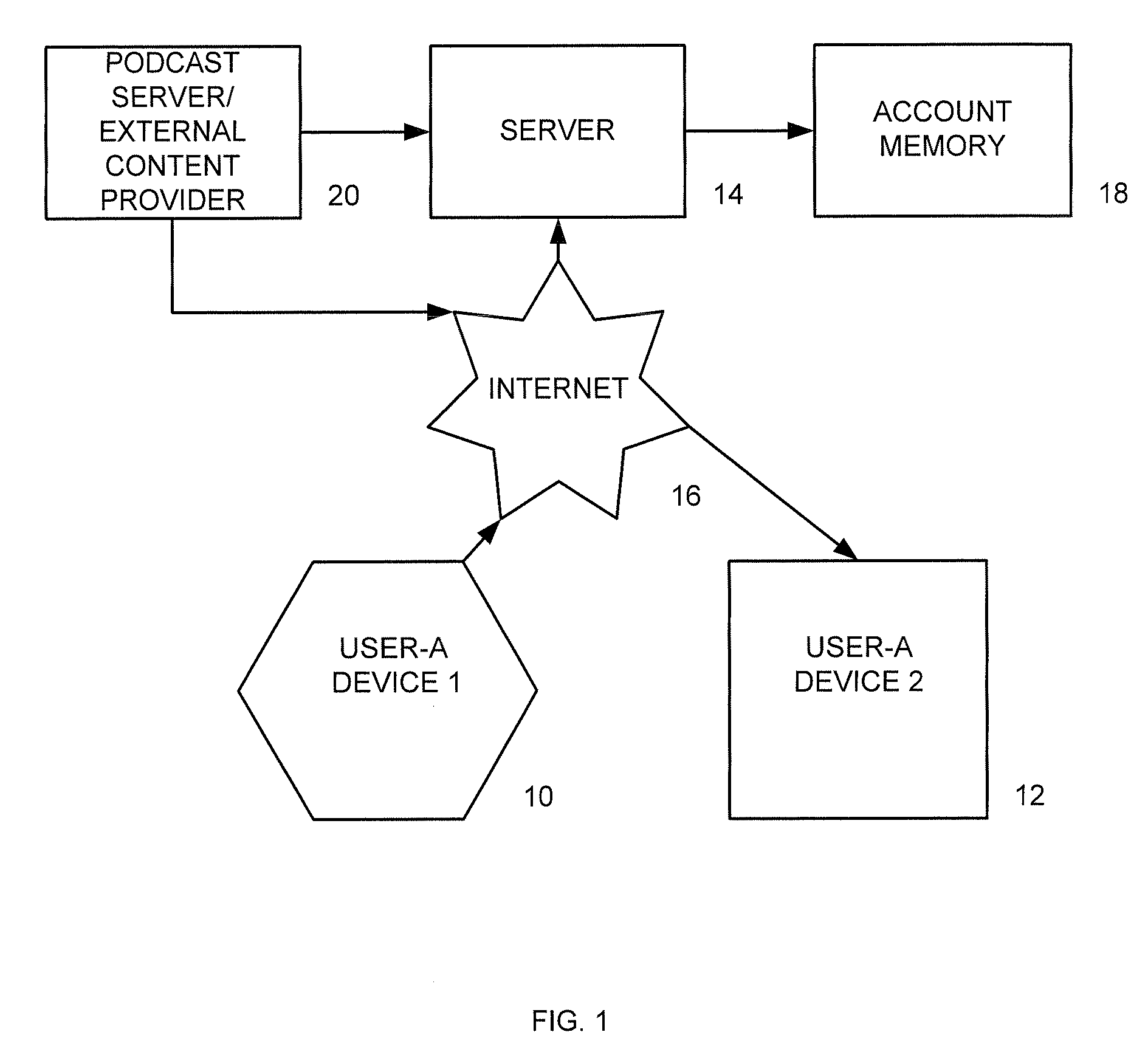
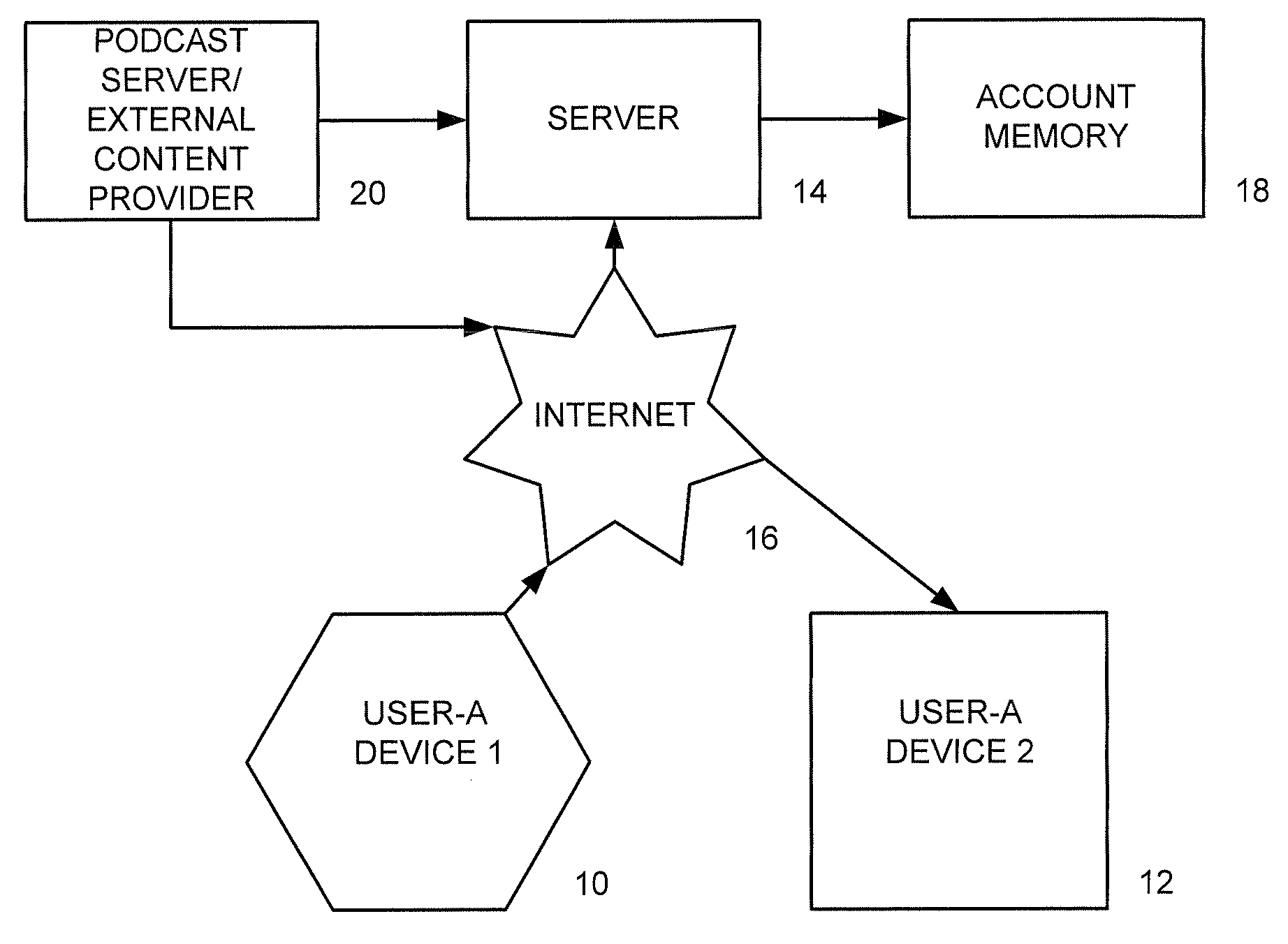
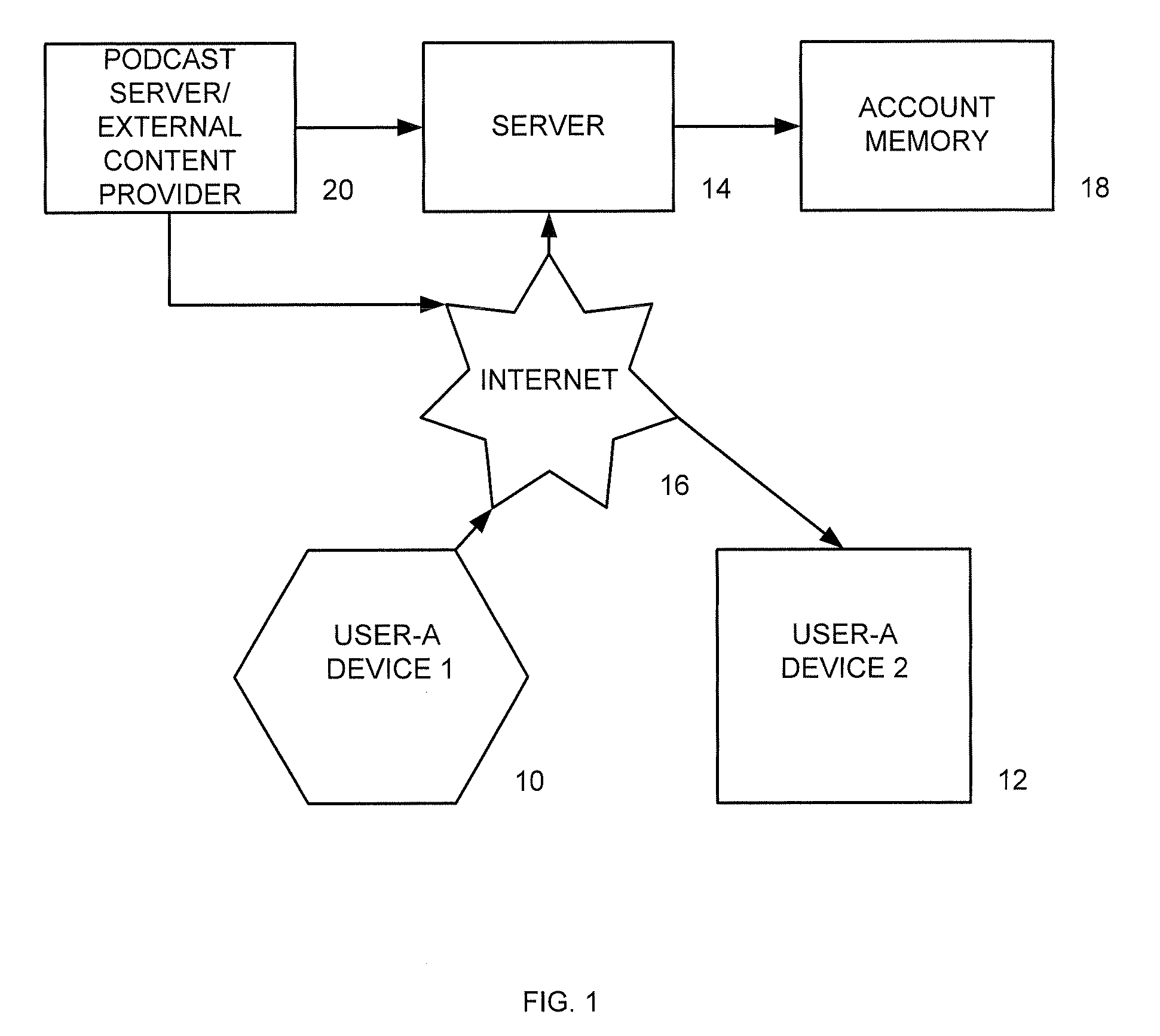
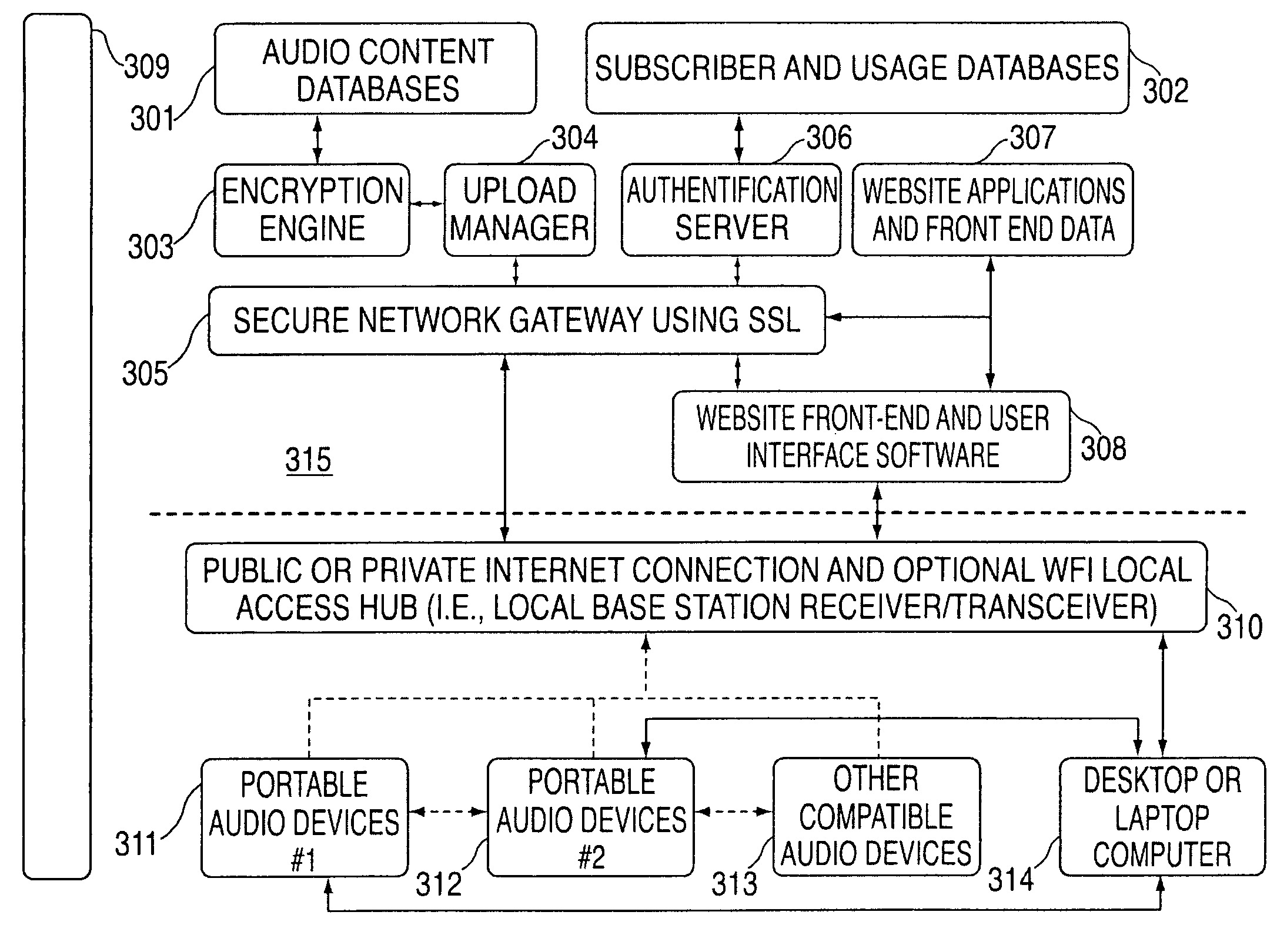
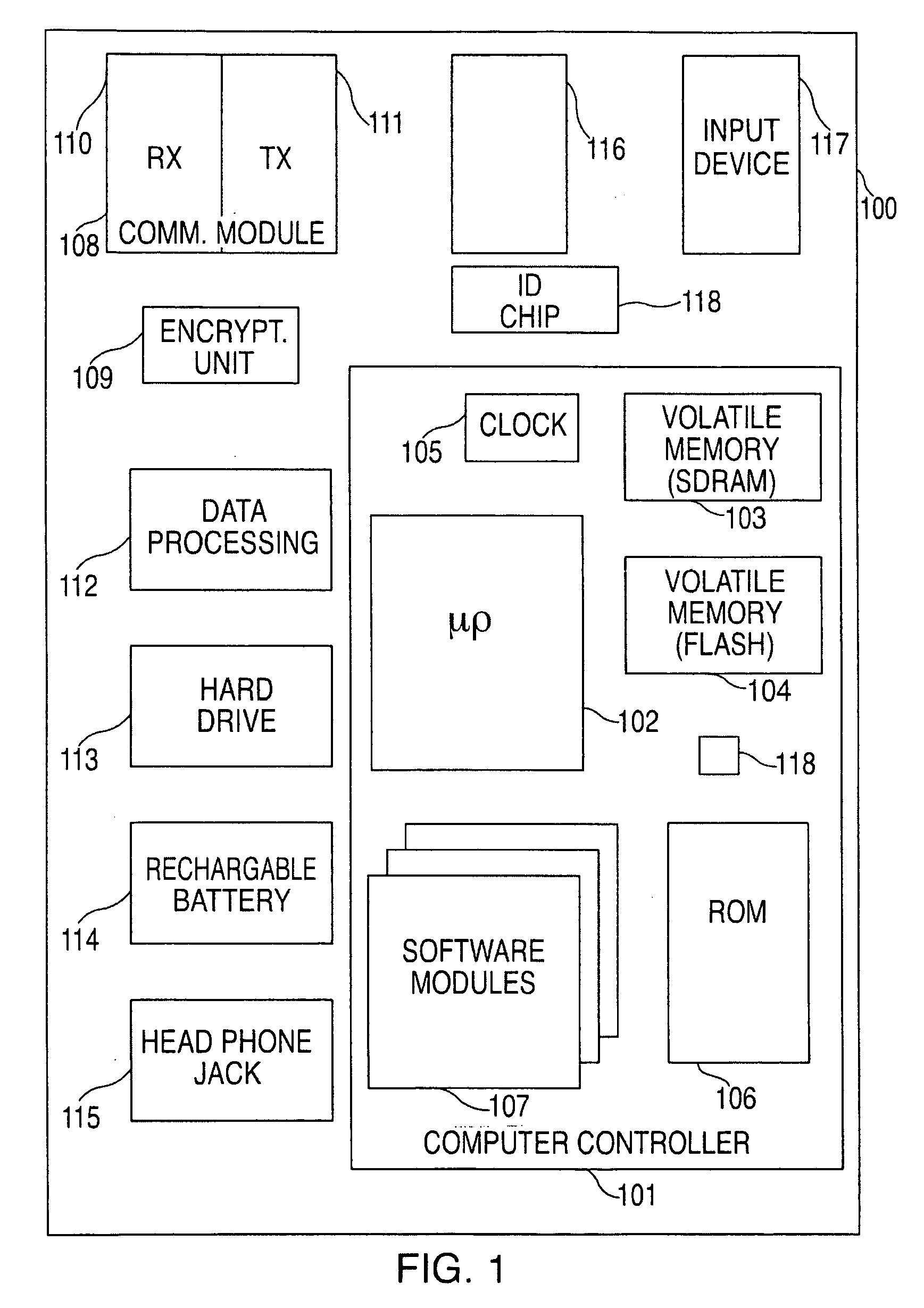
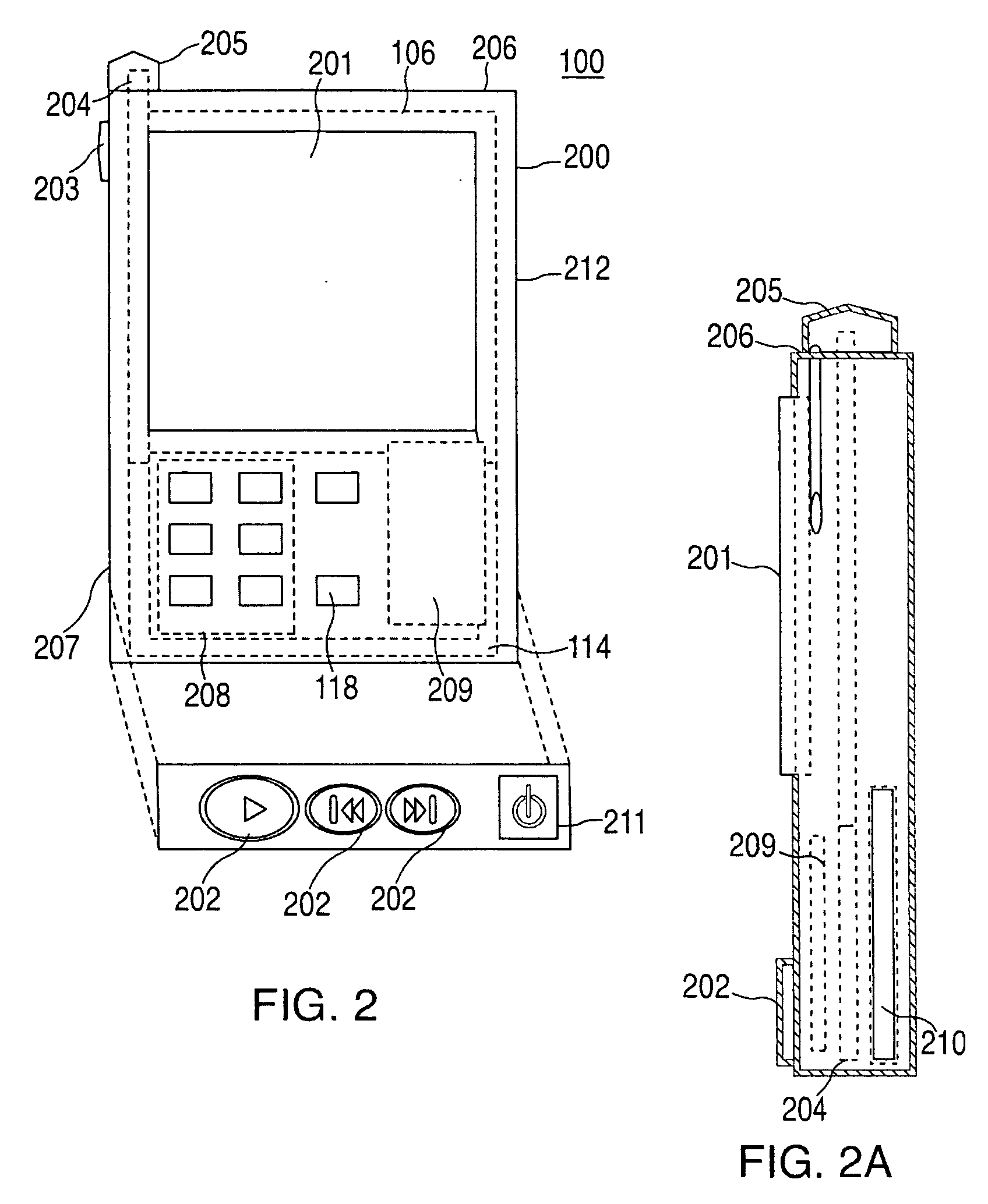
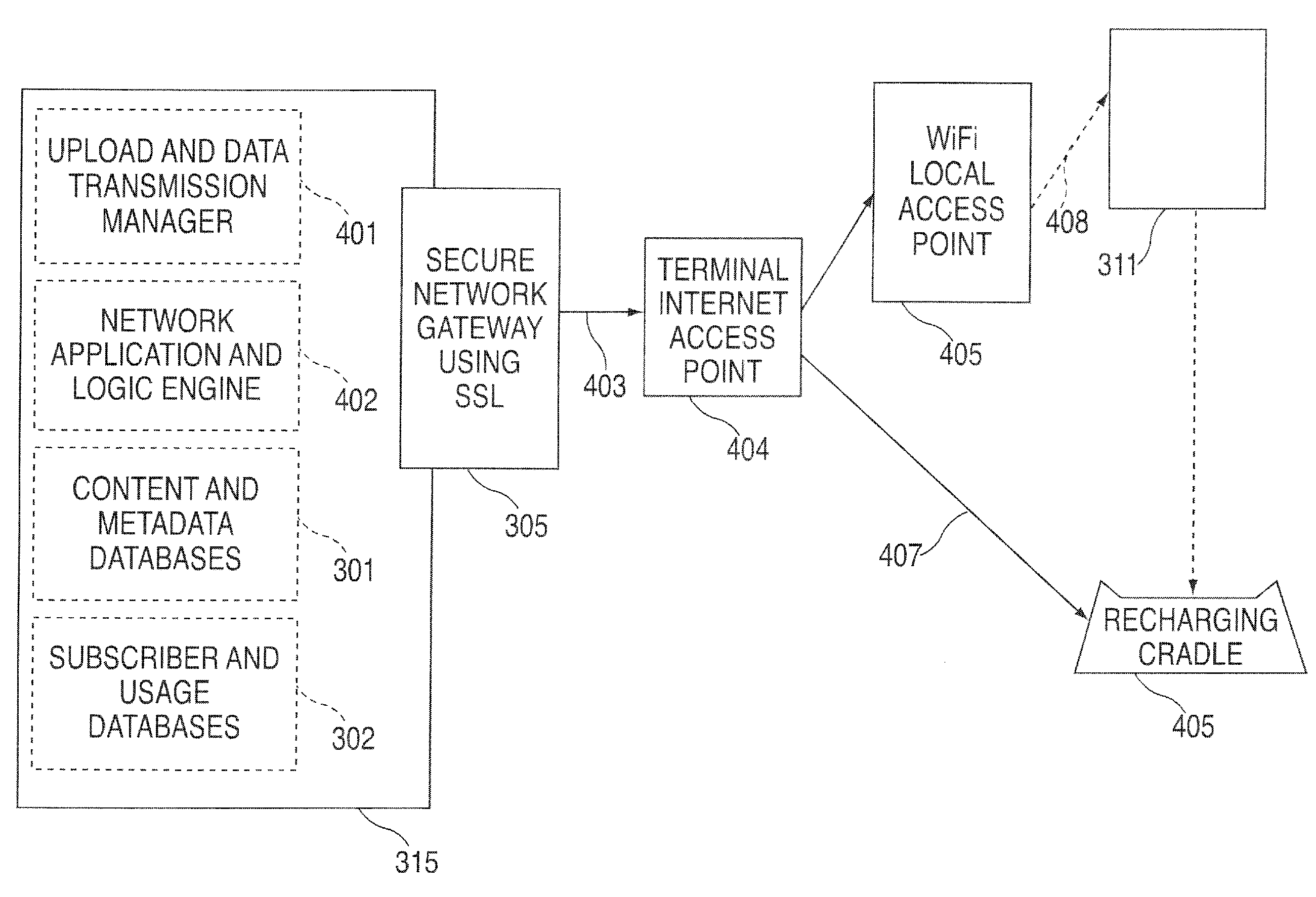
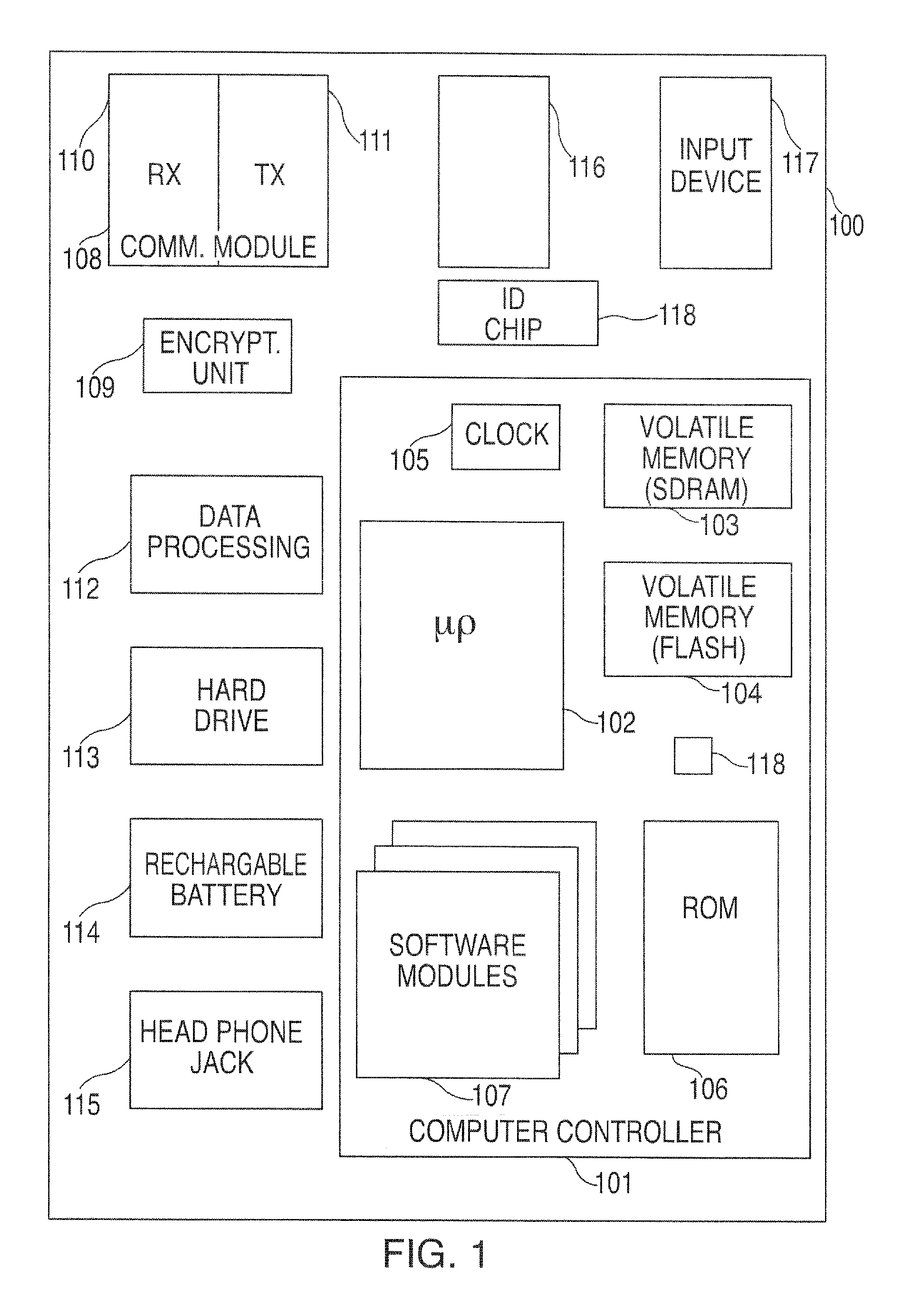
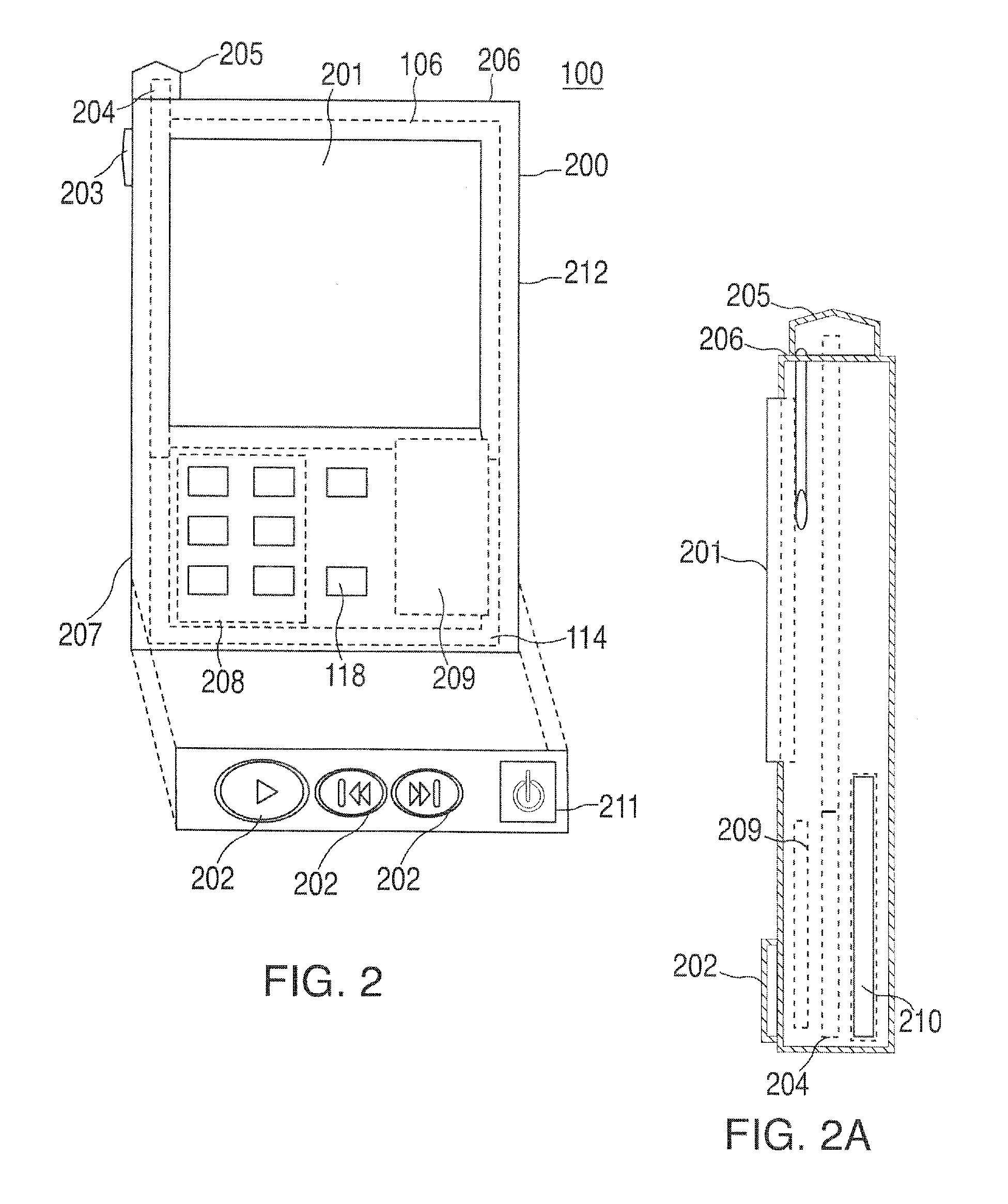
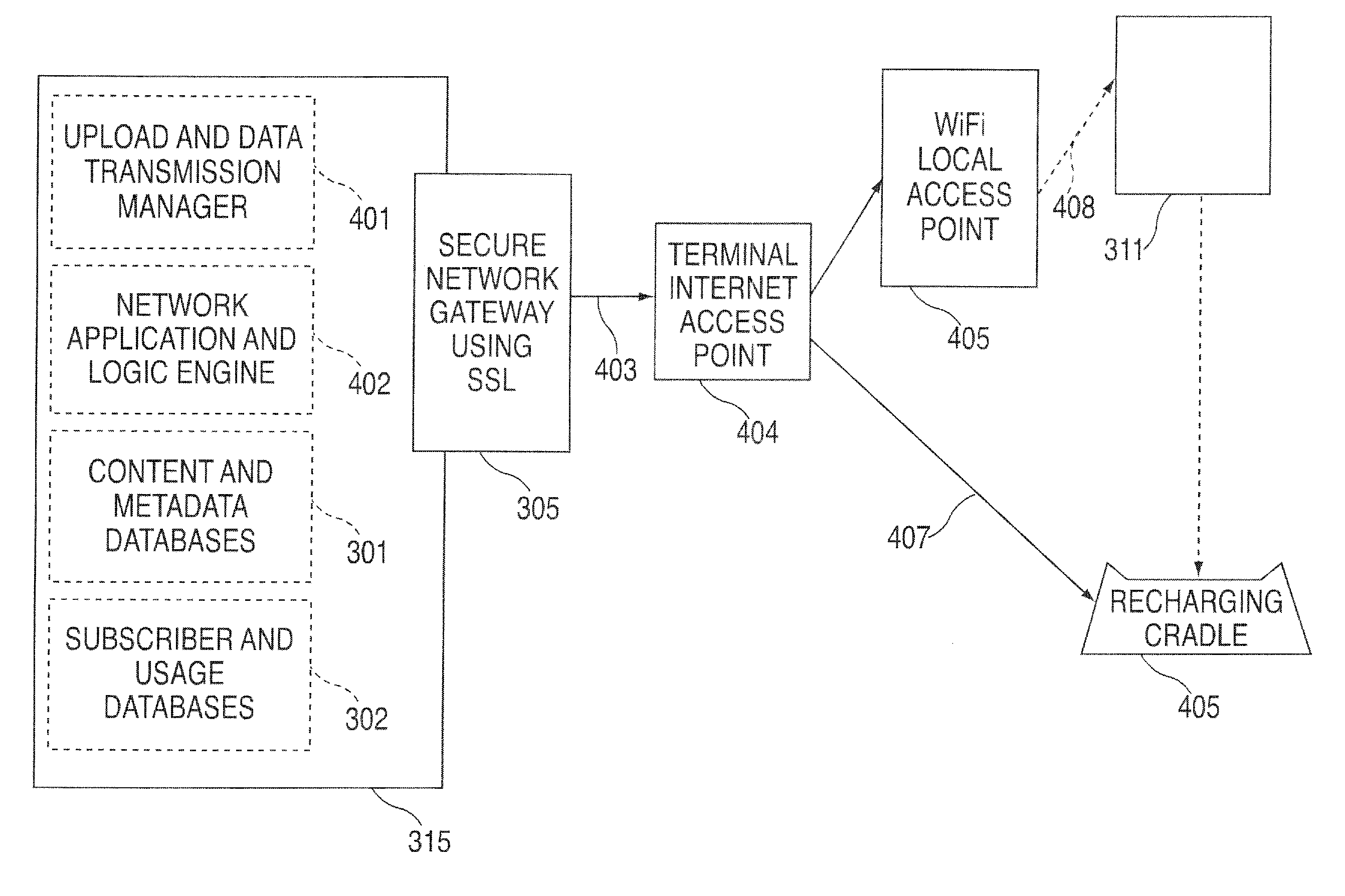
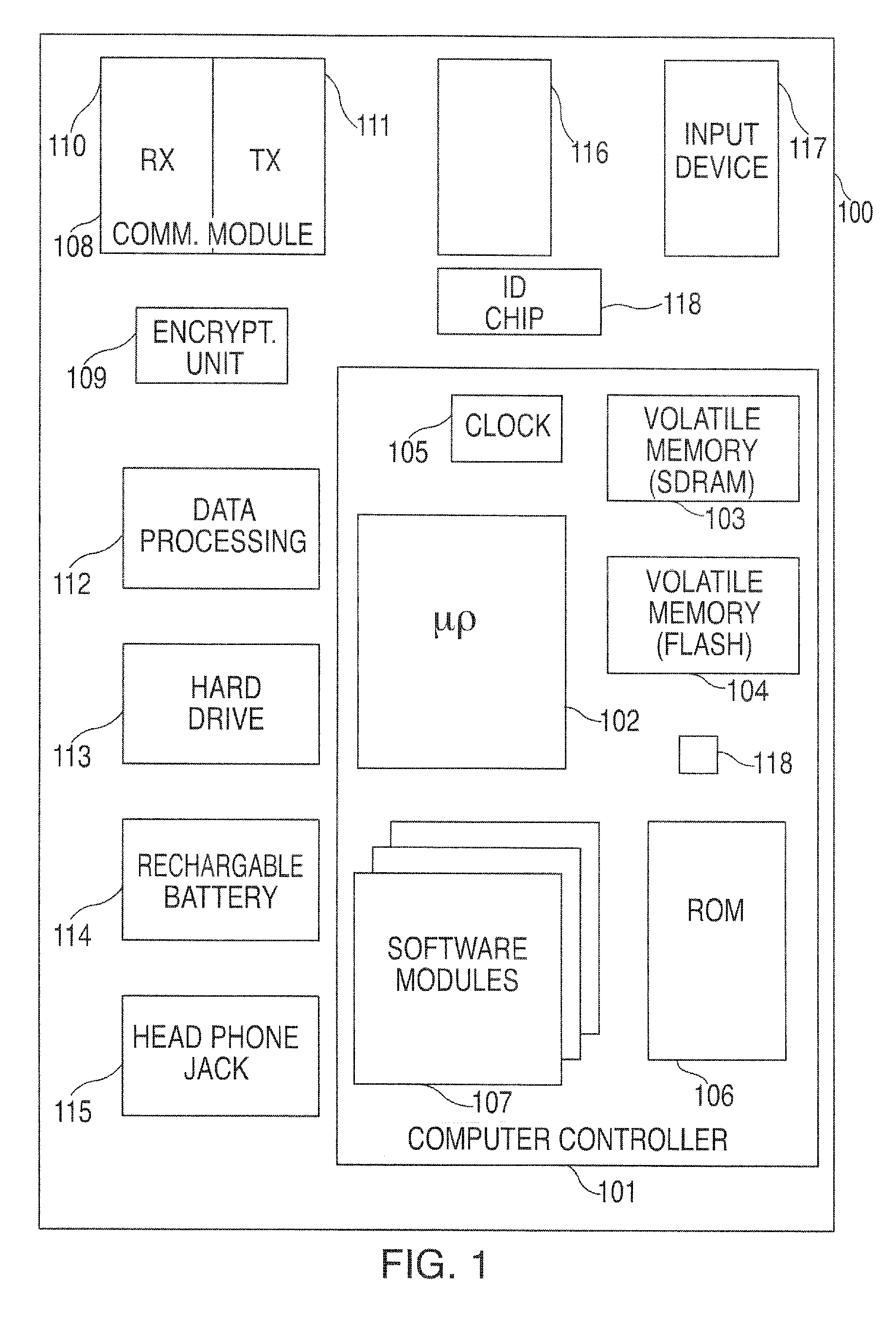
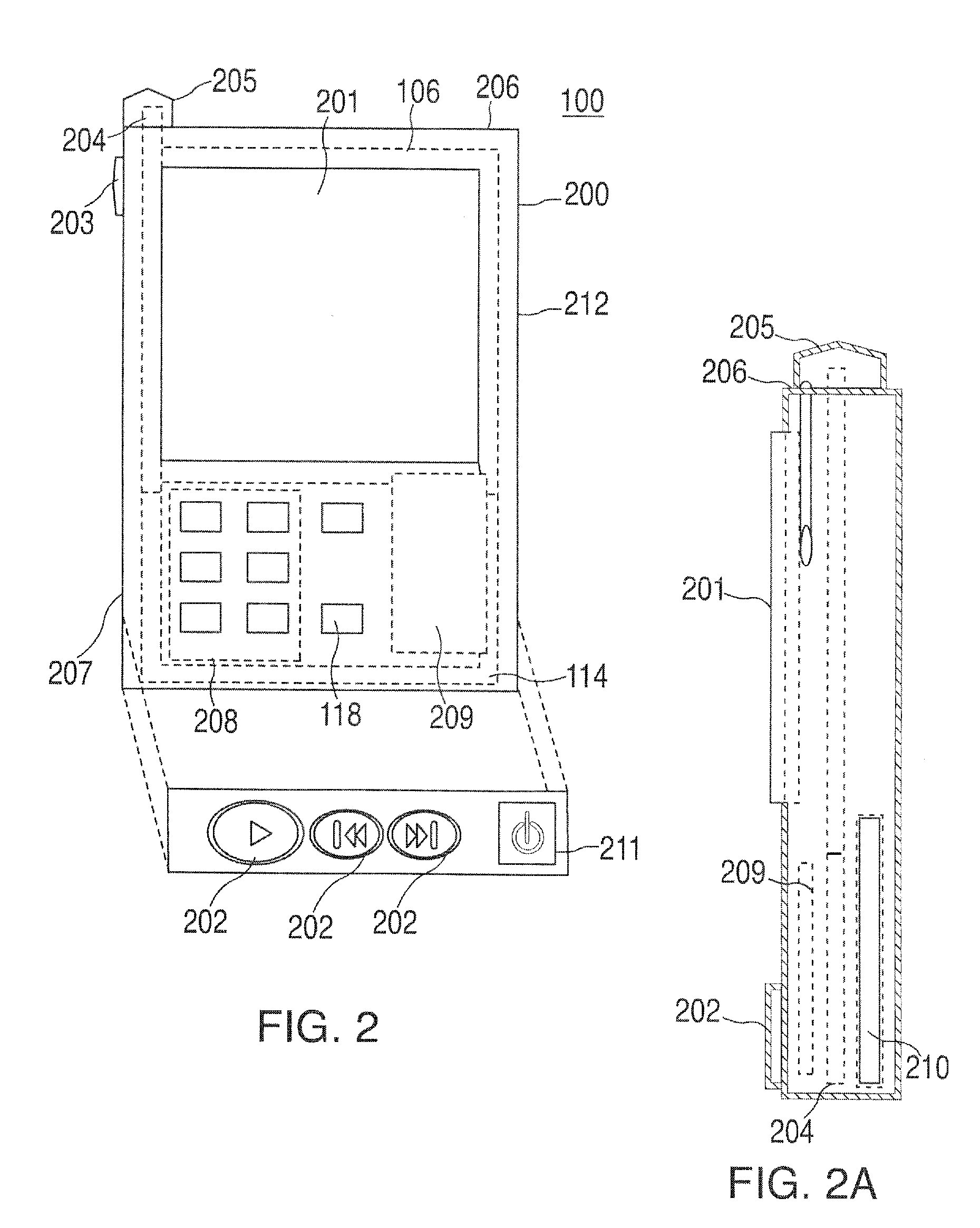
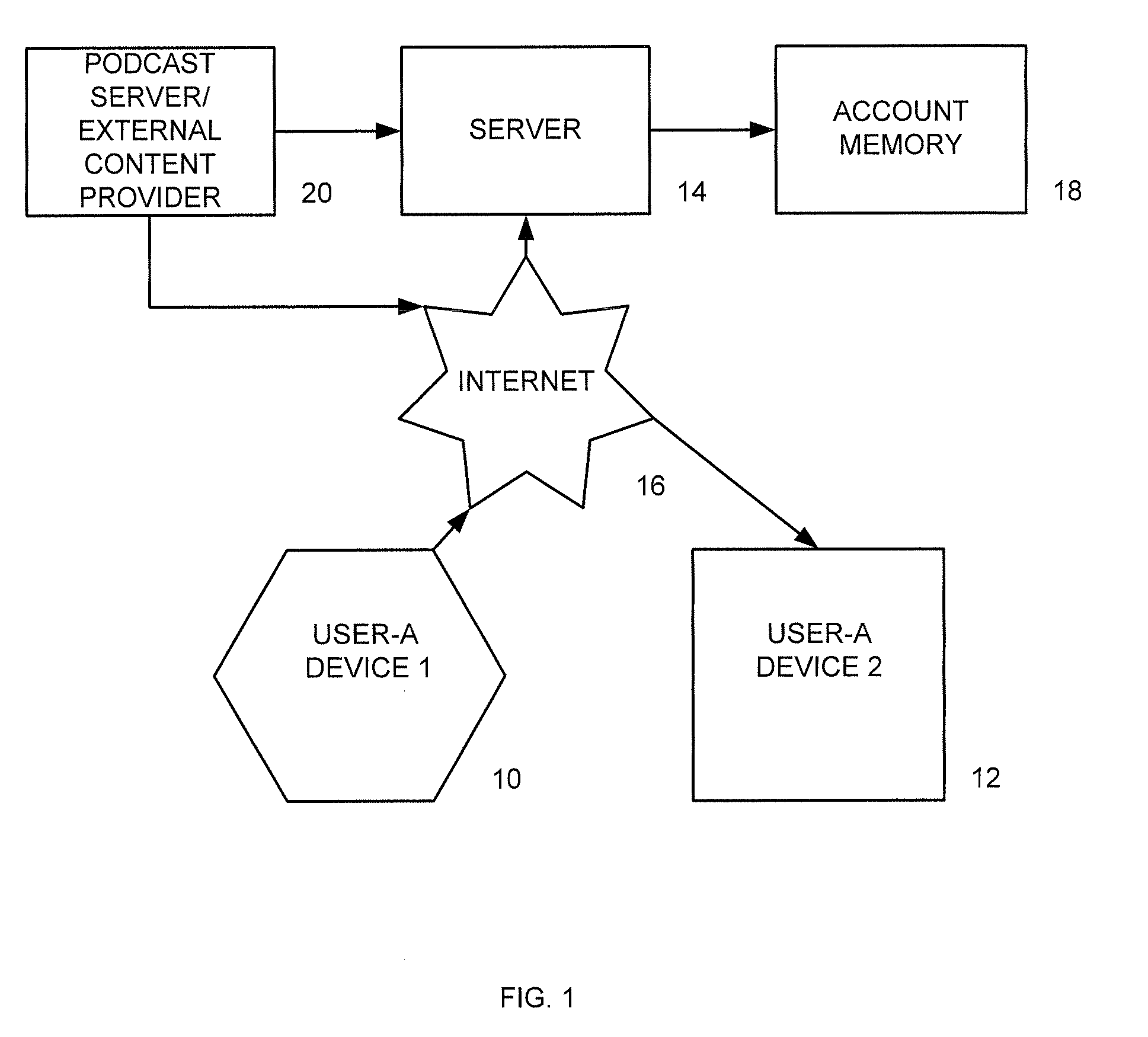
A portable wireless communications subscriber audio and / or video player apparatus and system and method for selecting, requesting, downloading, and playing audio and / or video data content files from an Internet-based database server. The wireless link is preferably implemented in accordance with the WiFi protocol, which allows connectivity to the Internet by being in proximity with a local base station or WiFi hotspot (i.e., publicly available local wireless access hub connected to the Internet). The portable wireless communications subscriber audio and / or video player apparatus and system preferably include a security means for monitoring and blocking unauthorized use of the player apparatus and system. The player apparatus further preferably has the capability to communicate with other neighboring player apparatus for the purpose of exchanging content data files, playlists and personal messages.
Owner:SANDISK TECH LLC
Audio visual player apparatus and system and method of content distribution using the same
InactiveUS20080010372A1None of methods is secureDigital data information retrievalElectronic editing digitised analogue information signalsWi-FiContent distribution
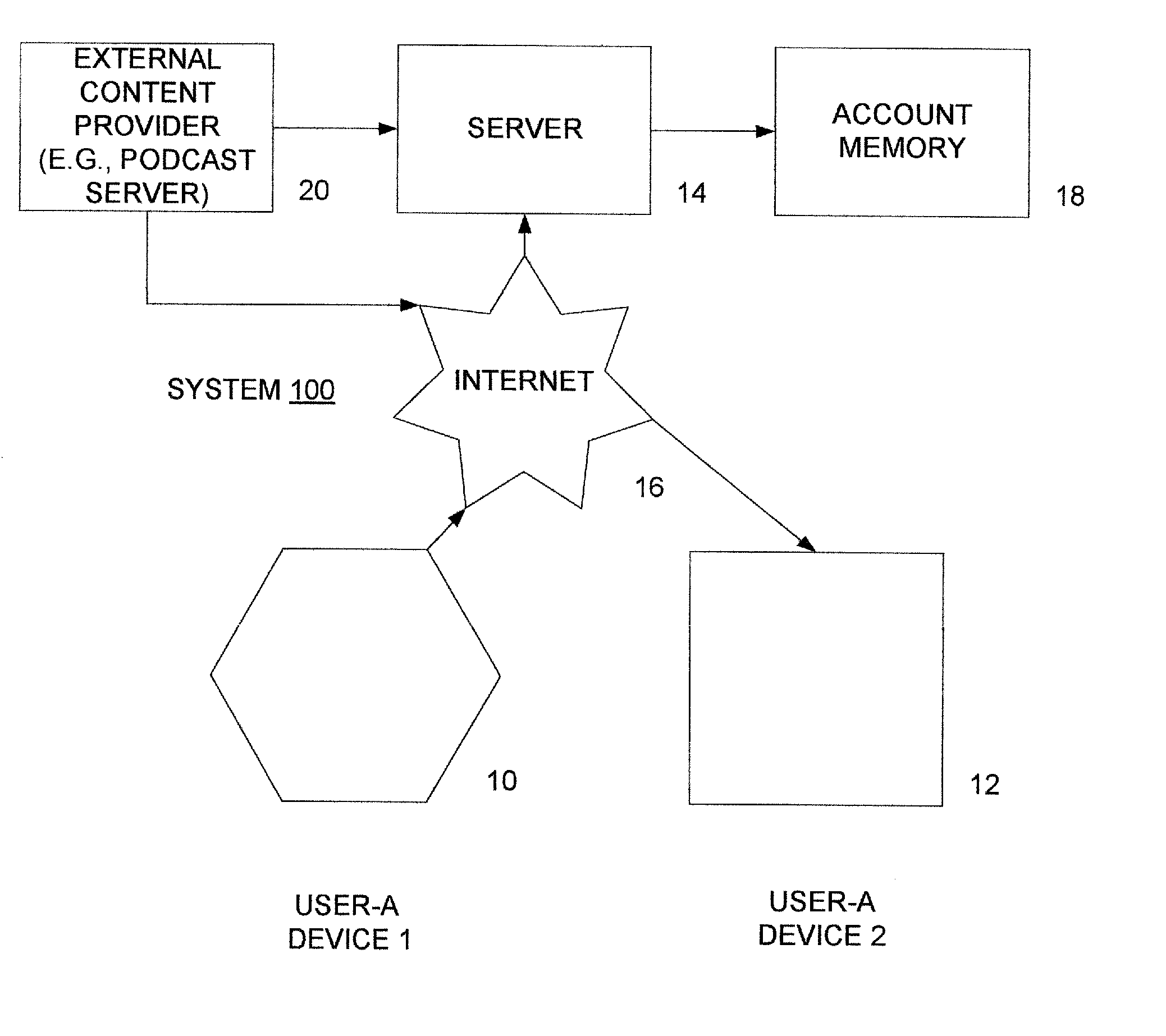
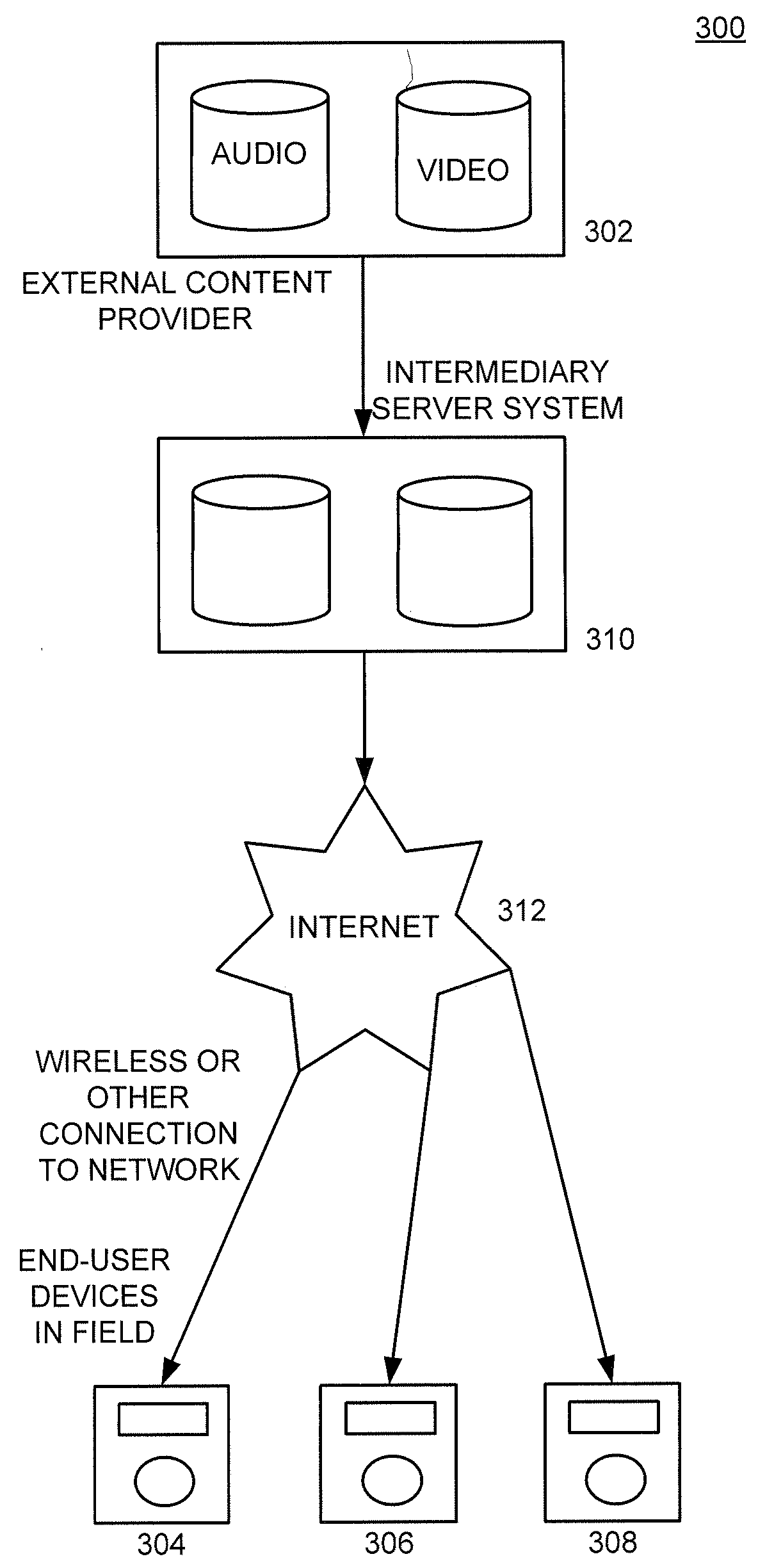
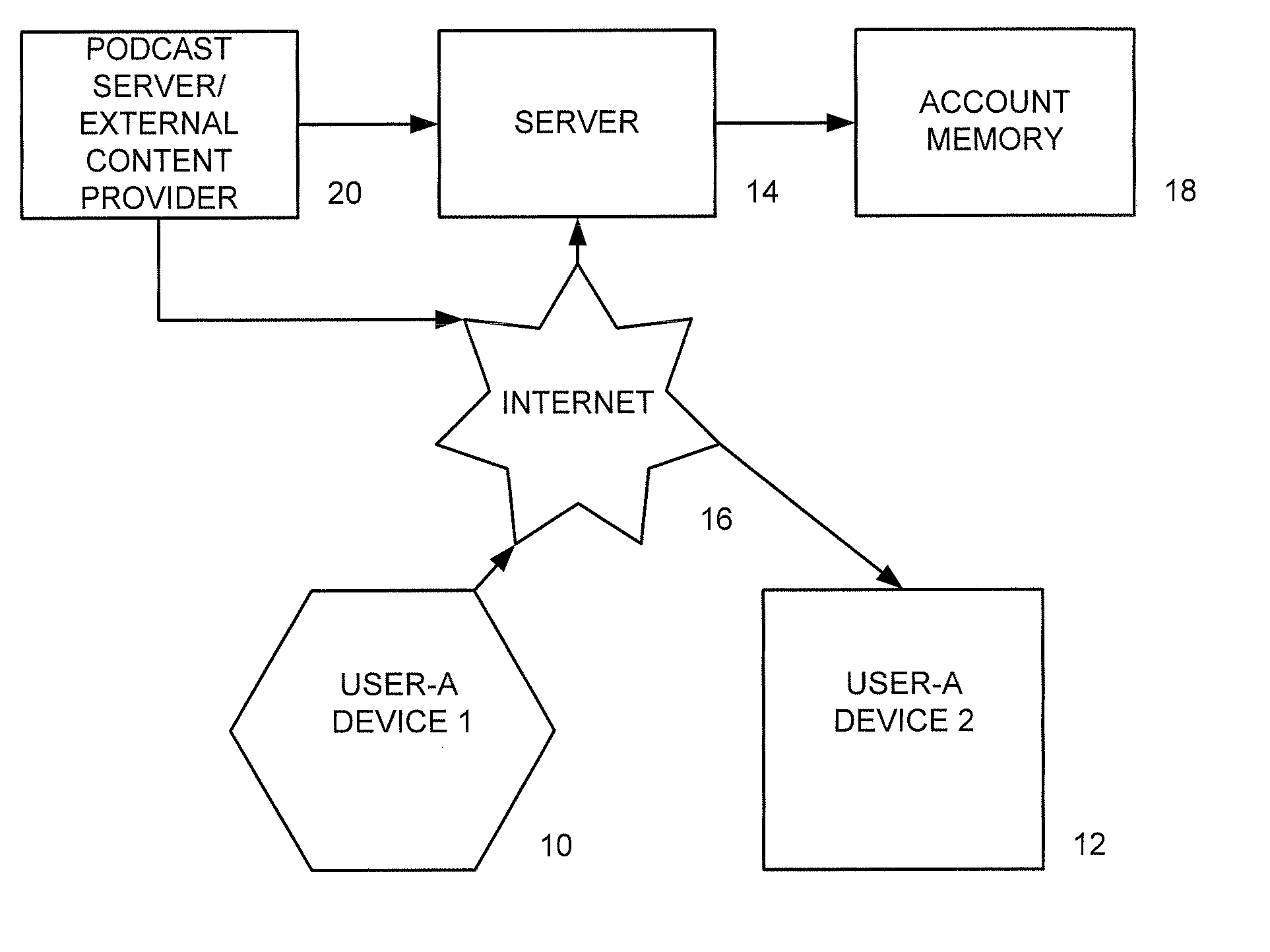
A system is presented providing content to a plurality of handheld devices (including musical selections). The devices can access a server over the Internet via a Wi-Fi or other similar wireless interconnection and can download songs requested by a user from the server or from other users using, e.g., a P2P protocol. All downloads may be governed by applicable DRM rules. Content and playlists may also be pushed by a server from other sources and means including, e.g., podcasting, based on predetermined rules, favorite preferences of users, and other criteria.
Owner:SANDISK TECH LLC
Identity theft protection and notification system
InactiveUS20060080263A1None of methods is secureDigital data authenticationElectronic credentialsInformation monitoringData mining
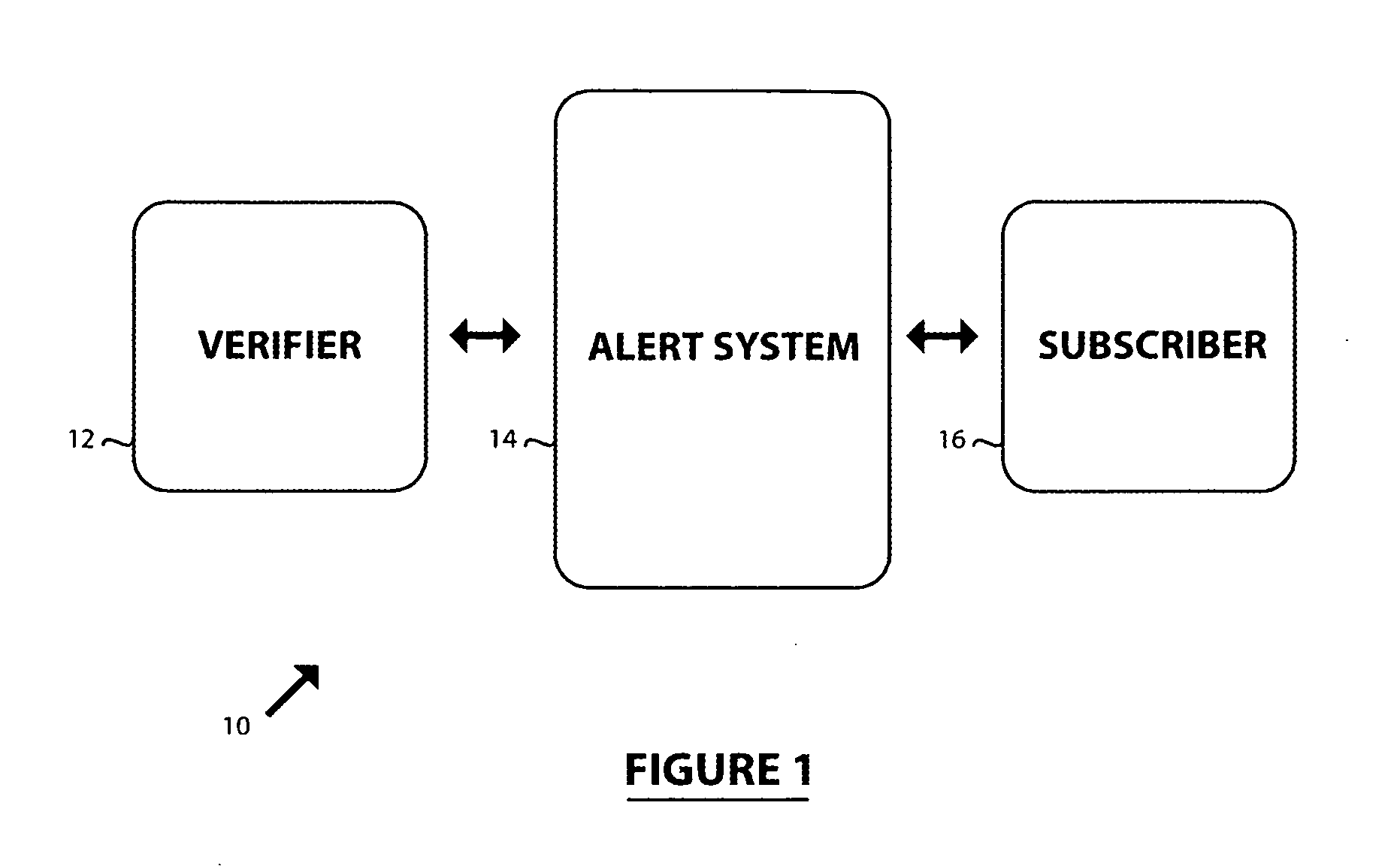
An information monitoring and alert system is provided which registers subscribers and verifiers with a central alert system. The alert system provides an interface for the verifiers to submit queries relating to identification information. Information in this query is compared to the stored data submitted by the subscriber during registration and if a match occurs the subscriber is notified that the identification has been used for a certain purpose. The alert system only stores an encrypted value of the identification with only contact information which is preferably anonymous. Any other information is deleted after registration. The subscriber upon being alerted of the use of the identification is instructed to authorize or reject the transaction pertaining to the query.
Owner:ID ALARM
Portable media device with list management tools
InactiveUS20080155470A1None of methods is secureMetadata multimedia retrievalMultiple digital computer combinationsVideo playerManagement tool
A portable wireless communications subscriber audio and / or video player apparatus and system and method for selecting, requesting, downloading, and playing audio and / or video data content files from an Internet-based database server. The wireless link is preferably implemented in accordance with the WiFi protocol, which allows connectivity to the Internet by being in proximity with a local base station or WiFi hotspot (i.e., publicly available local wireless access hub connected to the Internet). The portable wireless communications subscriber audio and / or video player apparatus and system preferably include a security means for monitoring and blocking unauthorized use of the player apparatus and system. The player apparatus further preferably has the capability to communicate with other neighboring player apparatus for the purpose of exchanging content data files, playlists and personal messages.
Owner:SANDISK TECH LLC
System sharing user content on a content-receiving device
InactiveUS20080155057A1None of methods is secureMetadata multimedia retrievalMultiple digital computer combinationsVideo playerDatabase server
A portable wireless communications subscriber audio and / or video player apparatus and system and method for selecting, requesting, downloading, and playing audio and / or video data content files from an Internet-based database server. The wireless link is preferably implemented in accordance with the WiFi protocol, which allows connectivity to the Internet by being in proximity with a local base station or WiFi hotspot (i.e., publicly available local wireless access hub connected to the Internet). The portable wireless communications subscriber audio and / or video player apparatus and system preferably include a security means for monitoring and blocking unauthorized use of the player apparatus and system. The player apparatus further preferably has the capability to communicate with other neighboring player apparatus for the purpose of exchanging content data files, playlists and personal messages.
Owner:SANDISK TECH LLC
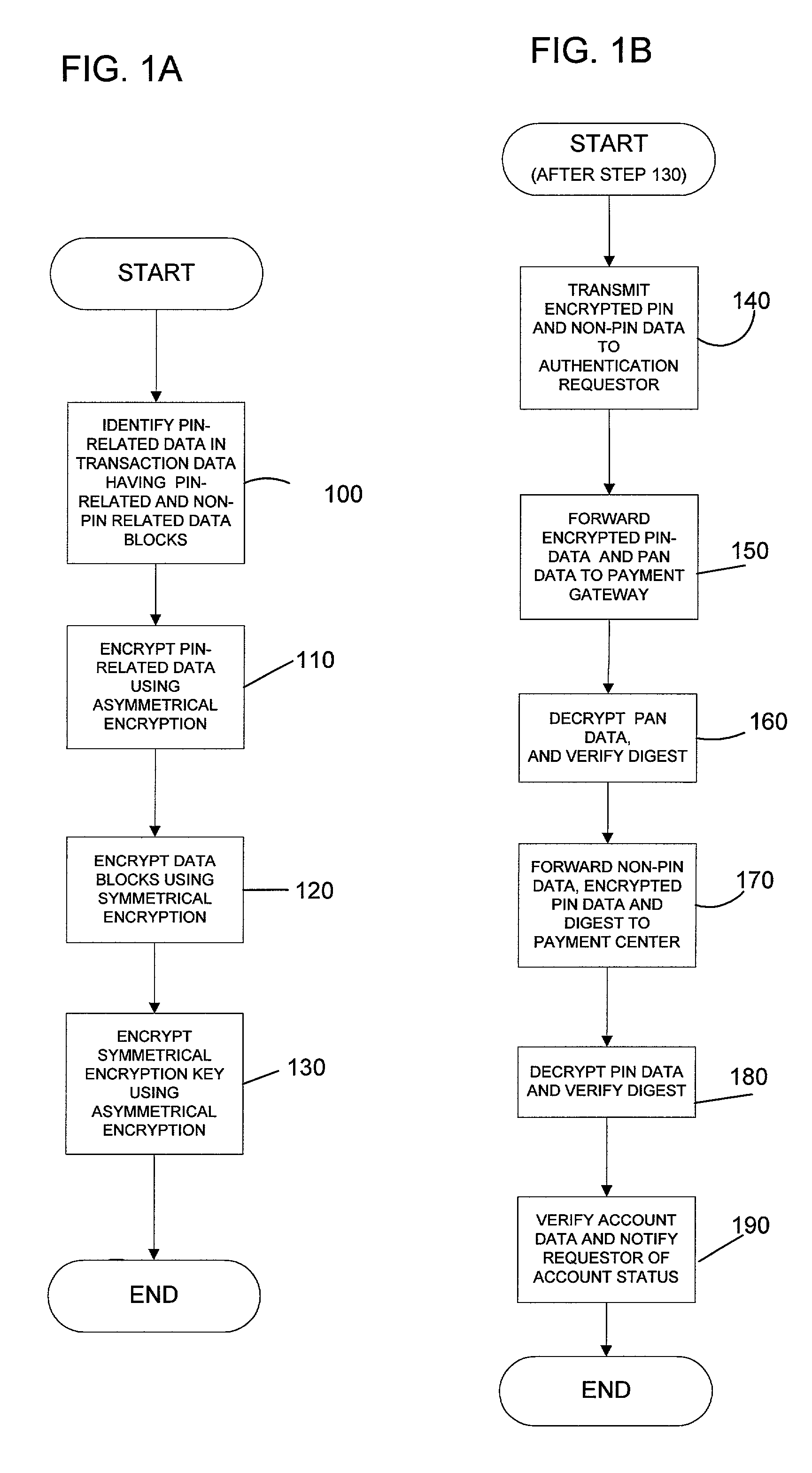
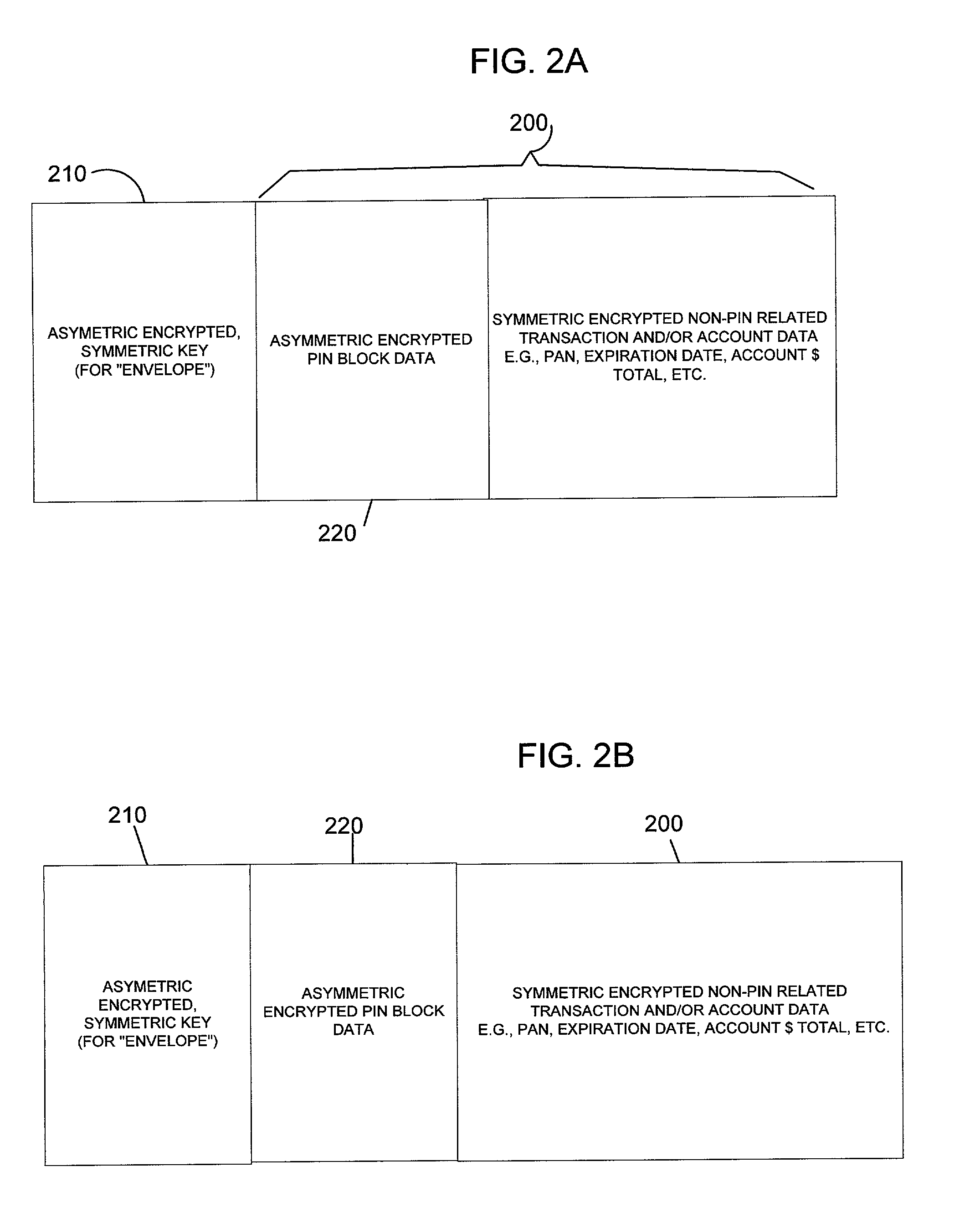
Asymmetric encrypted pin
InactiveUS7039809B1Improve securitySecure and efficientAcutation objectsDigital data processing detailsPersonal identification numberEncryption
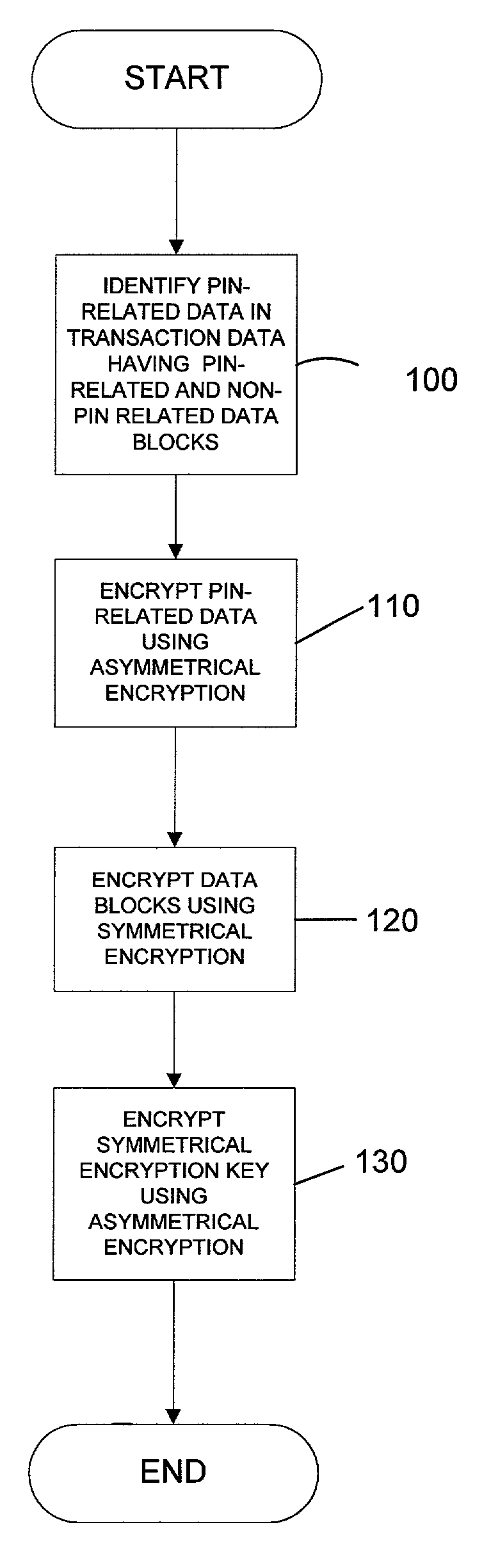
Secure protection and distribution of a personal identification number (PIN) is achieved by using a first encryption process only for PIN data and a second encryption process for non-PIN data. The first encryption process uses asymmetric encryption, where a public key is used for encryption of PIN data and a private key, held only by an authorizing agent, is used to decrypt the PIN data. The second encryption process uses a key which is available to an authentication requestor, such as merchants. A party seeking authentication of PIN data must forward the encrypted PIN data to an authorizing agent along with account data necessary to validate the PIN data. The authentication requestor is provided with a signal which is indicative of the verification status of the PIN data without being privy to the contents of the PIN data.
Owner:MASTERCARD INT INC
Video Surveillance Sharing System & Method
ActiveUS20120105632A1Simple setupEasy to controlColor television detailsClosed circuit television systemsVideo monitoringHuman–computer interaction
A surveillance system and method with at least one wireless input capture device ICD(s) and a corresponding digital input recorder (DIR) and / or another ICD, including the steps of providing base system; at least one user accessing the DIR via user interface either directly or remotely; the DIR and / or ICD searching for signal from the ICD(s) and establishing communication with them; providing DIR interface and setup options, for providing a secure surveillance system having wireless communication for monitoring a target environment.
Owner:SENSORMATIC ELECTRONICS CORP
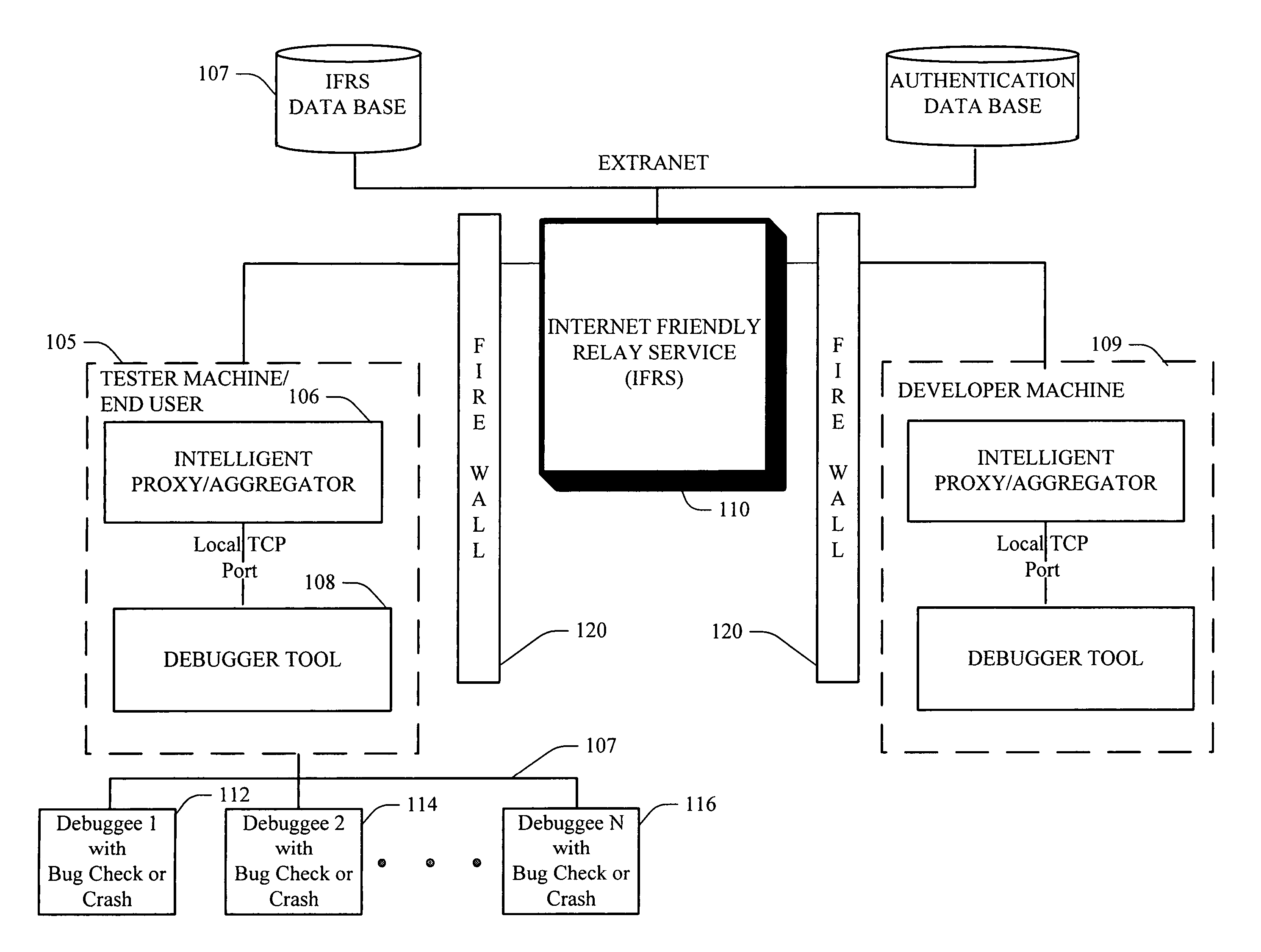
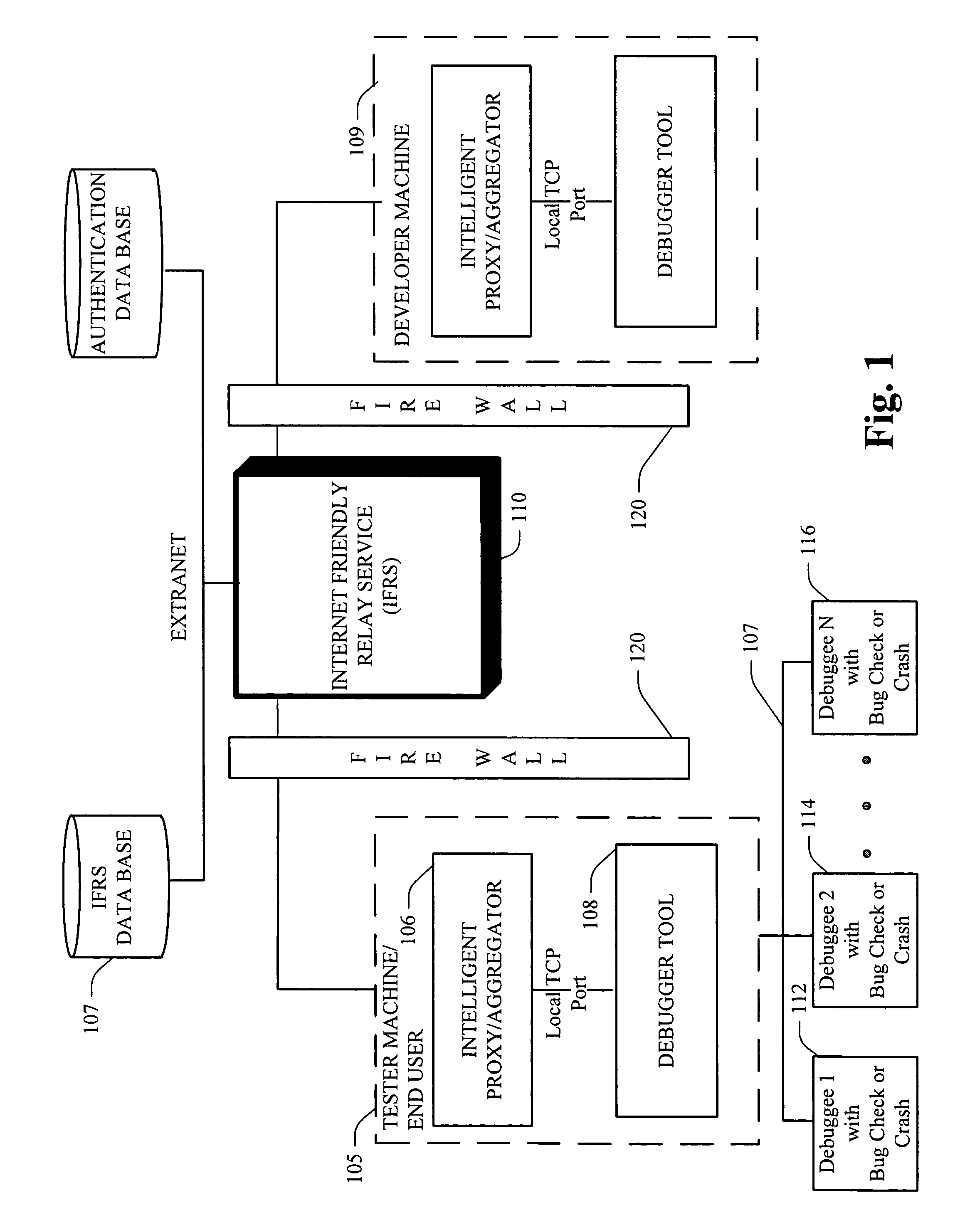
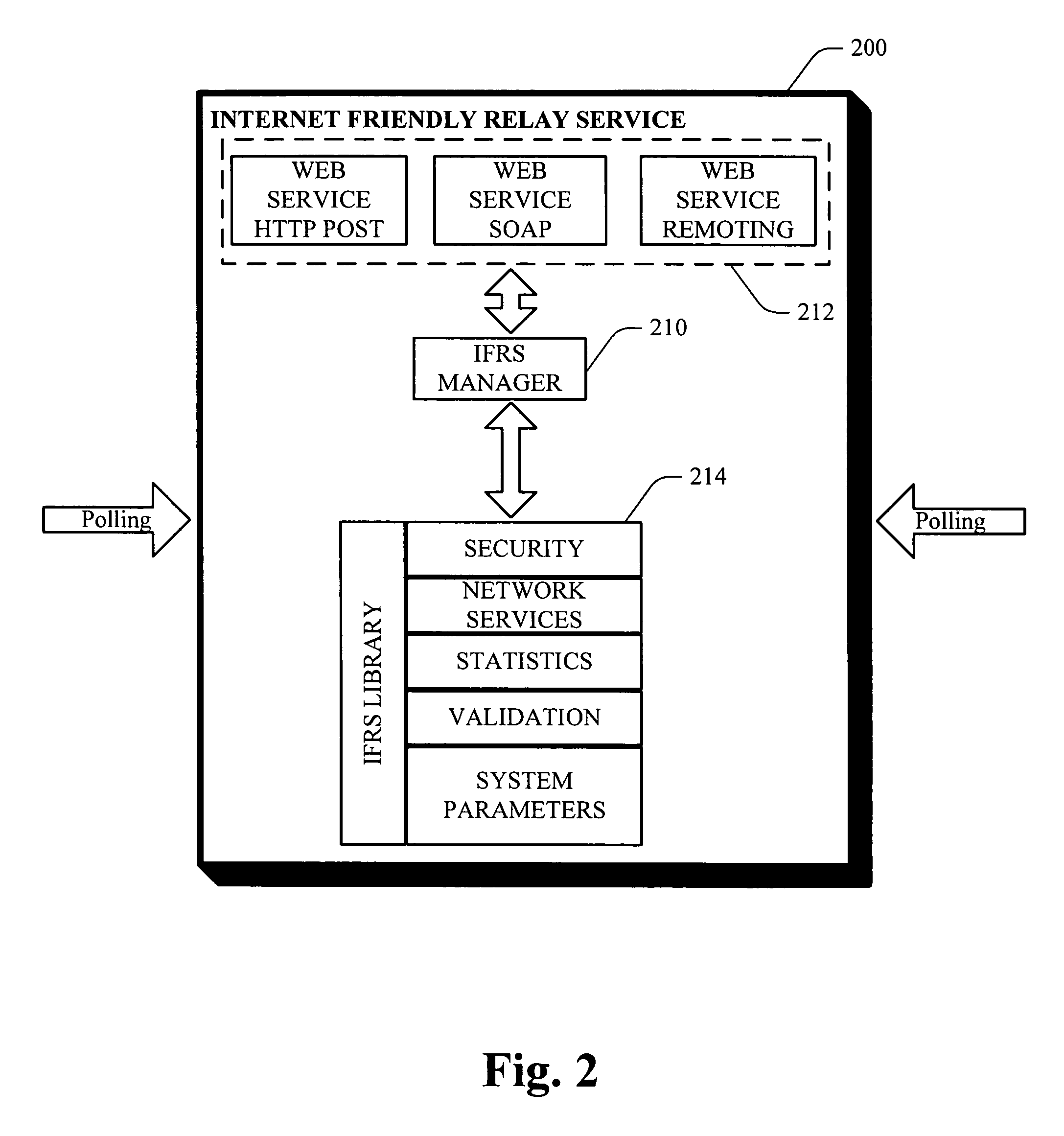
Windows remote debugger service
InactiveUS20060195894A1Improve balanceFacilitate regulationError detection/correctionMultiple digital computer combinationsClient-sideAuthorization
Systems and methodologies for a scalable remote debugging system that can debug machines positioned behind a firewall and thru the Internet, via employing an Internet Friendly Relay Service (IFRS). The IFRS can be positioned in a common reach location and provide a secure method of exchanging communication traffic over HTTP using SSL and security tokens in real time. Web server(s) of the IFRS can further employ an authorization and / or tracking system to verify connection of a client thereto, for debugging purposes.
Owner:MICROSOFT TECH LICENSING LLC
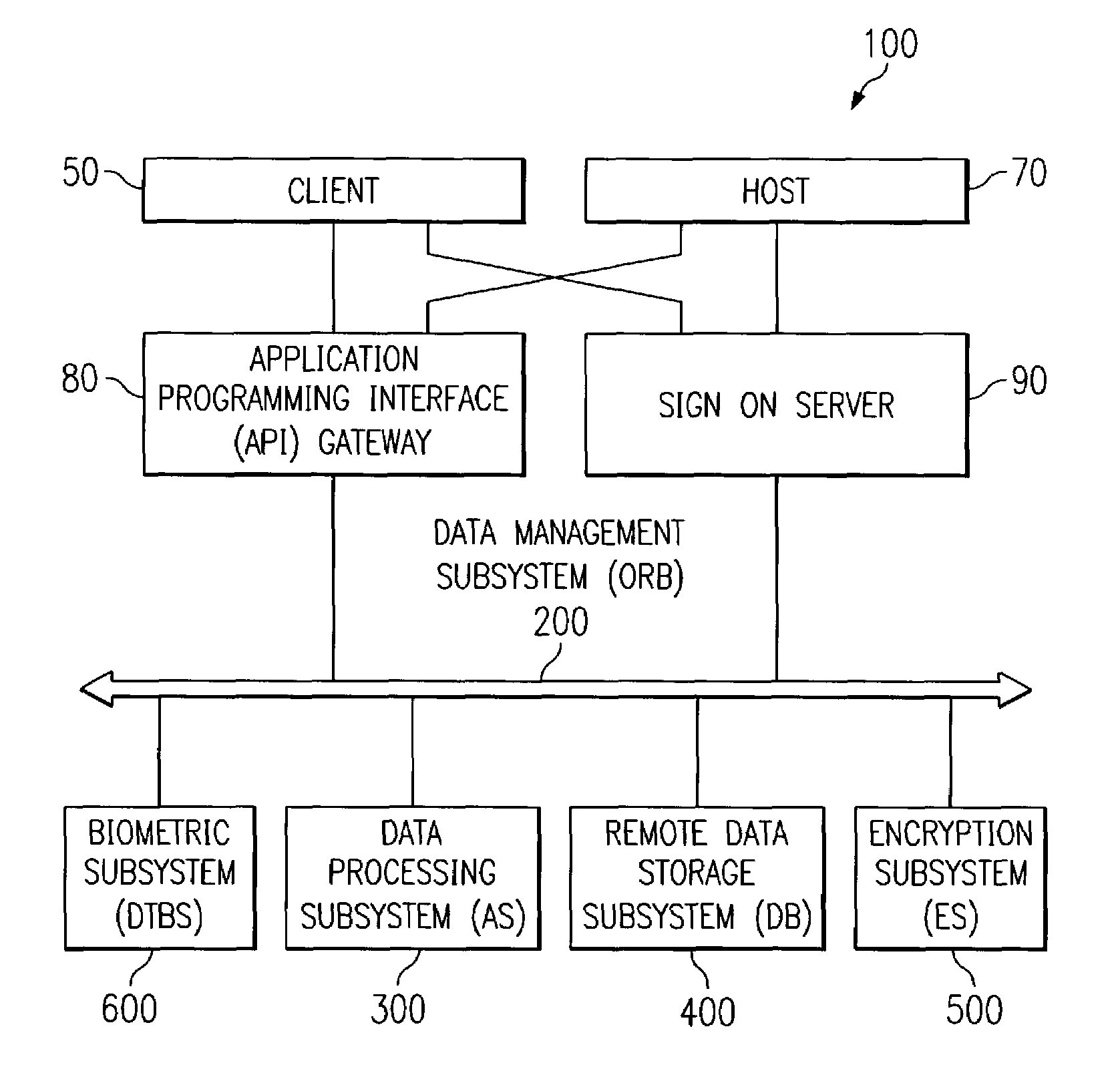
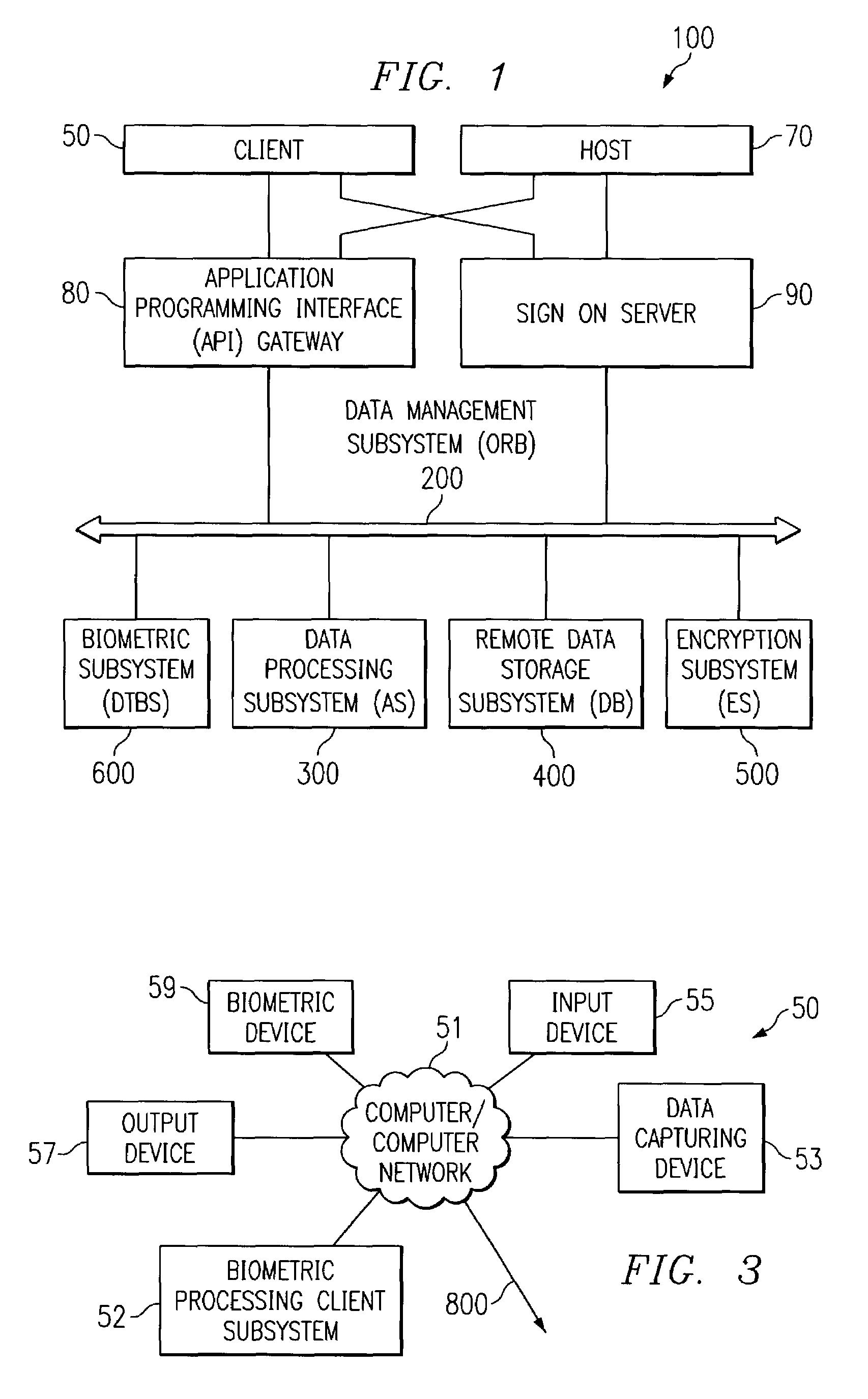
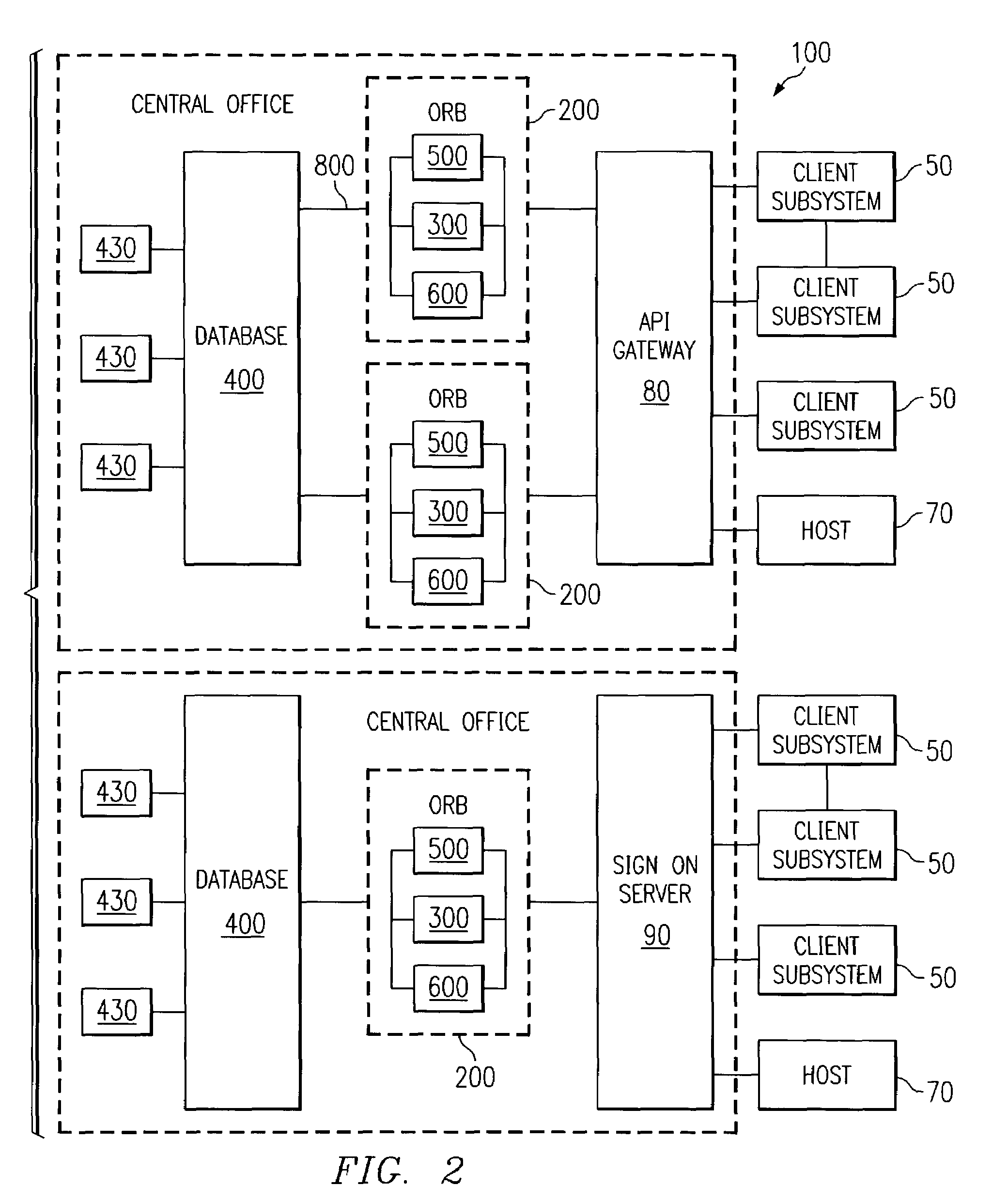
Biometrically enabled private secure information repository
InactiveUS7519558B2None of methods is secureCommunication securityFinanceCo-operative working arrangementsInformation repositoryBiometric data
A system for remote data acquisition and private and secure and authenticated, centralized processing and storage is disclosed called the DataTreasury™ Repository System. The DataTreasury™ Repository System provides a secure system for the storage and retrieval of data comprising personal information, financial information, and general information. The identity of the users are held private through the use of a biometric as the sole personal identifier. The system acquires transactional data at at least one remote locations, encrypts the data, transmits the encrypted data to a central location, transforms the data to a usable form, performs identification verification using biometric data, generates informative reports from the data and transmits the informative reports to the remote location(s), while maintaining privacy, security, and authenticity of the user's data and biometric. To ensure the complete security of the system, all data is re-encrypted while in storage, or when it is in a state of nonuse.
Owner:DATATREASURY CORP
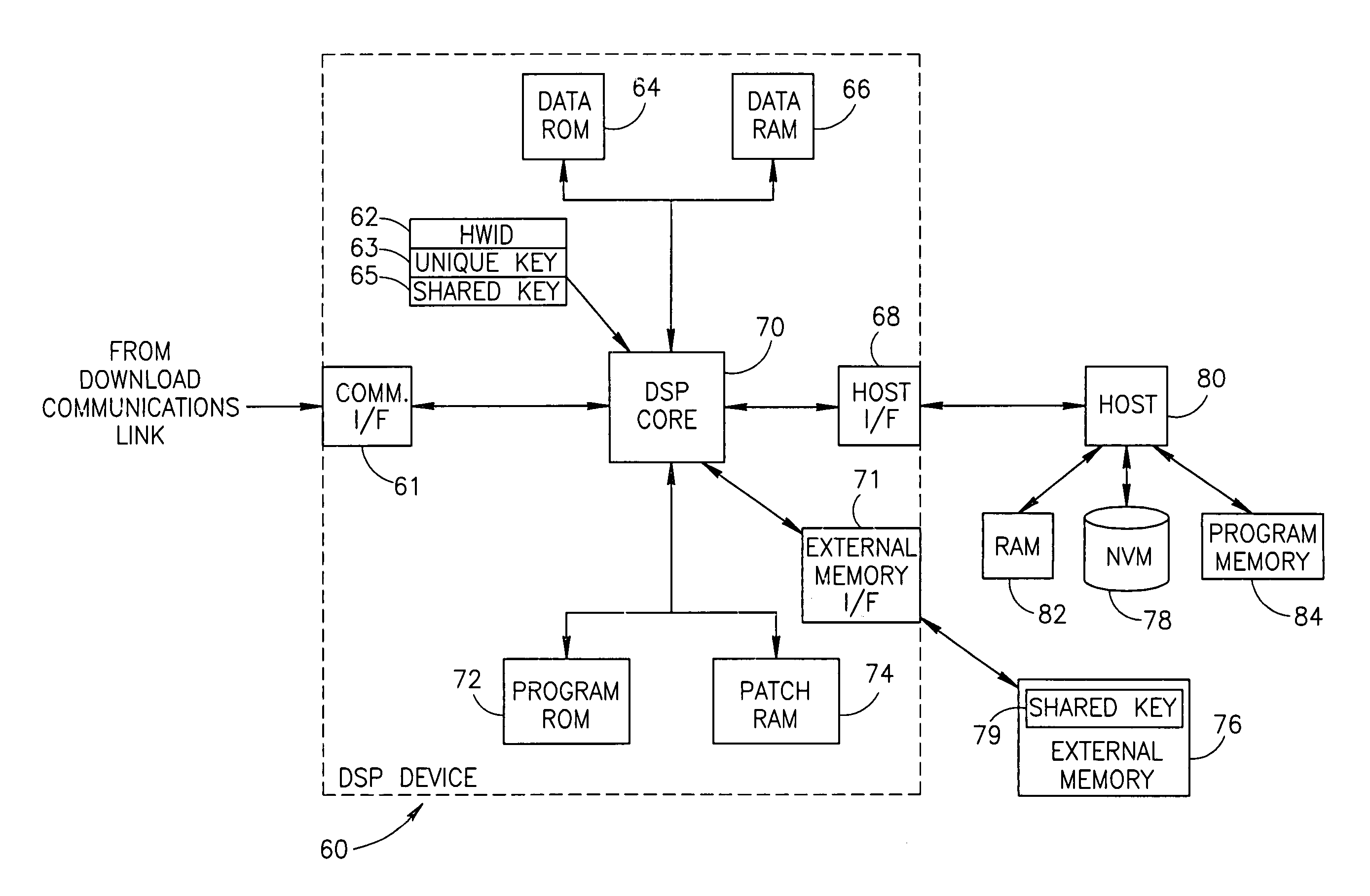
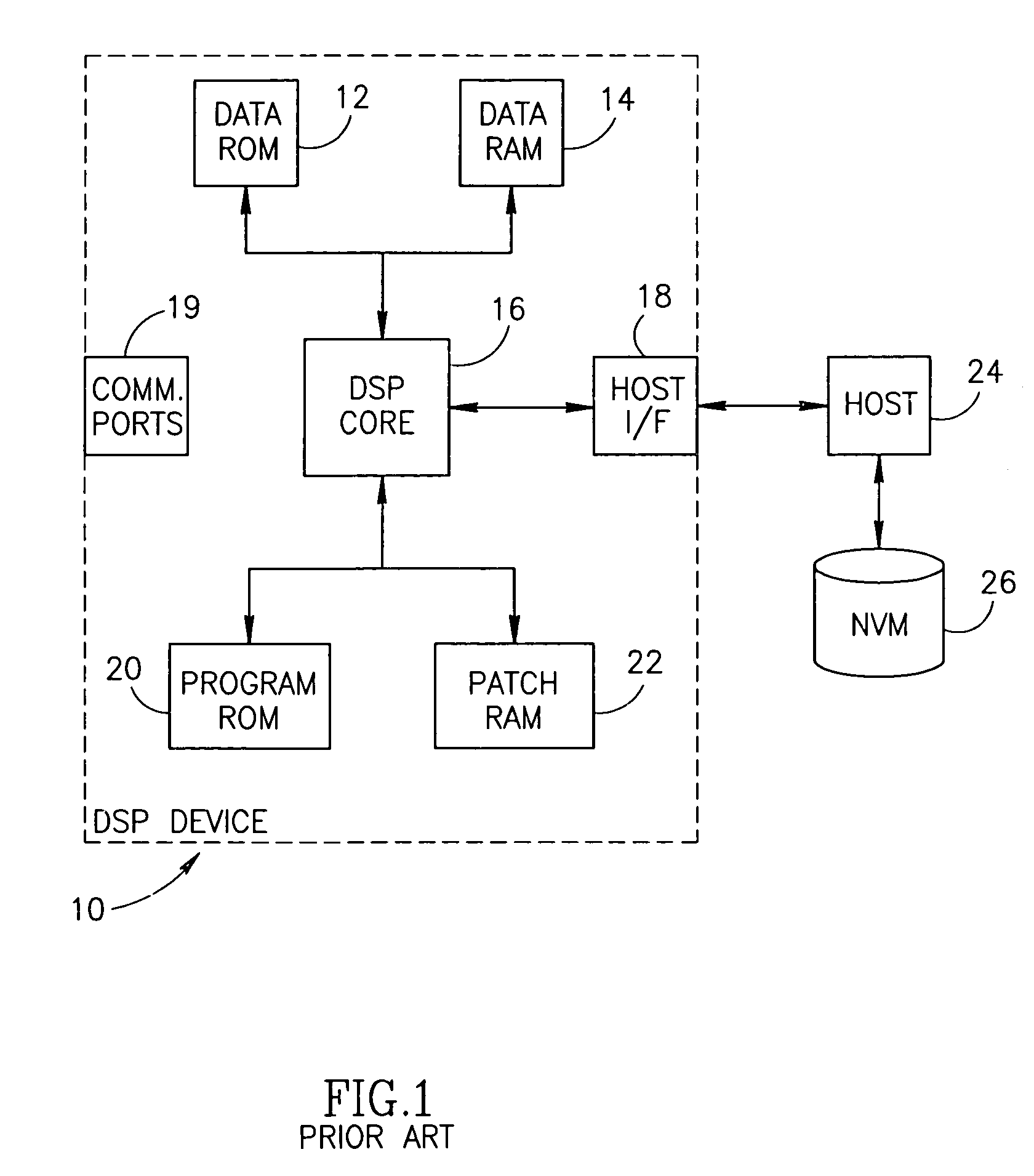
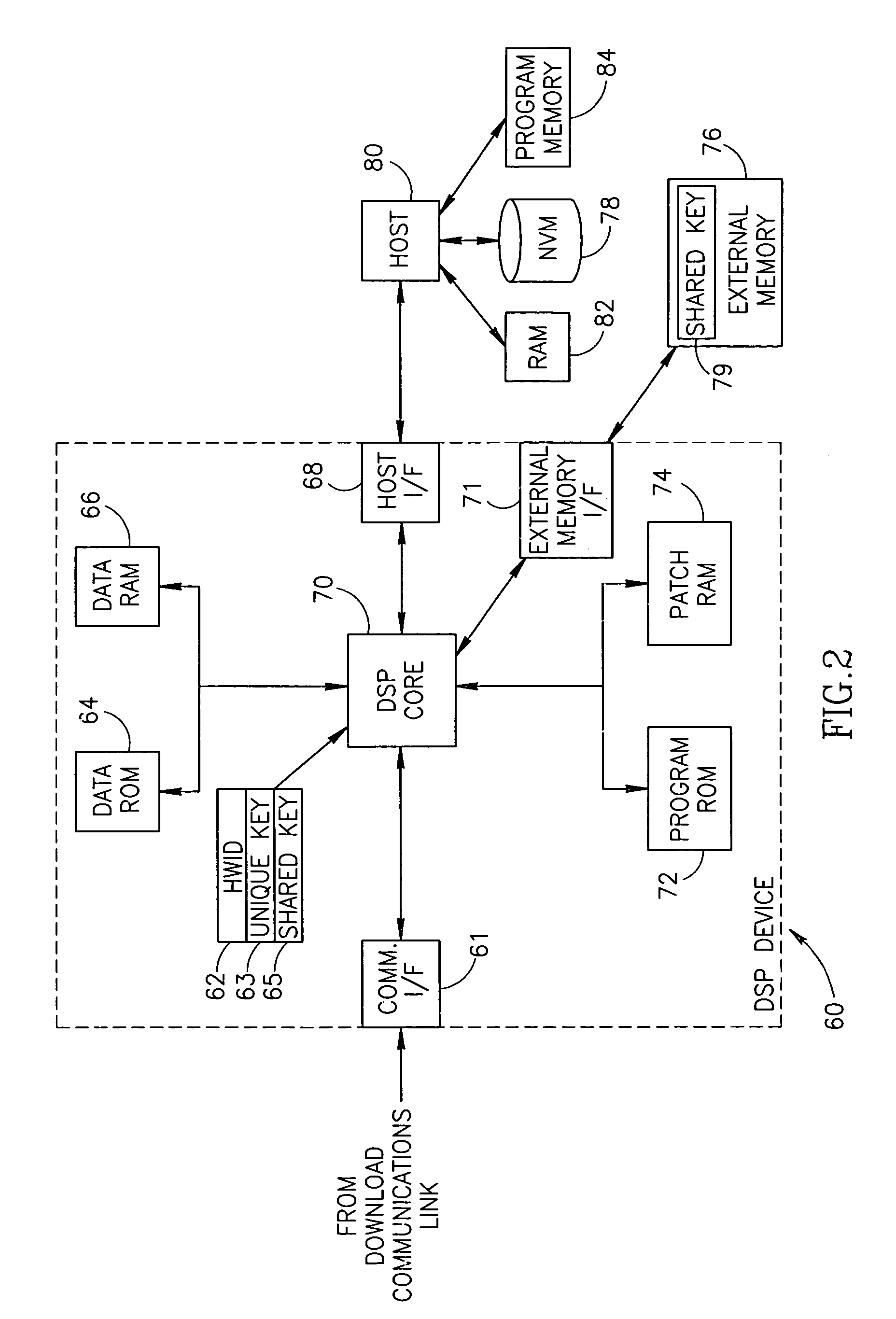
Apparatus for and method of securely downloading and installing a program patch in a processing device
InactiveUS6970565B1Reduce vulnerabilityNone of methods is secureSecret communicationPlatform integrity maintainanceSatellite radioTelecommunications link
A novel and useful apparatus for and method of securely downloading and installing a patch program in a processing device. Each processing device is assigned a unique key embedded therein during manufacture and has knowledge of a shared key. The program patch is encrypted using the shared key and transmitted over a communication link, such as a satellite radio link, to each device. The patch is decrypted using the shared key and re-encrypted using the unique key known only to the device itself. The re-encrypted patch program is stored in nonvolatile memory and upon reset of the device, the encrypted patch contents are read out of the nonvolatile memory, decrypted using the unique key and loaded into patch memory for execution by the processing device.
Owner:SIRIUS XM RADIO INC
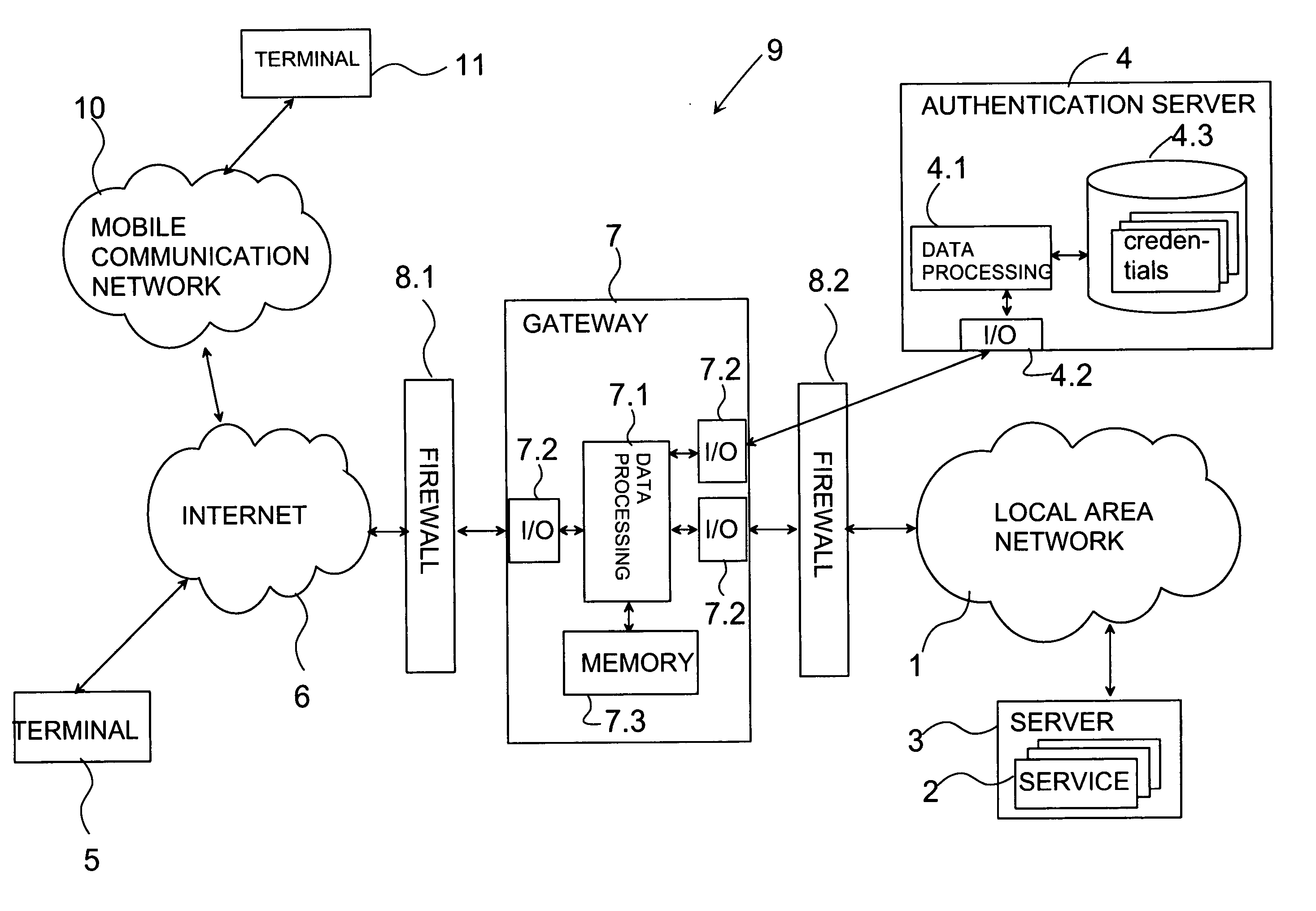
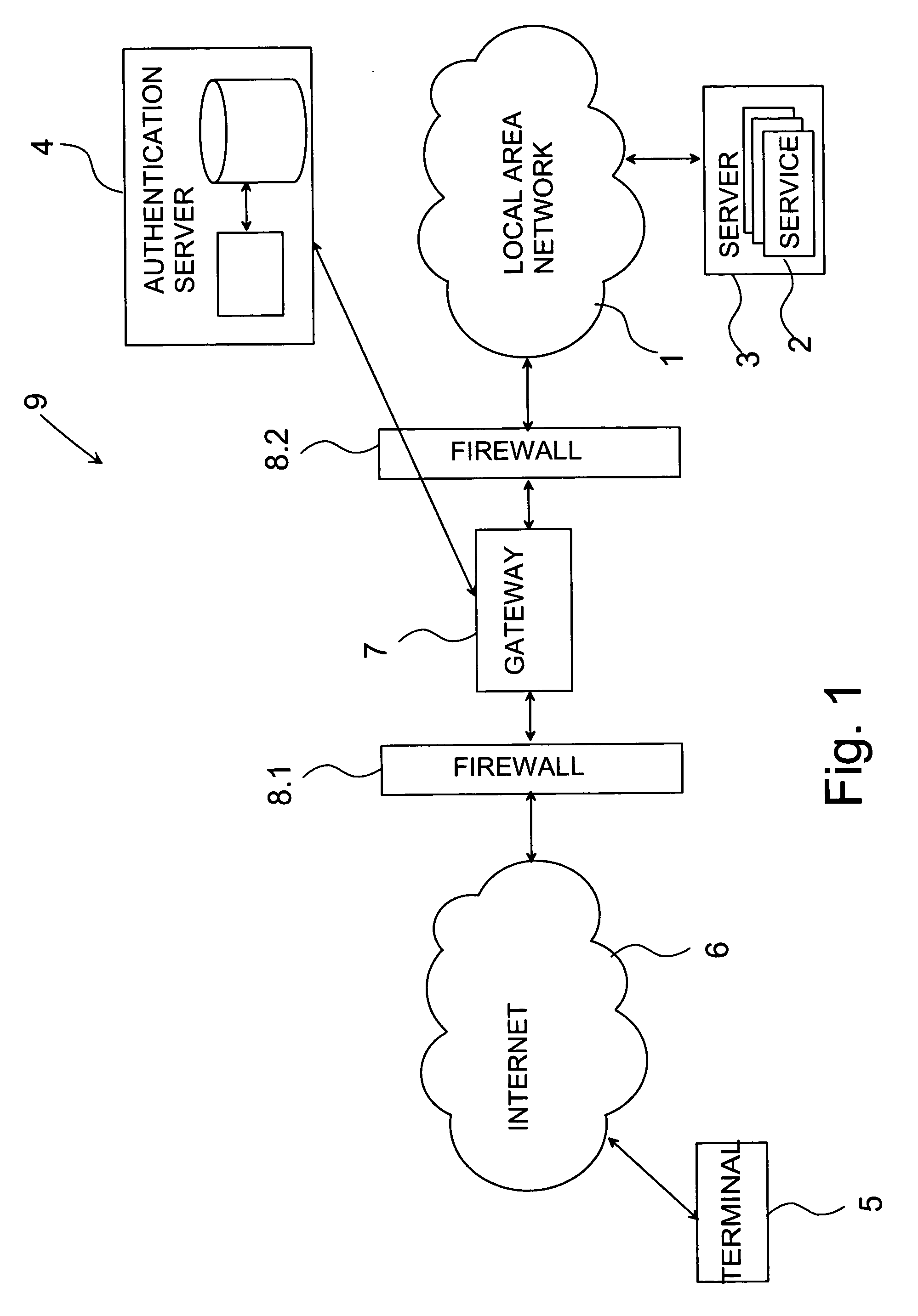
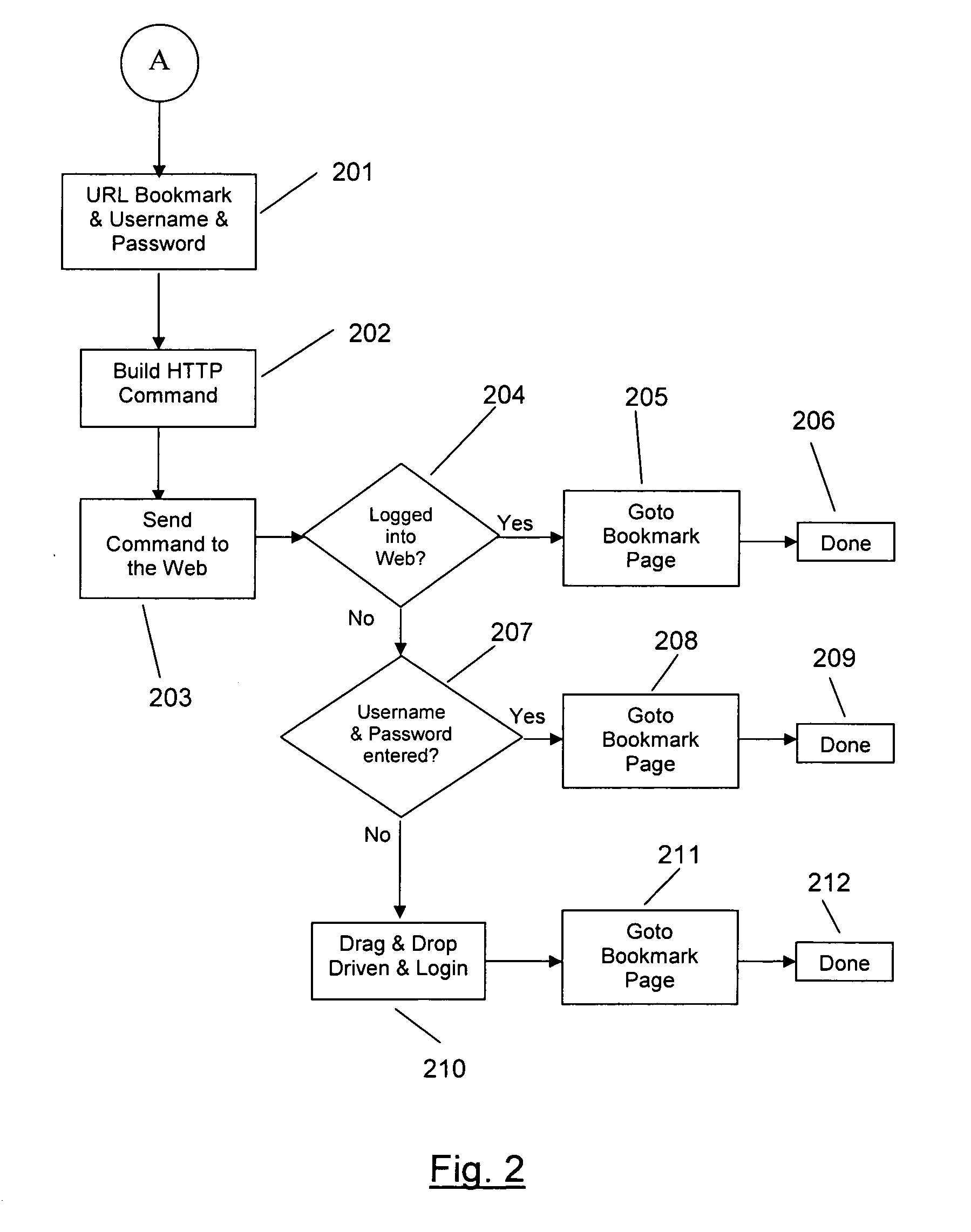
Providing credentials
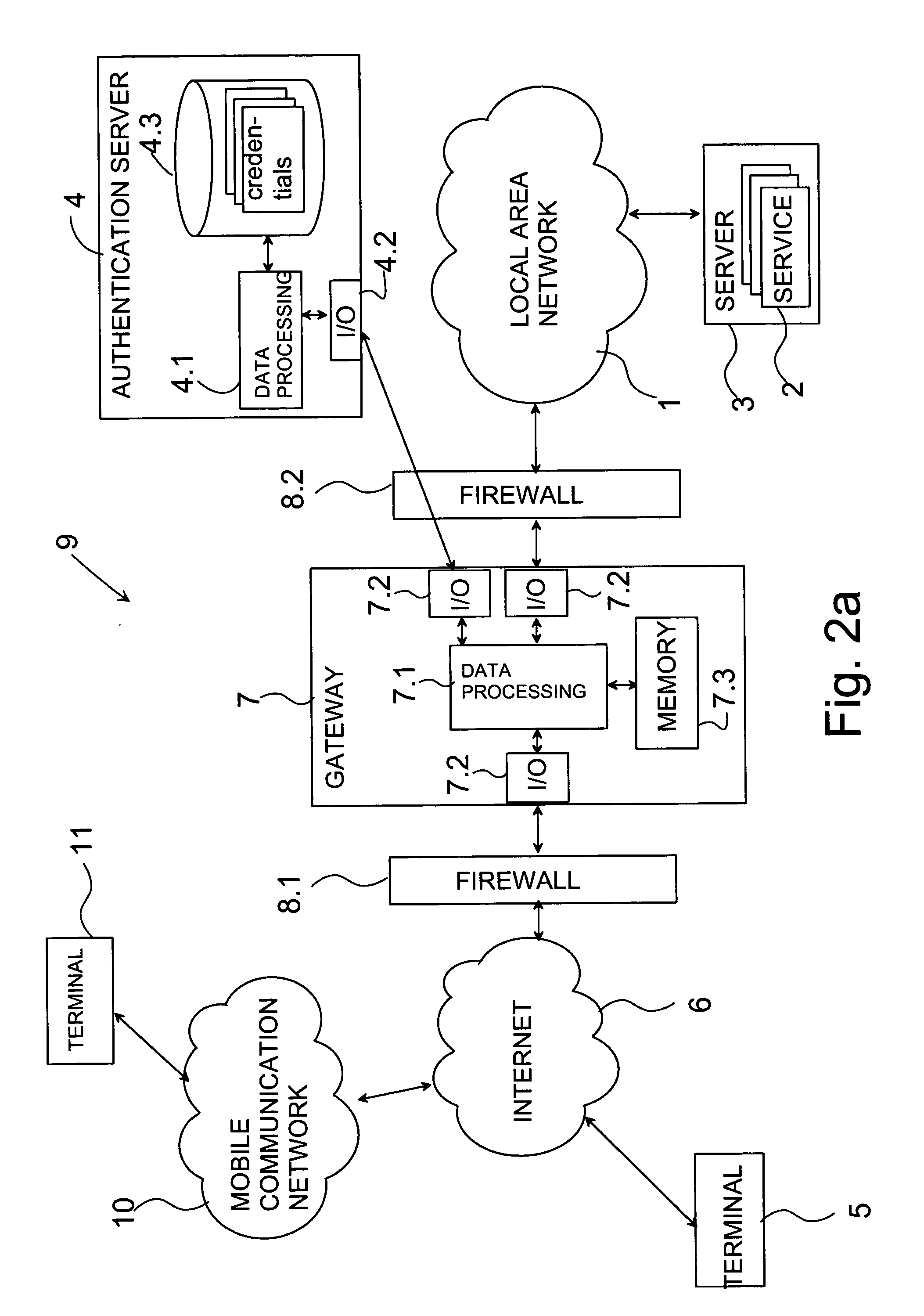
InactiveUS20050081066A1None of methods is secureIncrease speedDigital data processing detailsUser identity/authority verificationAuthentication serverUser identifier
The invention relates to a method and a system for providing credentials for using a service in a first data network. The user logs in to a second data network with a user identifier, which is transmitted from the second network via a gateway to an authentication server, where the user identifier is verified and information on a successful login is sent to the gateway. Information connected to the credentials is stored in connection with the authentication server, in which case the information connected to the credentials is transmitted from the authentication server to the gateway in the login phase. From the gateway the credentials are transmitted to the service in the first data network. The invention also relates to a authentication server to be used in the system, and a gateway.
Owner:NOKIA CORP
Document transmission techniques IV
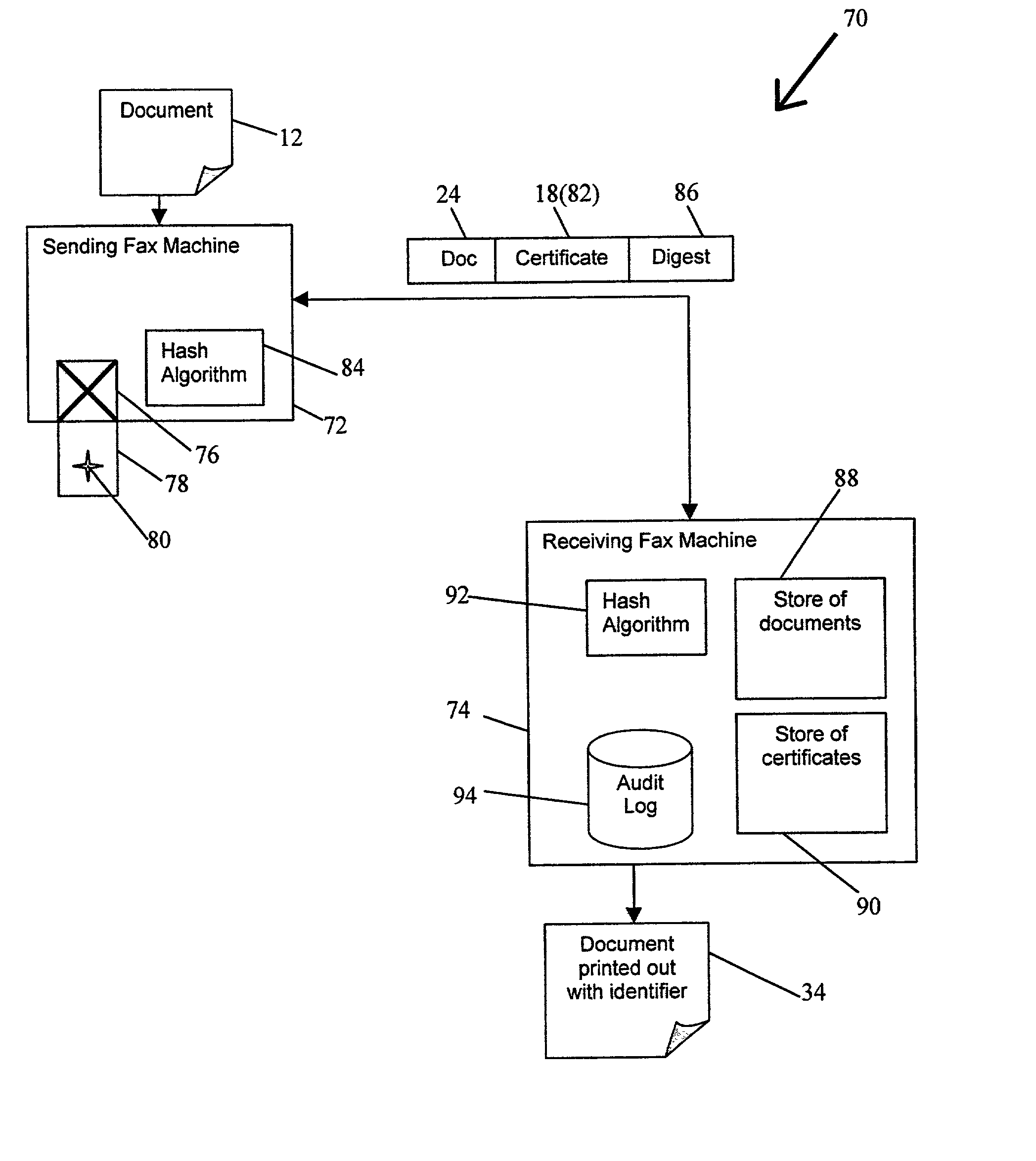
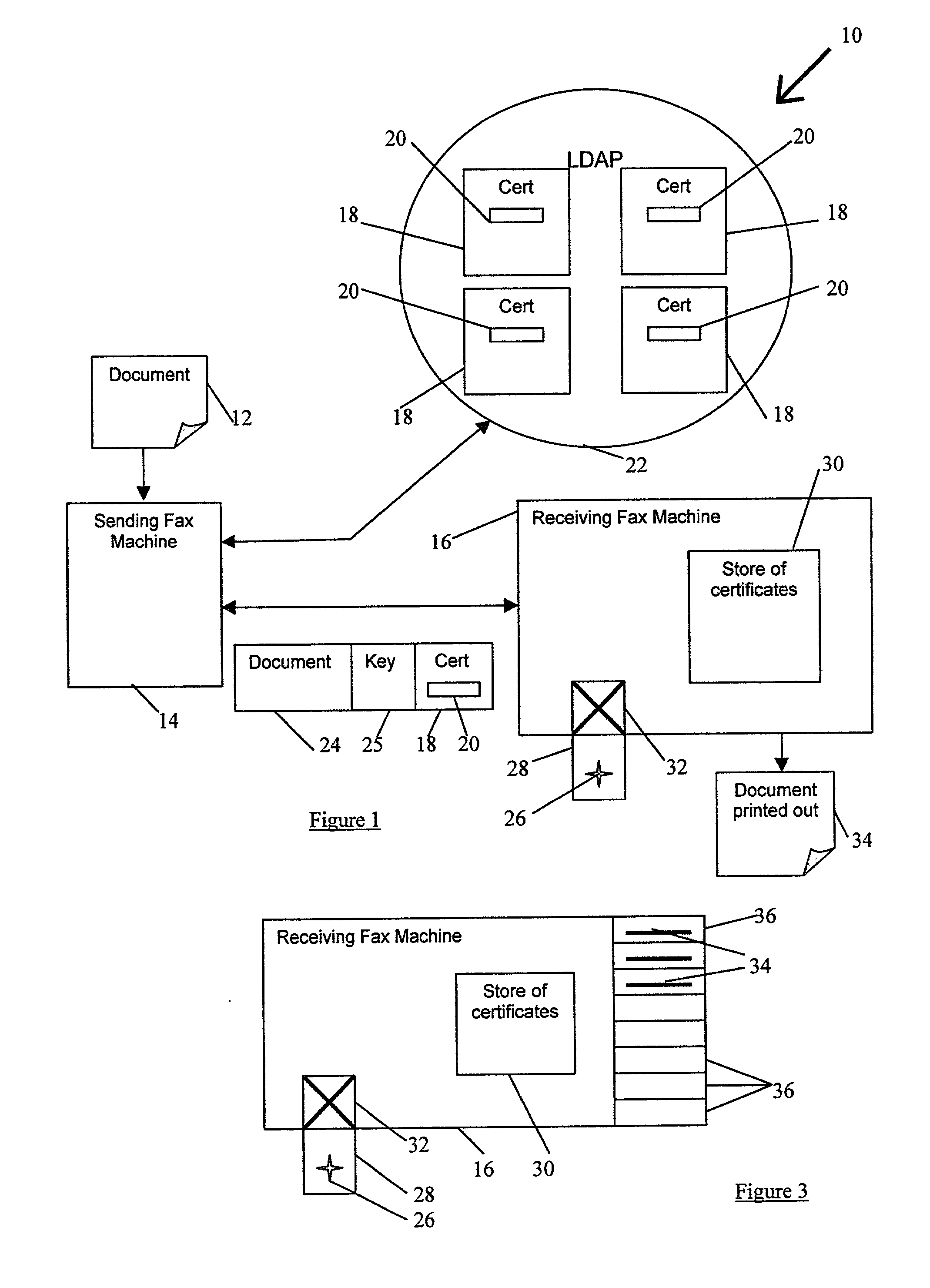
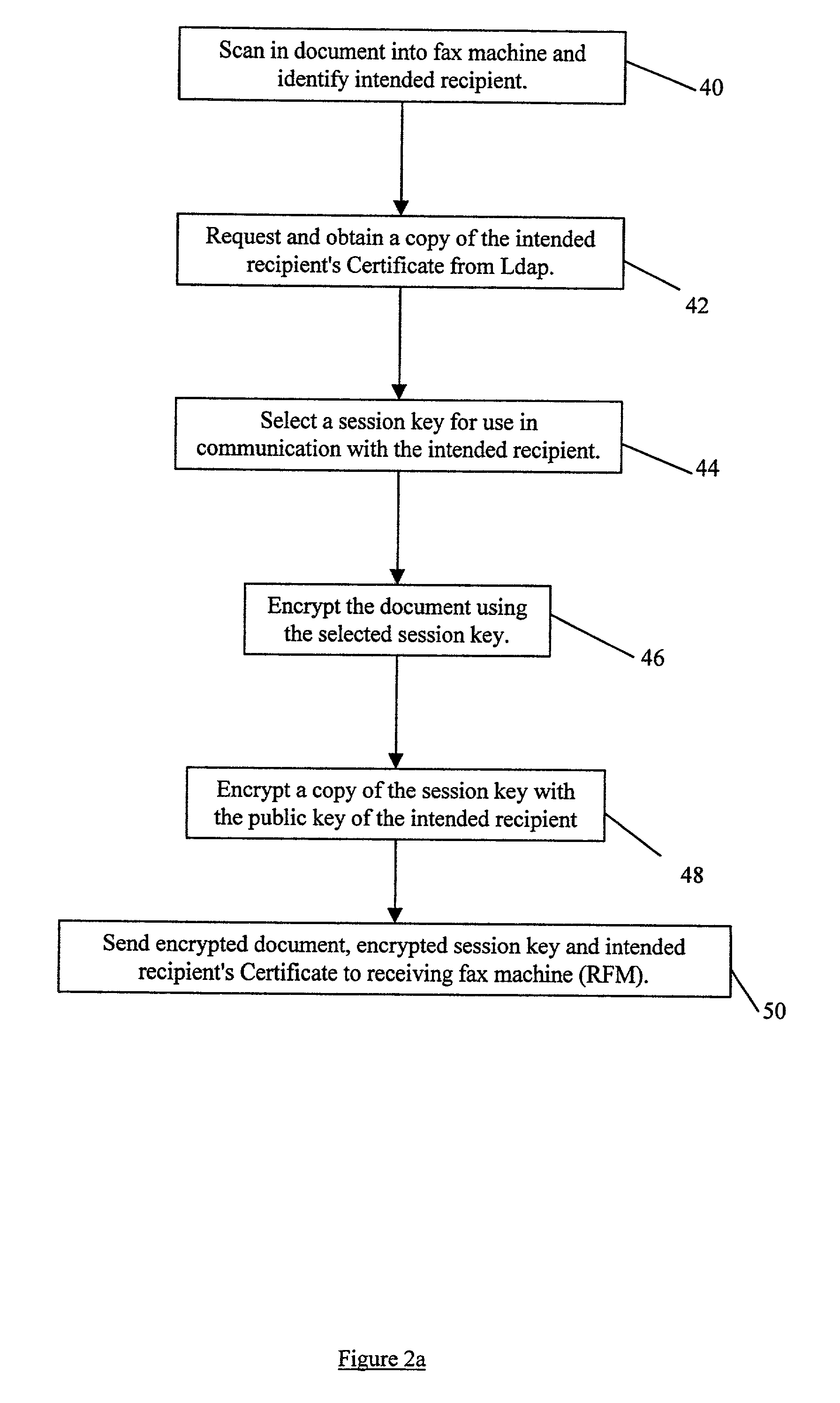
InactiveUS20020026583A1None of methods is secureConfidenceUser identity/authority verificationComputer securityFile transfer
A method of determining the authenticity of a digital document sent by an unknown sender. The method comprises receiving a digital document and an encrypted digest of the document created by the sender using a hash algorithm. The digest is encrypted using a first token, such as a private key, of the sender. The method also comprises obtaining a second token, such as a public key, relating to the first token, decoding the encrypted digest using the second token, using a hash algorithm to create a digest of the document; and comparing the decrypted received digest with the newly created digest to determine the authenticity of the sender and the document. The receiving step may comprise receiving a digital certificate of the sender within which the second token is contained as part of the sender's digital certificate. Also the validity of the sender's certificate can be checked on-line.
Owner:HEWLETT PACKARD DEV CO LP
Remotely configured media device
InactiveUS20080155129A1None of methods is secureMetadata multimedia retrievalPayment architectureVideo playerDatabase server
A portable wireless communications subscriber audio and / or video player apparatus and system and method for selecting, requesting, downloading, and playing audio and / or video data content files from an Internet-based database server. The wireless link is preferably implemented in accordance with the WiFi protocol, which allows connectivity to the Internet by being in proximity with a local base station or WiFi hotspot (i.e., publicly available local wireless access hub connected to the Internet). The portable wireless communications subscriber audio and / or video player apparatus and system preferably include a security means for monitoring and blocking unauthorized use of the player apparatus and system. The player apparatus further preferably has the capability to communicate with other neighboring player apparatus for the purpose of exchanging content data files, playlists and personal messages.
Owner:SANDISK TECH LLC
Audio visual player apparatus and system and method of content distribution using the same
InactiveUS20080163302A1None of methods is secureTelevision system detailsDigital data information retrievalContent distributionThe Internet
A system is presented providing content to a plurality of handheld devices (including musical selections). The devices can access a server over the Internet via a WIFI or other similar wireless interconnection and can download songs requested by a user from the server or from other users using, e,g, a P2P protocol. All downloads are governed by applicable DRM rules. Content and playlists may also be pushed by a server from other sources and means including, e.g., podcasting, based on predetermined rules, favorite preferences of users, and other criteria.
Owner:SANDISK CORP
Audio visual player apparatus and system and method of content distribution using the same
InactiveUS20080162655A1None of methods is secureDigital data information retrievalElectronic editing digitised analogue information signalsContent distributionThe Internet
A system is presented providing content to a plurality of handheld devices (including musical selections). The devices can access a server over the Internet via a WIFI or other similar wireless interconnection and can download songs requested by a user from the server or from other users using, e,g, a P2P protocol. All downloads are governed by applicable DRM rules. Content and playlists may also be pushed by a server from other sources and means including, e.g., podcasting, based on predetermined rules, favorite preferences of users, and other criteria.
Owner:SANDISK TECH LLC
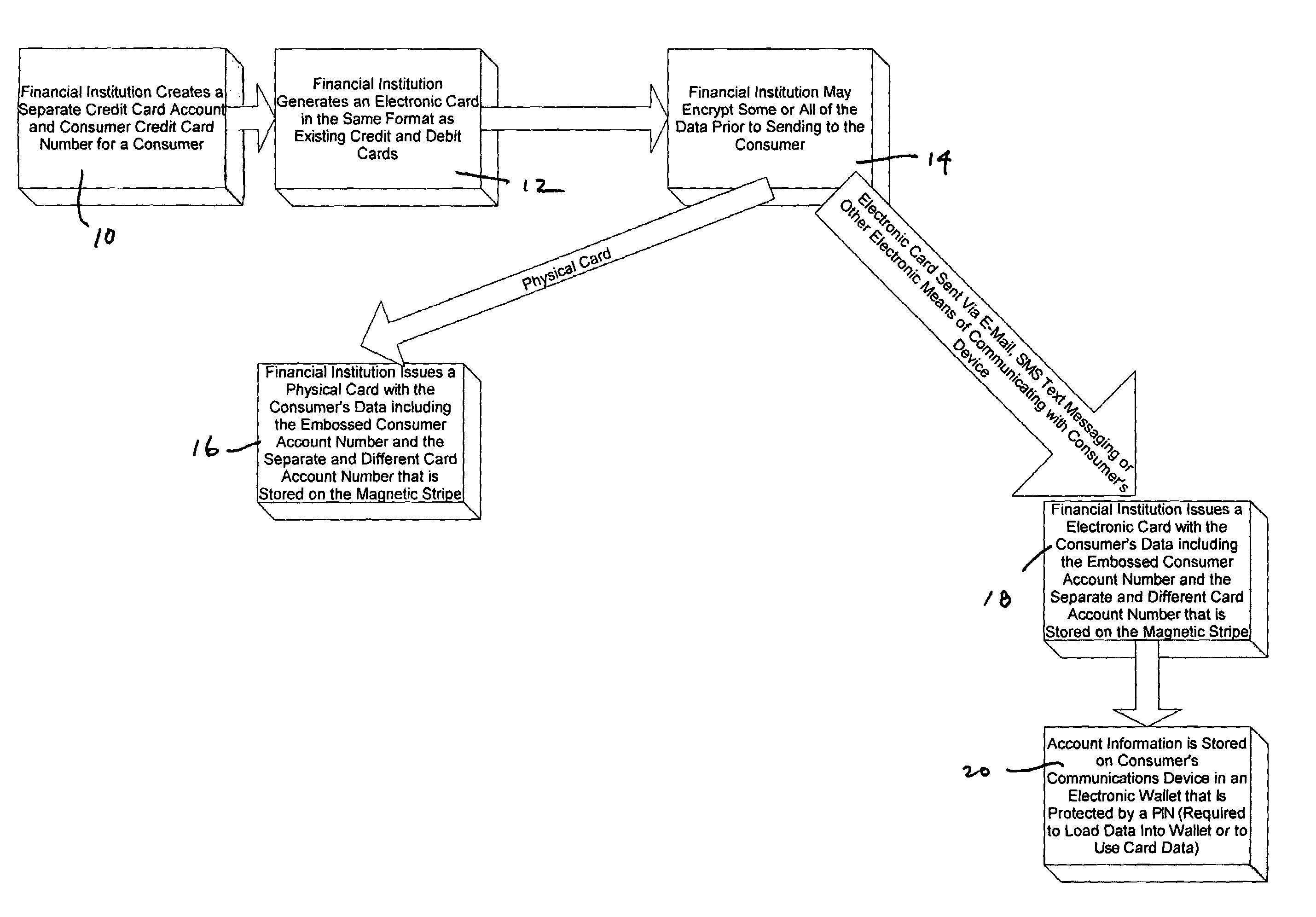
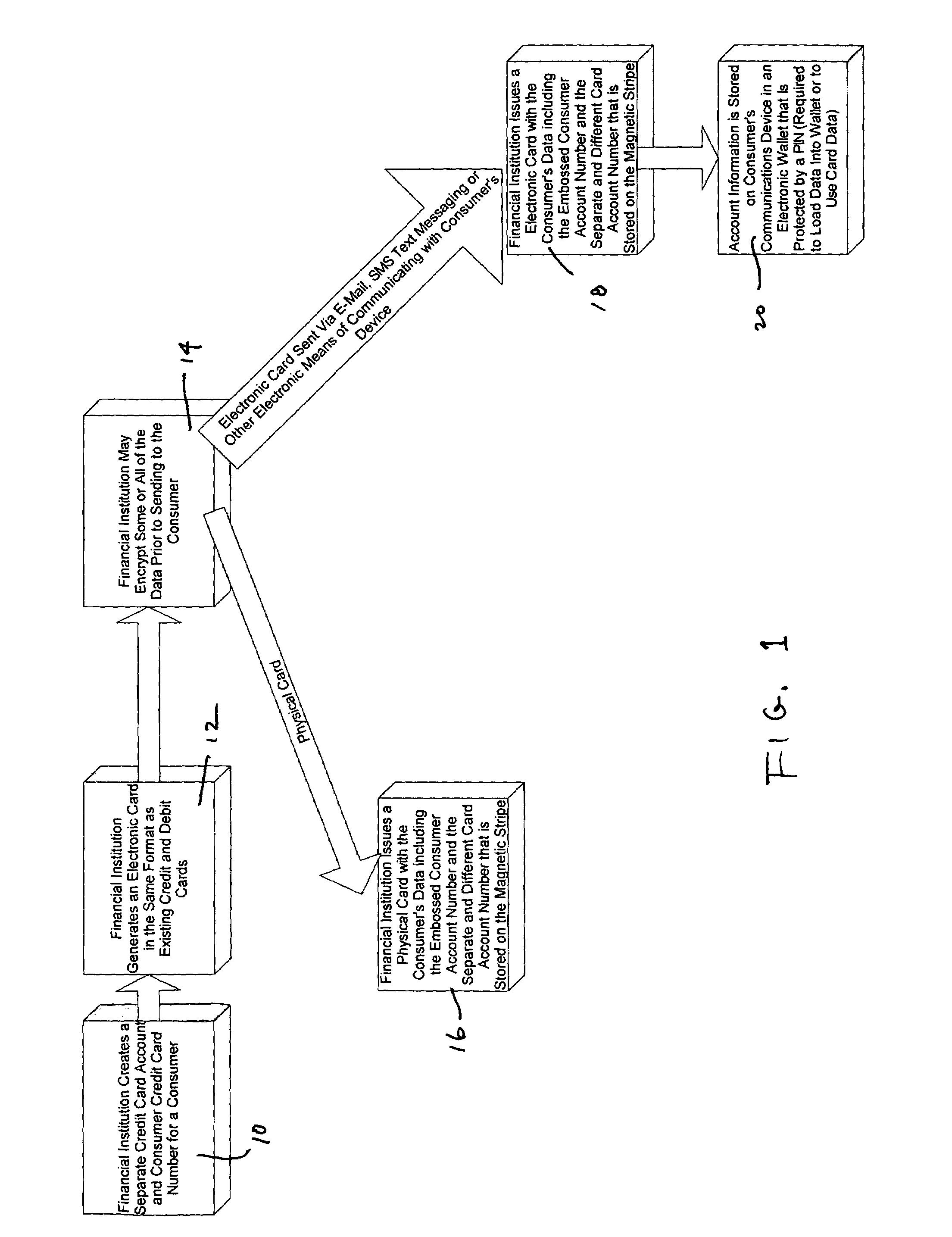
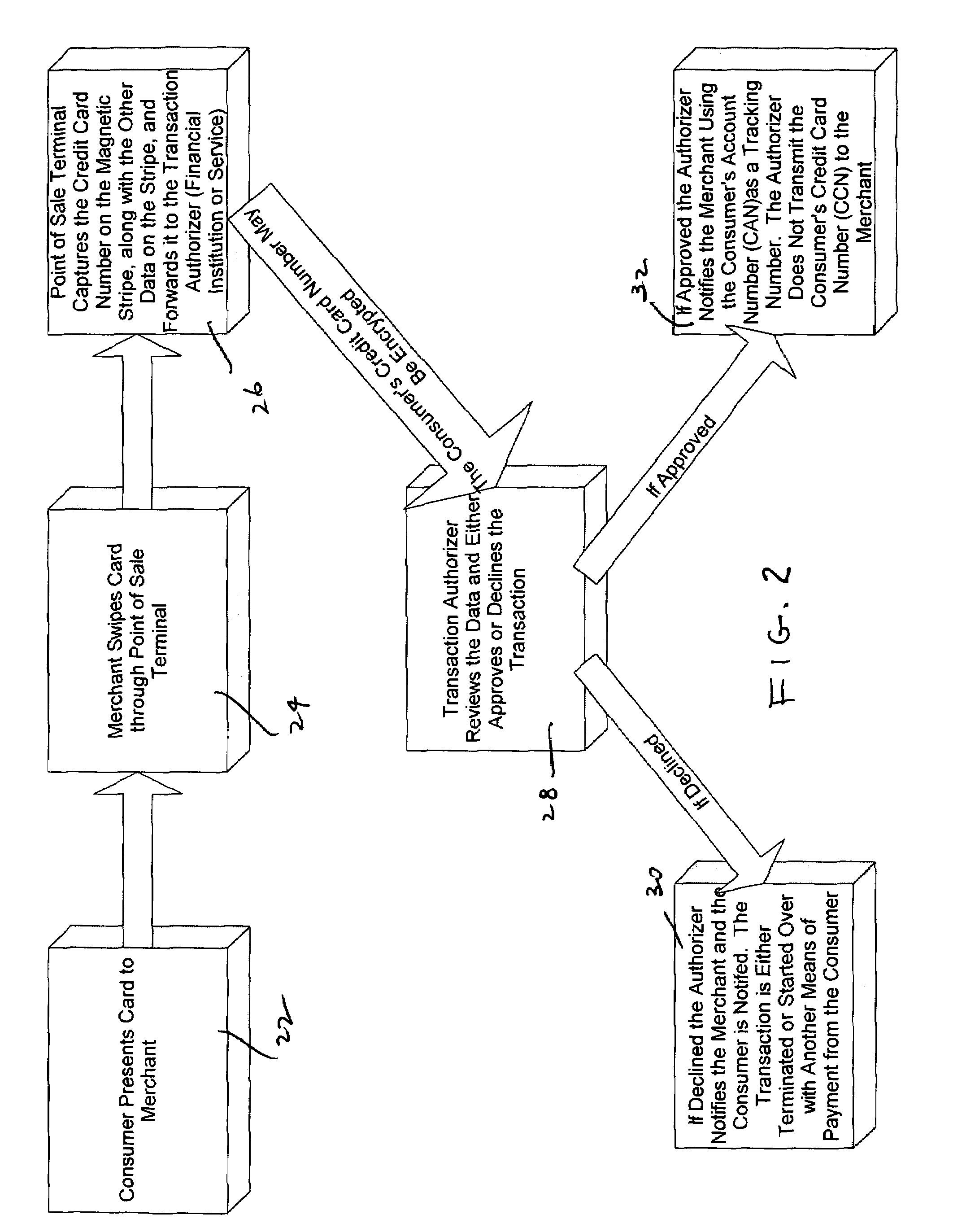
System for increasing the security of credit and debit cards transactions
A system for facilitating a commercial transaction by a consumer includes a card or electronic storage device which includes a first number for identifying a financial account of the consumer and a second number, related to the first number, for use in authorizing a transaction involving the financial account of the consumer.
Owner:ADVANCED TRANSACTIONS LLC
System sharing content
InactiveUS20080155634A1None of methods is secureMetadata multimedia retrievalPayment architectureVideo playerDatabase server
A portable wireless communications subscriber audio and / or video player apparatus and system and method for selecting, requesting, downloading, and playing audio and / or video data content files from an Internet-based database server. The wireless link is preferably implemented in accordance with the WiFi protocol, which allows connectivity to the Internet by being in proximity with a local base station or WiFi hotspot (i.e., publicly available local wireless access hub connected to the Internet). The portable wireless communications subscriber audio and / or video player apparatus and system preferably include a security means for monitoring and blocking unauthorized use of the player apparatus and system. The player apparatus further preferably has the capability to communicate with other neighboring player apparatus for the purpose of exchanging content data files, playlists and personal messages.
Owner:SANDISK TECH LLC
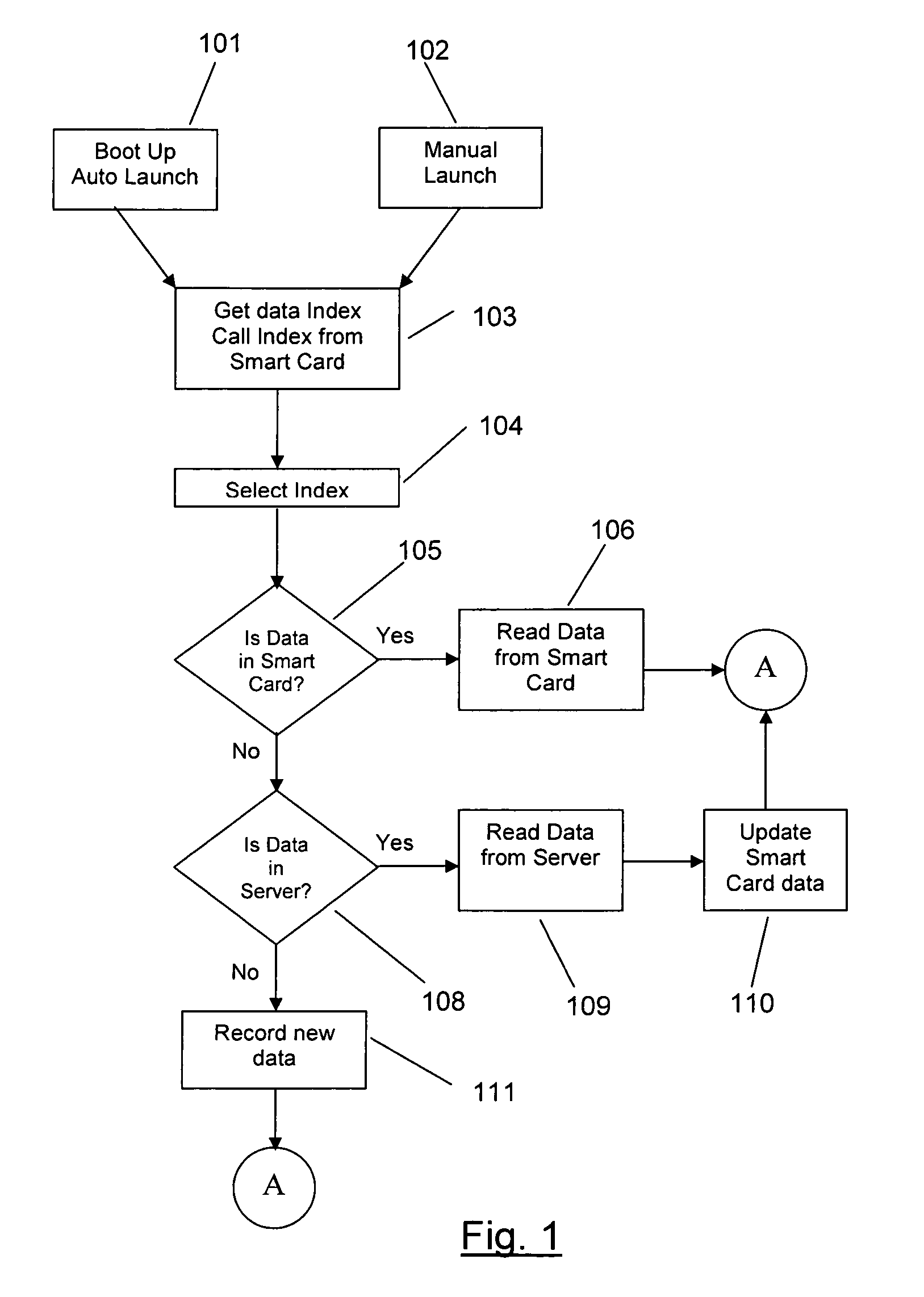
Smart card security information configuration and recovery system
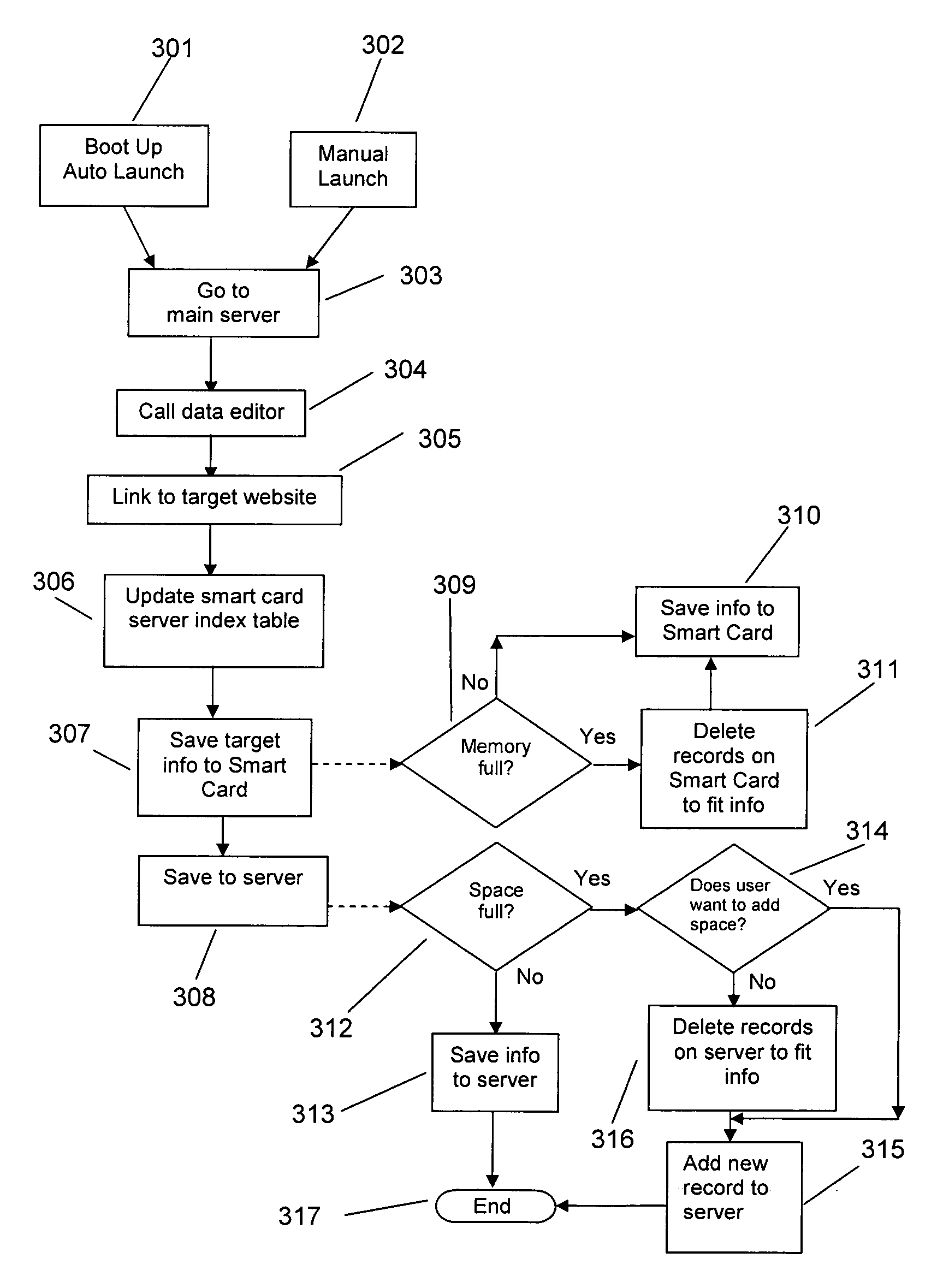
InactiveUS6981152B2None of methods is secureEasy to createUser identity/authority verificationUnauthorized memory use protectionWeb siteCMOS
A smart card security information configuration and recovery system provides a secure Web site and server that allows smart card users to easily create and obtain smart cards and passwords. The client program accesses the smart card inserted into the client computer and retrieves the smart card's ID and other user and system information and sends them to the server which creates an access key. The access key and the smart card ID are stored in the client computer's CMOS or non-volatile memory for boot-up access. The client computer will boot only if the proper smart card is installed or the proper access key is entered when the smart card is unavailable. If the user loses his smart card, then he must gain access to his computer through the access key which the server issues after the user logs in. When the user wants to get a new smart card issued, he logs onto the server which is sent the new smart card's ID that replaces the previous smart card's ID and the server generates a new access key and stores it. The new access key and the smart card's ID are stored in the client computer's CMOS or non-volatile memory for boot access.
Owner:O2 MICRO INT LTD
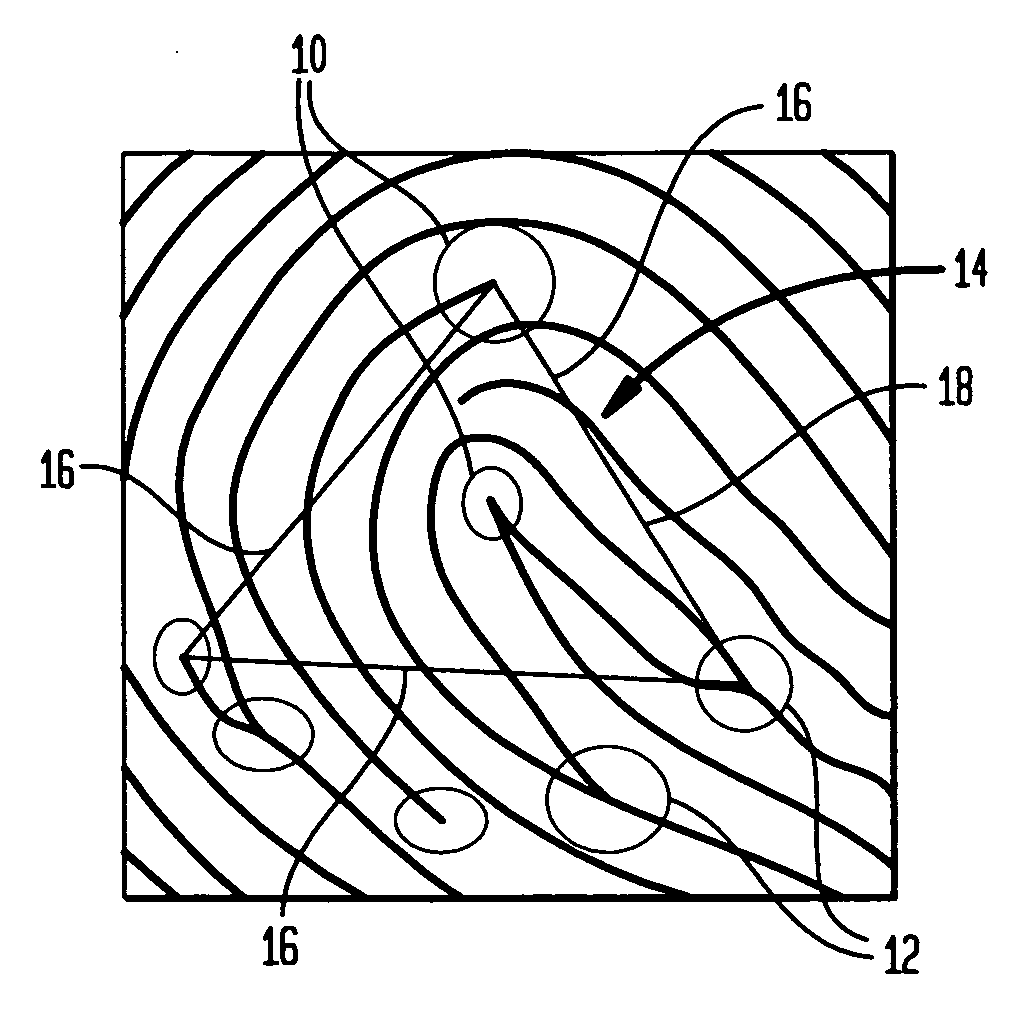
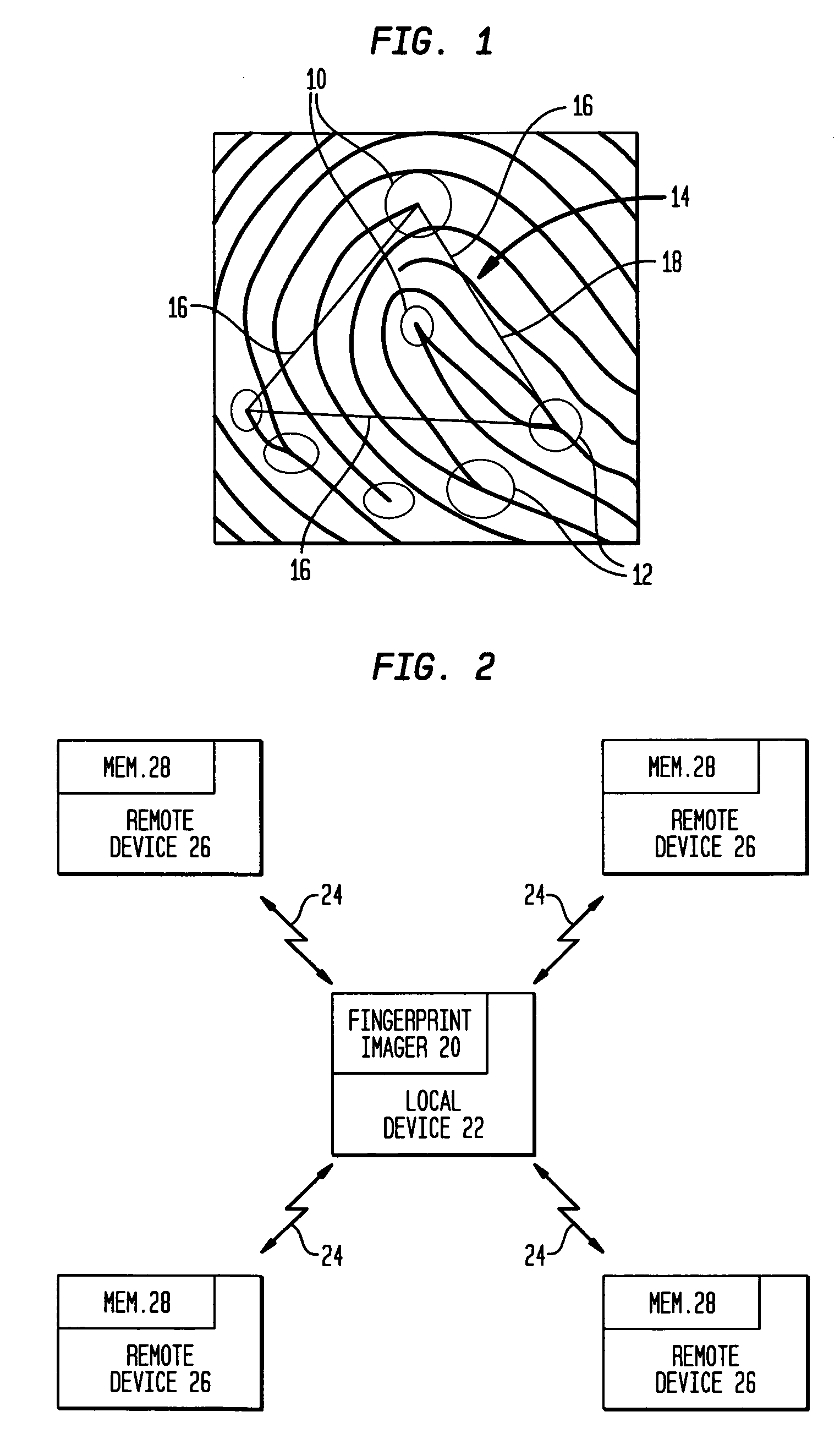
Minutiae fingerprint transactions
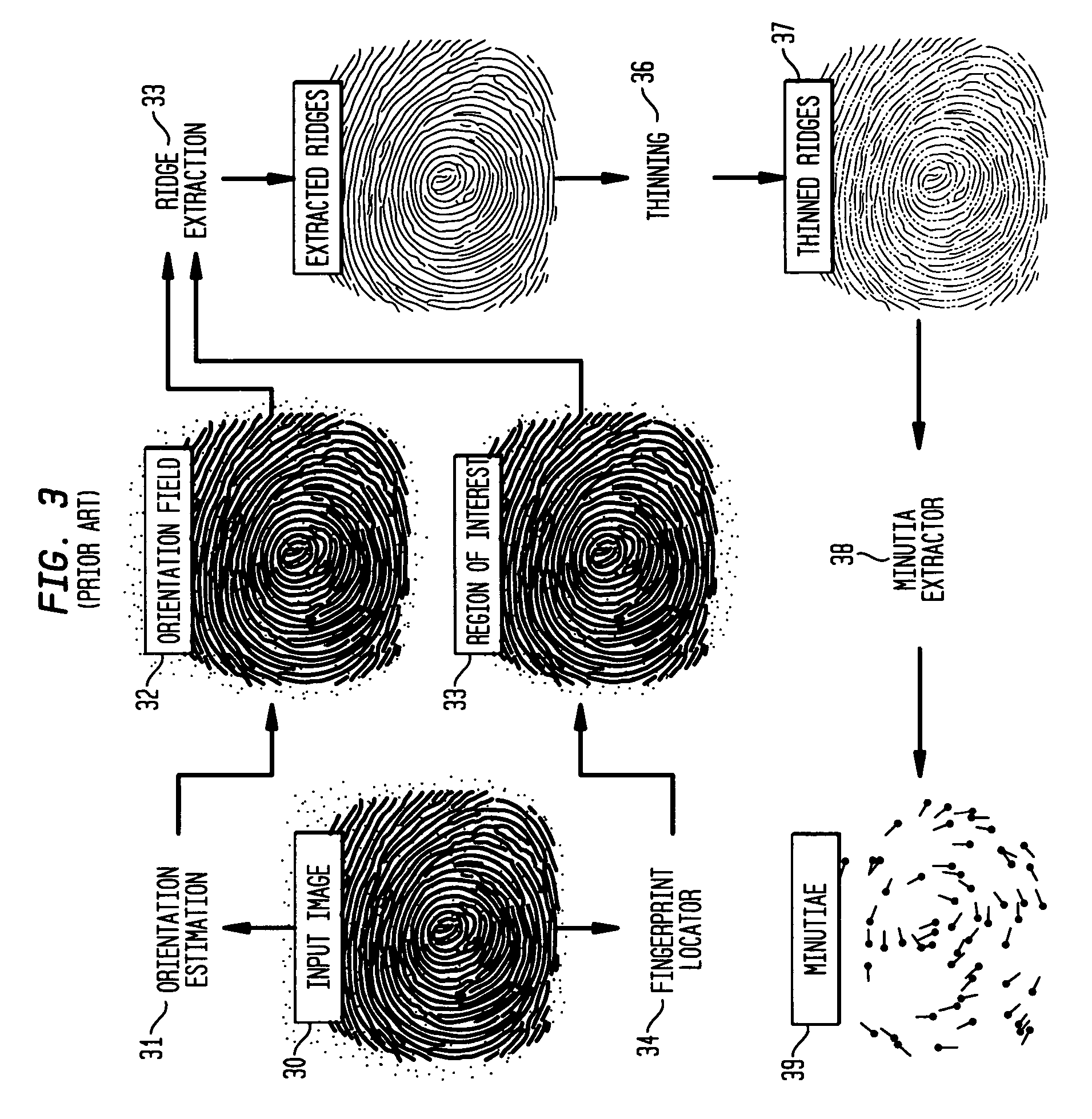
ActiveUS20060159316A1None of methods is secureCharacter and pattern recognitionPattern recognitionCommunications system
Minutiae based fingerprint transactions are validated and authenticated over wireless based communications systems, such as over a Bluetooth wireless based communication system. Minutiae points are unique identification points on a fingerprint where a ridge in the fingerprint joins another ridge or a ridge ends. The combination of any three minutiae points forms a triangle, and the method / algorithm of the present invention uses triangles of minutiae points because triangles are proportional regardless of possible differences in scale of two fingerprints being compared. A first method / algorithm uses a minutiae exchange where triplets of minutiae points are exchanged and form triangles for comparison between an original template of minutiae points and a stored template of minutiae points. A second method / algorithm exchanges three linear equations for three pairs of minutiae points that form triangles for comparison between an original template and a stored template.
Owner:LENOVO PC INT
Method and system for setting a secure computer environment
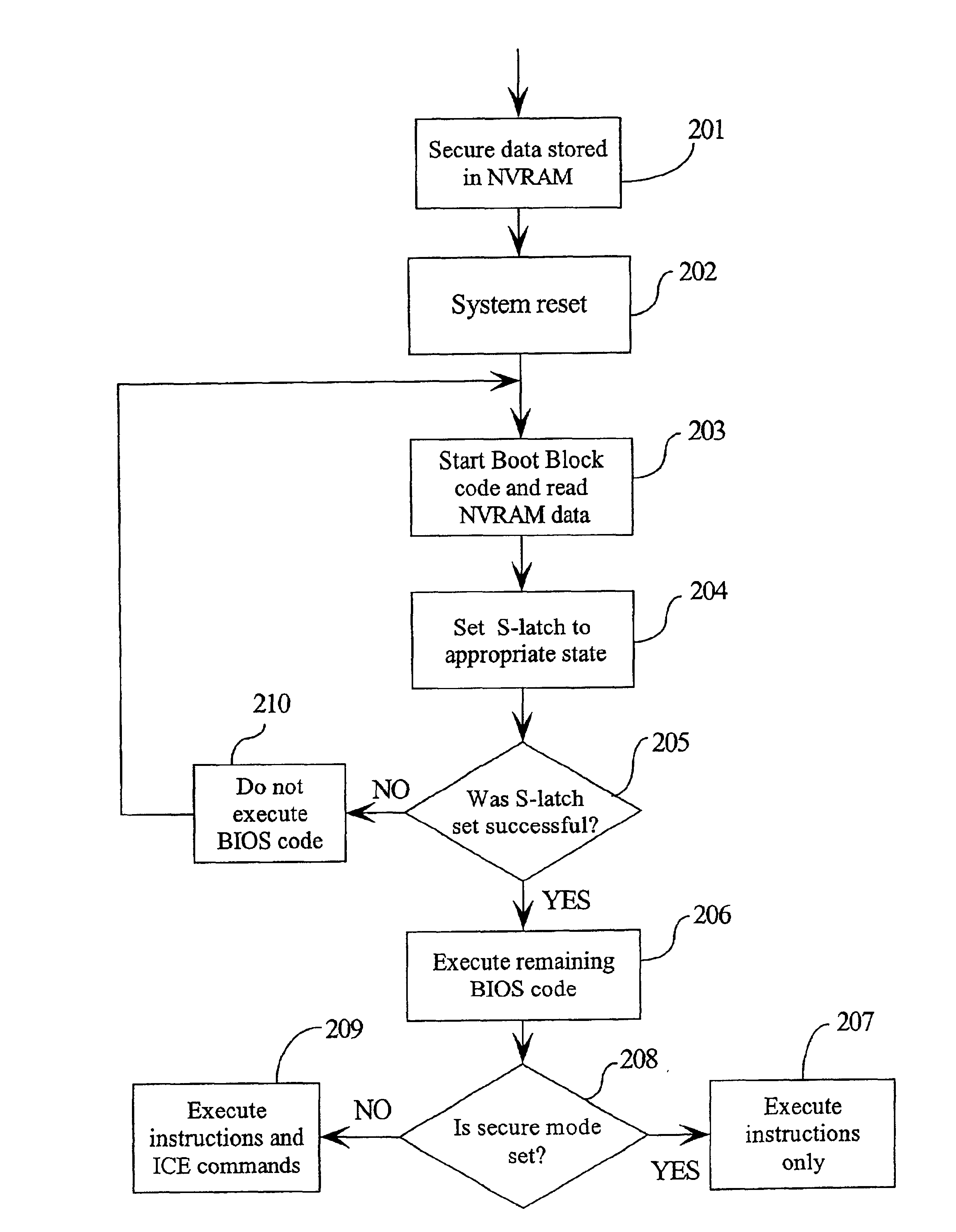
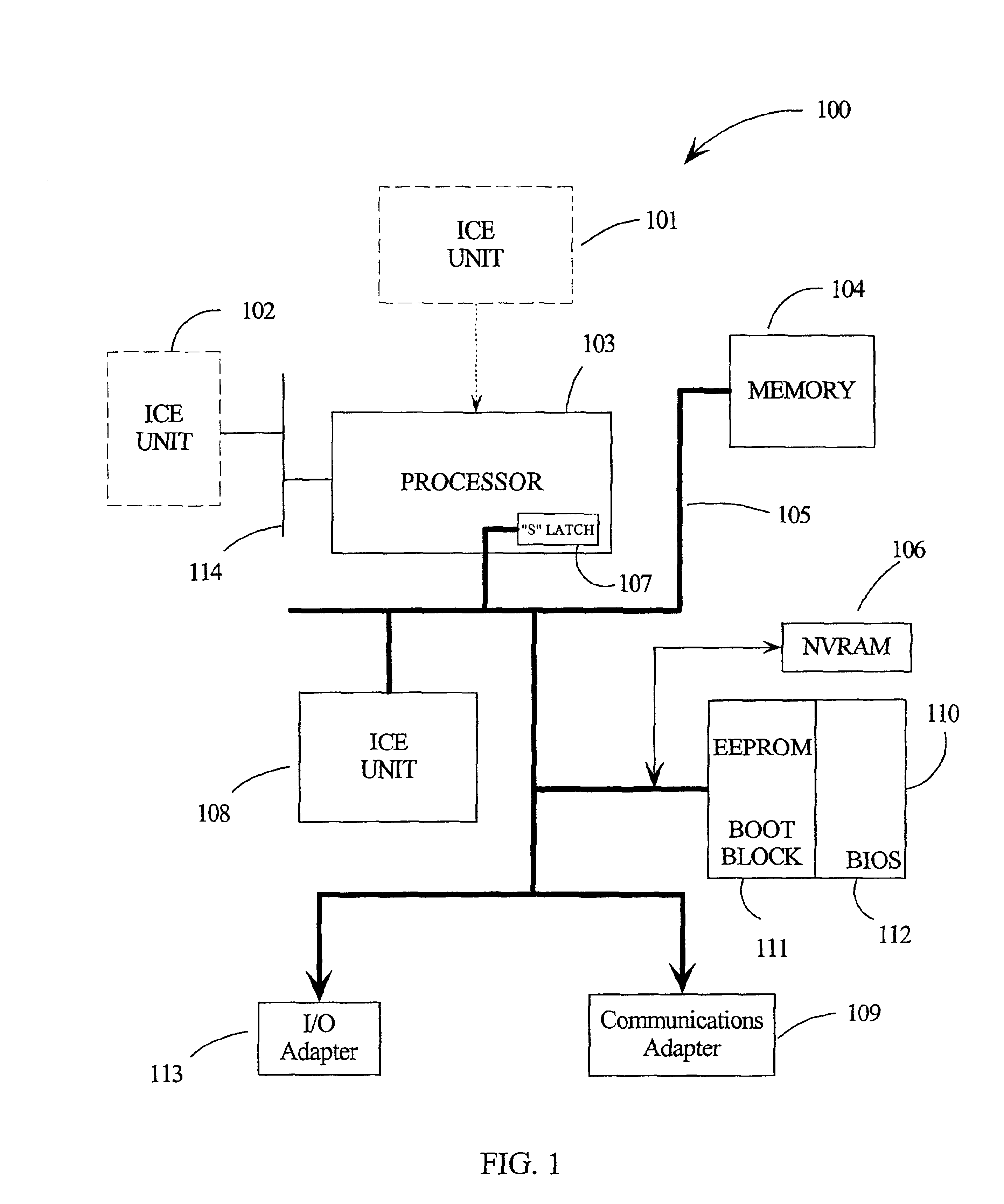
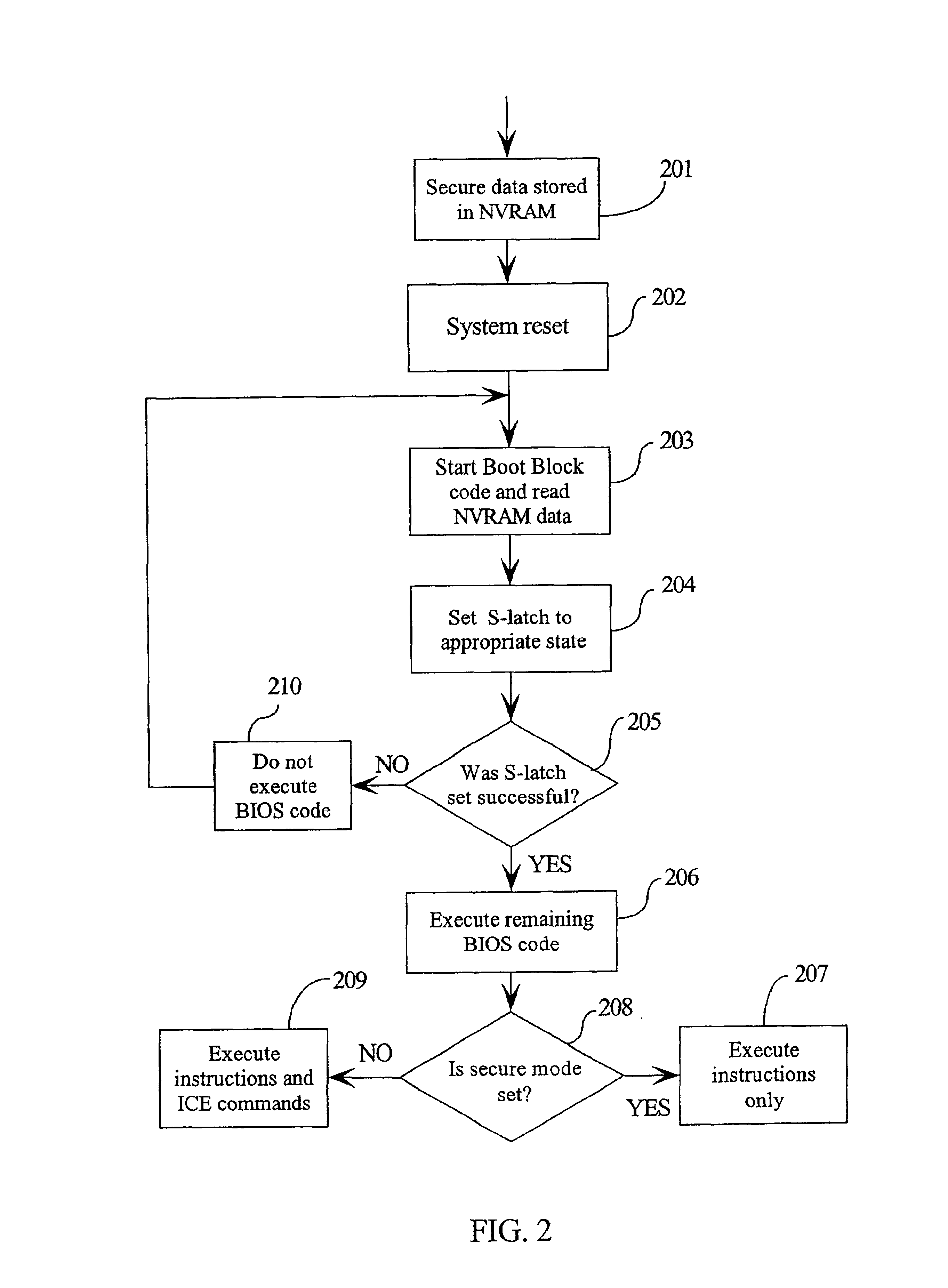
InactiveUS6925570B2None of methods is secureDigital data processing detailsDigital computer detailsBlock codeComputerized system
A computer system processor incorporates a special S-latch which may only be set by secure signals. One state of the S-latch sets the processor into a secure mode where it only executes instructions and not commands from an In Circuit Emulator (ICE) unit. A second state of the S-latch sets the processor into a non-secure mode. A non-volatile random access memory (NVRAM) is written with secure data which can only be read by boot block code stored in a BIOS storage device. The boot block code is operable to read the secure data in the NVRAM and set the S-latch to an appropriate security state. If the boot block code cannot set the S-latch, then remaining boot up with BIOS data is stopped. On boot up the boot block code reads the NVRAM and sets the S-latch into the appropriate security state.
Owner:LENOVO (SINGAPORE) PTE LTD
System for providing a digital media service
InactiveUS20080155109A1None of methods is secureMetadata multimedia retrievalMultiple digital computer combinationsVideo playerDatabase server
A portable wireless communications subscriber audio and / or video player apparatus and system and method for selecting, requesting, downloading, and playing audio and / or video data content files from an Internet-based database server. The wireless link is preferably implemented in accordance with the WiFi protocol, which allows connectivity to the Internet by being in proximity with a local base station or WiFi hotspot (i.e., publicly available local wireless access hub connected to the Internet). The portable wireless communications subscriber audio and / or video player apparatus and system preferably include a security means for monitoring and blocking unauthorized use of the player apparatus and system. The player apparatus further preferably has the capability to communicate with other neighboring player apparatus for the purpose of exchanging content data files, playlists and personal messages.
Owner:SANDISK TECH LLC
Method and apparatus for secure communication between mobile devices
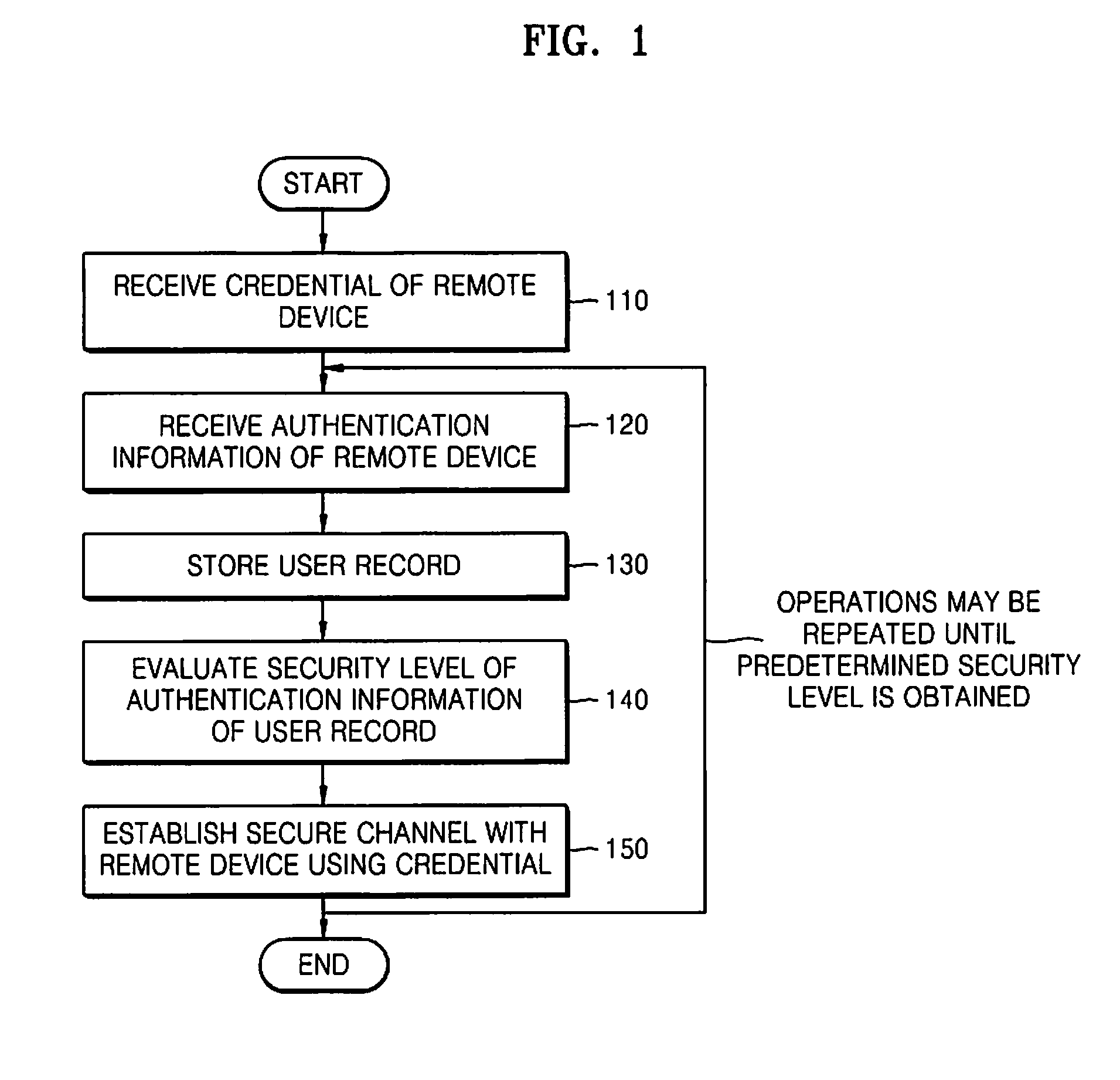
ActiveUS20110179473A1None of methods is secureDigital data processing detailsComputer security arrangementsSecure communicationMobile device
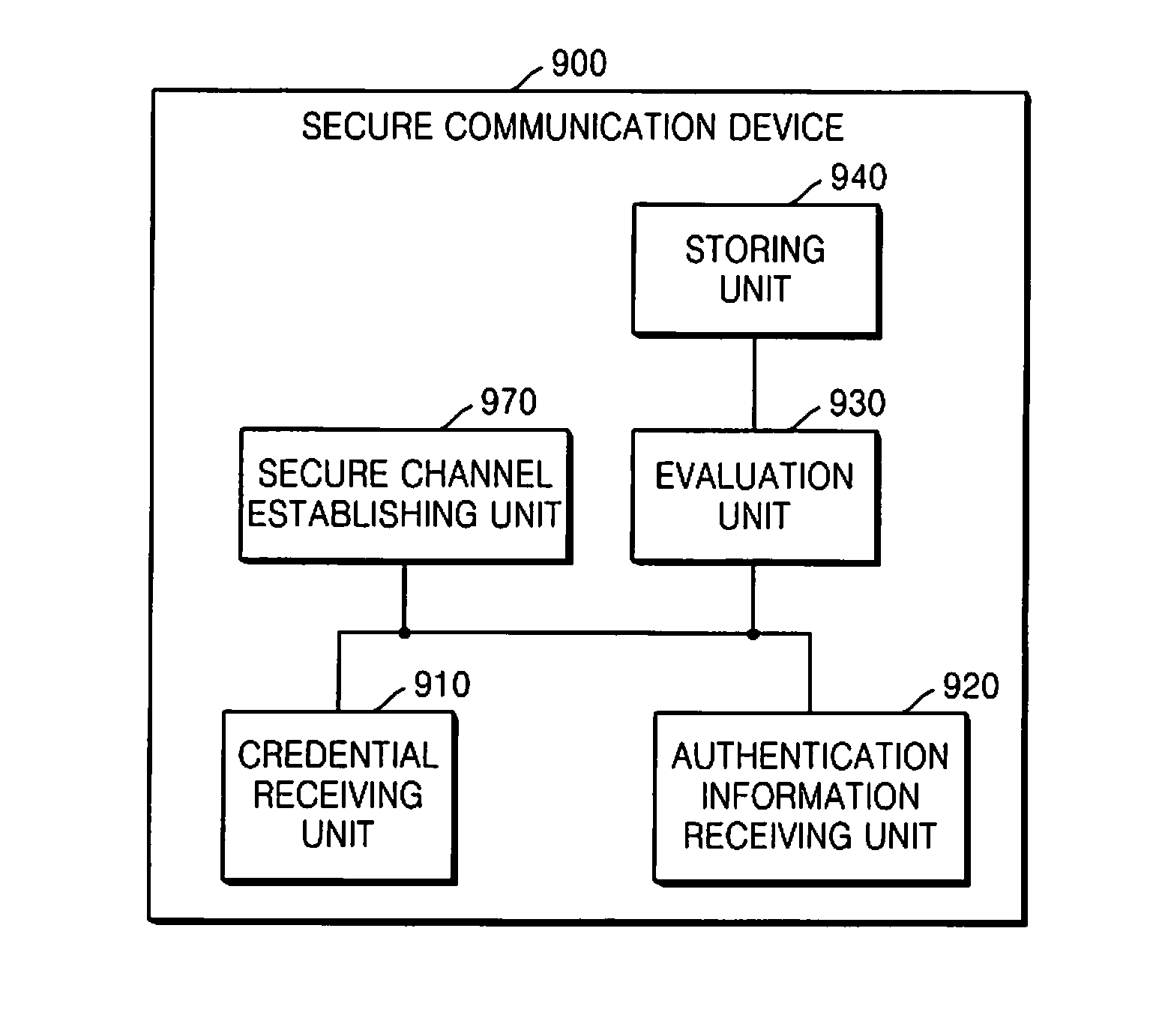
Methods and apparatuses for secure communication are provided. The secure communication method includes receiving a first credential of a remote device; receiving first authentication information of the remote device; storing a user record including the first credential and the first authentication information; and evaluating a security level of the received first authentication information.
Owner:SAMSUNG ELECTRONICS CO LTD
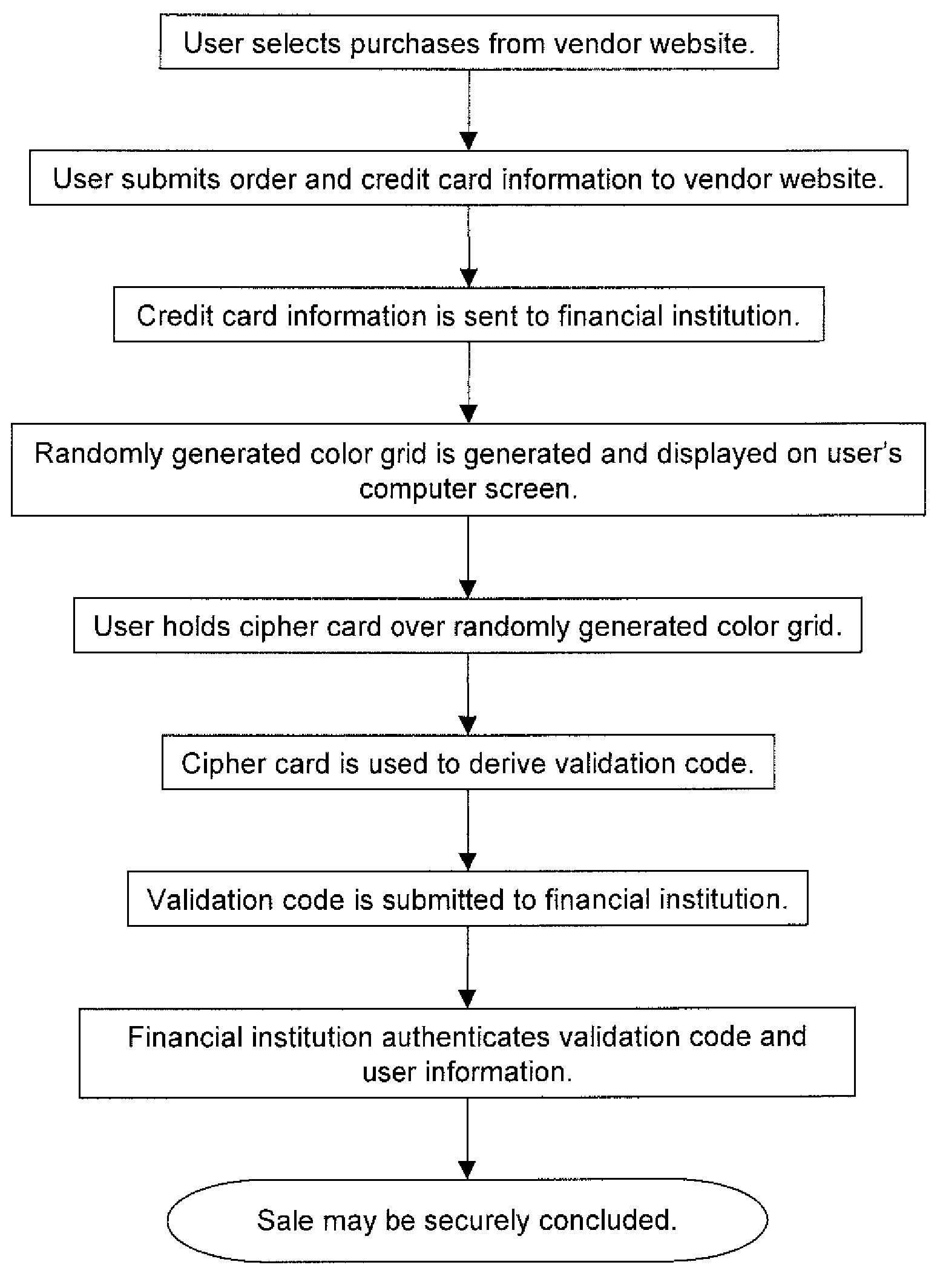
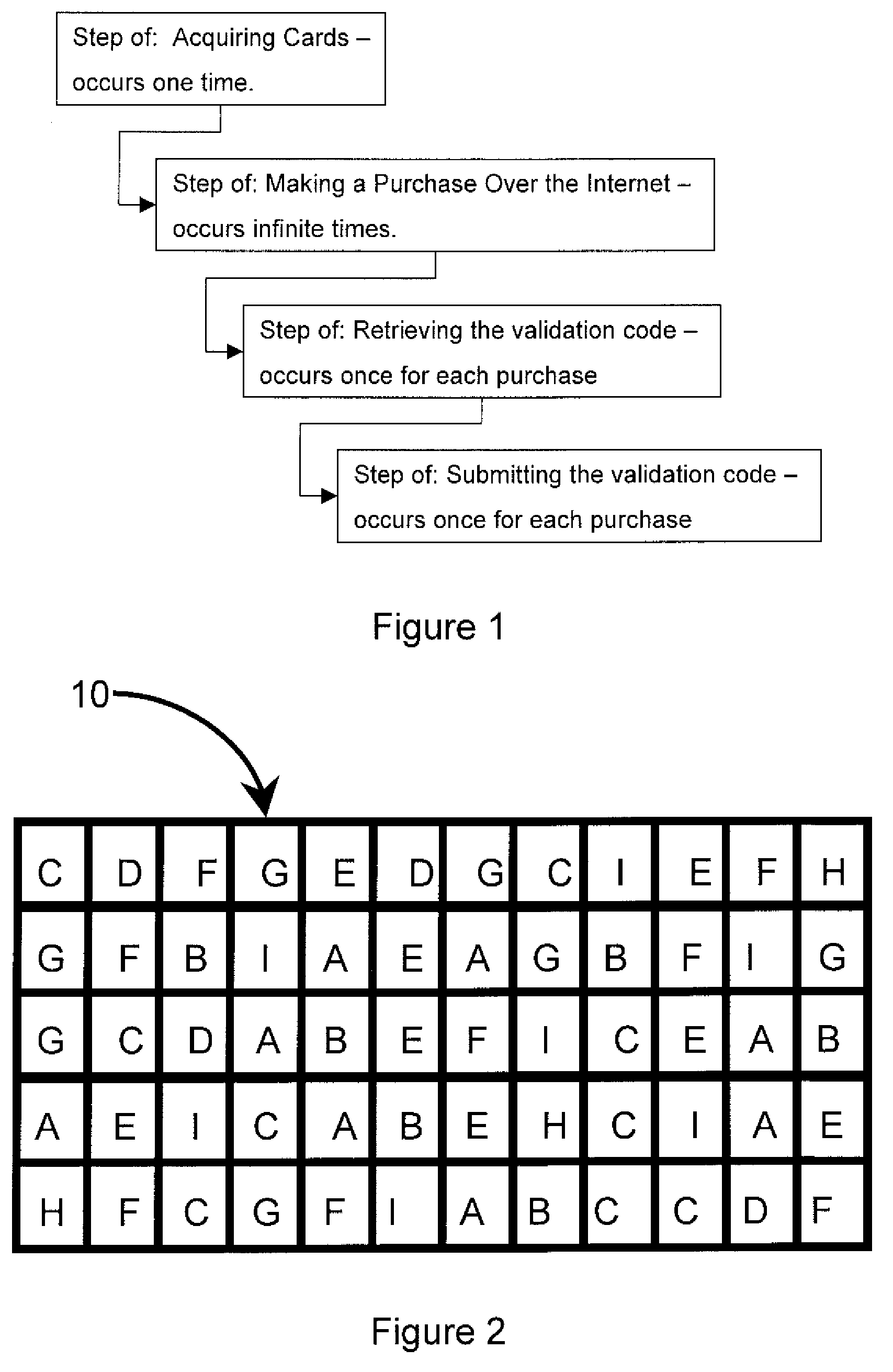
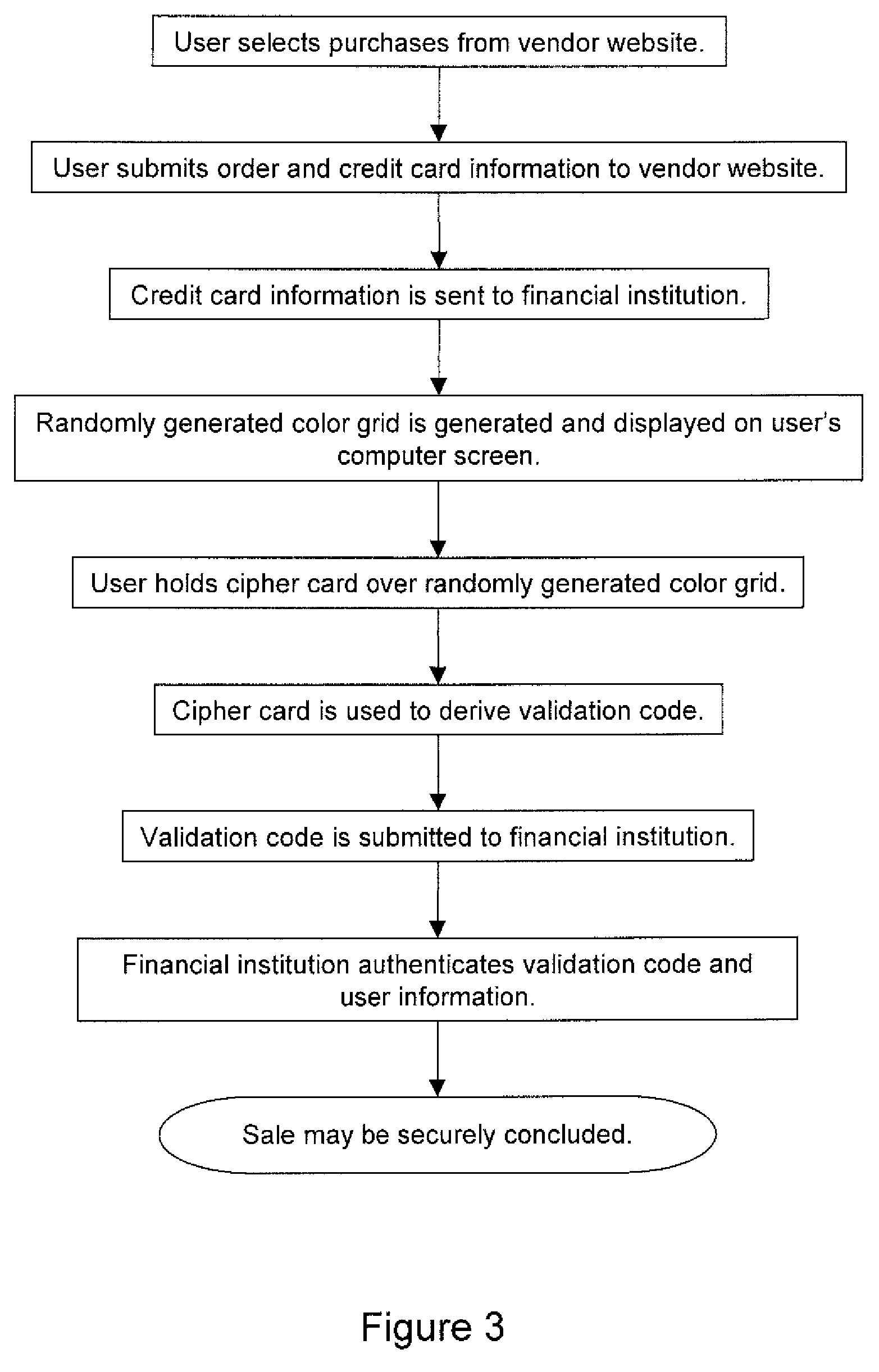
Randomly generated color grid used to ensure multi-factor authentication
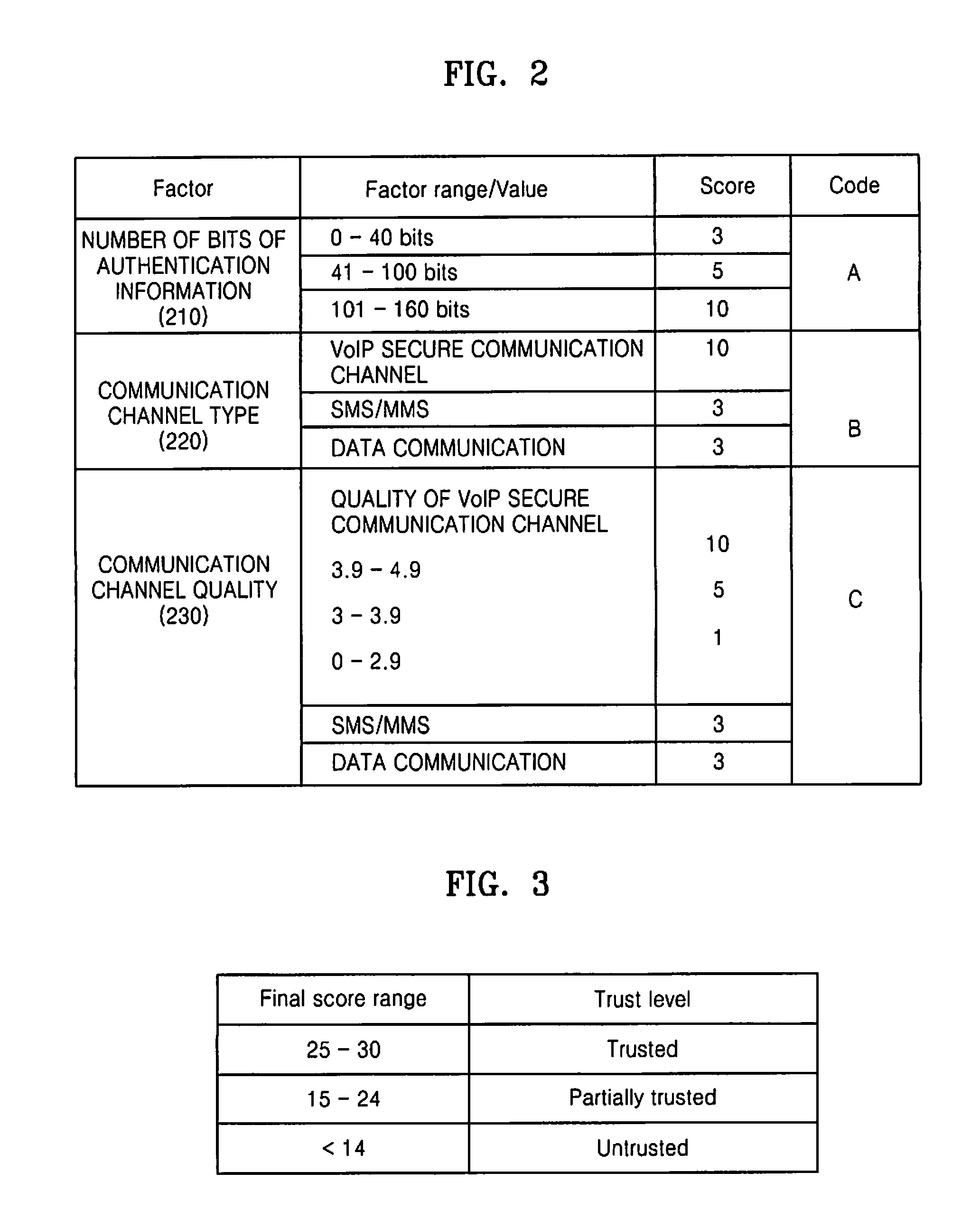
InactiveUS7672906B2Simple wayNone of methods is securePayment architectureDigital data authenticationComputer hardwareSecure authentication
Owner:SCHWARTZ ASSAF MR +1
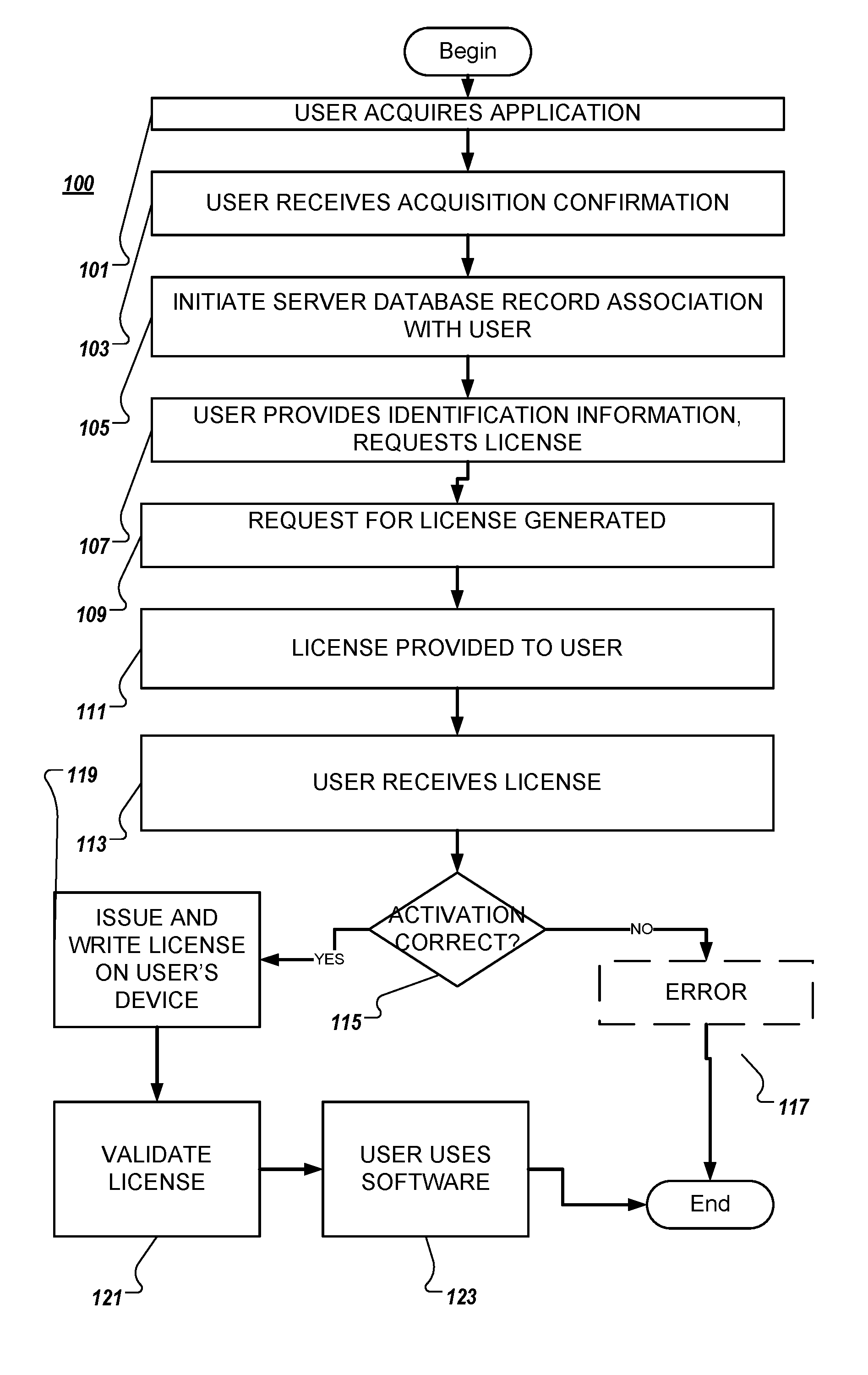
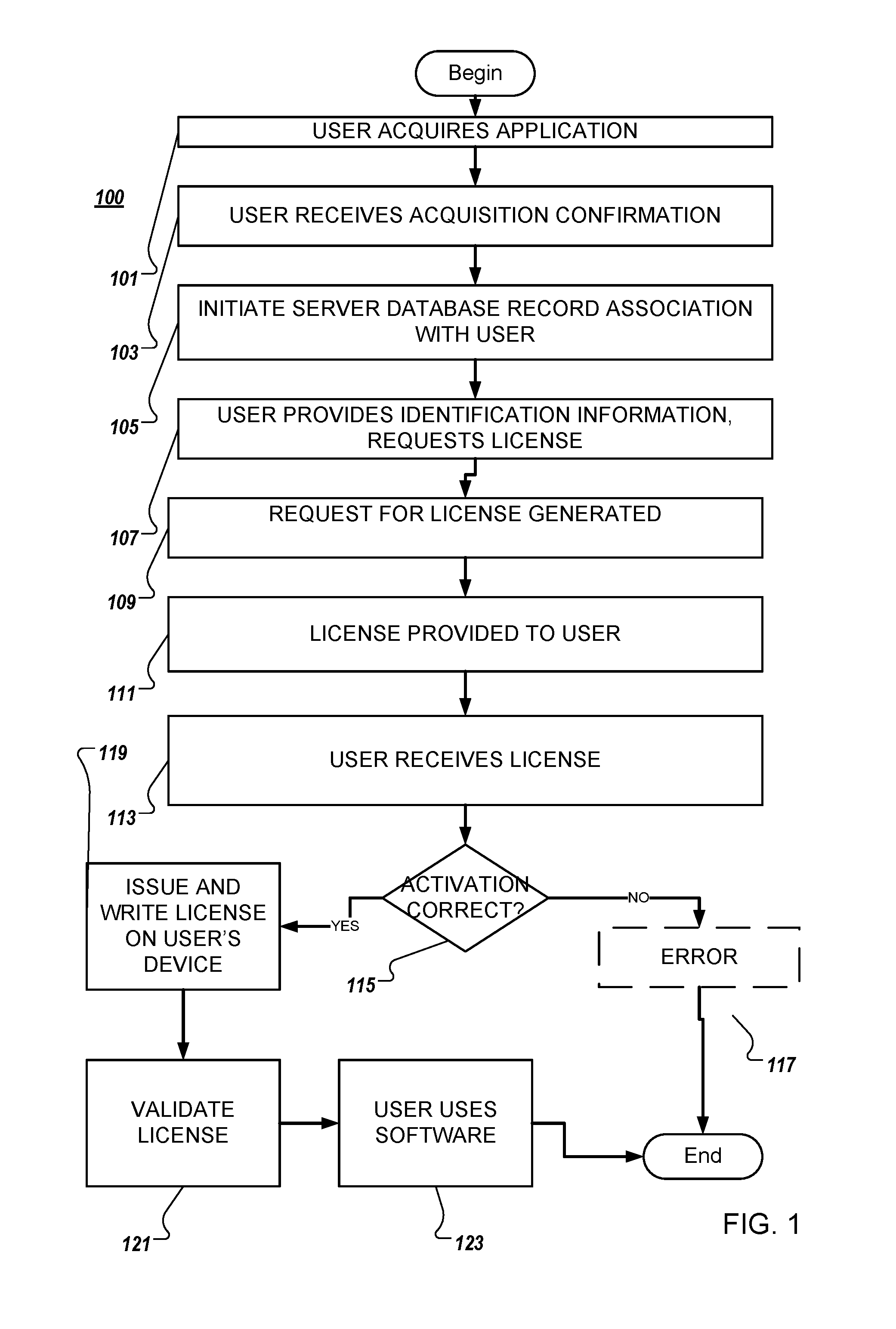
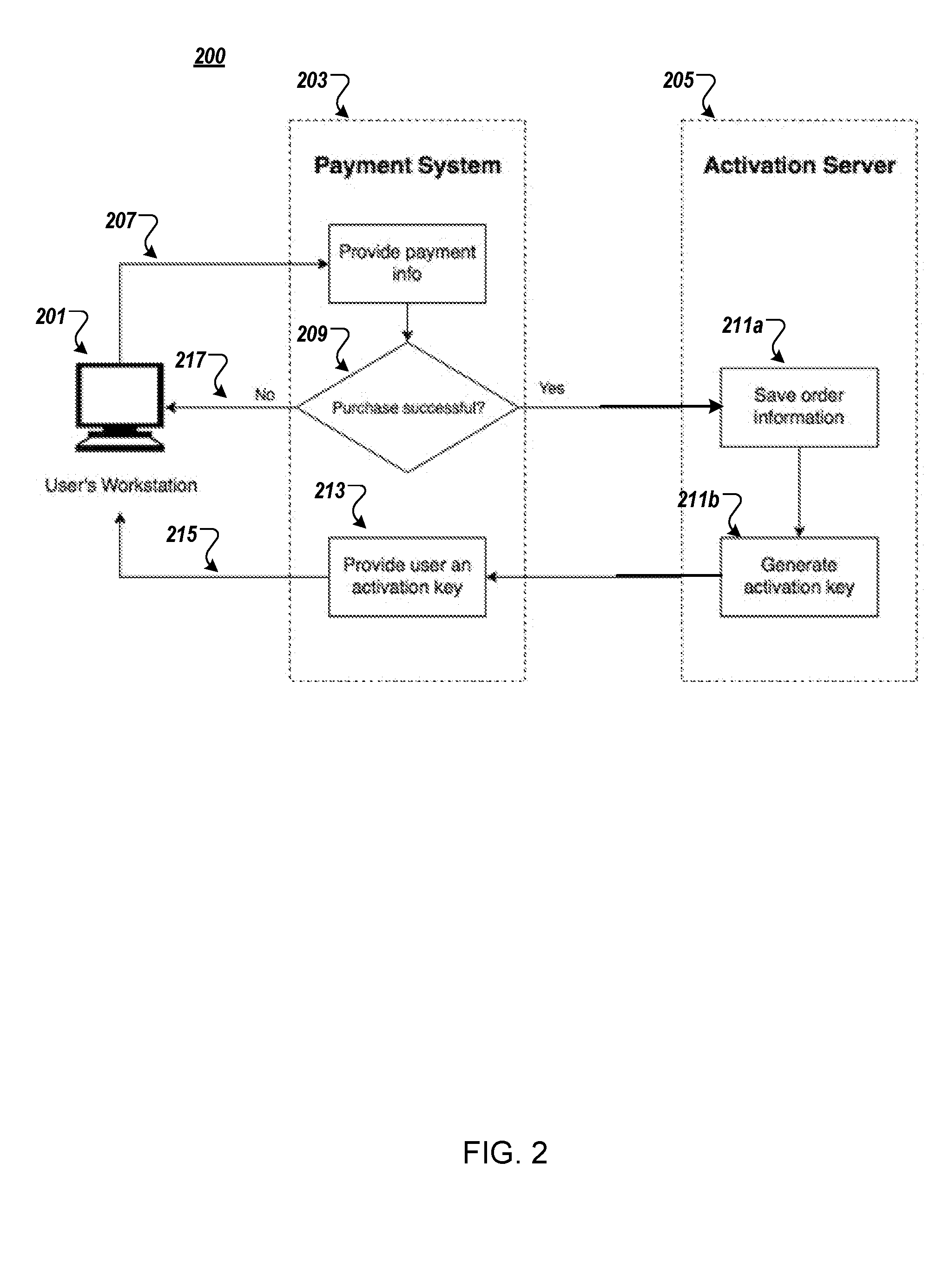
System and method for software activation and license tracking
ActiveUS20160232334A1Simplify the activation processPrevent unauthorizedUser identity/authority verificationProgram/content distribution protectionSoftware distributionSoftware development
System and method for software activation and further tracking of its states on an end-user computing device (computer) was developed to provide software developers a flexible and secure tool for software distribution and gathering statistics of usage of software activation. The method consists of the following logical steps: (a) obtaining an acquisition confirmation; (b) requesting for a license; (c) issuing and delivering the license to End User; (d) verification of license on the User's computer; (e) storing the license on the User's computer; (f) periodic tracking of activation state, (g) another action with the User's license.
Owner:MACPAW WAY LTD
Device for accessing a digital media service
InactiveUS20080160910A1None of methods is secureMetadata multimedia retrievalPayment architectureVideo playerDatabase server
A portable wireless communications subscriber audio and / or video player apparatus and system and method for selecting, requesting, downloading, and playing audio and / or video data content files from an Internet-based database server. The wireless link is preferably implemented in accordance with the WiFi protocol, which allows connectivity to the Internet by being in proximity with a local base station or WiFi hotspot (i.e., publicly available local wireless access hub connected to the Internet). The portable wireless communications subscriber audio and / or video player apparatus and system preferably include a security means for monitoring and blocking unauthorized use of the player apparatus and system. The player apparatus further preferably has the capability to communicate with other neighboring player apparatus for the purpose of exchanging content data files, playlists and personal messages.
Owner:SANDISK TECH LLC
Audio visual player apparatus and system and method of content distribution using the same
ActiveUS20080160908A1None of methods is secureDigital data information retrievalElectronic editing digitised analogue information signalsContent distributionThe Internet
A system is presented providing content to a plurality of handheld devices (including musical selections). The devices can access a server over the Internet via a WIFI or other similar wireless interconnection and can download songs requested by a user from the server or from other users using, e,g, a P2P protocol. All downloads are governed by applicable DRM rules. Content and playlists may also be pushed by a server from other sources and means including, e.g., podcasting, based on predetermined rules, favorite preferences of users, and other criteria.
Owner:SANDISK TECH LLC
System and method for securely storing and accessing credentials and certificates for secure VoIP endpoints
InactiveUS20070150726A1Low costNone of methods is secureSecuring communicationSession Initiation ProtocolSecure voice
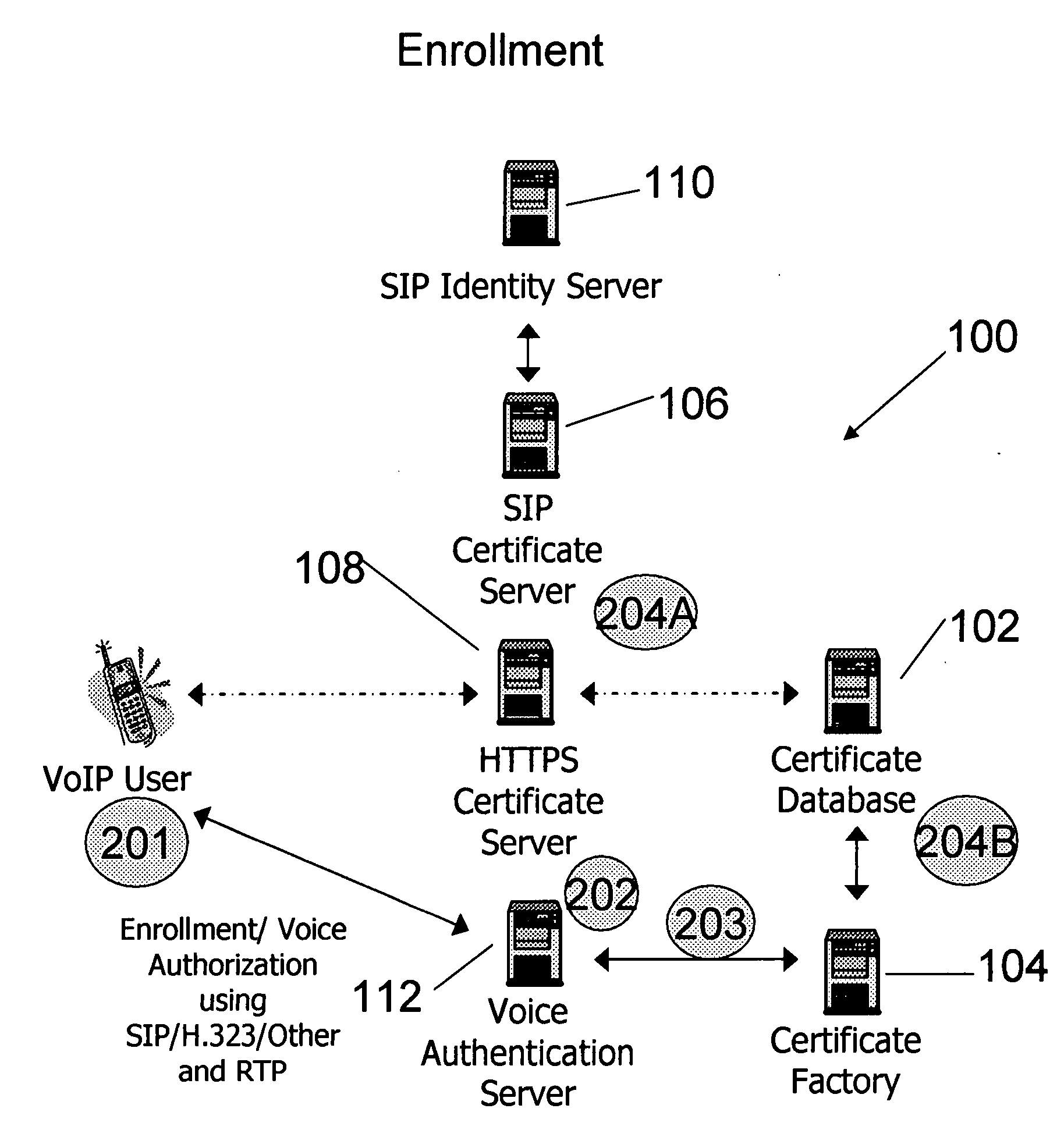
A system and method for enabling secure Voice over IP (VoIP) communication includes receiving a request for the generation of a certificate to be used in conjunction with a VoIP communication, generating a certificate in response to the request, the certificate being generated based, at least in part, on a voice sample of a user that made the request, and thereafter making the certificate available for use to enable secure VoIP communication. The system and method preferably leverages the session initiation protocol (SIP).
Owner:PULVER COM
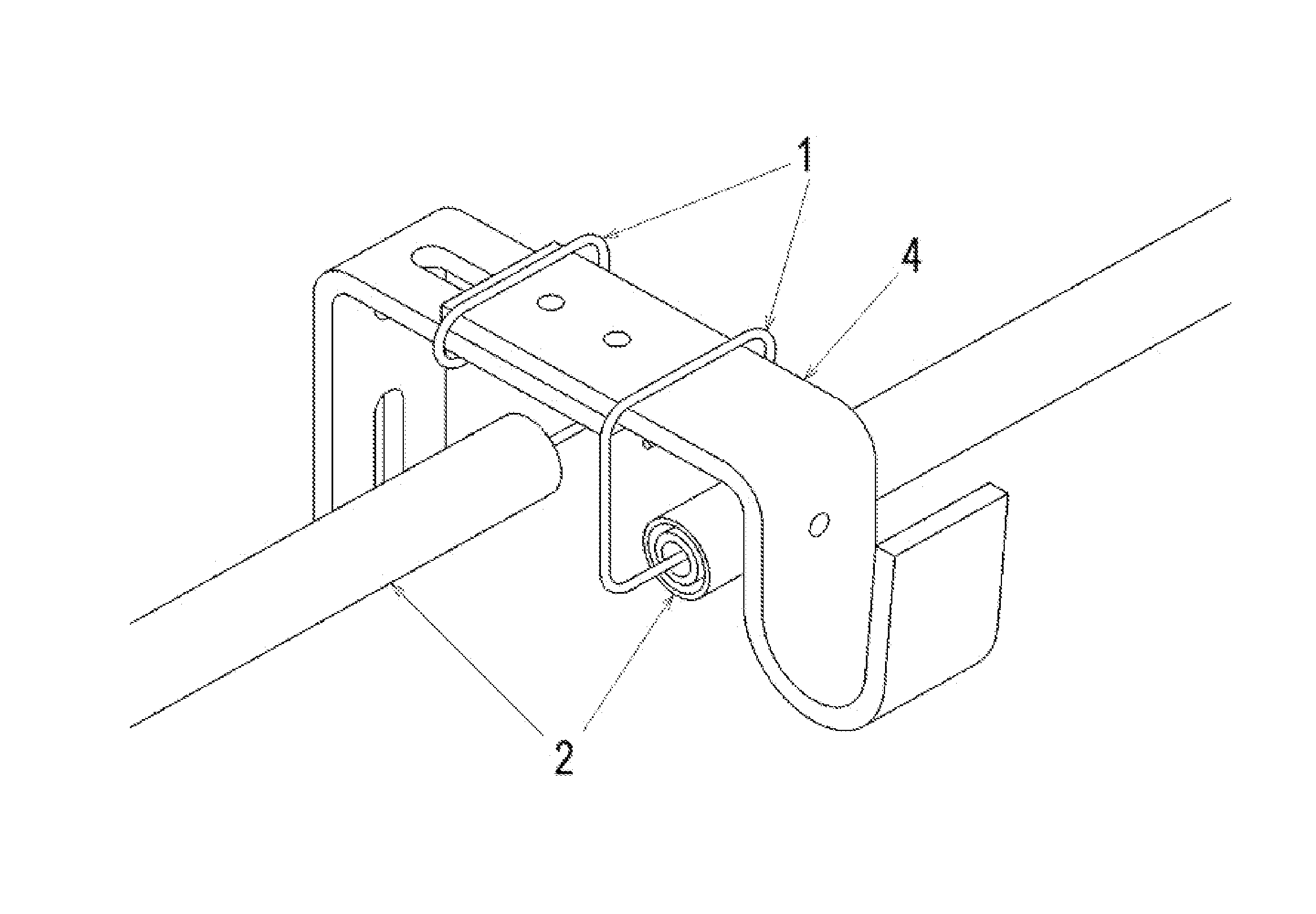
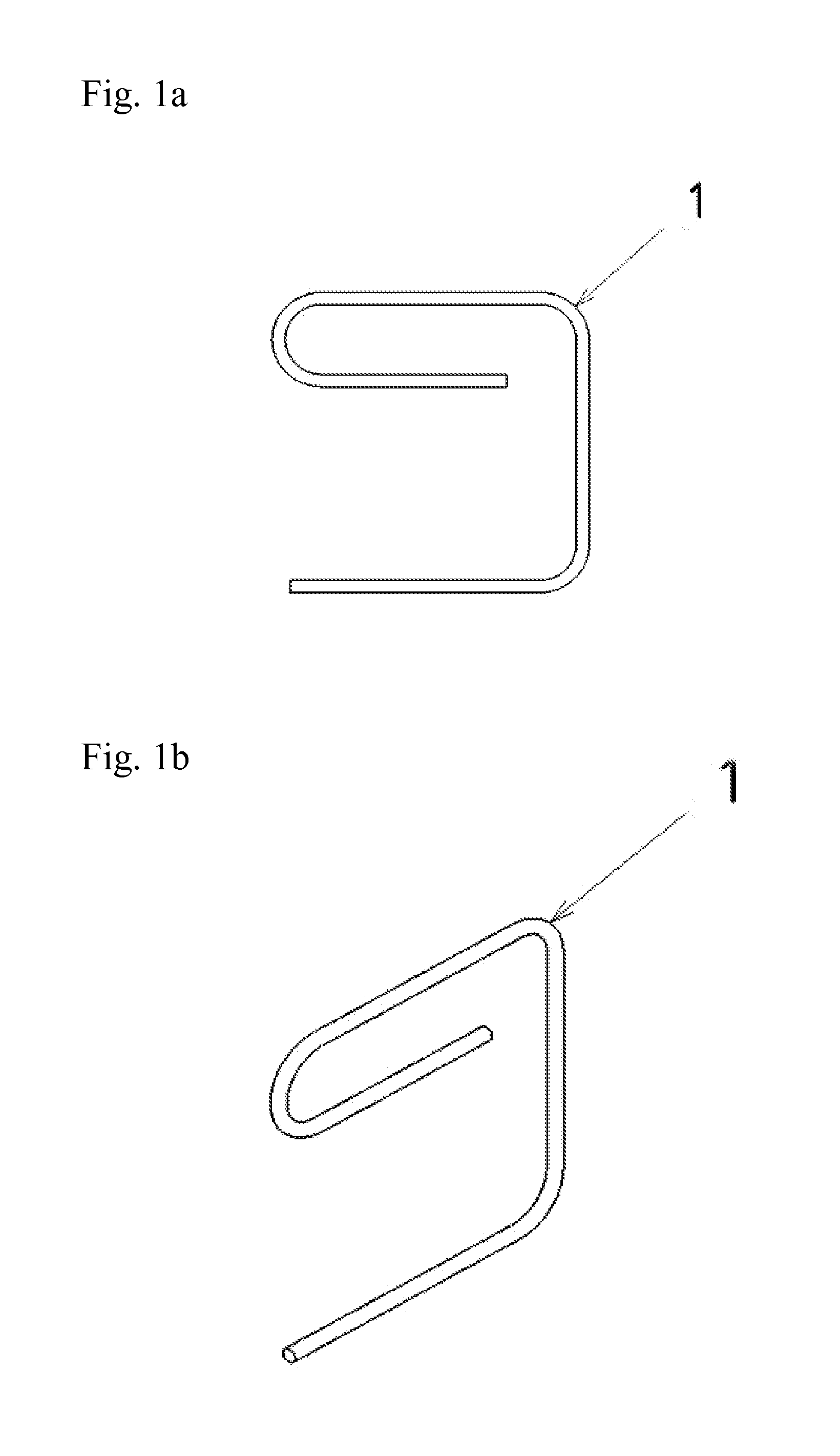
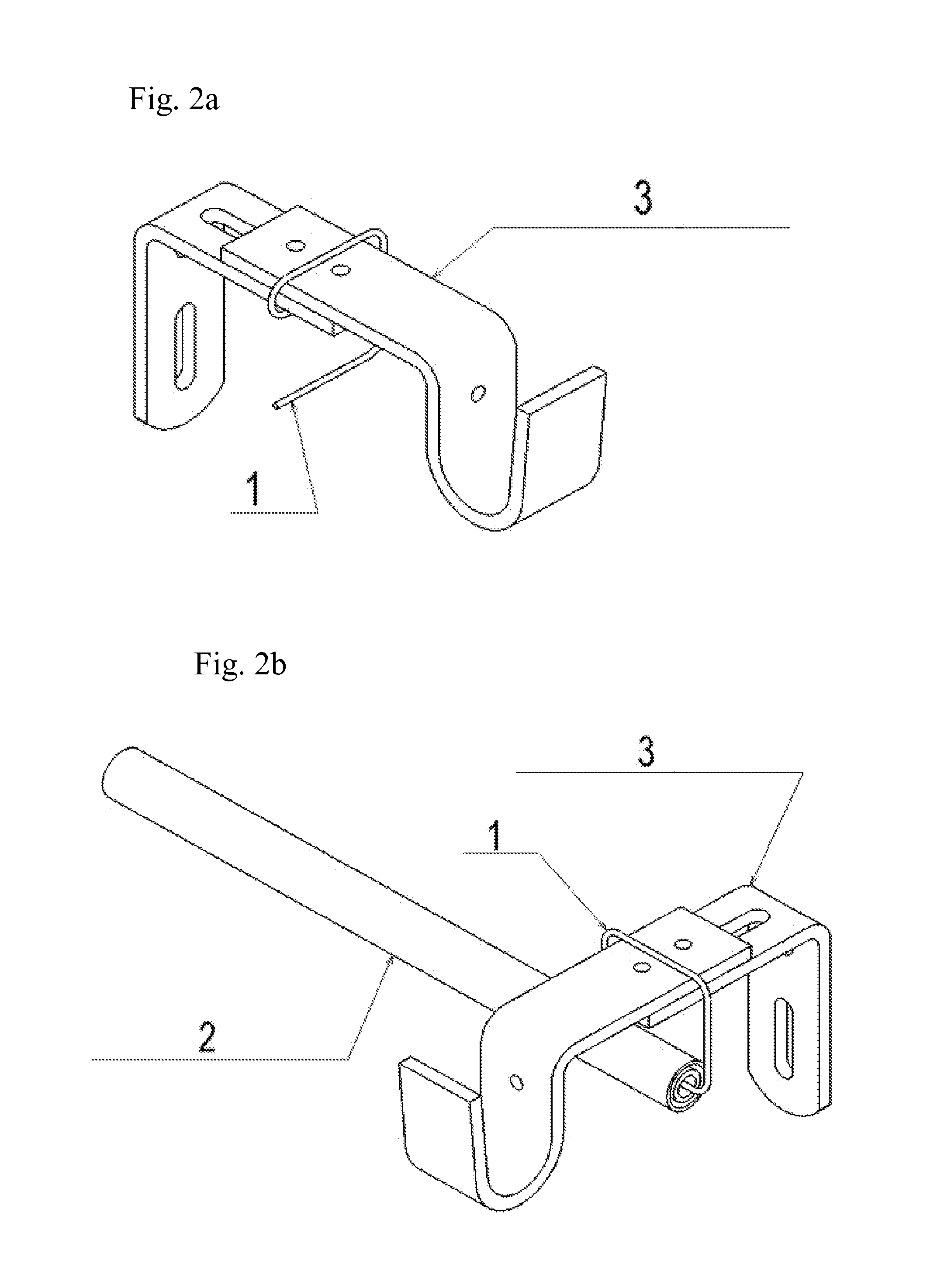
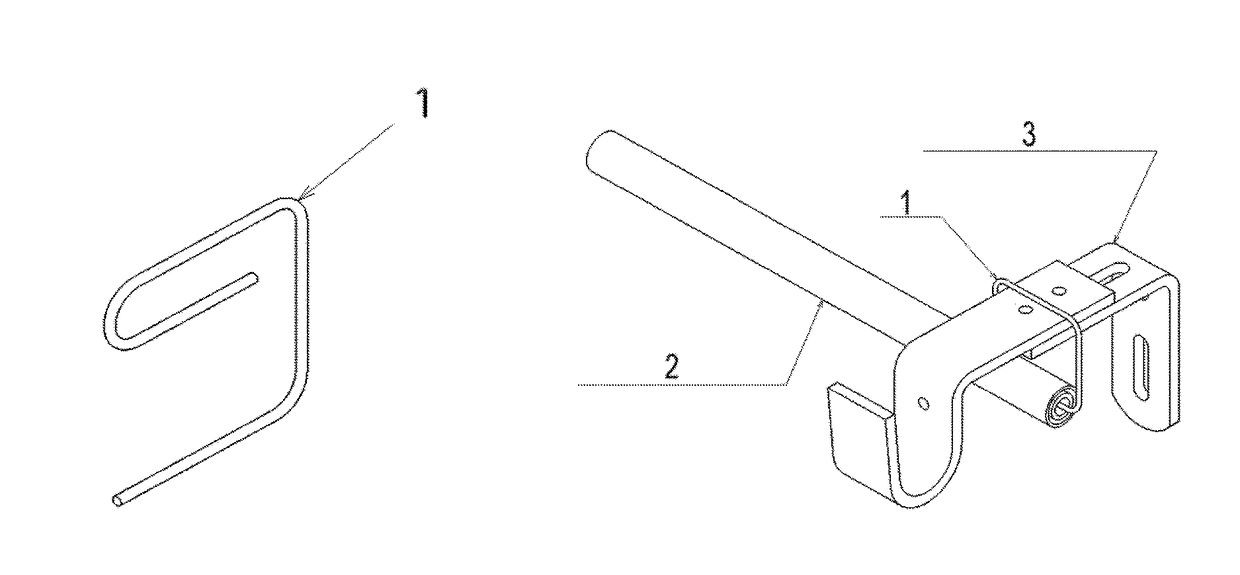
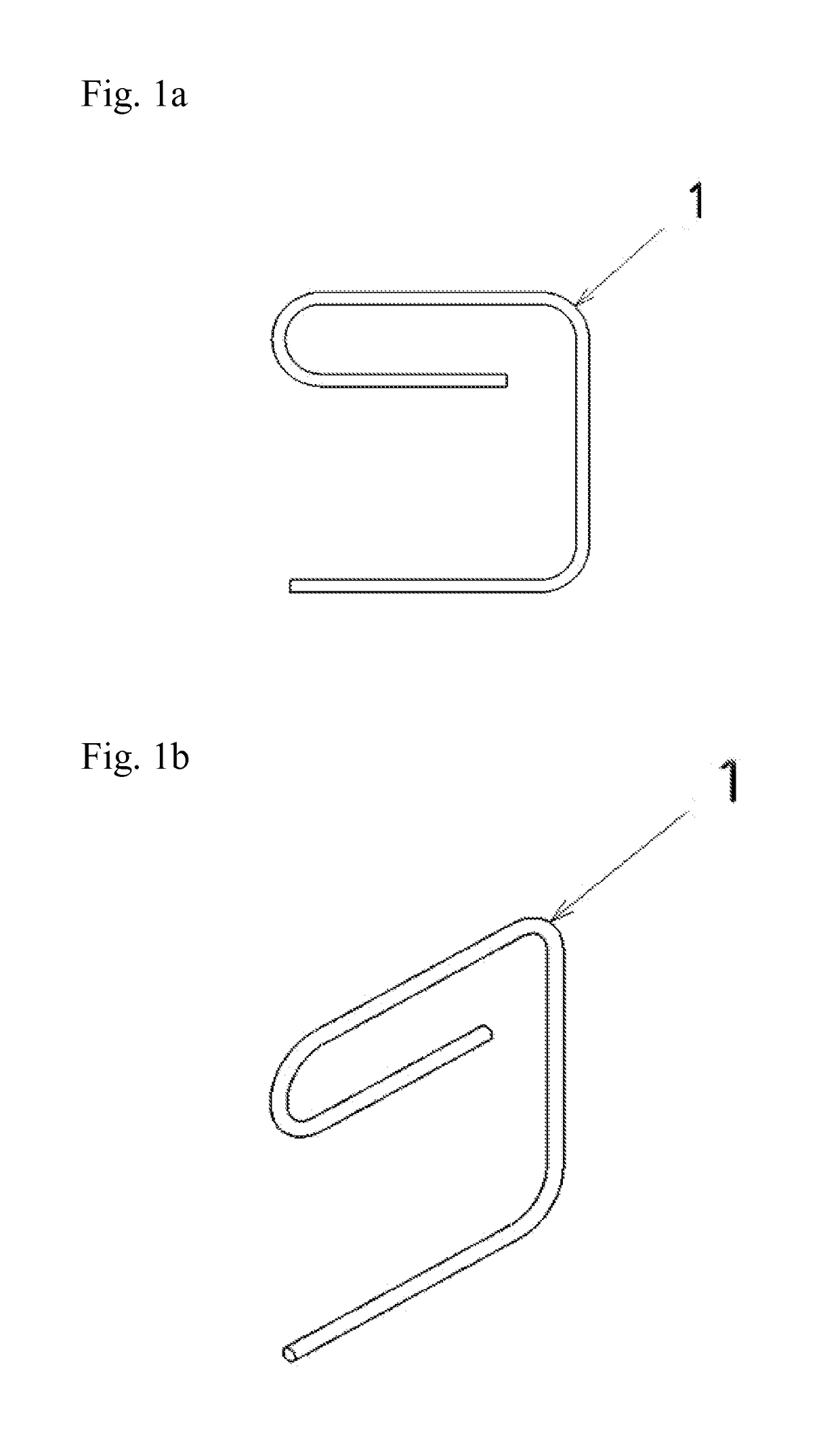
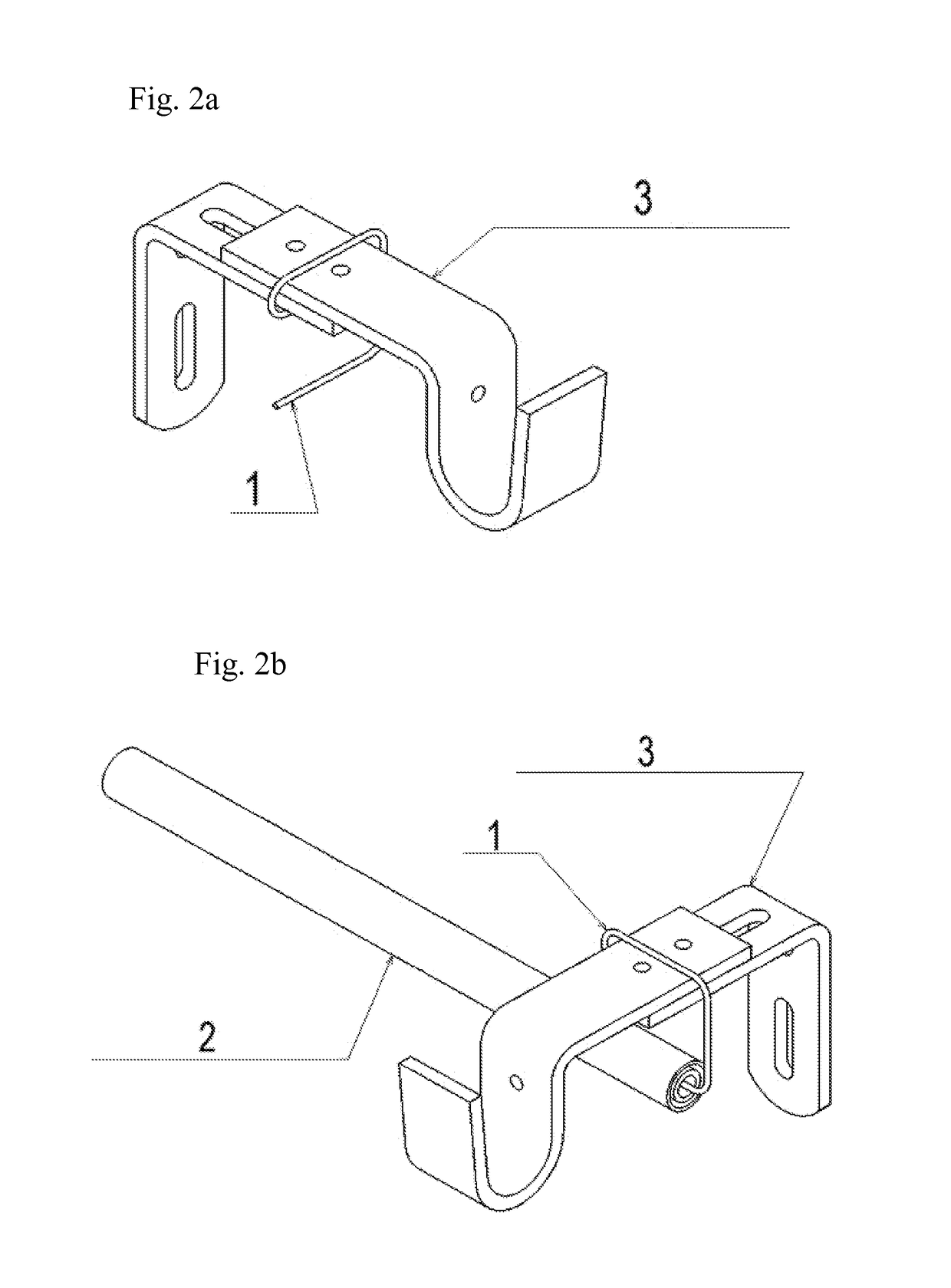
Hang-It-All Curtain System
ActiveUS20160242586A1Easy to installEasy to removeCurtain suspension devicesFriction grip releasable fasteningsCost effectivenessEngineering
An improved, simpler, and more cost effective method for hanging multiple layers of curtaining with reduced damage to the casement of a window or of the walls around a window. An e-shaped hook (1) wraps around an existing bracket (3) utilized to hang a primary curtain rod. The hook (1) then extends down from the bracket (3) ending in a lateral prong at a right angle to the bracket (3) and perpendicular to the original curtain rod, pointing toward the center of the window. This prong is then inserted into the aperture of a telescoping rod with an internal spring adjustment referred to as a spring tension rod (2). The spring tension rod (2), due to its internal spring, allows for the rod to be inserted onto the hook (1) and be released from the hook (1) without the removal of the hook (1) from the bracket (3).
Owner:MATEER SHELLEY MEGAN
Hang-it-all curtain system
ActiveUS9609974B2Easy to installEasy to remove and replaceCandle holdersLighting support devicesCost effectivenessEngineering
An improved, simpler, and more cost effective method for hanging multiple layers of curtaining with reduced damage to the casement of a window or of the walls around a window. An e-shaped hook (1) wraps around an existing bracket (3) utilized to hang a primary curtain rod. The hook (1) then extends down from the bracket (3) ending in a lateral prong at a right angle to the bracket (3) and perpendicular to the original curtain rod, pointing toward the center of the window. This prong is then inserted into the aperture of a telescoping rod with an internal spring adjustment referred to as a spring tension rod (2). The spring tension rod (2), due to its internal spring, allows for the rod to be inserted onto the hook (1) and be released from the hook (1) without the removal of the hook (1) from the bracket (3).
Owner:MATEER SHELLEY MEGAN
Apparatus and methods for playing digital content and displaying same
InactiveUS20080160909A1None of methods is secureDigital data information retrievalElectronic editing digitised analogue information signalsDigital contentThe Internet
A system is presented providing content to a plurality of handheld devices (including musical selections). The devices can access a server over the Internet via a WIFI or other similar wireless interconnection and can download songs requested by a user from the server or from other users using, e.g., a P2P protocol. All downloads are governed by applicable DRM rules. Content and playlists may also be pushed by a server from other sources and means including, e.g., podcasting, based on predetermined rules, favorite preferences of users, and other criteria.
Owner:SANDISK TECH LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com