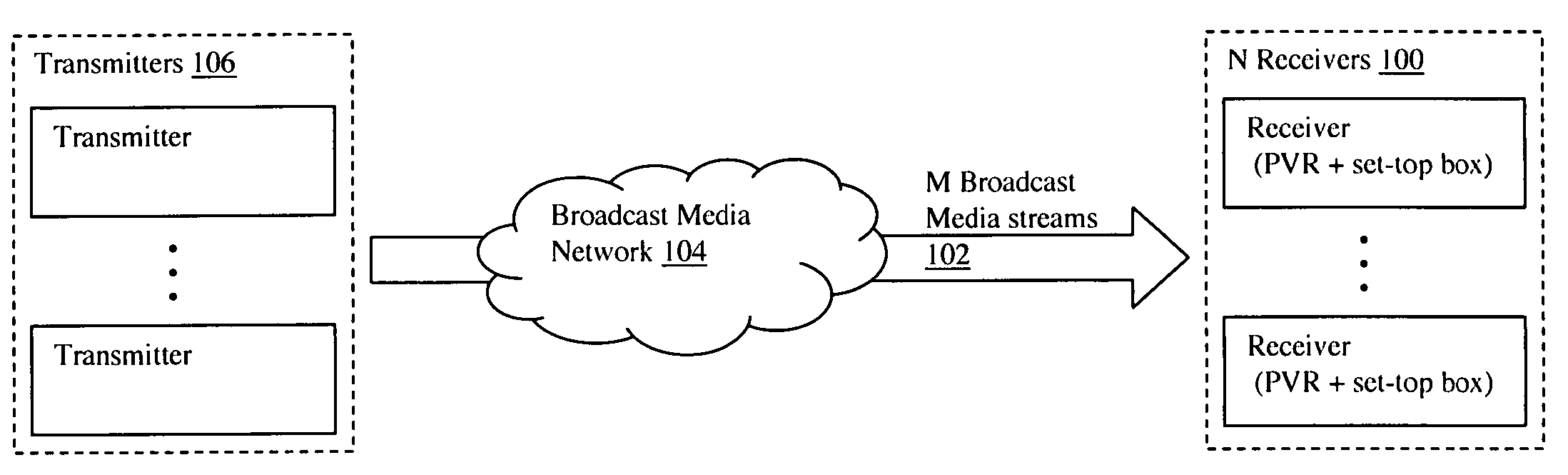Patents
Literature
608results about How to "Communication security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
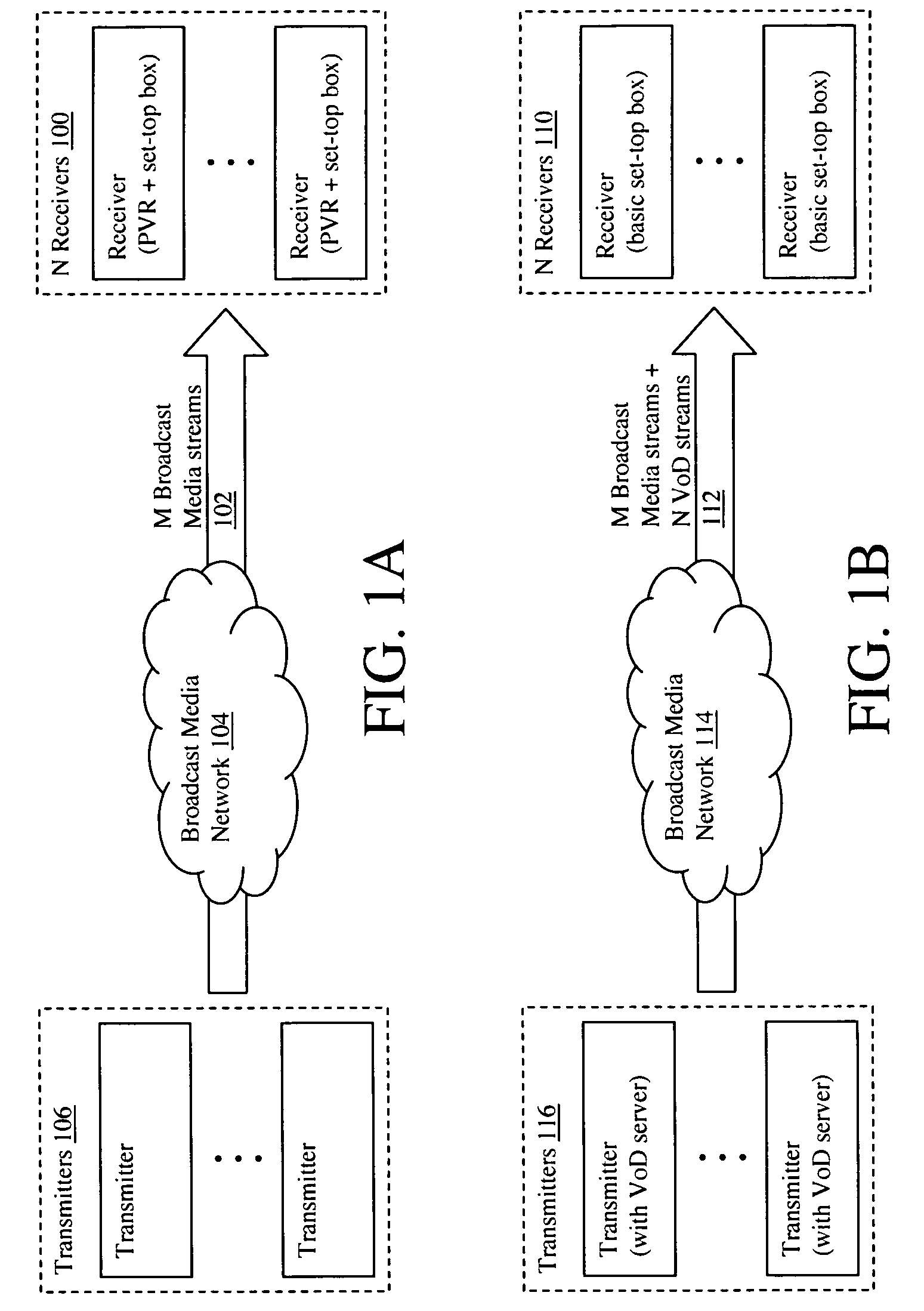
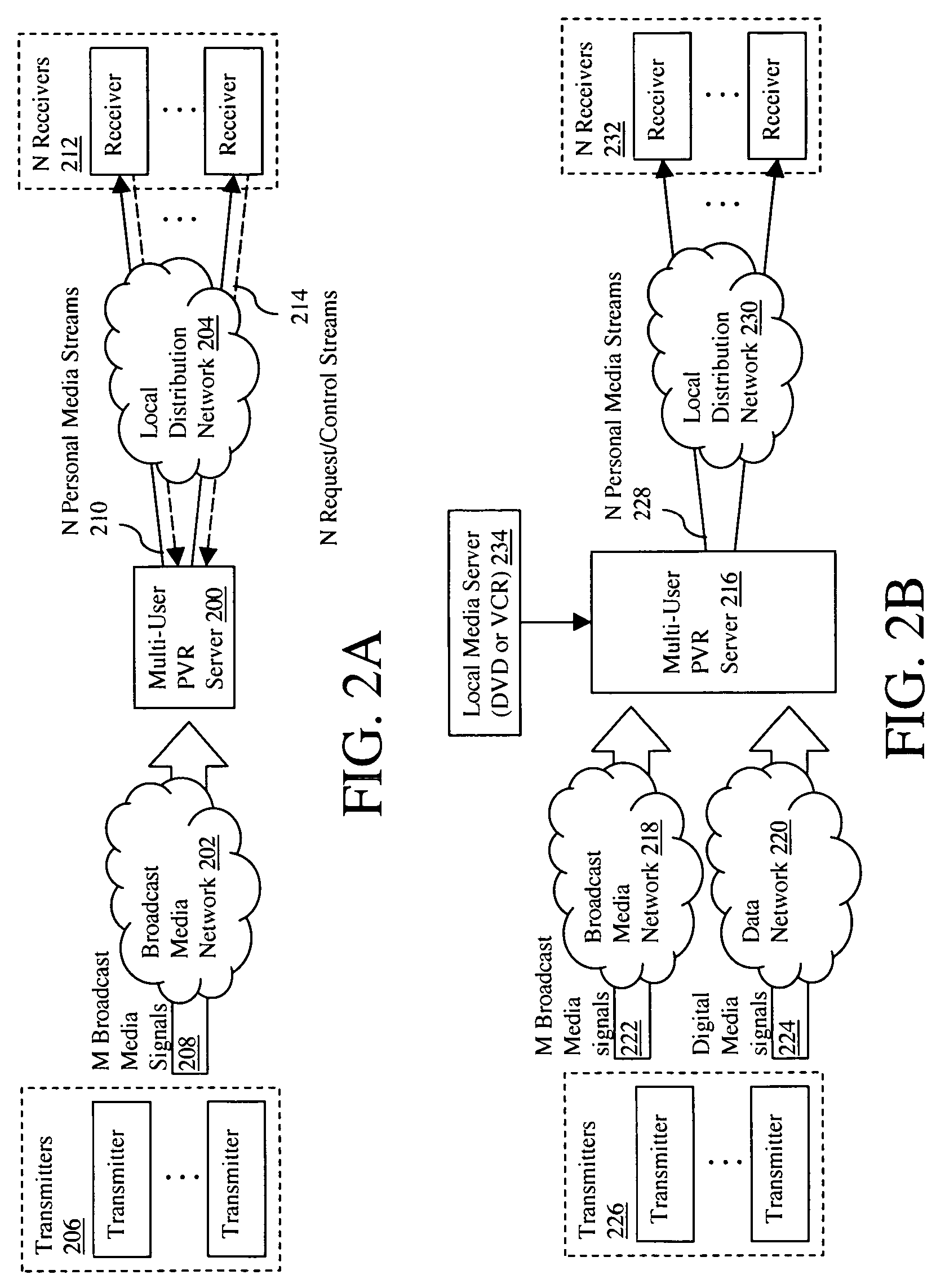
Multi-user personalized digital multimedia distribution methods and systems
InactiveUS20050183120A1Communication securityTelevision system detailsColor television detailsPersonalizationNetwork termination
A media distribution technique employs a multi-user server positioned at the terminal end of a broadcast media network. The server receives broadcast media signals and selectively captures a portion of the signals for live personalized media streaming and / or storage for later personalized media streaming and / or download over a local distribution network to a collection of user receivers. Request / control streams sent from the receivers to the server control real-time personalization of the media streams such as trick-play functions and channel selection. Buffering and data storage segmentation techniques are used to provide highly responsive personal video recorder-like functionality to the multiple end users.
Owner:IP VIDEO SYST
Wireless operation of a game device
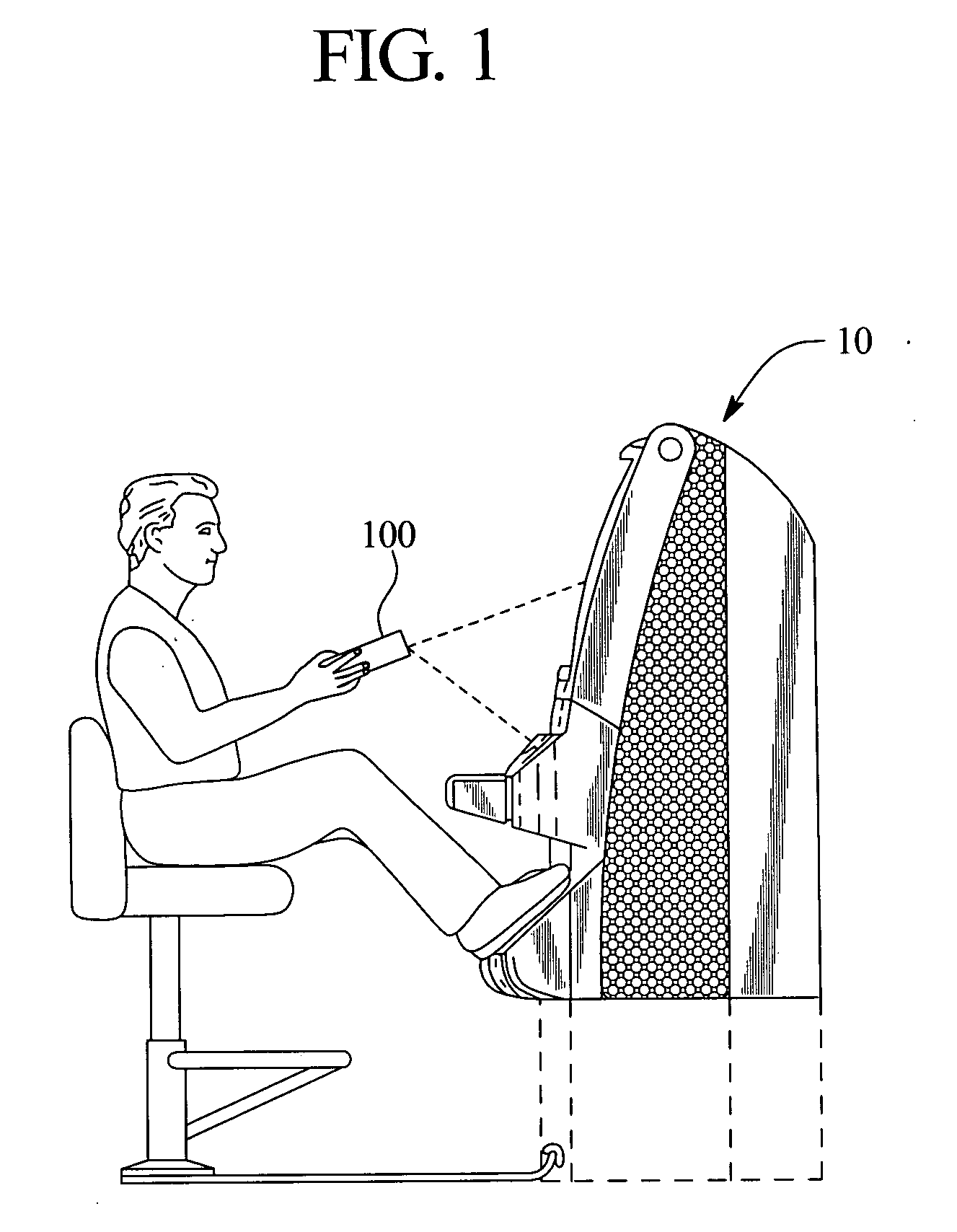
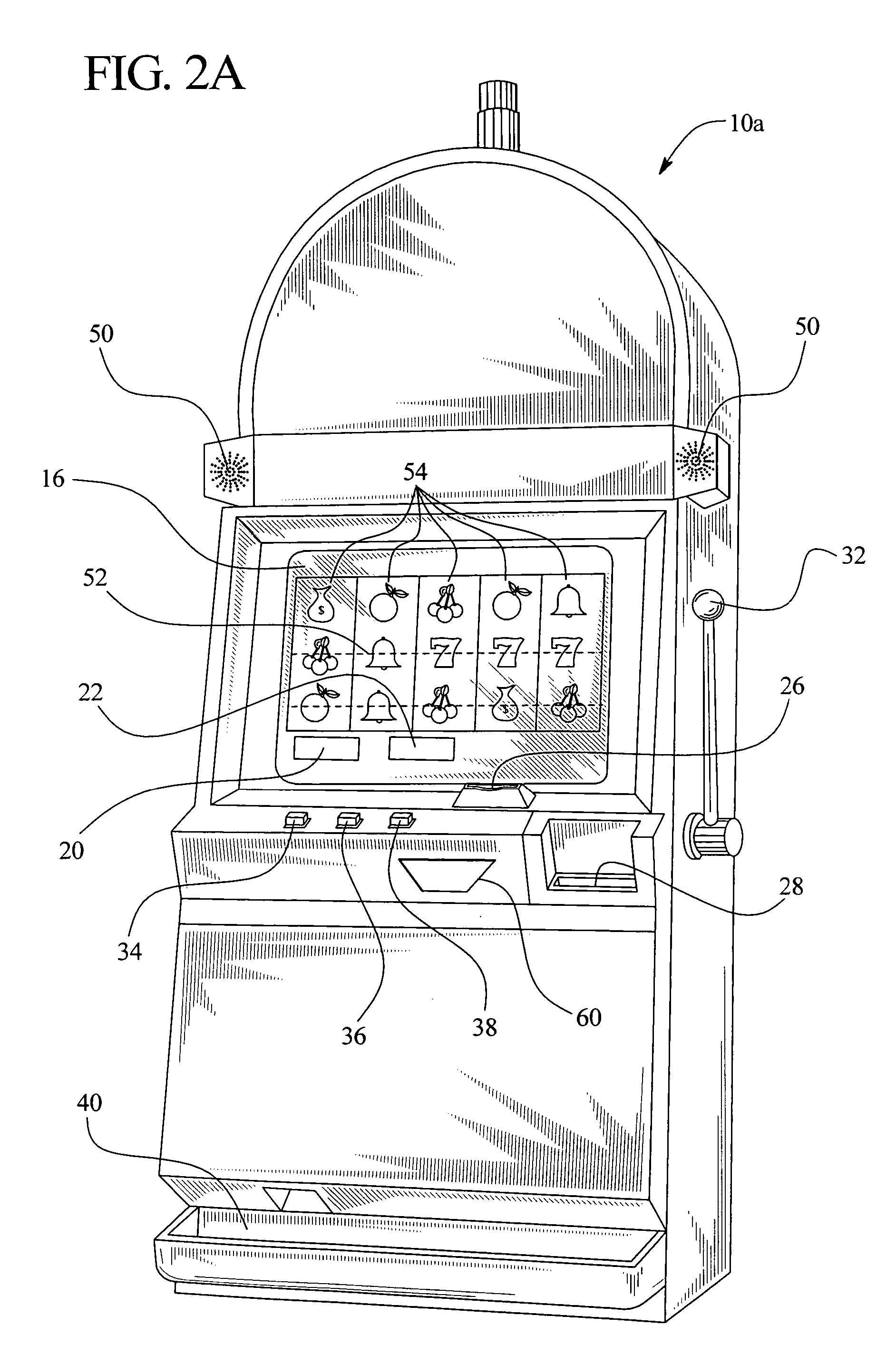
ActiveUS20060046849A1Improve securitySuitable for processingApparatus for meter-controlled dispensingVideo gamesRemote controlInit
A gaming device which can be operated by wireless signals provided by a remote control unit or device after an initialization process. The initialization process insures that the initialized gaming device accepts signals solely from the initialized remote control unit and that other players are prevented from operating the gaming device using a different remote control unit. The wireless signals contain gaming commands for play of a primary wagering game as well as player identification and / or player tracking information.
Owner:IGT
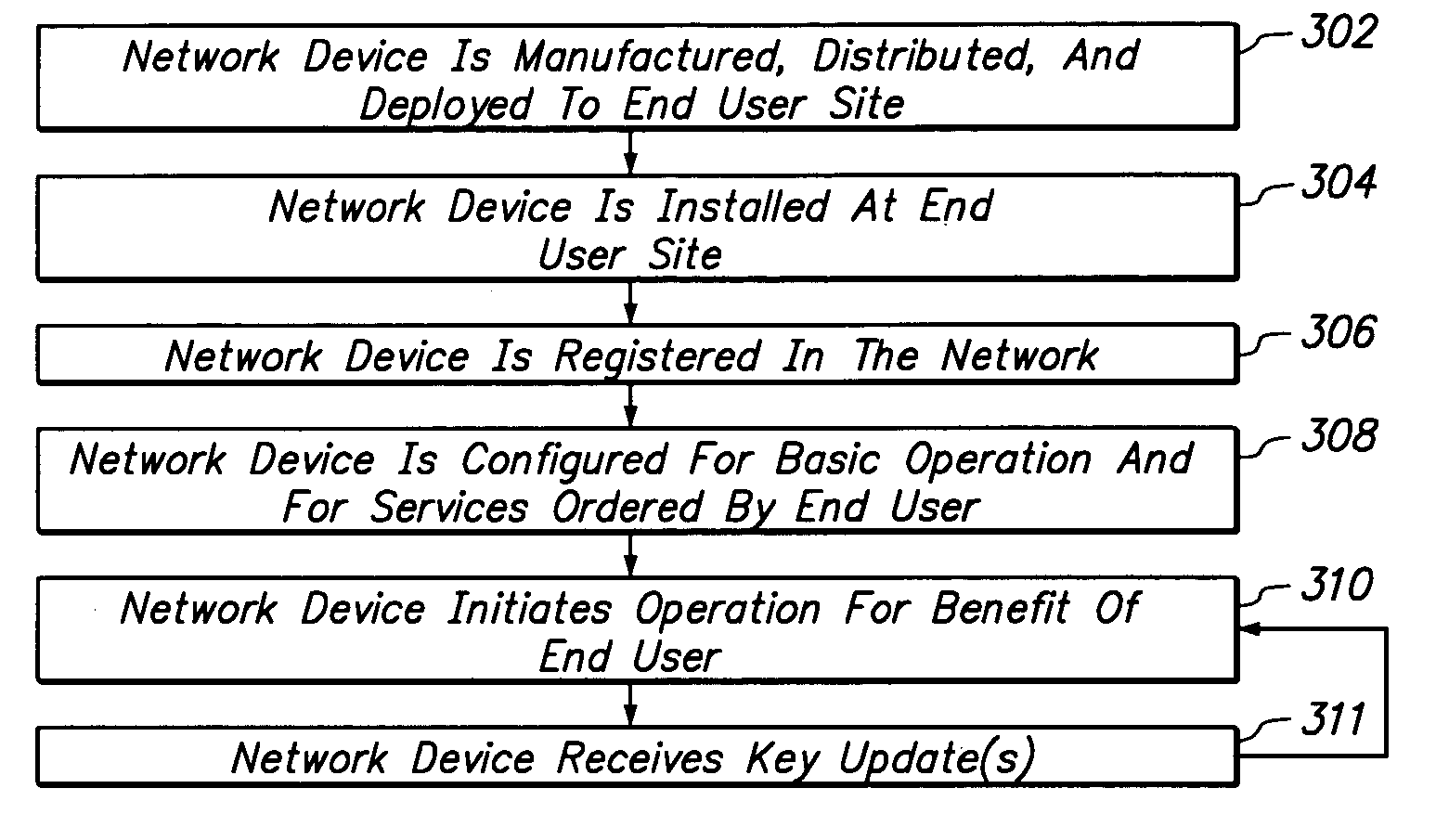
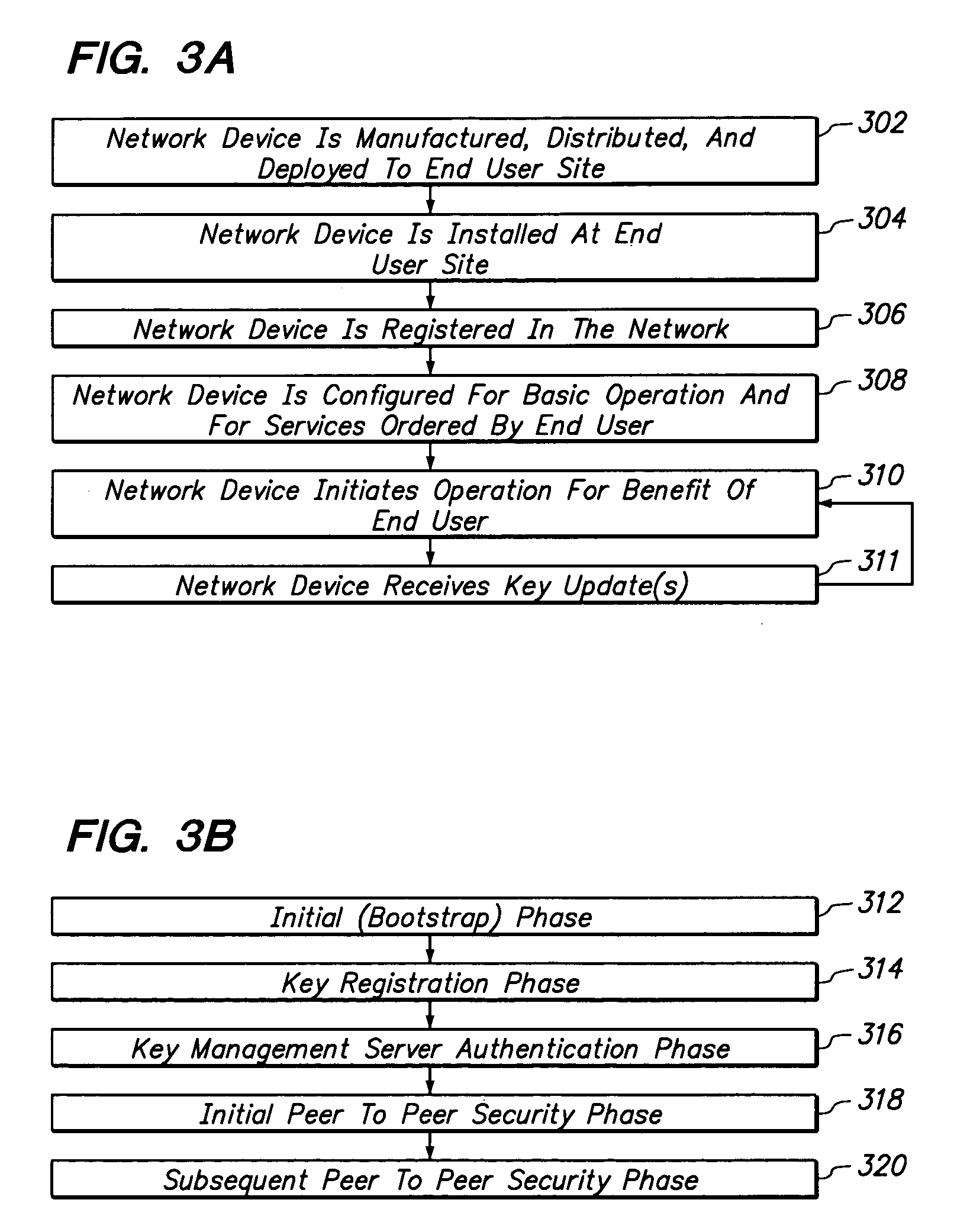
Method and apparatus providing secure initialization of network devices using a cryptographic key distribution approach
ActiveUS7181620B1Efficiently establishedCommunication securityKey distribution for secure communicationUser identity/authority verificationKey scheduleKey distribution
Registration of non-configured network devices in a distributed network is facilitated by a method of distributing cryptographic keys. A non-configured first device seeking to communicate securely with a second device acquires knowledge of a trusted registration service. The first device registers with the registration service and obtains a longer-lived symmetric key. Using the longer-lived key, the first device authenticates itself to a key management service, and receives a shorter-lived symmetric key encapsulated in a ticket that includes policy information. A second device carries out the same preparatory process. Using its ticket containing the shorter-lived key, the first device requests the second device to obtain a session key on behalf of both. The second device presents its own ticket and that of the first device to the key management service to authenticate the shorter-lived key, and then obtains a session key for use in communications among the first and second devices. The first device and second device then communicate by encrypting communications with the session key, and without further contact with the key management or registration services or any other online authoritative server or key database. Thus newly deployed network devices may be positively identified, registered in the network, and subjected to key schedule or other key management policies.
Owner:CISCO TECH INC
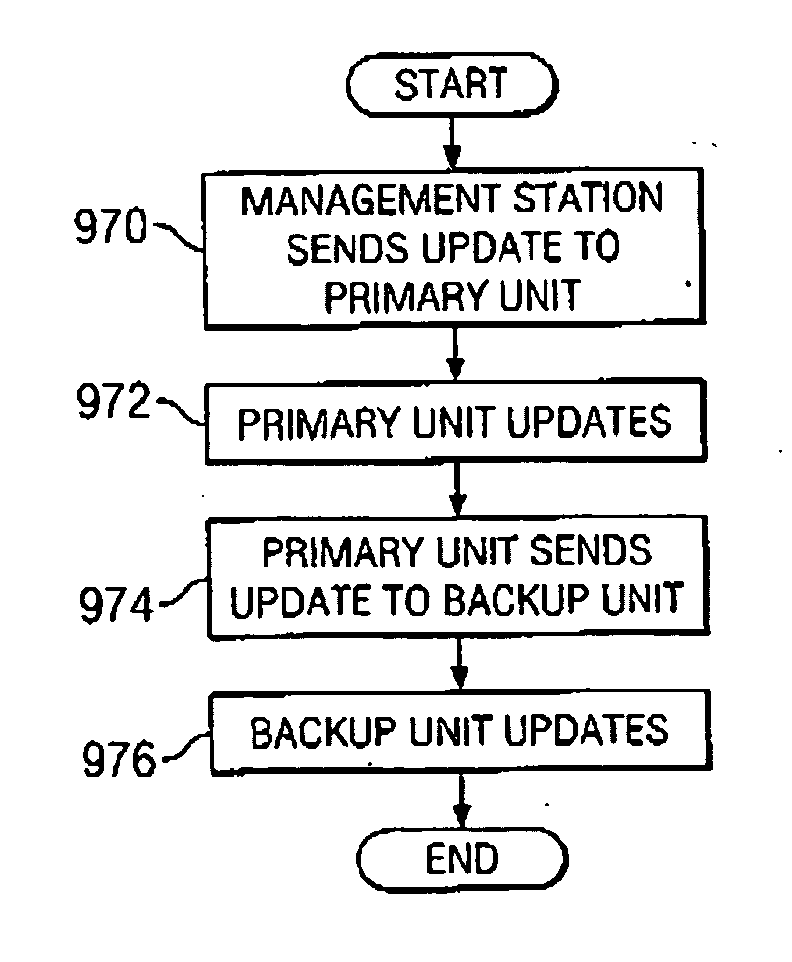
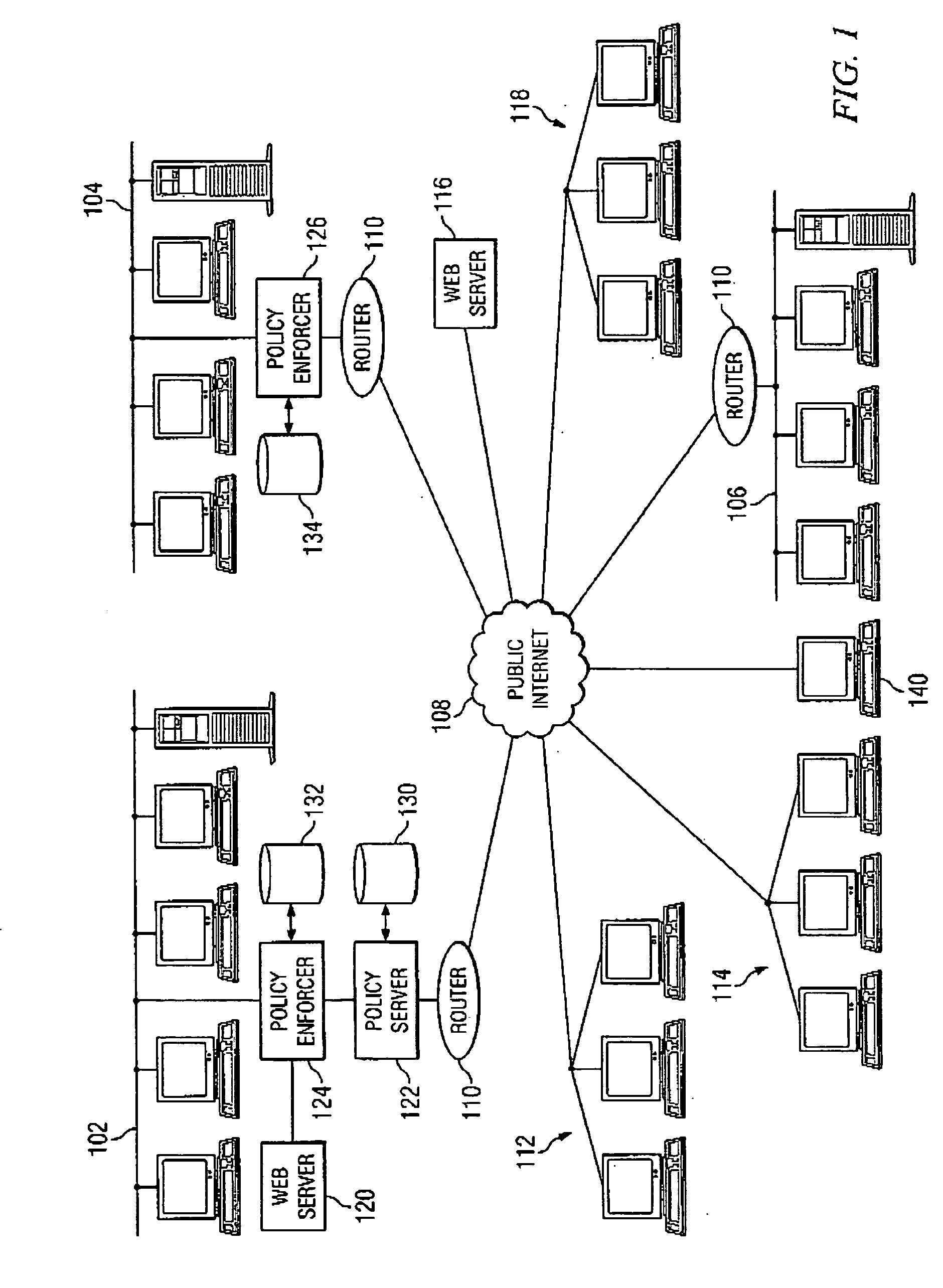
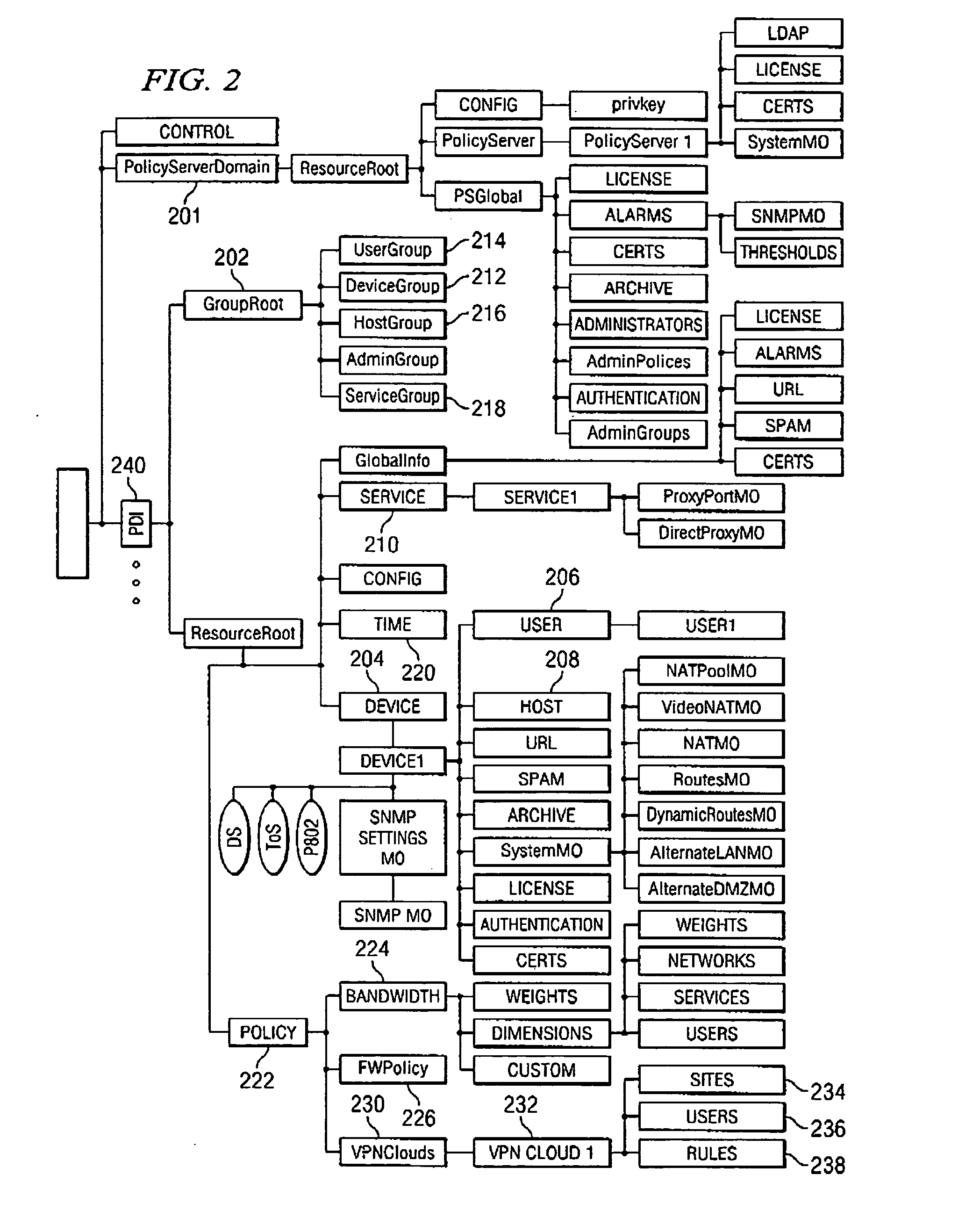
Virtual private network having automatic reachability updating
InactiveUS20050138204A1Easy to createCommunication securityEnergy efficient ICTDigital data protectionPrivate networkReachability
A unified policy management system for an organization including a central policy server and remotely situated policy enforcers. A central database and policy enforcer databases storing policy settings are configured as LDAP databases adhering to a hierarchical object oriented structure. Such structure allows the policy settings to be defined in an intuitive and extensible fashion. Changes in the policy settings made at the central policy server are automatically transferred to the policy enforcers for updating their respective databases. Each policy enforcer collects and transmits health and status information in a predefined log format and transmits it to the policy server for efficient monitoring by the policy server. For further efficiencies, the policy enforcement functionalities of the policy enforcers are effectively partitioned so as to be readily implemented in hardware. The system also provides for dynamically routed VPNs where VPN membership lists are automatically created and shared with the member policy enforcers. Updates to such membership lists are also automatically transferred to remote VPN clients. The system further provides for fine grain access control of the traffic in the VPN by allowing definition of firewall rules within the VPN. In addition, policy server and policy enforcers may be configured for high availability by maintaining a backup unit in addition to a primary unit. The backup unit become active upon failure of the primary unit.
Owner:IYER SHANKER V +3
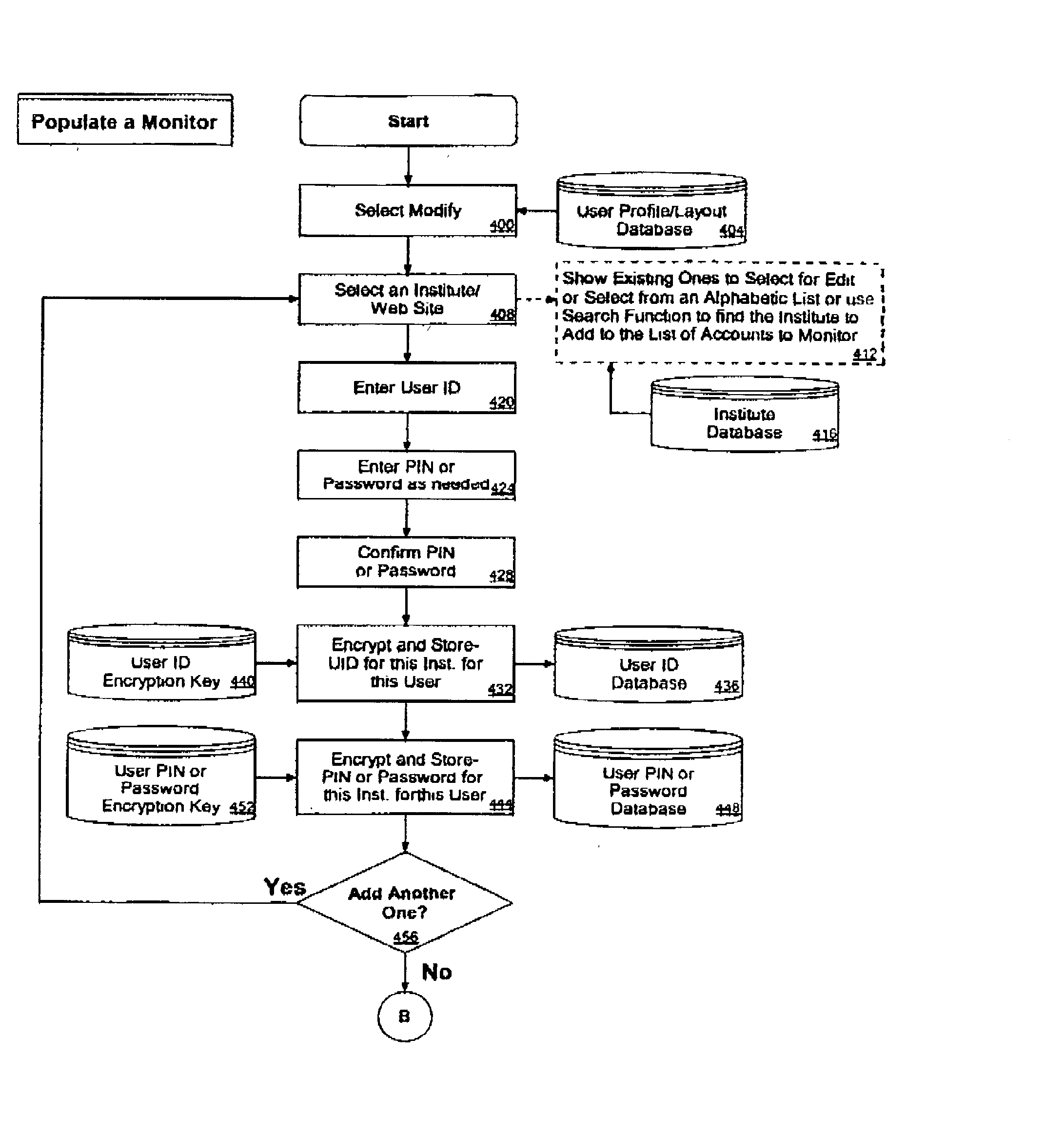
Secure selective sharing of account information on an internet information aggregation system
InactiveUS7120928B2Preserve security and confidentialityCommunication securityDigital data processing detailsUser identity/authority verificationThe InternetCode distribution
Owner:FINASTRA USA CORP
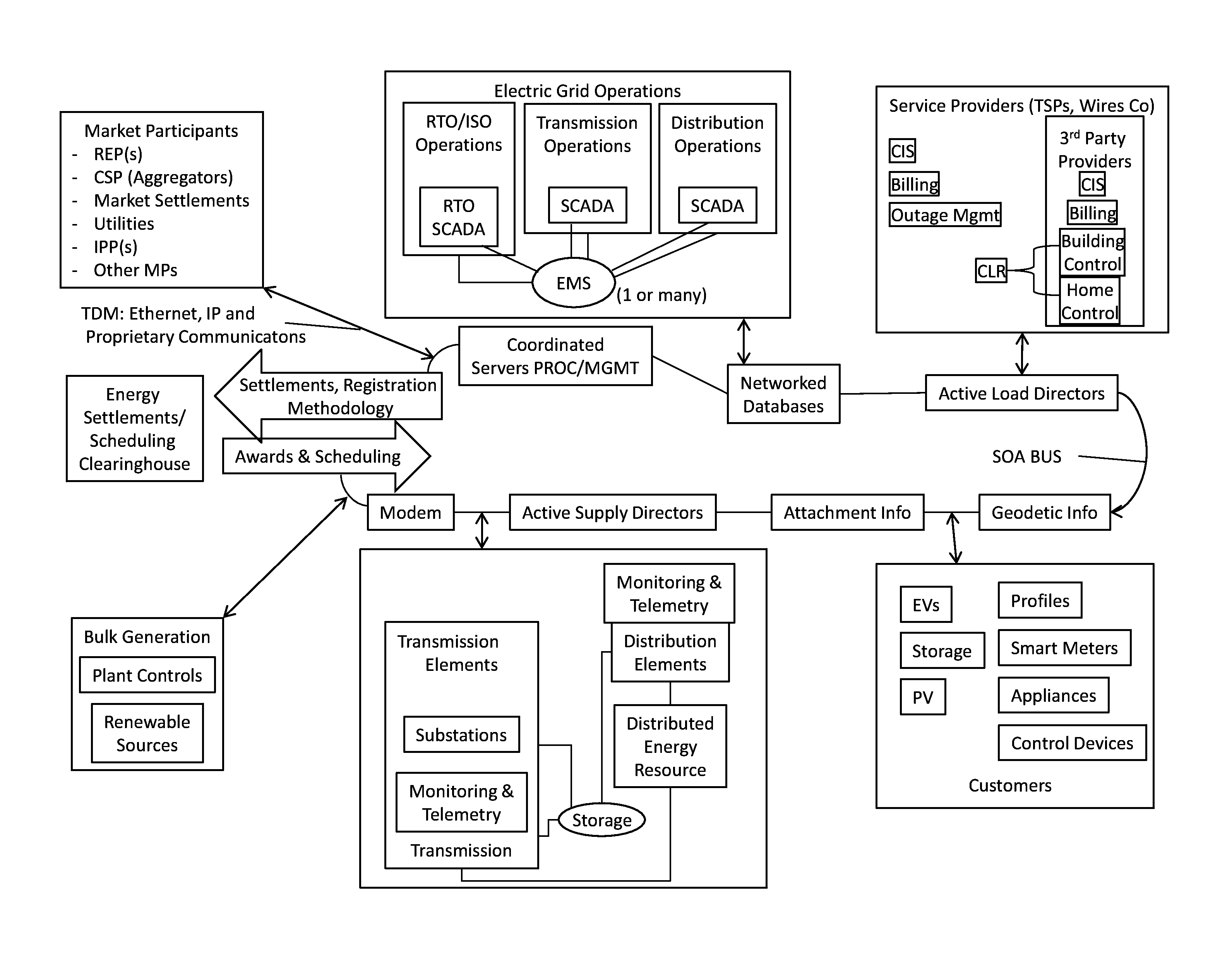
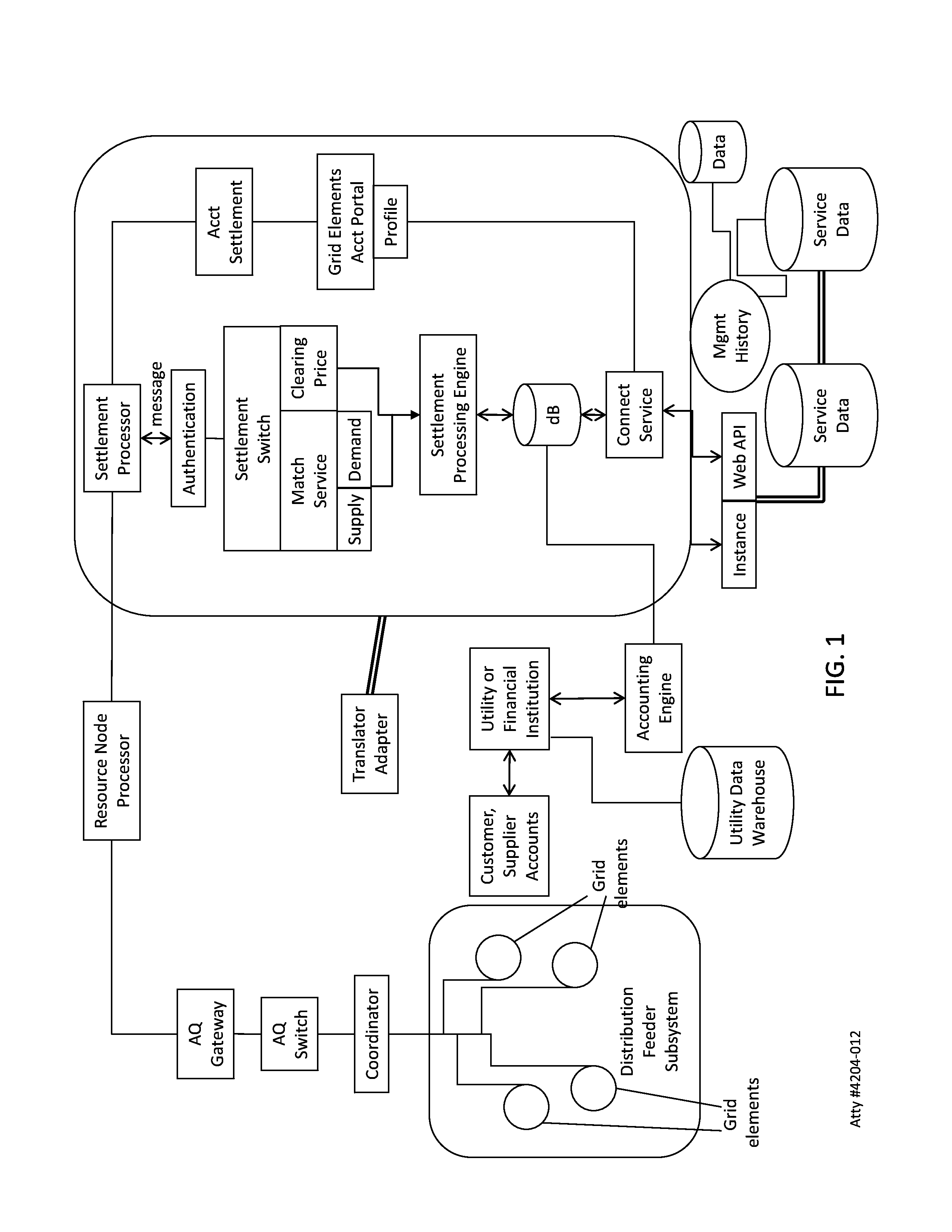
System, method, and apparatus for settlement for participation in an electric power grid
ActiveUS8583520B1Communication securityEasy to useLevel controlCoin-freed apparatusNetwork managementGrid operator
Systems, methods, and apparatus embodiments for electric power grid and network registration and management of physical and financial settlement for participation of active grid elements in supply and / or curtailment of power. Settlement is provided for grid elements that participate in the electric power grid following initial registration of each grid element with the system, preferably through network-based communication between the grid elements and a coordinator, either in coordination with or outside of an IP-based communications network router. A multiplicity of active grid elements function in the grid for supply capacity, supply and / or load curtailment as supply or capacity, and are compensated through settlement for their functional participation in the electric power grid. Also, messaging related to settlement is managed through a network by a Coordinator using IP messaging for communication with the grid elements, with the energy management system (EMS), and with the utilities, market participants, and / or grid operators.
Owner:CAUSAM ENERGY INC
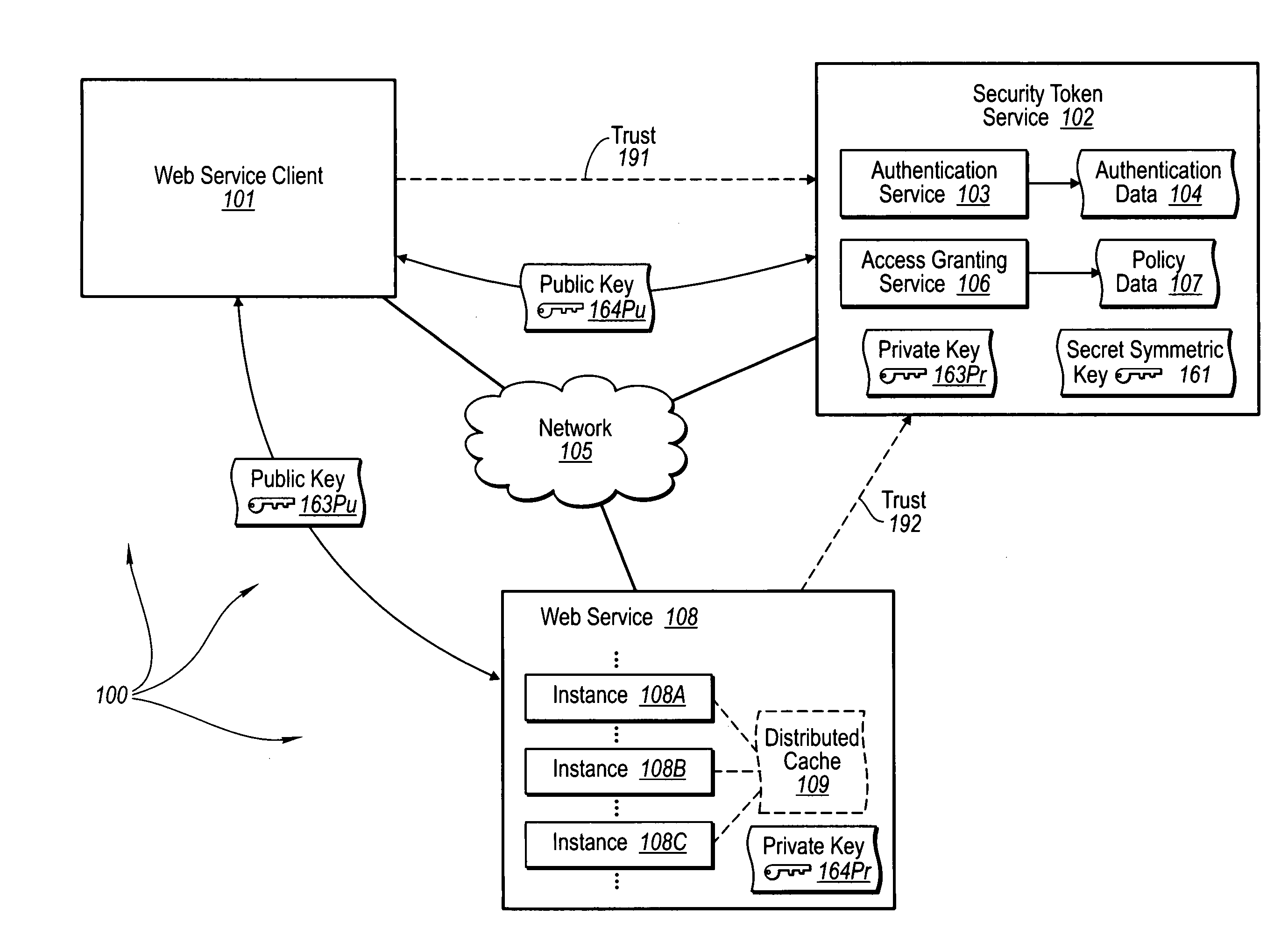
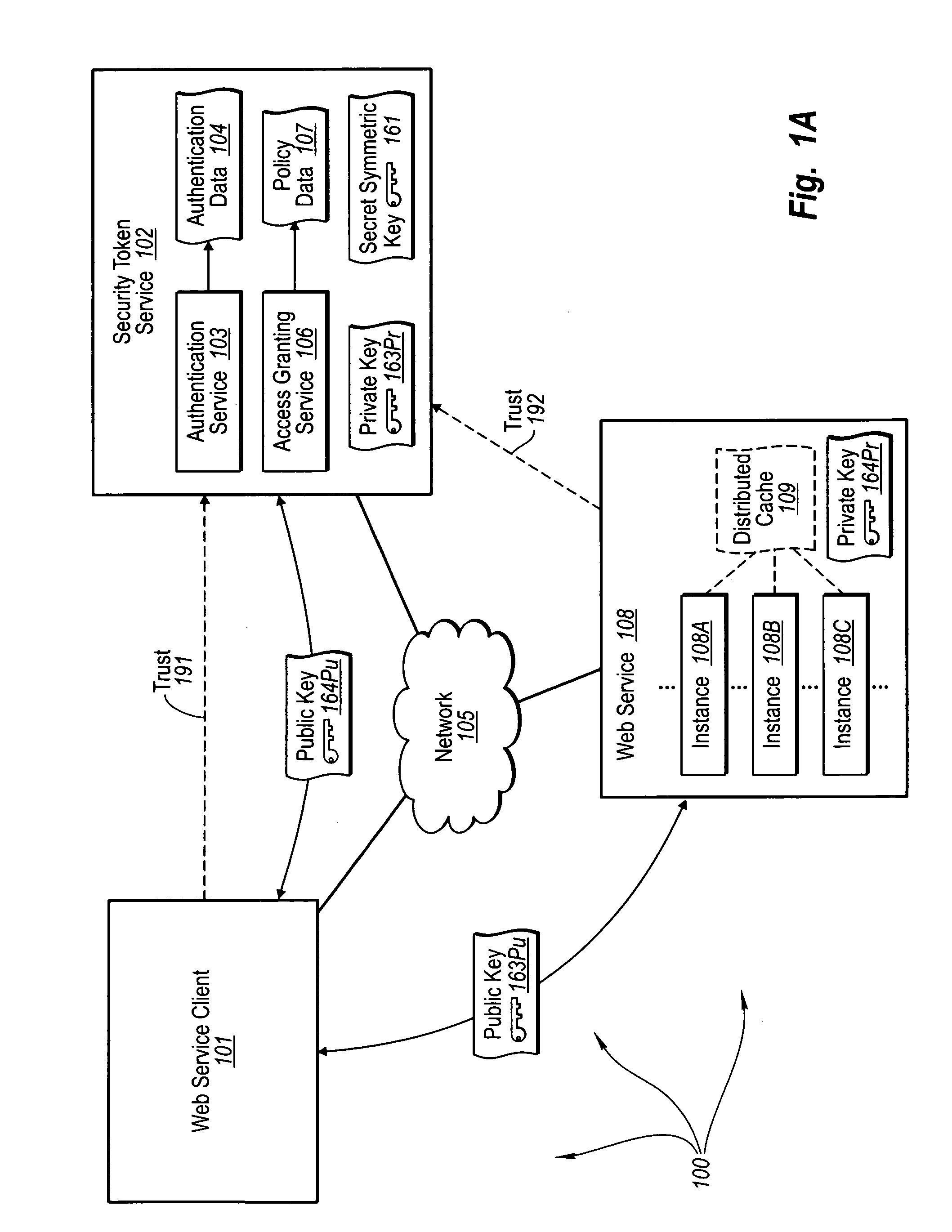
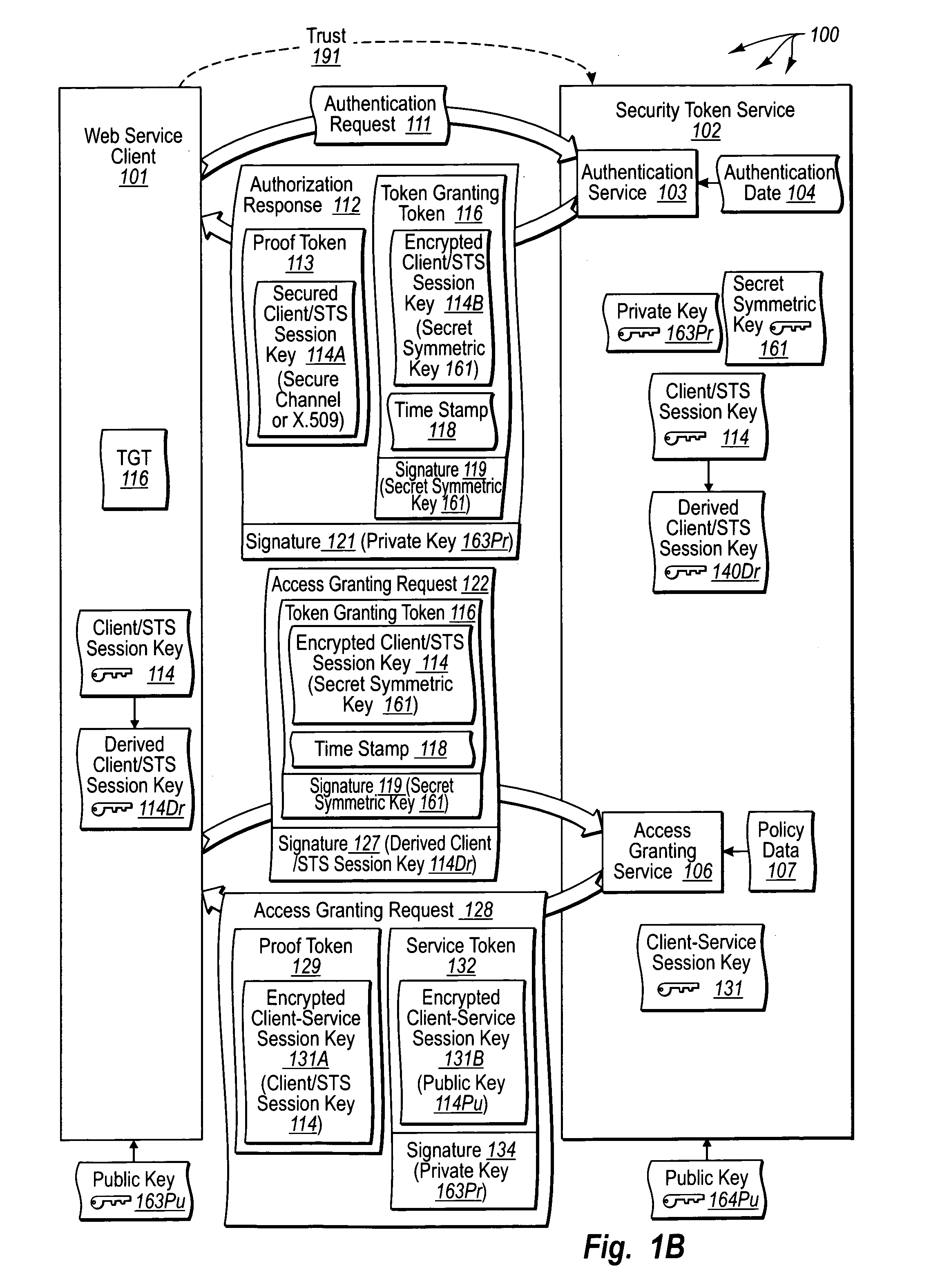
Trusted third party authentication for web services
InactiveUS20060206932A1Communication securityDigital data processing detailsUser identity/authority verificationWeb serviceInternet privacy
The present invention extends to trusted third party authentication for Web services. Web services trust and delegate user authentication responsibility to a trusted third party that acts as an identity provider for the trusting Web services. The trusted third party authenticates users through common authentication mechanisms, such as, for example, username / password and X.509 certificates and uses initial user authentication to bootstrap subsequent secure sessions with Web services. Web services construct user identity context using a service session token issued by the trusted third party and reconstruct security states without having to use a service-side distributed cache.
Owner:MICROSOFT TECH LICENSING LLC
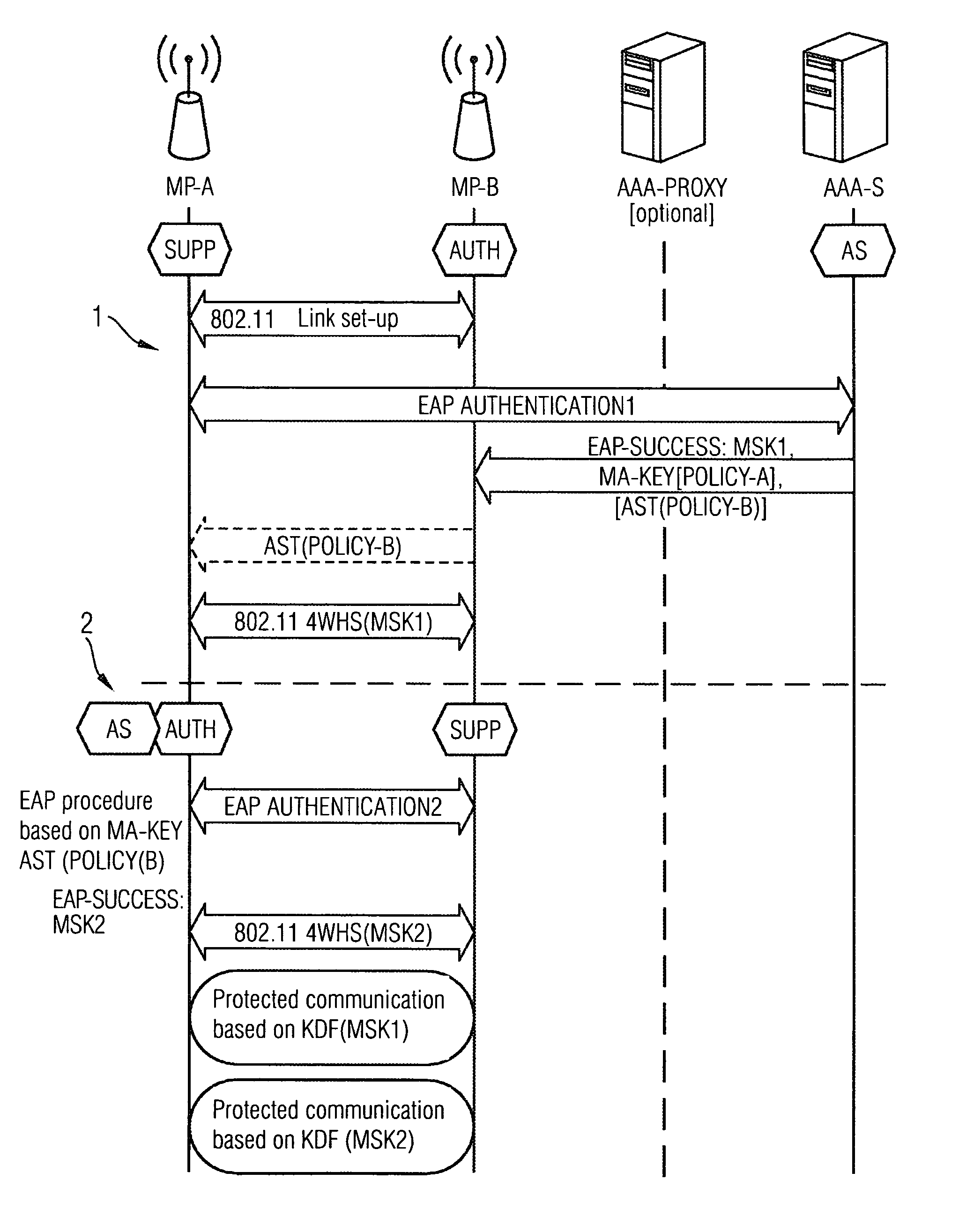
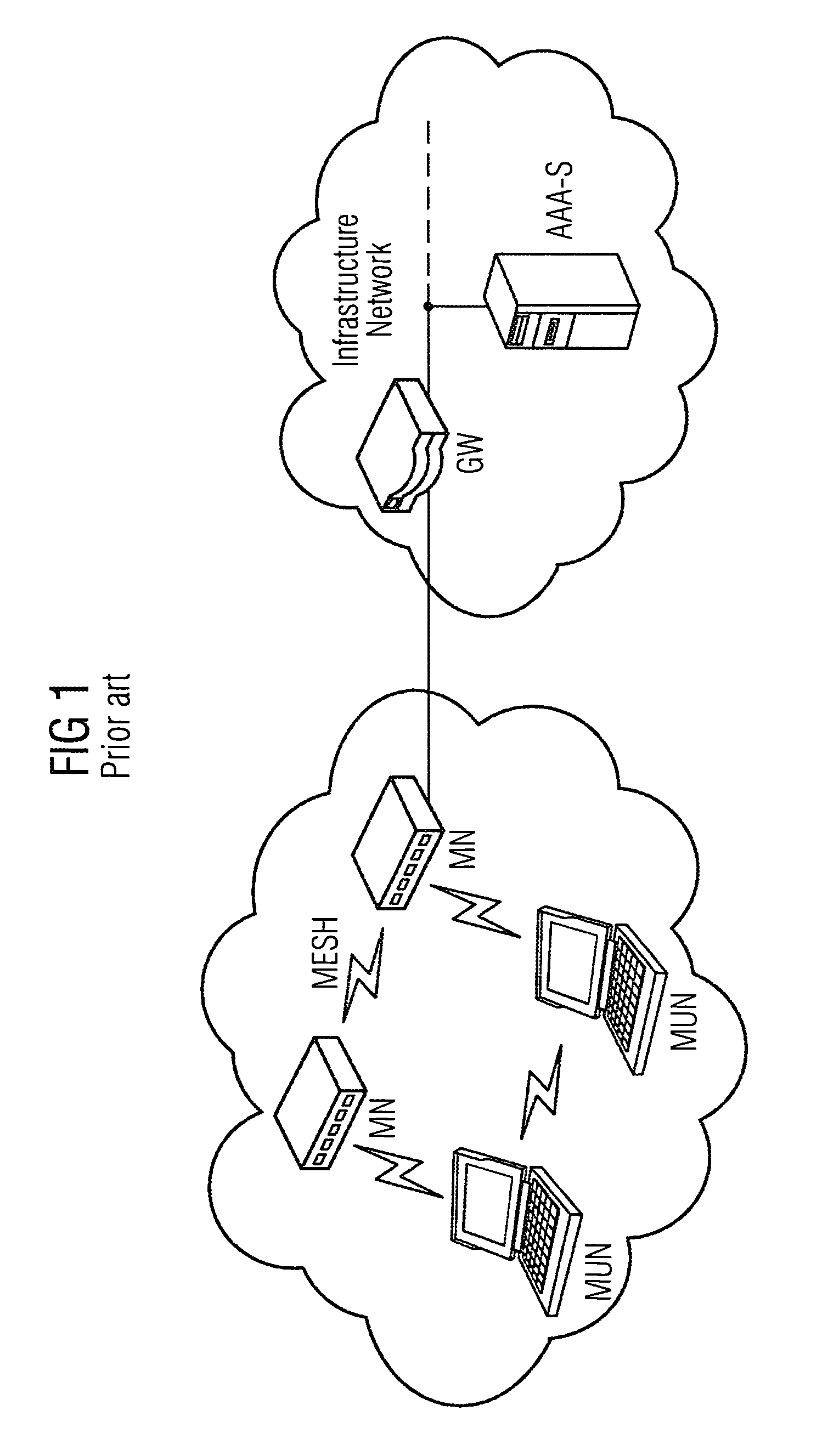
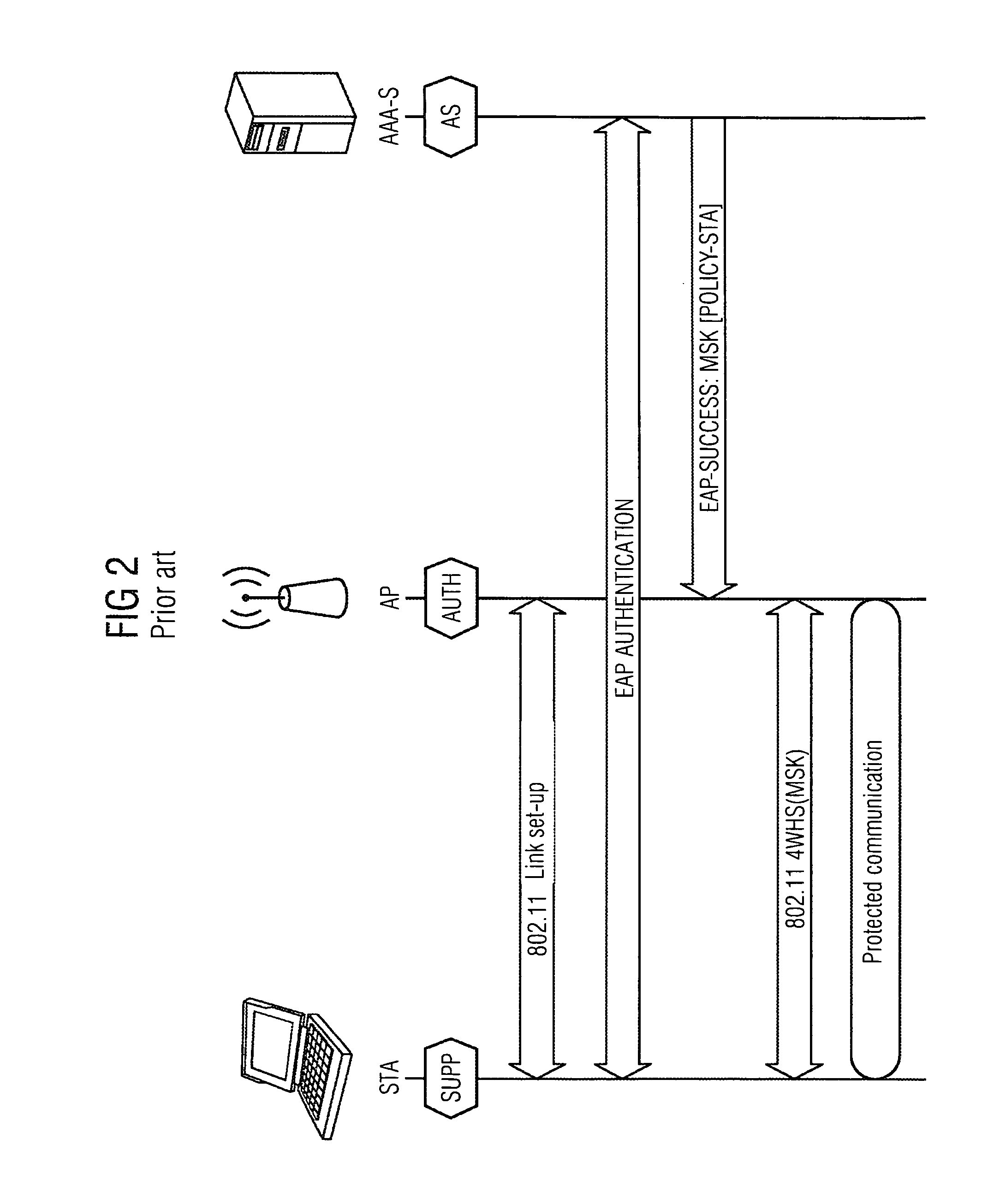
Method and arrangement for providing a wireless mesh network
ActiveUS8495360B2Communication securitySimple and appropriateDigital data processing detailsUser identity/authority verificationComputer scienceMesh node
A method and an arrangement are provided wherein a newly added mesh node does not require a link to the AAA server for the purpose of authentication. Authentication is carried out using a node which is already present in the mesh network and which has a link to the AAA server.
Owner:UNIFY PATENTE GMBH & CO KG
Portable wireless access to computer-based systems
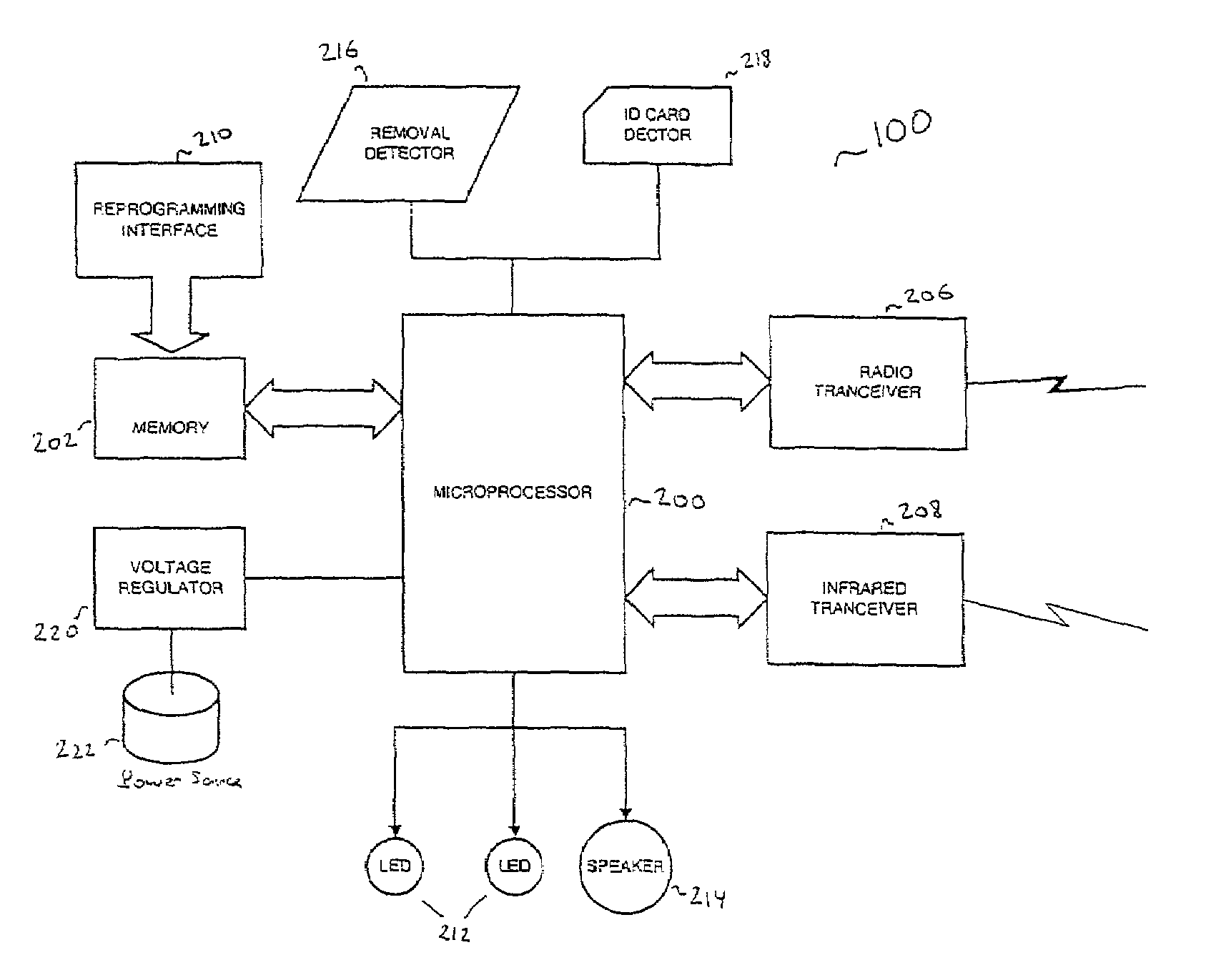
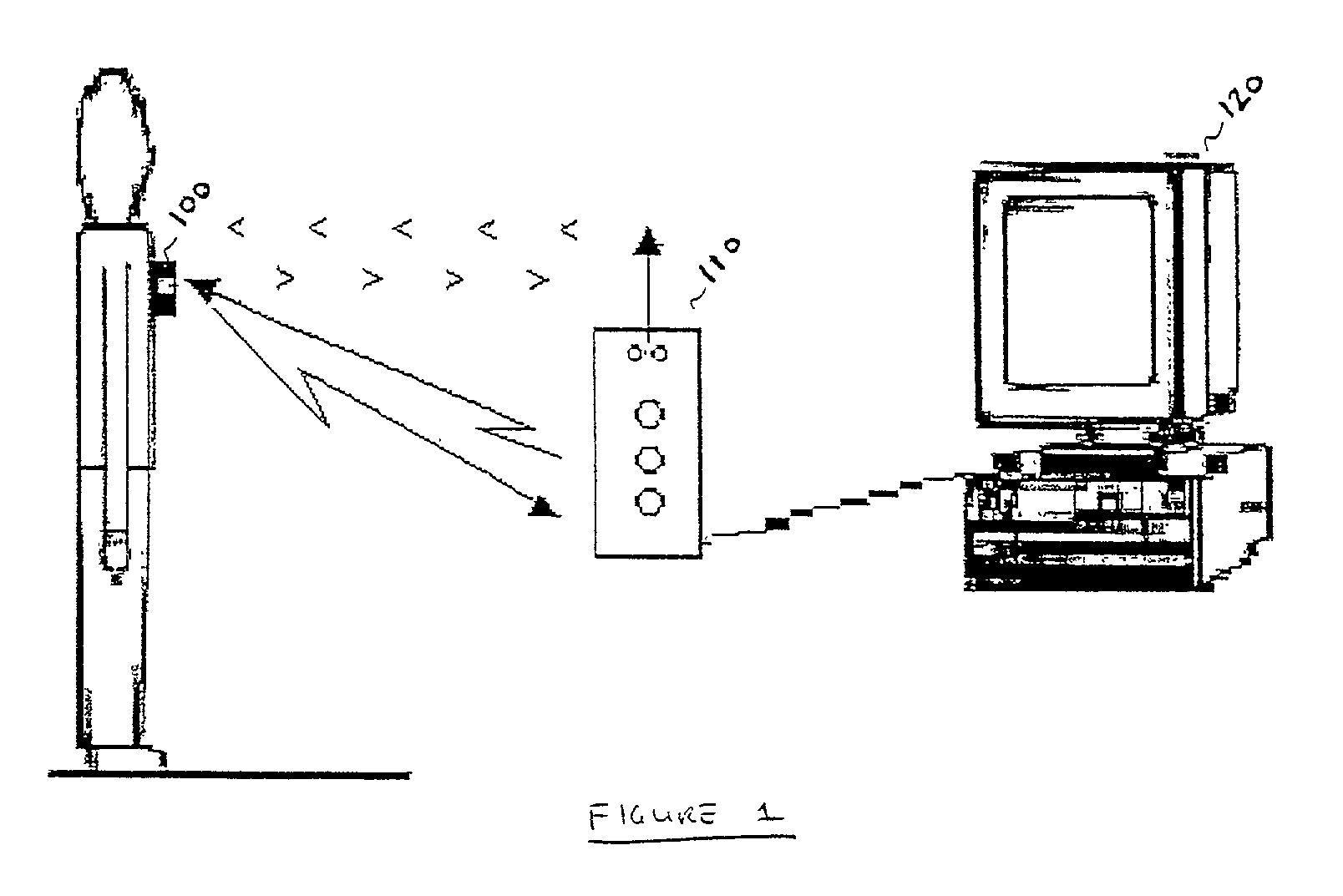
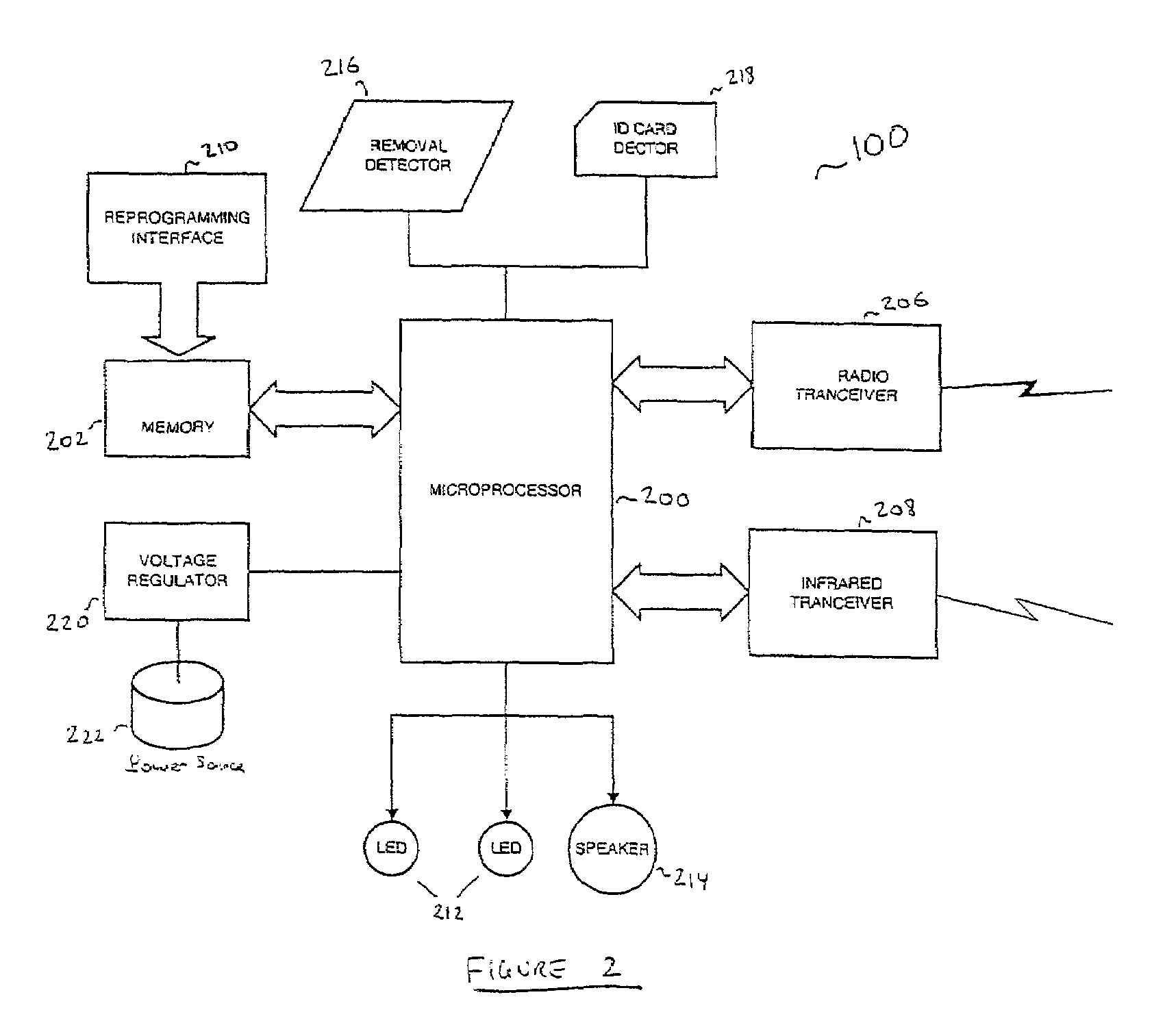
InactiveUS7069444B2Facilitates secure communicationCommunication securityMultiple digital computer combinationsDigital data authenticationSecure communicationTransceiver
A portable wireless system for providing a user with access to a computer-based system includes a BARB Badge to interface with the user's body, responsive to a disruption in the interface and including a transceiver to communicate with an external source, a BARB Base to detect a presence of said BARB Badge in a vicinity of said BARB Base and relay secure communications between said BARB Badge and said computer-based system; and an administrator subsystem to regulate interfacing operations of said BARB Badge and said computer-based system based on predetermined administrative protocols. In this way, the overall security of the computer-based system is enhanced while the amount of operational burdens associated with accessing the computer-based system are reduced.
Owner:LOWENSOHN BRENT
Secure selective sharing of account information on an internet information aggregation system
InactiveUS20020194502A1Preserve security and confidentialityCommunication securityDigital data processing detailsComputer security arrangementsThe InternetMobile device
Owner:FINASTRA USA CORP
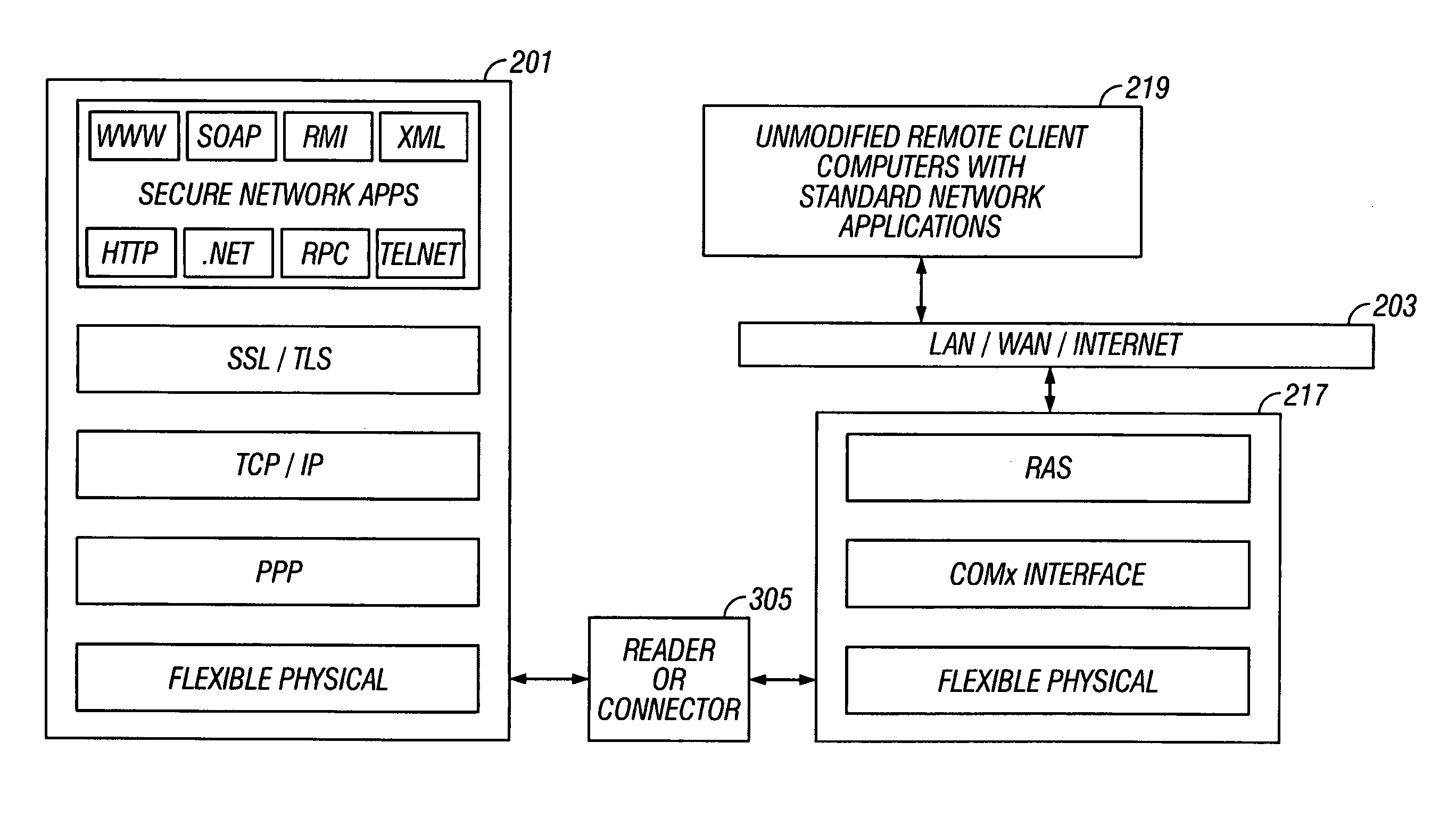
Secure networking using a resource-constrained device
ActiveUS20050108571A1Easy to adaptCommunication securityDigital data processing detailsHardware monitoringSecure communicationClient-side
Secure communication between a resource-constrained device and remote network nodes over a network with the resource-constrained acting as a network node. The remote network nodes communicate with the resource-constrained device using un-modified network clients and servers. Executing on the resource-constrained device, a communications module implements one or more link layer communication protocols, operable to communicate with a host computer, operable to communicate with remote network nodes and operable to implement network security protocols thereby setting a security boundary inside the resource-constrained device.
Owner:GEMPLU
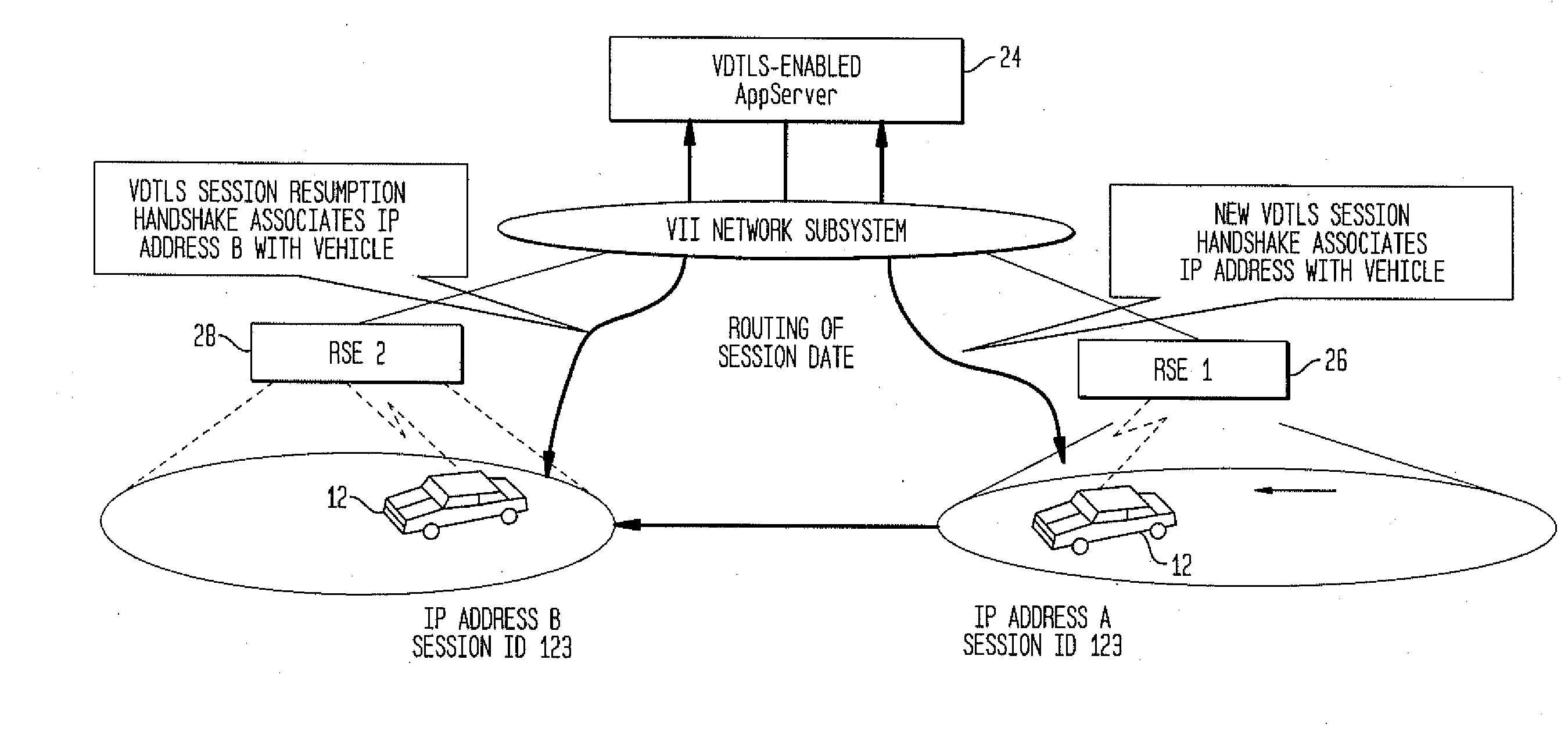
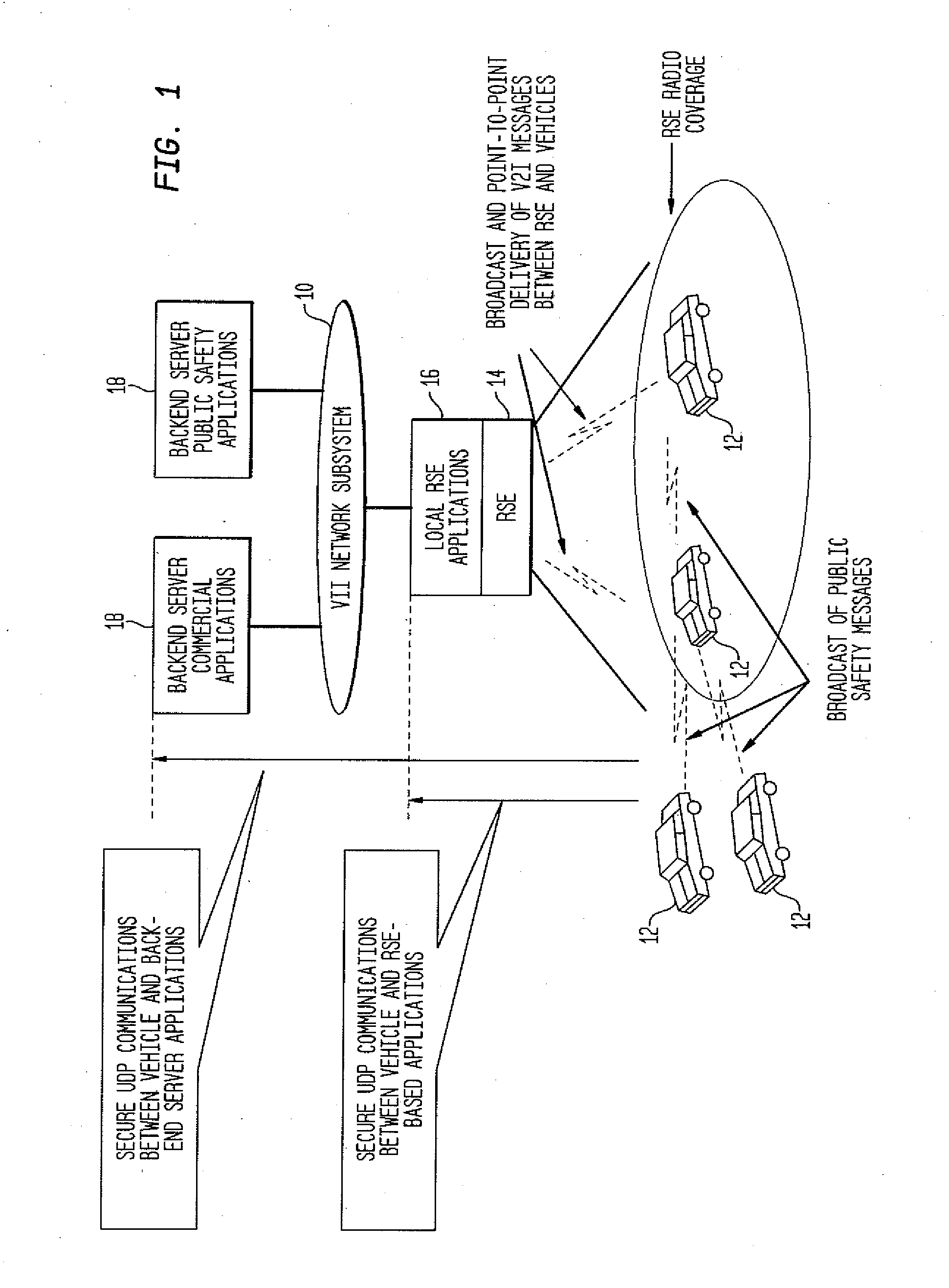
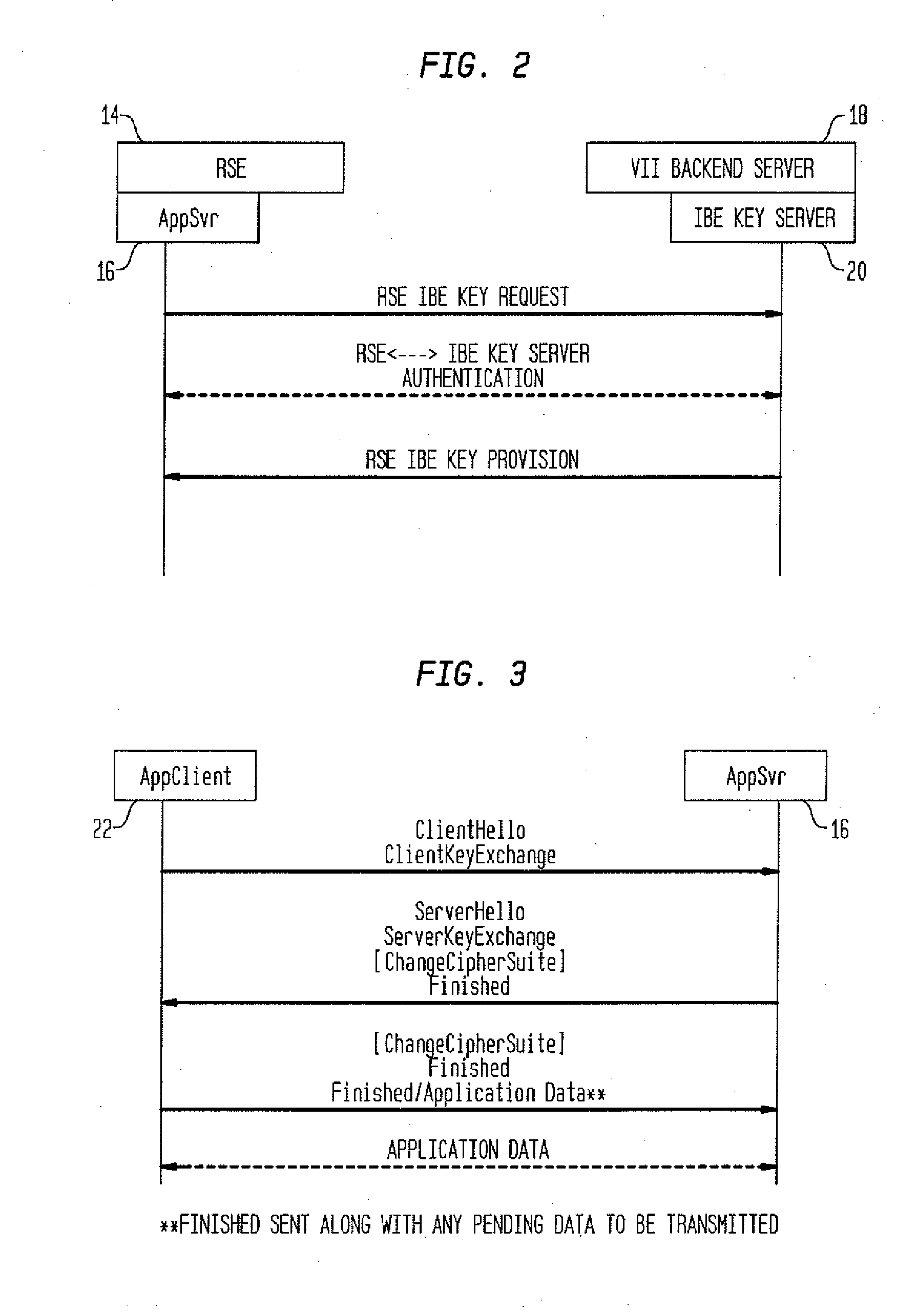
Method and System for Secure Session Establishment Using Identity-Based Encryption (VDTLS)
ActiveUS20100031042A1Communication securityPrivacy protectionUser identity/authority verificationSecurity arrangementID-based encryptionSecure communication
The inventive system for providing strong security for UDP communications in networks comprises a server, a client, and a secure communication protocol wherein authentication of client and server, either unilaterally or mutually, is performed using identity based encryption, the secure communication protocol preserves privacy of the client, achieves significant bandwidth savings, and eliminates overheads associated with certificate management. VDTLS also enables session mobility across multiple IP domains through its session resumption capability.
Owner:TELCORDIA TECHNOLOGIES INC
System and method for distributed ssl processing between co-operating nodes
ActiveUS20080307219A1Communication securityMultiple digital computer combinationsProgram controlSecure communicationClient-side
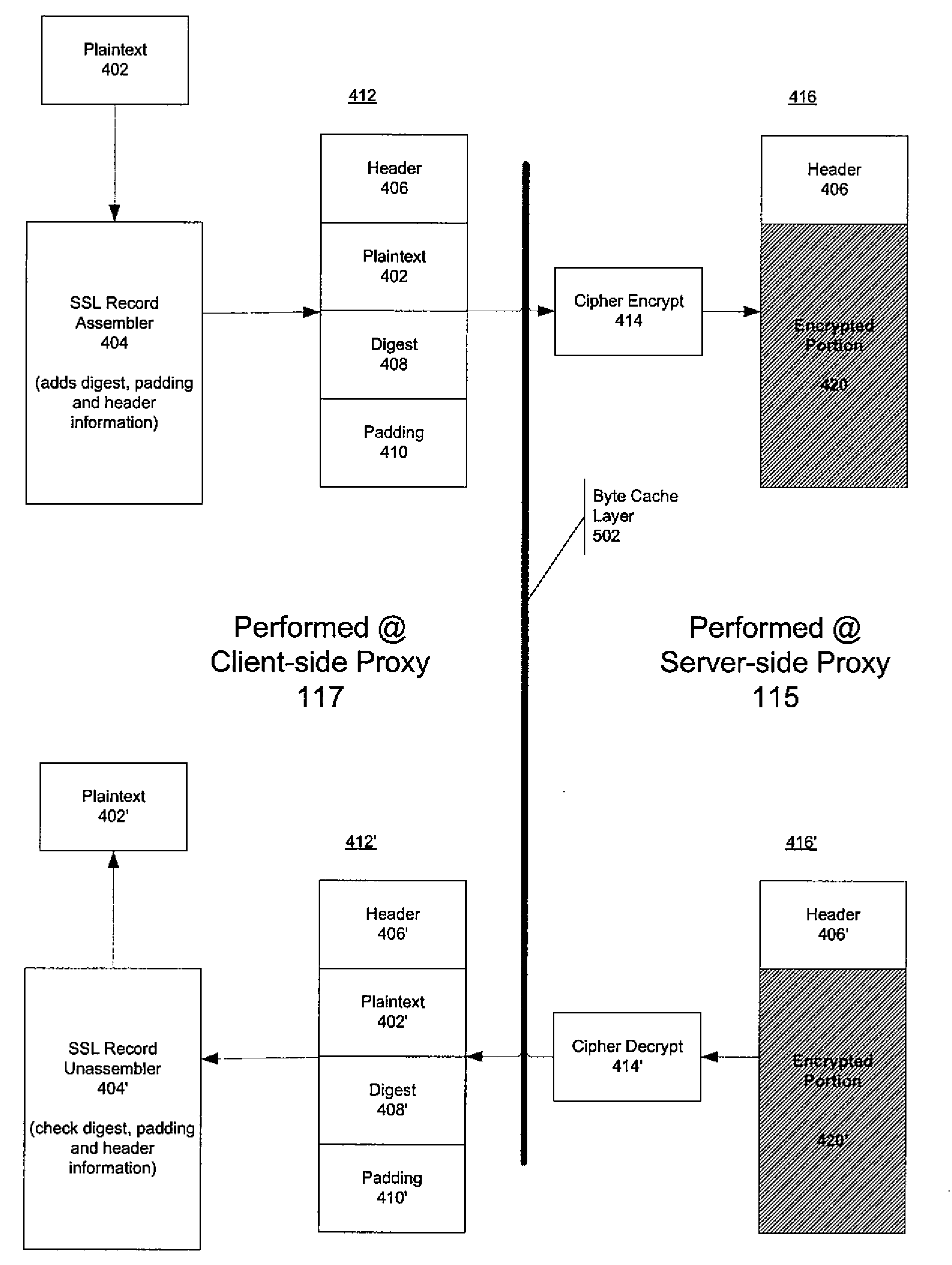
A secure communication protocol (e.g., SSL) transaction request from a client to a server is intercepted at a client-side proxy communicatively coupled to the client and logically deployed between the client and the server. The client-side proxy initiates a secure connection with the server and passes an attribute (e.g., a cryptographic key) associated with that secure connection to a server-side proxy communicatively coupled to the server and logically deployed between the client and the server. This enables the server-side proxy to engage in secure communications with the server in a transparent fashion.
Owner:CA TECH INC
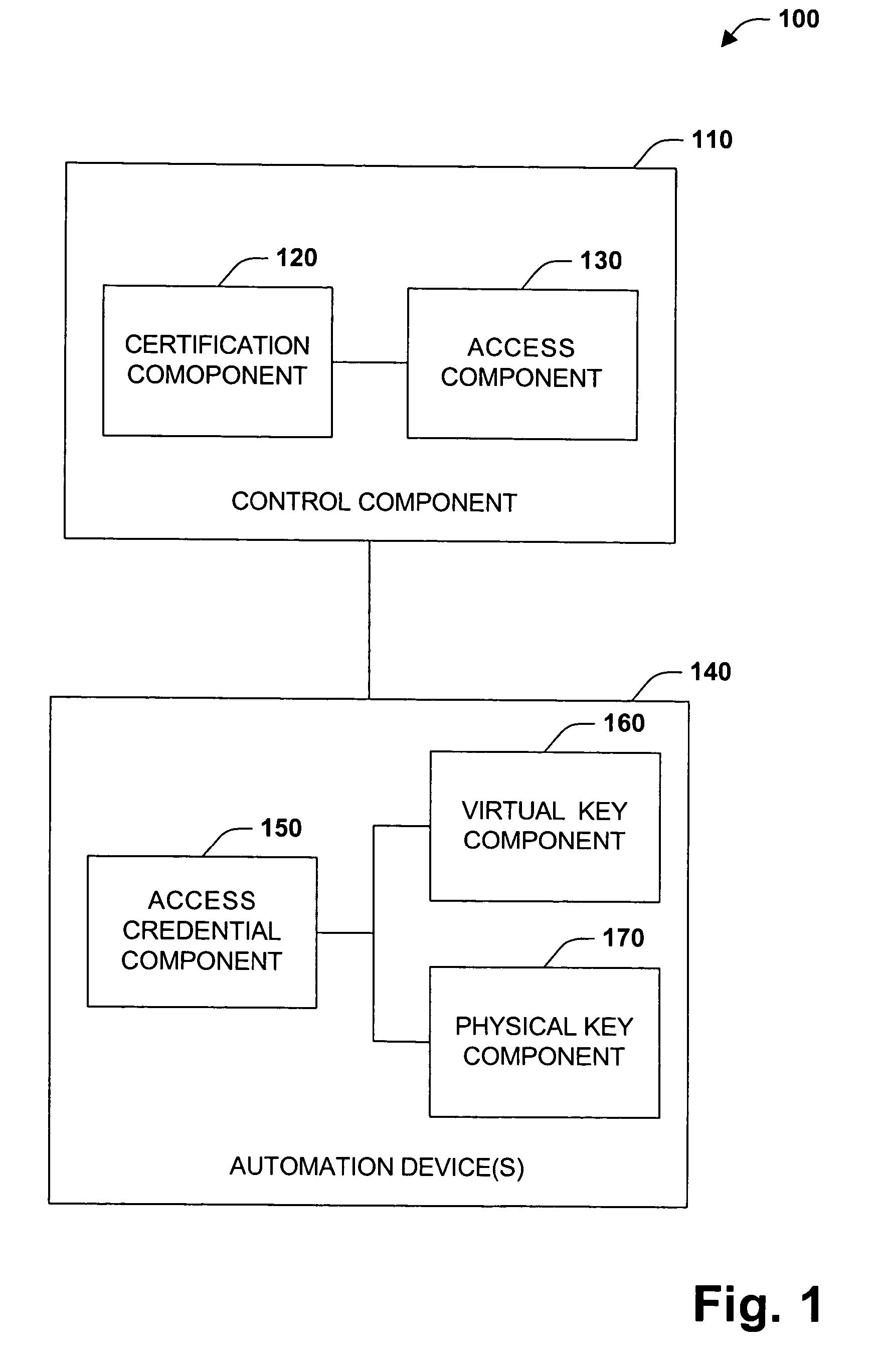
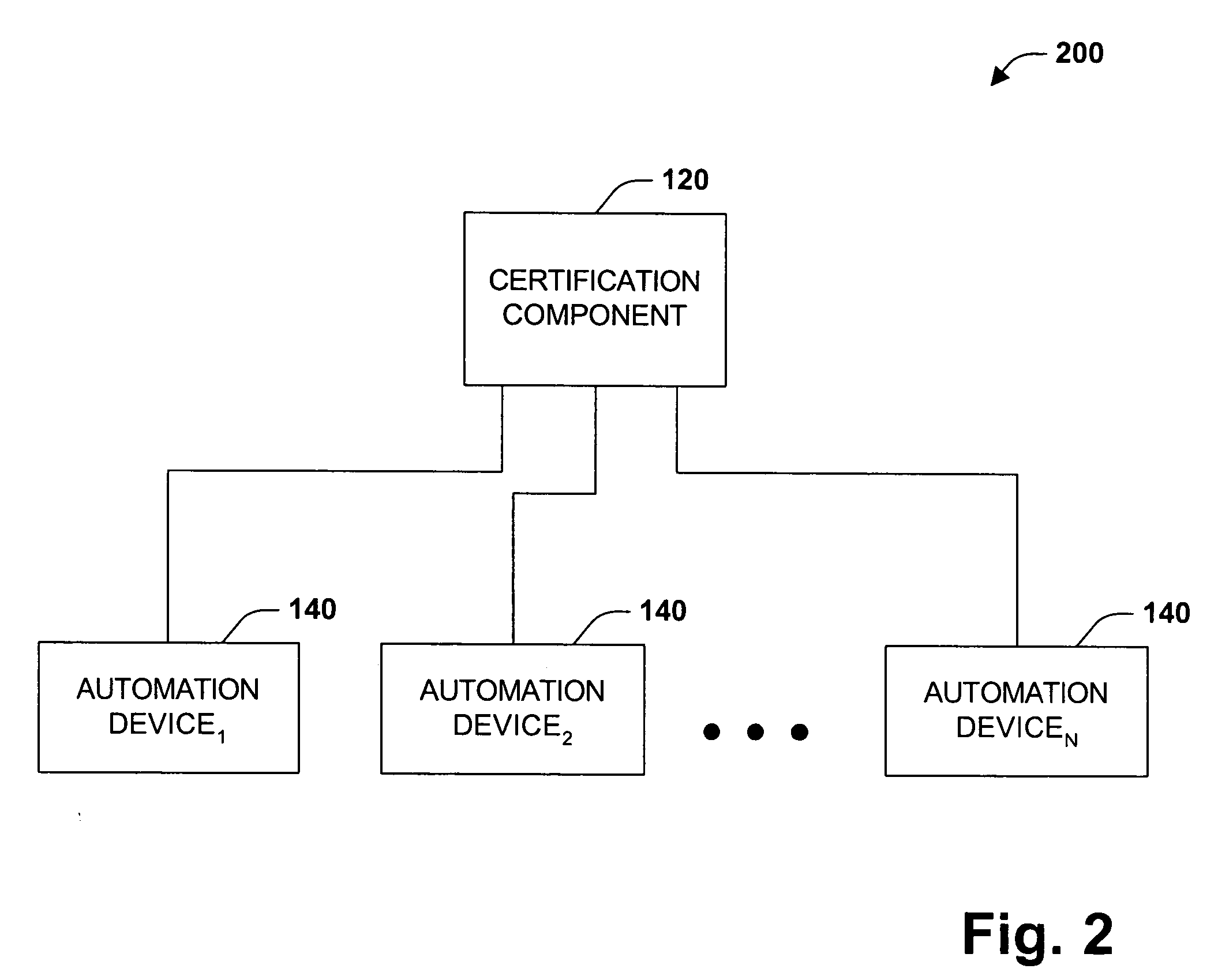
Digital rights management system and method
InactiveUS20050229004A1Improve securityCommunication securityProgramme controlComputer controlUser PrivilegeSecure transmission
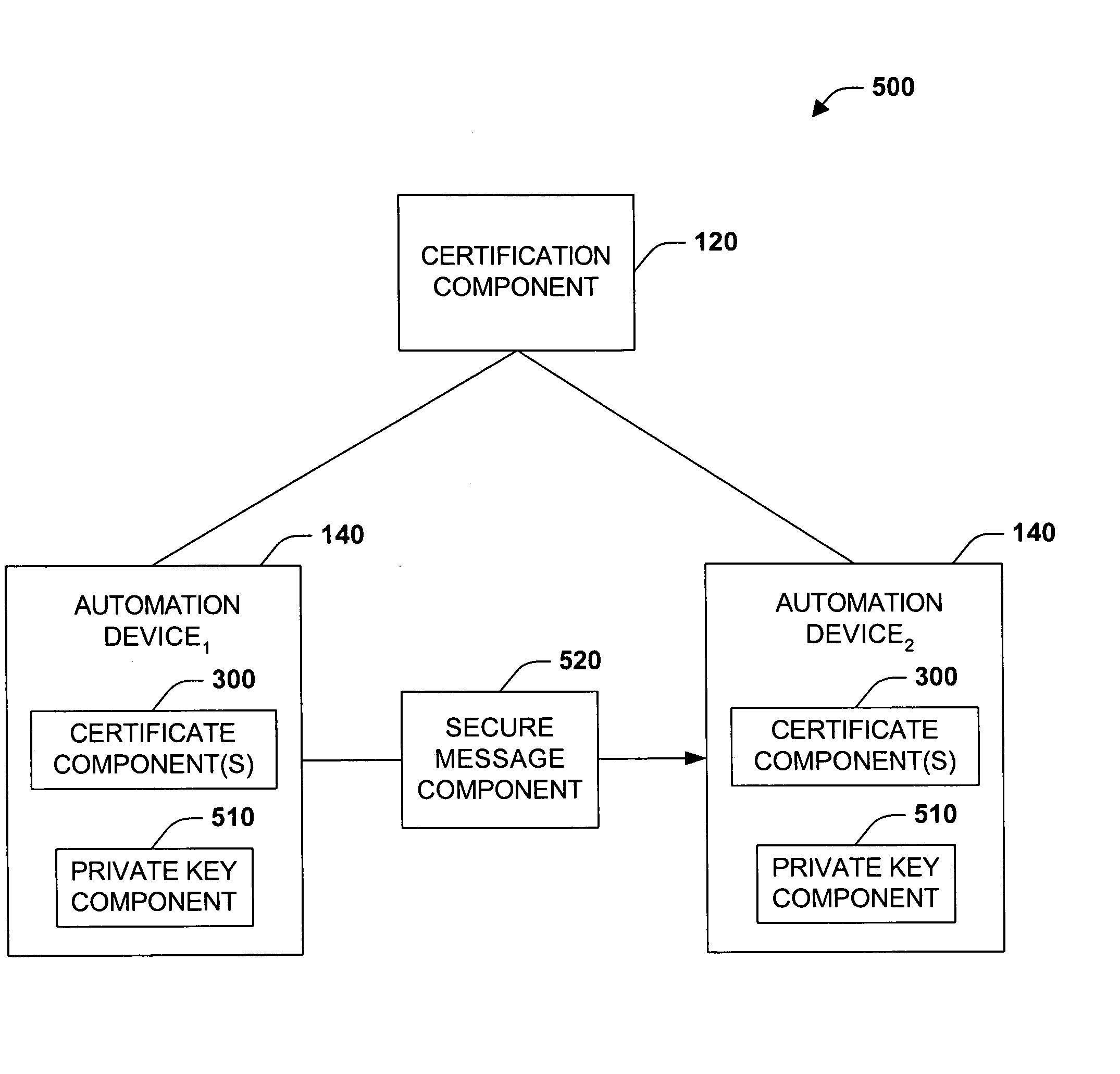
The present invention concerns application of digital rights management to industrial automation devices including programmable logic controllers (PLCs), I / O devices, and communication adapters. Digital rights management involves a set of technologies for controlling and managing access to device objects and / or programs such as ladder logic programs. Access to automation device objects and / or programs can be managed by downloading rules of use that define user privileges with respect to automation devices and utilizing digital certificates, among other things, to verify the identity of a user desiring to interact with device programs, for example. Furthermore, the present invention provides for secure transmission of messages to and amongst automation devices utilizing public key cryptography associated with digital certificates.
Owner:ROCKWELL AUTOMATION TECH
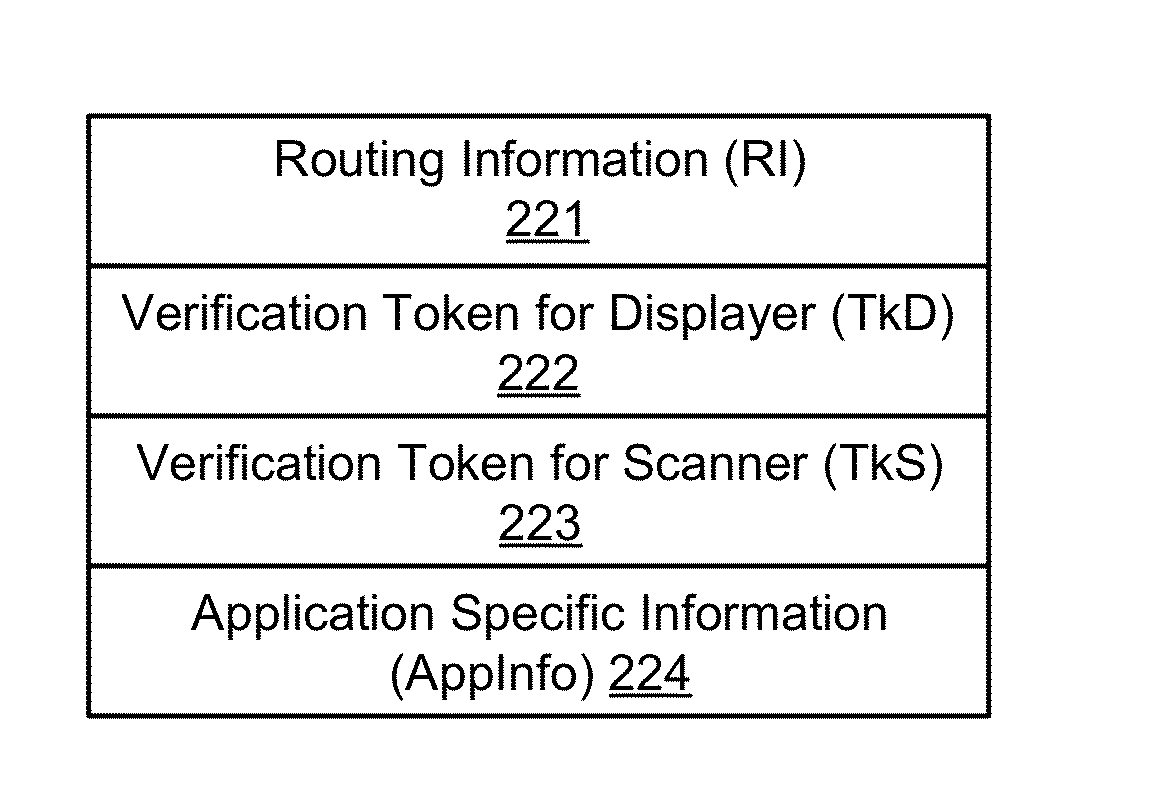
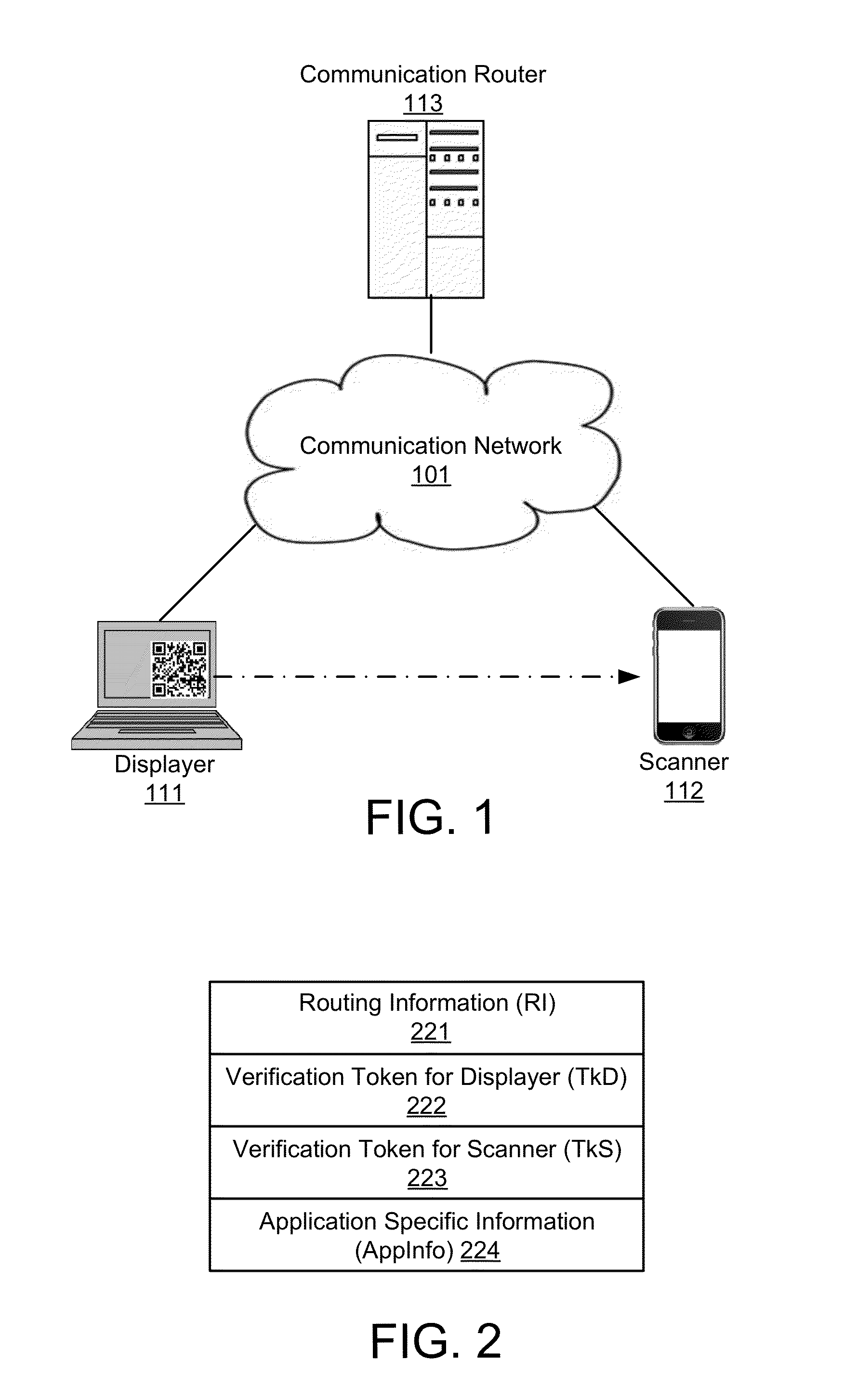
Secure and Authenticated Transactions with Mobile Devices
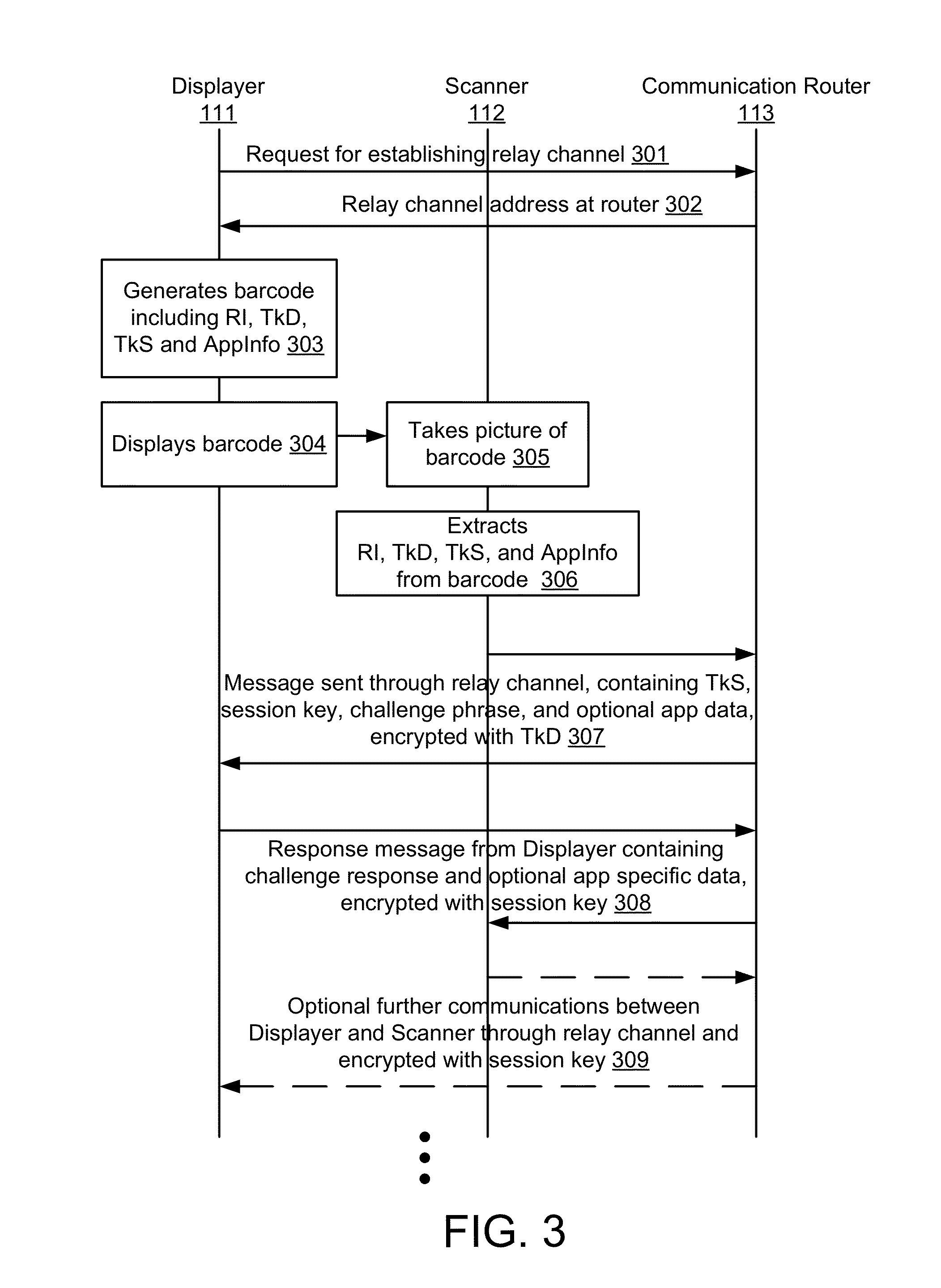
Embodiments of the invention include a platform for using 2D barcodes to establish secure authenticated communication between two computing devices that are in proximity to each other. A two-tier application architecture using a single base app and dynamic add-on applets is used. 2D barcodes can be distinctively visually branded. According to other aspects, the security of mobile payment systems are enhanced by (1) a triangular payment settlement in which the sender and receiver of payment each submit transaction information independently to the same payment server; (2) sensitive information is split into two parts, one of which is stored on a mobile device, and the other of which is stored on a payment server, and the two parts are only combined and exist transiently in the payment server's volatile memory when executing a transaction; and (3) a process to securely update profile pictures associated with payment accounts.
Owner:NETABPECTRUM
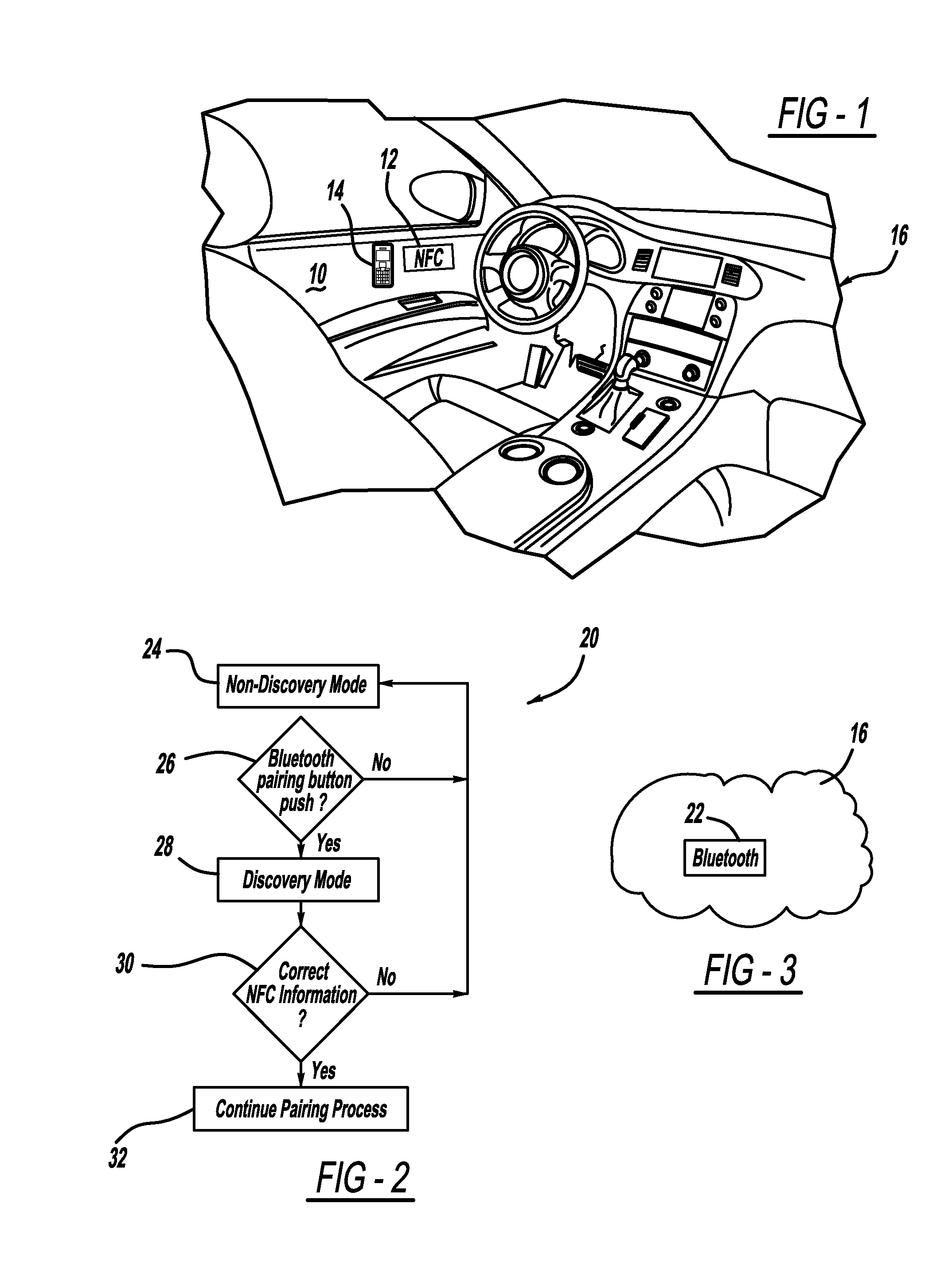
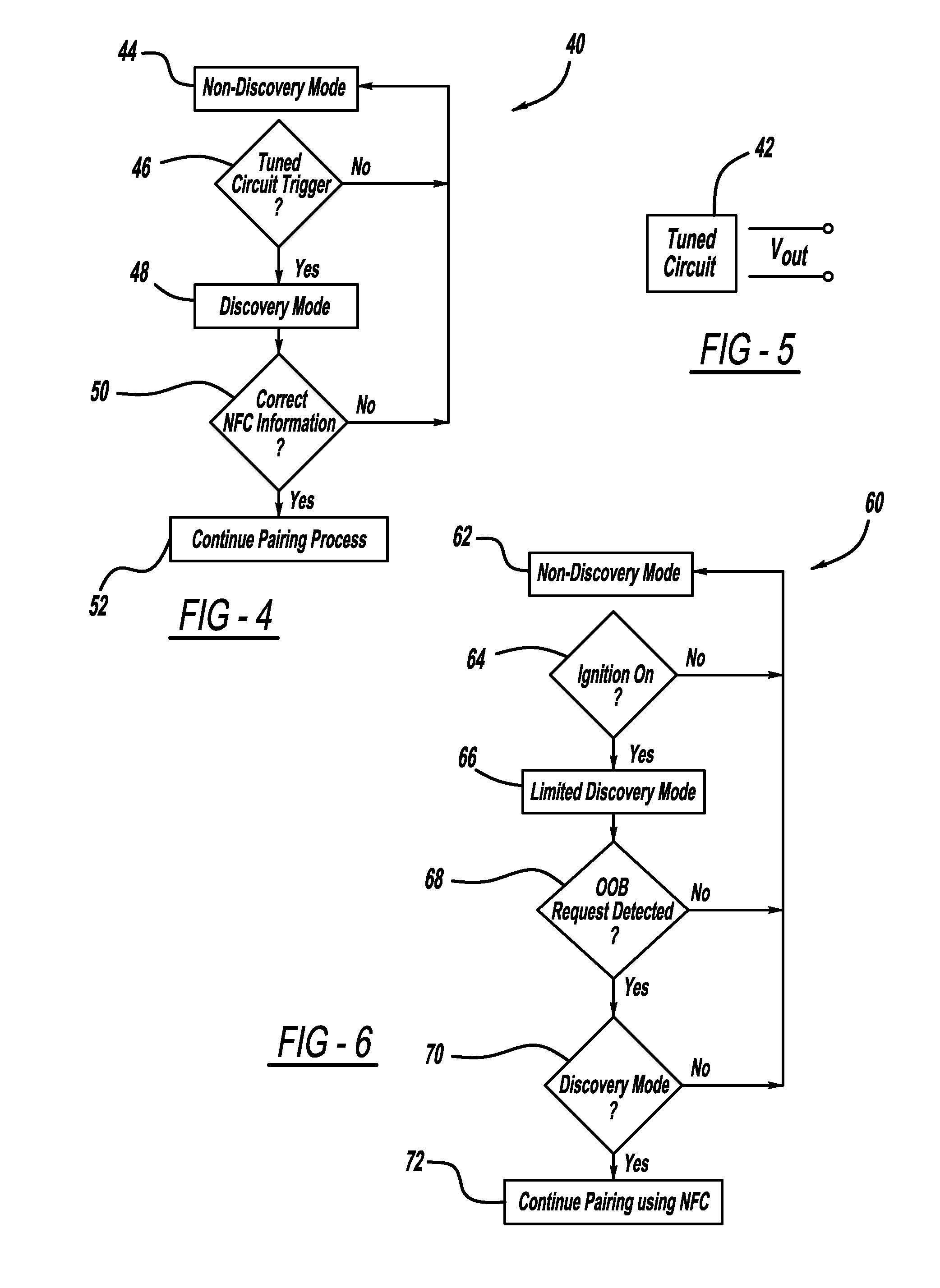
Simplified vehicle bluetooth pairing employing near field communication tags
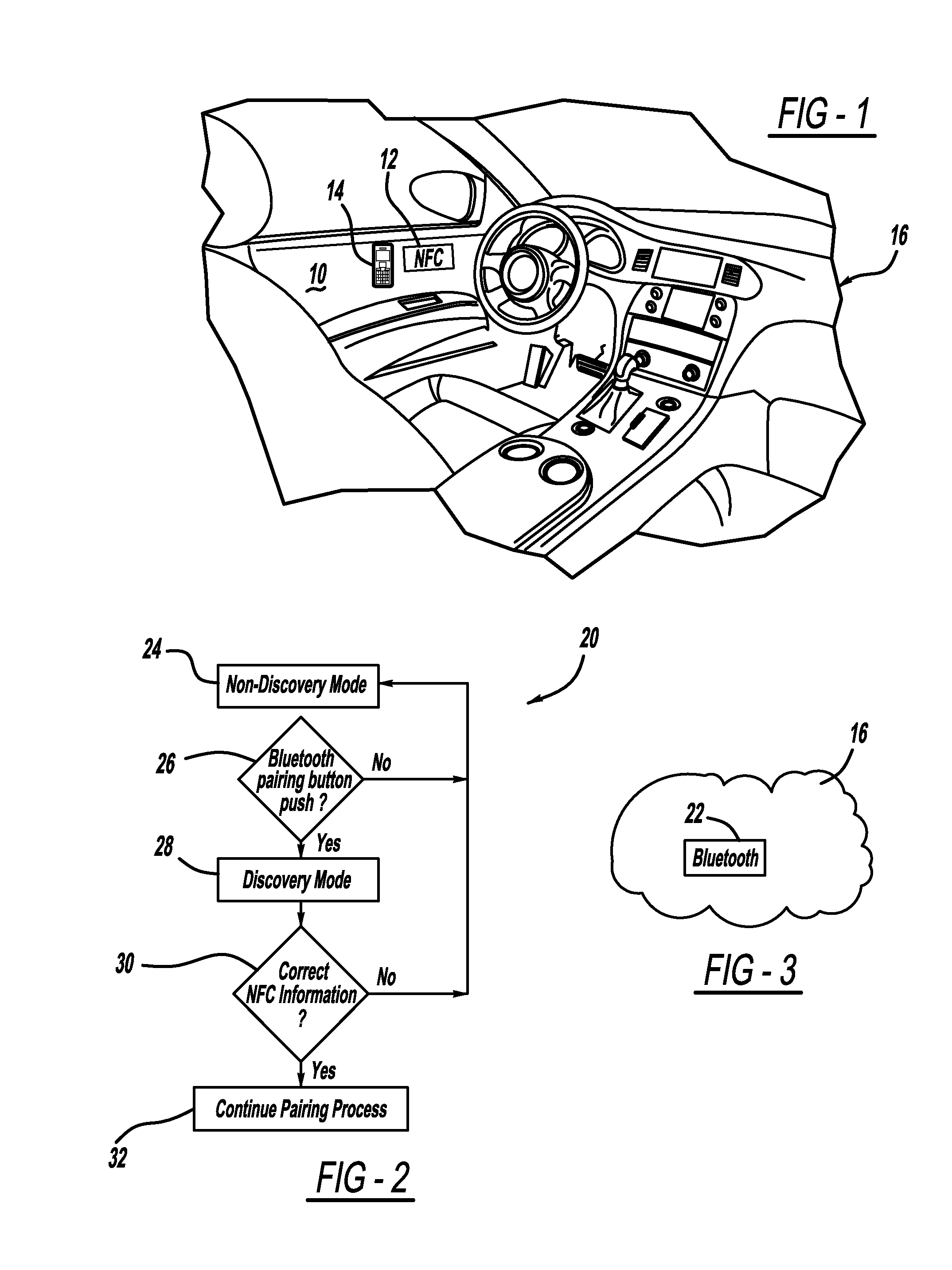
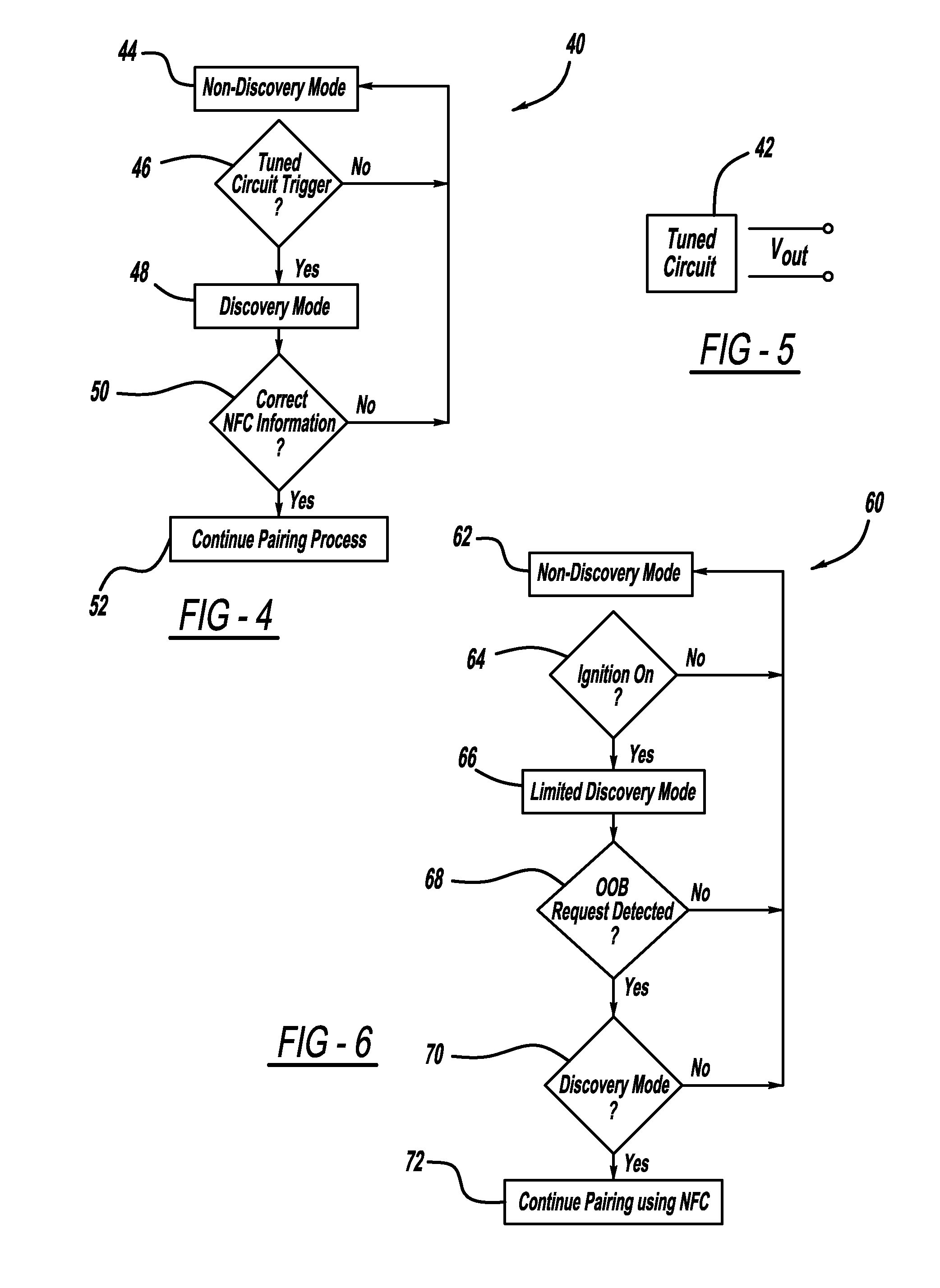
ActiveUS8432260B2Quickly and easily establishingCommunication securityNear-field transmissionParticular environment based servicesComputer hardwareData shipping
A system and method for simply and securely pairing Bluetooth devices in a vehicle. A Near Field Communication (NFC) read-only tag is placed in the vehicle such that a user can pass an NFC-enabled Bluetooth device near the tag, which then transfers encryption key data for the vehicle's Bluetooth device to the user's Bluetooth device. Various embodiments are disclosed for initiating the pairing process with the vehicle's Bluetooth device, which ordinarily remains in a silent mode for security reasons. Once the pairing process has been initiated, and the user's Bluetooth device has been passed near the NFC tag, the pairing process is completed with no further action required by the user.
Owner:GM GLOBAL TECH OPERATIONS LLC +1
Method and Apparatus for Accessing Corporate Data from a Mobile Device
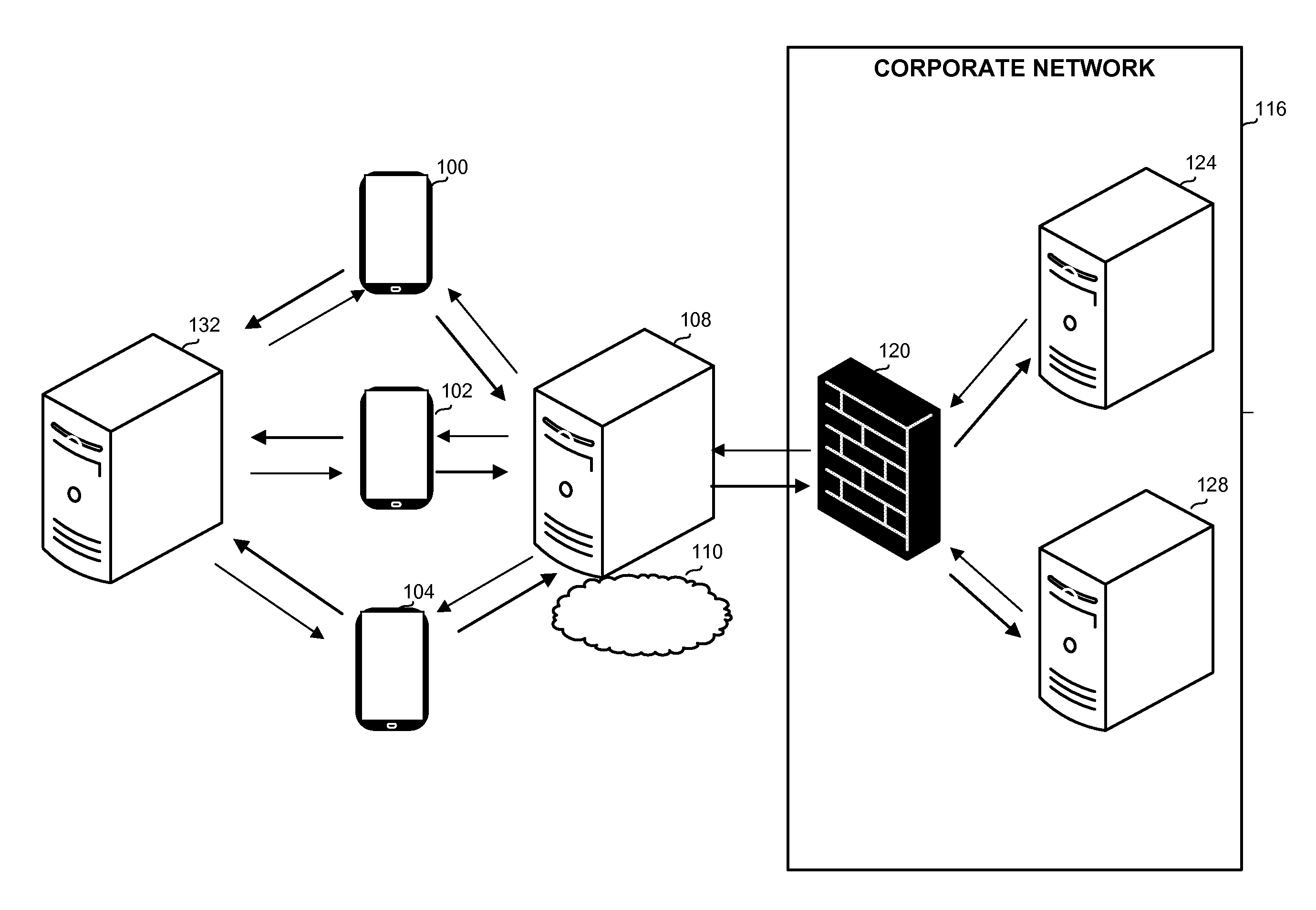
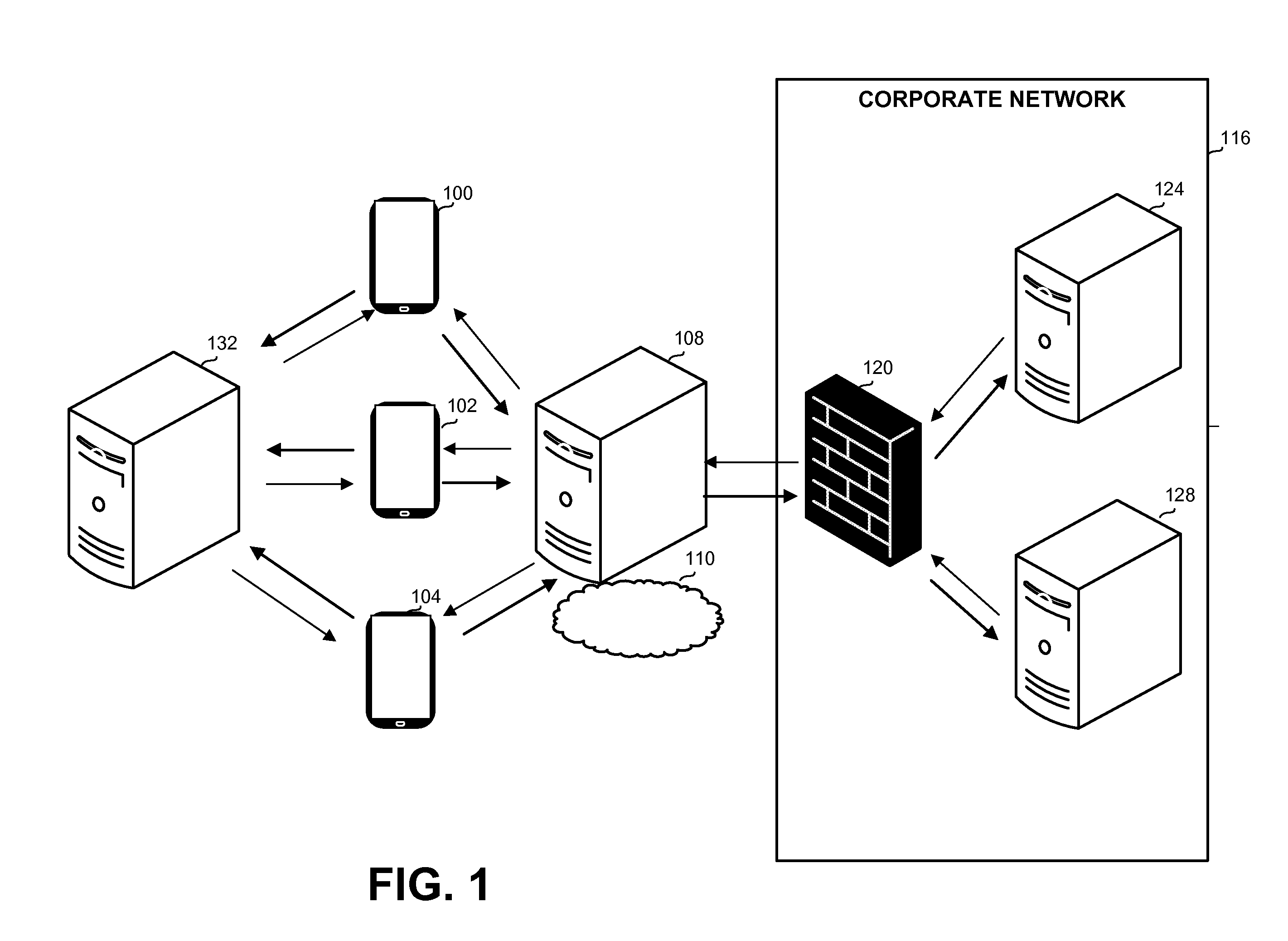
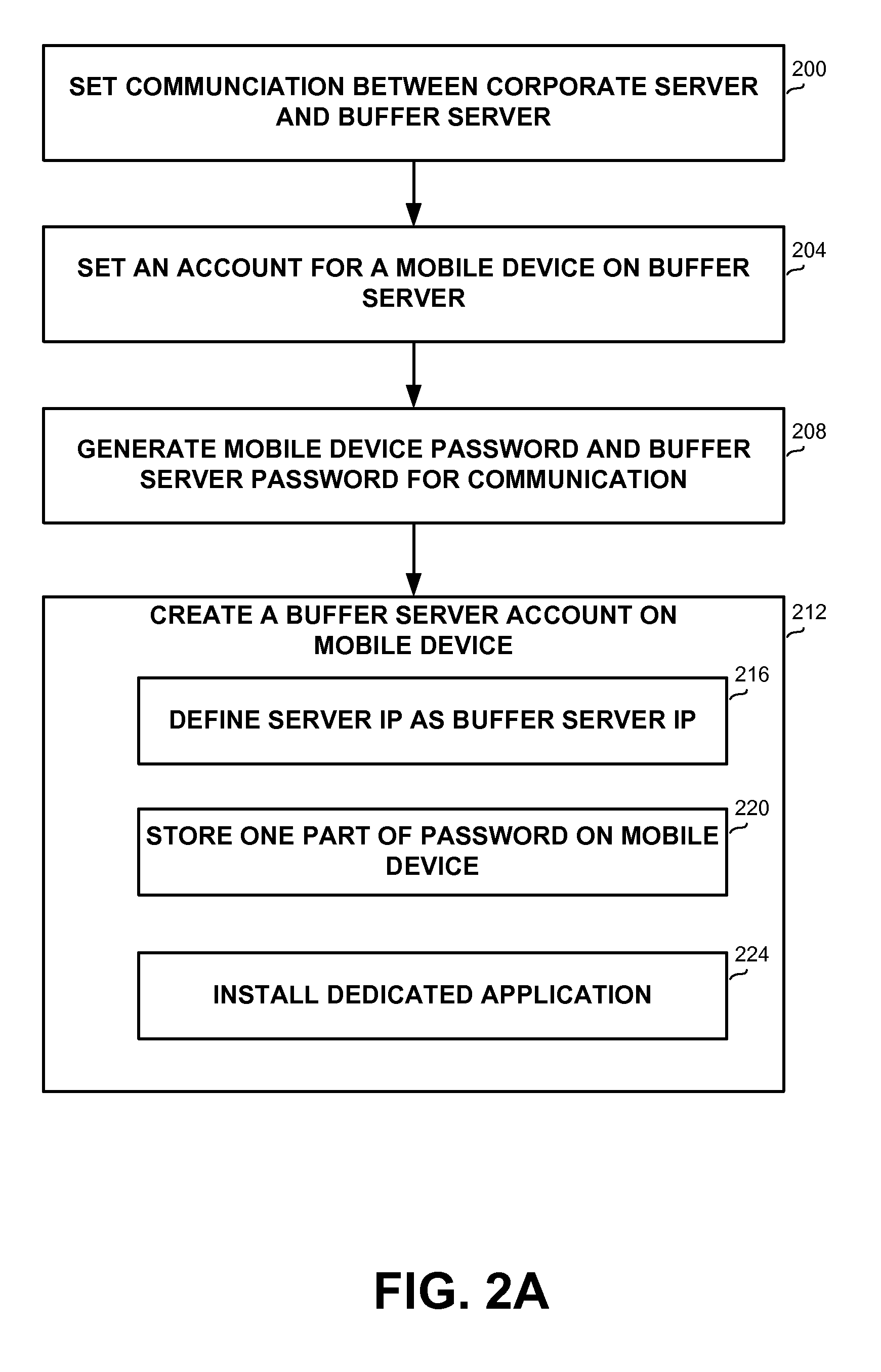
ActiveUS20130061307A1Communication securityDigital data processing detailsMultiple digital computer combinationsMobile deviceCommunication device
A computer-implemented communication method performed by a computerized device and a computerized communication apparatus, the method comprising: receiving by a buffer server a first communication request and a device key from a mobile device; verifying the device key and a buffer server key; sending a request with details associated with the device key and the buffer server key, to a corporate server; receiving a response from the corporate server; removing data from the response, and sending a reduced response to the mobile device; receiving a user identification and a second communication request from the mobile device, for the data that has been removed; and sending the data that has been removed to the mobile device, upon verifying the user identification.
Owner:IVANTI INC
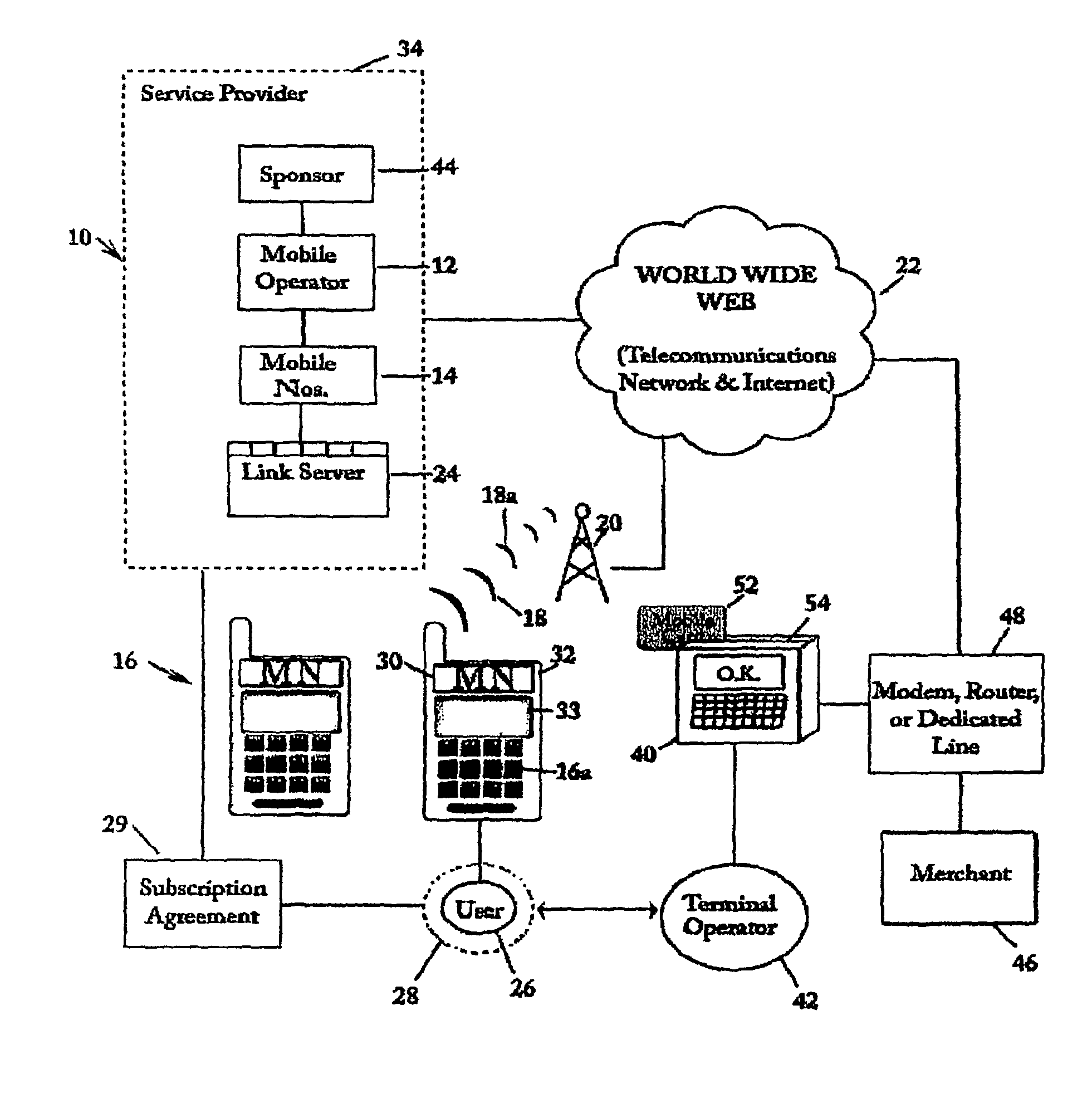
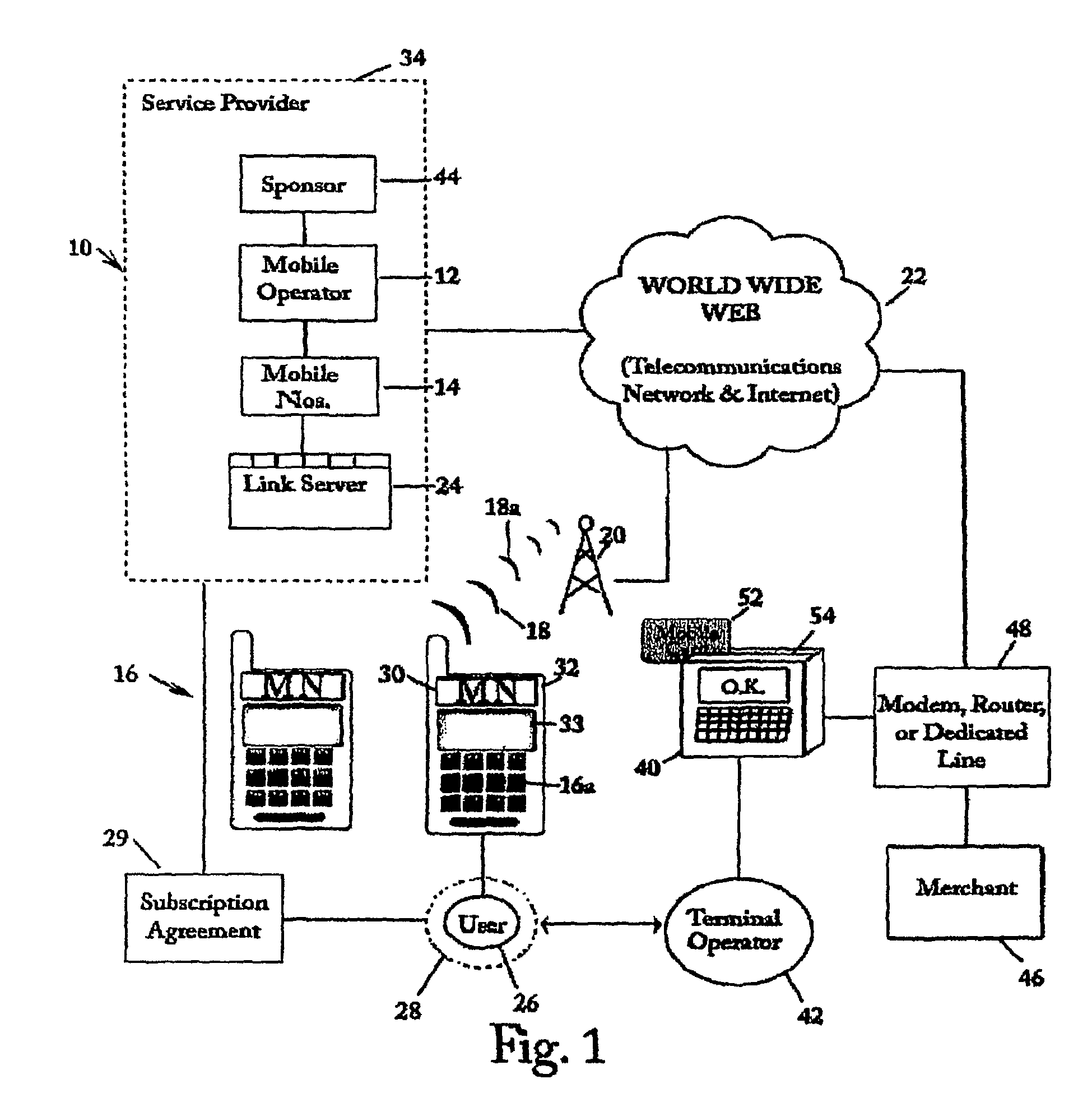
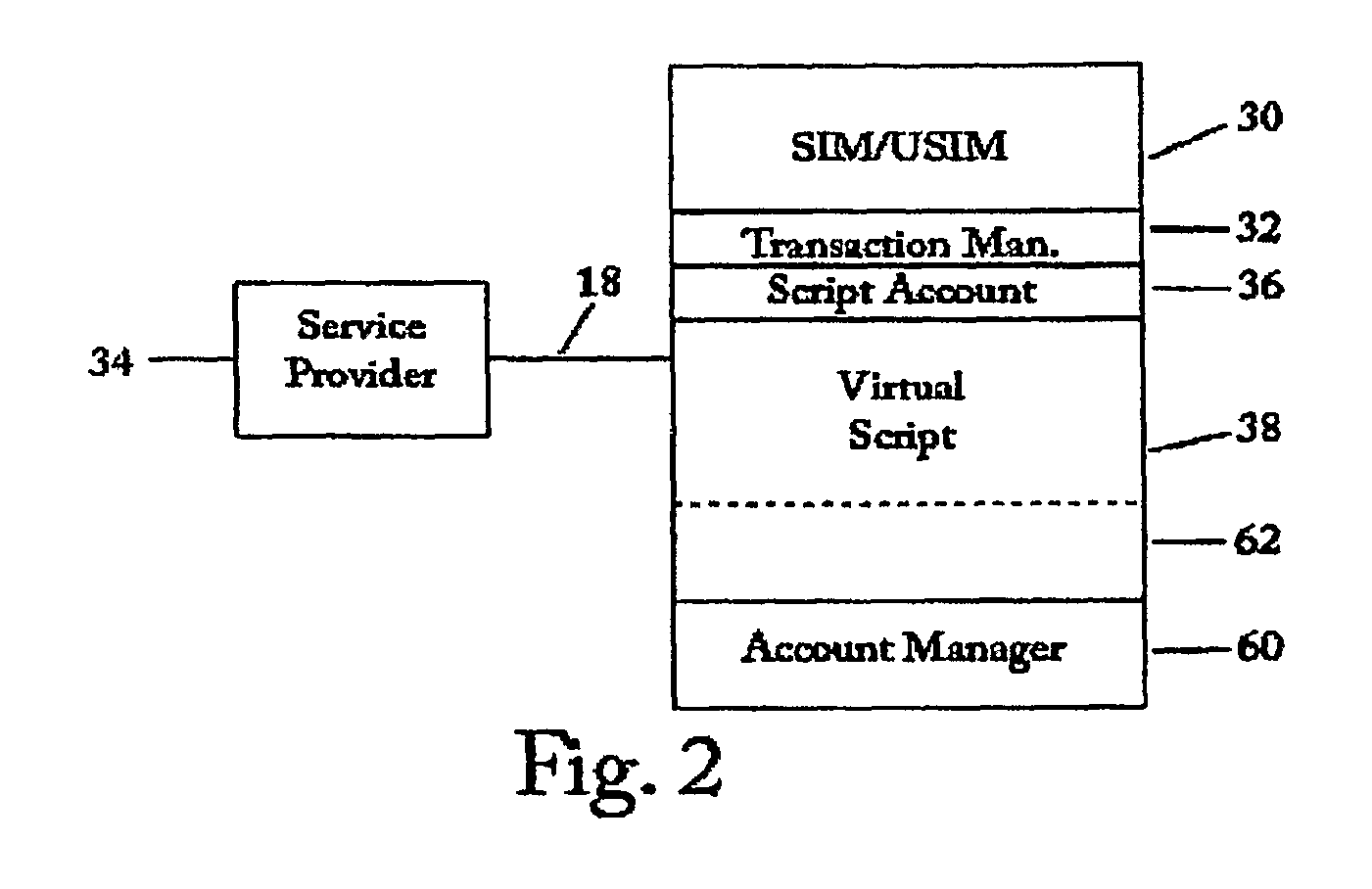
SIM-centric mobile commerce system for deployment in a legacy network infrastructure
InactiveUS8639215B2Improve securityUsage existComplete banking machinesFinanceComputer networkService provision
A financial transaction processing system in a legacy financial transaction network for wireless mobile handset devices having an internal SIM or USIM under control of a service provider in a wireless communication network connected to an open world communication network in which the SIM or USIM has a secure part of an account management application that manages a financial account in the handset and adjusts the financial account when the user of the handset communicates a number related to the mobile number of the handset to a legacy remote card terminal which routes the number and transaction data to the secure link server of the service provider.
Owner:MCGREGOR GREGORY M +2
System and method for network discovery and connection management
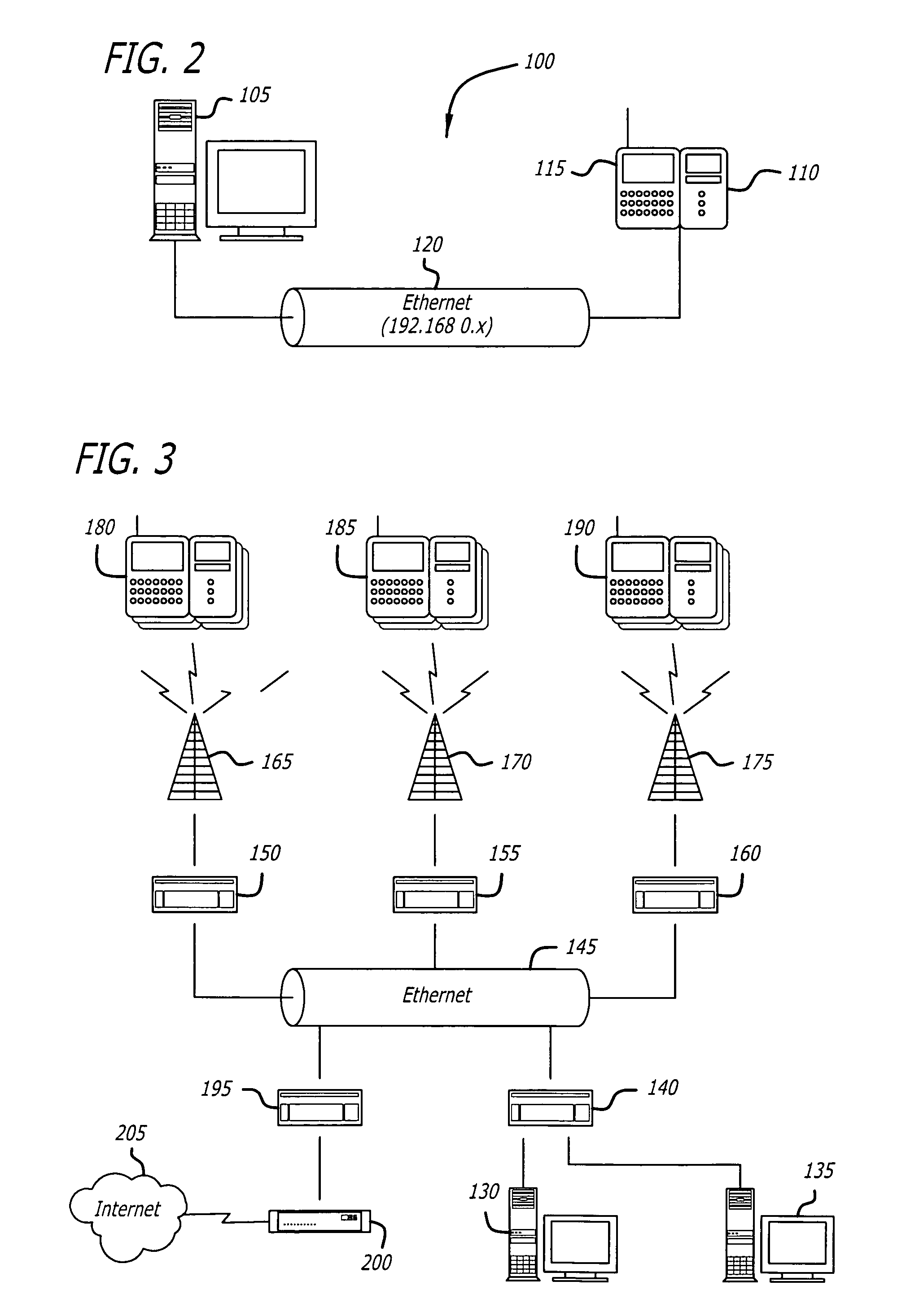
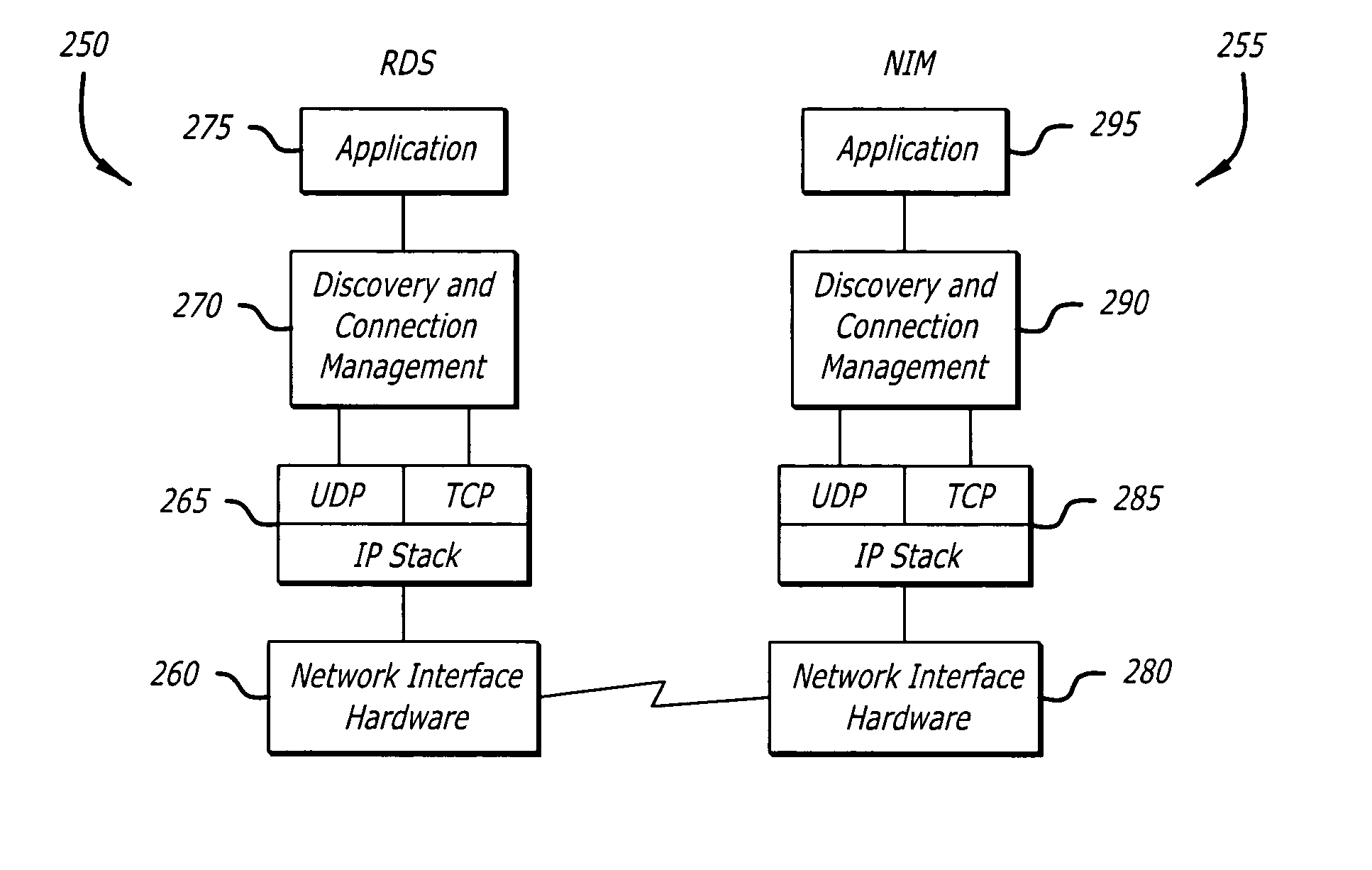
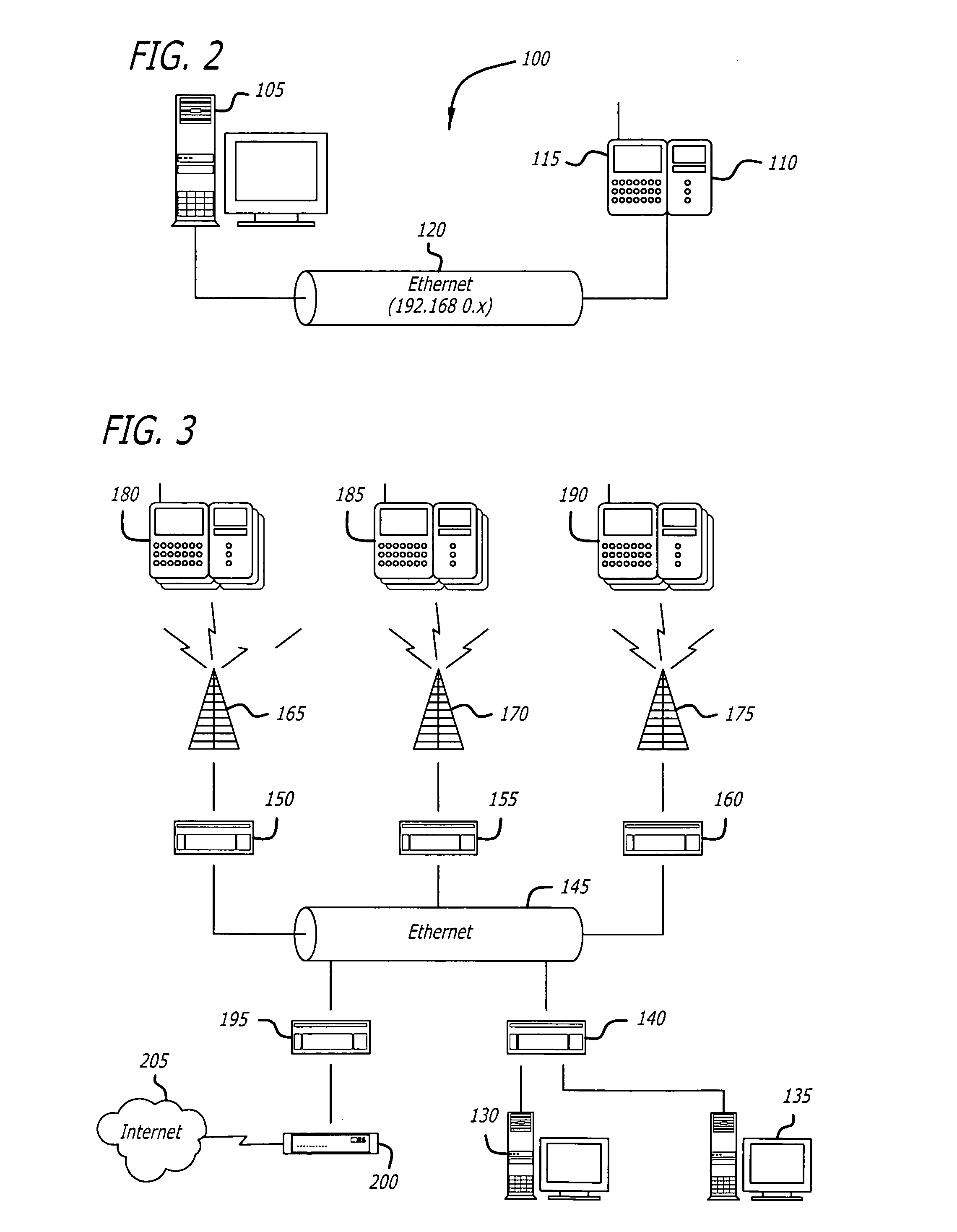
InactiveUS7788369B2Communication securityDigital data processing detailsHardware monitoringSecure communicationConnection management
Owner:CAREFUSION 303 INC
System and method for network discovery and connection management
InactiveUS20050138428A1Communication securityDigital data processing detailsHardware monitoringSecure communicationConnection management
The present invention provides for a system and method of discovering whether a medical device is connected to a network, establishing secure communications between and a server and the medical device, and communicating with the medical device. Also disclosed is a method of encryption to ensure secure communications within the network between a server and medical devices connected to the network. The invention also includes a system and method for determining the location of medical devices within an institution.
Owner:CAREFUSION 303 INC
Network and node for providing a secure transmission of mobile application part messages
ActiveUS20070127418A1Lower security levelCost efficientMultiple digital computer combinationsRadio/inductive link selection arrangementsTelecommunications networkSecure transmission
Owner:TELEFON AB LM ERICSSON (PUBL)
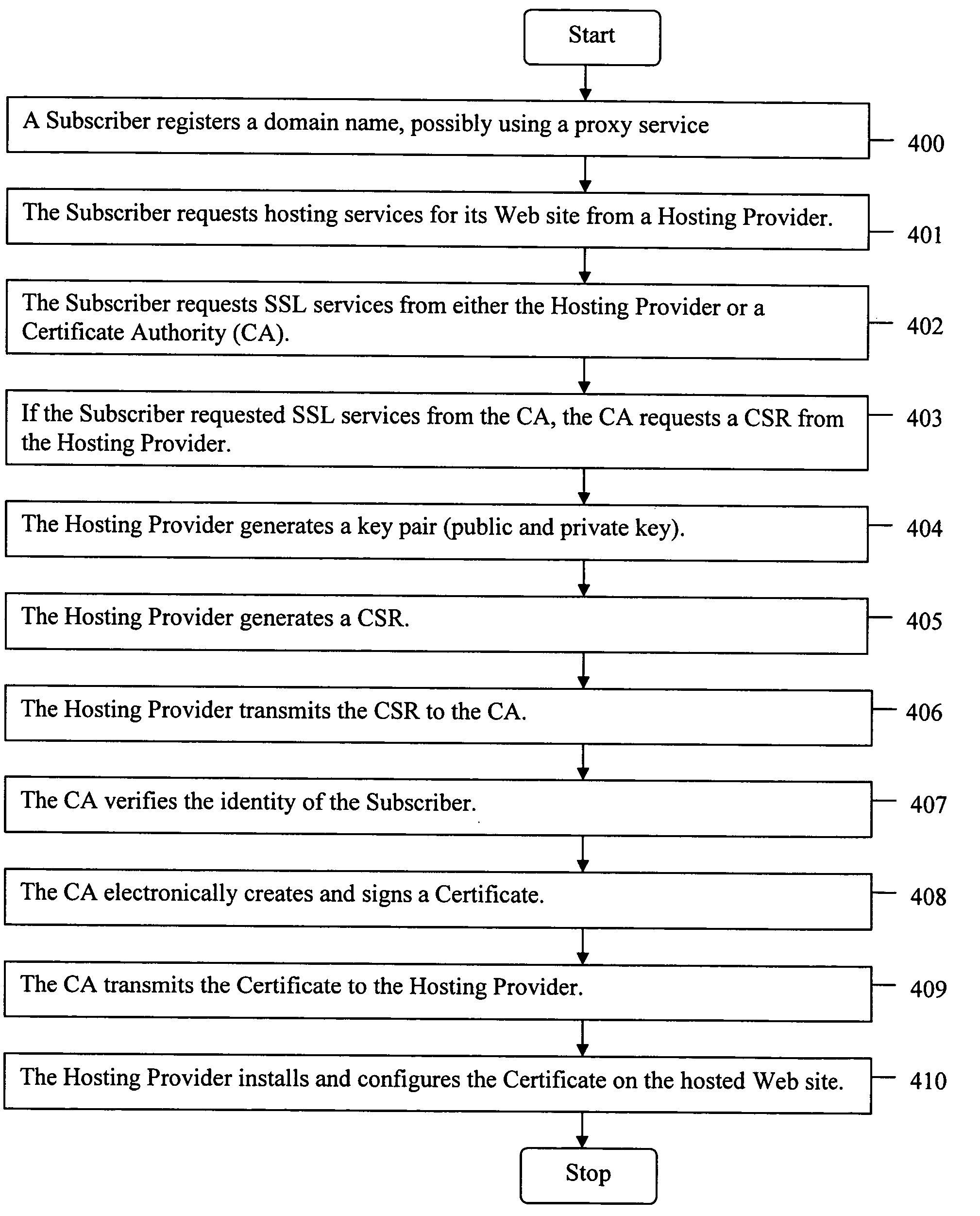
Method for a Web site with a proxy domain name registration to receive a secure socket layer certificate
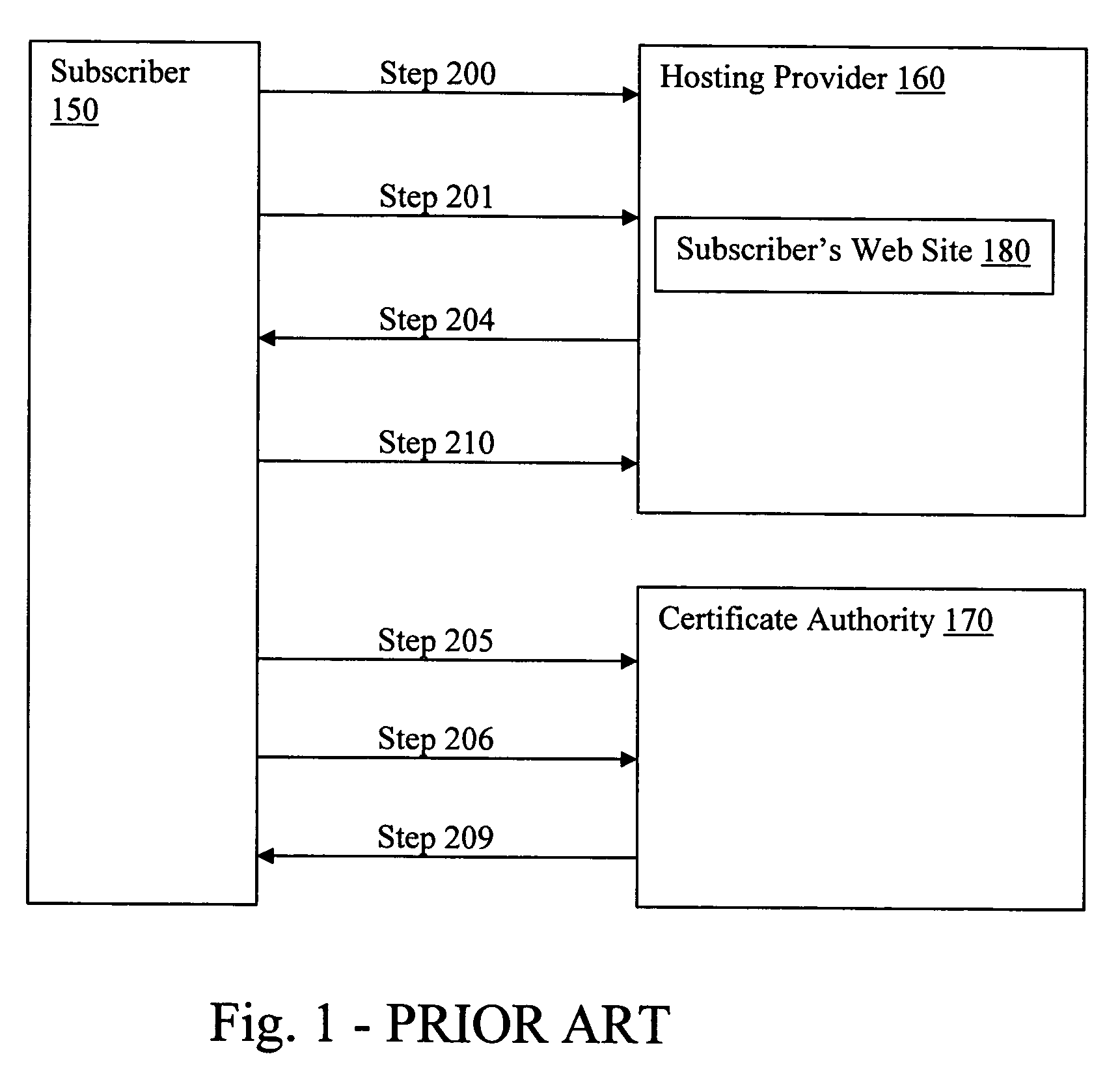
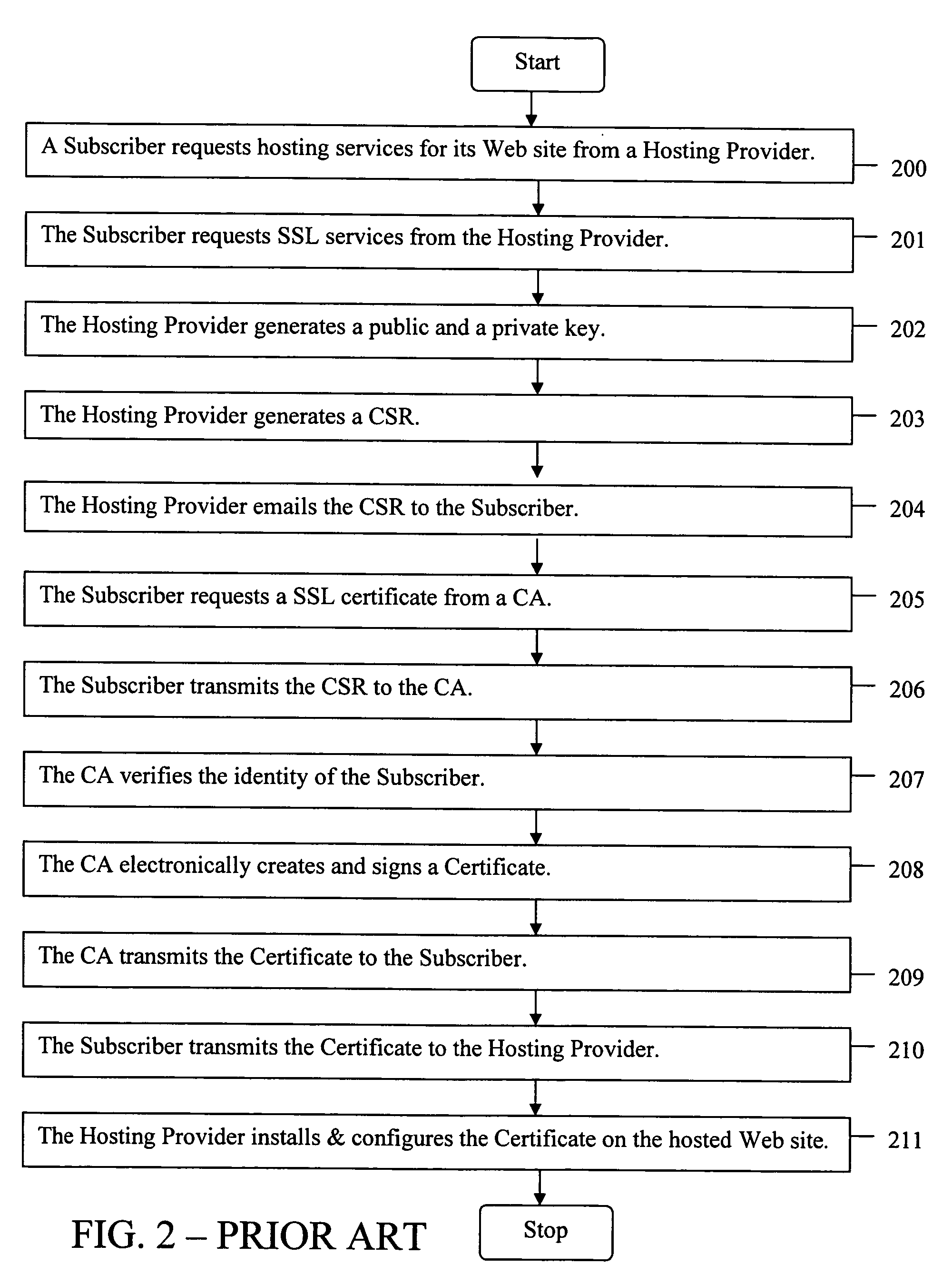
ActiveUS20050289084A1Improve securityMaximize efficiencyUser identity/authority verificationPayment architectureDomain nameWeb site
The present invention provides systems and methods for enabling encrypted communication capabilities for a Subscriber's Web Site, thereby allowing Customers to access the Subscriber's Web Site in a secure manner. The Subscriber may register a domain name associated with the Subscriber's Web Site using a proxy domain name service, thereby hindering its Customers ability to verify the owner of the Subscriber's Web Site. A Hosting Provider hosts the Subscriber's Web Site and a Certificate Authority (CA) verifies the identity of the Subscriber. In combination the Hosting Provider and CA provide the Subscriber's Web Site with Secure Sockets Layer (SSL) encrypted communications capability. The Hosting Provider and CA communicate directly with each other as needed, typically via the Internet, without using the Subscriber as an intermediary in their communications.
Owner:GO DADDY OPERATING
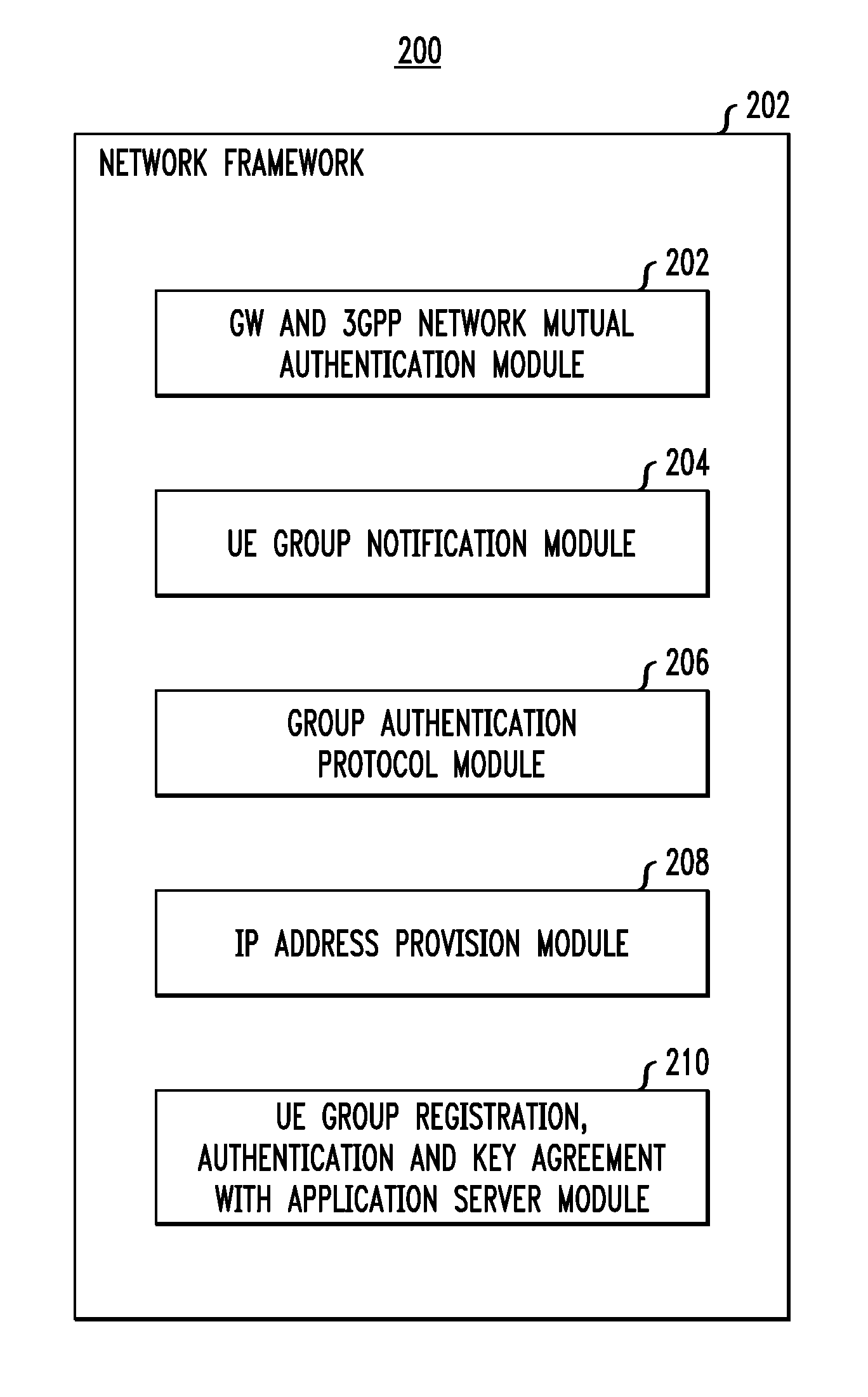
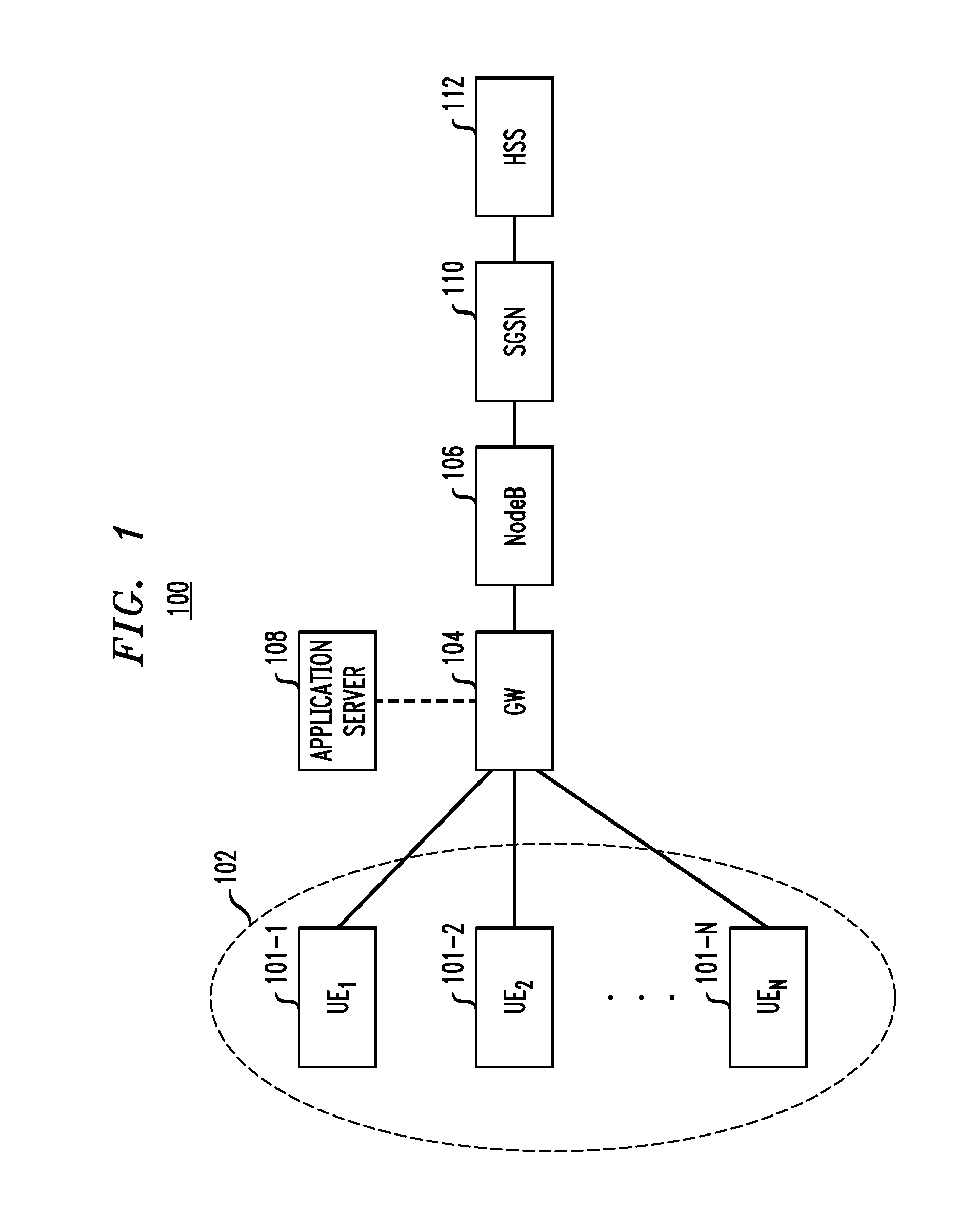
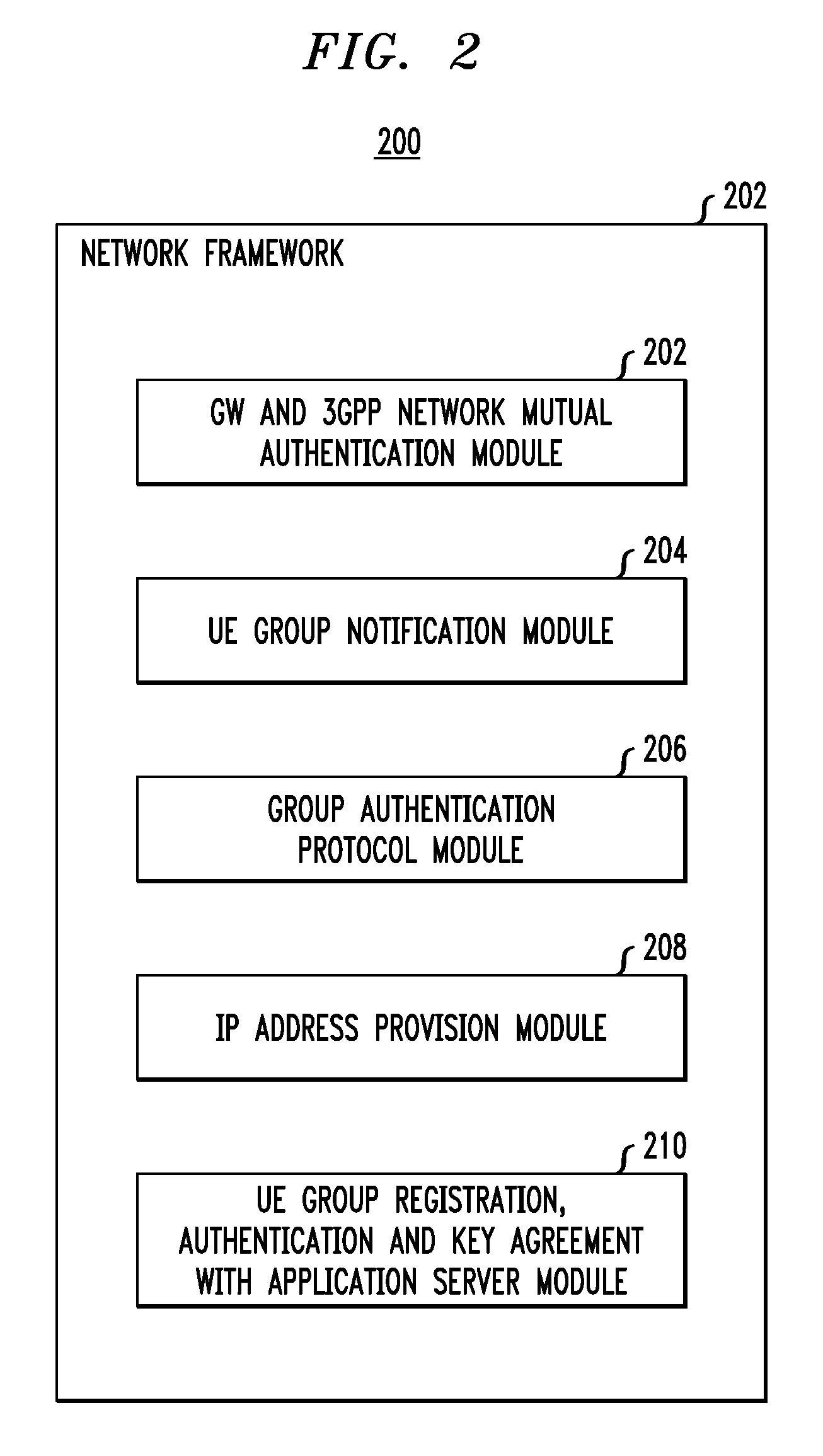
Secure Registration of Group of Clients Using Single Registration Procedure
ActiveUS20110307694A1Compromising privacyReduce signalingDigital data processing detailsUser identity/authority verificationCommunication deviceSingle sign-on
Automated secure registration techniques for communication devices are provided which address the problem of allowing multiple clients to gain access to one system, and thus provide a solution to the “reverse single sign-on” problem. For example, a method for registering a group of two or more communication devices in a communication network comprises the following steps. A group challenge message is sent from a network device to the group of two or more communication devices. The network device receives one or more response messages to the group challenge respectively from one or more of the group of two or more communication devices, wherein the response message from each of the responding communication devices in the group comprises a group credential corresponding to the group.
Owner:THALES DIS FRANCE SA
Simplified vehicle bluetooth pairing employing near field communication tags
ActiveUS20110210830A1Quickly and easily establishingCommunication securityNear-field transmissionParticular environment based servicesBluetoothData shipping
A system and method for simply and securely pairing Bluetooth devices in a vehicle. A Near Field Communication (NFC) read-only tag is placed in the vehicle such that a user can pass an NFC-enabled Bluetooth device near the tag, which then transfers encryption key data for the vehicle's Bluetooth device to the user's Bluetooth device. Various embodiments are disclosed for initiating the pairing process with the vehicle's Bluetooth device, which ordinarily remains in a silent mode for security reasons. Once the pairing process has been initiated, and the user's Bluetooth device has been passed near the NFC tag, the pairing process is completed with no further action required by the user.
Owner:GM GLOBAL TECH OPERATIONS LLC +1
Encrypted communication method and system
InactiveUS20050273843A1Maintain confidentialityMaintain integrityKey distribution for secure communicationDigital data processing detailsCommunications systemPassword
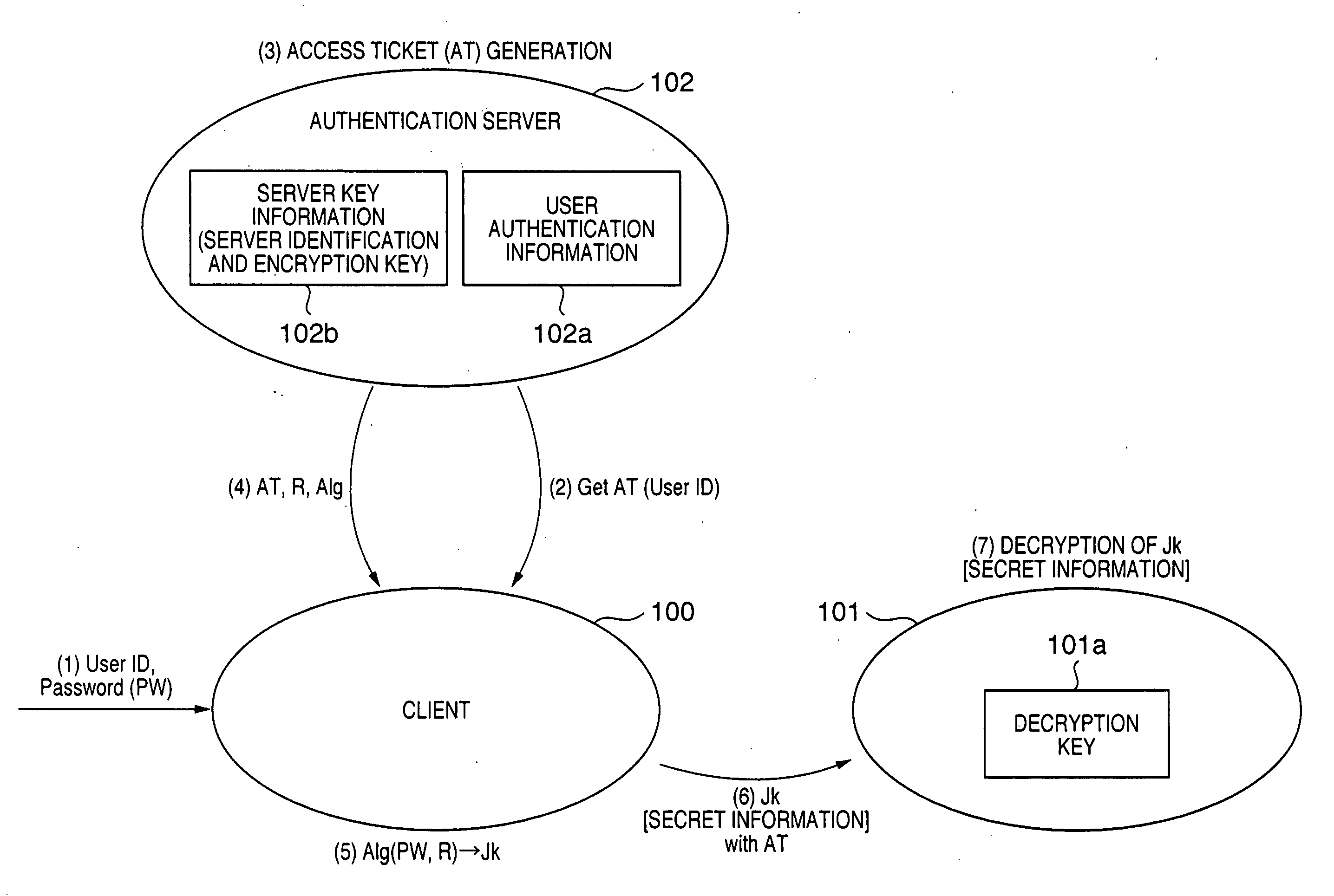
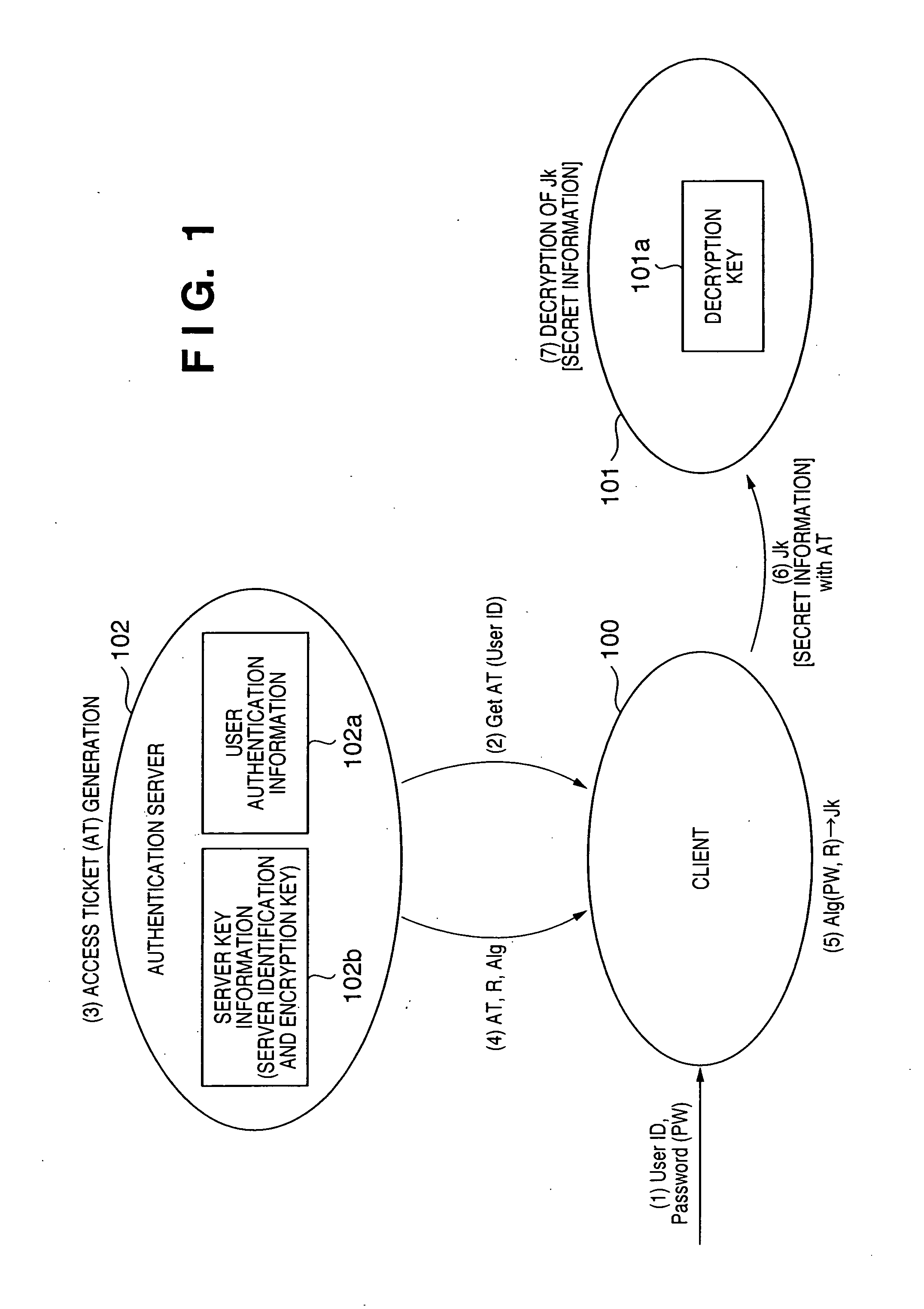
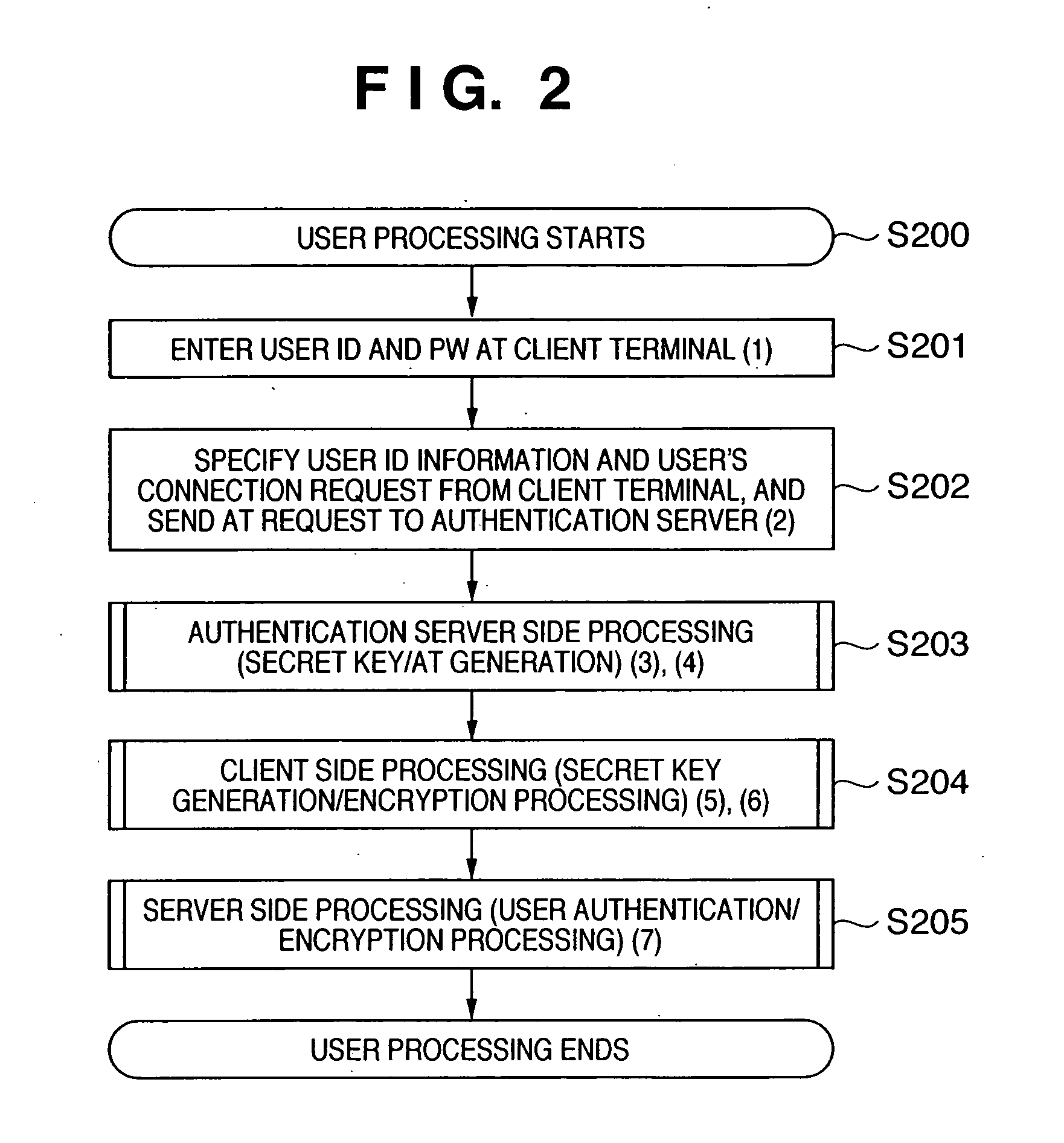
An encrypted communication system according to the present invention comprises an authentication server in which a user password and an encryption key of a server were registered, a client involved in utilization by a user, and a server providing a service. According to the encrypted communication system, shared credentials for the client and the server to conduct encrypted communication are generated separately by the authentication server and the client based on mutually shared information, a ticket is generated in which the credentials that were generated by the authentication server are encrypted with the encryption key by the authentication server, and the client encrypts information to be sent using the credentials generated by the client and attaches the ticket that was acquired from the authentication server to the encrypted information to send the encrypted information and the ticket to the server.
Owner:CANON KK
Dual-tier security architecture for inter-domain environments
InactiveUS6996716B1Communication securityUser identity/authority verificationDigital computer detailsCost effectivenessSecurity information
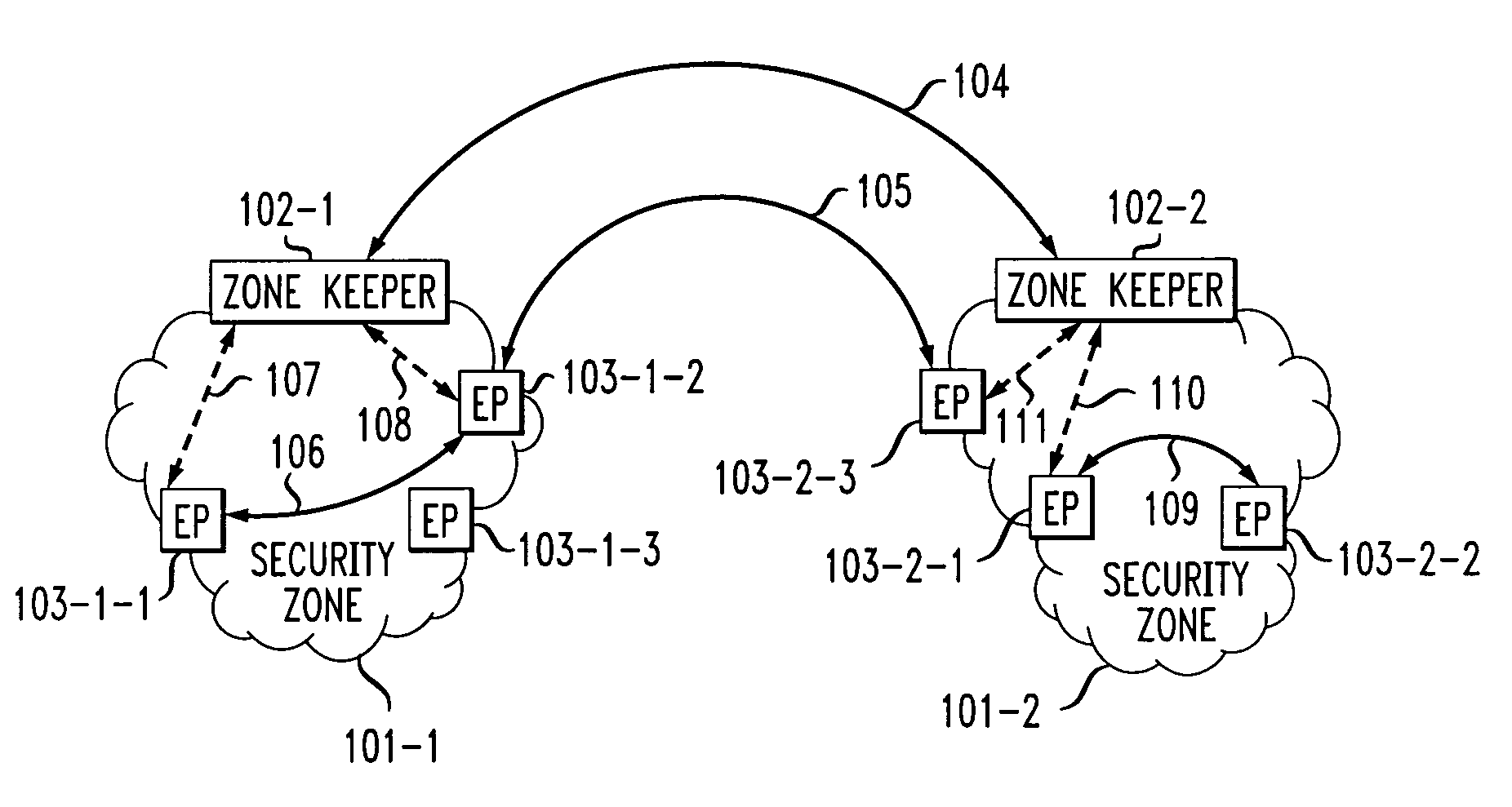
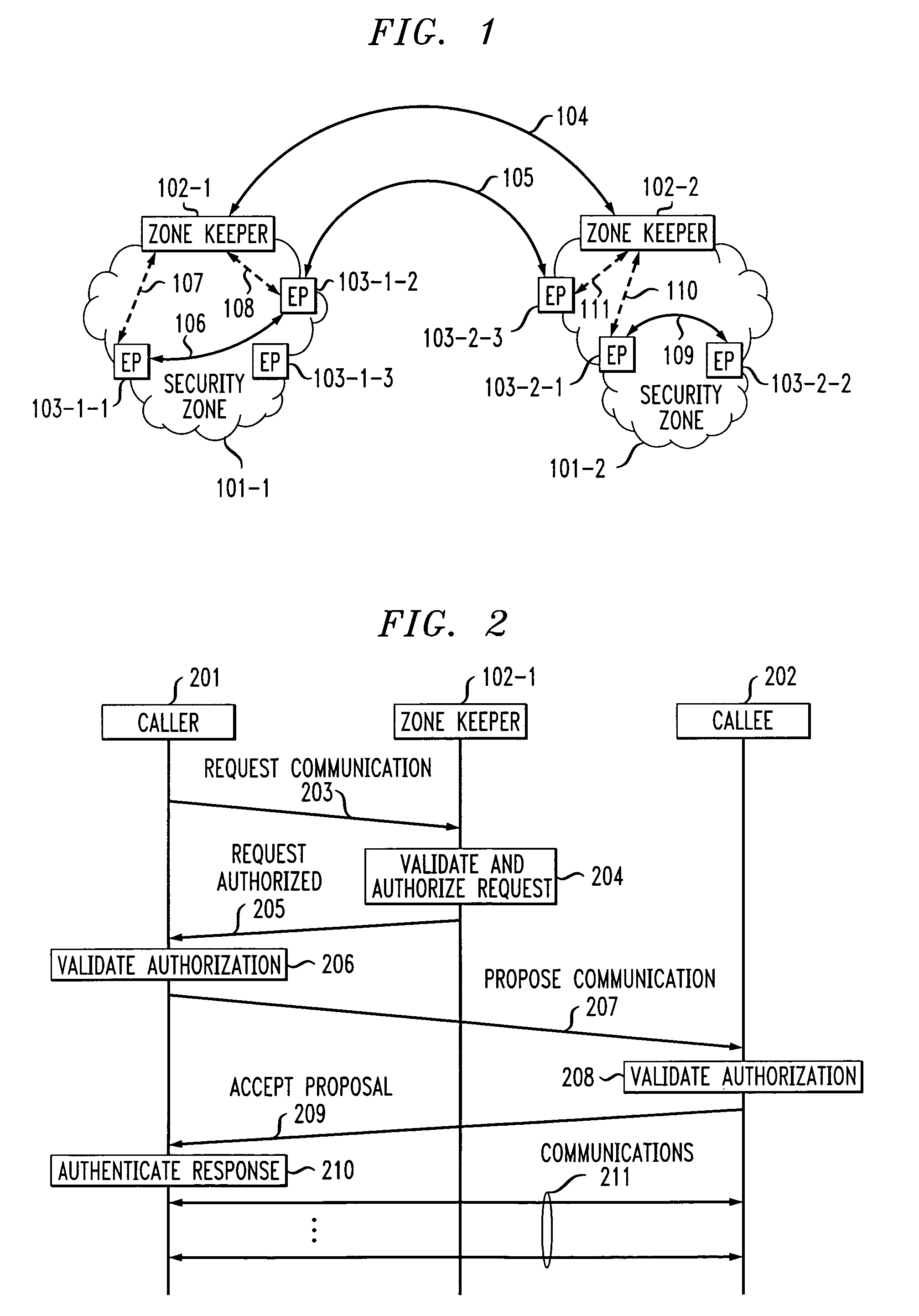
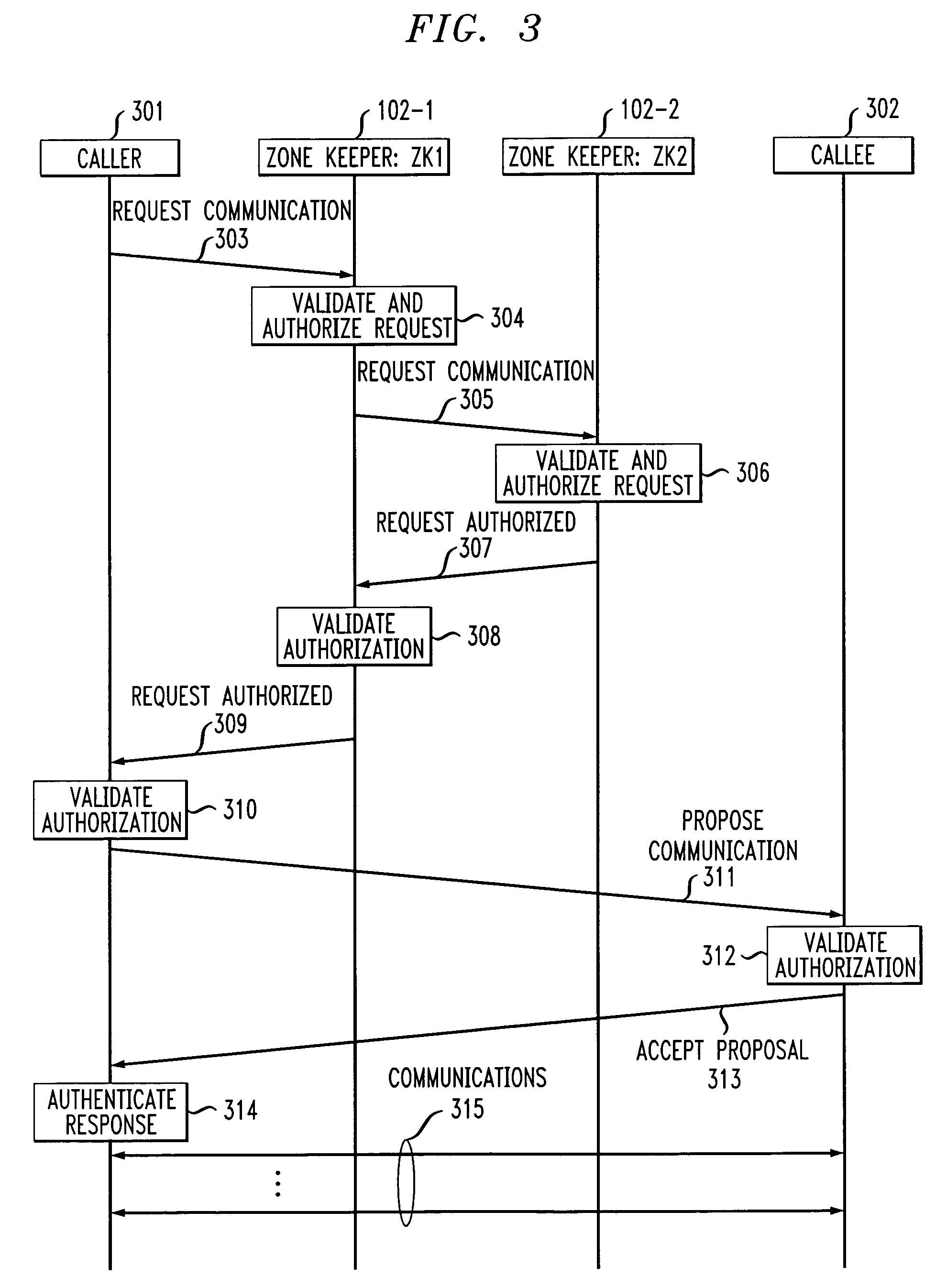
A two-tier security architecture that provides balance between the use of public and secret-key cryptography to realize cost-effectiveness and scalability of security. One tier is an intra-zone tier and the other tier is an inter-zone tier. The intra-zone tier addresses communication between users employing endpoints within a prescribed Security Zone and is designed to achieve cost-effectiveness. The inter-zone tier specifies how communication between users employing endpoints from different Security Zones can be established and is designed to provide scalability for intra-enterprise and / or inter-enterprise communications. Specifically, each Security Zone has a “Zone Keeper” and one or more endpoints that may be employed by users. The Zone Keeper authenticates, i.e., validates, users employing an endpoint in the Security Zone and determines whether a caller and a callee are security compatible. When setting up a communication, the caller provides the Zone Keeper security information in order for the caller to prove its identity. The callee supplies to the caller information confirming its identity. A proposal on how the communication is to be Set-up is sent from the caller to the callee, and if they agree to the proposal and their security is authenticated, the communication is started. For inter-zone, inter-domain, communications, the caller provides information as described above to its Zone Keeper. Then, the caller's Zone Keeper forwards the caller's request to the Zone Keeper of the security associated with the callee. Additionally, the caller's Zone Keeper also supplies the callee's Zone Keeper with its security identity so that the callee's Zone Keeper may authenticate that the request is from the caller's Zone Keeper. Then, the callee's Zone Keeper sends back an authorization to the Caller's Zone Keeper. This authorization includes the callee's Zone Keeper security identity so that the caller's Zone Keeper can authenticate that the authorization is from the callee's Zone Keeper.
Owner:AVAYA INC
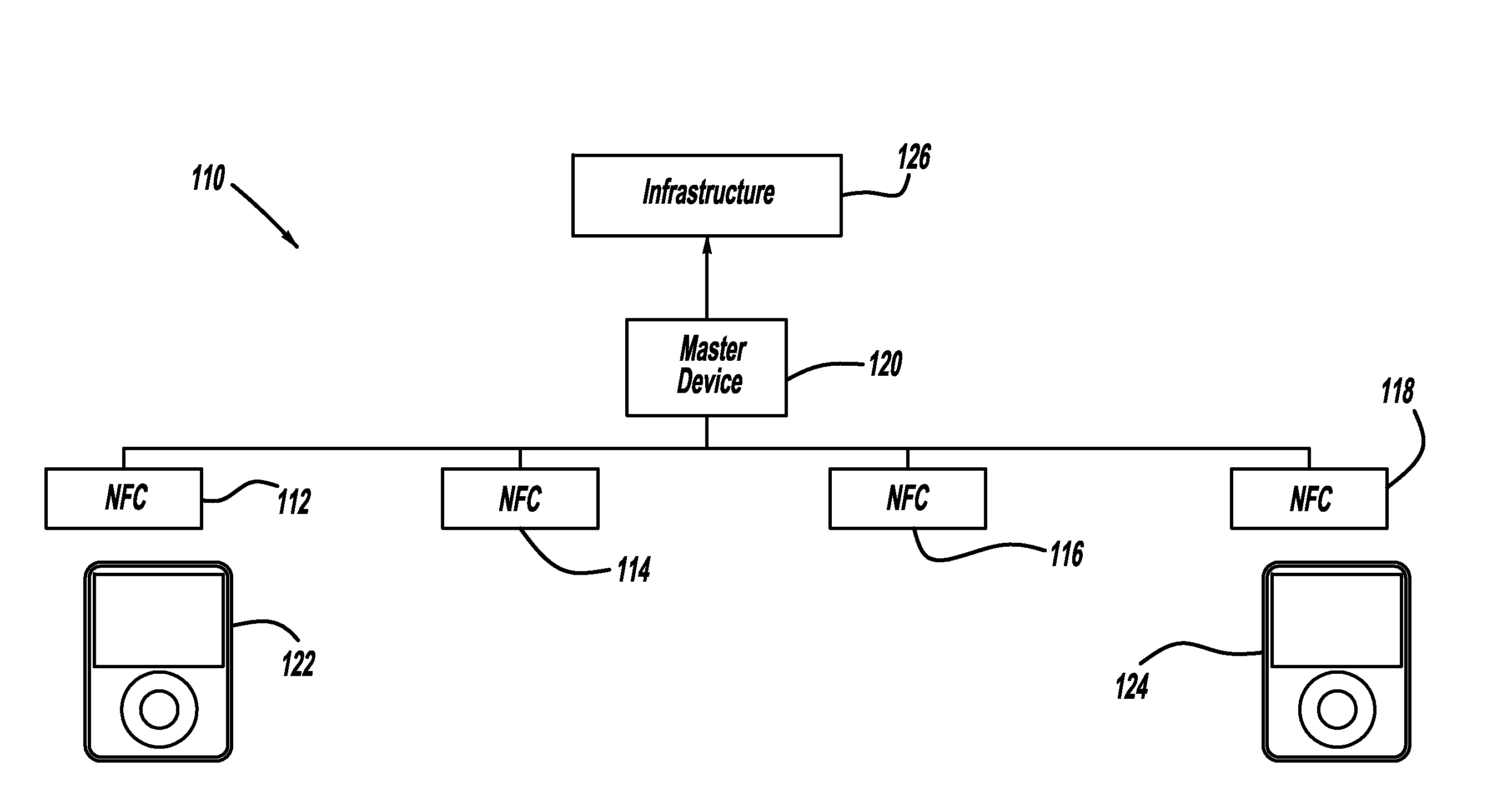
Method and system for distribution of voice communication service via a wireless local area network
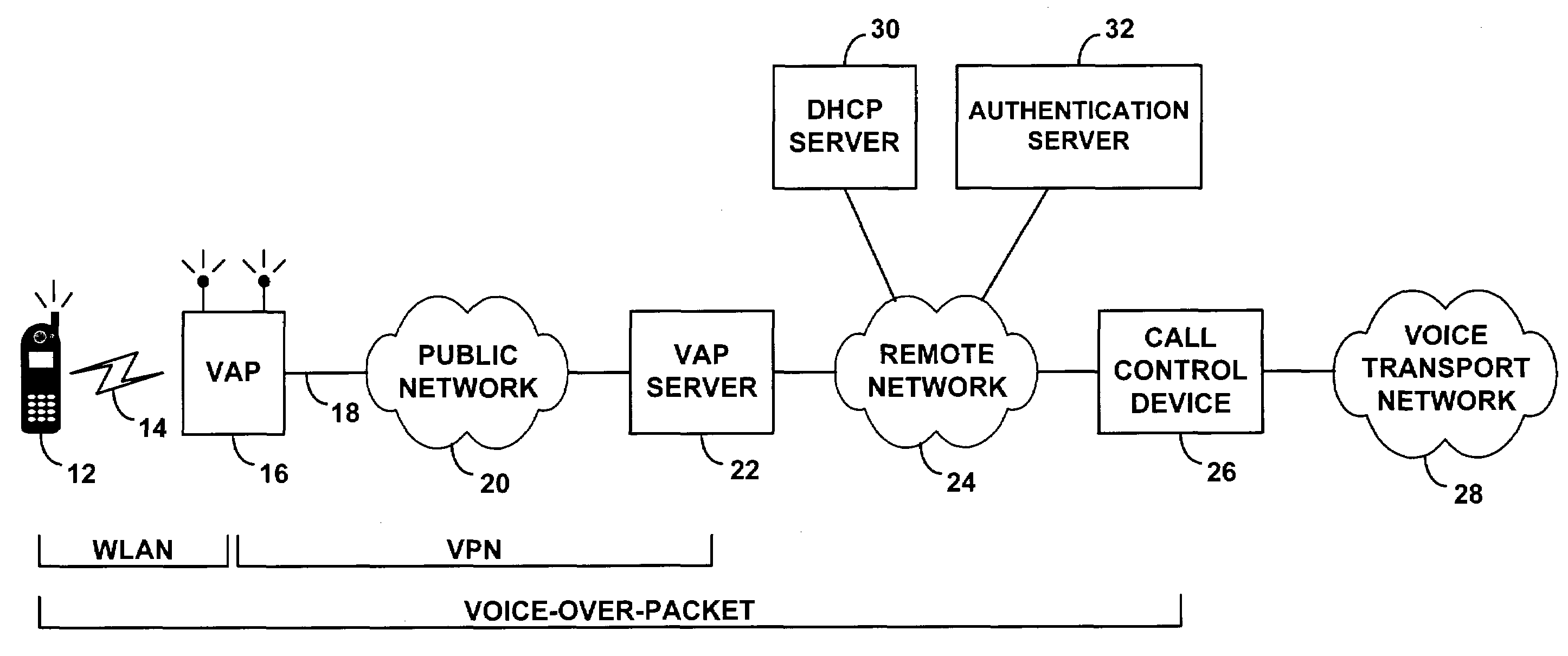
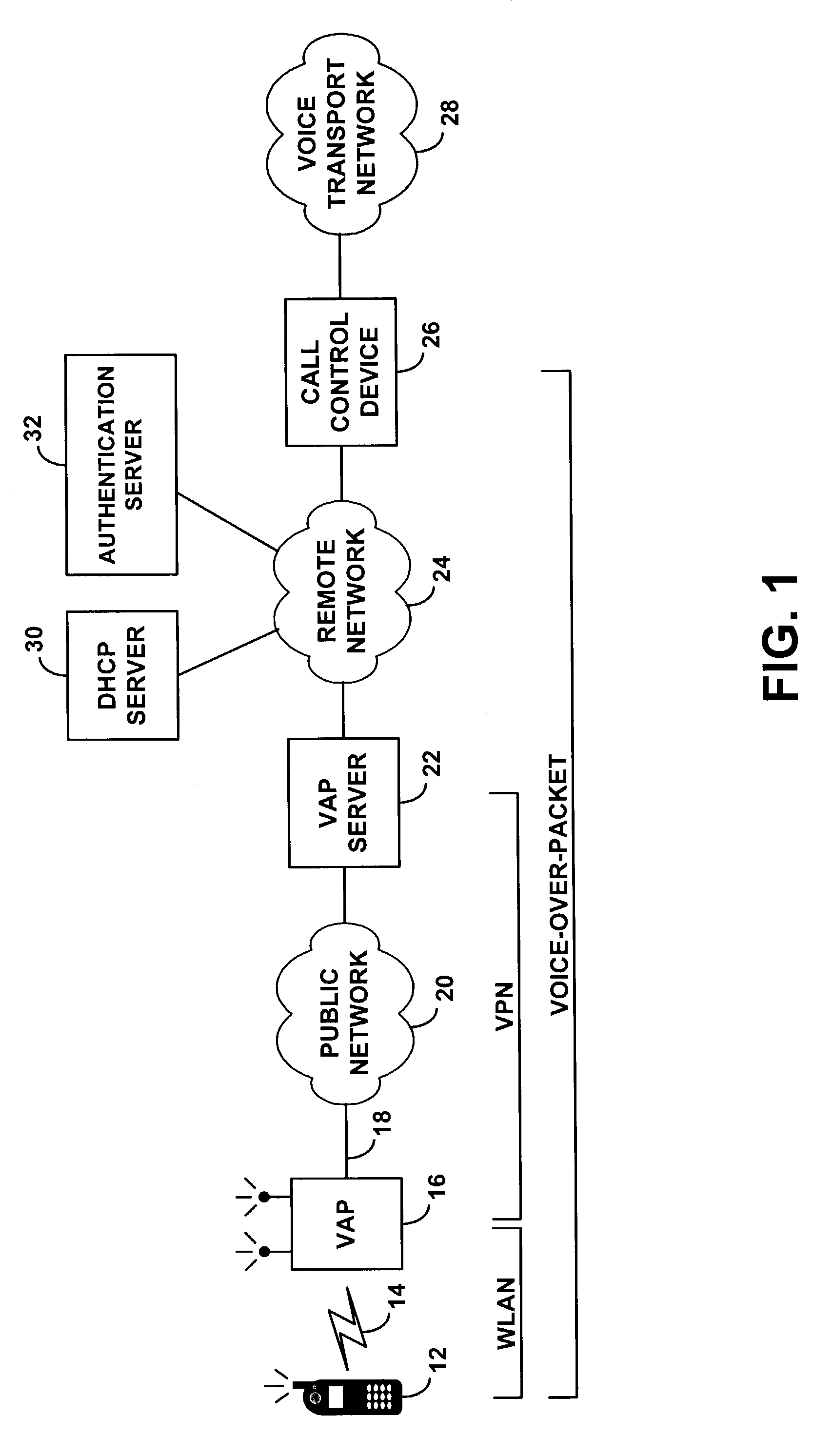
ActiveUS7349412B1Communication securityReadily engage in voice over packet (VoP) communicationData switching by path configurationNetwork connectionsPrivate networkVoice communication
A method and system for distributing voice communication services via wireless local area networks. An entity sells, loans, gives or otherwise distributes wireless access points, each of which is pre-configured with virtual private network (VPN) security settings to establish a VPN tunnel over a packet network with a VPN terminator on a remote telephony services network. A recipient may thus install the wireless access point on a local area network (LAN), to allow users of voice-capable wireless devices to engage in voice calls via the wireless access point, VPN tunnel and telephony services network. The distributor of the access point, or another entity, may then charge users for placing and receiving voice calls through this system.
Owner:SPRINT SPECTRUM LLC
A Secure Virtual Network Layer and Virtual Network Manager that Establishes a Comprehensive Business Reporting and Security Infrastructure as an Integral Part of the Network
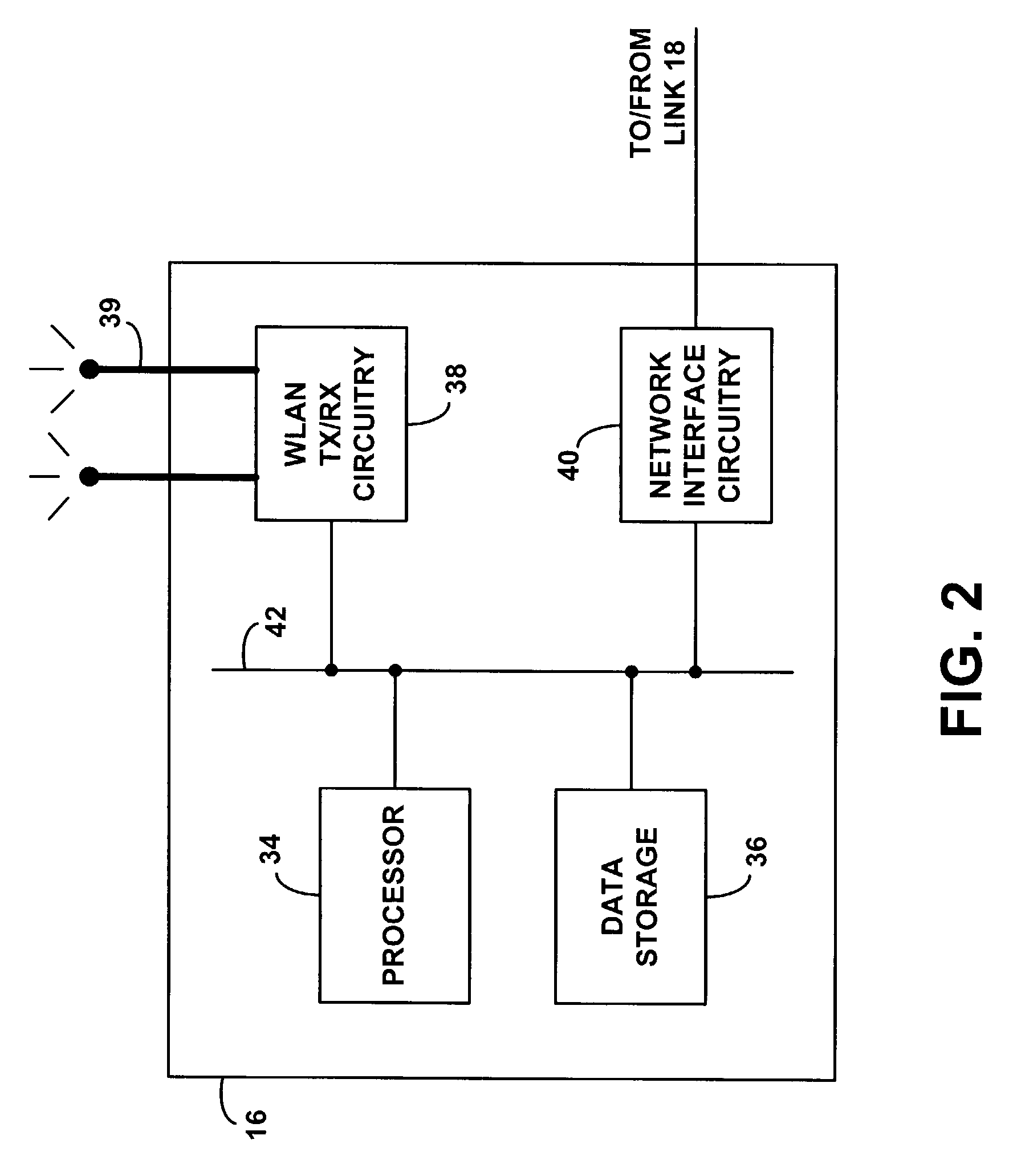
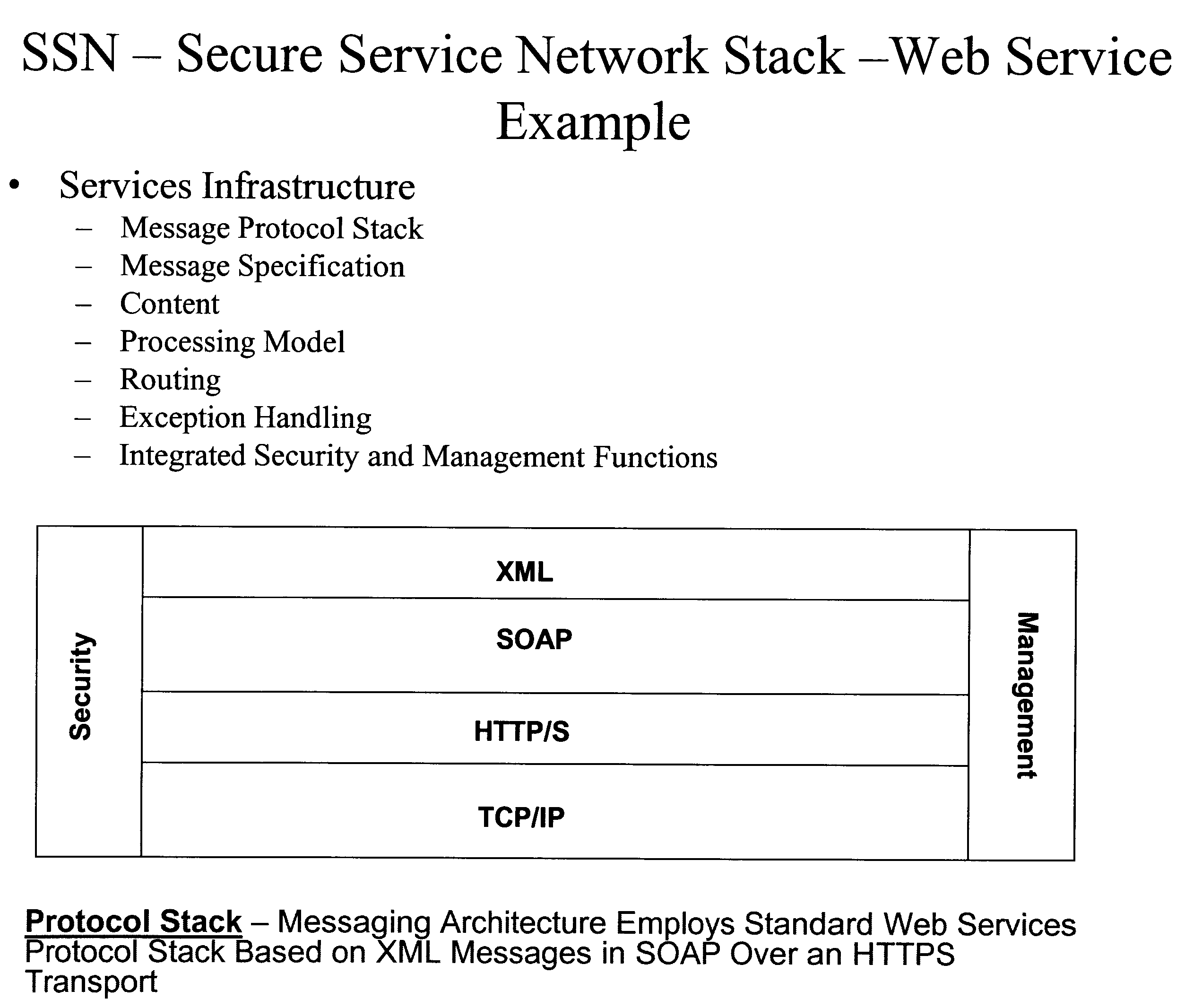
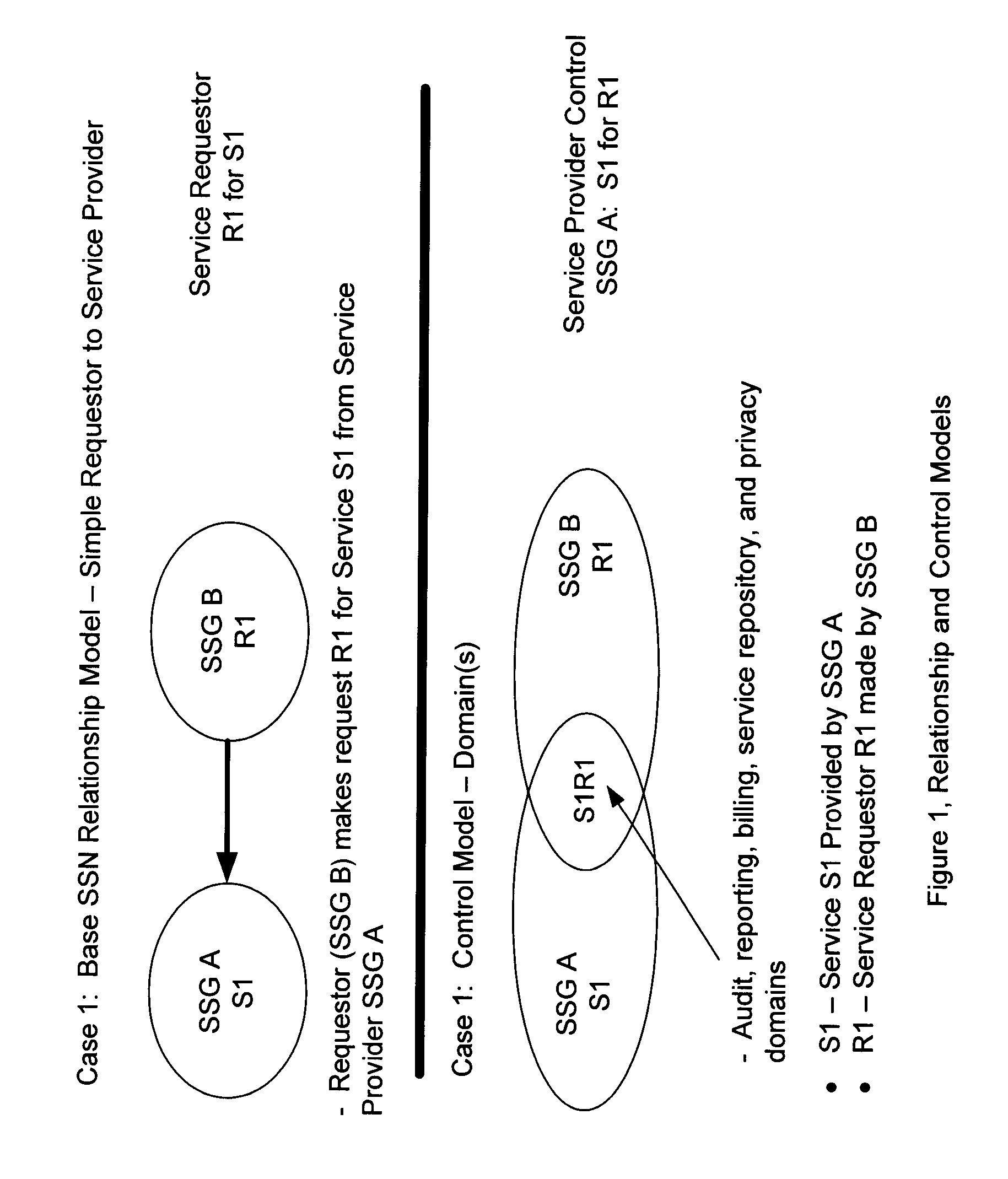
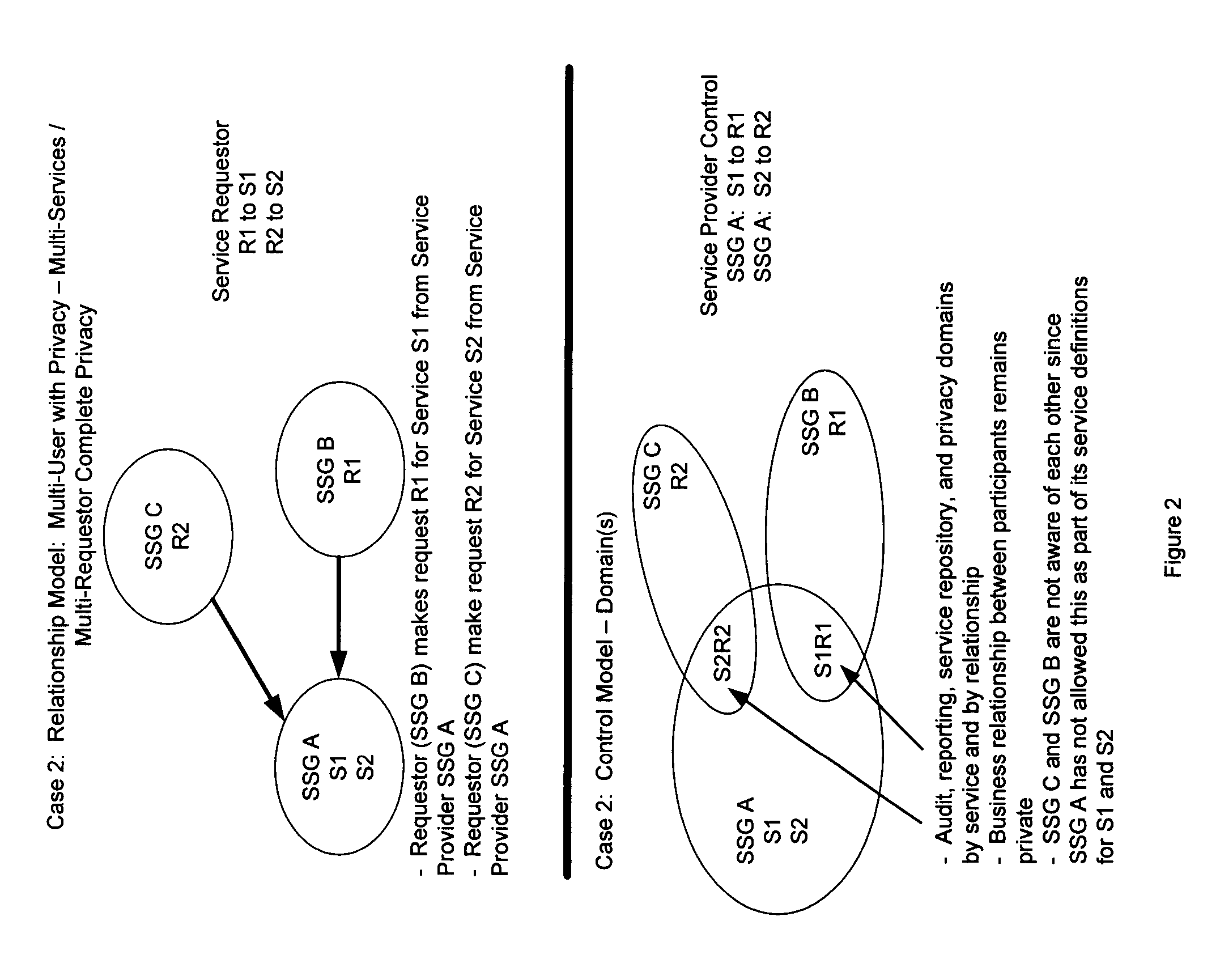
InactiveUS20060248205A1Increase valueMaintenance safetyMultiple digital computer combinationsTransmissionWeb serviceVirtual network topology
A Secure Service Network (SSN) in which at least two participants having a relationship are connected to a physical network by way of Secure Service Gateways and share information defined by one or more Service Definitions allowing for the creation of a secure Virtual Service Connection (VSC) between the participants in which the VSC is specific to the activity being performed and the participants provisioned for that activity. SSN enables the creation of a secure virtual network topology on any network transport that allows participants to exchange documents and transact business over the network real time, where all activity inherits a business and security infrastructure that is independent and in addition to the applications, devices, web services, users using the network.
Owner:RANDLE WILLIAM M +1
One arm data center topology with layer 4 and layer 7 services
ActiveUS7571470B2Expensive to operateExpensive to setComputer security arrangementsMultiple digital computer combinationsTraffic capacityData center
A one-arm data center topology routes traffic between internal sub-nets and between a sub-net and an outside network through a common chain of services. The data center topology employs layer 4 services on a common chassis or platform to provide routing and firewall services while reducing the number of devices necessary to implement the data center and simplifying configuration. Load balancing is provided by a load balancing device. In the one-arm topology, policy based routing or client network address translations or NAT pushes traffic to the CSM.
Owner:CISCO TECH INC
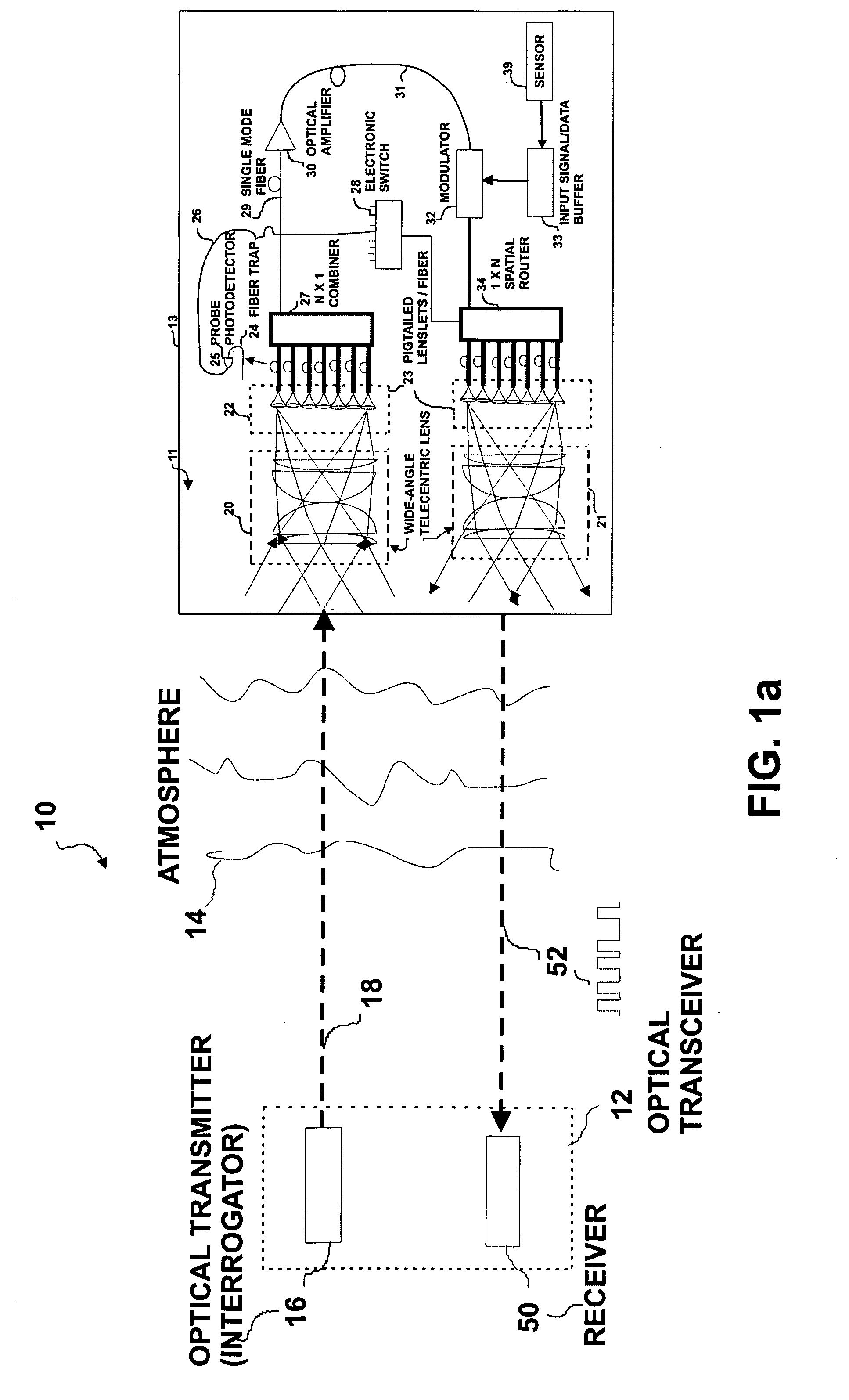
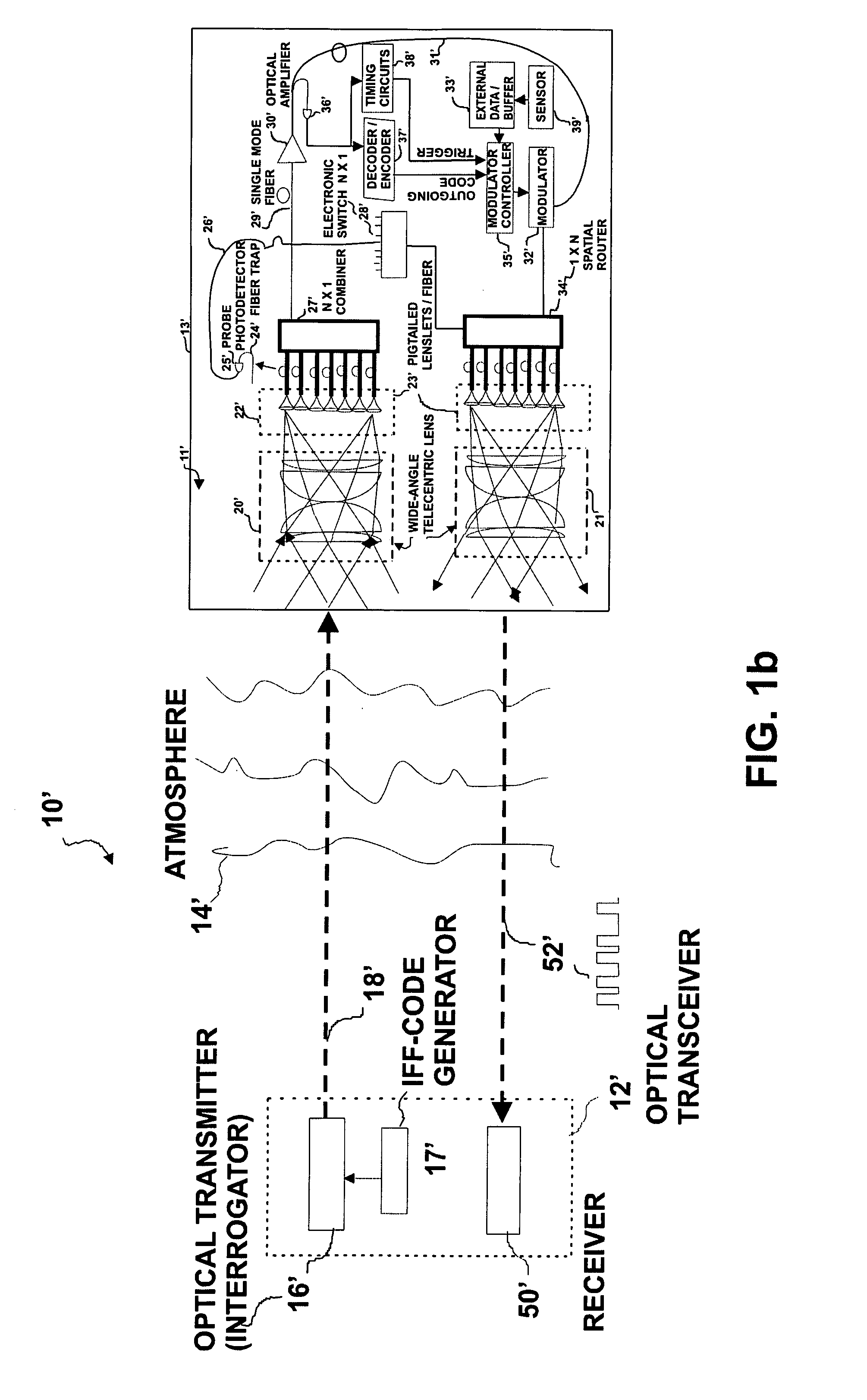
Wide field-of-view amplified fiber-retro for secure high data rate communications and remote data transfer
InactiveUS20090202254A1Increase data rateReduce power consumptionElectromagnetic transmissionSubscribers indirect connectionFiber arrayOptical communication
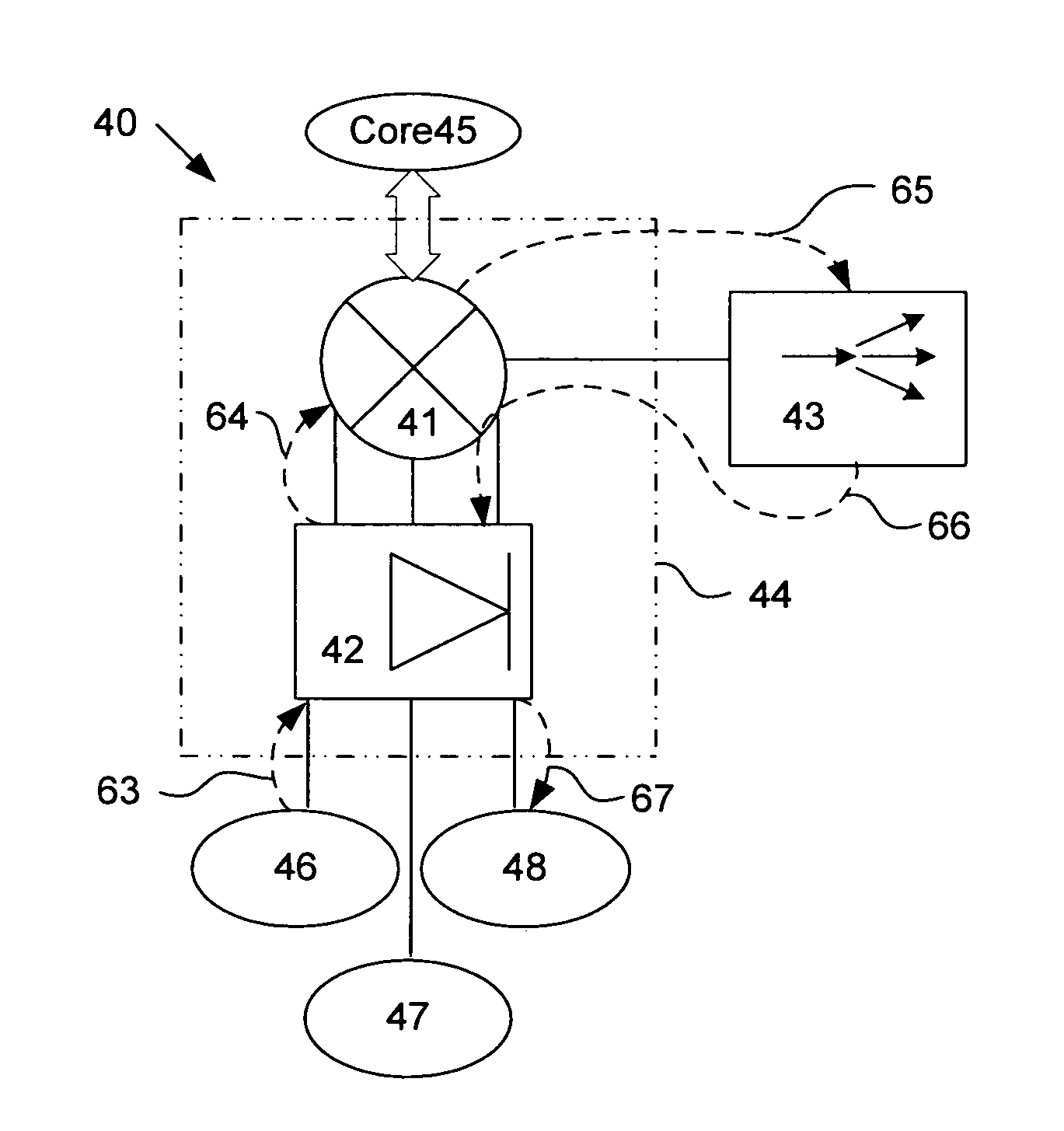
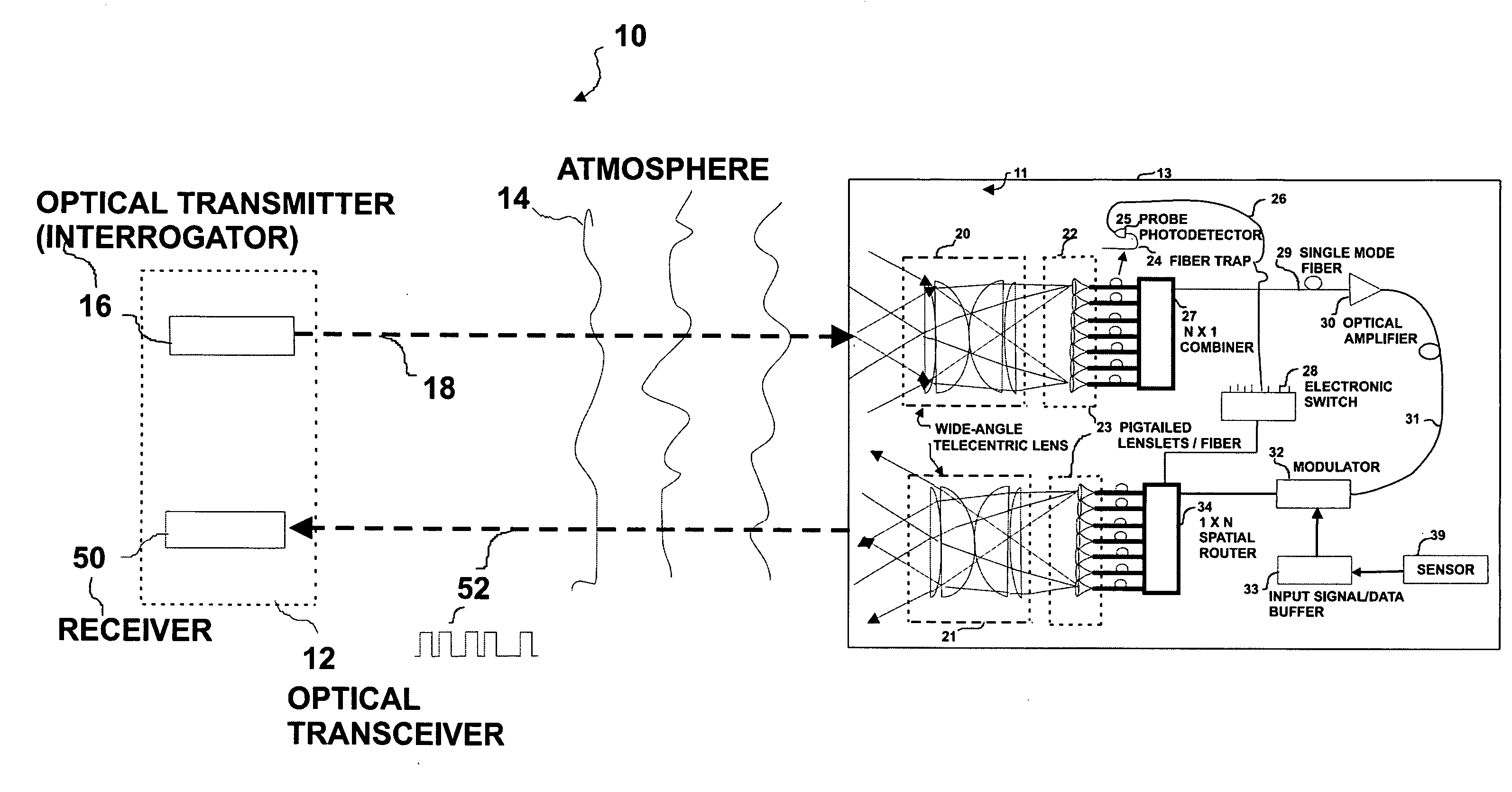
An optical system for remotely optical communications at a high data rate between a base station and a remote station under atmospheric turbulence conditions is disclosed. The remote station includes an entirely different type of retroreflector that does not use the conventional type of retroreflection, but instead consists of two sets of lenslets coupled with single-mode fiber array, called fiber “retro”. Amplified retromodulation is achieved requiring only one single optical amplifier and one single modulator. A transmitter located at the base station sends an interrogating optical beam to the fiber “retro” which modulates the optical beam according to the input signal / data, and redirects the modulated optical beam to the base station for detection by a receiver. The present invention includes the capabilities of providing Identification of Friend-or-Foe (IFF), secure communication, and a means of achieving a wide field-of-view (FOV) with a fiber-coupled lenselet array.
Owner:MAJUMDAR ARUN KUMAR +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com