Patents
Literature
5671 results about "User authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
User authentication is the verification of an active human-to-machine transfer of credentials required for confirmation of a user’s authenticity; the term contrasts with machine authentication, which involves automated processes that do not require user input.
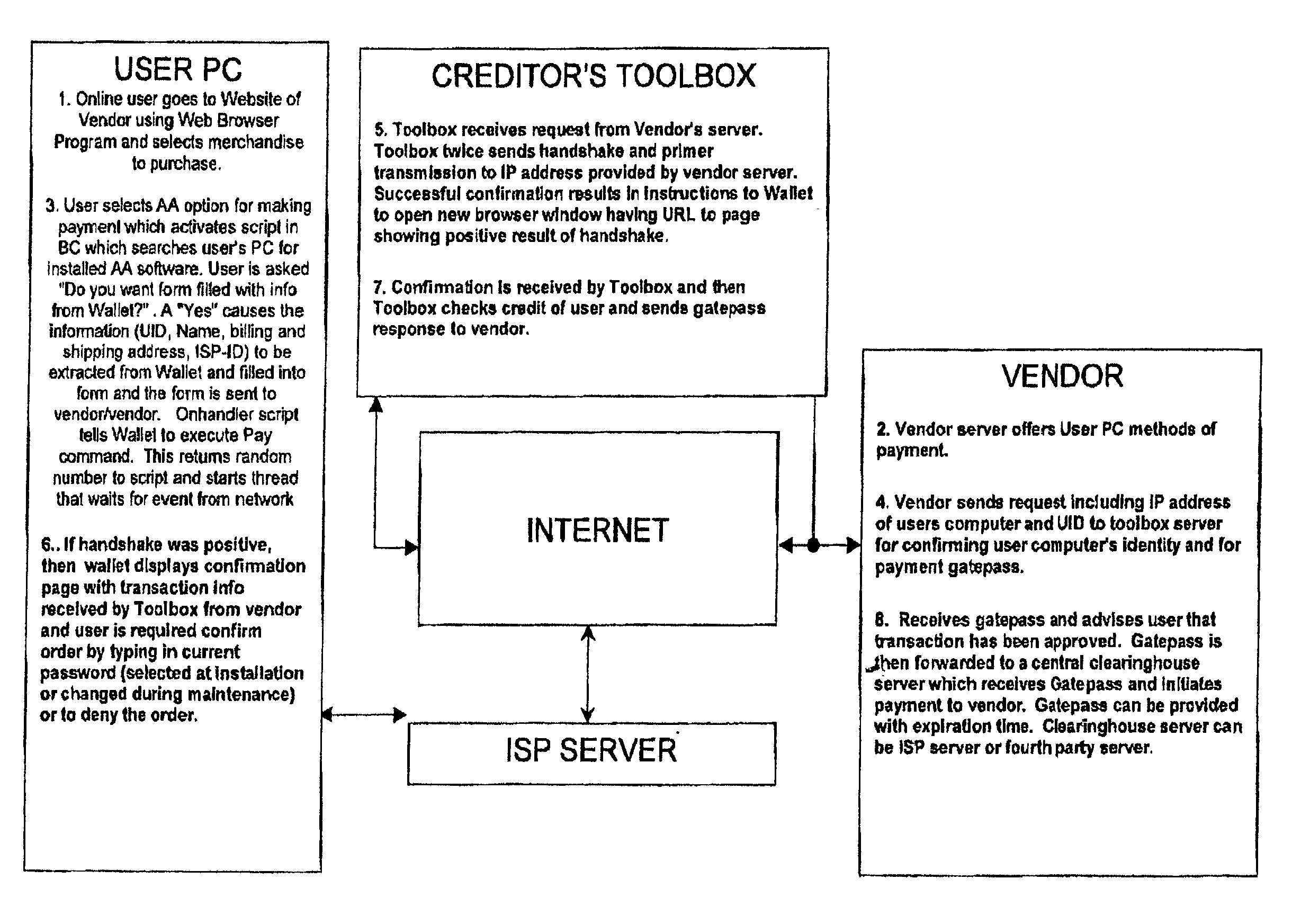
System and method for fraud monitoring, detection, and tiered user authentication
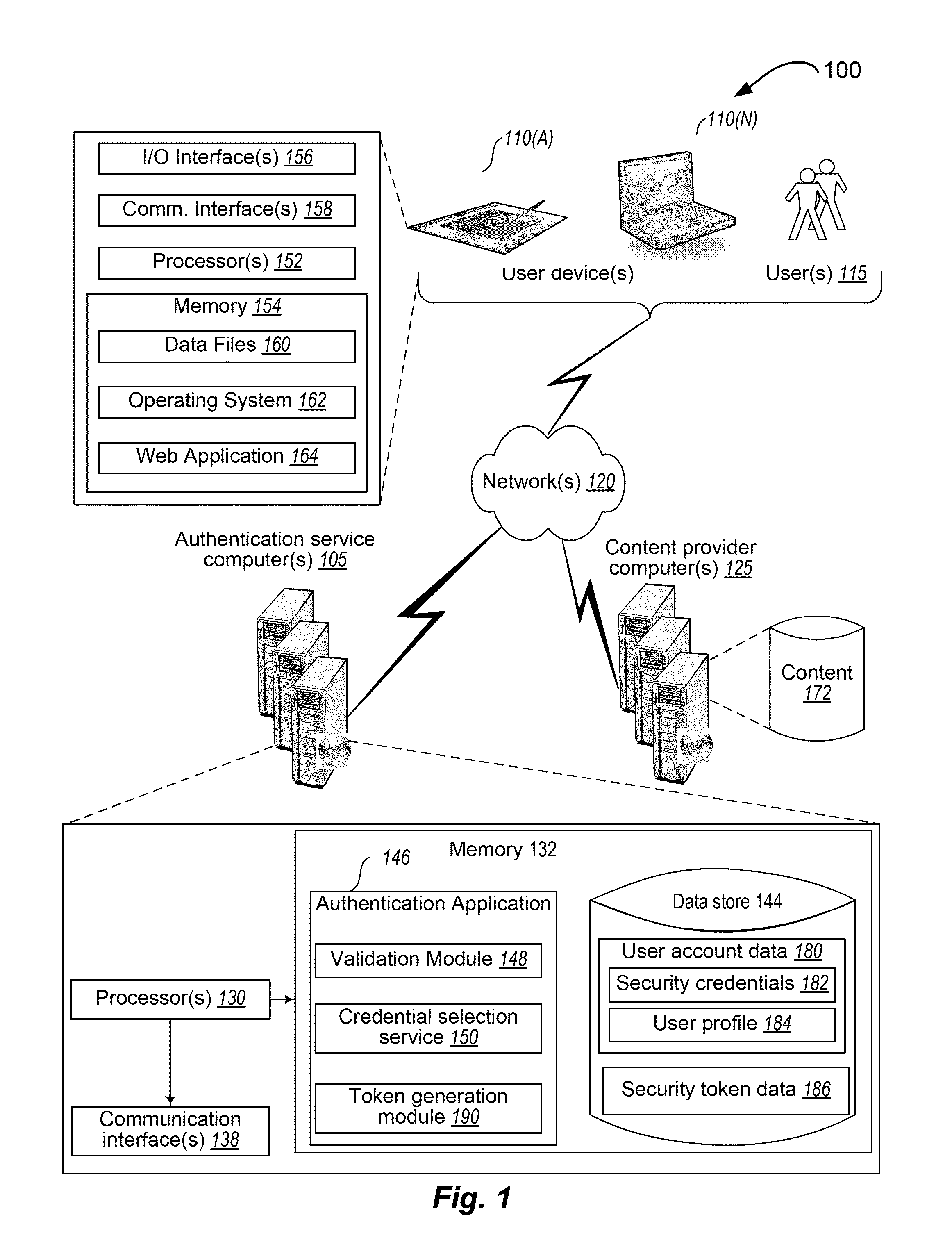
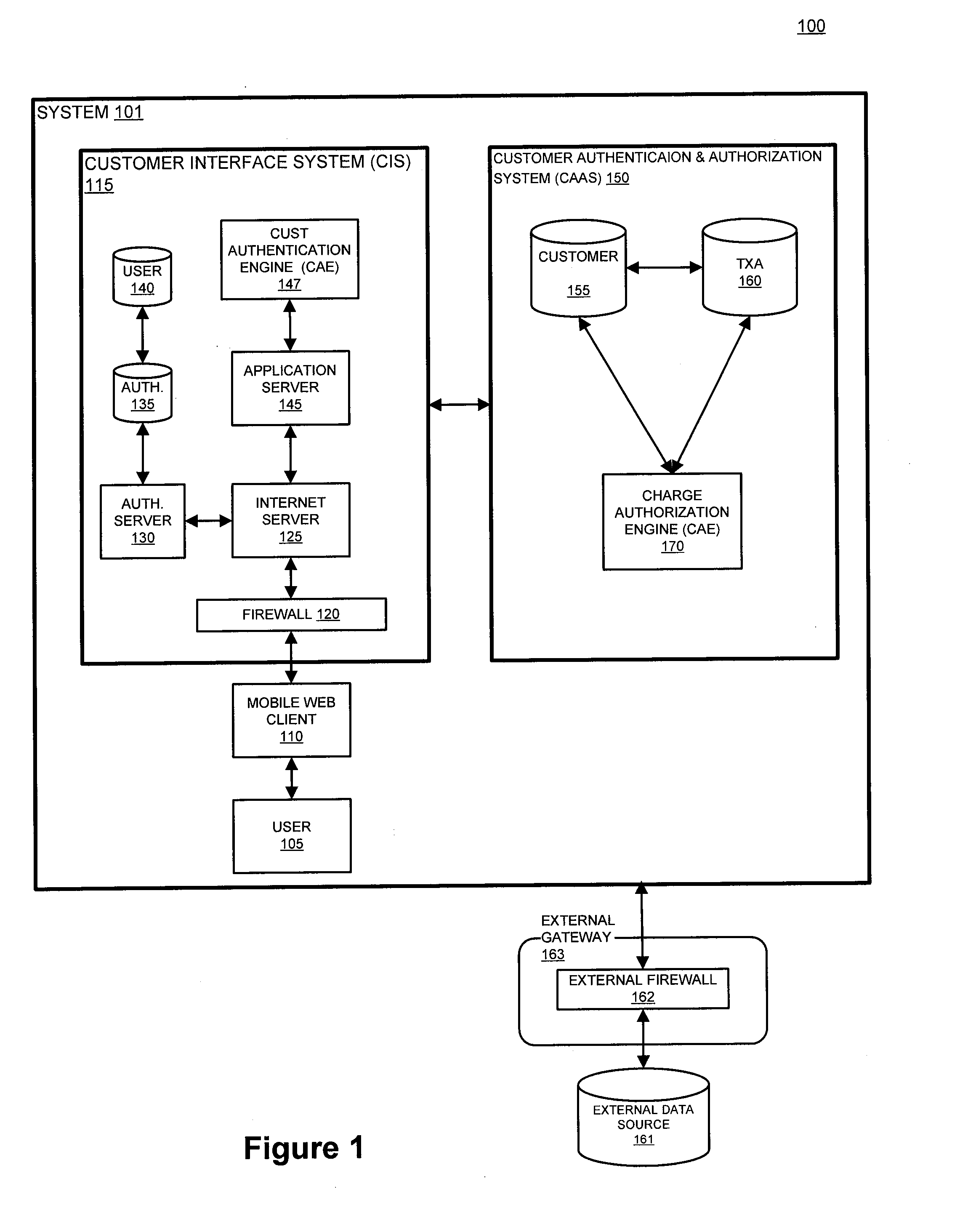
The present invention provides systems and methods for authenticating access requests from user devices by presenting one of a plurality of graphical user interfaces selected depending on a perceived risk of fraud associated with the devices. User devices are identified with fingerprinting information, and their associated risks of fraud are determined from past experience with the device or with similar devices and from third party information. In preferred embodiments, different graphical user interfaces are presented based on both fraud risk and, in the case of a known user, usability. In preferred embodiments, this invention is implemented as a number of communicating modules that identify user devices, assess their risk of fraud, present selected user interfaces, and maintain databases of fraud experiences. This invention also includes systems providing these authentication services.
Owner:ORACLE INT CORP
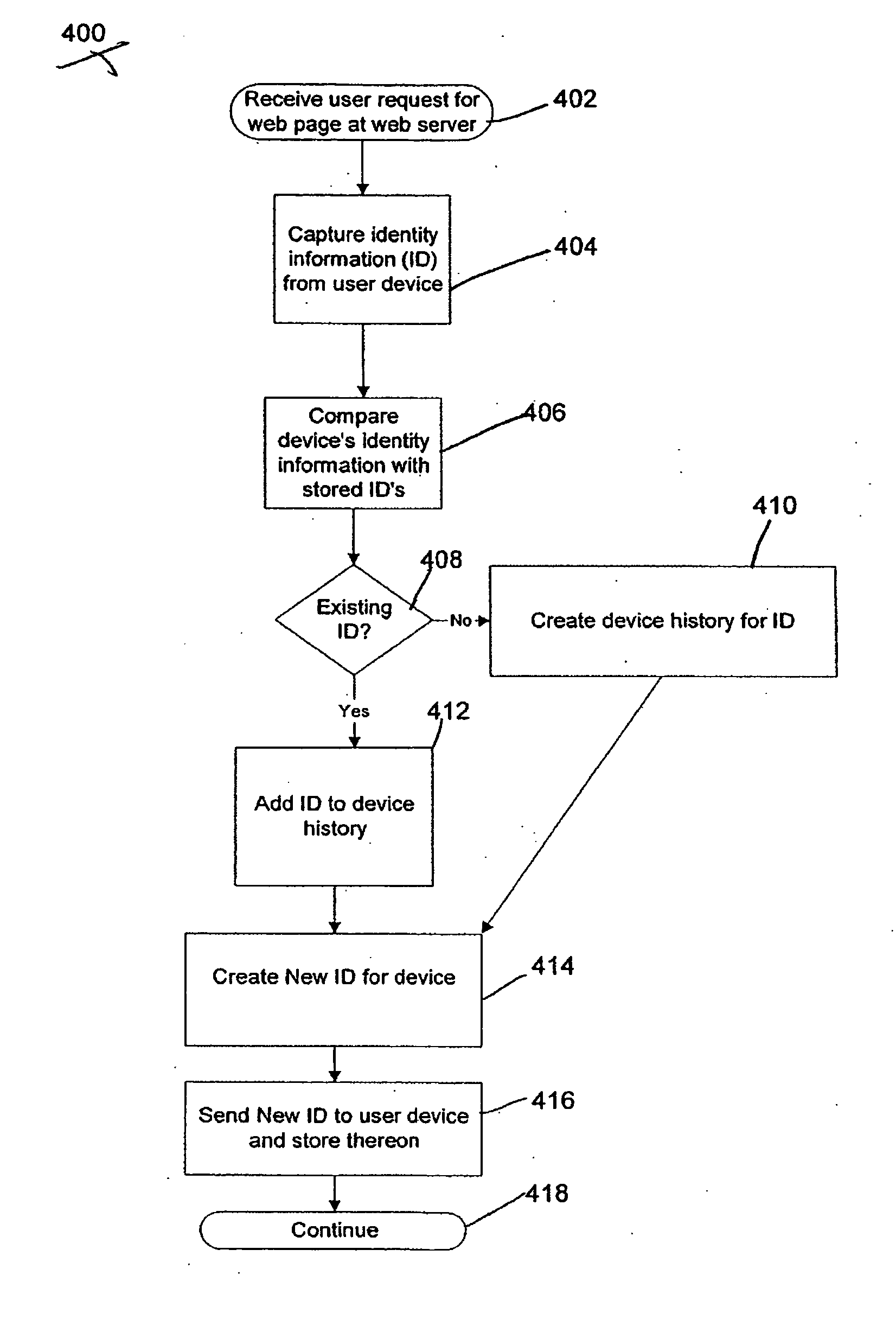
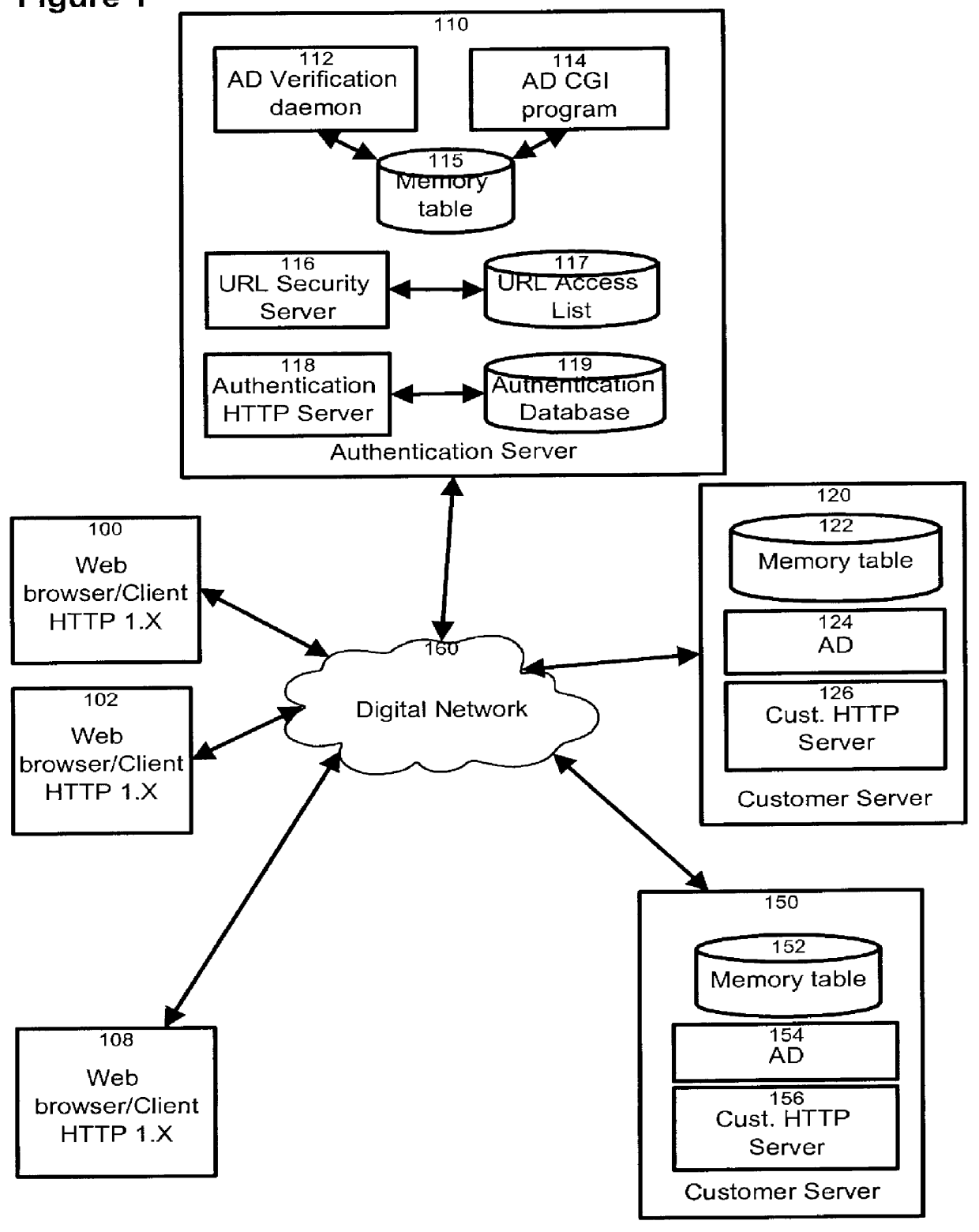
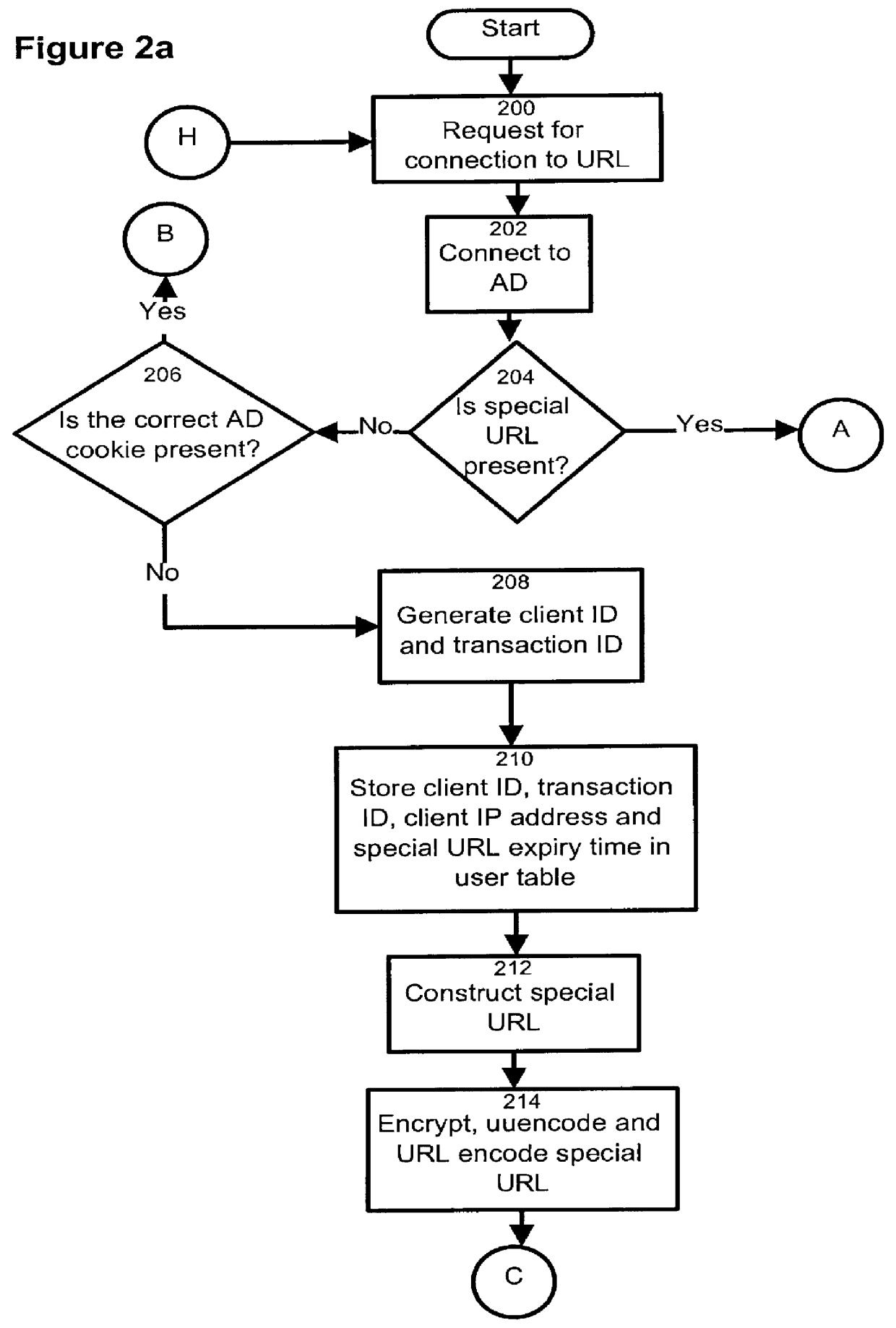
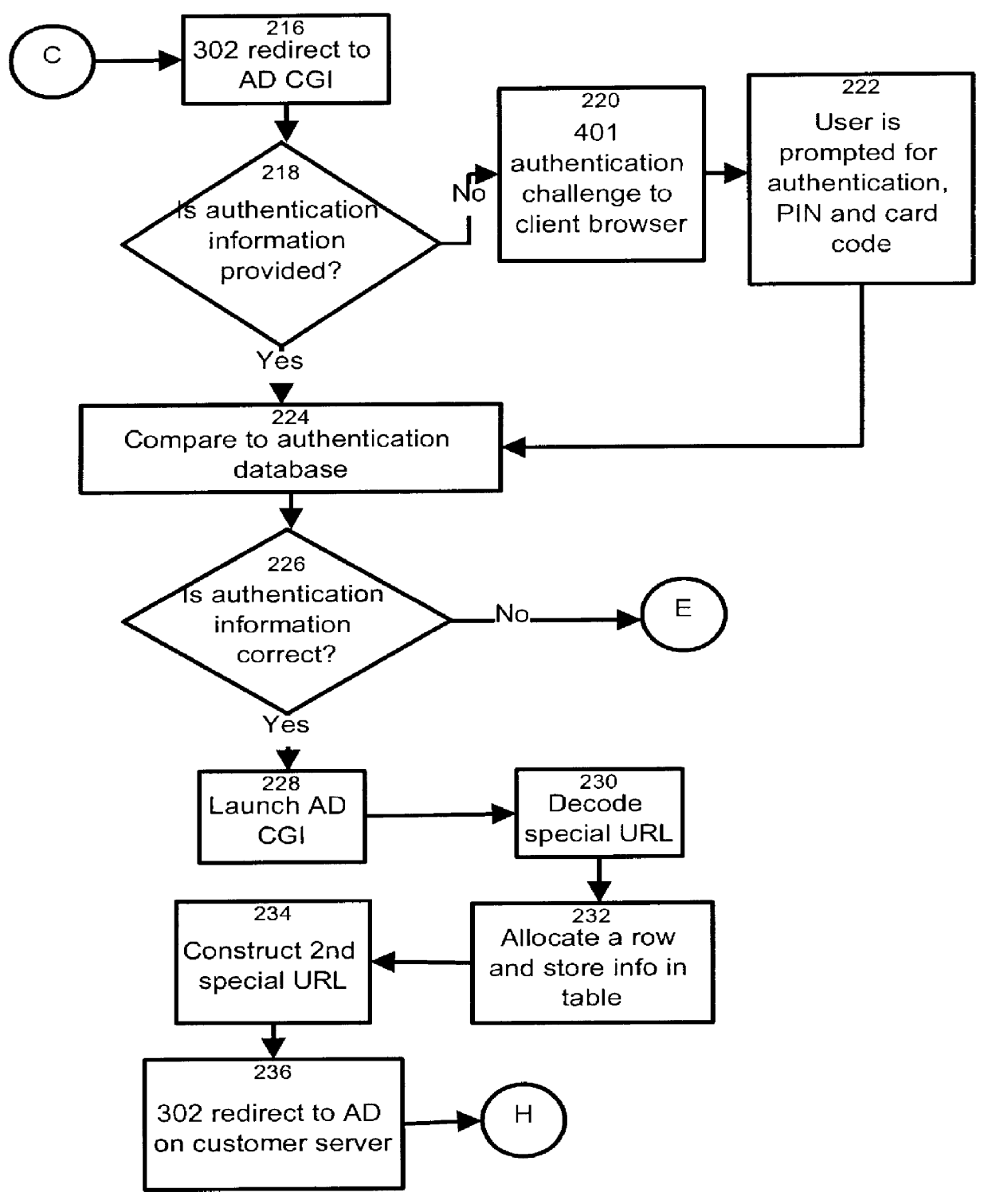
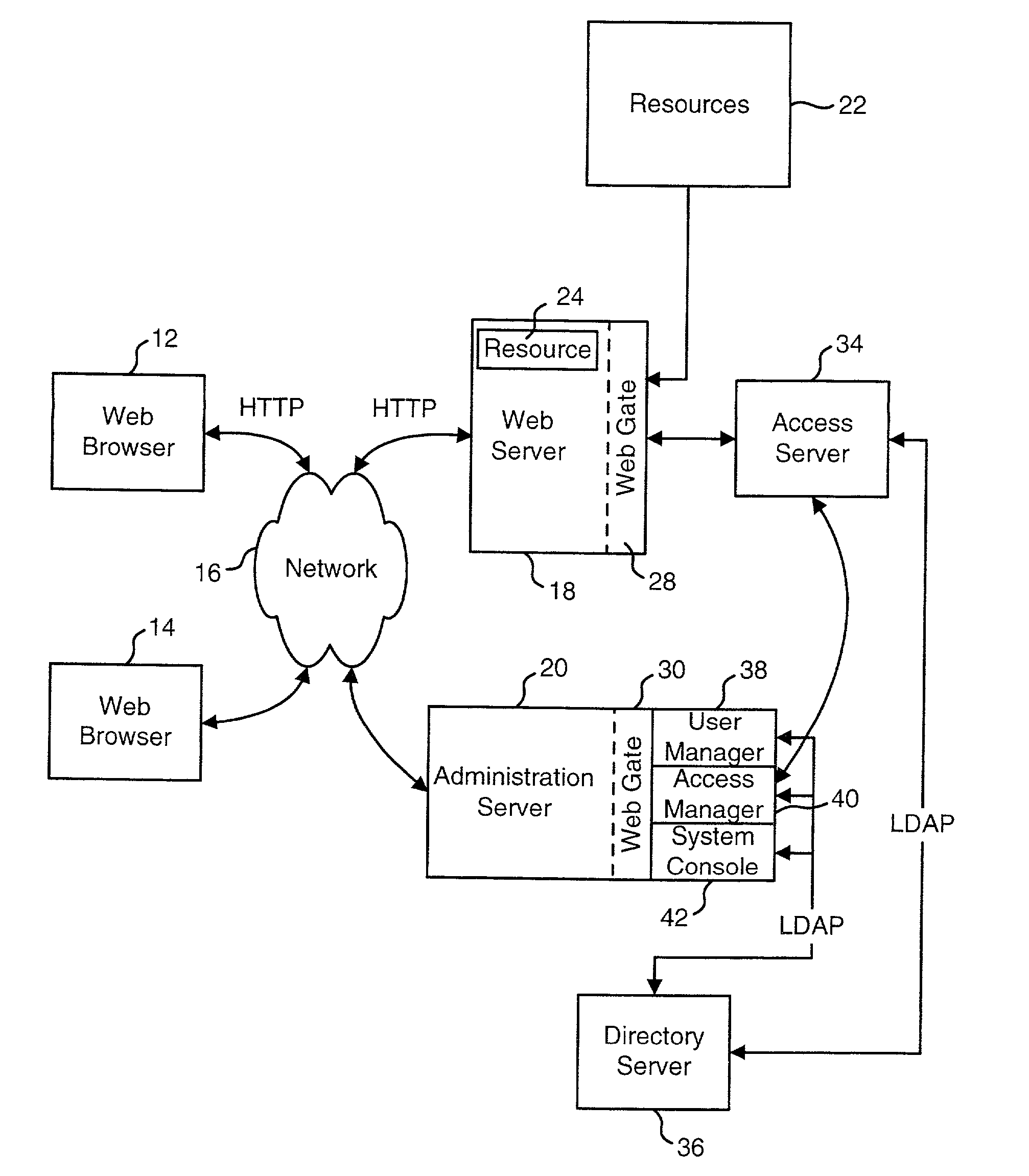
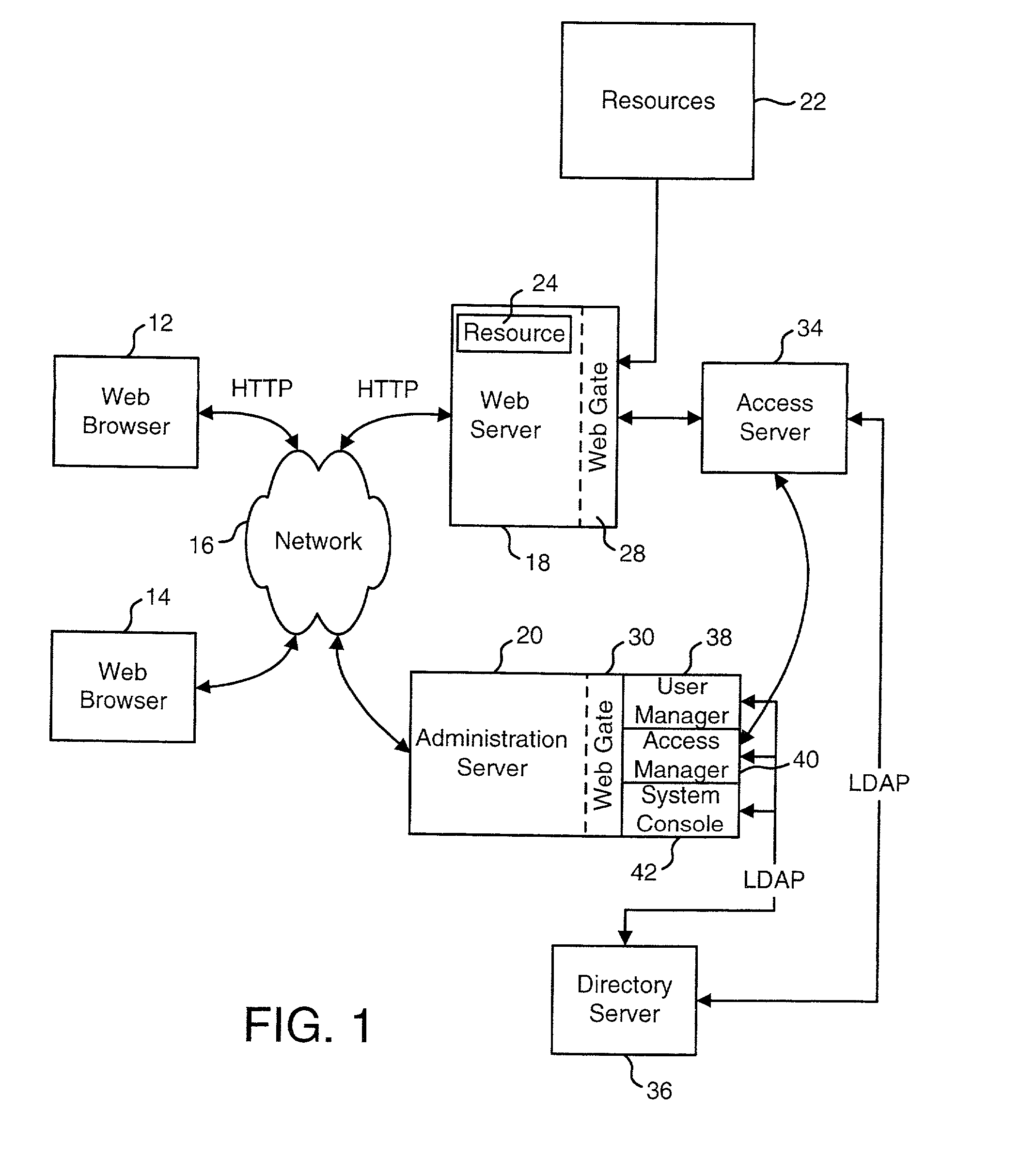
HTTP distributed remote user authentication system
InactiveUS6092196AExemption stepsAvoid necessityDigital data processing detailsUser identity/authority verificationUser authenticationUser identifier
The present invention relates to the field of data and computer network security. Data and computer network security is of the utmost importance to most organizations that possess such networks. One of the difficulties that users and managers of these networks face is that the users have to provide a user ID and password every time they wish to access one of the organization's secured HTTP servers or URLs. This creates a problem for users and managers since lists of numerous user IDs and passwords need to be maintained and therefore can easily be lost or their confidentiality compromised. This invention addresses these problems by providing a transparent, scalable, single point of authentication for remote users across any number of HTTP servers anywhere on a data network, such as an Intranet, using any user ID and password scheme implemented by a main authentication HTTP server.
Owner:RPX CLEARINGHOUSE
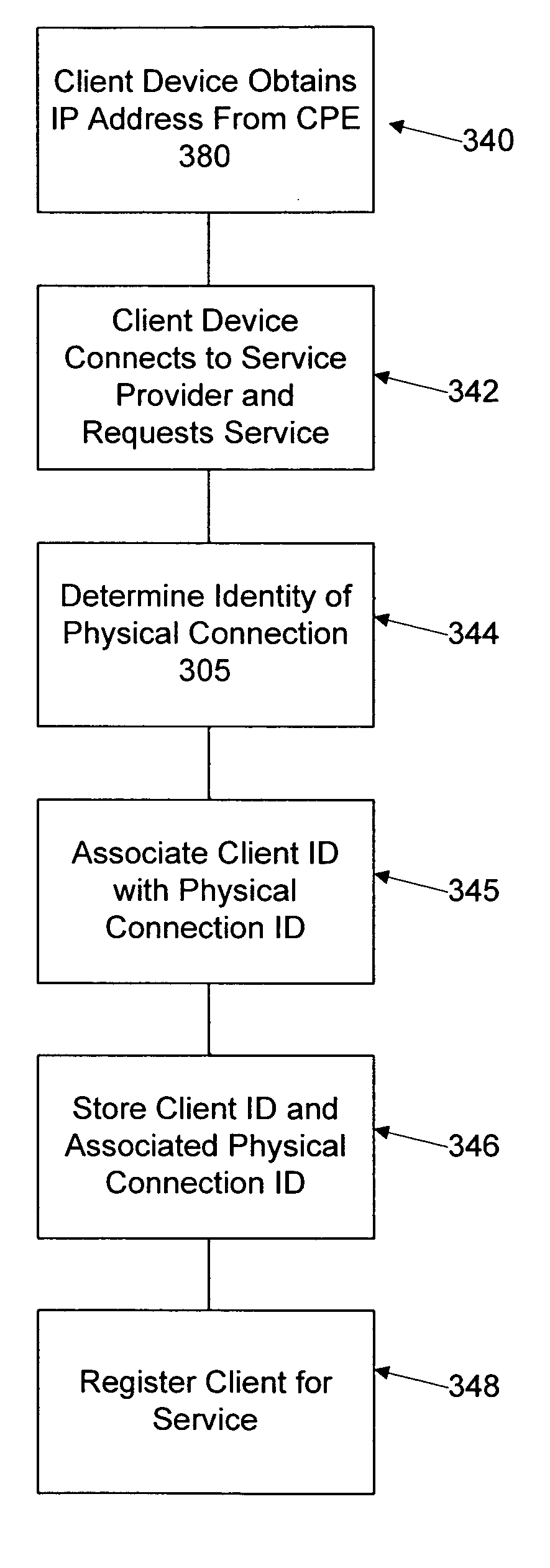
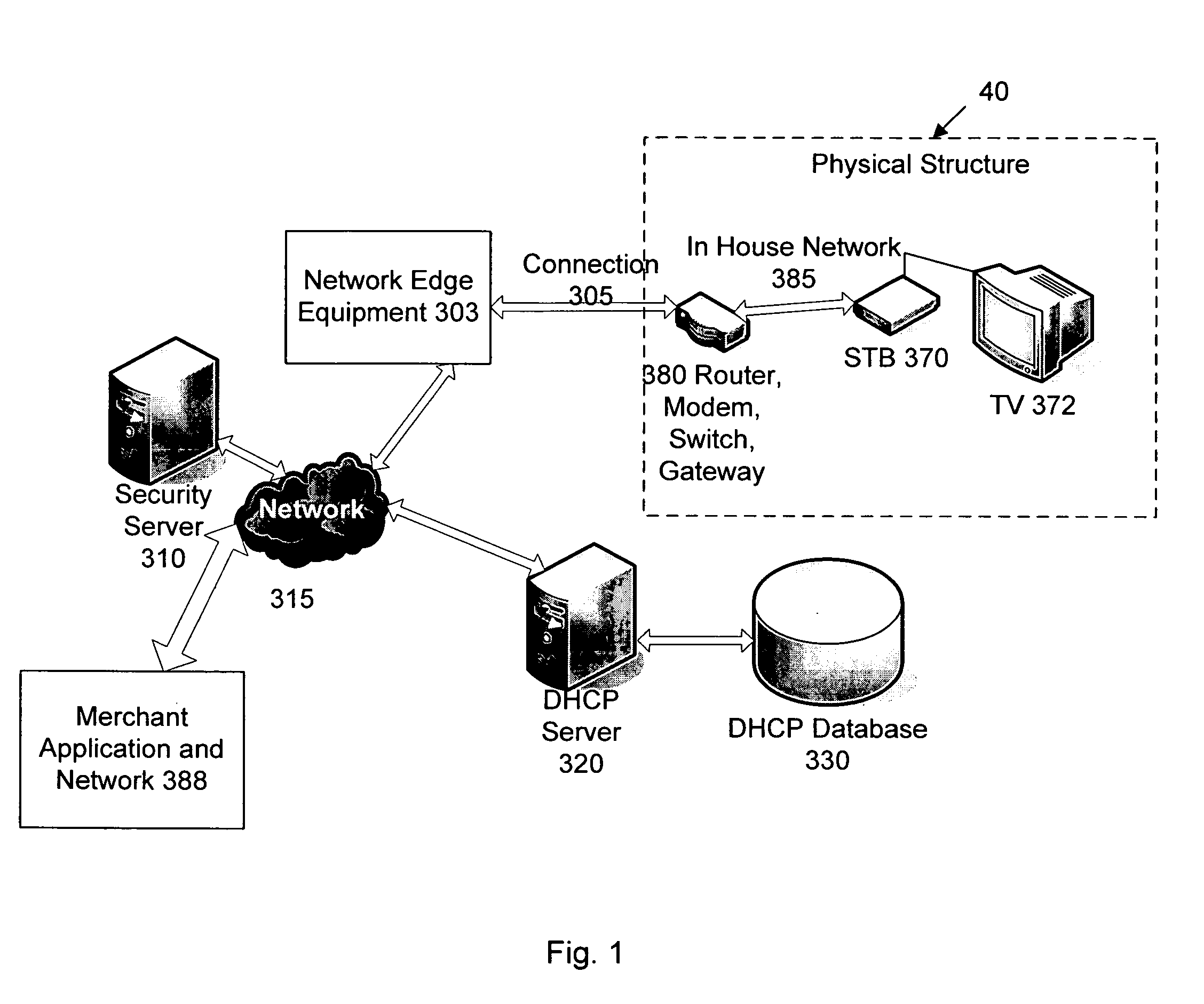
Network user authentication system and method
ActiveUS20070022469A1Removal difficult and impossibleThe certification process is reliableDigital data processing detailsUser identity/authority verificationUnique identifierAuthentication server
In a network user authentication system, a network user is identified for authentication purposes using the unique identifier for a dedicated physical communication line associated with the building in which the network user is located or a digital certificate which is associated with a secure component or communication line physically attached to a building. An authentication server initially verifies the identification of the dedicated communication line to be associated with a network service subscriber or issues a unique digital certificate to be associated with the dedicated communication line for authentication purposes. The digital certificate may be stored in a building gateway or in an edge site module which is connected to the secure components of a plurality of buildings and stores unique digital certificates for each building.
Owner:VERIMATRIX INC
Smart Device User Authentication
InactiveUS20110219427A1Little and no burdenImprove securityDigital data processing detailsComputer security arrangementsUser deviceWeb service
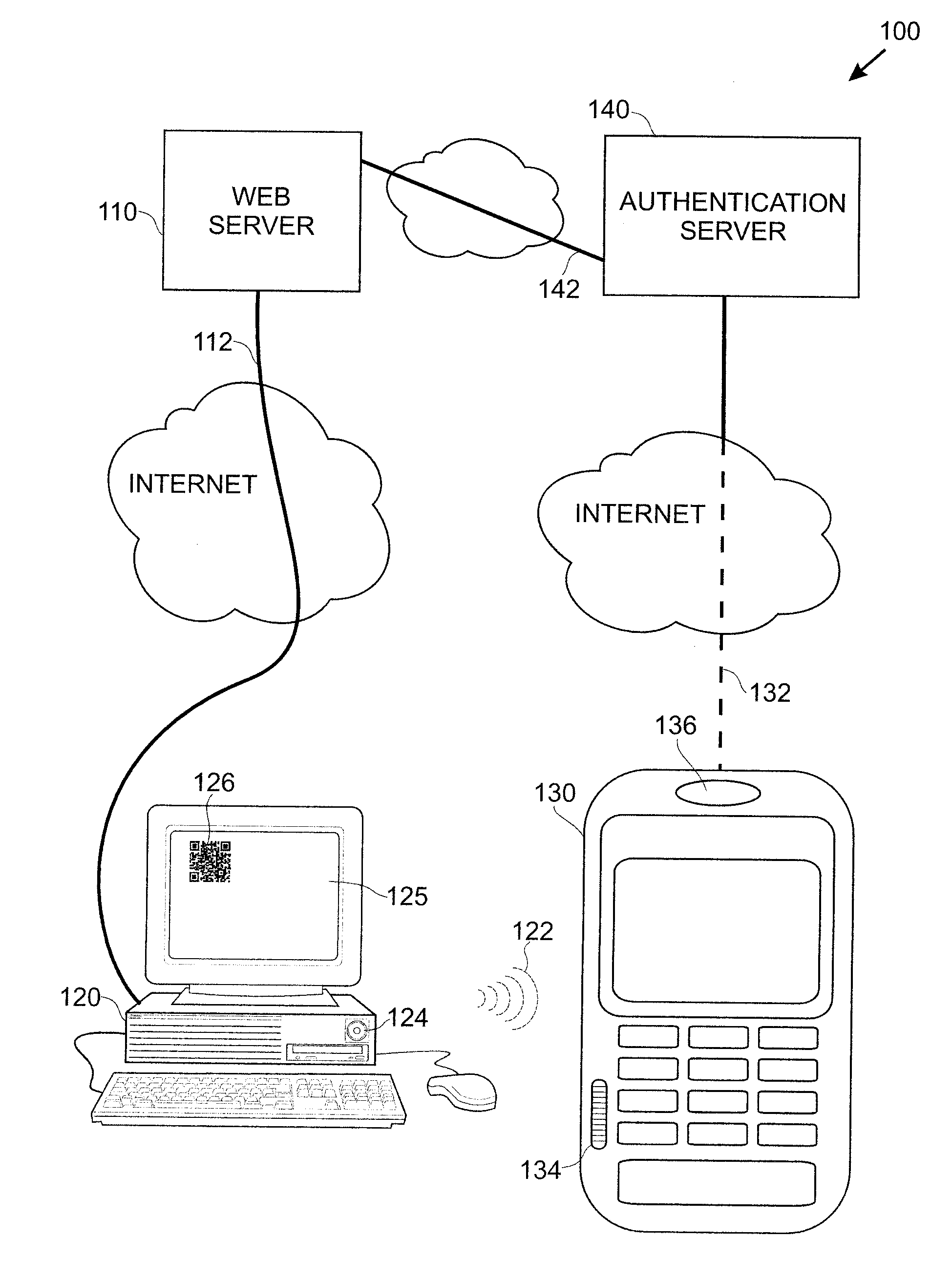
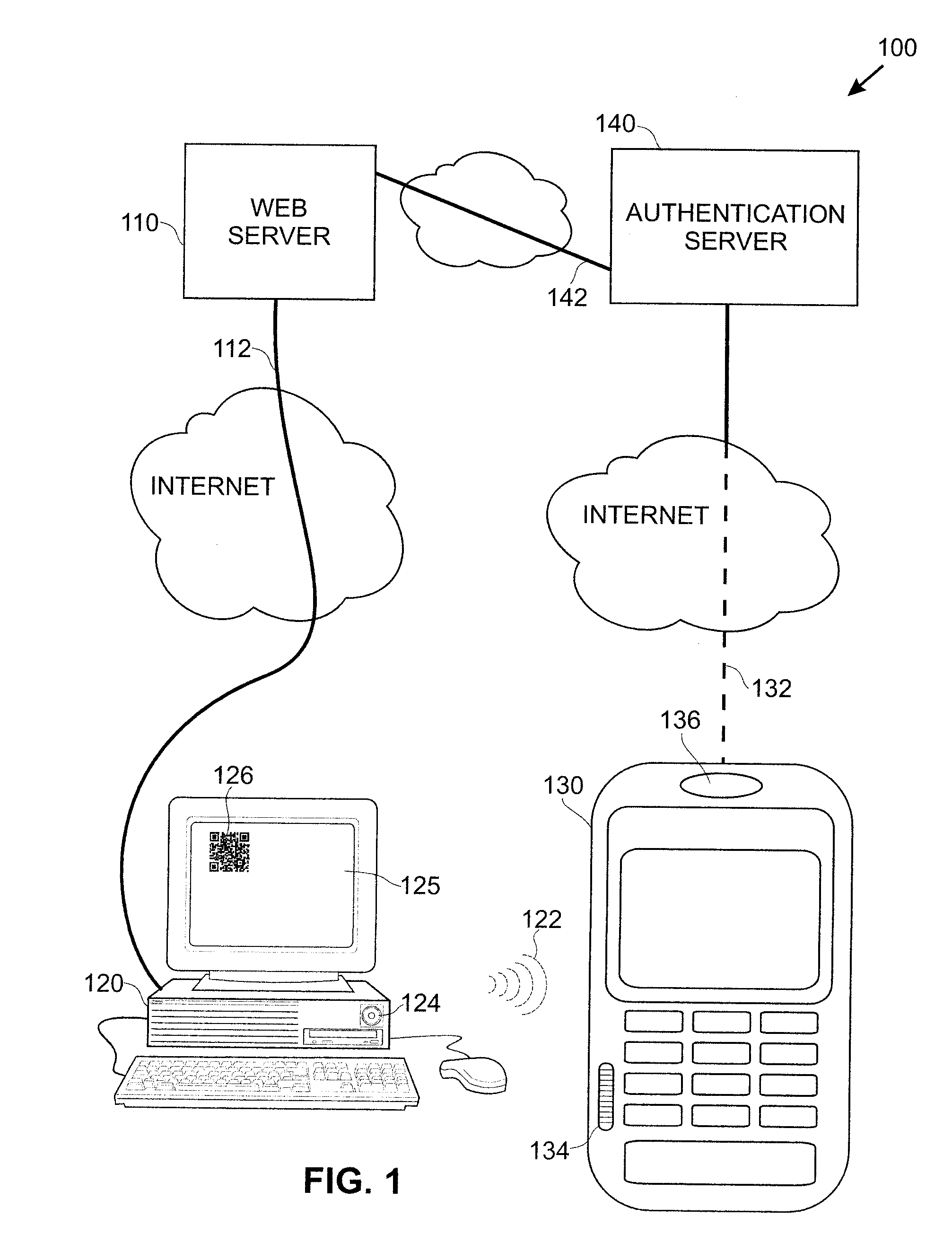
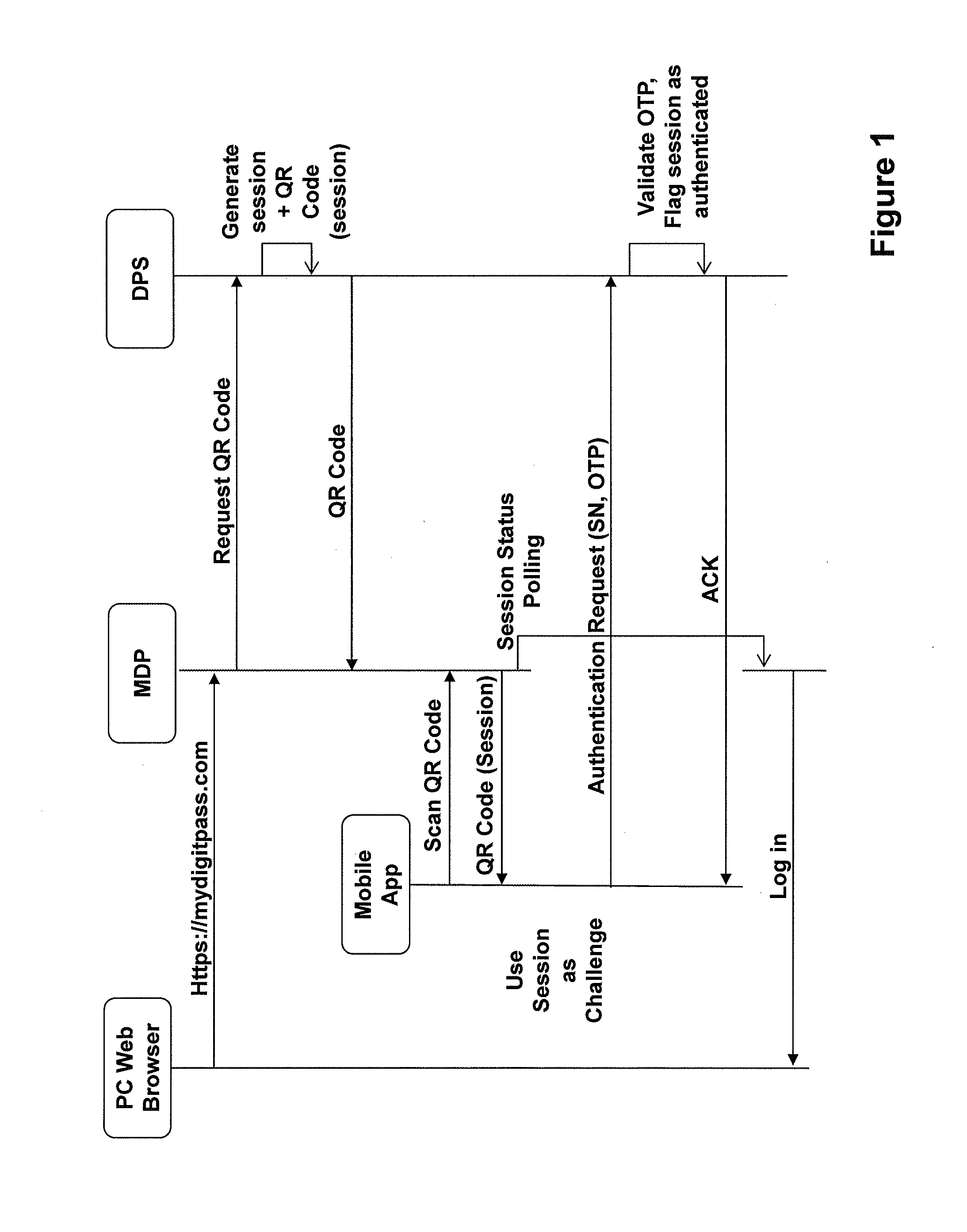
Techniques for simplifying an authentication process from the viewpoint of a user while providing improved security to the many users currently employing no or weak security techniques. In logging into a web site hosted by a web server, a session begins by a user connecting and logging in with a device, such as a personal computer. Rather than a user name and password approach which is presently typical, the personal computer communicates with another user device, such as a smart phone. In one approach, an encoded acoustic signal is employed for this communication. The smart phone securely communicates with an authentication server which informs the web server whether the user has been authenticated or not.
Owner:RSSBUS
User-convenient authentication method and apparatus using a mobile authentication application
ActiveUS20140040628A1Authentication process can be made convenientCost-effectiveDigital data authenticationCoding/ciphering apparatusUser authenticationApplication software
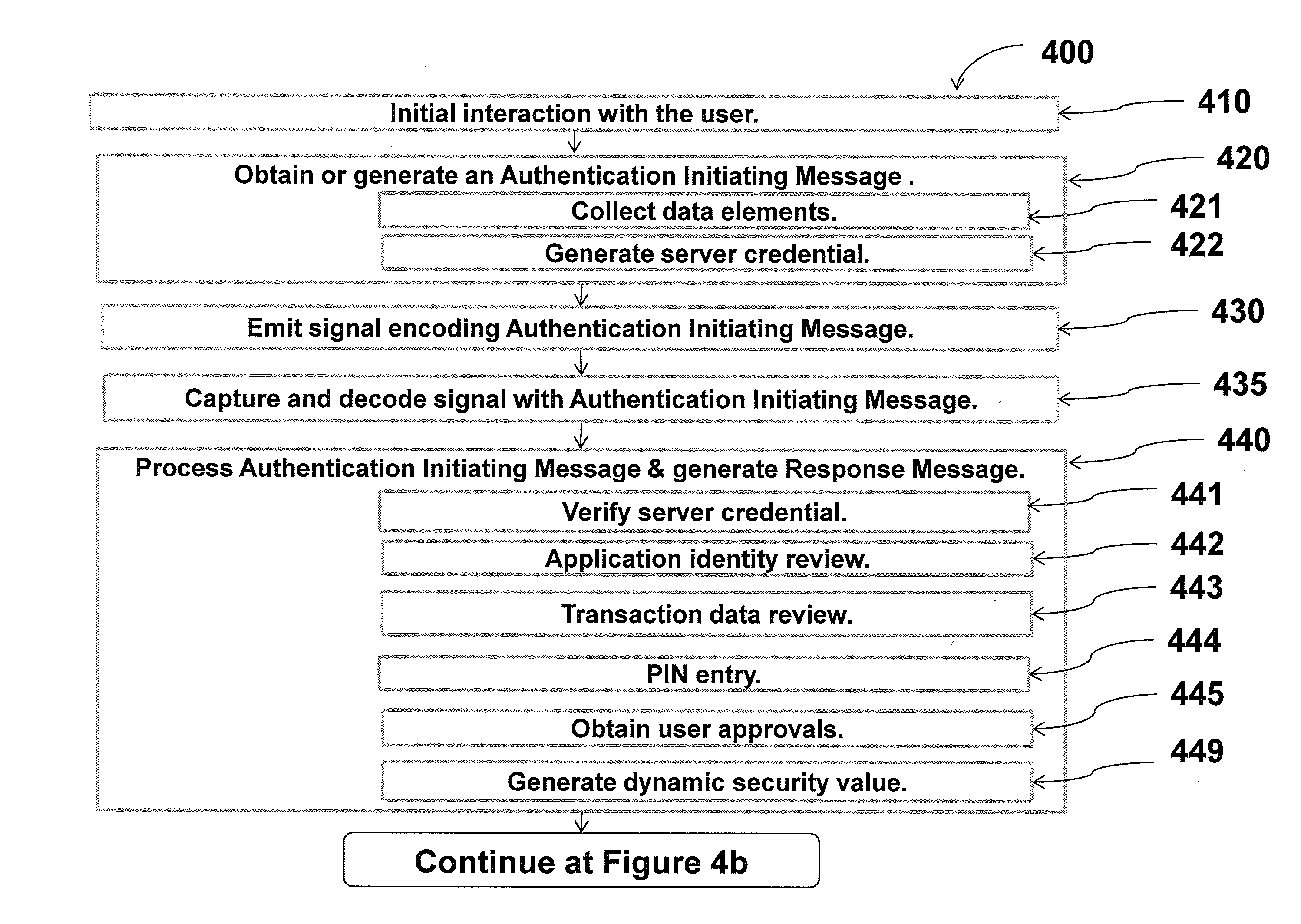
Methods, apparatus, and systems for securing application interactions are disclosed. Application interactions may be secured by, at a user authentication device, capturing a signal emitted by an access device encoded with an authentication initiating message including an application identifier, decoding the signal and obtaining the authentication initiating message, retrieving the application identifier, presenting a human interpretable representation of the application identity to the user, obtaining user approval to generate a response message available to a verification server, generating a dynamic security value using a cryptographic algorithm that is cryptographically linked to the application identity, and generating a response message including the generated dynamic security value; making the response message available to a verification server; and, at the verification server, receiving the response message, verifying the response message including verifying the validity of the dynamic security value, and communicating the result of the verification of the response message to the application.
Owner:ONESPAN NORTH AMERICA INC
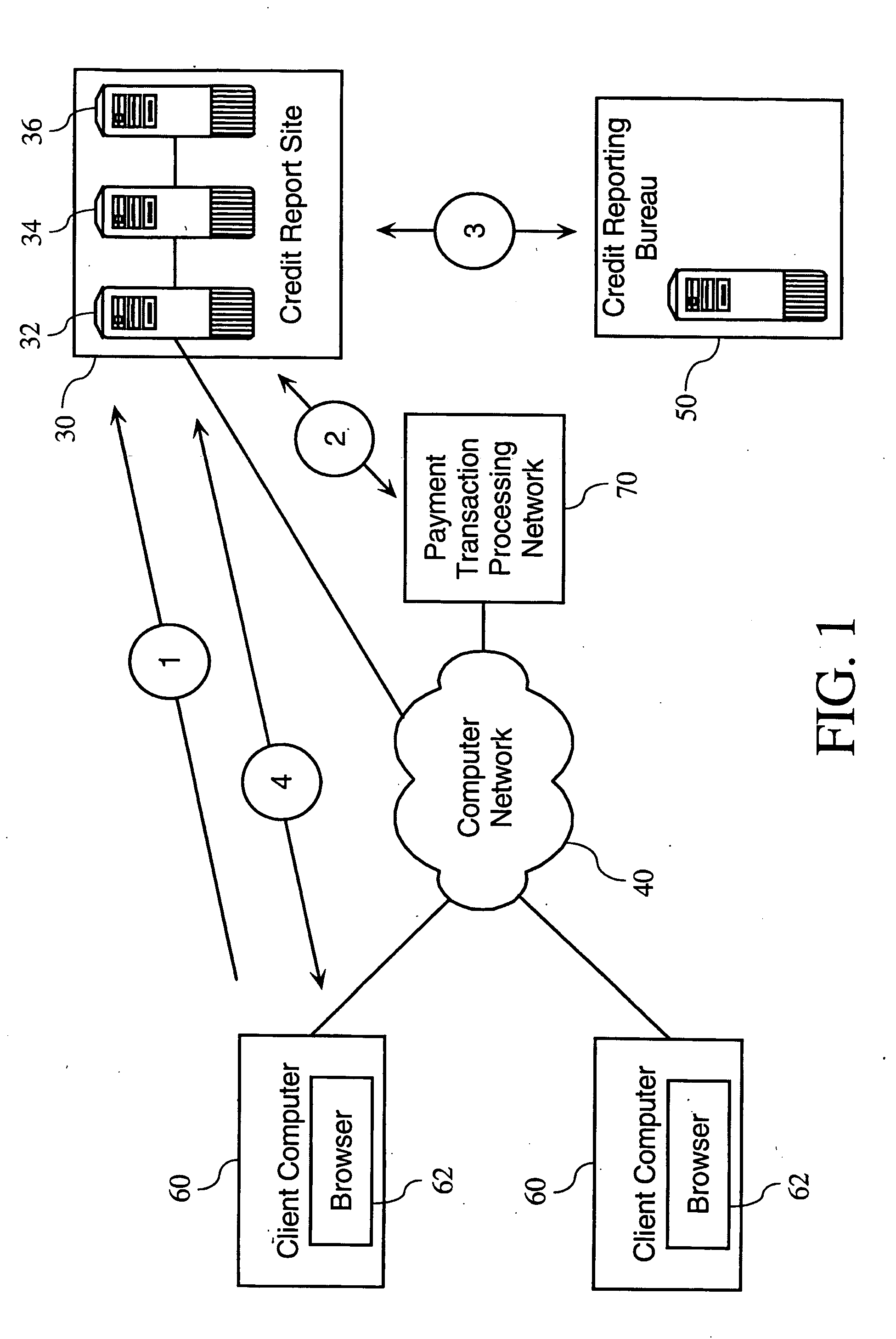
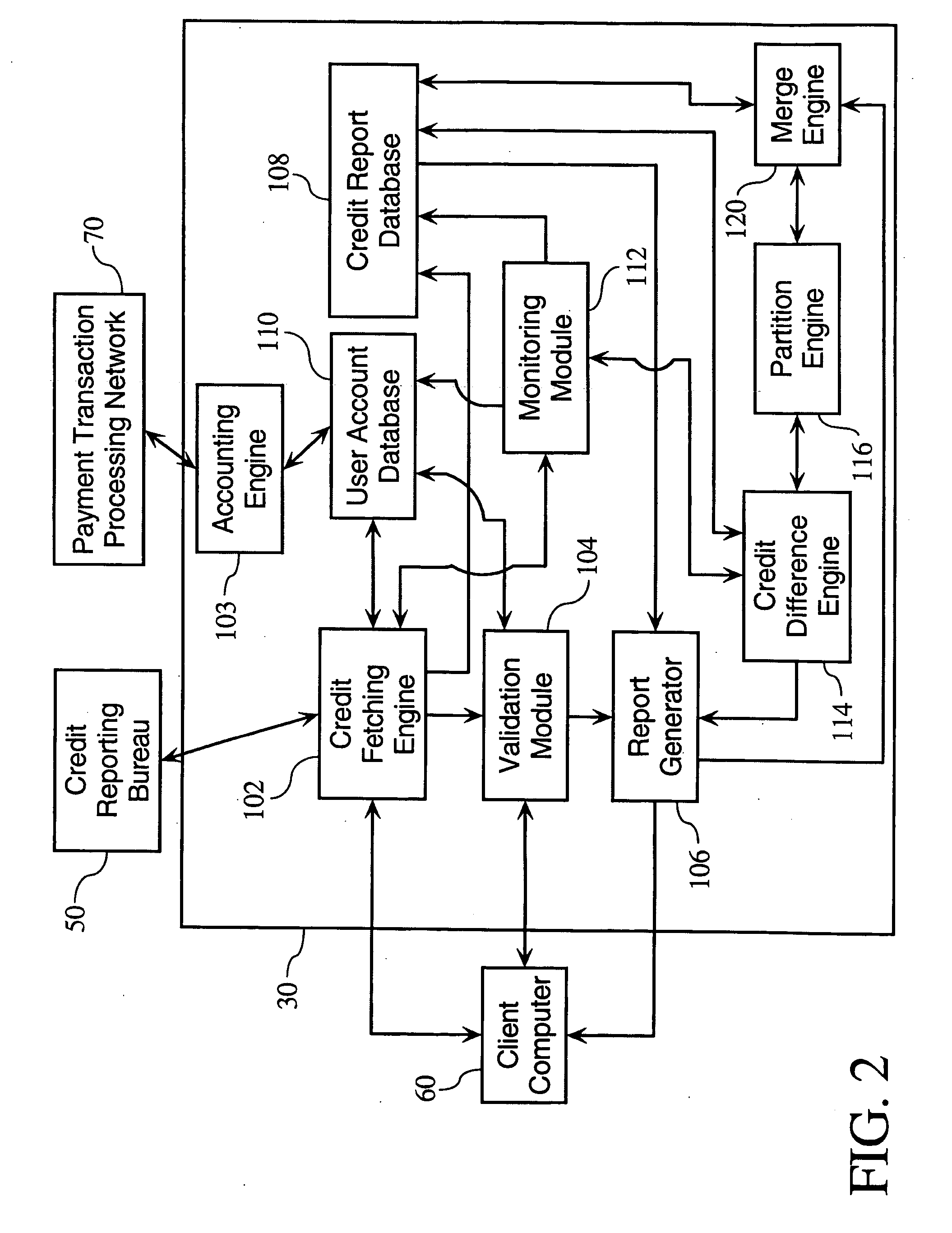
Credit and financial information and management system
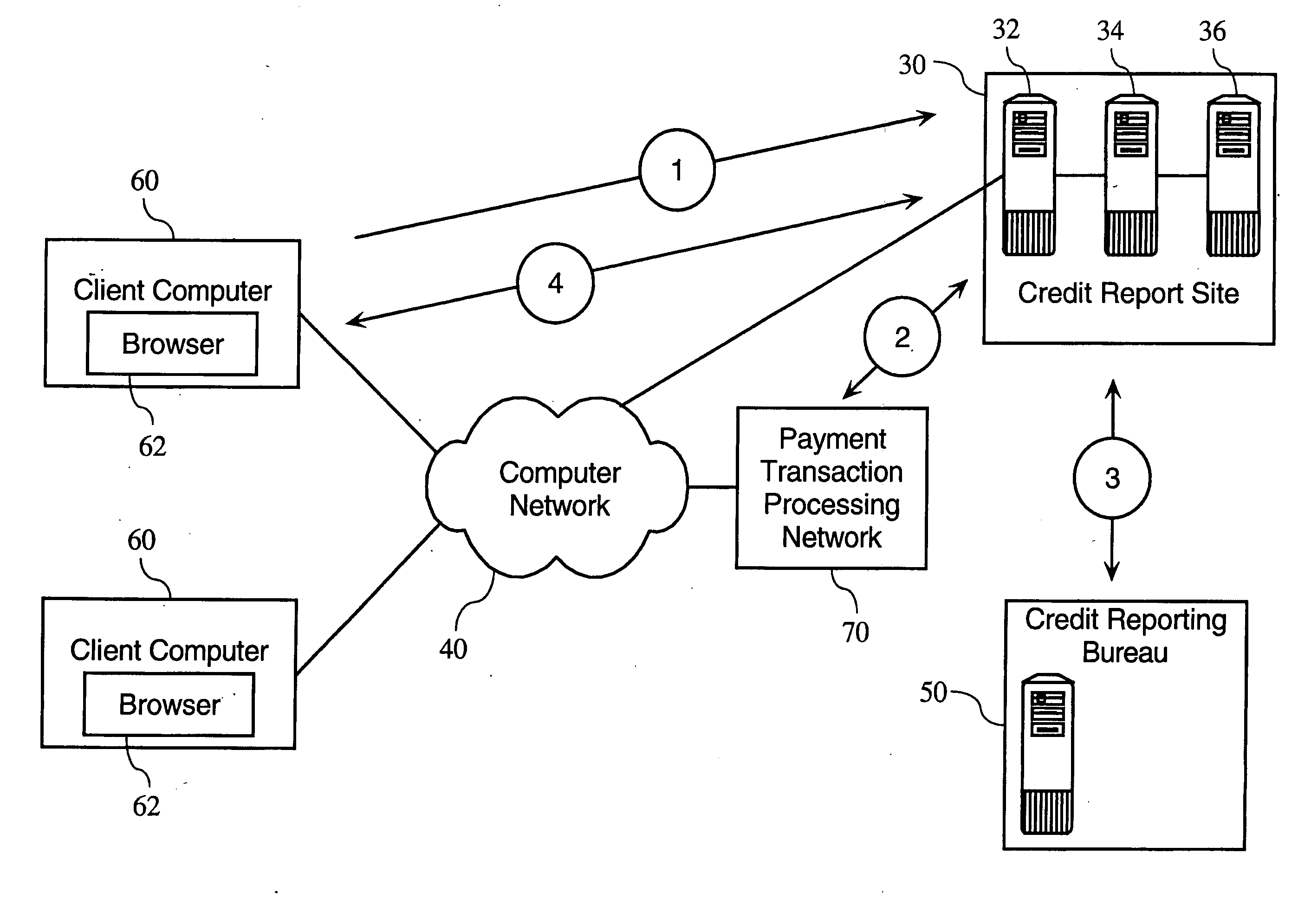
InactiveUS20050154664A1Facilitates correction of inaccuracyReduce deliveryFinanceDigital data processing detailsUser authenticationManagement system
Methods and apparatuses relating to the provision of credit and financial services. In one embodiment, the present invention provides-user authentication protocols facilitating the electronic delivery of credit reports over a computer network directly to users. According to one embodiment of the invention, a credit report comprises a particular user's credit history and other financial information, and / or a credit rating. Other embodiments of the present invention allow for the provision of services related to consumer and business credit report data.
Owner:TRANSUNION INTERACTIVE
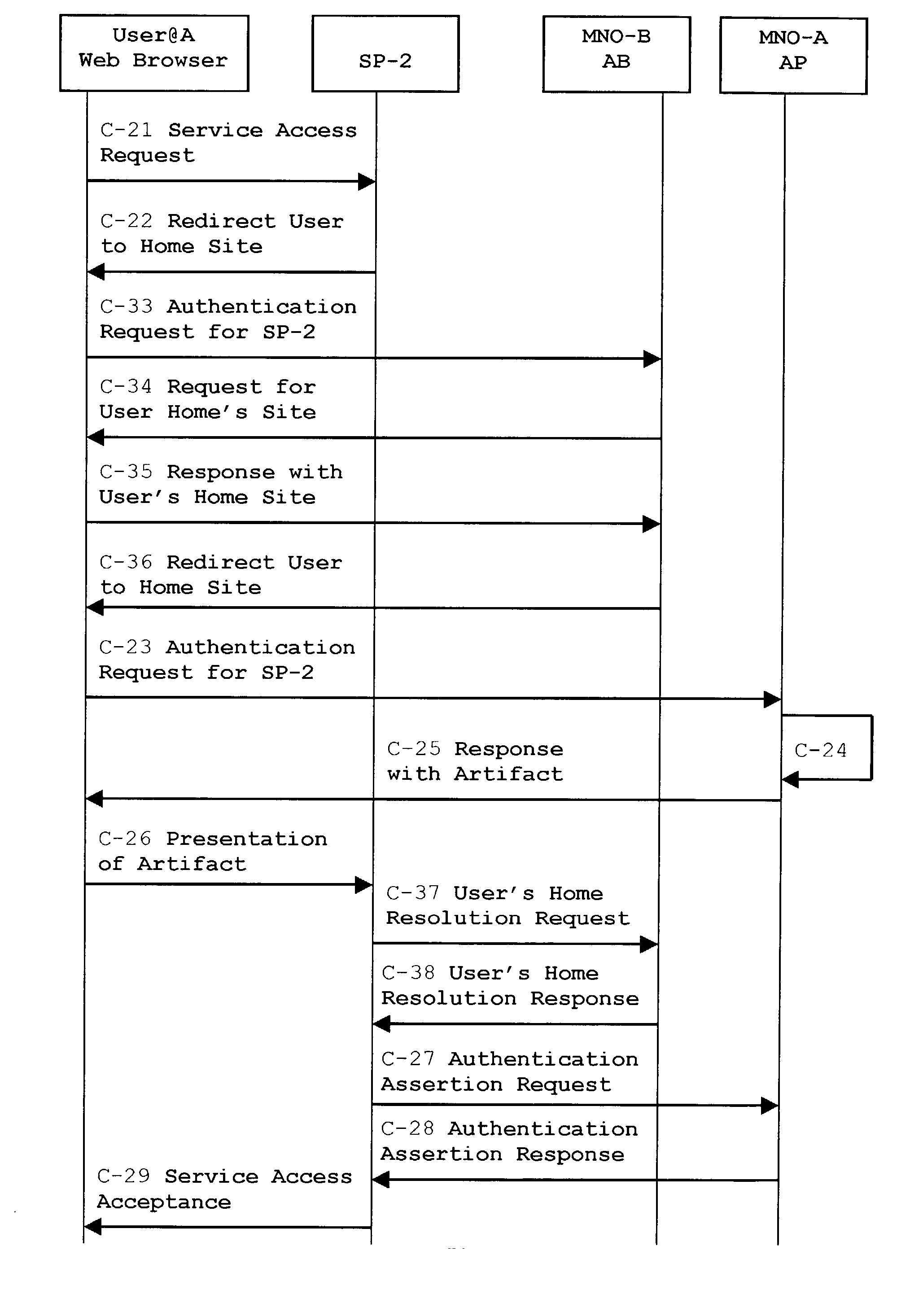
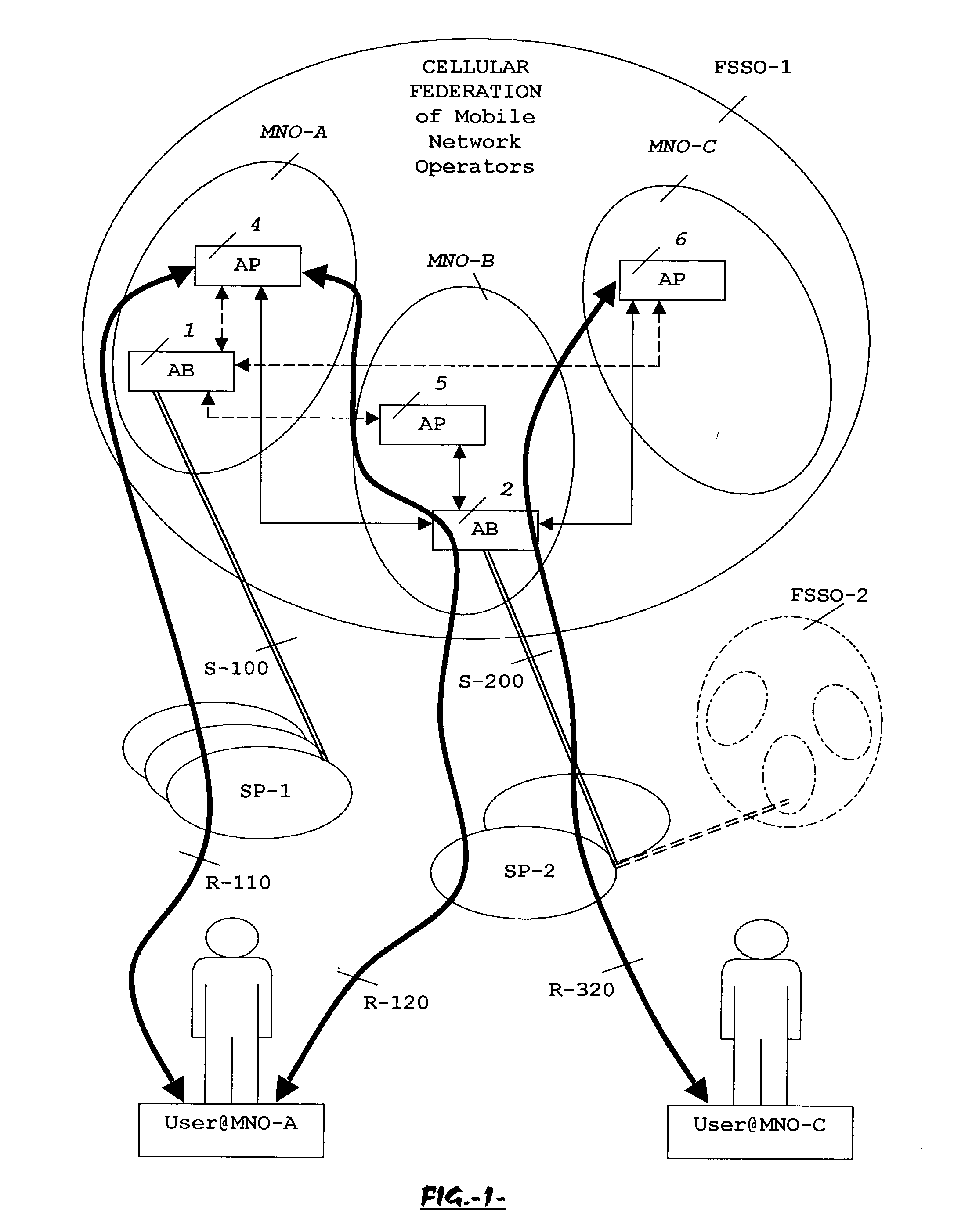
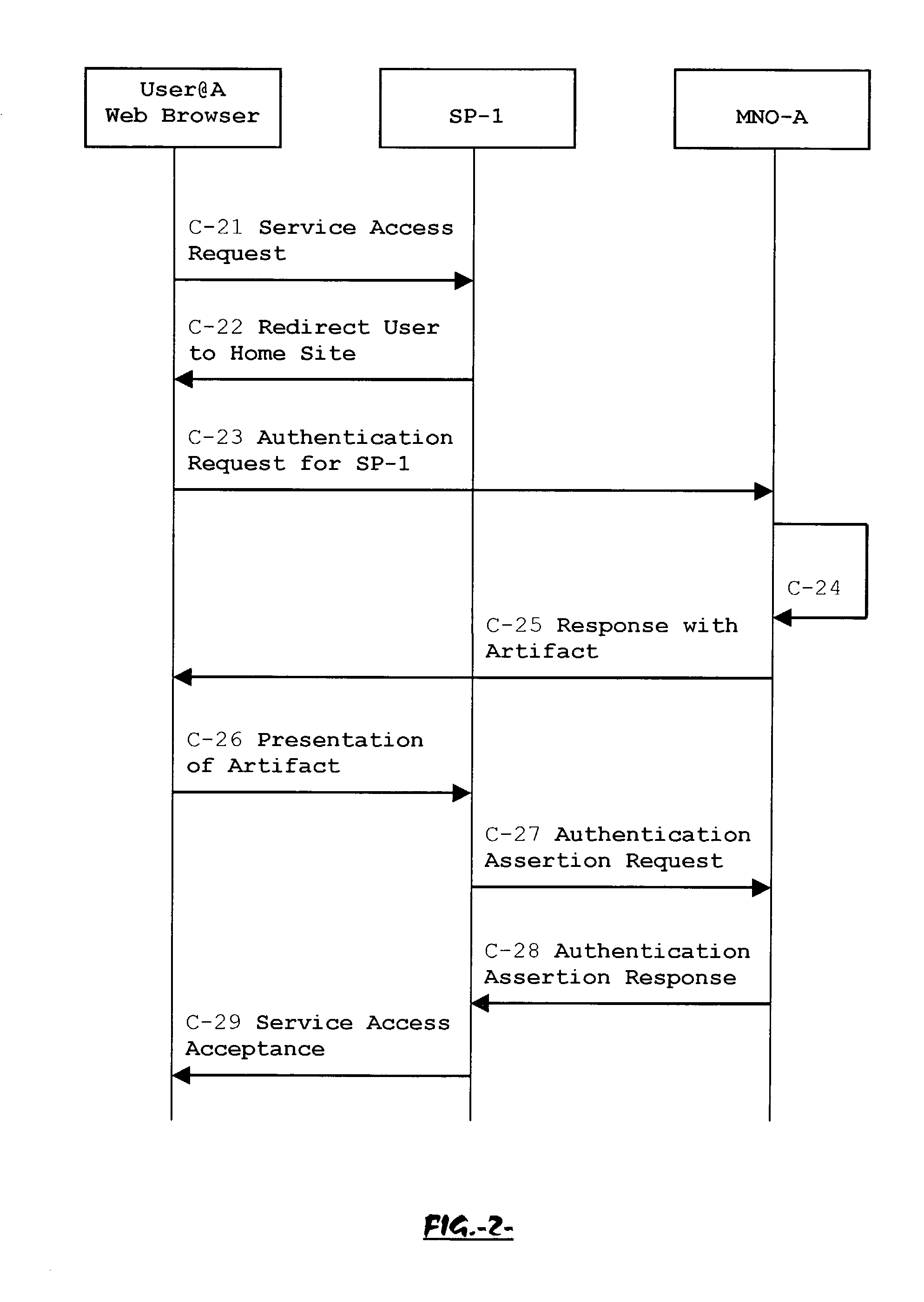
System, method and apparatus for federated single sign-on services
ActiveUS20030163733A1Unauthorised/fraudulent call preventionDigital data processing detailsCyber operationsService domain
The advent of new and sophisticated web services provided by Service Providers to users, services that individually require authentication of user and authorization of access, brings the needs for a new service to facilitate such authentication and access, a service referred to as Single Sign-On (SSO). The basic principle behind SSO is that users are authenticated once at a particular level, and then access all their subscribed services accepting that level of authentication. The present invention provides a system, method and apparatus wherein a cellular Federation of mobile network operators becomes an SSO authentication authority for subscribers of this Federation accessing Service Providers having such agreement with a mobile network operator of the Federation. In accordance with this invention, mobile network operators can leverage their operator-subscriber trust relationship in order to act as SSO authentication authority for those subscribers accessing Service Providers in a service domain other than the mobile network domain.
Owner:TELEFON AB LM ERICSSON (PUBL)
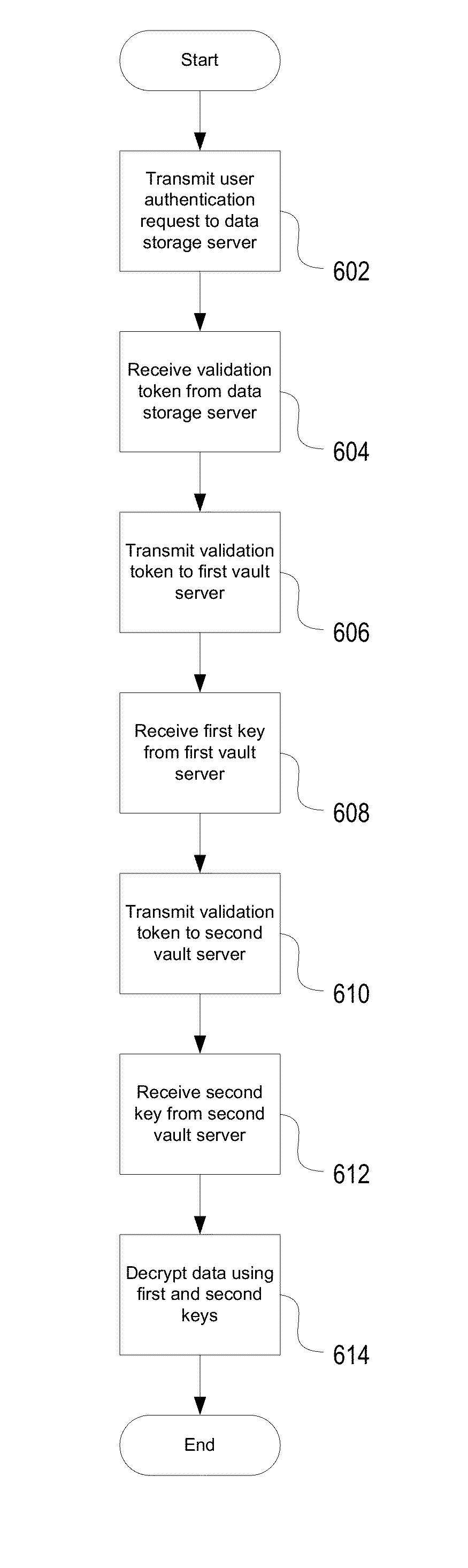
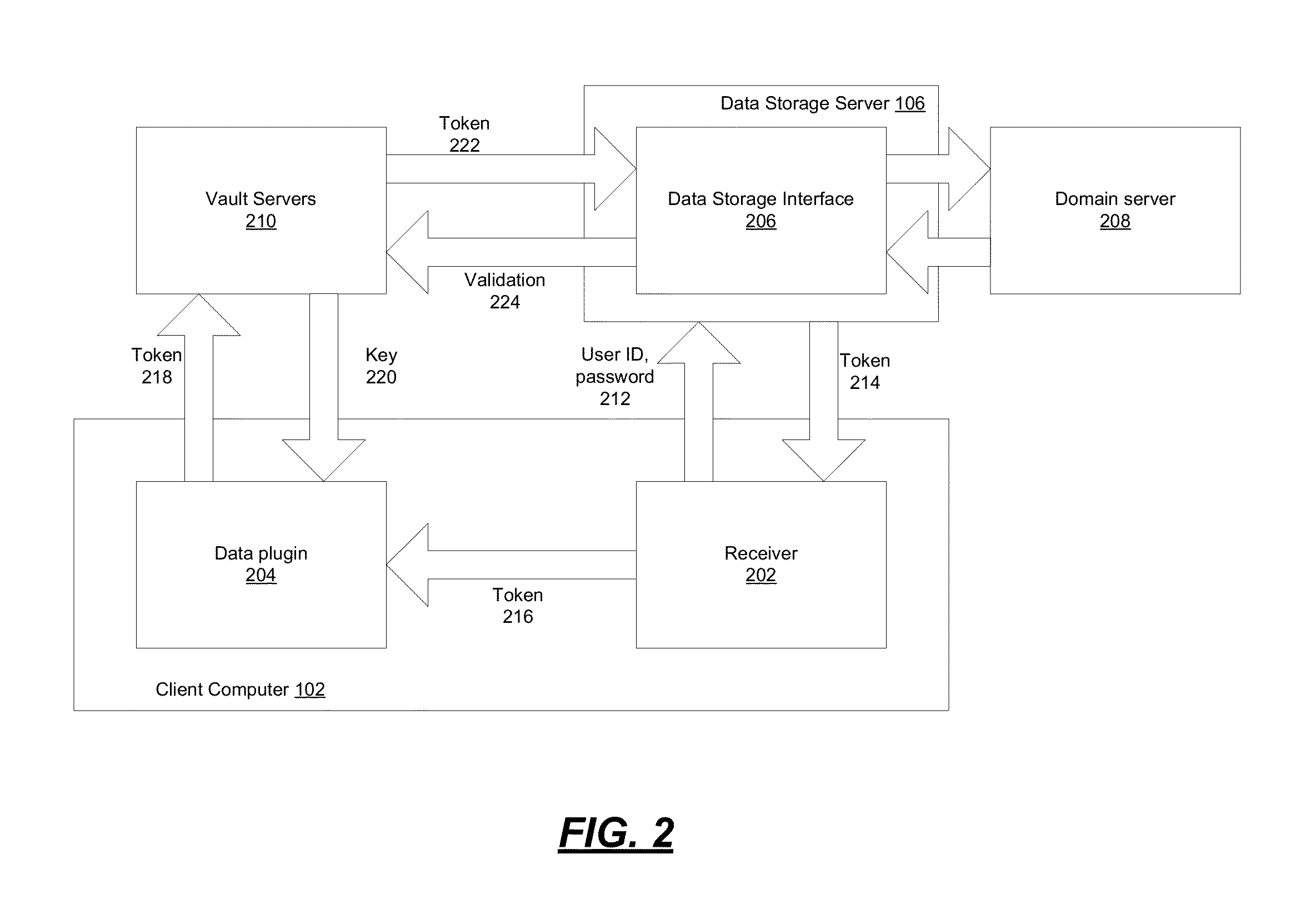
Encryption-Based Data Access Management
ActiveUS20140164774A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesKey serverData access
Encryption-based data access management may include a variety of processes. In one example, a device may transmit a user authentication request for decrypting encrypted data to a data storage server storing the encrypted data. The computing device may then receive a validation token associated with the user's authentication request, the validation token indicating that the user is authenticated to a domain. Subsequently, the computing device may transmit the validation token to a first key server different from the data storage server. Then, in response to transmitting the validation token the computing device may receive, from the first key server, a key required for decrypting the encrypted data. The device may then decrypt at least a portion of the encrypted data using the key.
Owner:CITRIX SYST INC
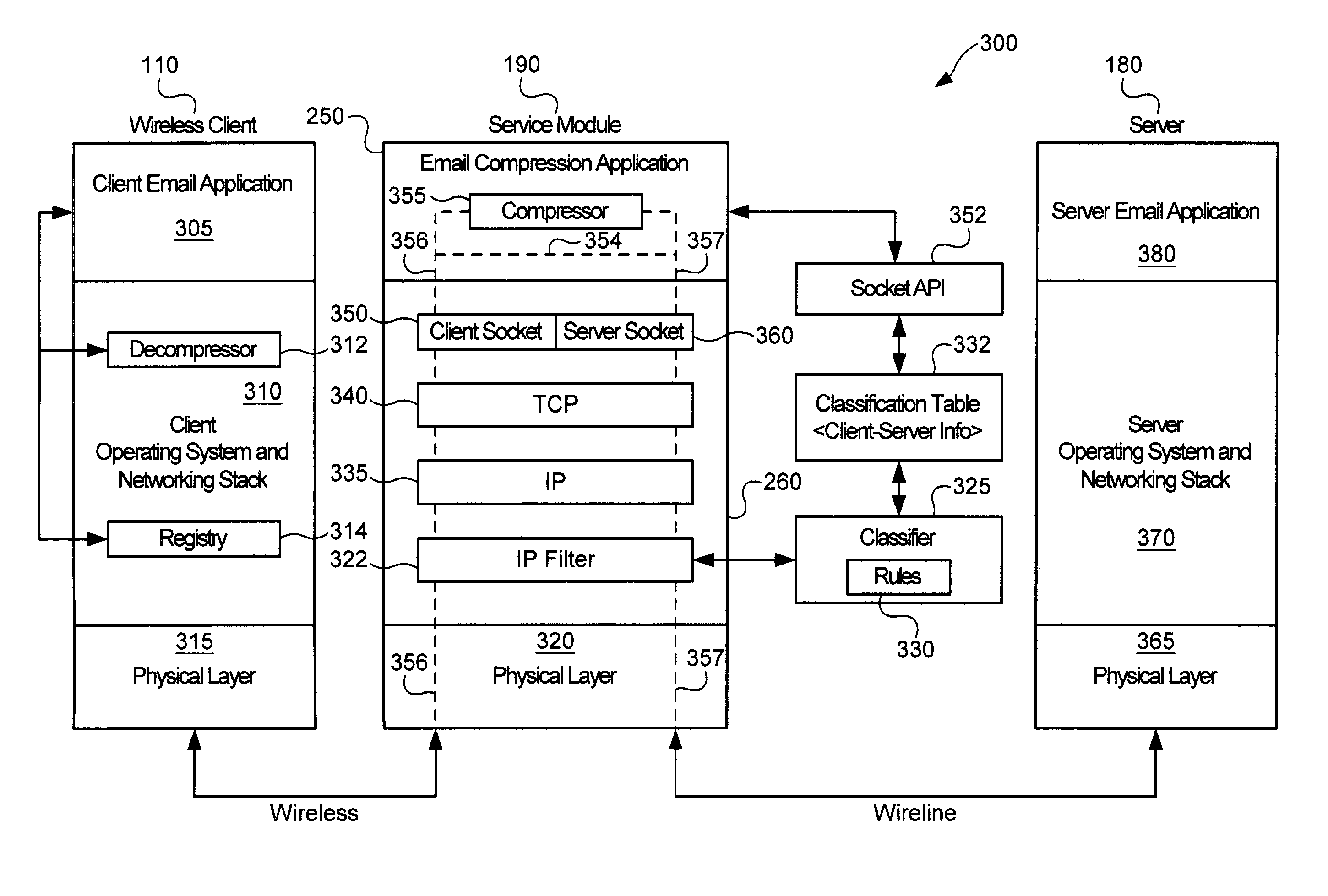
Service-based compression of content within a network communication system
ActiveUS7024460B2Easy to decompressMultiple digital computer combinationsData switching networksOperational systemData stream
A service module incorporated within the network infrastructure intercepts packets communicated between a client and a server to determine whether the connection corresponds to an email service. If so, the service module breaks the connection by terminating the connection with the client at the service module and opening a separate connection between the service module and the server. Packets communicated between the client and the server may then be redirected to an email compression application that monitors messages communicated between the client and the server and processes the messages in accordance with the state of the email session. For messages corresponding to connection establishment, user authentication and other protocol-specific messages, for example, the email compression application may be configured to forward the messages to the originally intended destination. Messages corresponding to an email message data, however, are buffered within the email compression application. Once the entire message has been received, the email compression application may strip the message headers and any protocol-specific data, compress the data and attach new message headers corresponding to the compressed email message. The compressed and reformatted email message is then reinserted into the data stream for transmission to the intended destination. Because compression may occur between the server and client, compression may be performed without requiring special processing by the server before email messages are sent. Furthermore, because the email messages may be compressed in a format that can be readily decompressed using decompression libraries incorporated within the operating system of client devices, such as the CAB format or GZIP format, the client may decompress received email messages utilizing software already incorporated within the operating system of the client device, without requiring download or installation of special decompression software and / or coordination of compression / decompression of email messages with the server or sending party.
Owner:OPTIMORPHIX INC
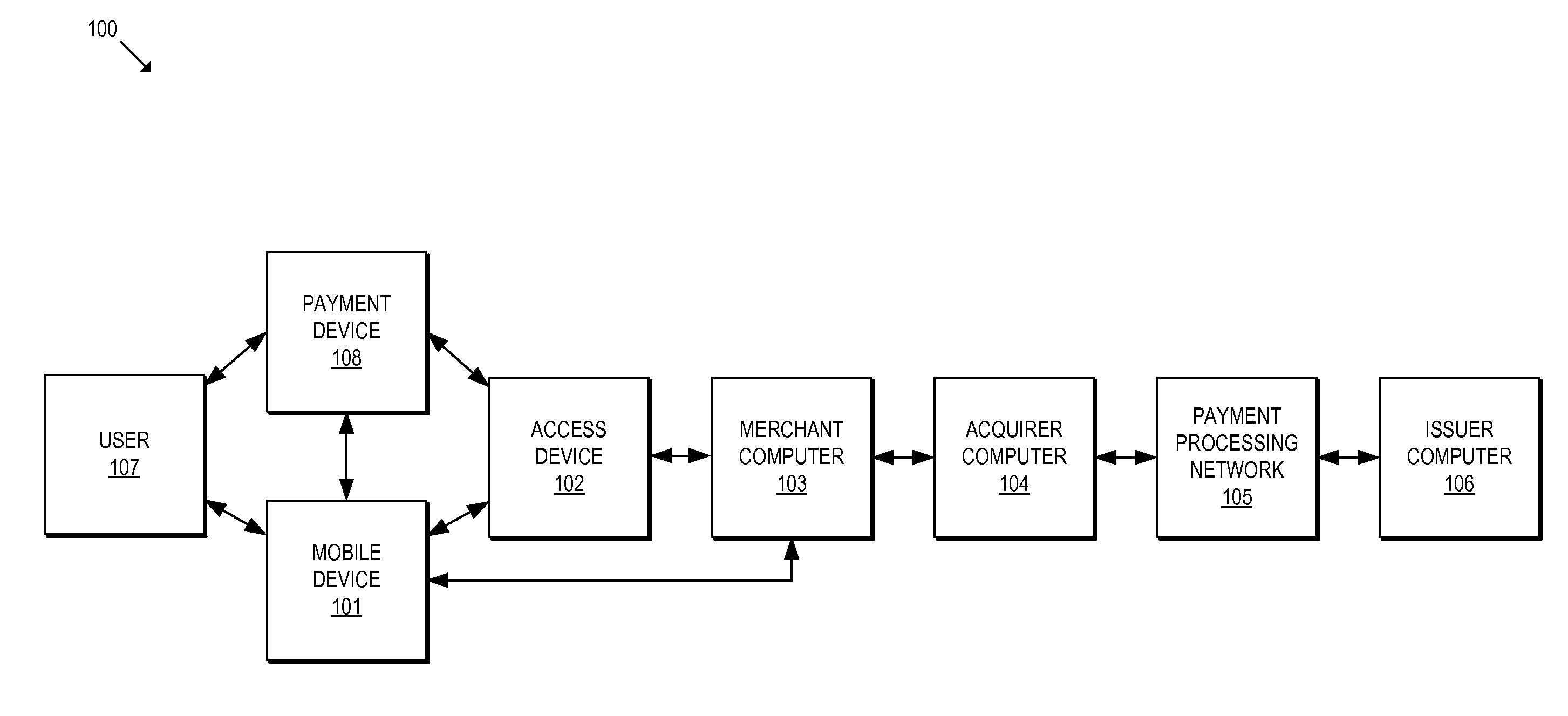
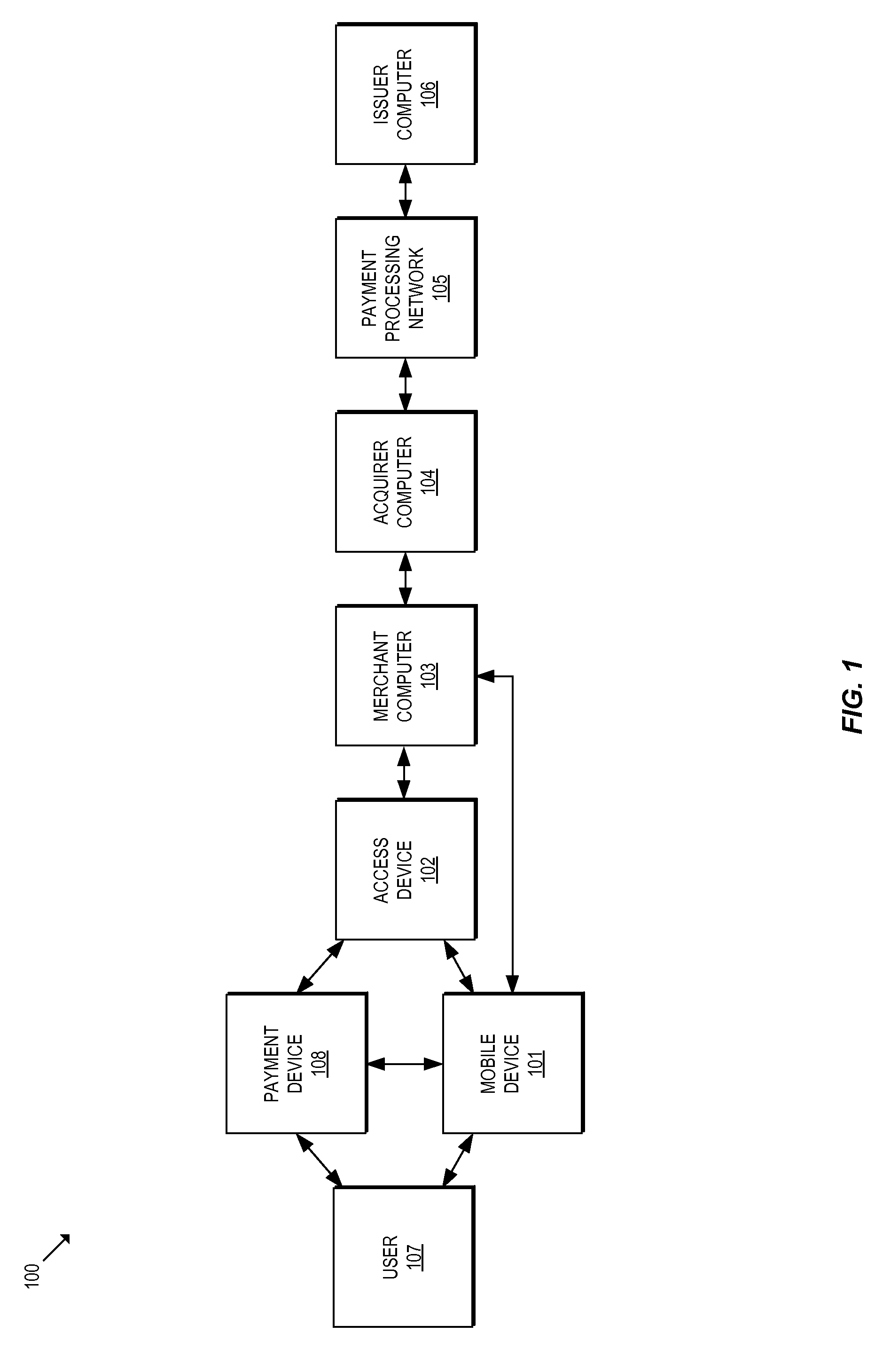
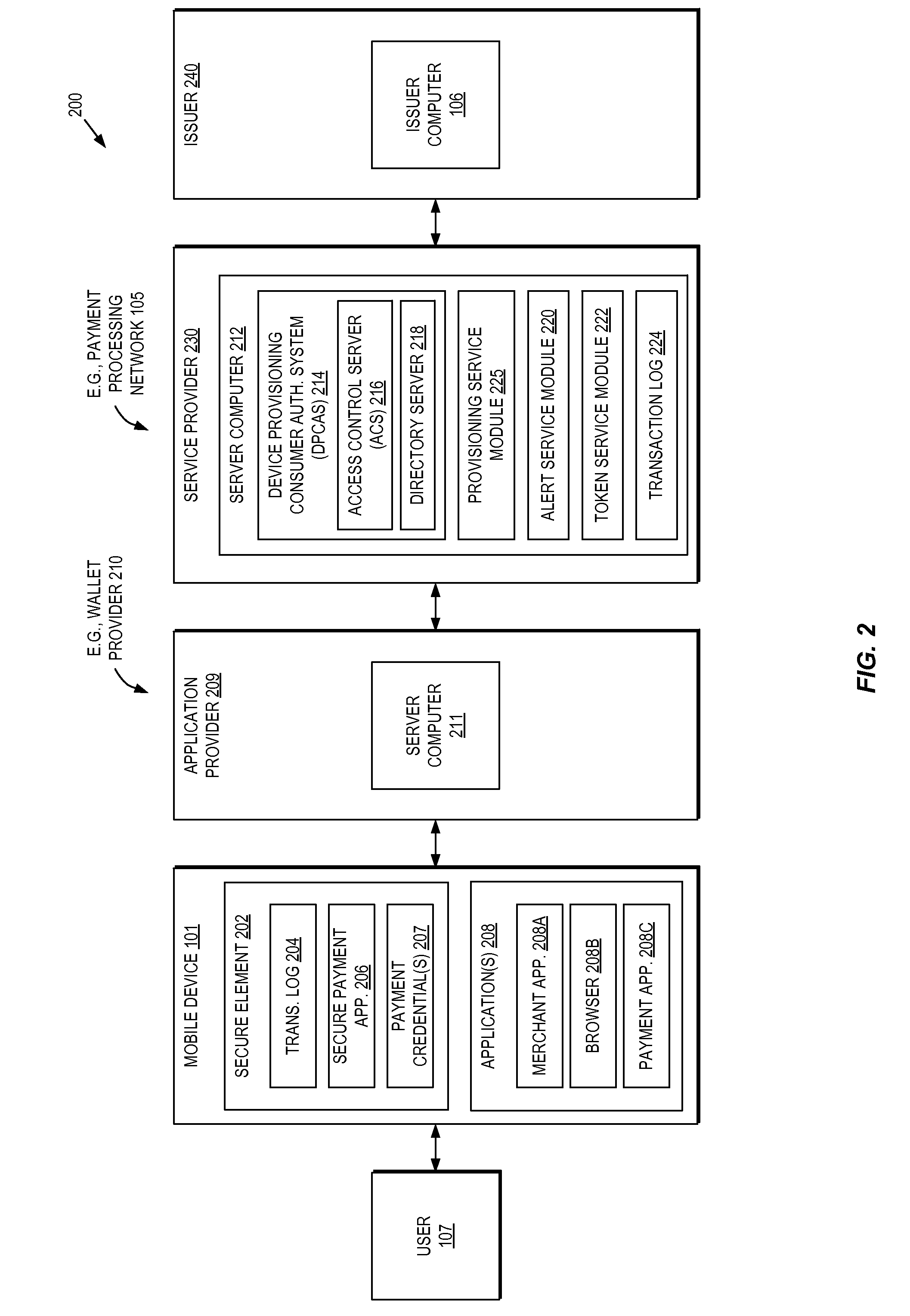
Methods and systems for provisioning mobile devices with payment credentials
ActiveUS20150046339A1Unnecessary delayProcessing speedFinanceElectronic credentialsPaymentMedium Risk
Embodiments are described that are directed to optimizing the provisioning of payment account credentials to mobile devices utilizing mobile wallets. In some embodiments, one of multiple provisioning schemes may be selectively chosen for payment account credential provisioning based upon a determined risk involved with a particular provisioning request. A low risk provisioning request leads to an immediate provisioning of a payment credential, whereas a provisioning request of high risk results in the provisioning request being denied. In some embodiments, medium risk provisioning requests will cause an additional user authentication to be performed before the payment account provisioning is finalized. The additional user authentication may occur using a separate communication channel than the channel in which the provisioning request was received.
Owner:VISA INT SERVICE ASSOC
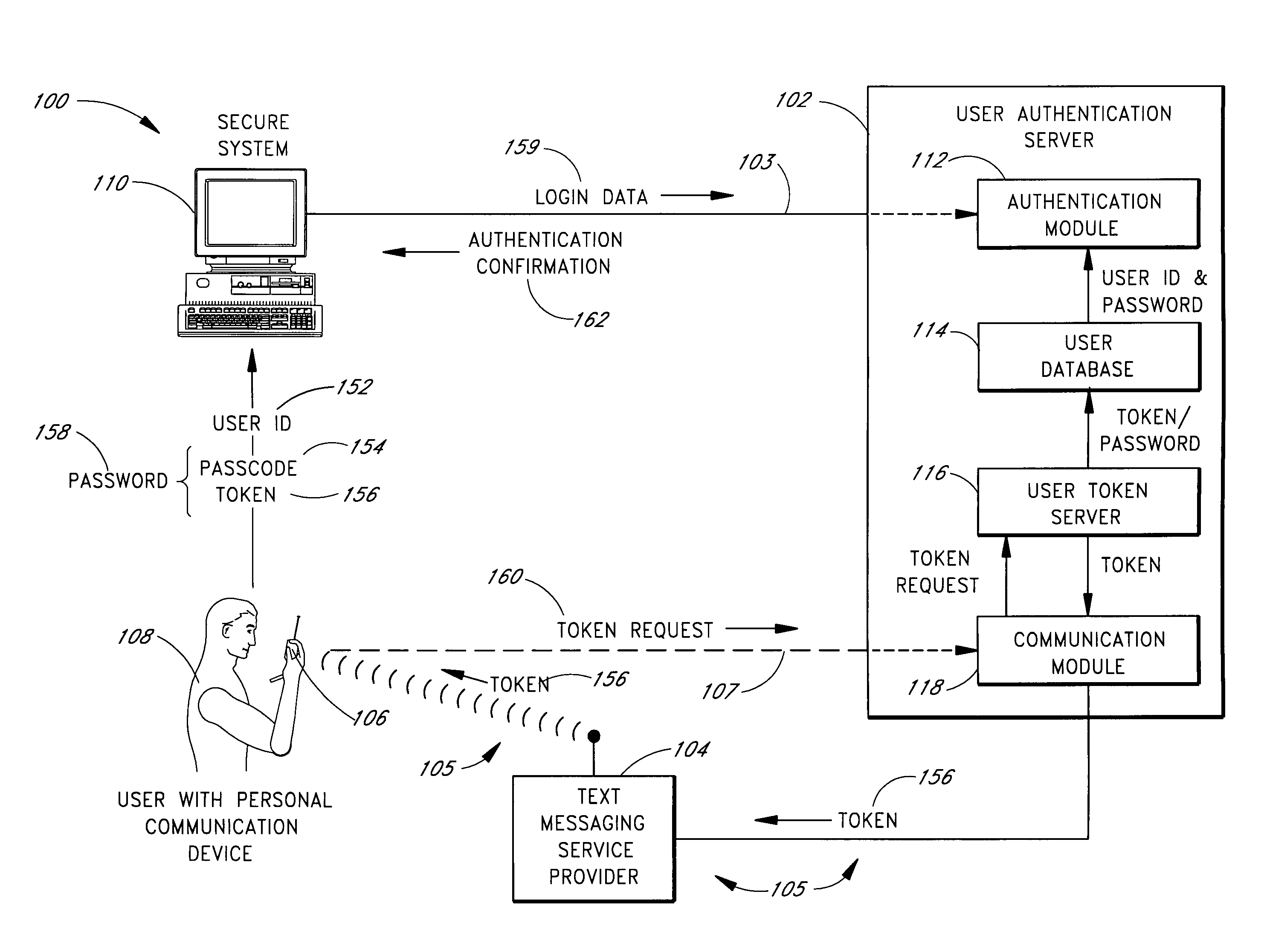
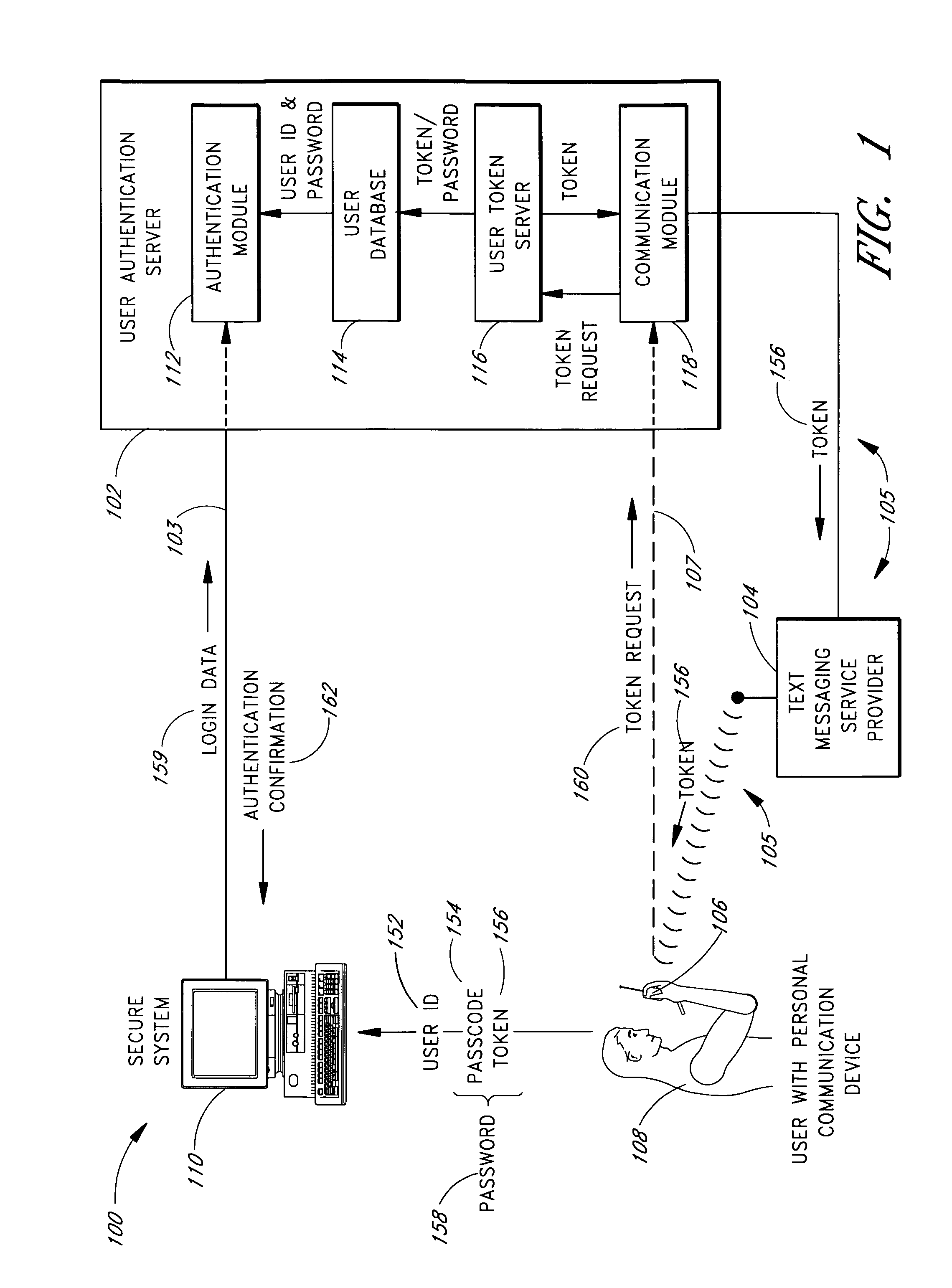
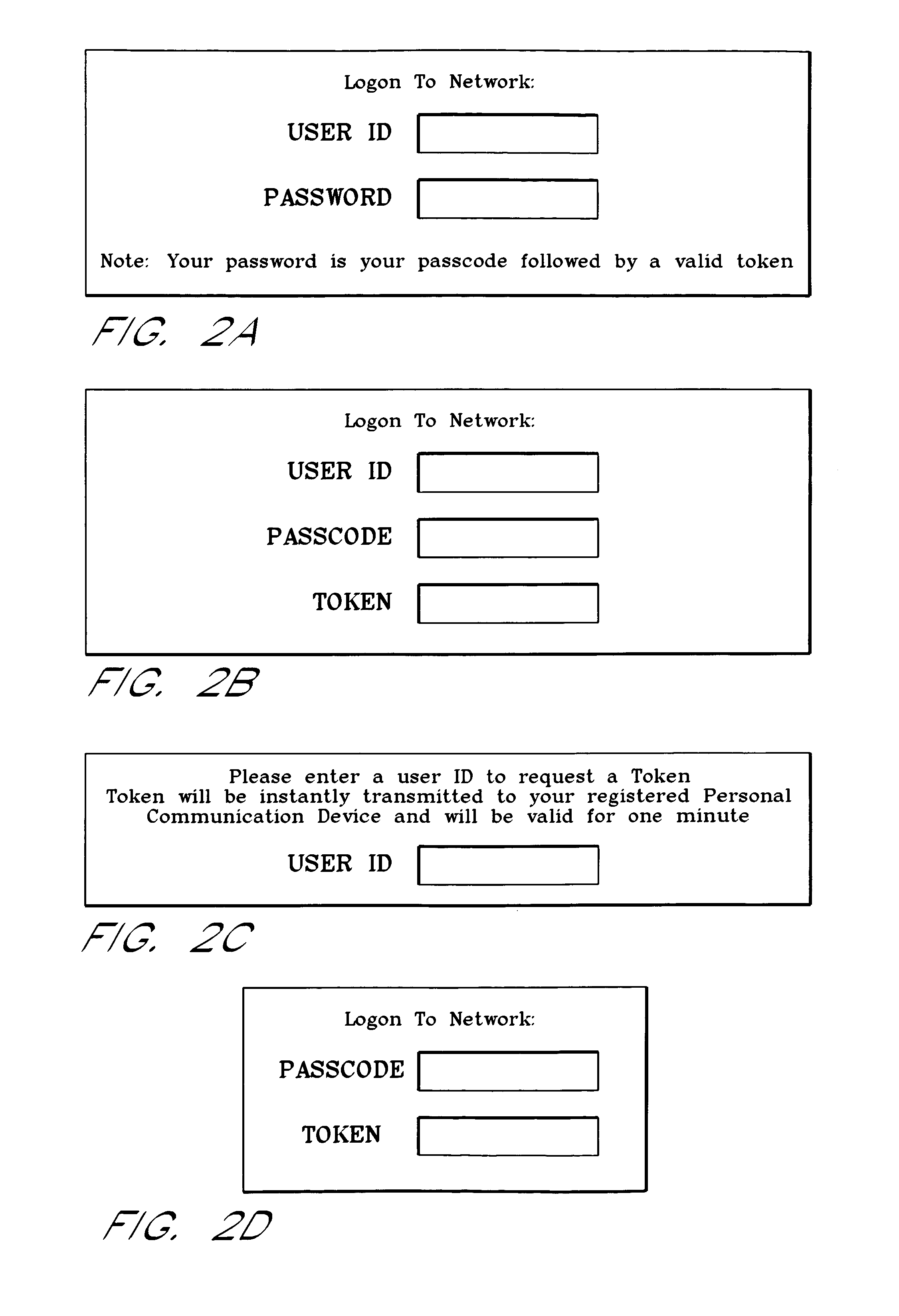
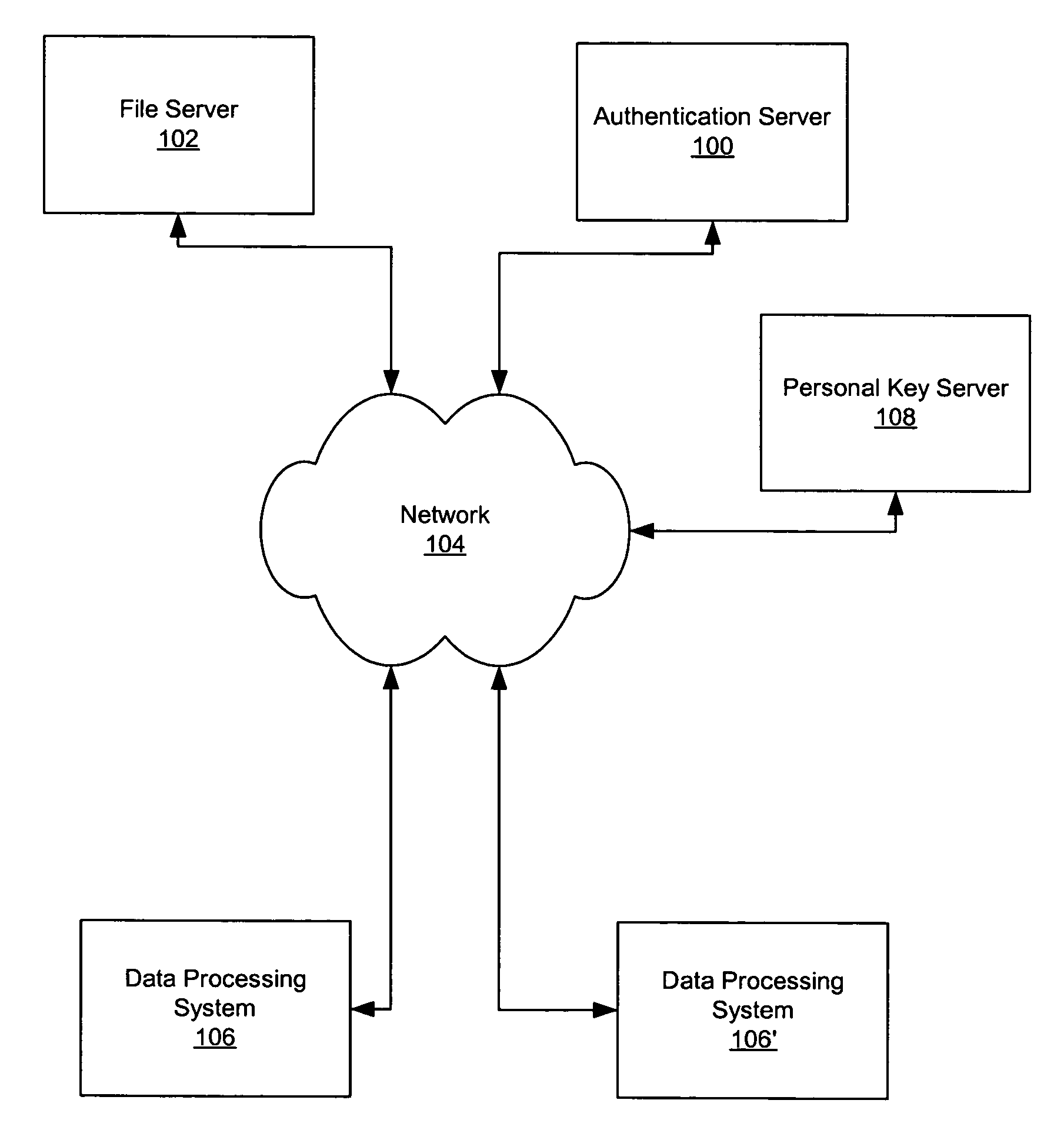
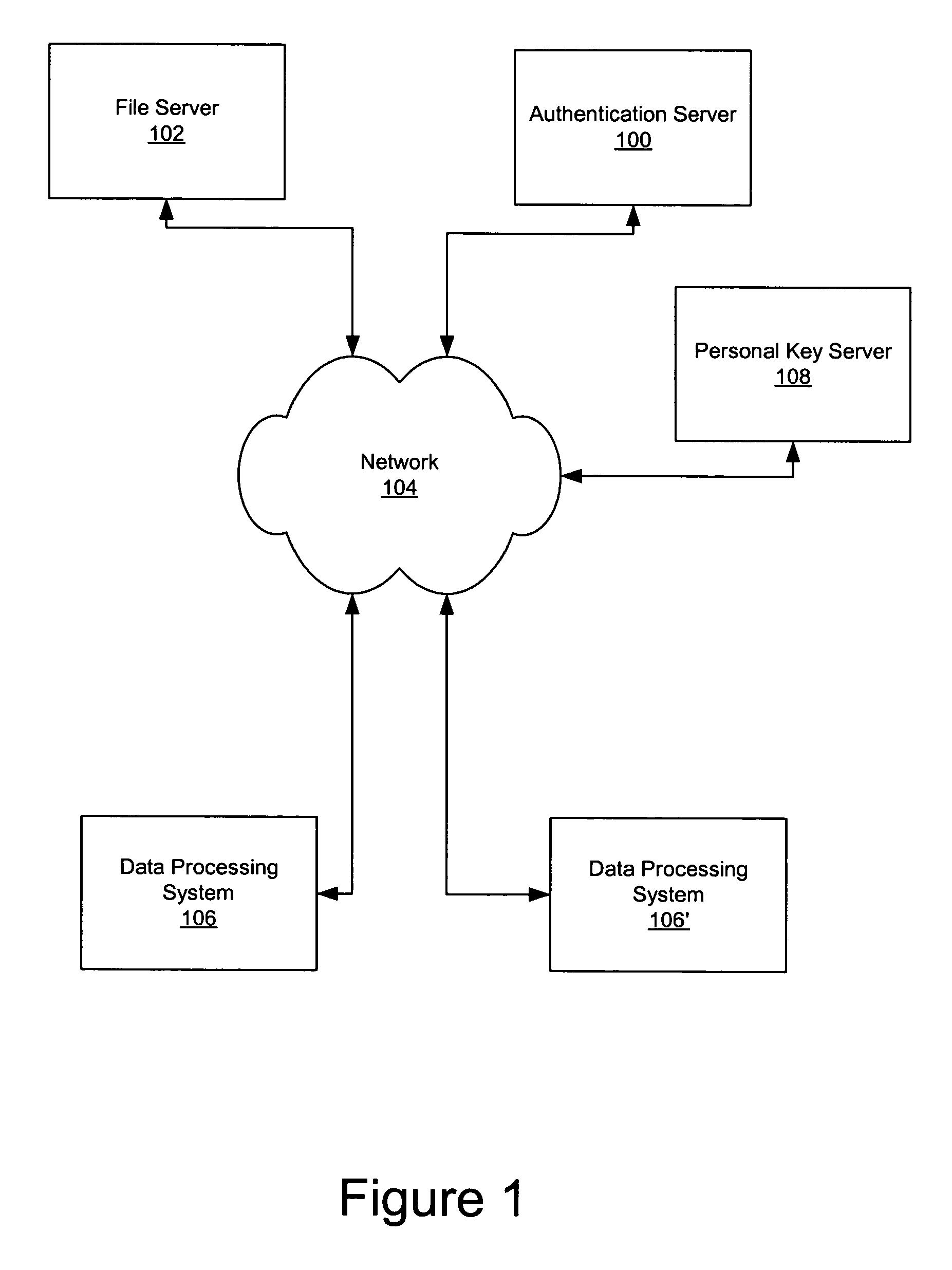
Use of personal communication devices for user authentication
InactiveUS6993658B1Metering/charging/biilling arrangementsDigital data processing detailsPagerInternet privacy
A password setting system for a secure system includes a user token server and a communication module. The user token server generates a random token in response to a request for a new password from a user. The server creates a new password by concatenating a secret passcode that is known to the user with the token. The server sets the password associated with the user's user ID to be the new password. The communication module transmits the token to a personal communication device, such as a mobile phone or a pager carried by the user. The user concatenates the secret passcode with the received token in order to form a valid password, which the user submits to gain access to the secure system. Accordingly, access to the system is based upon: nonsecret information known to the user, such as the user ID; secret information known to the user, such as the passcode; and information provided to the user through an object possessed by the user, such as the token.
Owner:DYNAPASS IP HLDG LLC
Secure data storage and retrieval with key management and user authentication
InactiveUS6947556B1Key distribution for secure communicationUser identity/authority verificationDigital dataPassphrase
Methods, systems and computer program products are provided which provide for controlling access to digital data in a file by encrypting the data with a first key, encrypting the first key with a second personal key generated from a password / passphrase associated with the file and further encrypting the encrypted first key with a control key which is managed by the system. In certain embodiments, user authentication may also be provided by issuing a ticket which is utilized to create, access and administer the files in the system.
Owner:IBM CORP
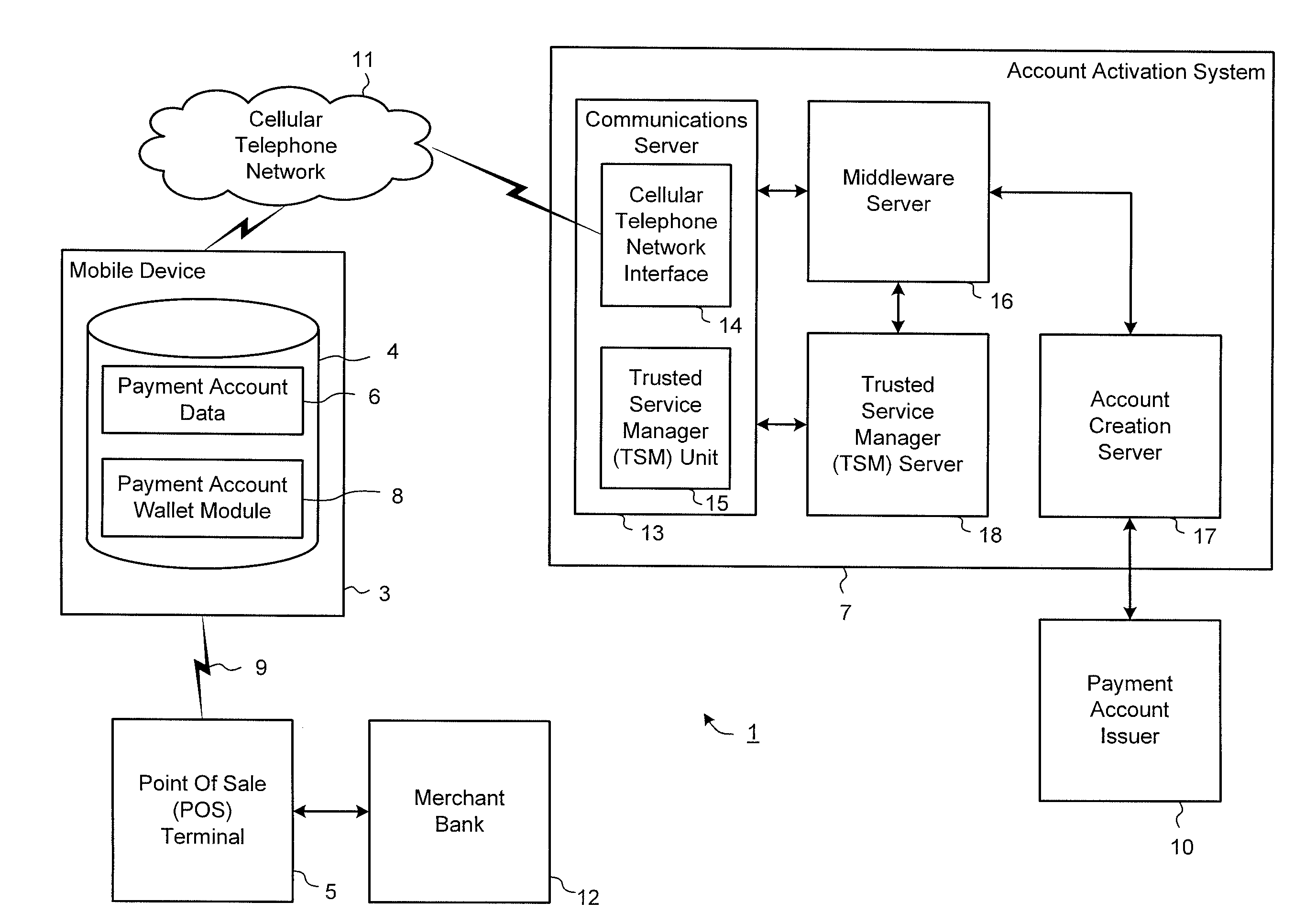
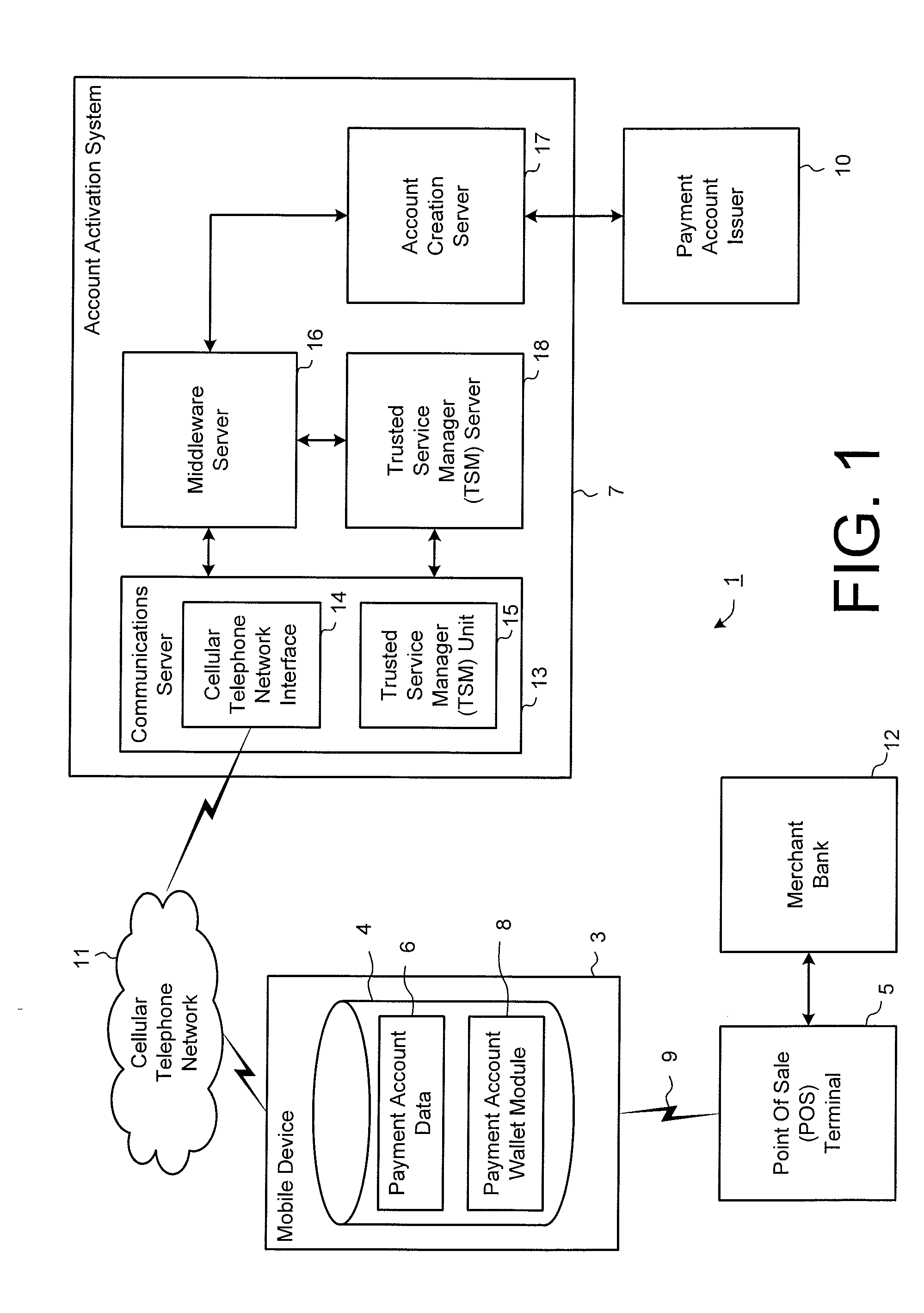
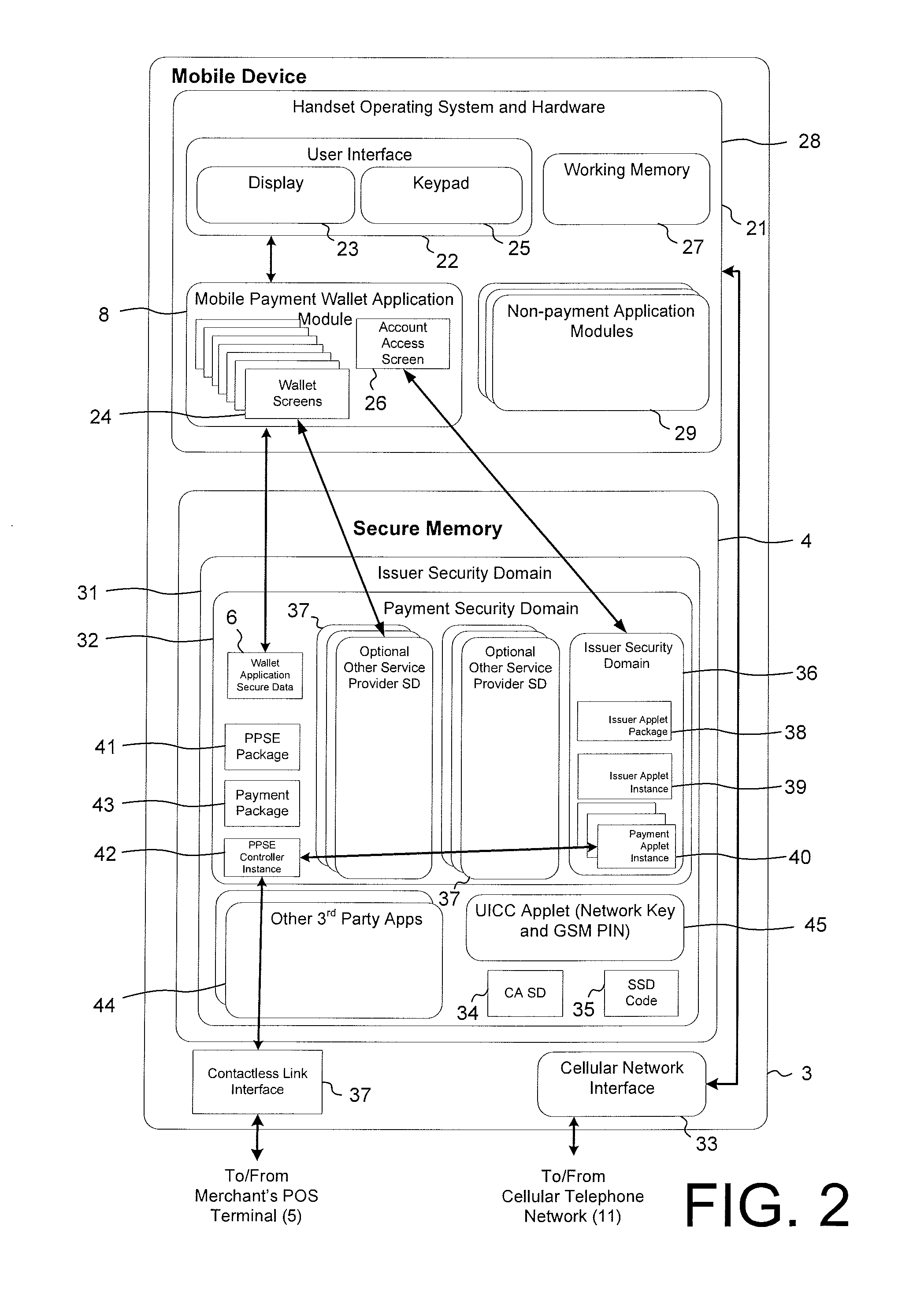
Secure account provisioning
ActiveUS20120078735A1Promote activationFinancePoint-of-sale network systemsComputer networkUser authentication
A mobile payment system and method are described that facilitates the secure and real time user authentication and activation of a mobile payment account for a user portable electronic device over a communications network.
Owner:BARCLAYS EXECUTION SERVICES LTD
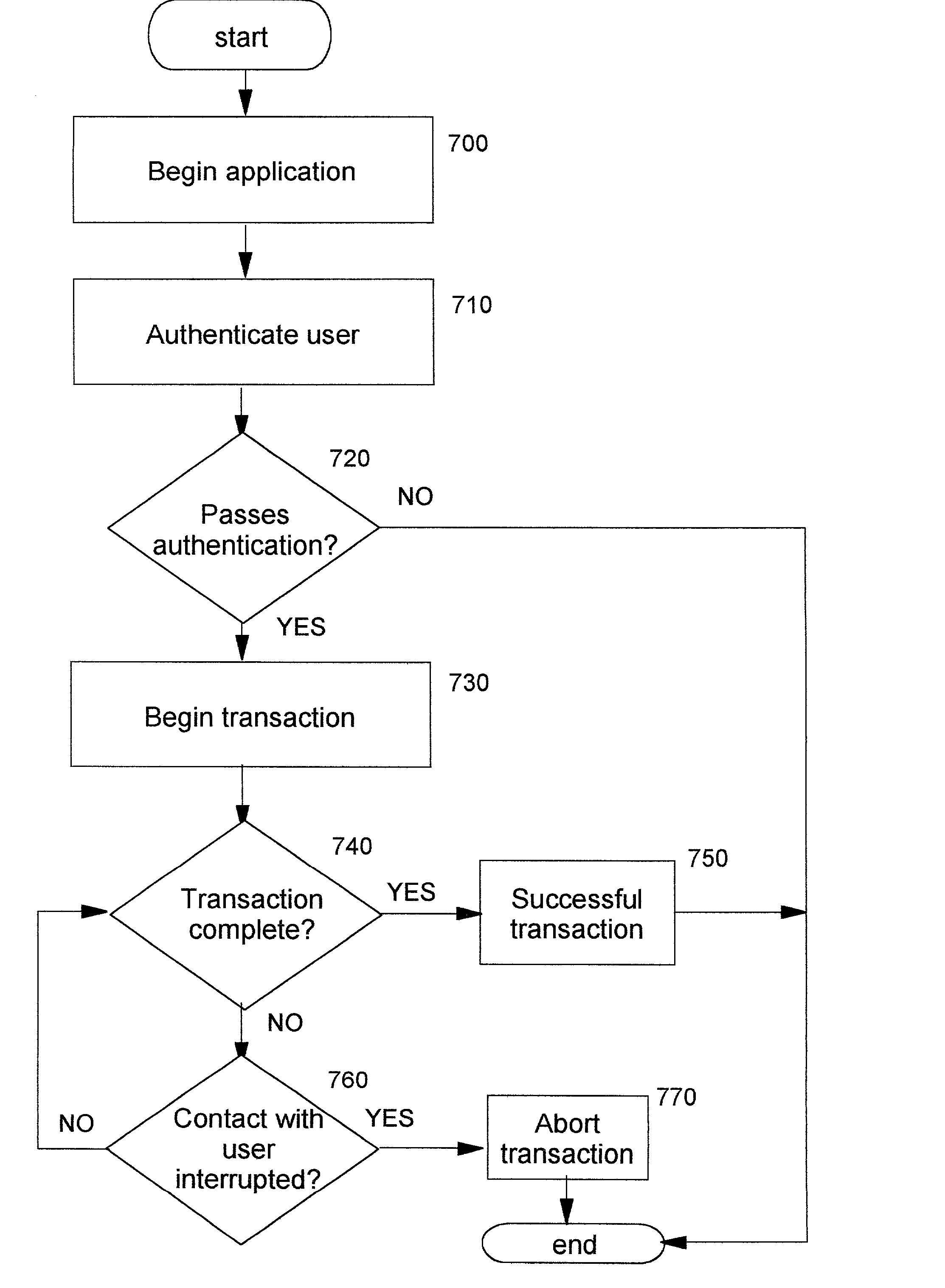
Technique for continuous user authentication
InactiveUS20020095586A1User identity/authority verificationDigital data authenticationInternet privacyUser authentication
A method, system, computer program product, and method of doing business by improving security of a computing device. Continuous authentication of a user of the computing device, which may be (for example) a portable or personal computing device (also known as a "pervasive computing device"), is performed. The disclosed techniques also improve the security of operations or transactions carried out with such computing devices. Biometric sensors are preferably used for obtaining identifying information from users of computing devices, and this obtained information is compared to previously-stored biometric information which identifies the legitimate owner of the device. If the information matches, then it can be assumed that this user is the device owner, and a security-sensitive transaction is allowed to proceed so long as the biometric input is uninterrupted. Otherwise, when the obtained information does not match, or when there is an interruption in the biometric input, then the device may be in the wrongful possession of an impostor. A transaction may therefore be prevented or aborted, or in other cases perhaps simply marked as suspect or not authenticated; or, it may be desirable to completely deactivate the computing device.
Owner:IBM CORP
Method and system for determining authentication levels in transactions
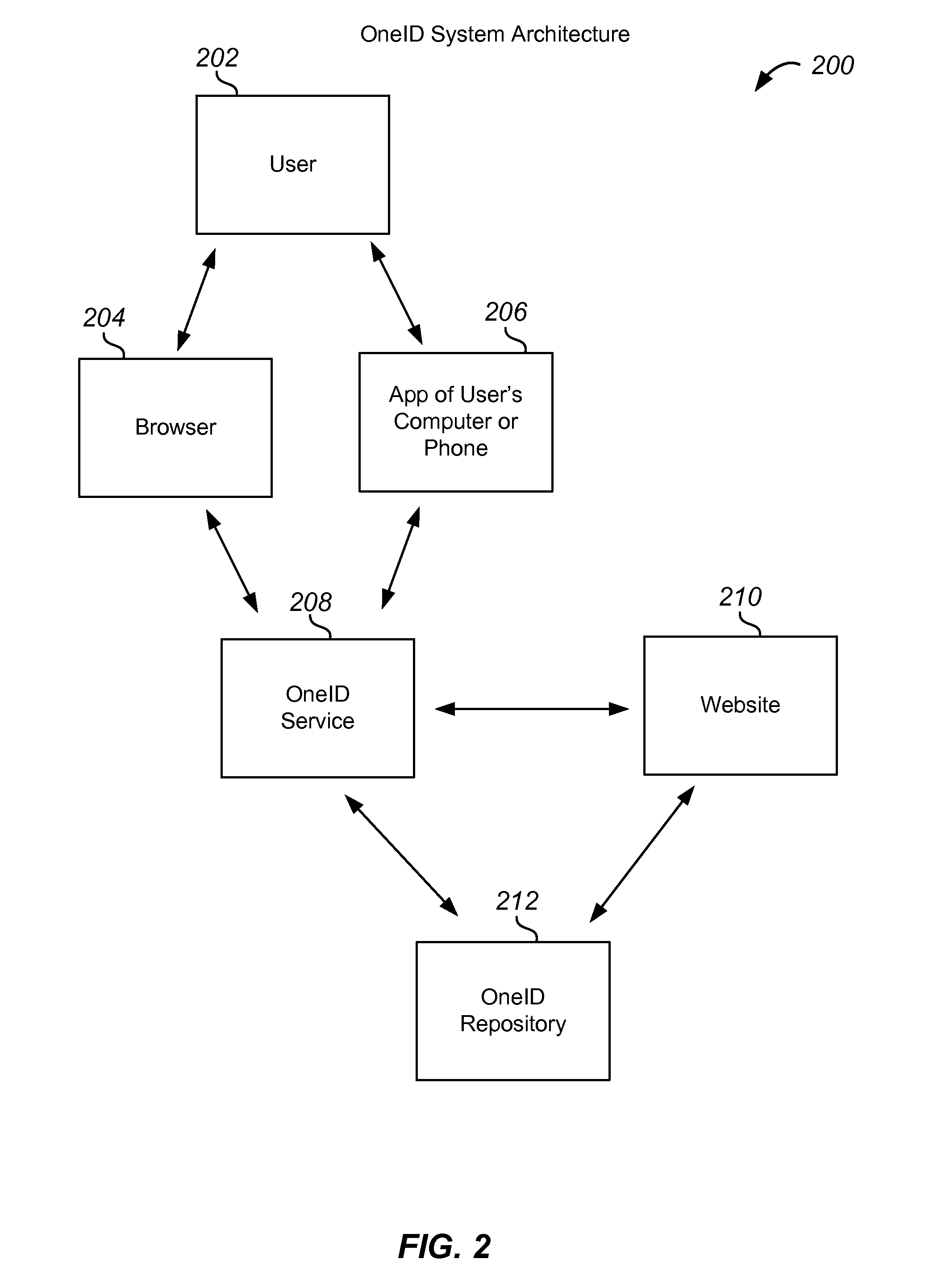
According to an embodiment of the present invention, a method for determining a transaction authentication level includes receiving transaction information associated with a transaction between a user and a relying party, receiving relying party preferences, and determining a relying party authentication level based on the transaction information and the relying party preferences. The method also includes accessing user preferences, and determining a user authentication level based the transaction information and the user preferences. The method further includes determining the transaction authentication level using the user authentication level and the relying party authentication level.
Owner:ONEID
User Authentication
InactiveUS20020112155A1Easy mappingDigital data processing detailsUser identity/authority verificationInternet privacyUser authentication
The present invention authenticates a user for multiple resources distributed across multiple domains through the performance of a single authentication. User access requests for a protected resource in a first domain are received and redirected to a second domain. User authentication is performed at the second domain. In one embodiment, the system transmits an authentication cookie for the second domain to the user after authentication at the second domain. In another embodiment, the system further redirects subsequent resource requests for resources in the first domain or a third domain to the second domain. The second domain confirms the user's authentication for applicable portions of the first, second, and third domains using the cookie.
Owner:ORACLE INT CORP
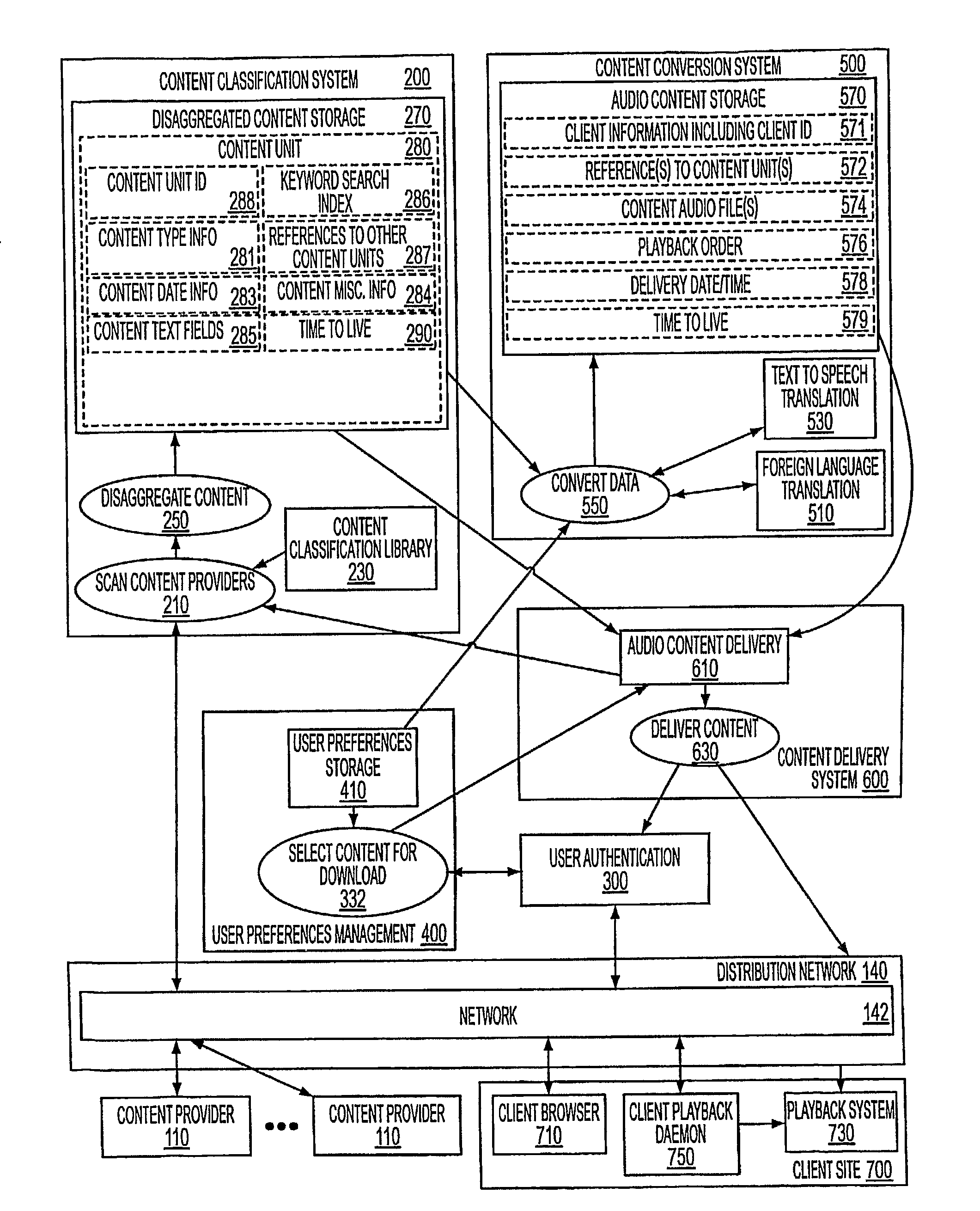
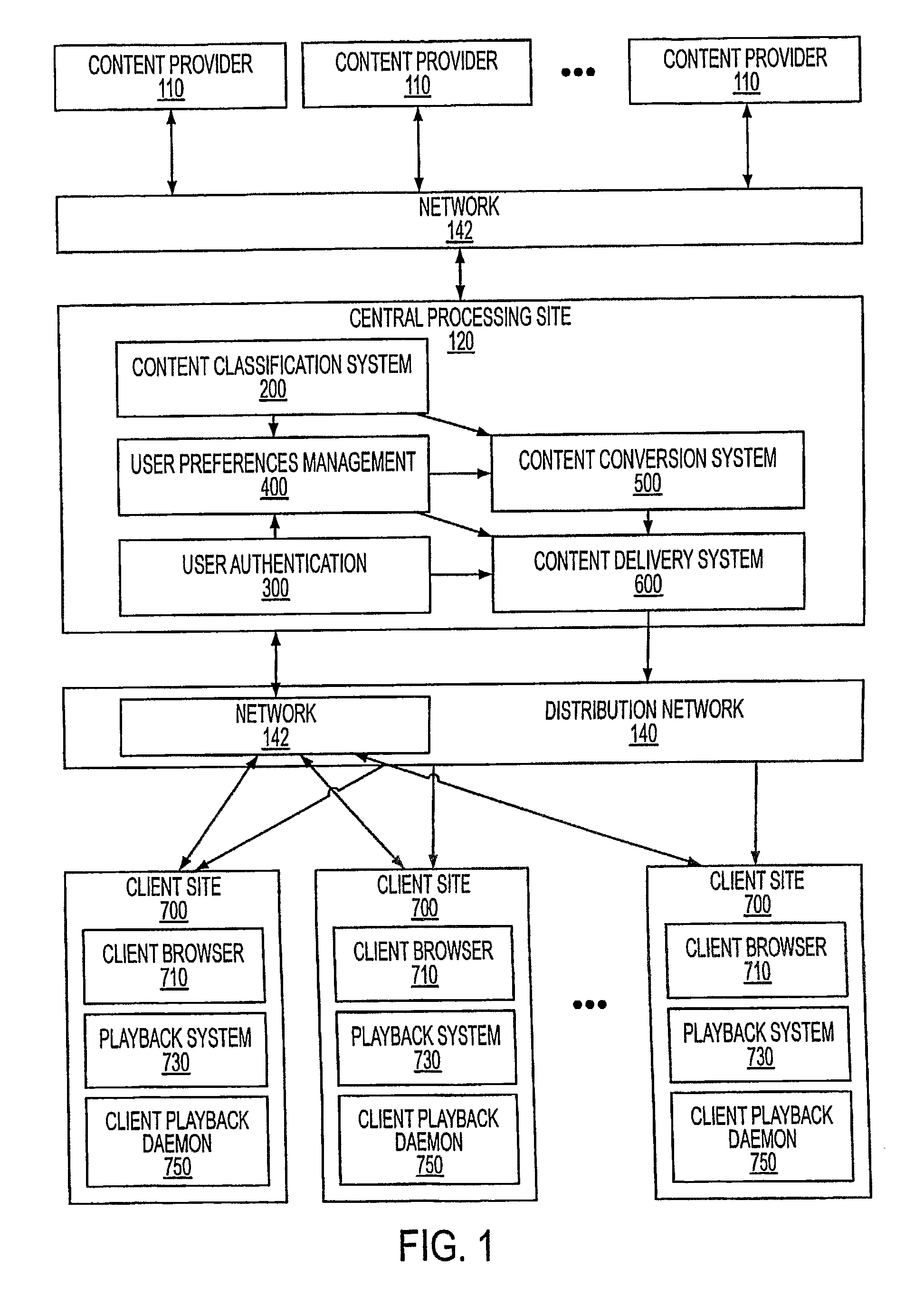
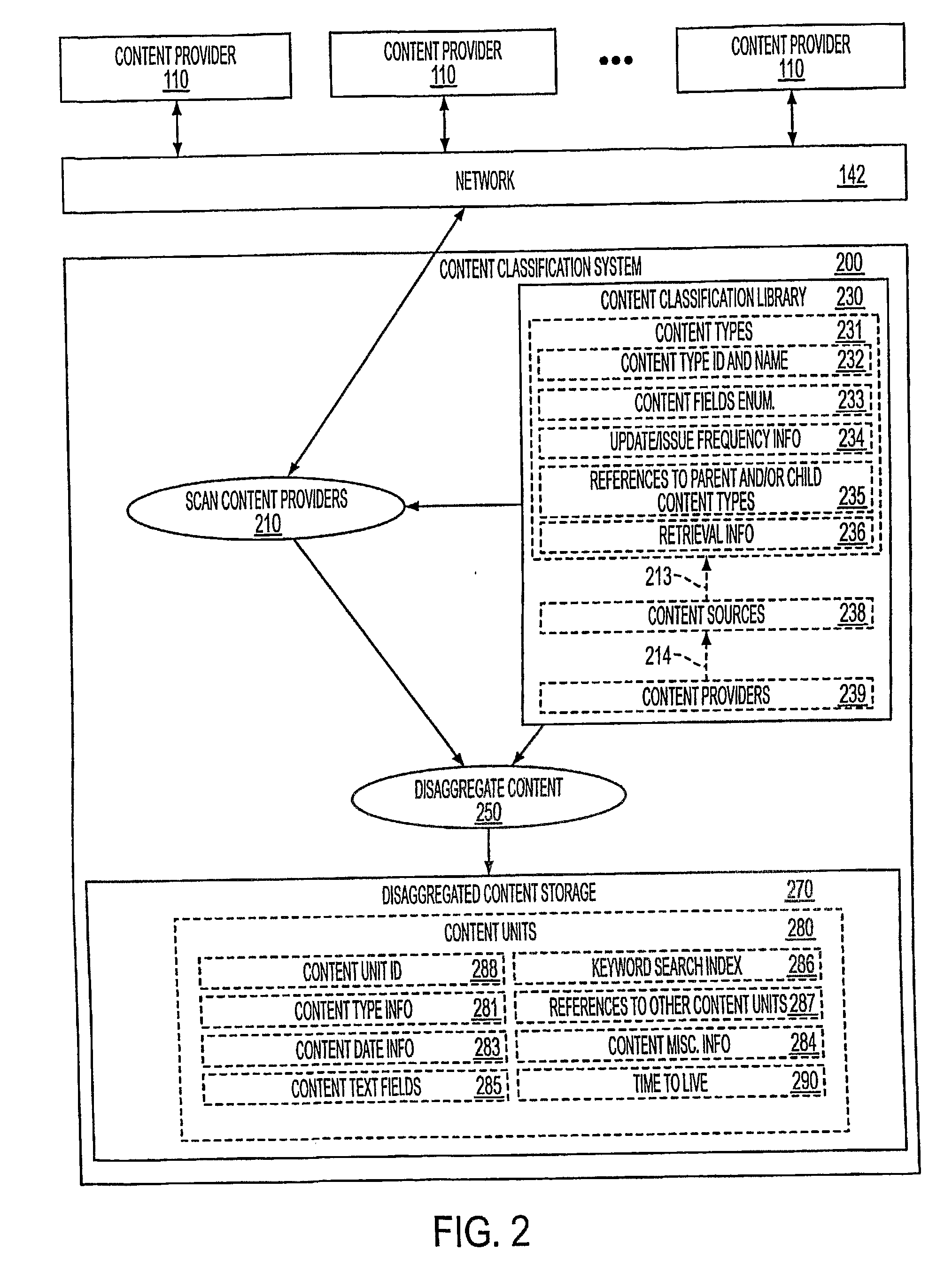
Customizable Delivery of Audio Information
InactiveUS20080189099A1Digital data information retrievalNatural language data processingUser authenticationProcessing Site
A system for delivering customized audio content to customers. A central processing site (120) is coupled with content providers (110) through a network (142). The central processing consists of a number of components, namely content classification system (200), user preference management (400), content conversion system (500), content delivery system (600), and user authentication (300).
Owner:FRIEDMAN HOWARD +1
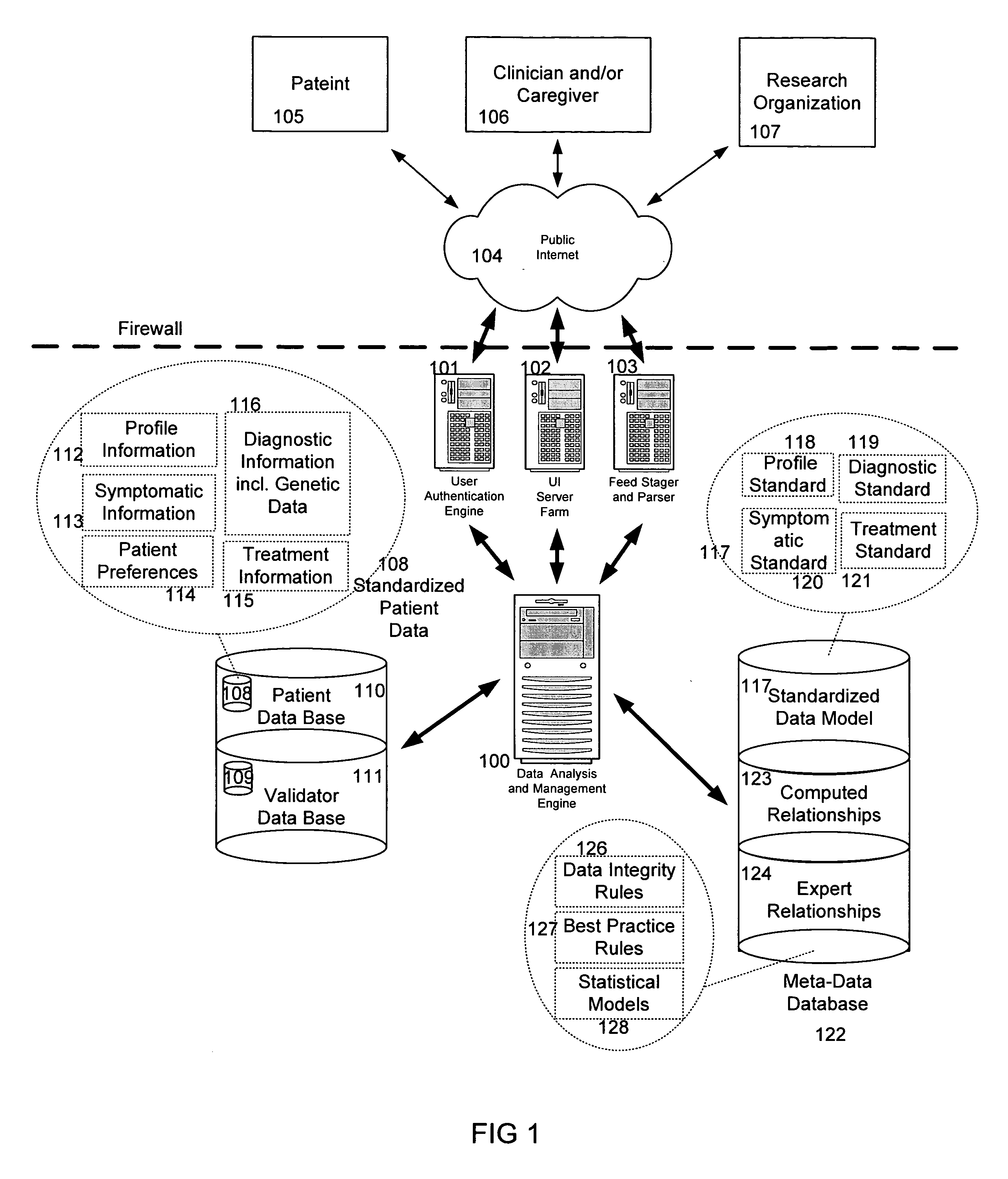
System and method for improving clinical decisions by aggregating, validating and analysing genetic and phenotypic data
The information management system disclosed enables caregivers to make better decisions, faster, using aggregated genetic and phenotypic data. The system enables the integration, validation and analysis of genetic, phenotypic and clinical data from multiple subjects who may be at distributed facilities. A standardized data model stores a range of patient data in standardized data classes that encompass patient profile information, patient symptomatic information, patient treatment information, and patient diagnostic information including genetic information. Data from other systems is converted into the format of the standardized data classes using a data parser, or cartridge, specifically tailored to the source system. Relationships exist between standardized data classes that are based on expert rules and statistical models. The relationships are used both to validate new data, and to predict phenotypic outcomes based on available data. The prediction may relate to a clinical outcome in response to a proposed intervention by a caregiver. The statistical models may be inhaled into the system from electronic publications that define statistical models and methods for training those models, according to a standardized template. Methods are described for selecting, creating and training the statistical models to operate on genetic, phenotypic and clinical data, in particular for underdetermined data sets that are typical of genetic information. The disclosure also describes how security of the data is maintained by means of a robust security architecture, and robust user authentication such as biometric authentication, combined with application-level and data-level access privileges.
Owner:NATERA
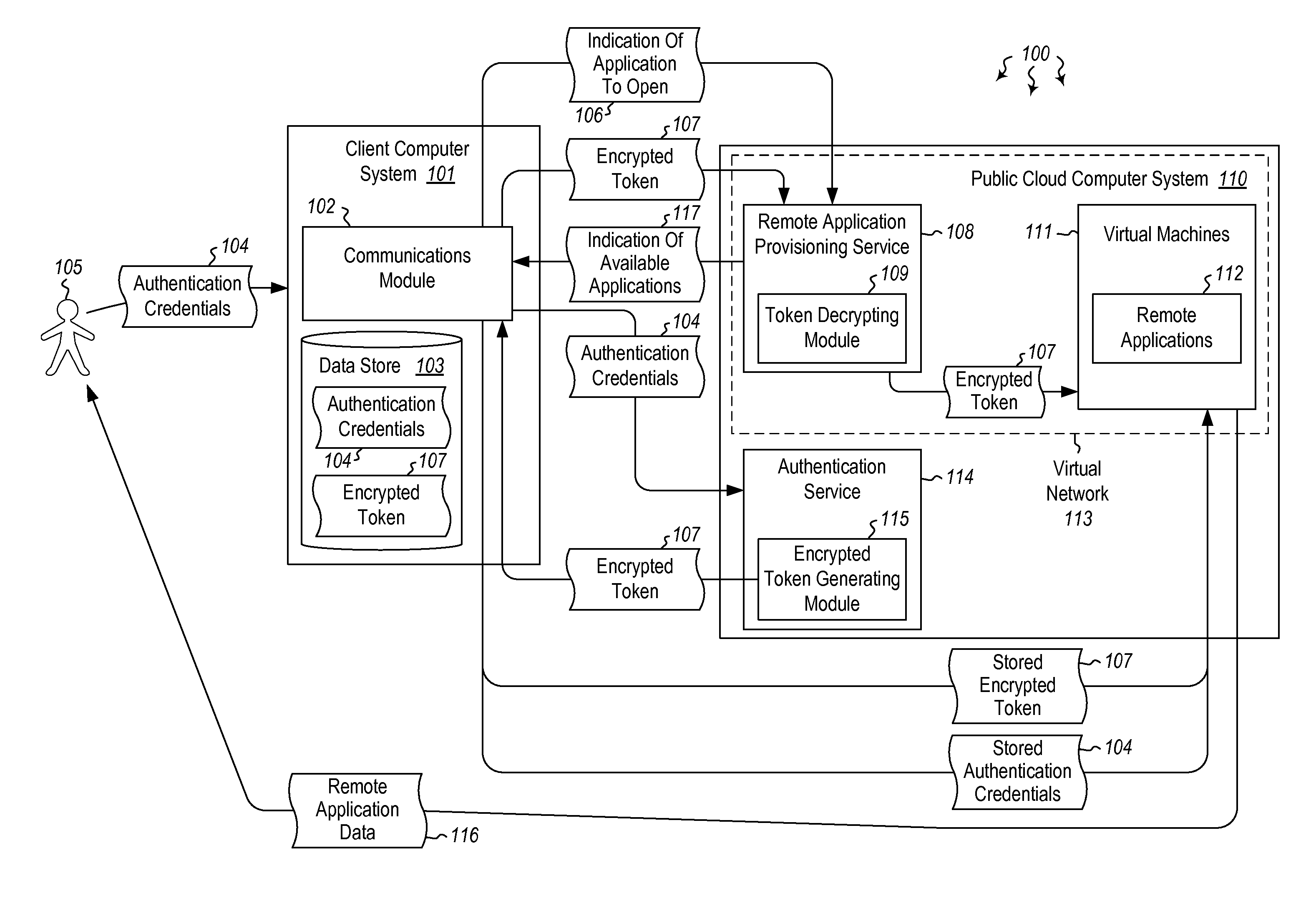
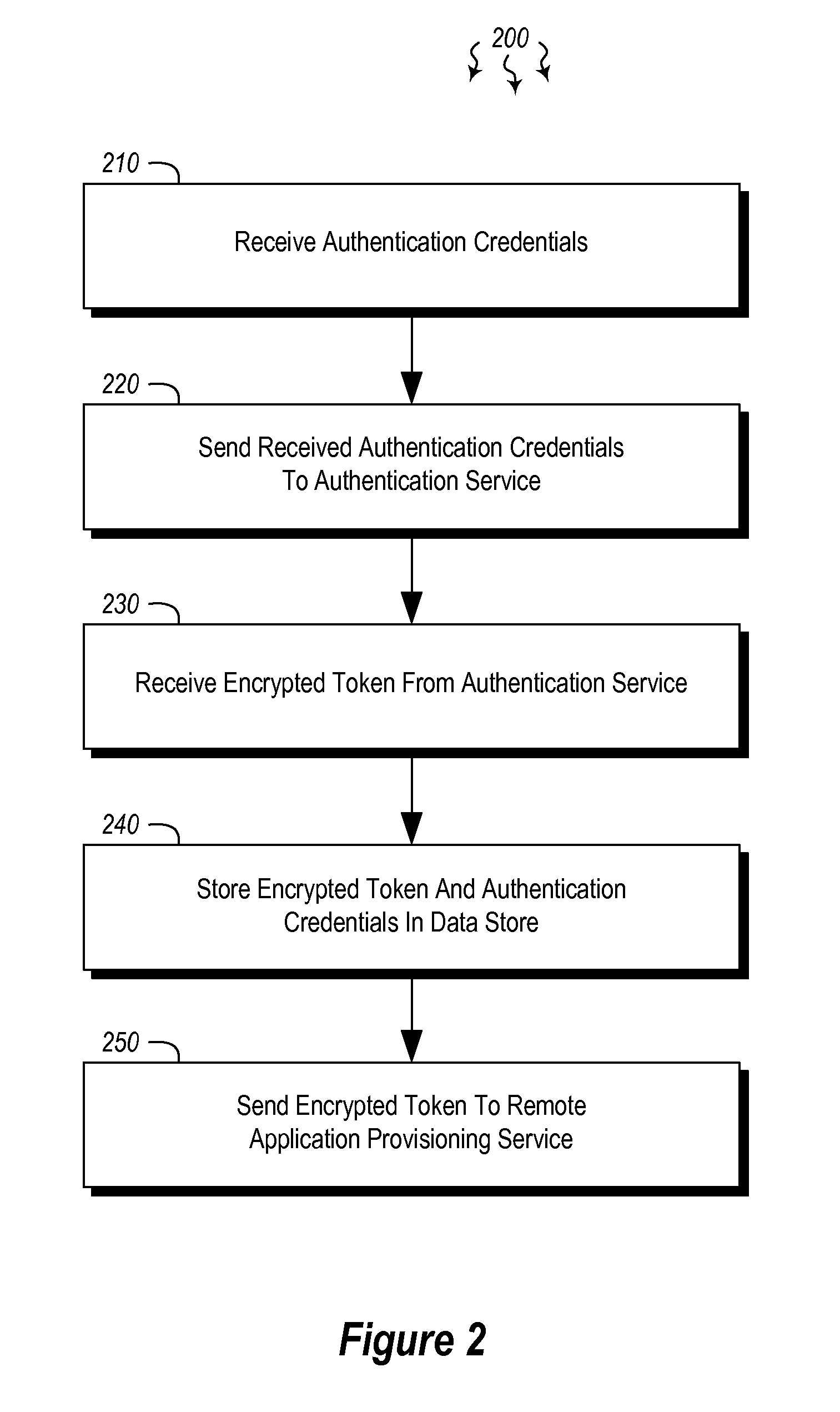
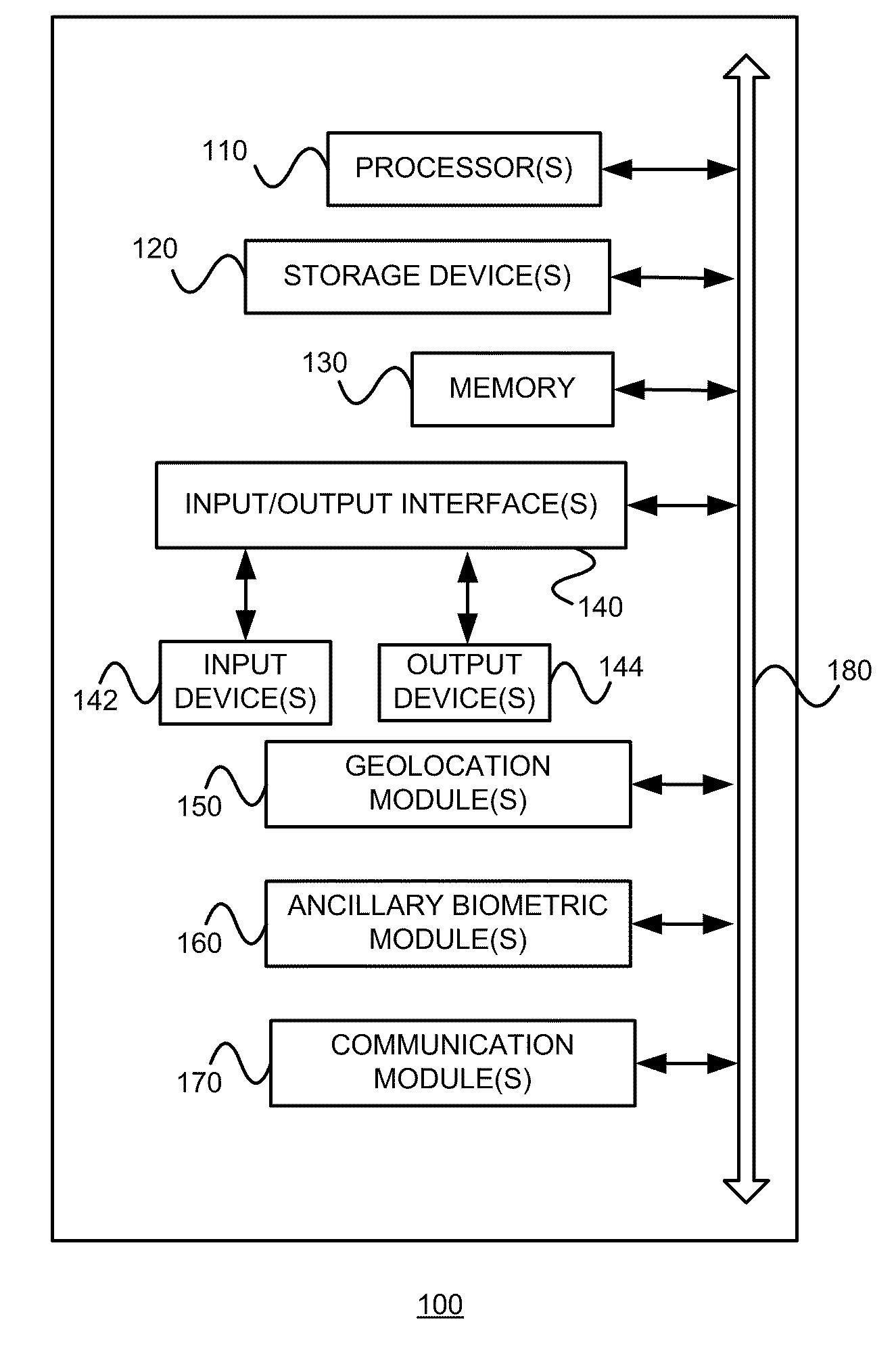
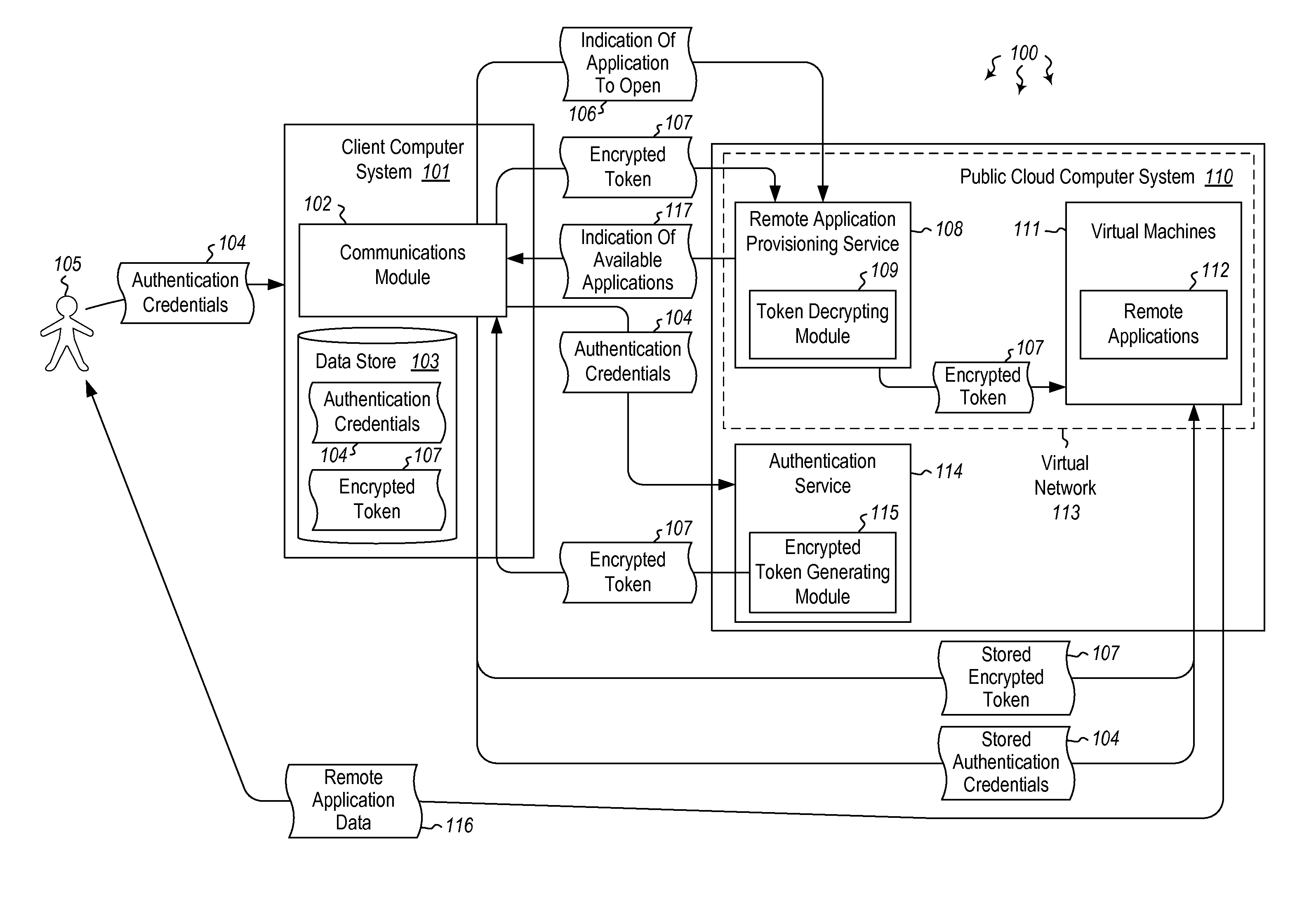
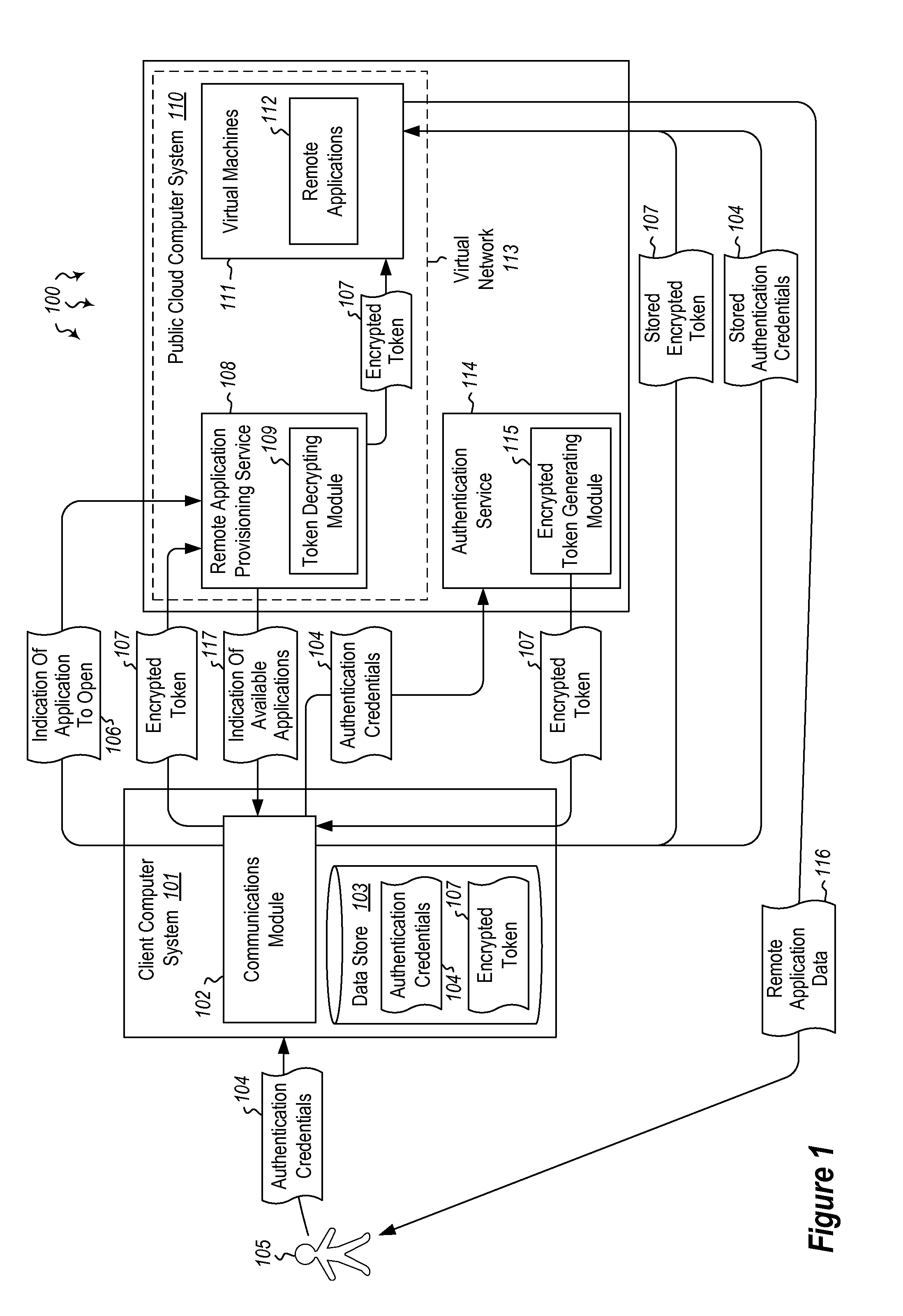
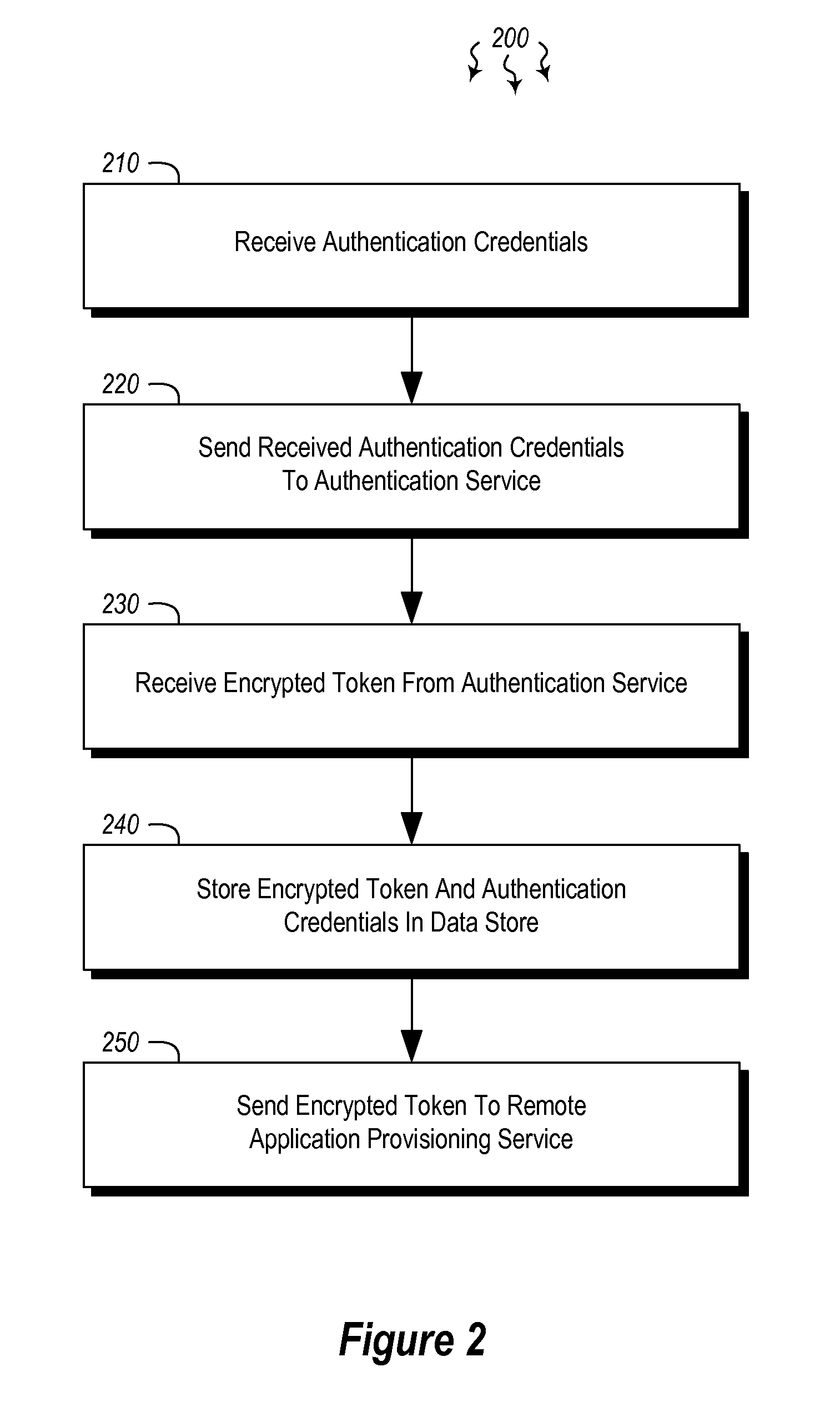
User authentication in a cloud environment
ActiveUS20140373126A1Well formedDigital data processing detailsComputer security arrangementsInternet Authentication ServiceData memory
Embodiments are directed to authenticating a user to a remote application provisioning service. In one scenario, a client computer system receives authentication credentials from a user at to authenticate the user to a remote application provisioning service that provides virtual machine-hosted remote applications. The client computer system sends the received authentication credentials to an authentication service, which is configured to generate an encrypted token based on the received authentication credentials. The client computer system then receives the generated encrypted token from the authentication service, stores the received encrypted token and the received authentication credentials in a data store, and sends the encrypted token to the remote application provisioning service. The encrypted token indicates to the remote application provisioning service that the user is a valid user.
Owner:MICROSOFT TECH LICENSING LLC
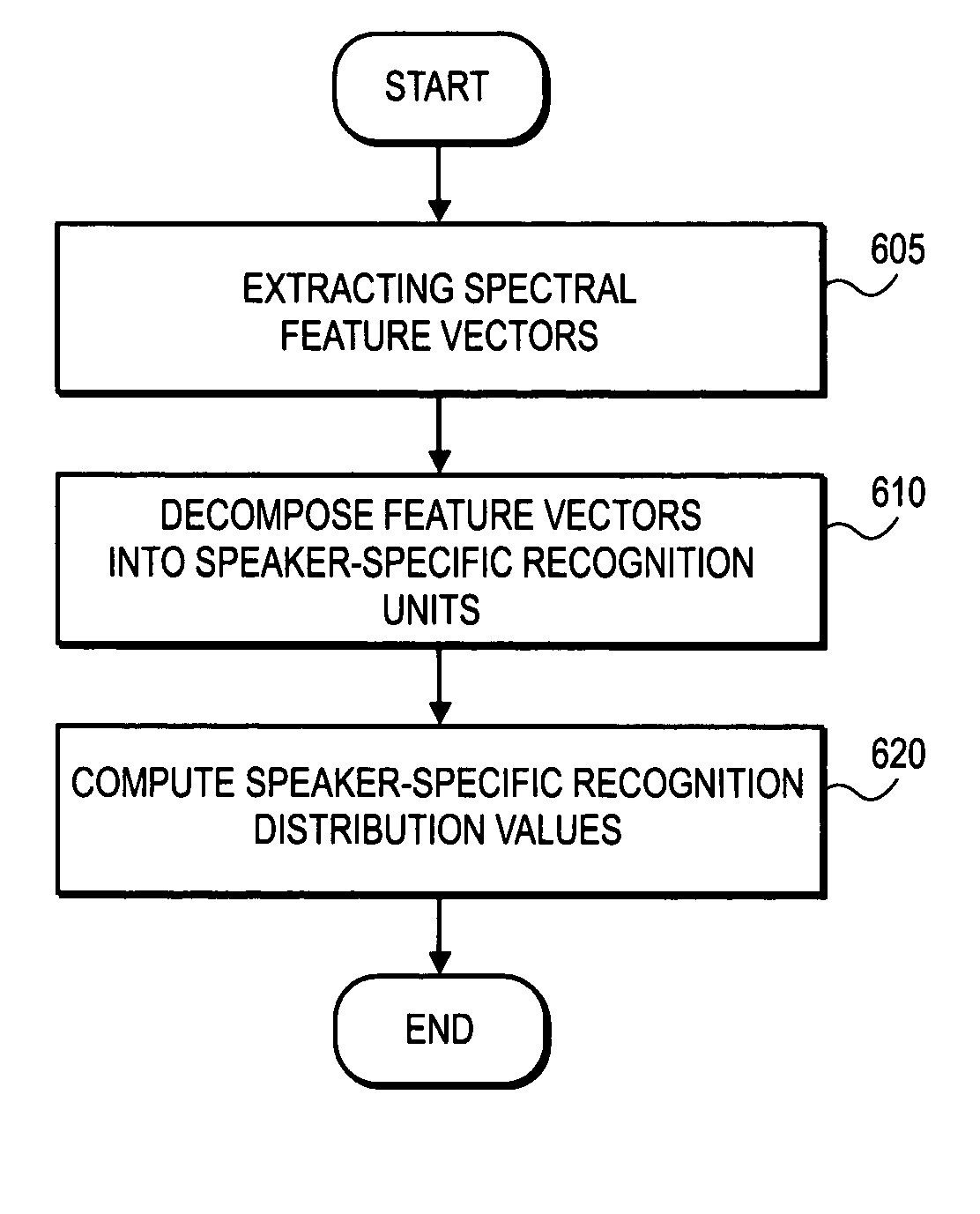
Fast, language-independent method for user authentication by voice
A method and system for training a user authentication by voice signal are described. In one embodiment, a set of feature vectors are decomposed into speaker-specific recognition units. The speaker-specific recognition units are used to compute distribution values to train the voice signal. In addition, spectral feature vectors are decomposed into speaker-specific characteristic units which are compared to the speaker-specific distribution values. If the speaker-specific characteristic units are within a threshold limit of the speaker-specific distribution values, the speech signal is authenticated.
Owner:APPLE INC
System and method for secure network purchasing
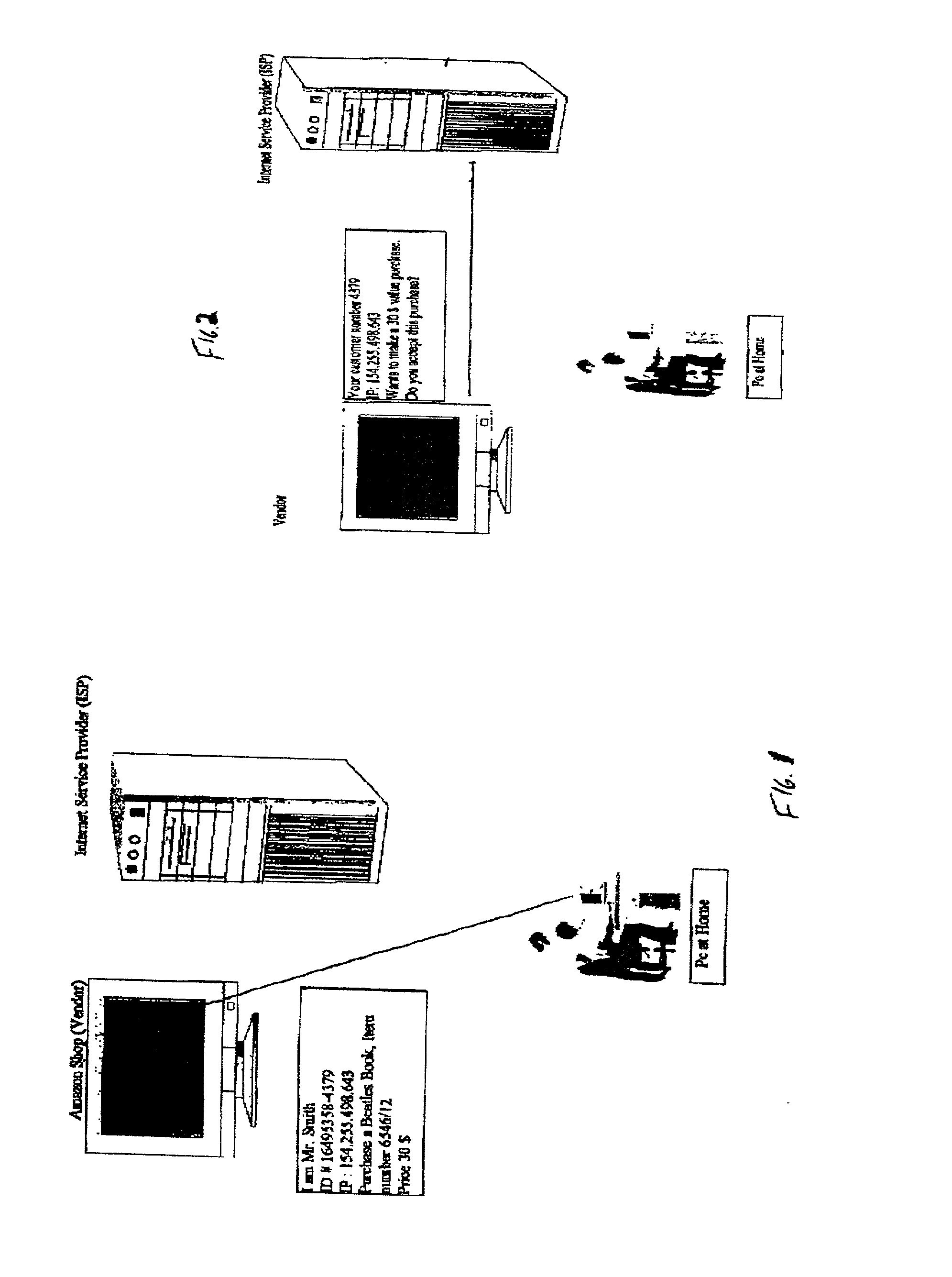
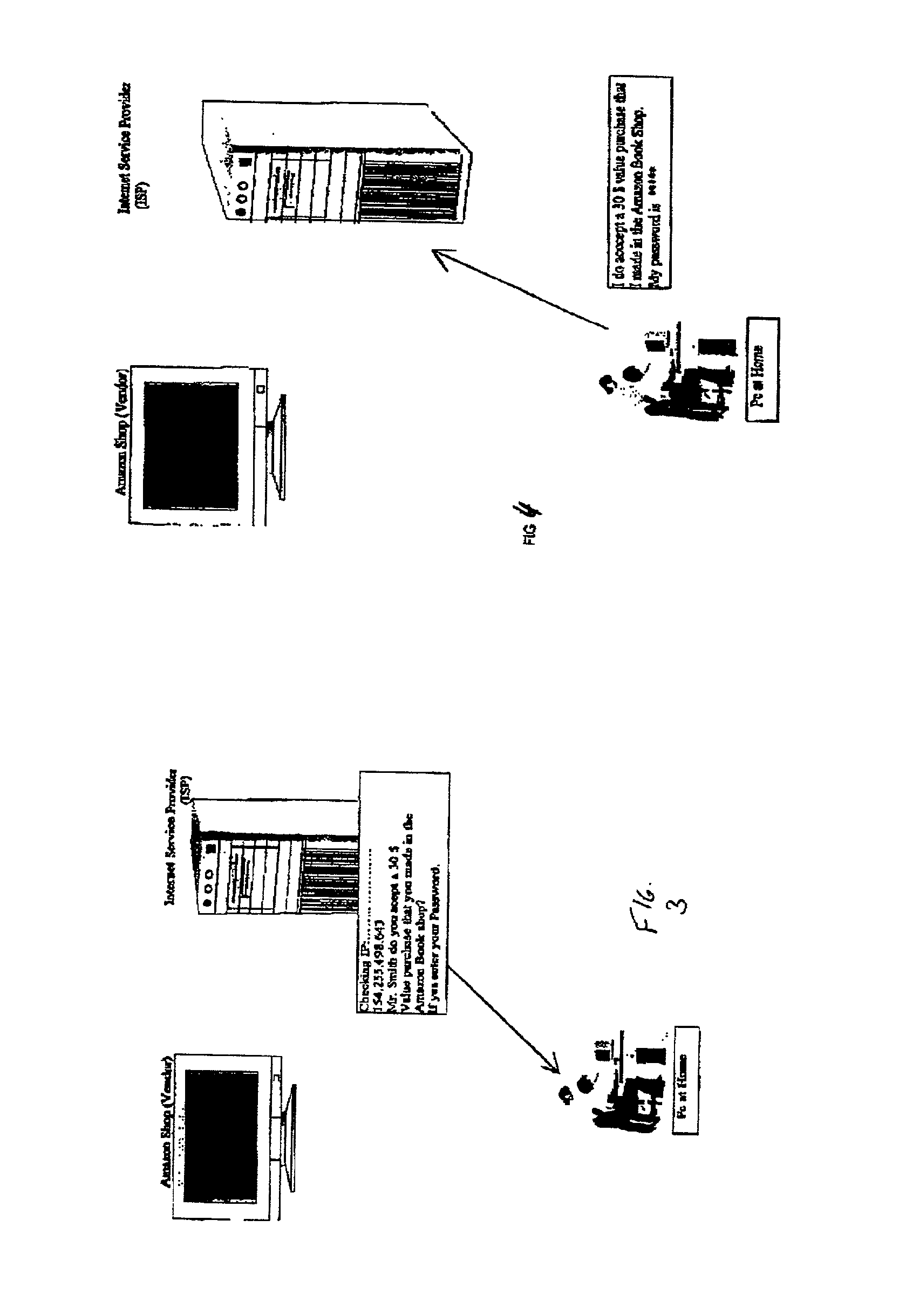
InactiveUS20020073046A1Improve securityCharacter and pattern recognitionDigital data authenticationSecure Electronic TransactionInternet privacy
A system for permitting a secure electronic transaction on a network is disclosed. The network has a user device having a fingerprint, a provider's server and a means for providing verification of user's identity. In response to a request by the provider's server the means for providing verification positively identifies the fingerprint of the user device. It thereupon requests a confirmation from the user device of the transaction and upon receiving the confirmation completes the transaction.
Owner:CHANNEL IP BV
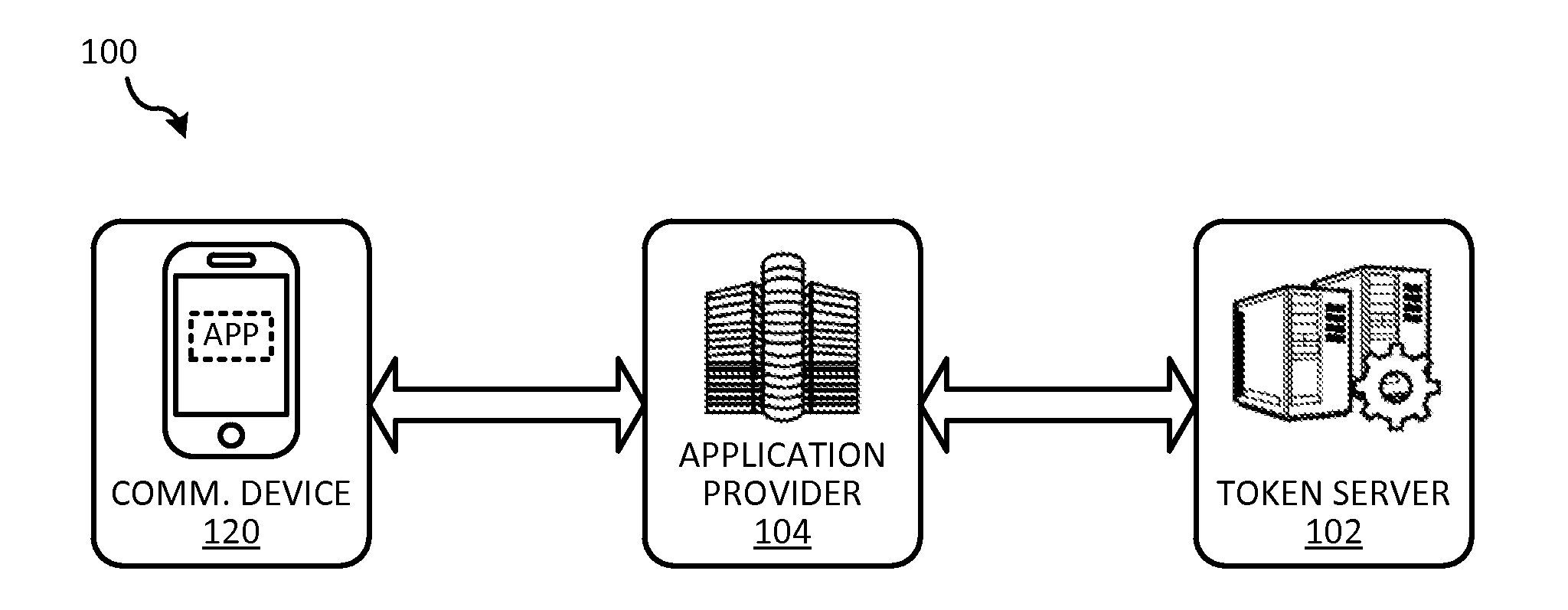
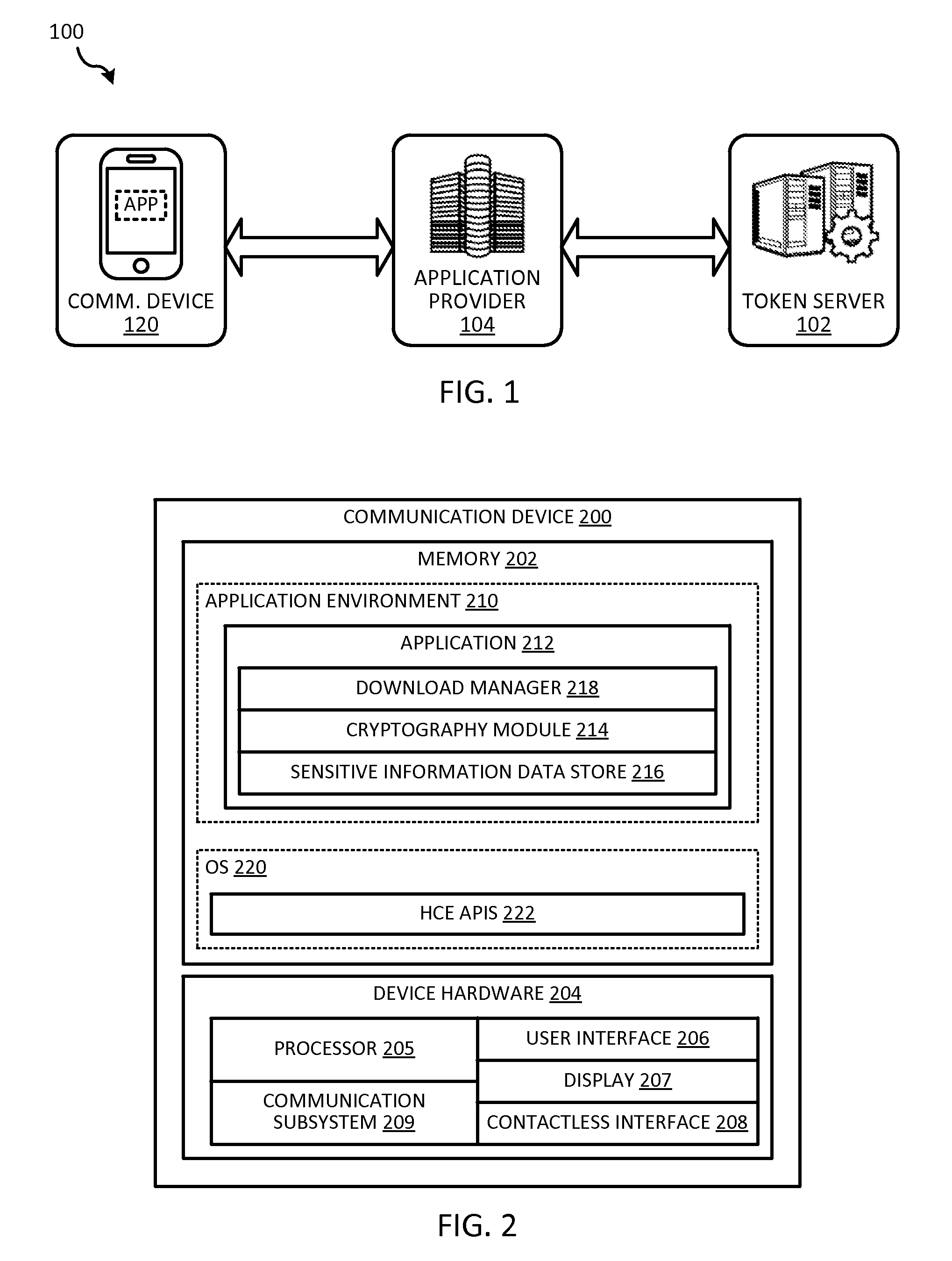
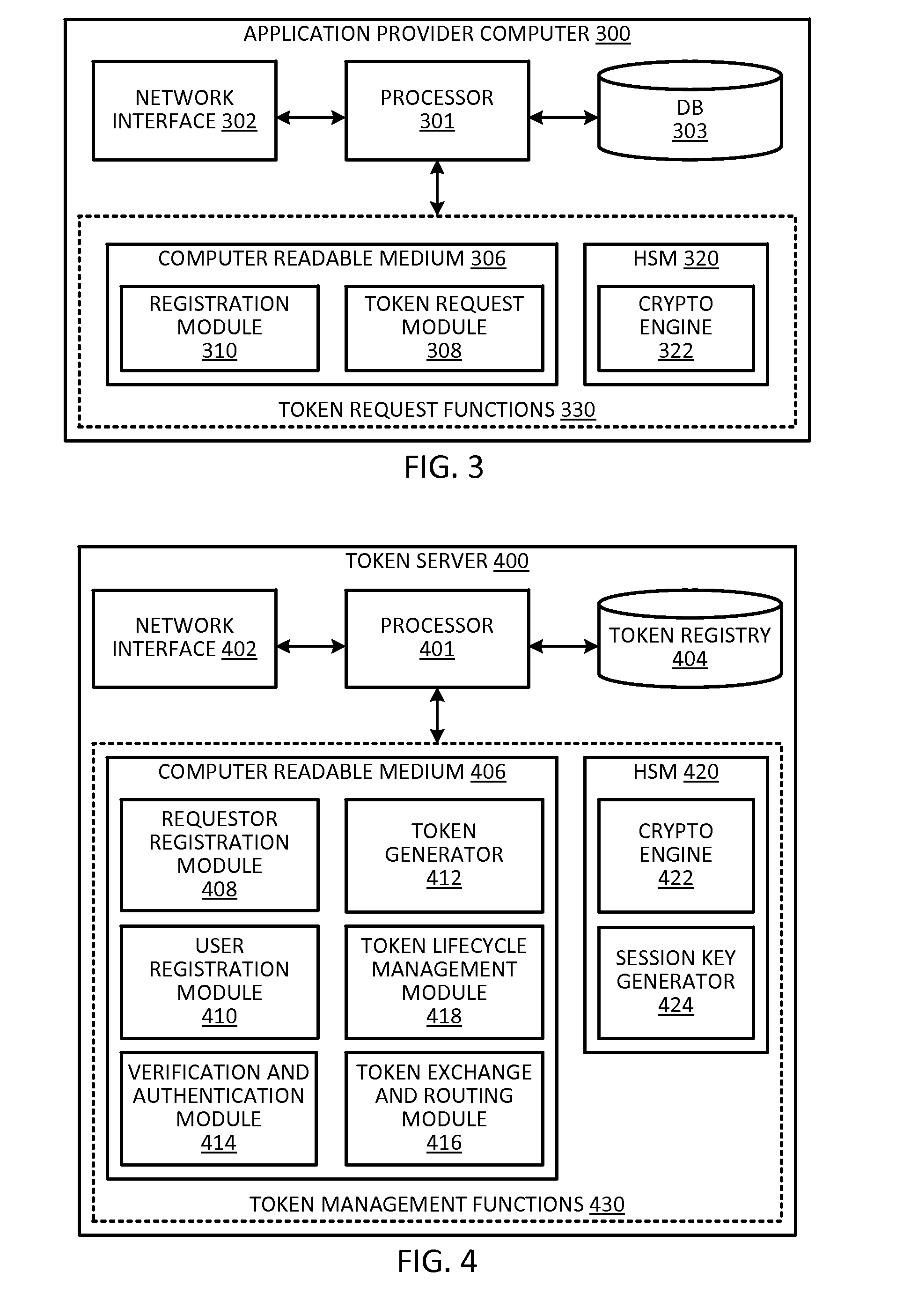
Token security on a communication device
ActiveUS20150312038A1Improve securityUser identity/authority verificationPayment architectureUser authenticationHash table
Techniques for enhancing the security of storing sensitive information or a token on a communication device may include sending a request for the sensitive information or token. The communication device may receive a session key encrypted with a hash value derived from user authentication data that authenticates the user of the communication device, and the sensitive information or token encrypted with the session key. The session key encrypted with the hash value, and the sensitive information or token encrypted with the session key can be stored in a memory of the communication device.
Owner:VISA INT SERVICE ASSOC
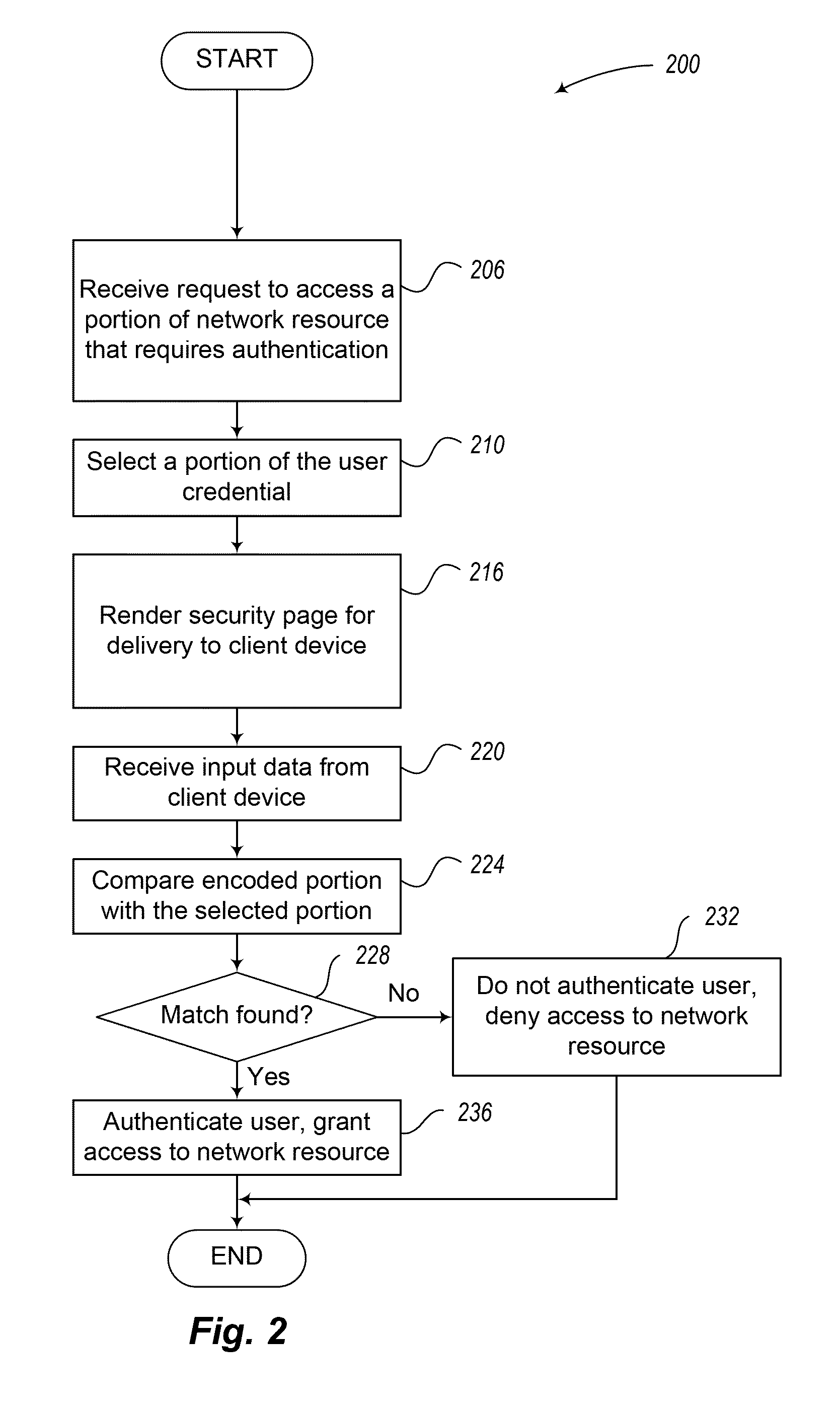
Techniques for user authentication
InactiveUS8613066B1Digital data processing detailsUser identity/authority verificationUser authenticationClient-side
Techniques for user authentication are disclosed. In some situations, the techniques include receiving, from a client device, an authentication request to access a network resource, the request including a user identifier, obtaining a security credential associated with the user identifier contained in the received request, generating an authorization code based on the obtained security credential, providing to the client device instructions to obtain first information corresponding to the generated authorization code, receiving, from the client device, the first information provided in response to the provided instructions, and, when the first information received from the client device corresponds to at least a portion of the generated authorization code, authorizing the client device to access the network resource.
Owner:AMAZON TECH INC
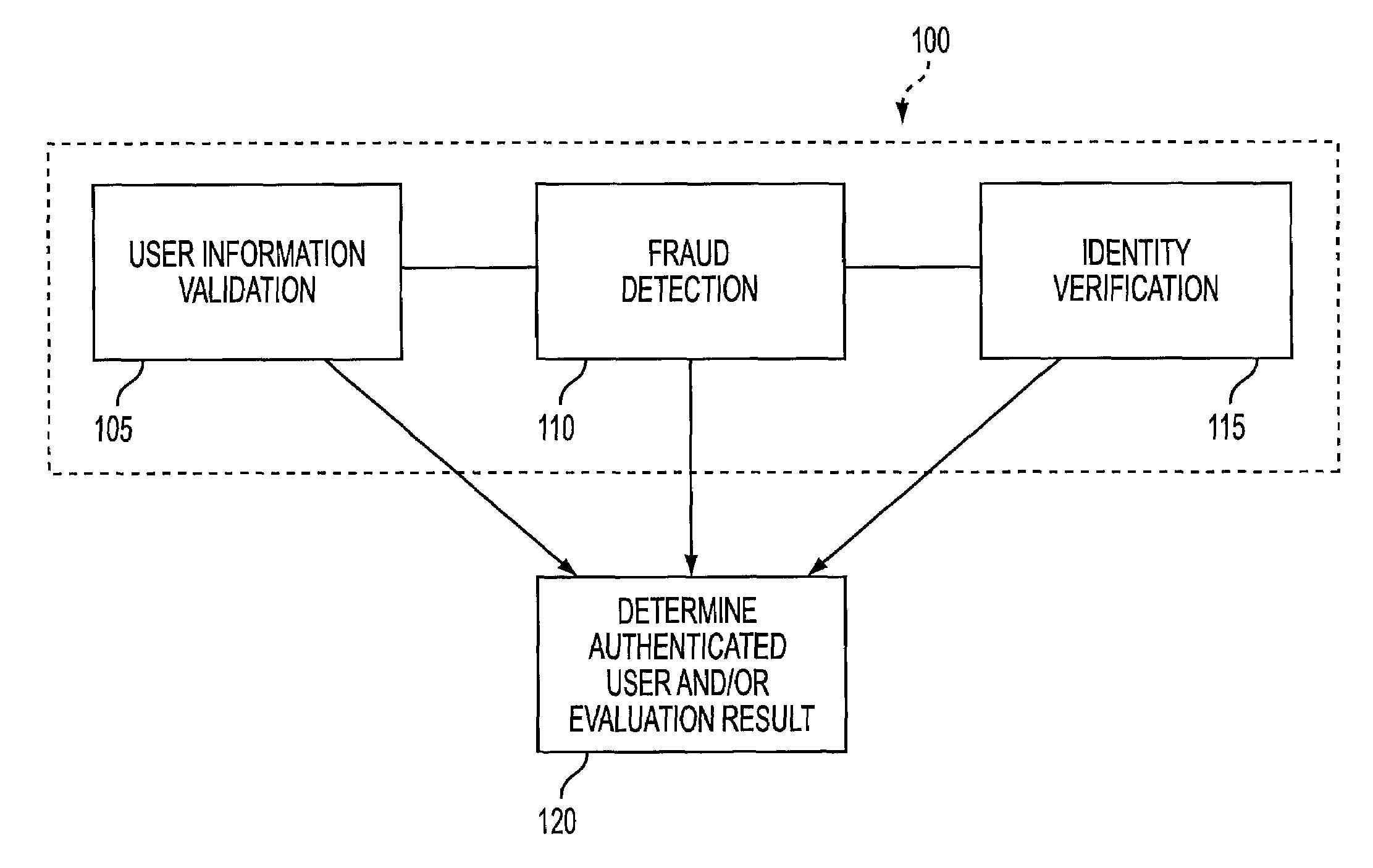
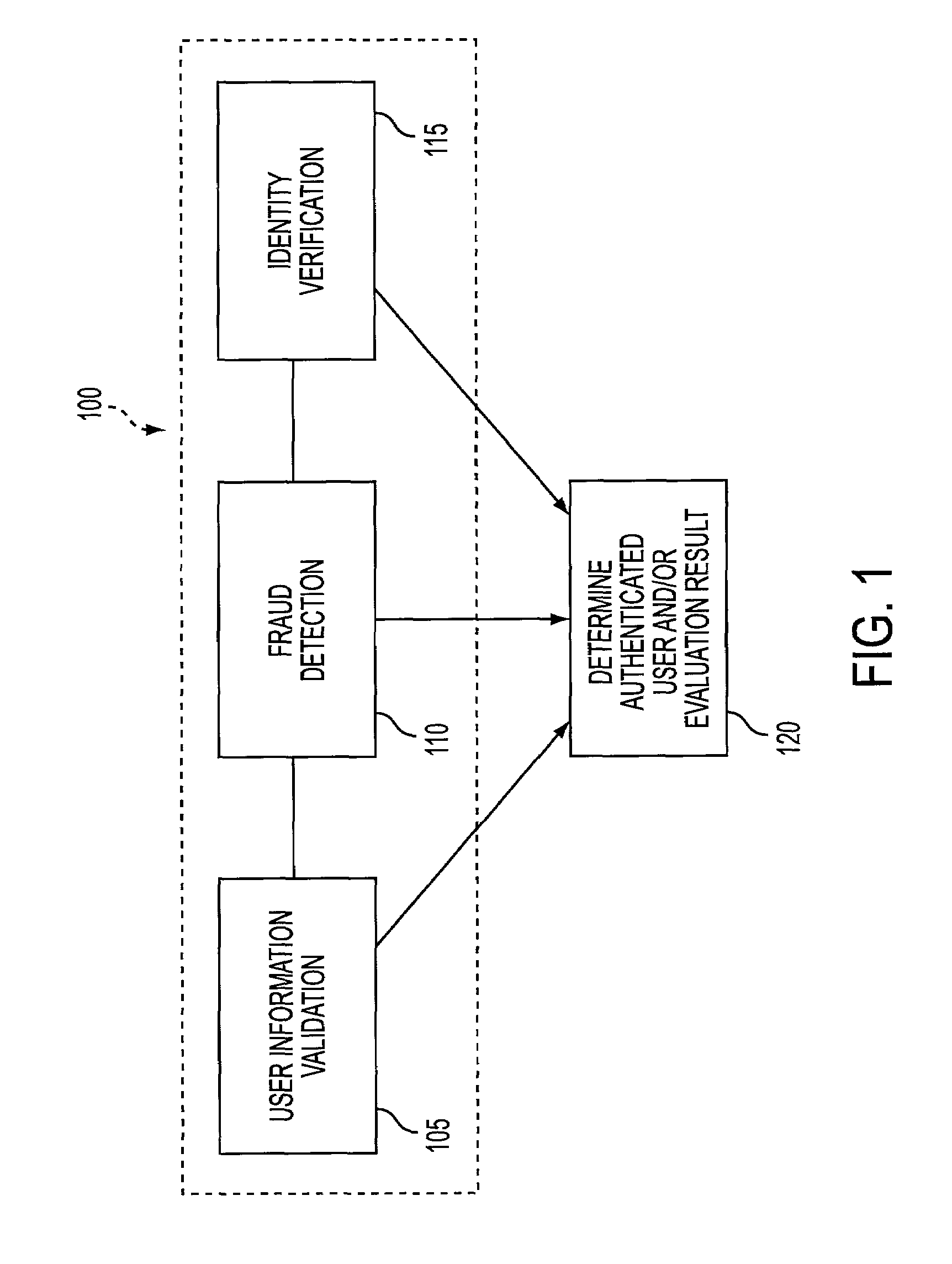
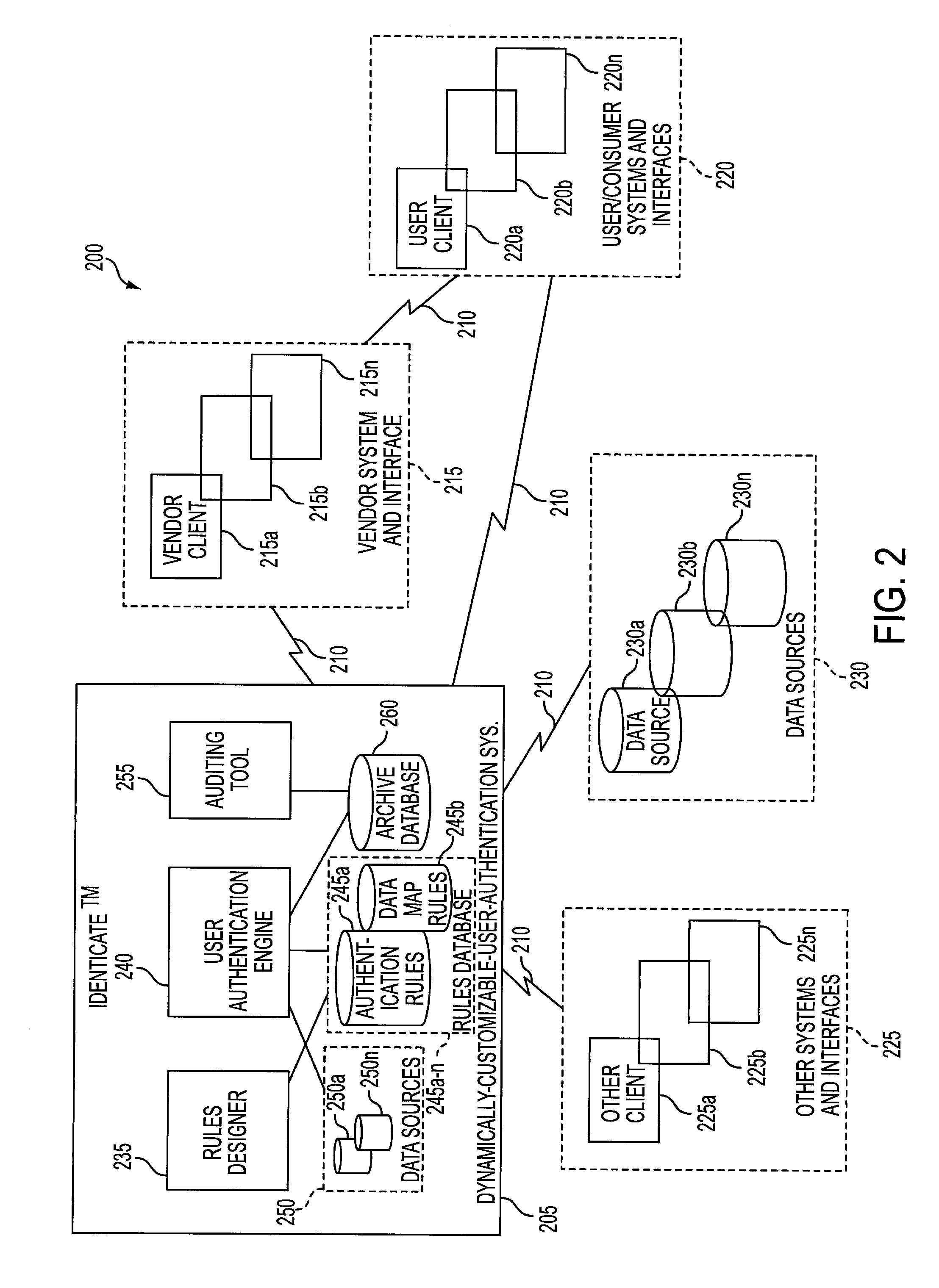
User authentication system and methods thereof
ActiveUS7231657B2Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyData source
A computer system to authenticate users of vendors supplying services and / or products to the users, the system having programmed processors providing authentication rules, authenticating users according to the authentication rules responsive to user authentication requests, configuring the authentication rules in real-time, thereby allowing real-time customization of the system, providing multi-factor user authentication processes, using any data sources providing information about and / or known to the users to authenticate the users, thereby providing a data agnostic system, and authentication strategies correspond to the authentication rules, thereby allowing the system to support authentication strategy experimentation.
Owner:CGI TECH & SOLUTIONS
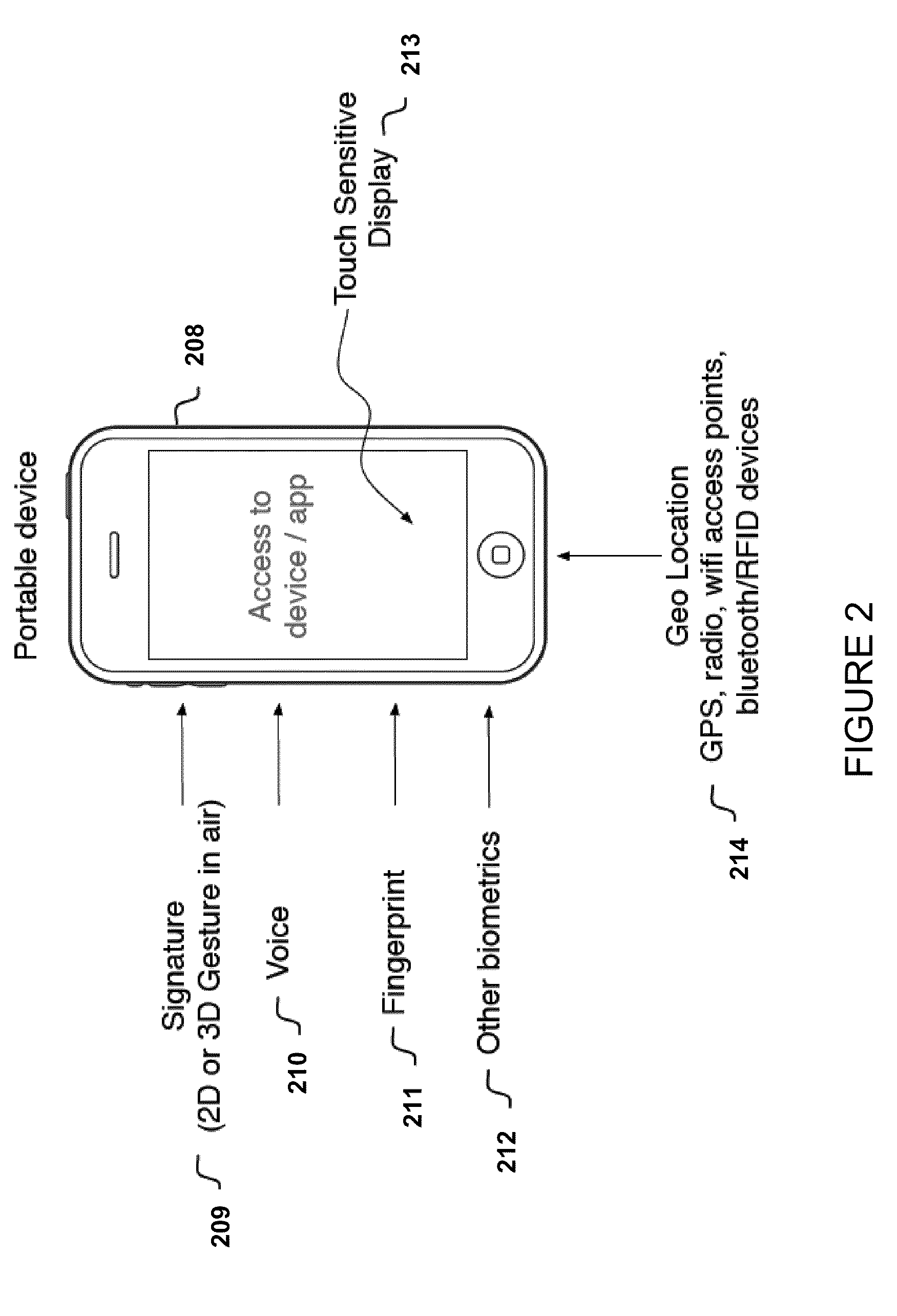
User authentication for devices with touch sensitive elements, such as touch sensitive display screens
ActiveUS20100225443A1Electric signal transmission systemsImage analysisUser authenticationFinger touch
For user authentication, finger touch information from a user is accepted via a touch sensitive element, the finger touch information including at least a time series of finger touch samples that define a trace of the user's signature, and each of the finger touch samples including centroid coordinates and non-centroid information, the non-centroid information including at least one of (A) a shape of the finger touch sample, (B) a size of the finger touch sample, (C) an orientation of the finger touch sample, and (D) characteristics of a multi-touch finger touch sample. A similarity of such finger touch samples with previously entered and stored finger touch samples is determined and compared with a threshold for purposes of user authentication.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
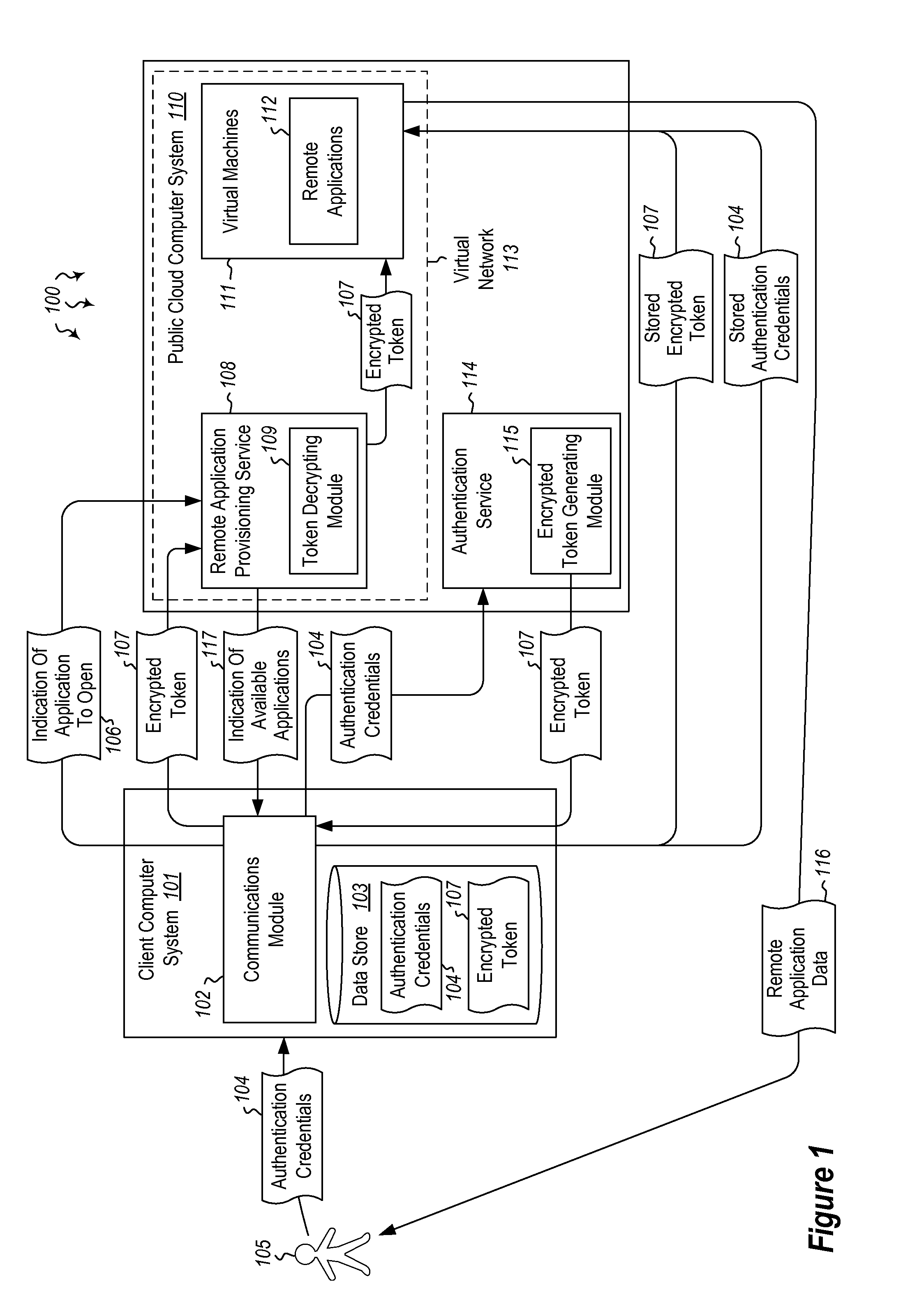
User authentication in a cloud environment
ActiveUS9124569B2Digital data processing detailsDigital data authenticationInternet Authentication ServiceData memory
Embodiments are directed to authenticating a user to a remote application provisioning service. In one scenario, a client computer system receives authentication credentials from a user at to authenticate the user to a remote application provisioning service that provides virtual machine-hosted remote applications. The client computer system sends the received authentication credentials to an authentication service, which is configured to generate an encrypted token based on the received authentication credentials. The client computer system then receives the generated encrypted token from the authentication service, stores the received encrypted token and the received authentication credentials in a data store, and sends the encrypted token to the remote application provisioning service. The encrypted token indicates to the remote application provisioning service that the user is a valid user.
Owner:MICROSOFT TECH LICENSING LLC
System and method for fraud monitoring, detection, and tiered user authentication
The present invention provides systems and methods for authenticating access requests from user devices by presenting one of a plurality of graphical user interfaces selected depending on a perceived risk of fraud associated with the devices. User devices are identified with fingerprinting information, and their associated risks of fraud are determined from past experience with the device or with similar devices and from third party information. In preferred embodiments, different graphical user interfaces are presented based on both fraud risk and, in the case of a known user, usability. In preferred embodiments, this invention is implemented as a number of communicating modules that identify user devices, assess their risk of fraud, present selected user interfaces, and maintain databases of fraud experiences. This invention also includes systems providing these authentication services.
Owner:ORACLE INT CORP
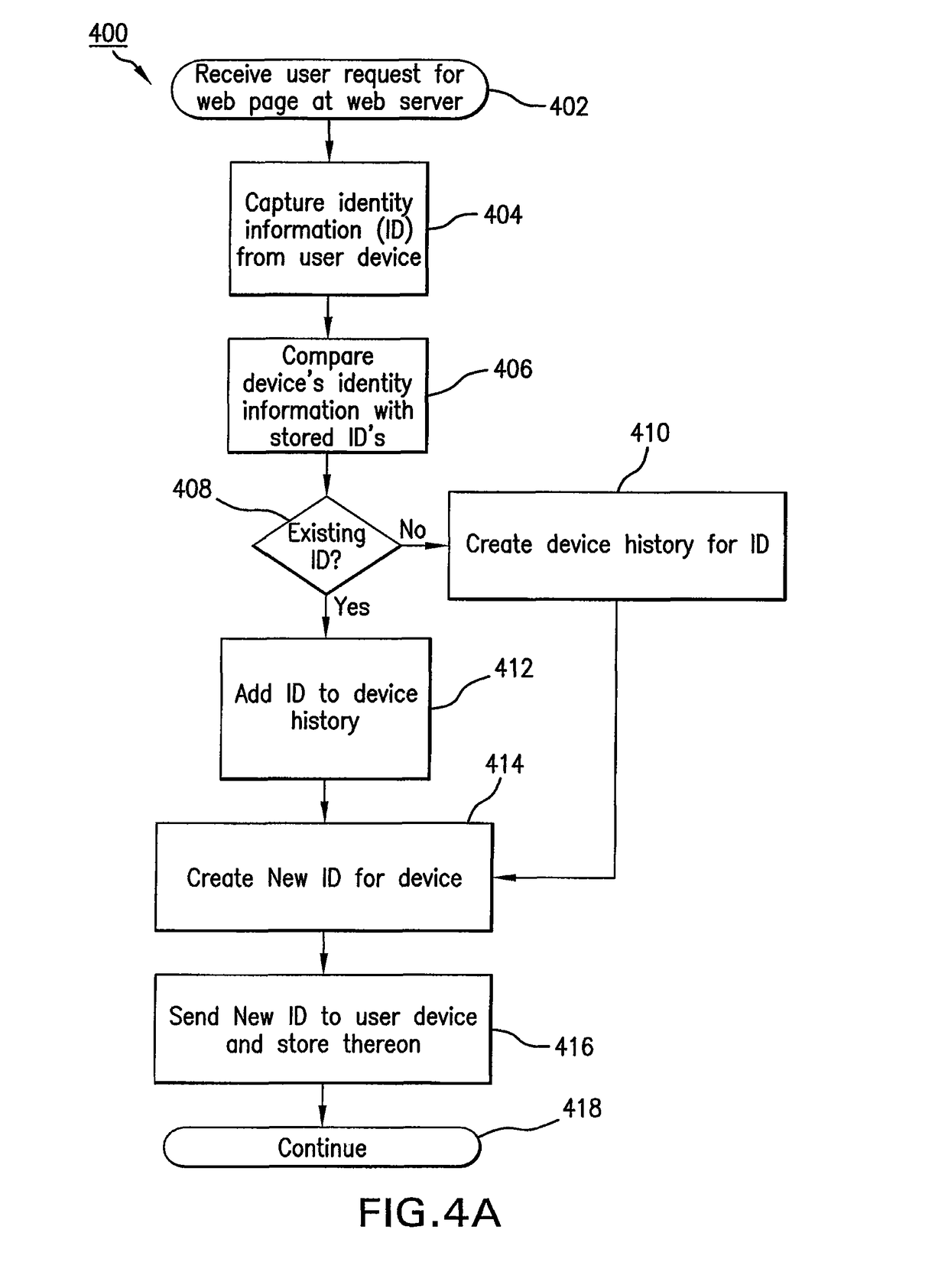
Automatic authentication method and system in print process
ActiveUS7313699B2Improve securityEliminate needDigital data processing detailsUser identity/authority verificationUser authenticationUser identifier
This invention provides an automatic authentication method and system in a print process, which can obviate the need for user's input operations of the user ID and password and can improve security since authentication is automatically done based on print information embedded in a file or information from an application program without any user's input.In a print process that requires user authentication, a printer driver extracts information related to an application and / or a document for the print process as attribute information, and user authentication is made by comparing the attribute information with information stored in a user registration information database of a server. If user authentication has succeeded, the printer driver controls a printer to print, and the server manages and stores accounting information and the like for respective departments in a department management information database.
Owner:CANON KK
Dynamic account authentication using a mobile device
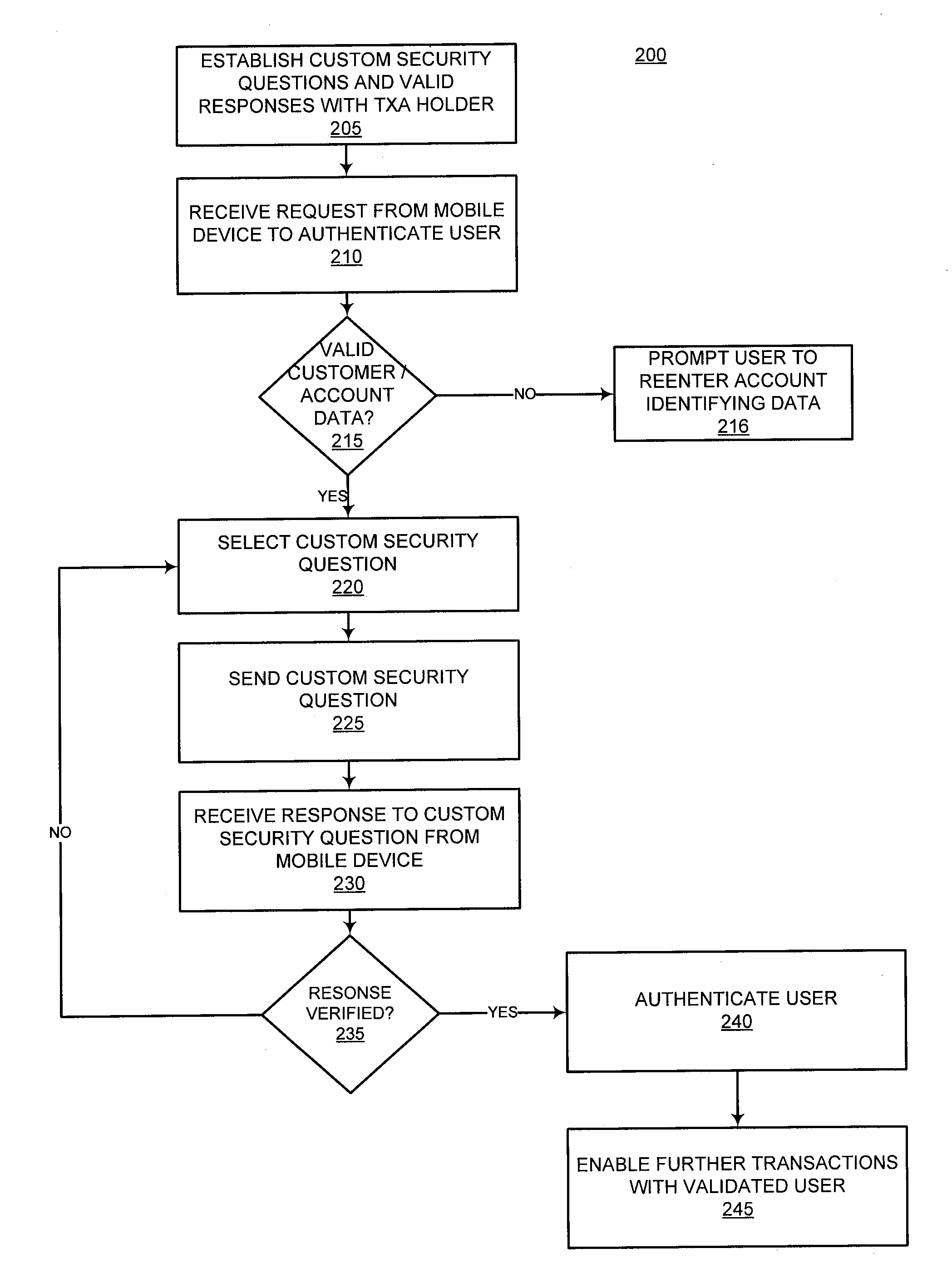
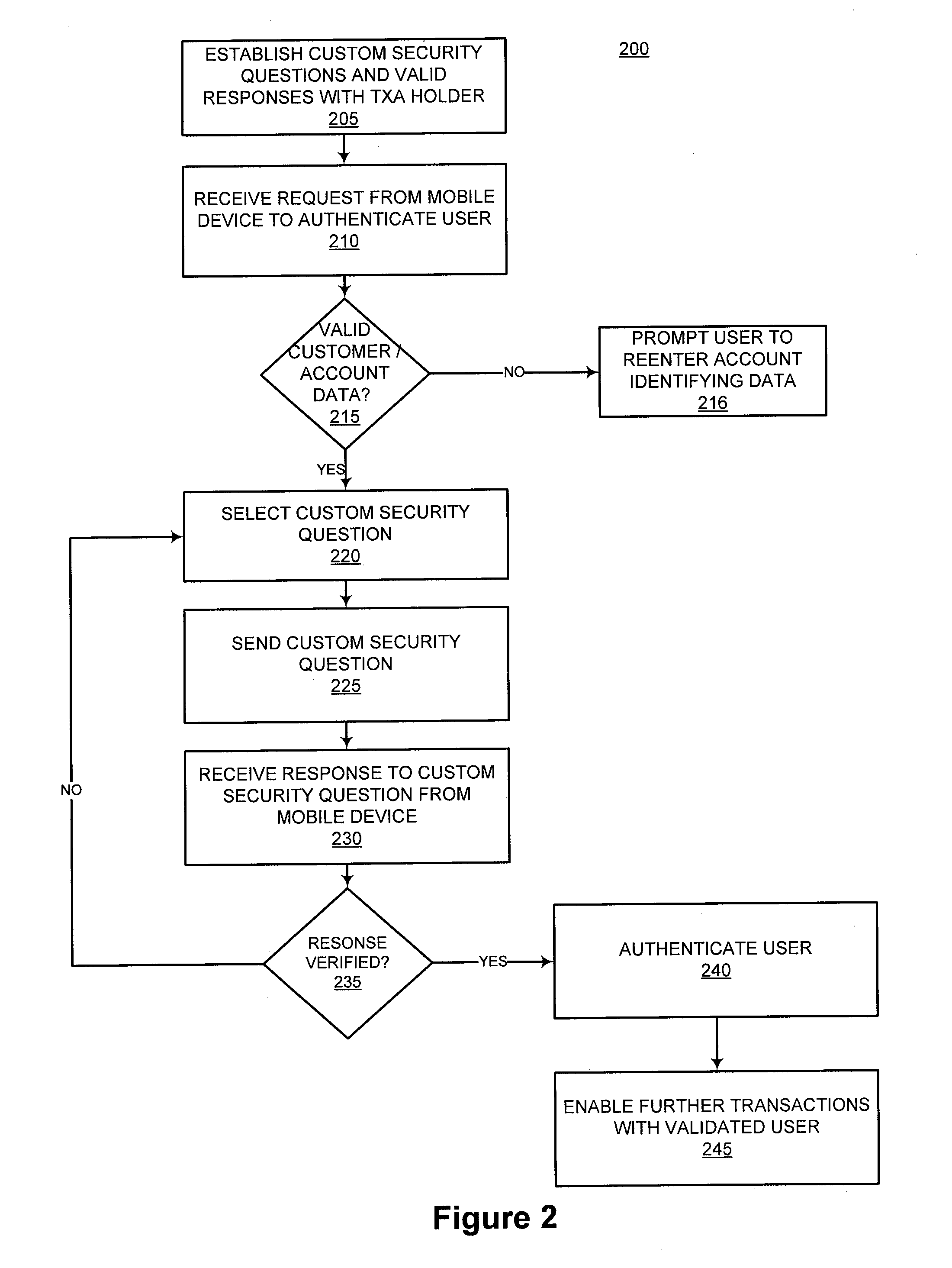
InactiveUS20090327131A1Authentication is convenientSimple methodFinanceDigital data processing detailsUser authenticationMobile device
Providing dynamic authentication of a user requesting access to a system via a mobile device is disclosed. An account holder tailors a set of customized security challenges and responses. When a request for account authentication is received from a mobile device, the system conducts a multi-step user authentication process that includes dynamically selecting and prompting the user with the custom security challenges.
Owner:LIBERTY PEAK VENTURES LLC
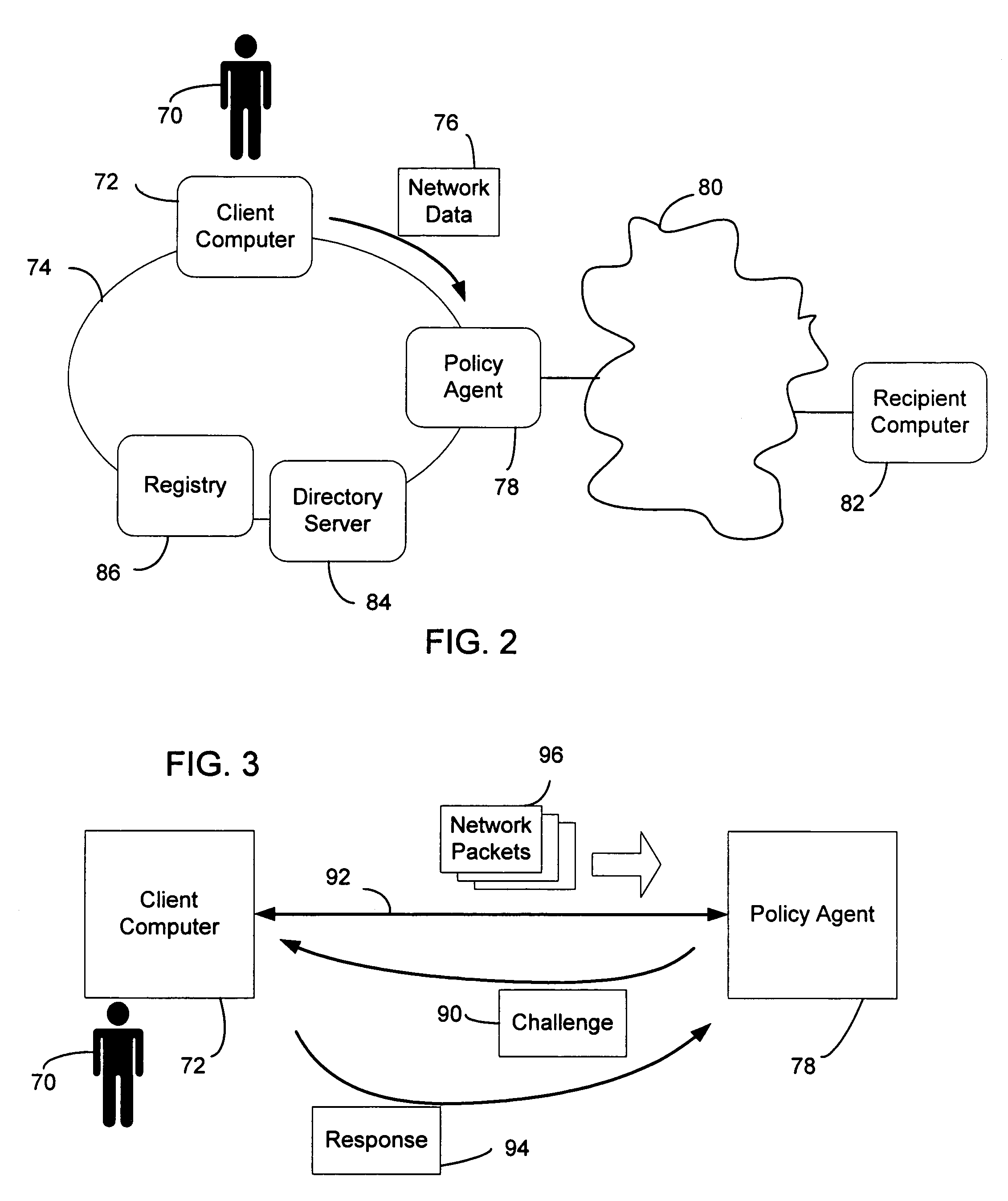
System and method of user authentication for network communication through a policy agent
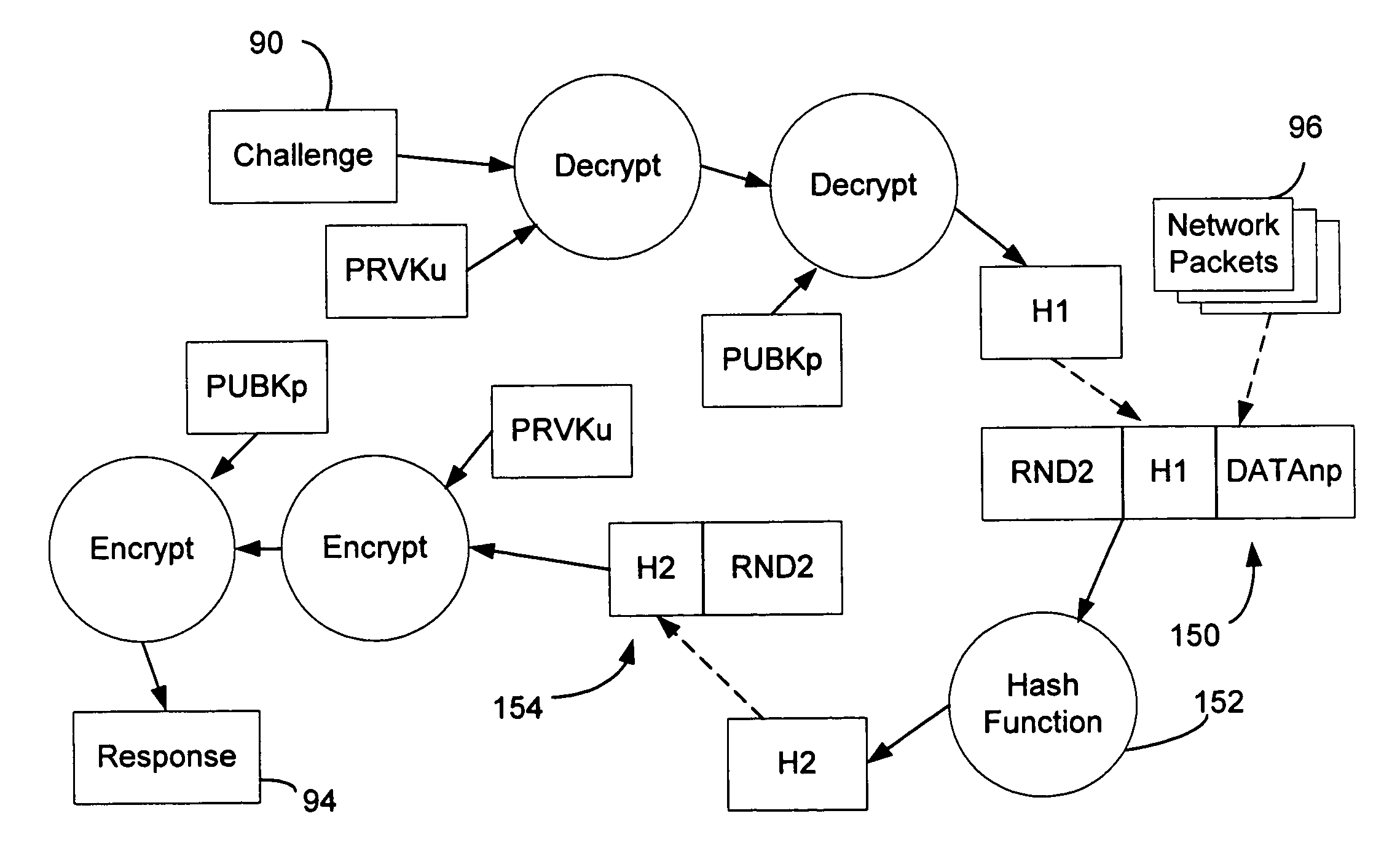
InactiveUS7039713B1Digital data processing detailsComputer security arrangementsData connectionUser authentication
A policy agent of a network performs an out-of-band user authentication process to verify the identity of a user of a client computer and associates the network data received from the client computer with the user. When the client computer initiates a network data connection to or through the policy agent, the policy agent sends an encrypted challenge to the client computer. The challenge is encrypted with a private key of the policy agent. When the client computer receives the challenge, it decrypts the challenge and prepares a message digest value based on the challenge and the network data sent by the user. The message digest value is then encrypted with the private key of the user to form a response, and the response is sent to the policy agent. The policy agent decrypts the response with the public key of the user to obtain the message digest value and calculates a digest value based on the challenge and the received network data. The policy agent then compares the calculated digest value with the decrypted digest value. A match between the two digest values indicates that the user is successfully authenticated and that the received network data are associated with the user. The policy agent may then apply network policies based on the credentials of the authenticated user.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com