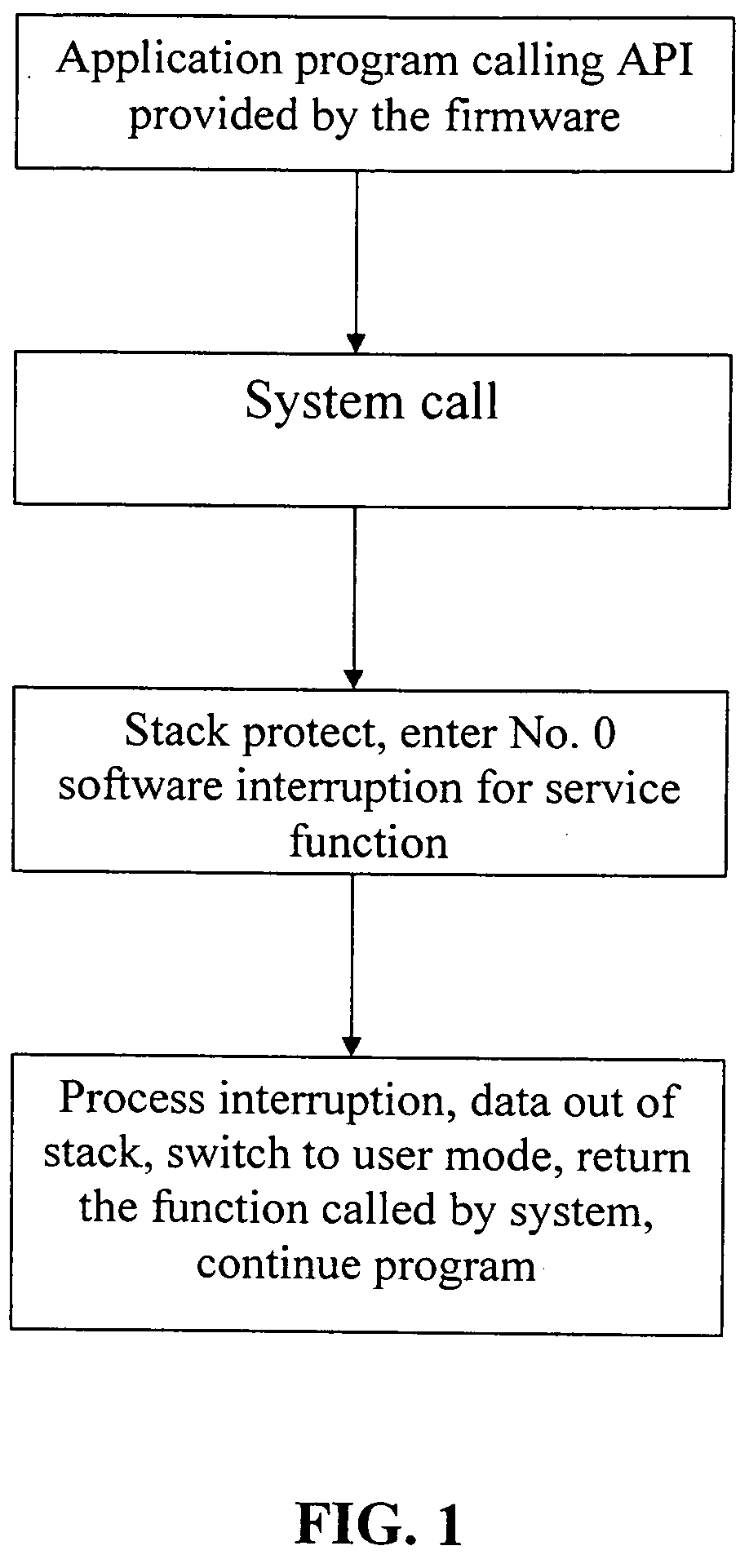
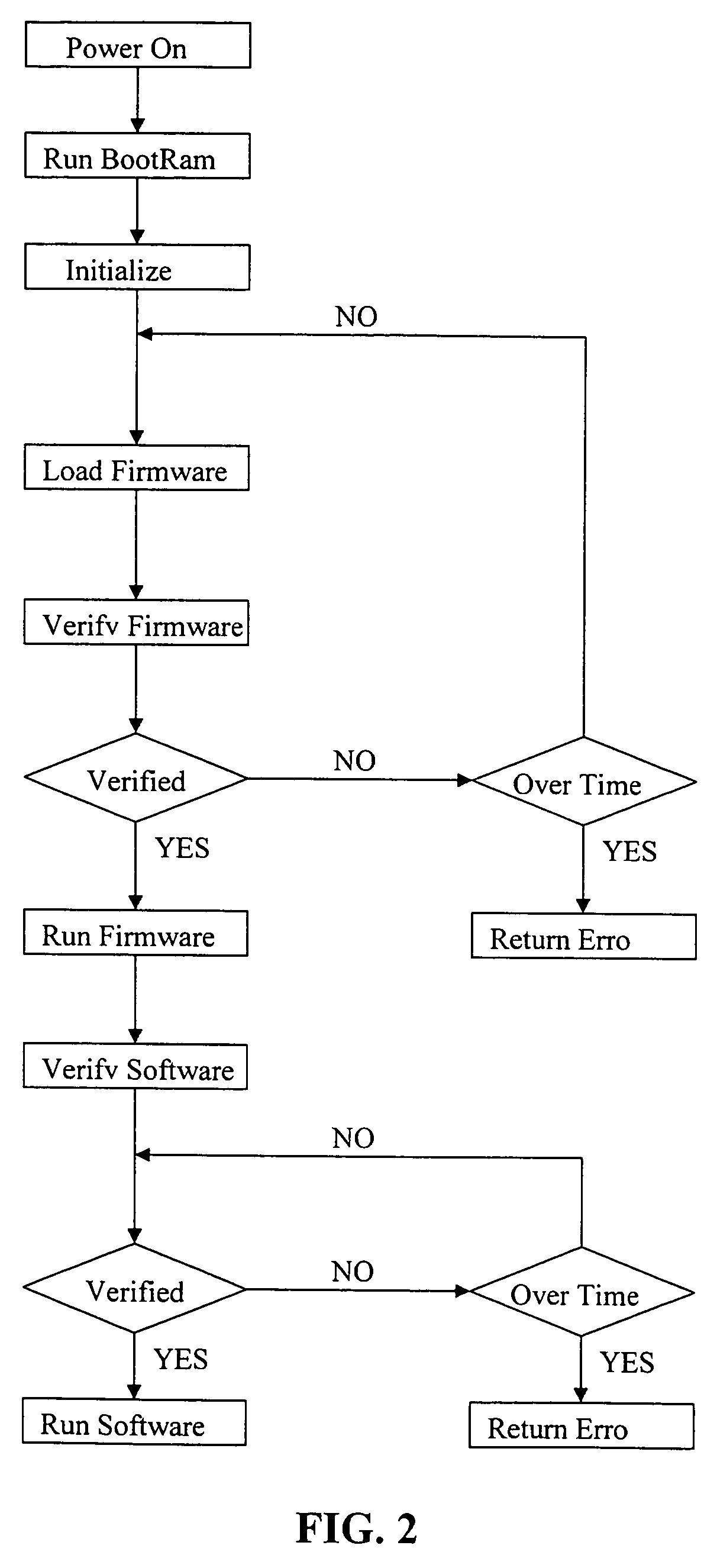
Patents
Literature
88 results about "Secure Electronic Transaction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
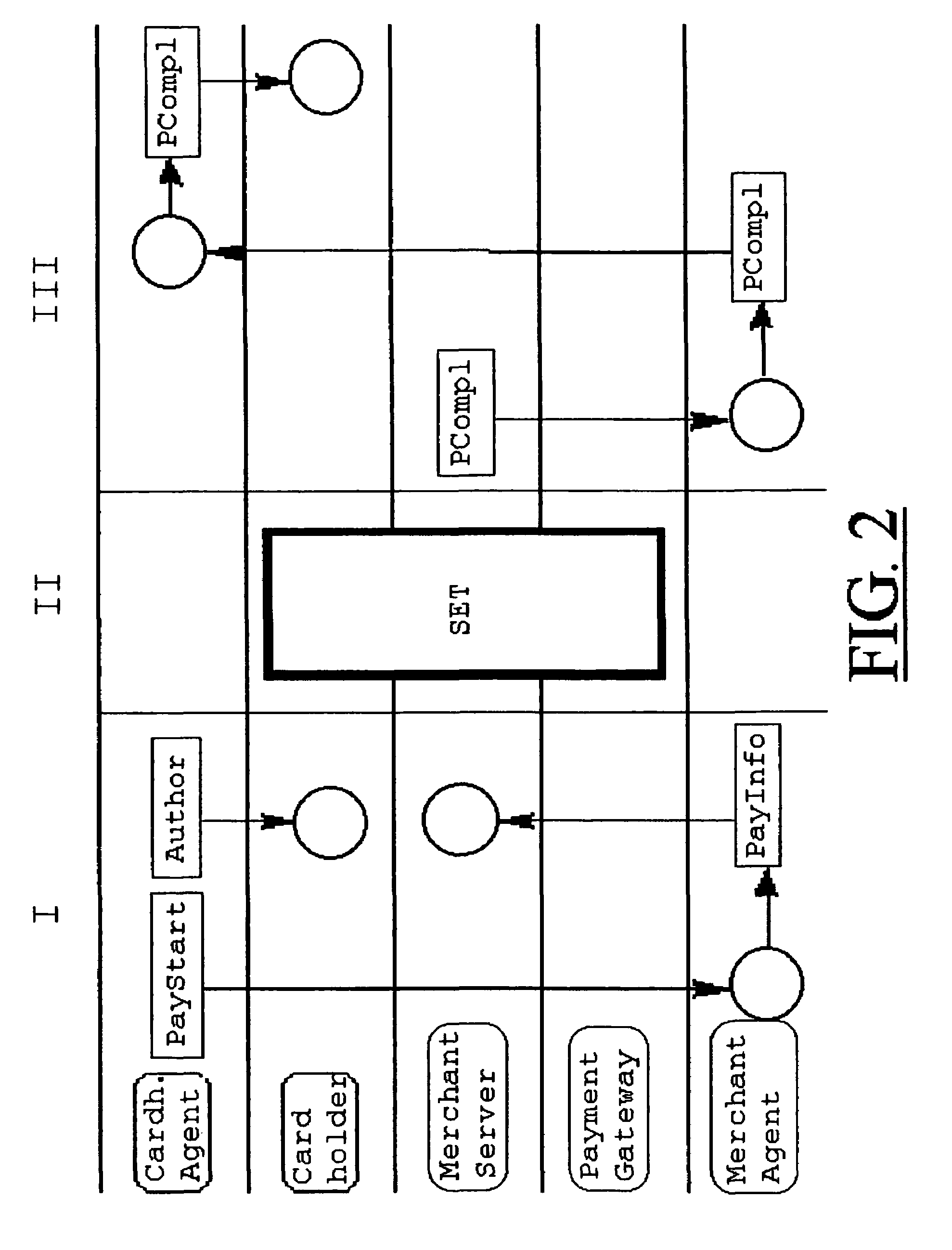
Secure Electronic Transaction (SET) is a communications protocol standard for securing credit card transactions over networks, specifically, the Internet. SET was not itself a payment system, but rather a set of security protocols and formats that enabled users to employ the existing credit card payment infrastructure on an open network in a secure fashion. However, it failed to gain attraction in the market. VISA now promotes the 3-D Secure scheme. Secure Electronic Transaction (SET) is a system for ensuring the security of financial transactions on the Internet. It was supported initially by Mastercard, Visa, Microsoft, Netscape, and others. With SET, a user is given an electronic wallet (digital certificate) and a transaction is conducted and verified using a combination of digital certificates and digital signatures among the purchaser, a merchant, and the purchaser's bank in a way that ensures privacy and confidentiality...
System and method for secure network purchasing
InactiveUS20020073046A1Improve securityCharacter and pattern recognitionDigital data authenticationSecure Electronic TransactionInternet privacy
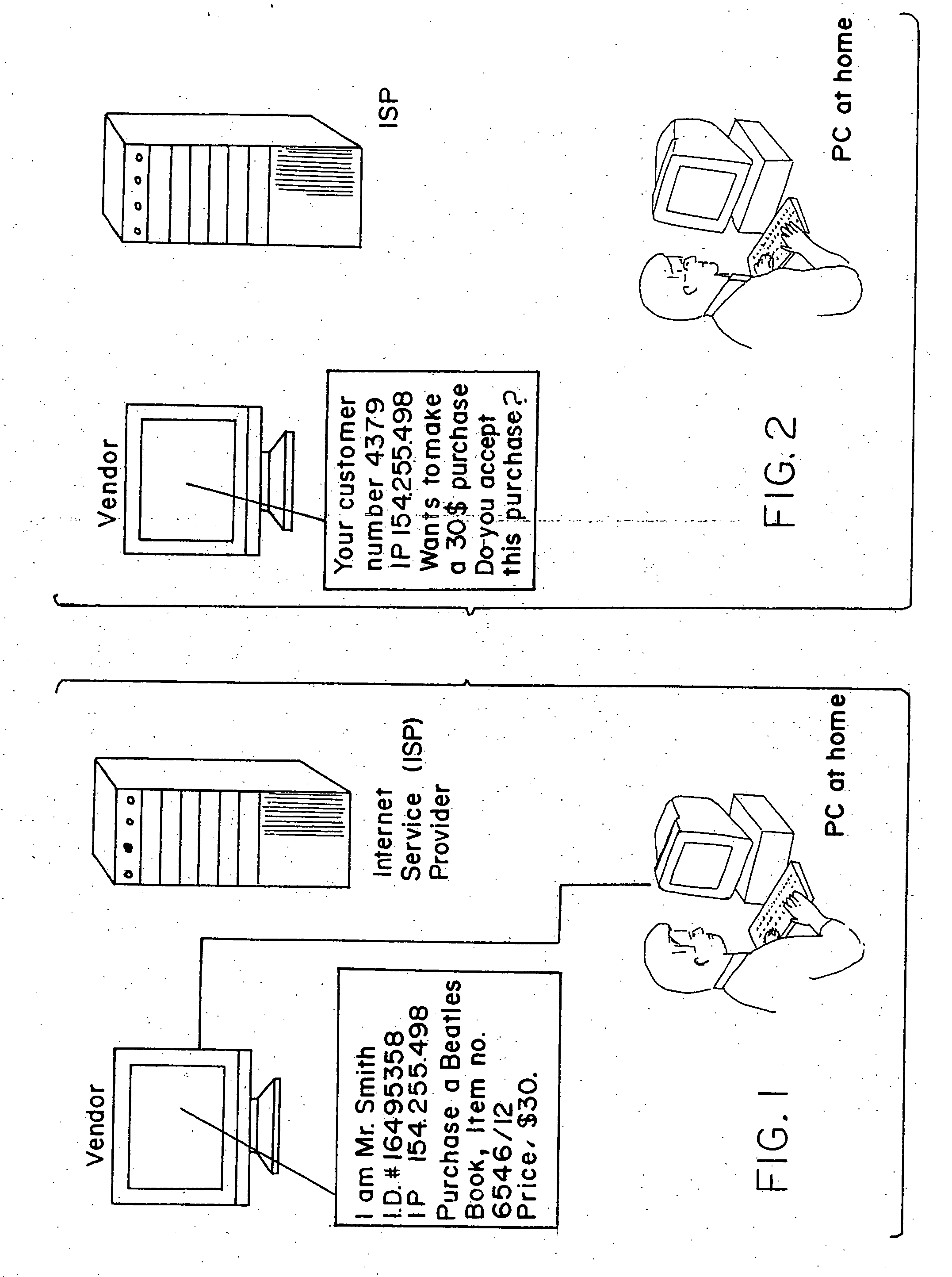
A system for permitting a secure electronic transaction on a network is disclosed. The network has a user device having a fingerprint, a provider's server and a means for providing verification of user's identity. In response to a request by the provider's server the means for providing verification positively identifies the fingerprint of the user device. It thereupon requests a confirmation from the user device of the transaction and upon receiving the confirmation completes the transaction.
Owner:CHANNEL IP BV
Cryptographic system and method for electronic transactions
InactiveUS7096494B1Key distribution for secure communicationFinanceCredit cardSecure Electronic Transaction
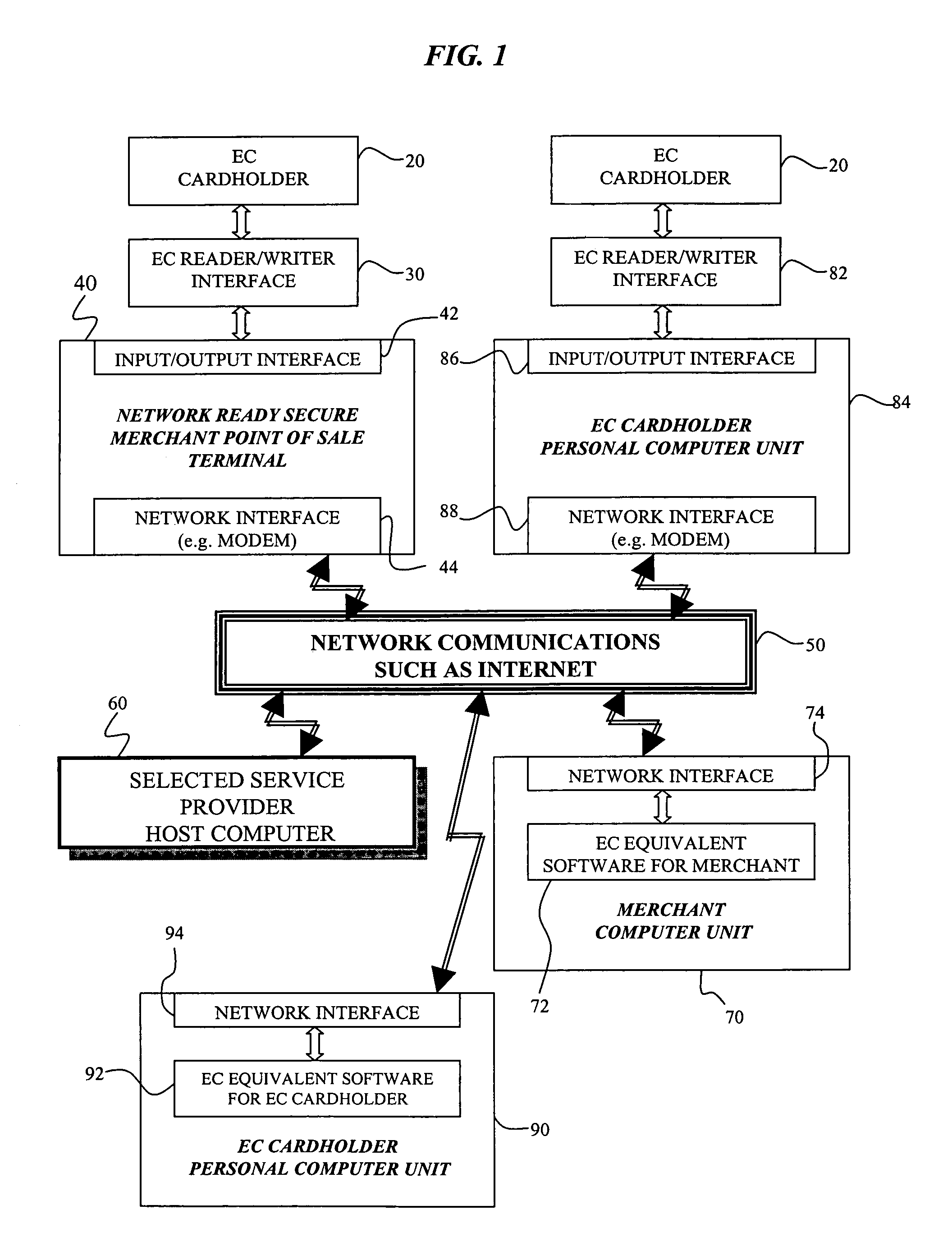
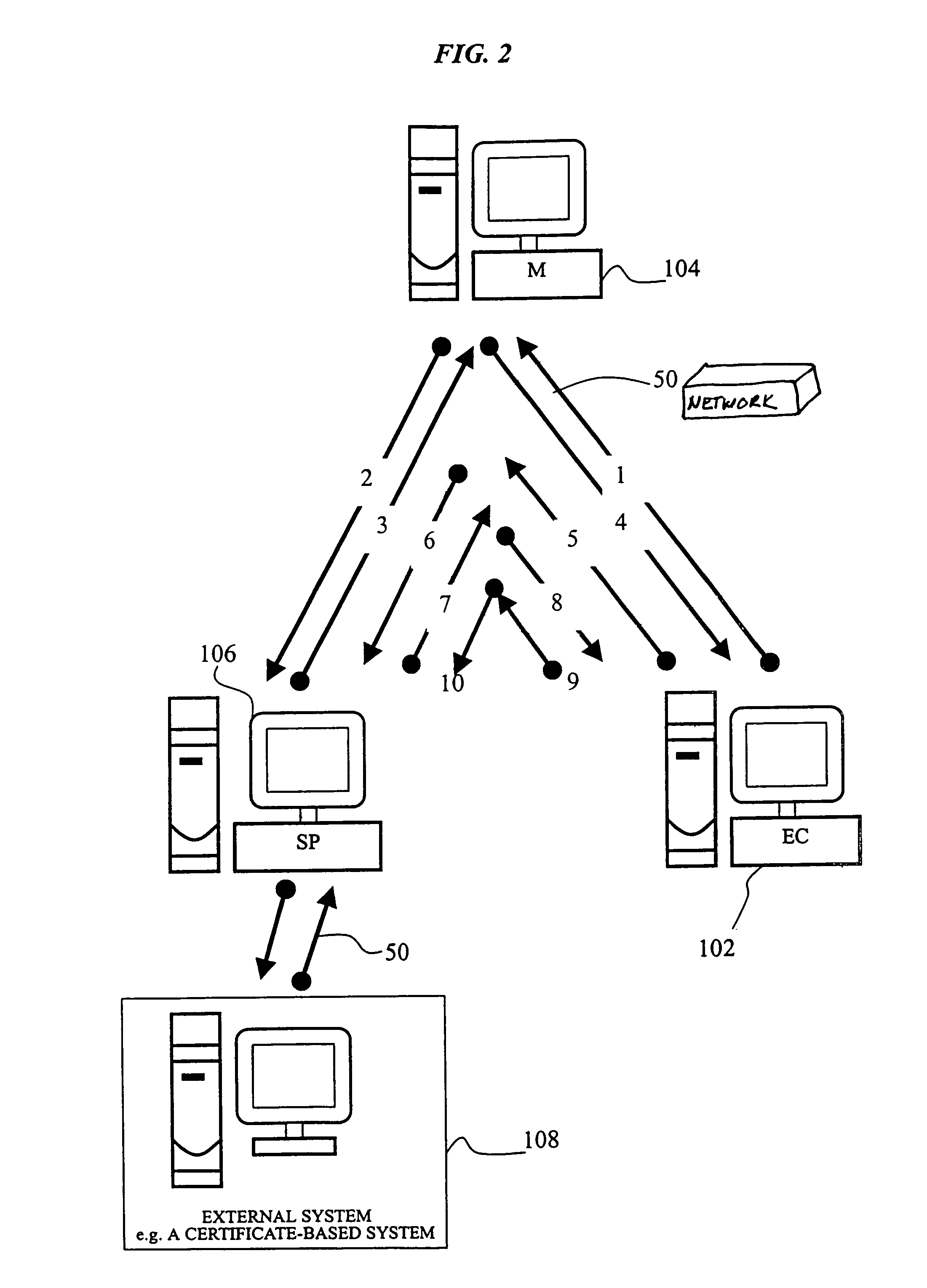
An electronic transaction system, which facilitates secure electronic transactions among multiple parties including cardholders, merchants, and service providers (SP). The system involves electronic cards, commonly known as smart cards, and their equivalent computer software package. The card mimics a real wallet and contains commonly seen financial or non-financial instruments such as a credit card, checkbook, or driver license. A transaction is protected by a hybrid key cryptographic system and is normally carried out on a public network such as the Internet. Digital signatures and challenges-responses are used to ensure integrity and authenticity. The card utilizes secret keys such as session keys assigned by service providers (SPs) to ensure privacy for each transaction. The SP is solely responsible for validating each participant's sensitive information and assigning session keys. The system does not seek to establish a trust relationship between two participants of a transaction. The only trust relationship needed in a transaction is the one that exists between individual participants and the SP. The trust relationship with a participant is established when the SP has received and validated certain established account information from that particular participant. To start a transaction with a selected SP, a participant must have the public key of the intended SP. Since the public key is openly available, its availability can be easily established by the cardholder. The SP also acts as a gateway for the participants when a transaction involves interaction with external systems.
Owner:CINGULAR WIRELESS II LLC
System and method for secure network purchasing
InactiveUS7366702B2Improve securityCharacter and pattern recognitionDigital data authenticationUser deviceSecure Electronic Transaction
A system for permitting a secure electronic transaction on a network is disclosed. The network has a user device having a fingerprint, a provider's server and a means for providing verification of user's identity. In response to a request by the provider's server the means for providing verification positively identifies the fingerprint of the user device. It thereupon requests a confirmation from the user device of the transaction and upon receiving the confirmation completes the transaction.
Owner:CHANNEL IP BV
System and method for secure network purchasing
InactiveUS20040117321A1Risk minimizationConfidenceDigital data authenticationBuying/selling/leasing transactionsSecure Electronic TransactionMethod selection
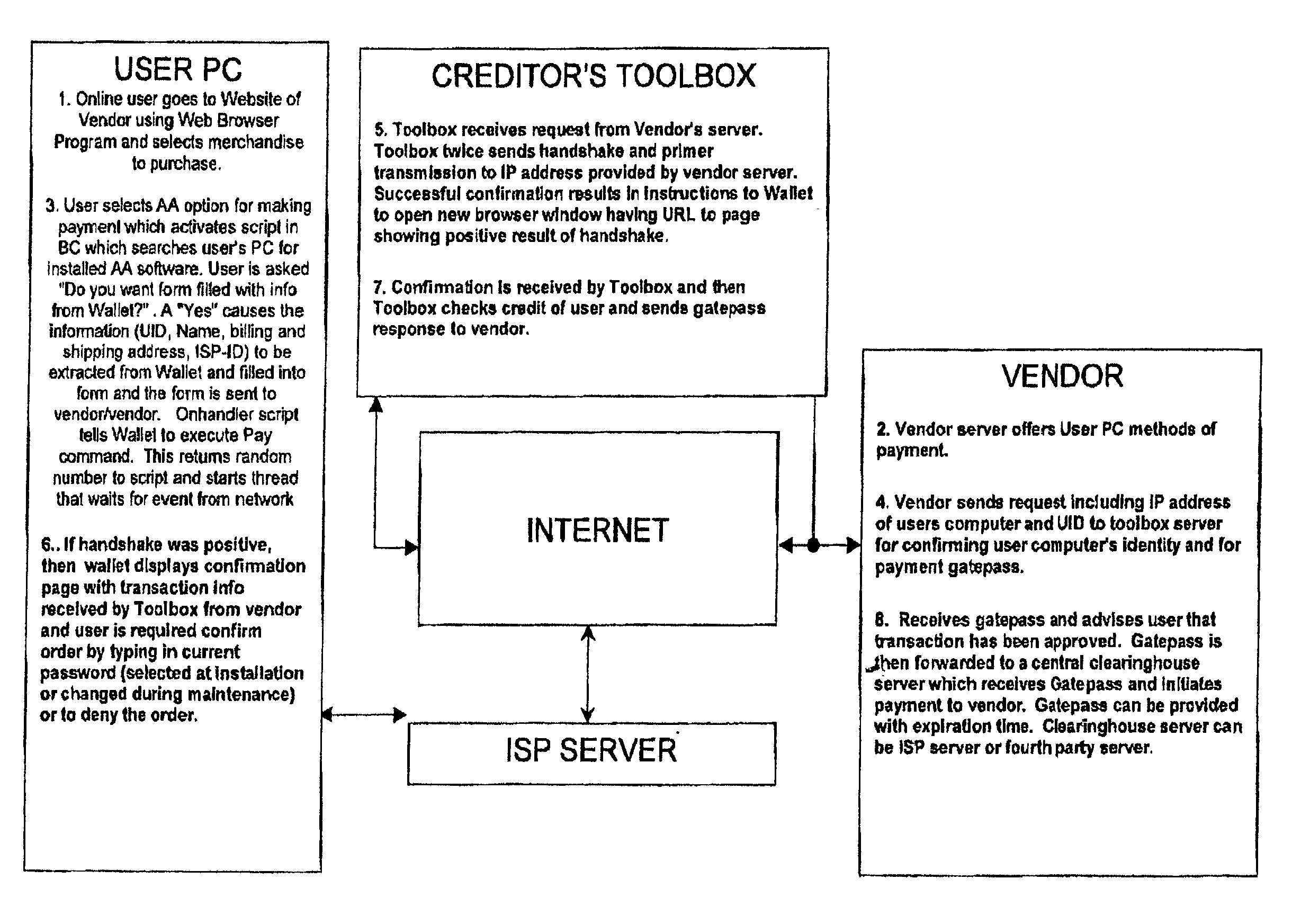
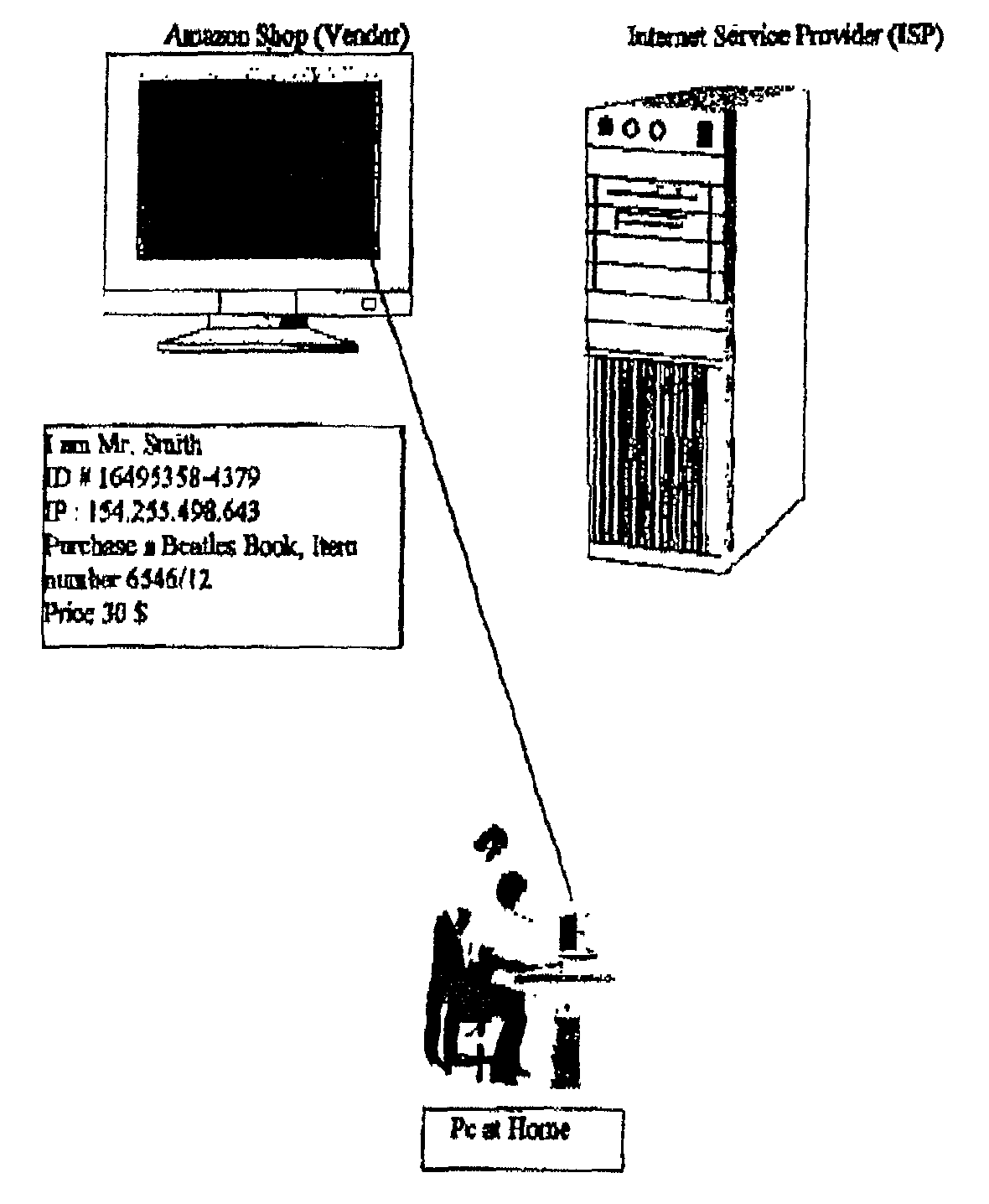
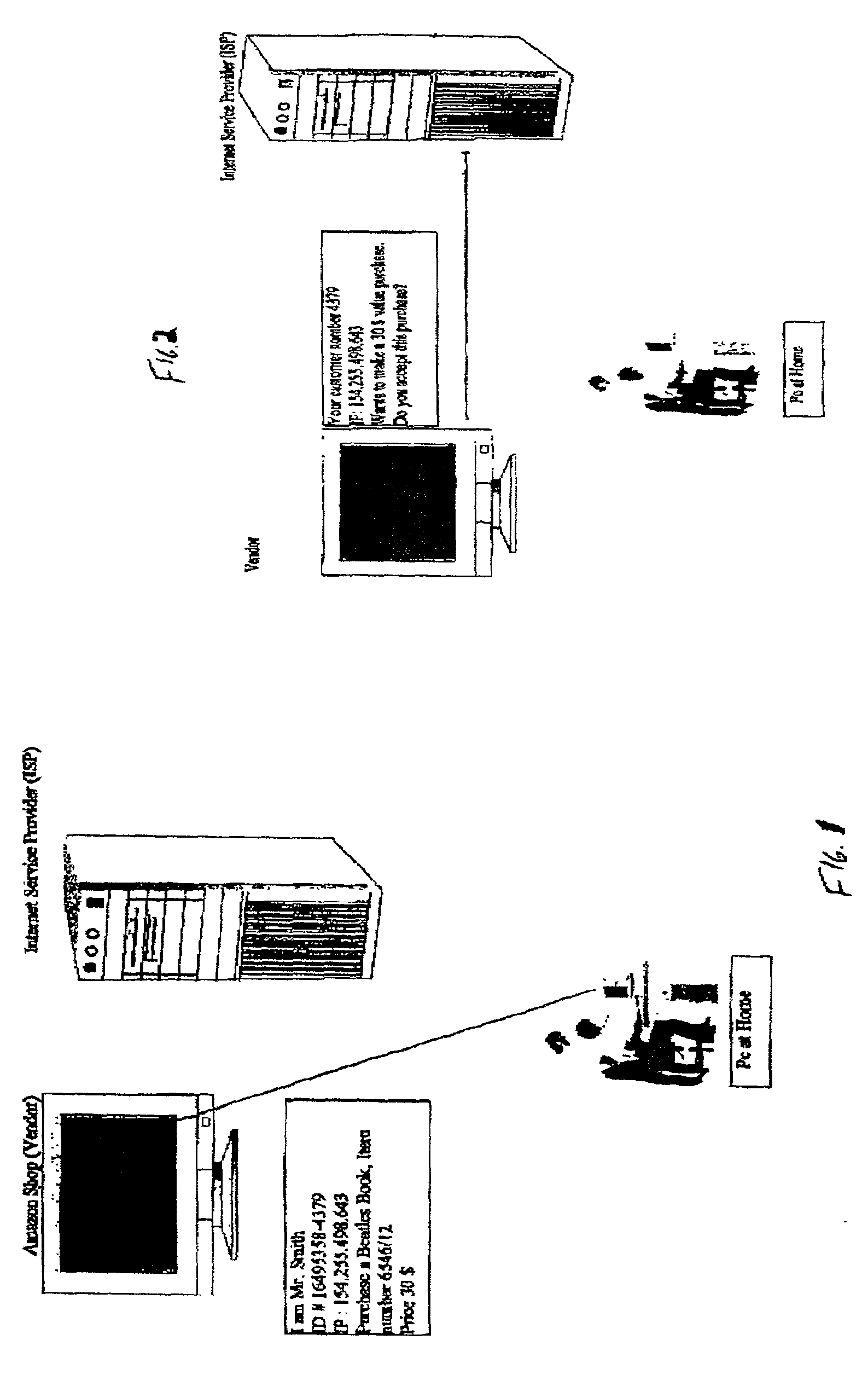
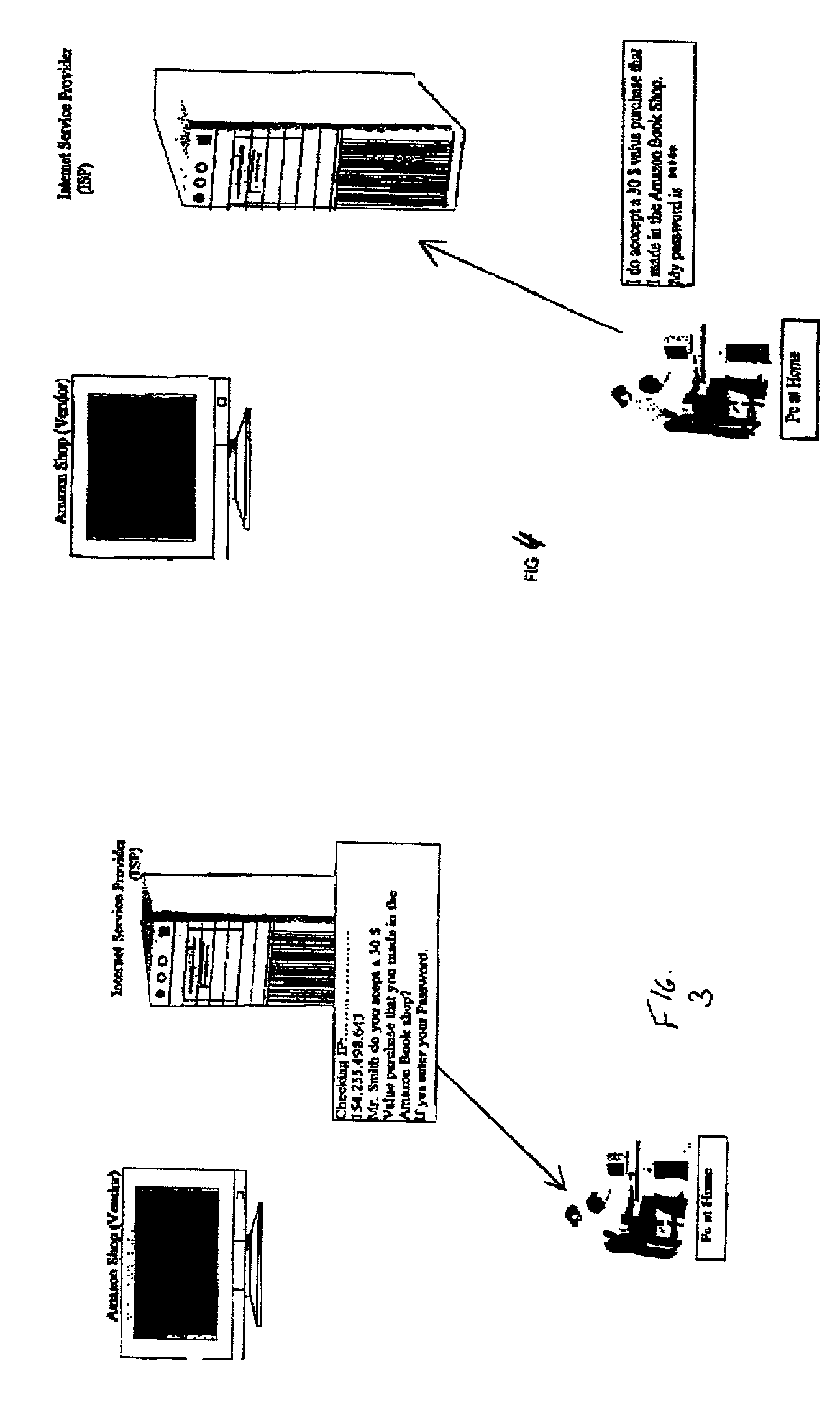
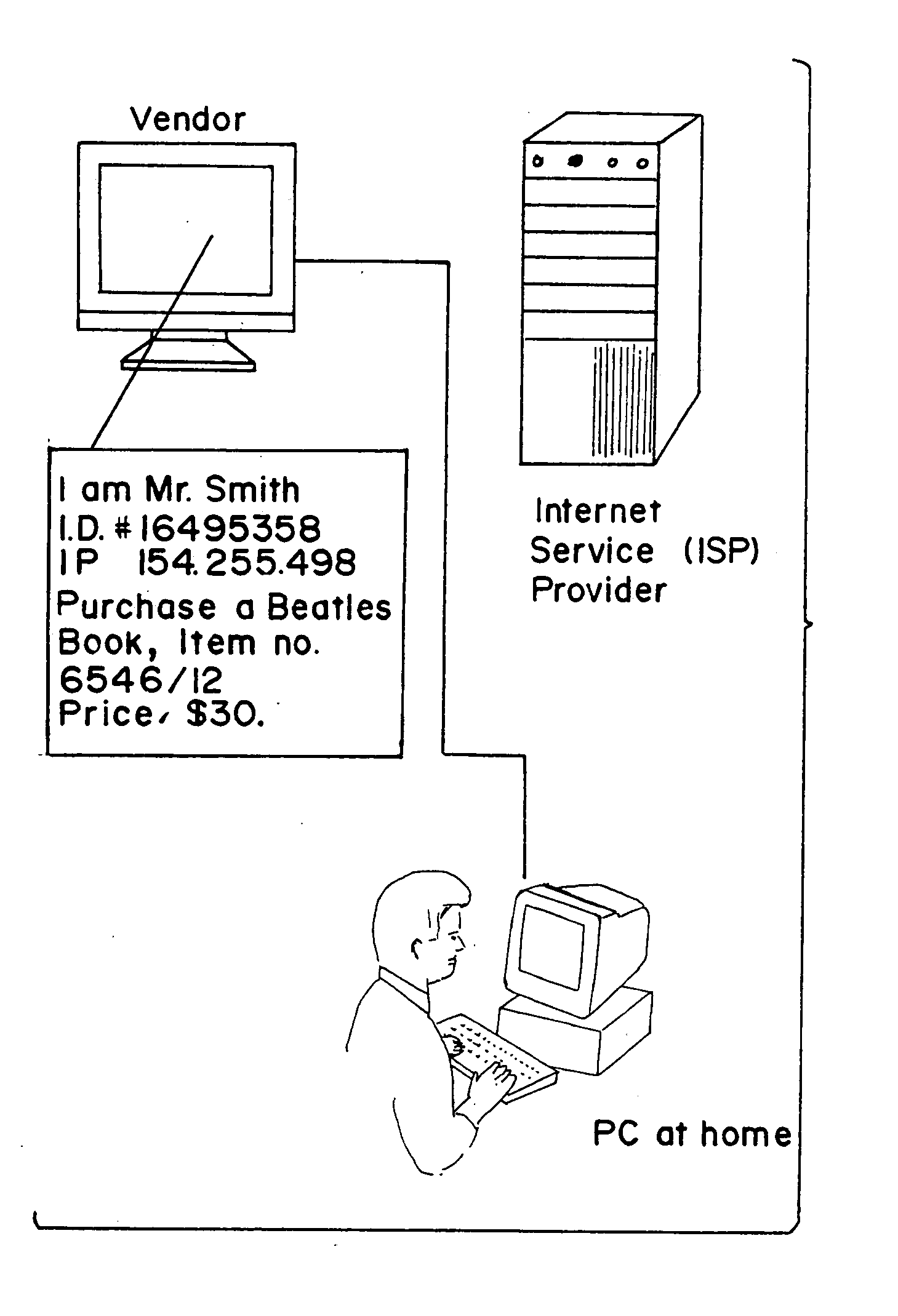
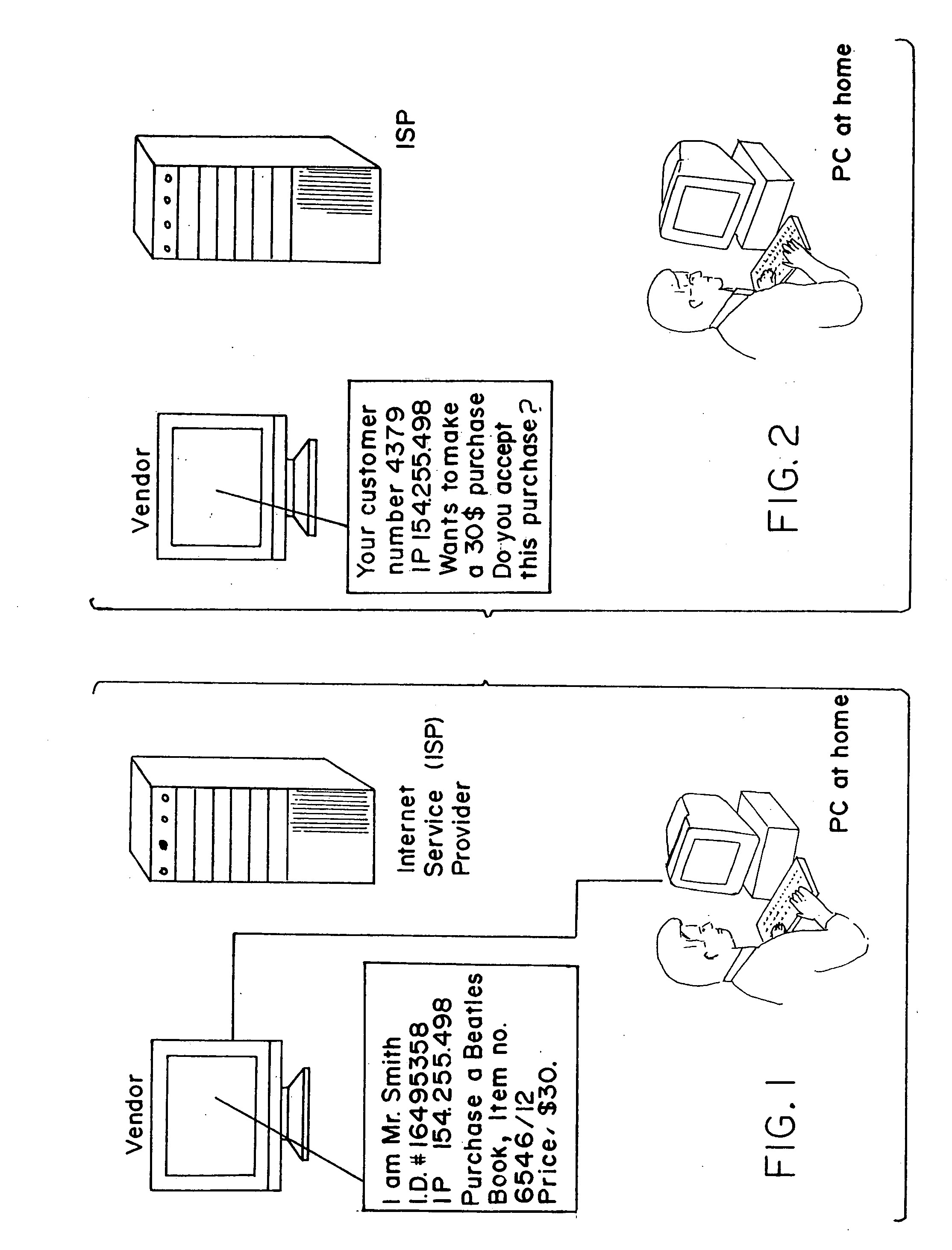
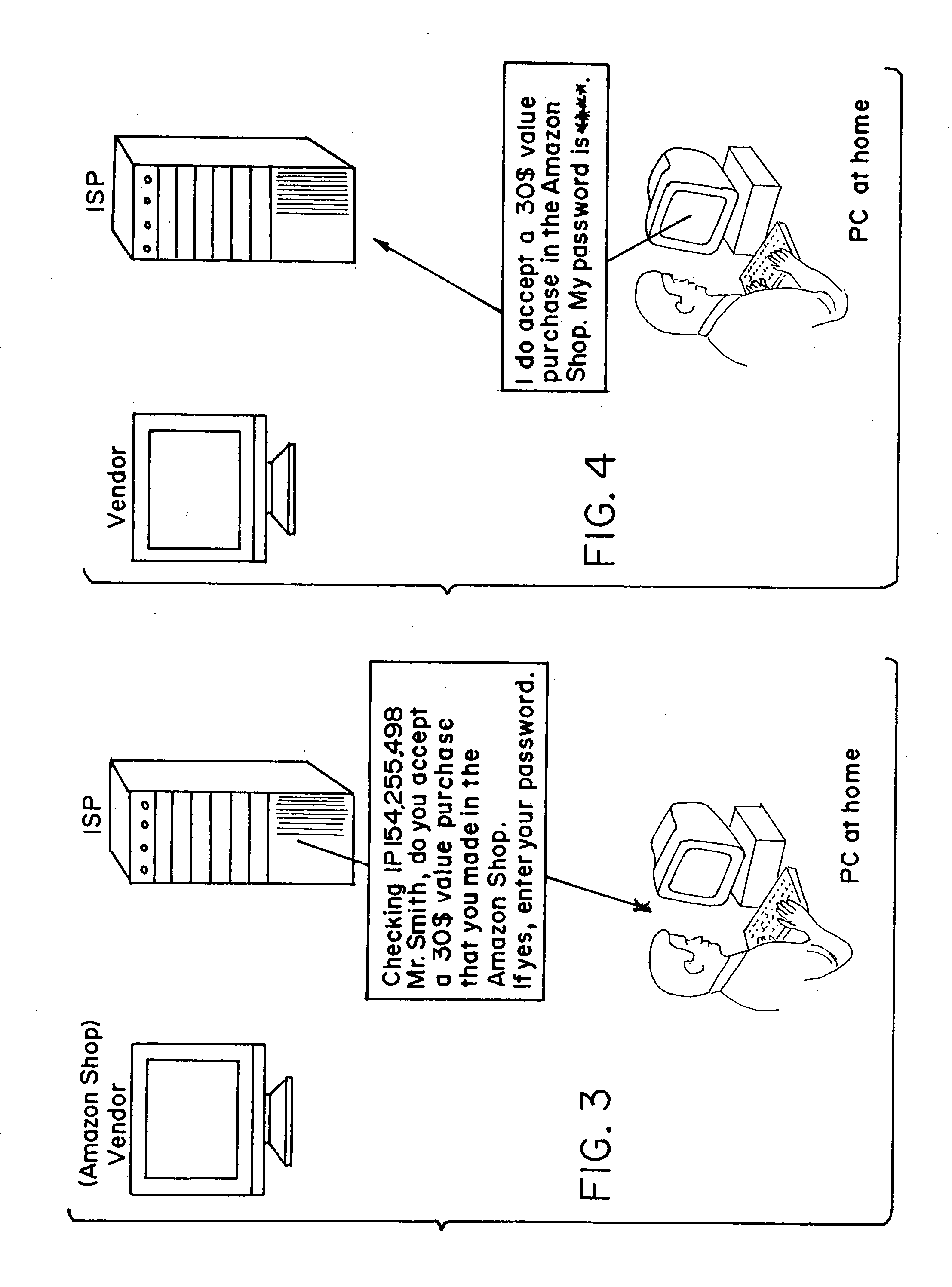
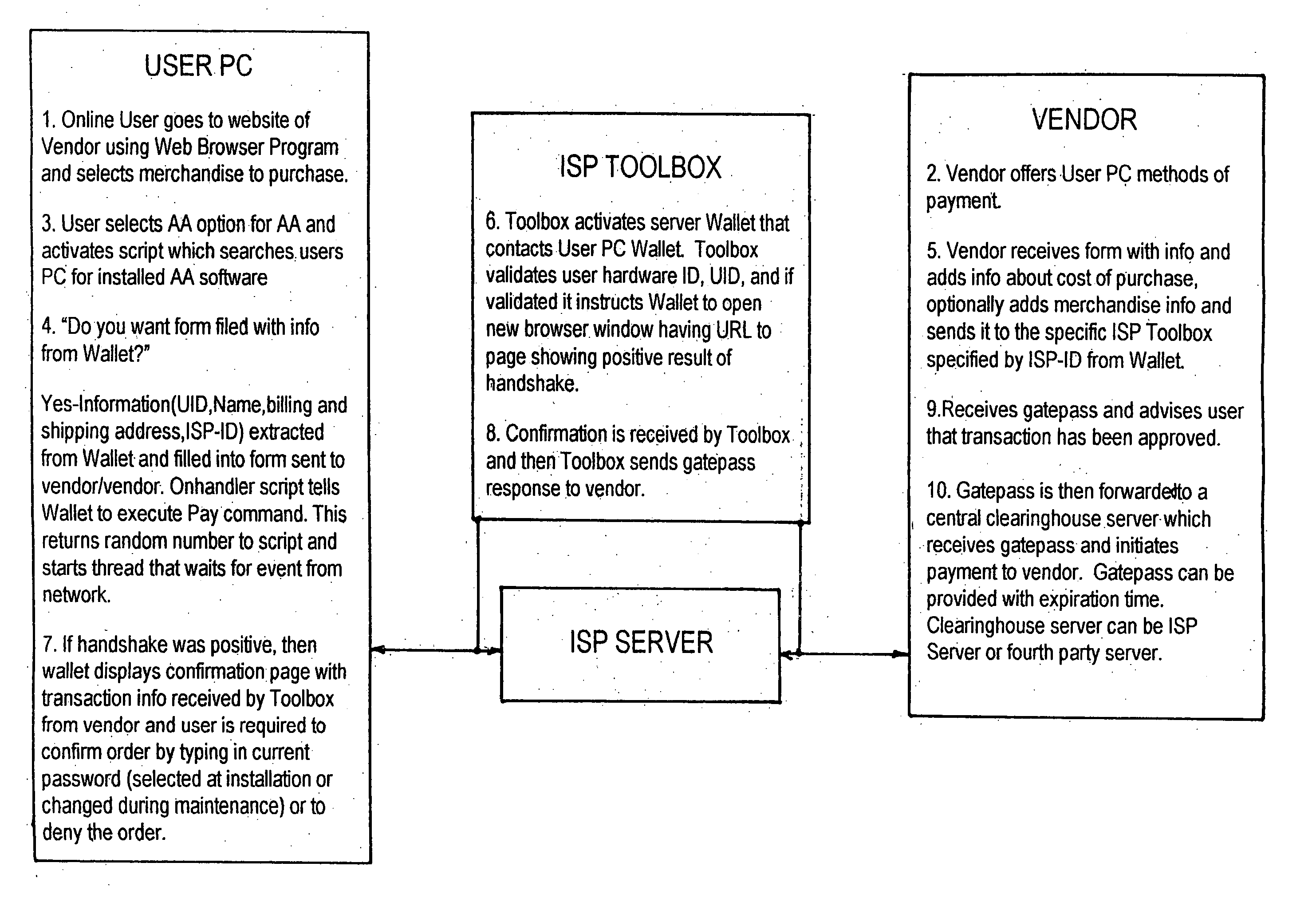
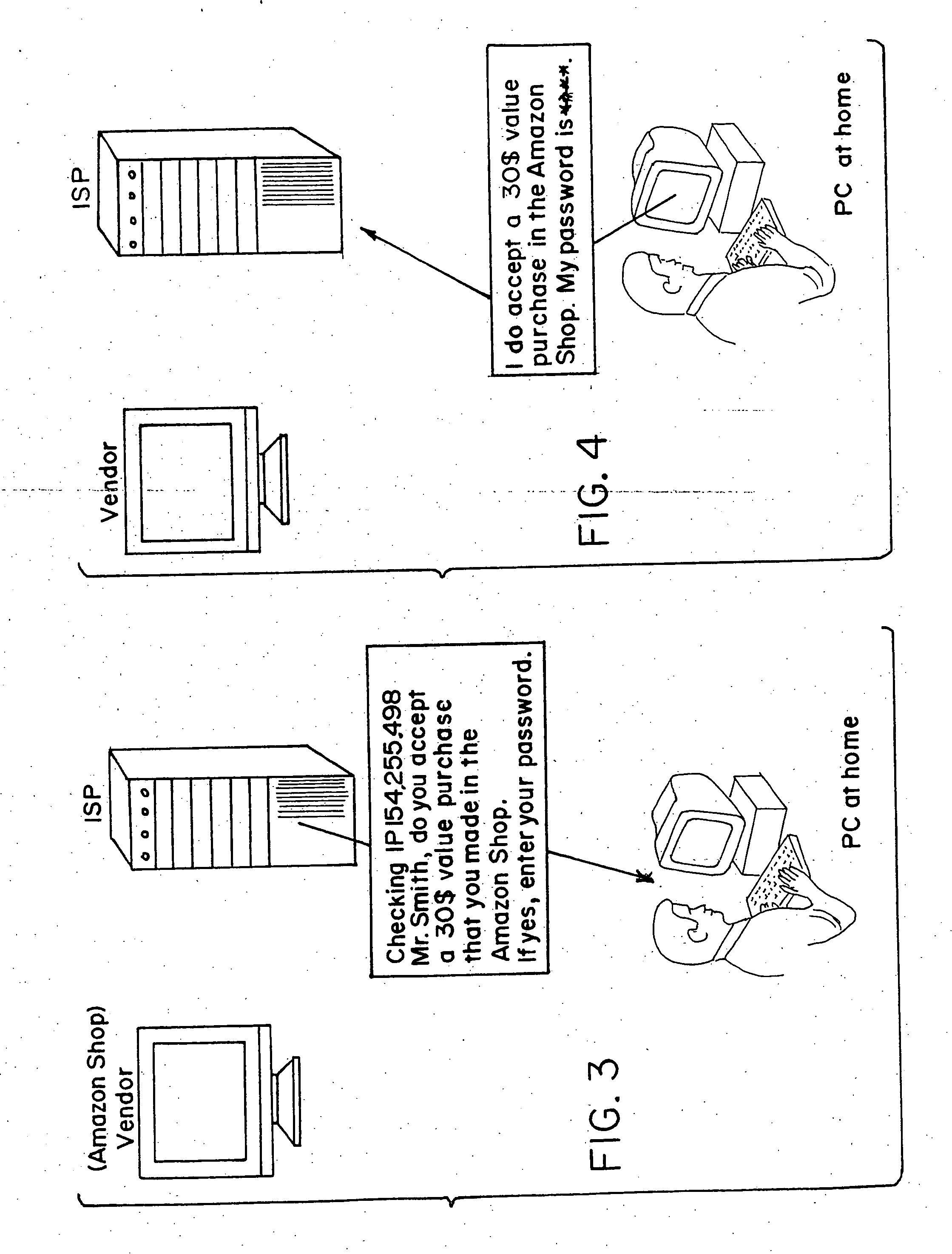
There is disclosed a method for performing secure electronic transactions on a computer network, the network comprising a buyer's computer, a vendor server, a creditor server and a security server. The buyer's computer has a fingerprint file stored in the memory thereof. The method includes the steps of: i) the buyer computer requesting to purchase merchandise to the vendor server, the purchase request including said buyer computer's IP address; ii) the buyer computer selecting a predetermined form of secured payment method; iii) the payment method selection causing the vendor server to transmit to the security server a request for confirmation of the buyer computer's identity at the buyer computer's IP address; iv) the confirmation request causing the security server to send a retrieval request to the IP address, the retrieval request including a retrieval program for detecting and retrieving the buyer's computer's fingerprint file, and the retrieval request further comprising a response request asking for confirmation of the purchase request; whereby a positive response from the buyer's computer to the security server accompanied by the fingerprint file causes the security server to confirm the buyer computer's identity to the vendor server and to approve the purchase.
Owner:IPASS
System and method for secure network purchasing
PendingUS20050108177A1Minimizing substantially exposure to riskConfidenceDigital data authenticationBuying/selling/leasing transactionsIp addressMethod selection
There is disclosed a method for performing secure electronic transactions on a computer network, the network comprising a buyer's computer, a vendor server, a creditor server and a security server. The buyer's computer has a fingerprint file stored in the memory thereof. The method includes the steps of: i) the buyer computer requesting to purchase merchandise to the vendor server, the purchase request including said buyer computer's IP address; ii) the buyer computer selecting a predetermined form of secured payment method; iii) the payment method selection causing the vendor server to transmit to the security server a request for confirmation of the buyer computer's identity at the buyer computer's IP address; iv) the confirmation request causing the security server to send a retrieval request to the IP address, the retrieval request including a retrieval program for detecting and retrieving the buyer's computer's fingerprint file, and the retrieval request further comprising a response request asking for confirmation of the purchase request; whereby a positive response from the buyer's computer to the security server accompanied by the fingerprint file causes the security server to confirm the buyer computer's identity to the vendor server and to approve the purchase.
Owner:IPASS
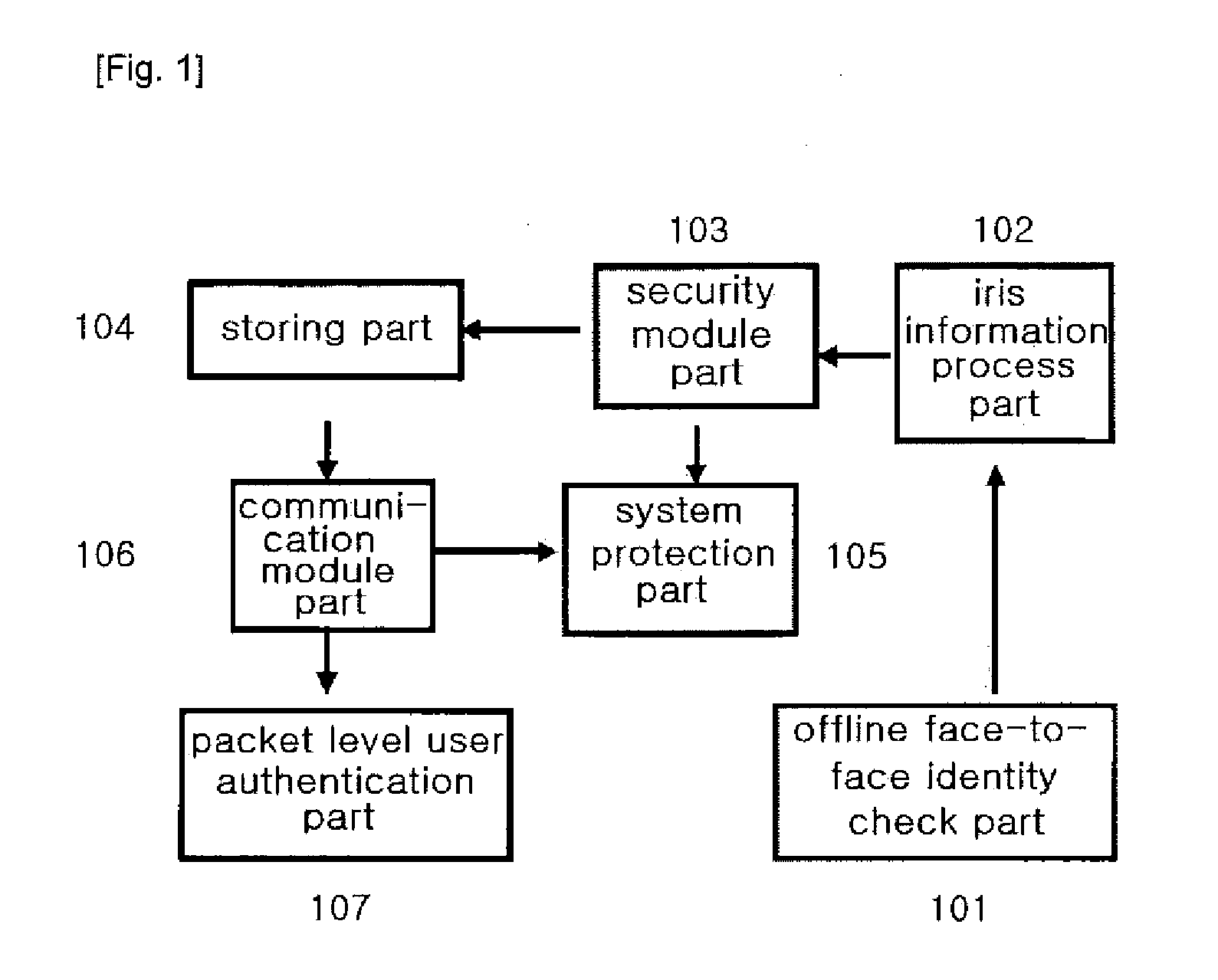
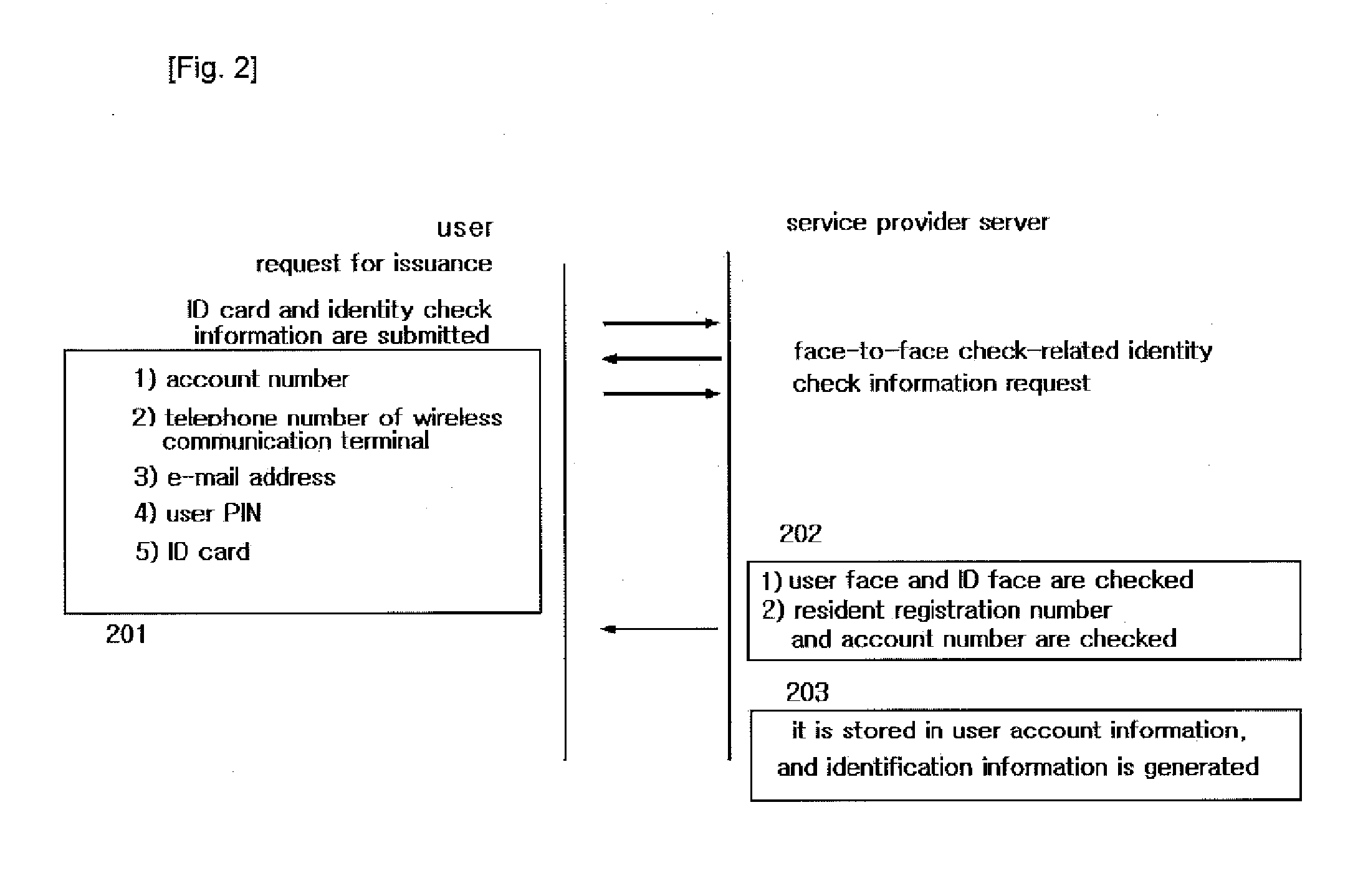
Three-factor user authentication method for generating otp using iris information and secure mutual authentication system using otp authentication module of wireless communication terminal
InactiveUS20130268444A1Simple and safe processMaximize convenienceDigital data processing detailsMultiple digital computer combinationsSecure Electronic TransactionService provision
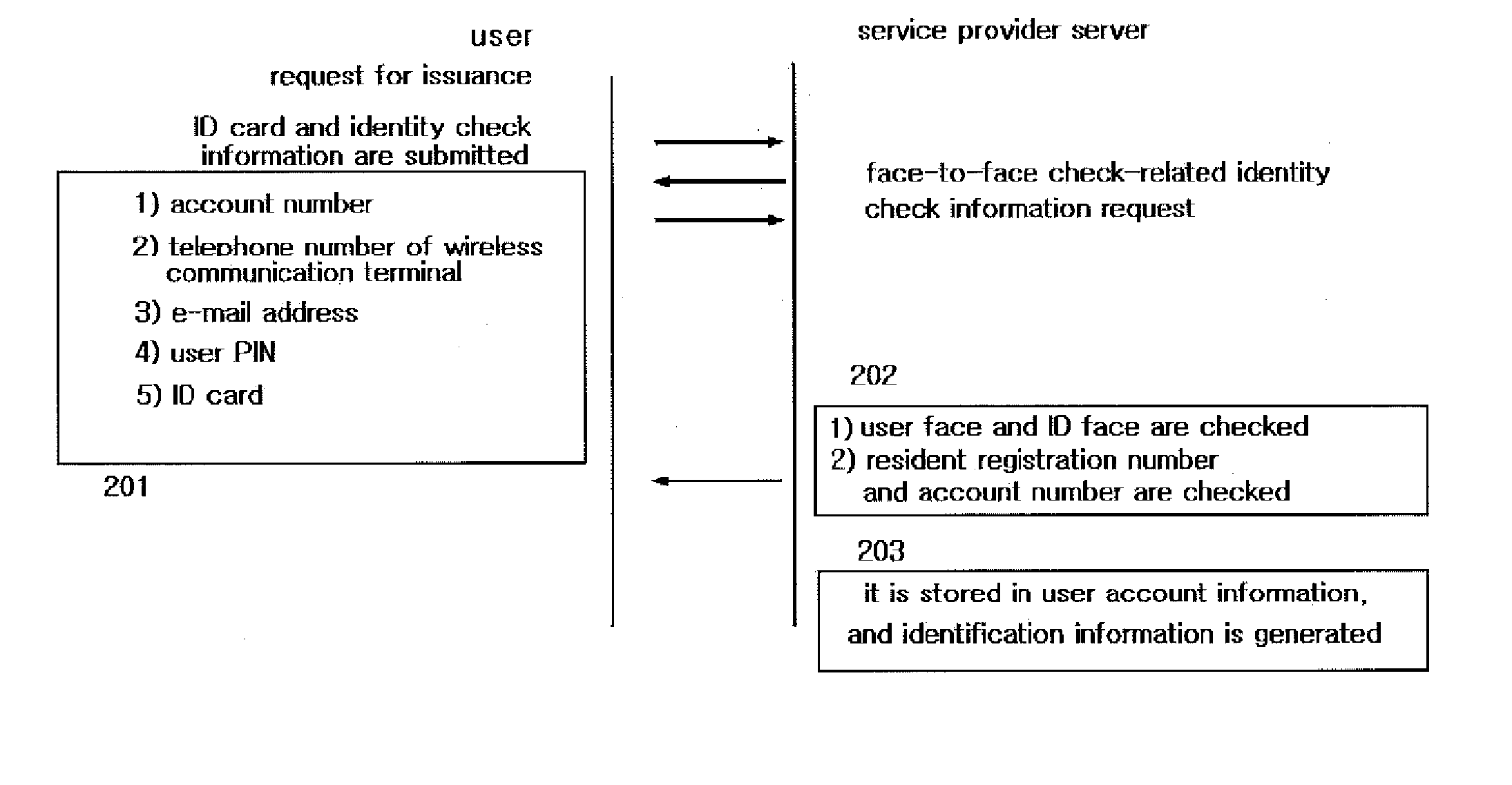
The present invention authenticates a user using iris information in order to generate OTP, generates OTP using a 3-factor authentication method based on HMAC, and performs encryption thereof, and also relates to a security system that secures and controls a wireless communication terminal owned by a user through the following methods: a method for managing the storage of a program memory having a management program and encrypted key values stored therein, by directly inputting the iris information in real-time; a method for authenticating a wireless communication terminal by mutually authenticating two methods having different directions, the methods being an authentication by an OTP integrated authentication server through a service providing server, and an authentication by a public authentication facility through a wireless authentication server; a method for enabling the service usage of packets for communication between a user and a server only through iris authentication in order to prevent a DoS attack during the communication; and a method for protecting the system by protecting the original and patch files of the applications and the drives using iris information and constantly monitoring same, thus enabling secure electronic transaction services.
Owner:NAMGOONG JONG +1
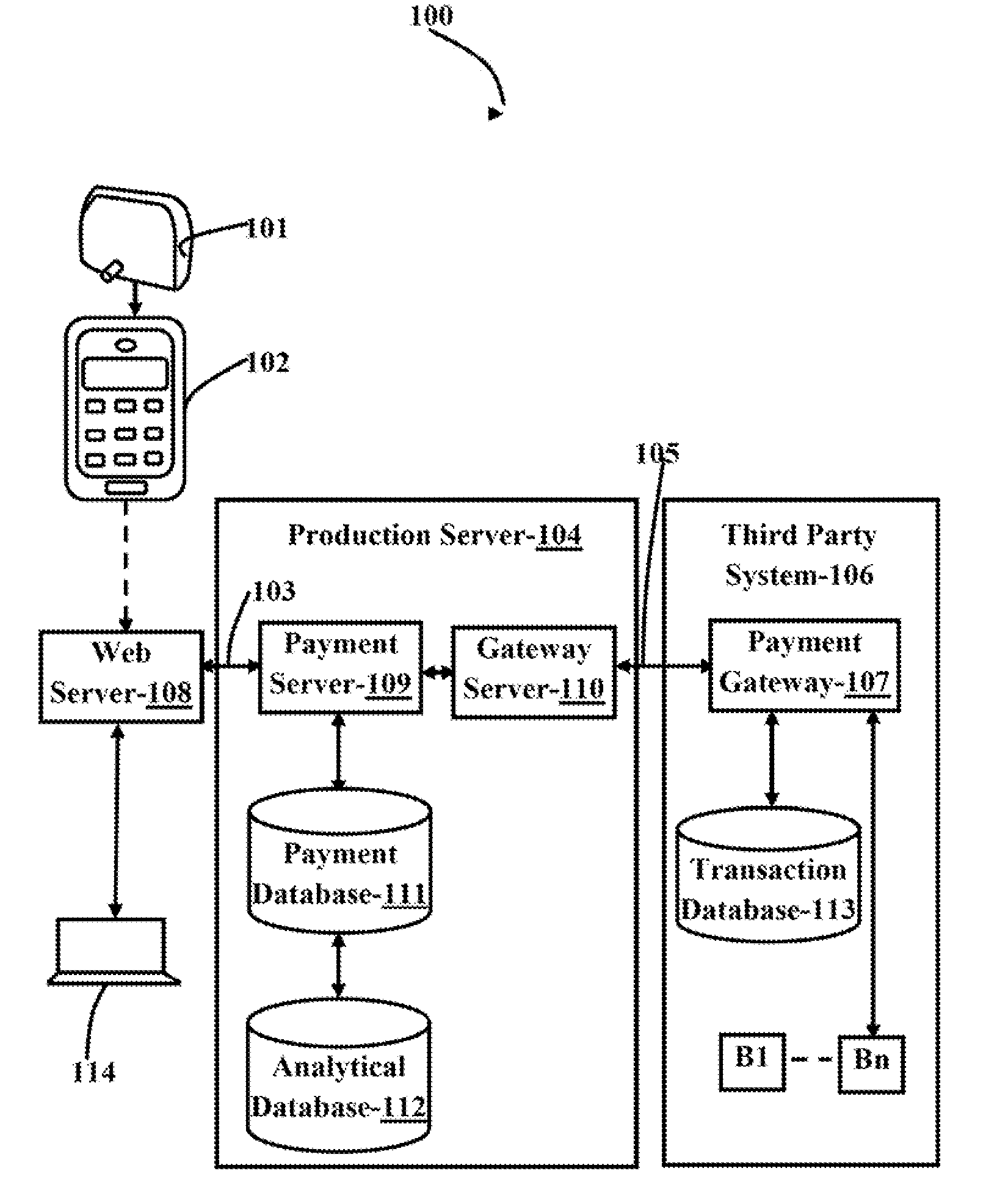
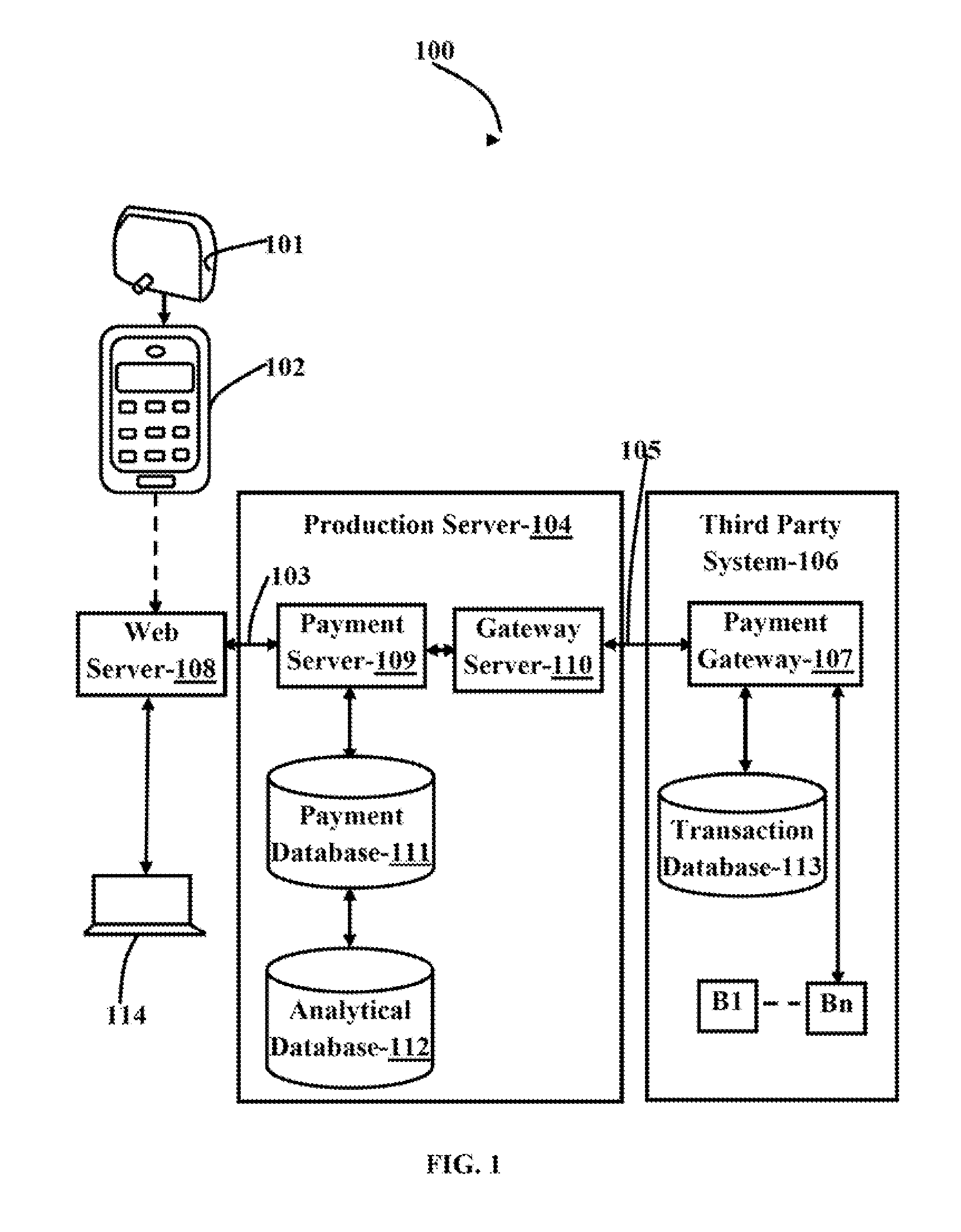
System and method for secure electronic transaction
InactiveUS20140258132A1Increase probabilityAcutation objectsCryptography processingNetwork connectionSecure Electronic Transaction
The various embodiments herein provide a system for a secure electronic transaction. The system comprises a dongle connected to a computing device for reading an electronic card data, a client application running on the client device for collecting a transaction information from a customer, a service provider system connected to the computing device through a first communication network for transmitting the collected transaction information and the audio signal from the computing device to the service provider system, a production server located at the service provider system for processing the received card data, a payment server for processing the audio signal, a second communication network for transmitting a processed card data from the production server to a payment system and a payment gateway running on the payment system for interfacing with the service provider system. The payment system performs the financial transaction by authenticating the customer and a merchant.
Owner:EZETAP MOBILE SOLUTIONS
System for secure transactions
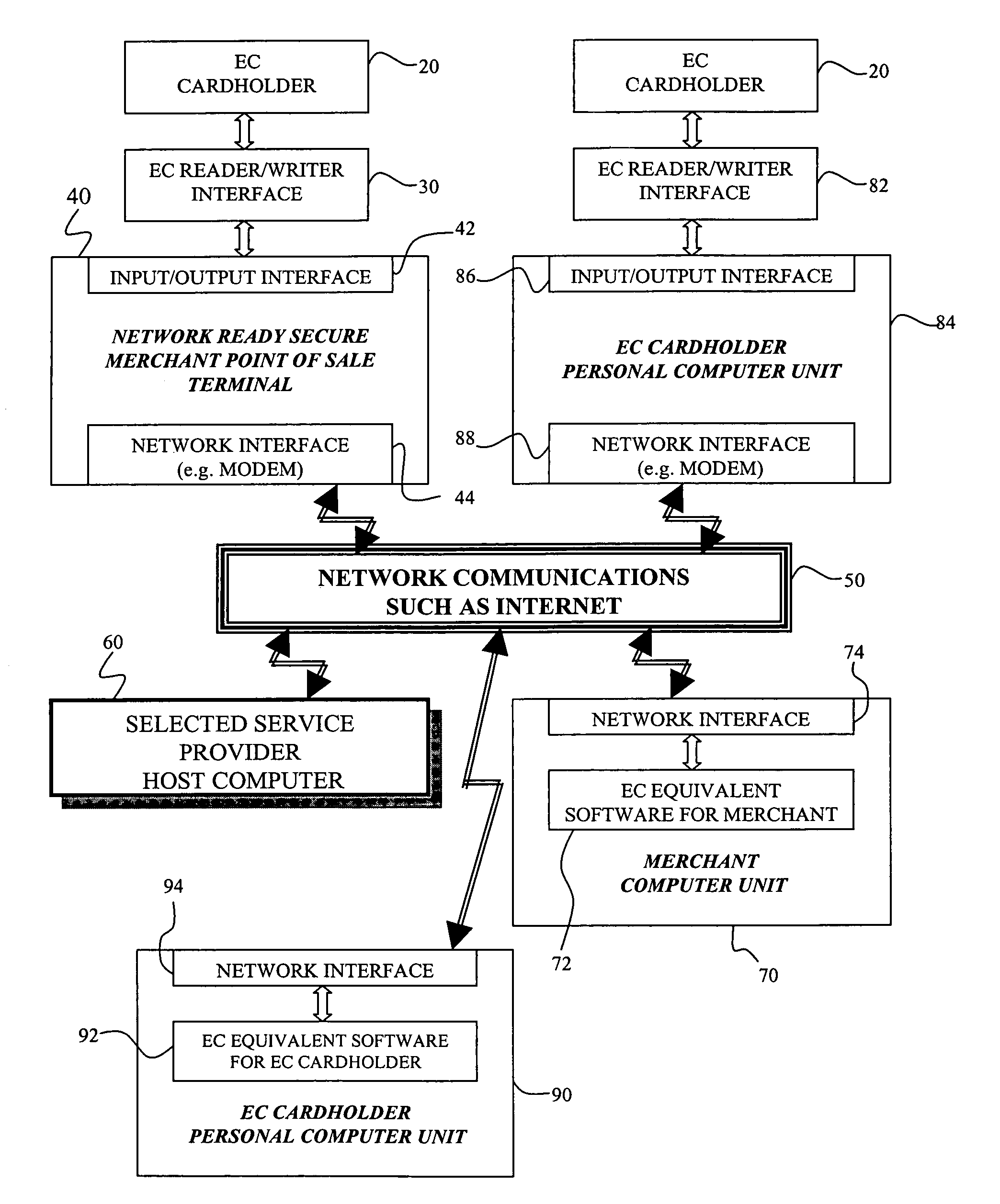
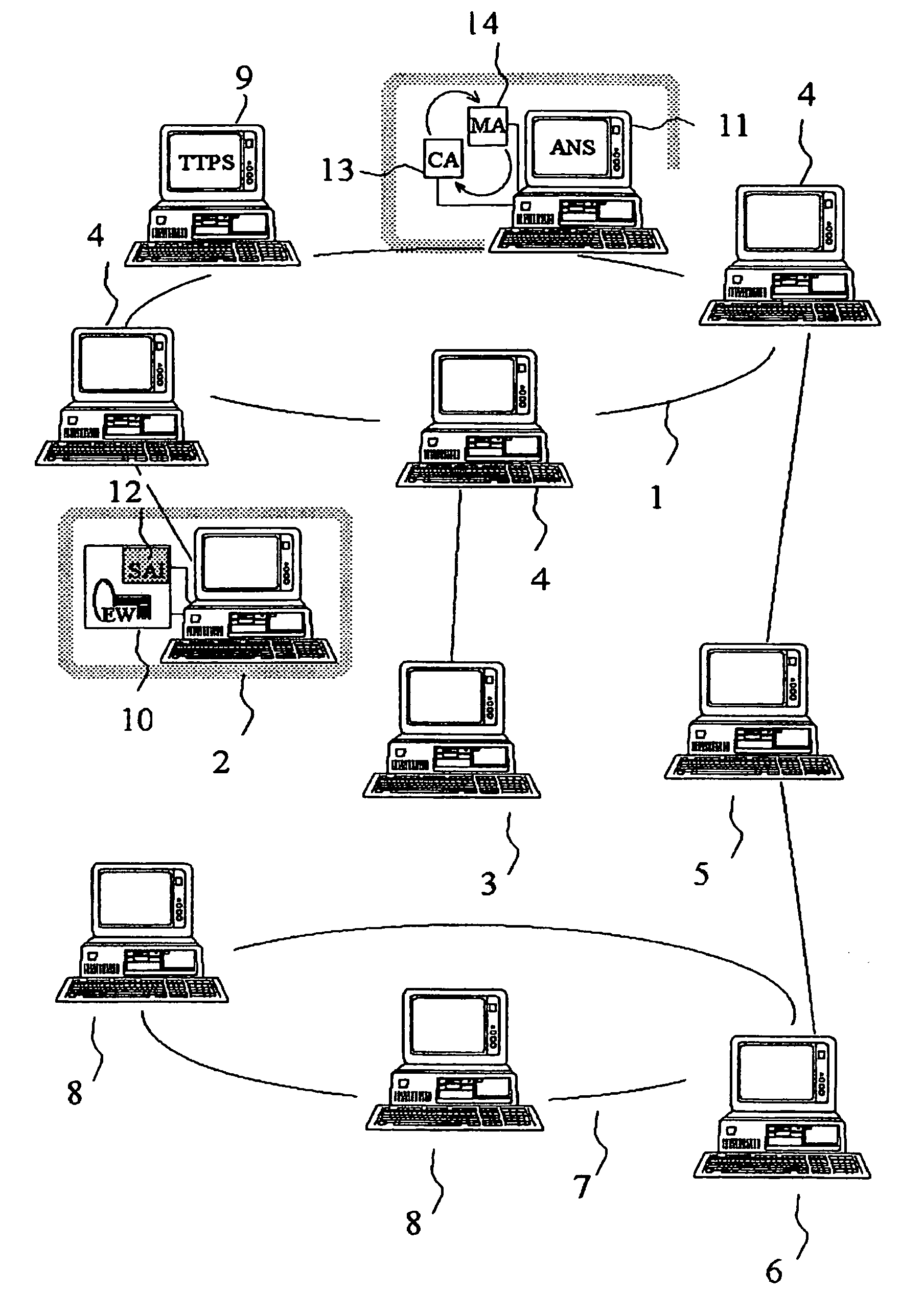
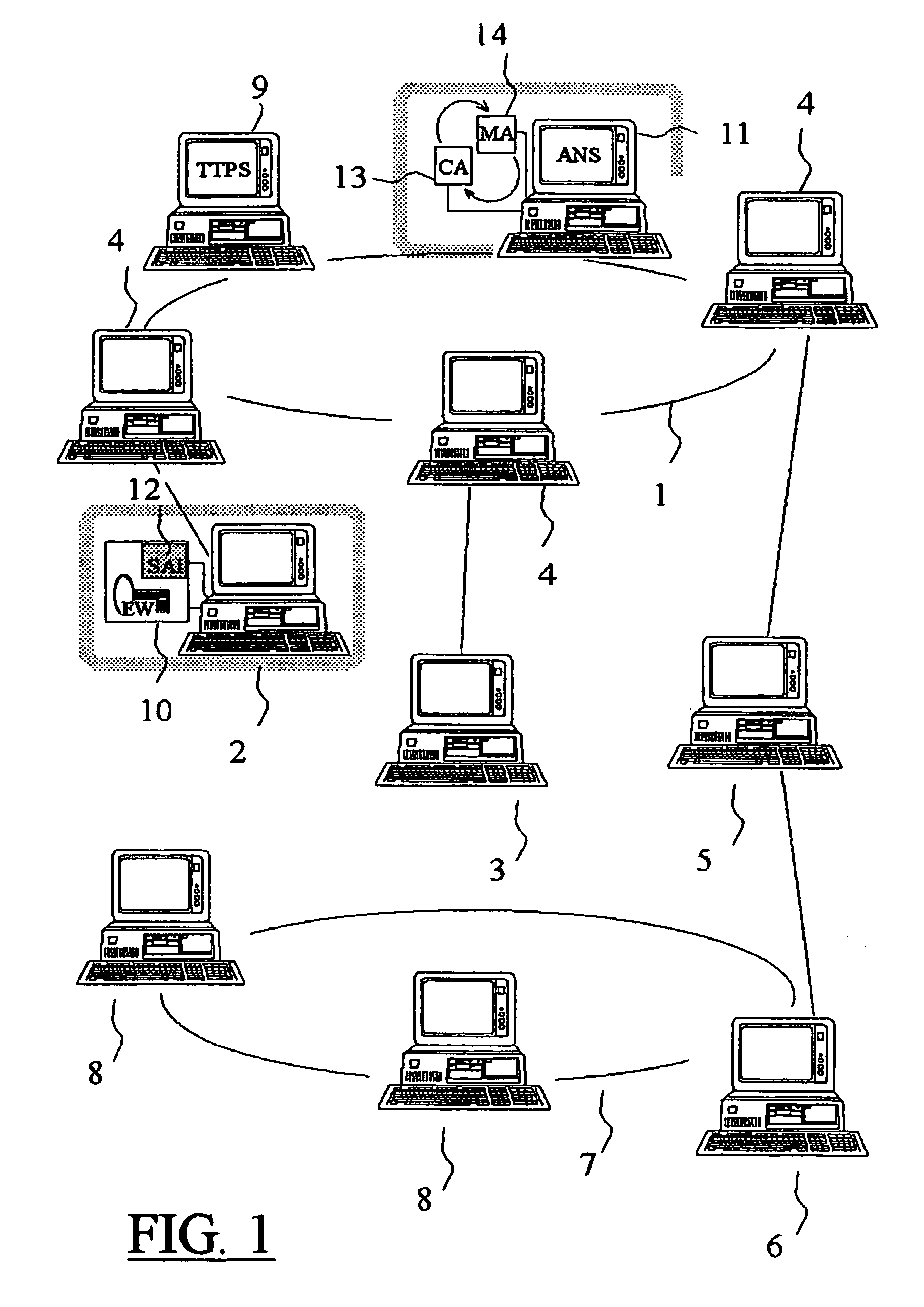
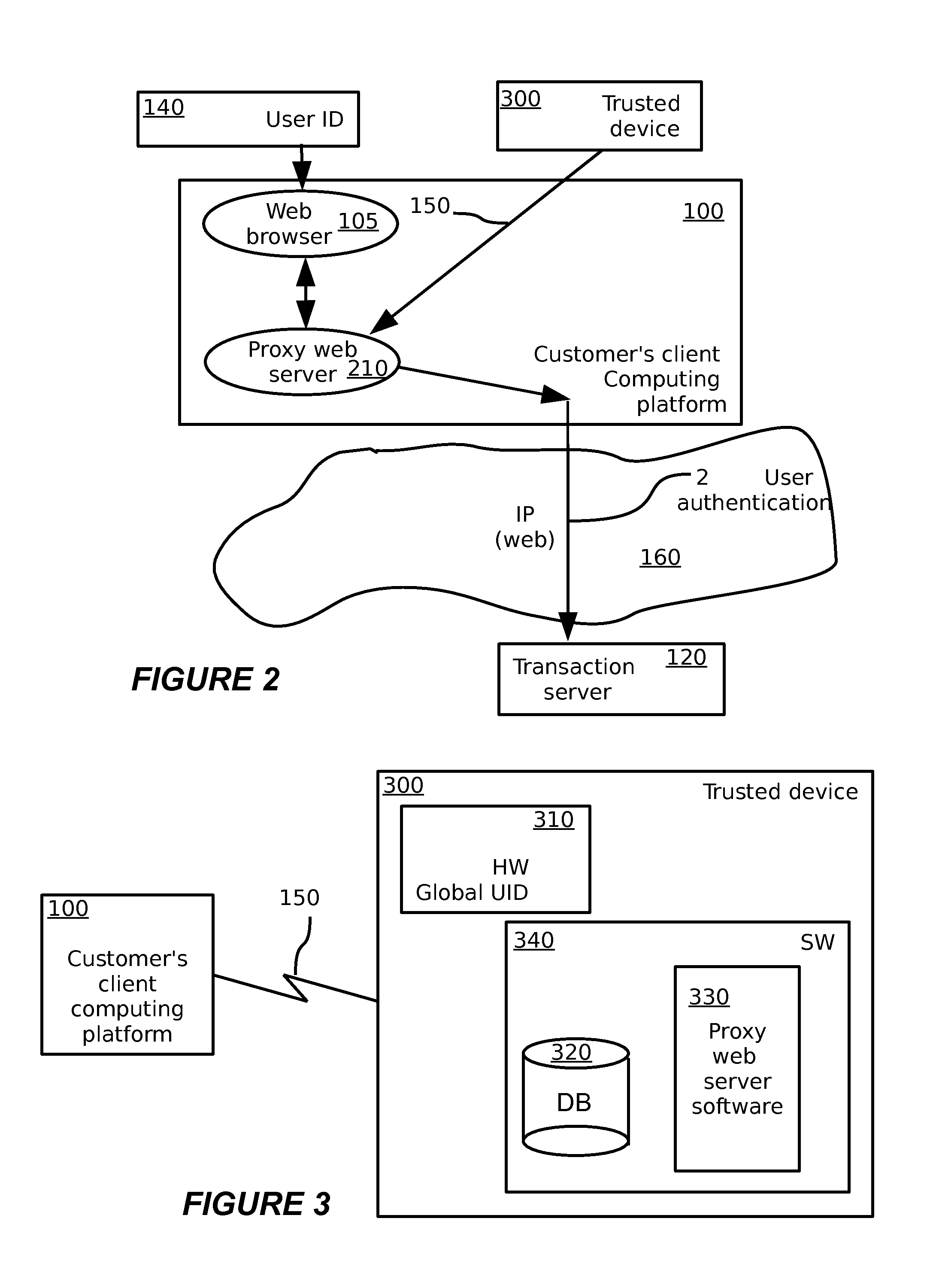
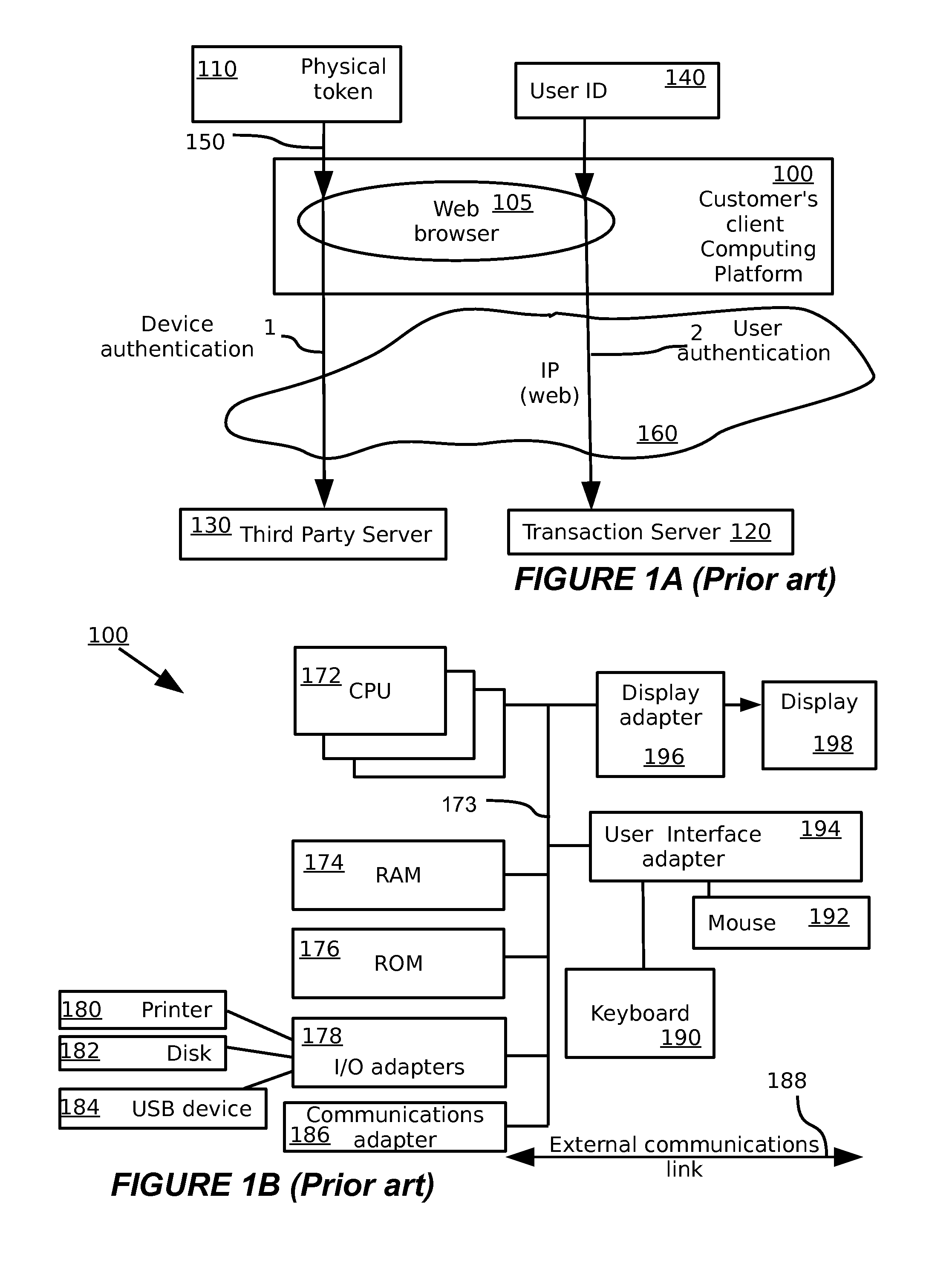
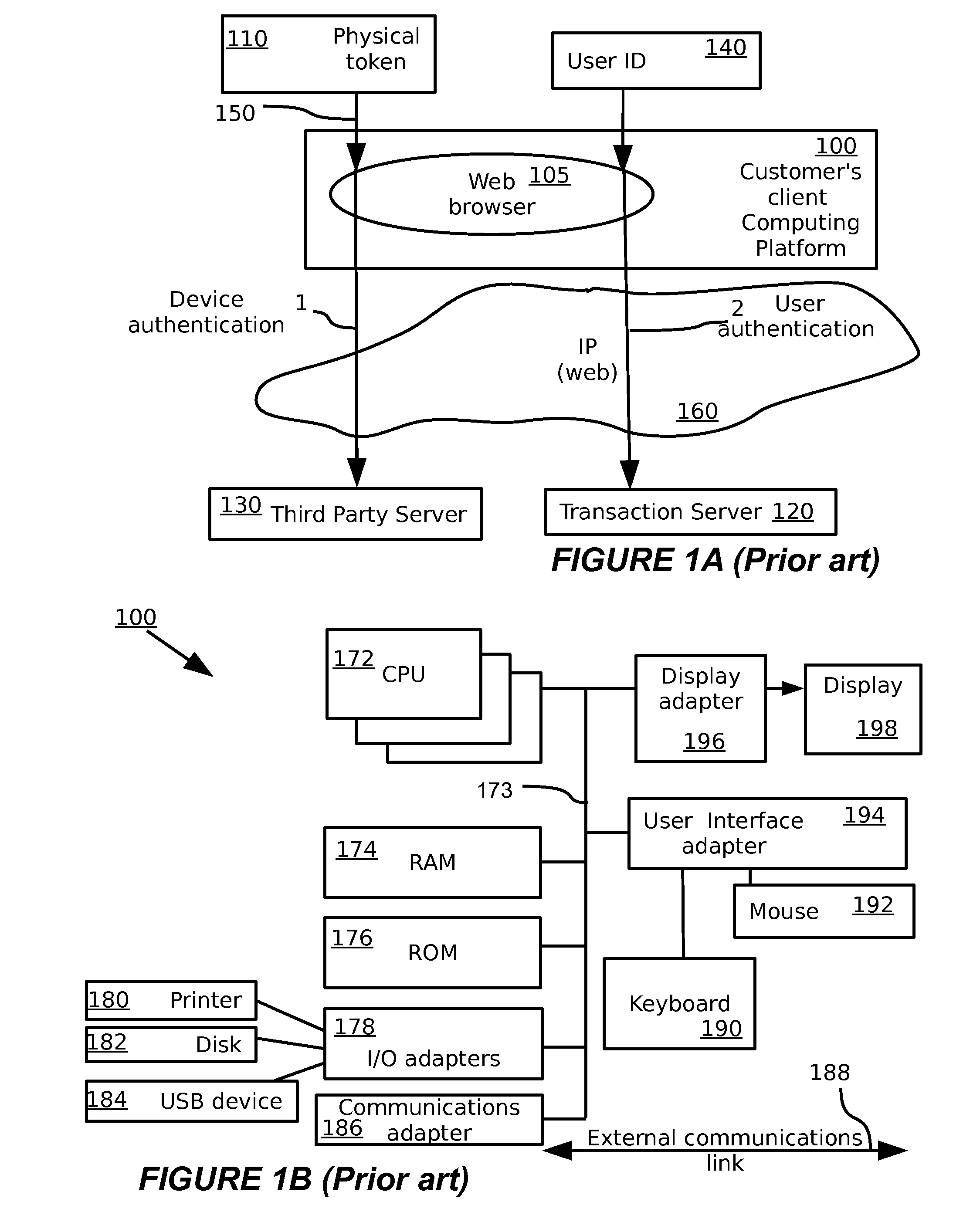
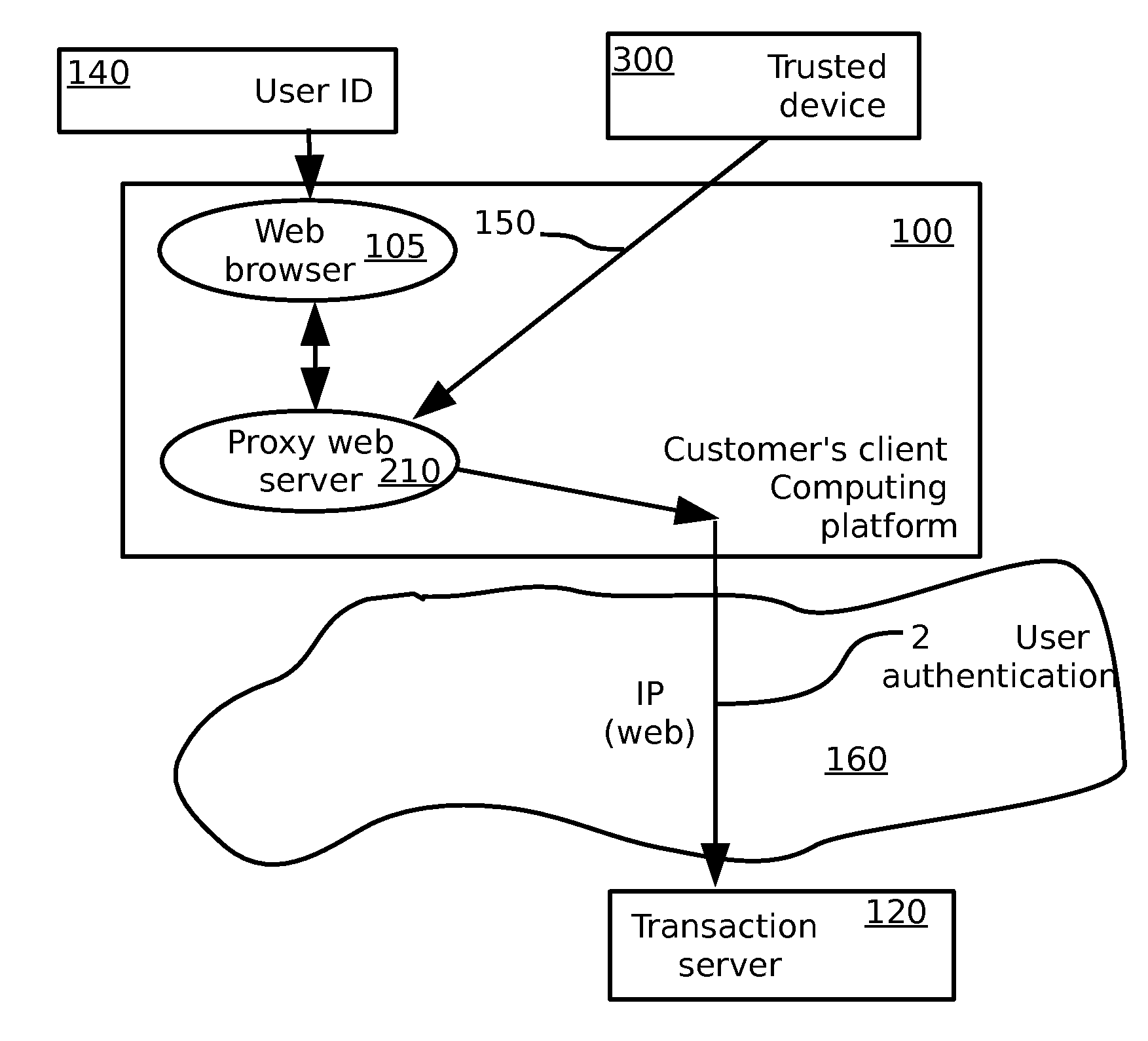
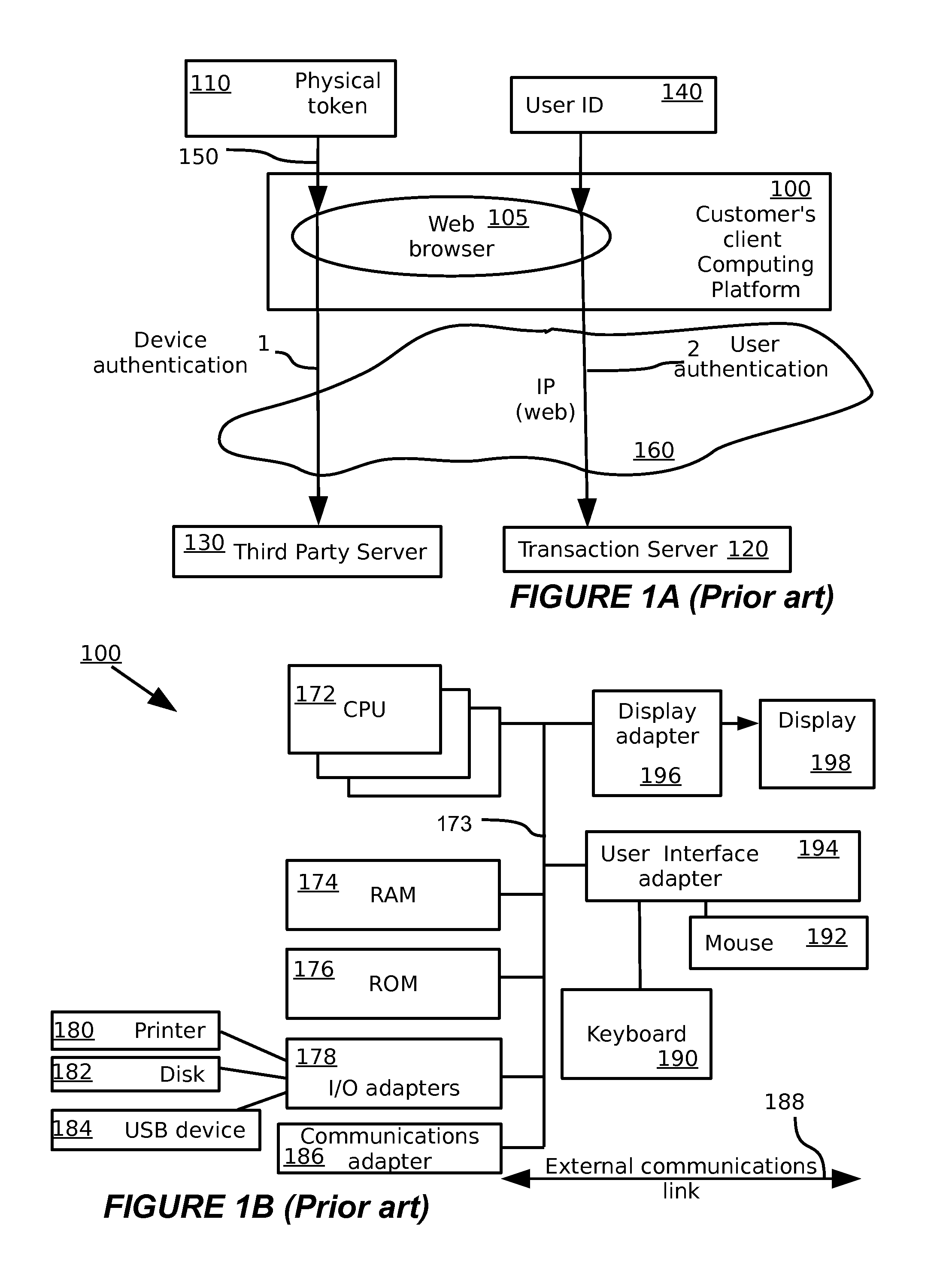
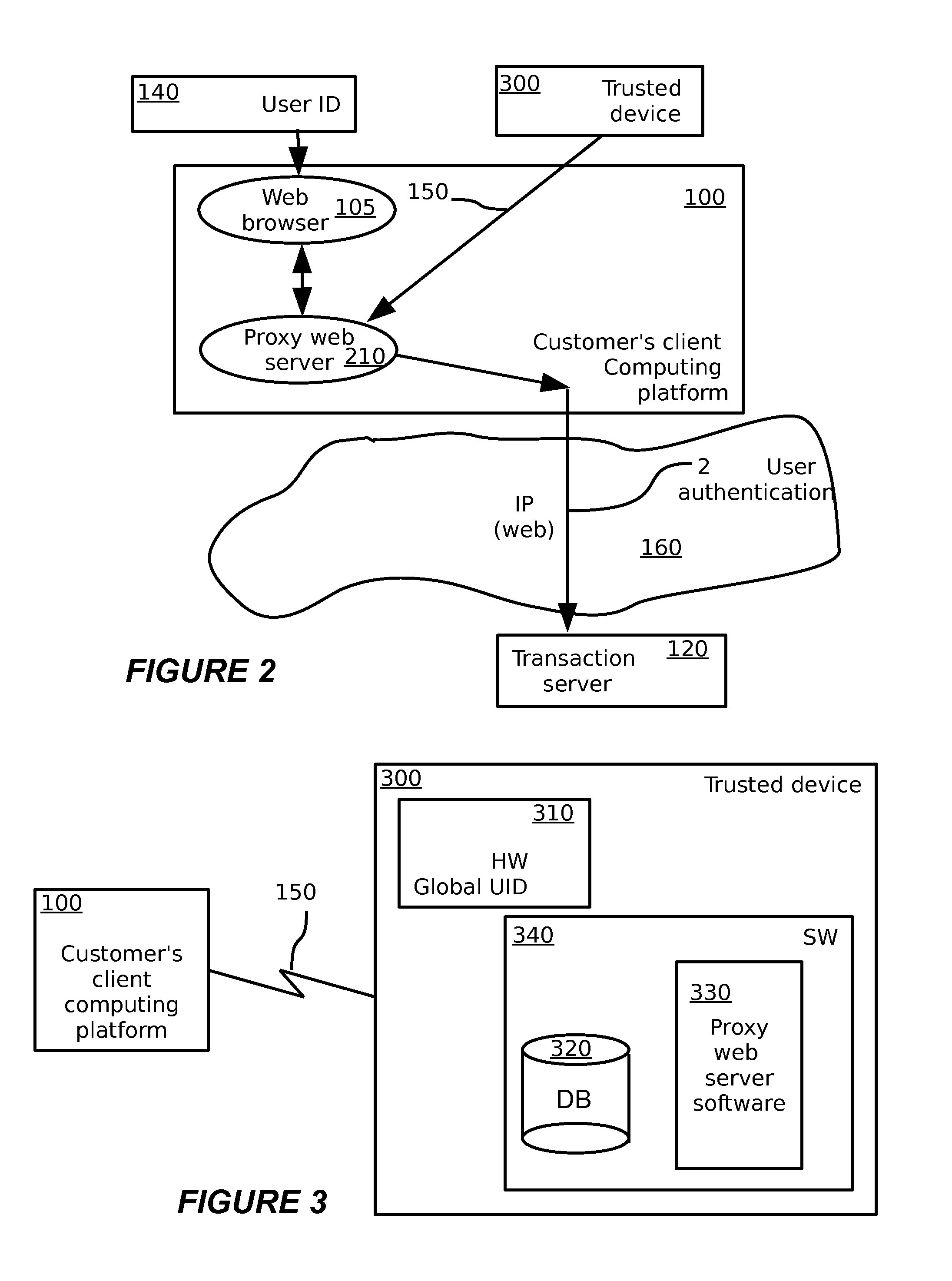
A multimedia network (1) with connected customer stations (2), merchant servers (3), and a payment server (5). Secure electronic transactions are performed using a secure electronic transactions protocol (SET), including exchange of digital certificates, managed by a Trusted Third Party Server (9). The customer stations comprise transactions management means (10), fit for performing said SET protocol and for managing said certificates for the customer station. A remote customer agent (13) represents the customer station in the negotiation and payment process. The customer station (2) comprises an agent interface (12), fit for transmission of codes, parameters and certificates between the customer agent (13) and the transactions management means (10). A remote merchant agent (14) represents the merchant station (3) in the negotiation and payment process with the customer agent (13) or the customer station (3), to have paid for the selected products in a secure way, under control of SET protocol.
Owner:NOKIA CORP
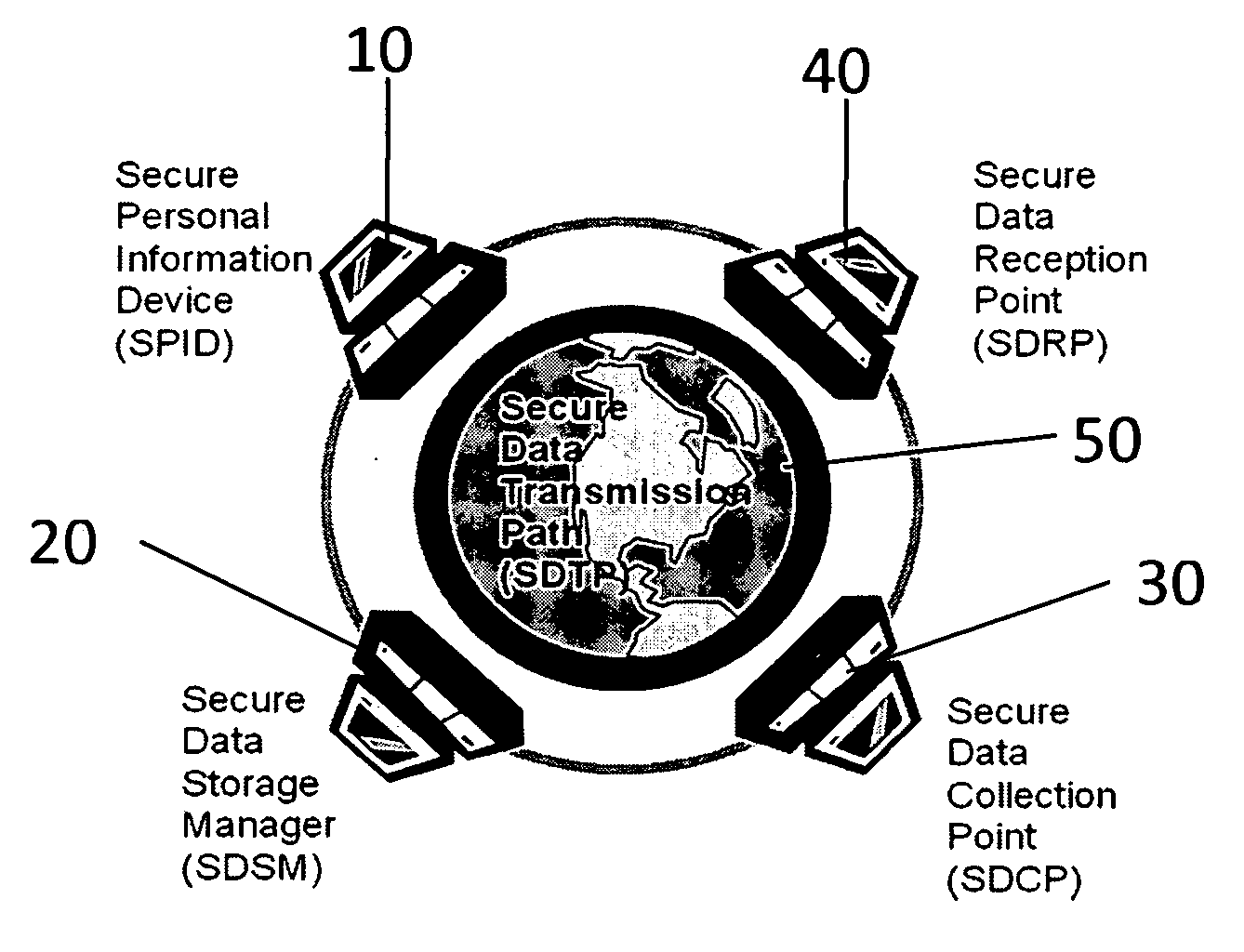
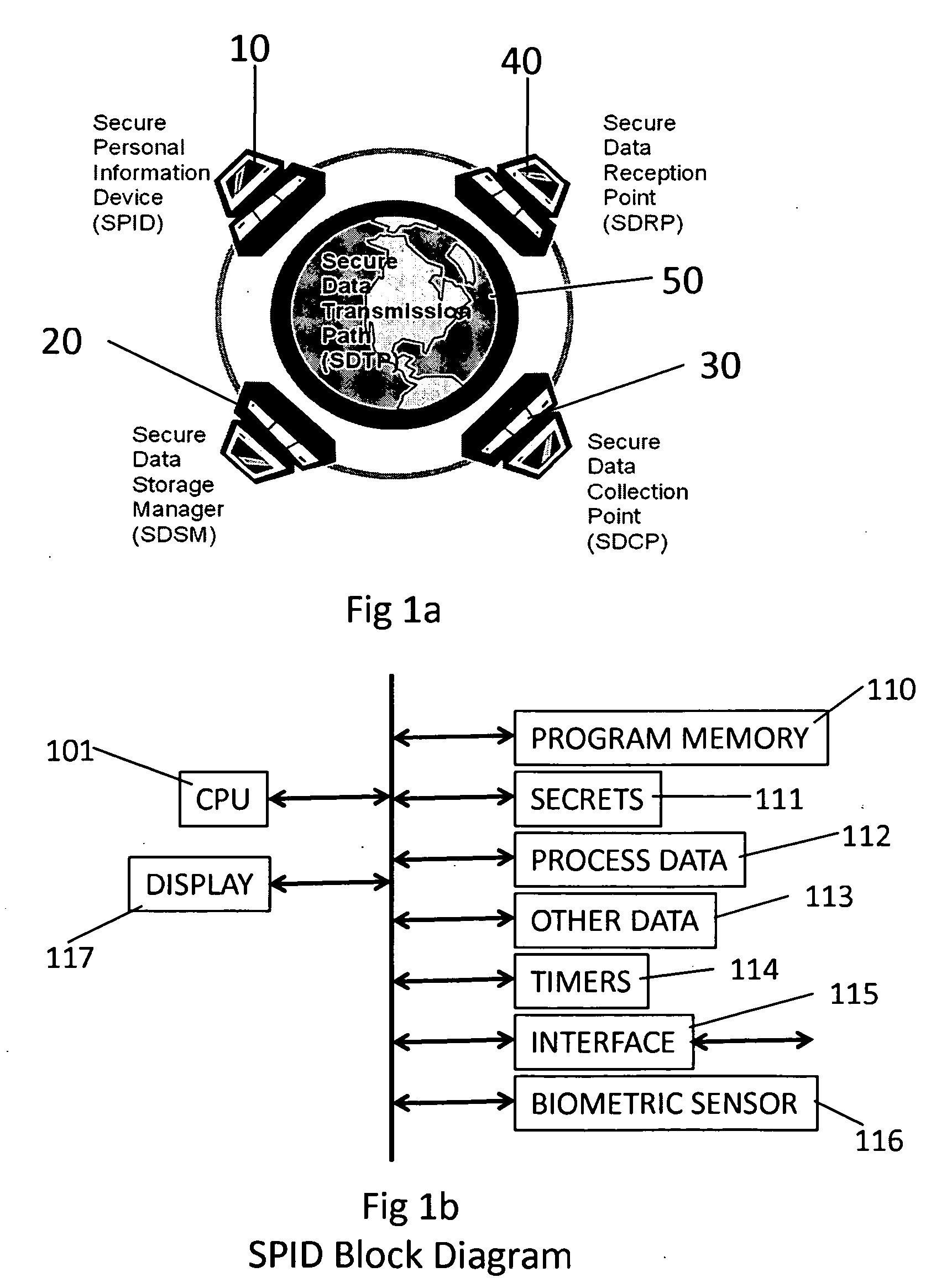
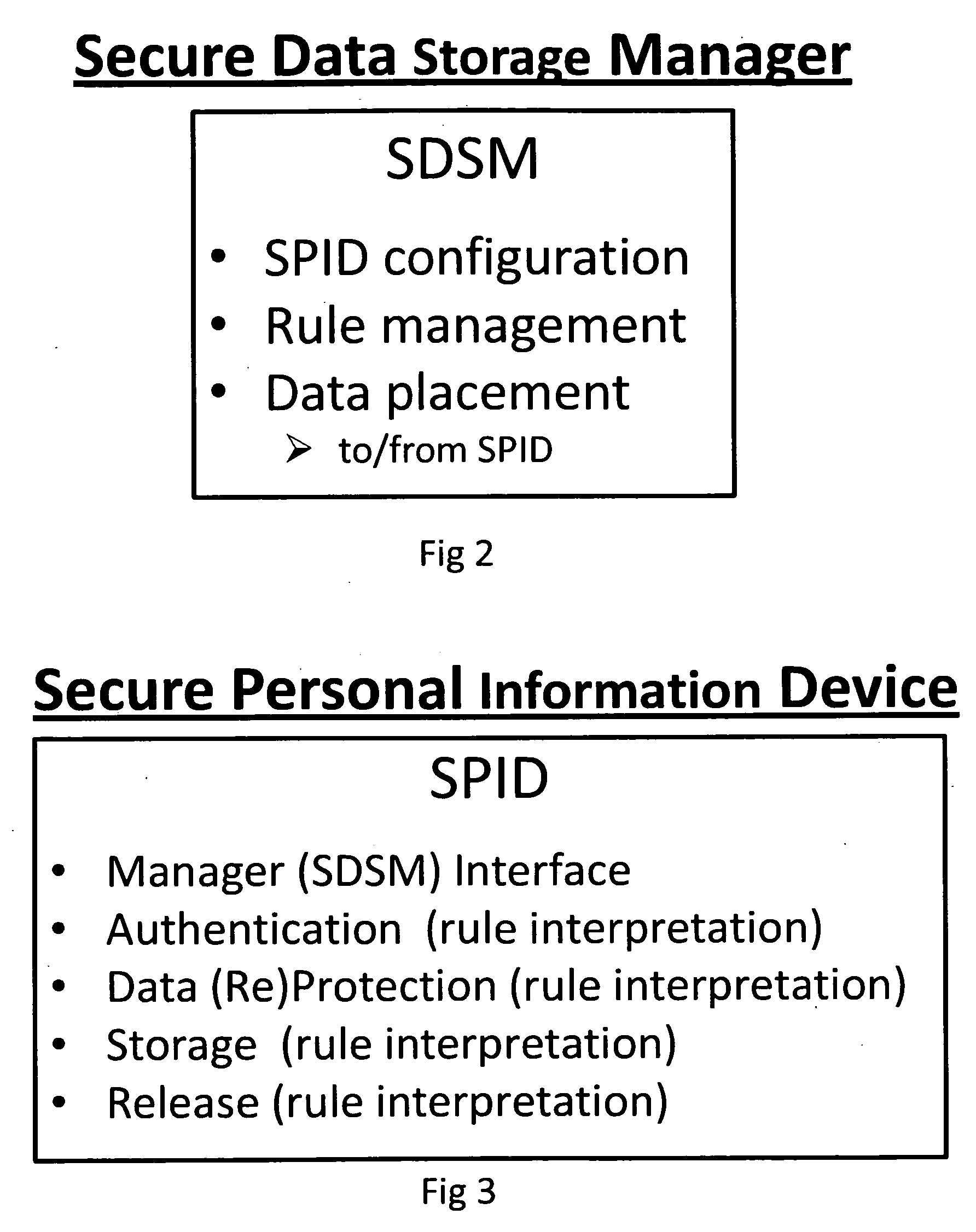
Security process for private data storage and sharing
InactiveUS20090083544A1Without riskEffectively transparentUser identity/authority verificationInternal/peripheral component protectionSecure Electronic TransactionPrivate network
A method and system for supplementing and / or replacing current security protocols and / or mechanisms used to store, manage and / or disseminate information for use on private data management devices and / or a private network and / or public network access provider's network. The system includes processing hardware, proprietary software, and firmware. The system protects private data without the need to trust the security or veracity of third parties and / or intermediate computers and / or networks. When a “user” stores data it is immediately protected from active and passive compromise attempts. Once protected and stored, data is never released and / or transferred unprotected. Only the authorized “receiver” of the data is capable of accessing the protected data. Encryption is used to enhance authentication of the participants and / or protection of the data. This method can be used in conjunction with other secure data transfer applications such as, but not limited to, Secure Socket Layer (SSL) encryption and / or the Secure Electronic Transaction (SET) protocol, etc. This method can also be used in conjunction with any data transfer mechanism such as, but not limited to, Ethernet, WiFi, Bluetooth, RFID transponders, etc.
Owner:SCHOLNICK ANDREW +1
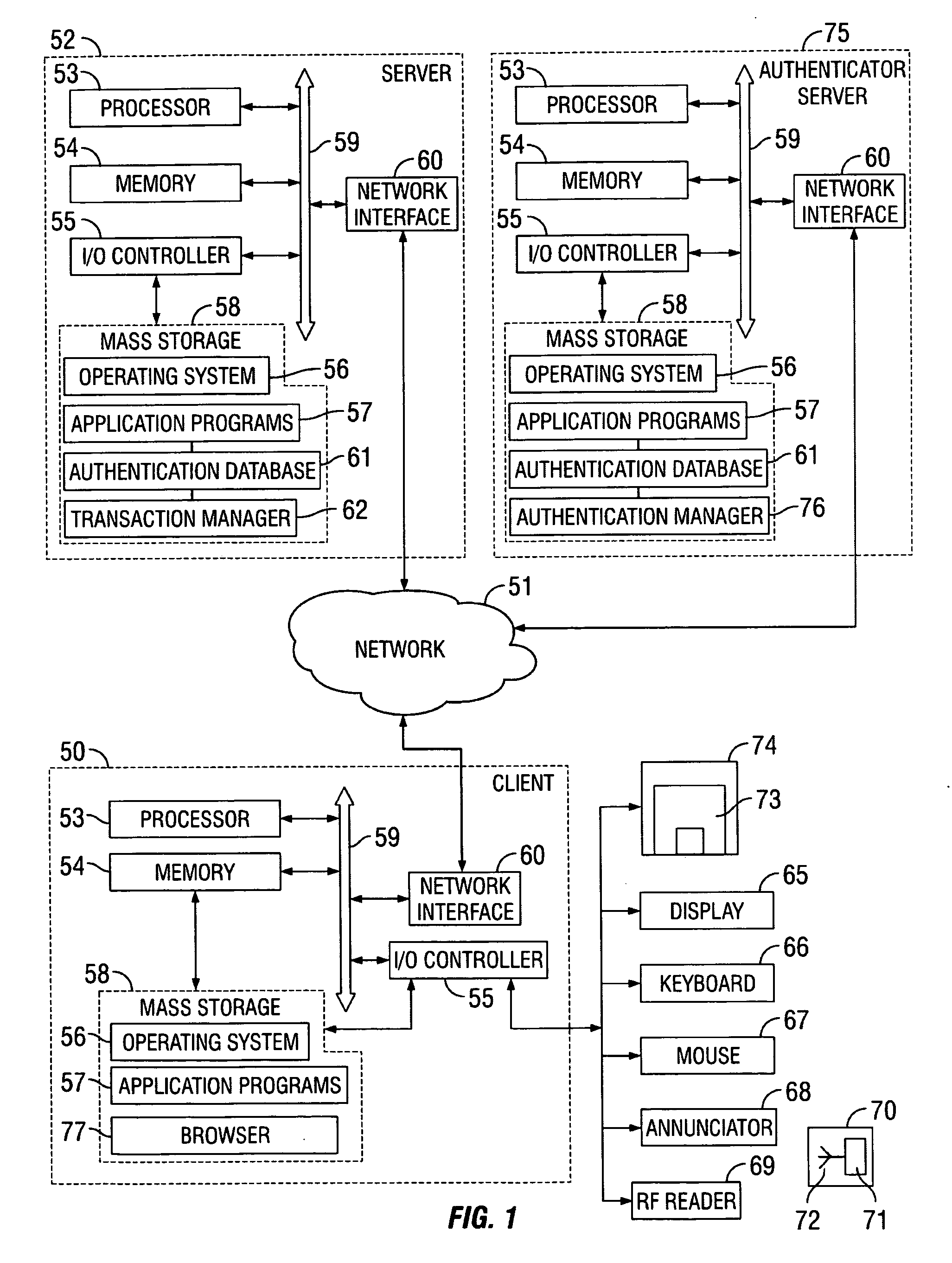
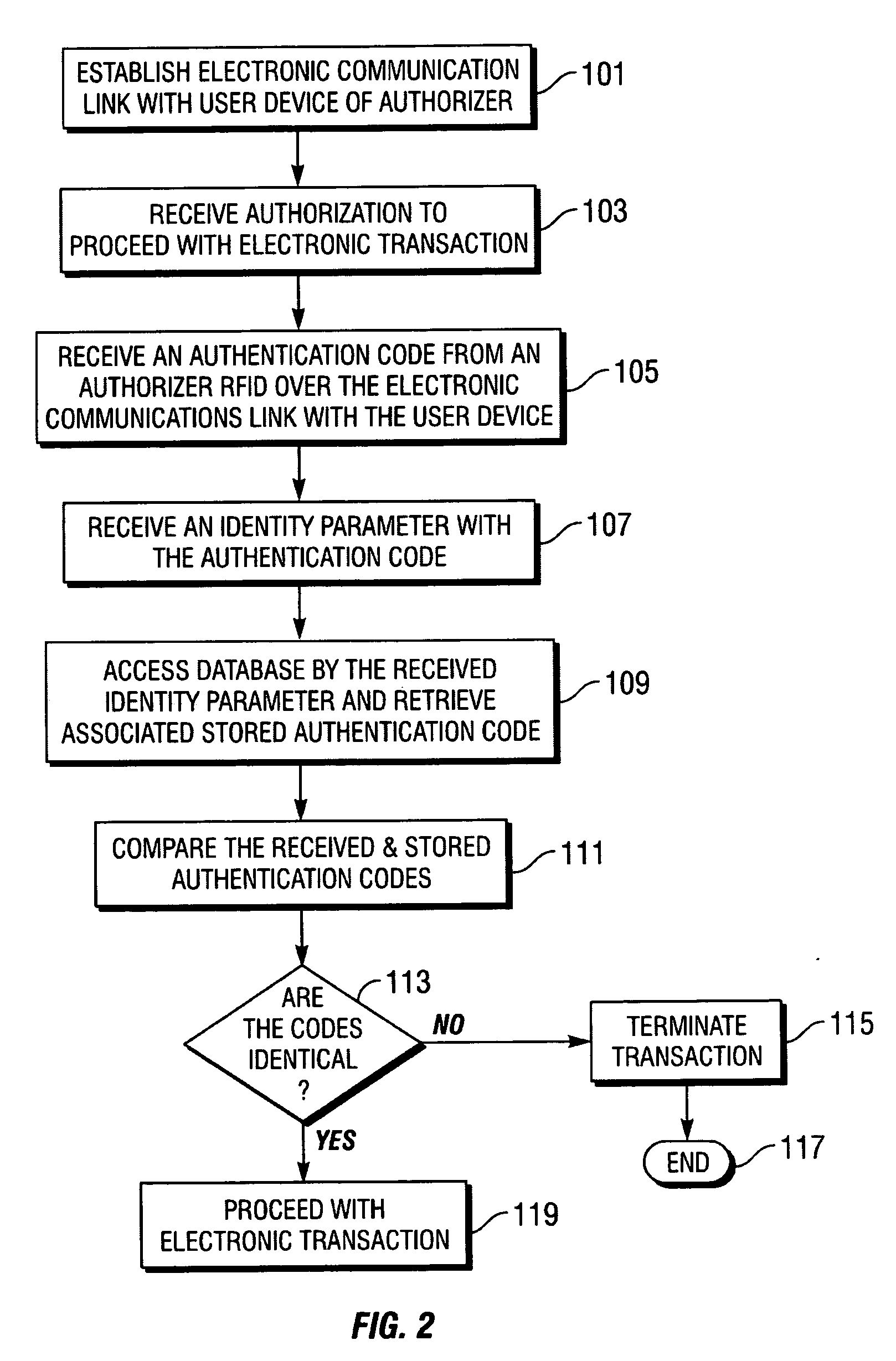
Secure electronic transaction authentication enhanced with RFID
InactiveUS20070094152A1Securing communicationPayments involving neutral partyUser deviceSecure Electronic Transaction
Methods, computer program products and systems for authenticating an electronic transaction conducted over an electronic communications link with a user device of a transaction authorizer. A method includes establishing the electronic communications link with the user device of the authorizer, receiving an authentication code from an authorizer RFID over the electronic communication link, and determining if the received authentication code matches a stored authentication code assigned to the authorizer. The electronic transaction may proceed if the stored authentication code matches the received authentication code. Also included may be the step of determining if one or more required personal attributes match stored personal attributes associated with the stored authentication code assigned to the authorizer. If so, then the method may include proceeding with the electronic transaction if the one or more required personal attributes match the stored personal attributes associated with the stored authentication code assigned to the authorizer.
Owner:IBM CORP
Method and system for securing electronic transactions
ActiveUS8468582B2Avoid and mitigate shortcomingFinanceDigital data processing detailsSecure Electronic TransactionTrusted Computing
Owner:INBAY TECH
Detecting man-in-the-middle attacks in electronic transactions using prompts
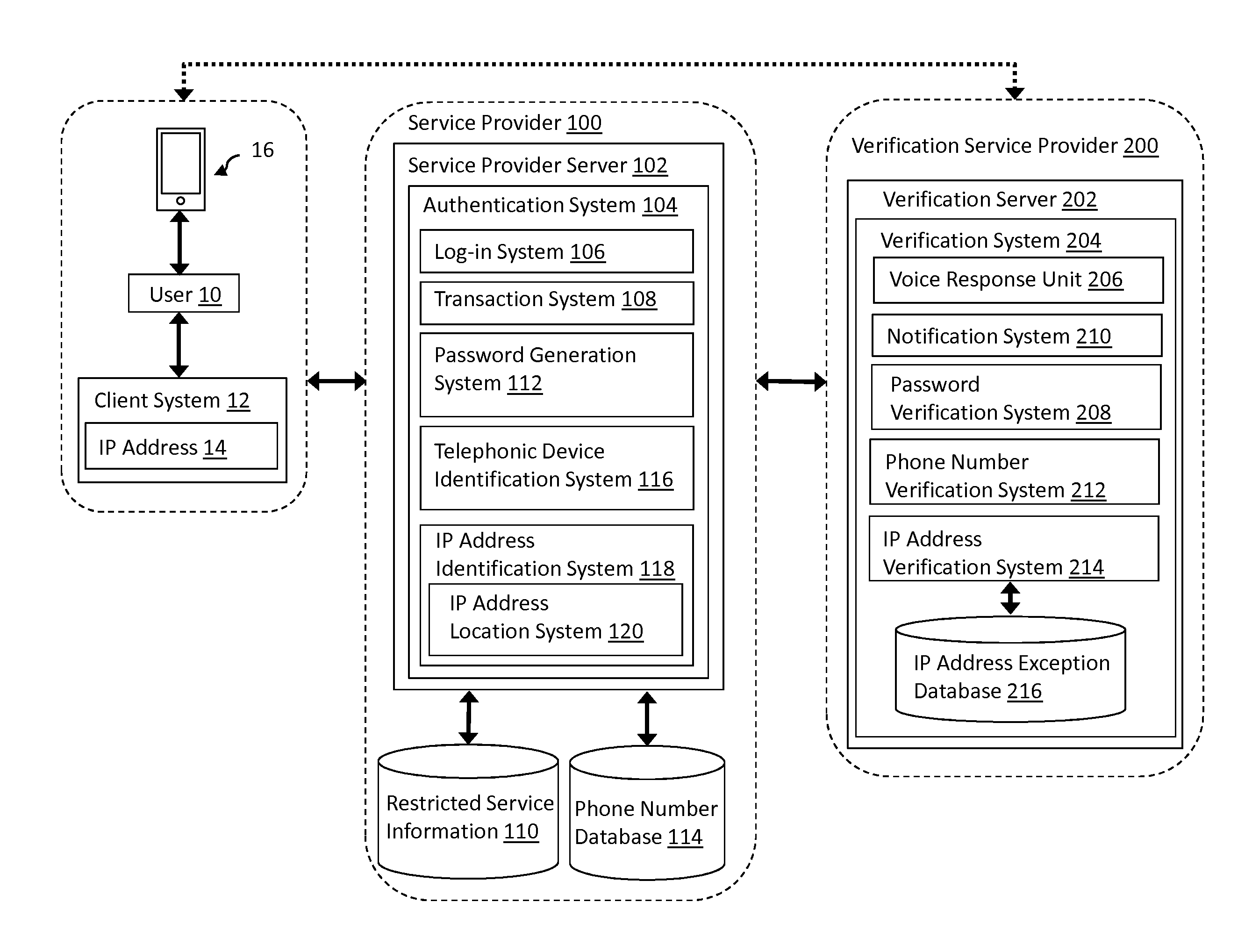
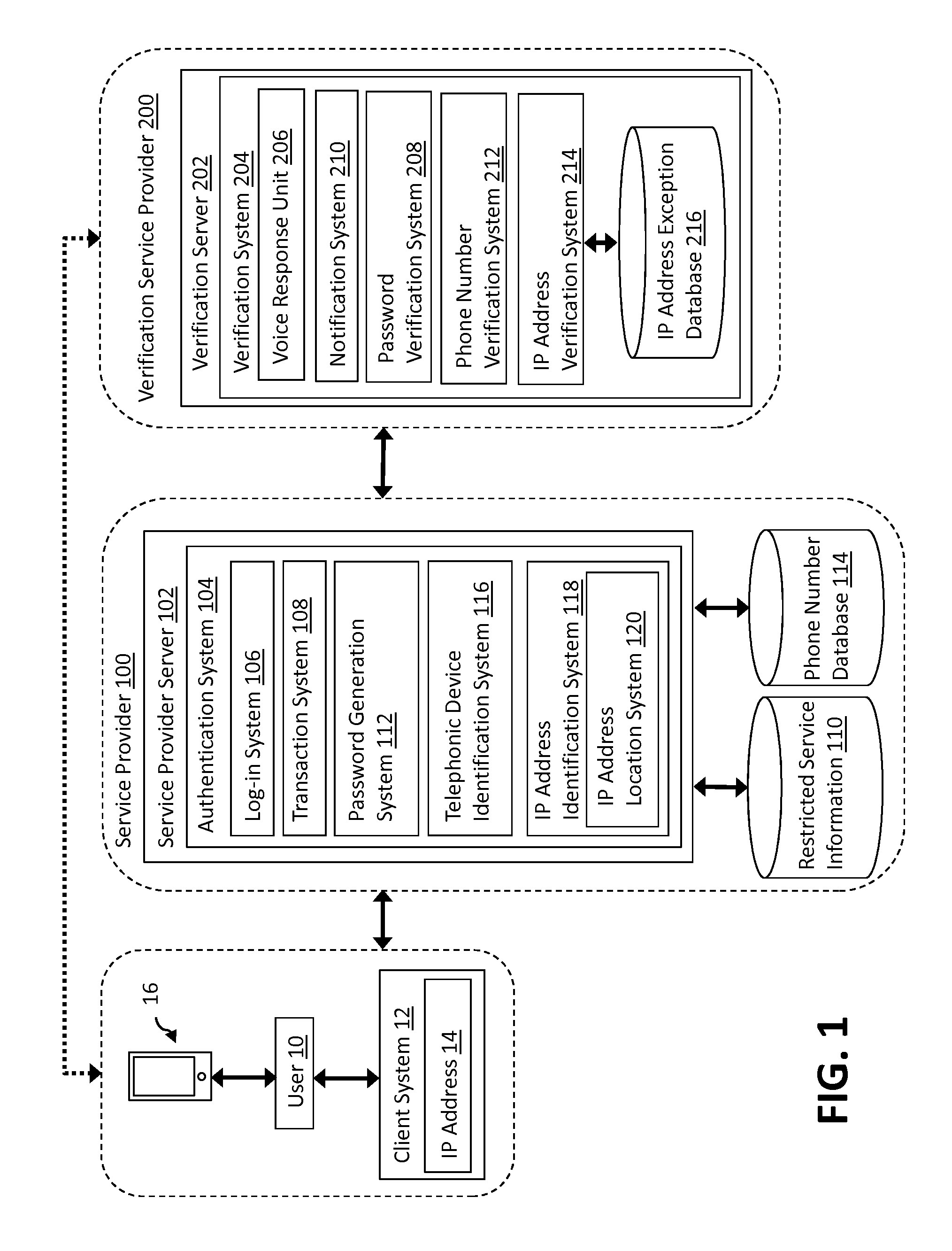
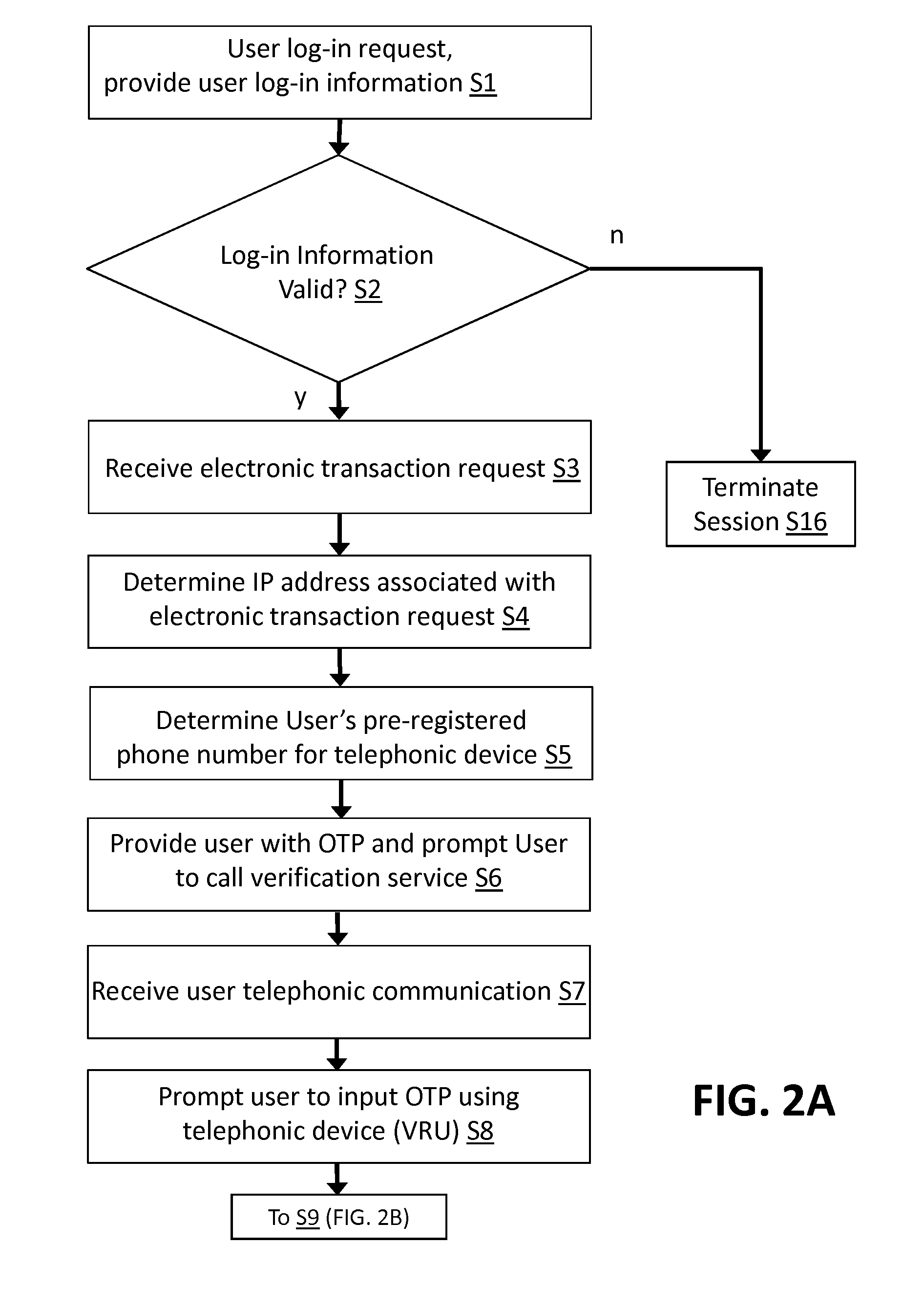
InactiveUS20140037074A1Automatic call-answering/message-recording/conversation-recordingLocation information based serviceMan-in-the-middle attackIp address
Aspects of the invention provide a solution for detecting man-in-the-middle attacks in electronic transactions using prompts. One embodiment includes a method for authenticating an electronic transaction. The method includes: receiving an electronic transaction request from a user, determining an IP address associated with a client system from which the electronic transaction request originates, providing the user with a password associated with the electronic transaction request, receiving a telephonic communication from a telephonic device associated with the user, prompting the user, via a voice response unit, to input the password using the telephonic device, authenticating the user by comparing the inputted password and the provided password, determining a probable location of the user based on the determined IP address of the client system, communicating to the user the probable location of the user based on the determined IP address, and prompting the user to confirm the probable location of the user.
Owner:IBM CORP
Smart authentication and identification via voiceprints
ActiveUS10074089B1Cure deficiencySpeech analysisProtocol authorisationBiometric dataSecure Electronic Transaction
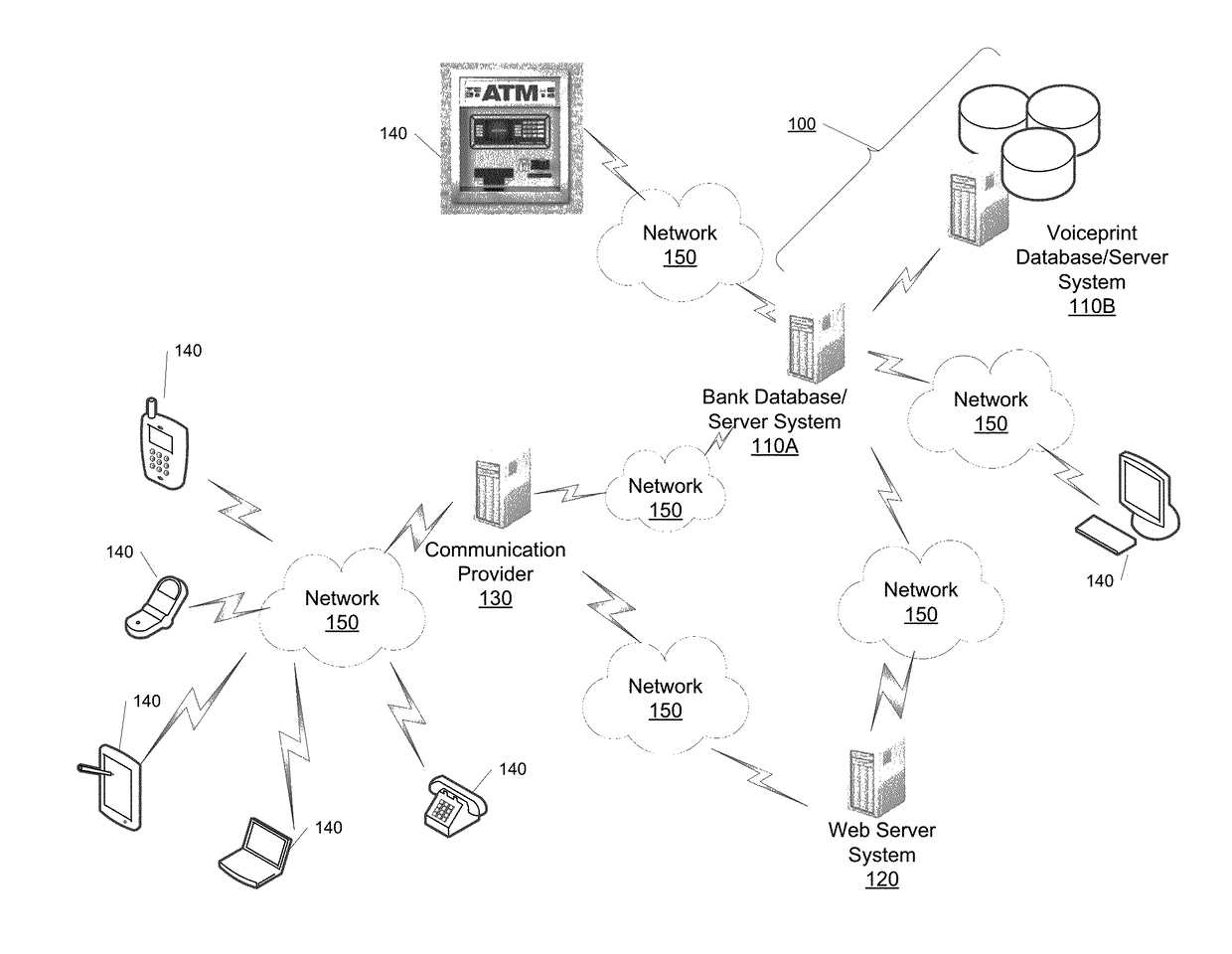
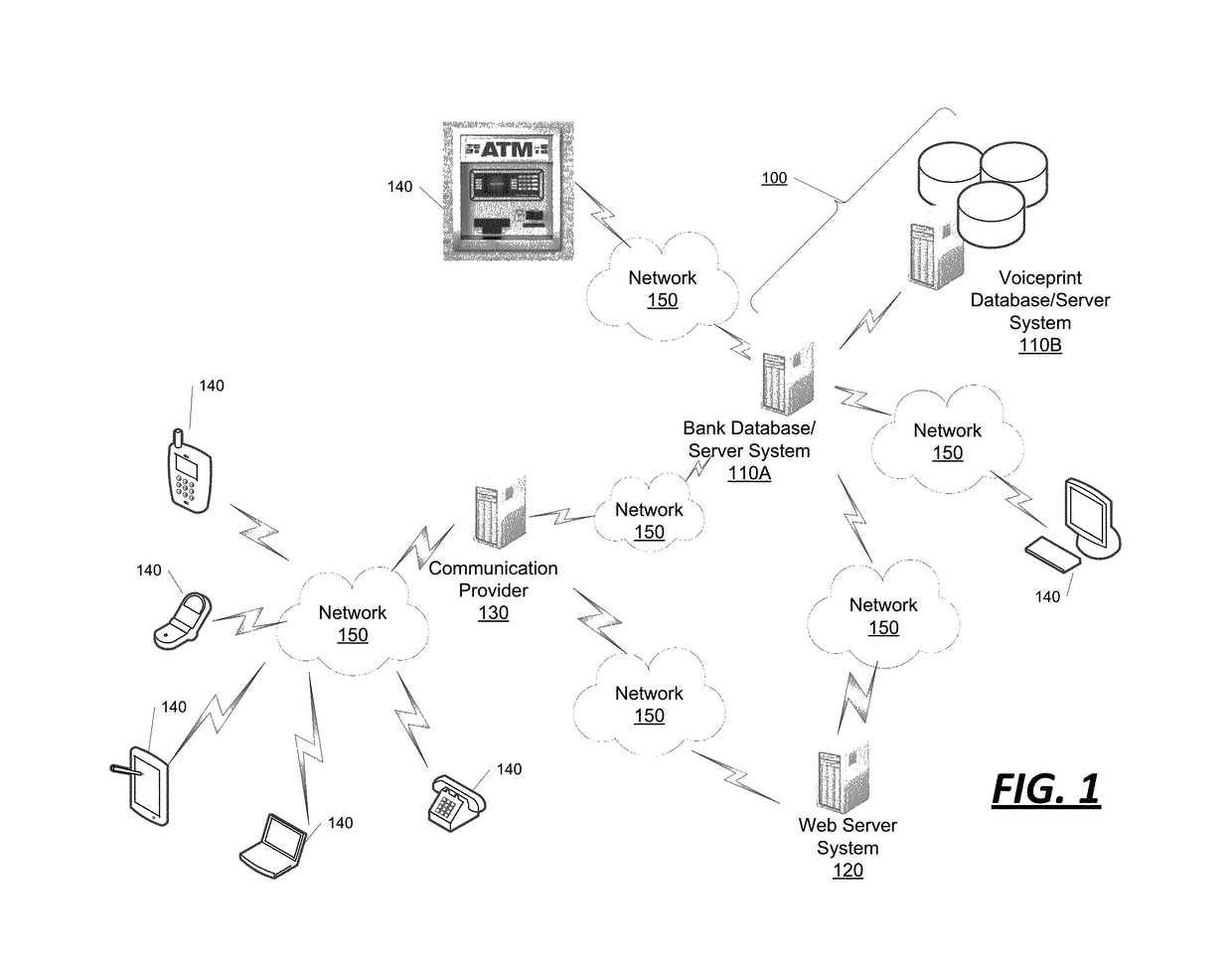
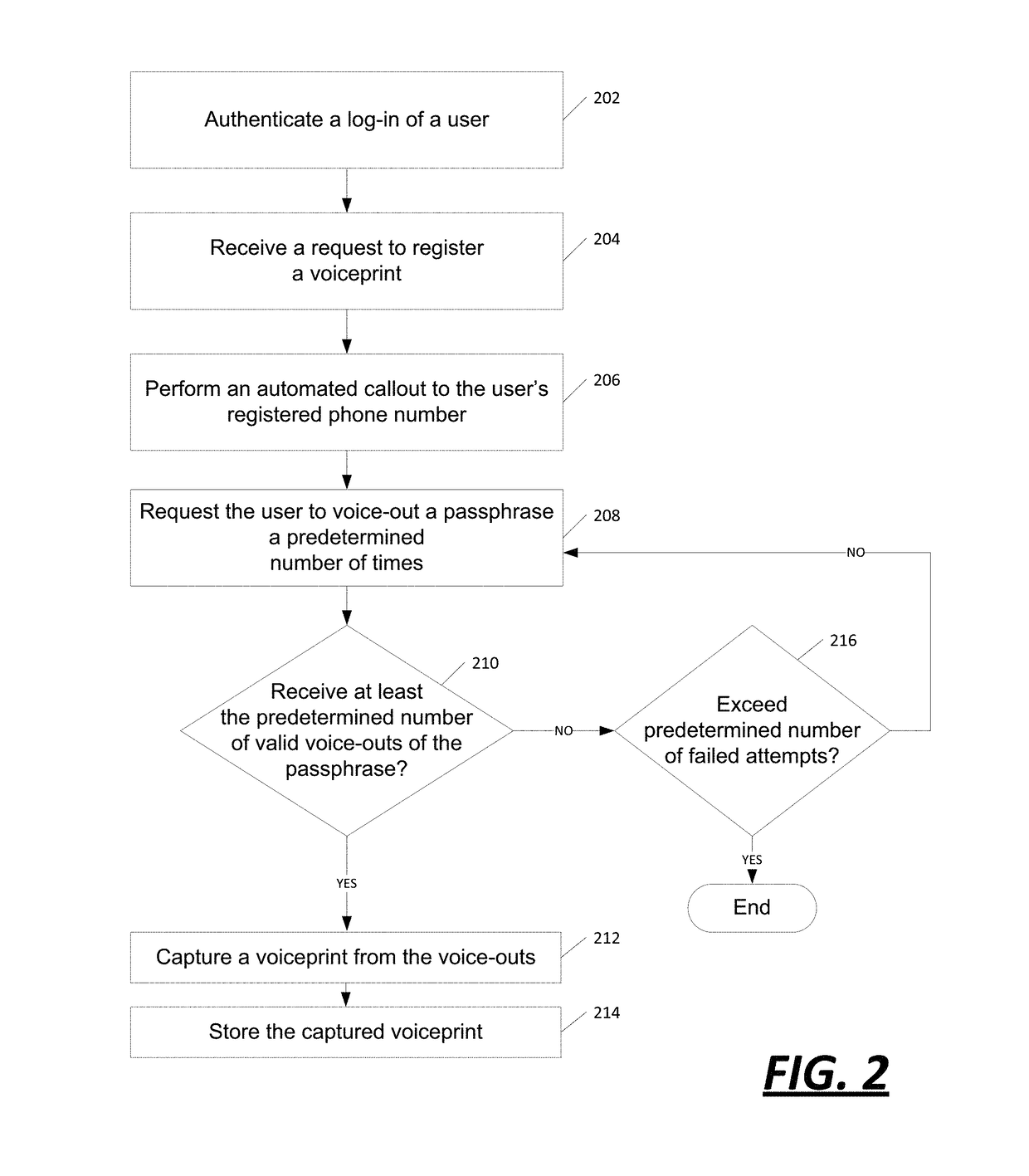
The systems and methods described herein allow an electronic transaction to be performed upon determining, via biometric data, that an authorized individual is conducting the transaction. This may involve receiving, by a computer system, a request to authorize an electronic transaction for an account. The computer system is configured to access a phone number, which is stored in computer memory and associated with the enrolled user of the account. An automated and outward call to the phone number is performed by the computer system. The computer system is configured to capture a voiceprint in association with voice data received from the automated call. The captured voiceprint is compared to a registered voiceprint, which is stored in the computer memory in association with the enrolled user. The computer system responds to the request to authorize the secure electronic transaction based on said comparison.
Owner:CITIGROUP TECH
Data storage key for secure online transactions
ActiveUS20150199684A1Reduce usagePayment protocolsInternal/peripheral component protectionSecure Electronic TransactionPhysical shape
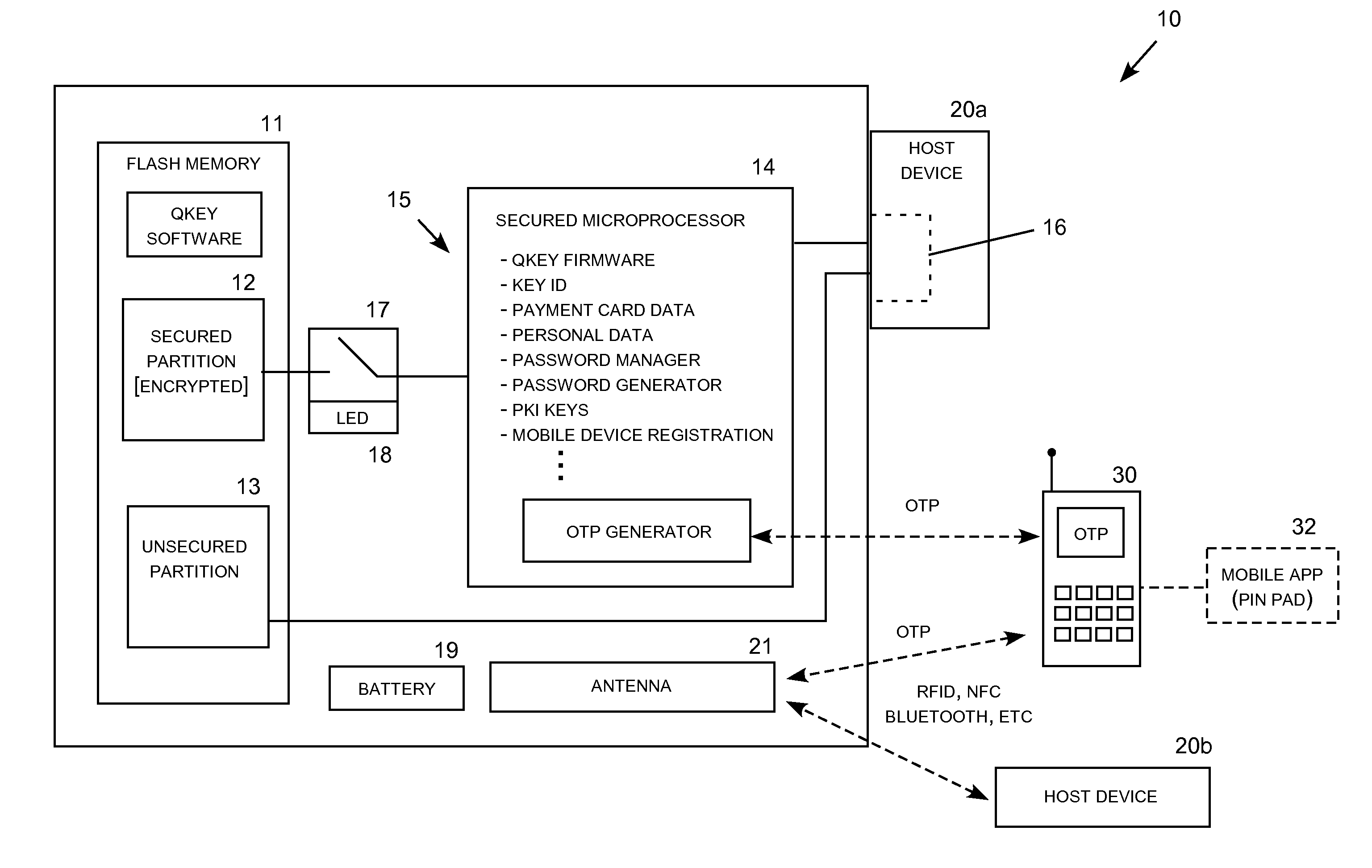
A secure non-volatile solid state memory data key appears similar to a conventional USB flash drive modified to have a physical shape resembling a door key with an eyelet for attaching the data key to a key ring or lanyard. The data key includes a USB port, a microprocessor (effectively serving as the “chip” in the chip-and-pin configuration), and a secure memory for holding secure transaction information, such as credit and debit card numbers, verified personal identification (federated ID), and other secure data. A biometric sensor (e.g., touch sensor or “capcha”) verifies that a person is in physical possession of the data key before permitting access to the secure memory. The touch sensor may be limited to use by a unique individual person through a biometric reader, such as a finger print reader, where the verification finger print is stored on the key rather than the connected host device.
Owner:UQONTROL
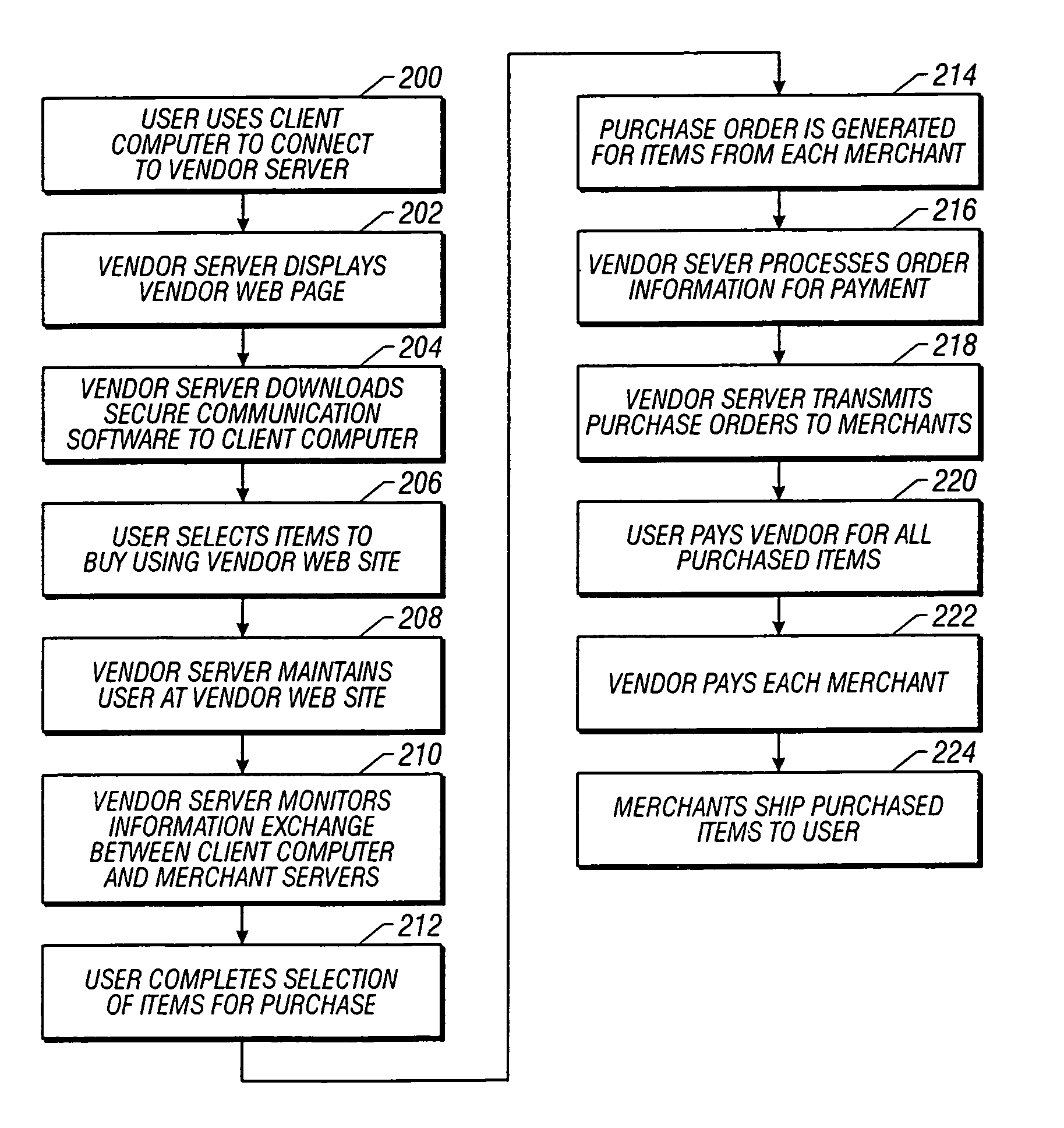
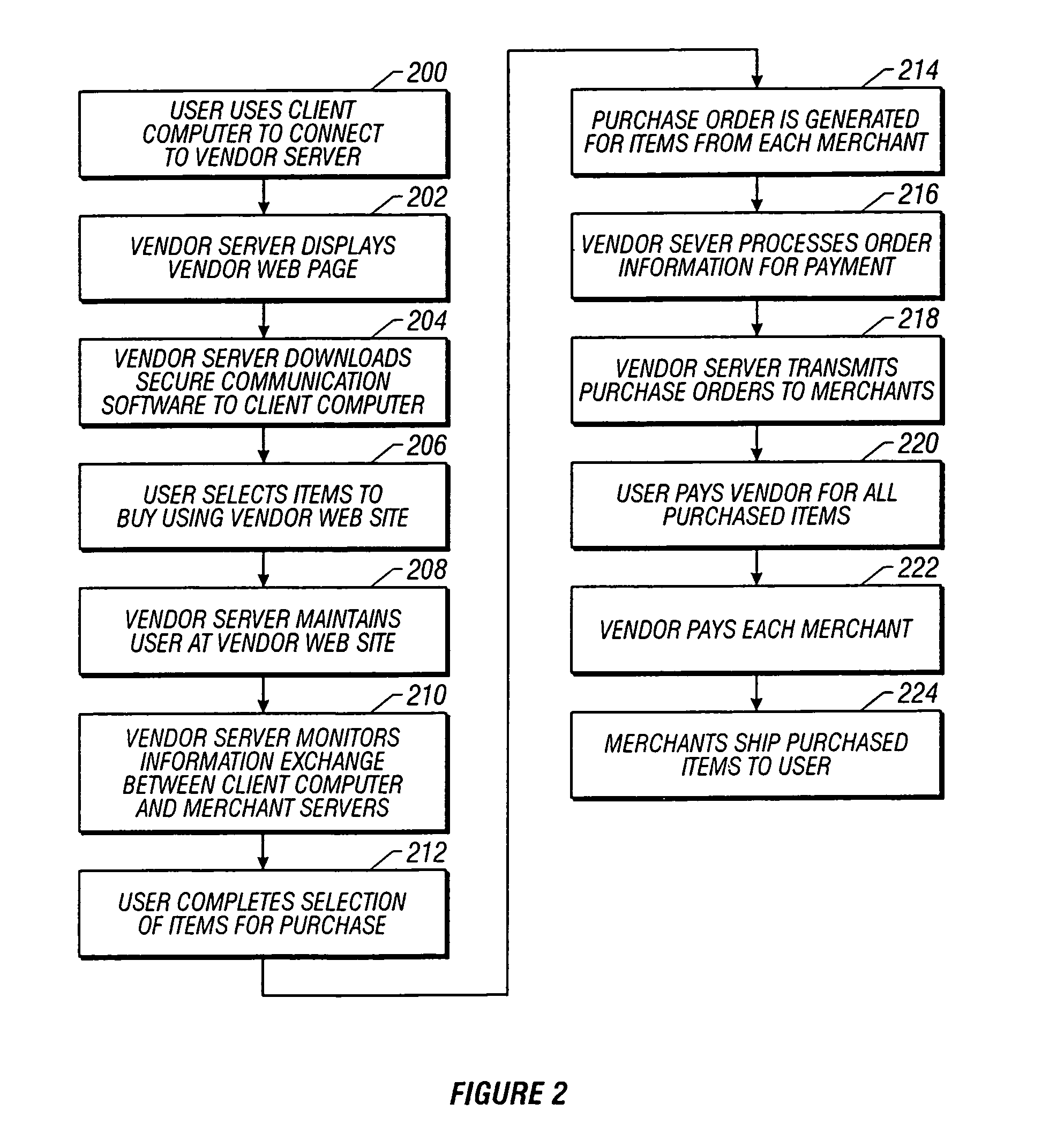
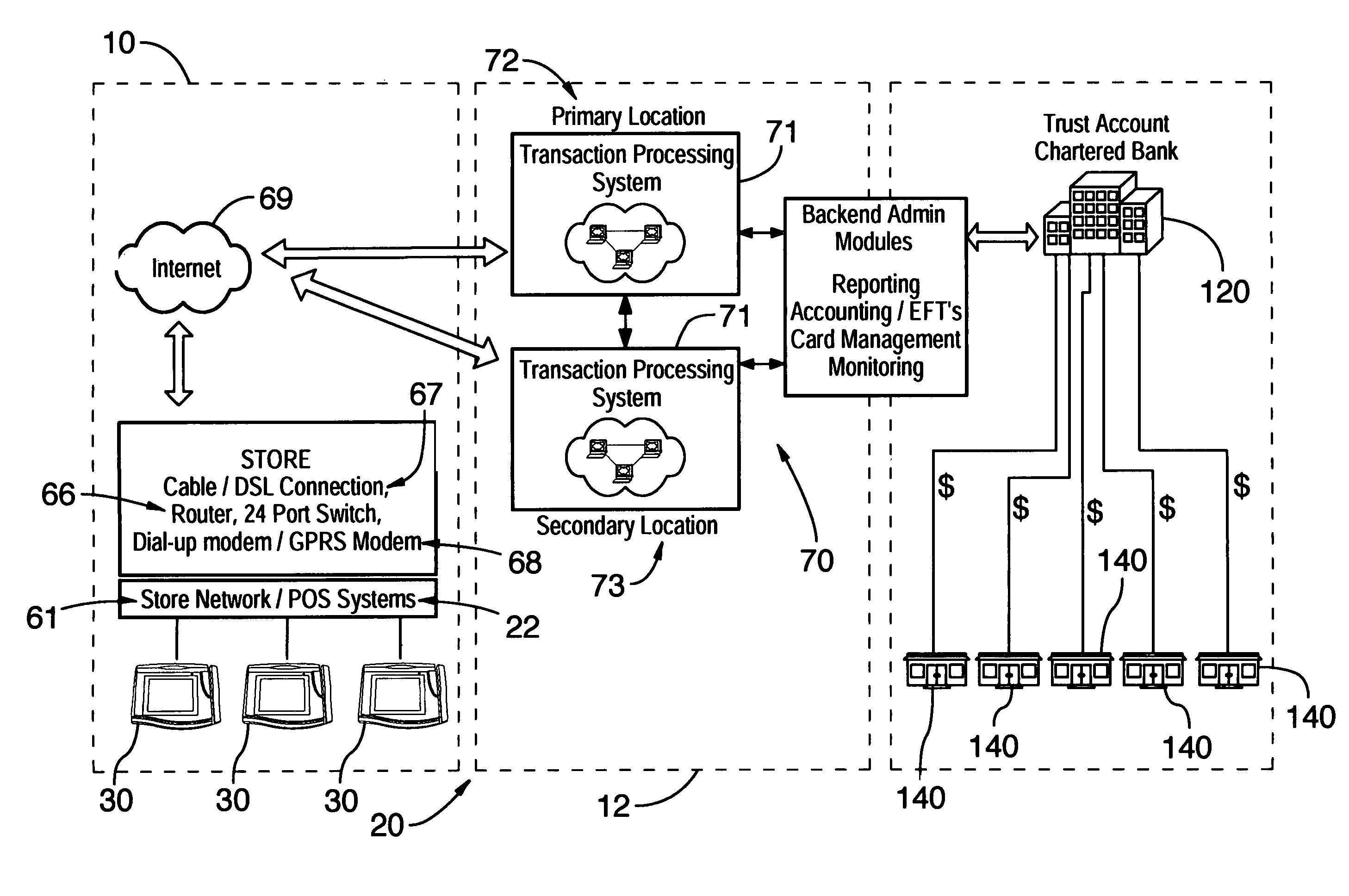
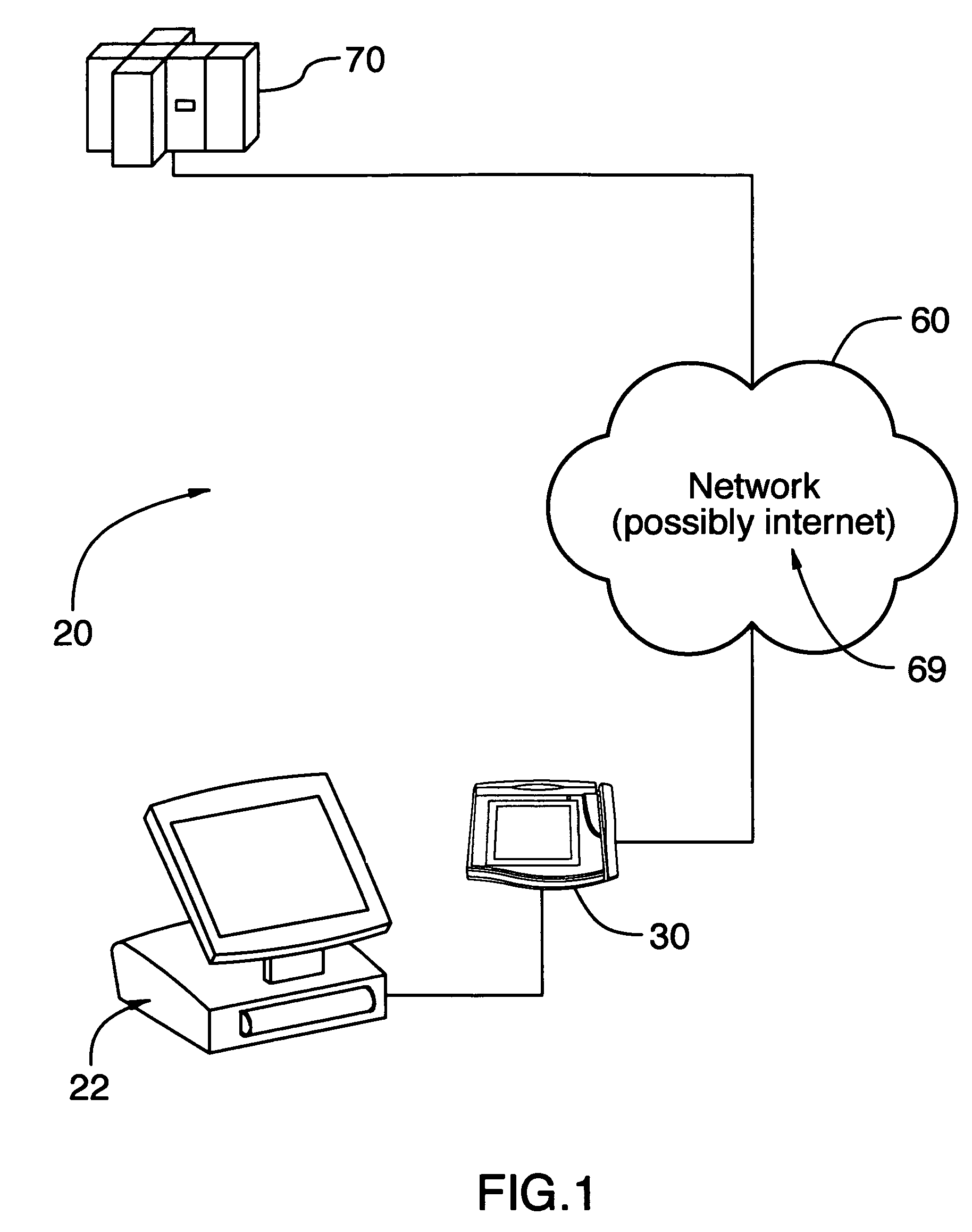
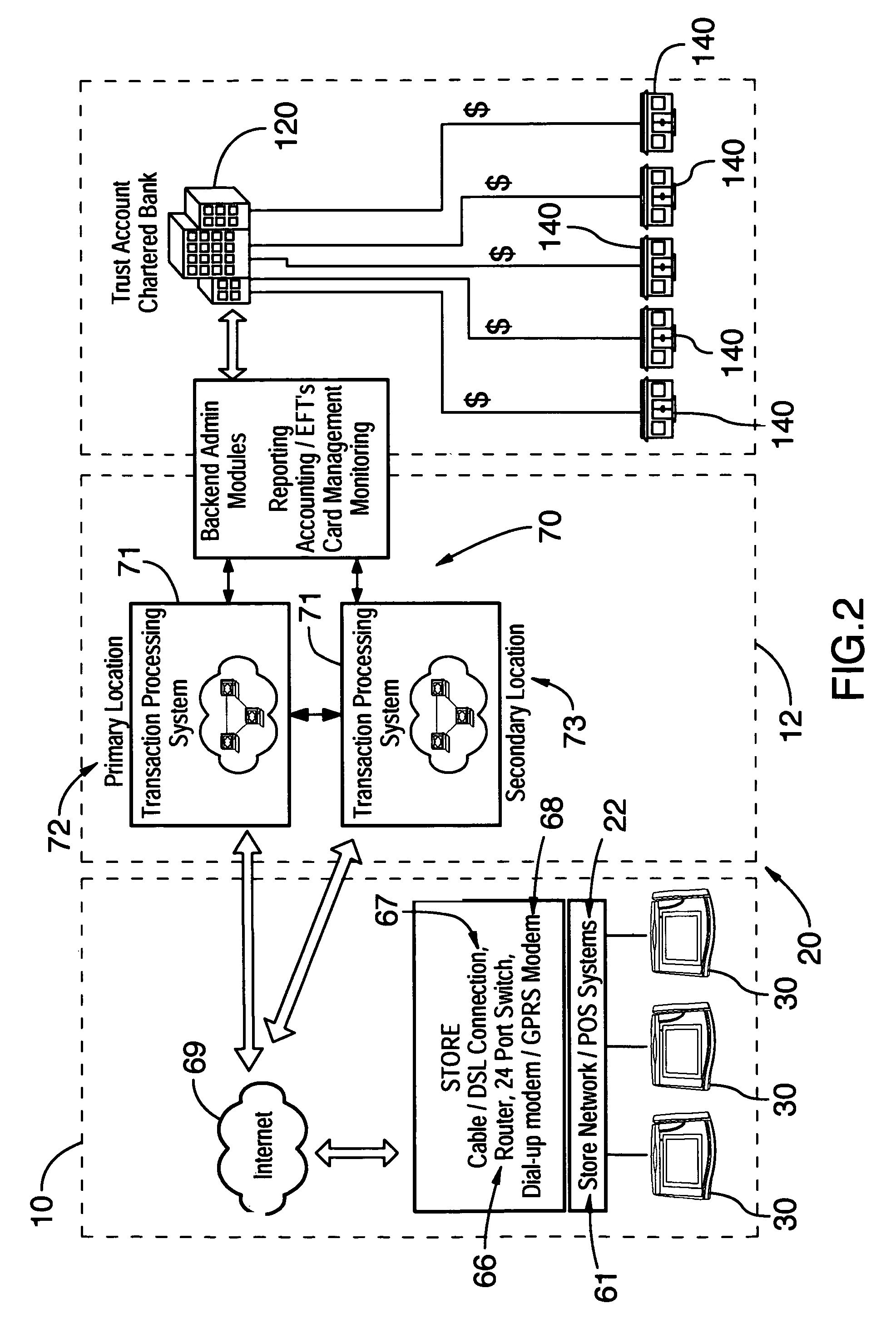
Method and system for facilitating secure electronic transactions with multiple merchants
InactiveUS7359869B1Payment protocolsBuying/selling/leasing transactionsTelecommunications linkSecure Electronic Transaction
A system for conducting electronic commerce comprising at least one client computer system, a vendor computer system and a merchant computer system, interconnected via the communication link. The client computer and the vendor computer system are configured to establishing a secure link communication between the client computer system and the vendor computer system and transmit transaction information between the client and vendor computer systems enabling a user at the client computer system to select and purchase, via the vendor computer system, items listed in at least the merchant computer systems by one or more merchants.
Owner:STAMPS COM
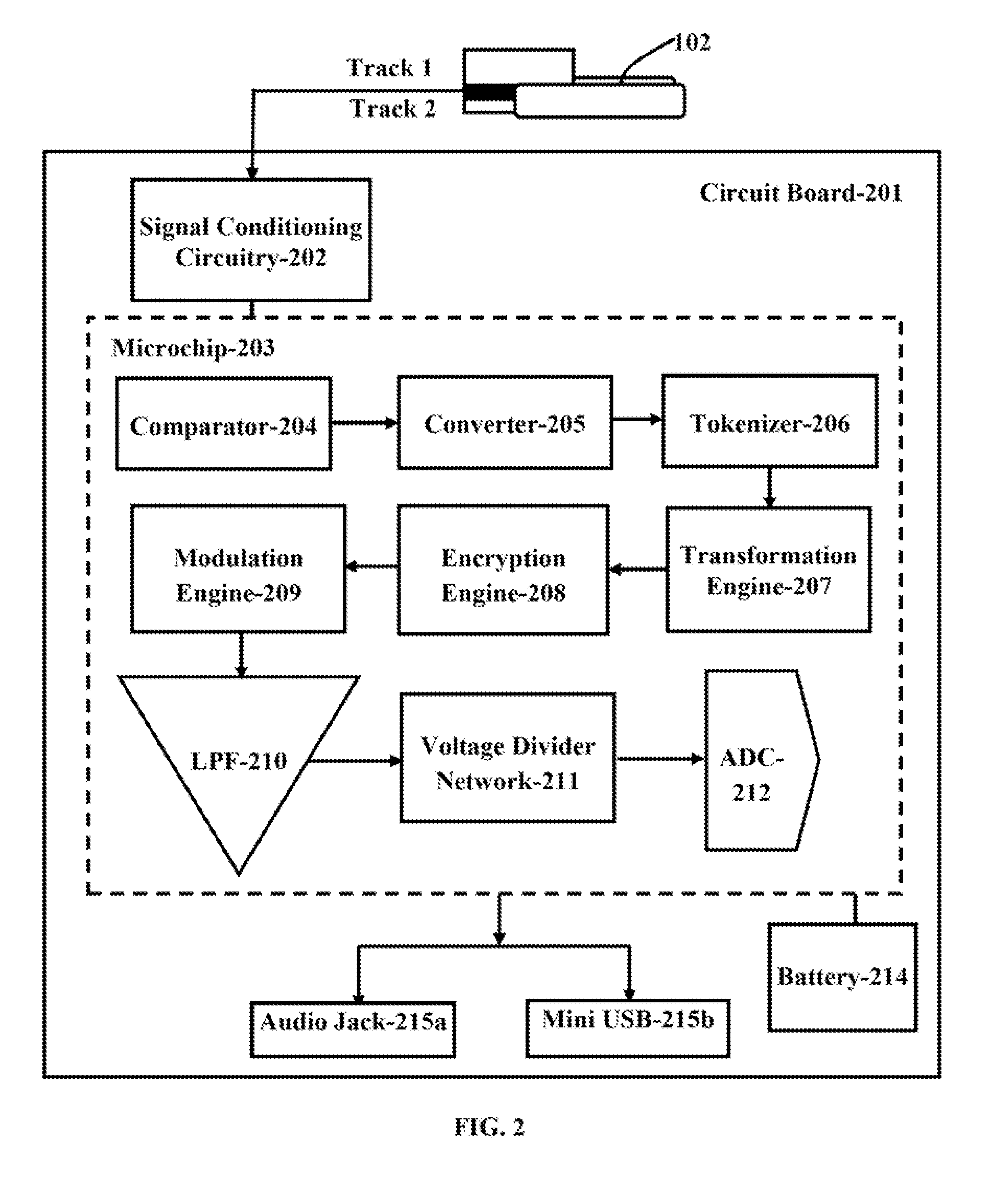
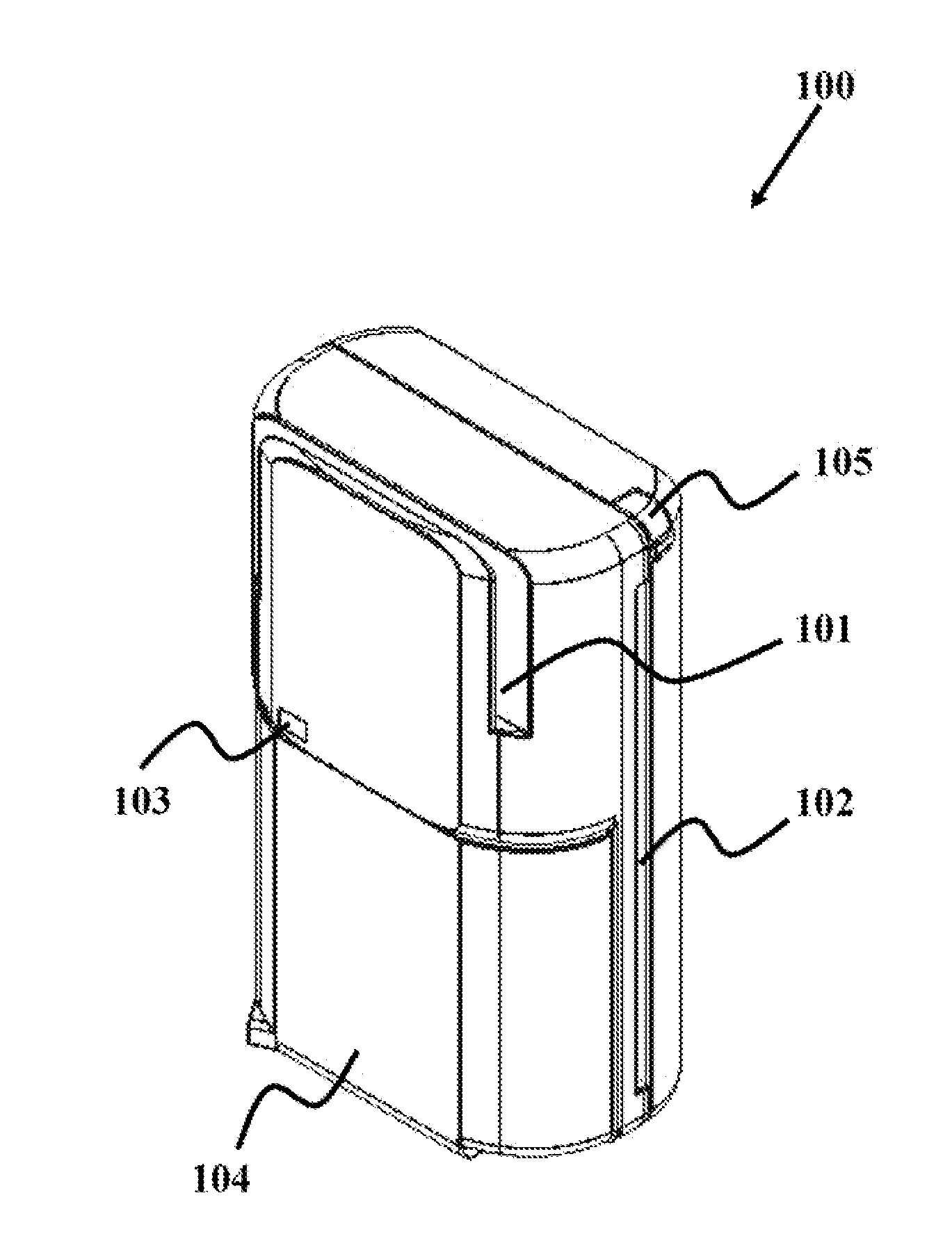
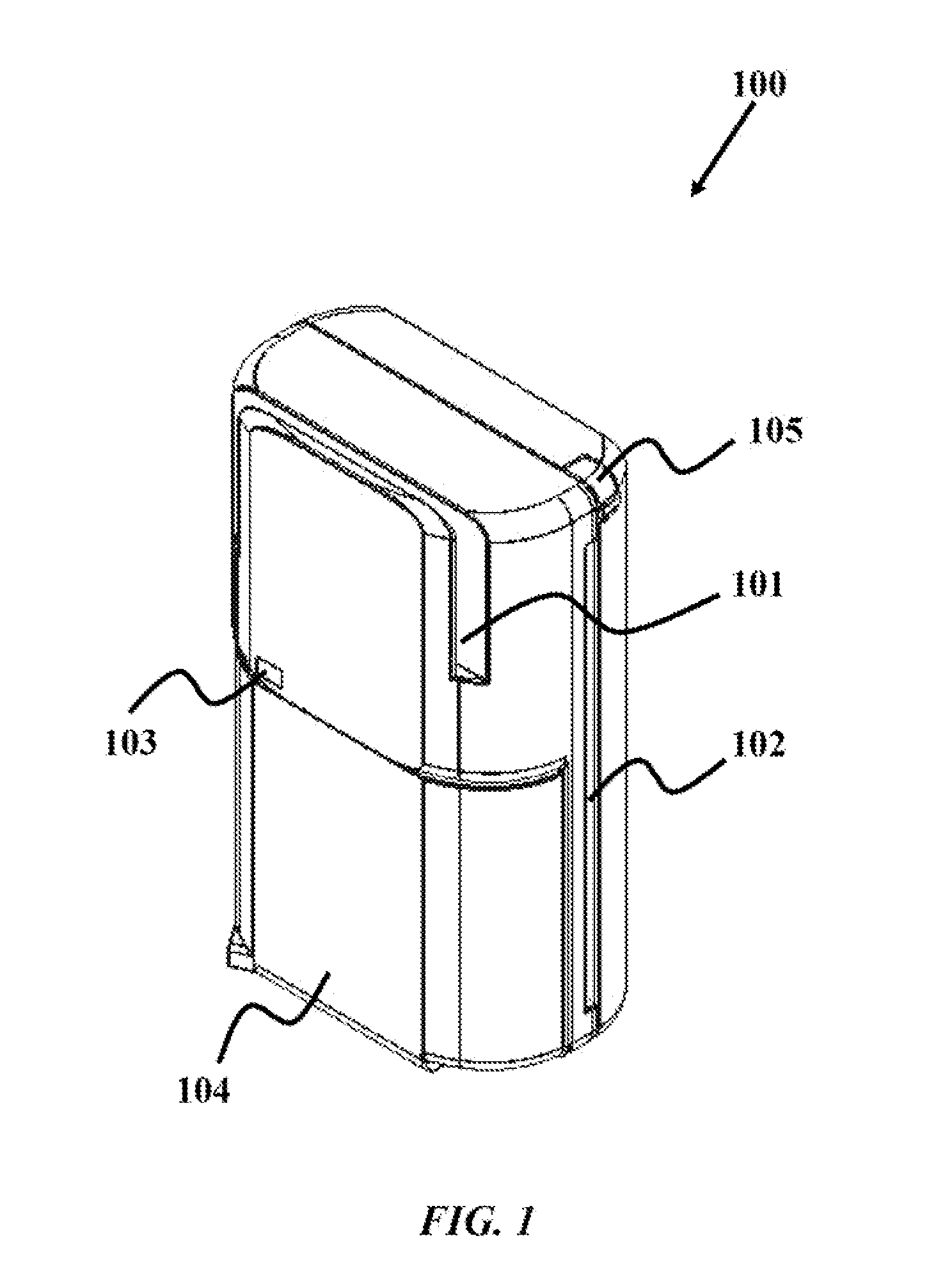
Dongle device with tamper proof characteristics for a secure electronic transaction
The various embodiments herein provide a dongle device with tamper proof characteristics for a secure electronic transaction. The dongle device comprises a housing which includes a first half comprising a main circuit board and a second half comprising a secondary circuit board, a slot for swiping a magnetic stripe card, a slot for inserting a contact type card, a communication module, a key pad, a connector, a cover for safeguarding the connector, a stylus, a universal serial bus (USB) port, a processor and a display. The processor continuously monitors a connection between the main circuit board and the secondary circuit board and kills the dongle device when processor detects a tampering. The first half and the second half of the dongle device are ultrasonically sealed together. The main circuit board and the secondary circuit board are electrically and electronically connected through a compressible connector.
Owner:EZETAP MOBILE SOLUTIONS
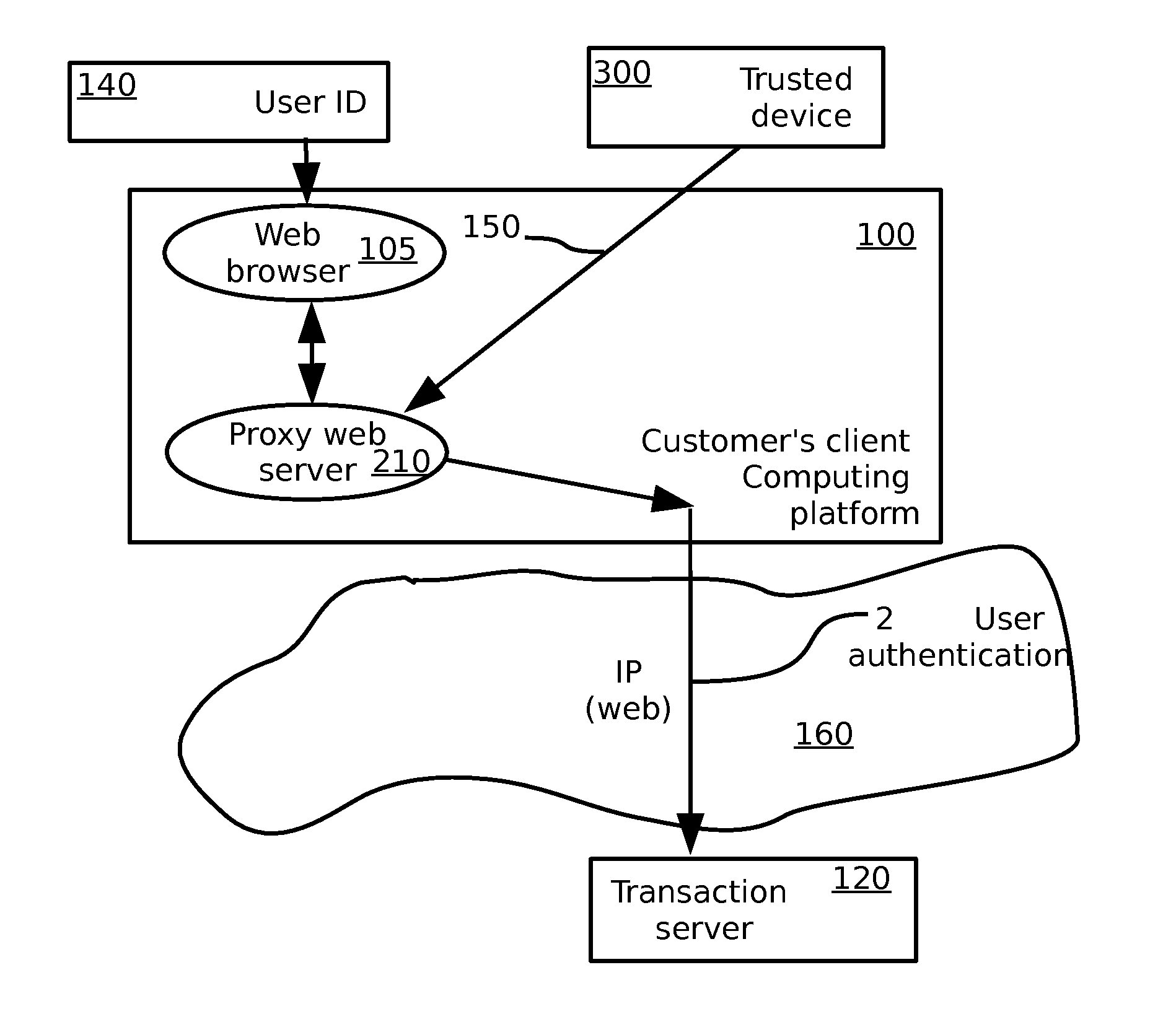
Method and system for securing electronic transactions
ActiveUS20110154459A1Avoid and mitigate shortcomingFinanceDigital data processing detailsSecure Electronic TransactionTrusted Computing
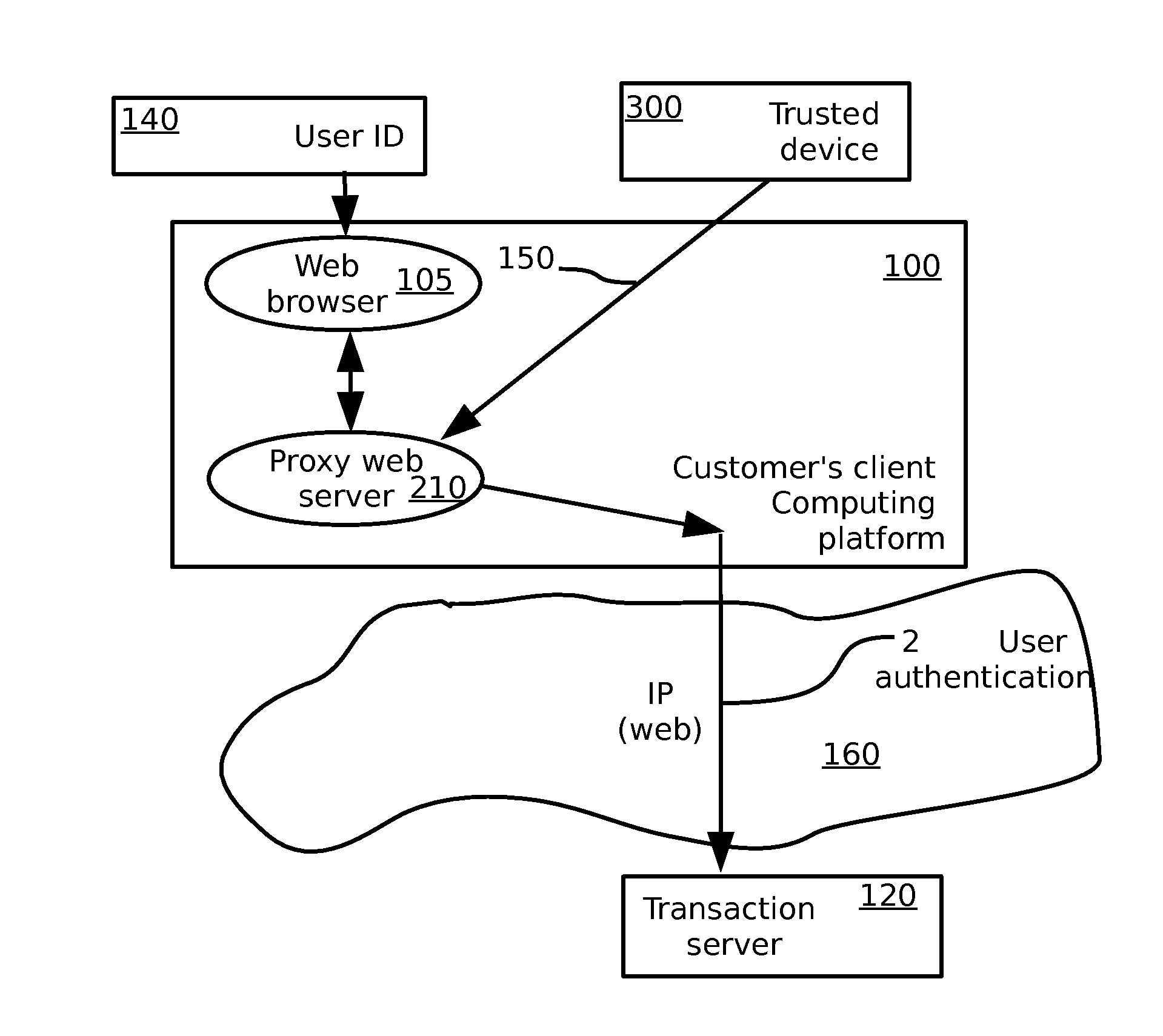
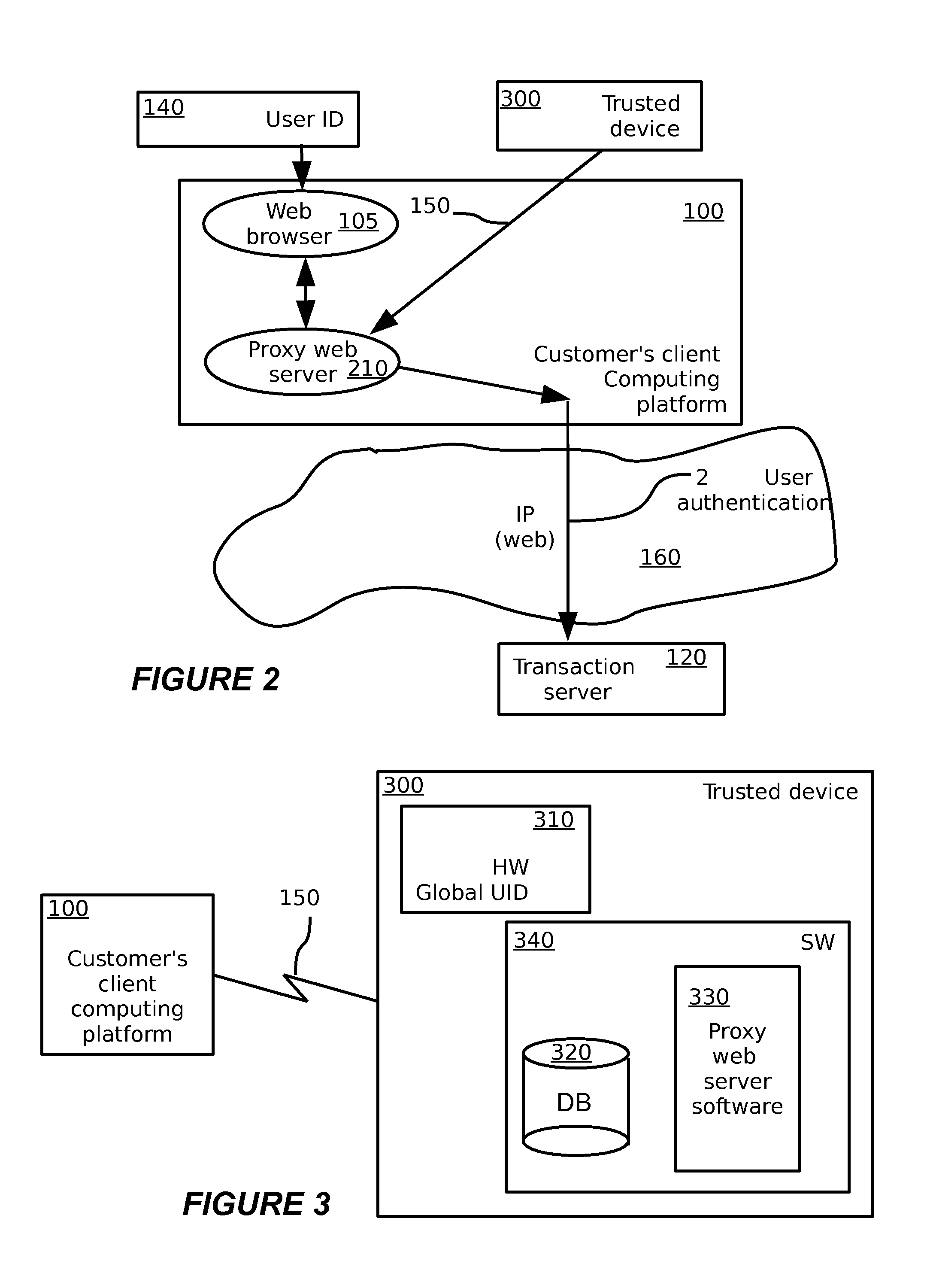
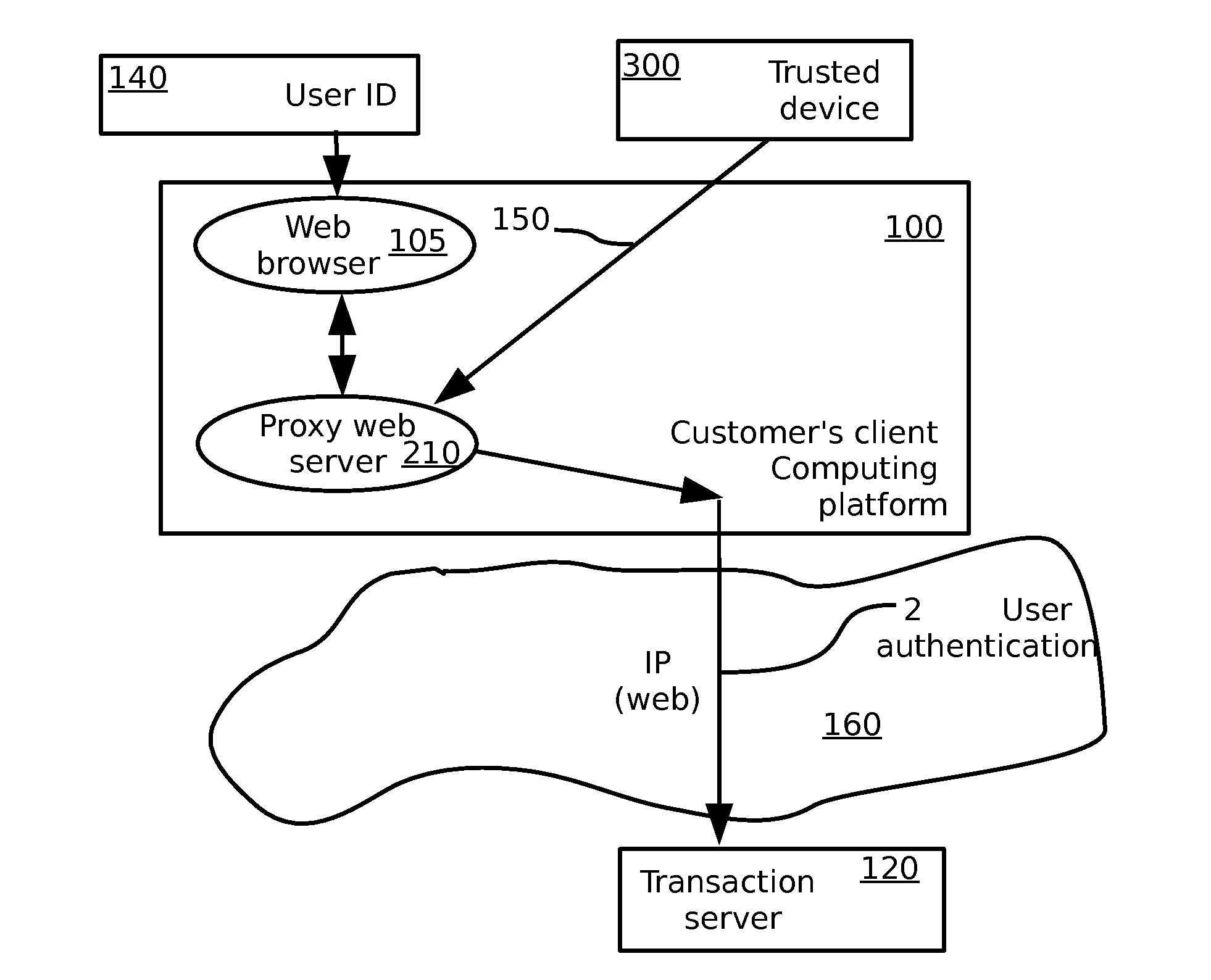
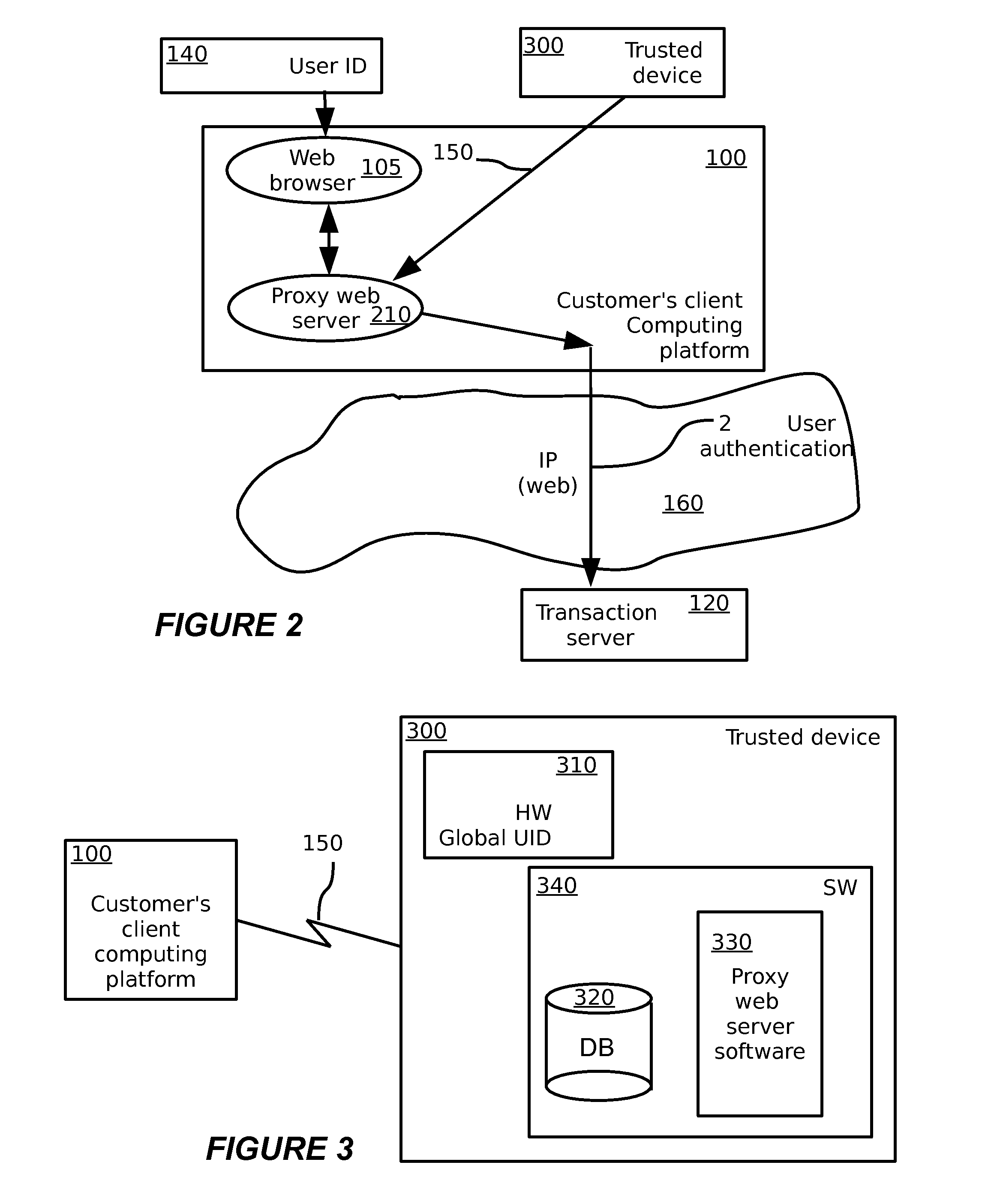
A method for secure electronic transaction over a computer network, comprising: at a trusted relationship profile server computer: storing a unique identity of a trusted computing unit; generating a confirmation message regarding the unique identity of the trusted computing unit in response to a request from the trusted computing unit; at a security proxy server computer: storing real credentials and local credentials of a customer in a secure vault; receiving the confirmation message and permitting a login process to be performed with the security proxy server using the local credentials, provided the confirmation message is valid; and replacing the local credentials submitted in the login process with the real credentials. A corresponding system for secure electronic transactions is also provided.
Owner:INBAY TECH
Method and system for authorizing secure electronic transactions using a security device having a quick response code scanner
ActiveUS20150326565A1Avoid and mitigate shortcomingDigital data information retrievalDigital data processing detailsSecurity softwareSecure Electronic Transaction
Methods and systems for authenticating a security device for providing a secure access and transaction authorization to a remote network location are provided. The security device is authenticated by installing private security software on the security device. In order to authorize a transaction, a transaction authorization is performed using the security device by display a QR (Quick Response) code from an authorization server on a user terminal and scanning the QR code into the security device. After scanning the QR code, an OTA (One-Time-Authorization) code is sent from the security device to the authorization server for verifying the transaction. Embodiments of the present invention provide increased security and privacy. A corresponding system for authenticating a security device and preforming secure and private transactions is also provided.
Owner:INBAY TECH
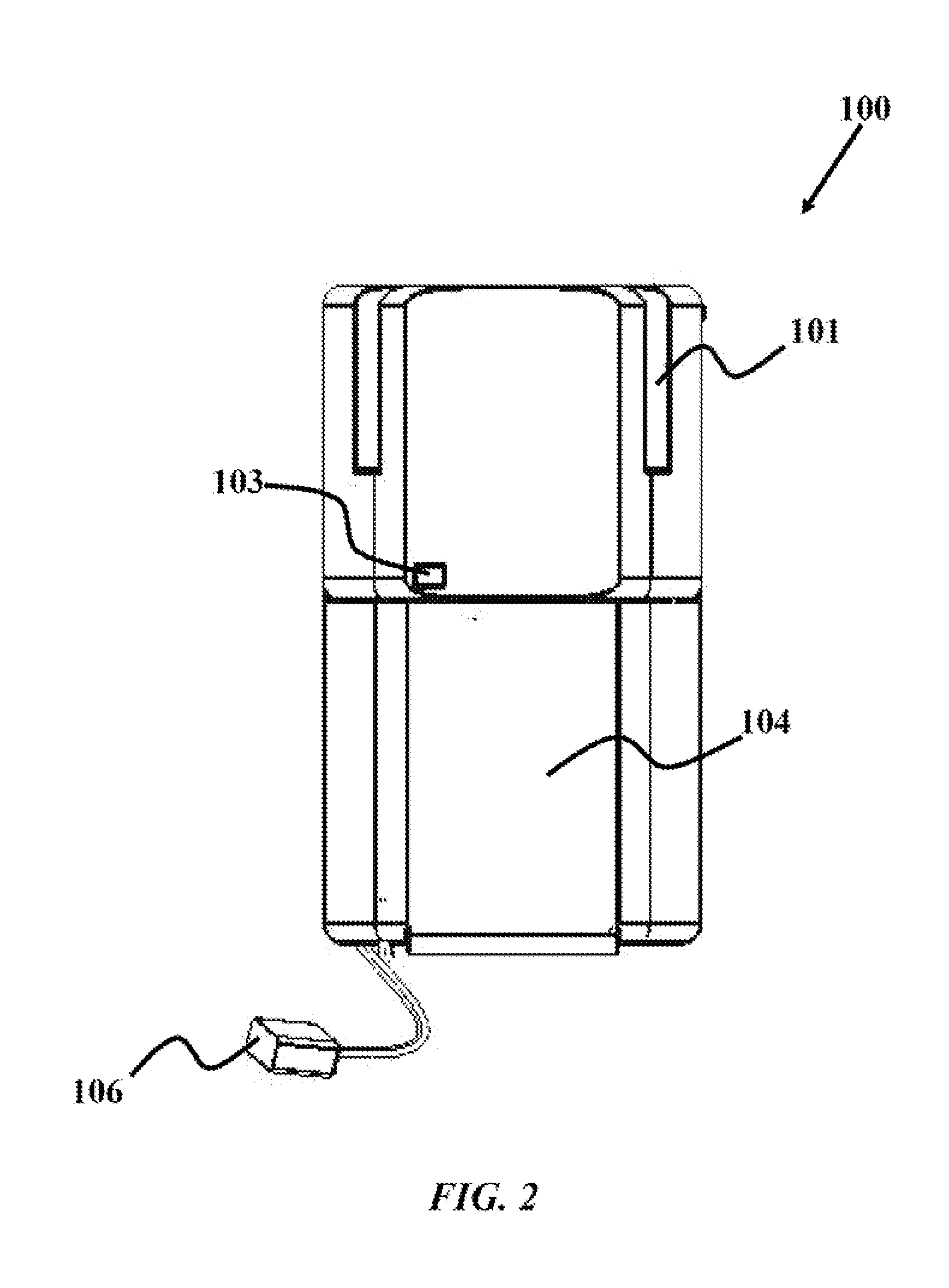
Dongle device with rechargeable power supply for a secure electronic transaction
InactiveUS20140297539A1Avoid viewingAcutation objectsCryptography processingSecure Electronic TransactionElectrical battery
The various embodiments herein provide a dongle device with rechargeable power supply for a secure electronic transaction. The dongle device comprises a slot for swiping a magnetic stripe card, a slot for inserting a contact type card, a rechargeable battery, a recharging circuit, a key pad, a key pad cover, a connector, wherein the connector is an audio jack, a cover for safeguarding the connector, a stylus, a universal serial bus (USB) port, a processor and a display. The rechargeable battery is powered by the recharging circuit when a residual battery level of the rechargeable battery falls below a preset value. The key pad is used to enter PIN and the key pad cover prevents an onlooker from viewing and learning the PIN entered by a user.
Owner:EZETAP MOBILE SOLUTIONS
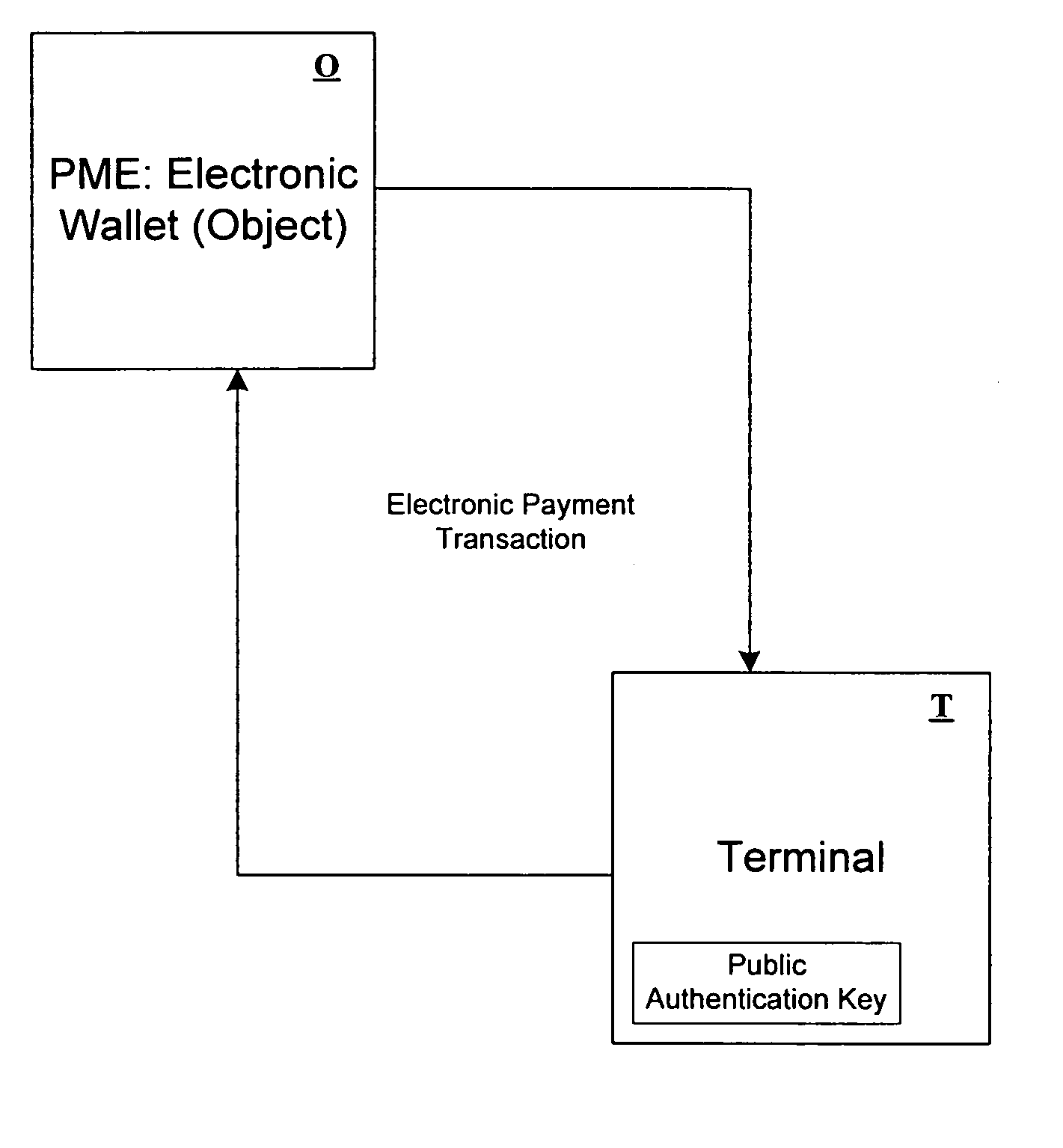
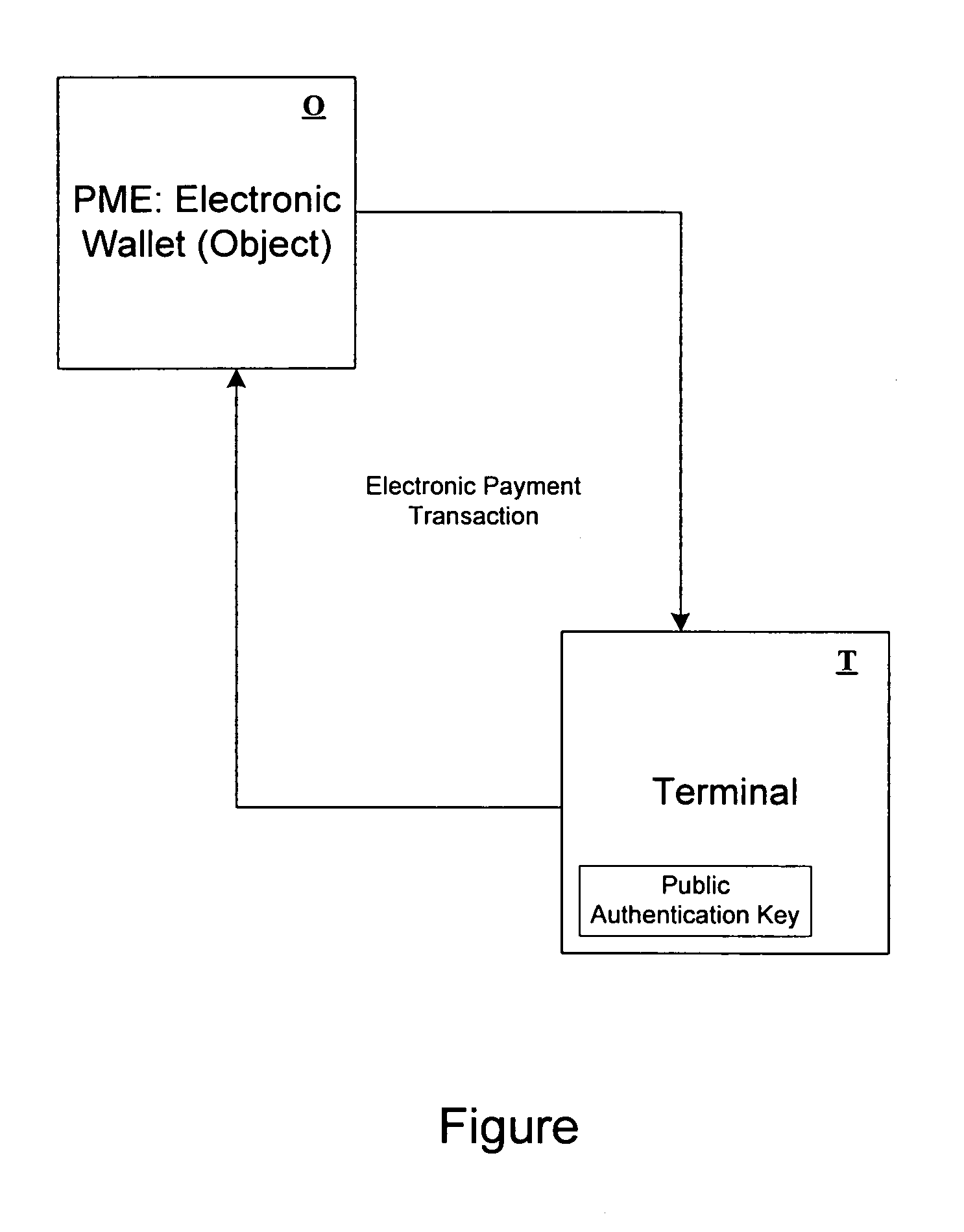
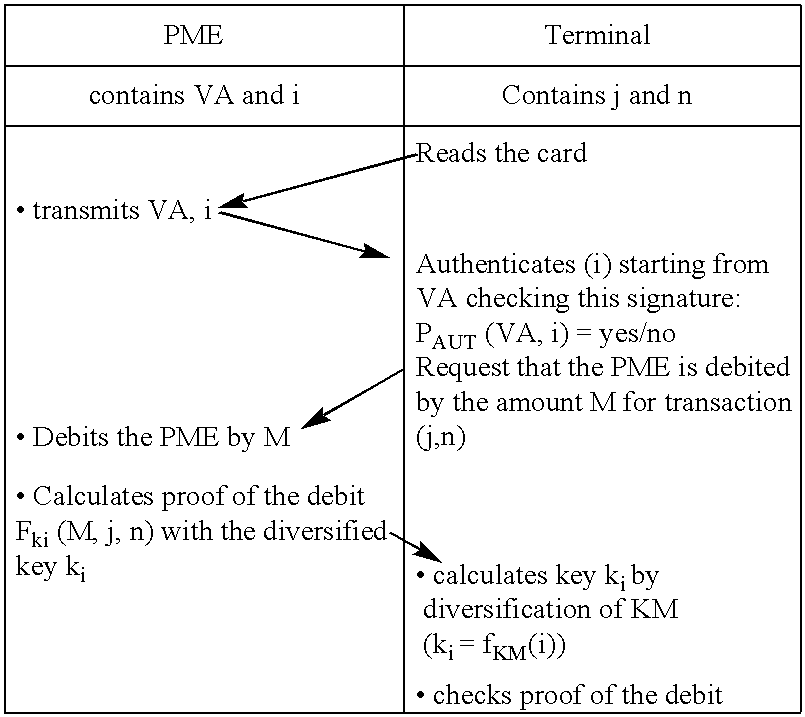
Method for secure electronic transaction and corresponding system
InactiveUS7240034B1Key distribution for secure communicationFinanceDigital signatureSecure Electronic Transaction
The transaction is made between an object and a terminal. According to the invention, an authentication value is inserted in the object which is a digital signature appearing on an identifier of the object. Each object also has a diversified key created from a base key diversified by the identifier. The terminal can thus authenticate the identifier and check that the debit has actually been made.Application to electronic payment.
Owner:FRANCE TELECOM SA
Electronic balance checking and credit approval system for use in conducting electronic transactions
InactiveUS8050991B2Maximize security and authenticityStrong authenticationFinancePoint-of-sale network systemsCredit cardSecure Electronic Transaction
Owner:DXSTORM COM
System and method for transparently providing certificate validation and other services within an electronic transaction
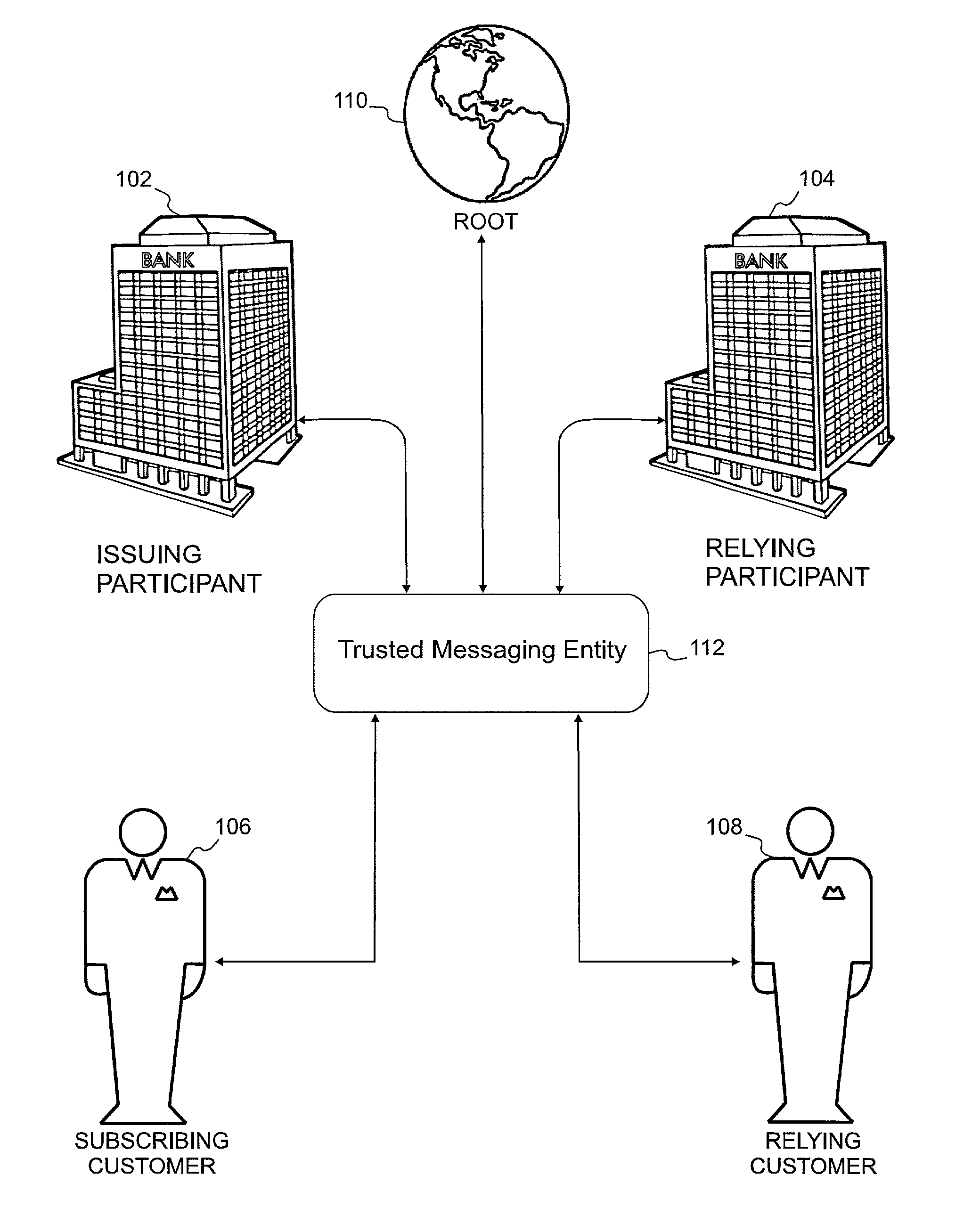
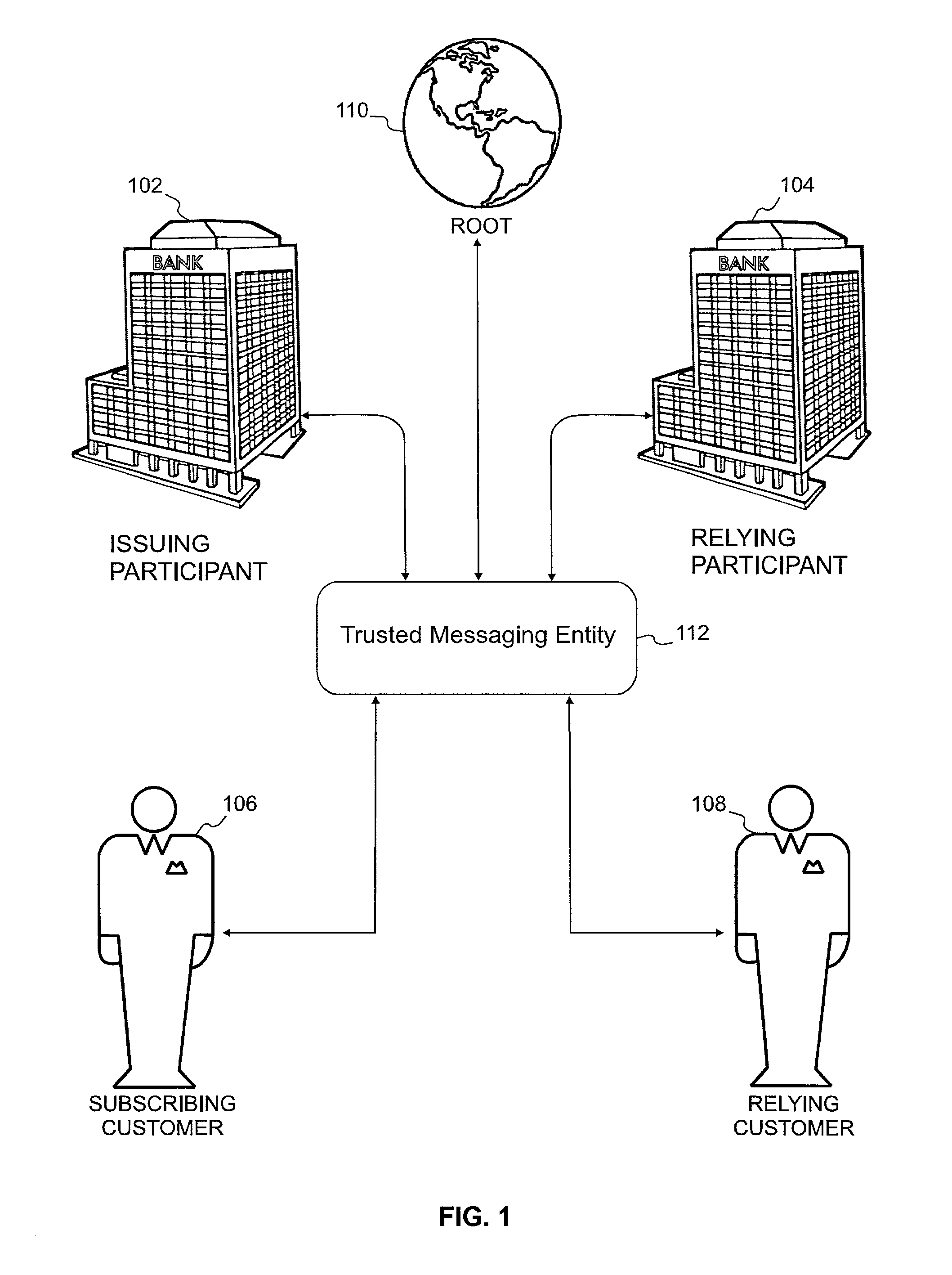
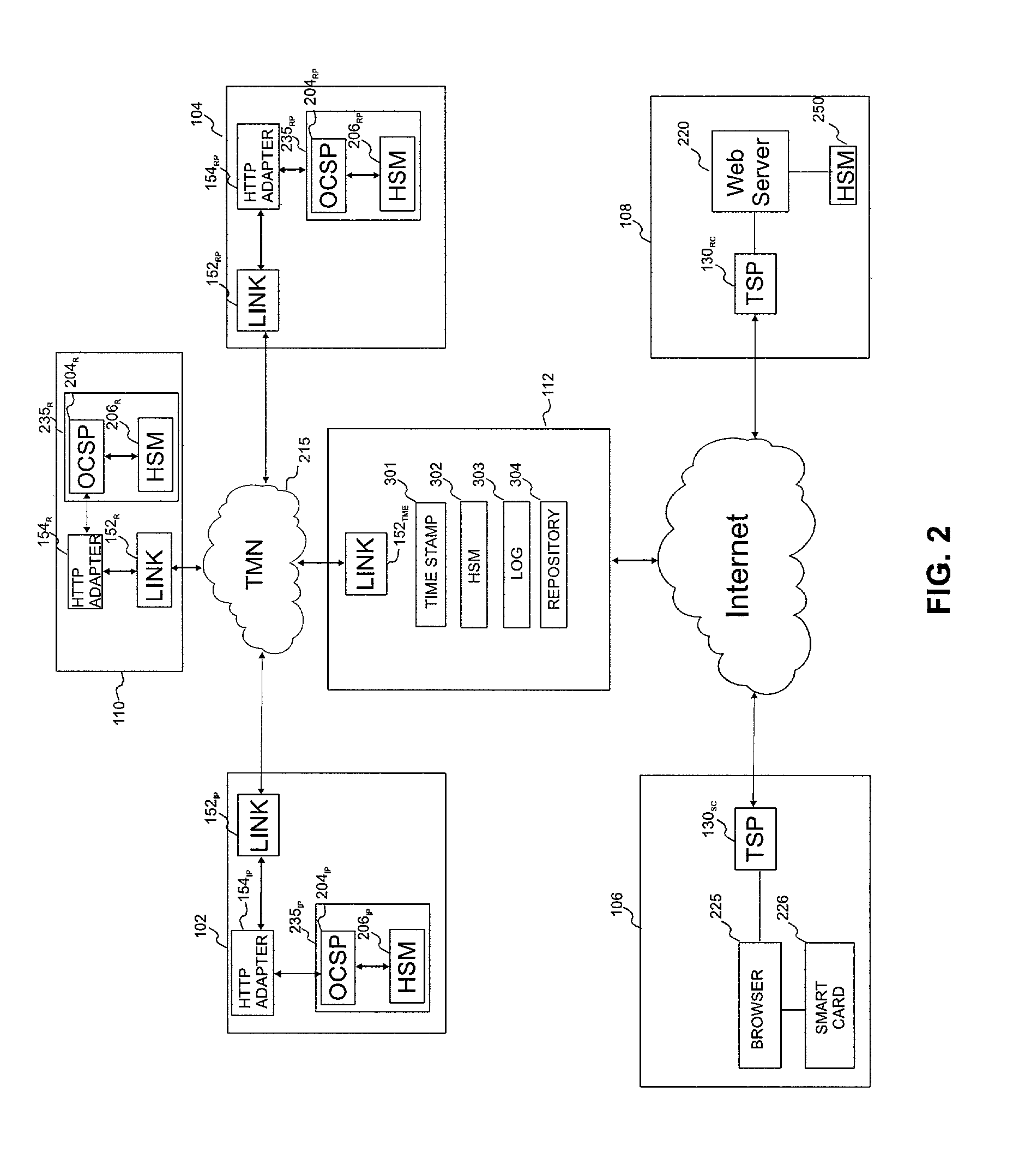
InactiveUS7000105B2Facilitating non-repudiationFinanceUser identity/authority verificationDigital signatureSecure Electronic Transaction
A system and method are disclosed for transparently providing certificate validation and other services without requiring a separate service request by either a relying customer or subscribing customer. In a preferred embodiment, after the subscribing customer digitally signs a document (e.g., a commercial document such as a purchase order), it forwards the document to a trusted messaging entity which validates the certificates of both the subscribing customer and relying customer and the respective system participants of which they are customers. If the certificates are valid, the trusted messaging entity appends a validation message to the digitally-signed document and forwards the document to the relying customer. A validation message is also preferably appended to a digitally-signed receipt from the relying customer and transmitted to the subscribing customer. In this way, both the relying customer and subscribing customer obtain certification of their respective counterparty to the transaction.
Owner:ZIONS BANCORPORATION +1
Secure electronic transaction method and system
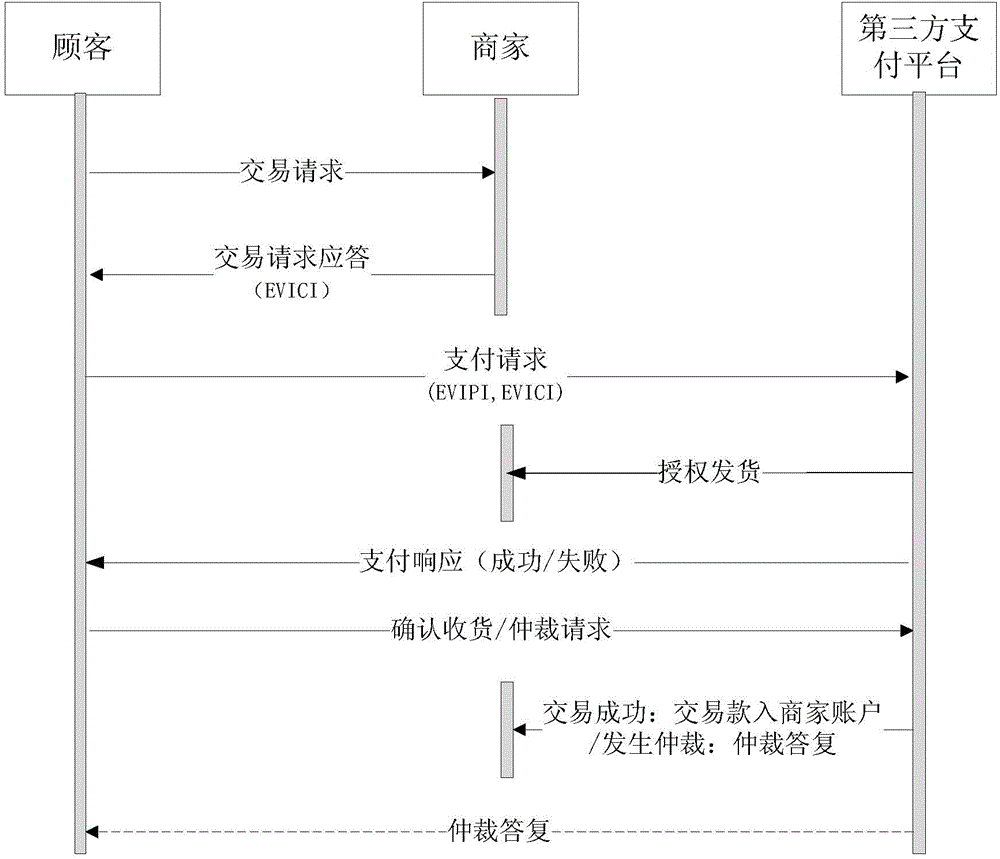
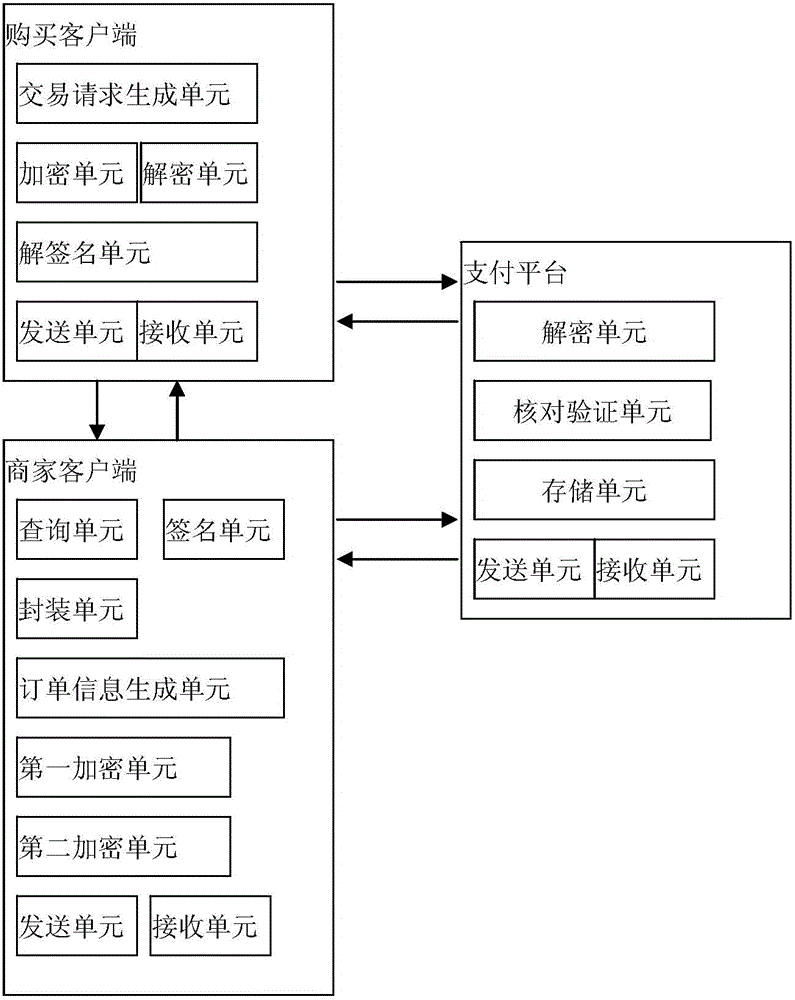
ActiveCN104463567AReduce the number of interactionsImprove efficiencyUser identity/authority verificationBuying/selling/leasing transactionsNon symmetricSecure Electronic Transaction
The invention relates to a secure electronic transaction method and system which are used for solving repudiation disputes existing in electronic transactions. According to the secure electronic transaction method and system of the invention, based on traditional secure electronic transactions, two kinds of electronic evidences containing signature values and signature time of important transaction data are provided, namely, commodity information evidences and payment information evidences, and therefore, non-repudiation can be provided for information which tends to cause repudiation disputes. In a transaction process, verified electronic evidences can be submitted, so that complex transaction authentication procedures can be reduced, and a non-symmetric encryption algorithm and a hash algorithm are utilized to ensure the confidentiality and integrity of data in the whole electronic transaction process.
Owner:AEROSPACE INFORMATION
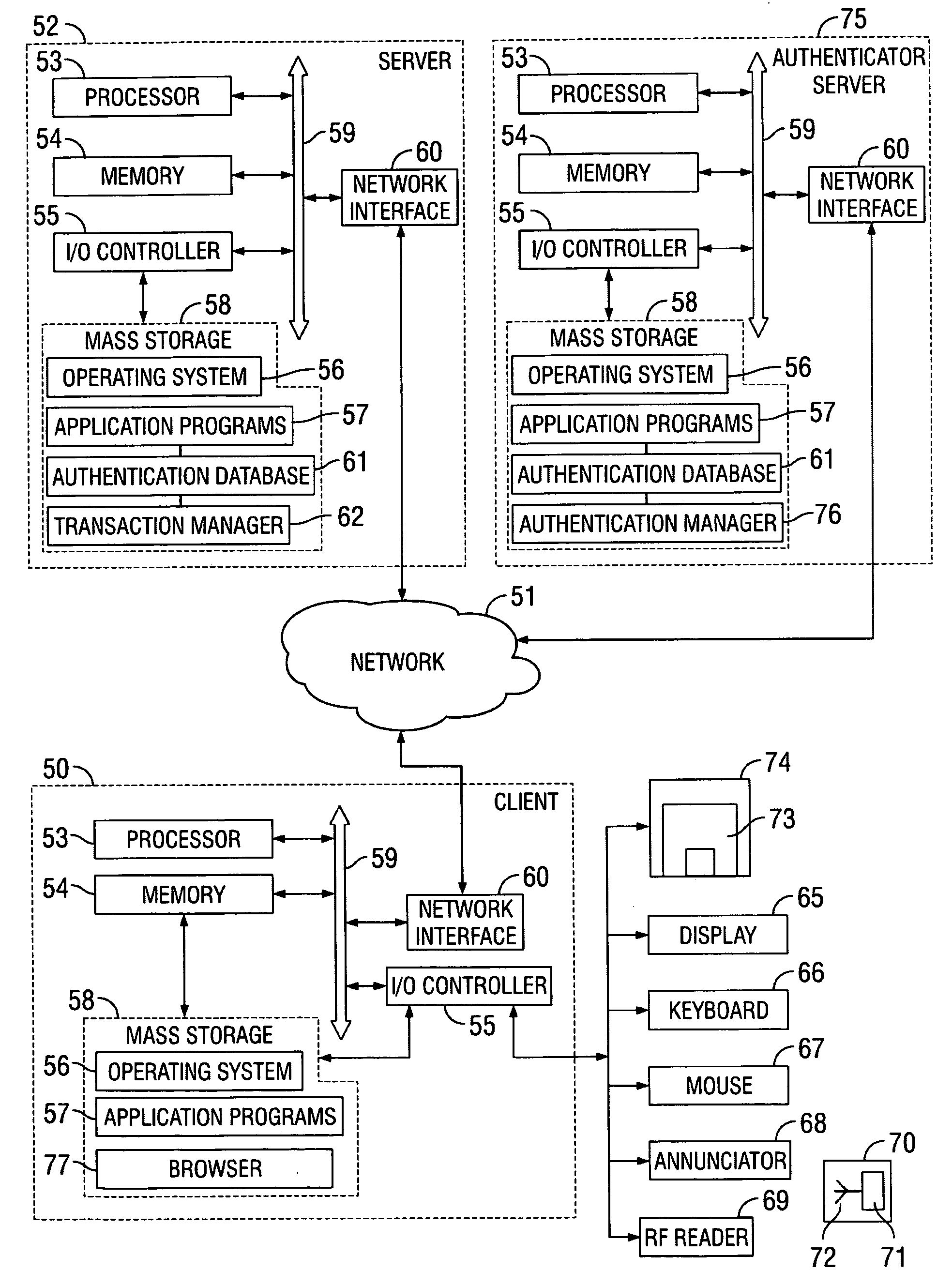
Methods and systems for securing electronic transactions
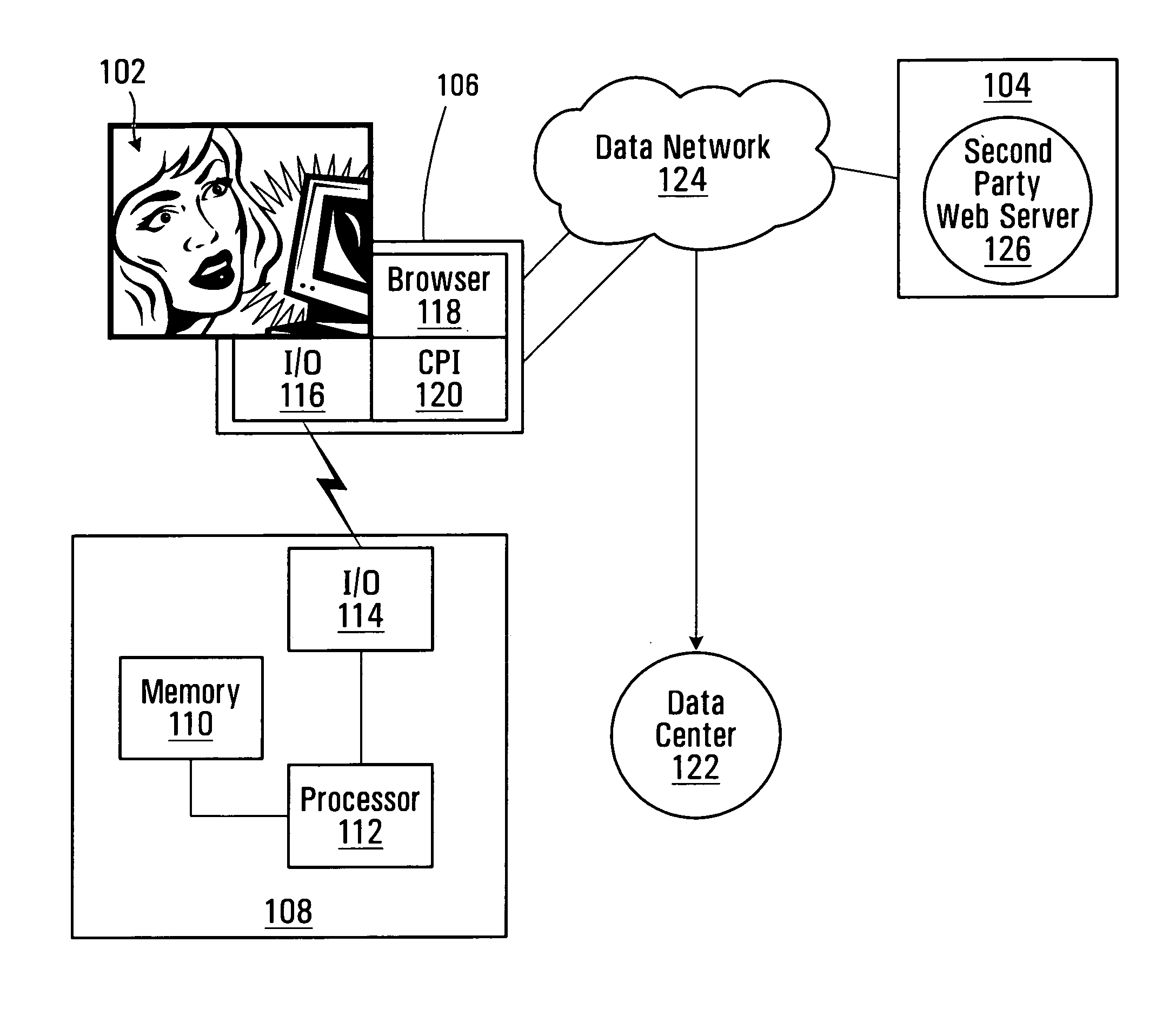
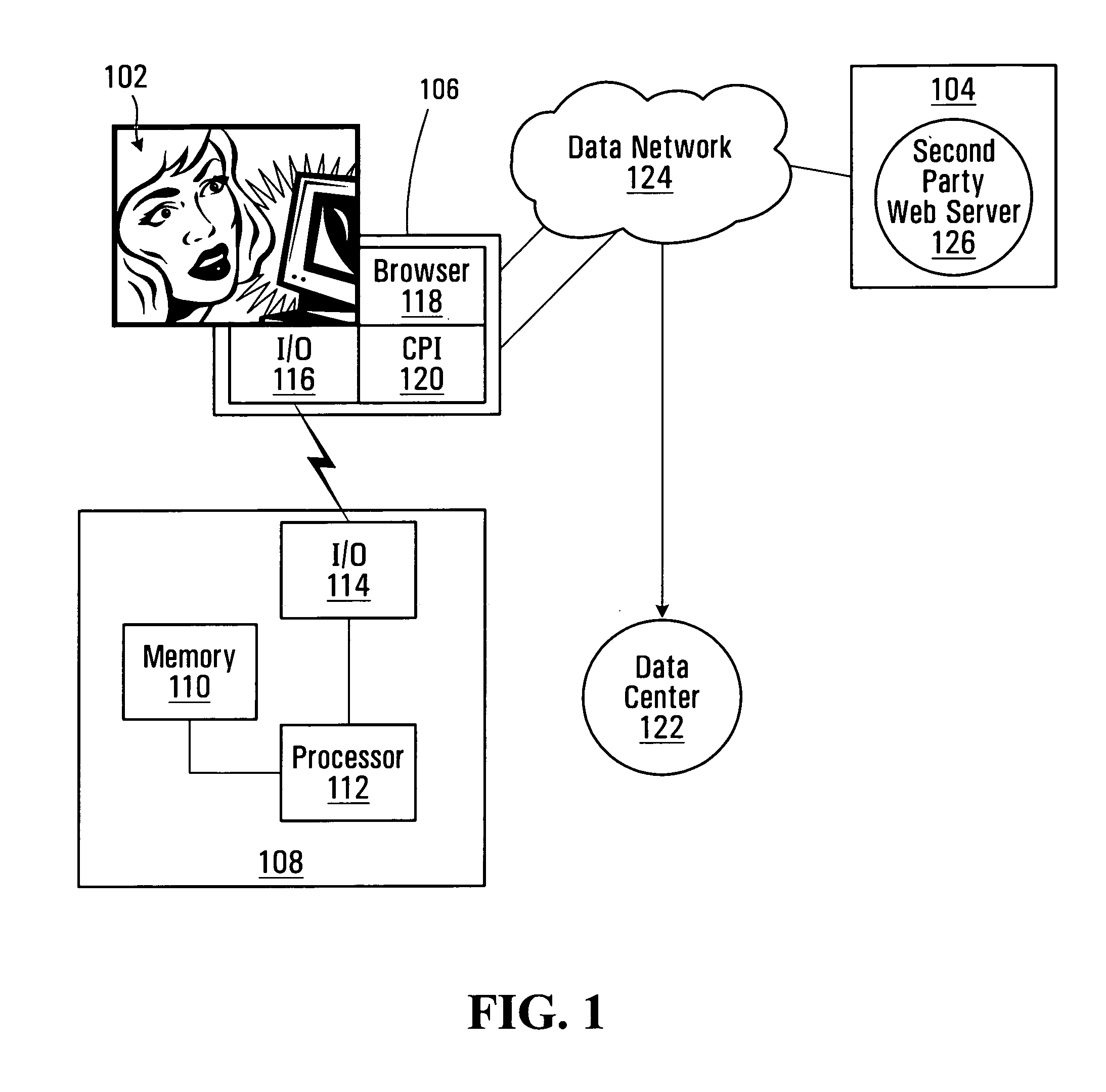
Methods and systems for securing a prospective electronic transaction between a first party and a second party. The system comprises an authentication entity adapted for generating a transaction indicia for the electronic transaction and sending the transaction indicia to the client computer, wherein receipt of the transaction indicia by a client computer used by the first party causes encryption of the transaction indicia and account information associated with the first party into encrypted data. Also, the system comprises a data center adapted for receiving the encrypted data from the client computer; decrypting the encrypted data to obtain the transaction indicia and the account information associated with the first party; and sending the transaction indicia and the account information to the authentication entity for completion of the electronic transaction on a basis of the account information.
Owner:ELHARAR AMIR +1
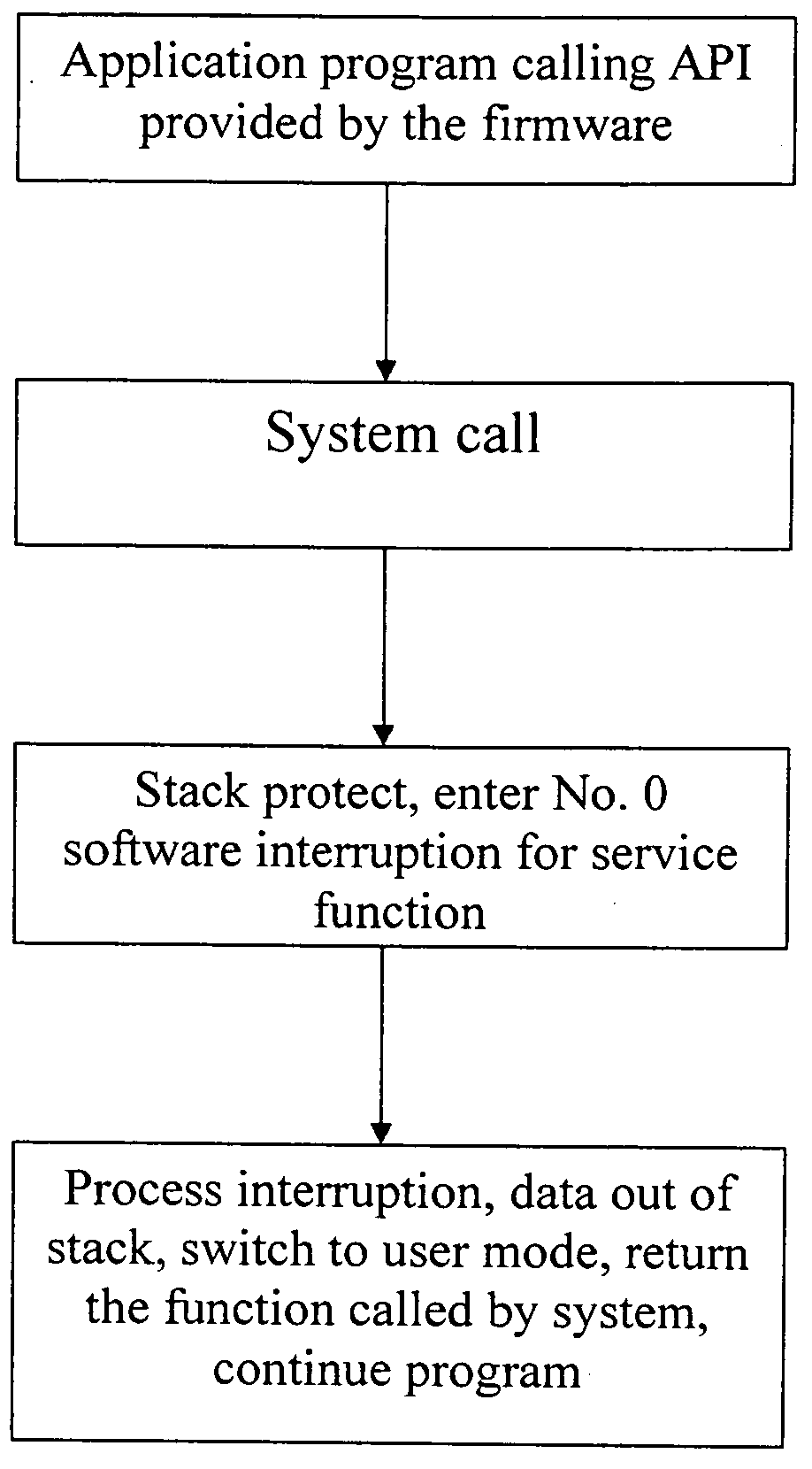
Secure device firmware
InactiveUS20100174631A1Setup safelyAcutation objectsFinanceSecure Electronic TransactionApplication software
Owner:ONBEST TECH HLDG
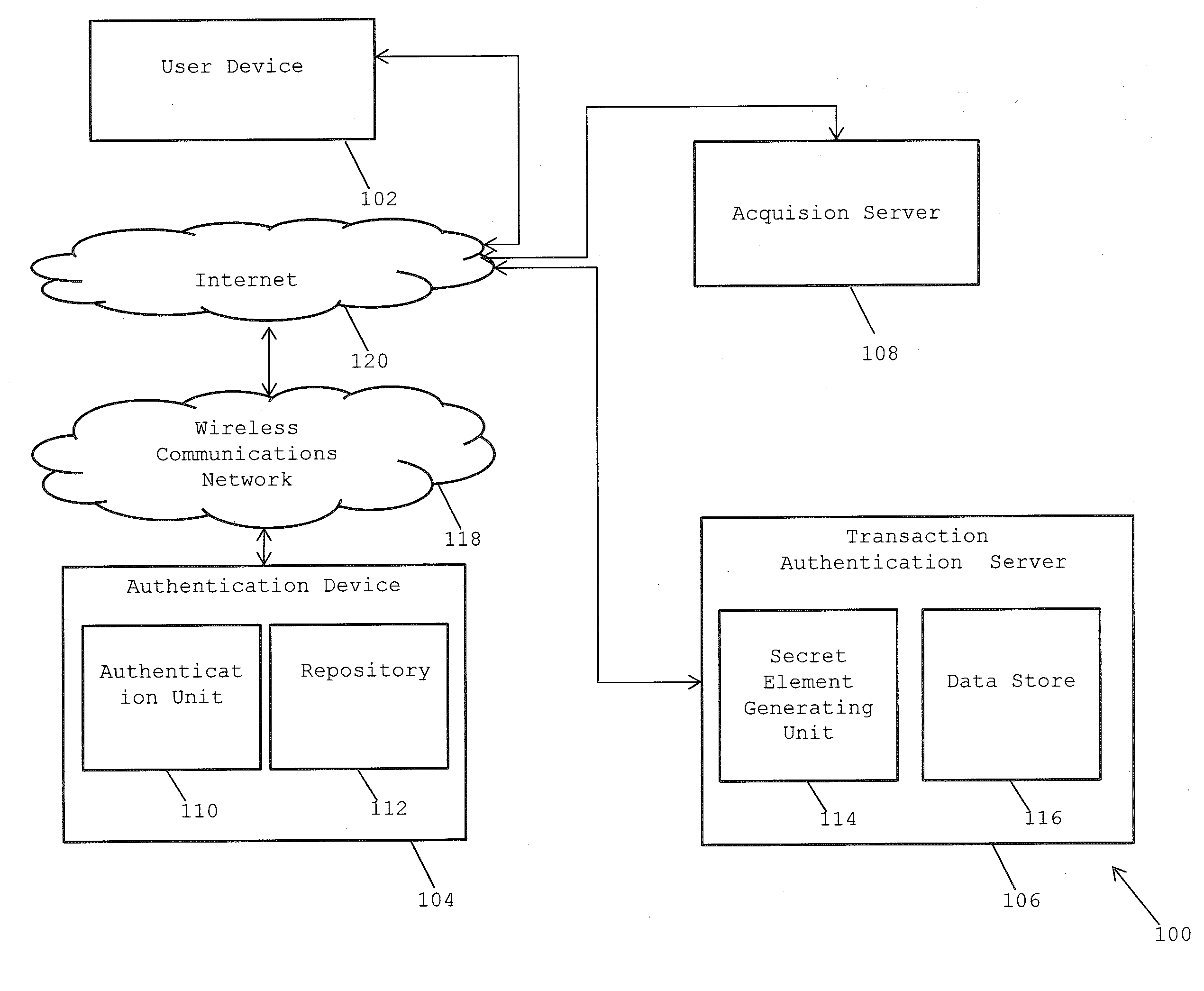
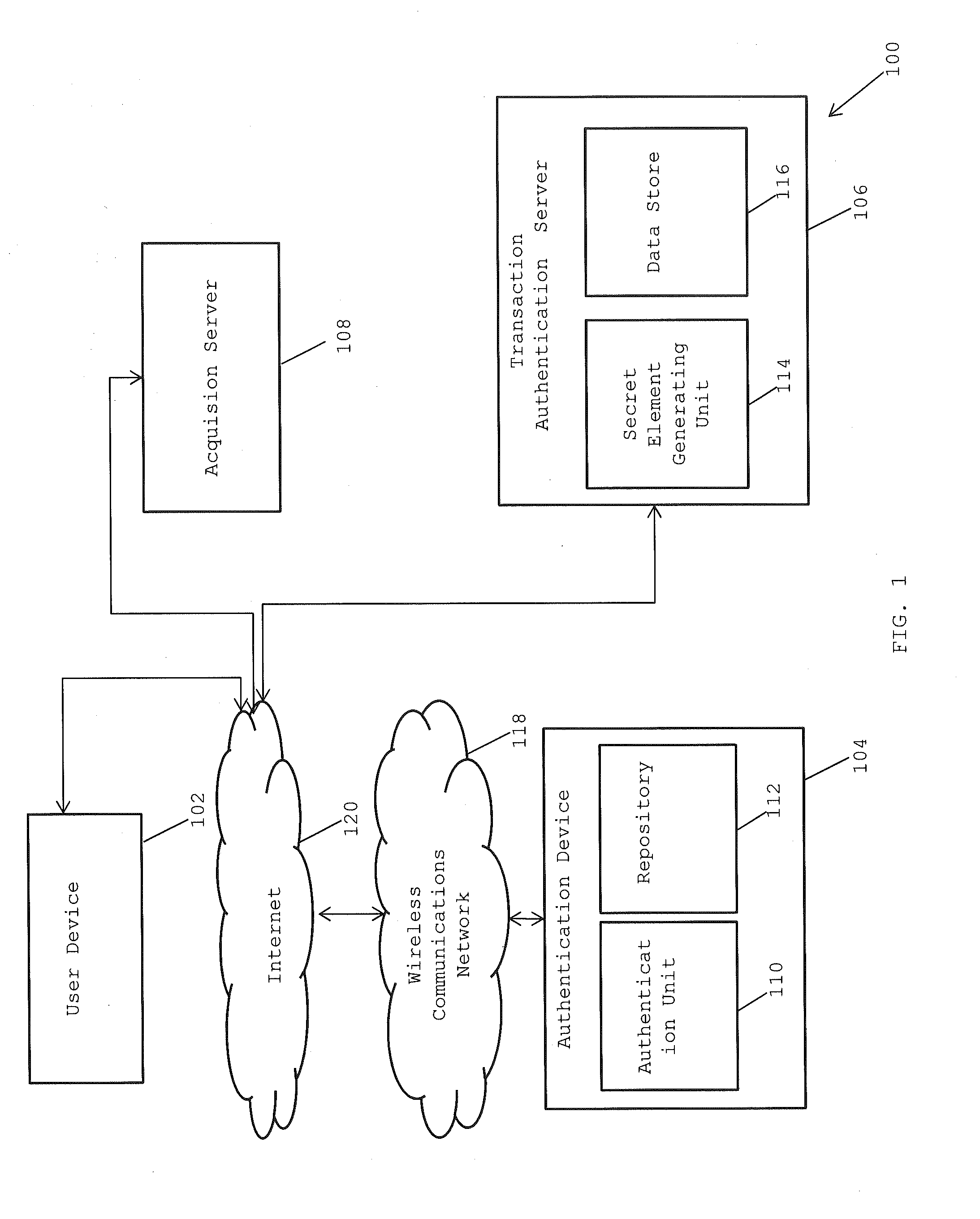
Method and system for providing secure end-to-end authentication and authorization of electronic transactions
InactiveUS20140149294A1Facilitate data exchangePayment protocolsPayments involving neutral partyUser deviceSecure Electronic Transaction
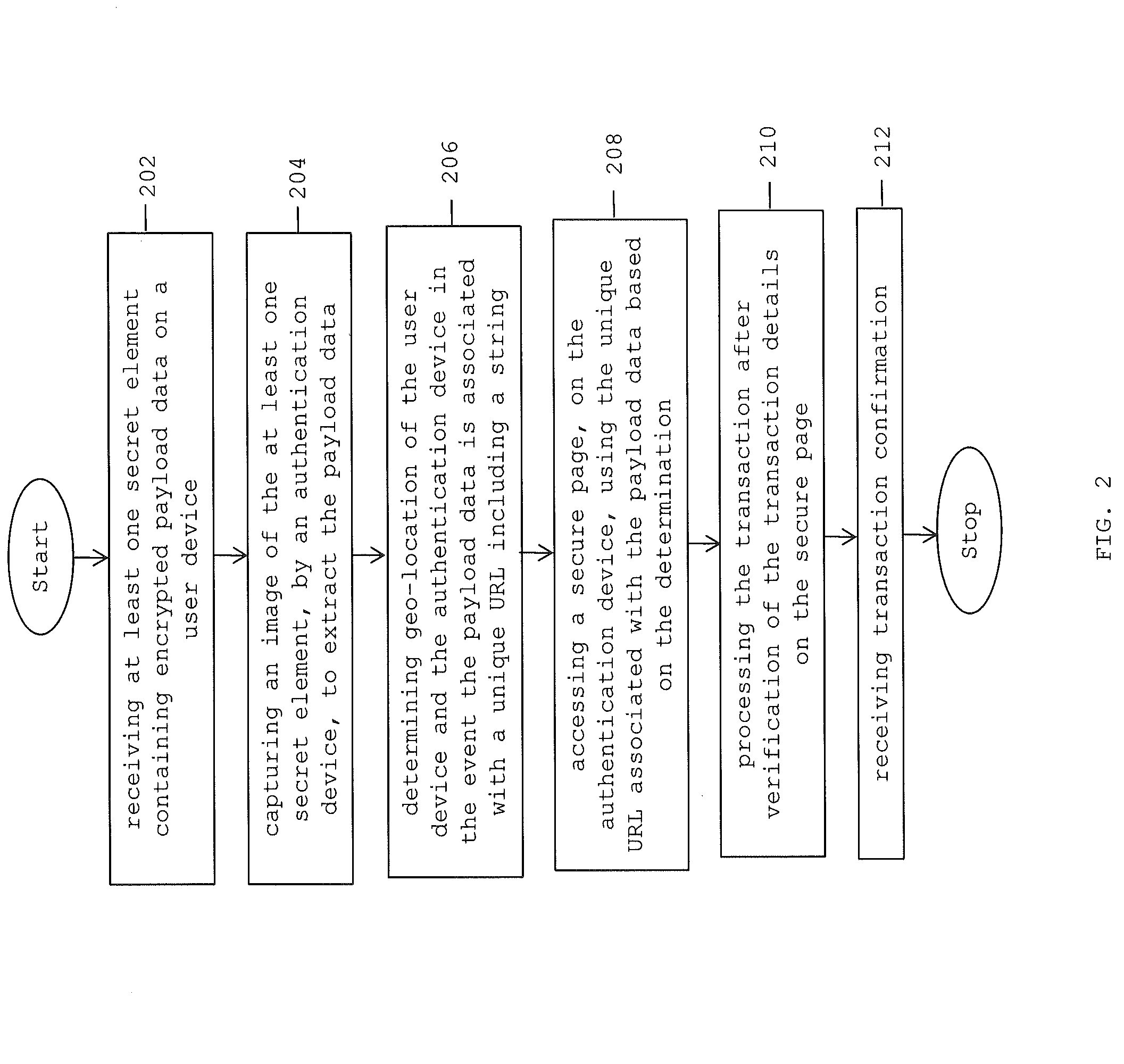
A method and system for performing secure end-to-end authentication of an electronic transaction initiated by a user using a user device is provided. At least one secret element comprising payload data encrypted using at least two cryptographic keys is generated and transmitted to the user device. An image of the at least one secret element is captured and analyzed by an authentication device. The image is analyzed to extract the payload data by decrypting the payload data using at least two cryptographic keys. Geo-location of the user device and the authentication device is determined if the extracted payload data is associated with a unique URL including a string. Based on the determination, a secure page displayed on the authentication is accessed using the unique URL. Finally, the transaction is processed after verification of the transaction details on the secure page and the transaction is confirmed.
Owner:COGNIZANT TECH SOLUTIONS INDIA PVT
Tamper-proofing and identity validation in a secure electronic transaction processing system
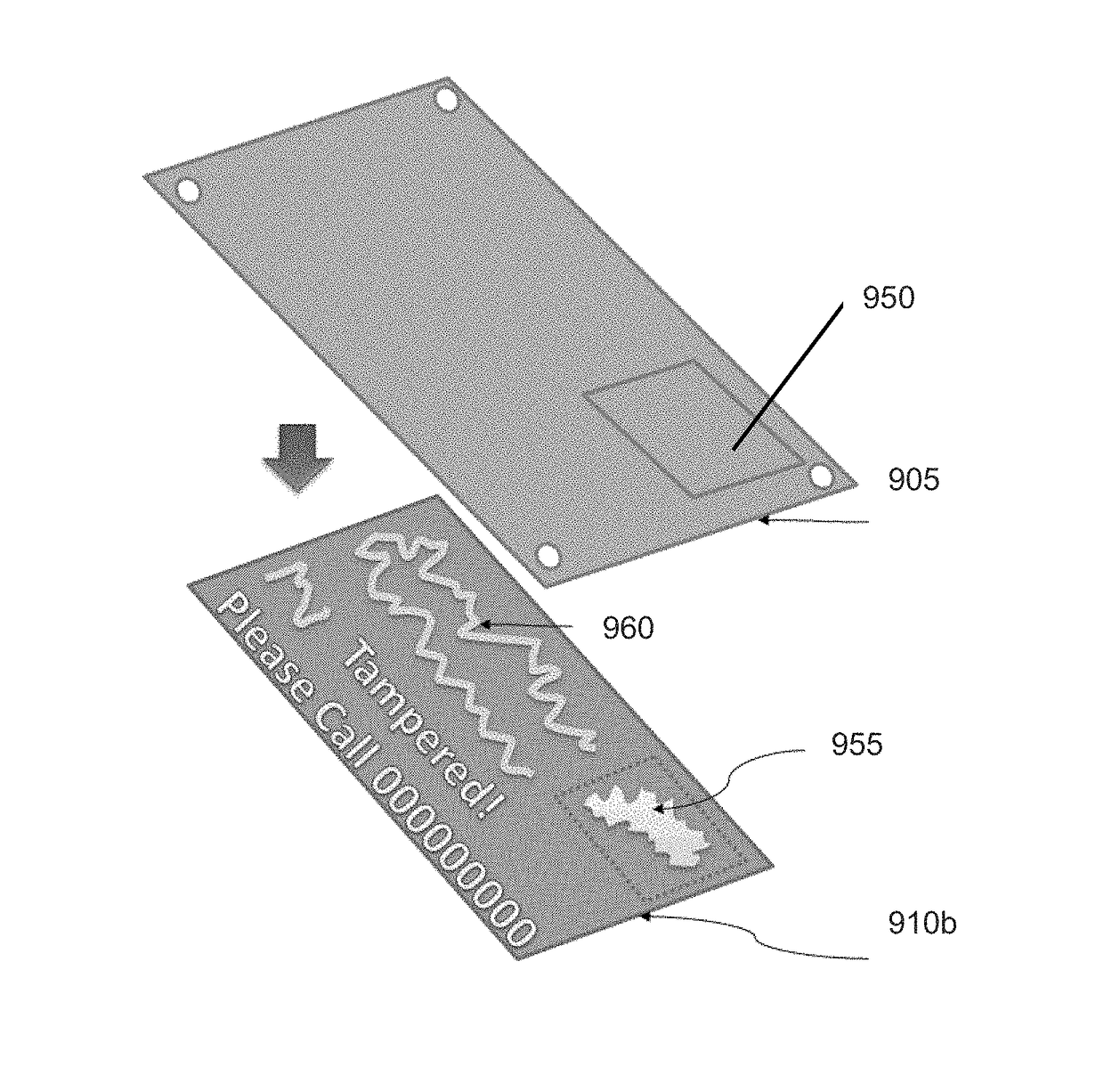
ActiveUS20170213218A1Point-of-sale network systemsRecord carriers used with machinesTamper resistanceComputer hardware
Tamper-proofing and secure identity validation techniques in a transaction processing system and secure electronic payment techniques are disclosed. A tamper-proof transaction processing device is provided and comprises at least two different strength adhesives to secure parts of the device together and a housing comprising at least a first and second protective layer. An electronic component comprising a secure element chip storing unique information relating to the chip is located between the first and second protective layer in the housing. In another aspect, a transaction processing system includes a payment instrument that is configured to approve only negative value and / or zero value transaction requests. Another aspect provides an identity card checking system and method where the identity card is brought into proximity of a data processing device and identity information is displayed on the screen of the data processing device for the period of time while the card is in proximity.
Owner:WORLDPLAY LTD
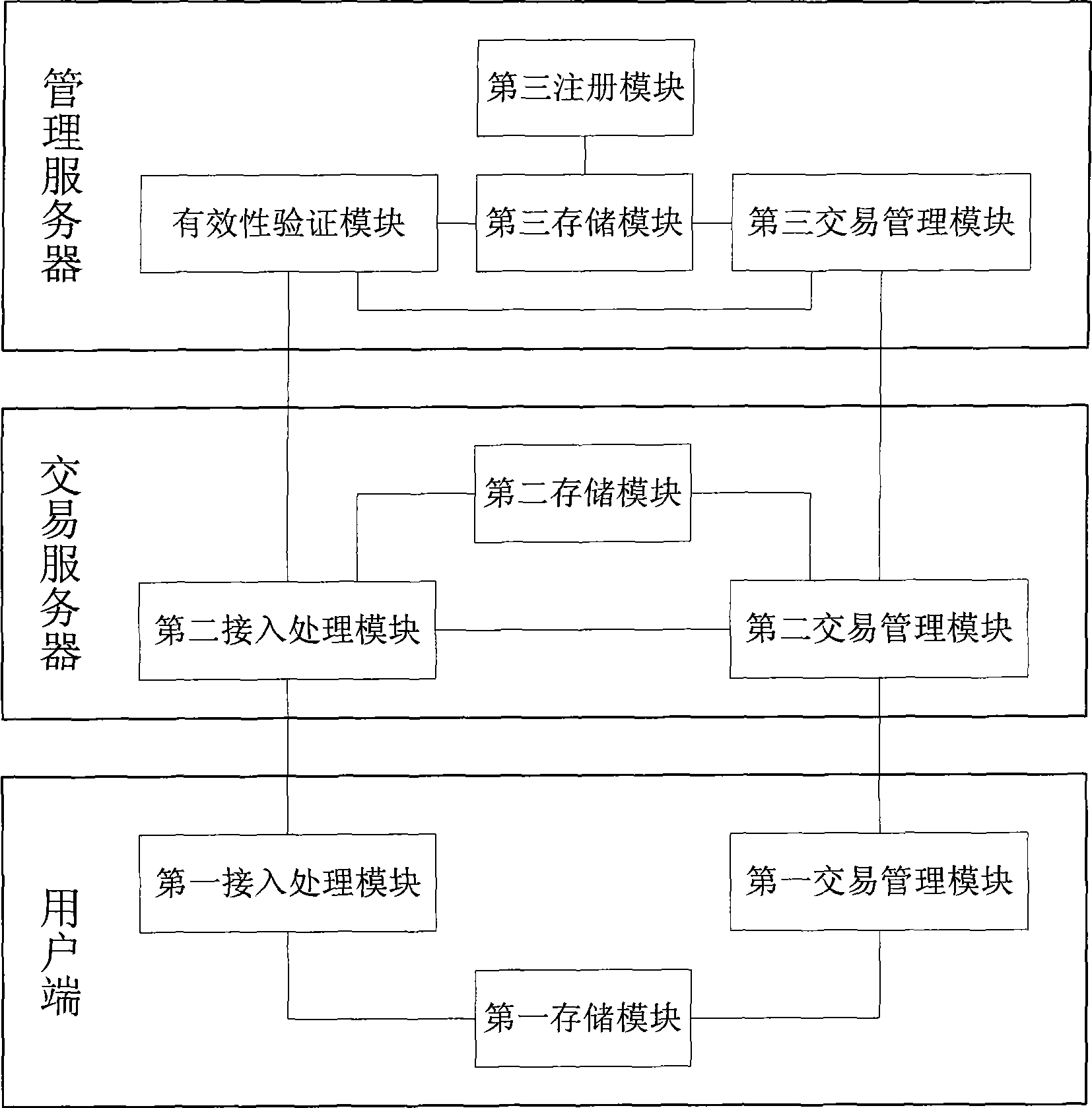
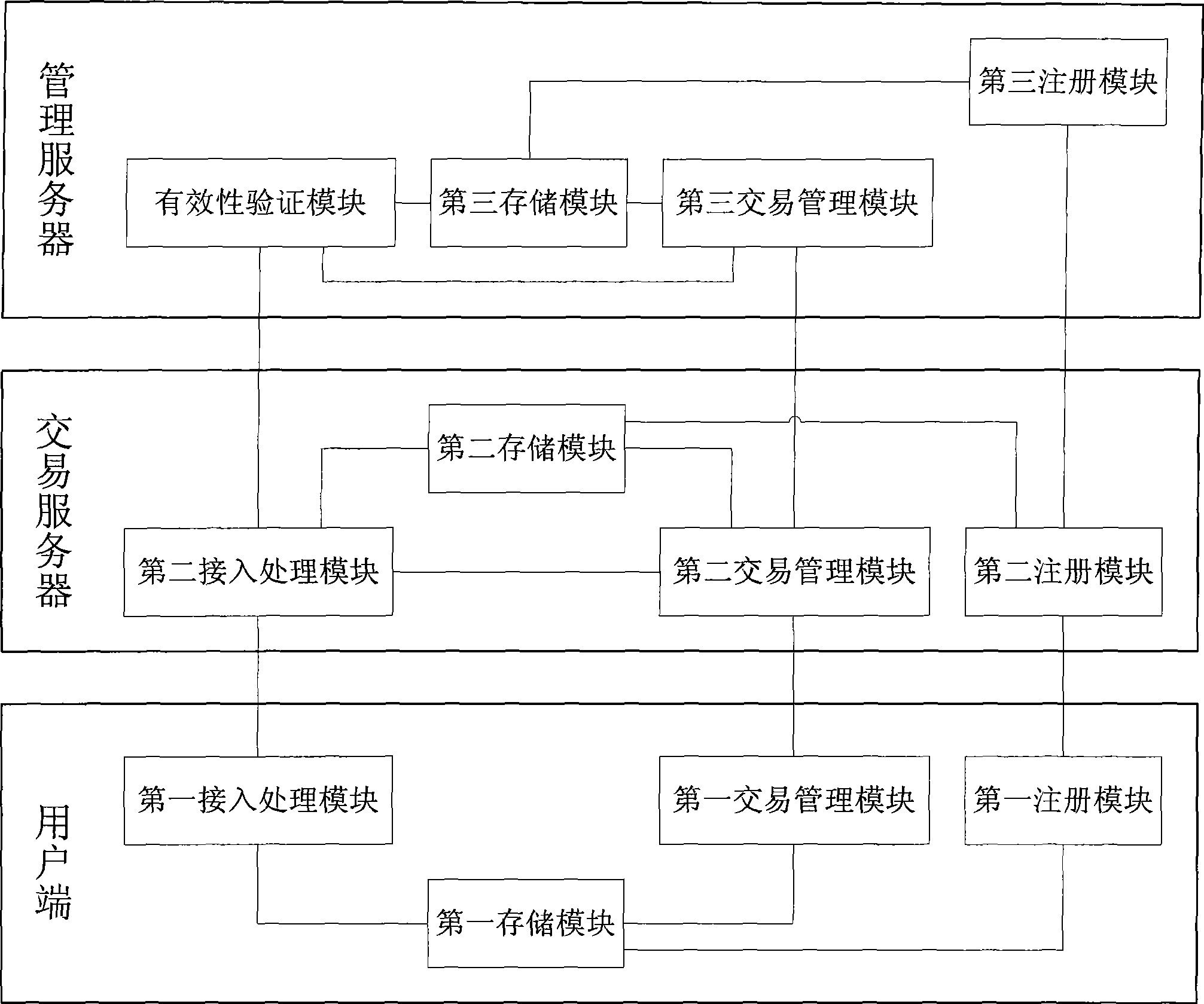
Electronic commerce system and management method thereof based on digital certificate
InactiveCN101546407AImprove securityAvoid damageUser identity/authority verificationDigital data authenticationElectronic contractsTransaction service
The invention relates to an electronic commerce system and a management method thereof based on a digital certificate. A management server issues certificates and corresponding certificate private keys for each user end and each transaction server; the user end can access different transaction servers according to the certificate issued by the management server and can be accessed to different transaction servers to carry out electronic commerce action without unnecessary logging operation; in addition, after the management server validates the identities of the user end and the transaction server, and when a concrete electronic transaction is carried out, the transaction server validates the validity of the content of an electronic contract, and the management server judges the validity of the transaction so as to realize uniform authentication and management for electronic commerce behaviors and ensure the trusty degree of network electronic transaction behaviors.
Owner:GCI SCI & TECH
Method and system for securing electronic transactions
ActiveUS20130276082A1Avoid and mitigate shortcomingDigital data processing detailsMultiple digital computer combinationsSecure Electronic TransactionTrusted Computing
A method for secure electronic transaction over a computer network, comprising: at a trusted relationship profile server computer: storing a unique identity of a trusted computing unit; generating a confirmation message regarding the unique identity of the trusted computing unit in response to a request from the trusted computing unit; at a security proxy server computer: storing real credentials and local credentials of a customer in a secure vault; receiving the confirmation message and permitting a login process to be performed with the security proxy server using the local credentials, provided the confirmation message is valid; and replacing the local credentials submitted in the login process with the real credentials. A corresponding system for secure electronic transactions is also provided.
Owner:INBAY TECH
Secure electronic transaction system
InactiveUS20100049658A1Multiple keys/algorithms usageUser identity/authority verificationSecure Electronic TransactionFinancial transaction
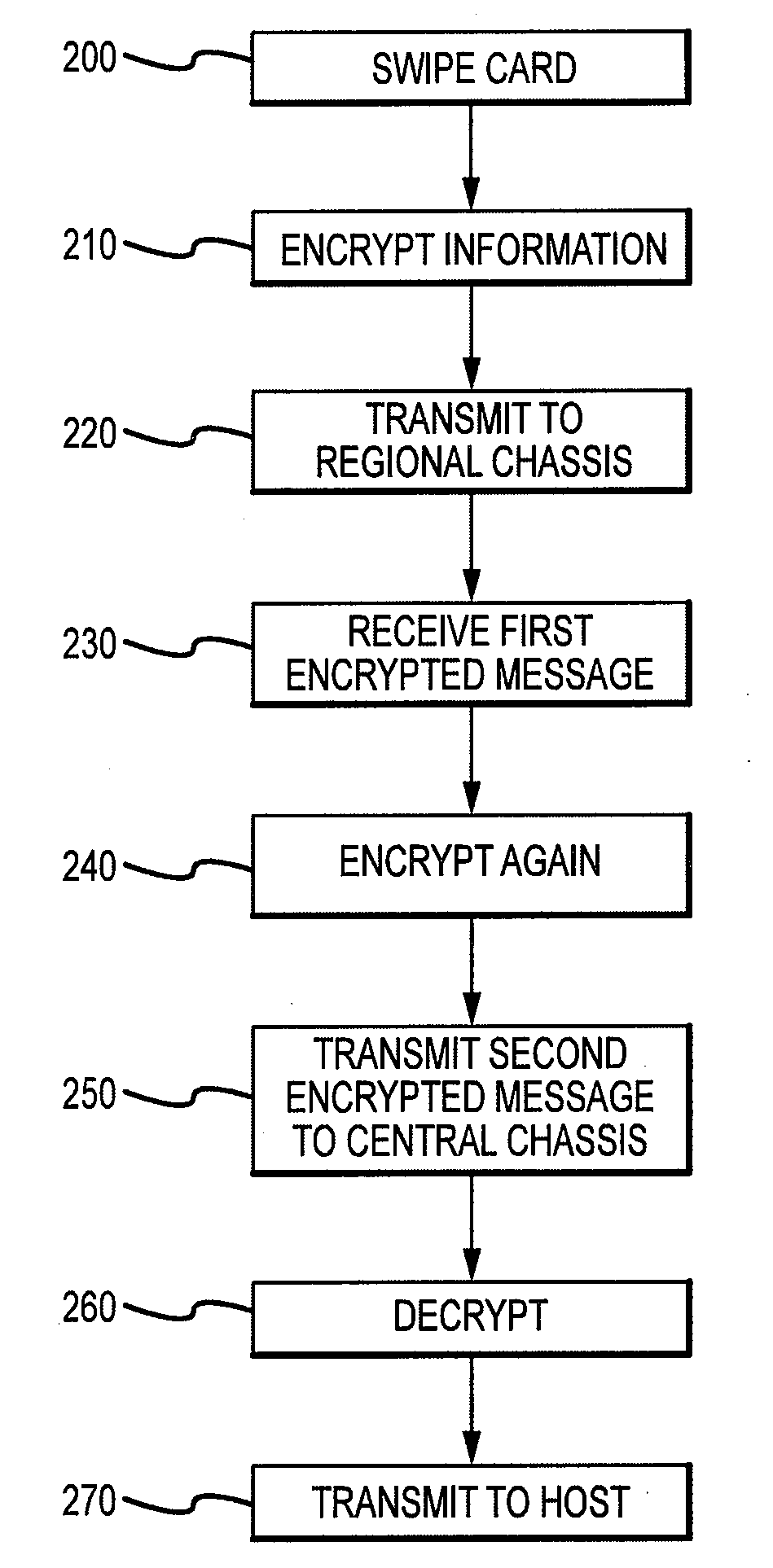
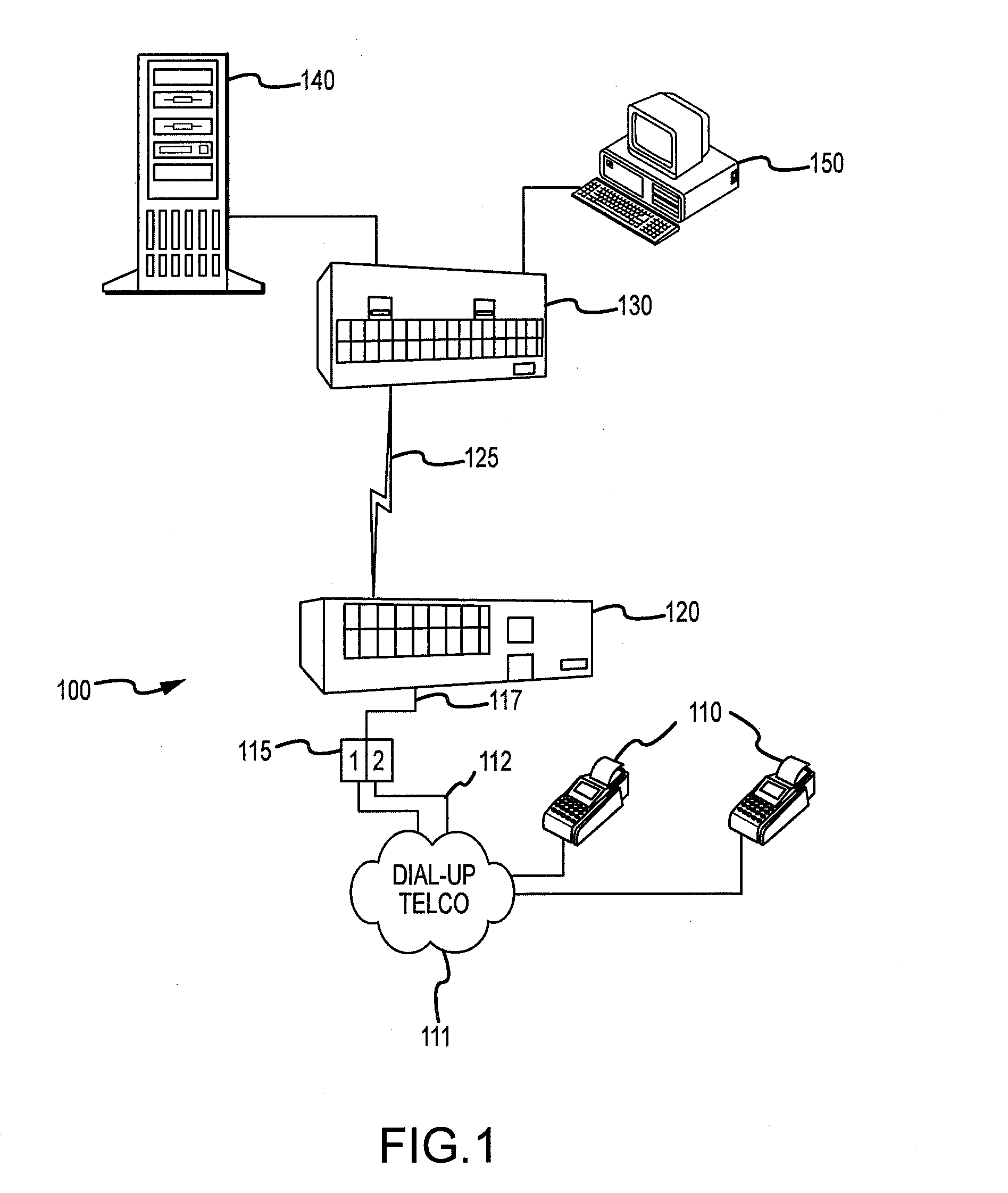
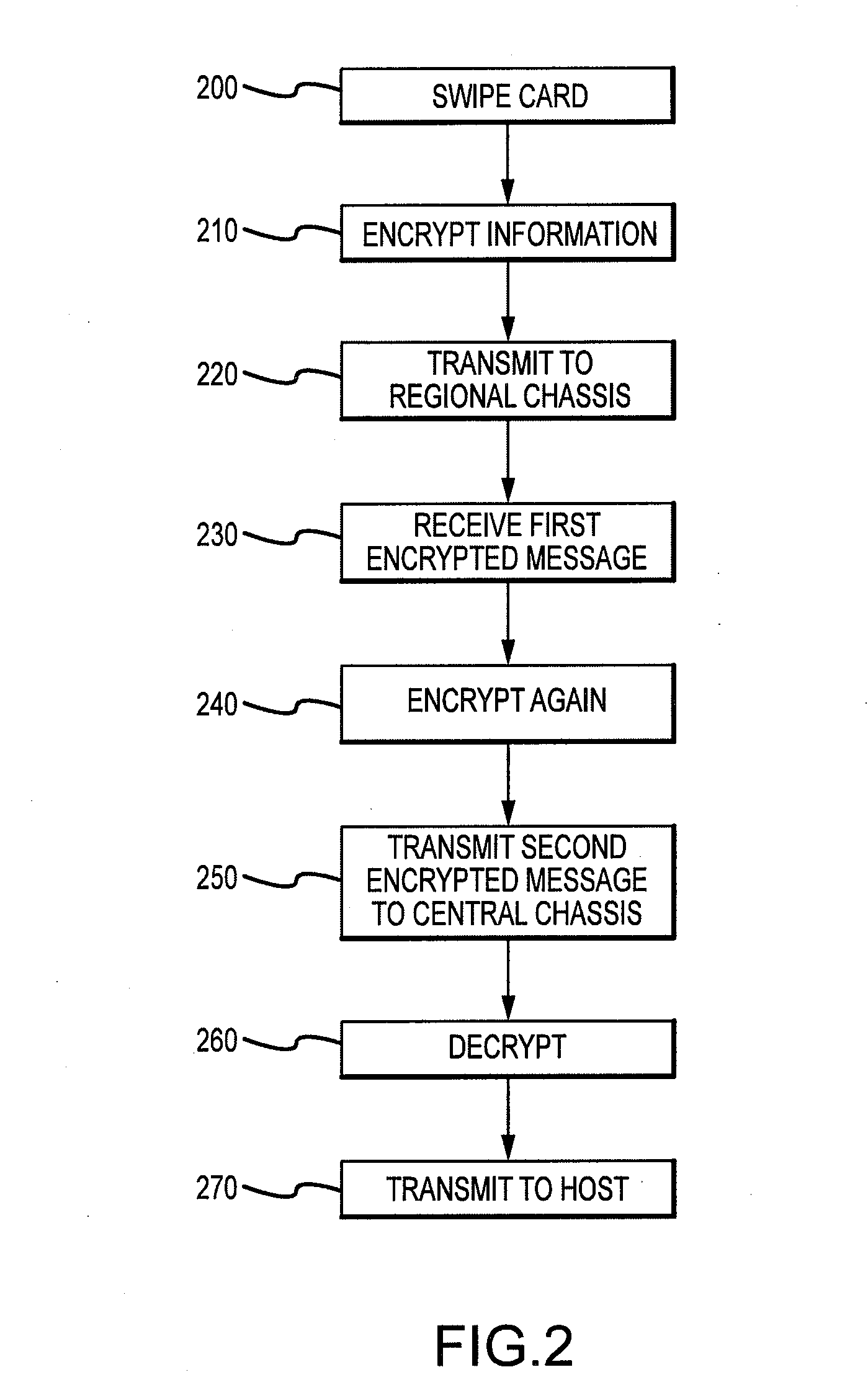
Systems and methods for the secure processing of electronic transactions are disclosed. In accordance with an exemplary embodiment, a system and method for the secure processing of electronic transactions comprises: receiving, by a POS terminal, information for a financial transaction card; receiving, by the POS terminal, information for a financial transaction; encrypting, by the POS terminal, the financial card information and the financial transaction information into a first encrypted message; transmitting the first encrypted message to a regional chassis; encrypting, by the regional chassis, the first encrypted message into a second encrypted message; transmitting the second encrypted message to a central chassis; decrypting, by the central chassis, the second encrypted message into a decrypted message; and transmitting the decrypted message to a host processor for authorization.
Owner:HYPERCOM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com