Patents
Literature
3142results about "Cryptography processing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
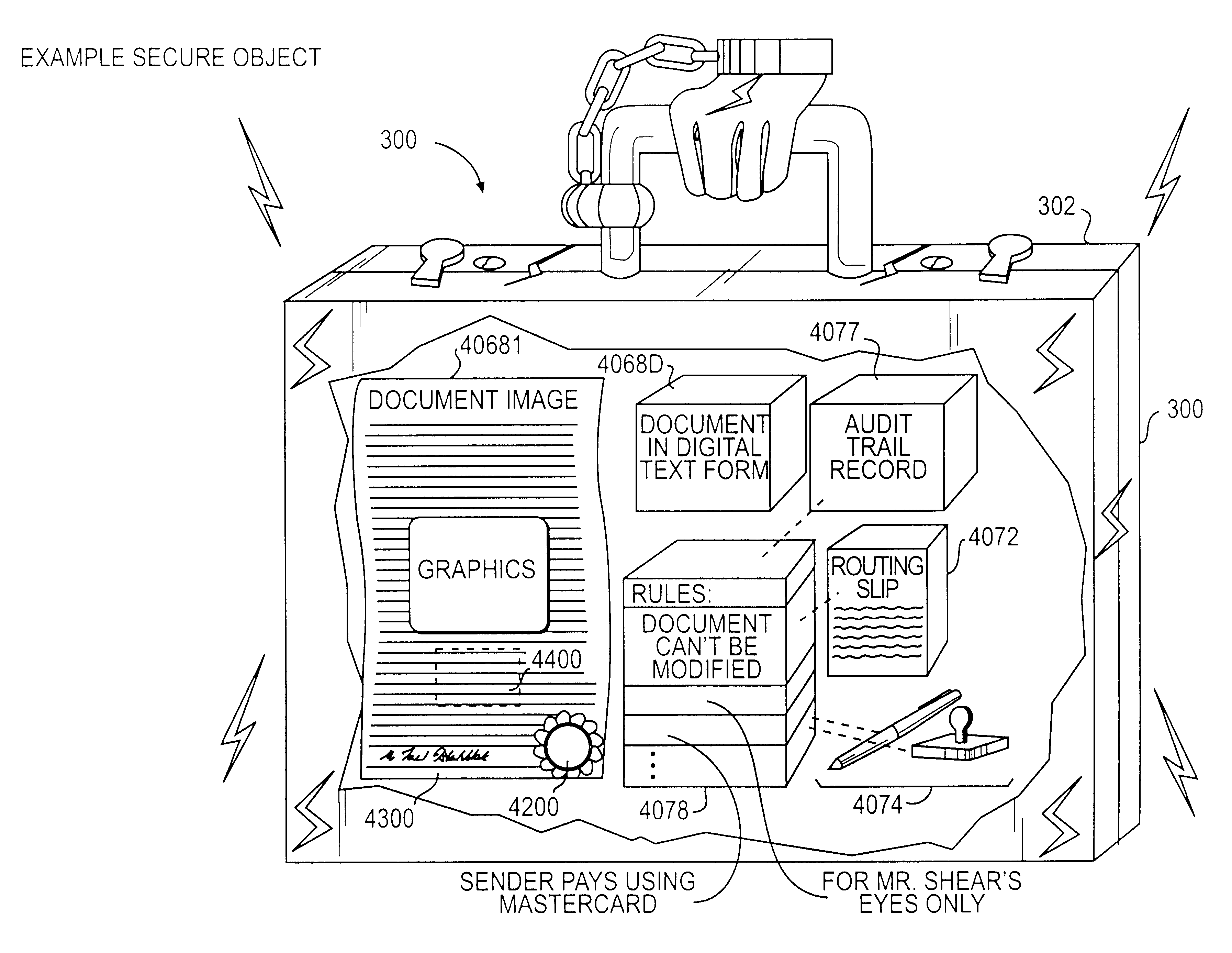
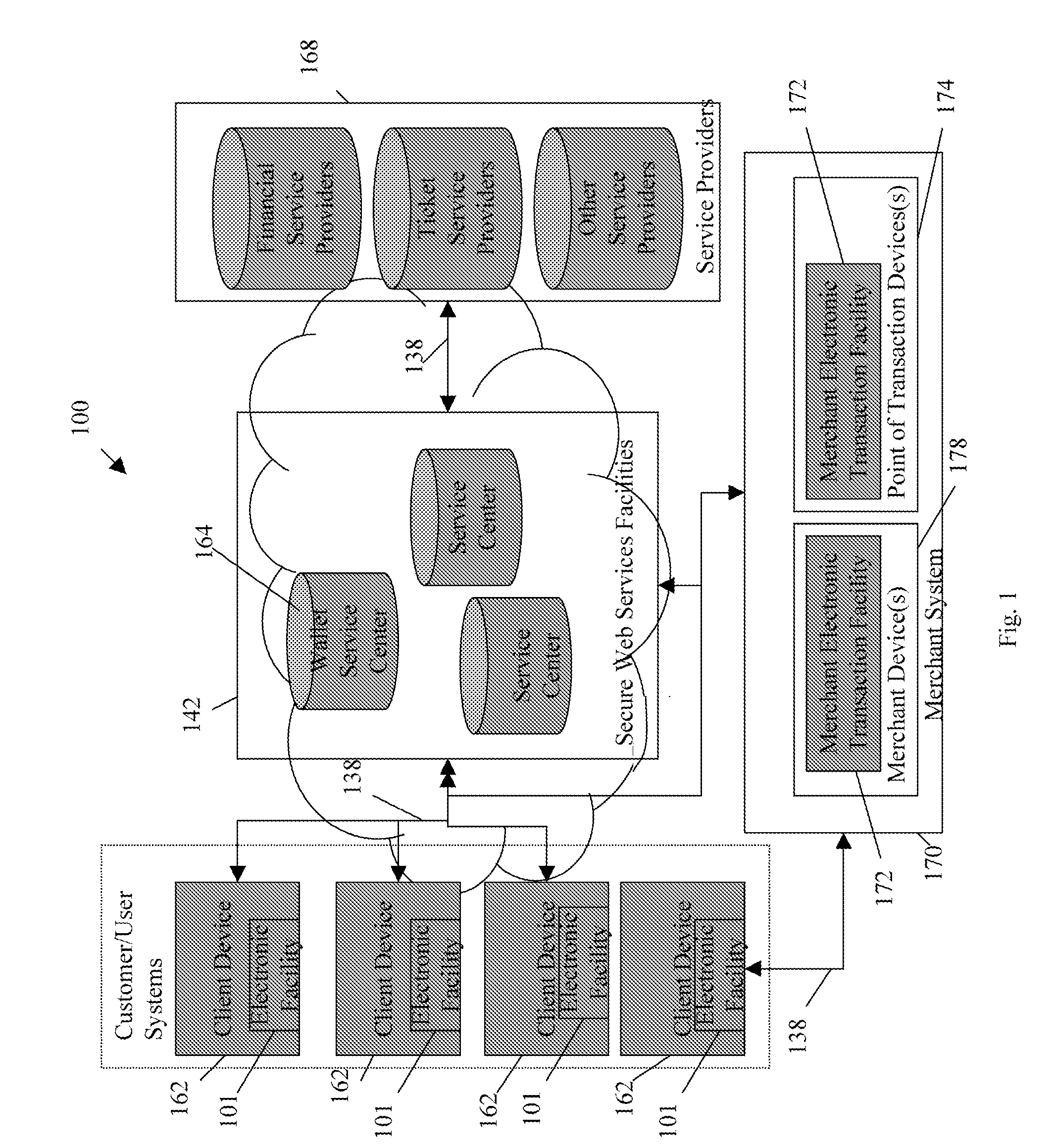
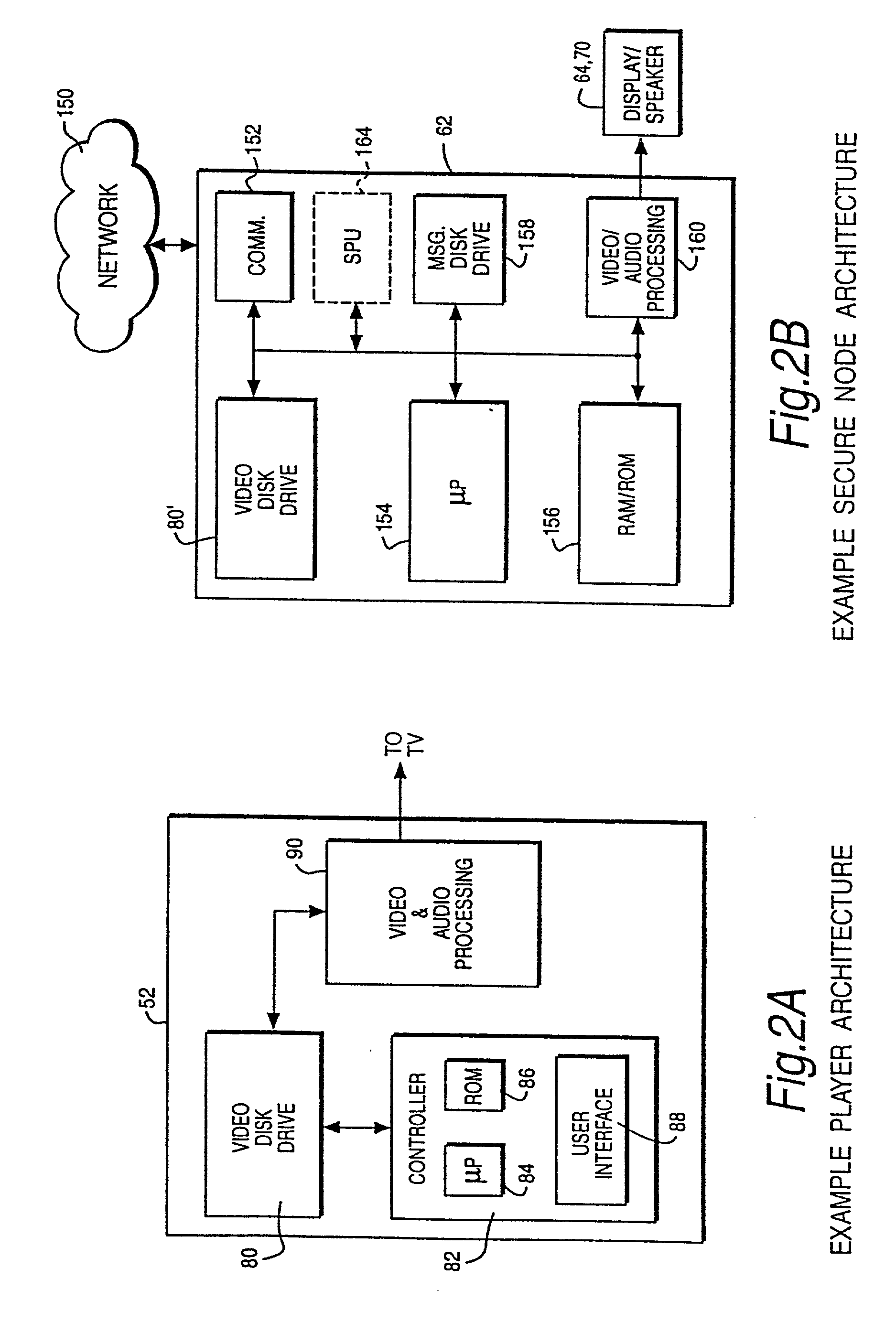
Trusted and secure techniques, systems and methods for item delivery and execution
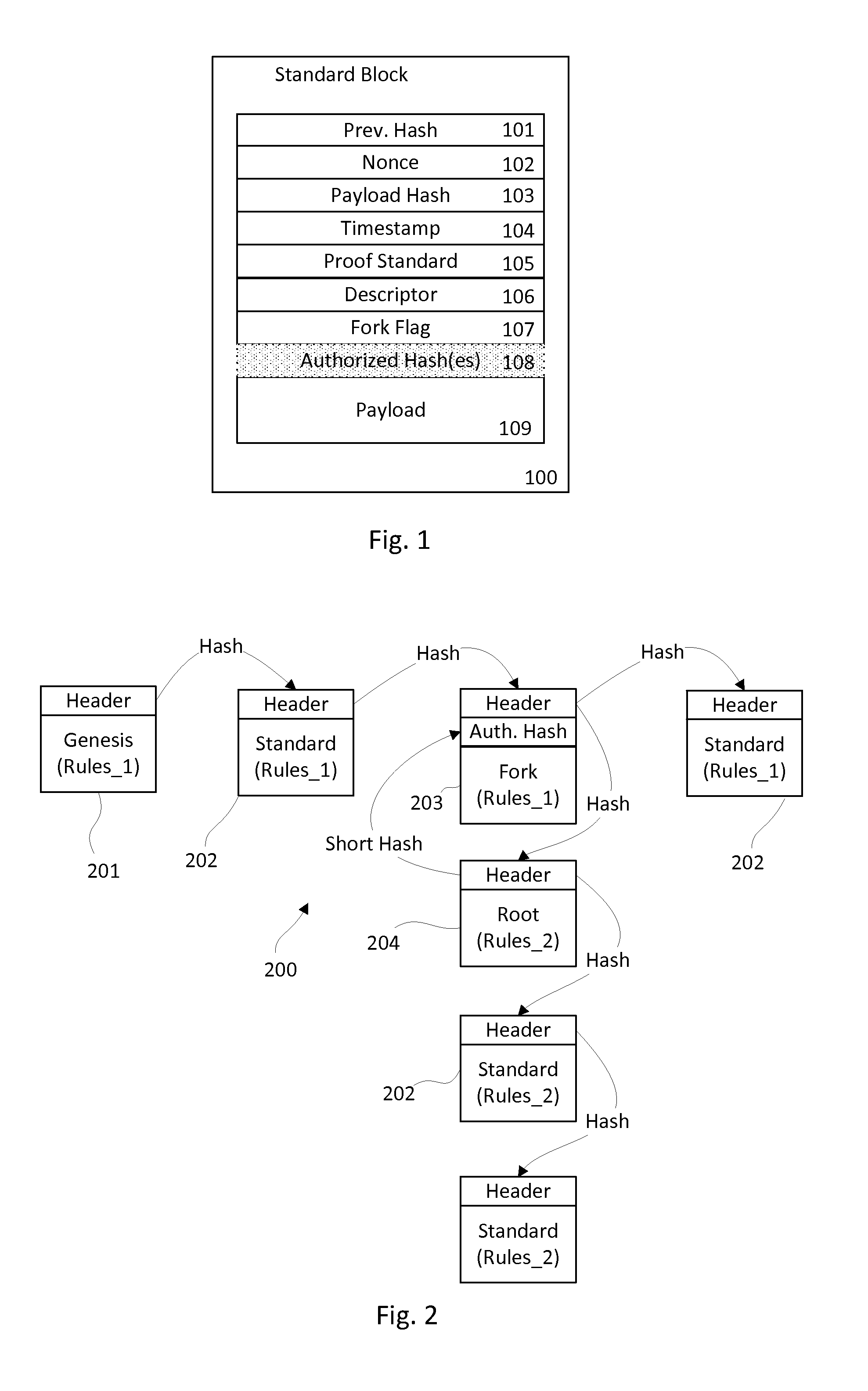
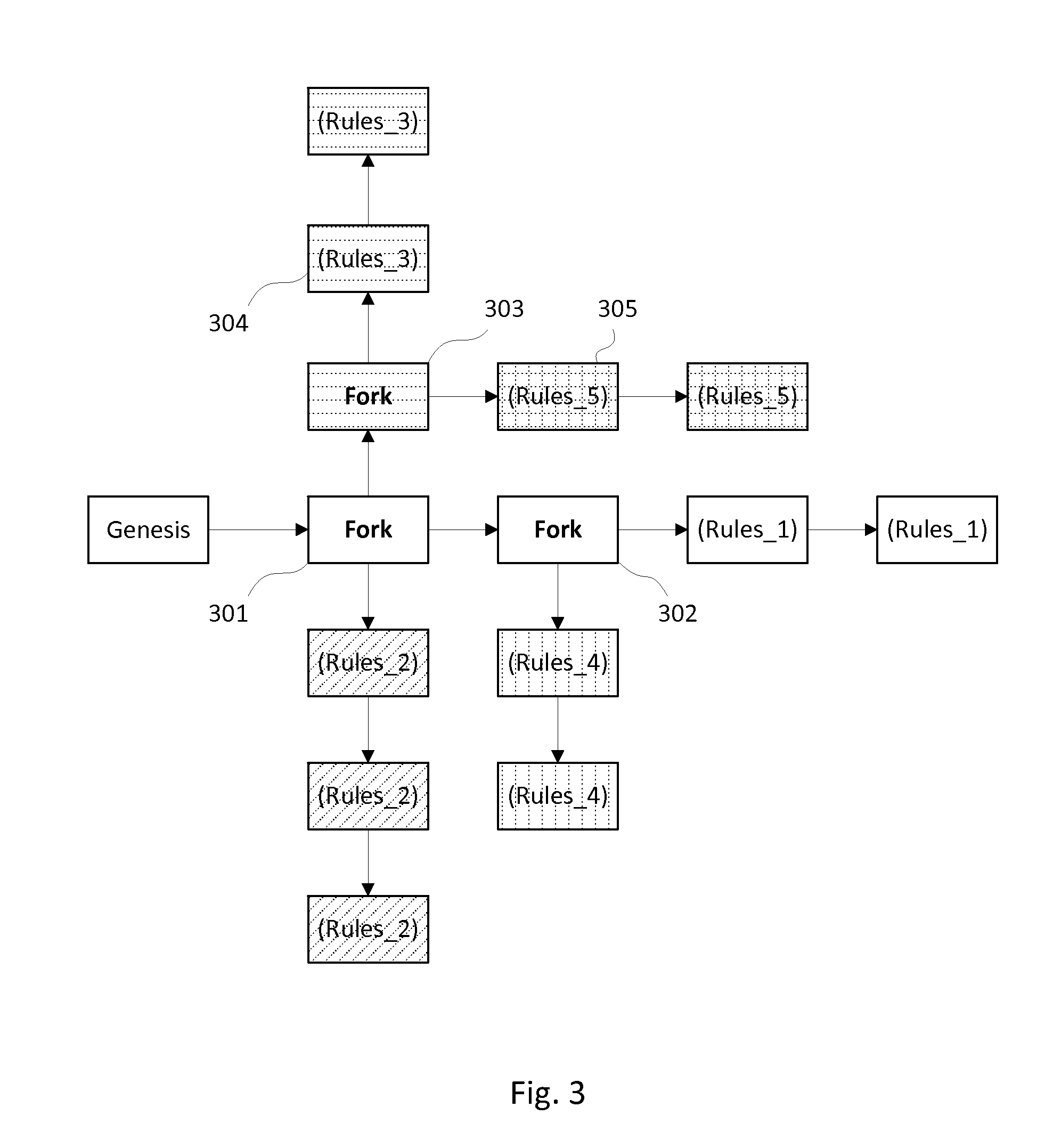
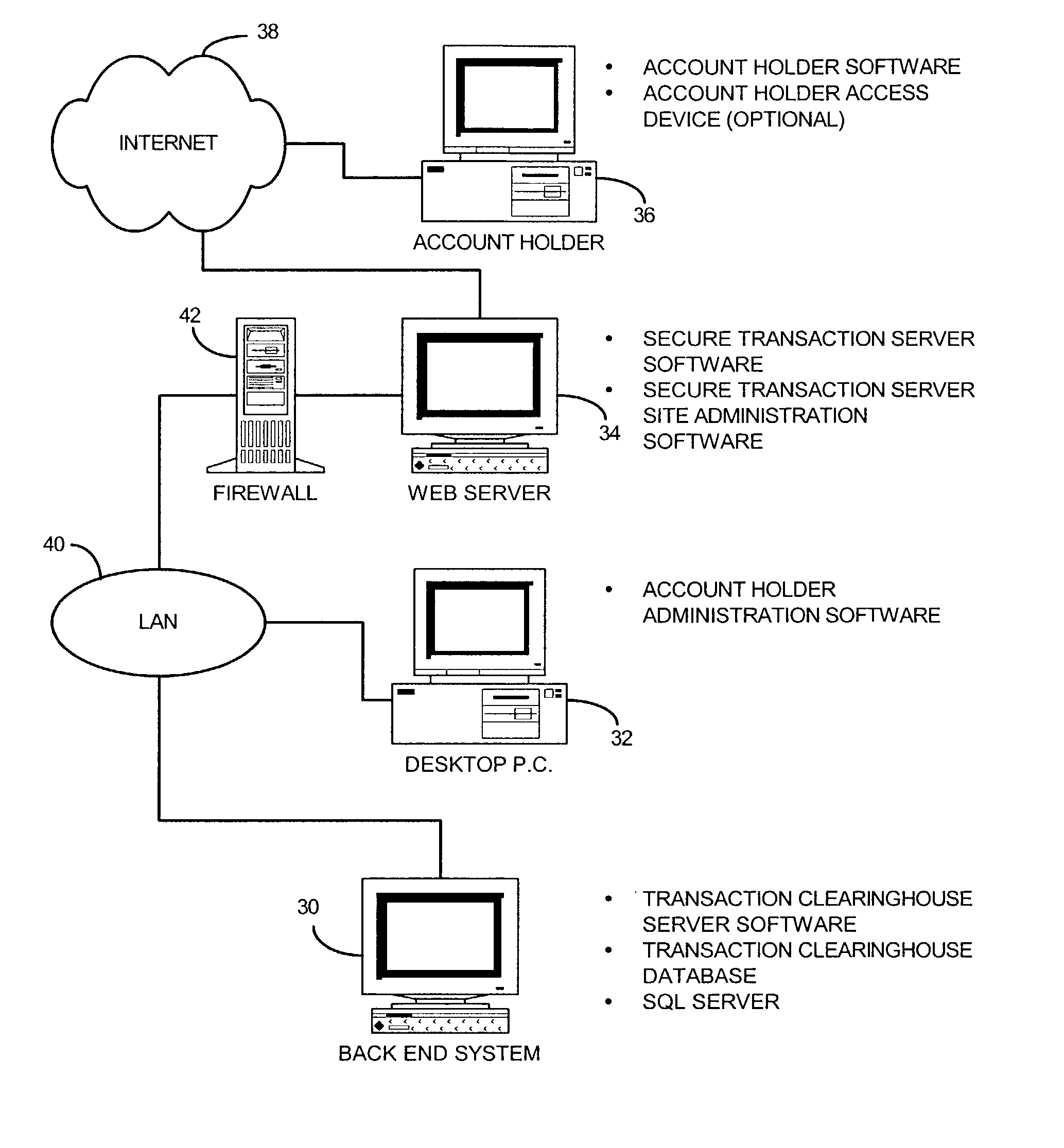
InactiveUS6185683B2Avoid deletionEasy to identifyTelevision system detailsPulse modulation television signal transmissionDocumentation procedureDocument preparation
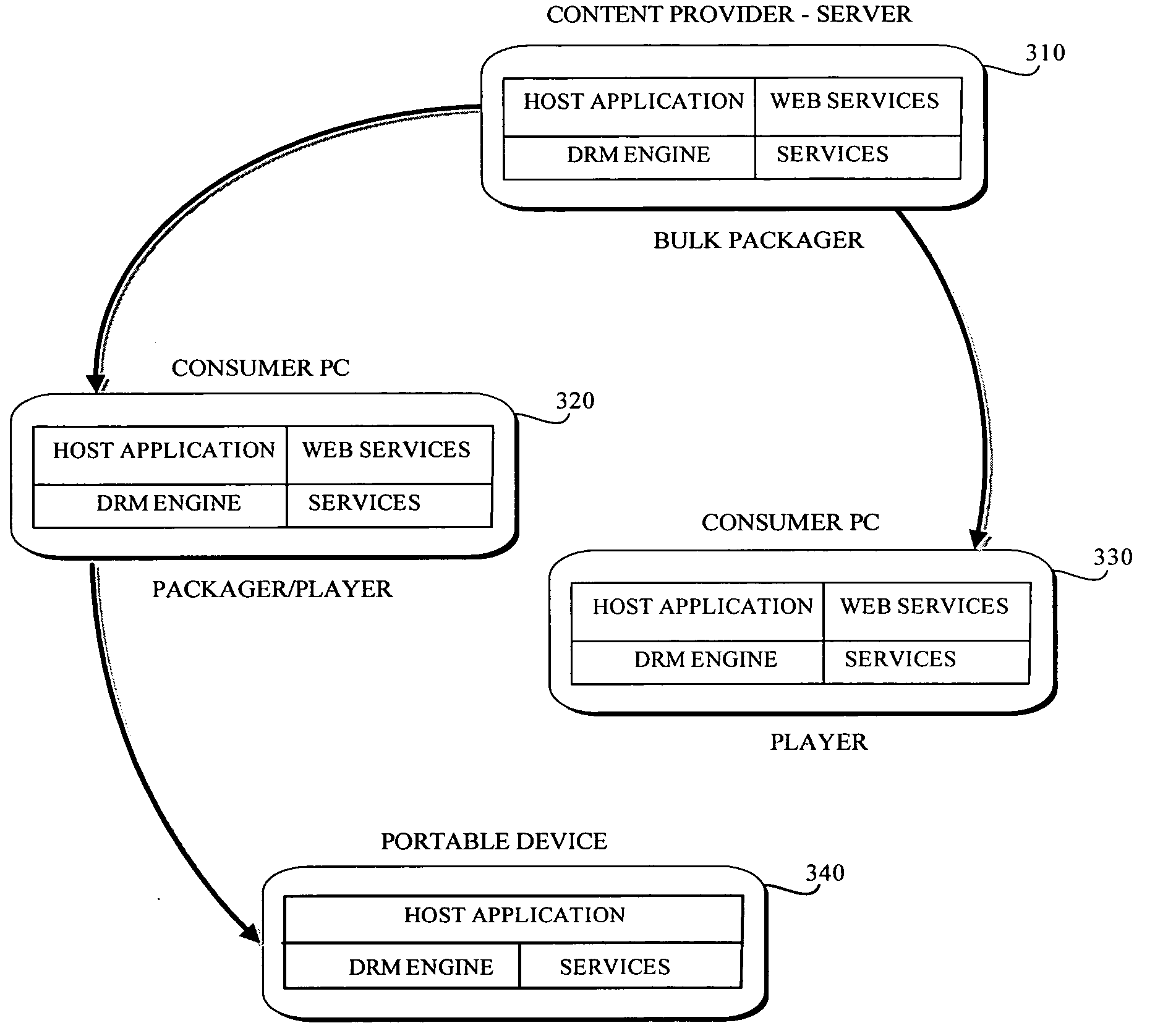
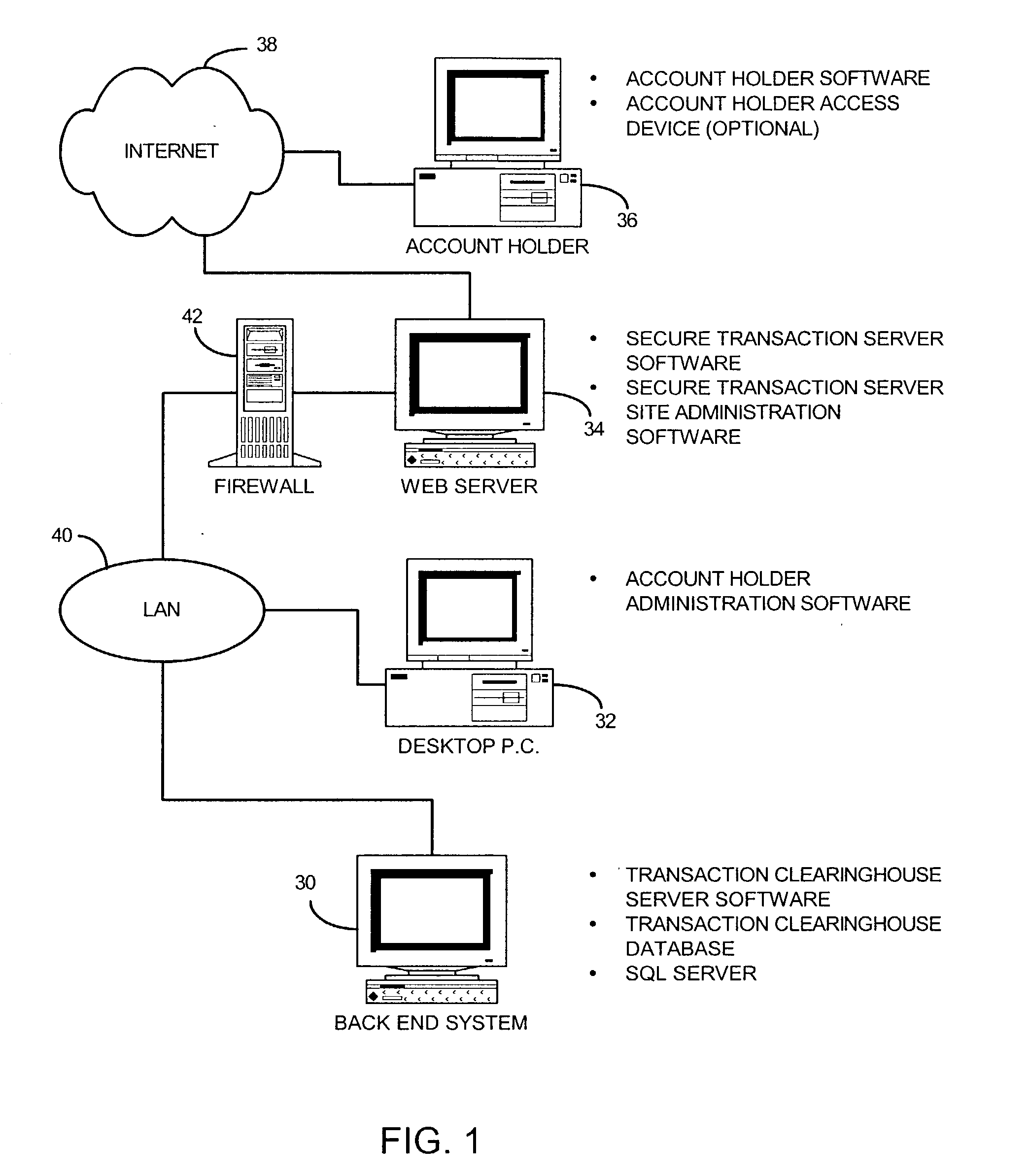
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, "trusted" virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
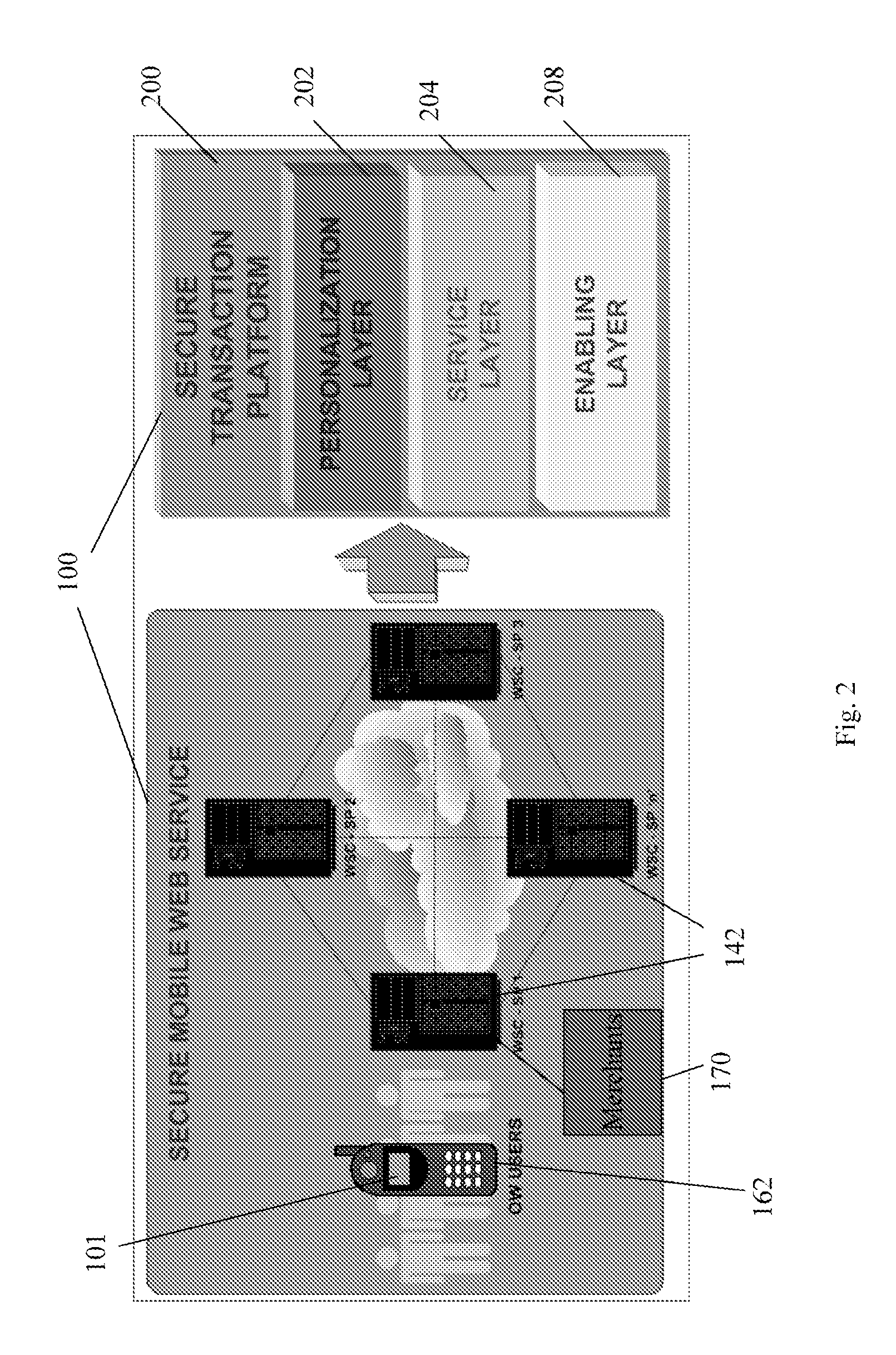
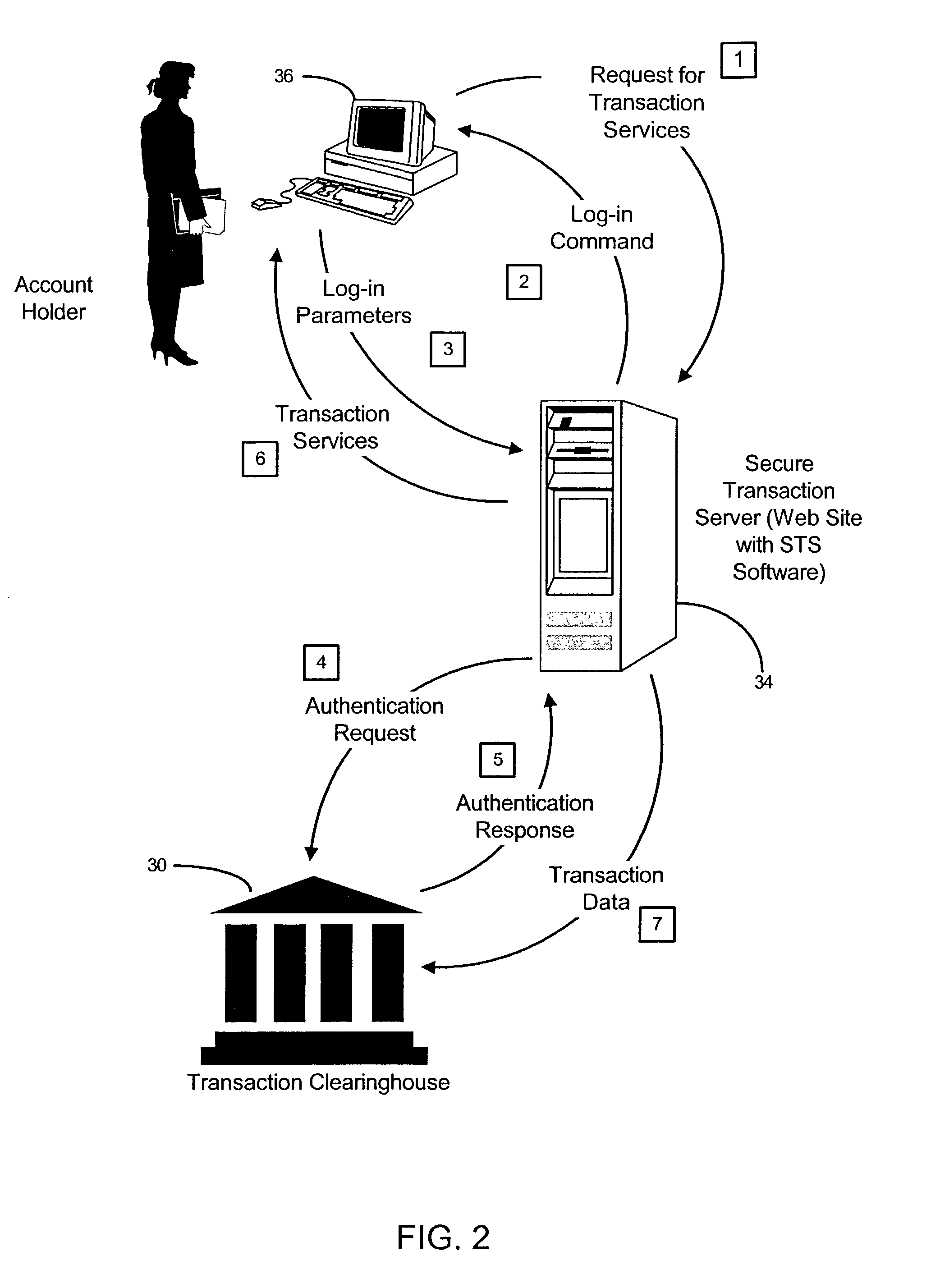
Transactional services
InactiveUS20070198432A1High level of throughputHigh level of efficiencyCryptography processingComputer security arrangementsTransaction serviceDatabase
Owner:MASTERCARD MOBILE TRANSACTIONS SOLUTIONS
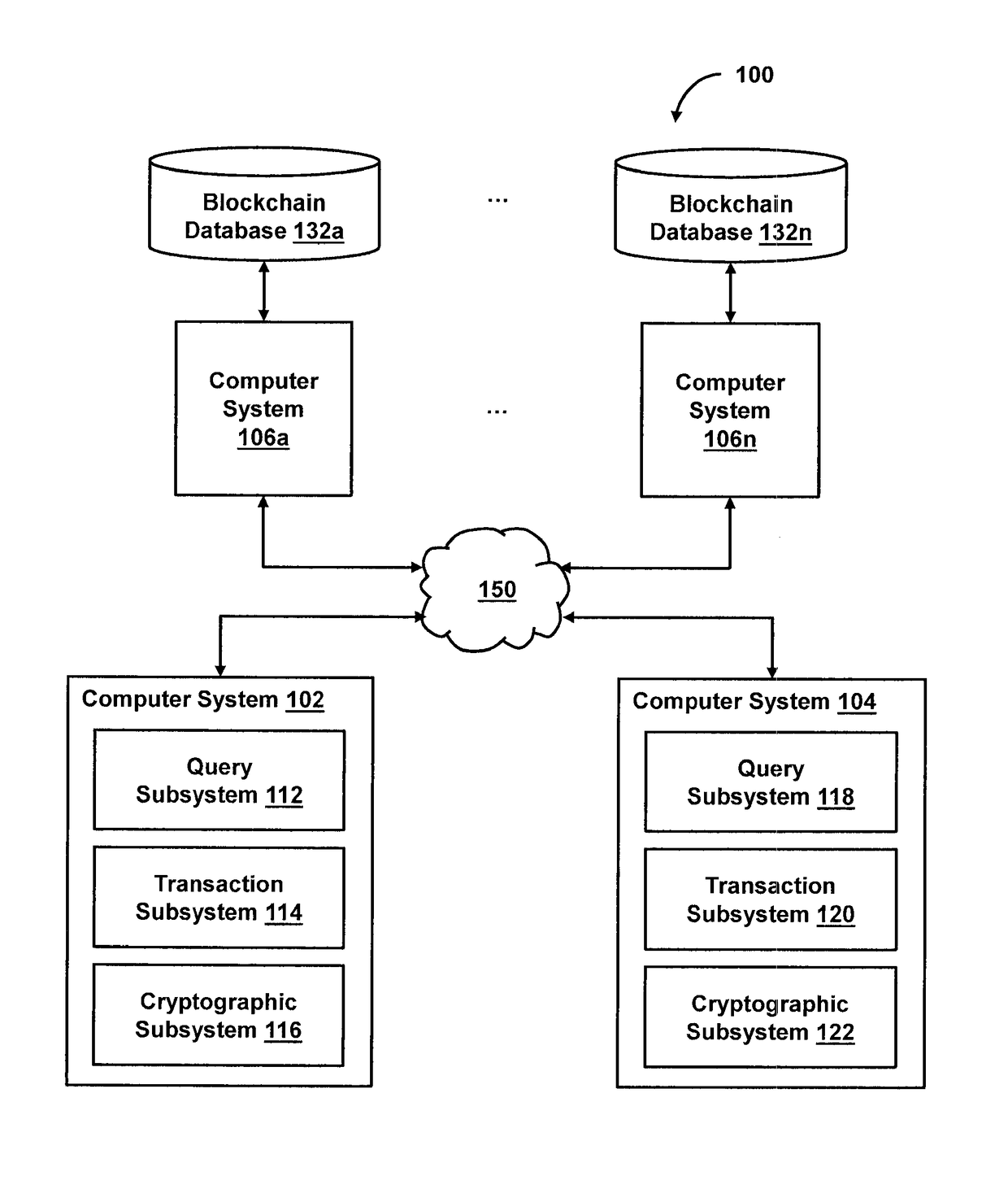
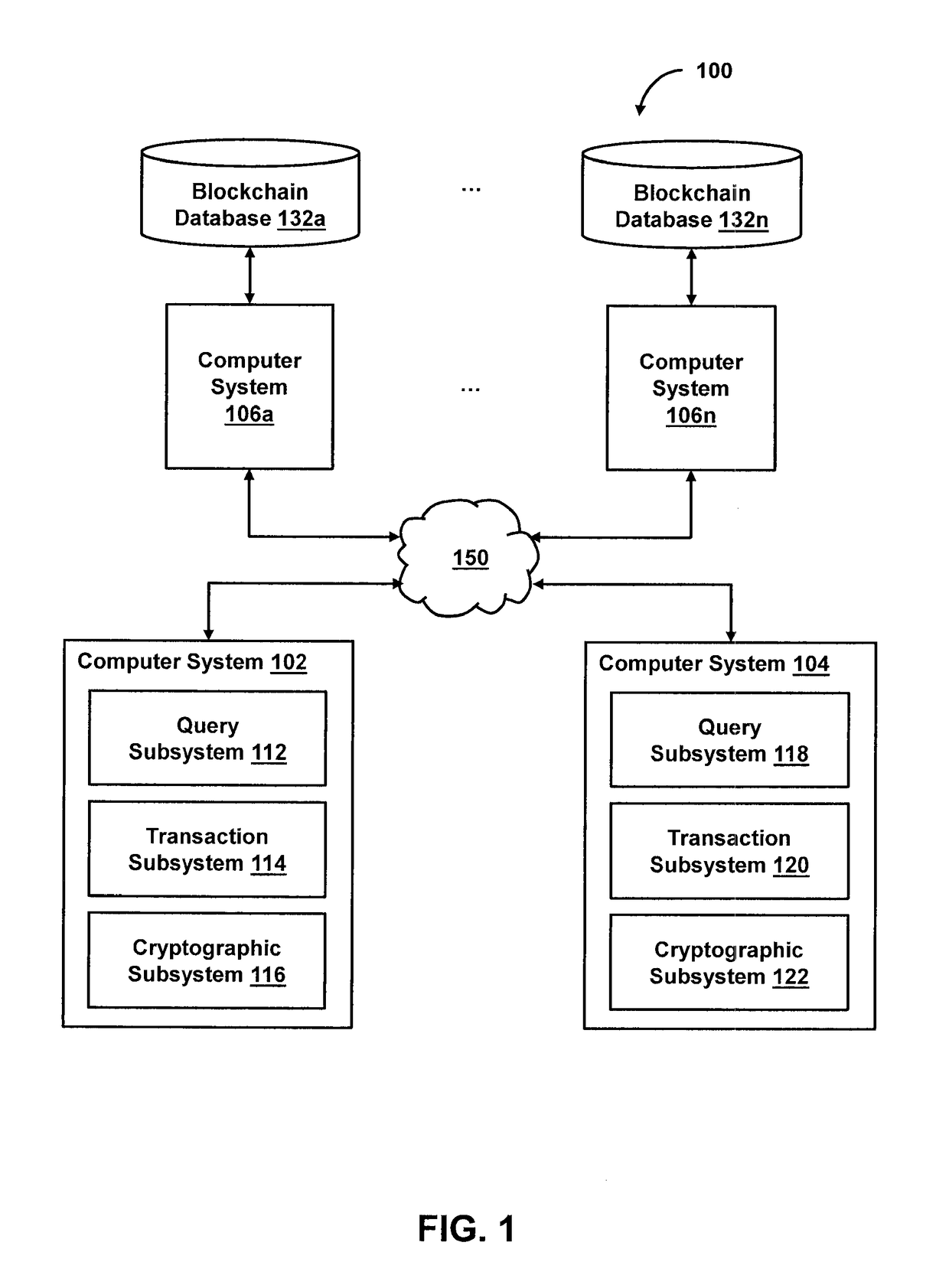
Systems and methods of blockchain transaction recordation
Owner:NASDAQ INC
Authentication and verification of digital data utilizing blockchain technology
InactiveUS20160283920A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital dataHuman interaction
A method for authenticating a chain of custody utilizing blockchain technology, whereby digital evidence or other digital content is acquired and then hashed to produce a hash fingerprint / signature and then immediately or instantly submitting said hash fingerprint / signature to the blockchain using the blockchain network protocol, forming an immediate verifiable chain of custody without human interaction or requiring a trusted third party.
Owner:FISHER JUSTIN +1
Interoperable systems and methods for peer-to-peer service orchestration
InactiveUS20050027871A1Facilitating commercial exchangeIncrease flexibilityWeb data indexingCryptography processingOperational systemWeb service
Systems and methods are described for performing policy-managed, peer-to-peer service orchestration in a manner that supports the formation of self-organizing service networks that enable rich media experiences. In one embodiment, services are distributed across peer-to-peer communicating nodes, and each node provides message routing and orchestration using a message pump and workflow collator. Distributed policy management of service interfaces helps to provide trust and security, supporting commercial exchange of value. Peer-to-peer messaging and workflow collation allow services to be dynamically created from a heterogeneous set of primitive services. The shared resources are services of many different types, using different service interface bindings beyond those typically supported in a web service deployments built on UDDI, SOAP, and WSDL. In a preferred embodiment, a media services framework is provided that enables nodes to find one another, interact, exchange value, and cooperate across tiers of networks from WANs to PANs.
Owner:INTERTRUST TECH CORP
Cryptographic methods, apparatus and systems for storage media electronic rights management in closed and connected appliances
InactiveUS20010042043A1Low costGuaranteed to continue to useTelevision system detailsDigital data processing detailsControl setGeneral purpose
A rights management arrangement for storage media such as optical digital video disks (DVDs, also called digital versatile disks) provides adequate copy protection in a limited, inexpensive mass-produceable, low-capability platform such as a dedicated home consumer disk player and also provides enhanced, more flexible security techniques and methods when the same media are used with platforms having higher security capabilities. A control object (or set) defines plural rights management rules for instance, price for performance or rules governing redistribution. Low capability platforms may enable only a subset of the control rules such as controls on copying or marking of played material. Higher capability platforms may enable all (or different subsets) of the rules. Cryptographically strong security is provided by encrypting at least some of the information carried by the media and enabling decryption based on the control set and / or other limitations. A secure "software container" can be used to protectively encapsulate (e.g., by cryptographic techniques) various digital property content (e.g., audio, video, game, etc.) and control object (i.e., set of rules) information. A standardized container format is provided for general use on / with various mediums and platforms. In addition, a special purpose container may be provided for DVD medium and appliances (e.g., recorders, players, etc.) that contains DVD program content (digital property) and DVD medium specific rules. The techniques, systems and methods disclosed herein are capable of achieving compatibility with other protection standards, such as for example, CGMA and Matsushita data protection standards adopted for DVDs. Cooperative rights management may also be provided, where plural networked rights management arrangements collectively control a rights management event on one or more of such arrangements.
Owner:INTERTRUST TECH CORP
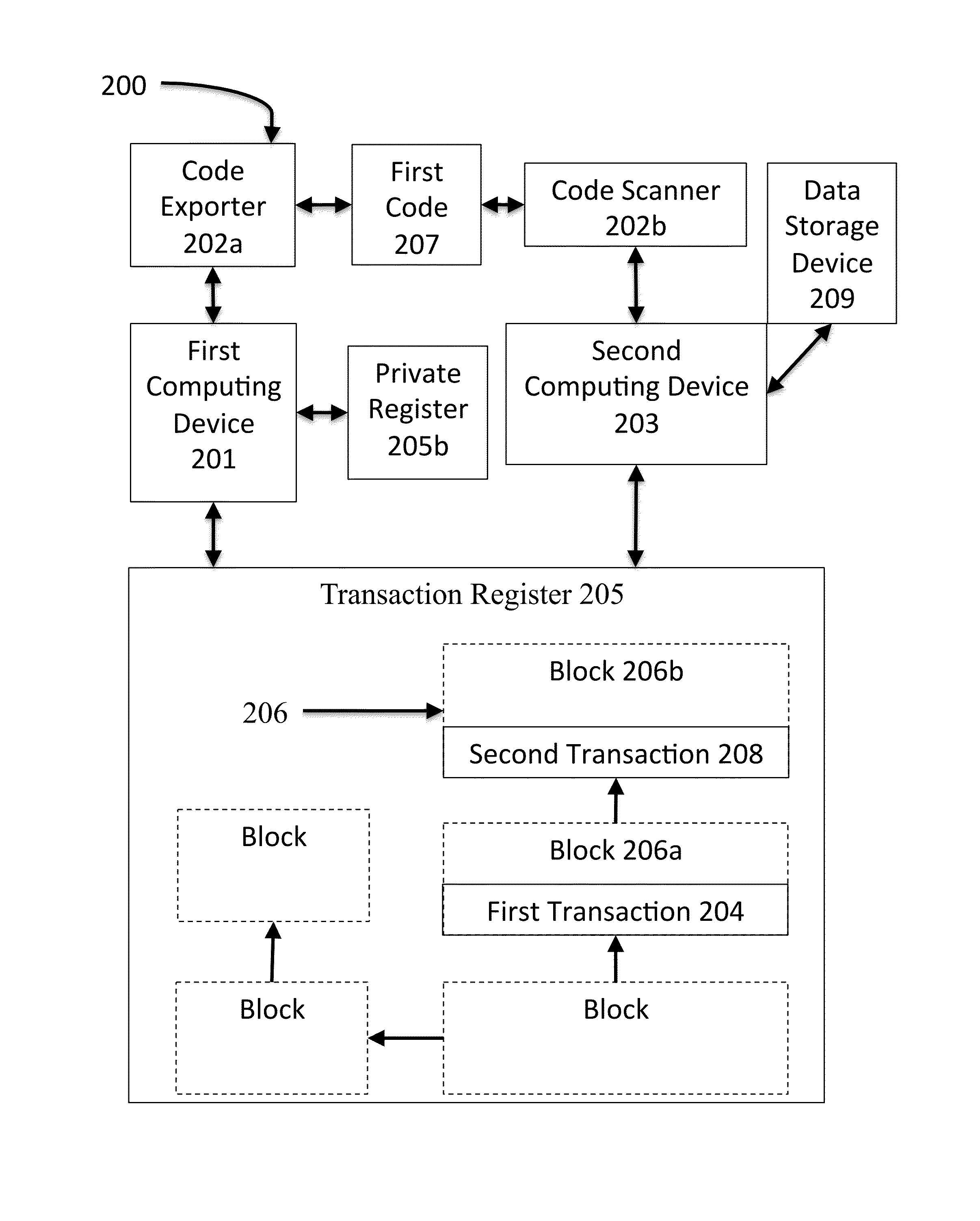
System and method for block-chain verification of goods
A method for block-chain verification of goods includes scanning, by a computing device, using a code scanner, an address from a code affixed to a product, verifying, by the computing device, that the address is associated with a crypto-currency transaction recorded at a transaction register, obtaining, by the computing device, at least one current transaction datum, and determining, based on the verification and the at least one current transaction datum, that the product is authentic.
Owner:THE FILING CABINET
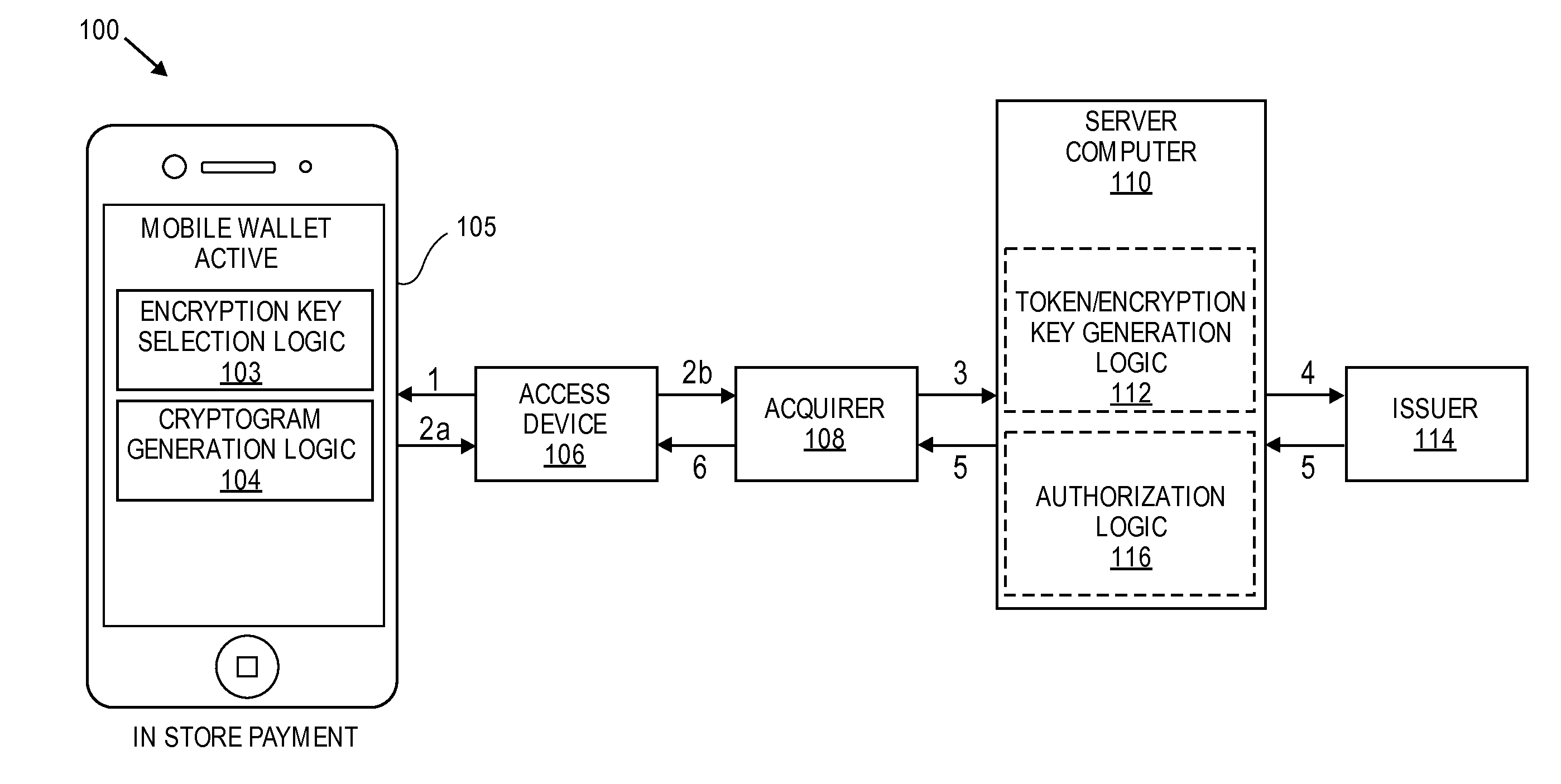
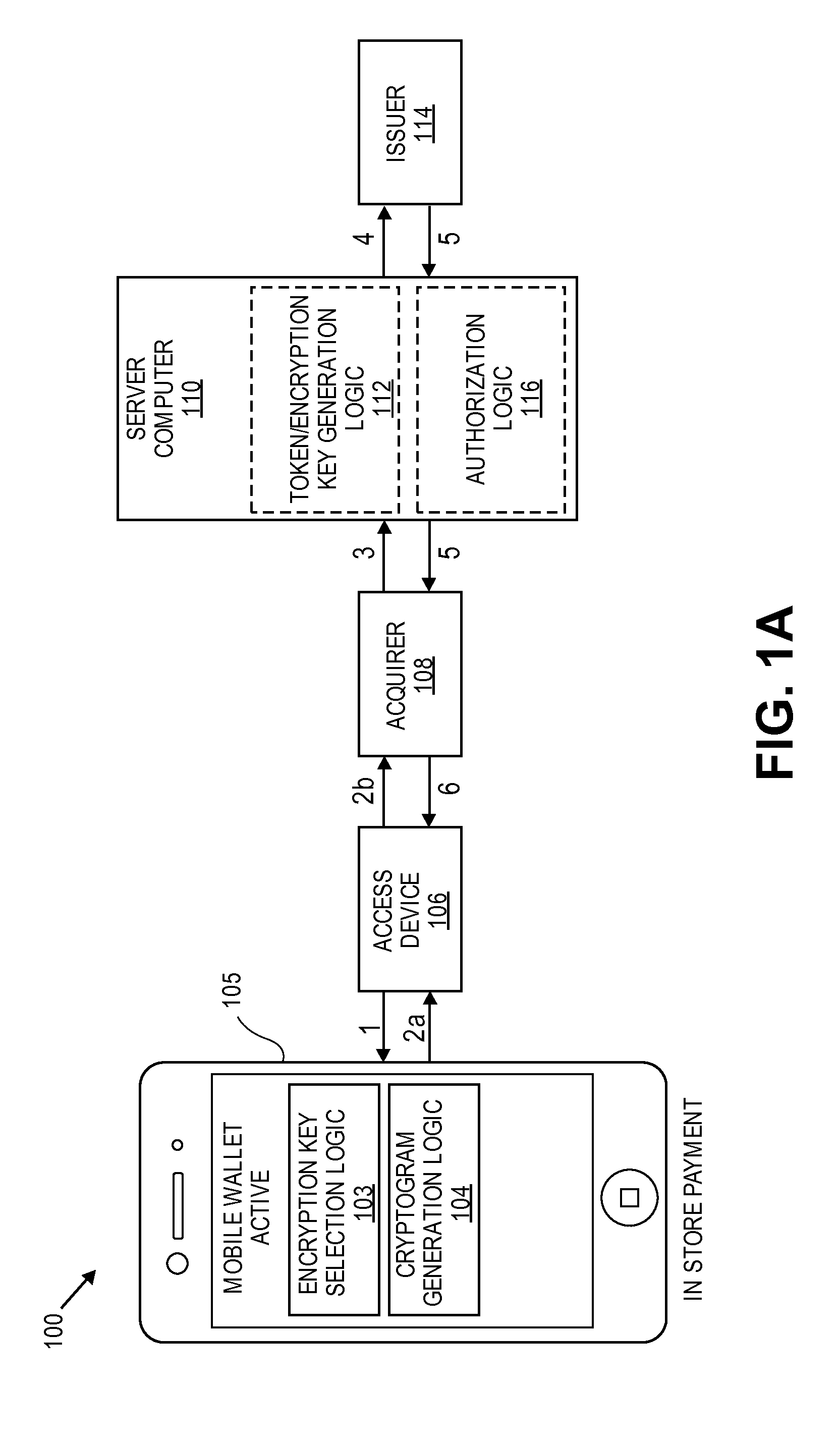
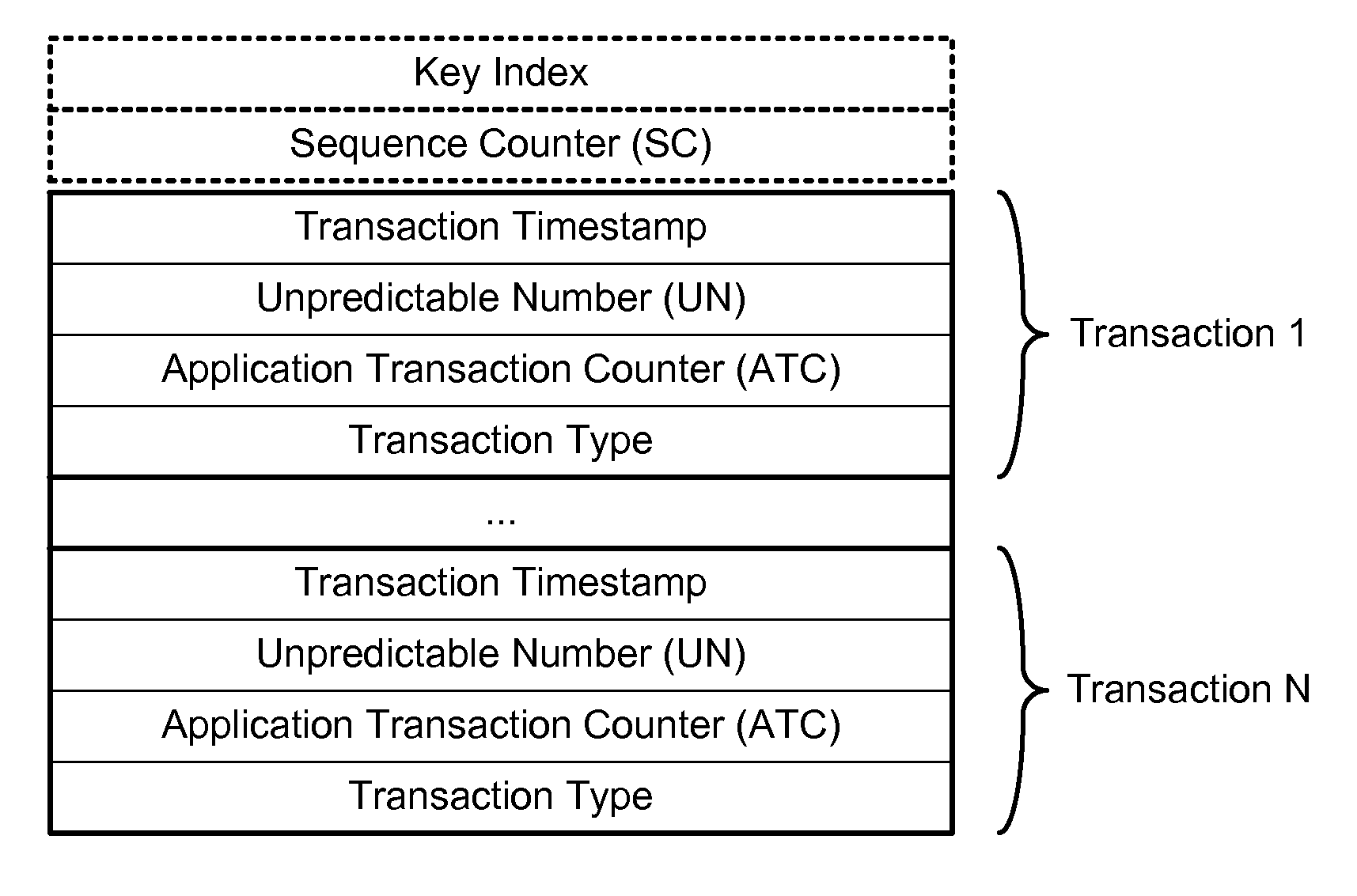
Limited-use keys and cryptograms
ActiveUS20150178724A1Promote generationImprove securityMultiple keys/algorithms usageCryptography processingCryptogramCommunication device
Techniques for enhancing the security of a communication device when conducting a transaction using the communication device may include encrypting account information with a first encryption key to generate a second encryption key, and encrypting key index information using the second key to generate a limited-use key (LUK). The key index information may include a key index having information pertaining to generation of the LUK. The LUK and the key index can be provided to the communication device to facilitate generation of a transaction cryptogram for a transaction conducted using the communication device, and the transaction can be authorized based on the transaction cryptogram generated from the LUK.
Owner:VISA INT SERVICE ASSOC
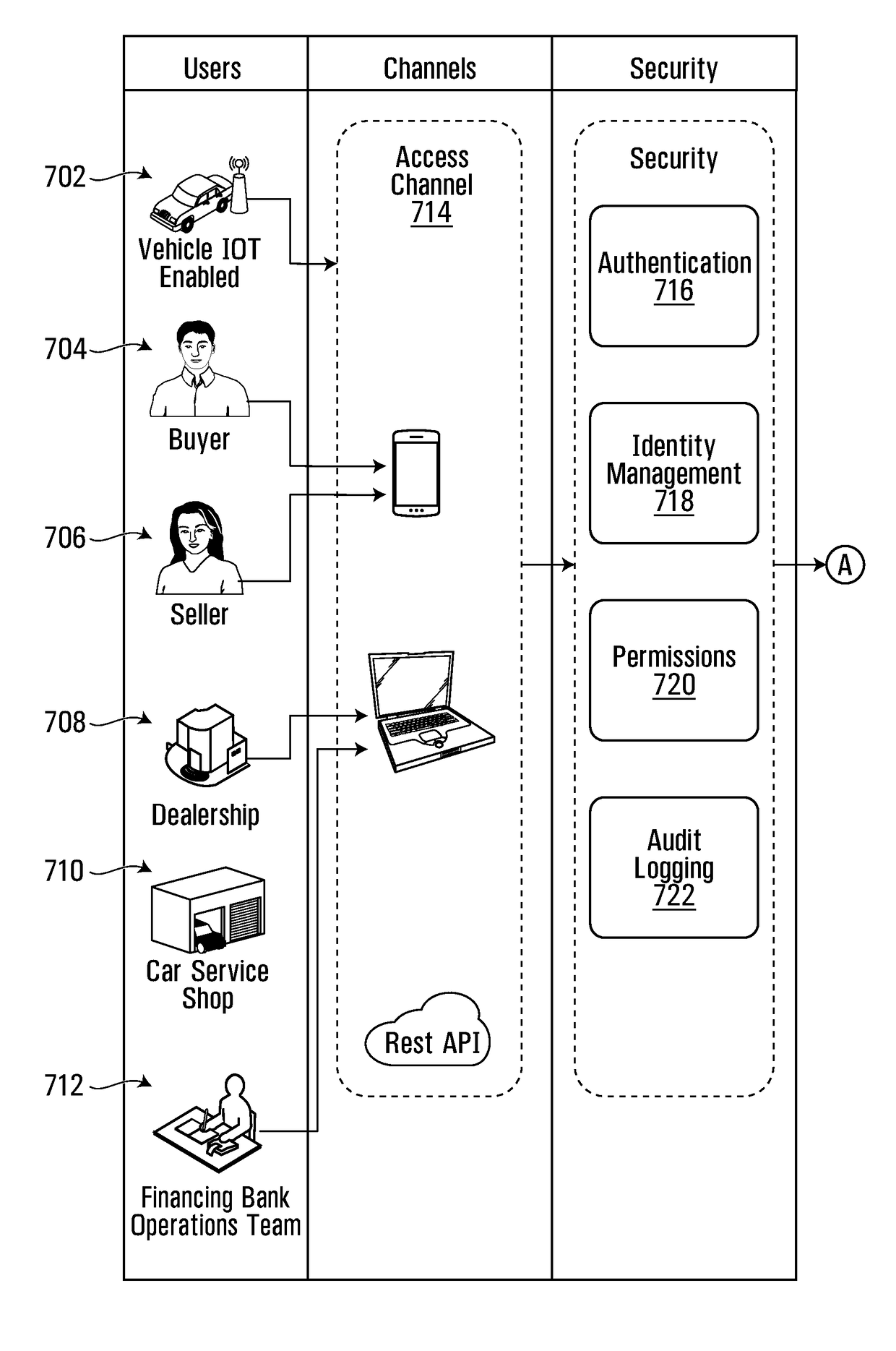
Distributed ledger platform for vehicle records
Embodiments described herein provide a vehicle record platform using blockchain technology. Vehicle records are recorded using blocks linked by vehicle identification number. The vehicle record stores historical information about vehicles, including collision information, financing information, transfer of ownership information, and other transaction information.
Owner:ROYAL BANK OF CANADA
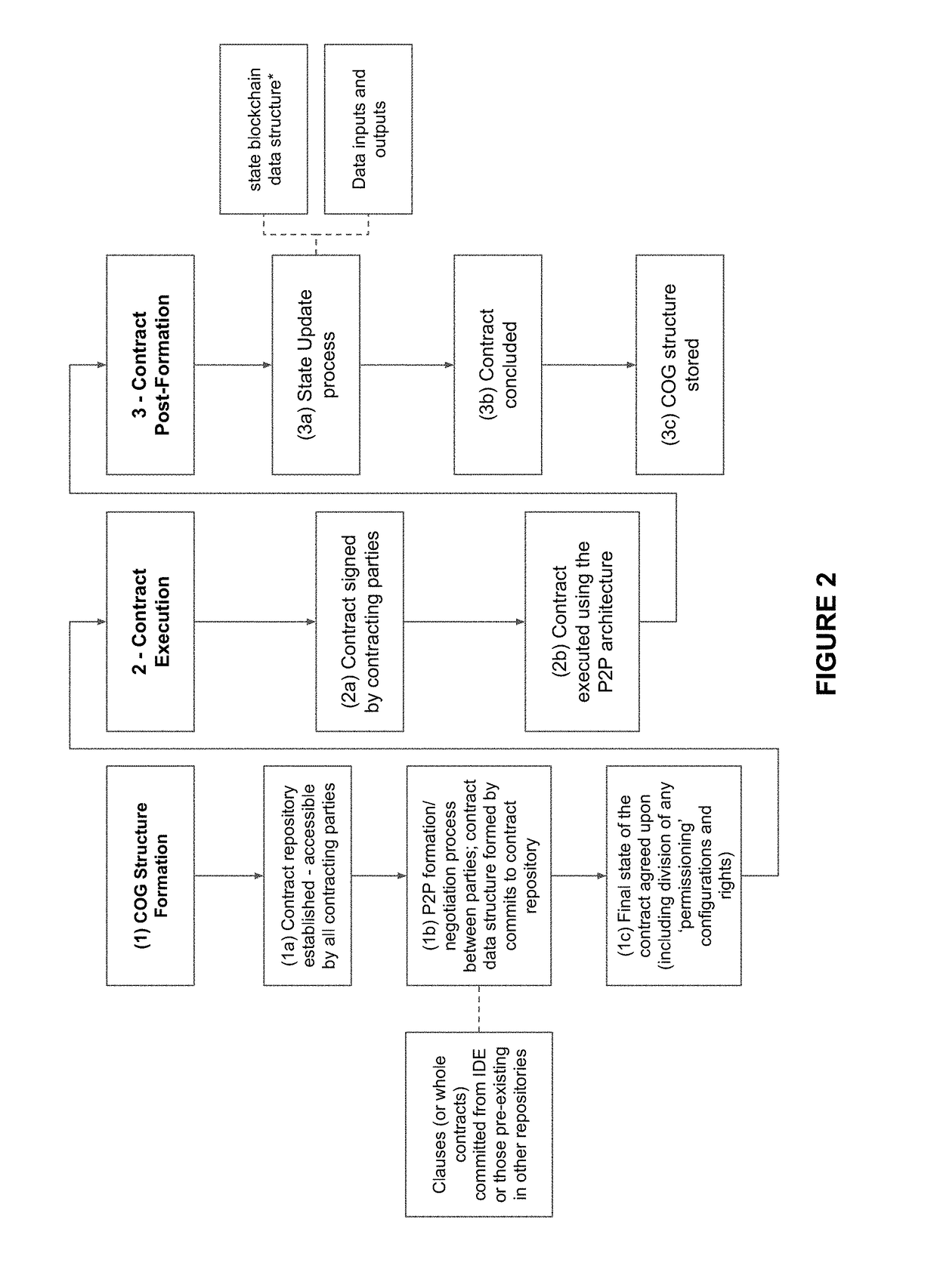
System and method for forming, storing, managing, and executing contracts
ActiveUS20180005186A1Efficiently and verifiably moveReduce dataDrawing from basic elementsCryptography processingDocumentationObject graph
A system and method for computable contracts that includes a contract management system accessible by involved parties, managing a formation stage of a contract document by obtaining object components, assembling a contract object graph from the object components, and committing the contract object graph to post formation execution; and in an execution environment during a post-formation stage, executing the contract object graph where instances of execution include receiving a contract state update, and appending at least one update object component to the contract object graph in accordance with the contract state update. Variations of the system and method may apply peer-to-peer negotiation and execution, use a cryptographic directed acyclic contract object graph, and / or interface with distributed ledgers.
Owner:DOCUSIGN
Method and system for storage and retrieval of blockchain blocks using galois fields
A method and system for storage and retrieval of blockchains with Galois Fields. One or more blocks for a blockchain are securely stored and retrieved with a modified Galois Fields on a cloud or peer-to-peer (P2P) communications network. The modified Galois Field provides at least additional layers for security and privacy for blockchains. The blocks and blockchains are securely stored and retrieved for cryptocurrency transactions including, but not limited to, BITCOIN transactions and other cryptocurrency transactions.
Owner:LESAVICH STEPHEN +1
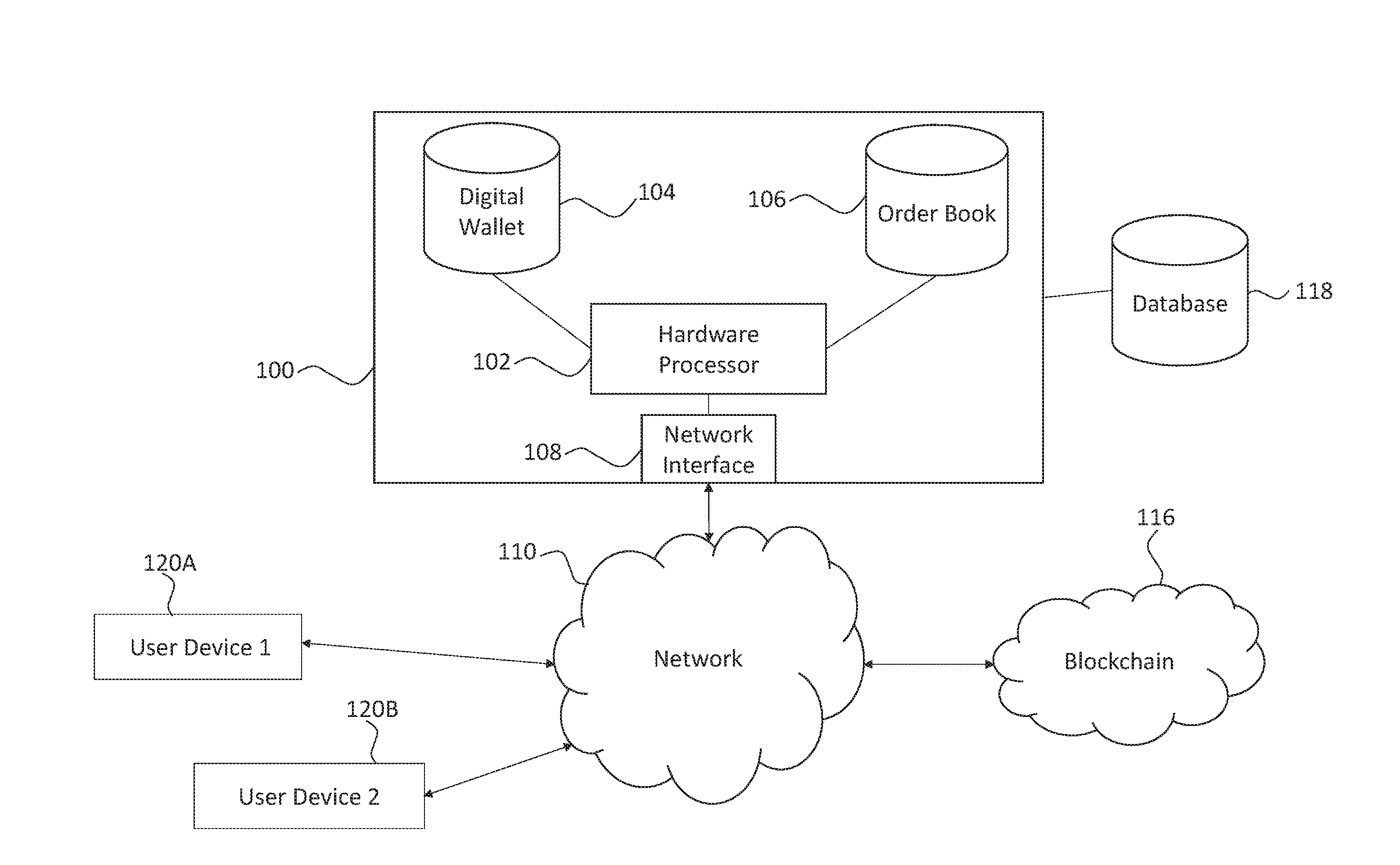
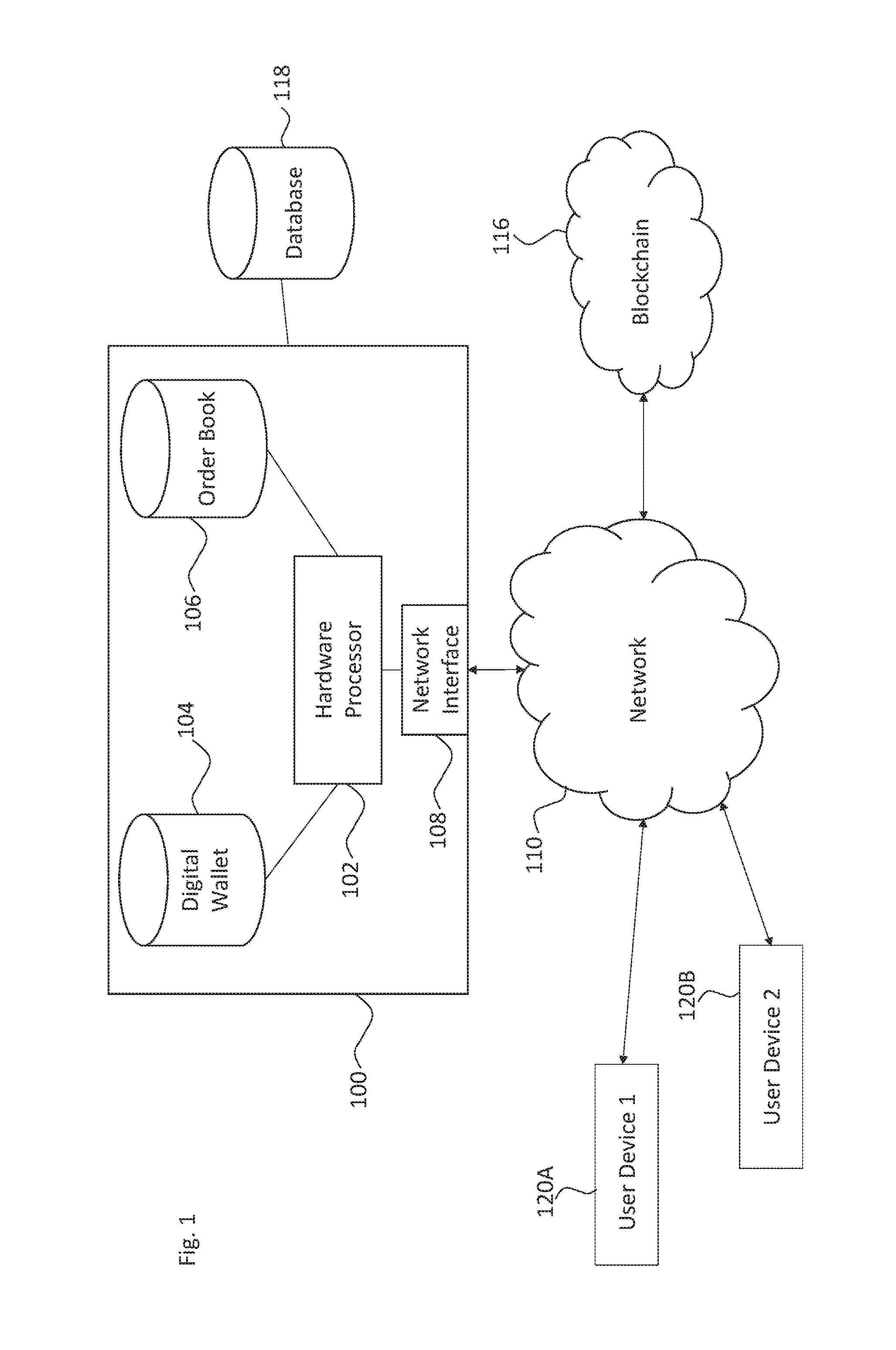
Cryptocurrency Virtual Wallet System and Method
InactiveUS20150324789A1Prevent unauthorized accessConvenient transactionCryptography processingPayment protocolsComputer hardwareUser device
The present disclosure describes a method in which an encrypted request to transfer a requested amount of cryptocurrency from a user address to a destination address is received. The request includes a destination address, a requested amount, a user device encryption key, and biometric data. A partially signed transaction to transfer a requested amount of cryptocurrency from the user address to the destination address is also received. The partially signed transaction is cryptographically signed and a multi-signed transaction is broadcast to a cryptocurrency network to transfer the requested amount of cryptocurrency from the user address to the destination address.
Owner:TOKENIZE INC
System and method for securely receiving and counting votes in an election
ActiveUS20160027229A1Improve securityPrevent fraudVoting arrangementKey distribution for secure communicationBarcodeNetwork communication
The present invention generally relates to blockchain technology. Specifically, this invention relates to adapting blockchain technology for the storage of voting data in an electronic voting system. The system includes a distributed network of voting machines in communication with each other. Each voting machine has a barcode scanner, a network communications device and a computer system running a voting client. Votes are received through the barcode scanner or a voter interface system and stored securely on a blockchain. The tally for various candidates in the election is updated and stored as each vote is received and counted. This creates an auditable trail of votes and the tally which can be used to detect, correct, and prevent fraud and error in the vote counting process.
Owner:BLOCKTECH LLC
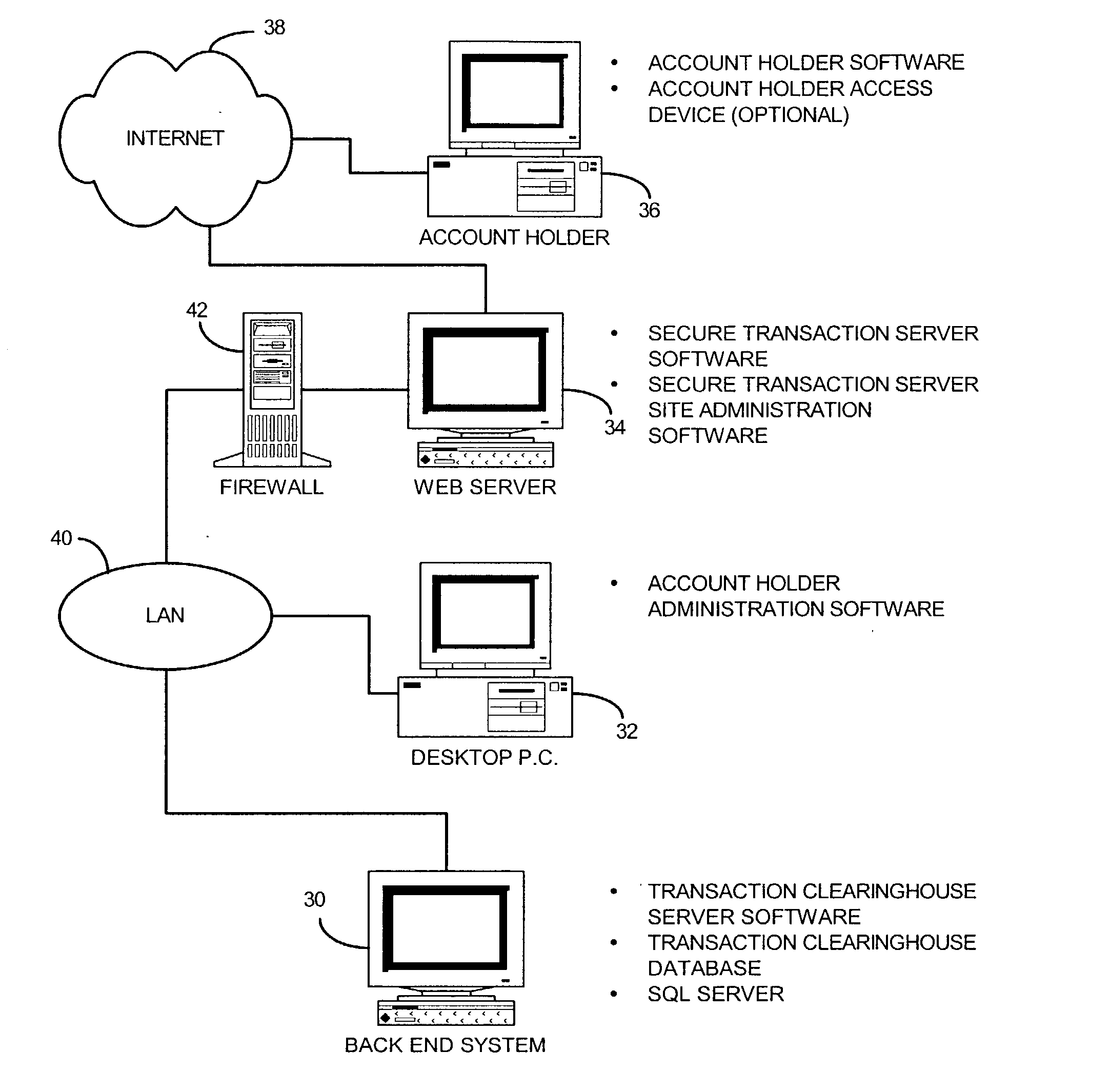
Method and system for controlling access, by an authentication server, to protected computer resources provided via an internet protocol network
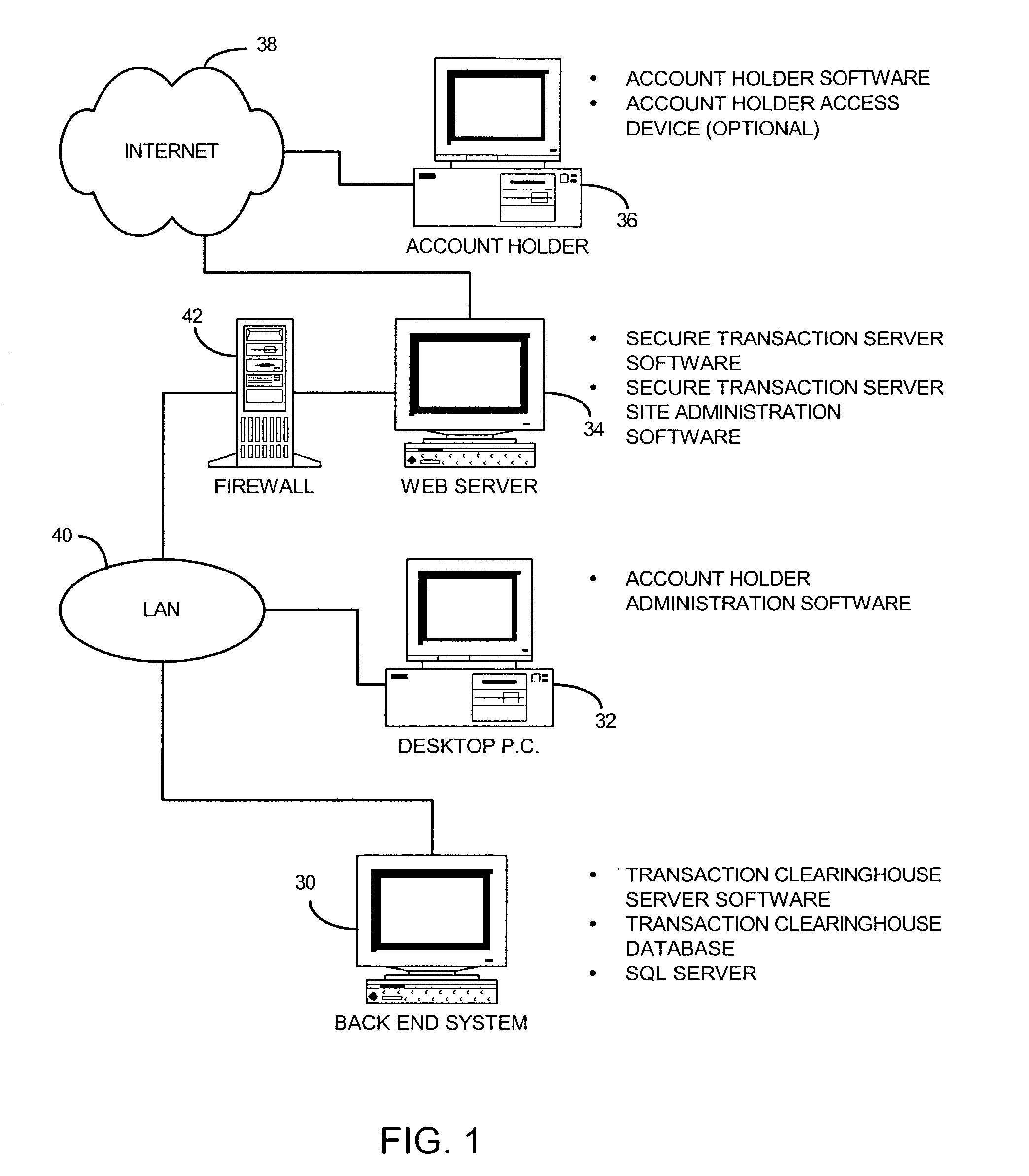
InactiveUS7290288B2Mosaic printer telegraph systemDigital data processing detailsComputer resourcesThe Internet
A method and system for controlling access, by an authentication server, to protected computer resources provided via an Internet Protocol network that includes storing (i) a digital identification associated with at least one client computer device, and (ii) data associated with the protected computer resources in at least one database associated with the authentication server; authenticating, by the authentication server, the digital identification forwarded by at least one access server; authorizing, by the authentication server, the at least one client computer device to receive at least a portion of the protected computer resources requested by the at least one client computer device, based on the stored data associated with the requested protected computer resources; and permitting access, by the authentication server, to the at least the portion of the protected computer resources upon successfully authenticating the digital identification and upon successfully authorizing the at least once client computer device.
Owner:PRISM TECH
Transaction Risk Based Token
Embodiments of the invention provision multiple payment tokens on a communication device. The communication device may be provisioned with multiple limited use keys (LUK), each LUK being associated with a specific type of transaction. When the communication device is used for a transaction, the communication device automatically determines a type of the transaction and selects an appropriate LUK based on the determined transaction type. The selected LUK may be used to create a cryptogram, which can be used to verify the transaction.
Owner:VISA INT SERVICE ASSOC
System and Method for Block-Chain Verification of Goods
A method for block-chain verification of goods includes obtaining, by a first computing device, a first address. The method includes exporting, by the first computing device, the first address to a first code affixed to a first product. The method includes filing, by the first computing device, a first crypto-currency transaction to the first address, at a transaction register. The method includes receiving, by a second computing device, from a code scanner, the first address, scanned from the first code affixed to the first product. The method includes verifying, by the second computing device, the first crypto-currency transaction at the transaction register, using the first address. The method includes identifying, by the second computing device, based on the verification, that the first product is authentic.
Owner:THE FILING CABINET
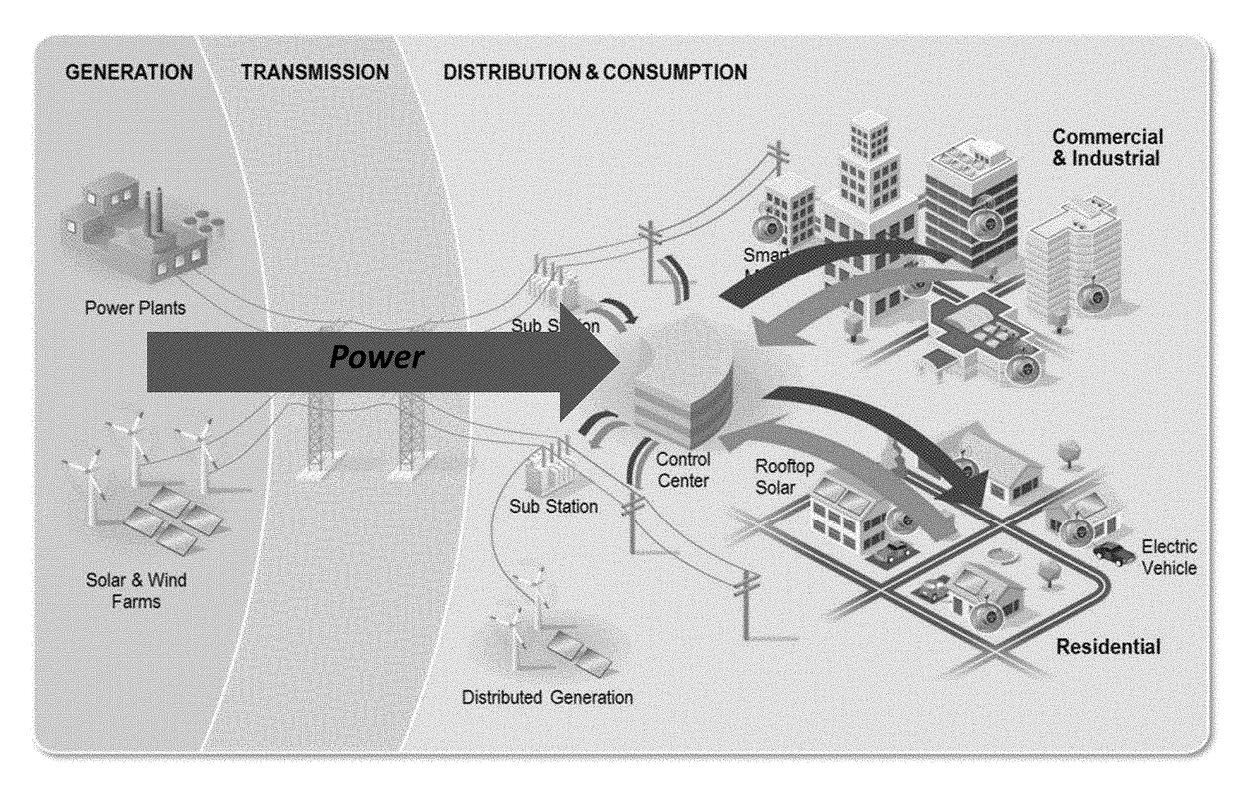
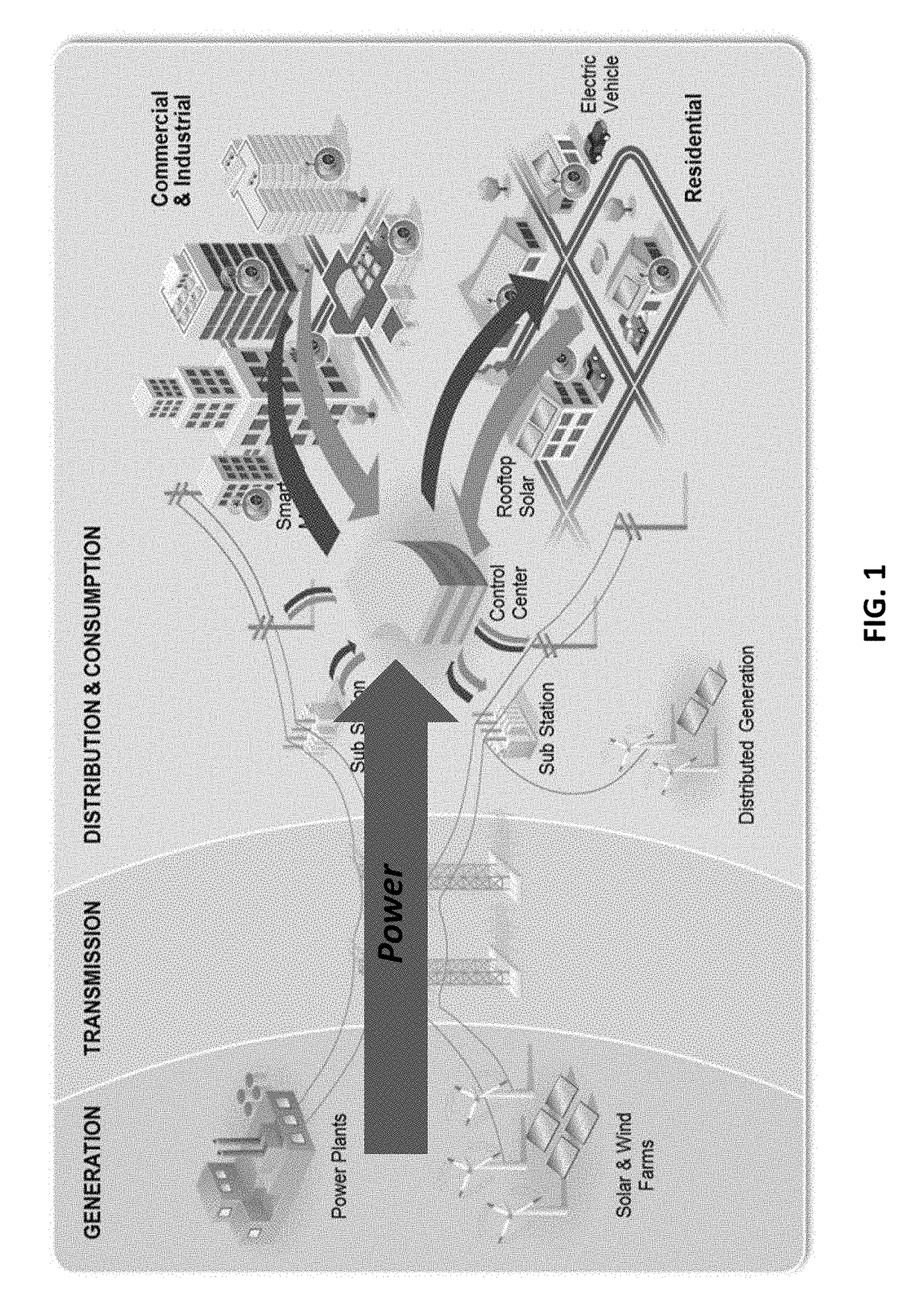
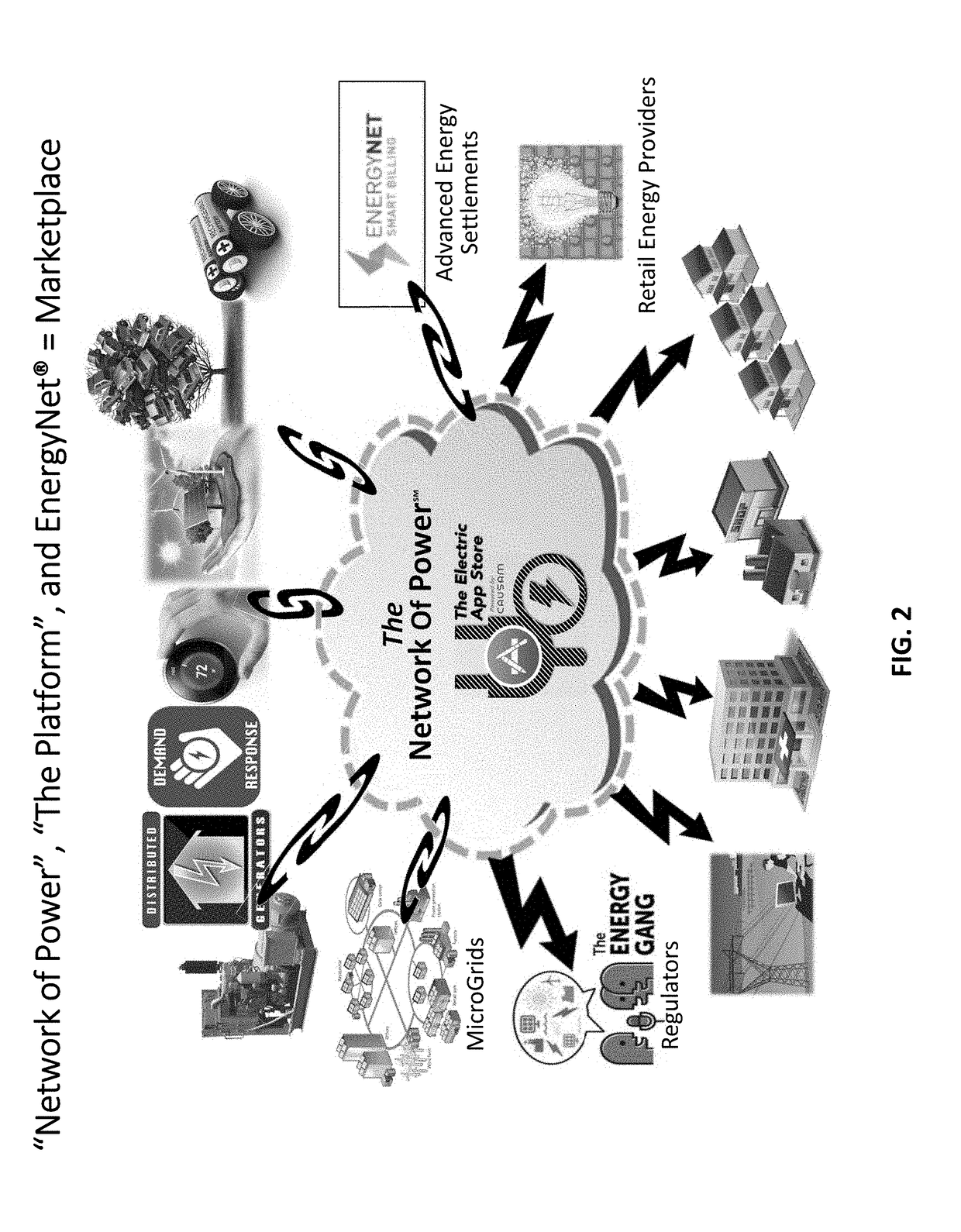
Systems and methods for advanced energy settlements, network-based messaging, and applications supporting the same on a blockchain platform
Systems and methods for financial settlement of transactions within an electric power grid network are disclosed. A multiplicity of active grid elements are constructed and configured for electric connection and network-based communication over a blockchain-based platform. The multiplicity of active grid elements are operable to make peer-to-peer transactions based on their participation within the electric power grid by generating and executing a digital contract. The multiplicity of active grid elements generate messages autonomously and / or automatically within a predetermined time interval. The messages comprise energy related data and settlement related data. The energy related data of the multiplicity of active grid elements are based on measurement and verification. The energy related data and the settlement related data are validated and recorded on a distributed ledger with a time stamp and a geodetic reference.
Owner:CAUSAM ENERGY INC
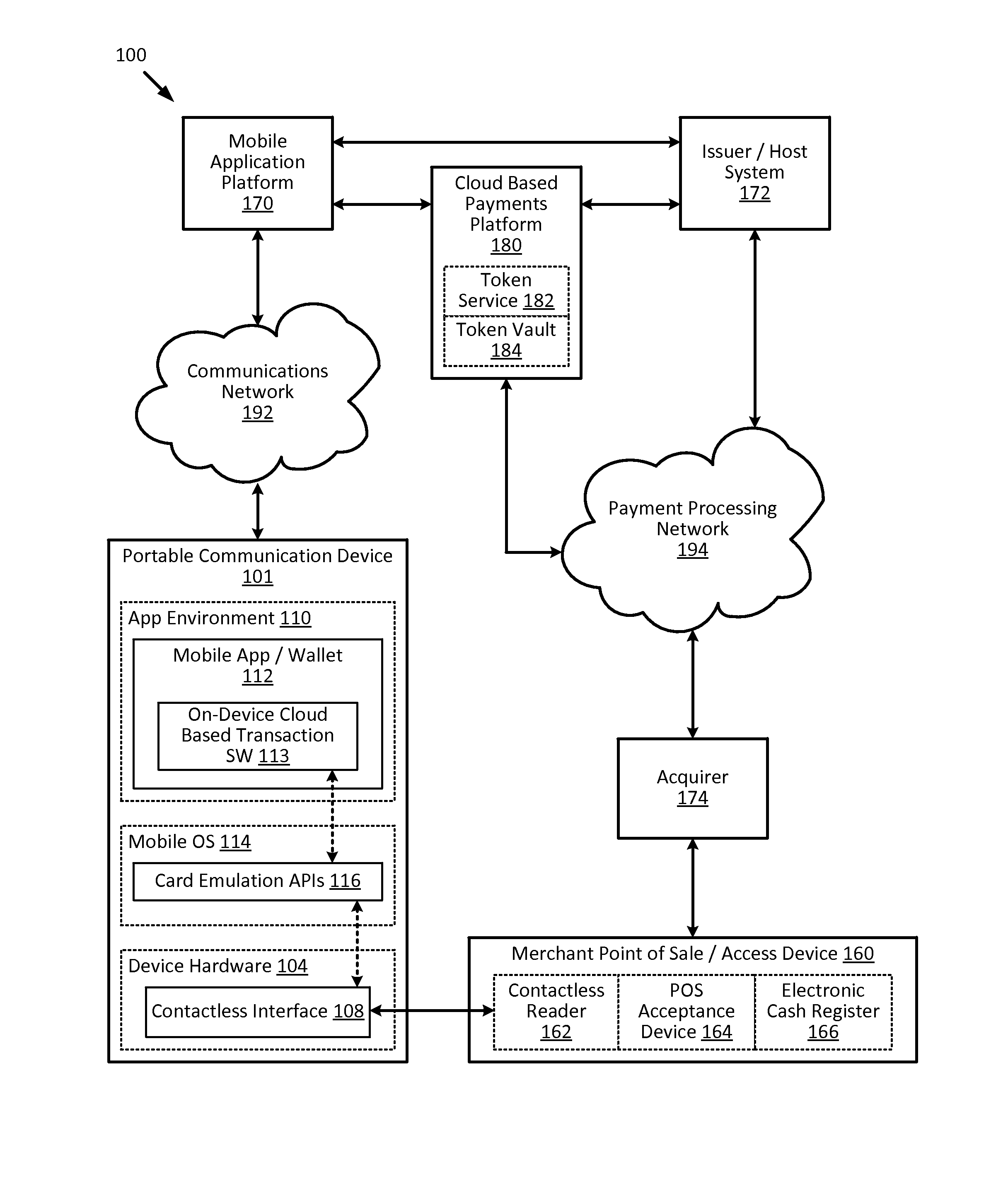
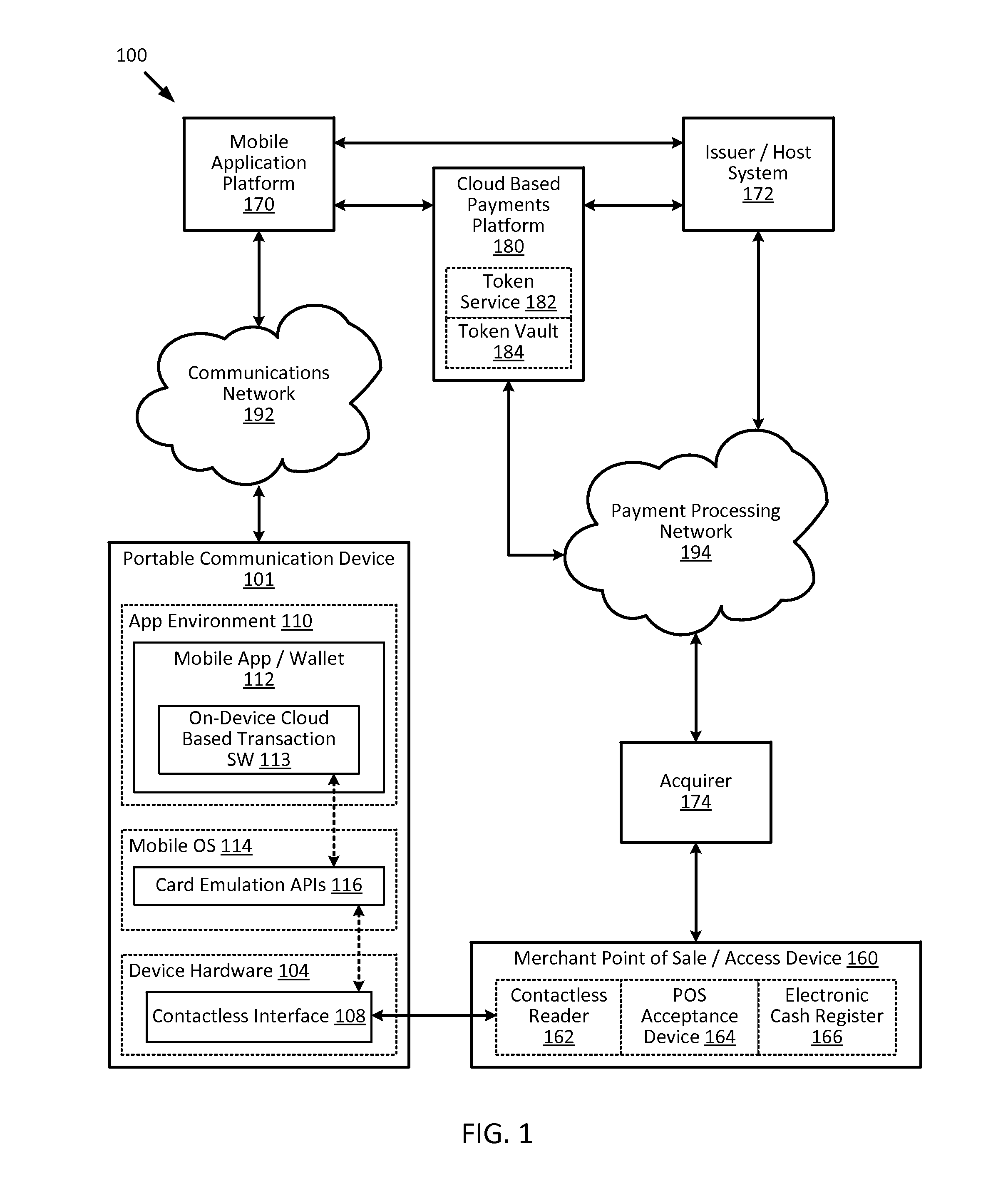
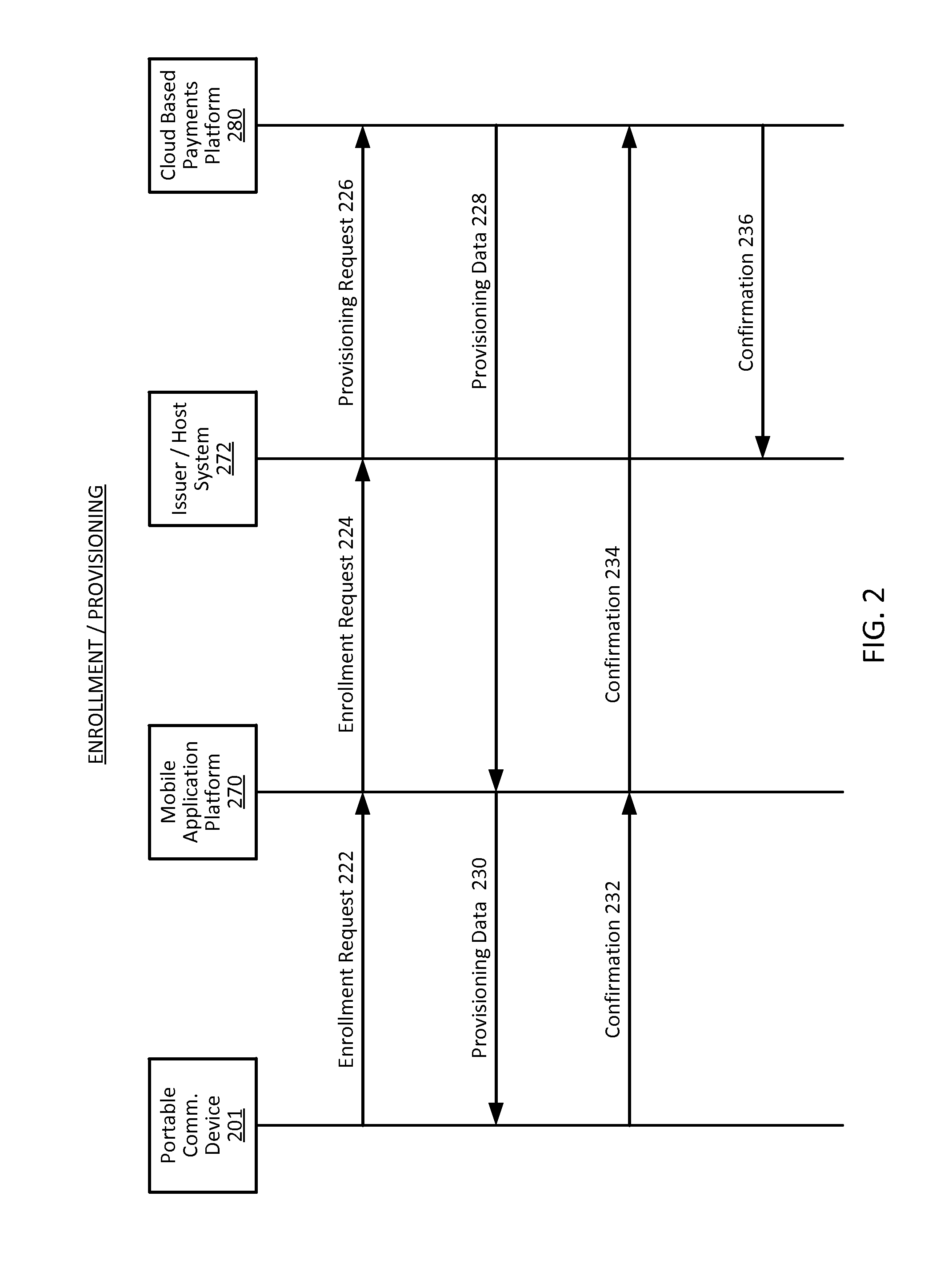
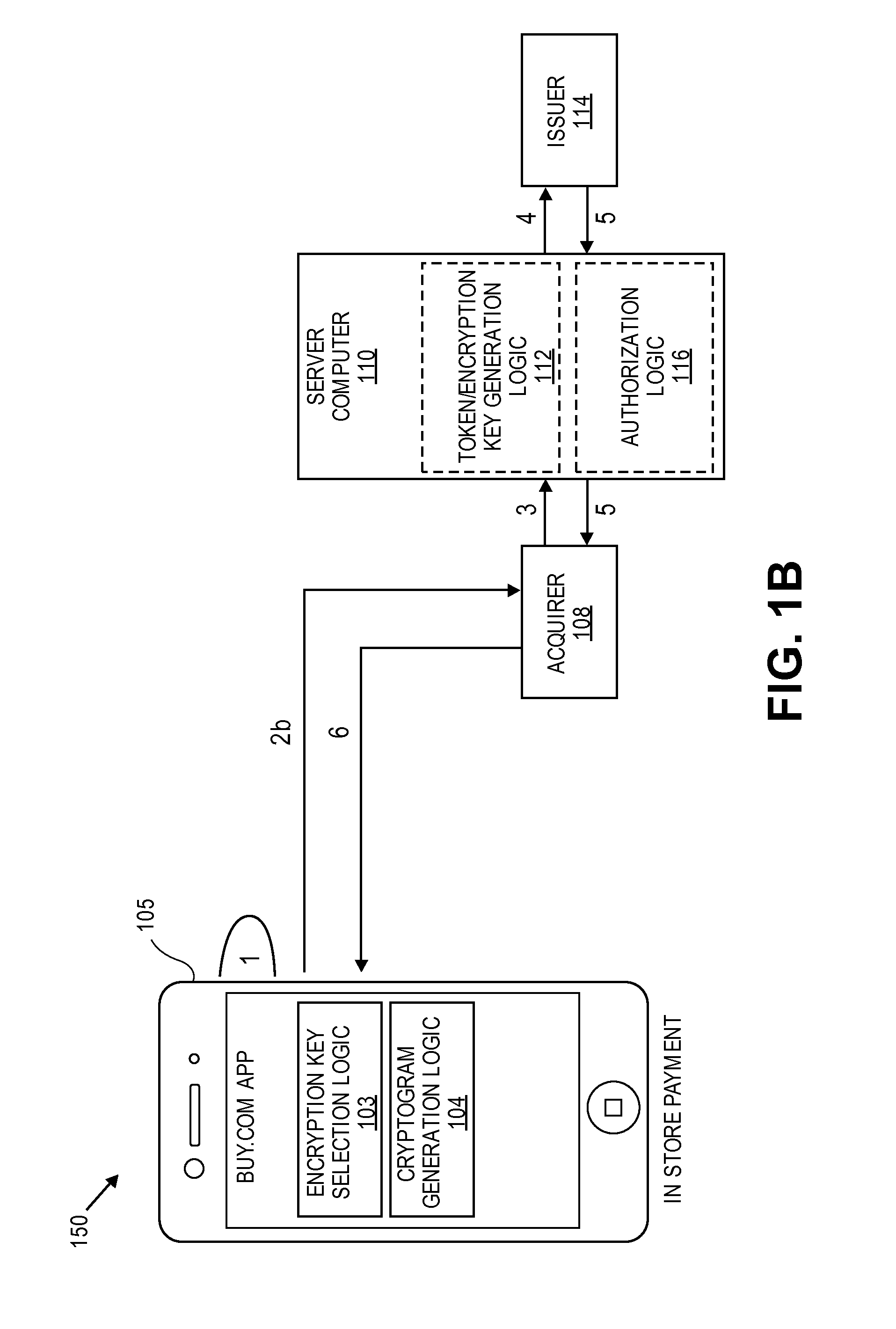
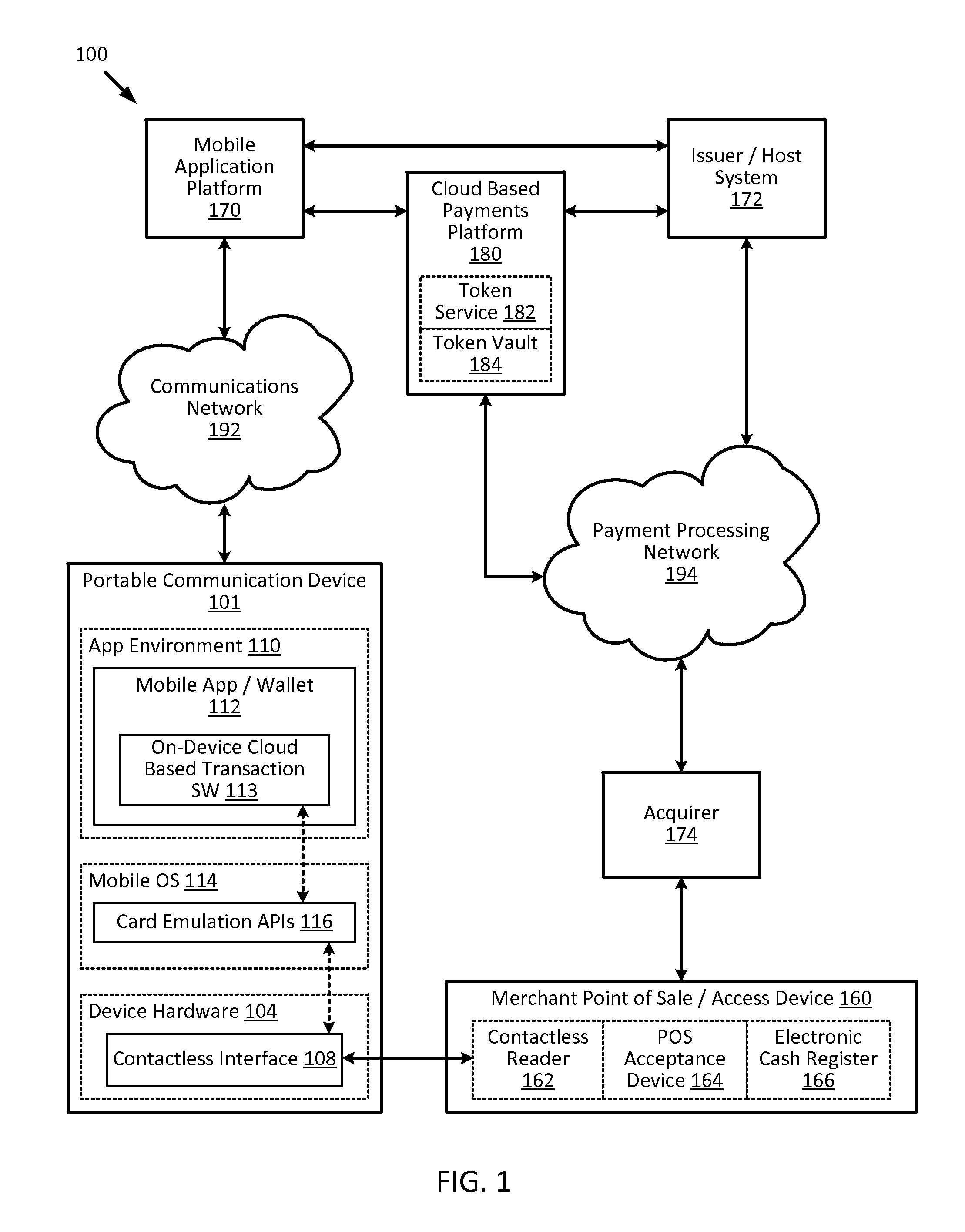
Cloud-based transactions methods and systems
ActiveUS20150180836A1Promote generationImprove securityKey distribution for secure communicationMultiple keys/algorithms usageCryptogramDatabase
Techniques for enhancing the security of a communication device when conducting a transaction using the communication device may include using a limited-use key (LUK) to generate a transaction cryptogram, and sending a token instead of a real account identifier and the transaction cryptogram to an access device to conduct the transaction. The LUK may be associated with a set of one or more limited-use thresholds that limits usage of the LUK, and the transaction can be authorized based on at least whether usage of the LUK has exceeded the set of one or more limited-use thresholds.
Owner:VISA INT SERVICE ASSOC
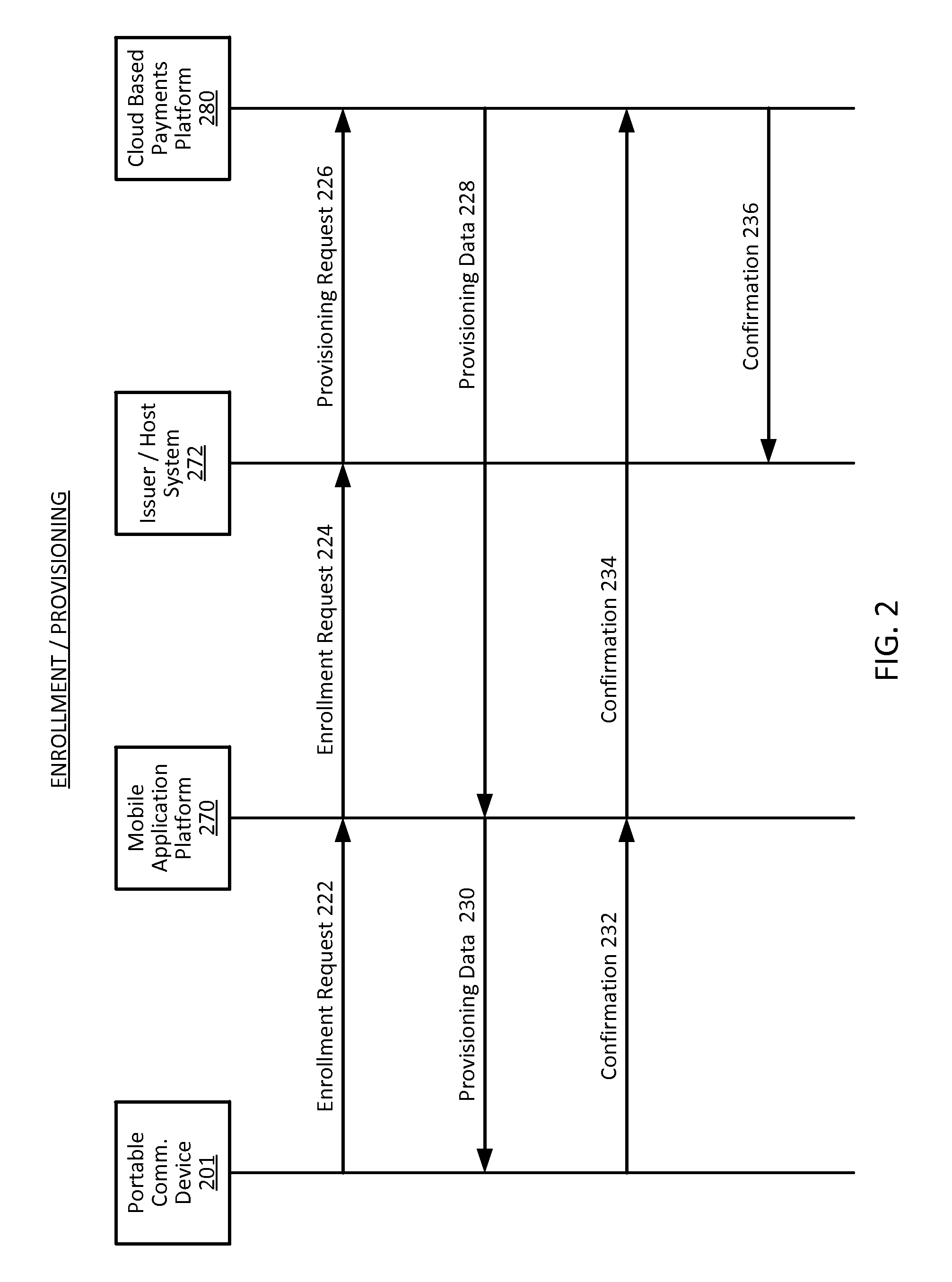
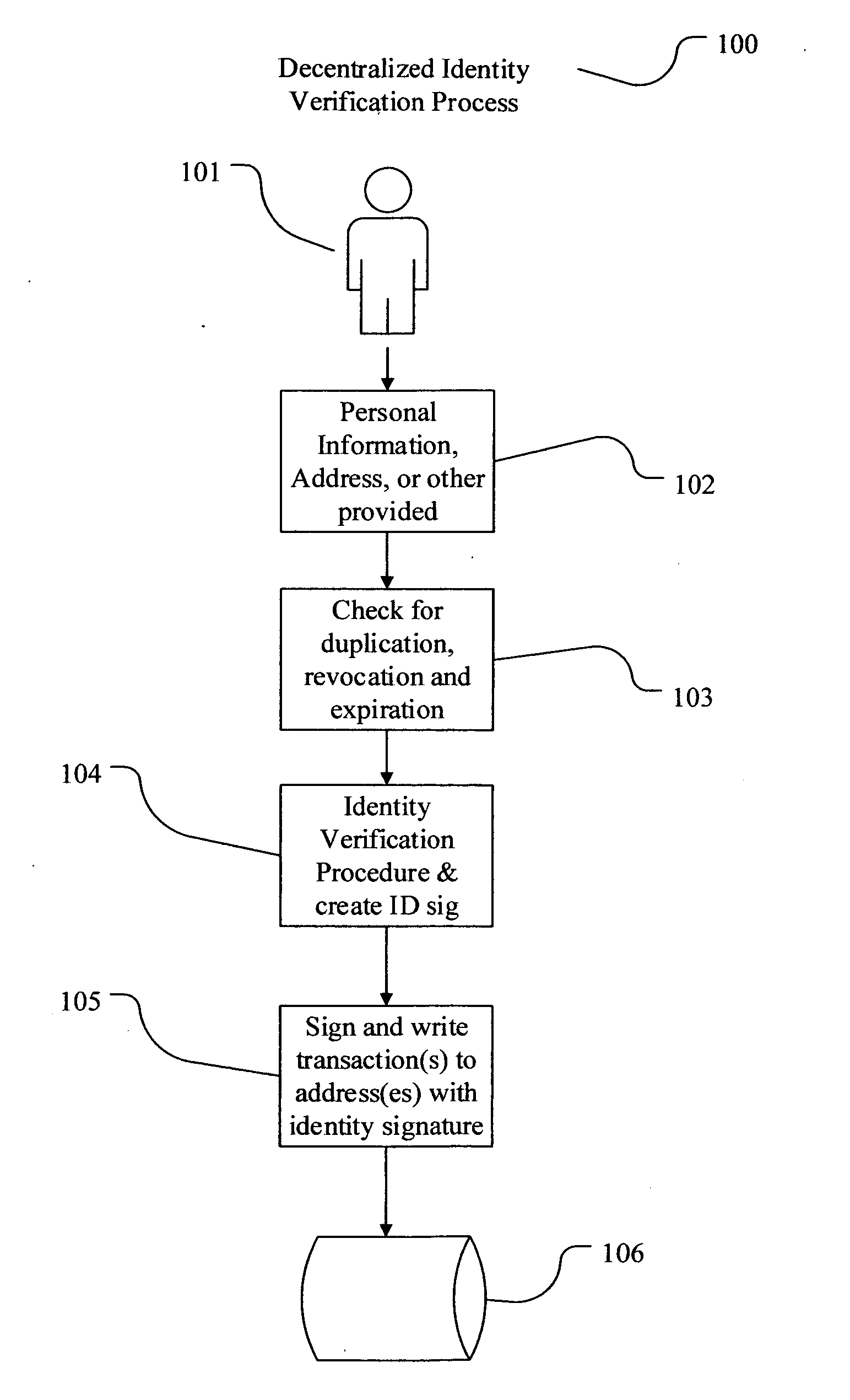
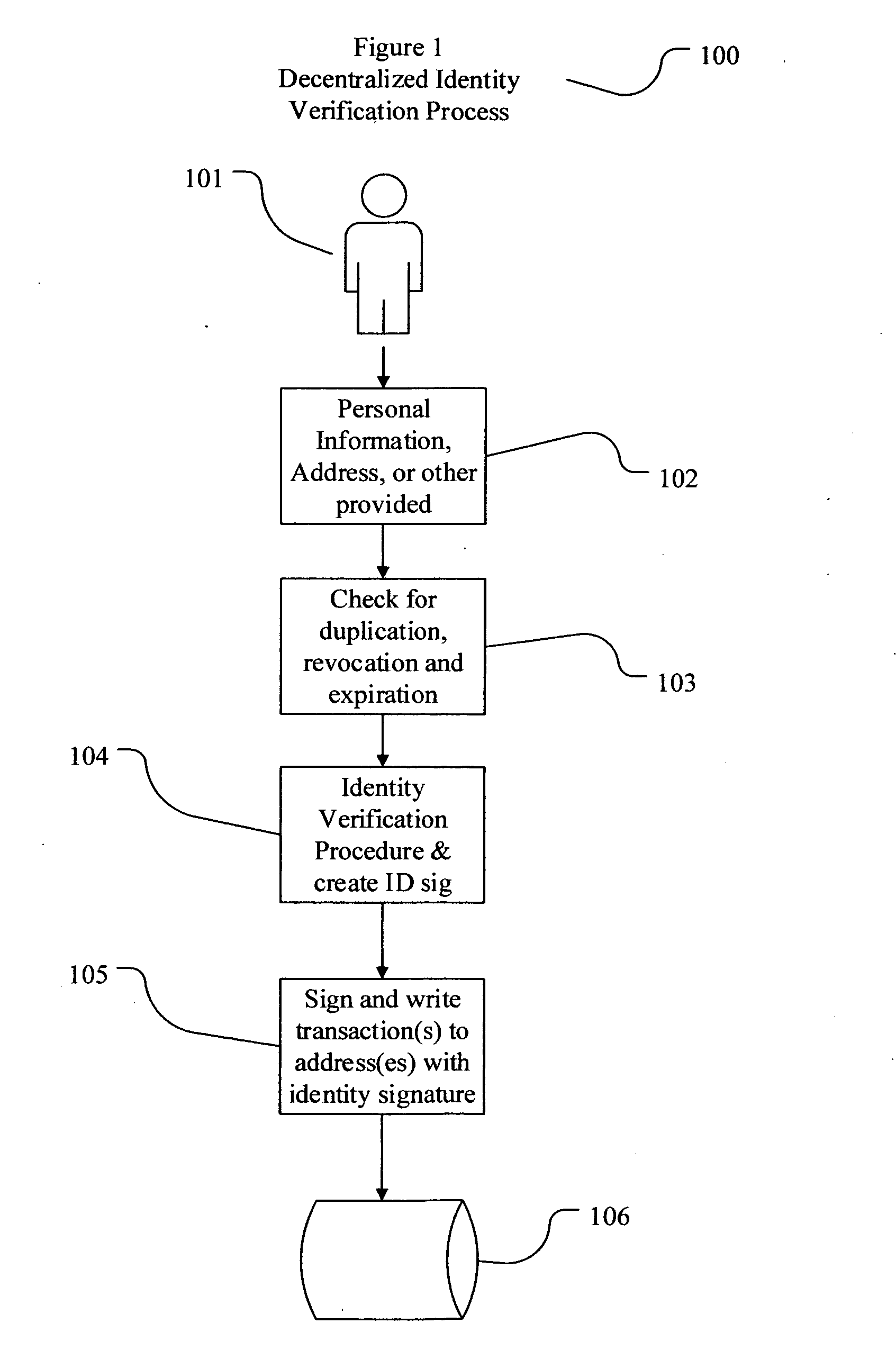
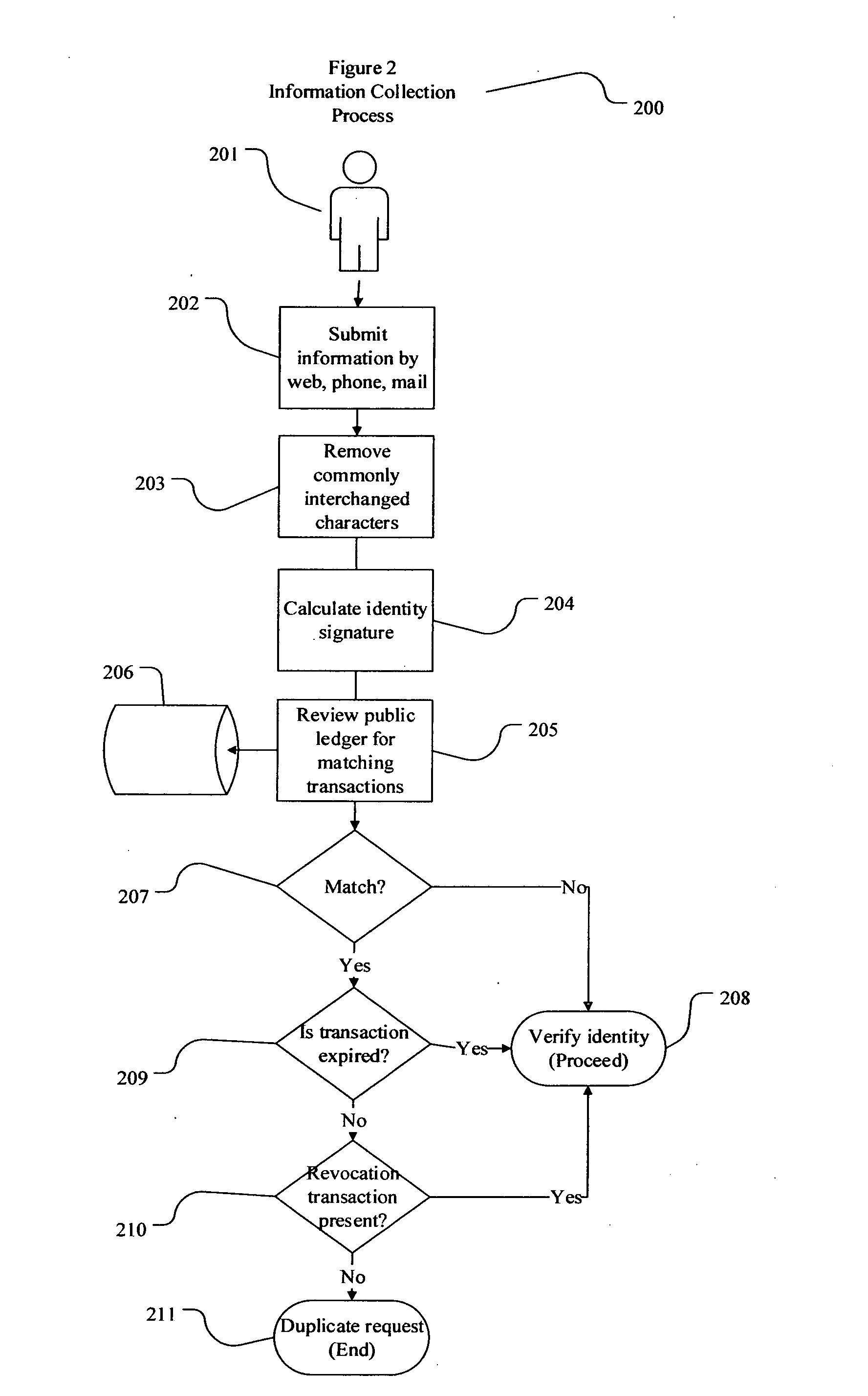
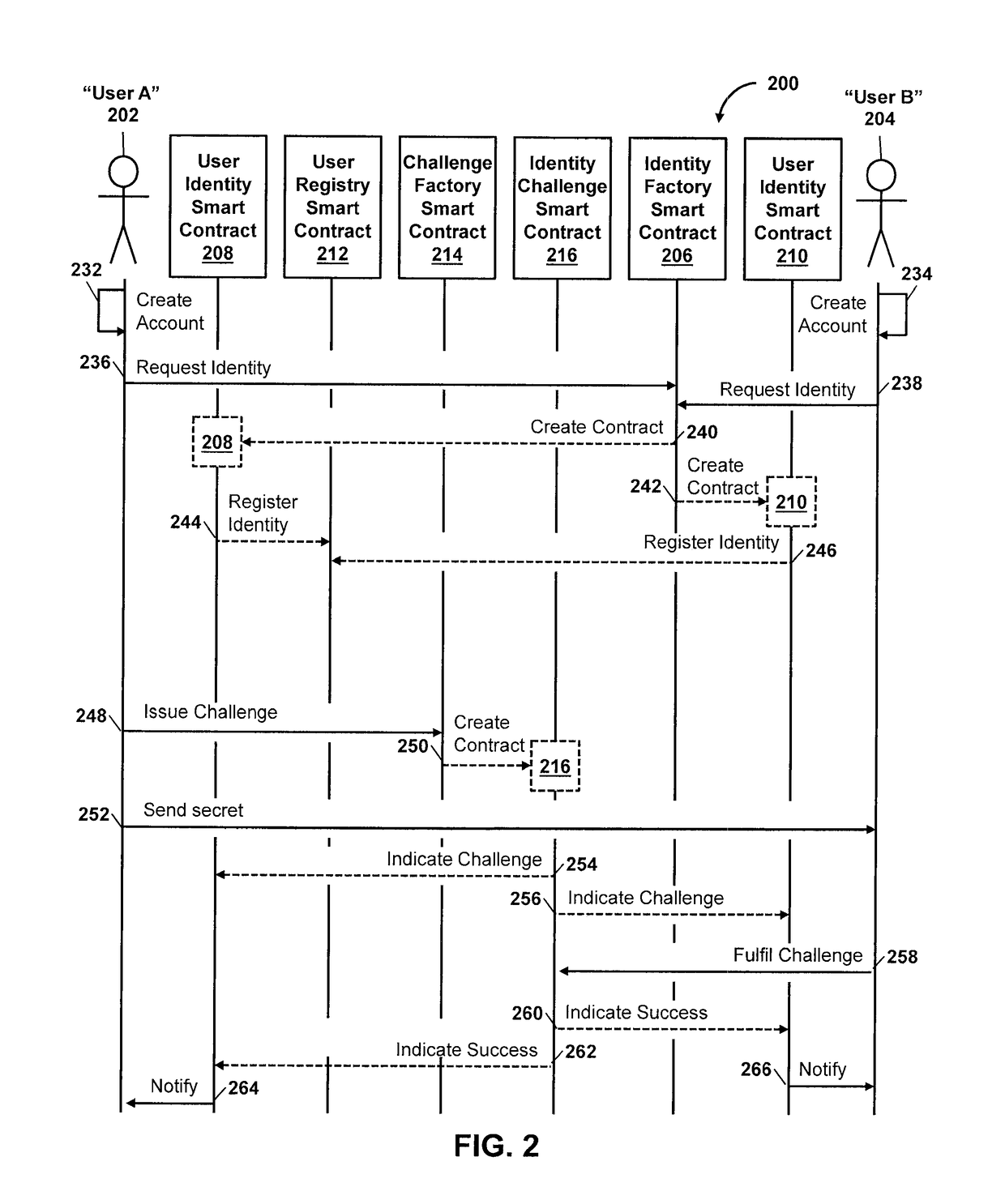
Decentralized identity verification systems and methods
InactiveUS20150356523A1Cryptography processingUser identity/authority verificationRegulatory authorityFinancial transaction
The present invention involves systems and methods that allow participants in cryptocurrency networks to exchange cryptocurrency for traditional currency legally and safely without requiring the use of a traditional exchange or online brokerage as a fiduciary. The invention accomplishes this through the use of a decentralized identity verification protocol that allows a service provider to verify the identity of a participant and then publish an identity signature on the participant's cryptocurrency address or addresses. The invention enables full compliance with Country specific customer identification program and anti-money laundering requirements, and maintains the ability to independently satisfy requests for information or data retention requirements if requested by legally authorized parties, but does not require that the participant store the private keys or access controls to their cryptocurrency on an exchange or brokerage service.The invention serves to verify a participant's identity in full compliance with US Bank Secrecy and Patriot Act provisions or similar regulations where identification may be achieved through non-documentary or documentary identity verification procedures. After passing the applicable verification procedure, the service provider stamps the participant's cryptocurrency address with a transaction containing an identity signature. This identity signature within the transaction consists of a public indicator of the participant's Country and subdivision, a compliance level code, an ID type indicator, and an identity hash. The identity hash is created from the digests of cryptographic hash functions where the participant's personal information is used as an input. The service provider signs the transaction with their authorized private key that corresponds to their publicly accessible public key. This serves as a publicly verifiable confirmation that the identity associated with the address in question was validated by the service provider authorized to act on behalf of the regulatory authority.The participant may then purchase and sell cryptographic currency from and to a third party exchange or brokerage service legally and safely when using their verified cryptocurrency address. This is because the third party is able to confirm compliance by openly referencing and verifying the identity verification transaction present on the address. Subsequent transactions where the third party sells or purchases cryptocurrency for the verified participant are similarly stamped with a transaction conforming to the identity verification protocol. This allows the third party interacting with the verified participant's address to observe any regulations limiting the amount or frequency of transactions over a variable period of time. It follows that this address could be used with any third party or participant in the cryptocurrency network that observes the decentralized identity verification protocol, all without requiring the third party or participant to collect and verify personal information redundantly. The ability to verify an identity remotely also eliminates the need for the third party to act as a fiduciary holding the private keys or access controls to the verified address. Lawful requests for information by authorized authorities are served to the service provider as digitally signed transactions that may then be linked to the participant's identity and transactions, allowing the protocol to observe subpoenas or similar lawful requests for information. The encrypted personal information may be held in escrow by the service provider indexed to the verified cryptocurrency address for such purposes. An alternate embodiment would store the encrypted personal information in a decentralized network of other participants, with the information accessible for retrieval using the public key of the verified cryptocurrency address and decryption using the corresponding private key, decentralizing the process entirely except for the identity verification step.
Owner:CHAINID
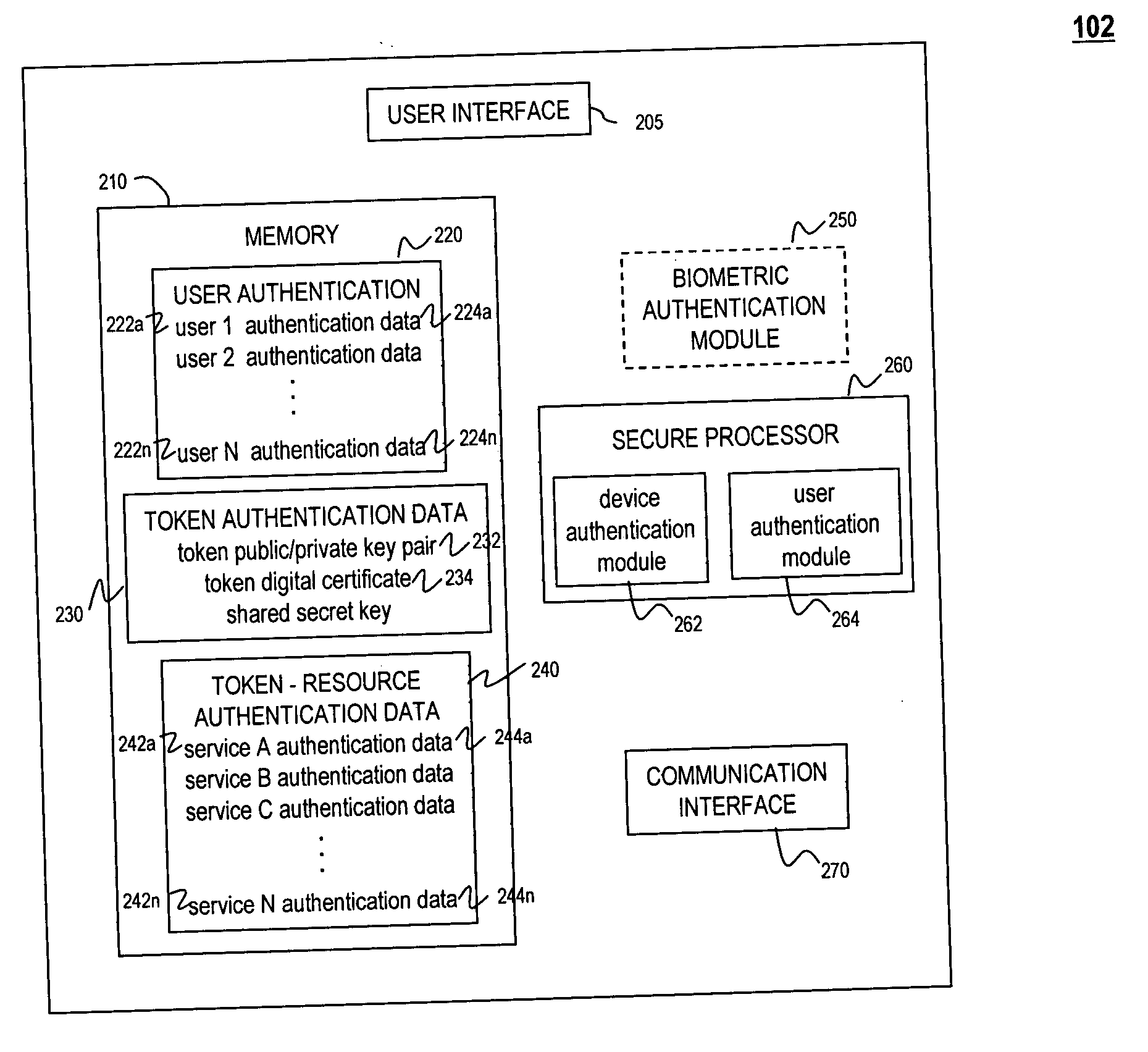
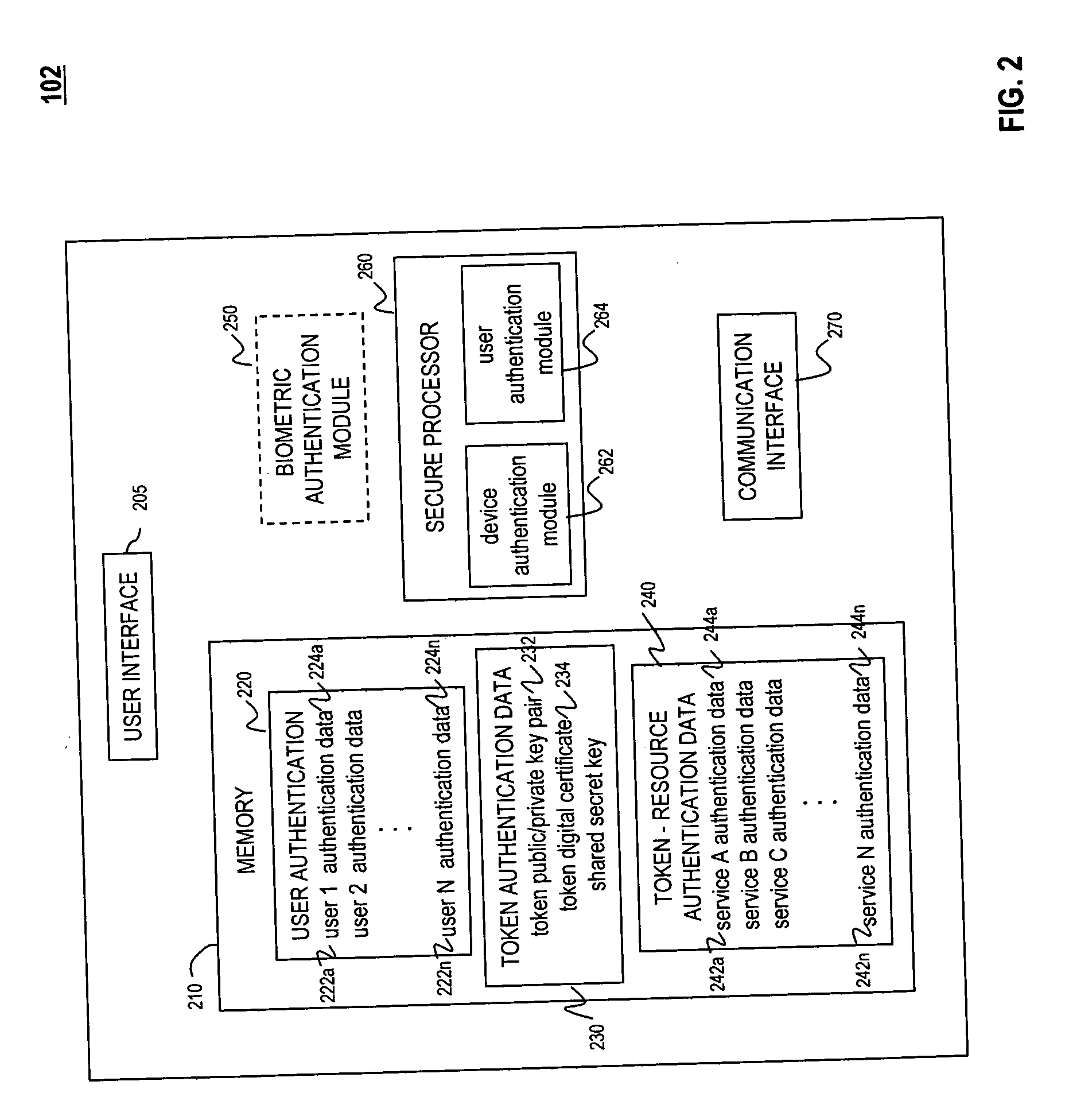
Universal authentication token
ActiveUS20070118891A1Key distribution for secure communicationDigital data processing detailsComputer scienceUser interface
A universal authentication token is configured to securely acquire security credentials from other authentication tokens and / or devices. In this manner, a single universal authentication token can store the authentication credentials required to access a variety of resources, services and applications for a user. The universal authentication token includes a user interface, memory for storing a plurality of authentication records for a user, and a secure processor. The secure processor provides the required cryptographic operations to encrypt, decrypt, and / or authenticate data that is sent or received by universal token. For example, secure processor may be used to generate authentication data from seed information stored in memory.
Owner:NXP BV
Systems and methods for blockchain virtualization and scalability
PendingUS20170337534A1Encryption apparatus with shift registers/memoriesCryptography processingVirtualizationComputer science
A virtualized blockchain forest includes a plurality of individual blockchains. Each individual blockchain of the plurality includes a blockchain height, a genesis block, and at least one additional block. The virtualized blockchain forest further includes a plurality of participating processors that make up a consensus pool, and a blockchain forest height having a time-sequenced start-to-finish length of blocks among the collective plurality of individual blockchains. The virtualized blockchain forest is configured to aggregate different ones of the plurality of individual blockchains, and is further configured to terminate individual ones of plurality of individual blockchains.
Owner:CABLE TELEVISION LAB
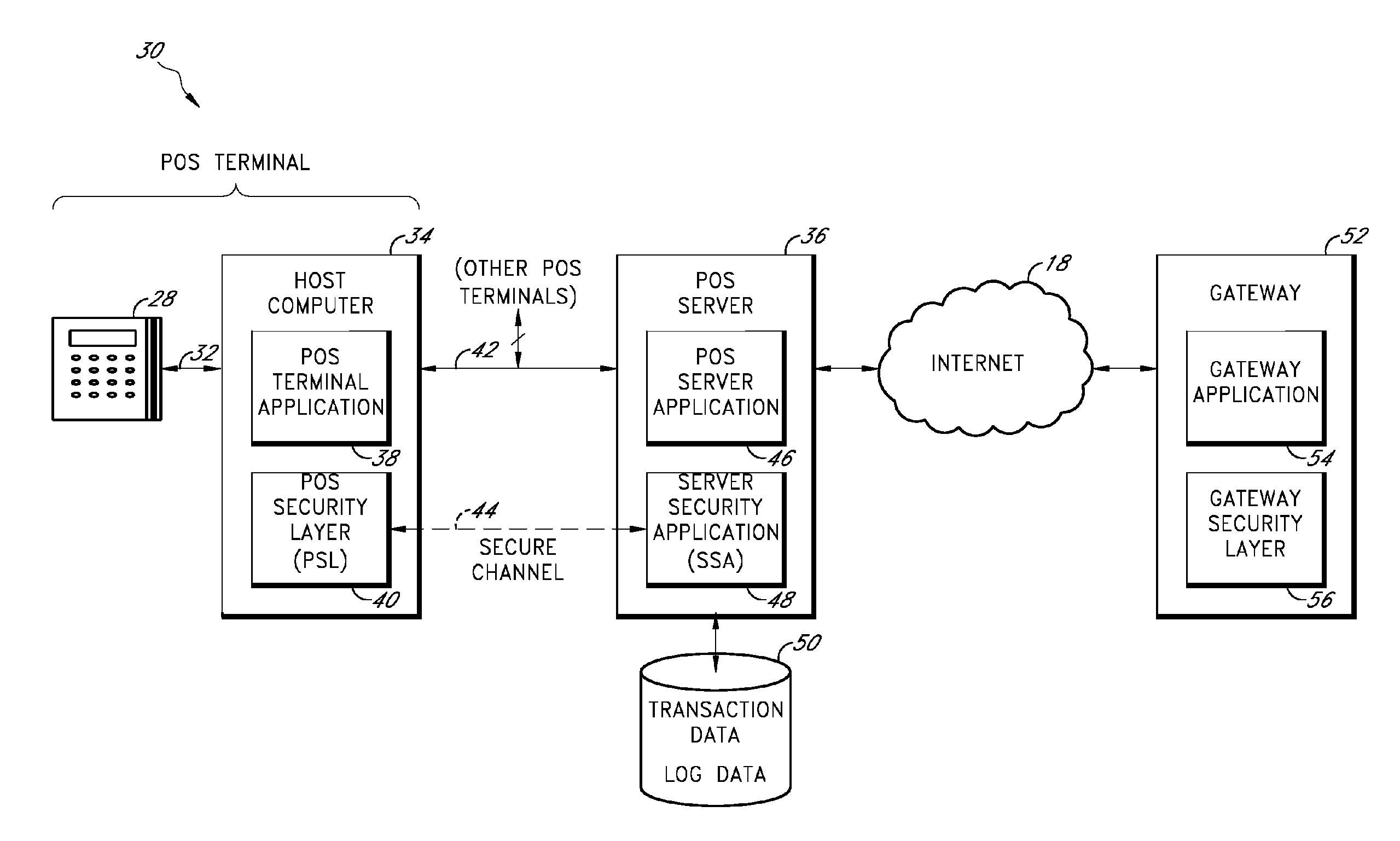
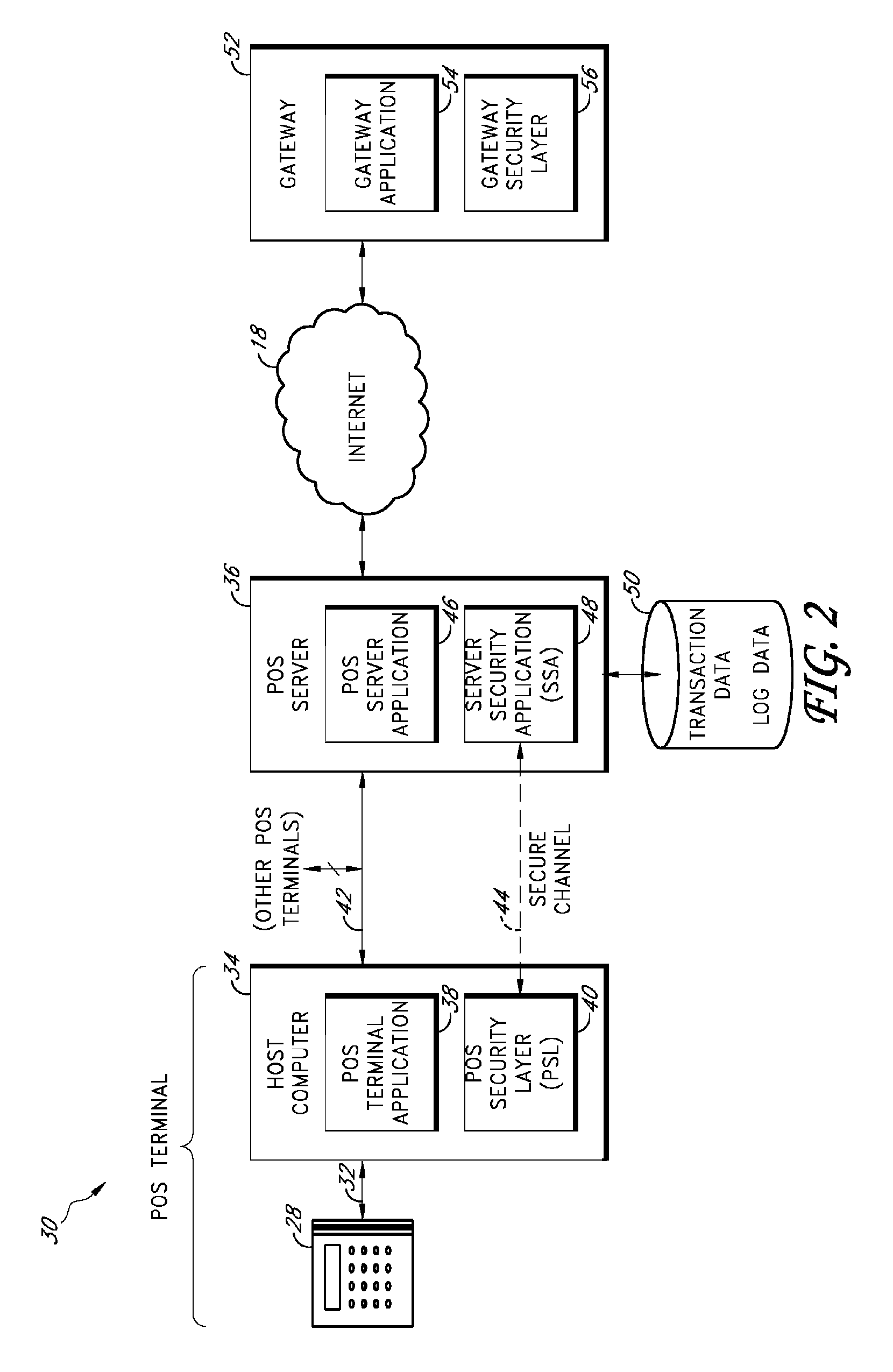
Secure payment card transactions
Payment card transactions at a point of sale (POS) are secured in certain embodiments by intercepting, with a POS security layer installed on a POS terminal, payment data from the POS terminal, transmitting the payment data from the POS security layer to a server security application installed on a POS server, and providing false payment data from the POS security layer to a POS terminal application installed on the POS terminal. The false payment data in various embodiments is processed as if it were the payment data, such that the POS terminal transmits an authorization request to the POS server using the false payment data. In addition, the authorization request may be transmitted from the POS server to a payment gateway.
Owner:SHIFT4 CORP
Method and system for storage and retrieval of blockchain blocks using galois fields
A method and system for storage and retrieval of blockchains with Galois Fields. One or more blocks for a blockchain are securely stored and retrieved with a modified Galois Fields on a cloud or peer-to-peer (P2P) communications network. The modified Galois Field provides at least additional layers for security and privacy for blockchains. The blocks and blockchains are securely stored and retrieved for cryptocurrency transactions including, but not limited to, BITCOIN transactions and other cryptocurrency transactions.
Owner:LESAVICH STEPHEN +1
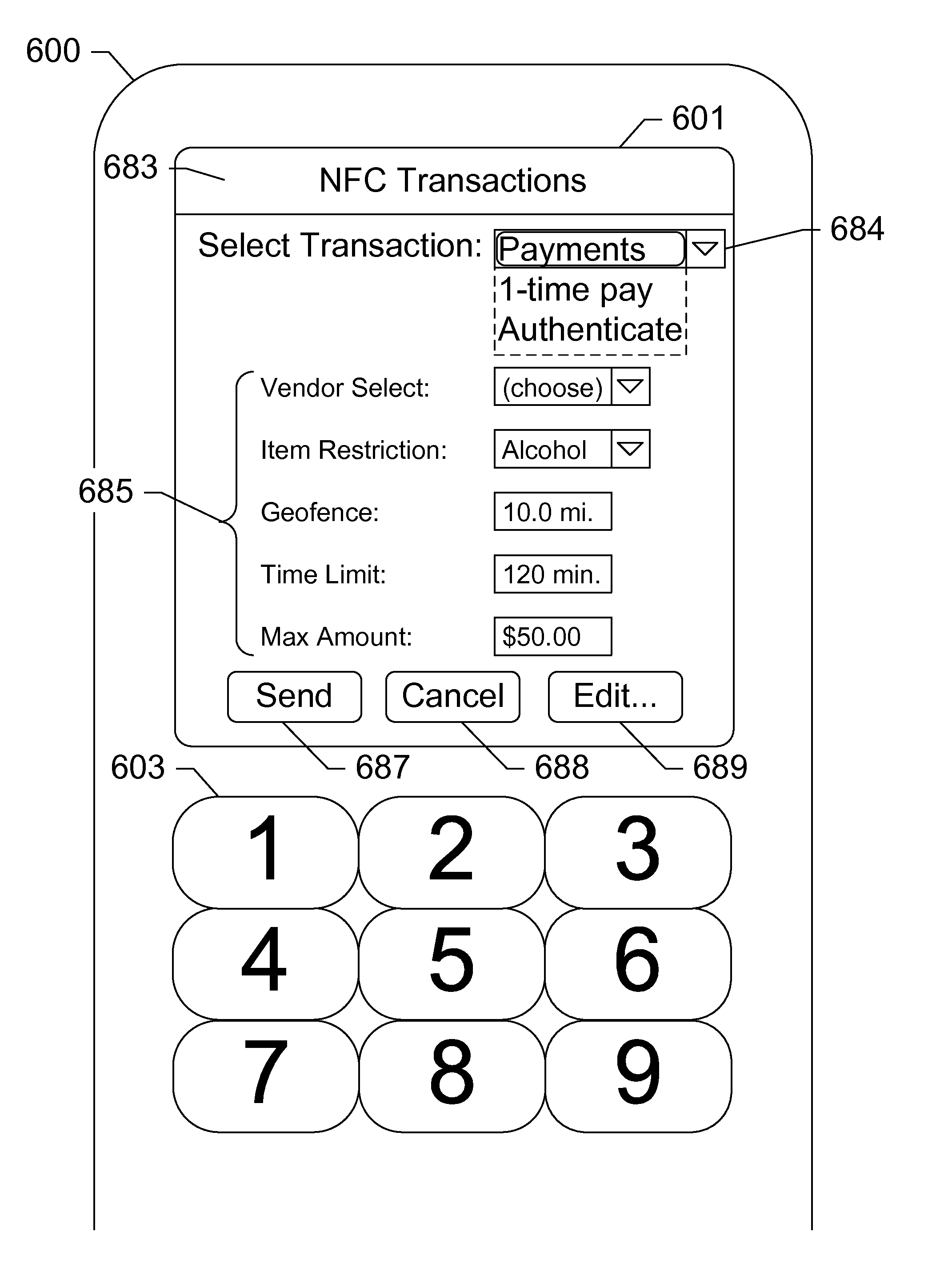
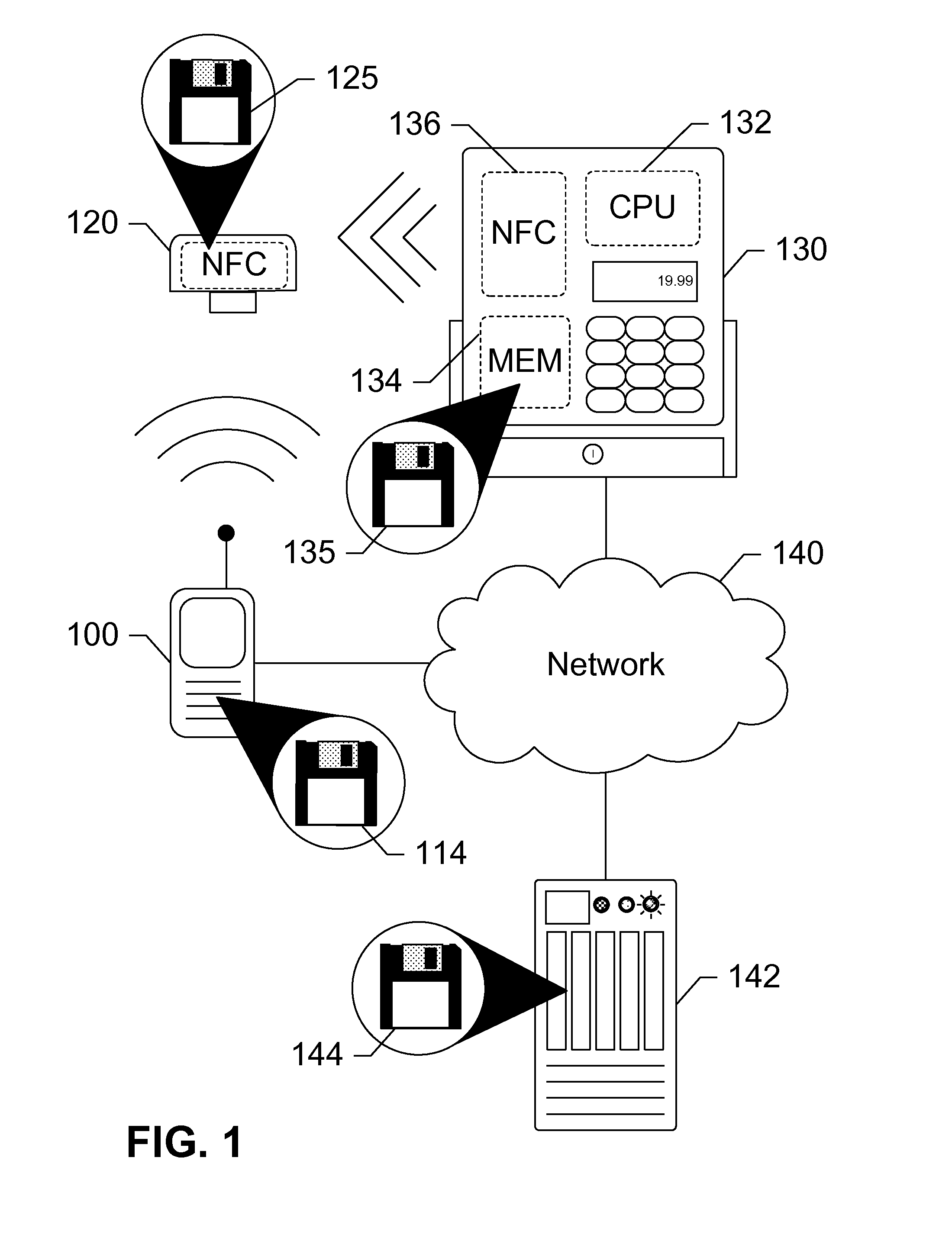
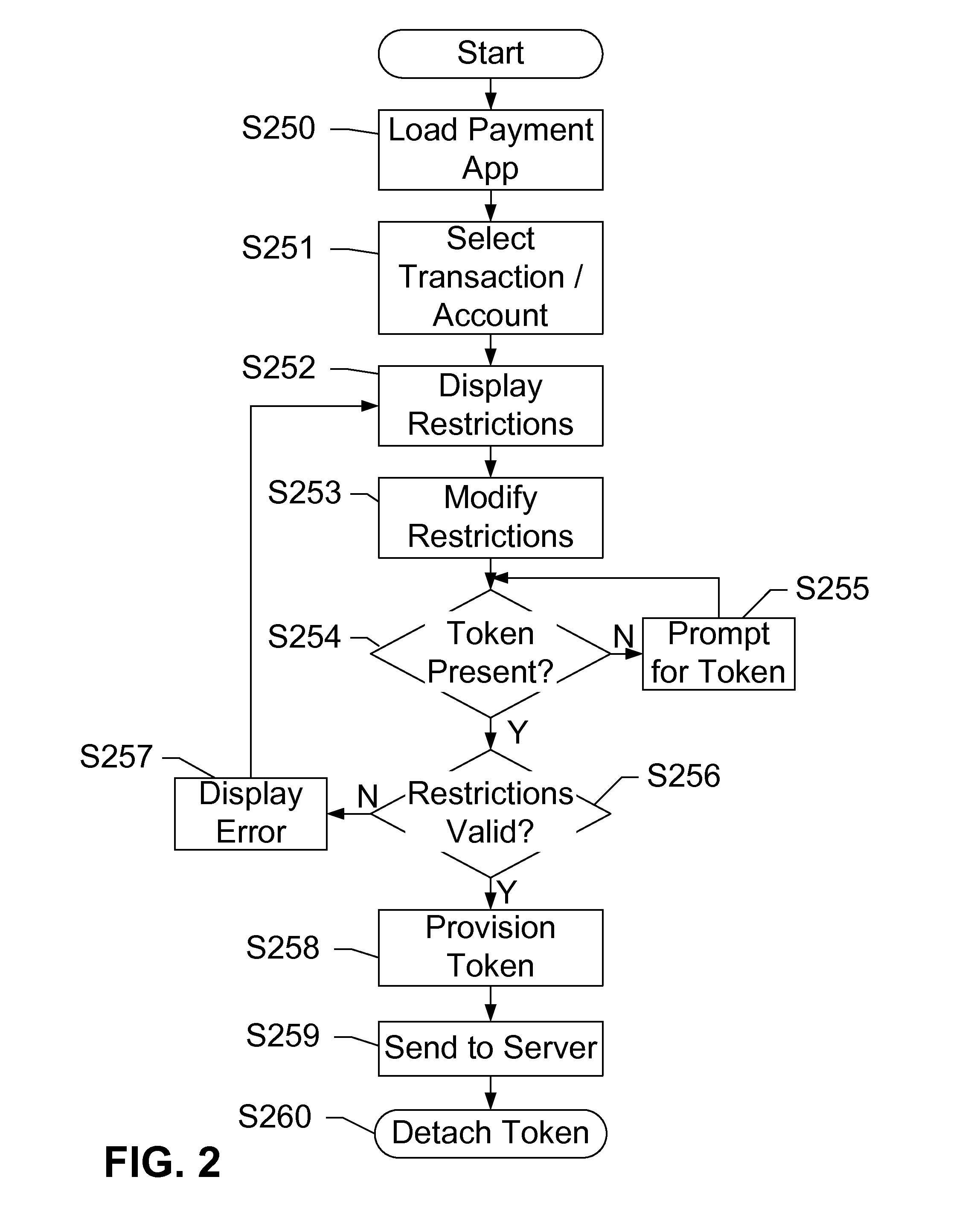
Security token for mobile near field communication transactions
Devices, systems, and methods are disclosed which relate to an NFC-enabled security token that is removably coupled to a mobile device. The security token may be provisioned with the information by the mobile device, then decoupled from the mobile device and used to authenticate the user or perform a transaction at a POS terminal equipped with an NFC reader. The security token includes logic for user-controlled restrictions on allowable purchases, such as payment limits, timeouts, vendor identifiers, allowed purchases, and location-based restrictions. The security token is further equipped with “self destruct” security features, such as deactivating itself or erasing any sensitive information upon being unable to contact the mobile device for a specified duration, or being subject to an unauthorized or restricted transaction, until such time as it is re-coupled to the mobile device.
Owner:AT&T INTPROP I LP
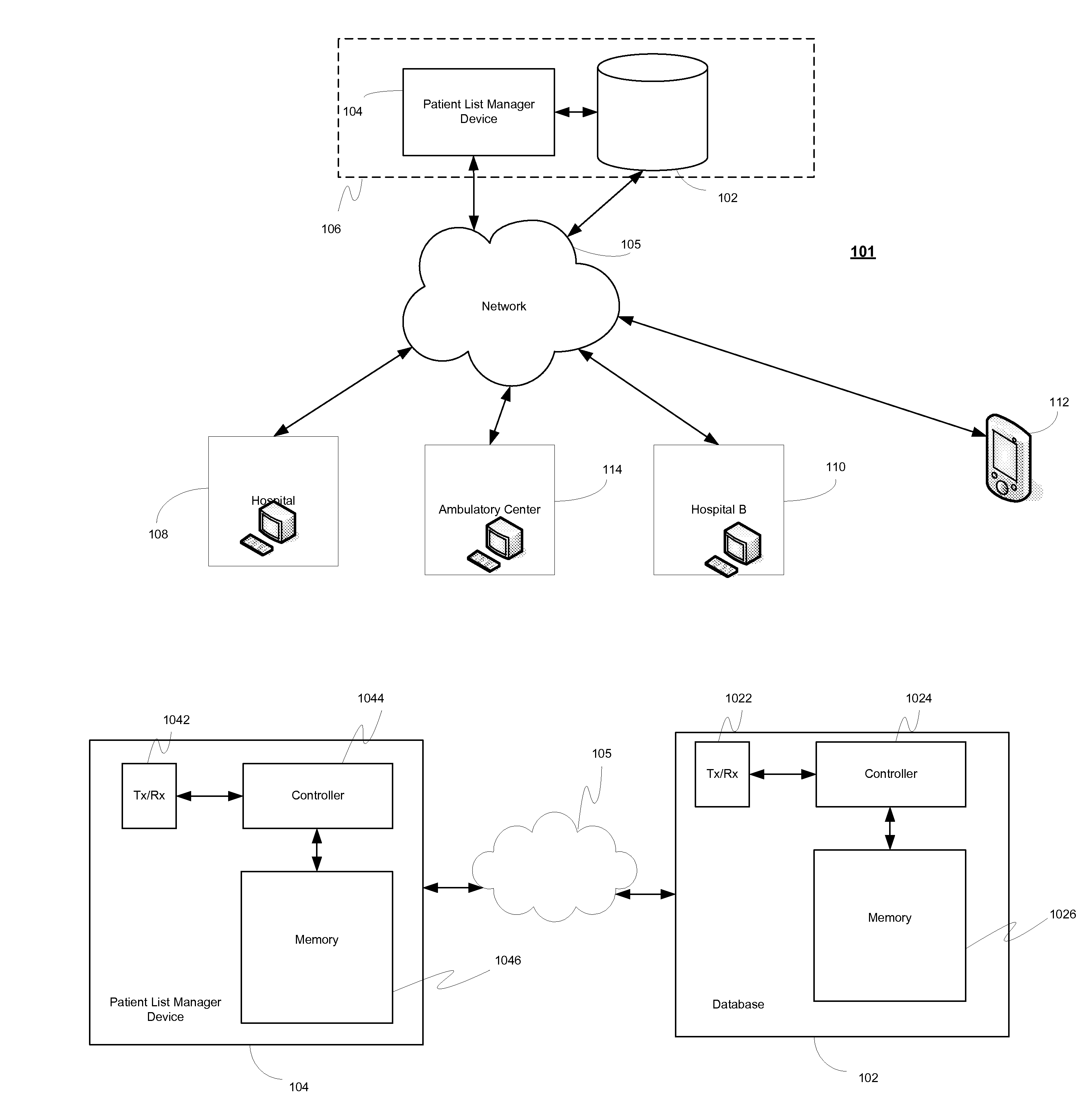
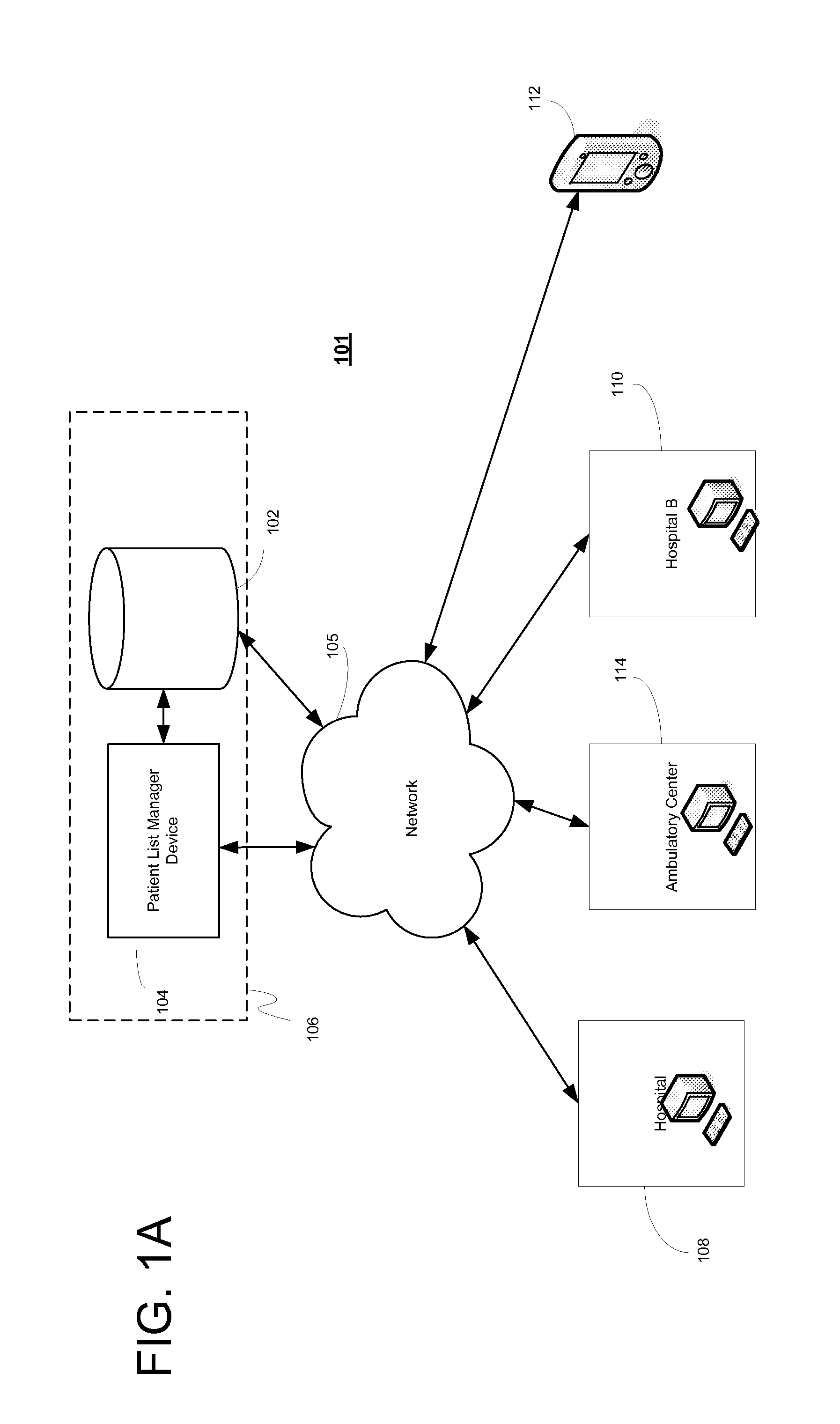
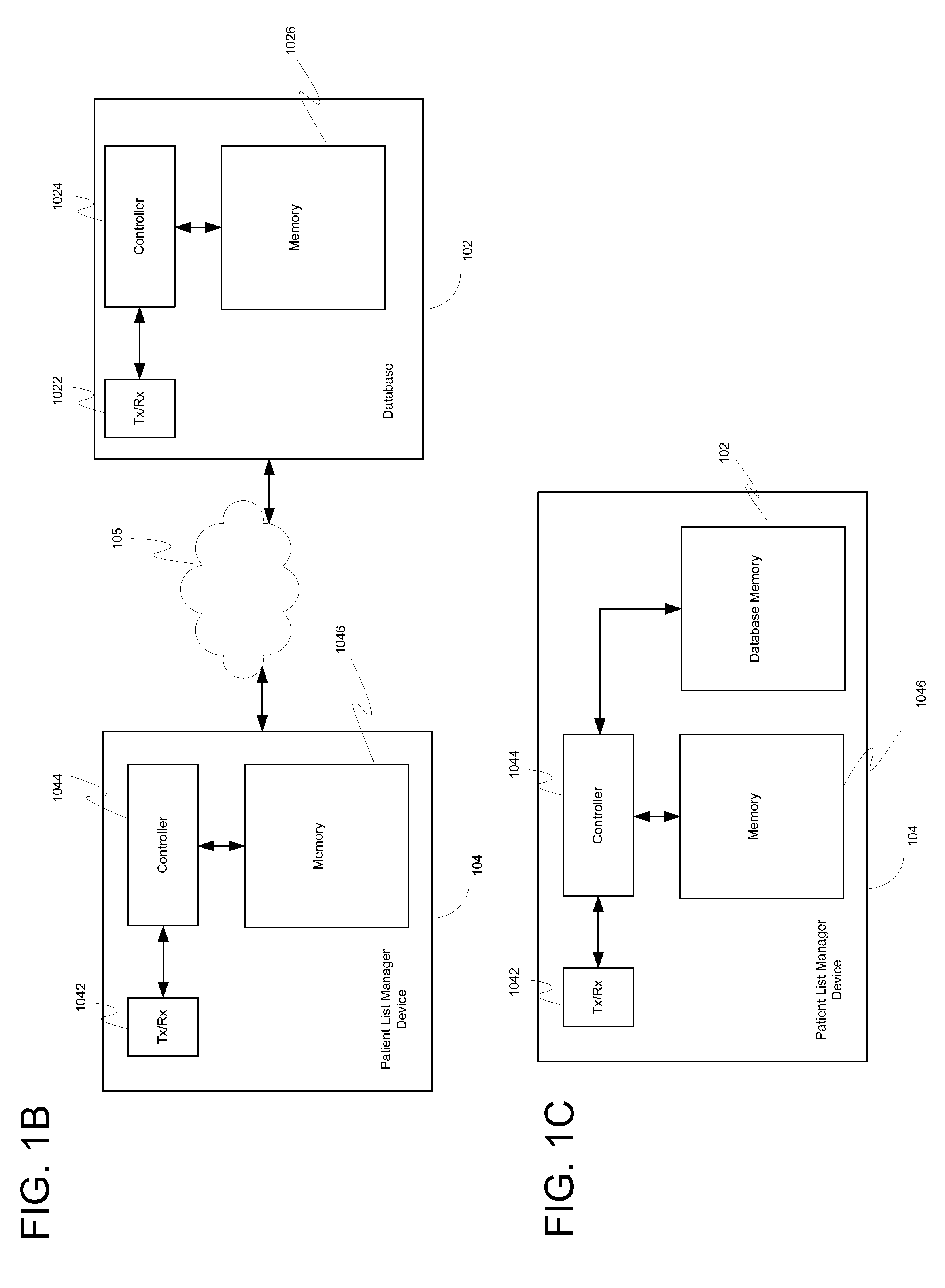
System, client device, server and method for providing a cross-facility patient data management and reporting platform
ActiveUS20150169827A1Readily annotatedAccurate billingKey distribution for secure communicationCryptography processingPoint of carePatient management
A system for providing a patient list manager includes a client device for point of care capture and access of patient data and a server for providing cloud based hosting. One or more modules can leverage the patient data to help users improve and facilitate the efficiency and safety of patient management, diagnostic imaging management, clinical work flows, charge capture, revenue cycle management, accreditation reporting, quality and outcomes monitoring and improvement, among other things.
Owner:ICONIC DATA
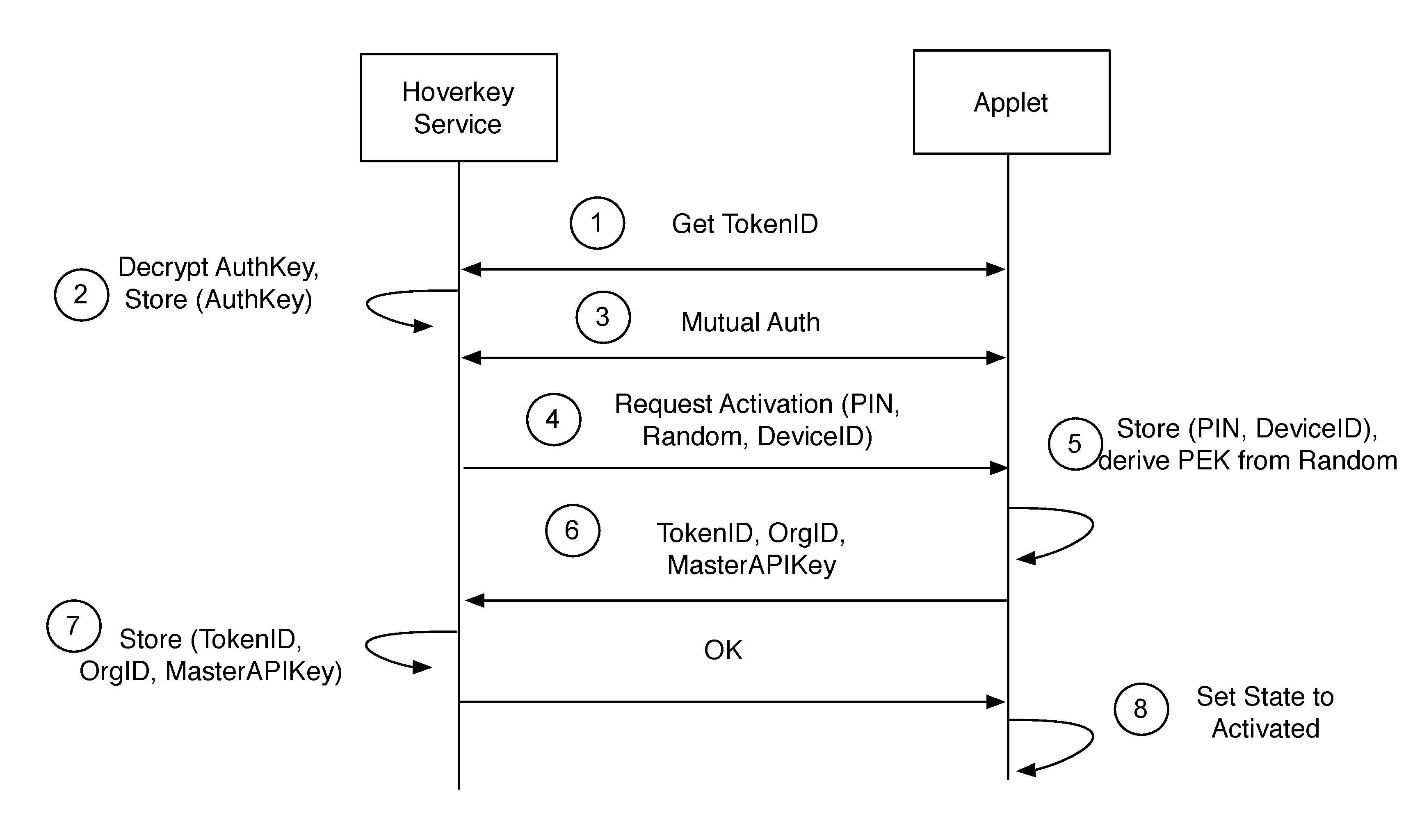
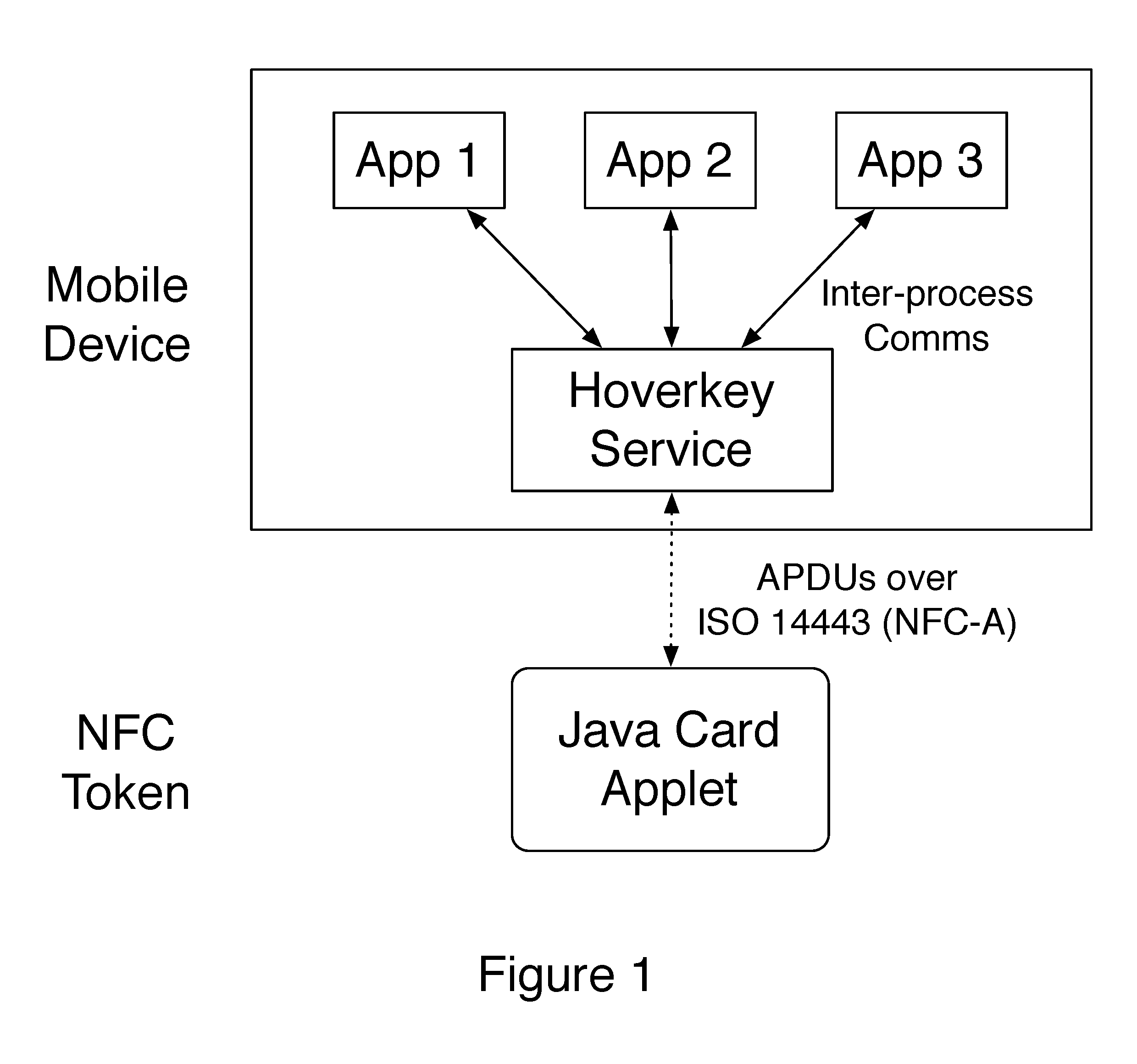
Method and system of providing authentication of user access to a computer resource via a mobile device using multiple separate security factors
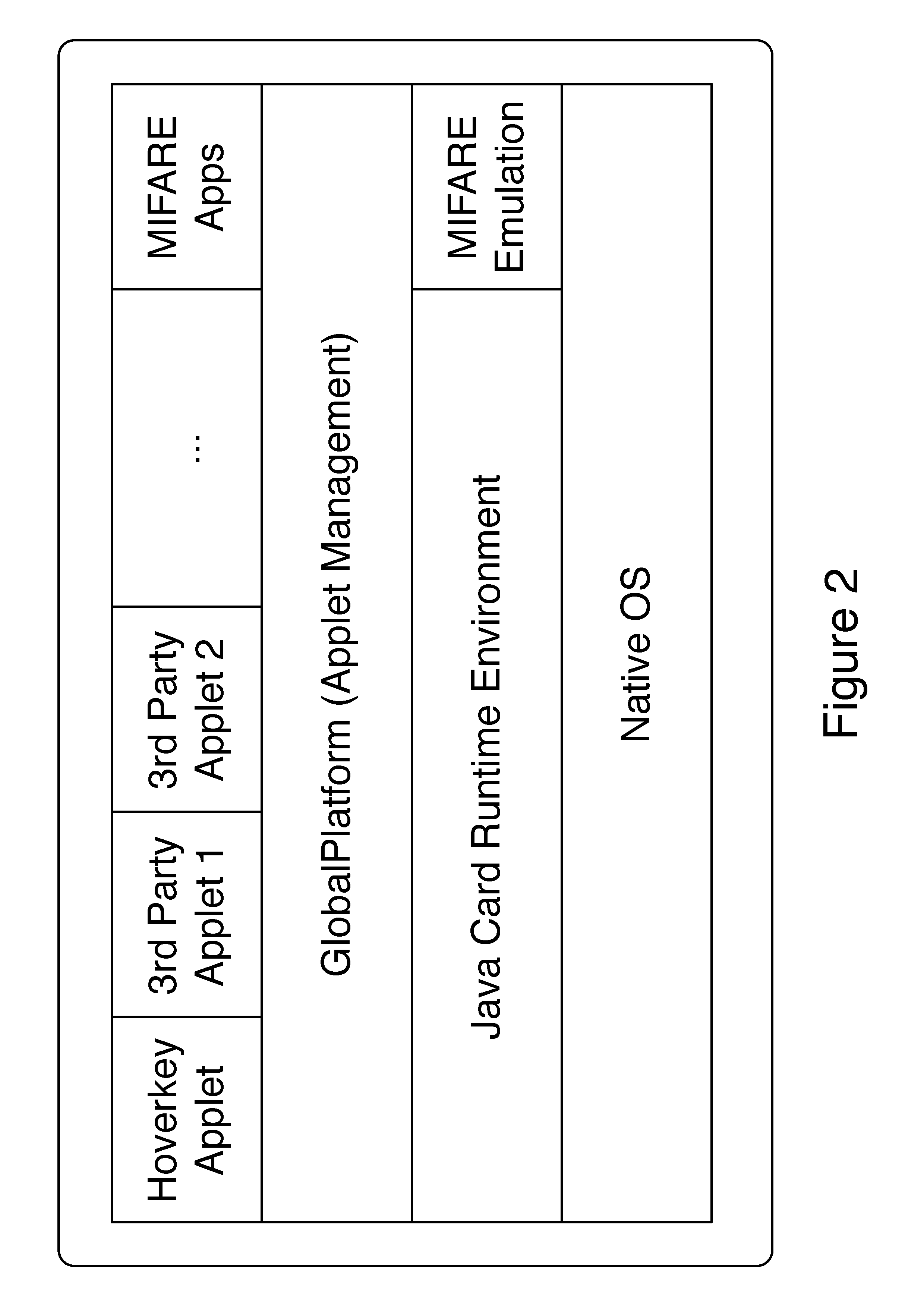
ActiveUS20160261411A1Easy to rememberPromote cloningKey distribution for secure communicationCryptography processingComputer resourcesPassword
A method and system of authenticating a computer resource such as an application or data on a mobile device uses a contactless token to provide multi-factor user authentication. User credentials are stored on the token in the form of private keys, and encrypted data and passwords are stored on the device. When an application user requires access to the resource an encrypted password is transmitted to and decrypted on the token using a stored key. An unencrypted data encryption key or password is then transmitted back to the device under the protection of a cryptographic session key which is generated as a result of strong mutual authentication between the device and the token.
Owner:HOVERKEY
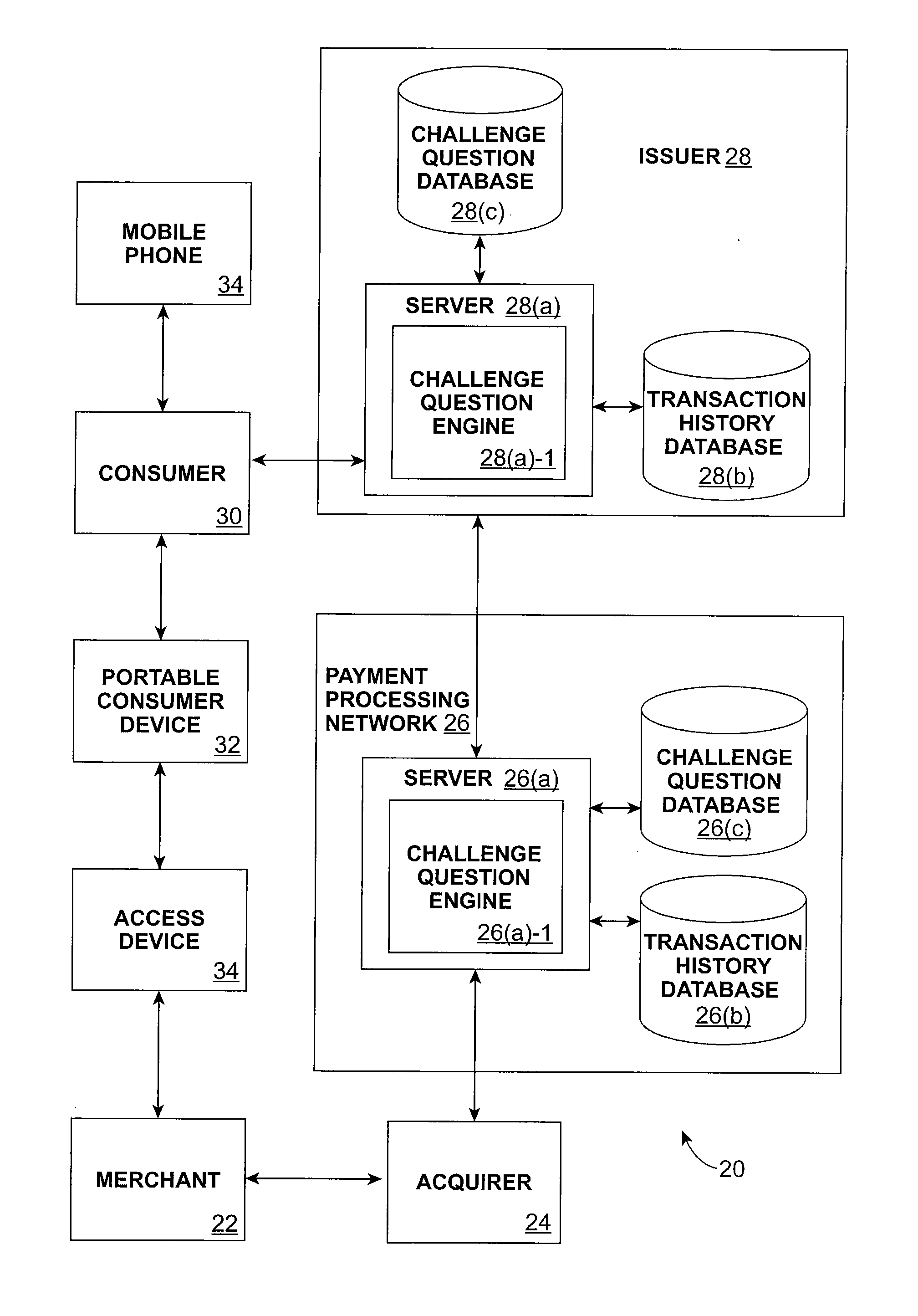
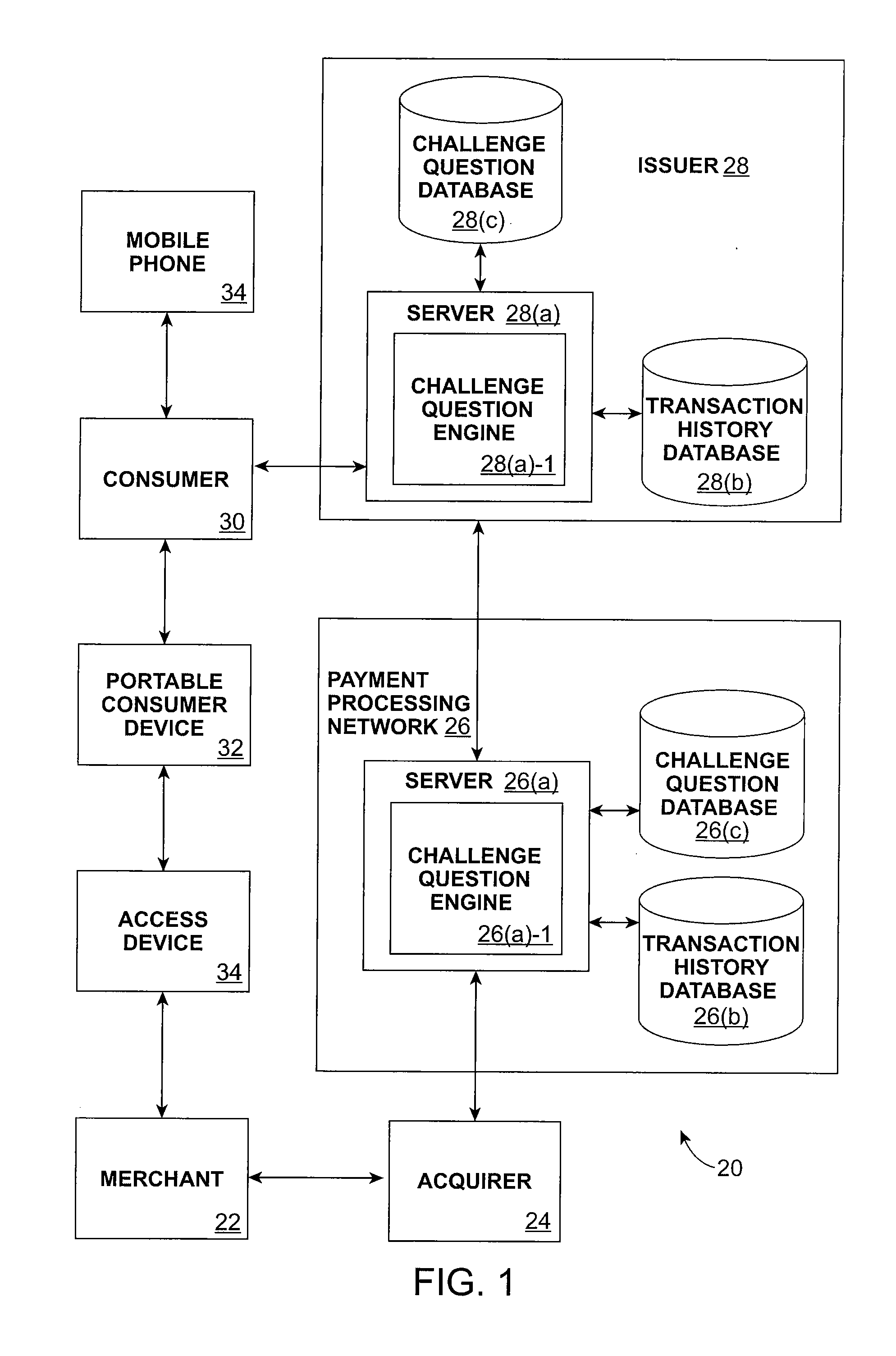
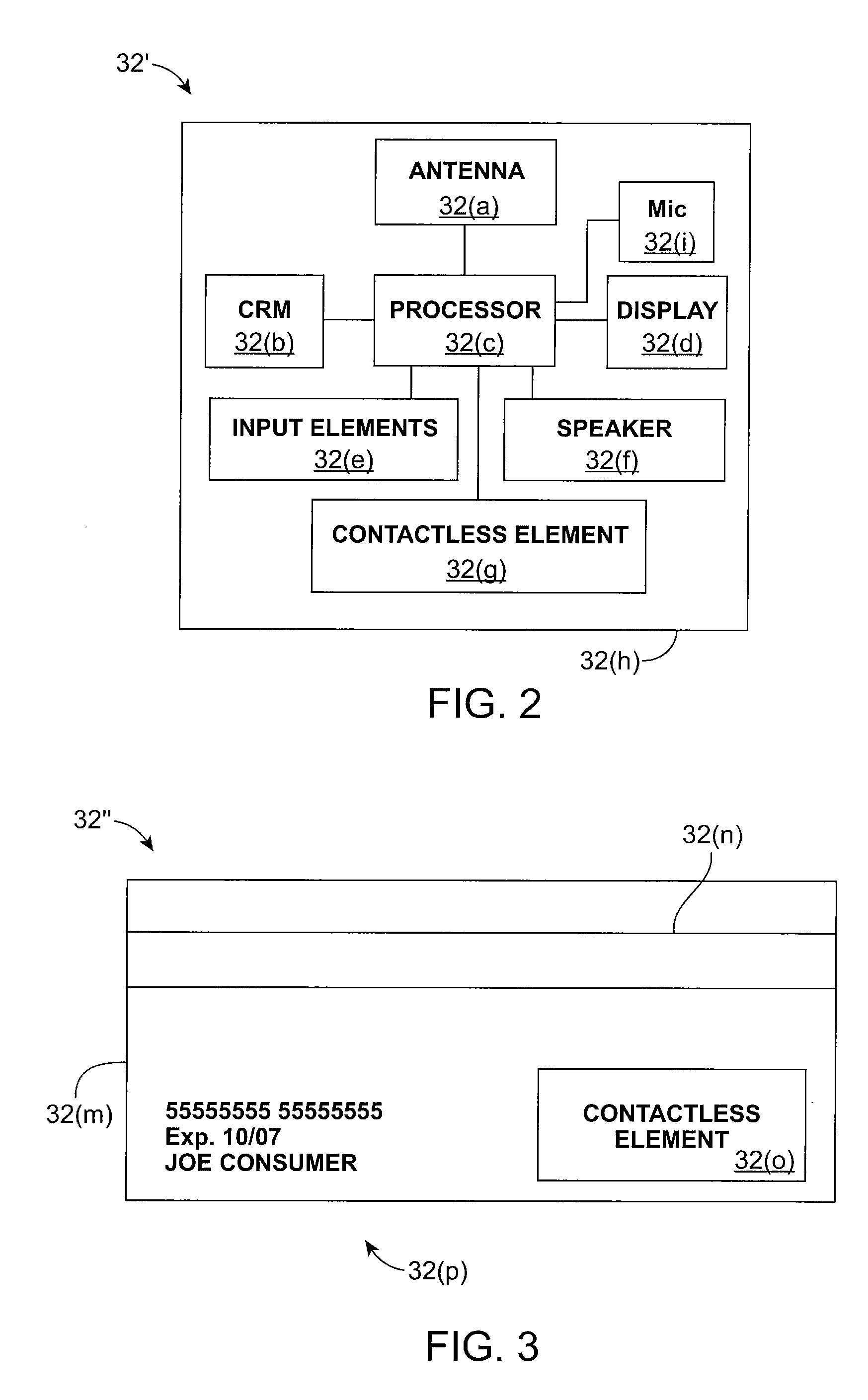
Consumer authentication system and method
A method for authenticating a consumer. The method includes receiving an authorization request message associated with a consumer conducting a transaction with a portable consumer device. A challenge message is sent to the consumer, where the challenge message is dynamic or semi-dynamic. A challenge response message is received from the consumer, and an authorization response message is sent to the consumer. The authorization response message indicates whether or not the transaction is authorized.
Owner:VISA USA INC (US)
System and method for facilitating blockchain-based validation
InactiveUS20170344988A1Key distribution for secure communicationDigital data information retrievalFinancial transactionSmart contract
In certain embodiments, blockchain-based validation of a bearer of a private key used to register a record on a blockchain may be facilitated. In some embodiments, reference information associated with a user and with a blockchain record may be obtained. The reference information may be based on a blockchain address associated with the user and with the record. The blockchain address may be based on a public key corresponding to a private key used to register the record, where the keys are a key pair associated with the user. A smart contract may be caused to be generated based on the reference information and provided on a blockchain. The smart contract may be configured to automatically validate a transaction using the public key. A notification indicating that the user registered the record may be obtained responsive to the smart contract validating a transaction signed using the private key.
Owner:UBS BUSINESS SOLUTIONS AG
System and method for securing transactions and computer resources with an untrusted network
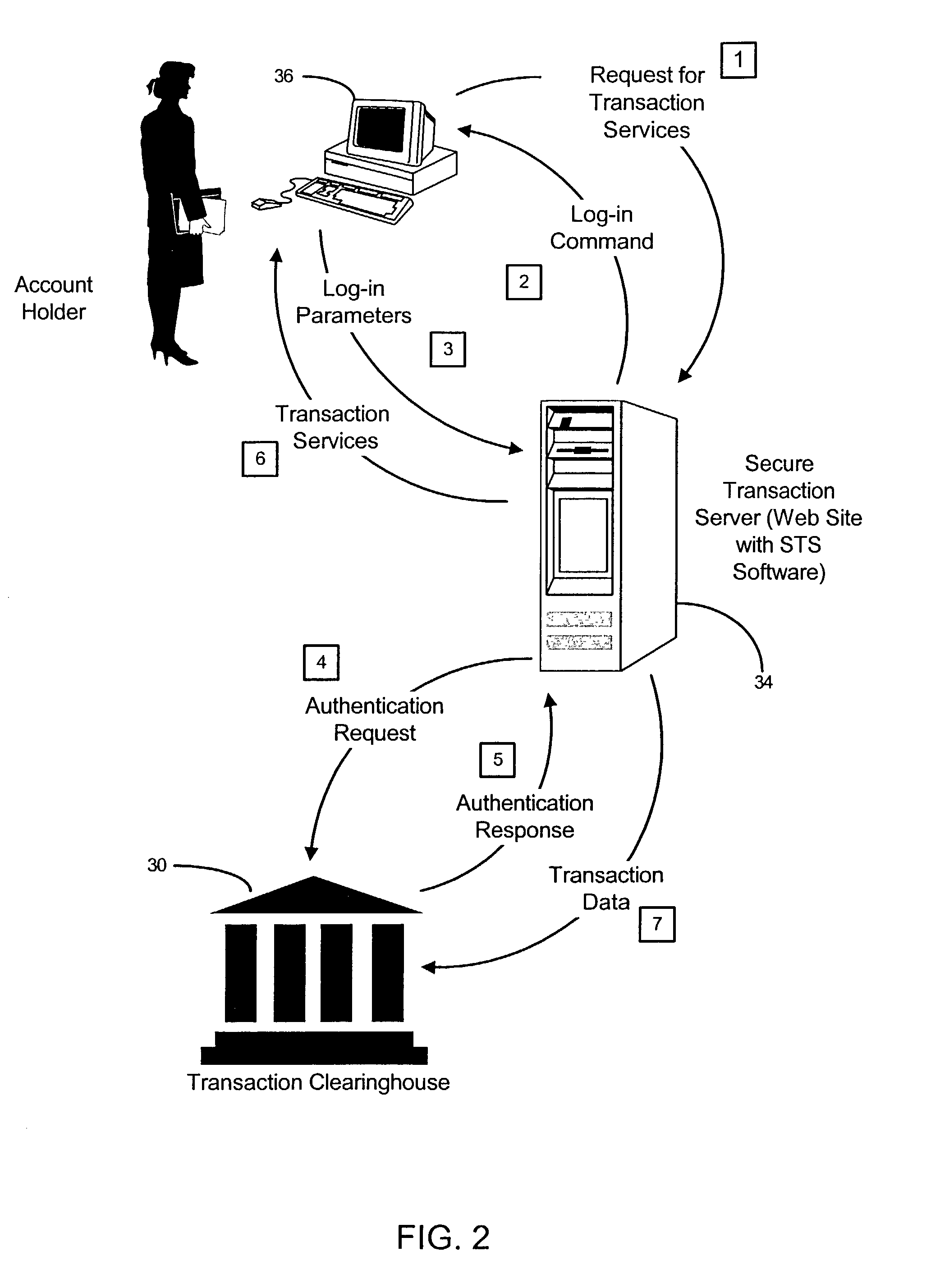
InactiveUS20030046589A1Digital data processing detailsCryptography processingComputer resourcesTransaction service
A system for securing and tracking usage of transaction services or computer resources by a client computer from a first server computer, which includes clearinghouse means for storing identity data of the first server computer and the client computer(s); server software means and client software means adapted to forward its identity data and identity data of the client computer(s) to the clearinghouse means at the beginning of an operating session; and a hardware key connected to the client computer, the key being adapted to generate a digital identification as part of the identity data; wherein the hardware key is implemented using a hardware token access system, a magnetic card access system, a smart card access system, a biometric identification access system or a central processing unit with a unique embedded digital identification.
Owner:PRISM TECH
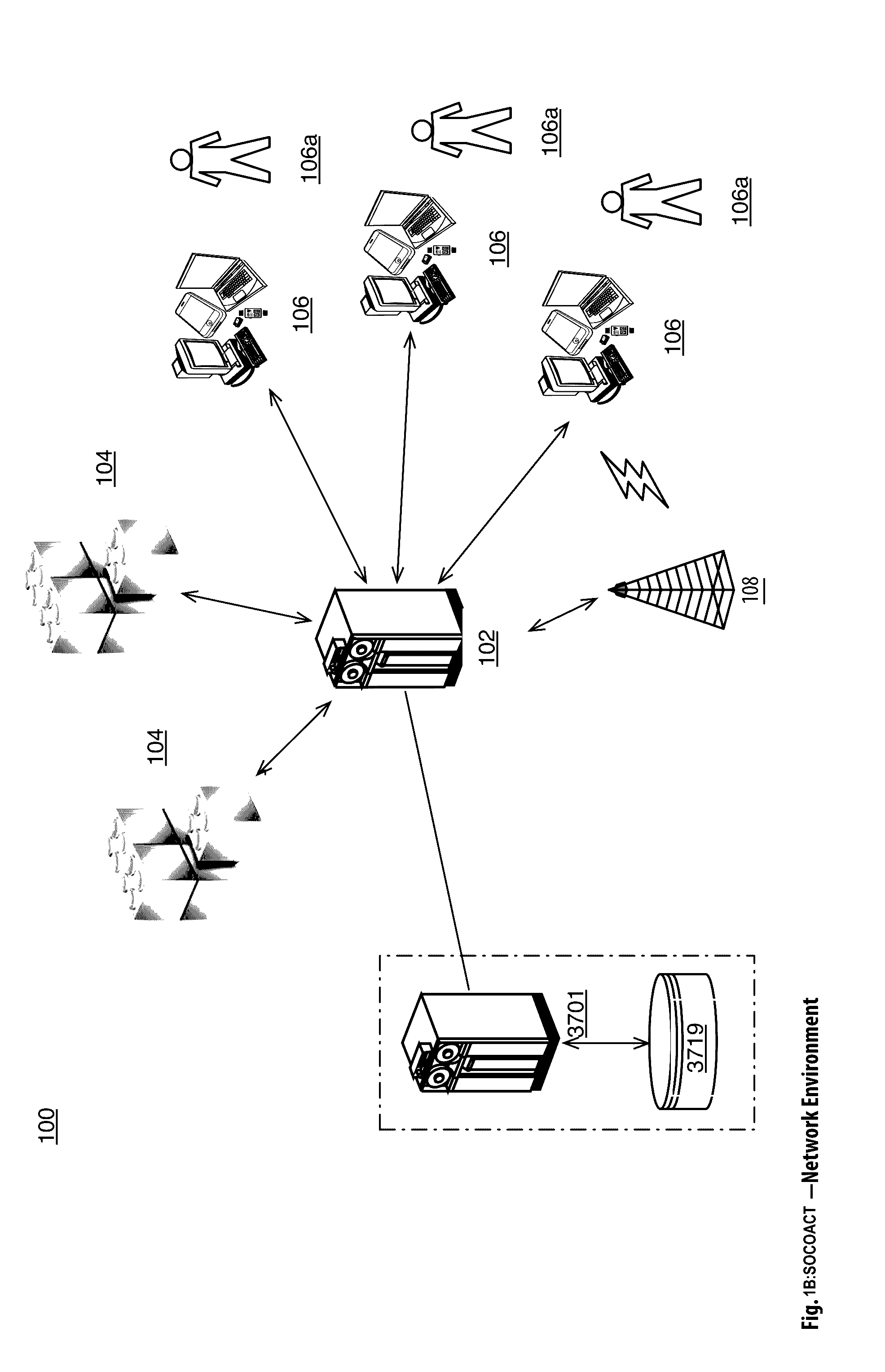
Crypto Key Recovery and Social Aggregating, Fractionally Efficient Transfer Guidance, Conditional Triggered Transaction, Datastructures, Apparatuses, Methods and Systems
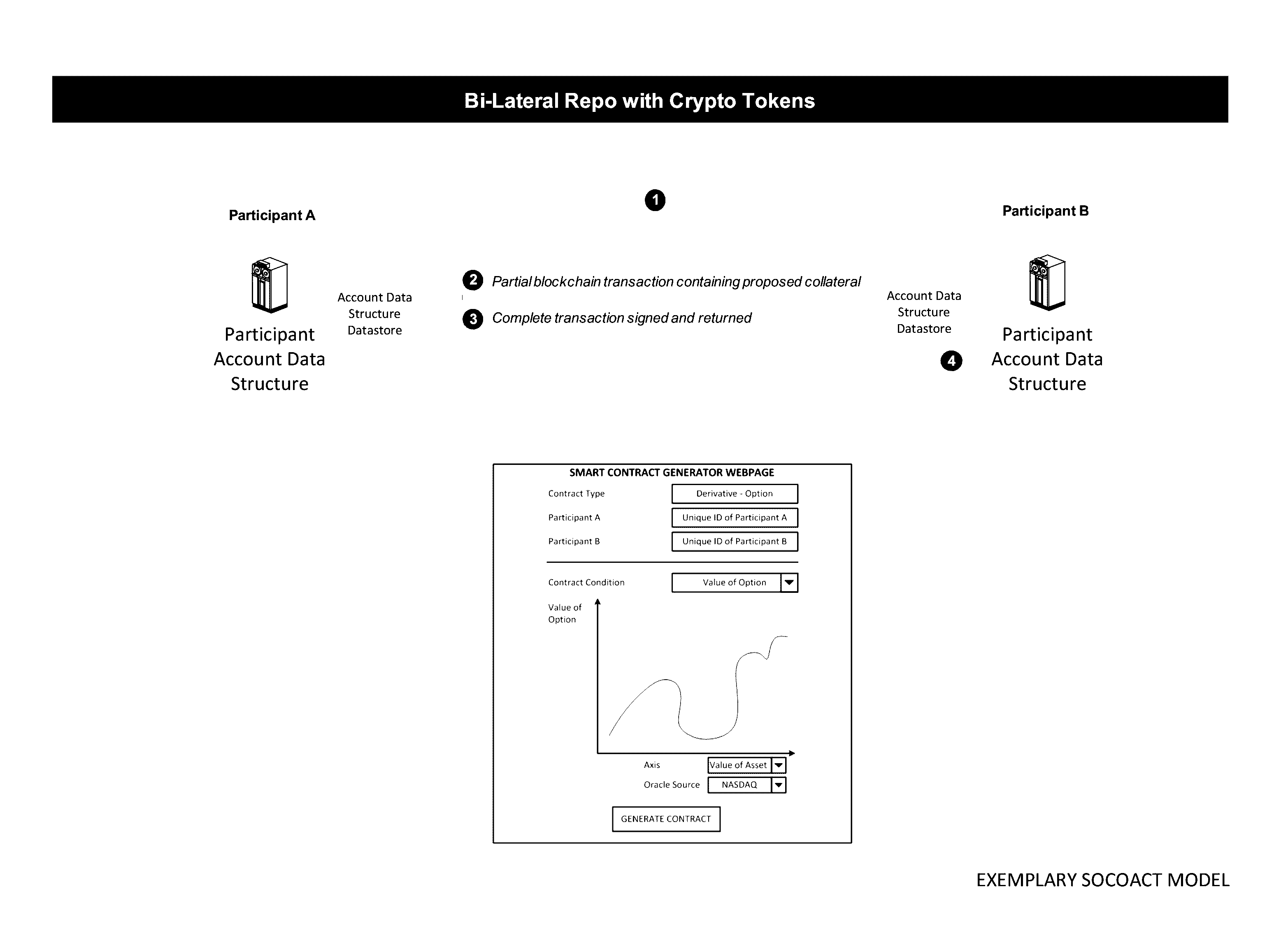
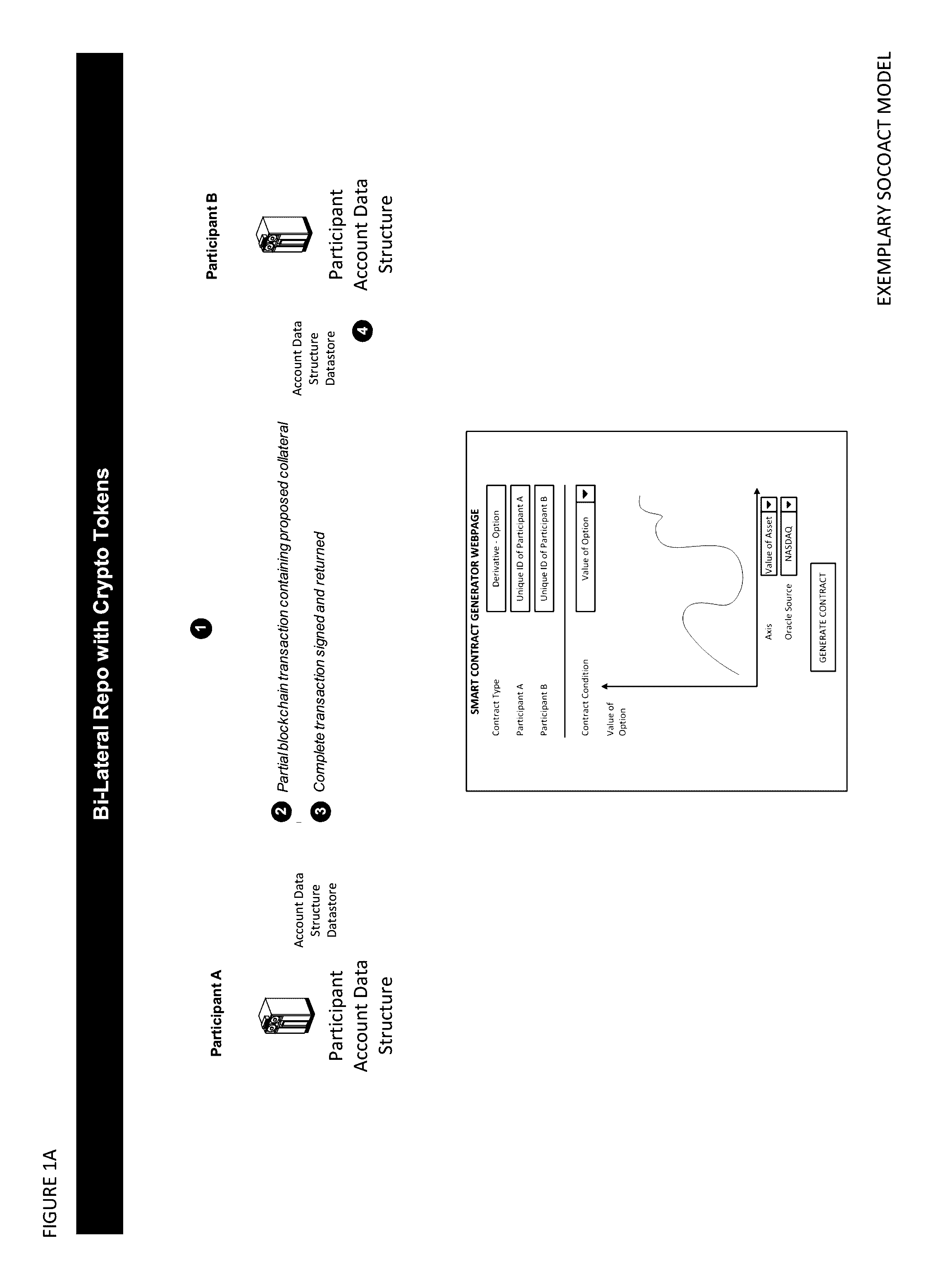
InactiveUS20170048209A1Multiple keys/algorithms usageCryptography processingData structureKey recovery
The Crypto Key Recovery and Social Aggregating, Fractionally Efficient Transfer Guidance, Conditional Triggered Transaction, Datastructures, Apparatuses, Methods and Systems (“SOCOACT”) transforms MKADSD generation request, trigger event message inputs via SOCOACT components into transaction confirmation, recovery notification outputs. A multiple key account data structure datastore (MKADSD) generation request may be obtained from a user. A set of crypto public keys for a MKADSD may be determined. The MKADSD may be instantiated in a socially aggregated blockchain datastructure using the determined set of crypto public keys. A crypto recovery private key may be associate with the MKADSD and trigger event recovery settings for the MKADSD may be set. A trigger event message associated with the MKADSD may be obtained and recovery settings associated with a trigger event may be determined. The crypto recovery private key may be retrieved and a recovery action may be facilitated.
Owner:FMR CORP
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com