Patents
Literature
238 results about "Self-destruct" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A self-destruct is a mechanism that can cause an object to destroy itself after a predefined set of circumstances has occurred. Self-destruct mechanisms are typically found on devices and systems where malfunction could endanger large numbers of people.
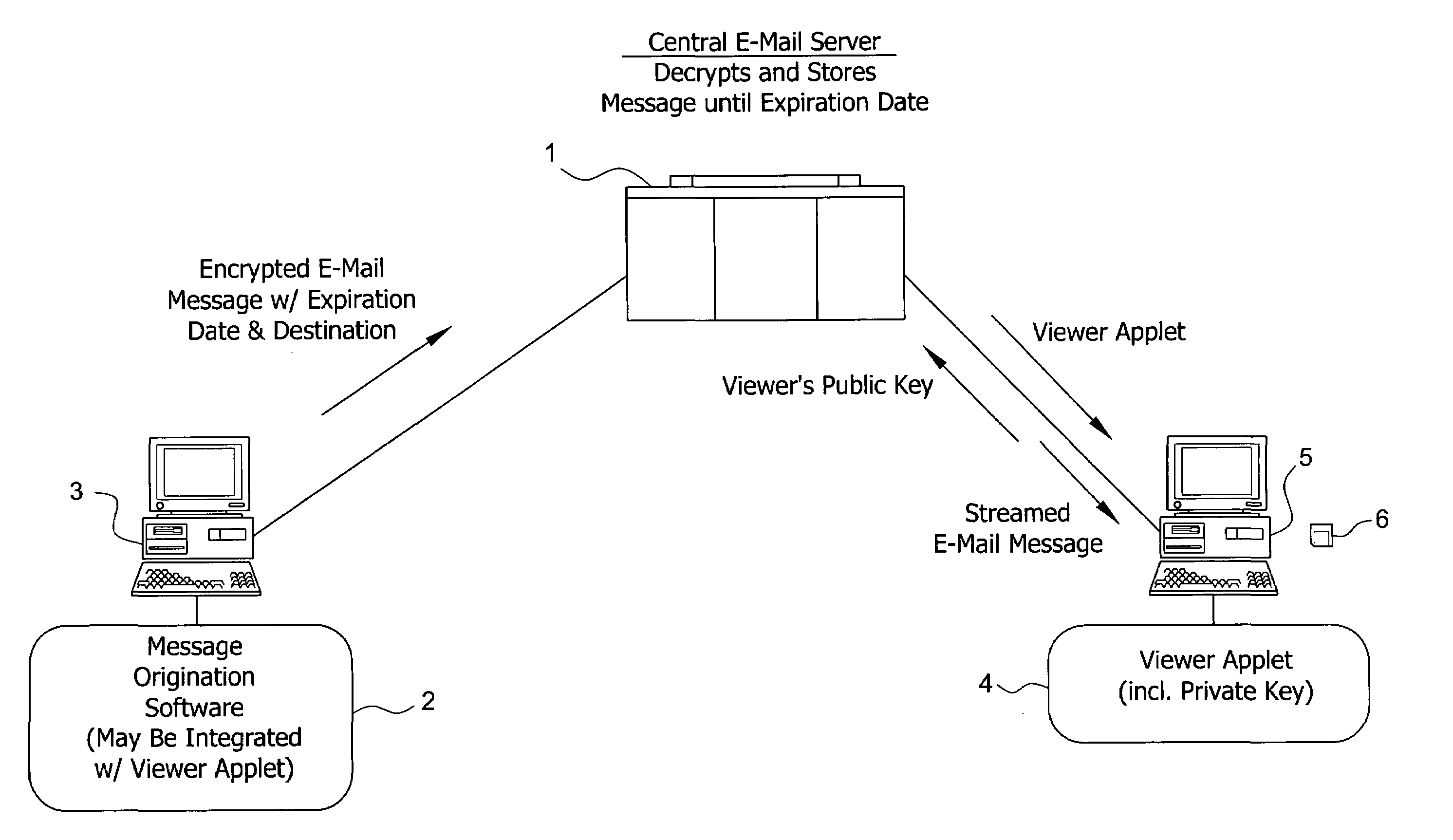
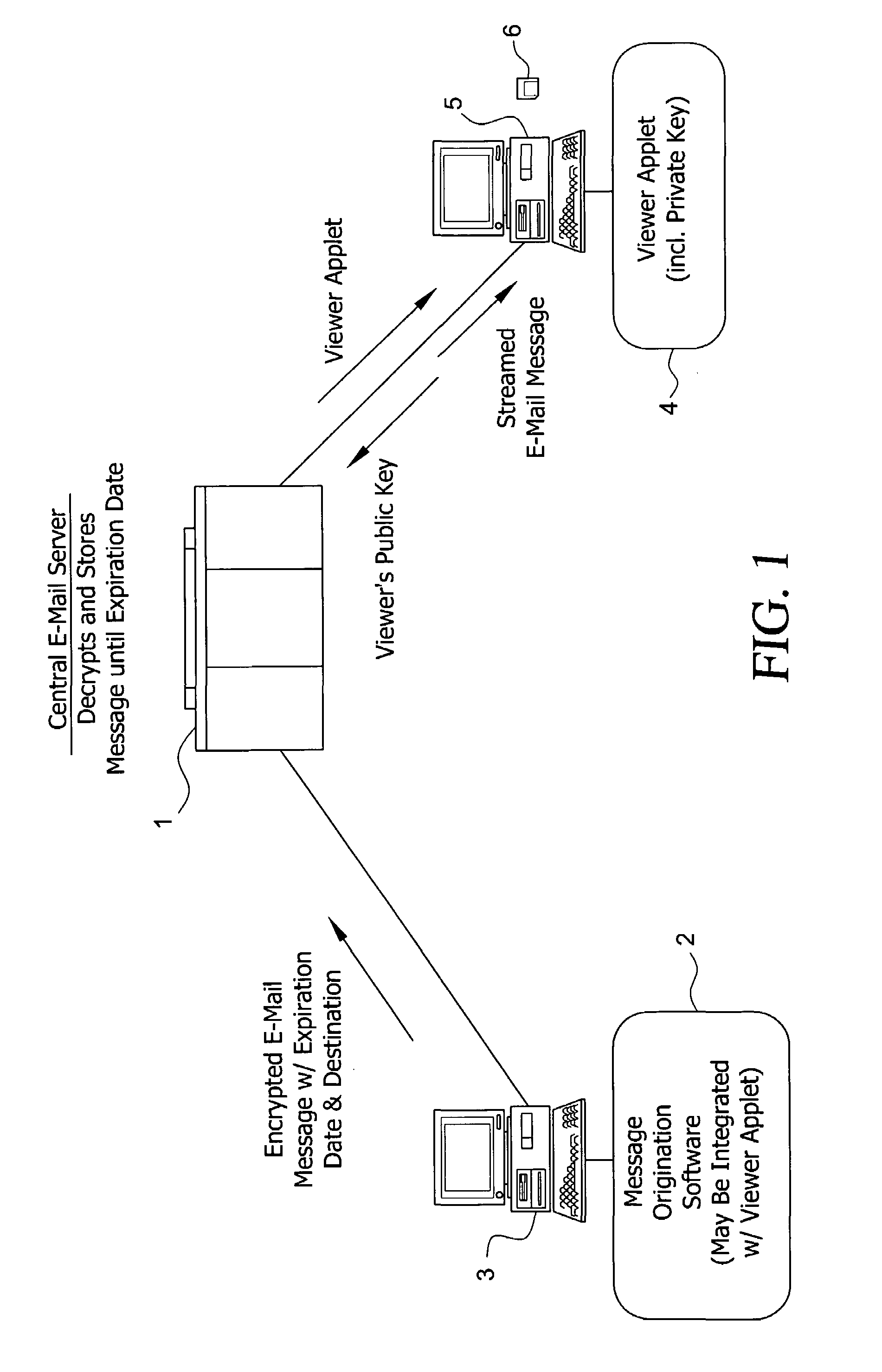
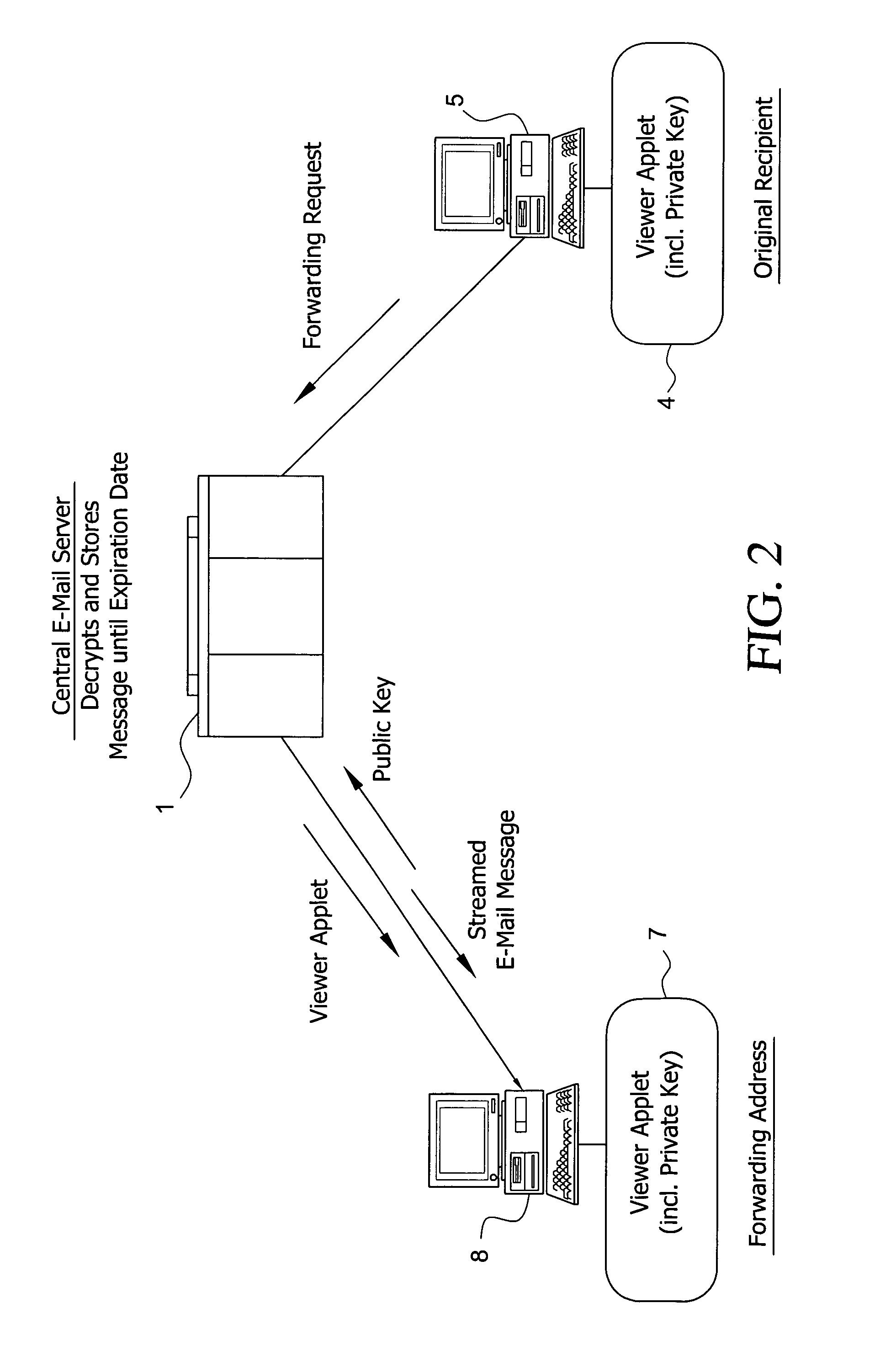
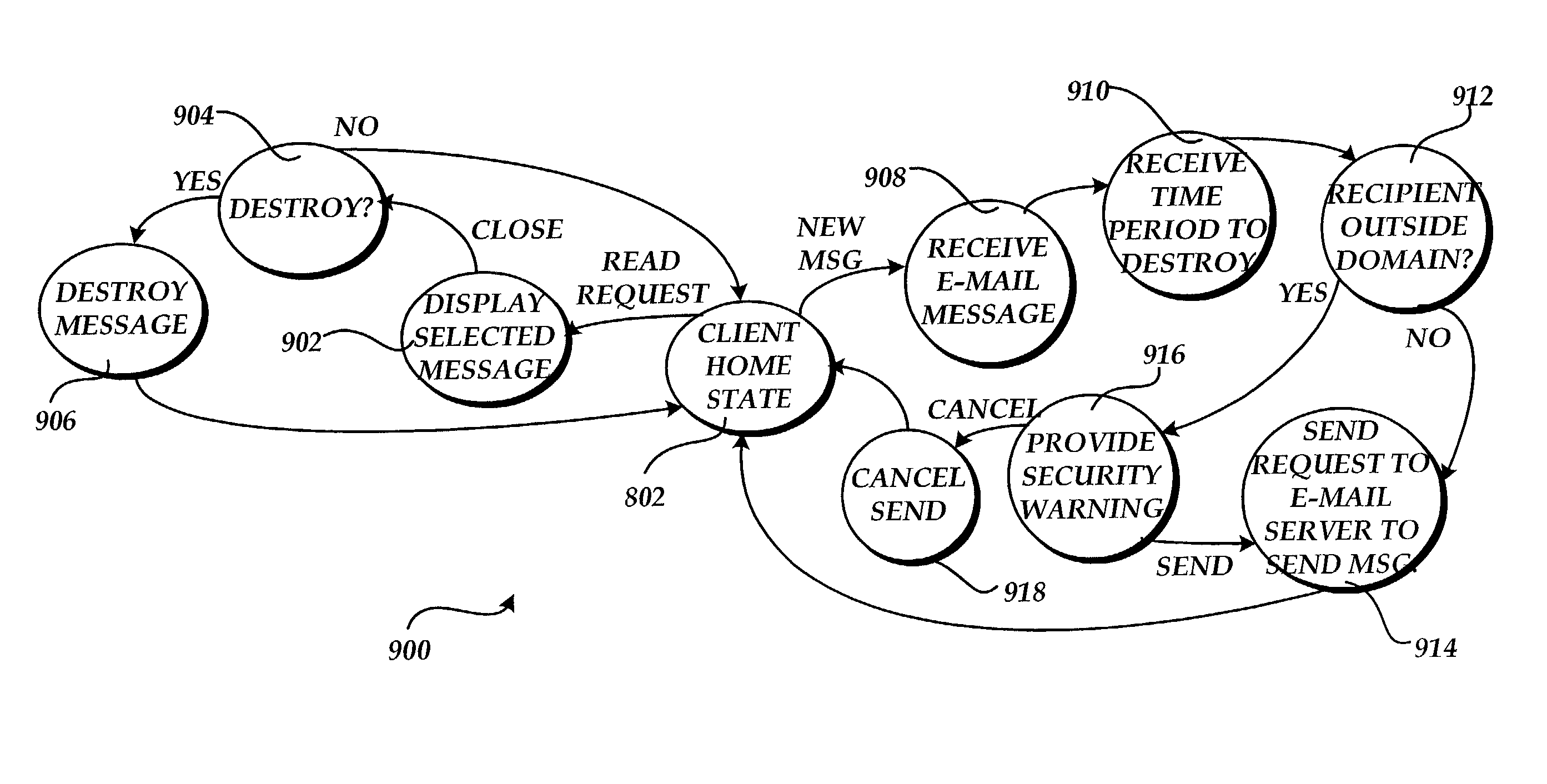
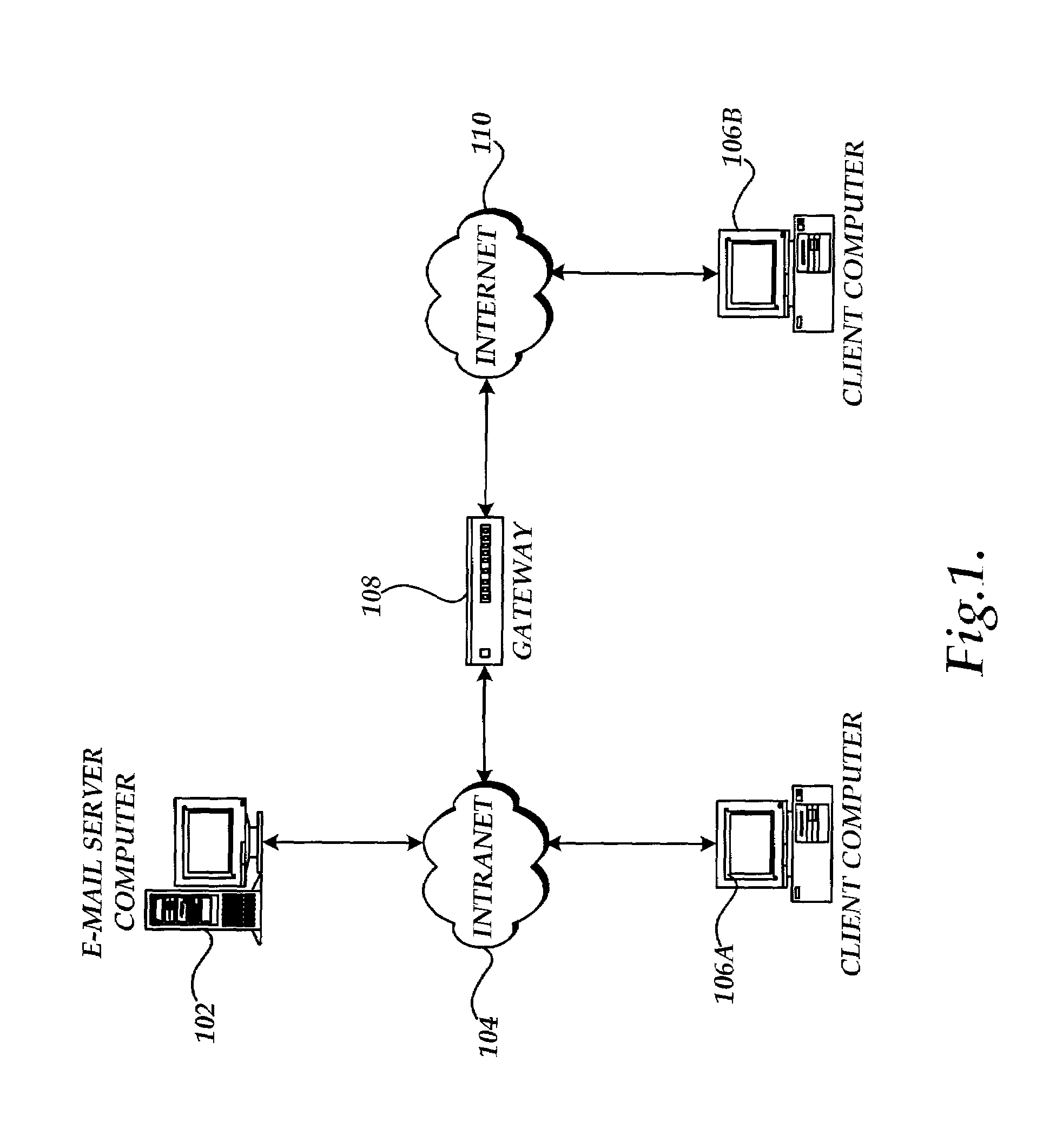
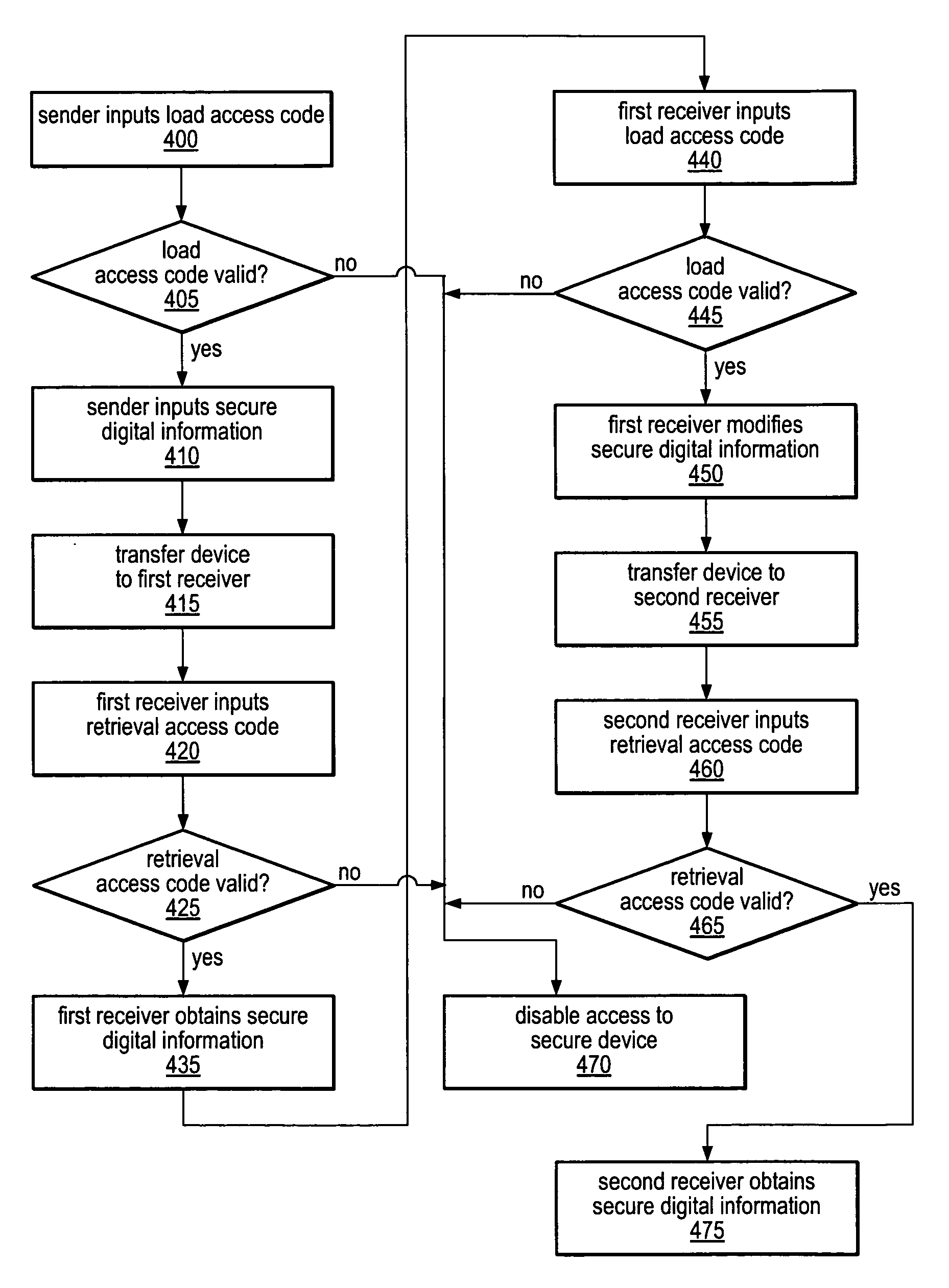
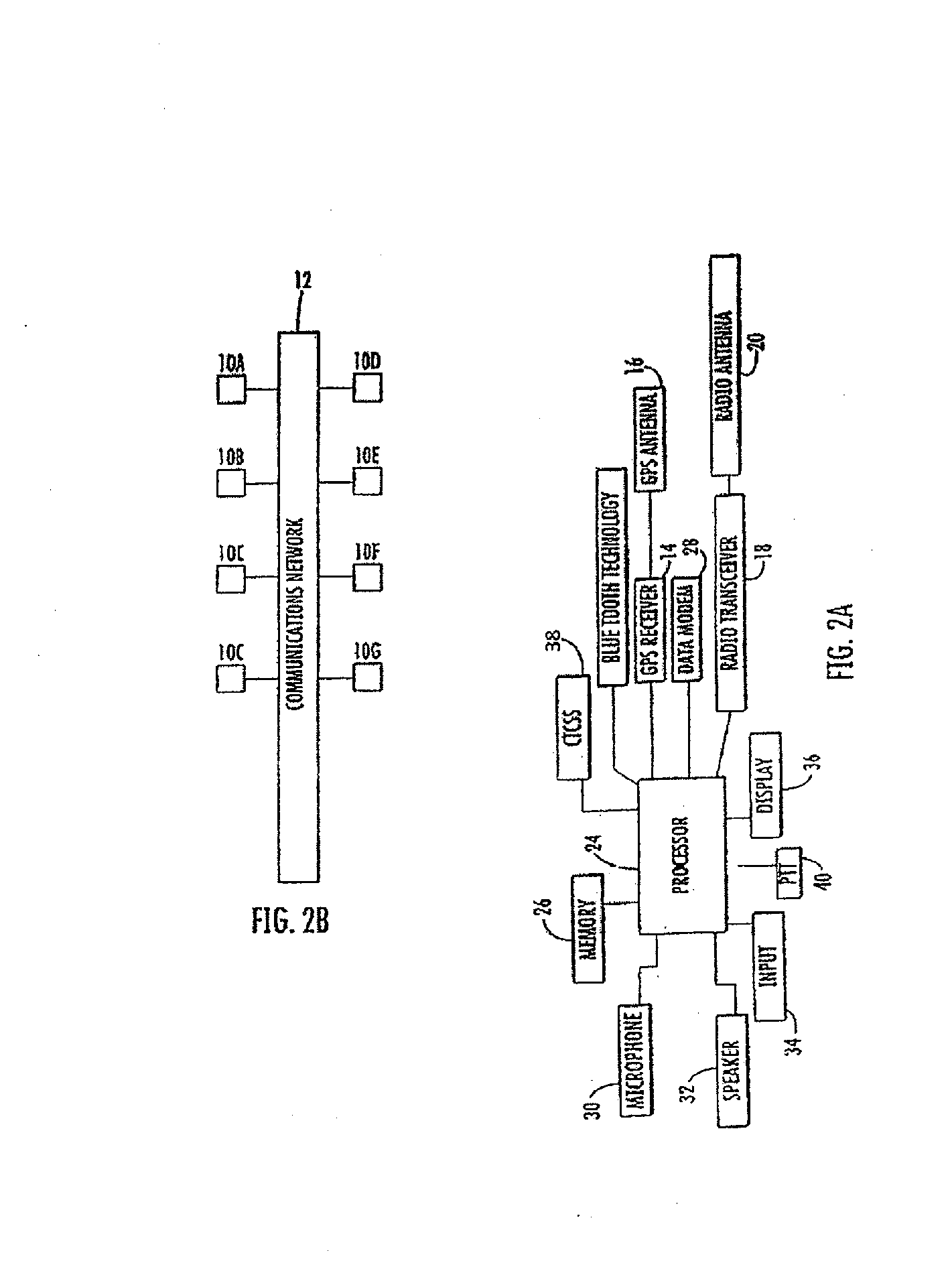
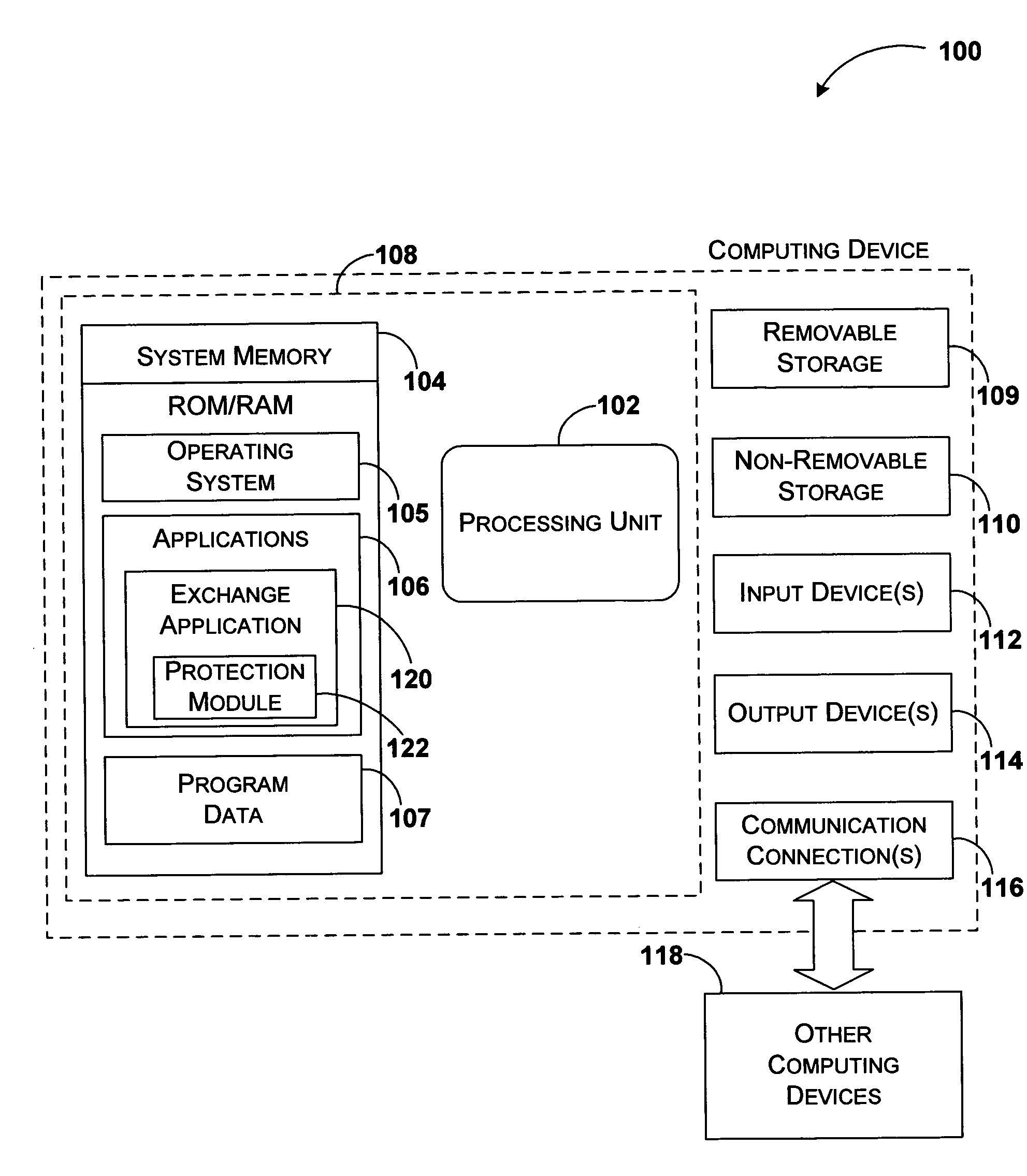
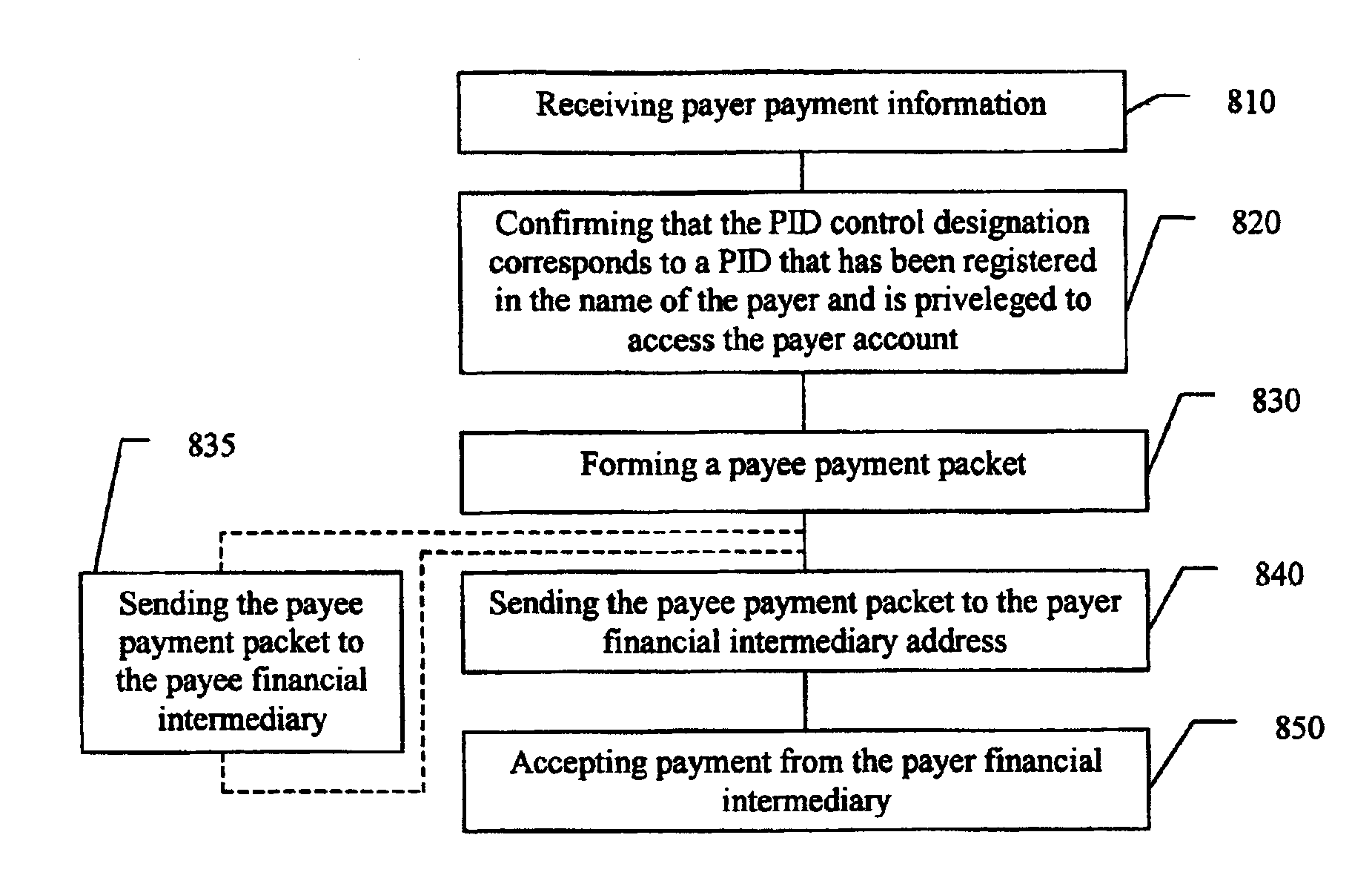
System and method for enabling the originator of an electronic mail message to preset an expiration time, date, and/or event, and to control processing or handling by a recipient
InactiveUS7149893B1Limited lifespanRapid and efficient mannerDigital data processing detailsAnalogue secracy/subscription systemsExpiration TimeComputer hardware
An electronic mail system and method enables the originator of a message sent by electronic mail to select a date, time, or event at which the message and all incarnations of the message to self-destruct, regardless of the number and types of computers or software systems that may have interacted with the message. The system and message also permits the originator to include processing and handling limitations. The necessary control over the message is achieved by encrypting the message and enabling viewing only through a viewer applet arranged to facilitate destruction of the message upon the occurrence of the selected expiration time, date, or event, and to implemented the handling and processing limitations. A central server can be used to exercise additional control over the message by serving as a proxy destination, and by streaming the encrypted message to the viewer applet. The viewer applet can be transmitted to new recipients with the message so that the system and method can direct mail to any electronic mail user.
Owner:RESOURCE CONSORTIUM LTD LLC
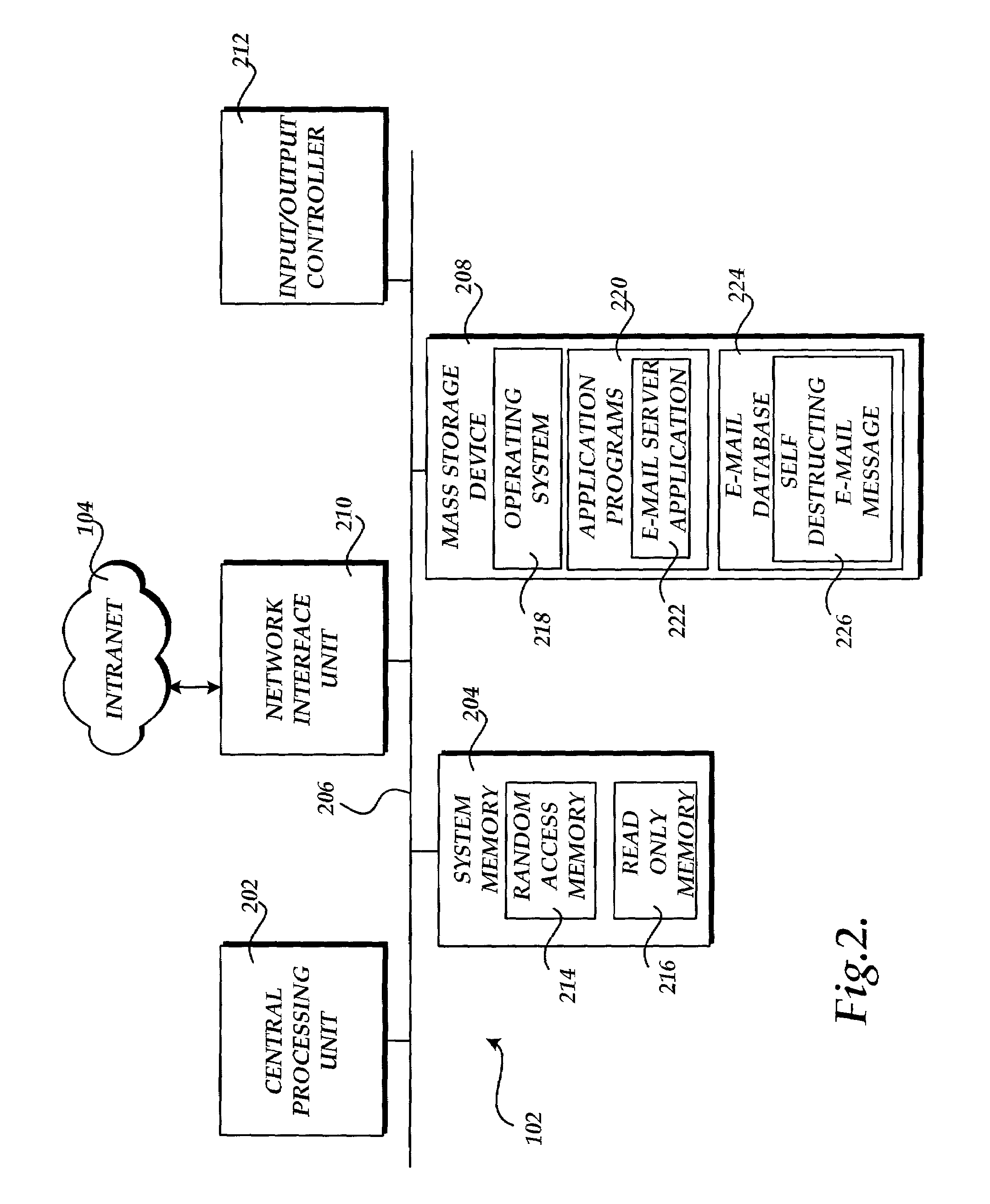
Method, system, and apparatus for providing self-destructing electronic mail messages
ActiveUS7356564B2Limited in numberLimited in typeDigital data processing detailsSpecial service for subscribersClient-sideApplication software
A method, system, and apparatus for providing a self-destructing e-mail messages are described. An e-mail client application provides a user interface through which the sender of an e-mail message can enter the message and a time period for destruction of the message. Once the sender has provided this information, the e-mail client application sends a request to an e-mail server application to transmit the self-destructing e-mail message. The e-mail client application may also receive self-destructing e-mail messages. When a self-destructing e-mail message is received, the destruction date associated with the e-mail message is identified and the message is destroyed at the specified time. The e-mail client application can also limit the number and type of operations that may be performed on a self-destructing e-mail. An e-mail server application is also provided that receives requests from the e-mail client application to transmit self-destructing e-mail messages and perform other functions.
Owner:BELLSOUTH INTPROP COR +1
Systems and methods for secure and private delivery of content
InactiveUS20140201527A1Inhibitory contentUser identity/authority verificationDigital data protectionSelf-destructTimer
The present solution provides a new tool for privately and securely delivering content from a send to a recipient. Additionally, the tool provides a system and method for ensuring the content is not seen by onlookers, retransmitted, or copied. The system described herein accomplishes the protection of content by several different means. For example, the system may never store unencrypted copies of content to a local device, such that content may not be viewed by a system other than the system described herein. Additionally, the system may overlay an obfuscating layer to the content when the content is displayed on a client device. Such an obfuscating layer prevents onlookers from unintentionally viewing the content. It may also prevent a recipient from capturing a screen shot or copying the content. Furthermore, the system may also set a number of expiring timers on the content. For example, a first expiration timer may automatically delete send content from a recipient device a set time after the content has been sent. A self-destruct expiring timer may delete the content a short time after a user begins to view the content.
Owner:KRIVOROT ZOHAR
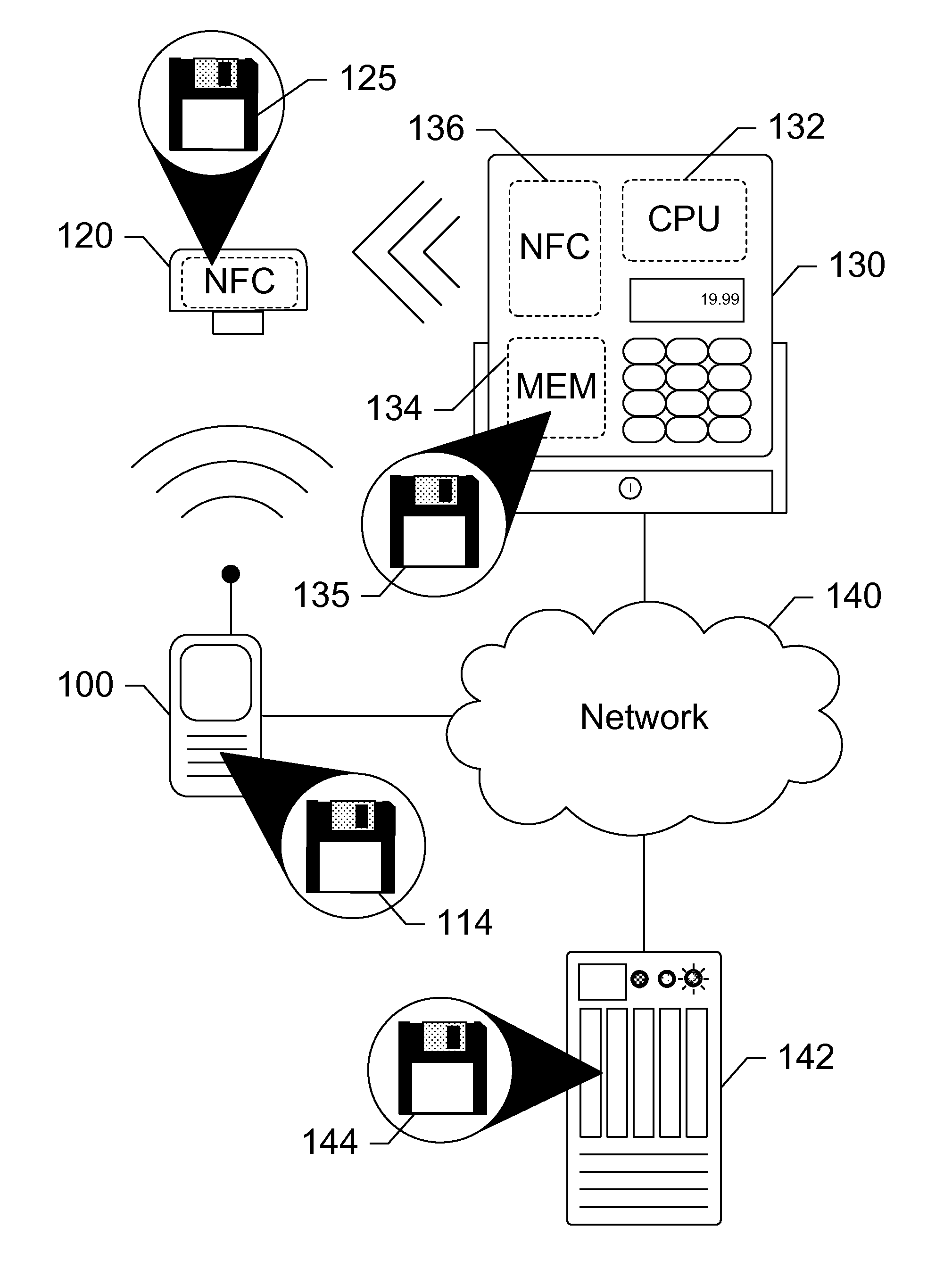
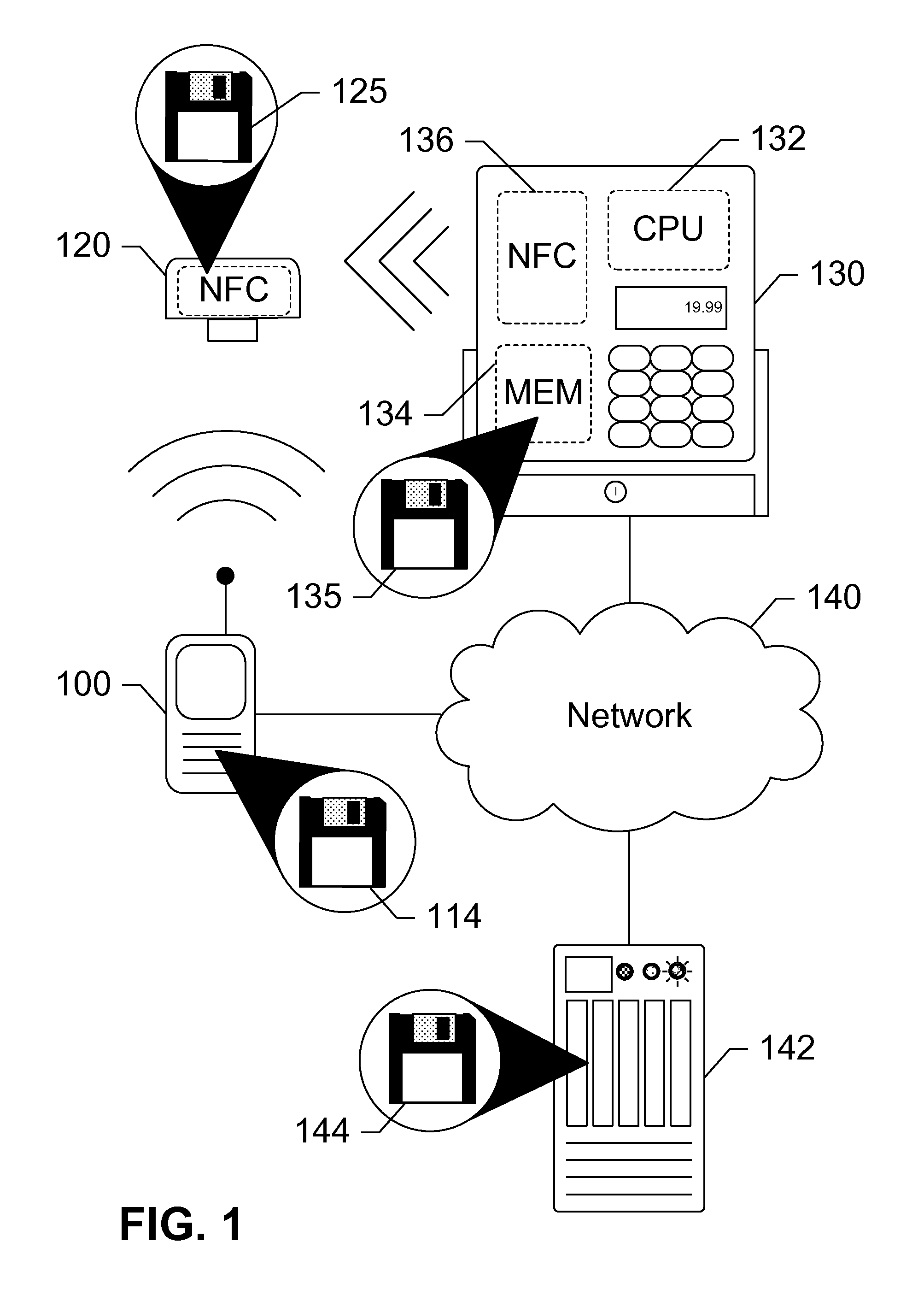
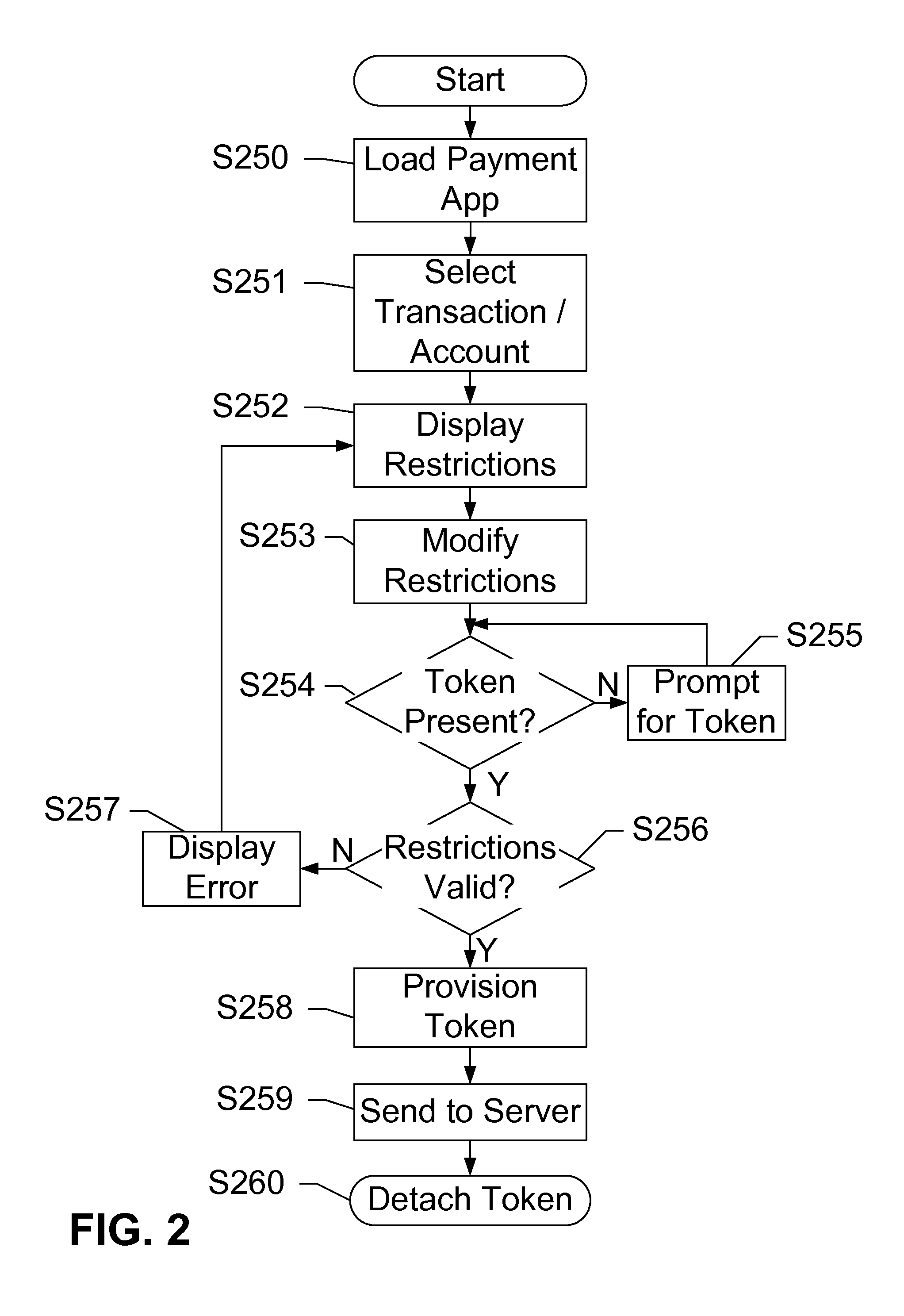
Security Token for Mobile Near Field Communication Transactions
ActiveUS20130124346A1Cryptography processingBuying/selling/leasing transactionsPaymentFinancial transaction
Devices, systems, and methods are disclosed which relate to an NFC-enabled security token that is removably coupled to a mobile device. The security token may be provisioned with the information by the mobile device, then decoupled from the mobile device and used to authenticate the user or perform a transaction at a POS terminal equipped with an NFC reader. The security token includes logic for user-controlled restrictions on allowable purchases, such as payment limits, timeouts, vendor identifiers, allowed purchases, and location-based restrictions. The security token is further equipped with “self destruct” security features, such as deactivating itself or erasing any sensitive information upon being unable to contact the mobile device for a specified duration, or being subject to an unauthorized or restricted transaction, until such time as it is re-coupled to the mobile device.
Owner:AT&T INTPROP I L P
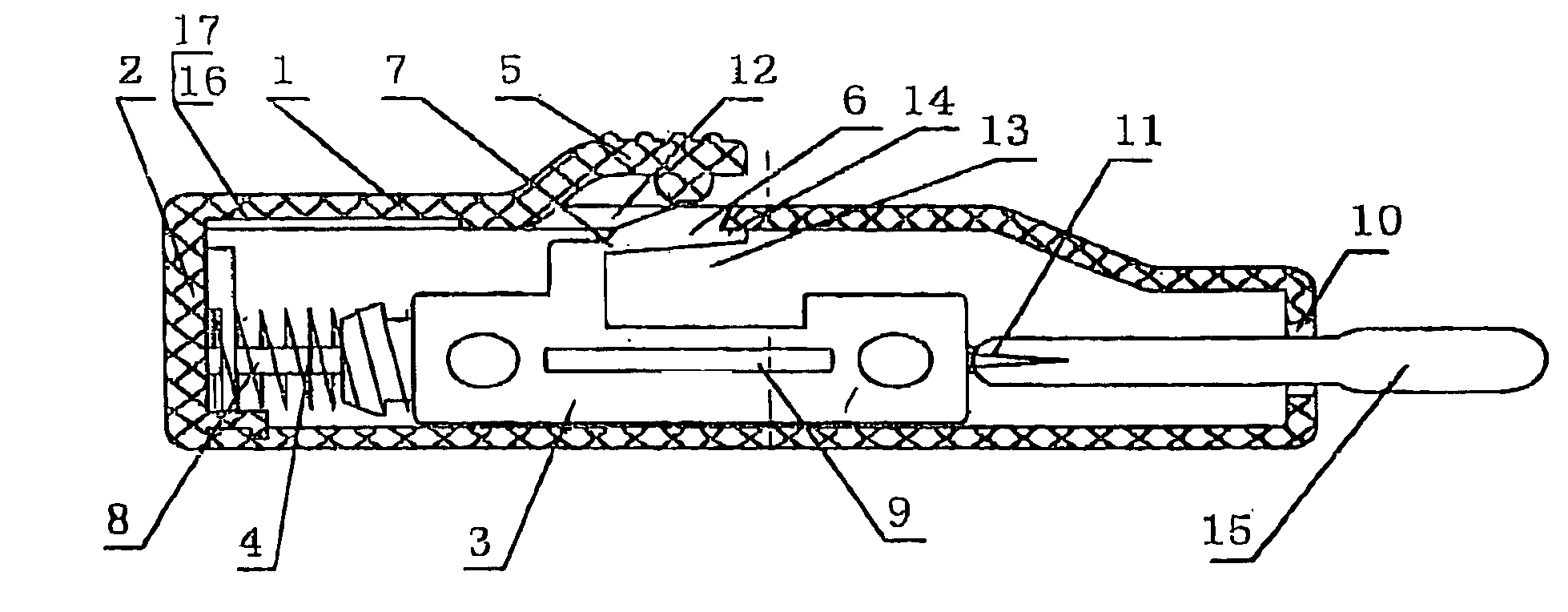
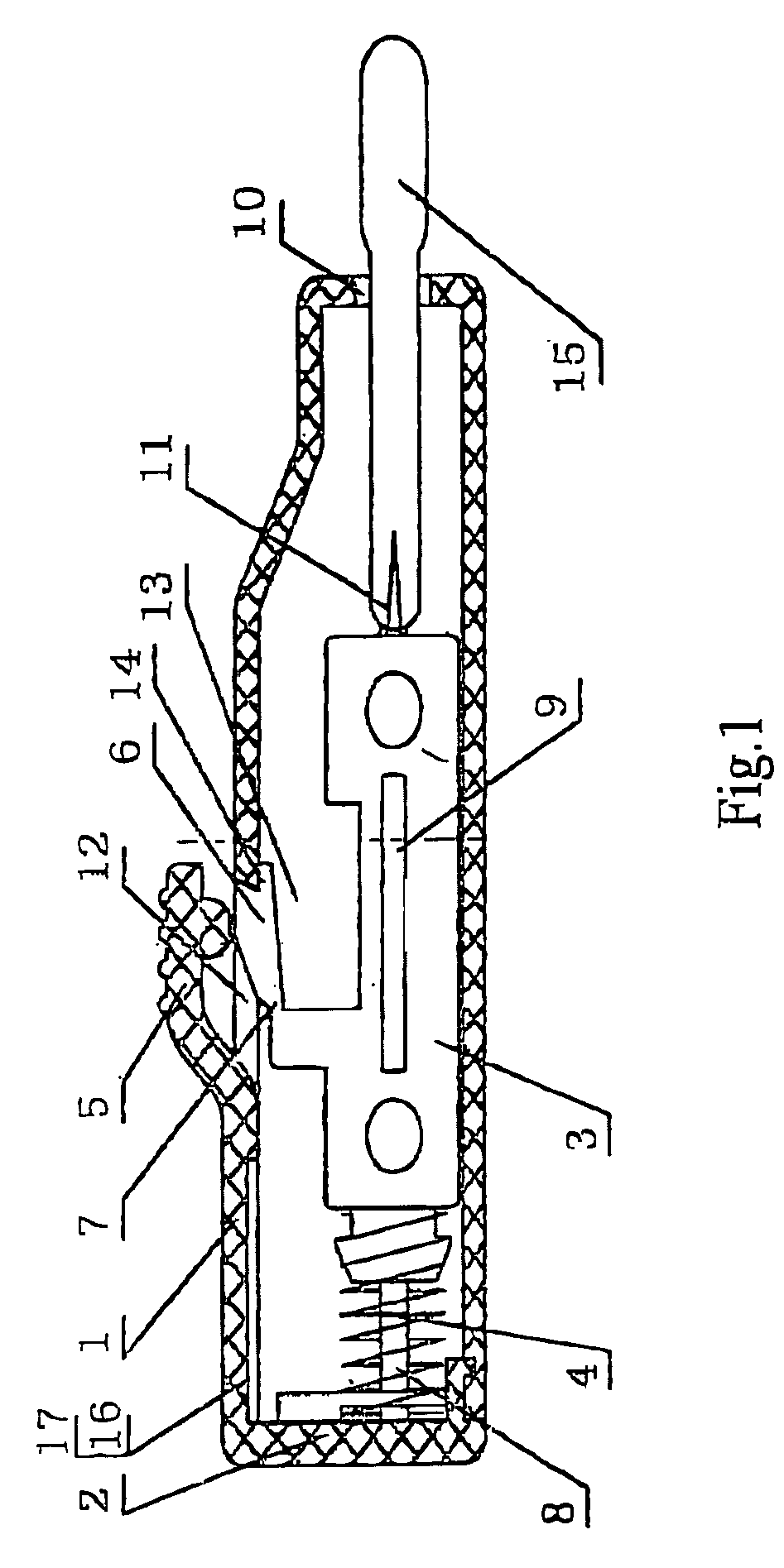
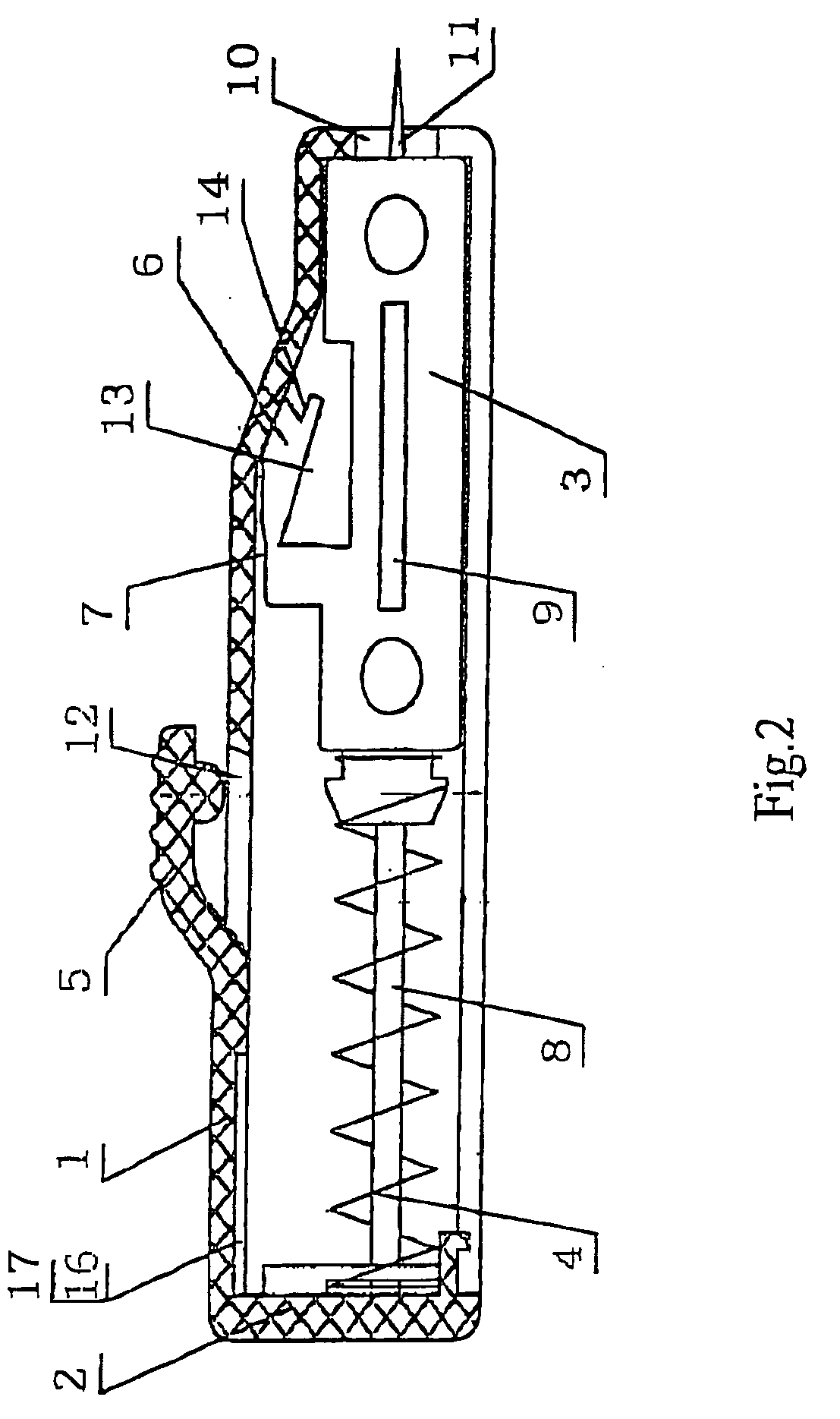
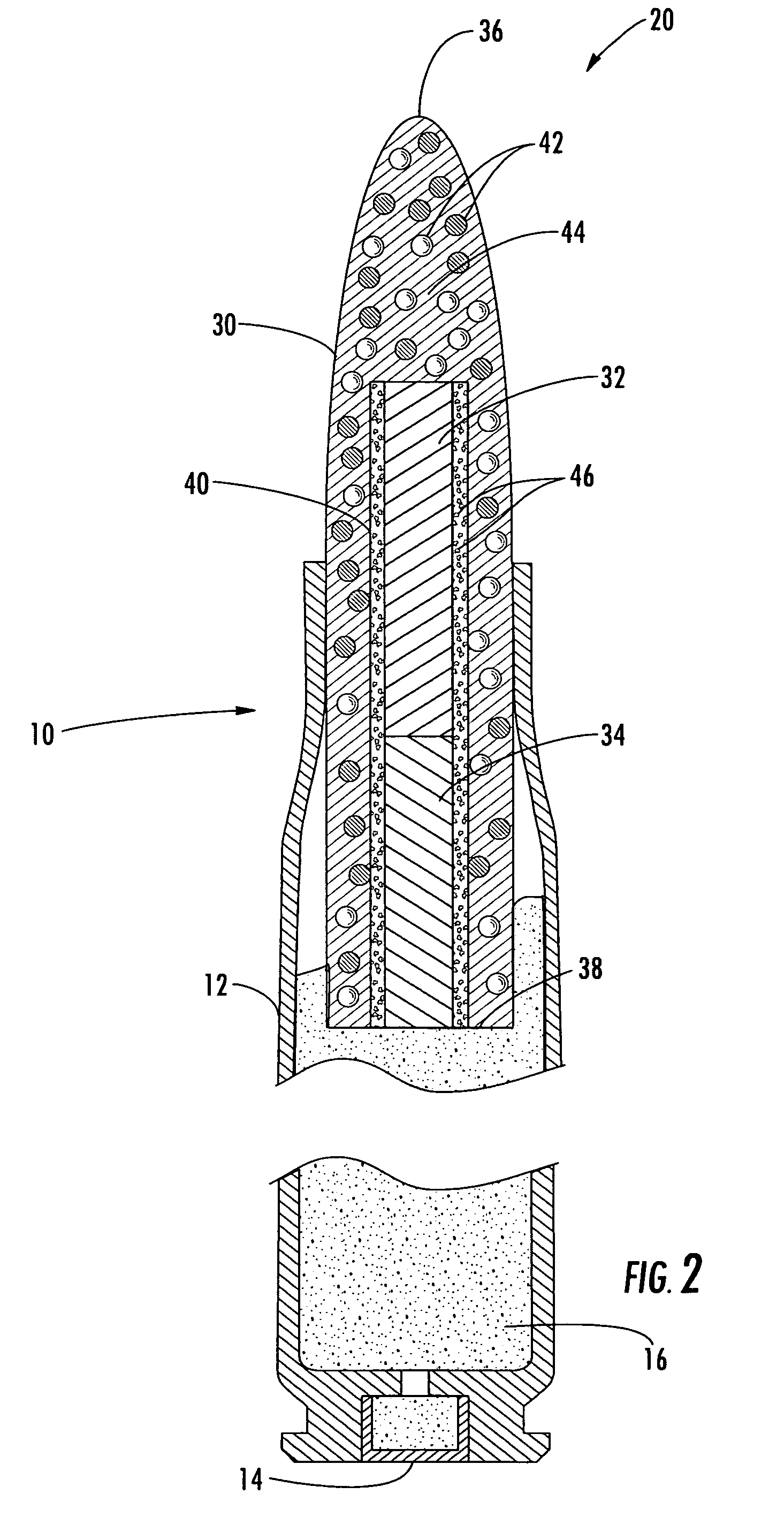
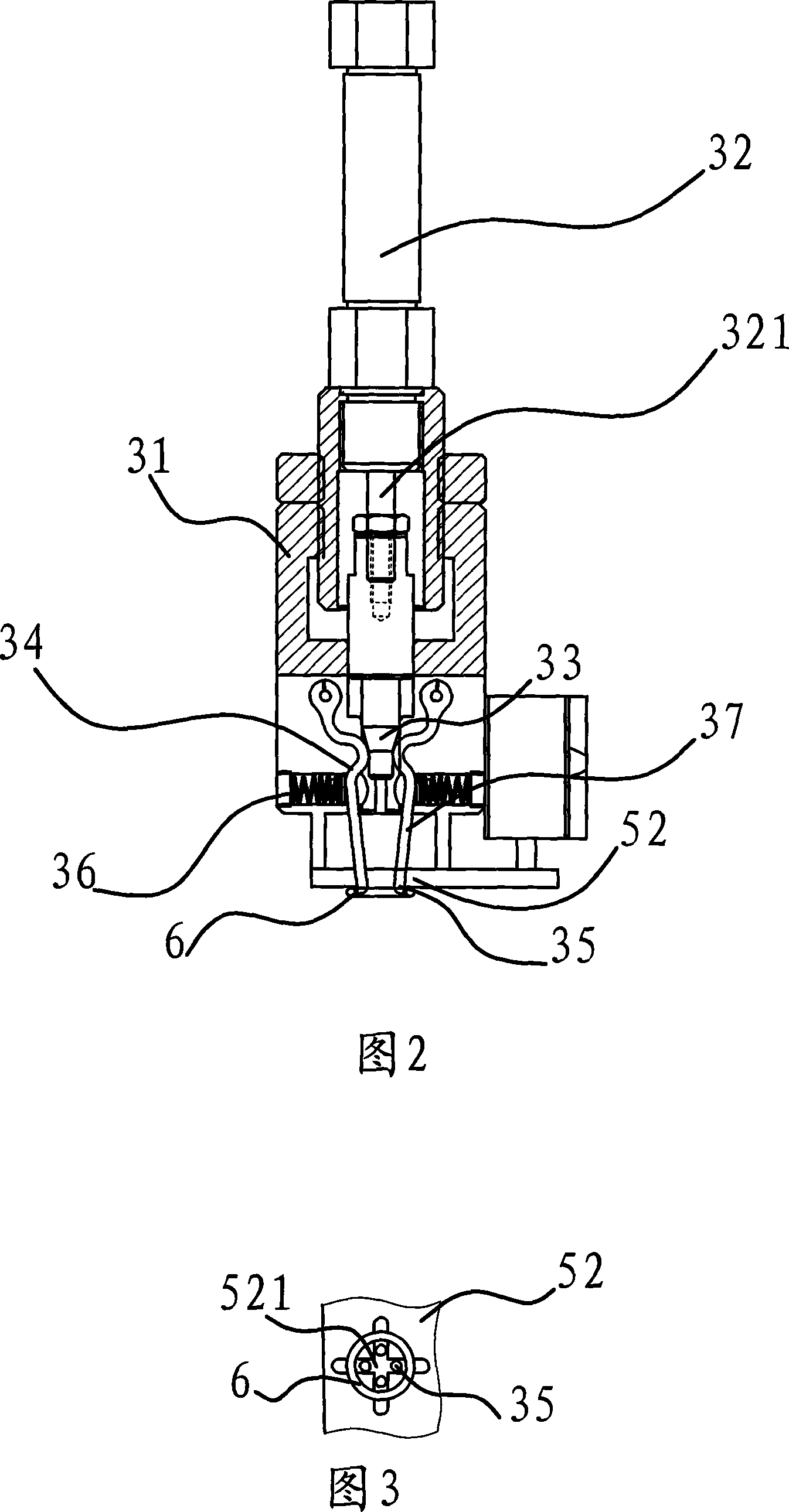
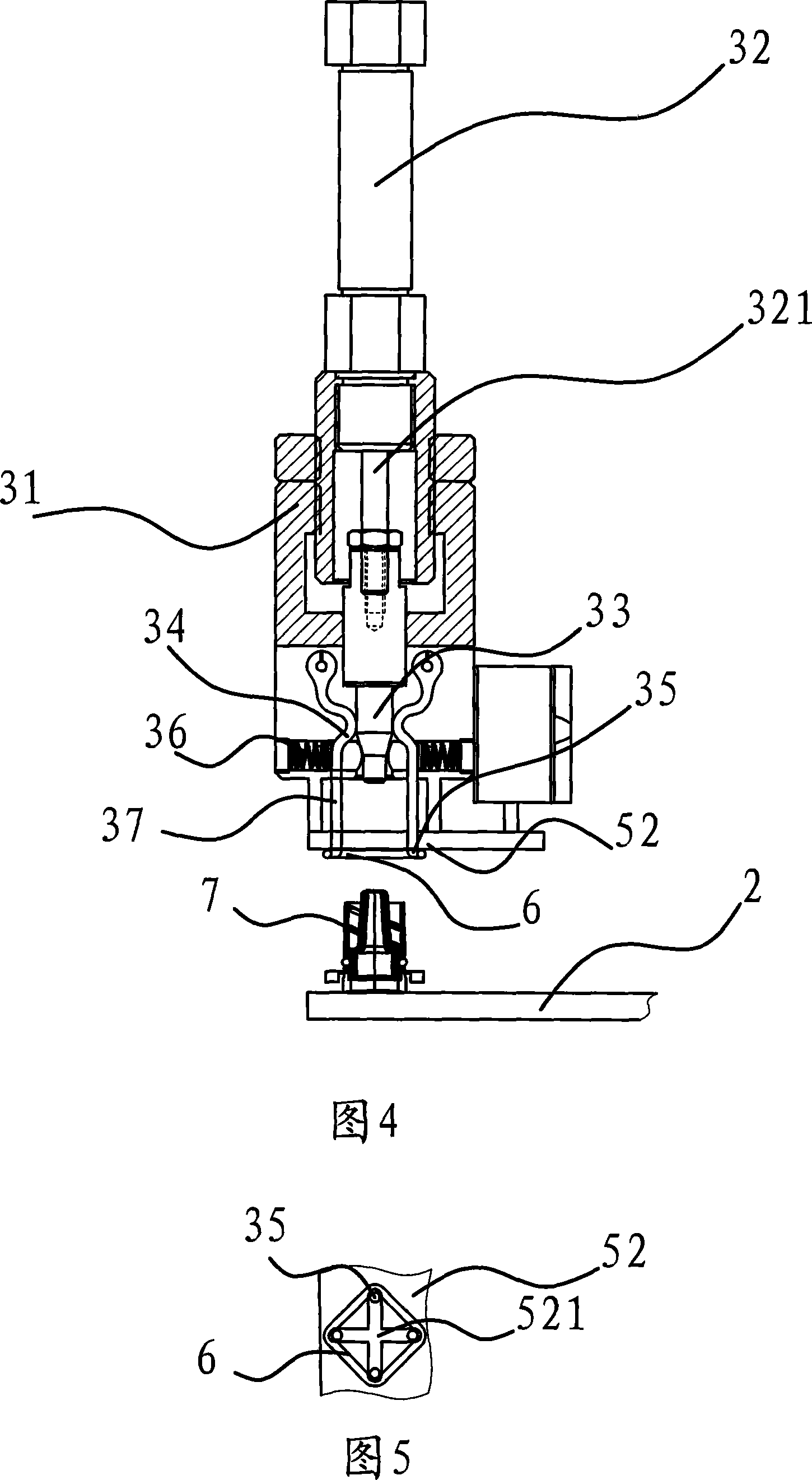
Automatic safe self-destructive disposable blood sampling device
An automatic safe disposable blood sampling device, comprising a case defining an shoot chamber, said shoot chamber being provided with a lancet-exiting hole at a front end thereof; a lancet disposed slidably in said shoot chamber and provided with a puncturing tip at a front portion thereof, said puncturing tip being pointed to said lancet-exiting hole in an alignment manner, a spring disposed at back of said lancet in a shooting direction of said lancet; a locking and shooting structure provided on a side of said lancet and said case along a compression path of said spring, said locking and shooting structure being composed of an elastic arm button on said case and an elastic arm on said lancet, said elastic arm button being an extended structure on a side of said case, a button engaging end of said elastic arm button facing a locking hole provided on a side wall of said case, said elastic arm being another extended structure on a side of said lancet corresponding to said side wall of said case, a free end of said elastic arm being engaged with said locking hole in a locking state, and a root portion of said elastic arm being provided with a notch or a shrink neck oil which stress is easy to concentrate. Since a notch or a shrink neck is provided at the root portion of the elastic arm, the elastic arm disengages from the locking hole after the elastic arm button is pressed, at the same time, the elastic arm is broken to be self-destructed due to the stress concentration on the notch, therefore, the present invention is beyond retrieval after one-off shooting.
Owner:SHI GUOPING
Method and apparatus for secure information distribution
ActiveUS20080091605A1Cryptography processingPayment architectureElectricityElectromagnetic radiation
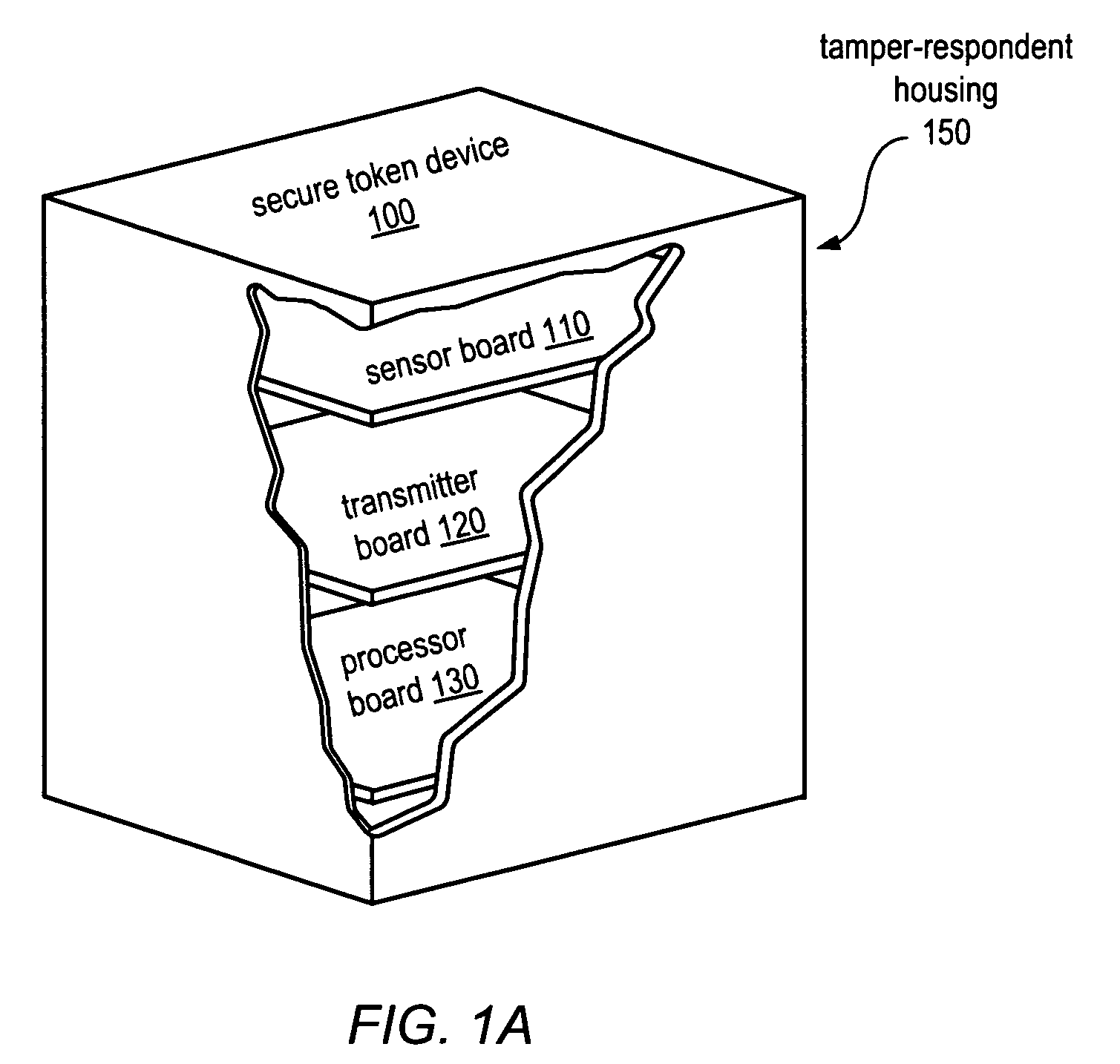
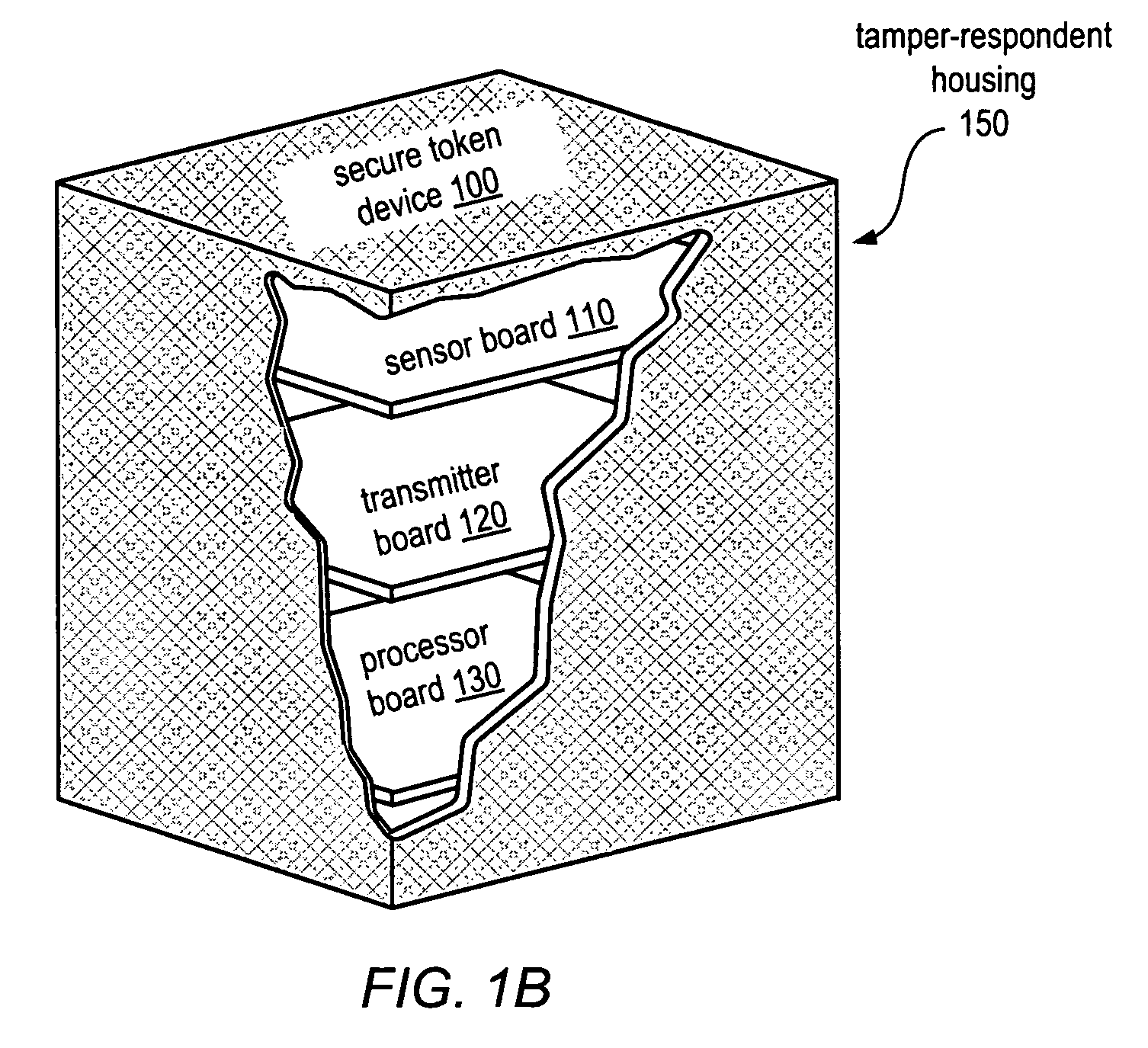
A system and method for secure generation and distribution of digital encryption keys is disclosed. The system may also be used to protect and distribute other types of secure information, including digital, audio, video, or analog data, or physical objects. The system may include a tamper-respondent secure token device, which may be configured to destroy or disable access to the secure information contained therein in response to attempts to physically or electronically breach the device. Outputs may be provided in a secure manner through various interfaces without using electricity (wires) or electromagnetic radiation. Inputs may be provided in a secure manner, including through the use of a gesture-based input interface. Destruction or disablement of the device and / or its secure contents may be provided upon detection of tamper attempts or upon input of a self-destruct command. Proof of the destruction or disablement of the device or its contents may be provided.
Owner:ORACLE INT CORP
Self-destructing document and e-mail messaging system
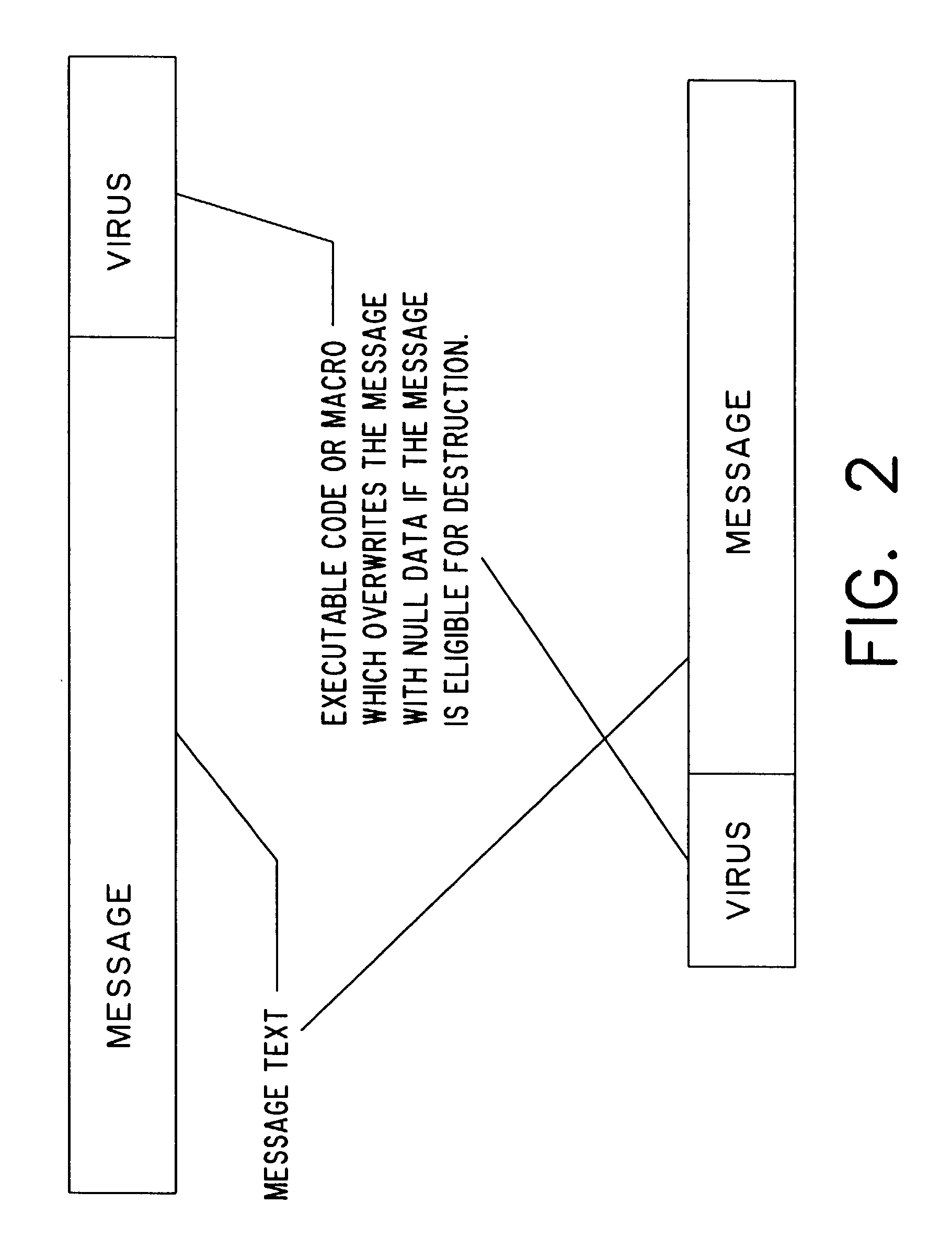
InactiveUS7191219B2Robust enforcement of lifetimeDigital data processing detailsUnauthorized memory use protectionMagnetic tapeDocumentation
A self-destruction document or e-mail massaging system is provided that automatically destroys documents or e-mail messages at a predetermined time by attaching a “virus” to the document or e-mail message. A virus in the form of a Trojan horse is attached to file (such as an e-mail message or document) when it is created. The virus contains a portion of executable code or an executable program which instructs the computer to overwrite and / or delete the file to which the virus is attached at a desired time. Since the virus is attached to the file, it will travel with the file even when the file is copied, forwarded, or saved to disks or tape drives.
Owner:HANGER SOLUTIONS LLC
Secure transaction processor
InactiveUS7568114B1User identity/authority verificationUnauthorized memory use protectionDocumentation procedureProcessor register
Owner:SCHLAFLY ROGER
Hand held wireless reading viewer of invisible bar codes
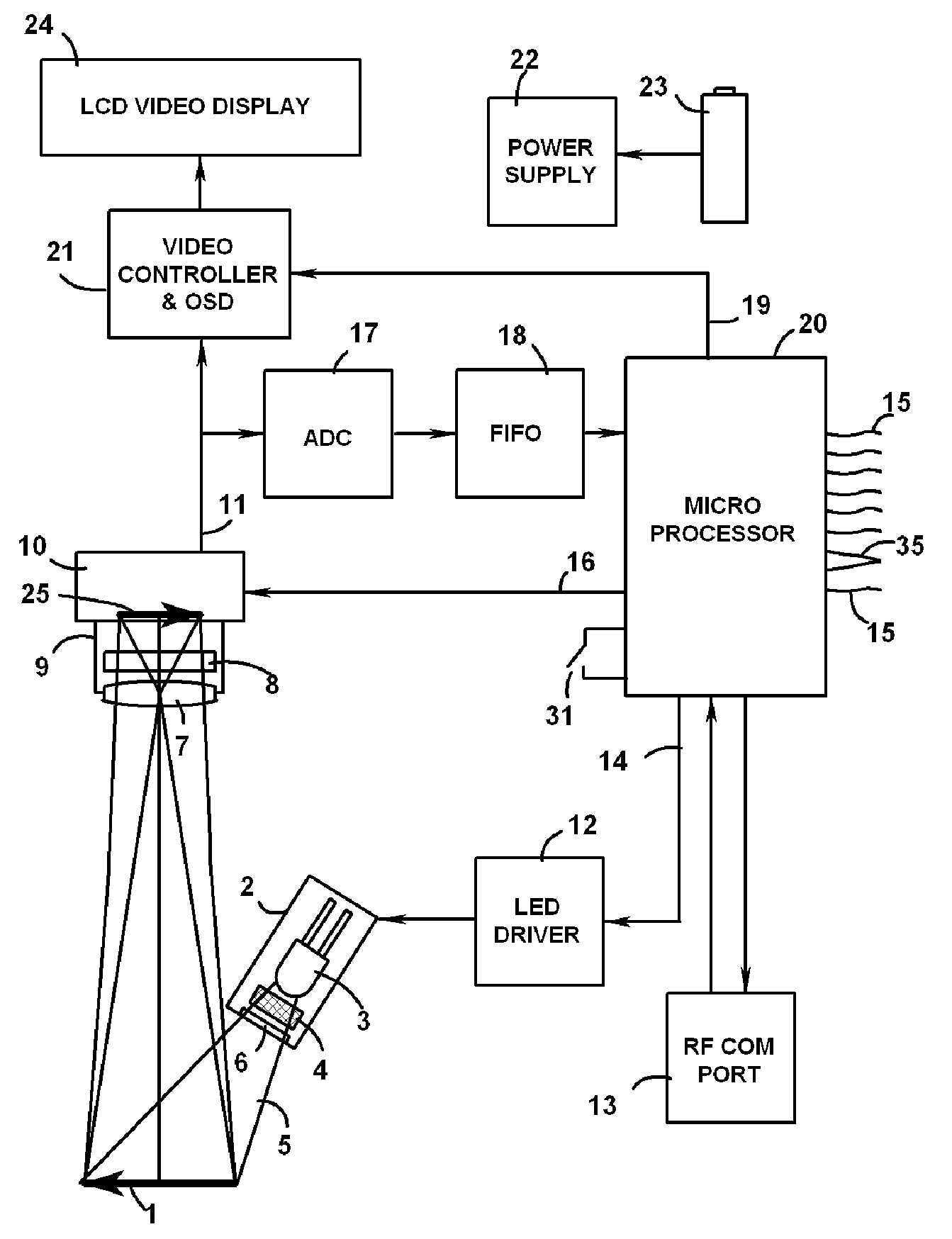
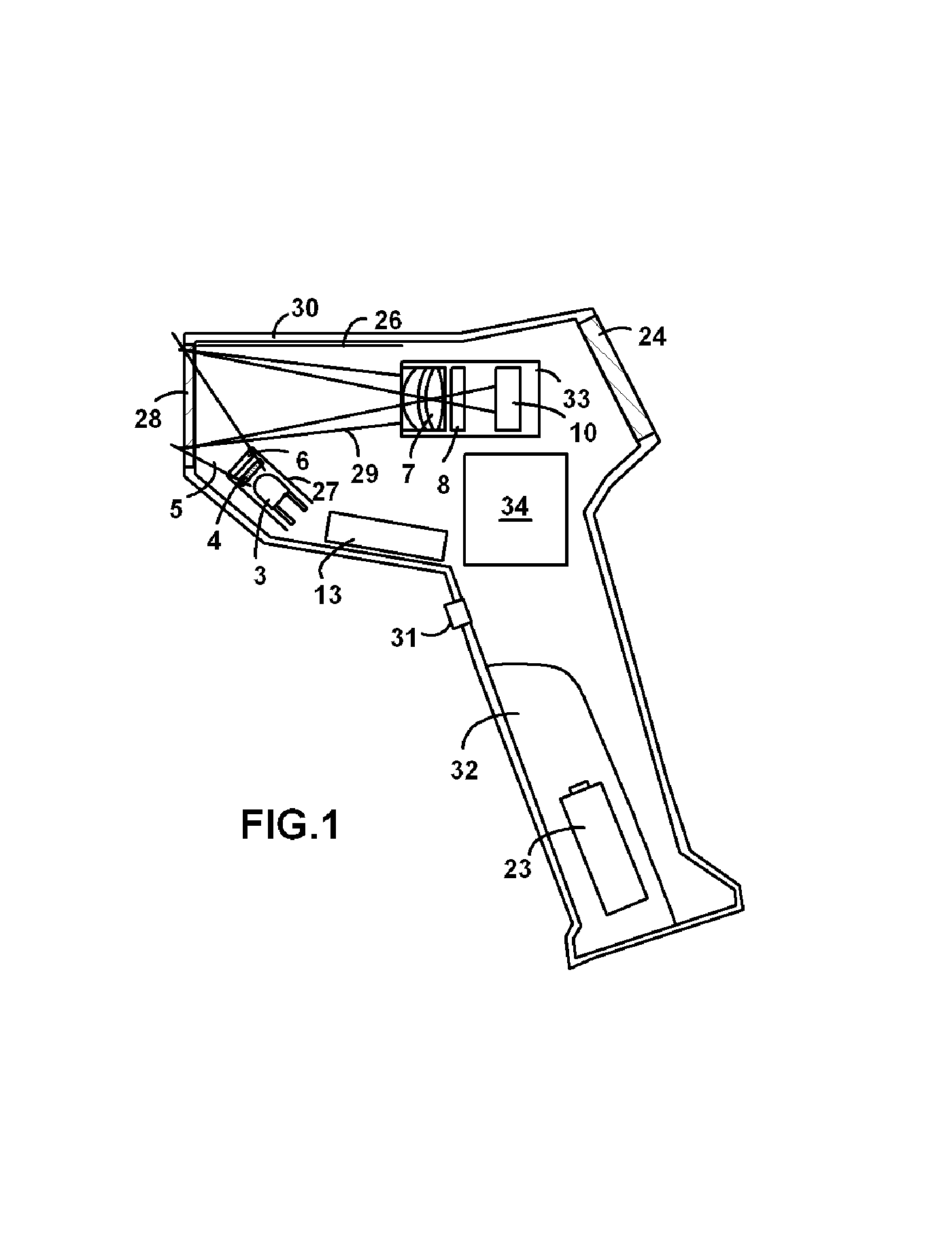
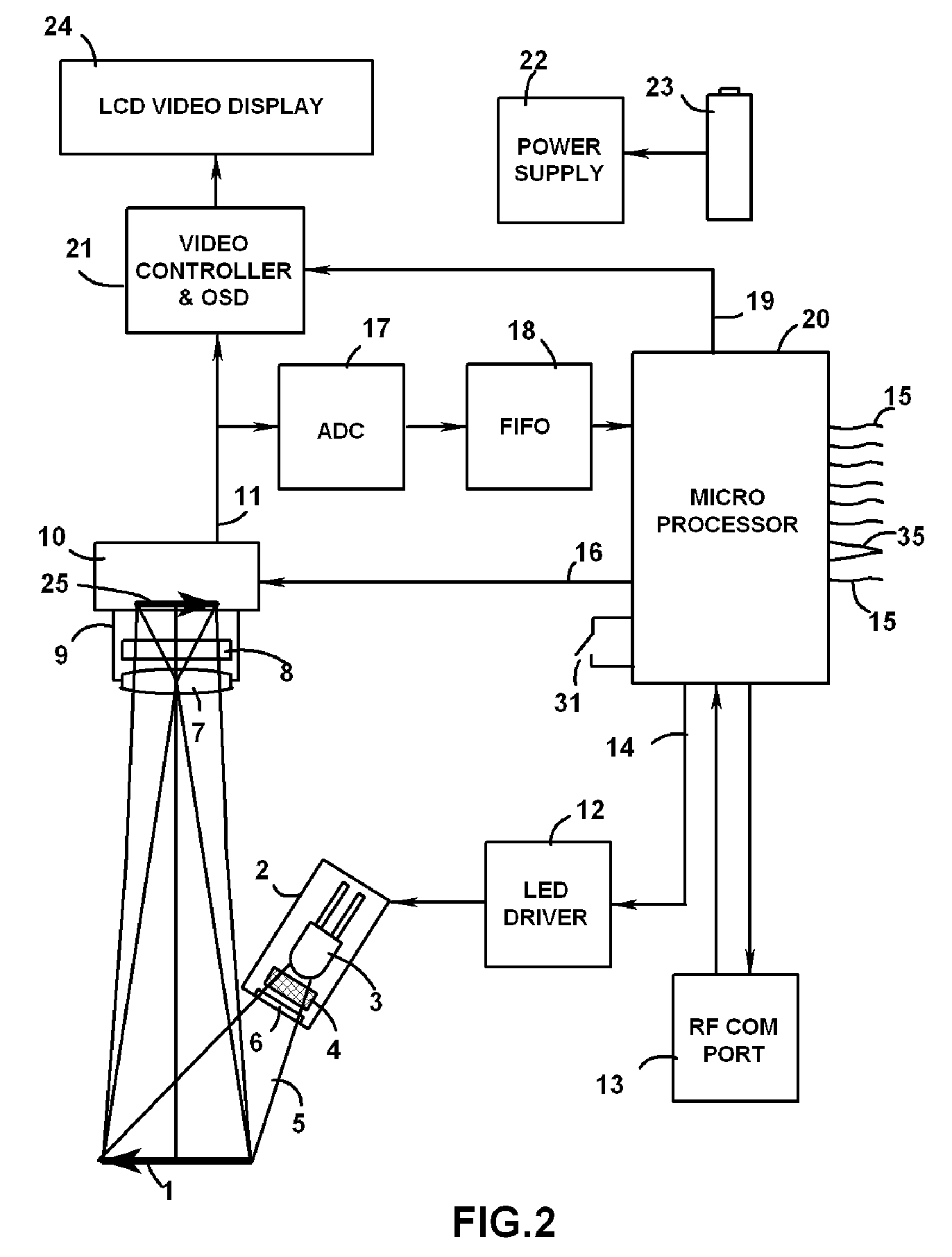
InactiveUS7516899B2Quickly and reliably decodeSensing by electromagnetic radiationSpectral bandsFluorescence
Hand held wireless reading viewer for bar codes printed with fluorescing inks that are invisible to the human eye. The reading viewer comprises a portable housing with a window transparent to the excitation and emission wavelengths, an LED or laser diode illuminator module having optical filter and diffuser, an image sensor module with a spectral band limited imaging optics, real time LCD video display, microprocessor with an image acquisition circuit, RF communications port, battery and self-destruct intrusion detector.
Owner:V L ENG
Virtual badge, device and method
ActiveUS20130048720A1Minimize threatEnhance subject materDigital data processing detailsIndividual entry/exit registersTime scheduleNot for profit
A system, method, and device comprising a virtual badge are disclosed. A virtual badge can be displayed on a cell phone or in another linked portable device, and for security purposes, has images which can be scanned, and the capability to alternate colors and / or self-destruct on a pre-set schedule. Whether for after a disaster or for daily use, the system uses cell phones or mobile devices loaded with specialized software. Using plugin technologies, the system optionally can enable field collected photos and notes on customizable forms to be mapped, tracked, and time / date stamped—including in a 100% disconnected environment. A modifiable virtual badge can aid in inventory, accountability, organization, and efficiency. The system can be employed by the “Whole Community”—citizens, businesses, not-for-profits, and government agencies—for social media, business, cleanup, insurance adjusters, or personnel focused on day to day operations or on mitigation, preparedness, response, and recovery.
Owner:DISASTER SOLUTIONS LLC
Virtual badge, device and method
ActiveUS20130218931A1Digital data processing detailsSpecial data processing applicationsTime scheduleNot for profit
A system, method, and device comprising a virtual badge are disclosed. A virtual badge can be displayed on a cell phone or in another linked portable device, and for security purposes, has images which can be scanned, and the capability to alternate colors and / or self-destruct on a pre-set schedule. Whether for after a disaster or for daily use, the system uses cell phones or mobile devices loaded with specialized software. Using plugin technologies, the system optionally can enable field collected photos and notes on customizable forms to be mapped, tracked, and time / date stamped—including in a 100% disconnected environment. A modifiable virtual badge can aid in inventory, accountability, organization, and efficiency. The system can be employed by the “Whole Community”—citizens, businesses, not-for-profits, and government agencies—for social media, business, cleanup, insurance adjusters, or personnel focused on day to day operations or on mitigation, preparedness, response, and recovery.
Owner:SPHINX IND INC
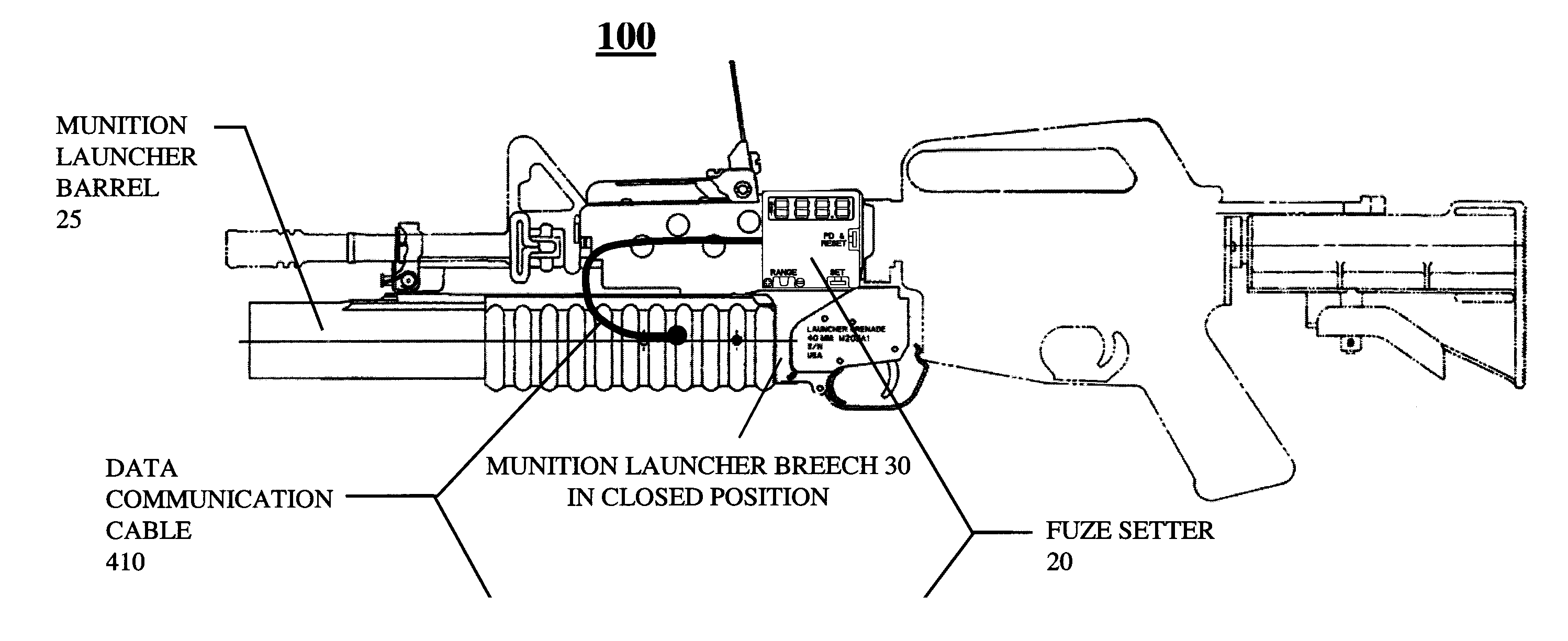
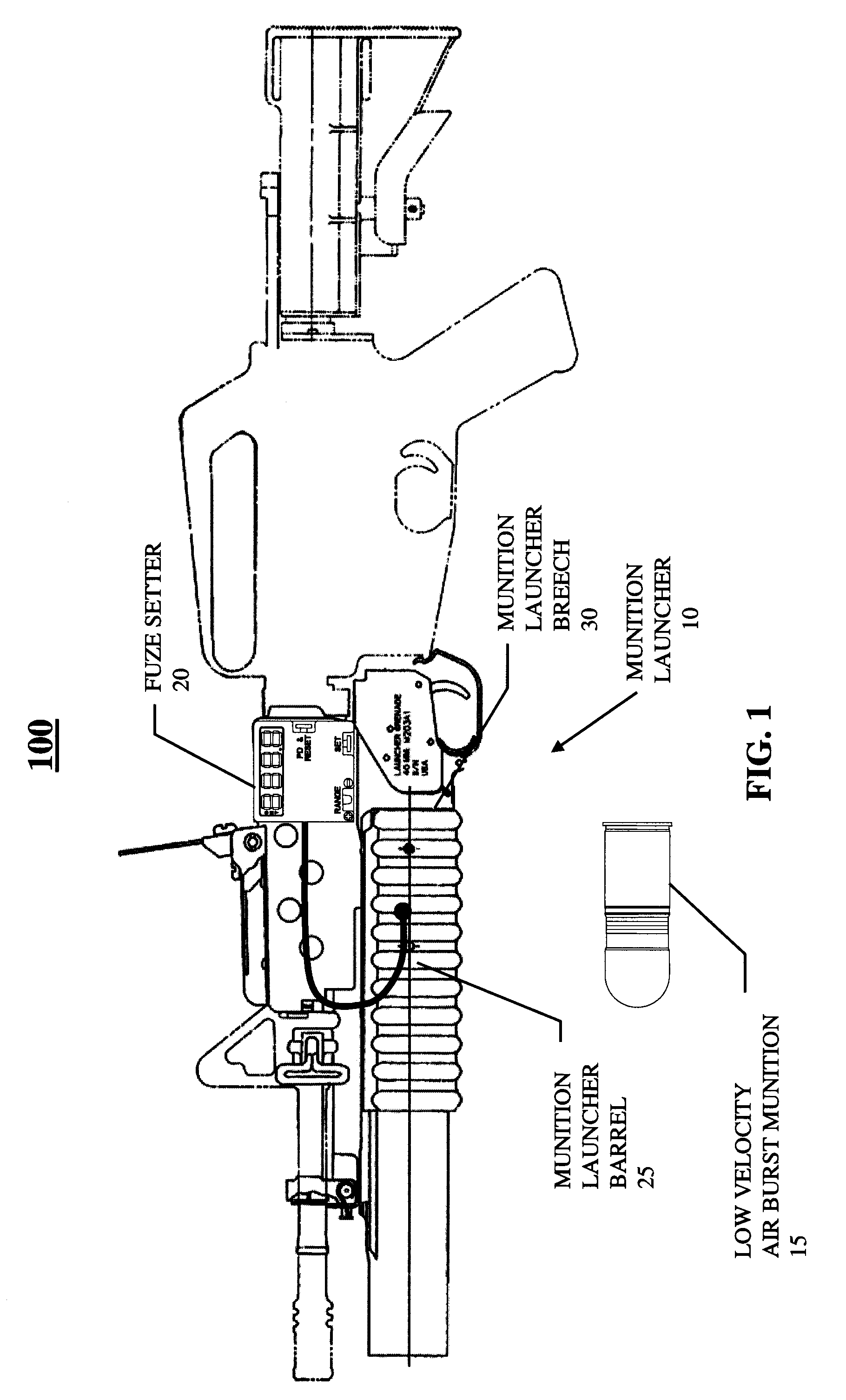
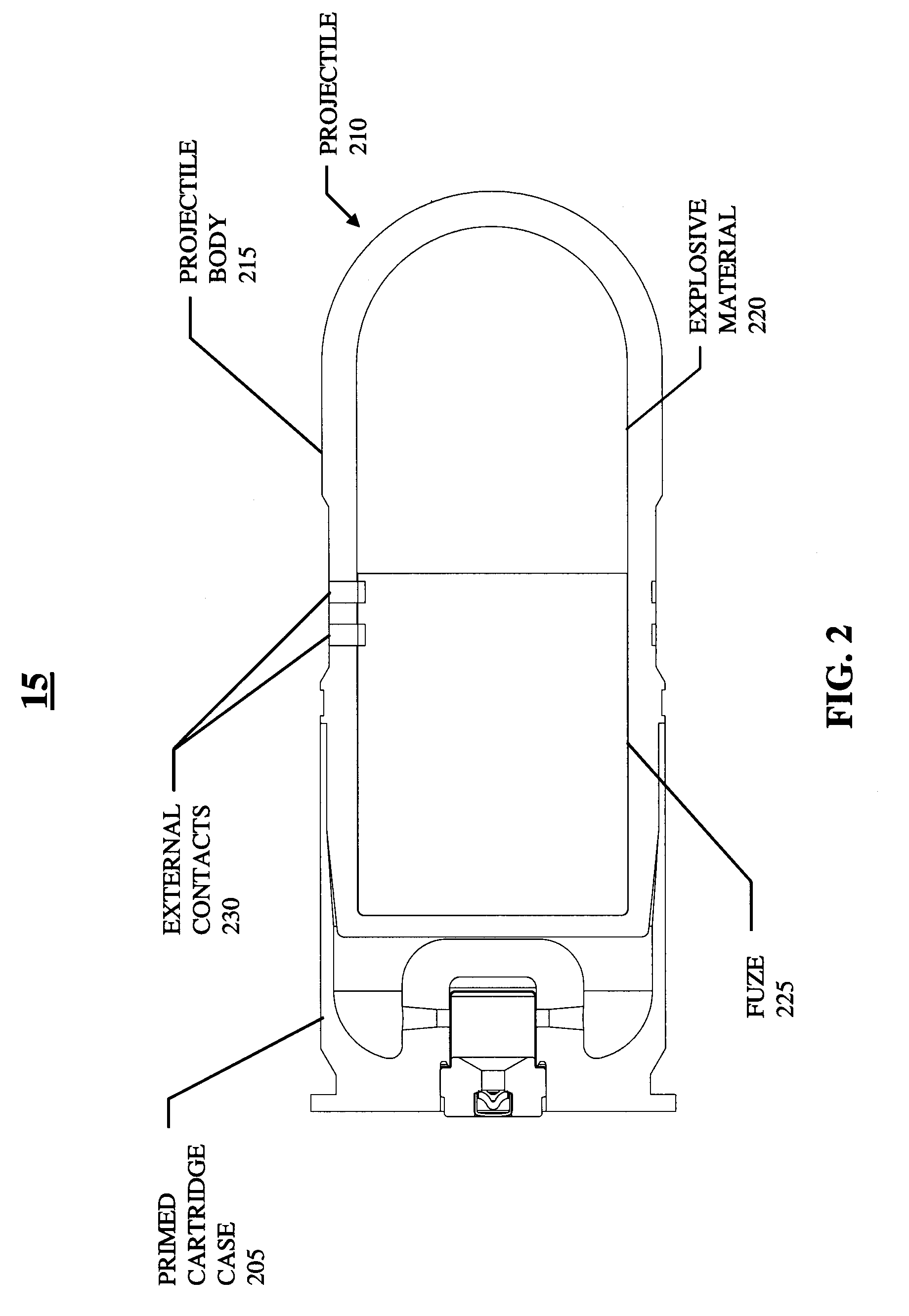
Low velocity air burst munition and launcher system implemented on an existing weapon
InactiveUS7021187B1Simple designReduce power consumptionAmmunition projectilesAmmunition fuzesElectricityAir burst
A low velocity air burst munition and launcher system allows the user to program the munition to detonate in the air at a specified range from the muzzle. The system further allows the munition to detonate upon impact or self-destruct if the target is missed. The system allows the user to program and reset the munition multiple times, and allows the user to perform this operation at night in cold weather conditions. The system requires the user to manually input the range into a fuze programming device prior to projectile launch. The fuze programming device is capable of direct interface with electronic range determining devices. The system employs electrical contacts in the chamber of the munition launcher barrel and on the projectile body to complete the circuit used for programming. Furthermore, this system is capable of integrating a magnetic induction method of programming.
Owner:UNITED STATES OF AMERICA THE AS REPRESENTED BY THE SEC OF THE ARMY
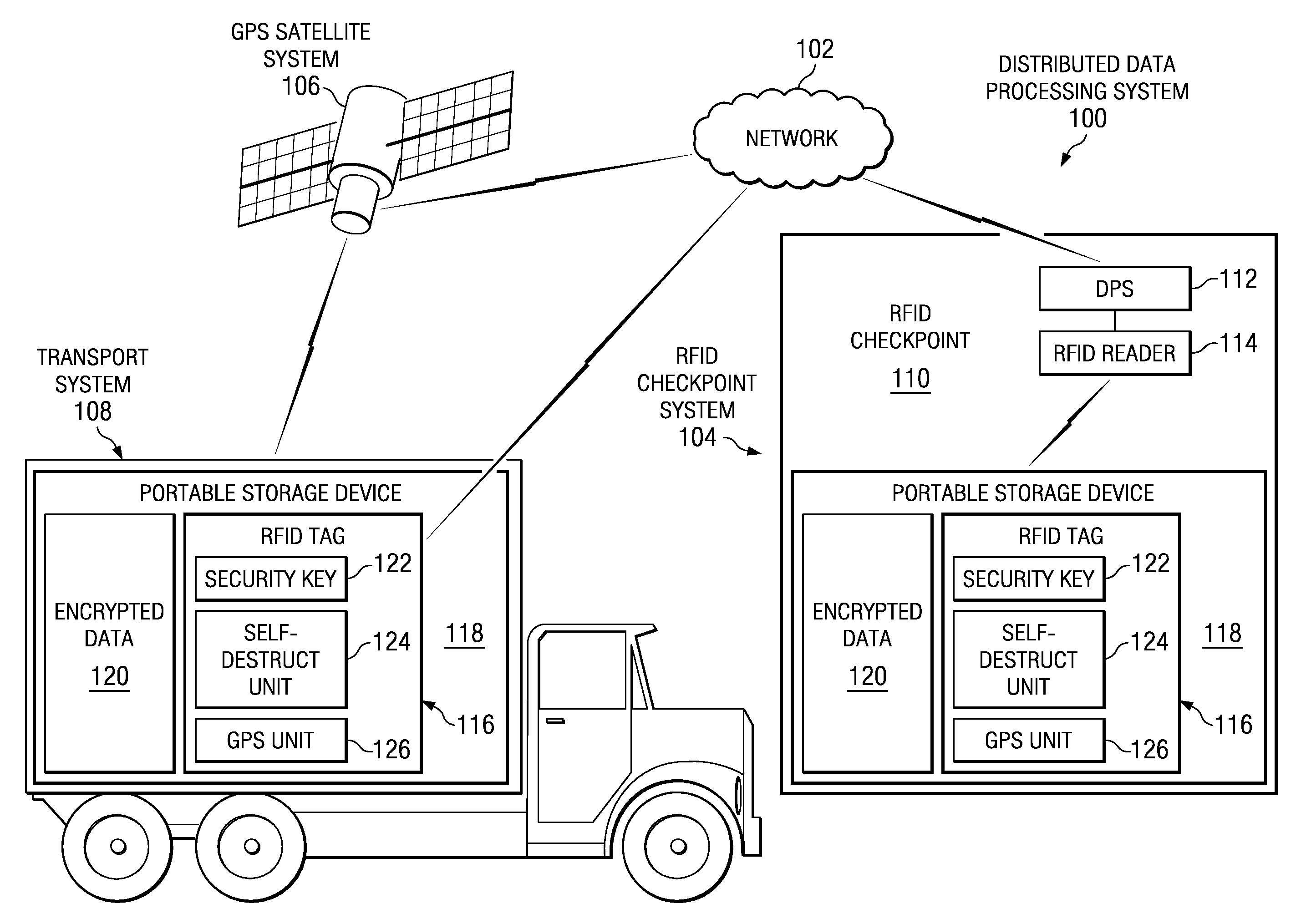
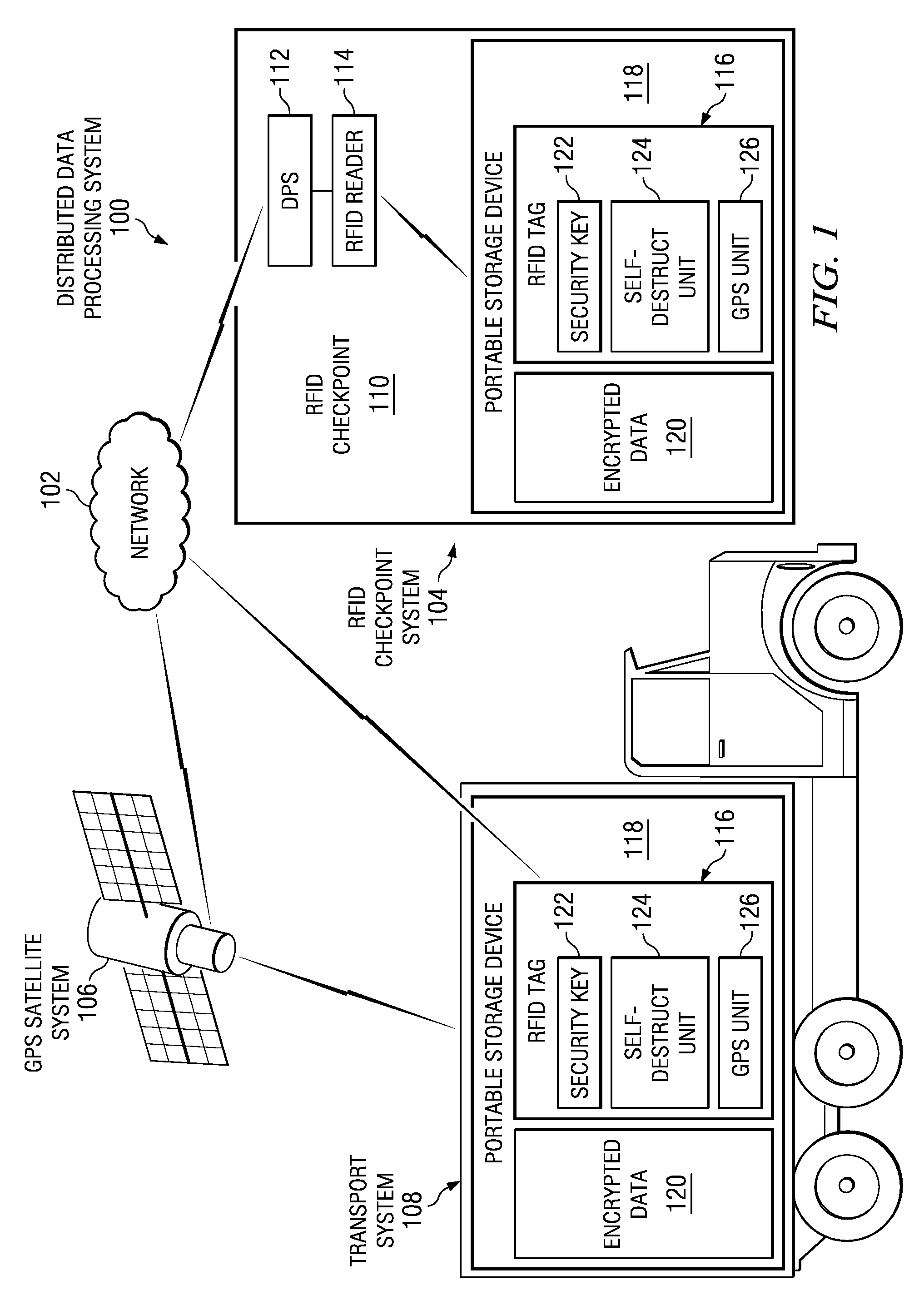
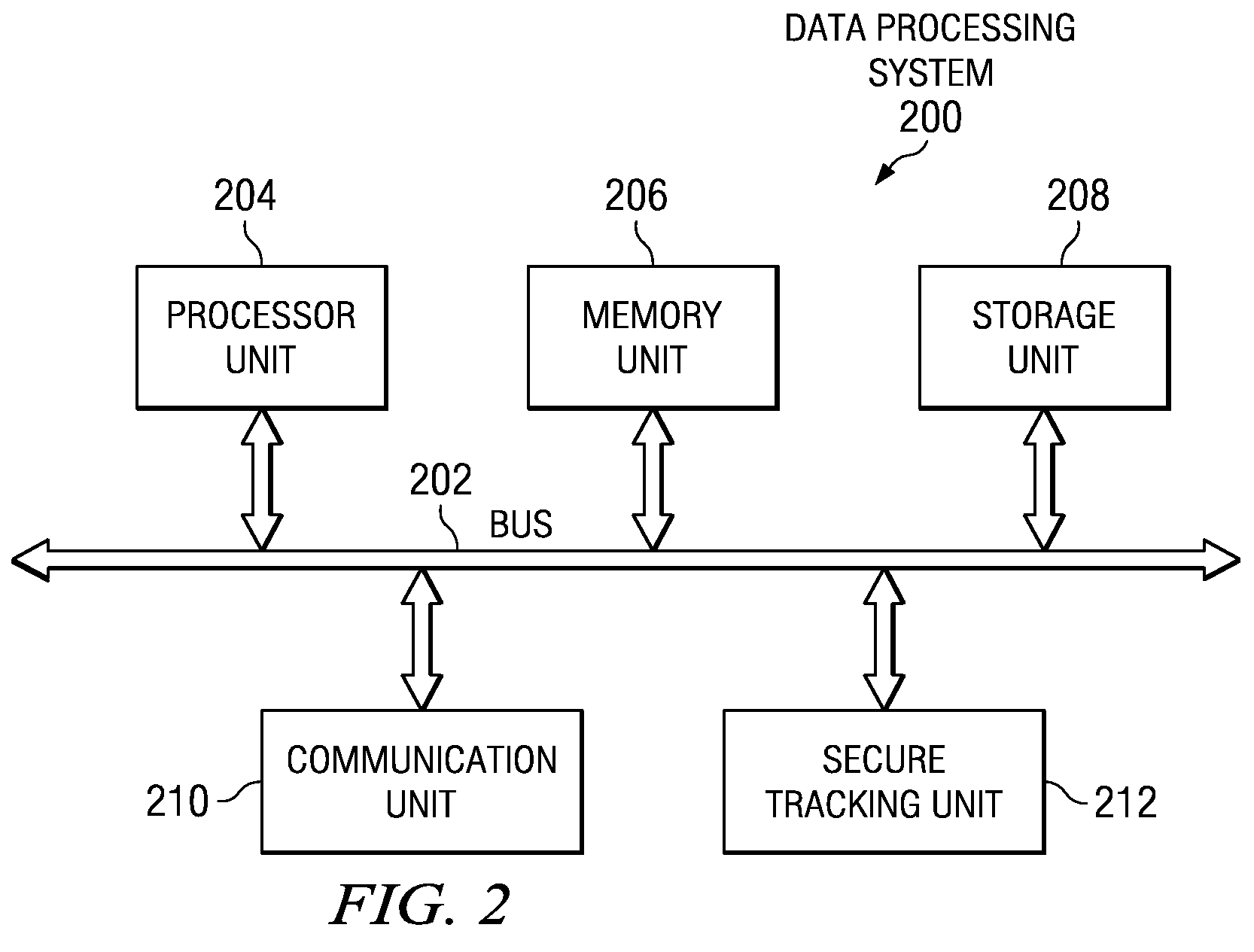
Method and system for protecting data
InactiveUS20080112300A1Electronic editing digitised analogue information signalsRecord information storageComputer hardwareElectromagnetic pulse
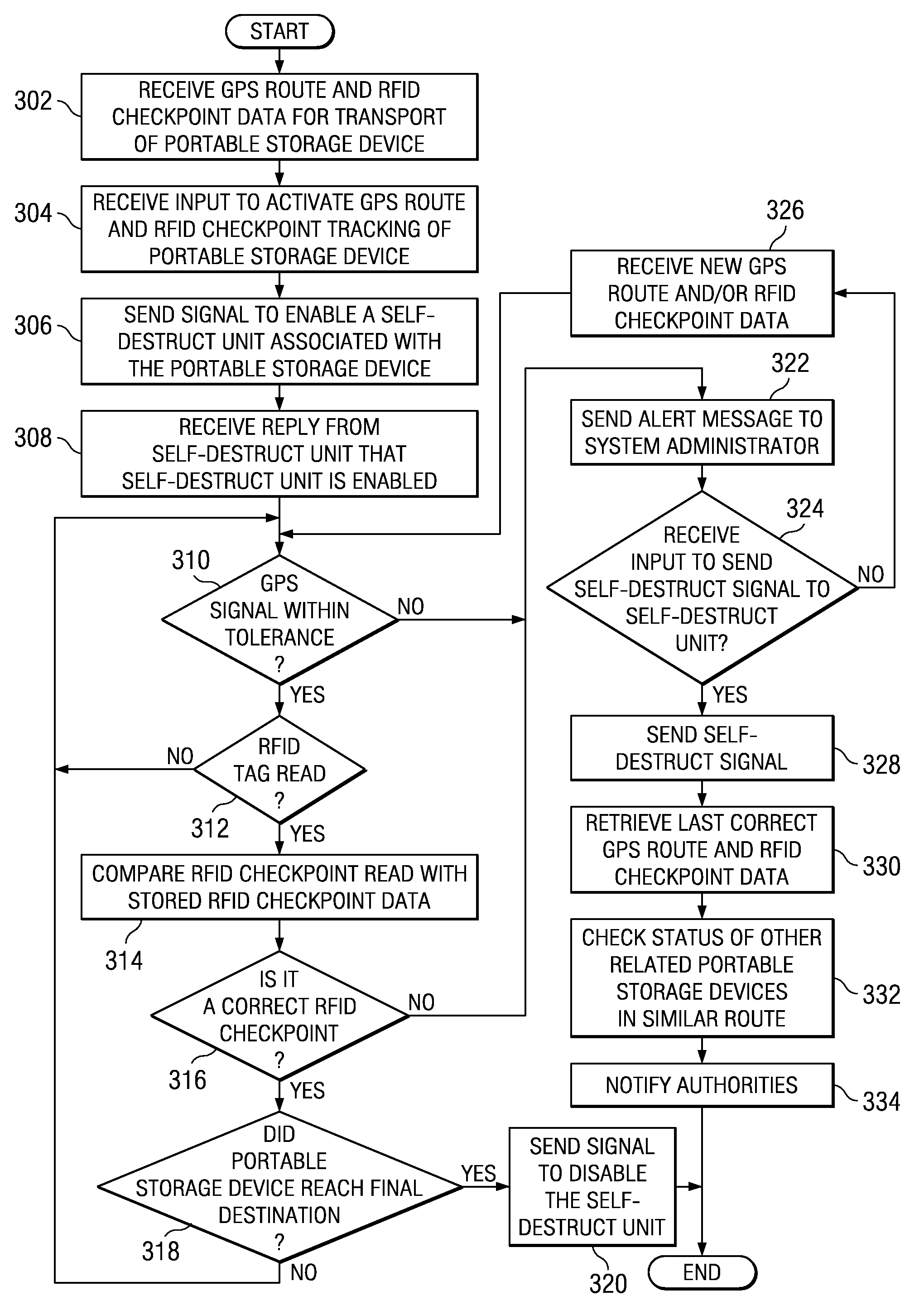
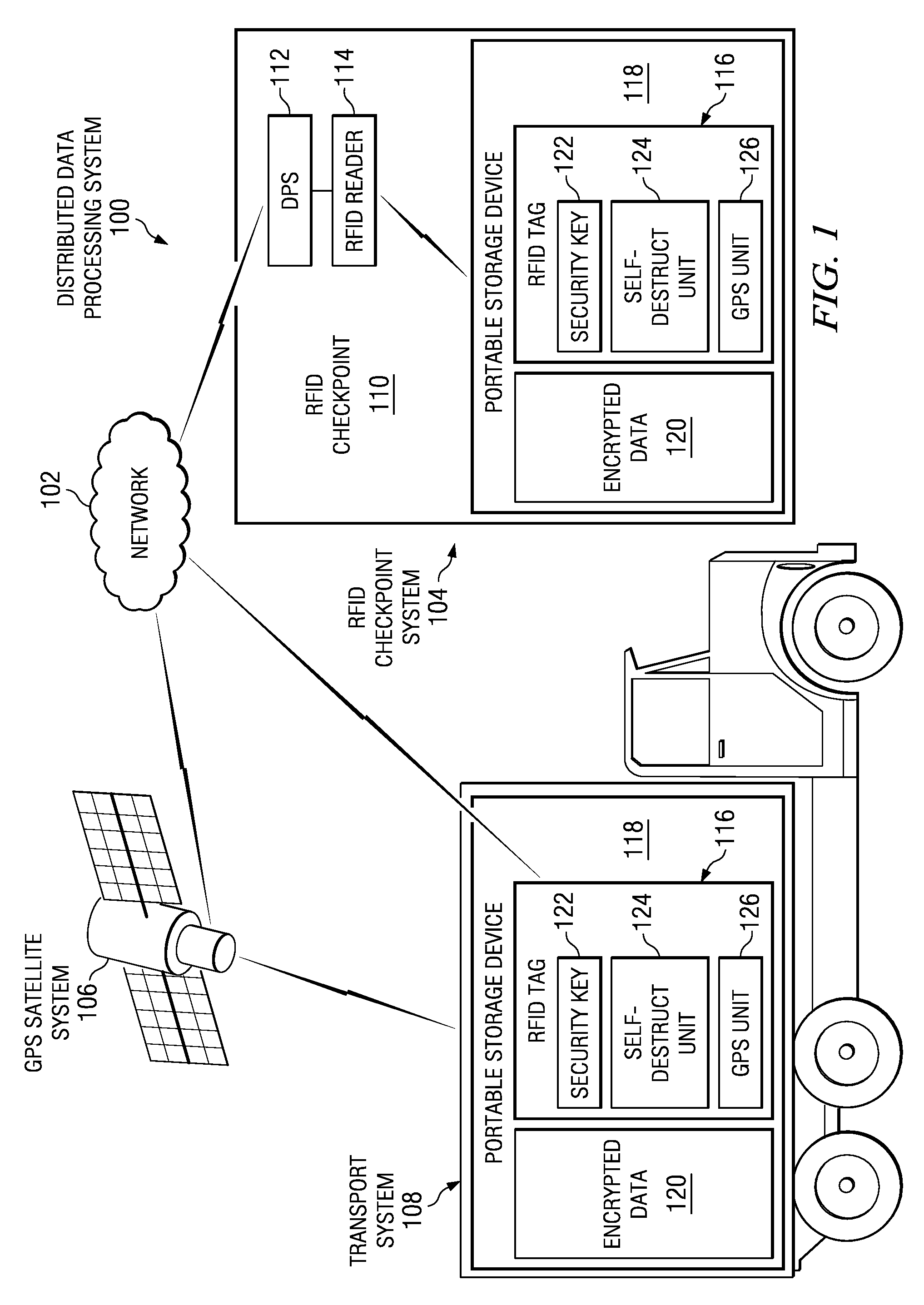
A system for protecting data within a portable storage device. A self-destruct unit associated with the portable storage device is enabled. If the portable storage device is not within a pre-specified route tolerance or if the portable storage device is not at a pre-selected identification checkpoint, an alert message is sent. In response to receiving a particular response, a self-destruct signal is sent to the enabled self-destruct unit. Then the enabled self-destruct unit creates an electromagnetic pulse from a xenon flash tube to render confidential data within the portable storage device unusable.
Owner:IBM CORP
System and method of data cognition incorporating autonomous security protection
ActiveUS20090007227A1Reduce errorsReduce incidenceDigital data processing detailsUser identity/authority verificationAuto-configurationSelf-destruct
Autonomous embedded data cognition enables data to perform real-time environmental configuration control, self-manage, perform analyses, determine its current situation, and evaluate behavior to respond accordingly. When created, security measures, and access controls are selected. Highly sensitive data can be extracted and substituted with creator label and / or functional representation. Data-to-data reasoning and analysis can be performed. The processing method comprises autonomous monitoring for a state change and analyzing the current user to determine if the instantiation should exist. If affirmed, the cognition engine automatically configures the computational environment in which it resides. If denied, environmental behavior is further analyzed for security problems or an erroneous situation. If detected, the creator is alerted and provided with incident information enabling remote creator control of the data. Cognitive data can decide to self-destruct mitigating risk of undesirable instantiations. Intelligent Agents, a comprehensive data structure, and intelligent document means are leveraged for implementation.
Owner:AZOS AI
Tamper-proof container
InactiveUS20060261259A1Reduce and alter light transmissibilityRadiation pyrometryMaterial analysis by optical meansNuclear radiationFiber
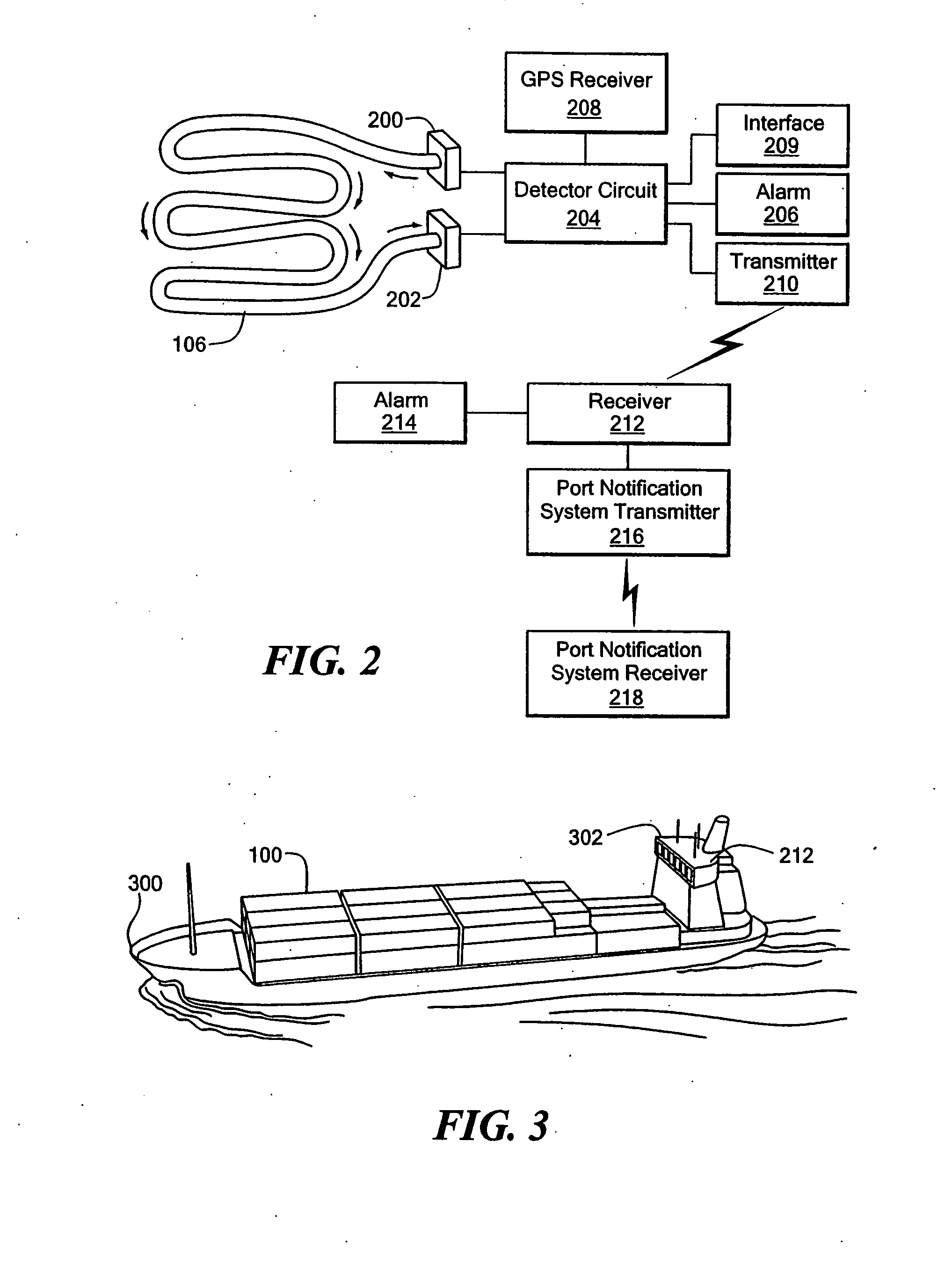
An inflatable sheet includes an optical fiber extending across at least a portion of its surface to detect a breach or nuclear radiation. The sheet can line at least a portion of a container or several such sheets can line several walls of the container. A breach of the sheet or radiation within or near the sheet reduces optical transmissibility of the fiber. The fiber integrates the radiation over time and / or over the length and volumetric mass of the fiber, making the fiber sensitive to even low-level radiation. The optical fiber is monitored for a change in its transmissibility. A reduction in the transmissibility, such as to below a threshold, can trigger an alarm, such as an annunciator, a self-destruct circuit or send a message that includes information about the time or the container's contents or location when the breach or radiation is detected to a central location, such as a ship's control room or port notification system.
Owner:3D FUSE TECH
System and method for scanning hosts using an autonomous, self-destructing payload
InactiveUS20160099960A1Memory loss protectionError detection/correctionSelf-destructComputer security
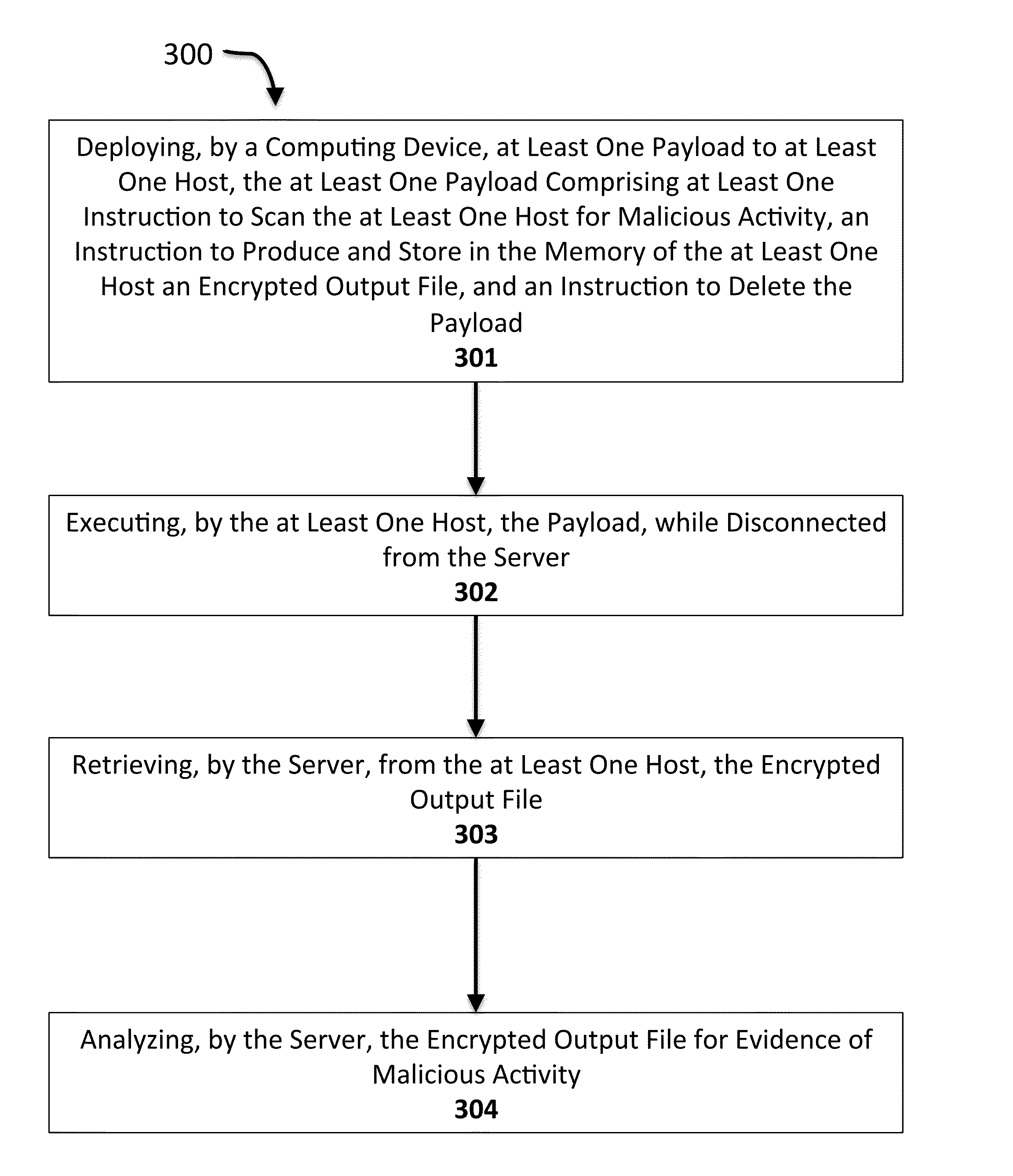
A method for scanning hosts using an autonomous, self-destructing payload, deploying, by a computing device, at least one payload to at least one host, the at least one payload comprising at least one instruction to scan the at least one host for malicious activity, an instruction to produce and store in the memory of the at least one host an encrypted output file, and an instruction to delete the payload. The method includes disconnecting, by the computing device, from the at least one host. The method includes executing, by the at least one host, the payload, while disconnected from the computing device. The method includes reconnecting, by the computing device, to the at least one host. The method includes retrieving, by the computing device, from the at least one host, the encrypted output file. The method includes analyzing, by the computing device, the encrypted output file for evidence of malicious activity.
Owner:INFOCYTE
Capacitance Structures for Defeating Microchip Tampering
ActiveUS20100026313A1Testing dielectric strengthResistance/reactance/impedenceCapacitanceActive sensing
Apparatus, method and program product may detect an attempt to tamper with a microchip by detecting an unacceptable alteration in a measured capacitance associated with capacitance structures proximate the backside of a microchip. The capacitance structures typically comprise metallic shapes and may connect using through-silicon vias to active sensing circuitry within the microchip. In response to the sensed change, a shutdown, spoofing, self-destruct or other defensive action may be initiated to protect security sensitive circuitry of the microchip.
Owner:IBM CORP
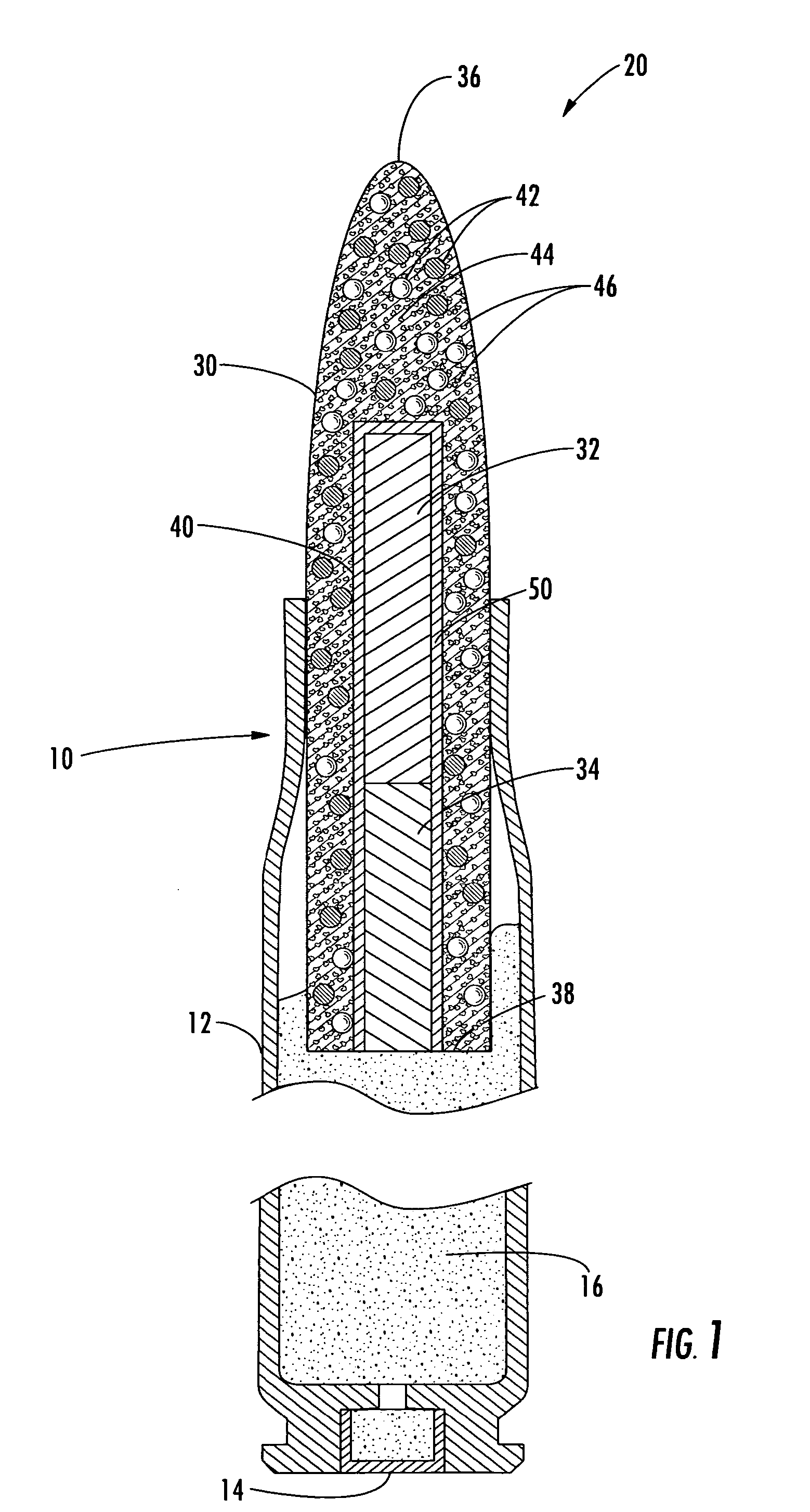
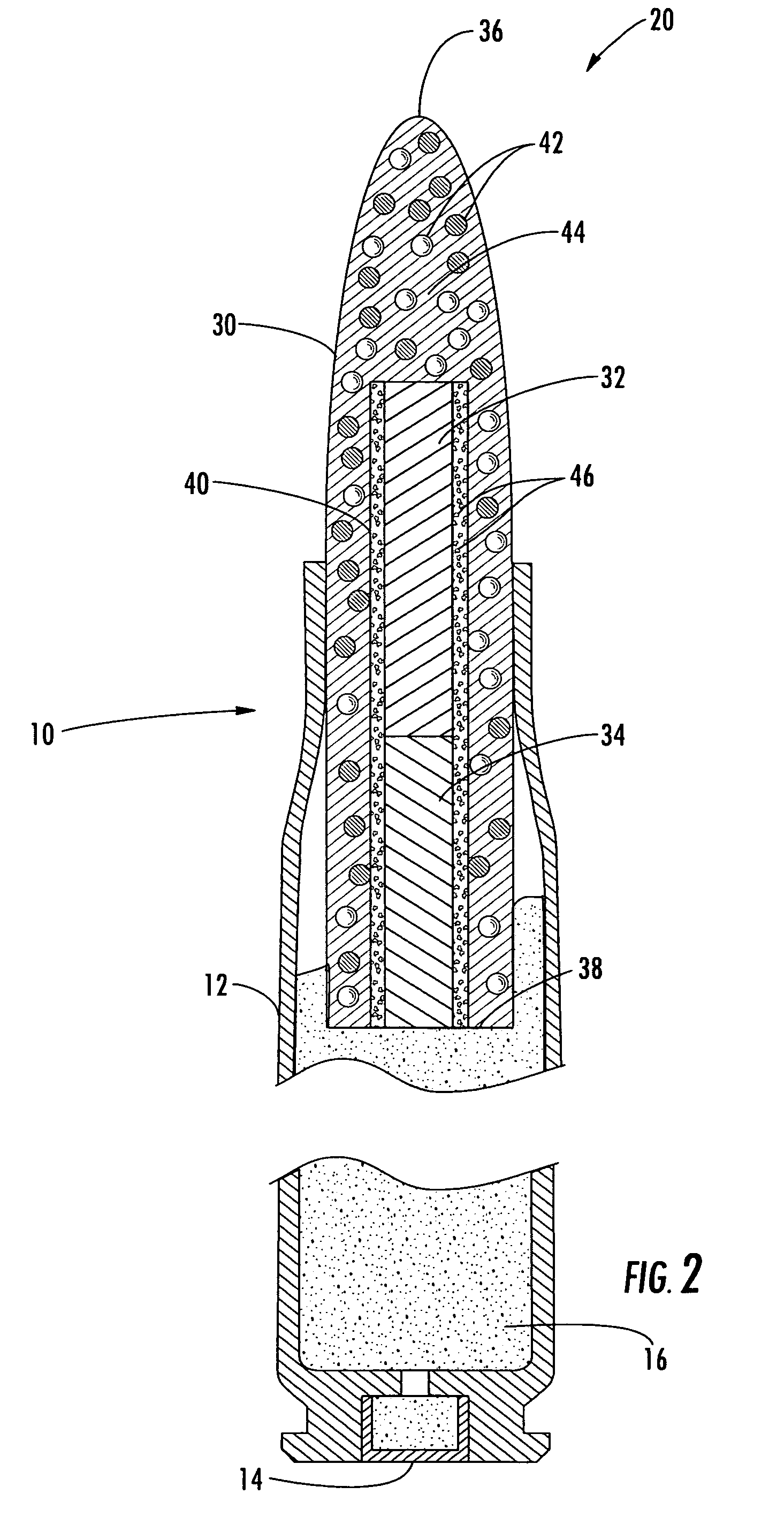
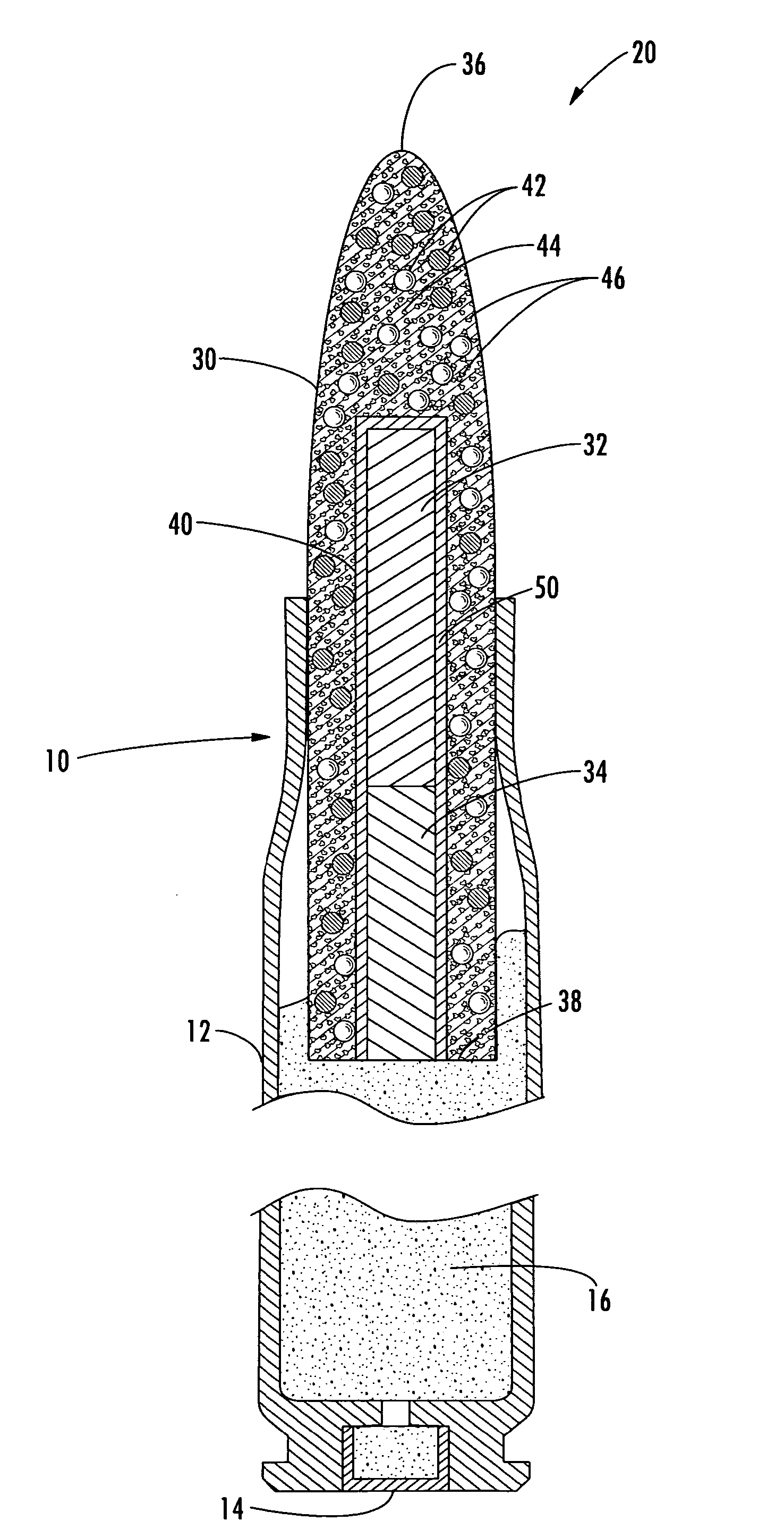
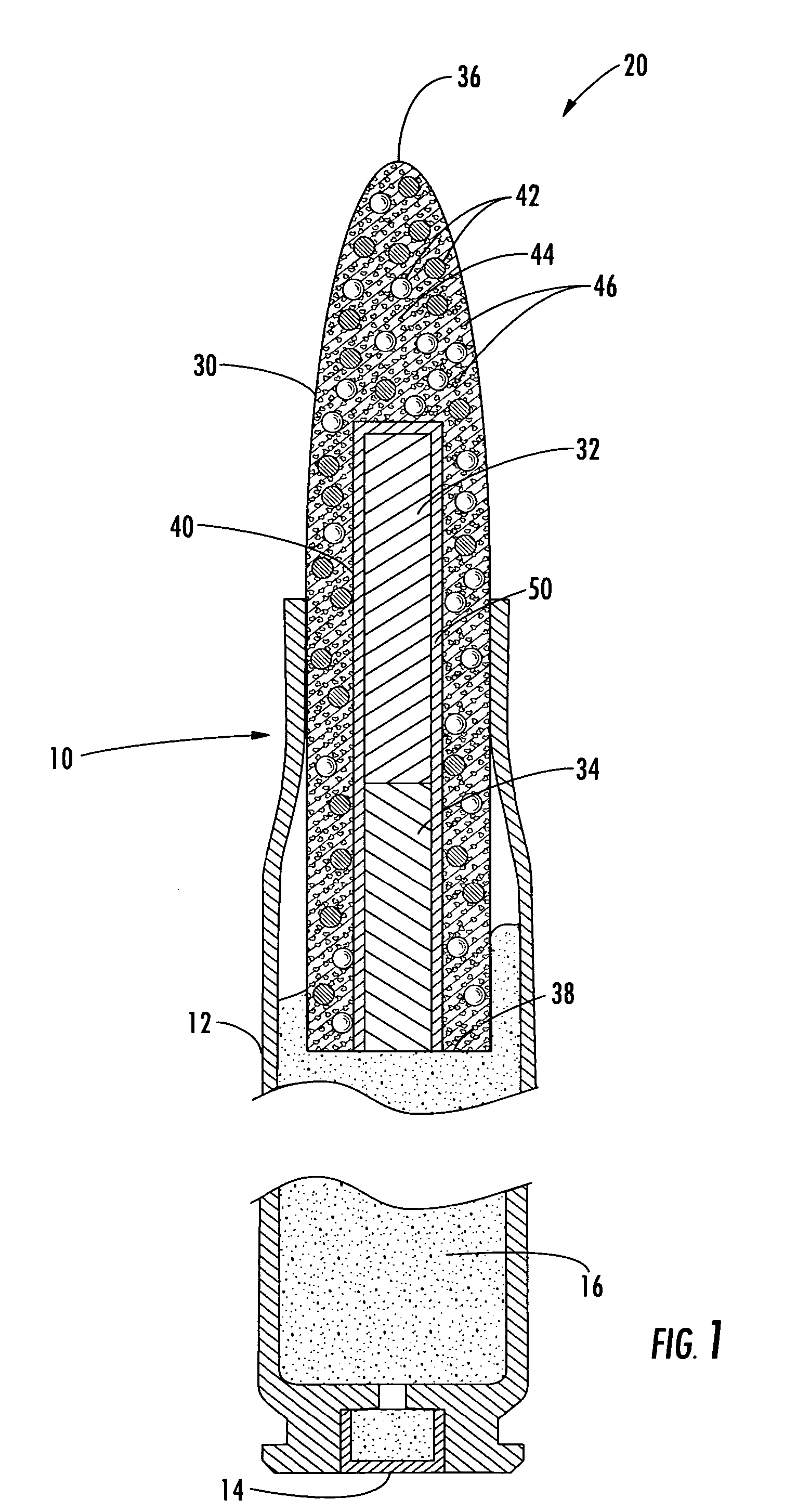
Method and apparatus for self-destruct frangible projectiles
Owner:NEWTEC SERVICES GROUP
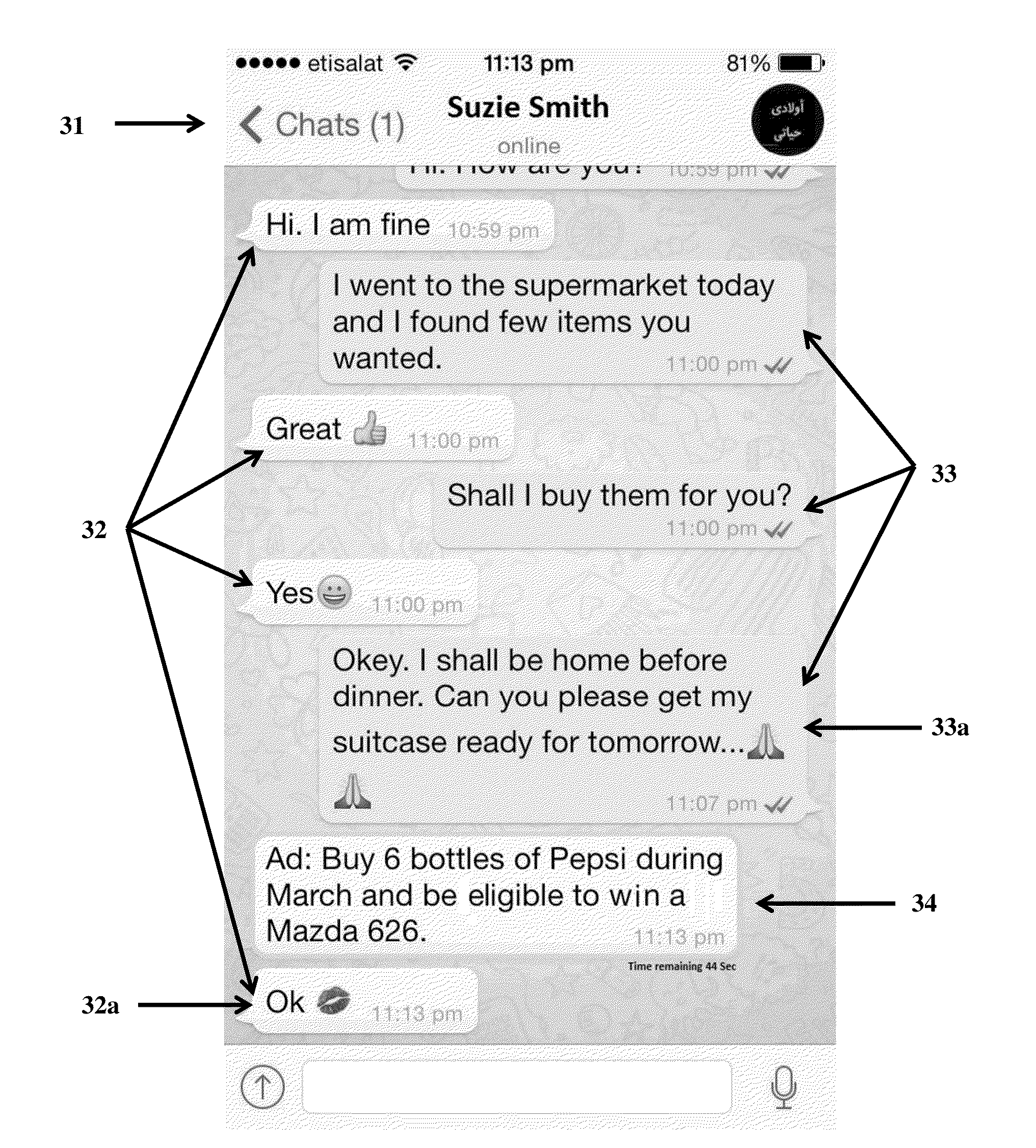
Self-destructing ad messages in messaging apps
InactiveUS20150332332A1Minimizing effect of advertisingAdvertisementsInput/output processes for data processingDisplay deviceMobile device
The present application is directed to systems and methods for providing and displaying advertising messages within applications running on smart phones, tablets and other mobile devices while minimizing the disruptive effect of those advertising messages. The application may include an instant messaging or chat function. Within the application, advertising content may be presented in the portion of the screen dedicated to displaying the instant messaging or chat conversation, or in the portion of the screen dedicated to displaying a list of conversations, contacts or other content. The advertising content is set to be displayed for a certain amount of time and the display may indicate the amount of time remaining before the advertising content will disappear. The advertising content may include, for example, a limited-time offer that the user may accept while the advertising content is displayed.
Owner:AL DARMAKI AHMED SAIF
System and method for password protecting an attribute of content transmitted over a network
InactiveUS20060230459A1Reduce riskDigital data processing detailsUser identity/authority verificationPasswordSelf-destruct
System and methods for password protecting an attribute of content transmitted over a network. Content such as a text file, an audio file, a video file, and the like, sent over a network is protected by a password. A sender setting up the protection may determine which attribute of the content is to be protected by the password. Attributes that may be protected include time to access, number of accesses, permission to forward, permission to store, and the like. In a time to view example, the received content may self-destruct unless the receiver enters the password within a specified time period. Protection may be set up such that every time the receiver attempts to access the content, the password has to be re-entered. Access by an unauthorized user who may have possession of the computing device with the received content is prevented by content level protection.
Owner:MICROSOFT TECH LICENSING LLC
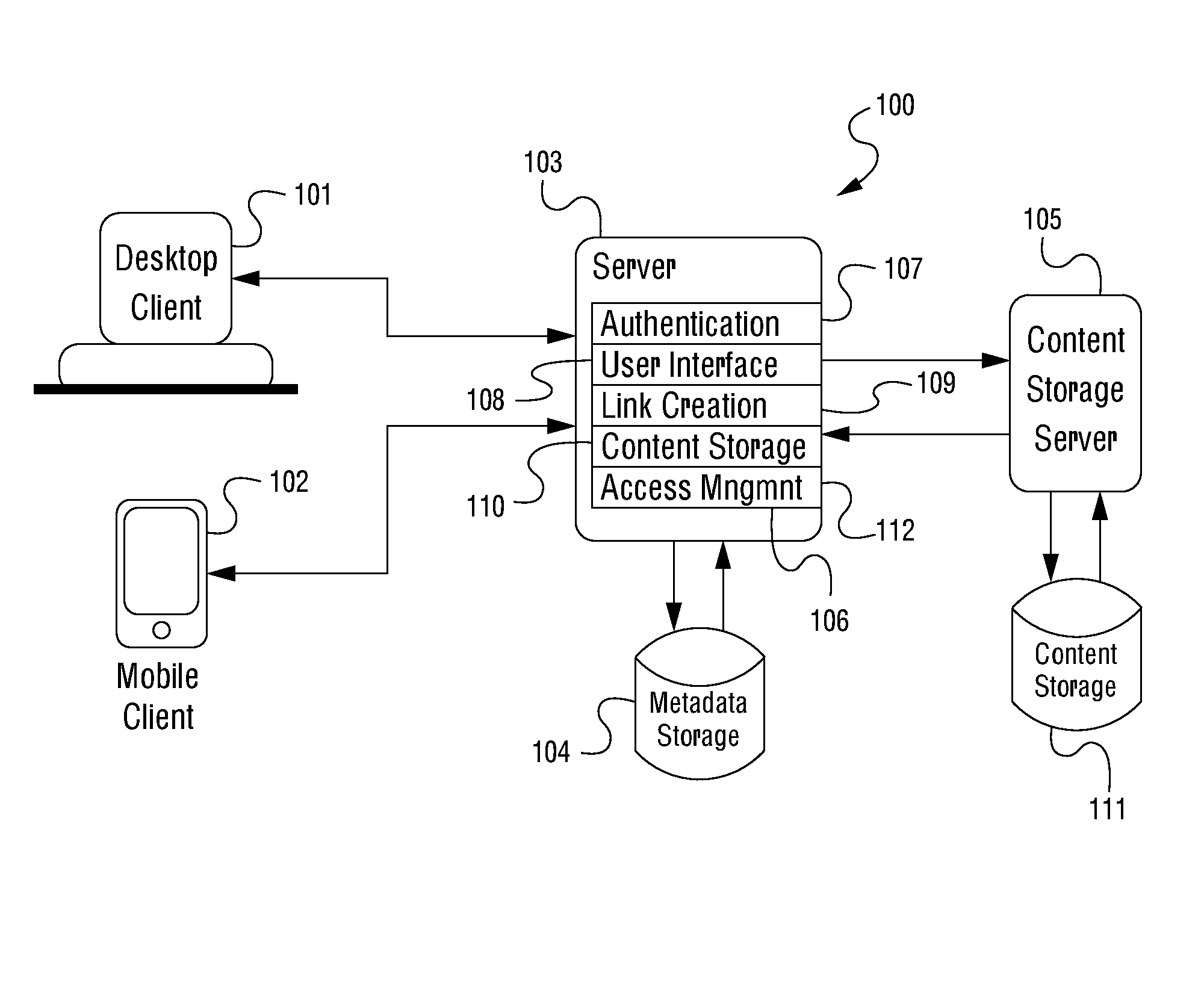
Systems and methods for implementing self-destructing content links
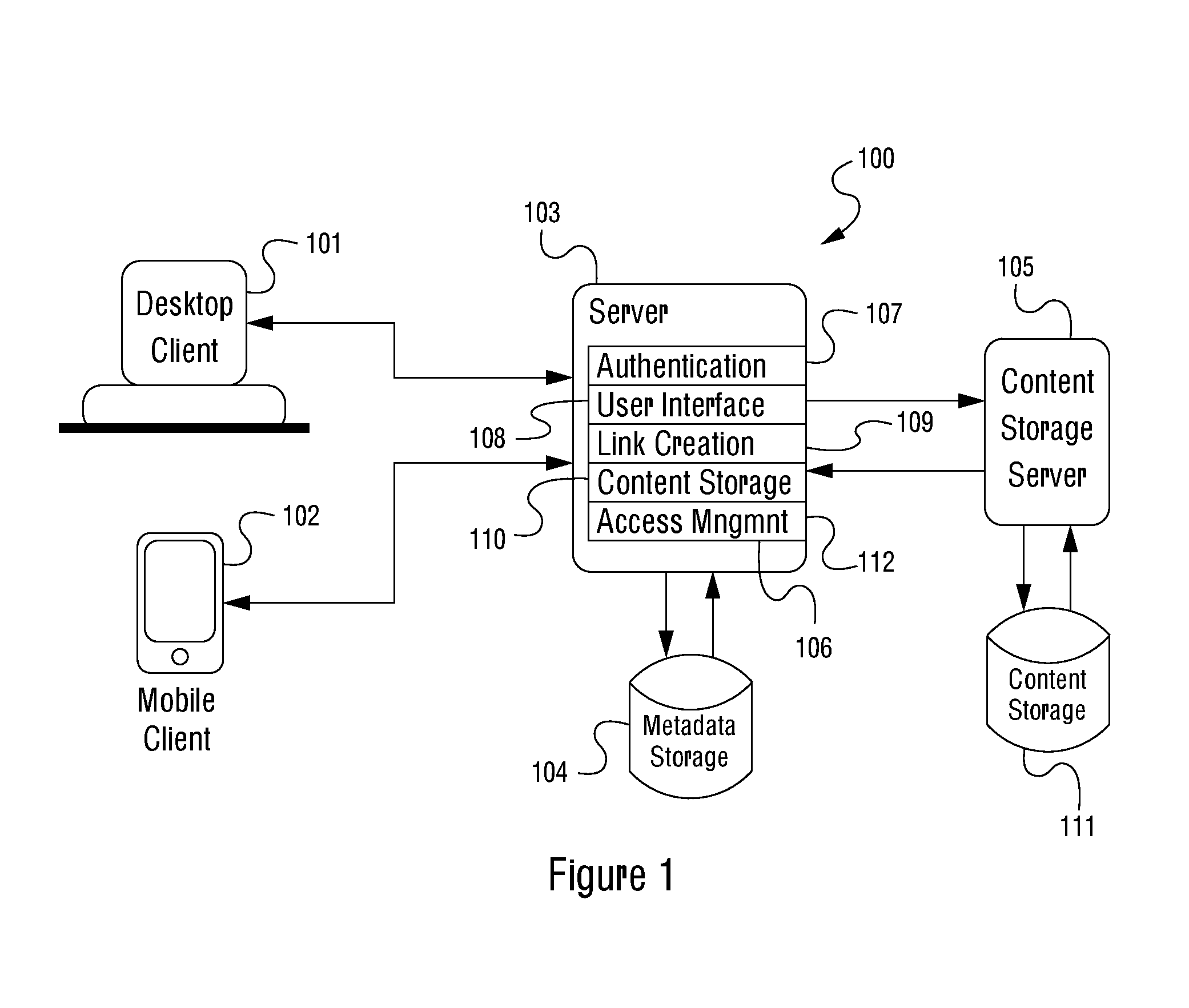
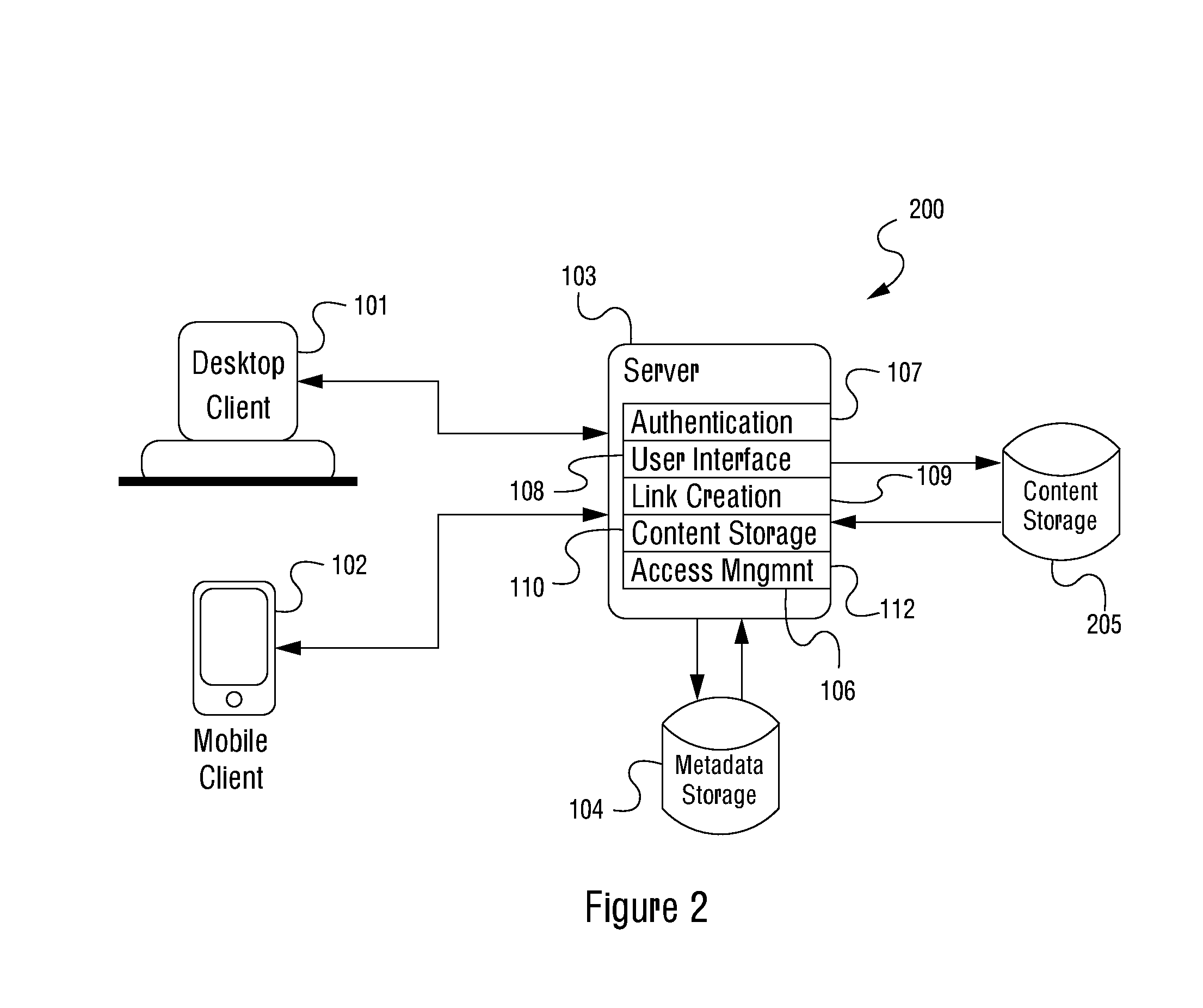
ActiveUS20150213236A1Eliminate the problemDigital data processing detailsAnalogue secracy/subscription systemsComputerized systemClient machine
A computer-implemented method performed in a computerized system incorporating a central processing unit, a network interface and a memory, the computer-implemented method involving: using the network interface to receive a content and an associated access restriction from a client computer system directly accessible by a user; causing the received content to be stored in a content storage system; using the central processing unit to generate a self-destructing content link for the stored content based on the received associated access restriction, wherein the generated self-destructing content link is configured to de-activate pursuant to the received associated access restriction; storing a metadata corresponding to the generated self-destructing content link for the stored content; and using the network interface to provide the generated self-destructing content link to the client computer system. The content storage system may be an online content storage system accessible via a network or a local content storage system.
Owner:AURA SUB LLC
Autonomic and apoptopic systems in computing, robotics, and security
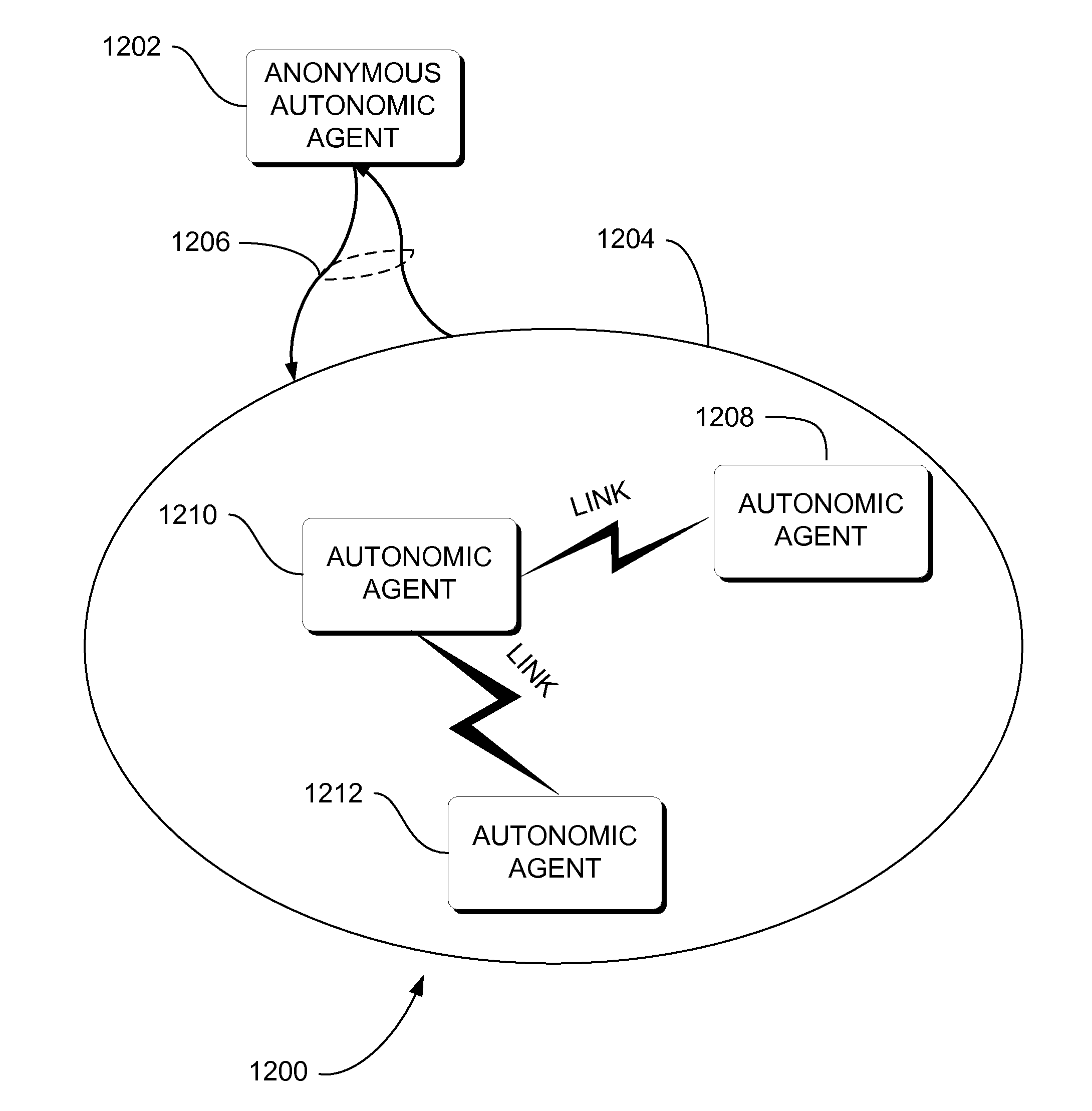
InactiveUS20130080360A1Effective recoveryLevel avoidComputer controlSimulator controlRoboticsSelf-destruct
Autonomic computing, robotics, and security devices, systems, and methods are provided. Agents of the system can communicate with one another and can self-destruct under event conditions that would render the agent detrimental to the overall system.
Owner:NASA
Social content integration
InactiveUS20150365395A1Digital data processing detailsMultiple digital computer combinationsPasswordIntegration platform
Herein disclosed is an integrated platform comprising at least one social network and one password to access the platform and the at least one social network. In some embodiments, the at least one social network comprises the integrated platform itself as a social network, Google+, Instagram, LinkedIn, Facebook, Twitter, Tumblr, or combinations thereof. In some embodiments, the integrated platform provides full function of the at least one social network. In some embodiments, the full function comprises logging in, registering, saving log-ins, following, posting, chatting, inviting friends, adding friends, sending messages, sending or uploading photos or videos, notifying, sharing, aggregating news feed. In some embodiments, the integrated platform provides a chatting function with a user-dictated timed self-destruct feature or instant self-destruct feature by shaking a mobile device on which the platform is installed. In some embodiments, the chatting function comprises photo or video correspondence.
Owner:WHATAGOOBER
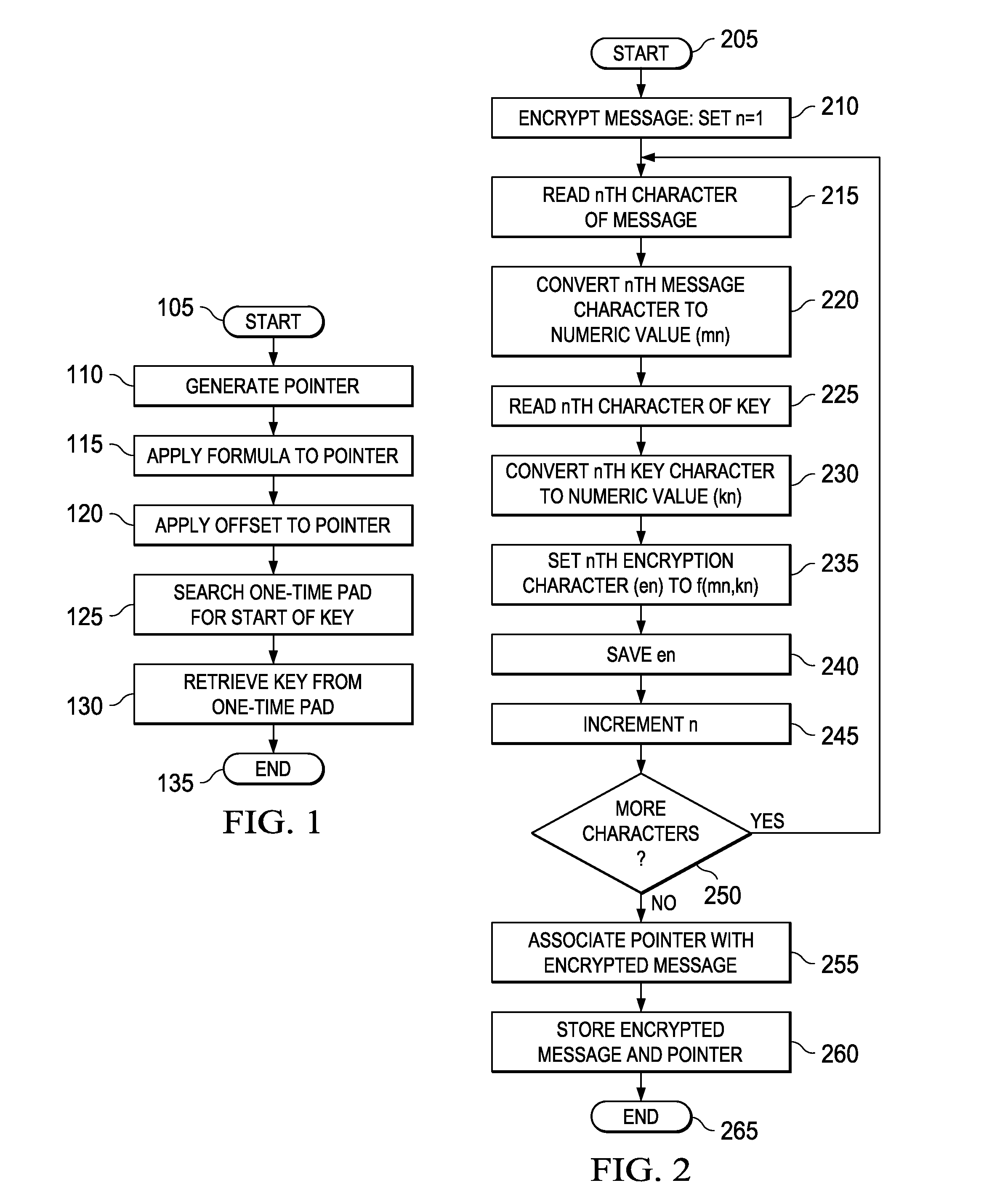
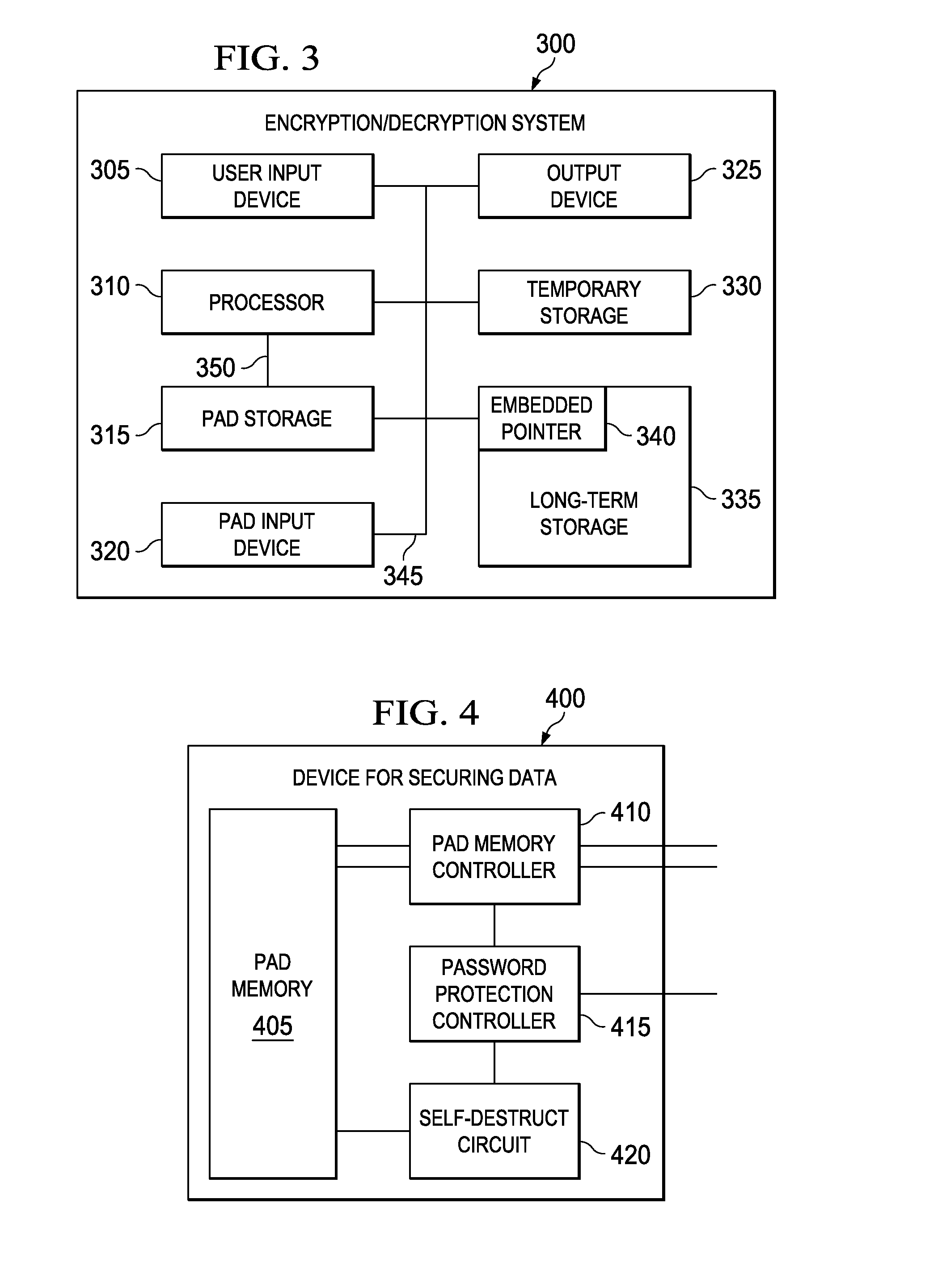
Device for data security using user selectable one-time pad
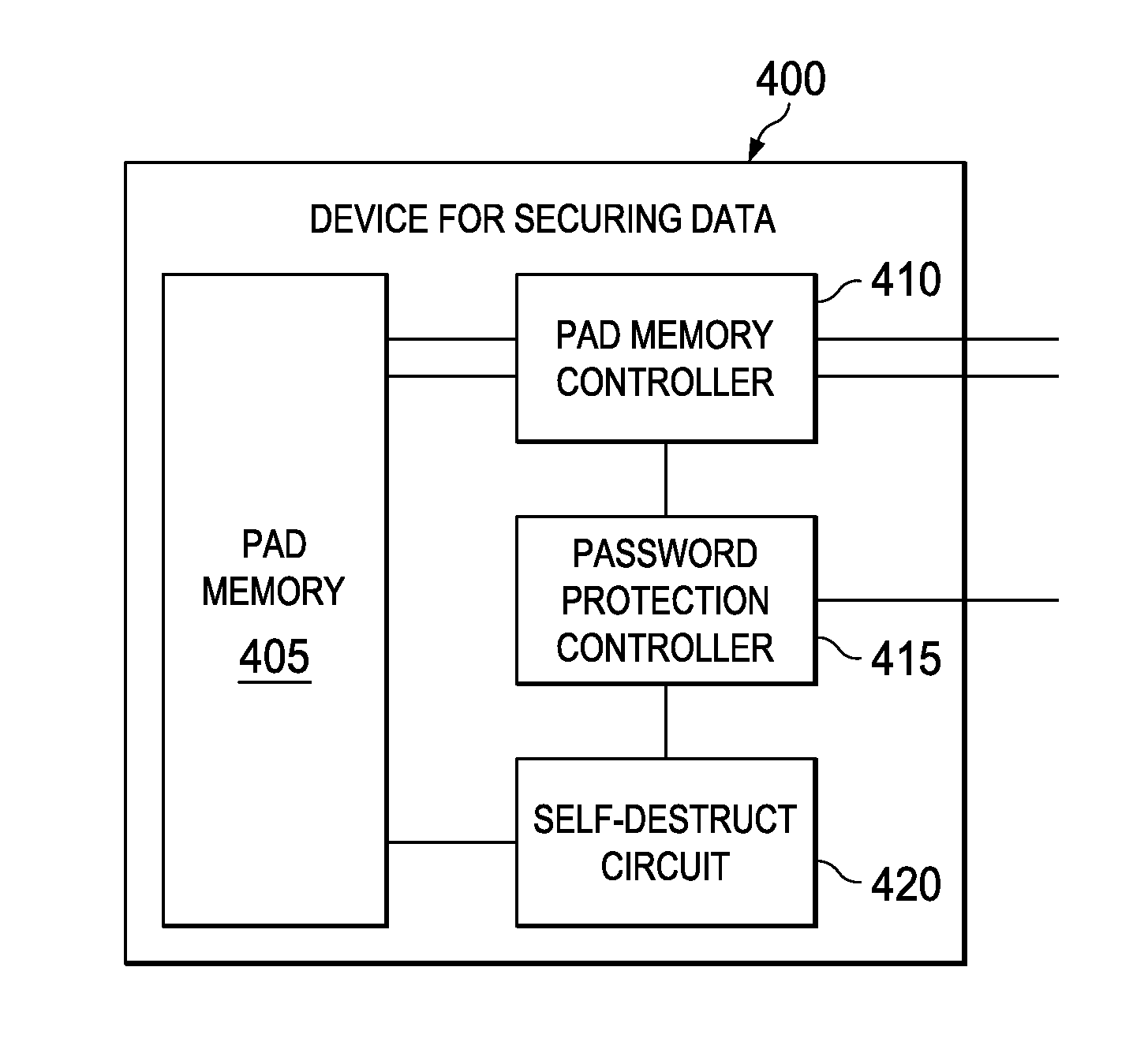
InactiveUS20100250968A1Digital data processing detailsUnauthorized memory use protectionPasswordMemory controller
Devices for securing data and method of managing a one-time pad stored in nonvolatile memory of a device. In one embodiment, the device for securing data includes: (1) a nonvolatile memory, (2) a nonvolatile memory controller coupled to the nonvolatile memory and configured to cooperate with the nonvolatile memory to make a key available when a password provided to the device is valid and (3) a self-destruct circuit coupled to the nonvolatile memory and configured to corrupt at least part of the nonvolatile memory when the password is invalid.
Owner:LSI CORPORATION
Method and apparatus for self-destruct frangible projectiles
The present invention discloses and claims an apparatus and method for delivering a wide array of selected agents to a target from stand-off distances. The apparatus includes a self-destruct frangible projectile made of primary, binding, and active components. The primary component generally has a specific gravity greater than lead, and the binding component generally has a specific gravity less than lead. The active component may be a metal for penetrating the target, a dye for optically marking the target, or another specially selected agent for delivery to the target, depending on the particular embodiment. The frangible projectile self-destructs upon contact with the target, in proximity to the target, or after passing the target, depending on the particular embodiment.
Owner:NEWTEC SERVICES GROUP
Method and system for protecting data
InactiveUS7717326B2Electronic editing digitised analogue information signalsRecord information storageComputer hardwareElectromagnetic pulse
Owner:IBM CORP
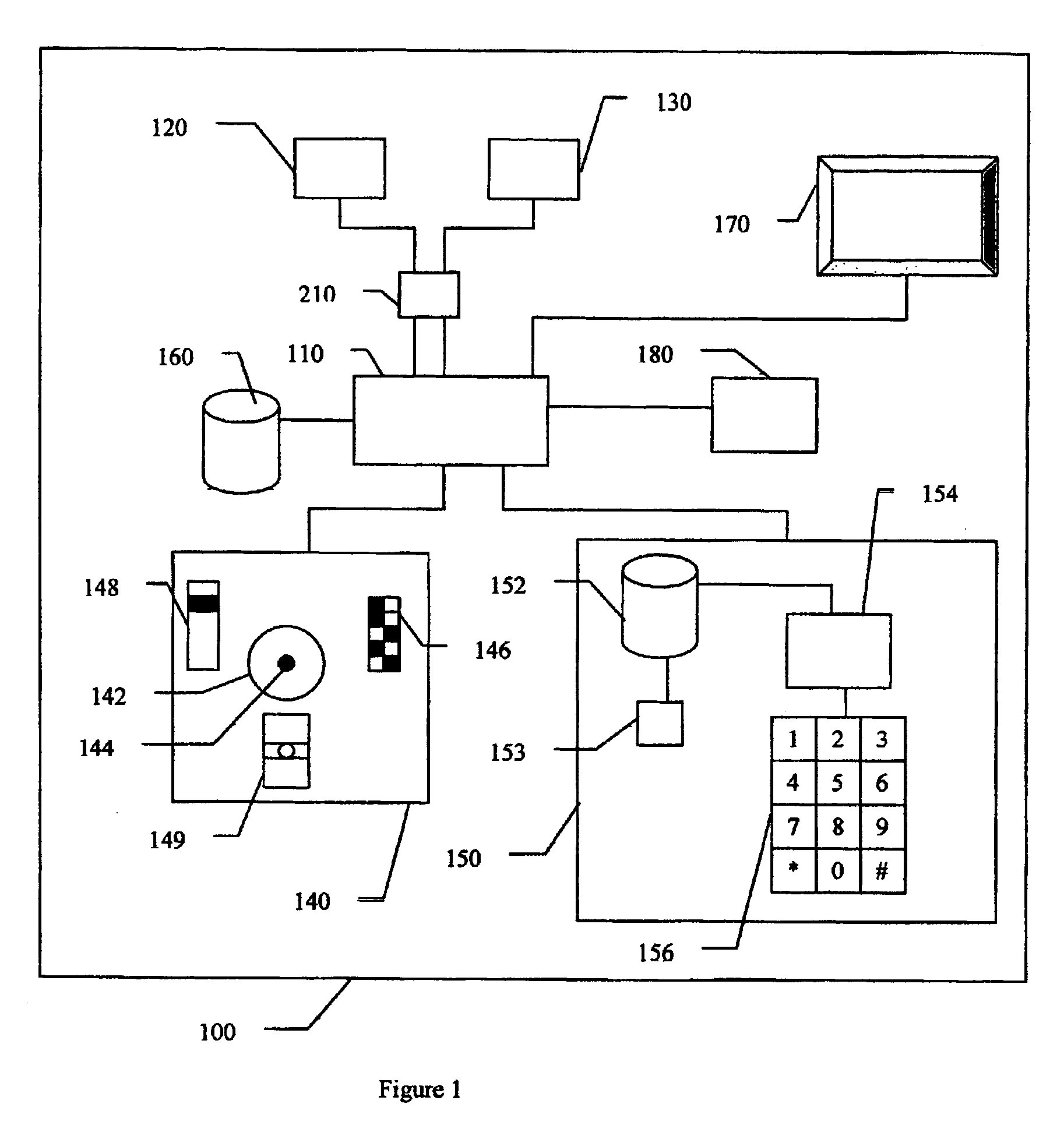
Biometric identification device and methods for secure transactions
InactiveUS20080319915A1Reduce chanceStrong assuranceElectric signal transmission systemsImage analysisInternet privacyIdentification device
The invention is directed towards methods, systems and apparatuses, see FIG. 1, (100) for providing secure and private interactions. The invention provides capability for verifying the identity of a party initiating an electronic interaction with another party through data input module (140) which is verified by the identity verification module (150), which further includes a self-destruct mechanism (153). Embodiments of the invention include secure methods for conducting transactions and for limiting the transfer and distribution of personal data to only those data that are absolutely necessary for the completion of the transactions. The invention facilitates the transfer of additional personal data contingent upon an agreement that appropriately compensates the provider of the personal data.
Owner:APPLE INC
Neilsbed seal ring assembling device of the safety type self-destructing syringe assembly machine
InactiveCN101081320AIncrease productivityReduce manufacturing costInfusion syringesInfusion needlesEngineeringTransfer mechanism
The present invention provides one device for assembling needle stand sealing ring in safe self-destructing syringe assembling machine, and belongs to the field of mechanical technology. The device for assembling needle stand sealing ring set between the turntable for fixing needle stand and the feeding mechanism for conveying sealing ring includes one frame, one ring opening mechanism, one ring transferring mechanism between the frame and the ring opening mechanism, and one ring shifting mechanism for setting the ring on the needle stand. The device has high assembling efficiency, high safety, being hygienic, and other features.
Owner:王兴章
Sensor and heater for stimulus-initiated self-destructing substrate
ActiveUS20180033742A1ThyristorSemiconductor/solid-state device detailsSelf-destructElectrical and Electronics engineering
A self-destructing device includes a stressed substrate with a heater thermally coupled to the stressed substrate. The device includes a power source and trigger circuitry comprising a sensor and a switch. The sensor generates a trigger signal when exposed to a trigger stimulus. The switch couples the power source to the heater in response to the trigger signal When energized by the power source, the heater generates heat sufficient to initiate self-destruction of the stressed substrate.
Owner:PALO ALTO RES CENT INC
Electronically expiring device
InactiveUS7048195B2Record carriers used with machinesTime interval measurement without driving mechanismStopped workTime segment
The present invention relates to a method and system for expiring a device after a predetermined time period has elapsed. A device, which contains its own internal time cell, is designed to stop working or self-destruct after a predetermined time period has expired. The device uses its own time cell so that the elapsed time period is not altered through an external time source. After the predetermined time period has elapsed, the device or a component of the device self-destructs when connected to a power source.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com