Patents
Literature
16027 results about "Processor register" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer architecture, a processor register is a quickly accessible location available to a computer's central processing unit (CPU). Registers usually consist of a small amount of fast storage, although some registers have specific hardware functions, and may be read-only or write-only. Registers are typically addressed by mechanisms other than main memory, but may in some cases be assigned a memory address e.g. DEC PDP-10, ICT 1900.
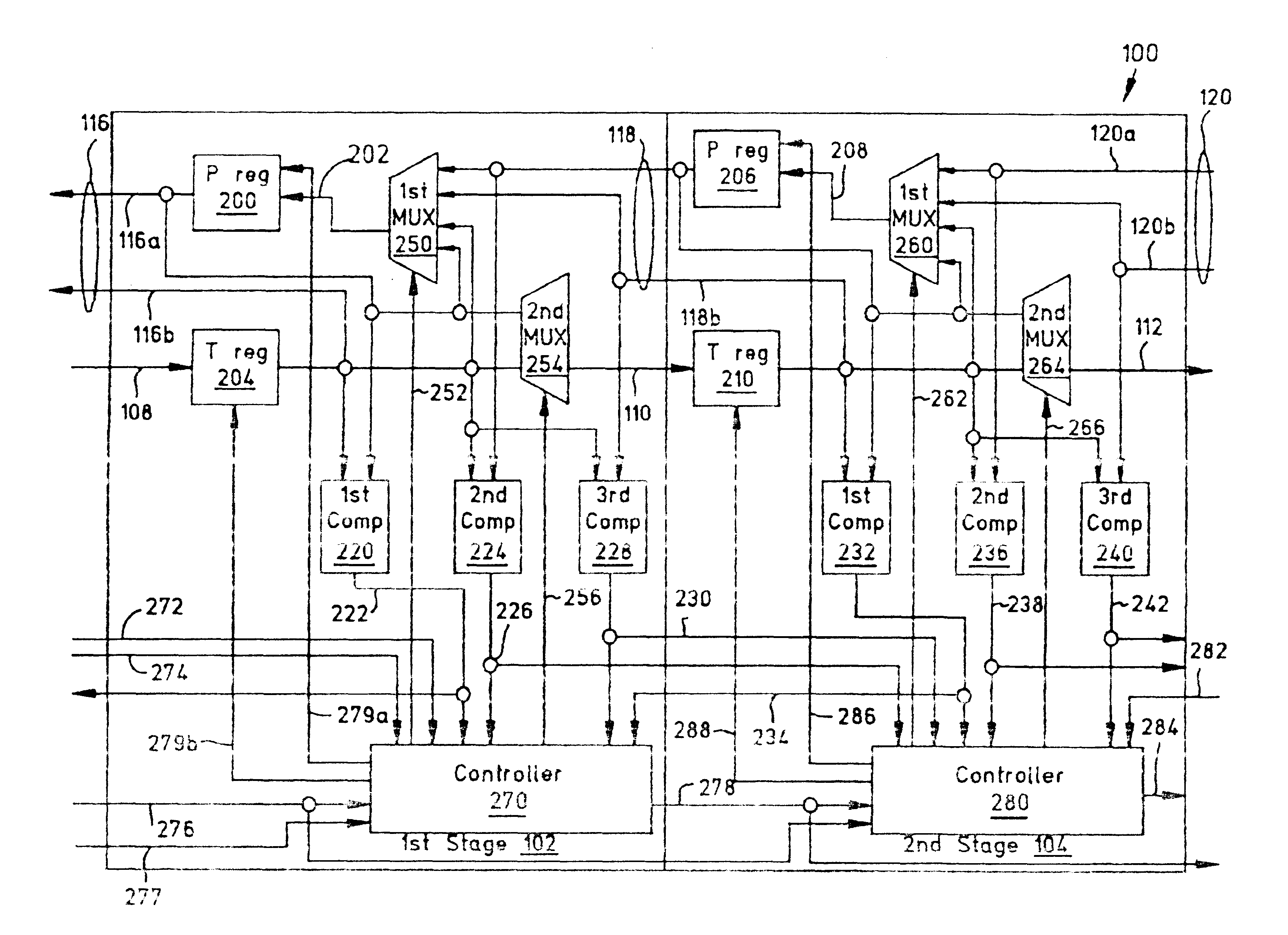
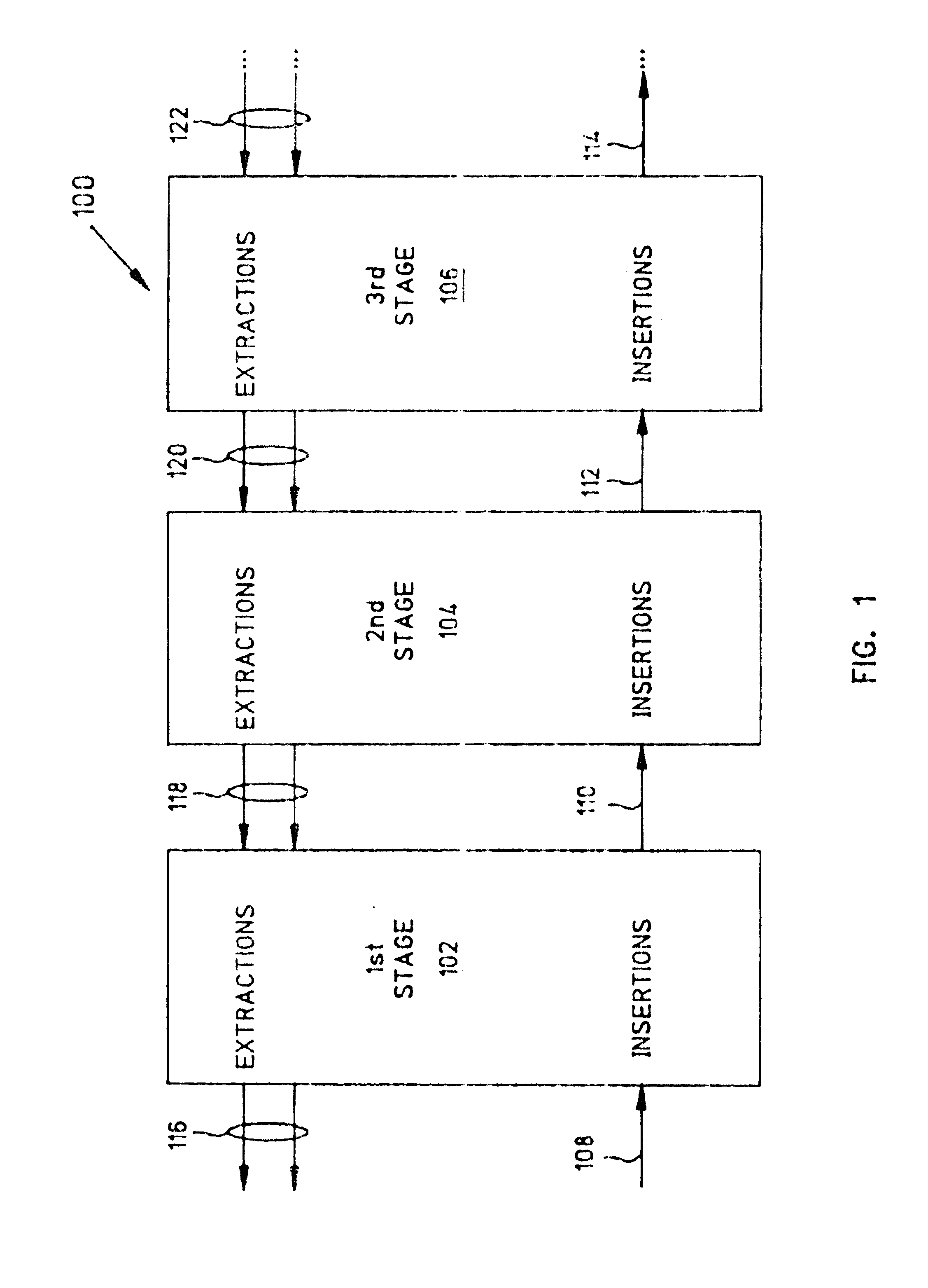
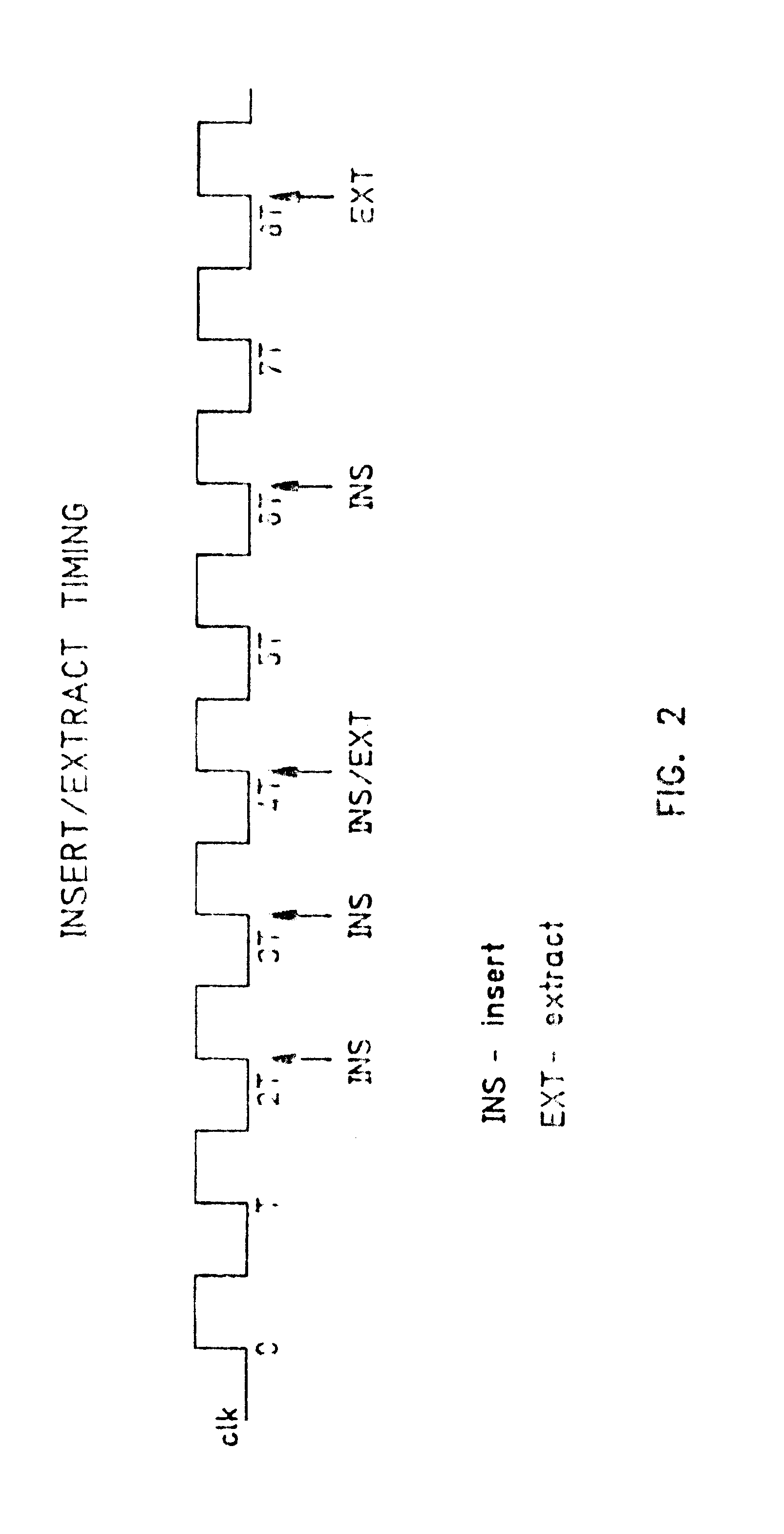
System and method for systolic array sorting of information segments
A system and method have been provided for sorting information segments in a packet / cell earliest deadline first queue circuit. The invention permits information segments to be inserted at a rate that is twice as fast as the maximum extraction rate. Pairs of permanent and temporary registers are organized into a hierarchical sequence of stages. Generally, information segments with lower field ranks move systolically through the stages to temporary registers in higher sequence stages. Information segments with higher field ranks move systolically through the stages to permanent registers lower in the sequence of stages. The invention permits the highest rank information segments to be sorted and extracted with great efficiency.
Owner:QUALCOMM INC
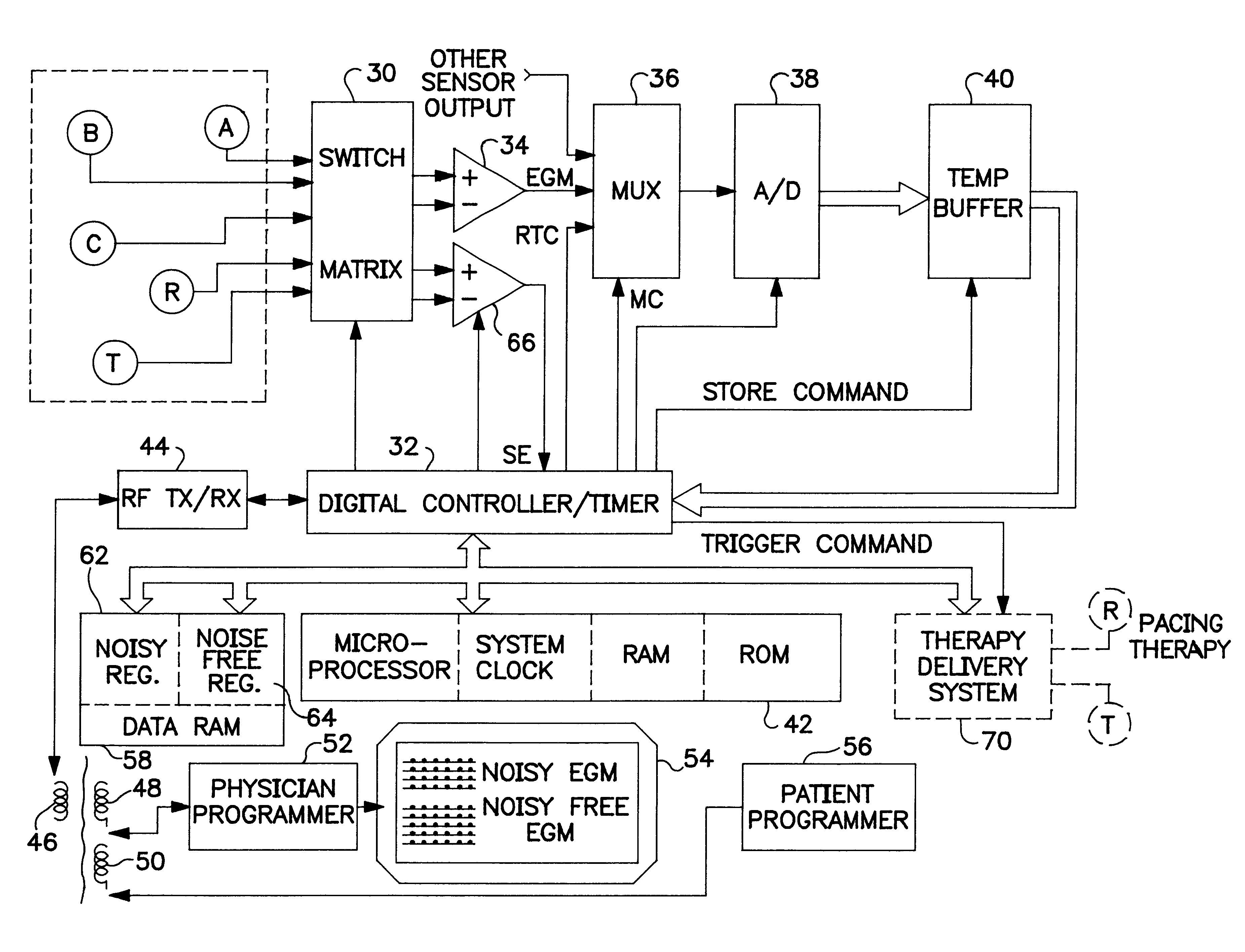
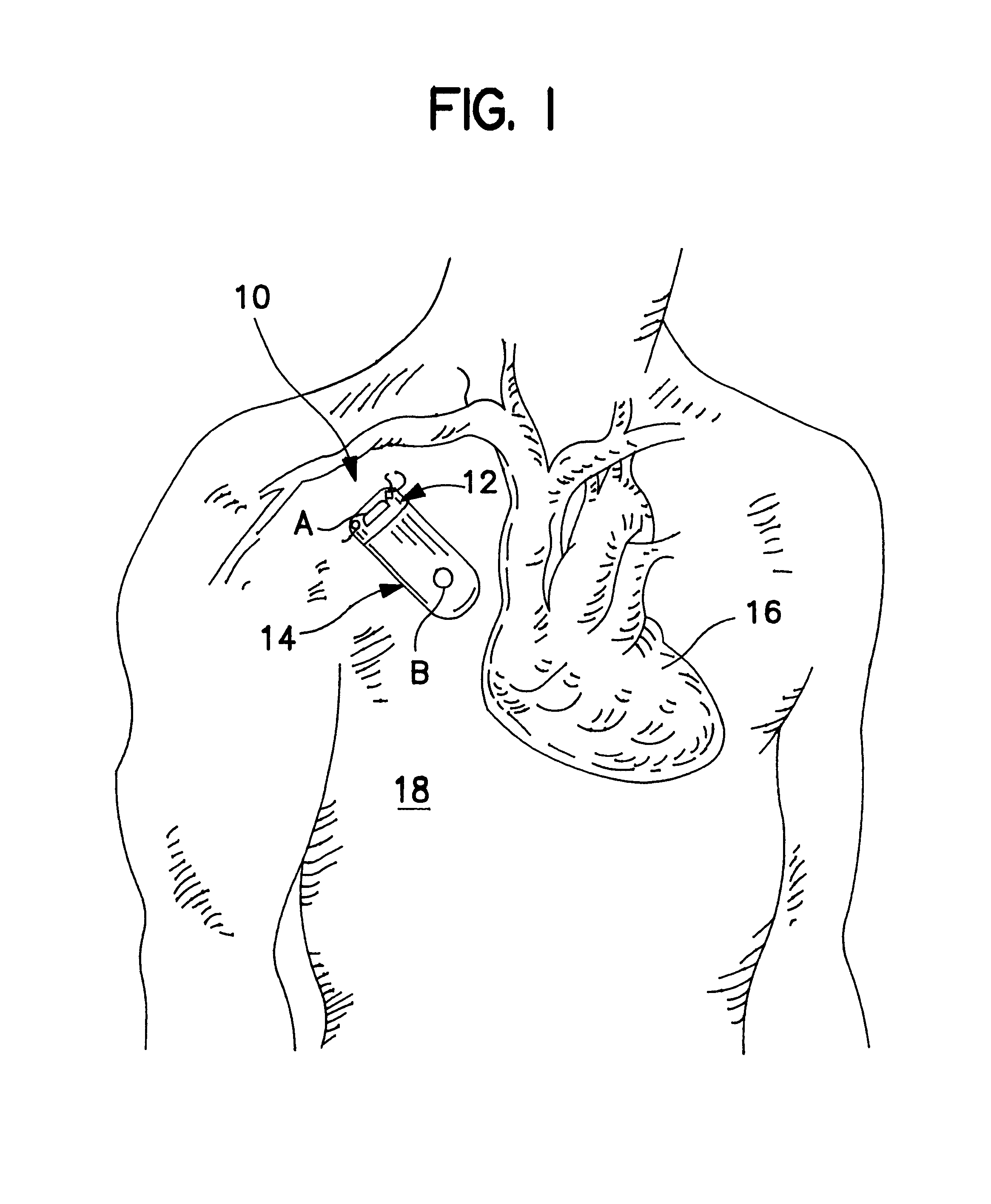
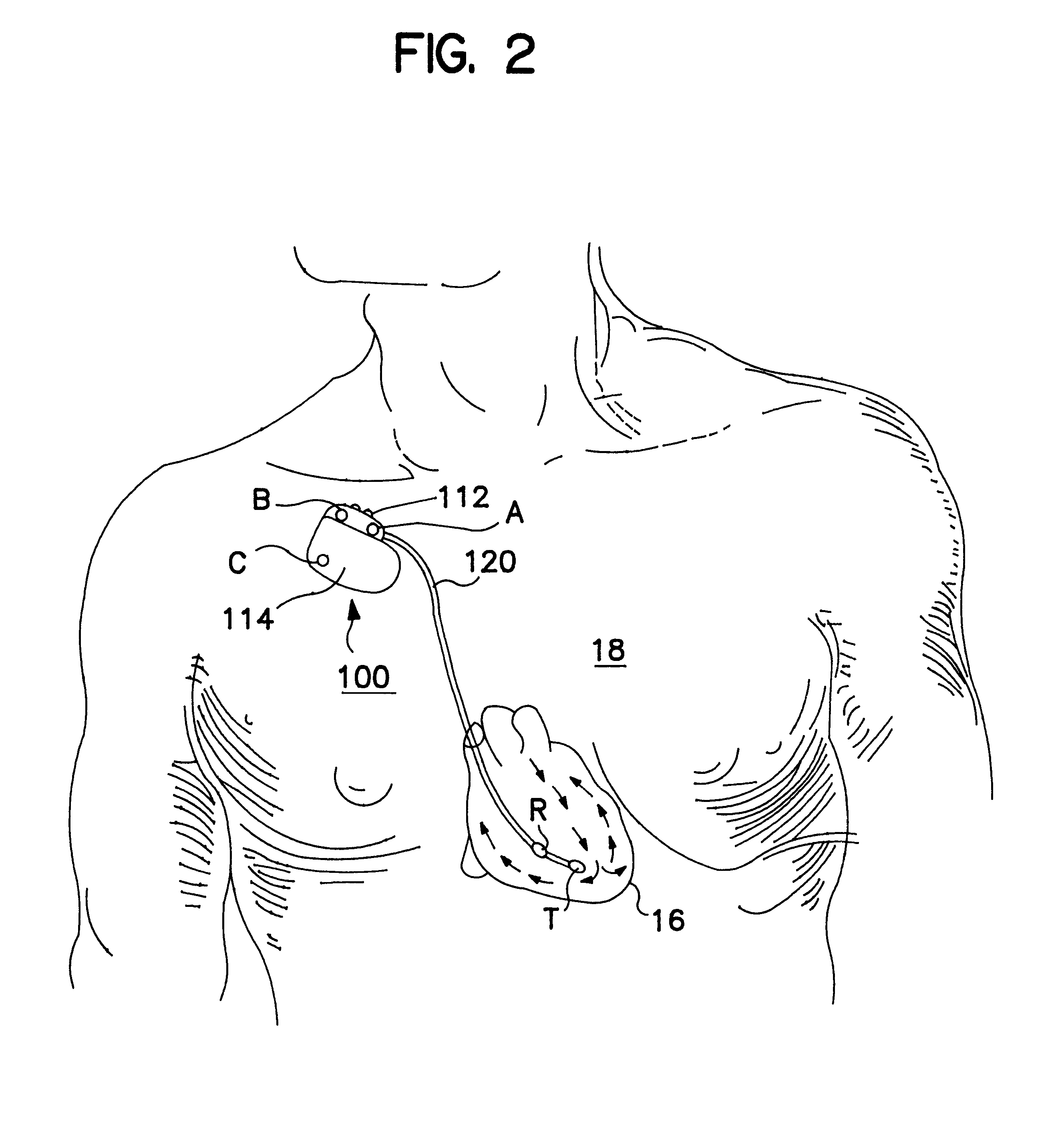
Implantable monitor
An implantable medical device (IMD) capable of monitoring physiologic data, distinguishing relatively noisy and noise free physiologic data, and recording noisy and relatively noise free segments of physiologic data in separate memory registers of a limited memory for retrieval and analysis at a later time. Preferably the physiologic data comprises the sampled EGM of the heart detected from sense electrode pairs that are implanted in the patient at sites where extraneous electrical noise, e.g., electromyographic signals, are also capable of being detected. The sense electrode pairs can constitute one or both sense electrodes located on or adjacent to the atrial and / or ventricular heart chambers and coupled to the IMD by a lead body or sense electrode pairs that are located remotely from the heart, e.g. at a subcutaneous implantation site of the IMD. A plurality of noisy EGM episode data registers store a corresponding plurality of noisy EGM episode data sets on a FIFO basis and another plurality of noise free EGM episode data registers to store a corresponding plurality of relatively noise free EGM episode data sets on a FIFO basis. Any form of discrimination of noisy data from relatively noise free data can be employed at the time of recording, but because the stored EGM episode data sets are subsequently viewed and analyzed by a physician, discrimination with absolute certainty is not required, and the physician can alter the detection criteria to fine tune it.
Owner:MEDTRONIC INC
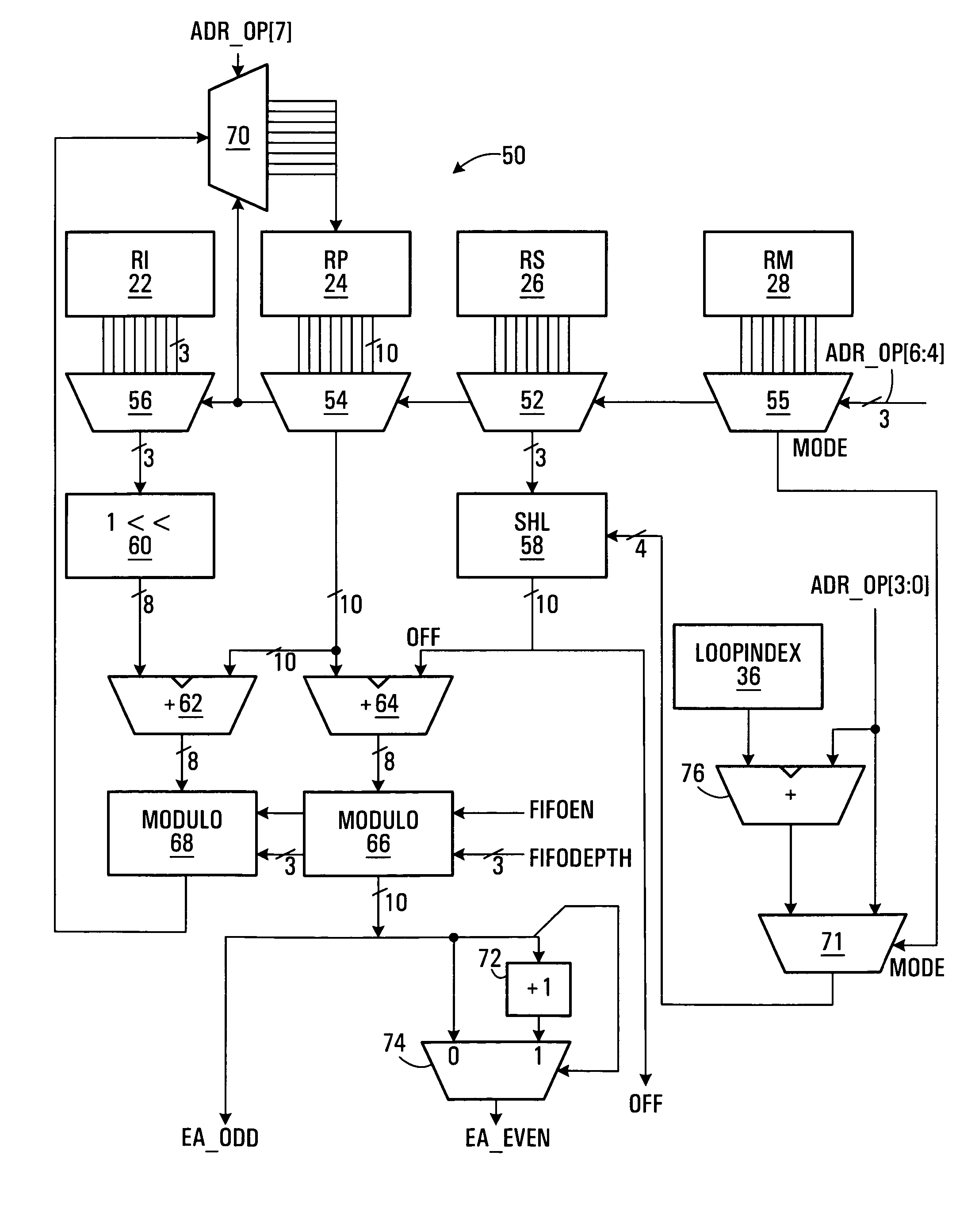
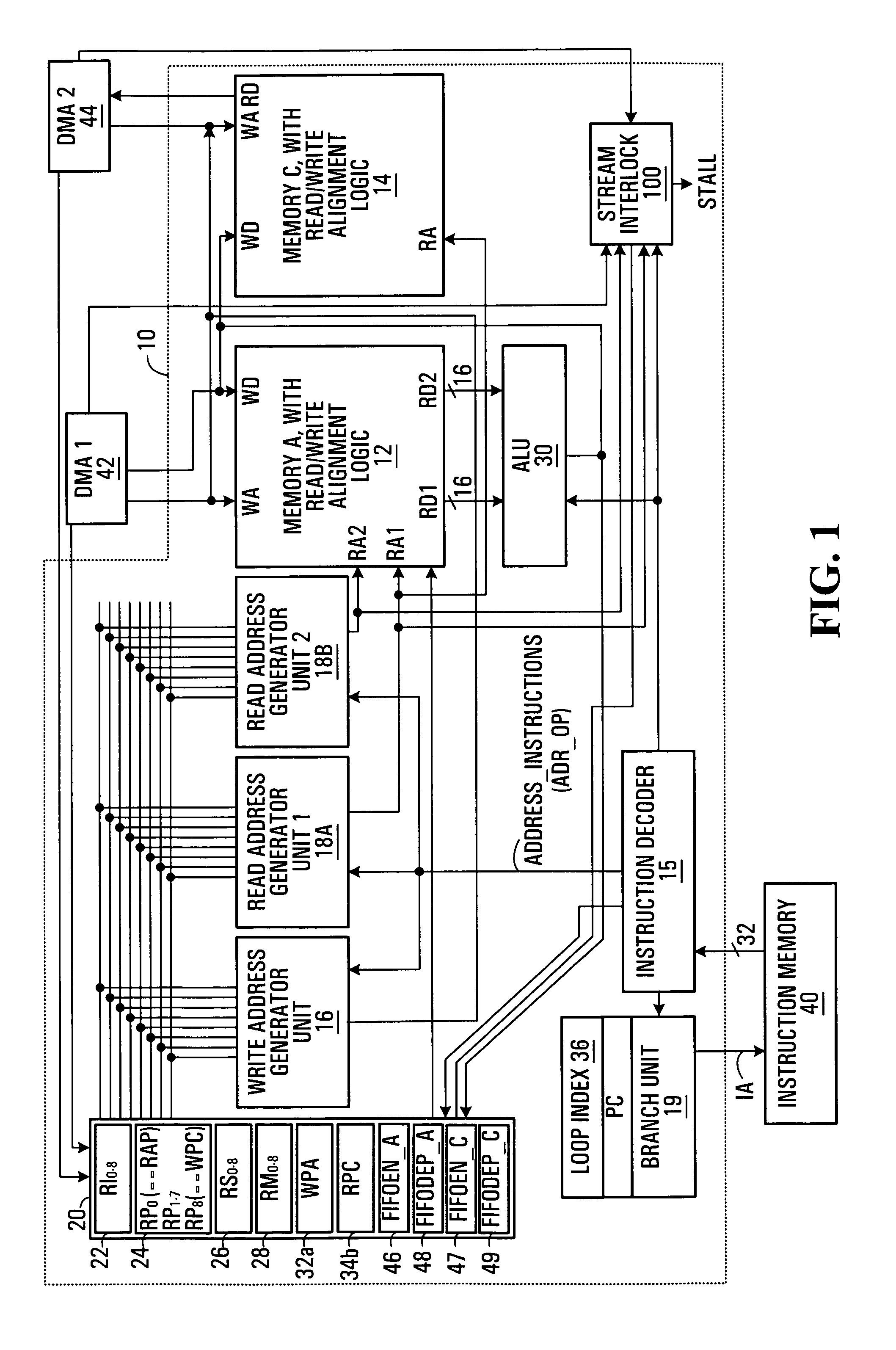
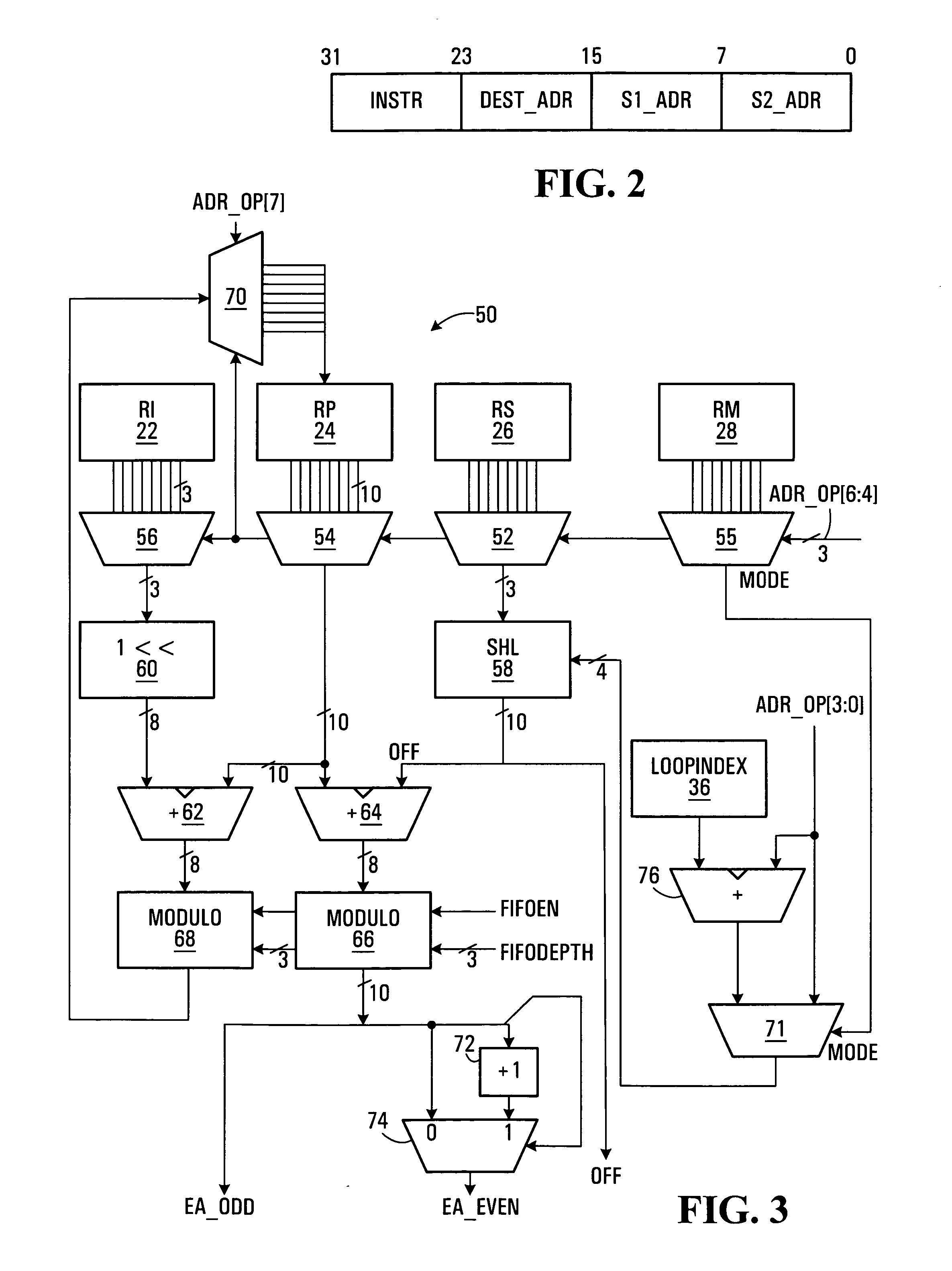
SIMD processor and addressing method
InactiveUS20060047937A1Without unduly consuming processor resourcesMemory adressing/allocation/relocationMicro-instruction address formationMemory addressProcessor register
A single instruction, multiple data (SIMD) processor including a plurality of addressing register sets, used to flexibly calculate effective operand source and destination memory addresses is disclosed. Two or more address generators calculate effective addresses using the register sets. Each register set includes a pointer register, and a scale register. An address generator forms effective addresses from a selected register set's pointer register and scale register; and an offset. For example, the effective memory address may be formed by multiplying the scale value by an offset value and summing the pointer and the scale value multiplied by the offset value.
Owner:AVAGO TECH INT SALES PTE LTD
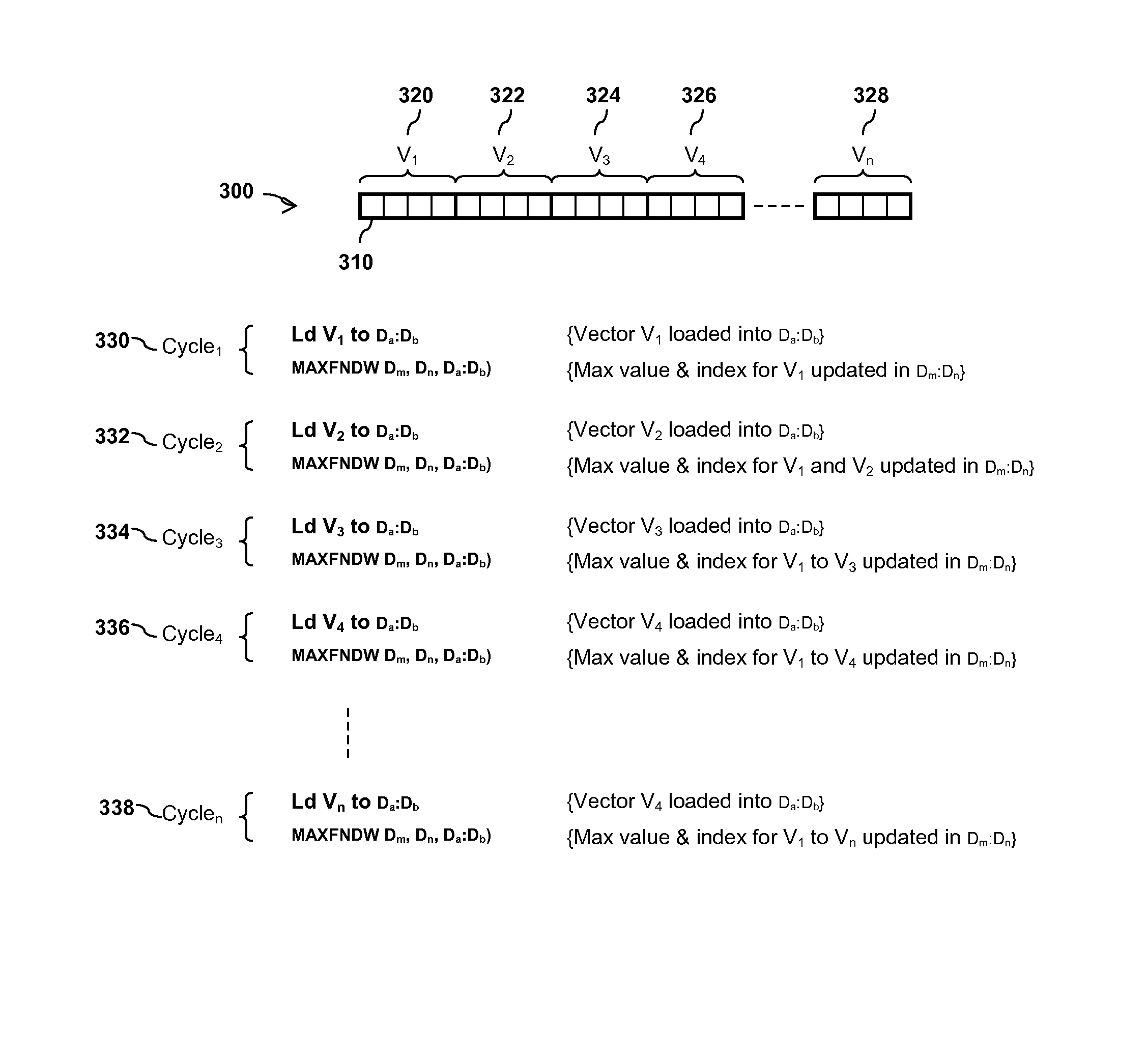
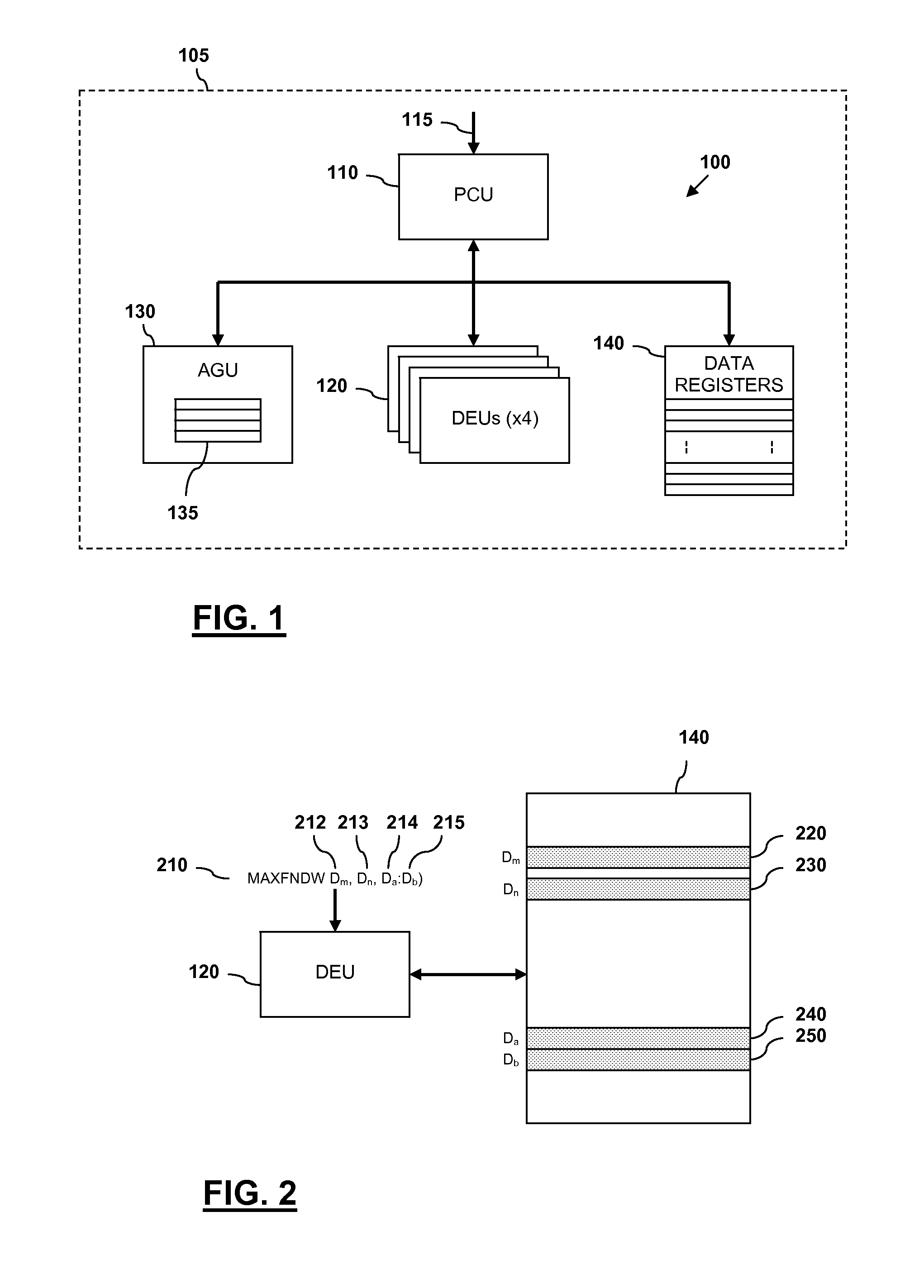
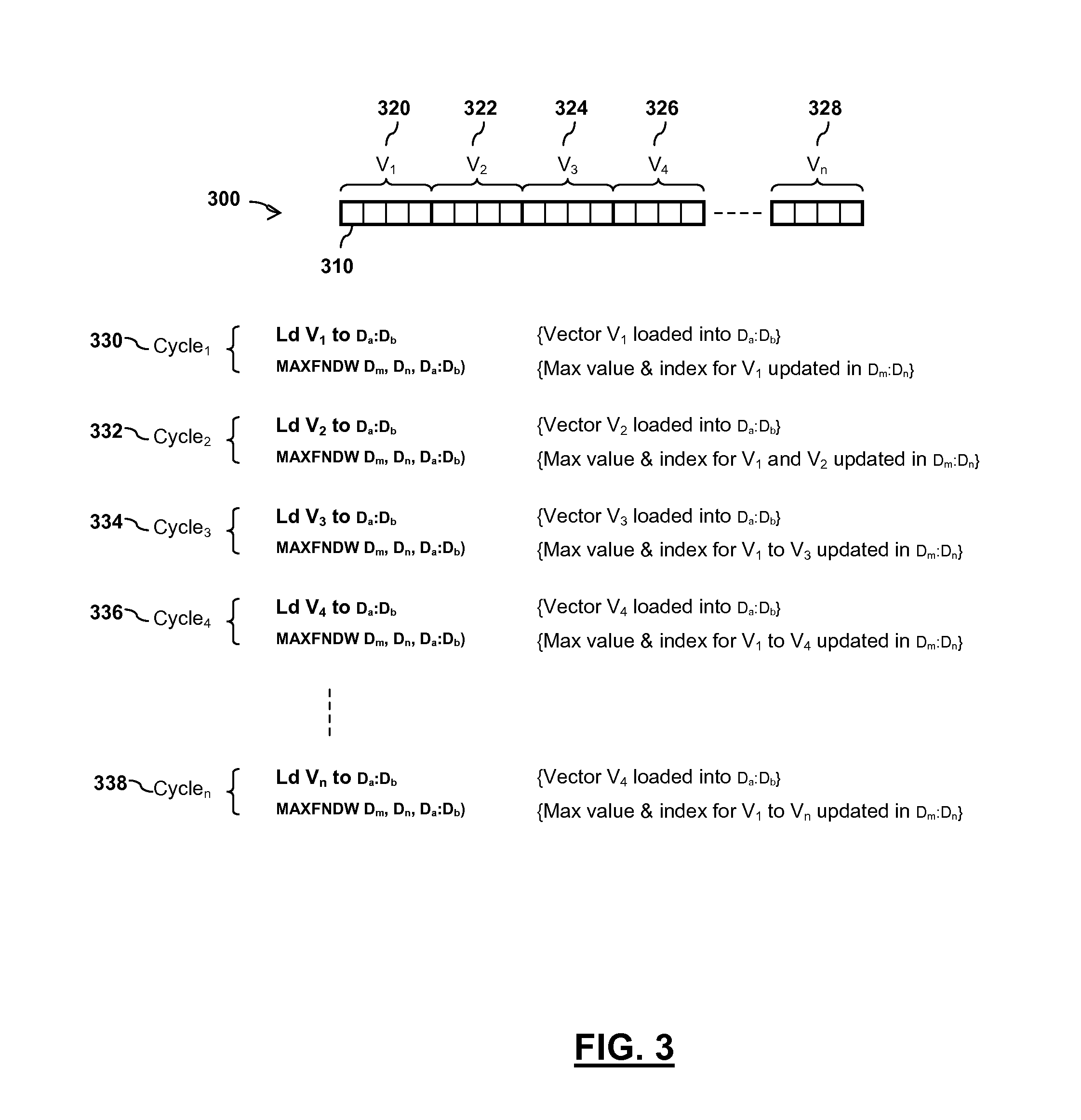
Integrated circuit device and method for determining an index of an extreme value within an array of values
InactiveUS9165023B2Digital data information retrievalDigital data processing detailsProcessor registerComputer module
An integrated circuit device comprises at least one digital signal processor, DSP, module, the at least one DSP module comprising a plurality of data registers and at least one data execution unit, DEU, module arranged to execute operations on data stored within the data registers. The at least one DEU module is arranged to, in response to receiving an extreme value index instruction, compare a previous extreme value located within a first data register set of the DSP module with at least one input vector data value located within a second data register set of the DSP module, and determine an extreme value thereof. The at least one DEU module is further arranged to, if the determined extreme value comprises an input vector data value located within the second data register set, store the determined extreme value in the first data register set, determine an index value for the determined extreme value, and store the determined index value in the first data register set.
Owner:NXP USA INC
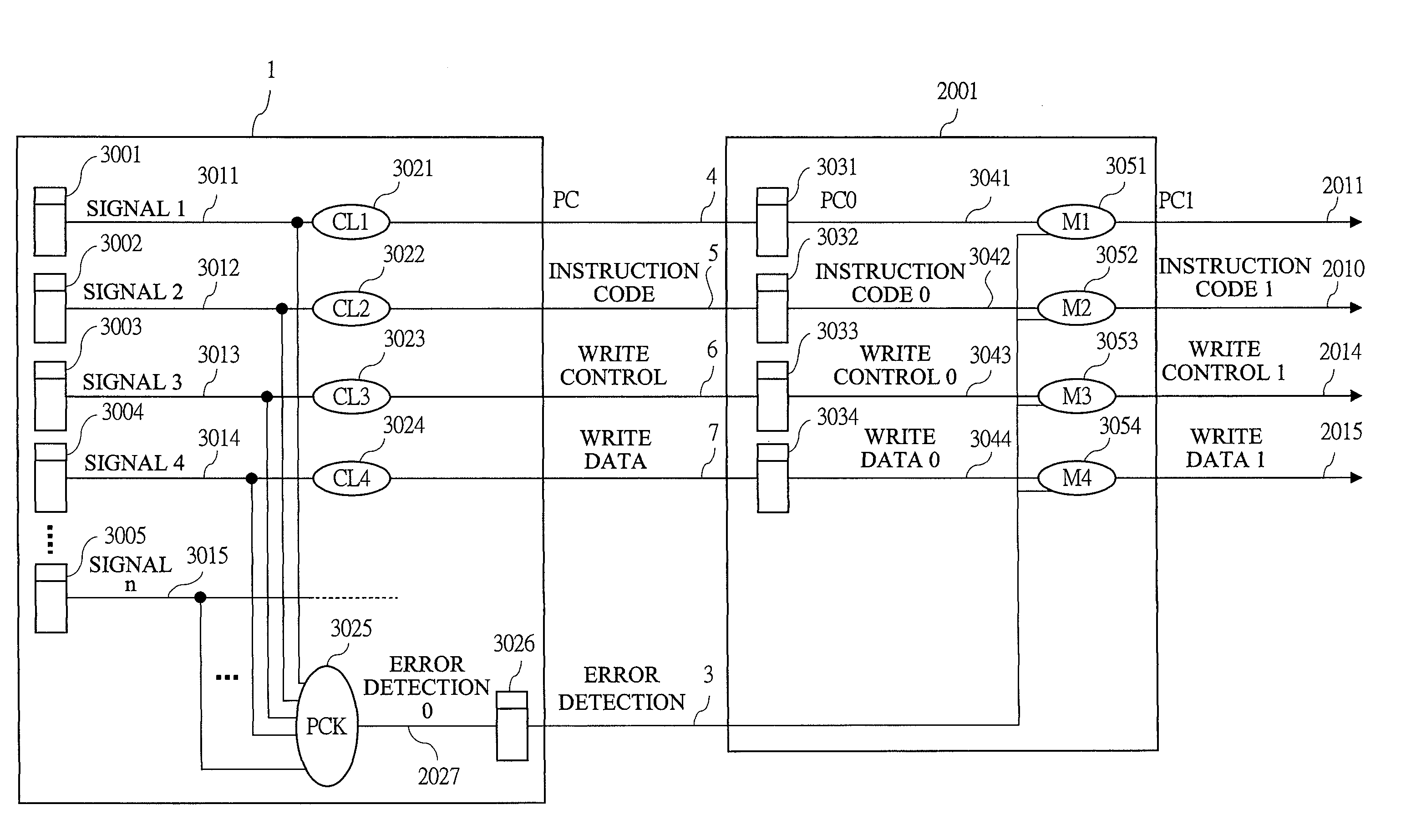
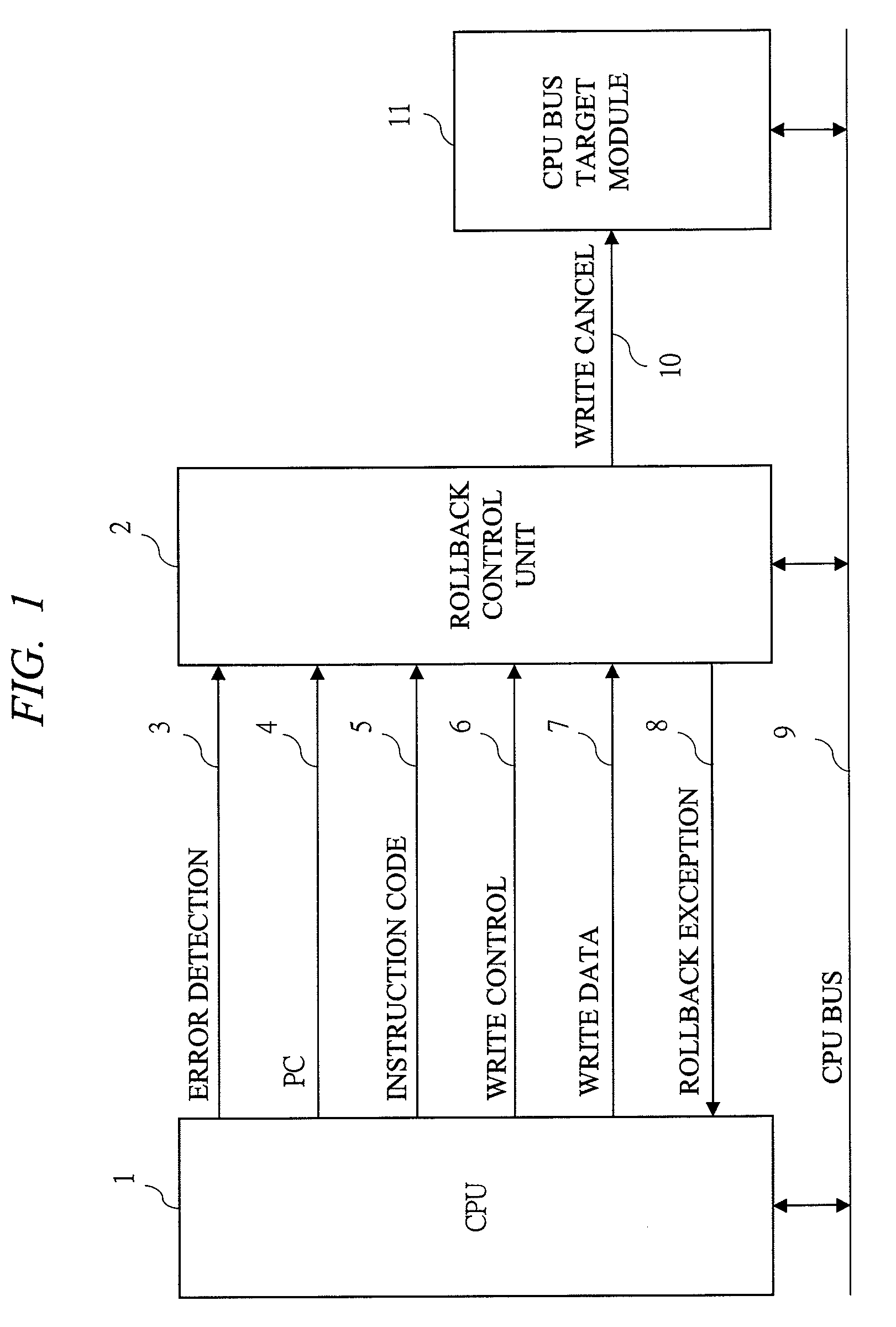
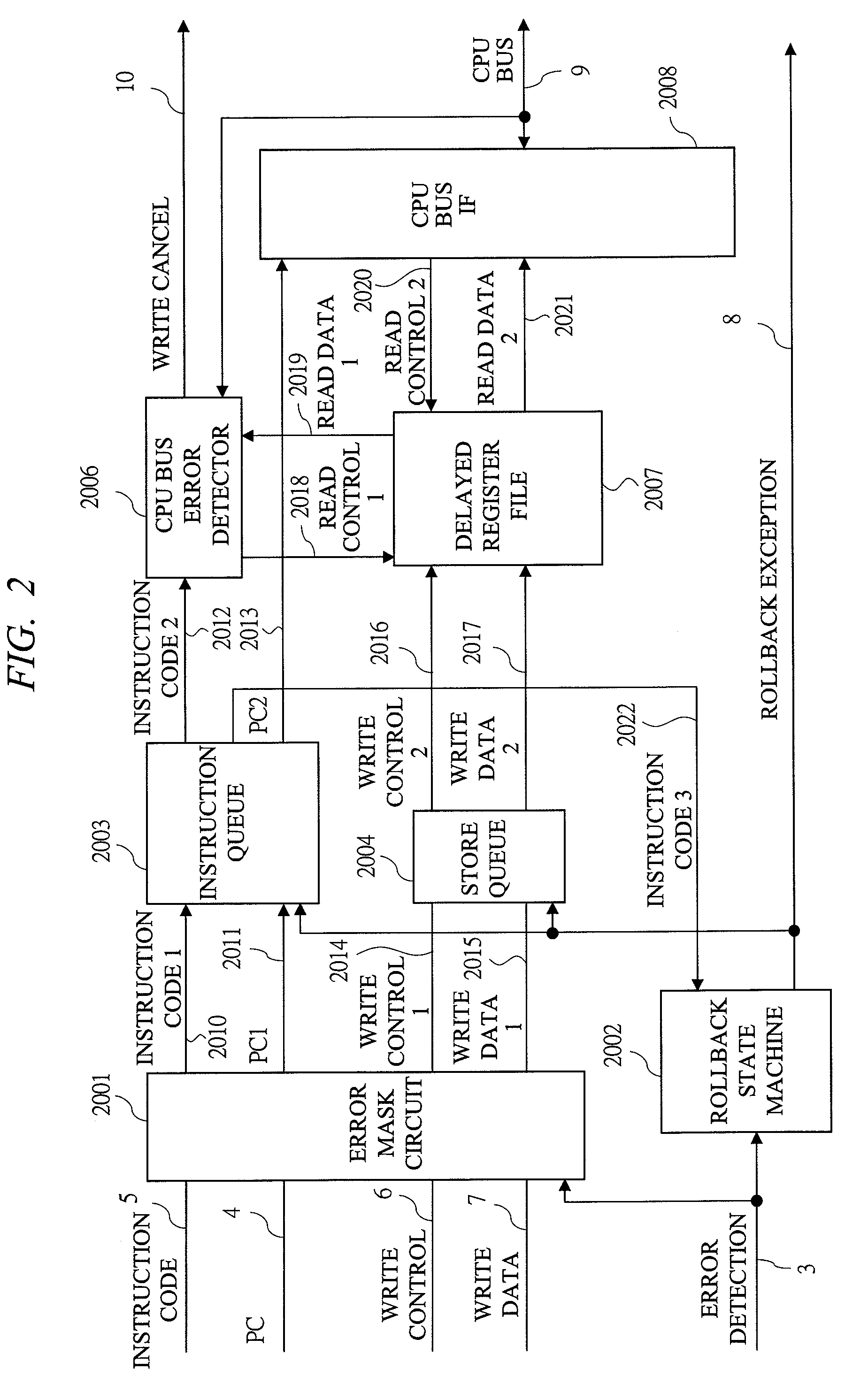
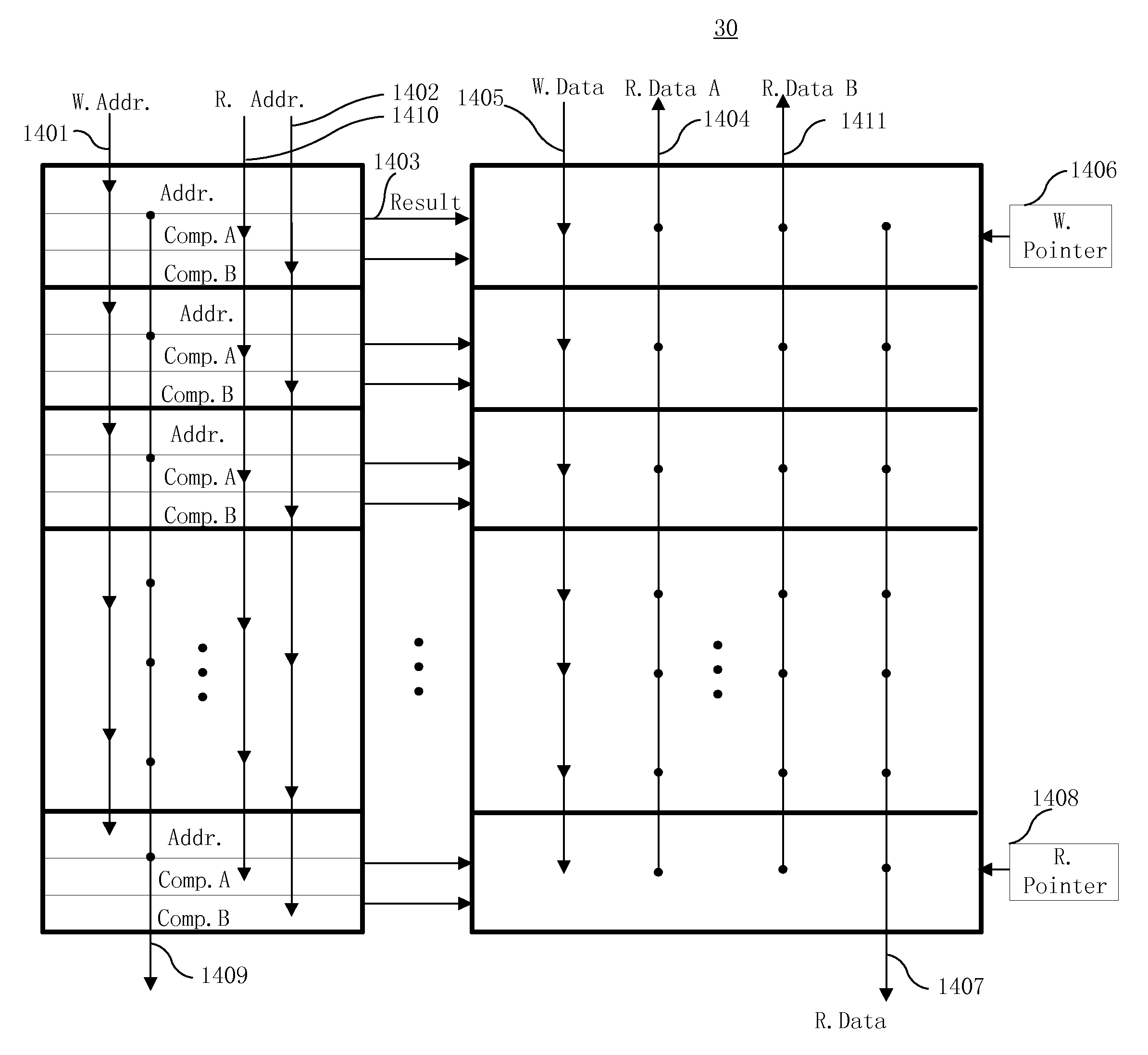
Error correction method with instruction level rollback
This method is an error correction method such that, when an error is detected in a CPU with pipeline structure, a content of a register file is restored by a delayed register file which holds an execute completion state of an [Instruction N] correctly executed before this error, and a rollback control that re-executes an instruction from the [Instruction N+1] which is the next instruction of the [Instruction N] is performed. The method collects a parity check result of arbitrary Flip-Flops existing inside the CPU, and detects an error. As a result, the content of the register file is restored into the instruction execute completion state preceding to the instruction range likely to malfunction by the error, and the instruction can be roll backed from the beginning of the instruction range likely having malfunctioned by the error.
Owner:RENESAS ELECTRONICS CORP
Processor-cache system and method
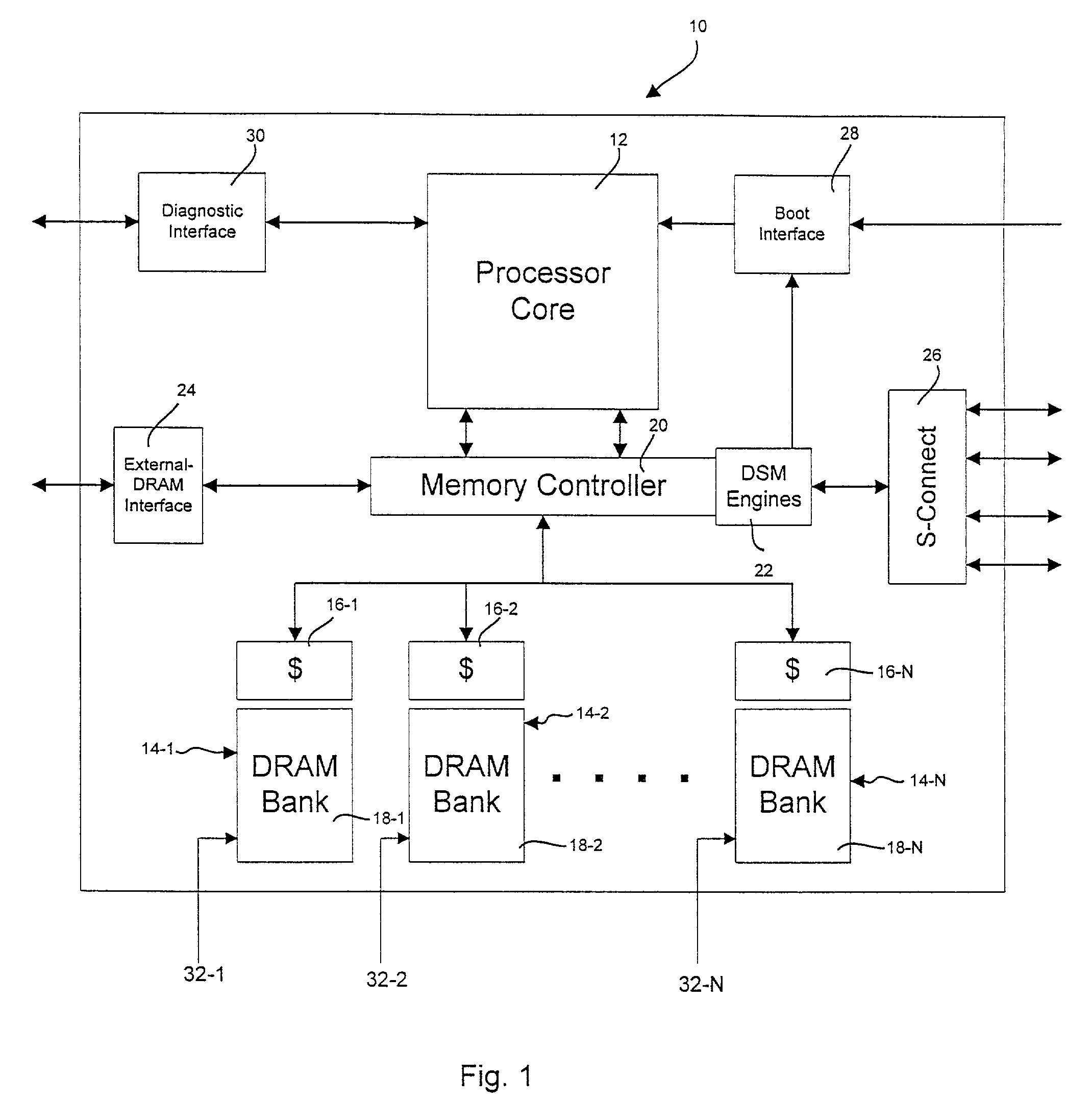
ActiveUS9047193B2Shorten the counting processEfficient and uniform structureEnergy efficient ICTRegister arrangementsAddress generation unitProcessor register
A digital system is provided. The digital system includes an execution unit, a level-zero (L0) memory, and an address generation unit. The execution unit is coupled to a data memory containing data to be used in operations of the execution unit. The L0 memory is coupled between the execution unit and the data memory and configured to receive a part of the data in the data memory. The address generation unit is configured to generate address information for addressing the L0 memory. Further, the L0 memory provides at least two operands of a single instruction from the part of the data to the execution unit directly, without loading the at least two operands into one or more registers, using the address information from the address generation unit.
Owner:SHANGHAI XINHAO MICROELECTRONICS
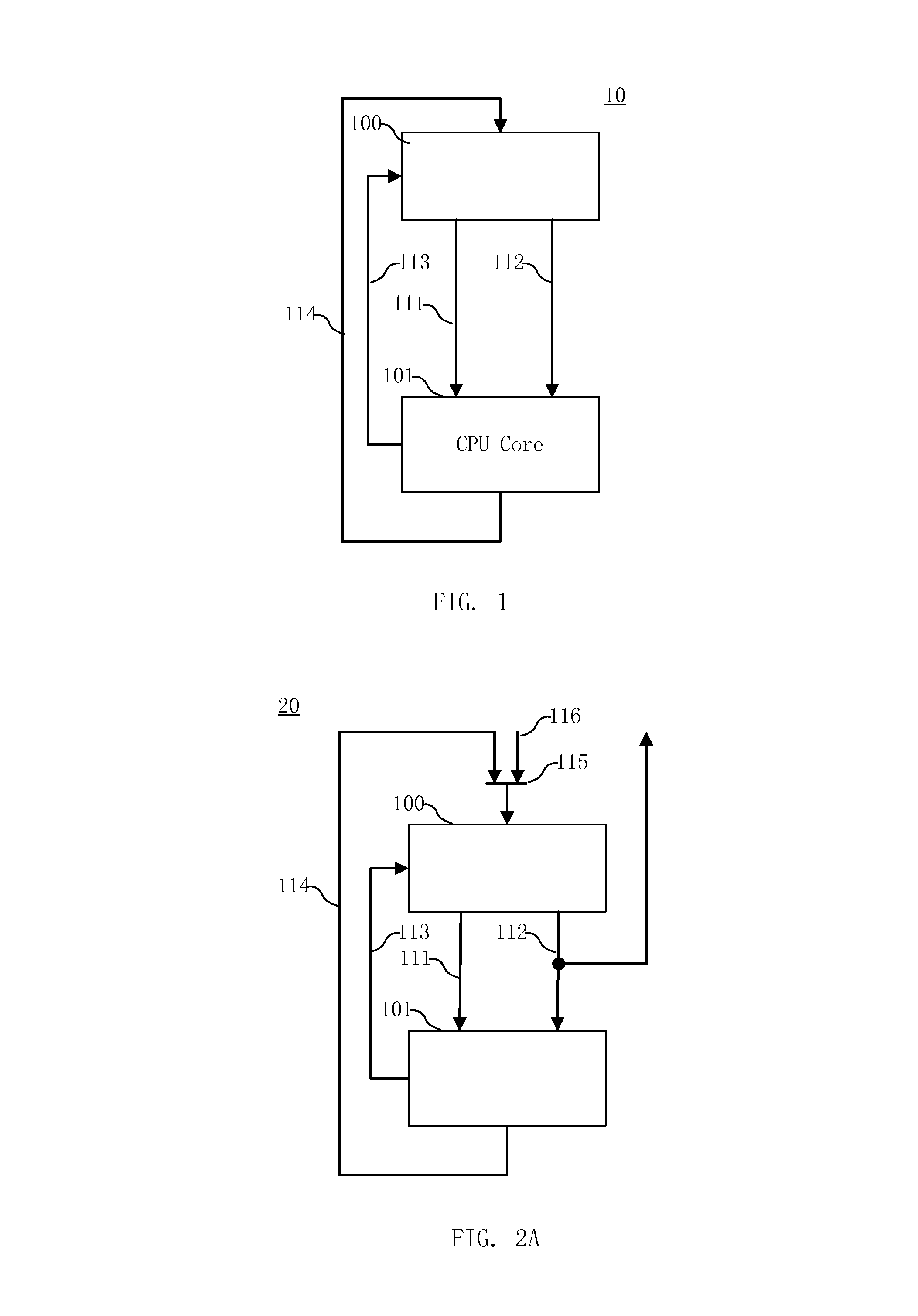
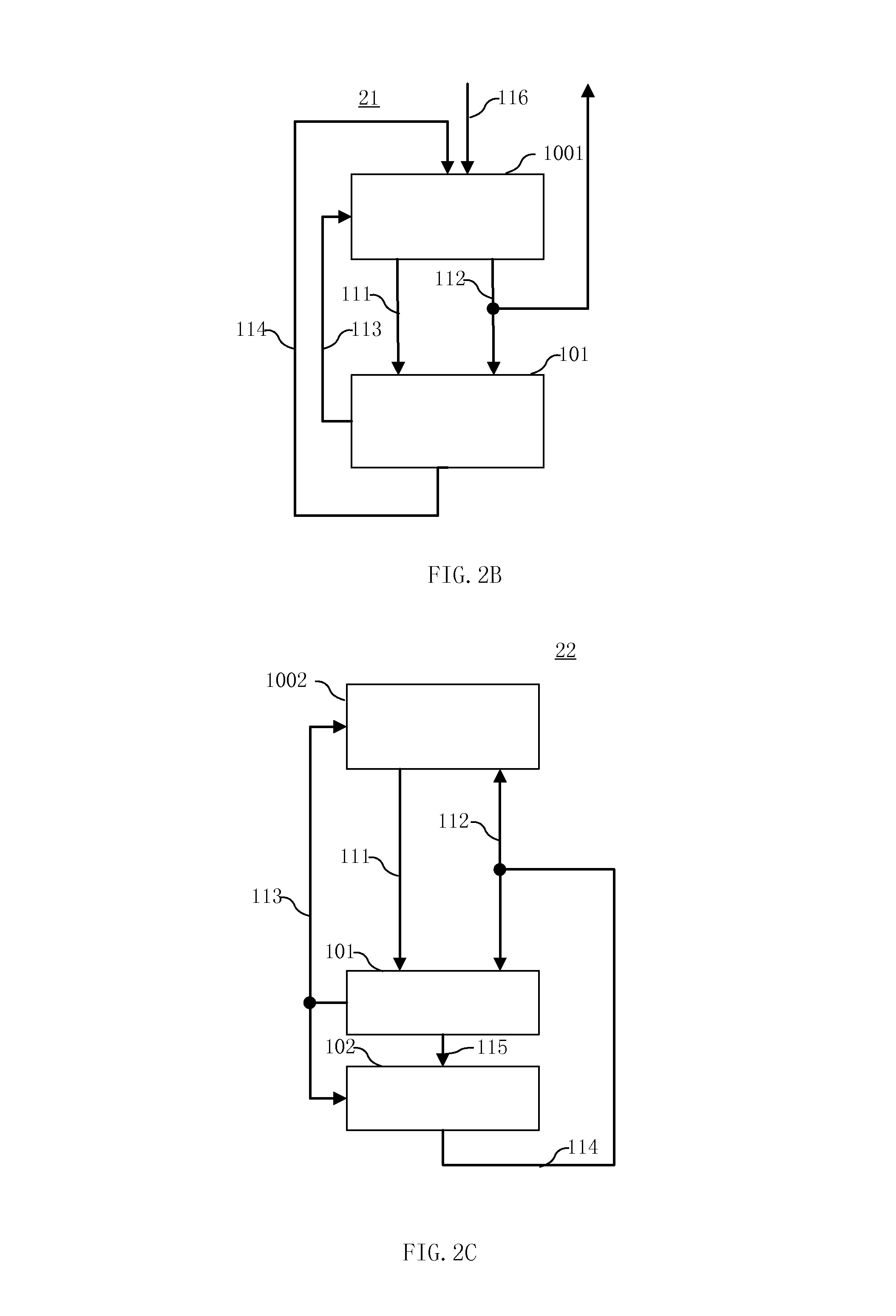
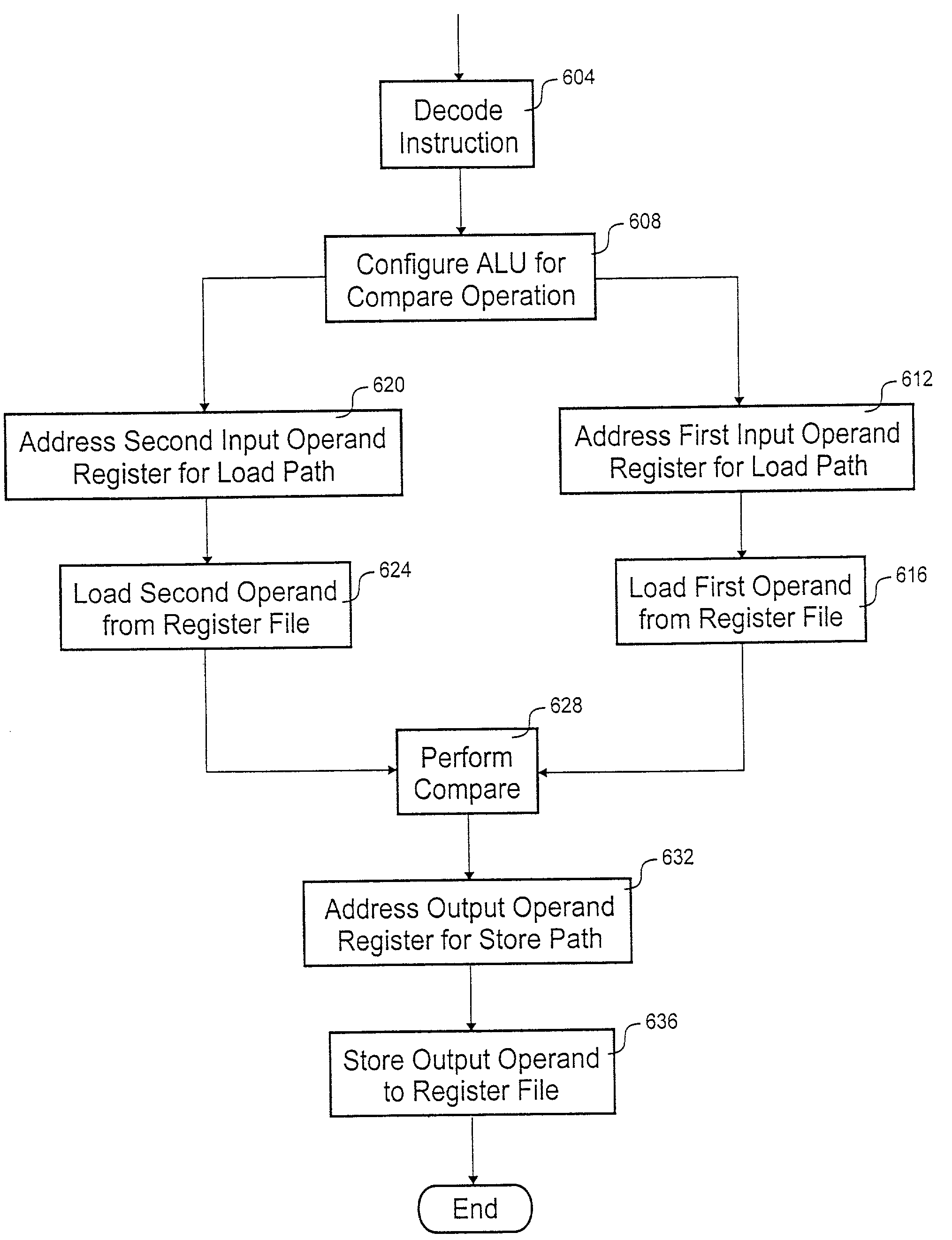
Processing architecture having a compare capability
According to the invention, a processing core that executes a compare instruction is disclosed. The processing core includes a register file, comparison logic, decode logic, and a store path. Included in the register file are a number of general-purpose registers. The general-purpose registers include a first input operand register, a second input operand register and an output operand register. Comparison logic is coupled to the register file. The comparison logic tests for at least two of the following relationships: less than, equal to, greater than and no valid relationship. The decode logic selects the output operand register from the plurality of general-purpose registers. The store path extends between the comparison logic and the selected output operand register.
Owner:ORACLE INT CORP
System and Method for Processor-Based Security
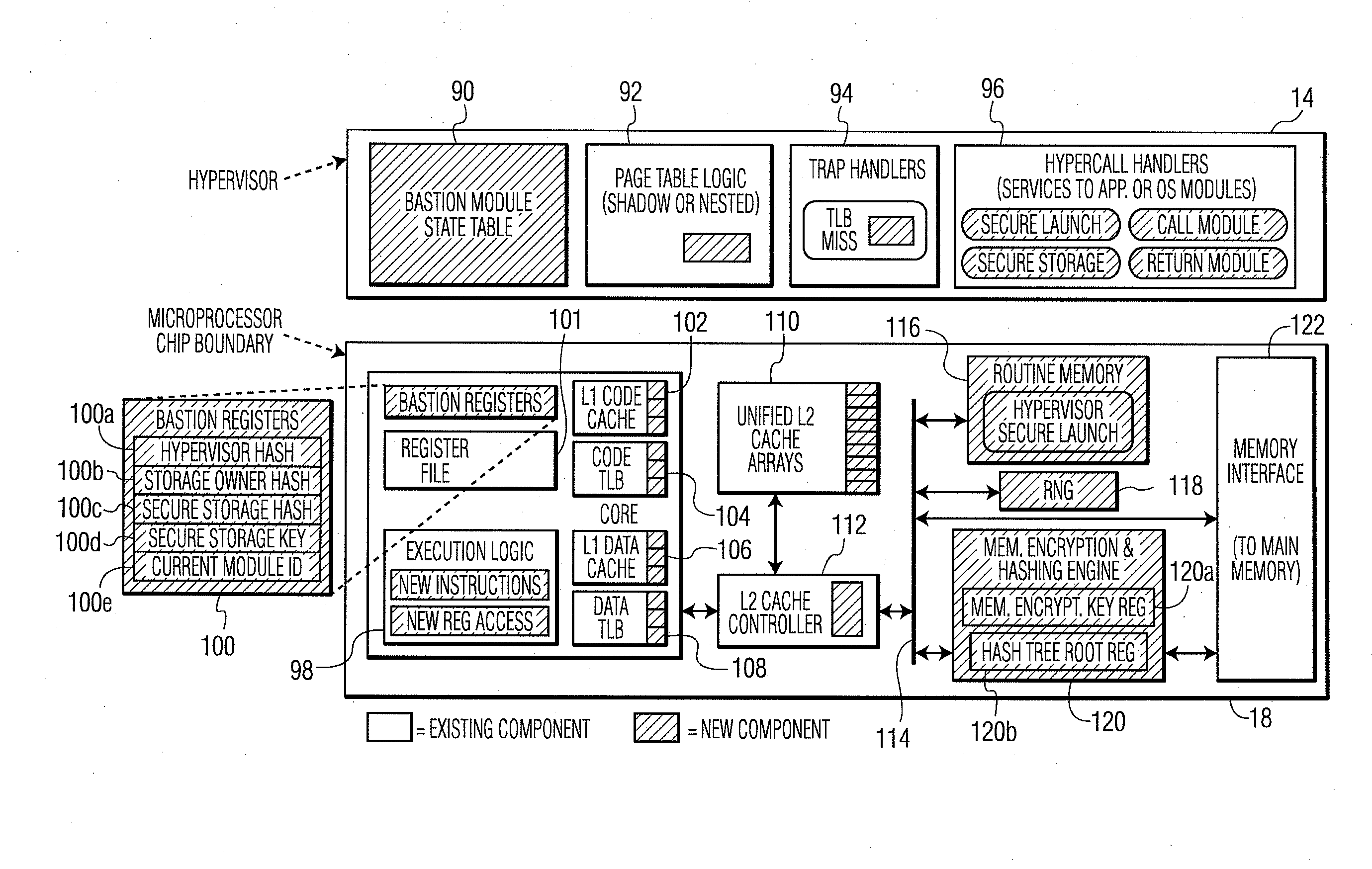
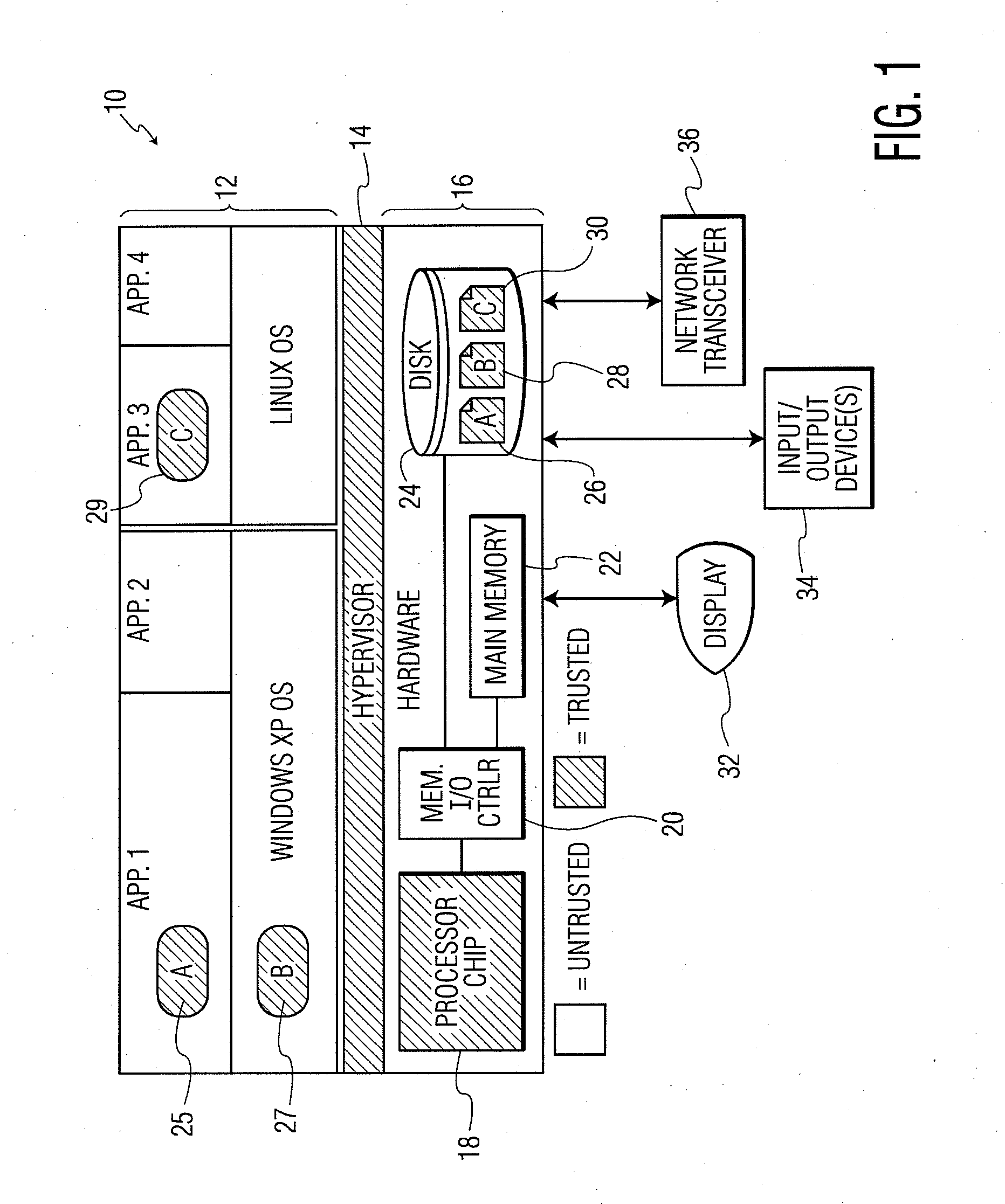
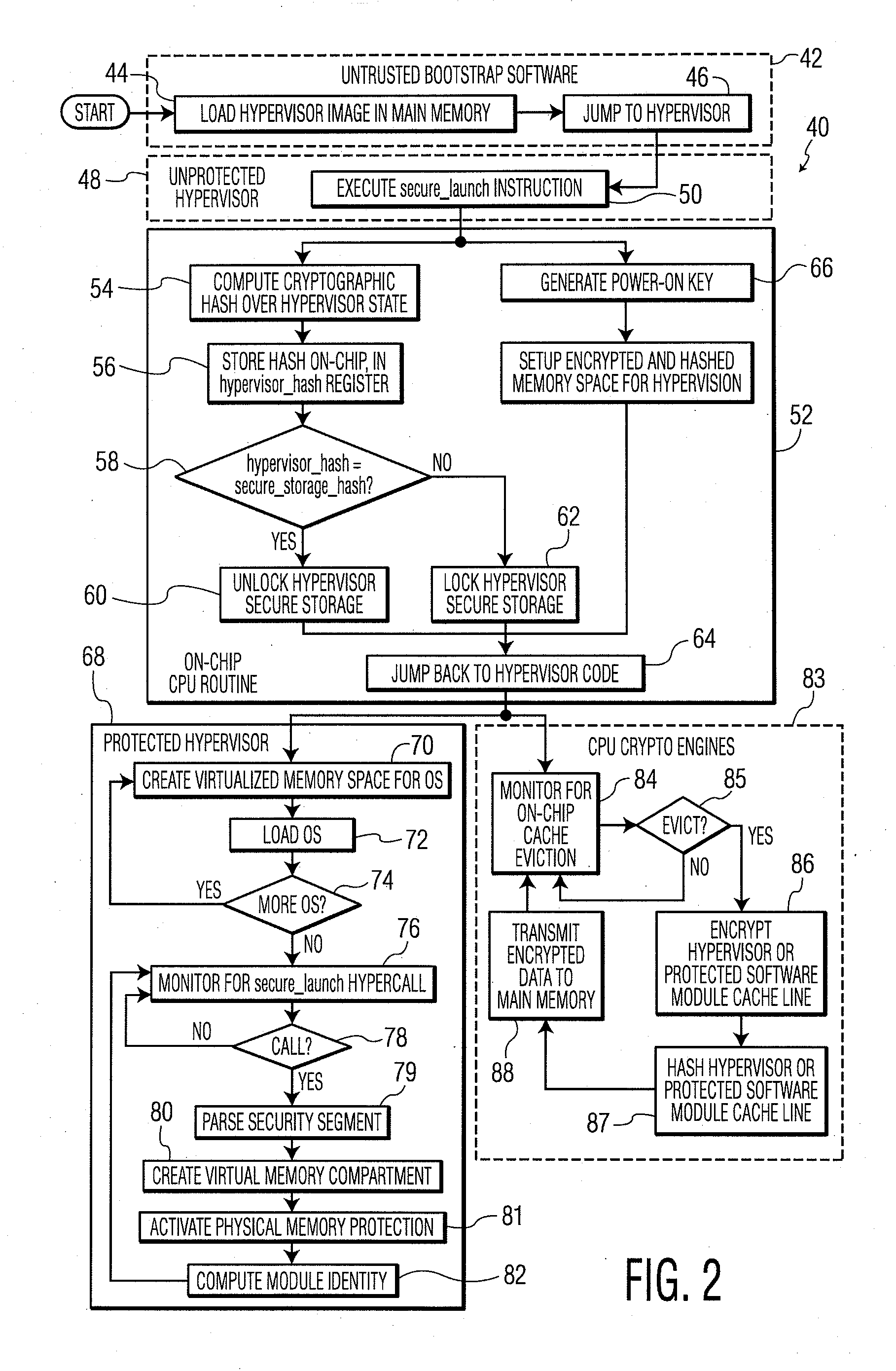
ActiveUS20100281273A1Avoid accessUnauthorized memory use protectionHardware monitoringExternal storageMemory interface
A system and method for processor-based security is provided, for on-chip security and trusted computing services for software applications. A processor is provided having a processor core, a cache memory, a plurality of registers for storing at least one hash value and at least one encryption key, a memory interface, and at least one on-chip instruction for creating a secure memory area in a memory external to the processor, and a hypervisor program executed by the processor. The hypervisor program instructs the processor to execute the at least one on-chip instruction to create a secure memory area for a software area for a software module, and the processor encrypts data written to, and decrypts data read from, the external memory using the at least one encryption key and the verifying data read from the external memory using the at least one hash value. Secure module interactions are provided, as well as the generation of a power-on key which can be used to protect memory in the event of a re-boot event. Lightweight, run-time attestation reports are generated which include selected information about software modules executed by the processors, for use in determining whether the processor is trusted to provide secure services.
Owner:CORESECURE TECH LLC
Storage traffic communication via a switch fabric in accordance with a VLAN
ActiveUS20130151646A1Improve performanceImprove efficiencyDigital computer detailsTransmissionTraffic capacityControl store
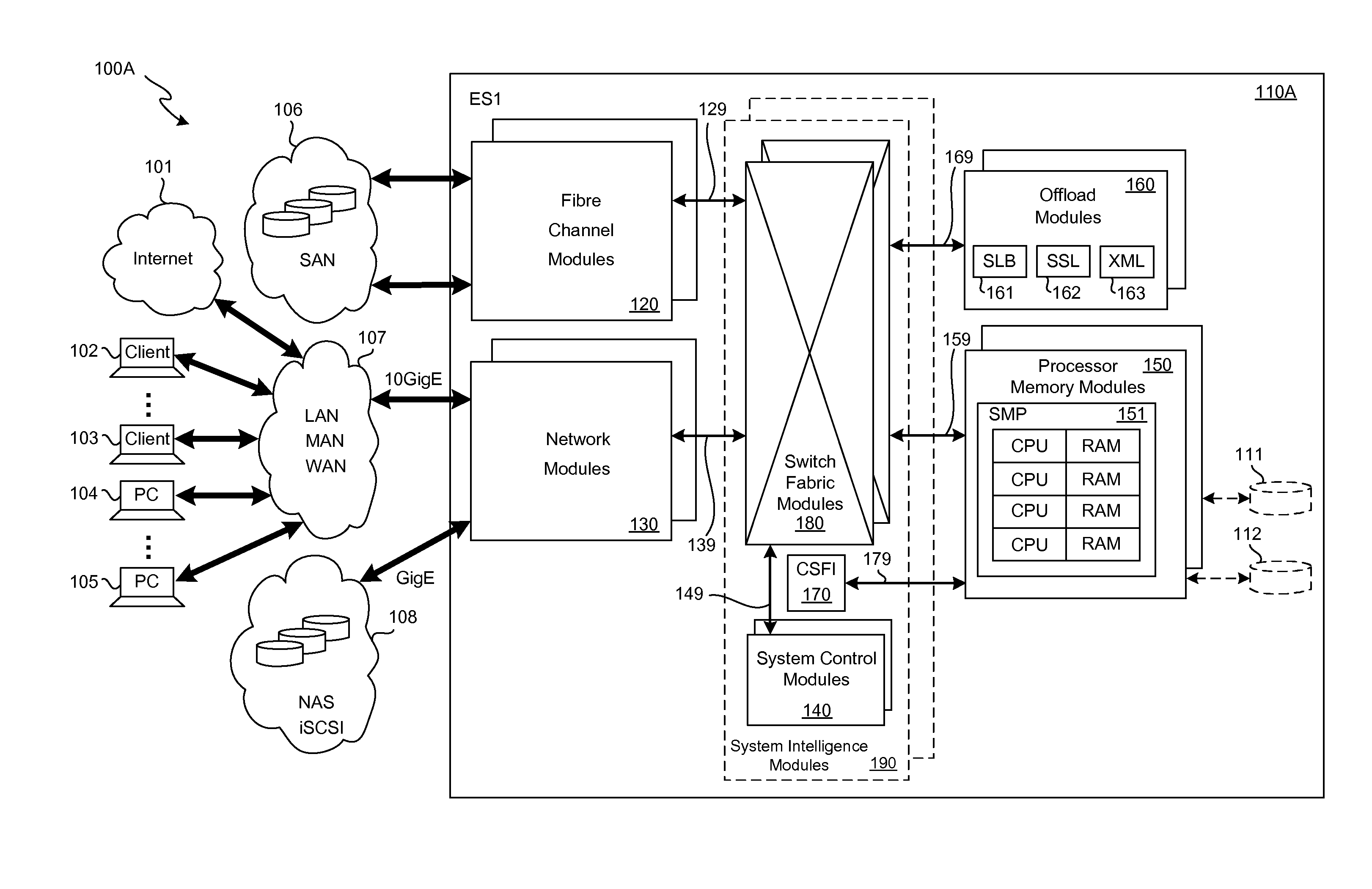
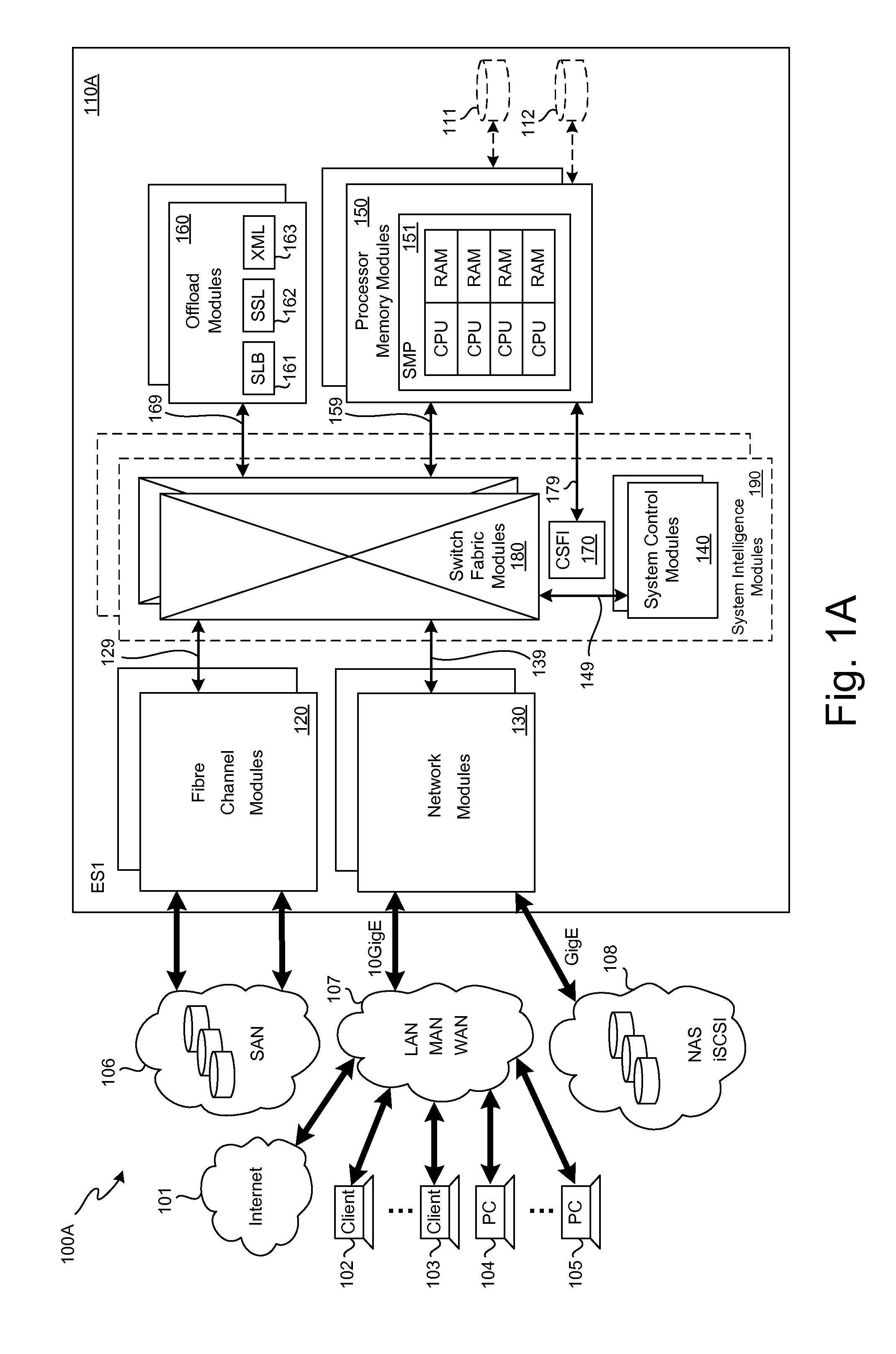
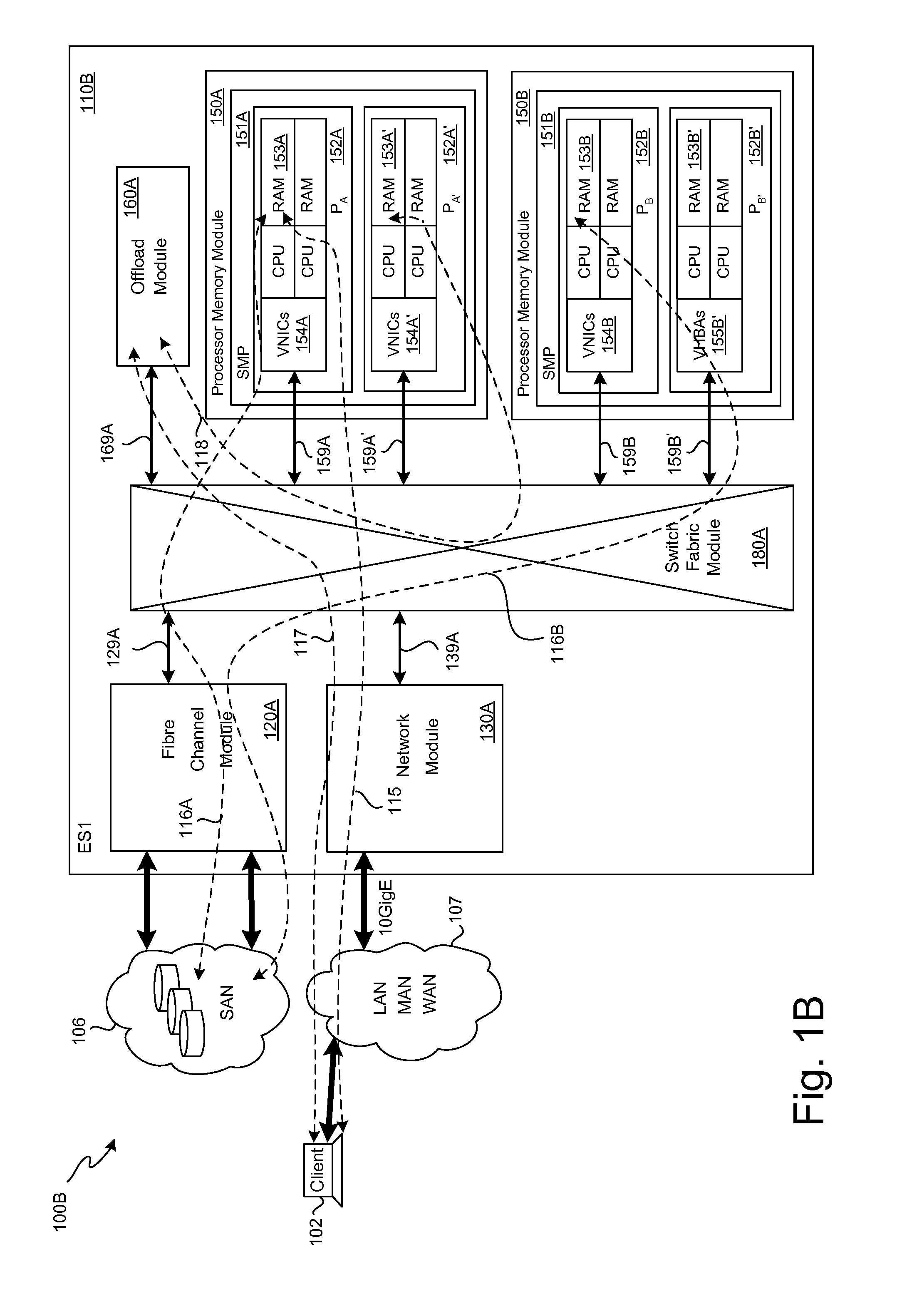
A plurality of SMP modules and an IOP module communicate storage traffic via respective corresponding I / O controllers coupled to respective physical ports of a switch fabric by addressing cells to physical port addresses corresponding to the physical ports. One of the SMPs executes initiator software to partially manage the storage traffic and the IOP executes target software to partially manage the storage traffic. Storage controllers are coupled to the IOP, enabling communication with storage devices, such as disk drives, tape drives, and / or networks of same. Respective network identification registers are included in each of the I / O controller corresponding to the SMP executing the initiator software and the I / O controller corresponding to the IOP. Transport of the storage traffic in accordance with a particular VLAN is enabled by writing a same particular value into each of the network identification registers.
Owner:ORACLE INT CORP
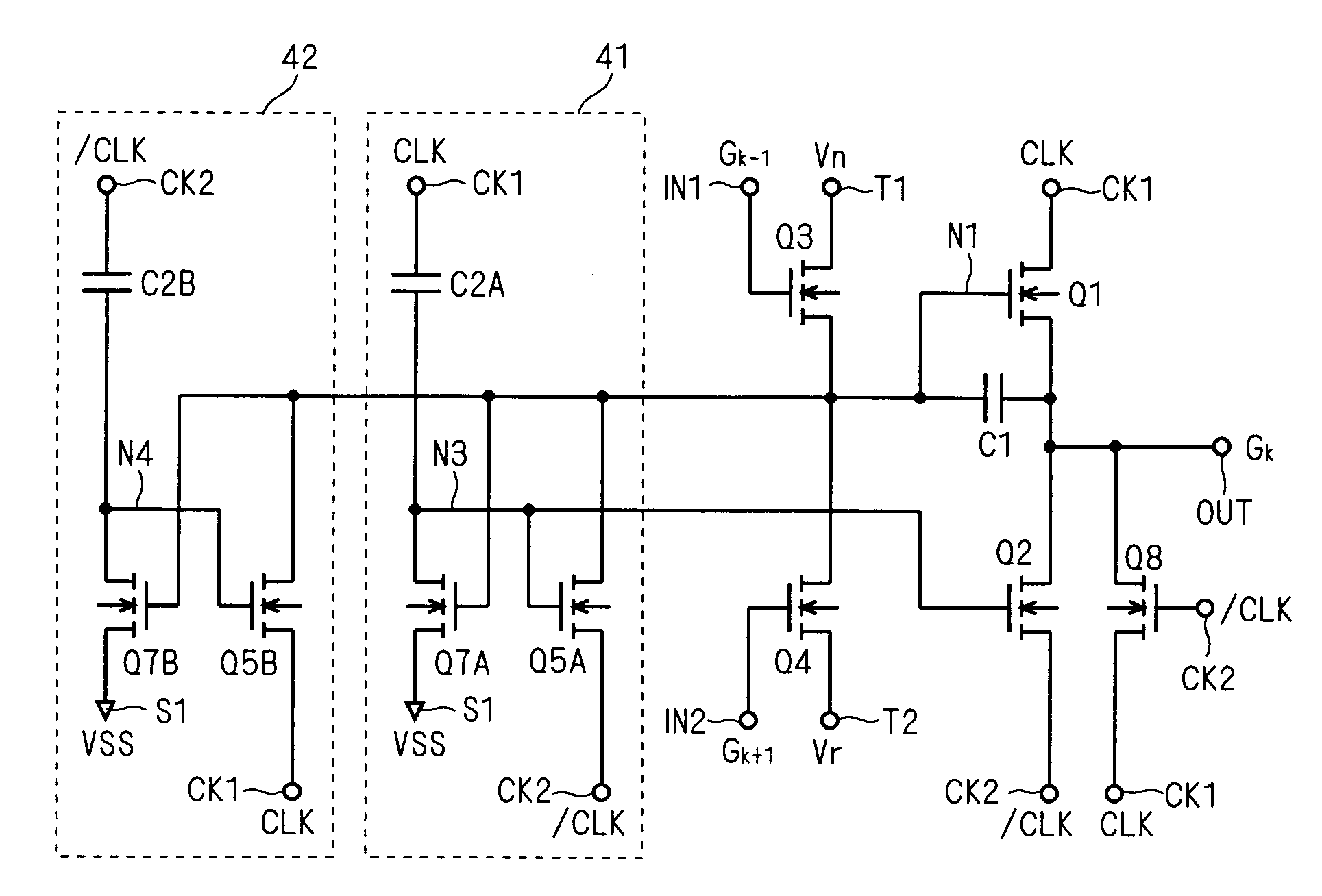
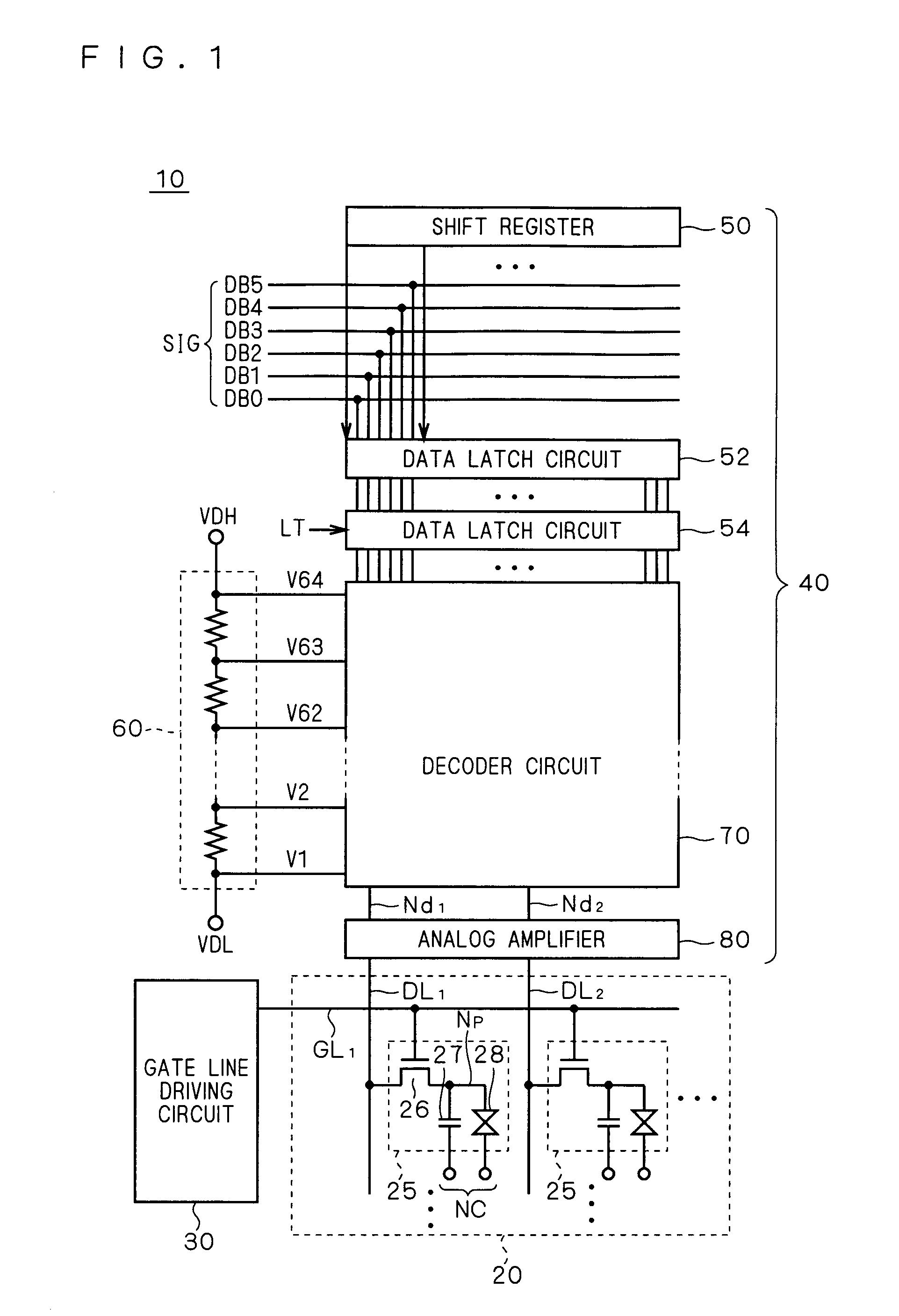
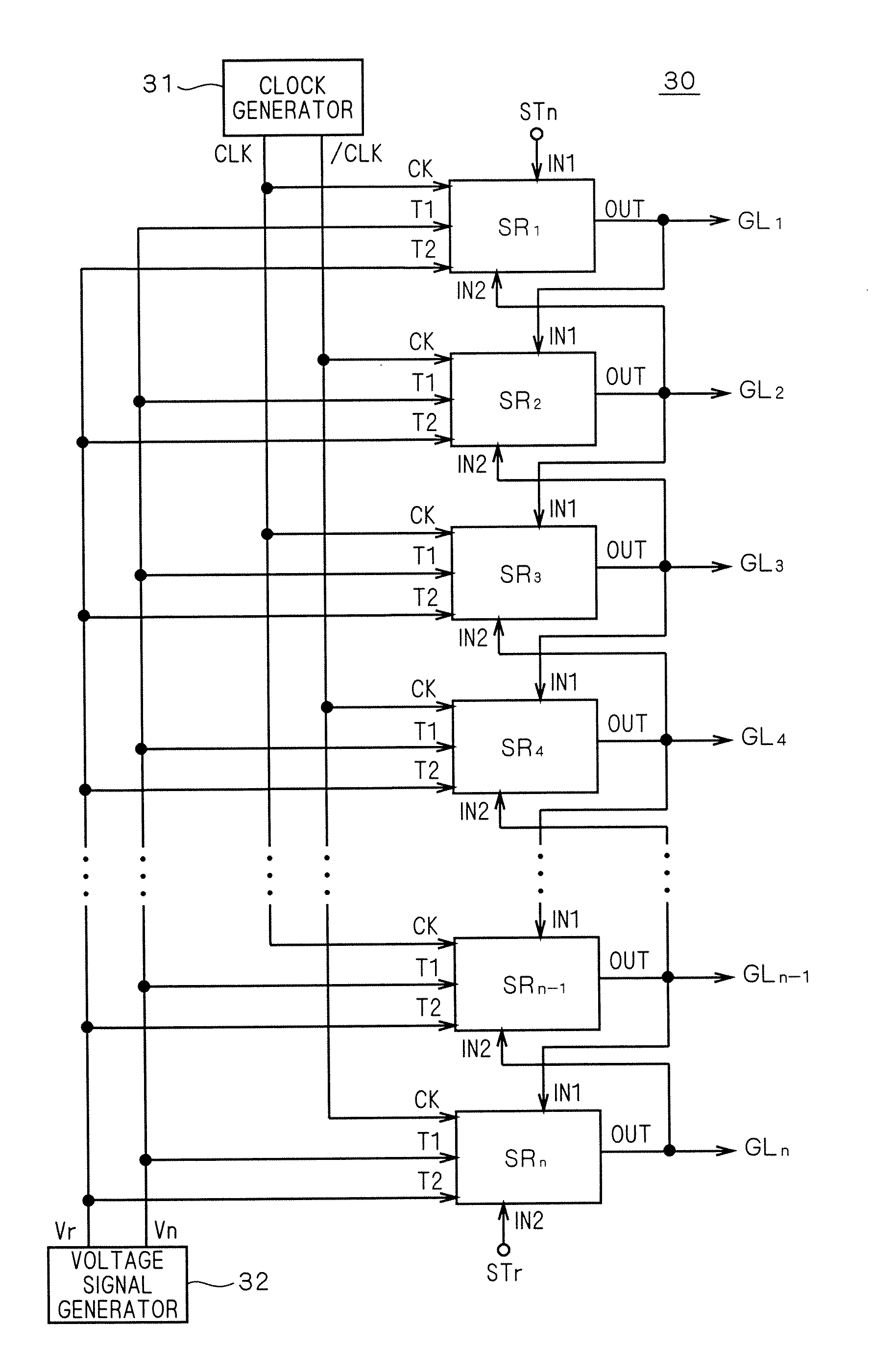
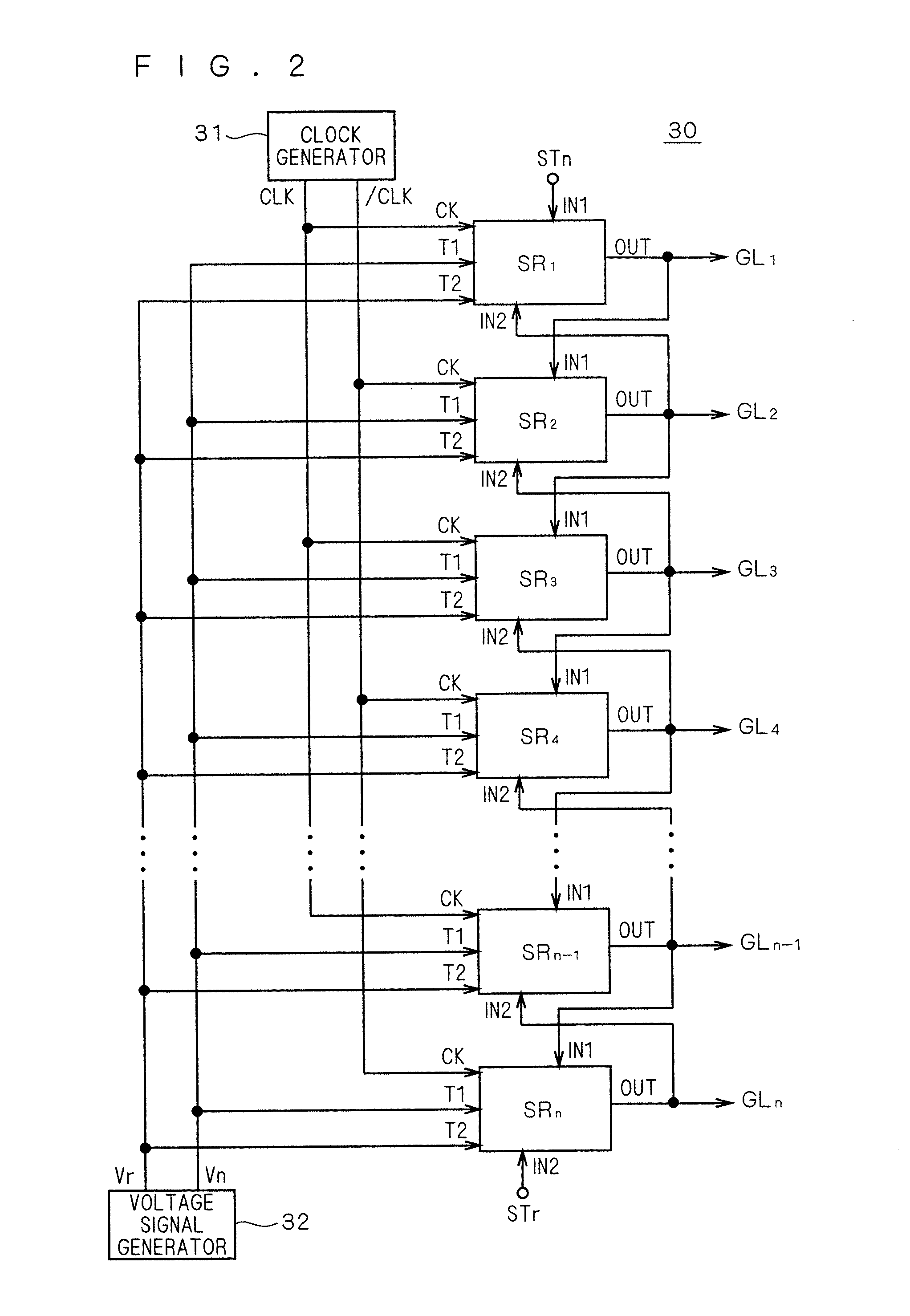
Shift register circuit and image display apparatus containing the same
InactiveUS20080219401A1Avoid failureReduced driving abilityStatic indicating devicesDigital storageShift registerProcessor register
Threshold voltage shifts of transistors which are constituents of a bidirectional shift register are reduced to prevent a malfunction in the shift register. A bidirectional unit shift register includes first and second pull-down circuits (41, 42) connected to the gate of a first transistor (Q1) that supplies a first clock signal (CLK) to an output terminal (OUT). The first pull-down circuit (41) includes a first inverter that uses the gate of the first transistor (Q1) as the input node and that is activated by the first clock signal (CLK), and a second transistor (Q5A) that discharges the gate of the first transistor (Q1) according to the output of the first inverter. The second pull-down circuit (42) includes a second inverter that uses the gate of the first transistor (Q1) as the input node and that is activated by a second clock signal ( / CLK) having a different phase from the first clock signal (CLK), and a third transistor (Q5A) that discharges the gate of the first transistor according to the output of the second inverter.
Owner:TRIVALE TECH LLC
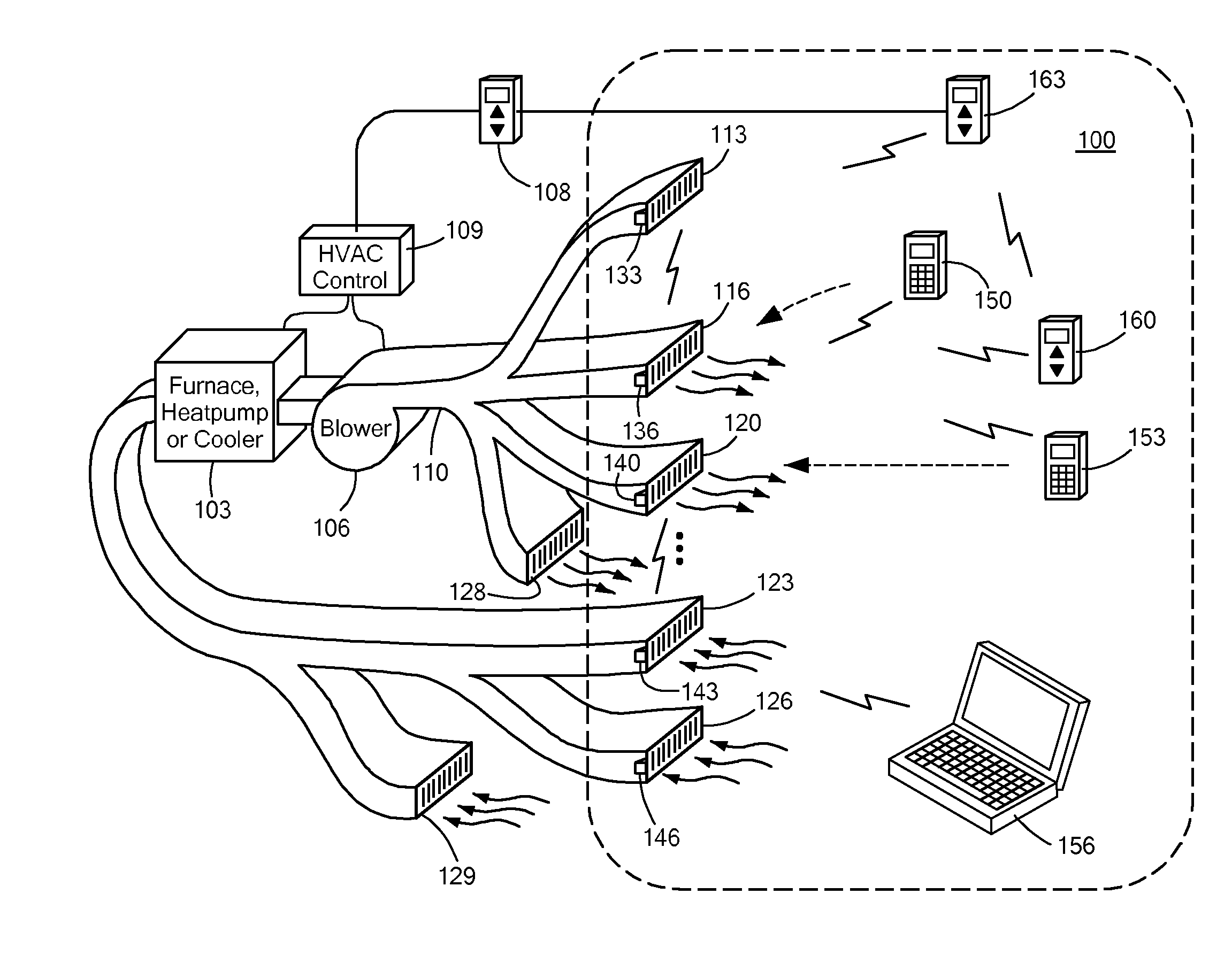
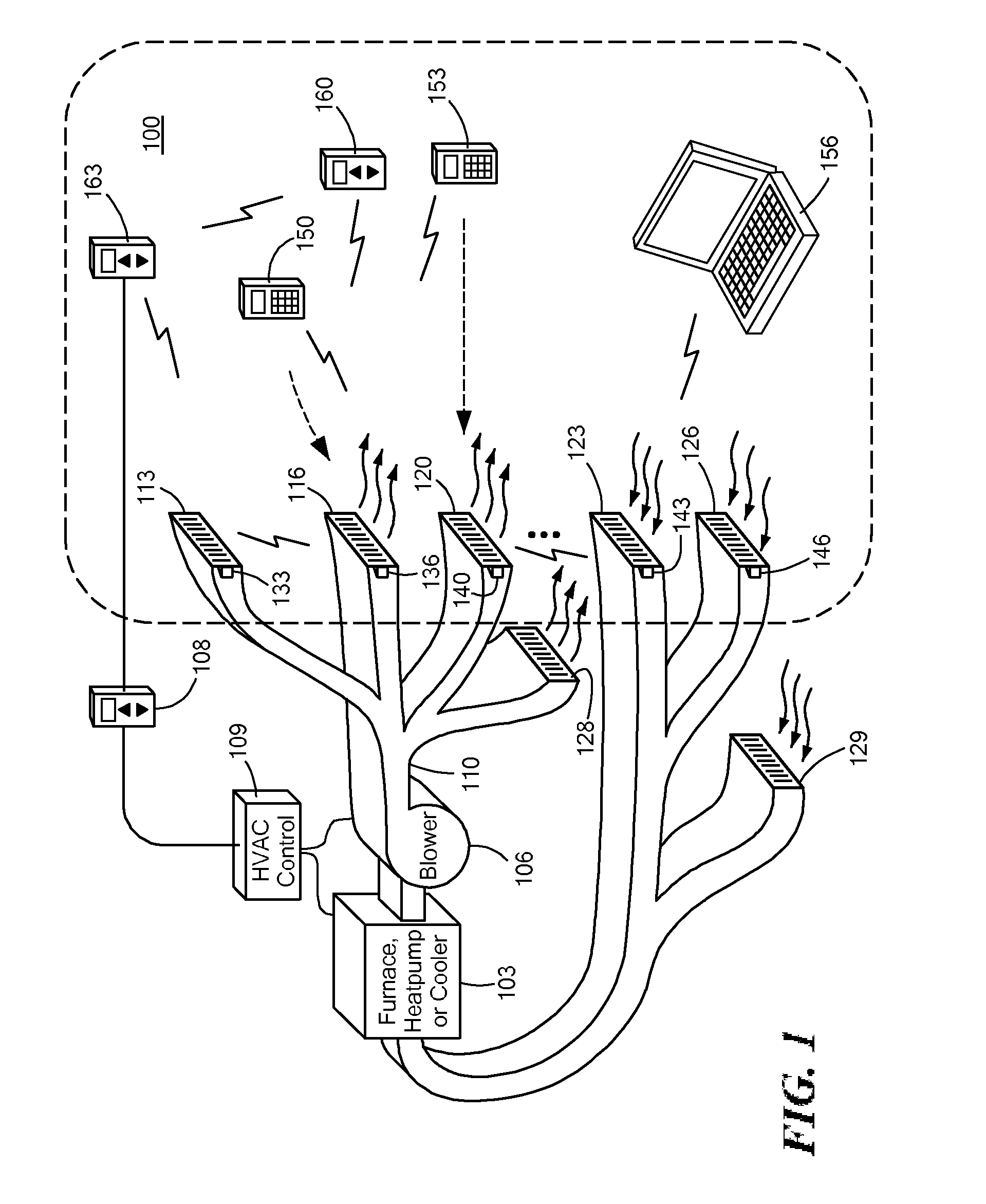
Automatically Balancing Register for HVAC Systems
Distributed nodes, such as intelligent register controllers, of a heating, ventilating and / or air conditioning (HVAC) system wirelessly communicate with each other on a peer-to-peer basis, forming a network, and collectively control the HVAC system, without a central controller. The intelligent register controllers collectively control the amount of conditioned air introduced into each region. Each node may base its operation at least in part on information about one or more (ideally all) of the other nodes. Each intelligent register controller automatically determines how much conditioned air to allow into its region, or how much return air to allow to be withdrawn from its region, based on information collected by the register controller, such as: current temperature of the region; desired temperature of the region; calculated amount of conditioned air required to change the region's temperature to the desired temperature; temperature of conditioned air begin supplied by a duct to the register; current time, day of week, vacation or other schedule data; temperatures of other regions and their respective desired temperatures; calculated amounts of air required to be supplied or withdrawn by the other controlled registers to change their respective regions' temperatures to their desired temperatures; or combinations thereof. Each register controller automatically determines when and to what extent to operate its respective controllable damper.
Owner:ZONER
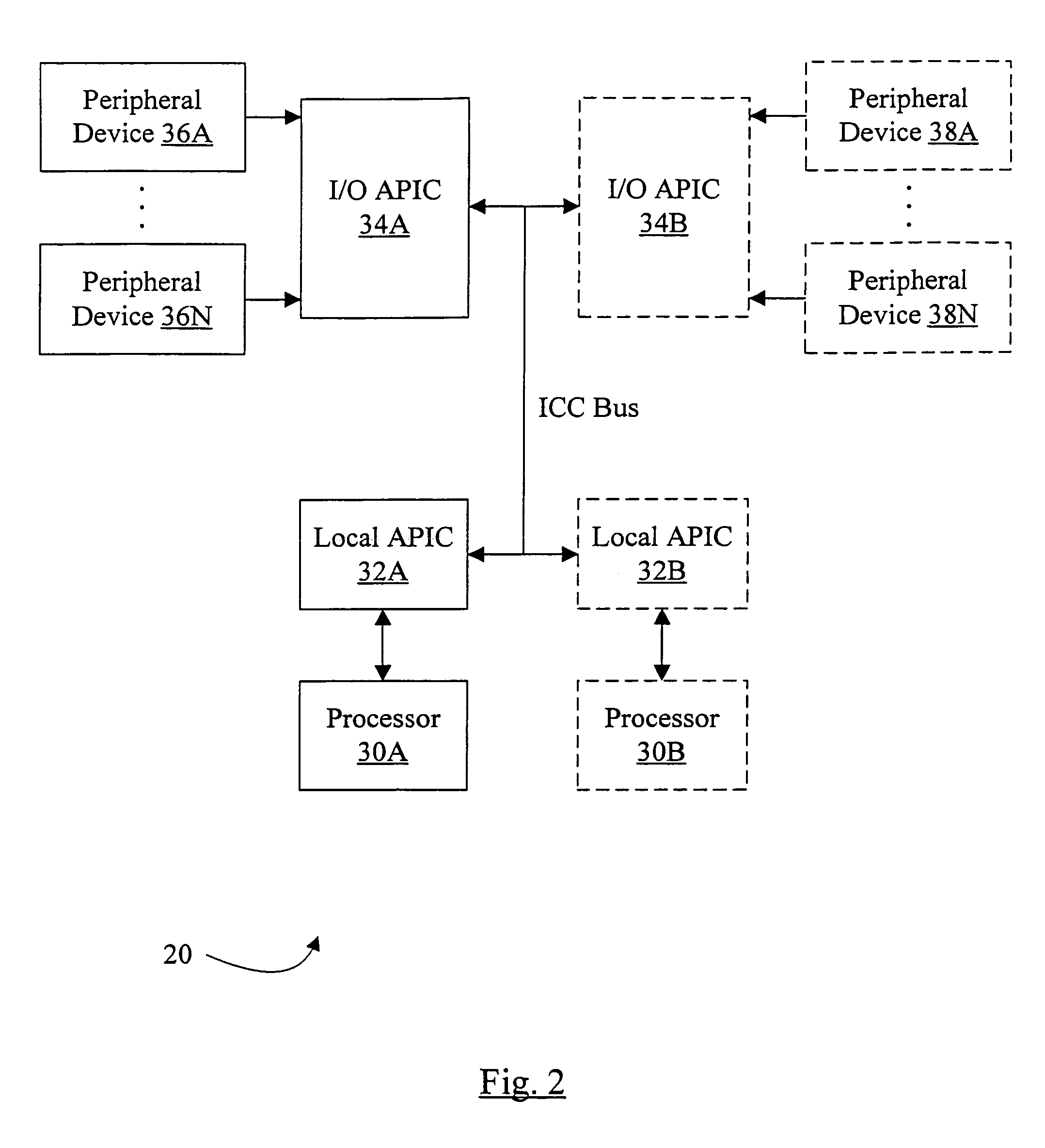
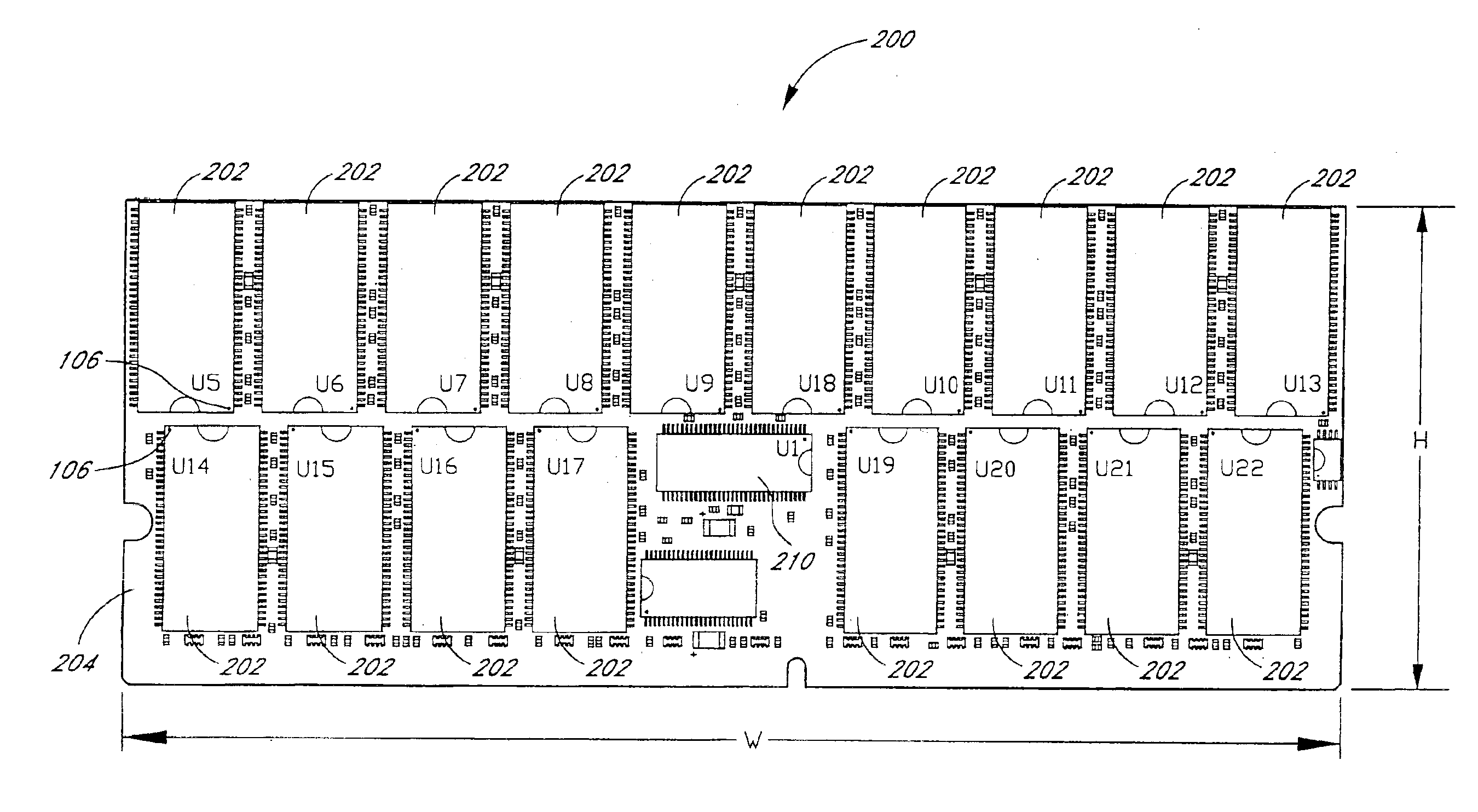
Arrangement of integrated circuits in a memory module
InactiveUS20050018495A1Final product manufactureCross-talk/noise/interference reductionGigabyteProcessor register
Abstract of the Disclosure Integrated circuits utilizing standard commercial packaging are arranged on a printed circuit board to allow the production of one-Gigabyte, two-Gigabyte, and four-Gigabyte capacity memory modules. A first row of integrated circuits is oriented in an opposite orientation to a second row of integrated circuits. The integrated circuits in the first row on a first lateral portion of the printed circuit board and in the second row on the first lateral portion are connected to a first addressing register with two register integrated circuits. The integrated circuits in the first row on the second lateral portion and in the second row on the second lateral portion are connected to a second addressing register with two register integrated circuits. Each addressing register processes a non-contiguous subset of the bits in each data word.
Owner:NETLIST INC
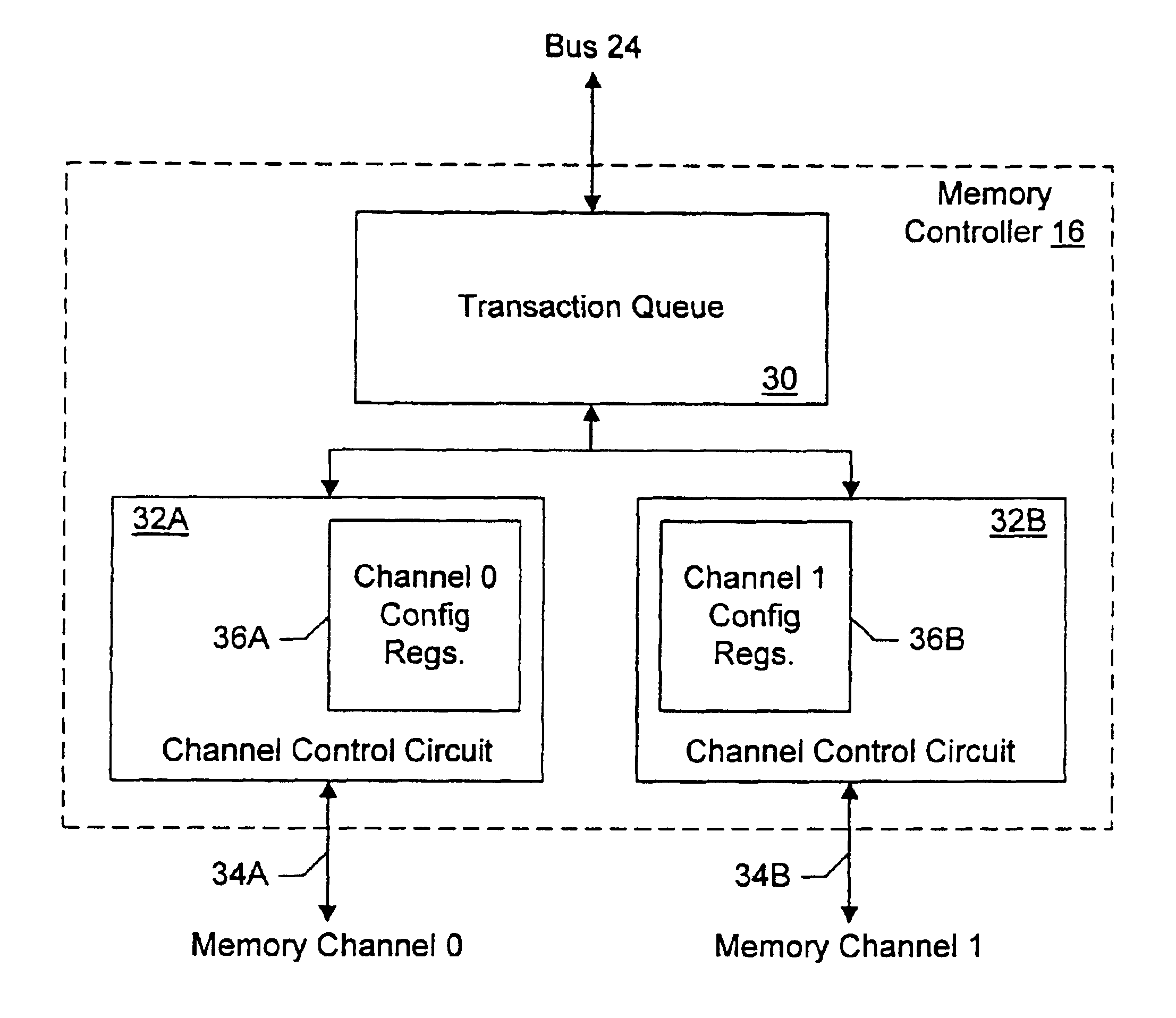
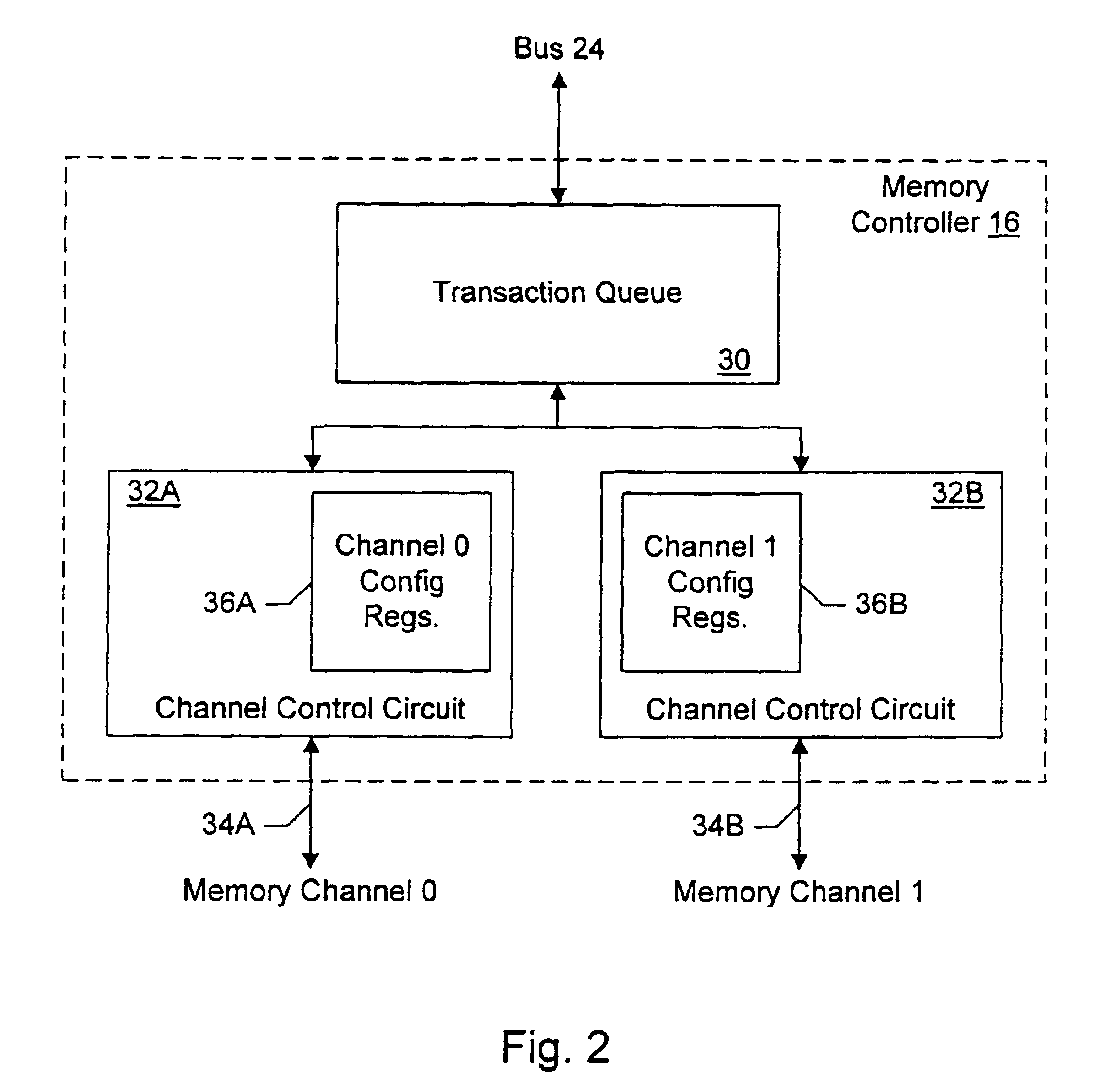
Memory controller with programmable configuration
InactiveUS6877076B1Flexible configurationOpen in timeMemory adressing/allocation/relocationMicro-instruction address formationProcessor registerParallel computing
Owner:AVAGO TECH INT SALES PTE LTD
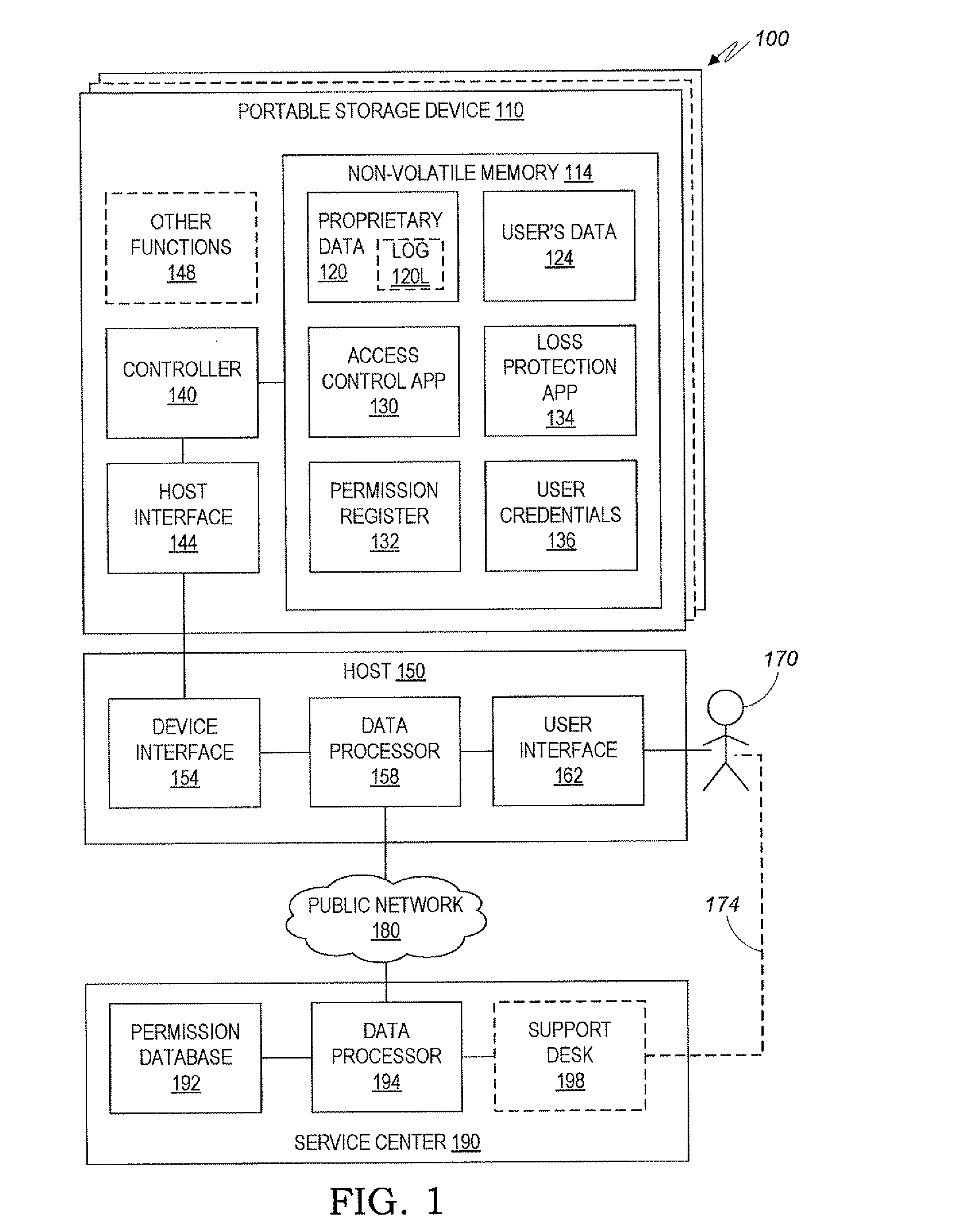
Portable Storage Device With Updatable Access Permission
ActiveUS20080059743A1Unauthorized memory use protectionInternal/peripheral component protectionCouplingProcessor register
Owner:WESTERN DIGITAL ISRAEL LTD
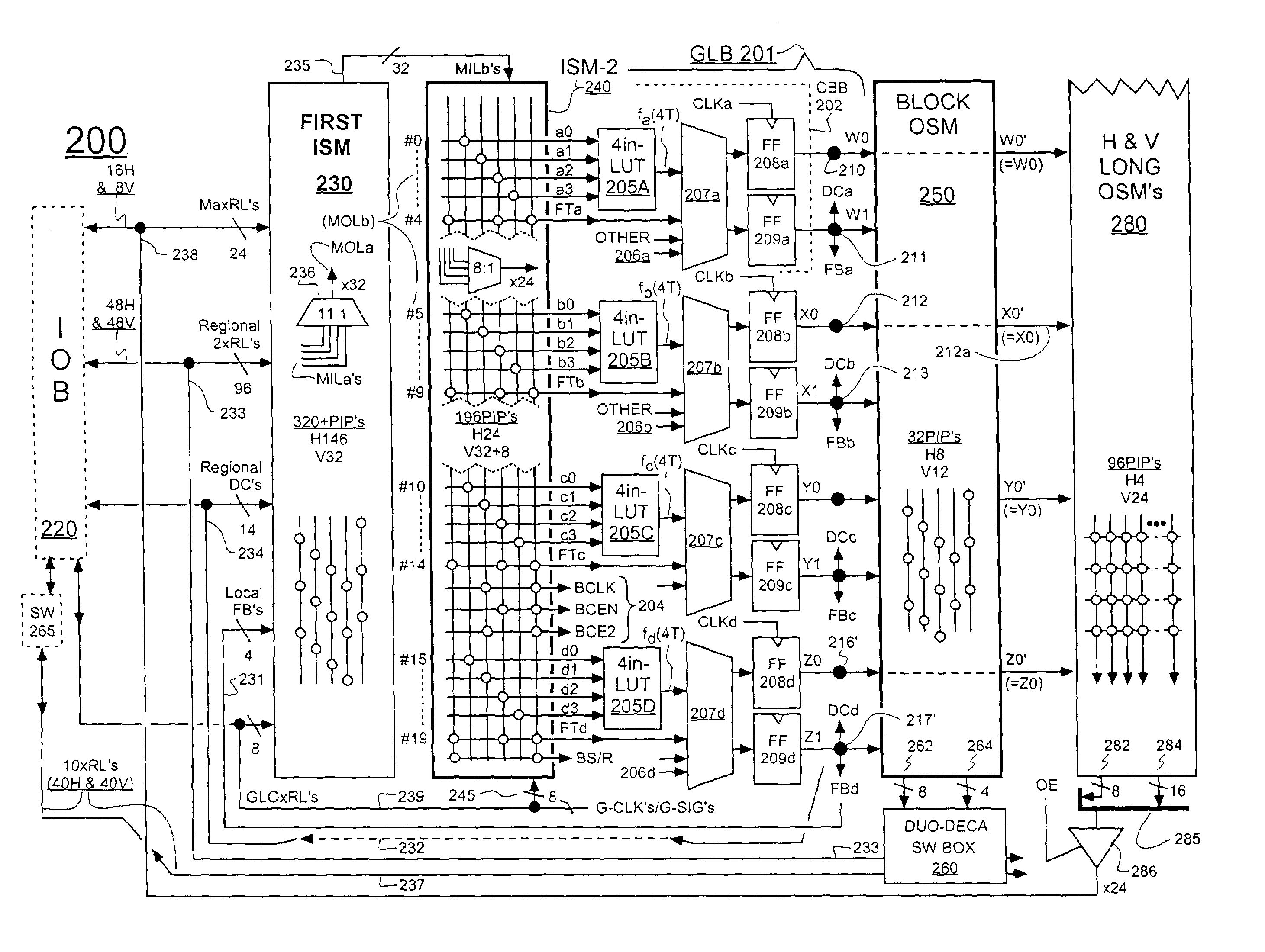
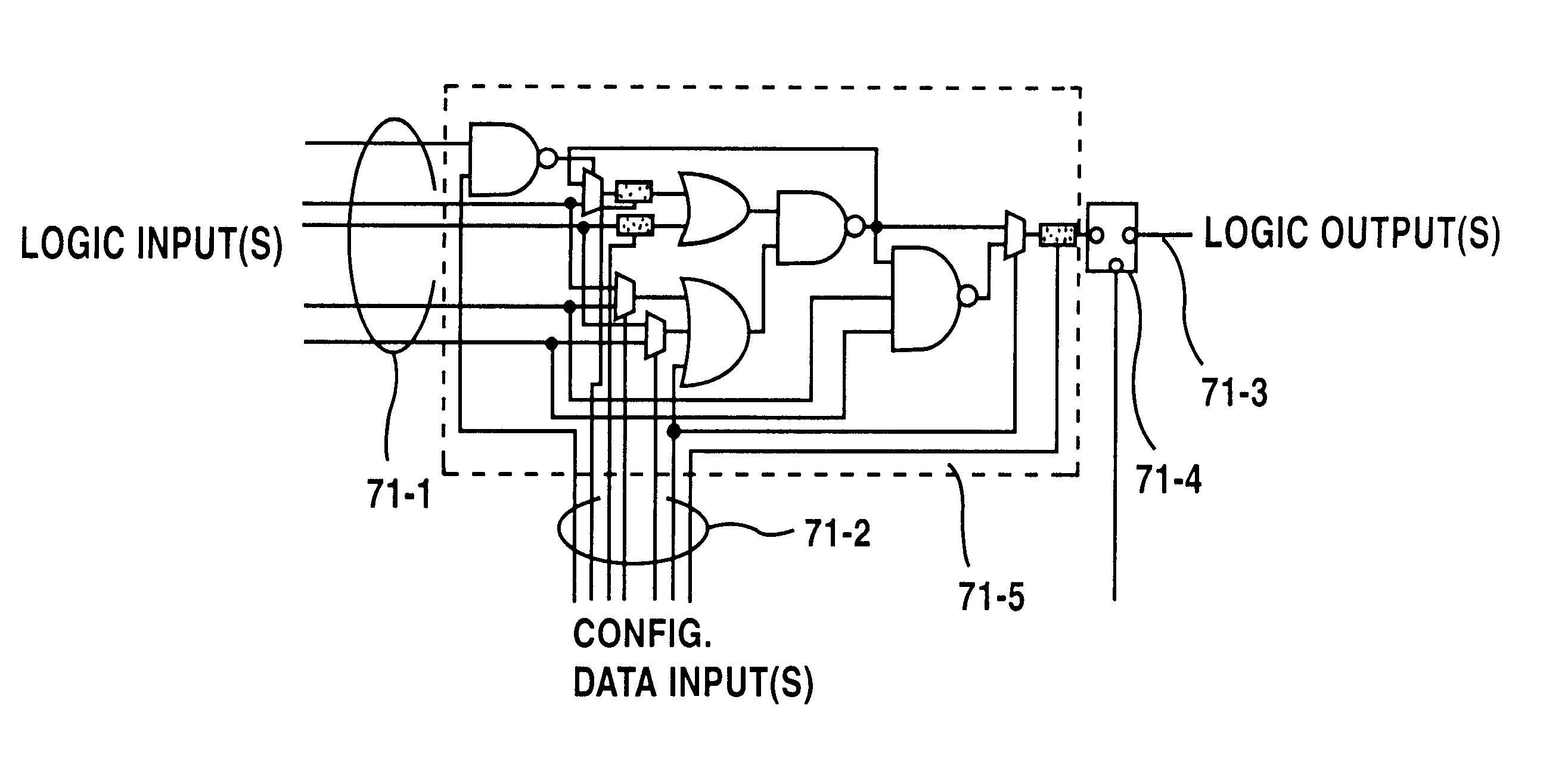
FPGA with register-intensive architecture
ActiveUS7028281B1Minimize resourceReduce consumptionSolid-state devicesCAD circuit designProcessor registerMultiplexer
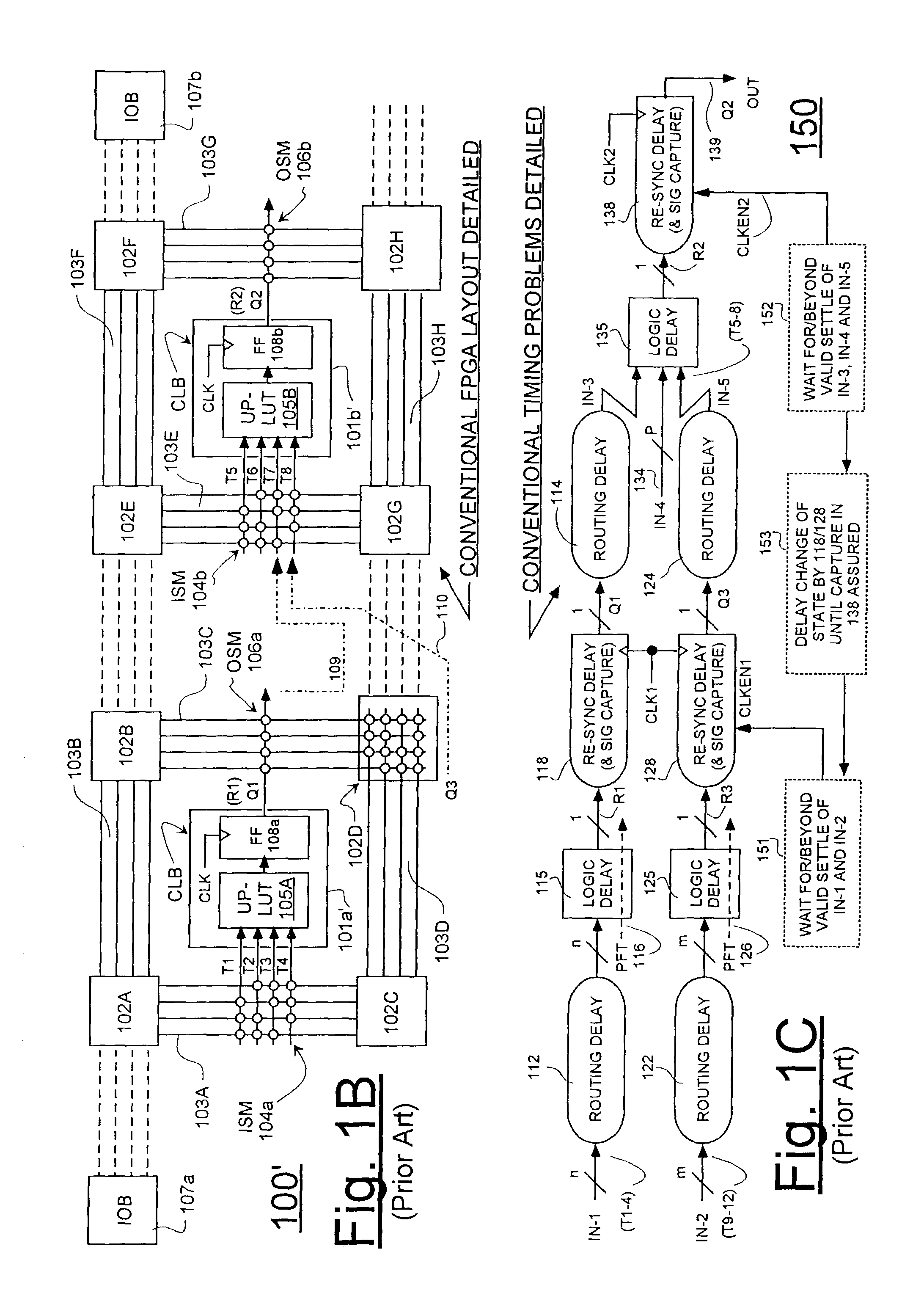
Field programmable gate arrays (FPGA's) may be structured in accordance with the disclosure to have a register-intensive architecture that provides, for each of plural function-spawning LookUp Tables (e.g. a 4-input, base LUT's) within a logic block, a plurality of in-block accessible registers. A register-feeding multiplexer means may be provided for allowing each of the plural registers to equivalently capture and store a result signal output by the corresponding, base LUT of the plural registers. Registerable, primary and secondary feedthroughs may be provided for each base LUT so that locally-acquired input signals of the LUT may be fed-through to the corresponding, in-block registers for register-recovery purposes without fully consuming (wasting) the lookup resources of the associated, base LUT. A multi-stage, input switch matrix (ISM) may be further provided for acquiring and routing input signals from adjacent, block-interconnect lines (AIL's) and / or block-intra-connect lines (e.g., FB's) to the base LUT's and / or their respective, registerable feedthroughs. Techniques are disclosed for utilizing the many in-block registers and / or the registerable feedthroughs and / or the multi-stage ISM's for efficiently implementing various circuit designs by appropriately configuring such register-intensive FPGA's.
Owner:LATTICE SEMICON CORP
SIMD datapath coupled to scalar/vector/address/conditional data register file with selective subpath scalar processing mode
InactiveUS6839828B2Not compromise SIMD data processing performanceReduce consumptionRegister arrangementsDigital data processing detailsProcessor registerOperation mode
There is provided a processor designed to operate in a plurality of modes for processing vector and scalar instructions. Register files are each for storing scalar and vector data and address information. A parallel vector unit, coupled to the register files, includes functional units configurable to operate in a vector operation mode and a scalar operation mode. The vector unit includes an apparatus for tightly coupling the functional units to perform an operation specified by a current instruction. Under a vector operation mode, the vector unit performs, in parallel, a single vector operation on a plurality of data elements. The operations performed on the plurality of data elements are each performed by a different functional unit of the vector unit. Under a scalar operation mode, the vector unit performs a scalar operation on a data element received from the register files in a functional unit within the vector unit.
Owner:INTEL CORP
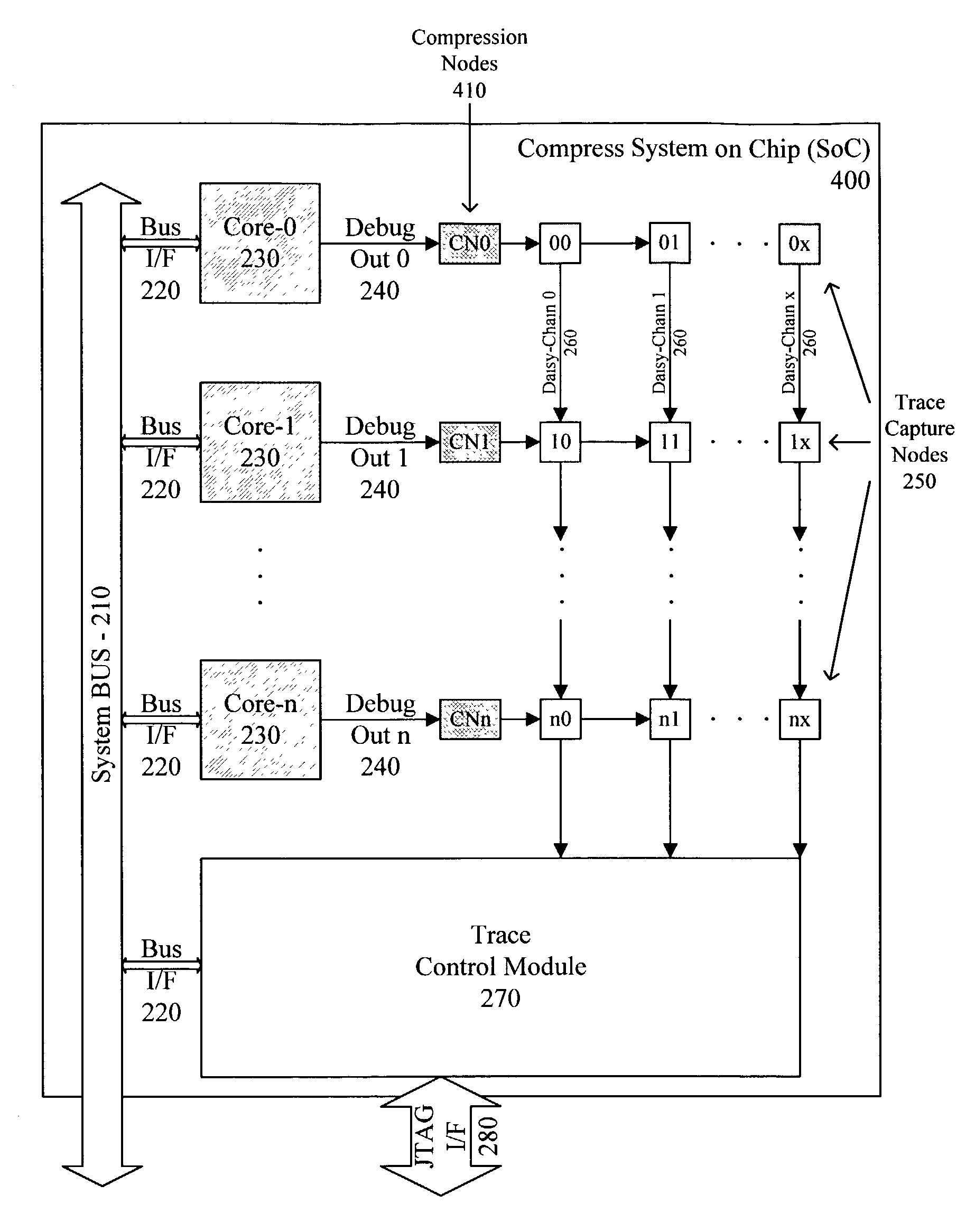
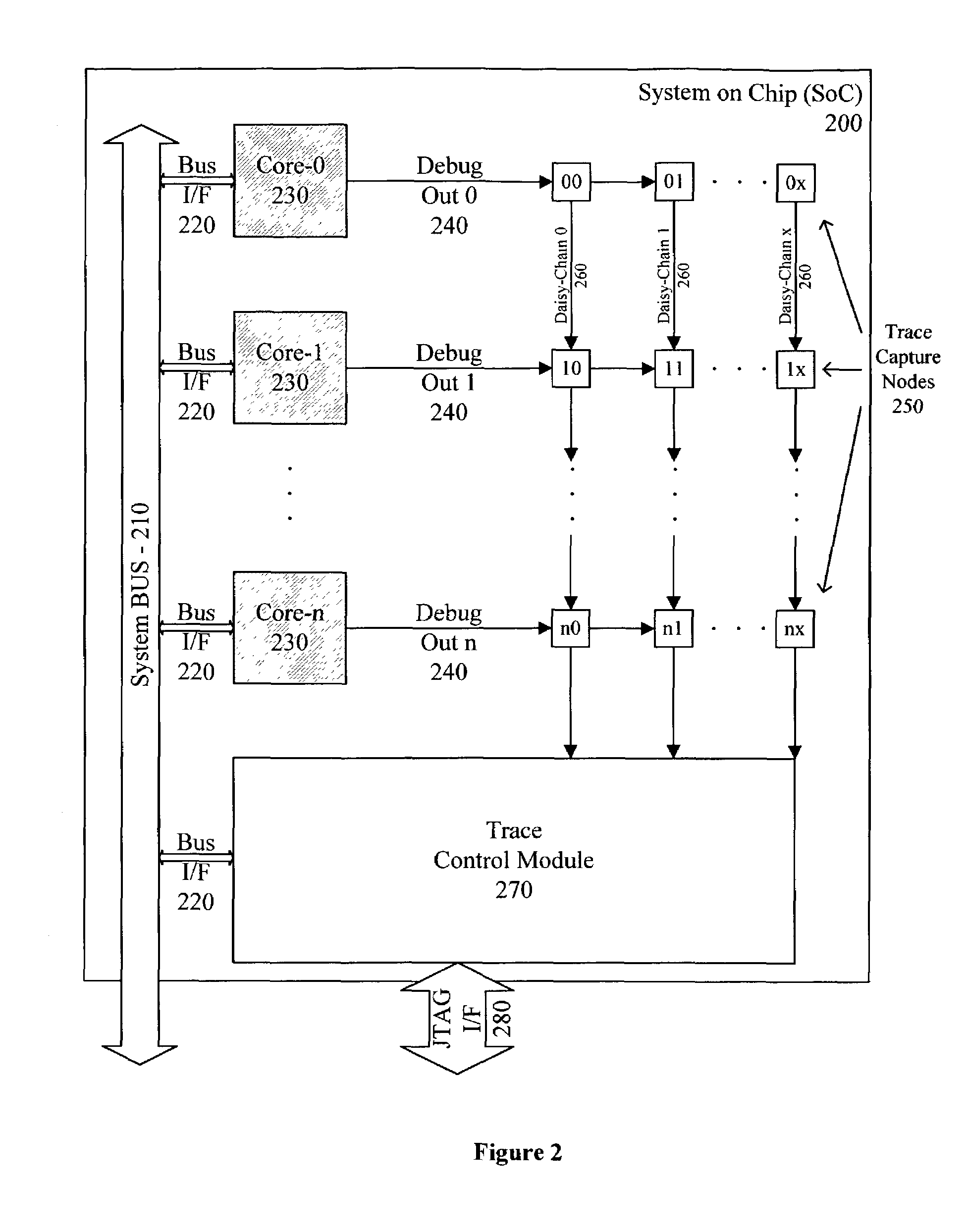
Simultaneous real-time trace and debug for multiple processing core systems on a chip
A system for providing simultaneous, real-time trace and debug of a multiple processing core system on a chip (SoC) is described. Coupled to each processing core is a debug output bus. Each debug output bus passes a processing core's operation to trace capture nodes connected together in daisy-chains. Trace capture node daisy-chains terminate at the trace control module. The trace control module receives and filters processing core trace data and decides whether to store processing core trace data into trace memory. The trace control module also contains a shadow register for capturing the internal state of a traced processing core just prior its tracing. Stored trace data, along with the corresponding shadow register contents, are transferred out of the trace control module and off the SoC into a host agent and system running debugger hardware and software via a JTAG interface.
Owner:TENSILICA
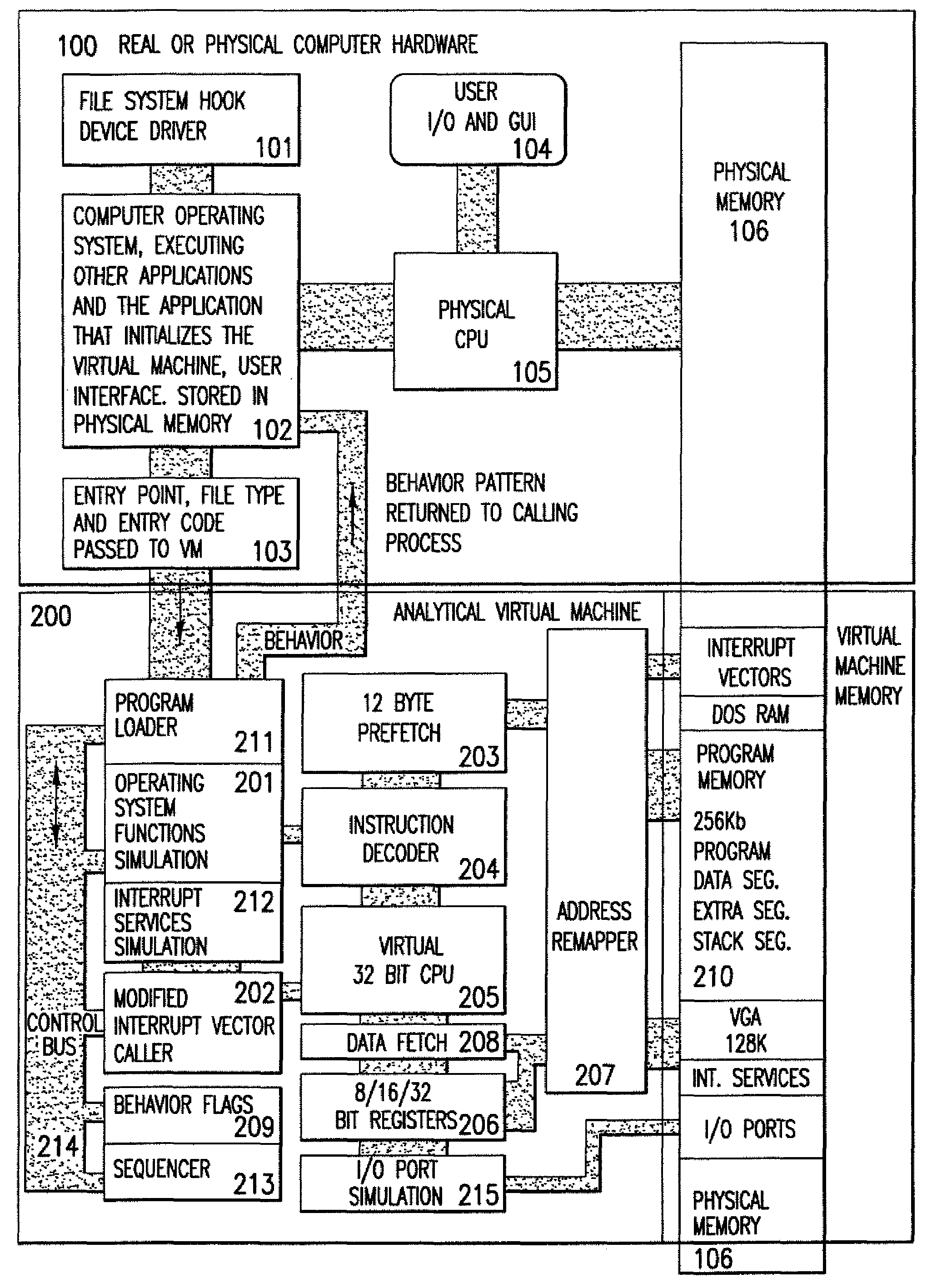
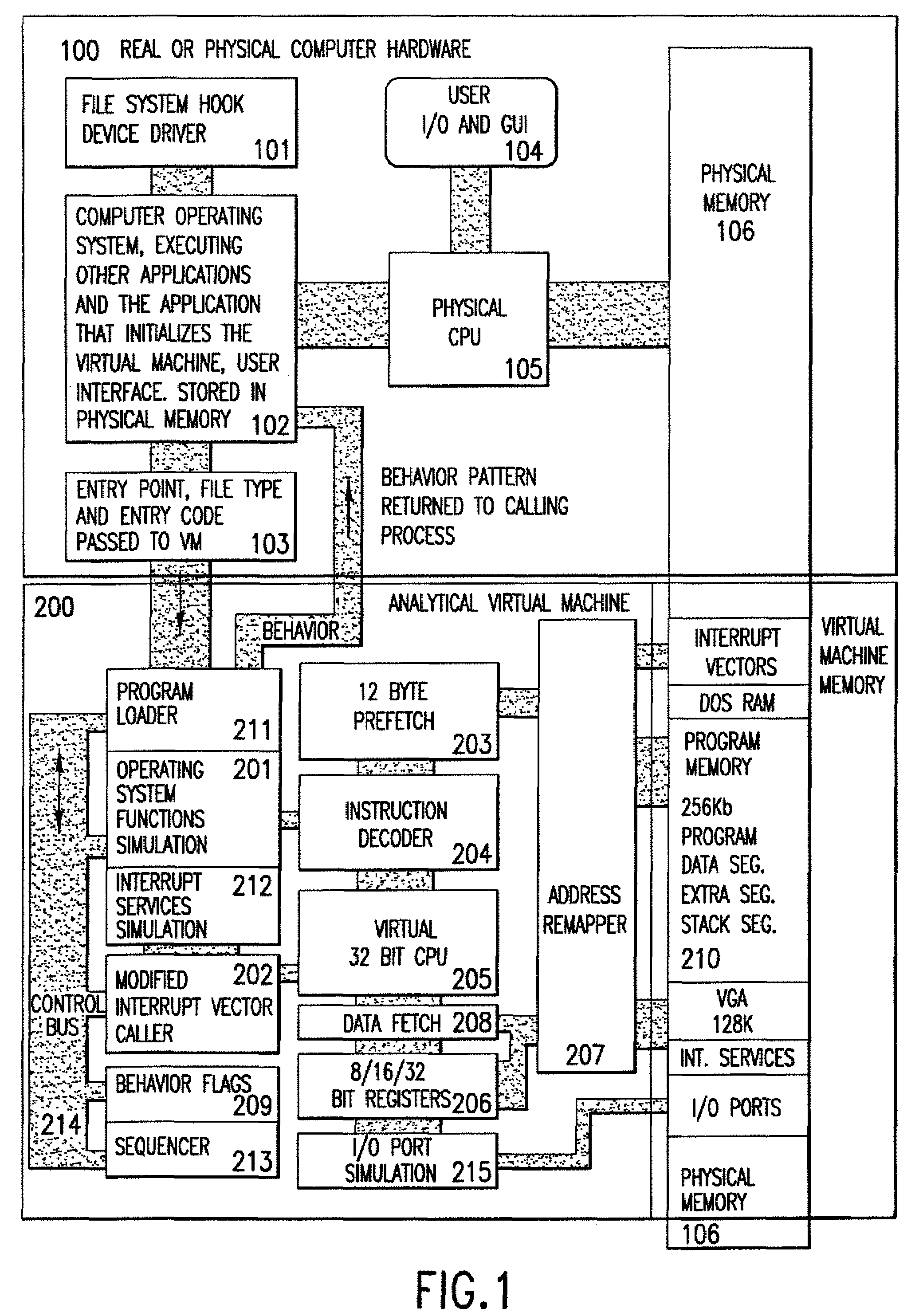
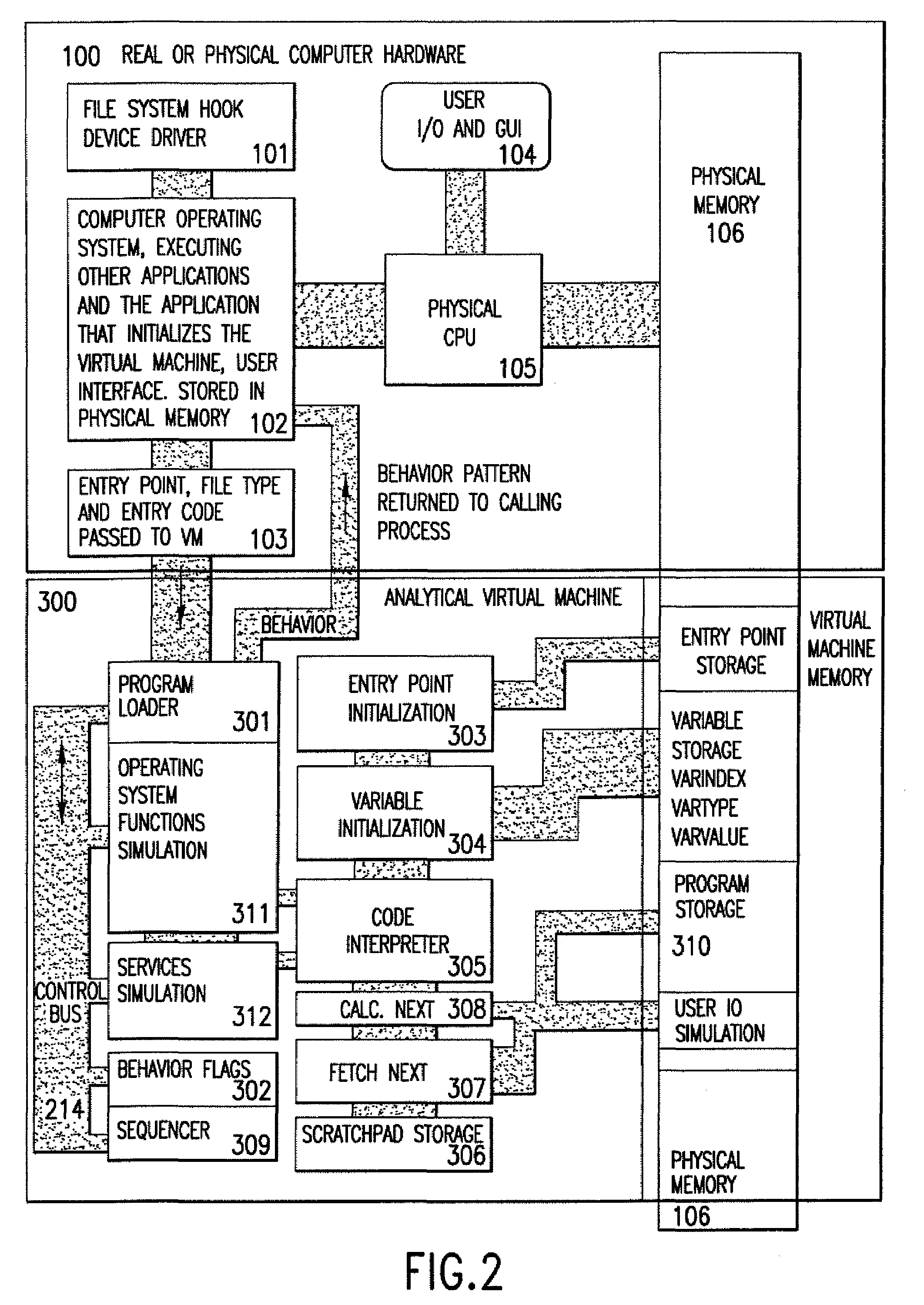
Analytical virtual machine
InactiveUS7657419B2Memory loss protectionError detection/correctionProcessor registerParallel computing
An analytical virtual machine (AVM) analyzes computer code using a software processor including a register that stores behavior flags indicative of behaviors identified by virtually executing the code within the virtual machine. The AVM includes a sequencer that stores the sequence in which behavior flags are set in the behavior flags register. The AVM analyzes machine performance by emulating execution of the code being analyzed on a fully virtual machine and records the observed behavior. When emulation and analysis are complete, the AVM returns the behavior flags register and sequencer to the real machine and terminates.
Owner:KYNDRYL INC
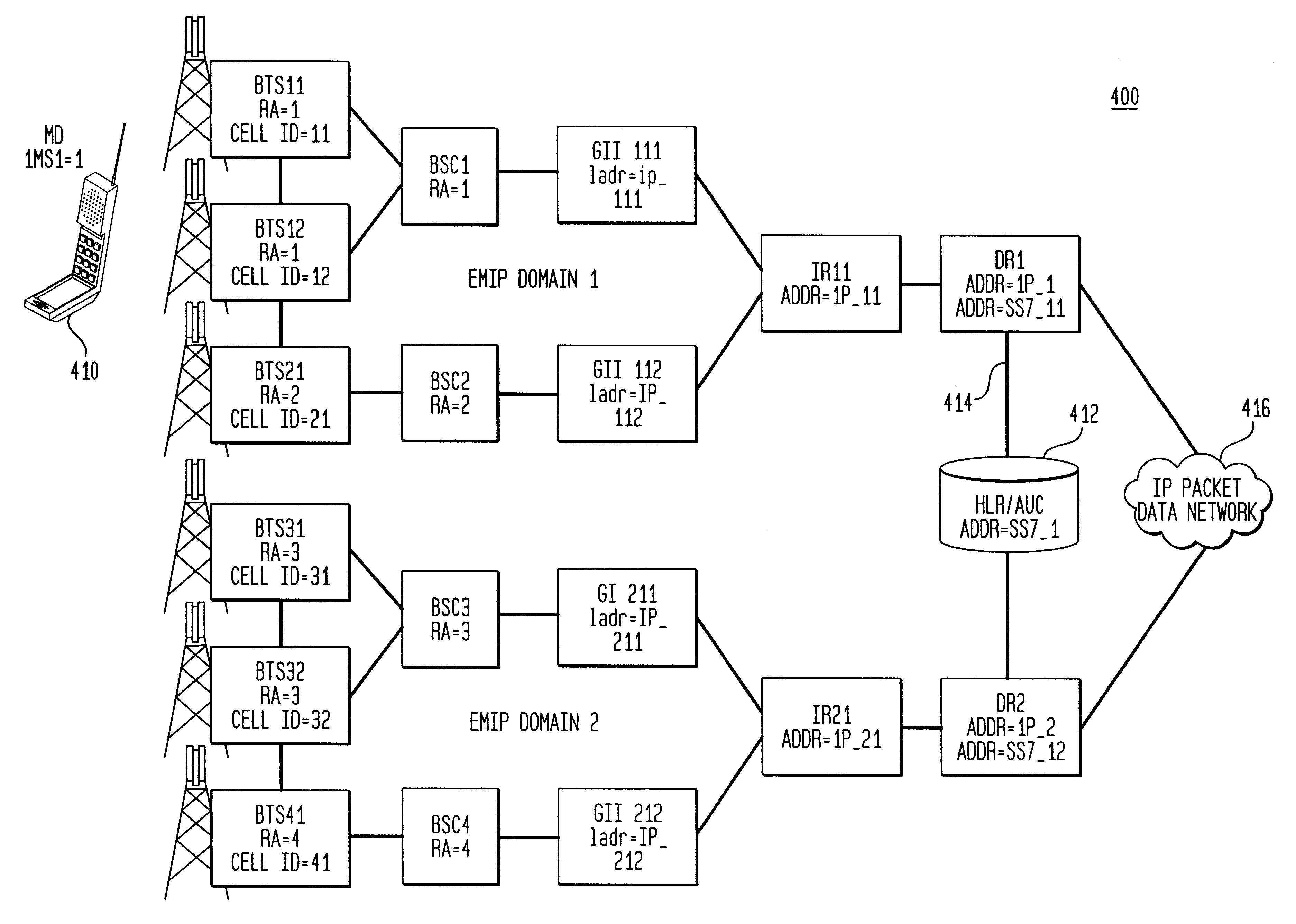
Wireless access of packet based networks
A General Packet Radio Service (GPRS) Accessed Extended Mobile Internet Protocol (EMIP) [G-EMIP] network is provided for wireless mobile device access to external packet data networks. Domains are defined to incorporate a subnet of standard GPRS and EMIP network entities accessed through a Domain Router. Packet access at the radio interface is provided using the base station portion of a GPRS network. Wireless link specific processing is relegated to this potion of the G-EMIP network. EMIP is utilized as a backbone network to provide mobility and service management and interconnection to external networks. A GPRS-IP Interworking entity (GII) interworks IP and GPRS protocols between GPRS and IP addressable network entities (i.e., translates messages of each protocol to corresponding messages of the other protocol). Mobility-related functionality is handled at the IP (network) layer. Mobile IP is used to support the macro-mobility and Handoff-Aware Wireless Access Internet Infrastructure (HAWAII) is used to support micro-mobility and paging. The Domain Router provides packet service management and interacts with a Home Location Register / Authentication Center, which provides GRPS registration, authentication and encryption.
Owner:LUCENT TECH INC +1
Arithmetic processing apparatus
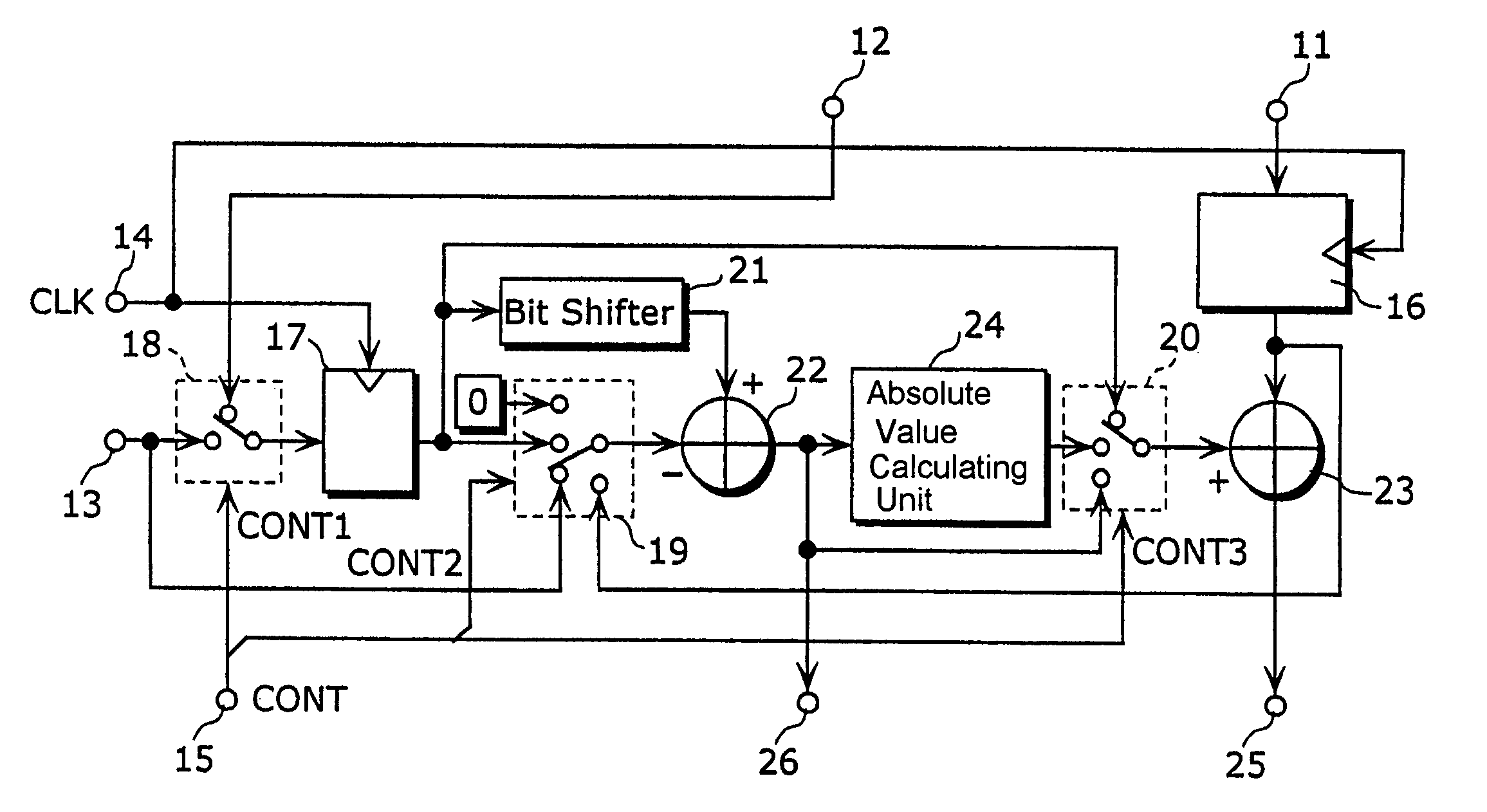
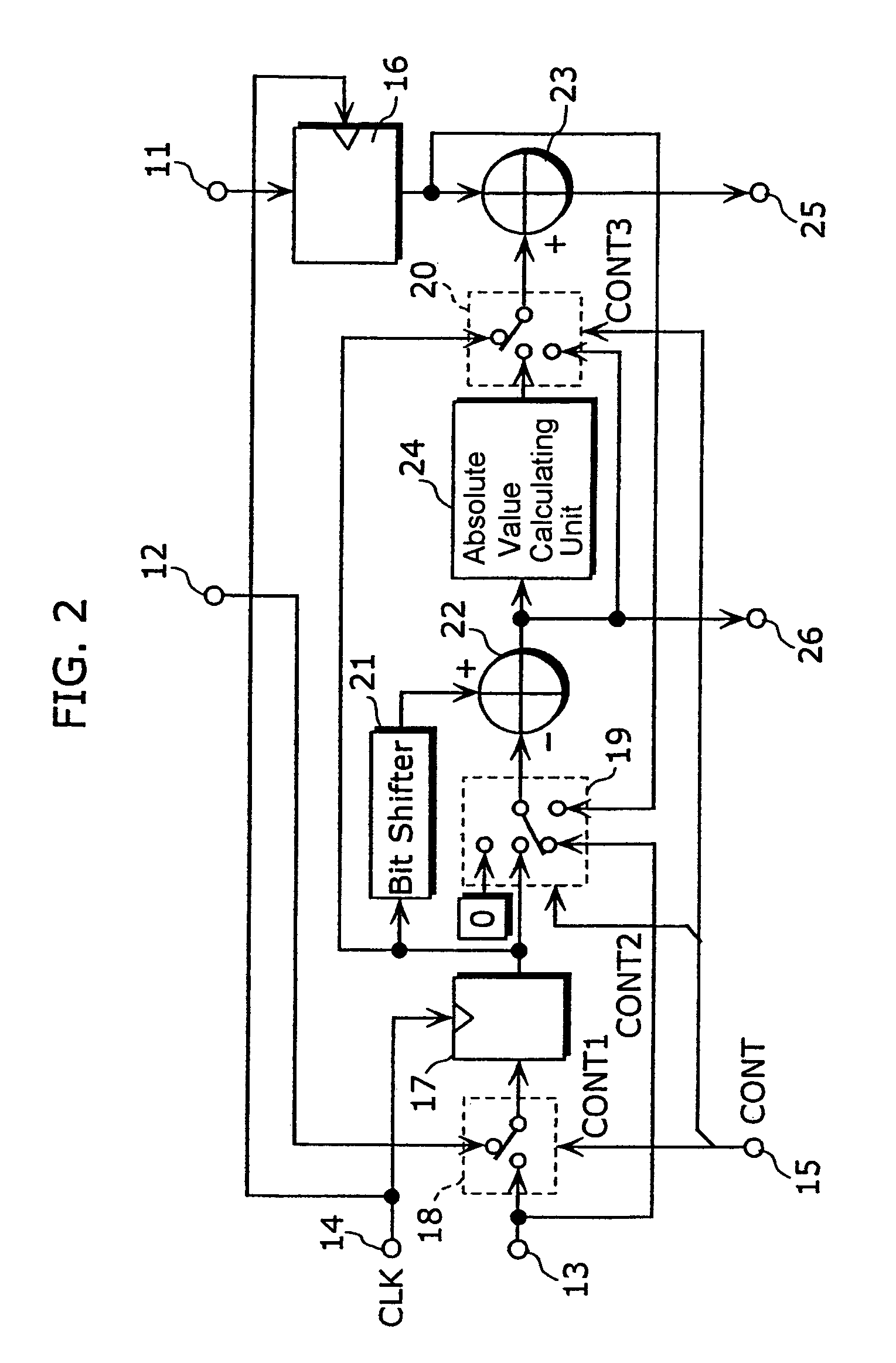
InactiveUS7412470B2MiniaturizationReduce power consumptionDigital data processing detailsPicture reproducers using cathode ray tubesProcessor registerComputer science
The arithmetic processing apparatus of the present invention is an arithmetic processing apparatus that can be reconfigured in accordance with a processing mode and has a plurality of arranged unit arithmetic circuits. Each unit arithmetic circuit includes at least one input terminal, at least one output terminal, a first register which holds data, an adder which calculates a sum of two pieces of data, a second register which holds data, a bit shifter which shifts data left or right, a subtractor which calculates a difference between two pieces of data, an absolute value calculating unit which calculates an absolute value of data, and a path setting unit which sets a path according to the processing mode connecting among these circuit elements.
Owner:GK BRIDGE 1
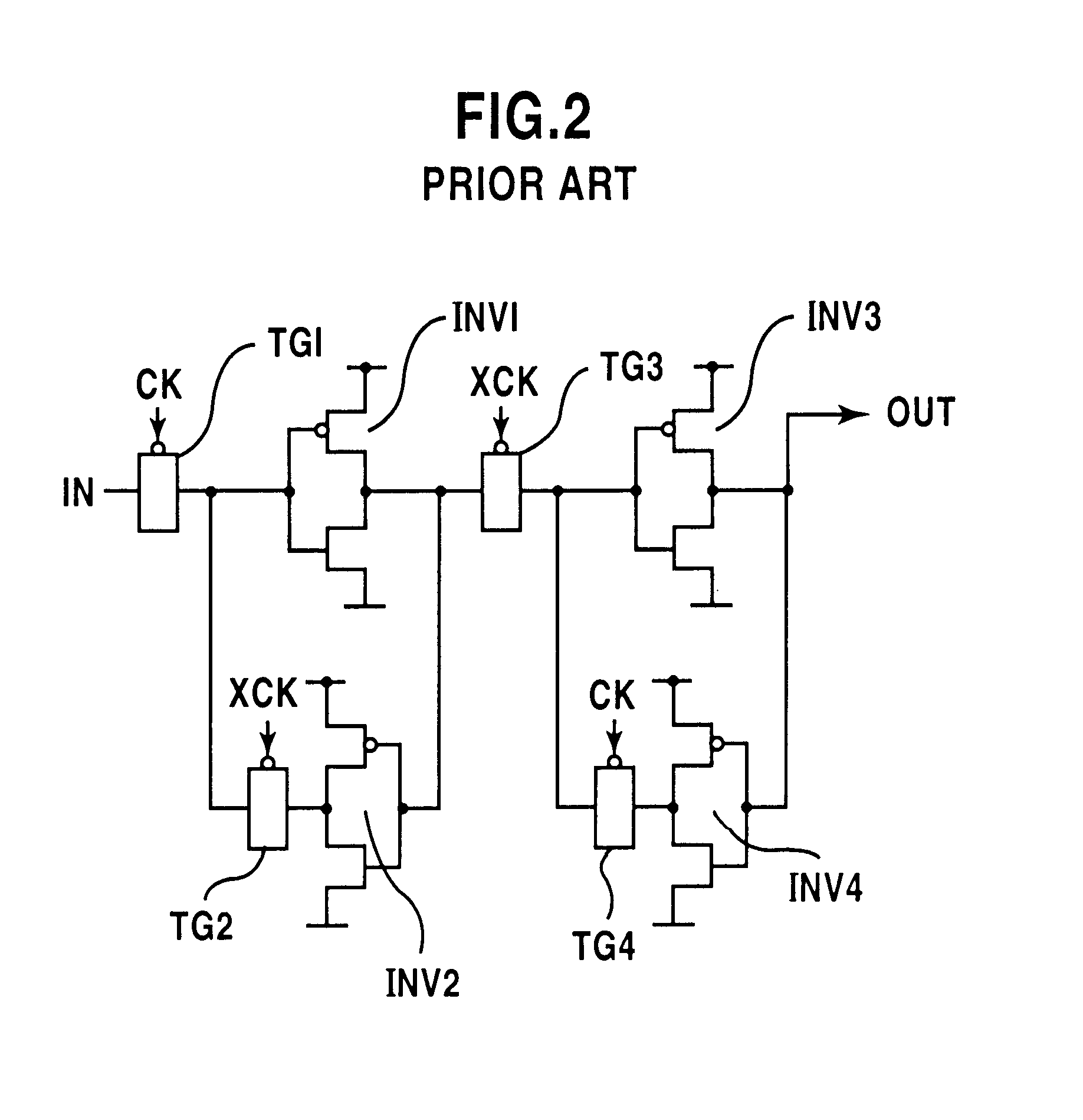
Chain-connected shift register and programmable logic circuit whose logic function is changeable in real time
A shift register having a plurality of circuit cells successively connected in a chain formation is proposed. Each of the circuit cells includes a first inversion gate, a first transmission gate, connected to an output of the first inversion gate, being switched by a clock, and a second inversion gate connected to an output of the first transmission gate. The circuit cell further includes a first P-channel transistor, connected between an output of the second inversion gate and an input of the first inversion gate, being switched by the clock, a second transmission gate, connected to the output of the second inversion gate, being switched by an inversion clock, and a second P-channel transistor, connected to the output of the first transmission gate, being switched by the inversion clock. In the shift register, the plurality of circuit cells are successively connected such that the input of the first inversion gate of the circuit cell is connected to an output of a second transmission gate of a former-stage circuit cell, and the output of the first inversion gate of the circuit cell is connected to an output of a second P-channel transistor of the former-stage circuit cell.
Owner:FUJITSU LTD
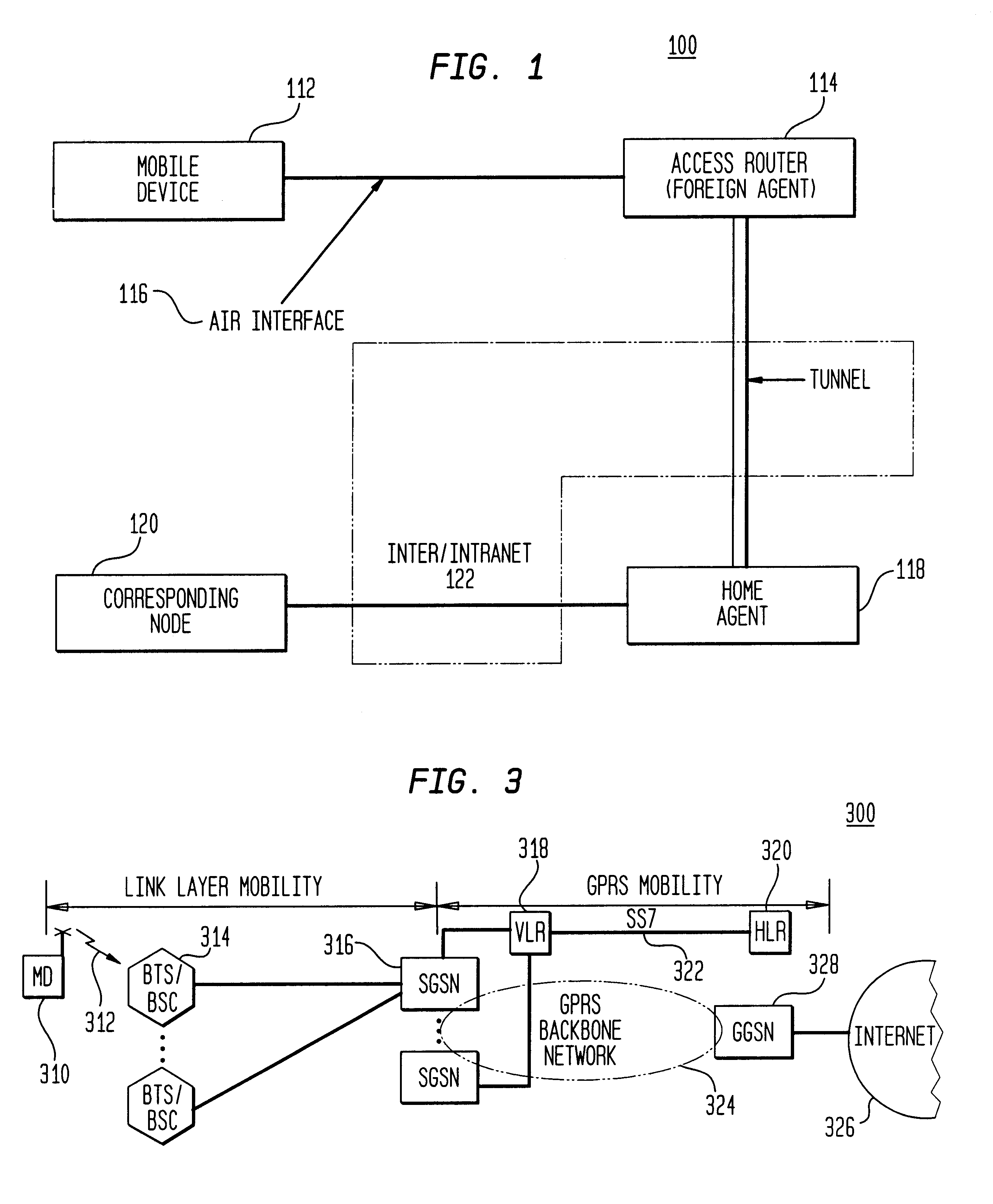
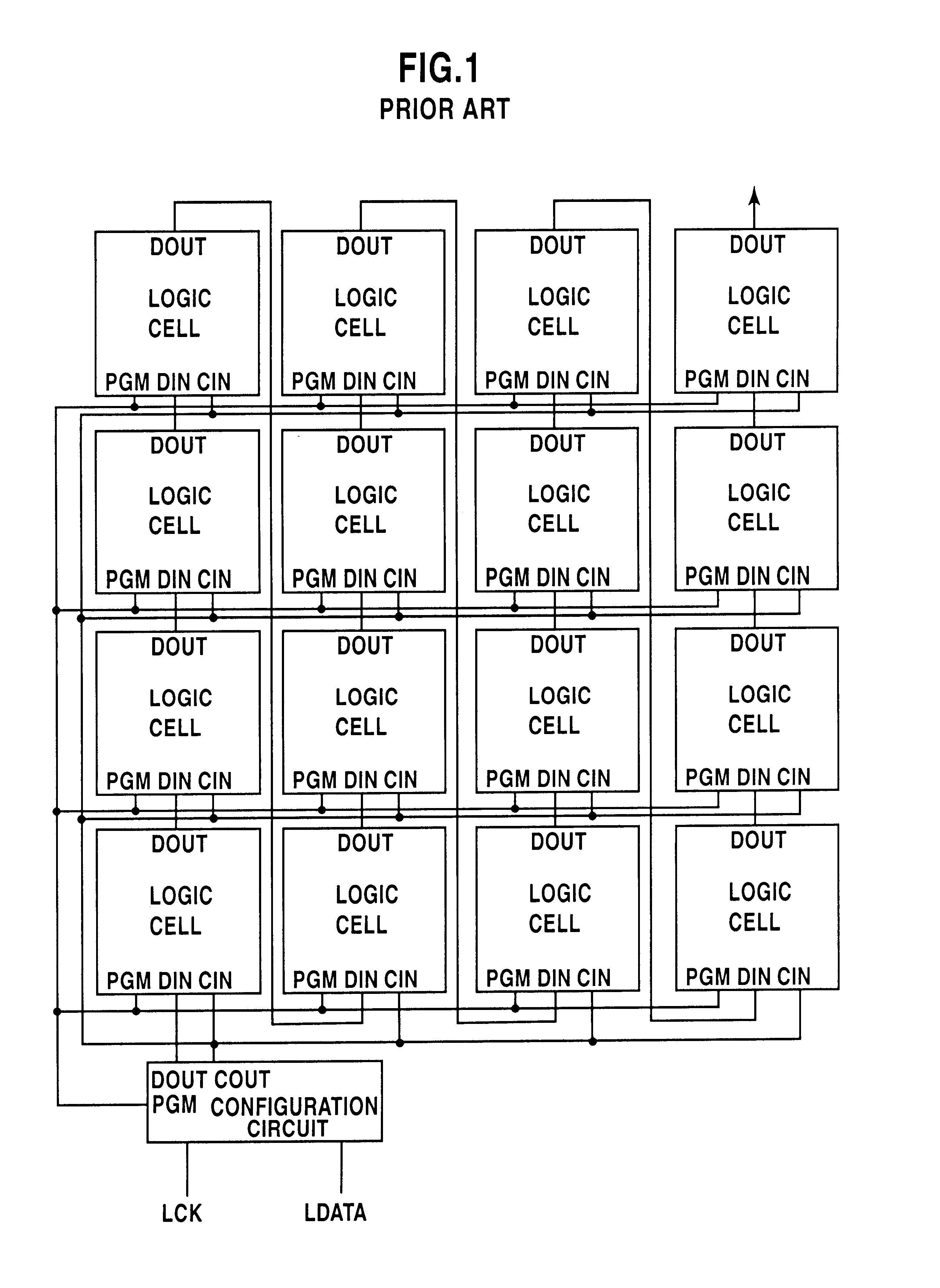
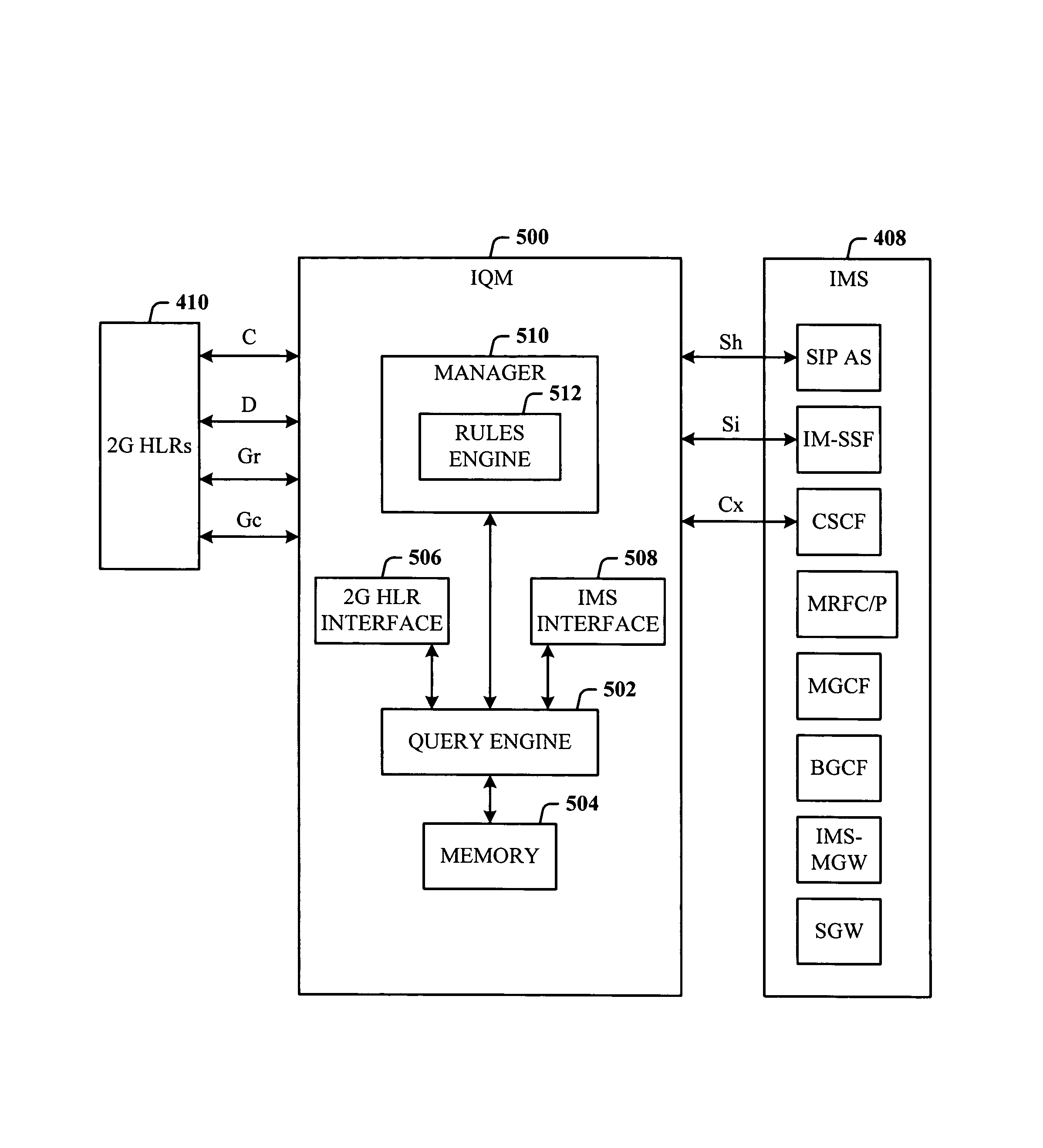
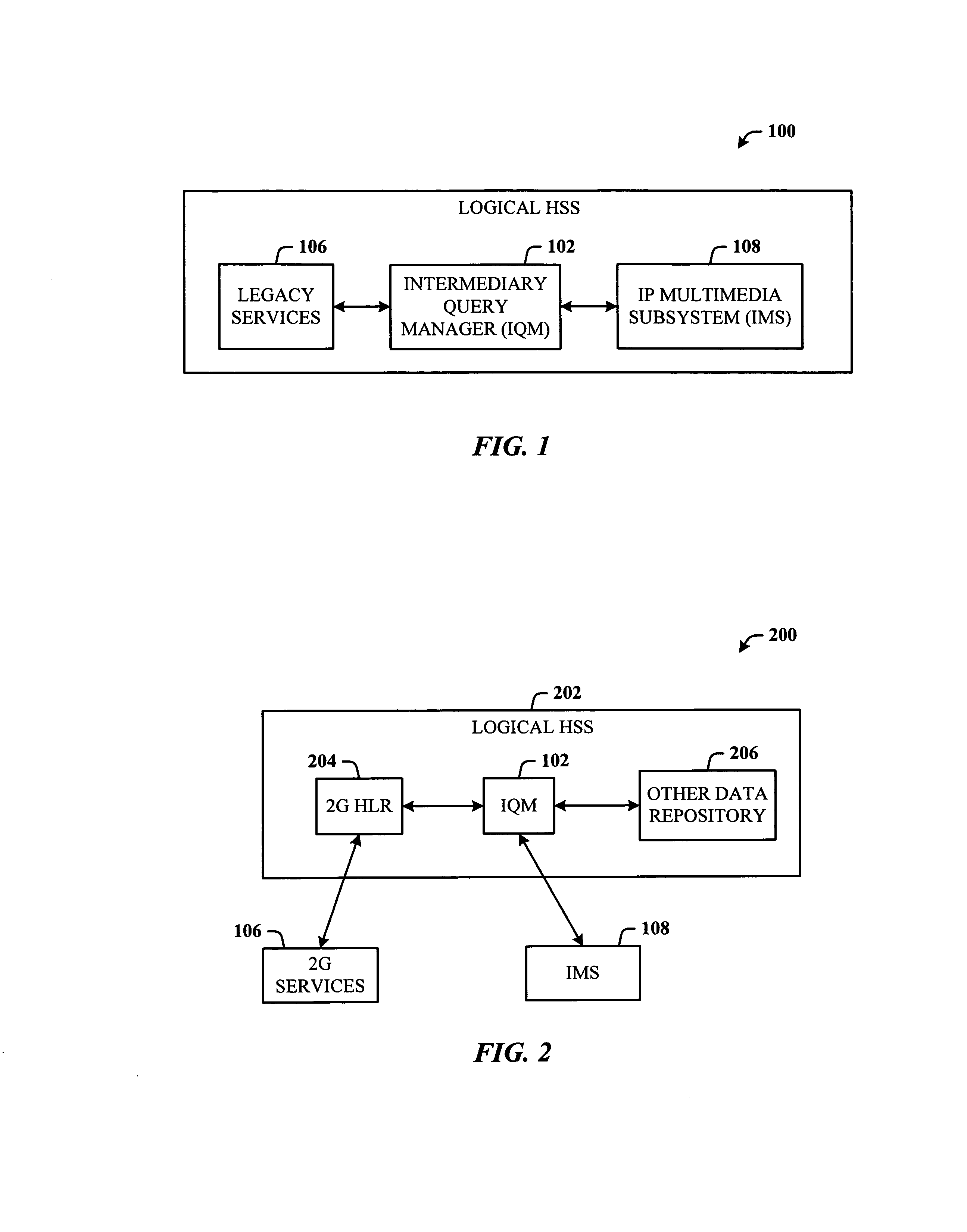
Intermediary query manager for 2G and 3G services
InactiveUS7920529B1Smooth transitionWireless commuication servicesTransmissionProcessor registerService control
An intermediary system that seamlessly evolves the 2G / 2.5G storage mediums to the 3G entities (e.g., a logical HSS) and provides subscriber data to 3G services such as IMS, from legacy data sources. An Intermediary Query Manager (IQM) is provided that functions as intermediary / broker system, and supports defined standard 3GPP interfaces specific to the IMS system (utilizing the existing storage medium servicing the PS domain) and also allows the continued support of the 2G / 2.5G interfaces to 2G HLRs (servicing the CS domain). The IQM provides the capability to leverage usage of the current subscriber databases without requiring extraordinary efforts to migrate subscriber information to a new dedicated HSS element. The IQM provides data from multiple sources and processes requests necessary to fulfill these requests. The IQM can look like a MSC (Mobile Switching Center), VLR (Visitor Location Register), and / or SCP (Service Control Point) to the HLRs depending on the type of queries.
Owner:CINGULAR WIRELESS LLC
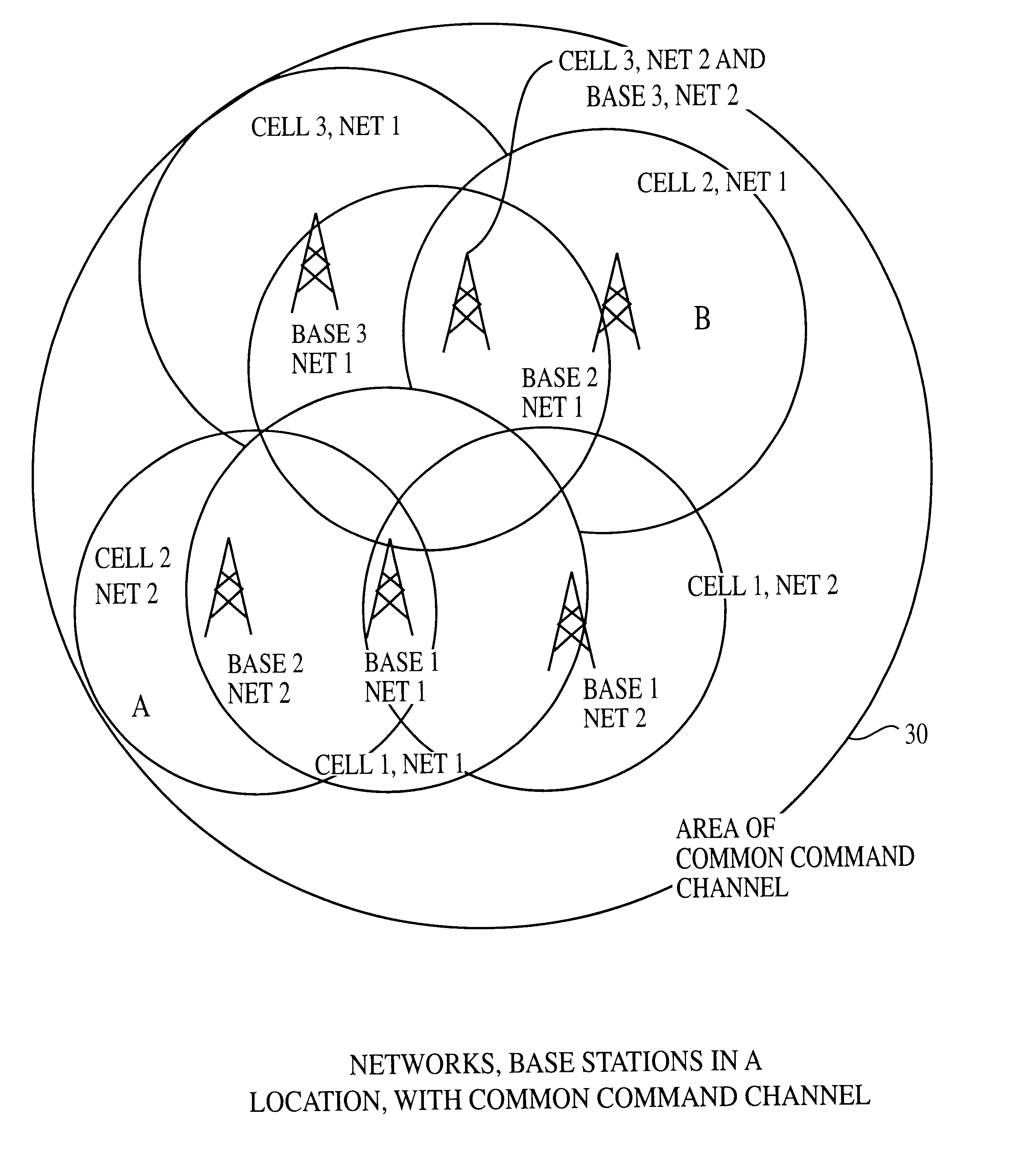
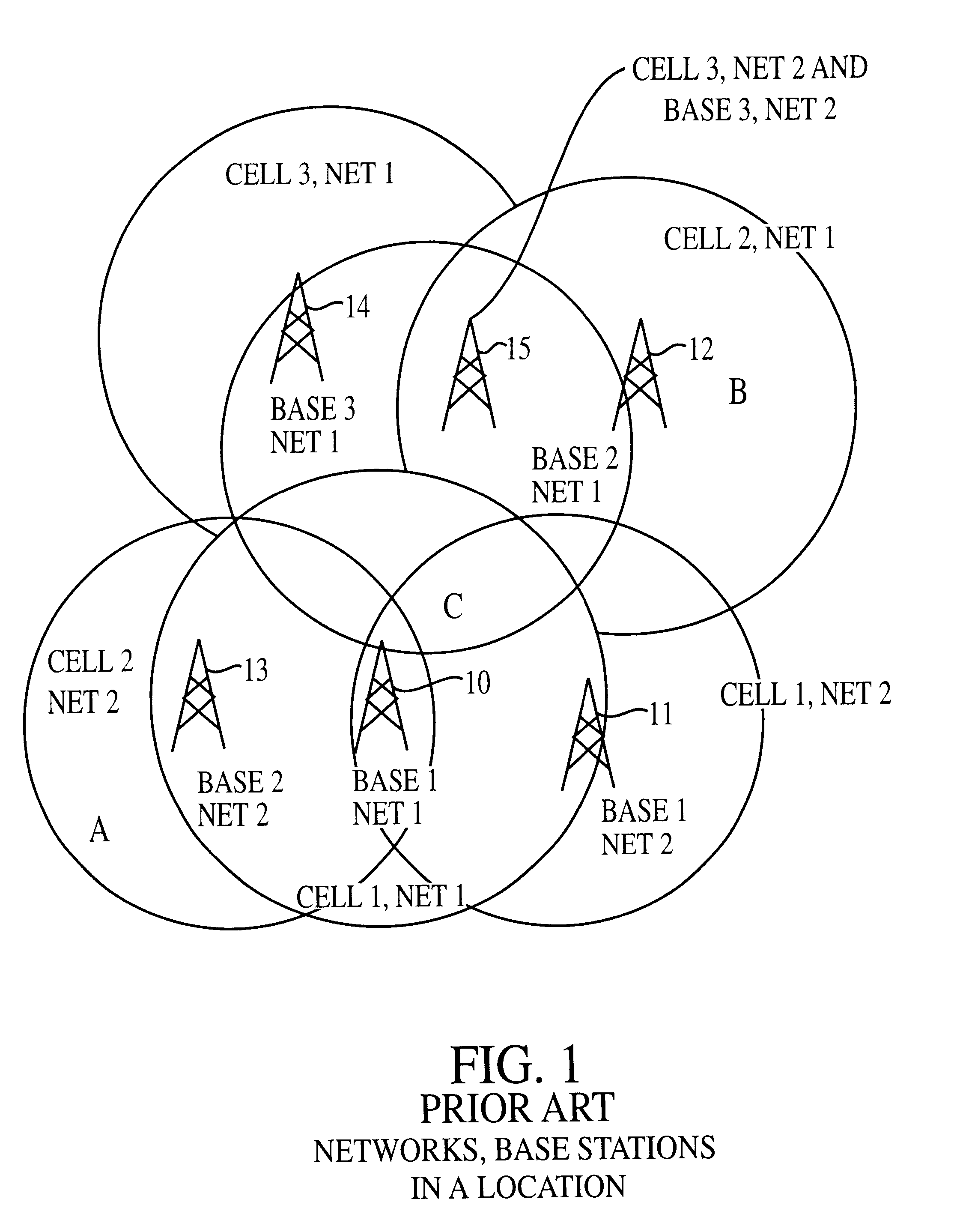
Wireless telecommunications system and method of operation providing users' carrier selection in overlapping hetergenous networks
InactiveUS6591103B1Improve securityAssess restrictionNetwork topologiesProcessor registerCarrier signal
An improved wireless telecommunication system enables a user to obtain communication services in overlapping wireless heterogeneous or homogeneous cellular networks at the most economical cost and bandwidth. A plurality of overlapping cellular networks includes a common command channel, a Central Selection Agency (CSA), a home location register, a visitor location register, and a user device positional location mechanism. In one embodiment the user device is equipped with a Global Positioning System (GPS) to determine its location. In placing a call, the user device broadcasts its ID, location and connection capability requirements on the common command channel. When a base station for the command channel bears the request, the CSA and the home location register for the user are informed. The CSA capability / requirements determine which network and base station selections are potential carriers for the call. Based on user preferences established by a profile stored in an accessible database, the CSA assigns a network and base station to handle the connection. The user device is informed and tunes to the appropriate network and protocols. For incoming calls, the calling party checks the home location register to determine the last known location. The user device is informed that a called is waiting. The user device selects the network and base station to receive the call in a fashion similar to that of placing the call. A call may be transferred from one network to a different network, the networks using different protocol. The user device may be programmed to change networks at random times to provide enhanced security for a call.
Owner:IBM CORP
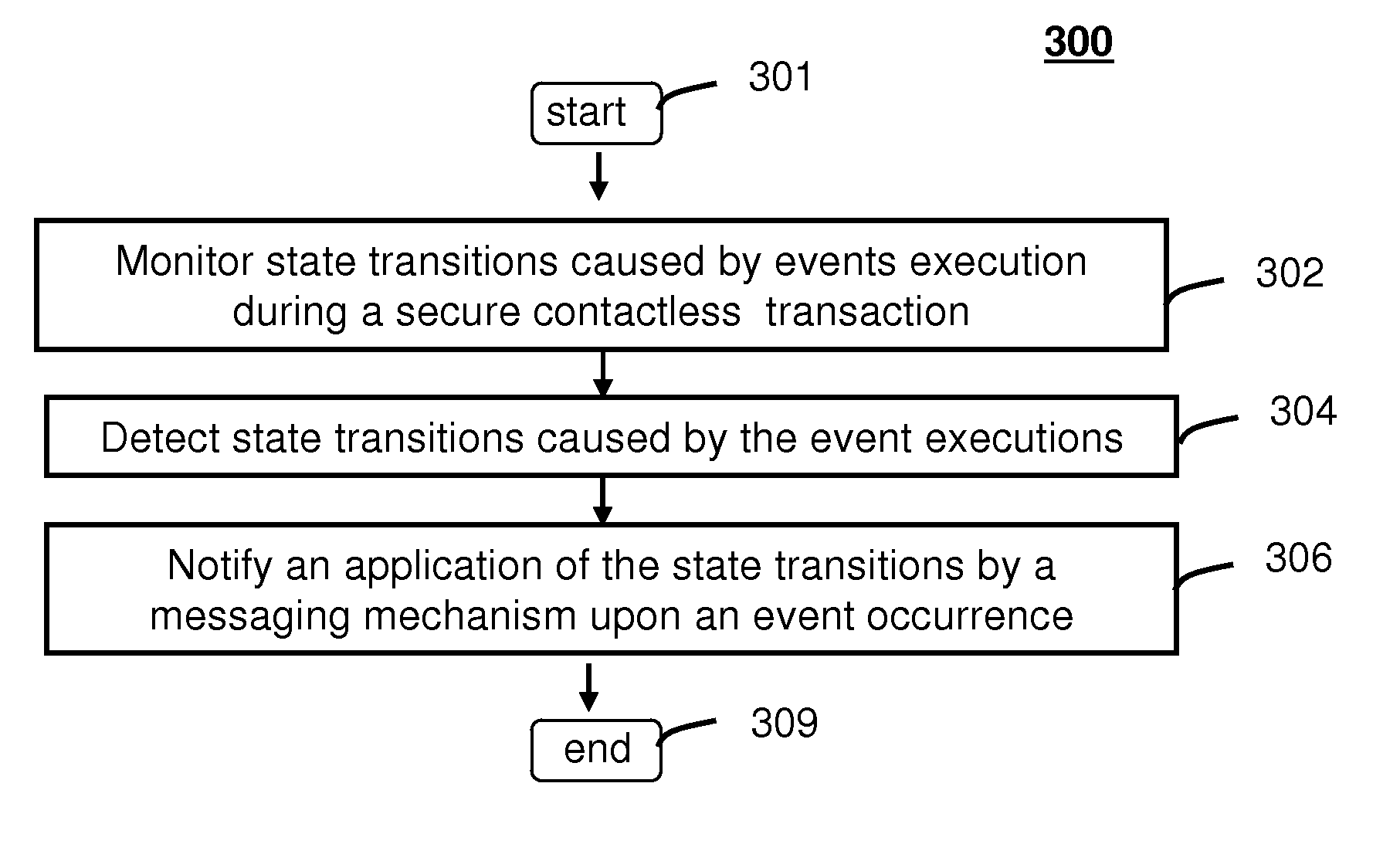
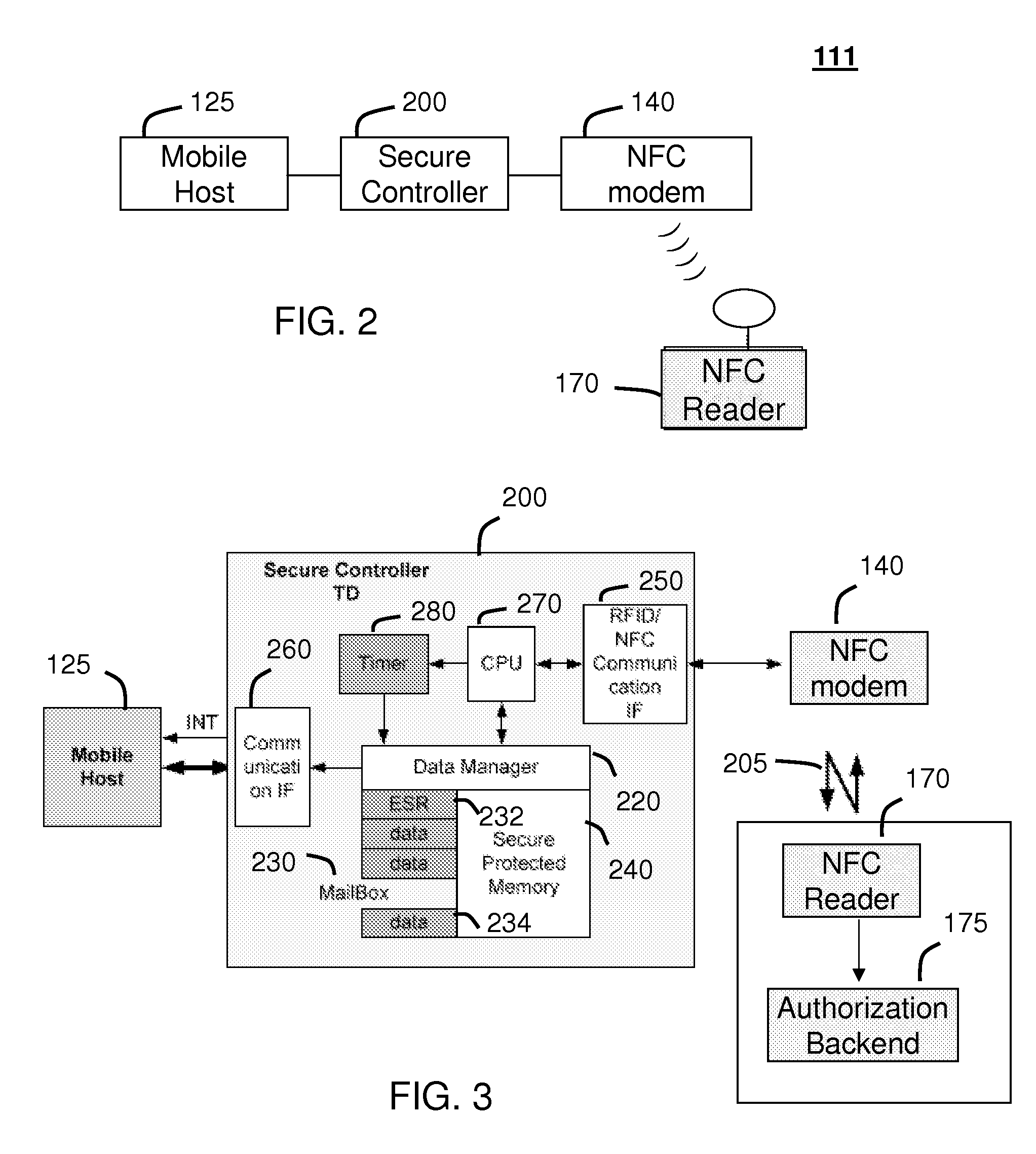
Method and system for monitoring secure application execution events during contactless rfid/nfc communication
ActiveUS20080162361A1Radio transmissionSecuring communicationCommunications securityTechnical communication
A system (211) and method (300) for reliable monitoring of secure application execution events is provided. The system can include a Near Field Communication (NFC) modem (140) for communicating transaction events of a secure contactless transaction (358) with a NFC reader (170), a secure controller (200) for monitoring state transitions caused by the transaction events, and a mobile host communicatively coupled to the secure controller for receiving hardware event notifications of the state transitions. The secure controller can generate message using a hardware interrupt to a mobile host based on secure applet state transition monitoring by setting up the events flag such as a Transaction Completion Flag (TCF) (372) into an Events Status Register (232) to identify a status of a secure contactless transactions
Owner:GOOGLE TECH HLDG LLC
Techniques for processing out-of -order requests in a processor-based system
InactiveUS20030093630A1Memory systemsInput/output processes for data processingShift registerProcessor register
A mechanism for executing requests in a system. More specifically, a technique for processing requests to a memory system is provided. A shift register may be used to store an index associated with requests, such as read and write requests, to a memory system. Each request is stored in a respective queue depending on the source of the request and the request type (e.g. read or write). Each request includes flags which may be set to determine the processing order of the requests, such that out-of-order processing is feasible. An index corresponding to each of the requests is stored in an index shifter to facilitate the out-of-order processing of the requests. Alternatively, a shift register may be used to store each of the requests. Rather than shifting the indices to facilitate the out-of-order processing of requests, depending on the state of the corresponding request flags, the entire entry may be shifted.
Owner:VALTRUS INNOVATIONS LTD +1
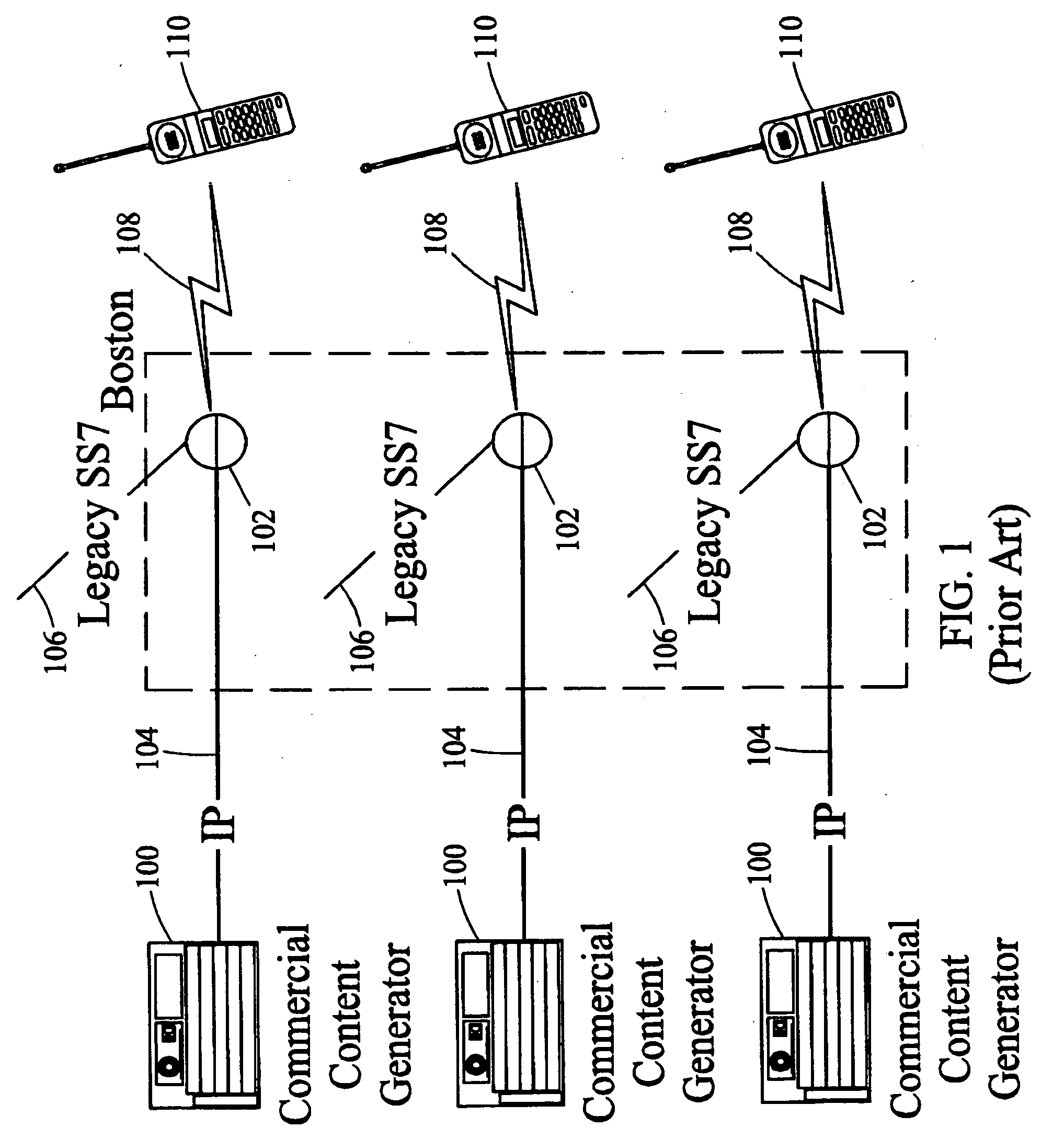
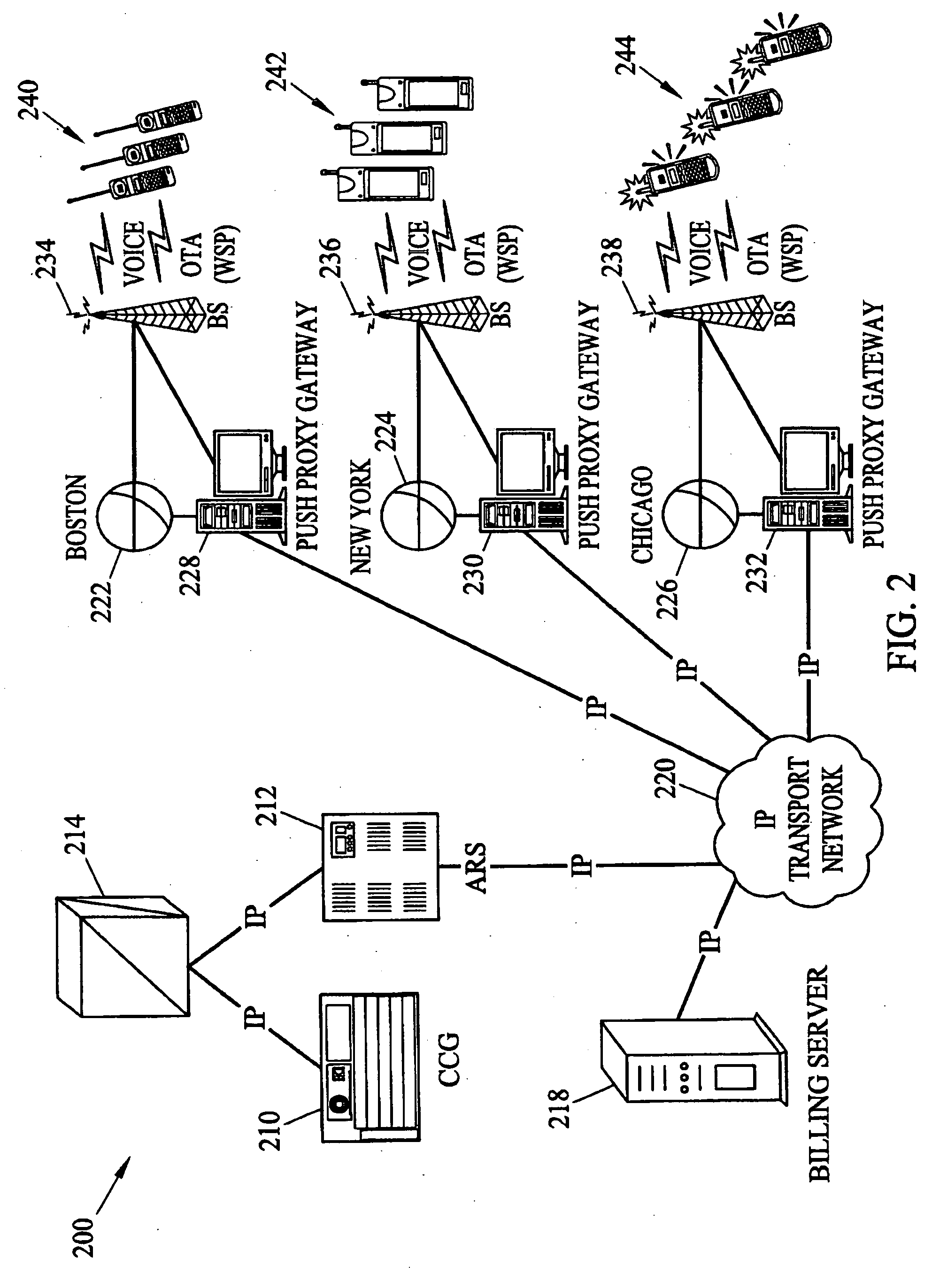
Methods and systems for generating, distributing, and screening commercial content
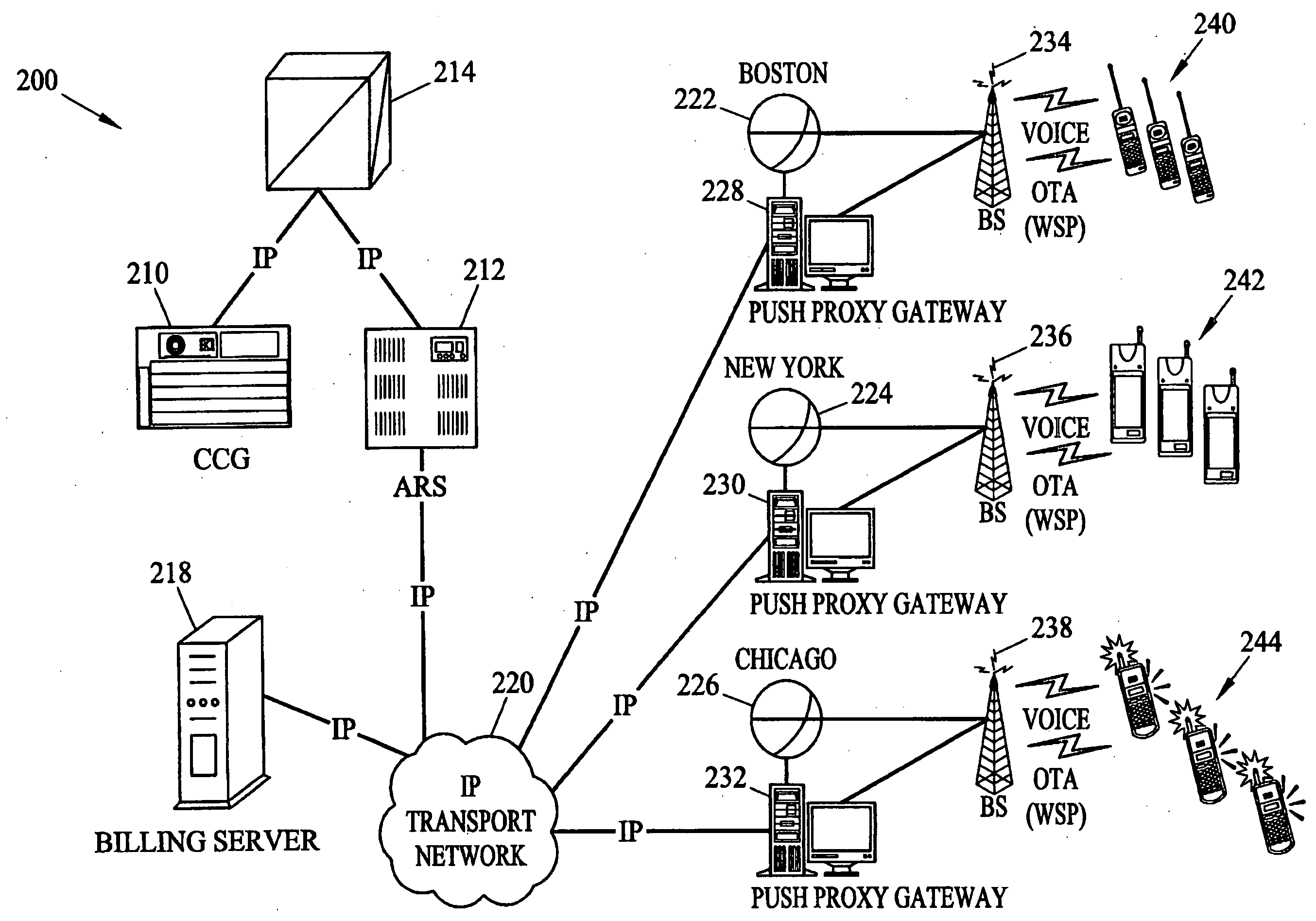
ActiveUS20040259553A1Broadcast systems characterised by addressed receiversBroadcast transmission systemsProcessor registerAddress resolution
Methods and systems for generating, distributing, and screening commercial content are disclosed. A commercial content generator (CCG) generates commercial content message and obtains from a push proxy agent address resolution server the network routing address of each push proxy agent that is required for distribution of the message to the target mobile subscriber audience. A push proxy agent receives a message containing commercial content and resolves a mobile subscriber identifier for each mobile subscriber who is to receive the commercial content information using subscriber information obtained from a subscriber location register, such as a visitor location register (VLR). The push proxy agent may also negotiate media format characteristics for each member of the target mobile subscriber audience and facilitate delivery of the commercial content to each member of the target mobile subscriber audience.
Owner:TEKELEC
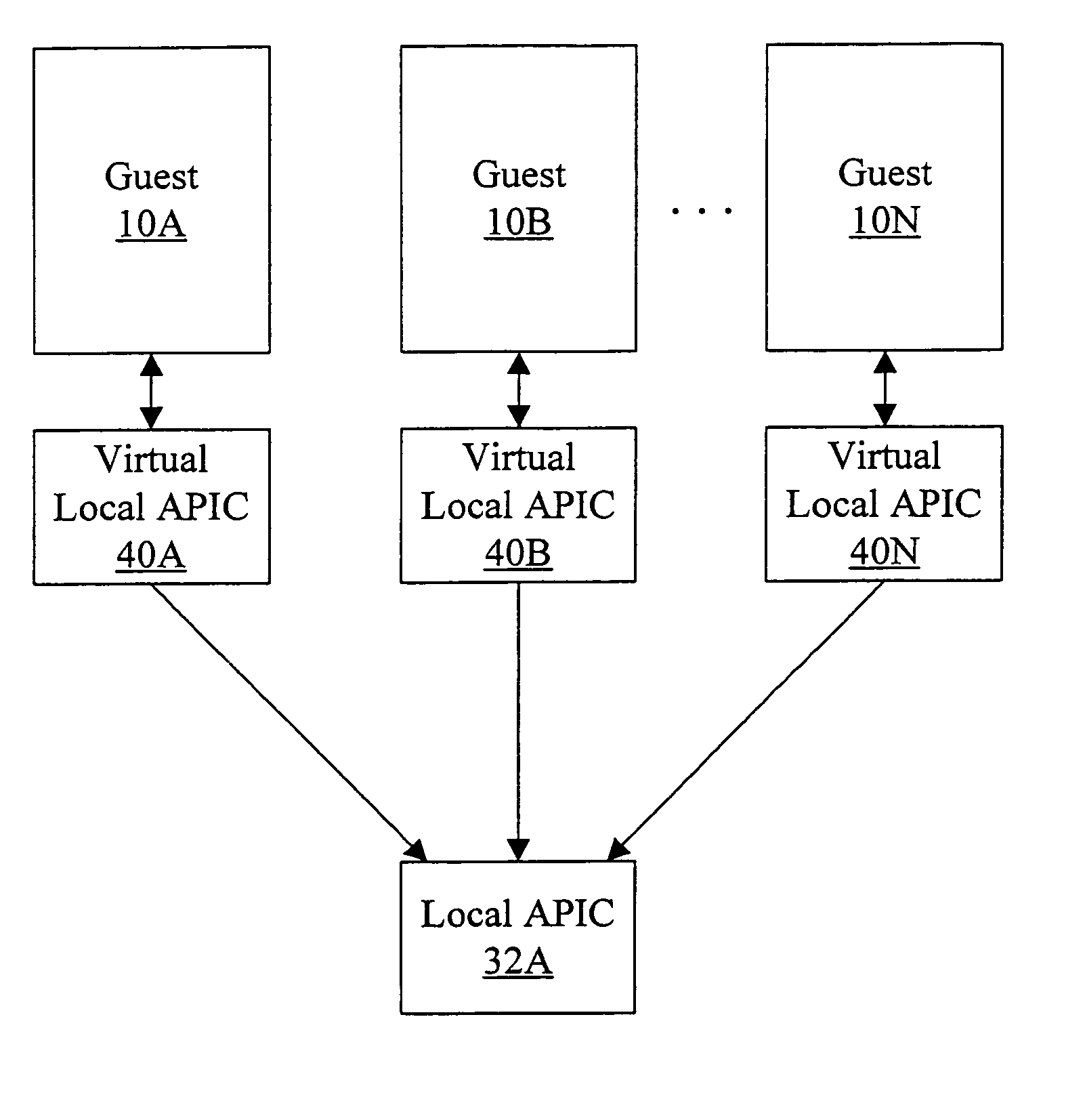
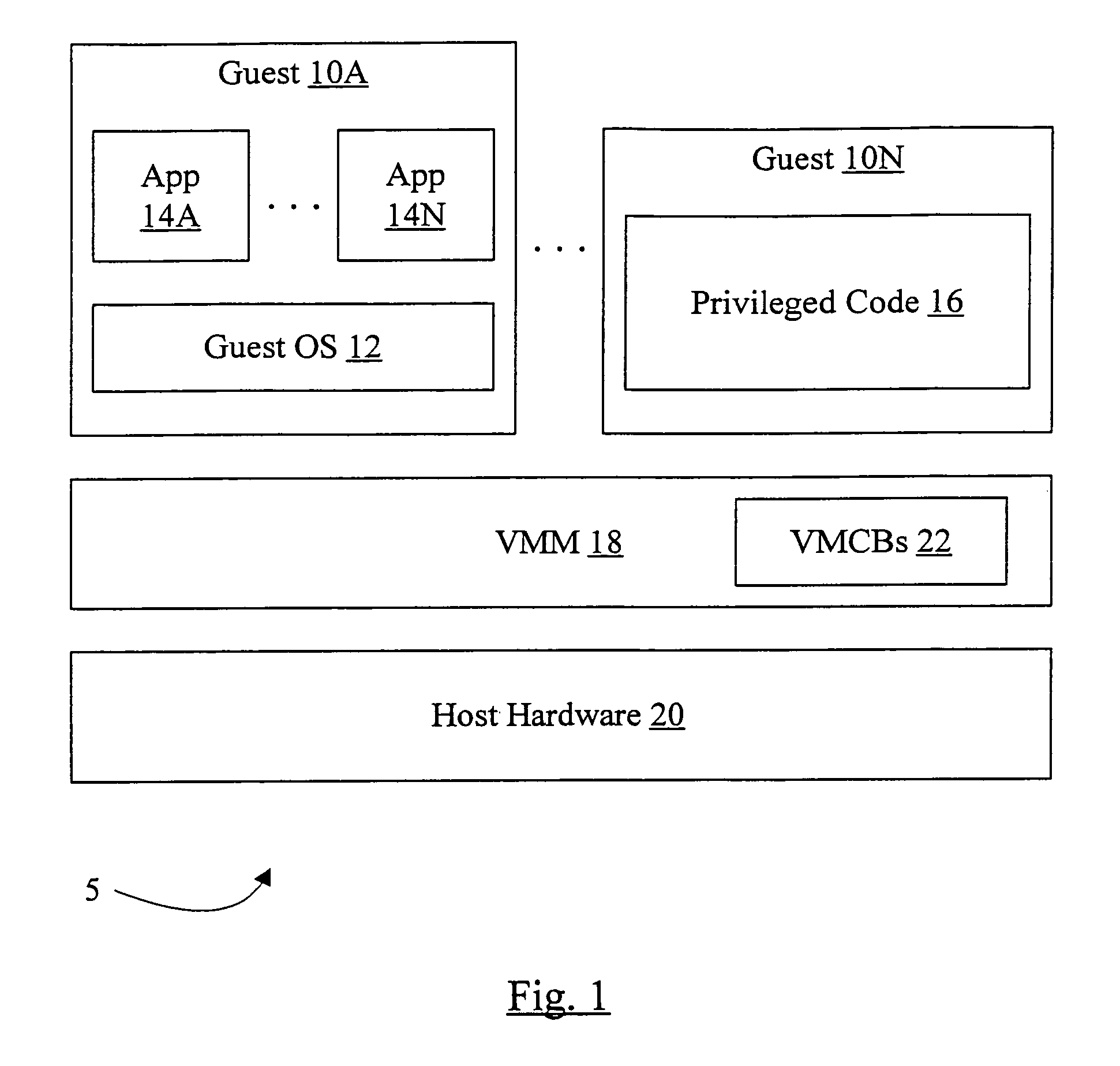
Processor that maintains virtual interrupt state and injects virtual interrupts into virtual machine guests
In one embodiment, a processor comprises one or more registers and a control unit. The registers are configured to store interrupt state describing a virtual interrupt. The control unit is configured to initiate the virtual interrupt responsive to the interrupt state. In another embodiment, a method comprises storing an interrupt state describing a virtual interrupt in a storage area allocated to a guest. A processor initiates the virtual interrupt subsequent to initiating execution of the guest, responsive to the interrupt state. In still another embodiment, a computer accessible medium stores a plurality of instructions comprising instructions which, when executed on a processor in response to a physical interrupt: determine a guest into which a virtual interrupt corresponding to the physical interrupt is to be injected; and store an interrupt state describing the virtual interrupt in a storage area allocated to the guest.
Owner:GLOBALFOUNDRIES US INC
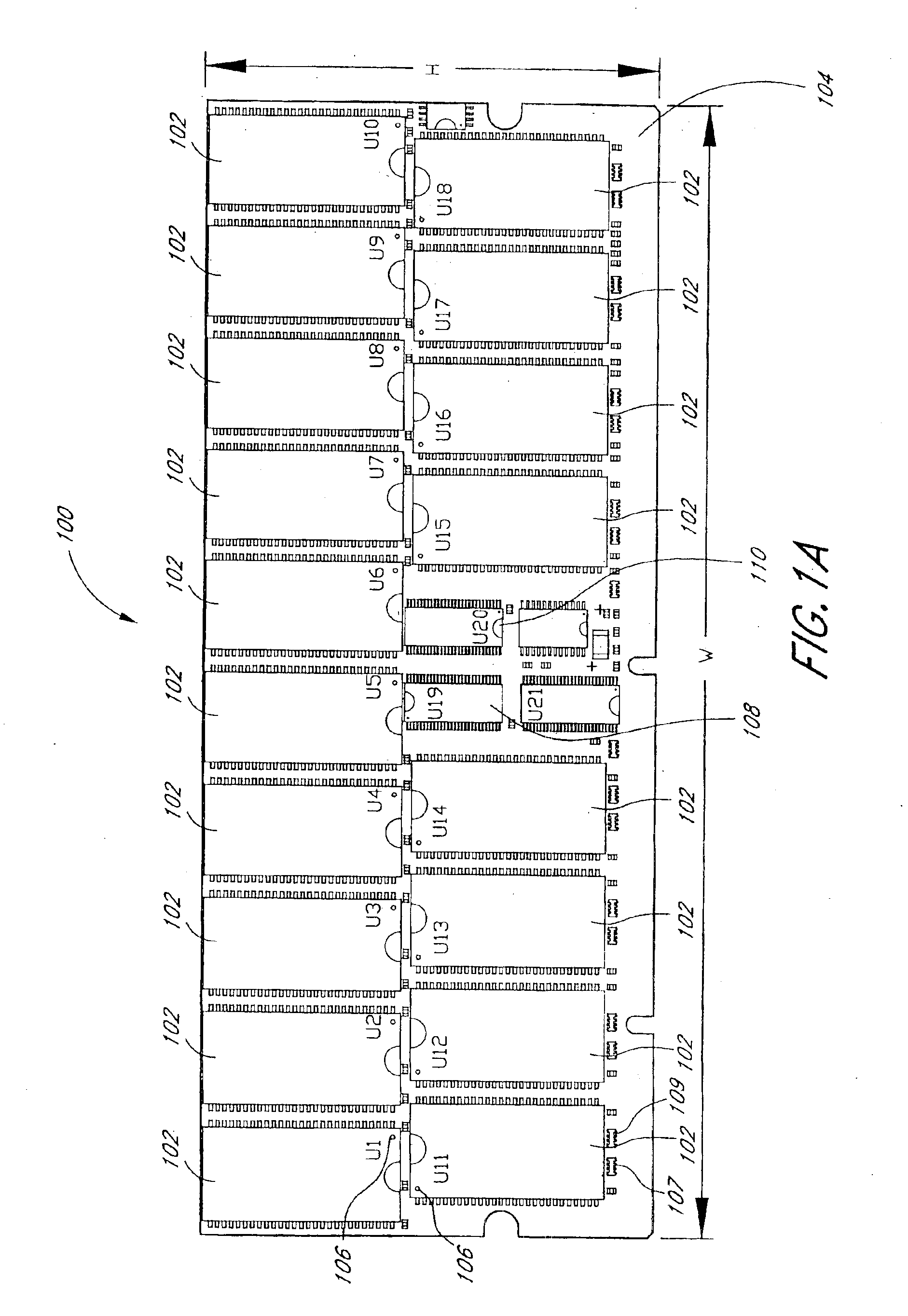
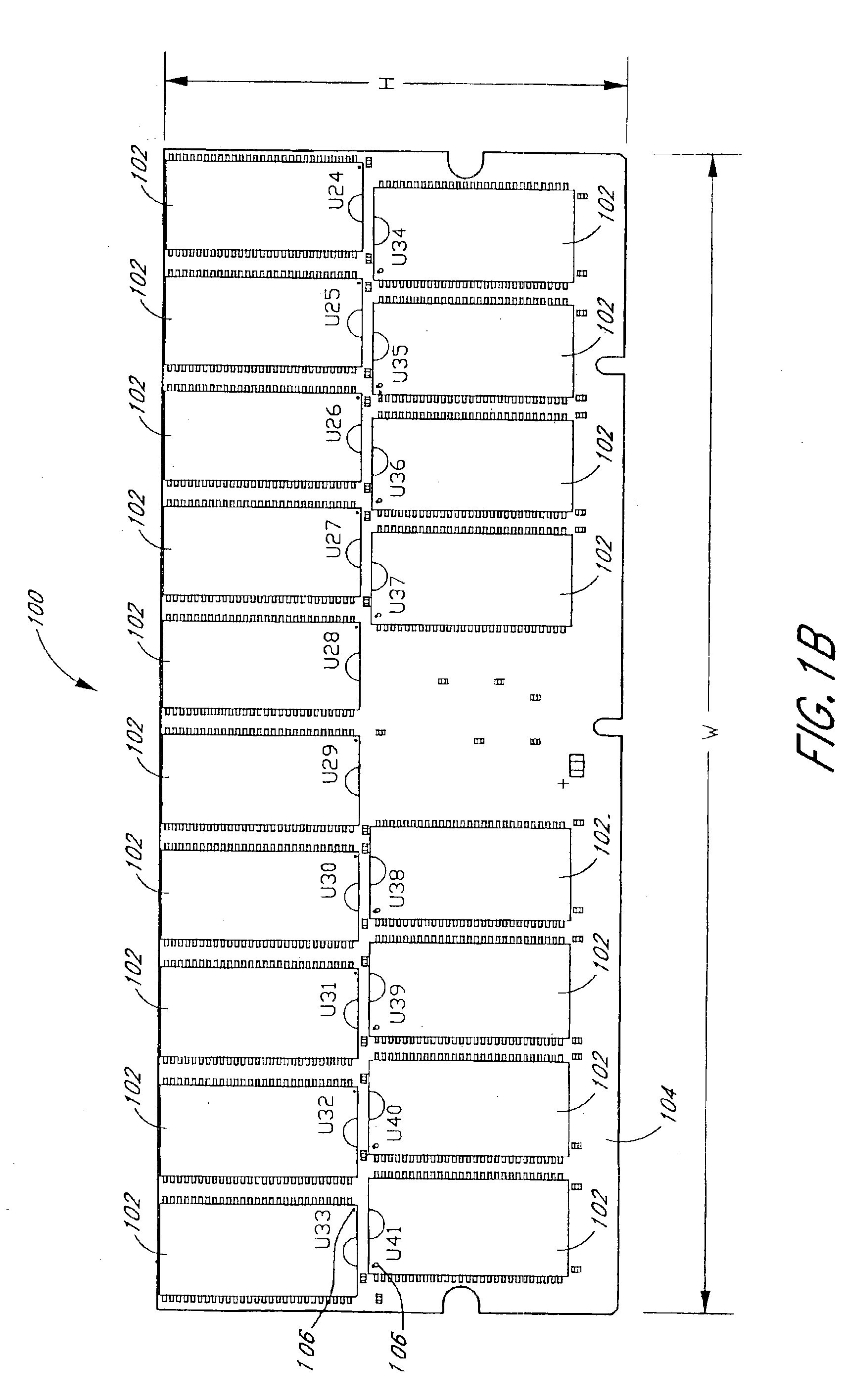
Arrangement of integrated circuits in a memory module
Integrated circuits utilizing standard commercial packaging are arranged on a printed circuit board to allow the production of 1-Gigabyte and 2-Gigabyte capacity memory modules. A first row of integrated circuits is oriented in an opposite orientation to a second row of integrated circuits. The integrated circuits in a first half of the first row and in the corresponding half of the second row are connected via a signal trace to a first register. The integrated circuits in a second half of the first row and in the corresponding half of the second row are connected to a second register. Each register processes a non-contiguous subset of the bits in each data word.
Owner:NETLIST INC
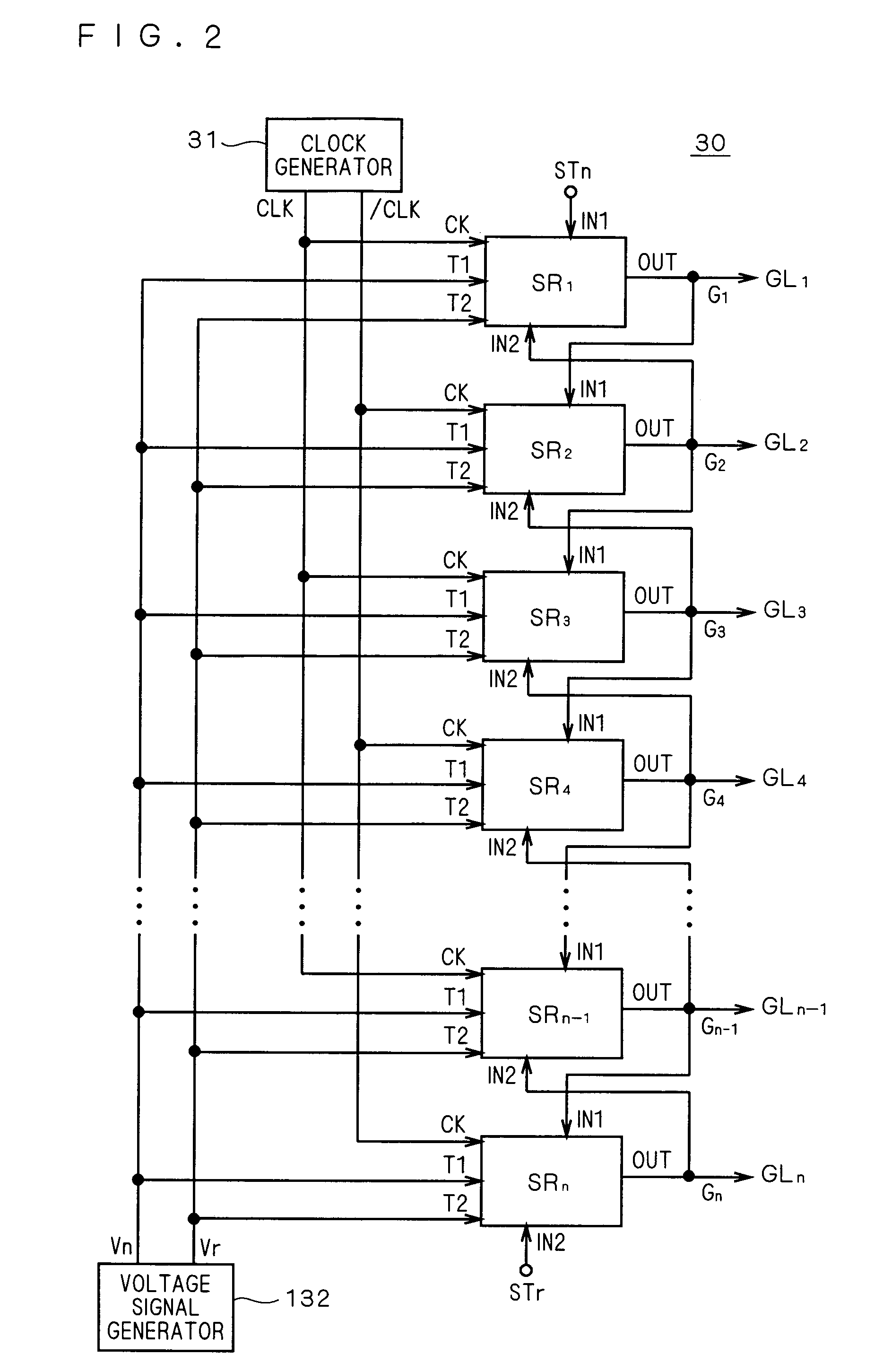
Shift register circuit and image display apparatus equipped with the same
InactiveUS20070274433A1Suppress failureIncrease computing speedStatic indicating devicesDigital storageShift registerElectricity
Malfunction caused by leakage current of the transistor and shift in threshold voltage is prevented in the shift register in which the signal can be shifted bi-directionally. The bi-directional unit shift register includes a first transistor Q1 for providing a first clock signal CLK to an output terminal OUT, a second transistor Q2 for discharging the output terminal OUT based on a second clock signal, third and fourth transistors Q3, Q4 for providing first and second voltage signals Vn, Vr complementary to each other to a first node, which is a gate node of the first transistor Q1, and a fifth transistor Q5 connected between the first node and the output terminal OUT. The fifth transistor Q5 is in an electrically conducted state based on the first clock signal CLK when the gate of the transistor Q1 is at L (Low) level.
Owner:MITSUBISHI ELECTRIC CORP
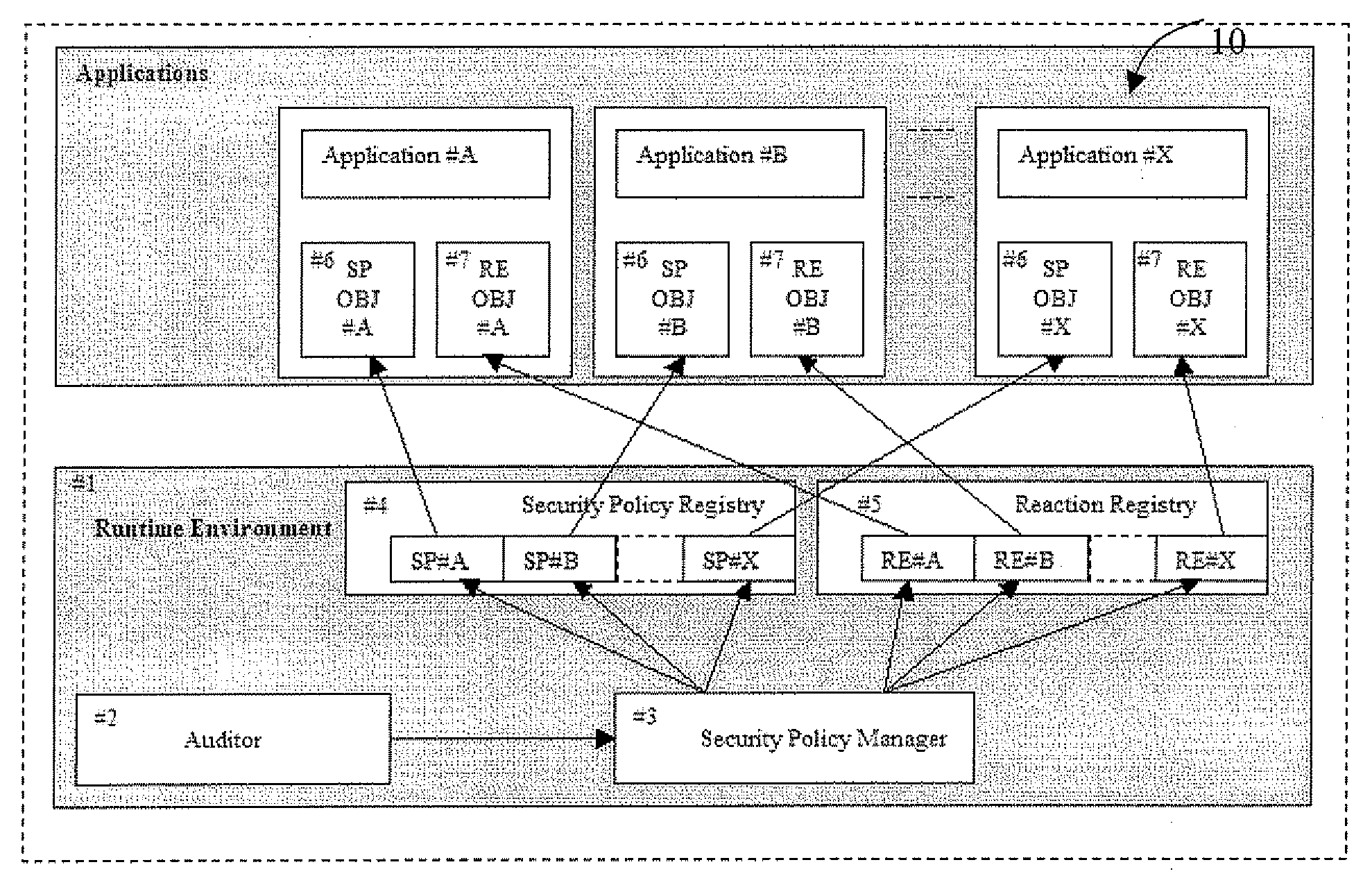
Multi-application IC card with secure management of application
ActiveUS20080128515A1Avoid spreadingAcutation objectsPayment architectureProcessor registerSecurity policy management
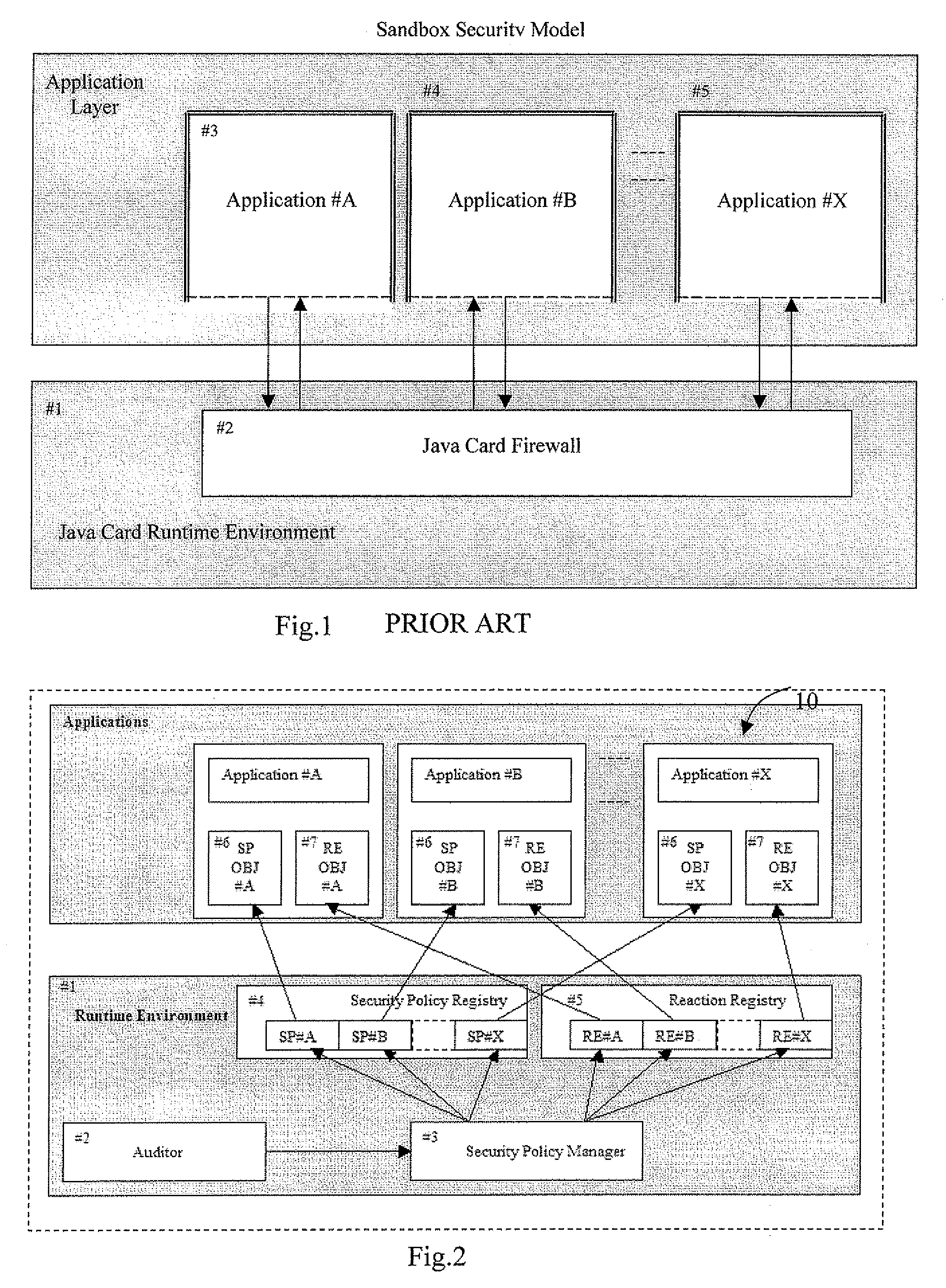
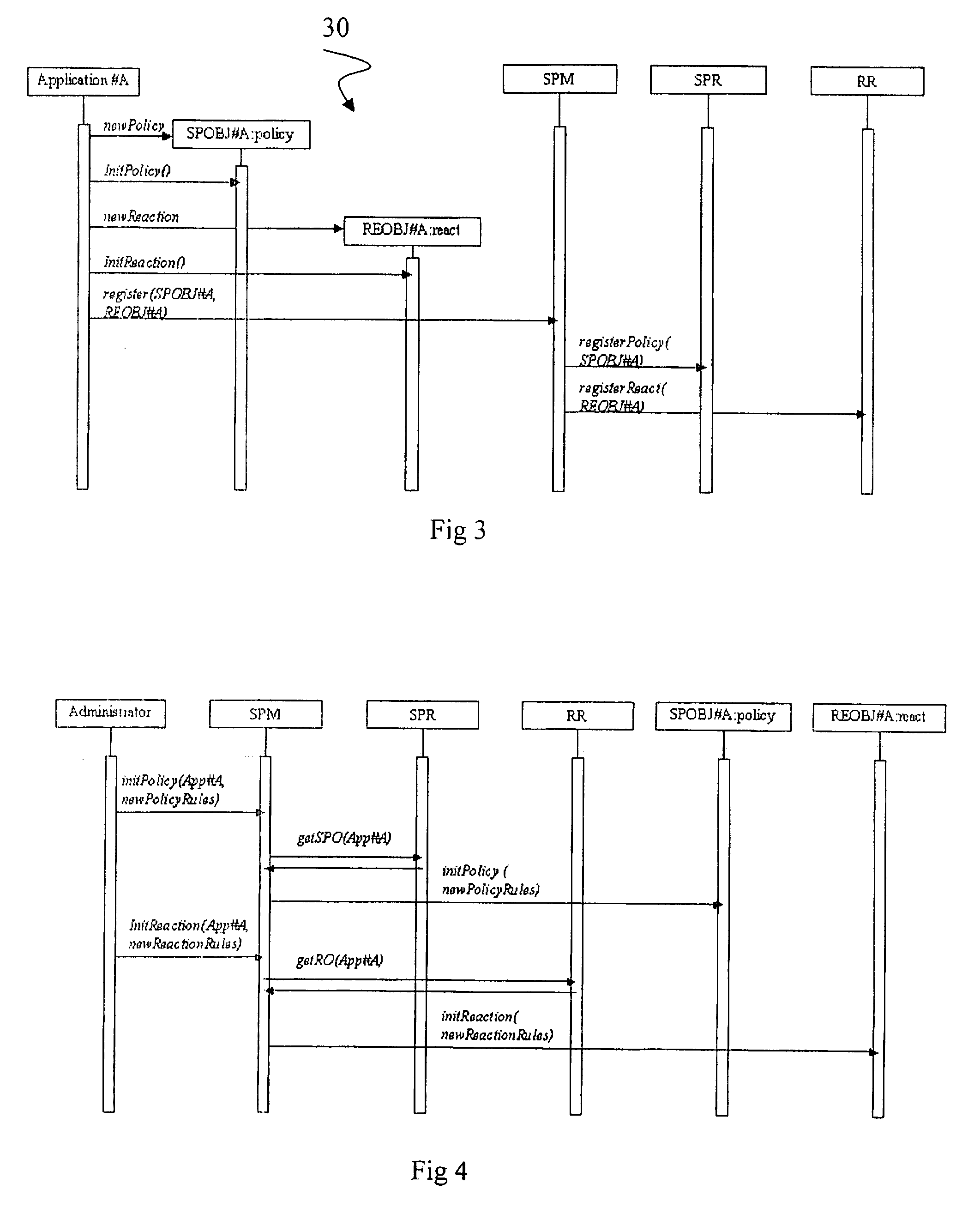
A multi-application IC card may include a runtime environment for managing executions of a plurality of stored application. Each application may include a set of rules, to be satisfied by their execution, and a corresponding set of reactions, to be taken if the rules are not satisfied. The runtime environment may include security and reaction registers to reference, respectively, the set of rules and reactions associated with the applications. A security policy manager may initialize, for each application, a reference between the security registers and the rules set between the reactions register and the reactions set. Checking the rules set and / or an activation of the reactions set is controlled by the security policy manager through the security registers and reaction registers. The security policy manager may include a registration function for initializing the security and reaction registers. The registration function may be called from the applications or an administrative user.
Owner:STMICROELECTRONICS INT NV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com