Patents
Literature
1098 results about "Network identification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
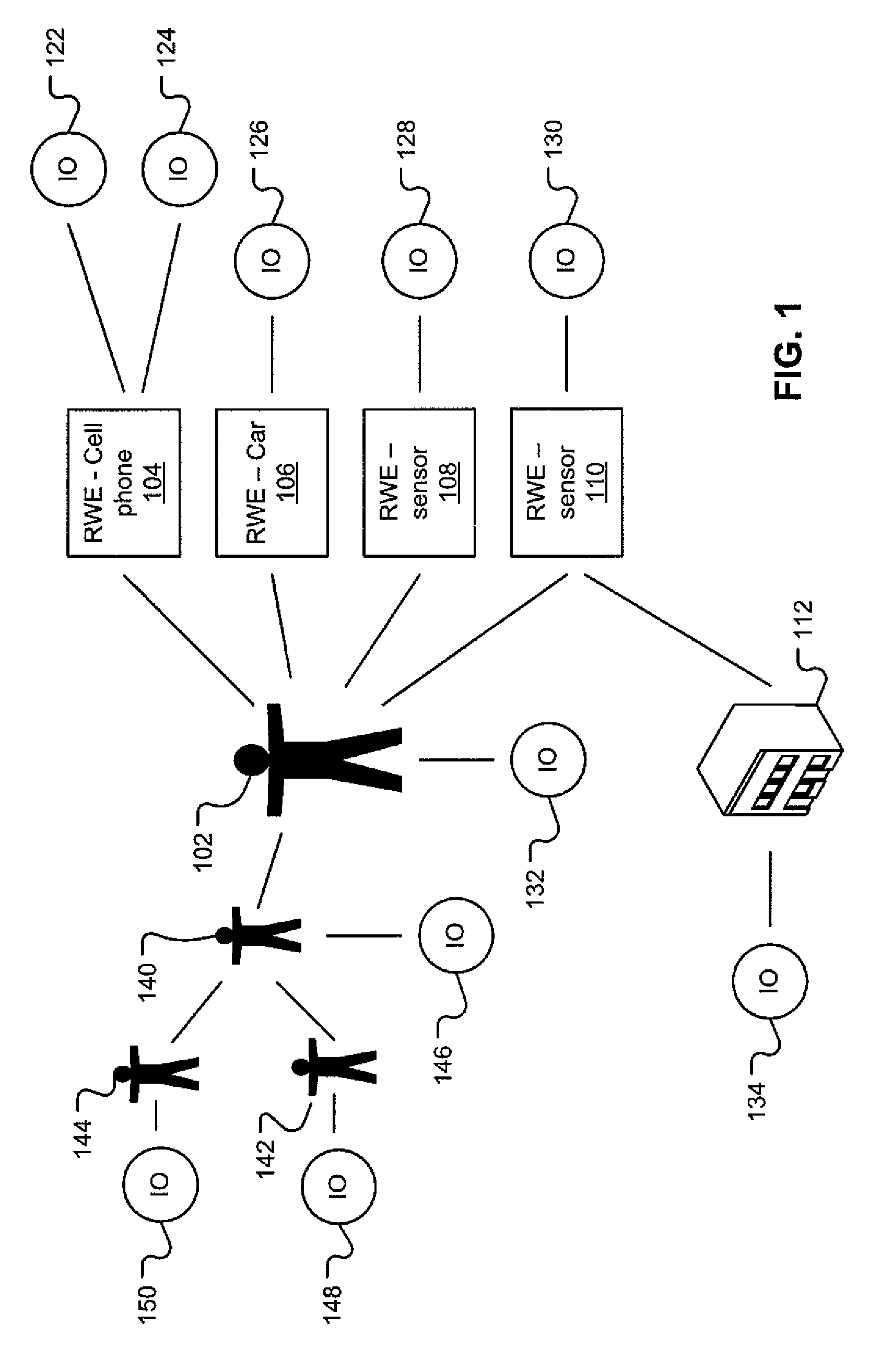
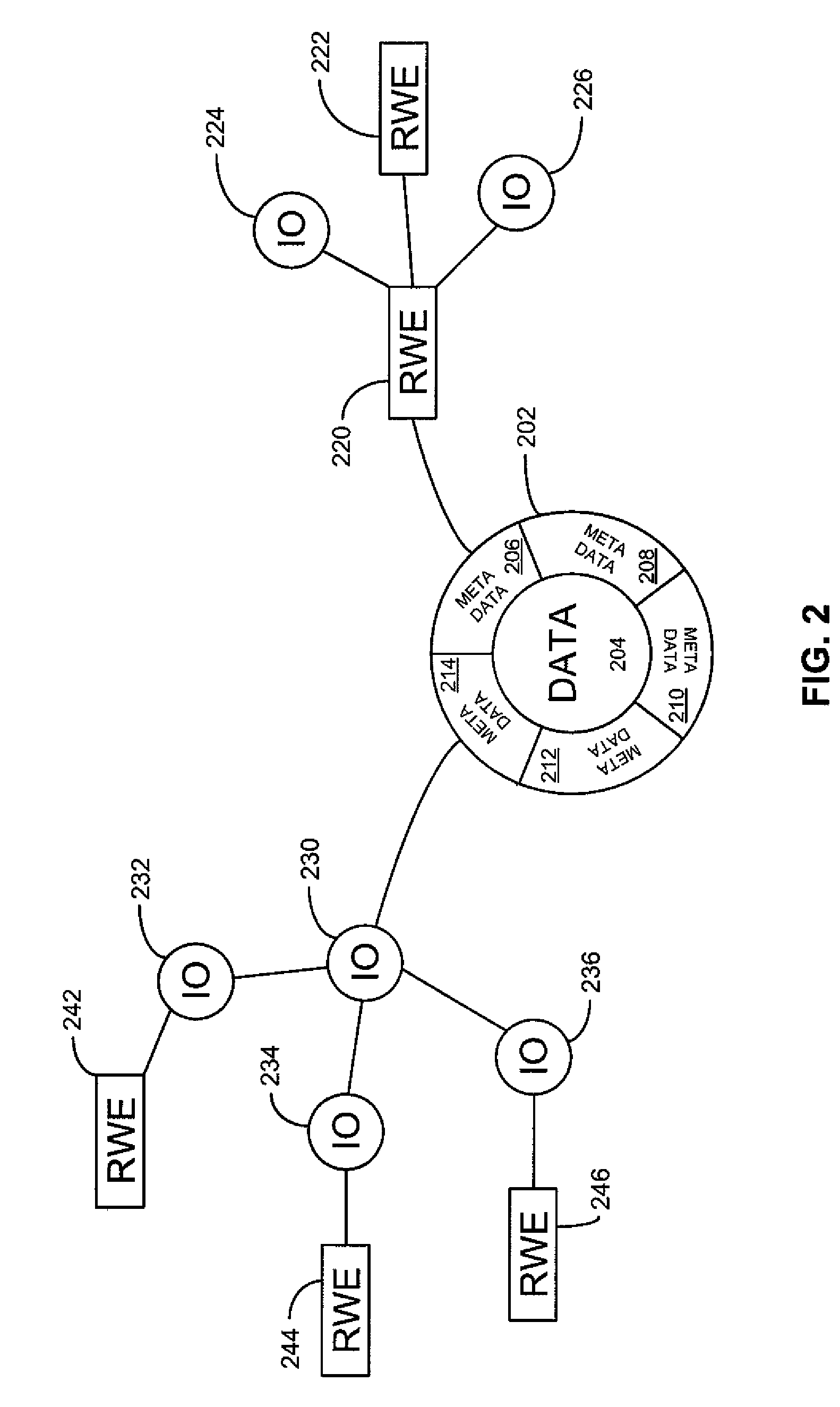
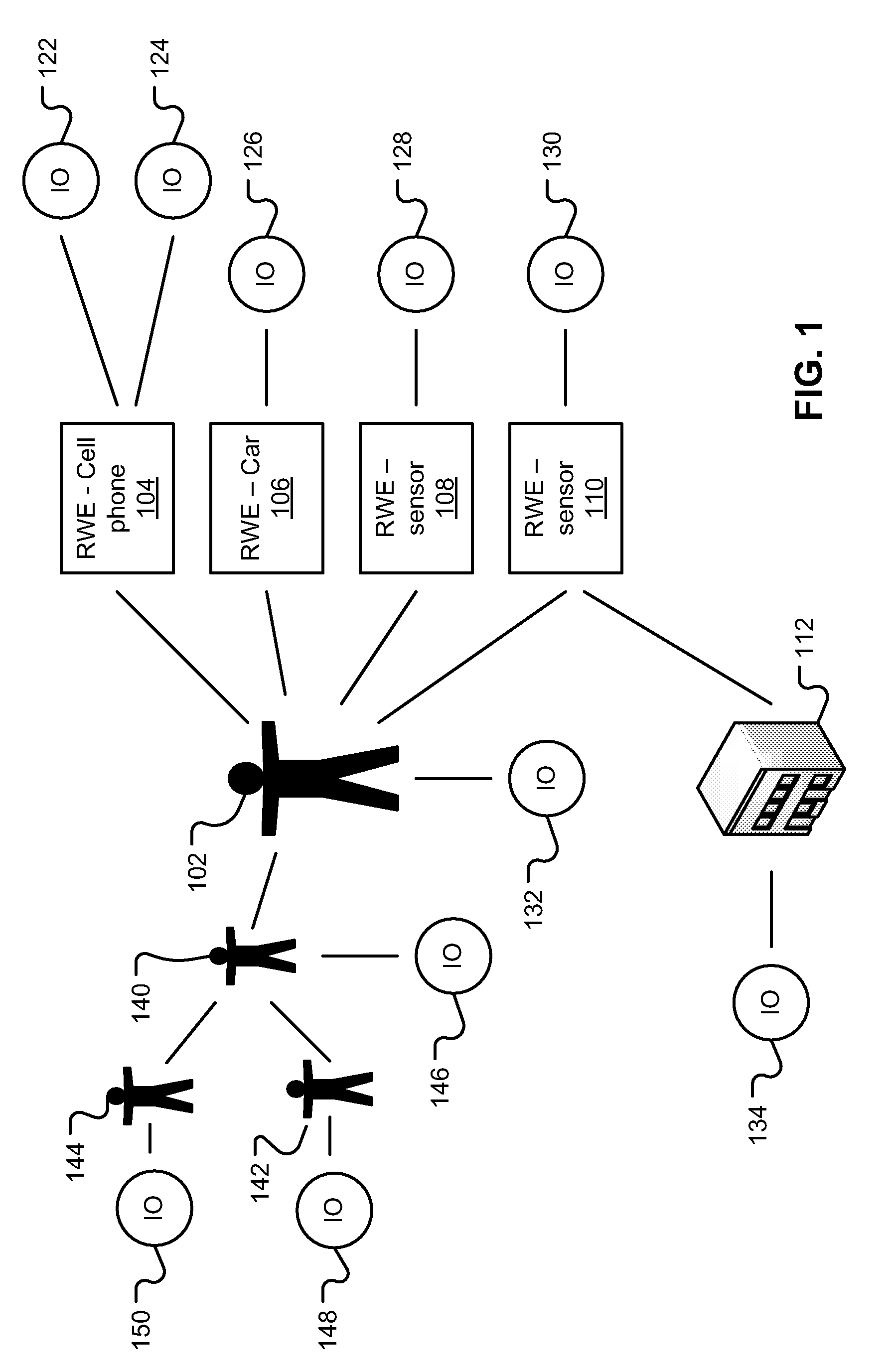
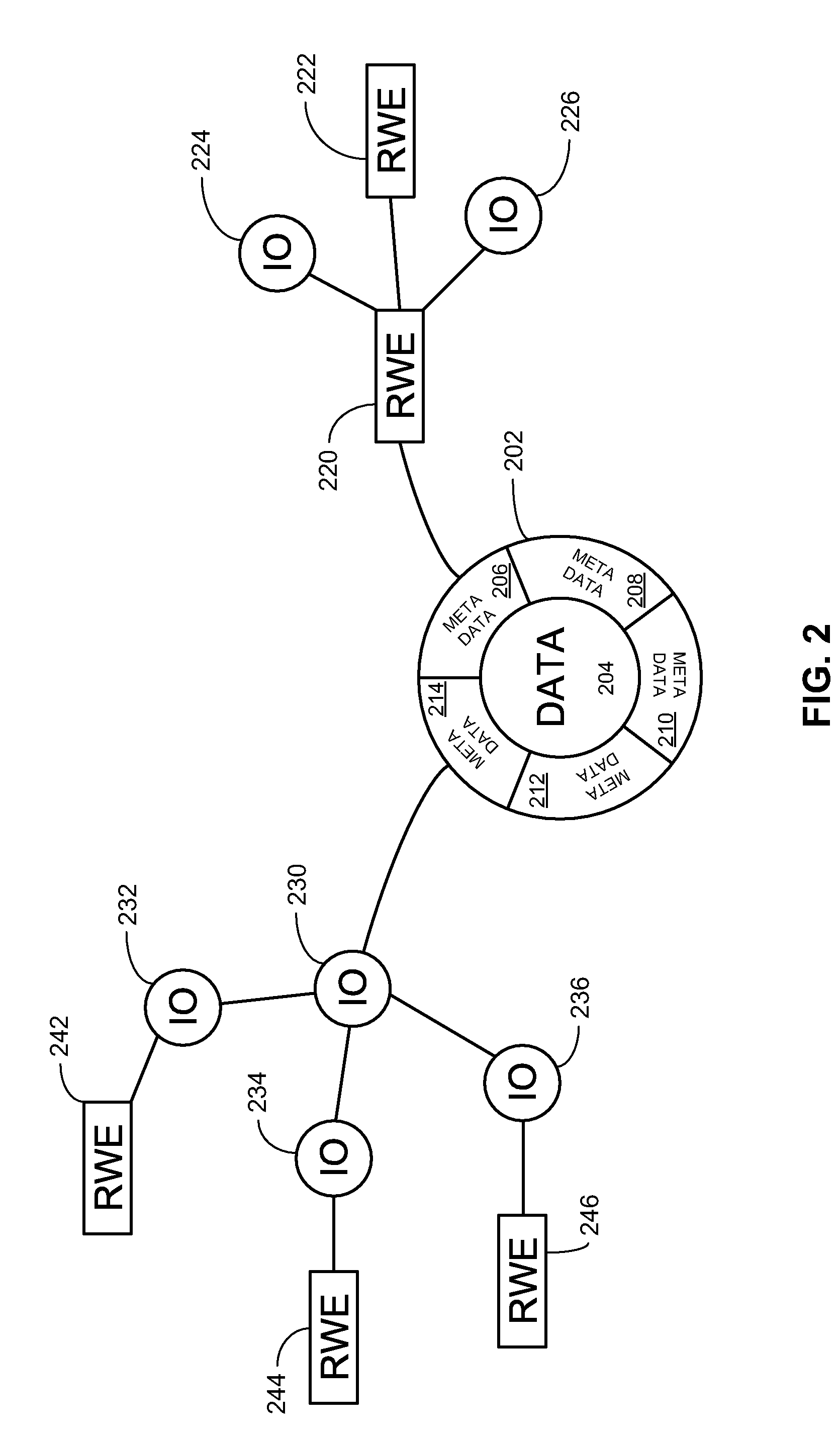
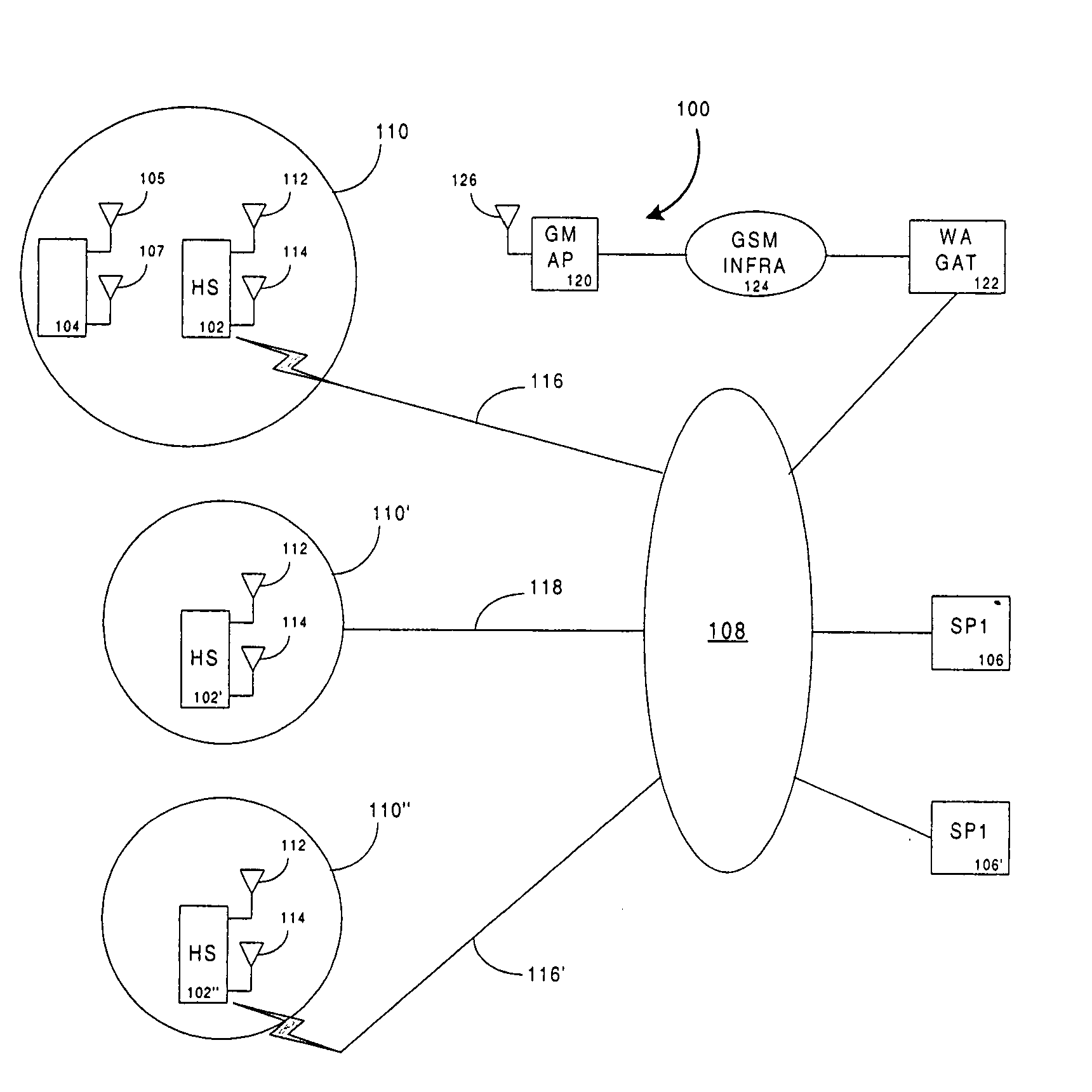
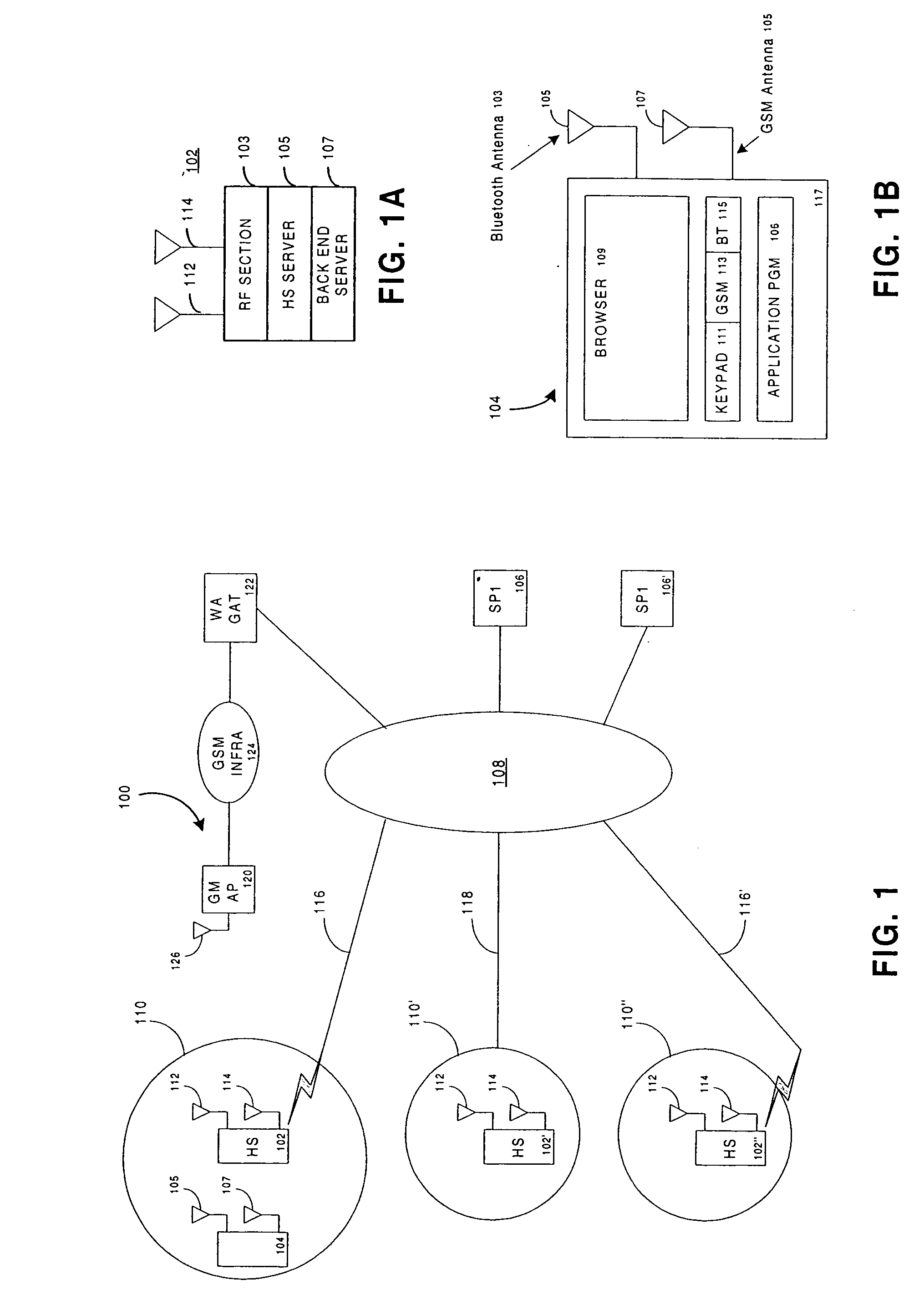
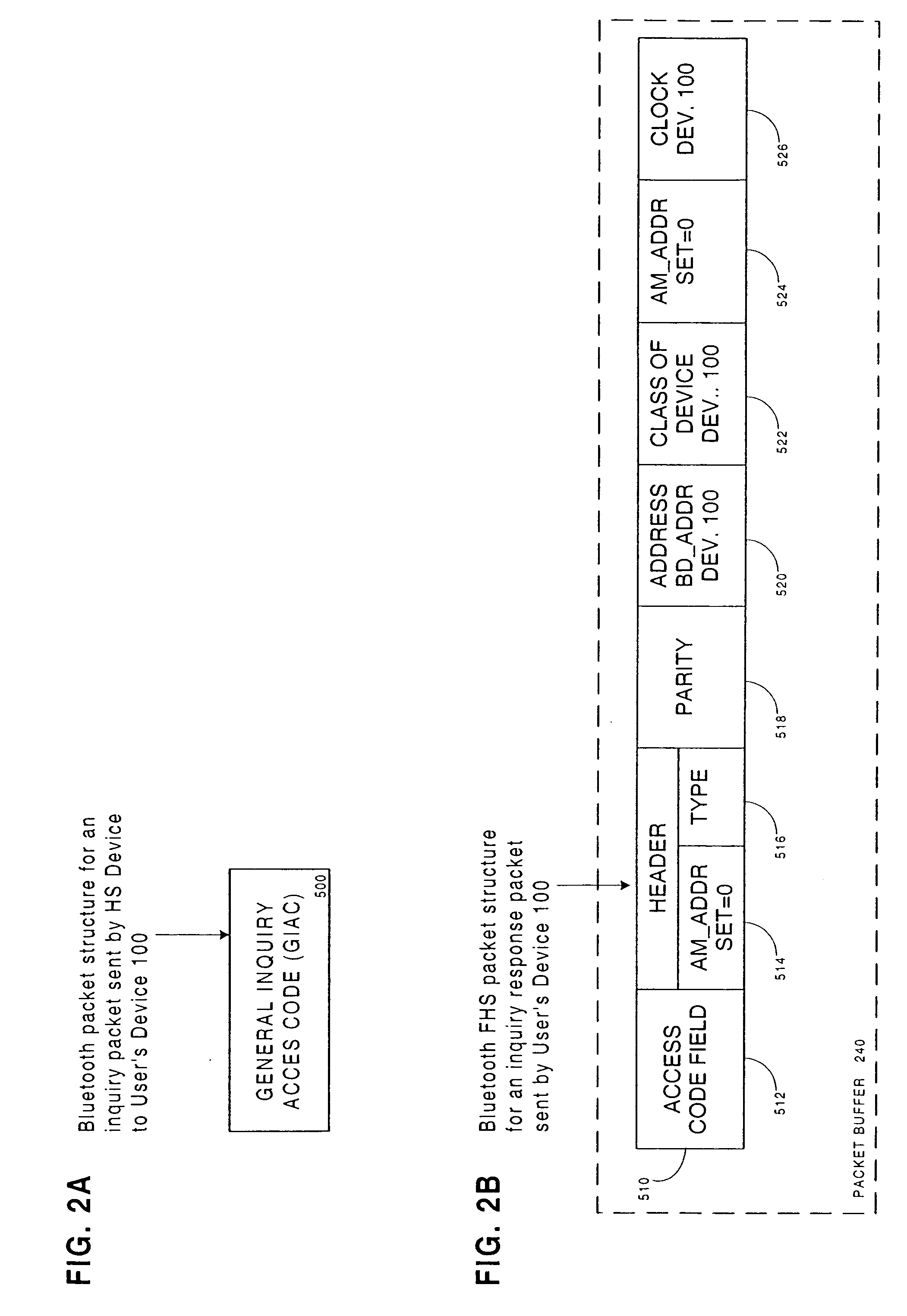
Network identity (network ID) is a portion of the TCP/IP address that is used to identify individuals or devices on a network such as a local area network or the Internet. Network ID is designed to ensure the security of a network and related resources.
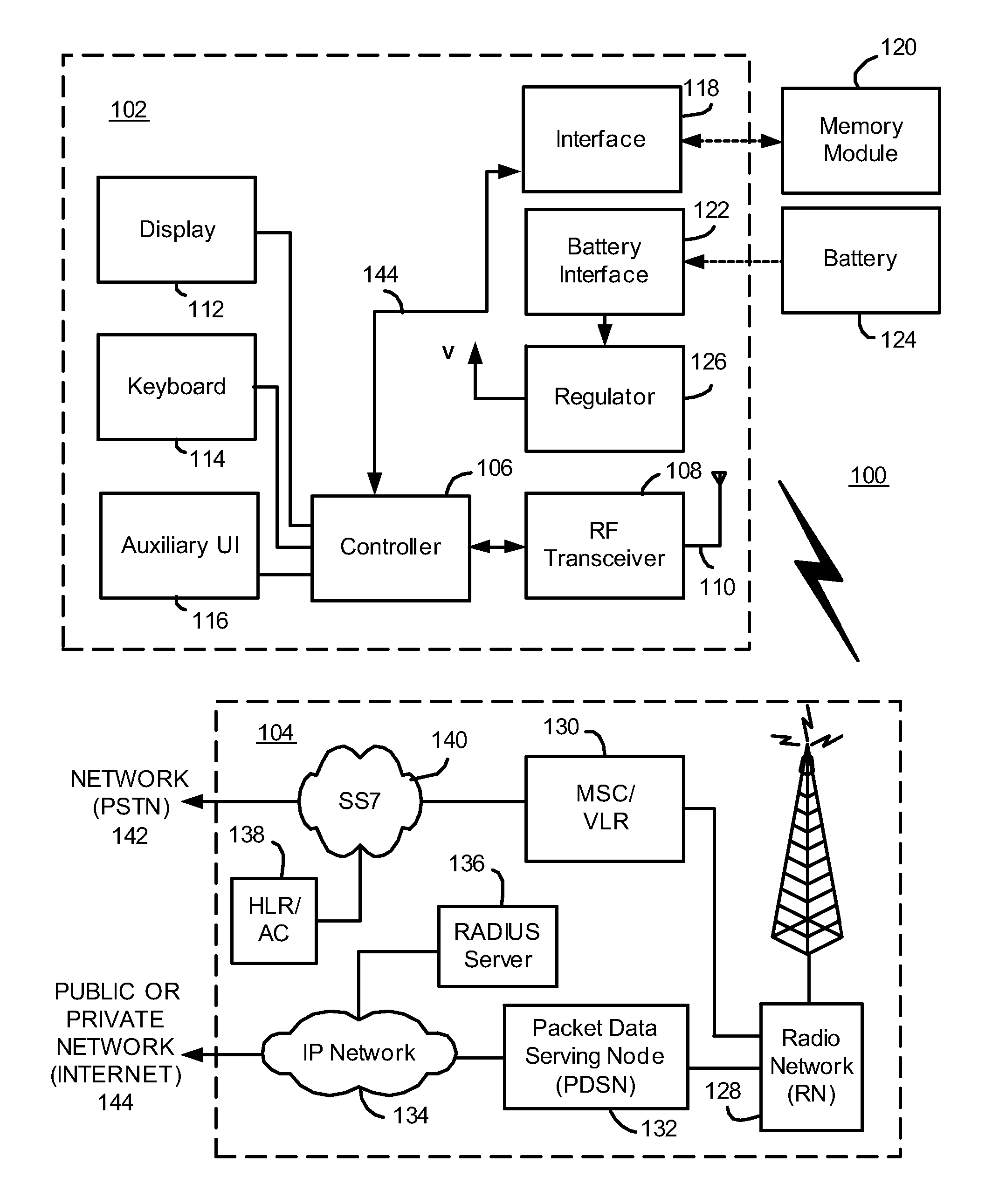
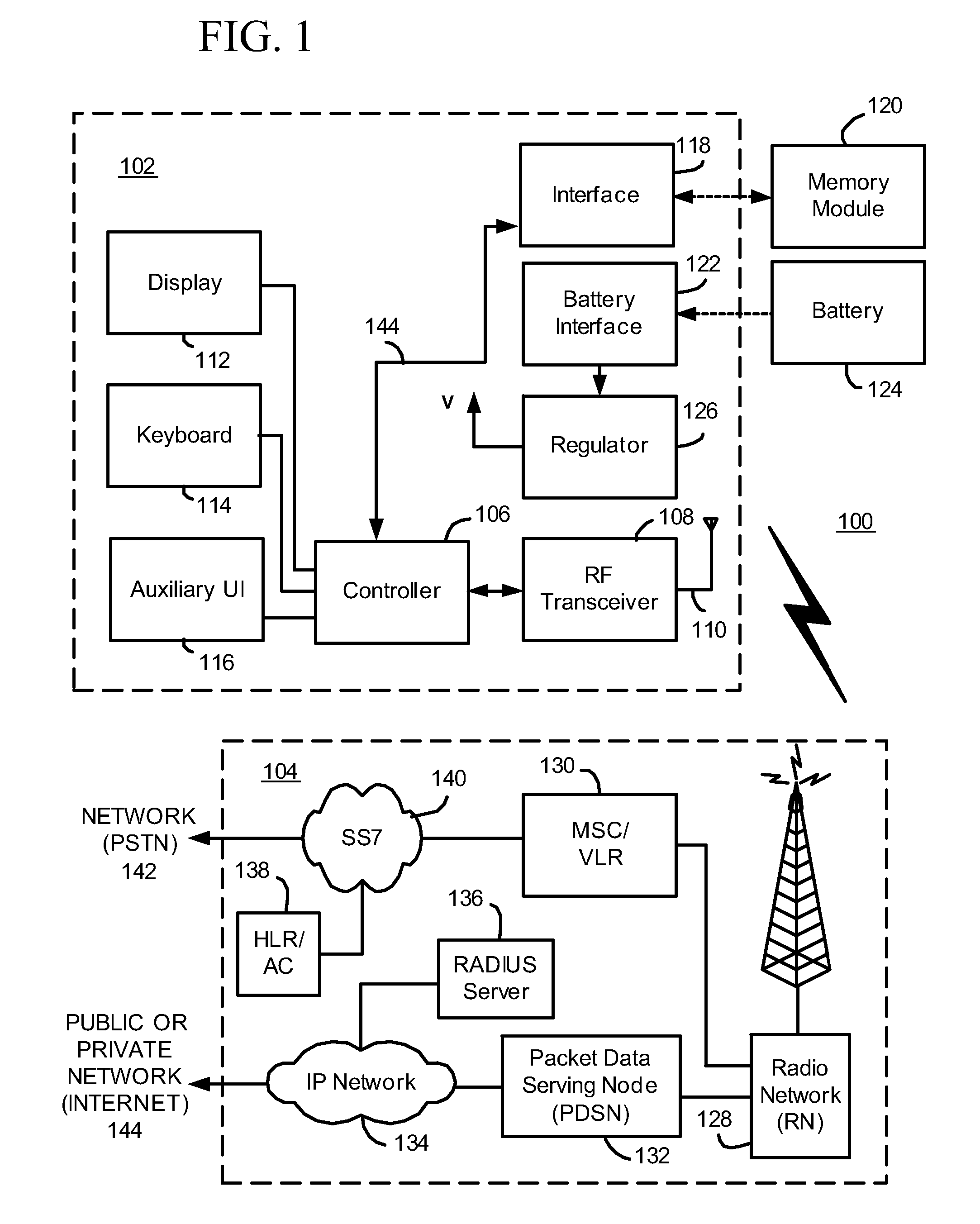
System and method for an application provider framework
InactiveUS6904449B1Broaden applicationMultiple digital computer combinationsOffice automationService provisionElectronic form
Owner:ACCENTURE GLOBAL SERVICES LTD
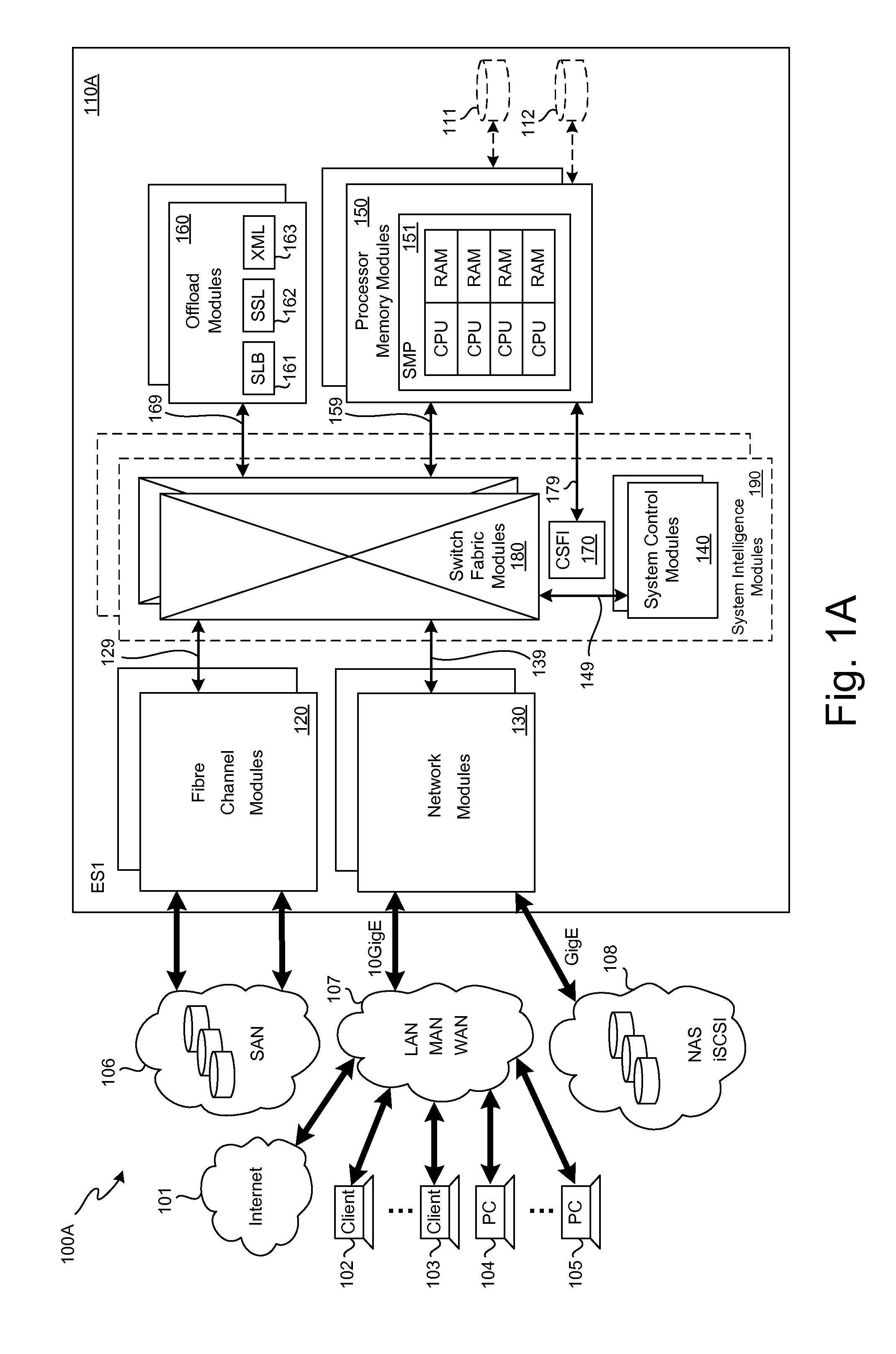
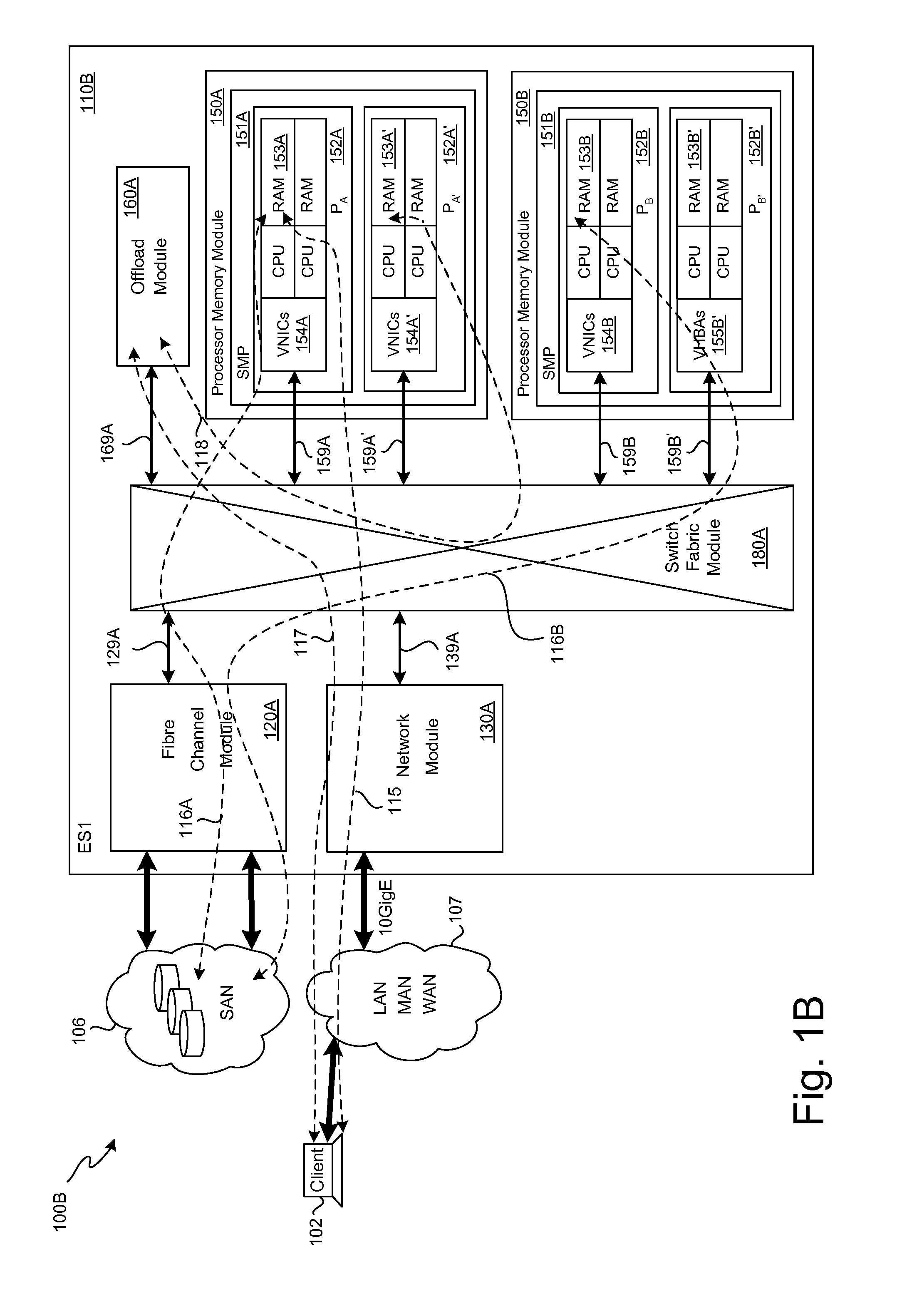
Storage traffic communication via a switch fabric in accordance with a VLAN
ActiveUS20130151646A1Improve performanceImprove efficiencyDigital computer detailsTransmissionTraffic capacityControl store
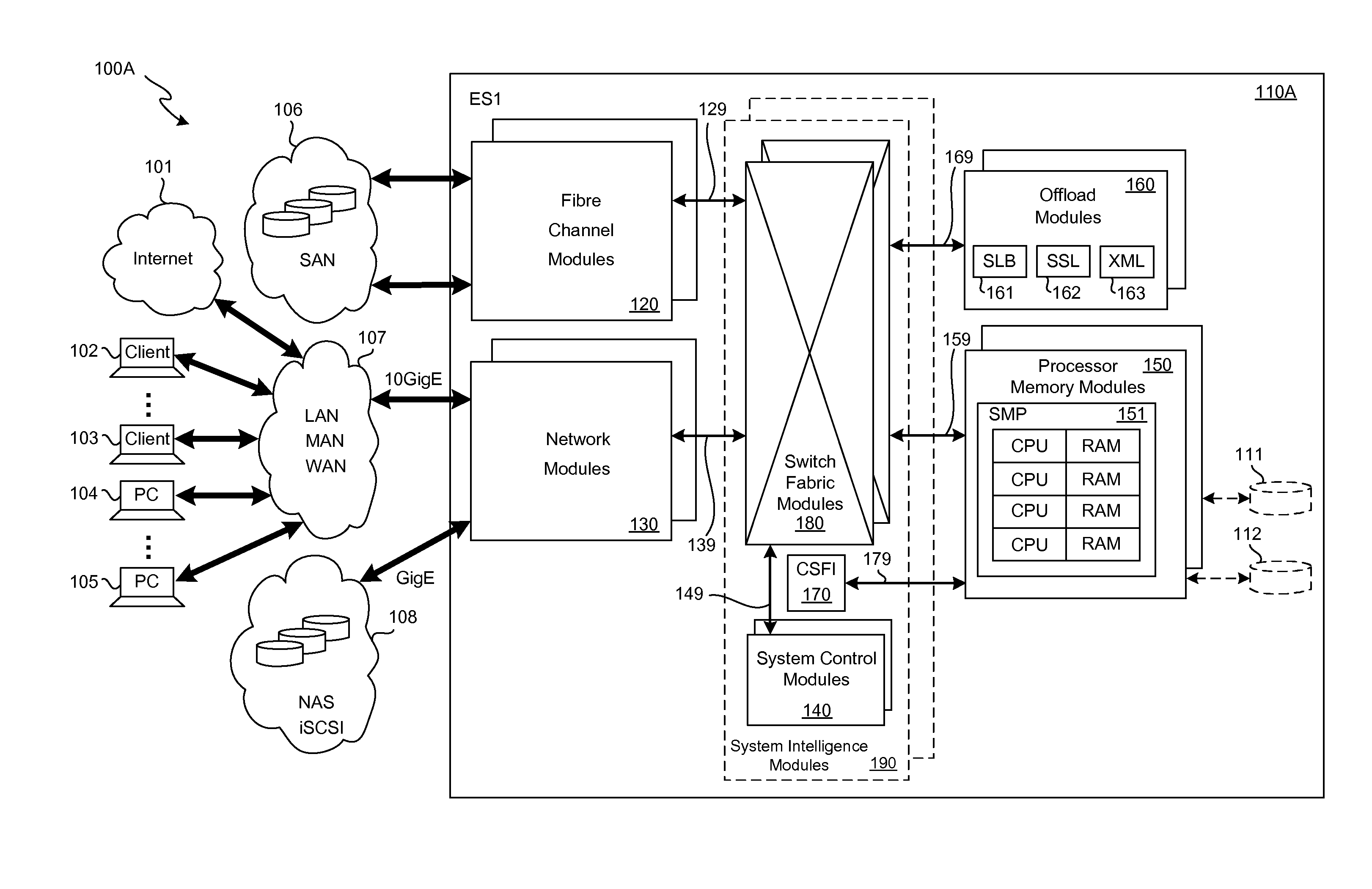
A plurality of SMP modules and an IOP module communicate storage traffic via respective corresponding I / O controllers coupled to respective physical ports of a switch fabric by addressing cells to physical port addresses corresponding to the physical ports. One of the SMPs executes initiator software to partially manage the storage traffic and the IOP executes target software to partially manage the storage traffic. Storage controllers are coupled to the IOP, enabling communication with storage devices, such as disk drives, tape drives, and / or networks of same. Respective network identification registers are included in each of the I / O controller corresponding to the SMP executing the initiator software and the I / O controller corresponding to the IOP. Transport of the storage traffic in accordance with a particular VLAN is enabled by writing a same particular value into each of the network identification registers.
Owner:ORACLE INT CORP
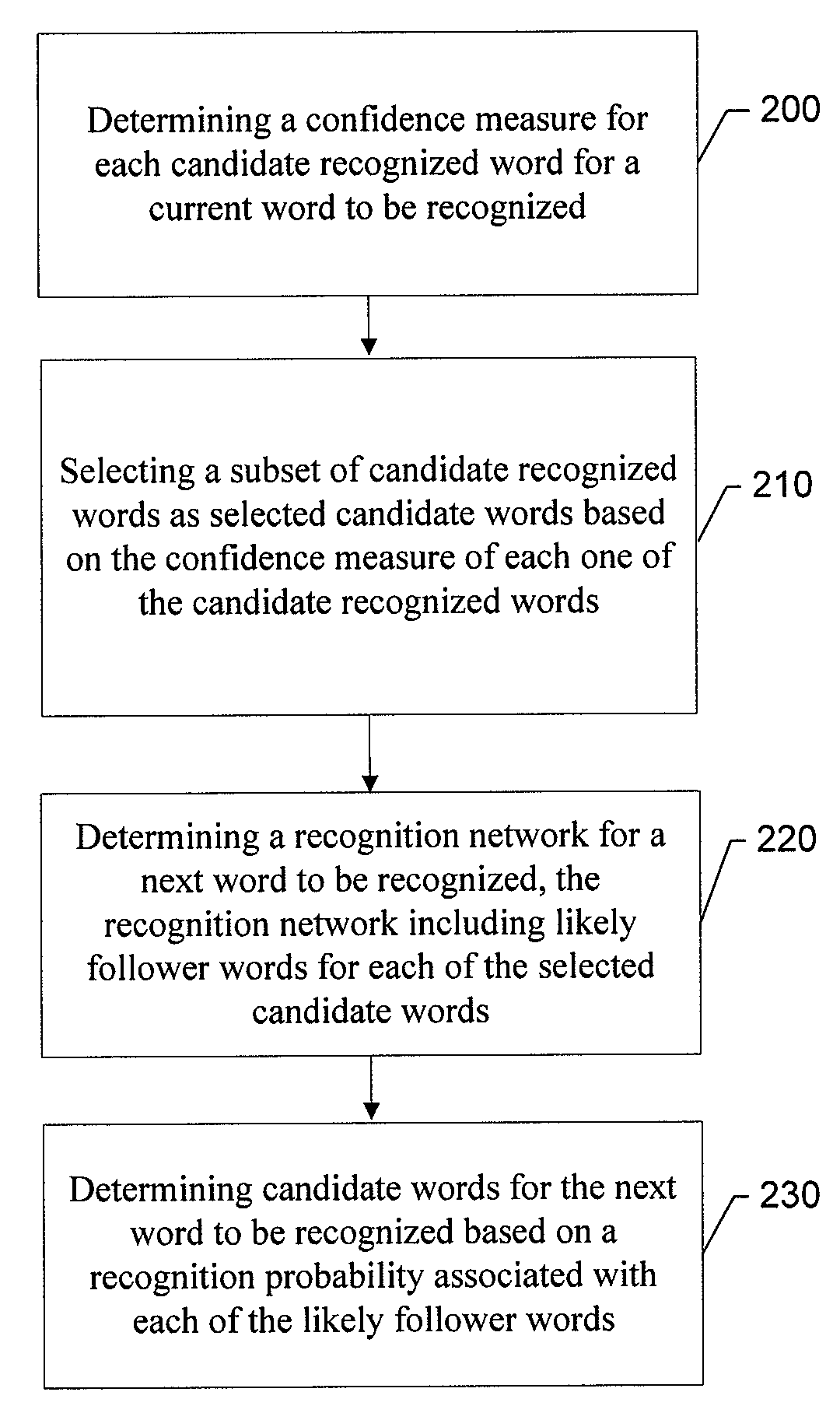
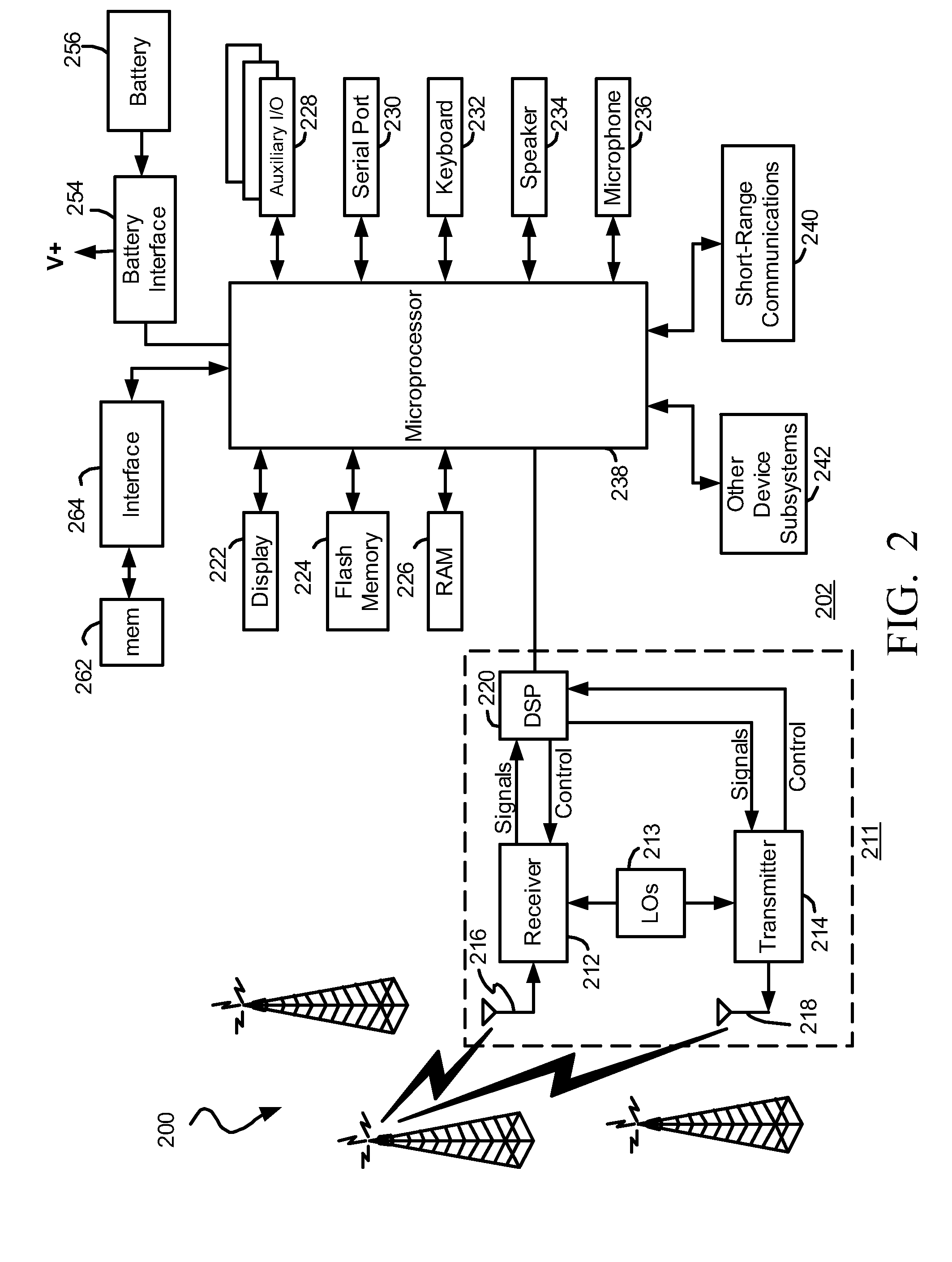
System, Method, Apparatus and Computer Program Product for Providing Dynamic Vocabulary Prediction for Speech Recognition
InactiveUS20080154600A1Improve speech processingAccurate word recognitionSpeech recognitionNatural language processingConfidence measures
An apparatus for providing dynamic vocabulary prediction for setting up a speech recognition network of resource constrained portable devices may include a recognition network element. The recognition network element may be configured to determine a confidence measure for each candidate recognized word for a current word to be recognized. The recognition network element may also be configured to select a subset of candidate recognized words as selected candidate words based on the confidence measure of each one of the candidate recognized words, and determine a recognition network for a next word to be recognized, the recognition network including likely follower words for each of the selected candidate words, e.g. using language model and highly frequently used words.
Owner:NOKIA CORP
Method and apparatus for multi-level distributed speech recognition
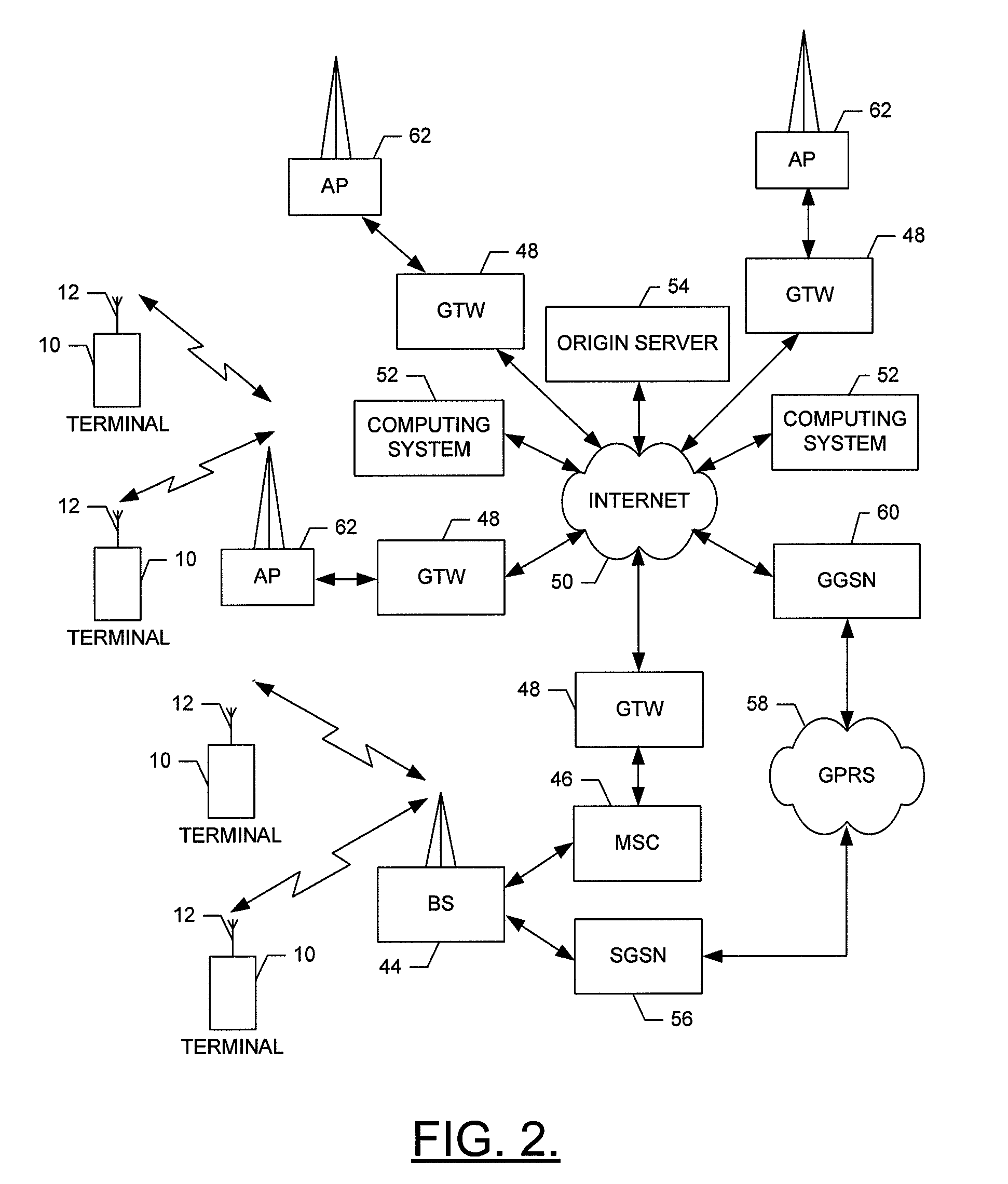
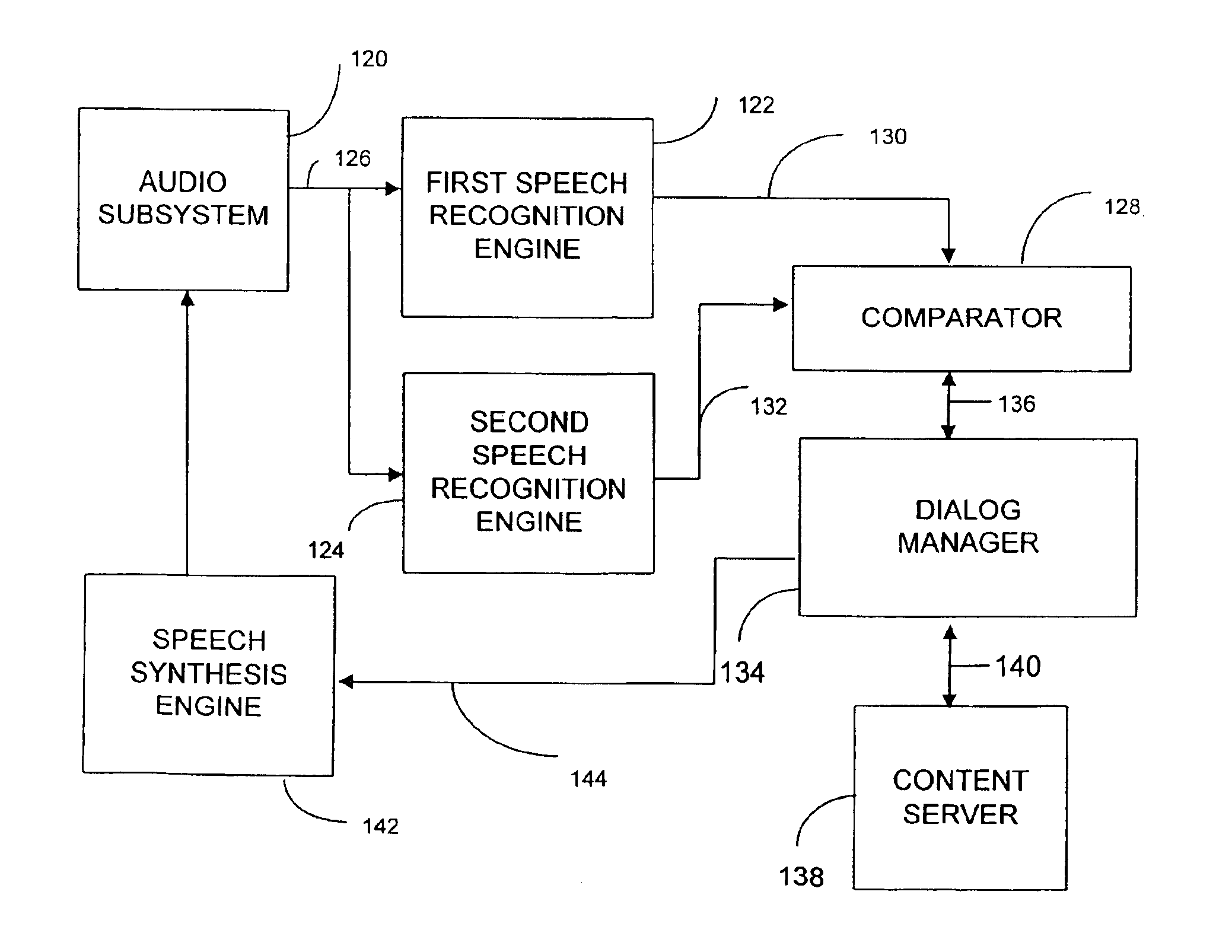
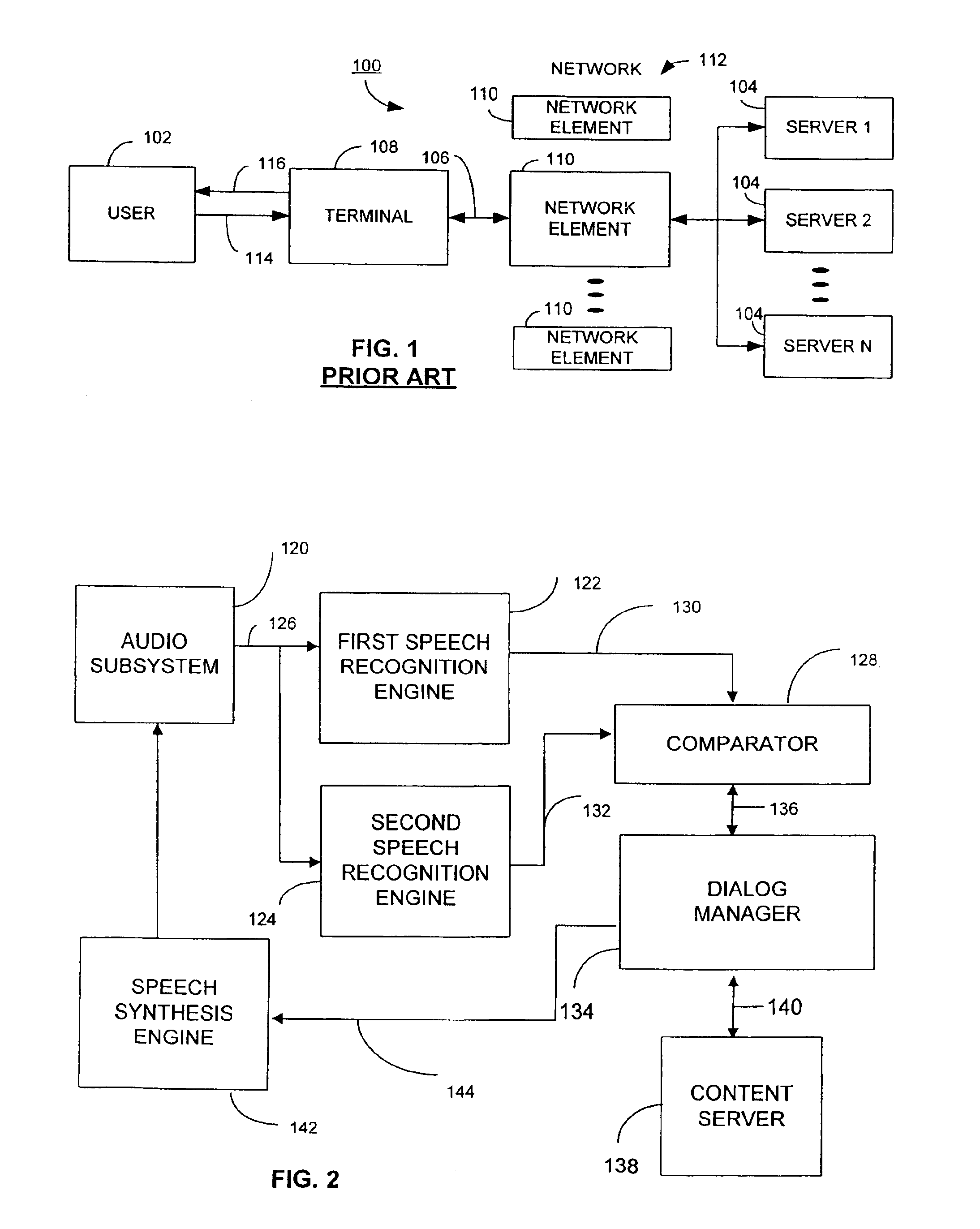
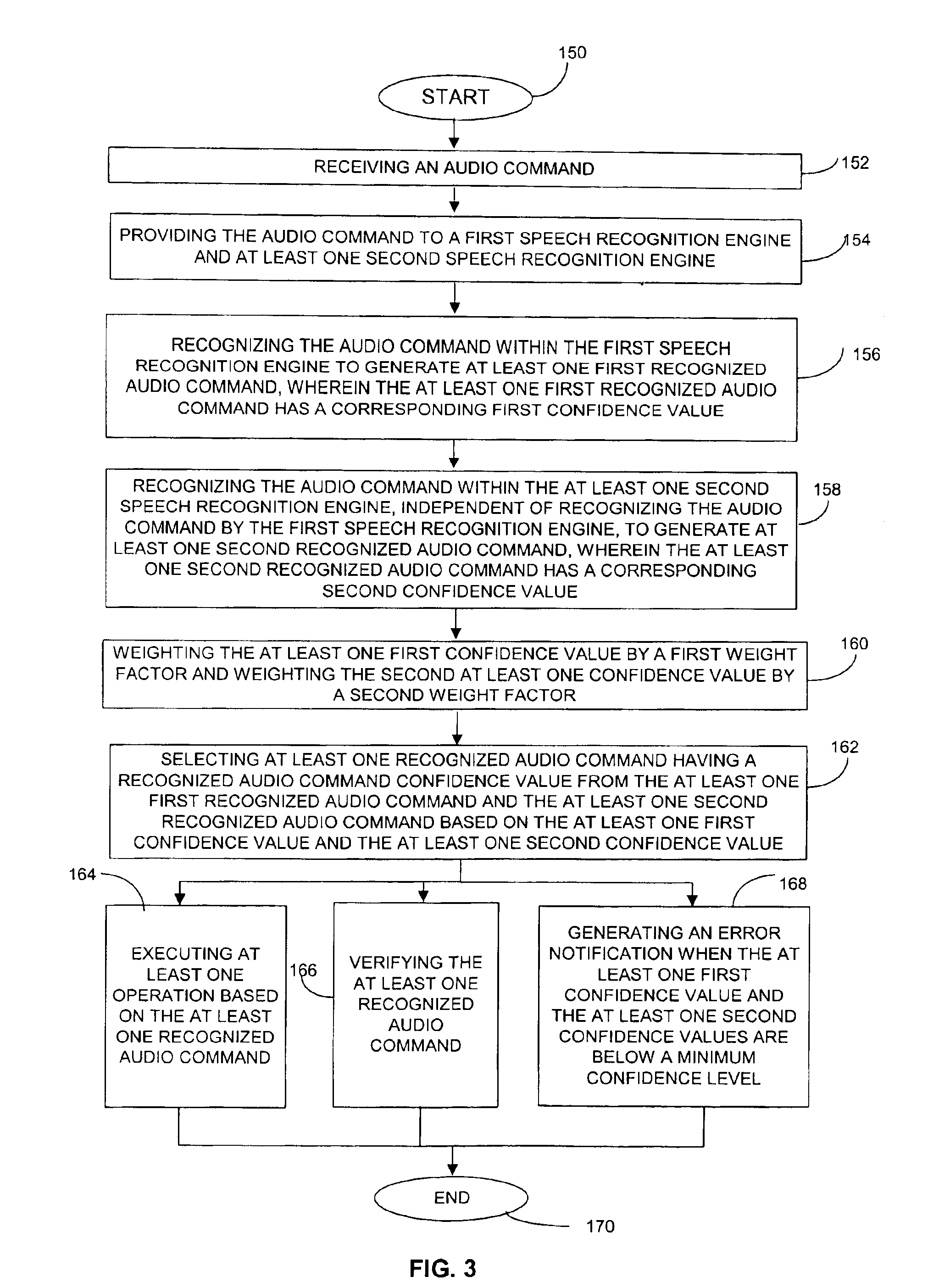
A system and method for multi-level distributed speech recognition includes a terminal (122) having a terminal speech recognizer (136) coupled to a microphone (130). The terminal speech recognizer (136) receives an audio command (37), generating at least one terminal recognized audio command having a terminal confidence value. A network element (124) having at least one network speech recognizer (150) also receives the audio command (149), generating a at least one network recognized audio command having a network confidence value. A comparator (152) receives the recognized audio commands, comparing compares the speech recognition confidence values. The comparator (152) provides an output (162) to a dialog manager (160) of at least one recognized audio command, wherein the dialog manager then executes an operation based on the at least one recognized audio command, such as presenting the at least one recognized audio command to a user for verification or accessing a content server.
Owner:GOOGLE TECH HLDG LLC
Methods and apparatus for selecting a wireless network based on quality of service (QoS) criteria associated with an application
In one illustrative example, a mobile communication device has a plurality of software applications including an Internet browser application, an electronic mail (e-mail) communication application, and an audio or video player application. The mobile device is adapted to receive, from wireless communication networks or through use thereof, available quality of service data for the wireless networks and store the corresponding data in association with each network identification. The available quality of service data includes at least a bandwidth criterion and a delay criterion associated with each wireless network. For each one of the software applications, the mobile device is adapted to execute the software application; identify, based on the stored quality of service data, one or more wireless networks having a bandwidth criterion and a delay criterion that best match a bandwidth requirement and a delay requirement, respectively, of the executed software application; and select, based on the identifying, an available wireless network for communication using the executed software application.
Owner:MALIKIE INNOVATIONS LTD
System and method for location based media delivery
InactiveUS20090328087A1Information formatAnalogue secracy/subscription systemsEnd userNetwork identification
A system and method for selecting and presenting media on a network to tune an environment to the tastes of the users within that environment, thus improving the experience of that location. A physical location of a media presentation device is received over a network. The physical location of a plurality of end users are identified via the network, wherein each of plurality of users associated are with a plurality of media files stored on the network. A least one of the end users that are within a defined proximity to the media presentation device are identified. At least one media file associated with the end users that are within a defined proximity to the media presentation device are identified and transmitted over the network to the media presentation device.
Owner:R2 SOLUTIONS
Automatic network selection methods and apparatus using a steered PLMN
ActiveUS20070191006A1Assess restrictionRadio/inductive link selection arrangementsTelecommunicationsUser equipment
Methods and apparatus for automatically selecting a wireless communication network by user equipment using a “steered” PLMN are disclosed. A home network identification, a list of prioritized roaming network identifications, and a steered network identification are stored in memory (e.g. a SIM or USIM) of the user equipment. In an automatic network selection procedure, a scanning operation is performed to receive one or more network identifications corresponding to one or more available wireless communication networks in a coverage area. The user equipment attempts to select a wireless communication network in the coverage area by comparing the received network identifications from the scanning operation with the steered network identification. If a match between a received network identification and the steered network identification is identified, a wireless communication network corresponding to the received network identification that matches the steered network identification is selected and registered with by the user equipment. This procedure is performed in lieu of use of the list of prioritized roaming network identifications of the user equipment. By setting the steered network identification via an over-the-air programming procedure when necessary (e.g. on a per region basis), a home network operator may “steer” user equipment to any desired network immediately and efficiently.
Owner:LEPATENT (BEIJING) CONSULTING CORP LTD
System and method for automatic detection and configuration of network parameters
ActiveUS7051087B1Automatically network operationReduce errorsMultiple digital computer combinationsTransmissionComputerized systemAutomatic testing
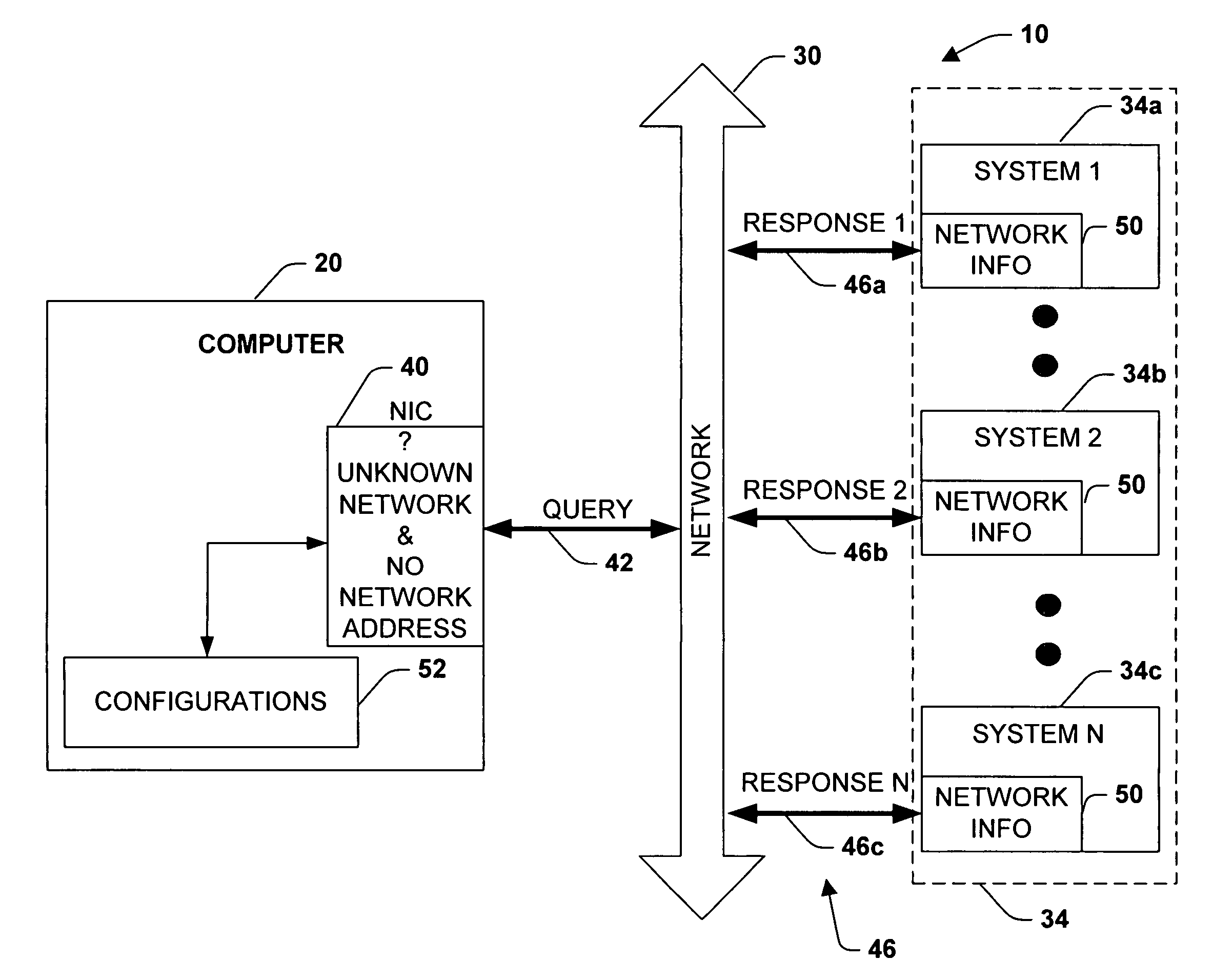
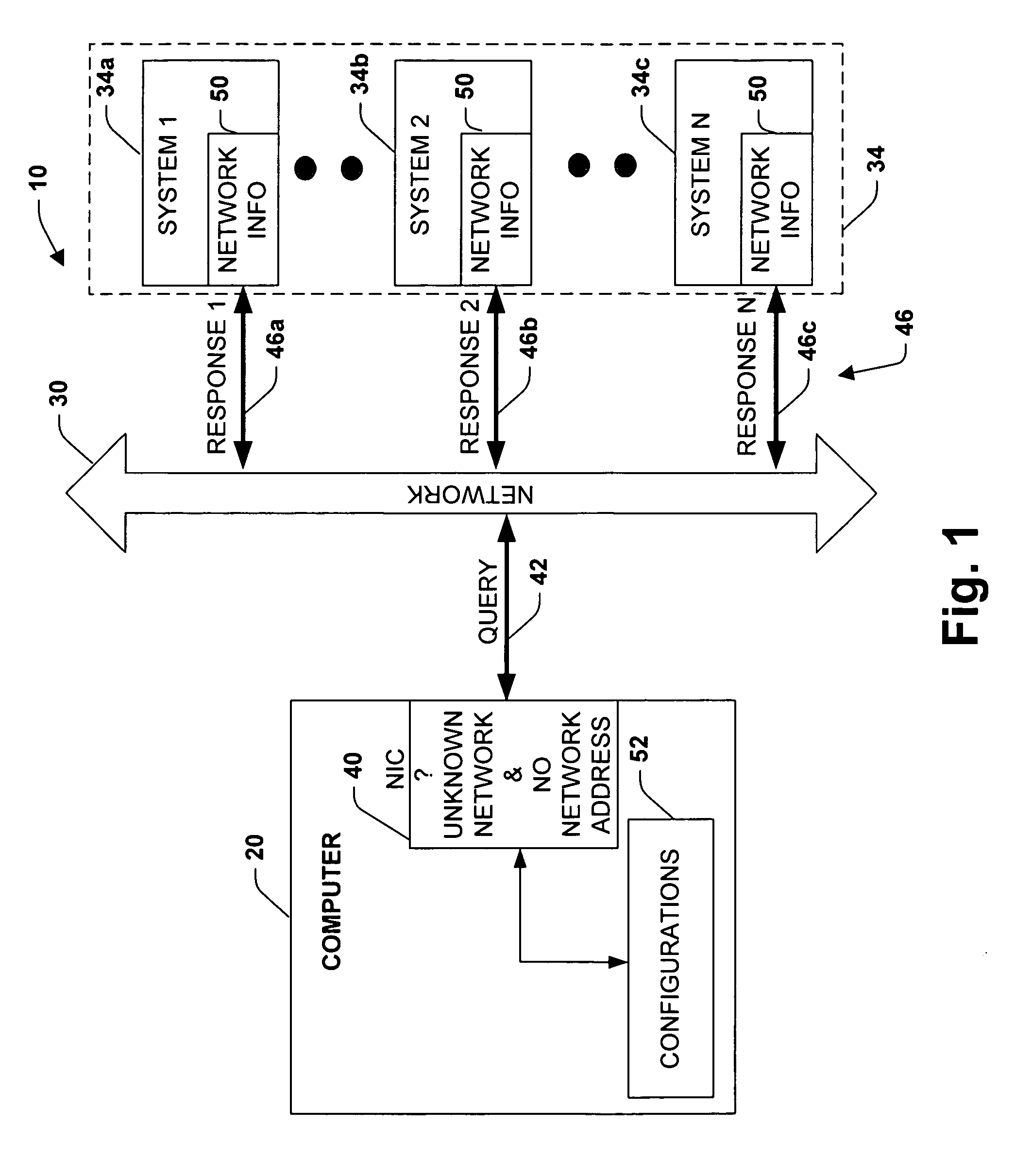
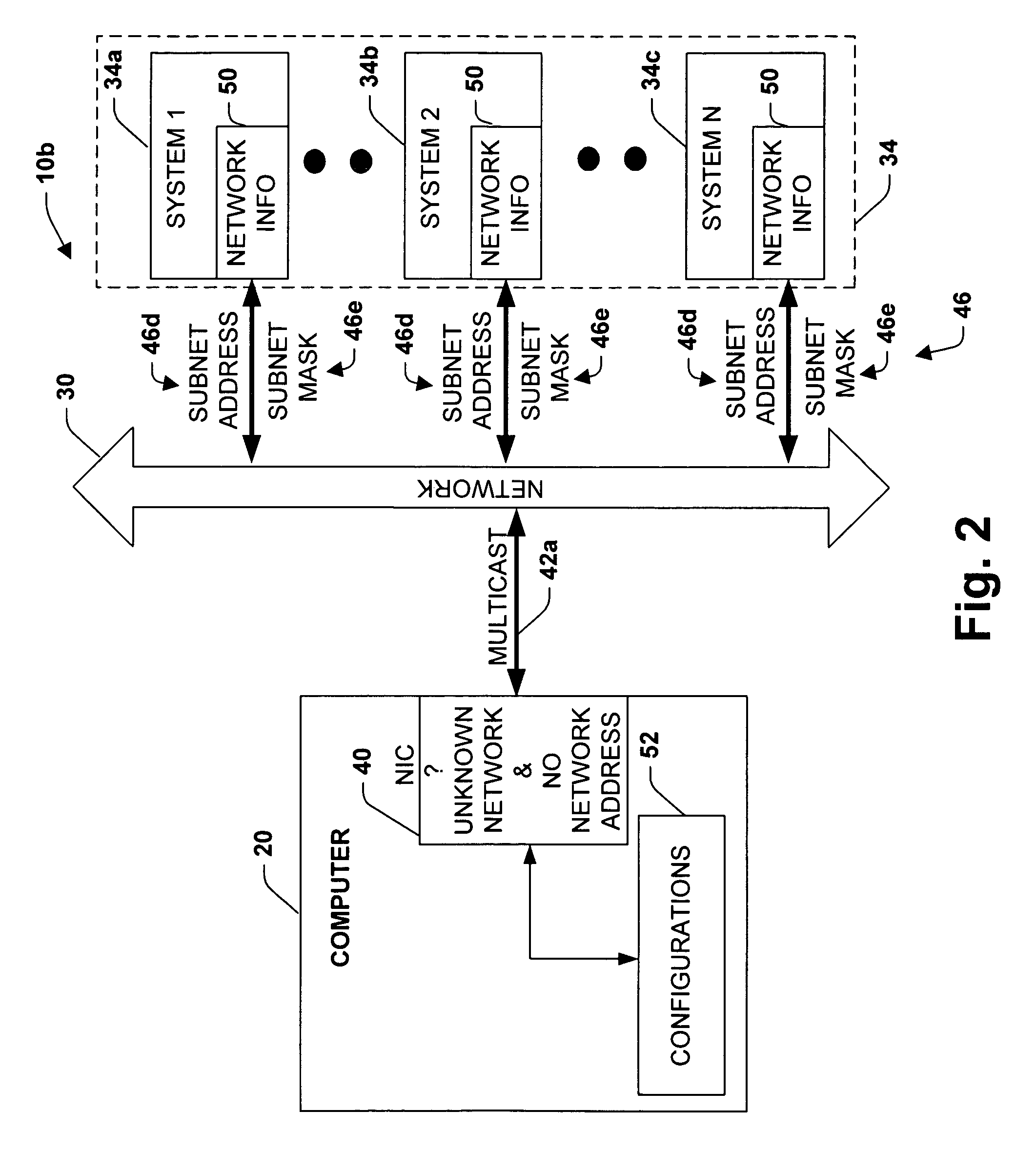
The present invention relates to a system for automatic detection and configuration of network parameters. The system includes a first computer system for communicating to a network and at least a second computer system for providing network information. The first computer system queries the network and receives network information from the at least a second computer system before a network identification has been established for the first computer system. The system further includes a storage for storing at least one configuration associated with a network interface. The first computer system configures the network interface based upon the network information received from the at least a second computer system. Also, the first computer system may configure the network interface by determining a network identification associated with the network information and matching the at least one configuration with the network identification.
Owner:MICROSOFT TECH LICENSING LLC
System and method for determining availability of radio access technology associated with a wireless network
InactiveUS20050202828A1Eliminate needAssess restrictionTransmissionRadio access technologyTransceiver
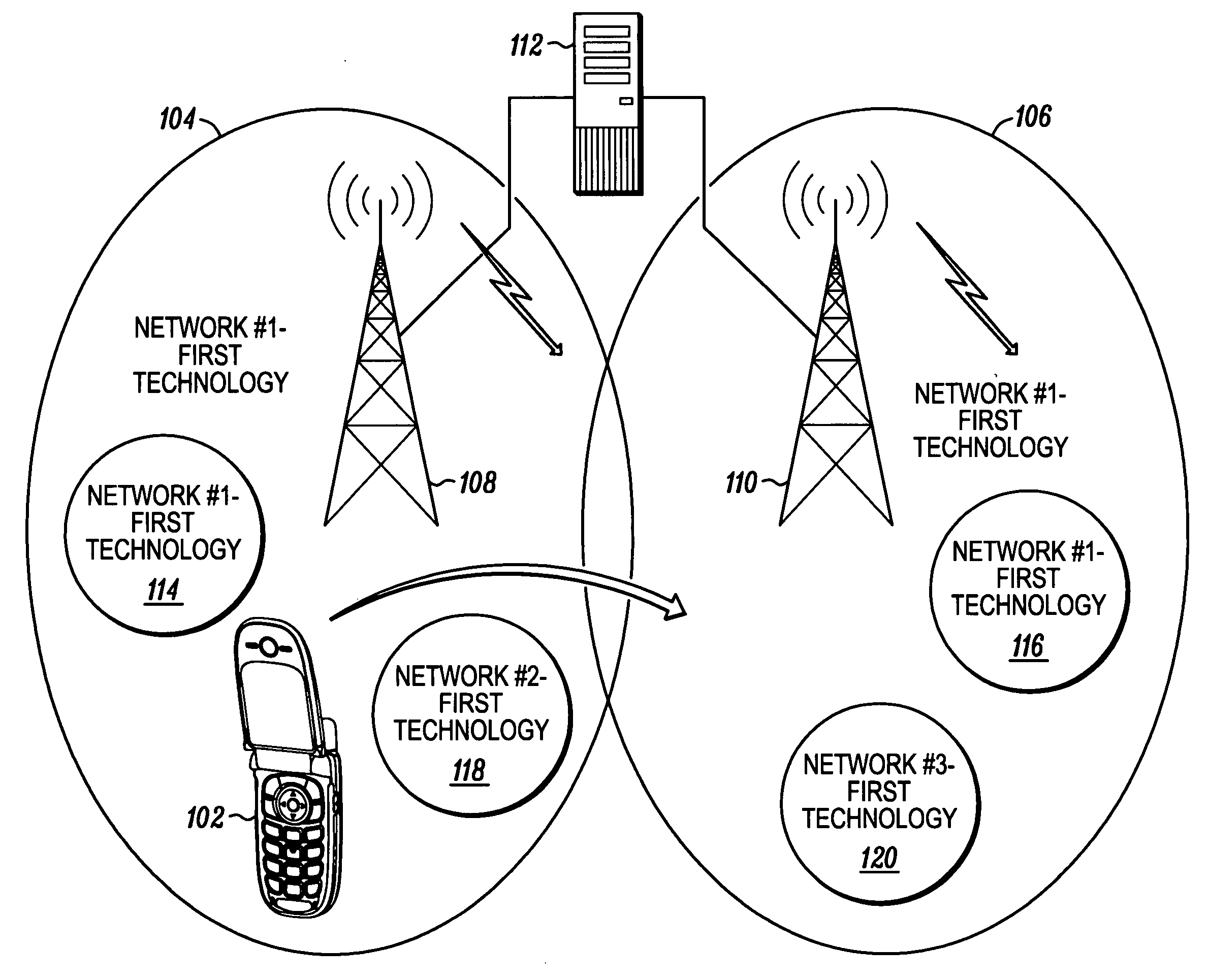
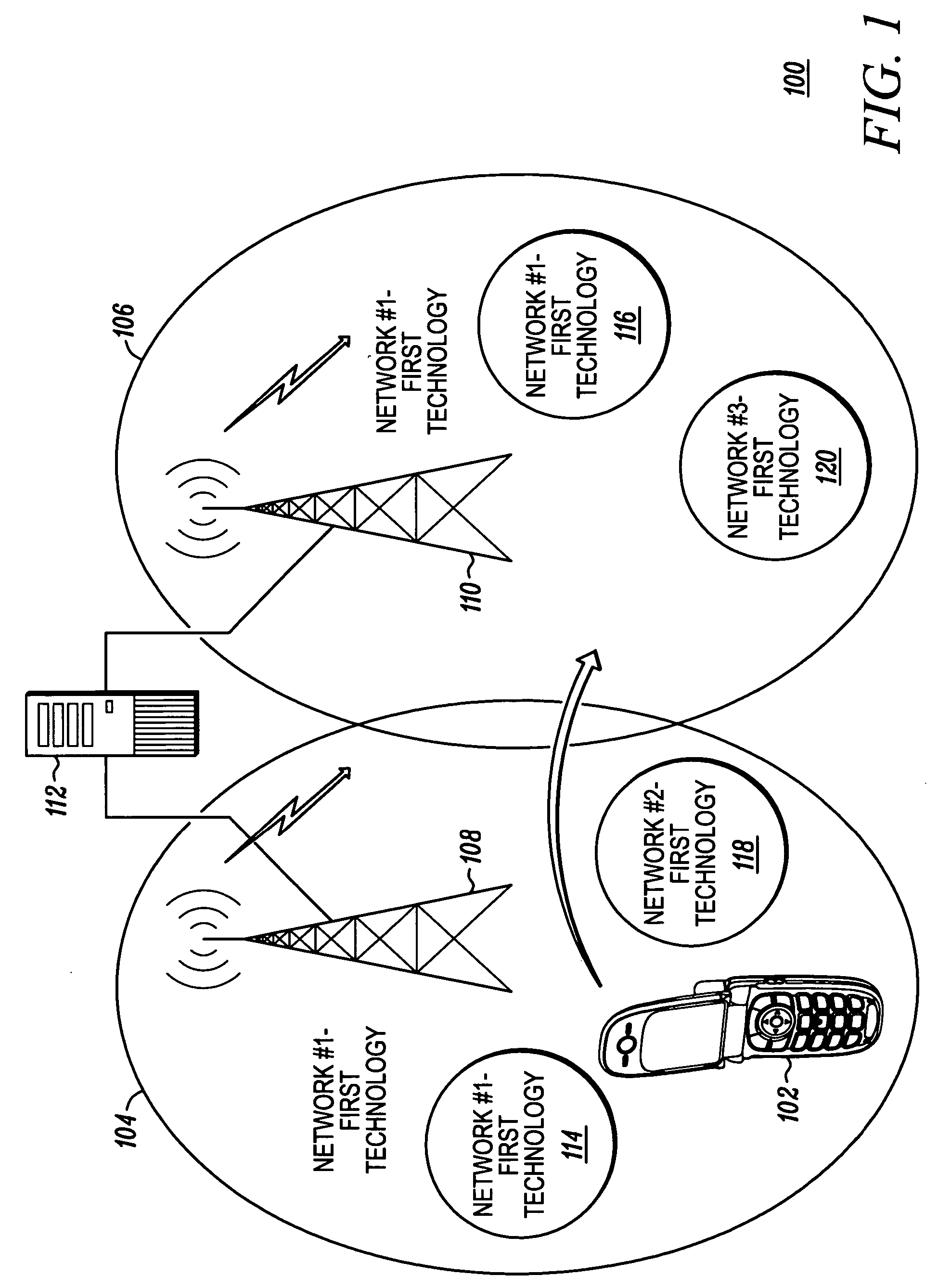
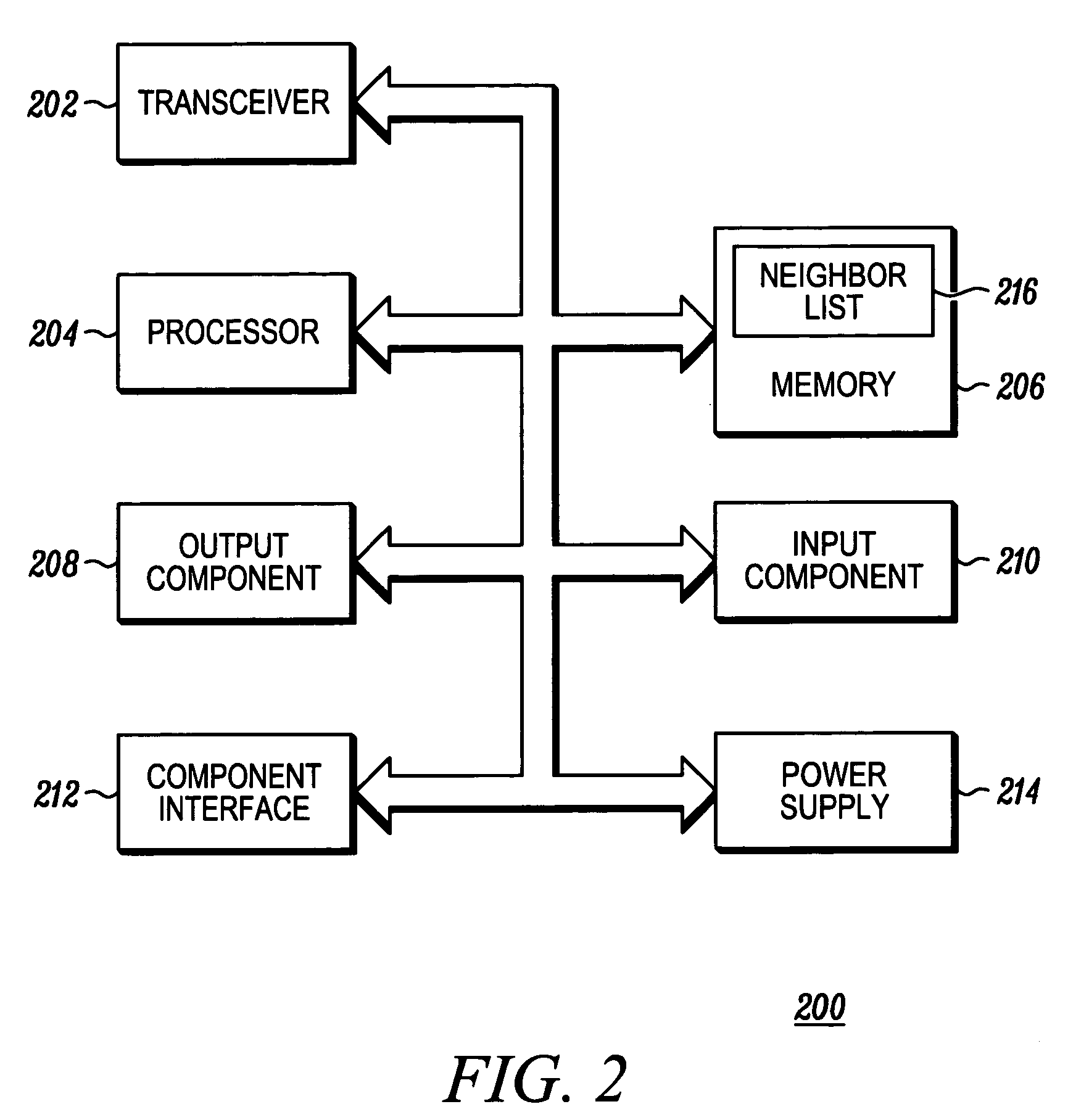
A wireless communication device (102), a wireless communication network and methods therefor. The wireless communication device (102) comprises a transceiver (202) configured to receive a neighbor list (216) from a remote source (108, 110, 112). The device (102) receives the neighbor list (216) that includes one or more technology type indicators and determines availability of technology based on the neighbor list. The wireless communication network comprise a server (112) and a base station (108, 110) communicating with the server. The server (112) inserts network identification and technology type to the neighbor list (216), and the base (108, 110) station provides the neighbor list to a remote device (102).
Owner:MOTOROLA INC
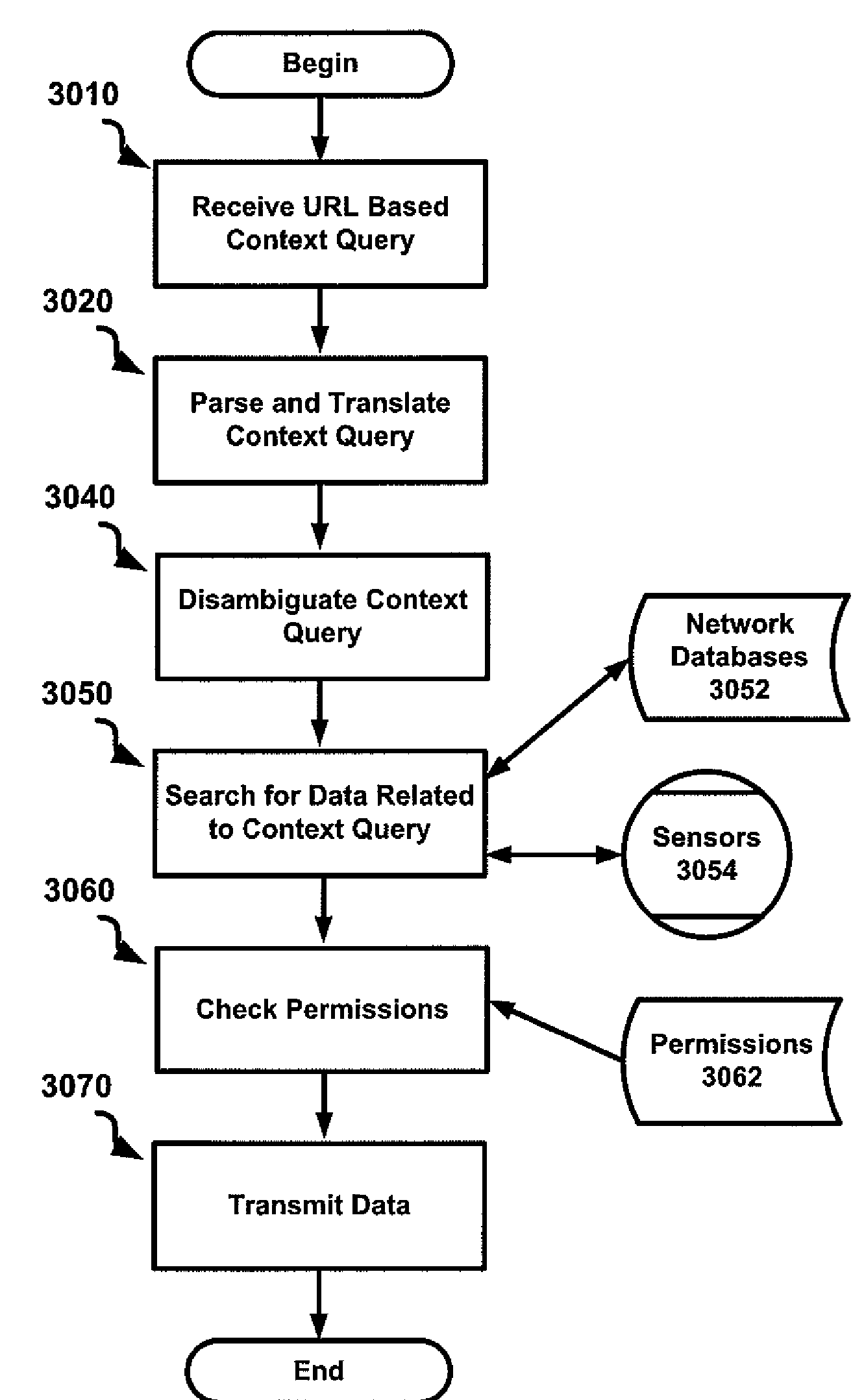
System and method for data privacy in URL based context queries
InactiveUS20100125605A1Digital data information retrievalOrganic chemistryContextual inquiryInternet privacy
A system and method for data privacy in URL based context queries. A reference to a data object is received from a user. At least one entity that controls the data object is identified via the network. At least one permission for the data object is retrieved via the network, wherein the permission is associated with the entity that controls the data object. It is then determined, via the network, if the user is permitted to access to the data object using the permission for the data object and spatial data, temporal data social data and logical data available to the network that relates to the user and to the permission for the data object. If the user is permitted access to the data object, access is granted to the data object, and if the user is nor permitted access to the data object, access is denied to the data object.
Owner:R2 SOLUTIONS
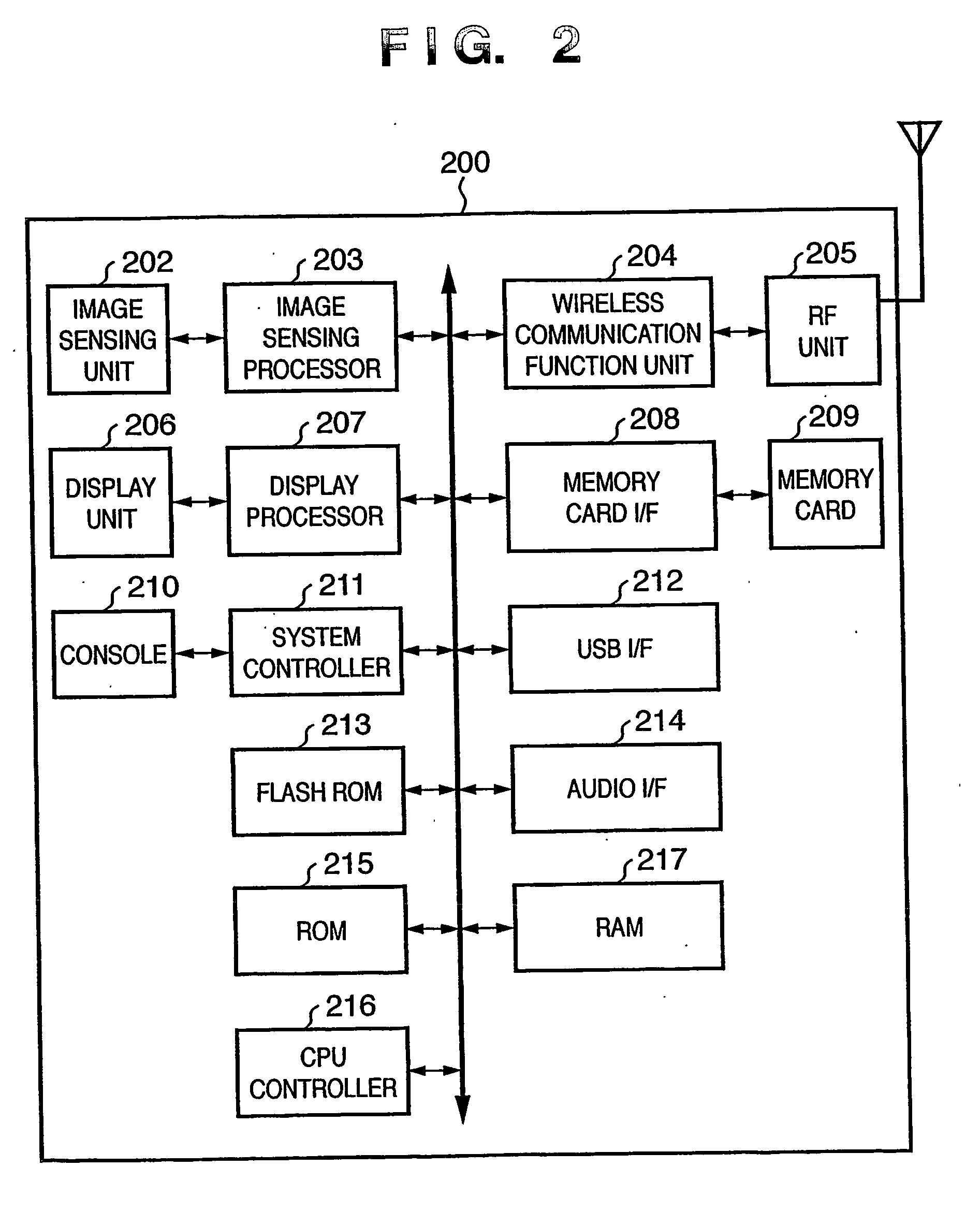
Wireless communication system and wireless communication device and control method
ActiveUS20060206592A1Easy to operateEasy searchElectric signal transmission systemsAssess restrictionCommunications systemComputer printing
This invention has as its object to establish a wireless communication between wireless communication devices and to provide a desired service without any troublesome setup operations. To this end, a digital camera and printer of this invention have wireless communication functions. When it is determined that a wireless communication instruction is issued by a console of the digital camera, a beacon from a network is detected. Upon detection of the beacon, search request information used to confirm the presence of a wireless communication processing device on a network identified by network identification information included in the beacon is transmitted in accordance with that network identification information. If response information to this transmitted request information is detected, identification information of a partner wireless communication device included in the response information is stored, and is displayed to allow the user to select a connection target device.
Owner:CANON KK
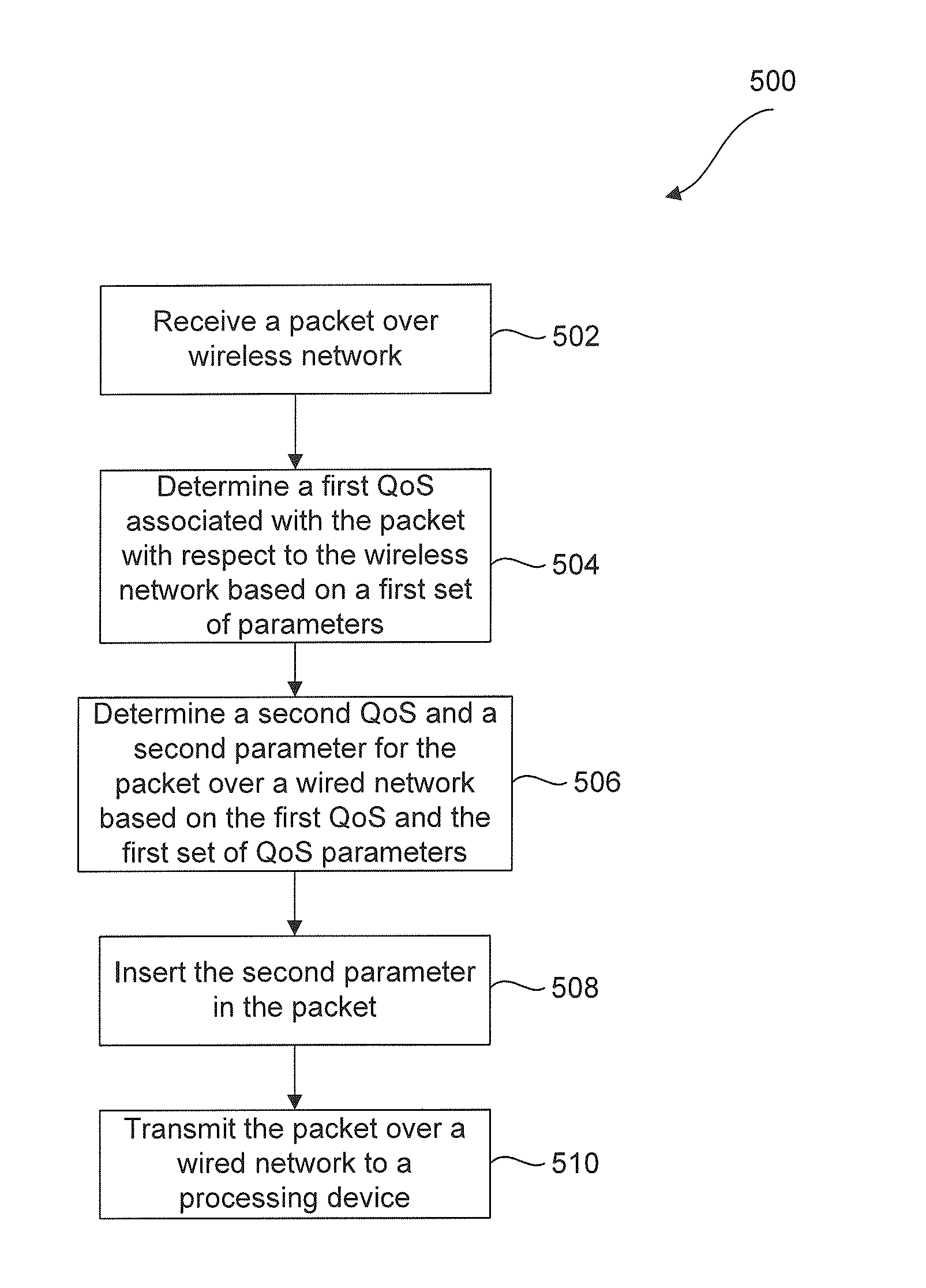
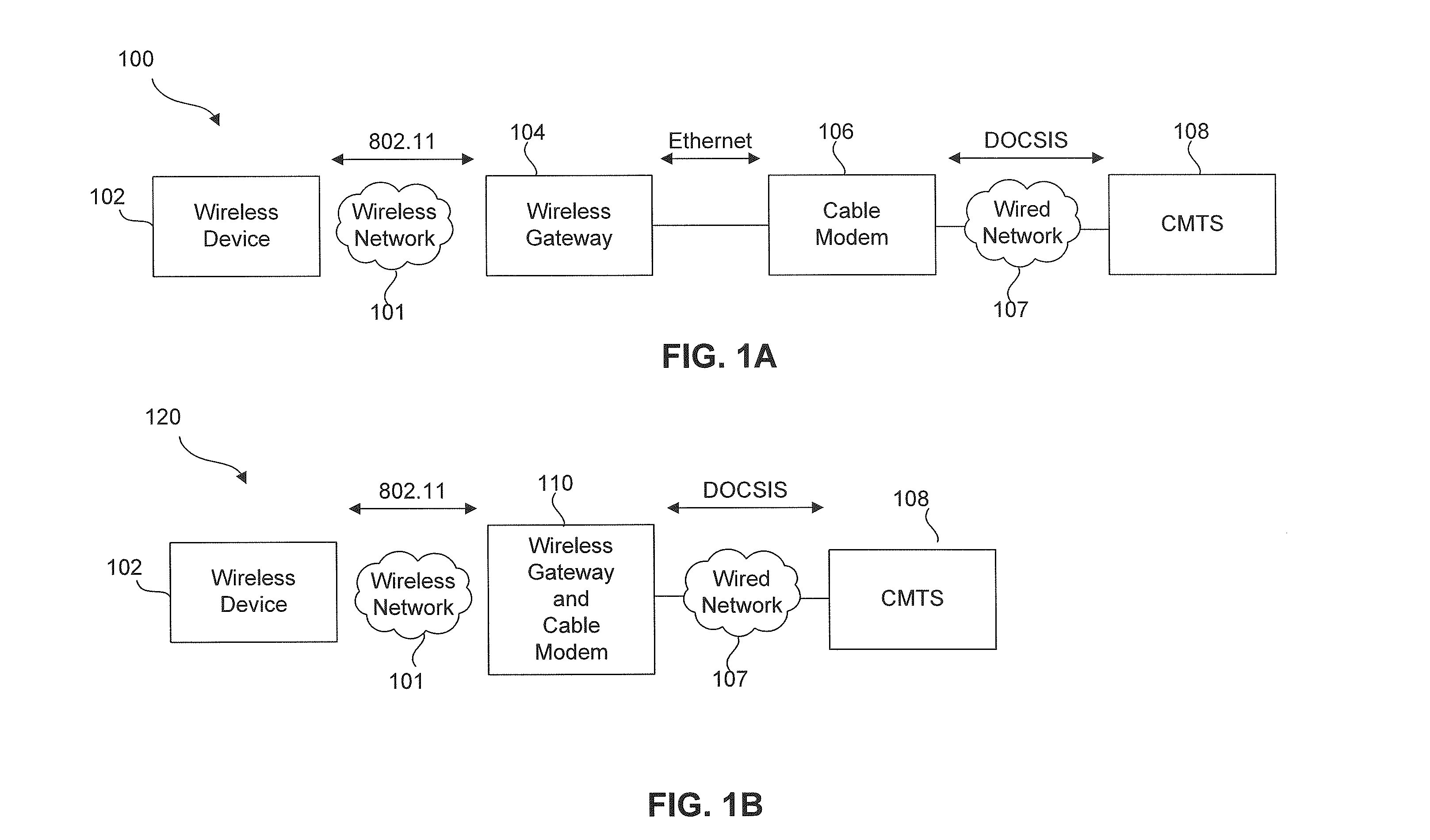
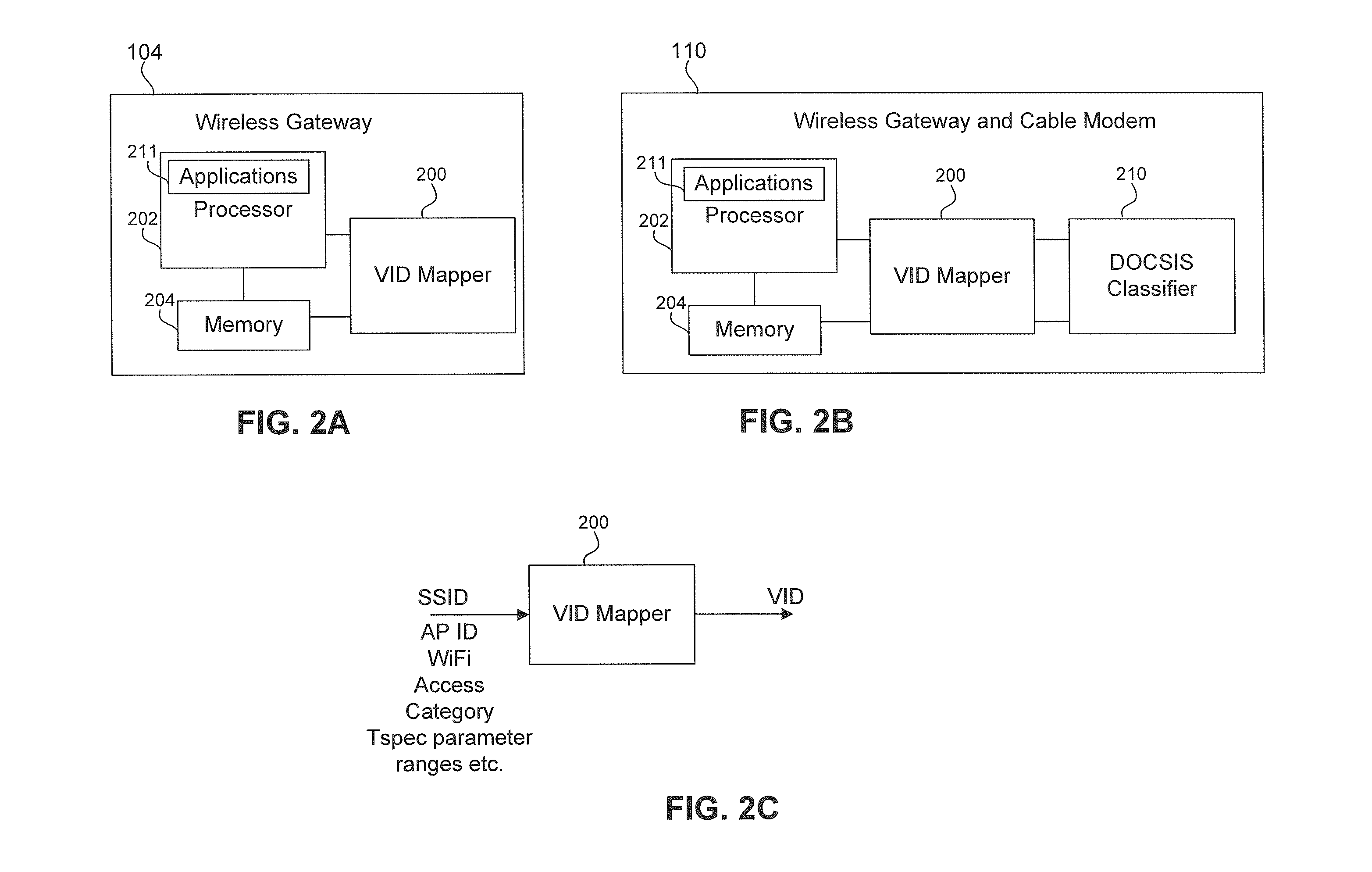
Methods quality of service (QOS) from a wireless network to a wired network
A system and method to map a Quality of Service (QoS) of a traffic flow from a wireless network to a wired network is described herein. The method comprises the steps of receiving a packet of the traffic flow over the wireless network and determining a first Quality of Service associated with the traffic flow over the wireless network based on a first set of parameters associated with the packet. The method further comprises the step of determining a second parameter that identifies a second Quality of Service over the wired network, wherein the second Quality of Service is substantially equivalent to the first Quality of Service. The method also comprises inserting the second parameter in a field of the packet based on the determined second Quality of Service and transmitting the packet over the wired network.
Owner:AVAGO TECH INT SALES PTE LTD
Messaging system involving wireless communications and methods therefor
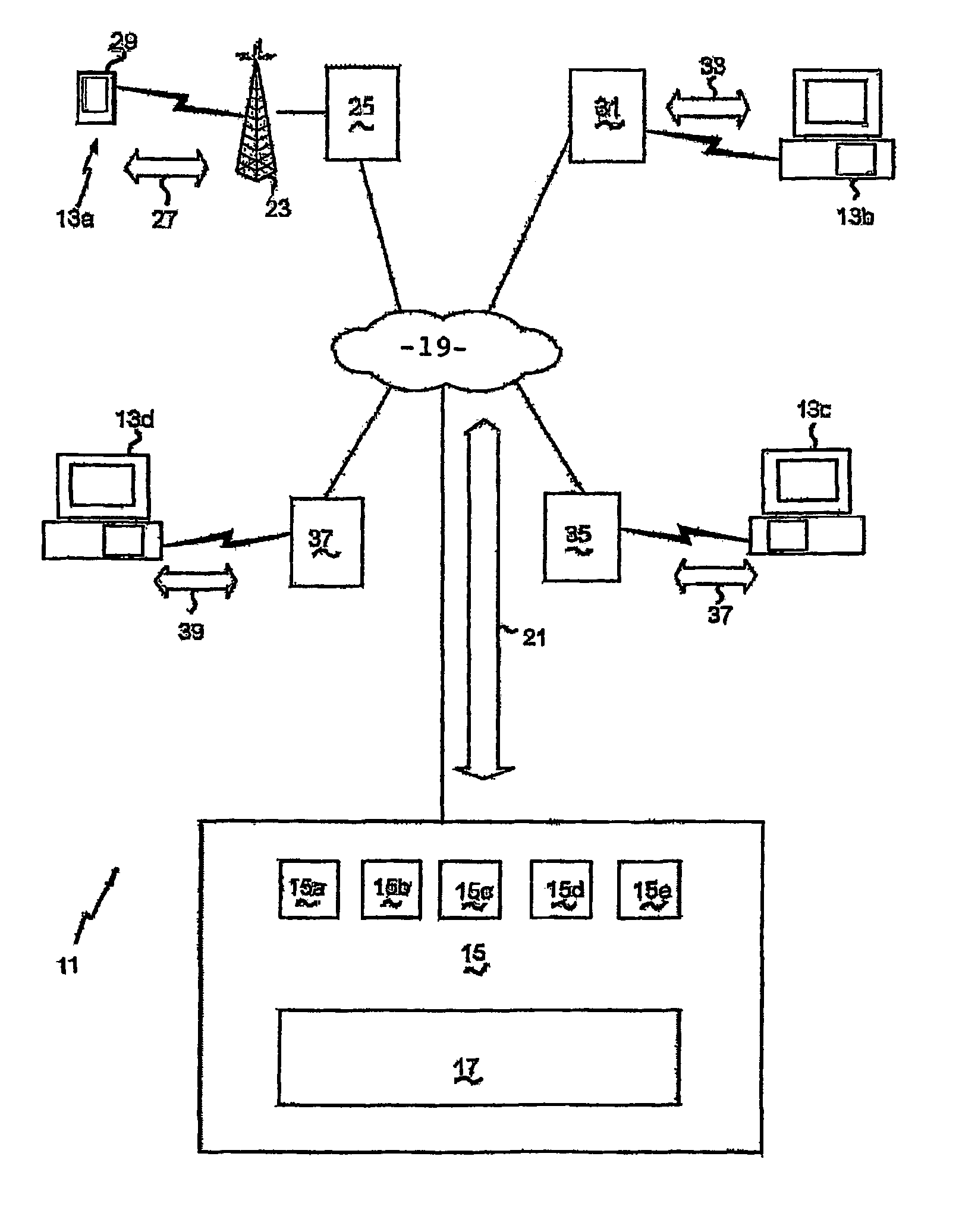
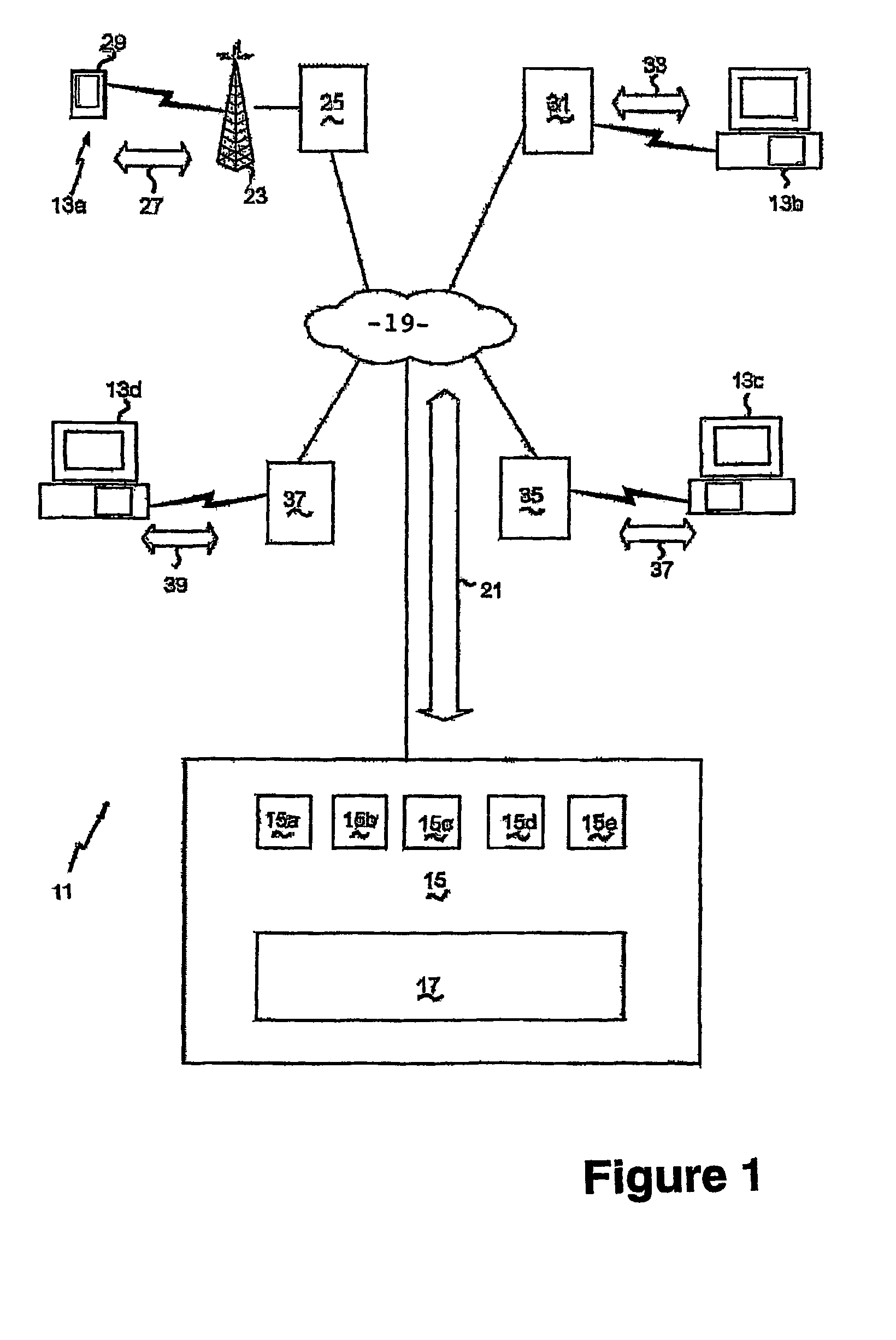
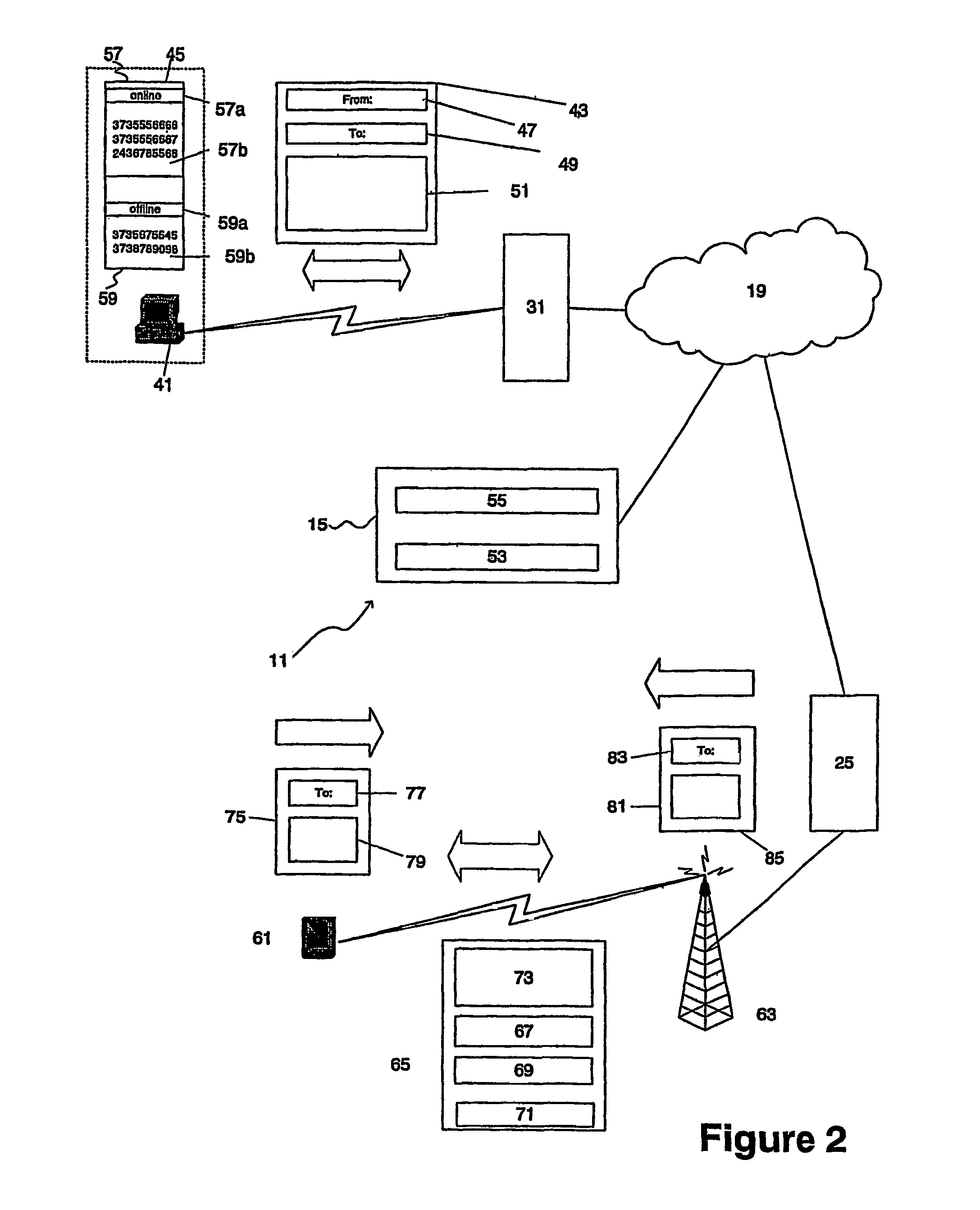
InactiveUS7319882B2Efficient and convenient communication of messageSpecial service for subscribersMultiple digital computer combinationsWireless communication systemsNetwork identification
A messaging system (11) for conveying messages between a host server (15) and a client (13a) that is part of a GSM network and a method therefor. The GSM network includes an SMS facility to convey messages between its clients using an SMSC (25), each wireless client having a network identifying number (NIN) associated with it to uniquely identify the client within the GSM network. Each message comprises a message packet (43) including the address (49) of an intended recipient, the address (47) of the sender of the message and the message itself (51). The host server (15) may be selectively connected to a plurality of different client types (13) via the Internet (19) to convey messages therebetween. Each client has a client identifying number (CIN) associated with it to uniquely identify it to the host server (15). The host server (15) and the SMSC (25) are interconnected by the Internet (19) or another computer network to provide for communications therebetween. One of the clients (13) of the host server (15) is a wireless client (13a) and has its CIN corresponding to its NIN. The host server (15) has an access code (AC) to uniquely identify it to the SMSC (25) and a unique identification number (UIN) ascribed to: (i) a prescribed action performed by it, and (ii) an entity that is the subject of the prescribed action. The messages sent in message packet (43) between the host server (15) and the wireless client (13a) in connection with a particular prescribed action and entity include: (i) a combination of the AC and the UIN ascribed to the particular action and entity as the address of the host server (15); and (ii) the NIN as the address of the wireless client. The SMSC (25) also uses the AC in the address of the intended recipient or the sender to recognize messages sent to or received from the host server (15) and routs the messages accordingly.
Owner:CHIKKA PTE LTD
System and method for distributing media related to a location
ActiveUS20100077017A1Multiple digital computer combinationsTransmissionUser devicePosition dependent
A system and method for distributing media related to a location. The physical location of a media presentation device is received over a network. The physical location of a plurality of end users are identified, via the network, wherein each of plurality of users is associated with a user device capable of storing media files. At least one of the end users is identified who is located in such proximity to the media presentation device that the user can perceive media that presented on the media presentation device. At least one media file that is currently being presented on the media presentation device is identified and transmitted over the network to each of the identified end users.
Owner:R2 SOLUTIONS
Methods and apparatus for producing a user-controlled PLMN list for a SIM/USIM card with use of a user agent application
ActiveUS20070254646A1Assess restrictionRadio/inductive link selection arrangementsRankingUser equipment
Methods and apparatus for producing a user-controlled PLMN list for a SIM / USIM card with use of a user agent application are disclosed. Selection indication data corresponding to at least one of a plurality of network attribute type preferences is received at the user agent application. The selection indication data may be received through a user interface of the user equipment, a user application of the user equipment, or both. The at least one selected network attribute type preference is indicative of a preference to prioritize network selection based on at least one network attribute type of a plurality of network attributes types (e.g. cost, bandwidth, quality, number of available features, etc.). A list of network identifications associated with a plurality of wireless communication networks is ranked in accordance with a ranking of network attributes of the at least one selected network attribute type made available by the plurality of wireless communication networks. The ranked list of network identifications is then stored as a user-controlled PLMN list in the SIM / USIM. An automatic network selection process may then be performed with use of the user-controlled PLMN list. As apparent, network selection may be controlled and facilitated by the end user in a more conceptual fashion. Other additional and alternative advantageous features are described in the detailed description.
Owner:MALIKIE INNOVATIONS LTD
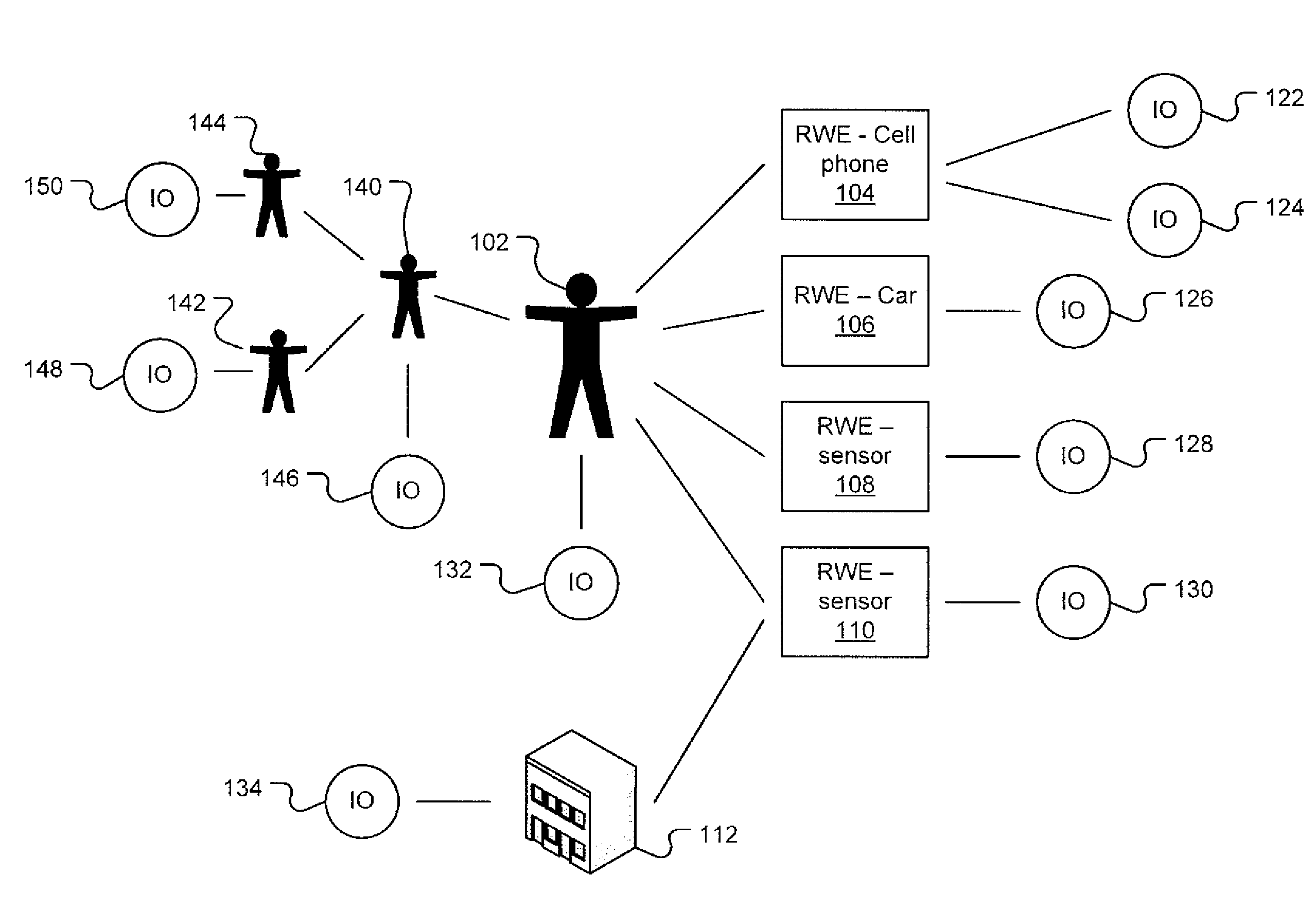
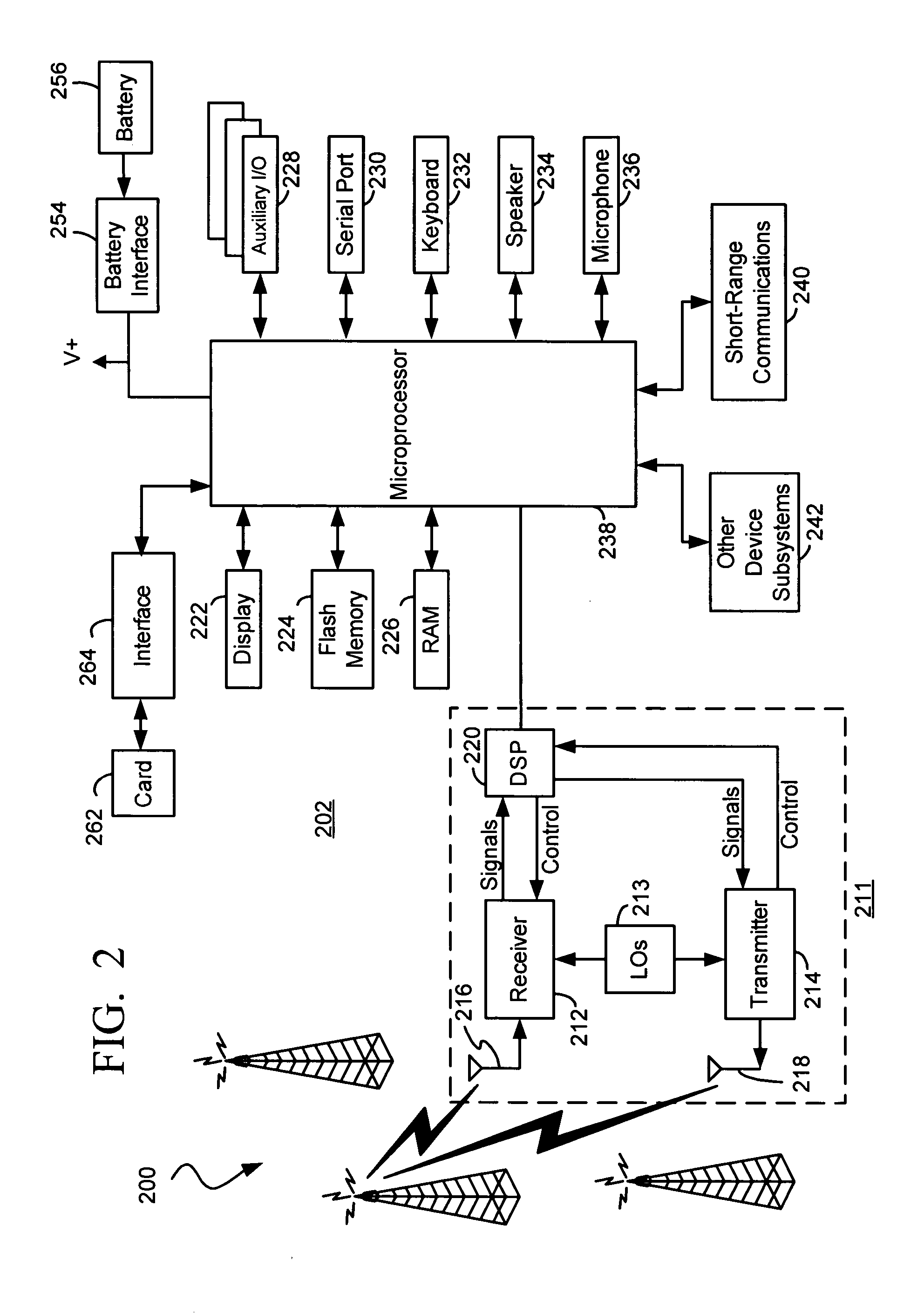
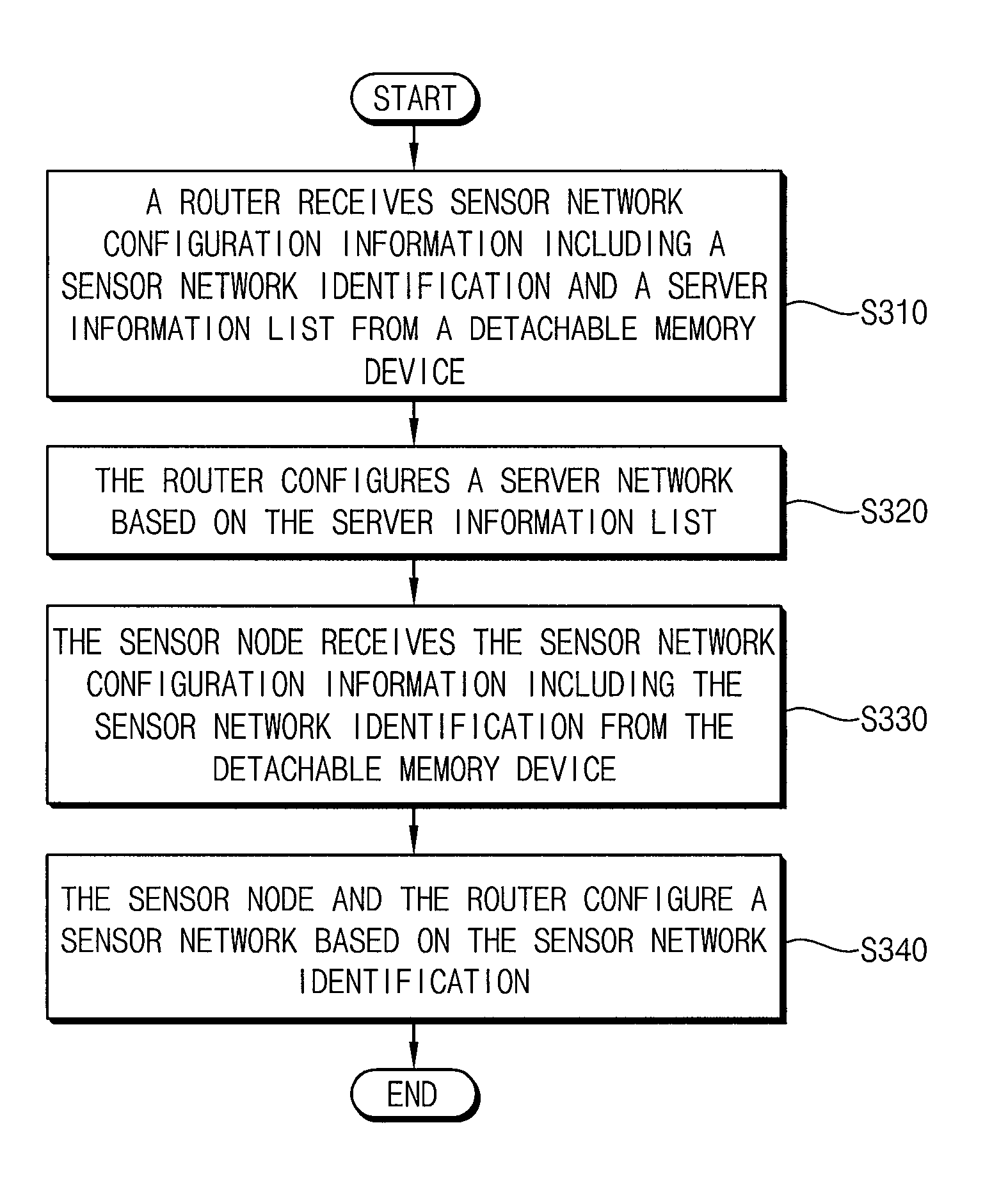
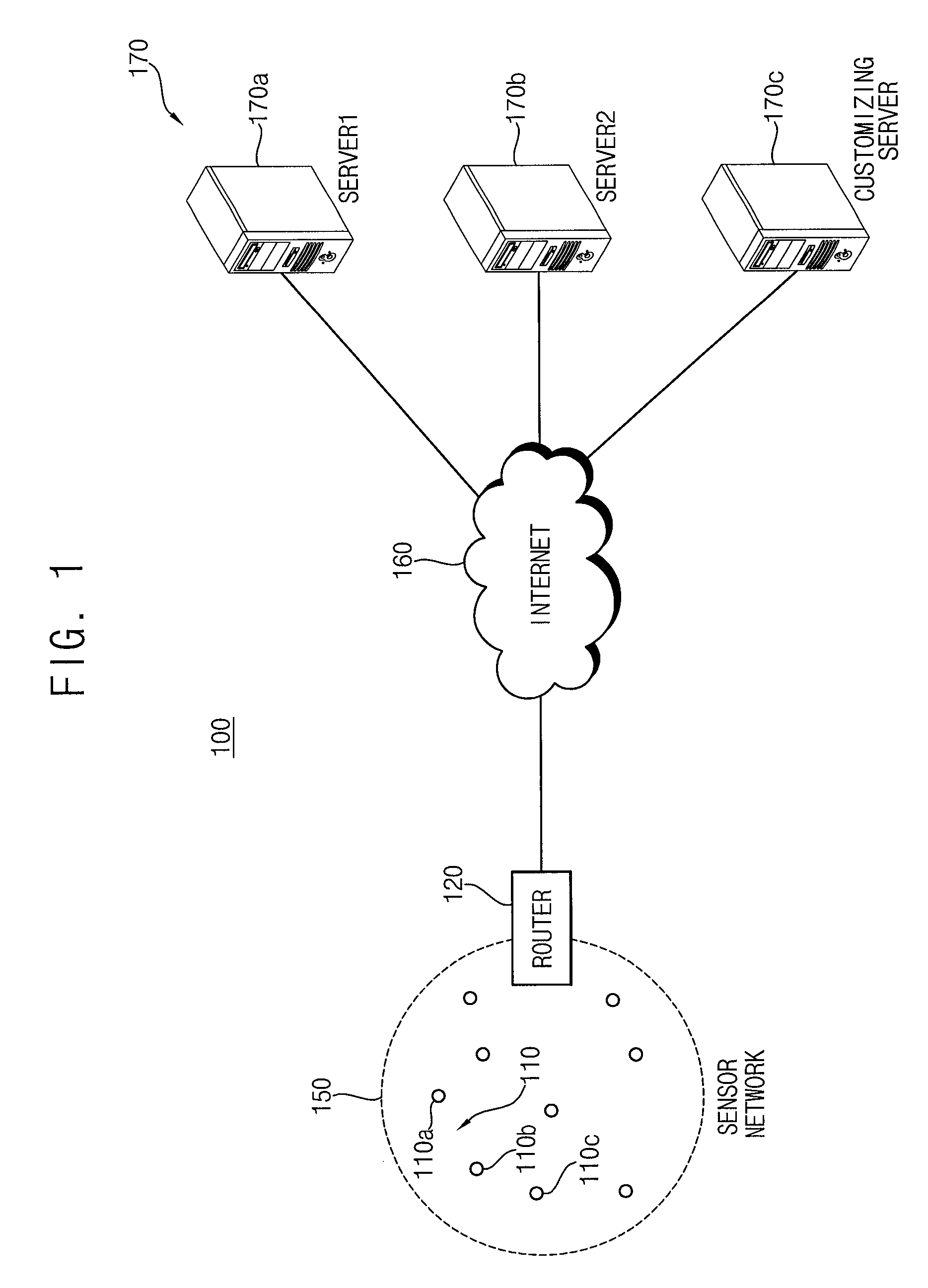
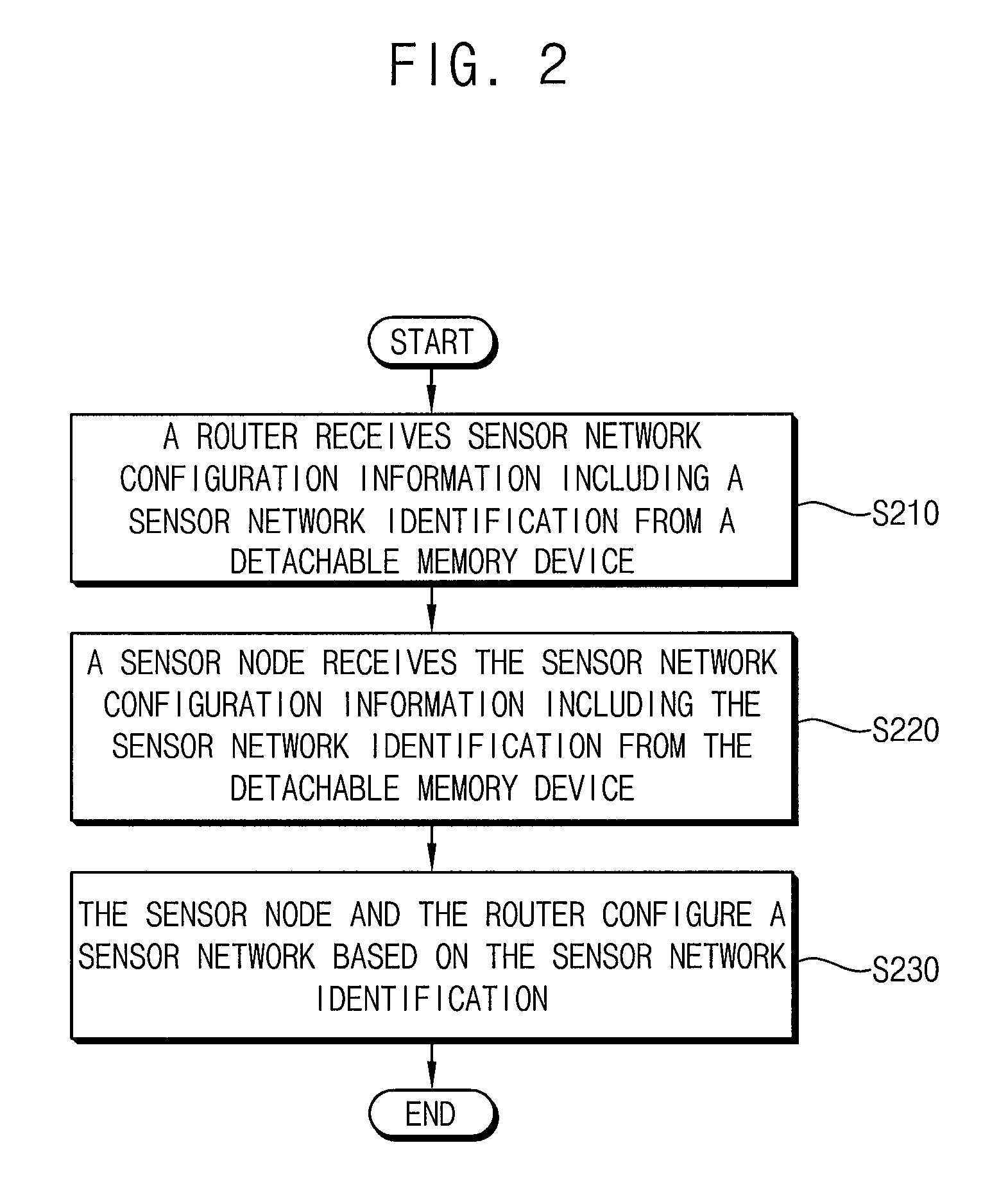
Ubiquitous sensor network system and method of configuring the same
In a ubiquitous sensor network (USN) system having a router and a sensor node connectable to a detachable memory device, a sensor network configuration information including a sensor network identification is received from the detachable memory device under control of the router. The sensor network configuration information including the sensor network identification is received from the detachable memory device under control of the sensor node. A sensor network is configured based on the sensor network identification under control of at least one of the router and the sensor node. Accordingly, the USN system may be automatically configured by using the detachable memory devices including the sensor network configuration information.
Owner:AJOU UNIV IND ACADEMIC COOP FOUND
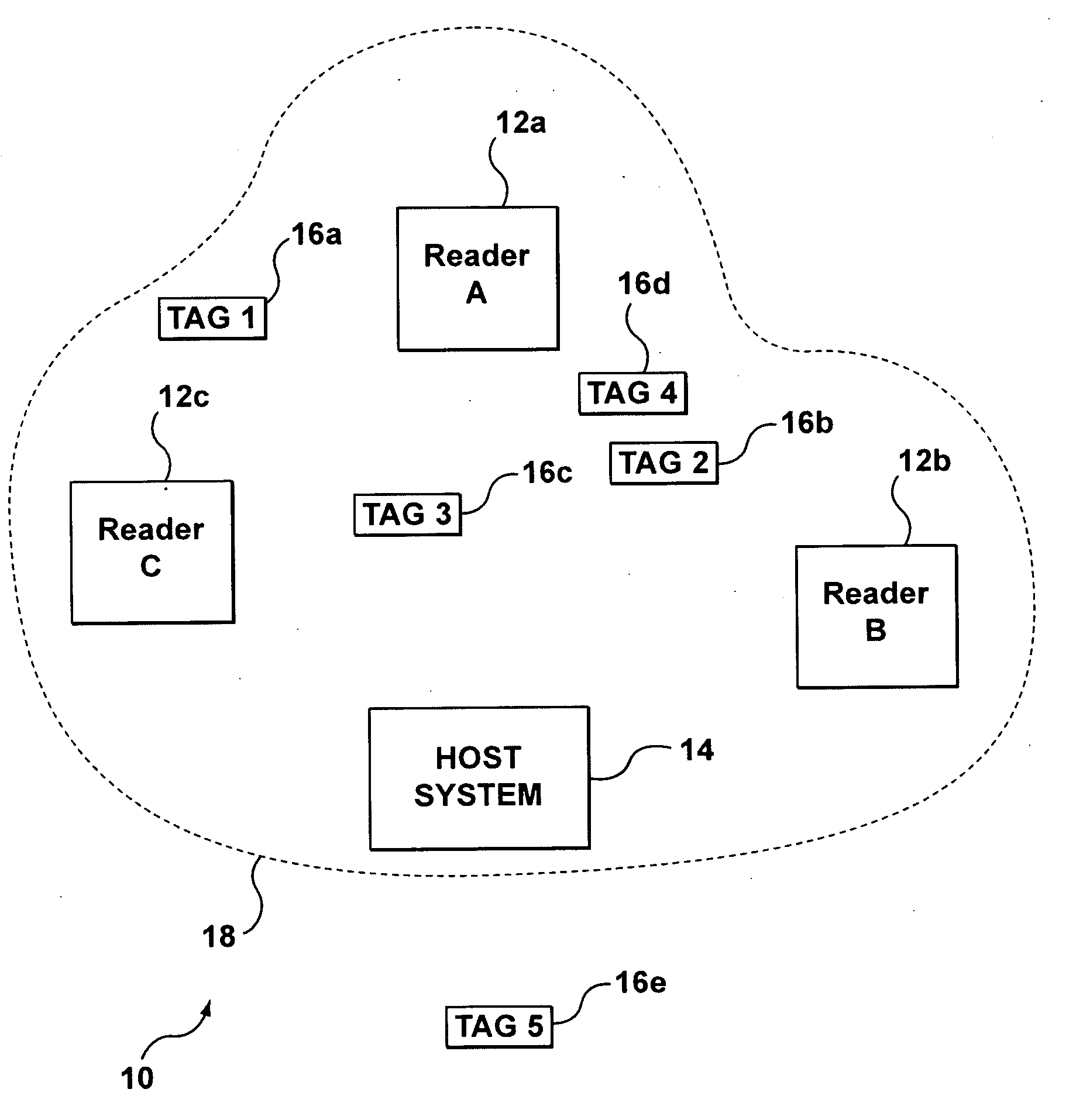
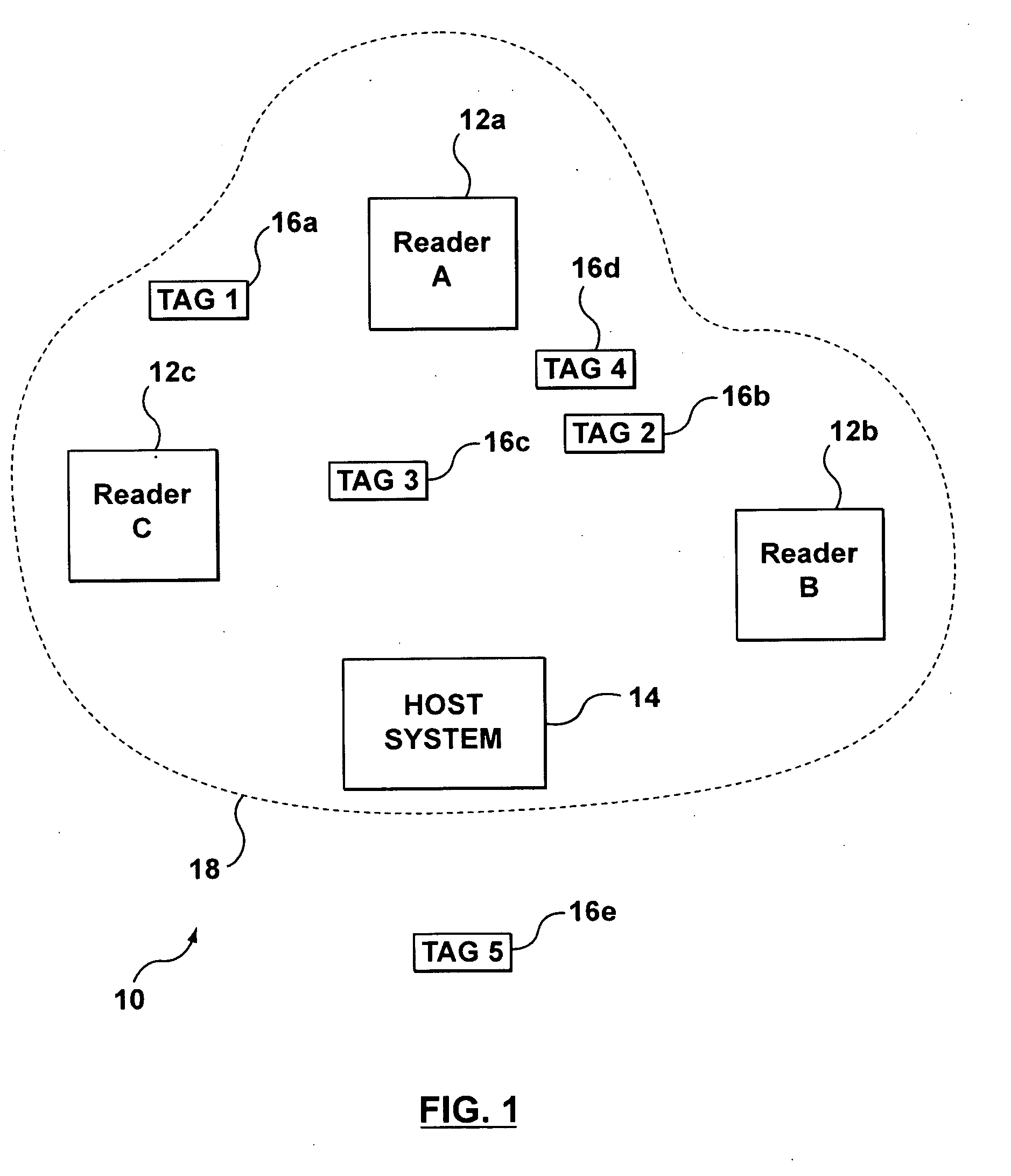
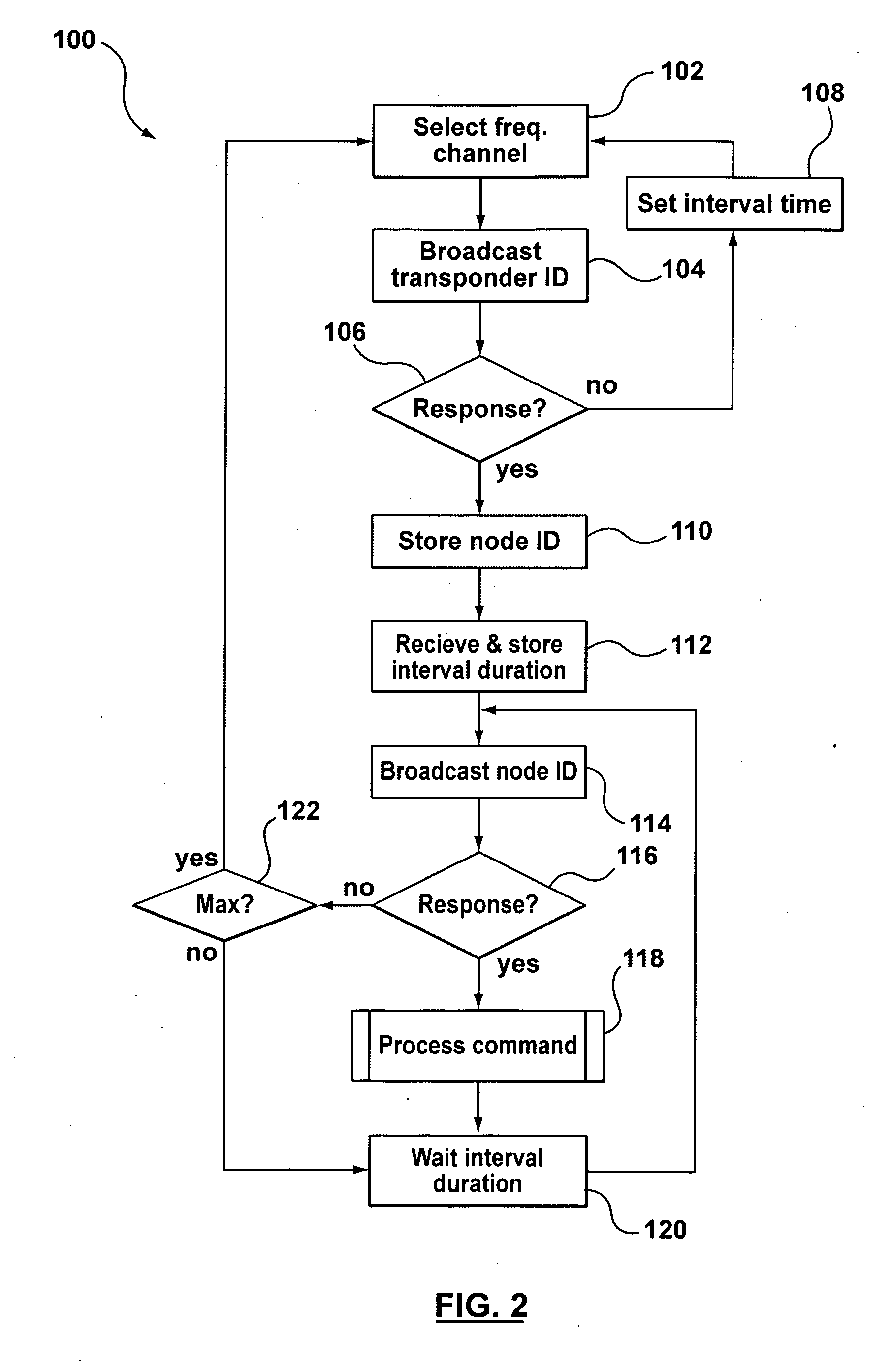
Real-Time Location Systems and Methods
InactiveUS20090201169A1Eliminate the effects ofElectric/electromagnetic visible signallingAlarmsMultilaterationReal-time locating system
A real-time location system for identifying and locating tagged items. The system may include an identification protocol that tracks in-network transponders and assigns dynamic in-network identification numbers to in-network transponders. The system includes a locator function that employs time-of-arrival analysis. Rather than attempt to synchronize the time base at each reader, the system and process eliminate the need to sync the readers and also eliminate the impact of differential receive delays in the respective readers. Both the transponder and a master reader transmit locate signals, which are measured at slave readers. The system relies on differences in time-of-arrival of the two signals at the respective slave readers to determine the likely location of the transponder.
Owner:MARK IV INDS
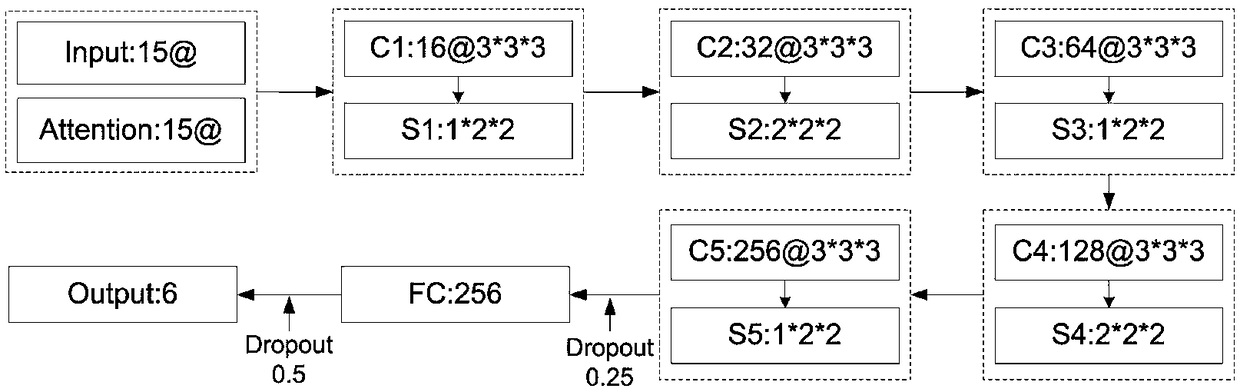
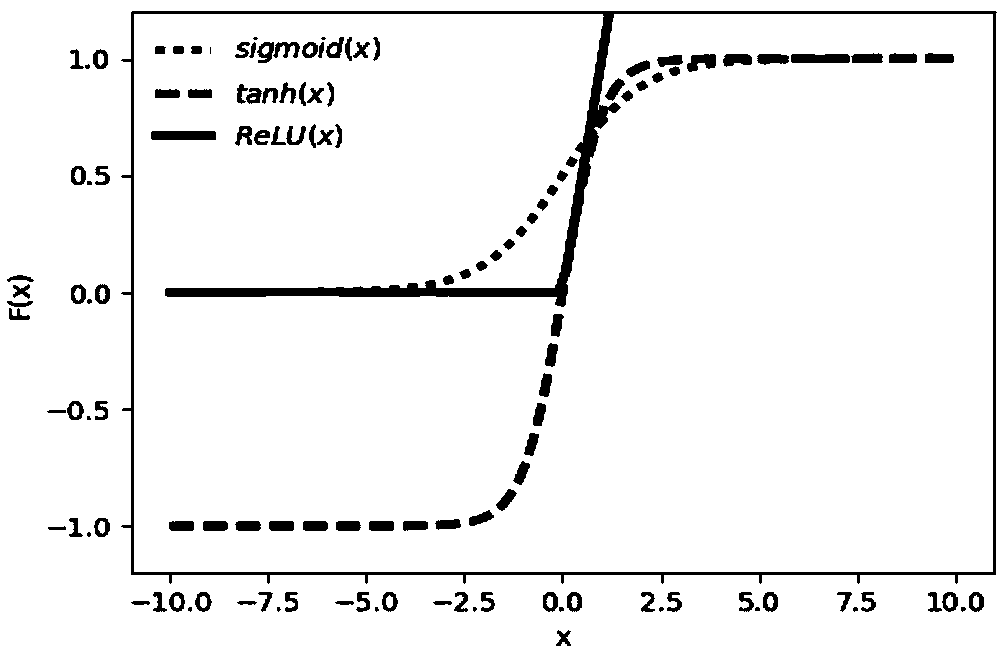
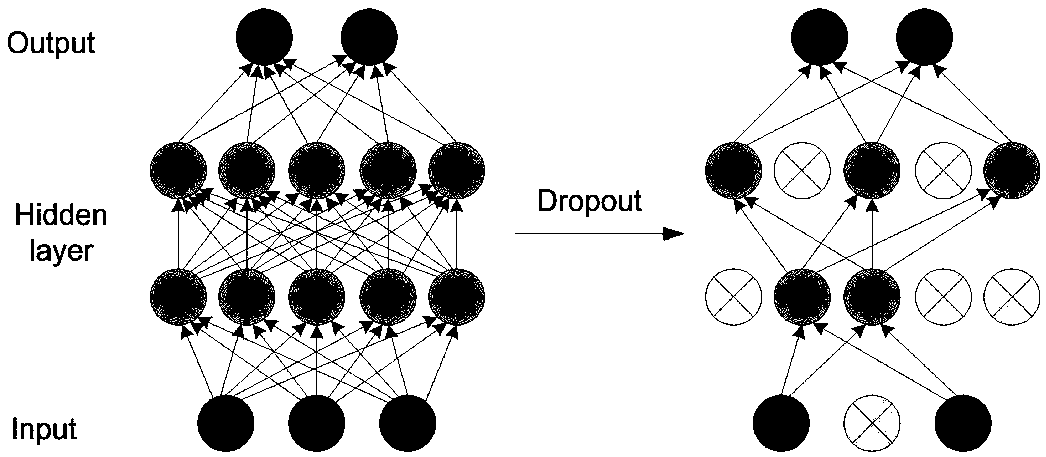
Human behavior recognition method based on attention mechanism and 3D convolutional neural network
ActiveCN108830157AImprove the accuracy of behavior recognitionEfficient use ofCharacter and pattern recognitionNeural architecturesHuman behaviorActivation function
The invention discloses a human behavior recognition method based on an attention mechanism and a 3D convolutional neural network. According to the human behavior recognition method, a 3D convolutional neural network is constructed; and the input layer of the 3D convolutional neural network includes two channels: an original grayscale image and an attention matrix. A 3D CNN model for recognizing ahuman behavior in a video is constructed; an attention mechanism is introduced; a distance between two frames is calculated to form an attention matrix; the attention matrix and an original human behavior video sequence form double channels inputted into the constructed 3D CNN and convolution operation is carried out to carry out vital feature extraction on a visual focus area. Meanwhile, the 3DCNN structure is optimized; a Dropout layer is randomly added to the network to freeze some connection weights of the network; the ReLU activation function is employed, so that the network sparsity isimproved; problems that computing load leap and gradient disappearing due to the dimension increasing and the layer number increasing are solved; overfitting under a small data set is prevented; and the network recognition accuracy is improved and the time losses are reduced.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING) +1
System for securely communicating amongst client computer systems
InactiveUS6973477B1Protect normal transmissionEasy to integrateMultiple digital computer combinationsAutomatic exchangesOperational systemModem device
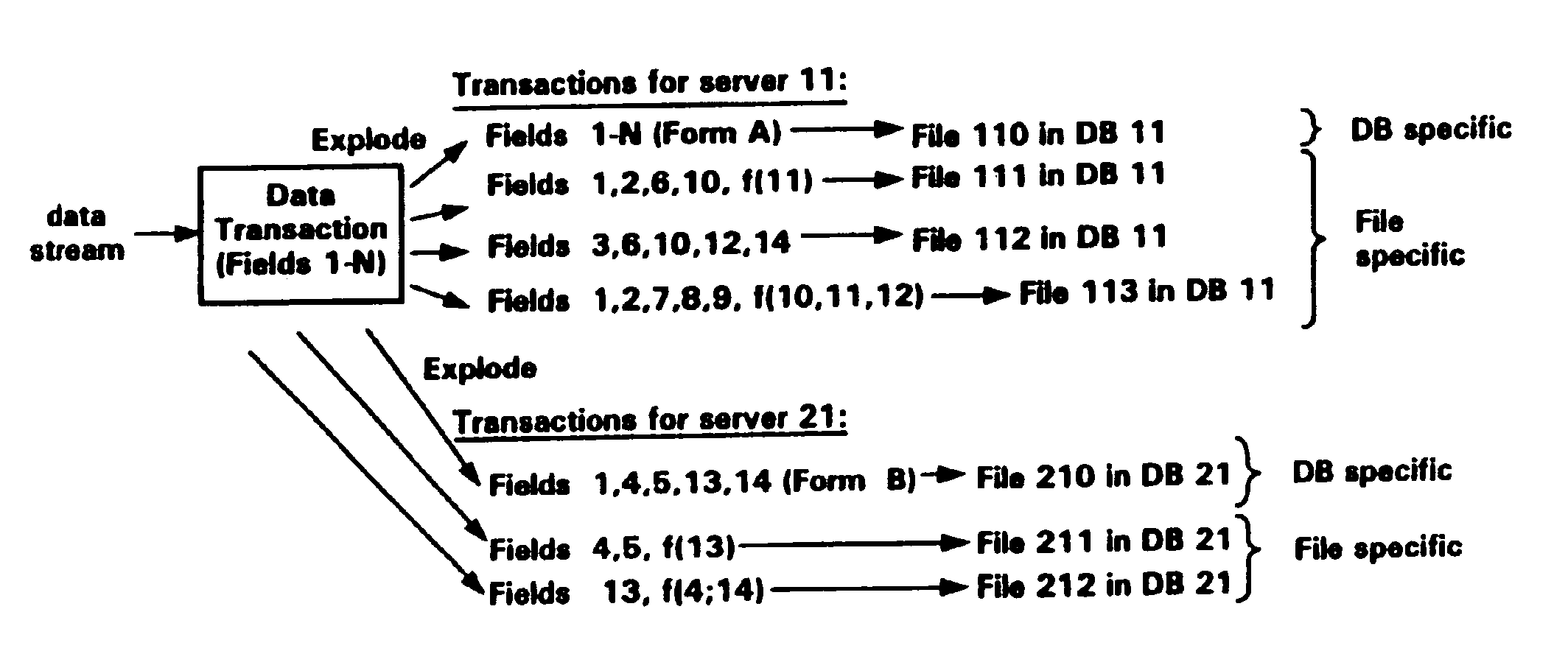
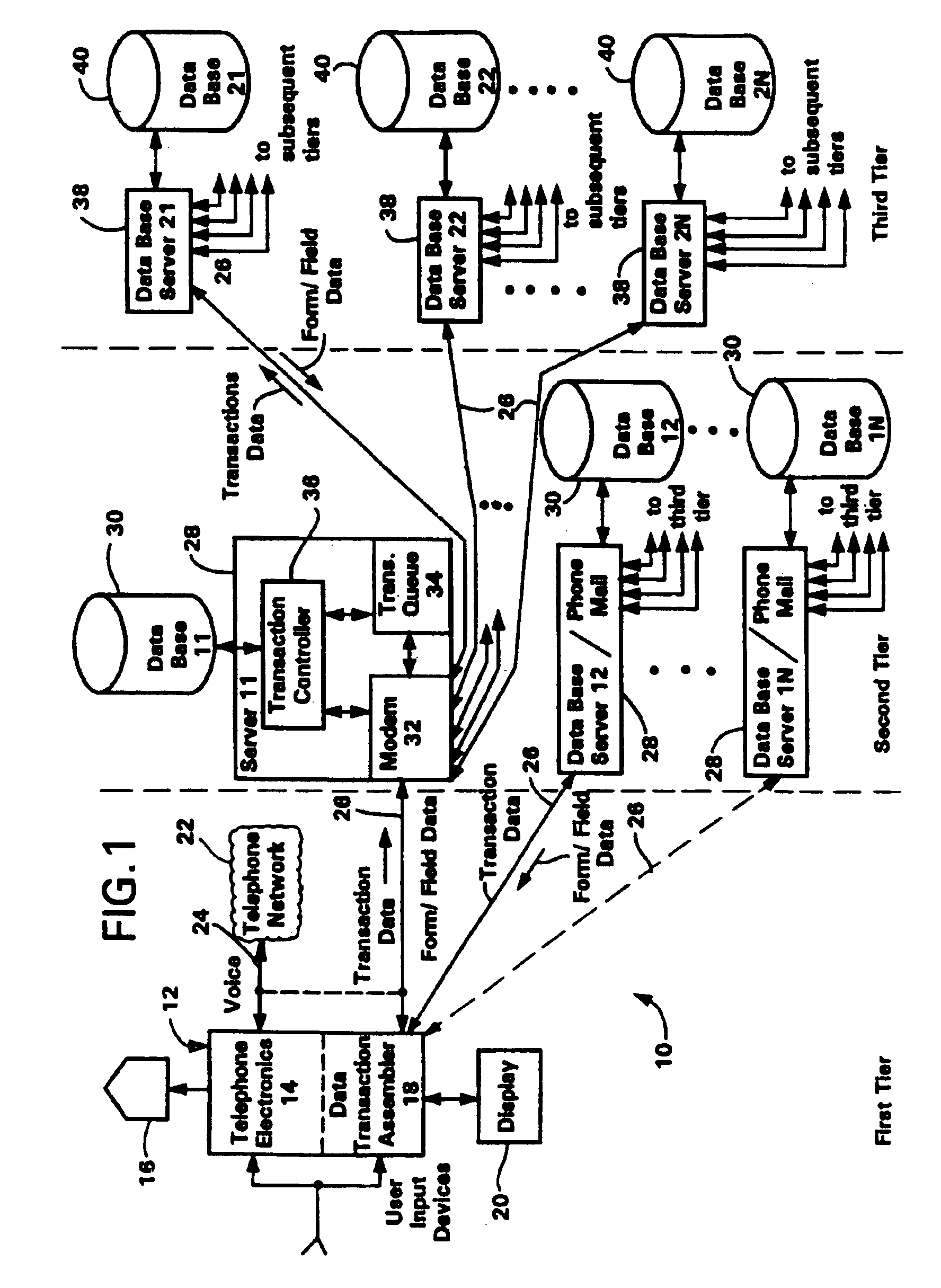
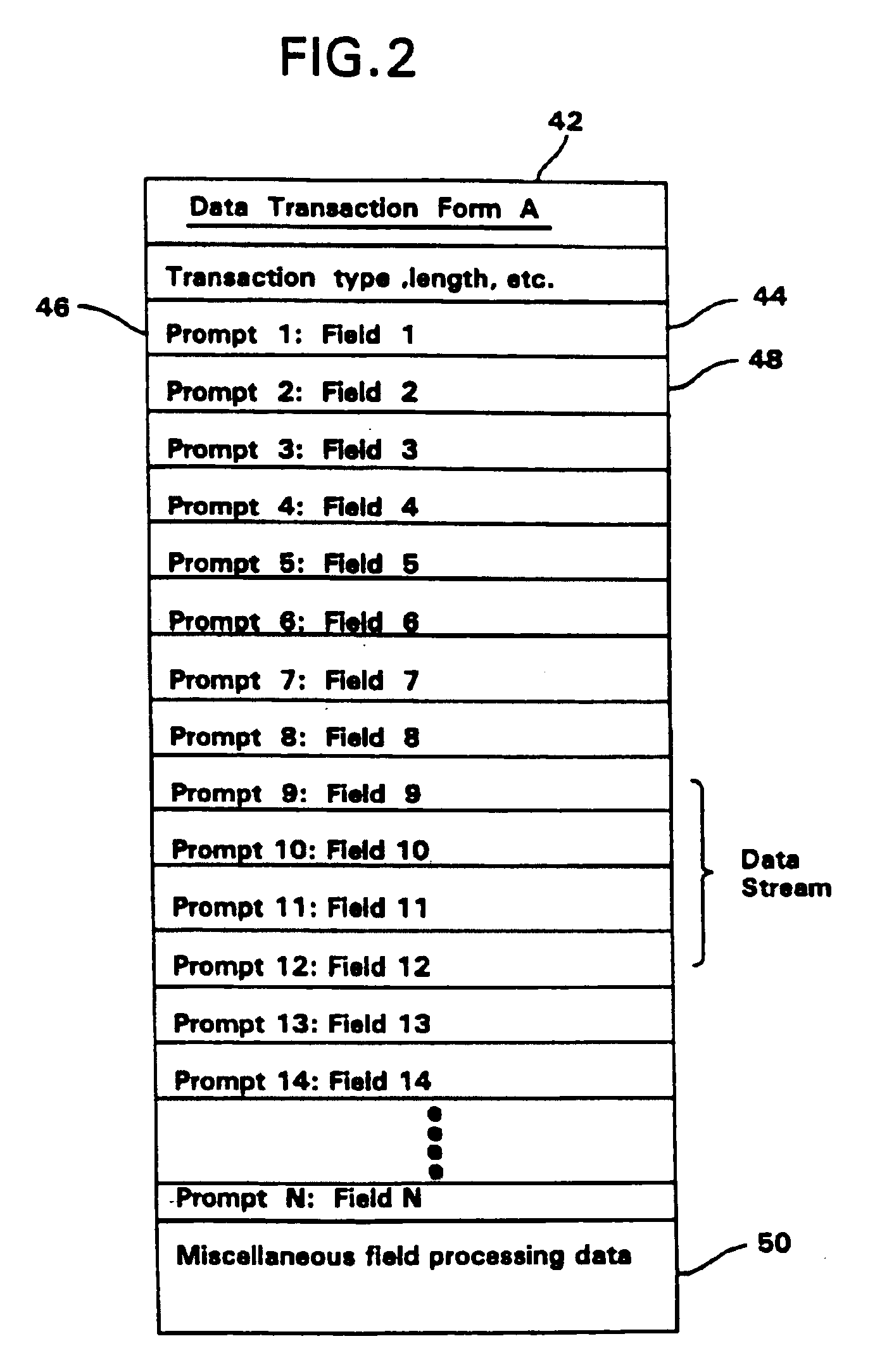
A data transaction processing system in which transaction data is entered by the user in response to prompts in a template which is tailored to each user application. The template and entered data are accumulated into data transactions that are immediately transmitted upon completion to an external database server for processing and storage. The data transaction is received via standard protocols at the database server which, depending upon the application, stores the entire data transaction, explodes the data transaction to produce ancillary records which are then stored, and / or forwards the data transaction or some or all of the ancillary records to other database servers for updating other databases associated with those database servers. In response to requests from the transaction entry device, the database server may return data streams for use in completing the fields in the data transaction or in presenting a menu on the display which was read in from the database server or a remote phone mail system. The transaction entry device is integrated with a telephone and is accessed via a touch screen, an optional keyboard, a magnetic card reader, voice entry, a modem, and the like.A plurality of such database servers under the control of broad operations system server (BOSS) software and a plurality of form-driven client computing devices are provided to create an open platform system for receiving and transmitting transaction data to or from the client devices, other applications and databases. Advantageously, a locator server computer serves to retrieve IP address numbers, PSTN numbers and other network identification information for use in identifying and locating, e.g., an originating user and a destination client device. A robust security and authentication scheme along with robust storage protects the transmission of sensitive or confidential data.
Owner:CYBERFONE TECH
System and method for distributing media related to a location
A system and method for distributing media related to a location. The physical location of a media presentation device is received over a network. The physical location of a plurality of end users are identified, via the network, wherein each of plurality of users is associated with a user device capable of storing media files. At least one of the end users is identified who is located in such proximity to the media presentation device that the user can perceive media that presented on the media presentation device. At least one media file that is currently being presented on the media presentation device is identified and transmitted over the network to each of the identified end users.
Owner:R2 SOLUTIONS
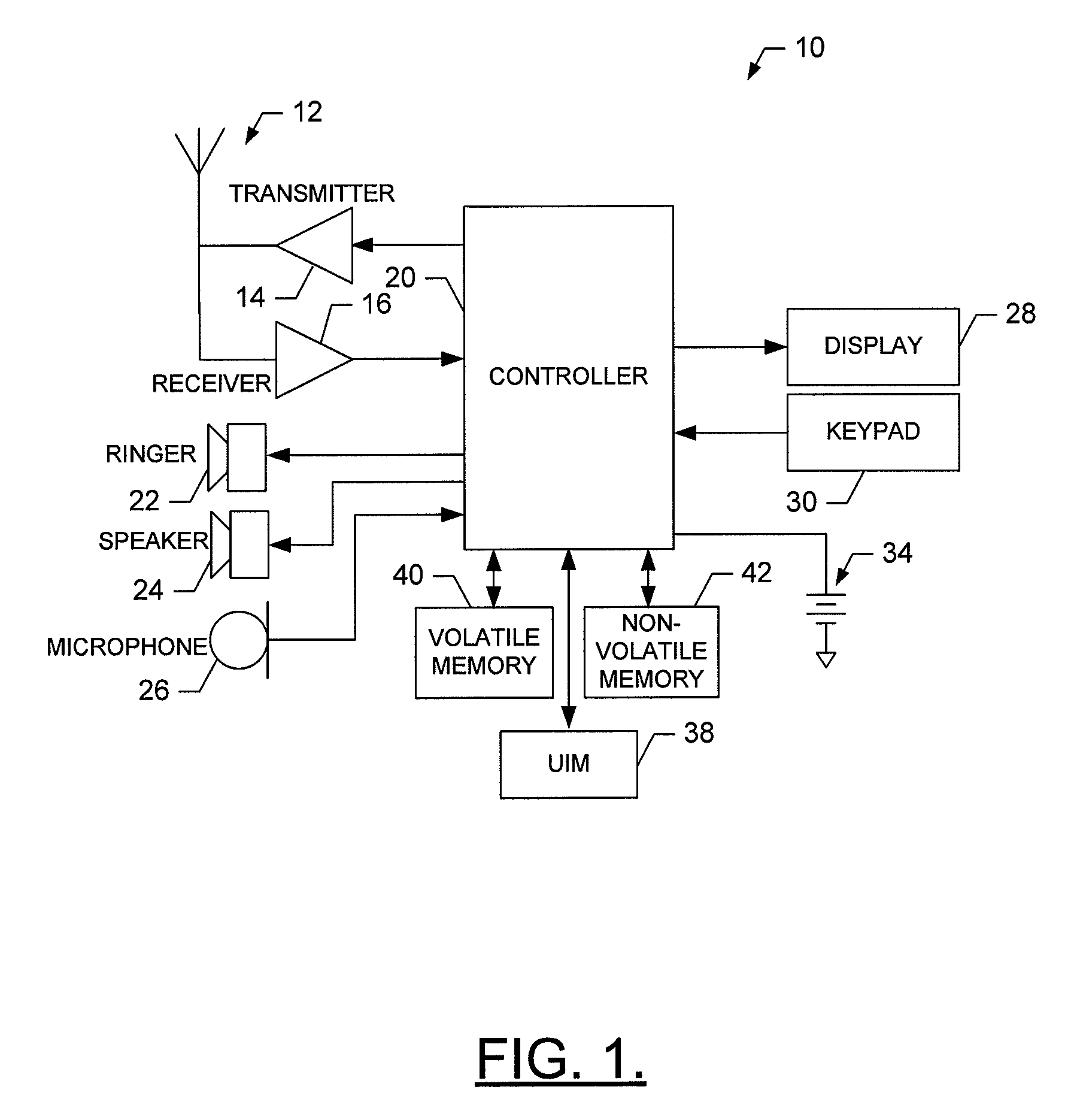
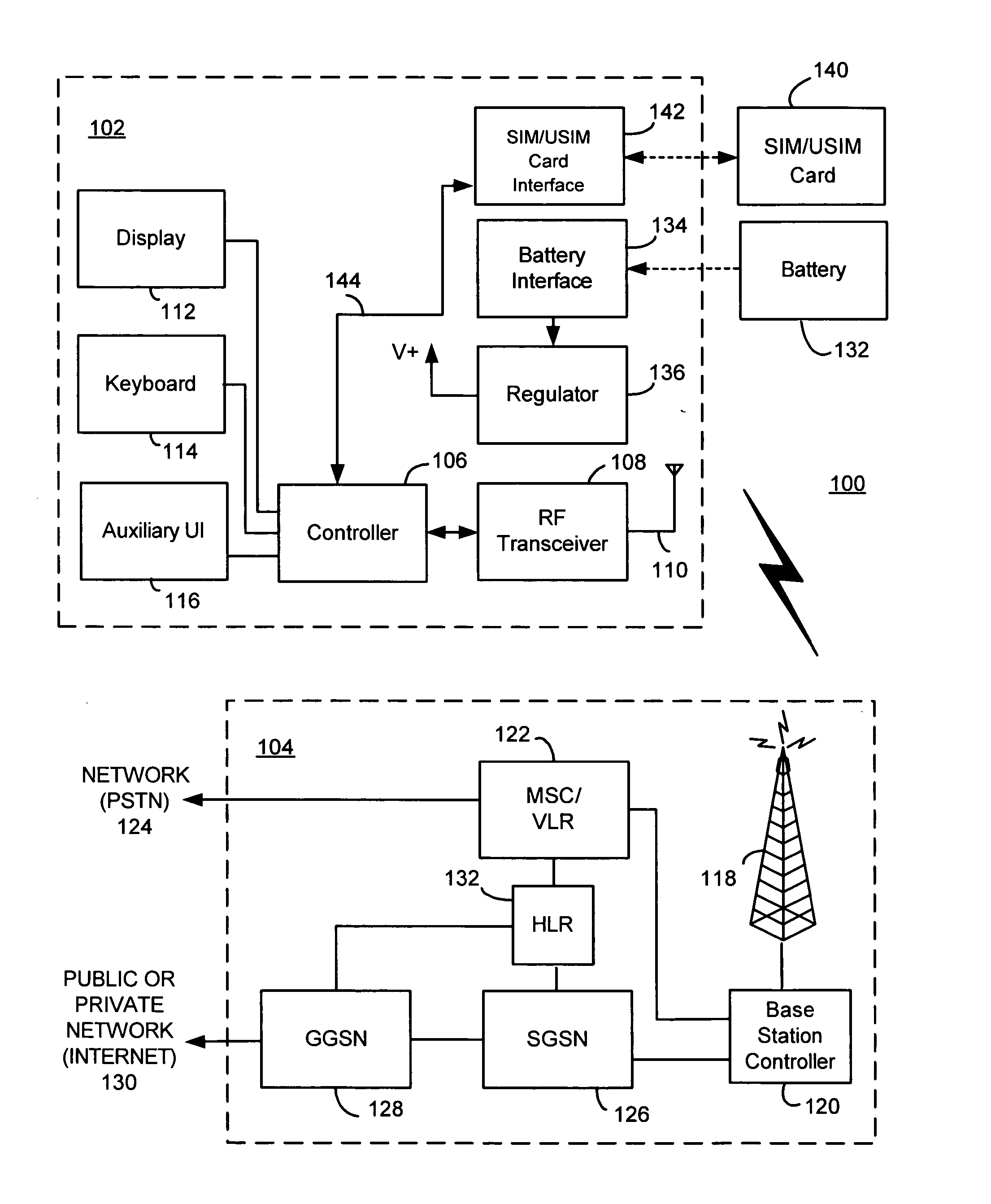
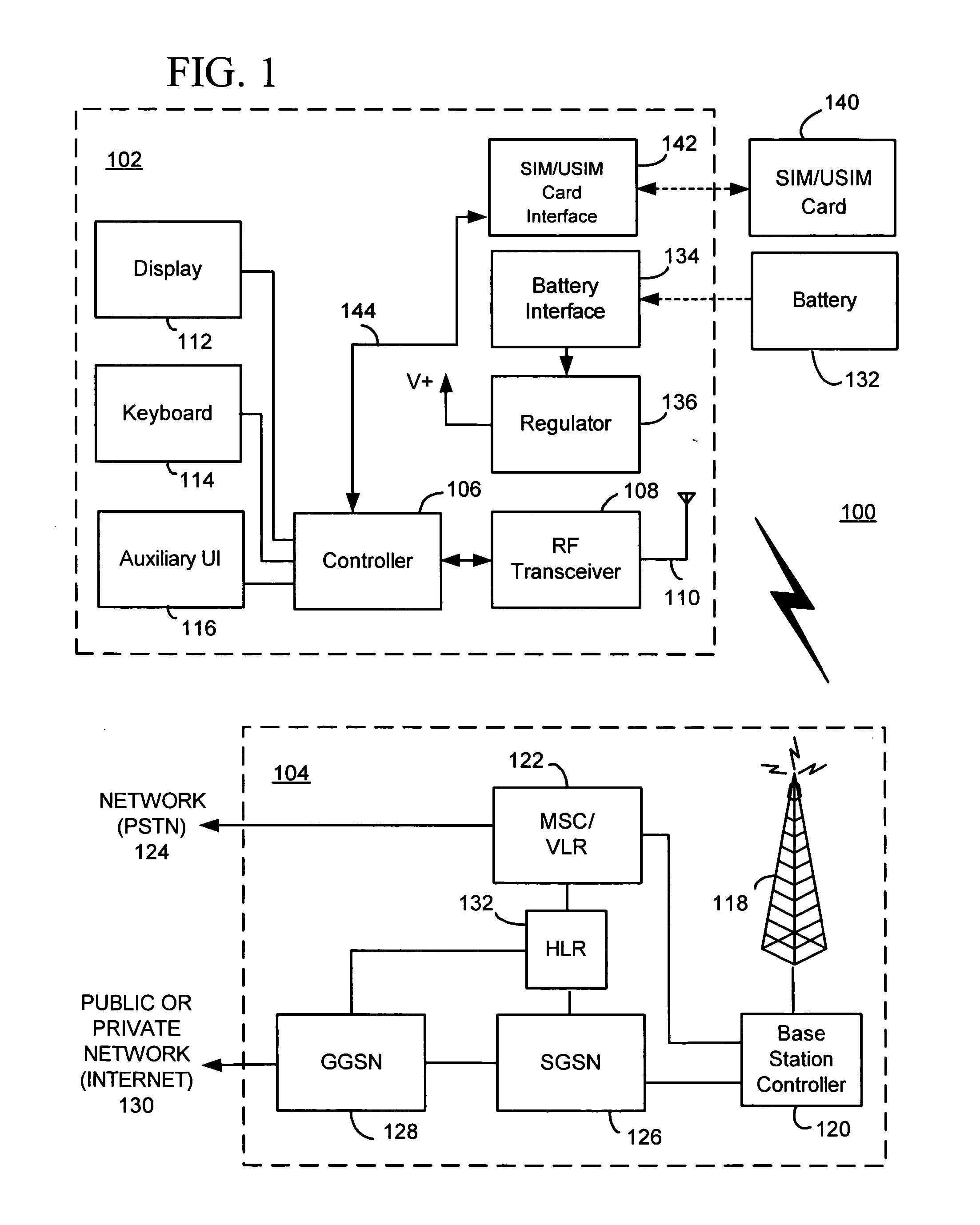
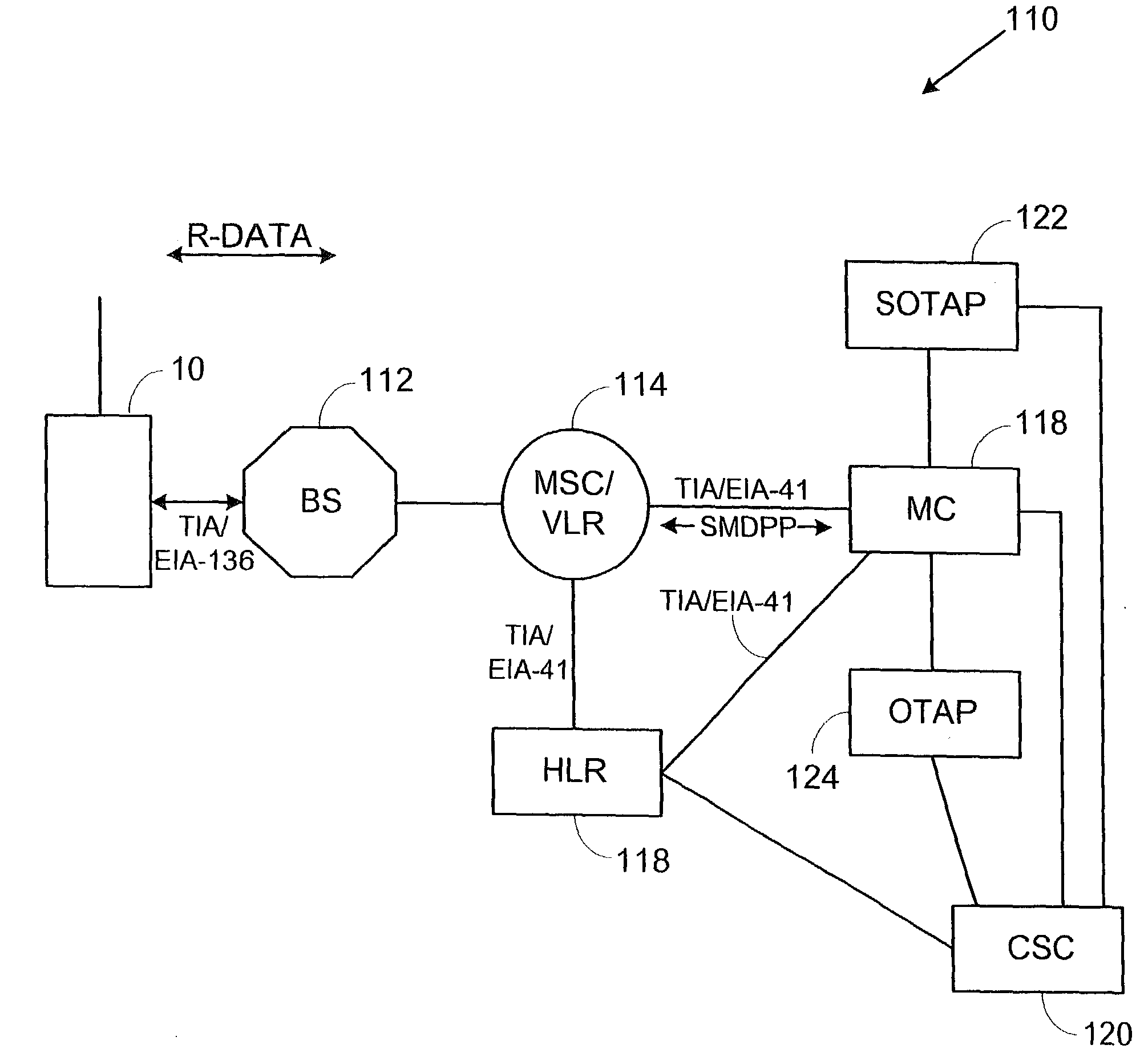
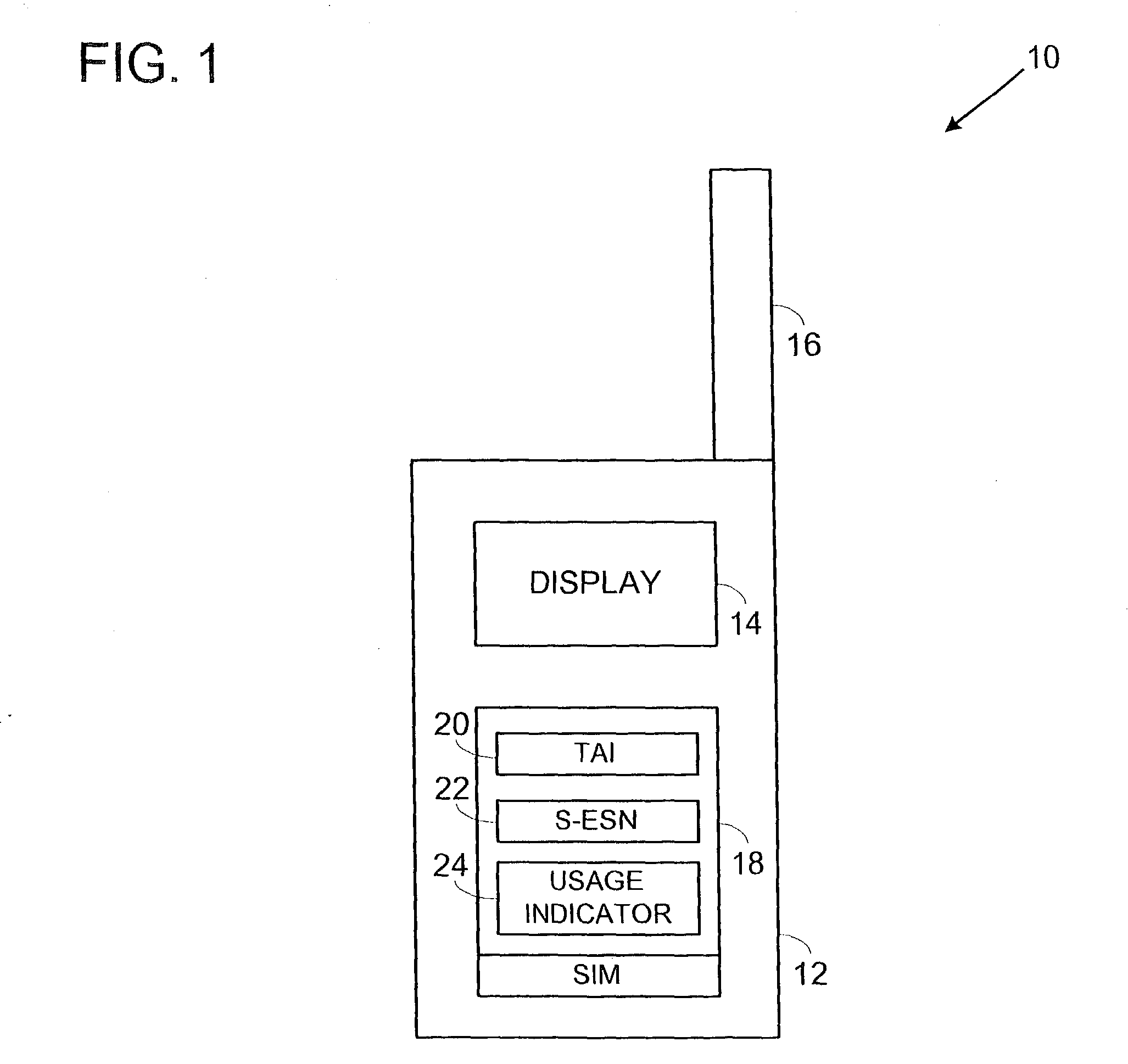
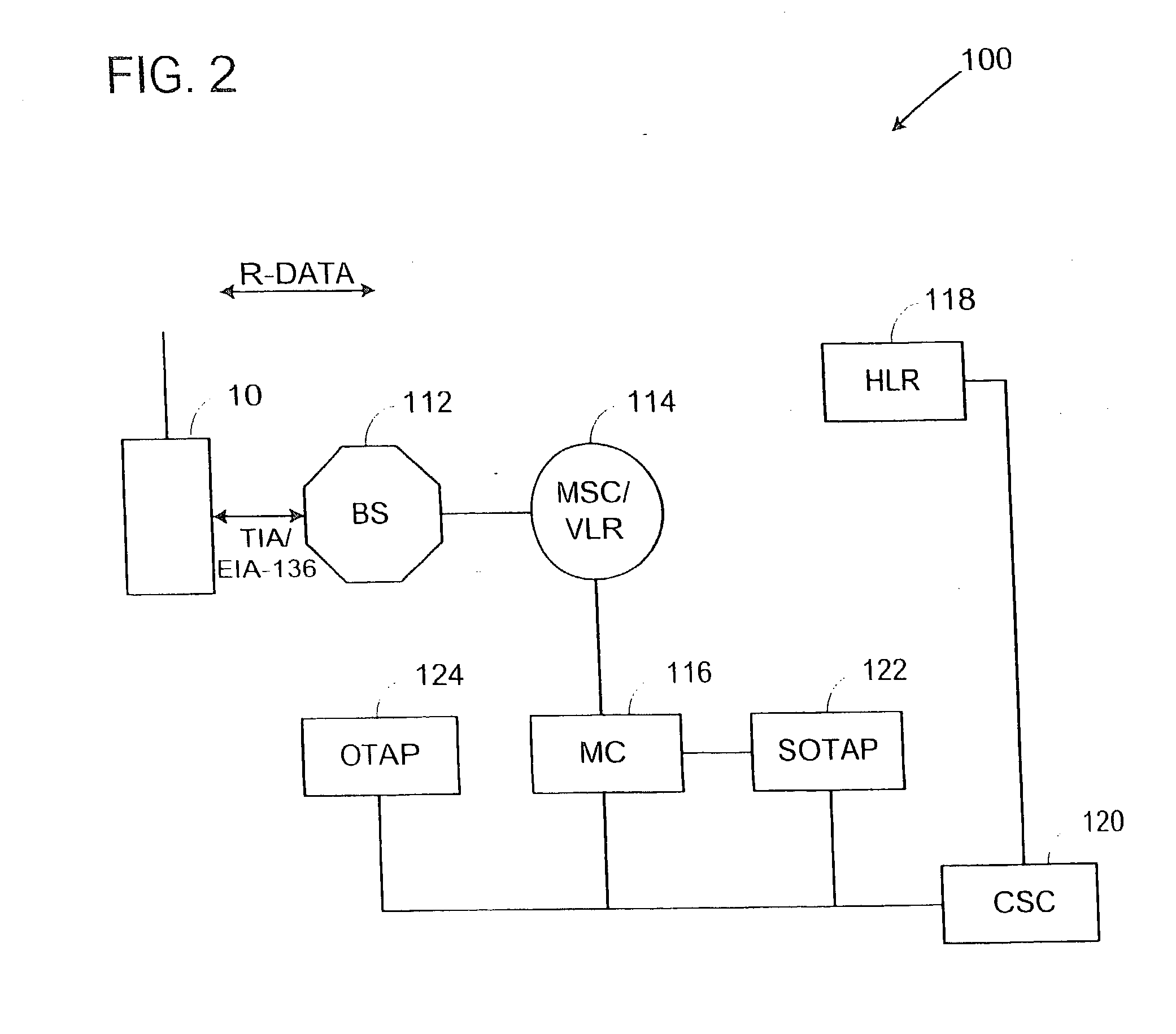
System and method for using a temporary electronic serial number for over-the-air activation of a mobile device
InactiveUS20080171532A1Accurate procedureUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile identification numberElectronic serial number
A system and method for activating a subscriber identification module (SIM) based mobile device in a PCS / ANSI type wireless network. The method comprises pre-programming the SIM card of the mobile device with temporary activation identifiers, such as an international mobile station identity (IMSI) and / or a mobile identification number (MIN), and a temporary electronic serial number. The temporary electronic serial number, rather than the mobile device actual electronic serial number, is used to identify the mobile device during registration and activation. The network identifies the temporary electronic serial number associated with the SIM vendor and invokes an over-the-air activation procedure especially for the SIM card mobile devices. A SIM-over-the-air-activation processor is notified to perform the activation for that mobile device on the PCS wireless network. Authentication of the mobile device may be bypassed and the mobile device is instructed to transmit its actual electronic serial number for future registrations. Once the activation process is completed, the temporary activation identifiers are overwritten.
Owner:AT&T WIRELESS SERVICES
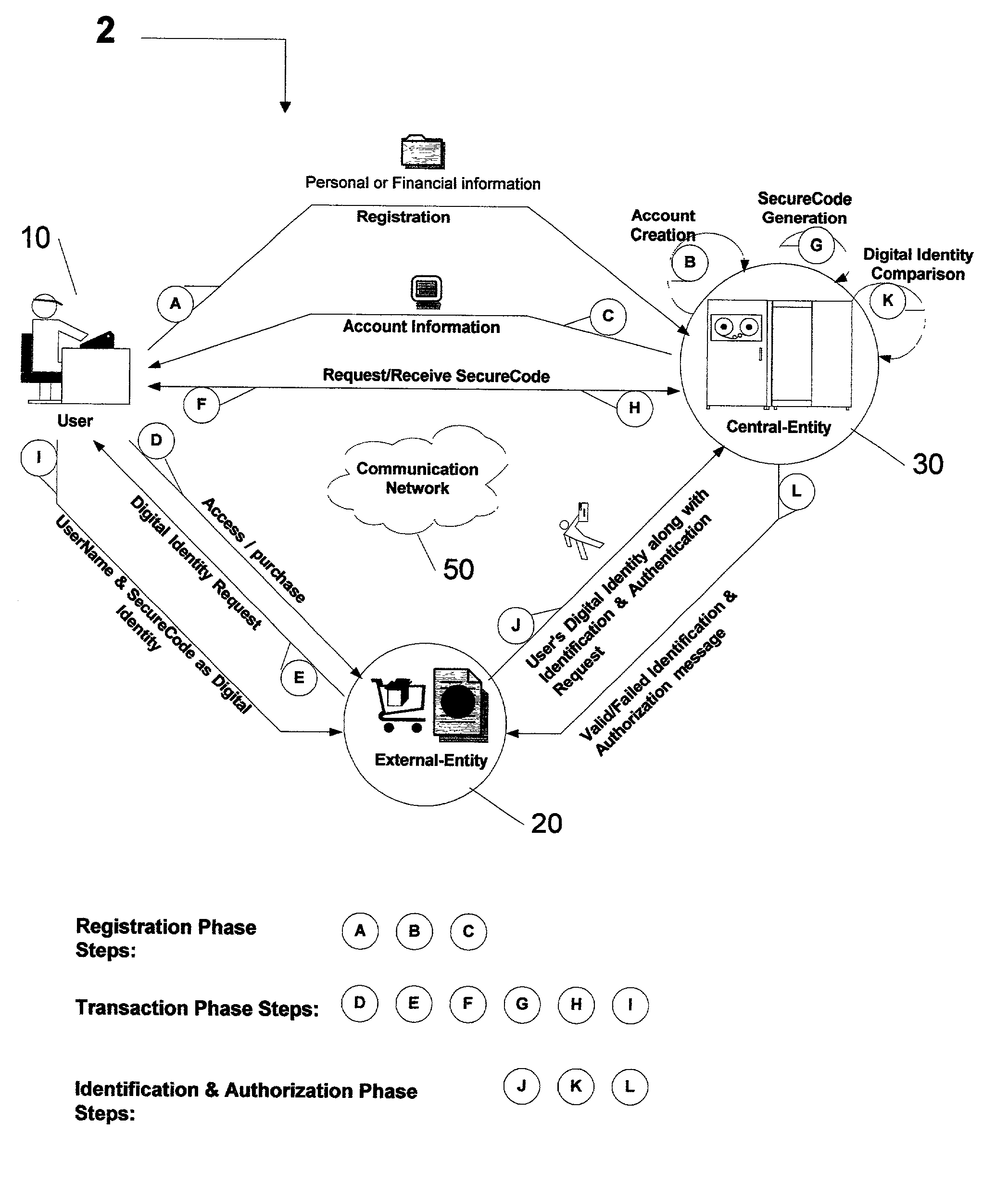
Centralized identification and authentication system and method
ActiveUS7356837B2Reduce fraudImprove securityFinanceDigital data processing detailsDigital identityService provision
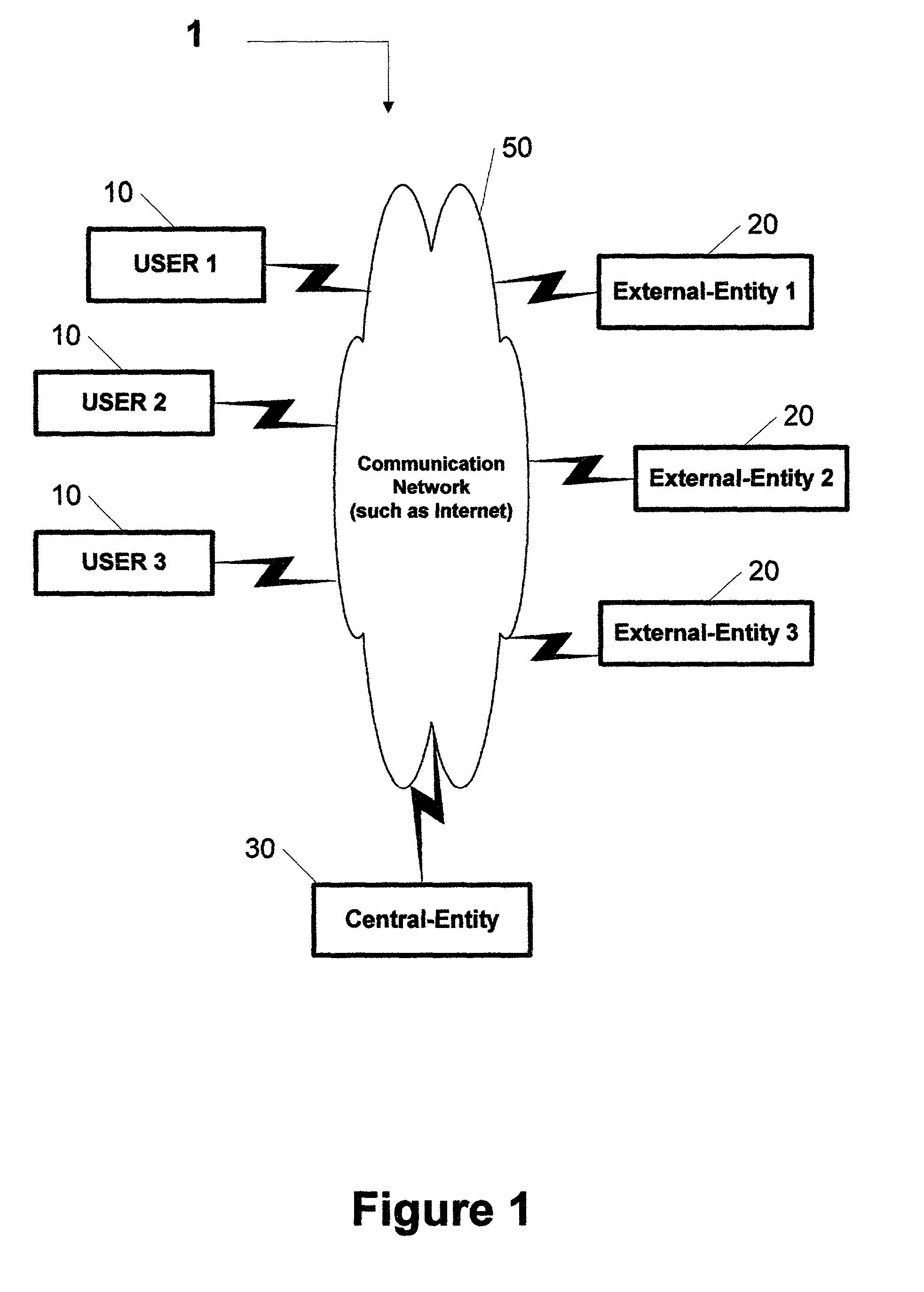
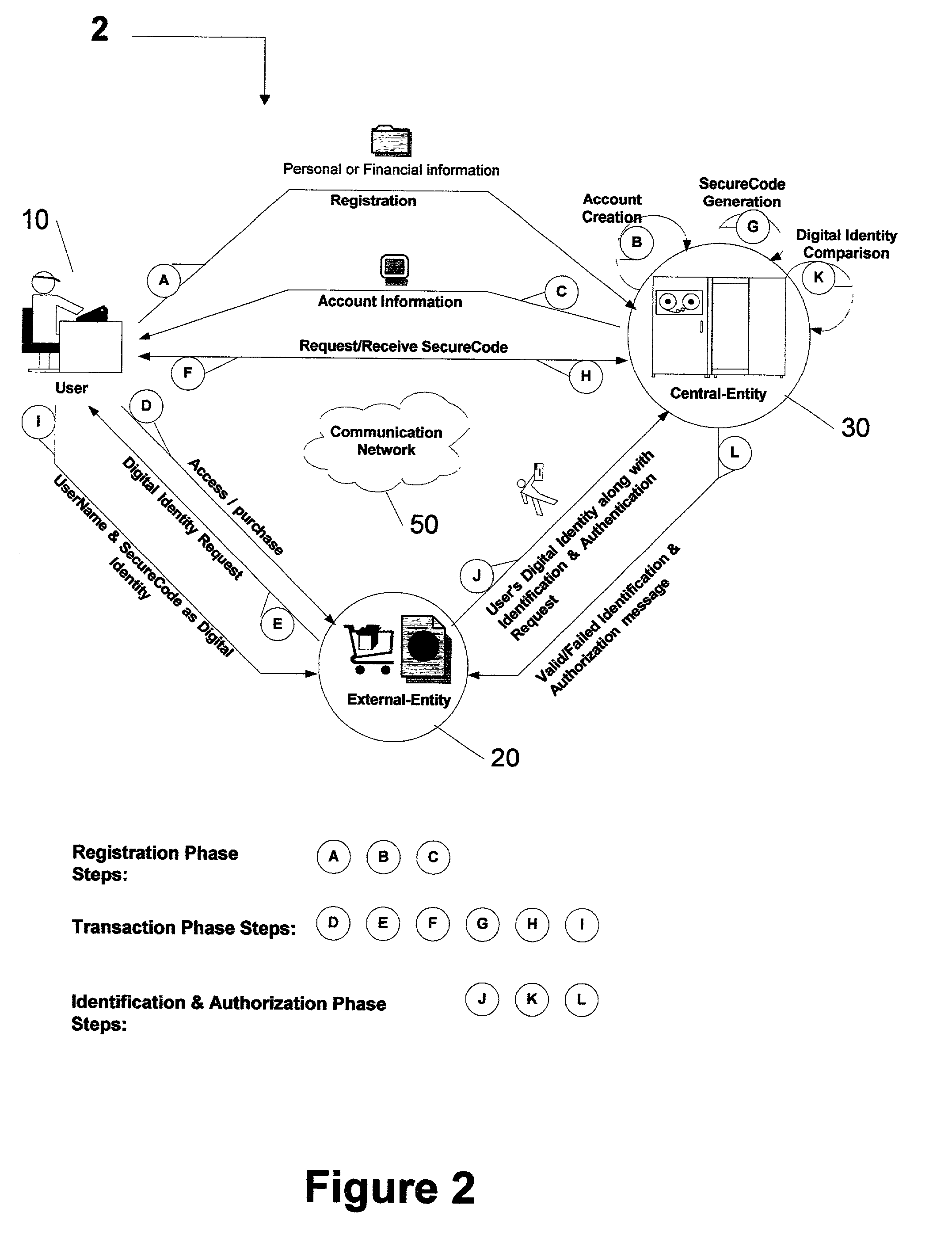
A method and system is provided by a Central-Entity, for identification and authorization of users over a communication network such as Internet. Central-Entity centralizes users personal and financial information in a secure environment in order to prevent the distribution of user's information in e-commerce. This information is then used to create digital identity for the users. The digital identity of each user is dynamic, non predictable and time dependable, because it is a combination of user name and a dynamic, non predictable and time dependable secure code that will be provided to the user for his identification.The user will provide his digital identity to an External-Entity such as merchant or service provider. The External-Entity is dependent on Central-Entity to identify the user based on the digital identity given by the user. The External-Entity forwards user's digital identity to the Central-Entity for identification and authentication of the user and the transaction.The identification and authentication system provided by the Central-Entity, determines whether the user is an authorized user by checking whether the digital identity provided by the user to the External-Entity, corresponds to the digital identity being held for the user by the authentication system. If they correspond, then the authentication system identifies the user as an authorized user, and sends an approval identification and authorization message to the External-Entity, otherwise the authentication system will not identify the user as an authorized user and sends a denial identification and authorization message to the External-Entity.
Owner:AMERITECH SOLUTIONS INC
Method and apparatus for configuring a network topology with alternative communication paths
InactiveUS20080013453A1Increase the number ofError preventionTransmission systemsCommunications systemNetwork management
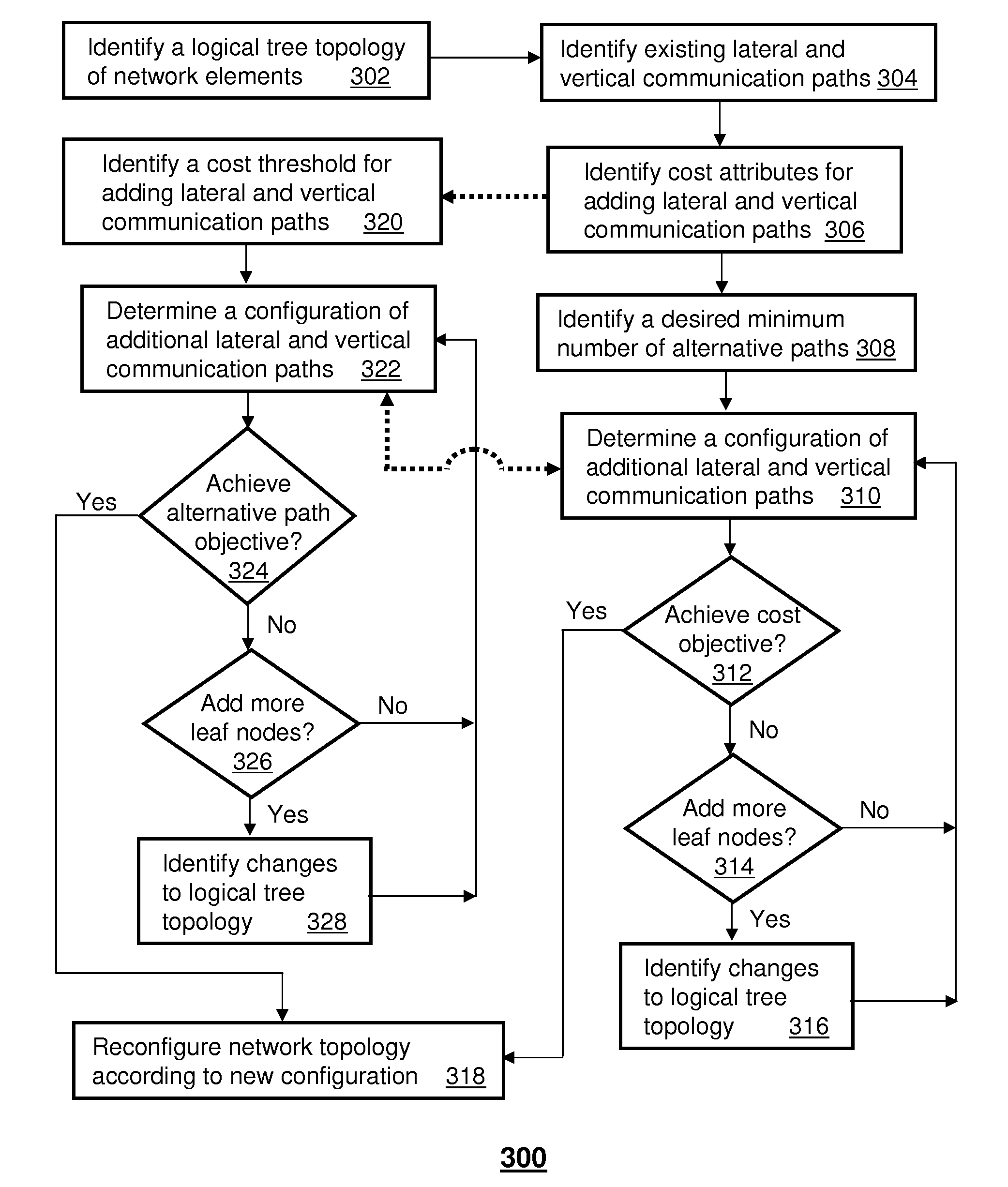
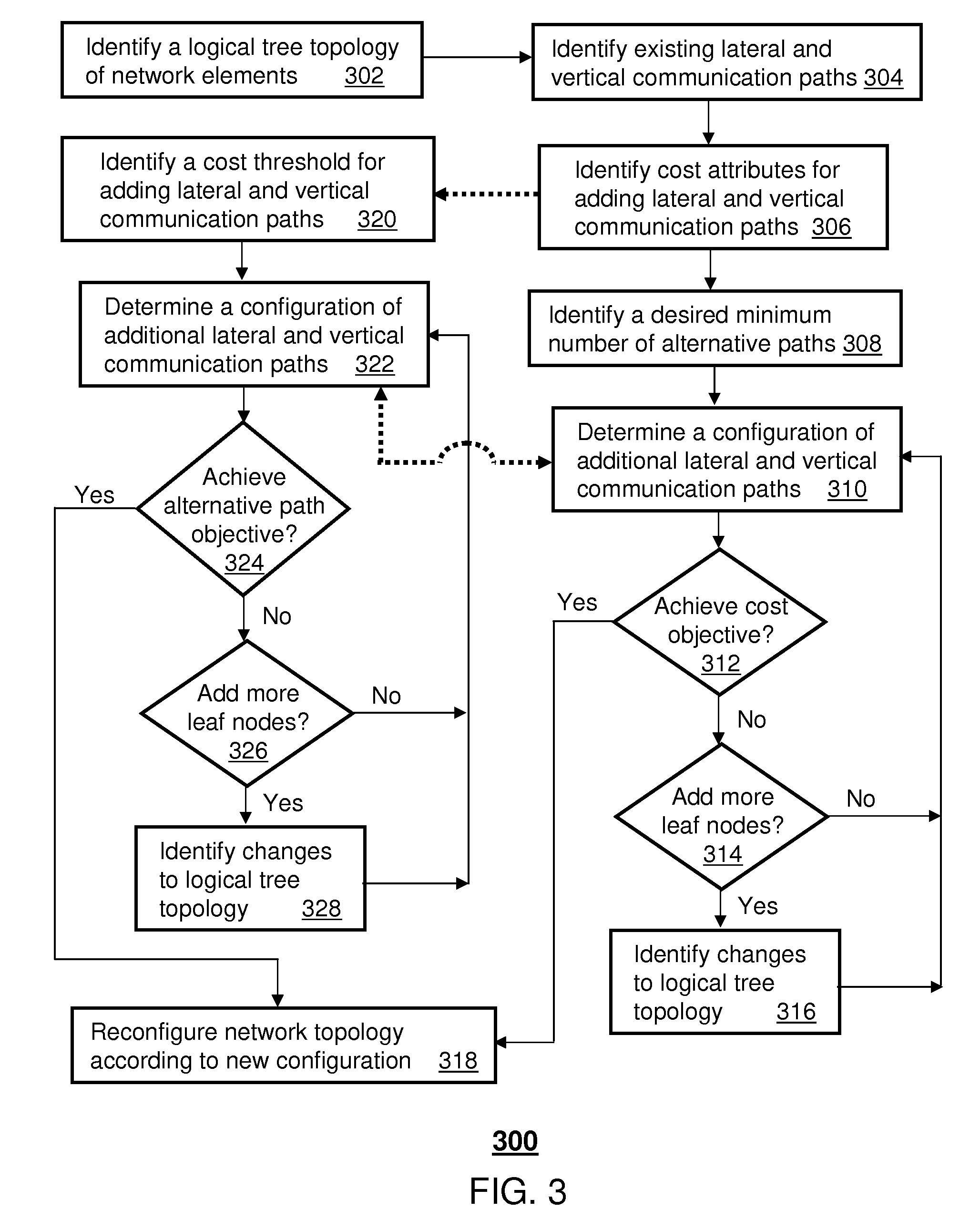
A method and apparatus for configuring a network topology with alternative communication paths. An apparatus that incorporates teachings of the present disclosure may include, for example, a network management system (NMS) having a network identification element that identifies a tree topology of network elements in a communication system comprising a root node and a plurality of leaf nodes, a network configuration element that specifies a desired number of alternative communication paths between each of the plurality of leaf nodes and the root node, and a network restructuring element that determines a configuration of additional lateral and vertical communication paths superimposed on a portion of the plurality of leaf nodes that achieves a desired cost objective according to the desired number of alternative paths and associated cost attributes. Additional embodiments are disclosed.
Owner:SBC KNOWLEDGE VENTURES LP
Apparatus, system, and method for routing data to and from a host that is moved from one location on a communication system to another location on the communication system
InactiveUS7970929B1Multiple digital computer combinationsWireless network protocolsCommunications systemRouting table
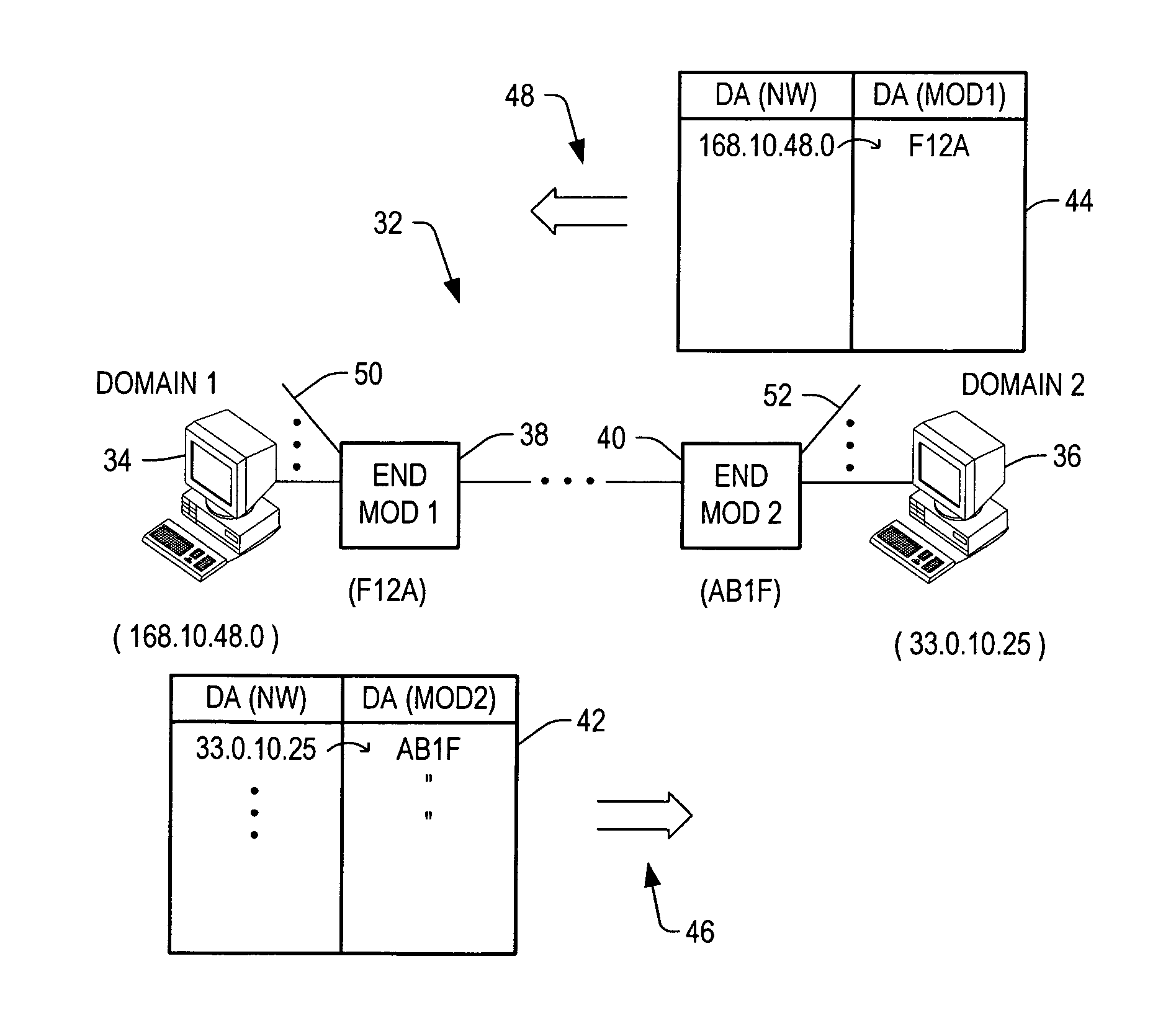
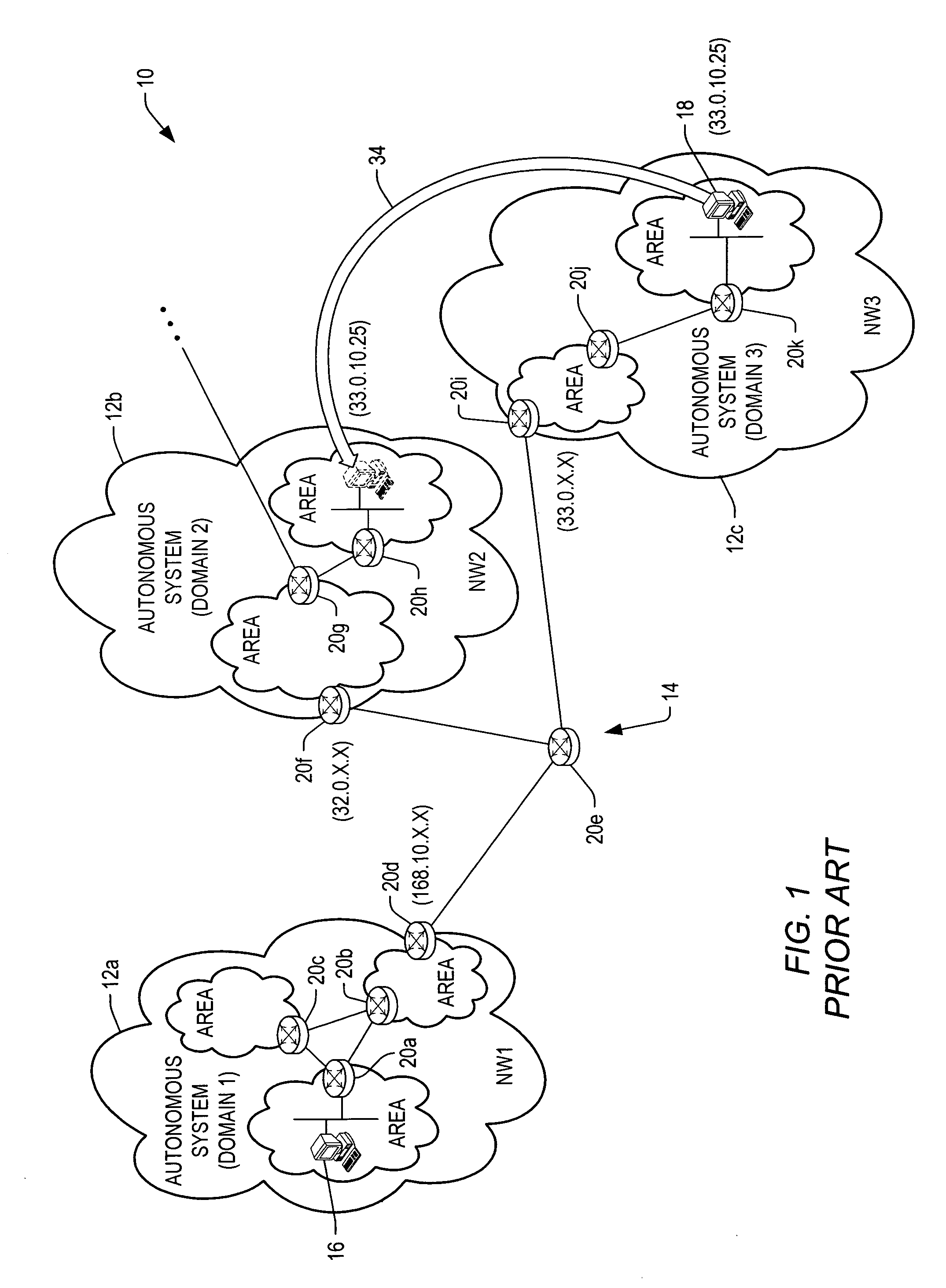
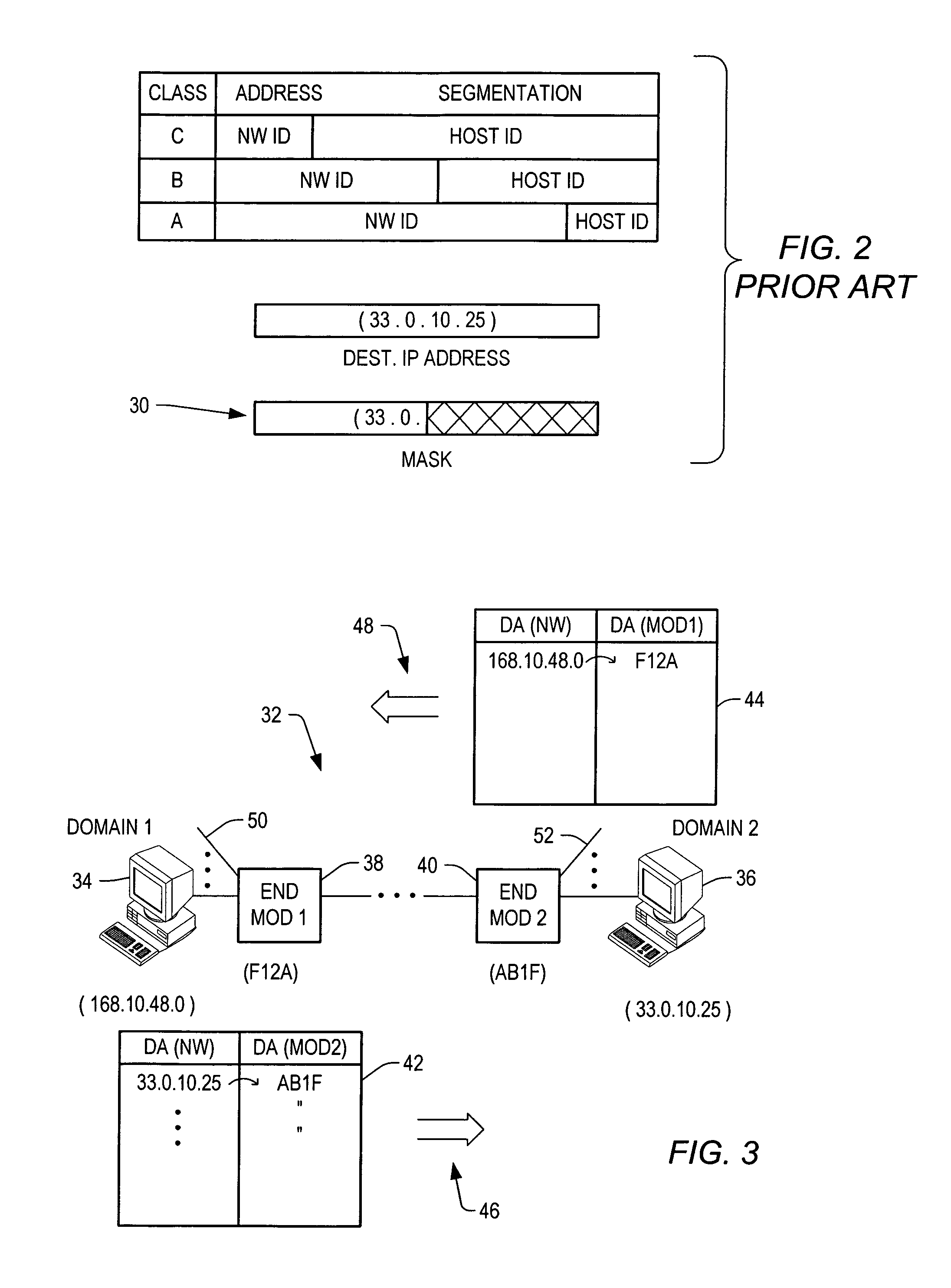
An architecture, system, and method are provided for transparently mapping a network identification number of a host to an access point of an internet. The host can be moved from a first point to a second point on the internet without having to reconfigure routing tables or to update routing protocols. The network identification number of the host does not change as it is moved from the first point to the second point. Thus, the network identification number of the host does not perform routing. Instead, routing occurs by targeting the exit end module onto which the host is connected, i.e., at the second point. The exit end module thereby contains configuration registers which store mapping tables that note the new destination address of any data being sent to the new host location, and properties such as security and priority codes.
Owner:RPX CORP
Conflated seal affix authentication method having electronic seal digital certification
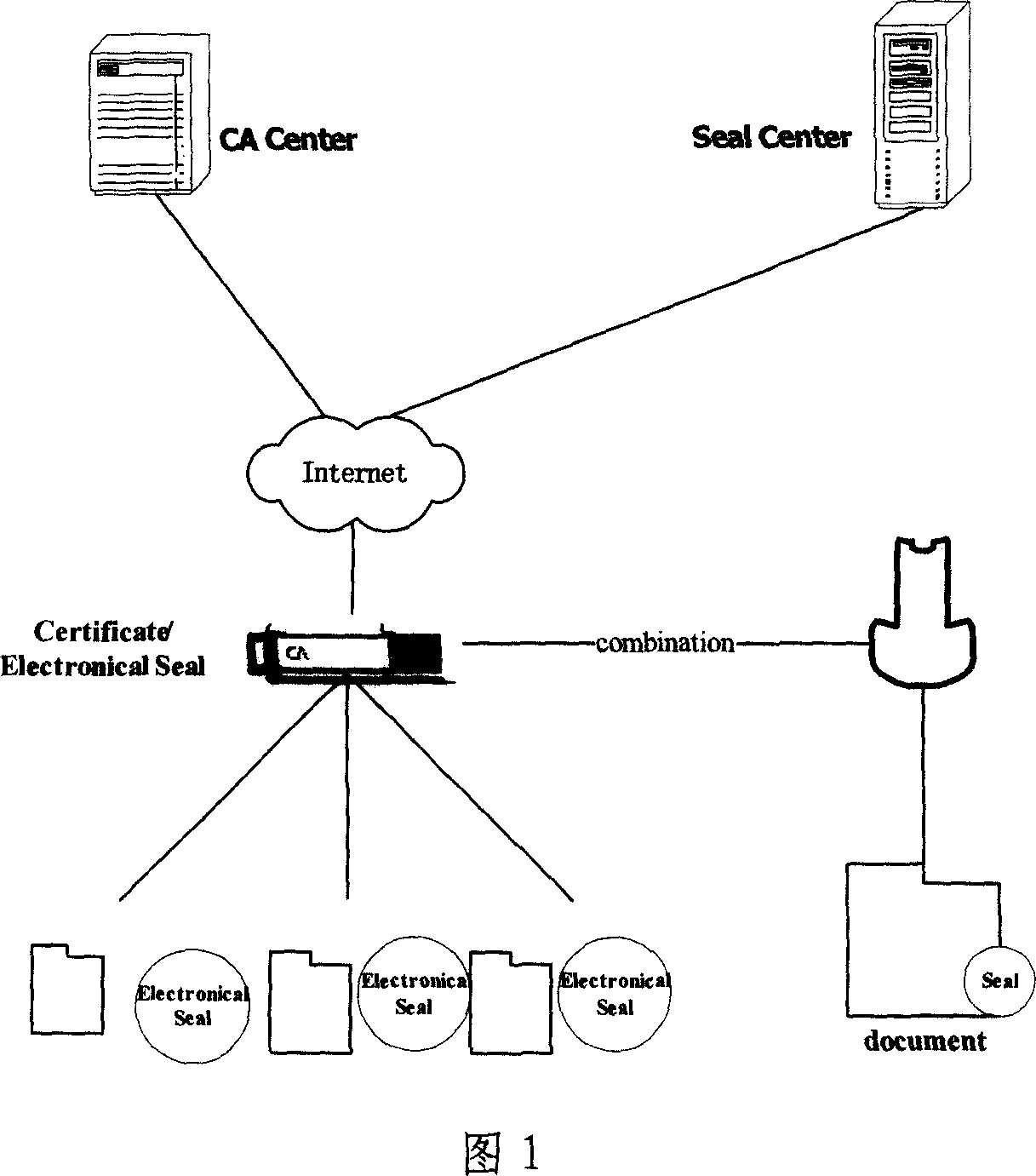
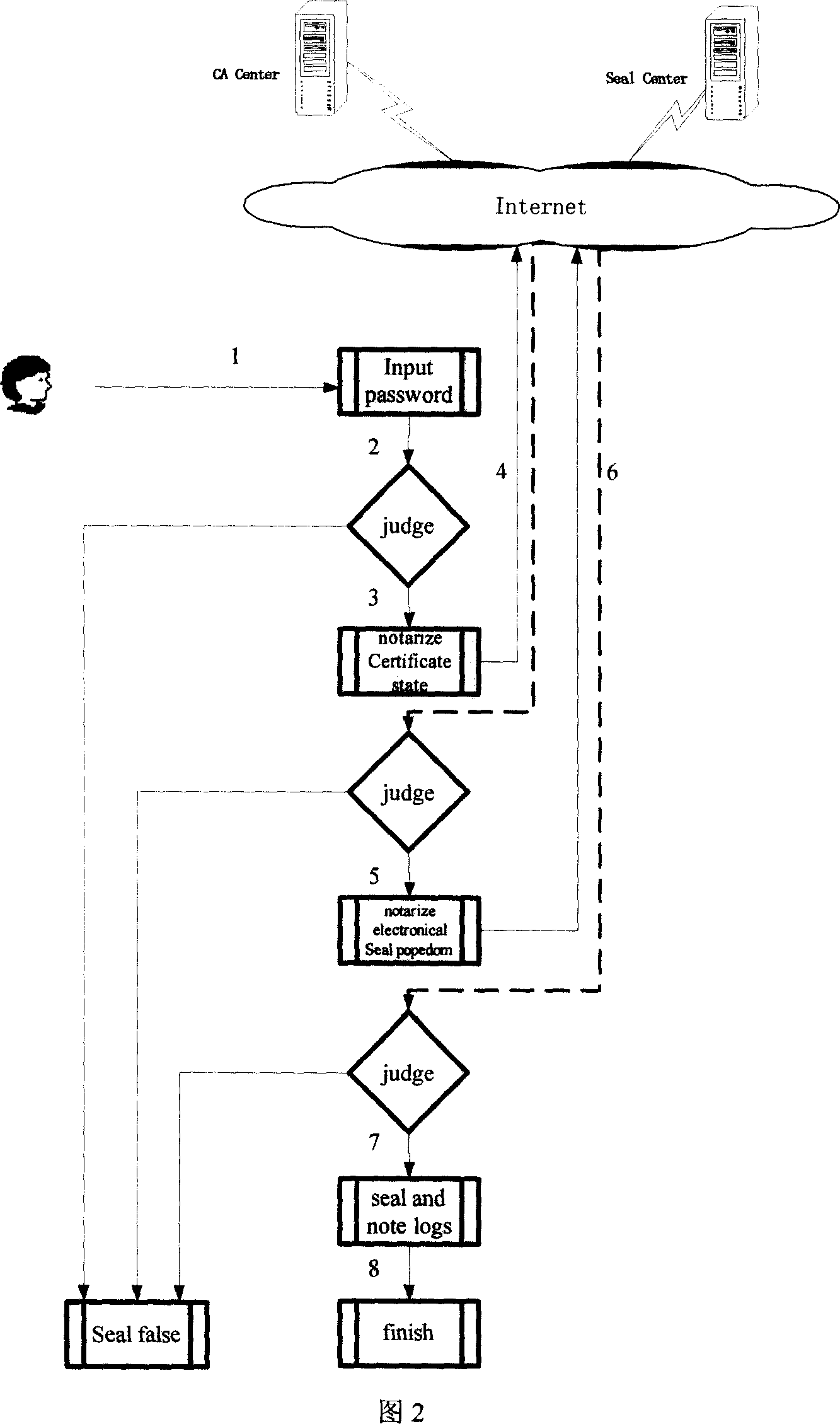
InactiveCN101017544AEnsure unforgeableEnsure non-repudiationComputer security arrangementsOffice automationElectronic documentAffix
This invention relates to one legal seam signature method with electron stamp digital certificate in network identification technique field, which comprises the following steps: through opening, requiring, determining, transferring, sending and stamping steps to realize legal stamp, stamp customer end and servo, CA center certificate servo electron stamp signature operation; through receiving, separating, comparing to realize customer end and stamp servo validating steps to ensure the electron stamp and physical body integral part with combination by traditional physical stamp and modern digital certificate.
Owner:江苏国盾科技实业有限责任公司
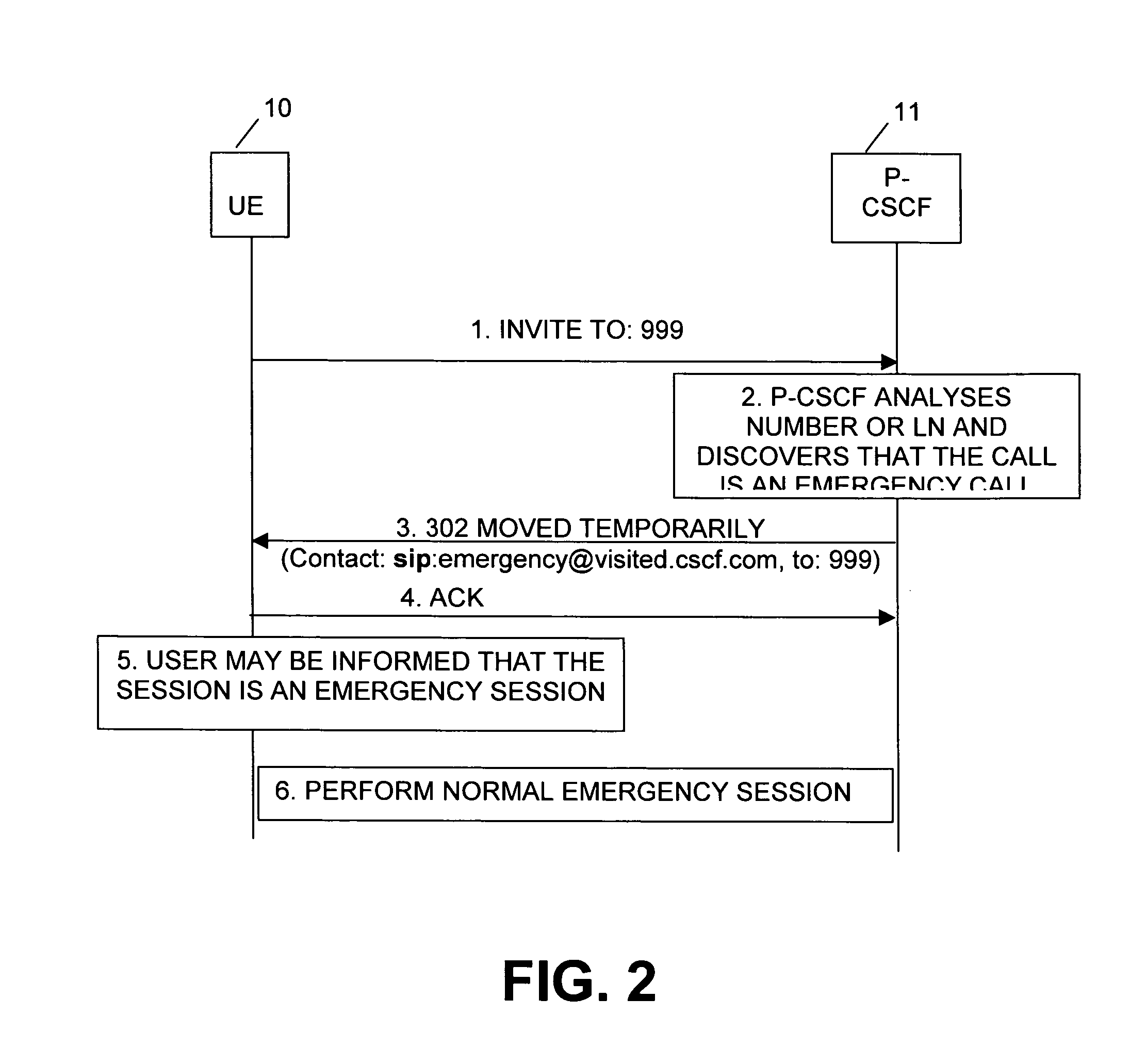
Method and system for handling a network-identified emergency session
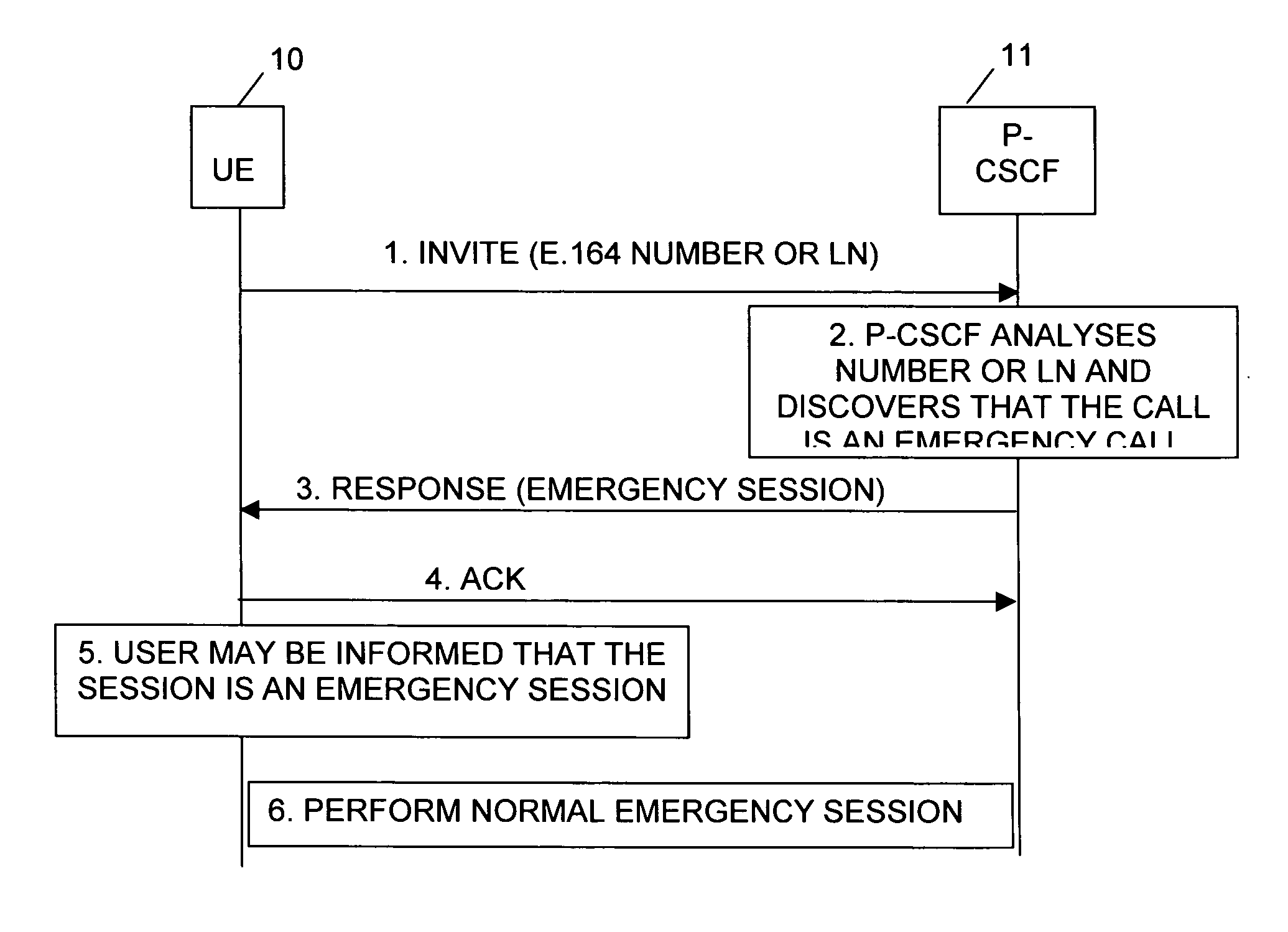
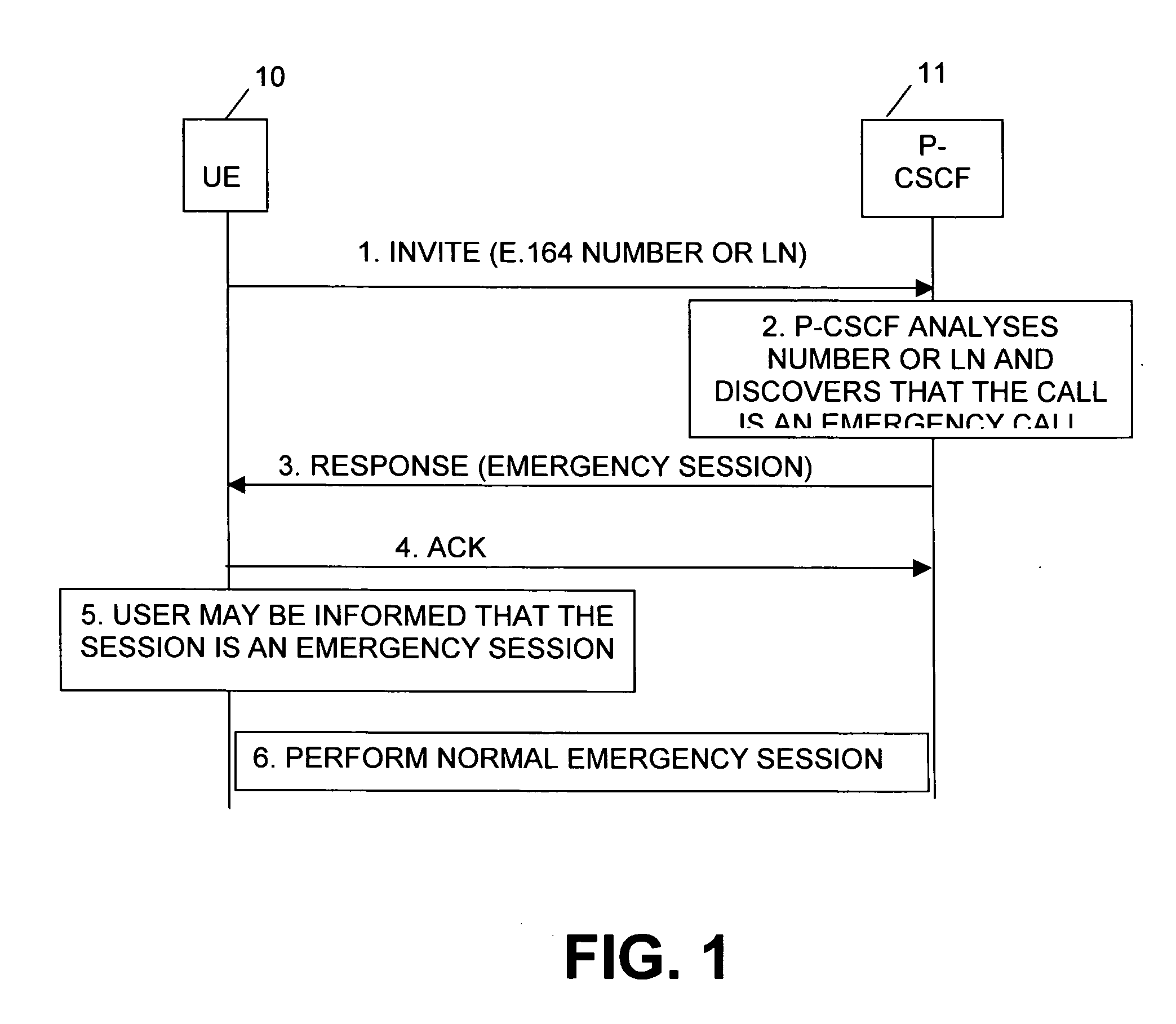
InactiveUS20040137873A1Guaranteed resourcesAddressing slow performanceEmergency connection handlingConnection managementCommunications systemUser equipment
The invention relates to a method and system for establishing an emergency session in a communication system which includes at least one user equipment and one or more network entities involved in establishing an emergency session. When the user equipment initiates a session by sending a message to a network entity indicating an identifier, e.g. the call number or logical name of a called entity, one of said network entities analyses the received identifier. When detecting that the session to be initiated is an emergency session, an information is returned to the user equipment for informing the latter that the initiated session is an emergency session. The user equipment thereupon initiates the execution of an emergency session. Thus, even when the user equipment is unable to detect, by itself, that the intended session is an emergency session, the network will inform the user equipment on the emergency session for ensuring appropriate handling thereof.
Owner:NOKIA TECHNOLOGLES OY
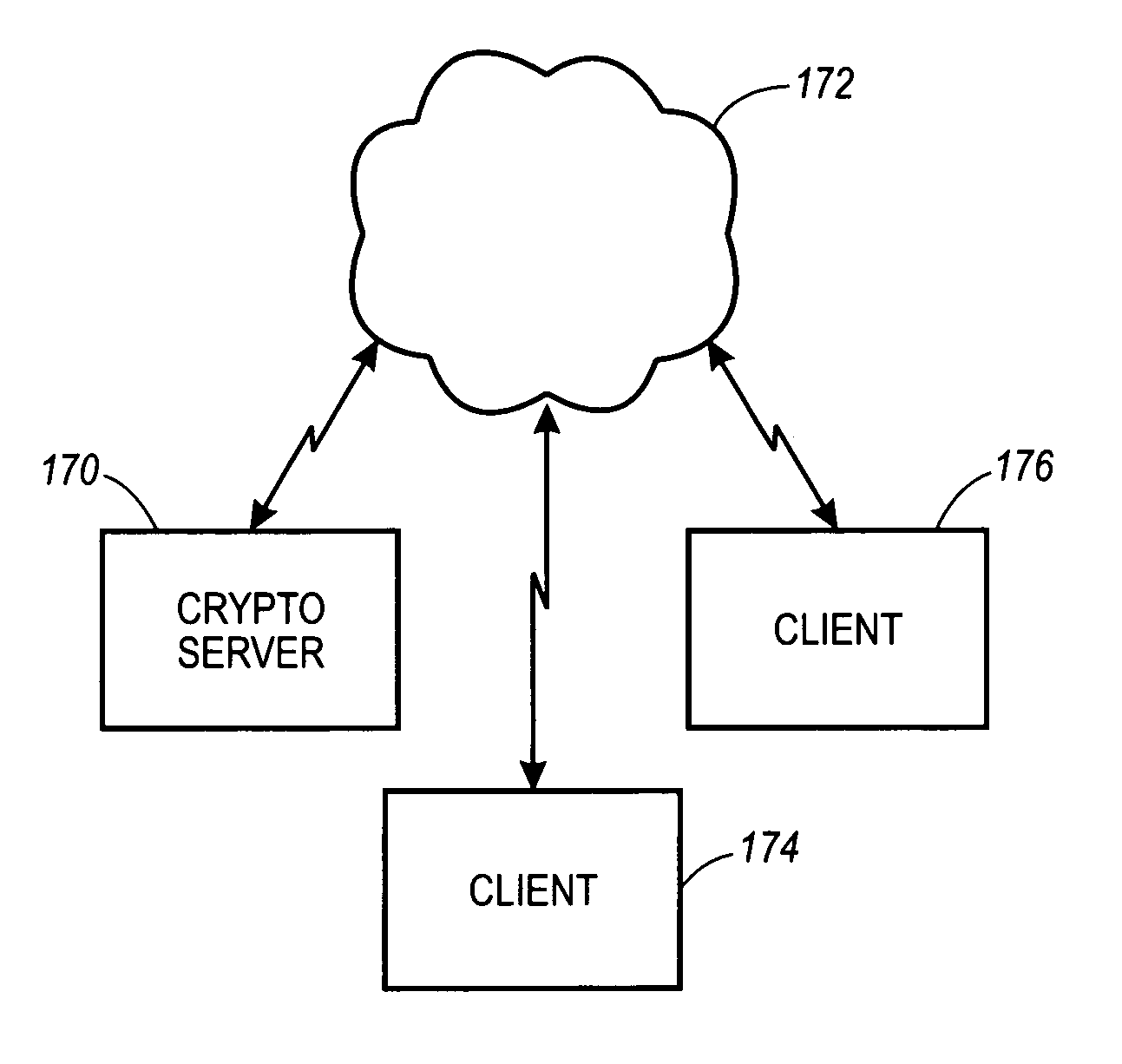
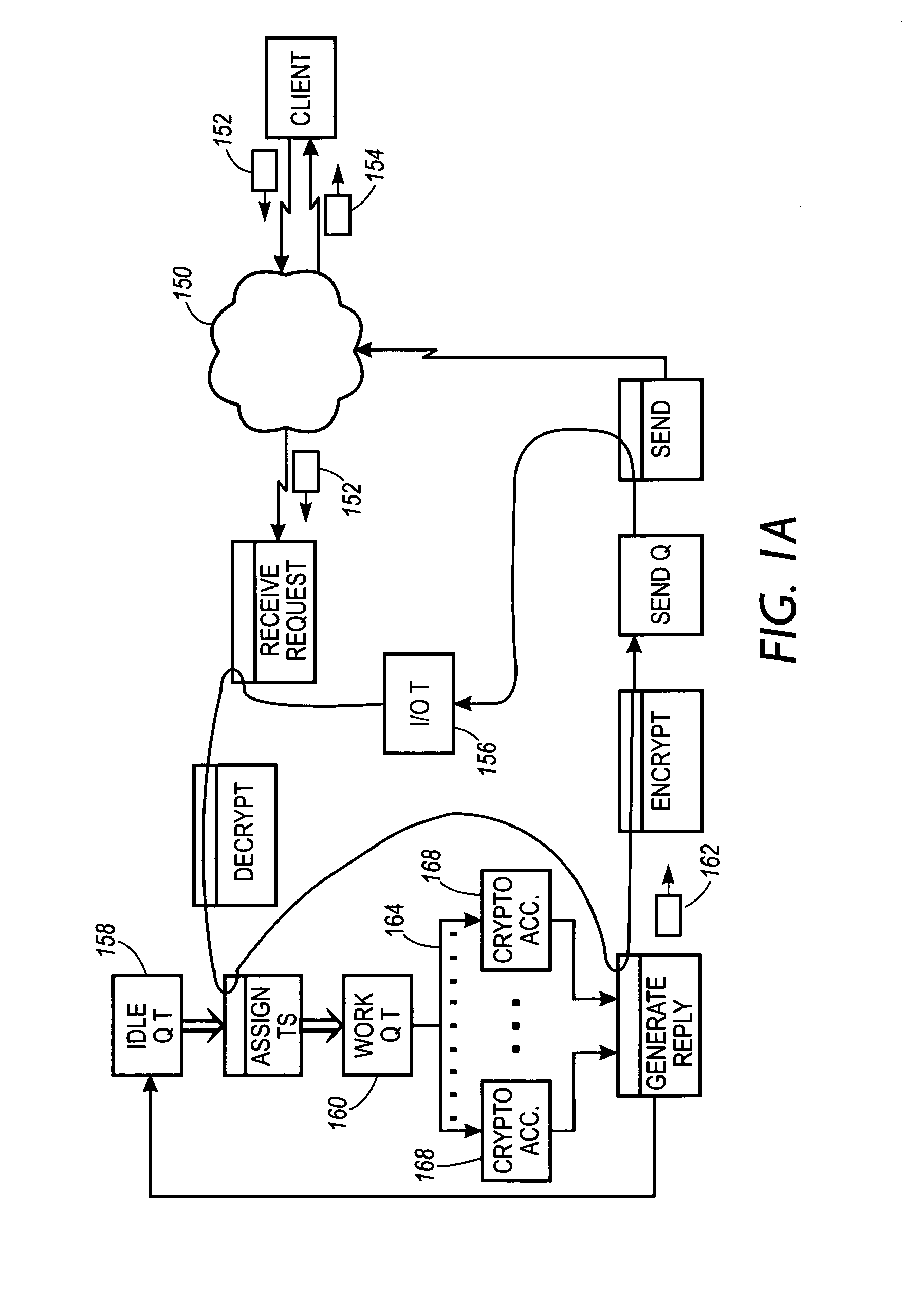
System, method and article of manufacture for providing cryptographic services utilizing a network
InactiveUS7051199B1Faster turn around timeCost-effectiveKey distribution for secure communicationCryptographic nonceClient-side
A system, method and article of manufacture are provided for affording a cryptographic service utilizing a server on a network. Initially, a client is identified utilizing the network. A first key is established, and a tunnel is generated on the network. Thereafter, information is received at the server from the client utilizing the tunnel. Such information is encrypted by the client using the first key. At the server, cryptographic work is performed using the first key.
Owner:CISCO TECH INC
Mapping wireless proximity identificator to subscriber identity for hotspot based wireless services for mobile terminals
ActiveUS20050097356A1Lowering hardwareReduce communication costsDigital data processing detailsTime-division multiplexWide areaCommunication link
A hotspot access point enables a mobile wireless device to resume a service with a network server when service is interrupted by the mobile device moving out of the coverage area of the access point. A short-range communication link is established by the access point with the mobile device based on a local identification of the device. The access point requests additional information from the wireless device. The additional information relates to a wide area network identification of the device. The mobile device transmits additional information to the access point which stores the local area identification and additional identification. The access point transmits to the mobile device a coded identificator of the wireless device based upon the local area identification and a network identification of the device. The access point determines whether service with the mobile device is open and establishes a wide area connection with the mobile device.
Owner:INTELLECTUAL VENTURES ASSETS 19
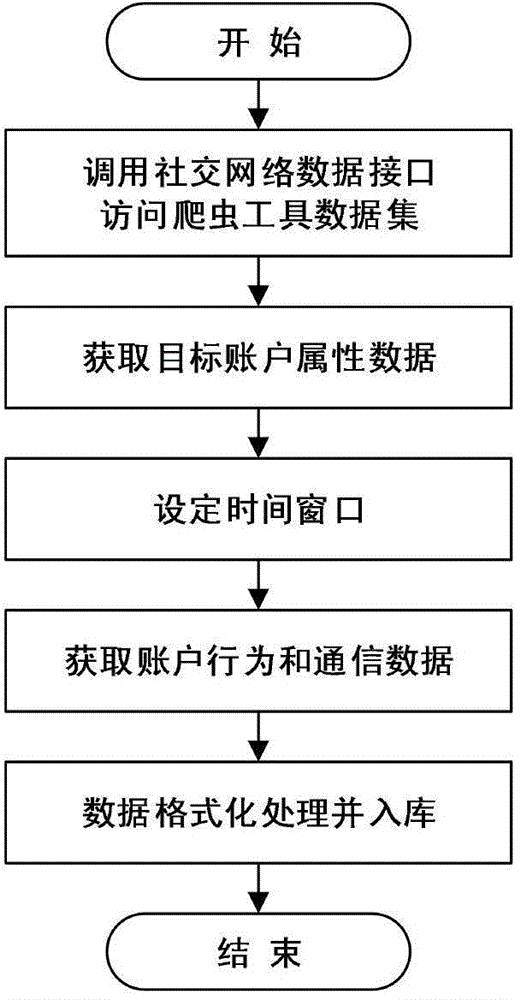
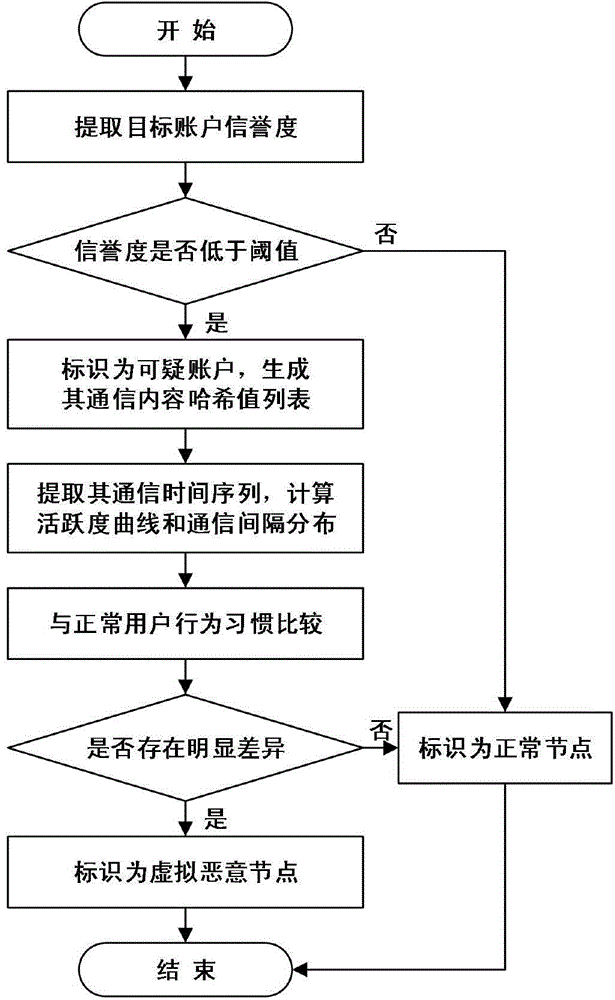
Method for identifying virtual malicious nodes and virtual malicious node network in social networks
The invention discloses a method for identifying virtual malicious nodes and a virtual malicious node network in social networks. The method includes the following steps: (1) obtaining the attribute data, behavioral data and communication data of unidentified accounts from target social networks; (2) calculating the creditworthiness of each unidentified account according to the credibility model feature vector calculated using the extracted data; (3) making a comparison between the user behavioral habit statistic data of each unidentified account with the credibility being lower than a set threshold value and that of a normal user, and judging whether the unidentified account is a virtual malicious node or not; (4) sorting the virtual malicious node set and establishing association for the virtual malicious node in each sort result, so as to form a virtual malicious node network; then evaluating by using the Bayesian network algorithm to determine the final virtual malicious node network. The method provided by the invention can be used to effectively identify highly-disguised malicious nodes and a collaborative virtual malicious node network.
Owner:INST OF INFORMATION ENG CAS
Method for risk analysis using information asset modelling
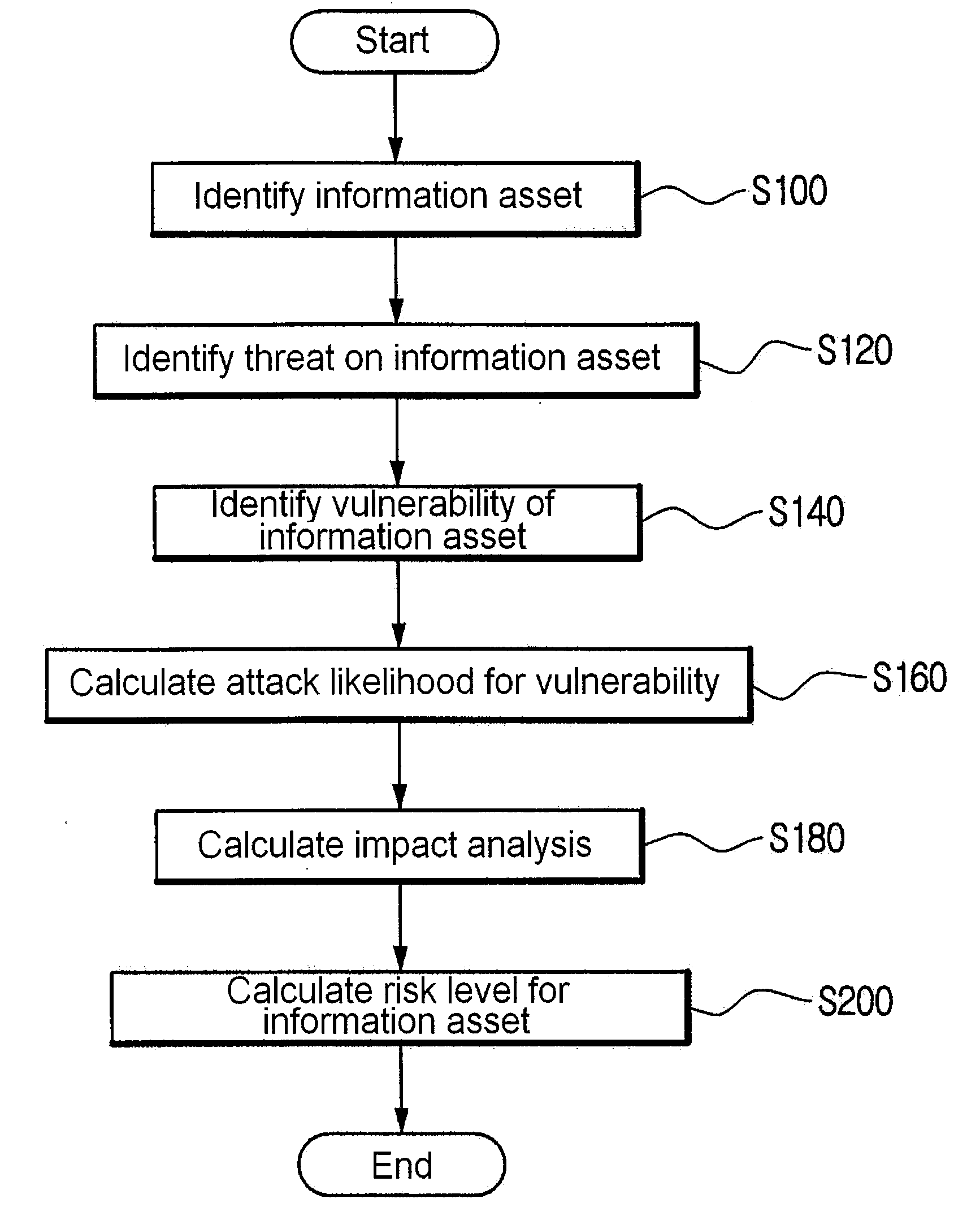
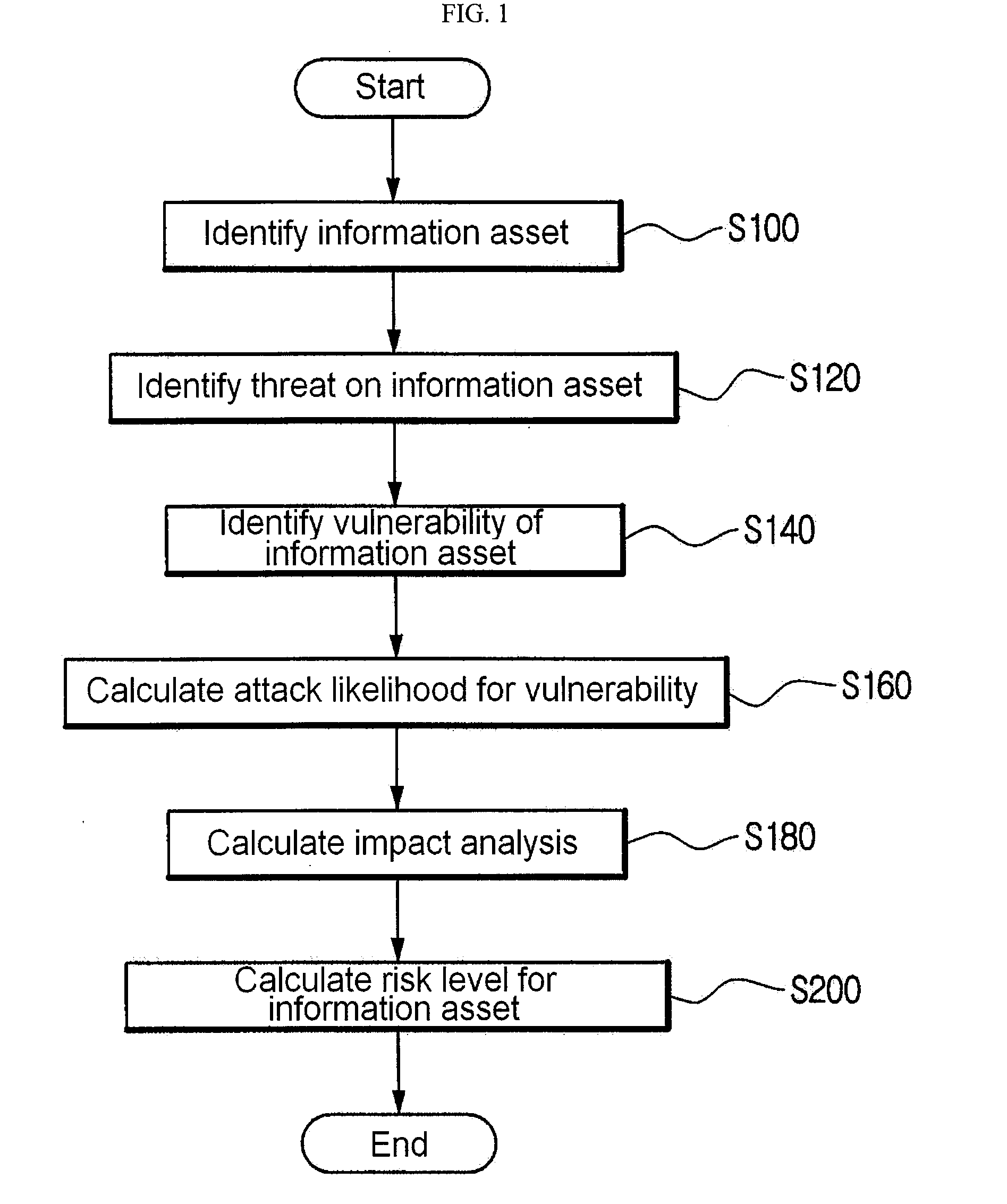
InactiveUS20090099885A1Minimizing interventionMemory loss protectionError detection/correctionRisk levelNetwork service
A method for risk analysis using information asset modeling. The method has the steps of: (a) identifying an information asset which uses or provides a network service; (b) identifying a threat on the information asset through a computer network; (c) identifying a vulnerability of the information asset; (d) calculating an AL (attack likelihood) by using a CVSS (Common Vulnerability Scoring System) score obtained by converting a severity caused by a success of an attack on the vulnerability into a standardized value; (e) computing the value of the information asset so as to calculate an IM (impact analysis); and (f) multiplying the calculated AL and IM so as to determine an RL (risk level) for the information asset.
Owner:KOREA INTERNET & SECURITY AGENCY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com