Method for identifying virtual malicious nodes and virtual malicious node network in social networks
A malicious node and social network technology, which is applied in the field of virtual malicious nodes and their network identification, can solve the problems of limited detection types of identification methods, difficulty in finding high camouflage, collaborative virtual malicious nodes, etc., to meet the recognition rate and real-time requirements Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
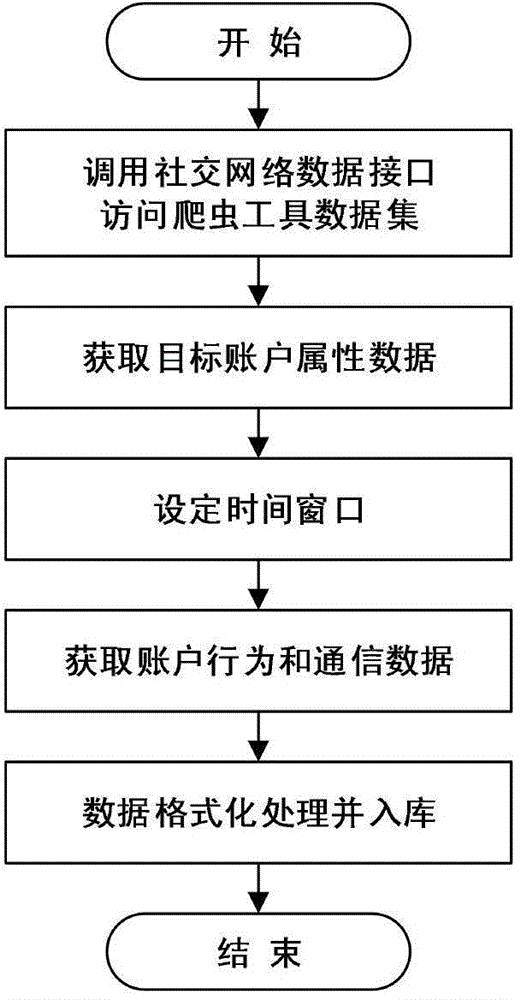
[0053] figure 1 A flowchart of step (1) is given, and the specific implementation is as follows:
[0054] a) According to the account data structure and form of the target social network system, realize the corresponding data interface and crawler tool to form the original data set. This method is suitable for mainstream social networks that focus on user interaction activities, such as Facebook, Twitter, Sina Weibo, Tencent WeChat, etc.; it is not suitable for social networks that focus on information publishing, such as forums and post bars.
[0055] b) Obtain the attribute data of the target account based on the accessible target social network original data set, including: user identification, user nickname, user associated account, real-name authentication, account creation time, and real identity information.
[0056] c) According to the set time window, extract the behavior data and communication data of the target account from the original data set. The behavior data has a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com