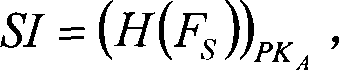Patents
Literature
73results about How to "Protect normal transmission" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
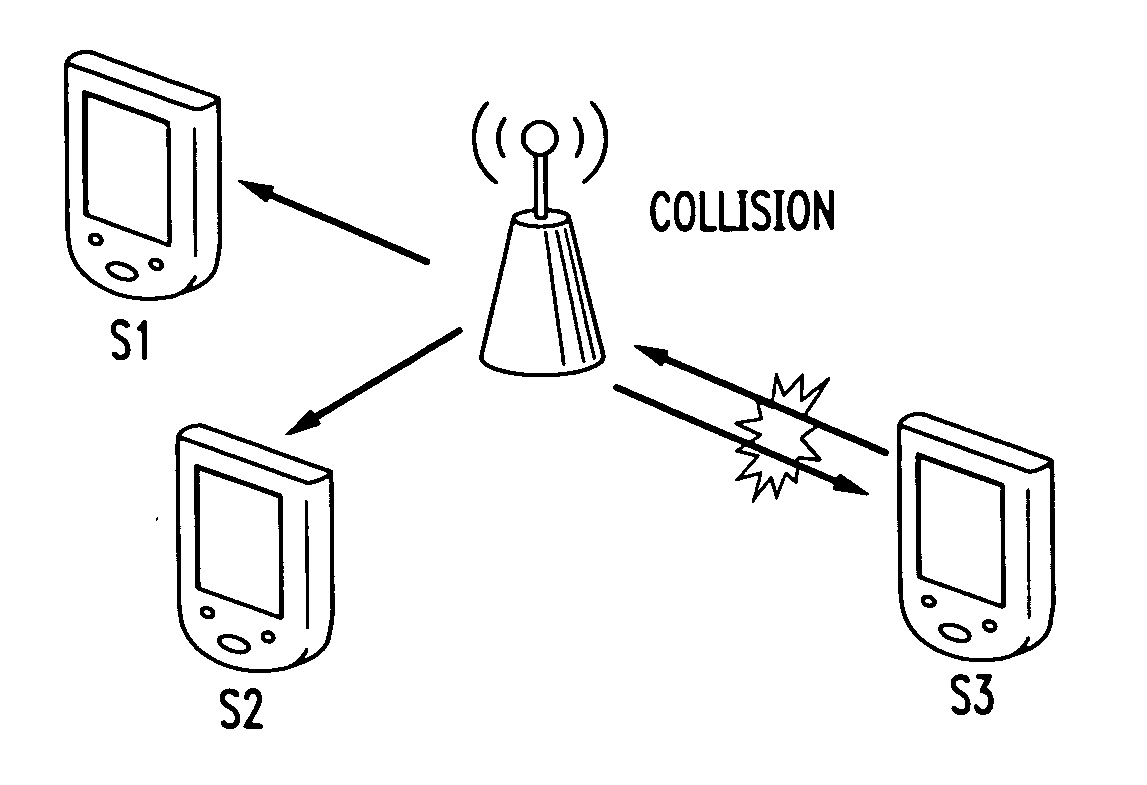
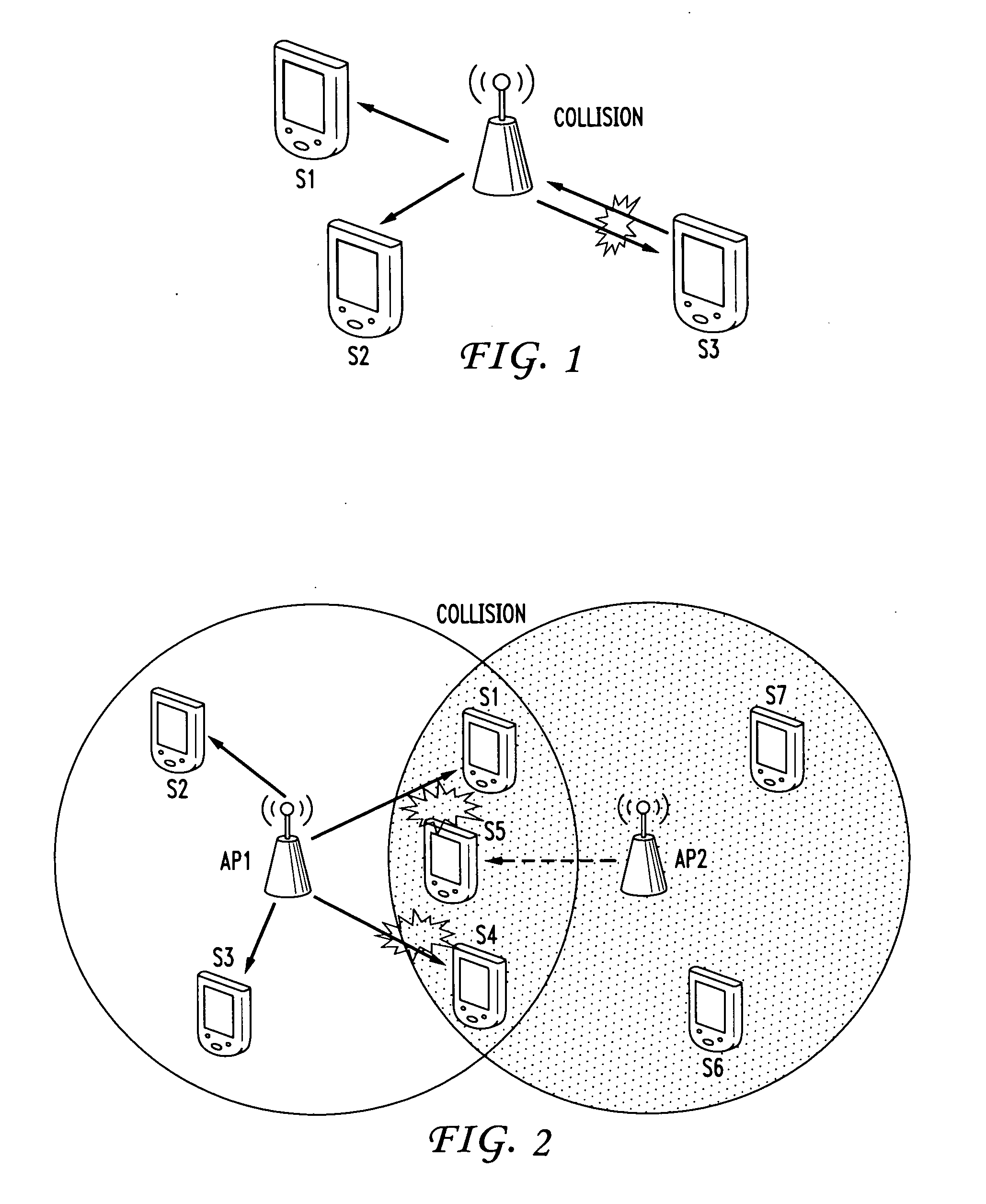
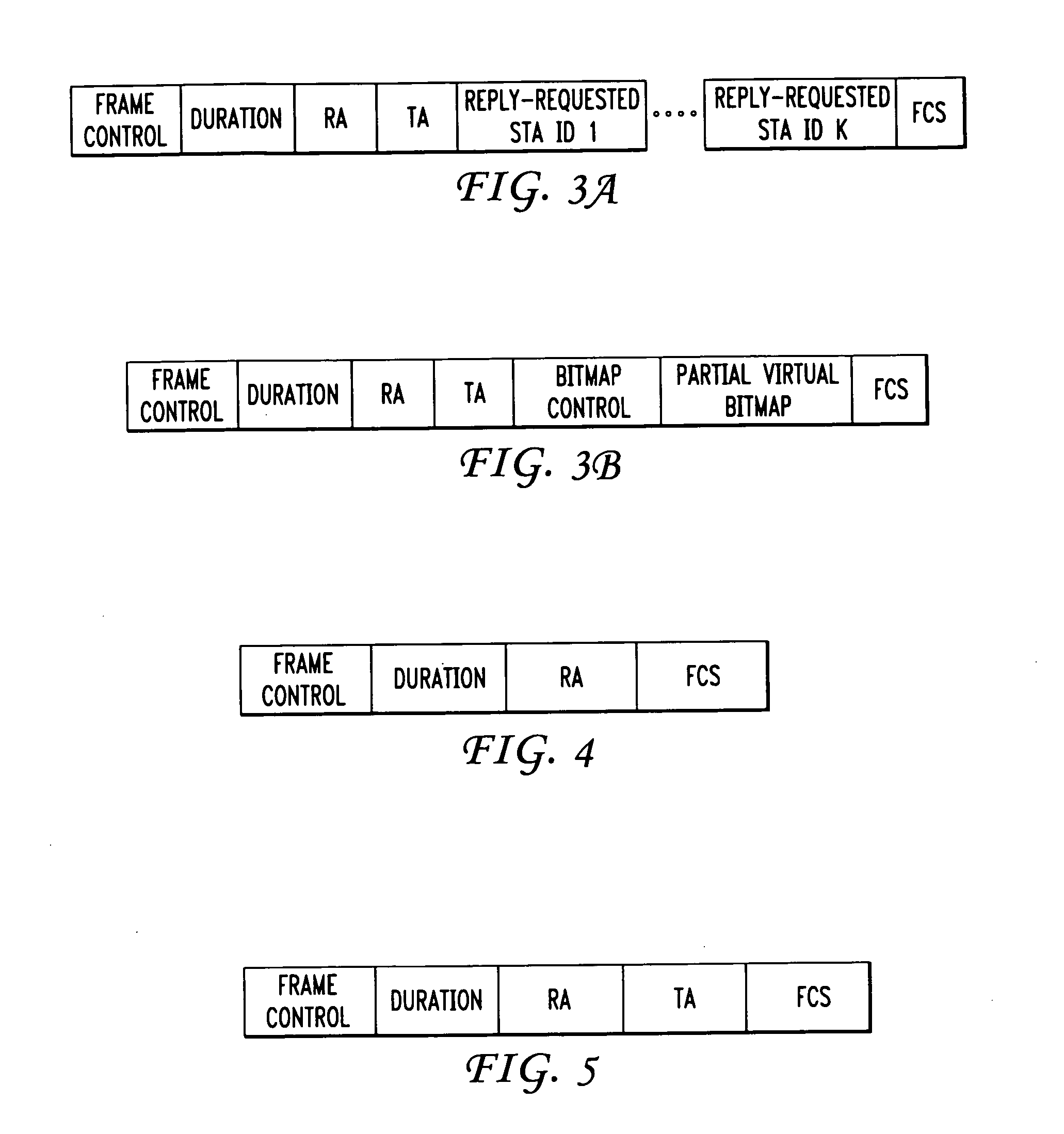
Collision mitigation for multicast transmission in wireless local area networks
InactiveUS20110064013A1Reduce the probability of collisionProtect normal transmissionError preventionNetwork topologiesLocal area networkMulticast transmission
A method and apparatus are described including multicasting a medium reservation message, receiving responses to the medium reservation message and determining if a ratio of the received responses to an expected number of responses exceeds a threshold. Also described are a method and apparatus including receiving a medium reservation message, determining if the medium reservation message specifies this receiver in a list of receivers from which a response is requested, determining if a medium is idle and transmitting the response to the medium reservation message responsive to the second determination.
Owner:MAGNOLIA LICENSING LLC
TLS tunneling
InactiveUS7529933B2Reduce interceptionProtect normal transmissionUser identity/authority verificationSecret communicationSecure communicationWireless mesh network
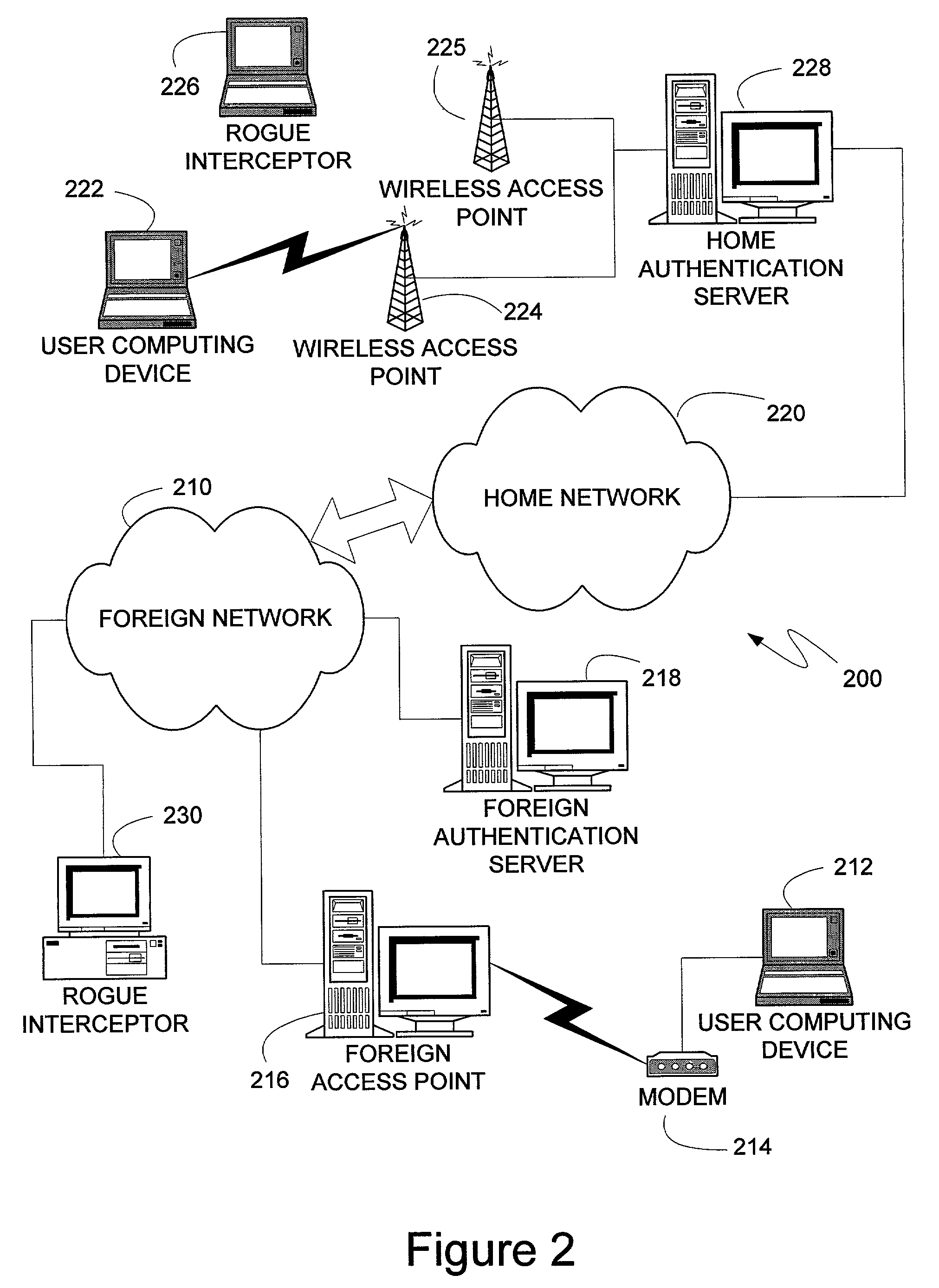
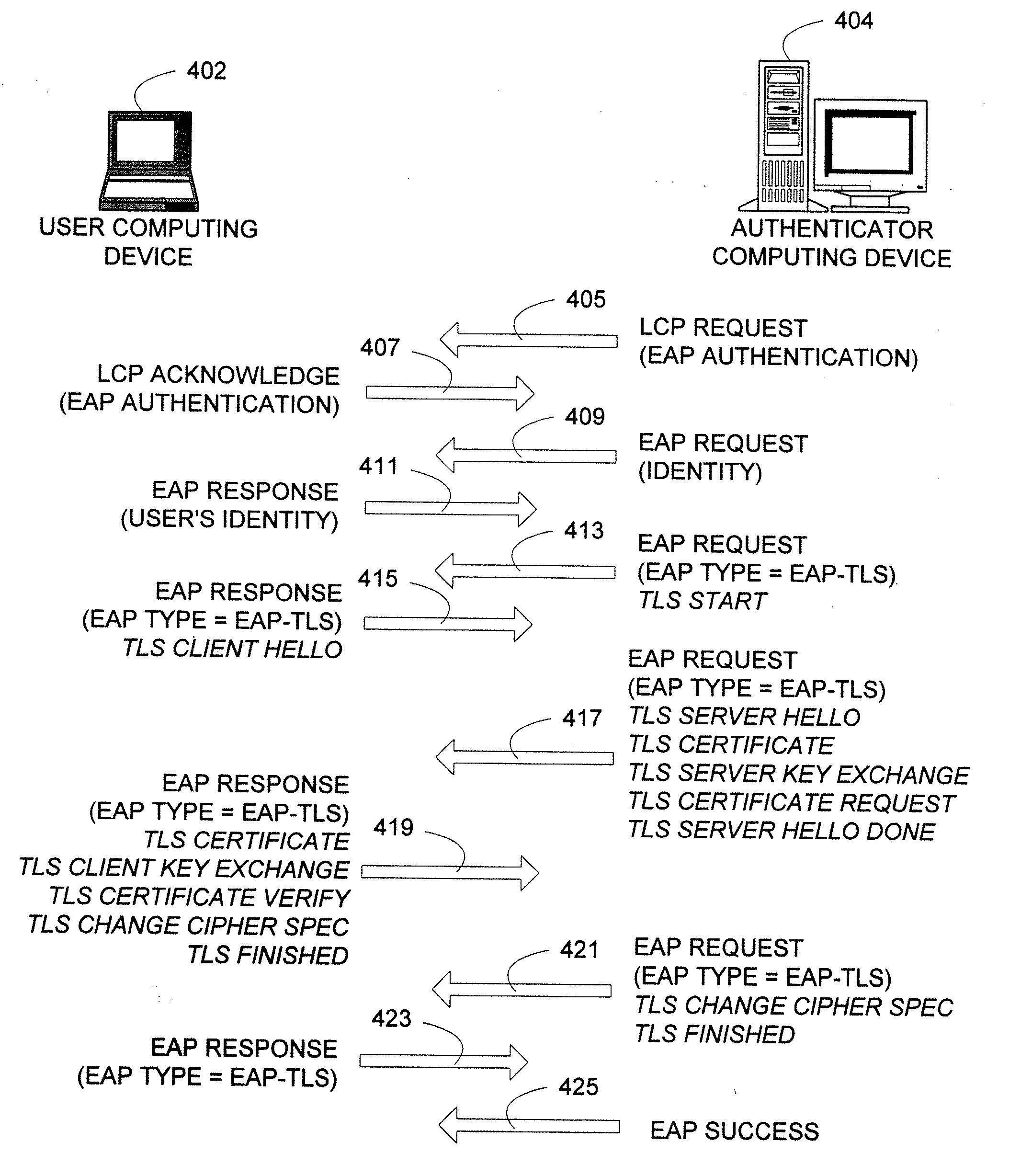
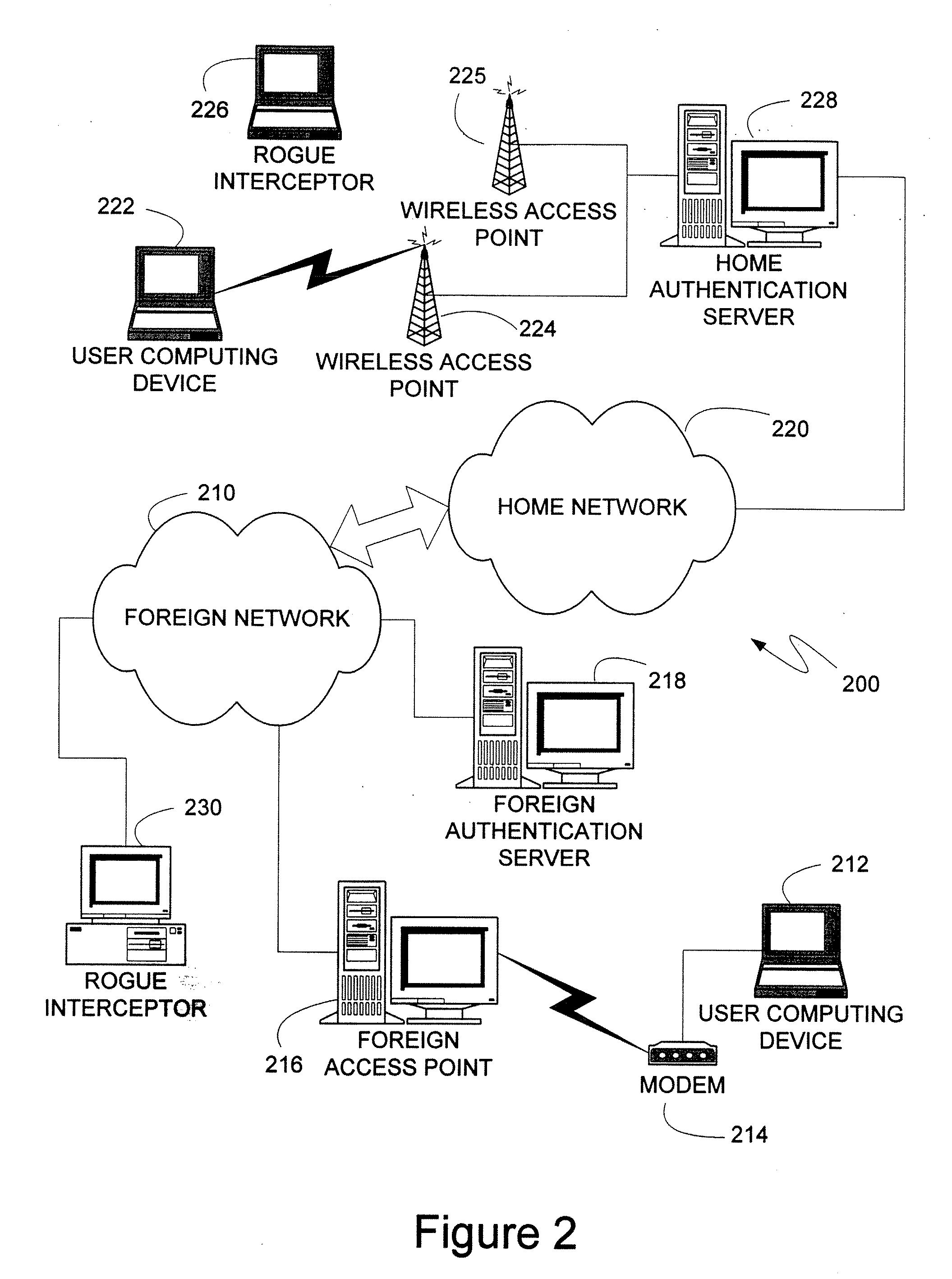
An authentication protocol can be used to establish a secure method of communication between two devices on a network. Once established, the secure communication can be used to authenticate a client through various authentication methods, providing security in environments where intermediate devices cannot be trusted, such as wireless networks, or foreign network access points. Additionally, the caching of session keys and other relevant information can enable the two securely communicating endpoints to quickly resume their communication despite interruptions, such as when one endpoint changes the access point through which it is connected to the network. Also, the secure communication between the two devices can enable users to roam off of their home network, providing a mechanism by which access through foreign networks can be granted, while allowing the foreign network to monitor and control the use of its bandwidth.
Owner:MICROSOFT TECH LICENSING LLC
Tls tunneling
ActiveUS20070157027A1Reduce interceptionProtect normal transmissionUser identity/authority verificationMultiple digital computer combinationsSecure communicationRelevant information
An authentication protocol can be used to establish a secure method of communication between two devices on a network. Once established, the secure communication can be used to authenticate a client through various authentication methods, providing security in environments where intermediate devices cannot be trusted, such as wireless networks, or foreign network access points. Additionally, the caching of session keys and other relevant information can enable the two securely communicating endpoints to quickly resume their communication despite interruptions, such as when one endpoint changes the access point through which it is connected to the network. Also, the secure communication between the two devices can enable users to roam off of their home network, providing a mechanism by which access through foreign networks can be granted, while allowing the foreign network to monitor and control the use of its bandwidth.
Owner:MICROSOFT TECH LICENSING LLC
EPA industrial bus and time sensitive network adaptation system and method
ActiveCN110943899AProtect normal transmissionEfficient use ofTime-division multiplexNetworks interconnectionLow jitterLow delay
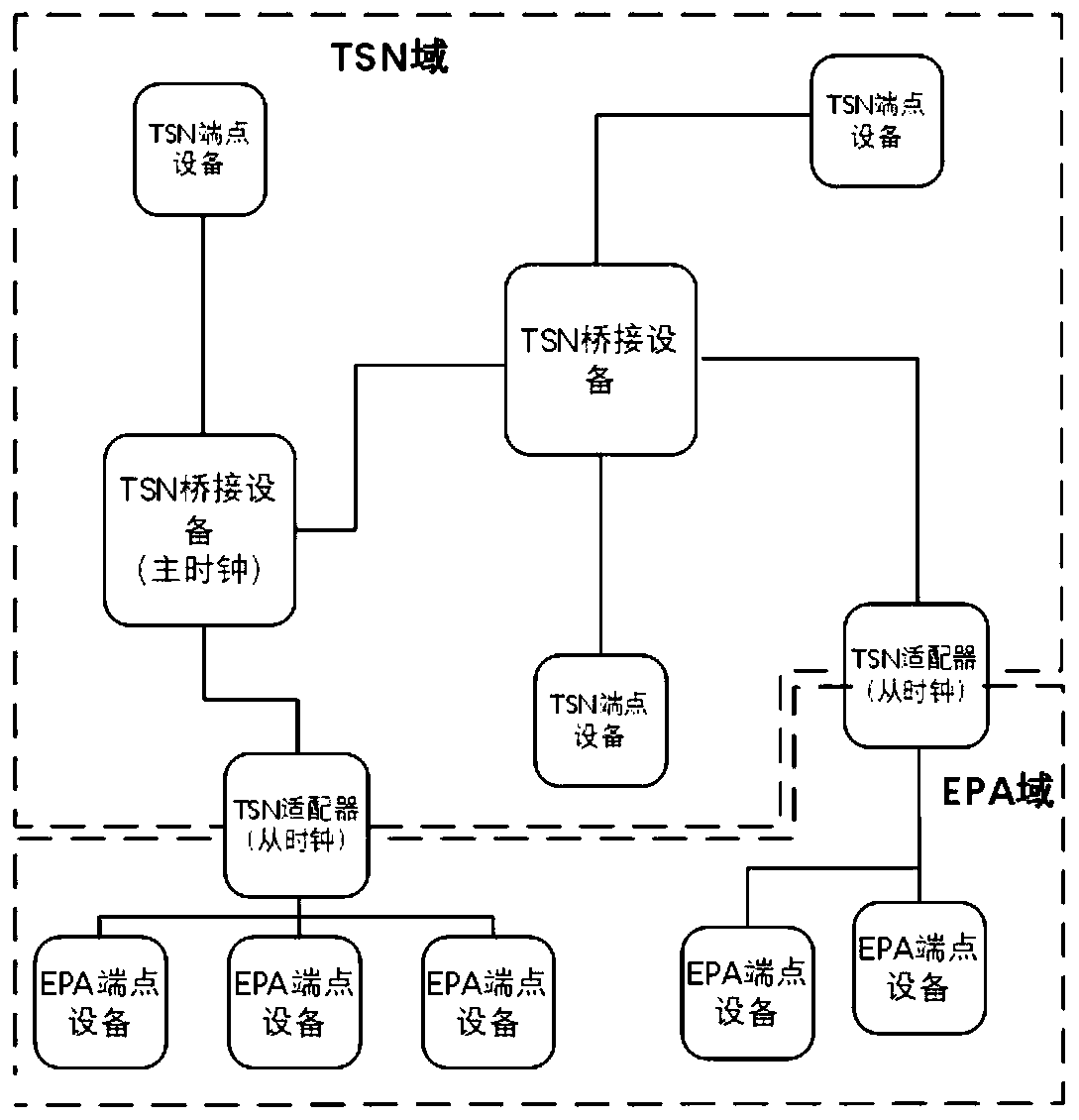
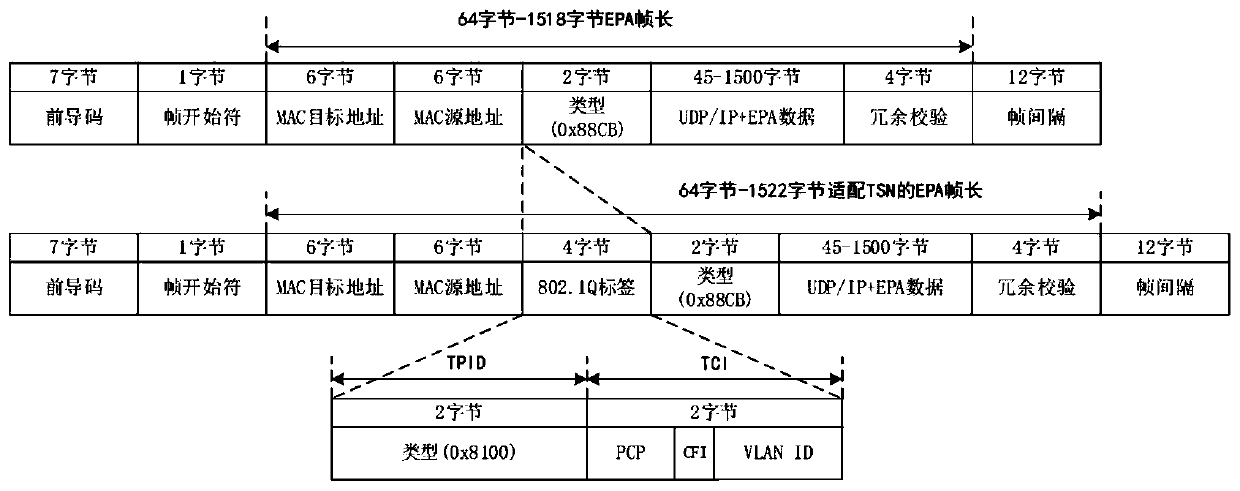
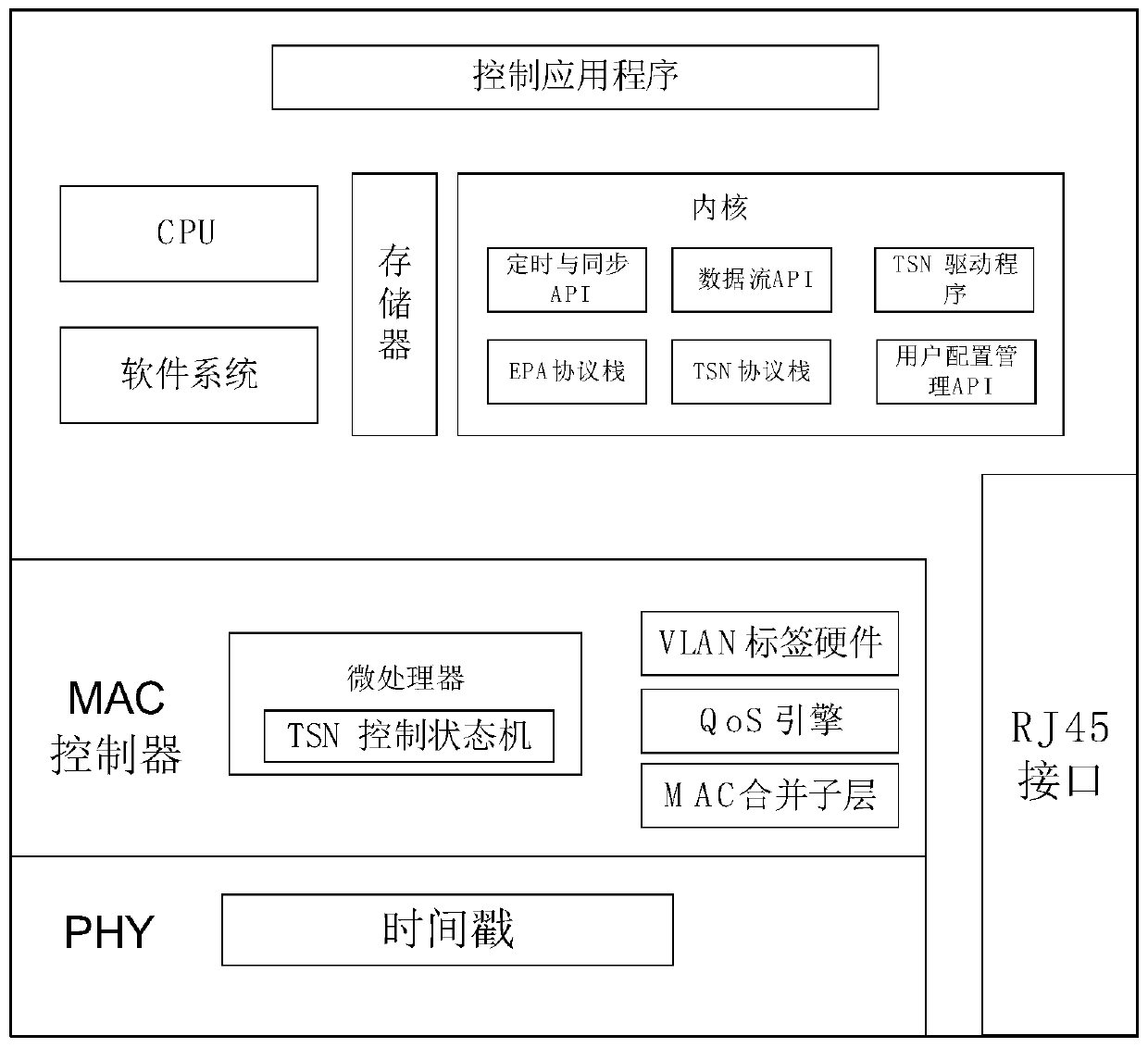
The invention relates to an EPA industrial bus and time sensitive network adaptation system and method, solves the technical problem that an EPA Ethernet cannot be connected with a time sensitive network in real time to construct a fast channel, and comprises an EPA endpoint device and a TSN endpoint device. The EPA endpoint device is in communication connection with a TSN bridging device througha TSN adapter, and the TSN bridging device is connected with the TSN endpoint device; the TSN adapter receives the time data issued by the main clock from the TSN bridging device, and adds a timestampin the process of receiving or transmitting the clock synchronization data to complete clock synchronization; and the TSN bridging device is used for providing time synchronization, low delay, low jitter and flow bandwidth guarantee, so that the problem is better solved, and the method can be applied to the EPA industrial technology.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Software real name authentication system and its safe checking method
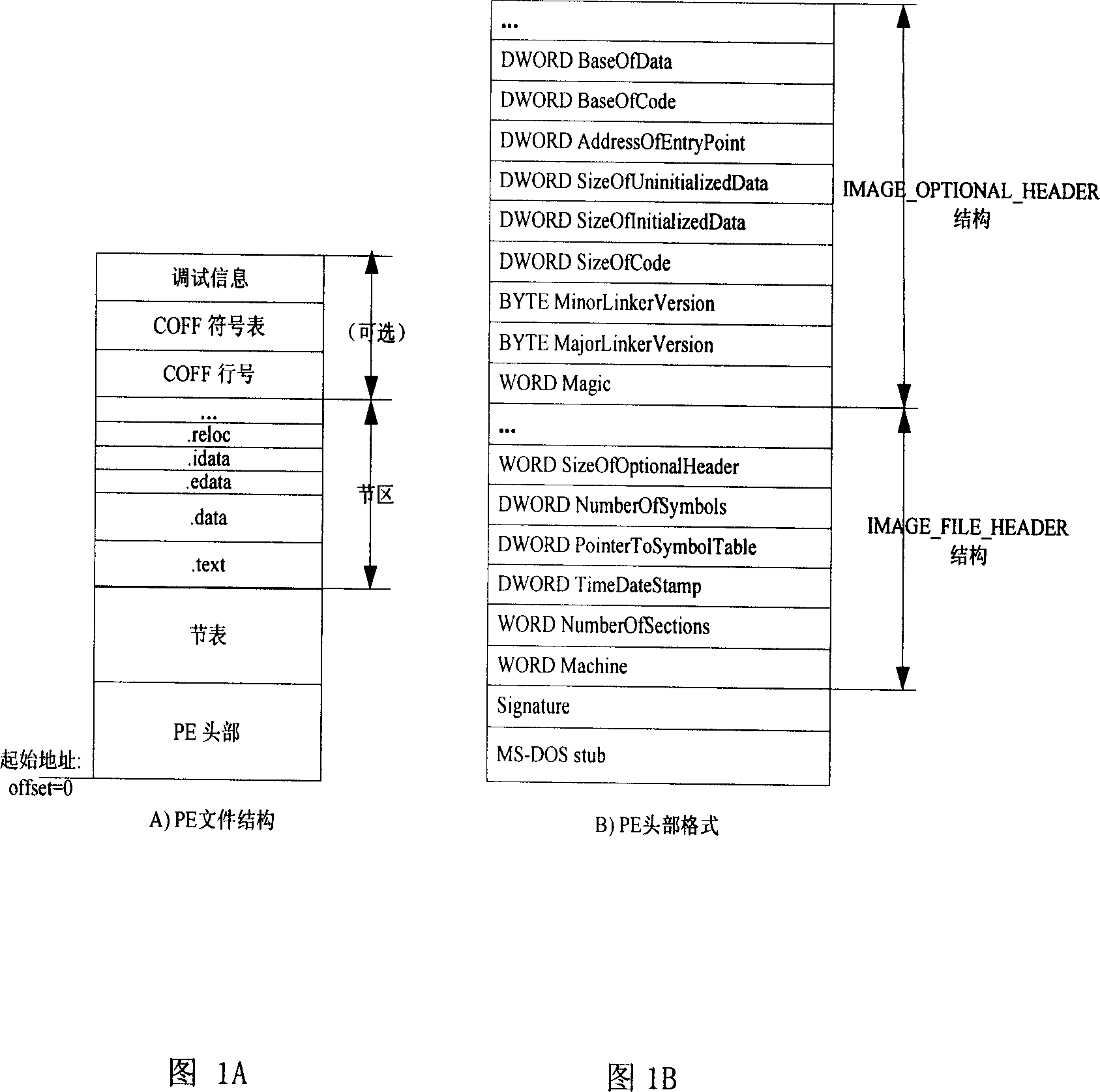
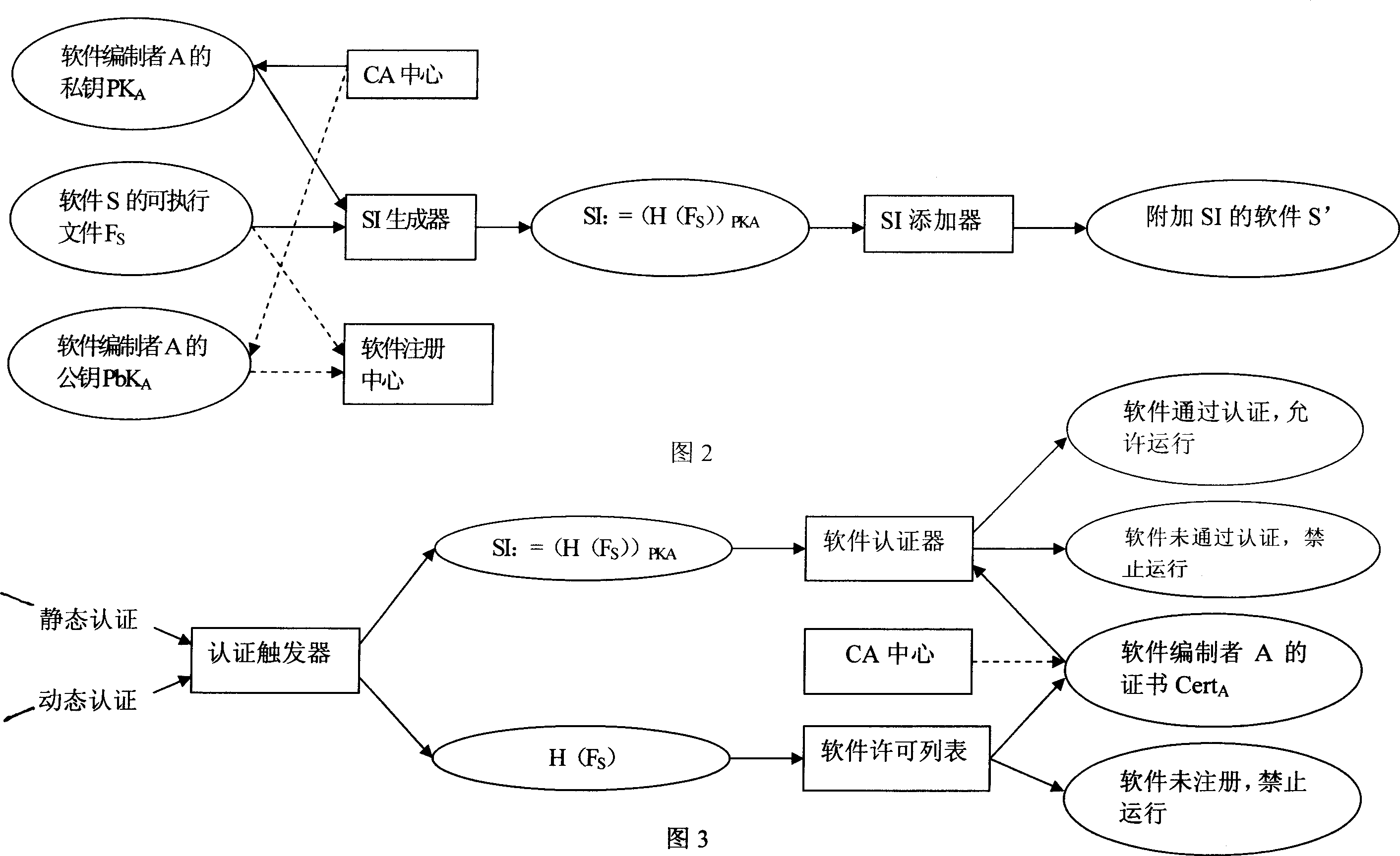
InactiveCN101149773AStop runningAvoid modificationComputer security arrangementsOperational systemSoftware engineering
The invention relates to a system based on software real-names and its safety verification method, the system comprises software concentrator marker used to add software identification for authorized software, software certification device used to identify if the software identification of executable file in system was legal, the software concentrator marker and software certification device were saved in the disk of the computer. The method is: when the Windows operating system runs the loader will first deal with the target document, in this process, the software certification device of the software real-name certification system break in the loading process of Windows executable programs, thus transfer to the software certification device to identify and inspect, finally install and use through certificated executable file. The invention can prevent operation of unauthorized malicious code, prevent malicious code change authorized executable code on the disk, avoid malicious code revise the running executable code in memory, identify malicious acts individual software manufacturers.
Owner:CHINESE PLA AIR FORCE ELECTRONICS TECH INST
Bluetooth electronic key system and control method thereof
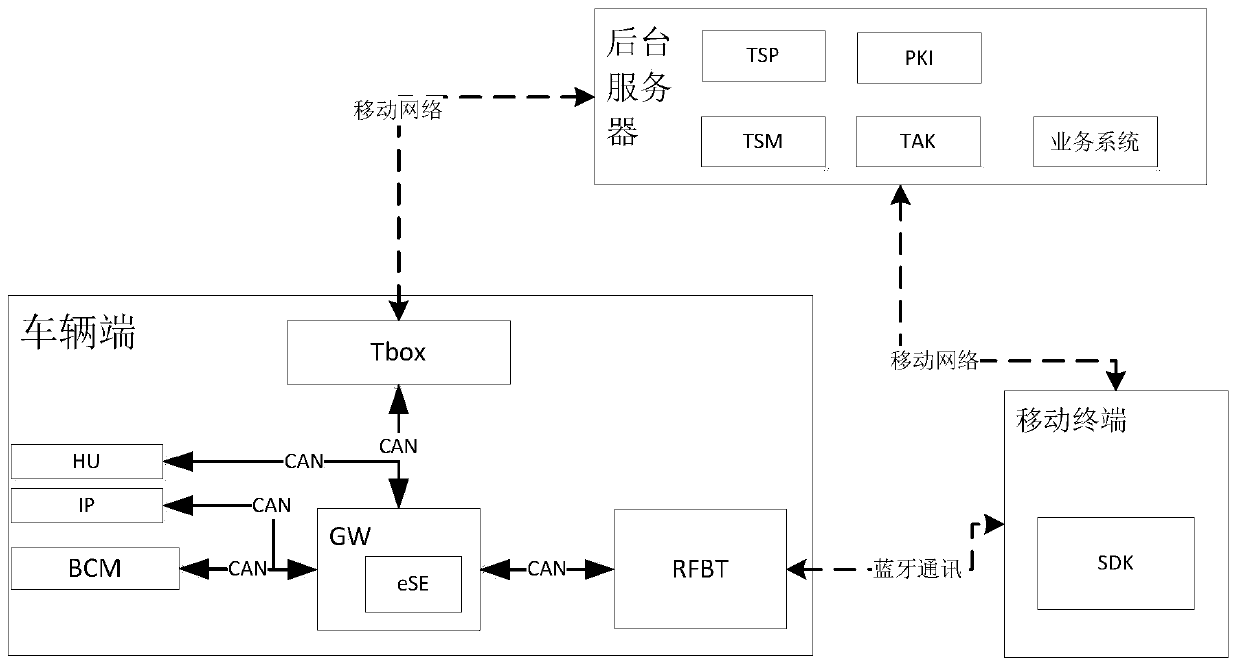
ActiveCN109808643AFind a carAchieve normal startupAnti-theft devicesIndividual entry/exit registersMobile data terminalComputer terminal
The invention discloses a Bluetooth electronic key system and a control method thereof. The system comprises a mobile terminal, a background server and a vehicle terminal, wherein the vehicle terminalcomprises a vehicle-mounted communication controller, a vehicle-mounted Bluetooth radio frequency module, a gateway and a vehicle controller; the background server communicates with the mobile terminal through a mobile network; the mobile terminal communicates with the vehicle terminal through a Bluetooth. By adopting the system, the use right of a vehicle can be acquired by using the mobile terminal, and safe transmission of information can be protected.
Owner:CHONGQING CHANGAN AUTOMOBILE CO LTD
Protection for wind power station
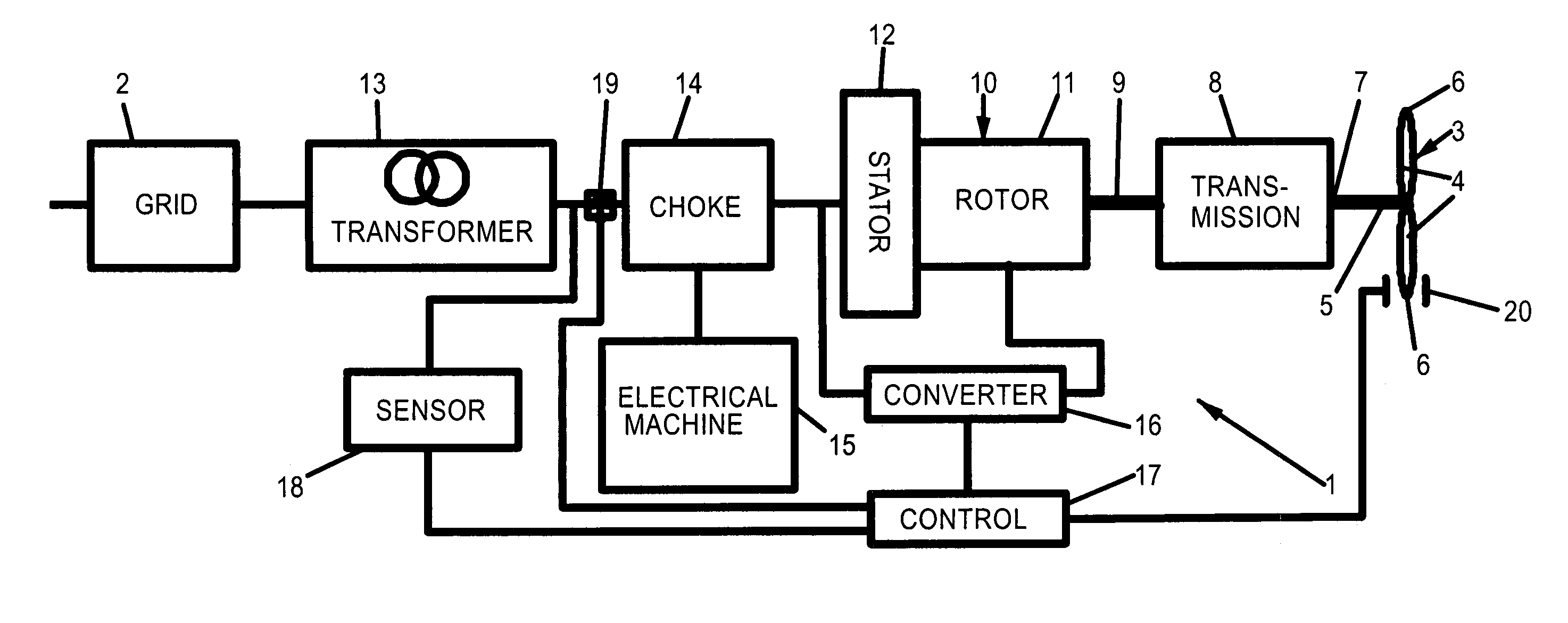
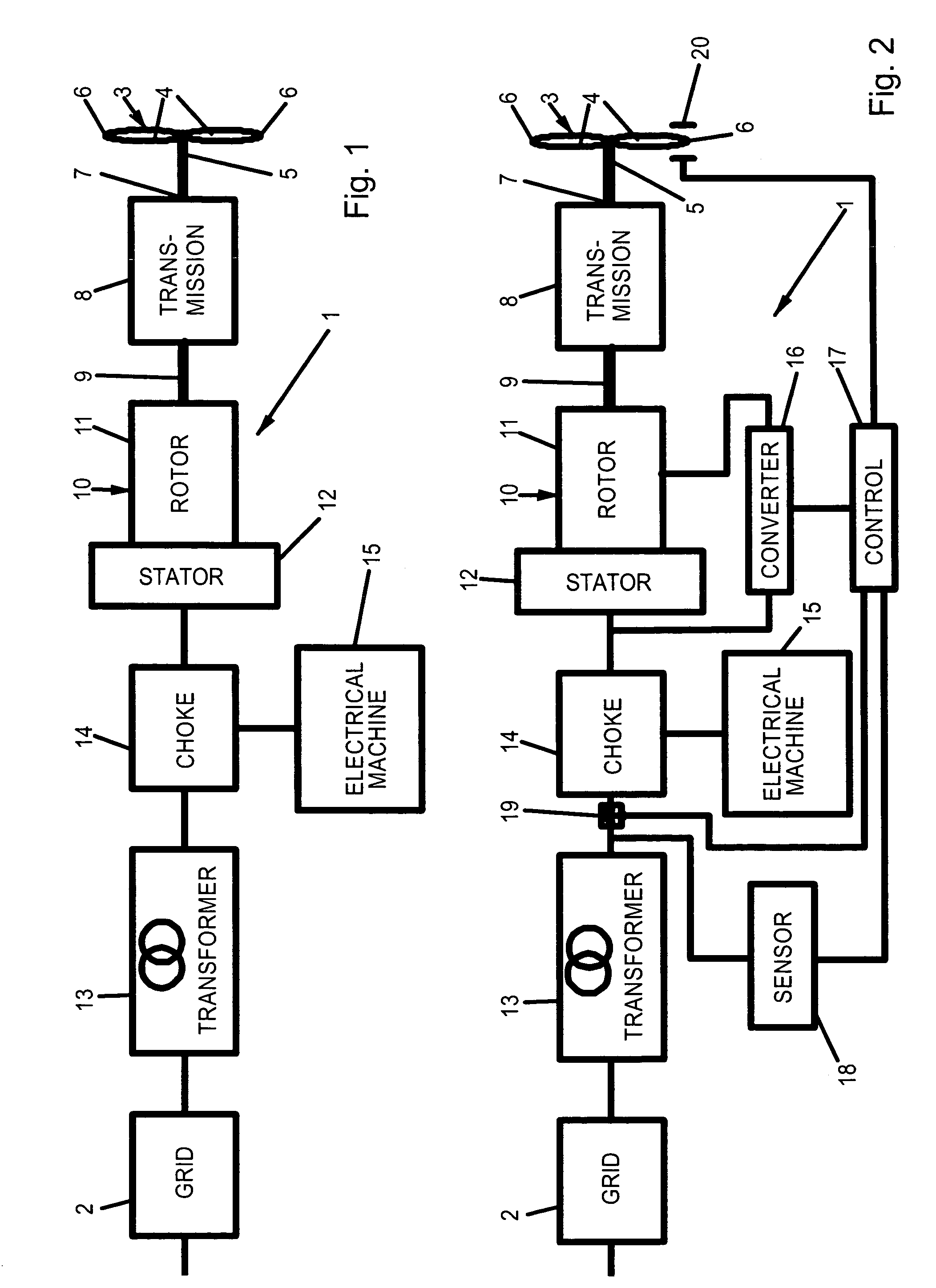
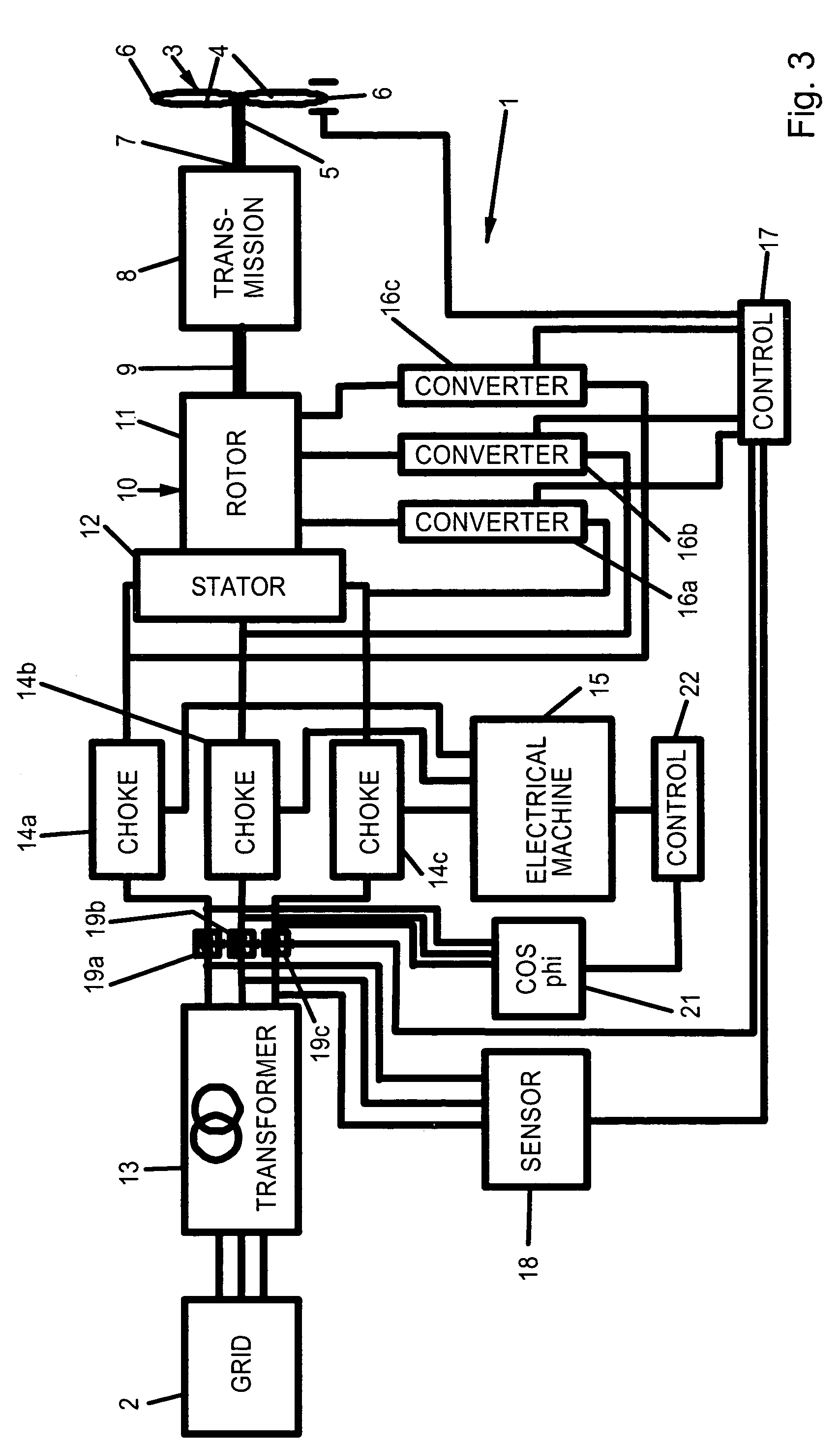
InactiveUS7038330B2Protect normal transmissionDc network circuit arrangementsSingle network parallel feeding arrangementsPower stationPower grid
A wind power station comprises a wind rotor; a transmission mechanically coupled to the wind rotor; an asynchronous generator having a generator rotor mechanically coupled to the transmission, and a generator stator electrically coupled to a power grid; and a protection unit protecting the generator and the transmission against accidental breakdowns of an alternating voltage provided by the power grid. The Protection unit includes at least one choke electrically arranged between the power grid and the generator stator, and a synchronous electrical machine electrically coupled to the choke.
Owner:PILLER GMBH
Control device for automatic transmission and control method for automatic transmission
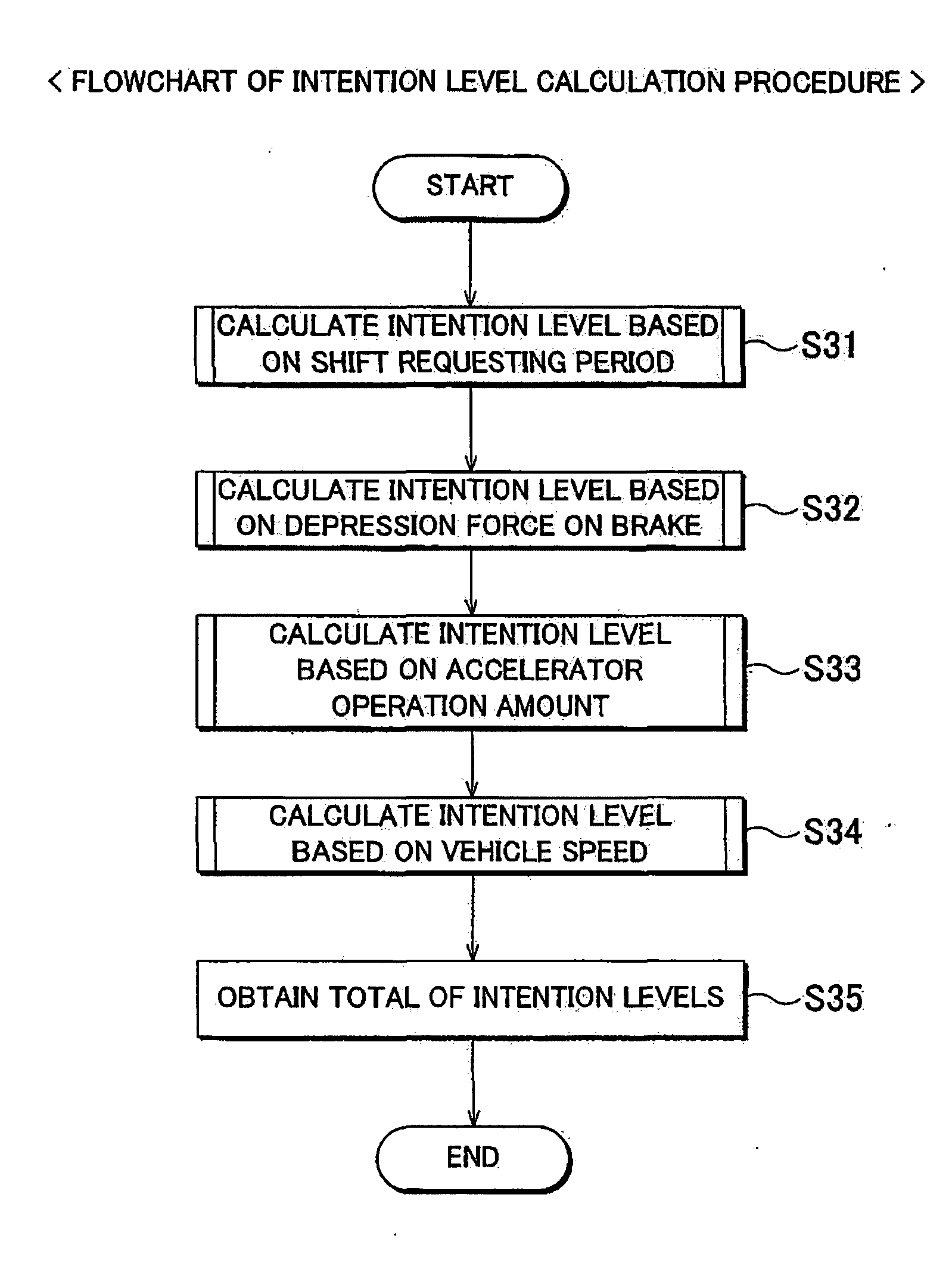
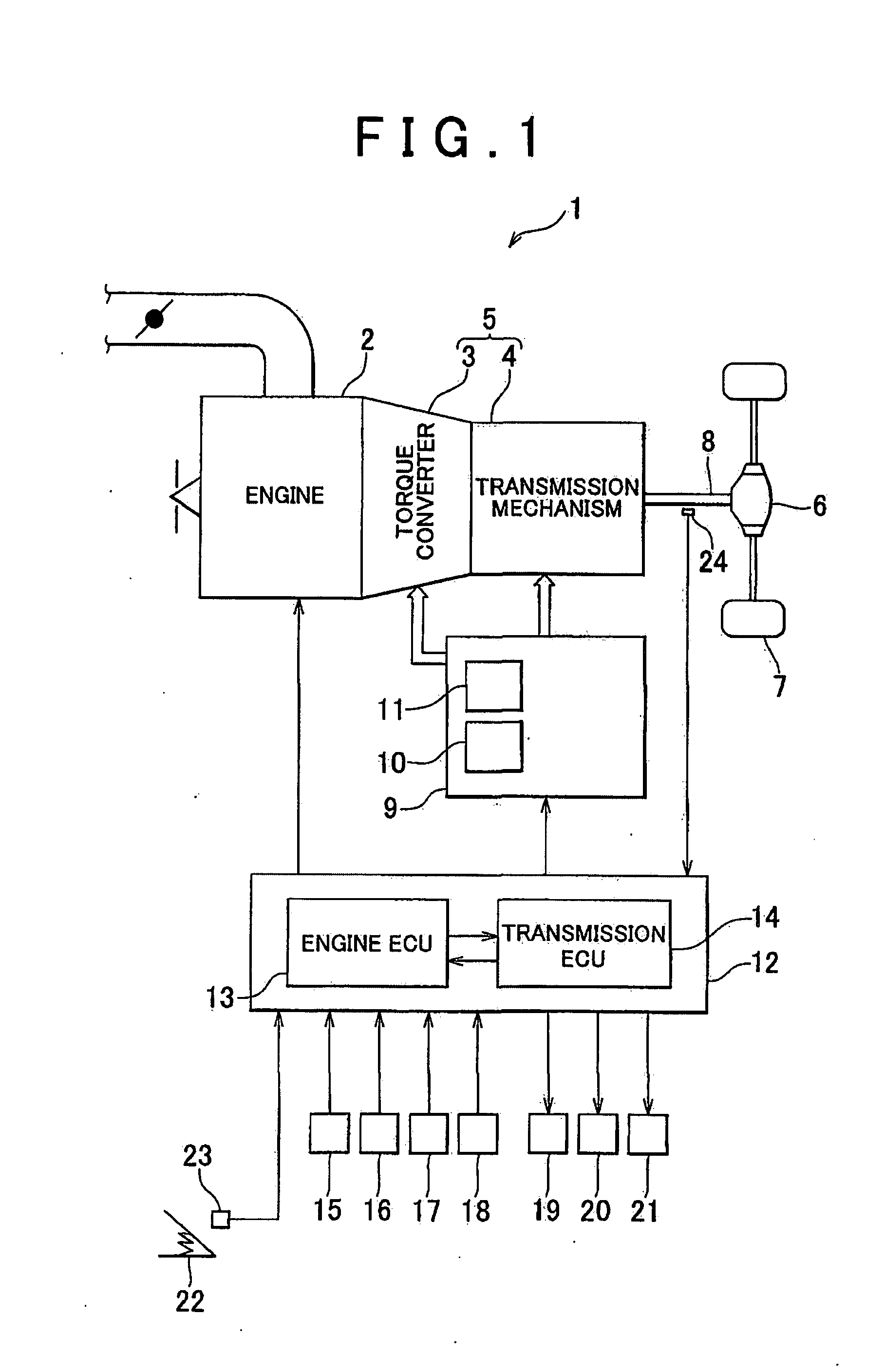
InactiveUS20080182718A1Easy to operateProtect normal transmissionGearing controlEngine controllersAutomatic transmissionExecution control
A control of a control device and control method of an automatic transmission provided on a vehicle to shift the automatic transmission between forward, reverse and neutral gears, includes the steps of: detecting a shift request from one of the forward or reverse gear to the other of the forward or reverse gear; acquiring an operating condition relating to a shift from one of the forward or reverse gear to the other of the forward or reverse gear; acquiring a running condition from a vehicle speed sensor of the vehicle; determining whether to permit a gear shift based on the operating condition and the running condition when a shift request is detected; and executing a control to shift from one of the forward or reverse gear to the other of the forward or reverse gear when the shift determination device determines that a gear shift is permissible.
Owner:TOYOTA JIDOSHA KK
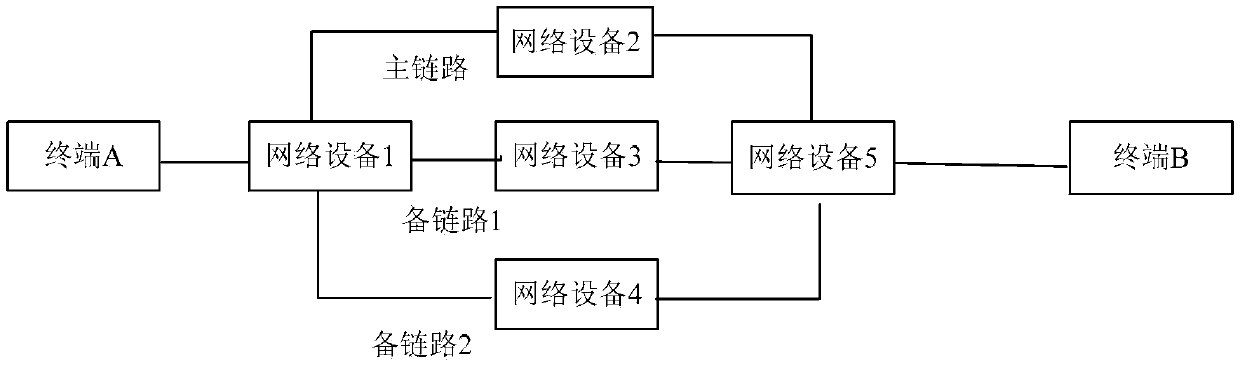
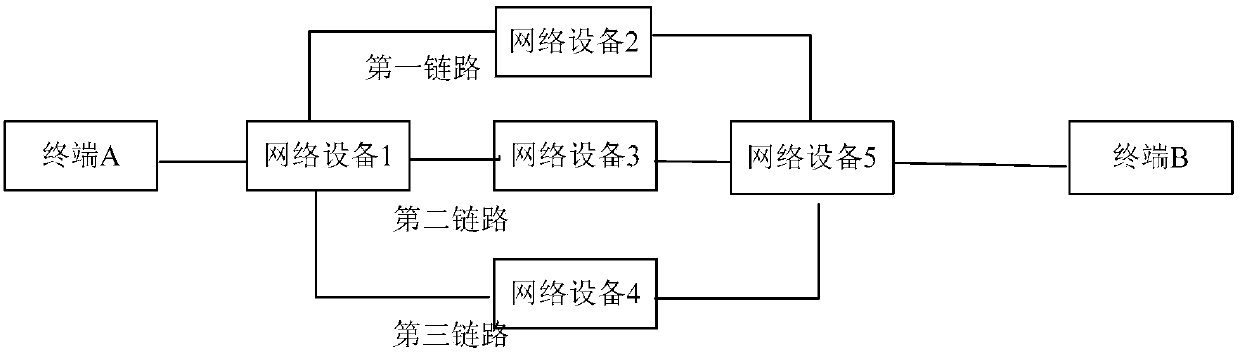
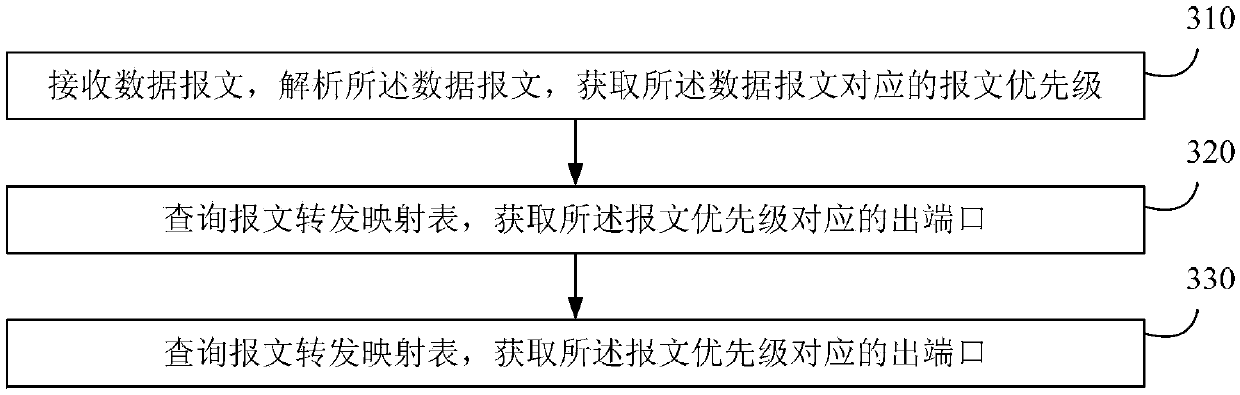
Load sharing method and device
InactiveCN103428101AReduce the likelihood of discardingProtect normal transmissionData switching networksMassageDistributed computing
The invention relates to a load sharing method and device. The method comprises steps of receiving a data message, and analyzing the data message to obtain a message priority corresponding to the data message; inquiring a massage forward mapping table to obtain an out interface corresponding to the message priority; forwarding the data message to an opposite terminal through a link corresponding to the out interface. By means of the method, the corresponding link is chosen for the massage to achieve transmission according to the message priority, and massage forward paths of different message priorities are controlled.
Owner:HUAWEI TECH CO LTD
Enhanced DLS and HCCA principles
InactiveUS20070002782A1Transmission power useProtect normal transmissionNetwork topologiesConnection managementTelecommunicationsOperation mode
An improved system and method for enabling communication among devices in wireless networks. The present invention involves the introduction of a new terminal class, referred to herein as an accessory class, to a WLAN network. The present invention allows for direct transmissions between accessories and terminals as a part of the service period. According to the present invention, the terminal transmits a request for stream setup to an access point. The access point provides a response to the terminal, after which the terminal prepares an accessory stream setup request to be transmitted to the accessory based upon the received response. The accessory stream setup request indicates the desired operation mode of the accessory.
Owner:NOKIA CORP
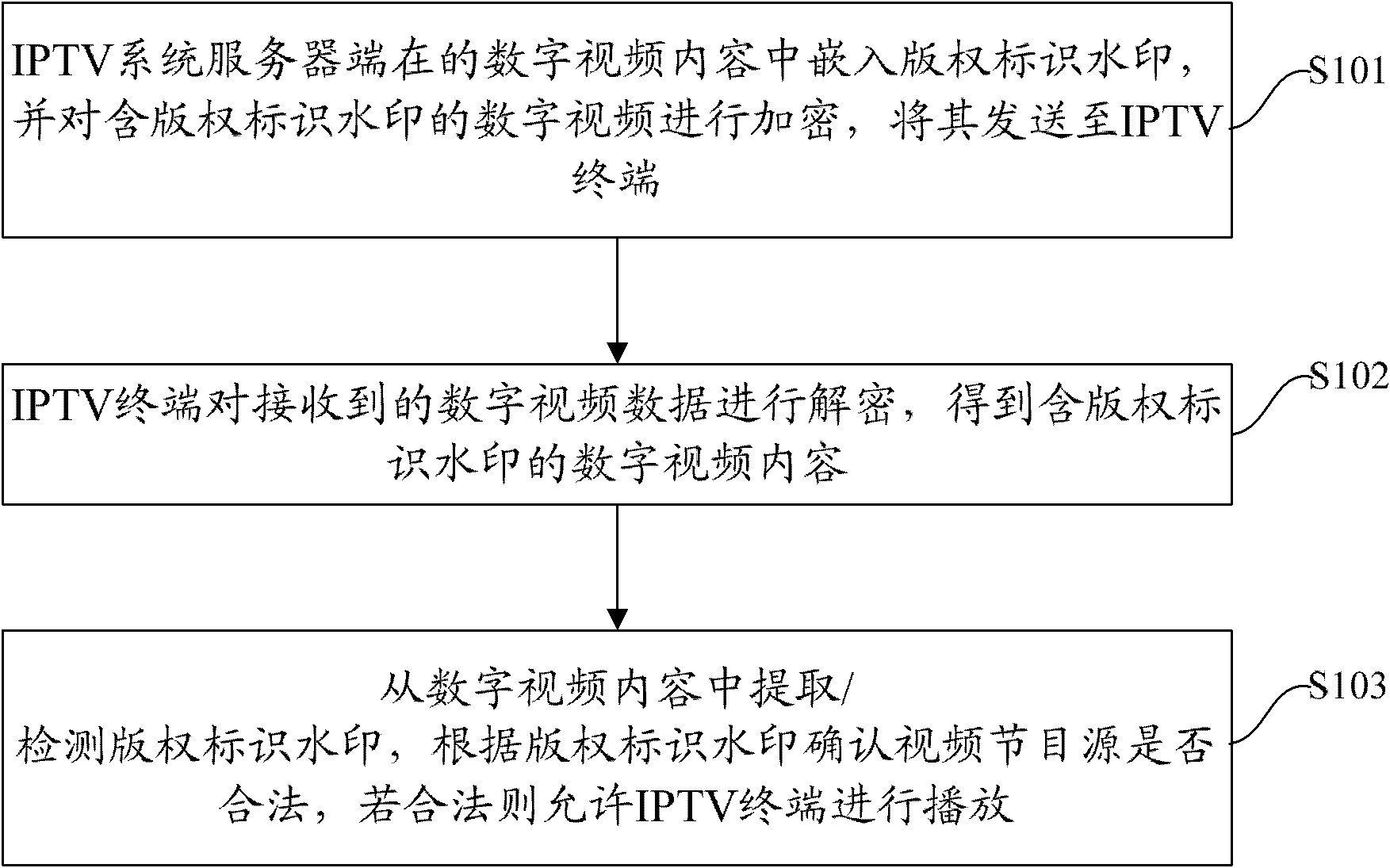
IPTV (Internet Protocol Television) digital rights management (DRM) method and device based on digital watermarking and encryption
ActiveCN102760221AGuarantee the legality of copyrightProtect normal transmissionComputer security arrangementsImage data processing detailsDigital videoDigital rights management
The invention discloses an IPTV (Internet Protocol Television) digital rights management (DRM) method and device based on digital watermarking and encryption, wherein the method comprises the following steps that: an IPTV system server side inserts copyright watermarking into a digital video content, encrypts the digital video containing the copyright watermarking, and sends the encrypted digital video containing the copyright watermarking to an IPTV terminal; the IPTV terminal decrypts the received digital video data, to obtain the digital video content containing the copyright watermarking; and the copyright watermarking is extracted / detected from the digital video content, whether the video program is legal is confirmed according to the copyright watermarking, if yes, the video program is allowed to be played at the IPTV terminal.
Owner:AEROSPACE INFORMATION
Stowable laser eye protection
ActiveUS20050280897A1Protect normal transmissionEasy extractionMirrorsAntiglare equipmentWavelengthEye protection
A stowable laser eye protection system is provided as a solution for protecting the eyes of pilots and other vehicle operators and optical sensors such as during critical phases of flight and for general protection against a wide range of spectral wavelengths. A stowable laser eye protection system provides protection that can be manually or automatically extended and retracted. For example, by installing flexible laser protective films on rollers at each window of an aircraft cockpit, the protection can be put in place during taxi before take-off and stowed when the aircraft is a safe distance away from a potential threat area such as after reaching a particular altitude. A similar activity could be used for approach and landing, where the protection is extracted when the aircraft approaches a threat condition or critical phase of flight and retracted after landing.
Owner:THE BOEING CO
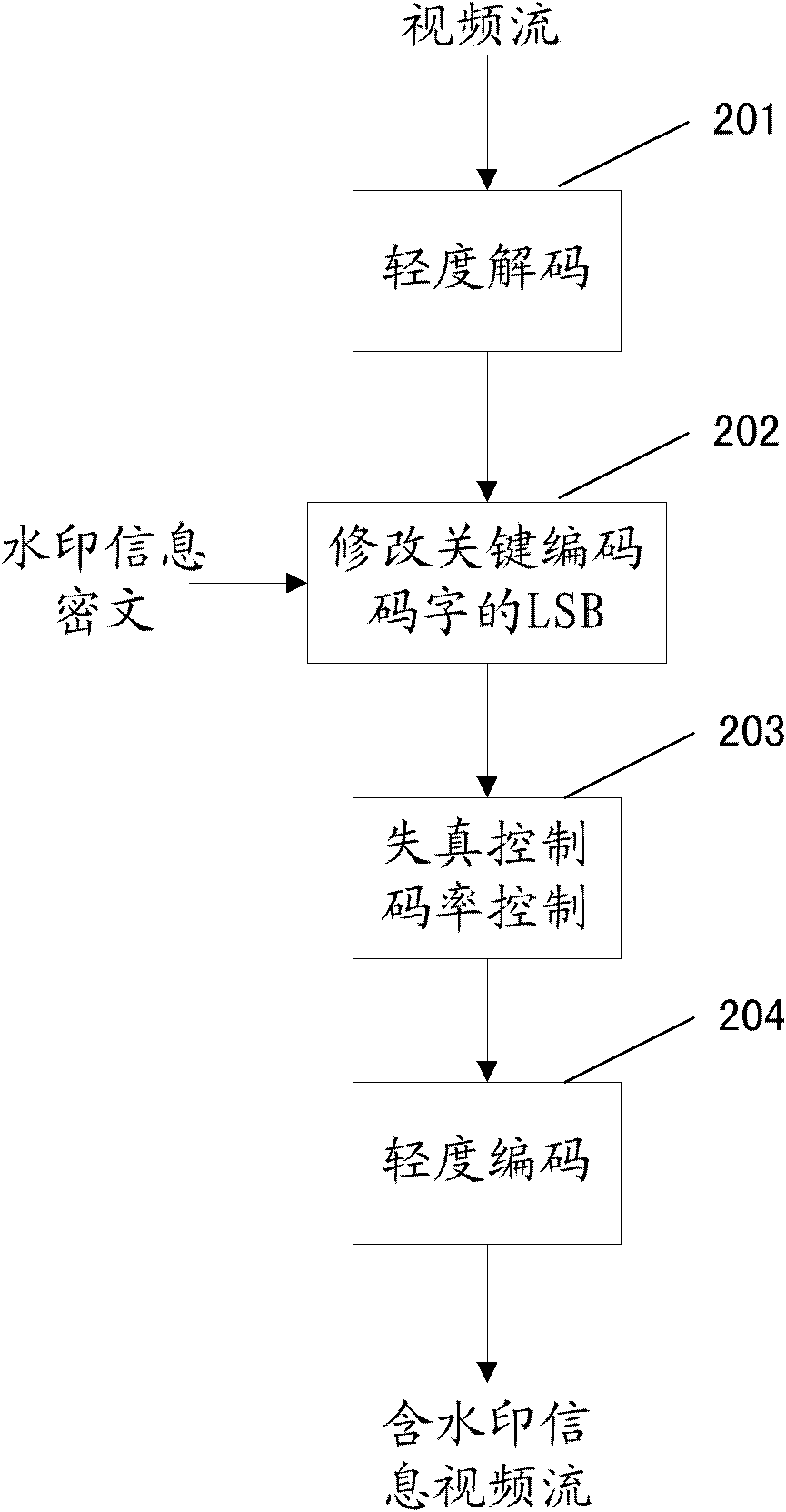
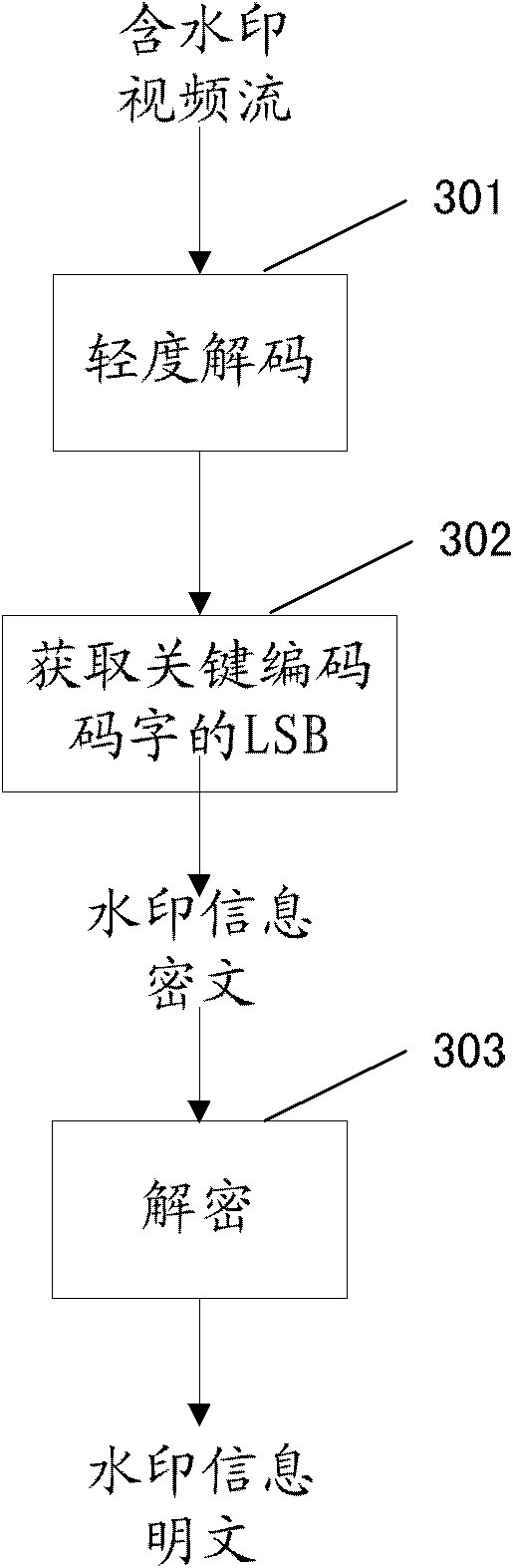
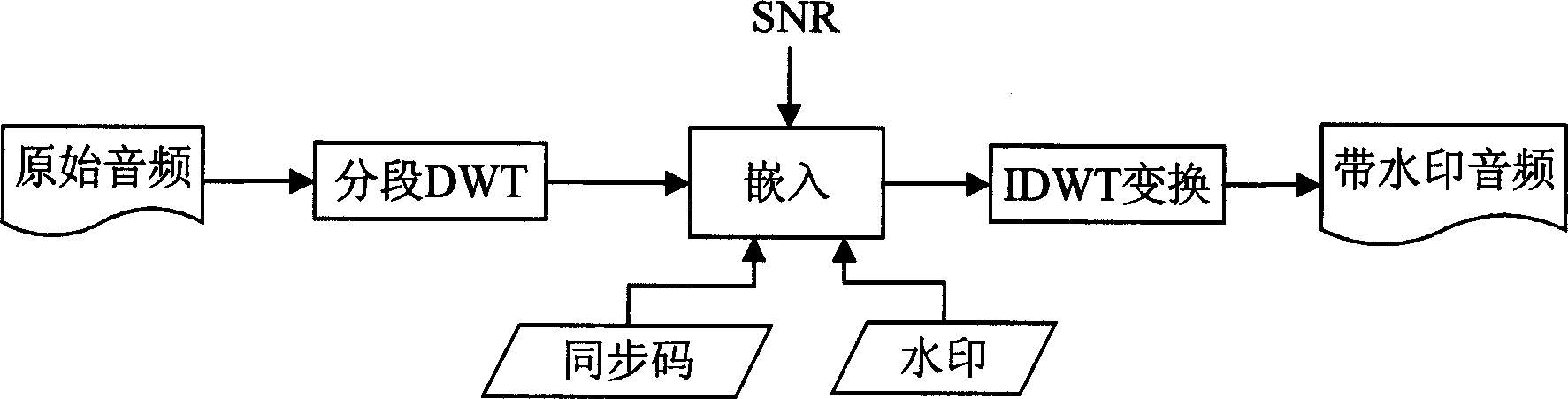
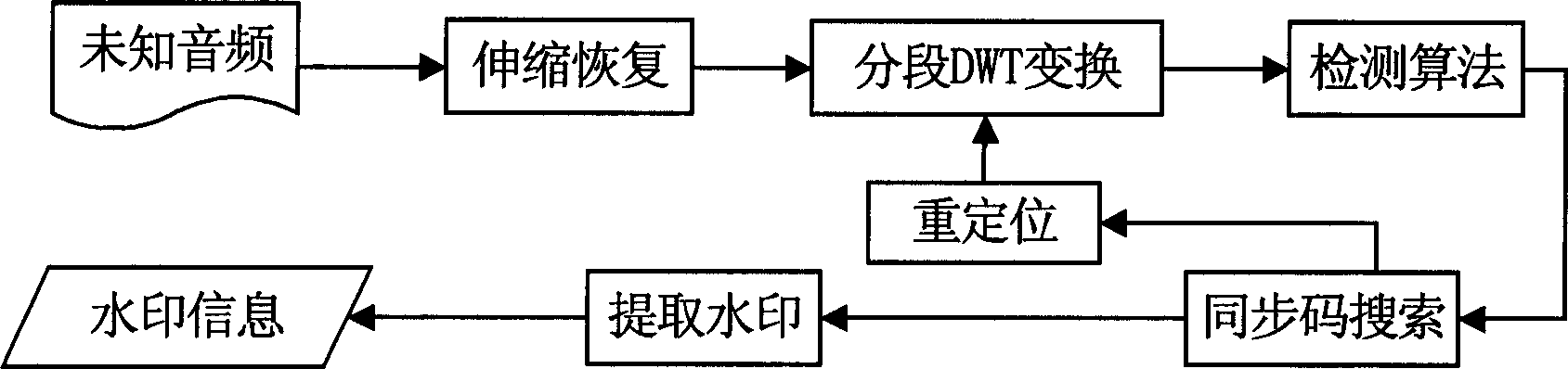
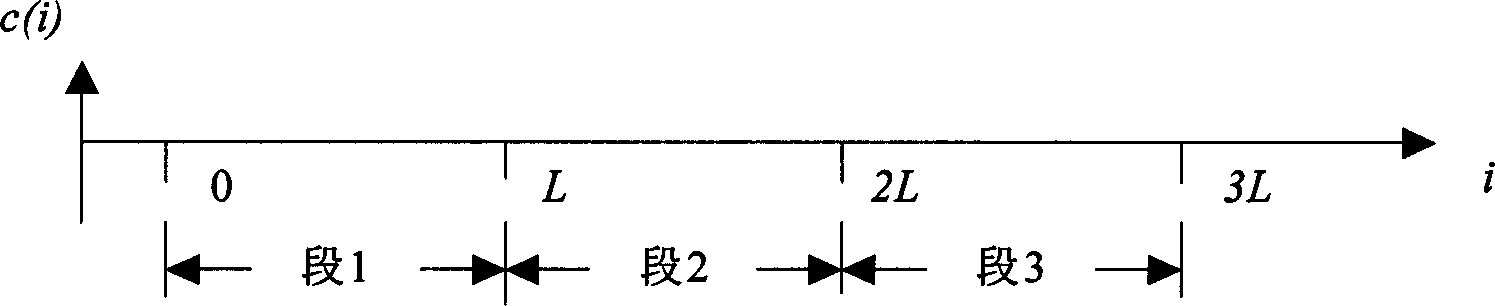
Anti-DA/AD converting audio-frequency watermark processing method
InactiveCN1889176ASolve the problem of anti-DA/AD transformation that cannot be solvedProtect normal transmissionSpeech analysisEnergy variationSolidity
The invention is a method of the audio frequency watermark handling which is based on DWT, resisting DA / AD transposition; it belongs to the safety field of multi-media information. The invention has two processes, one is watermark insertion, the other is watermark monitor; the watermark is inserted in the low frequency sub-strip of minor wave modulus to resist the attack against overlaying noise; three section of minor wave modulus are a group to insert a bit watermark information to remove the effect of energy change, the multiunit insert many bits of watermark; designing the re-synchronization technology based on the synchronization code and interpolation operation to remove the effect of the stretch of time axis. The invention can not only resist the effect on watermark brought by DA / AD transposition in effect , but also have great solidity against common attack operation (such as MP3 compression , noise etc.). Besides to protect the audio frequency production to transmit in digital route, the invention can protect the audio frequency data crossed the DA / AD equipment, and be used to monitor advertisement of the music broadcasting station.
Owner:SUN YAT SEN UNIV
Transmission control module
ActiveUS20140362535A1Reduce thicknessHigh bonding strengthCasings with connectors and PCBSemiconductor/solid-state device detailsElectrical conductorComputer module
A transmission control module includes a printed circuit board. The circuit board has conductor tracks routed on at least one layer of the circuit board and configured to electrically connect a carrier substrate to electrical components. The circuit board has an inner conductor track layer arranged between two insulating layers. A first outer insulating layer, at least on a first side of the circuit board, has a recess. Surfaces of conductor track sections of conductor tracks of the at least one inner conductor track layer are arranged at the bottom of the recess. The carrier substrate is inserted into the recess and makes electrical contact with the surfaces of the conductor track sections. The recess is filled with a moulding compound which covers at least the carrier substrate and the conductor track sections to protect the carrier substrate and the conductor track sections from transmission fluid.
Owner:ROBERT BOSCH GMBH
Data collection device enclosure
ActiveUS20080295932A1Capture and manipulate imageProtect normal transmissionFlexible coversWrappersEngineeringData transmission
An enclosure for housing a portable data transfer device, such as a bar code scanner, data collection device, or other equipment, for use in environments requiring a certain level of cleanliness, for protection against transmission of infection or merely dust or dirt, while allowing a full range of functional capability of such devices and equipment.
Owner:HAND HELD PRODS
Light funnel illumination system based on conical fiber light guide
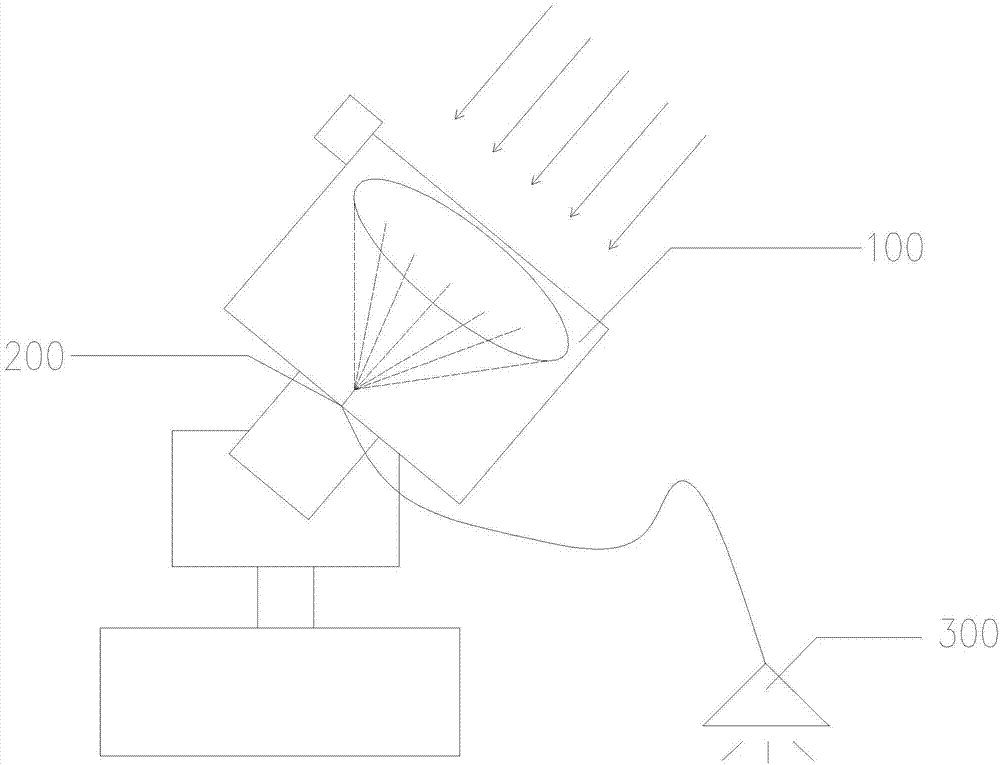
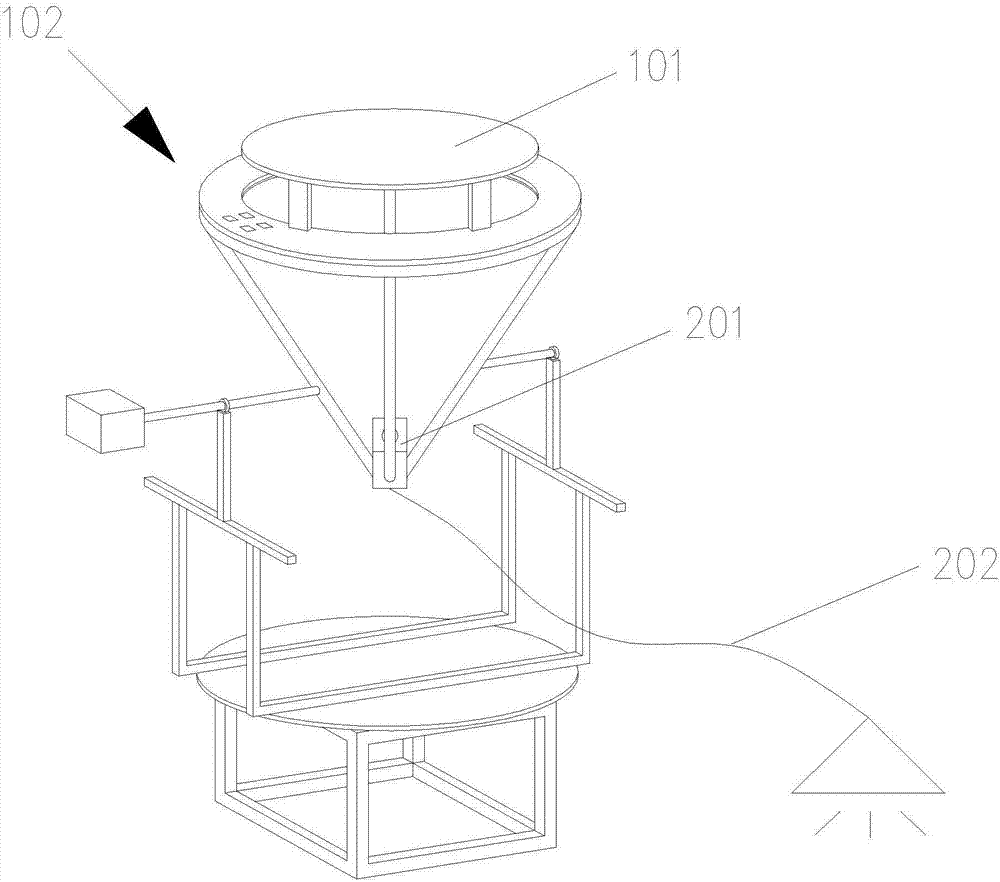
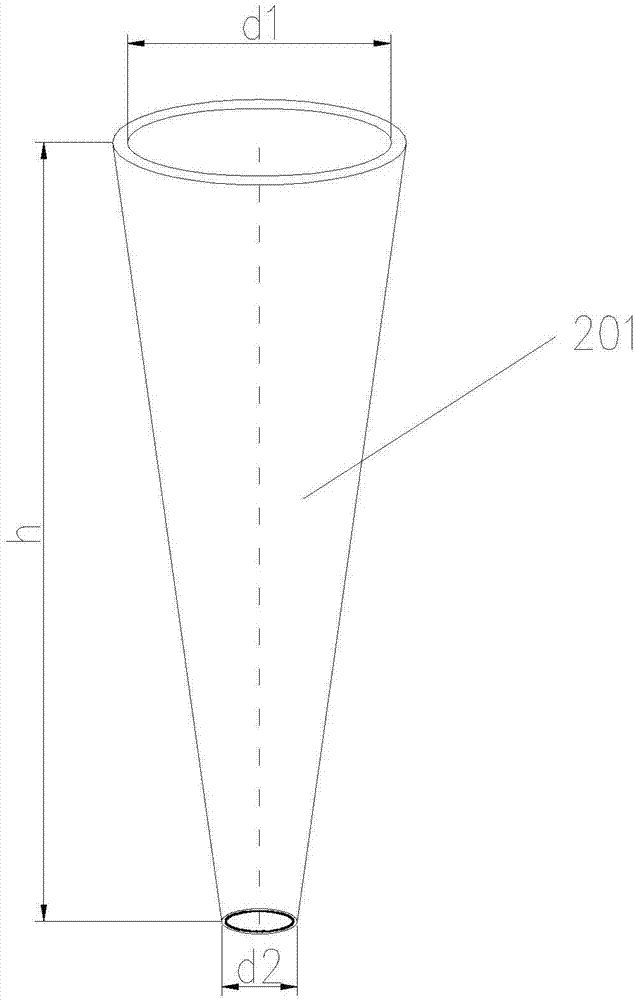
ActiveCN107218576AImprove temperature resistanceProtect normal transmissionMechanical apparatusLighting support devicesFiberLight guide
The invention discloses a light funnel illumination system based on conical fiber light guide. The light funnel illumination system comprises a condensing device, a light guide device and an illumination device; the condensing device comprises a condensing lens for collecting sunlight, and a photoelectric type tracking device for controlling the condensing lens to rotate; the photoelectric type tracking device controls the condensing lens to move collect the sunlight; after the sunlight penetrates through the condensing lens, a light spot is formed, and the light guide device transmits the light spot to the illumination device to realize illumination; the light guide device comprises a first optical fiber arranged below the center of the condensing lens and used for transmitting the sunlight, and a second optical fiber connected with the first optical fiber and the illumination device. The light funnel illumination system adopts the conical fiber as the light guide device, and the aperture of the large end of the conical fiber is greater than the diameter of the light spot, so that even if the light spot shifts, light can enter the conical fiber very well, and no energy loss appears; and the small end of the conical fiber is connected with the second optical fiber in an adapted manner, so that the brightness of an outlet optical fiber of the second optical fiber is improved, manufacturing materials are saved, and the cost is lowered substantially.
Owner:HUAQIAO UNIVERSITY
Secure transmission method and circuit of chip security information
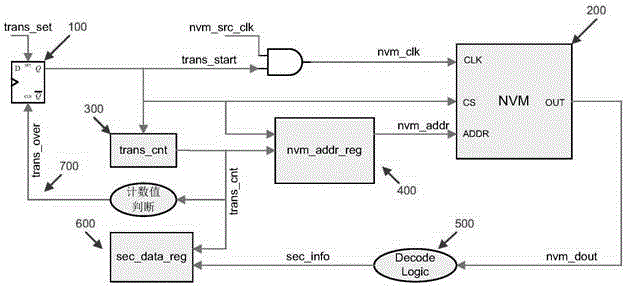
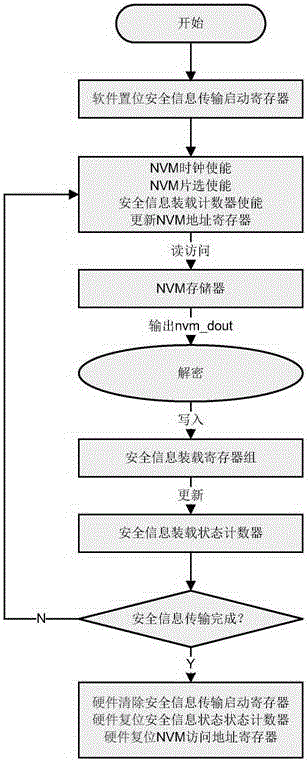
ActiveCN106372540AAchieve protectionTo achieve non-interferenceDigital data protectionInternal/peripheral component protectionProcessor registerSecure transmission
The invention discloses a secure transmission method and circuit of chip security information. The circuit comprises a control register used for starting security information transmission, an NVM used for storing the security information, a data register set used for loading the chip security information, a register used for generating an NVM access address, a counter used for recording a security information loading state, and a related combined logic unit. When the chip security information is accessed, firstly software sets the register used for starting the security information transmission to start access and transmission of the chip security information; hardware automatically performs read operation on the NVM used for storing the security information, decrypts returned data, and writes the data in the data register set used for loading the chip security information; and if the security information transmission is not finished (by judging a value of the counter used for recording the security information loading state), an access address register of the NVM is updated and the access and transmission of a next group of security information are started. The method provided by the invention can effectively protect the transmission of the chip security information.
Owner:BEIJING CEC HUADA ELECTRONIC DESIGN CO LTD
Data collection device enclosure
ActiveUS7987979B2Protect normal transmissionCapture and manipulate imageFlexible coversWrappersBarcodeEngineering
An enclosure for housing a portable data transfer device, such as a bar code scanner, data collection device, or other equipment, for use in environments requiring a certain level of cleanliness, for protection against transmission of infection or merely dust or dirt, while allowing a full range of functional capability of such devices and equipment.
Owner:HAND HELD PRODS
Information server and communication apparatus
ActiveUS20060045084A1Avoid communicationEasily restrainedLoop networksControl communicationsControl manner
A communication apparatus as one of first communication apparatuses belonging to a first communication network, for communicating with another of the first communication apparatuses via the first communication network, and with one or more second communication apparatuses via a second communication network, the communication apparatus as the one first communication apparatus including a communication portion which communicates with the different first communication apparatus via the first communication network, and with the one or more second communication apparatuses via the second communication network, and a control portion which controls the communication portion to communicate with the different first communication apparatus via the first communication network, in a first control manner, and controls the communication portion to communicate with the one or more second communication apparatuses via the second communication network, in a second control manner different from the first control manner.
Owner:BROTHER KOGYO KK
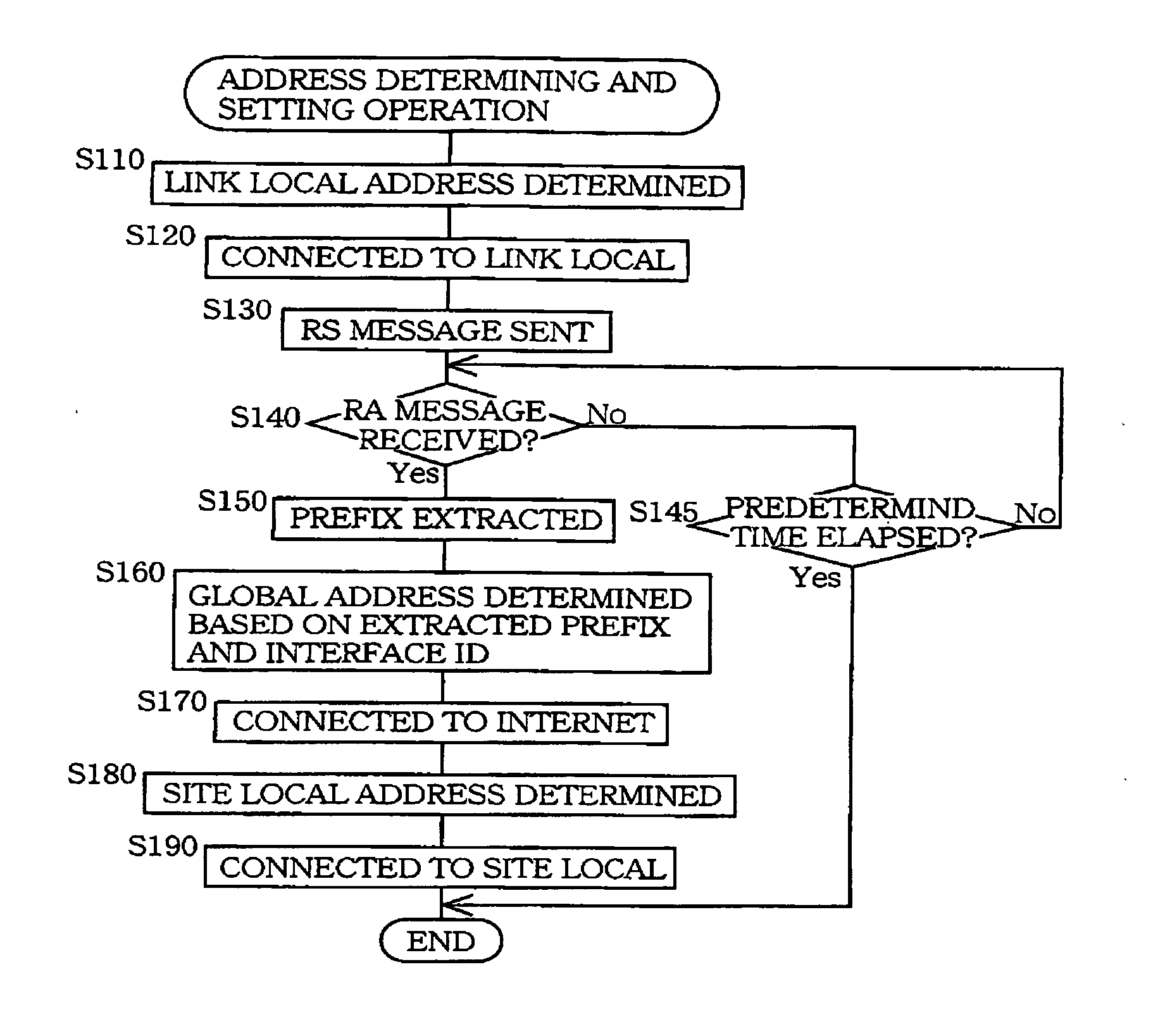
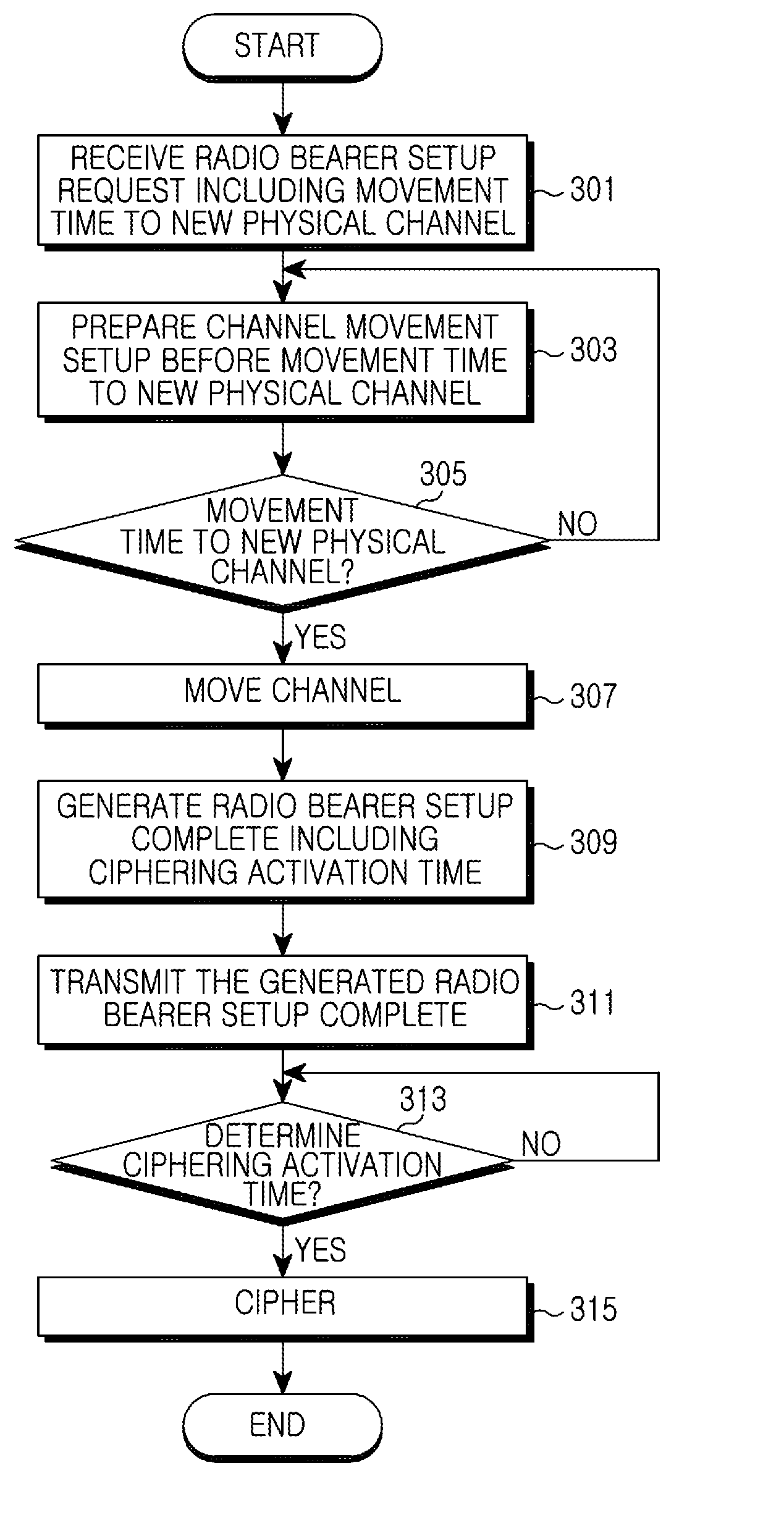
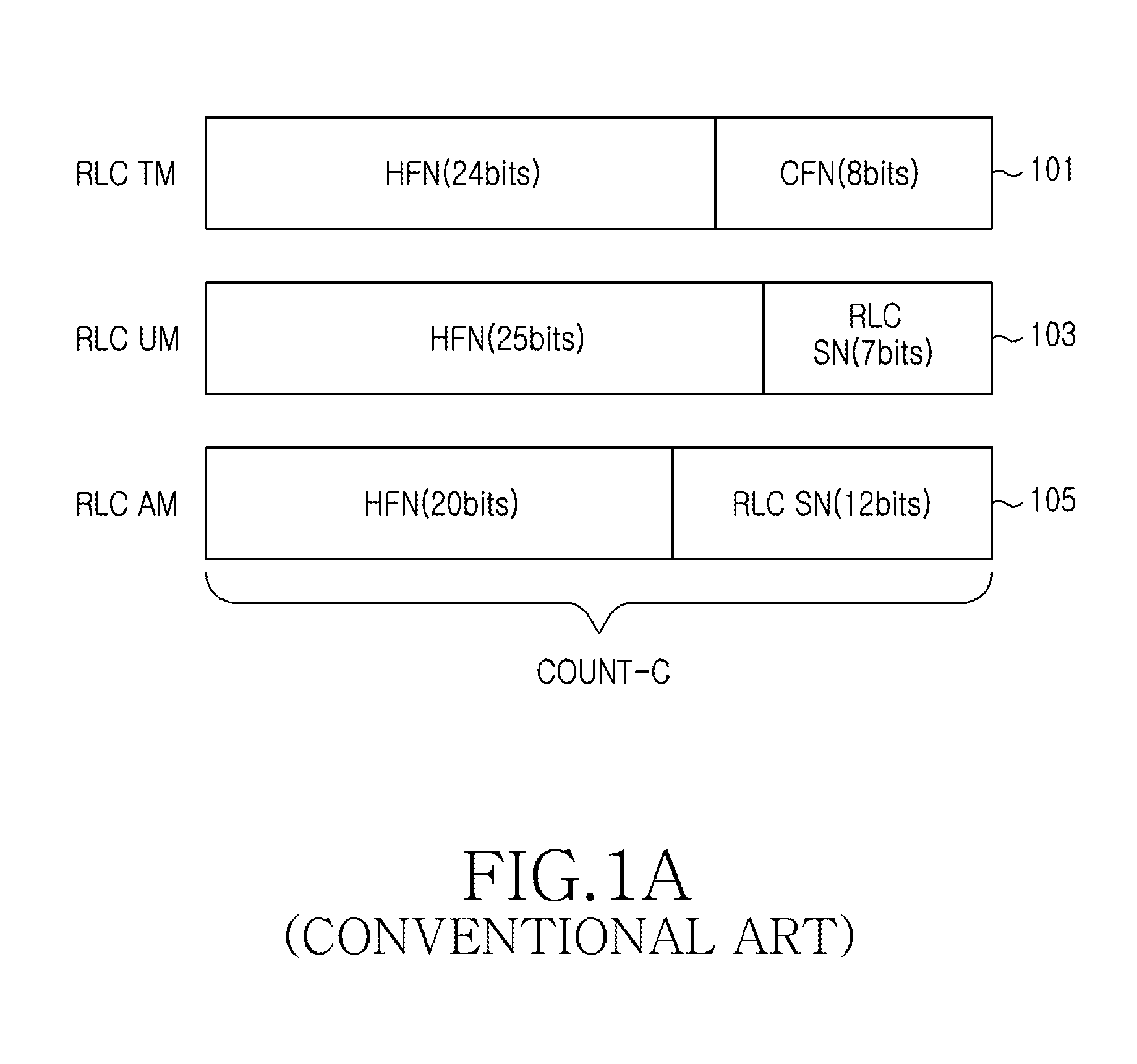
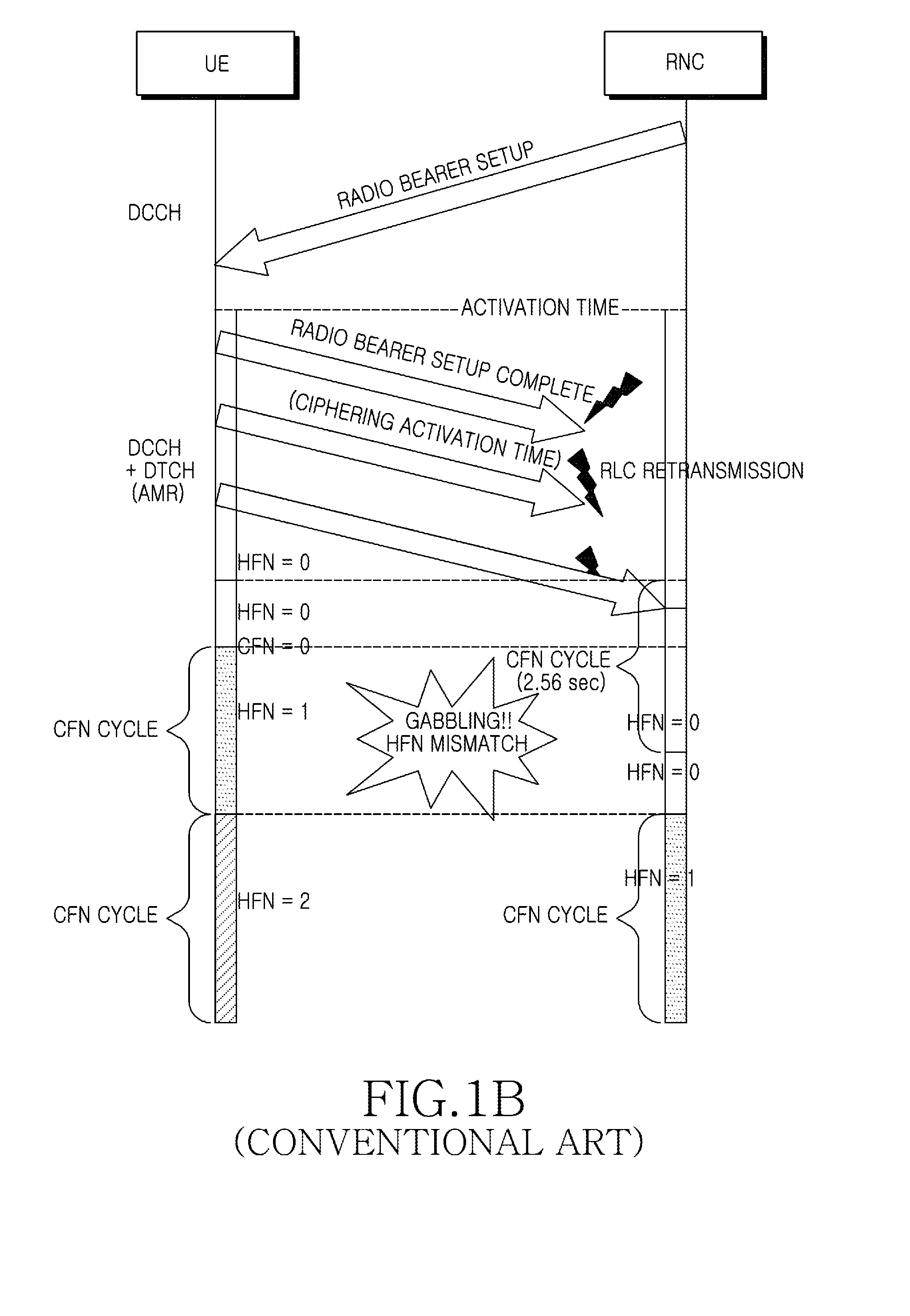
Apparatus and method for ciphering of uplink data in mobile communication system
InactiveUS20100202614A1Protect normal transmissionSynchronising transmission/receiving encryption devicesSecret communicationTelecommunicationsMobile communication systems
An apparatus and method for ciphering uplink data in a mobile communication system are provided. The apparatus includes a Radio Network Controller (RNC) for, when receiving a Radio Bearer Setup Complete after a ciphering activation time, determining a Hyper Frame Number (HFN) value of a User Equipment (UE) and changing an HFN value of the RNC to the same HFN value determined of the UE.
Owner:SAMSUNG ELECTRONICS CO LTD
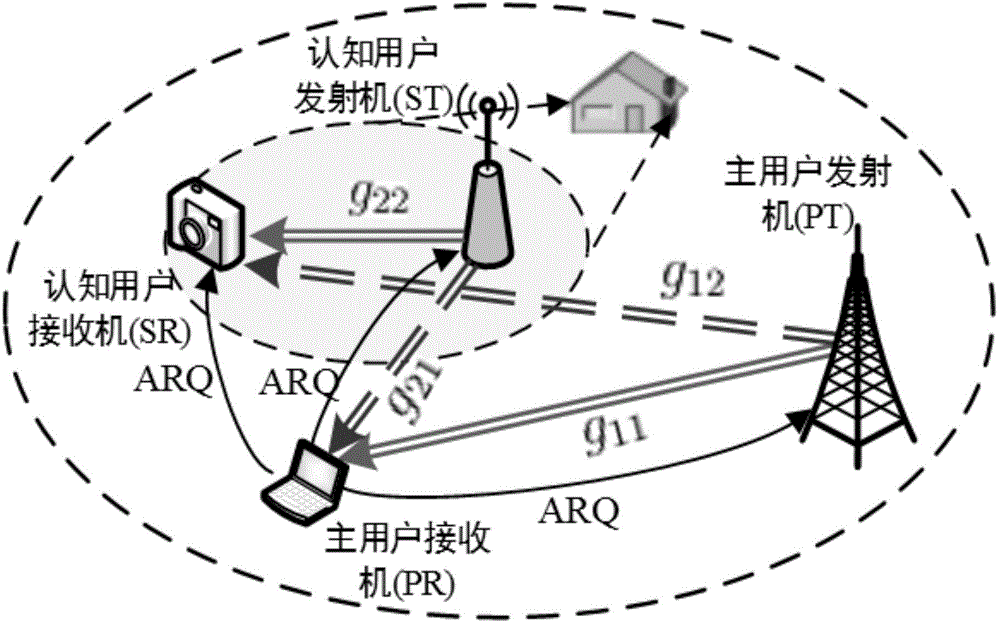
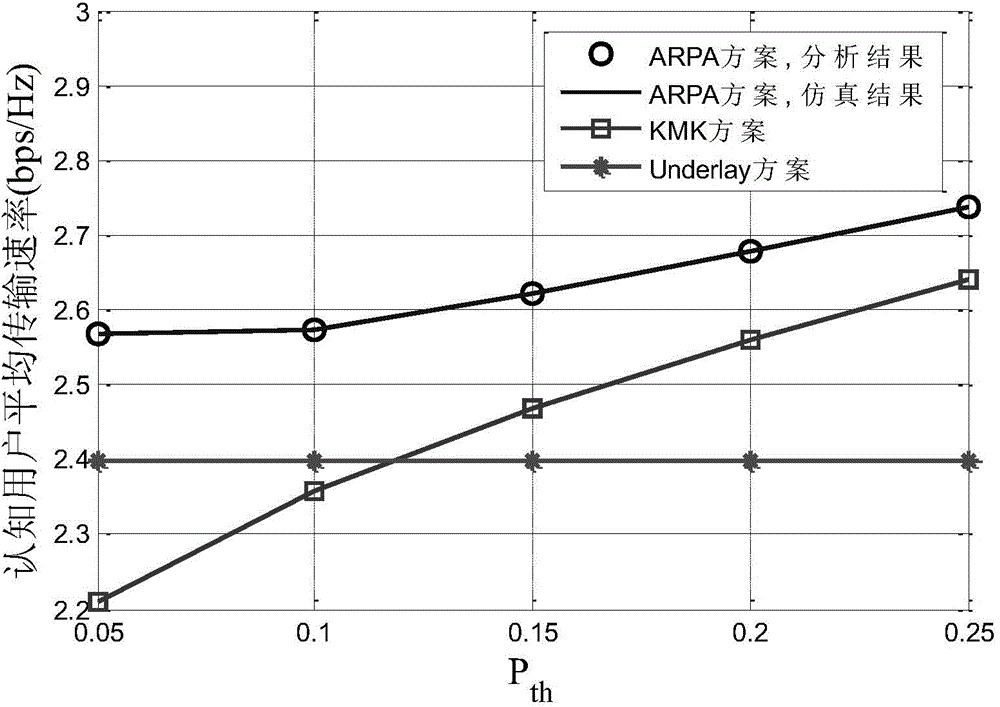
Frequency spectrum resource sharing method for authorized user oriented automatic repeat request in cognitive radio network
ActiveCN104936191AProtect normal transmissionGuaranteed transmission qualityNetwork planningCognitive userFrequency spectrum
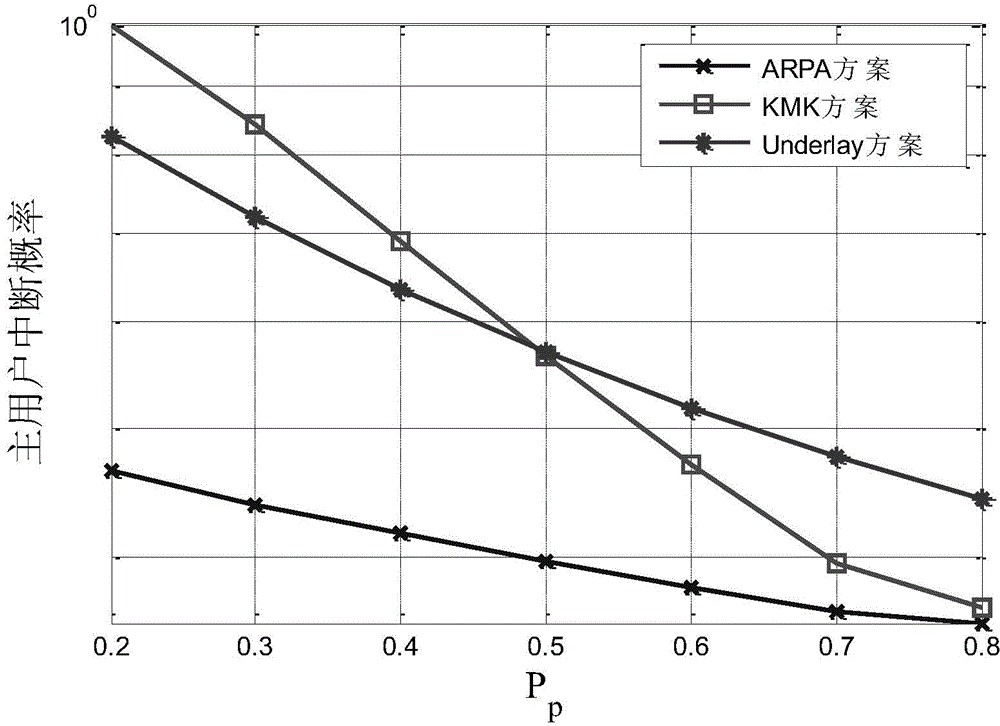
The invention discloses a frequency spectrum resource sharing method for an authorized user oriented an automatic repeat request in cognitive radio network, and belongs to the technical field of radio communication. A time division mechanism is used, and each data frame of the cognitive radio network is halved into two time slots; in the first time slot, the authorized user carries out first transmission, and a cognitive user shares a channel in the Underlay transmission manner; and in the second time slot, the authorized user carries out repeated transmission according to information of automatic repeat request, and the cognitive user shares the channel under the condition that the interruption performance of the authorized user is ensured. The problem of maximizing the average transmission speed of the cognitive user is established, and solved to obtain the power distribution scheme of the cognitive user in the repeat transmission time slot; and interference is eliminated, so that the cognitive user can obtain high transmission speed, and the ARQ information of the authorized user can be used by the cognitive user to protect transmission of the authorized user and further to reduce the interruption possibility of the authorized user.
Owner:XI AN JIAOTONG UNIV
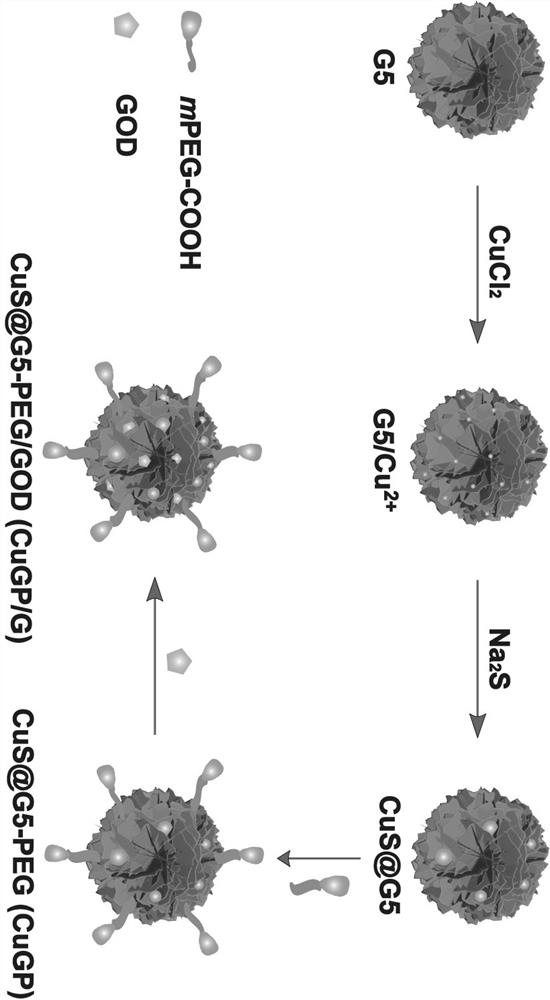
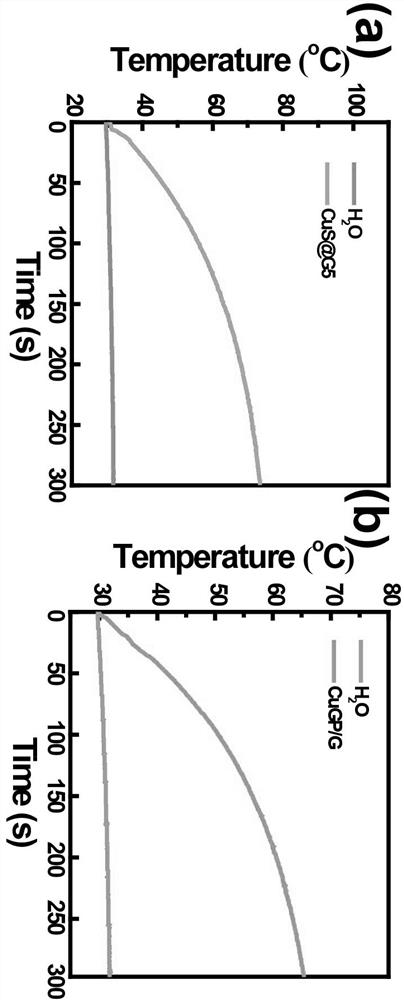
Preparation method and application of copper sulfide/hyperbranched macromolecular nano bionic enzyme
ActiveCN112089836AEnhanced near-infrared absorption propertiesStrong near-infrared absorption propertiesPeptide/protein ingredientsEnergy modified materialsPtru catalystTumor therapy
The invention relates to a preparation method and application of a copper sulfide / hyperbranched macromolecular nano bionic enzyme. An intelligent nano enzyme system is constructed to realize pH-controllable chemical kinetics enhanced photo-thermal anti-tumor therapy so as to solve the problem of high recurrence of lethal cancer. According to the nano bionic enzyme system, a copper sulfide nano particle core is used as a photo-thermal agent and a Fenton-like catalyst, and a hyperbranched macromolecular polymer is used as a template to wrap copper sulfide and graft glucose oxidase. Research results prove that the prepared nano bionic enzyme system has excellent chemical kinetics and photo-thermal therapy performance in a slightly acidic environment of tumors, can efficiently inhibit growth and recurrence of the tumors, and provides a new strategy for clinical treatment of high-recurrence middle and advanced stage cancers.
Owner:WENZHOU MEDICAL UNIV
Self-supporting cicada-preventing butterfly cable and production equipment for processing same
PendingCN111399151AOptimize the space areaIncrease fiber densityFibre mechanical structuresCore (optical fiber)Electrical and Electronics engineering
The invention discloses a self-supporting cicada-preventing butterfly cable which comprises an optical cable body. The optical cable body comprises an outer sheath, a communication unit and a reinforcer, and the outer sheath wraps the communication unit and the reinforcer; the communication unit comprises a winding optical fiber ribbon and two symmetrically arranged protection sheets, and the winding optical fiber ribbon is arranged between the two protection sheets; the two sides of the outer sheath are respectively provided with two tearing grooves, and the distance between the two tearing grooves at one side is greater than the width of the protection sheet, thereby solving the problem that the optical fiber attenuation exceeds the standard or the structure of the optical cable is damaged because cicadas are attached to the optical cable. The invention also discloses production equipment for processing the self-supporting cicada-preventing butterfly cable, the protection sheet pay-off rack is additionally arranged, and the extrusion molding die core and the extrusion molding die sleeve of the plastic extruding machine are improved so that the production process of integrated extrusion molding can be completed, the integrated molding of the novel optical cable is realized, and the production efficiency is relatively high.
Owner:FURUKAWA ELECTRIC XIAN OPTICAL COMM
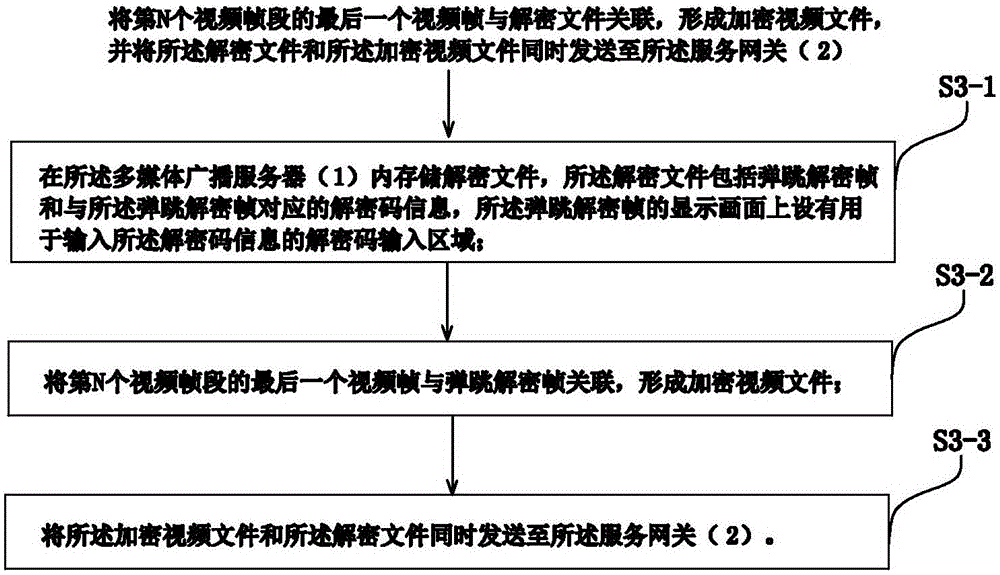
Safety transmission method and system for multi-media broadcast video
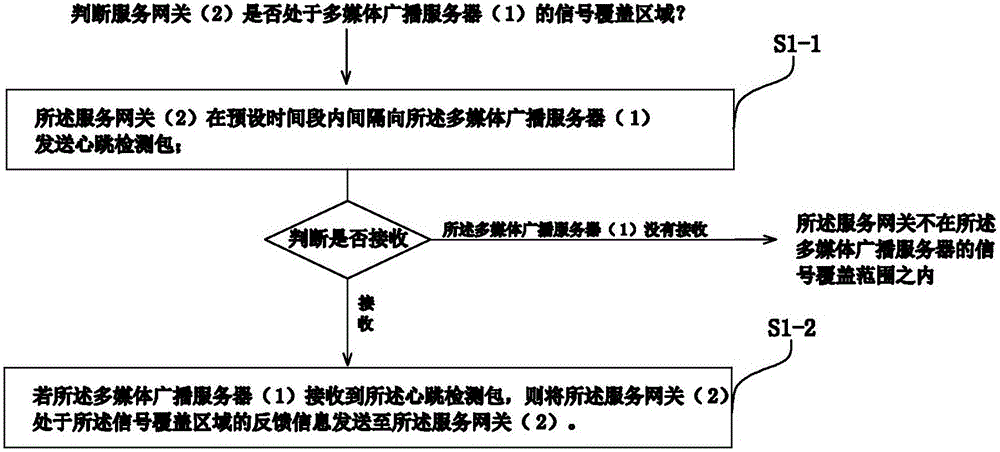
ActiveCN106851338ALow costProtect normal transmissionSelective content distributionSecure transmissionTerminal equipment
The invention provides a safety transmission method and a safety transmission system for a multi-media broadcast video. The safety transmission method comprises the following steps: whether a service gateway is within a signal coverage area of a multi-media broadcast server is judged; the multi-media broadcast server divides the multi-media broadcast video into N video frame segments; the last video frame of the N video frame segments is associated with a decryption file to form an encrypted video file, and the file is sent to the service gateway; the service gateway demodulates the file according to a demodulation method with the multi-media broadcast server, and the demodulated file is transmitted to terminal equipment; and after decrypting the file, the terminal equipment plays the multi-media broadcast video. According to the method and the system provided by the invention, cost of the terminal equipment can be effectively reduced, meanwhile video encryption is effectively performed during a data transmission process to prevent the received video from being illegally attacked, tampered, downloaded and pirated, effectively protection is performed on the transmission of the mobile multi-media broadcast video, and safety transmission is achieved.
Owner:ZHONGGUANG REDIANYUN TECH CO LTD
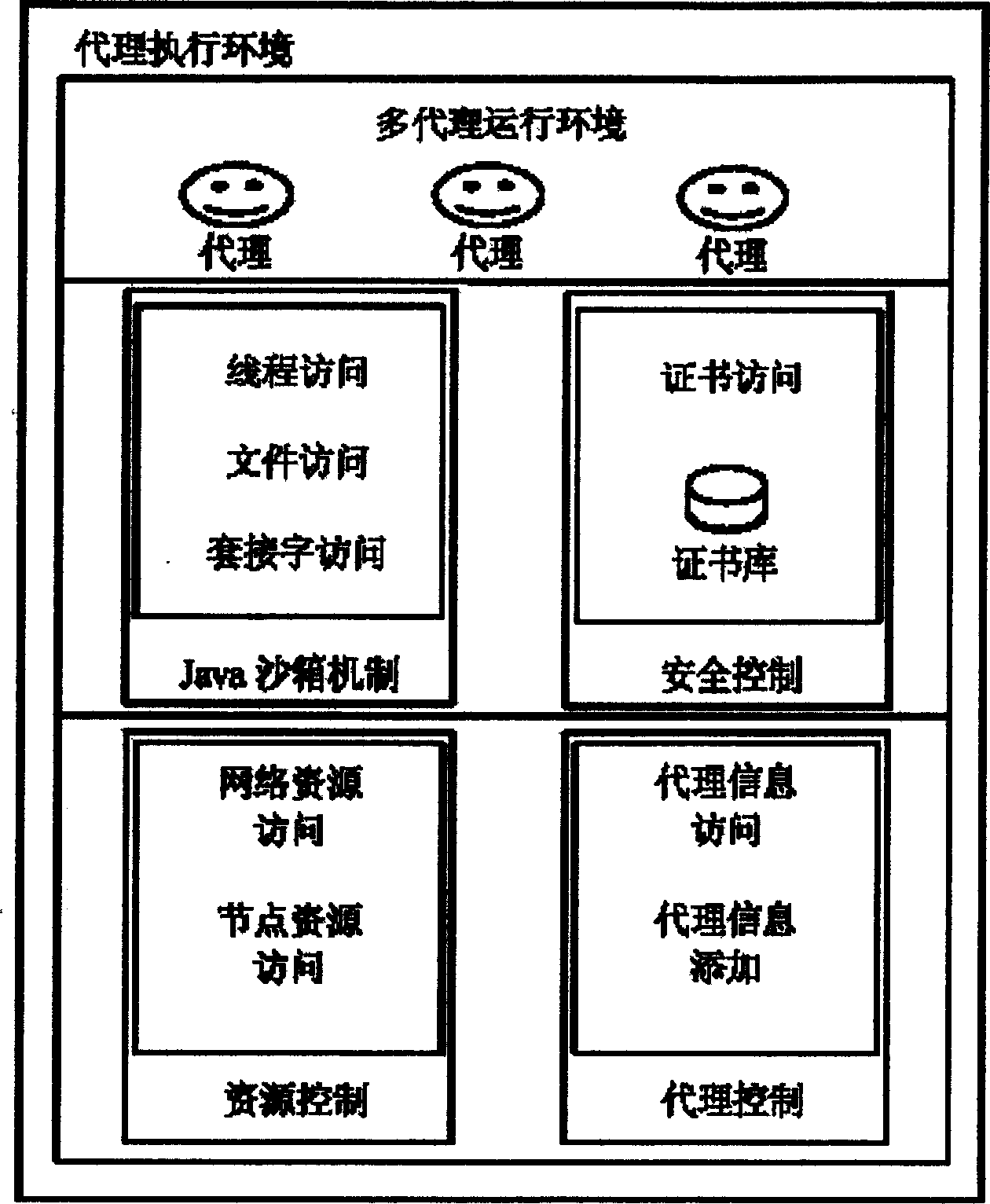
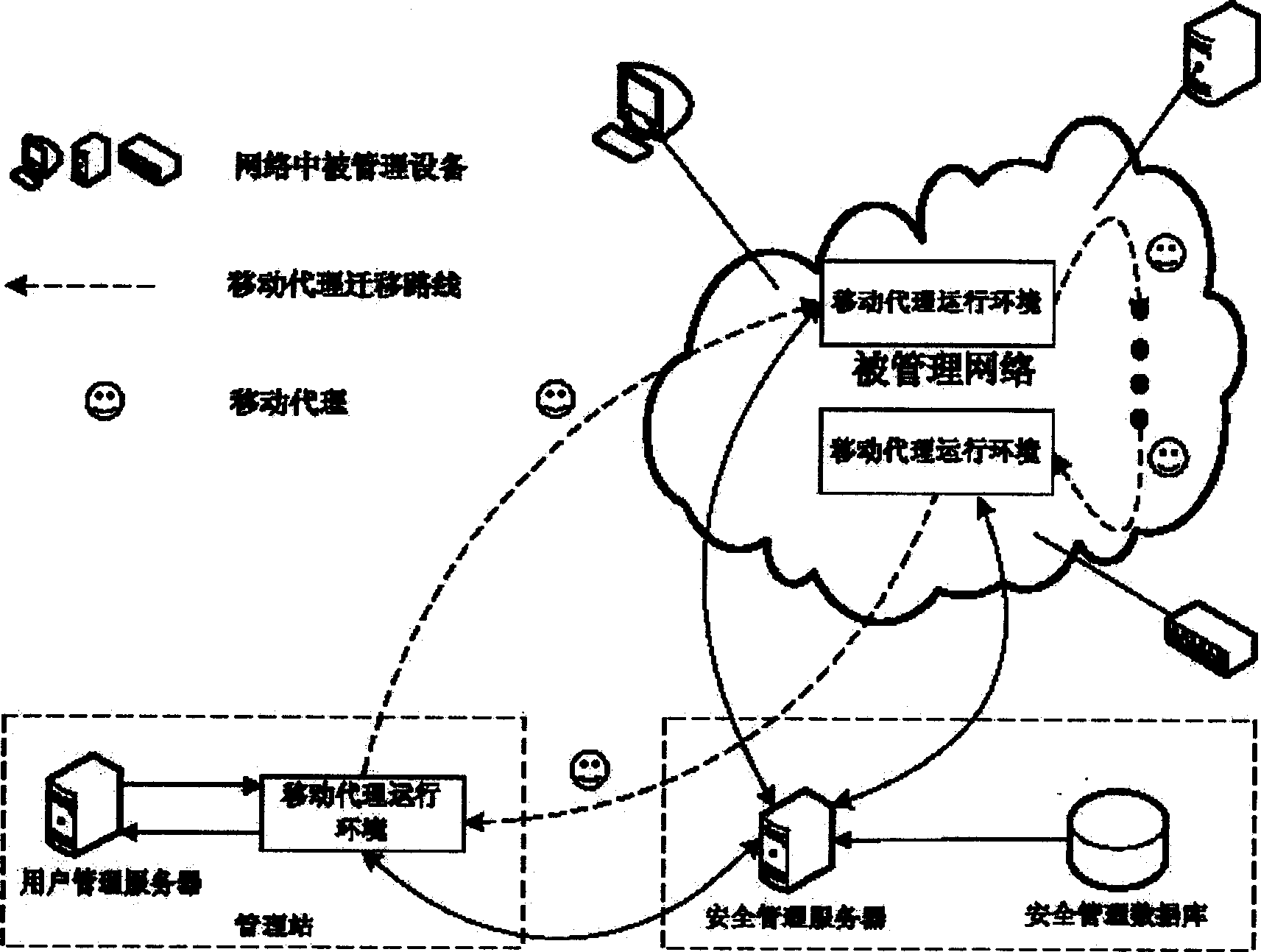
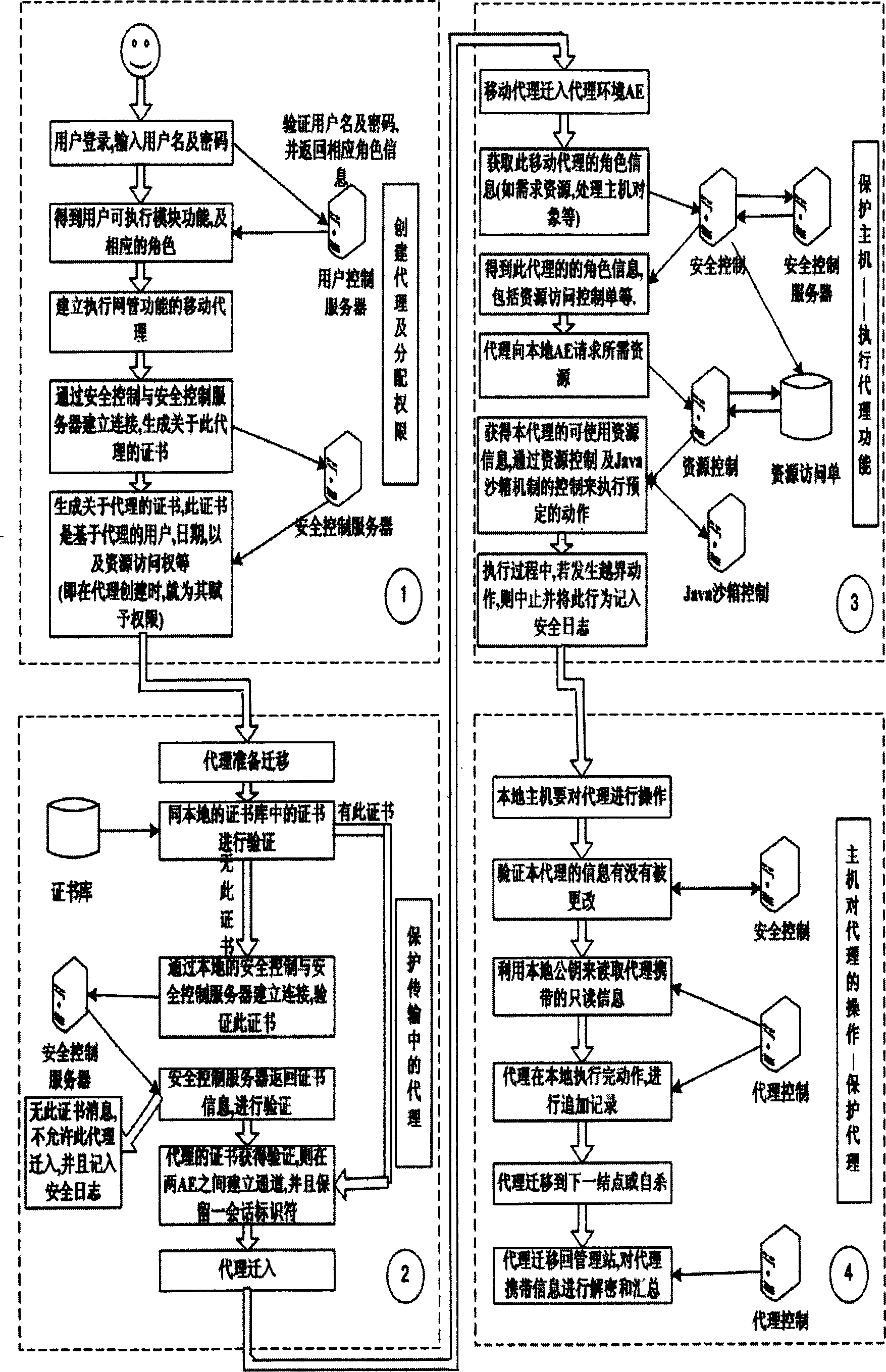
Safety structure of all-around protecting mobile proxy network management application
InactiveCN1845508AAvoid complexityIncrease flexibilityData switching networksExtensibilityNetwork management application
The security framework to protect mobile agent network manage application fully comprises: user logs on agent running environment to create mobile agent and assign right according to task request; the agent transfers the protection to be transmission to the target host for execution; while, it should prevent host resource from malicious destroy as well as the agent from malicious host attack. This invention improves network management security, and reduces protection difficulty and source consumption.
Owner:NANJING UNIV OF POSTS & TELECOMM
A cross-platform information input and output protection system
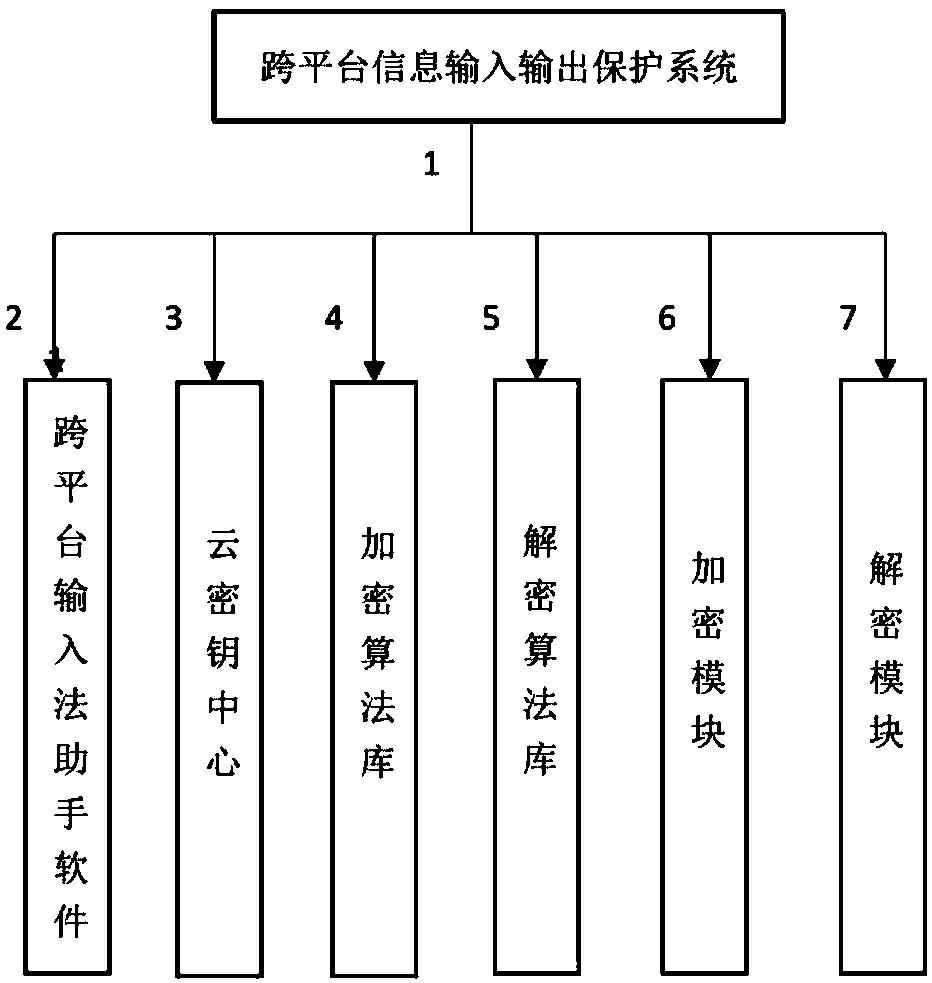
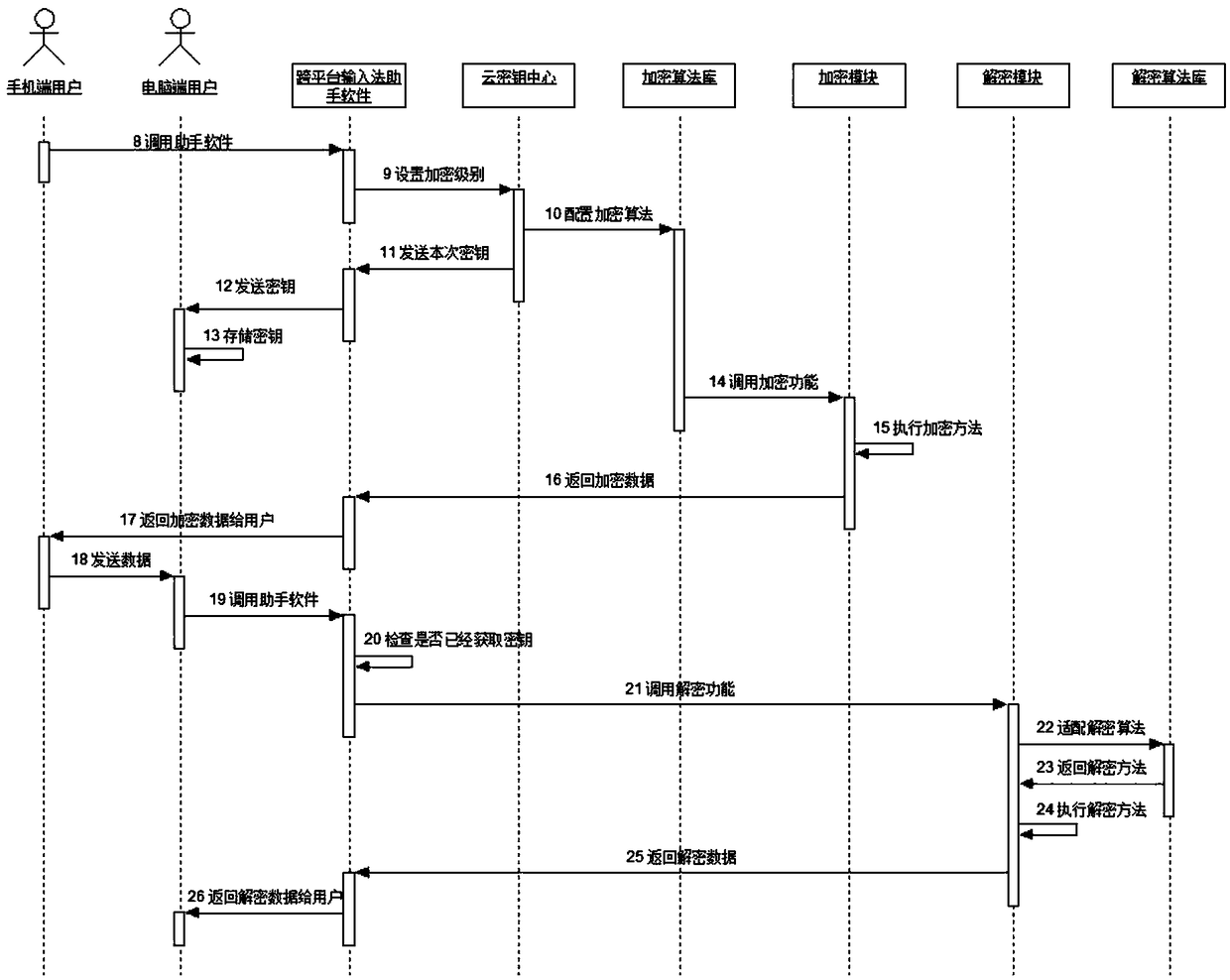
InactiveCN109067700AFully protected transmissionProtect normal transmissionKey distribution for secure communicationComputer hardwareData synchronization
The invention discloses a cross-platform information input and output protection system, comprising: 1. a cross-platform input method assistant software, which can be installed on a plurality of operating systems, is used for setting encryption / decryption keys and managing key information, encrypting data and decrypting data, 2. a cloud key cent, including key generation, key distribution and keymanagement modules, can synchronize data between the local key database and the remote key database system, 3. an encryption algorithm library, which can use or combine multiple encryption algorithms,4. a decryption algorithm library, which can automatically match and combine the decryption algorithm according to the parameters of the key, 5. an encryption module which can quickly encrypt the information data input into the buff area by the system of the device through calling the encryption function by the cross-platform input method assistant software, and 6. a decryption module, which cancall the decryption function to decrypt the information data in the system output buffer of the device quickly. The invention can effectively protect various kinds of privacy information of people innetwork communication, and has strong practicability.
Owner:JIANGSU UNIV OF SCI & TECH
Protective flavored thong
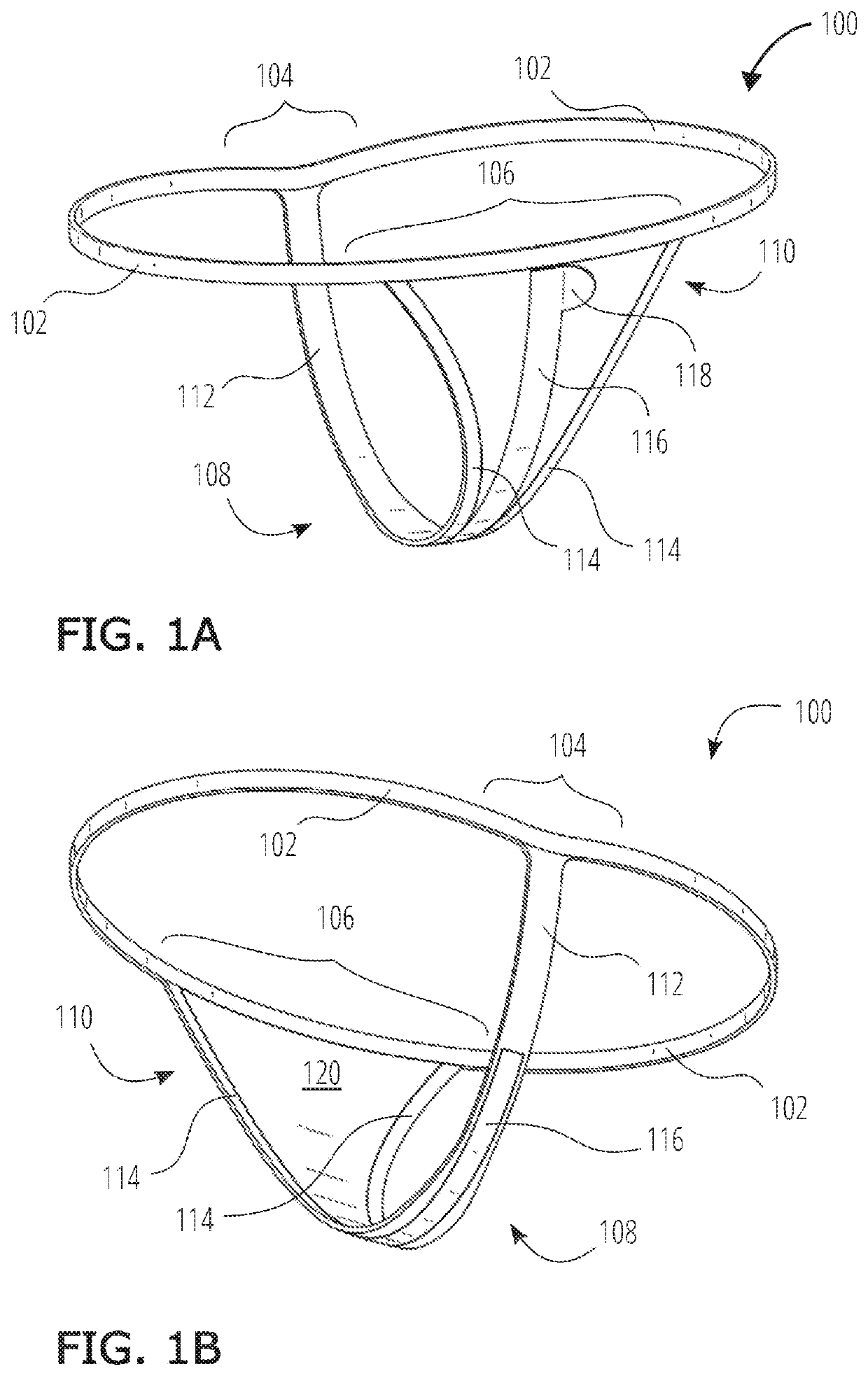
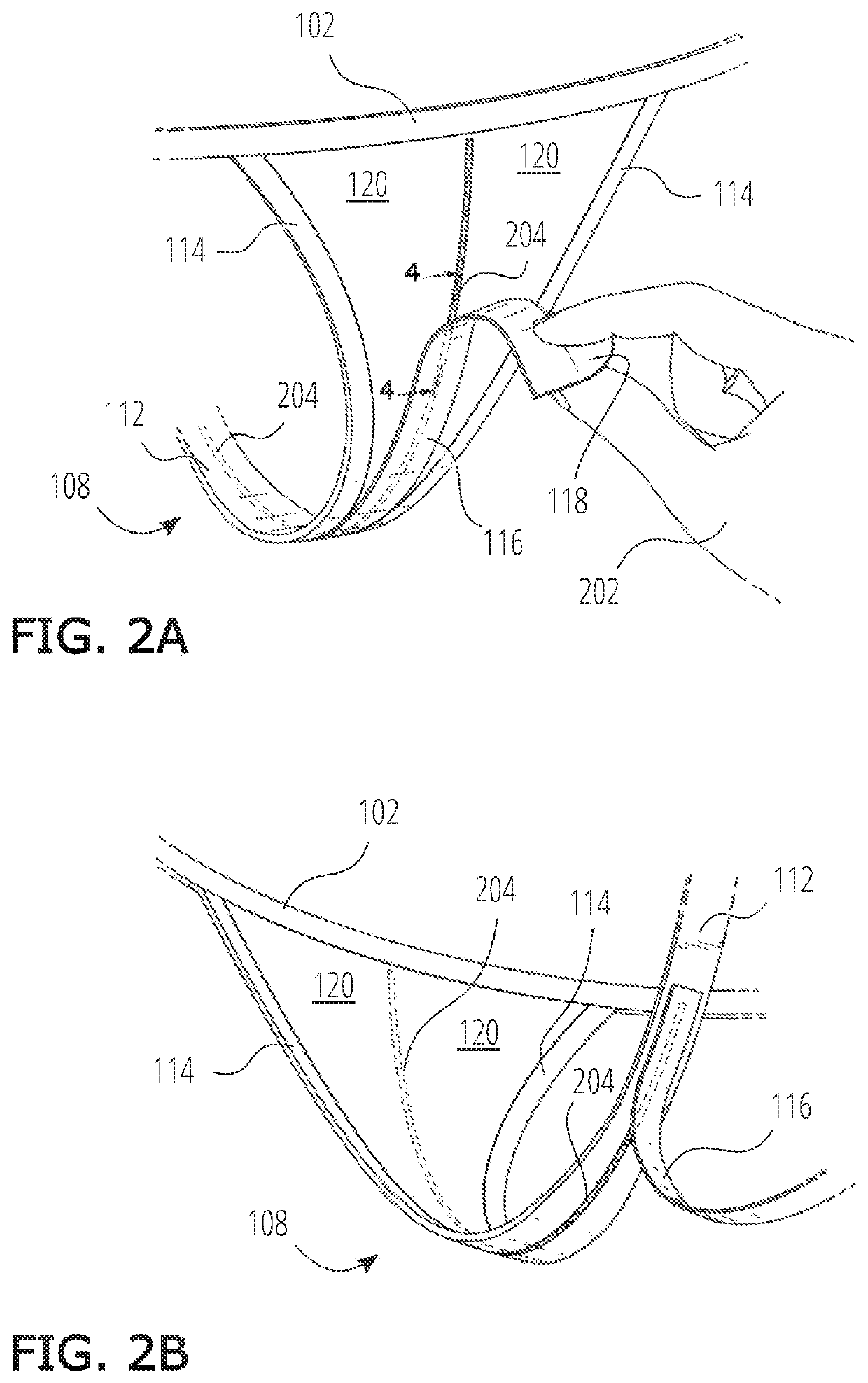
InactiveUS20200297039A1Easy to wearAccentuatesConfectioneryFemale contraceptivesLow-density polyethyleneTactile sensation
A protective flavored thong including a waistband configured to extend around the waist of a wearer, a crotch band, and at least one flavor ridge applied centrally along the crotch band. The thong provides an erotic female under-garment that is convenient to wear, visually appealing, accentuates the wearer's womanly curves, and provides protection against sexually transmitted diseases during cunnilingus for both the wearer and her sexual partner. Additionally, the thong includes a flavor ridge that imparts a pleasant flavor, also providing lingual and tactile guidance to the woman's partner during cunnilingus in an environment with possibly limited visual guidance. The flavor ridge can be applied to a backing layer that is applied centrally along the crotch band. The crotch band can include a panel of low-density polyethylene (LDPE) to serve as a protective barrier against transmission of STDs between the wearer and her partner during cunnilingus.
Owner:PARKER JEFFREY DEAN +2
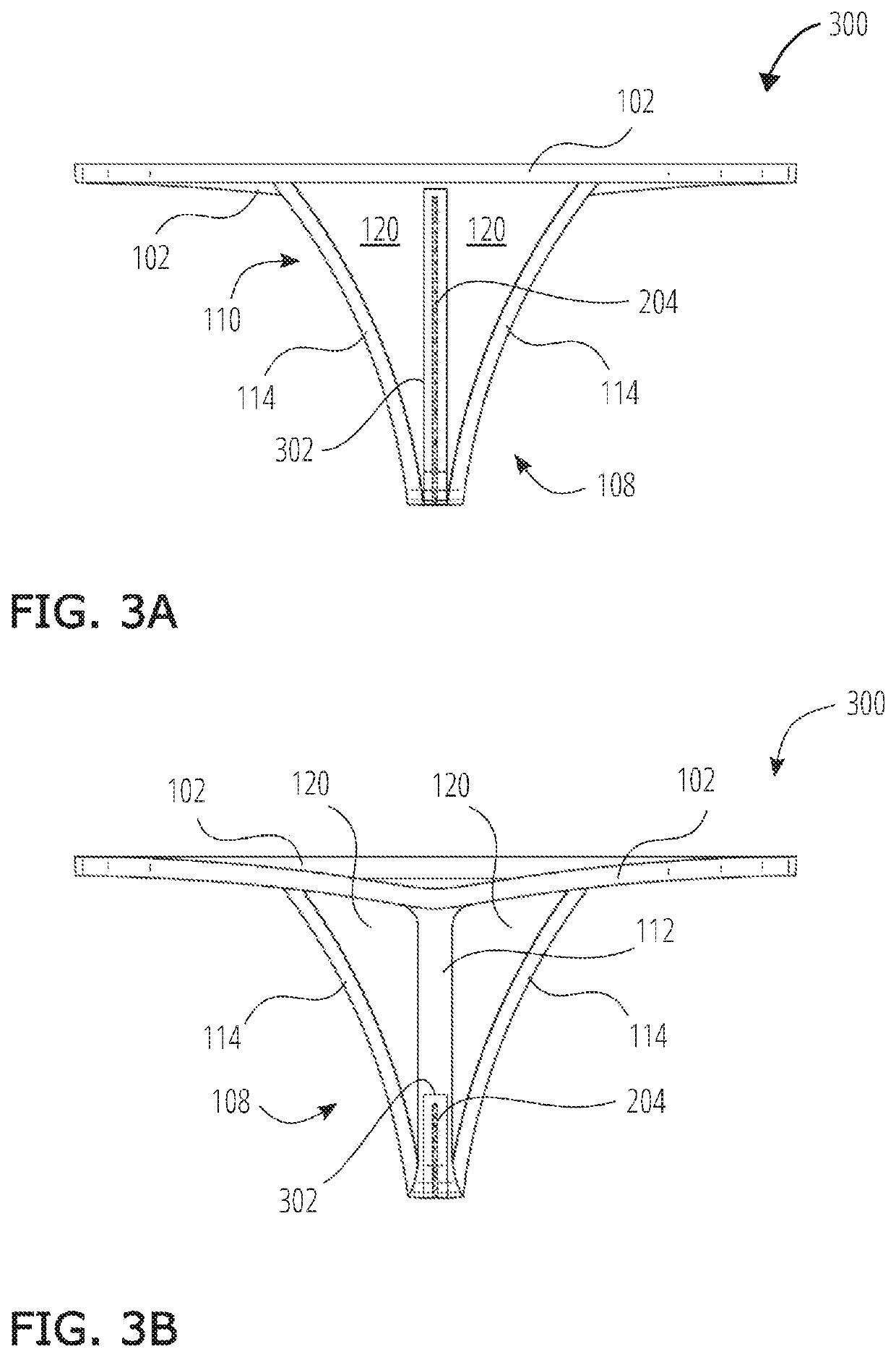
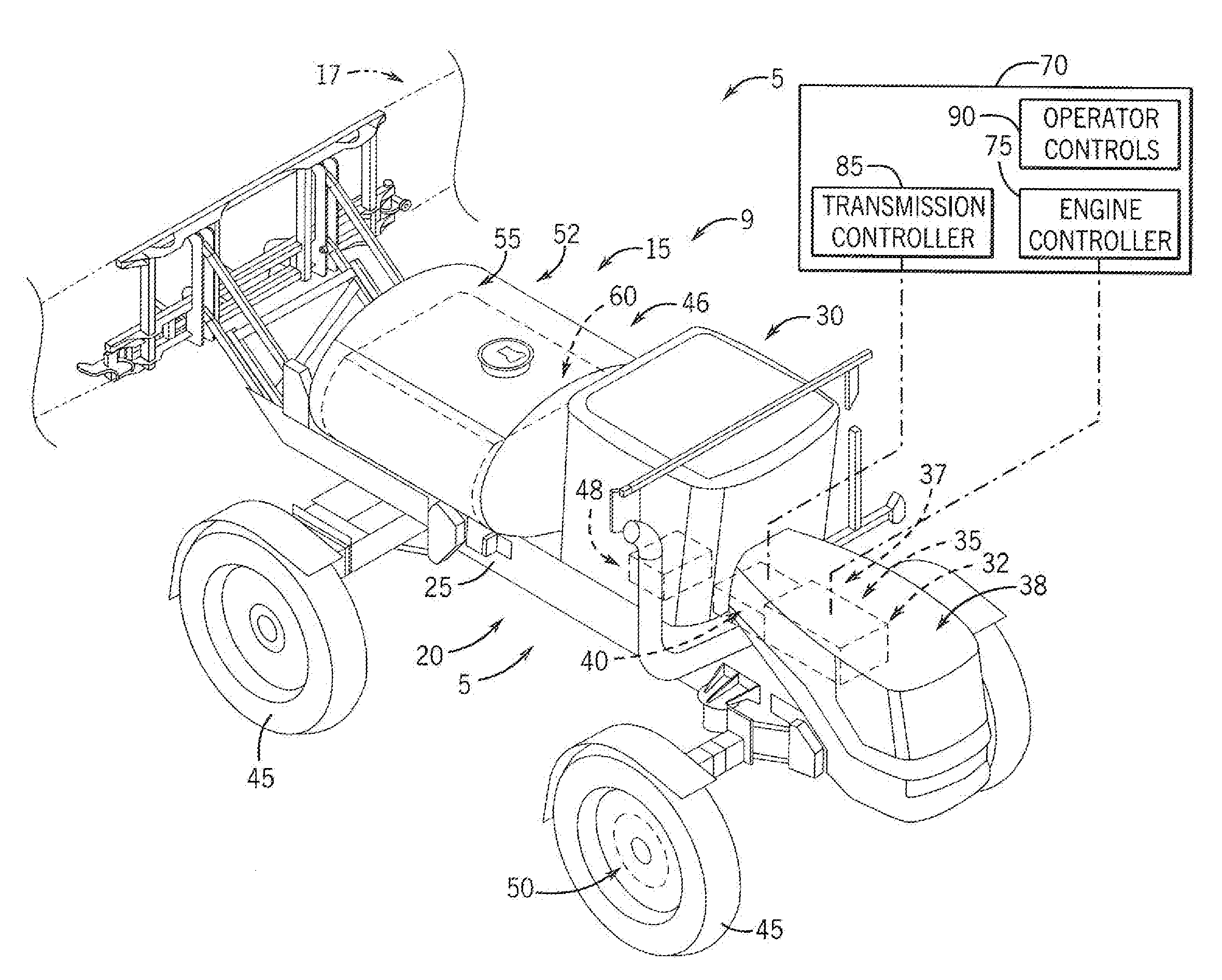
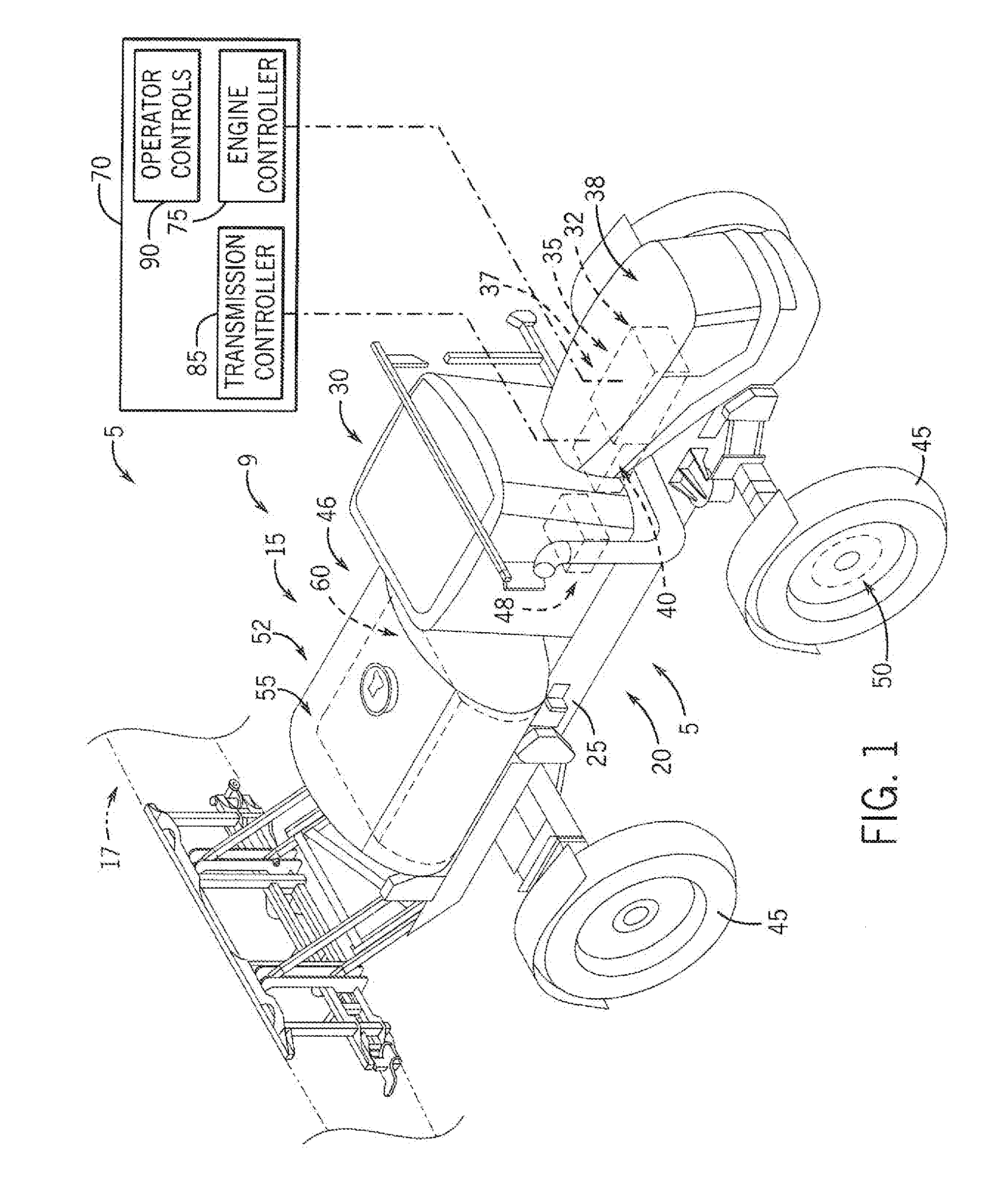
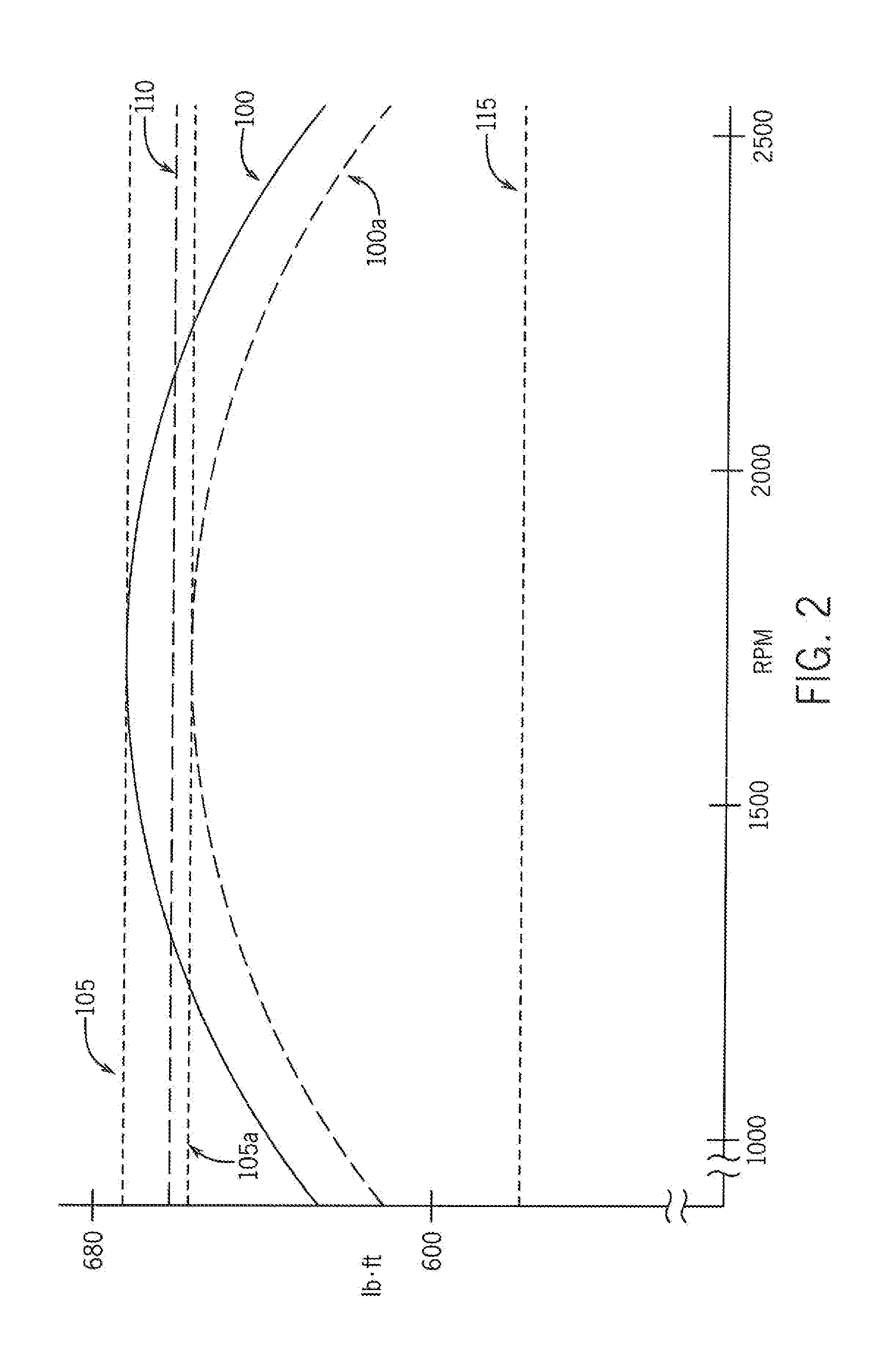
Self-Propelled Off-Road Vehicle With System For Torque Control At Shift Points
ActiveUS20160318517A1Protect normal transmissionAgricultural vehiclesElectrical controlControl systemDrivetrain
A self-propelled off-road agricultural vehicle such as a product applicator is provided with a system for torque control at shift points. The self-propelled applicator has a drivetrain configured with two power levels of its engine. One power level limits engine power output to a value at or below a shifting-state clutch rating of the transmission to protect the transmission while shifting. The second power level allows engine power to exceed a shifting-state clutch rating of the transmission when the transmission is not shifting.
Owner:BLUE LEAF I P INC
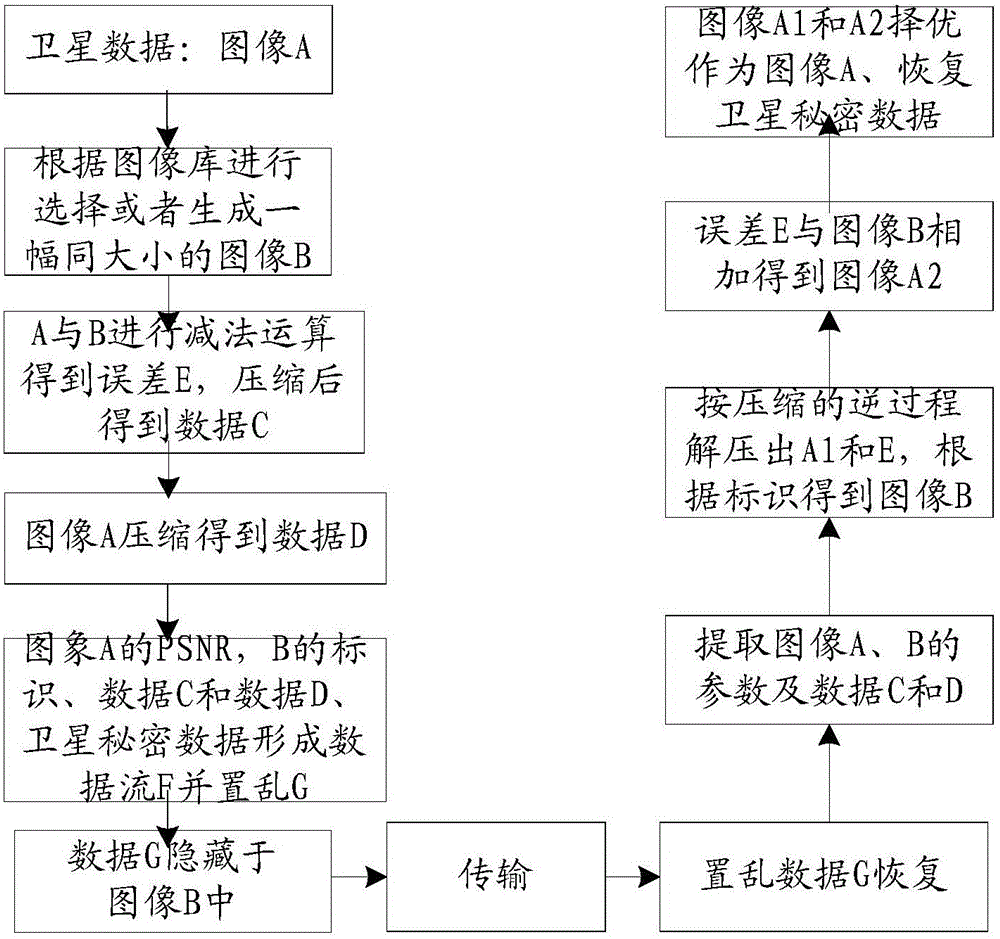
Real-hidden and fake-display satellite data transmission method
ActiveCN105025195AEasy to implementImprove concealmentDigital video signal modificationSatellite dataImaging processing
The invention provides a real-hidden and fake-display satellite data transmission method, and aims at solving the problems in data transmission safety and secrecy. After being processed by the method, satellite image data seems like other image data, and satellite secrete data is hidden; and after the transmission data is received, fake data processed by the transmitting end is directly obtained, and the reception end can directly recover the fake data to obtain real satellite image data and secret data. The method is based on information hiding and image processing, real data is hidden and fake data is displayed in the information transmission process, and the method is characterized by disguising information, hiding information, keeping information secret and preventing information from interception.
Owner:XIAN INSTITUE OF SPACE RADIO TECH
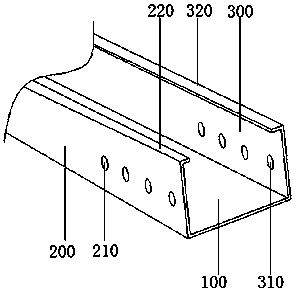
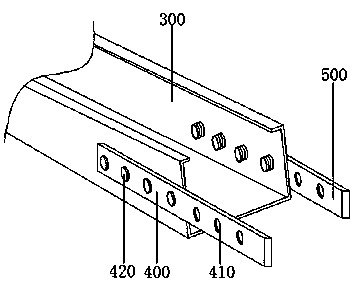
Integrally formed stainless steel cable bridge and preparation method thereof
ActiveCN110137870AImproves Strength and ToughnessAvoid local settlement deformationElectrical apparatusInformation transmissionCombustion
The invention discloses an integrally formed stainless steel cable bridge and a preparation method thereof in the technical field of cable fittings. The integrally formed stainless steel cable bridgecomprises a bottom plate, a left folded plate, a right folded plate, a left mounting plate and a right mounting plate. A left side wall of the bottom plate is integrally formed and is connected to theleft folded plate, and a right side wall of the bottom plate is integrally formed and is connected to the right folded plate. According to the integrally formed stainless steel cable bridge and the preparation method thereof, the cable bridge can be quickly and effectively prepared by the combination of accessories and the improvement of preparation process, the steps are simplified, a compression plate containing a top pad and a bottom pad is added inside, the strength and toughness of stainless steel are increased, the local settlement deformation of the stainless steel with strong ductility after bearing weight is avoided, the compression plate is made of expanded graphite powder which can be released from ports of a left folded side and a right folded side after being exposed to hightemperature, the internal space of the cable bridge is filled, the cable is protected, the risk of open flame combustion is reduced, the loss is effectively reduced, and the safety of information transmission is protected.
Owner:ANHUI JINDI ELECTRIC APPLIANCES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com