Secure transmission method and circuit of chip security information
A security information and chip technology, applied in computer security devices, electrical digital data processing, record carriers used by machines, etc., can solve problems such as chip security information leakage, and achieve the effect of enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
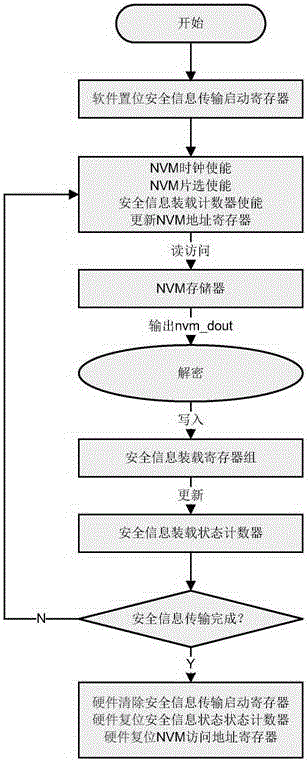
[0017] Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
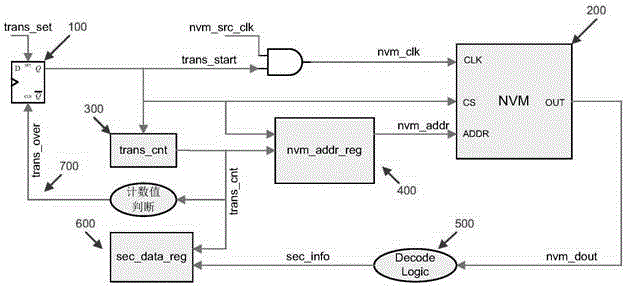
[0018] Such as figure 1 As shown in the schematic diagram of the hardware circuit of the present invention, 100 represents the security information transmission start register, 200 represents the NVM memory for storing security information, 300 represents the security information transmission state counter, 400 represents the NVM access address memory, 500 represents the security information decoding circuit, and 600 represents The security information is loaded into the register set, and 700 represents a sign that the transmission of the security information is completed.
[0019] figure 1 100 in represents the security information transmission start register, which is in an invalid state after the chip is initially powered on or the security information transmission operation is completed.
[0020] figure 1 The 200 in it represents NVM me...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com