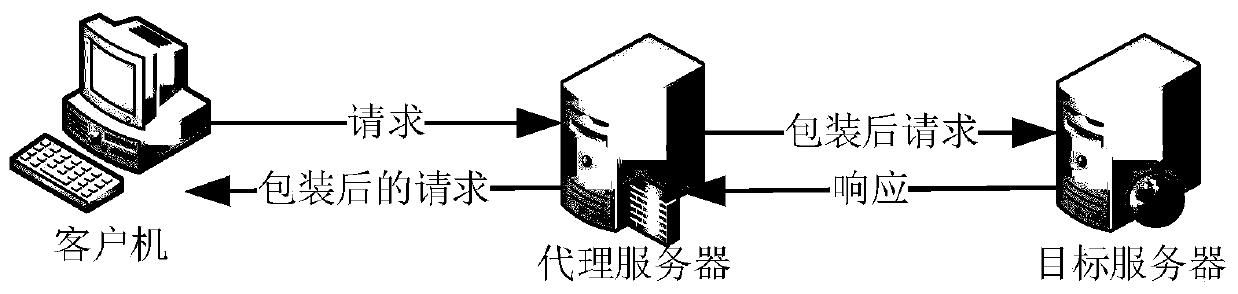
Patents
Literature
50results about How to "Realize security management and control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
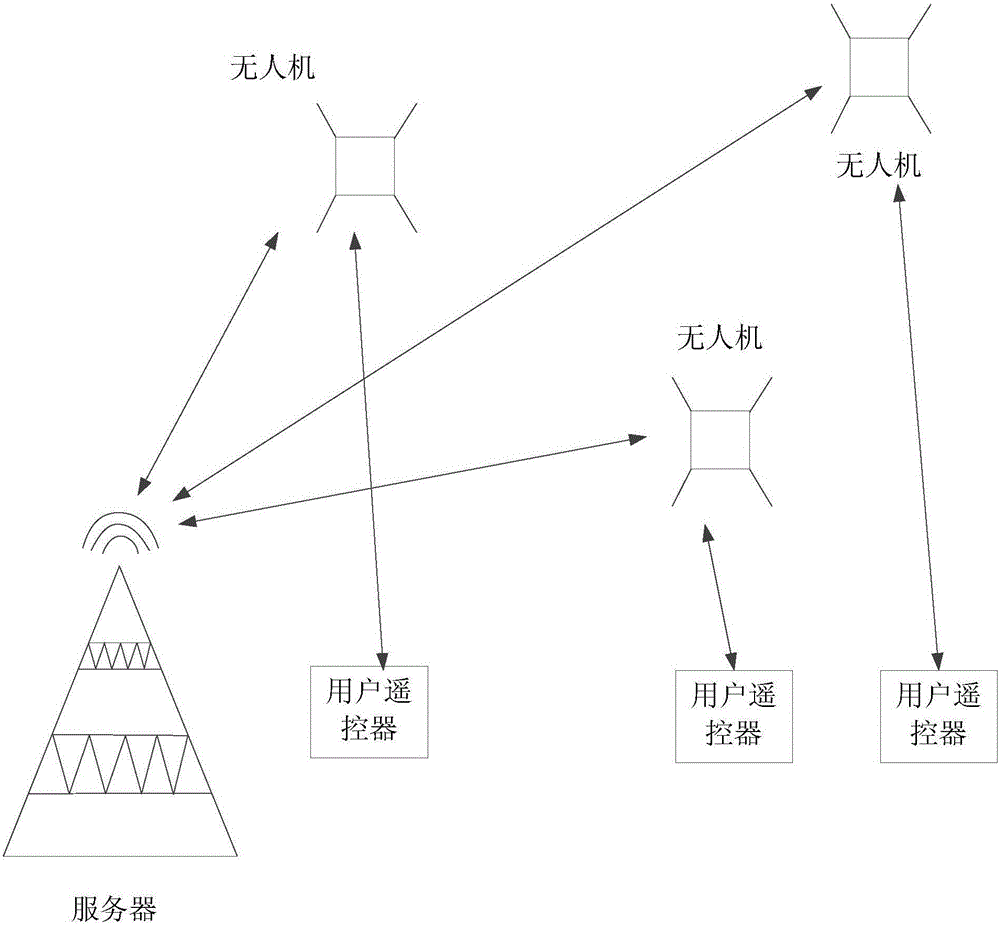
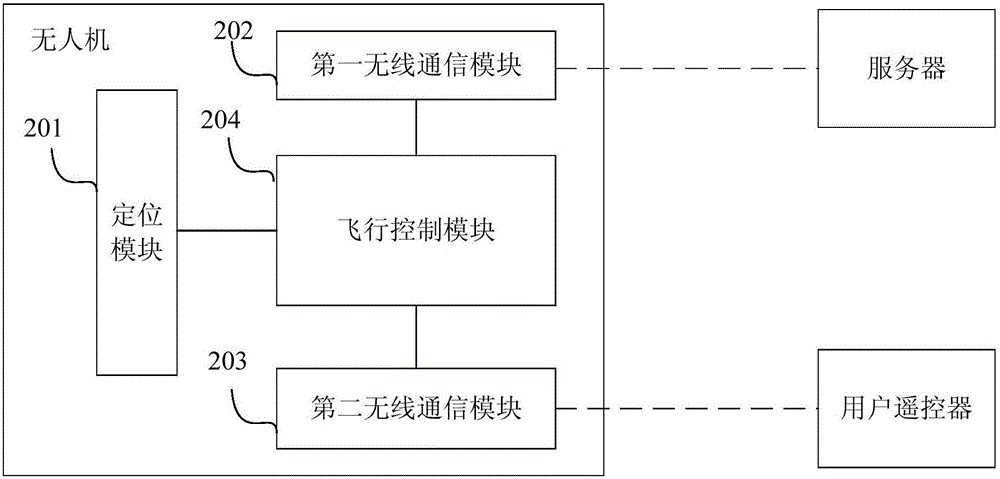
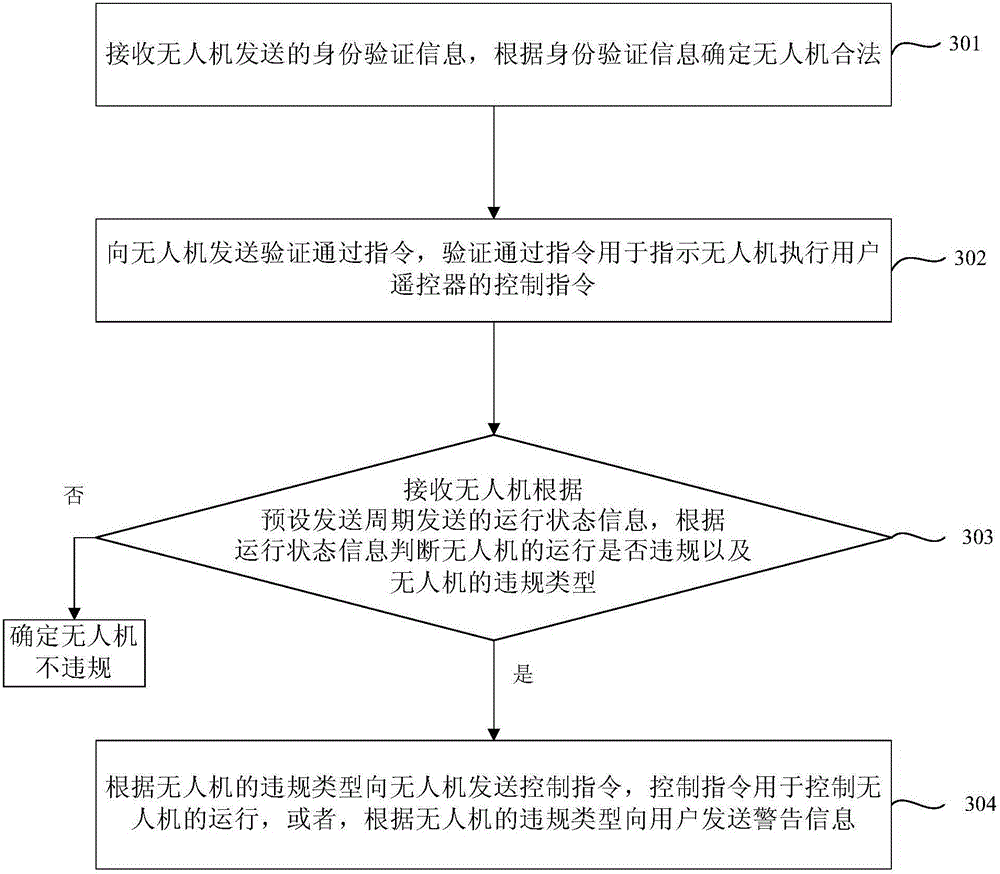
Unmanned aerial vehicle (UAV) air operation security control method, UAV and server
InactiveCN105761550ARealize security management and controlReduce riskAircraft traffic controlRemote controlComputer science
The invention provides an unmanned aerial vehicle (UAV) air operation security control method, a UAV and a server. The method comprises the steps of receiving identity authentication information transmitted by a UAV, and determining whether the UAV is legal according to the identity authentication information; transmitting, to the UAV, an authentication pass-through command for indicating the UAV to execute a control command of a user remote control; receiving operation state information transmitted by the UAV according to a preset transmission cycle, and determining whether the operation of the UAV violates a rule and the type of violation of the UAV according to the operation state information; and if so, transmitting a control command for controlling the operation of the UAV to the UAV according to the type of violation of the UAV, and otherwise, transmitting alarm information to the user according to the type of violation of the UAV. Through the above method, the takeoff of an illegal UAV and the operation of a legal UAV can be restricted, the security operation control of the UAV is achieved, and the risk of UAV operation is reduced.
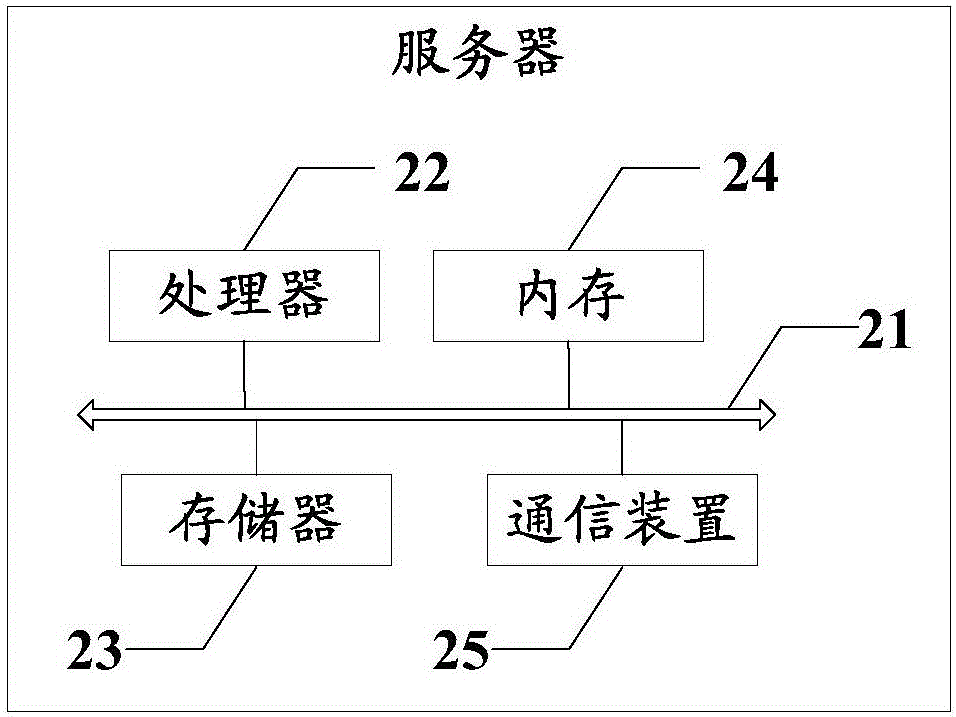
Owner:BEIHANG UNIV
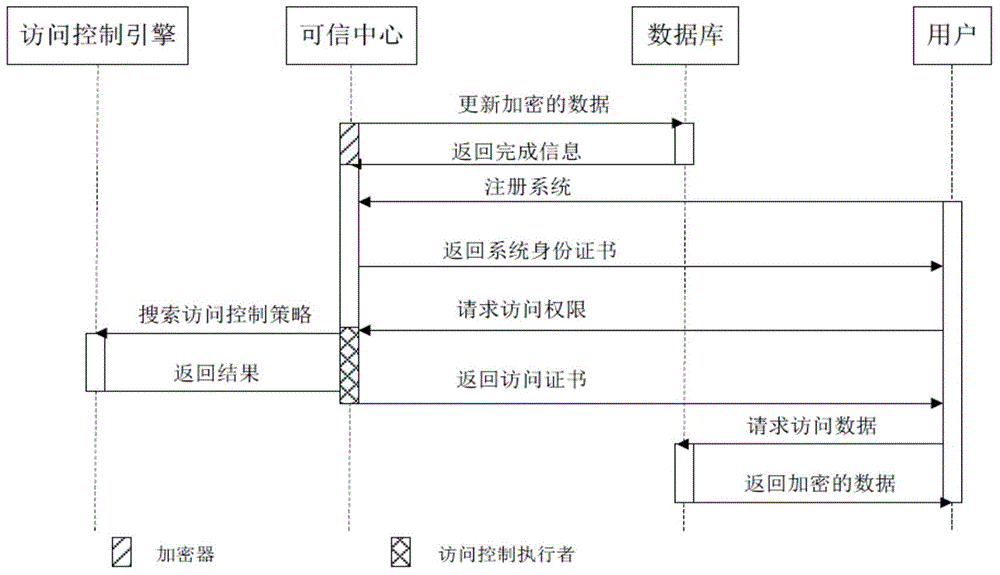
Data security control method and data security control platform
ActiveCN104796290AReflect business valueIncrease profitData switching networksSpecial data processing applicationsFull life cycleEncryption
The invention discloses a data security control method and a data security control platform. The method includes S1, partitioning data according to type and security classification; S2, performing encryption, identity authentication, access control, security audit, tracking and forensics on the data according to a data partitioning result, and distributing corresponding security protection tools for security protection; S3, collecting and normalizing log information generated by the security protection tools, and creating a full-life-cycle security view of the data. The data security control method and the data security control platform have the advantages that fine-grained differential full-life-cycle protection of big data can be achieved, utilization rate of the security protection tools can be increased, and the big data can be subjected to tracking and forensics.
Owner:GUANGDONG POWER GRID CO LTD INFORMATION CENT
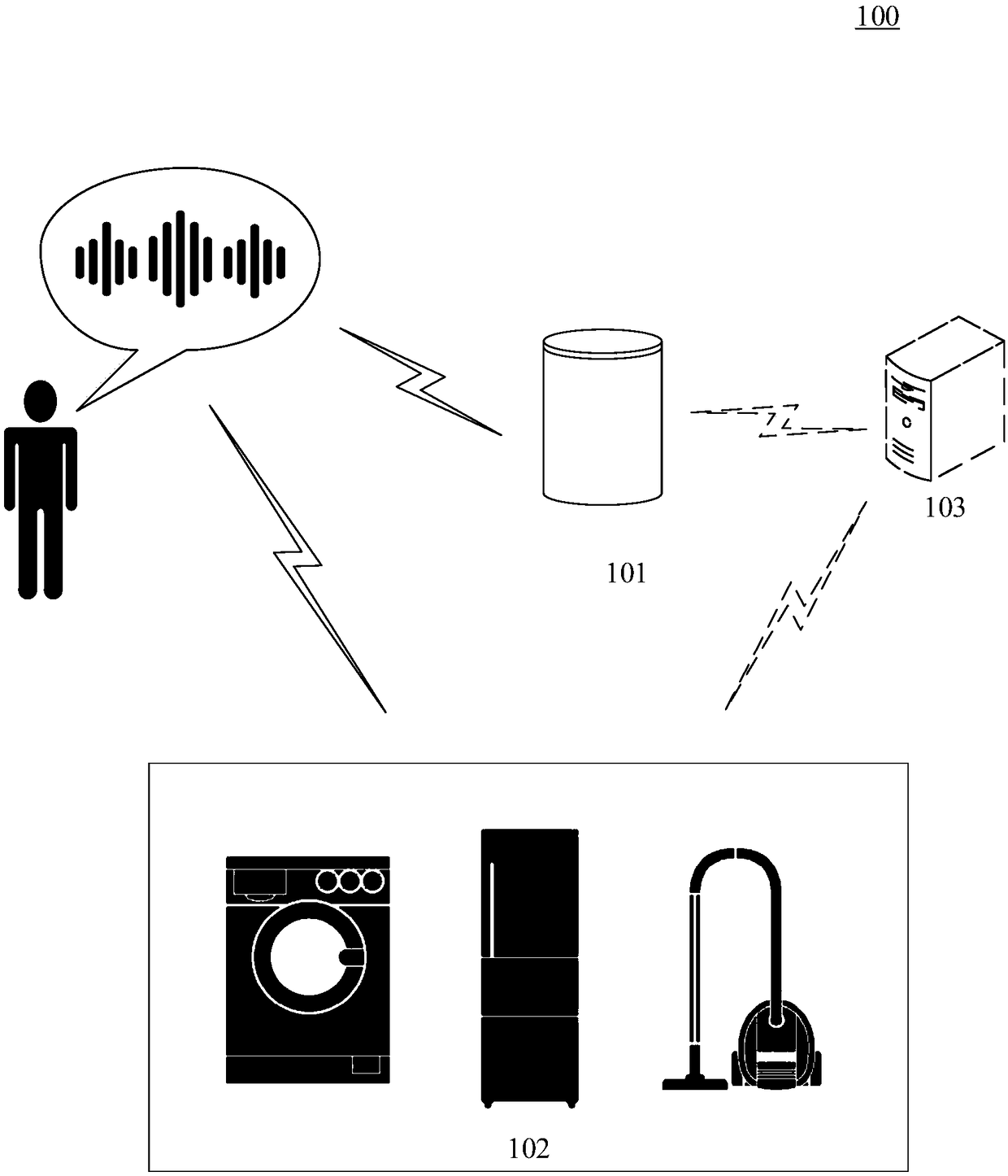
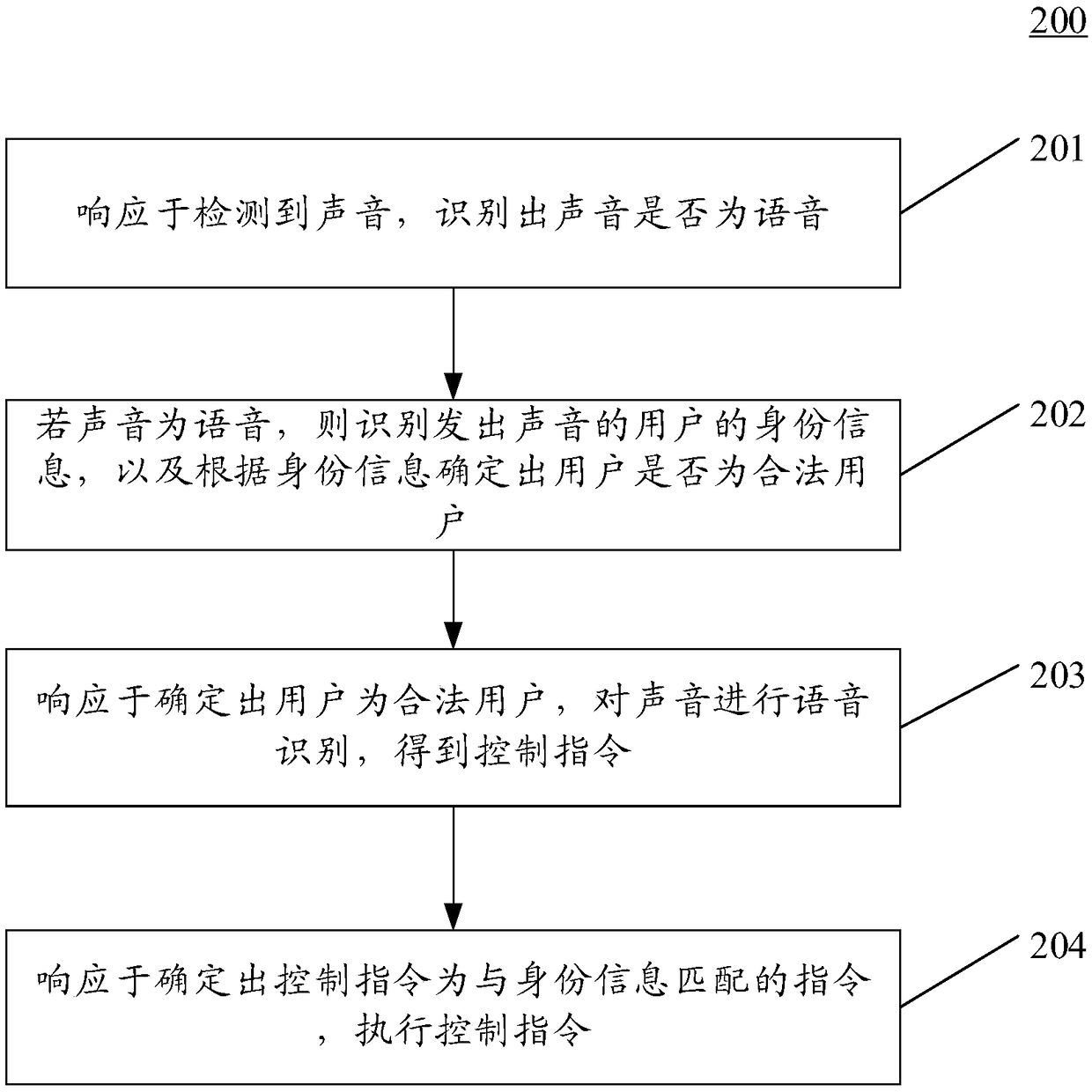
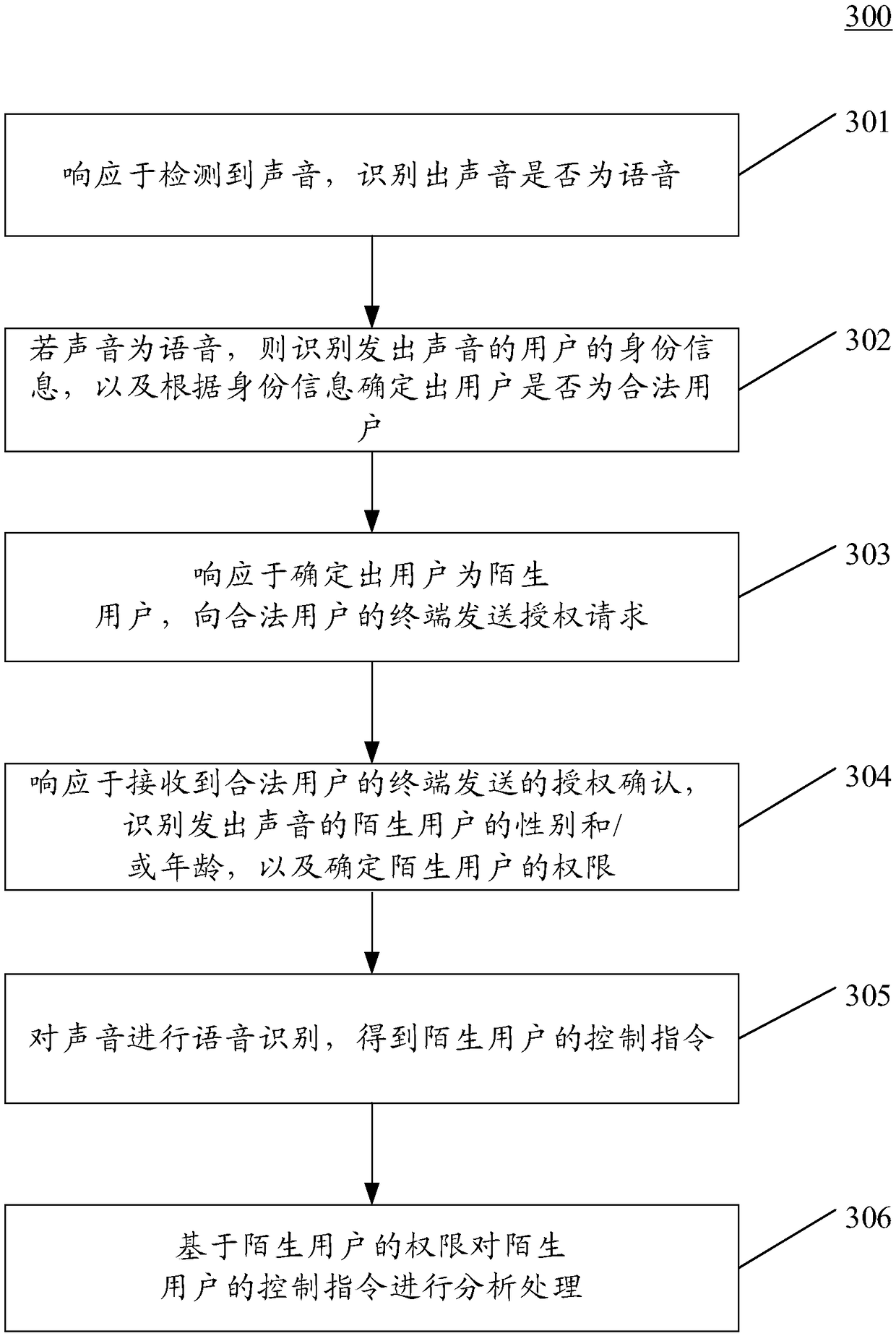
Method and apparatus for controlling smart home appliance
InactiveCN109412910ARealize security management and controlAchieve securitySpeech analysisHome automation networksExecution controlSpeech identification
The embodiment of the application discloses a method and apparatus for controlling a smart home appliance. One specific embodiment of the method includes steps: recognizing whether a sound is a voicein response to detection of the sound; if yes, recognizing identity information of a user emitting the sound, and determining whether the user is a legal user according to the identity information; performing speech recognition on the sound in response to determination that the user is the legal user, and obtaining a control instruction; and executing the control instruction in response to determination that the control instruction is an instruction matched with the identity information. According to the method and apparatus, security management and control of the smart home appliance and security management and security protection of a speaker can be realized.
Owner:SAMSUNG ELECTRONICS CHINA R&D CENT +1
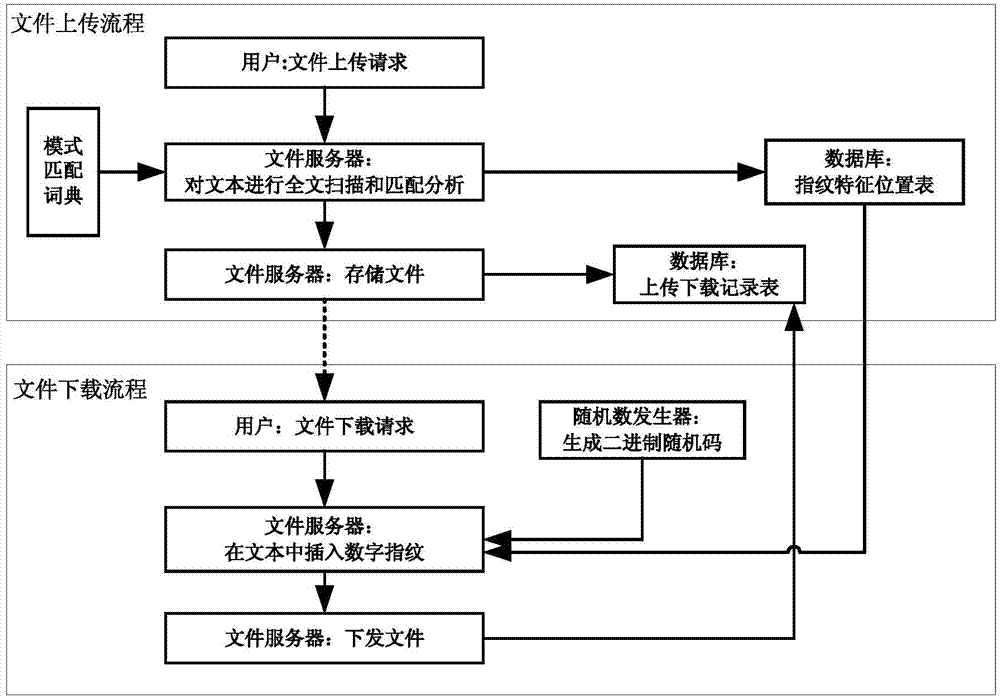
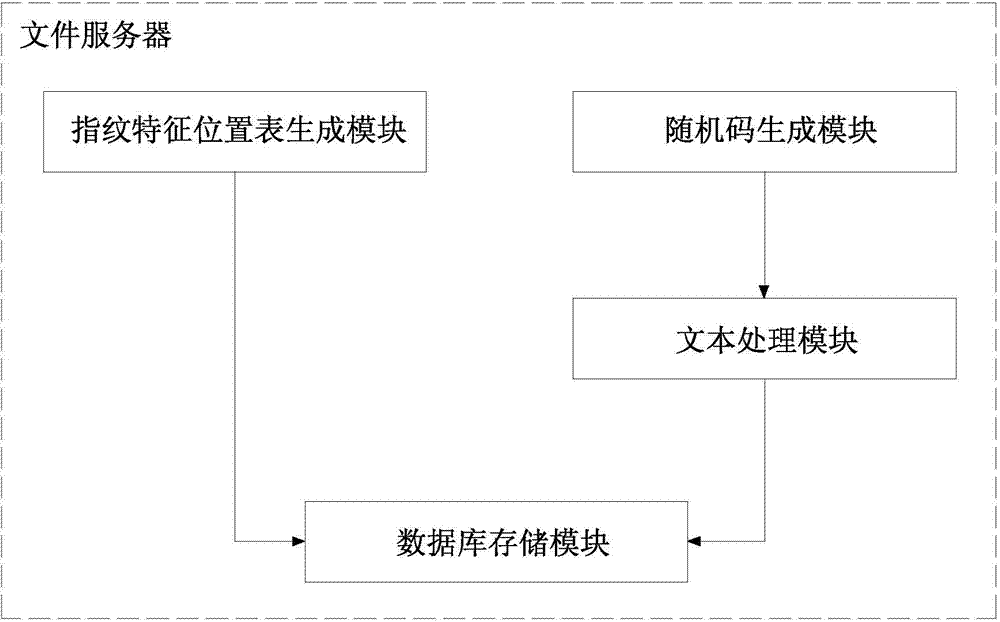
File security control and trace method and system based on digital fingerprints
InactiveCN104715168AImprove robustnessAvoid Malicious ModificationsProgram/content distribution protectionNatural language analysisFile server
The invention discloses a file security control and trace method and system based on digital fingerprints. The method includes the file uploading procedure and the file downloading procedure. In the file uploading procedure, when a user uploads files to a file server, the file server starts a natural language analysis program and conducts full-context scanning and matched analysis on file contexts, a position where the digital fingerprints can be inserted is found, a fingerprint feature position list is generated, the fingerprint feature position list and original files are stored in the file server together, the uploading and downloading record list is generated, and information uploaded this time is recorded. In the file downloading procedure, when the user sends a file downloading request to the file server, the file server generates binary random codes with the same length according to the length of the fingerprint feature position list, when the random code corresponding position is 1, the digital fingerprints are inserted in the contexts at the corresponding position, a new file is generated and sent to the user, and meanwhile the downloaded information is recorded in the uploading and downloading record list. By means of the method and system, the context files can be traced back, and the security of the context files is managed.
Owner:陈佳阳 +1
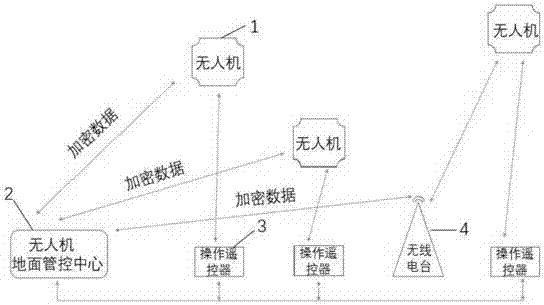
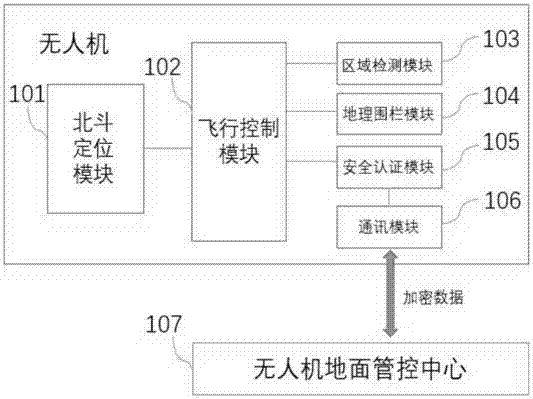
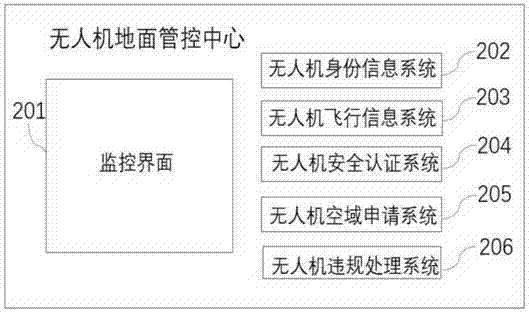
Unmanned aerial vehicle air operation safety control system and method
PendingCN107516437ARealize security management and controlAircraft navigation/guiding aidsTakeoffOperation safety
The invention discloses an unmanned aerial vehicle air operation safety control system and a method. The unmanned aerial vehicle air operation safety control system comprises the unmanned aerial vehicle, a radio station, an unmanned aerial vehicle ground control center and an operation remote controller, wherein the unmanned aerial vehicle has a unique production number, the production number is used for recognizing the identity of the unmanned aerial vehicle, and the identity of a user is bound for realizing a real name system; the radio station is used for long distance communication relay in a control region; the unmanned aerial vehicle ground control center is used for controlling the unmanned aerial vehicle to fly normatively in the control region, receiving the takeoff certification and the cross-region flight certification of the unmanned aerial vehicle from the control region and acquiring the identity information and the flight information of the unmanned aerial vehicle, and the unmanned aerial vehicle ground control center can carry out safety control on the unmanned aerial vehicle based on the flight information; and the operation remote controller receives and sends the flight information from the unmanned aerial vehicle and the indication information from the unmanned aerial vehicle ground control center. A data encryption function is also set, and the unmanned aerial vehicle safety system can be prevented from being deciphered or hacked to a certain extend.
Owner:HARBIN UNIV OF SCI & TECH
Network security management and control system for accessing social video networks to video private network
InactiveCN106027358ARealize security management and controlSafe and reliable connectionClosed circuit television systemsNetworks interconnectionDigital videoData stream
The invention discloses a network security management and control system for accessing social video networks to a video private network. The network security management and control system comprises the video private network, multiple social video networks and multiple access equipment arranged among the video private network and the social video networks; and an integrated management platform is arranged on the video private network. According to the network security management and control system disclosed by the invention, security management and control of a network is realized through the access equipment and the integrated management platform; an illegal data flow and access of an illegal user are intercepted in a physical isolation manner from a bottom protocol level of a network data packet while real-time transmission requirements of digital video information are ensured; and thus, the access security from the social video networks to the video private network is ensured.
Owner:SHANGHAI HORIZON INFORMATION TECH
Electric power line external-damage-preventive intelligent monitoring system
InactiveCN102646313ASolve operational problemsChange passive stateAlarmsBuilding material handlingElectricityRadar
The invention discloses an electric power line external-damage-preventive intelligent monitoring system, which comprises a nearly electric alarm sensor. The nearly electric alarm sensor is disposed on an operation moving arm of a large machine, is connected with an nearly electric alarm device and is further connected with a radar range unit disposed on the operation moving arm of the large machine, and the radar range unit is connected with a protecting device capable of leading the large machine to stop operation. The electric power line external-damage-preventive intelligent monitoring system is reasonable in structure, operation conditions of the construction machine in a power facility protecting area can be controlled in real time, effective safety monitoring is realized, and accidents are effectively prevented.
Owner:STATE GRID CORP OF CHINA +1
Intelligent seal system and method
ActiveCN107967593AEnsure safetyImplement remote authorizationOffice automationIndividual entry/exit registersEngineeringControl circuit
The invention discloses a safe seal sleeve internally provided with a driving device which has the advantages of simple structure, convenient use and high safety. The safe seal sleeve internally provided with the driving device is arranged inside an intelligent seal machine for fixedly mounting a seal, and comprises a shell, a driving device and a protective cover, wherein the driving device comprises a driving block, a guiding rod and a connecting block arranged inside the shell sequentially from top to bottom; the driving block and the guiding rod are respectively connected onto two ends ofthe guiding rod; the guiding rod is sleeved with a spring; the spring is located between the driving block and the connecting block; the upper end of the shell is internally provided with a first electronic lock matched with the driving block; the first electronic lock is electrically connected with a control circuit of the intelligent seal machine; the protective cover is fixedly connected onto the lower end of the shell; and the seal is mounted inside the protective cover and is connected with the connecting block. The safe seal sleeve internally provided with the driving device is applied to the technical field of intelligent seal machines.
Owner:珠海思格特智能系统有限公司
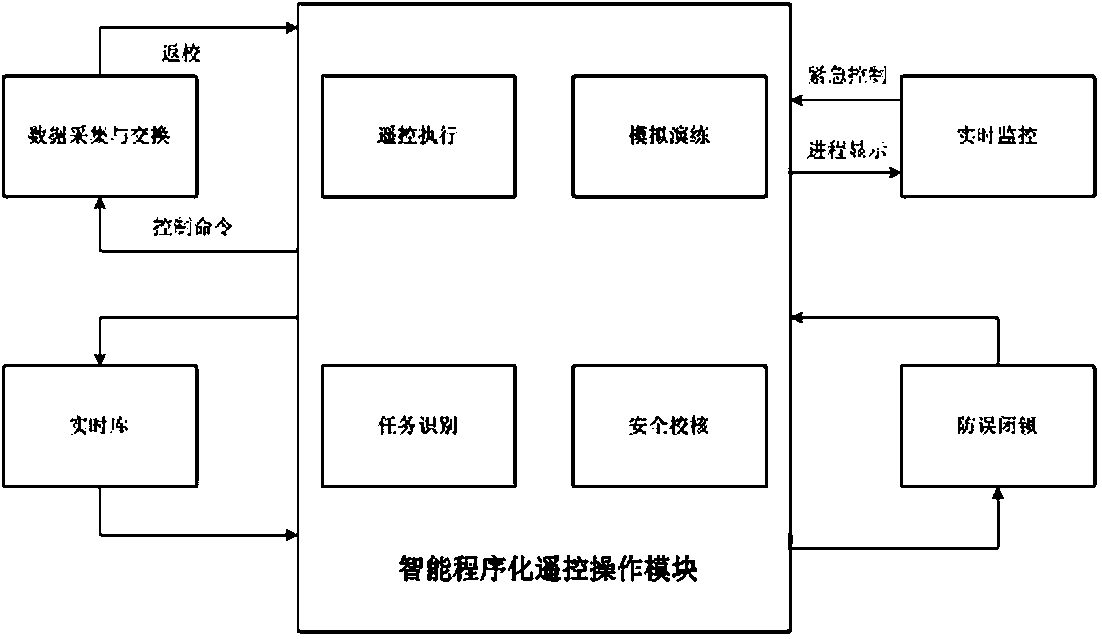
Intelligent procedural remote control operation system
InactiveCN108233536AAvoid misuse accidentsGenerate automatic shortcutsCircuit arrangementsRemote controlPower grid
The invention discloses an intelligent procedural remote control operation system. A topological fail-safe system of a D5000 automatic platform is arranged according to a topological relationship between an electrical island state and electrical equipment to realize fail-safe locking of equipment operation; the extraction of the topological fail-safe system is based on basic rules of operative locking between equipment as required by 'fail-safe', mutual operative locking equipment is found out through topological search so as to automatically adapt to the changes of the electrical equipment and a topological structure of a power grid. The intelligent procedural remote control operation system is a brand-new remote control technology researched and developed specific to a large operationalmode, has very strong innovativeness, safety and high efficiency, is quite beneficial to improving the working quality and efficiency of remote control operation, and can be wholly used for guaranteeing safe and stable operation of the power grid.
Owner:STATE GRID CORP OF CHINA +1
Flight safety management and control service method
ActiveCN105913693ARealize security management and controlAircraft traffic controlHuman–computer interactionLow altitude
The invention discloses a flight safety management and control service method. In the invention, through correlatively processing a low-altitude aircraft course, a flight path and a spatial domain, an air traffic controller uses a man-machine interaction mode to complete flight conflict processing of a low altitude airspace aircraft and spatial domain conflict management so as to realize safety management and control of low-altitude spatial domain flight. The method has an advantage that through correlatively processing the low-altitude aircraft course, the flight path and the spatial domain, the air traffic controller uses the man-machine interaction mode to complete flight conflict processing of the low altitude airspace aircraft and spatial domain conflict management so as to realize safety management and control of low-altitude spatial domain flight.
Owner:北京威胜通达科技有限公司
Webpage document watermark embedding method and device
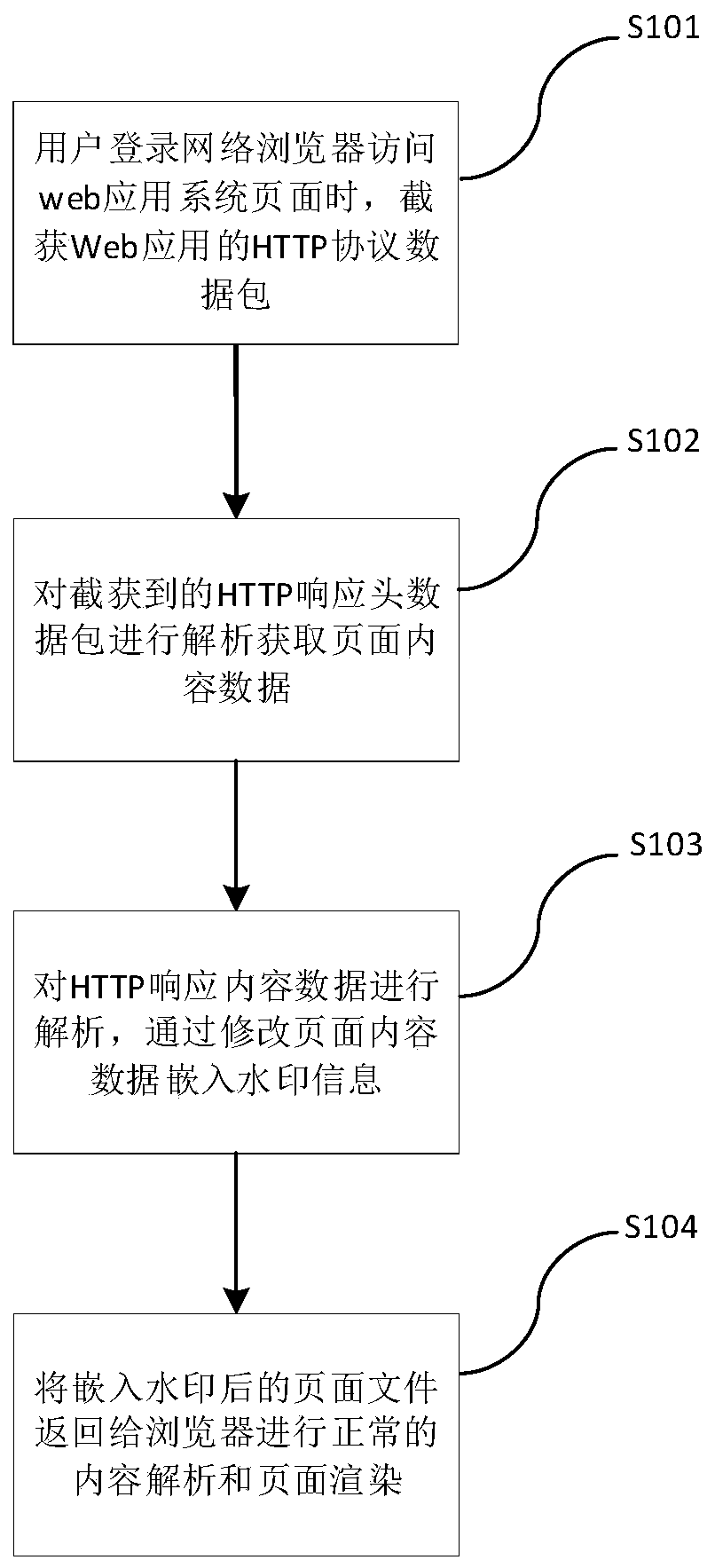
PendingCN110348182AAchieve the purpose of verificationRealize security management and controlImage data processing detailsTransmissionWeb browserWeb application
The invention relates to a webpage document watermark embedding method and device. The method comprises the steps that 1, when a user logs in a web browser to access a web application system page, intercepting an HTTP protocol data packet of a web application; step 2, analyzing an HTTP response header data packet in the intercepted HTTP protocol data packet to obtain HTTP response content data; 3,analyzing the HTTP response content data, and embedding watermark information by modifying the page content data; and 4, returning the page file embedded with the watermark to the browser for normalpage content analysis and page content rendering. According to the method, the embedded text traceability tracking information is visually invisible, so that visual interference caused by an existingscreen dominant watermarking technology is avoided; and meanwhile, the watermark information is embedded by taking the text content in the webpage document as a carrier, is not easy to erase manually,and can resist screen shooting or screen capture, so that the safety performance is higher.
Owner:李晓妮
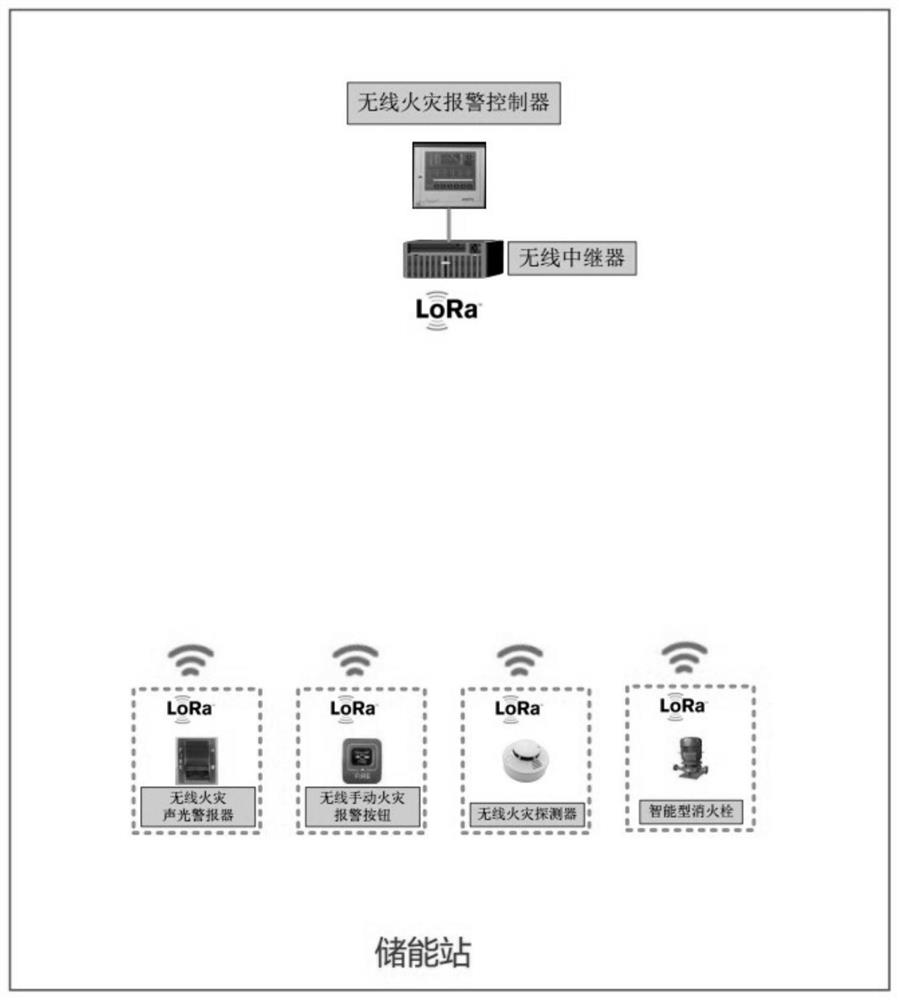
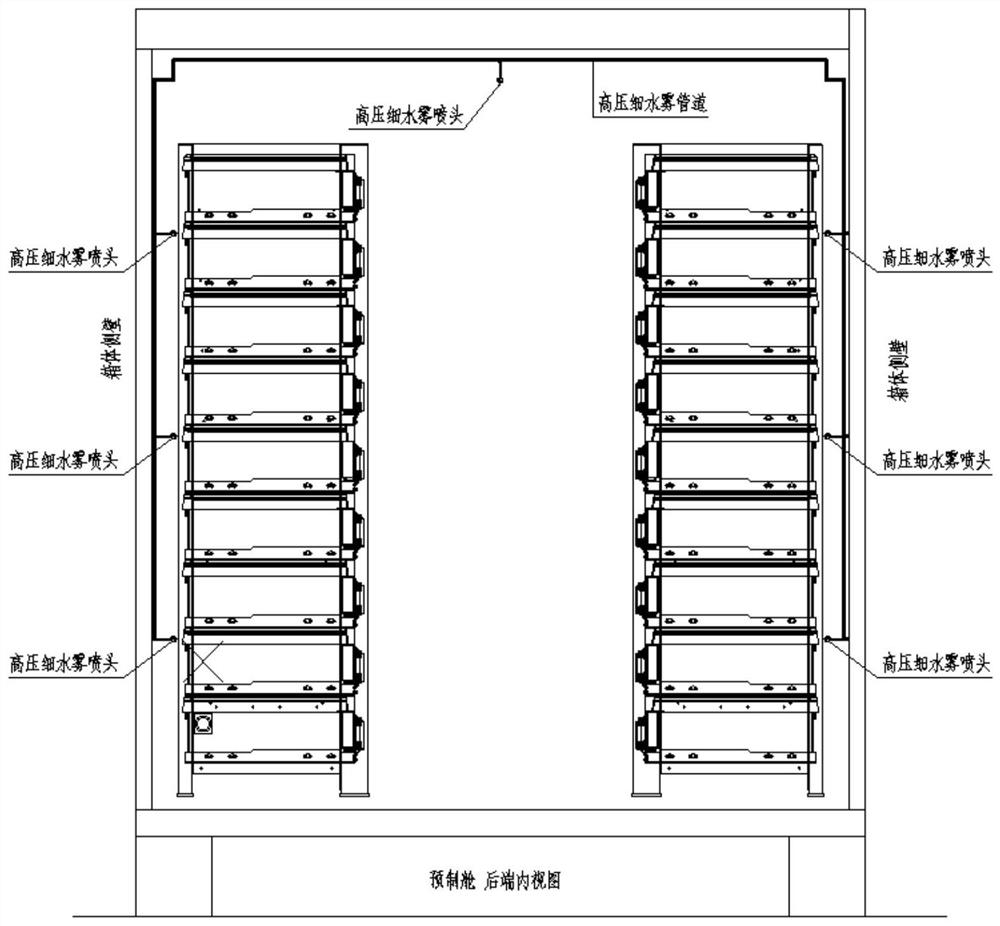
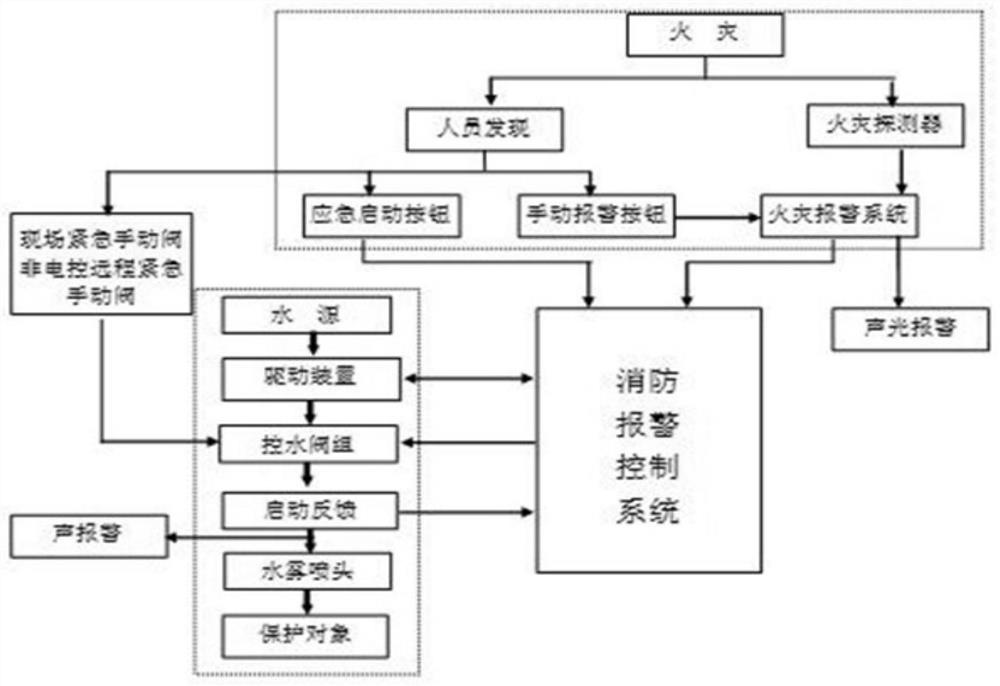
Wireless fire extinguishing system for energy storage station and control method thereof
InactiveCN111870843ASave on cable and construction costsOptimize system operation control methodFire rescueFire alarmsAutomotive engineeringFire detector
The invention discloses a wireless technology-based fire extinguishing system for an energy storage station. The fire extinguishing system is composed of all or parts of equipment such as a wireless fire alarm controller, a wireless fire detector, a wireless manual fire alarm button, a wireless fire acousto-optic alarm, a wireless module and a wireless repeater; a LoRa wireless communication function of the system is compounded into each component in the system to be realized; and based on fire characteristics of a lithium battery, an online early warning decision system, a multi-combination high-sensitivity detection system, a total-flooding automatic fire extinguishing system, a long-time protection cooling system, a manual backup means and other omnibearing, multi-angle and comprehensive control schemes are adopted. The fire extinguishing system has the functions of fire real-time detection and automatic fire extinguishing of the energy storage station.
Owner:NR ELECTRIC CO LTD +1
Oil-gas pipeline pre-warning system based on decision fusion and pre-warning method
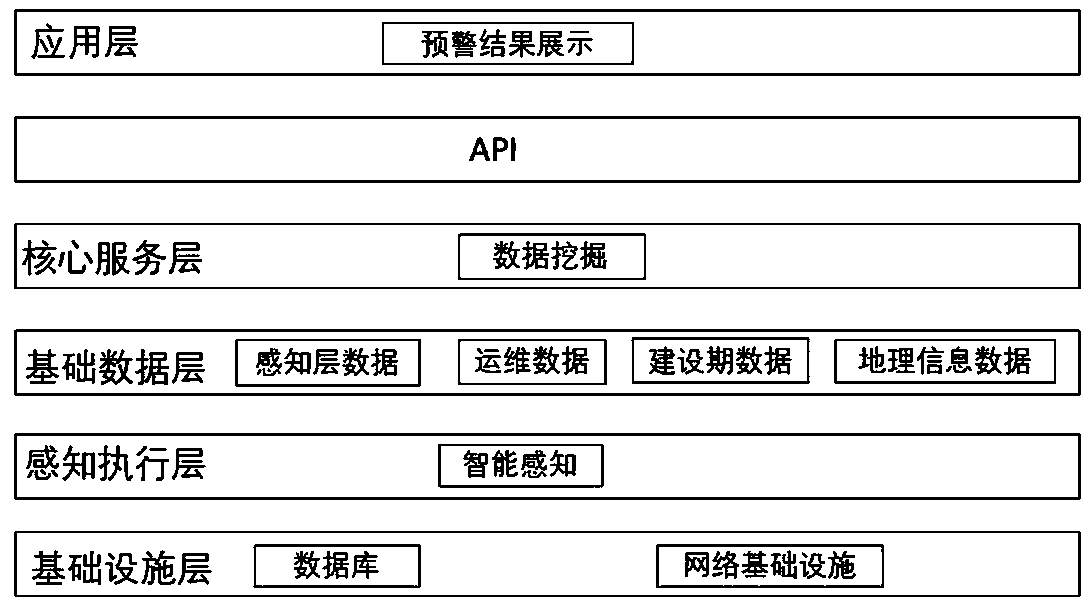
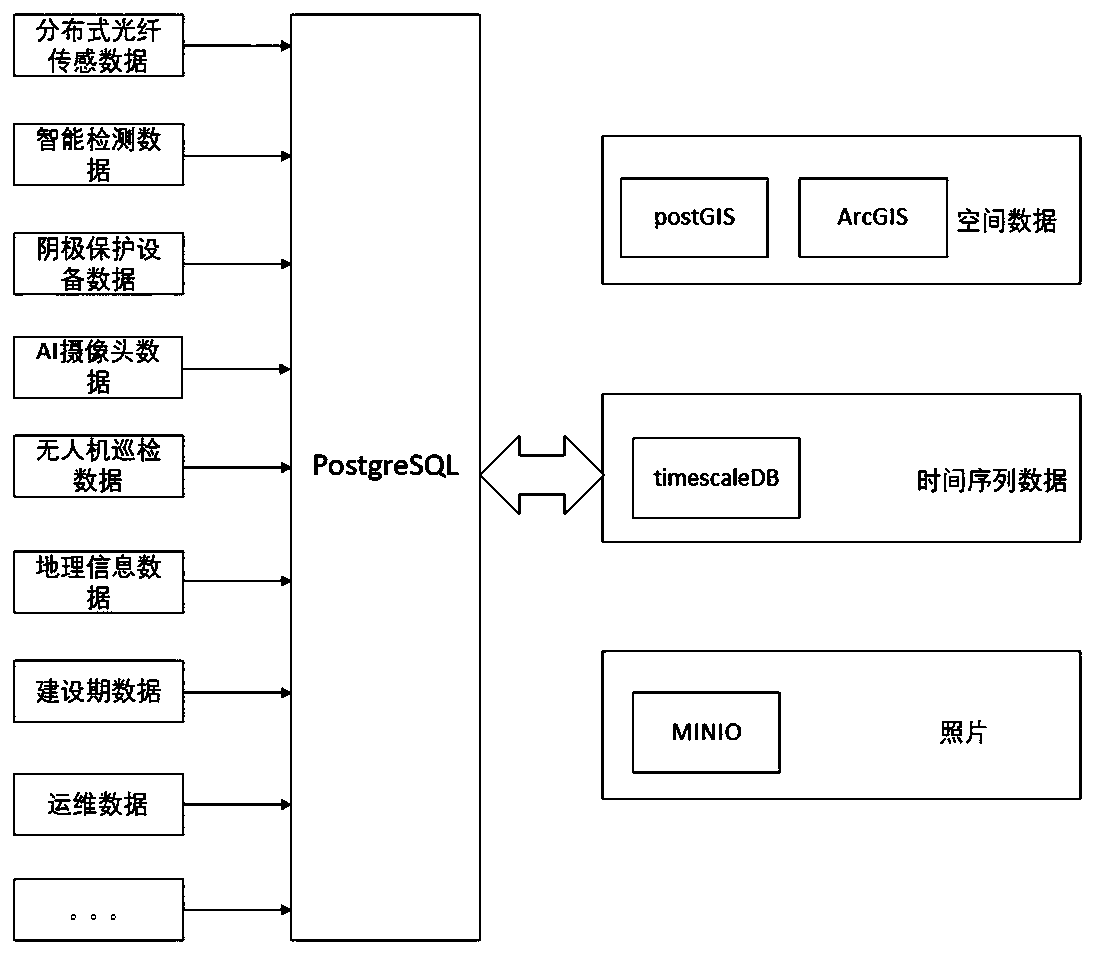
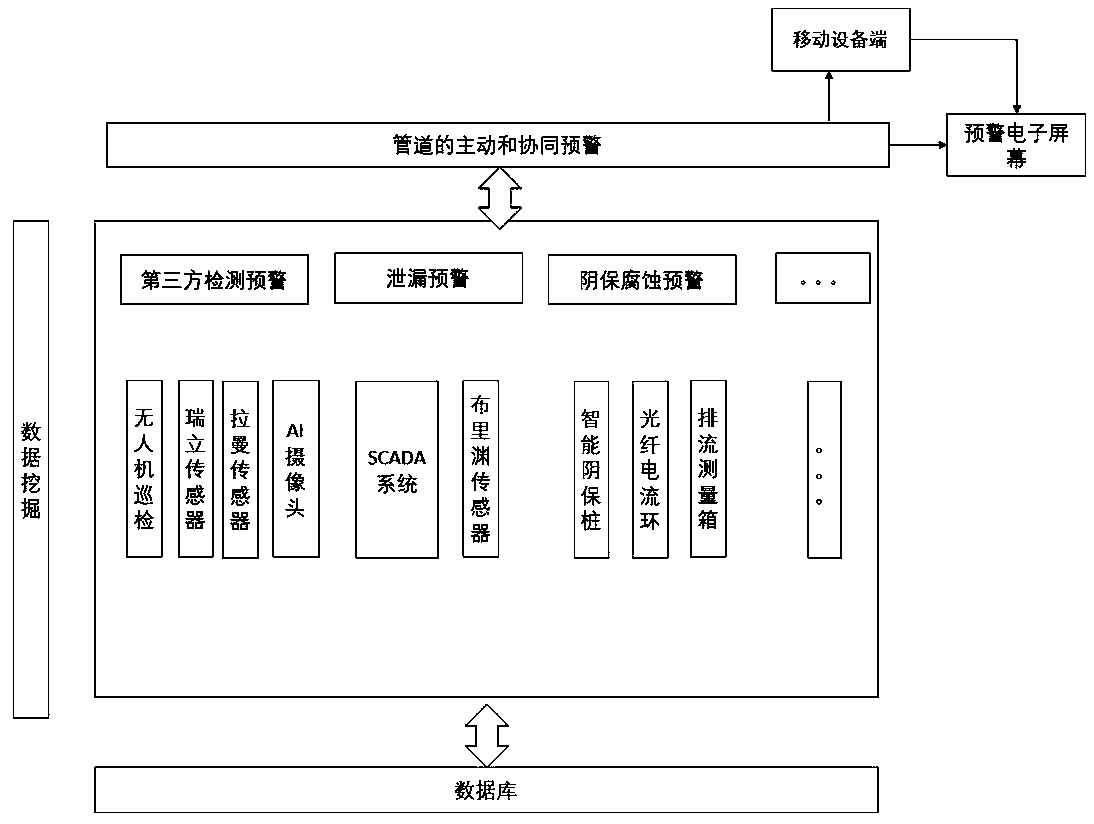
ActiveCN111536429AImprove performanceImprove integrityChecking time patrolsPipeline systemsInformation processingData acquisition
The invention belongs to the technical field of oil-gas pipeline monitoring and pre-warning systems, and particularly relates to an oil-gas pipeline pre-warning system based on decision fusion and a pre-warning method. The system comprises an infrastructure layer, a sensing actuation layer, a basic data layer and a core service layer. The infrastructure layer comprises intelligent sensing equipment. The sensing actuation layer carries out monitoring and data acquiring on an oil-gas pipeline through the intelligent sensing equipment. The basic data layer is used for storing data acquired by thesensing actuation layer and data in the full life circle of the oil-gas pipeline in a database. The core service layer is used for mining the data of the database. Multiple pre-warning grades of multiple pre-warning methods corresponding to different pre-warning tasks are subjected to decision fusion, and the pre-warning grades of the corresponding pre-warning tasks are obtained; the importance orders of all the pre-warning tasks and pre-warning methods are obtained through accident tree analysis, and active pre-warning is achieved; and multi-source data can be fused, the performance of information processing is effectively improved, the pre-warning accuracy is high, and the pre-warning system and the pre-warning method have higher pertinence for pre-warning of the oil-gas pipeline.
Owner:浙江浙能天然气运行有限公司 +2
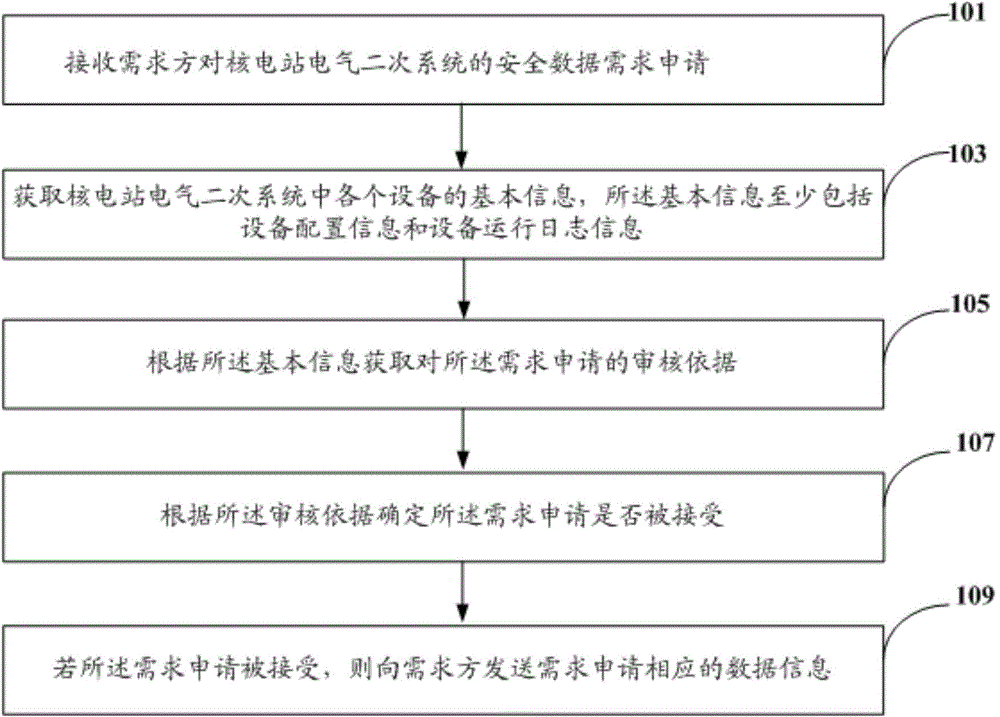
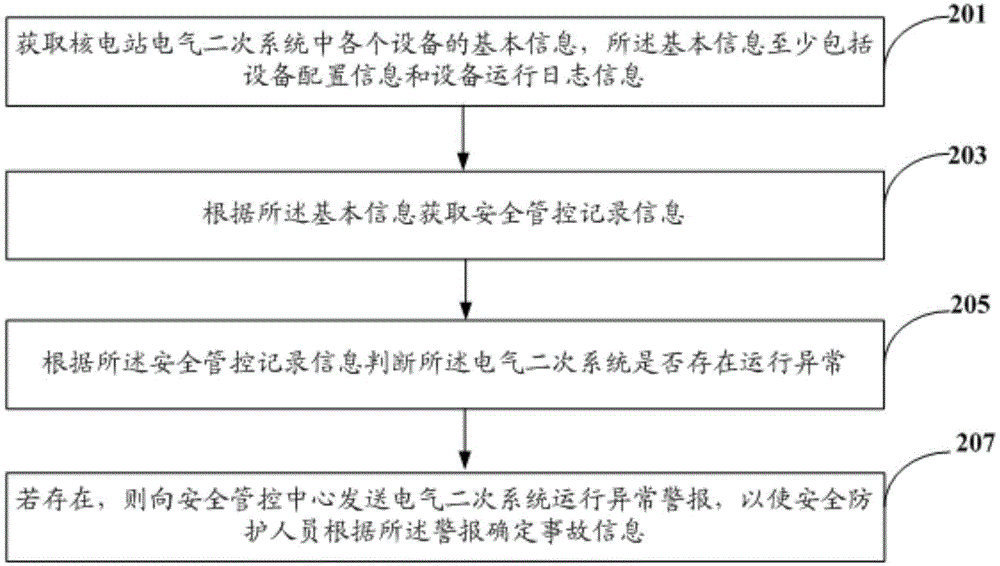
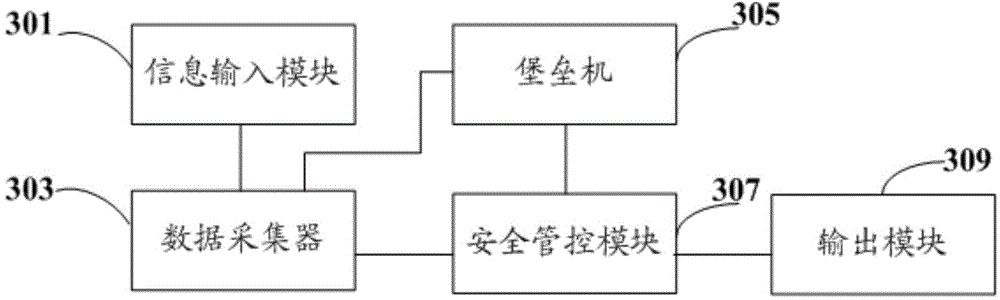
Safe control method and platform based on electrical secondary system of nuclear power station
InactiveCN104915762ARealize security management and controlSecurity management active and passiveResourcesData informationNuclear power plant
The invention discloses a safe control method and platform based on an electrical secondary system of a nuclear power station. The method comprises that demand application for safe data of the electrical secondary system of the nuclear power station from a demand side is received; basic information, which at least comprises configuration information and operation log information, of each device in the electrical secondary system of the nuclear power station is obtained; check basis of the demand application is obtained according to the basic information; whether the demand application is accepted is determined according to the check basis; and if the demand application is accepted, data information corresponding to the demand application is sent to the demand side. The safe control method is convenient to realize, safe and reliable.
Owner:中广核工程有限公司 +1
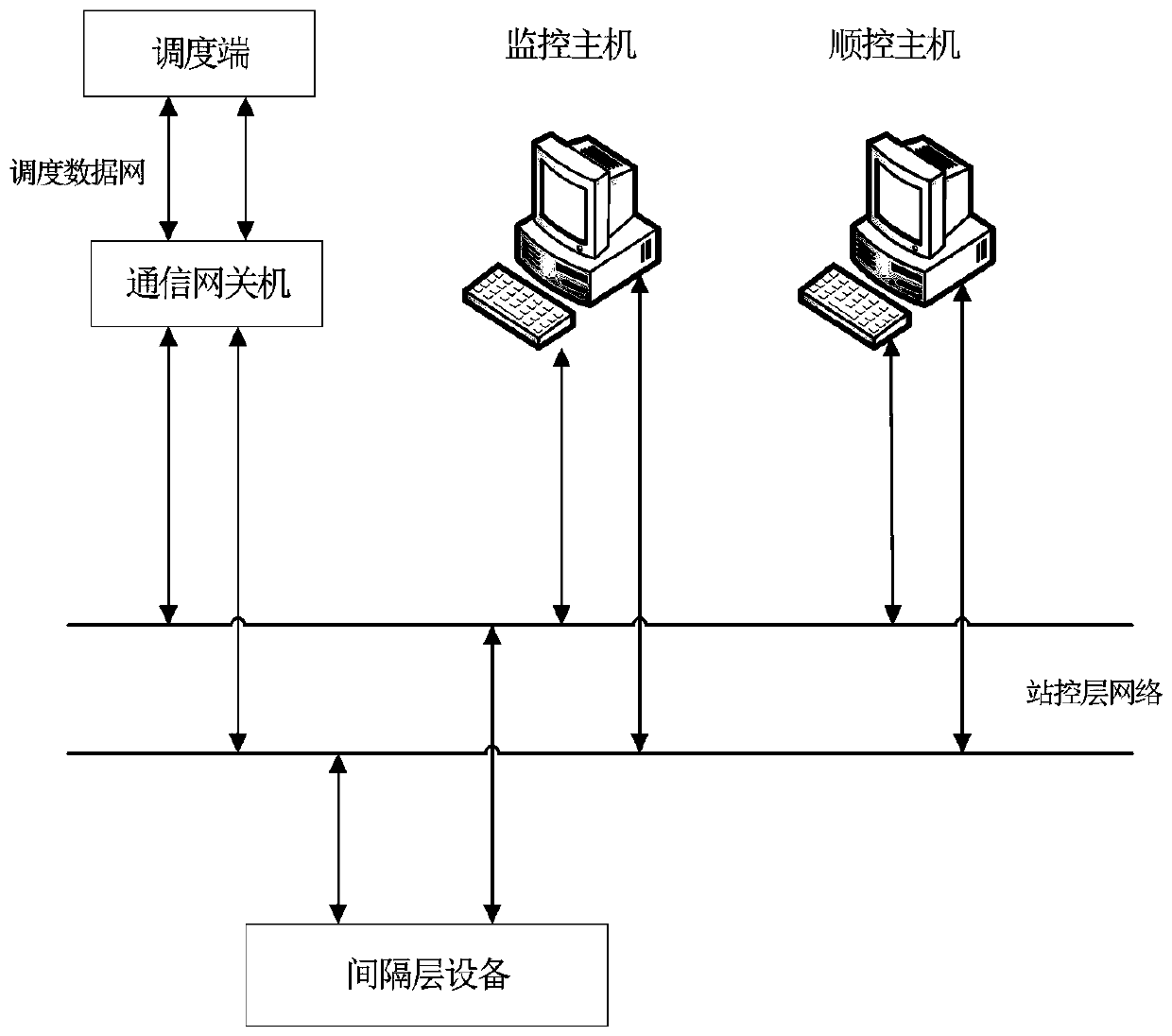
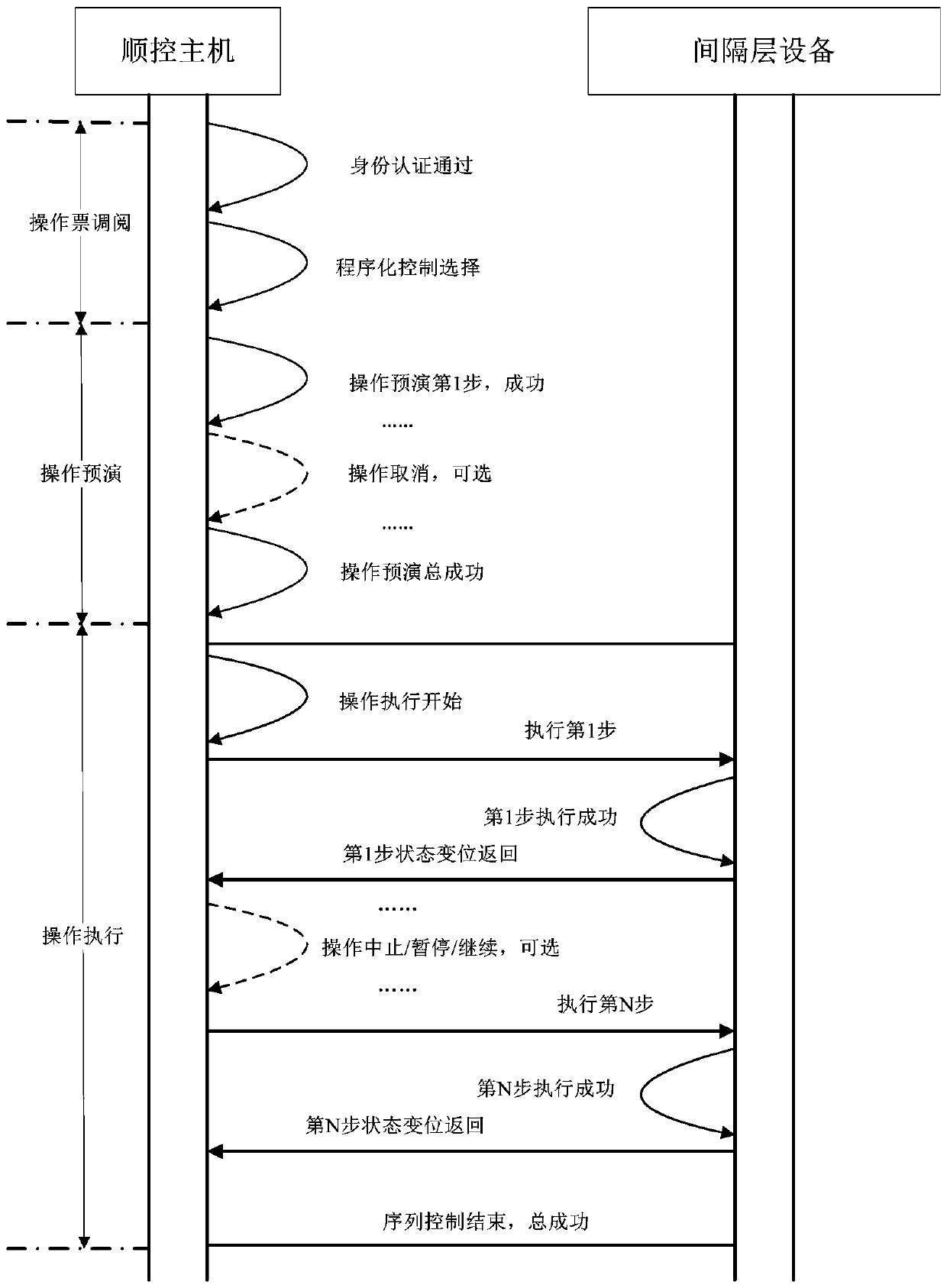
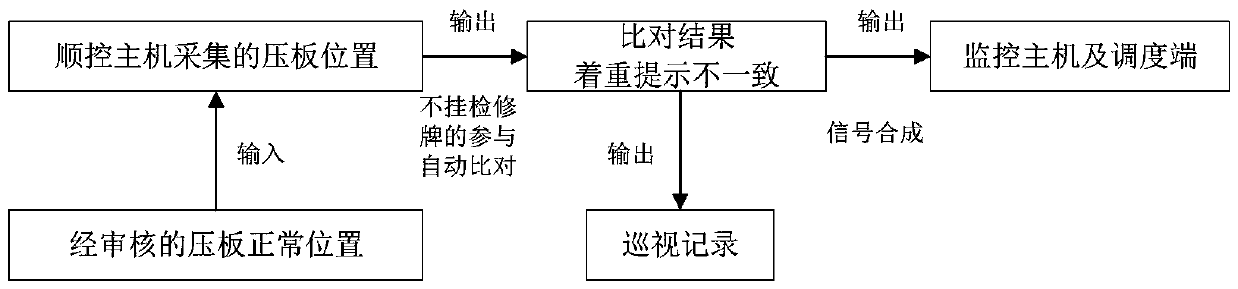
Intelligent inspection system and method for secondary equipment of 500kV transformer substation
InactiveCN110994797ARealize security management and controlEasy to useCircuit arrangementsInformation technology support systemEmbedded systemPower management
The invention discloses an intelligent inspection system and method for secondary equipment of a 500kV transformer substation, and relates to the technical field of power management. The system comprises a monitoring host, a scheduling end, a communication gateway machine, a station control layer network, spacer layer equipment and a sequential control host which are connected with one another, wherein the sequential control host is connected with the station control layer network and is in bidirectional communication with the station control layer network; the method is based on the equipmentand comprises the steps of S1, soft pressing plate one-key sequential control, the sequential control host initiates station end programmed control, the steps sequentially comprise three steps of S1.1 operation ticket retrieval, S1.2 operation rehearsal and S1.3 operation execution, and manual intervention is carried out through operation cancellation, operation pause, operation continuing and operation ending in the process of flow proceeding. Through the monitoring host, the scheduling end, the communication gateway machine, the station control layer network, the spacer layer equipment, thesequential control host and the like, the safety management and control of the soft strap are realized.
Owner:STATE GRID CORP OF CHINA +1
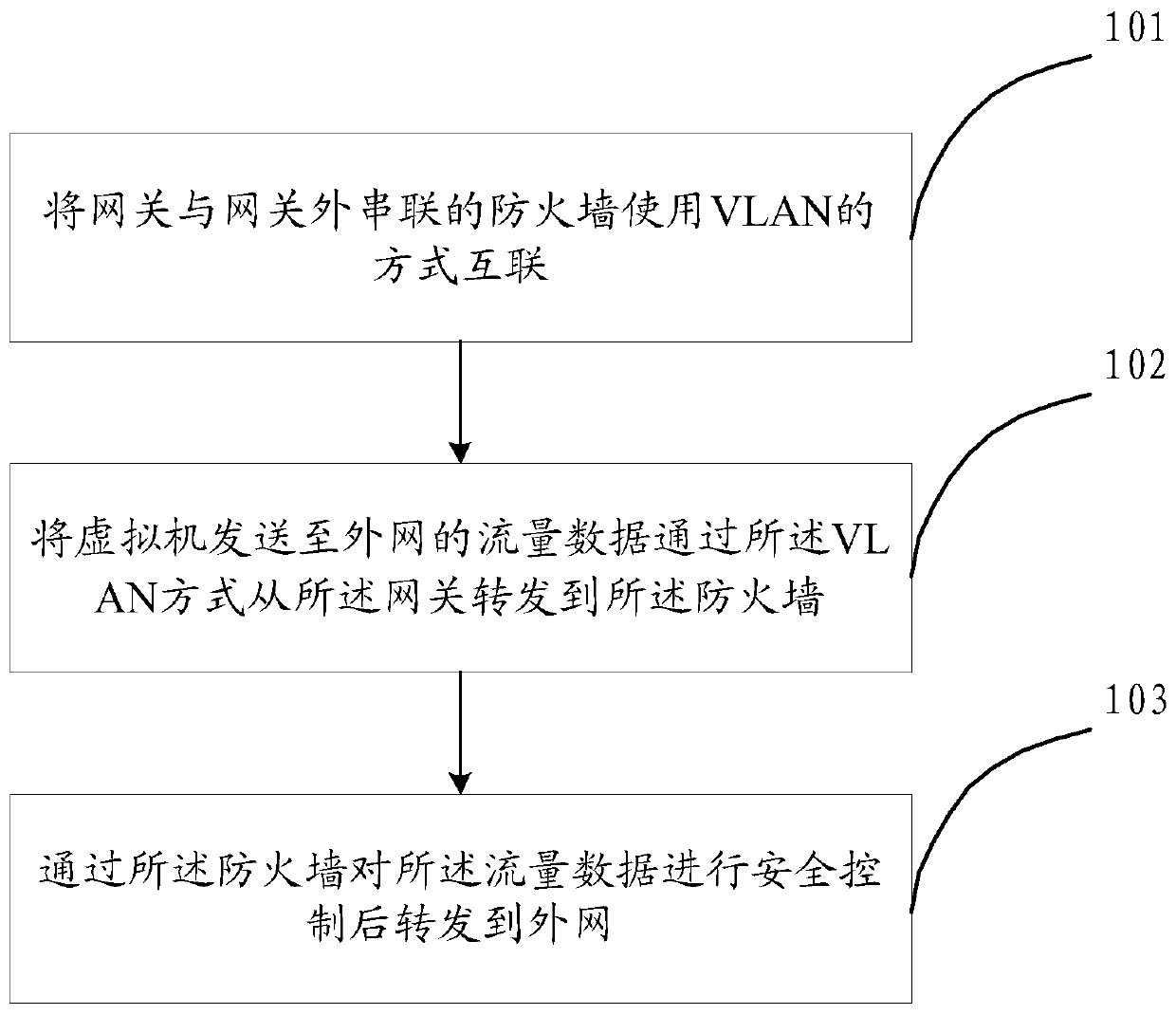
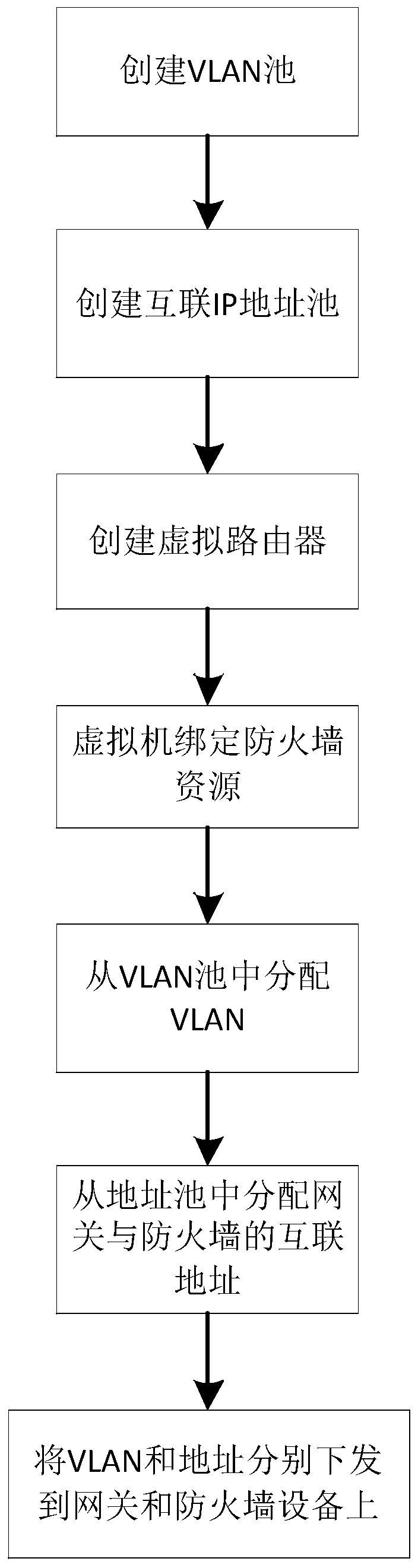
Security resource management and control method and device in SDN network
InactiveCN110417774ARealization of security resource management and controlEasy to controlTransmissionTraffic capacityResource management
The embodiment of the invention discloses a security resource management and control method and device in an SDN (Software Defined Network). The method comprises the following steps: interconnecting agateway with firewalls connected in series outside the gateway in a VLAN (Virtual Local Area Network) manner; forwarding the flow data sent to the external network by the virtual machine from the gateway to the firewall in the VLAN mode; and performing security control on the flow data through the firewall, and forwarding the flow data to an external network. The security management and control of the network flow of the virtual machine are realized.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
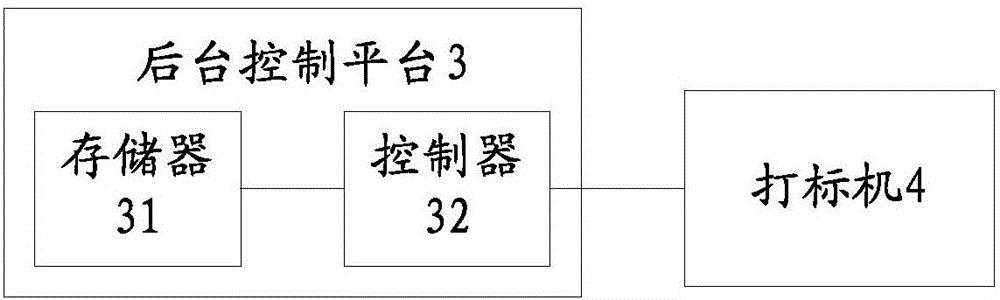
Item marking system, item management system, apparatuses and methods
ActiveCN106570551ARealize security management and controlImprove securityCommerceRecord carriers used with machinesGraphicsIdentity management
The invention discloses an item marking system, an item management system, an item marking apparatus, an item management apparatus, an item marking method and an item management method. According to the systems, apparatuses and methods of the invention, the memory of a background control platform is adopted to store graph setting strategies, the corresponding relations of elements of a management serial number numerical value sequence and an identification graph and mapping relations of a plurality of regions of the identification graph and the numerical value sequence; and a controller controls a printer to set the identification graph according to the graph setting strategies and controls the printer to set identification points in corresponding regions of the identification graph according to the management serial number numerical value sequence, the corresponding relations of the identification graph and the elements of the management serial number numerical value sequence and the mapping relations of the plurality of regions of the identification graph and the numerical value sequence. With the systems, apparatuses and methods adopted, a new item identity management mode is realized; the identification graph set on an item through the mode is completely different from identifiers such as two-dimensional codes, other people can only see a simple graph on the item, and cannot obtain the identity information of the item, and therefore, the safety and diversity of item management can be improved.
Owner:NUBIA TECHNOLOGY CO LTD
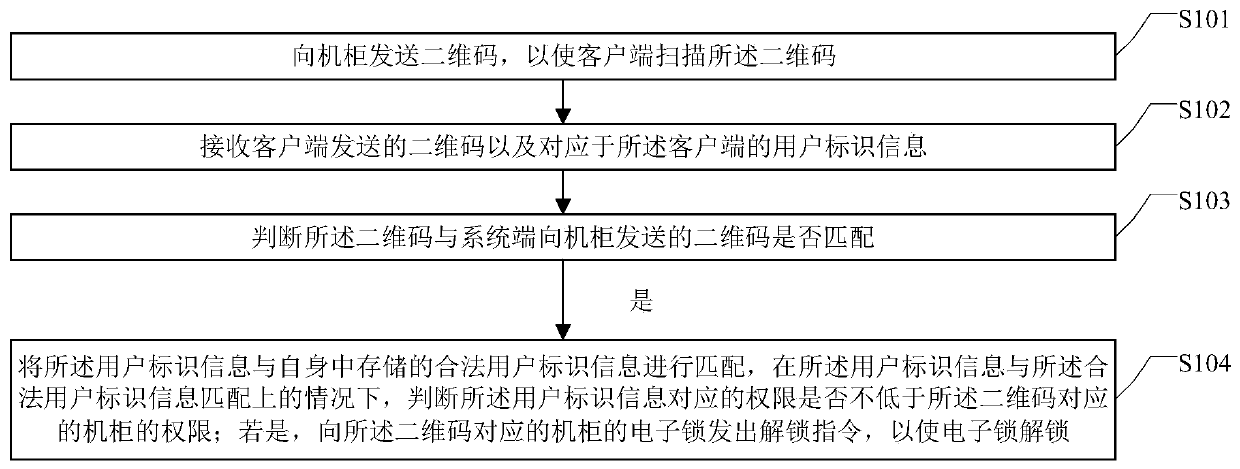
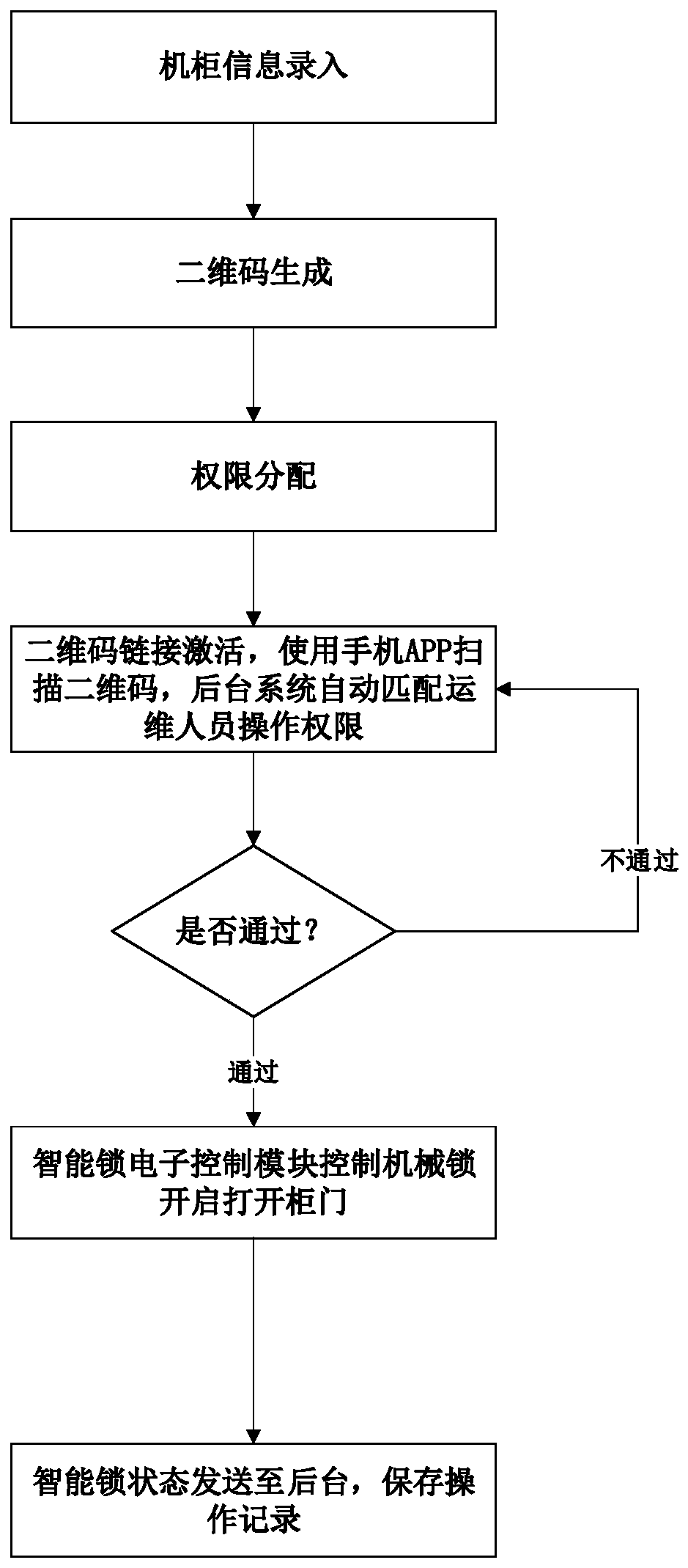
Control method, device and system of QR code cabinet remotely controlled by Internet of Things
InactiveCN110853202APrevent openingRealize security management and controlIndividual entry/exit registersComputer hardwareThe Internet
The embodiment of the invention provides a control method, device and system for a QR code cabinet remotely controlled by the Internet of Things, and the method, device and system are applied to a system end. The method comprises the steps: transmitting a QR code to the cabinet, so as to enable a client to scan the QR code; receiving the QR code sent by the client and user identification information corresponding to the client, wherein the QR code information is uniquely corresponding to the cabinet; judging whether the QR code is matched with the QR code sent to the cabinet by a system end ornot: if yes, enabling the user identification information to be matched with legal user identification information stored in the user identification information, and under the condition that the useridentification information is matched with the legal user identification information, judging whether the authority corresponding to the user identification information is not lower than the authority of the cabinet corresponding to the QR code or not: if yes, sending an unlocking instruction to an electronic lock of the cabinet corresponding to the QR code to unlock the electronic lock. By applying the embodiment of the invention, the safety of the cabinet is ensured.
Owner:HEFEI YOUO ELECTRONICS TECH
Indoor positioning method of intelligent safety helmet
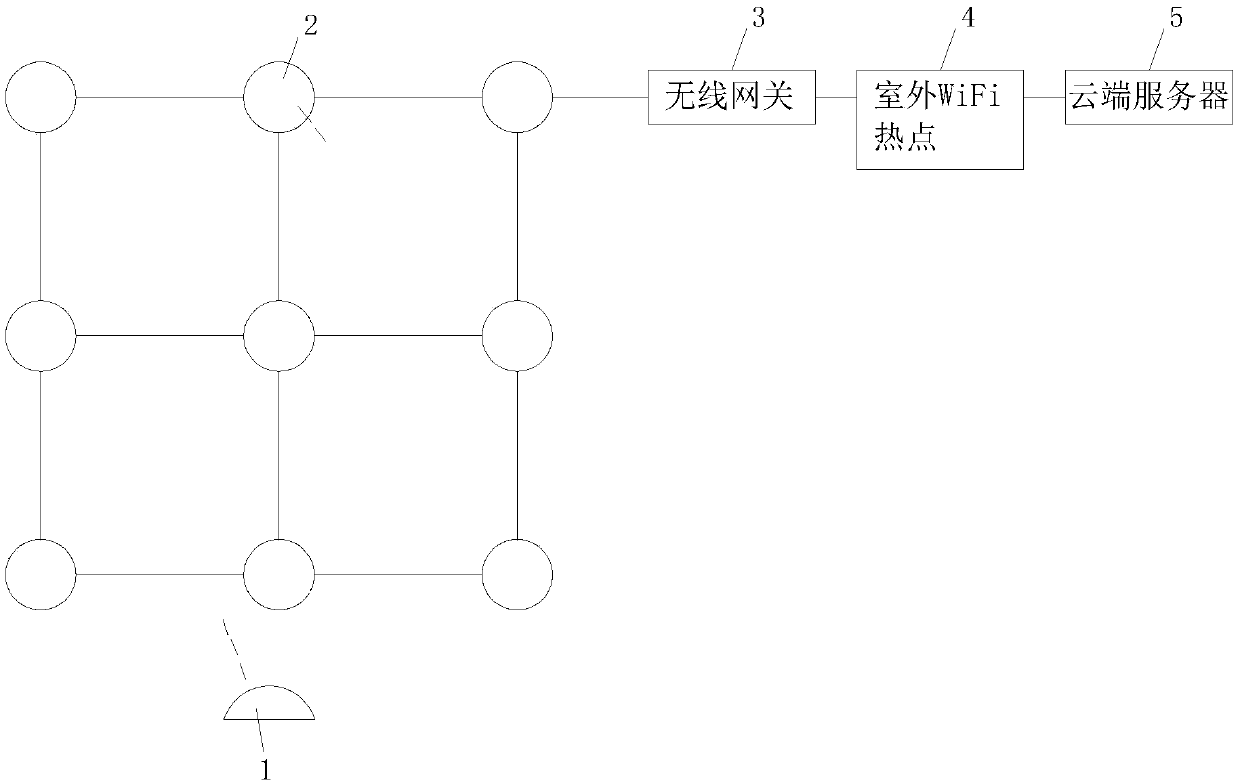
InactiveCN107634796APrecise Indoor PositioningSimple structureClose-range type systemsShort range communication serviceEngineeringBluetooth
The invention discloses an indoor positioning method of an intelligent safety helmet. The indoor positioning method of the intelligent safety helmet is implemented by devices including a safety helmet, intelligent LED lamps, a wireless gateway, an outdoor WiFi hotspot and a cloud server, wherein the intelligent LED lamps are installed on the top in a room and distributed on the same in an array; Bluetooth modules are installed in the intelligent LED lamps and form a network via an ad-hoc network protocol, the network formed by the intelligent LED lamps is connected with the outdoor WiFi hotspot via the wireless gateway, and the outdoor WiFi hotspot is connected with the cloud server. The Bluetooth modules arranged in the safety helmet read position information of the Bluetooth modules in the five closest intelligent LED lamps, the safety helmet uploads the position information to the cloud server via an ad-hoc network, and the cloud server computes the position information of the safety helmet via an algorithm routine. According to method provided by the invention, the devices are simple in structure and convenient to arrange, implementation of the method is facilitated, and indoorpositioning can be accurately performed on the safety helmet.
Owner:毛扬
Online project management and control system and method of electric power internet of things
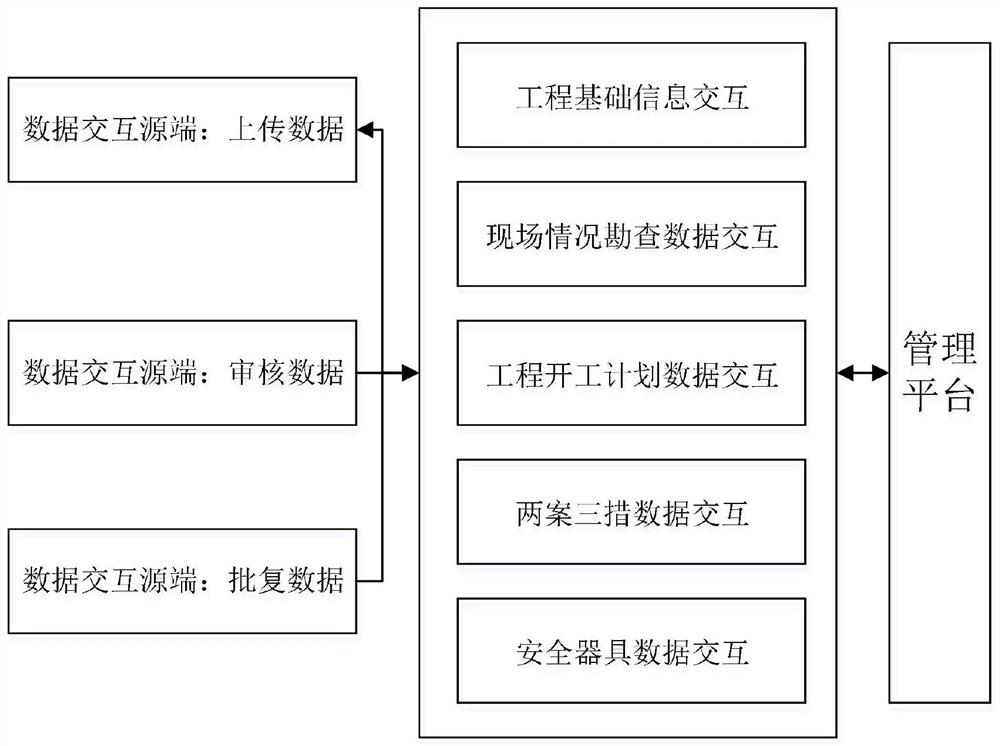
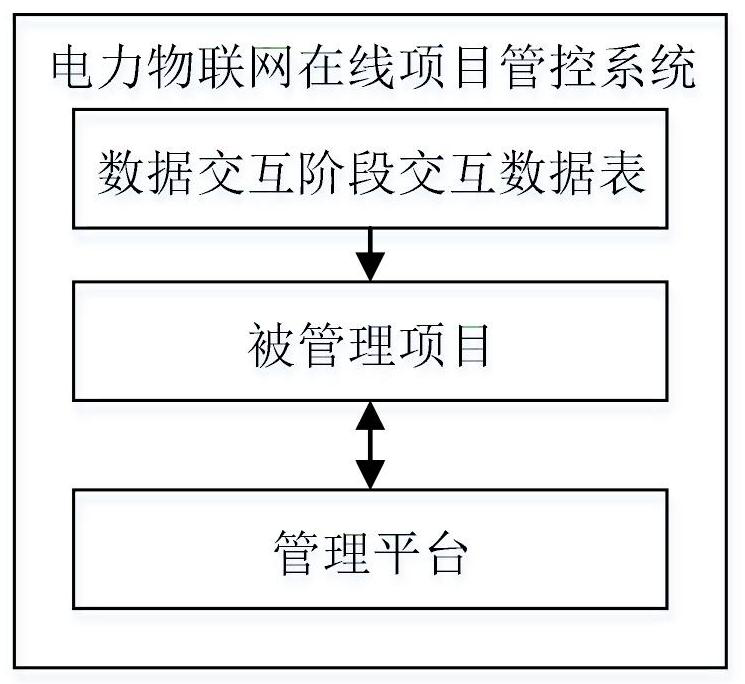
PendingCN113191632AEfficient managementTimely controlCharacter and pattern recognitionNeural architecturesDatasheetControl system
The invention discloses an electric power Internet of Things online project management and control system and method, and the system comprises a data interaction stage interaction data table which comprises a plurality of interaction data projects of a plurality of tasks in different interaction data stages of a project; the managed project is preset in a data interaction stage interaction data table and assigns a value to an interaction source end of the interaction data project, and the interaction source end of the interaction data project performs stage data interaction based on preset data interaction time setting; and the management platform stores an interactive data stage data table correspondingly consistent with the managed project, and the management platform receives and analyzes the interactive data of the managed project according to the interactive data stage data table. According to the invention, through real-time uploading, auditing and analysis of data of different stages of an electric power project, efficient management of various data in the project and timely and comprehensive management and control of a plurality of construction operation sites are realized.
Owner:HAIBEI POWER SUPPLY COMPANY STATE GRID QINGHAI ELECTRIC POWER +2
Anti-misoperation control system and method for switching process in chemical process
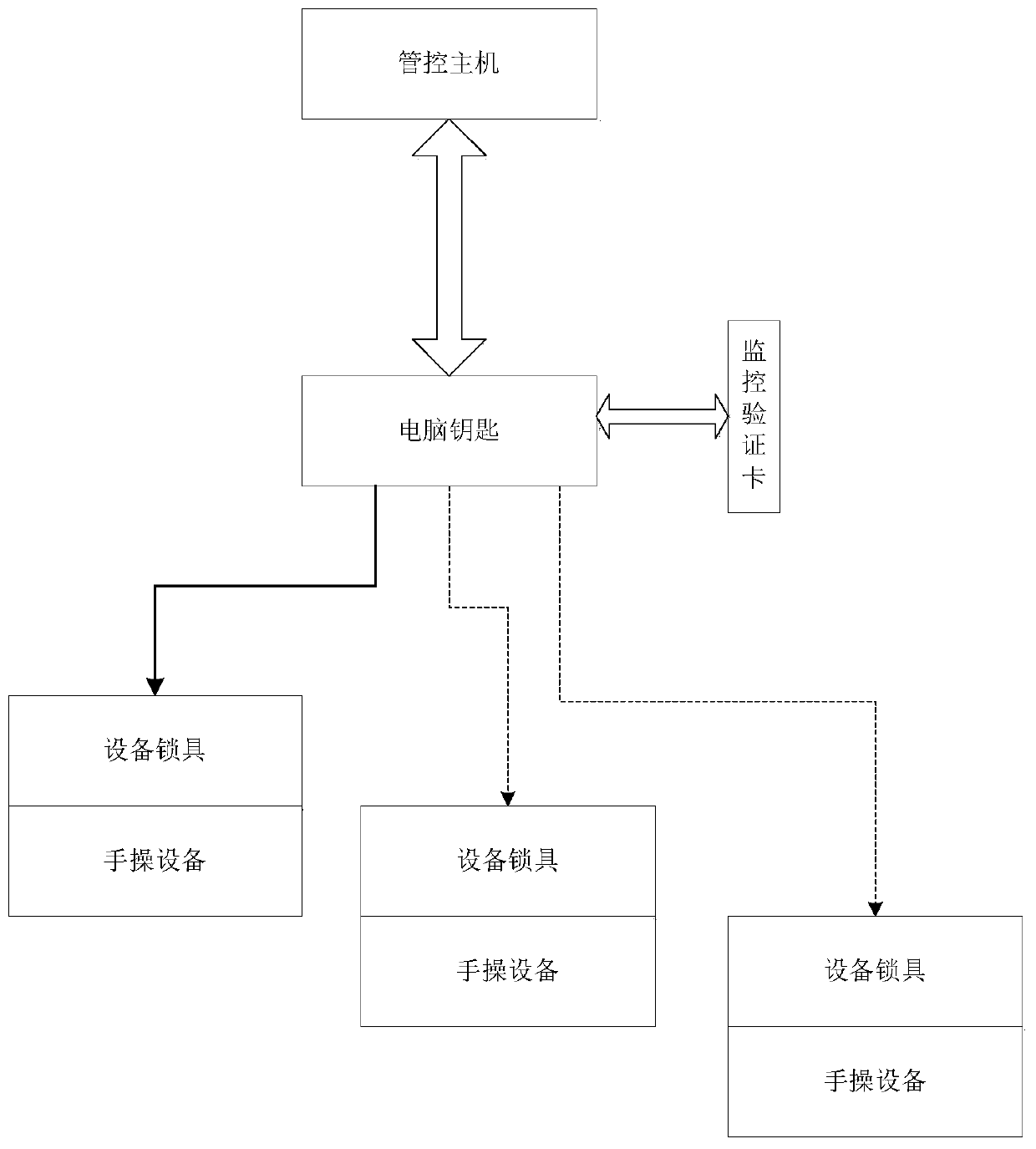
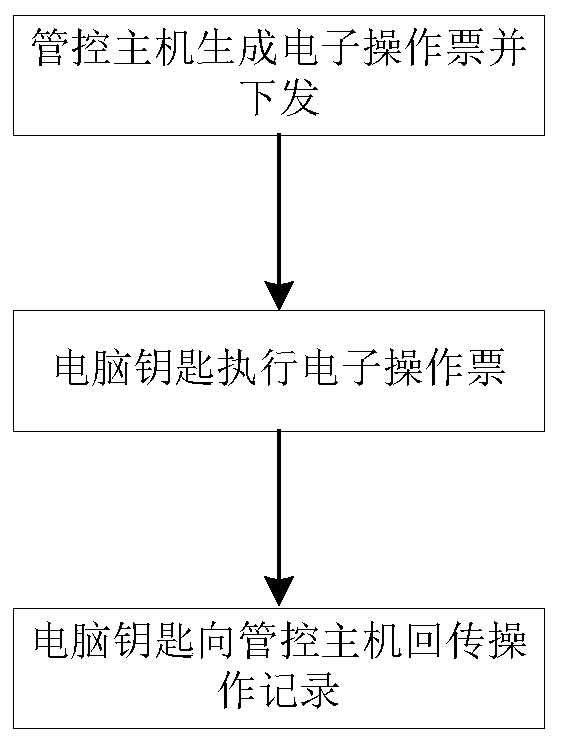
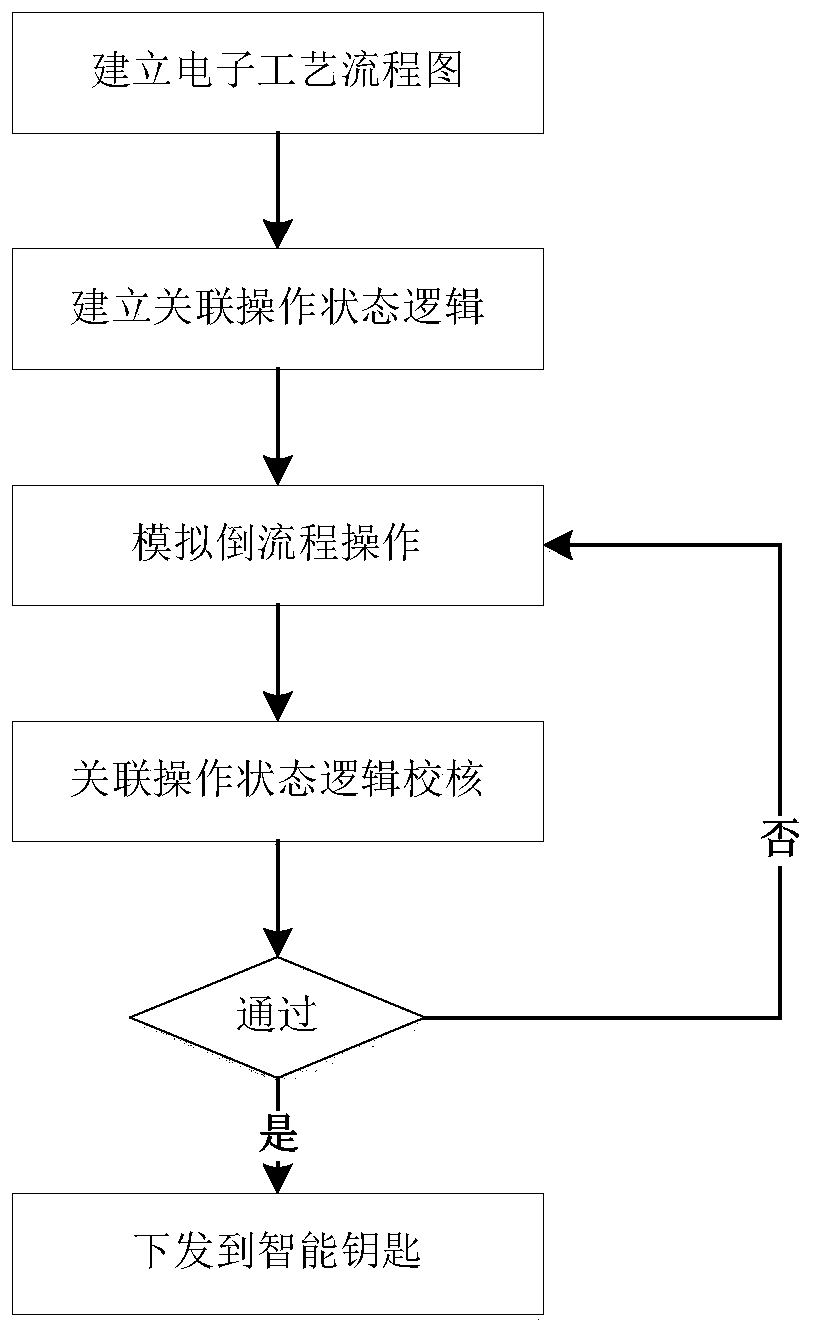
PendingCN110941249ARealize security management and controlTotal factory controlProgramme total factory controlTicketAutomatic control
The invention discloses an anti-misoperation control system and method for a switching process in a chemical process, and belongs to the technical field of automatic control and process misoperation prevention. According to the invention, when the operation ticket is generated, targeted operation prompting is carried out on the manual operation equipment of a specific manual operation point, so that the intelligent key for executing the operation ticket must execute corresponding operation according to the corresponding operation prompting during field operation so as to complete a correct operation process, otherwise, the operation is not allowed to be continuously executed; the operation prompting and the corresponding operation comprise means of monitoring the reading of the verification card, detecting the state, waiting for observation, obtaining the observation result, judging whether the operation is sent or not and the like. According to the invention, the operation process canbe subjected to forced standardization through various technical means, and the safety control of the manual operation equipment during the process switching in the chemical process is realized.
Owner:CYG CONTRON
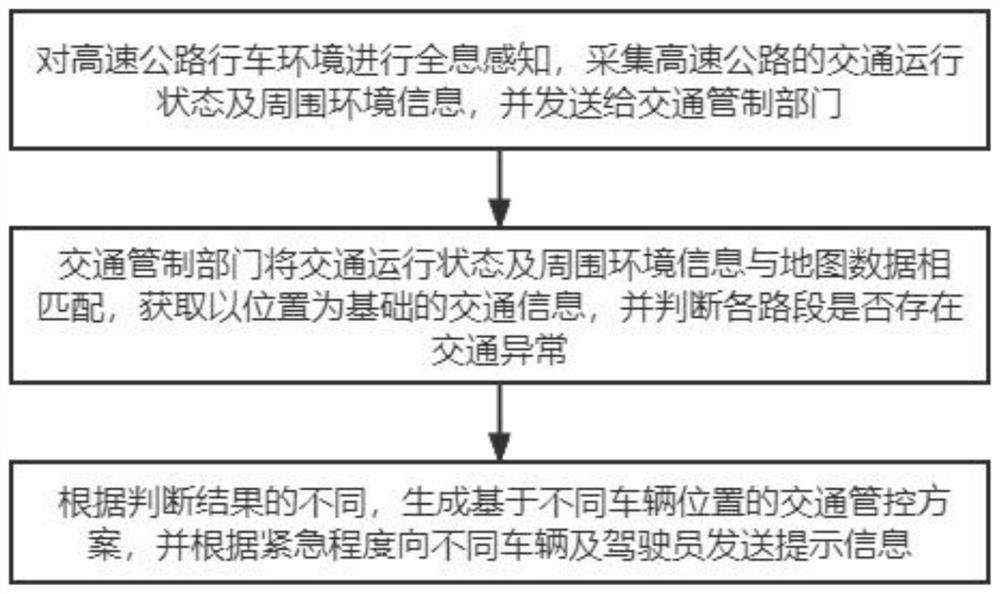
Safety control method and system based on smart road and storable medium
PendingCN114387785ARegulate driving behaviorImprove management efficiency and automation levelArrangements for variable traffic instructionsDetection of traffic movementDriver/operatorRoad traffic control
The invention discloses a safety management and control method and system based on a smart highway and a storable medium, and relates to the technical field of smart highways, and the method comprises the following steps: carrying out the holographic perception of a highway driving environment, collecting the traffic operation state and surrounding environment information of a highway, and transmitting the information to a traffic control department; the traffic control department matches the traffic operation state and the surrounding environment information with map data, obtains traffic information based on the position, and judges whether traffic abnormity exists in each road section or not; and according to the difference of the judgment results, generating a traffic control scheme based on the vehicle position, and sending prompt information to different vehicles and drivers according to the emergency degree. According to the invention, sufficient data can be obtained, the road can be comprehensively perceived, the safety control of the intelligent road is realized, and the management efficiency and the automation level are improved.
Owner:陕西交通职业技术学院
Visual electronic fence and control method thereof
PendingCN112396787AImprove securityConvenient operation and maintenance of equipmentTelevision system detailsFencingInfraredStructural engineering
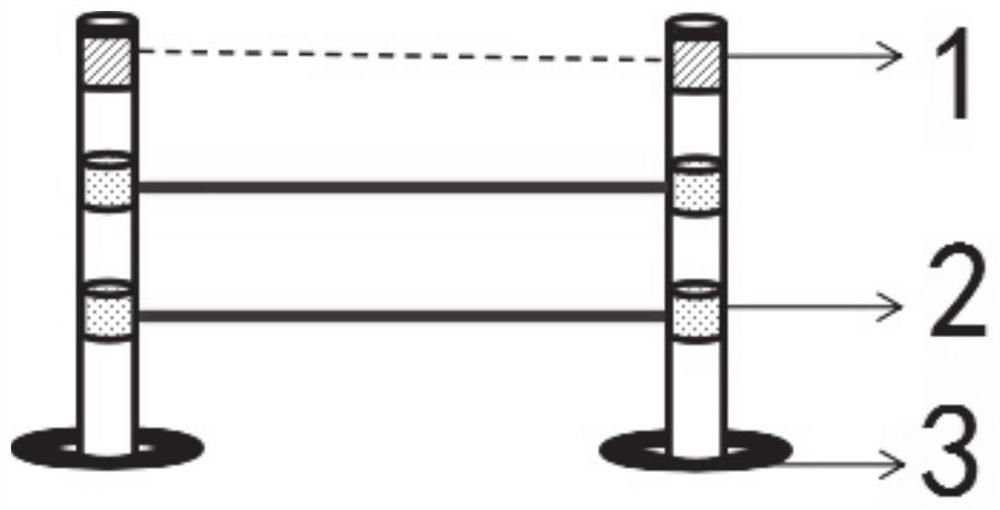
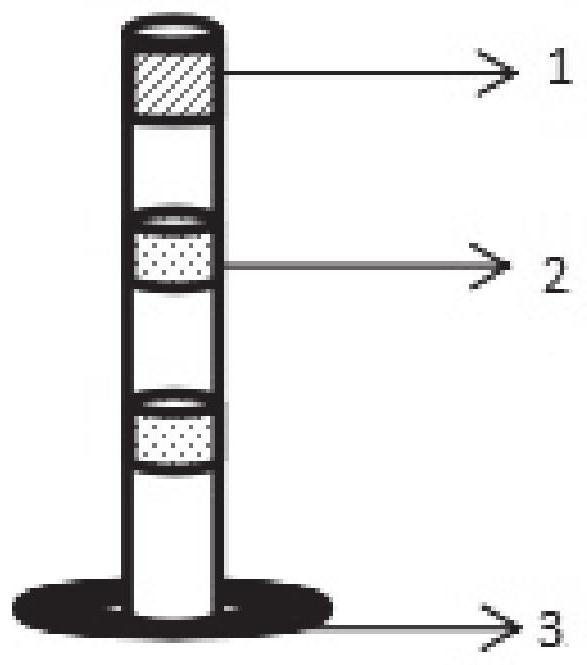
The invention discloses a visual electronic fence and a control method thereof. The visual electronic fence comprises a plurality of electronic fence supporting columns. All the electronic fence supporting columns are numbered, a working area for all the electronic fence supporting columns is defined according to the sequence of the numbers from small to large, and infrared rays and at least two telescopic belts are arranged between adjacent electronic fence supporting columns, wherein the area between the first electronic fence supporting column and the last electronic fence supporting columnis an entrance and exit, and the entrance and exit is not provided with a telescopic belt.
Owner:STATE GRID CORP OF CHINA +4
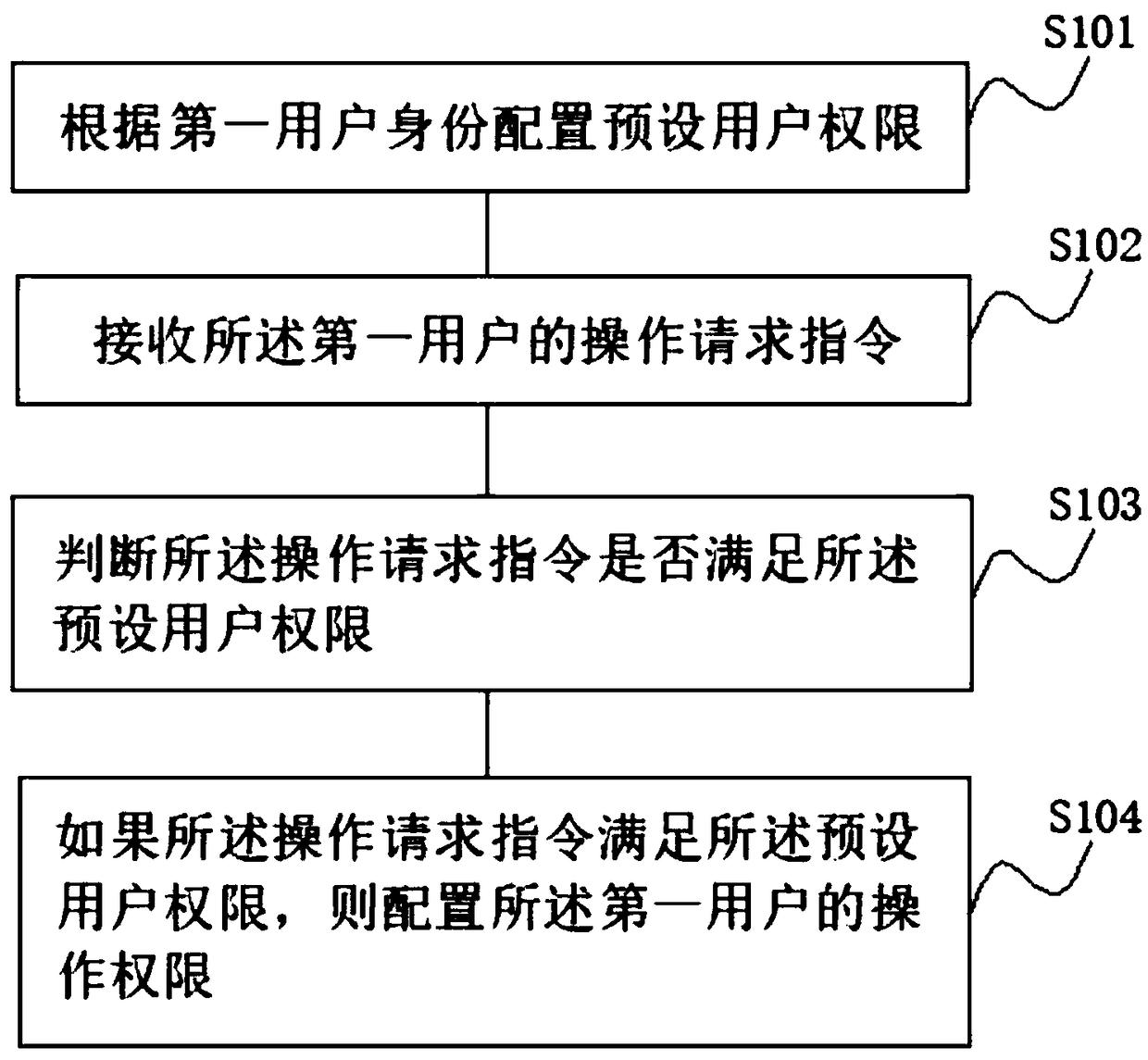
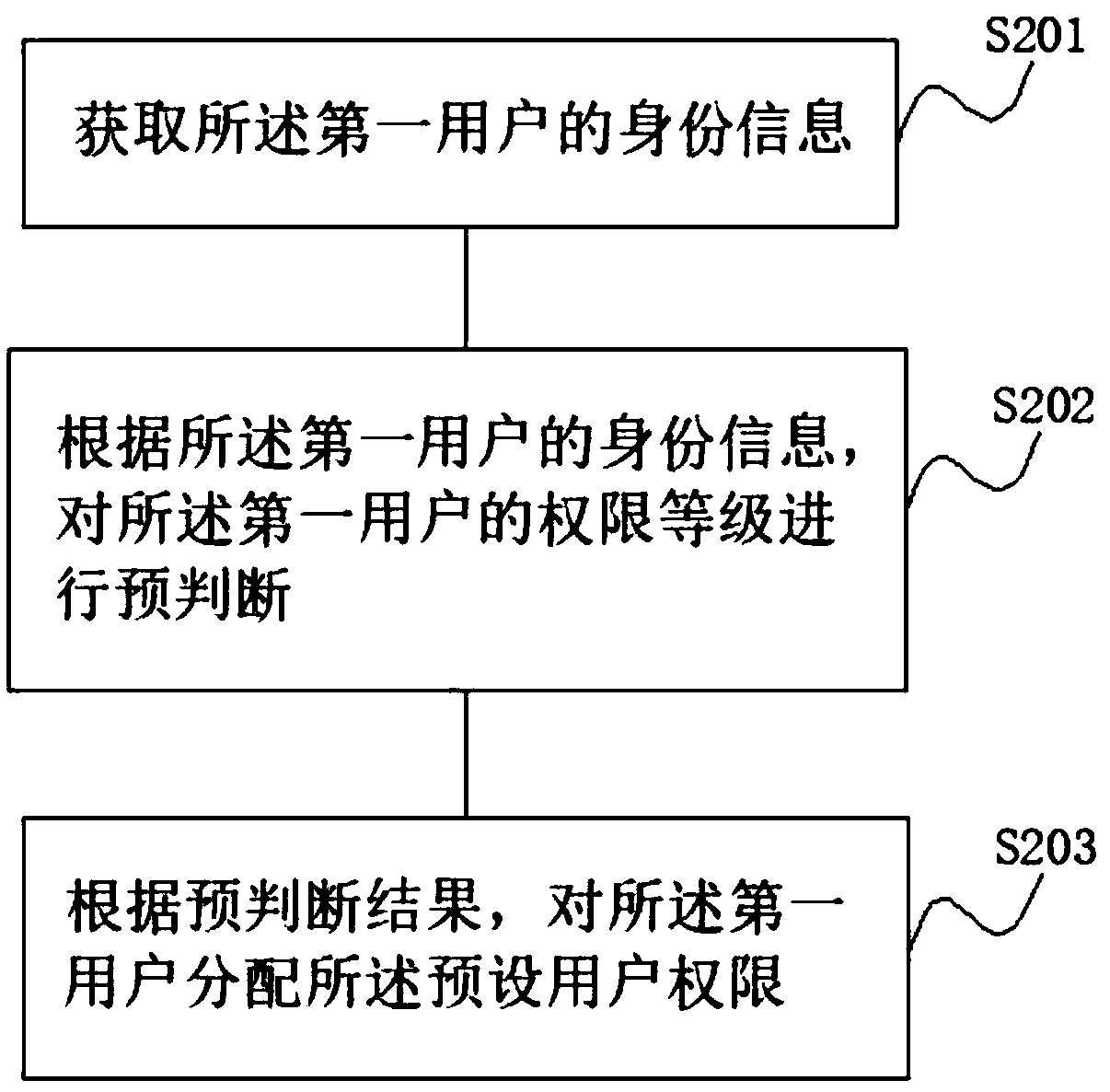
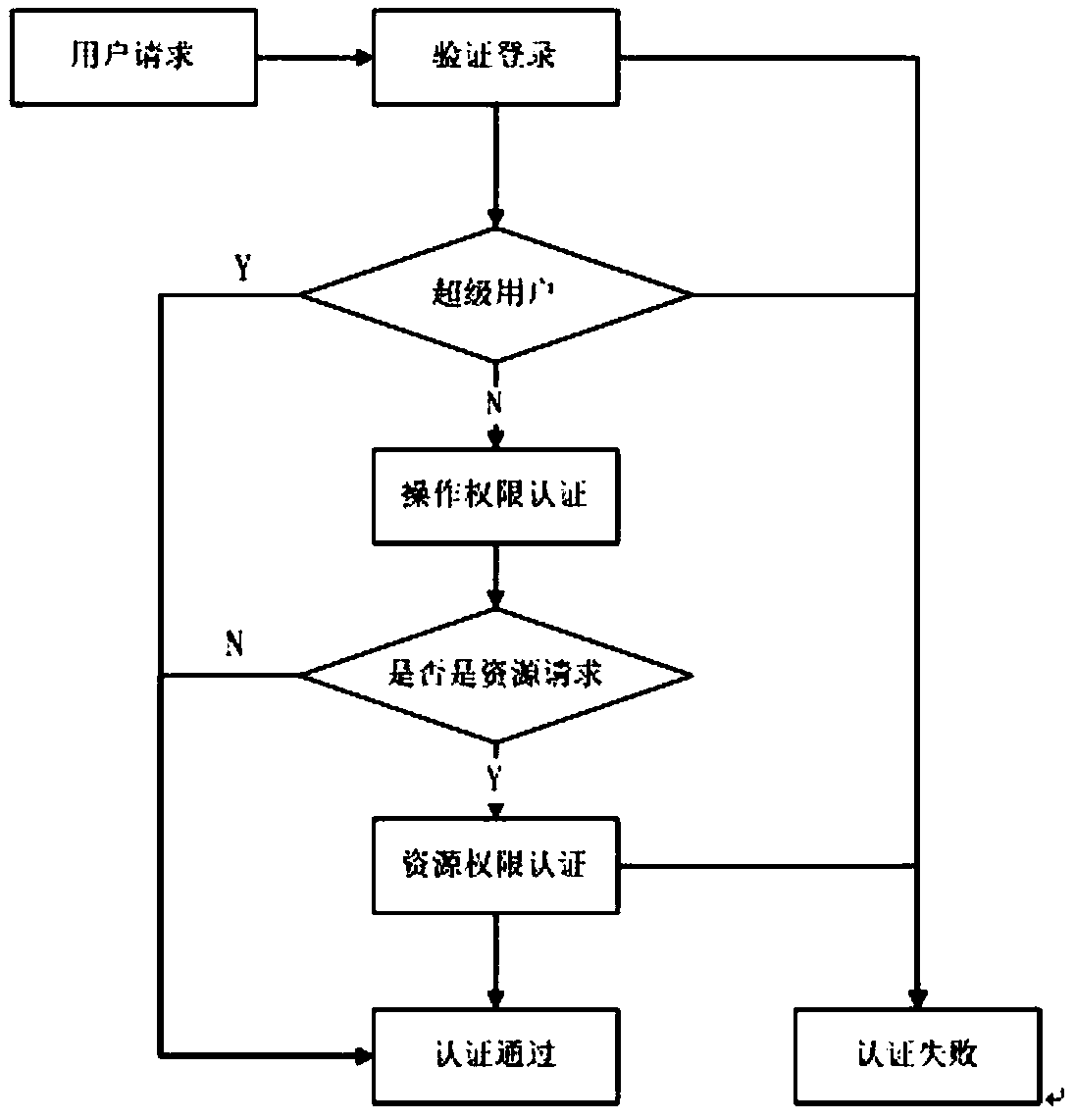
User permission management method and device
ActiveCN108809930AImprove securityRealize security management and controlUser identity/authority verificationUser PrivilegeInformation acquisition
The application discloses a user permission management method and device. The user permission management method and device comprises the following steps: configuring preset user permission according to a first user identity; receiving an operation request instruction of the first user; judging whether the operation request instruction satisfies the preset user permission; and configuring the operation permission of the first user if the operation request instruction satisfies the preset user permission. Through the user permission management method disclosed by the application, the technical problem that the intelligent terminal is low in information security and free from information acquisition permission setting is solved.
Owner:北京易代储科技有限公司
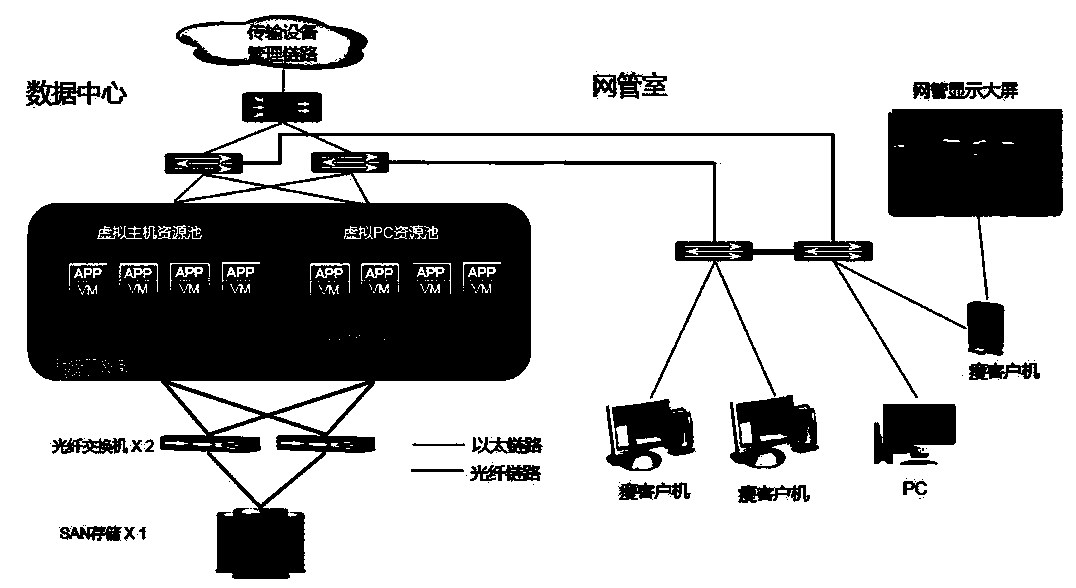
A railway communication centralized network construction method based on a cloud computing technology
InactiveCN109818779AImprove reliabilityReduce operation and maintenance workloadData switching networksSystem administratorNetwork management
The invention relates to a railway communication centralized network construction method based on a cloud computing technology, which comprises the following steps of: concentrating user desktop dataoriginally dispersed on each PC (Personal Computer) to a cloud data center, establishing a resource pool through a desktop virtualization technology, and accessing network management users and officeworkers as users through various terminals. According to the invention, the terminal is separated from the data, the local terminal is only a display device and has no local storage, and all desktop operation data are centrally stored in the rear-end desktop cloud data center in a centralized manner, so that data asset leakage does not need to be worried; A communication network management systemadministrator can efficiently access a network management software desktop at any time and any internal place to obtain network operation data and obtain maximum service flexibility, and due to the fact that the data and the desktop operate in a centralized mode and are stored in a data center, a user can operate the application without interrupting, and seamless switching of office places is achieved.
Owner:CHINA RAILWAY FIRST SURVEY & DESIGN INST GRP
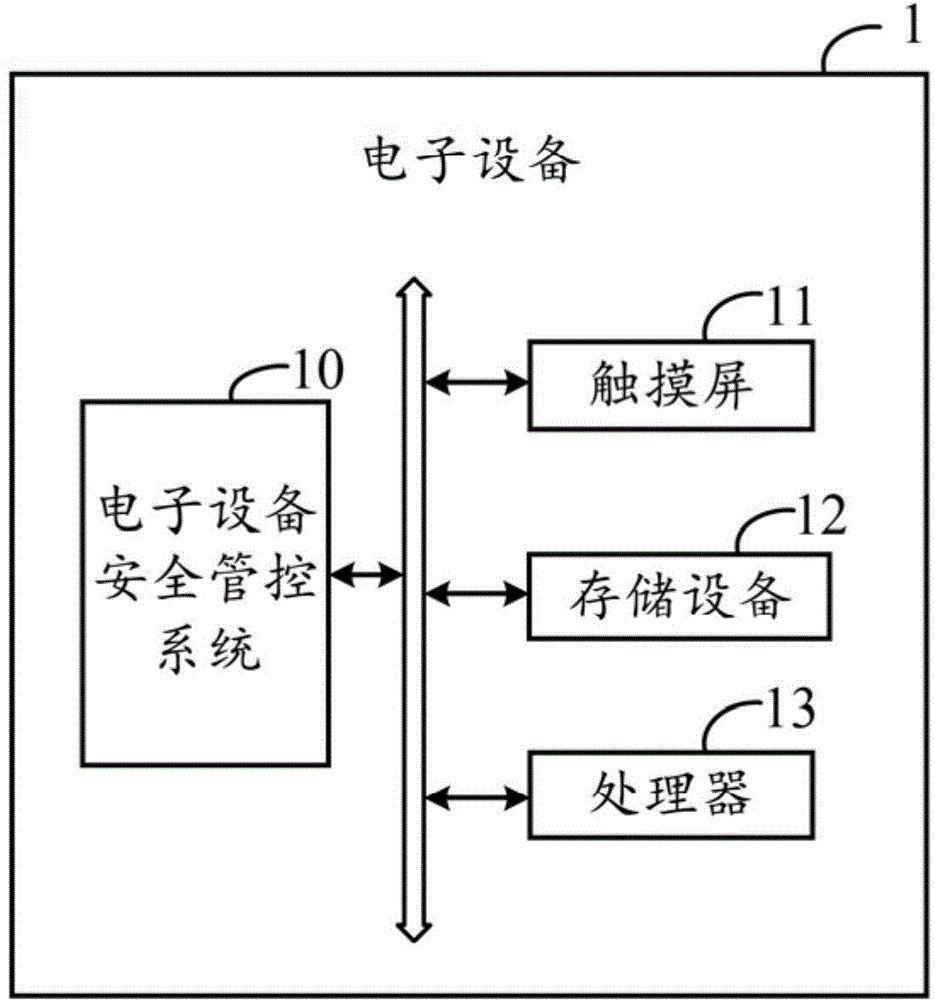
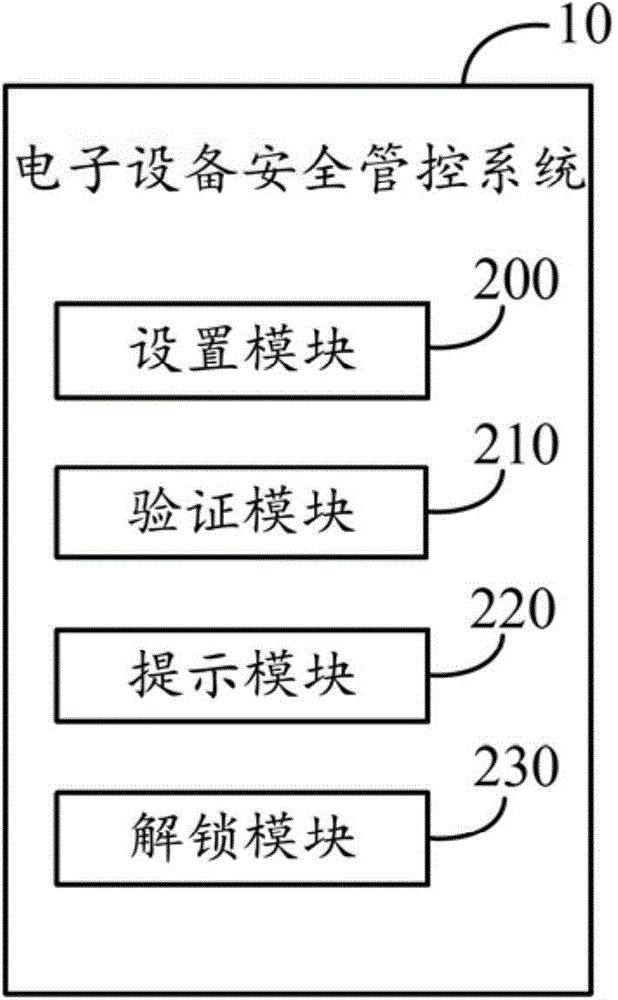
Electronic device safety management system and method
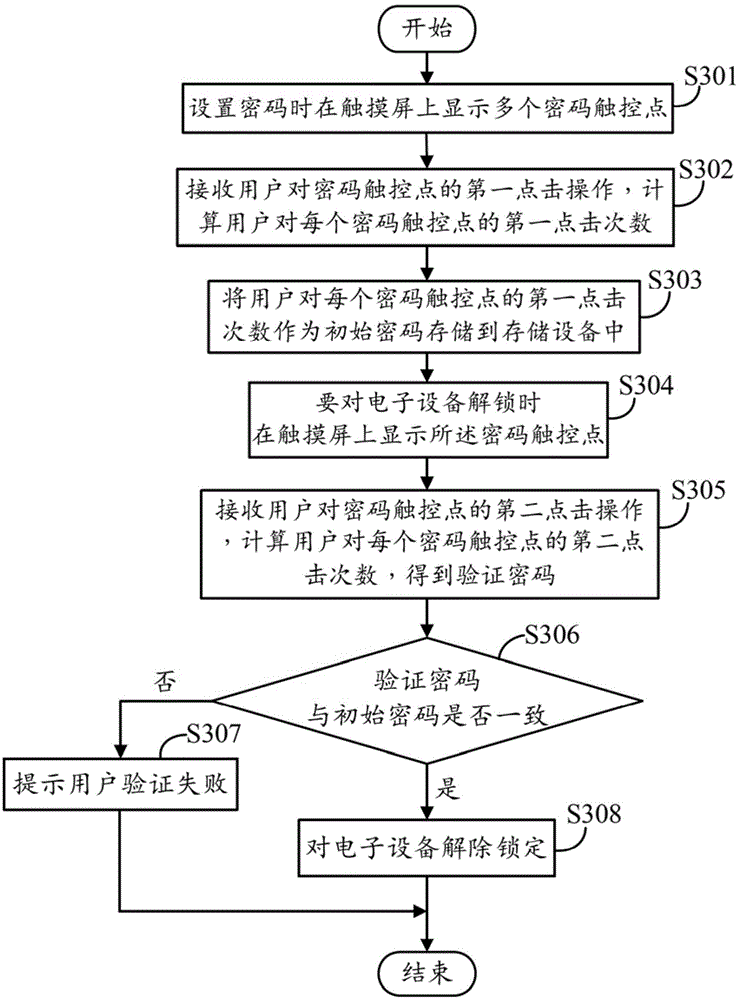
InactiveCN105740665AMeet individual needsRealize security management and controlDigital data authenticationSafety management systemsPassword
The invention discloses an electronic device safety management system, run in an electronic device which comprises a touch screen. The system comprises a setting module, a verification module and an unlocking module, wherein the setting module is used for displaying a plurality of password touch points on the touch screen, computing the first click number of each password touch point on which the user clicks, and thereby obtaining an initial password of the user; the verification module is used for displaying the password touch points on the touch screen, computing the second click number of each password touch point on which the user clicks, thus obtaining a verification password, and judging that whether the verification password is accordant with the initial password when the user is to unlock the electronic device; and the unlocking module is used for unlocking the electronic device when the verification password is accordant with the initial password. The invention also provides an electronic device safety management method. According to the system and method, the password can be set and verified according to the click number of the specific touch points, thus the safety management of the electronic device is achieved.
Owner:FU TAI HUA IND SHENZHEN +1
Personnel safety management and control system for 3D personnel positioning
PendingCN114245294AEasy to track in real timeReal-time precise centimeter-level positioningClosed circuit television systemsLocation information based serviceControl systemPositioning technology
The invention discloses a personnel safety management and control system for 3D personnel positioning, a plurality of UWB positioning base stations are distributed in a positioning area and used for receiving, capturing and analyzing ultra-bright band signals emitted by positioning tags in the positioning area, the positioning tags are connected with exciters, the plurality of UWB positioning base stations are interconnected through communication base stations, and the communication base stations are connected with the UWB positioning base stations. And a communication base station is connected with a positioning engine server, and operation and maintenance work visual management of a positioning area is realized through UWB positioning technology, three-dimensional display and monitoring linkage. The production state of personnel is controlled in real time based on advanced technologies such as a UWB personnel positioning technology, a virtual reality technology and big data analysis, the production state is dynamically displayed on a three-dimensional model, comprehensive monitoring of personnel basic information, personnel position information and production operation information is achieved, and the purpose of safe closed-loop management is achieved through personnel qualification auditing, area management and control, safety alarm and the like.
Owner:XINJIANG TIANCHI ENERGY SOURCES CO LTD +1
Internet of Things equipment security control method, device and system
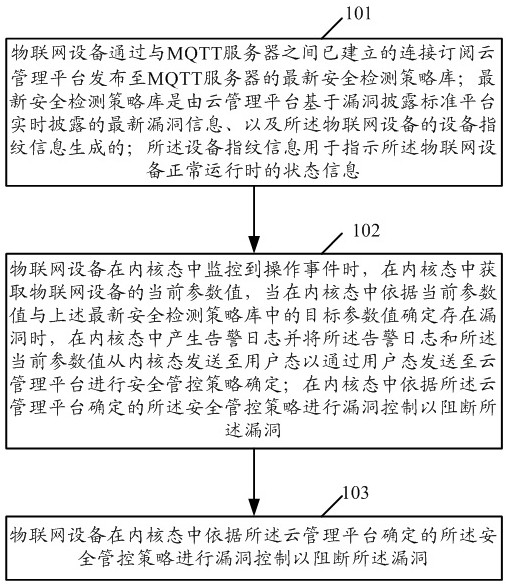
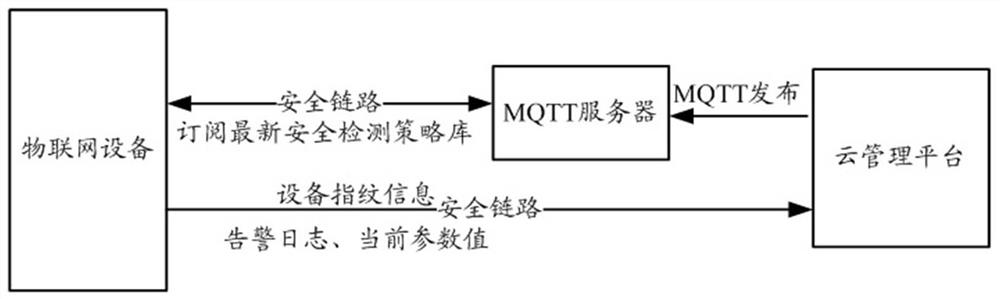
ActiveCN112995236AEnsure safetyImprove securityMachine learningTransmissionComputer networkInternet privacy
The embodiment of the invention provides an Internet of Things equipment security control method, device and system. In the embodiment of the invention, the method comprises the following steps that the Internet of Things equipment determines whether a vulnerability exists or not based on a real-time latest security detection strategy library in a kernel mode, and sends the vulnerability to the Internet of Things equipment when determining that the vulnerability exists in the kernel mode; and the alarm log is generated in the kernel mode, and the alarm log and the current parameter value are sent to the user mode from the kernel mode so as to be sent to the cloud management platform through the user mode for security control strategy determination, so that security control of the Internet of Things equipment is realized, and the security of the Internet of Things is guaranteed. Moreover, the Internet of Things equipment determines vulnerabilities and security control in a kernel mode, so illegal tampering is prevented, the security control of the Internet of Things equipment is further effectively improved, and the security of the Internet of Things is guaranteed.
Owner:HANGZHOU HIKVISION DIGITAL TECH
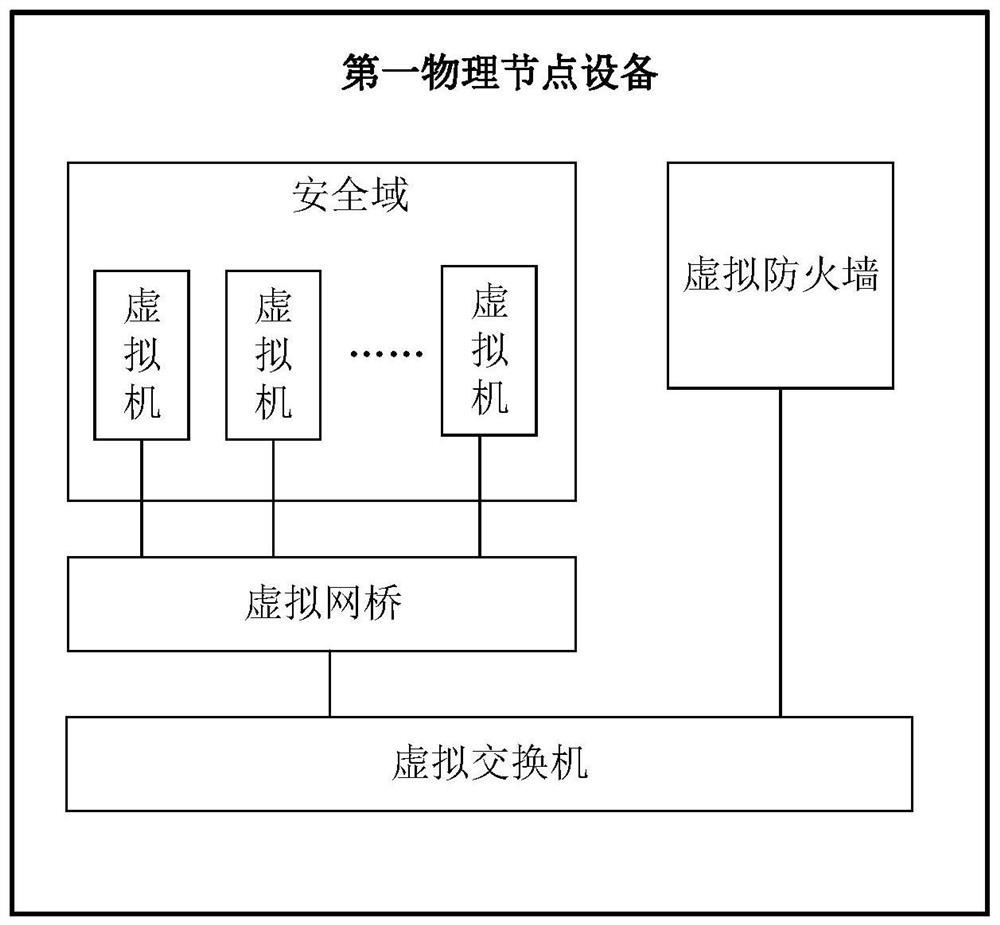
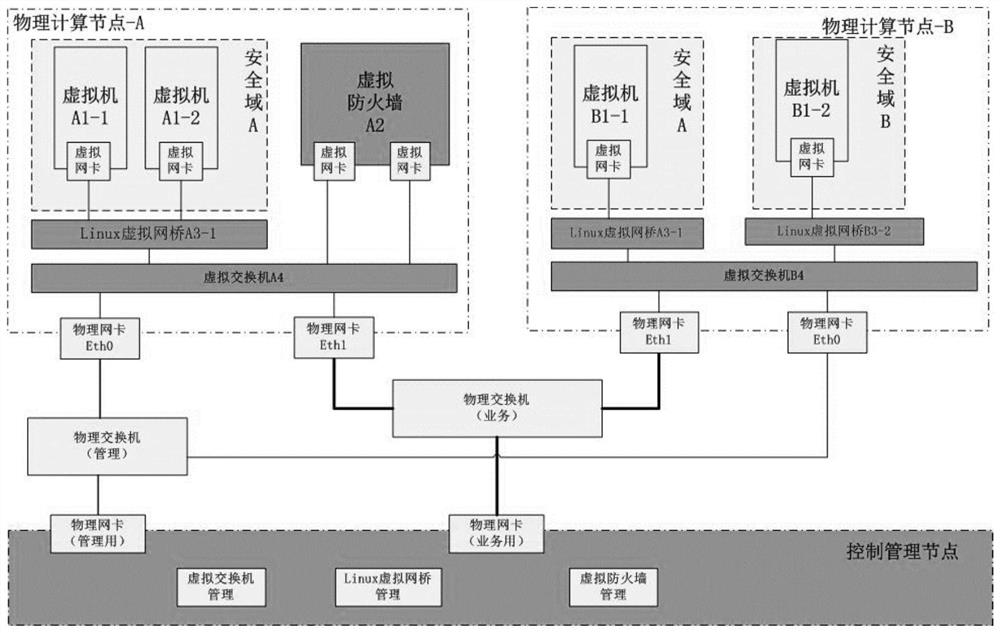
Network shooting range security management and control system and method
ActiveCN114422196ARealize access management and controlRealize in-depth management and controlNetworks interconnectionSecuring communicationSecurity domainEngineering
The invention provides a network shooting range security management and control system, which comprises a plurality of physical node devices and virtual network bridges established on the physical node devices and used for performing access control in the same security domain, the virtual firewall built on the physical node equipment is used for performing access control in different security domains; and the virtual switch built on the physical node equipment is used for carrying out communication service between the physical node equipment and other physical node equipment. According to the invention, a security management and control mechanism with a network access layer, a convergence layer and a core layer is constructed through the established virtual network bridge, virtual switch and virtual firewall, multi-dimensional depth management and control of the network target range are realized, and convenience is provided for large-scale resource and complex network access. The invention further provides a network shooting range security control method.
Owner:永信至诚科技集团股份有限公司
Data processing method, system and equipment and computer readable storage medium
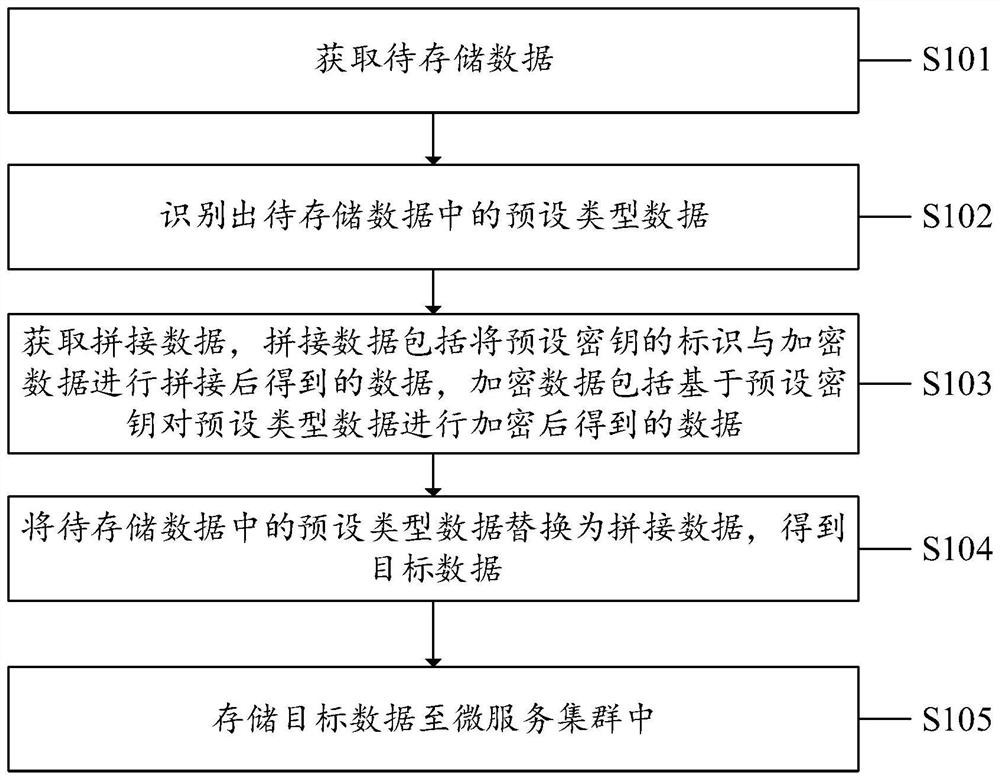
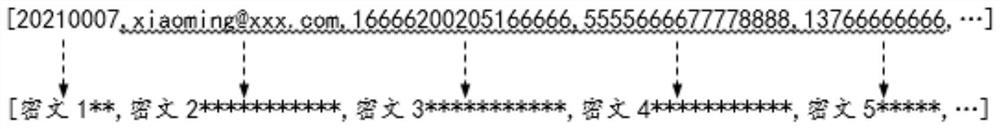
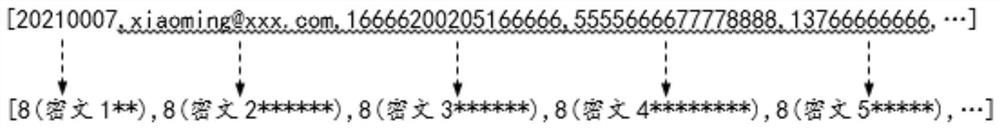
InactiveCN114244606AEnable secure storageRealize security management and controlKey distribution for secure communicationDigital data protectionData packEngineering
The invention discloses a data processing method, system and device and a computer readable storage medium, which are applied to a micro-service gateway, and the method comprises the following steps: obtaining to-be-stored data; identifying preset type data in the to-be-stored data; obtaining spliced data, the spliced data comprising data obtained by splicing the identifier of the preset key and the encrypted data, and the encrypted data comprising data obtained by encrypting the preset type of data based on the preset key; replacing the preset type of data in the to-be-stored data with the spliced data to obtain target data; and storing the target data into the micro-service cluster. In the application, the micro-service gateway can automatically identify the preset type of data in the to-be-stored data, obtain the corresponding spliced data, then obtain the target data based on the spliced data, and store the target data in the micro-service cluster, so that automatic secure storage of the to-be-stored data is realized, and the security of the to-be-stored data is improved. Therefore, the micro-service system can automatically perform security control on the data.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com