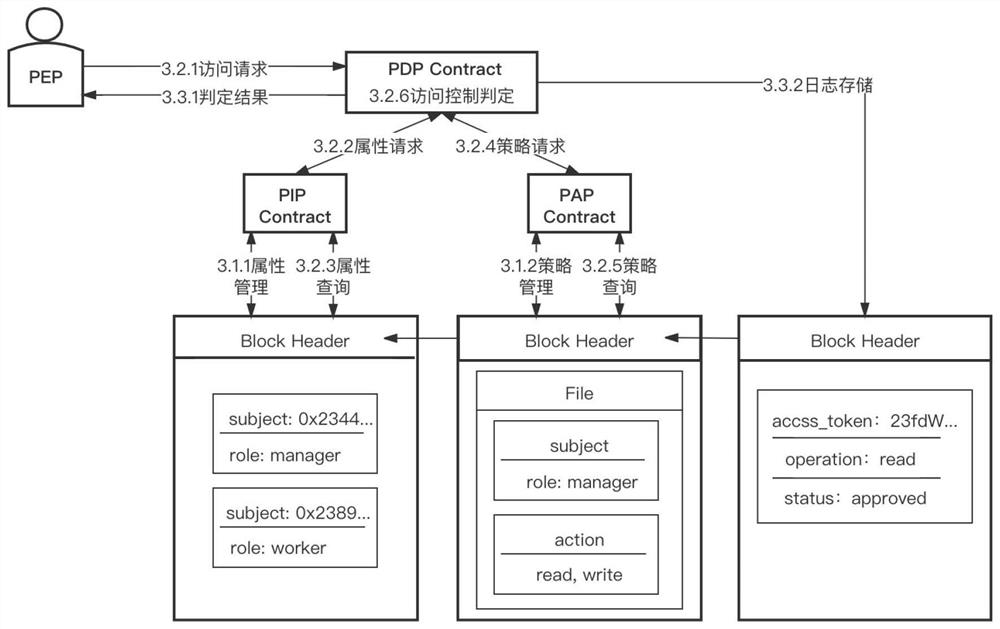
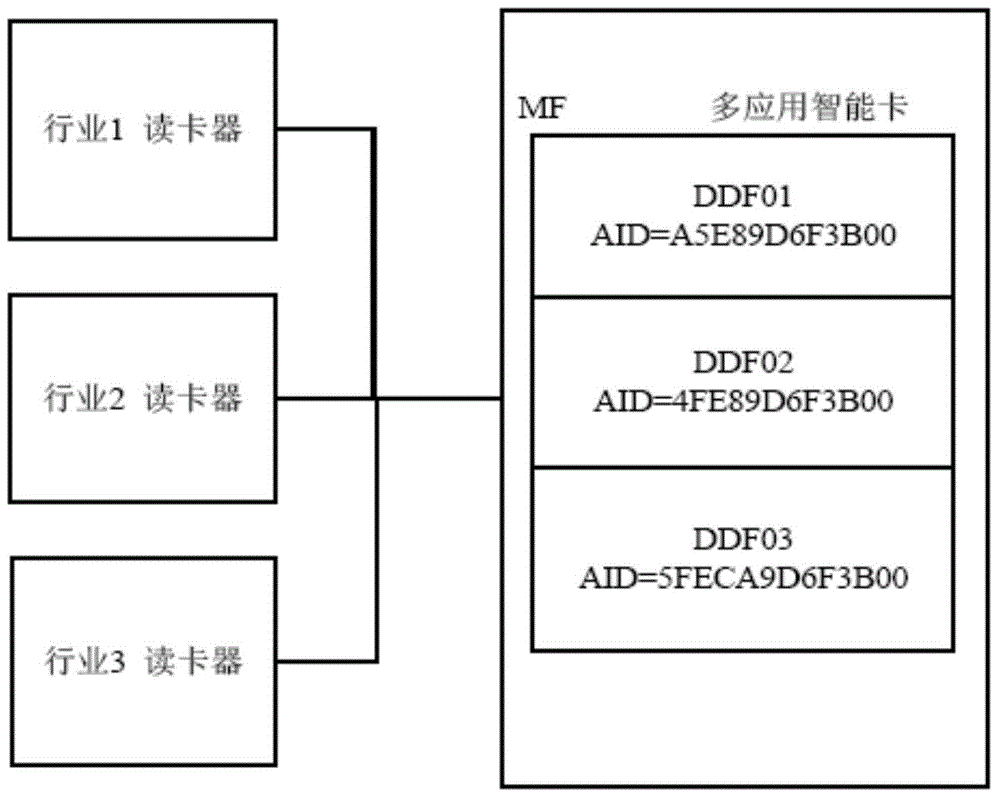
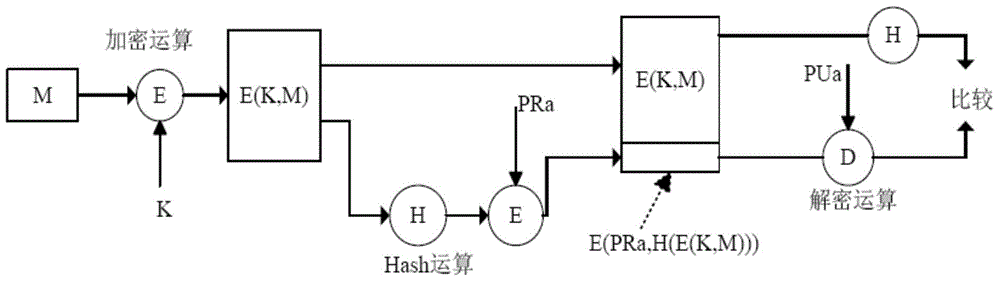
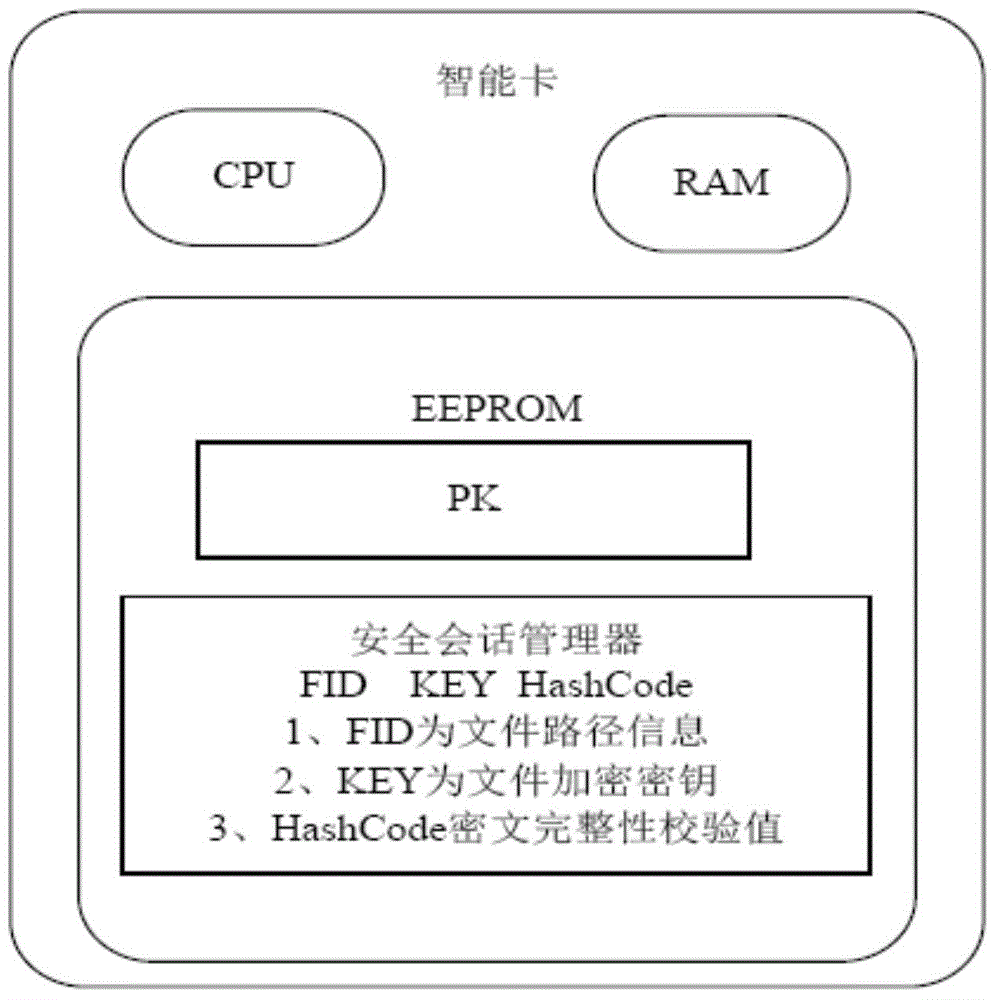
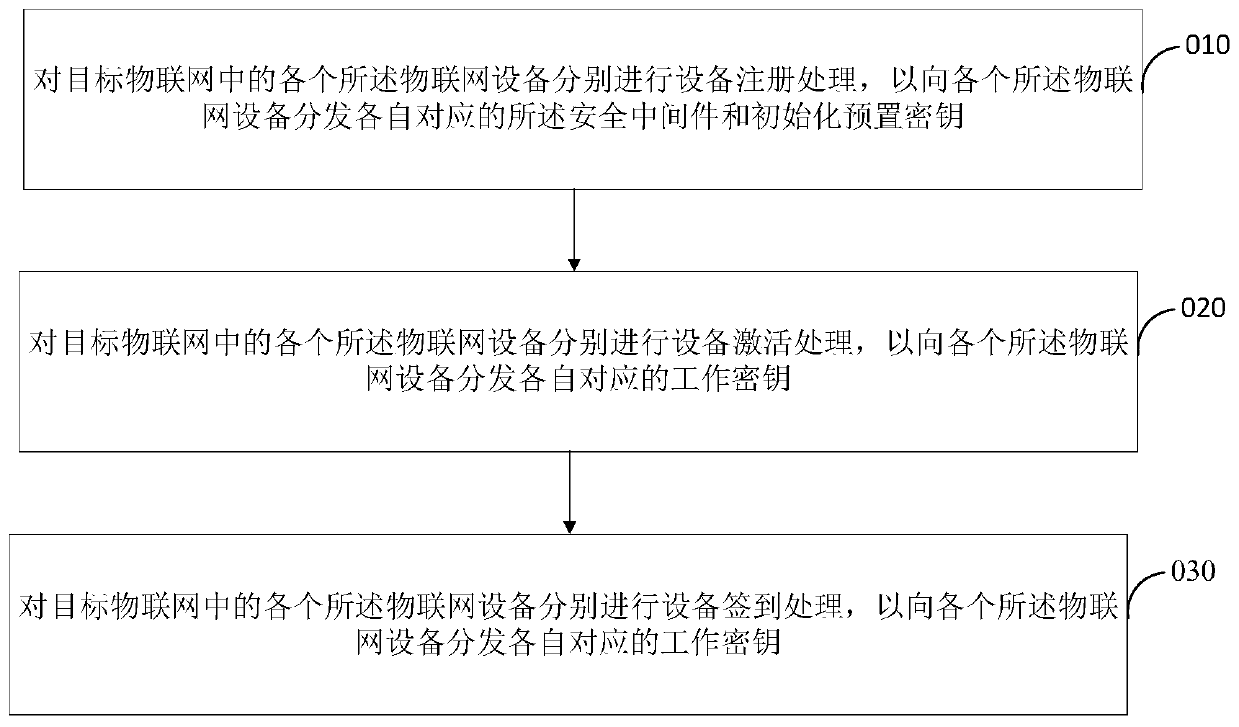
Patents
Literature
97results about How to "Enable secure storage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
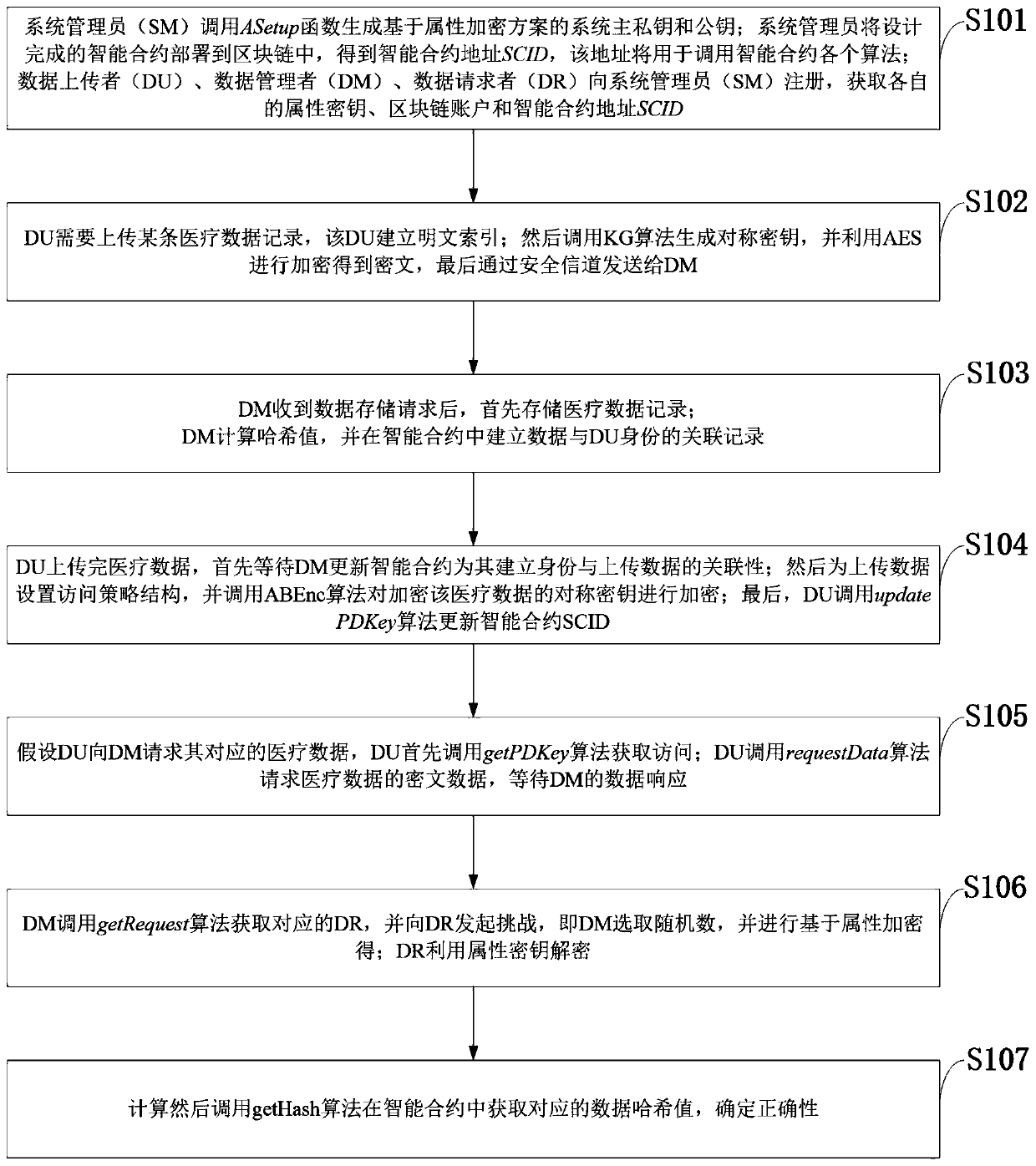
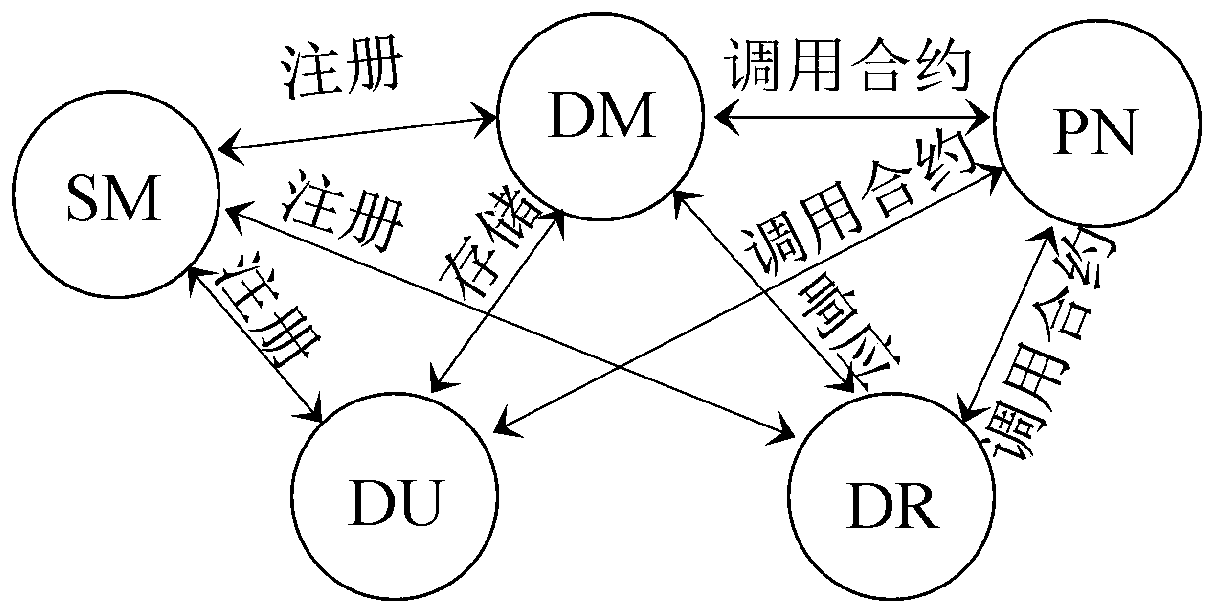
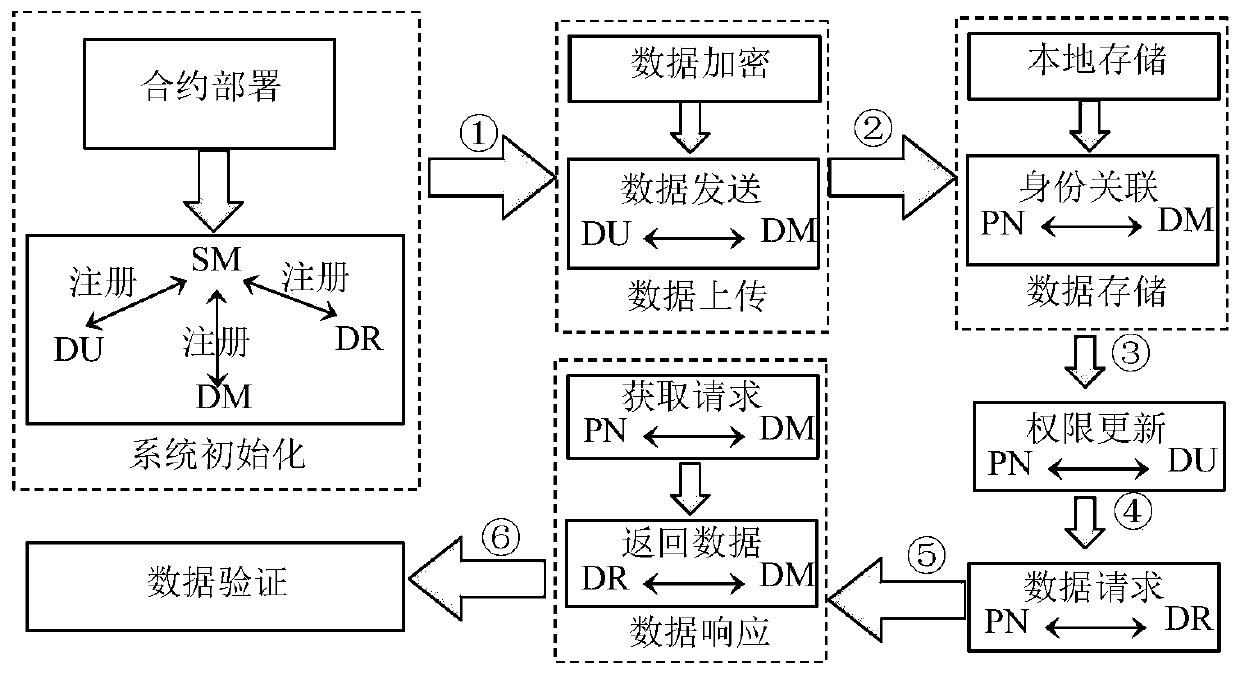
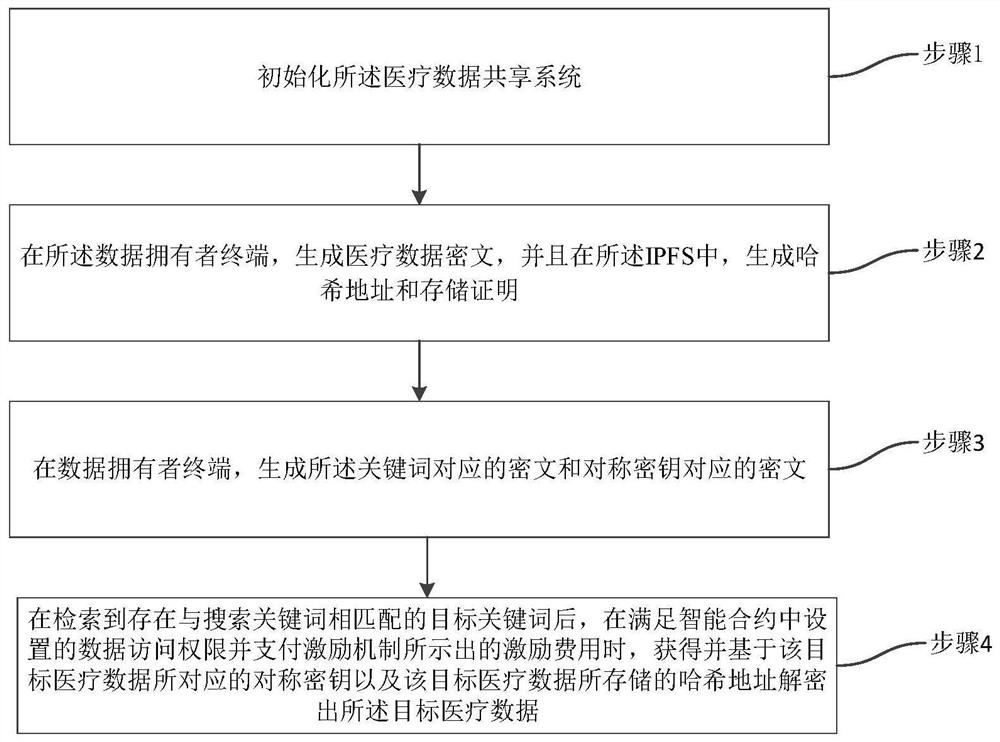
Medical data sharing system based on Blockchain technology and designing method
PendingCN110400642APrivacy protectionAchieve sharingMedical communicationDigital data protectionData informationStructure of Management Information
The invention belongs to the field of data information safety technology, and discloses a medical data sharing system based on Blockchain technology and a designing method. The medical data sharing system based on the Blockchain technology comprises components of a data uploader, a data manager, a data requester, alliance chain nodes and a system administrator. In the system, the data uploader utilizes AES for encrypting the medical data, thereby effectively protecting medical data privacy, and realizing high-efficiency medical data storage. Furthermore according to a symmetric key in the AESis encrypted according to the CPABE, thereby ensuring a fact that only the data requestor with an attribute that satisfies a preset accessing strategy structure can perform deciphering for obtaining the symmetric key, realizing fine-grained access control of the medical data, and realizing supports for accessing control of the temporary request data in an emergency. Obviously, the system and the method effectively settle existing problems based on a Blockchain medical data sharing system and safely and efficiently provides services such as medical data storage, fine-grained access control andsharing.
Owner:梁胤豪
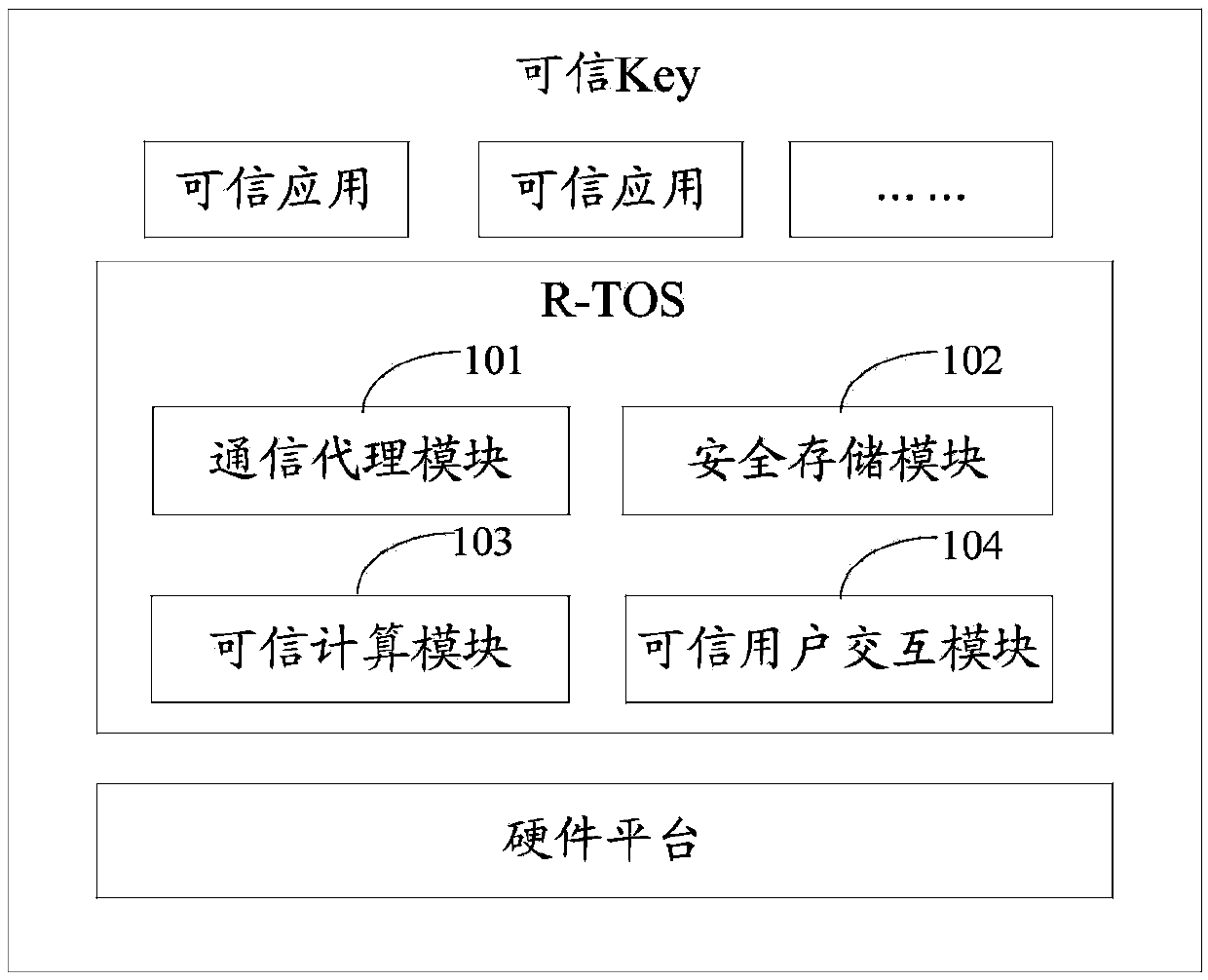
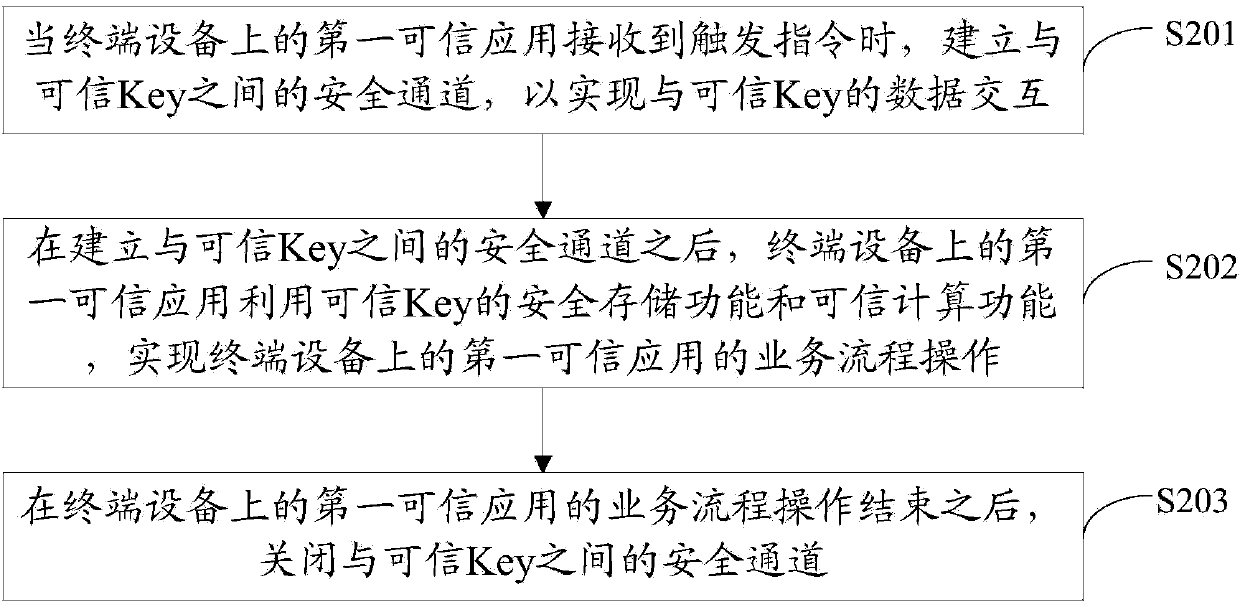
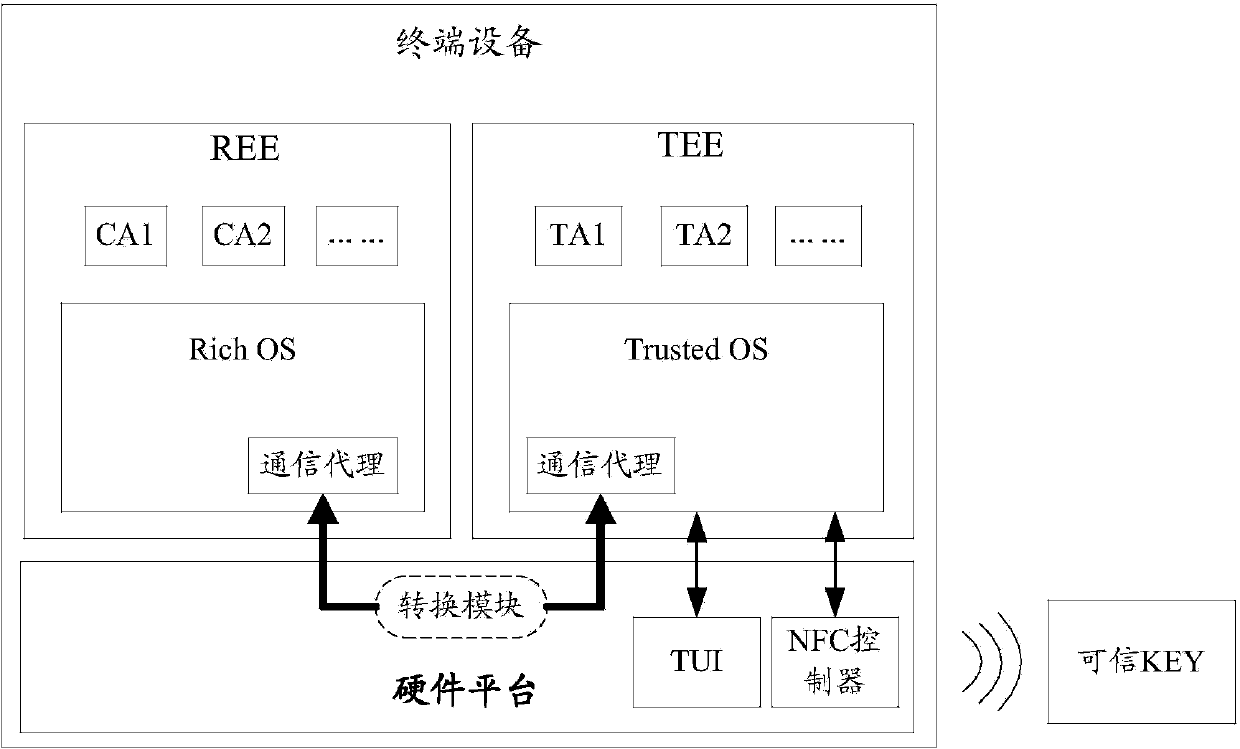
Credible Key and safe operation method thereof
InactiveCN103745155ASimple designEasy to operatePayment architectureDigital data authenticationPaymentOperational system
The invention provides a credible key and a safe operation method thereof. The credible Key comprises a communication agent module, a safe storage module, a credible computation module and a credible interaction module, wherein the communication agent module is used for establishing a safe channel between the credible Key and a credible operating system of terminal equipment; the safe storage module is used for providing a safe storage API (Application Program Interface) for developing a credible application, and providing a safe storage function for the credible Key; the credible computation module is used for providing a credible computation API for the credible application, and providing a credible computation function for the terminal equipment; the credible interaction module is used for transmitting an interaction command to the credible operating system of the terminal equipment through the communication agent module on the basis of user operation. The credible KEY can be used together with a credible running environment on the terminal equipment, thereby realizing credible services such as remote payment, online transfer, safe storage and credible computation.
Owner:EASTCOMPEACE TECH
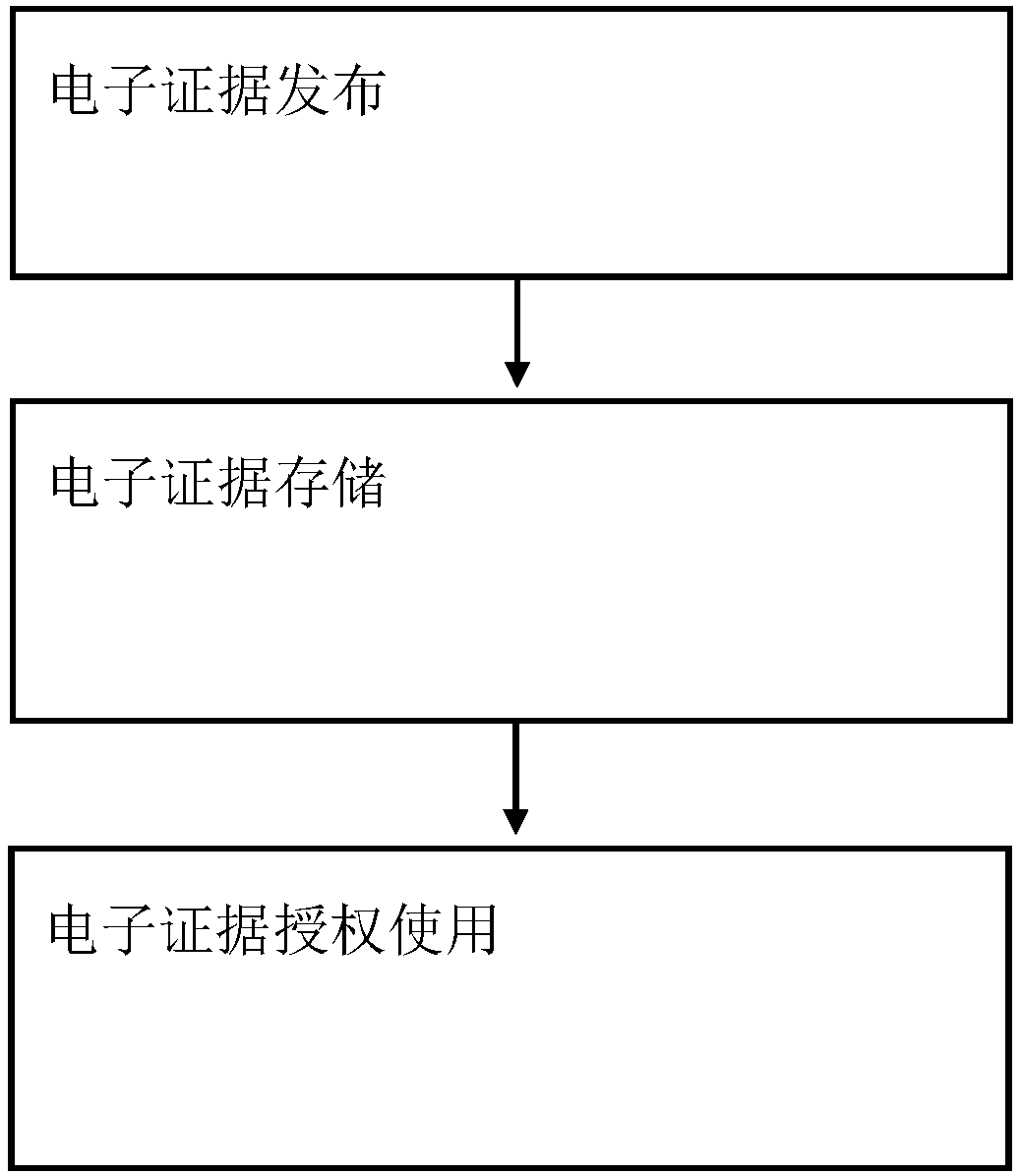
Blockchain-based trusted data calculation method
InactiveCN108471350AEnable secure storageKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCalculation methodsBlockchain
The invention provides a blockchain-based trusted data calculation method. The method includes the following steps: electronic evidence issuance, electronic evidence storage, and authorized use of electronic evidences. According to the blockchain-based trusted data calculation method proposed by the invention, the secure storage and effective use of the electronic evidences of users can be effectively realized.
Owner:CHENGDU RES INST OF UESTC
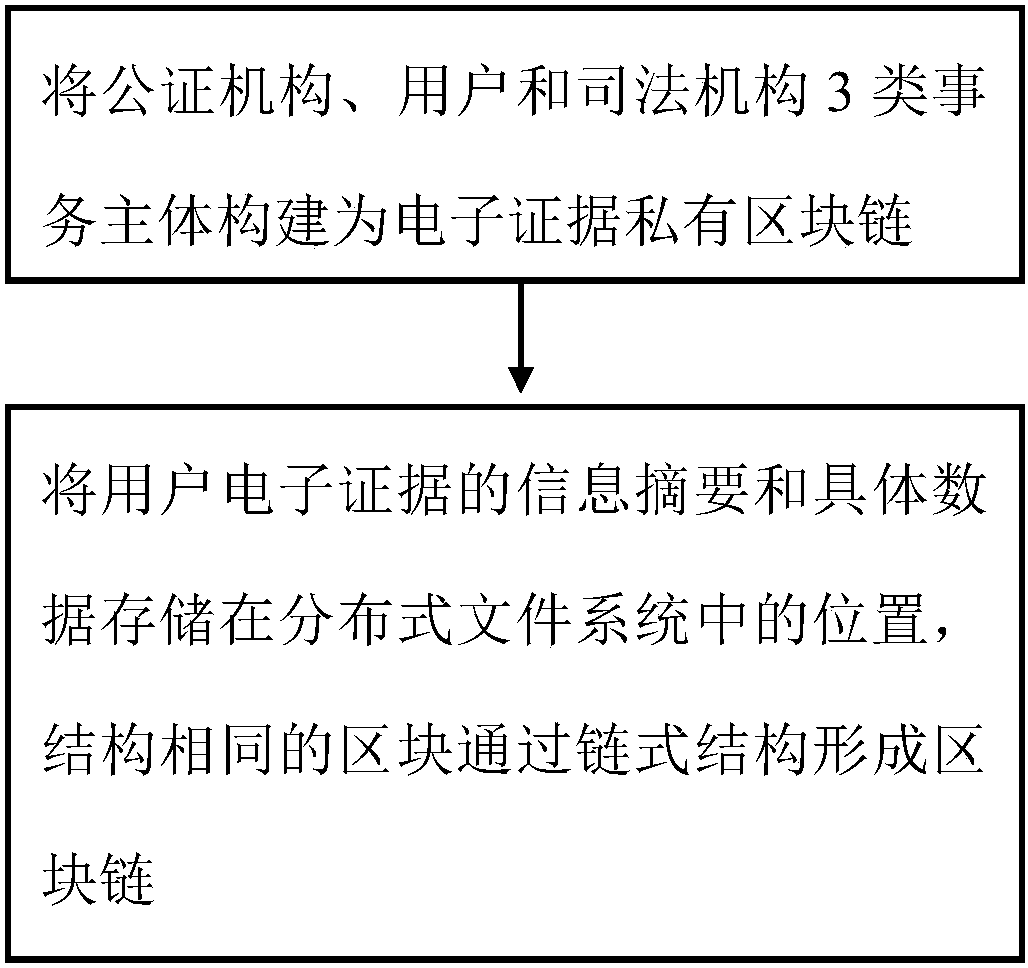
Decentralized storage security implementation method
ActiveCN108429759ASafe for secure storageSafe to useEncryption apparatus with shift registers/memoriesUser identity/authority verificationStorage securityChain structure
The invention provides a decentralized storage security implementation method. The method comprises the following steps: building an electronic evidence private block chain by three types of affair main bodies, namely a notary organization, a user organization and a judicial organ; and storing information abstracts and specific data of electronic evidences of users into positions in a distributedtype file system, and forming a block chain by blocks of same structures through chain structures. The invention provides the decentralized storage security implementation method, which effectively implements secure storage and effective use of the electronic evidences of the users.
Owner:CHENGDU RES INST OF UESTC
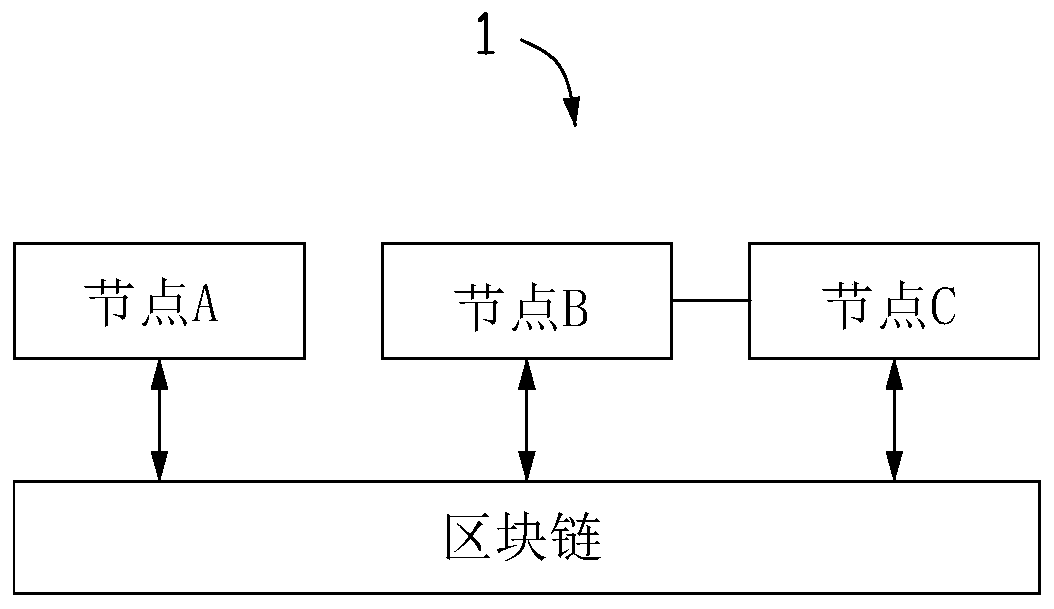
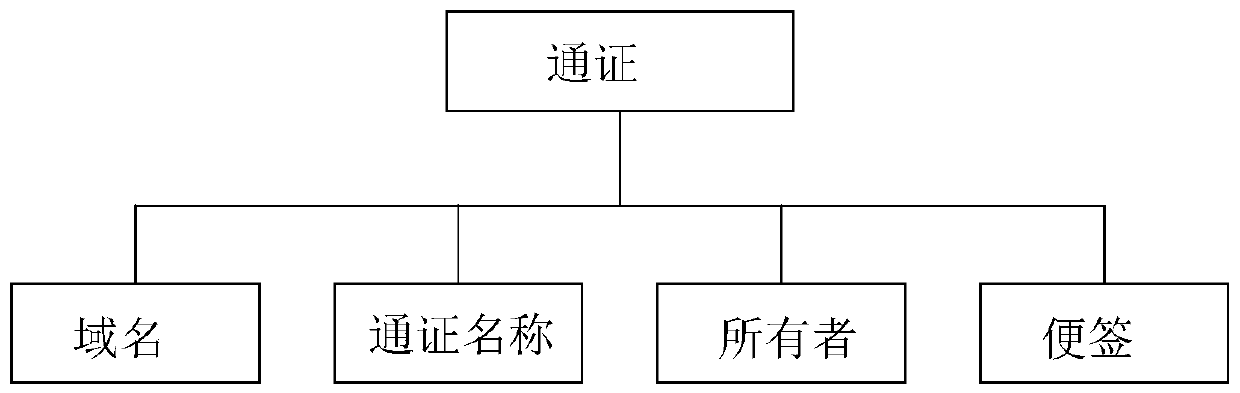
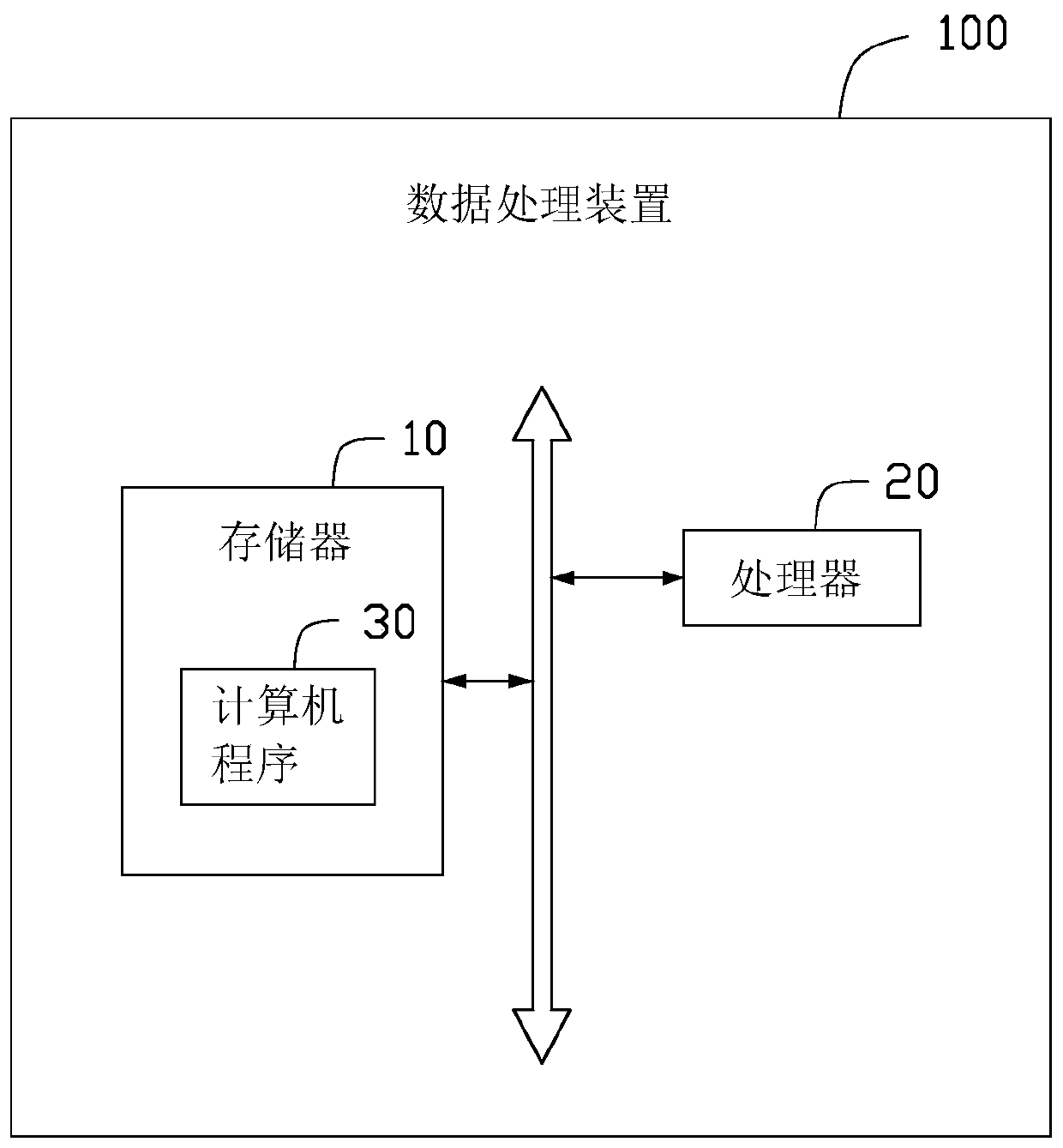
Data processing device and method based on block chain and computer readable storage medium
The invention discloses a data processing method based on a block chain. The method comprises the following steps: encrypting private data according to a data key of a signer and a preset encryption algorithm to obtain a data ciphertext; recording a timestamp generated by carrying out block generation on the privacy data at this time; obtaining a new data block according to the data ciphertext, the timestamp and the hash value of the previous data block of the privacy data; sending the signature message of the new data block to a verification node for verification; when the verification node passes the verification, adding the new data block into a pass issued by the signer in a block chain system; wherein the pass comprises an excrement field, and basic information of private data bound with the pass is recorded in the excrement field. The invention further provides a data processing device based on the block chain and a computer readable storage medium. The privacy data of the user can be stored through the block chain, and the privacy data can be safely stored.
Owner:卓尔智联(武汉)研究院有限公司
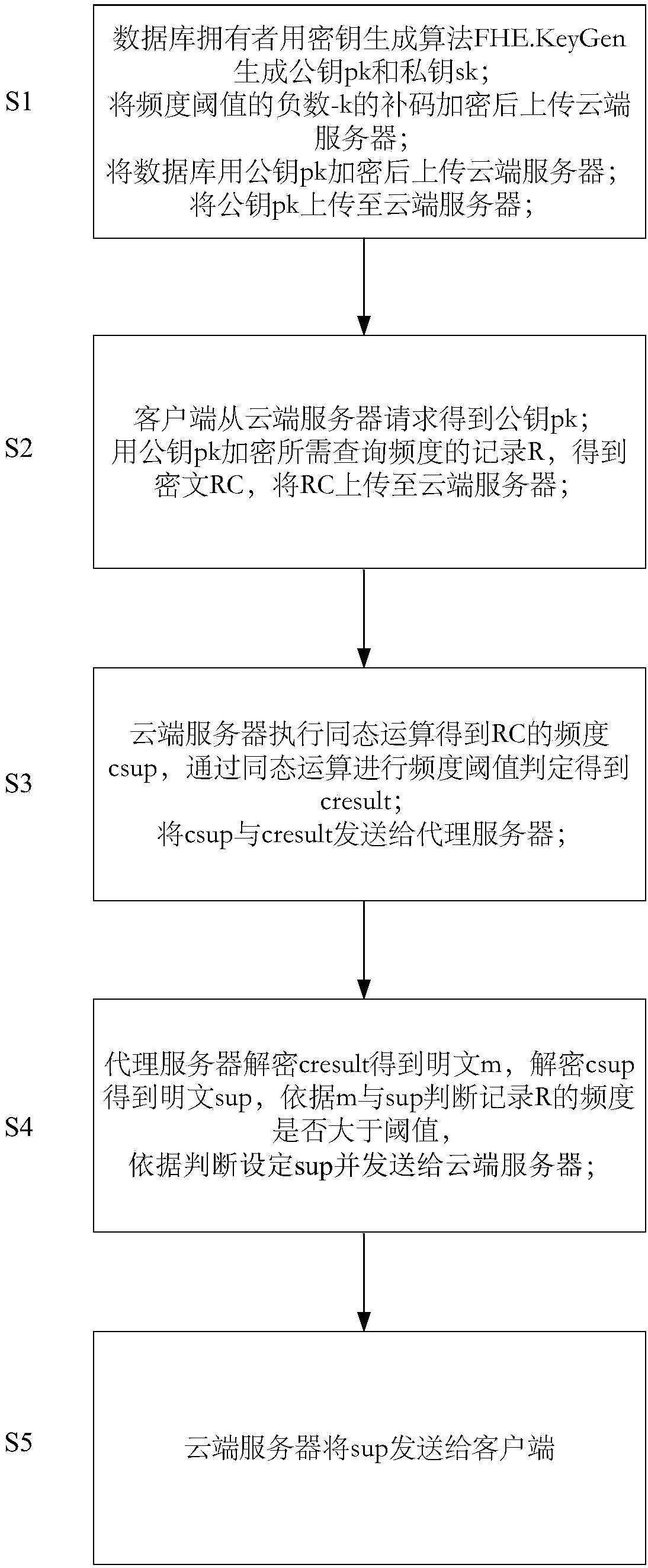
Frequentness measuring method and system for security and privacy protection facing cloud data issuing
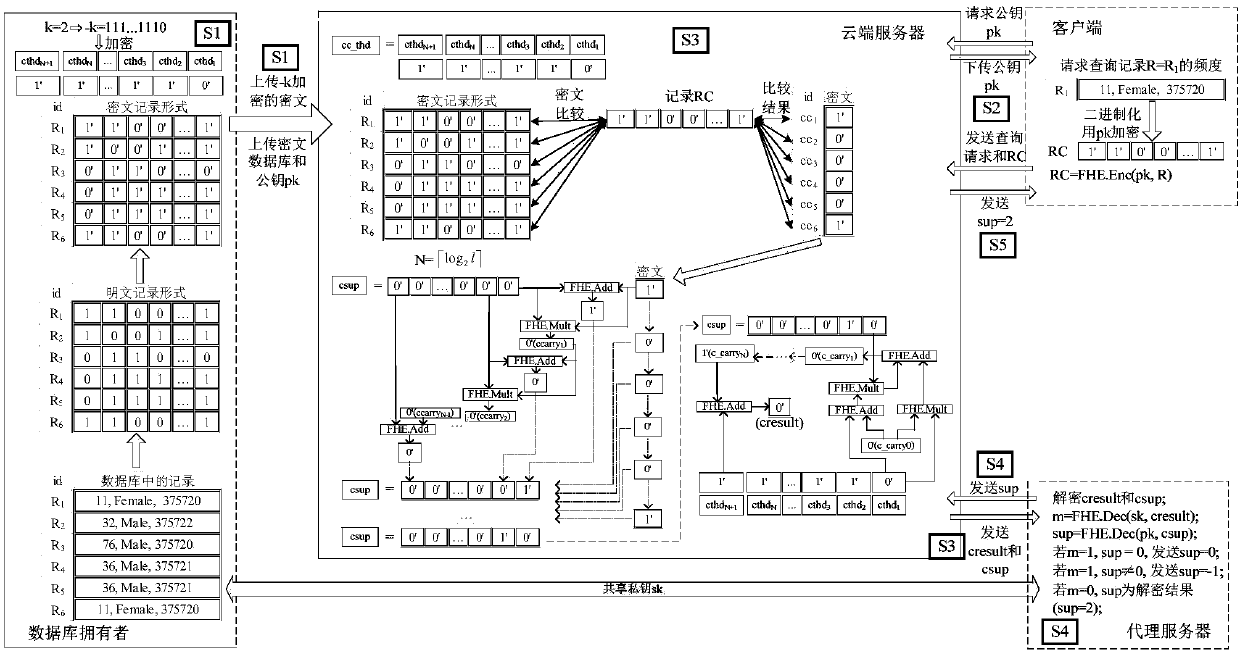
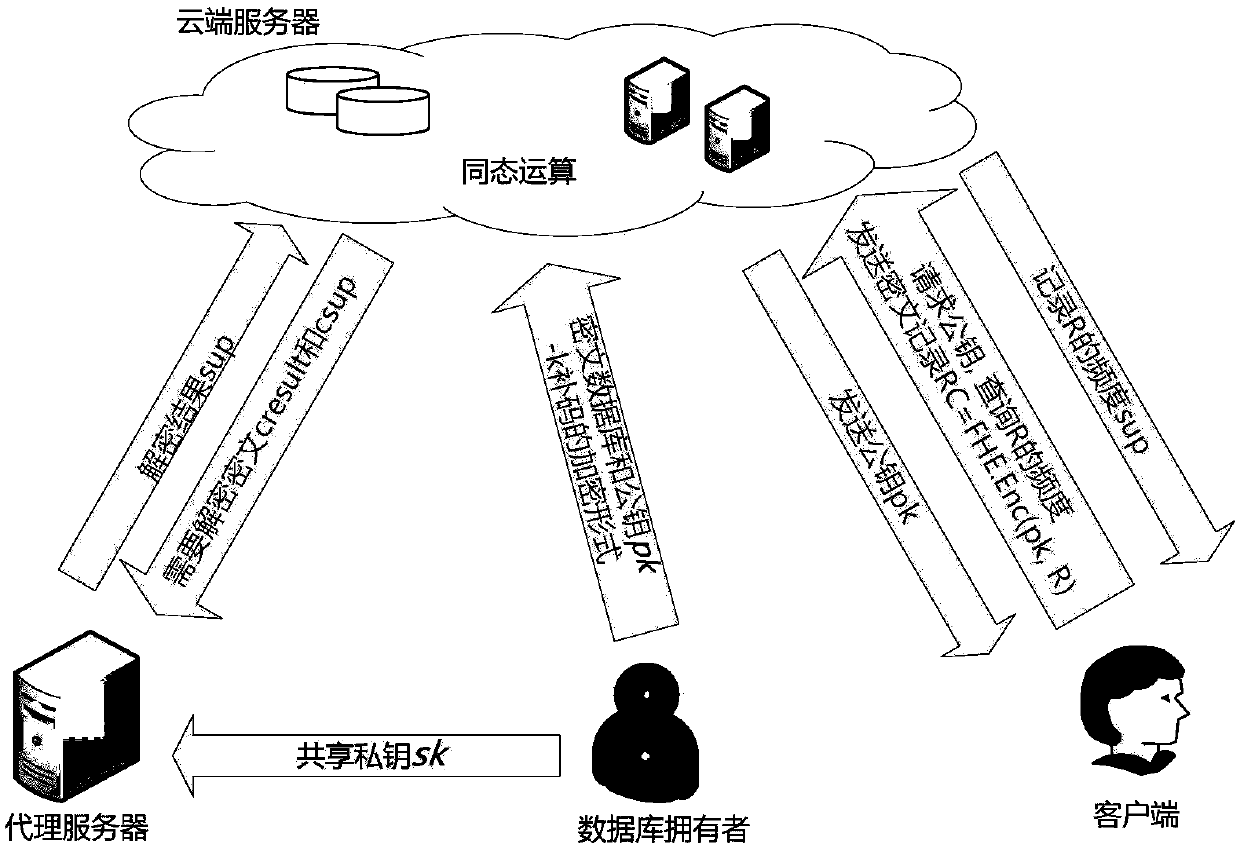
ActiveCN106534313AEnable secure storageDetermination of protection frequencyKey distribution for secure communicationCiphertextPrivacy protection
The invention discloses a frequentness measuring method and system for security and privacy protection facing cloud data issuing. A database owner generates a secret key pair, encryption outsourcing processing is carried out on the database, encryption operation is carried out on complement of a frequentness threshold negative -k, the encrypted complement is uploaded to a cloud server, and a private key sk is authorized to a proxy server; a client applies to inquire the frequentness of a record R; the proxy server obtains permission from the database owner and assists the database owner in dealing with a transaction. The cloud server is used for storing a ciphertext database and carrying out a homomorphic operation on the ciphertext. According to the method and system disclosed by the invention, with the full-homomorphic encryption technology, the frequentness ciphertext in a data recording manner is obtained in a cloud environment and whether the frequentness of the record meets a privacy protection requirement is determined; and leaking of a recorded content inquired by a client as well as sensitive recorded content with the frequentness lower than a threshold in the database can be prevented during the whole process. Therefore, secure storage of data can be realized; and frequentness measurement for privacy protection can be carried out by the cloud conveniently.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Safety storage method for data
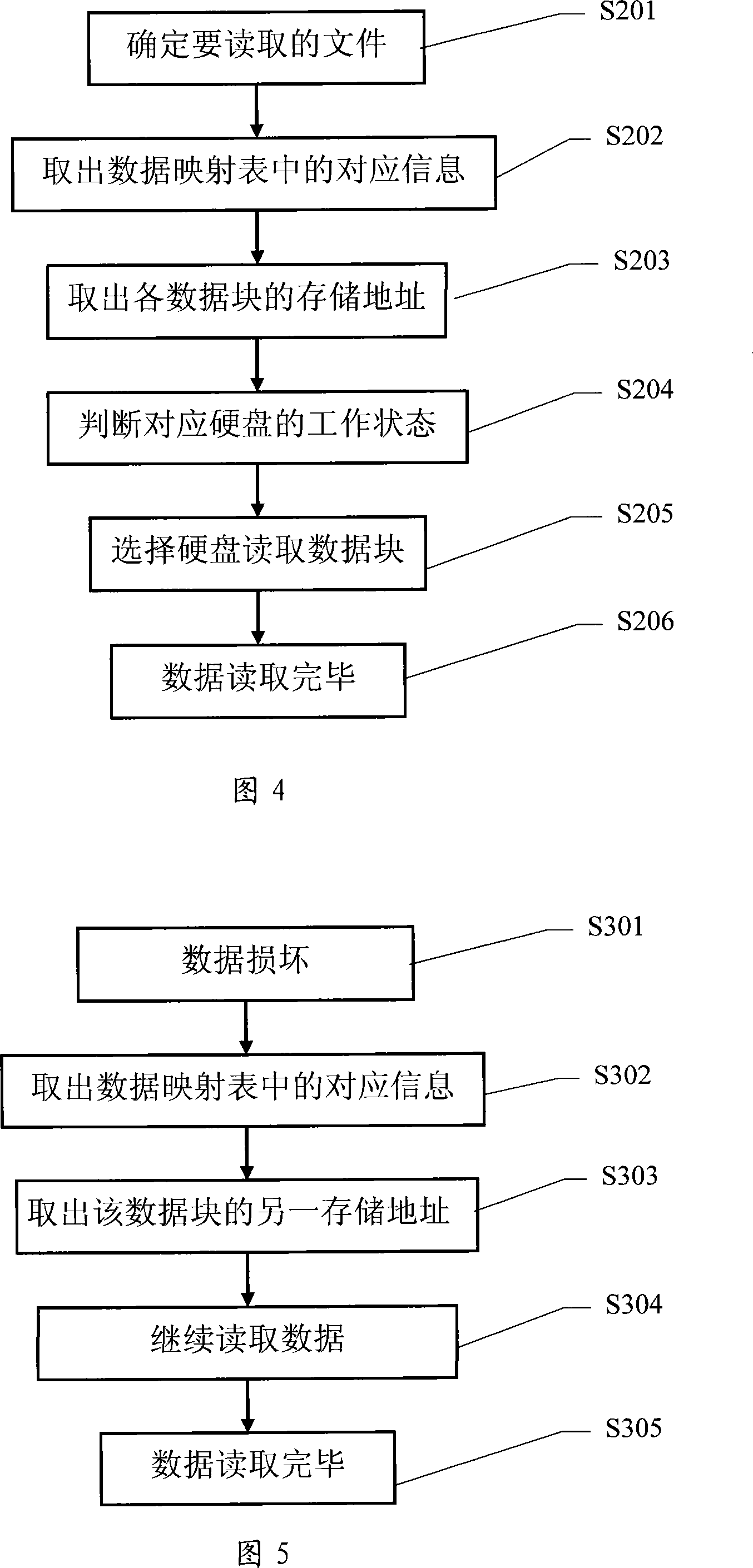
ActiveCN101118508ALow costEnable secure storageRedundant operation error correctionSpecial data processing applicationsPresent methodComputerized system
The present invention discloses a safe data storing method. By connecting with a plurality of storage device, the computer system can store any one data into two separate storage devices simultaneously to form a relationship; when the data in one of the storage device is damaged, or the storage device is damaged, the present invention can take out the data from the other storage device which stores the corresponding data and stores the data into other storage device, to guarantee that any one of the data has usable data in two storage devices simultaneously. When reading data from the two storage devices, the present method can select one, and when one storage device storing the data is damaged, the method can read data from the other storage device. The present invention has low cost, strong data safety and strong expansibility, can increase or decrease the capacity of the storage device at will, and is applicable to the storage system formed by multi hard disks and multiserver, and has high data read rate. No recreating time is needed, when finding data damaged during the course of data reading, the present method can retrieve on line, without influence for the data reading and running.
Owner:CHENGDU SOBEY DIGITAL TECH CO LTD
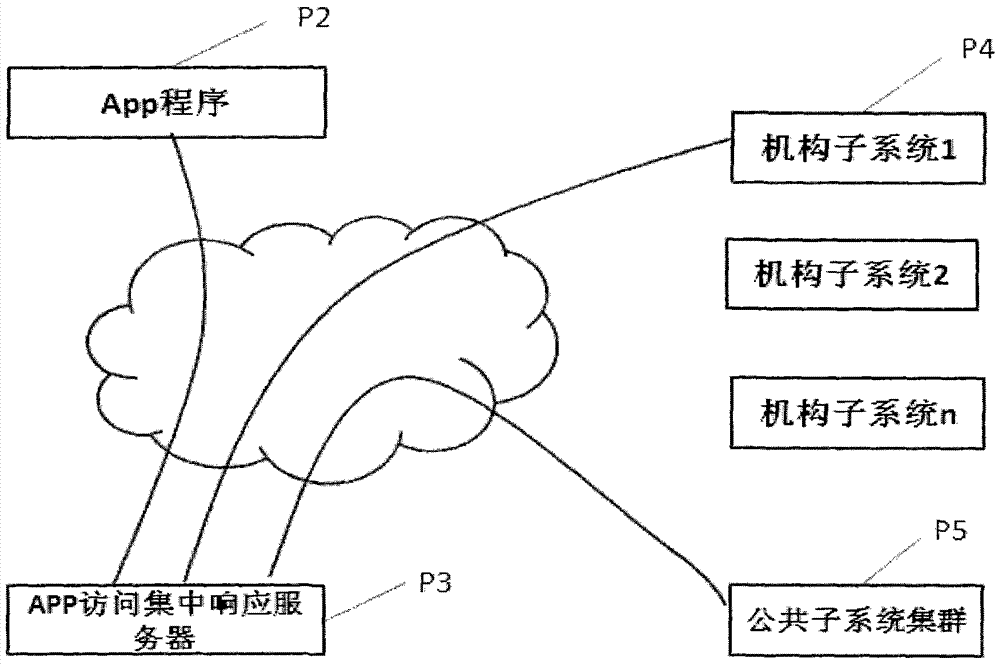
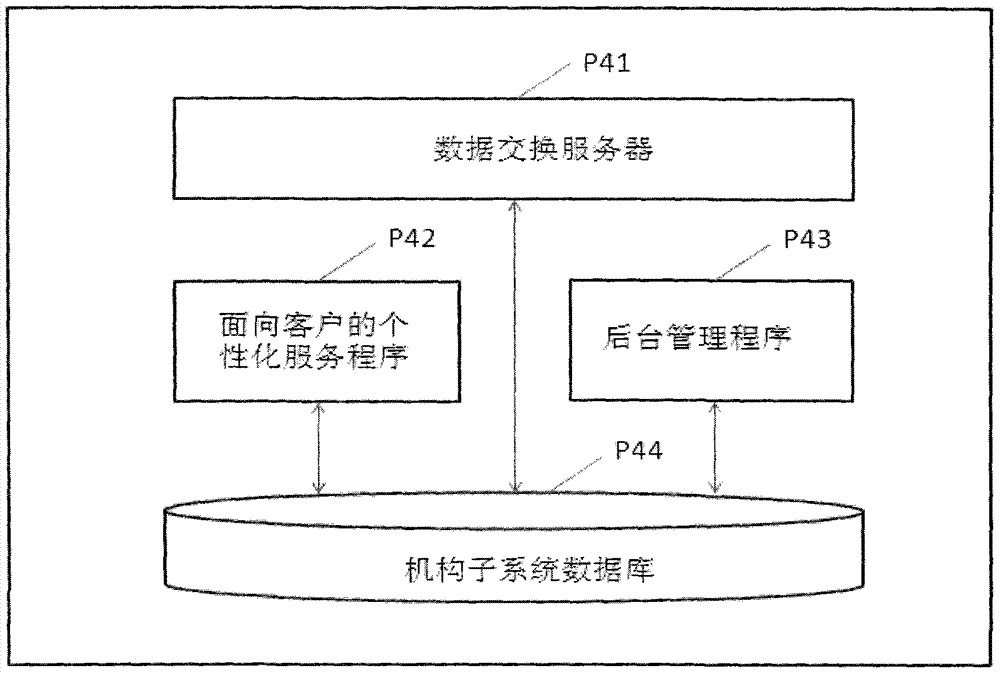
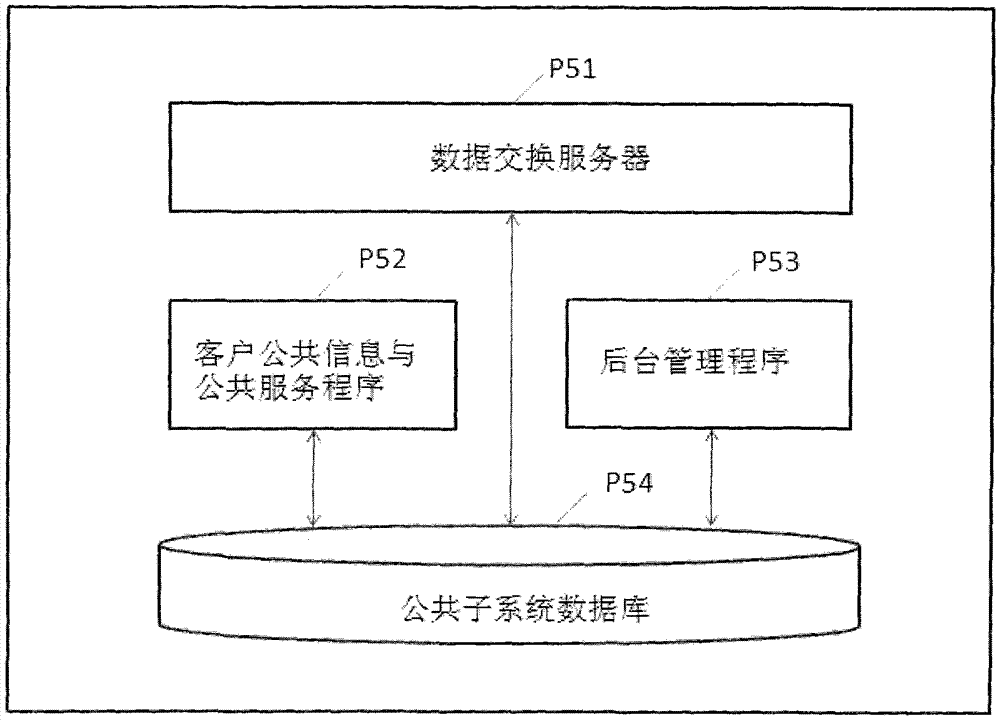
Method and system for accessing multiple subsystems and public subsystem with distributed storage personalized data through single APP program
InactiveCN103929473AImplement storageEnable secure storageTransmissionStructure of Management InformationOrganizational framework
The invention relates to a method and system for accessing multiple subsystems and a public subsystem with distributed storage personalized data through a single APP program. According to the method and system, in the interagency networking service system, the personalized data of clients are distributed and stored in different agency databases, independent management and safety of the data are ensured, a special service is provided, and agency subsystems are formed; public data and service are focused on the public subsystem, and public service extension, development and synergism are achieved; the agency subsystem and client access authentication information structures are planned, a client login access verification mirror image is generated on the public subsystem, the uniform mobile internet APP program (Client) is provided for the clients, the APP program interacts with an APP access centralized response server (Server), the APP access request is analyzed, client login access verification is conducted, personalized service client agency subsystems and a service content organizational framework are determined, personalized data are obtained and processed, the personalized and public service is provided, and the clients can synergistically access agency private systems and a public system.
Owner:冯力新 +1
Distributed storage-based object storage method
ActiveCN106506668AImprove reliabilityImprove usabilityUser identity/authority verificationSpecial data processing applicationsStorage securityAuthentication server
The present invention discloses a distributed storage-based object storage method. The method comprises the steps of building an authentication server by using a distributed storage technology, and completing secure authentication of a user end and a server end; and then optimizing a background IO model for recording fragmented logs so as to improve object storage security. Compared with the prior art, the distributed storage-based object storage method ensures data storage security and the security of a storage cluster, and improves the reliability, availability, security and practicability of the distributed storage cluster.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
A method to realize a global network real name system based on ID authentication
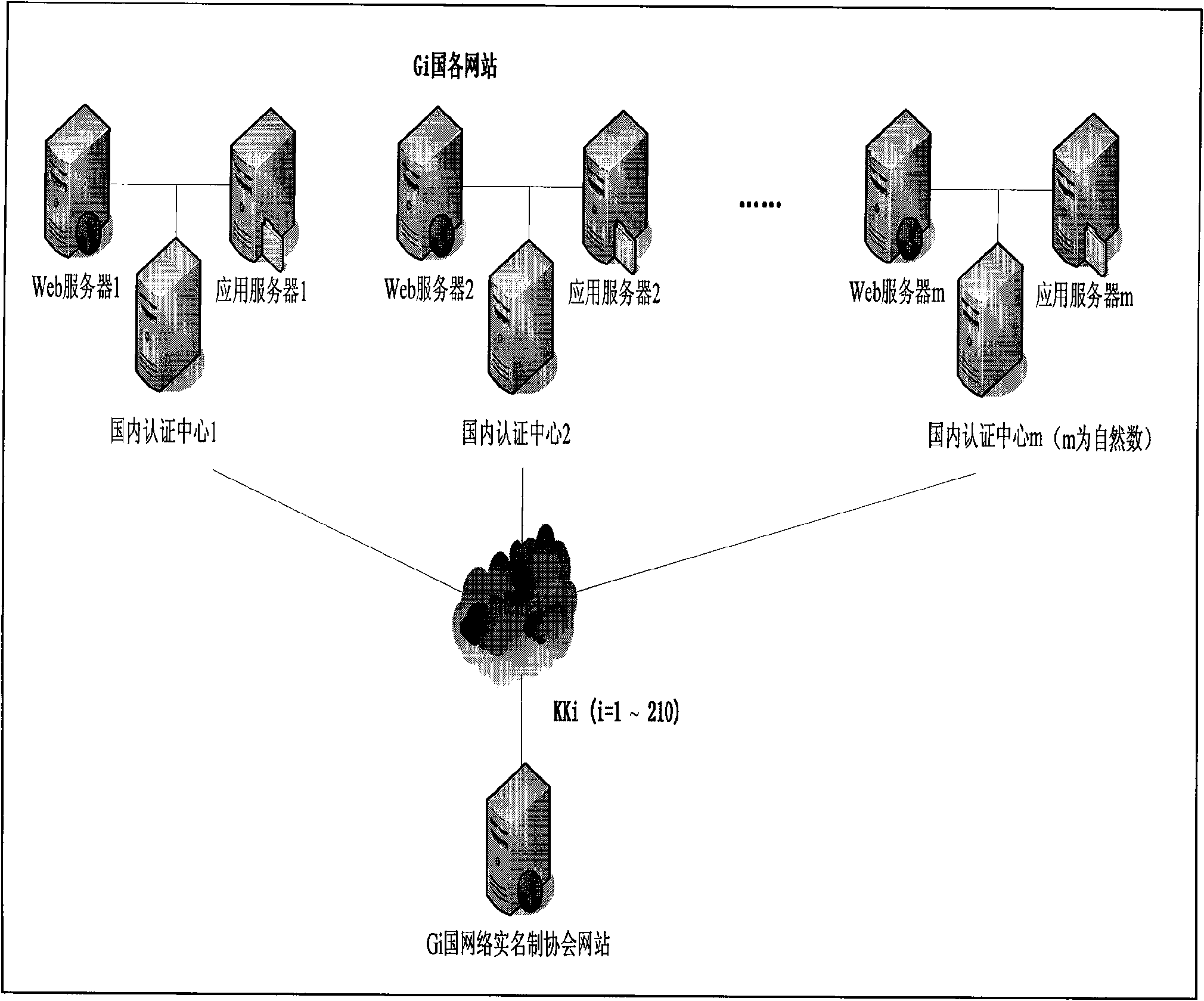
InactiveCN101552672AImprove security levelReduce operating costsUser identity/authority verificationThird partyUser authentication
A method to realize a global network real name system based on ID authentication is to classify network user identity authentication at each network into two types, establish one-to-one domestic authentication center at each website to provide authentication service for domestic network users when they logon domestic websites, establish 10-30 international authentication centers in the country to provide third-party centralized authentication service for foreign network users (from other countries or regions) when they access and logon domestic websites, adopt ID authentication means to solve the 'bottleneck' of mass authentication of authentication centers, update and maintain the network user authentication parameters of domestic authentication centers through the encrypted transmission established between the network real name system association (or society) of each country and domestic website technicians, and meanwhile update and maintain the network user authentication parameters of international authentication center of each country through encrypted transmission established between the network real name system associations (or societies) of different countries, thus realizing a global network real time system.
Owner:胡祥义
Wheel-leg-arm-tank combined explosive disposal robot
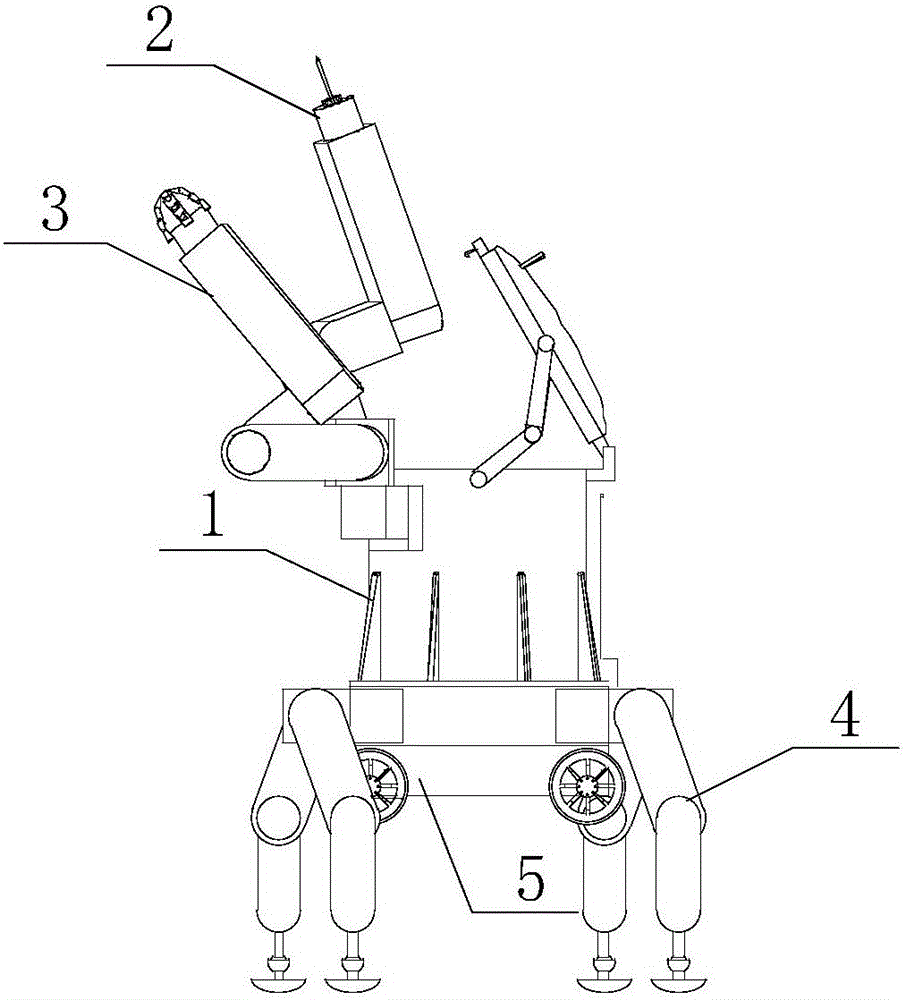
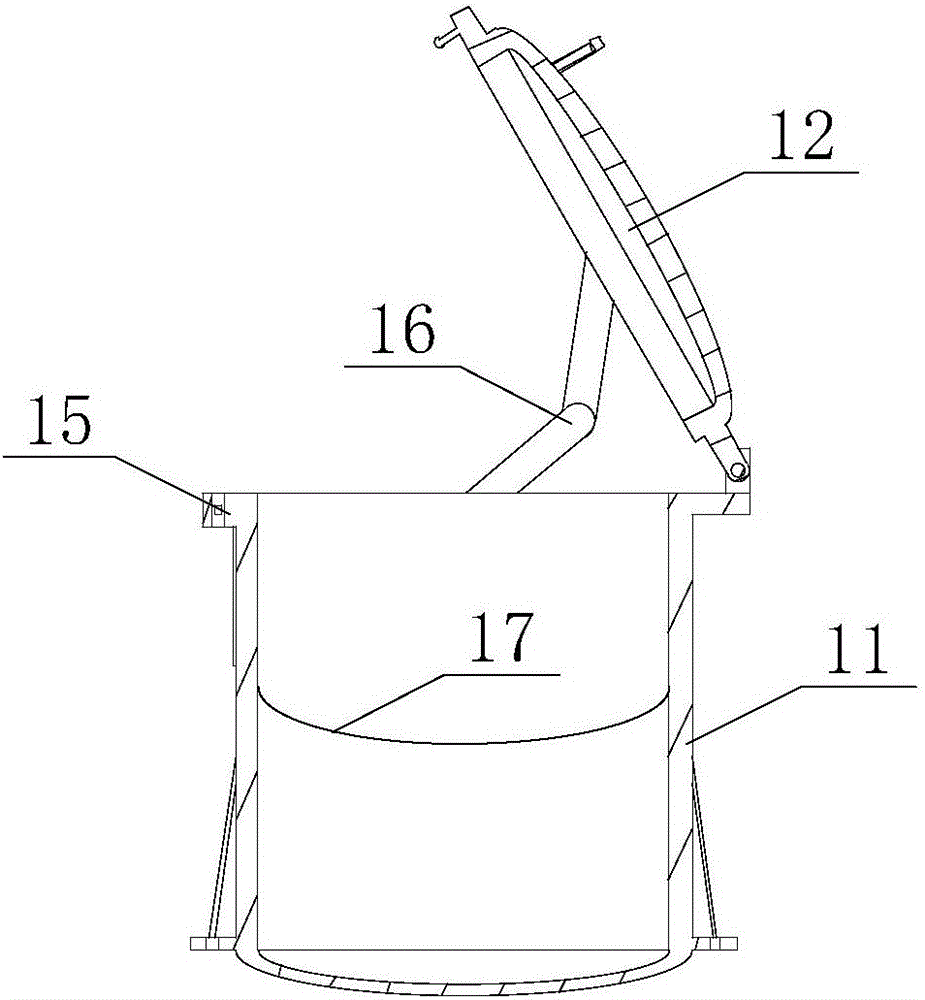
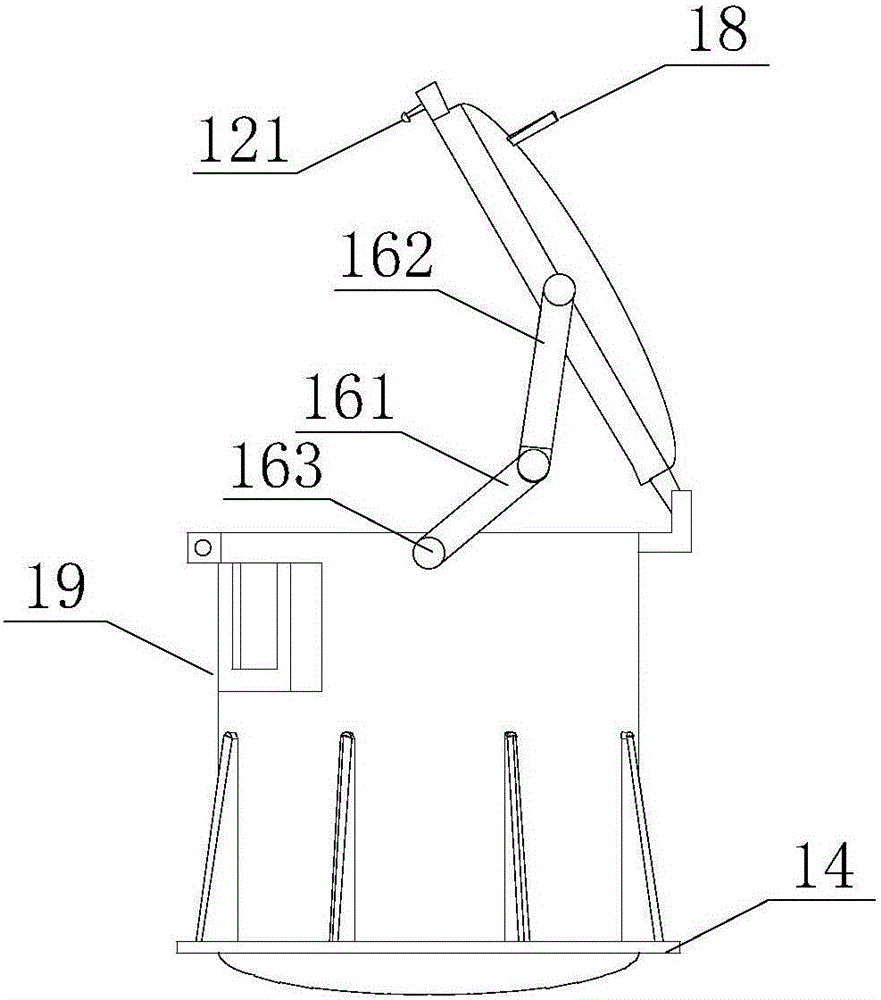
ActiveCN105758271AEnable secure storageRealize transportationBlastingManipulatorControl theoryExplosive material
The invention relates to a robot and particularly relates to an explosive disposal robot. According to the technical scheme, a wheel-leg-arm-tank combined explosive disposal robot comprises an explosion-proof tank (1), a dismounting mechanical arm (2), a grasping mechanical arm (3), mechanical legs (4) and a frame (5) with rolling wheels; after questionable explosives are found, the proper dismounting mechanical arm (2), grasping mechanical arm (3), and mechanical legs (4) can be mounted according to early-stage information; according to the field environment, the robot can reach the adjacent side of the questionable explosives in a manner of selecting the wheels and the mechanical legs (4) or combining the wheels and the mechanical legs (4); the explosives are dismounted through the dismounting mechanical arm (2) and then the questionable explosives are put into the explosion-proof tank (1) through the grasping mechanical arm (3); even if the questionable explosives explode, damages to the surrounding and the explosive disposal robot are not caused; and after the explosion-proof tank (1) is replaced, the explosive disposal robot can be repeatedly utilized.
Owner:BEIJING INST OF SPACECRAFT SYST ENG
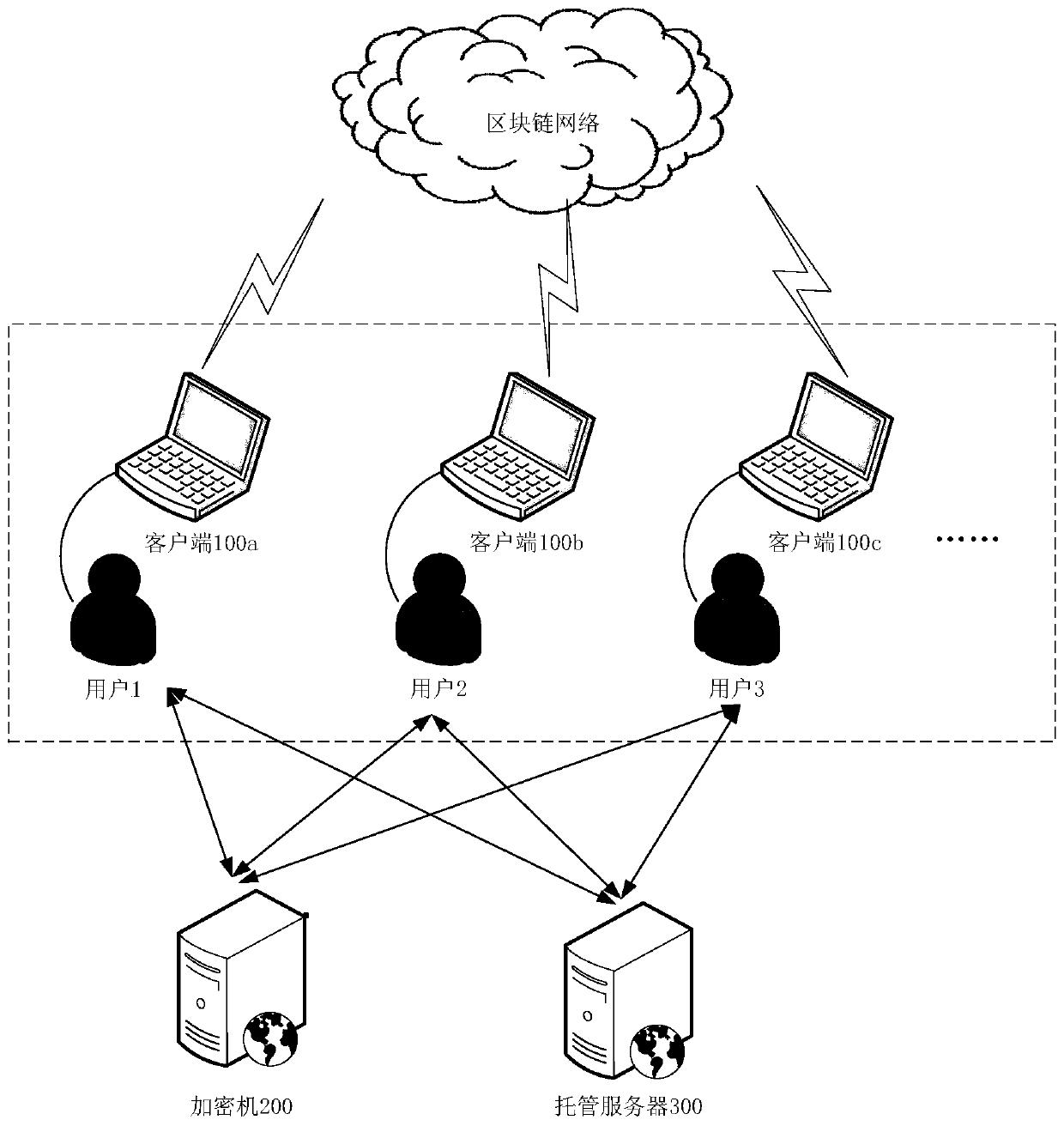
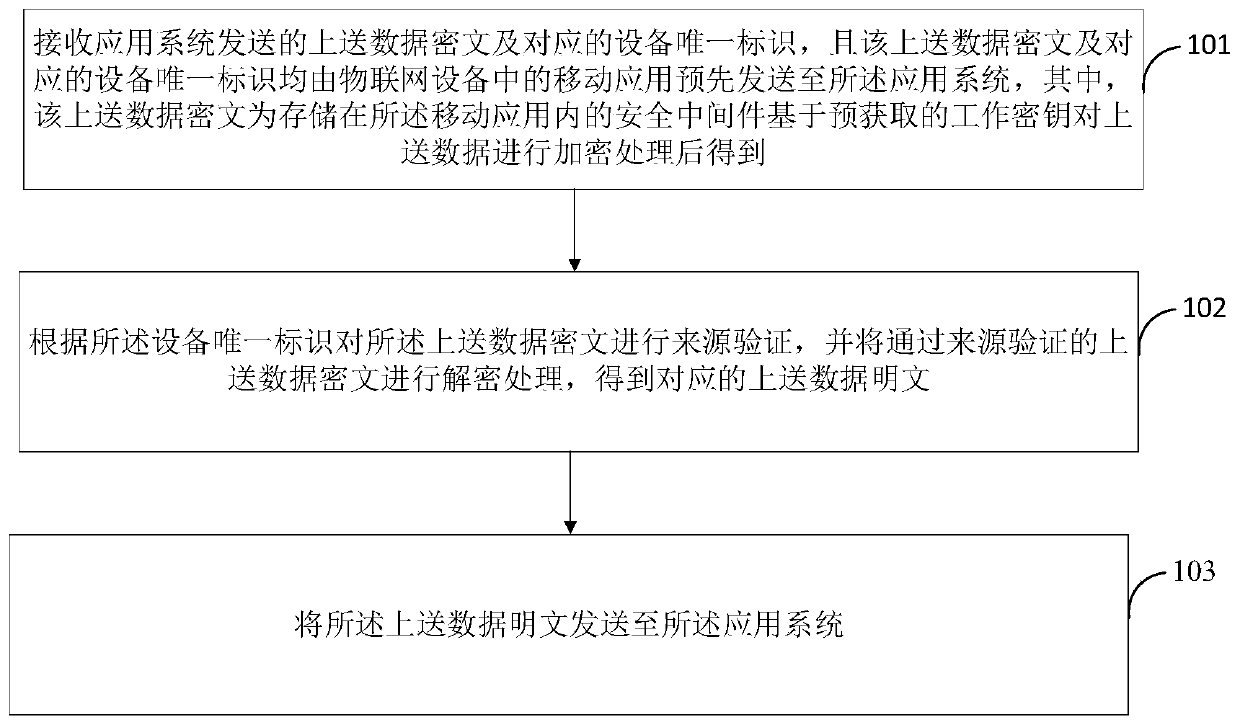
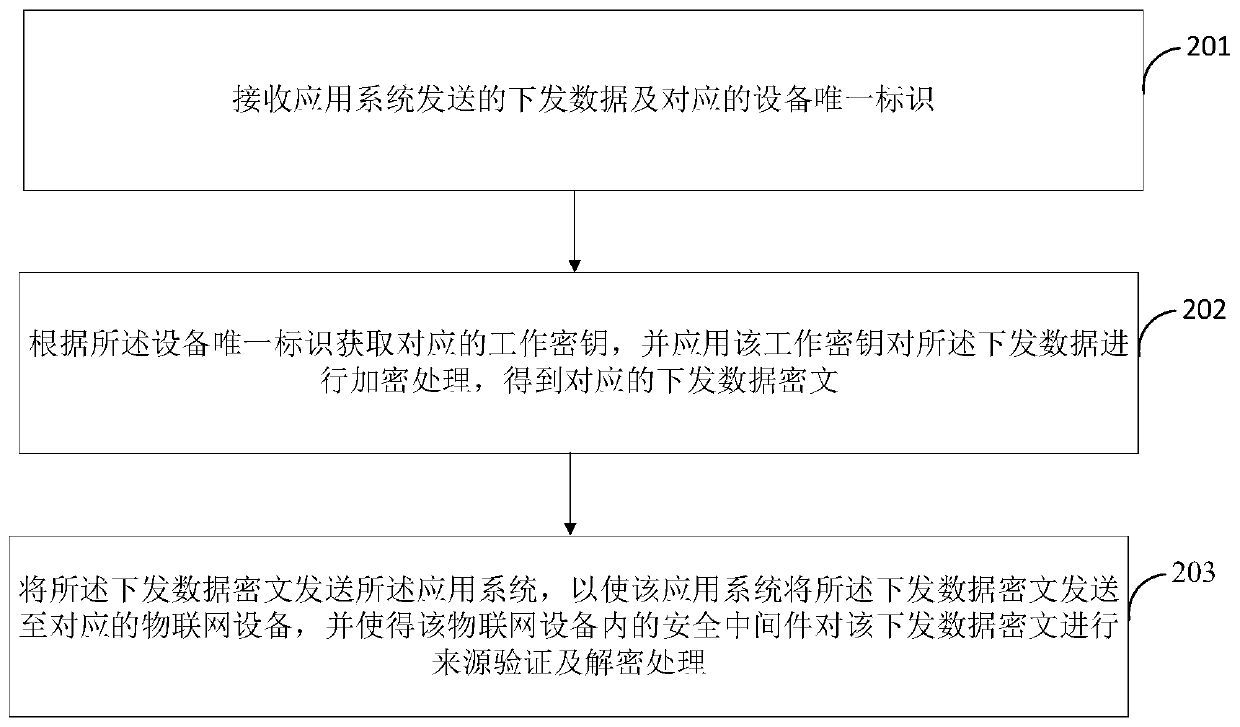
Private key storage method and device and related equipment
ActiveCN111431713AImplement storageEnable secure storageKey distribution for secure communicationInternet privacyCiphertext
The invention discloses a private key storage method and device, and related equipment. The private key storage method comprises the steps that a key negotiation application sent by a client is received, a corresponding key position is formulated according to the key negotiation application, a corresponding encryption key is generated at the key position, and the key position is a key position inan encryption machine; a private key of a target user sent by the client is received, and the private key is encrypted according to the encryption key to obtain an encrypted ciphertext corresponding to the private key; wherein the private key is used for signing, encrypting and decrypting transaction data in a target account so as to use virtual assets in the target account; and the encrypted ciphertext corresponding to the private key is sent to a trusteeship server, so that the trusteeship server stores the encrypted ciphertext corresponding to the private key. By adopting the embodiment ofthe invention, the user private key can be encrypted through the encryption machine, and the leakage of the user private key is effectively prevented, so that the security of the virtual assets of theuser in the blockchain network is ensured.
Owner:TENPAY PAID TECH
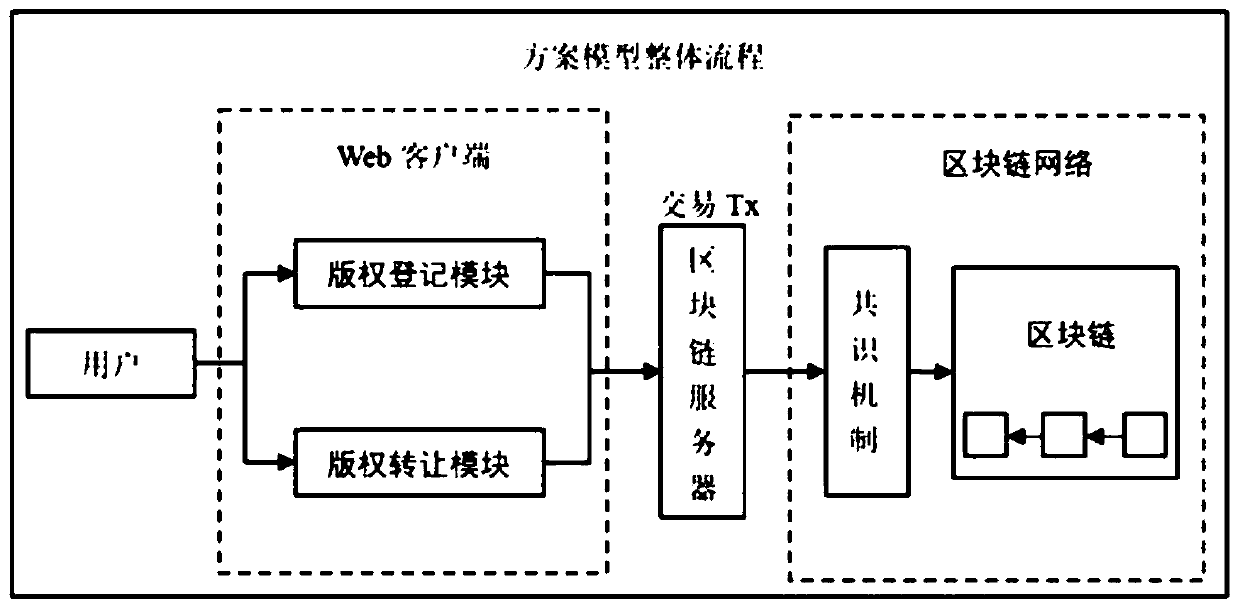
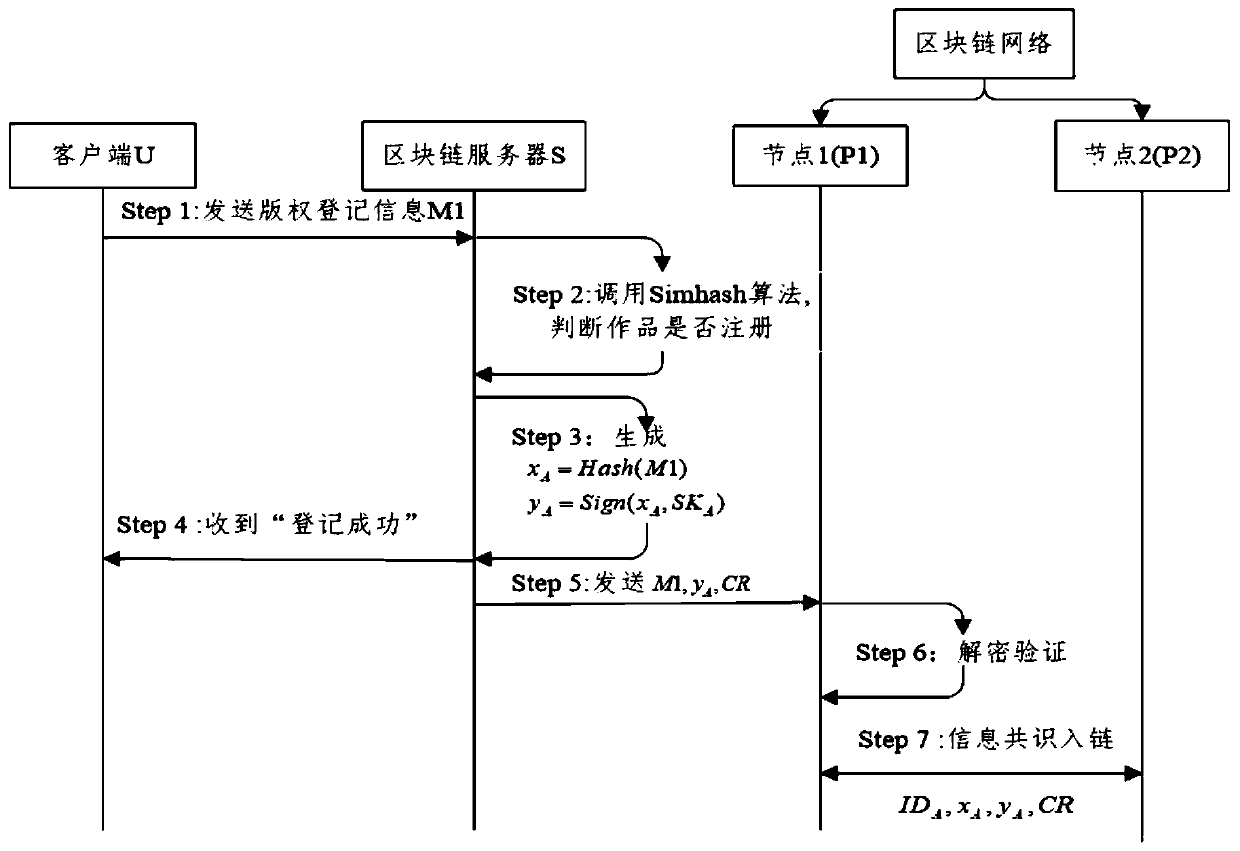
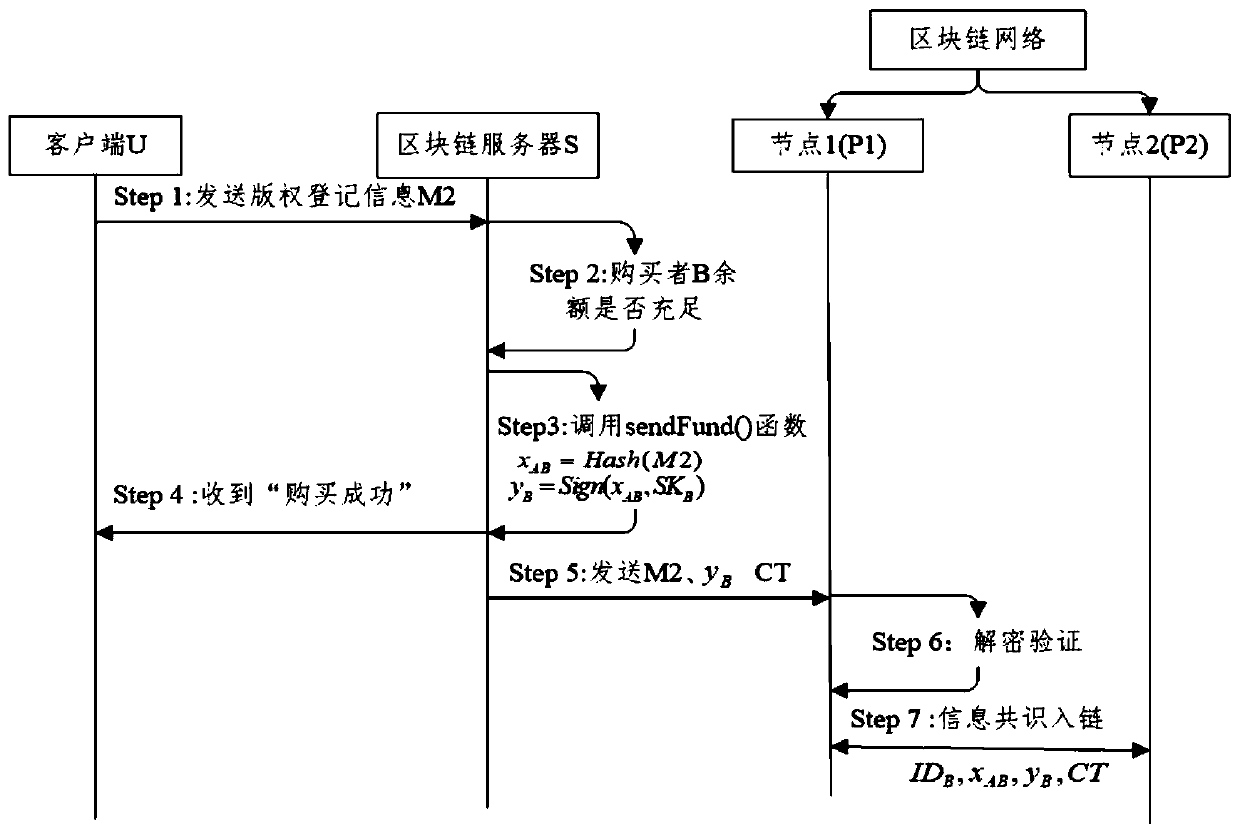
Digital rights protection method based on block chain technology
InactiveCN110968842AEnable secure storageRealize immutableUser identity/authority verificationProgram/content distribution protectionInternet privacyEngineering
The invention discloses a digital copyright protection method based on a block chain technology. The digital copyright protection method comprises a digital copyright protection model based on the block chain technology and a copyright protection protocol. The digital copyright protection model comprises a user, a Web client, a block chain server and a block chain network. A user registers and identifies through the Web client, generated transaction information Tx is processed through the block chain server, and information consensus is carried out through a consensus mechanism of the block chain network; the copyright protection protocol comprises a digital copyright registration sub-protocol and a digital copyright transfer sub-protocol. Information leakage cannot be caused even if the scheme is attacked; according to the method and the system, piracy and copying behaviors of the digital works are prevented, malicious users cannot perform camouflage attacks, piracy infringement behaviors can be solved, the real uniqueness of the digital works is ensured, and the calculation cost of a Simhash (locality sensitive hash) algorithm is greatly reduced.
Owner:NANTONG UNIVERSITY
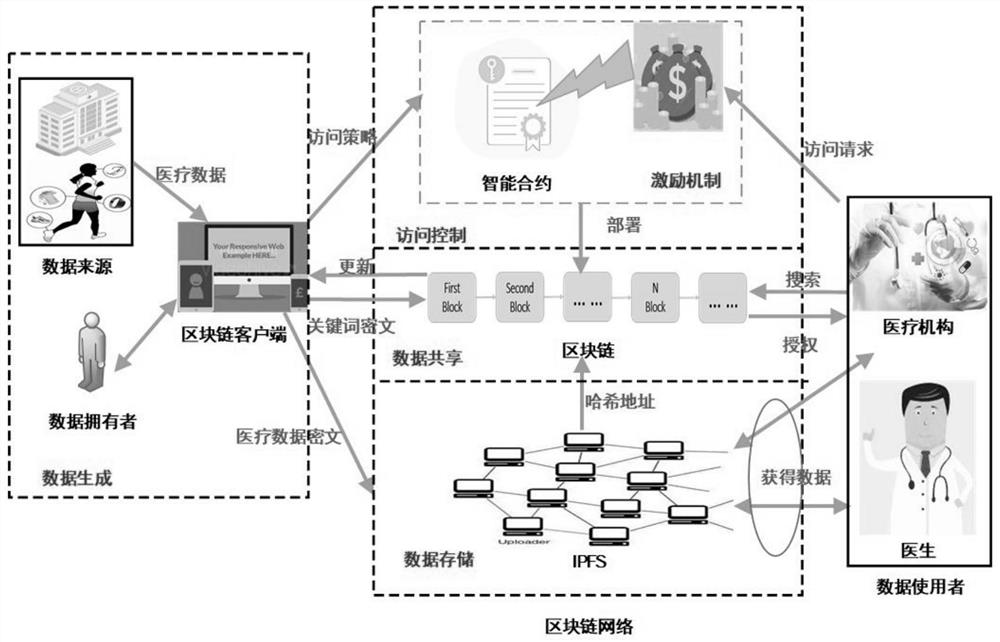
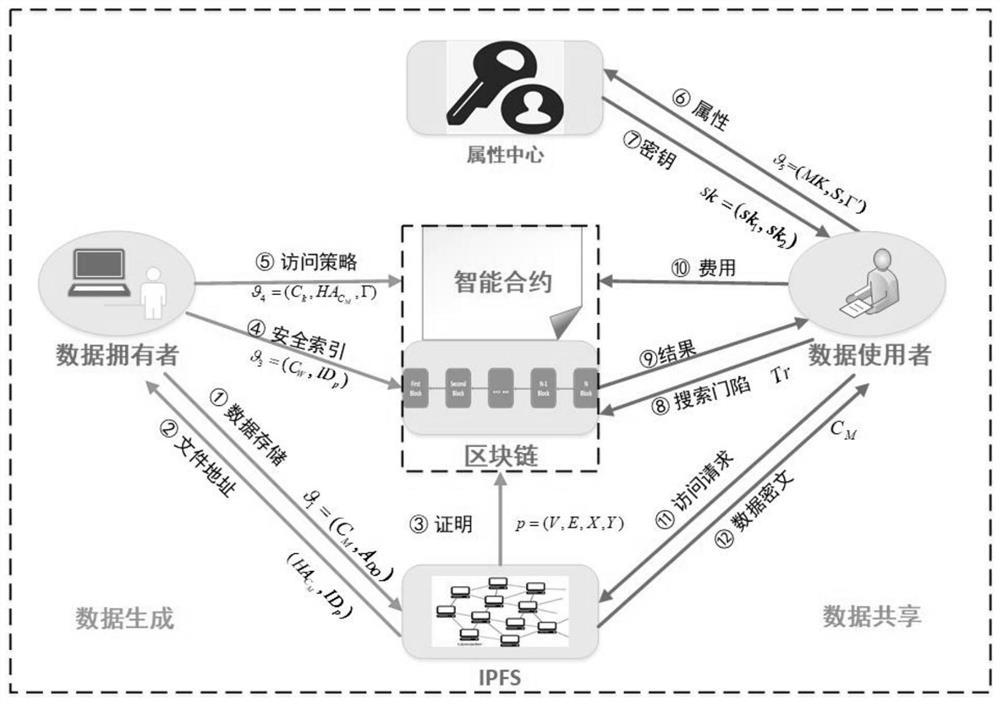
Medical data security sharing system and method based on IPFS and alliance chain
PendingCN111916173AEnable secure storageImplement fine-grained access controlDigital data protectionFile metadata searchingSafe storageData security
Owner:ANHUI NORMAL UNIV
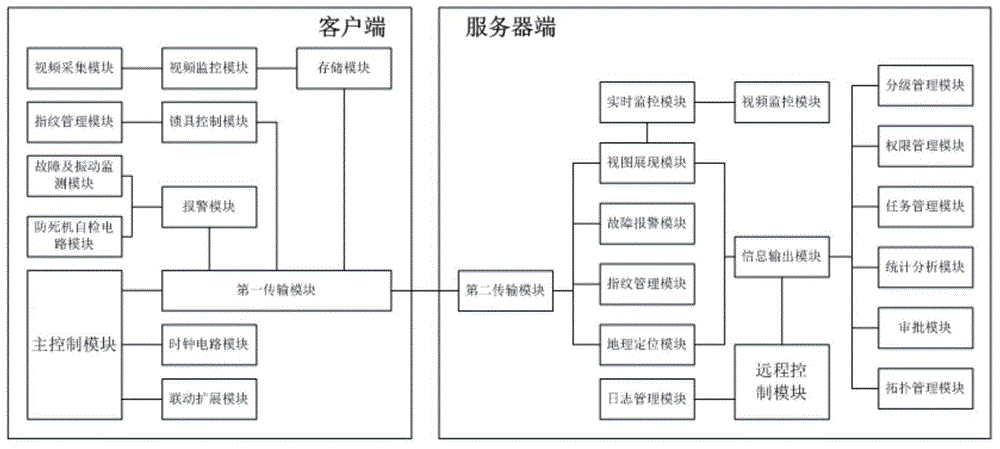
Remote monitoring system
InactiveCN104168459AReduce the risk of failureGuarantee data securityClosed circuit television systemsData switching networksVideo monitoringTopology management
The invention relates to a remote monitoring system which comprises a client-side and a server-side. According to the client-side, a video acquisition module is connected with a video monitoring module; a storage module is connected with the video monitoring module and a first transmission module; a lockset control module is connected with a fingerprint management module and the first transmission module; an alarm module is connected with the first transmission module, a fault and vibration monitoring module and an anti-crash self-checking circuit module; a master control module is connected with a clock circuit module, a linkage extension module and the first transmission module. According to the server-side, a second transmission module is connected with a view display module, a fault warning module, a fingerprint management module and a geographic module; a real-time monitoring module is connected with a video monitoring module and the view display module; an information output module is connected with the view display module, a geographic positioning module, a level-to-level management module, an authority management module, a task management module, a statistic analysis module, an approval module and a topology management module; a remote control module is connected with the information output module and a log management module.
Owner:北京神舟航天软件技术股份有限公司
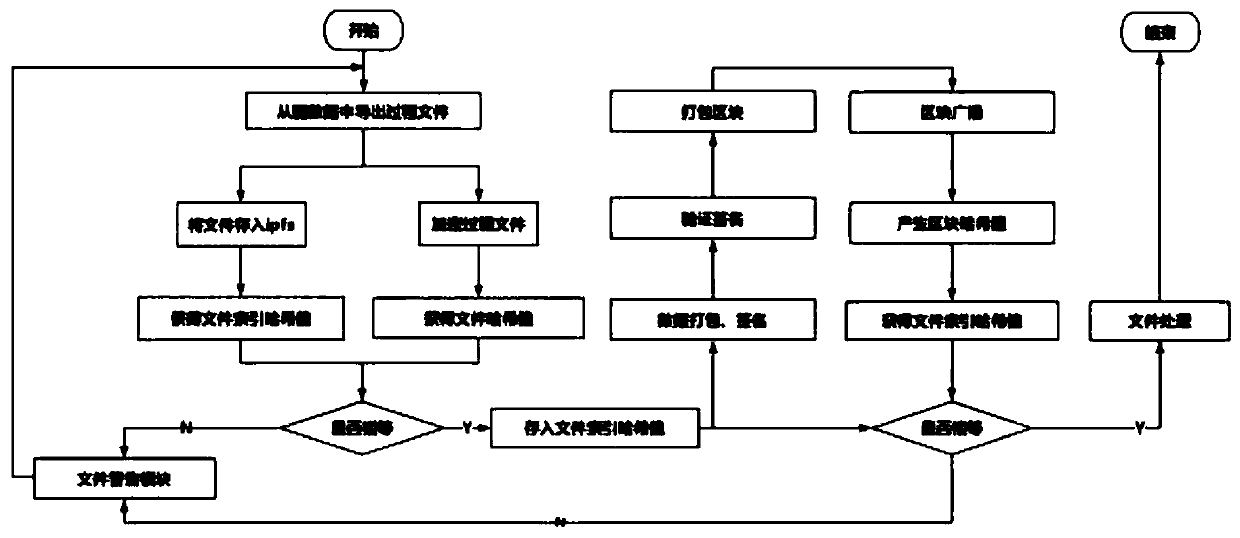
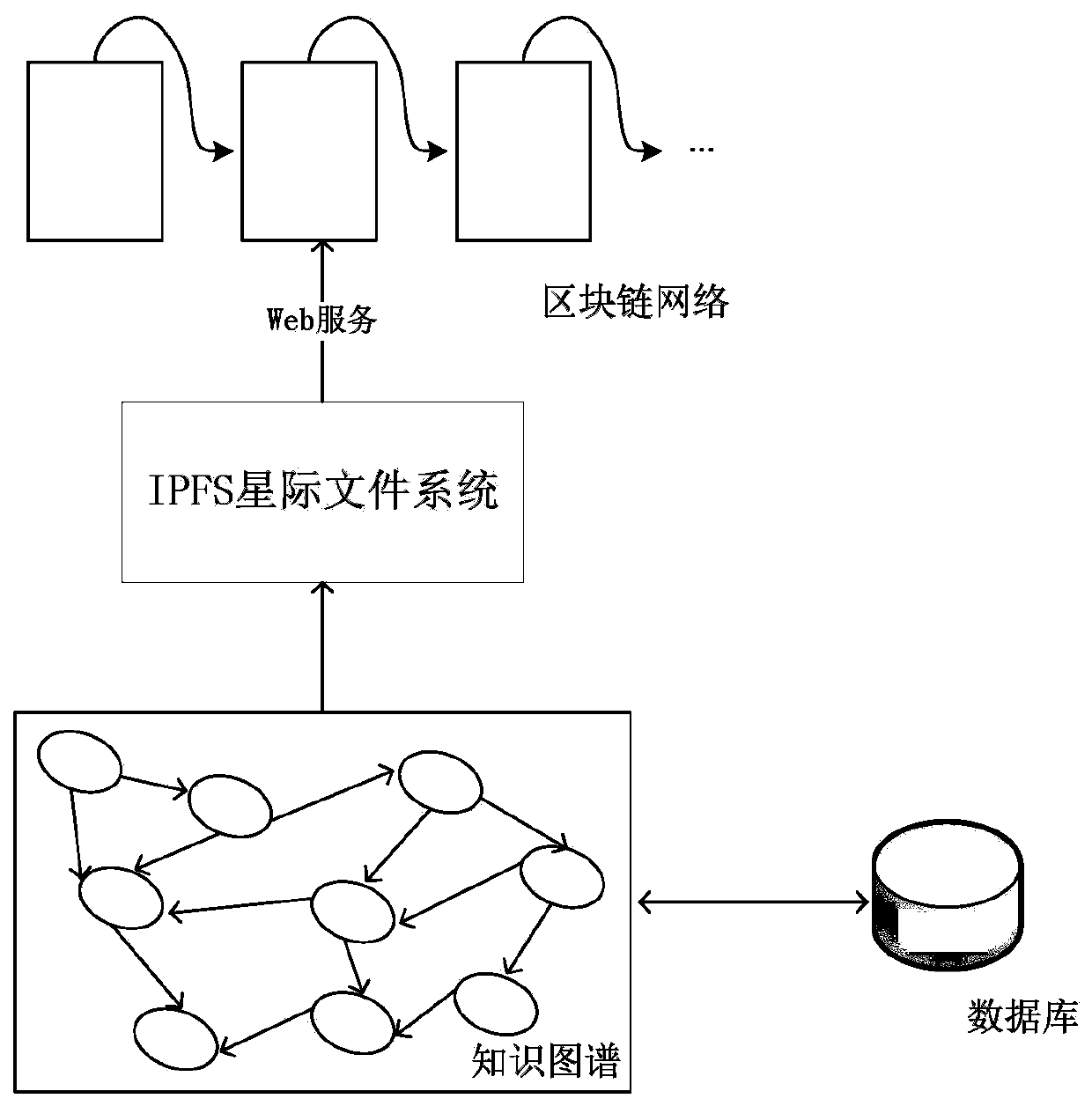
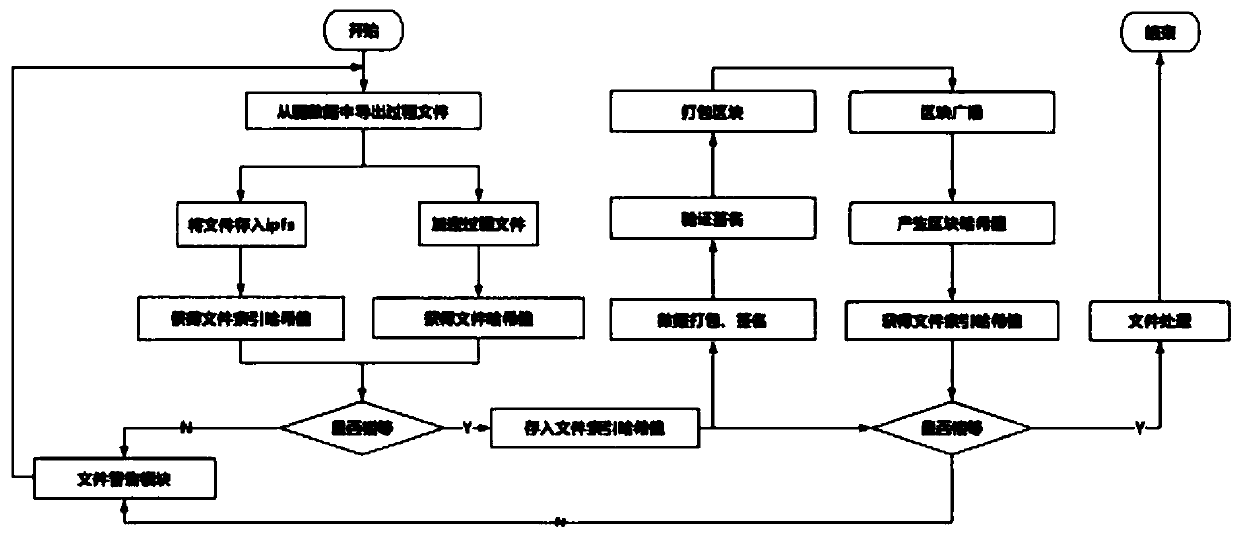
Knowledge graph storage and verification method based on blockchain and IPFS
ActiveCN111177080AEnable secure storageTraceableDatabase distribution/replicationDigital data protectionFile systemTheoretical computer science
The invention discloses a knowledge graph storage and verification method based on a blockchain and an IPFS. The method specifically comprises the steps that firstly, a process file of the knowledge graph is exported from a graph database, a file hash value is calculated, the process file is stored in an IPFS inter-satellite file system, a file index hash value returned by the IPFS is compared with the previously calculated hash value, and if the file index hash value is equal to the previously calculated hash value, the file index hash value is stored in a block chain, and safety of the process file is guaranteed. The file index hash value is stored into the blockchain through processes of data packaging, signing, block packaging, block broadcasting and the like, querying the file index hash value in the blockchain, comparing the file index hash value with a file index hash value obtained from an IPFS before, if the file index hash value is the same as the file index hash value, entering a file processing module, and otherwise, entering a file warning module. Through combination of the blockchain and the IPFS, reliable and rapid storage of the knowledge graph can be realized, andthe security and traceability of knowledge graph process files are ensured.
Owner:XIAN UNIV OF TECH
Data safety storage and processing method of mobile storage equipment
InactiveCN1794210APrevent leakageGreat Mobile Storage FreedomDigital data processing detailsUnauthorized memory use protectionRemovable mediaData store
This invention relates to a safely storage and a process method for data of a mobile storage device, which utilizes tools of a mobile safe system to set up virtual ciphered file catalogs belonging to legal users only to data necessary to be ciphered in the mobile storage device and legal users can set up, modify and delete files in it, put the un-ciphered data in the device to the safe to be ciphered and puts the ciphered data in the safe to the un-ciphered public region in the device to be deciphered, yet illegal users cannot open it or get content from the safe forever.
Owner:北京中讯锐尔科技有限公司
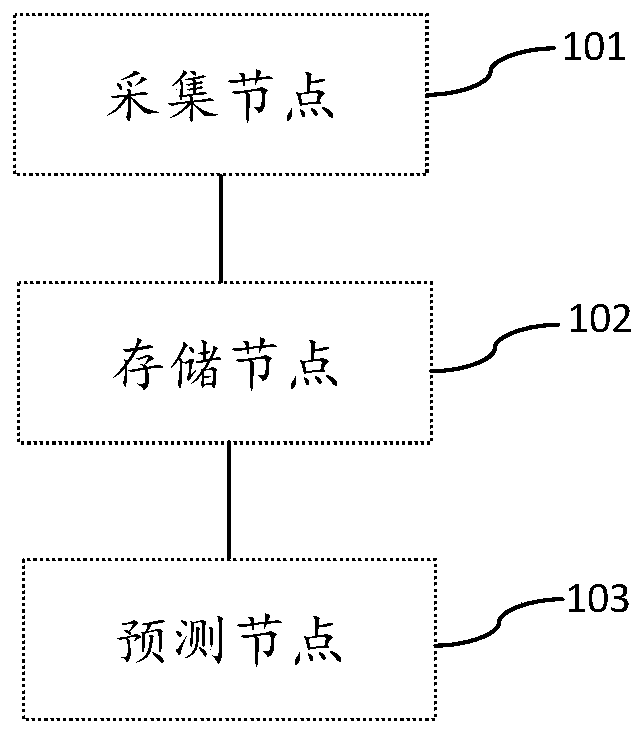
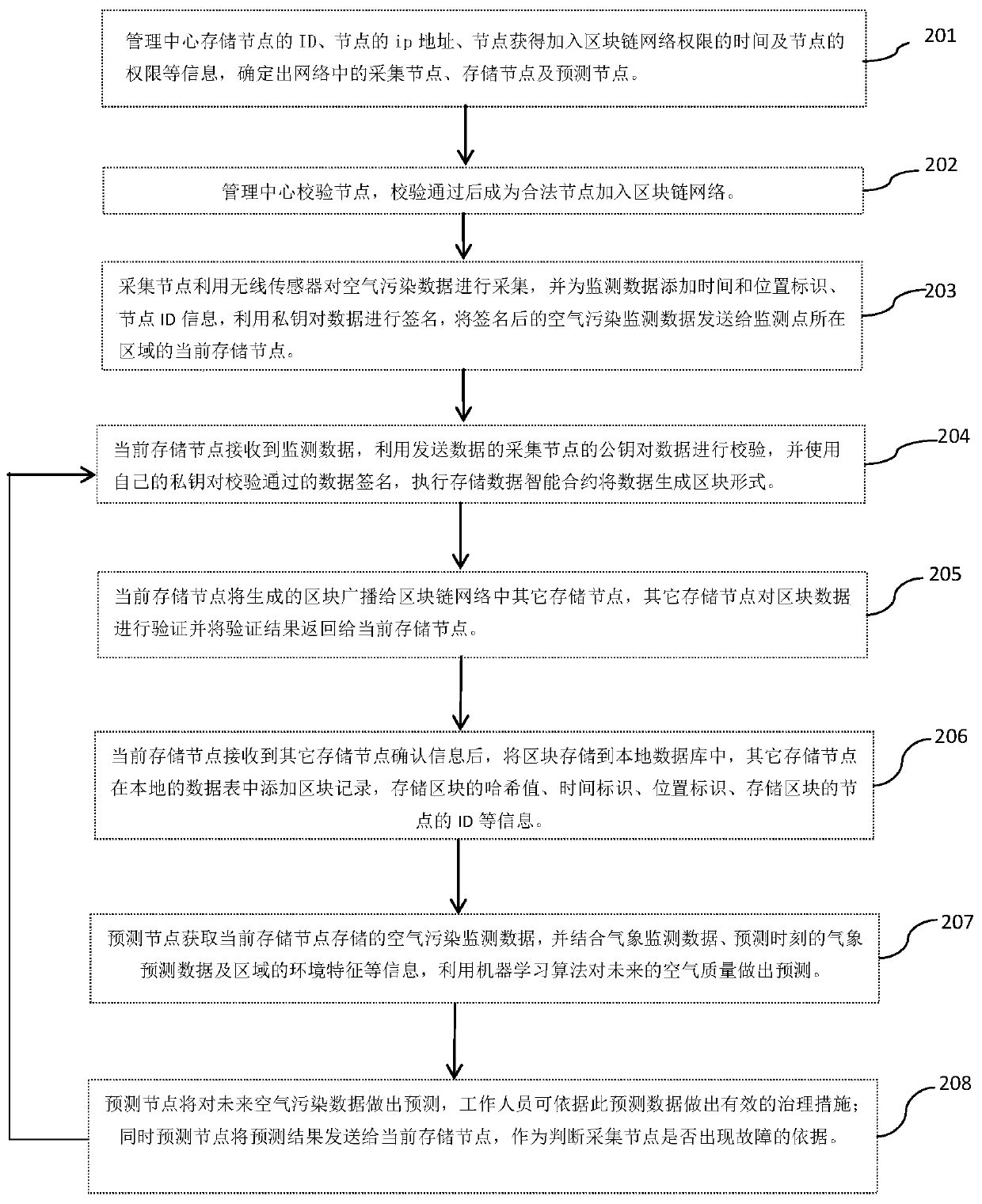
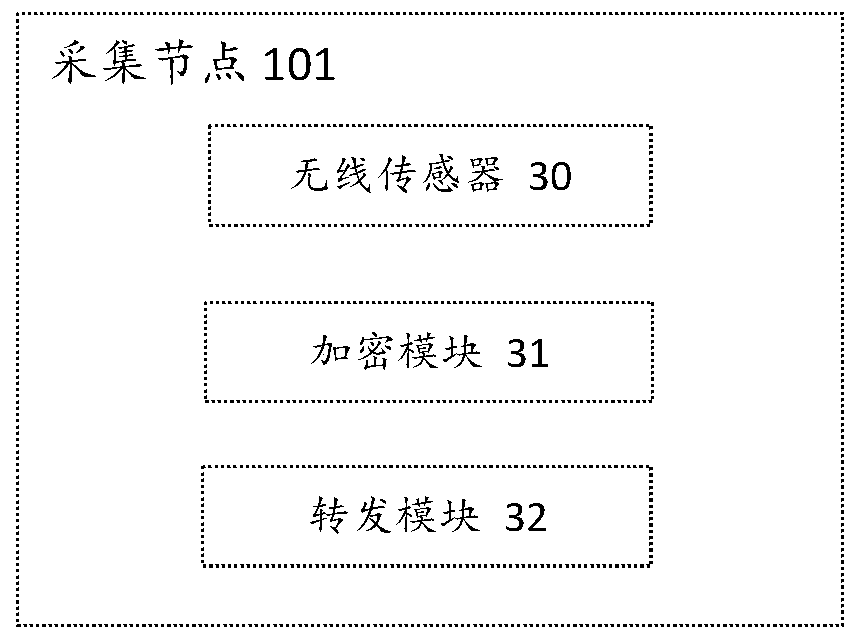
Air quality monitoring and predicting system and method
PendingCN111157682APrevent forgeryPrevent tamperingWeather condition predictionMaterial analysisMonitoring sitePrediction system
The invention provides an air quality monitoring and prediction system and method, and the system comprises a collection node, a storage node, and a prediction node, and the collection node, the storage node, and the prediction node form a blockchain network. The collection nodes are used for acquiring air pollution monitoring data and sending the monitoring data to the storage nodes in the area where the monitoring points are located. After receiving the monitoring data, the storage node verifies the data, generates a block from the data after passing the verification, and broadcasts the block in the system. Other storage nodes verify the blocks, and after the blocks pass the verification, the current storage node receives verification information of the other storage nodes and stores theblocks locally according to a time sequence to form a chain structure. Other storage nodes store the hash value, the time identifier and the position identifier of the block and the information of the storage node of the block locally for monitoring and querying the monitoring data, and the prediction nodes acquire monitoring data and predict future air quality in combination with a machine learning algorithm.
Owner:SHANGHAI INST OF TECH
Test data-based storage method and medium
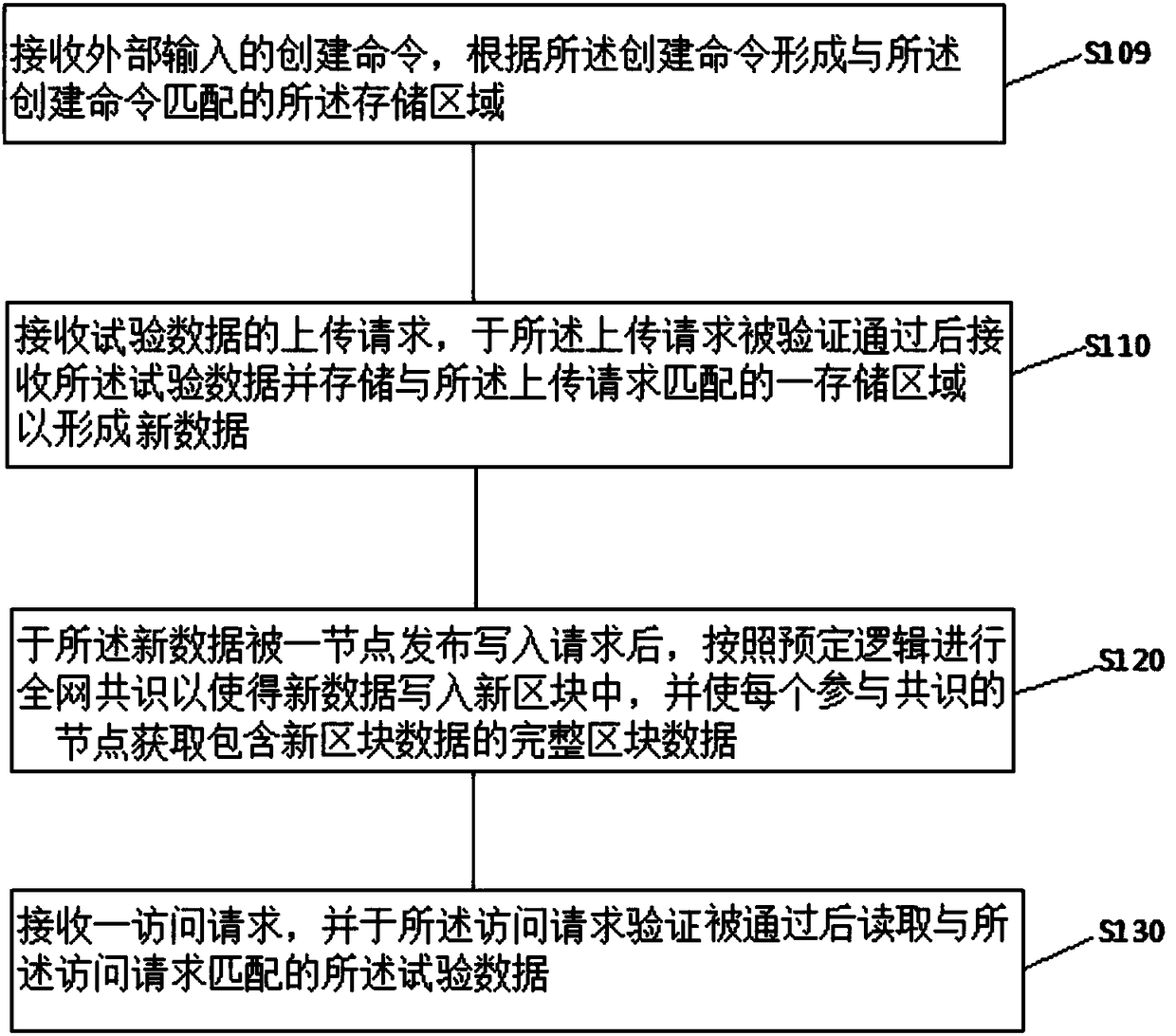
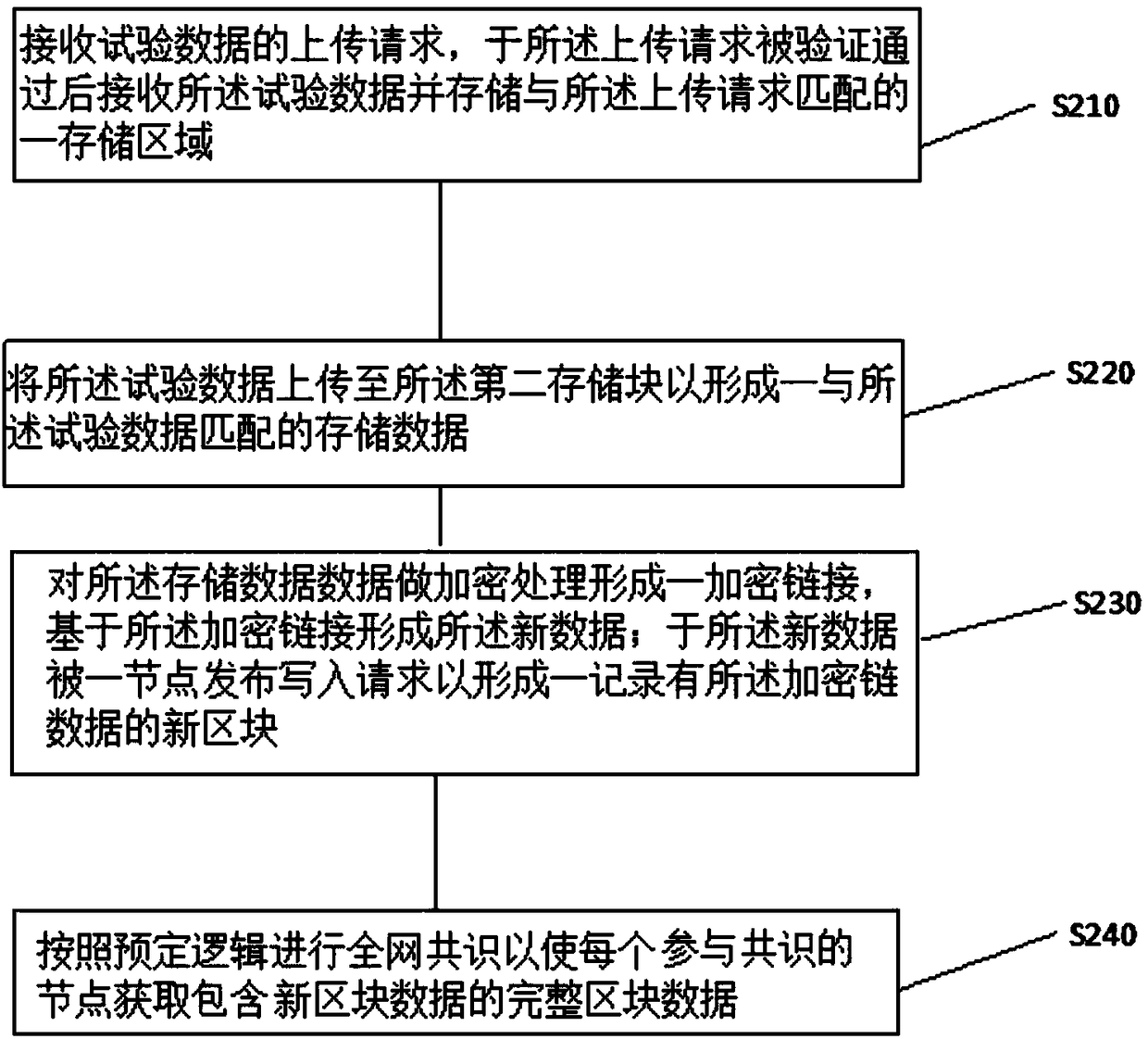
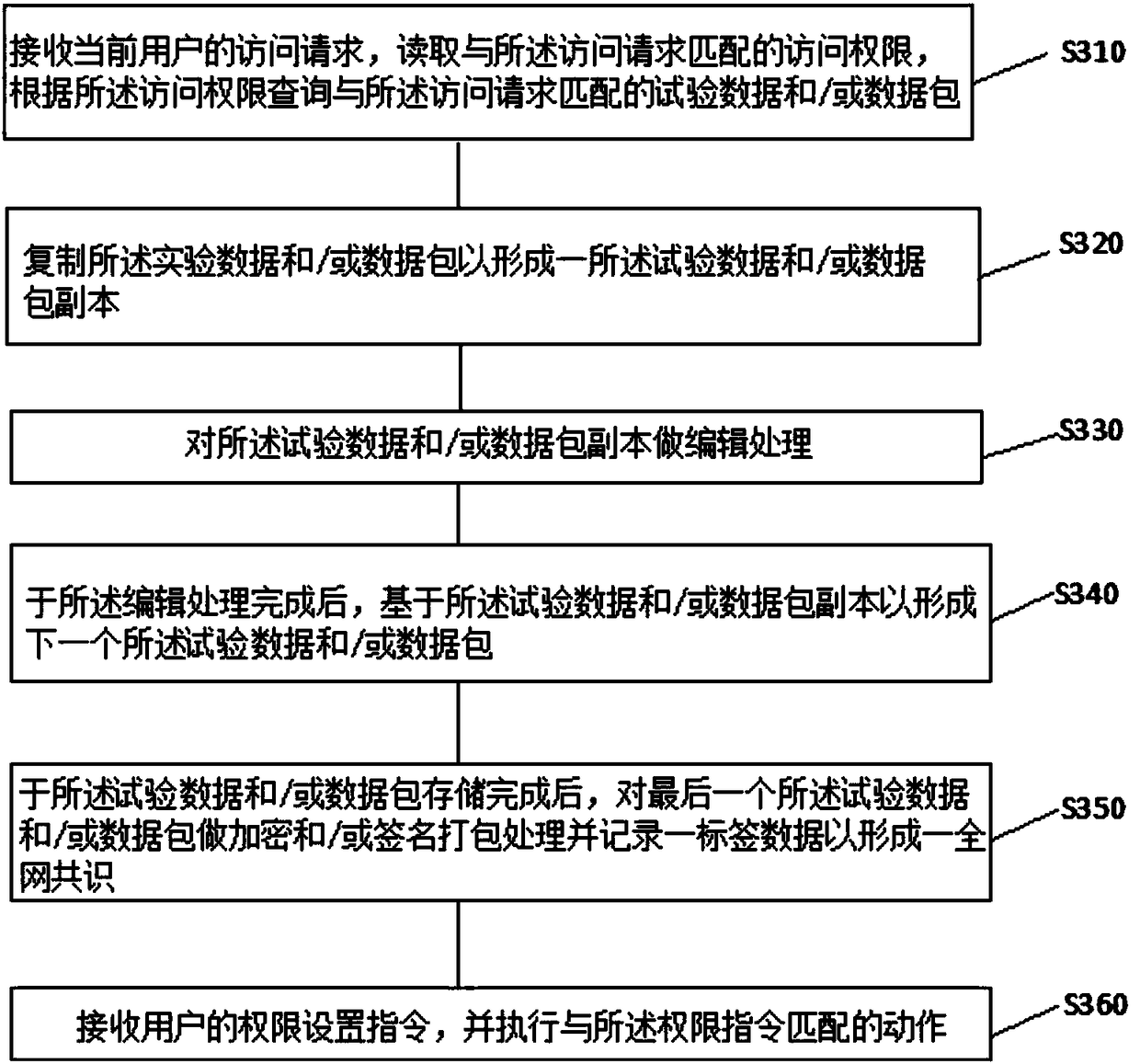
ActiveCN108256354ATroubleshoot tampered technical issuesEnable secure storageDigital data protectionTimestampOperating system
The embodiment of the invention relates to the data storage technology, particularly to a test data-based storage method and medium. The test data-based storage method comprises receiving an uploadingrequest of test data, after the uploading request is verified, receiving and storing the test data into a storage area matched with the uploading request to form new data; after the new data are released and written into a request by a node, performing whole-network common recognition according to preset logic so that the new data can be written into a new block and every node involved in commonrecognition acquiring complete block data containing new block data. By writing the new data into the new block through whole-network common recognition according to the preset logic, enabling every node involved in common recognition to acquire the complete block data containing the new block data and combining timestamp standards and block height also known as blockchain age which are carried bythe blockchain technology, the test data-based storage method and medium solves the technical problem that the test data can be tampered.
Owner:张天
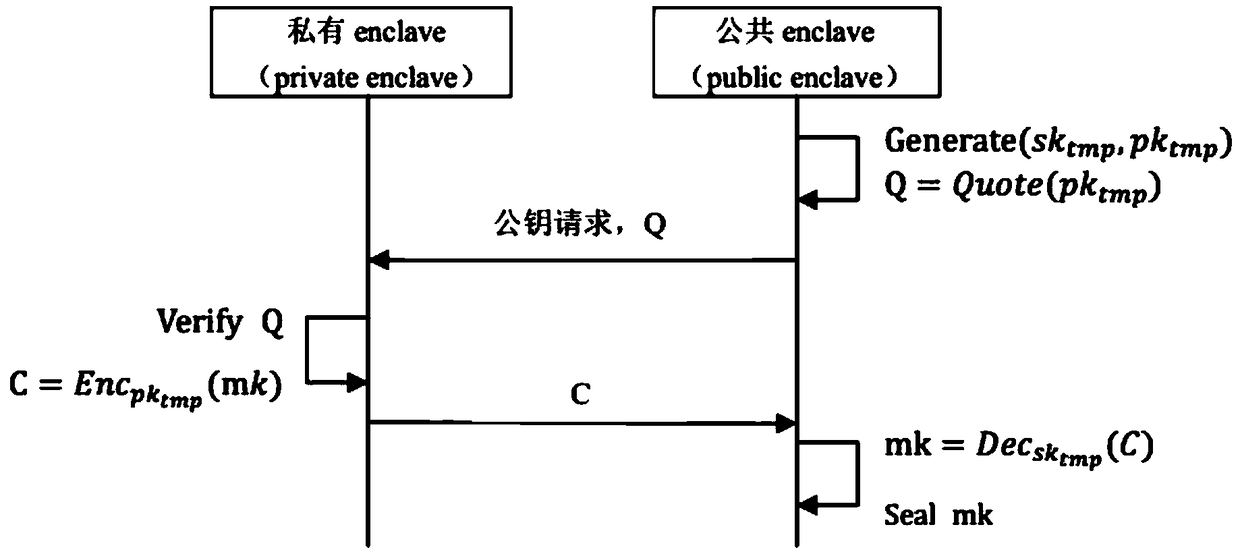
Public key password calculation method and system based on Intel SGX mechanism
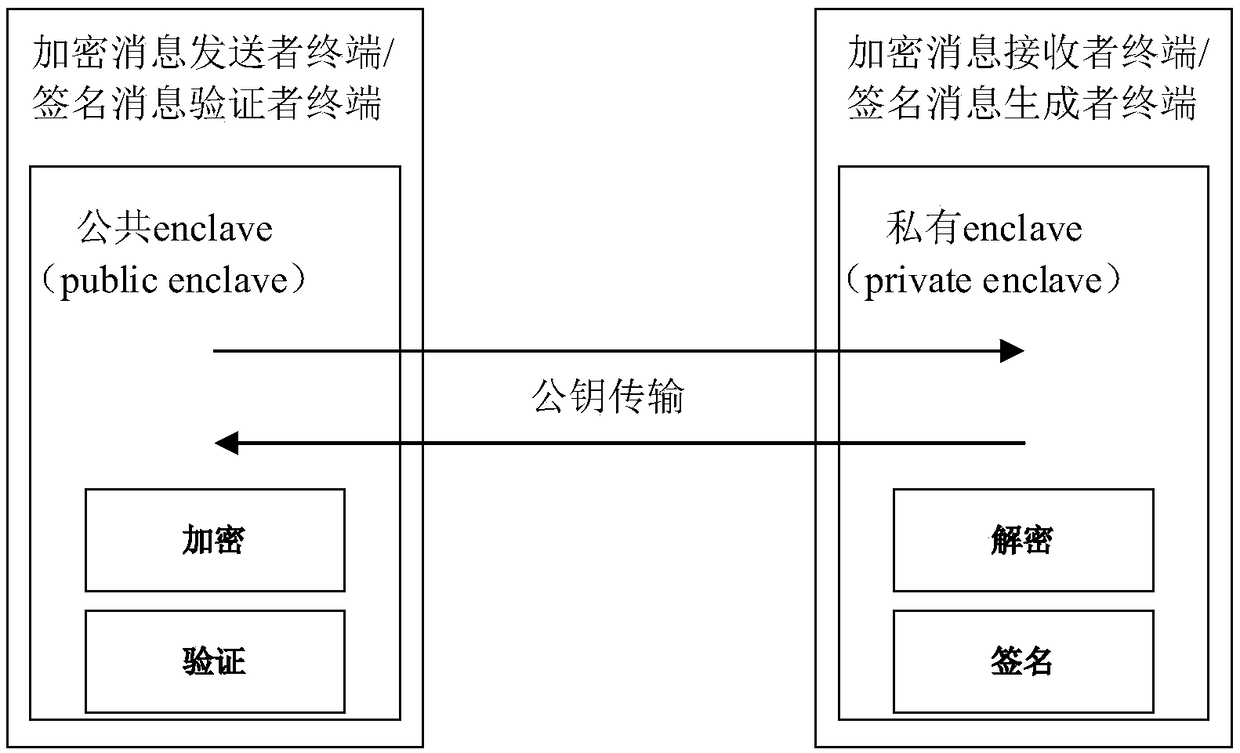
ActiveCN109510708AEnable secure storageSimplify the acquisition processKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPasswordCalculation methods
The invention discloses a public key password calculation method and system based on an Intel SGX mechanism. The method comprises the following steps of 1) generating Public enclave and Private enclave independent of each other, which are application running environments providing isolated execution based on the Intel SGX mechanism respectively; deploying the Public enclave in an encrypted messagesender terminal or a signed message verifier terminal, and deploying the Private enclave in an encrypted message receiver terminal or a signed message generator terminal; and 2) when the Private enclave is started for the first time, generating a private key; and when the Public enclave is started for the first time, executing SGX remote authentication for the Private enclave to request for a public key identical to the private key. According to the public key password calculation method and system, the public key password calculation is realized securely and efficiently.
Owner:INST OF INFORMATION ENG CAS
Classified and graded fitness health big data sharing system and method
PendingCN114513533ASecurityEnsure safetyCharacter and pattern recognitionSecuring communicationPrivacy protectionIndividual data
The invention provides a classification and grading fitness health big data sharing system and method. The system comprises a user management module, a data management module, an access control module, a data sharing module, a block chain and a distributed file system. The user management module is used for managing users; the data management module is used for encrypting by adopting different encryption levels according to the data sensitivity level; the access control module manages an access strategy of personal data generated by a data owner and realizes access control of the personal data at the same time, and the data sharing module is used for performing authority verification on a data visitor; the block link is used for storing an access control strategy and serving as an access control server; and the distributed file system is used for storing the encrypted personal data. According to the system disclosed by the invention, construction and optimization from data storage to data sharing are carried out based on the block chain, and auditing of the access control record is realized while data classification and grading privacy protection is ensured.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY +1
Multi-application intelligent card with encryption and decryption functions
ActiveCN104484628AGuaranteed independenceImplement access controlDigital data protectionInternal/peripheral component protectionProtocol for Carrying Authentication for Network AccessSystem maintenance
The embodiment of the invention provides a multi-application intelligent card with encryption and decryption functions. The intelligent card comprises a transmission management module, a command parsing module, an encryption / decryption module and a secure conversation management module, wherein the transmission management module is used for inputting a command or returning a response according to a preset transfer protocol; the command parsing module is used for parsing the received command; the encryption / decryption module is used for executing encryption or decryption operation on the application content in an application card; the secure conversation management module is used for managing the contents in the application card based on conversation information, and controlling the state transition of the content. The multi-application intelligent card not only can be used for solving the security problem of the intelligent card well, but also has the advantages of short development period, convenience in system maintenance and update, lower cost and the like.
Owner:陕西埃菲克能源科技有限公司
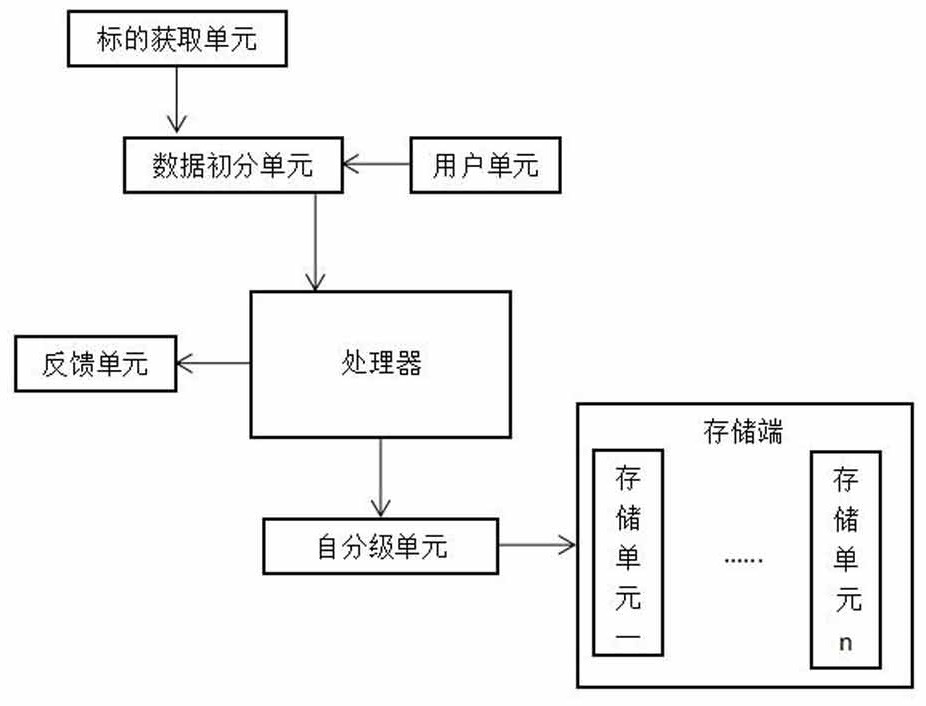
Multi-dimensional data security storage system based on big data
ActiveCN113378202ARealize separate storageEnable secure storageDigital data protectionNatural language data processingComputer hardwareData transport
The invention discloses a multi-dimensional data security storage system based on big data. The multi-dimensional data security storage system comprises an object acquisition unit, a data initial classification unit, a user unit, a processor, a self-classification unit and a storage end, the object acquisition unit is used for acquiring to-be-stored data, the object acquisition unit is used for transmitting the to-be-stored data to the data initial division unit, and the data initial division unit receives the to-be-stored data transmitted by the object acquisition unit. According to the method, the content in the data to be stored is averagely split into the number corresponding to the dispersion number, each split data to be stored is marked as a dispersion segment, each dispersion segment is randomly placed in a document with a specified attribute according to the content, and a new dispersion segment is obtained; and a storage document can be preliminarily encrypted.
Owner:湖南盈聚信息技术有限公司
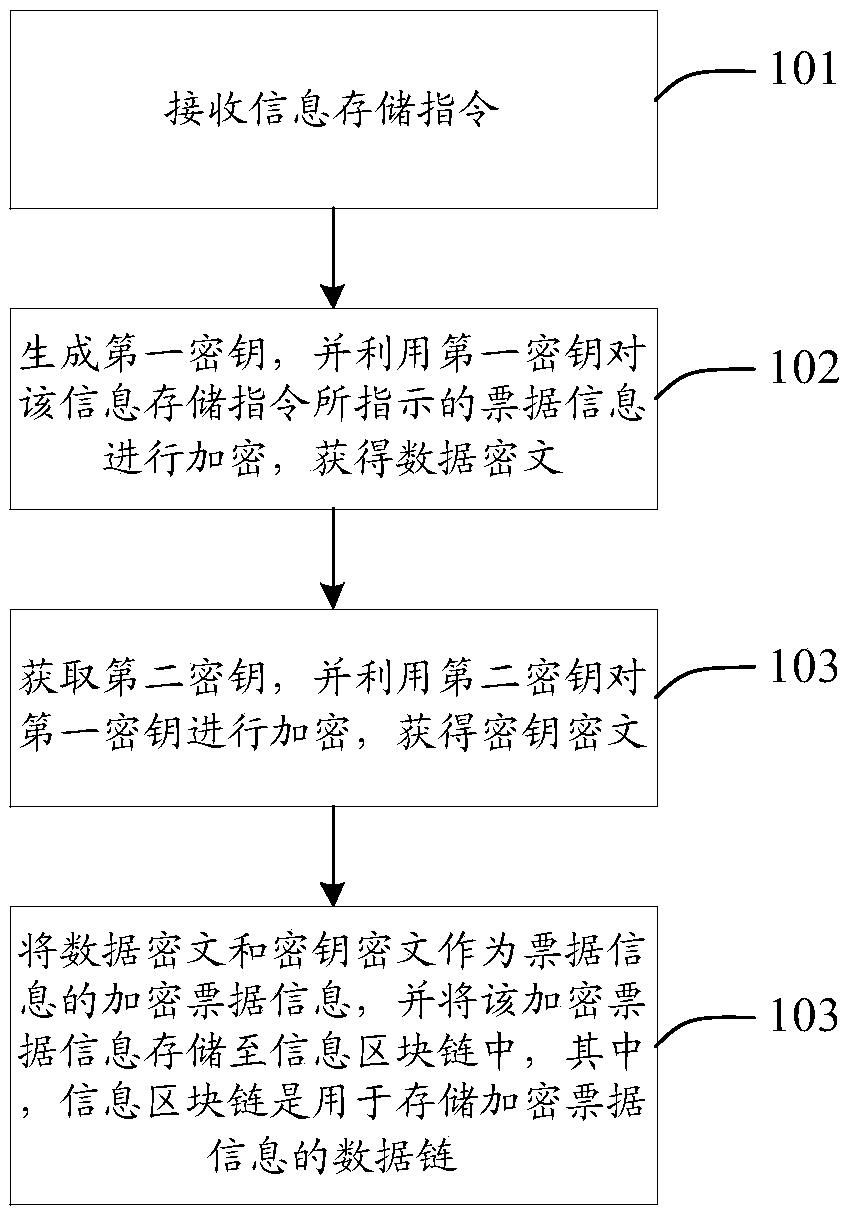
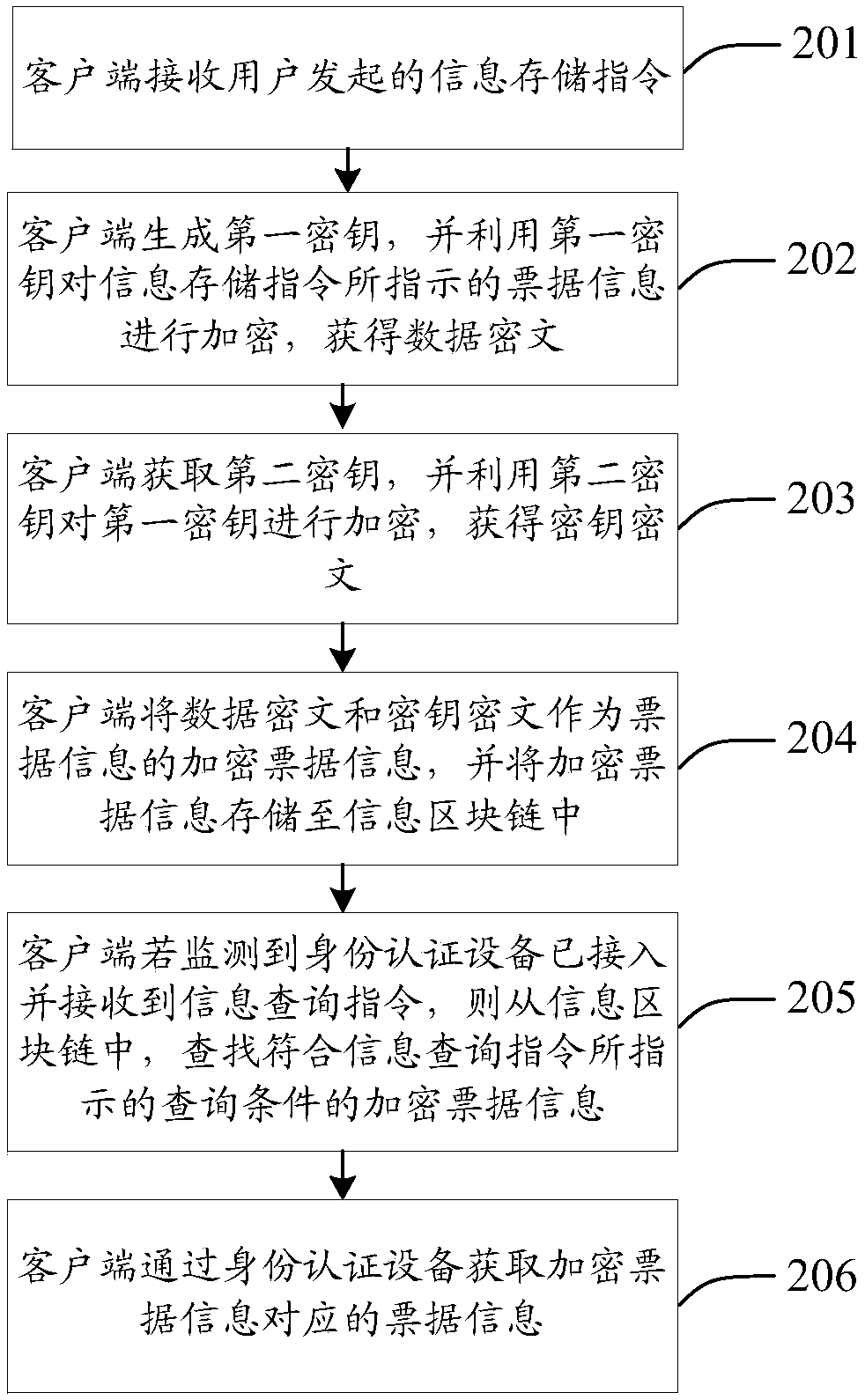
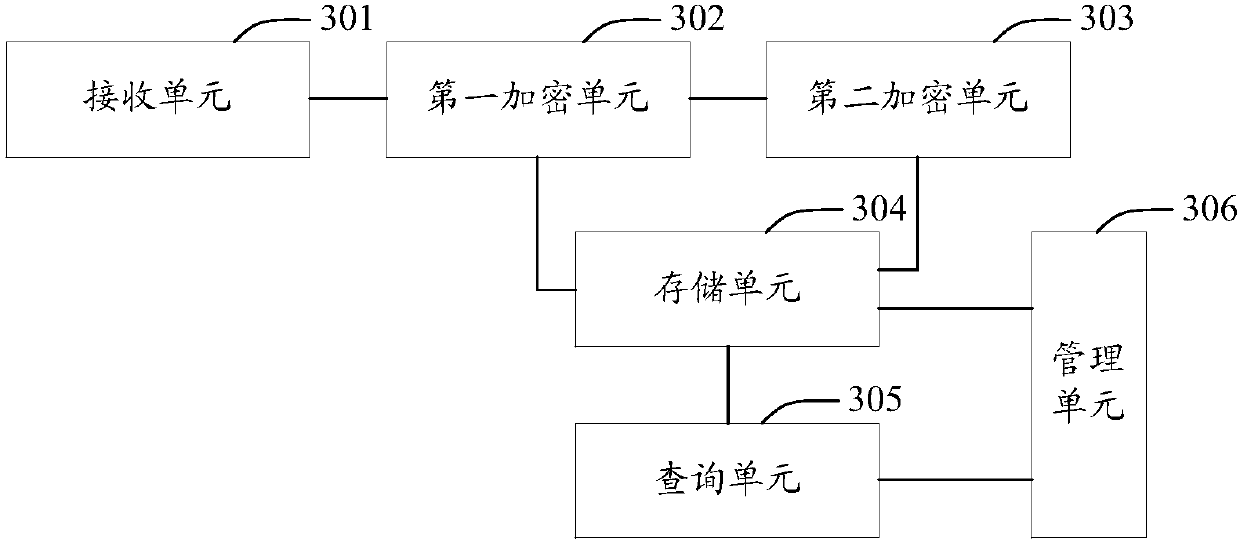
Information processing method, device and equipment and medium
InactiveCN109918937AImprove securityPrevent leakageKey distribution for secure communicationDigital data protectionInformation processingComputer hardware
The invention discloses an information processing method and device, equipment and a medium, which are used for solving the problem of low security of bill information in the prior art. The method specifically comprises the steps of receiving an information storage instruction; generating a first secret key, encrypting the bill information indicated by the information storage instruction by usingthe first secret key to obtain a data ciphertext; obtaining a second secret key, encrypting the first secret key by using the second secret key to obtain a secret key ciphertext; and storing the dataciphertext and the key ciphertext as encrypted bill information of the bill information in an information block chain. Therefore, double encryption is carried out on the bill information through the first secret key and the second secret key. Compared with the prior art, the security of the bill information is improved, the bill information is prevented from being leaked as much as possible, and once the bill information is stored in the information block chain, the bill information cannot be tampered or repudiated, so that the security of the bill information is further improved by storing the bill information through the information block chain.
Owner:AEROSPACE INFORMATION
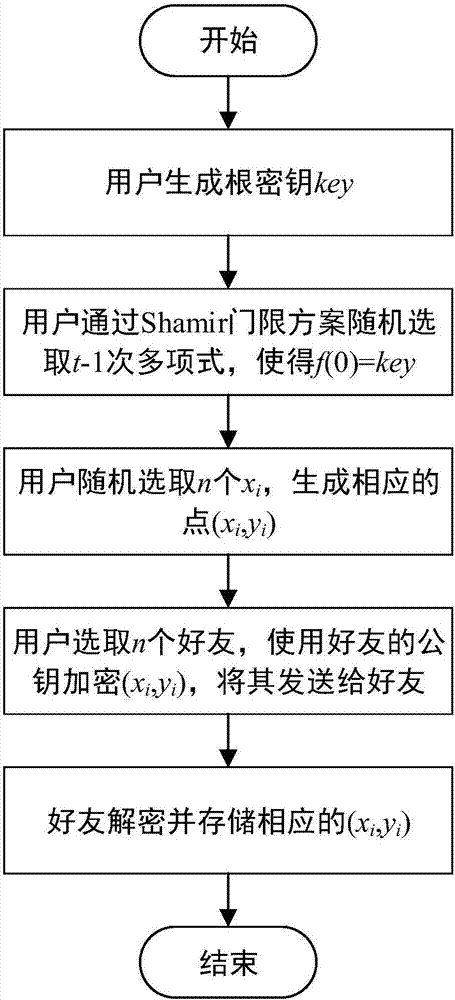
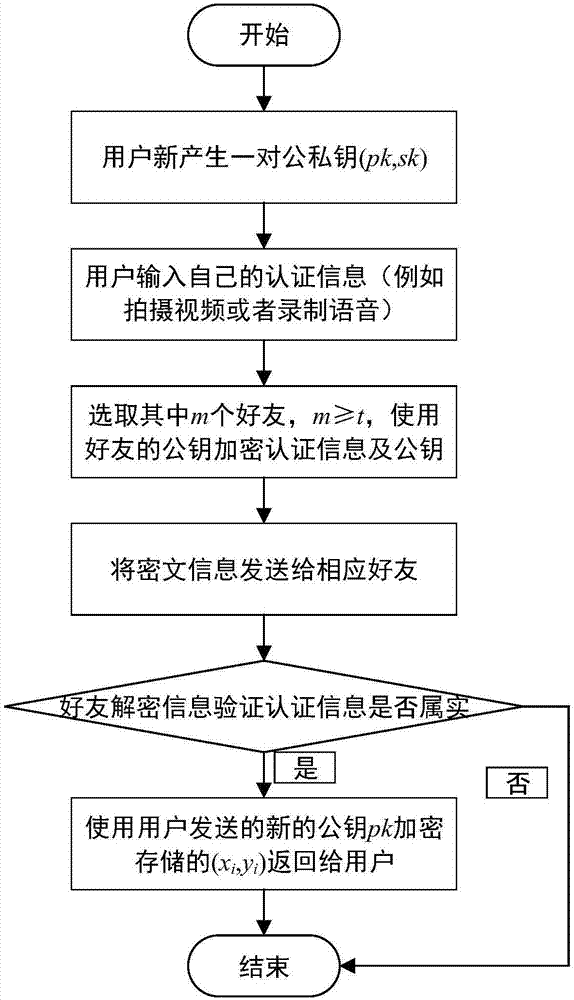
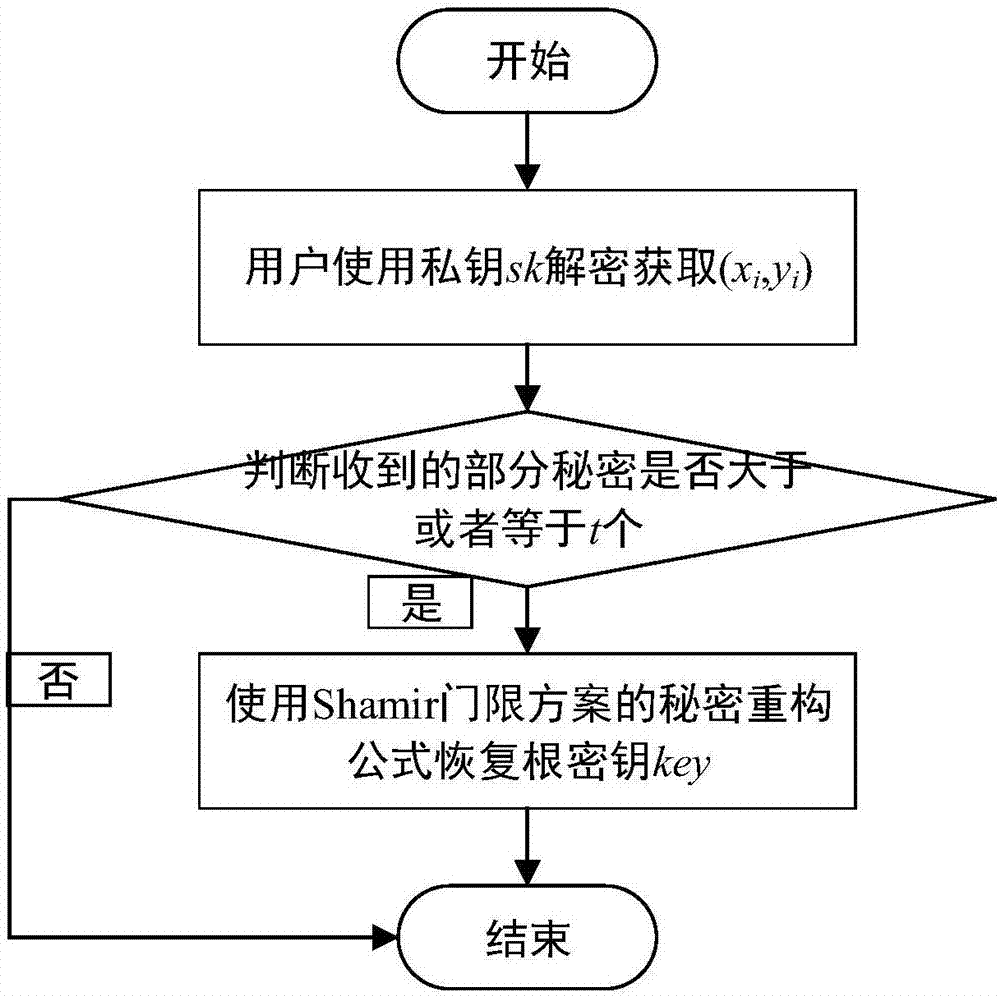
Root key management method and apparatus based on network friends
ActiveCN106878005AEnable secure storagePromote recoveryKey distribution for secure communicationPasswordSpeech sound
The invention relates to the field of secrete key management and provides a root key management method and apparatus based on network friends aiming at the problems in the prior art. By means of the network friends, a user's password is decomposed into a plurality of parts by means of a Shamir threshold scheme and then is stored at different friends, once the user forgets the root key, the user's root key can be recovered by part of friends by means of video and voice, so that the security of the root key can be guaranteed. When the user forgets his / her root key and the public key and the private key for root key protection are lost, the user generates a pair of public key and private key (pk1,sk1); the public key and the private key (pk1,sk1) are in data interaction with the friends storing the part of the root key data to acquire t part of the root key data (xi,yi), and the root key can be recovered by means of the secrete reconstruction formula of the Shamir threshold scheme.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
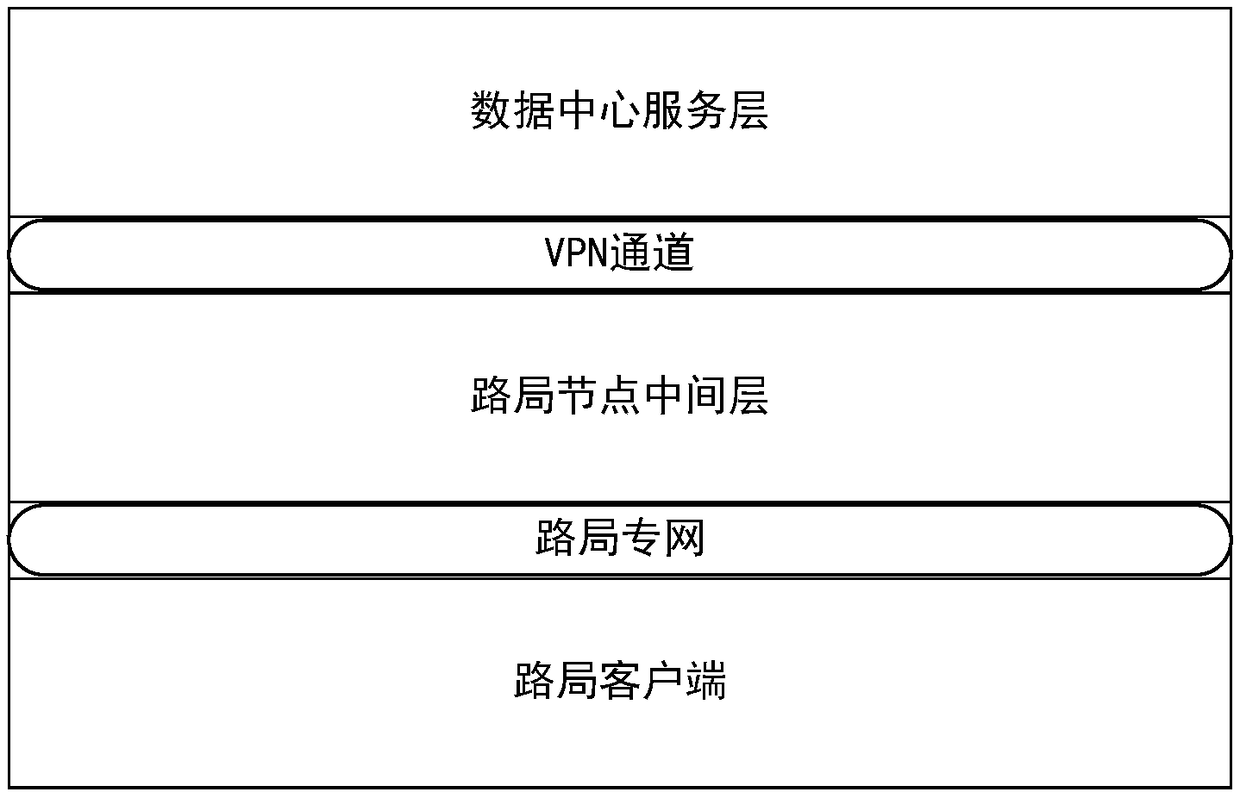
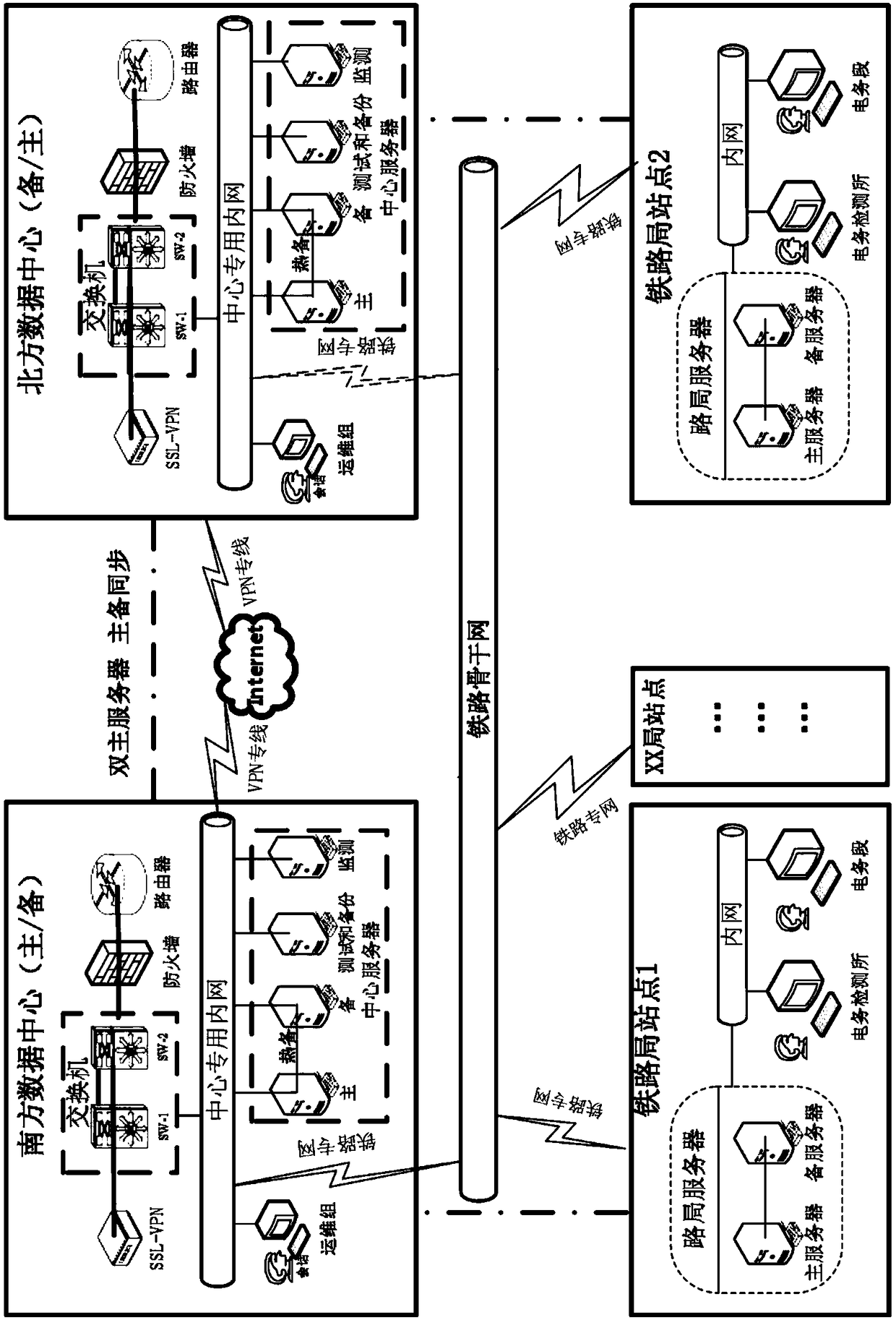
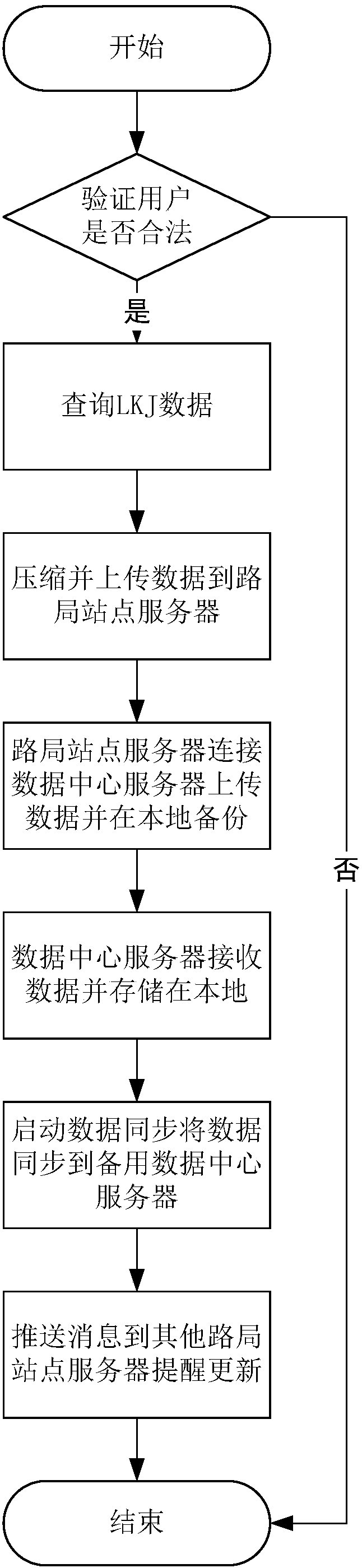
Storage system for remotely backing up data of train operation monitoring device
InactiveCN108116456ARemote backup implementationEnable secure storageRailway traffic control systemsNetworks interconnectionClient-sideData center services
The invention discloses a storage system for remotely backing up data of a train operation monitoring device. Real-time synchronization of remote data across a local area network is achieved based ondata replication of a data center and remote master and standby servers. According to the technical scheme, the system comprises a railway administration client, a railway administration site server,two data center servers and a computer program. The railway administration client, the railway administration site server and the data center servers are in communication connection, and after a computer program runs, the follow steps are executed: train operation monitoring device data queried by the railway administration client is uploaded to the railway administration site server; the railwayadministration site server receives the train operation monitoring device data and then performs local backup and forwards the data to a first data center server; the first data center server receivesthe train operation monitoring device data and then performs local backup and synchronizes the data to a second data center server for remote backup.
Owner:HUNAN CRRC TIMES SIGNAL & COMM CO LTD +1
Internet of Things data encryption transmission method and system
InactiveCN111431922AImprove securityImprove reliabilityKey distribution for secure communicationThe InternetHealth examination
The embodiment of the invention provides an Internet of Things data encryption transmission method and system, and the method comprises the steps: calling a health examination assembly corresponding to a target micro-service architecture system, wherein the health examination assembly comprises a preset health examination core assembly and a received pluggable health examination assembly defined by a user; performing health examination on each target service component corresponding to the target micro-service architecture system by applying the health examination assembly to obtain a health examination result corresponding to each target service component; and determining whether the health examination result corresponding to each target service component meets a preset health condition ornot, and if so, scheduling each target service component based on a preset scheduling rule. According to the application, encrypted transmission of the Internet of Things data can be realized by effectively utilizing a data encryption mode, the encrypted transmission process is high in reliability and high in security, and the security and reliability of the Internet of Things data can be effectively improved.
Owner:CHINA CONSTRUCTION BANK +1
Data storage method and device, electronic equipment and computer readable medium
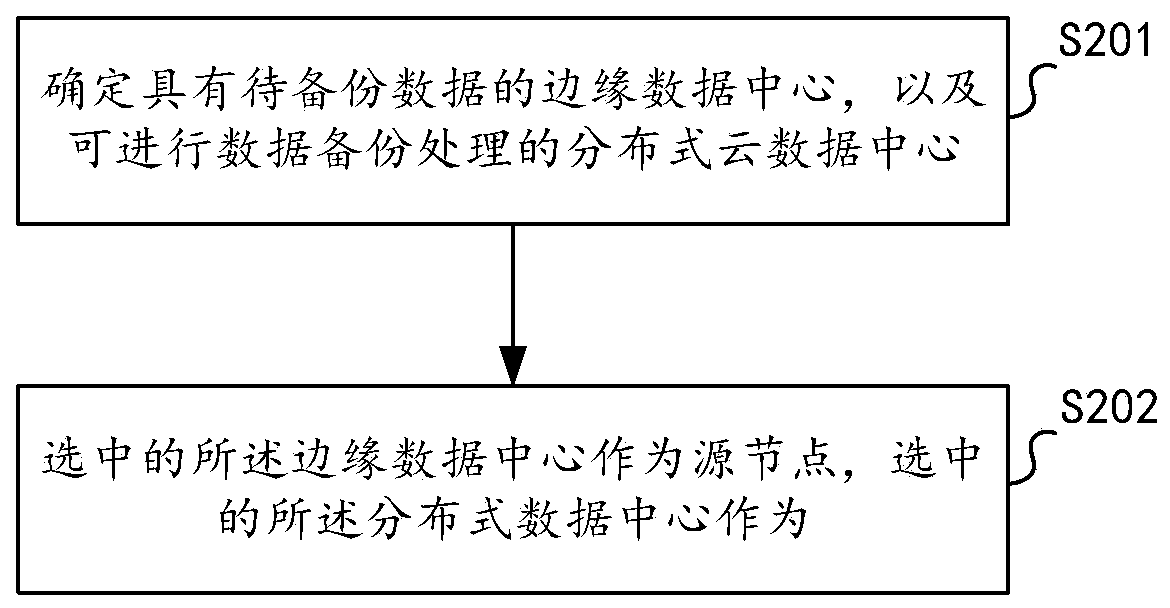
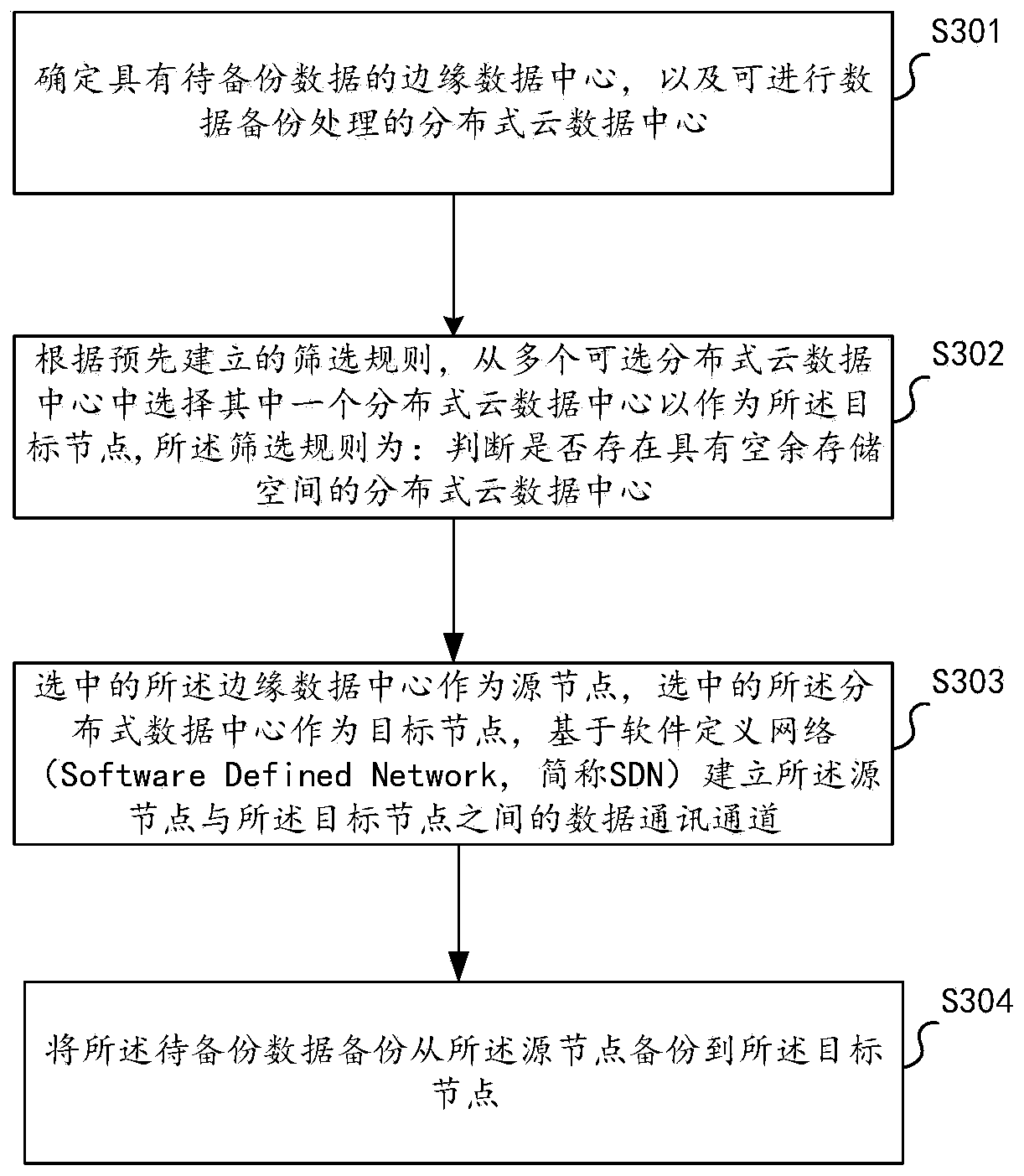
InactiveCN109739927AEnable secure storageDatabase distribution/replicationDigital data protectionCloud data centerData store
The invention discloses a data storage method and device, electronic equipment and a computer readable medium, and the data storage method comprises the steps: determining an edge data center with to-be-backed-up data and a distributed cloud data center capable of carrying out data backup processing, for example, judging whether a distributed cloud data center with an unoccupied storage space exists or not; The selected edge data center is used as a source node; and selecting the distributed data center as a target node to back-up the to-be-backed-up data from the source node to the target node, for example, transmitting the to-be-backed-up data from the source node to the target node through a data communication channel established by a software defined network, thereby realizing secure storage of the data.
Owner:BEIJING 21VIANET DATA CENT
Method and equipment for building connection between client sides
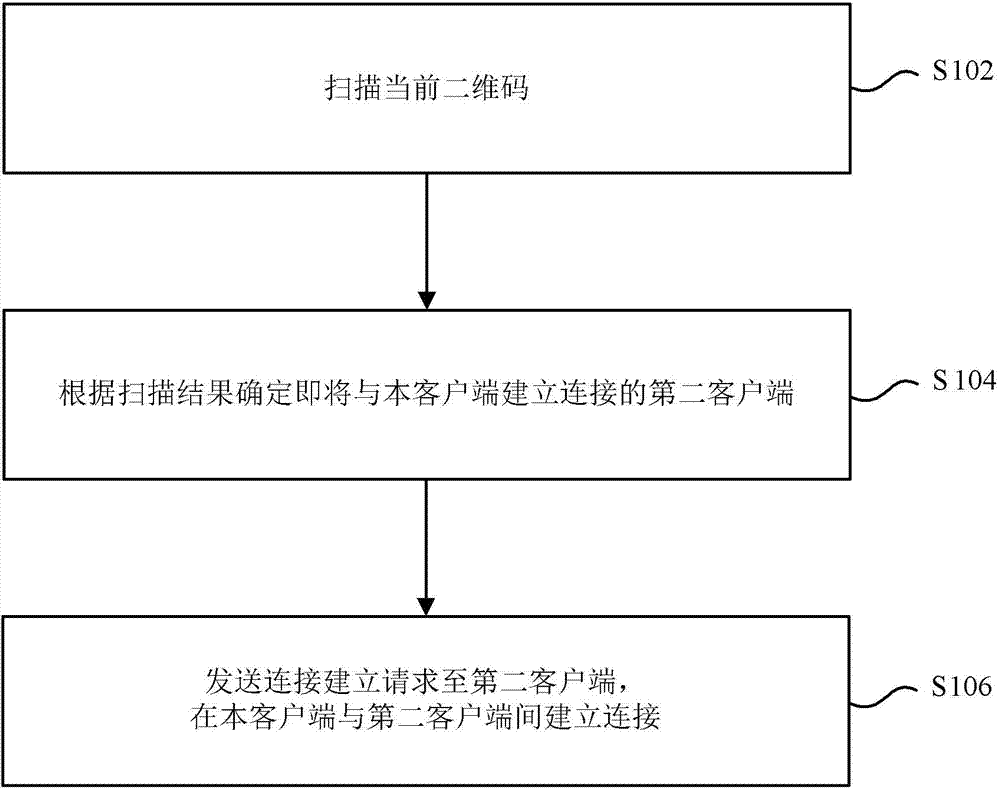
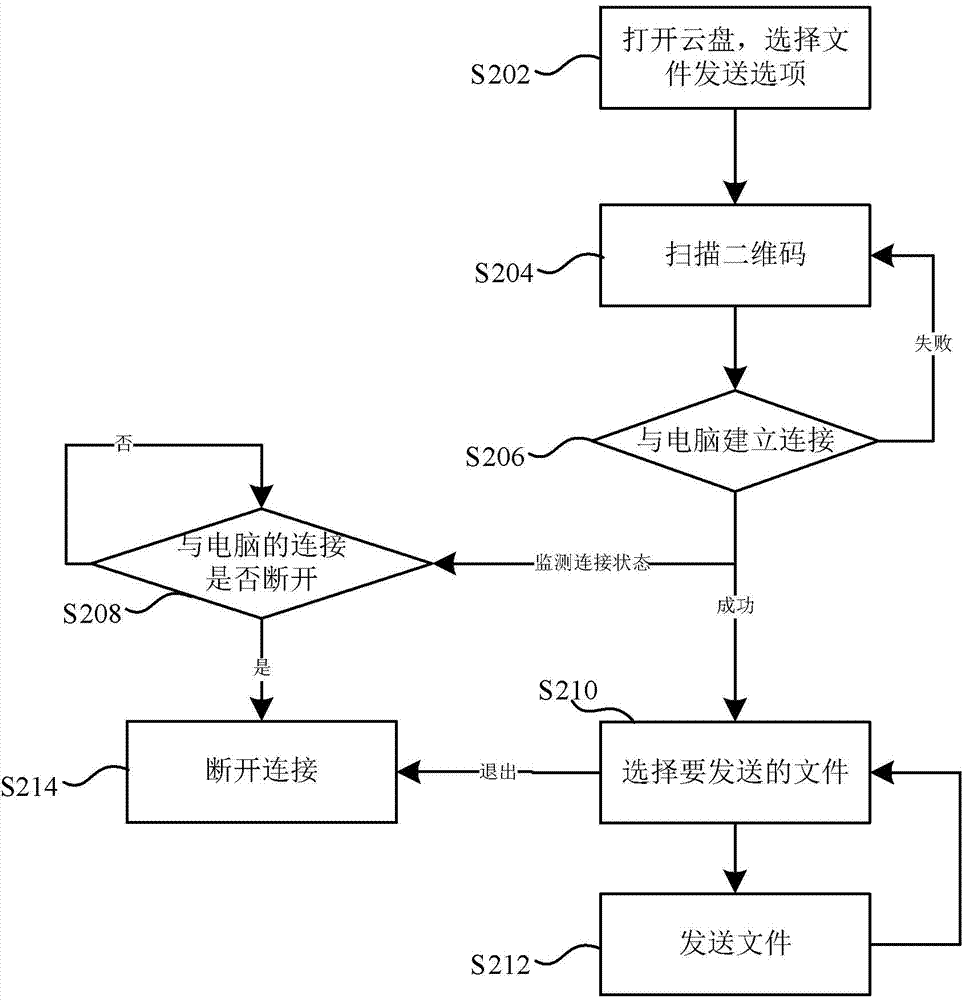
ActiveCN103618789AEnsure safetyHigh densityTransmissionSensing by electromagnetic radiationProgramming languageHigh density
The invention provides a method and equipment for building the connection between client sides. The method comprises the steps of scanning a current two-dimension code, determining the second client side about to be connected with the client side according to a scan result, sending a connection building request to the second client side, and the connection is built between the client side and the second client side. In the method and equipment, the two-dimension code is used for determining the second client side about to be connected with the client side, the safety of the connection can be guaranteed through the advantages of high density and high reliability of the two-dimension code, furthermore, the advantages of achieving safe storage, convenient carrying and automatic recognition and reading can be achieved, and therefore user experience is improved.
Owner:BEIJING QIHOO TECH CO LTD
Automatic storage express cabinet for unmanned aerial vehicle distribution
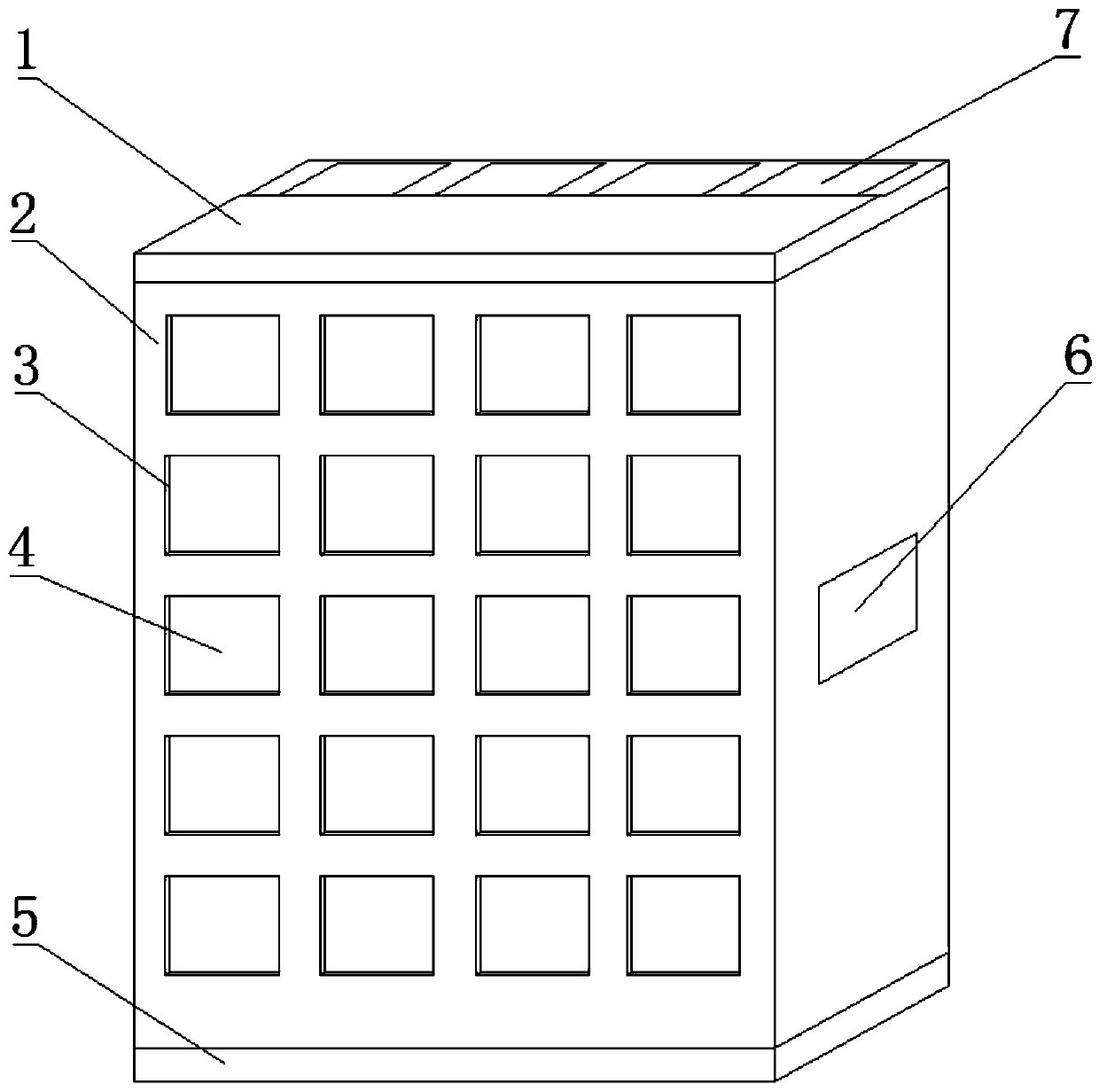
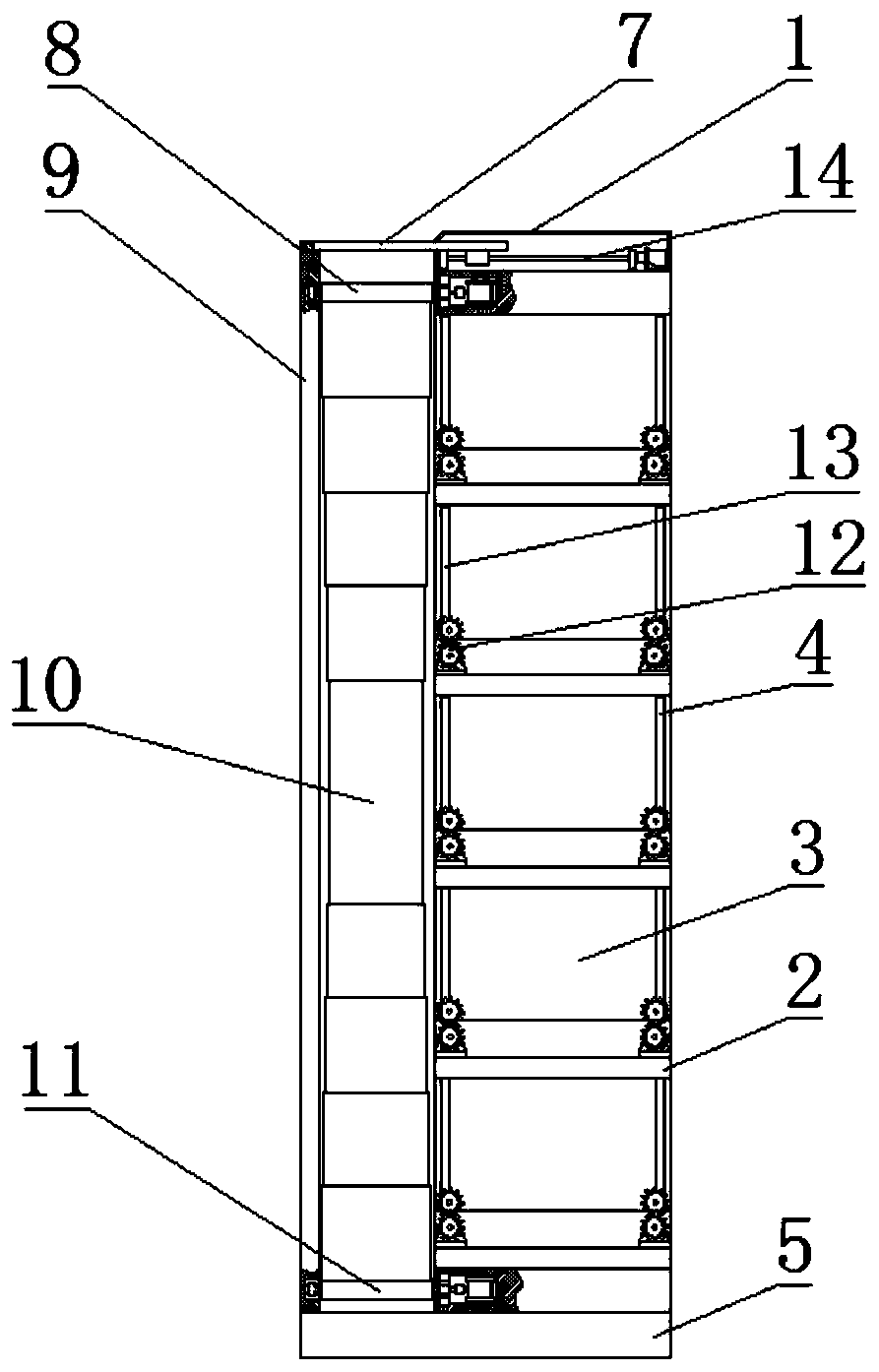
PendingCN110276914ARealize automatic sortingRealize automatic storagePower-operated mechanismCabinetsUncrewed vehicleSelf adaptive
The invention discloses an automatic storage express cabinet for unmanned aerial vehicle distribution. The structure design is simplified and the goods storage safety is improved during the automatic storage of goods. In particular, the express cabinet has a function of performing the automatic communication with the unmanned aerial vehicle, and can send an instruction according to the storage condition to enable the unmanned aerial vehicle to place the goods at the corresponding top door opening position, thereby solving the problem of disorder of goods placement of the unmanned aerial vehicle; (2) the express cabinet is provided with a self-adaptive goods slow descending device, so that the goods can be slowly conveyed into a specified storage grid by a corresponding mechanism after being released by the unmanned aerial vehicle, thereby solving the problems that the goods distributed by the unmanned aerial vehicle are difficult to sort and place, and the goods possibly fall off and are damaged when being released are solved; (3) the express cabinet is provided with the storage grids for automatically storing and opening the goods, and employs a full-automatic mechanism design, so that the problems of safe storage of the goods without unmanned distribution and possible forgetting to close the outer doors of the storage grids when a user takes the goods are solved.
Owner:FUJIAN UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com