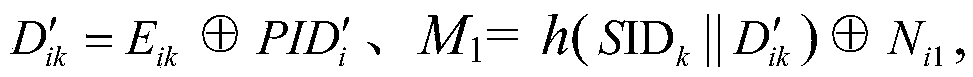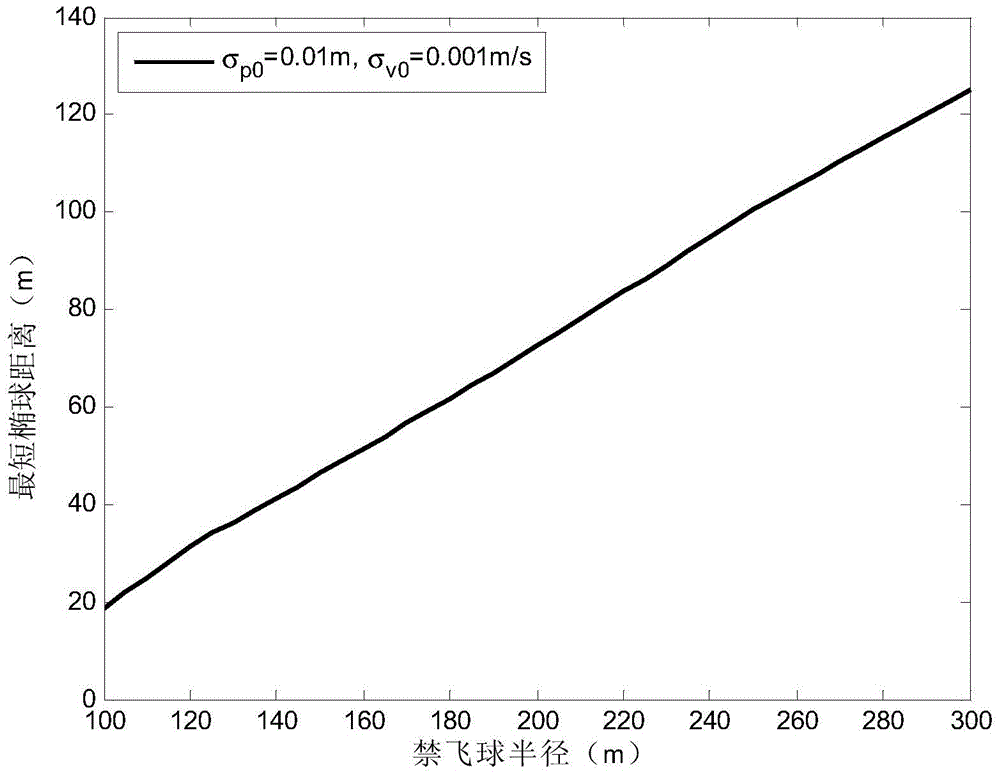Patents
Literature
53results about How to "Security does not affect" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
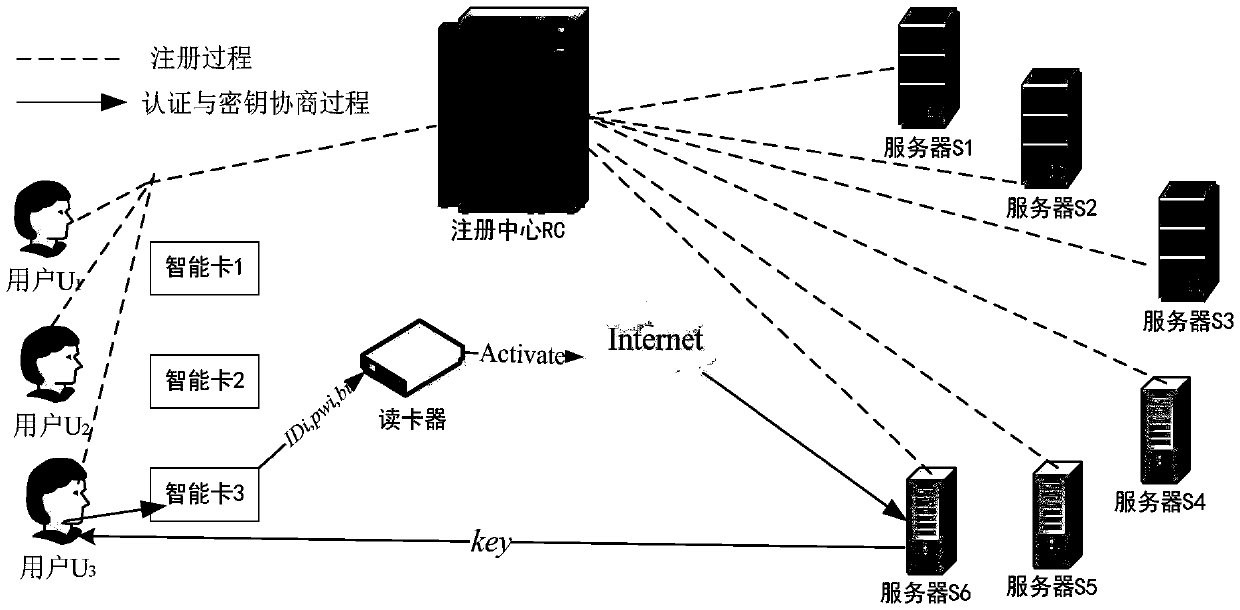
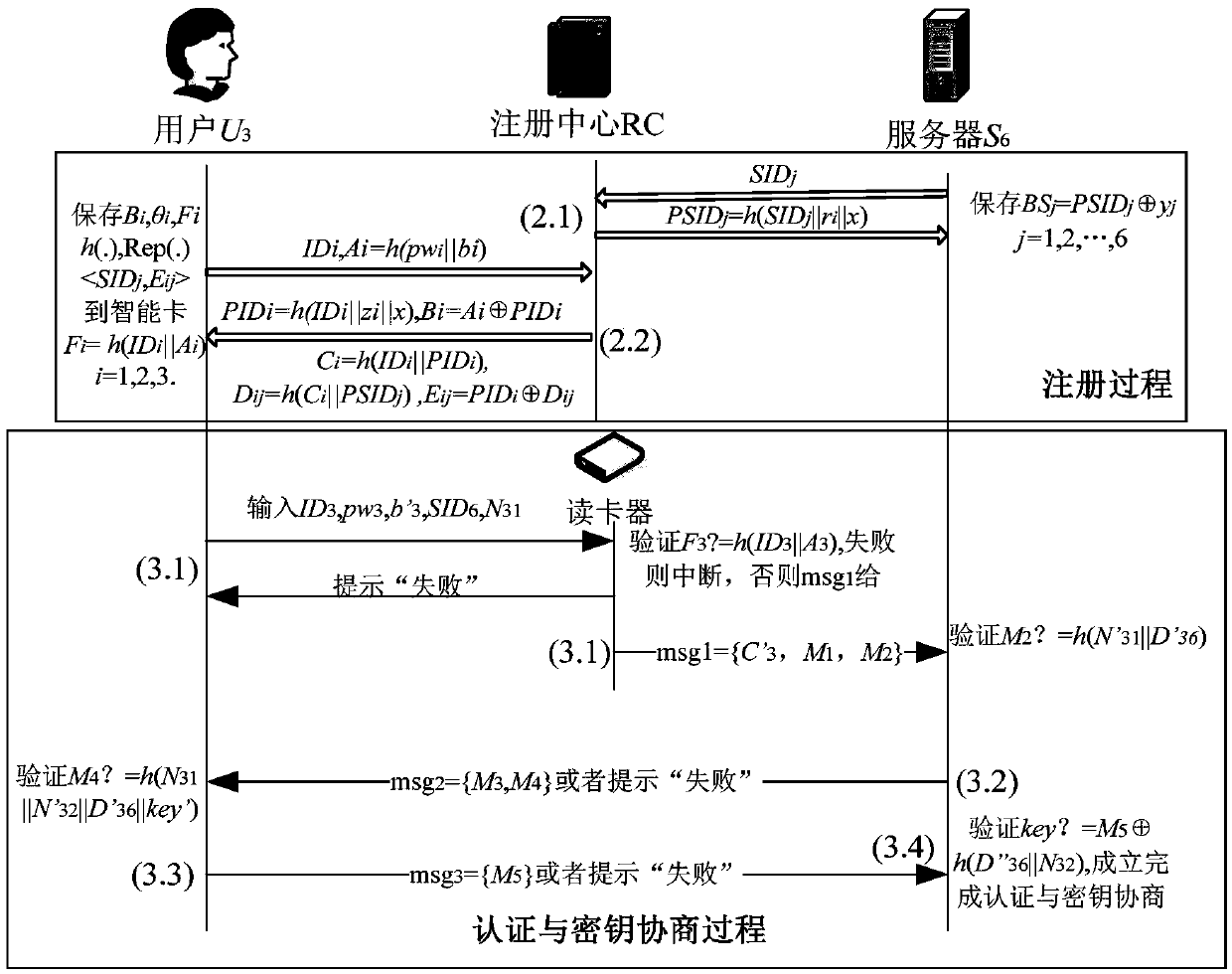
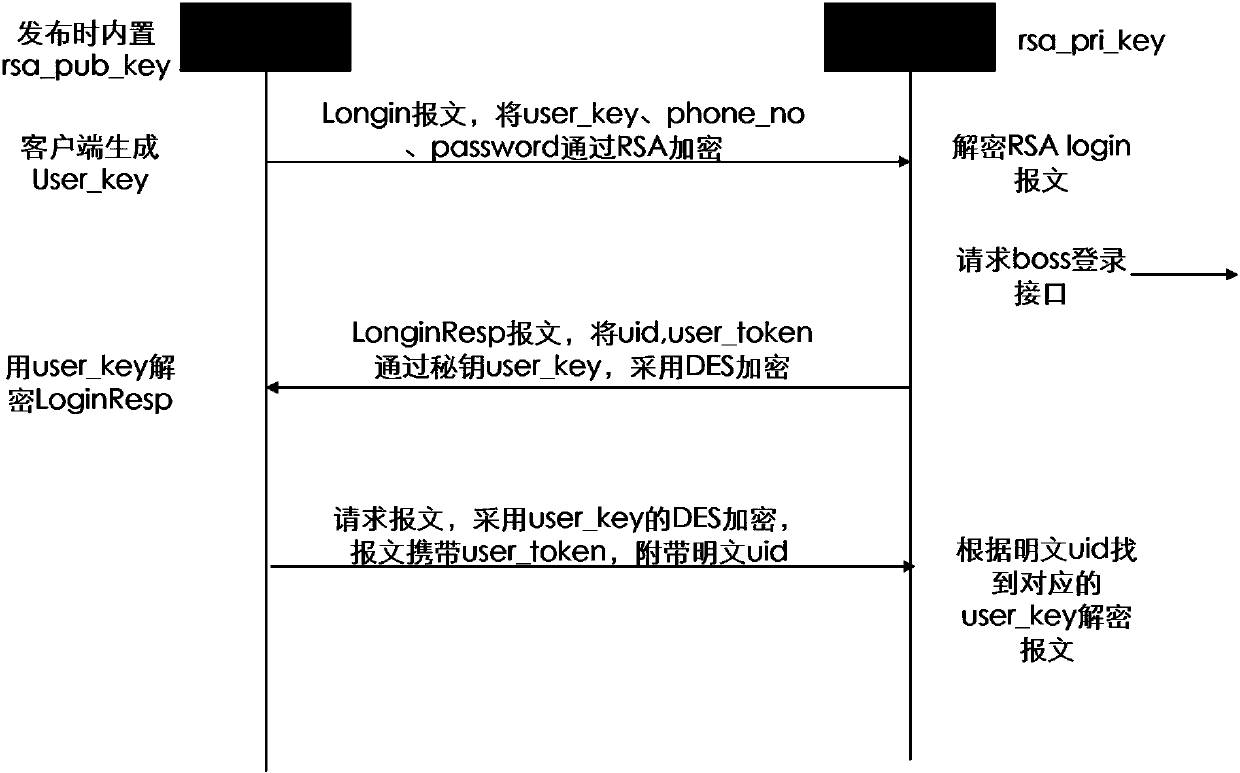
Lightweight anonymous authentication and key negotiation method in multi-server environment
The invention relates to a lightweight anonymous authentication and key negotiation method in a multi-server environment and belongs to the technical field of information safety. The method is characterized by achieving the anonymous authentication and key negotiation in the multi-server environment by means of the following three steps: (1) building a system and selecting system parameters; (2) registering in a registering center RC by a server and a user; (3) carrying out authentication and key negotiation by the user and a remote server so as to provide subsequent communication session keys. The lightweight anonymous authentication and key negotiation method is applicable to remote authentication of a mobile terminal and servers with low calculation capability, memory space and communication capability; the mobile terminal can log in any server registered by RC through a user name and a password; the server only can authenticate that the user is a valid user and cannot know the specific identity of the user, so that the privacy of the user is protected; the lightweight anonymous authentication and key negotiation method is excellent in expansibility; the two-party negotiation session keys are determined by random numbers Ni1 and Ni2 selected by authenticating for each time by two parties; the independence and the forward and backward security of the session keys are ensured.
Owner:深圳市迅威恒达信息技术有限公司
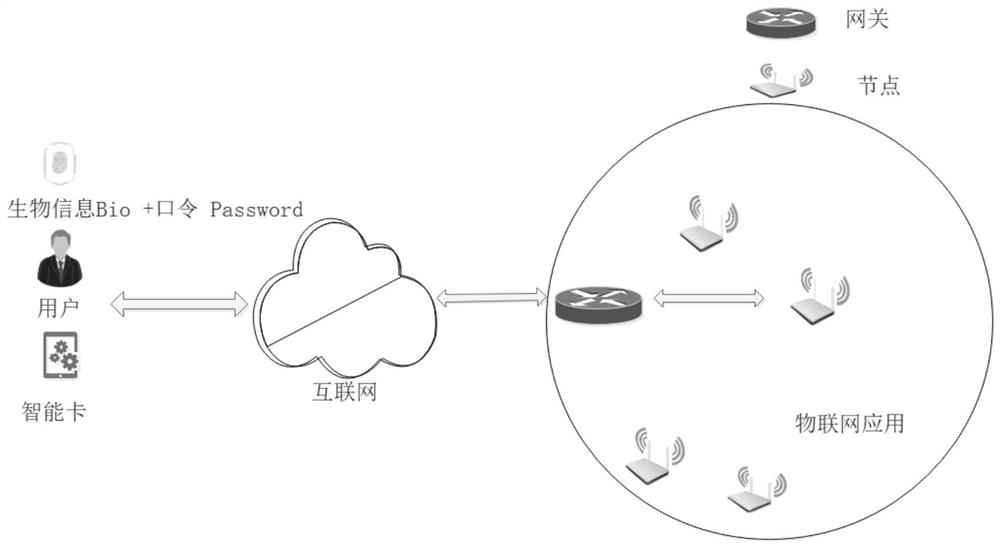
PUF-based three-factor anonymous user authentication protocol method in Internet of Things
ActiveCN111818039ASave memorySave computing powerKey distribution for secure communicationSecurity arrangementAttackThe Internet
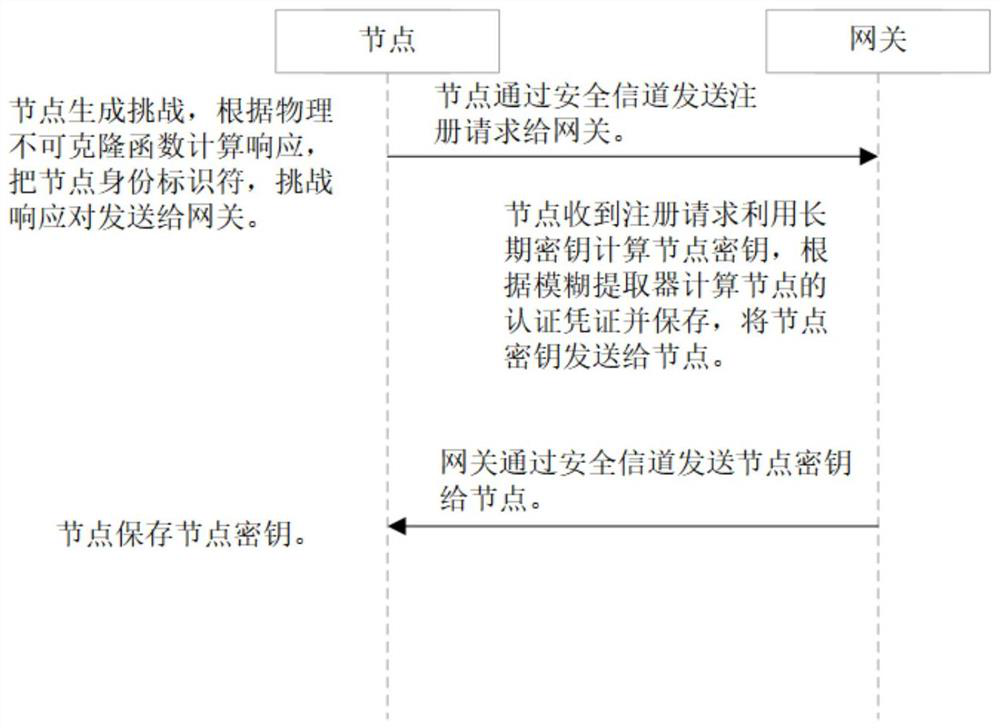
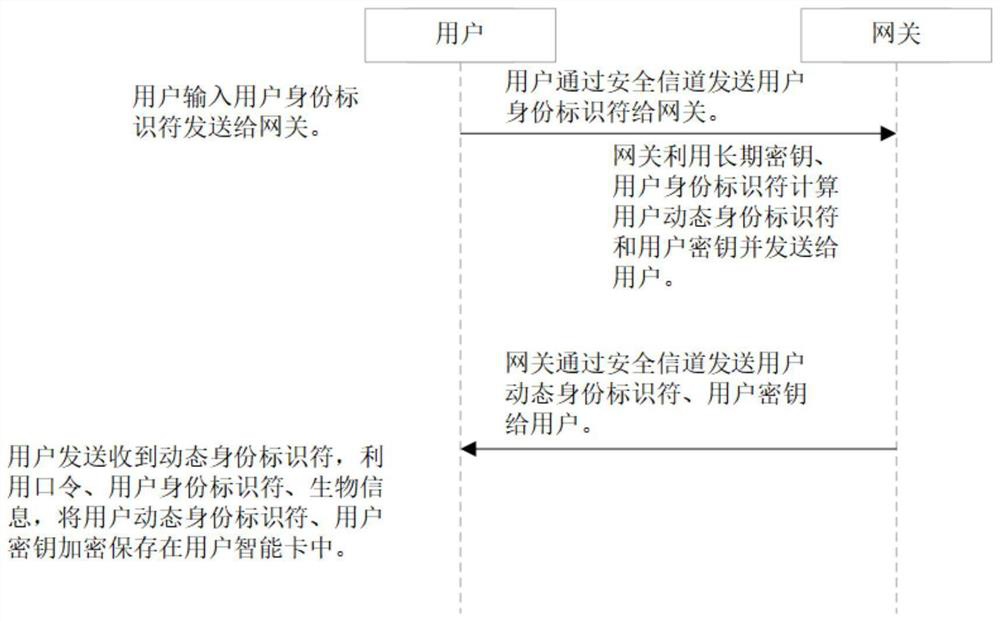
The invention discloses a PUF (Physical Unclonable Function)-based three-factor anonymous user authentication protocol method in the Internet of Things, which solves the security problems such as physical clone attacks and the like, and is implemented by the following steps that: a gateway generates a long-term key for registration and key negotiation of nodes and users; the node sends a PUF-basedchallenge and response to the gateway, and the gateway generates an authentication certificate and sends a node key to the node to complete registration; the user sends the identity identifier to thegateway, the gateway generates a user dynamic identity identifier and a user key and sends the user dynamic identity identifier and the user key to the user, and the user encrypts and stores the userdynamic identity identifier and the user key in the smart card to complete registration; and the user, the gateway and the node perform mutual authentication and key agreement to form a PUF-based three-factor anonymous user authentication protocol method in the Internet of Things. Based on three-factor authentication, smart card loss, password guessing attack and the like can be resisted; the method achieves the anonymity of the user and the node, is small in calculation amount, is high in efficiency, is suitable for IOT nodes with limited resources, and is used for IOT safety communication.
Owner:XIDIAN UNIV
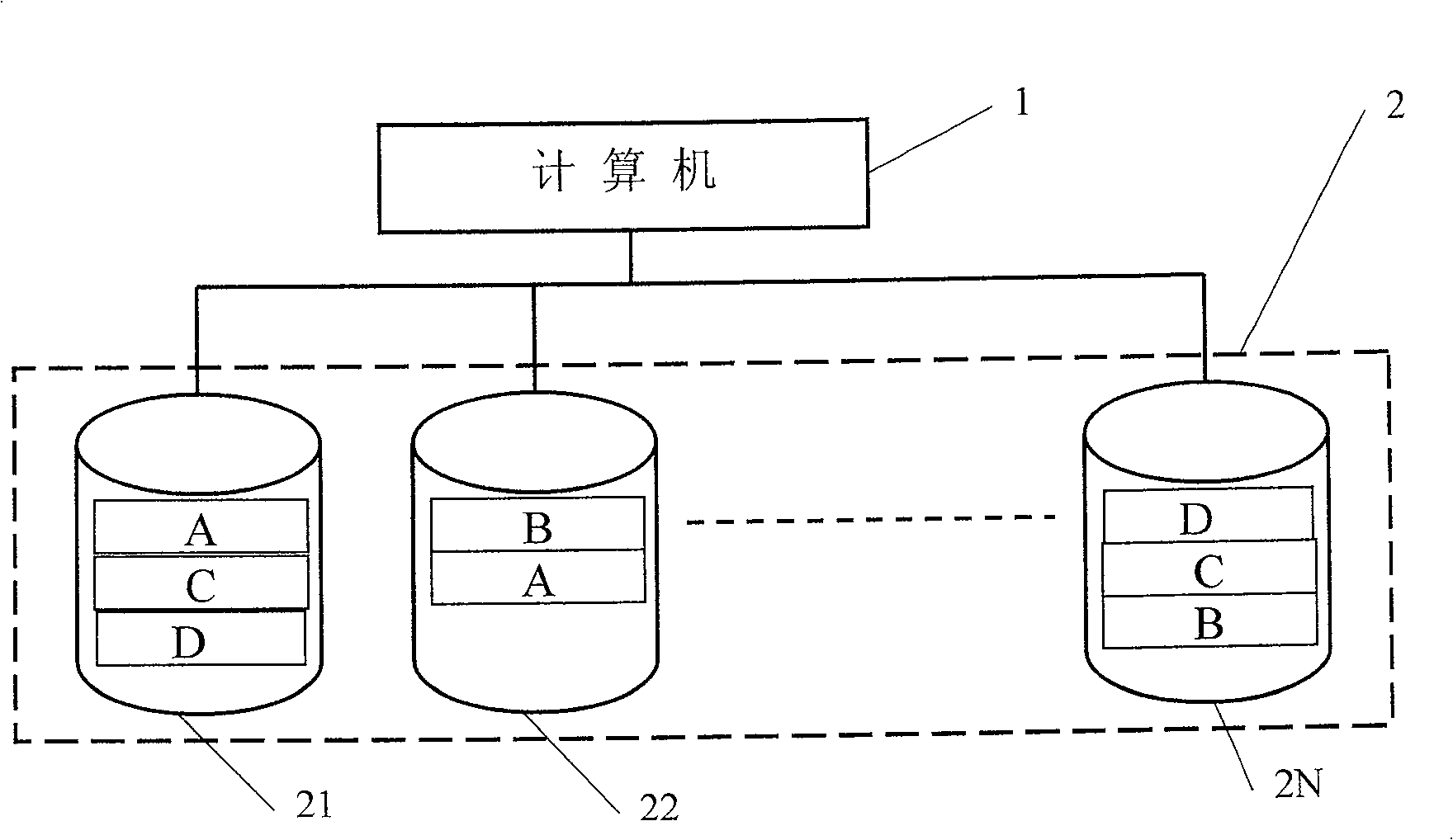
Safety storage method for data
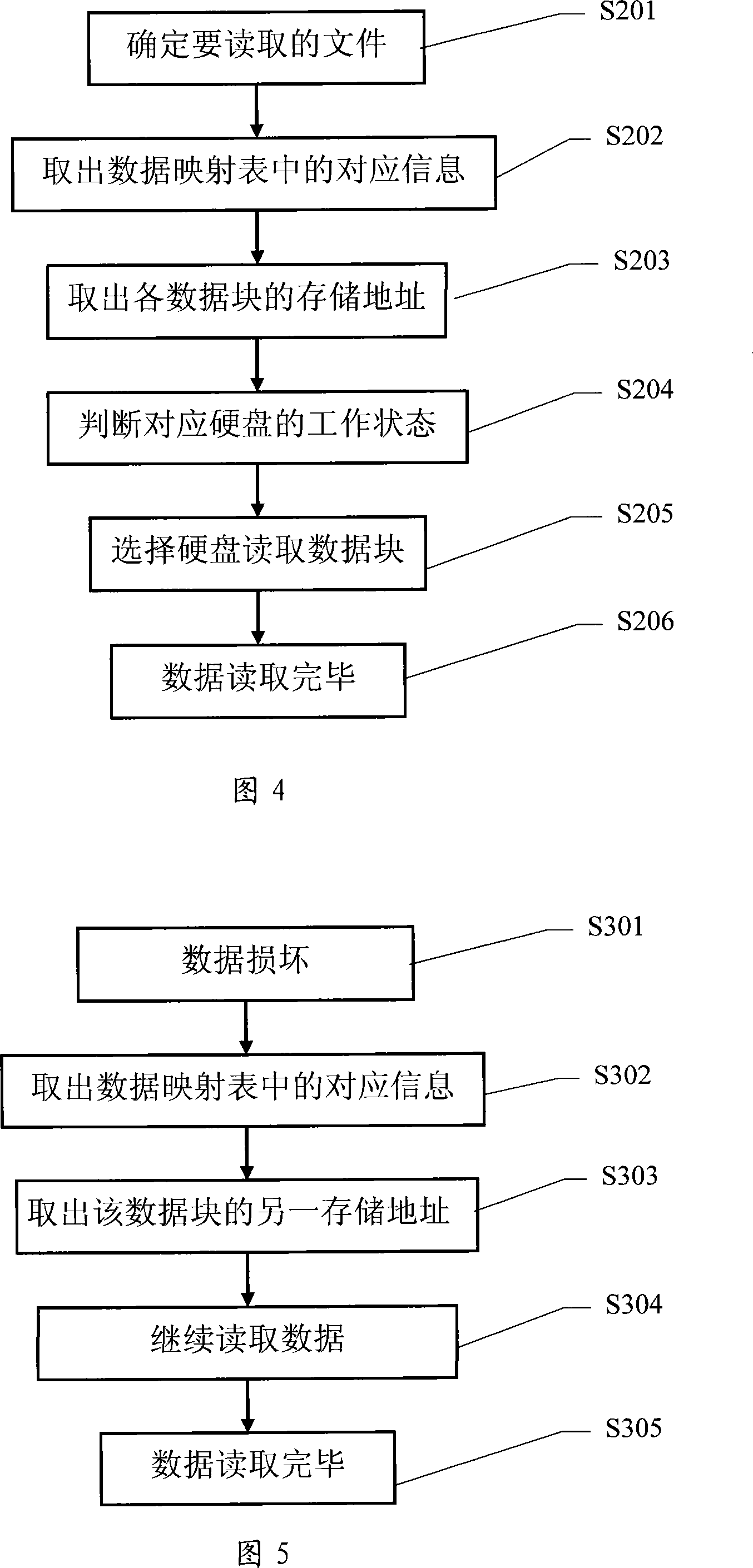
ActiveCN101118508ALow costEnable secure storageRedundant operation error correctionSpecial data processing applicationsPresent methodComputerized system
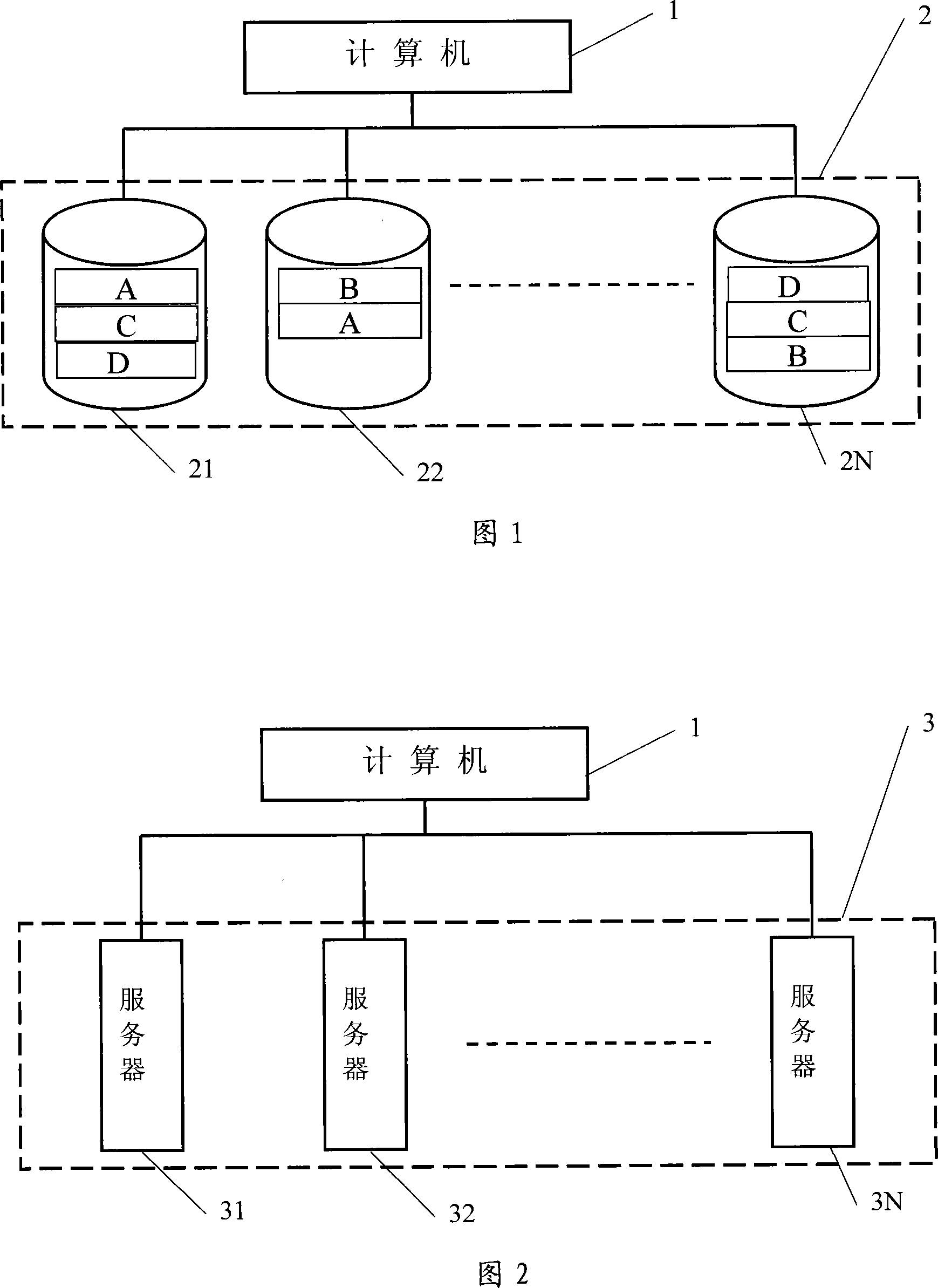
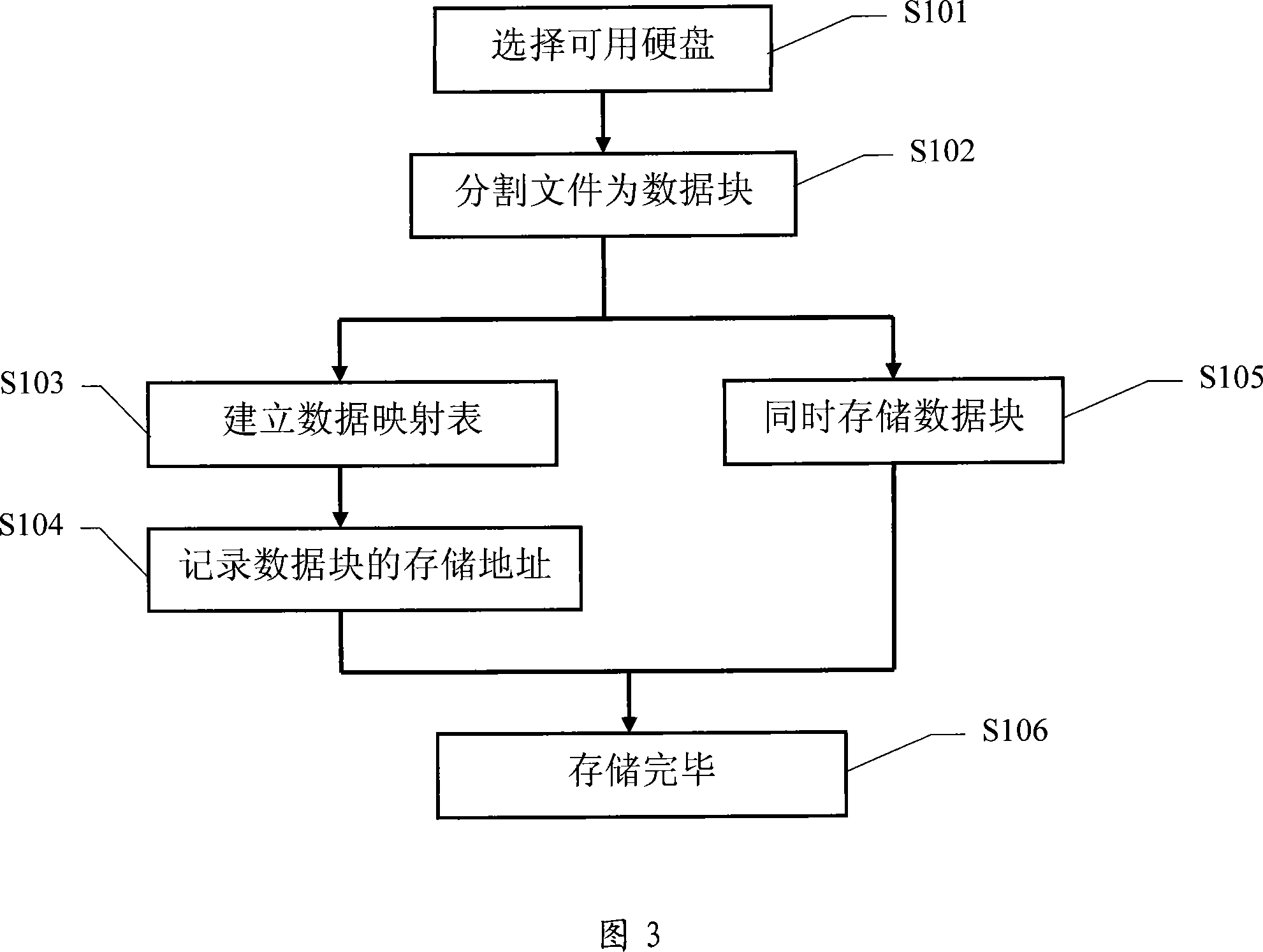
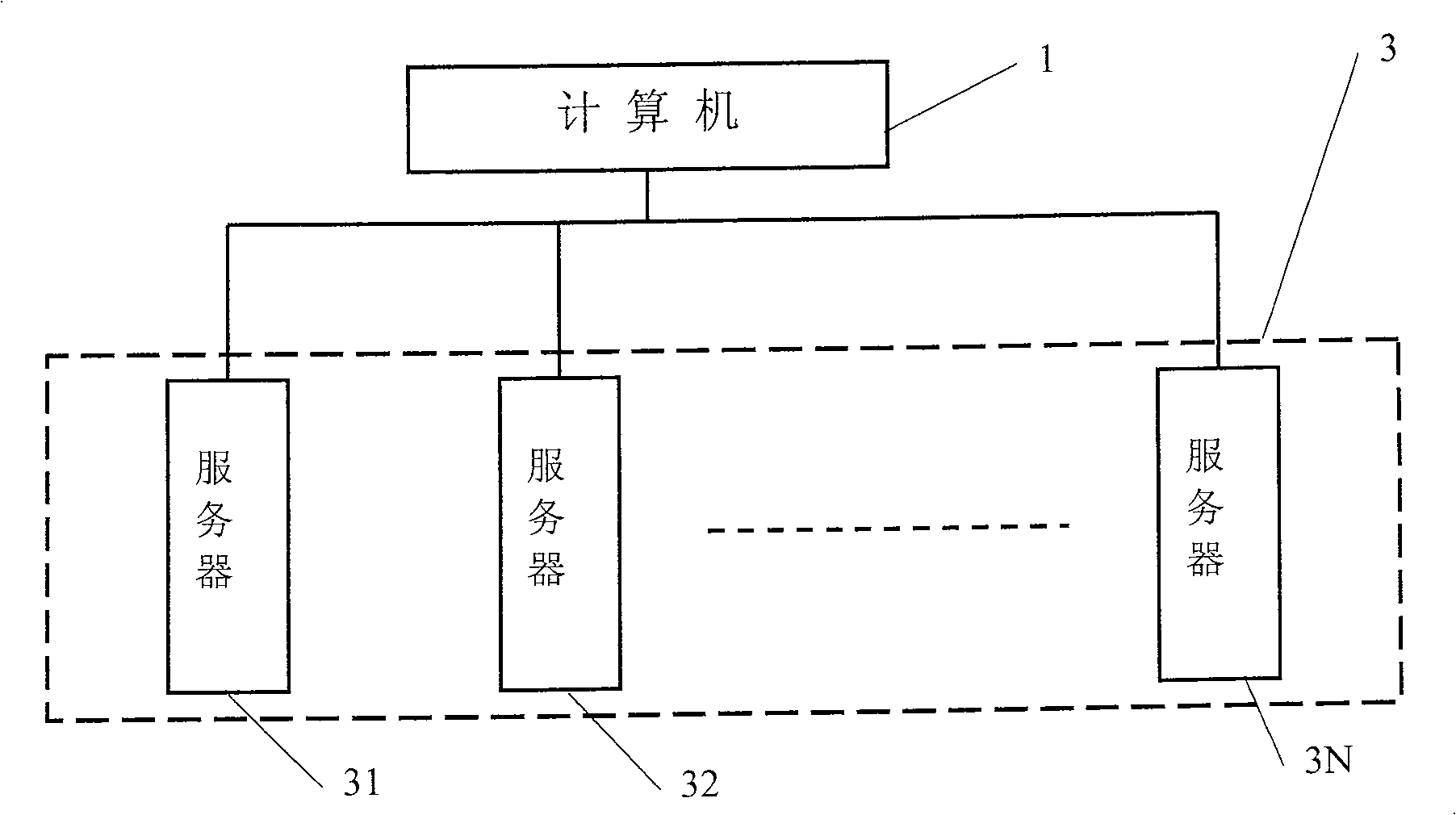
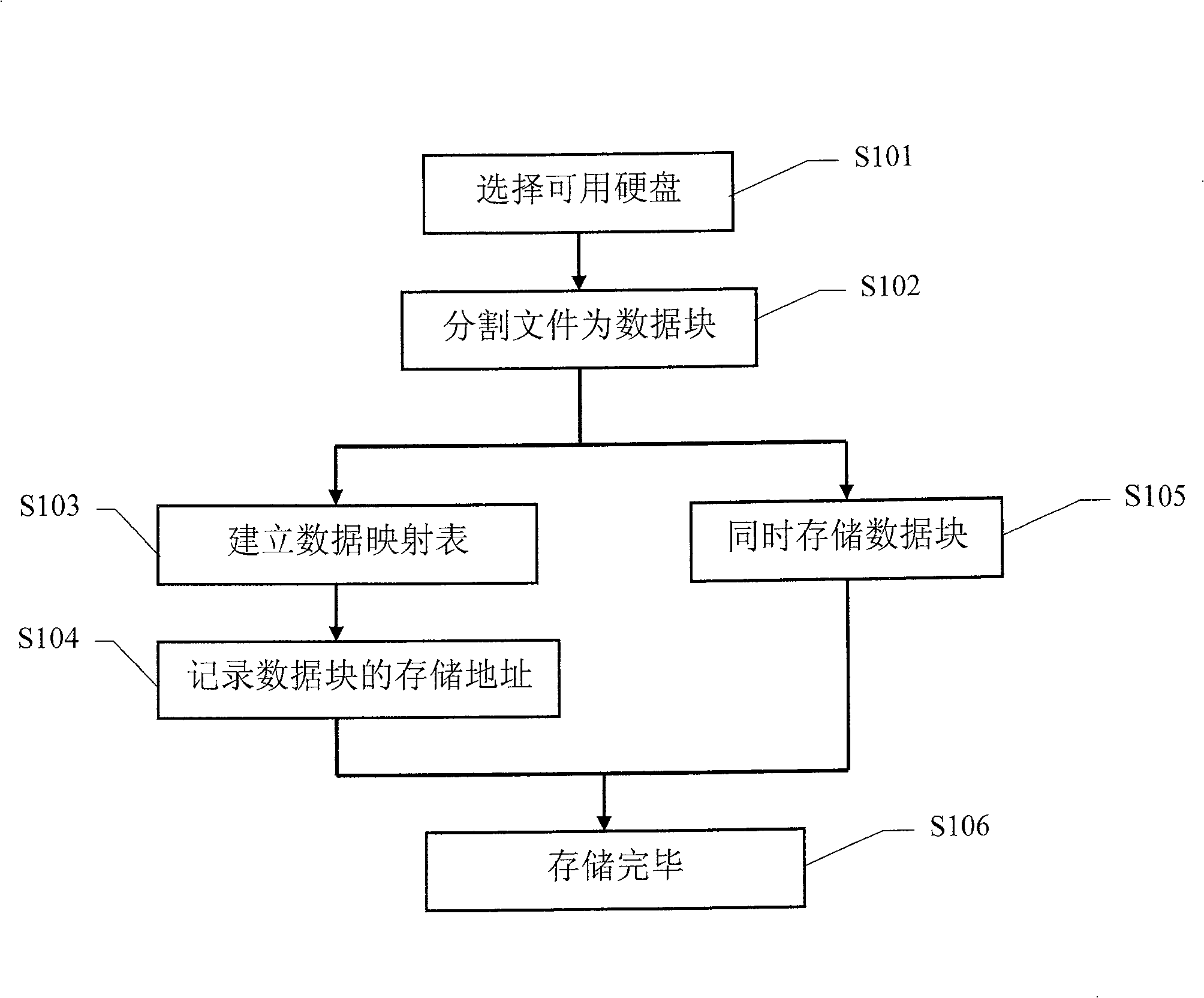
The present invention discloses a safe data storing method. By connecting with a plurality of storage device, the computer system can store any one data into two separate storage devices simultaneously to form a relationship; when the data in one of the storage device is damaged, or the storage device is damaged, the present invention can take out the data from the other storage device which stores the corresponding data and stores the data into other storage device, to guarantee that any one of the data has usable data in two storage devices simultaneously. When reading data from the two storage devices, the present method can select one, and when one storage device storing the data is damaged, the method can read data from the other storage device. The present invention has low cost, strong data safety and strong expansibility, can increase or decrease the capacity of the storage device at will, and is applicable to the storage system formed by multi hard disks and multiserver, and has high data read rate. No recreating time is needed, when finding data damaged during the course of data reading, the present method can retrieve on line, without influence for the data reading and running.
Owner:CHENGDU SOBEY DIGITAL TECH CO LTD
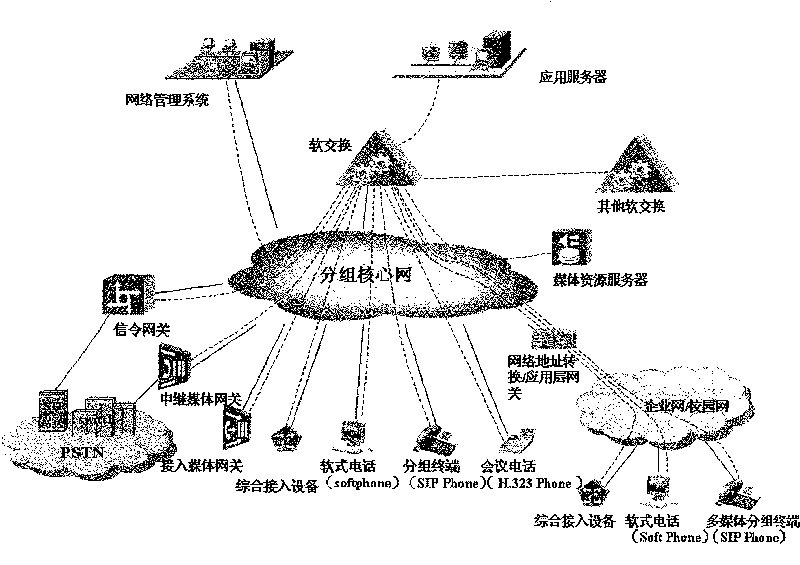
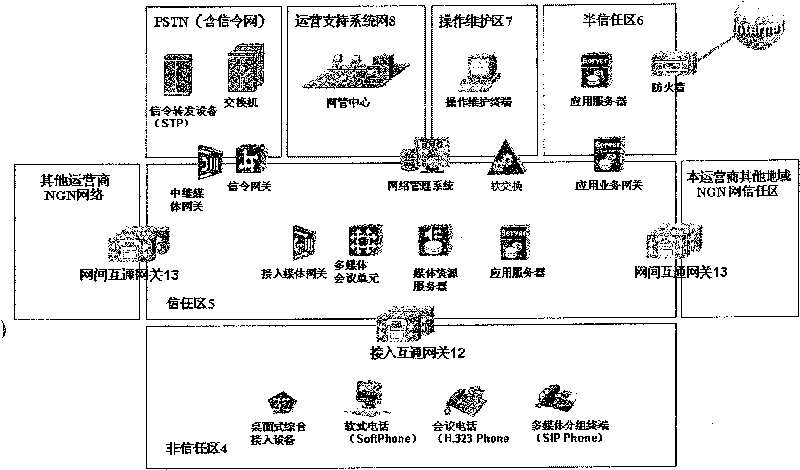
Networking system for next generation network
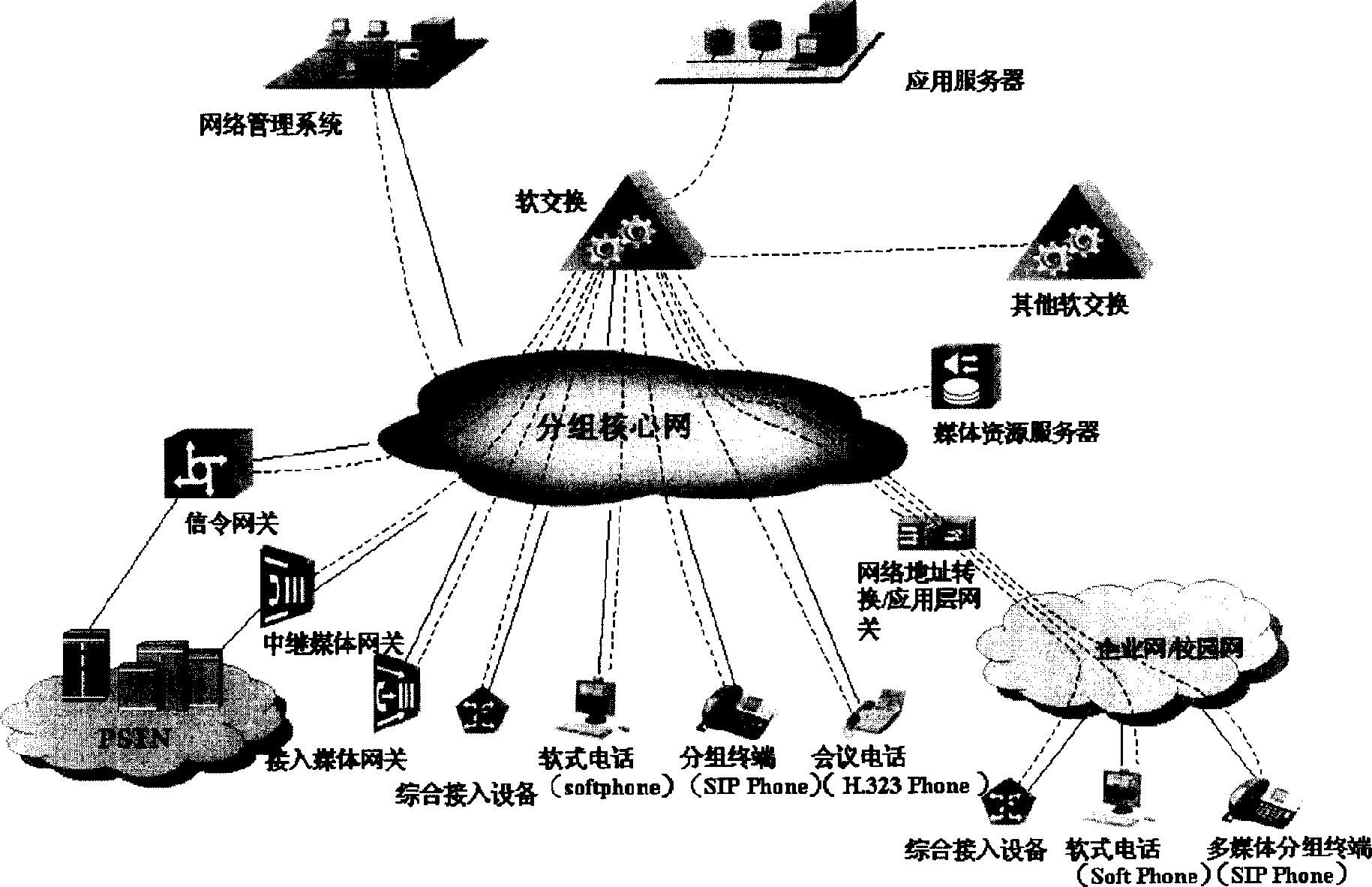
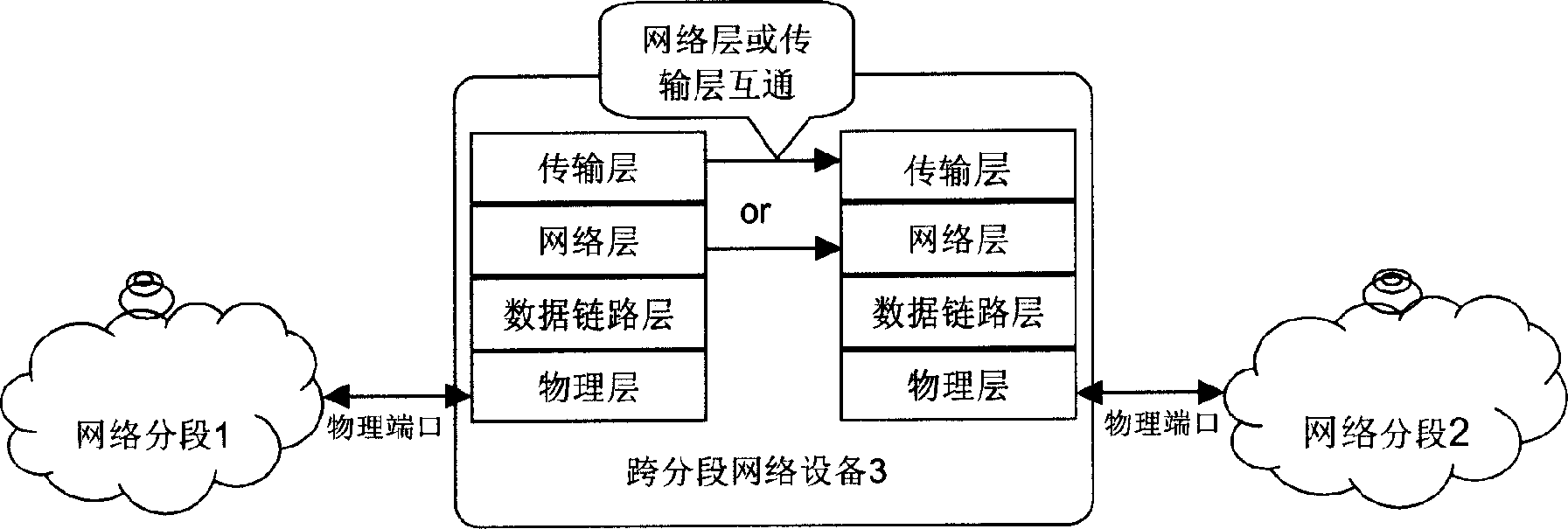
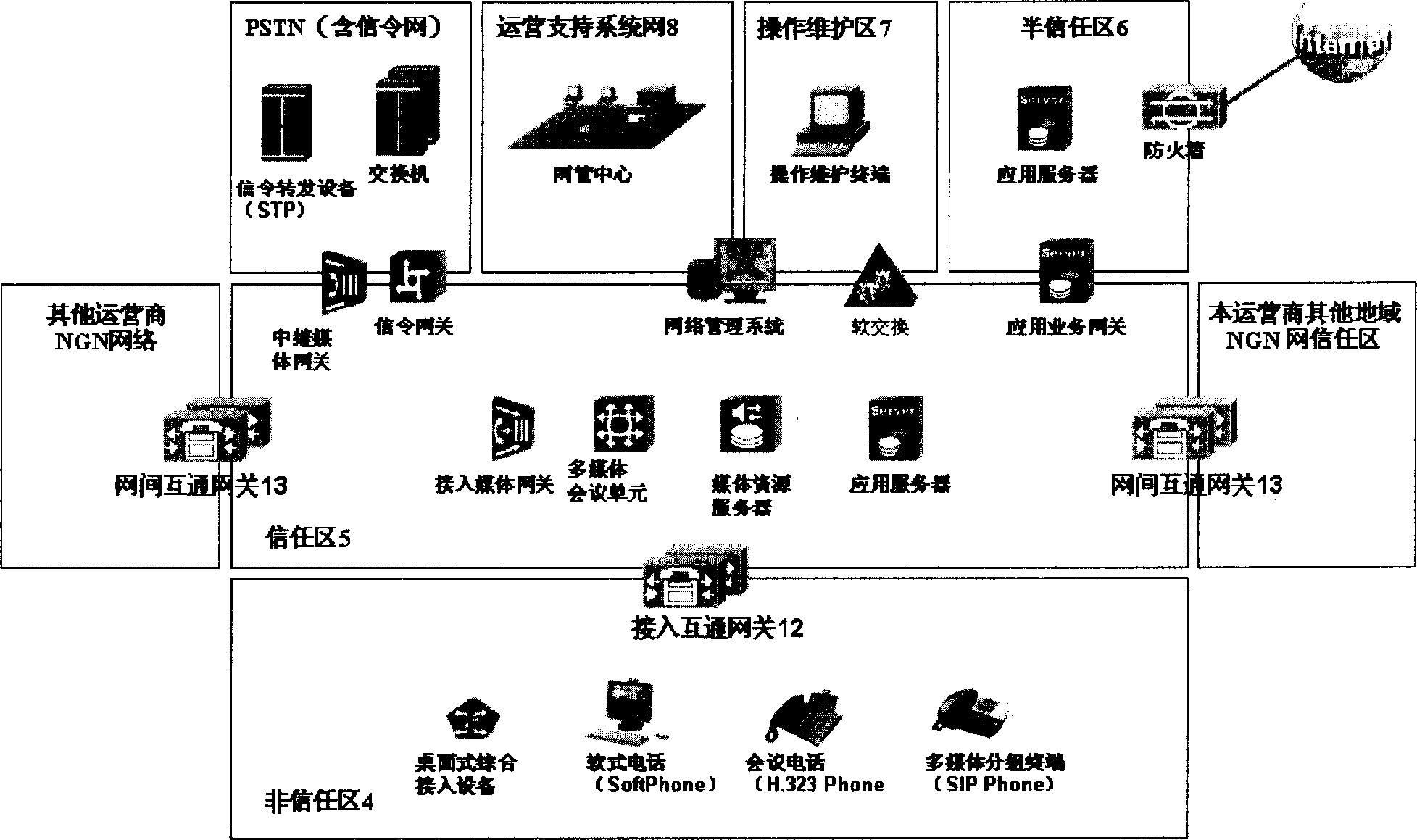
InactiveCN1665238AImprove securityAchieve securityTransmissionOperational maintenanceApplication server
The invention discloses a networking system for next-generation network, comprising several network subregions, all connected by transregional network components, where these components only implement intercommunication between the application layers of all the network subregions and then implement their service intercommunication. The networking system comprises the below network subrgions: non-trust region, meaning the network the users can directly access to as well as the network with undetermined safety; trust region, meaning the service special network for the next-generation network; semi-trust region, the IP network region connected with the external data network by the firewall; operation maintaining region, an independent IP network, one side connected with the equipment at the operation maintaining server end and the other side connected with client ends; operation supporting network, a special network, managing the whole network equipment of the operator. The networking system has feasibility and implements the safety of access network and application server, implementing the intercommunication of all the network subregions.
Owner:HUAWEI TECH CO LTD
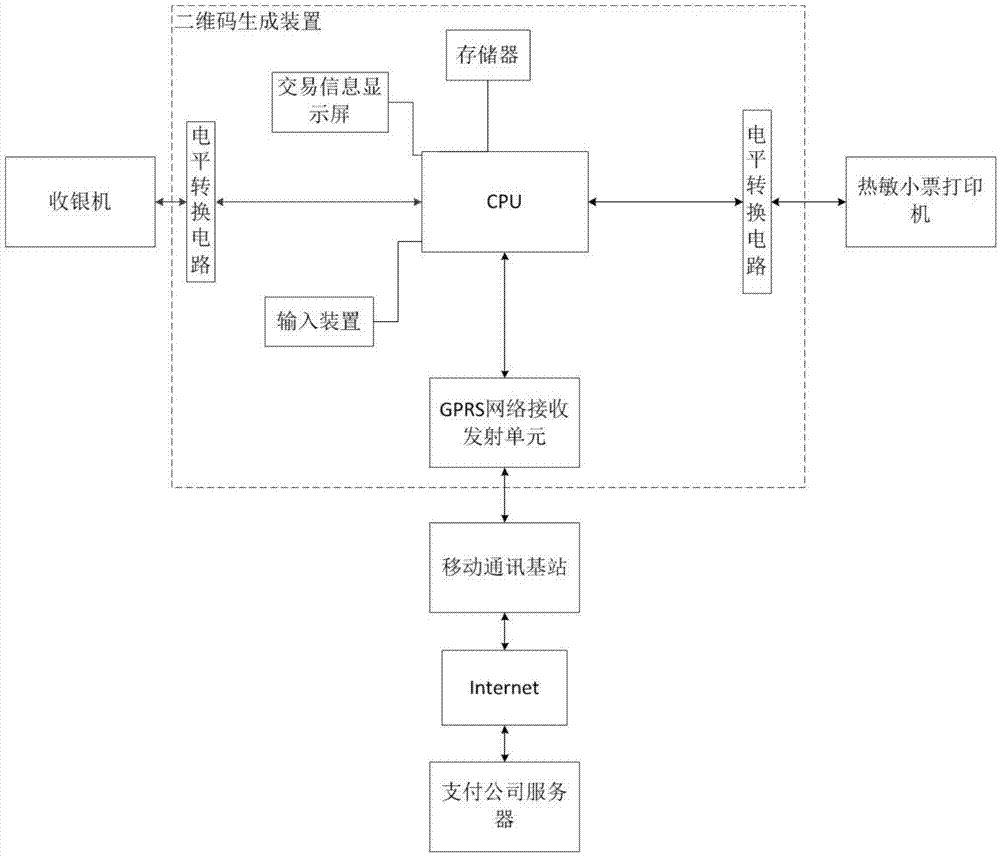
Quick-response matrix code receipt paying method and system
InactiveCN103617522ALow costImprove stabilityPayment architectureApparatus for meter-controlled dispensingPaymentProgramming language
The invention discloses a quick-response matrix code receipt paying method and system. According to the quick-response matrix code receipt paying method, a consumption receipt is printed with quick-response matrix code consumption information including a primary account number, a transaction processing code, a transaction amount, transaction transmission time, the type of a merchant, an identification code of a processing machine terminal, a transaction money code and the like, the phenomenon that a consumer align a displayer of a cash register to conduct code scanning payment is not needed, and the consumer can directly align the printed consumption receipt printed with a quick-response matrix code to conduct code scanning payment. The quick-response matrix code receipt paying system comprises the cash register, a two-dimension code generating device and a thermal printer, wherein the cash register, the two-dimension code generating device and the thermal printer are connected in sequence. The quick-response matrix code receipt paying method and system can be effectively applied to all types of cash registers. By the adoption of the quick-response matrix code receipt paying method and system, payment operation is easy, convenient and fast, low cost is achieved, the efficiency of payment is greatly improved, the practical value is high, and the practical significance is important.
Owner:王冉 +1
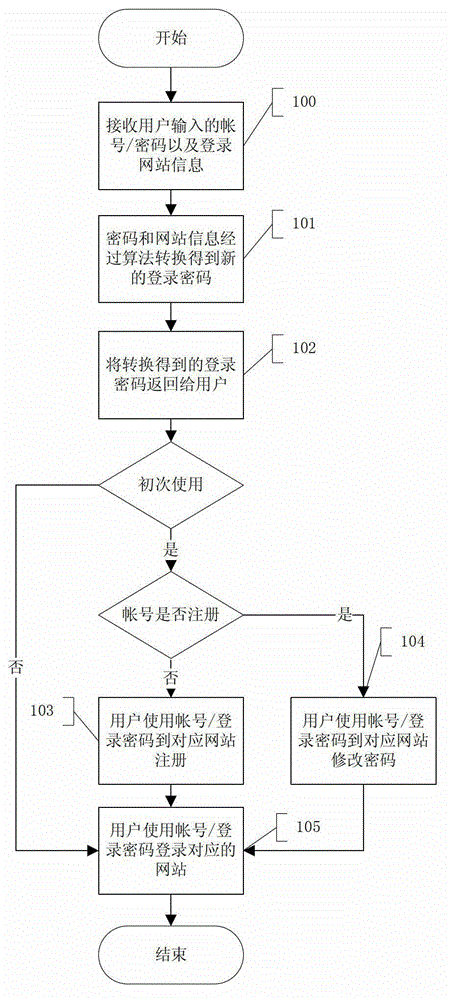
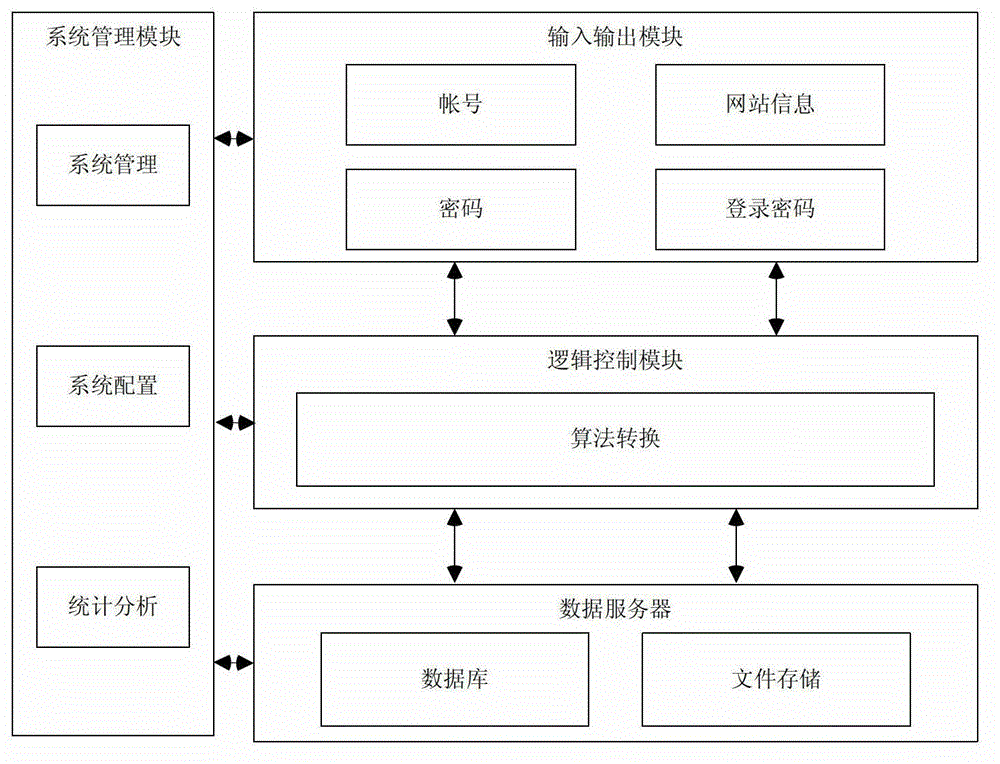
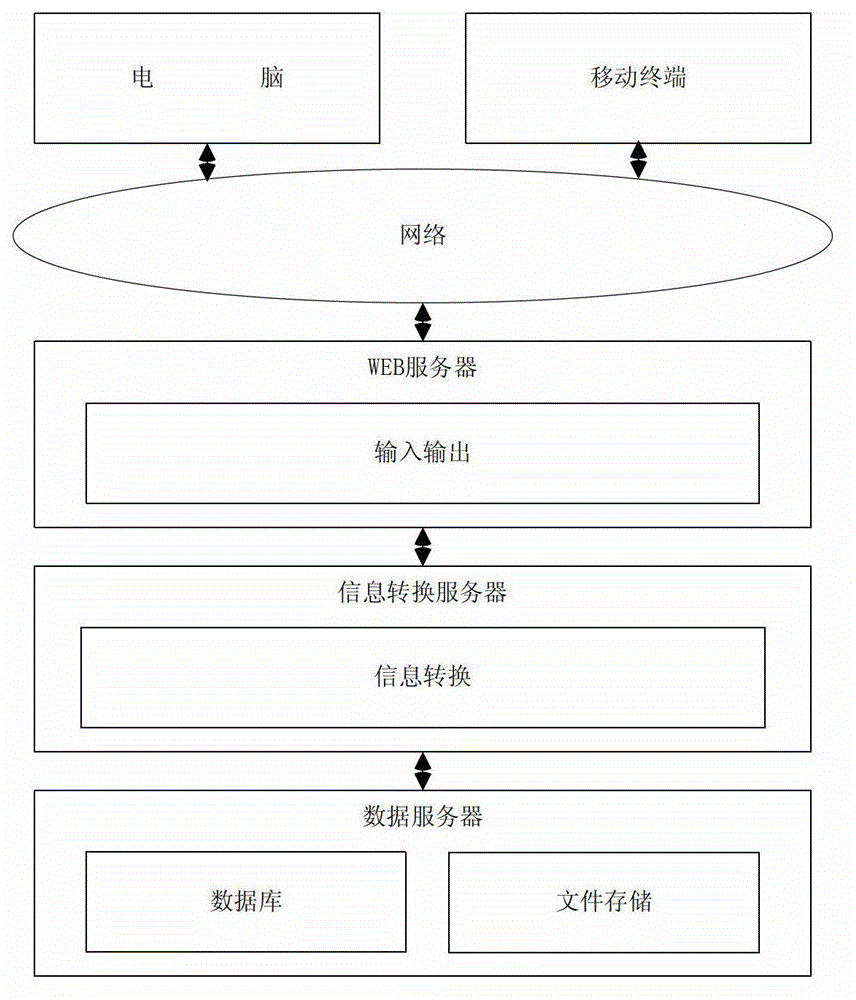
Internet account number and password information management method and system
The invention relates to an internet account number and password information management method and a system. The internet account and password information management method comprises the following steps: inputting login information through a user terminal, wherein the login information comprises an original password and a website identification; combining the inputted original password with the website identification for algorithm conversion to generate a login password; returning the generated login password to the user terminal; and logging a corresponding website by using an account number and the generated login password. The internet account number and password information management method and the system solve the problem that as a majority of existing internet users gets used to applying and using the same set of account number and password on different internets, when the safety problem occurs in a certain website to cause the account number and password leakage of the website, the safety risk problem exists in the account number and the password of the user in other websites.
Owner:胡浩 +1
Mobile client user dynamic secret key encrypted communication method based on HTTP protocol
InactiveCN108040048AEnsure safetyGuaranteed efficiencyTransmissionProtocol for Carrying Authentication for Network AccessMobile client
The invention relates to a mobile client user dynamic secret key encrypted communication method based on the HTTP protocol. A unique secret key is allocated dynamically after each App is successfullylogged in, therefore, the security of other Apps is not be affected even if the secret key is leaked; and the secret key is updated automatically after the user logs in again, therefore, the timeliness of the secret key is controlled, so that the security is improved.
Owner:福建福诺移动通信技术有限公司
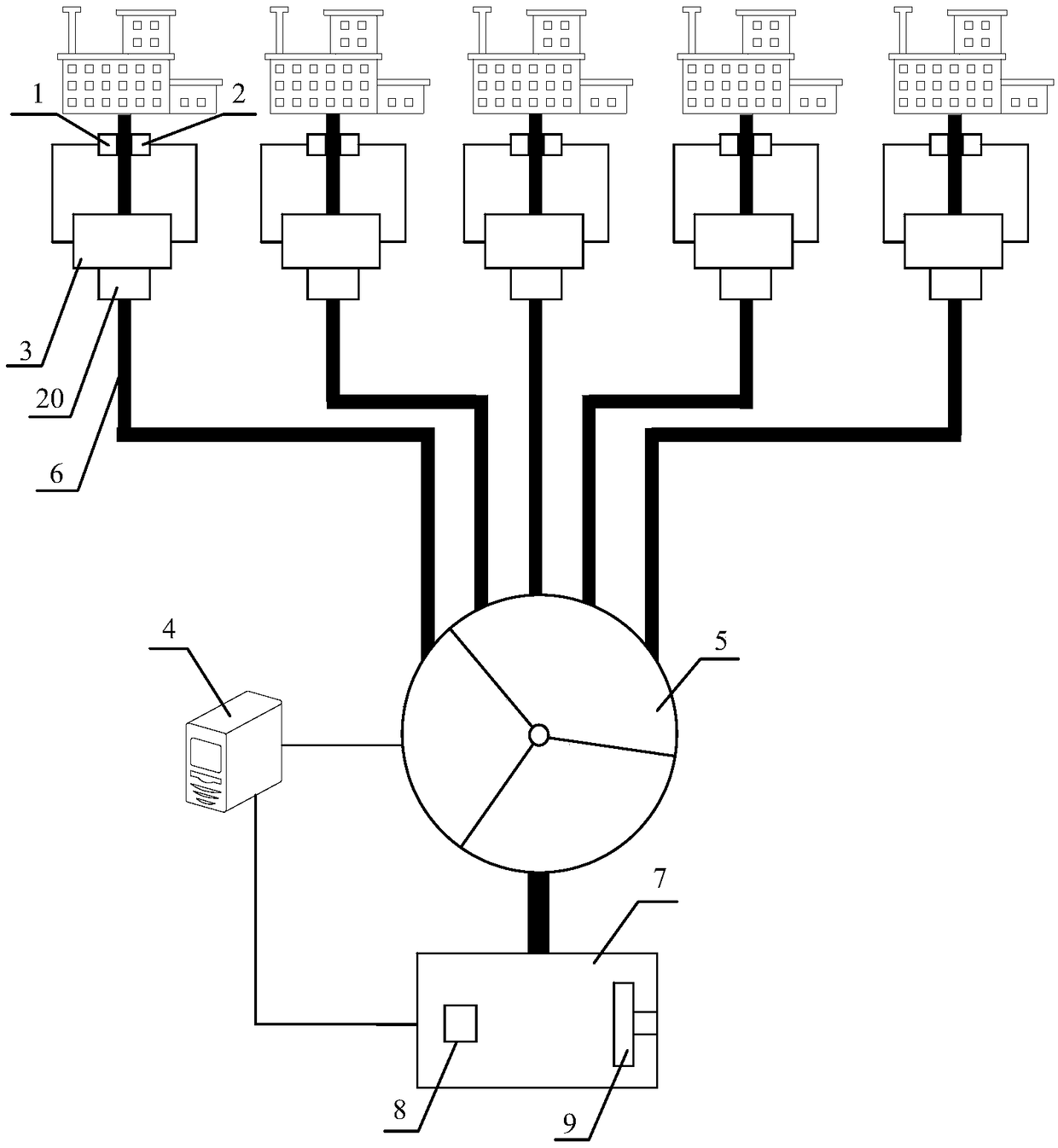
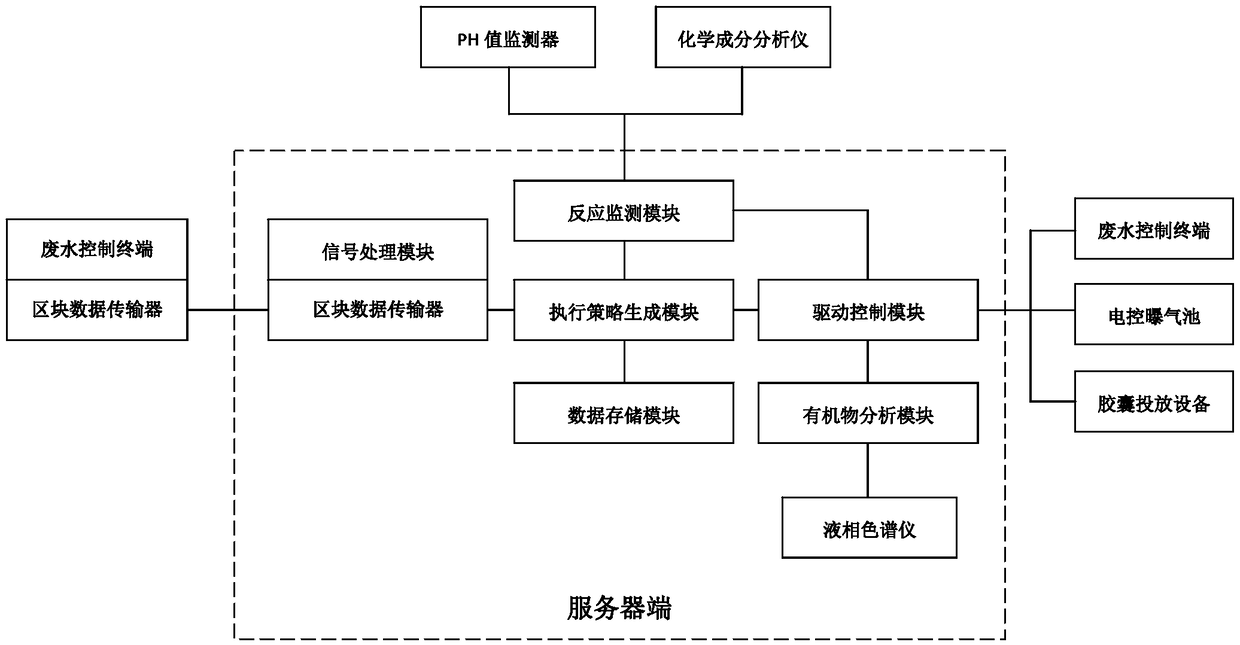
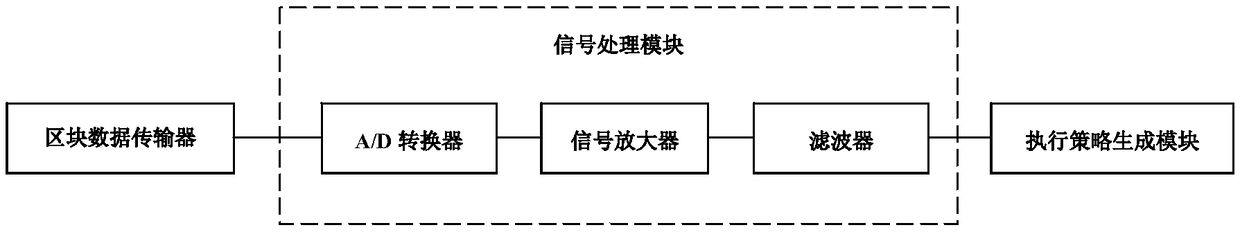
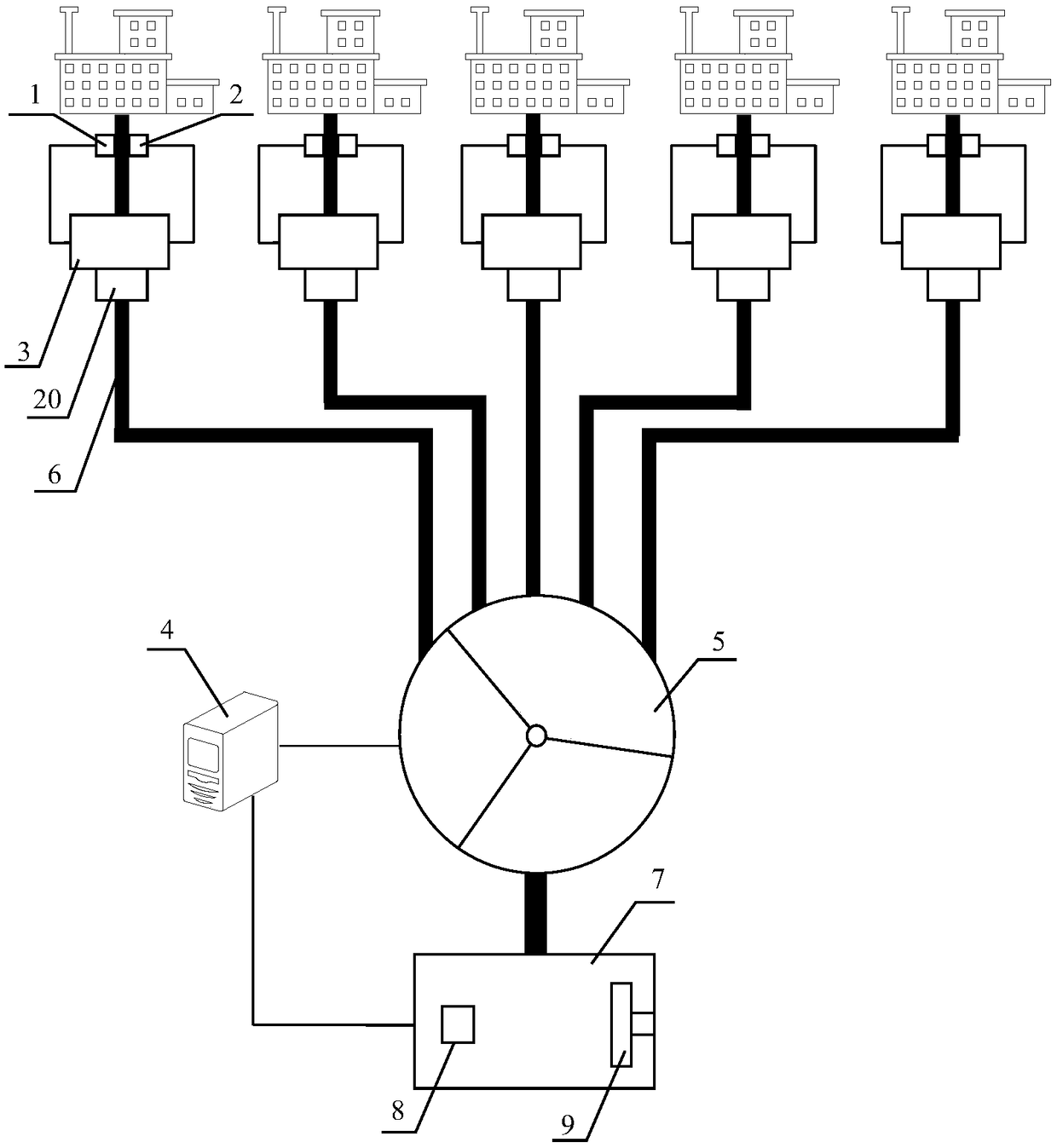
Intelligent industrial wastewater treatment system
InactiveCN108793289AReduce processing costsImprove purification efficiencyWater treatment parameter controlTesting waterIndustrial wastewater treatmentData entry
The invention relates to an intelligent industrial wastewater treatment system. The intelligent industrial wastewater treatment system comprises PH value monitors (1), chemical component analysis meters (2), wastewater control terminals (3), a serer (4) and an electronic control aeration tank (5). According to the system, firstly, through the PH value monitors and the chemical component analysis meters, the wastewater PH values and chemical components of various drainage outlets are monitored, then monitored data is fed back to the server, the wastewater monitored data of various plants is summarized by the server, secondly, based on a big data analysis and processing technology, after the monitored data is input to a trained model, a system executive strategy is automatically generated, through a numerical control technology, the wastewater control terminals are driven to conduct drainage according to the set strategy, the electronic control aeration tank is driven to run, the acid wastewater and the alkaline wastewater are neutralized by each other, and mutual neutralization of the acid wastewater and the alkaline wastewater is fully used for achieving the aim of using the wastewater to treat the wastewater; meanwhile, the intelligent industrial wastewater treatment system is based on a blockchain technology to achieve interaction of the monitored data, so that the safety ofthe data is improved.
Owner:刘守凯 +2
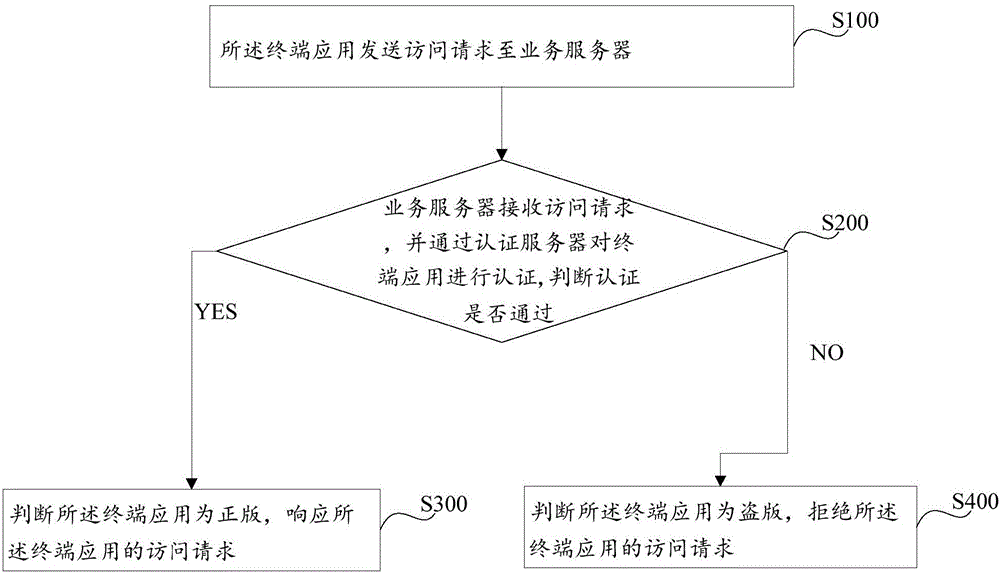
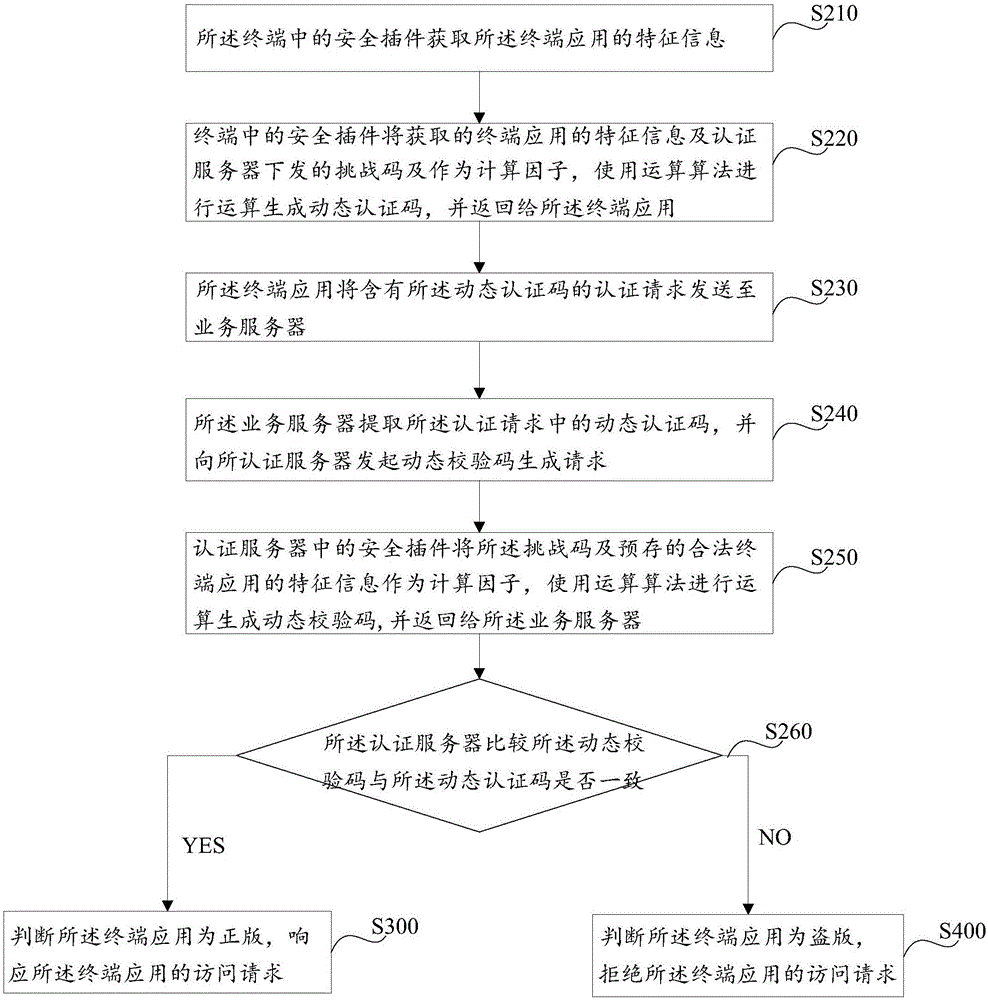
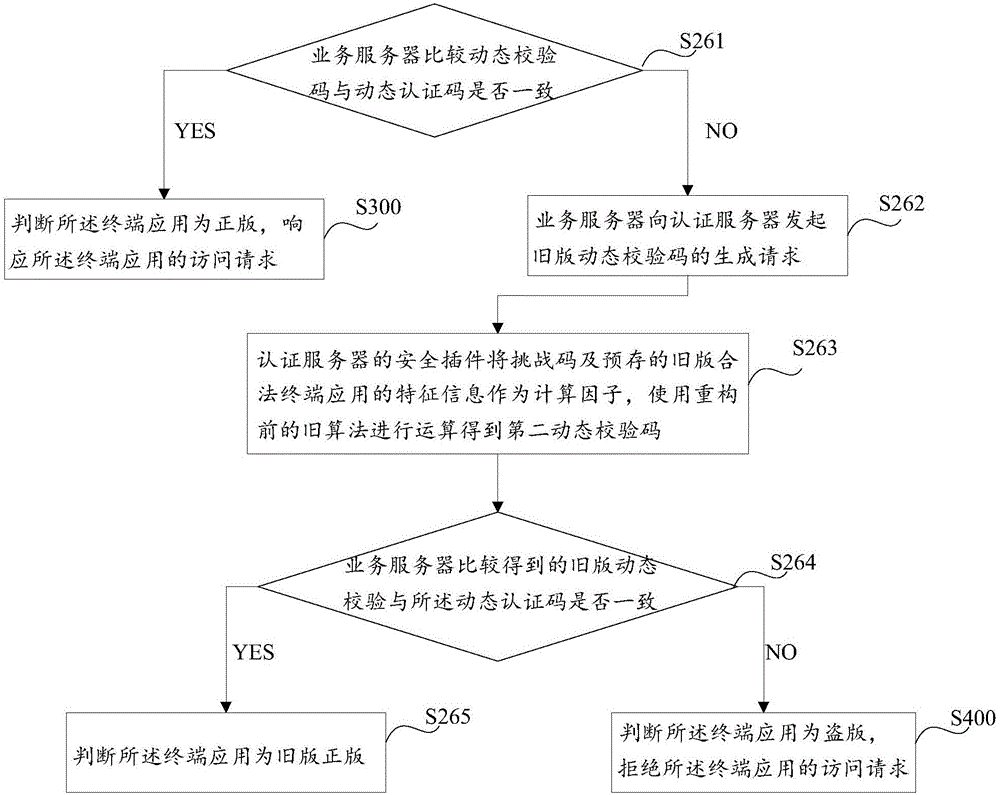
Terminal application legal-copy authentication method and system
ActiveCN106549957AProtection of legal rightsImprove securityTransmissionAuthentication serverAuthentication system
The invention discloses a terminal application legal-copy authentication method. The terminal application legal-copy authentication method comprises the following steps: a terminal application sends an access request to a service server; the service server receives the access request, and authenticates the terminal application through an authentication server; if authentication is passed, the service server judges that the terminal application is the legal copy, and responds to the access request of the terminal application; and otherwise, the service server judges that the terminal application is pirated, and refuses the access request of the terminal application. On the other hand, the invention further discloses a terminal application legal-copy authentication system. The terminal application legal-copy authentication system comprises a terminal, the terminal application, the service server and the authentication server; the terminal application is positioned on the terminal; the service server is separately in communication connection with the terminal application and the authentication server, wherein the terminal application comprises a first information transceiving module; and the service server comprises a second information transceiving module and an information verification module connected with the second information transceiving module. By means of the terminal application legal-copy authentication method and system disclosed by the invention, the terminal application legal-copy authentication security is greatly improved; and the rights and interests of general legal-copy terminal applications can be effectively maintained.
Owner:SHANGHAI PEOPLENET SECURITY TECH
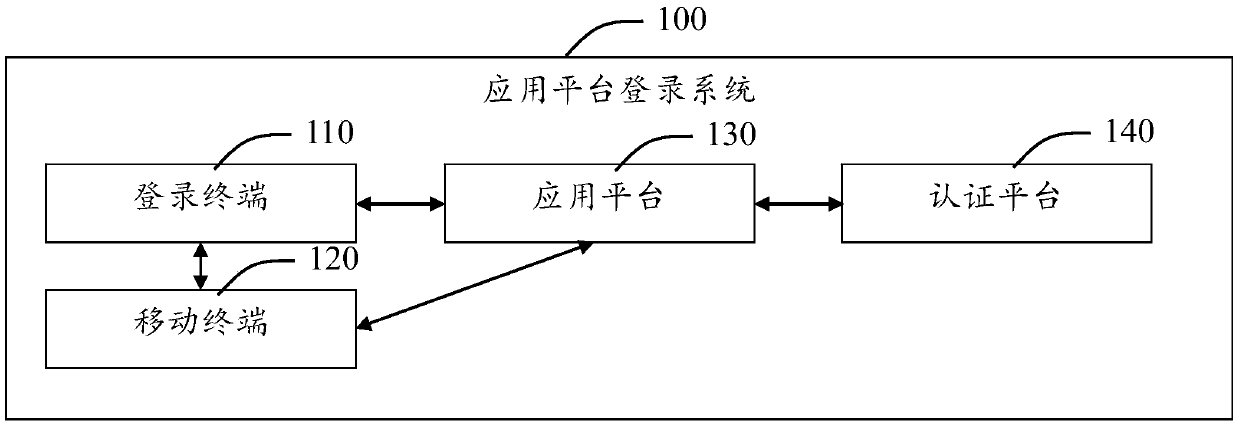
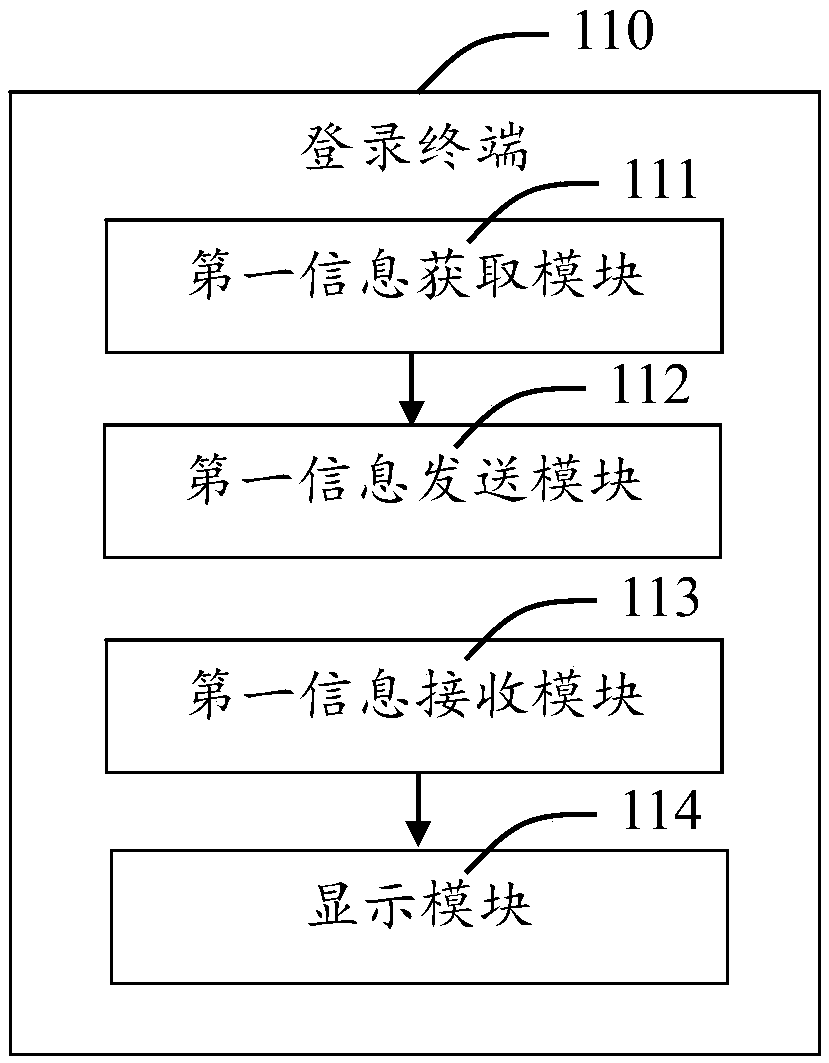
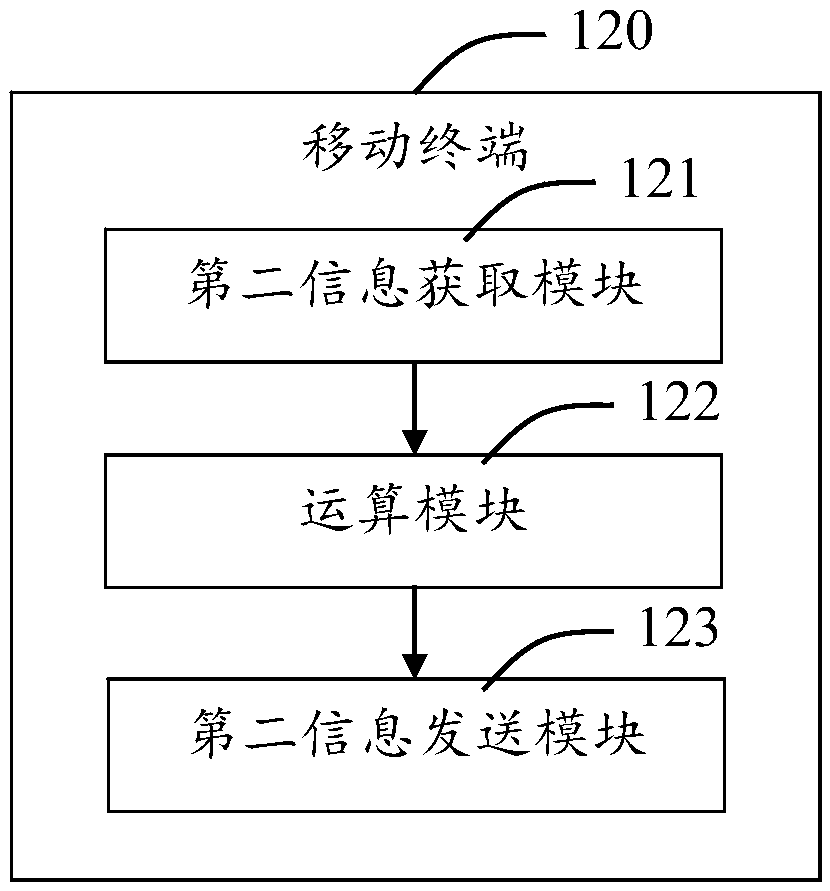
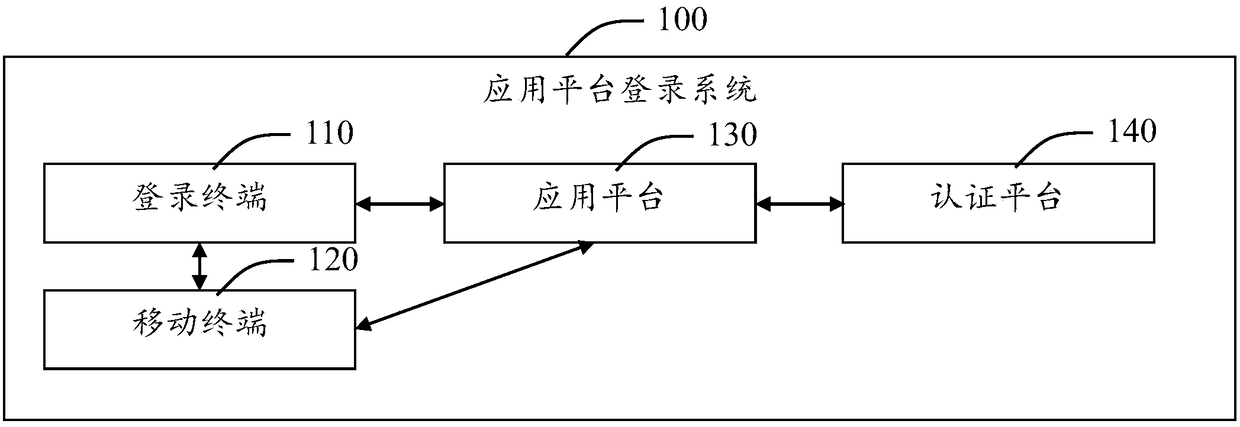
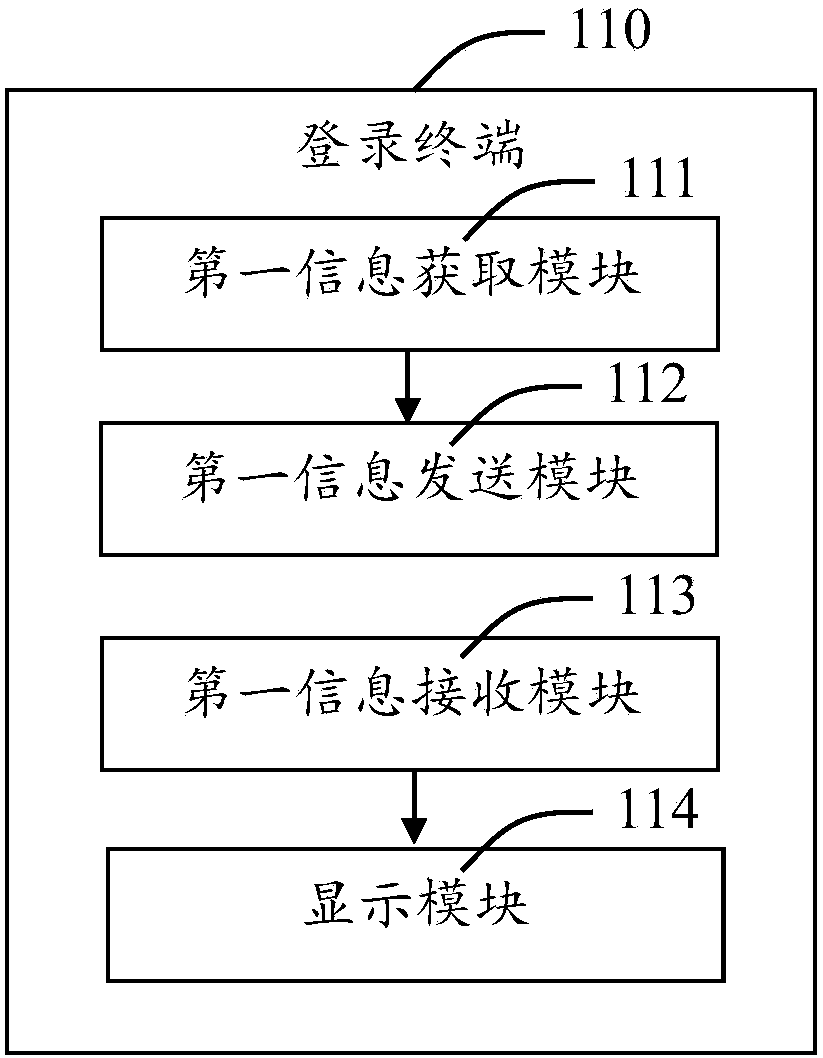
Login system of application platform and login method thereof
ActiveCN105515781AWith randomnessImprove securityUser identity/authority verificationAuthenticationComputer engineering
The invention provides a login system of an application platform and a login method thereof. The login system of the application platform comprises a login terminal, a mobile terminal, the application platform and an authentication platform. The login terminal is used for obtaining the requesting information of users for logging in the application platform and receiving the identification information automatically distributed by the application platform on the basis of the requesting information. The mobile terminal is in communication connection with the login terminal, obtains the identification information from the login terminal while obtaining the user information, and generates a first authentication code on the basis of the user information and the identification information. The application platform is in communication connection with the login terminal, the mobile terminal and the authentication platform respectively, receives the requesting information sent by the login terminal and automatically distributes the identification information which is fed back to the login terminal; and at the same time, the application platform receives the first authentication code and sends it to the authentication platform for authentication. The authentication platform is in communication connection with the application platform and is used for achieving authentication of the first authentication code. The login system greatly reduces the risk caused by the leakage of a user account to a user, and is safe and reliable.
Owner:SHANGHAI PEOPLENET SECURITY TECH
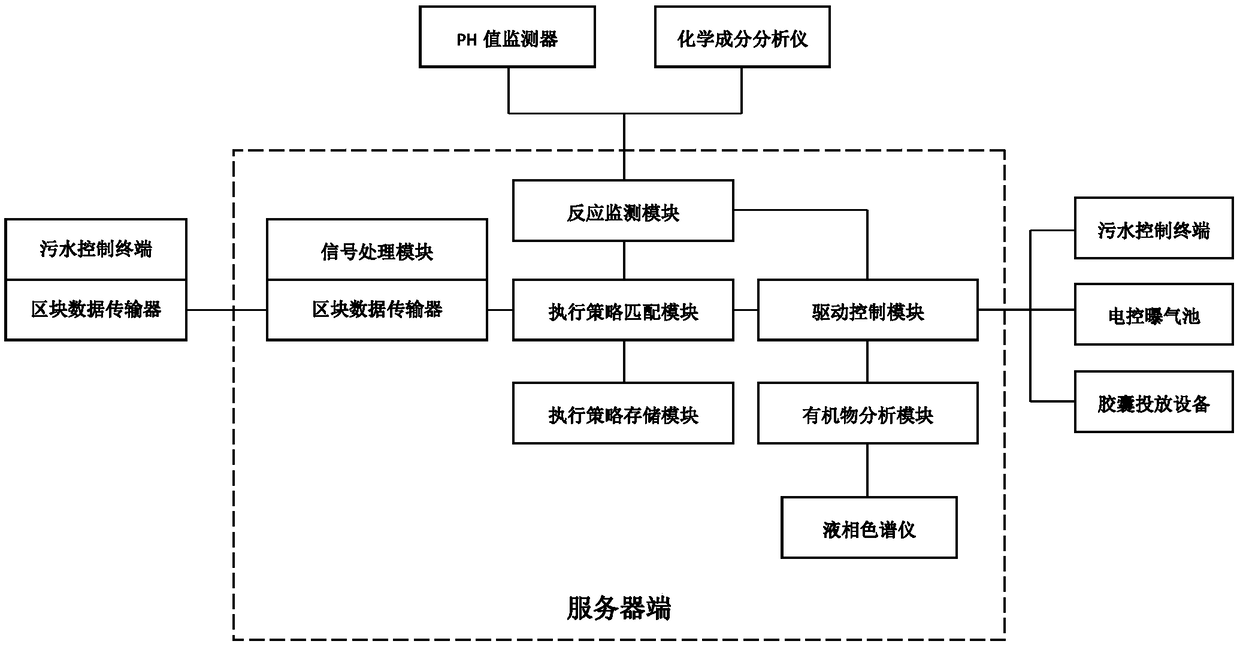
Sewage processing method based on big data
InactiveCN108821425AReduce processing costsPrevent arbitrary tamperingWater treatment parameter controlParticular environment based servicesNumerical controlChemical composition
The invention relates to a sewage processing method based on big data. According to the method, at first, the pH values and chemical components of sewage from each drain outlet are monitored by a pH value monitor and a chemical component analyzer; then the monitor data is fed back to a service terminal, which summarizes the sewage monitor data of all factories and matches two or more kinds of sewage that can carry out neutralization reactions; through a numerical control technology, a sewage control terminal is driven to discharge the sewage based on a designed strategy, at the same time, an electric control aeration tank is driven to start, and the acidic sewage and the alkaline sewage carry out neutralization reactions. The acidic sewage and alkaline sewage are neutralized by each other,or the acidic sewage is neutralized by waste alkali (slag). The waste is processed by waste, thus the sewage processing cost is reduced, and the purification efficiency is improved. At the same time,based on a block chain technology, the interaction of monitor data is realized, the de-centralization of data interaction is realized, enterprises will not be able to falsify the data, and the data safety is improved.
Owner:李泓
Intelligent cloud data safety protection system and method based on block chain
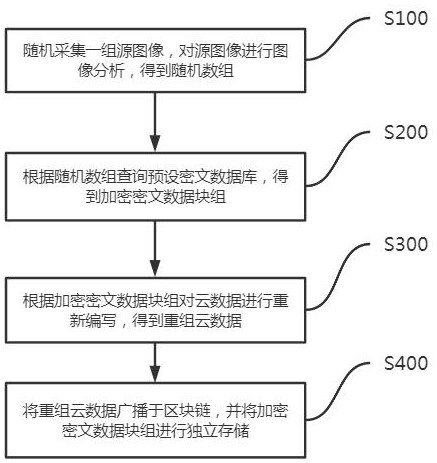
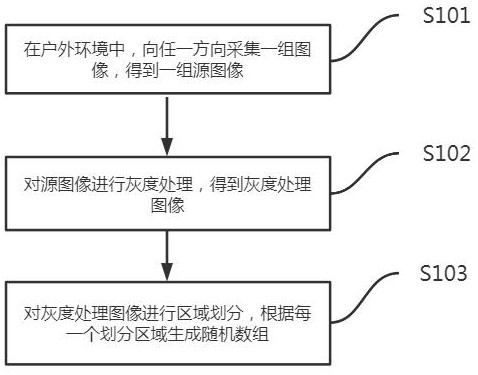
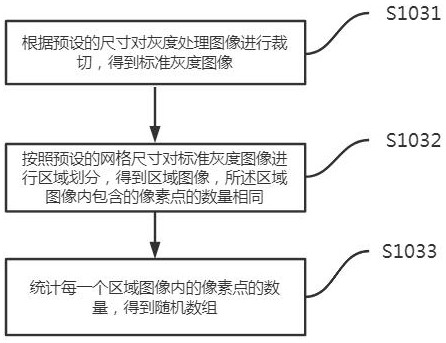
ActiveCN113742765AImprove protectionImprove securityDigital data protectionCiphertextTheoretical computer science
The invention is suitable for the technical field of computers, and particularly relates to a intelligent cloud data safety protection system and method based on a block chain. The system comprises a random number generation module which is used for randomly collecting a group of source images, carrying out the image analysis of the source images, and obtaining a random number group; a ciphertext query module is used for querying a preset ciphertext database according to the random number group to obtain an encrypted ciphertext data block group; a data reorganization module is used for recompiling the cloud data according to the encrypted ciphertext data block group to obtain reorganized cloud data; a data broadcasting module is used for broadcasting the recombined cloud data to the block chain and independently storing the encrypted ciphertext data block group. According to the method and the device, the encrypted ciphertext for encryption is generated in a true random mode to encrypt the cloud data needing to be protected, so that the specific content of the cloud data is changed, the encrypted ciphertext is independently stored, the cloud data can be decrypted by using the encrypted ciphertext, and the transportation safety is improved.
Owner:北京丰台永定消毒设备厂
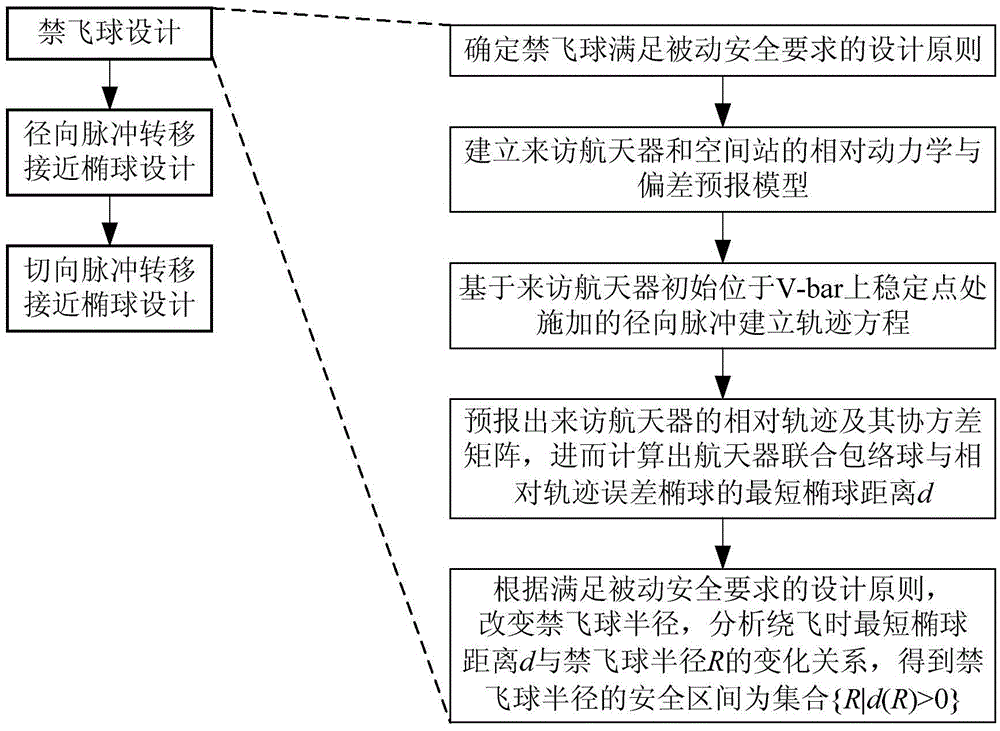
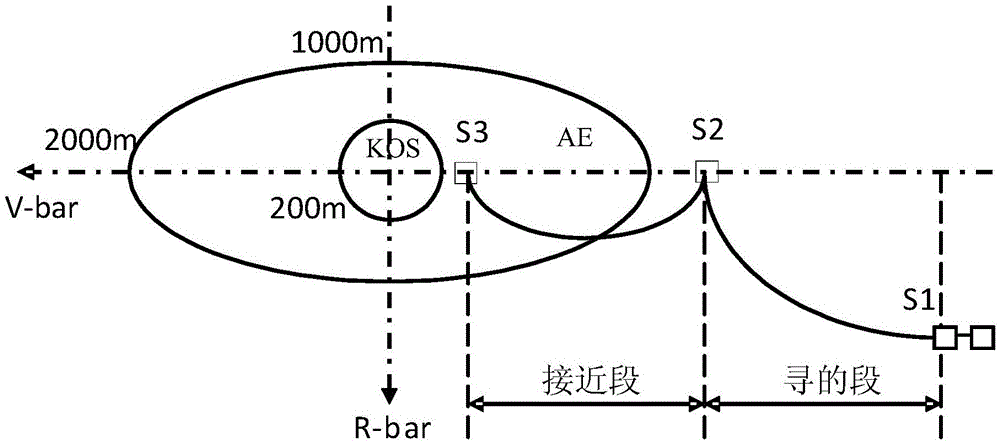
Space station safe region design method capable of satisfying passive safety requirement
ActiveCN105678061AVerify rationalitySecurity does not affectInformaticsSpecial data processing applicationsSufficient timeRadial pulse
The invention discloses a space station safe region design method capable of satisfying the passive safety requirement. The space station safe region design method comprises steps of the design of a keep out sphere, the design of a radial pulse transfer approach ellipsoid and the design of tangential pulse transfer approach ellipsoid. The design of the keep out sphere comprises steps of determining the design principle that the keep out sphere satisfies the passive safety requirement, establishing a relative dynamics and deviation forecast model of a visiting spacecraft and a space station, calculating the shortest ellipsoid distance between a spacecraft united enveloping sphere and a relative track error ellipsoid, assuming that the visiting spacecraft begins to fly around the V-bar boundary of the keep out sphere in dependence on the design principle that the keep out sphere satisfies the passive safety requirement, changing the radius of the keep out sphere, analyzing the relationship between the shortest ellipsoid distance when the visiting spacecraft flies around the keep out sphere and the change of the radius of the keep out sphere, and completing the design of the keep out sphere. The pace station safe region design method is advantaged in that the design method is correct and reasonable, safety of the space station is guaranteed, sufficient time is provided for the visiting spacecraft to remove the fault, and the design result is suitable for practical engineering tasks.
Owner:NAT UNIV OF DEFENSE TECH
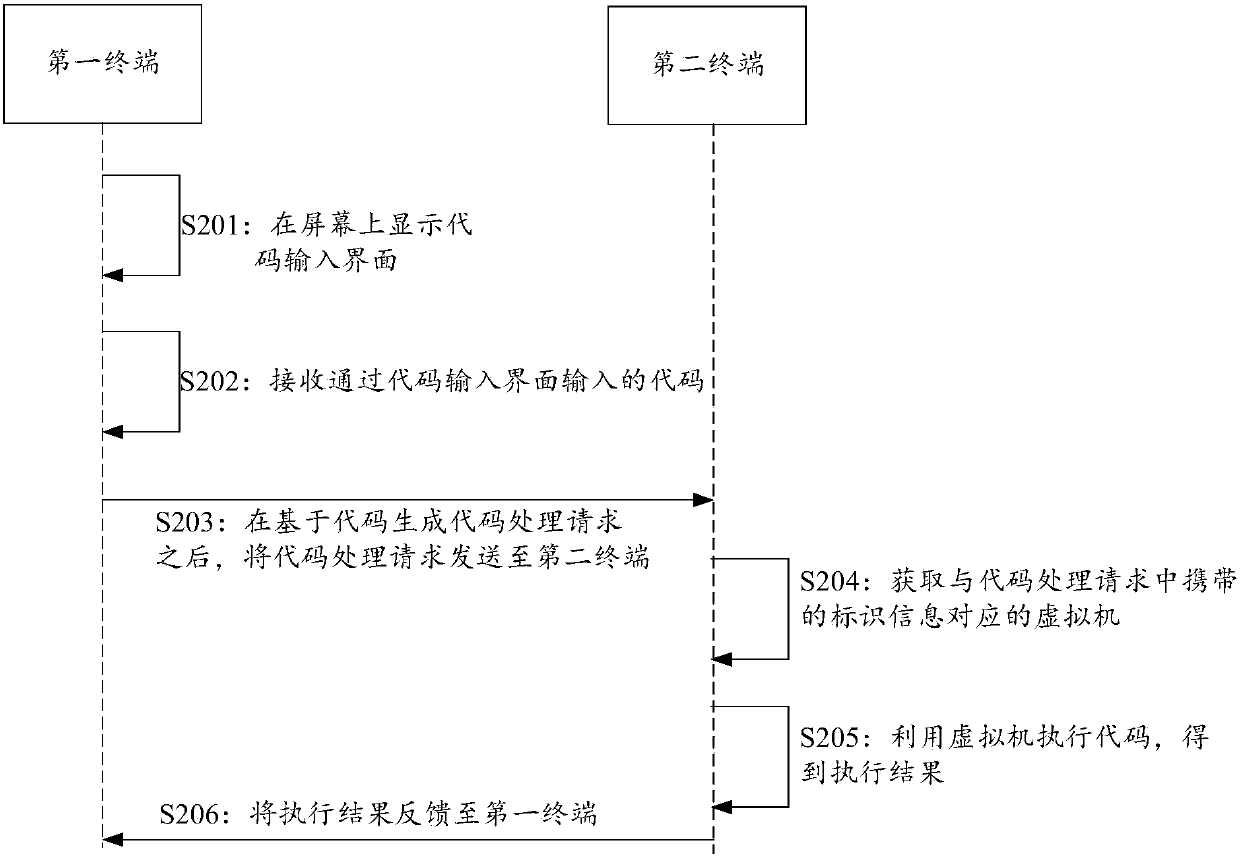
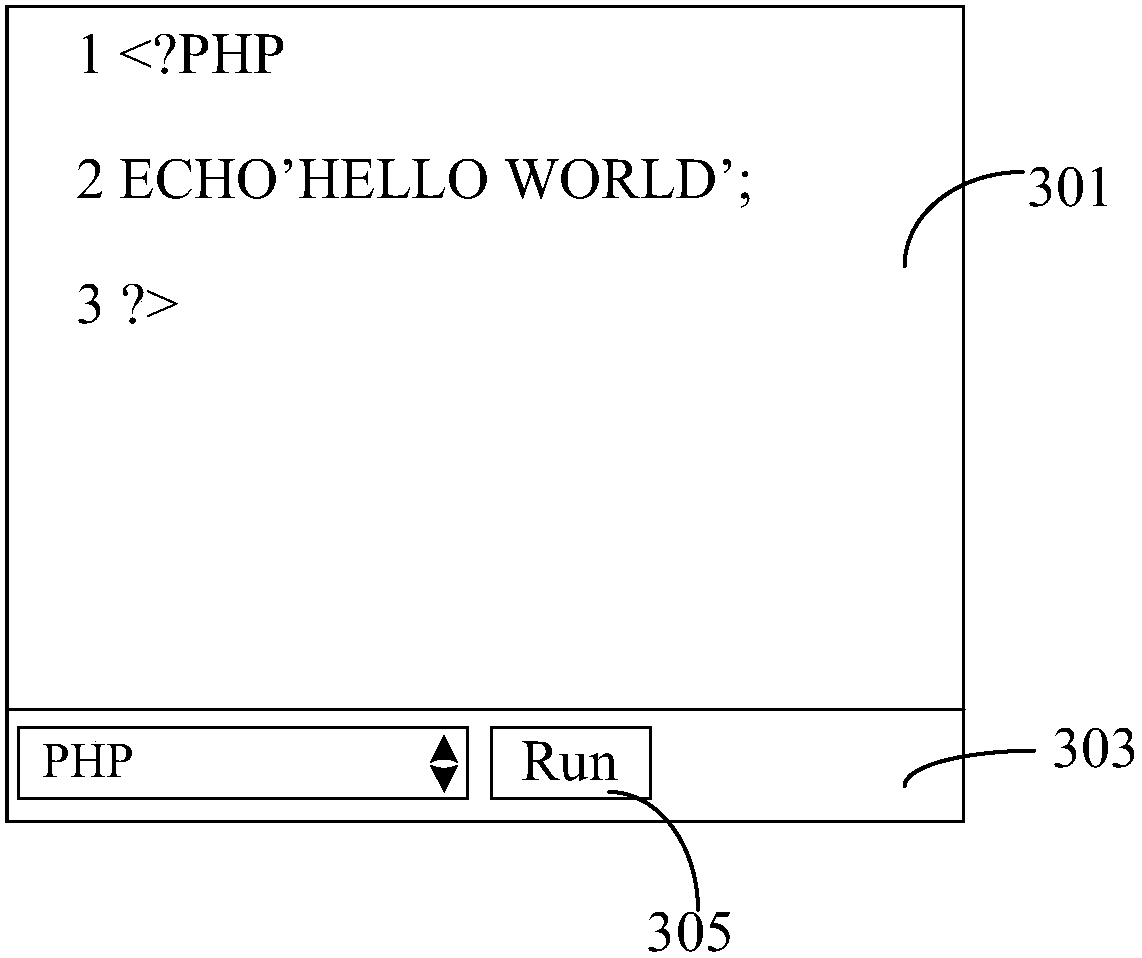
Code processing method, device and system
PendingCN107657172ASystem Environment GuaranteeEnsure safetyPlatform integrity maintainanceSoftware simulation/interpretation/emulationComputer terminalComputer engineering
The invention discloses a code processing method, device and system. The method comprises the steps of receiving a code processing request sent by a first terminal, wherein the code processing requestis used for making a request for performing code, and the code processing request carries identification information of the first terminal; obtaining a virtual machine corresponding to the identification information; performing the code through utilization of the virtual machine, thereby obtaining a performing result; and feeding back the performing result to the first terminal. According to themethod, the device and the system, at least the technical problem that the programming learning environment security is low is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
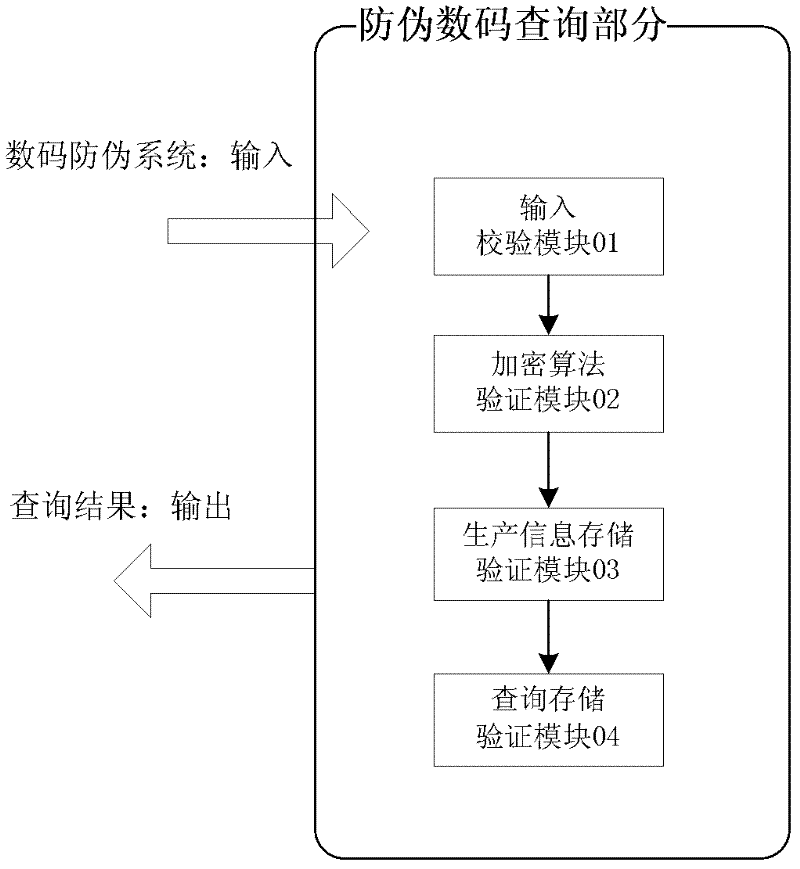
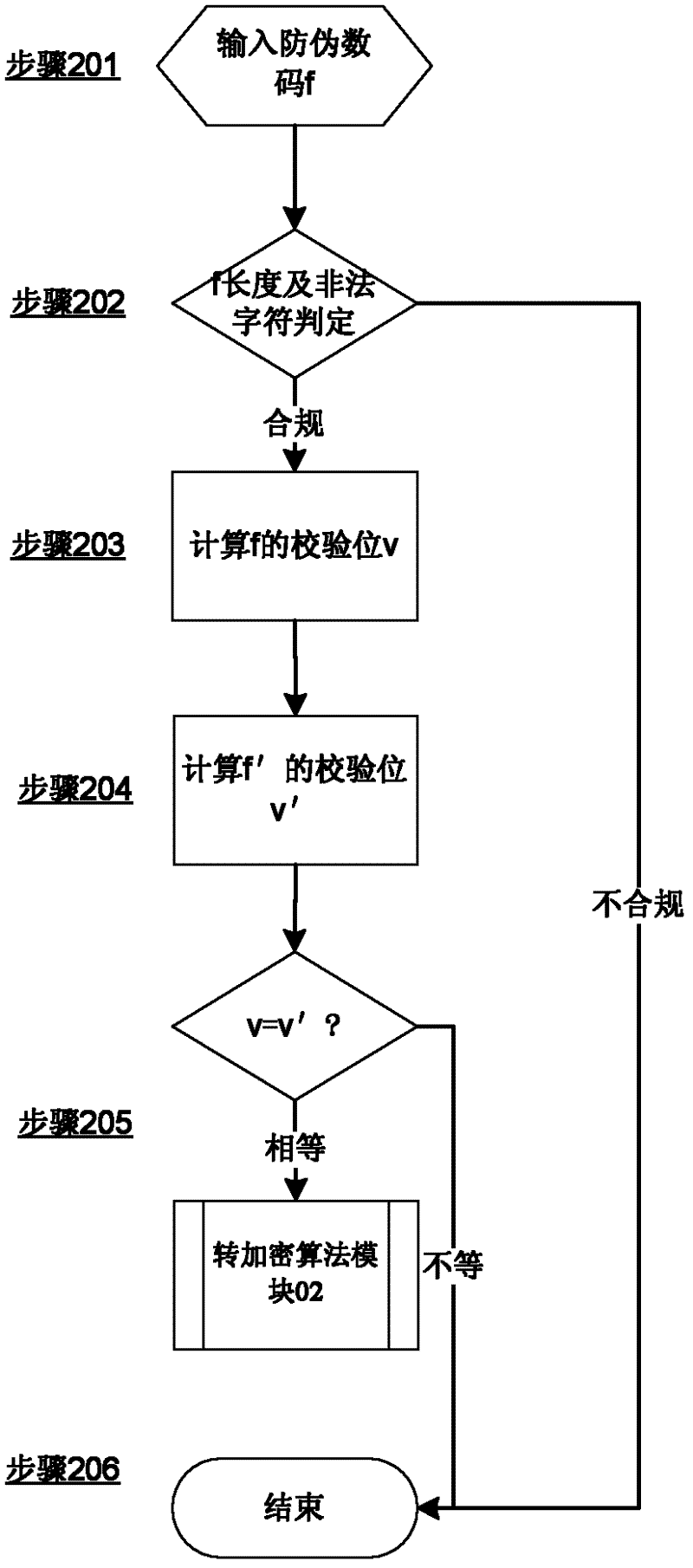
A digital anti-counterfeiting method for multiple security cigarettes
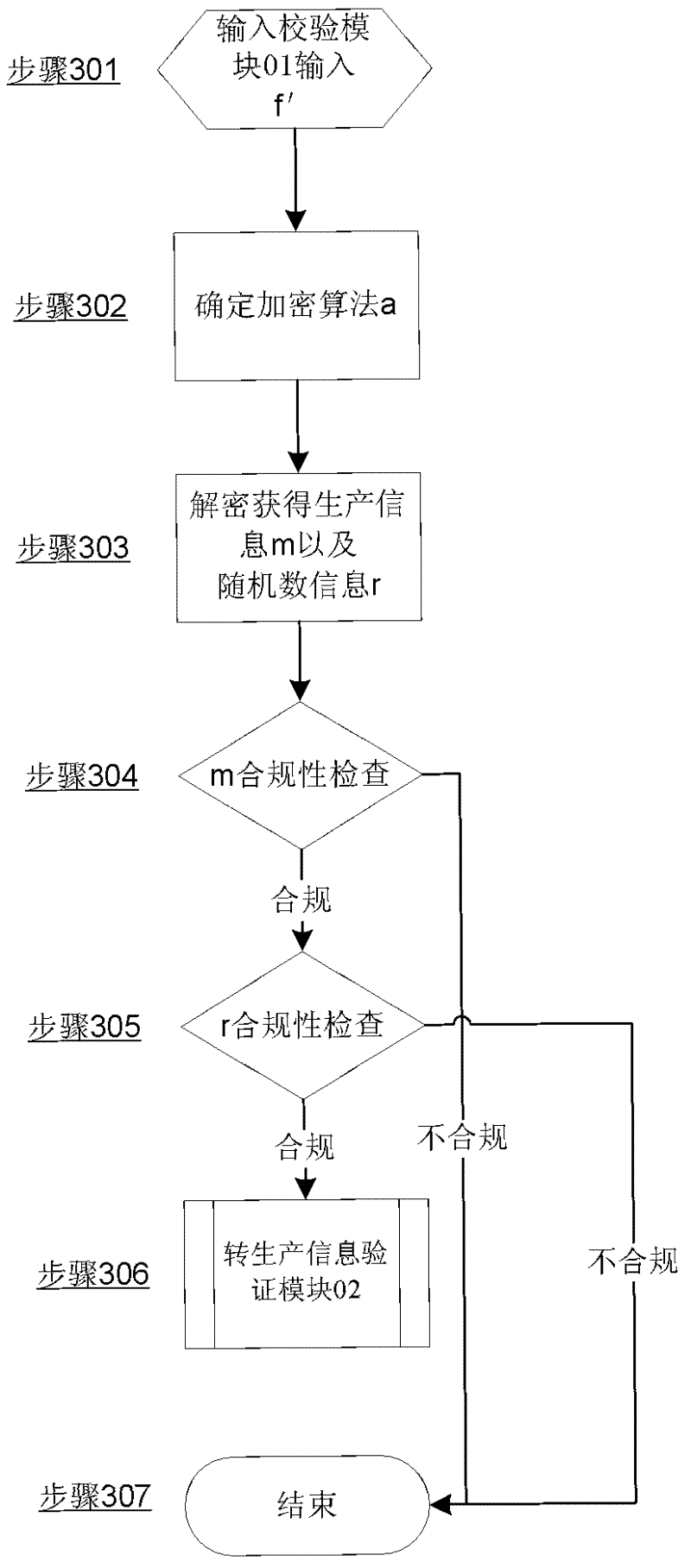
InactiveCN102270323AImprove securitySecurity does not affectData processing applicationsSpecial data processing applicationsComputer moduleModular design
The invention discloses a digital anti-counterfeiting method for multiple security cigarettes, which comprises four overlapping steps of input verification based on redundancy check, algorithm verification step, production information verification step and inquiry record verification step plus security verification steps. The multi-security cigarette digital anti-counterfeiting method has multiple anti-counterfeiting functions, and significantly reduces loopholes in the existing anti-counterfeiting technology. This method most likely eliminates the failure of the cigarette digital anti-counterfeiting query caused by the potential security loopholes in the digital query. At the same time, the method adopts a modular design and is embedded in the relevant digital anti-counterfeiting system. When some security verification modules fail, mutual detection and custom upgrade or adjustment can be realized to further enhance security.
Owner:CHINA TOBACCO HUNAN INDAL CORP
Terminal charge method and system, and network payment system
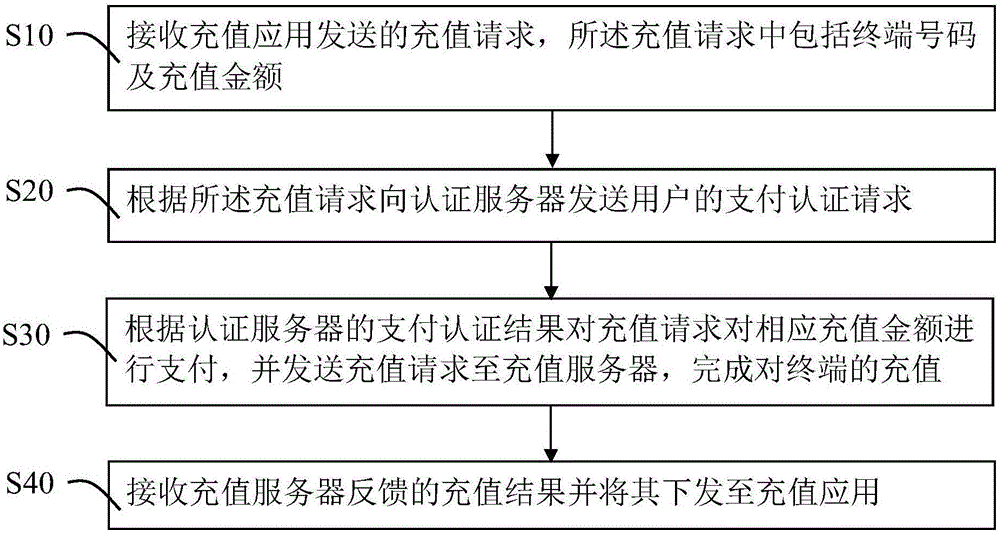
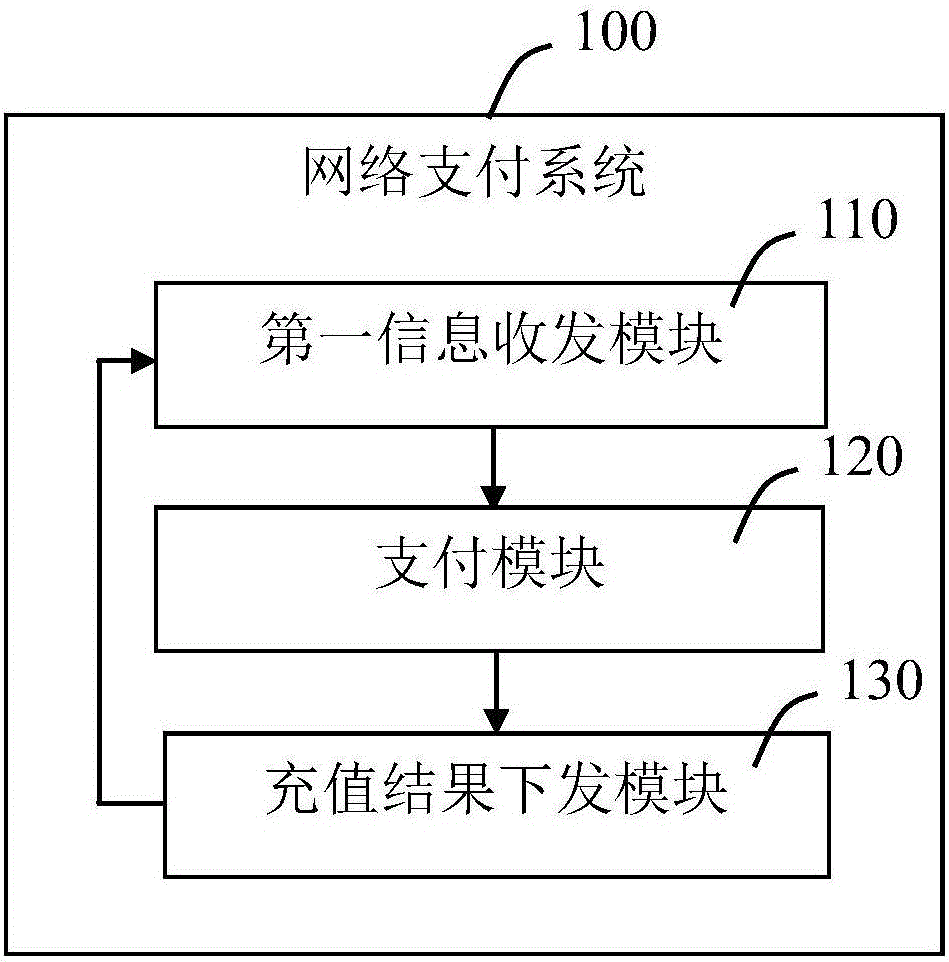
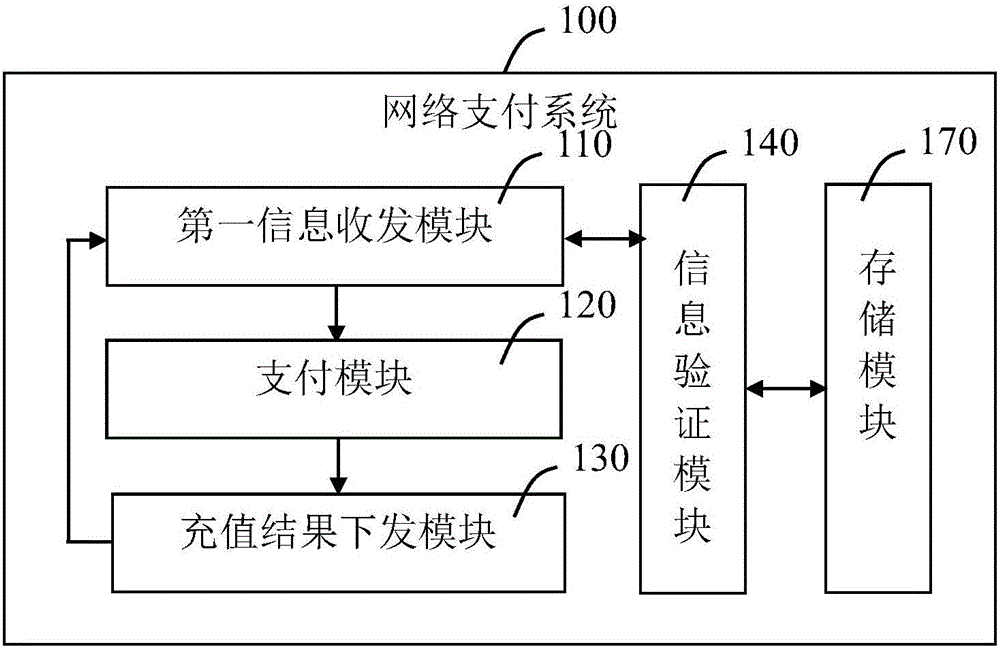
InactiveCN106485480AImprove experienceUniqueness guaranteedProtocol authorisationAuthentication serverComputer science
The invention provides a terminal charge method and system, and a network payment system. The terminal charge method comprises the following steps of S10 receiving a charge request sent by a charge application, wherein the charge request comprises a terminal number and a charge amount; S20 sending a payment authentication request of a user to an authentication server according to the charge request; S30 performing payment on the corresponding charge amount in the charge request according to a payment authentication result of the authentication server, and sending the charge request to the charge server, thereby finishing terminal charge; and S40, receiving a charge result fed back by the charge server and sending the charge result to the charge application. Therefore, the problem on fund security performance in the terminal charge process is effectively solved.
Owner:SHANGHAI PEOPLENET SECURITY TECH
Vehicle with external display device
InactiveCN101786419AImprove securitySecurity does not affectVehicle componentsDisplay deviceHuman engineering
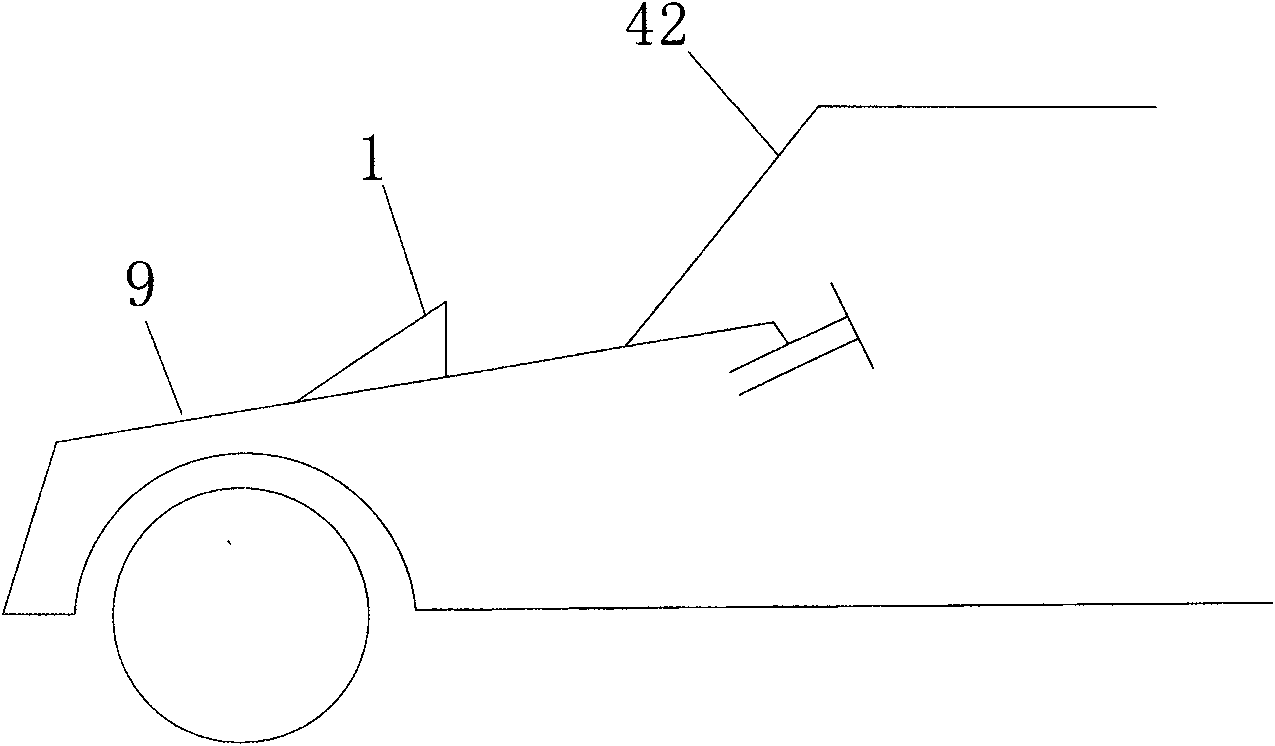
The invention provides a vehicle with an external display device. The vehicle comprises a vehicle body and the external display device which is arranged on an engine cover or a front wheel fender outside a front windshield of the vehicle body and is driven by a driving device to move up and down. Therefore, the visual line of a driver to observe vehicle information is basically at eye level and the degree of downward inclination of visual line is lower than that of the existing instrument panel in the vehicle, so the vehicle is more accordant with human engineering and is more beneficial for driving safety.
Owner:段海
Method for opening thrust-reversing system of power device of aircraft
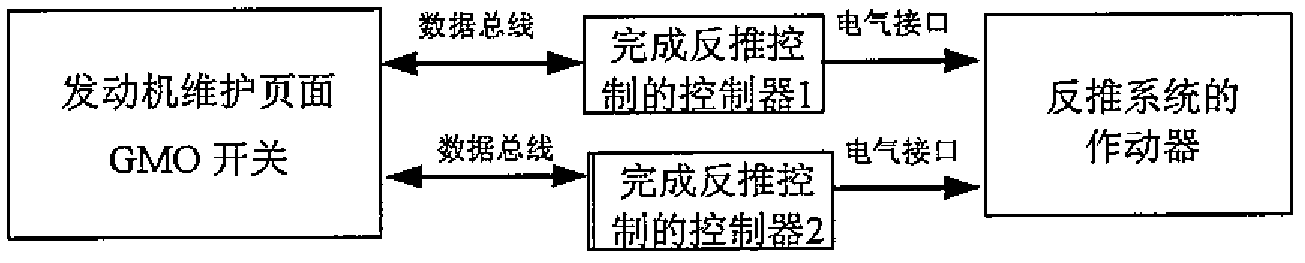
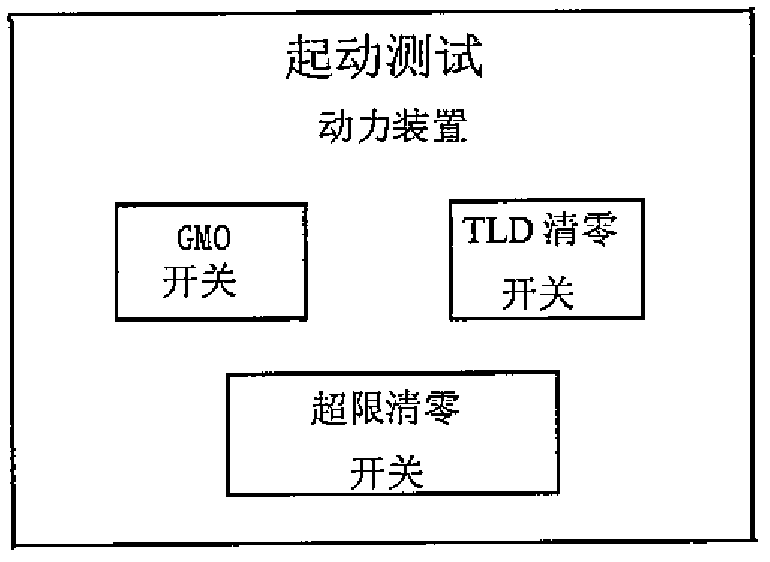
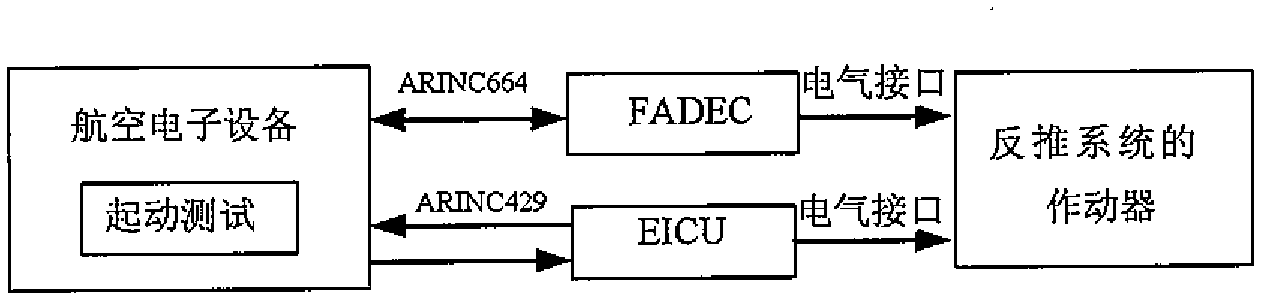
ActiveCN102621899ASecurity does not affectReduce connectionsProgramme control in sequence/logic controllersSoft switchingInteraction interface
The invention provides a method for opening a thrust-reversing system of a power device of an aircraft. The method comprises the following steps: providing a man-computer interaction interface of a flight motor-mounted maintenance system in a cockpit of the aircraft; setting a ground maintenance override software switch on the man-computer interaction interface; communicating the ground maintenance override software switch with at least one controller for realizing thrust-reversing control; and using the controller to receive a signal of the ground maintenance override software switch, and judging an actuator for controlling the thrust-reversing system through control logic according to the current state of an engine so as to open a thrust-reversing cover of the thrust-reversing system. According to the method disclosed by the invention, the function of the ground maintenance override switch of the thrust-reversing system is realized by adopting a soft switching way, the connection of hard wires is reduced, and the maintenance steps, the workload of ground service staff and maintenance tools are reduced.
Owner:COMAC +1
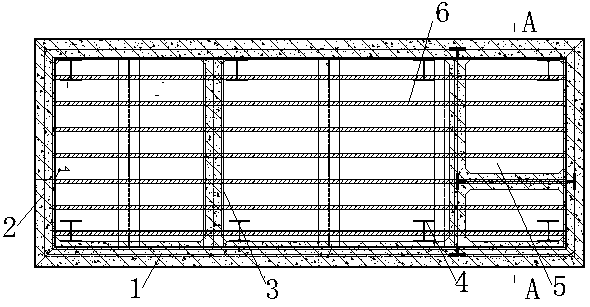
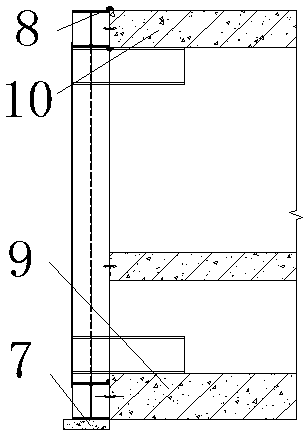
Temporary blocking wall structure of comprehensive pipe rack and construction method
PendingCN108049425AImprove construction progressImprove construction qualityArtificial islandsUnderwater structuresLower faceMaterials science
The invention discloses a temporary blocking wall structure of a comprehensive pipe rack and a construction method. The structure comprises H1 structural steel, H2 structural steel, H3 structural steel, H4 structural steel and a sealing plate; the H1 structural steel, the H2 structural steel and the H3 structural steel are welded and connected to form a plugging framework; the bottom of the plugging framework is provided with a waterproof mortar cushion layer; the joint of the plugging framework and the comprehensive pipe rack is provided with a polysulfide sealing paste layer; the plugging framework is connected with the upper face and the lower face of the comprehensive pipe rack in a sealed manner through the waterproof mortar cushion layer and the polysulfide sealing paste layer; the sealing plate is arranged on the plugging framework in a welded manner; the H4 structural steel is fixedly arranged on the inner side of the sealing plate; the two ends of the H4 structural steel are both fixed in a comprehensive pipe rack wall body through bolts; and a temporary blocking wall is fixed. The temporary blocking wall structure of the comprehensive pipe rack is simple, the construction process is mature, safe and reliable, the polysulfide sealing paste and the waterproof mortar cushion layer are adopted, the sealing performance is good, the safety performance is high, the waterproof performance is good, the safety of an original structure cannot be affected after disassembling, and thus the temporary blocking wall structure of the comprehensive pipe rack is suitable for application and popularization.
Owner:HANGZHOU MUNICIPAL CONSTR GRP CO LTD
Liquid-cooling power battery with battery box with immersed external bottom face
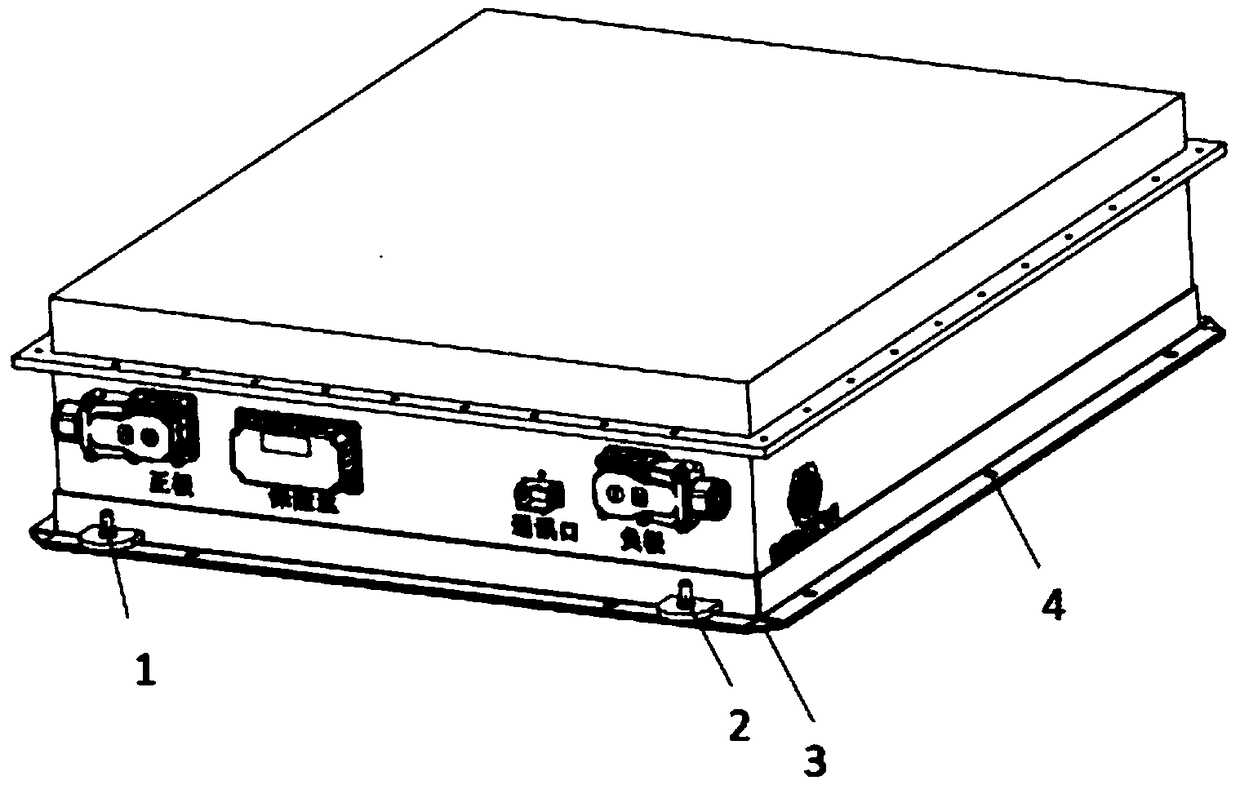
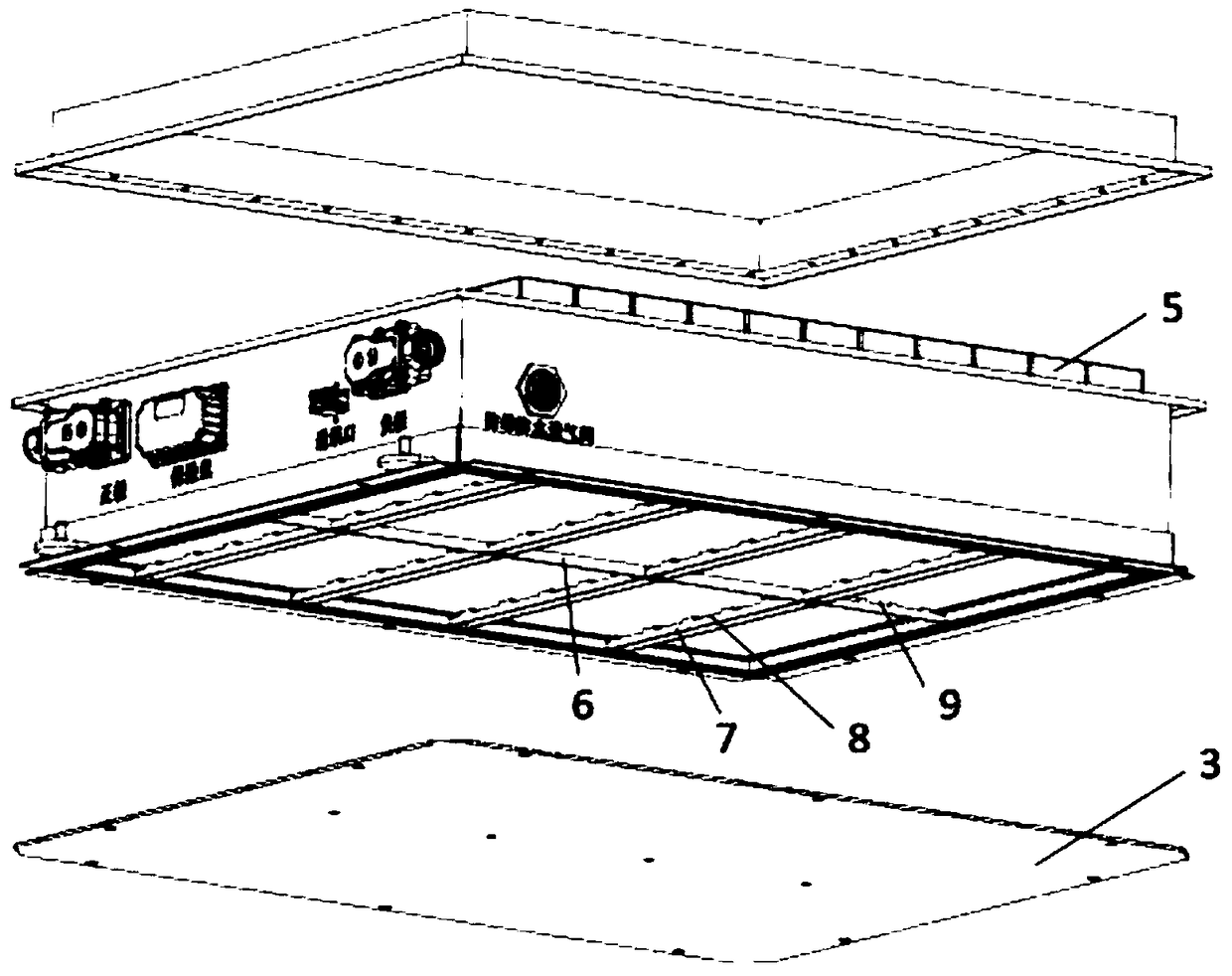
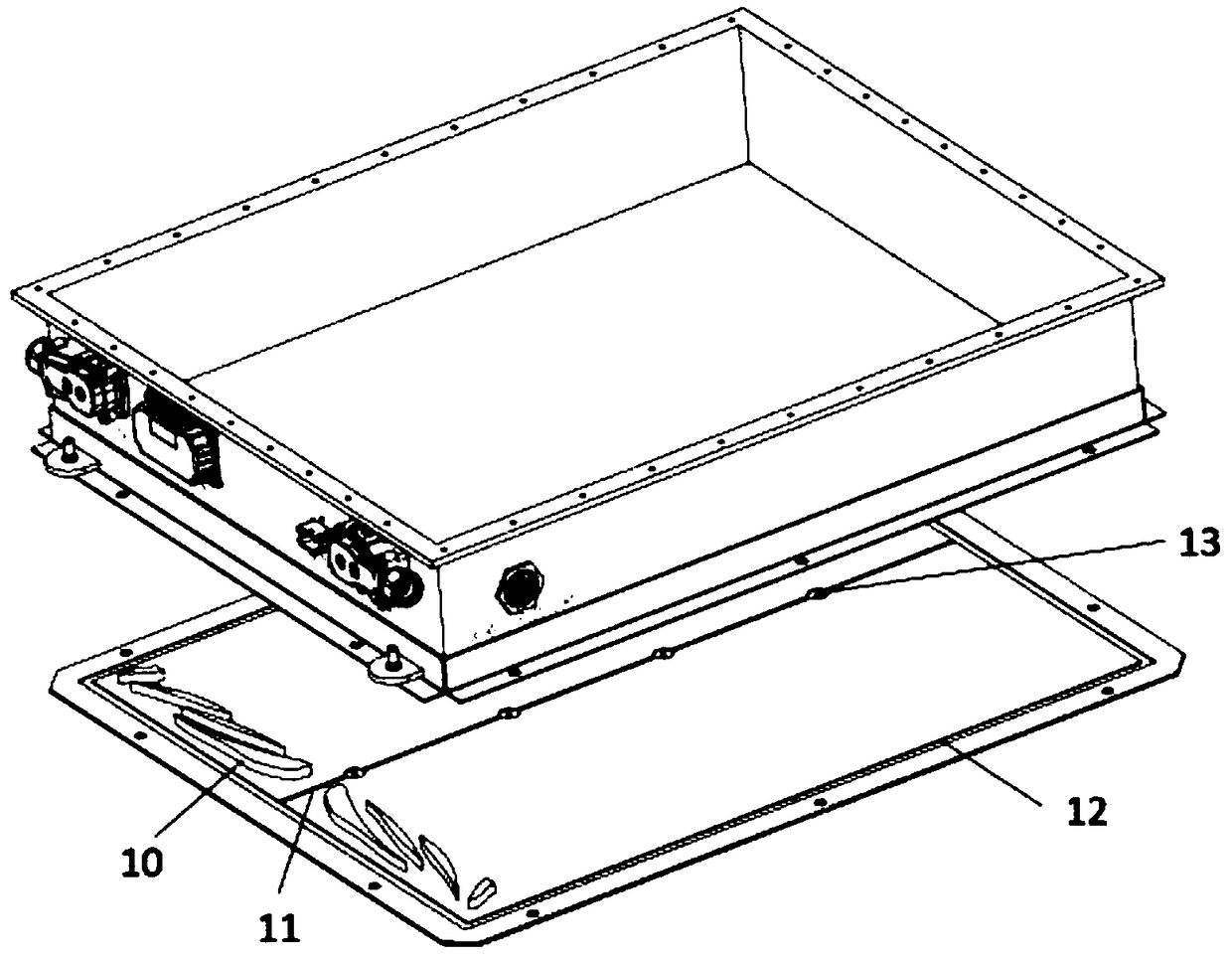
ActiveCN109509851AFlexible configurationImprove securitySecondary cellsCell component detailsCooling powerEngineering
The invention discloses a liquid-cooling power battery with a battery box with immersed external bottom face. The liquid-cooling power battery comprises a liquid inlet joint, a liquid outlet joint, asealing supporting plate, bolt holes, a monomer battery cell, a baffle plate, divided-flow reinforcing ribs, reinforcing rib flow passages, a baffle plate flow passage, a liquid outlet, a liquid inlet, baffle plate sealing bolt holes and a battery box bottom face sealing table, wherein the liquid inlet joint and the liquid outlet joint are positioned above the sealing supporting plate; the liquidinlet joint is connected with a liquid heat management medium inlet pipeline; the liquid outlet joint is connected with a liquid heat management medium outlet pipeline; the sealing supporting plate iscombined with the bottom of the power battery box to form a sealed cavity; the bolt holes are formed in the periphery of the sealing supporting plate; the baffle plate is positioned at the bottom ofthe battery box to make liquid in the bottom face of the battery box divided into inflowing liquid and outflowing liquid; divided-flow reinforcing ribs are positioned at the bottom of the battery box,and is perpendicular to the baffle plate; reinforcing rib flow passages are arranged on the divided-flow reinforcing ribs; and the baffle plate flow passage is arranged on the baffle plate. Accordingto the invention, the flexible configuration of the power battery with or without heat management can be achieved.
Owner:开沃新能源汽车集团股份有限公司
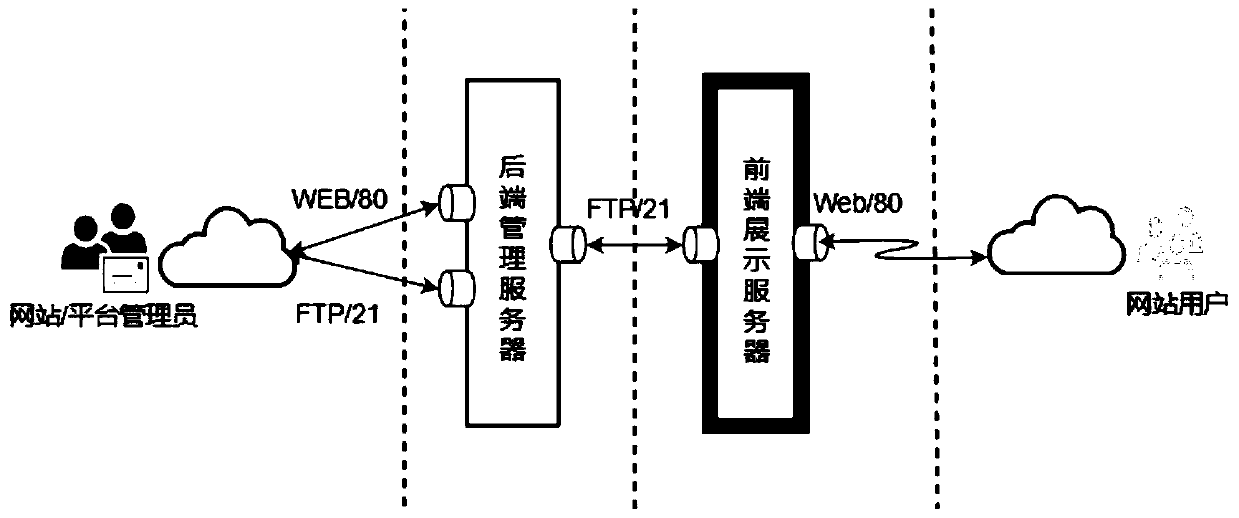
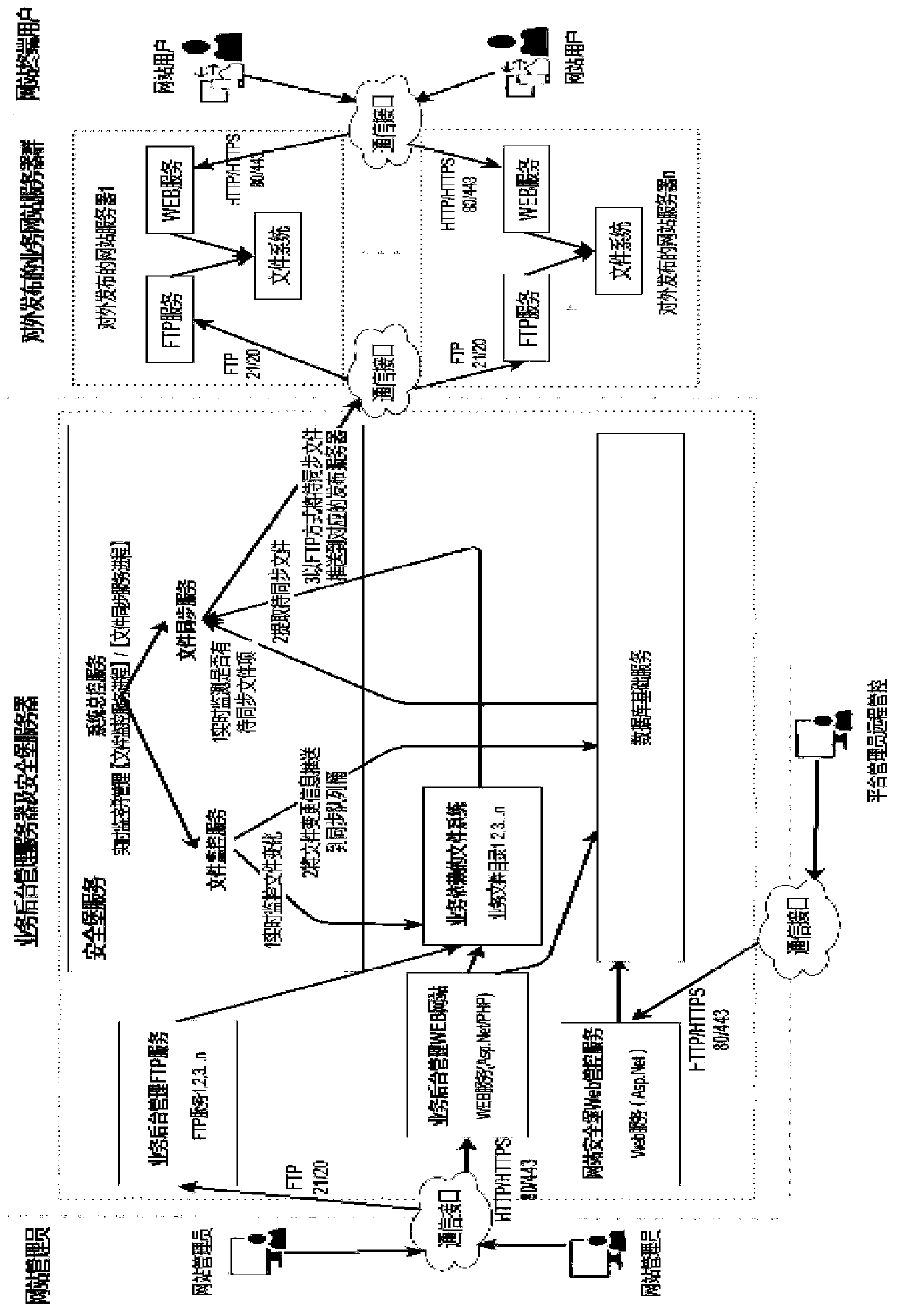
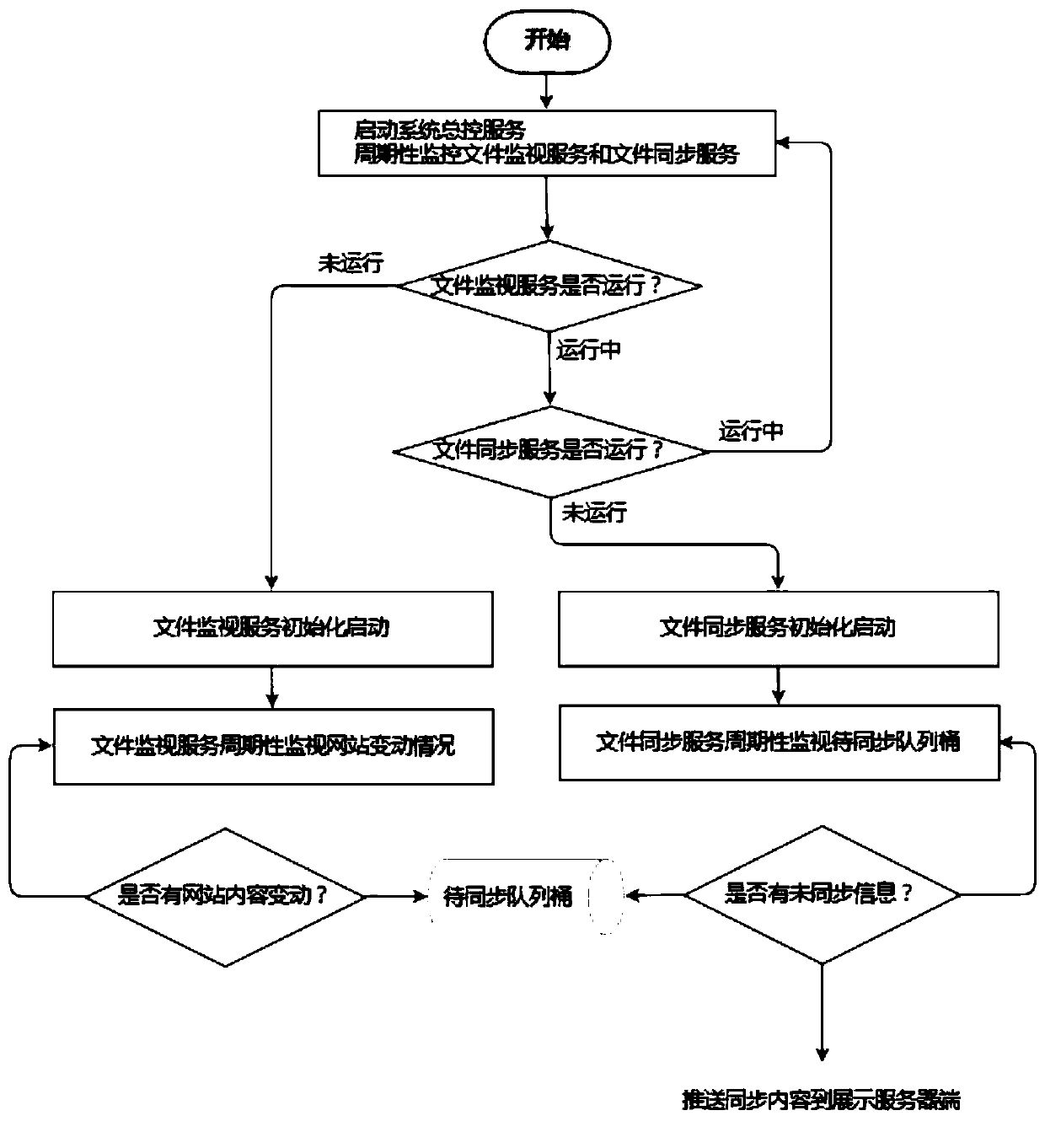
A website security management system and a website security management and control method
The invention discloses a website security management system and a website security management and control method, and relates to the technical field of website management, the website security management system comprises a management end facing a manager and used for deploying website resources and managing website contents, wherein the website resources comprise services supporting website operation; The display end which faces a terminal user and is used for displaying the information issued by the management end; The synchronous queue barrel unit which is used for synchronizing the information published by the management end to the display end. The management end and the display end are physically isolated, and information synchronization is carried out through the synchronous queue barrel unit; The display end opens the static WEB service and the FTP service; And the WEB service is set to be read-only to shield the writable authority. According to the invention, the system servicereliability and security of the website hosting service provider and the access performance of the website can be effectively improved.
Owner:天津开发区沃思电子商务有限公司
Application platform login system and login method thereof
ActiveCN105515781BImprove securitySecurity does not affectUser identity/authority verificationAuthentication protocolUser information
Owner:SHANGHAI PEOPLENET SECURITY TECH
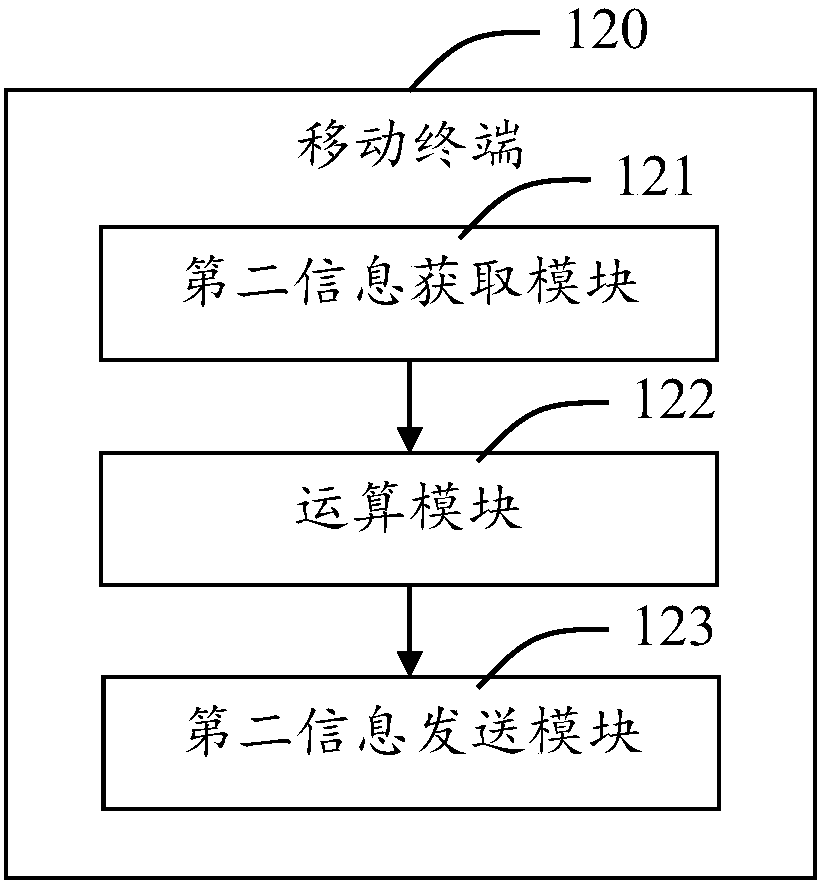
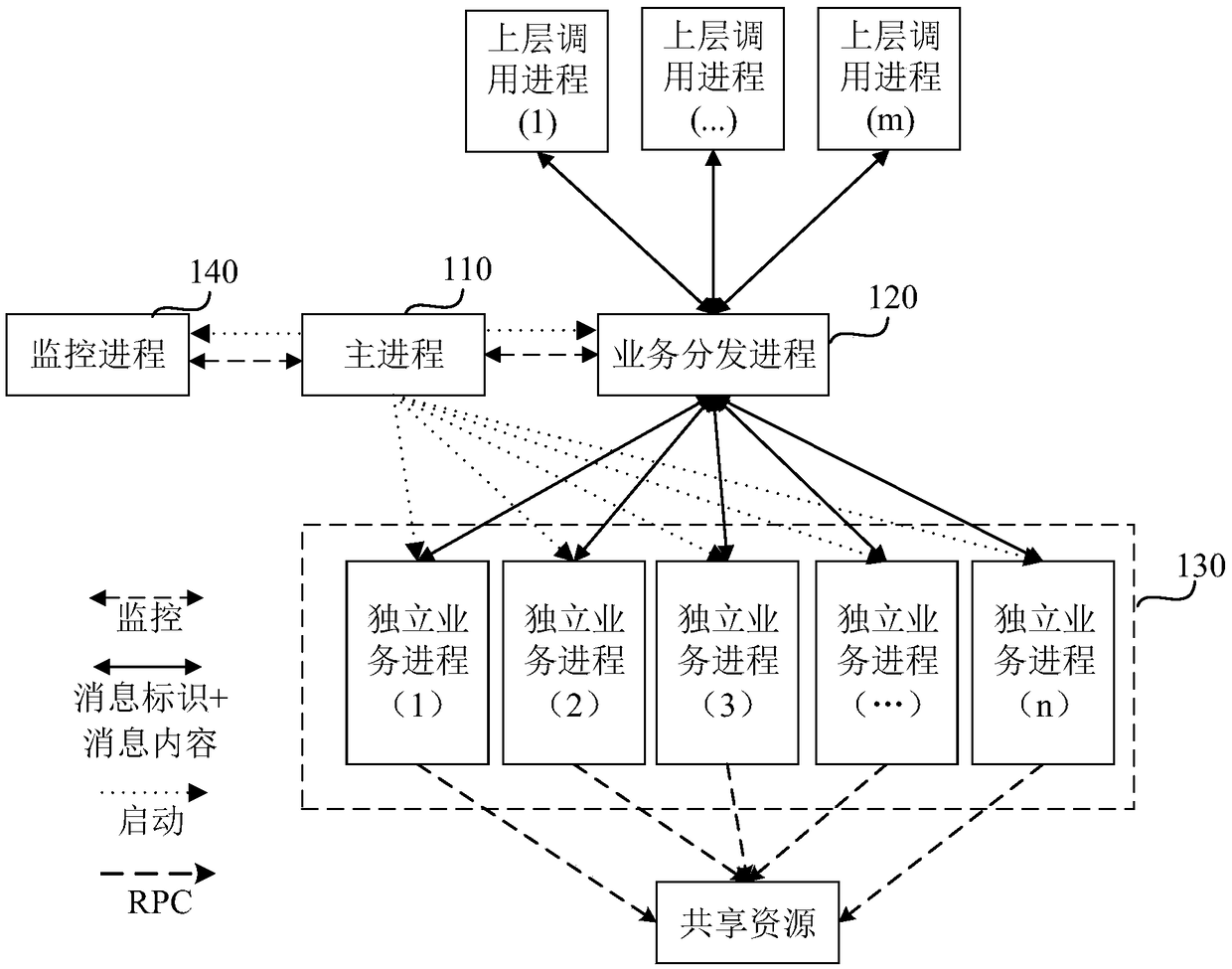
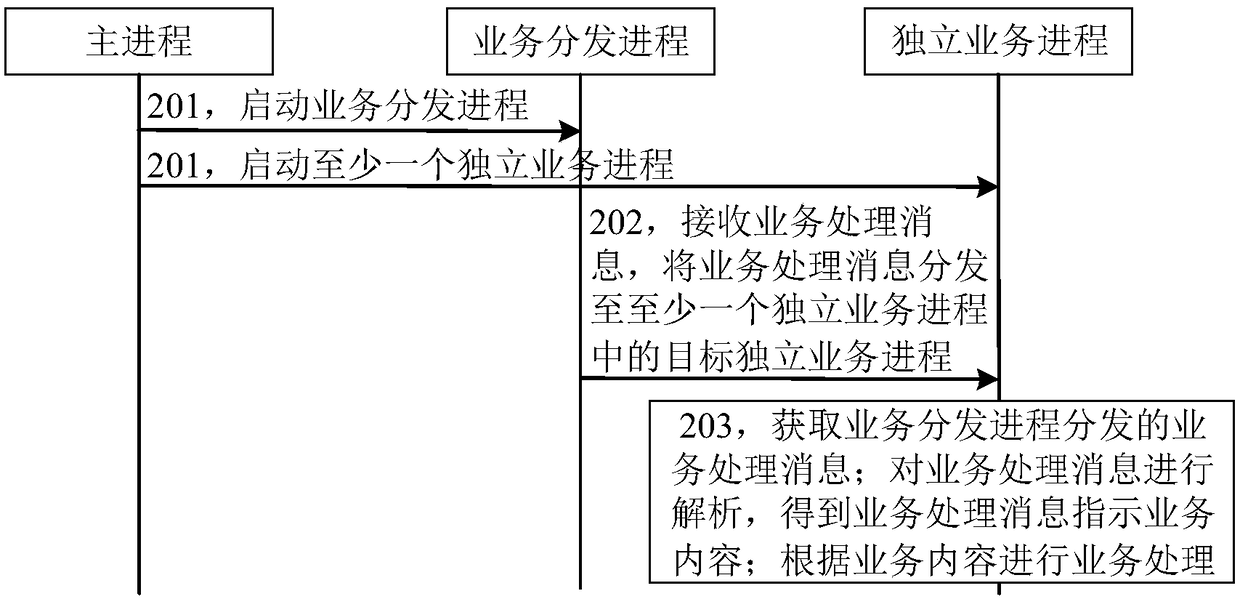
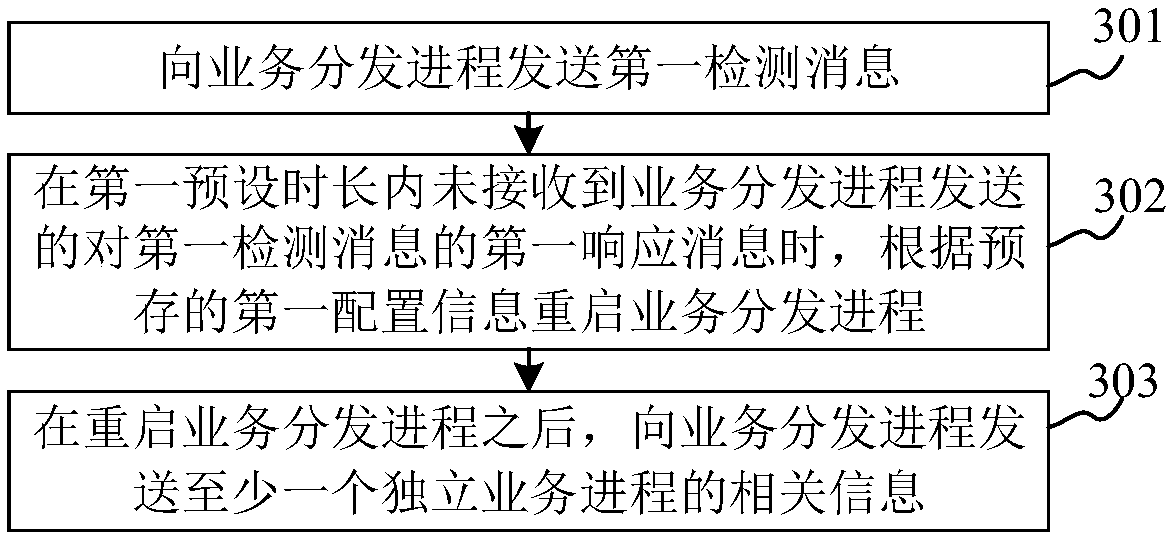
Asynchronous multi-process service processing system, method, apparatus, and storage medium
ActiveCN109032767AImprove securitySecurity does not affectProgram synchronisationInterprogram communicationTreatment systemBusiness logic
The present application relates to an asynchronous multi-process service processing system. The system comprises a main process for starting a service distribution process and at least one independentservice process, wherein each independent service process corresponds to a service logic, and the at least one independent service process subscribes to a service processing message in the service distribution process; the service distribution process is configured to receive a service processing message; distributing the service processing message to a target independent business process in at least one independent business process, wherein the target independent service process is used for obtaining service processing messages distributed by the service distribution process; analyzing the service processing message to obtain the service content indicated by the service processing message; carrying out service processing according to the service content; solving the problem of low process security in the existing asynchronous multi-process architecture; improving process security in an asynchronous multi-process architecture.
Owner:SUZHOU KEDA TECH
Networking system for next generation network
The invention discloses a networking system for next-generation network, comprising several network subregions, all connected by transregional network components, where these components only implementintercommunication between the application layers of all the network subregions and then implement their service intercommunication. The networking system comprises the below network subrgions: non-trust region, meaning the network the users can directly access to as well as the network with undetermined safety; trust region, meaning the service special network for the next-generation network; semi-trust region, the IP network region connected with the external data network by the firewall; operation maintaining region, an independent IP network, one side connected with the equipment at the operation maintaining server end and the other side connected with client ends; operation supporting network, a special network, managing the whole network equipment of the operator. The networking system has feasibility and implements the safety of access network and application server, implementing the intercommunication of all the network subregions.
Owner:HUAWEI TECH CO LTD
Safety storage method for data
ActiveCN100530125CLow costEnable secure storageRedundant operation error correctionSpecial data processing applicationsComputerized systemData Corruption
The invention discloses a data safe storage method. By accessing multiple storage devices in a computer system, any data is stored in two independent storage devices at the same time and associated. When the data in a certain storage device damage, or after the storage device is damaged, take out the data from another storage device that stores the corresponding data and store it in another storage device, so as to ensure that any data has available data in the two storage devices at the same time. When reading data, read from one of the two storage devices. If a storage device storing data is damaged, read data directly from the other storage device. The invention has low hardware cost, strong data security, and strong expansibility, and can increase or decrease storage device capacity arbitrarily. If data corruption is found in the system, it can also be restored online without affecting the reading and running of data.
Owner:CHENGDU SOBEY DIGITAL TECH CO LTD
Emergency rescue equipment for new energy automobile falling into water
ActiveCN111891064AEfficient destructionQuick detonationPedestrian/occupant safety arrangementEmergency rescueNew energy
The invention discloses emergency rescue equipment for a new energy automobile falling into water, which structurally comprises a vehicle body, wherein an inner cavity is formed in the vehicle body; aplurality of accommodating cavities are formed in the front and rear end walls of the inner cavity; open cavities in bilateral symmetry are formed in the left end wall and the right end wall of the inner cavity; protruding blocks in bilateral symmetry are fixedly arranged on the front end wall and the rear end wall of the inner cavity. A matching cavity with an opening is formed between the convex blocks; bottom bulges in bilateral symmetry are fixedly arranged on the left and right end walls of the matching cavity; and an electric crushing device handheld escape device used for crushing theaccommodating cavities and the open cavities is arranged in the matching cavity. According to the equipment, the electric crushing device handheld escape device and a skylight crushing device top escape device are adopted, an automobile skylight is broken in an explosive detonating mode, skylight glass is pushed out of the equipment through a spring and connecting rod type structure, and a handheld glass breaking device convenient for people to use is utilized, so that people can efficiently break and damage glass in other areas in an automobile.
Owner:泰山启帆山东创业投资管理有限公司
Intelligent child folding bed
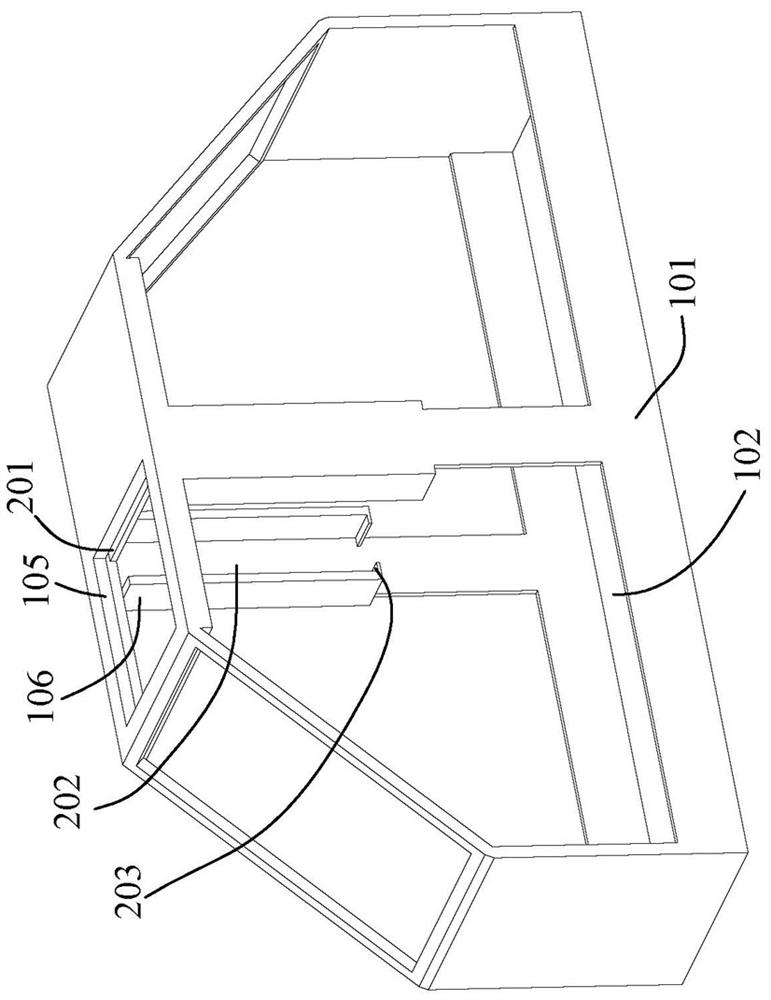
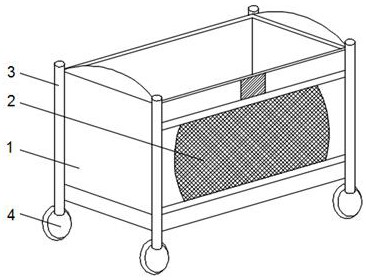
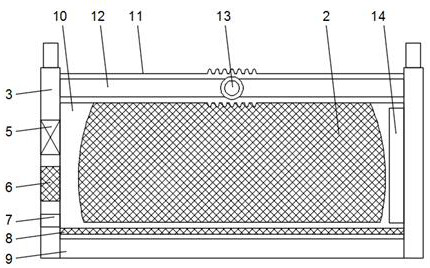
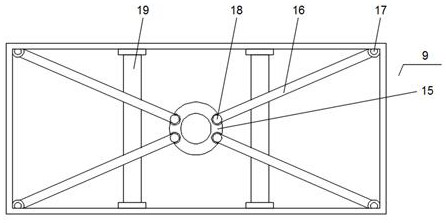
PendingCN112369862AImprove stabilityEnsure safetyThermometer detailsKids bedsDetectorStructural engineering
The invention discloses an intelligent child folding bed which comprises two sets of connecting plates, connecting rods are installed on the two sides of each connecting plate, guide wheels are installed at the bottom ends of the connecting rods, elastic cloth is installed on one sides of the two sets of connecting rods, and a protective curtain is installed between the two sets of elastic cloth.A signal transmitter and a decibel detector are installed in one set of connecting plates, a connecting groove is formed in one side penetrating through one set of connecting plates, an elastic net pad and a folding layer are installed between the two sets of connecting plates, the folding layer is located below the elastic net pad, and a protective sleeve is installed between the two sets of connecting rods. And a folding rod is mounted on the inner side of the protective sleeve. According to the folding bed, the folding process is fast and convenient, the stability of the folding bed is alsoimproved, so that the safety of children is guaranteed; meanwhile, the body temperature and the condition of the children can be intelligently monitored.
Owner:七彩人生集团有限公司
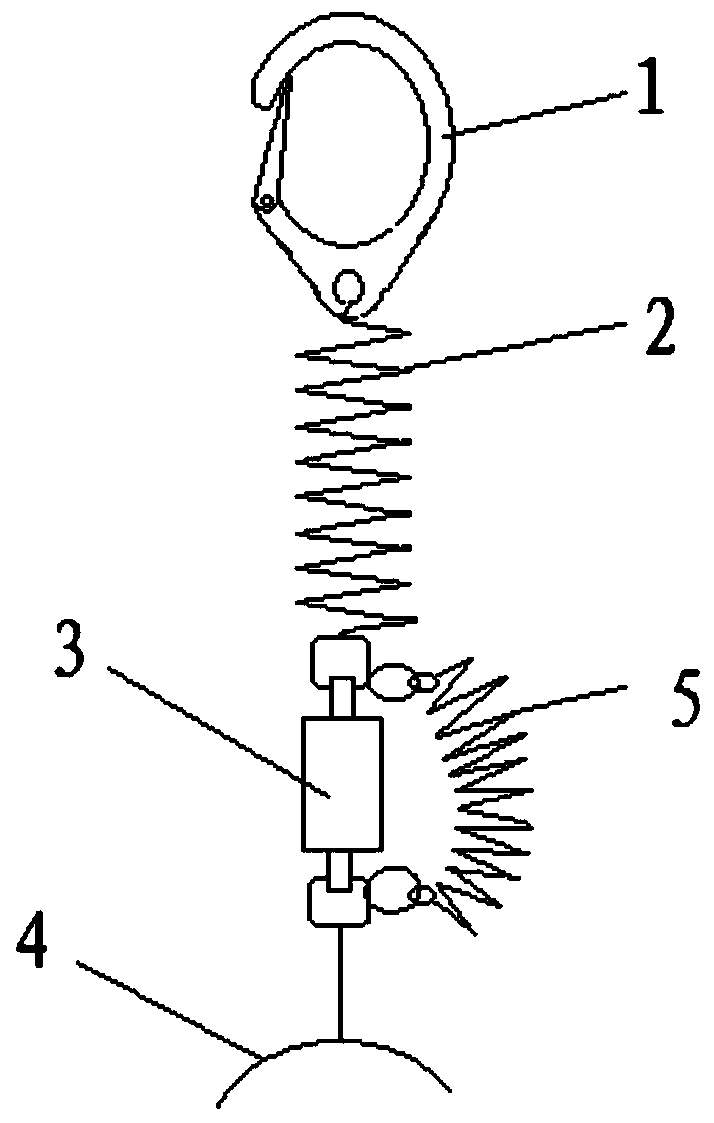
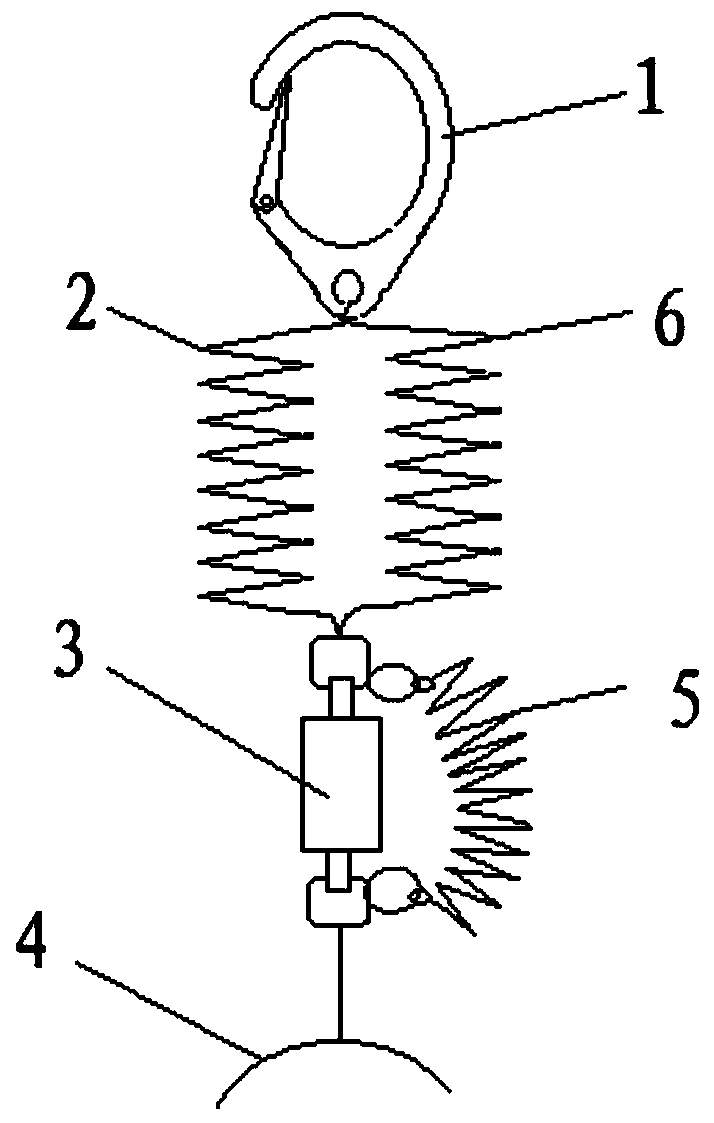
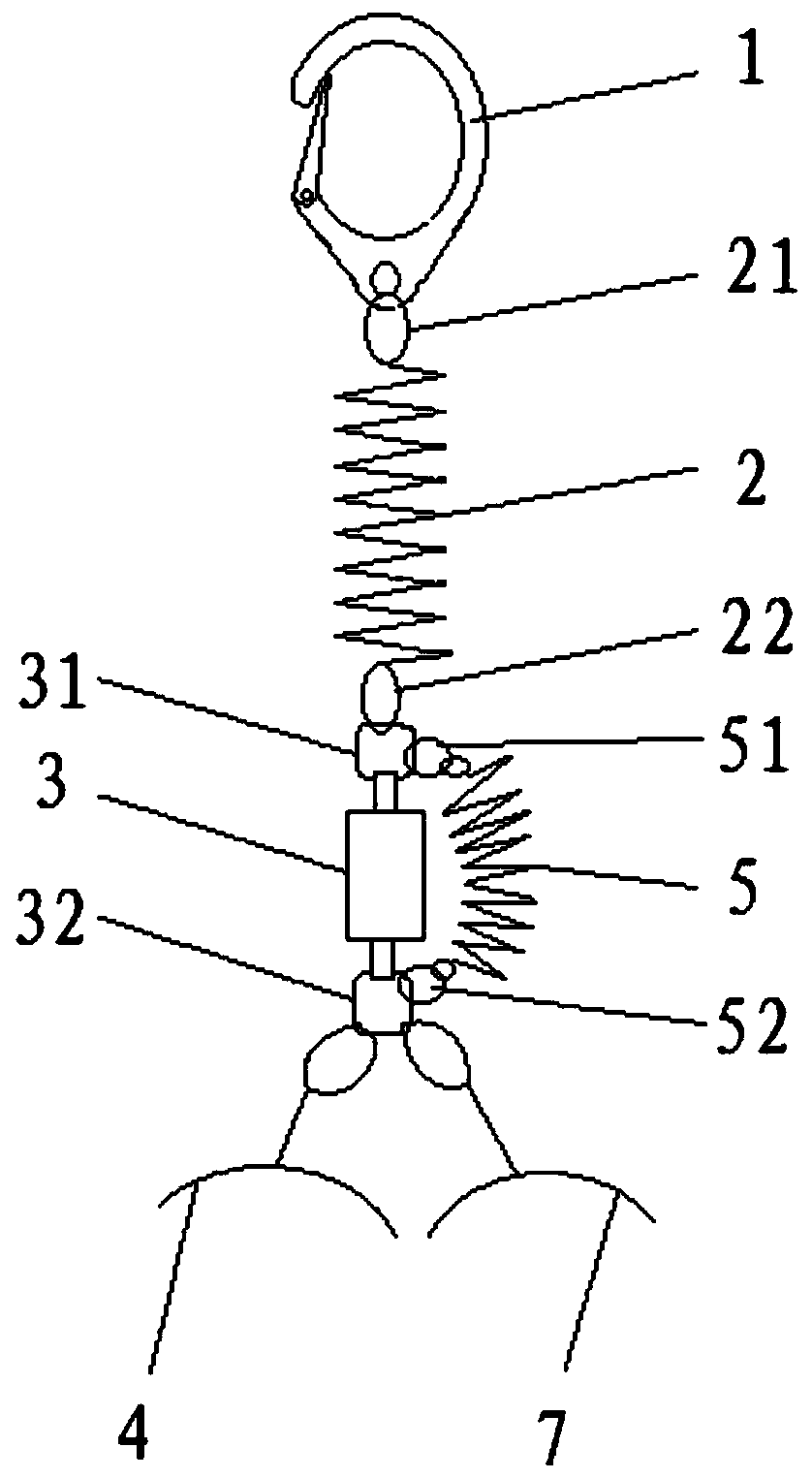
Composite reinforced safety belt
The invention discloses a composite reinforced safety belt. The composite reinforced safety belt comprises a safety hook, a first safety rope, a buffer bag and a first binding belt, a second safety rope connected with the buffer bag in parallel is also connected between the first safety rope and the first binding belt, and the extension length of the second safety rope is larger than or equal to the maximum length of the buffer bag after being collided to open. During normal use, the safety hook, the first safety rope, the buffer bag and the first binding belt form a safe suspension system toprotect the safety of a worker, the second safety rope cannot affect normal use of the buffer bag, when the buffer bag is abnormal, the second safety rope can have a function of replacing the buffer bag, that is, the safety hook, the first safety rope, the second safety rope and the first binding belt form another safe suspension system to ensure safety of the worker, and the safety in use is significantly improved.
Owner:秦向东
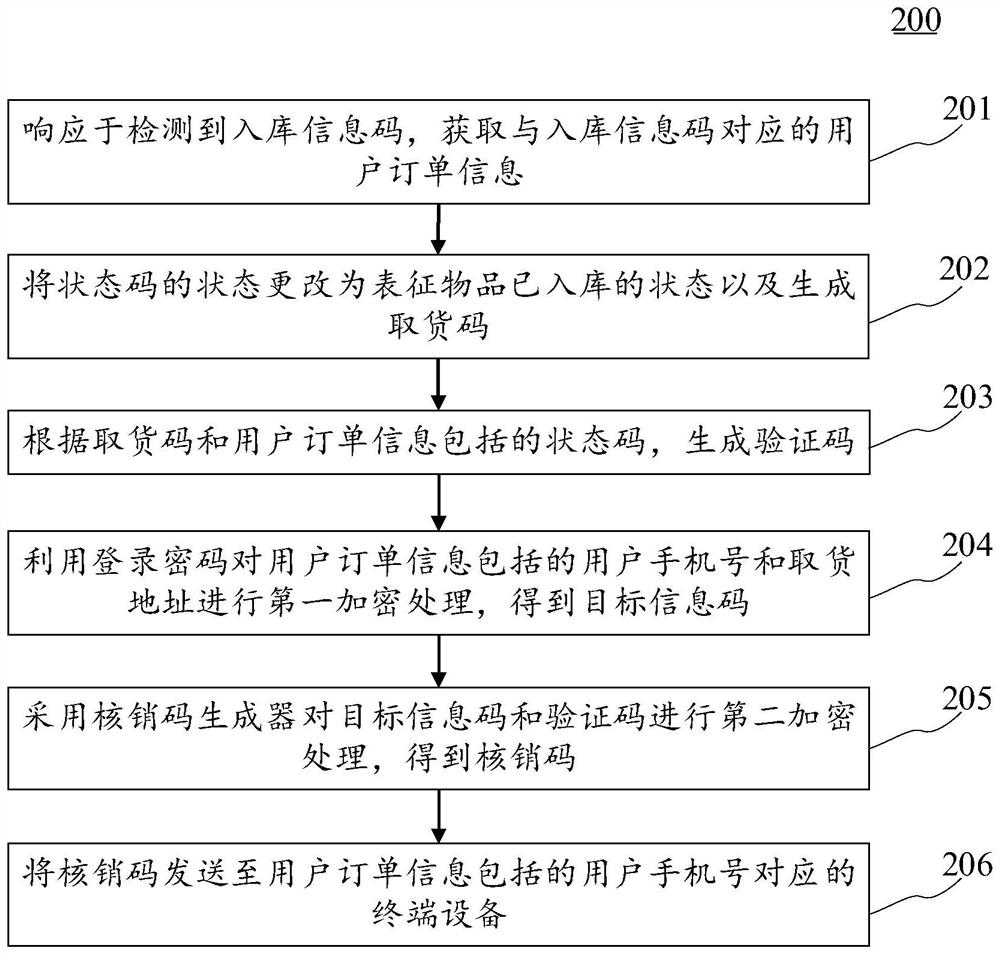
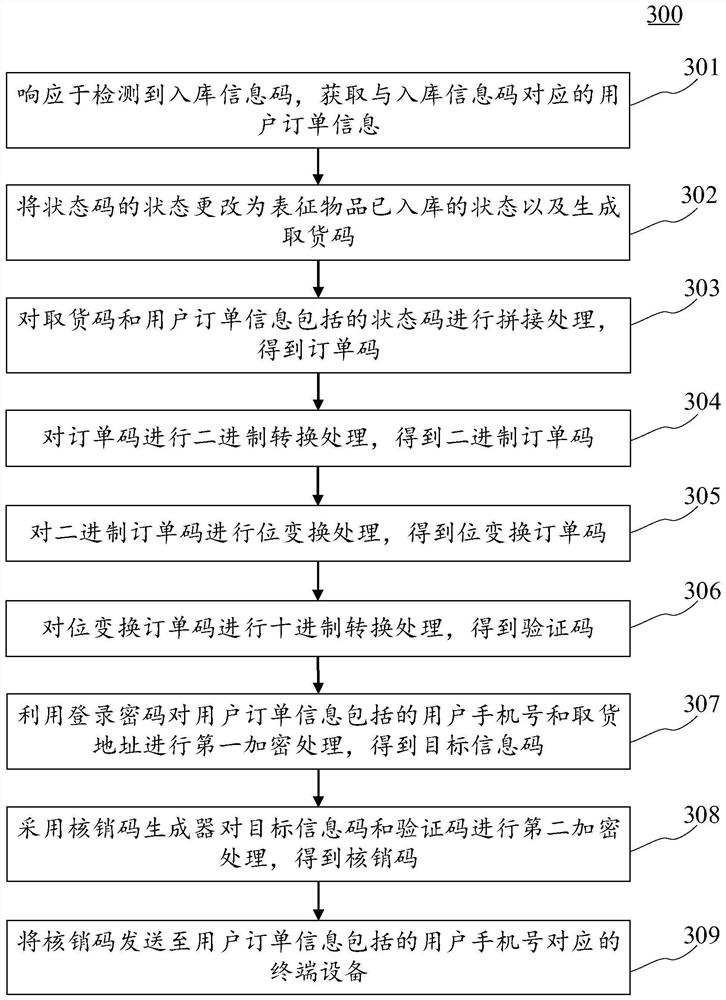
Verification code sending method and device, electronic equipment and computer readable medium
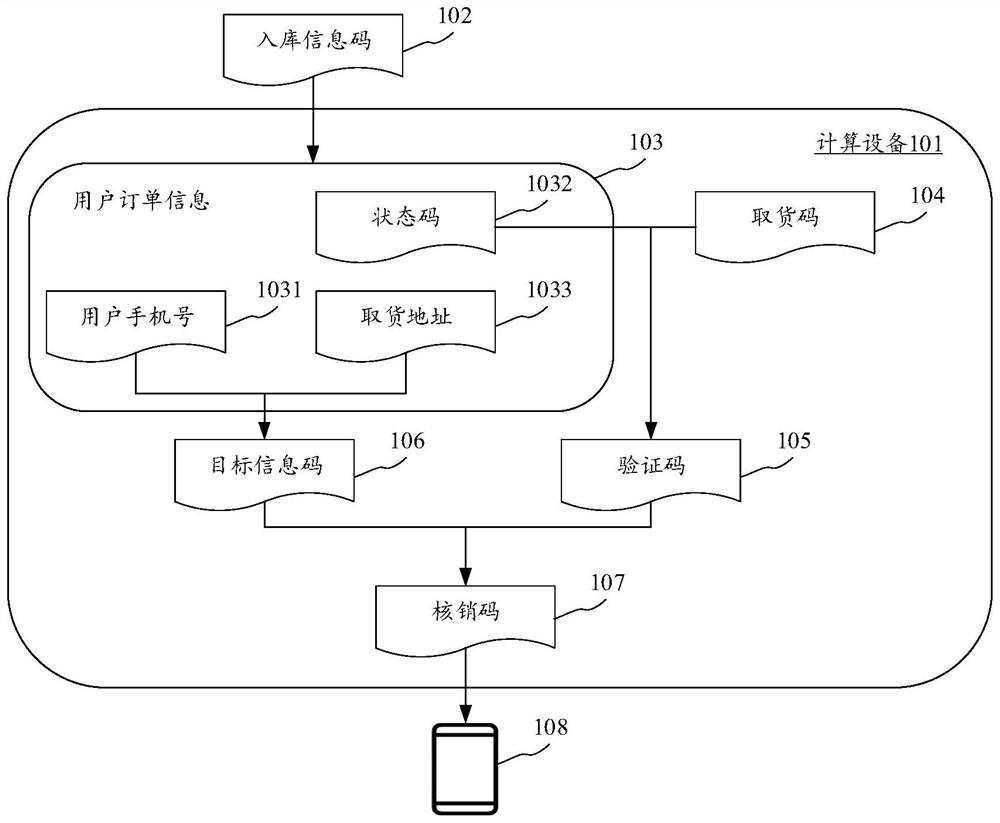
PendingCN113919922ADoes not compromise securityImprove securityDigital data protectionBuying/selling/leasing transactionsProgramming languagePassword
The embodiment of the invention discloses a verification code sending method and device, electronic equipment and a computer readable medium. A specific embodiment of the method comprises the steps of obtaining user order information corresponding to a warehousing information code; changing the state of the state code into a state representing that the article is put in storage, and generating an article taking code; generating a verification code according to the pickup code and a state code included in the user order information; performing first encryption processing on a user mobile phone number and a pickup address included in the user order information by using the login password to obtain a target information code; performing second encryption processing on the target information code and the verification code by adopting a verification code generator to obtain a verification code; and sending the verification code to a terminal device corresponding to the user mobile phone number included in the user order information. According to the embodiment, the verification codes are generated by using different secret keys at different verification points, so that after the secret key of one verification point is cracked, the security of the verification codes generated by other verification points is not influenced, and the overall security of the verification codes is improved.
Owner:杭州拼便宜网络科技有限公司
Multi-party security calculation method based on OverDrive
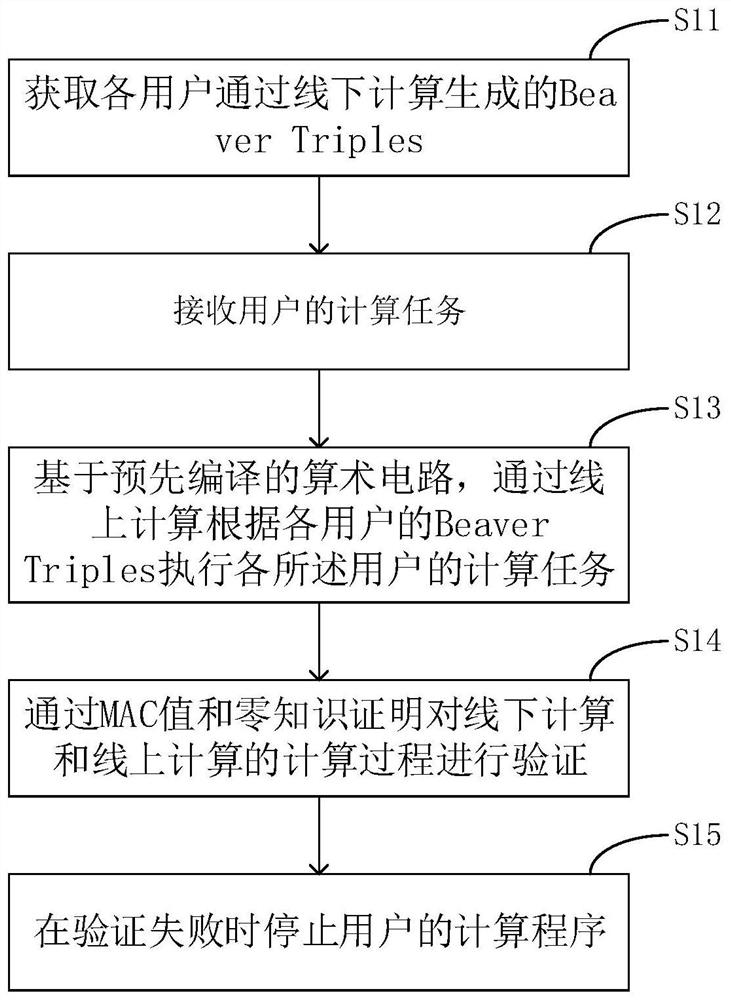
PendingCN114036498ASecurity does not affectRandom number generatorsDigital data protectionAlgorithmTheoretical computer science
The invention relates to a multi-party security calculation method based on OverDrive. Multi-party security calculation is carried out based on an OverDrive protocol; in the OverDrive protocol, the multi-party security calculation is divided into two parts of offline calculation and online calculation, wherein the offline calculation is used for generating BeaverTriples required by subsequent online calculation, and the online calculation carries out calculation based on a pre-compiled arithmetic circuit according to the BeaverTriples. In the calculation process of offline calculation and online calculation, the calculation process is verified through a MAC value and zero-knowledge proof, and a calculation program of a user is stopped when the verification fails, so that only the calculation program of the user can be stopped even if a certain user actively disables, does not comply with a protocol, and even tampers the input, the security of other honest user data is not influenced.
Owner:续科天下(北京)科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com